Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
311results about How to "Keep full control" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
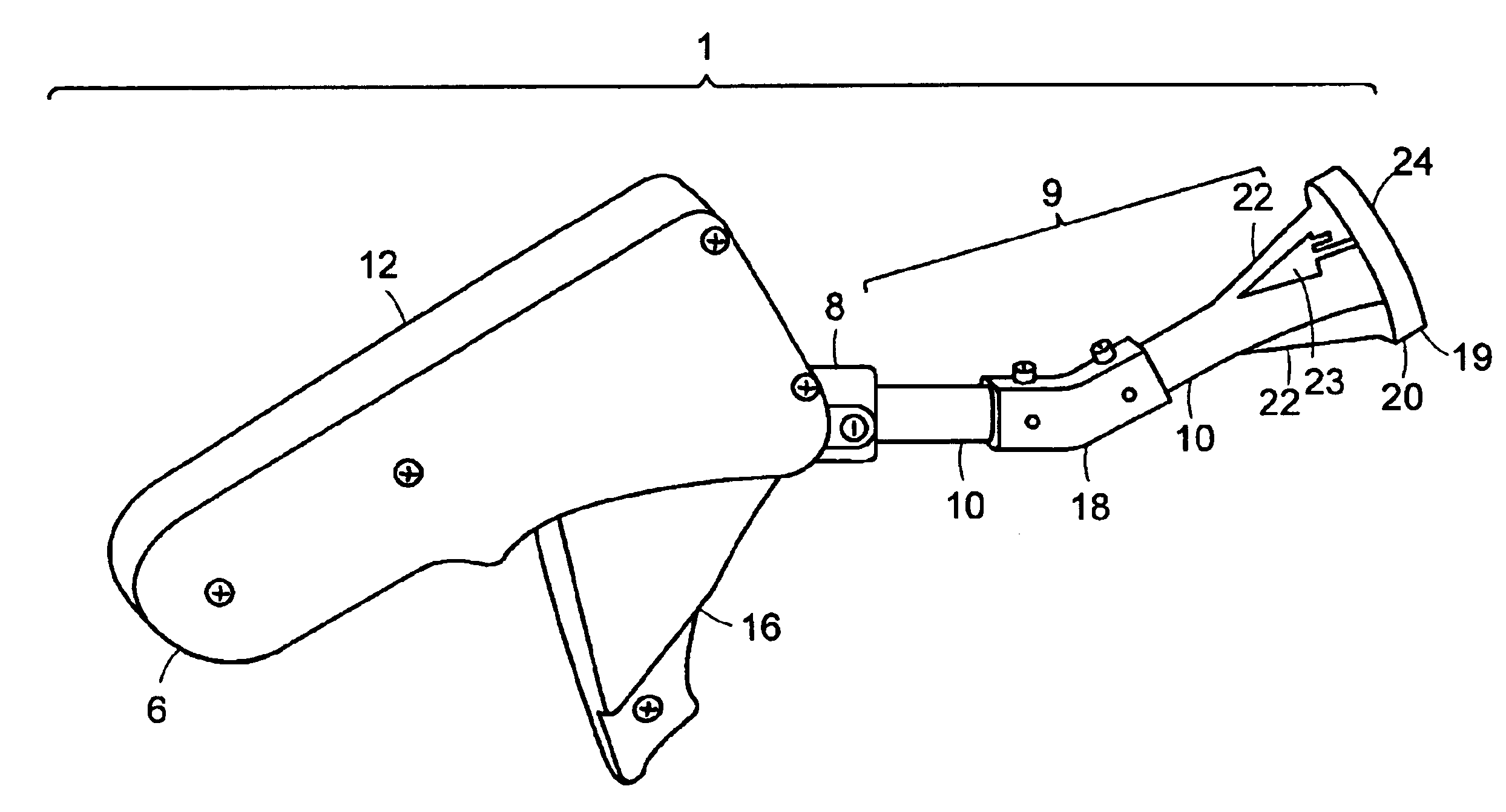
