Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
209 results about "Server agent" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
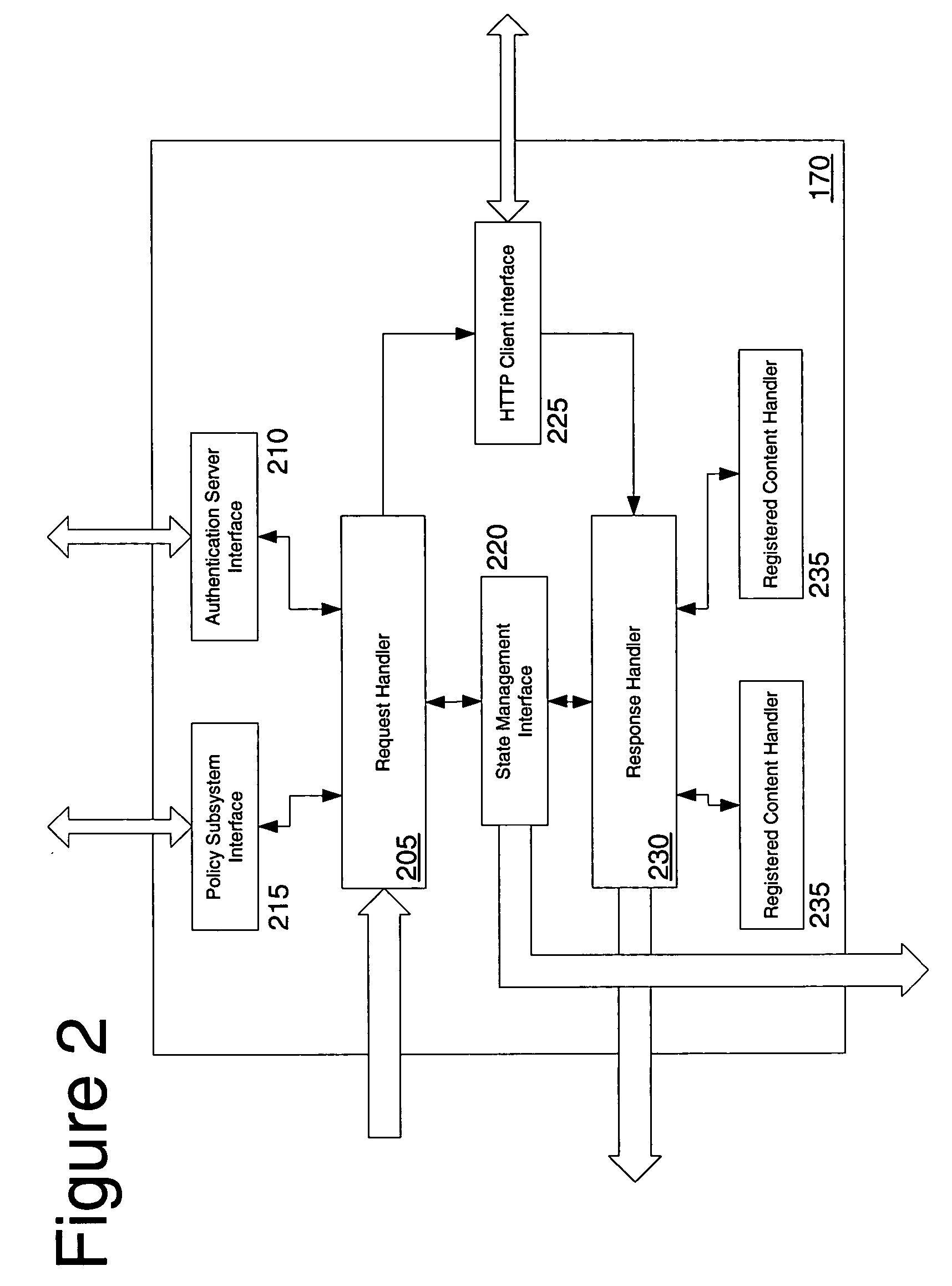
User Agent Server (UAS) is a Voice over Internet Protocol (VoIP) application that responds to User Agent Client (UAC) service requests based on input or other external stimuli in Session Initiation Protocol (SIP) systems.
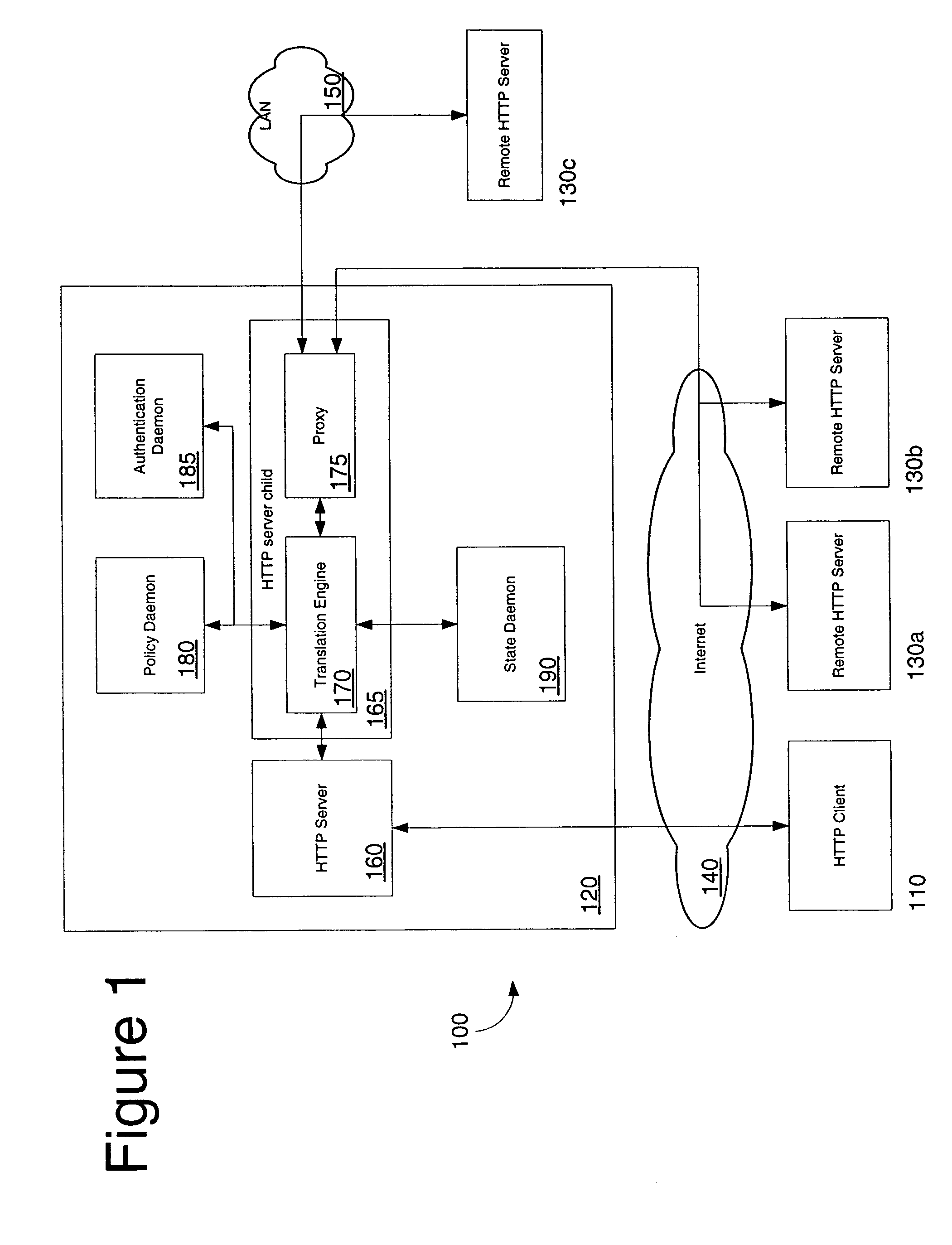
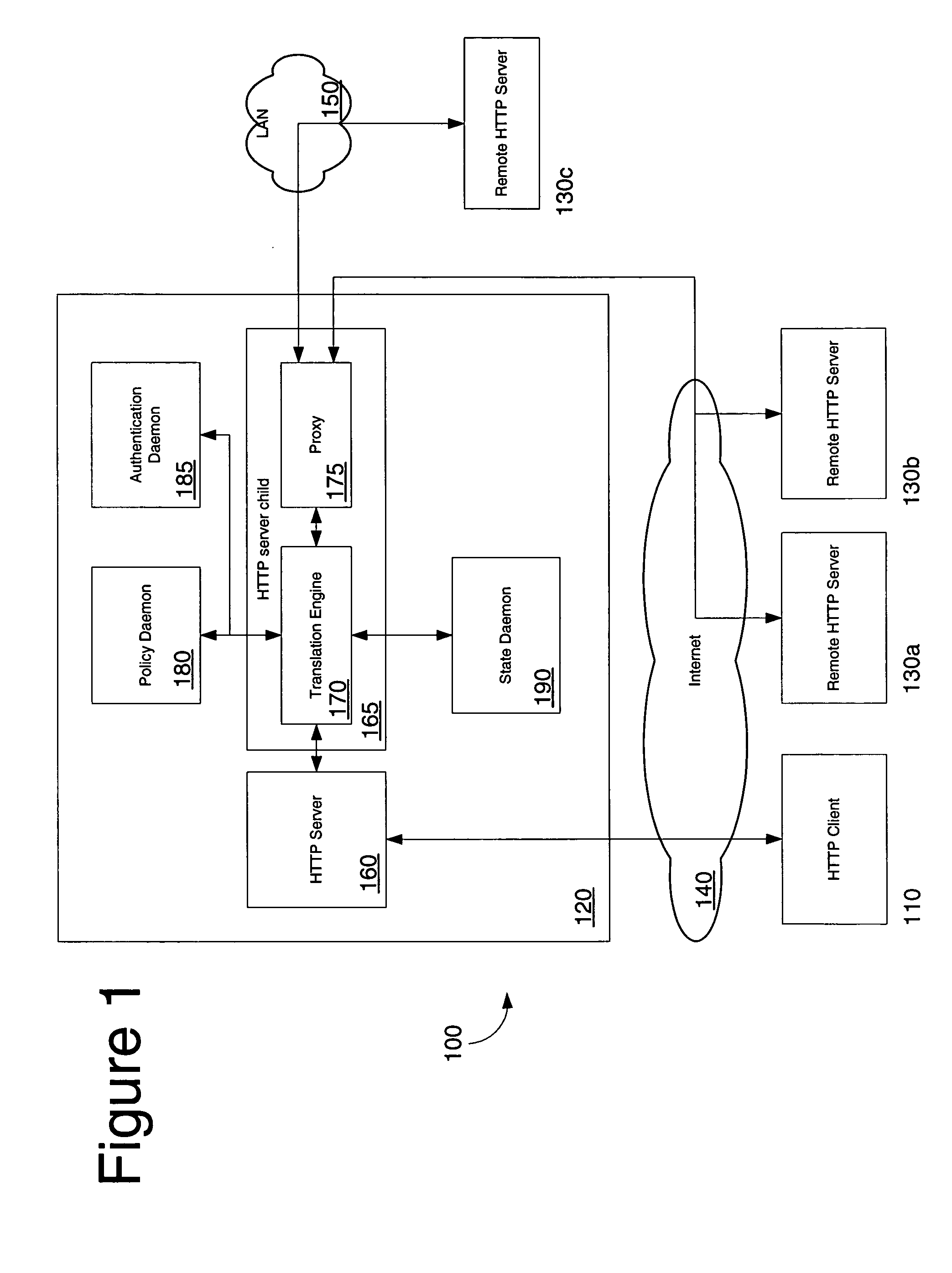
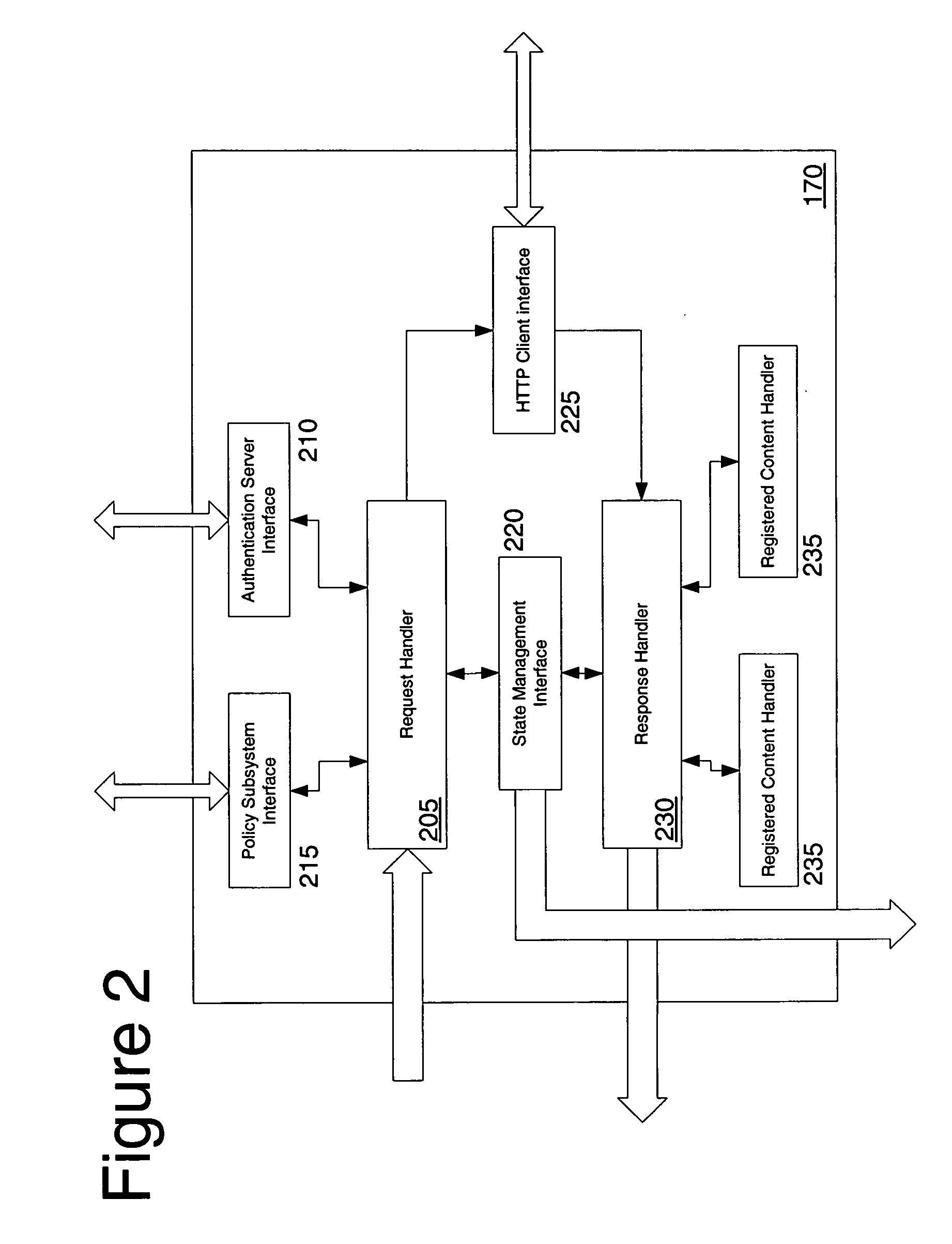
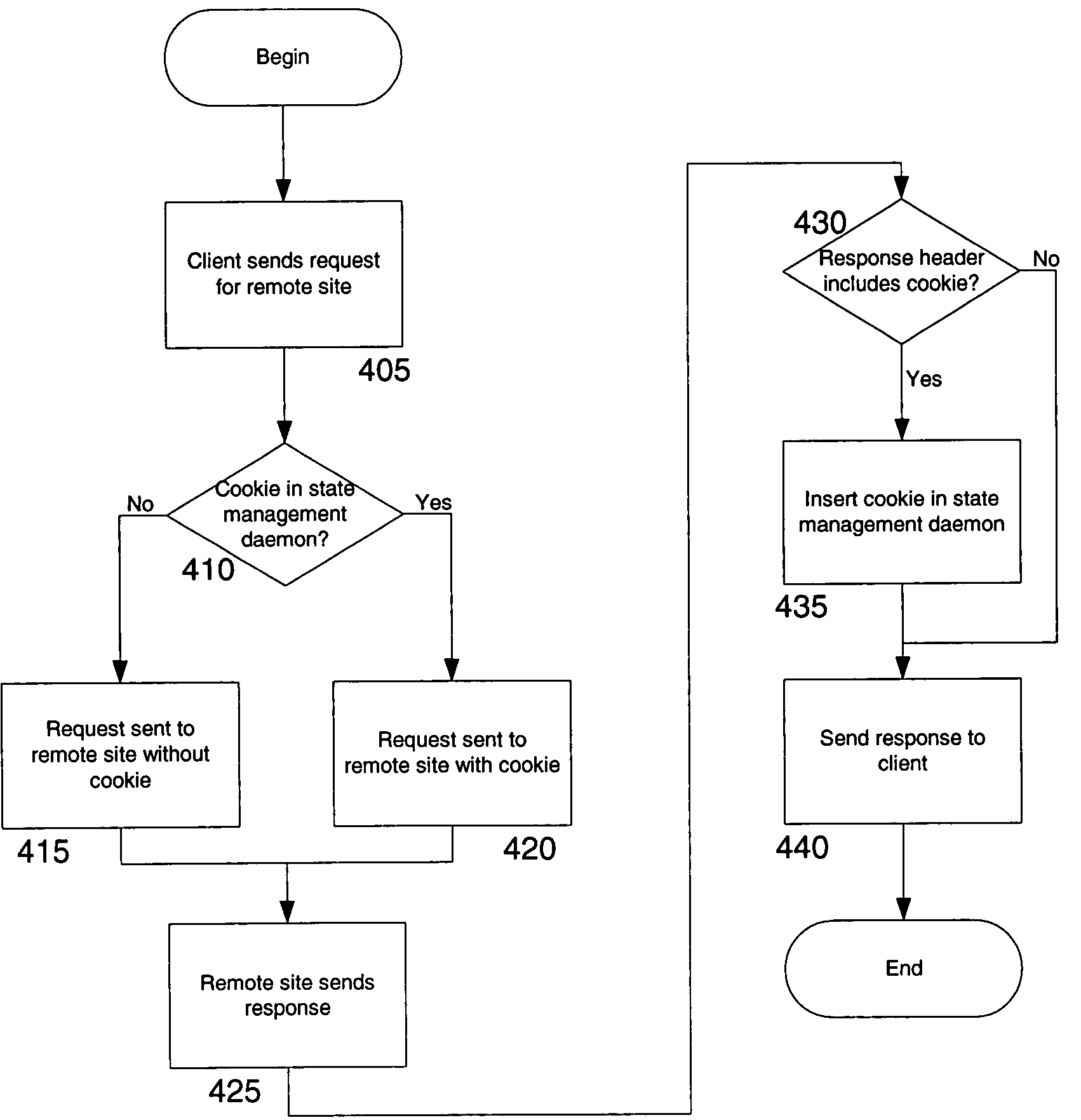
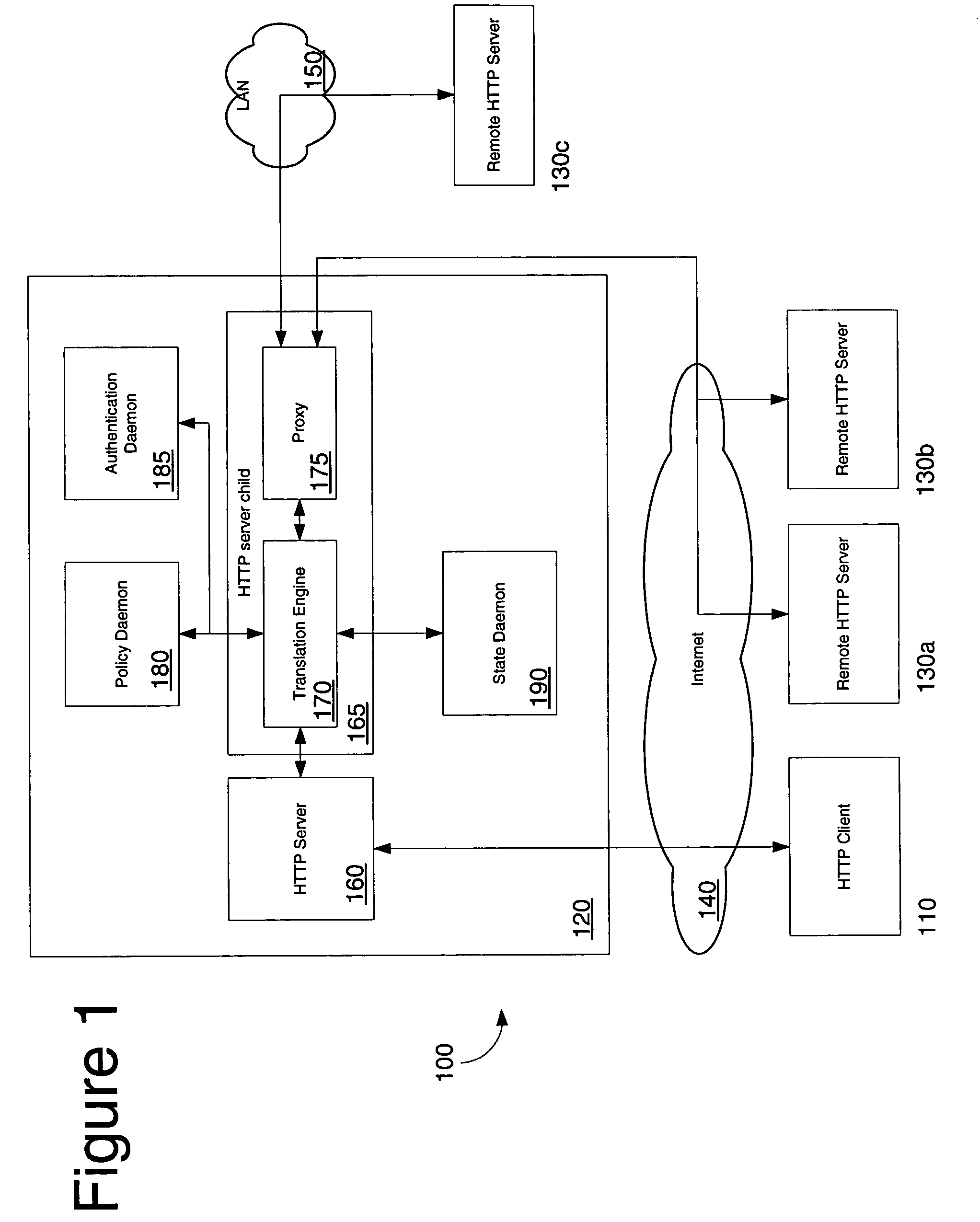
Protocol and system for firewall and NAT traversal for TCP connections
ActiveUS20060215684A1Time-division multiplexData switching by path configurationServer agentNAT traversal
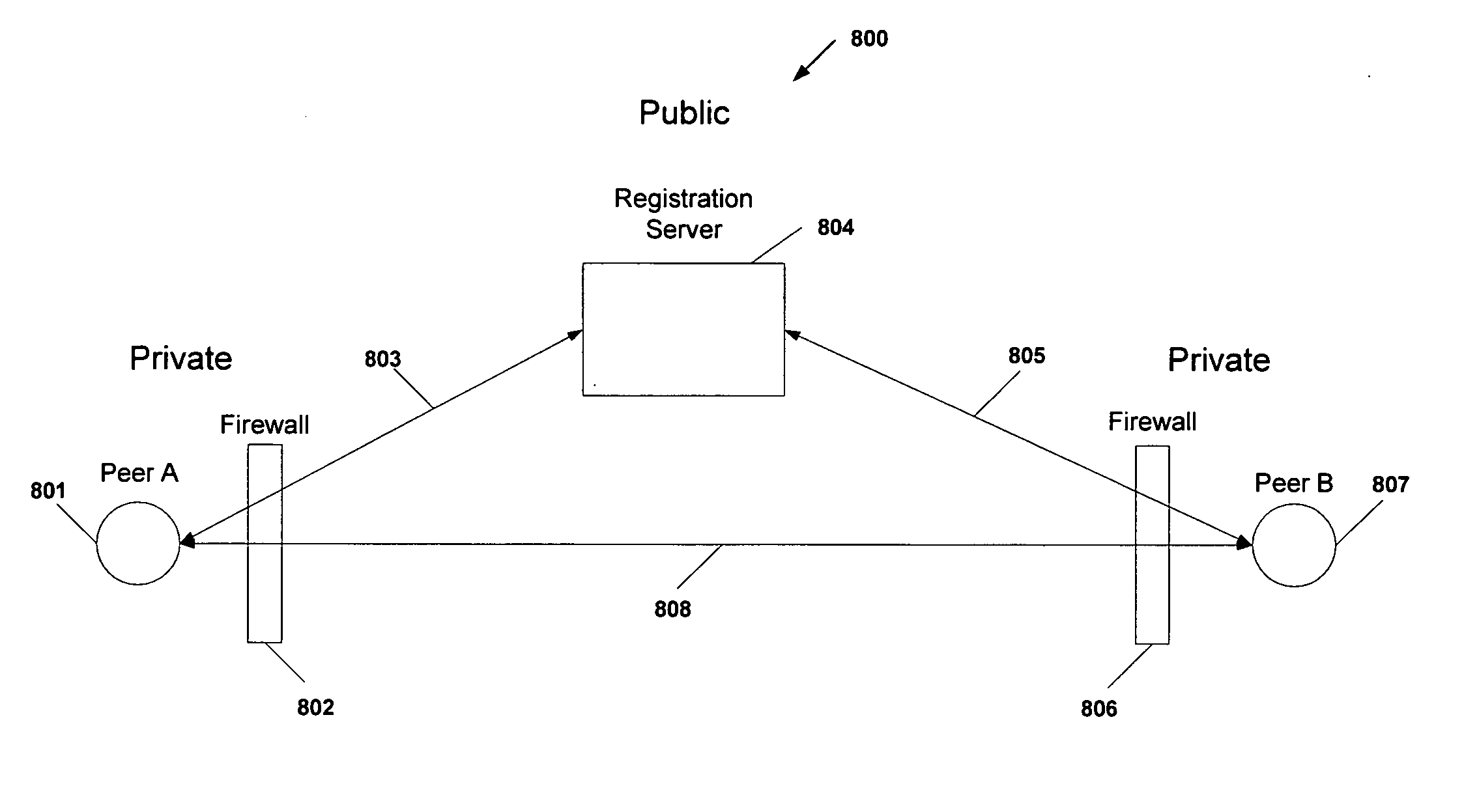
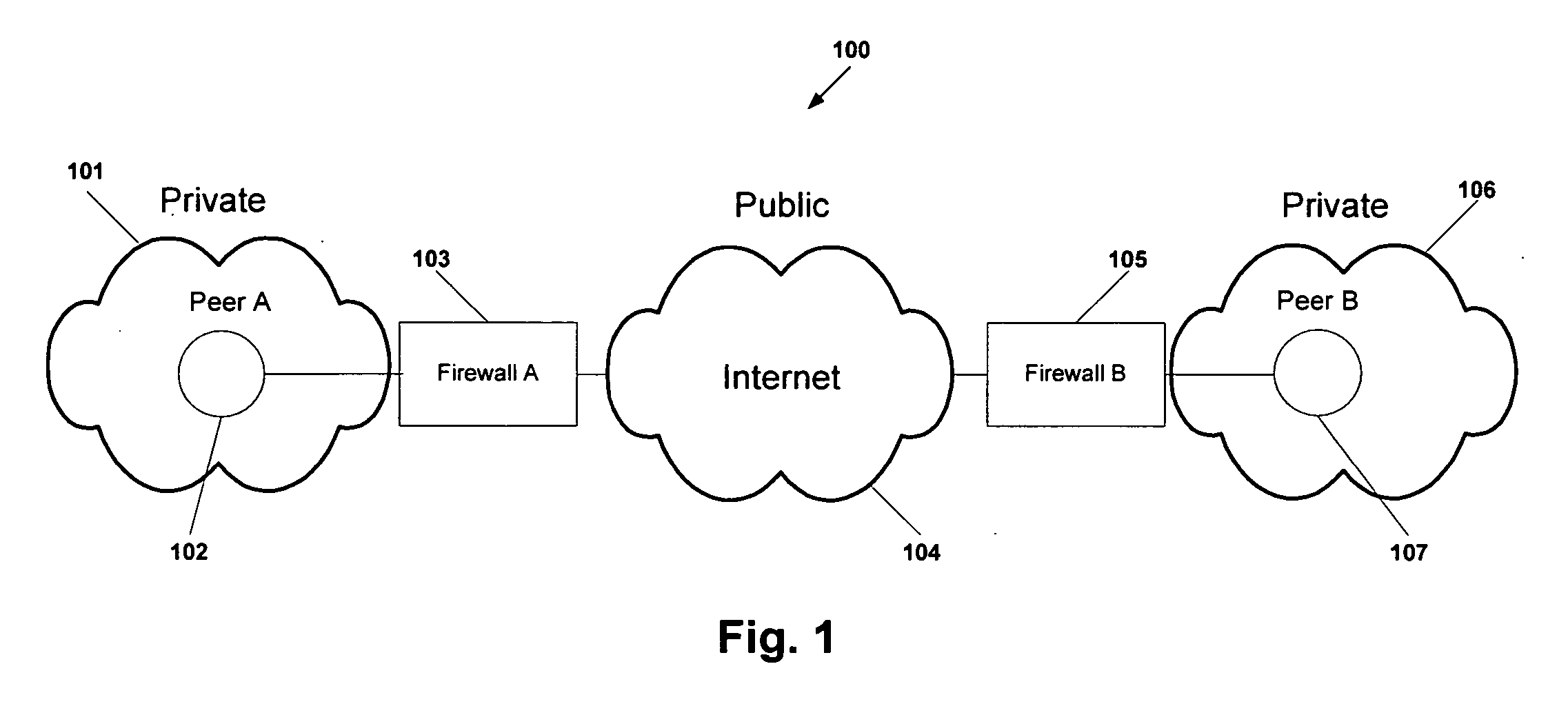
Firewalls and network address translators (NAT) provide many advantages for client and the Internet itself, however, these devices break many existing transmission control protocol (TCP) / Internet Protocol (IP) applications, since they conceal the identity of IP clients (i.e., peers) and block transmission control protocol (TCP) call setup requests. Firewalls and NATs make it impossible for one TCP peer to discover another and establish a connection. Embodiments of this invention provides a system and a protocol to enable two TCP peers that exist behind one or more firewalls and NATs to automatically setup a true peer-to-peer TCP connection and exchange data without making changes to the firewall or NAT devices or existing TCP-based applications. In embodiments of this invention, the synchronization between the blind TCP peers is achieved using a system that consists of a registration server, an agent application, and a virtual network interface that together relay and replicate the control signals between the two TCP peers. In addition, embodiments of this invention are also used to traverse the NAT and establish a bi-directional peer-to-peer TCP connection in the firewall.
