Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
80 results about "Fat client" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
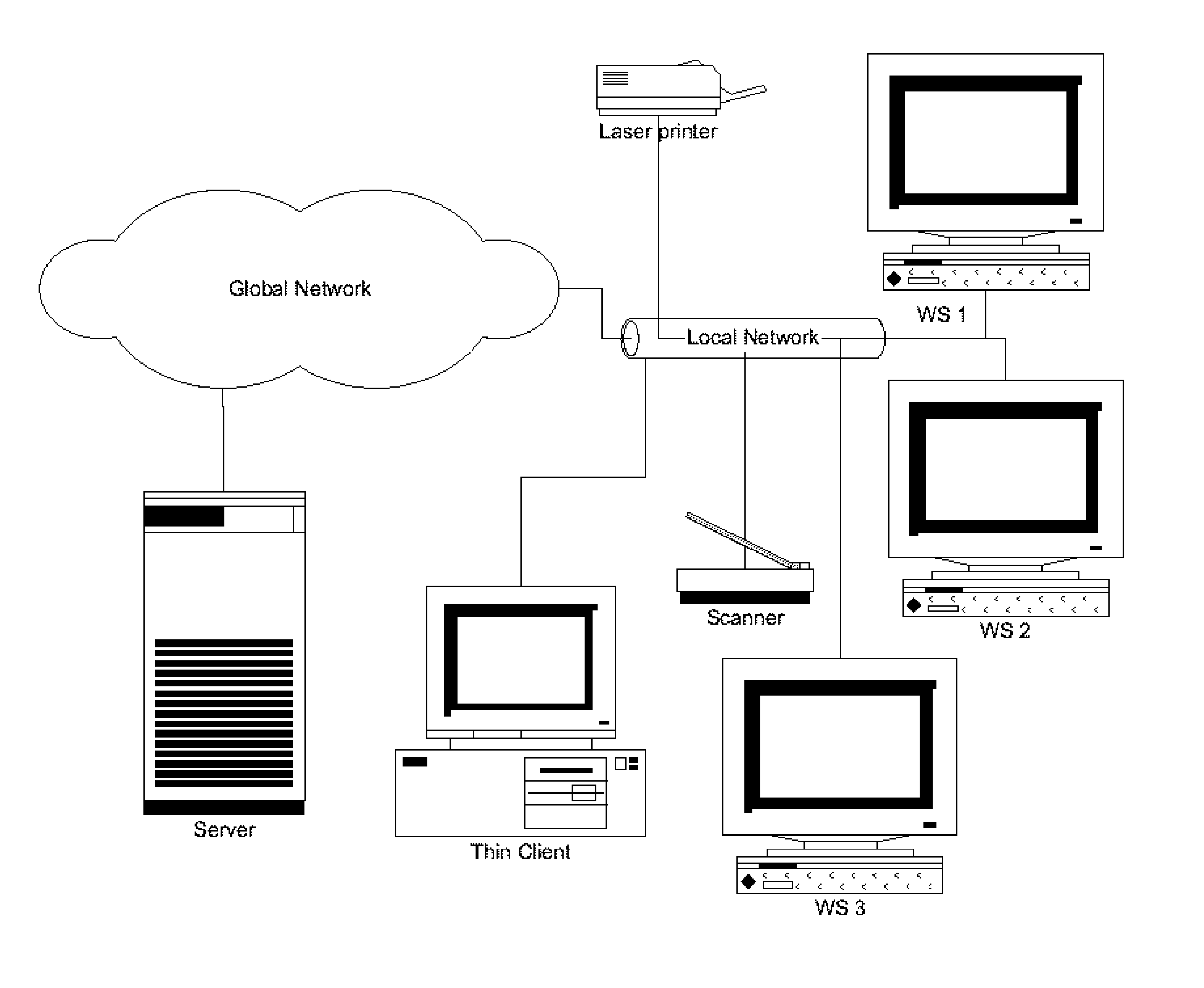
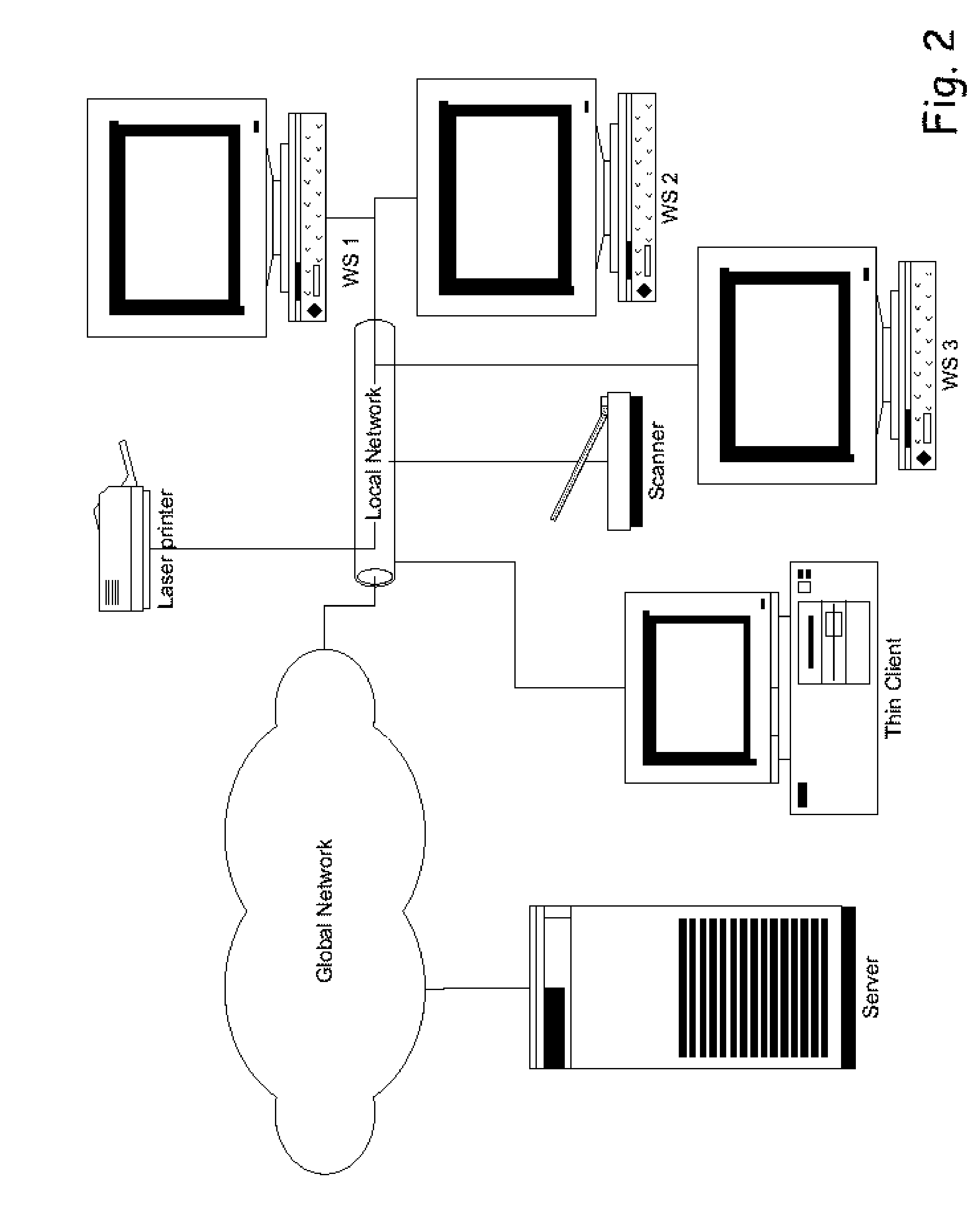
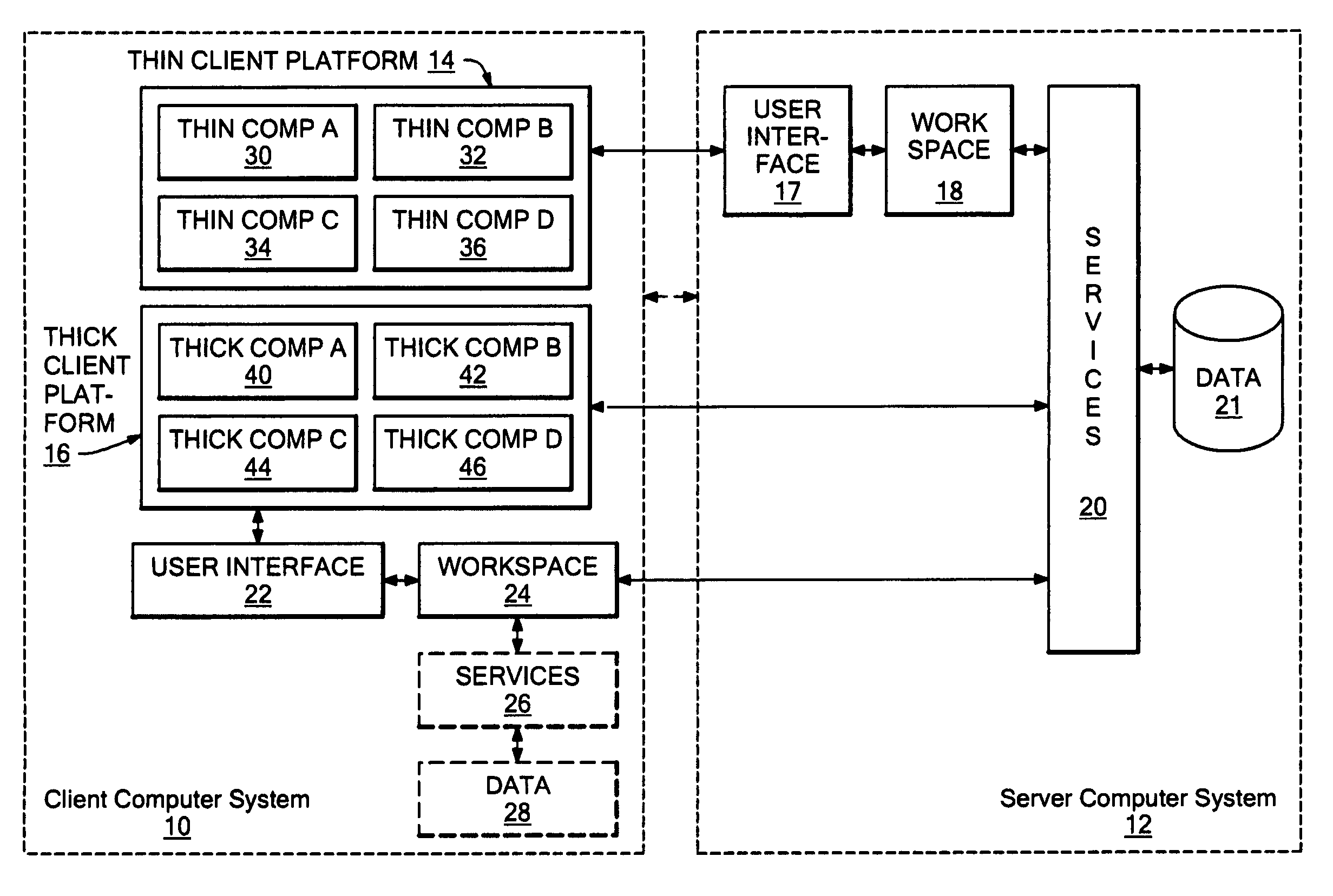
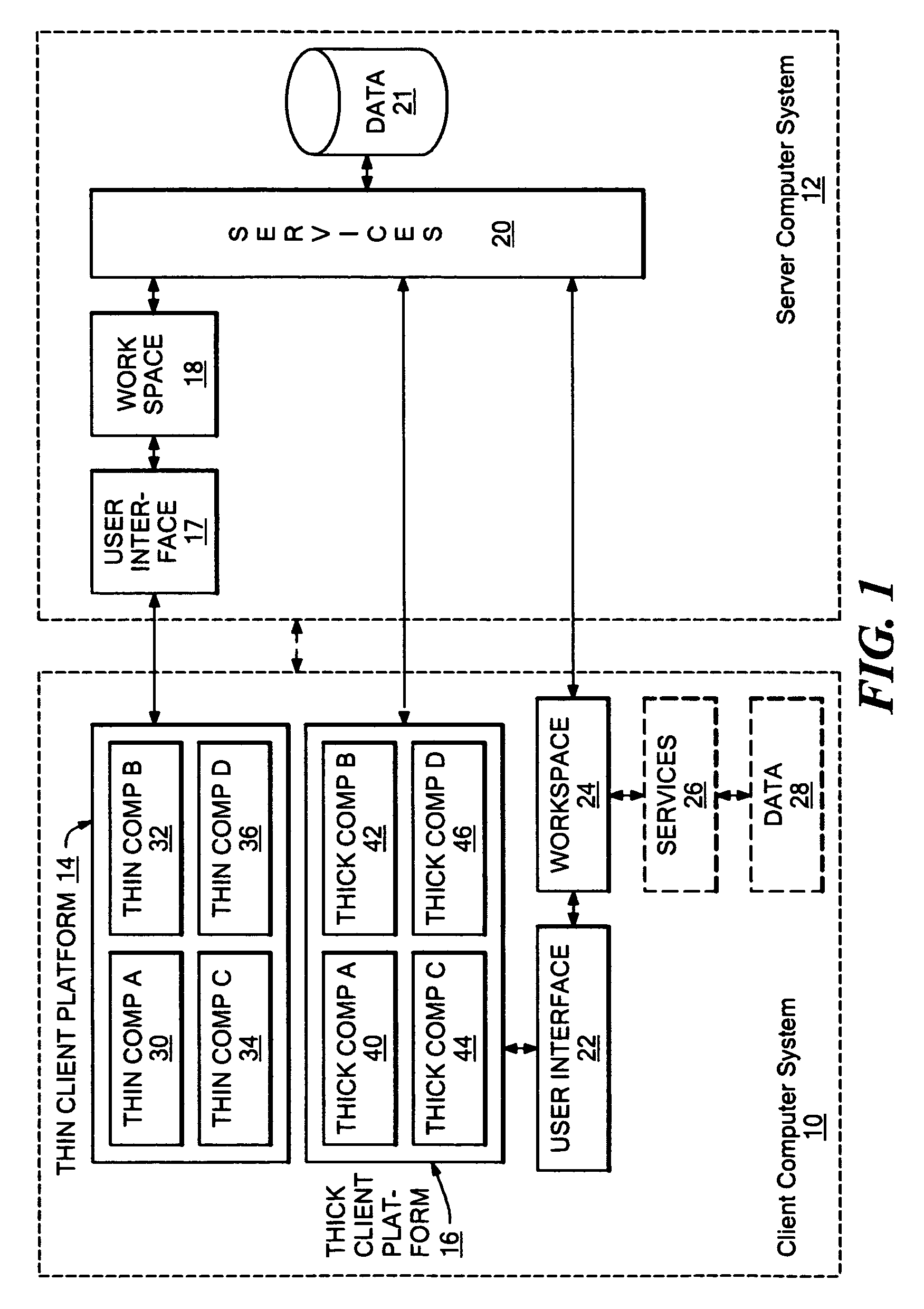
A fat client (also called heavy, rich or thick client) is a computer (clients), in client–server architecture or networks, that typically provides rich functionality independent of the central server. Originally known as just a "client" or "thick client," the name is contrasted to thin client, which describes a computer heavily dependent on a server's applications. A fat client may be described as having a rich user interaction.
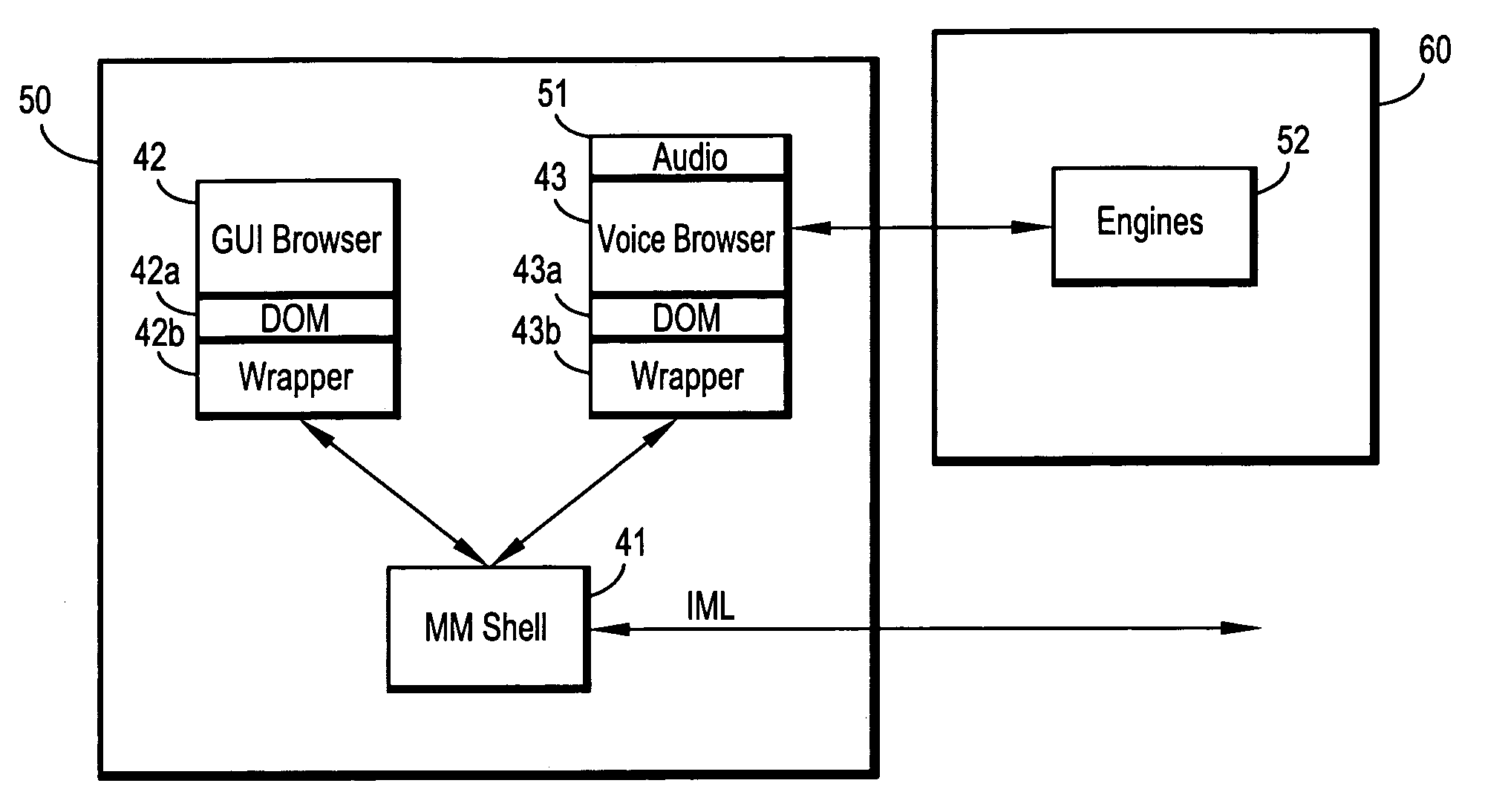
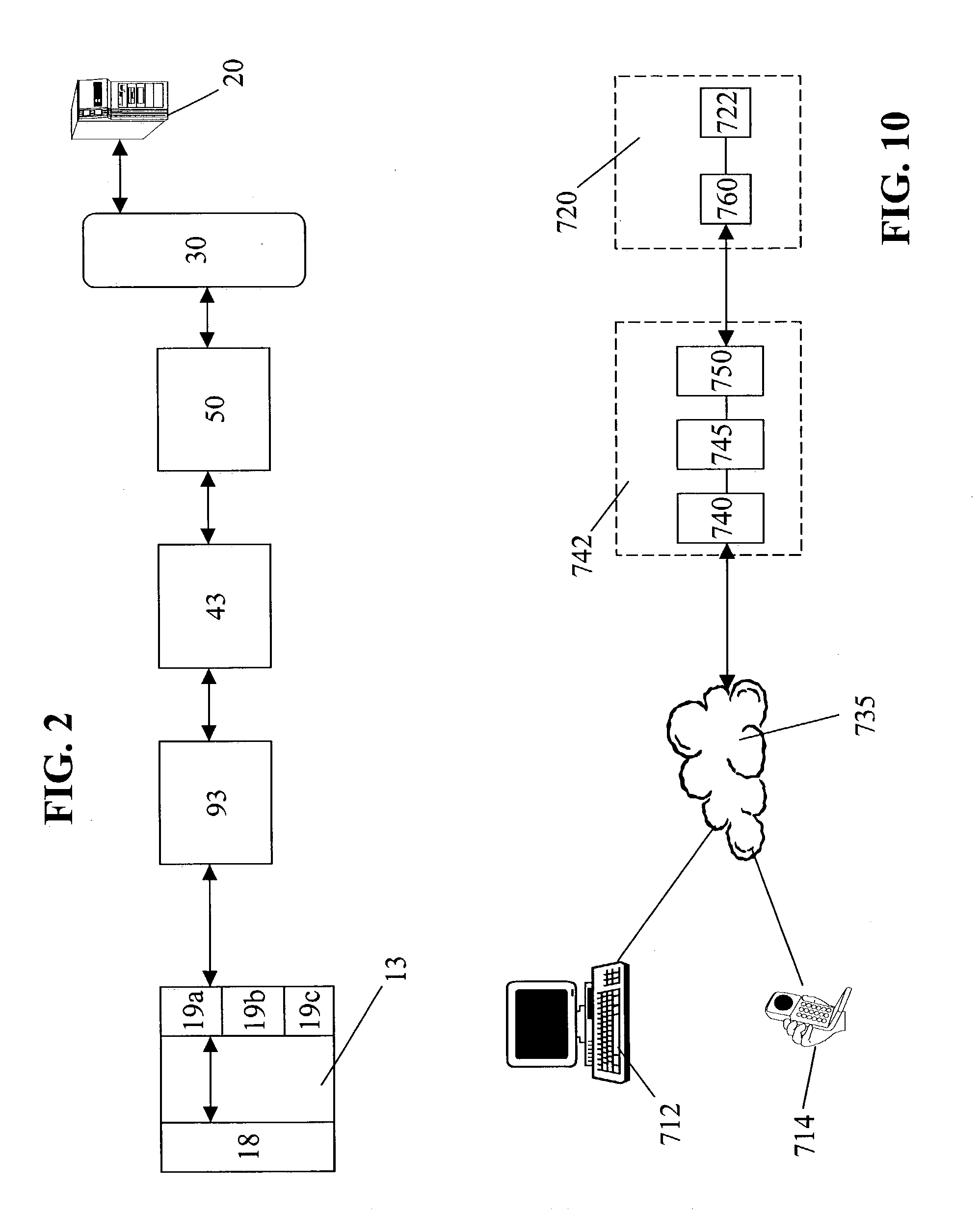
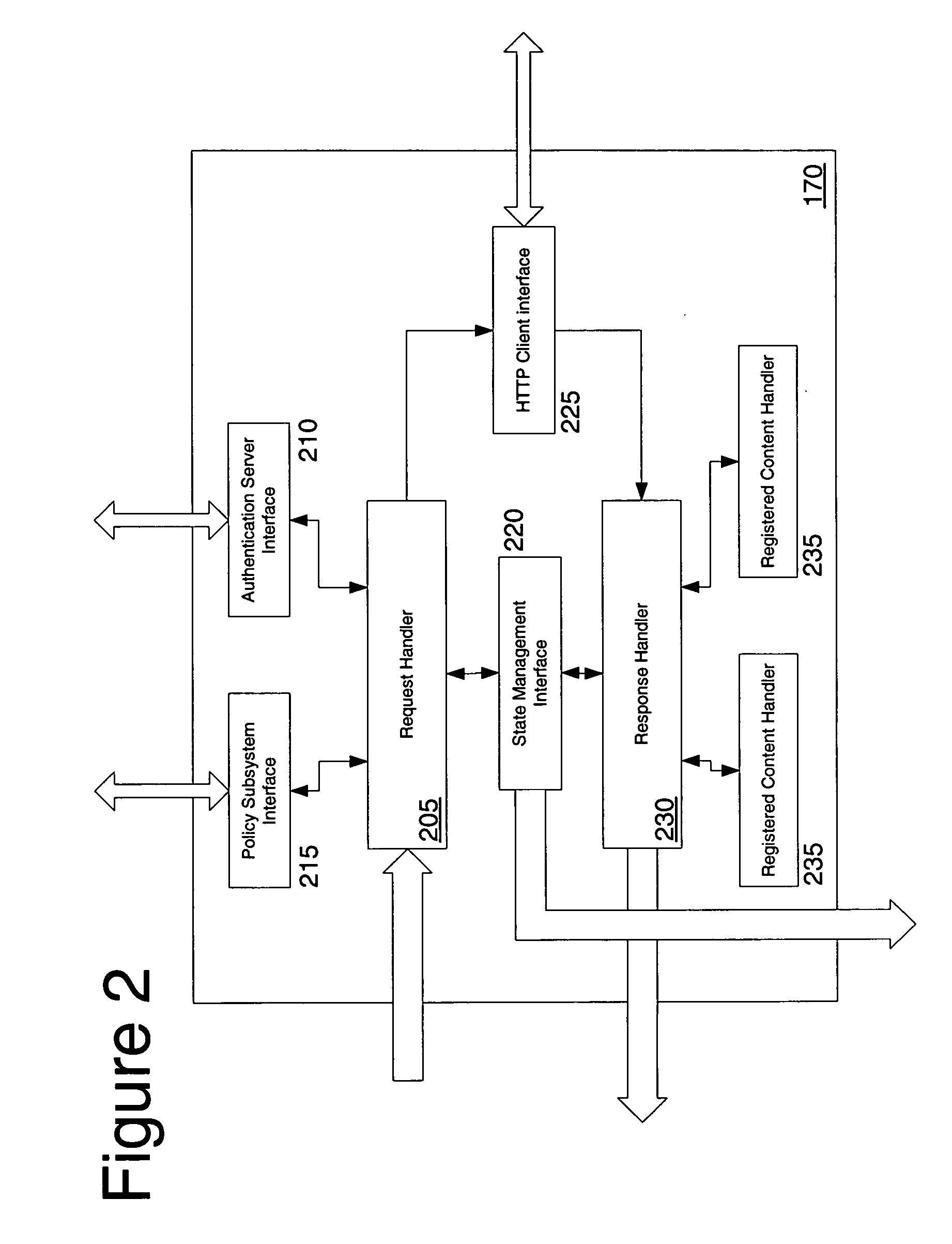
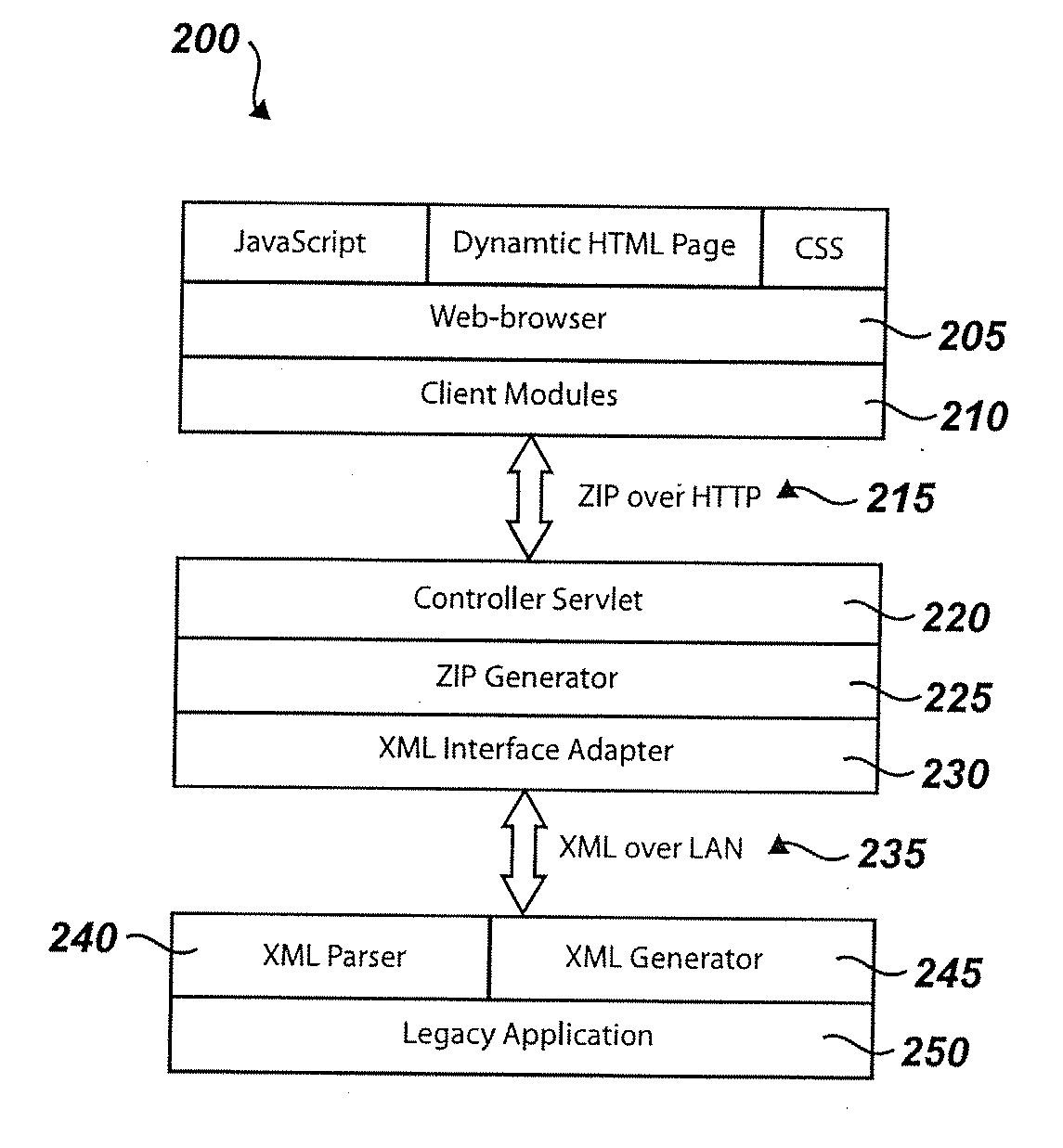
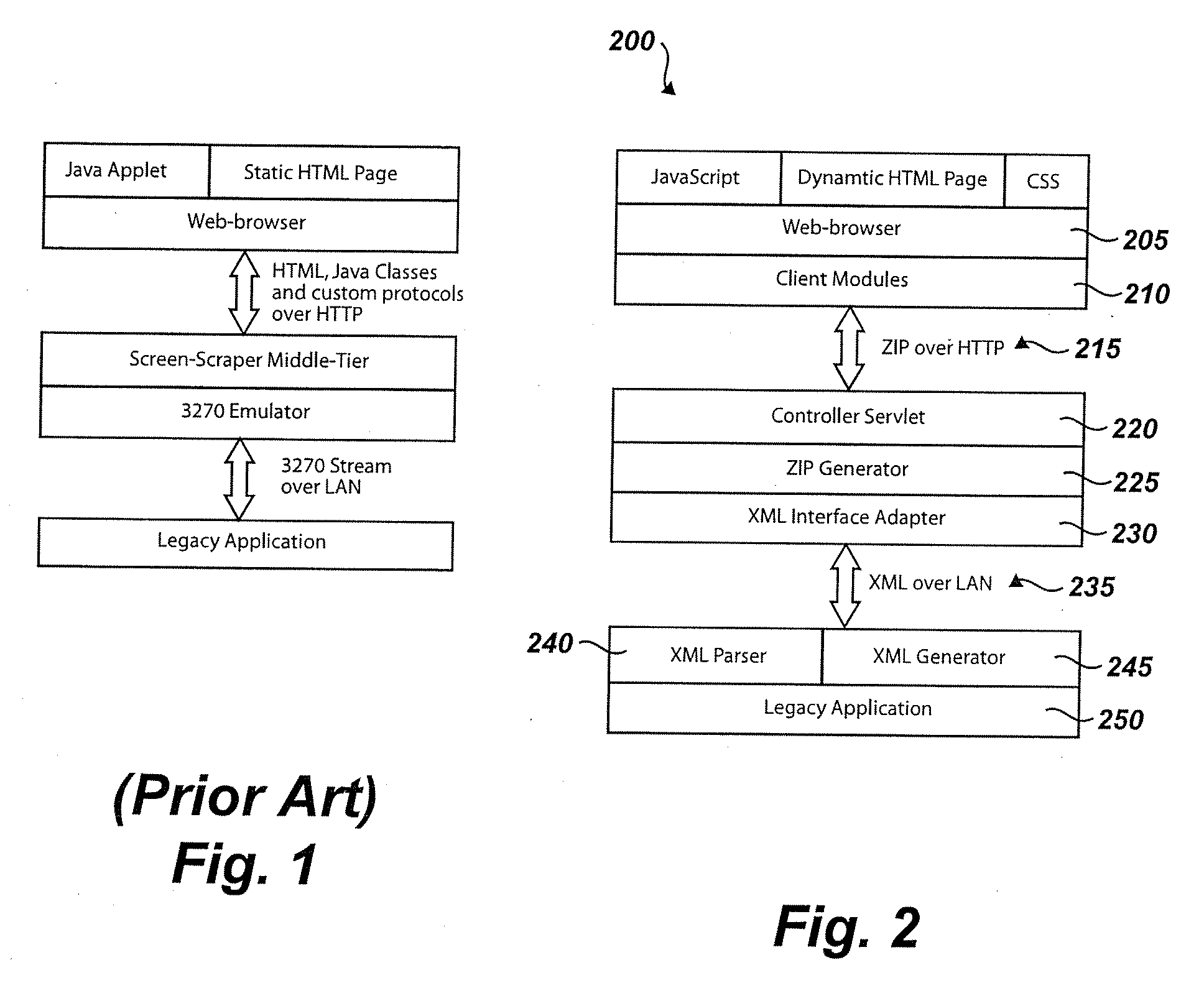
Systems and methods for implementing modular DOM (Document Object Model)-based multi-modal browsers
Systems and methods for building multi-modal browsers applications and, in particular, to systems and methods for building modular multi-modal browsers using a DOM (Document Object Model) and MVC (Model-View-Controller) framework that enables a user to interact in parallel with the same information via a multiplicity of channels, devices, and / or user interfaces, while presenting a unified, synchronized view of such information across the various channels, devices and / or user interfaces supported by the multi-modal browser. The use of a DOM framework (or specifications similar to DOM) allows existing browsers to be extended without modification of the underling browser code. A multi-modal browser framework is modular and flexible to allow various fat client and thin (distributed) client approaches.