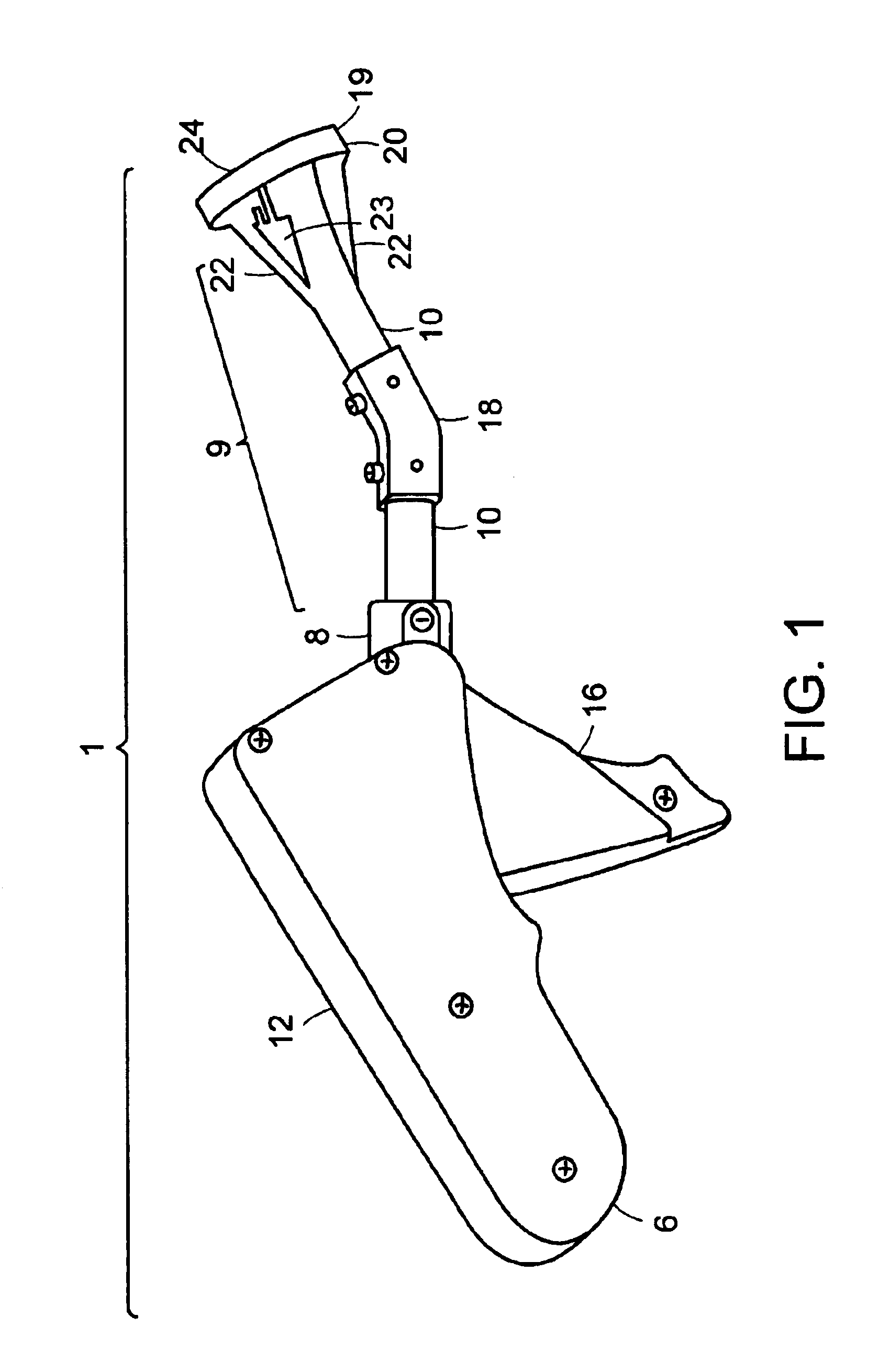
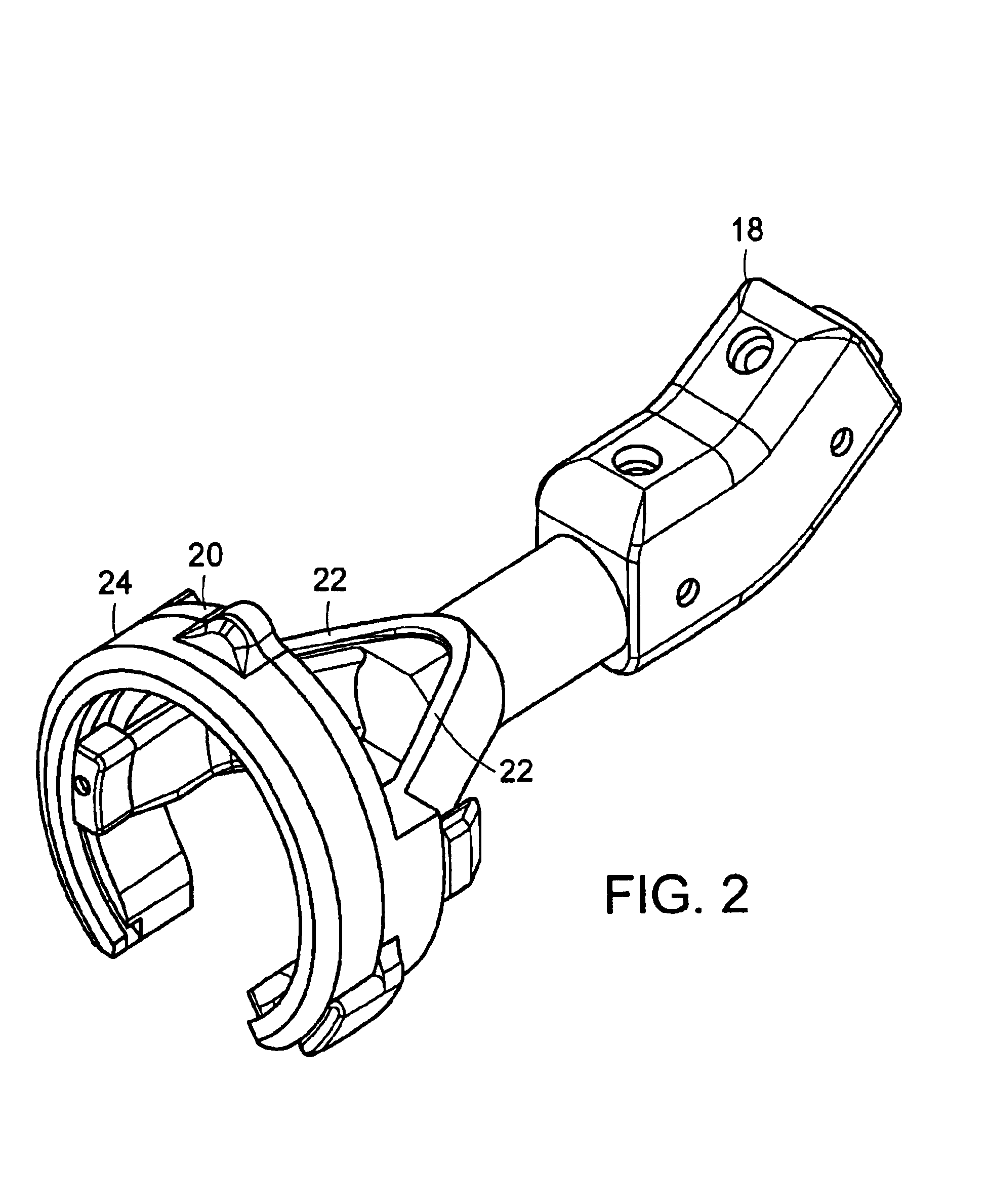
