Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
383 results about "Virtual network interface" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
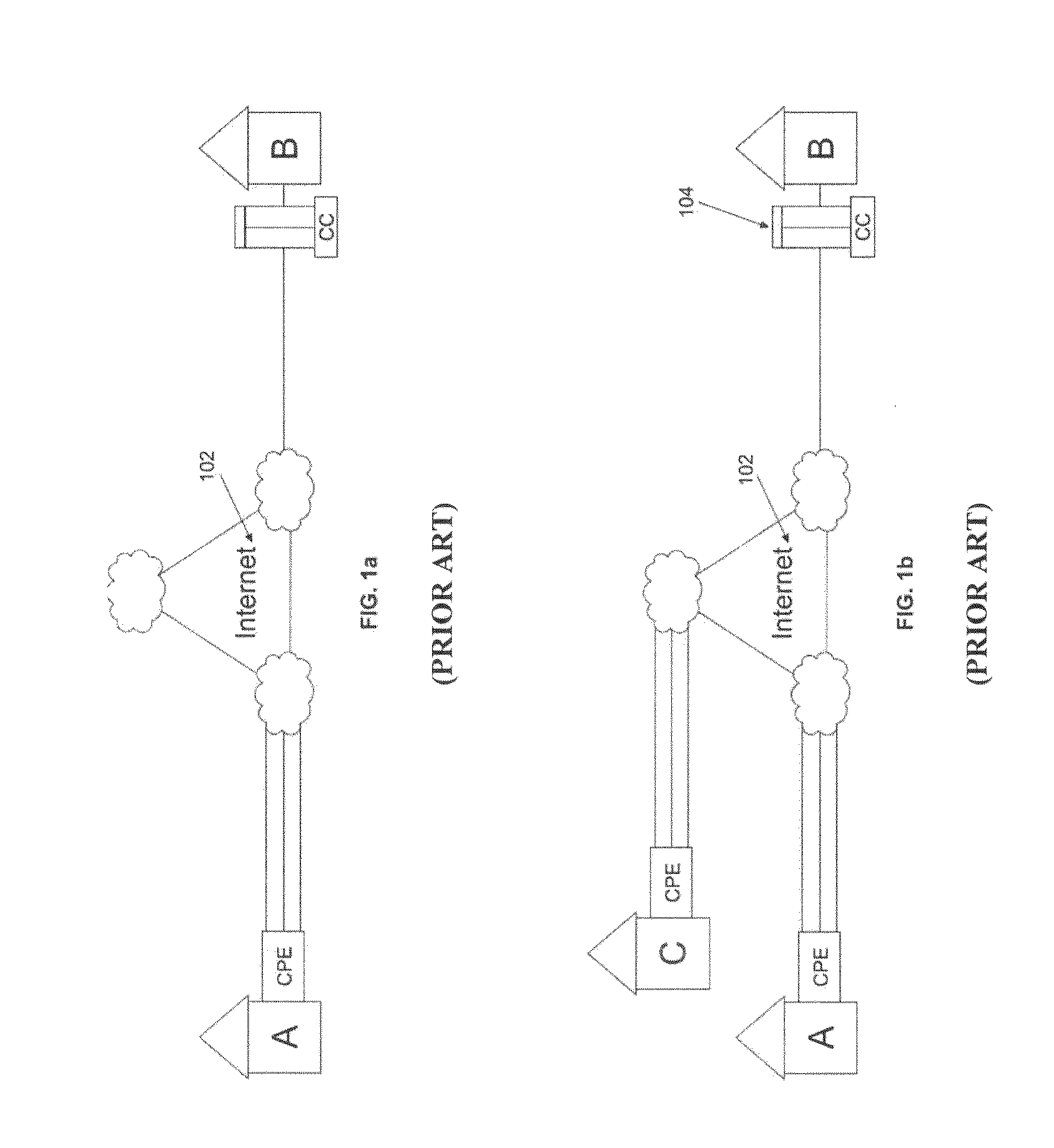
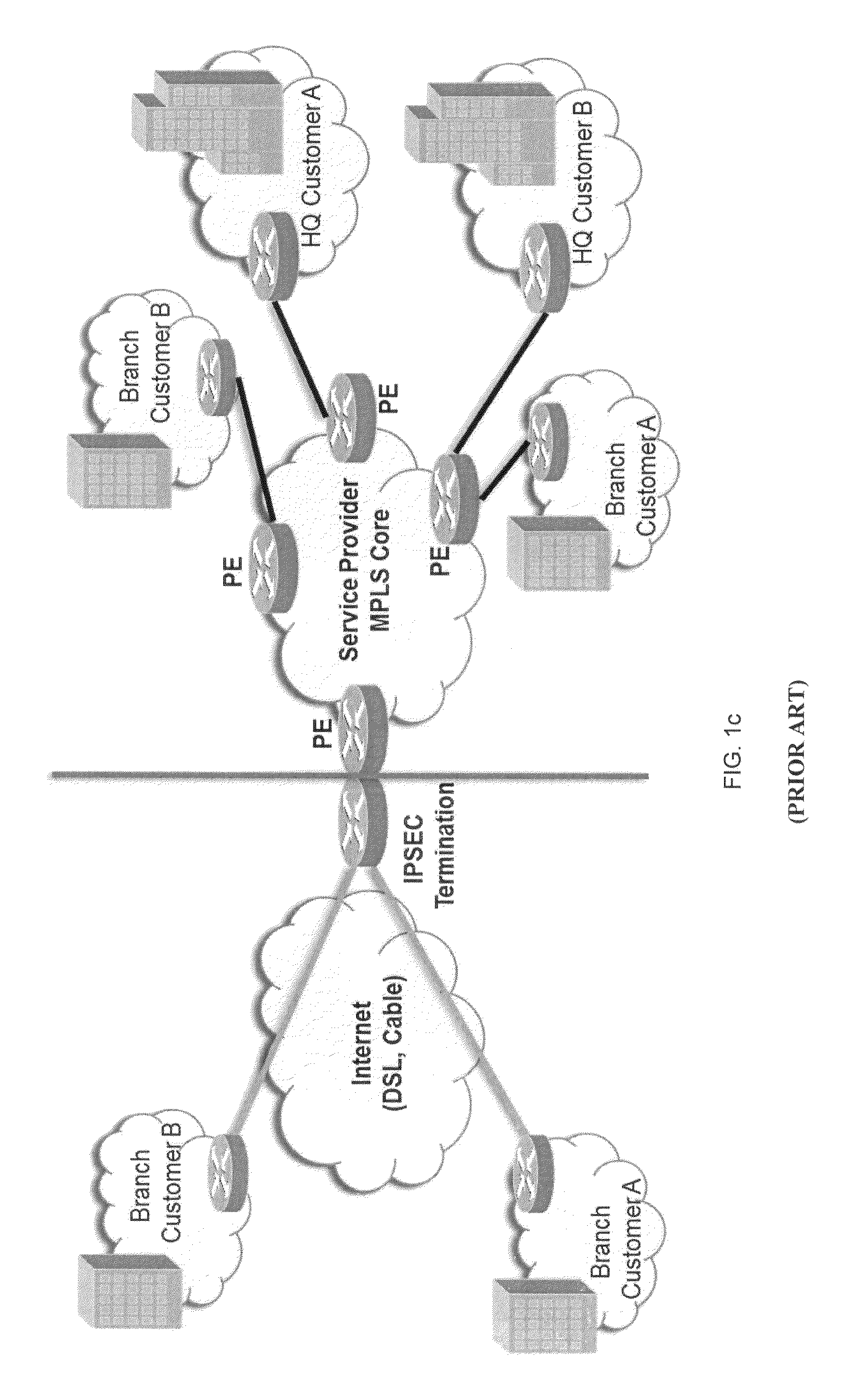
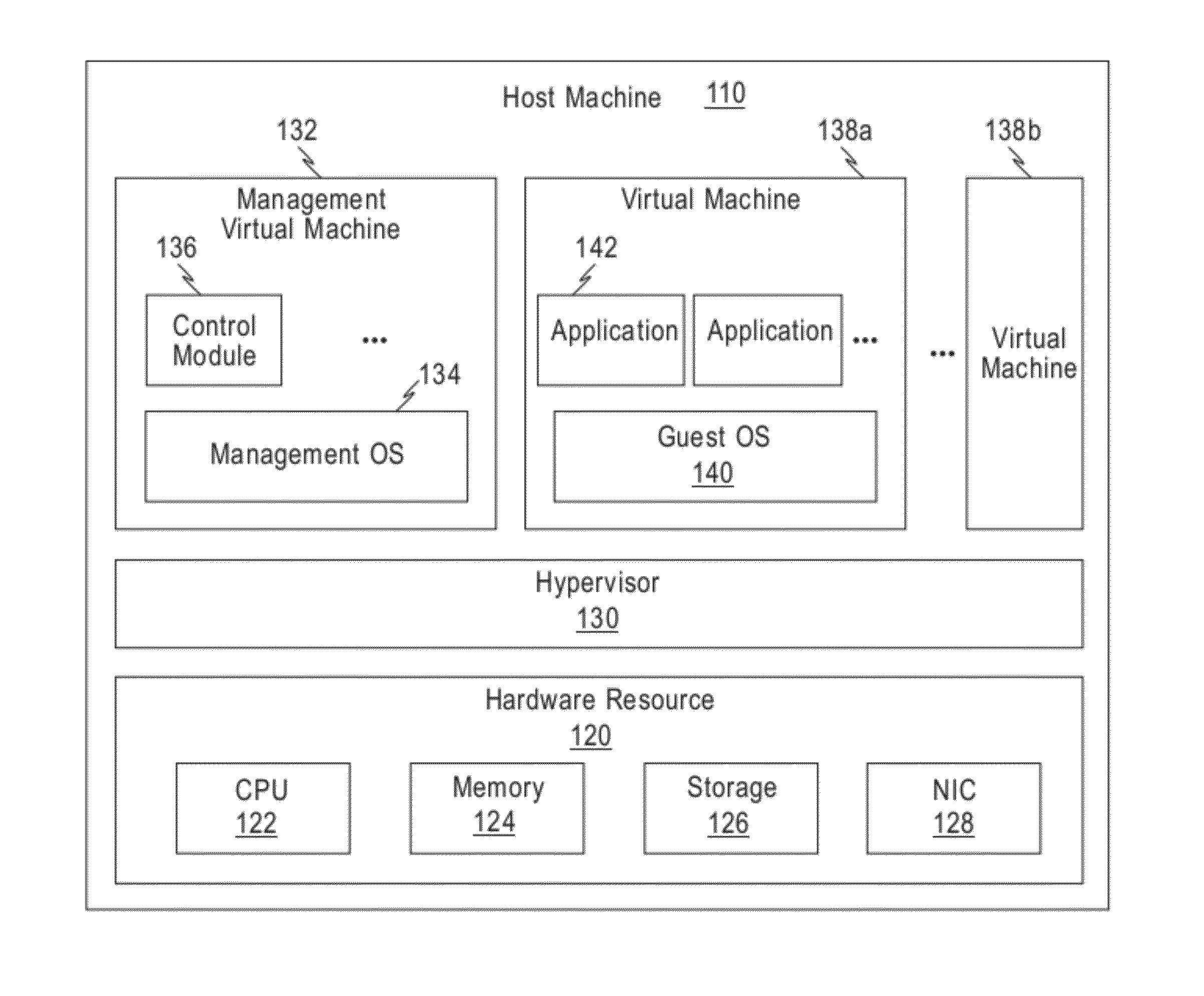
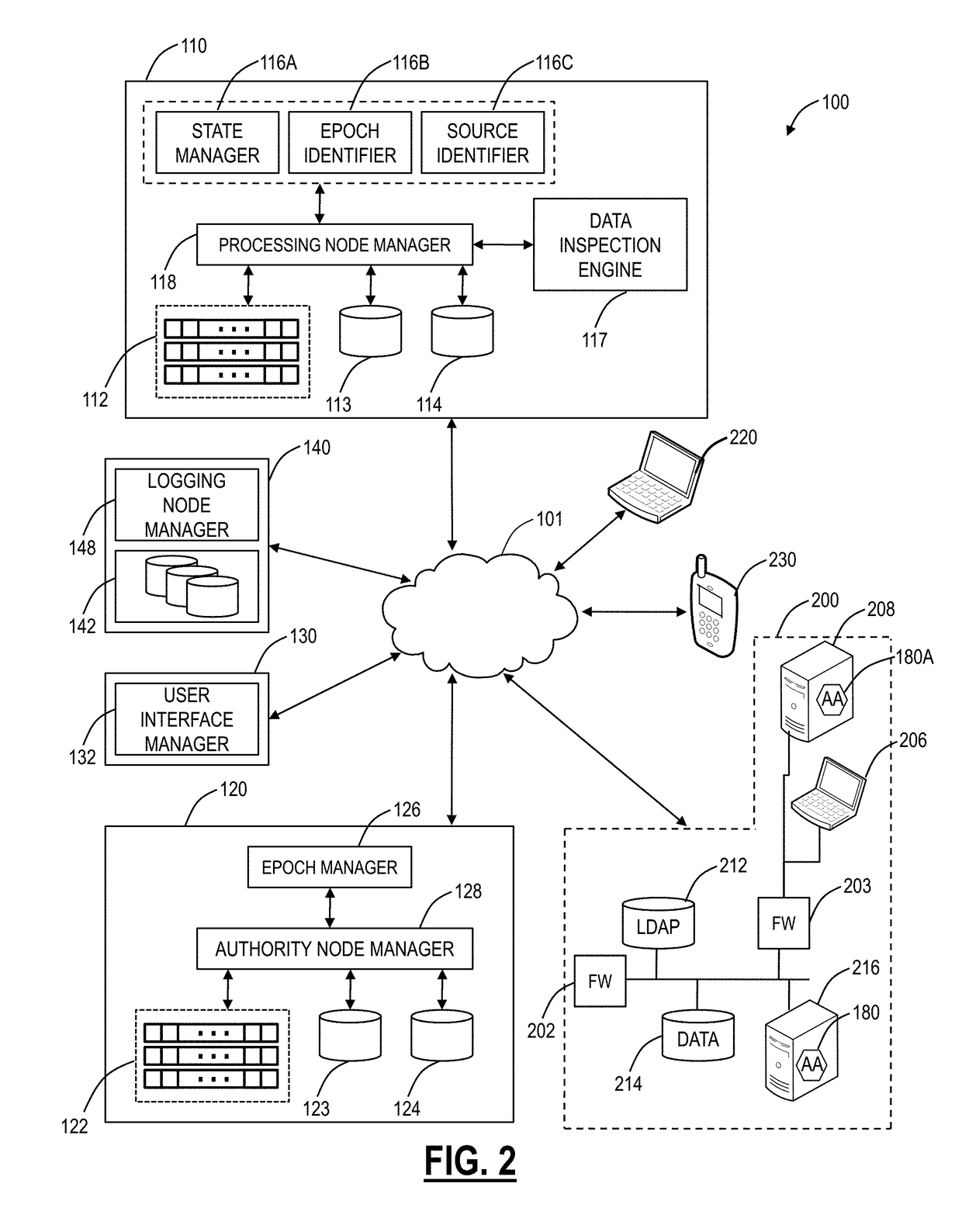
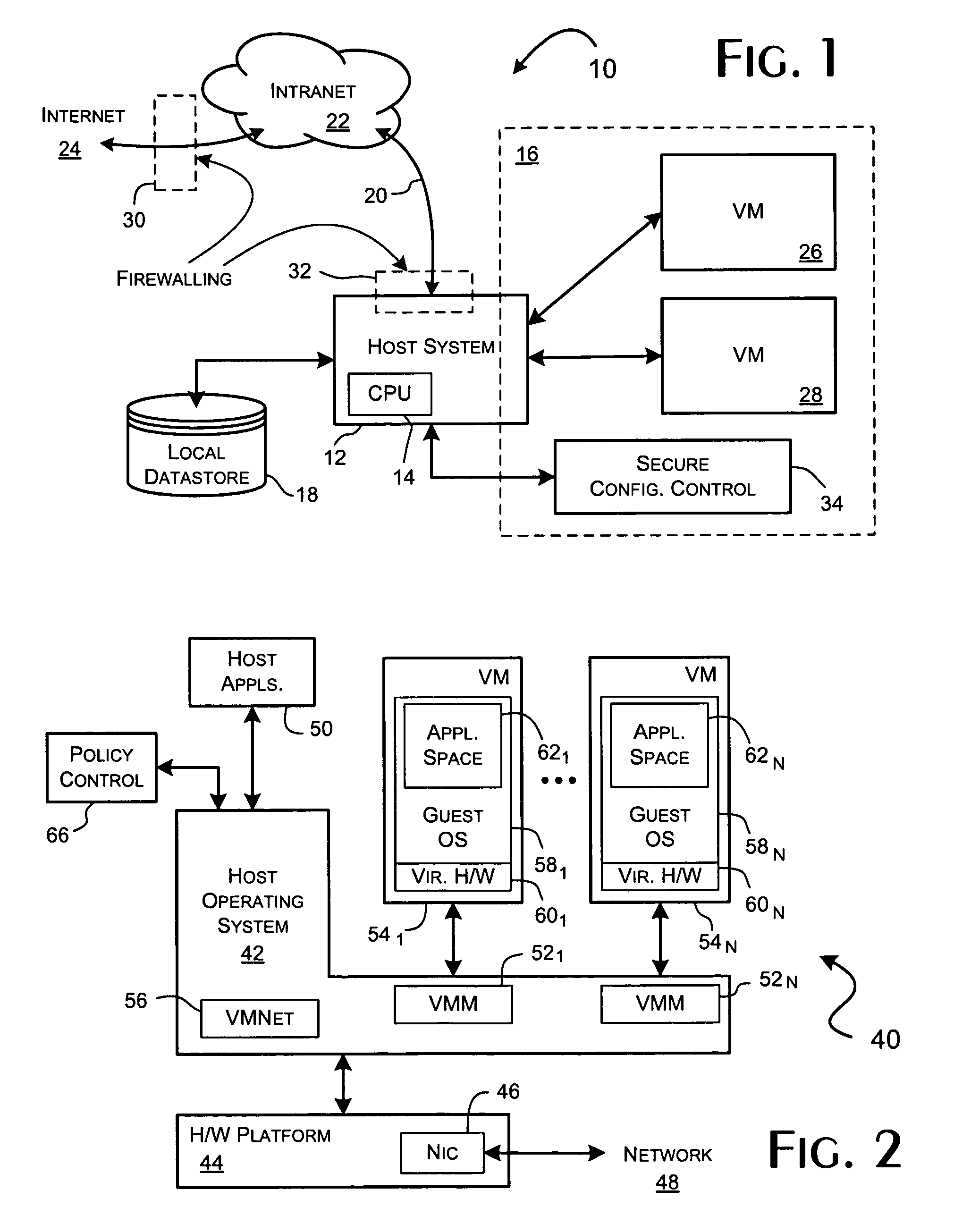
A virtual network interface (VIF) is an abstract virtualized representation of a computer network interface that may or may not correspond directly to a network interface controller.
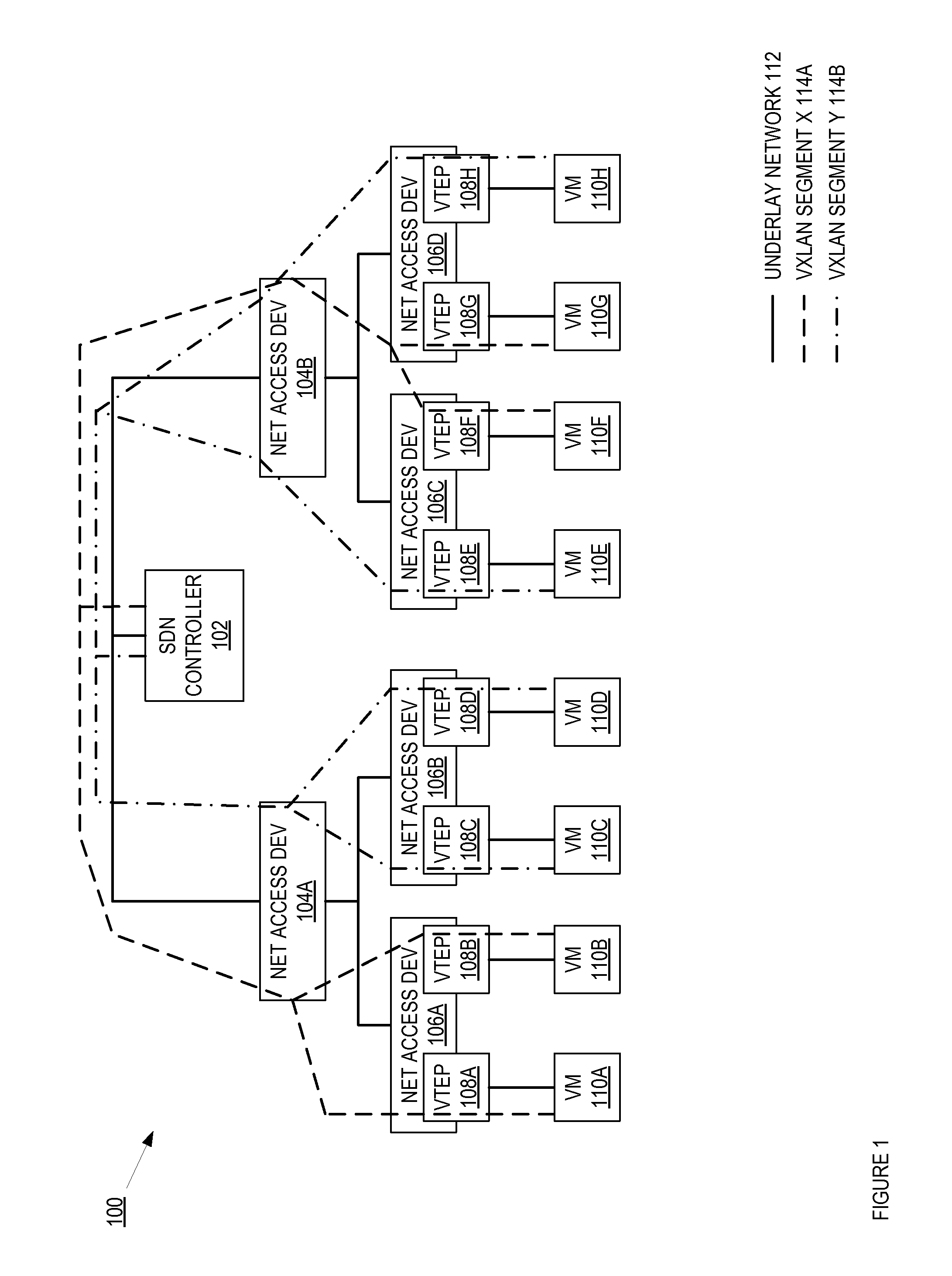
System and method for implementing and managing virtual networks
ActiveUS20140195666A1Digital computer detailsData switching networksVirtual network topologyDecision taking
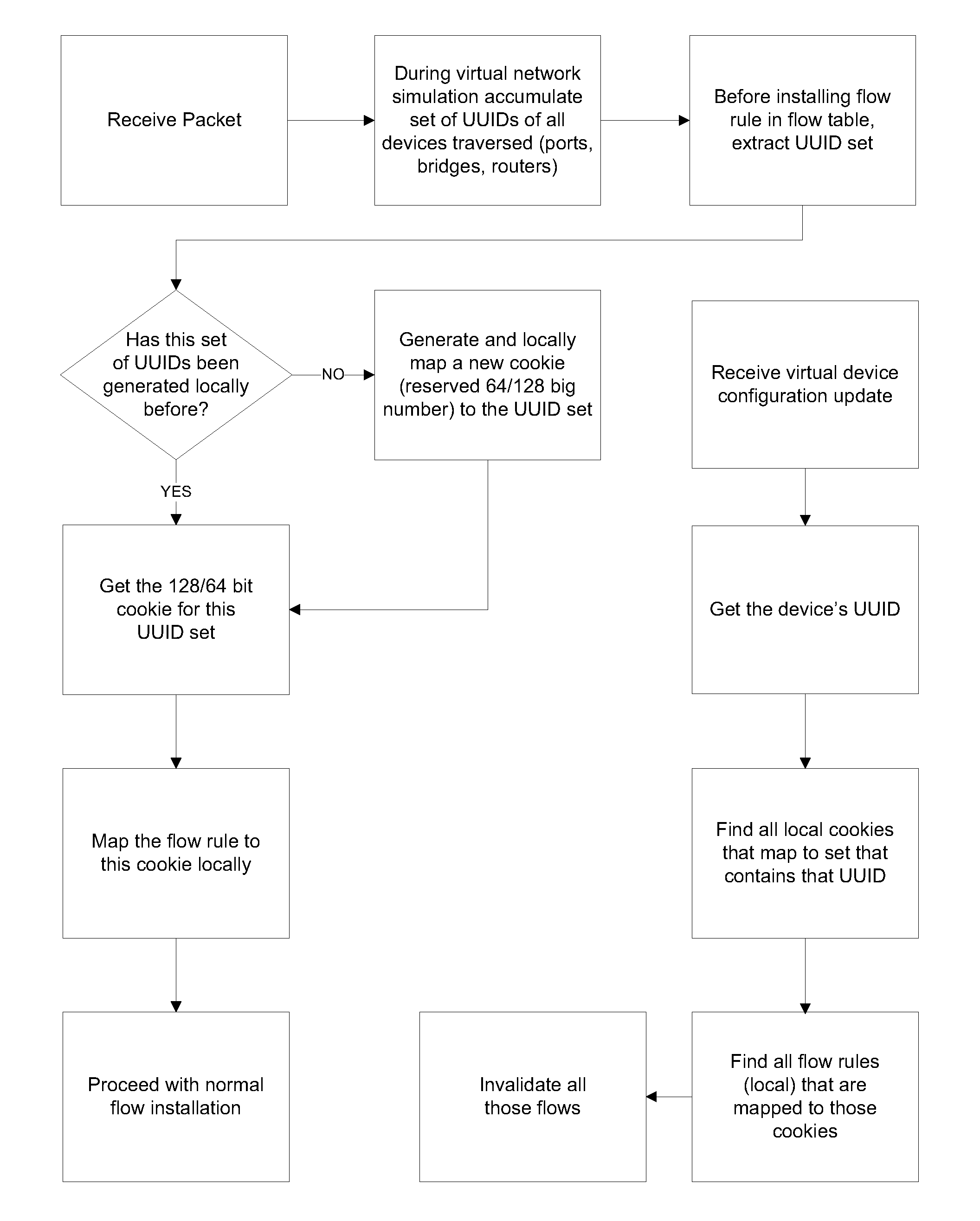
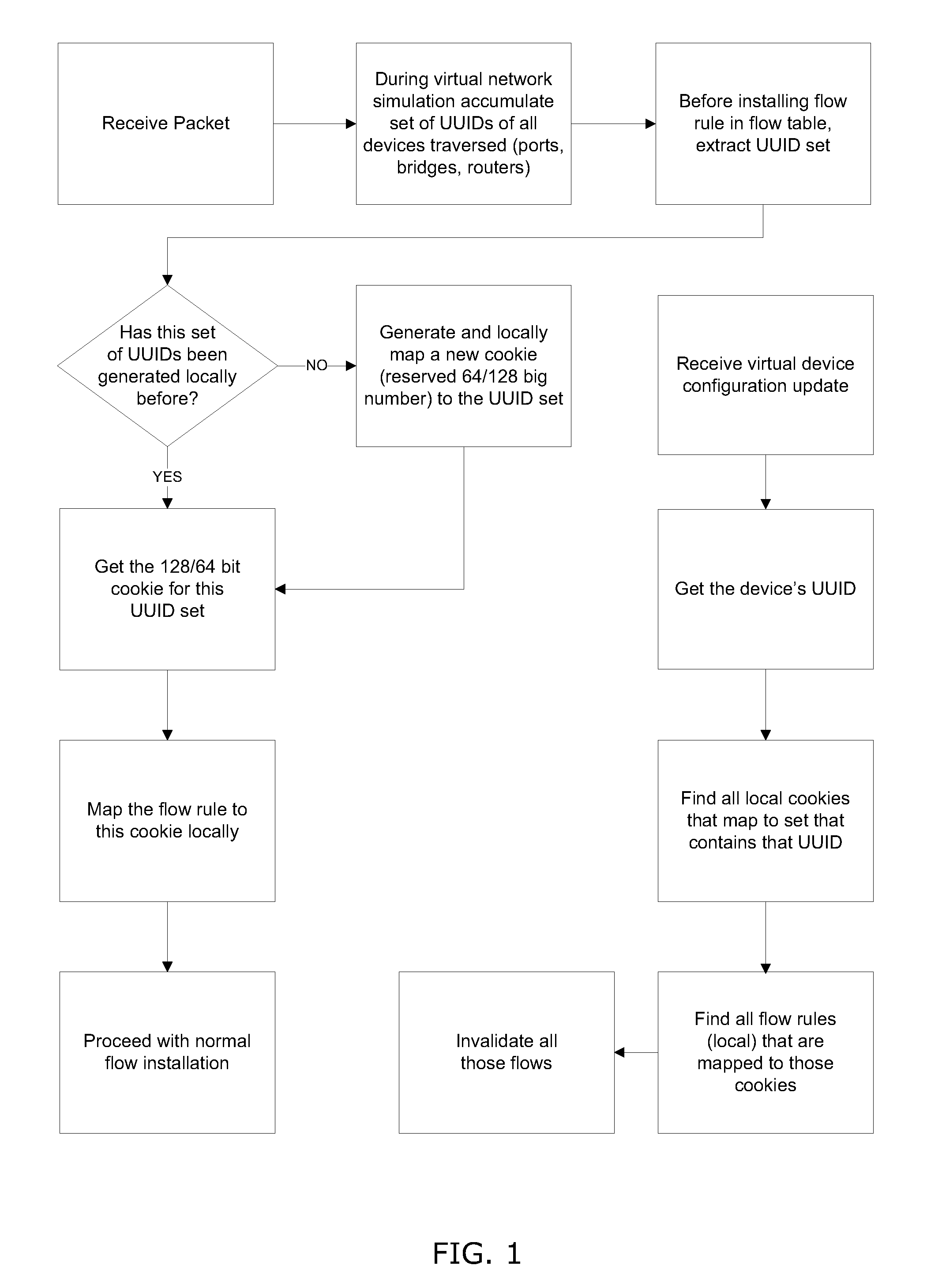
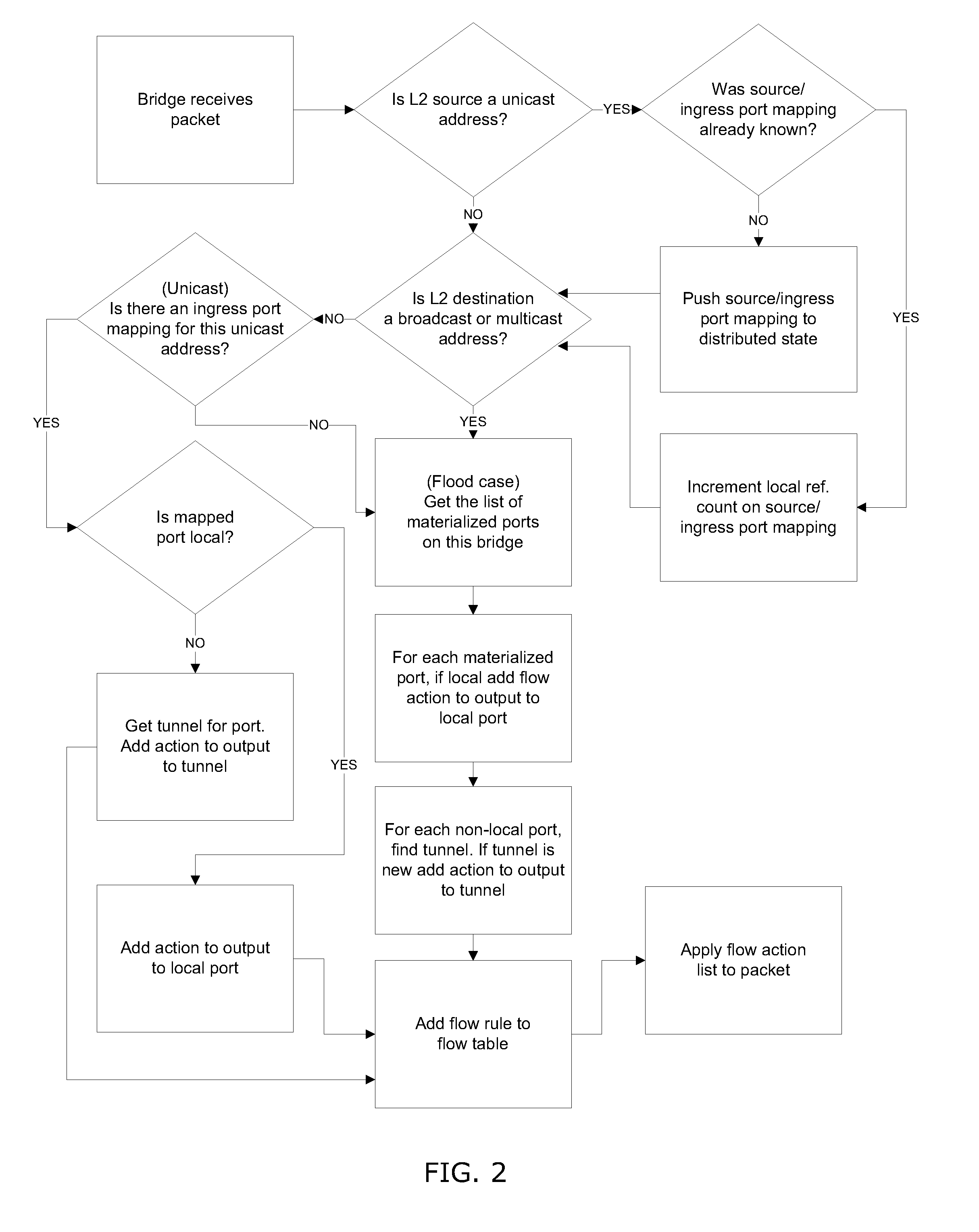
A system and method for implementing and management virtual networks is disclosed. A method includes receiving a network packet arriving at a first network interface of a first node of an underlying network, communicating at least the packet and an identifier of the first network interface to a decision engine, determining how the packet should be processed based on a simulation by the decision engine of a traversal of a virtual network topology including a plurality of virtual network devices, wherein the decision engine communicates with a shared database accessible from the underlying network that stores the virtual network topology and virtual device configurations for the plurality of virtual network devices; and processing the packet based upon the simulation.