Owner:IBM CORP
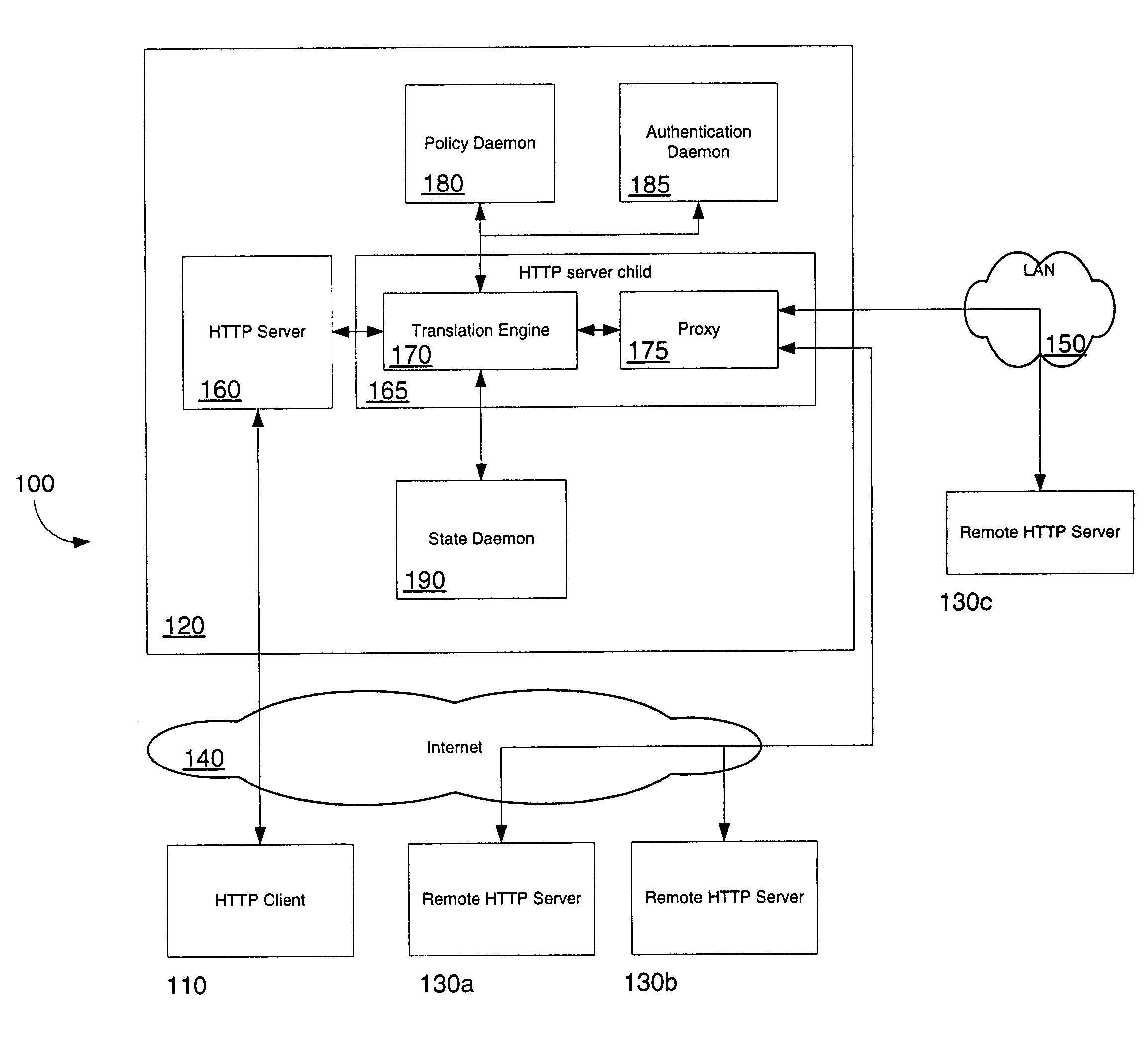
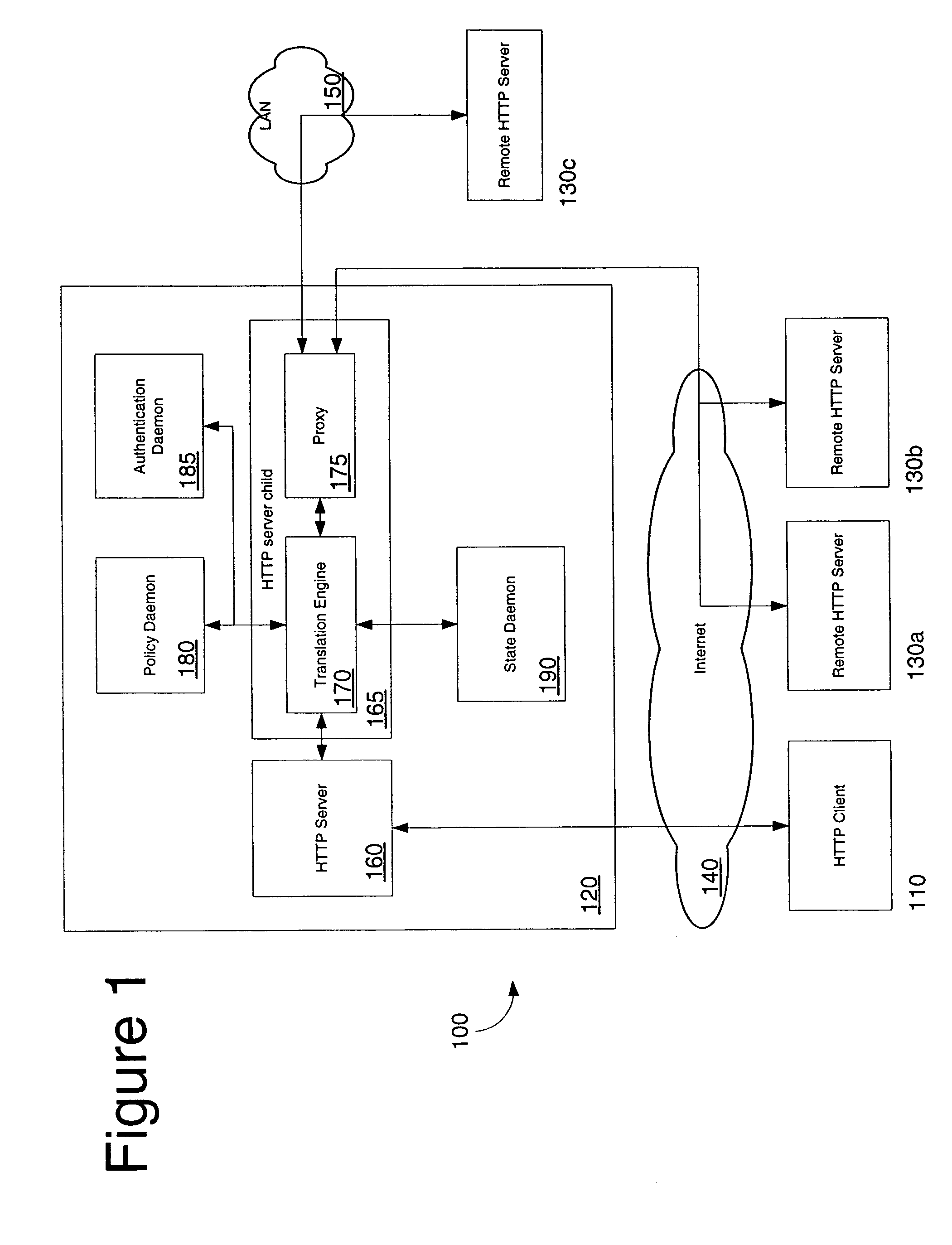
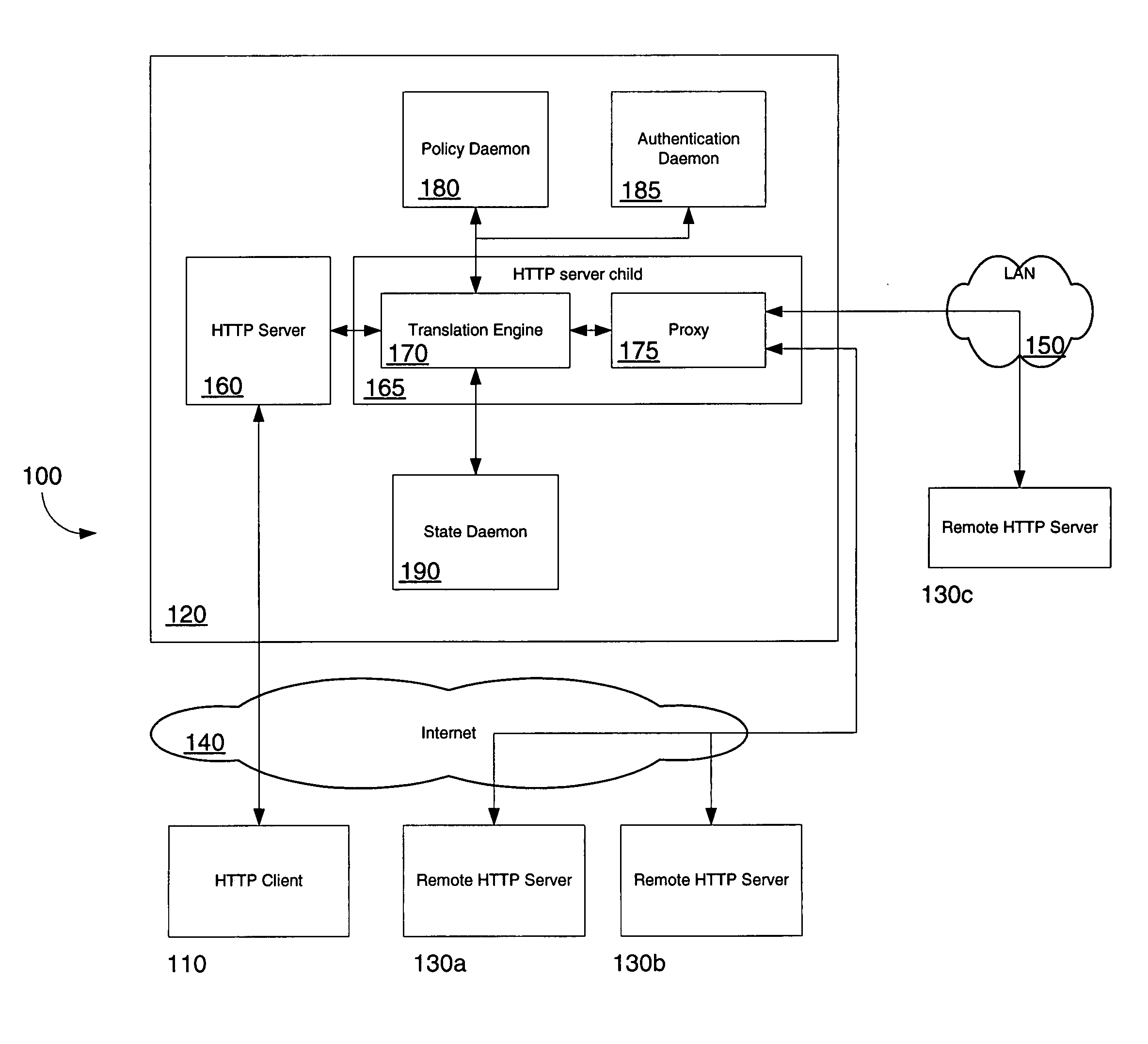
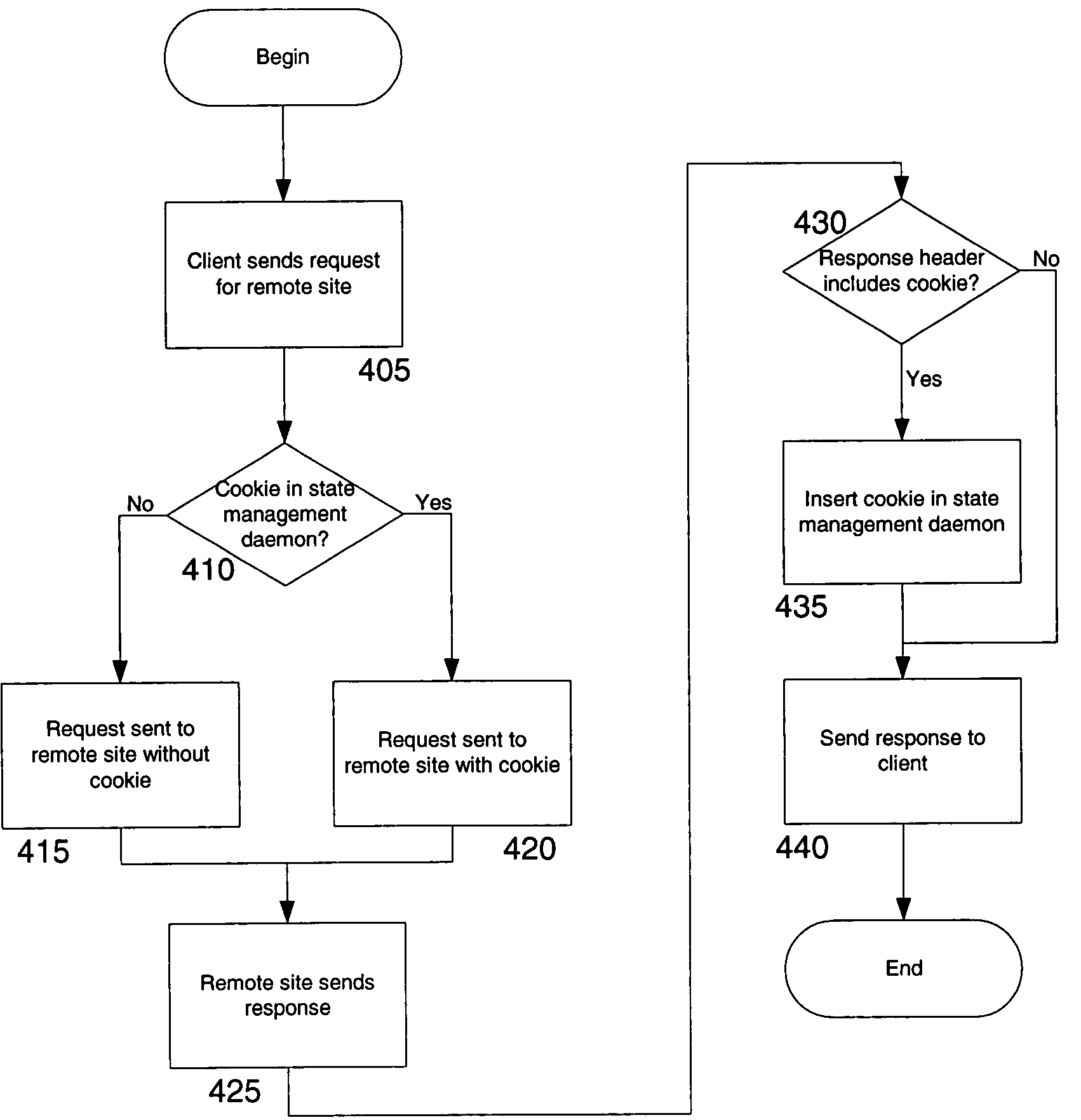
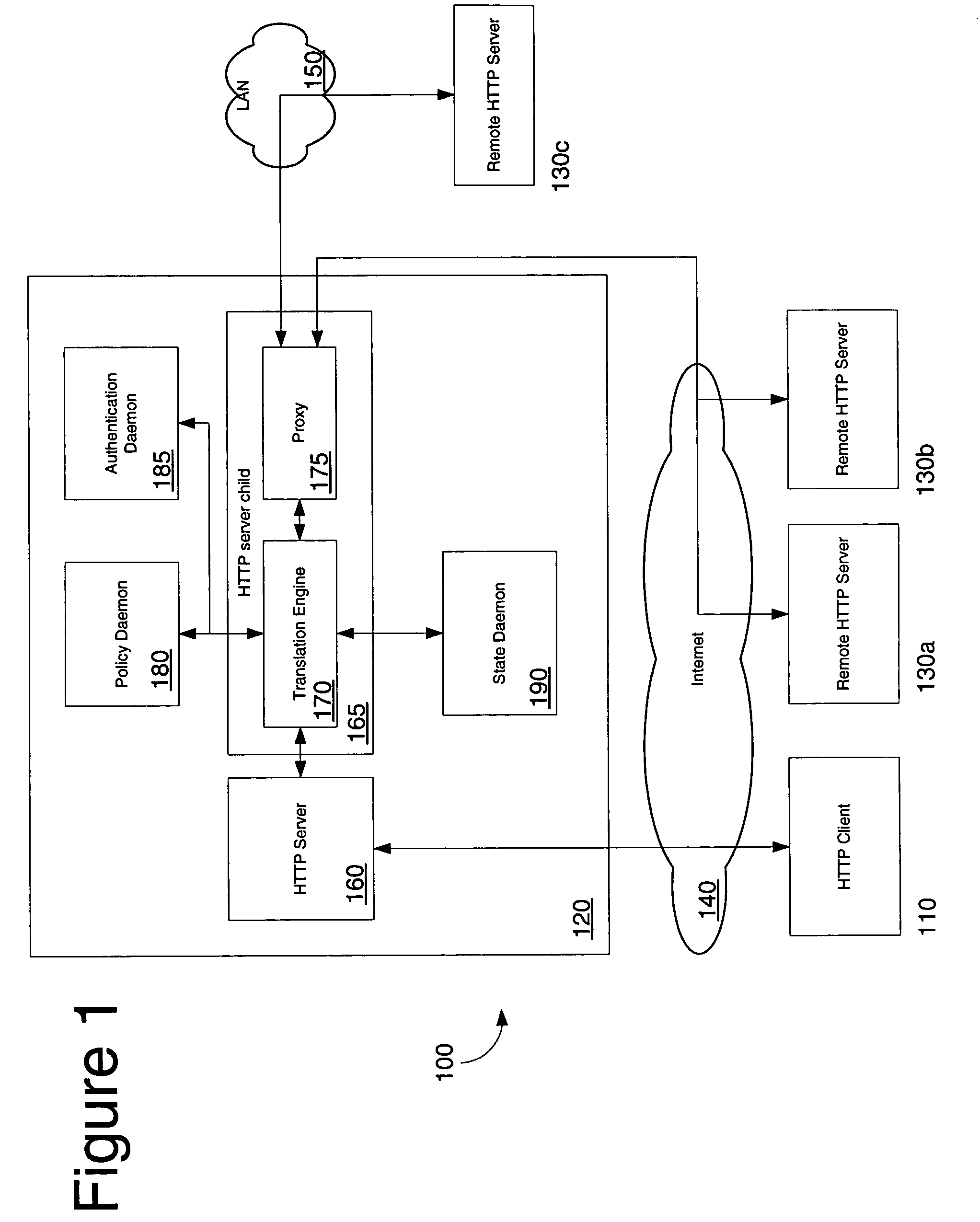
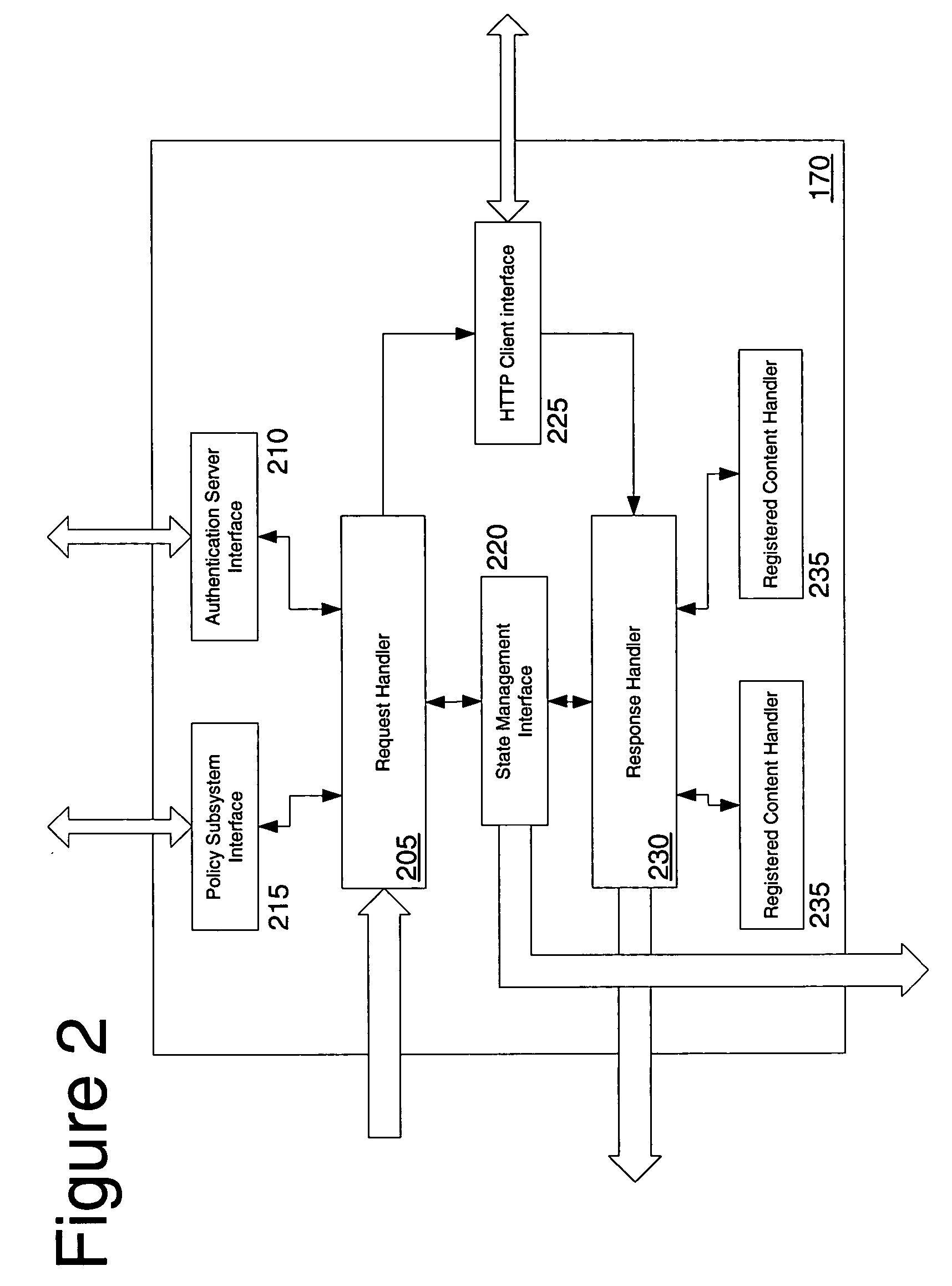
Network access using secure tunnel
InactiveUS20050273849A1Multiple digital computer combinationsProgram controlServer agentSecure communication
A security platform connected to a private network permits access to the private network from a public network (such as the Internet) through a variety of mechanisms. A reverse proxy system operating as part of the security platform provides access to web-enabled applications from a browser connected to the public network. The reverse proxy rewrites requests and responses so that the browser directs requests to the reverse proxy, from which the requests can be directed to the appropriate server on the public network or the private network. Responses come back to the reverse proxy, and are then forwarded to the browser. An SSL tunneling system permits fat clients to access the private network through an SSL connection. The SSL tunneling system employs a server component operating on the security platform and components downloaded to the client computer from the security platform. The client components include a control component operating in a browser window, a server-proxy component that sets up secure communications with the private network, and an adapter component between the server-proxy and the fat client. The adapter component operates in kernel space. Data is directed from the fat client to the adapter, and then forwarded to the server-proxy; data from the server-proxy is directed to the adapter, and then forwarded to the fat client. Security is provided through the use of multiple authentication realms, each of which provides a set of authentication stages for authenticating users and providing client integrity validation.