Owner:NETGEAR INC
Network access using secure tunnel
InactiveUS20050273849A1Multiple digital computer combinationsProgram controlServer agentSecure communication
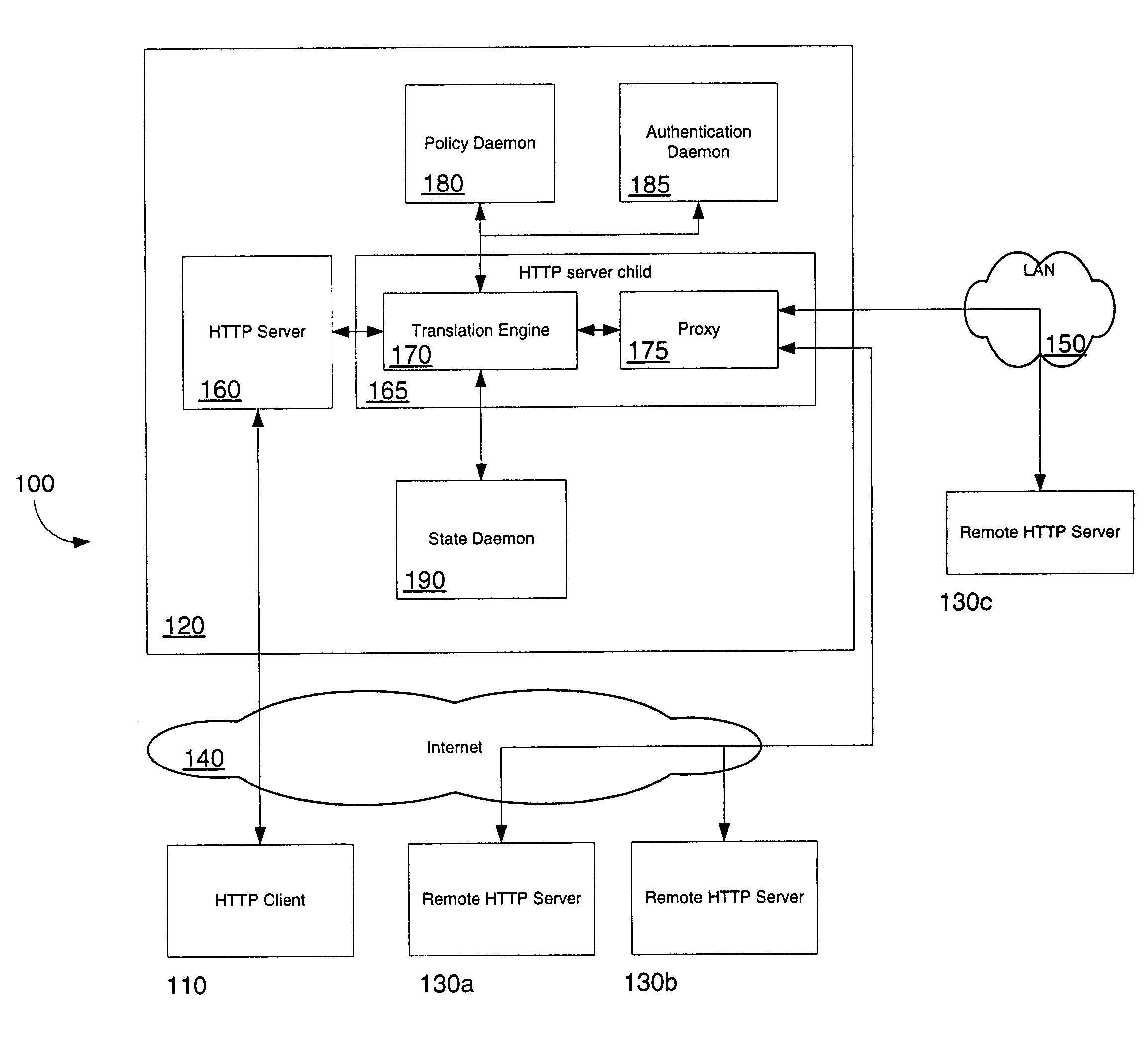
A security platform connected to a private network permits access to the private network from a public network (such as the Internet) through a variety of mechanisms. A reverse proxy system operating as part of the security platform provides access to web-enabled applications from a browser connected to the public network. The reverse proxy rewrites requests and responses so that the browser directs requests to the reverse proxy, from which the requests can be directed to the appropriate server on the public network or the private network. Responses come back to the reverse proxy, and are then forwarded to the browser. An SSL tunneling system permits fat clients to access the private network through an SSL connection. The SSL tunneling system employs a server component operating on the security platform and components downloaded to the client computer from the security platform. The client components include a control component operating in a browser window, a server-proxy component that sets up secure communications with the private network, and an adapter component between the server-proxy and the fat client. The adapter component operates in kernel space. Data is directed from the fat client to the adapter, and then forwarded to the server-proxy; data from the server-proxy is directed to the adapter, and then forwarded to the fat client. Security is provided through the use of multiple authentication realms, each of which provides a set of authentication stages for authenticating users and providing client integrity validation.
Owner:AEP NETWORKS
Apparatus, method and system for aggregrating computing resources
ActiveUS7380039B2Reduce the ratioBuild a scalable parallel computing infrastructureEnergy efficient ICTGeneral purpose stored program computerServer agentApplication software
Owner:COMP ASSOC THINK INC
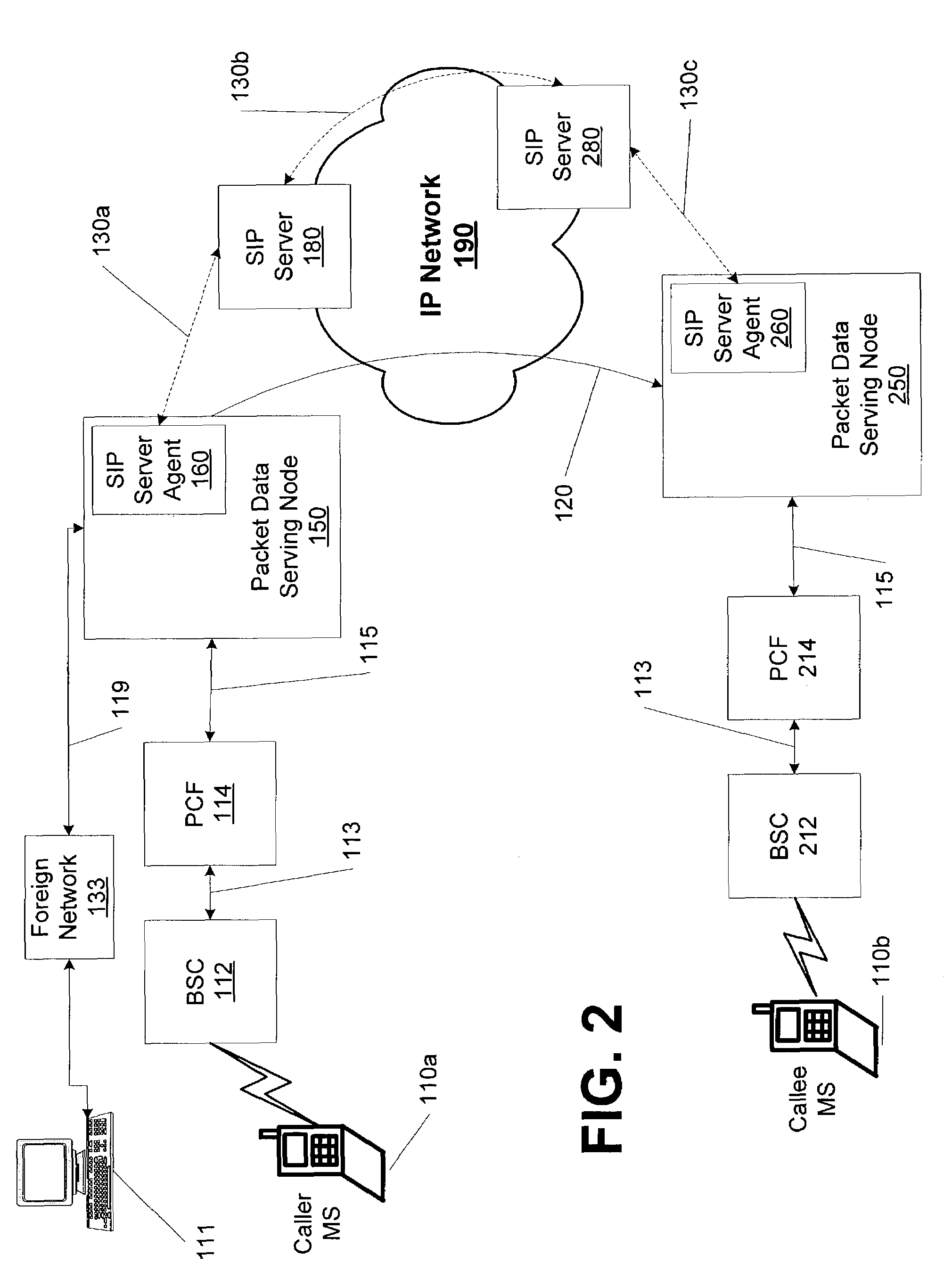
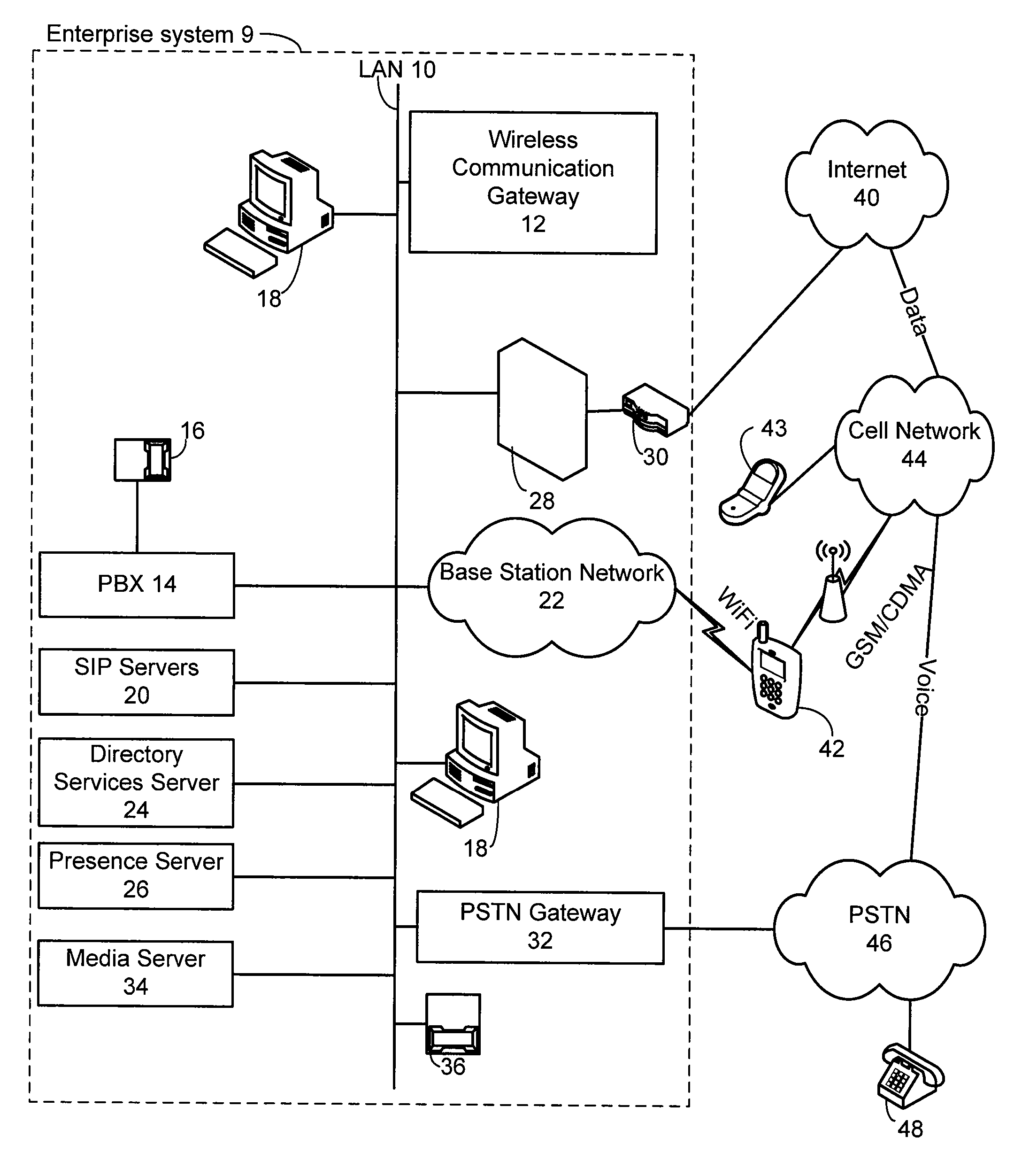
Method and system for extending services to cellular devices
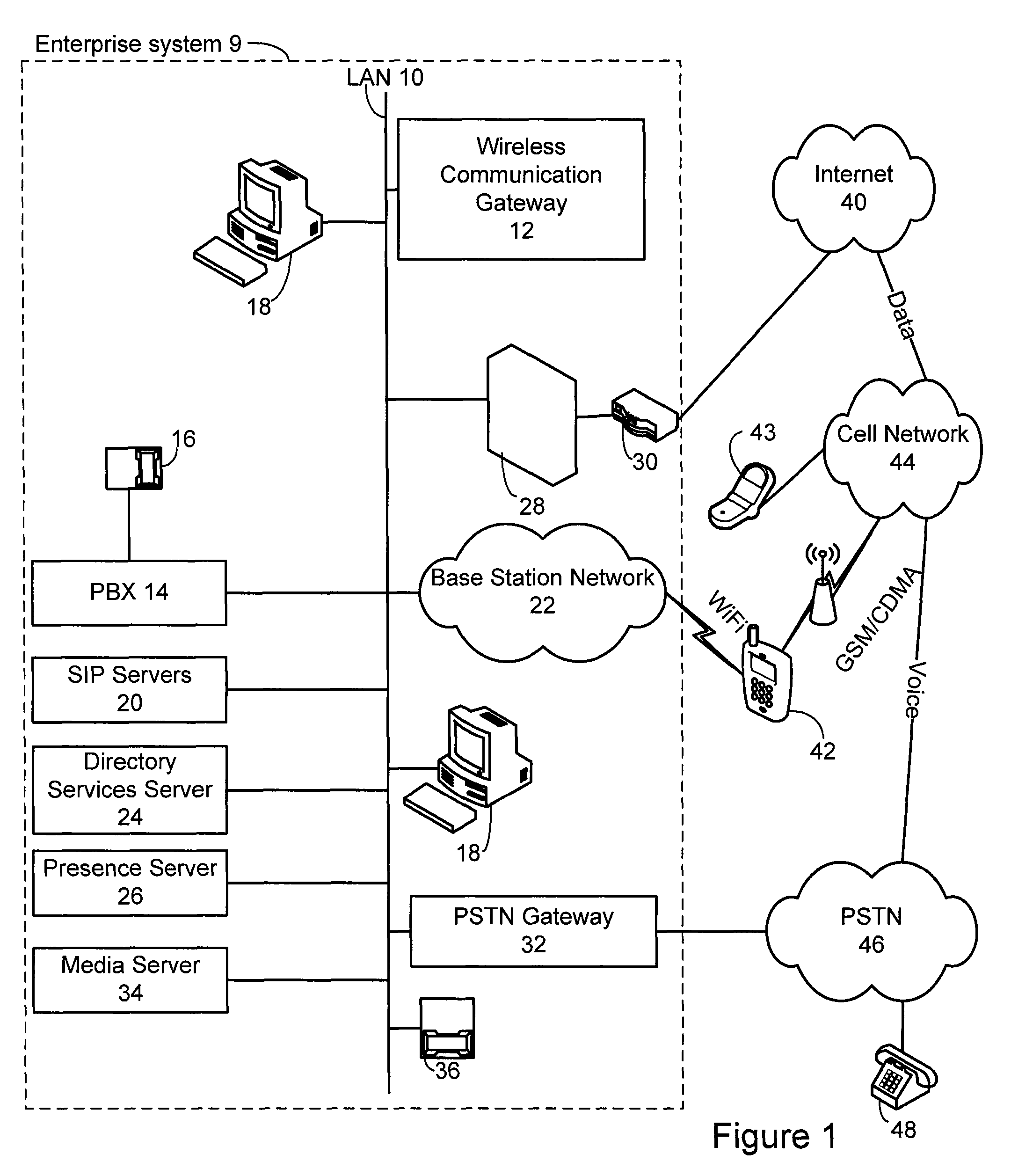
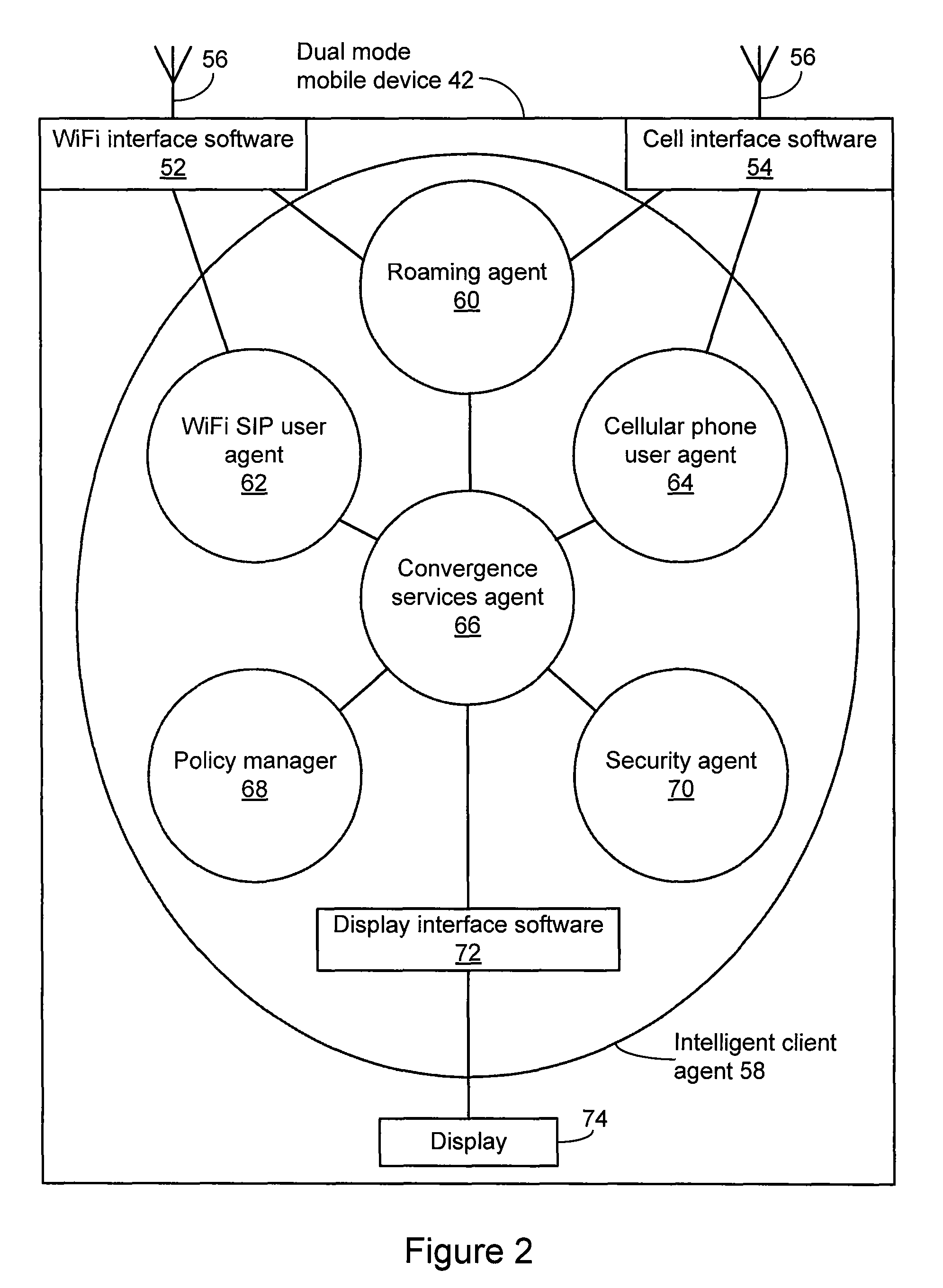
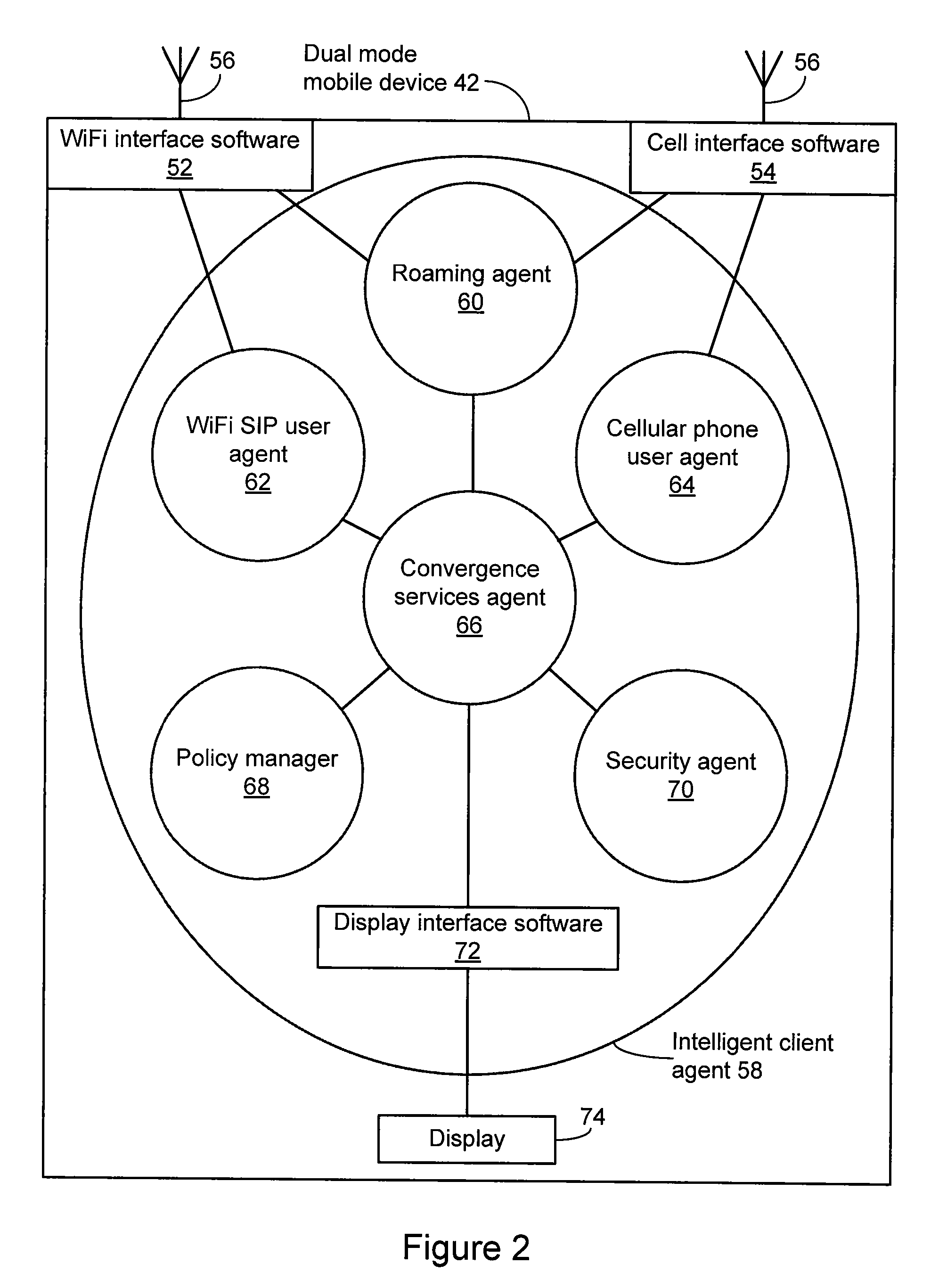
A system is provide for extending services to cellular devices. The system includes a wireless gateway having a client side with an intelligent client agent and a server side with an intelligent server agent, a wireless device having a first mode operable in a cellular system and a second mode operable in a wireless local area network and including an intelligent client agent for determining operation mode and for communicating with the intelligent client agent of the wireless gateway and a communications protocol for communication between the wireless gateway intelligent client agent and the wireless device intelligent client agent to effect services. The services include one or more of voice, directory, presence, and media services. The voice service includes at least one of call waiting, call forwarding conferencing, and caller identification. The media service includes at least one of interactive voice response (IVR), text-to-speech, speech recognition, play, record. The directory service includes a public switched telephone network (PSTN) directory, a cellular network directory, an Internet directory and a private branch exchange (PBX) directory. The communications protocol includes encapsulation for at least one of directory, mobility and security services and other protocols. The other protocols include at least one of Internet protocol (IP), session initiation protocol (SIP), and lightweight directory access protocol (LDAP).
Owner:COUNTERPATH TECH
Meta-data based method for local cache utilization
ActiveUS20050138176A1Lower the volumeDigital data information retrievalDigital computer detailsServer agentClient-side
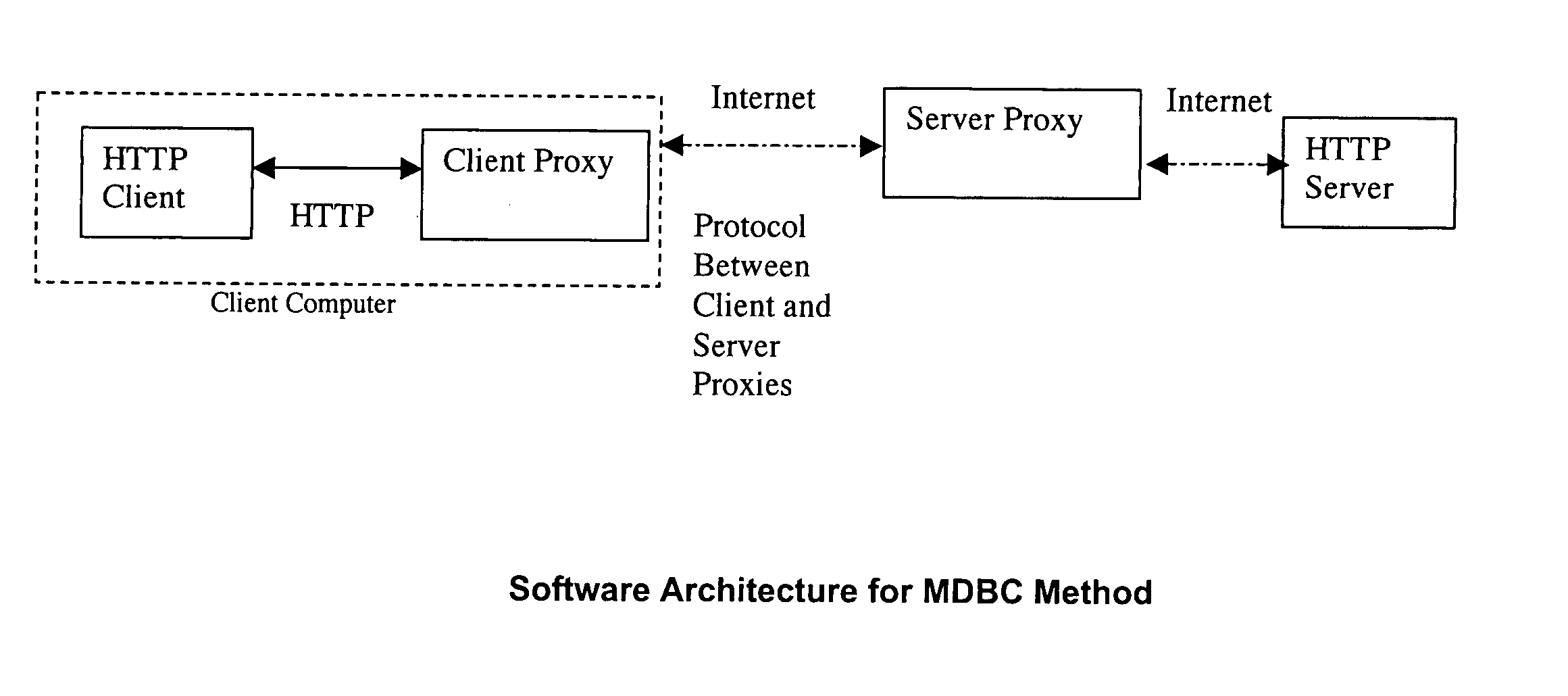
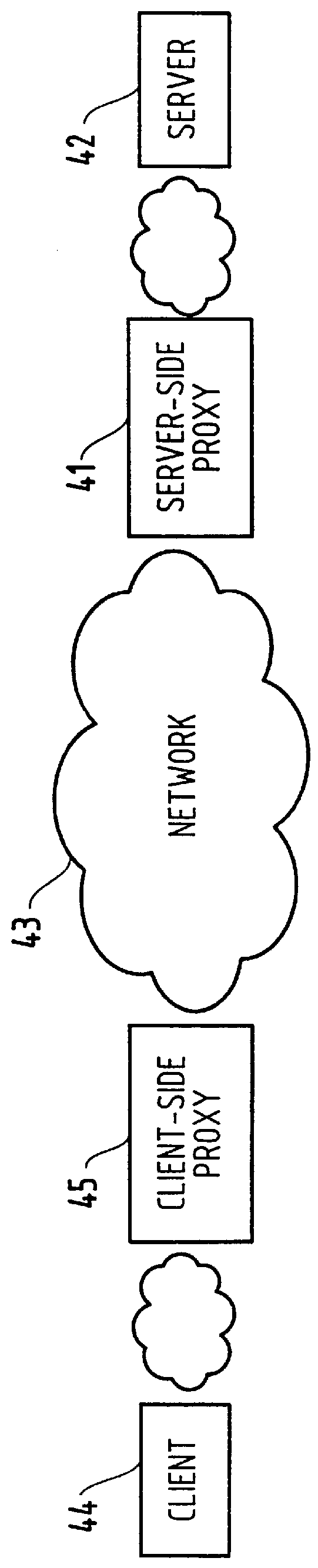
A system and method for caching data and verifying cached data using a client-server model and meta-data. In particular, a client proxy and a server proxy are in communication with each other and with the client and the server, respectively; client proxy meta-data and server proxy meta-data related to the data cached by the client proxy and server proxy, respectively, are calculated and communicated between the client proxy and the server proxy; and the client proxy meta-data and the server proxy meta-data are compared to determine a cache hit or miss.