Owner:MIDO HLDG LTD
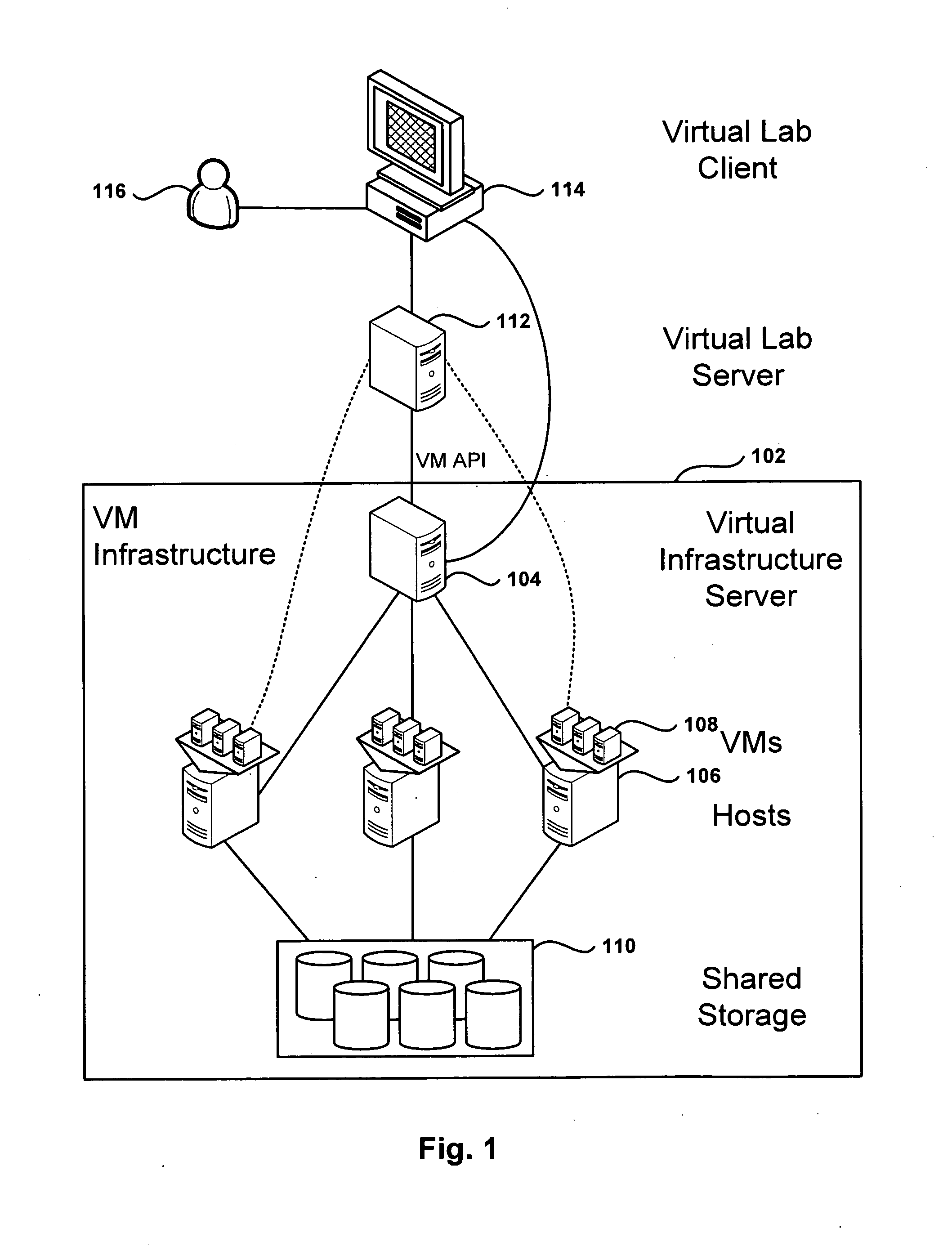
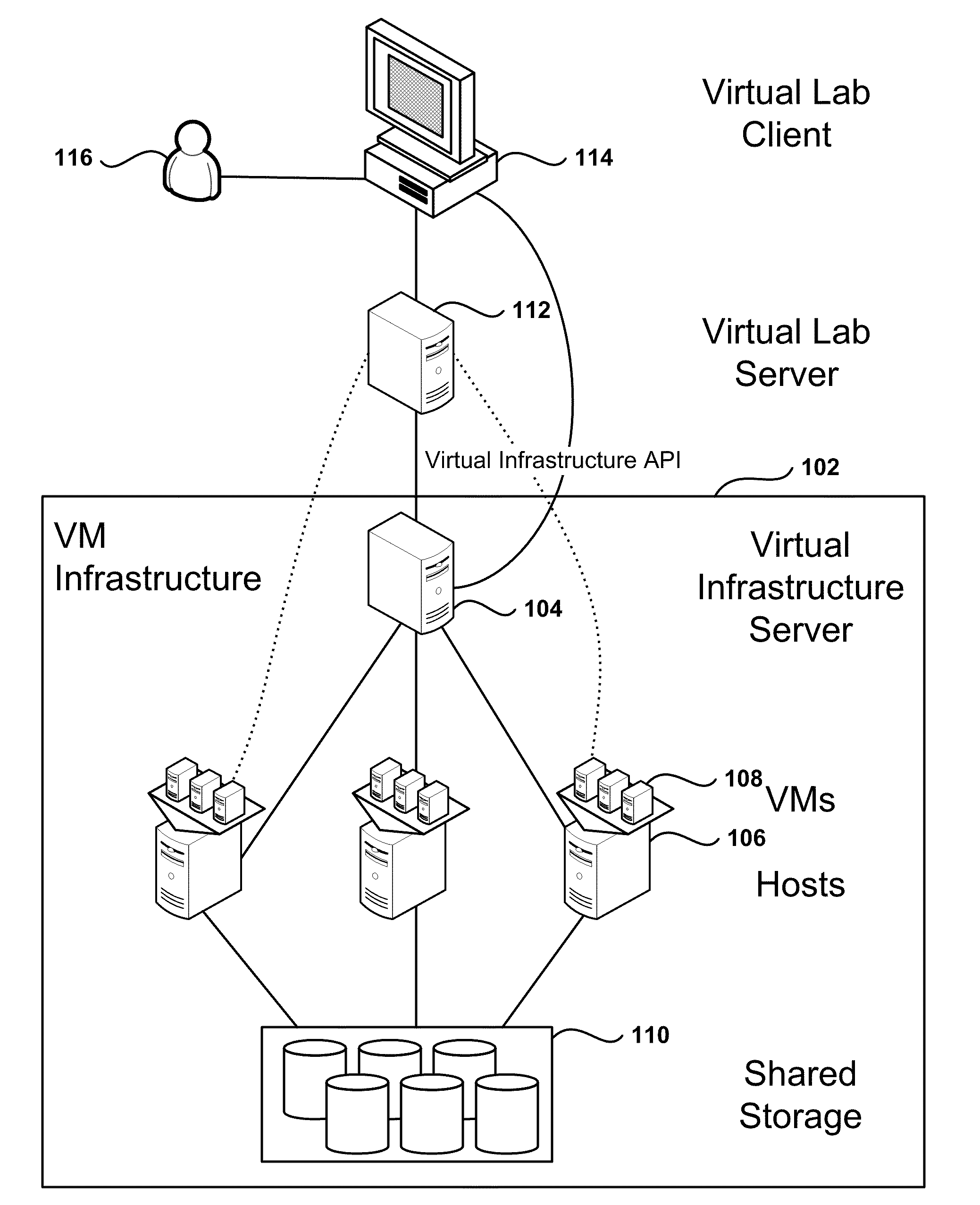
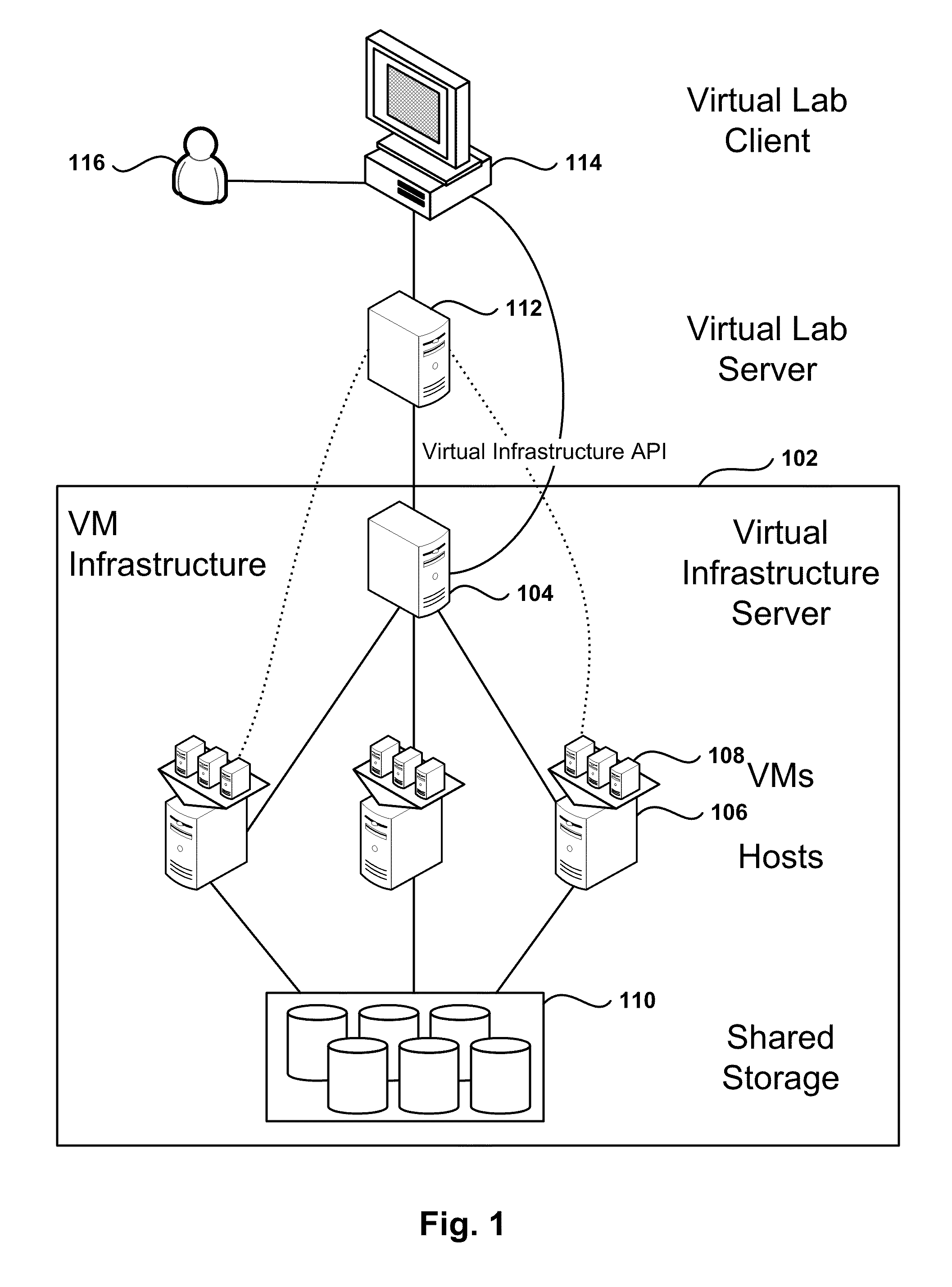
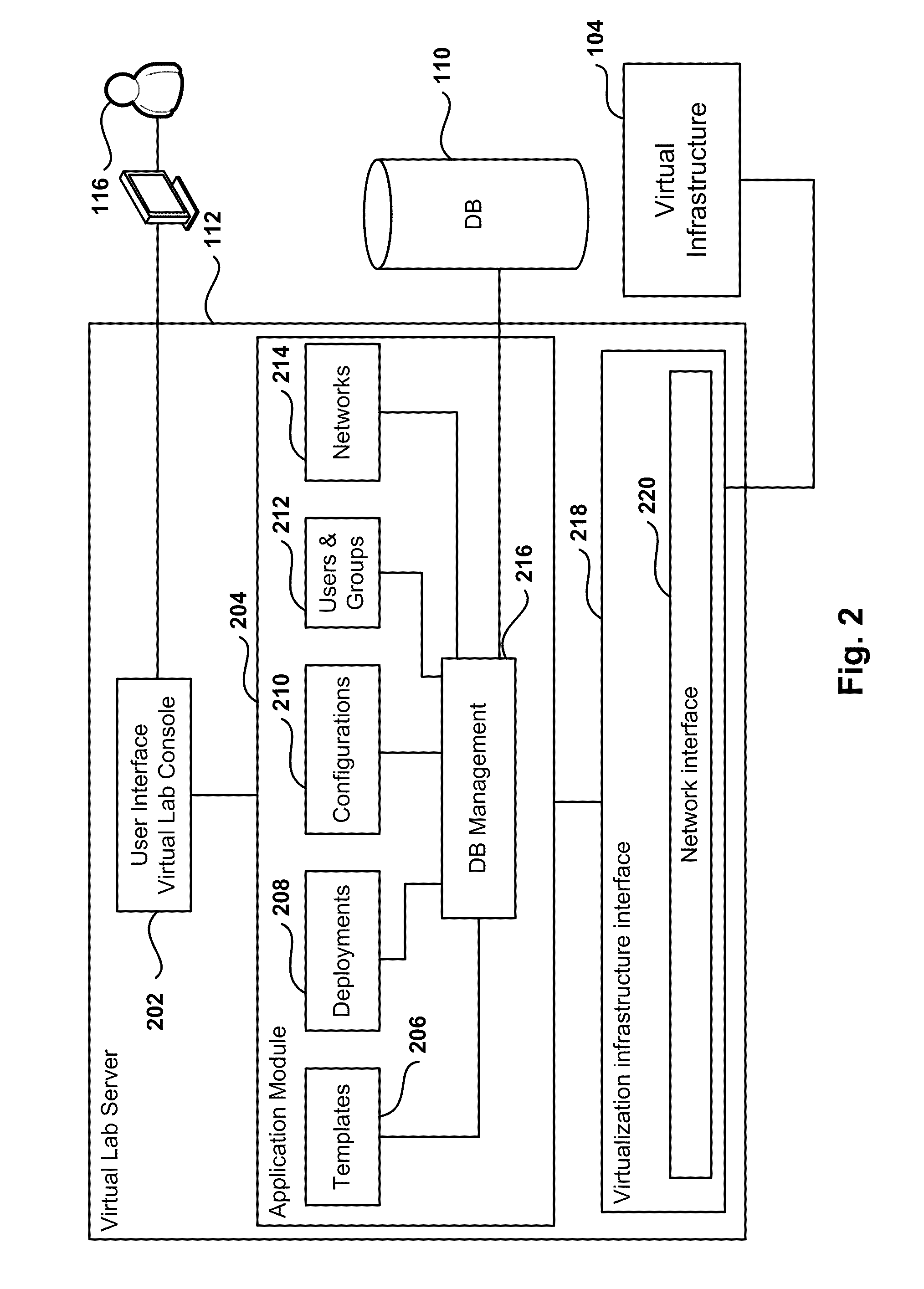
Management and Implementation of Enclosed Local Networks in a Virtual Lab
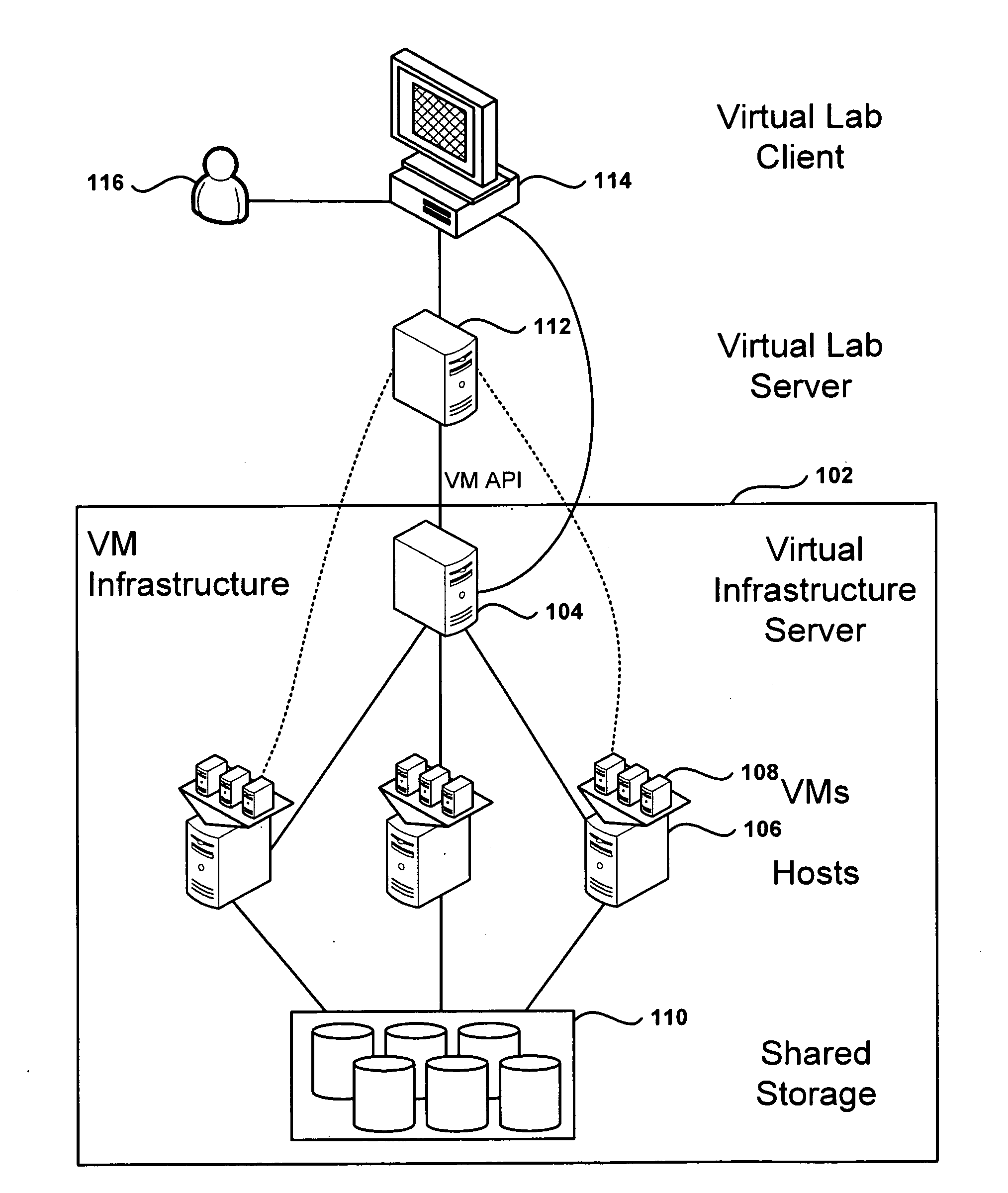
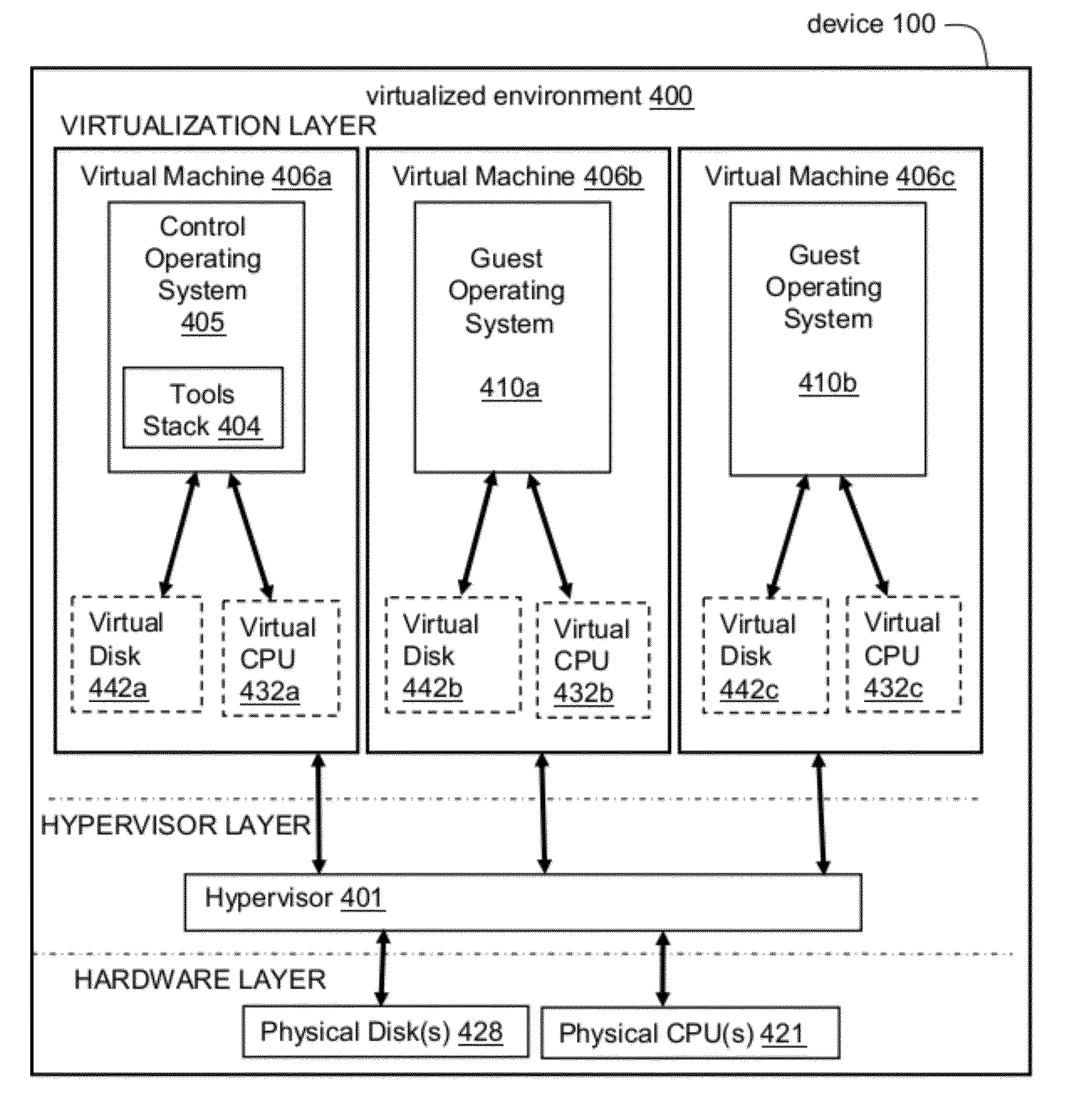
Methods, systems, and computer programs for creating isolated environments that include virtual machines (VM) and networks in a virtual infrastructure are presented. The method includes an operation to define a configuration of a virtual system which includes VMs, virtual network interface cards (VNIC) in the VMs, and configuration local networks (CLN). Further, the method associates each VNIC with one of the CLNs and transmits instructions to the virtual infrastructure for deploying the configuration. Deploying the configuration includes instantiating VMs and CLNs in the virtual infrastructure. Each VM is instantiated in a host monitored by a virtual lab server, and the CLNs are instantiated in the same hosts where the VMs have been instantiated. Only VMs from the configuration can connect to the instantiated CLNs. The method further transmits instructions to the virtual infrastructure to customize the VMs by executing the customization instructions in the guest operating systems of the VMs to configure the VMs' VNICs.