Owner:AEP NETWORKS
Lottery management system
InactiveUS20030228910A1Easy to integrateImprove reliabilityPaper-money testing devicesPayment architectureSystems managementSoftware development
A lottery management system provides the ability to integrate various lottery system types into a single lottery management solution so as to allow the customized deployment of various lottery system attributes. In one embodiment, lottery system attributes include game types, reporting functions, system administration, point-of-sale integration, device and network-specific interfaces and retail management. The present invention can include a lottery transaction server, a message exchange component, thin client components, thick client components and software development kits.
Owner:GTECH RHODE ISLAND CORP
Network access using multiple authentication realms
InactiveUS20050251856A1Multiple digital computer combinationsProgram controlServer agentSecure communication
A security platform connected to a private network permits access to the private network from a public network (such as the Internet) through a variety of mechanisms. A reverse proxy system operating as part of the security platform provides access to web-enabled applications from a browser connected to the public network. The reverse proxy rewrites requests and responses so that the browser directs requests to the reverse proxy, from which the requests can be directed to the appropriate server on the public network or the private network. Responses come back to the reverse proxy, and are then forwarded to the browser. An SSL tunneling system permits fat clients to access the private network through an SSL connection. The SSL tunneling system employs a server component operating on the security platform and components downloaded to the client computer from the security platform. The client components include a control component operating in a browser window, a server-proxy component that sets up secure communications with the private network, and an adapter component between the server-proxy and the fat client. The adapter component operates in kernel space. Data is directed from the fat client to the adapter, and then forwarded to the server-proxy; data from the server-proxy is directed to the adapter, and then forwarded to the fat client. Security is provided through the use of multiple authentication realms, each of which provides a set of authentication stages for authenticating users and providing client integrity validation.
Owner:AEP NETWORKS
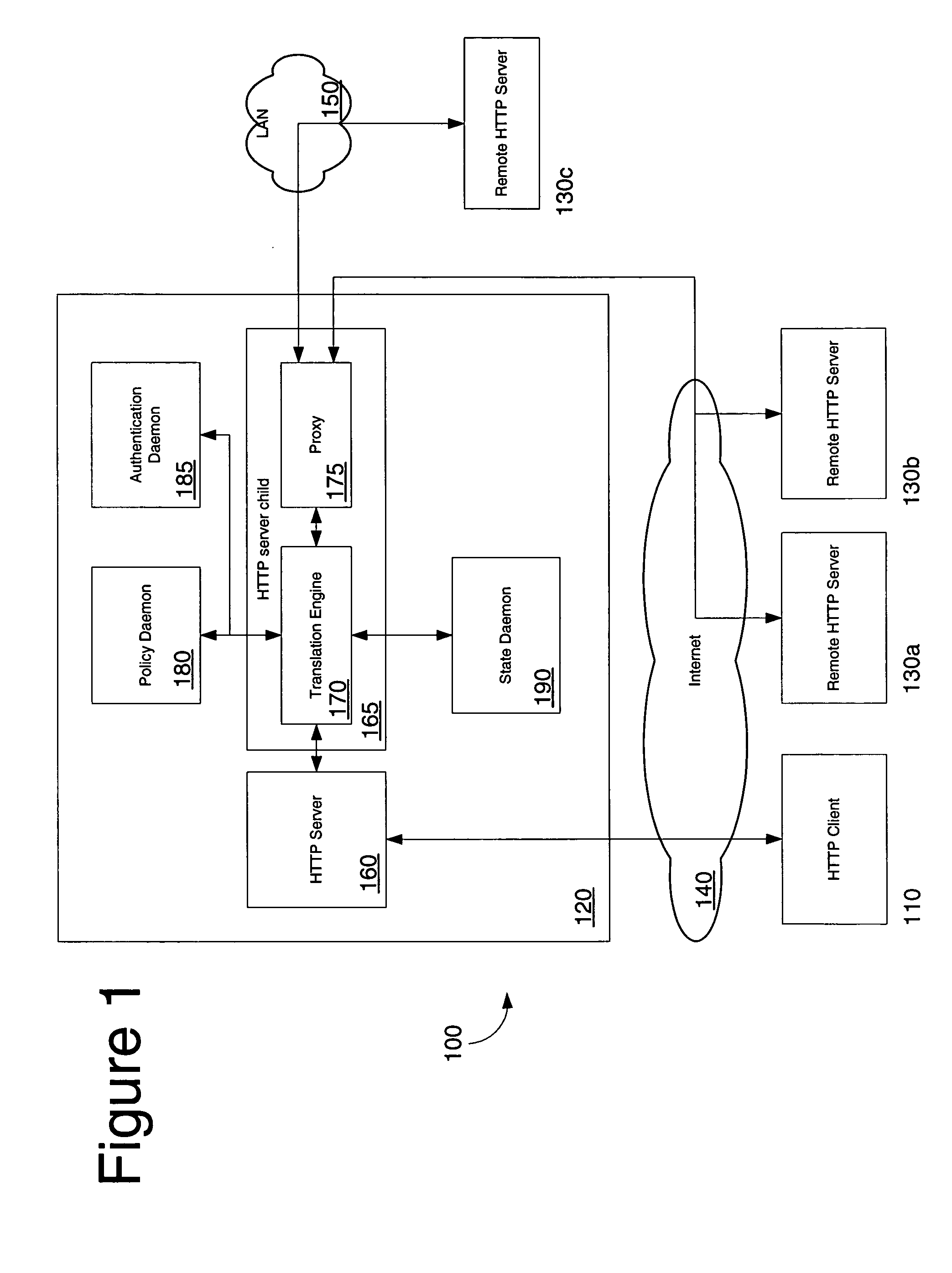
Network access using reverse proxy
InactiveUS20050262357A1Computer security arrangementsSecret communicationSecure communicationServer agent
A security platform connected to a private network permits access to the private network from a public network (such as the Internet) through a variety of mechanisms. A reverse proxy system operating as part of the security platform provides access to web-enabled applications from a browser connected to the public network. The reverse proxy rewrites requests and responses so that the browser directs requests to the reverse proxy, from which the requests can be directed to the appropriate server on the public network or the private network. Responses come back to the reverse proxy, and are then forwarded to the browser. An SSL tunneling system permits fat clients to access the private network through an SSL connection. The SSL tunneling system employs a server component operating on the security platform and components downloaded to the client computer from the security platform. The client components include a control component operating in a browser window, a server-proxy component that sets up secure communications with the private network, and an adapter component between the server-proxy and the fat client. The adapter component operates in kernel space. Data is directed from the fat client to the adapter, and then forwarded to the server-proxy; data from the server-proxy is directed to the adapter, and then forwarded to the fat client. Security is provided through the use of multiple authentication realms, each of which provides a set of authentication stages for authenticating users and providing client integrity validation.
Owner:AEP NETWORKS
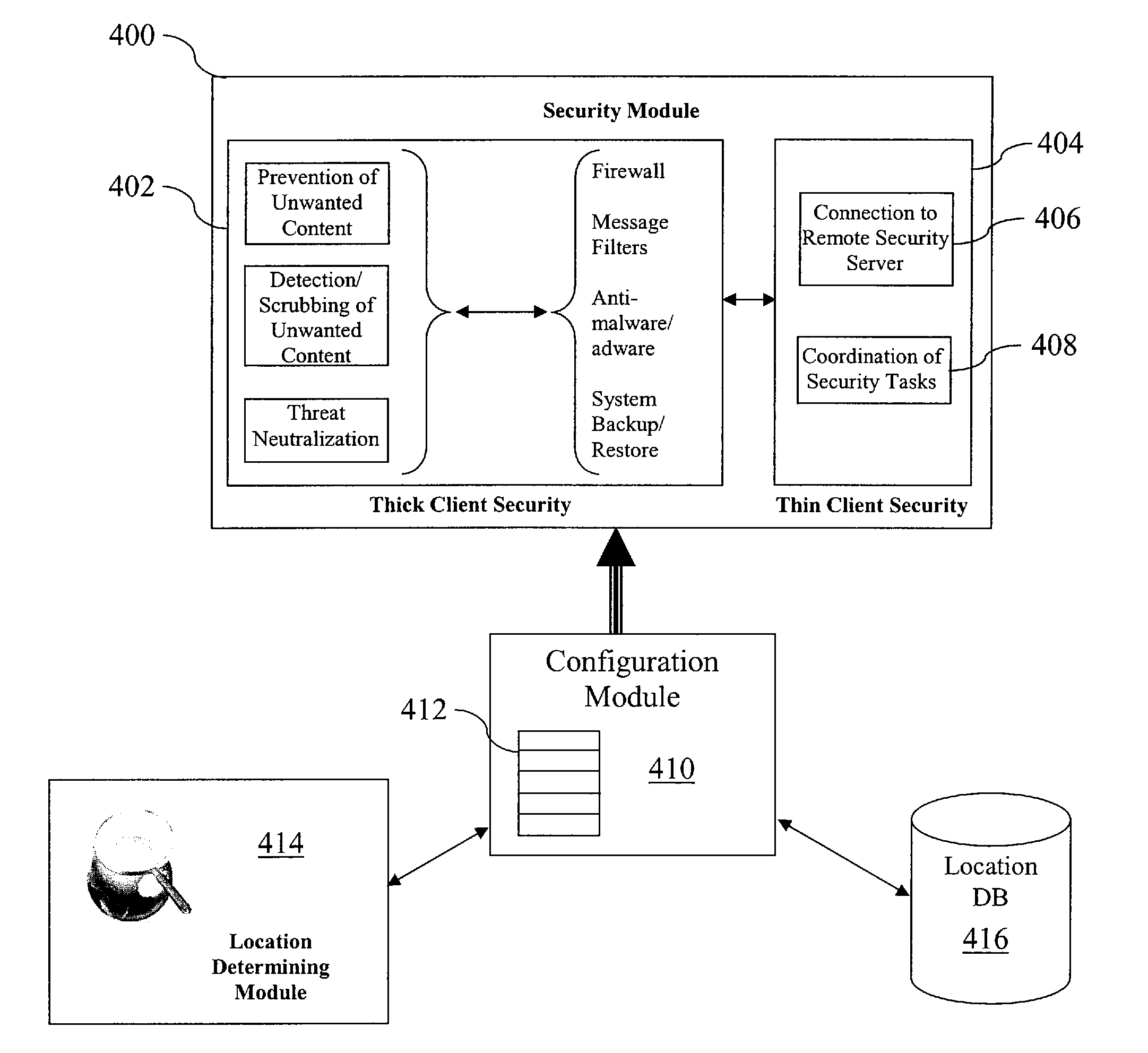
Adaptive security for portable information devices
ActiveUS7607174B1Facilitates selectively providing security serviceMemory loss protectionError detection/correctionInformation deviceClient-side
A portable information device includes a dynamically configurable security arrangement in which operational settings are automatically and dynamically configured for either thick client or thin client protection schemes based at least in part on the current location of the device.
Owner:AO KASPERSKY LAB
Application instrumentation and monitoring
ActiveUS20060123101A1Cost effectiveAvoid the needDigital computer detailsComputer security arrangementsApplication softwareData store
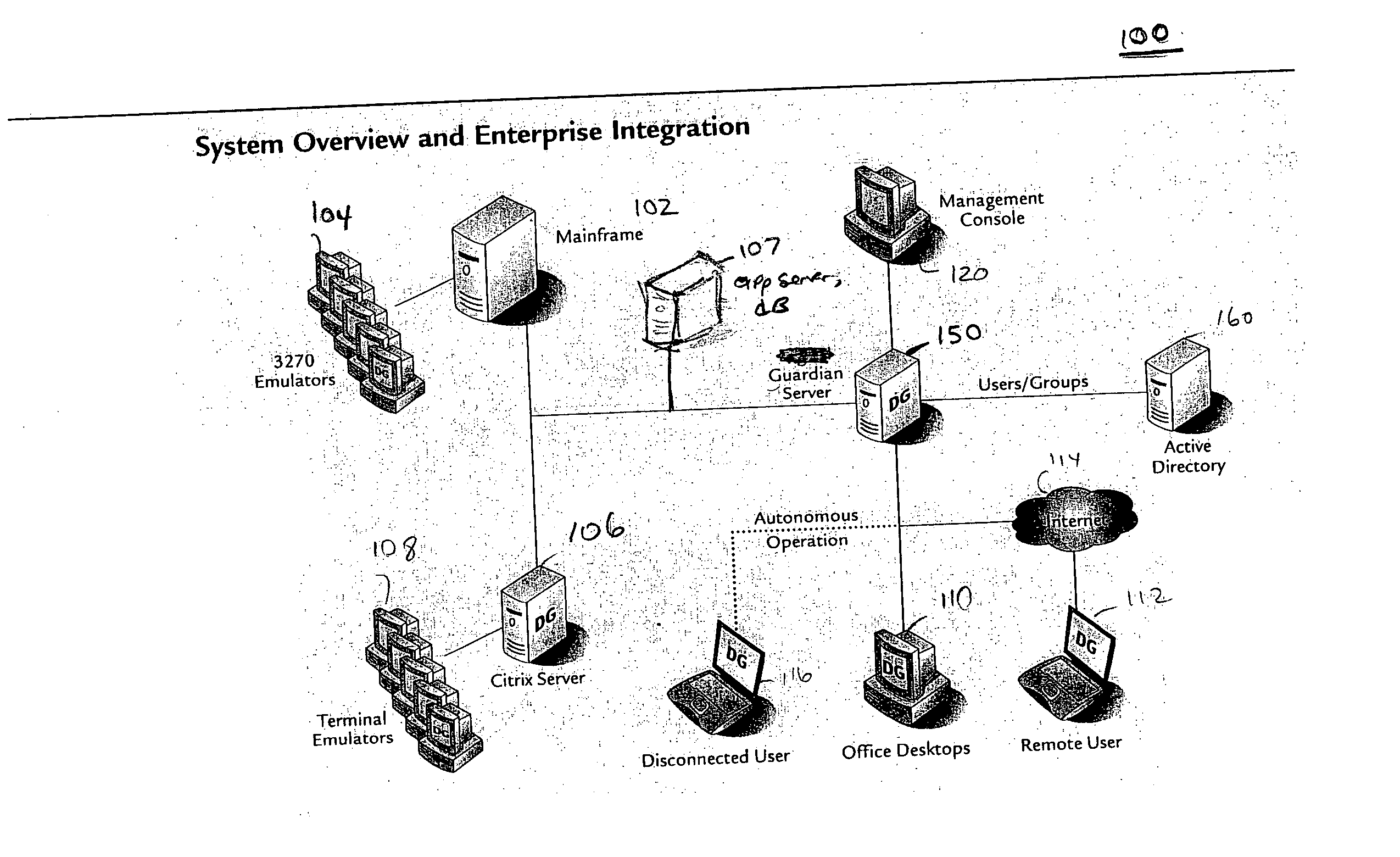
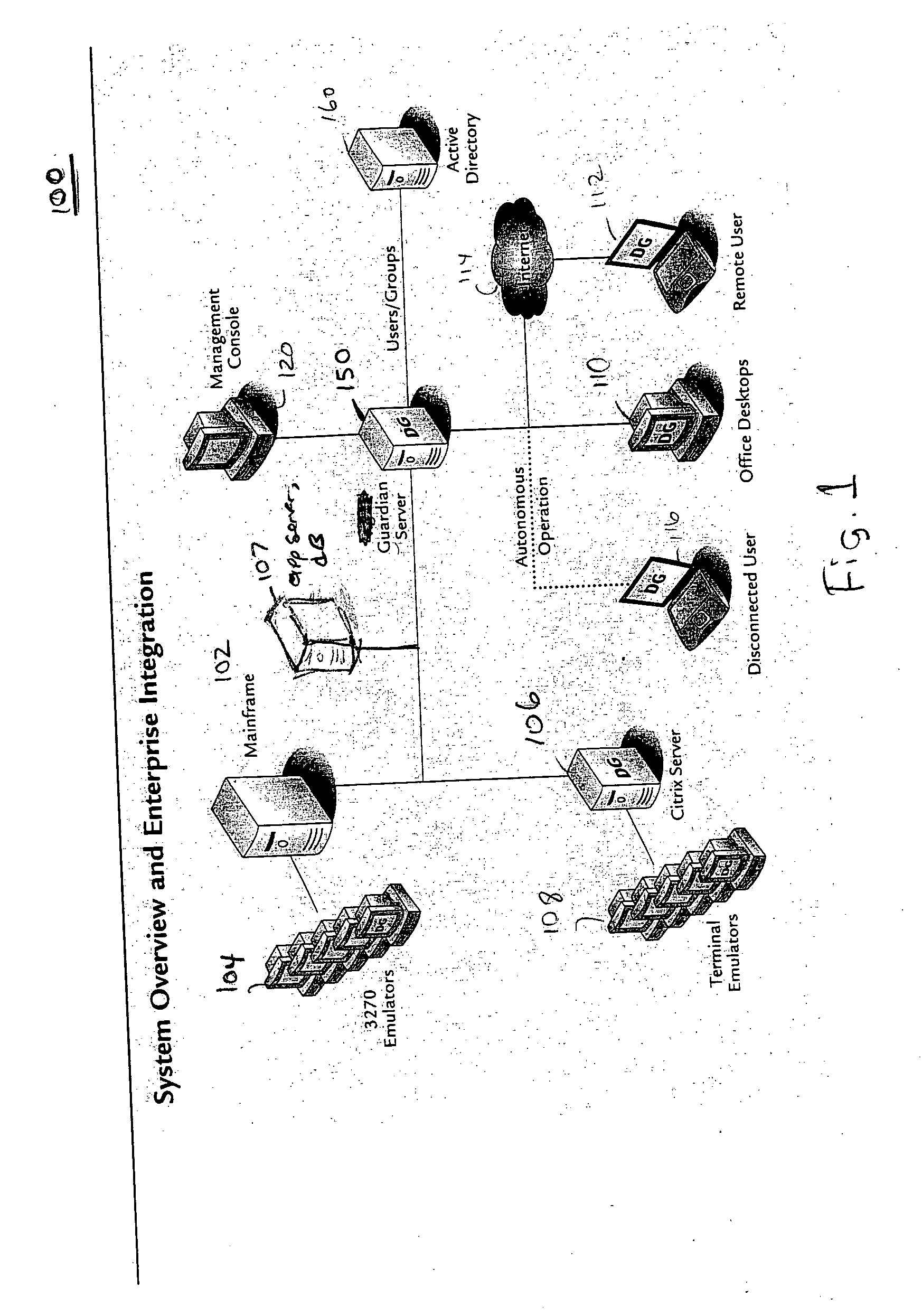
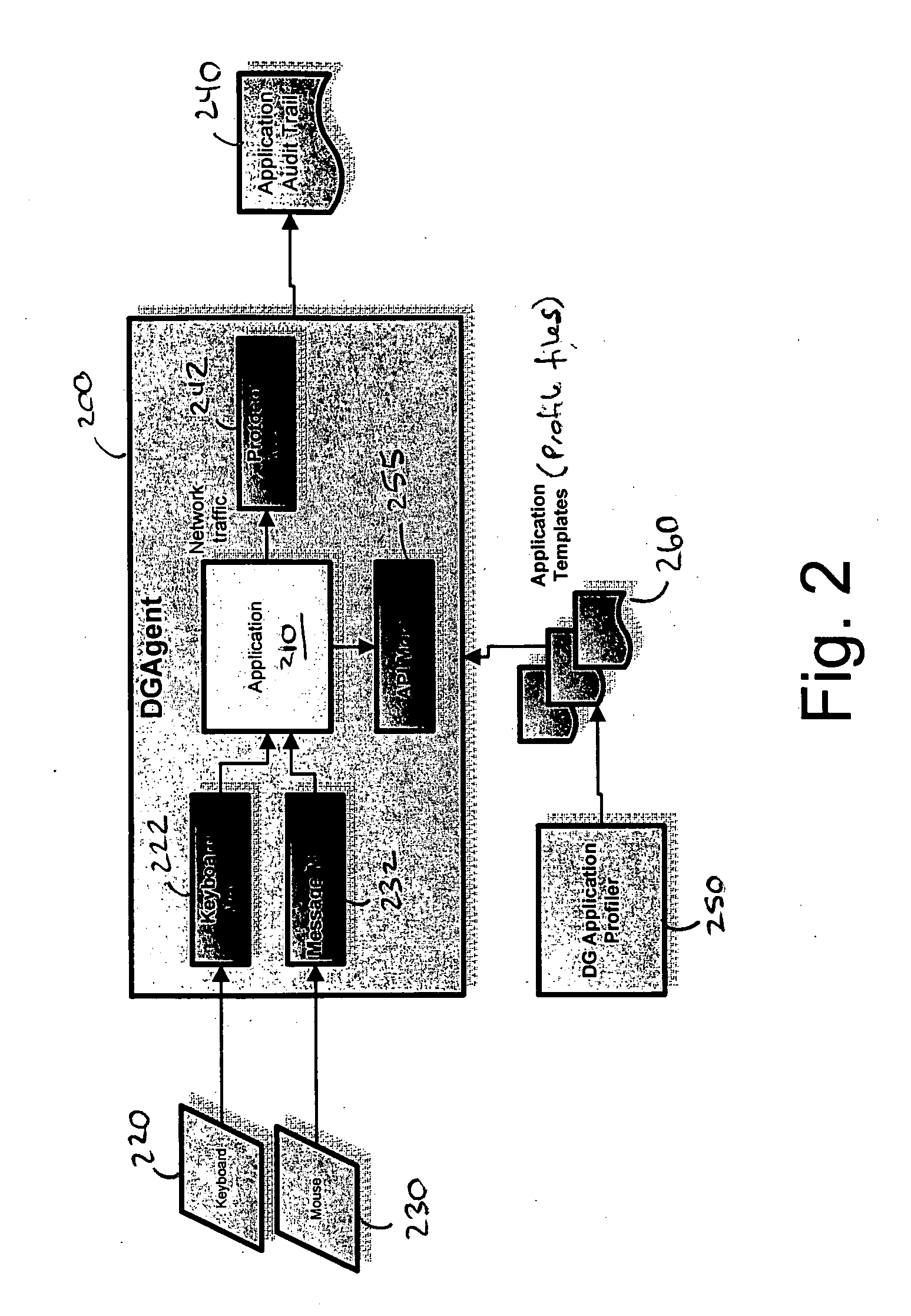
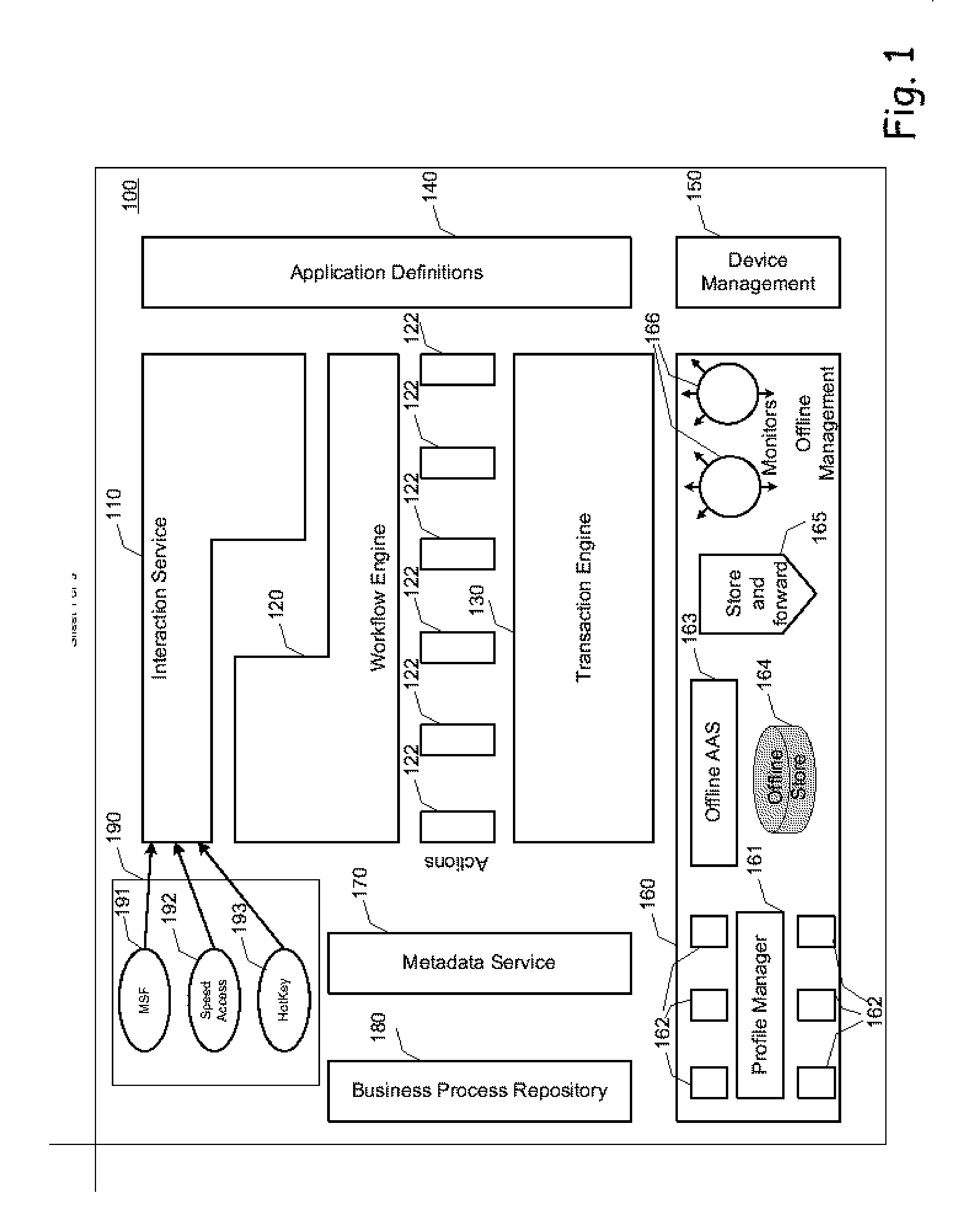
A data processing application logging, recording, and reporting process and infrastructure. Compliance with regulatory directives such as HIPAA, internal organizational and corporate, personal information privacy, and other security policies can thus be enforced without the need to recode legacy application software. In one preferred embodiment, a core agent process provides “listener” functionality that captures user input events, such as keyboard and mouse interactions, between a user and a legacy application of interest. The agent obtains instructions for how to deal with such events, accessing information that describes the application's behavior as already captured by an application profiler tool. Keyboard and mouse data entry sequences, screen controls and fields of interest are tagged during application profiling process. This data is stored in application profile developed for each mode of a legacy application. The technique can be implemented in various Information Technology (IT) environments including mainframe / terminal applications and / or client / server applications. Thus, full coverage of “fat” client, “thin” client, and legacy “mainframe” applications can be provided with a common approach across an enterprise.