Owner:MALIKIE INNOVATIONS LTD
Method for supporting different service levels in a network using web page content information
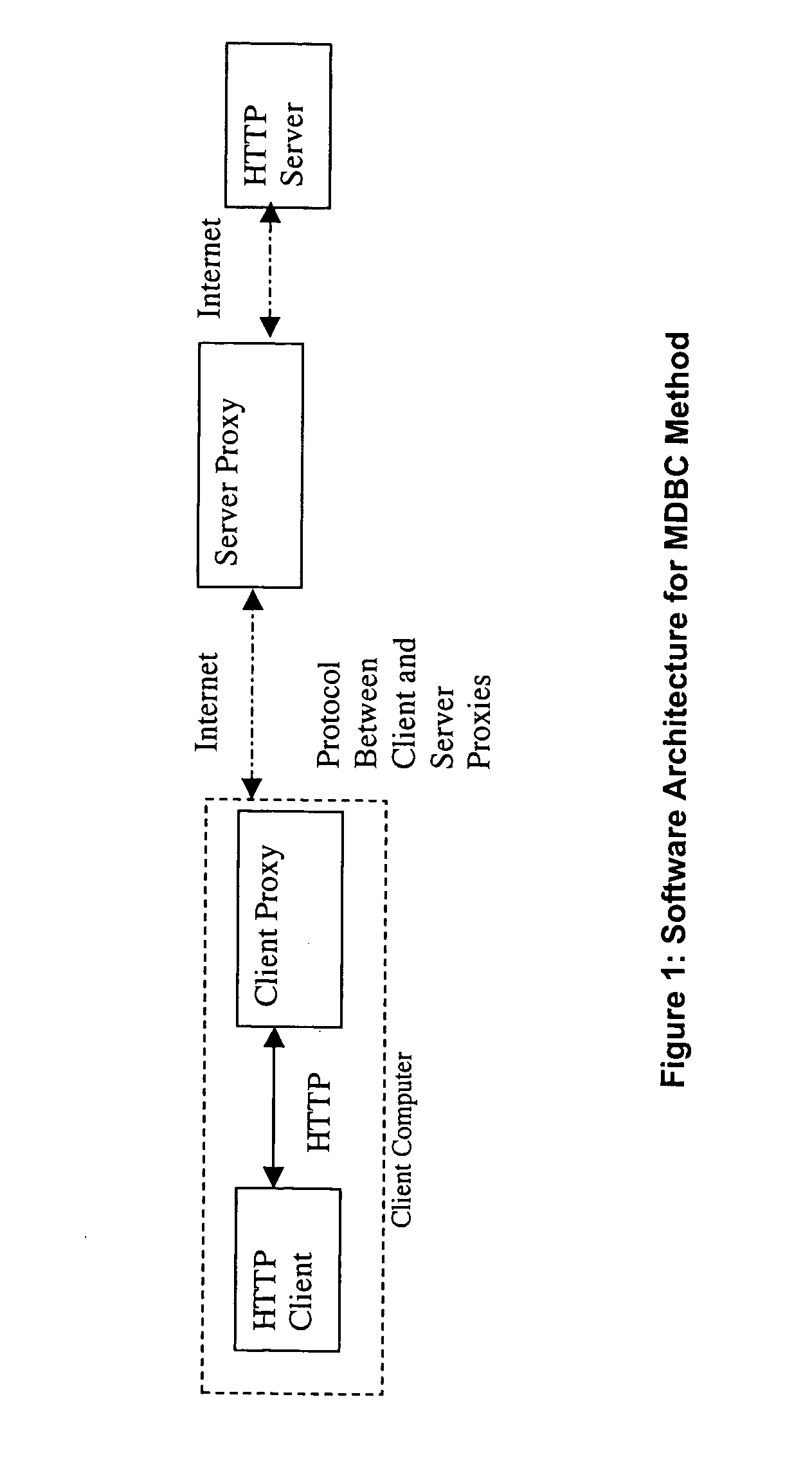
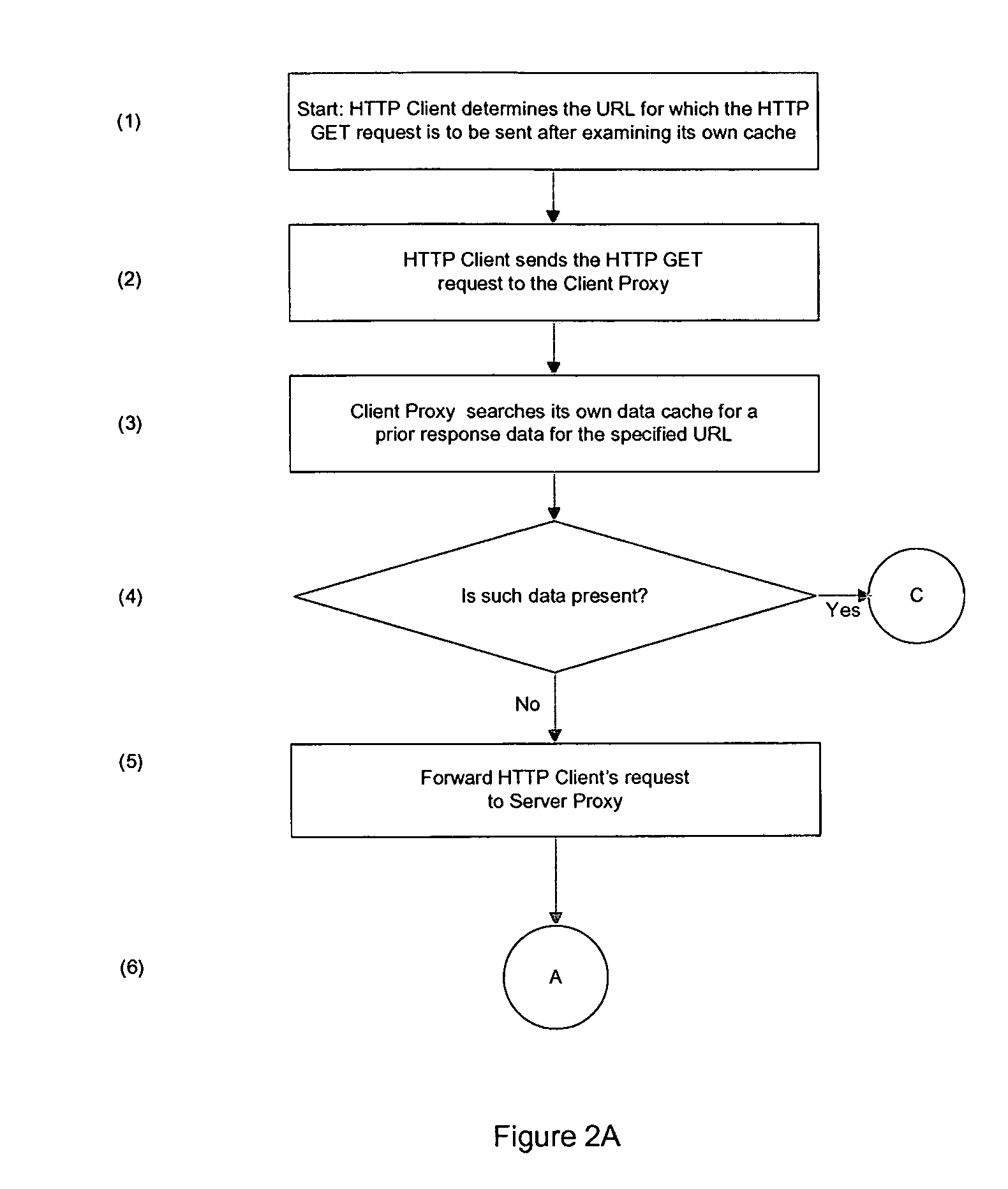
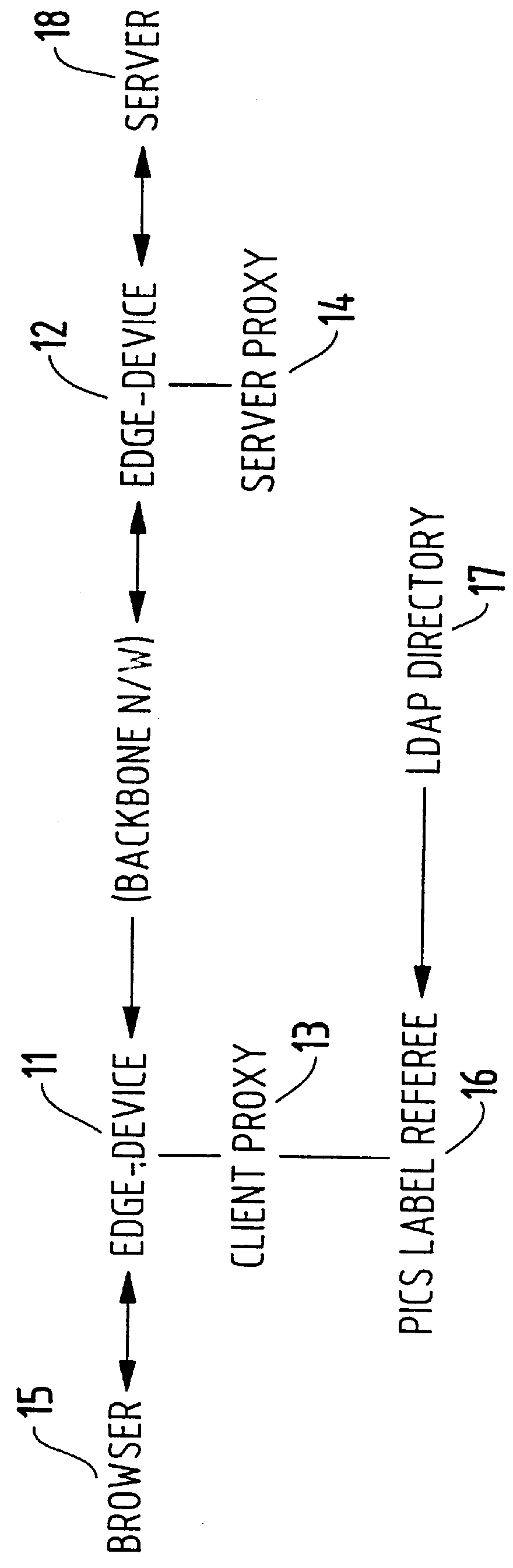
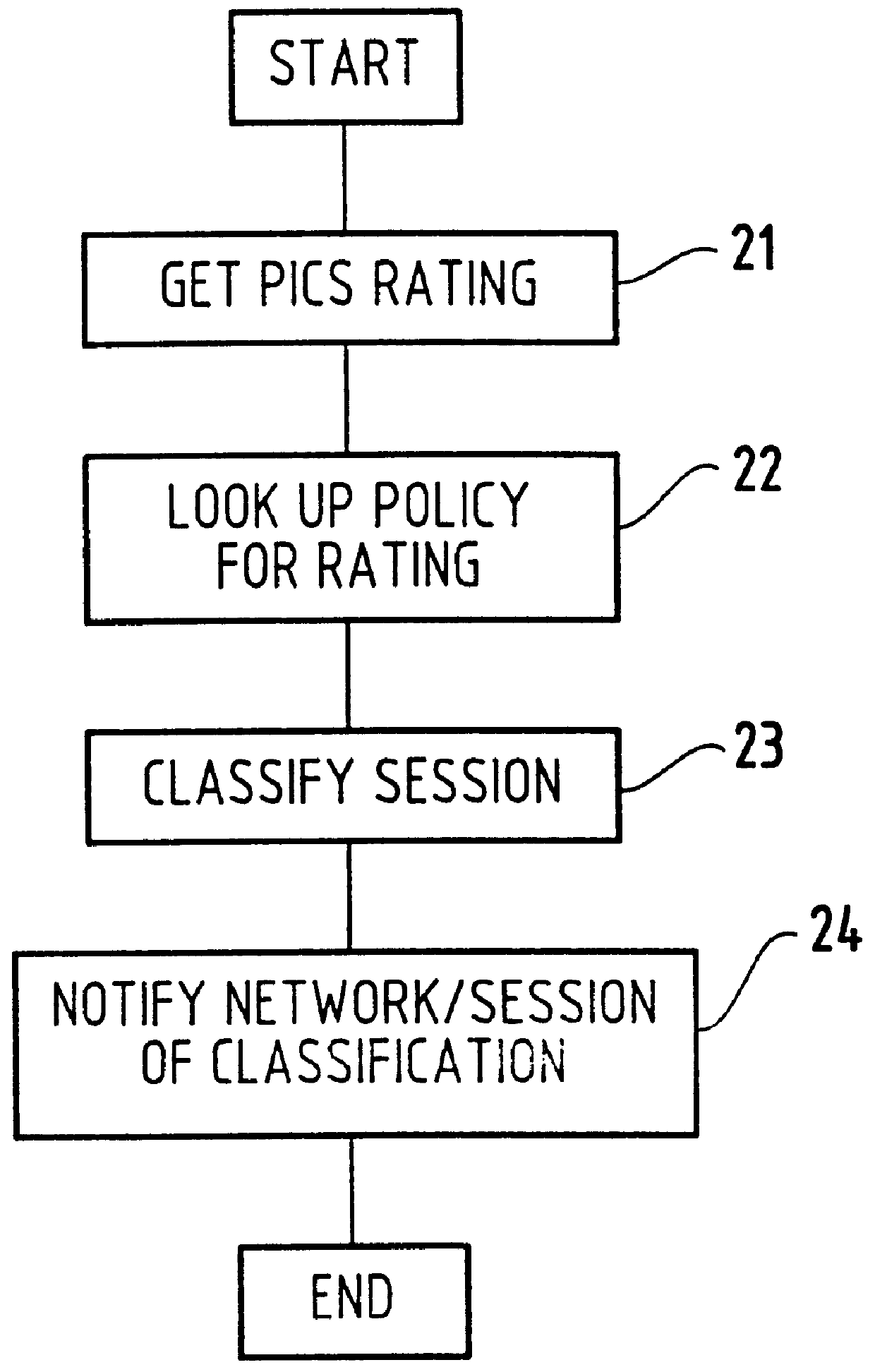
A method for classifying different pages accessed by a web-browser into different service-levels on a granularity finer than that of the connection. The method augments each edge device with two applications, a Client-Proxy and a Server-Proxy. The Client-Proxy obtains identifying information from the client's request, and the obtain PICS labelling information from a label referee. This information is used to obtain a service level from an LDAP based SLA directory, and this service level information is then imbedded along with a unique identifier for the network operator organization in the HTTP header request which is transferred to the Server-Proxy. The Server-Proxy then strips the header containing the PICS information from the request and forwards the request to the server. When the Server-Proxy gets a response, it uses the PICS information to mark the packets.
Owner:IBM CORP
Domain name resolution for a hybrid cloud cluster
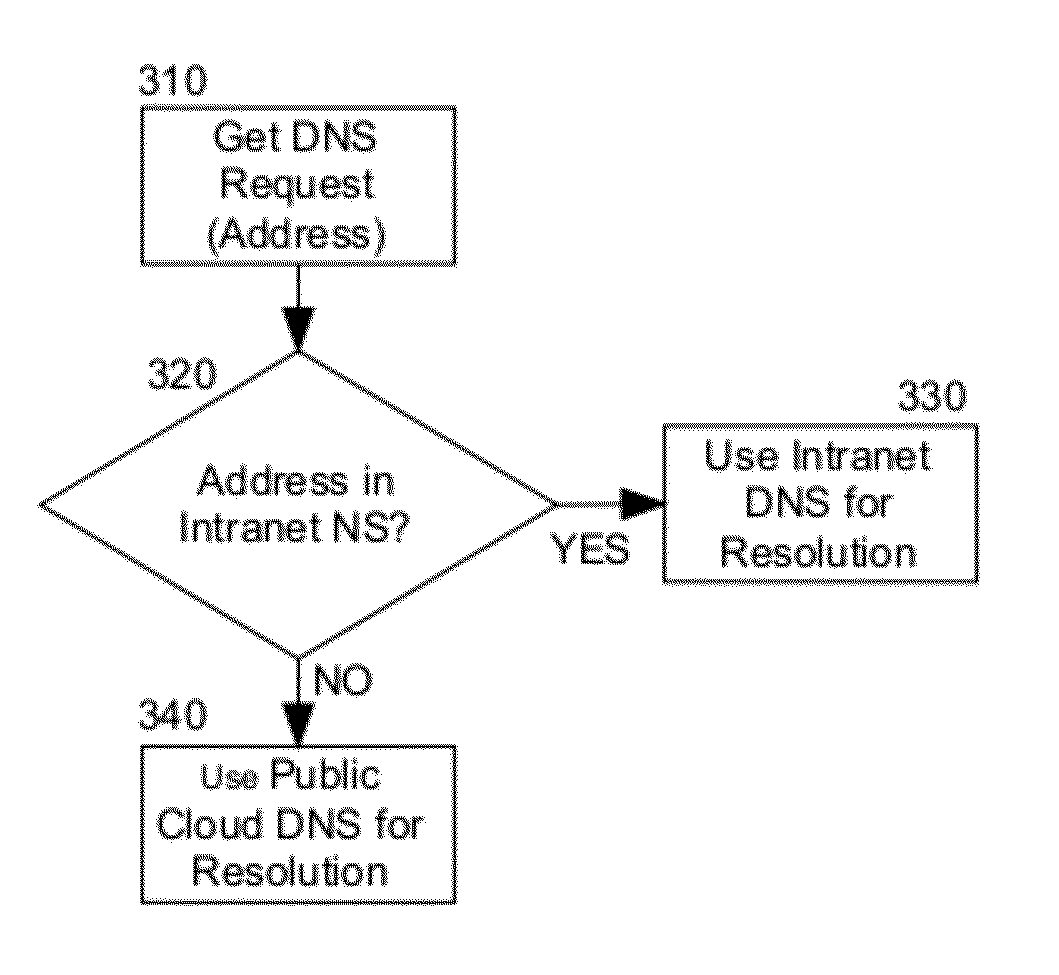
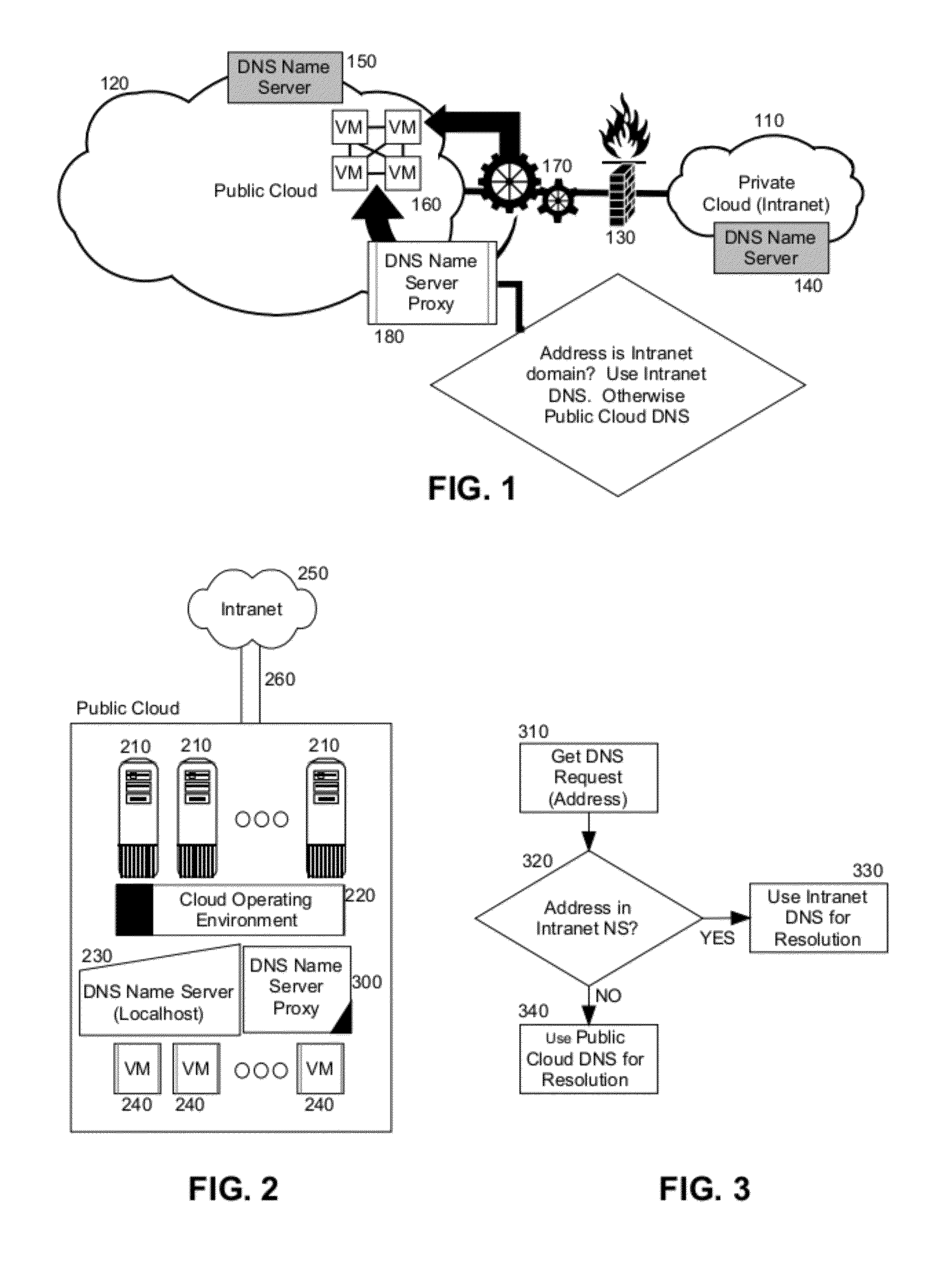
Embodiments of the present invention provide a method, system and computer program product for domain name resolution for a hybrid cloud cluster. In an embodiment of the invention, a method for domain name resolution for a hybrid cloud cluster includes receiving a request for name resolution in a DNS name server proxy executing in memory of a host computer in a public cloud. Thereafter, it can be determined whether or not the request for name resolution implicates a domain name within an Intranet coupled to the proxy over a communications network. Finally, the request for name resolution can be resolved in a DNS name server disposed in the Intranet in response to determining the request to implicate a domain name within the Intranet. Otherwise, the request for name resolution can be resolved in a DNS name server for the public cloud in response to determining the request not to implicate a domain name within the Intranet.
Owner:IBM CORP
Network access using multiple authentication realms
InactiveUS20050251856A1Multiple digital computer combinationsProgram controlServer agentSecure communication
A security platform connected to a private network permits access to the private network from a public network (such as the Internet) through a variety of mechanisms. A reverse proxy system operating as part of the security platform provides access to web-enabled applications from a browser connected to the public network. The reverse proxy rewrites requests and responses so that the browser directs requests to the reverse proxy, from which the requests can be directed to the appropriate server on the public network or the private network. Responses come back to the reverse proxy, and are then forwarded to the browser. An SSL tunneling system permits fat clients to access the private network through an SSL connection. The SSL tunneling system employs a server component operating on the security platform and components downloaded to the client computer from the security platform. The client components include a control component operating in a browser window, a server-proxy component that sets up secure communications with the private network, and an adapter component between the server-proxy and the fat client. The adapter component operates in kernel space. Data is directed from the fat client to the adapter, and then forwarded to the server-proxy; data from the server-proxy is directed to the adapter, and then forwarded to the fat client. Security is provided through the use of multiple authentication realms, each of which provides a set of authentication stages for authenticating users and providing client integrity validation.
Owner:AEP NETWORKS
Network access using reverse proxy
InactiveUS20050262357A1Computer security arrangementsSecret communicationSecure communicationServer agent
A security platform connected to a private network permits access to the private network from a public network (such as the Internet) through a variety of mechanisms. A reverse proxy system operating as part of the security platform provides access to web-enabled applications from a browser connected to the public network. The reverse proxy rewrites requests and responses so that the browser directs requests to the reverse proxy, from which the requests can be directed to the appropriate server on the public network or the private network. Responses come back to the reverse proxy, and are then forwarded to the browser. An SSL tunneling system permits fat clients to access the private network through an SSL connection. The SSL tunneling system employs a server component operating on the security platform and components downloaded to the client computer from the security platform. The client components include a control component operating in a browser window, a server-proxy component that sets up secure communications with the private network, and an adapter component between the server-proxy and the fat client. The adapter component operates in kernel space. Data is directed from the fat client to the adapter, and then forwarded to the server-proxy; data from the server-proxy is directed to the adapter, and then forwarded to the fat client. Security is provided through the use of multiple authentication realms, each of which provides a set of authentication stages for authenticating users and providing client integrity validation.
Owner:AEP NETWORKS
Network Connection Hand-off Using State Transformations
ActiveUS20120239725A1Improve scalabilityImprove resource usageMultiple digital computer combinationsTransmissionServer agentNetwork connection
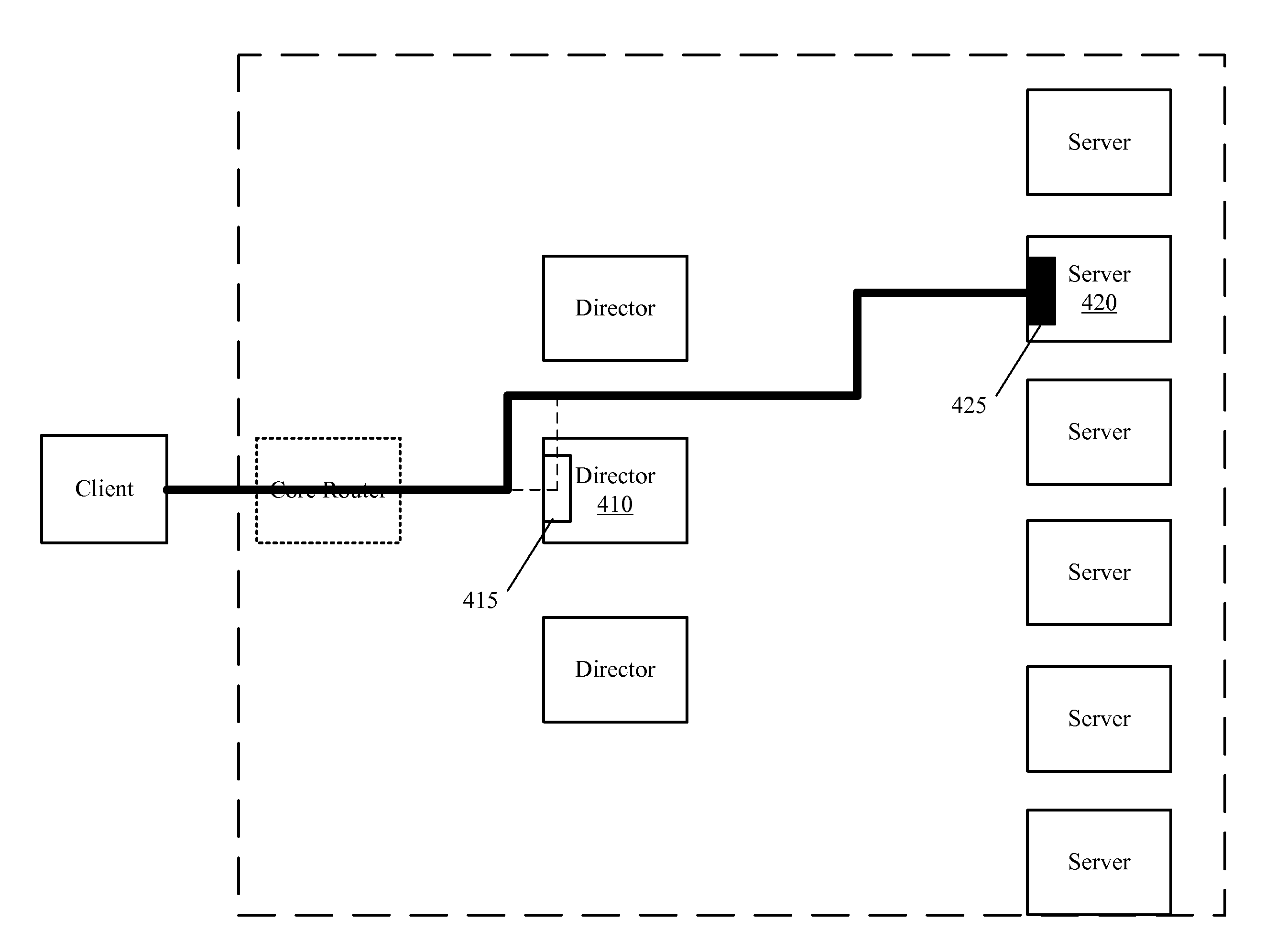
Some embodiments provide a director agent, a server agent, and a specialized hand-off protocol for improving scalability and resource usage within a server farm. A first network connection is established between a client and the director agent in order to receive a content request from the client from which to select a server from a set of servers that is responsible for hosting the requested content. A second network connection is established between the server agent that is associated with the selected server and a protocol stack of the selected server. The first network connection is handed-off to the server agent using the specialized hand-off protocol. The server agent performs network connection state parameter transformations between the two connections to create a network connection through which content can be passed from the selected server to the client without passing through the director.
Owner:EDGIO INC
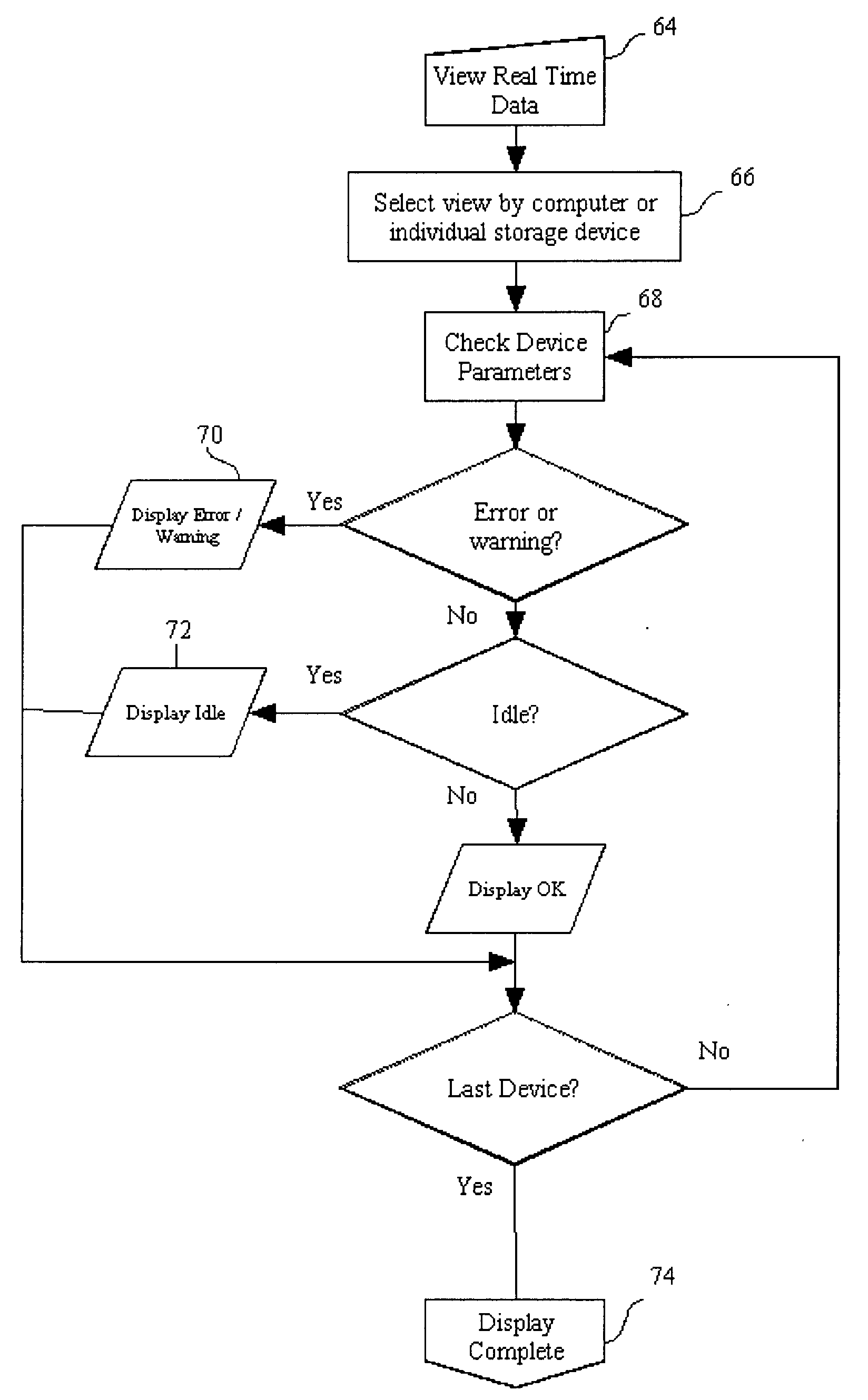
Method and apparatus for monitoring data storage devices
InactiveUS20050091369A1Early detectionAvoid lostNuclear monitoringHardware monitoringServer agentGraphics
The monitoring apparatus includes administrator level software installed in one computer of a computer network, and server agent level software installed in other computers of the computer network having corresponding data storage devices. Log page data of monitored data storage devices is retrieved by the server agent level software and then transmitted to the administrator level software. The log page data is stored in a database at the administrator level software and user interface information is generated from the data stored in the database to provide information to a user regarding the status of each monitored data storage device in the computer network. The user interface information may include explanatory text, predictive analysis, and / or graphical information of both realtime and historical performance of the data storage devices. Accordingly, a very large computer network can be monitored at a single location to determine the general status of each data storage device in the network thereby providing early warning of actual or potential failures of the data storage devices.