Owner:VMWARE INC
Automated Network Configuration of Virtual Machines in a Virtual Lab Environment
Methods, systems, and computer programs for creating virtual machines (VM) and associated networks in a virtual infrastructure are presented. The method defines virtual network templates in a database, where each virtual network template includes network specifications. A configuration of a virtual system is created, which includes VMs, virtual lab networks associated with virtual network templates, and connections from the VMs to the virtual lab networks. Further, the configuration is deployed in the virtual infrastructure resulting in a deployed configuration. The deployment of the configuration includes instantiating in the virtual infrastructure the VMs of the configuration, instantiating in the virtual infrastructure the virtual lab networks, retrieving information from the database, and creating and executing programming instructions for the VMs. The database information includes the network specifications from the virtual network templates associated with the virtual lab networks, and network resources for the virtual lab networks from a pool of available network resources. The programming instructions are created for the particular Guest Operating System (GOS) running in each VM based on the GOS and on the retrieved database information. When executed in the corresponding VM GOS, the programming instructions configure the VMs network interfaces with the corresponding network specifications.
Owner:NICIRA
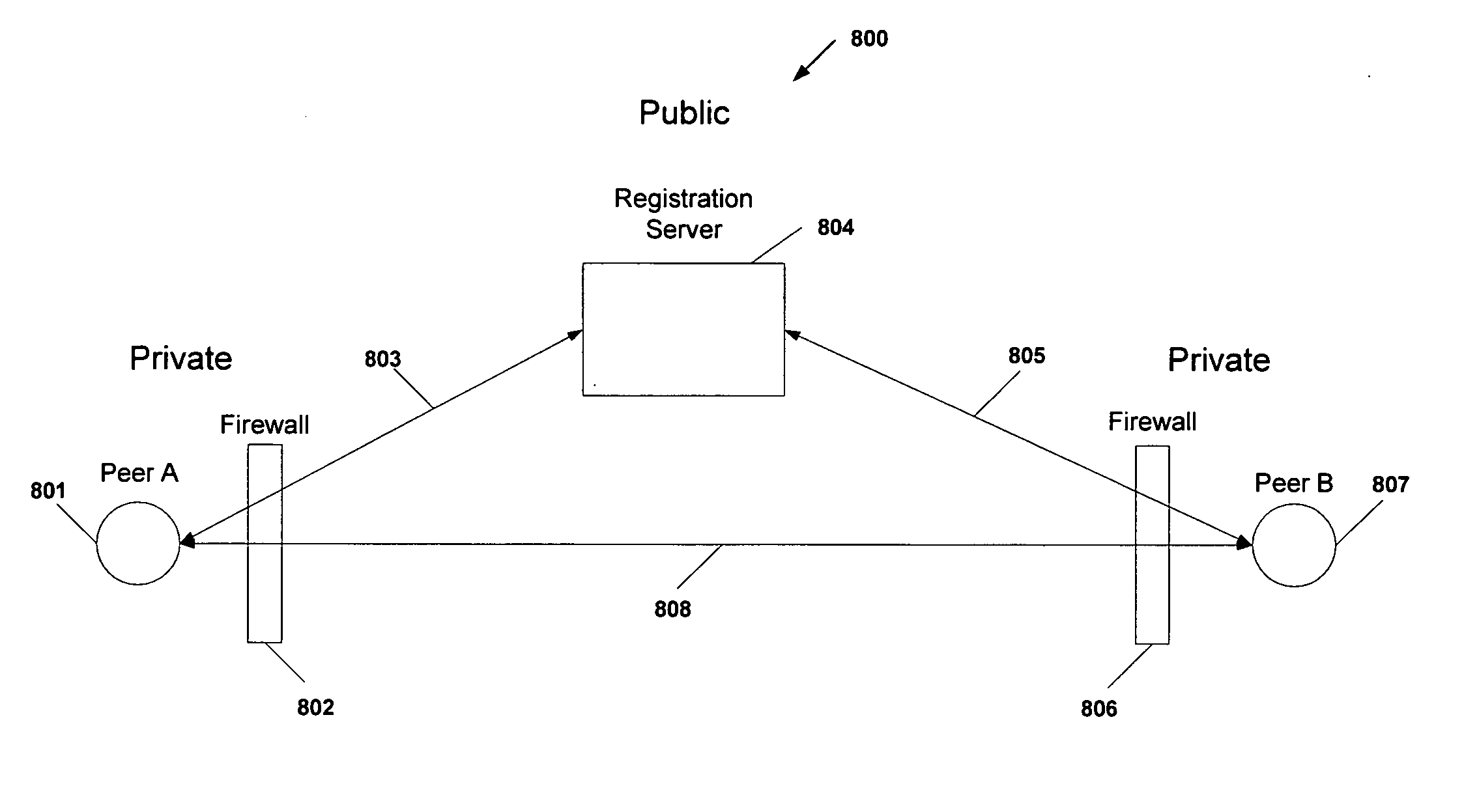
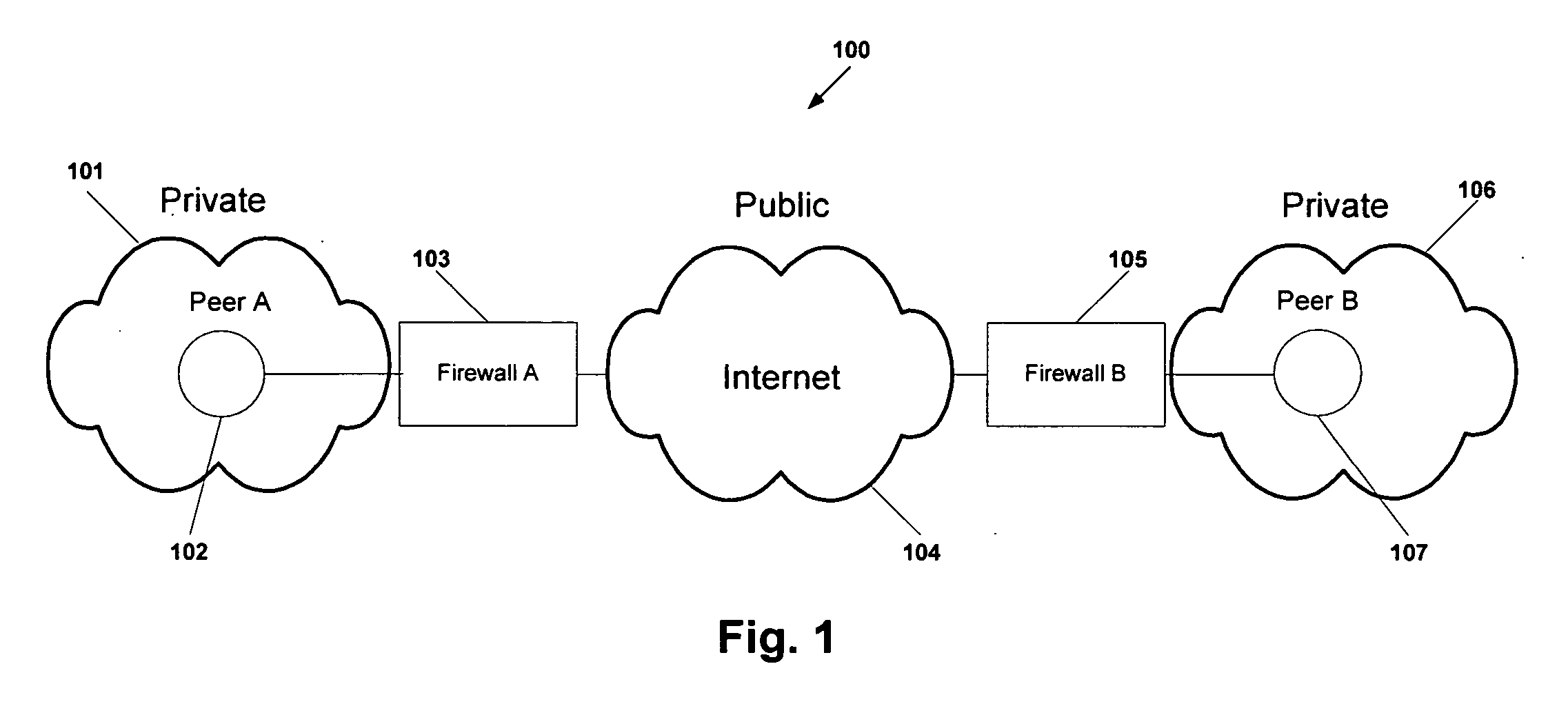
Protocol and system for firewall and NAT traversal for TCP connections
ActiveUS20060215684A1Time-division multiplexData switching by path configurationServer agentNAT traversal
Firewalls and network address translators (NAT) provide many advantages for client and the Internet itself, however, these devices break many existing transmission control protocol (TCP) / Internet Protocol (IP) applications, since they conceal the identity of IP clients (i.e., peers) and block transmission control protocol (TCP) call setup requests. Firewalls and NATs make it impossible for one TCP peer to discover another and establish a connection. Embodiments of this invention provides a system and a protocol to enable two TCP peers that exist behind one or more firewalls and NATs to automatically setup a true peer-to-peer TCP connection and exchange data without making changes to the firewall or NAT devices or existing TCP-based applications. In embodiments of this invention, the synchronization between the blind TCP peers is achieved using a system that consists of a registration server, an agent application, and a virtual network interface that together relay and replicate the control signals between the two TCP peers. In addition, embodiments of this invention are also used to traverse the NAT and establish a bi-directional peer-to-peer TCP connection in the firewall.
Owner:NETGEAR INC
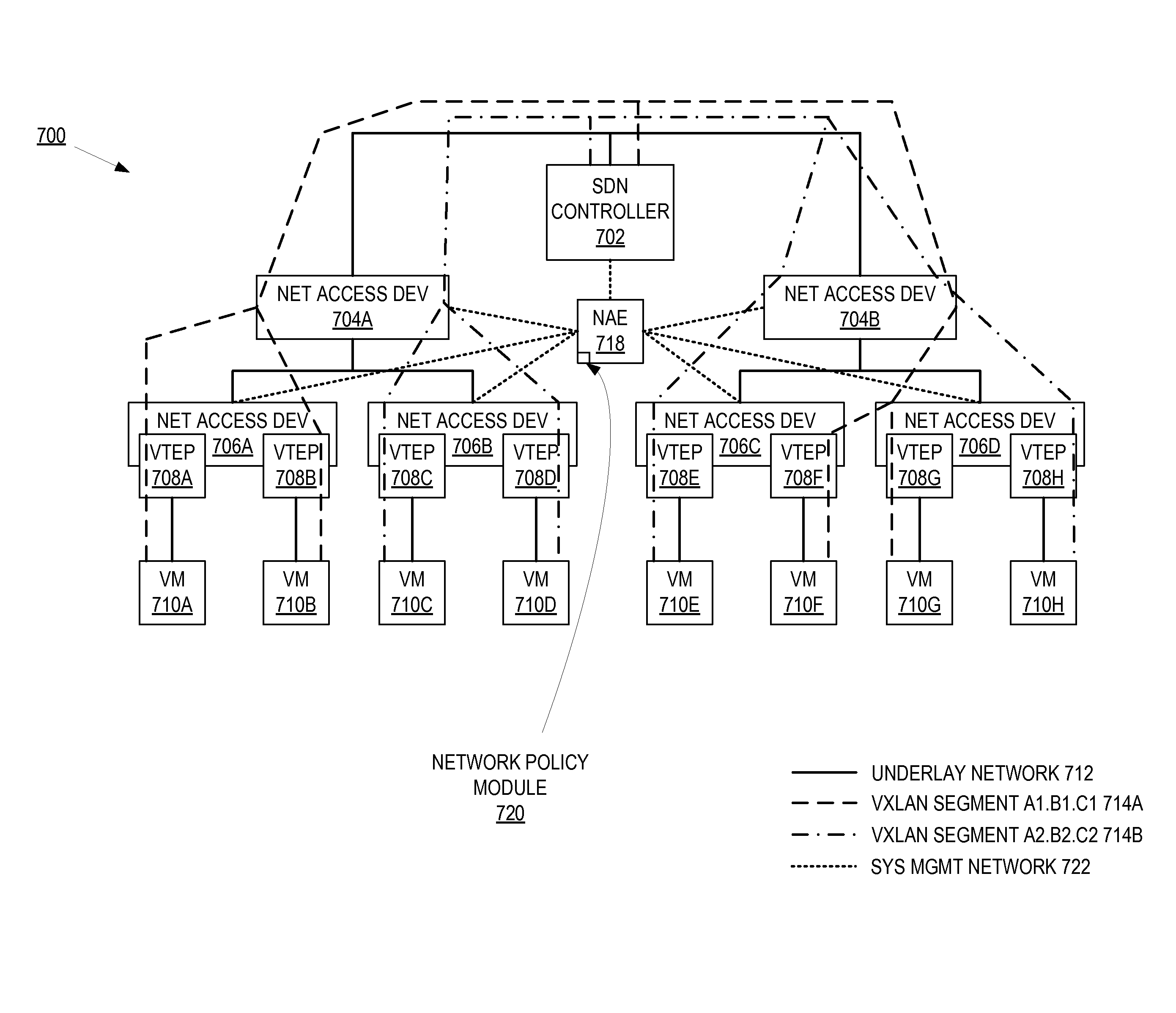
System, apparatus and method for providing a virtual network edge and overlay with virtual control plane
ActiveUS20160072669A1Improve communication performanceImprove throughputDigital computer detailsNetworks interconnectionTraffic capacityNetwork connection
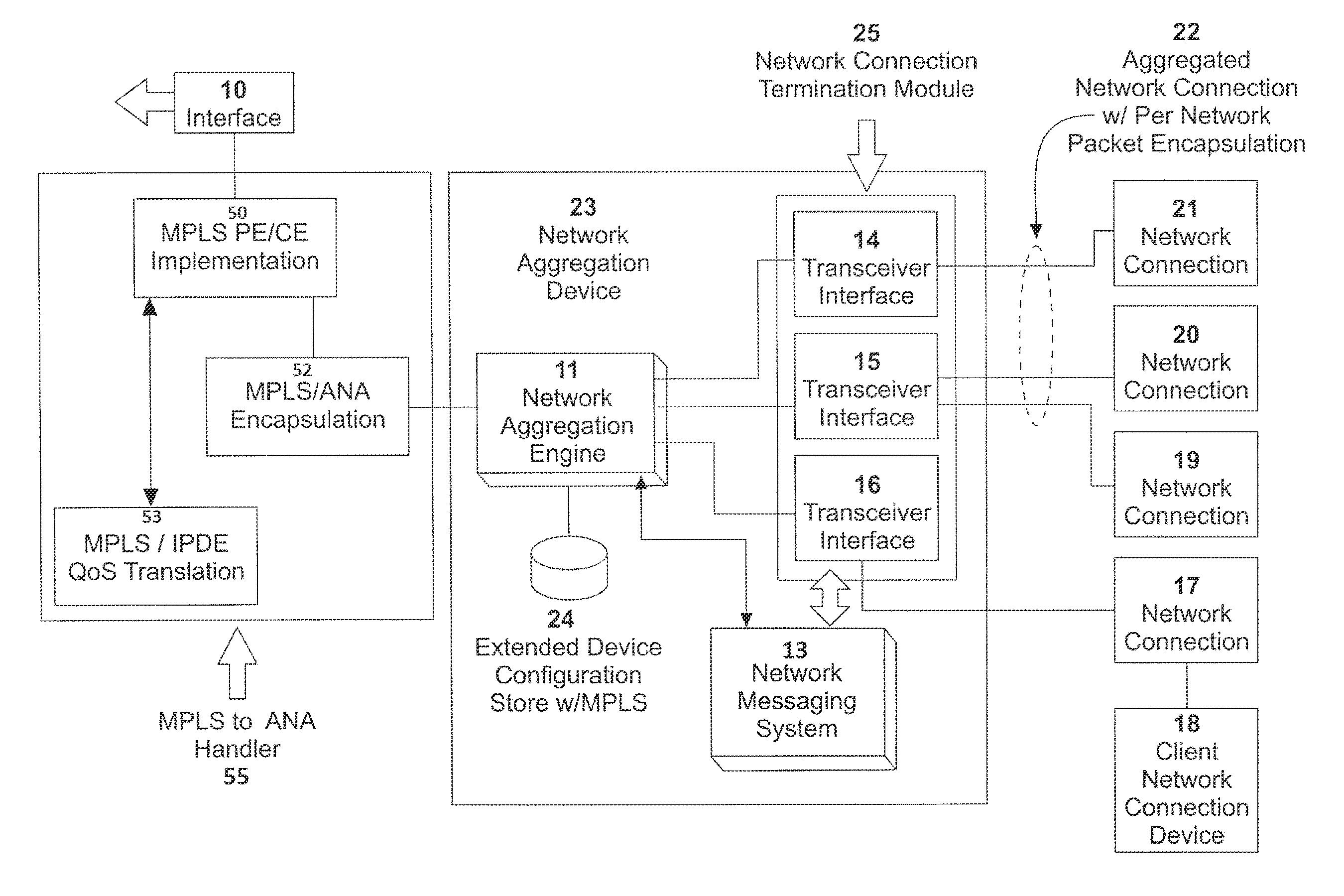
A network system is provided between at least a first client site and a second client site. A client site network component is implemented at least at the first client site, the client site network component aggregating one or more diverse network connections so as to configure an aggregated connection that has increased throughput. At least one network server component may be configured to connect to the client site network component using the aggregated connection. A cloud network controller may be configured to manage the data traffic and a virtual edge providing transparent lower-link encryption for the aggregated connection between the client site network component and the network server component. The network server component includes a virtual control plane interface configured to establish a unicast path between the network server component and each of a plurality of remote network server components.
Owner:ADAPTIV NETWORKS INC
Hypervisor Level Distributed Load-Balancing
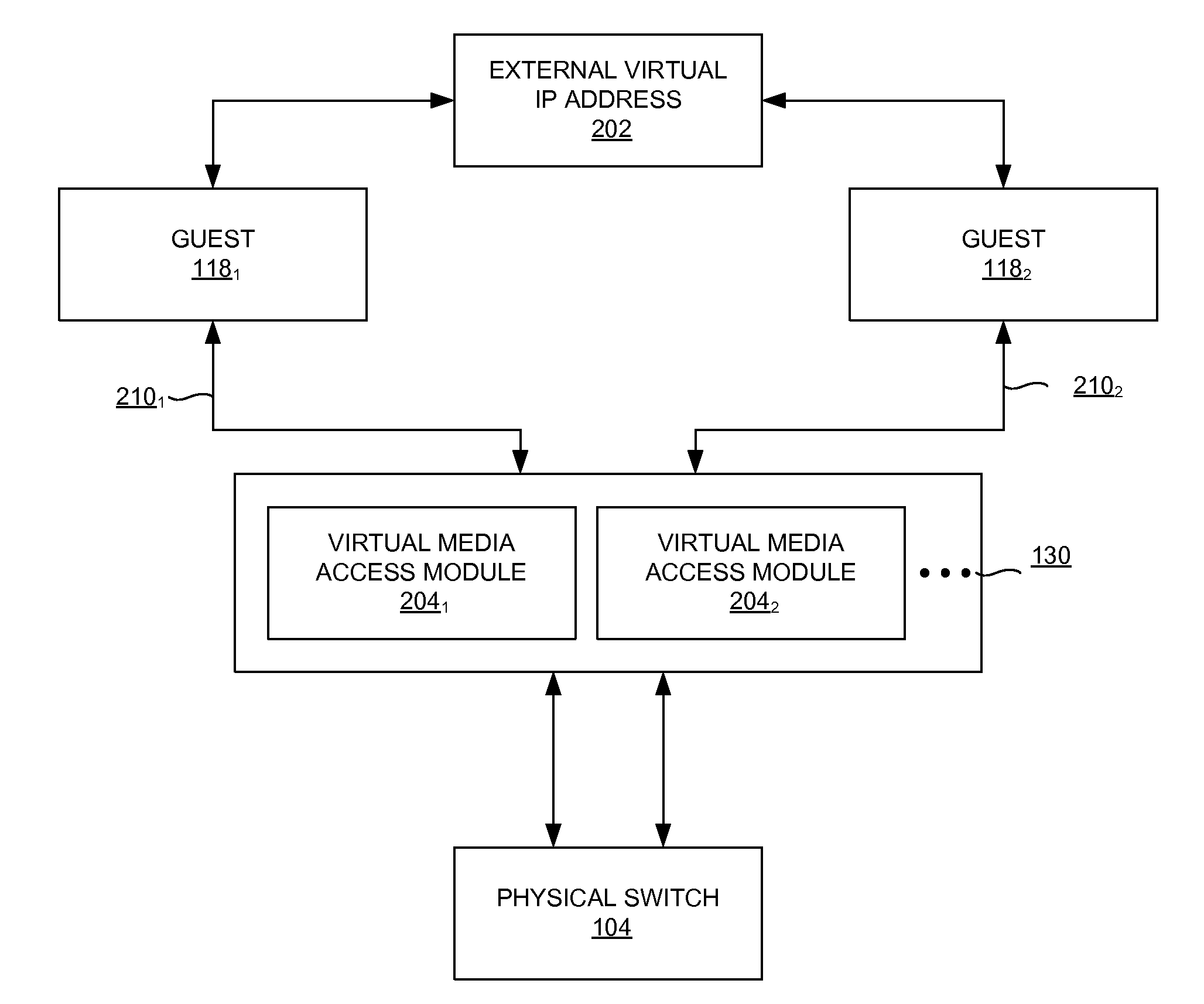
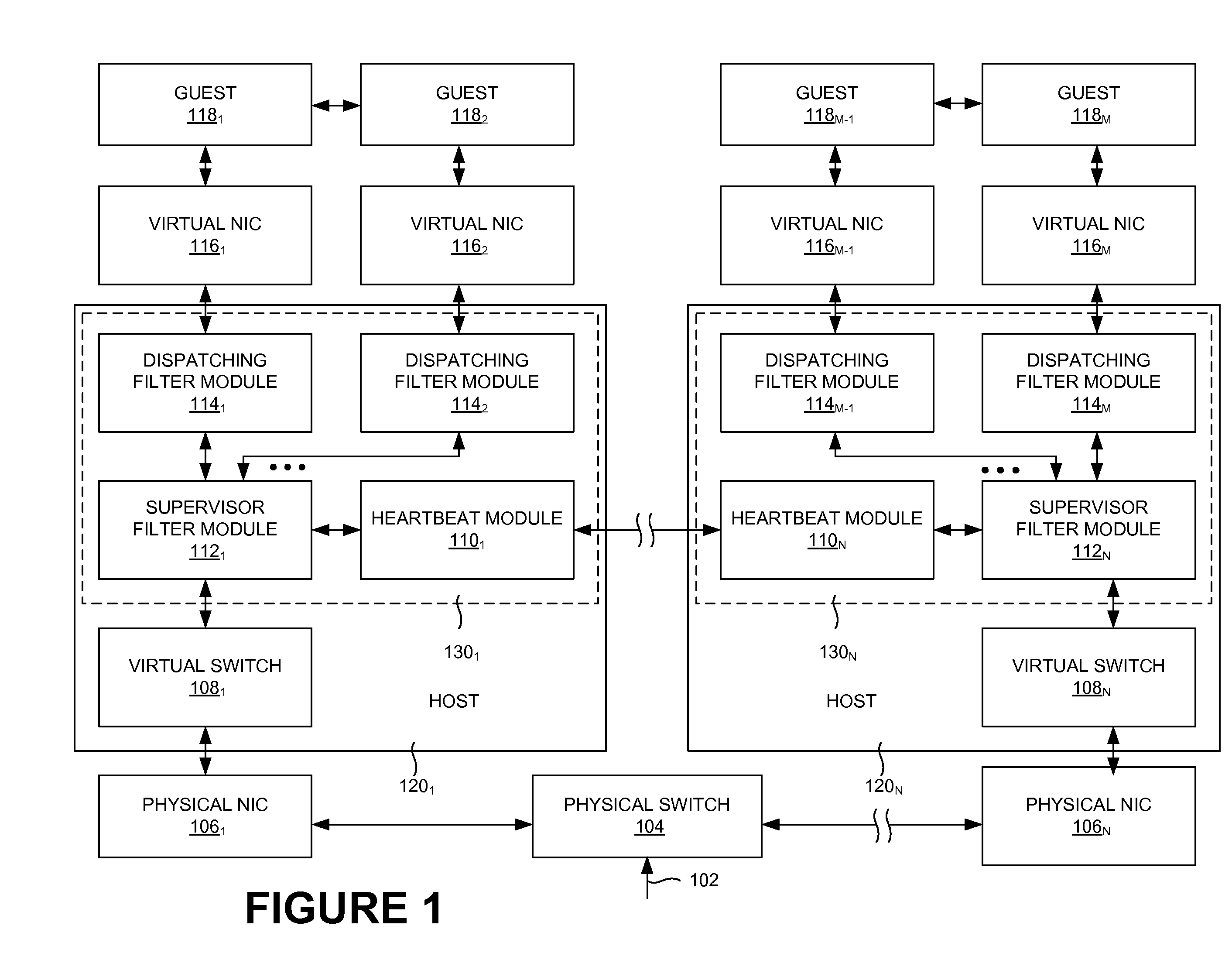
ActiveUS20110194563A1Reduce loadTime-division multiplexHardware monitoringVirtual switchVirtual network interface
A method and an apparatus of hypervisor level distributed load-balancing are disclosed. In one aspect, a method includes determining a location to direct a packet. The method also includes distributing the packet to process the packet through a processor. The method also includes assigning the packet to a guest such that a distribution of the packet to the guest is based on an algorithm. The method further includes altering a first destination address of the packet to a second destination address. The second destination address may be based on a virtual network interface of the guest. The method further includes convincing the guest the packet is from a virtual switch based on the second destination address. In addition, the method includes adjusting the distribution of the packet to the guest. The method also includes reducing a load of the guest through the adjustment.
Owner:VMWARE INC
Systems and methods for sr-iov pass-thru via an intermediary device
ActiveUS20120284712A1OptimizationUpgrade and downgrade capacityDigital computer detailsHybrid transportVirtualizationVirtual device
This disclosure describes a system for Single Root I / O Virtualization (SR-IOV) pass-thru for network packet processing via a virtualized environment of a device. The system includes a device comprising a virtualized environment and a plurality of virtual machines having a virtual network interface for receiving and transmitting network packets. A driver for the physical network interface of the device creates a plurality of virtual devices corresponding to the physical network interface, which appear as a Peripheral ComponentInterconnect (PCI) device to the virtualized environment. A virtual device of the plurality of virtual devices is assigned via the virtualized environment to each virtual machine of the plurality of virtual machines. The virtual machine uses the virtual device assigned to the virtual machine, to receive and transmit network packets via the physical network interface of the device.