Owner:DIGITAL GUARDIAN LLC
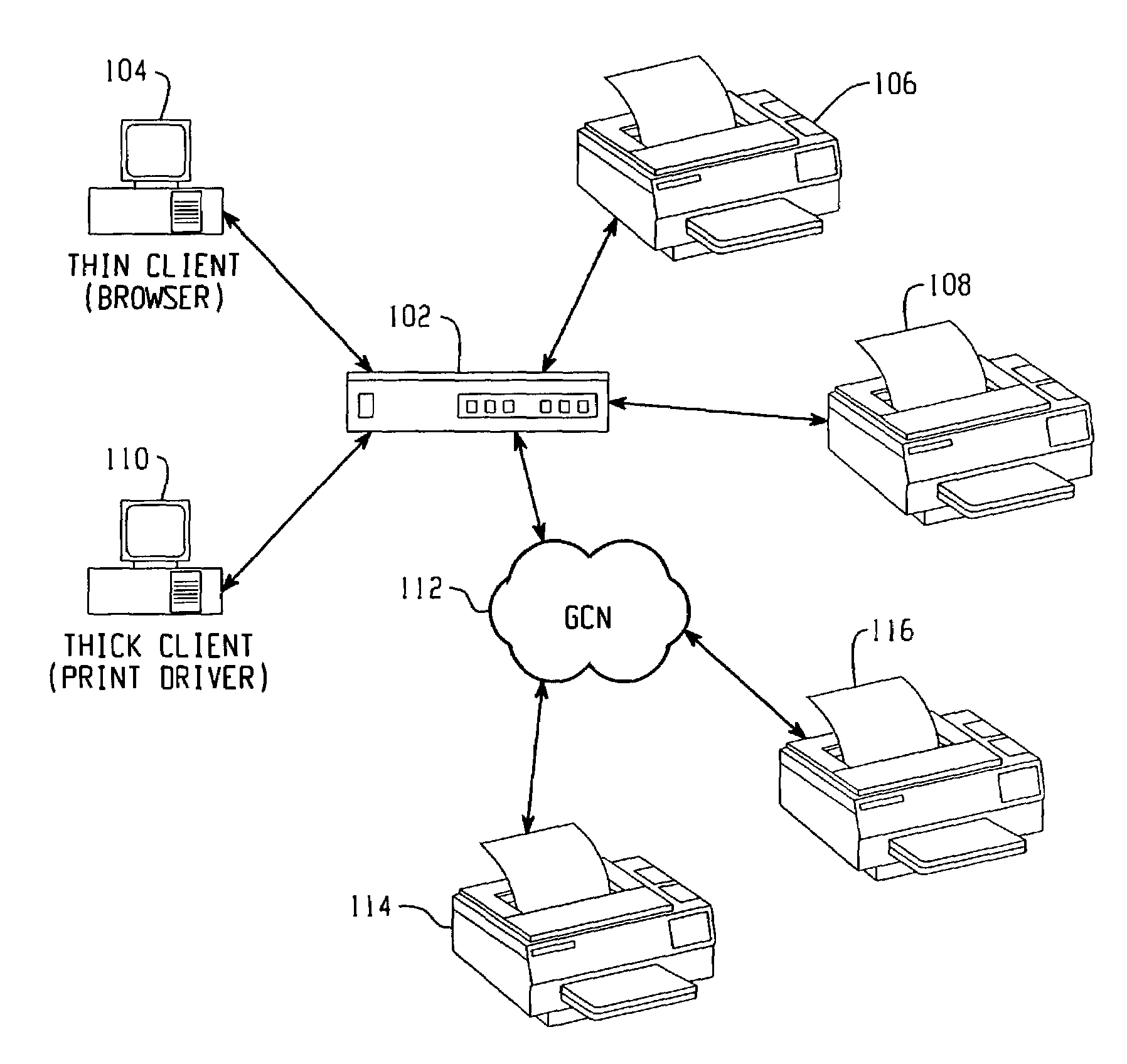
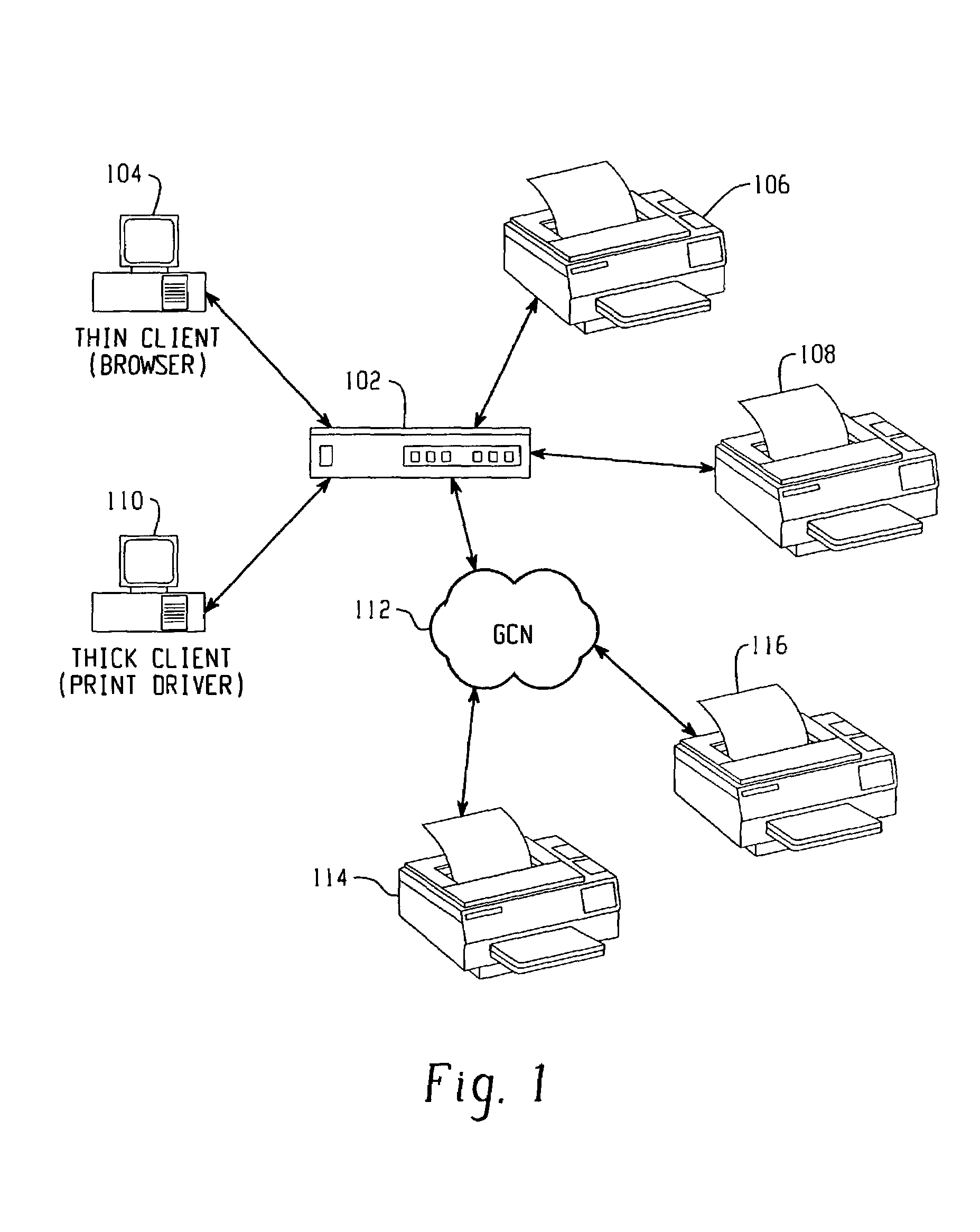
Novel distributed grid super computer system and method
InactiveCN101453398AMultiprogramming arrangementsData switching by path configurationBusiness enterpriseParallel computing
The invention relates to a novel system and a method for distributed grid supercomputing, which establish globally distributed applications in an organized mode and focus on supercomputing capacity to form an architecture, thereby forming a computing grid consisting of heterogeneous distributed computer systems, implementing communication and computer networks and providing an effective mode for using the prior unorganized internet architecture. The distributed network consists of the fat clients of different operational levels in a network architecture and establishes a communication replacement proposal applicable to the internet, enterprises and social communication framework according to the network standards of a credit expansion grade layer. The system and the method use a NetAlter manager to realize the communication of distributed networks and control the activities and computing of the networks in a plurality of modes such as a point-to-point mode, an off-line mode, an on-line mode and an intelligent equipment mode. The novel system and the method for distributed network supercomputing completely overcome the drawbacks of the prior internet architecture and point-to-point technology and grid computing.
Owner:WHITE WEISHENG SOFTEWARE
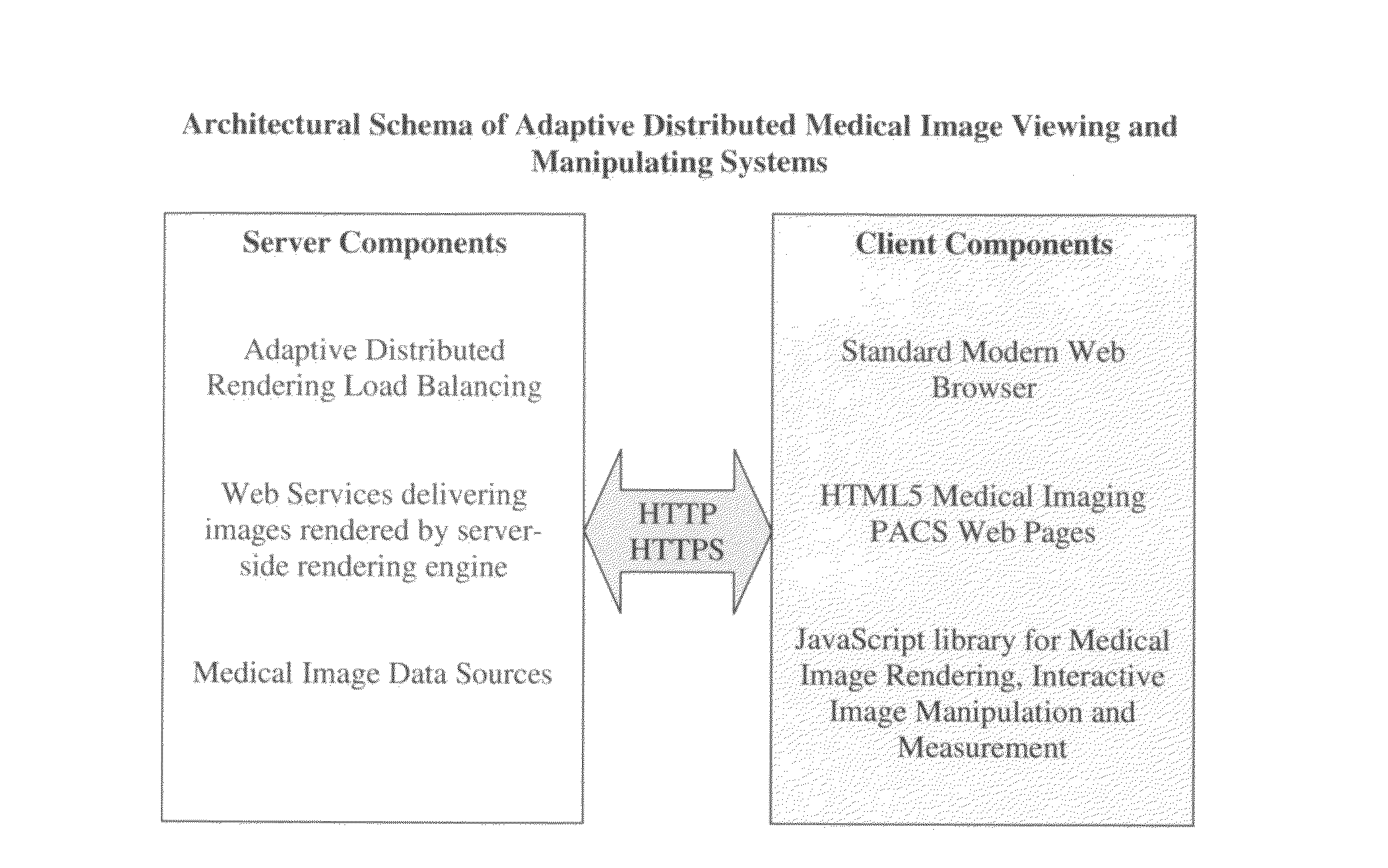
Adaptive distributed medical image viewing and manipulating systems
A pure web browser based medical imaging system that requires no installation of application software or any browser plug-in and functions in the same way as traditional full blown medical imaging PACS (Picture Archiving and Communication Systems) viewer fat clients. In addition, the system intelligently distributes the computing tasks of image rendering between browser and servers from complete server-side rendering to complete client-side rendering and anything between. It comprises a JavaScript medical image rendering library that can process original DICOM (Digital Imaging and Communications in Medicine) data sets and all standard web images at pixel level, a medical imaging server and a rendering load balancing component that can dynamically split the rendering computing from server to client according to their capabilities.
Owner:XIE LIANG
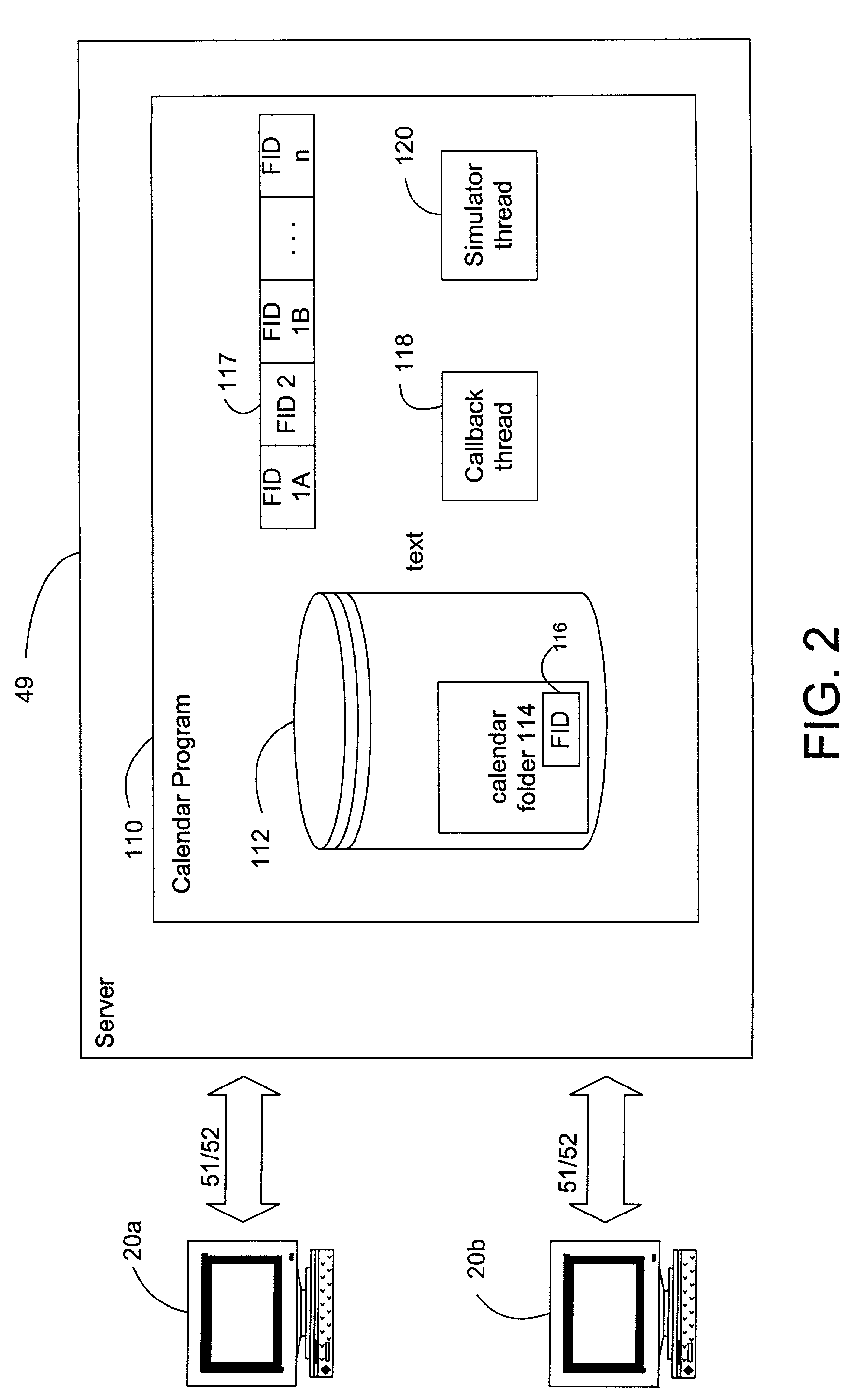
Method and system for expansion of recurring calendar events
A system and method for expanding recurring calendar events such that the retrieval of recurring calendar appointments is expedited. A recurring appointment is saved as a data structure including a recurrence pattern. When a recurring appointment is saved by a client that has sufficient processing and memory resources to perform the computations necessary to expand recurring appointments (i.e., a thick client), a background thread is notified. The background thread increases its priority to normal when idle processing capacity is available and calls a routine requesting calendar information for a defined time period. The routine causes the expansion of the data structure into the individual instances of the recurring appointment for a defined time period, and the individual instances are saved for later retrieval. A later query from a client without sufficient processing and memory resources to perform the calculations necessary to expand recurring appointments (i.e., a thin client), therefore, does not require that the expansion computations be performed contemporaneously.
Owner:MICROSOFT TECH LICENSING LLC
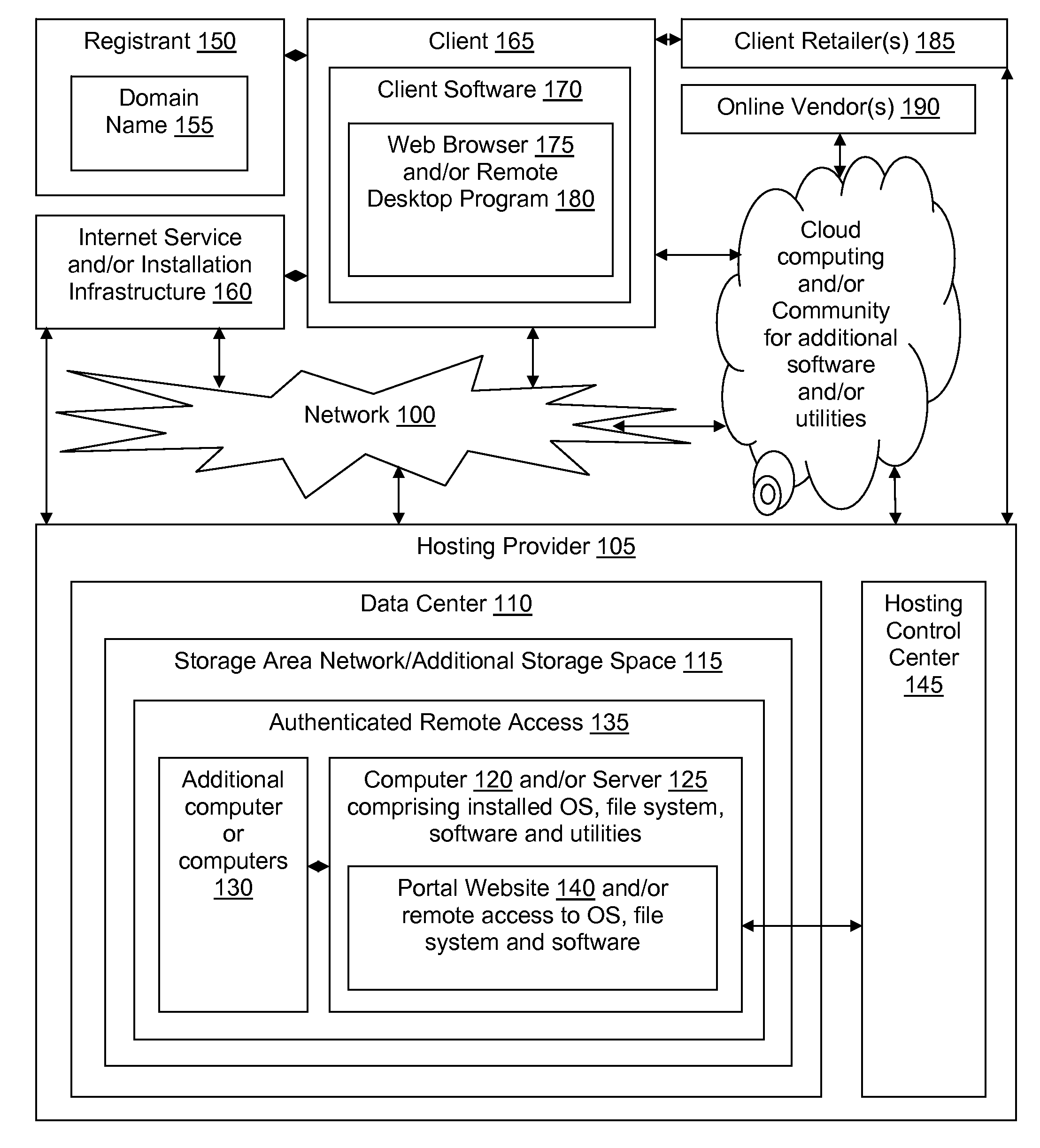
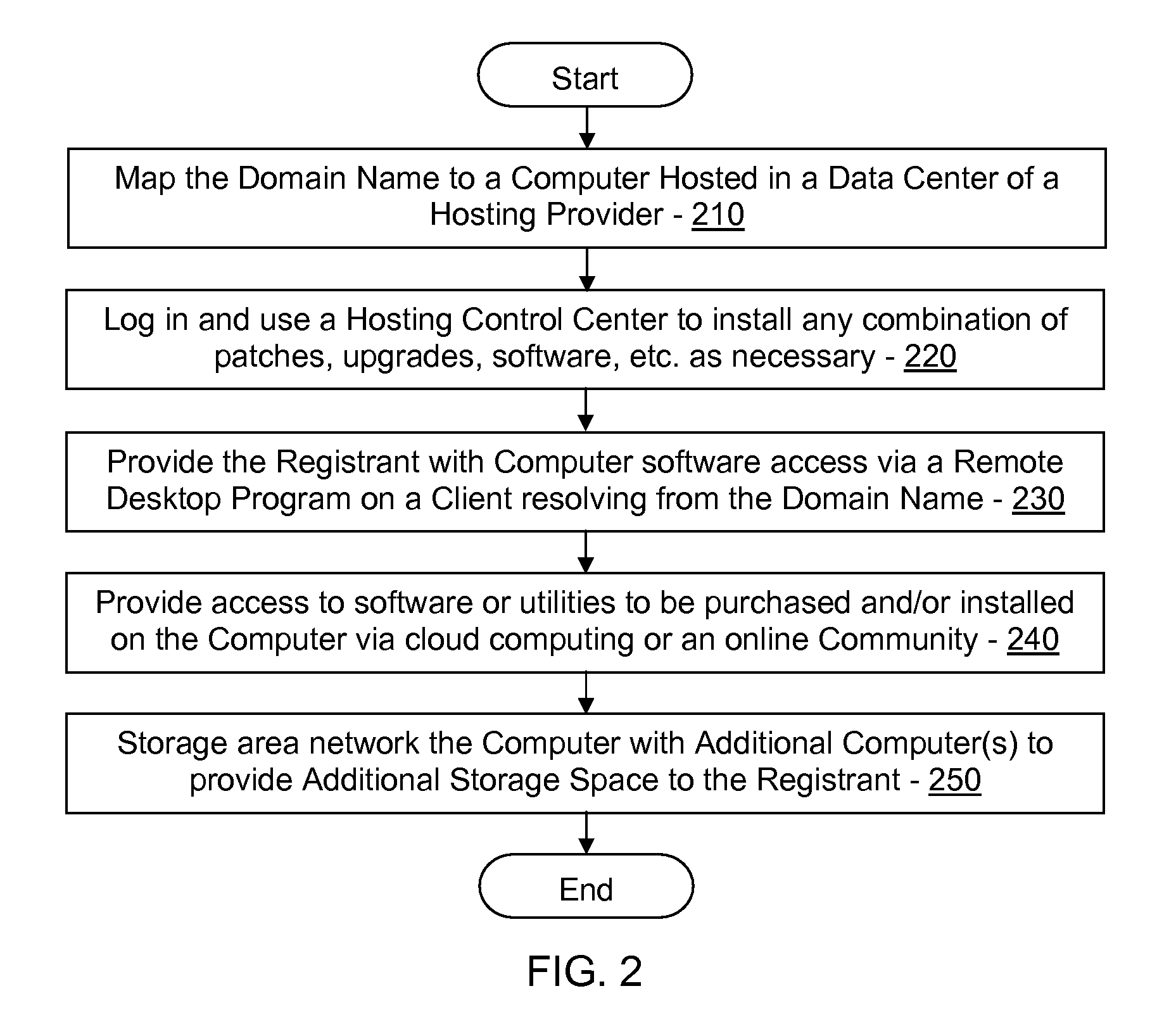
Branded and comarketed domain-based thick client system
ActiveUS20090313320A1Significant limitationMultiple digital computer combinationsTransmissionDomain nameData center
Systems and methods of the present invention allow for a thick client which may be provided with a domain name in a partnership between a hosting provider, an ISP and / or a thick client retailer. The client may be used to access a remote computer or server in the hosting provider's data center.