Owner:JONES MICHAEL D
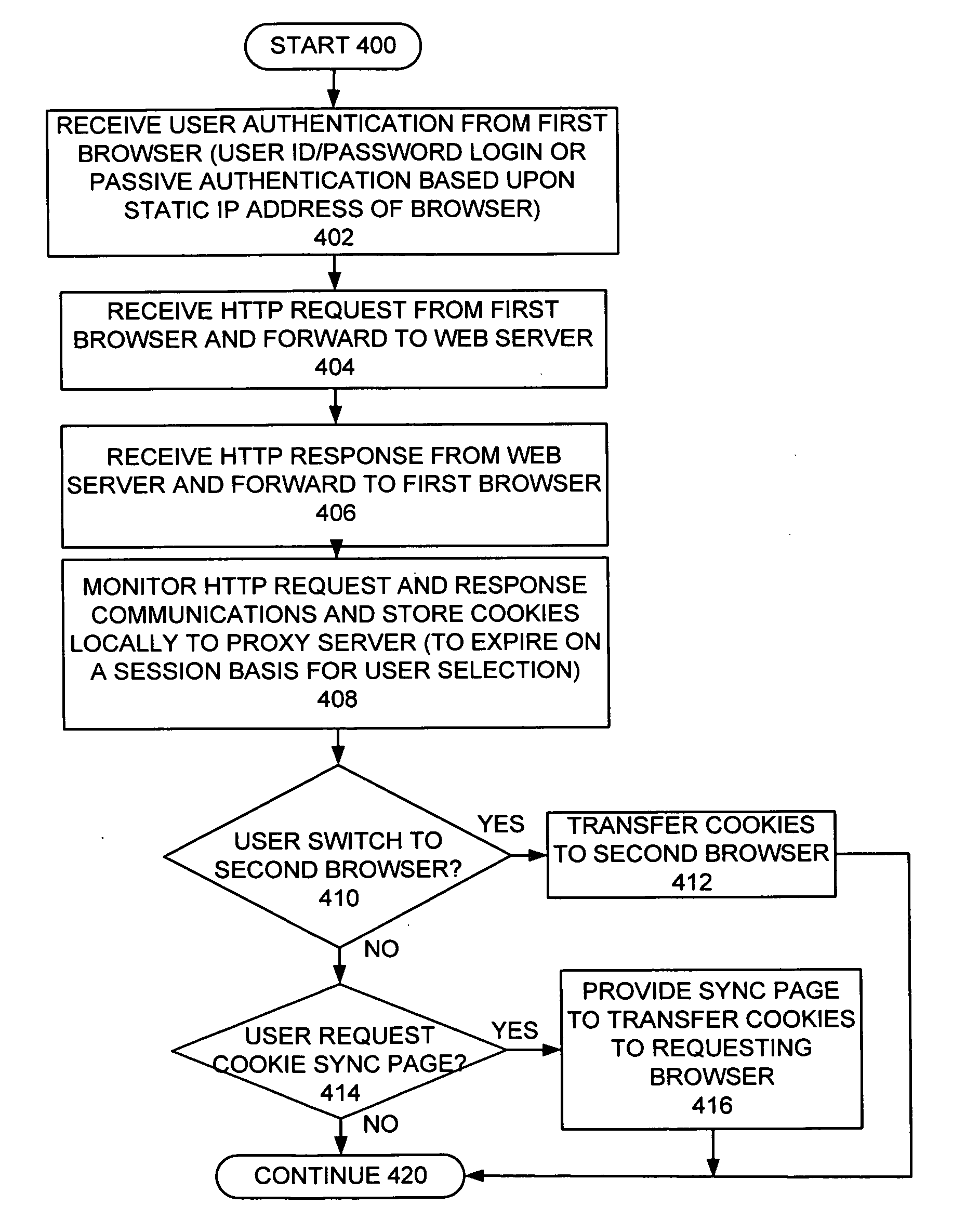
Method, apparatus and computer program product for automatic cookie synchronization between distinct web browsers
InactiveUS20070157304A1Negative effectMultiple digital computer combinationsProgram controlServer agentWeb browser
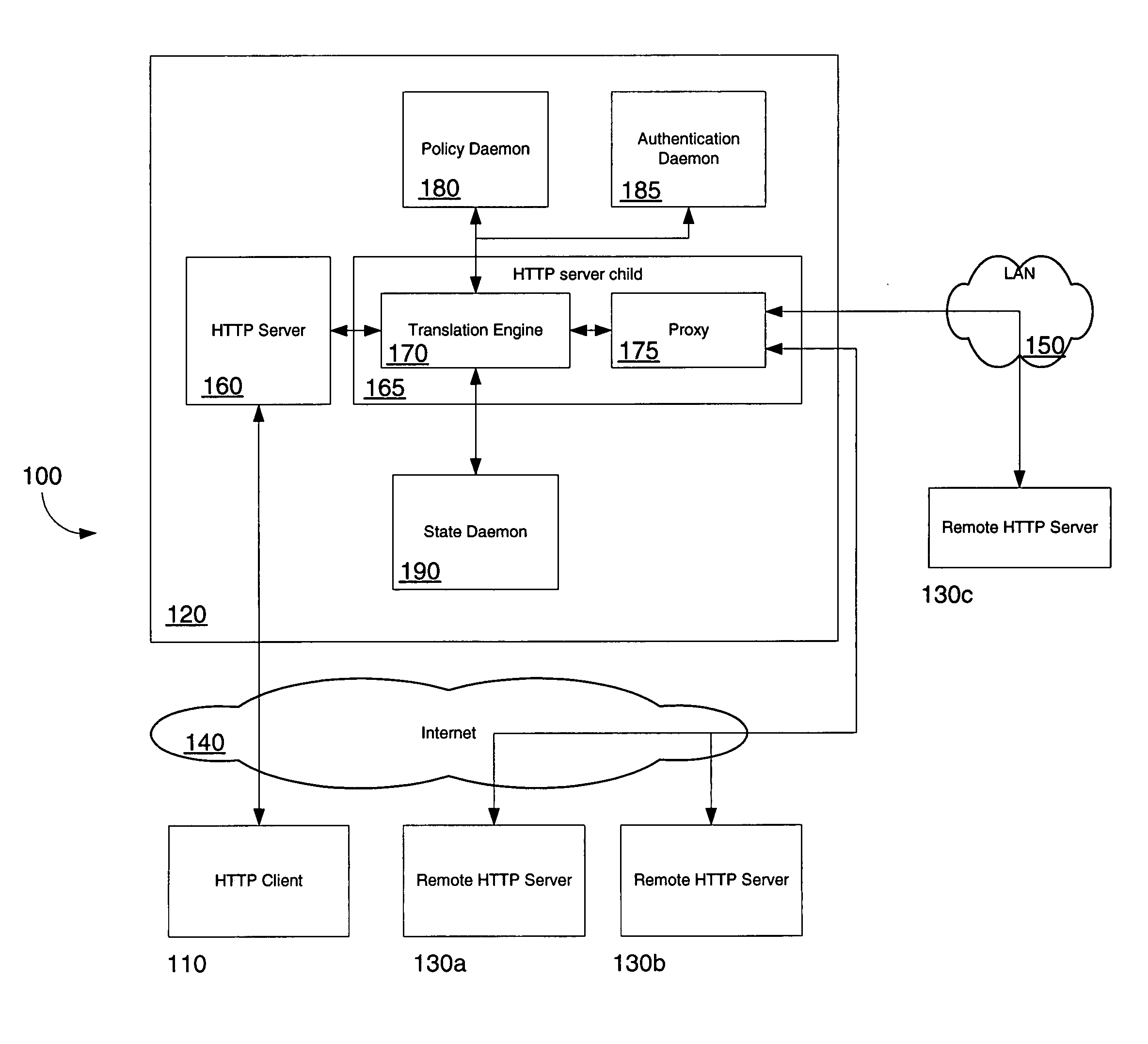
A method, apparatus and computer program product are provided for implementing automatic cookie synchronization between distinct web browsers. A proxy server is used to allow a user to synchronize cookies for the user among a plurality of browsers. A user first authenticates to the proxy server, which could be a traditional user id / password login or a passive authentication based upon a static IP address of a client browser. The proxy server receives a HTTP request from a client browser and forwards the HTTP request to a web server. The proxy server receives a HTTP response from a Web server and forwards the HTTP response to the client browser. The proxy server monitors the HTTP request and response communications, and stores cookies locally to the proxy server. When the user switches from one browser to another browser, the cookies created for the first browser automatically transfer to the second browser.
Owner:IBM CORP
Method for prefetching of structured data between a client device and a server device
InactiveUS20040215717A1Effective transmission speedSpeed efficientMultiple digital computer combinationsTransmissionClient agentServer agent
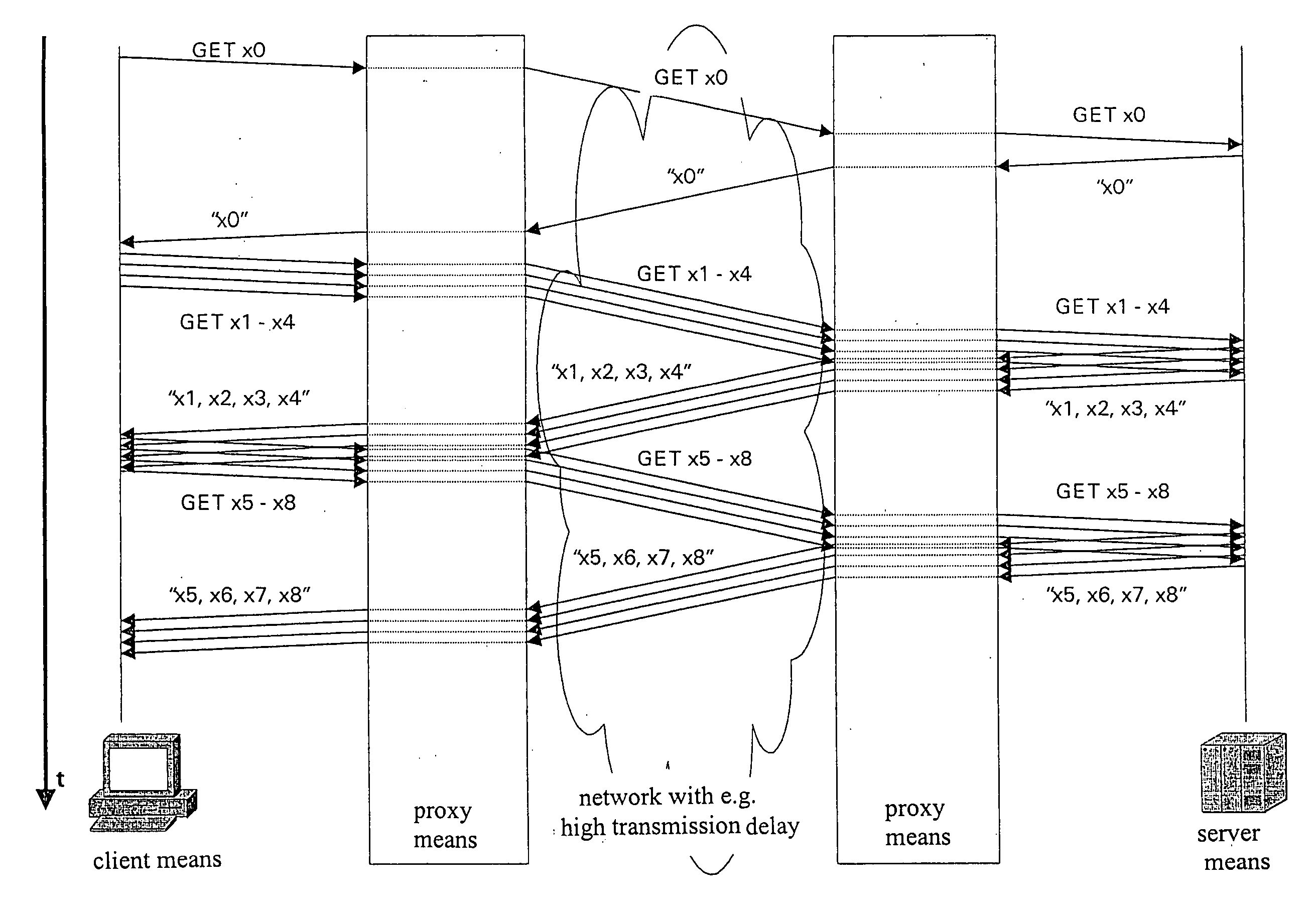
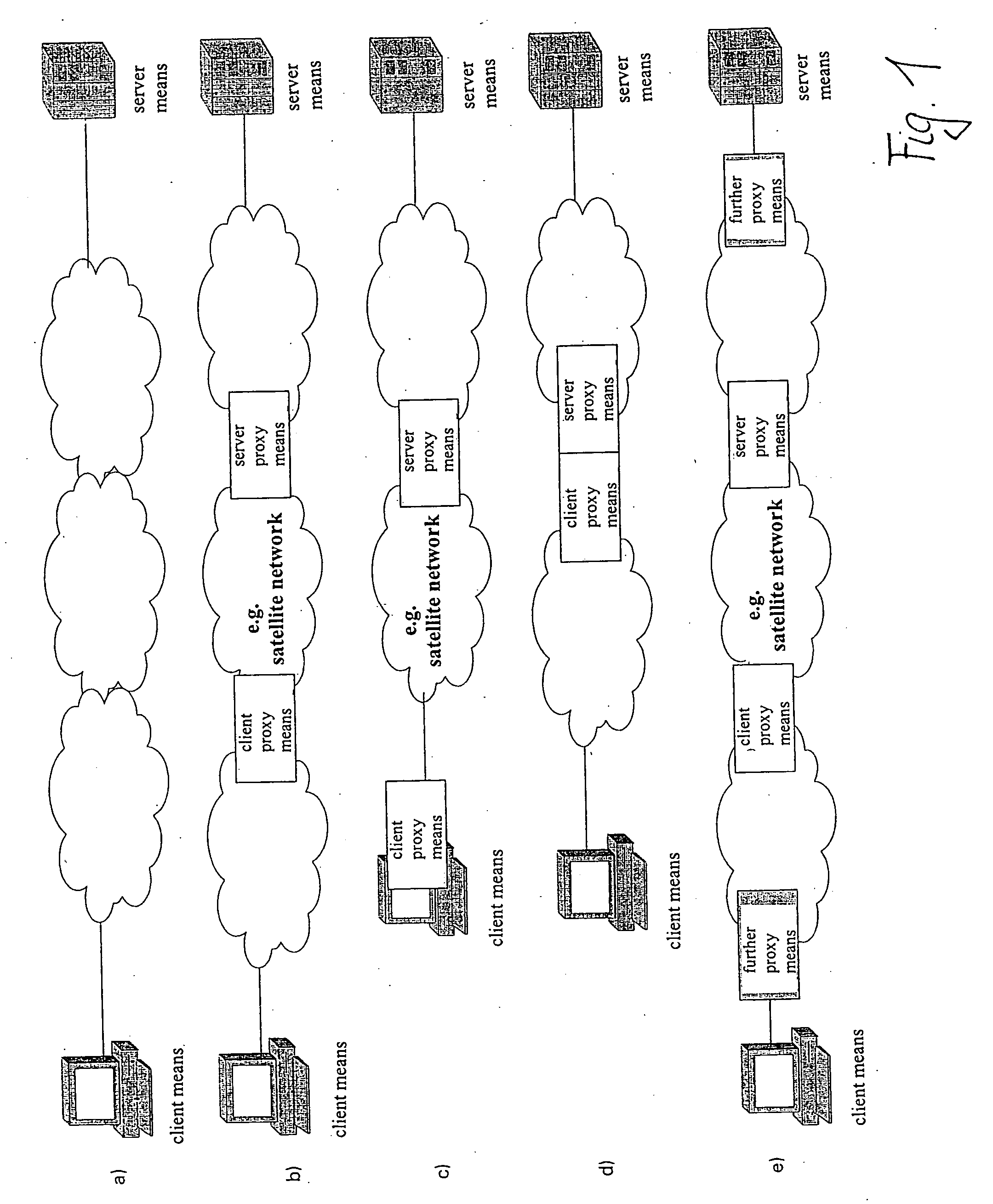
The invention relates to a method of more efficient data transmission, in particular transmission of structured data, such as web pages, in a system comprising a server means and a client means which are interconnected via a plurality of proxy means, including a server proxy means and a client proxy means.
Owner:TELLIQUE KOMMUNIKATIONSTECHN
Inter-applet communication using an applet agent
InactiveUS20030140089A1Communication securityAchieve persistenceMultiple digital computer combinationsSecuring communicationServer agentNetwork connection
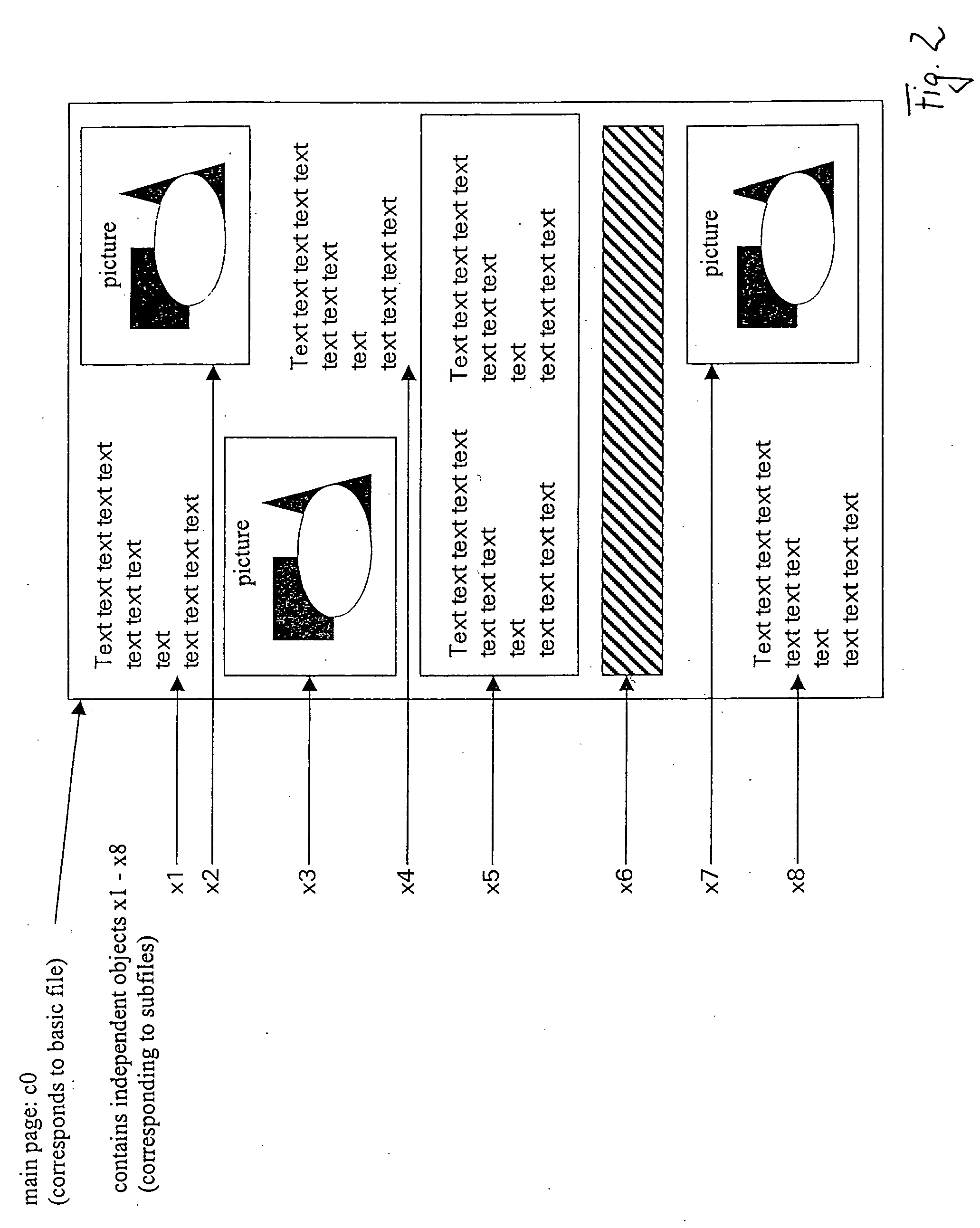
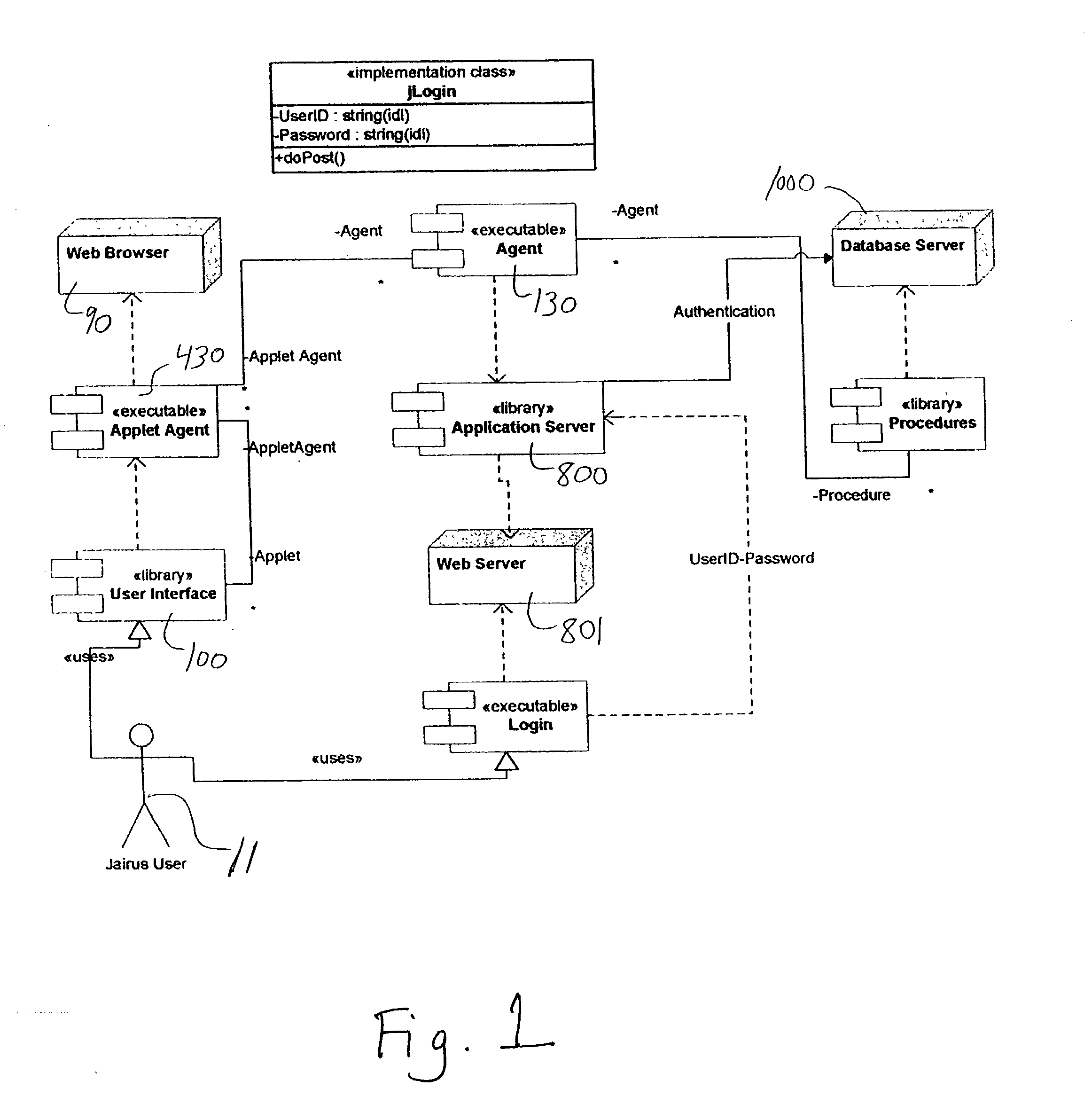
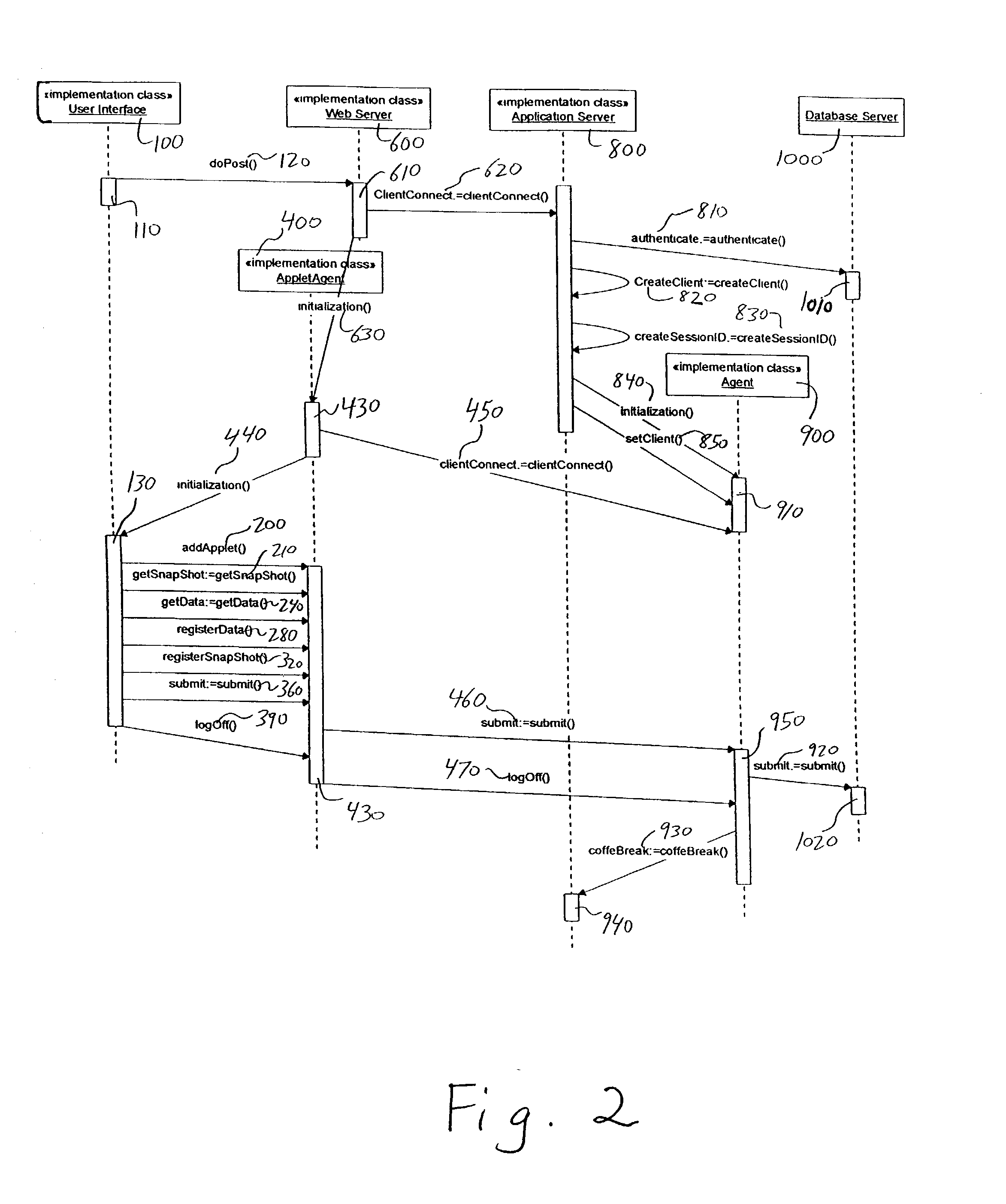
An Applet Agent on a browser of a client processor communicates with a server processor exclusively through a server agent on the server processor. Via this secure network connection, the server agent retrieves Client Applets and client applet data from a server database and sends them to the Applet Agent. The Applet Agent sends the Client Applets and data to the browser of the client processor. The Applet Agent stores the Client Applets, data, and amended data in the client processor, whereby the Client Applets and their data can be retrieved without accessing the server processor. Upon conclusion of a session, the Applet Agents sends the Client Applet data to the server agent, which stores the data on the server database. A plurality of Client Applets are preferably arranged in a logical unit of work, whereby a finite set of the Client Applets accomplish multiple functions.
Owner:HINES KENNETH J +1
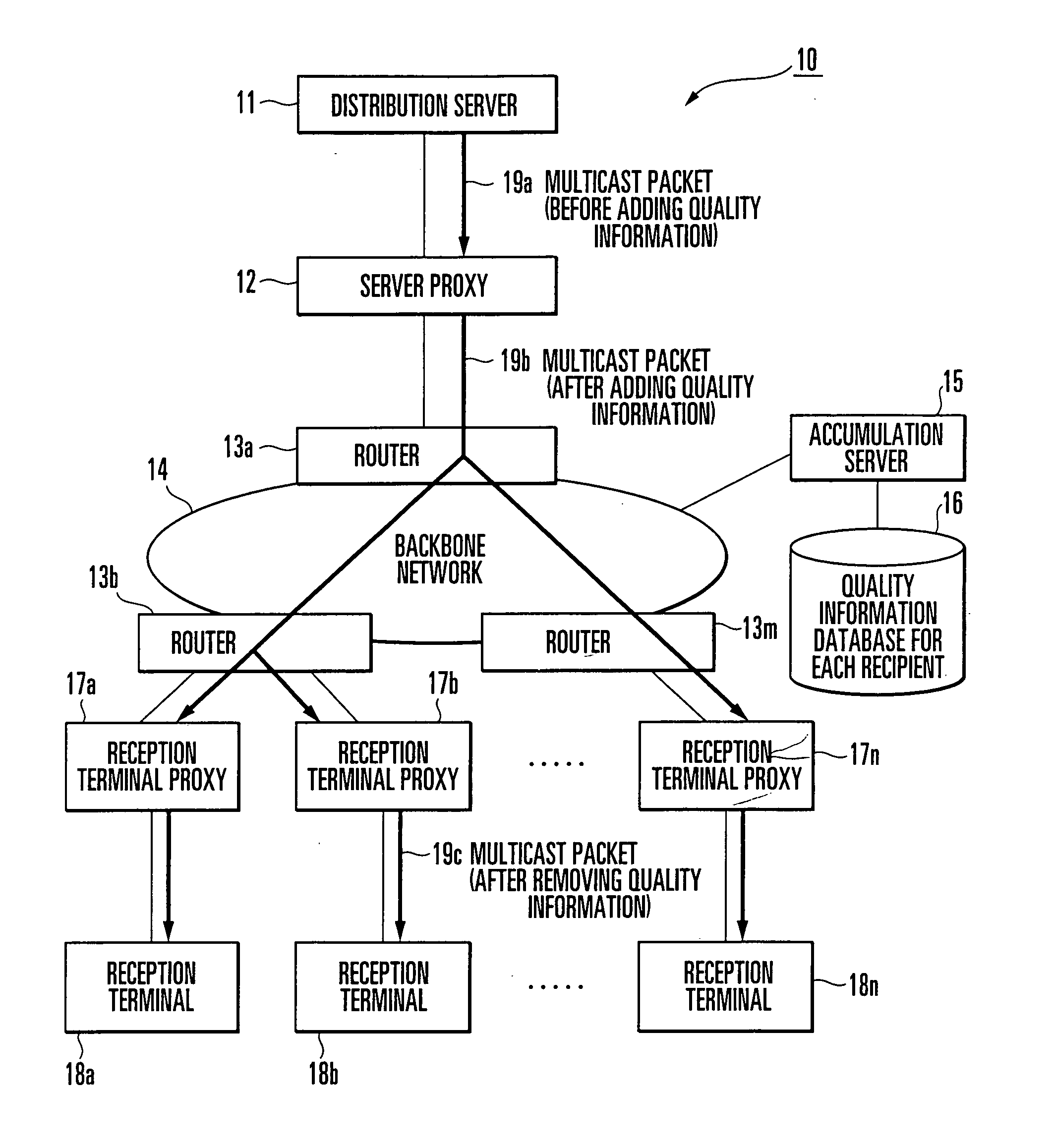
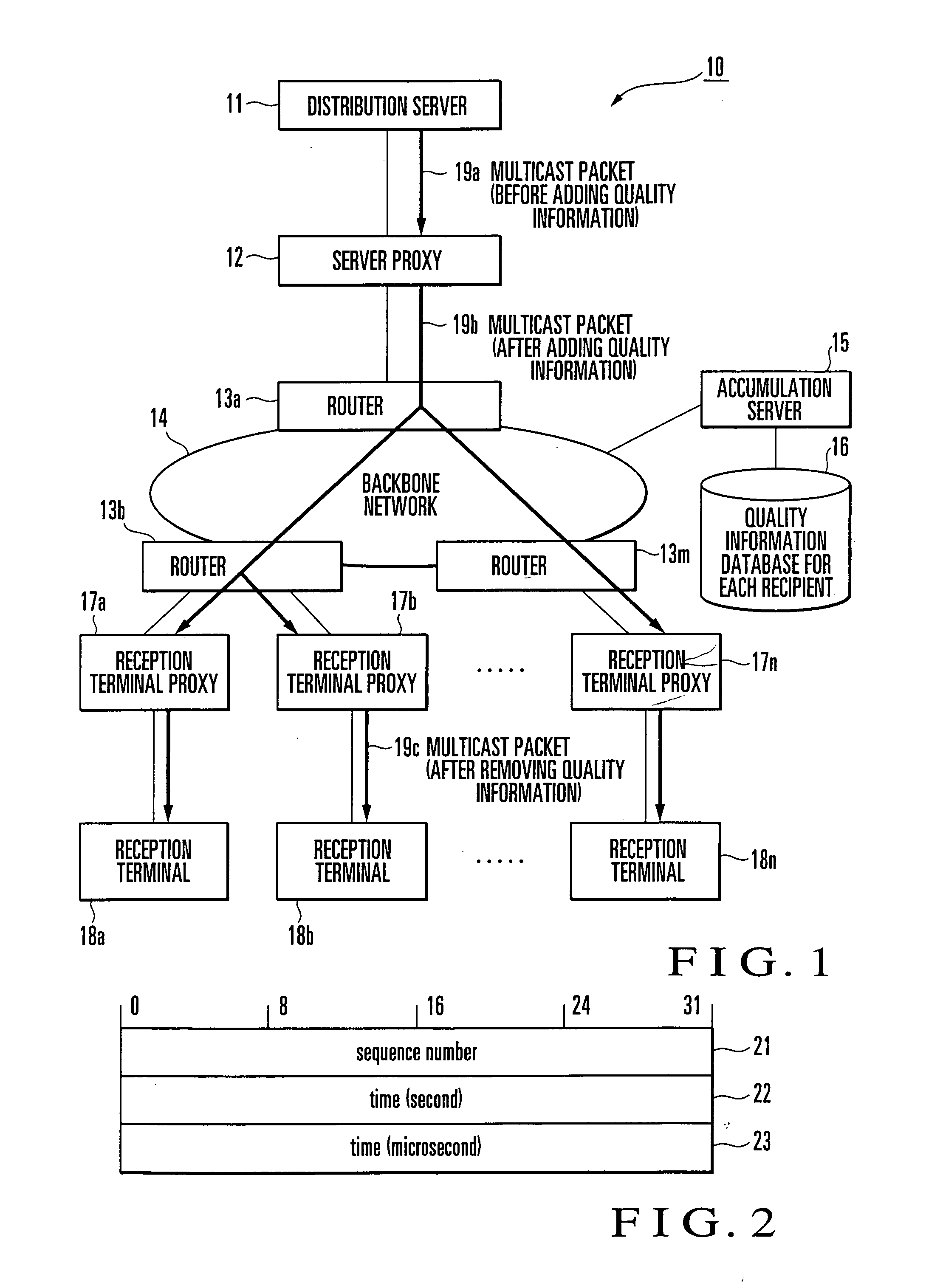
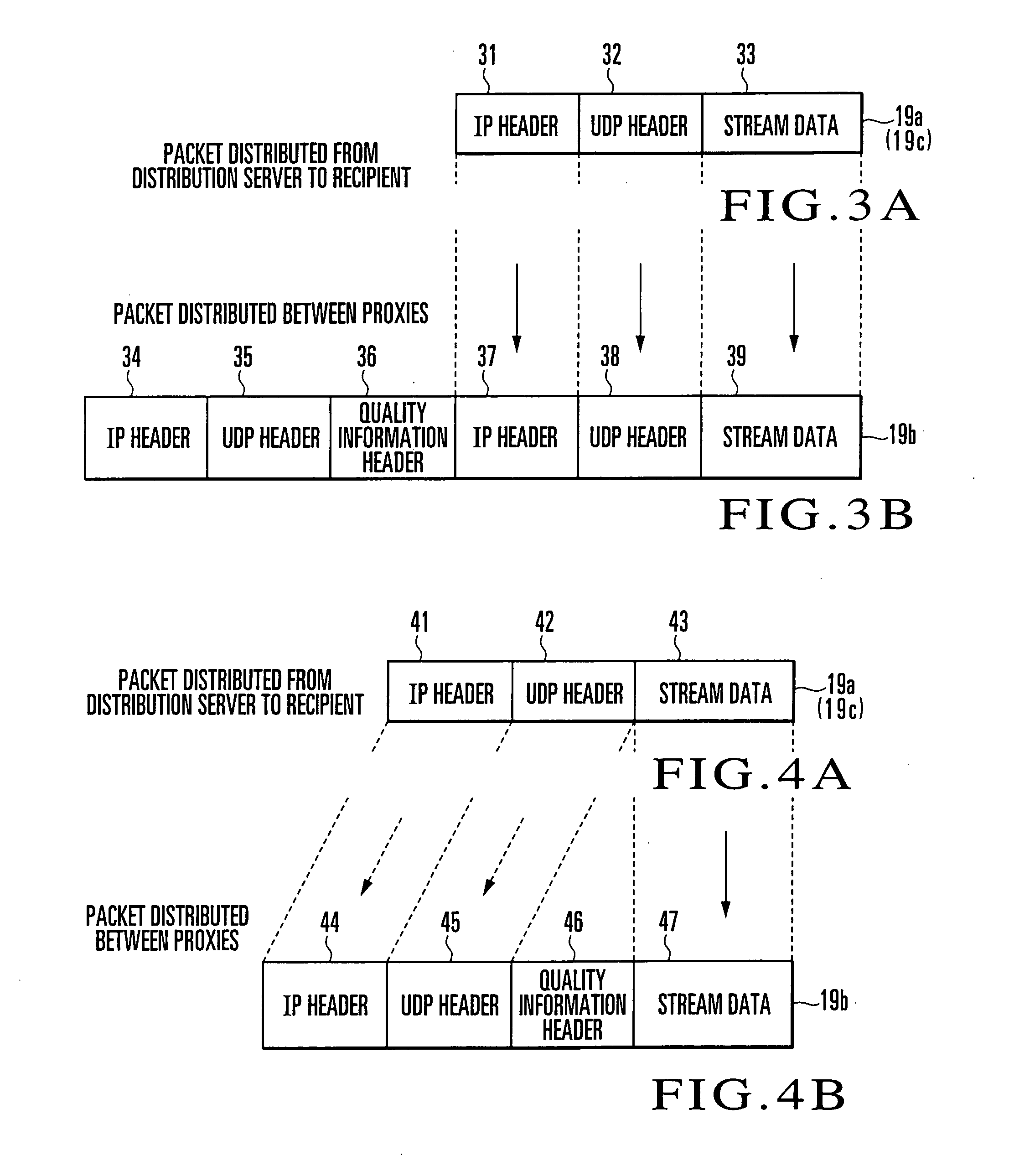
Communication quality management and apparatus
A server proxy (12), which is arranged between a distribution server (11) and a router (13a), adds quality information to a packet (19a) from the distribution server (11) to output a packet (19b). A plurality of reception terminal proxies (17a-17n), which are arranged immediately before respective reception terminals (18a-18n), remove the quality information from the packet (19b) distributed via a network (14) and routers (13b-13m), and distribute only necessary information to the respective reception terminals (18). Each reception terminal proxy (17) which includes a quality information acquisition unit (17A) acquires the quality information to transmit, from a quality information calculation / transmission unit (17B), the quality information (51) to an accumulation server (15). The accumulation server (15) saves, in a quality information database, packet quality information (52) for each reception terminal (18).