Owner:CITRIX SYST INC
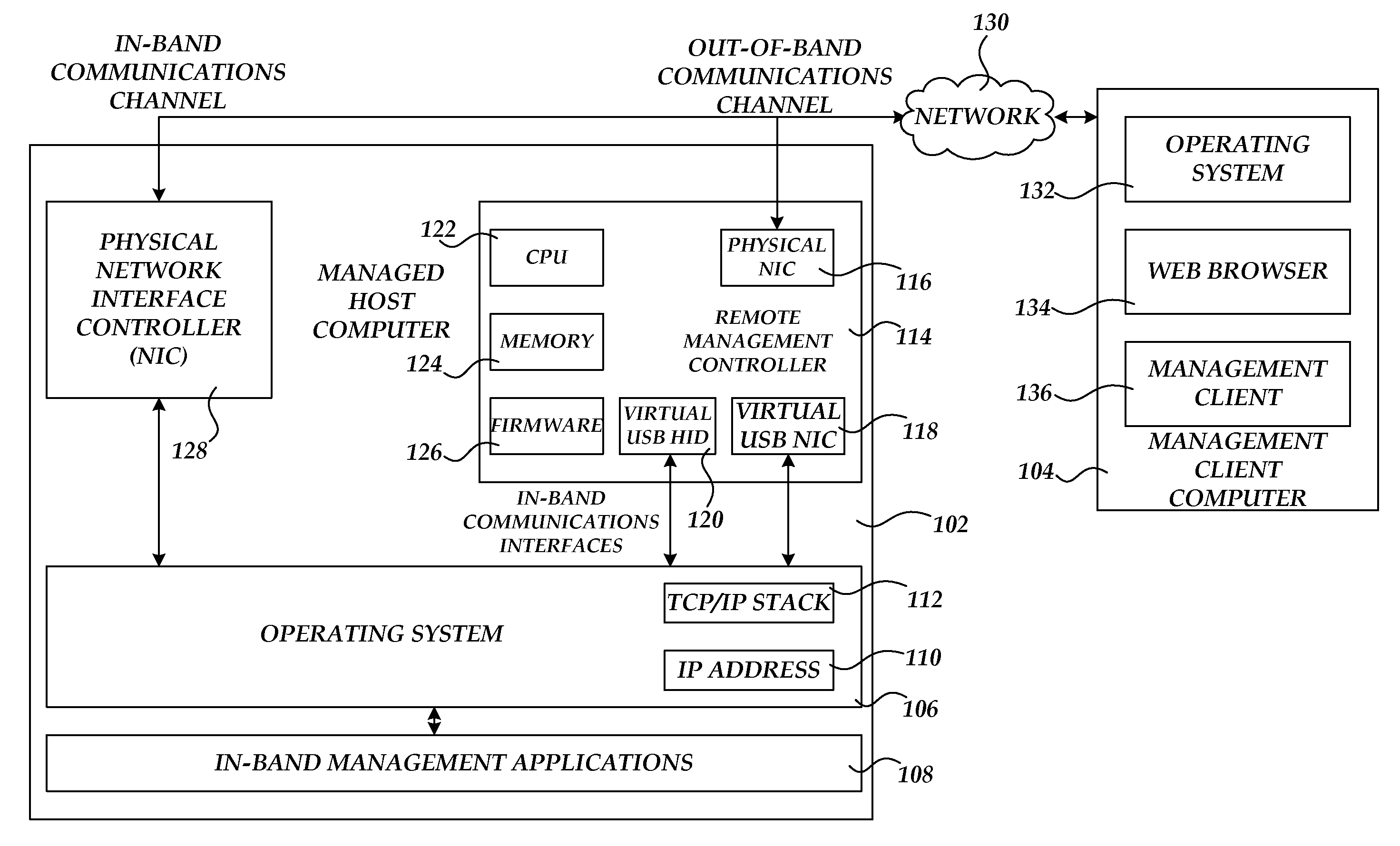
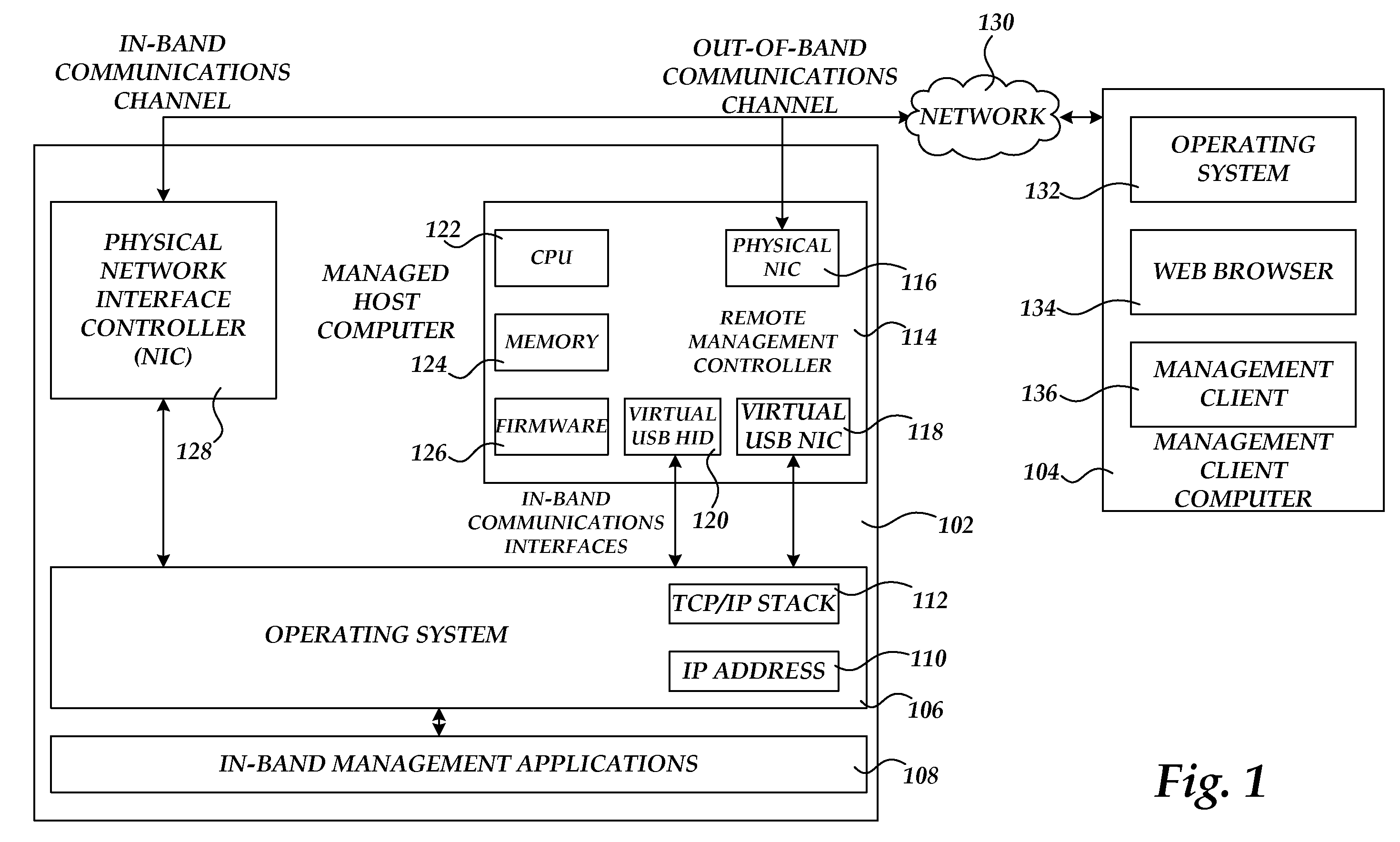
Communicating with an in-band management application through an out-of-band communications channel
ActiveUS20110283006A1Multiple digital computer combinationsData switching networksCommunication interfaceNetwork management application
A remote management controller is provided for use in conjunction with a managed host computer. The remote management controller exposes a virtual network interface controller, such as a driverless virtual USB network interface controller, to the managed host computer. Through the in-band connection provided by the virtual network interface controller, the remote management controller can communicate with in-band management applications executing on the managed host computer. The managed host computer can also access services executing on the remote management controller through the in-band communications interface. The remote management controller can also enable communication between the management client computer and in-band management applications executing on the managed host computer. The managed host computer can also access an out-of-band communications network between the remote management device and a management client computer.
Owner:AMERICAN MEGATRENDS
System, apparatus and method for providing a virtual network edge and overlay
ActiveUS20160006672A1Improve communication performanceImprove throughputData switching by path configurationHigh level techniquesTraffic capacityNetwork connection
A network system is provided between at least a first client site and a second client site, the first and the second client site are at a distance from one another. A client site network component is implemented at least at the first client site, the client site network component bonding or aggregating one or more diverse network connections so as to configure a bonded / aggregated connection that has increased throughput. At least one network server component may be configured to connect to the client site network component using the bonded / aggregated connection. A cloud network controller may be configured to manage the data traffic and a virtual edge providing transparent lower-link encryption for the bonded / aggregated connection between the client site network component and the network server component.
Owner:ADAPTIV NETWORKS INC
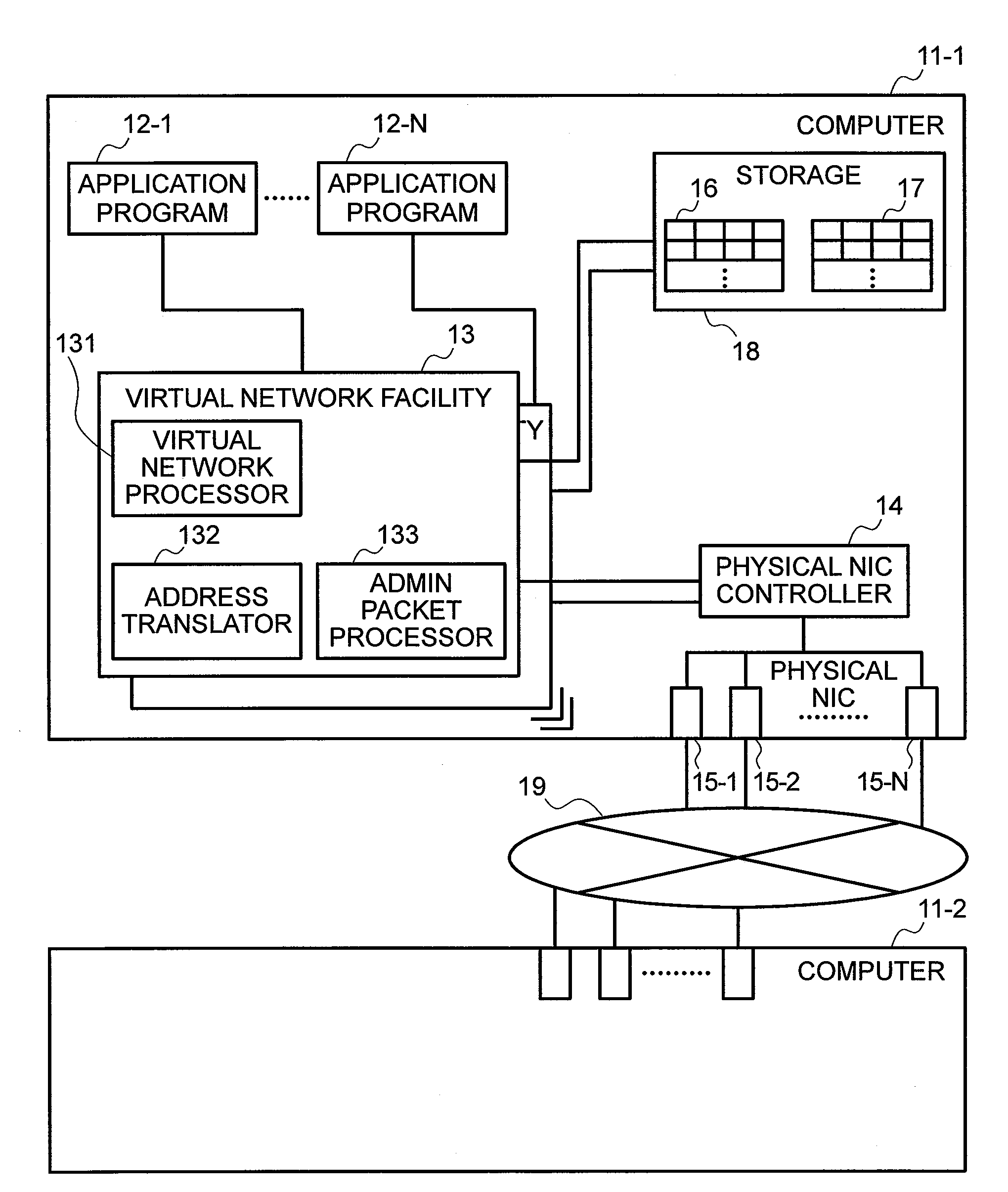
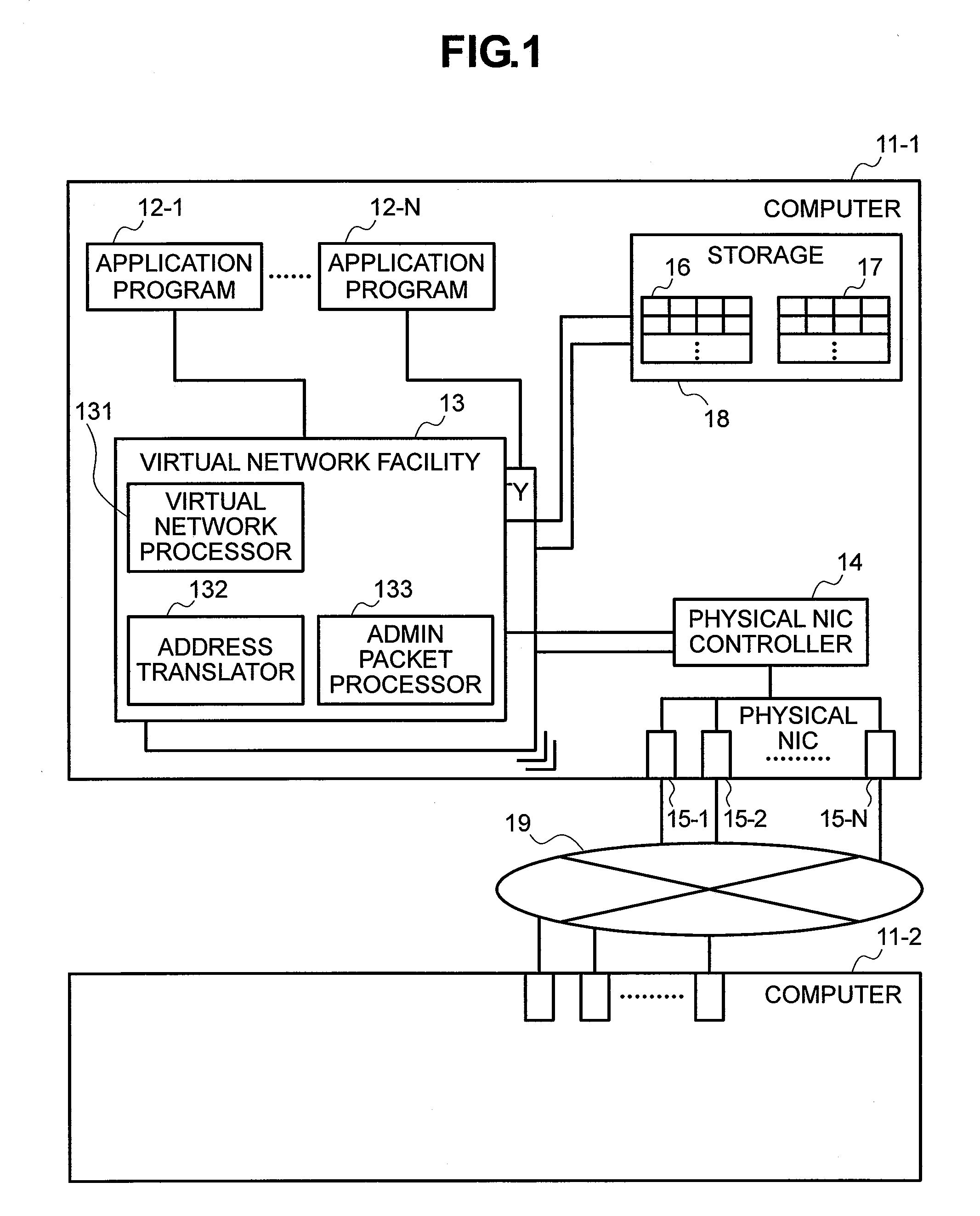
Method for configuring virtual network and network system
A first computer stores a correspondence between a virtual channel and a physical channel(s) in physical channel information and transmits the correspondence between the virtual channel and the physical channel(s) to a second computer having a virtual network interface to which a data transmission instruction is addressed. Upon receiving the correspondence between the virtual channel and the physical channel(s), the second computer stores the received correspondence in the physical channel information. The first computer transmits data in accordance with the data transmission instruction, using one or more physical channels associated with the virtual channel, based on the correspondence stored.
Owner:HITACHI LTD
Distributed data center access switch
ActiveUS8213336B2Data switching by path configurationNetwork connectionsData centerUnique identifier
Owner:CISCO TECH INC
Provisioning a virtual machine
InactiveUS20120144391A1Software simulation/interpretation/emulationMemory systemsInformation processingComputer module
An information processing system which includes: a storage controlling module in any of computer apparatuses that runs a clone origin virtual machine, where the storage controlling module controls: booting up the clone origin virtual machine when the clone origin virtual machine is detached from a virtual network interface; acquiring running state information indicating a running state of the clone origin virtual machine; and storing an image including the running state information and virtual disk information in a storage apparatus; and a boot controlling module in any of computer apparatuses that creates a clone virtual machine, where the boot controlling module controls: resuming at least one of the clone virtual machines with the image when each of the clone virtual machines is detached from the virtual network interface; and attaching the virtual network interface to the at least one clone virtual machine.
Owner:IBM CORP
Local service chaining with virtual machines and virtualized containers in software defined networking
ActiveUS20150370586A1Memory architecture accessing/allocationMemory adressing/allocation/relocationVirtualizationVirtual switch
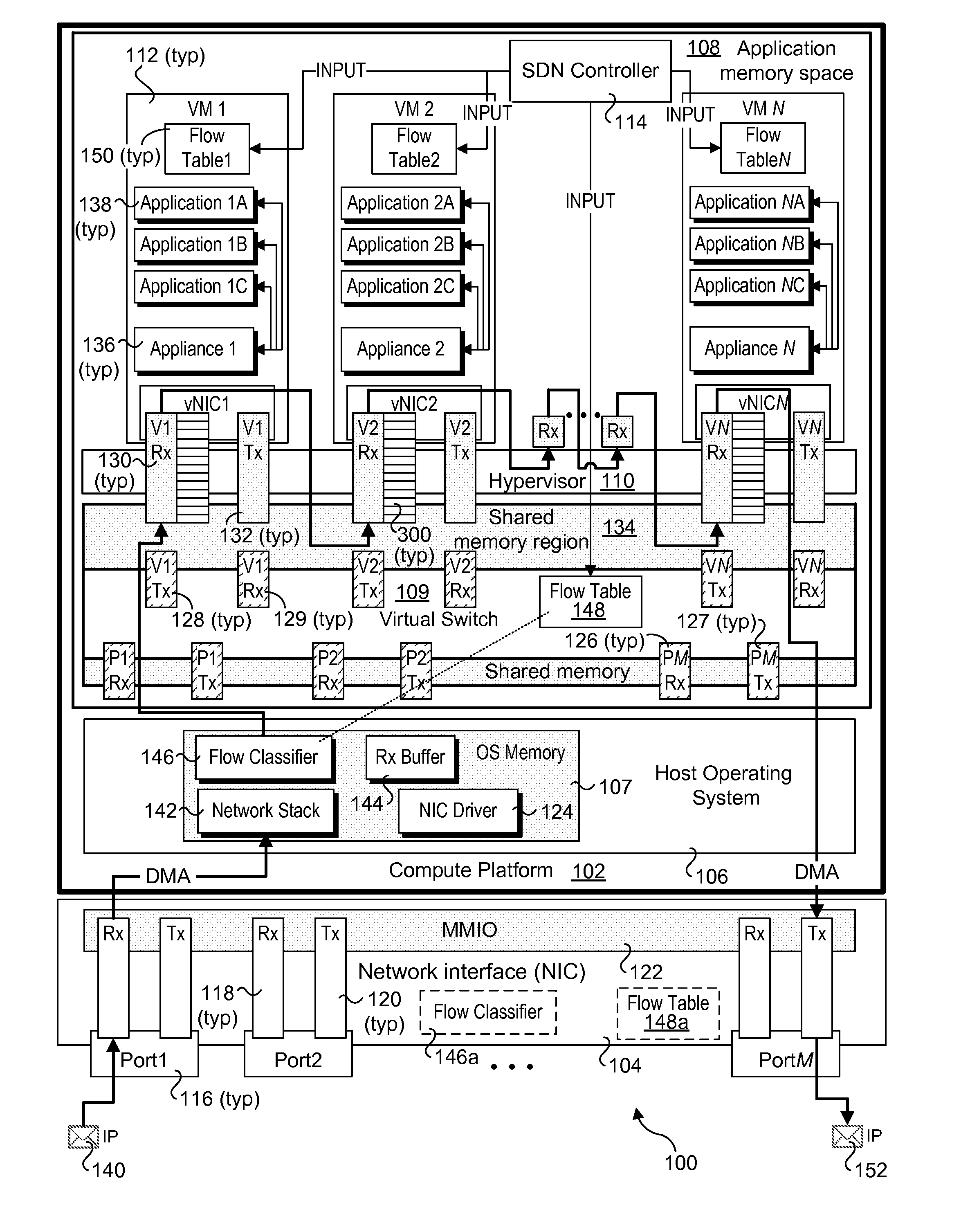
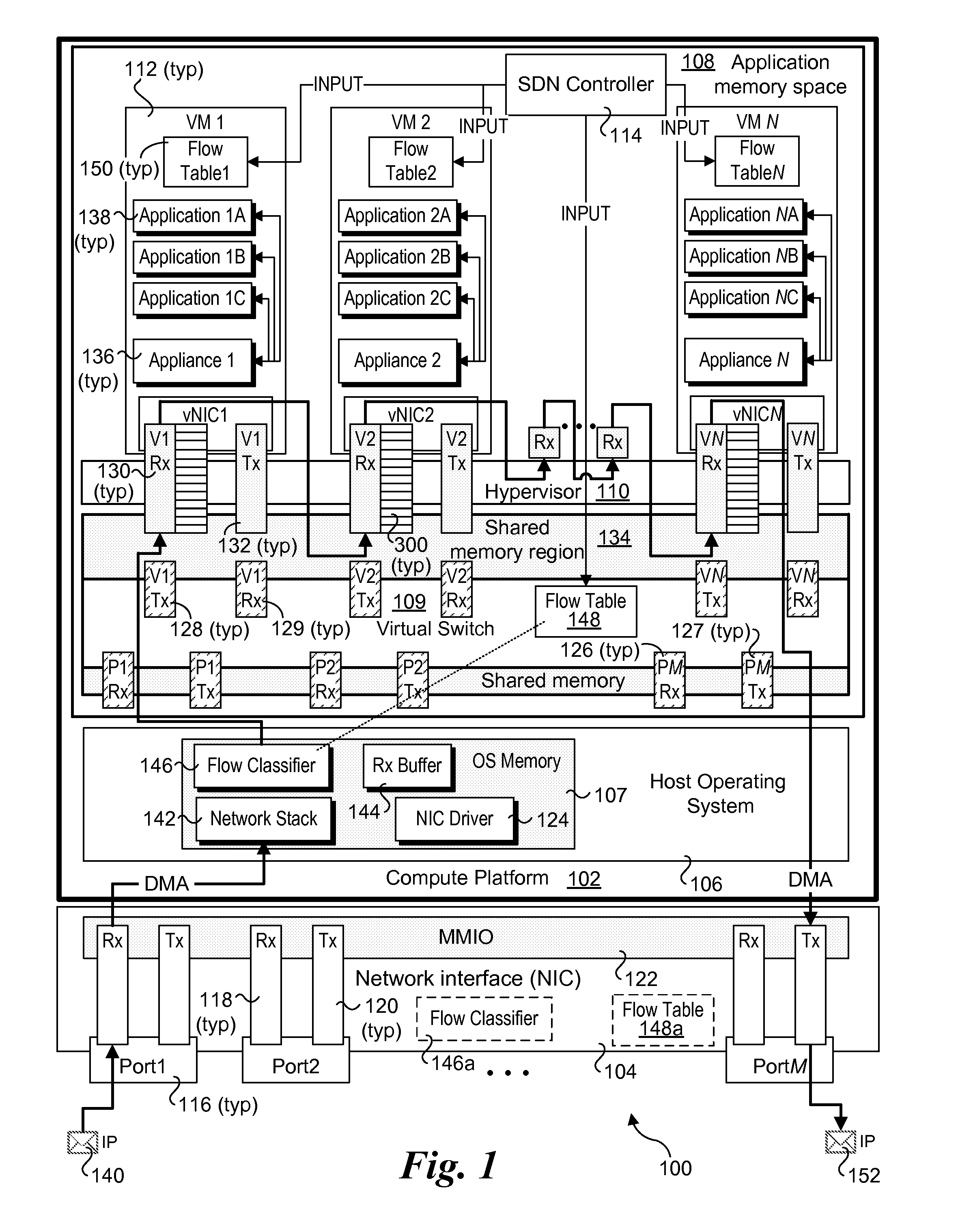
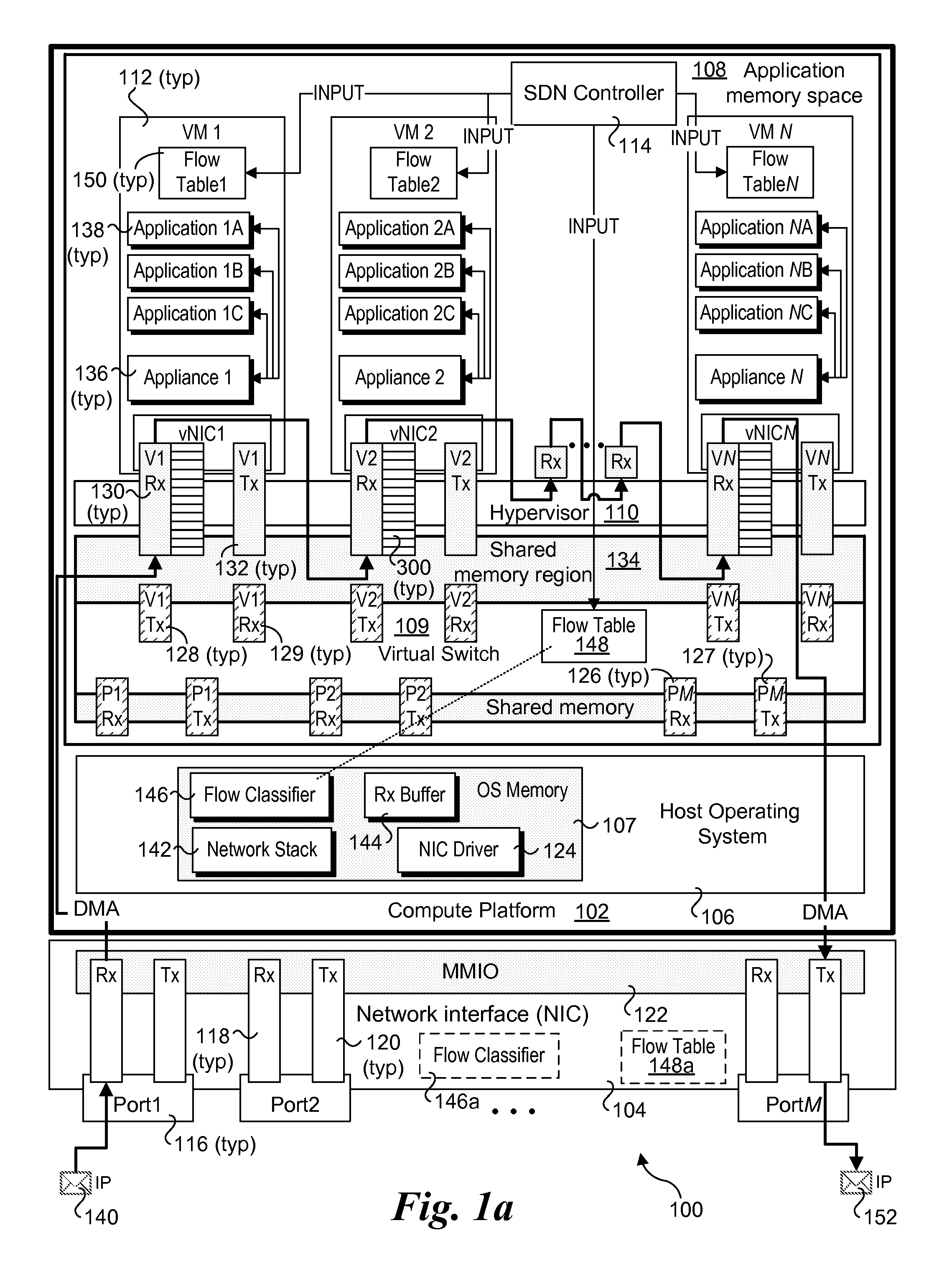
Methods, software, and apparatus for implementing local service chaining (LSC) with virtual machines (VMs) or virtualized containers in Software Defined Networking (SDN). In one aspect a method is implemented on a compute platform including a plurality of VMs or containers, each including a virtual network interface controller (vNIC) communicatively coupled to a virtual switch in an SDN. LSCs are implemented via a plurality of virtual network appliances hosted by the plurality of VMs or containers. Each LCS comprises a sequence (chain) of services performed by virtual network appliances defined for the LSC. In connection with performing the chain of services, packet data is forwarded between VMs or containers using a cut-through mechanisms under which packet data is directly written to receive (Rx) buffers on the vNICs in a manner that bypasses the virtual switch. LSC indicia (e.g., through LSC tags) and flow tables are used to inform each virtual network appliance and / or or its host VM or container of the next vNIC Rx buffer or Rx port to which packet data is to be written.