Owner:GO DADDY OPERATING
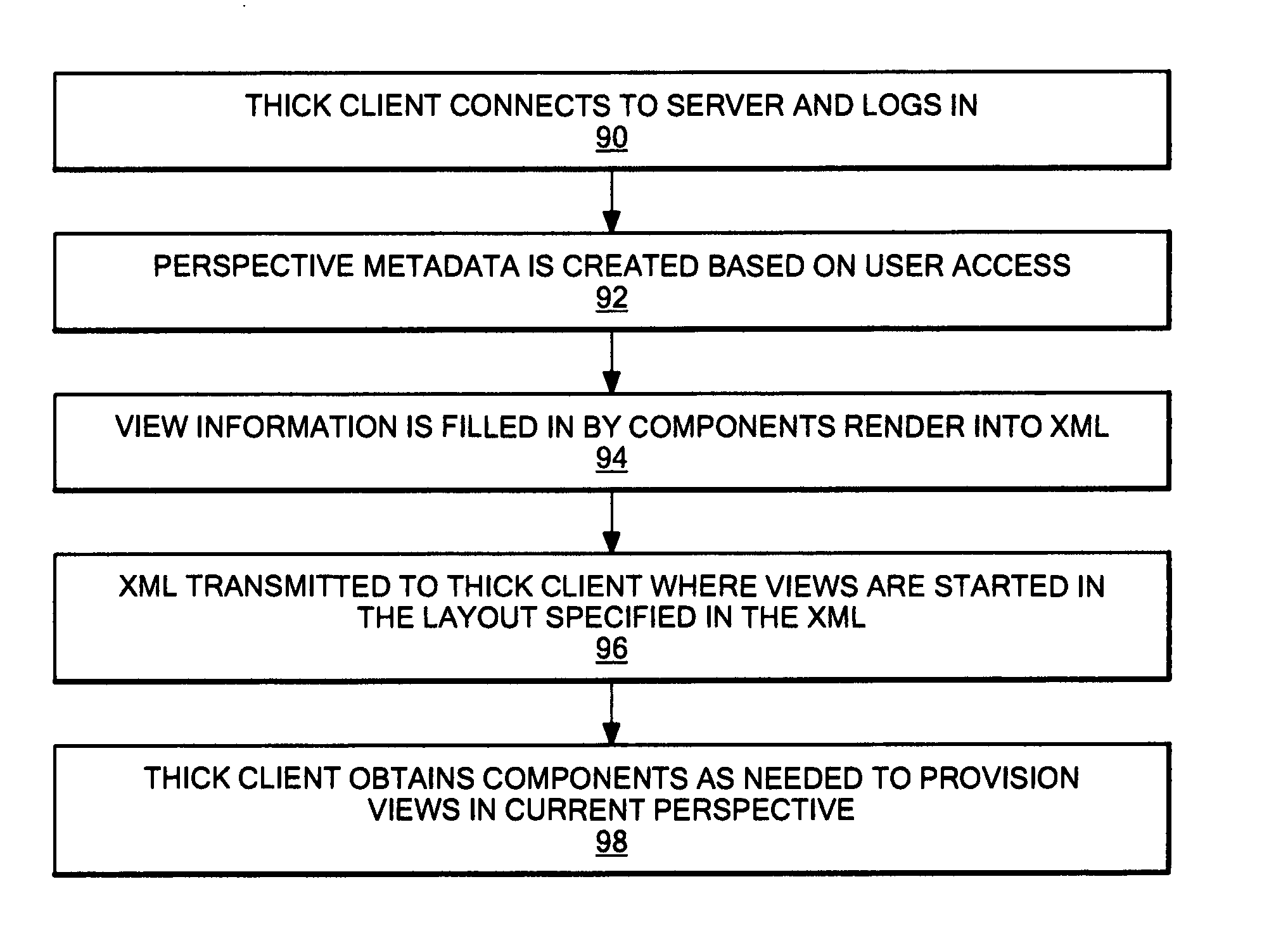
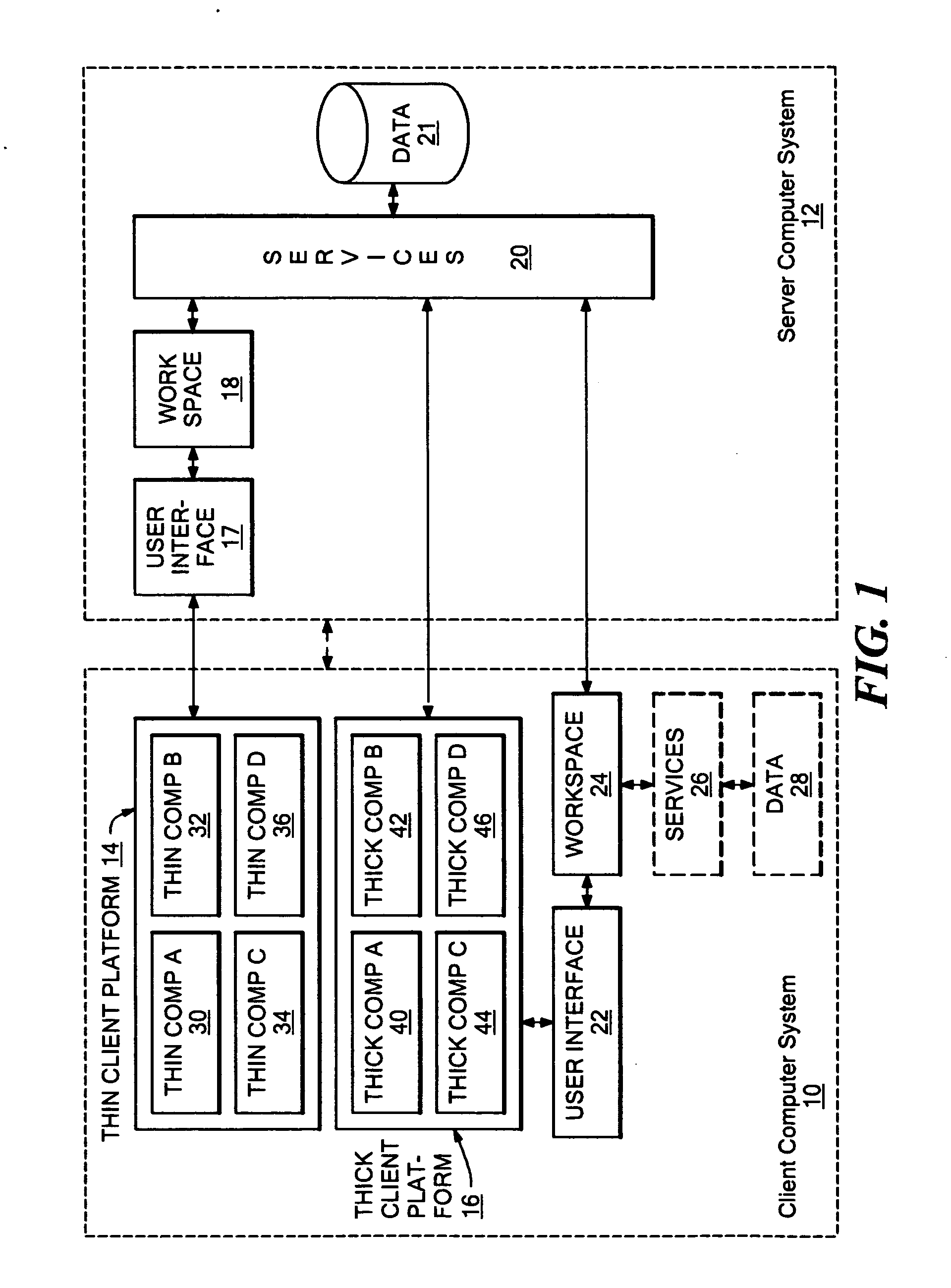
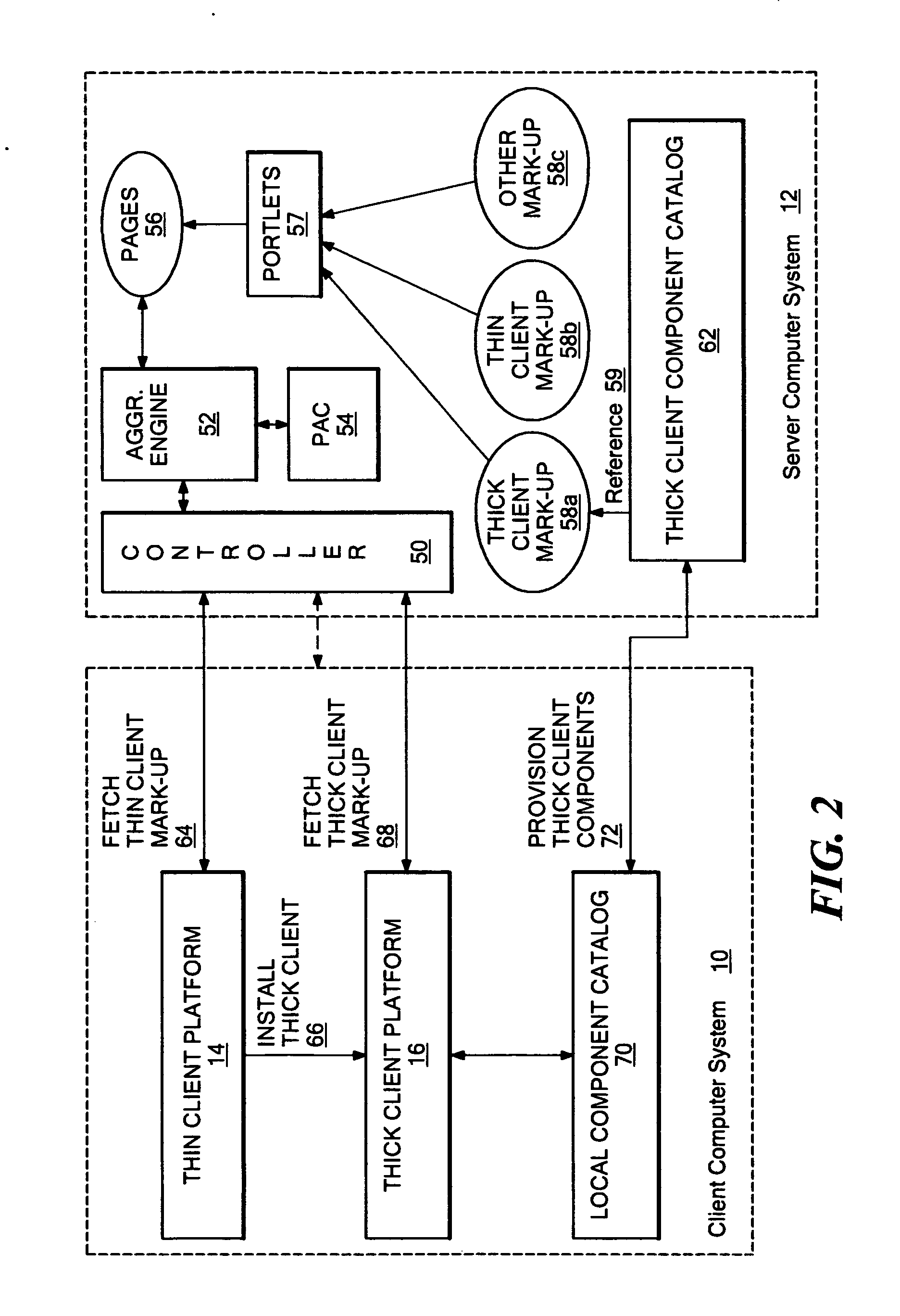
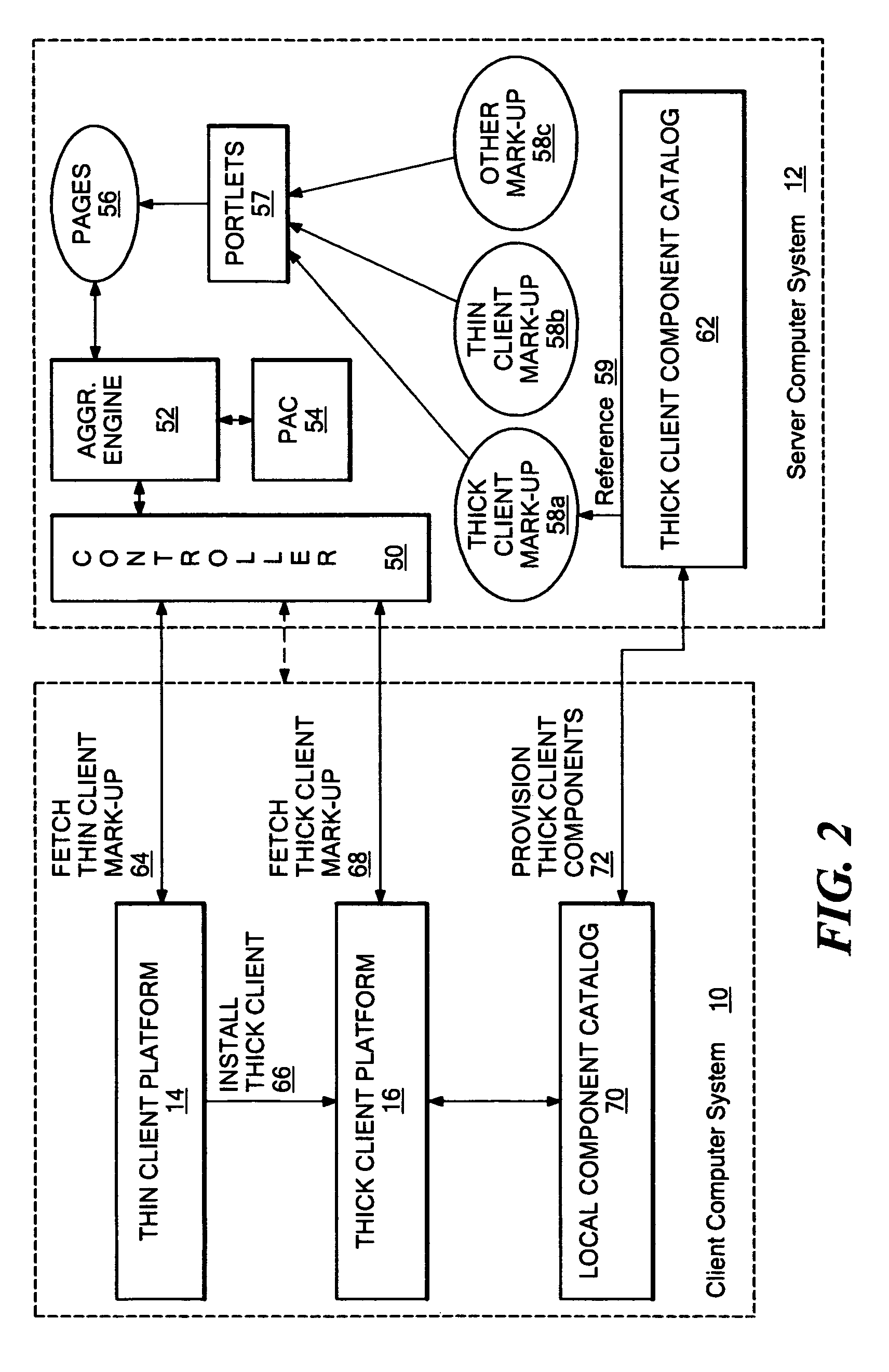
Markup method for managing rich client code and experiences using multi-component pages
ActiveUS20060168512A1Natural language data processingMultiple digital computer combinationsClient-sideCentralized management
A mark-up method and system that enables server-managed thick client capabilities using a thin client server, framework, and administration. Active content such as program code, service, and data components, are driven to a thick client platform. The thick client platform is defined through a combination of thick client components, while the thick client components and user interface experience are centrally managed. The thick client container can operate to embed thin client container components, such as a browser, and the thick client container itself can be initially deployed over a network using a thin client.
Owner:TWITTER INC
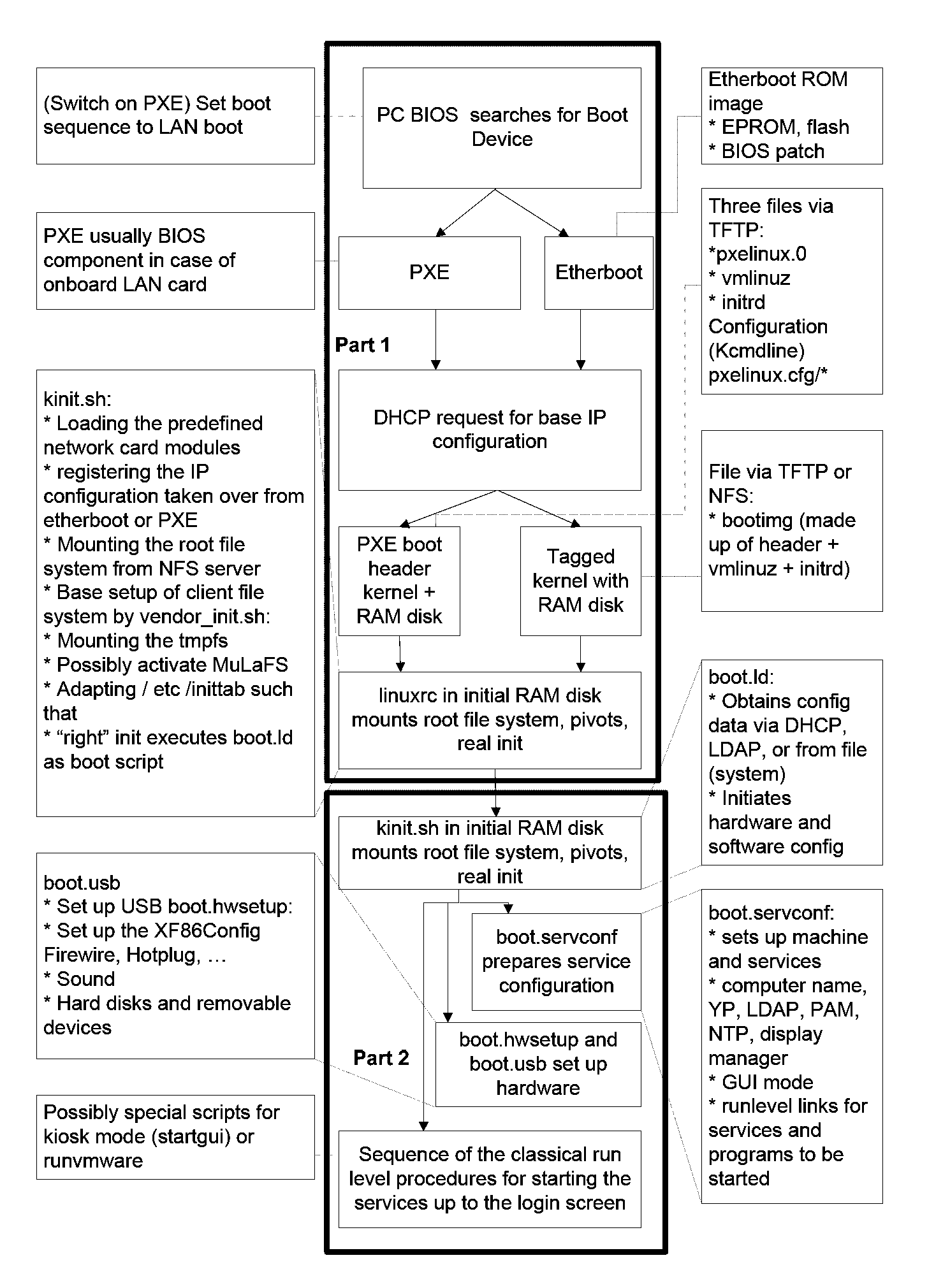
Method and system for the distribution of configurations to client computers
InactiveUS20090172136A1Significant positive effectSave storage spaceDigital data processing detailsUser identity/authority verificationOperational systemComputer configuration
A method for distributing computer configurations to at least one client from a server, comprising the following steps: Network-booting a first operating system for the clients from a server, automatically loading a virtual machine having an elective second operating system on the basis of the booted (first) operating system while taking into consideration one or more of the following parameters: user login, network address. Consequently, providing a full fat client (standard PC) functionality under an elective operating system on a (diskless) client hardware by using exclusively volatile storage media (on the new thin client system).
Owner:SCHULZ ULRICH +1
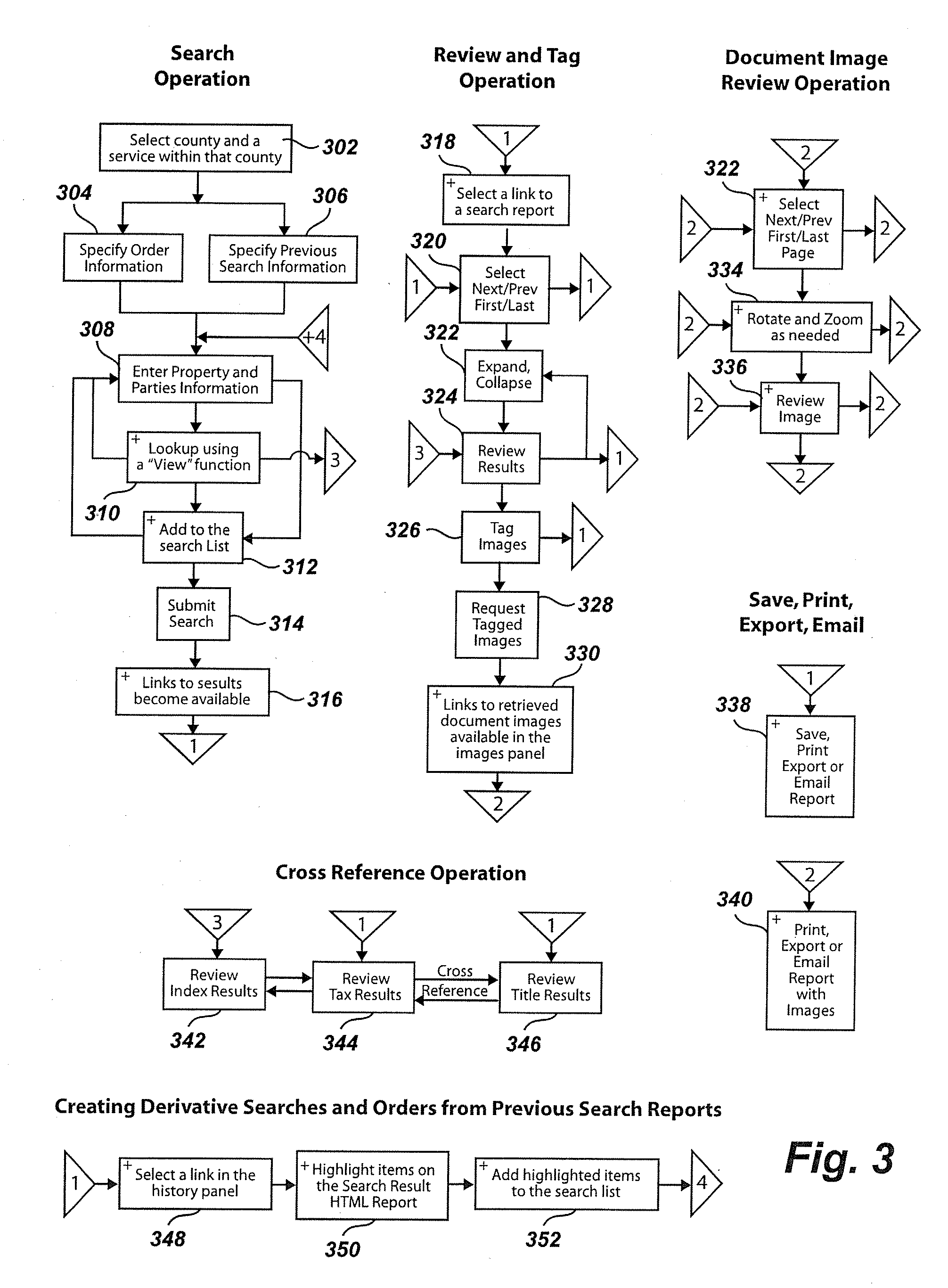
Property tax and title chain document ordering system and method
InactiveUS20070106647A1Improve performanceReduce network trafficFinanceMultiple digital computer combinationsSoftware updateIntegration platform
The present invention is an integration platform providing access to property tax and title document index (a.k.a. title plant) backend. The present invention is to provide the benefits of so-called thick-client architecture, with their real-time responsiveness and ability to browse through large numbers of huge reports and image collections, with so-called thin-client architectures, with their seamless software update capabilities and reduce centralized maintenance costs. The present invention serves as a title chain report and scanned document image ordering and download gateway. The present invention allows submission of requests in a batch and subsequent off-line browsing and analysis of fulfilled orders, and operates under challenging conditions of intermittent connections performing automatically data download resumption, therefore minimizing the dependency on live connections to situations where new data is required.
