System and method for realizing VPN protocol at application layer
A technology of application layer and protocol, applied in the direction of transmission system, digital transmission system, data exchange through path configuration, etc., can solve problems such as core layer system crash, unfavorable adaptability and impact of VPN client application environment, etc., to avoid conflicts , Improve the adaptability of the network environment
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
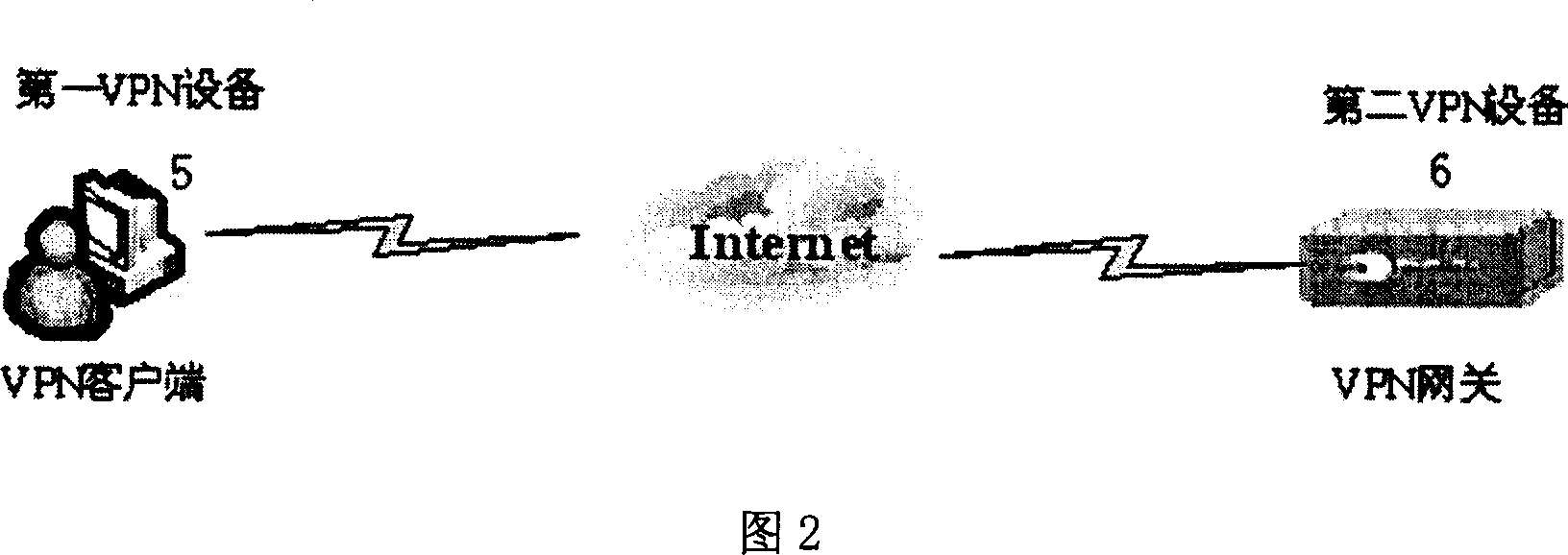
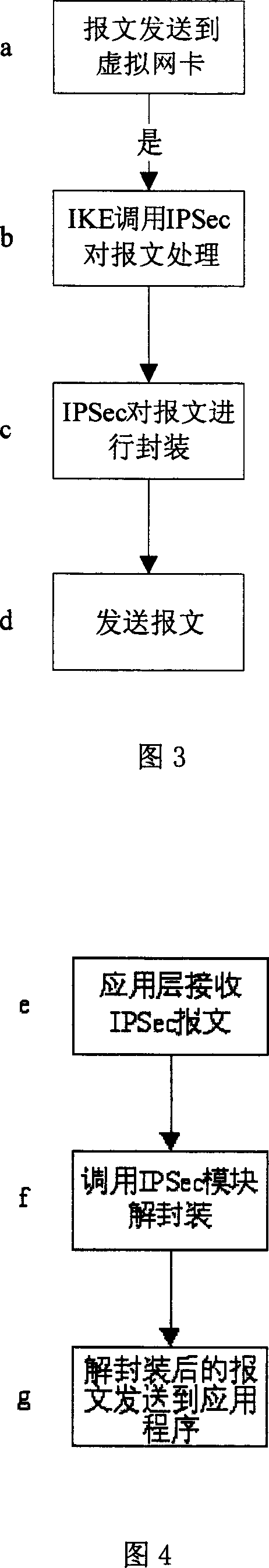
[0042] Further explain below in conjunction with accompanying drawing:
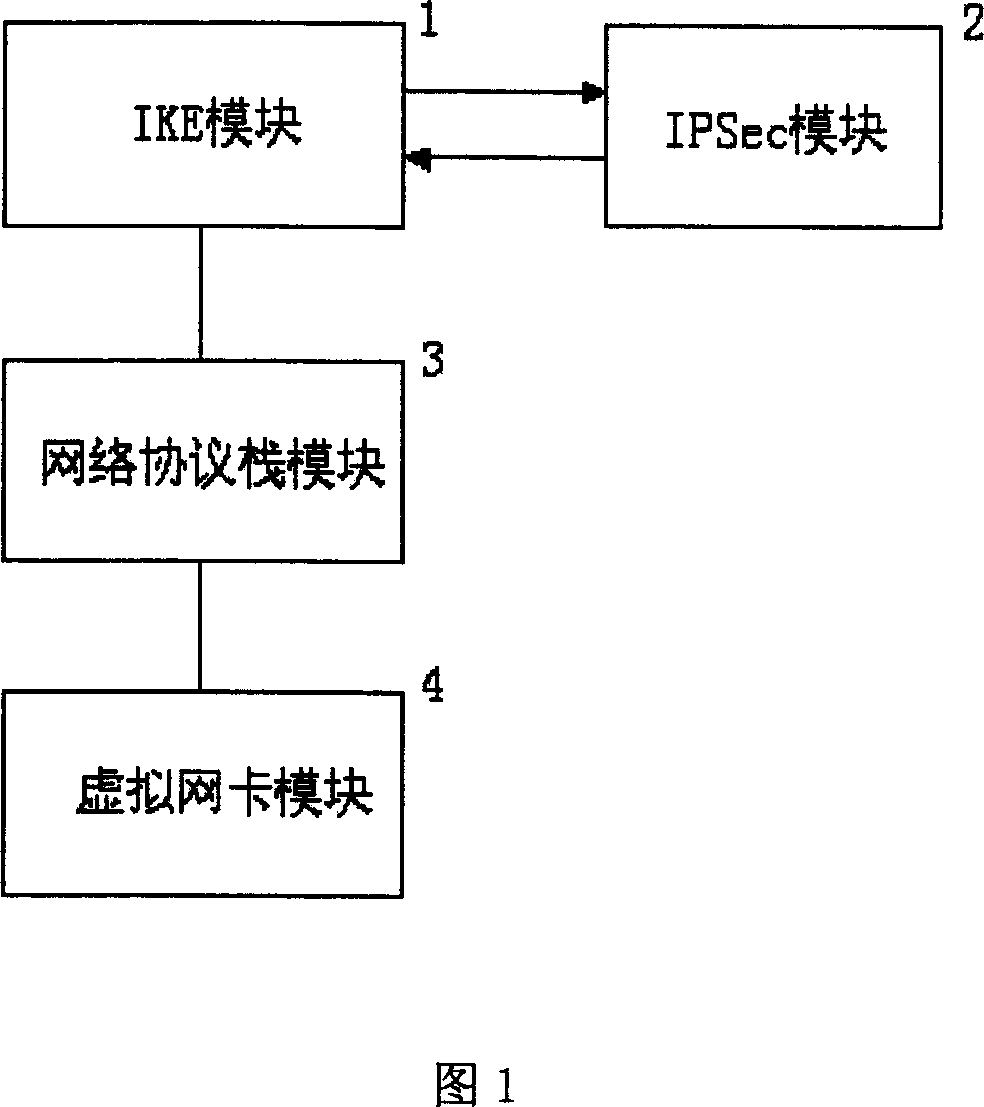
[0043] 1. A system that implements the VPN protocol at the application layer
[0044] (1) IKE module 1
[0045] The typical implementation of IKE module 1 is the Internet open source software FreeSWAN; FreeSWAN is a software of IPSec and Internet key exchange protocol implemented on the Linux operating system.
[0046] (2) IPSec module 2
[0047] The typical implementation of IPSec module 2 is the Internet open source software FreeSWAN; FreeSWAN is a software of IPSec and Internet key exchange protocol implemented on the Linux operating system.
[0048] (3) Network protocol stack module 3
[0049] Typical representatives of the network protocol stack module 3 are network operating systems such as Windows, UNIX, and Linux.
[0050] (4) Virtual network card module 4
[0051] The virtual network card module 4 can obtain the information of the virtual network interface by checking the system interface an...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com