Owner:INTEL CORP
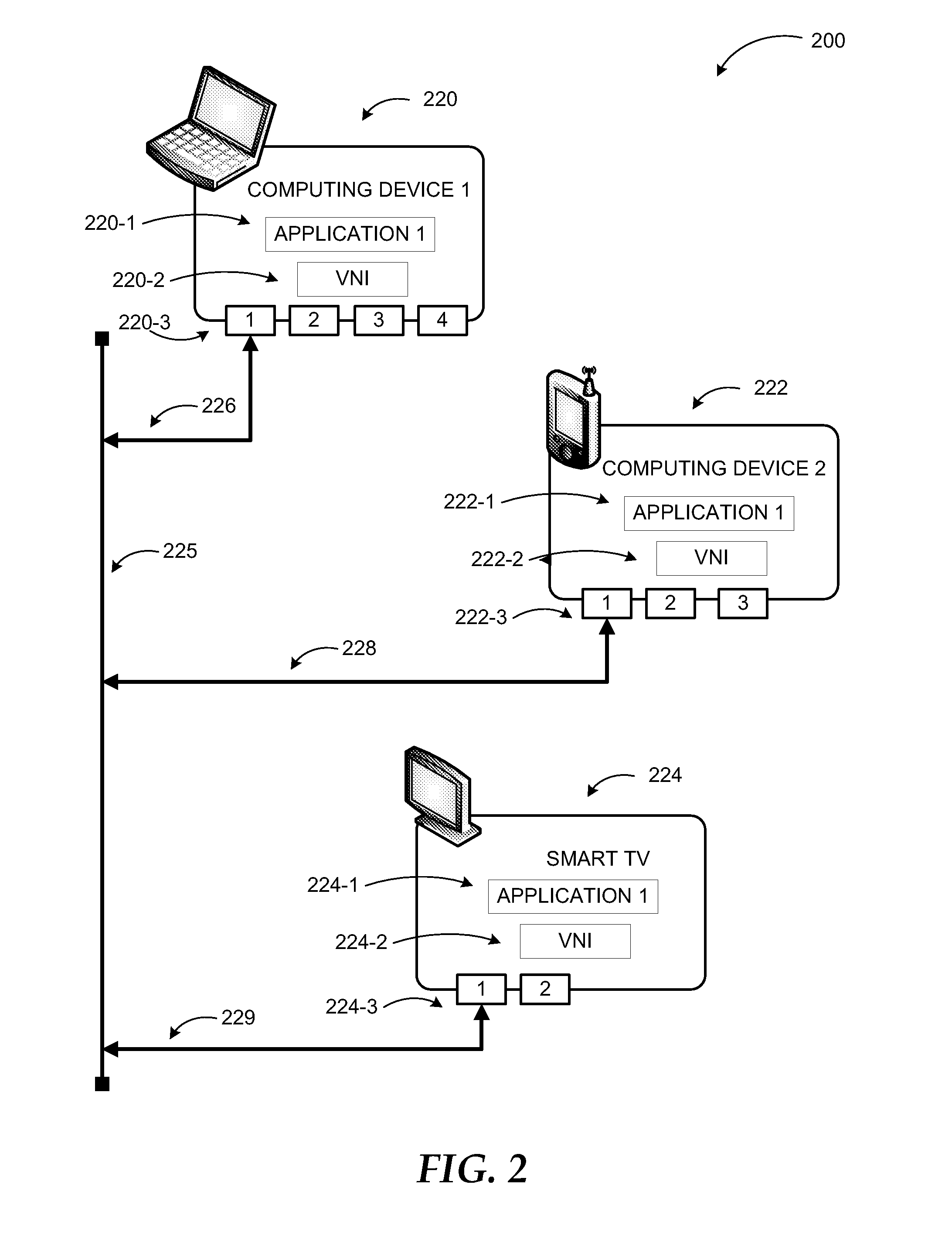
Mobile Devices Having Plurality of Virtual Interfaces
ActiveUS20110314467A1Multiprogramming arrangementsComputer security arrangementsService provisionApplication software
Mobile devices, systems and methods are described with a plurality of virtual machines, wherein each virtual machine executes a separate virtual interface, or guest operating system. Each guest operating system corresponds to a different virtual device having its own contact list, applications, and so on. A virtual “device” can be controlled by an employer or service provider, and is a secure space that provides authenticated applications that are walled off from another virtual device. A host operating system provides a hardware abstraction layer. A proxy server on the host operating system receives an incoming signal from a remote device on the external network, and routes the incoming signal to one of the first and second virtual machines based on a call context. A method and computer program product for providing a plurality of virtual interfaces on a mobile device are also disclosed.
Owner:AT&T INTPROP I L P
High-performance virtual machine networking
InactiveUS7620955B1Digital computer detailsSoftware simulation/interpretation/emulationComputer hardwarePhysical address
Owner:VMWARE INC
Virtual machine system and method of network communication between virtual machines
ActiveUS20070140263A1More flexiblyMore flexibly copeMultiprogramming arrangementsMultiple digital computer combinationsComputer hardwareNetwork communication
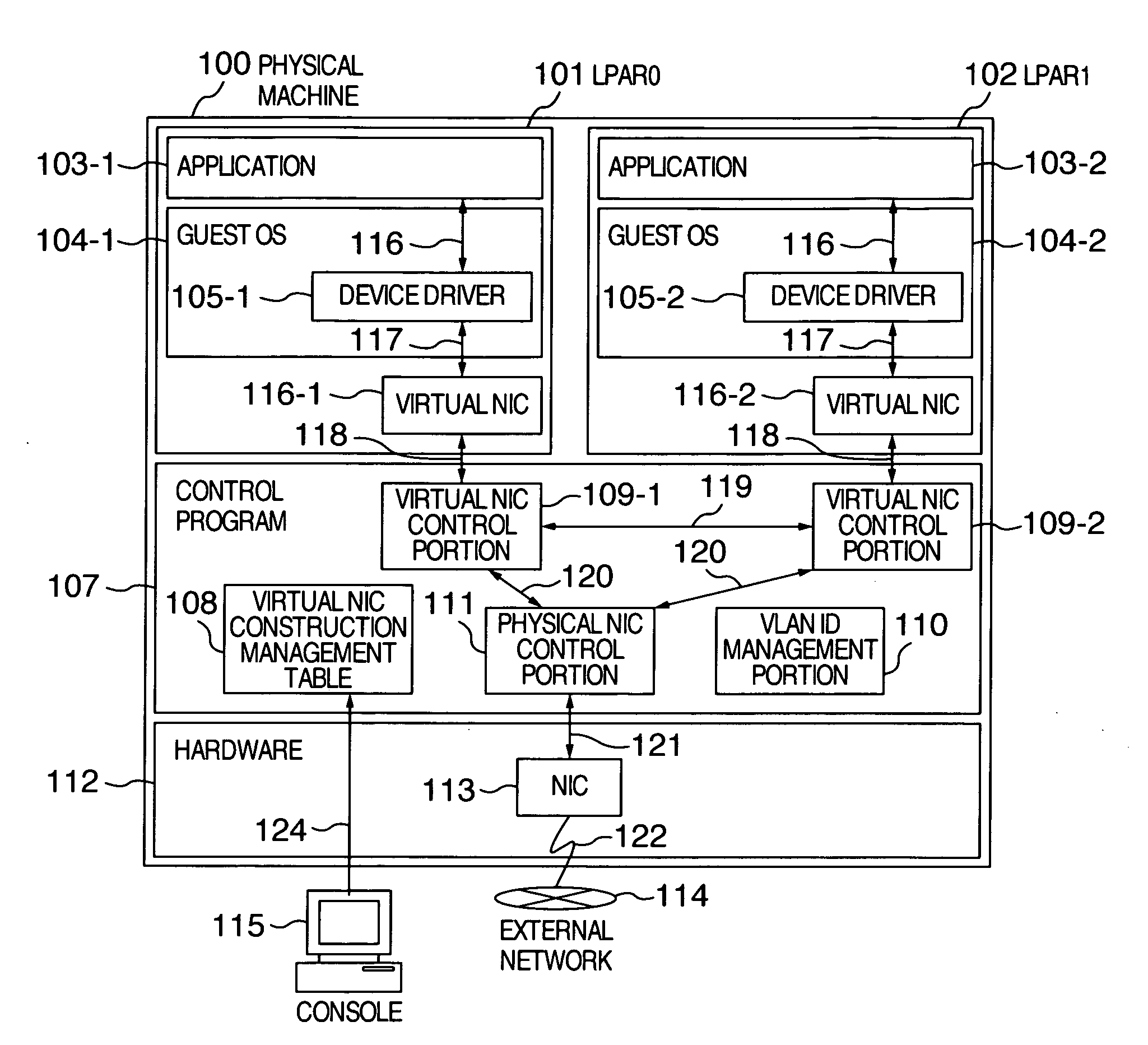
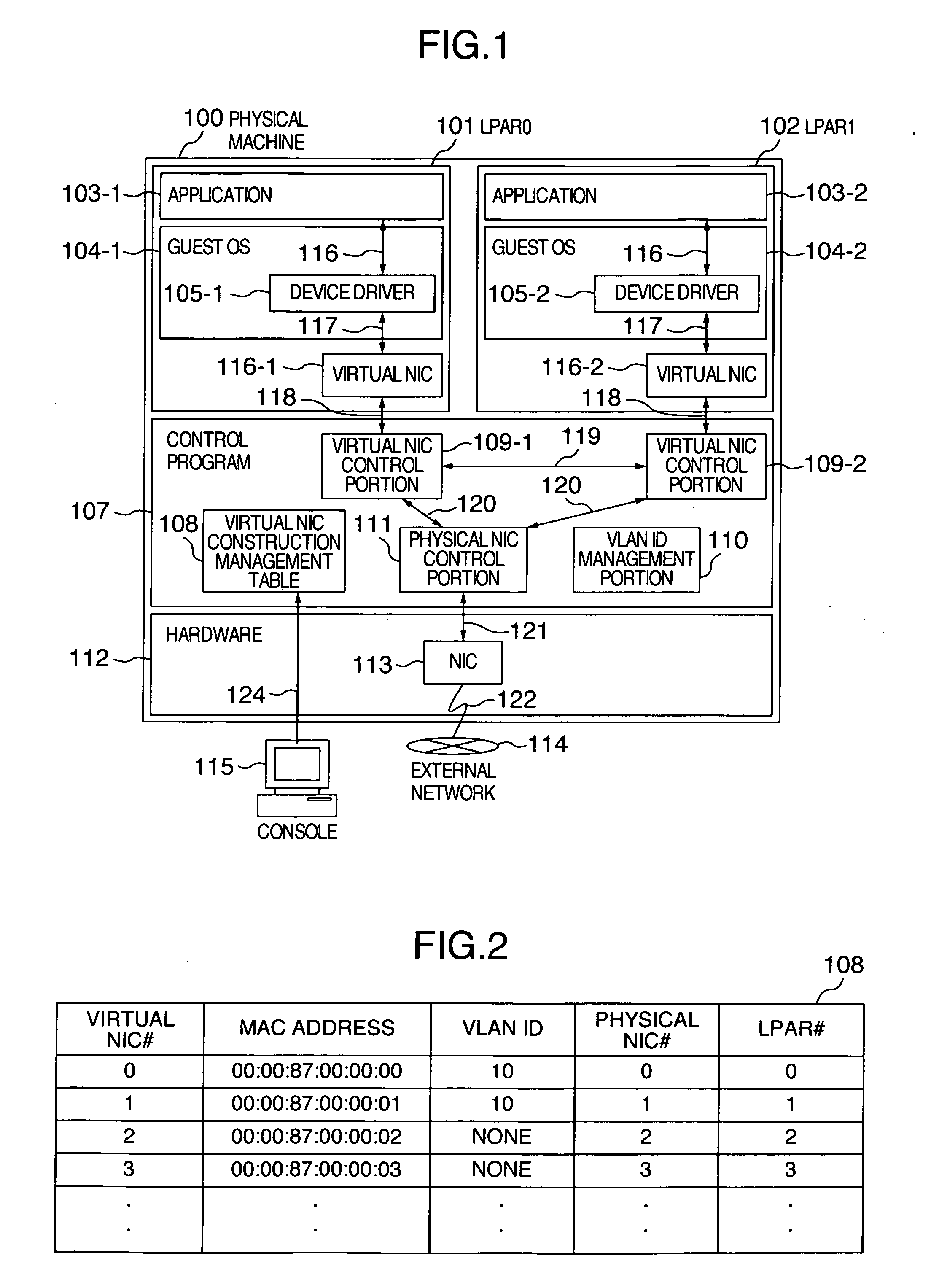
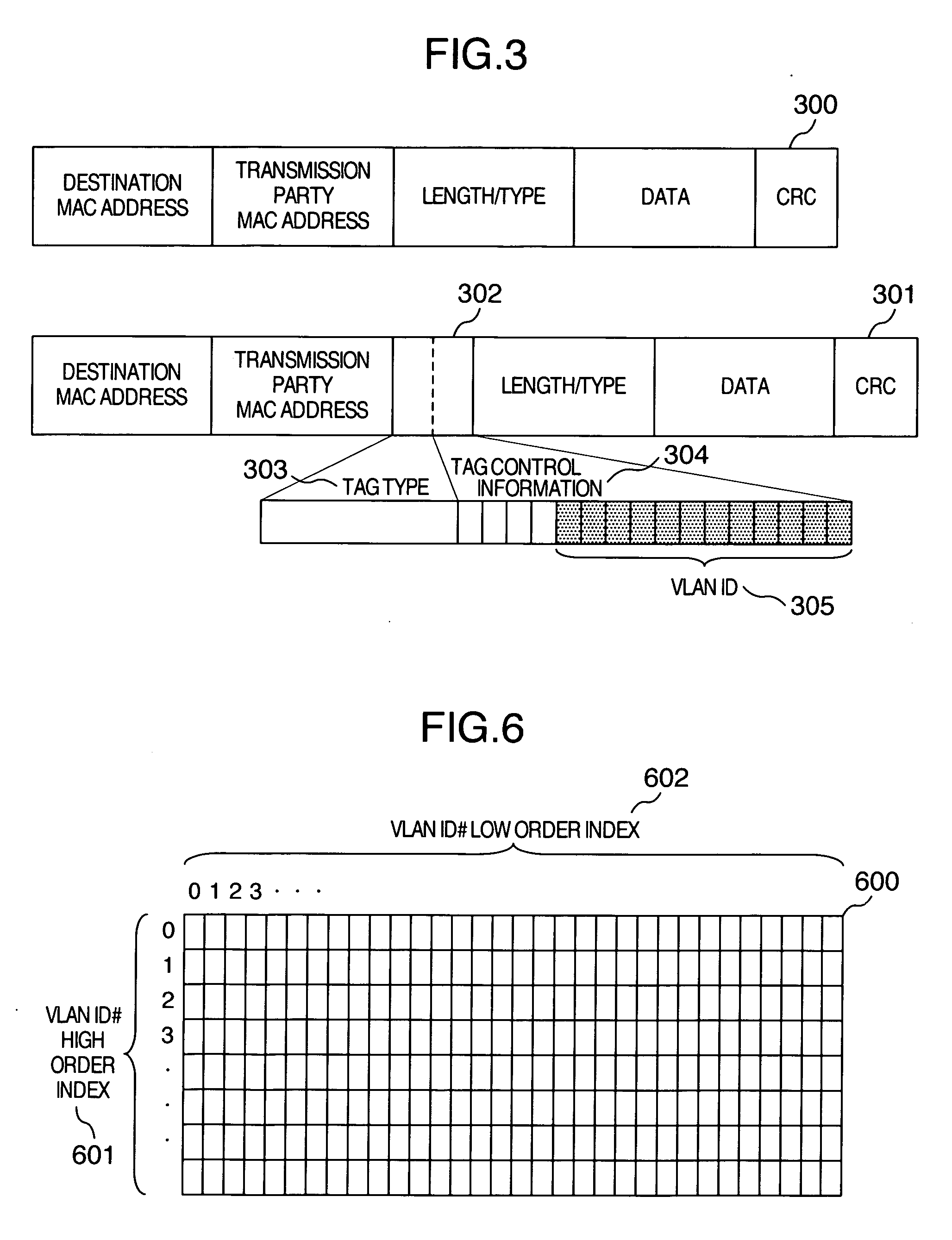
A plurality of machine systems constituted by different VLAN constitution methods are integrated on one machine system by using virtual machines. An operation can be switched for virtual network interface cards to VLAN communication corresponding to VLAN ID set to a virtual network interface card or to VLAN communication corresponding to VLAN ID set by OS on a virtual machine using the virtual network interface card depending on whether or not VLAN ID is set.
Owner:HITACHI LTD
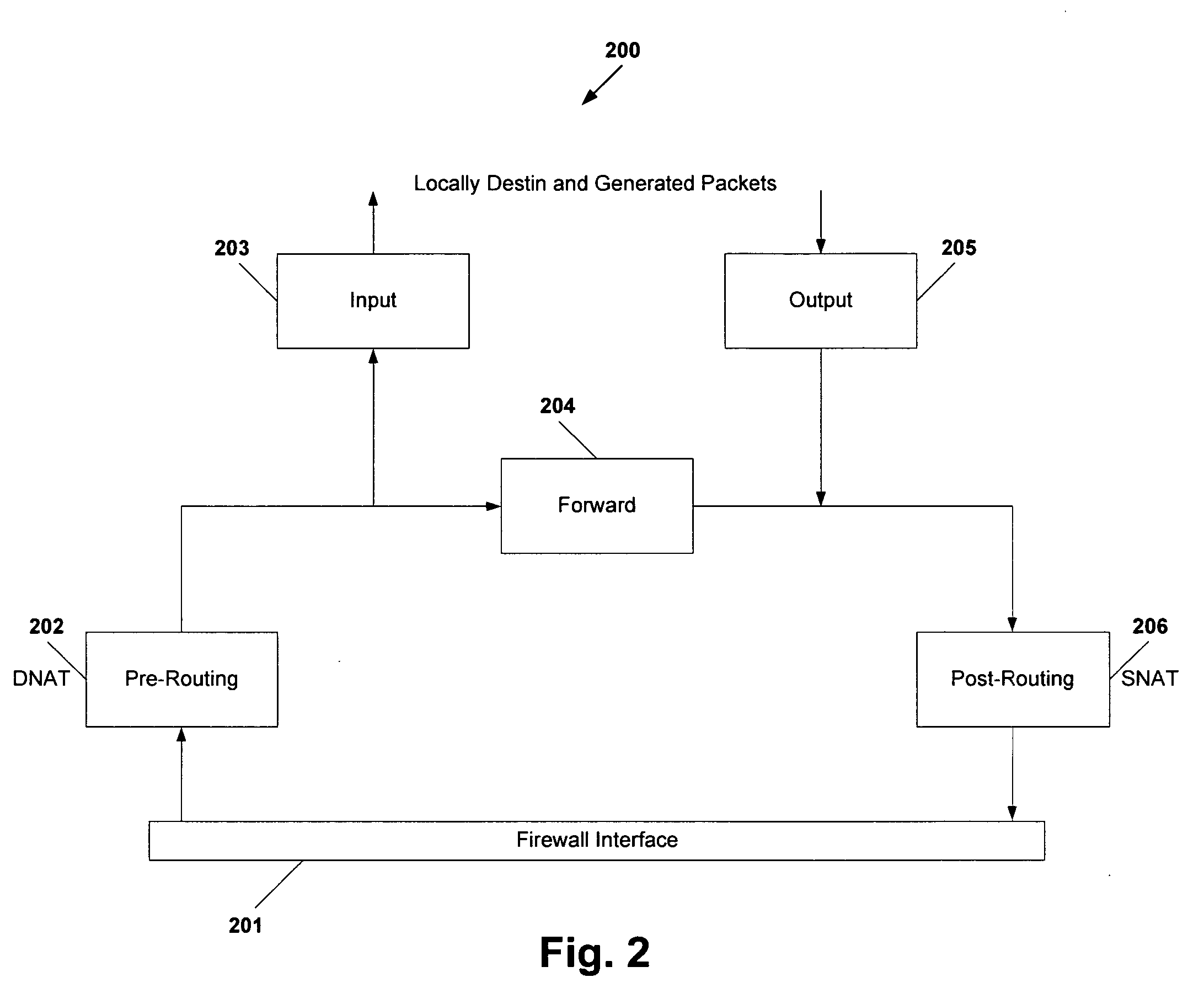
System and method for behavior-based firewall modeling
InactiveUS7610621B2Easy constructionMultiple digital computer combinationsProgram controlClient-sideTraffic flow
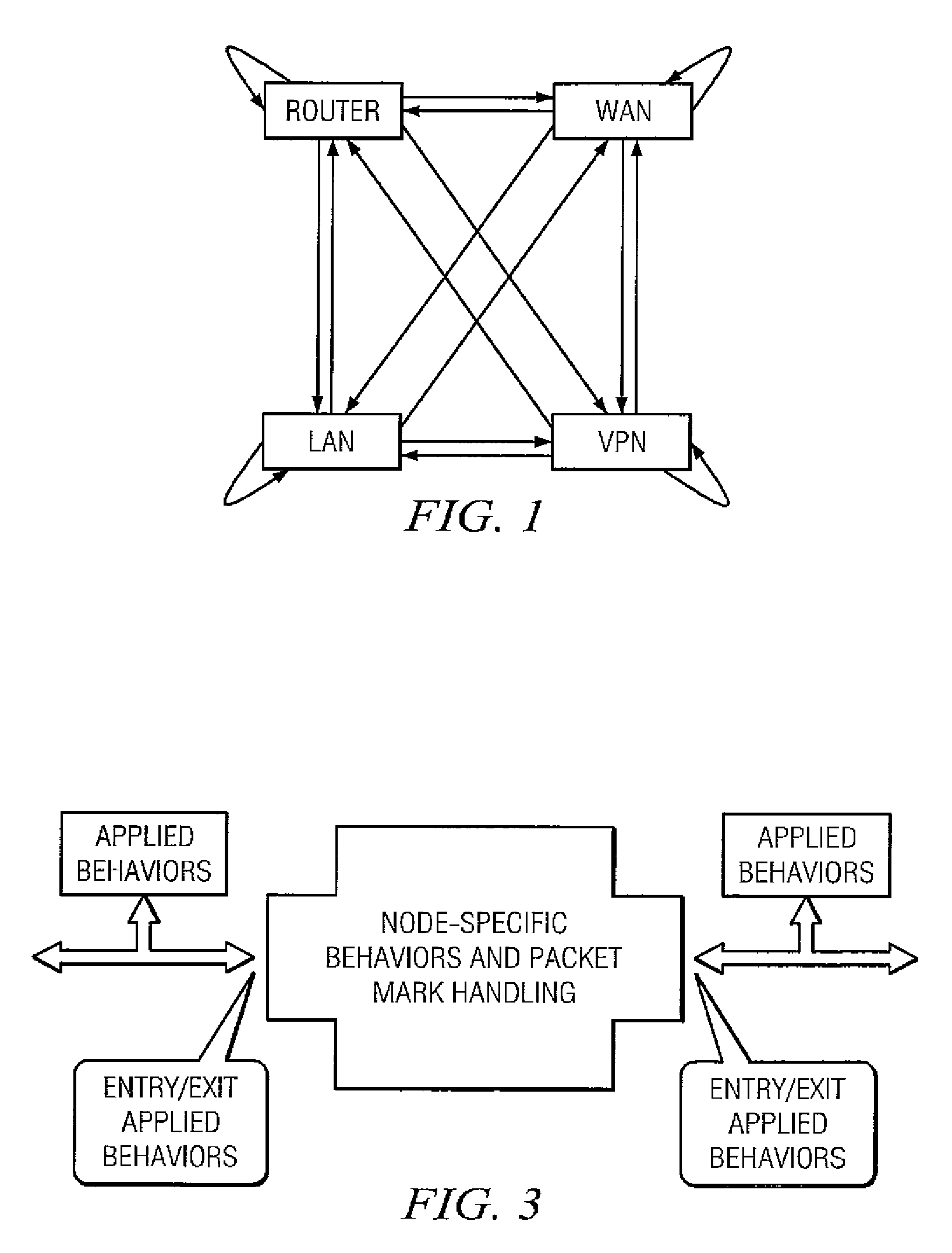
One embodiment of the present invention creates a model of the traffic through a network firewall and uses that model to dynamically manipulate the network firewall based on human intervention or based on the automatic invocations of processes and protocols that implement firewall policy. Another embodiment of the invention creates a model of the physical and virtual network interfaces that a firewall system controls and presents abstracted entities representing both the interface abstractions and the processing nodes (network segments or network client devices) to and through which network traffic flows.
Owner:RPX CORP
Systems and methods for cloud based unified service discovery and secure availability
Systems and methods implemented by a unified agent application executed on a mobile device, for unified service discovery and secure availability include authenticating a user into a plurality of cloud services including a proxy service and a Virtual Private Network (VPN) service, wherein the proxy service is utilized for Internet traffic and the VPN service is for Intranet traffic; creating and operating a link local network at the mobile device with a virtual network interface and multiple listening sockets; and intercepting traffic at the virtual network interface from one or more client applications on the mobile device and splitting the traffic between the proxy service, the VPN service, and the Internet based on a type of the traffic, a destination, and the one or more client applications.
Owner:ZSCALER INC
Wireless video camera and connection methods including a USB emulation
Systems and methods for connecting wireless cameras are provided. A computing device may include a network interface, and a processor configured to establish a virtual USB bus available to an operating system of the computing device, establish a virtual USB camera device, and report to the operating system that the virtual USB camera device is connected to the virtual USB bus. The virtual USB camera may be configured to establish a network connection to a network camera using the network interface, receive video data from the network camera via the network interface, and send the video data via the virtual USB bus. Alternatively, the virtual USB camera may send the video data to the operating system as USB packets, without establishing a virtual USB bus.