Owner:DATA TRACE INFORMATION SERVICES
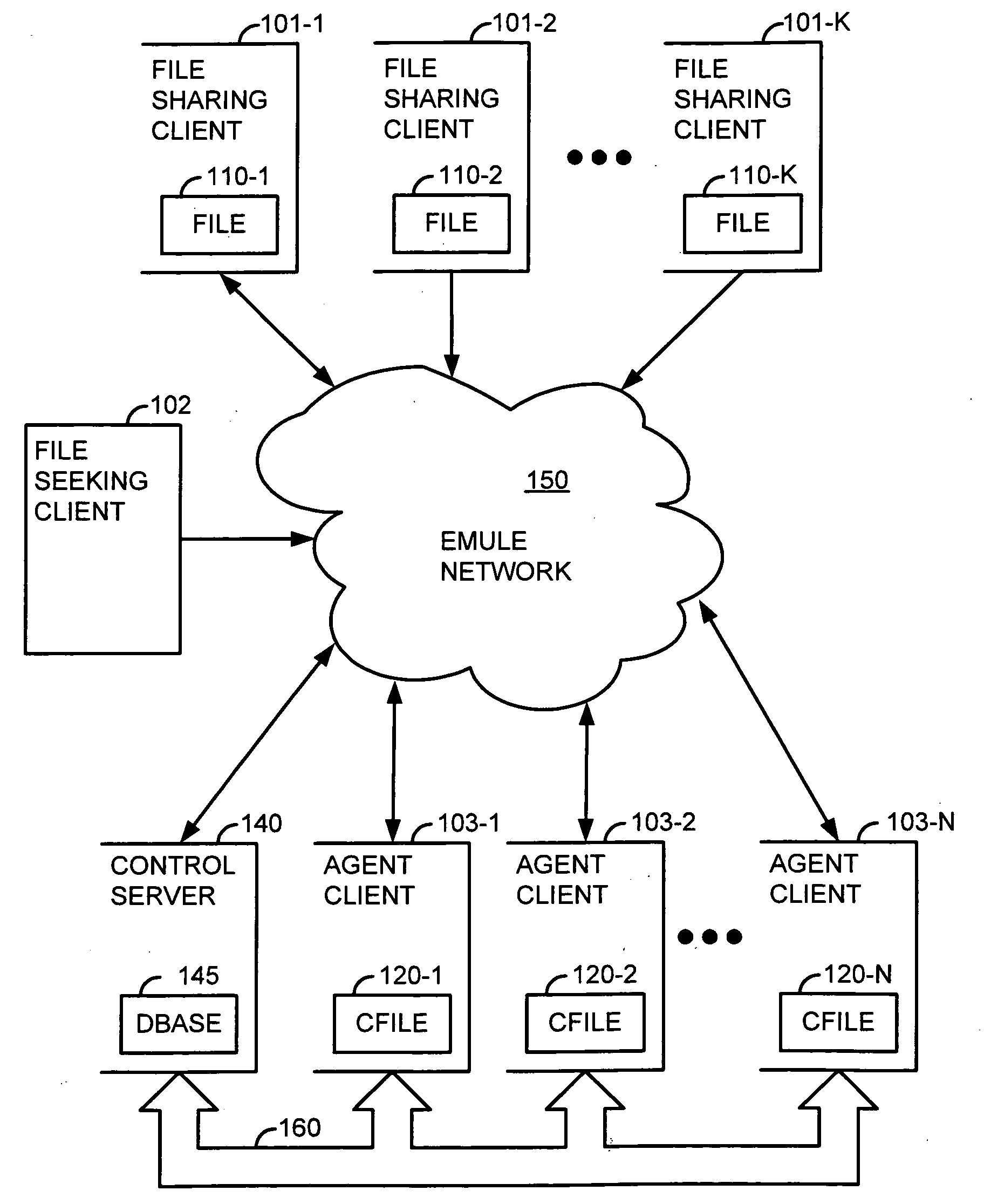
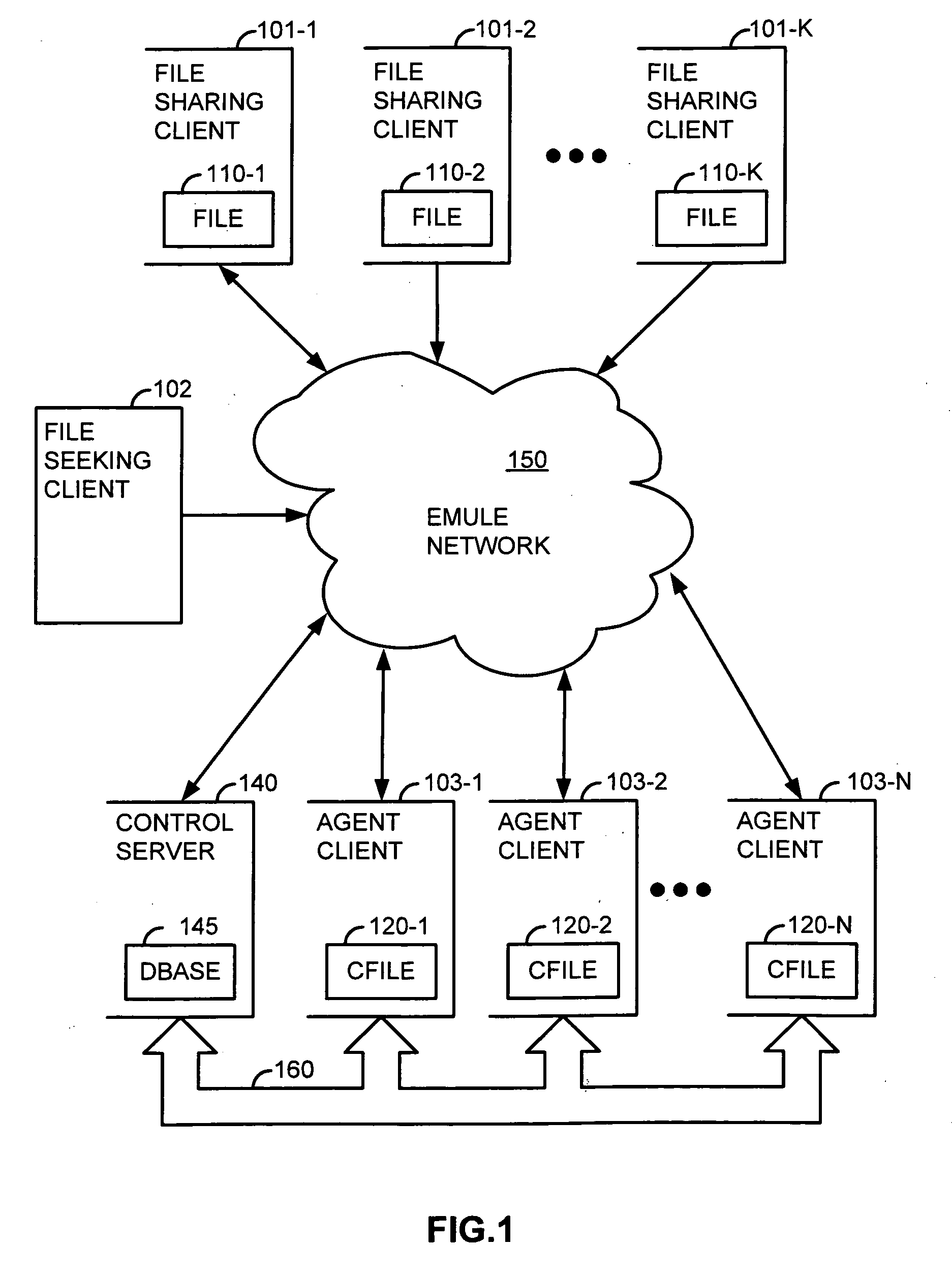
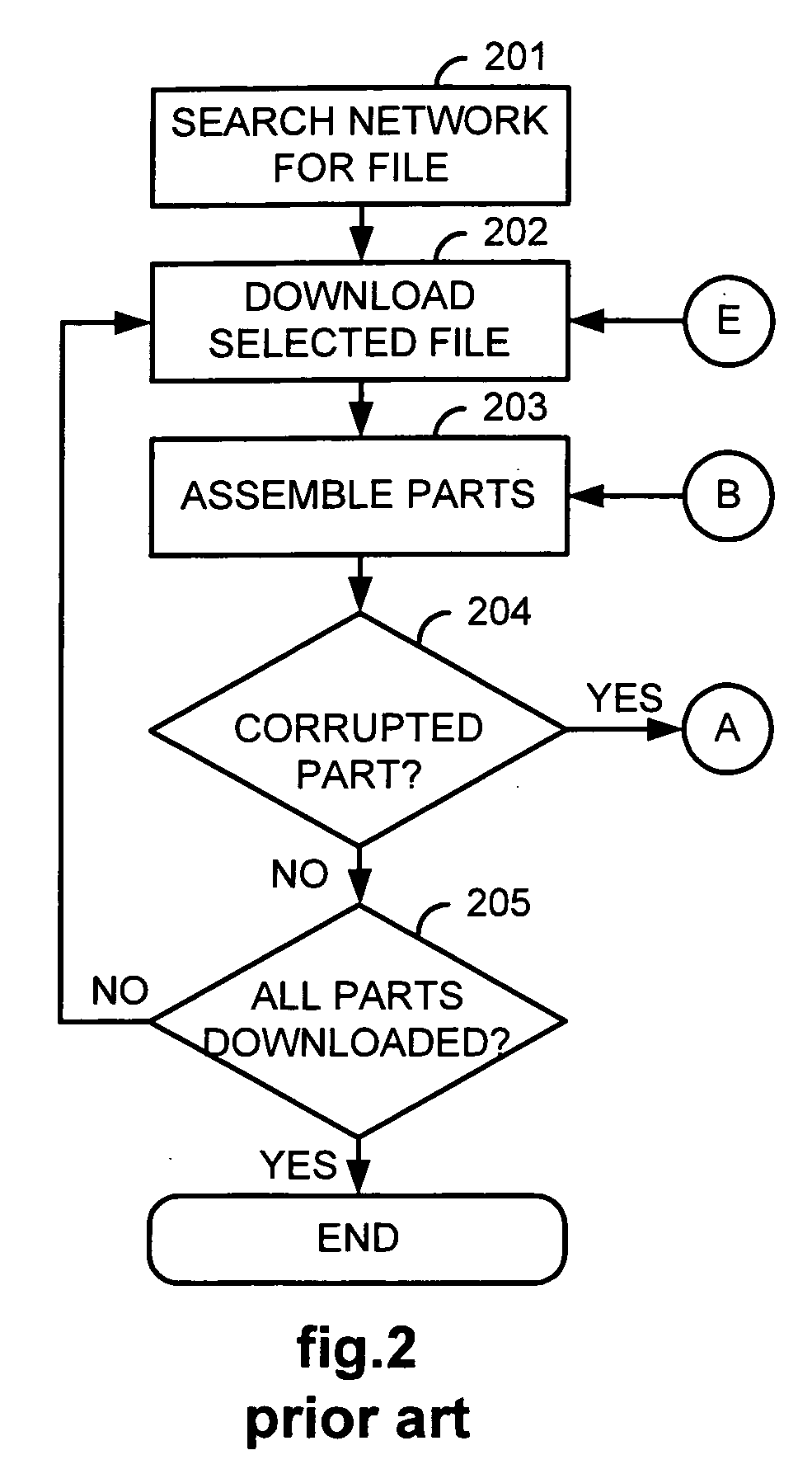
Corruption of swarm downloads in a decentralized network employing advanced intelligent corruption handling
InactiveUS20090172824A1Increase the number ofDigital data processing detailsUser identity/authority verificationNetwork packetClient-side
An eMule network employs Advanced Intelligent Corruption Handling (AICH). Agent clients offer copies of a corrupted version of content. When the corrupted copies participate in swarm downloads with uncorrupted copies, the AICH is triggered. The agent clients are sufficient in number to out vote all other clients in a trusted root hash determination performed by the AICH. As a result, one of the agent clients provides a recovery packet used by the AICH to determine good and bad blocks. Since the recovery packet includes block hashes for the corrupted version of the content, blocks uploaded by clients providing uncorrupted versions are determined to be bad blocks and the clients identified as bad sources. The agent clients, on the other hand, either fail to upload a requested block or do so in a manner to discourage a user of the downloading client to wait for completion of the upload.
Owner:MACROVISION CORP
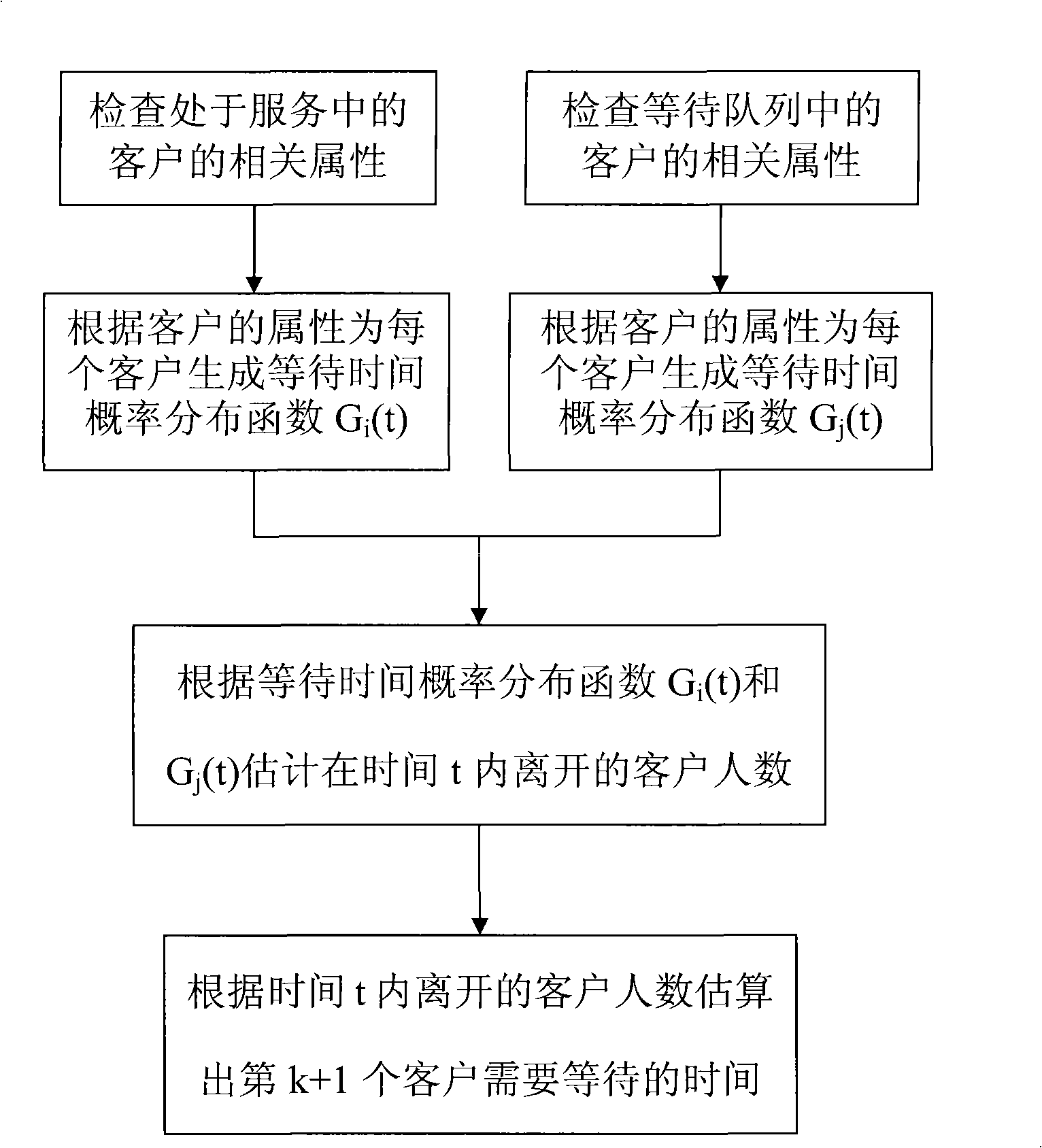
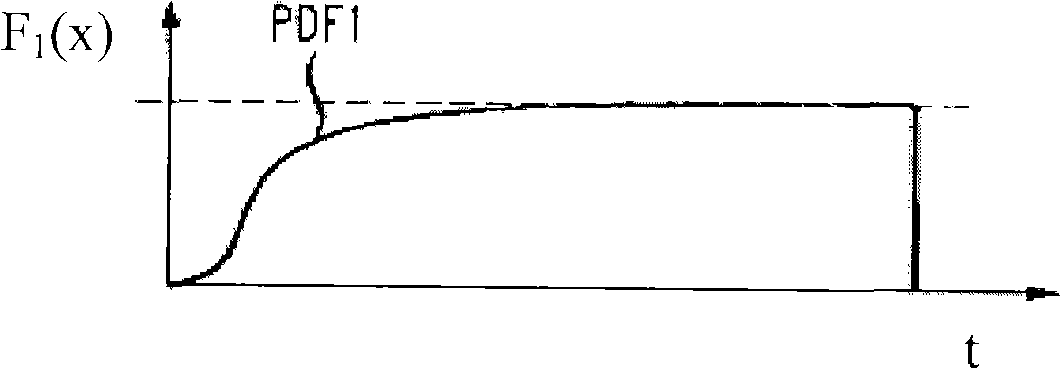
Queueing time estimation method
InactiveCN101540016AThe waiting time is accurateIncrease profitChecking apparatusDistribution functionUtilization rate
The invention relates to a queueing time estimation method for estimating the queueing time of clients in a service system. The queueing time estimation method includes the steps of client classification and providing queueing time probability distribution functions of various clients; when more than five clients wait, the attributes of the clients being served and the clients to be served are respectively checked, and the corresponding queueing time probability distribution function is generated; the number of the left clients is estimated according to the function, and the queueing time is estimated according to the number of the left clients and is provided for the clients; and when less than five clients wait, the queueing time of maximum probability of the clients to be served is added to obtain the queueing time of the clients directly according to the queueing time probability distribution function. The number of the left clients is estimated through the client classification and the probability distribution functions, and the estimated service queueing time can be more accurately provided for the clients compared with the prior art; and based on the estimated service queueing time provided for the clients, the utilization rate of the queueing time can be improved by the clients, and the trust, the satisfaction and the loyalty for the service quality of service improvers can be improved by the clients.
Owner:SHENZHEN AOTO ELECTRONICS
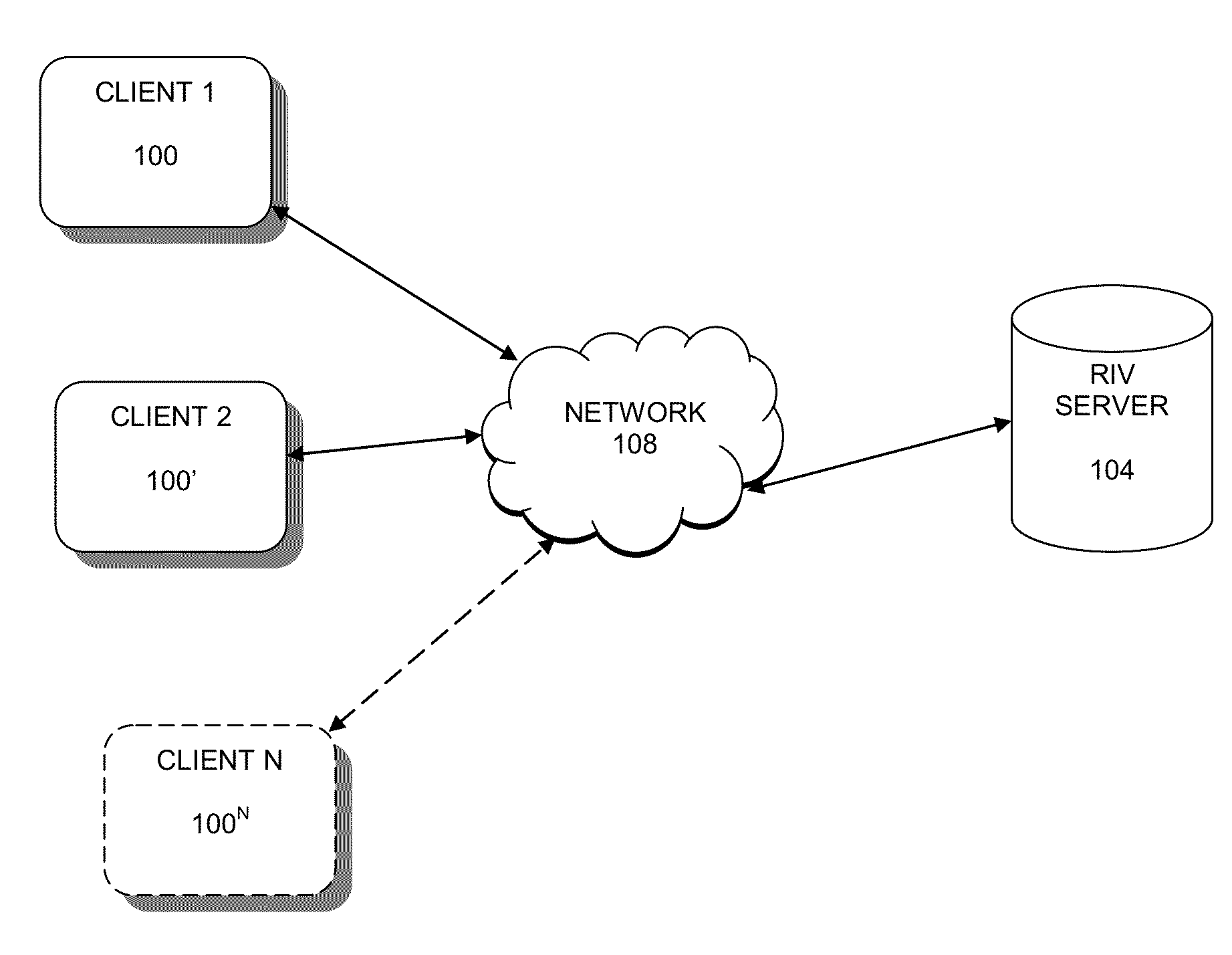
Methods and systems for remote interactive viewing
InactiveUS20160072858A1Facilitate browser sharingWebsite content managementTransmissionWeb browserClient-side
Browser sharing technology, i.e., sharing a window of a web browser or a portion thereof. This browser sharing is lightweight, in that it does not require the installation of a thick or thin client. The browser downloads and executes code to facilitate browser sharing in the same way that it downloads and interprets HTML for webpage rendering. Embodiments of the present invention permit all of the viewers of the shared browser window to interact with the window as it is shared, and their interactions appear concurrently in all of views.
Owner:RIV TECH
Client platform architecture
InactiveUS20060218228A1Low costMinimize waiting timeMultiple digital computer combinationsBuying/selling/leasing transactionsWorkstationClient-side
A client platform architecture enabling workstations to operate in an ASP type environment, but reap the benefits available to a rich or fat client. The client platform interfaces to a server and receives an image of its operational software from the server using JNLP or OSGI technology. The client device the necessary processing power and software to perform requested tasks regardless of whether the server is online or offline. Thus, the client device is fully or substantially fully functional without the need to interface to the server. The server contains the same functionality as is loaded into the client device and thus, can support thin clients. Any changes to the server software are subsequently loaded into the client platform.
Owner:SECURITY FIRST TECH
Chat system and its information processing method
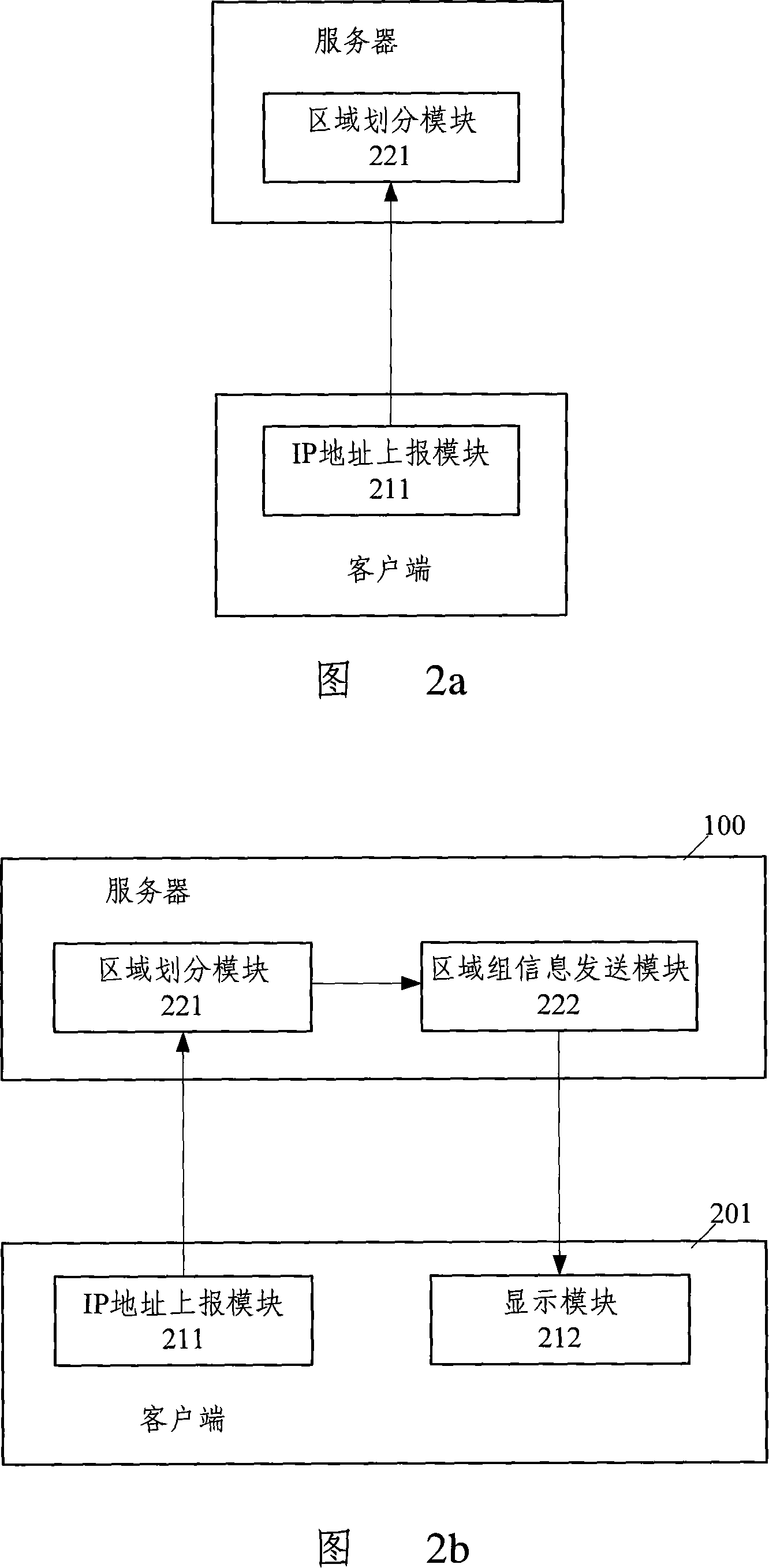
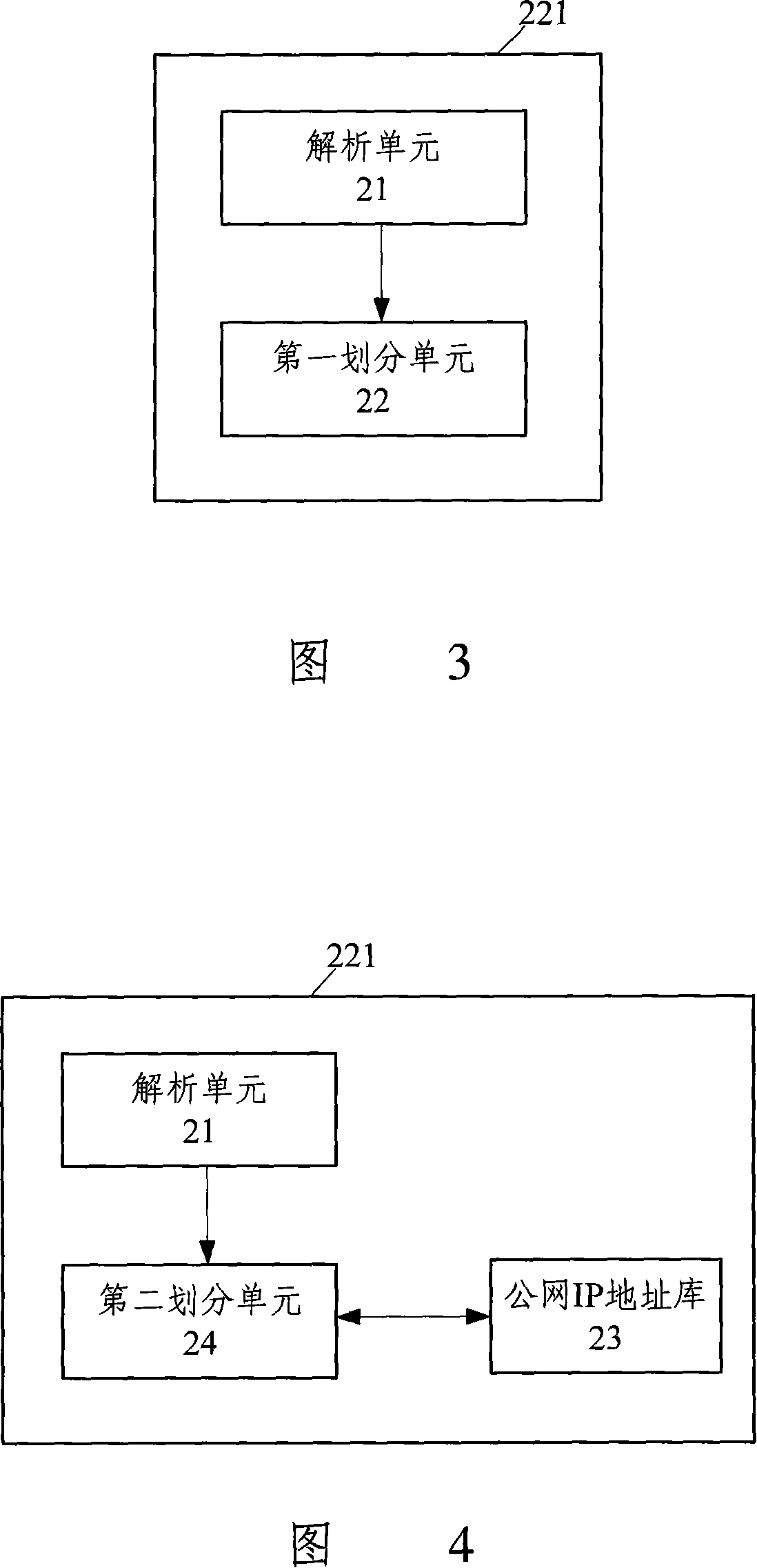
InactiveCN101123591ASave resourcesEasy to understandData switching networksInformation processingIp address
The invention discloses a chat system and an information processing method of the chat system. The chat system comprises a client and a server, the client comprises an IP address submission module, which is used for submitting the IP address of the client; the server comprises a region division module, which is used for analyzing the submitted IP address from the client and carrying out the region division of the client according to the analyzing result. The method comprises that A. the client end submits the IP address to the server; B. the server analyzes the submitted IP address from the client and carries out the region division of the client according to the analyzing result. By using the invention, the region belonging to the chat client is divided in the chat system, thus a function of the same network segment IP address chat is realized. Particularly, an intranet chat among the clients in a same local area network is implemented without occupying public network resources. The invention can also locate the IP address of the client precisely.