Owner:NEC CORP
Distributed computing system installation
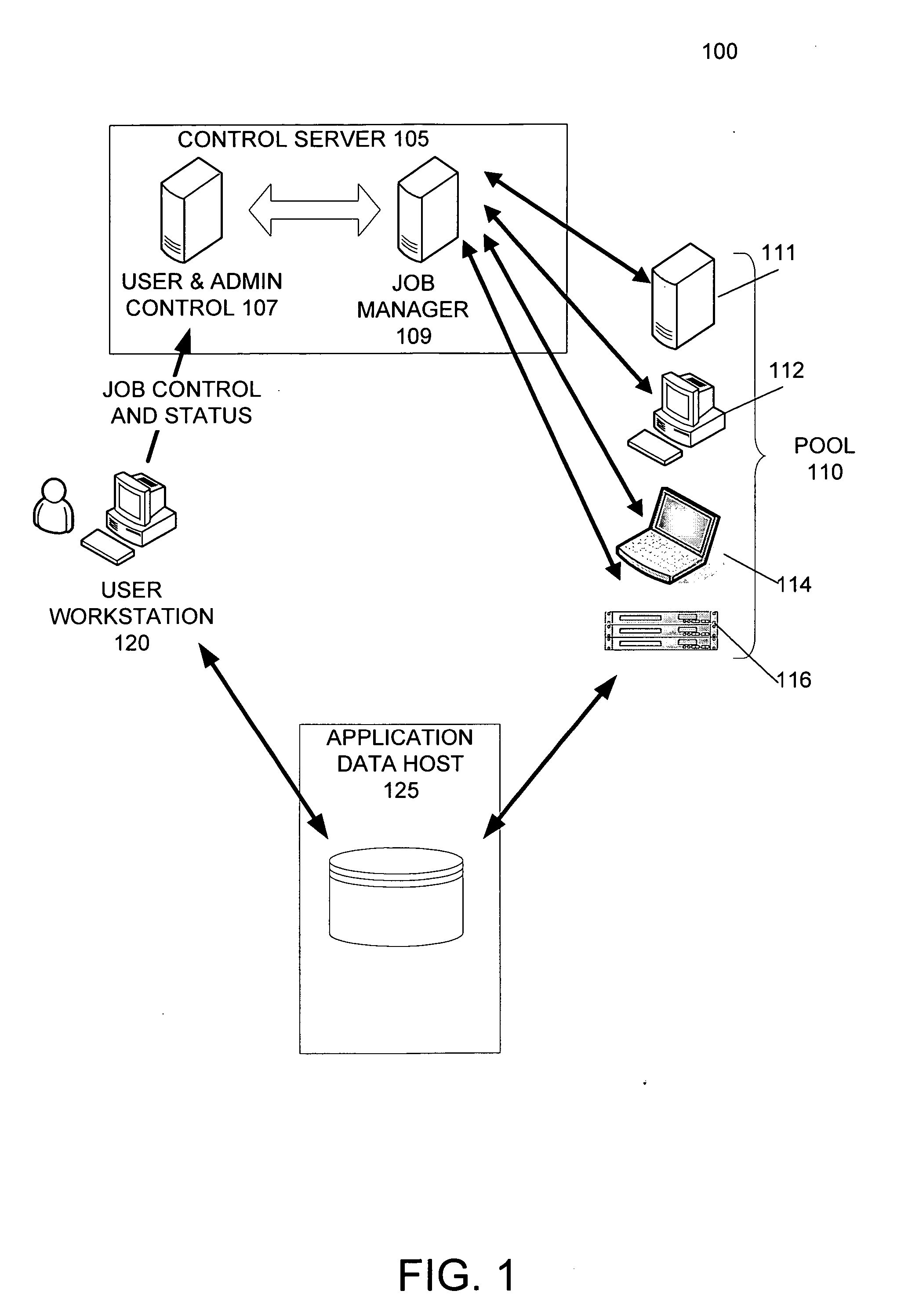
A distributed processing system delegates the allocation and control of computing tasks to intelligent agent applications running on computing resources. The distributed processing system includes agents and a server. The agents are run on or associated with any computer system contributing computing resources to the distributed processing system. An installation package facilitates the creation and maintenance of distributed computing systems. An installation software package is loaded and installed on to a computer that will be the server for the distributed computing system, thereby activating a server for the distributed processing system. The installation package creates an installation web site on the server accessible to other computers potentially suitable for inclusion in the distributed processing system. These other computers can manually or automatically access the installation web site to retrieve and install agent applications, thereby adding themselves to the distributed computing system.
Owner:DIGIPEDE TECH LLC
System and method for enabling asynchronous push-based applications on a wireless device
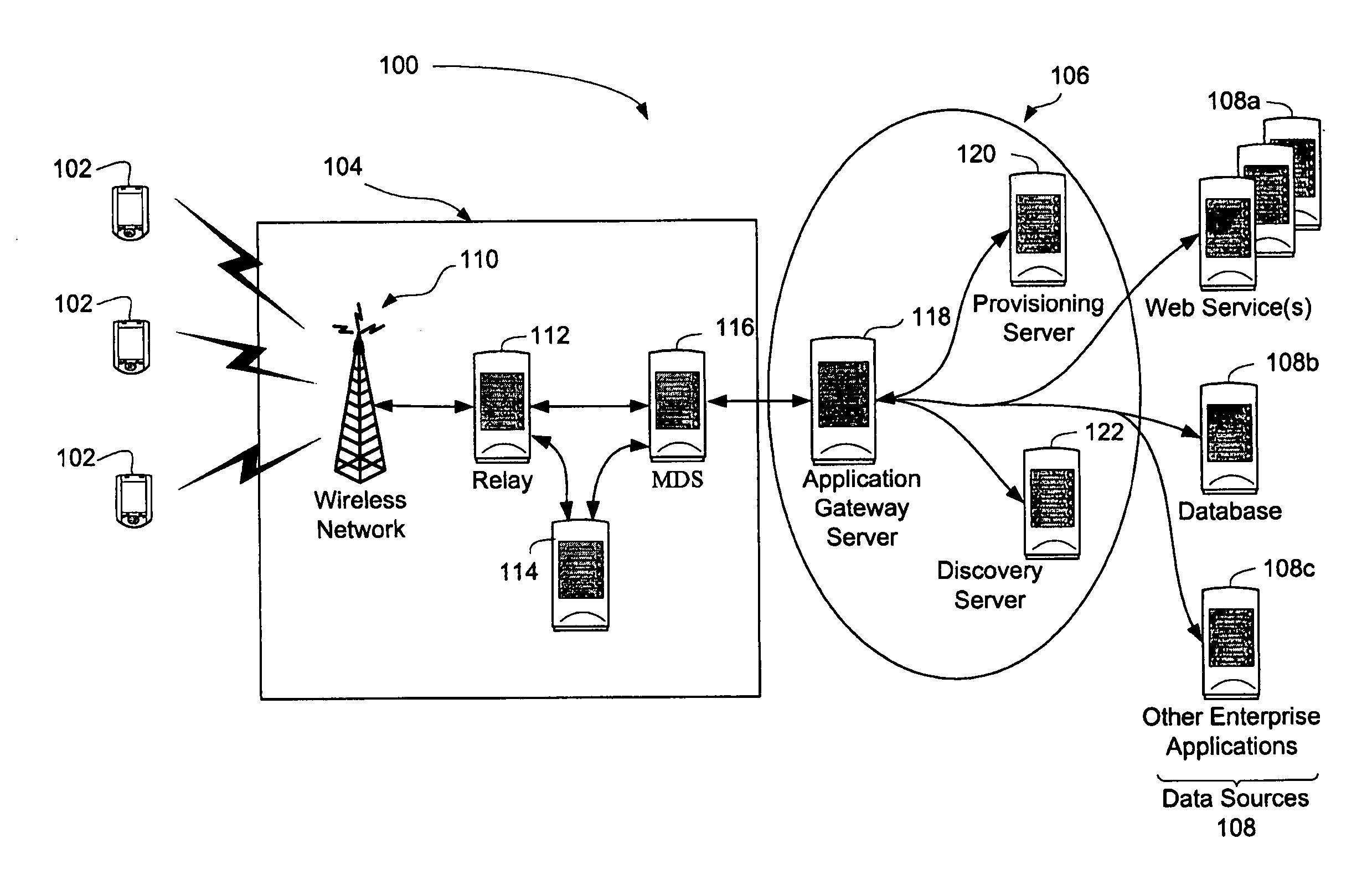
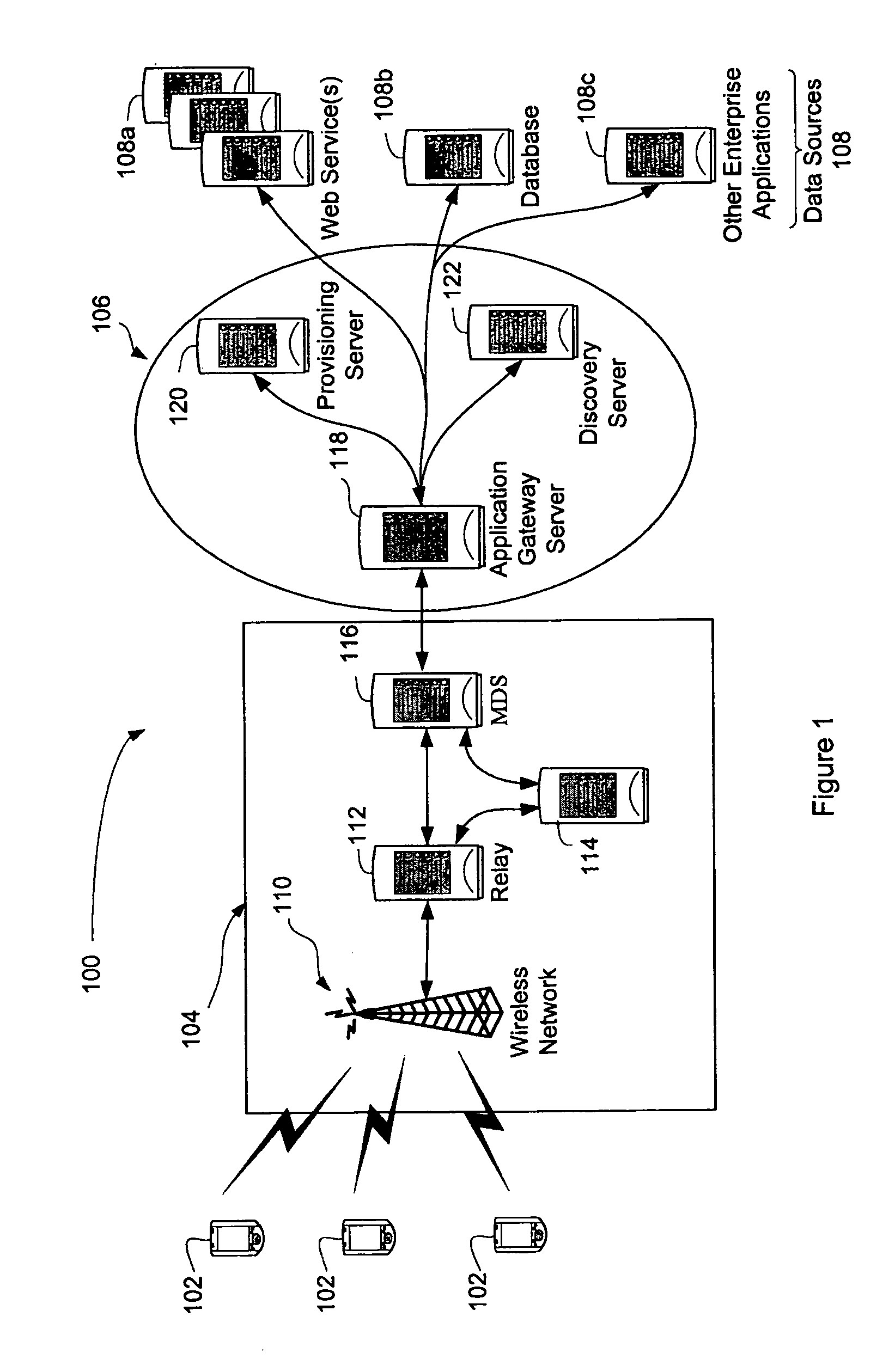
ActiveUS20070011292A1Digital computer detailsElectric digital data processingServer agentWeb service
There is provided a system and method of enabling asynchronous push-based applications on a wireless device in a system having an application gateway server including an application repository and a server proxy including an event sink for communicating between the system and the device. The method comprises reading a Web service interface, generating a Web service interface therefrom conforming to a notification protocol, creating a notification-based application bundle for the Web service, publishing the notification-based application bundle, creating an event source. The system comprises an application gateway server, an application repository and an application registry. The application gateway includes an event sink for communicating between the system and the device. The application gateway server is configured for communication with a backend server including an event source.
Owner:MALIKIE INNOVATIONS LTD
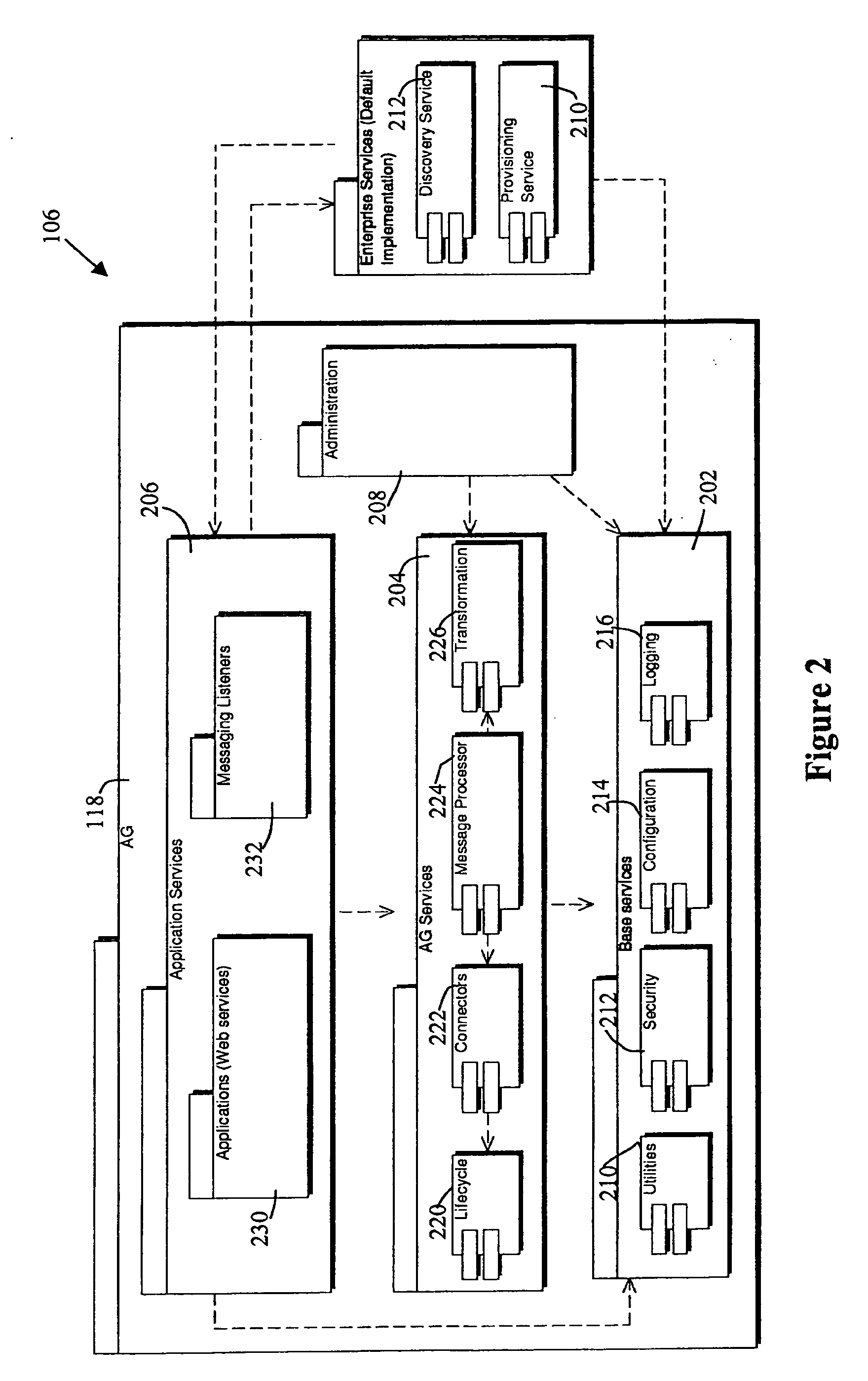
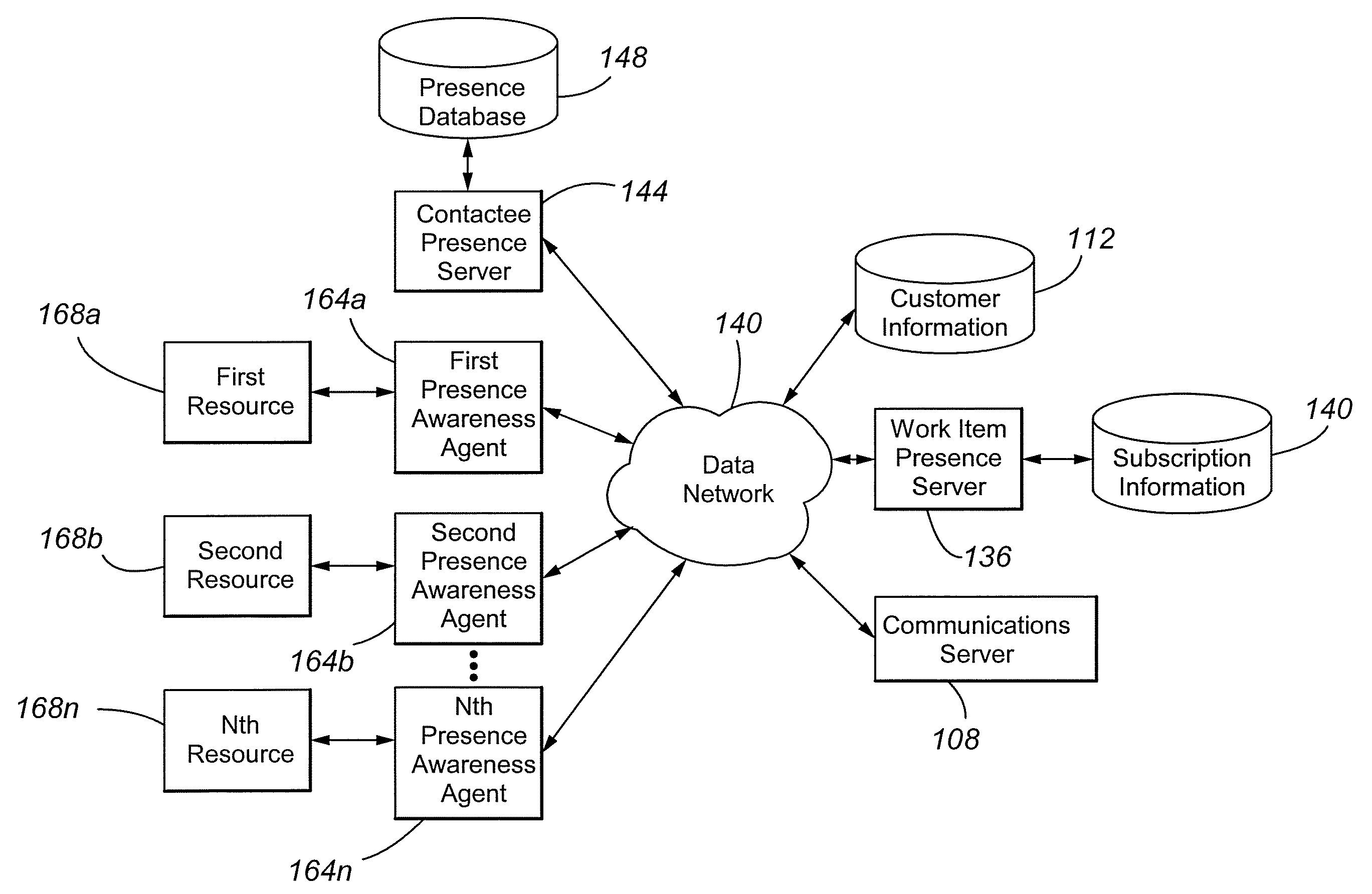
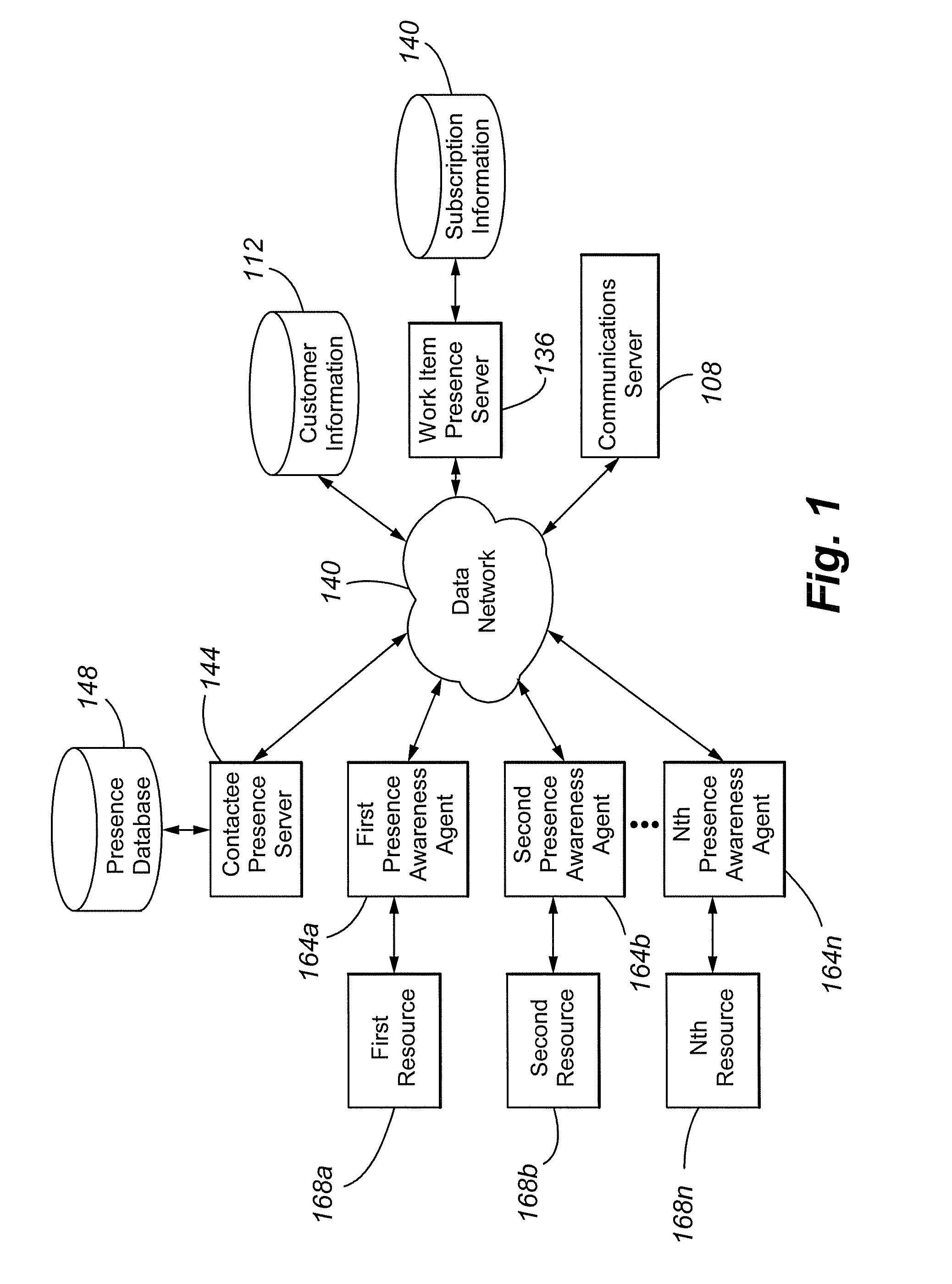
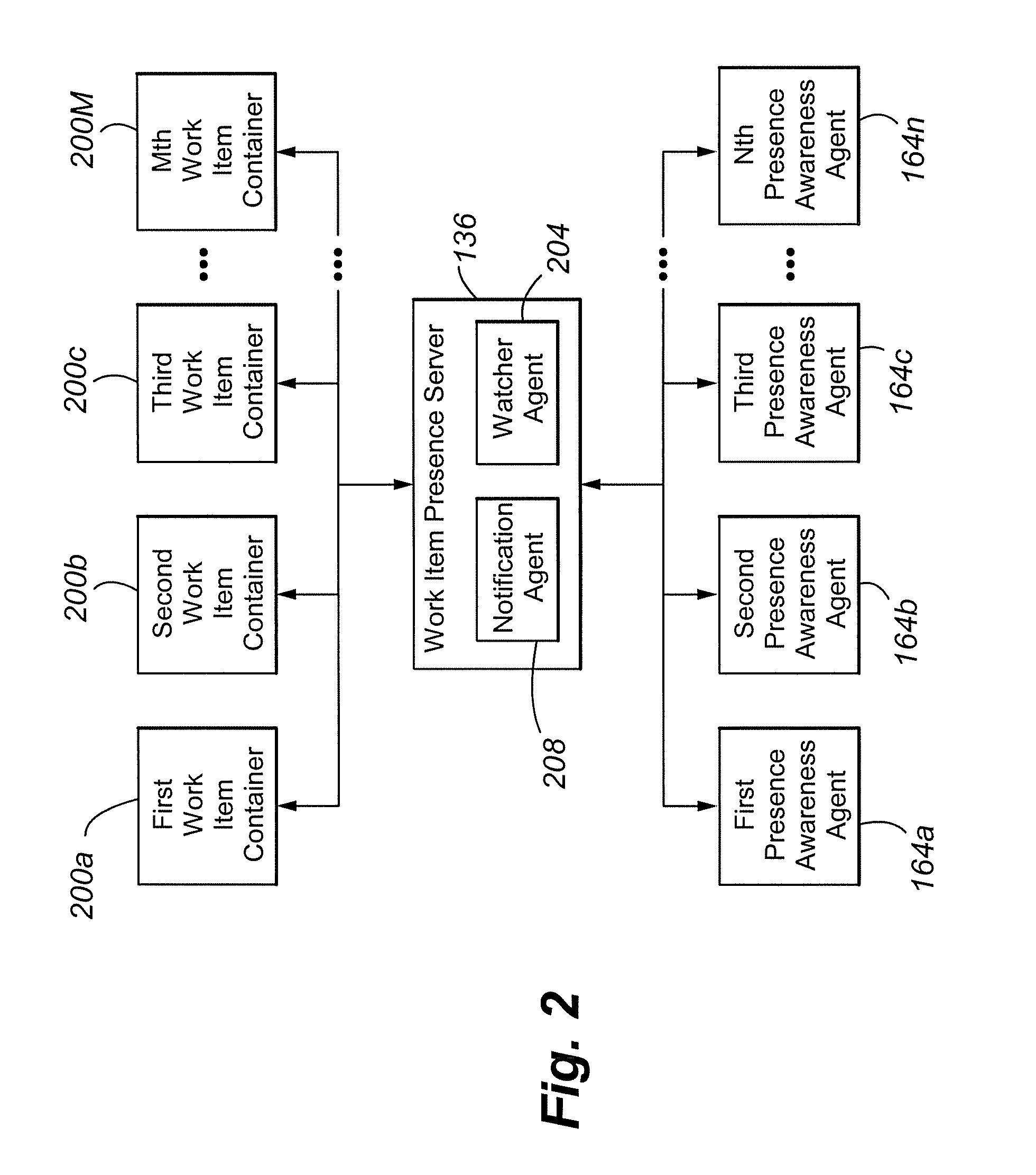
Contact center agent work awareness algorithm
InactiveUS20080120164A1Simple and efficient interfaceImprove customer satisfactionMarket predictionsAutomatic exchangesServer agentContact center
A contact center is provided that includes an input operable to receive work items 204a-w, a work item processing agent 200 to populate work item containers 212a-I with information respecting the received work items, and an Aagent Work Awareness Algorithm (AWAA) server notification agent 216 to notify subscribing AWAA agent entities of state changes in the work item containers. The processing AWAA server agent transfers work items to a subscribing AWAA agent entity when requested by the subscribing entity.