Owner:LOGITECH EURO SA
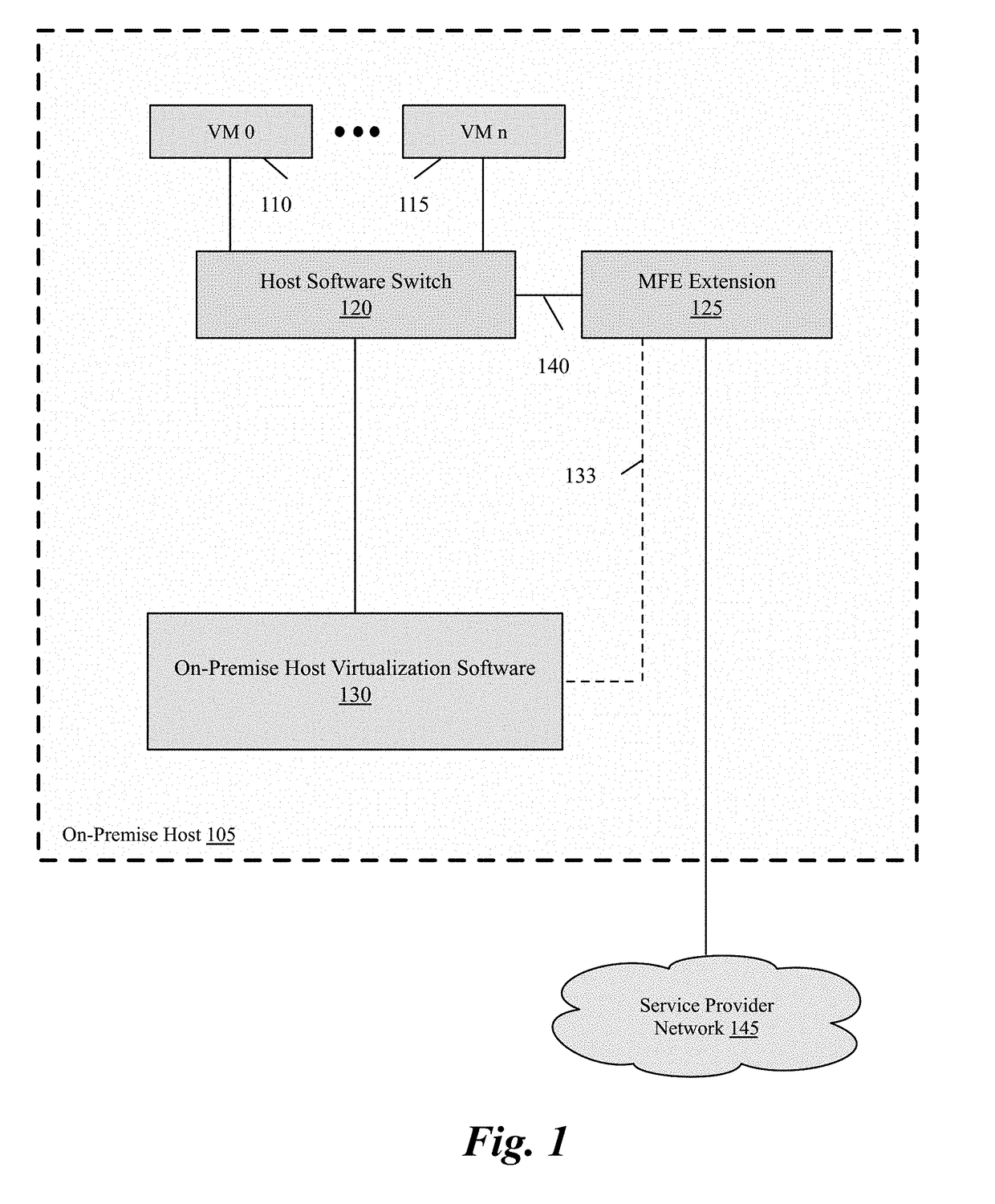
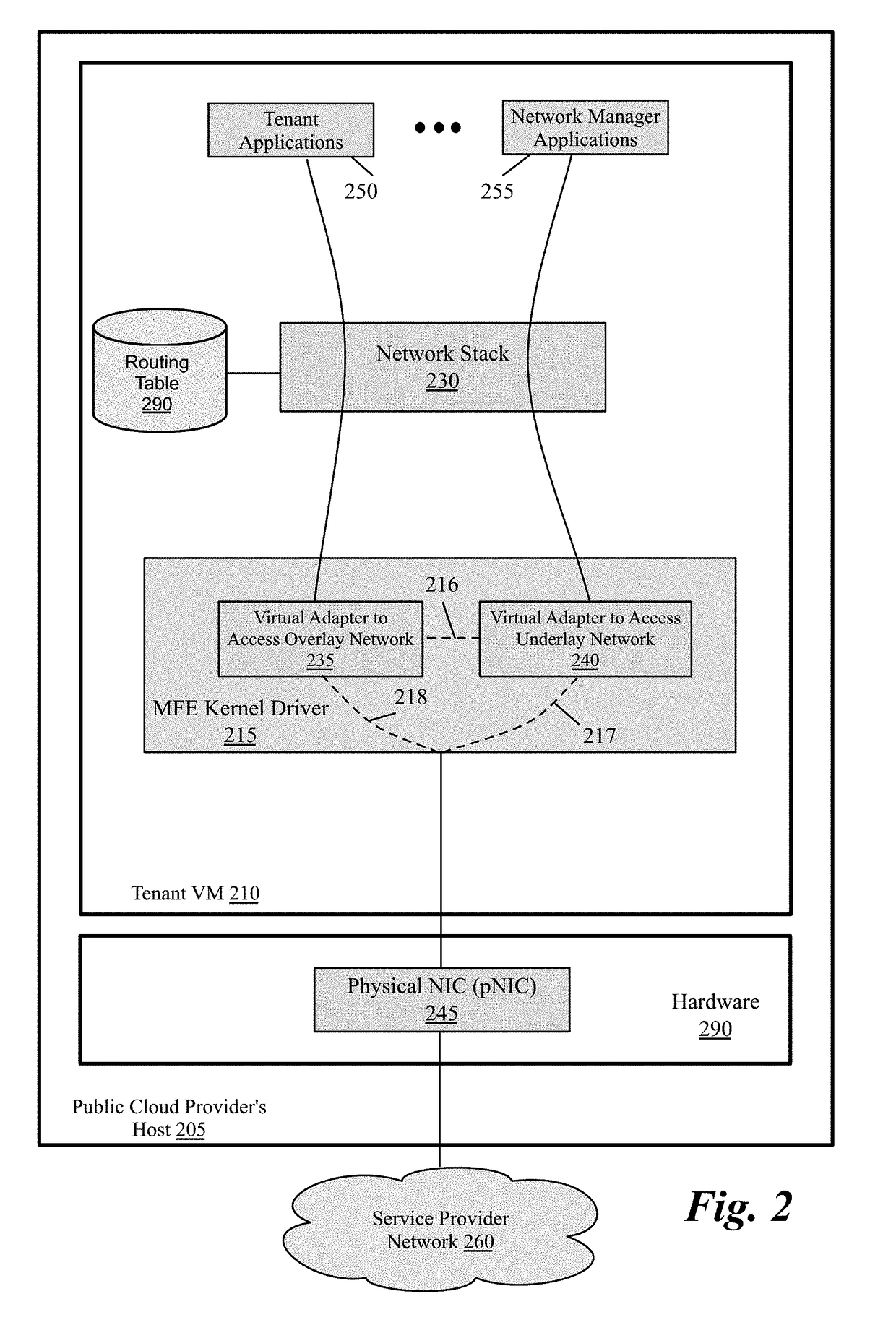
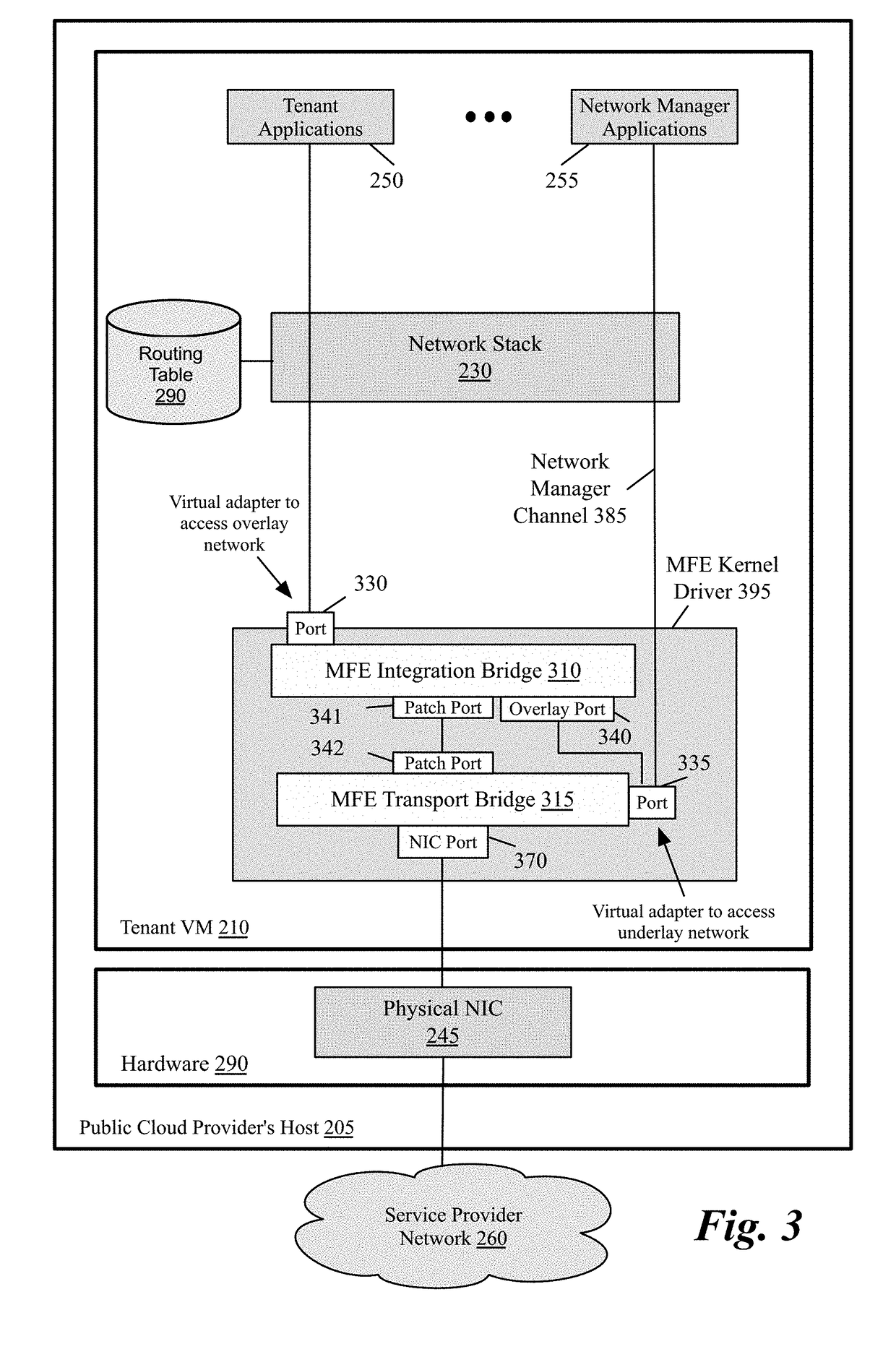
Packet communication between logical networks and public cloud service providers native networks using a single network interface and a single routing table
A data compute node executes (i) a set of tenant applications connected to a third party overlay network, (ii) a set of network manager applications, and (iii) a managed forwarding element that includes a pair of overlay and underlay network virtual adapters. A packet that is received from a network manager application and addressed to an underlay network destination is sent to the underlay network destination address through a physical NIC of the host without network address translation or encapsulation. A packet that is received from a tenant application and addressed to an underlay network destination is subject to SNAT and is sent to the underlay network destination address. A packet that is received from a tenant application and is addressed an overlay destination address is encapsulated with the header of the overlay network and is sent to the overlay network destination address through the underlay virtual adapter.
Owner:NICIRA
System and methods for implementing network traffic management for virtual and physical machines
ActiveUS8166474B1Ensure safetyEasy to useDigital computer detailsSoftware simulation/interpretation/emulationVirtualizationTraffic capacity
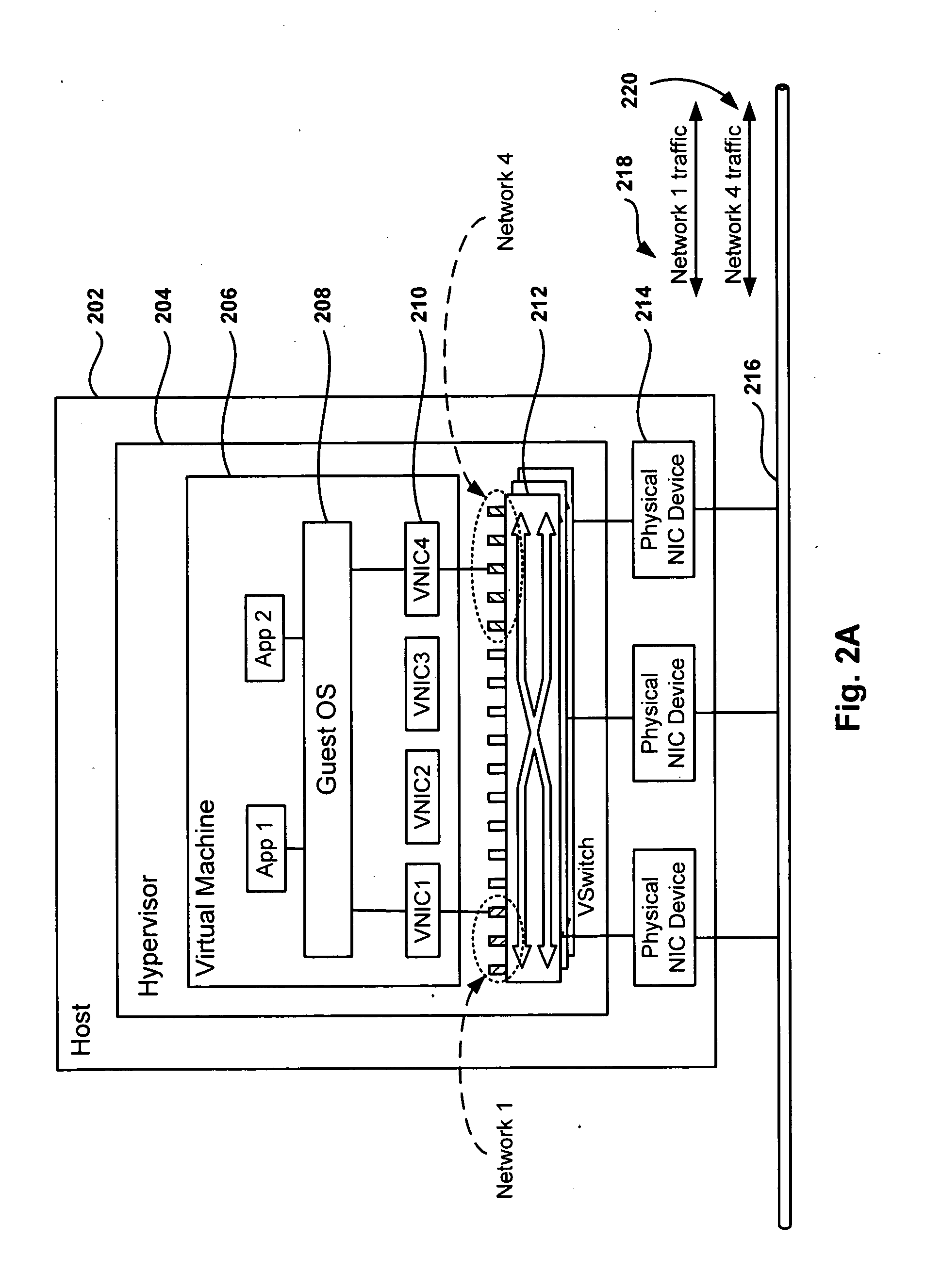
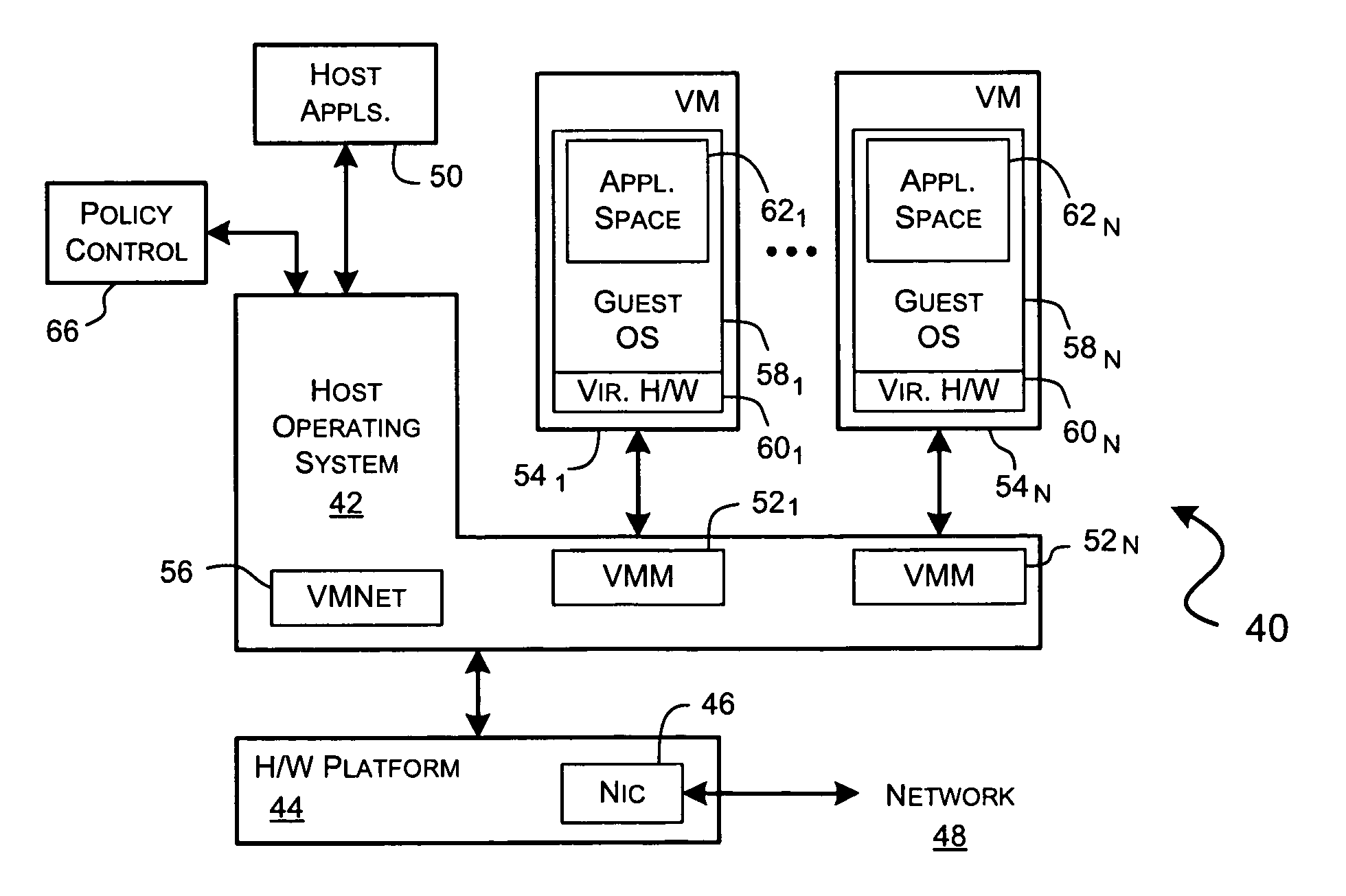
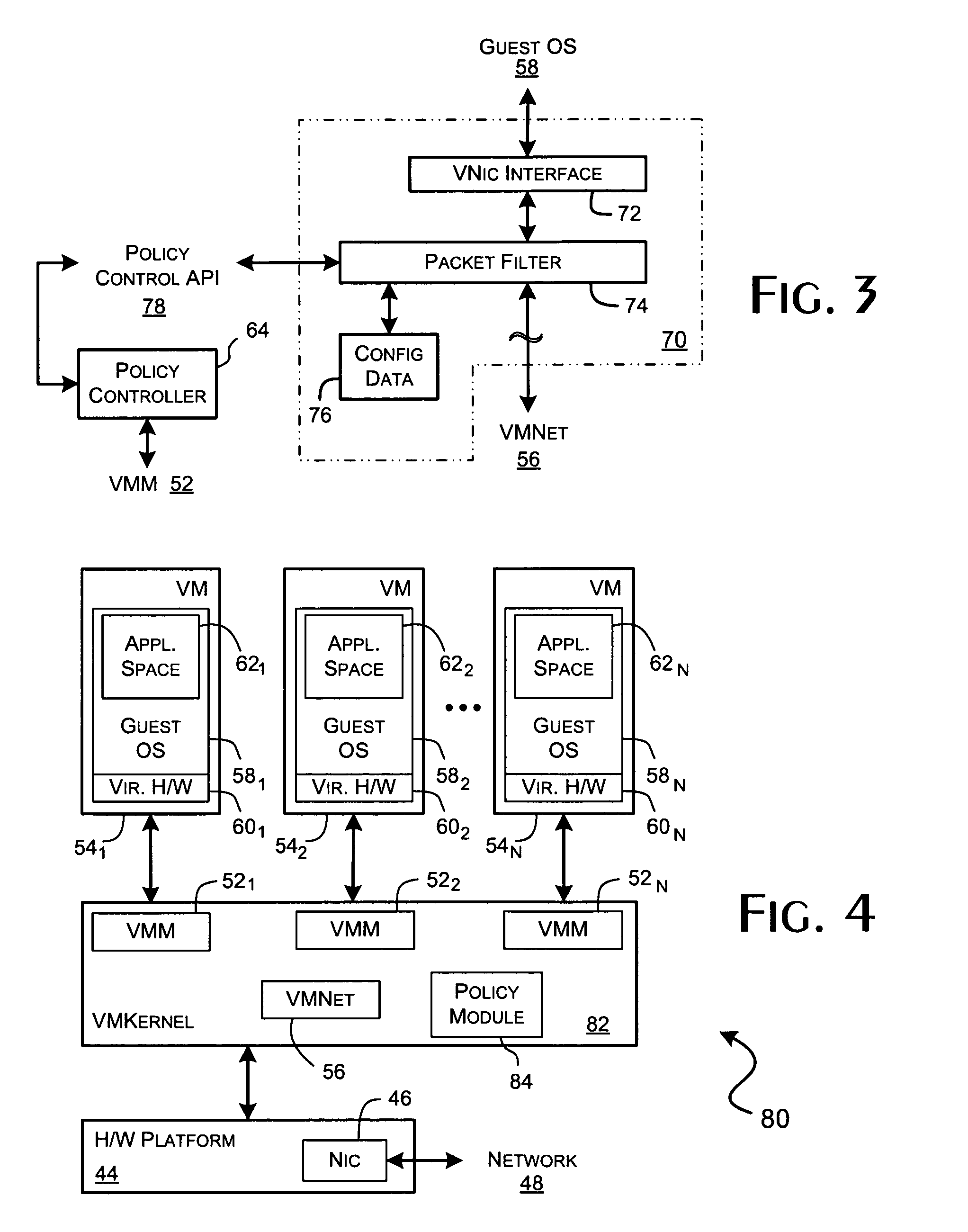
A virtualization framework provides security between multiple virtual machines with respect to network communications between the virtual machines and between the virtual machines and a physical network coupled to the underlying physical computer platform. The virtualization framework includes a network interface controller driver that provides an interface to the platform network interface controller and supports execution of a plurality of virtual machines. Each virtual machine includes a virtual network interface controller that provides a network communications path between the virtual machines and to the network interface controller driver. Each virtual network interface controller further contains a programmable network packet filter that controls the selective transfer of network packets with respect to a corresponding virtual machine.
Owner:VMWARE INC
Systems, Methods and Computer Readable Medium To Implement Secured Computational Infrastructure for Cloud and Data Center Environments
InactiveUS20170005990A1Implement securityInput/output to record carriersMultiple keys/algorithms usageData centerNetwork key
Systems, methods, and non-transitory computer-readable medium are provided to secure data centers and cloud computing. A method receives network identifiers for functions, requests a network key for each function, allocates network interfaces, requests a virtual network interface controller allocation, requests a network key for each cloud function, receives storage identifiers for functions, requests a storage key for each cloud function, allocates virtual storage disks, requests a storage interface controller allocation, requests a storage key for each cloud function. Methods secure migration of a virtual machine from a source to a target server. A server includes multiple cores where each core is dedicated to a compute function and a unique key encrypts data of each compute function. A non-transitory computer-readable medium encodes programs that execute the above methods.