Owner:TENCENT TECH (SHENZHEN) CO LTD
Data client
ActiveUS9124601B2Multiple digital computer combinationsTransmissionComputer scienceDistributed computing
Owner:CONVIVA
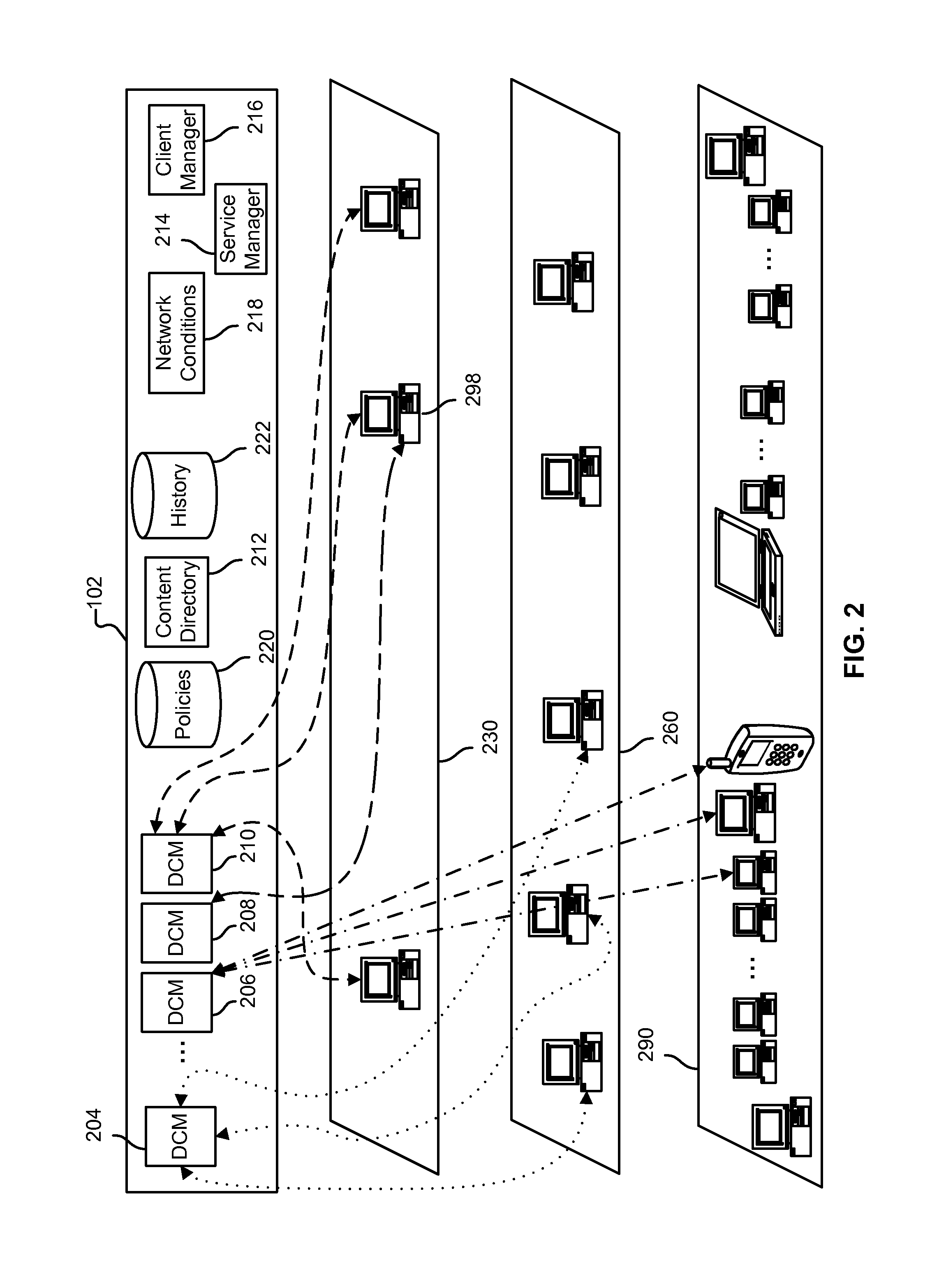
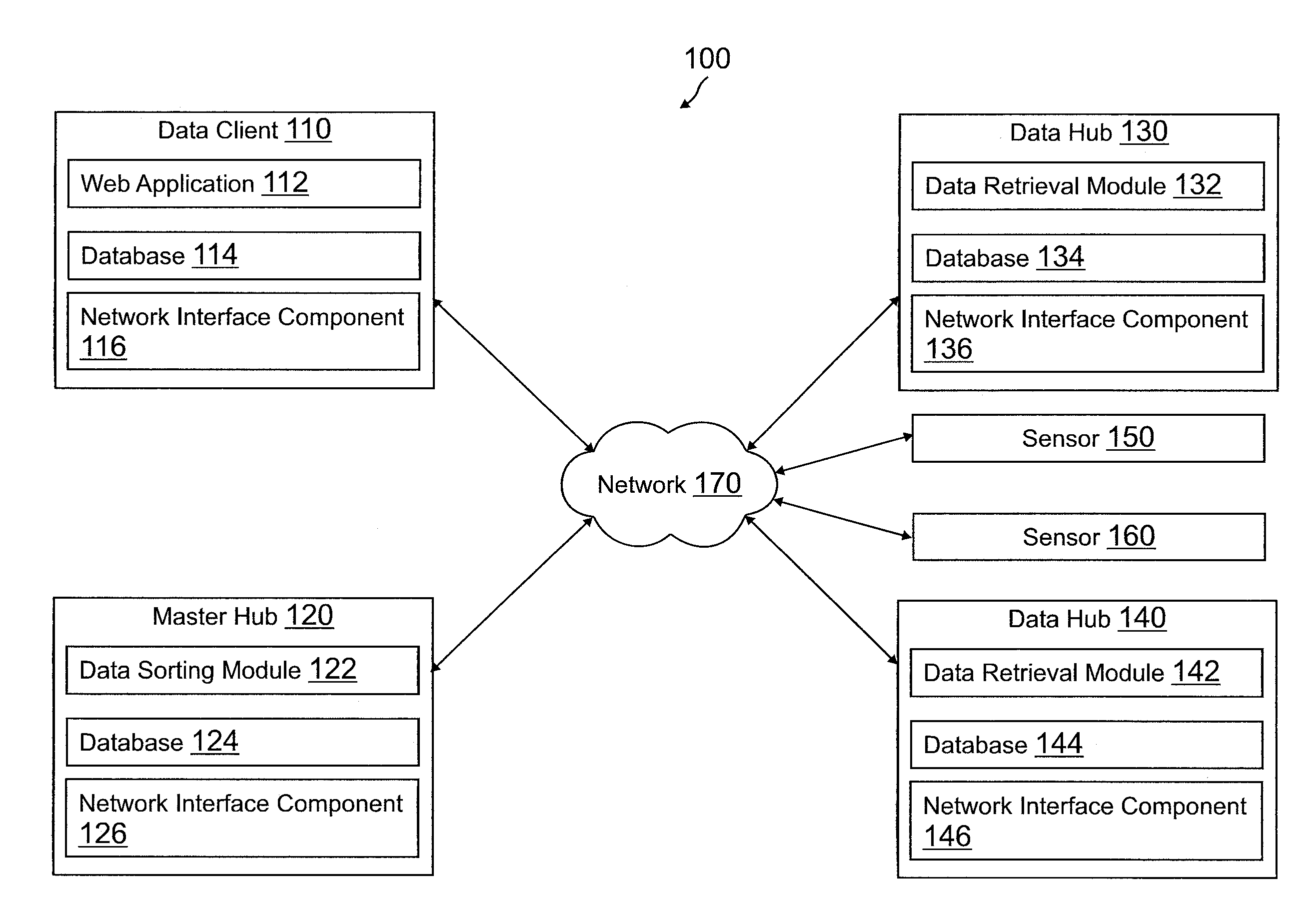
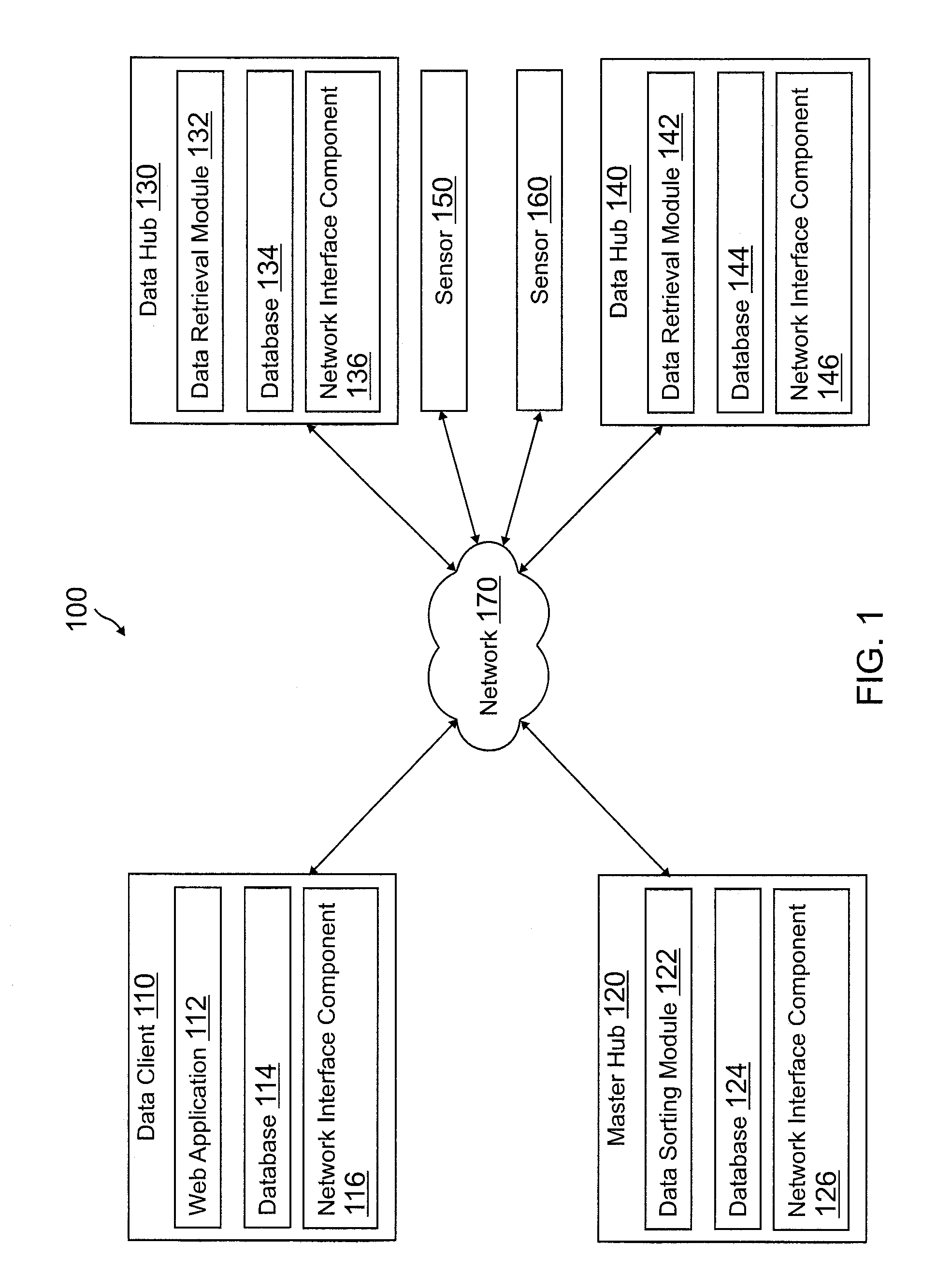
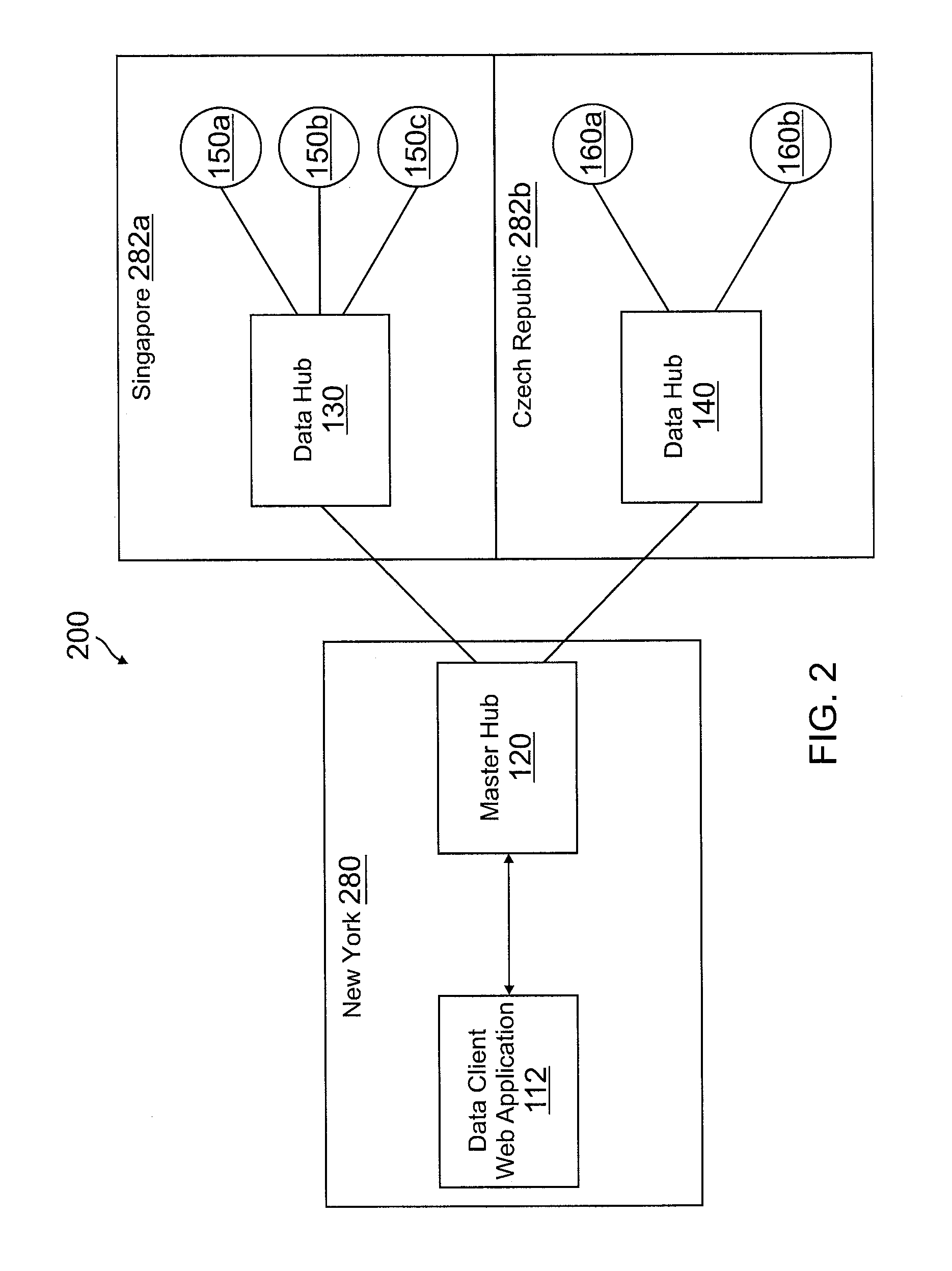
Data hub architecture to provide actionable data from remote sensor feeds
Systems and methods are provided for data hub architecture to provide actionable data from remote sensor feeds. An exemplary method includes receiving, by a master hub of a plurality of data hubs, a request to access at least one first sensor in a first location and at least one second sensor in a second location from a data client, wherein the master hub is closest to the data client of the plurality of data hubs on a network, determining a first data hub that is closest to the at least one first sensor on the network, and determining a second data hub that is closest to the at least one second sensor on the network. The method further includes querying the first data hub and the second data hub for data and communicating the data to the data client.
Owner:RED HAT
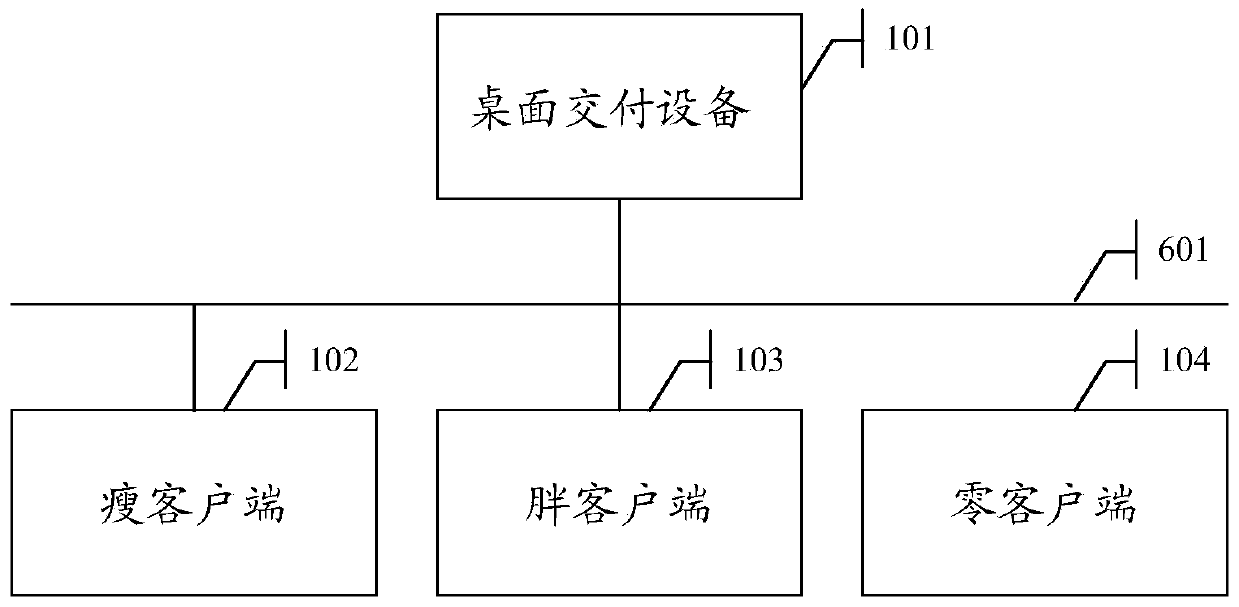
System and method for achieving desktop delivery device based on virtualization technology
InactiveCN103677962AEasy to buildSoftware simulation/interpretation/emulationVirtualizationOperational system
The invention discloses a system and method for achieving a desktop delivery device based on the virtualization technology. The desktop delivery device comprises a host machine operating system, virtualization software, a virtual desktop delivery management engine, a virtual server and a virtual desktop or a desktop image or a client side image. The host machine operating system is installed inside the desktop delivery device, the virtualization software and the virtual desktop delivery management engine are installed inside the host machine operating system, and the desktop delivery device creates the virtual desktop and manufactures the desktop image through the virtual desktop delivery management engine, allocates the virtual desktop to a thin client side to be recycled by the thin client side when the thin client side has a request, allocates the desktop image to a rich client side to be recycled by the rich client side when the rich client side has a request and sends the client side image to a zero client side when the zero client side has a request to work in a thin client side or rich client side mode. Various client sides can be supported under virtual desktop architecture.
Owner:SHANGHAI DIANJI UNIV
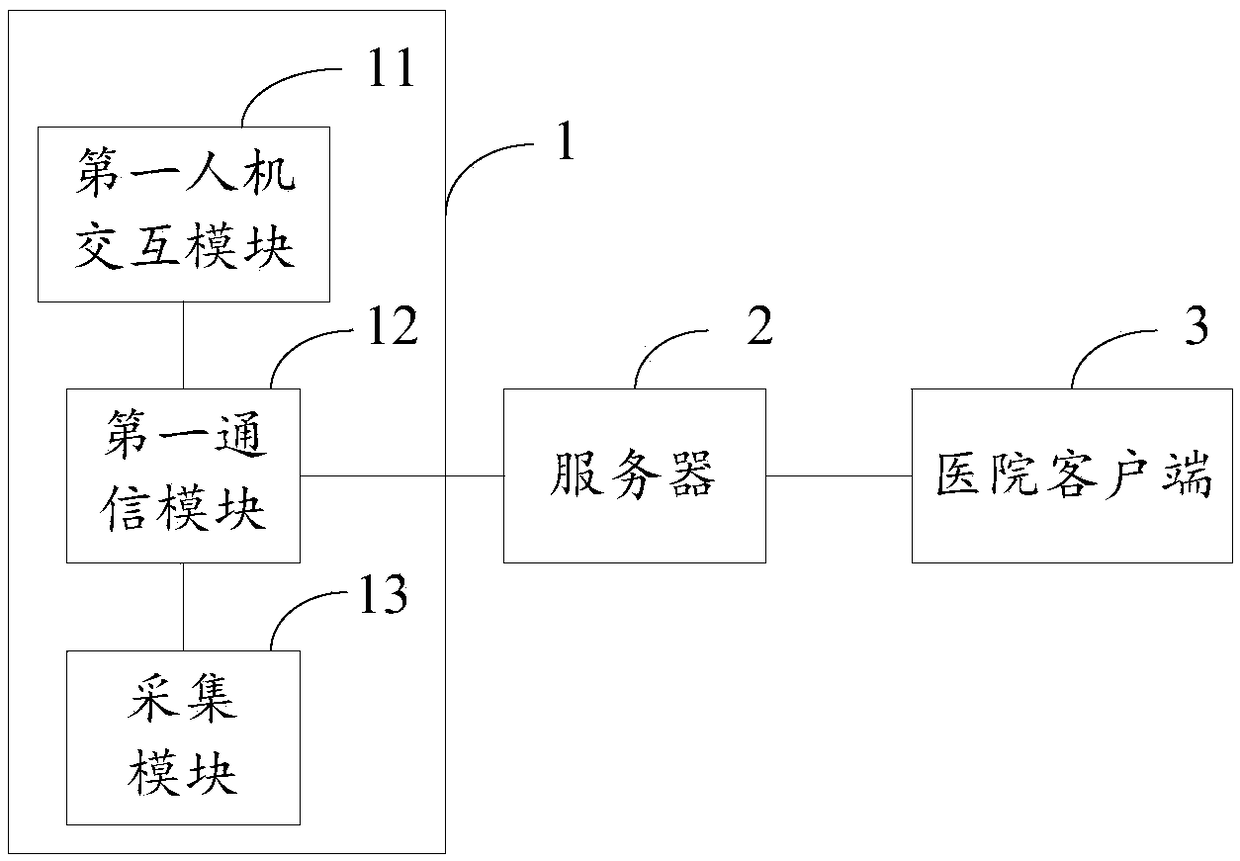
First-aid information management system
ActiveCN108335739ASolve delivery unpreparedSolve efficiency problemsMedical communicationInstruments for road network navigationClient-sideComputer science
The invention discloses a first-aid information management system. The system is used for solving the problems that present first-aid patient information transmission is not complete or the efficiencyof first aid is low. The first-aid information management system includes a first-aid client side, a server and a hospital client side. The first-aid client side is used for creating patient information and sending the patient information and an assigned hospital identifier to the server. The server is linked with the first-aid client side through a network and used for receiving the patient information and the assigned hospital identifier which are sent by the first-aid client side, saving the patient information and the identifier as a first-aid information archive and sending the first-aidinformation archive to the hospital client side corresponding to the assigned hospital identifier, wherein the first-aid information archive comprises a first-aid archive network serial number, the patient information and the corresponding hospital identifier. The hospital client side is linked with the server through the network and used for receiving the first-aid information archive sent by the server and providing the first-aid information archive to a current hospital client side user. The system can improve the efficiency of first aid, particularly the efficiency of the first aid for patients suffering from cardiovascular and cerebrovascular diseases.
Owner:THE AFFILIATED HOSPITAL OF QINGDAO UNIV +1
E-map search result displaying method and E-map client
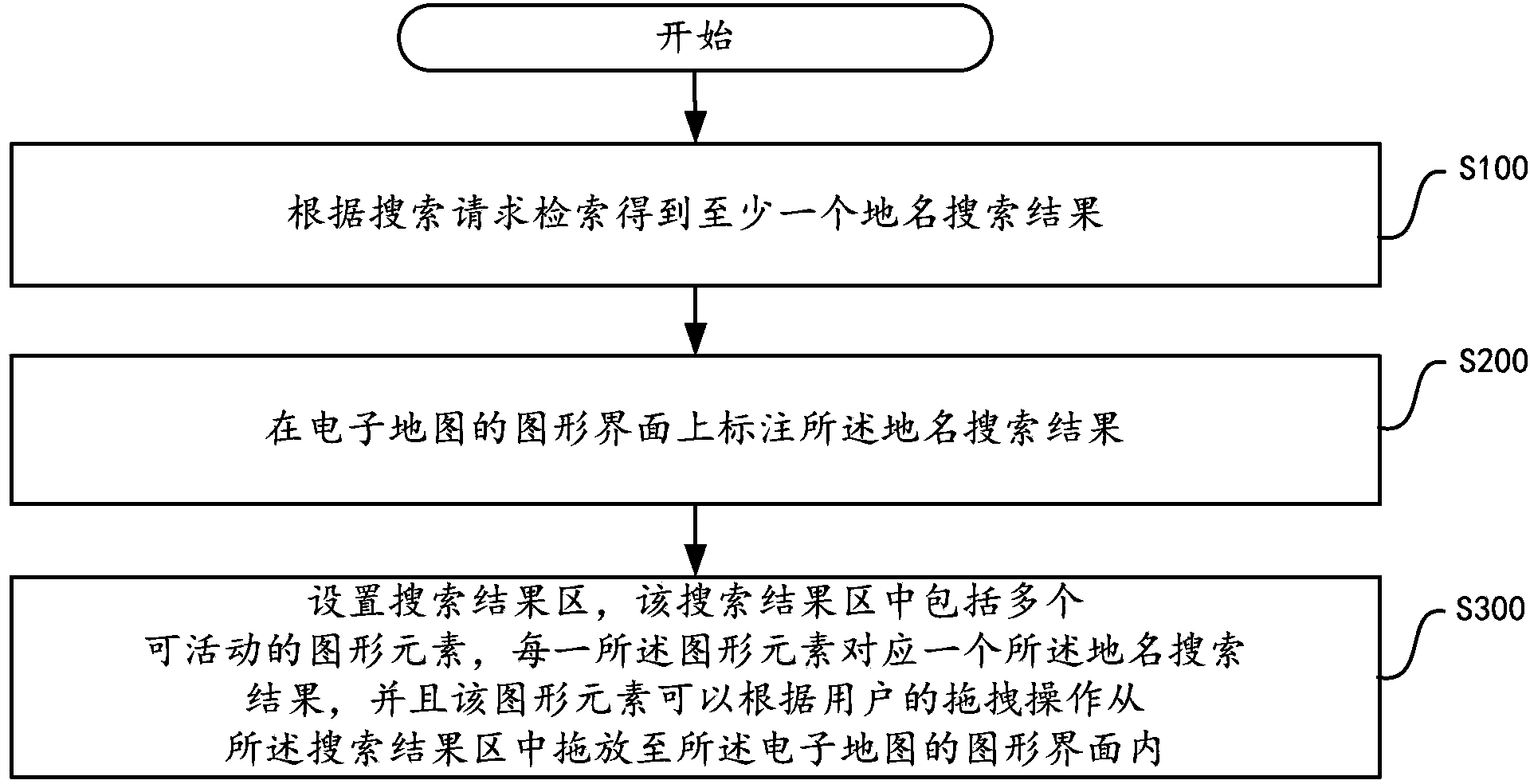
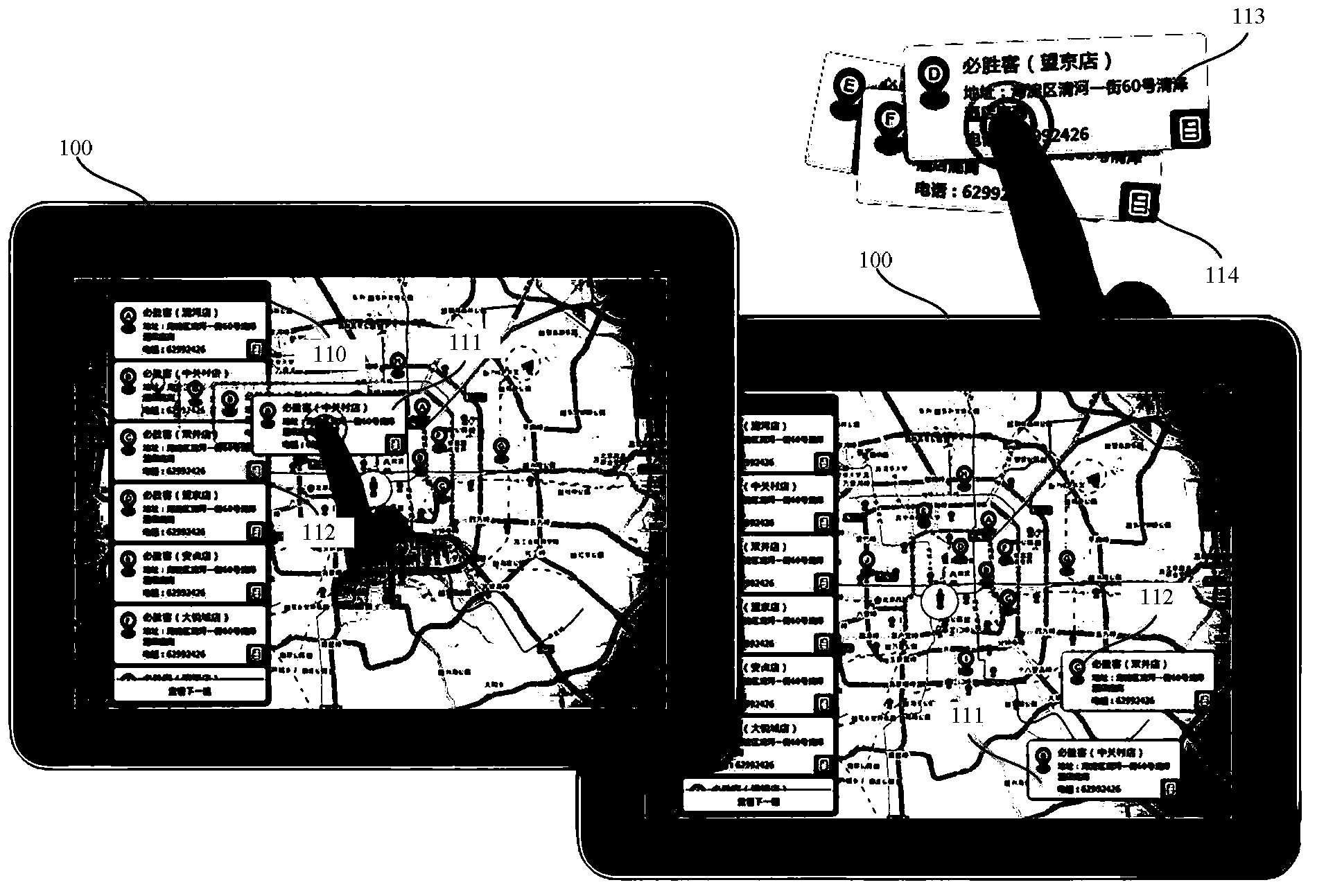
ActiveCN104111934AEasy to switchEasy for users to switch quicklyGeographical information databasesSpecial data processing applicationsGraphicsMarking out
The invention provides an E-map search result displaying method. The method includes: performing searching according to a search request to obtain at least one place name search result; marking out the place name search results on a graphical interface of an E-map; setting a search result area. The search result area includes a plurality of movable graphic elements; each graphic element corresponds to one place name search result; the graphic elements can be dragged into the graphical interface of the E-map according to drags performed by a user. Correspondingly, the invention further provides an E-map client. The E-map search result displaying method and the E-map client have the advantages that convenience is provided for the user to compare different results generated after the user performs multiple searches on the E-map, and the convenience is also provided for the user to quickly switch the multiple search results.