Owner:AVAYA INC
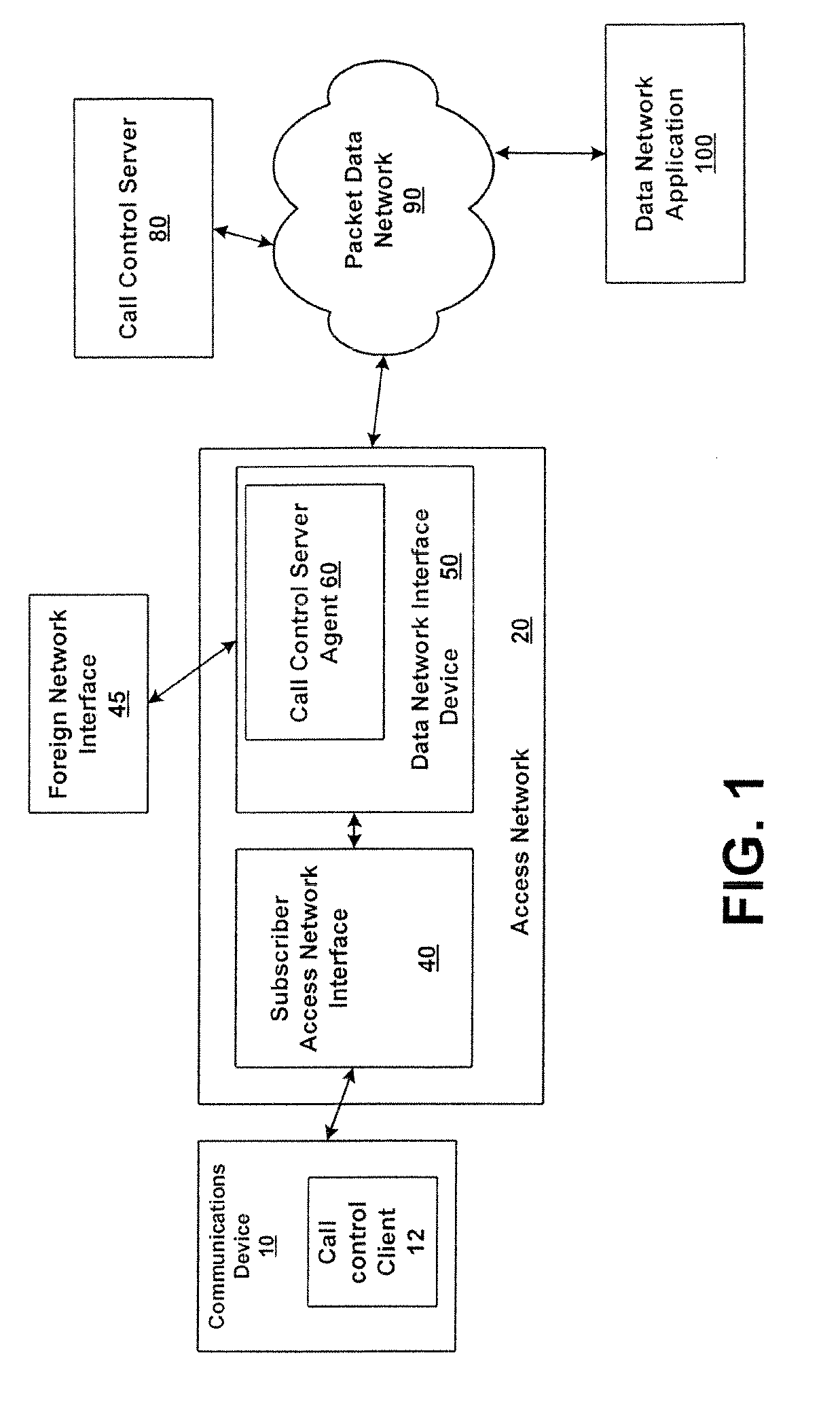
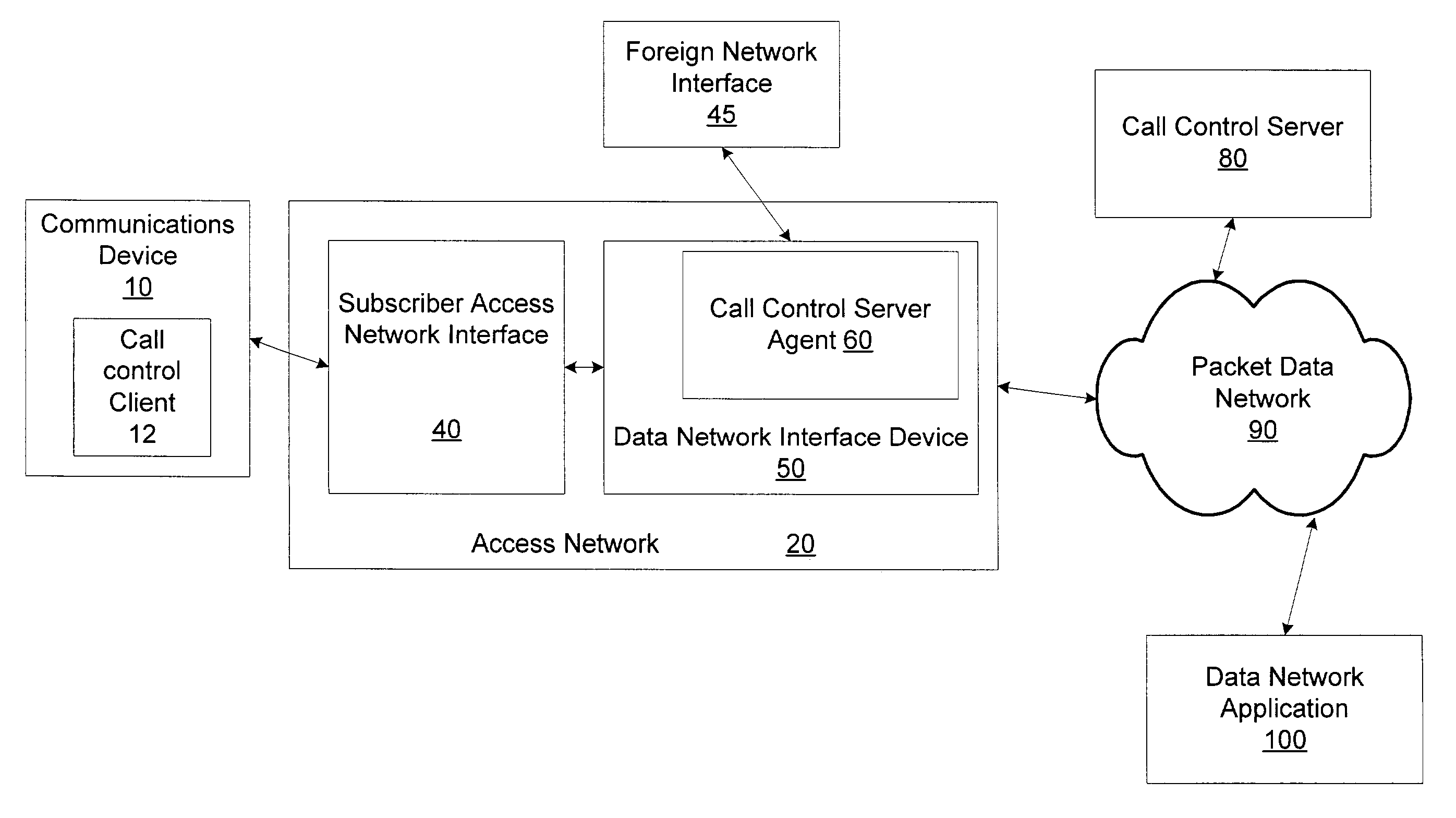
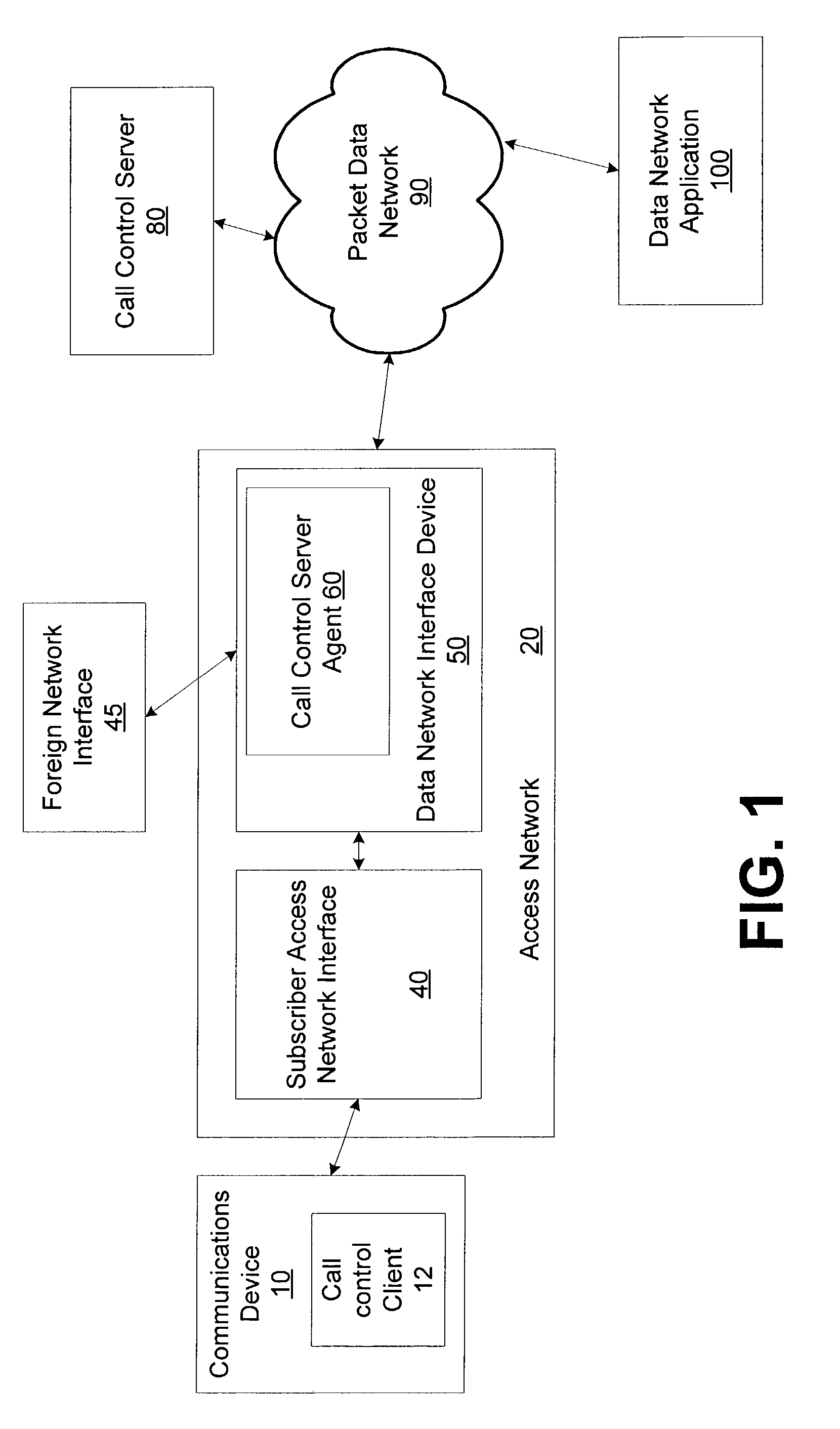
System and method for integrating call control and data network access components
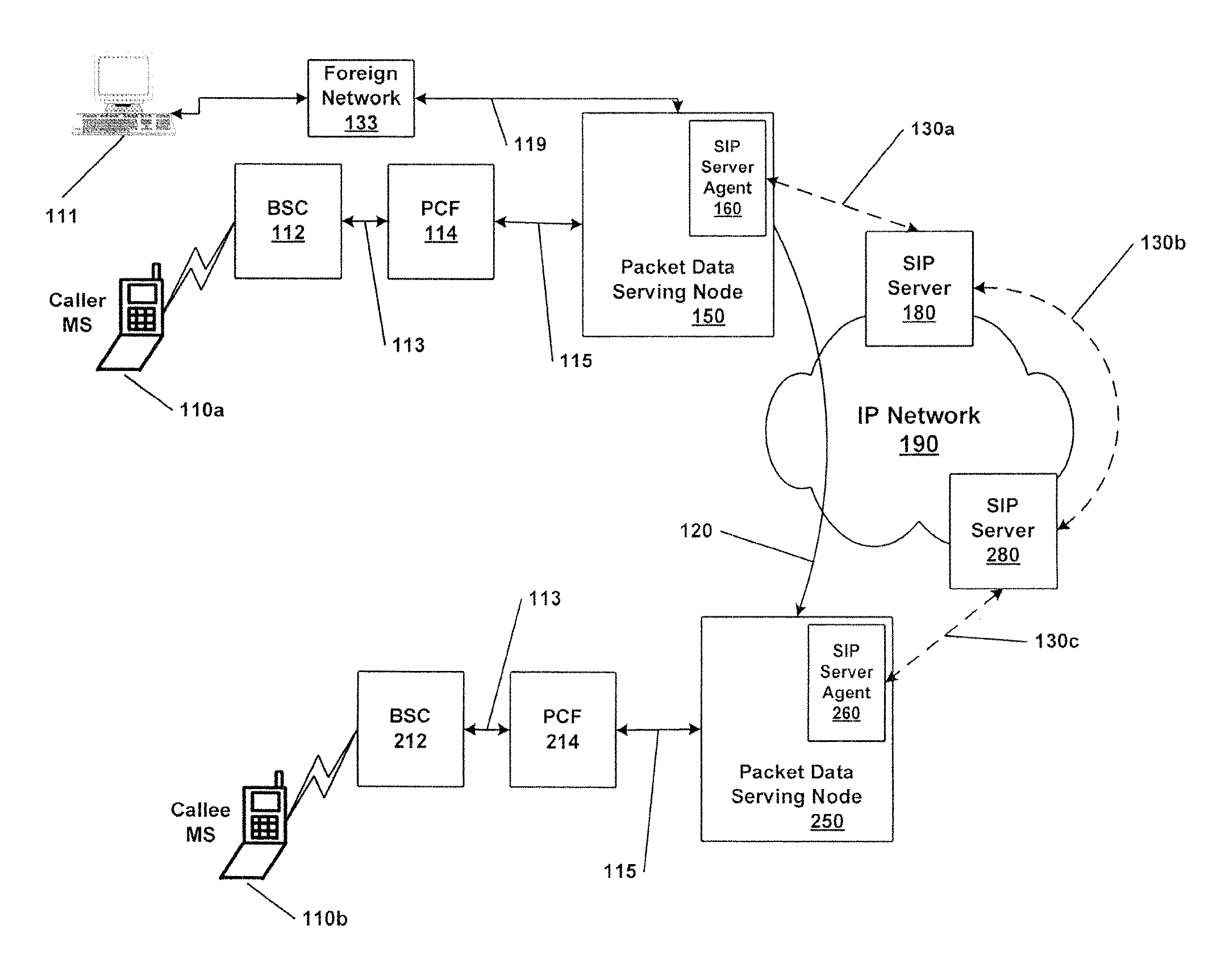
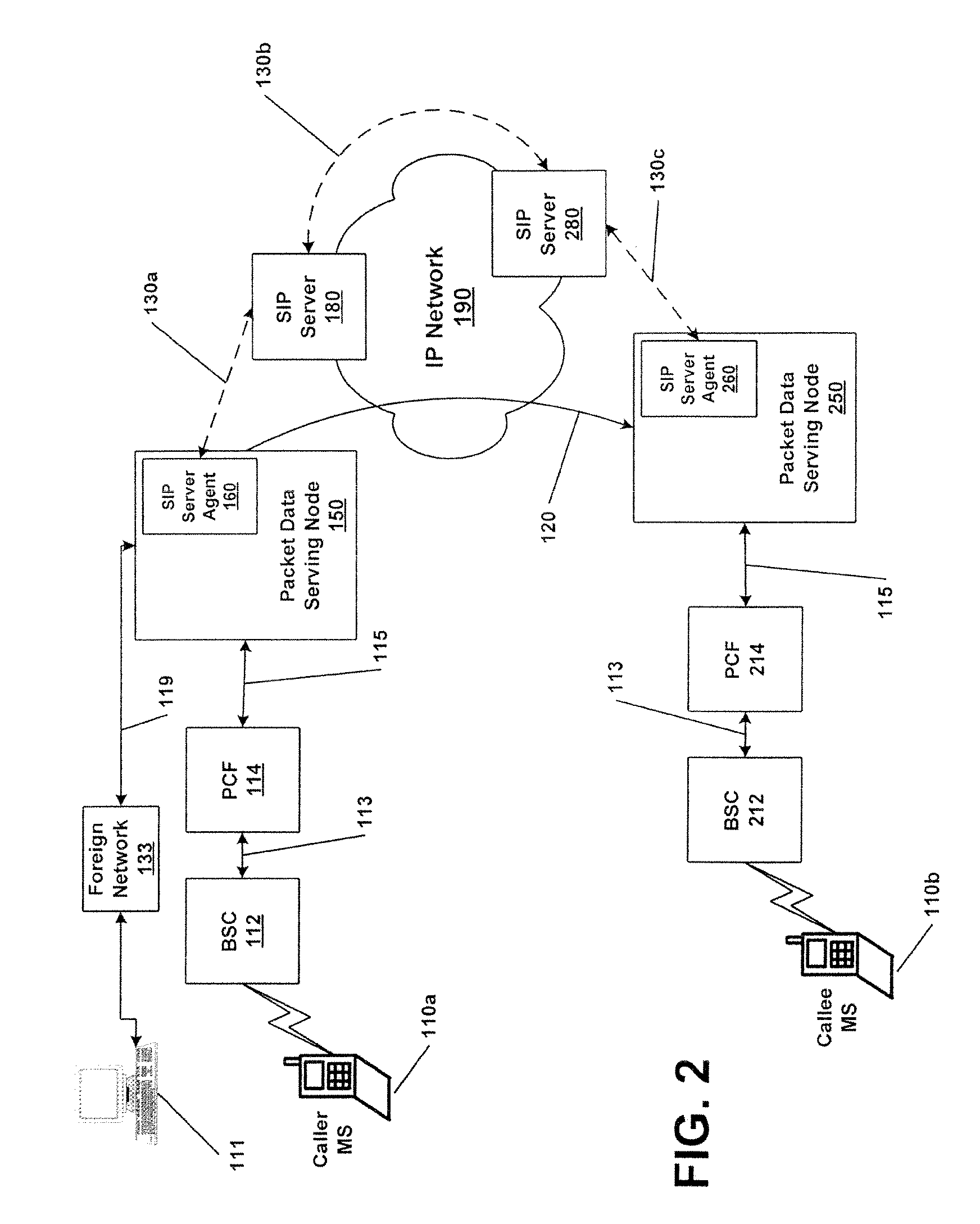
ActiveUS20080107094A1Metering/charging/biilling arrangementsConnection managementAccess networkServer agent
A system and method for integrating the call control signaling pathway with data network access components. A call control server agent is resident on a network device that provides a first interface from an access network to a packet-switched data network. The call control server agent receives data session initiation requests and passes the requests to the call control server agent. The call control server agent also performs proxy server functions and provides a source of information relating to data sessions directly to the access network.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
System and method for integrating call control and data network access components
ActiveUS7330453B1Metering/charging/biilling arrangementsConnection managementAccess networkServer agent
A system and method for integrating the call control signaling pathway with data network access components. A call control server agent is resident on a network device that provides a first interface from an access network to a packet-switched data network. The call control server agent receives data session initiation requests and passes the requests to the call control server agent. The call control server agent also performs proxy server functions and provides a source of information relating to data sessions directly to the access network.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
Method and system for extending services to cellular devices
ActiveUS20070281682A1Connection managementRadio/inductive link selection arrangementsServer agentClient agent
A system is provide for extending services to cellular devices. The system includes a wireless gateway having a client side with an intelligent client agent and a server side with an intelligent server agent, a wireless device having a first mode operable in a cellular system and a second mode operable in a wireless local area network and including an intelligent client agent for determining operation mode and for communicating with the intelligent client agent of the wireless gateway and a communications protocol for communication between the wireless gateway intelligent client agent and the wireless device intelligent client agent to effect services. The services include one or more of voice, directory, presence, and media services. The voice service includes at least one of call waiting, call forwarding conferencing, and caller identification. The media service includes at least one of interactive voice response (IVR), text-to-speech, speech recognition, play, record. The directory service includes a public switched telephone network (PSTN) directory, a cellular network directory, an Internet directory and a private branch exchange (PBX) directory. The communications protocol includes encapsulation for at least one of directory, mobility and security services and other protocols. The other protocols include at least one of Internet protocol (IP), session initiation protocol (SIP), and lightweight directory access protocol (LDAP).
Owner:COUNTERPATH TECH
Synchronizing an active feed adapter and a backup feed adapter in a high speed, low latency data communications environment
InactiveUS20080010487A1Increase speedLower latencyError detection/correctionData switching networksServer agentMessage flow
Owner:IBM CORP
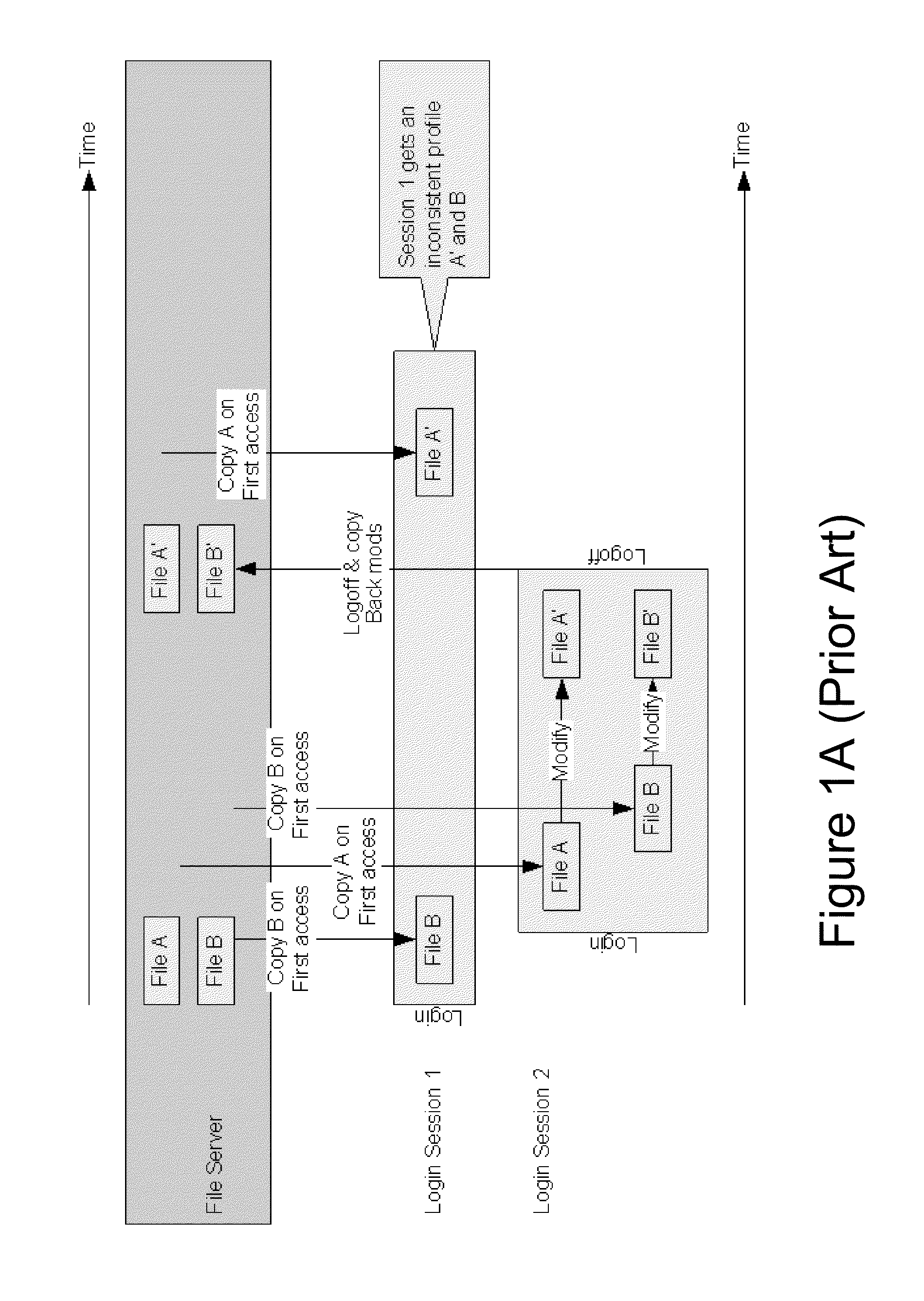
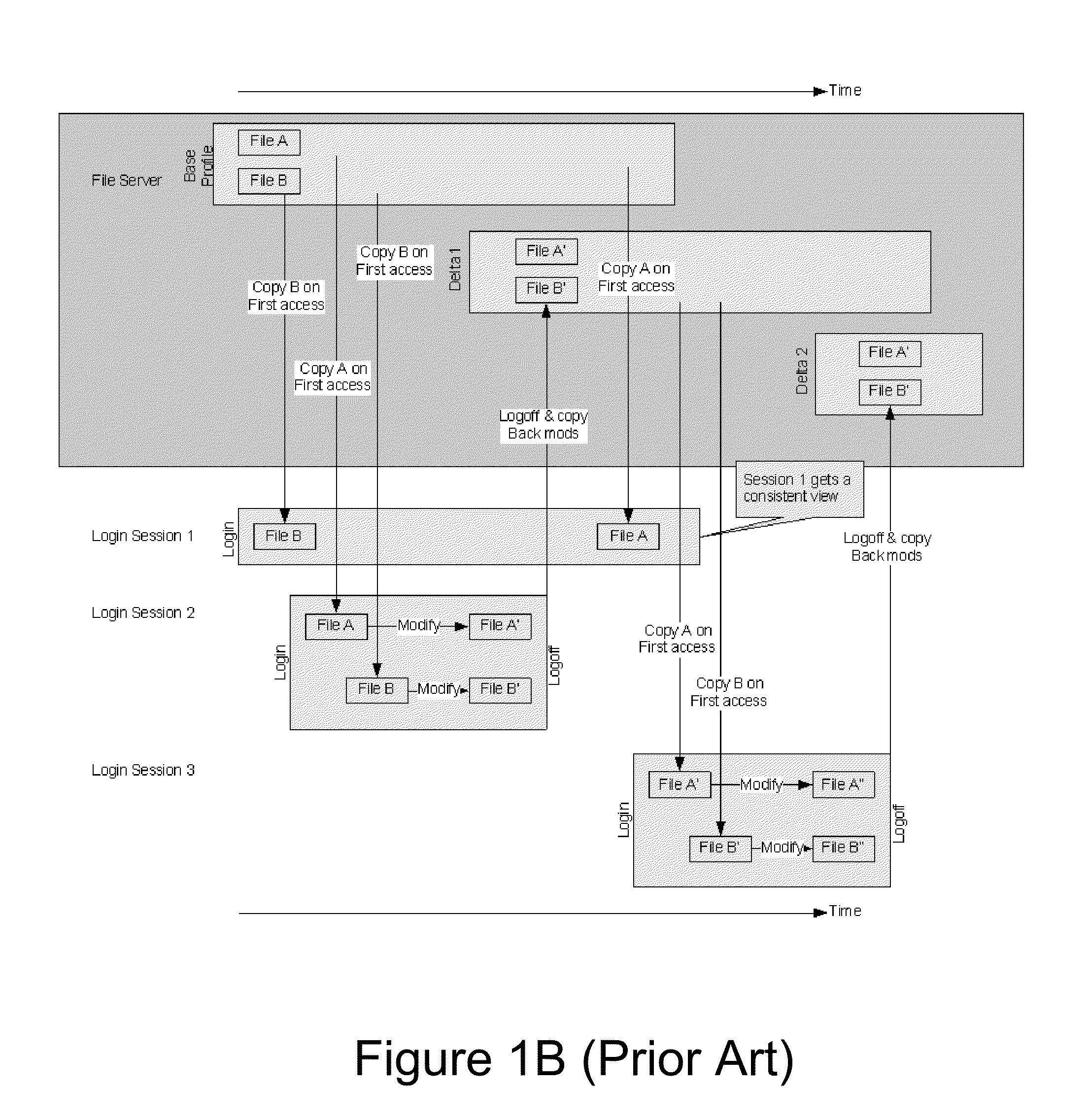
Methods and systems for providing a consistent profile to overlapping user sessions
Just in time delivery of a consistent user profile to overlapping user sessions, where a first user session issues a request for a first file of a user profile to a server agent. Upon receiving the request, the server agent retrieves the first file from a base user profile, and just in time delivers the retrieved first file to the first user session. The user, via a second user session executing simultaneously with the first user session, issues a request to the server agent for the first file and a second file of the user profile. Upon receiving the request, the server agent identifies a modified version of the first file in a provisional user profile, retrieves the modified first file from the provisional user profile and the second file from the base user profile, and just in time delivers both files to the second user session.