Owner:BIRGER ARI
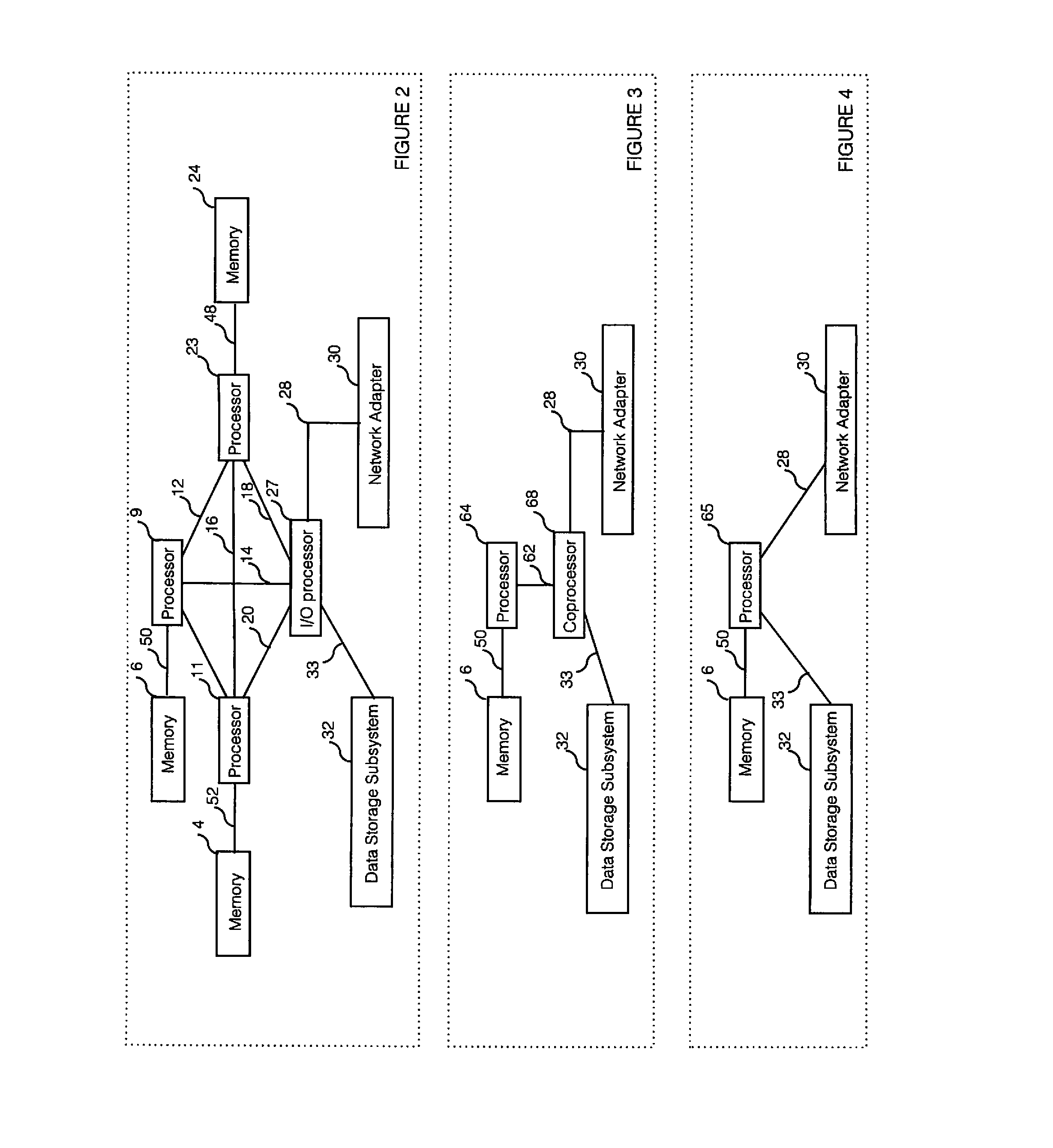
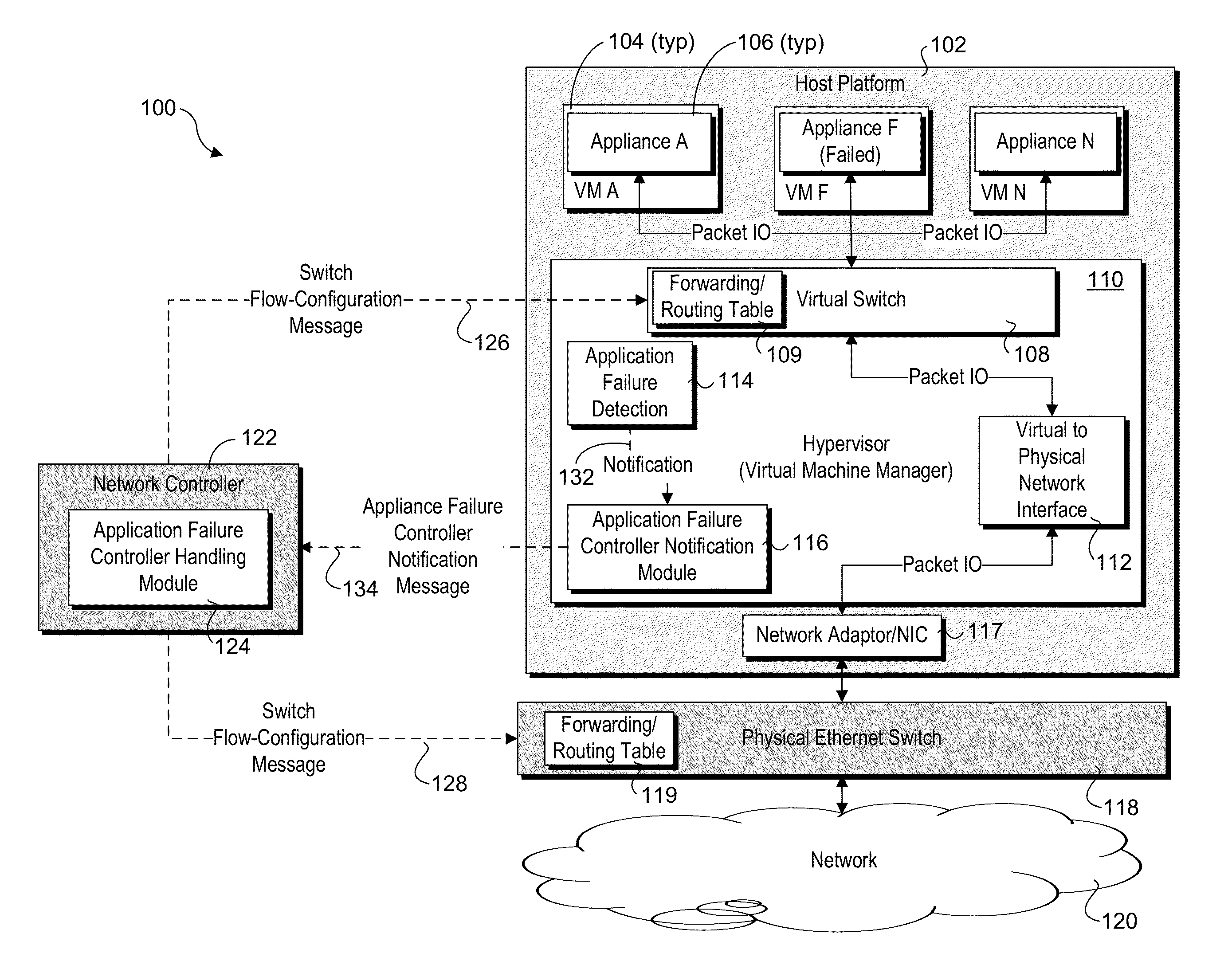
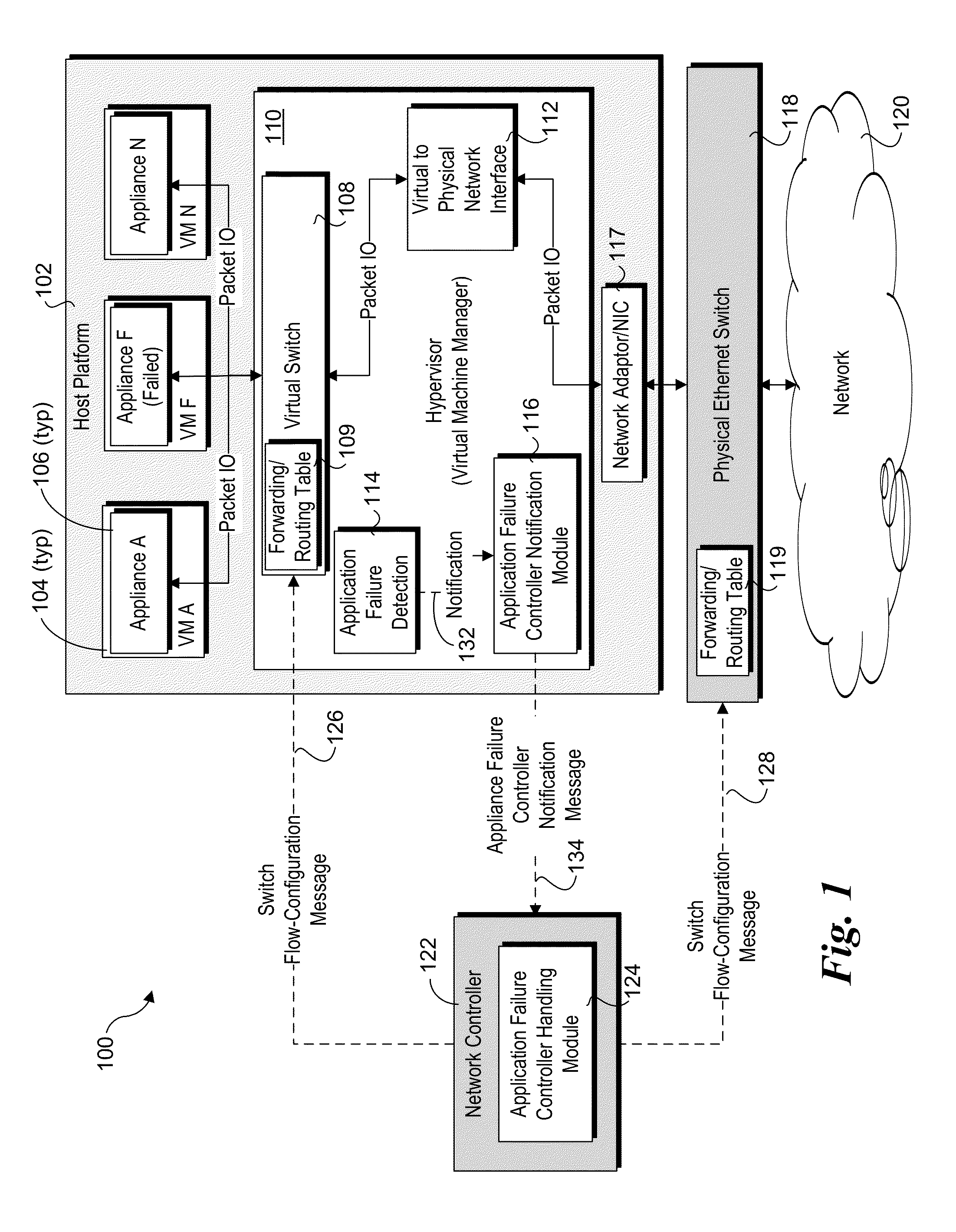
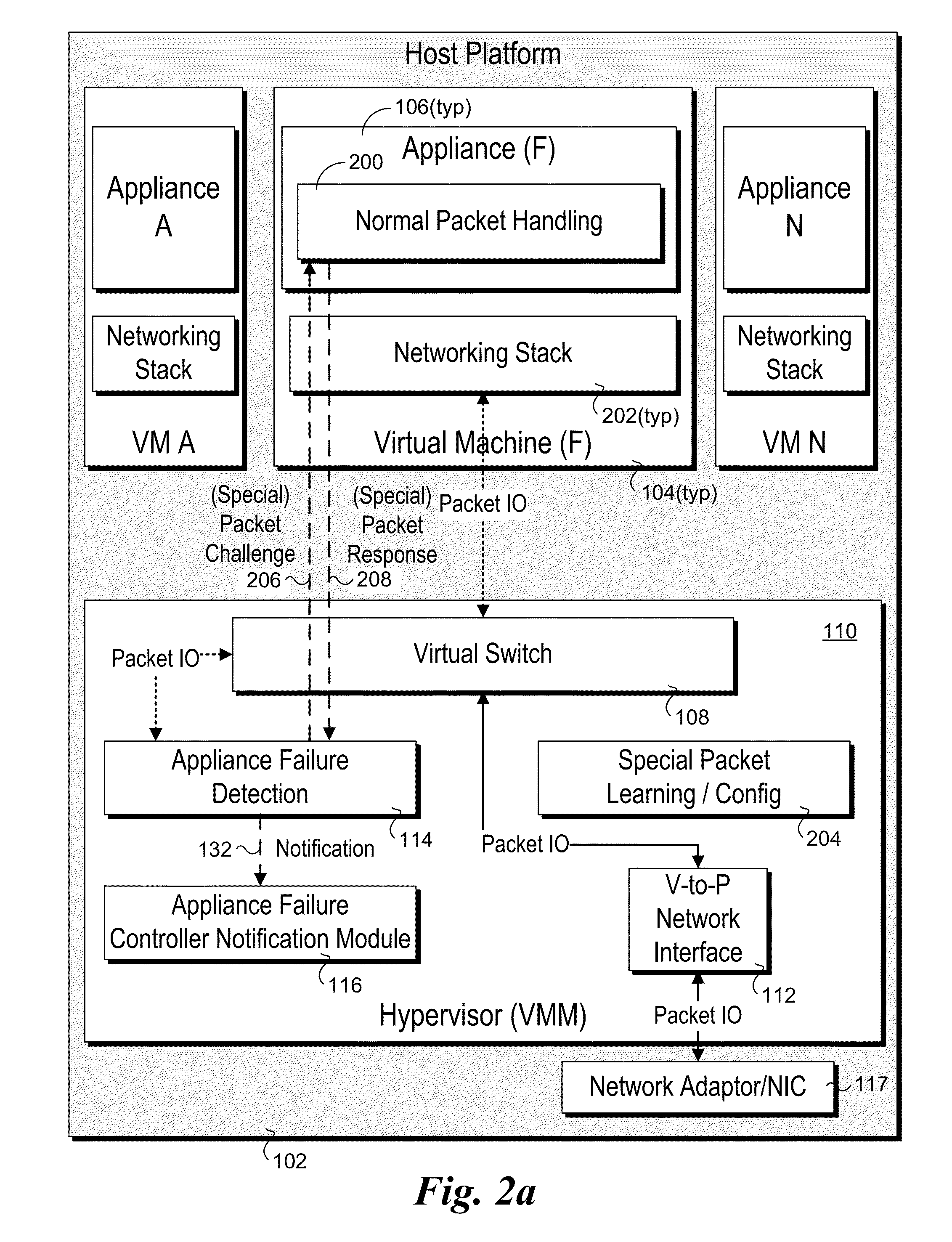
Detection and handling of virtual network appliance failures
InactiveUS20150089331A1Error preventionTransmission systemsVirtual applianceVirtual network interface
Methods and apparatus for detection and handling of virtual appliance failures. In one aspect, a method is implemented on a host platform on which a hypervisor (aka Virtual Machine Manager) and a plurality of virtual machines (VMs) are running, the plurality of VMs collectively hosting a plurality of Software Defined Networking (SDN) and / or Network Function Virtualization (NFV) appliances that are communicatively coupled via a virtual network. A software-based entity running on the host platform is configured to monitor the plurality of virtual network appliances to detect failures of the virtual network appliances. In response to detection of a virtual network appliance failure, messages containing configuration information are implemented to reconfigure packet flows to bypass the virtual network appliance that has failed.
Owner:INTEL CORP
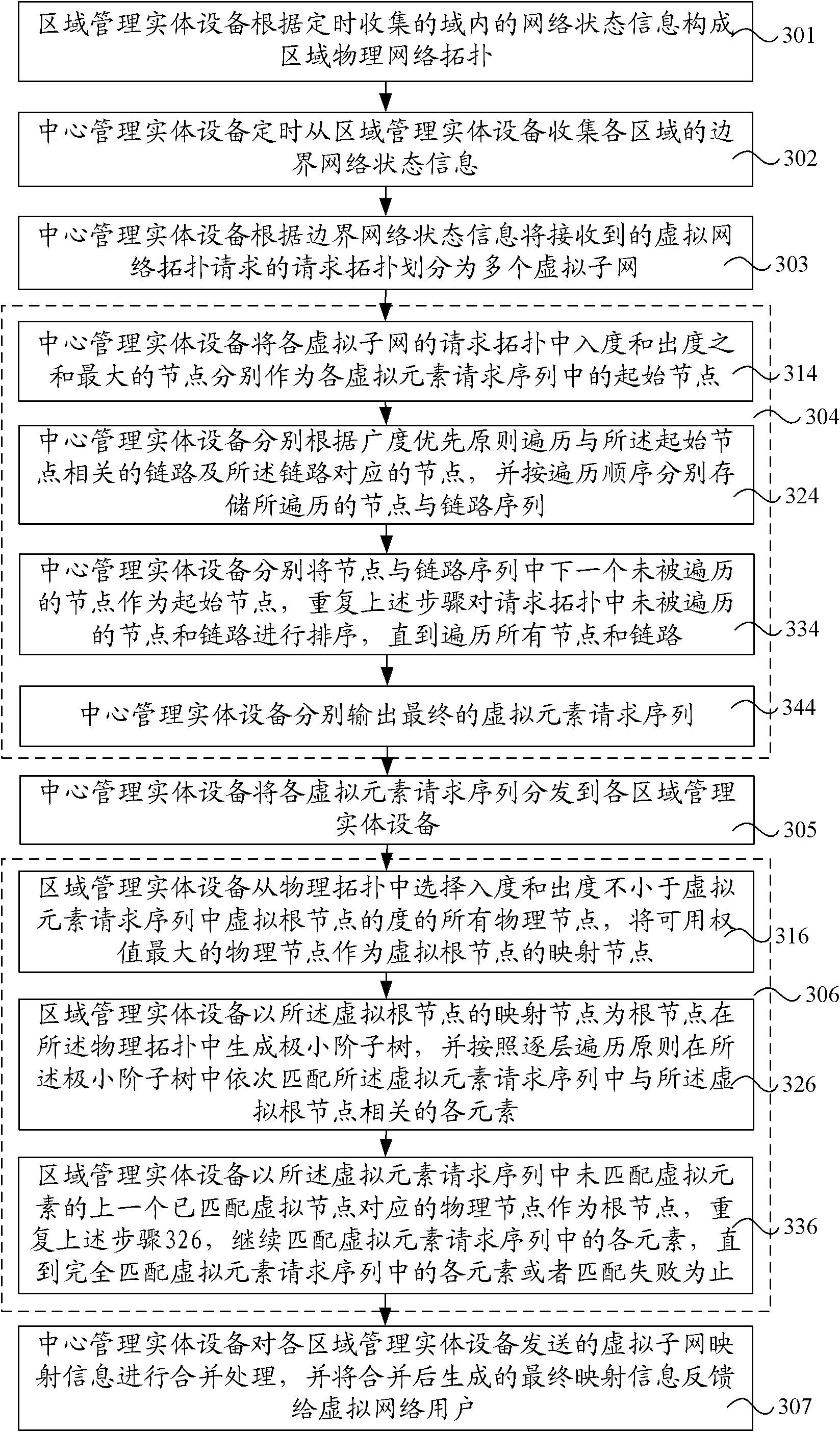
Virtual network mapping processing method and system
InactiveCN102075402AReduce requestsReduce deployment timeNetworks interconnectionResource consumptionVirtual network topology
The embodiment of the invention discloses a virtual network mapping processing method and system. The method comprises the following steps: according to perimeter network status information of each region sent by management entity equipment in each region, dividing the request topology of a received virtual network topology request into a plurality of virtual subnets, and decomposing each virtualsubnet into a virtual element request sequence respectively; distributing each virtual element request sequence to the management entity equipment in each region, and carrying out mapping matching onthe logical topology and physical topology of each virtual subnet by the management entity equipment in each region in accordance with each virtual element request sequence; and merging virtual subnet mapping information sent by the management entity equipment in each region, and feeding back generated final mapping information after merging to virtual network users. The system comprises central management entity equipment and a plurality of regional management entity equipment. By utilizing the method and system provided by the invention, the processing bottleneck problem caused by overhigh computing resource consumption in the prior art is solved.
Owner:HUAWEI TECH CO LTD
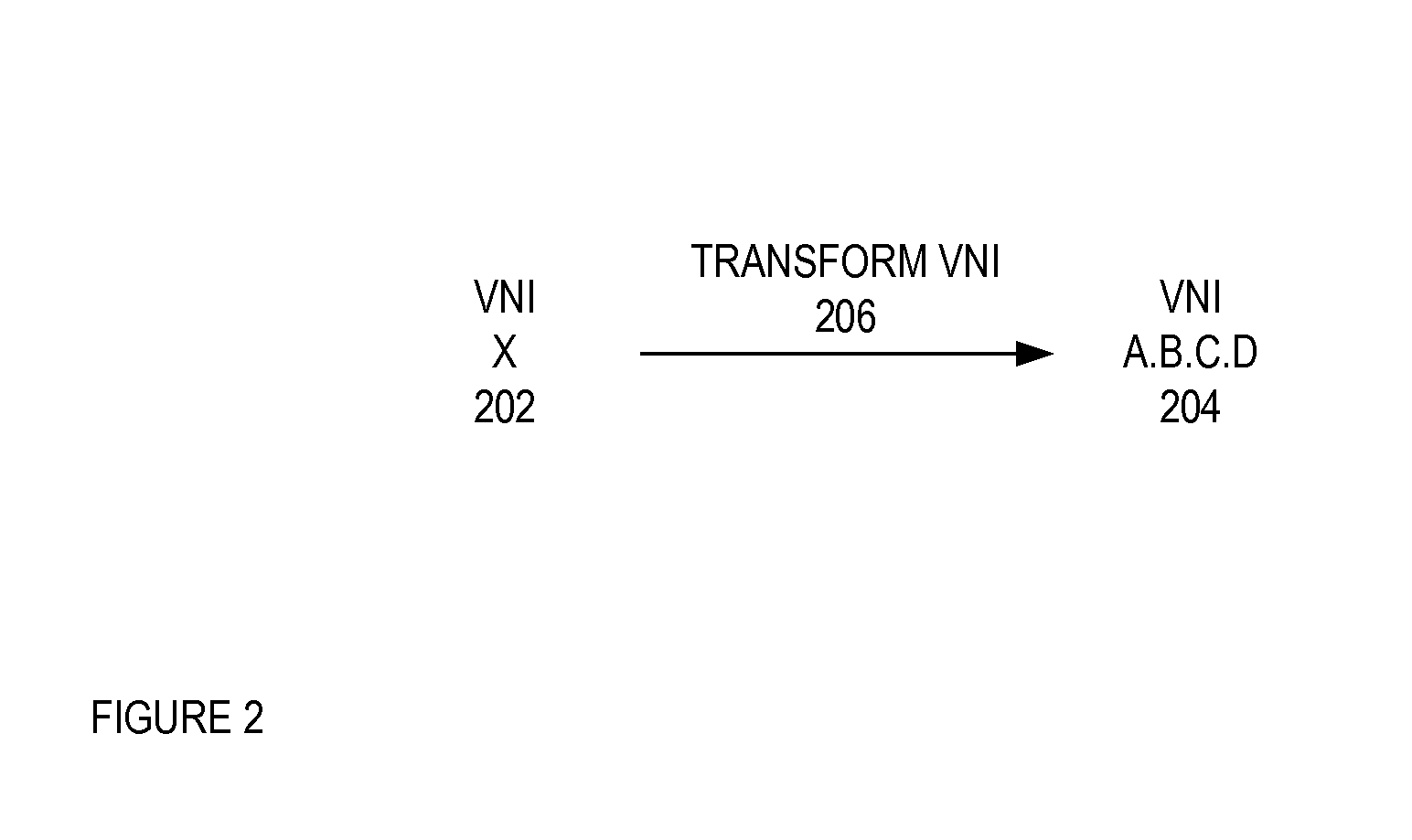
System and method of subnetting a virtual network identifier
ActiveUS20140337497A1Digital computer detailsData switching networksVirtualizationVirtual network interface
A method and apparatus that determines a plurality of matching policies for a segment of a dynamic virtualized network is described. A device retrieves a virtual network identifier of the segment, where the virtual network identifier includes a plurality of bits and a plurality of subnets and each of the plurality of subnets is a different subset of the plurality of bits. In addition, the dynamic virtualized network is a virtualized layer 2 network that is overlaid on a layer 3 physical network, where the layer 3 physical network includes a plurality of network access devices, and the segment includes a plurality of endpoints. The device further determines the plurality of matching policies for the segment from the plurality of subnets of the virtual network identifier, where each of the plurality of subnets corresponds to one of the plurality of matching policies. The device additionally applies the plurality of matching policies to each network access device that corresponds to one of the plurality of matching endpoints.
Owner:FORTINET
Framework for optimizing and simplifying network communication in close proximity networks
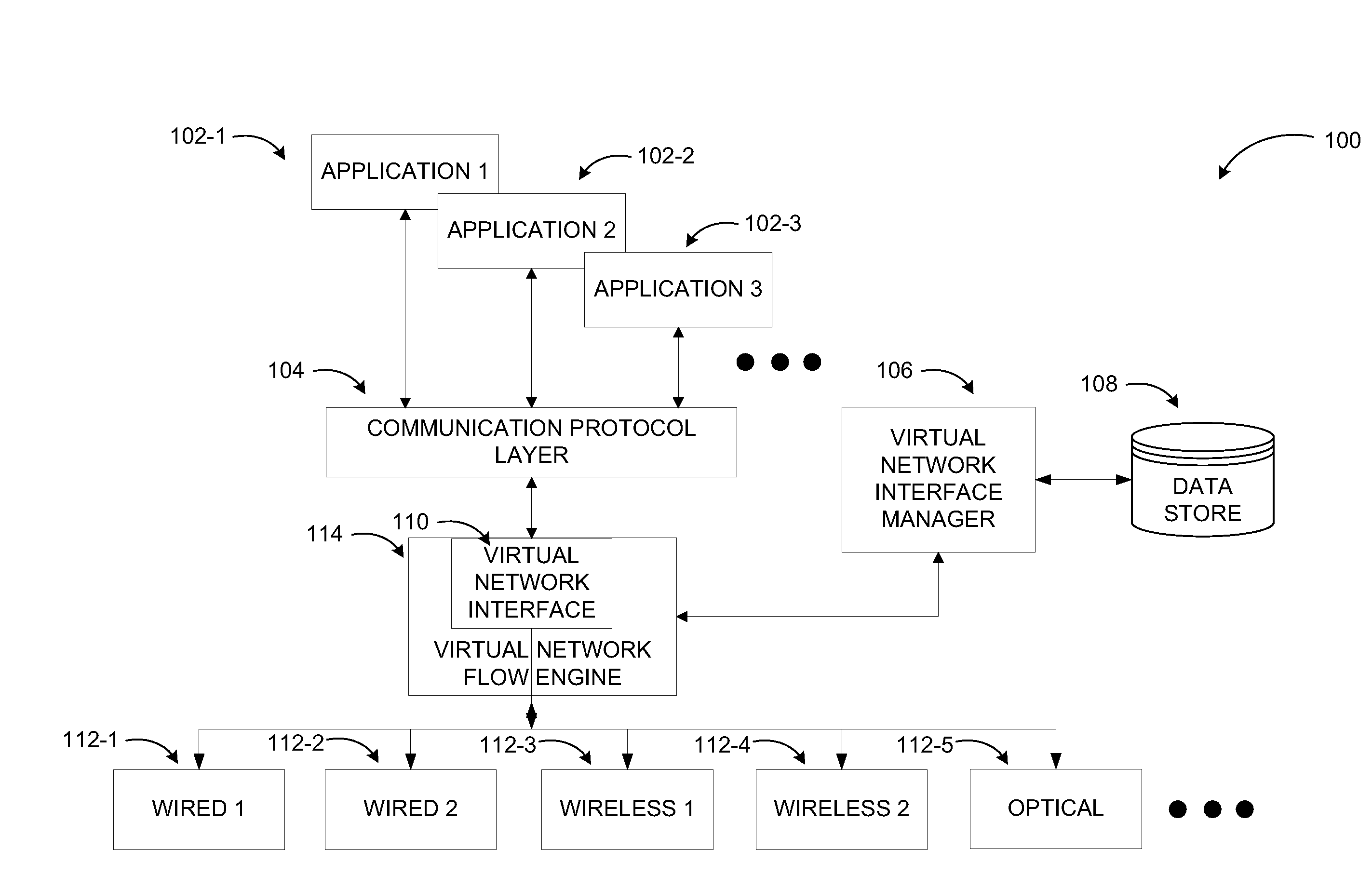
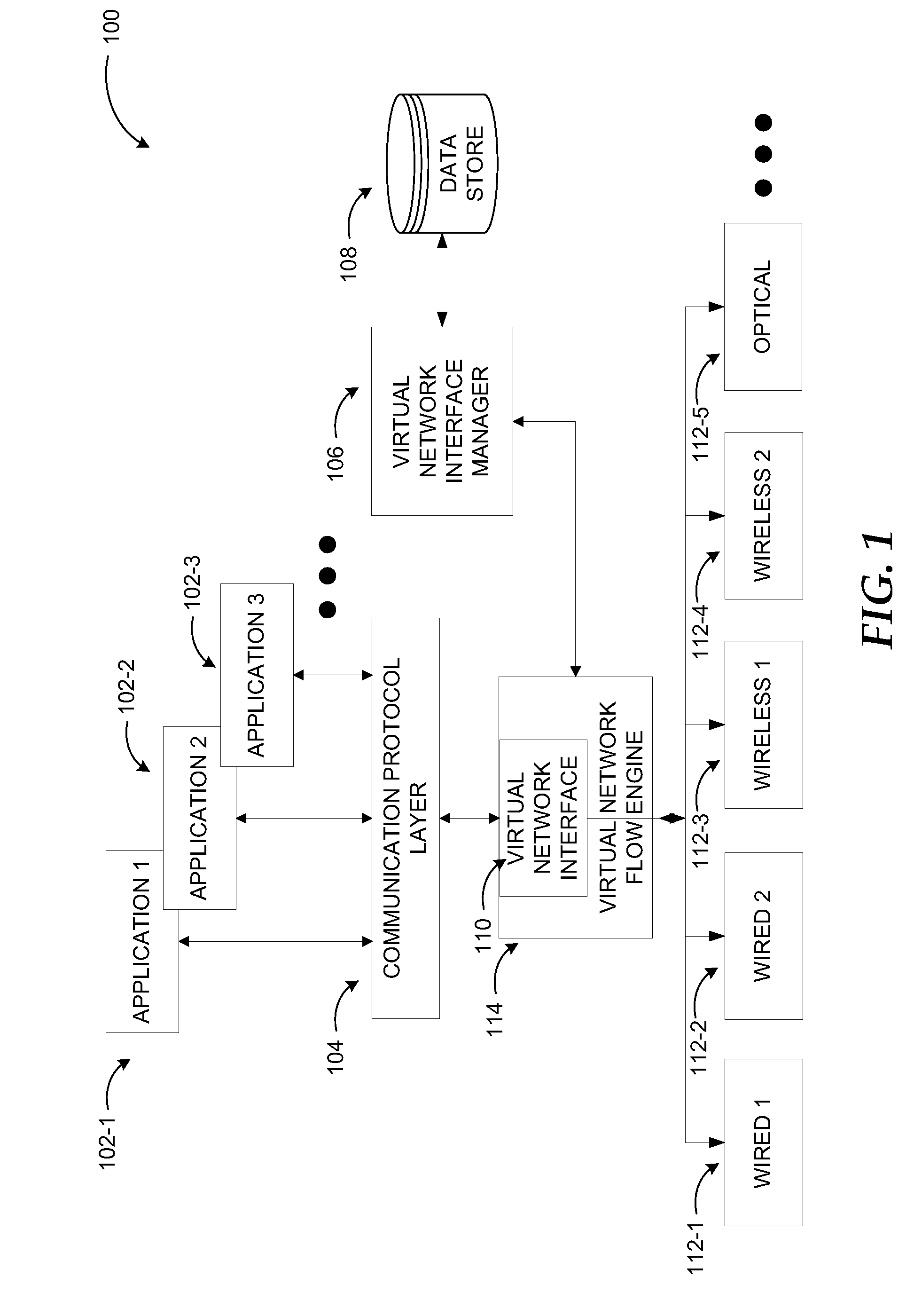
A framework capable of providing transparent handling of network traffic in close proximity networks such as home networks is provided. A single virtual network interface is exposed to users / applications on connected devices. A virtual network interface manager determines available physical network interfaces and switches to a different physical network interface or a different configuration on the same physical network interface in a transparent manner to the communicating application(s). This enables the framework to optimize network communications for the communicating applications, devices, and users based on predefined criteria, application requirements such as different data throughput, or changing environment conditions such as interference. Network communication operations are also simplified for users since they are no longer required to have the necessary knowledge for configuring physical network interfaces manually in response to changing conditions.