Owner:BEIJING BAIDU NETCOM SCI & TECH CO LTD
Simulation system, PC side simulator and mobile phone side agent client
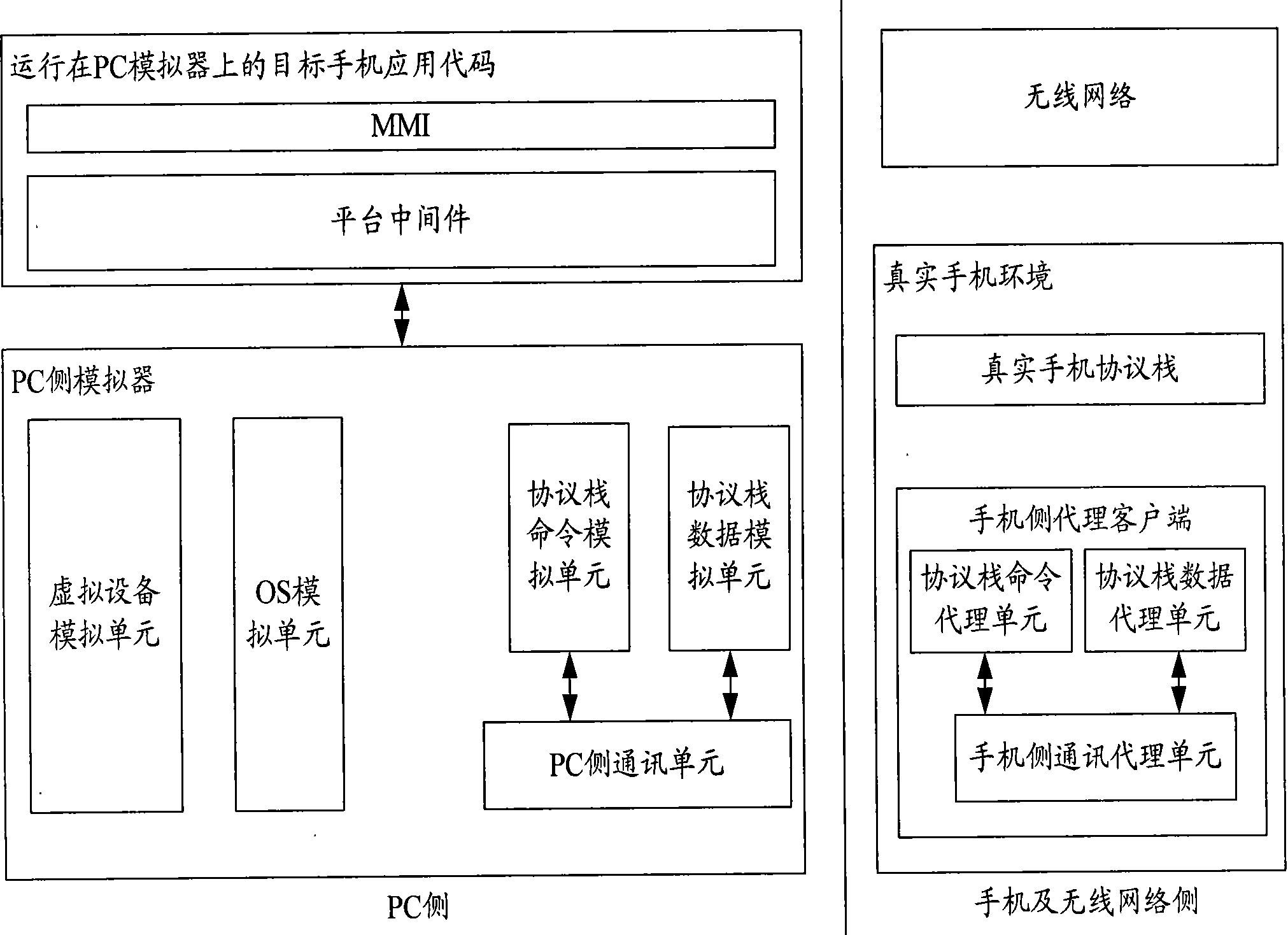
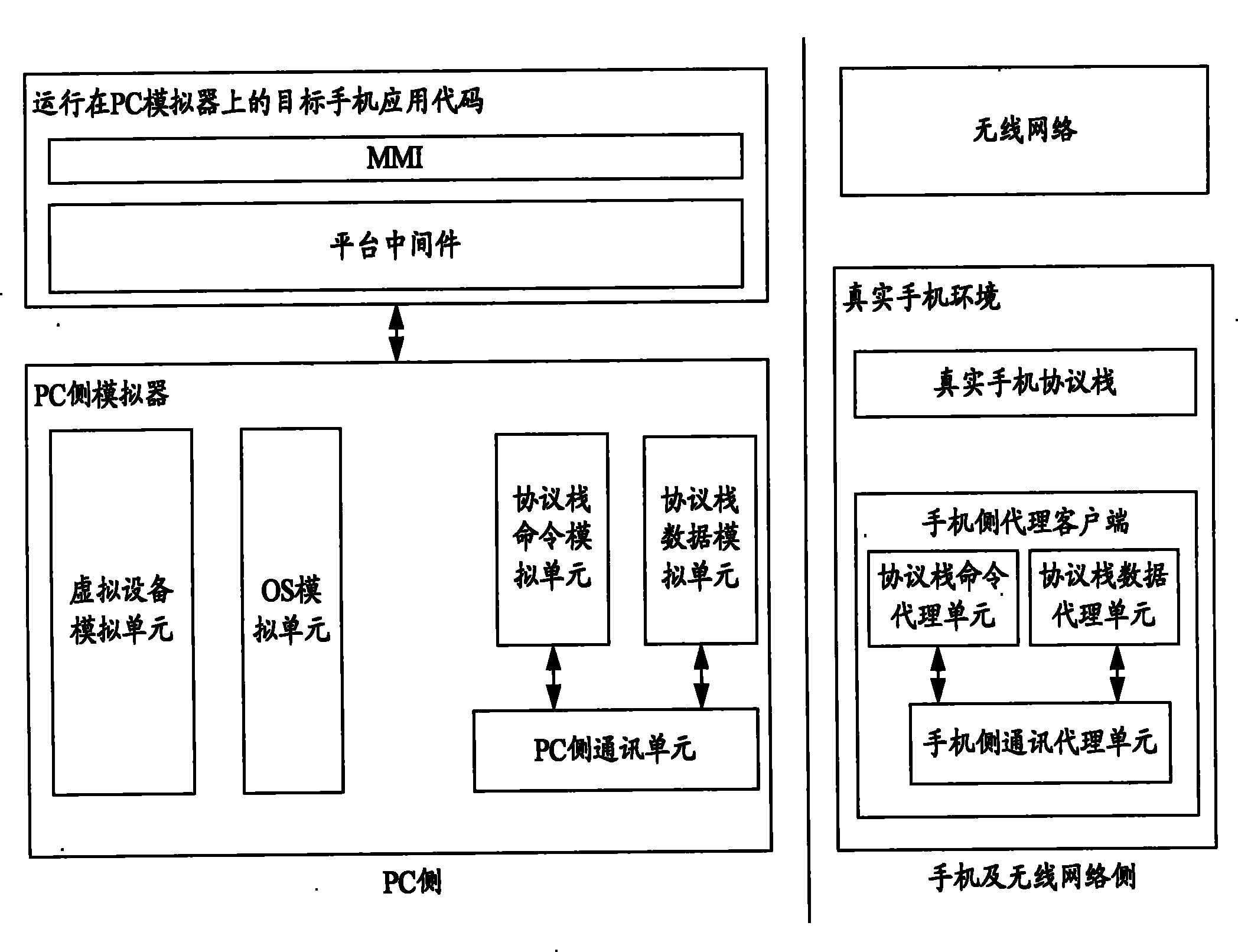
InactiveCN101800910AGet Wireless Networking CapabilitiesReduce the number of on-board debuggingWireless communicationSelection arrangementsProtocol stackMobile phone
The invention discloses a simulation system, a PC side simulator and a mobile phone side agent client, wherein in the simulation system, the PC side simulator is used for acquiring wireless network capacity same as a real mobile phone environment by message interaction with the mobile phone side agent client in the process of simulation; the mobile phone side agent client is used for message interaction with the PC side simulator, so that the PC side simulator acquires the wireless network capacity same as the real mobile phone environment; and the mobile phone side agent client is positioned in the real mobile phone environment and is connected with a real mobile phone protocol stack. The system, the PC side simulator and the mobile phone side agent client of the invention greatly improve the development efficiency of mobile phone softwares.
Owner:ZTE CORP
Cloud distributed real-time database system
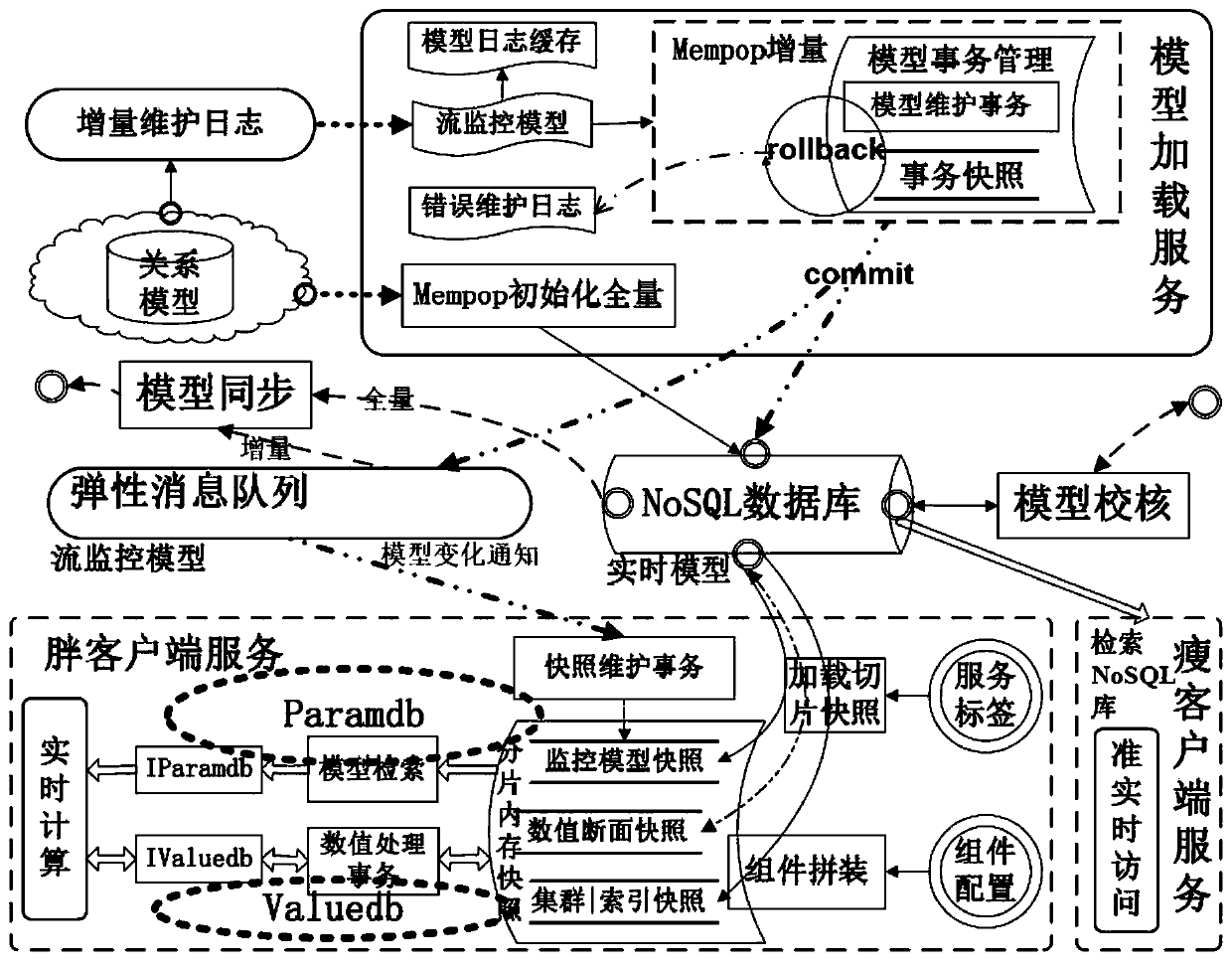
ActiveCN110196885AImprove scalabilityDoes not affect operationDatabase management systemsDatabase distribution/replicationRelational modelSmart grid
The invention discloses a cloud distributed real-time database system which comprises a real-time database and a real-time service bus. The real-time database comprises a storage layer with a distributed hierarchical structure, a positioning layer and an interface layer; the storage layer stores a real-time model based on a distributed NoSQL database, and the real-time model corresponds to a relational model of a relational database of the power grid system; the positioning layer is used for storing fragmented memory snapshots, and the fragmented memory snapshots comprise monitoring model snapshots, numerical section snapshots, transaction snapshots and the like; the interface layer provides a transaction type component and is used for realizing establishment, access and processing of a fragmented memory snapshot; and the real-time service bus comprises a model loading service, a fat client service and the like. Based on the intelligent power grid regulation and control system CIM model grouping and slicing technology, fat client service real-time calculation processing and thin client quasi-real-time access are achieved, model checking and synchronization functions are expanded, and concurrent control and extension expansibility of the system are improved.
Owner:DONGFANG ELECTRONICS
Online operation management method and system based on ship three-dimensional model and terminal
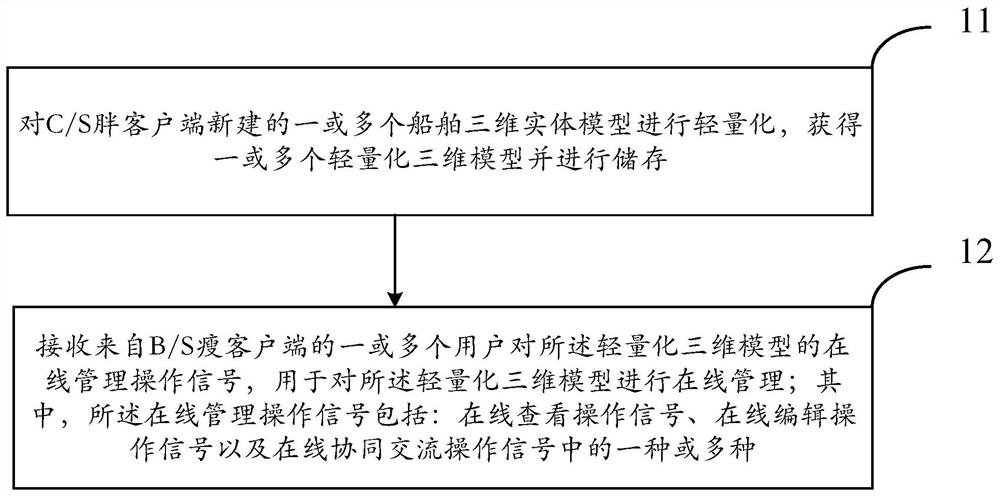
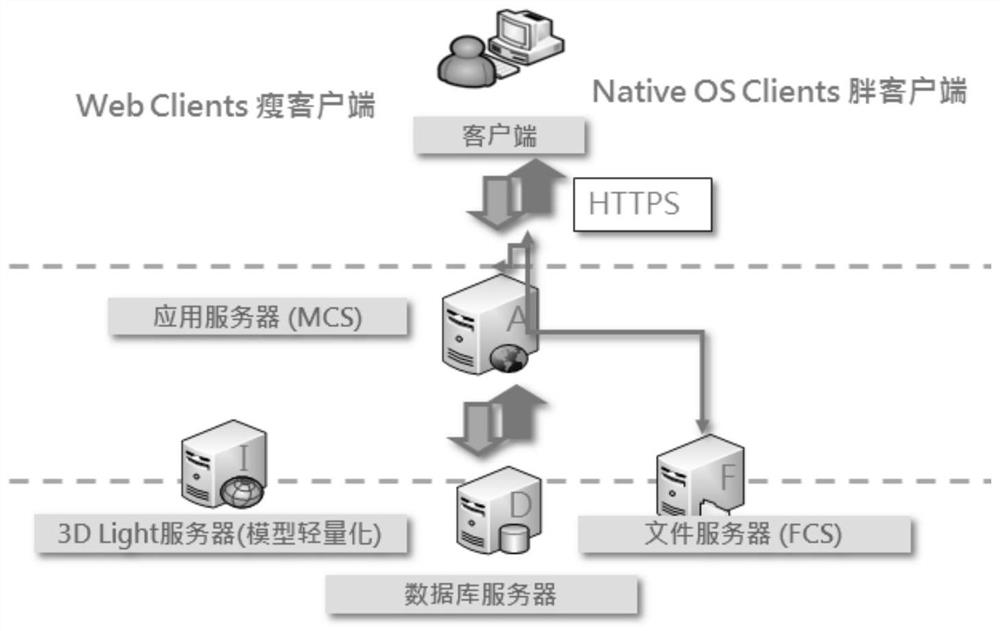
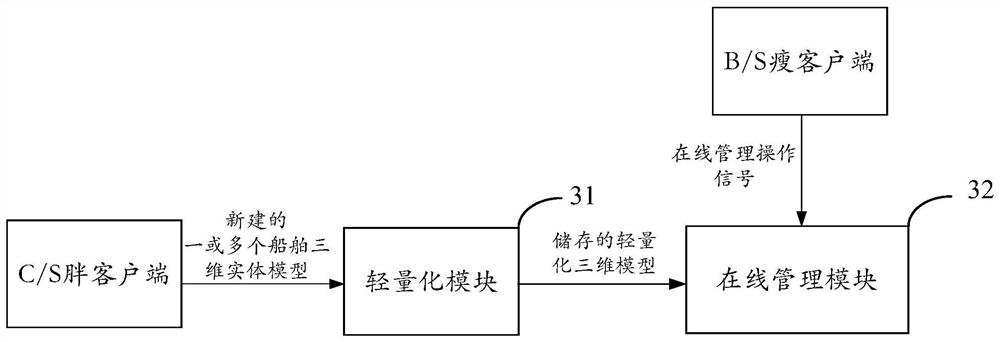
PendingCN111915276AAchieve fast and lightweightLower requirementGeometric CADOffice automationReworkIndustrial engineering
The invention provides an online operation management method and system based on a ship three-dimensional model and a terminal. The method comprises the steps: lightening a ship three-dimensional entity model newly built at a C / S fat client to acquire a light-weight three-dimensional model, and storing the light-weight three-dimensional model; receiving online management operation signals of one or more users from a B / S thin client, wherein the online management operation signals are used for carrying out online management on the lightweight three-dimensional model; wherein the online management operation signal comprises one or more of an online viewing operation signal, an online editing operation signal and an online cooperative communication operation signal. The problems that in the prior art, the requirement for field terminal application equipment is high, the application cost is high, and online cooperation between design and manufacturing cannot be achieved for a three-dimensional model are solved. Online cooperation between ship design and manufacturing is achieved, online communication between field manufacturing personnel and designers is supported, the design problem existing in the manufacturing field is rapidly solved, design change and manufacturing rework are reduced, and the production and construction cost is saved.
Owner:JIANGNAN SHIPYARD GRP CO LTD
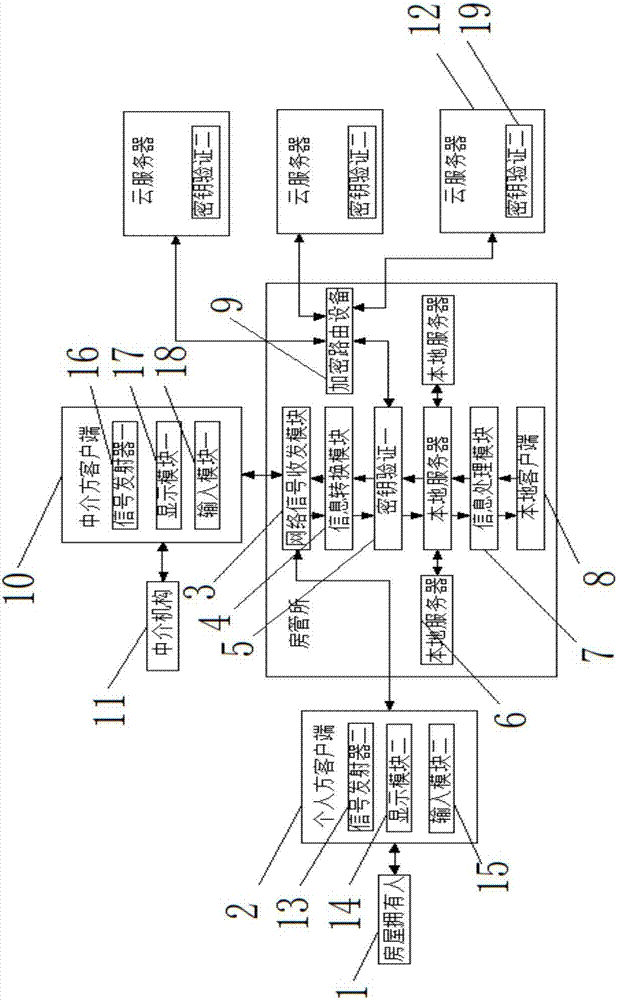
Multitime encryption system of house information of block link
The invention discloses a multitime encryption system of house information of a block link. The system comprises a house owner. The output end of the house owner is connected with the input end of a personal client. The input end of the house owner is connected with the output end of the personal client. The output end of the personal client is connected with the input end of a network signal transceiving module. The output end of the network signal transceiving module is connected with the input end of an information conversion module. The input end of the network signal transceiving module is connected with the output end of the information conversion module. According to the invention, by setting a personal client, an agent client and a local client, and using relations between different clients and a housing management office, information is encrypted for many times, thereby ensuring the safety; by setting multiple local servers, the information obtained by the housing management office is stored and processed, so requirements of the people are well met; and by backing up the information for many times, safety of the information is improved.
Owner:陈少峰
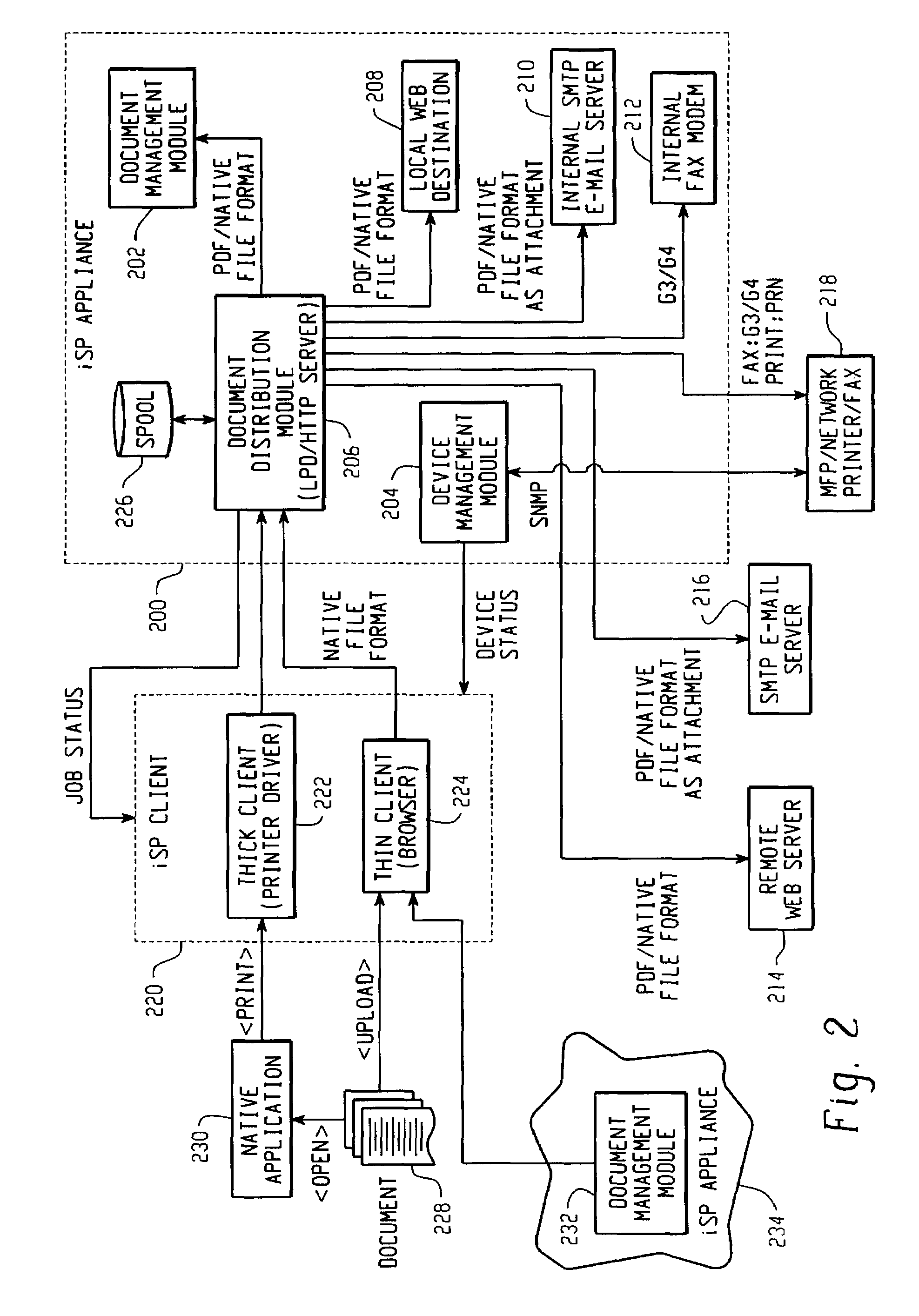
Method and system for preserving user identification when generating image data from a remote location
InactiveUS7565400B2Multiple digital computer combinationsOffice automationClient-sideDocument preparation
A method for a user using a thick client to send a print job to a server wherein the user name is preserved and can be determined by the server. When the image file is processed, the processing comprising appending a user identification to the file. A destination driver is invoked, which creates raw print data from the image file for each selected driver. The raw print data is sent to the server, wherein the server parses the raw data and determines the user identification. The raw print data can then be sent to the user's inbox on the server. In a preferred embodiment, the user identification comprises the sequence of ASCII 60 (or 3C hex), the username, and ASCII 62 (or 3E hex), or “<username>”. Preferably, the user identification is appended to the document name.
Owner:TOSHIBA TEC KK
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com