Owner:CITRIX SYST INC
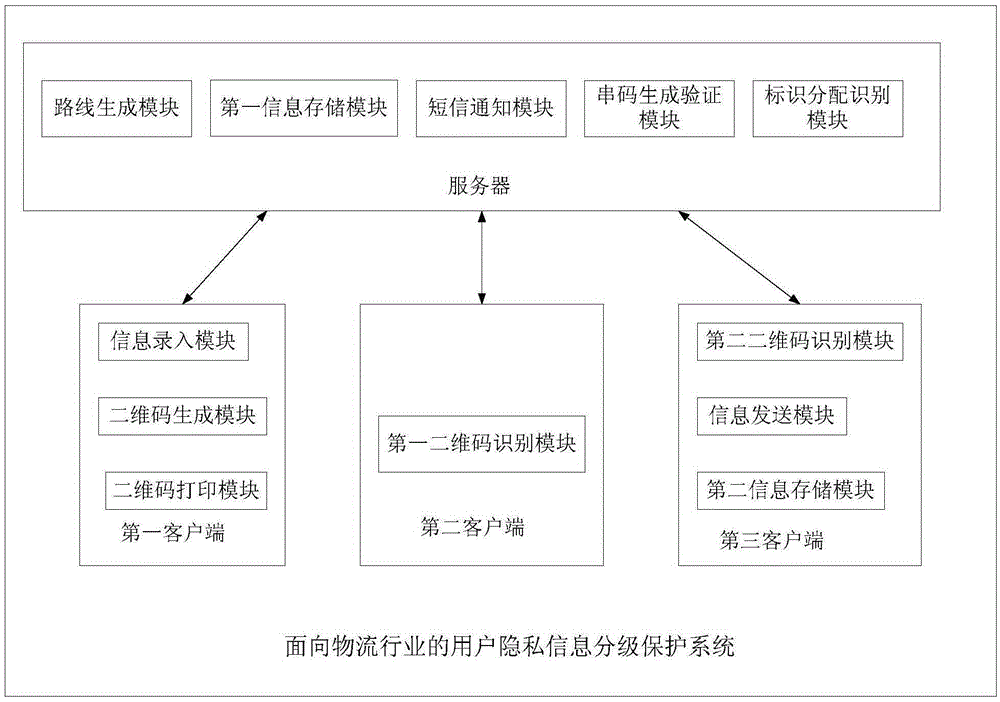
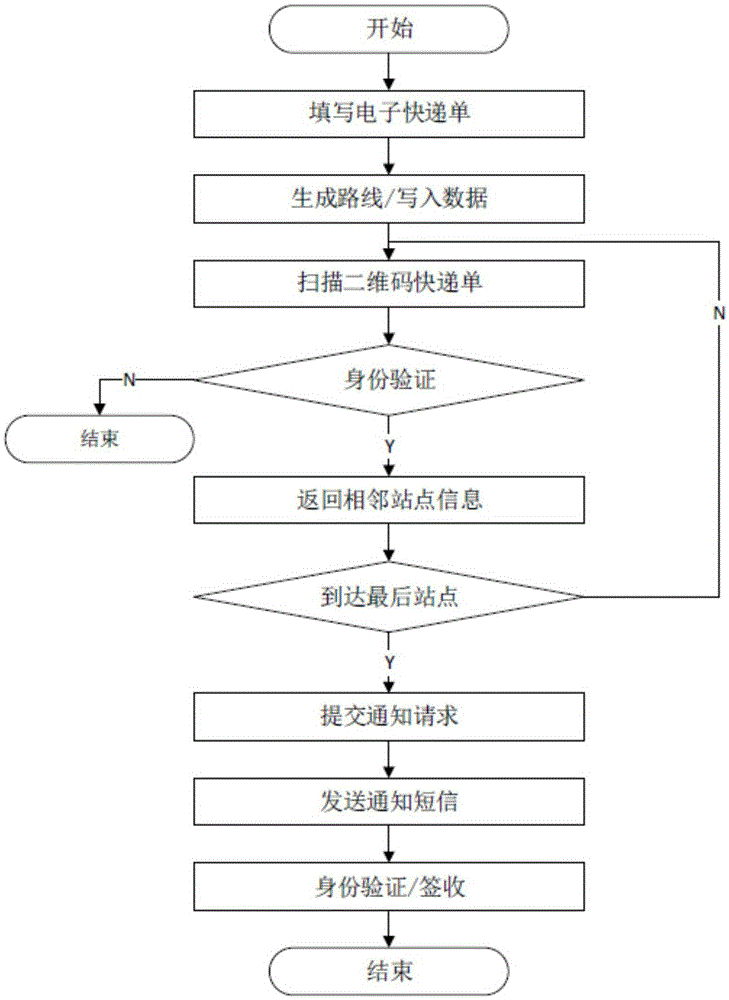
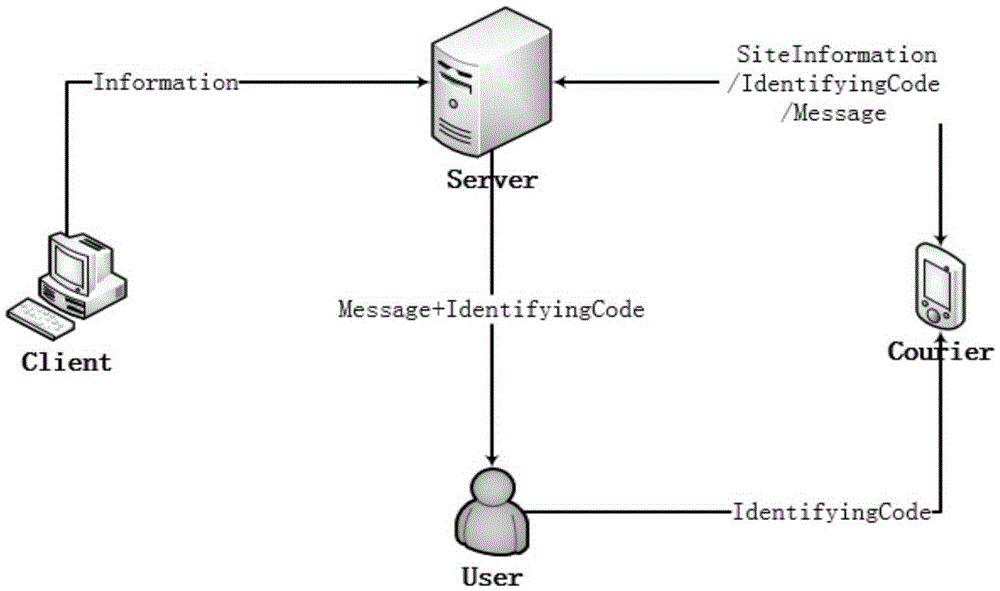
Logistics industry-oriented system and method for cascade protection of user privacy information
InactiveCN105354693ANot to be leakedReduce the probability of leakageTransmissionLogisticsServer agentLogistics management
The present invention discloses a logistics industry-oriented system and method for cascade protection of user privacy information. The method comprises: in a collection stage, using an electronic express form instead of a conventional express form, thereby ensuring that user information is transparent to a courier; in an express delivery transfer stage, applying an idea of secret division, so that each station can acquire only part of station information; in an express delivery notification stage, using a server proxy notification method, so that a courier can issue a notification without knowing contact information of a recipient; in a signing-for-accepting-the-express-delivery stage, verifying the identity of the recipient by using a verification code that is generated by the server in the previous stage; and at the same time, encrypting a content in network communication by combining symmetric encryption and asymmetric encryption.
Owner:CENT SOUTH UNIV
Method and apparatus for providing secure communication
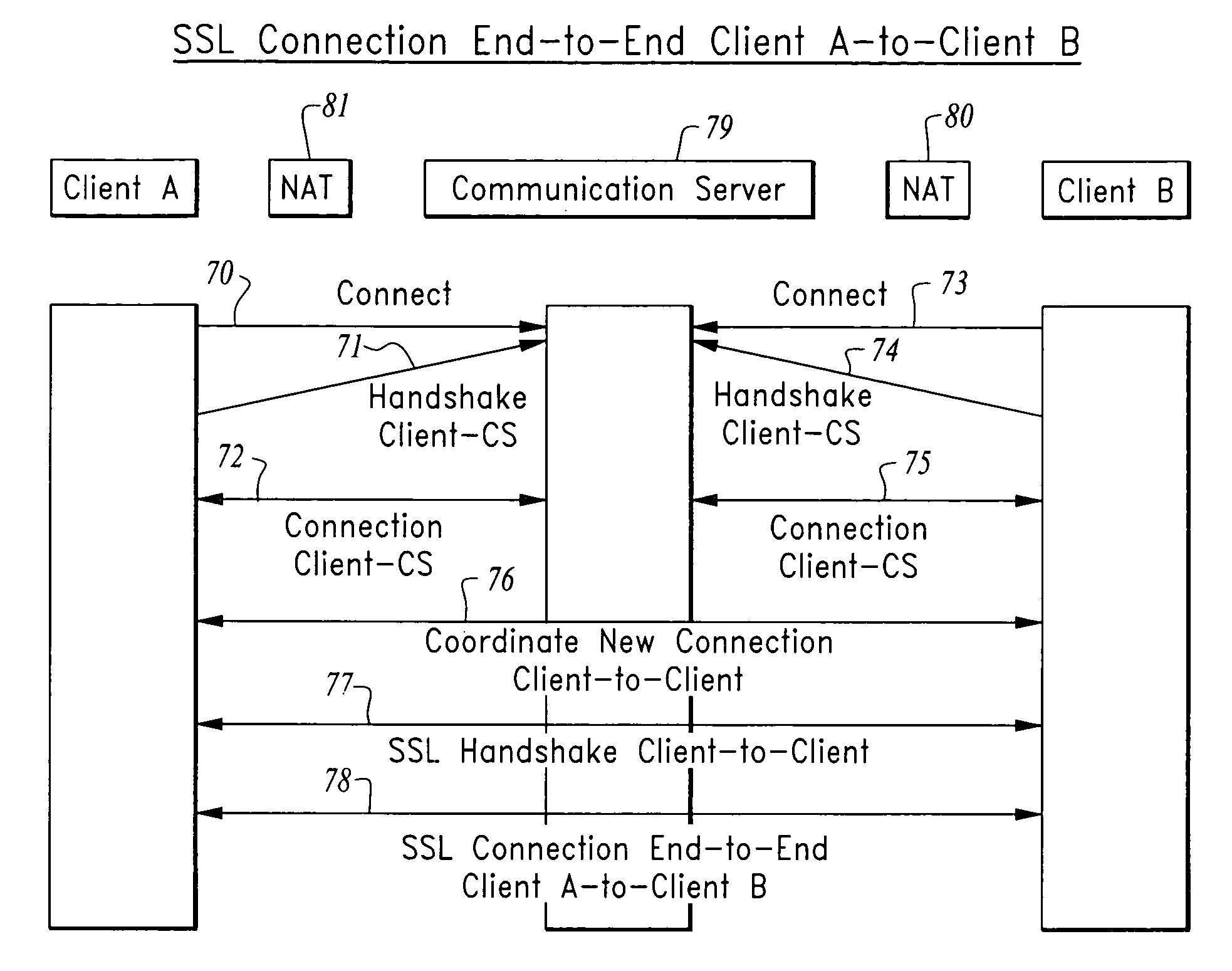
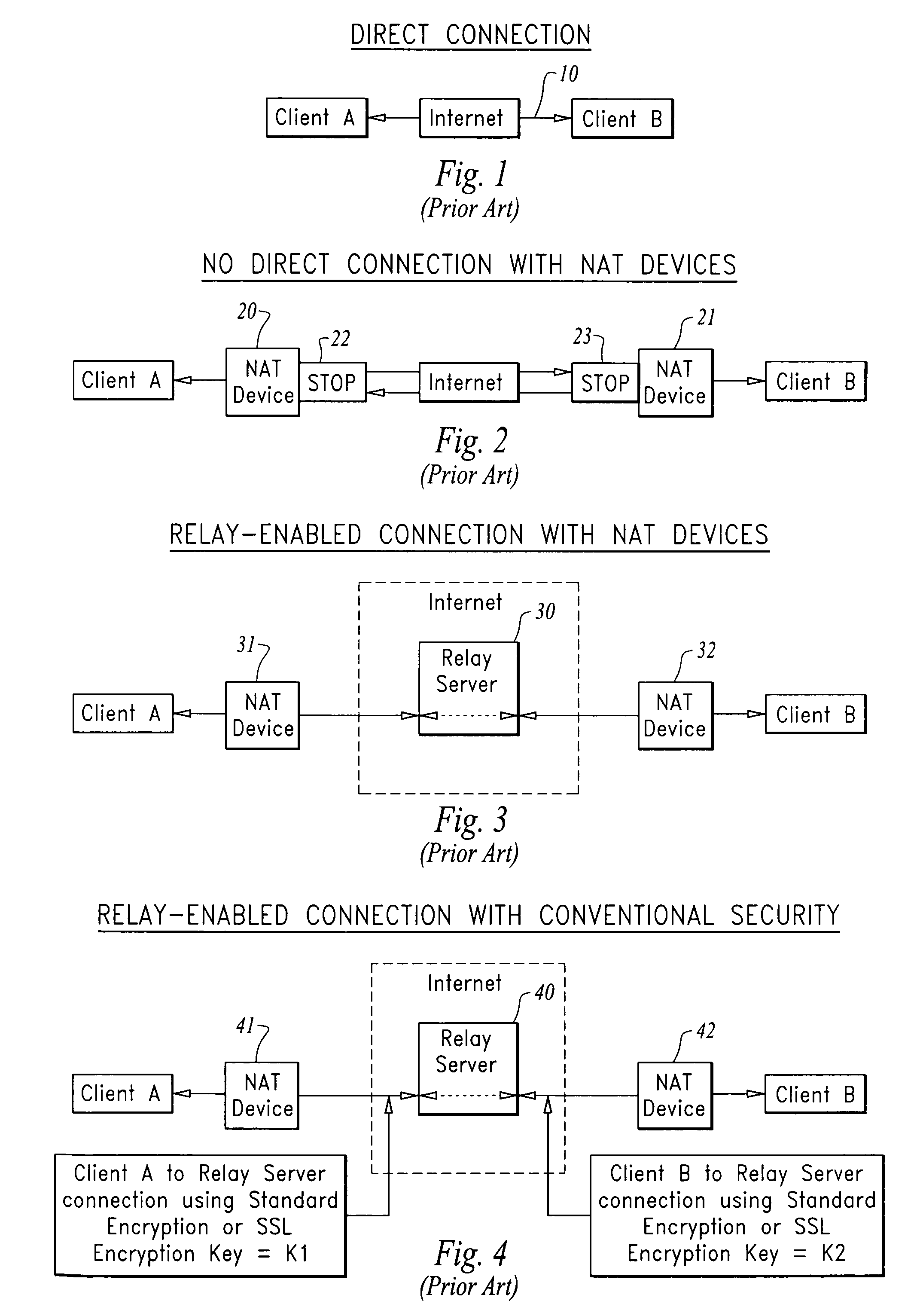
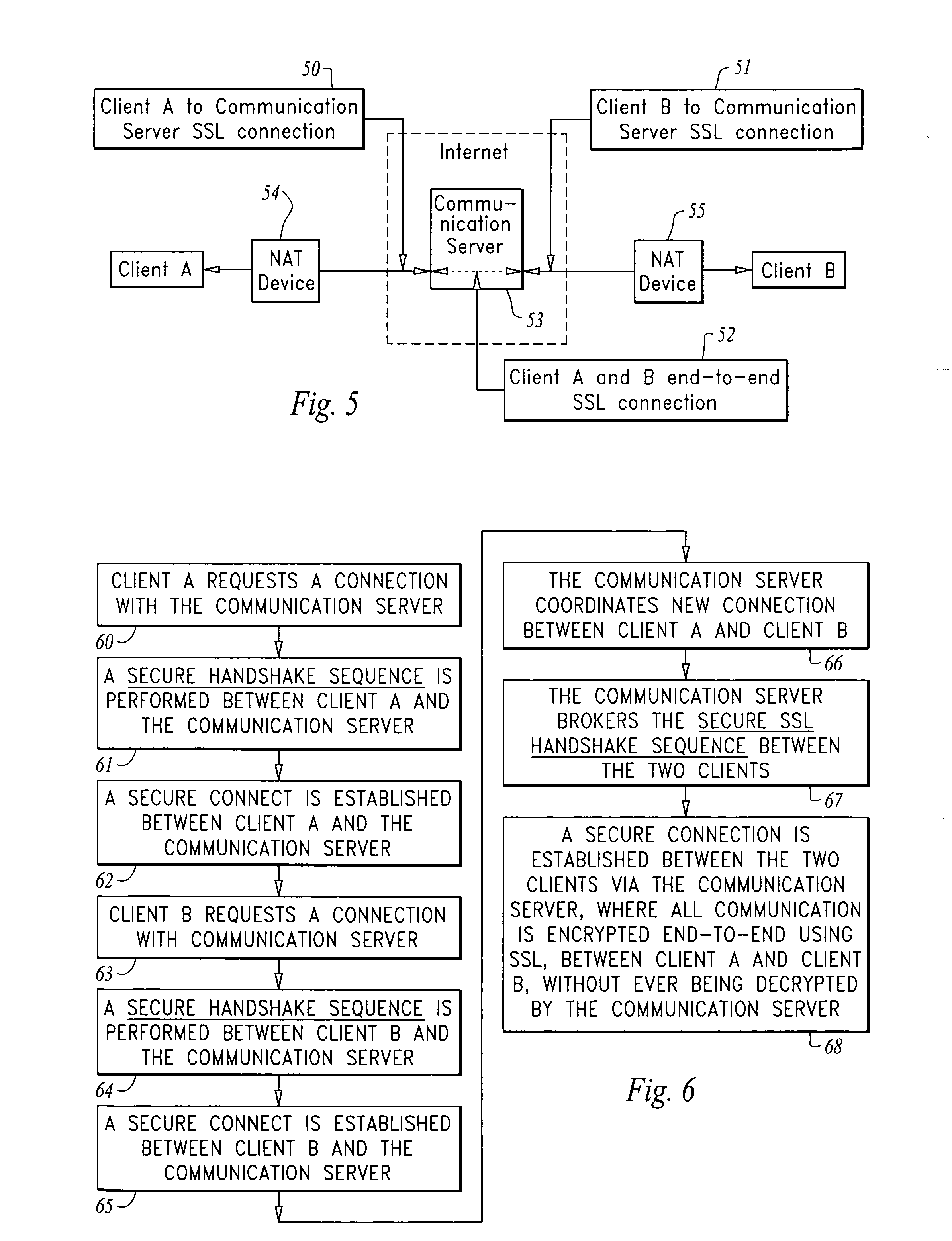
InactiveUS20080130900A1Facilitate communicationKey distribution for secure communicationDigital data processing detailsServer agentKey exchange
A method for providing secure communication in a computer system or network is disclosed where two or more clients, connect by firewalls and / or network address translation devices where no direct connection is possible, communicate via a proxy communication server using secure message transmission protocols such as the Secure Socket layer (SSL). Public-Private Key Exchange and secured data transfer are brokered by the proxy communication server as if the two clients are connected via the network directly without the need of decrypting the data and protocol communication traffic. The method provides enhanced security as no encryption key is disclosed on the proxy side and no data is transmitted or stored on the proxy unencrypted and improved performance is achieved as no data encryption or decryption is required by the proxy, and reduces network management requirements.
Owner:HSIEH VINCENT W
Internet business gateway for digital household network and audio/video program request method
ActiveCN101466022ALow technical requirementsImprove developmentData switching by path configurationTwo-way working systemsServer agentInternet business
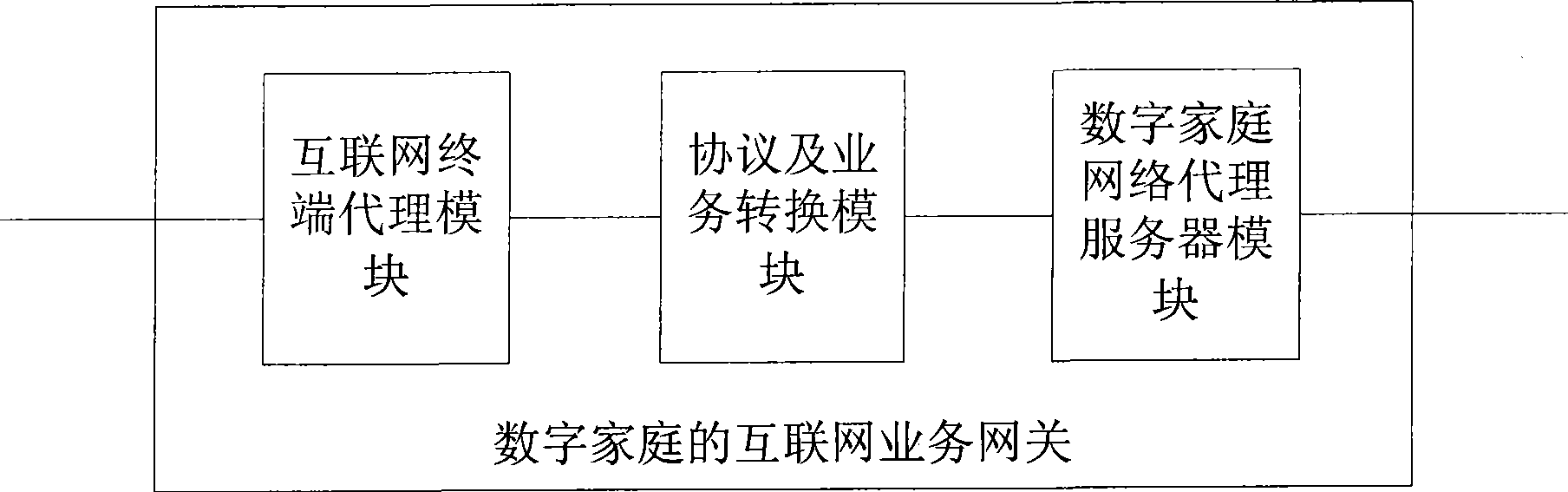
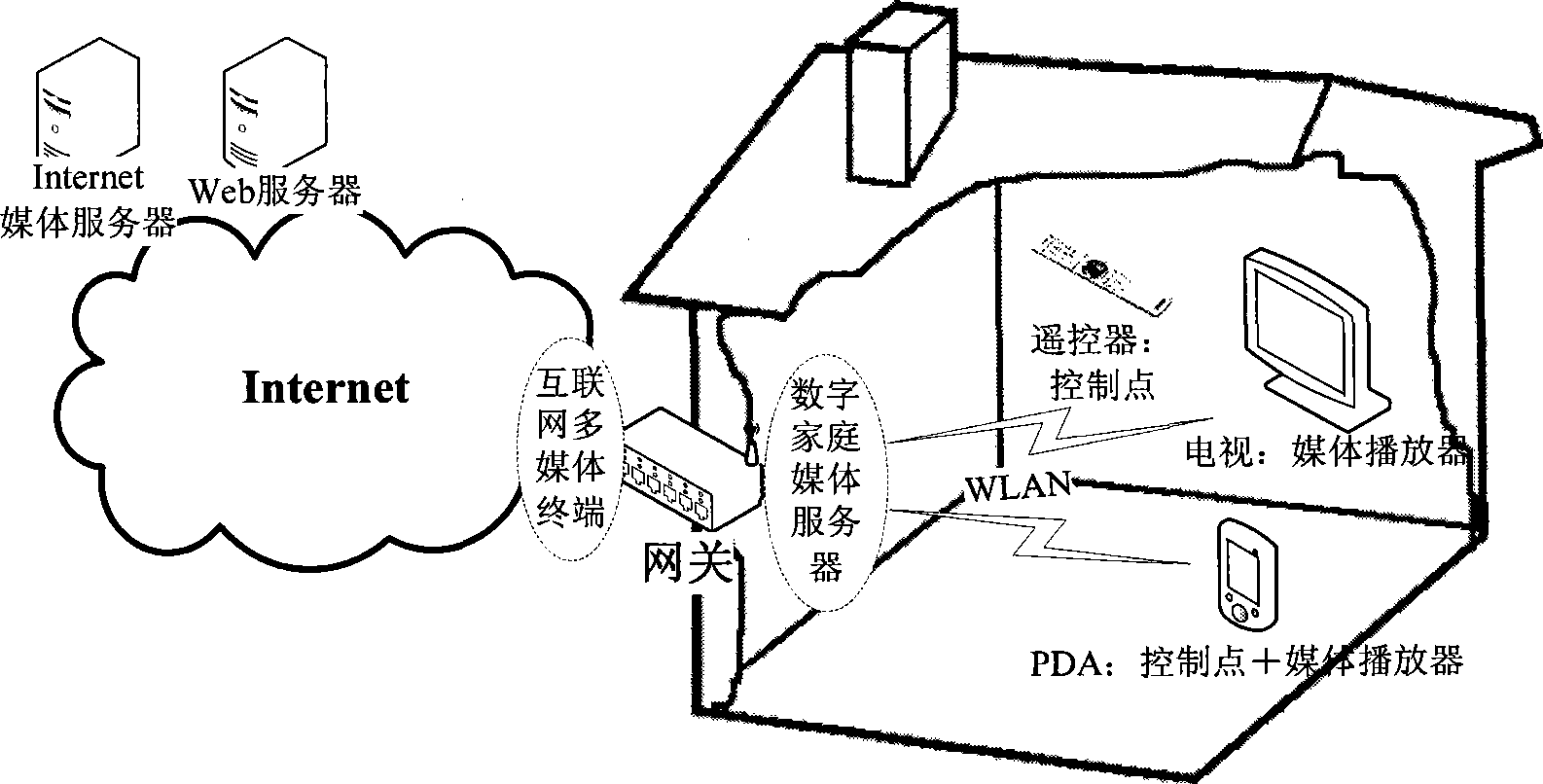
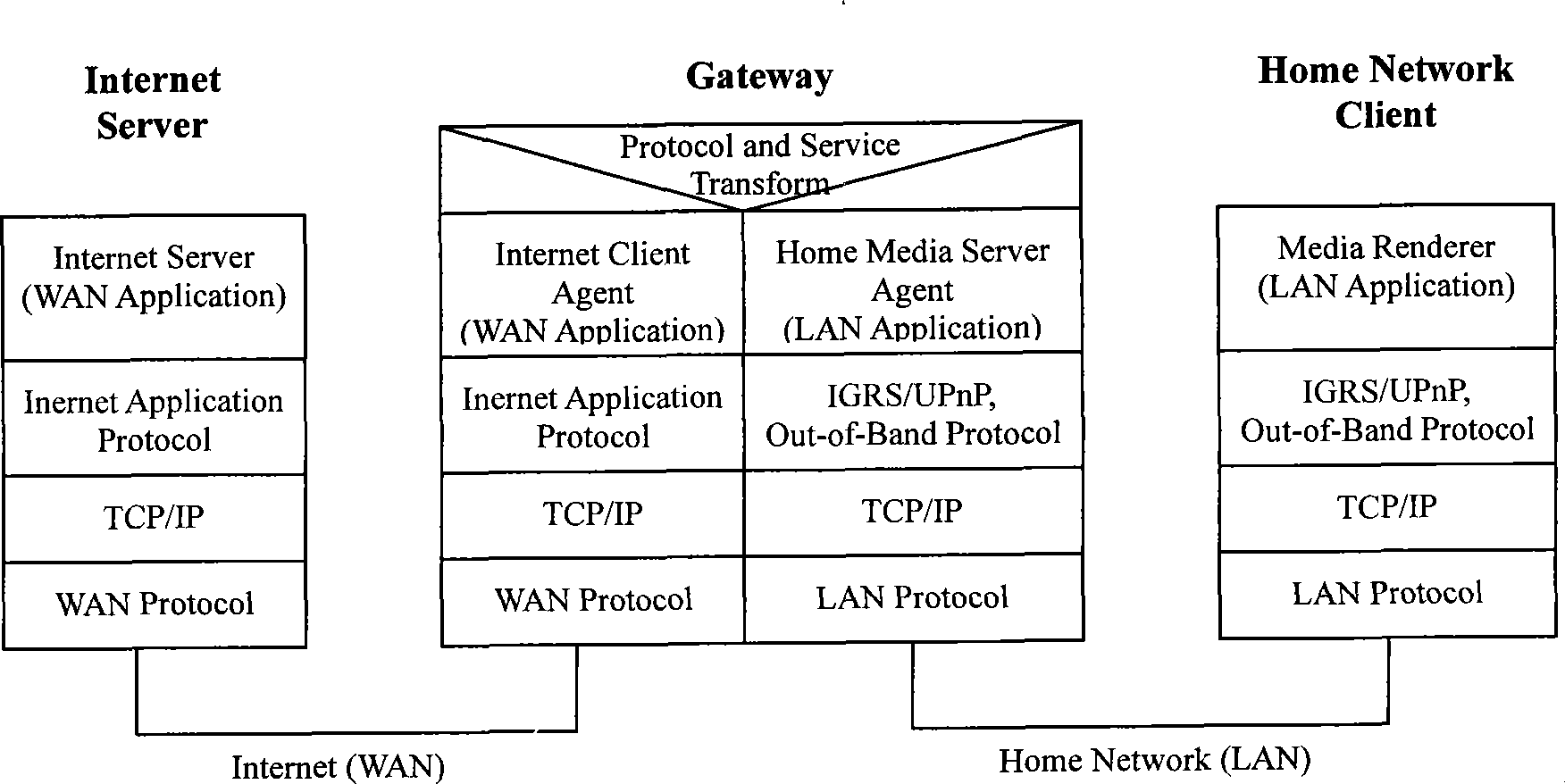
The invention discloses an internet terminal agent module, an application protocol and business conversion module and a digital family network server agent module which are sequentially connected. The internet terminal agent module is used for carrying out adaptation on the internet protocol and business, interacting with an external internet business server and acquiring the specific business from the internet server by an internet application protocol; the digital family network server agent module is used for carrying out adaptation on the digital family network protocol and business and providing the internet business which is converted into digital family network business for internal equipment of the digital family network by the mutual operation protocol of the digital family network; the application protocol and business conversion module is used for carrying out data forwarding, data format conversion, protocol conversion and business realizing mode conversion between the internet terminal agent module and the digital family network server agent module.
Owner:KONKA GROUP
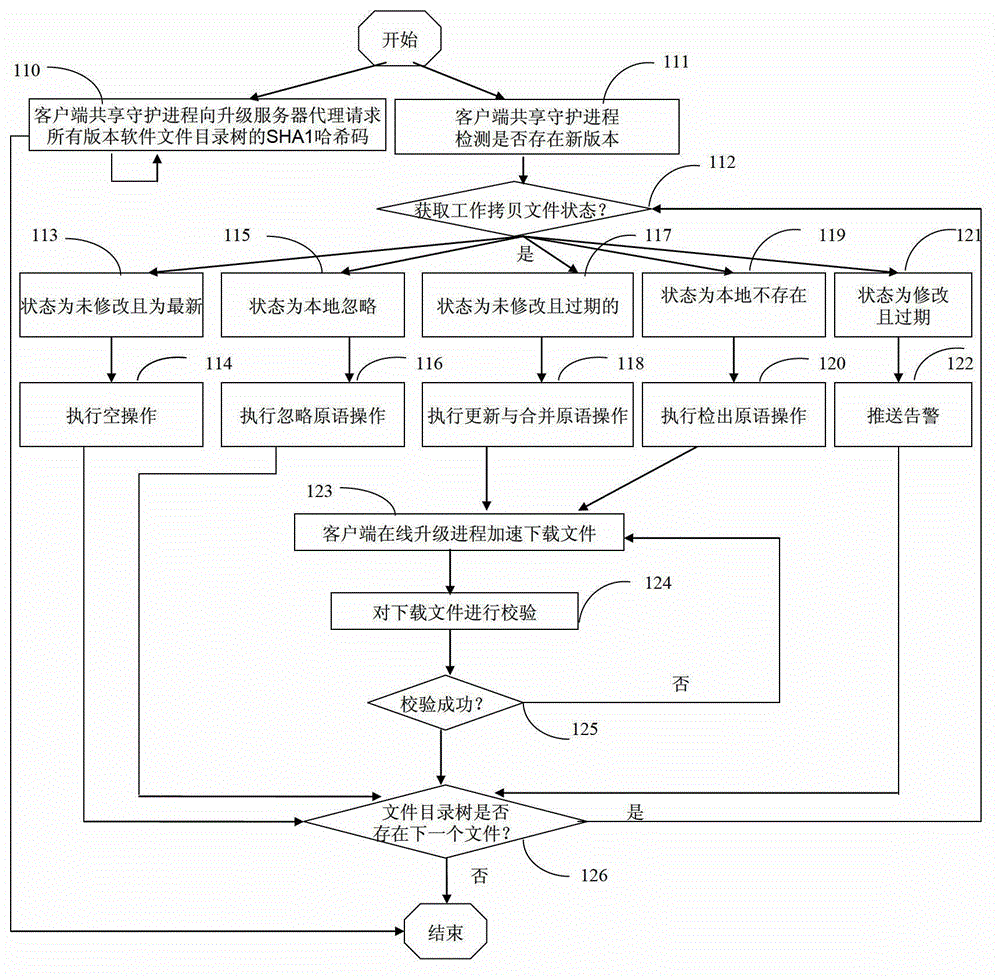
Method and device for software online updating and downloading acceleration
ActiveCN102868731AImplement addressingImplement storageProgram loading/initiatingTransmissionServer agentPrimitive operation
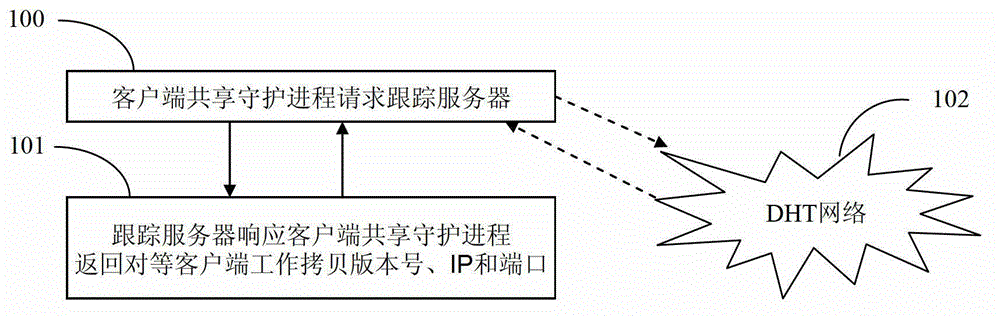
The invention relates to a method and a device for software online updating and downloading acceleration. The device comprises a client end online updating process device, a client end shared guard process device, a tracking server device, a updating server agent device and a plurality of updating server devices, stored contents in each updating server device are completely same to form an updating server pool in an annular queue, and real-time synchronization is realized via implementing a synchronizing primitive operation for version control by a version warehouse on each updating server device. The method is suitable for a situation of a large concurrency of client ends, the occupied updating server source is small, pressure of the updating servers is relieved, and the efficiency and service quality of the software online updating are improved.