Owner:MICROSOFT TECH LICENSING LLC
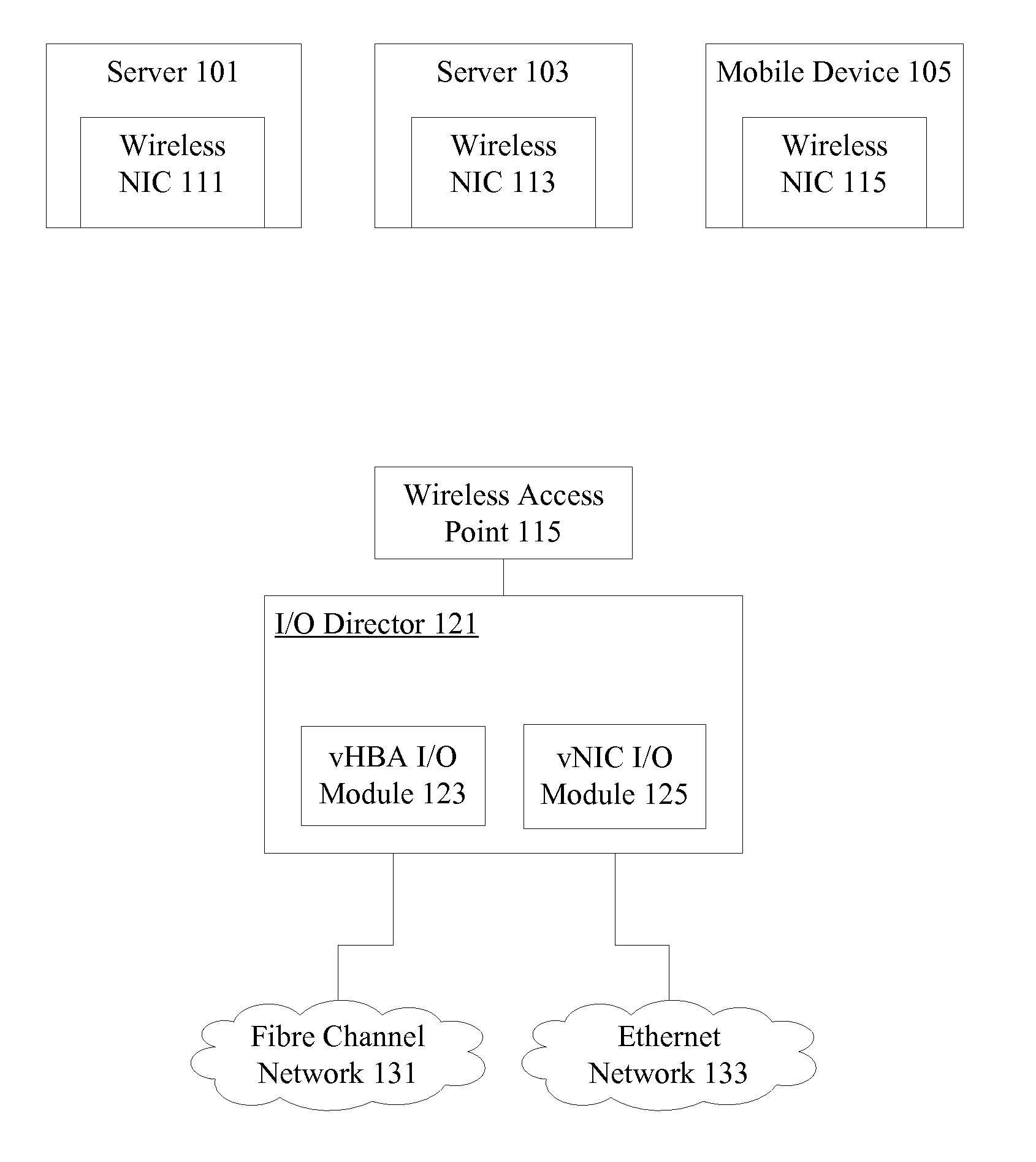
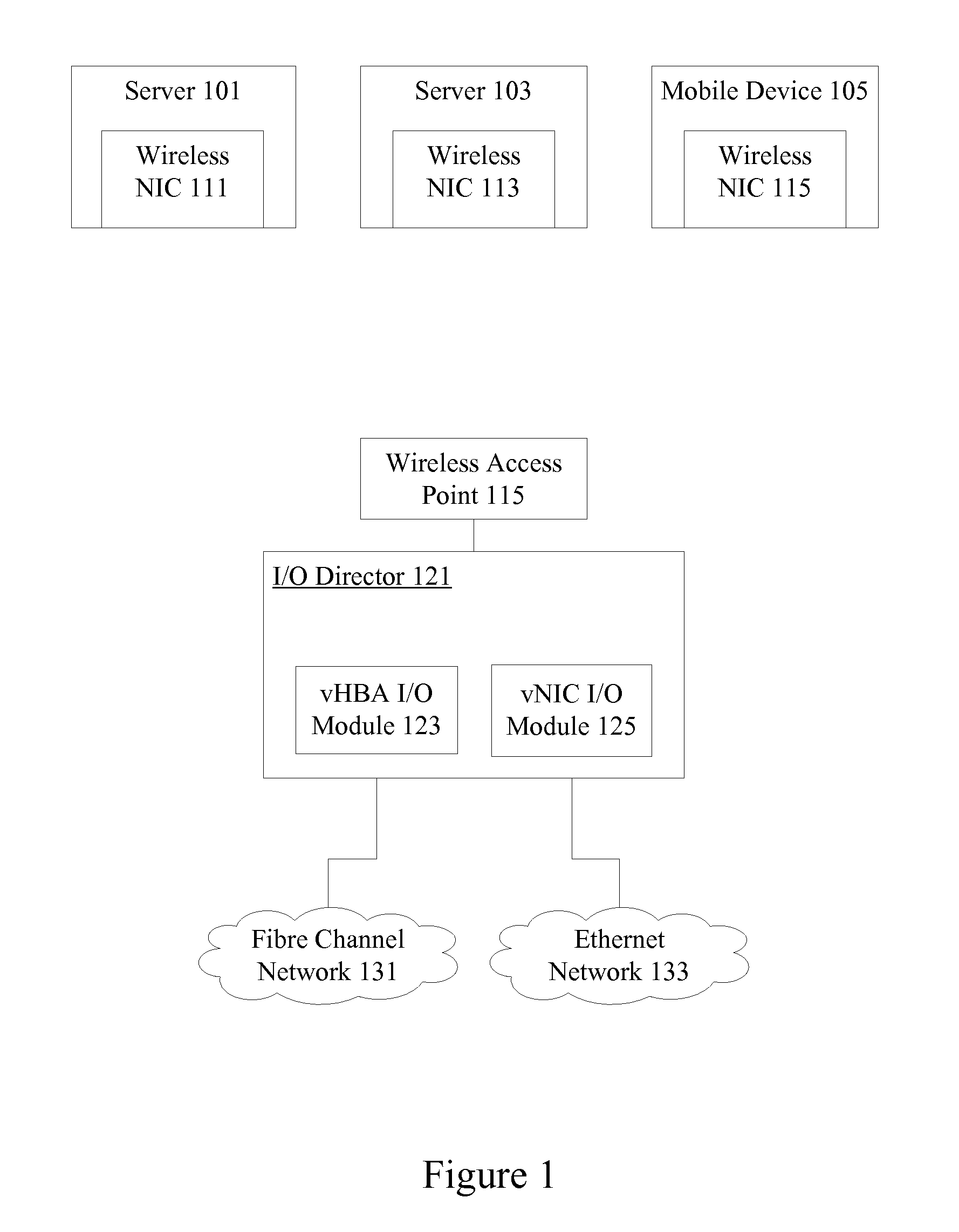
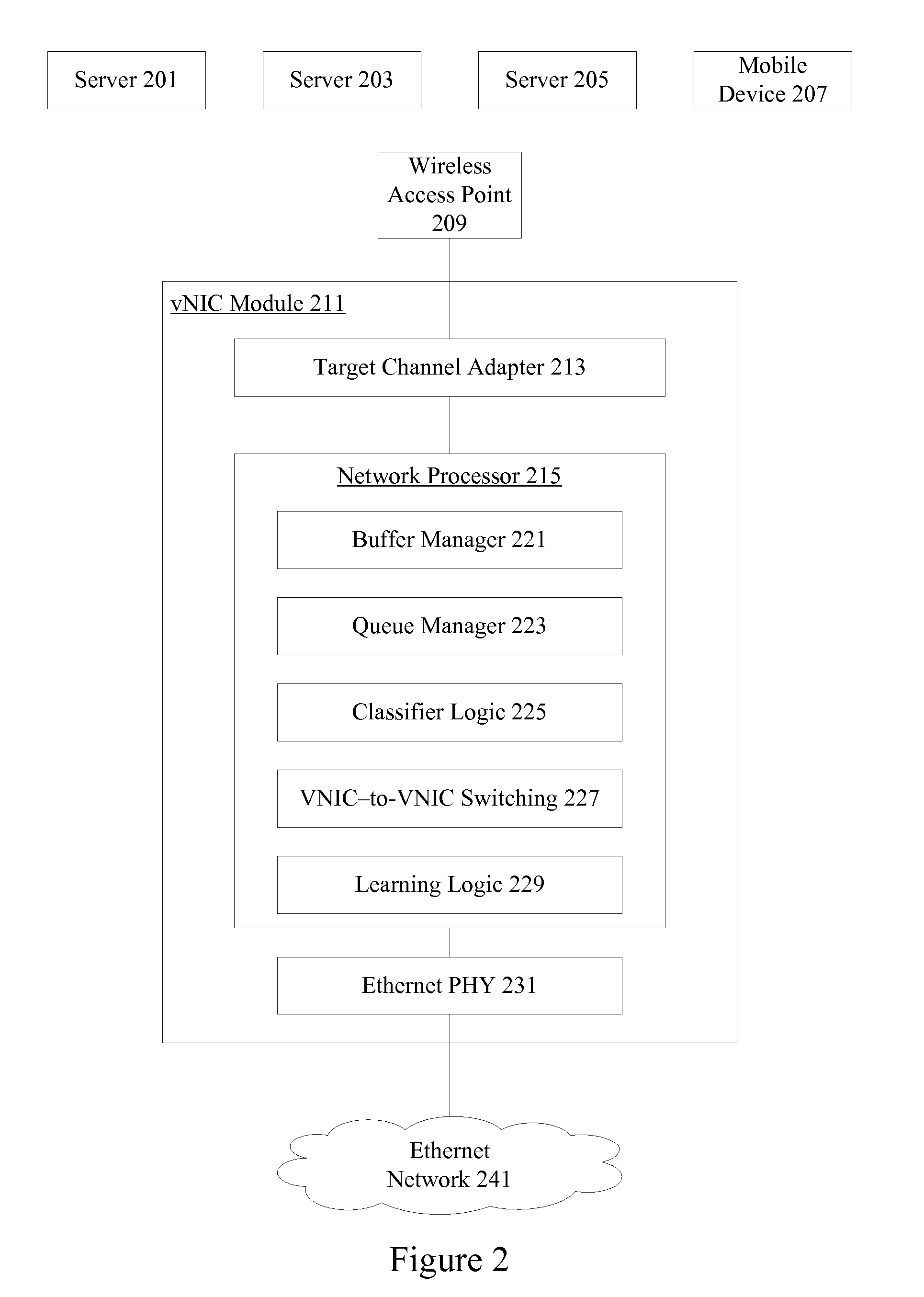
Wireless host I/O using virtualized I/O controllers
Mechanisms provide hosts such as servers and mobile devices with access to virtualized I / O resources including virtual Host Bus Adapters (vHBAs) and virtual Network Interface Cards (vNICs) over a wireless I / O interconnect. Host applications access virtualized I / O resources using virtual device drivers that communicate with virtualized I / O resources on an I / O director using a reliable communication protocol running over a wireless network. I / O data is throttled if necessary based on wireless network considerations.
Owner:ORACLE INT CORP
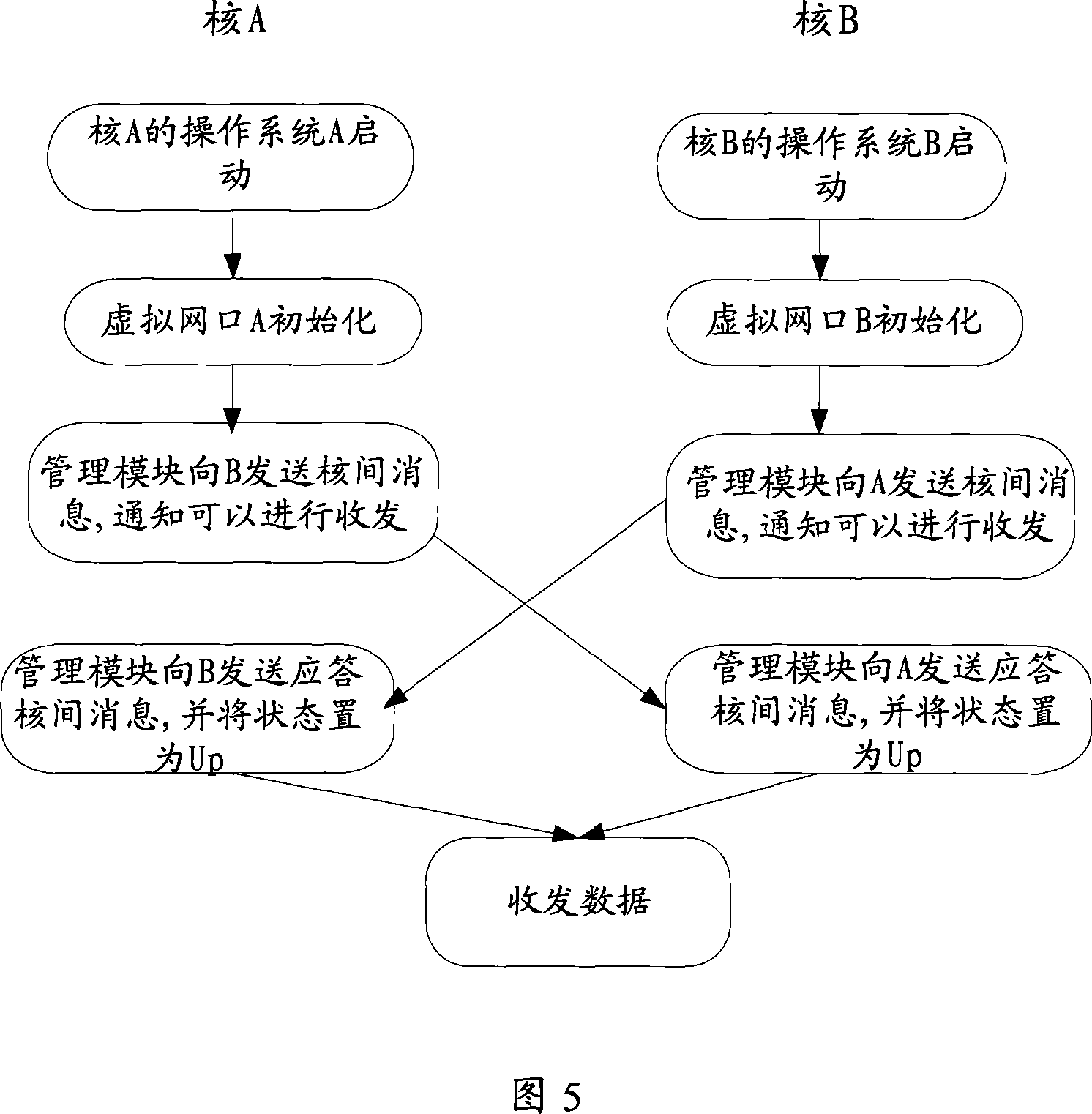
Communication method and system of multi-nuclear multi-operating system
ActiveCN101216814ALow costReduce transplant costsDigital computer detailsElectric digital data processingThird partyCommunications system
The invention discloses a communication system used among polykaryon multi-operating systems. The data transmission is completed among the operating systems through a virtual data channel, and the virtual data channel comprises a virtual interface (such as a virtual network interface) corresponding to the operating systems which are mutually connected. The invention also discloses a communication method among polykaryon multi-operating systems. The invention dose not use a hardware chip, thus the hardware cost is lowered; third party software can be migrated without alteration, thus the software migrating cost is lowered; the data receiving and sending can be realized by adopting shared memory and inter-karyon information, thus no copy of the data is realized, and the data receiving and sending efficiency is increased.
Owner:NEW H3C TECH CO LTD
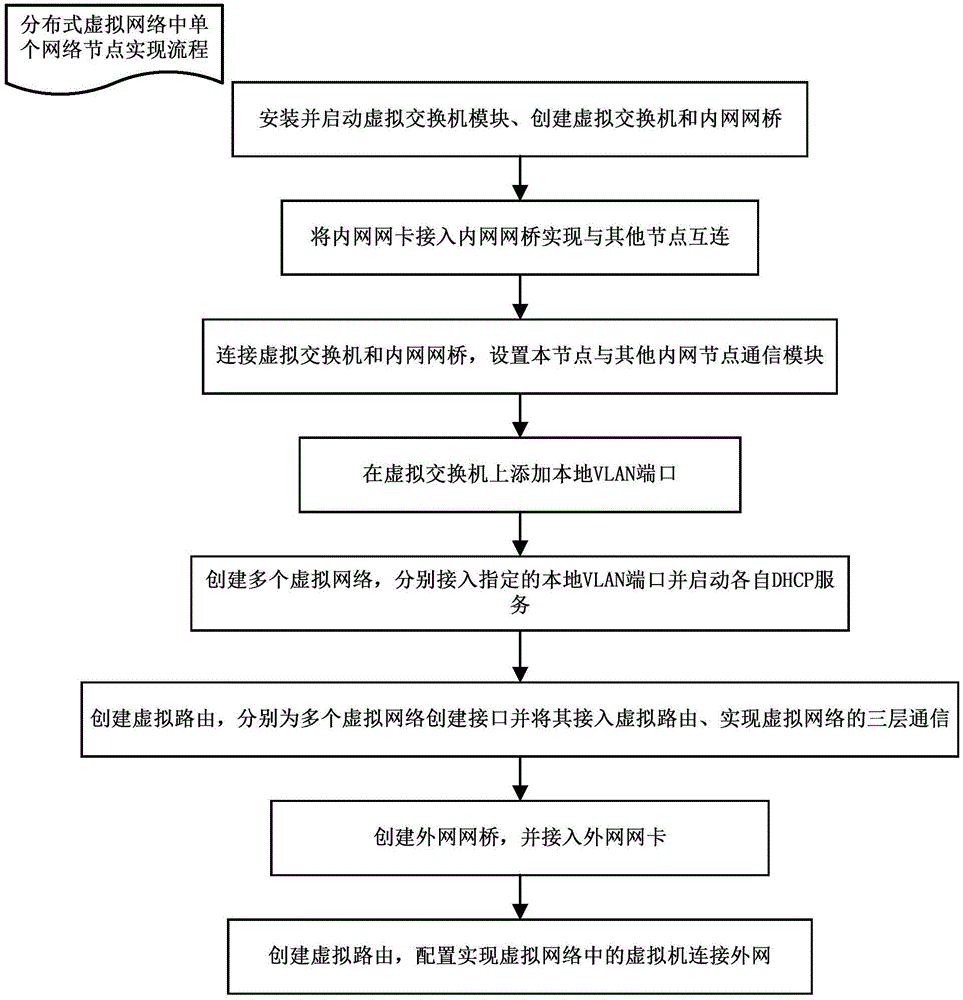
Method for realizing distributed virtual networks applicable to cloud platform
InactiveCN104468746AAvoid single point of failure problemsDoes not affect the normal provision of network servicesNetworks interconnectionComputer moduleVirtual switch
The invention relates to the technical field of cloud computing management, in particular to a method for distributed virtual networks applicable to a cloud platform. According to the method, any number of physical nodes are selected as network nodes of the cloud platform, and the network nodes establish and provide virtual network service; establishment of the network nodes includes the steps that (1), a virtual switch module is installed and started, and a virtual switch and an intranet network bridge are established; (2), an intranet network card is connected into the intranet network bridge; (3), the virtual switch and the intranet network bridge are connected, and a communication module for the node and other intranet nodes is set; (4), local VLAN ports are added; (5), the multiple virtual networks are established; (6), a virtual route is established; (7), an extranet network bridge is established, and an extranet network card is connected in; (8), a virtual route is established. Single-point failures of centralized network service of the cloud platform can be avoided, load balance of the network service nodes is achieved, the virtual networks can be managed flexibly and conveniently, and the method can be used for realizing the distributed virtual networks.
Owner:G CLOUD TECH
Integrated intrusion deflection, detection and introspection
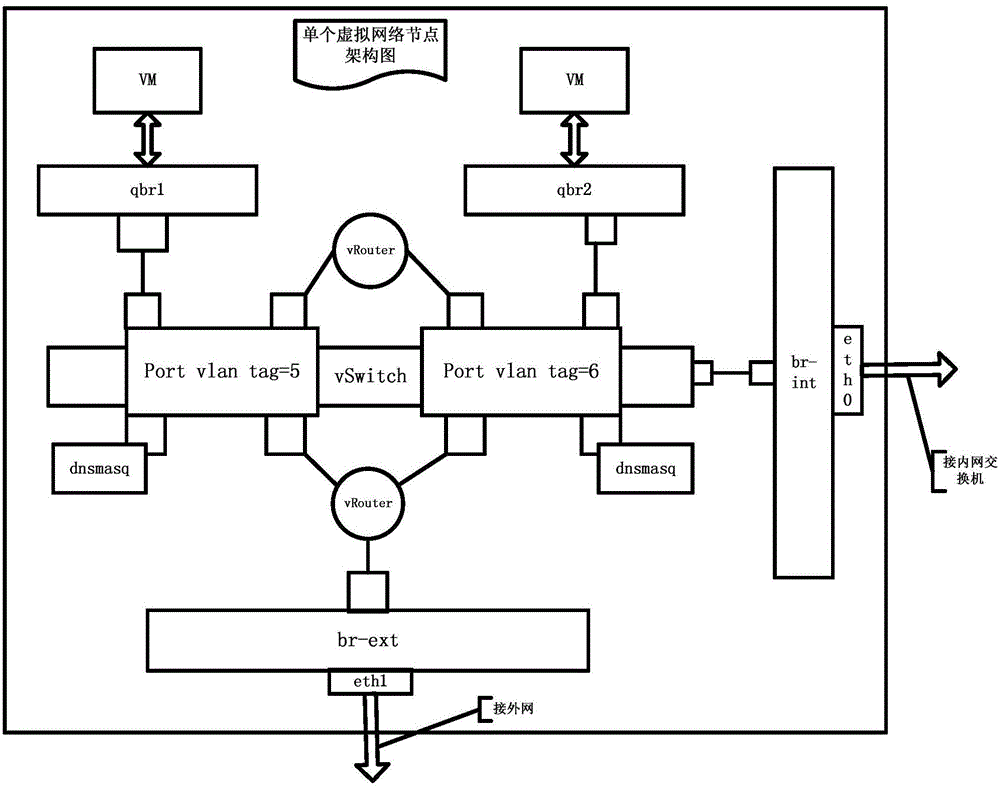
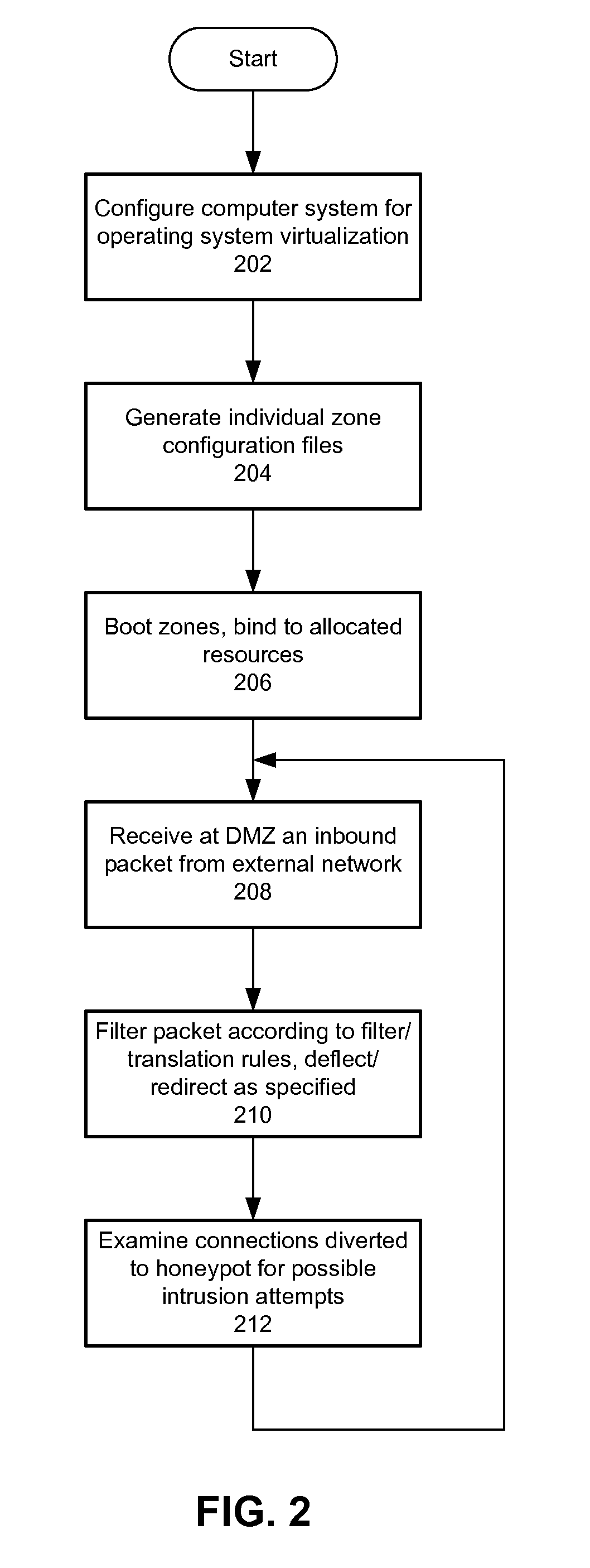
ActiveUS20110067107A1Easy to manageImprove securityError preventionFrequency-division multiplex detailsVirtualizationLimited resources
Methods and apparatus are provided for integrated deflection, detection and intrusion. Within a single computer system configured for operating system virtualization (e.g., Solaris, OpenSolaris), multiple security functions execute in logically independent zones or containers, under the control and administration of a global zone. Such functions may illustratively include a demilitarized zone (DMZ) and a honeypot. Management is facilitated because all functions work within a single operating system, which promotes the ability to configure, monitor and control each function. Any given zone can be configured with limited resources, a virtual network interface circuit and / or other features.
Owner:ORACLE INT CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com