Owner:UNIV OF JINAN
Smart road-toll-system
ActiveUS20110131238A1Convenient and accurateEasy to compressTicket-issuing apparatusRegistering/indicating working of vehiclesServer agentTime information
A road pricing smart client and method for a road pricing system enabling the removal of information from the positioning data describing the itinerary which suggest private data such as travelling speed and itinerary of the originator of the data. Accordingly, the smart client and method is configured to re-sample the original positioning points of the route into equidistant sections, remove timing information from the positioning data, slice the re-sampled route into slices shaped as those provided by other road users by employing a common “virtual grid”. By transmitting the slices in randomized order with an arbitrary delay, coherence of slices corresponding to formerly neighboring portions of the itinerary, are not correlated anymore. However, there is still enough information provided to the toll system to send an excerpt of the fee database allowing the smart pricing client or method to calculate the occurred fees.The main advantage of the smart client and method is that it delegates in a secure and privacy-preserving way the costly operations to the external toll server proxy. Thus, storage of digital maps in the client is not required, and tariff updates are only transmitted when necessary in a way that preserves privacy. Finally the data transmitted by the smart client can be preprocessed and compressed in order to remove all unnecessary personal information, thereby reducing the bandwidth requirements on the telecommunication network. Further, the proposed solution enables to raise statistics on road usage, i.e. traffic appearance by road-section without endangering privacy of the individual road users.
Owner:TITAN INTELLIGENCE TECH LTD
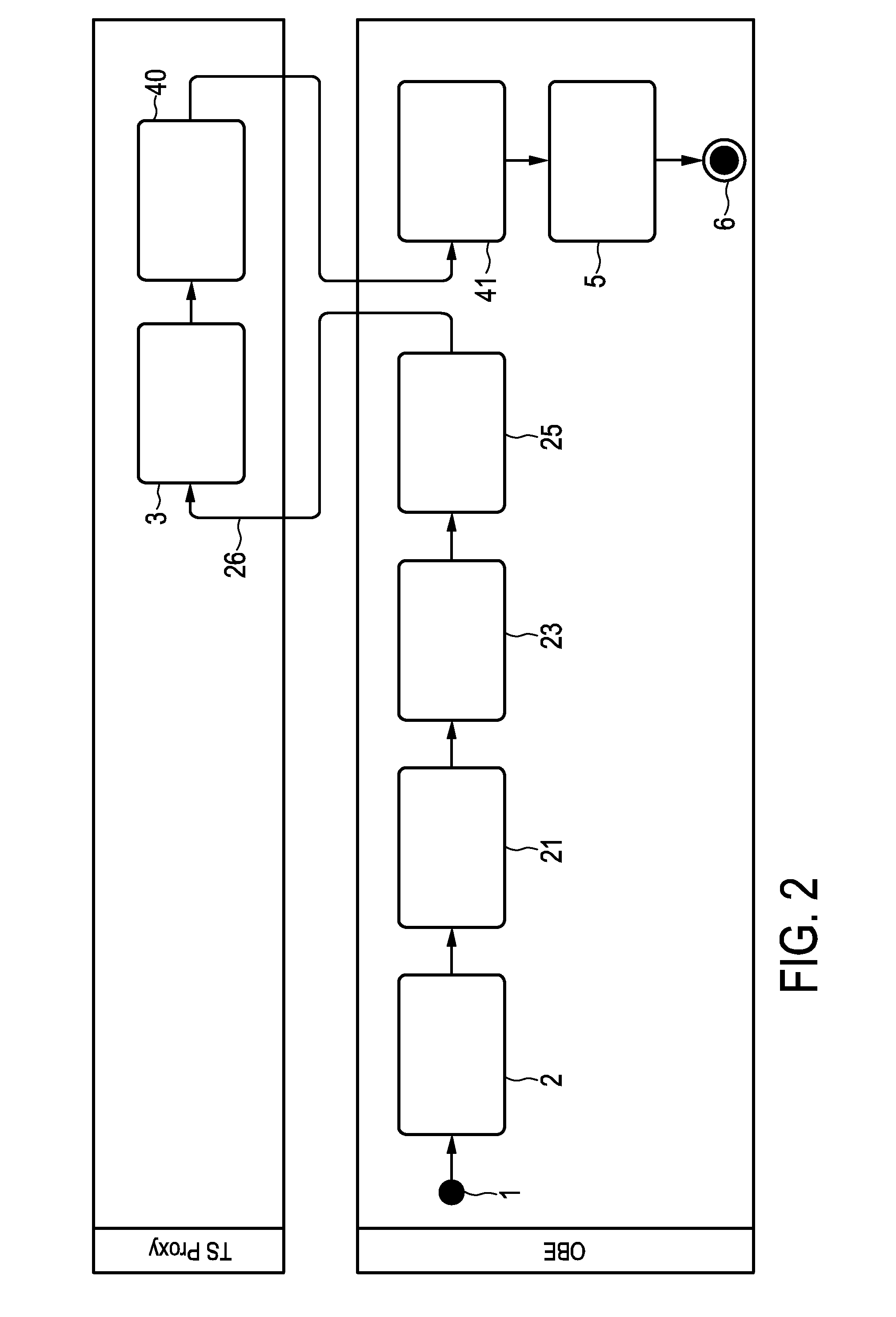
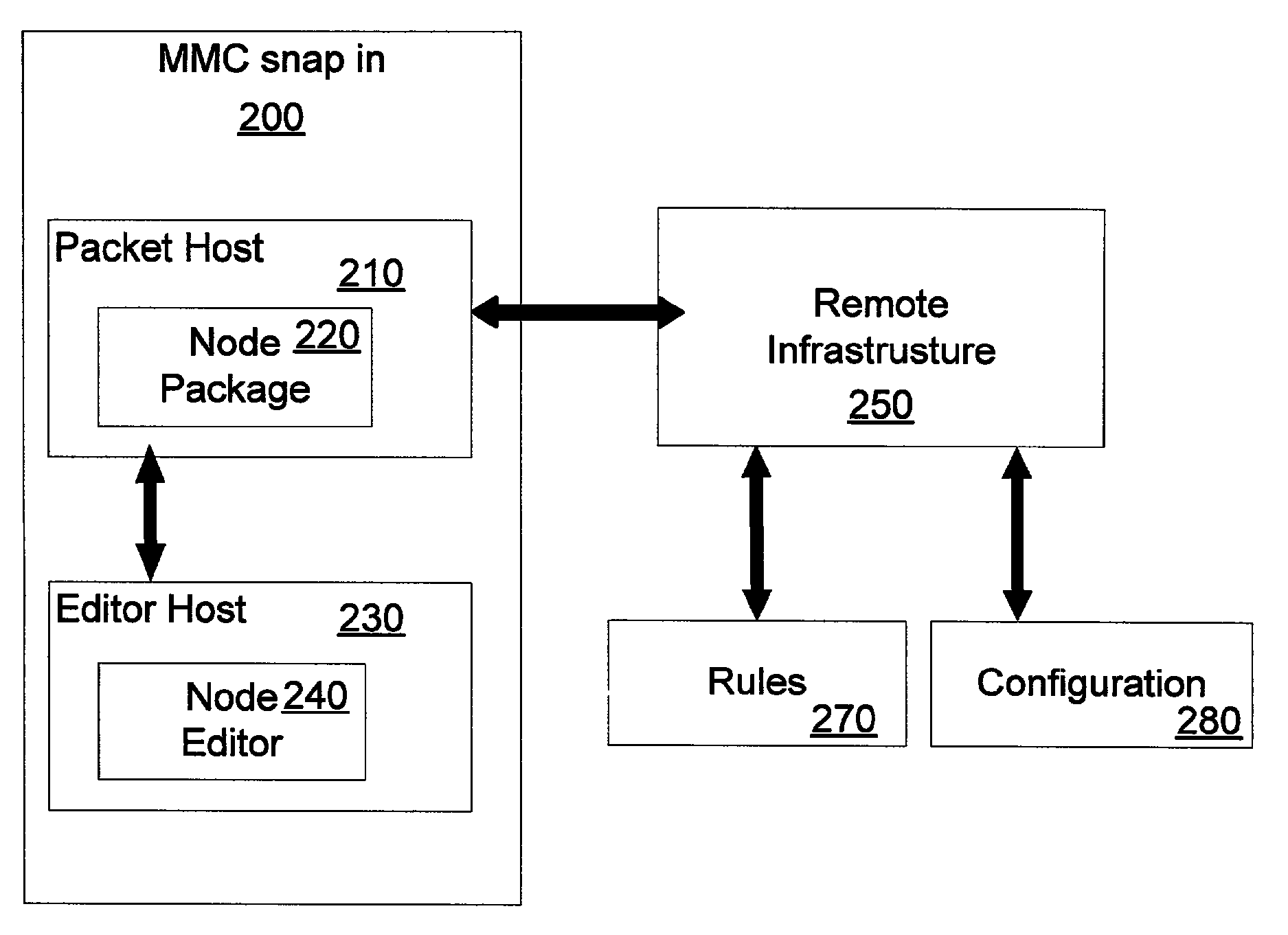
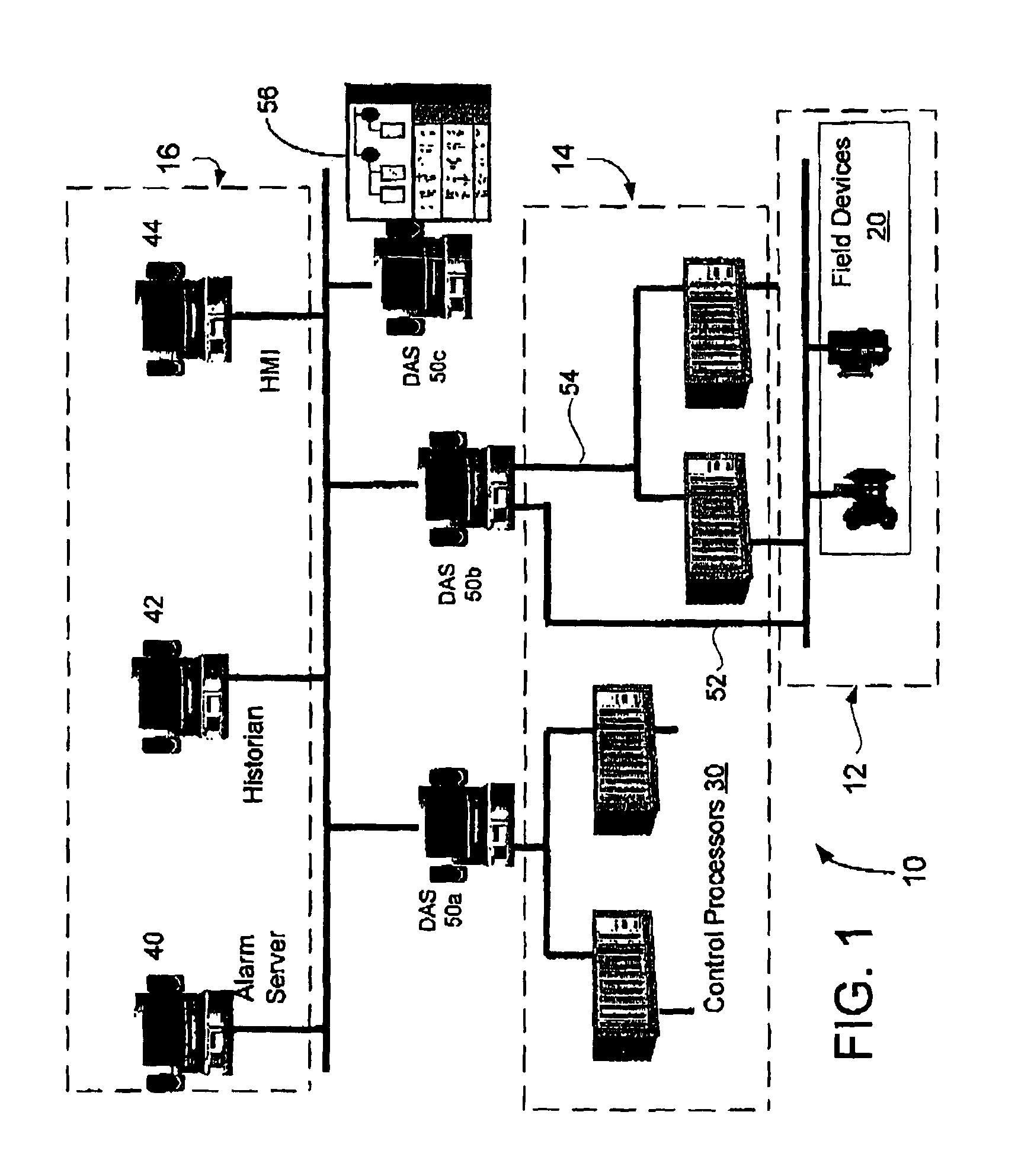
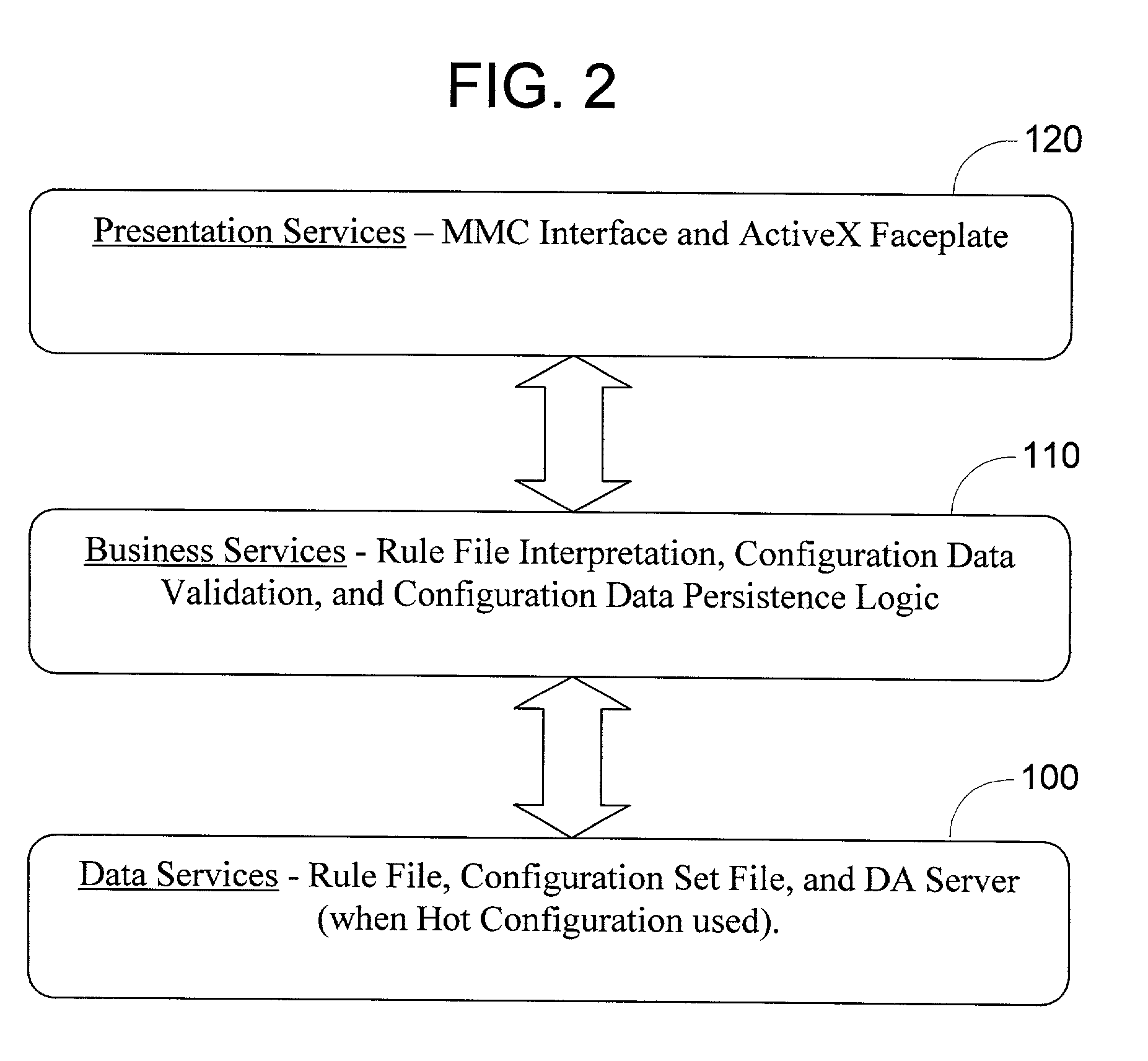
Method and system for remote configuration of process data access servers
ActiveUS7779089B2Facilitates remote configurationProgramme controlDigital computer detailsServer agentControl system
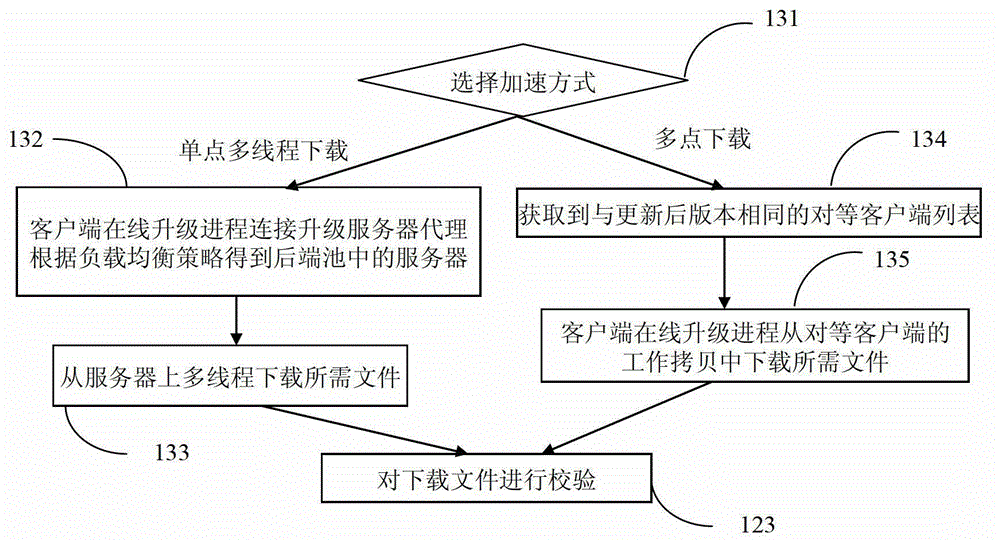
A remote configuration utility architecture is disclosed for a manufacturing / process control system data access server. Server agents, located on remote nodes, notify a configuration console of existing data access servers on the system. The configuration utility includes a control console from which a user selects one of the identified data access servers. Thereafter, the configuration console, via remote interfaces, obtains configuration parameters and associated rules associated with the selected data access server. The configuration utility thereafter displays the retrieved configuration information within a user interface faceplate defined for a type of configuration node selected for display / editing from the selected DAS. Using various faceplates for selected node types, the user creates, clears, examines and / or manipulates hierarchically arranged nodes for a configuration associated with the selected data access server.
Owner:SCHNEIDER ELECTRIC SOFTWARE LLC
Method and System for Transmission-Based Billing Applications
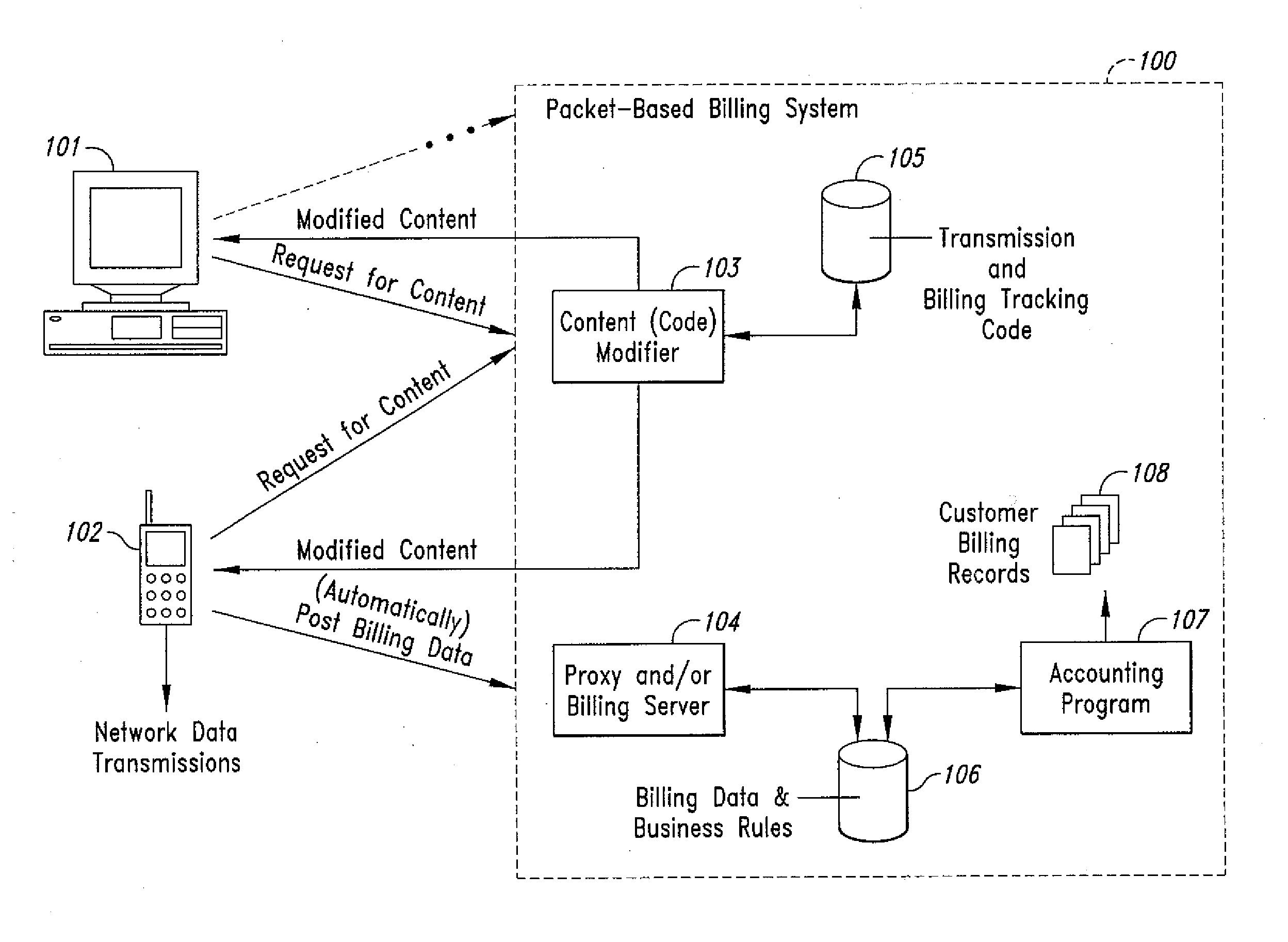
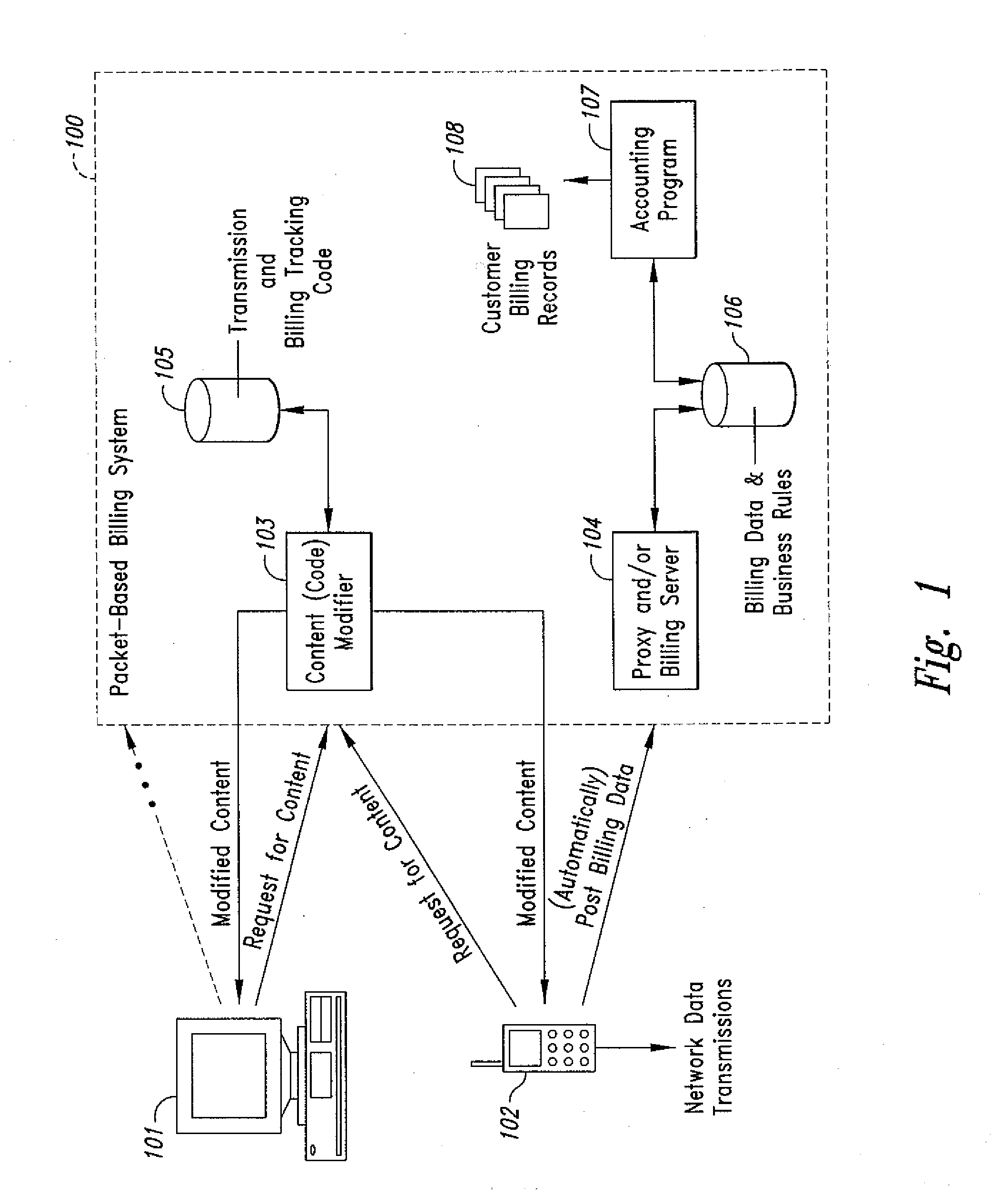
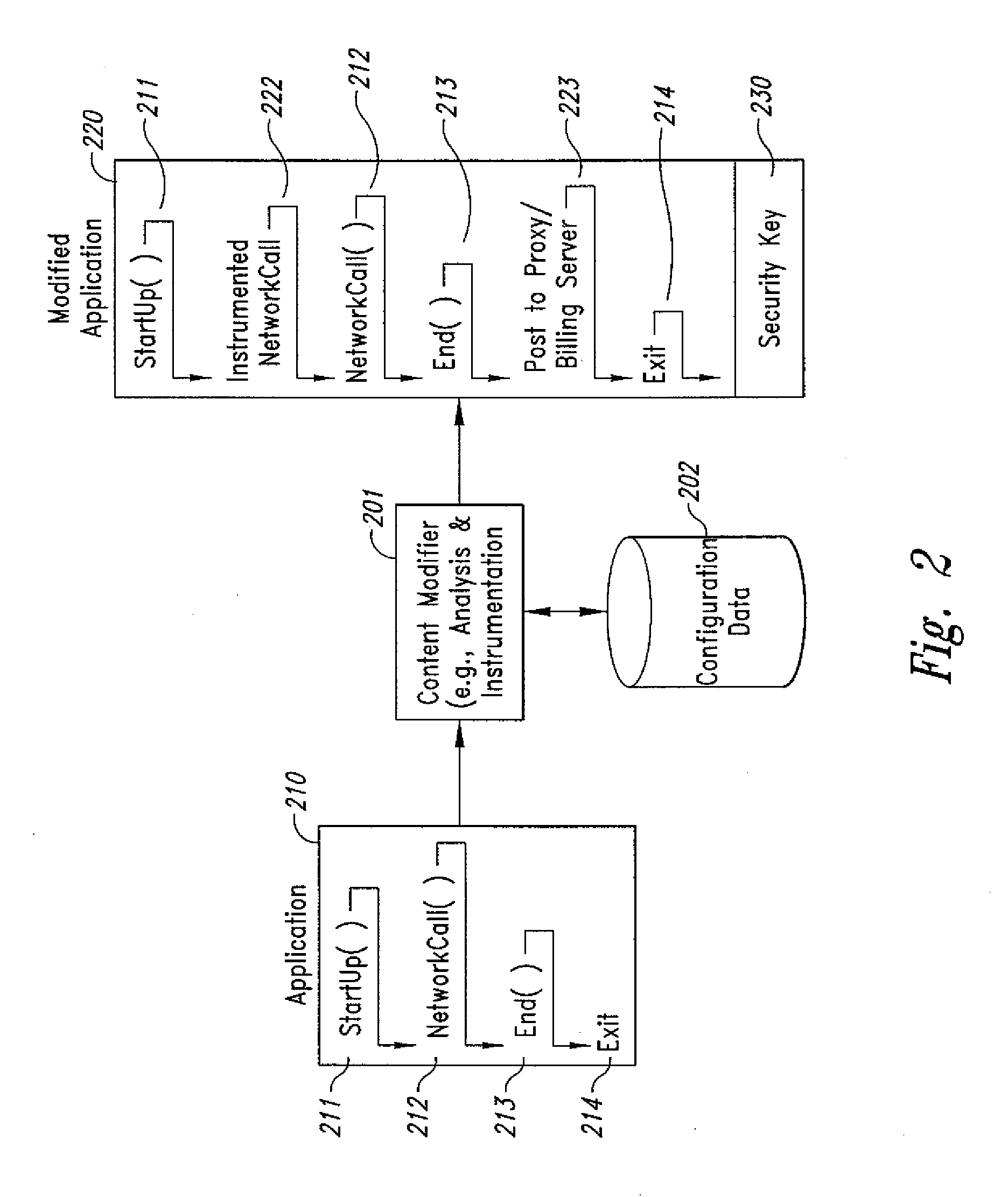
InactiveUS20070189514A1Short response timeImprove efficiencyMetering/charging/biilling arrangementsError preventionServer agentApplication computers
Computer- and network-based methods and systems for transmission-based billing are provided. Example embodiments provide a Packet-Based Billing System (“PBBS”), which enables application providers, such as carriers and content providers, to bill subscribers for the use of content on mobile subscriber devices, such as wireless devices, on a per-application, per-user basis based upon the extent of the usage. Embodiments of the present invention can also be used to bill subscribers for the use of content on a per-application, per-user basis for wired subscriber devices as well, using the same techniques. In operation, the PBBS provides modified content by inserting billing and tracking code into content returned to a requesting device. The modified content, when executed, tracks the amount of data sent and received between the content and a network and posts the accumulated data to a proxy / billing server according to business rules for an interval / frequency to post such data. The proxy / billing server stores the raw billing data and an accounting program retrieves the billing data to generate customer (call) data records. Business rules that specific different charges for different content or users can be incorporated into the system.
Owner:MOTOROLA MOBILITY LLC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com