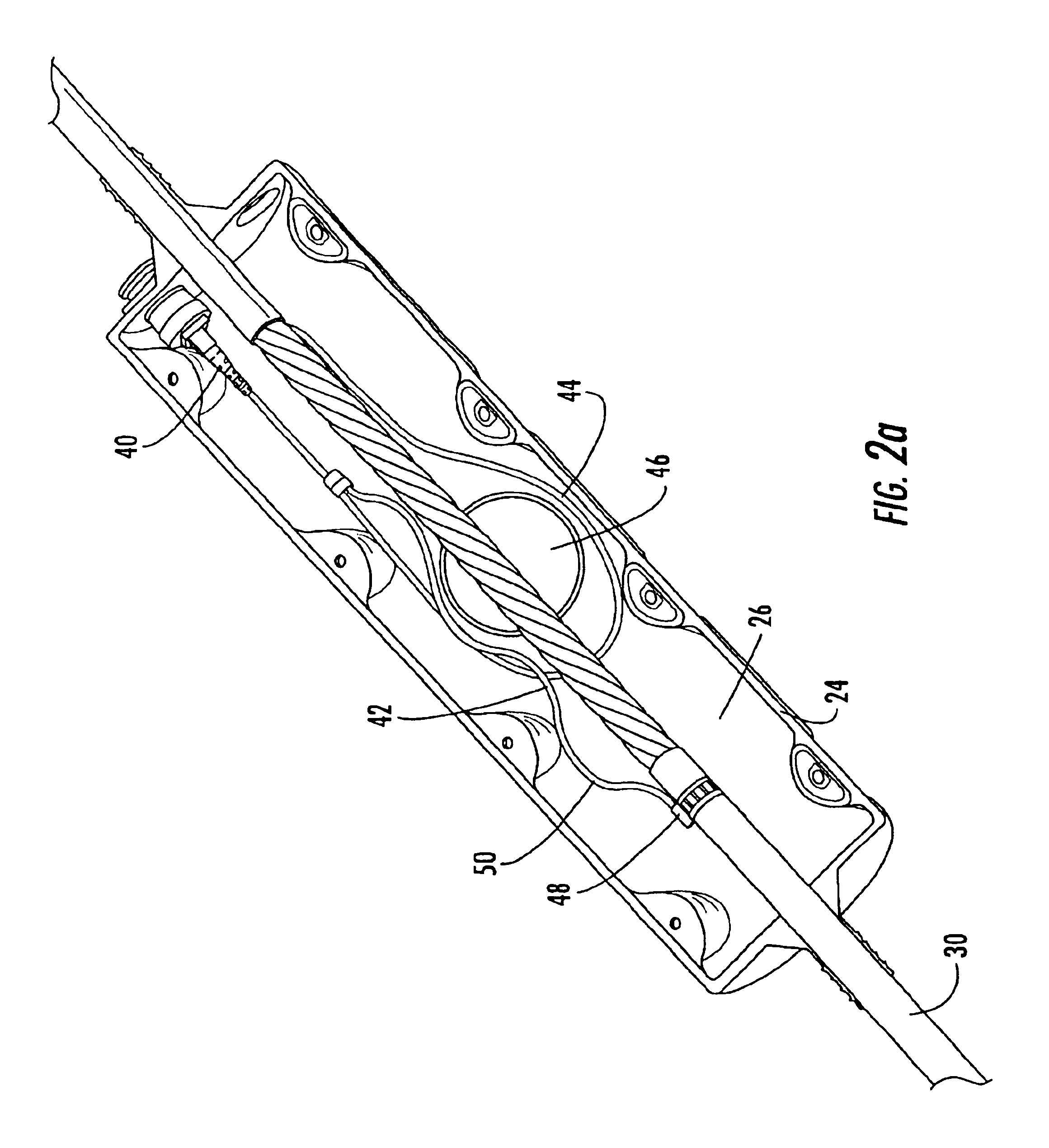
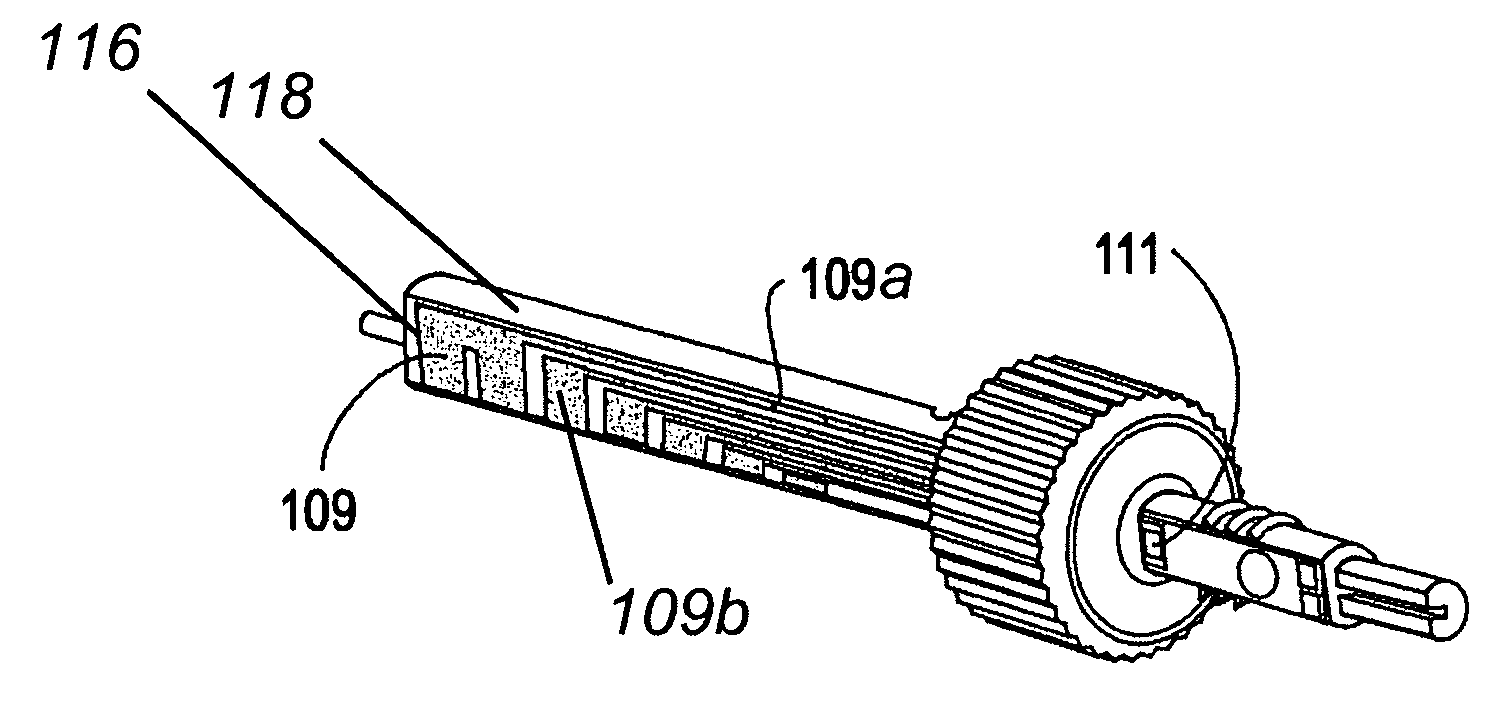
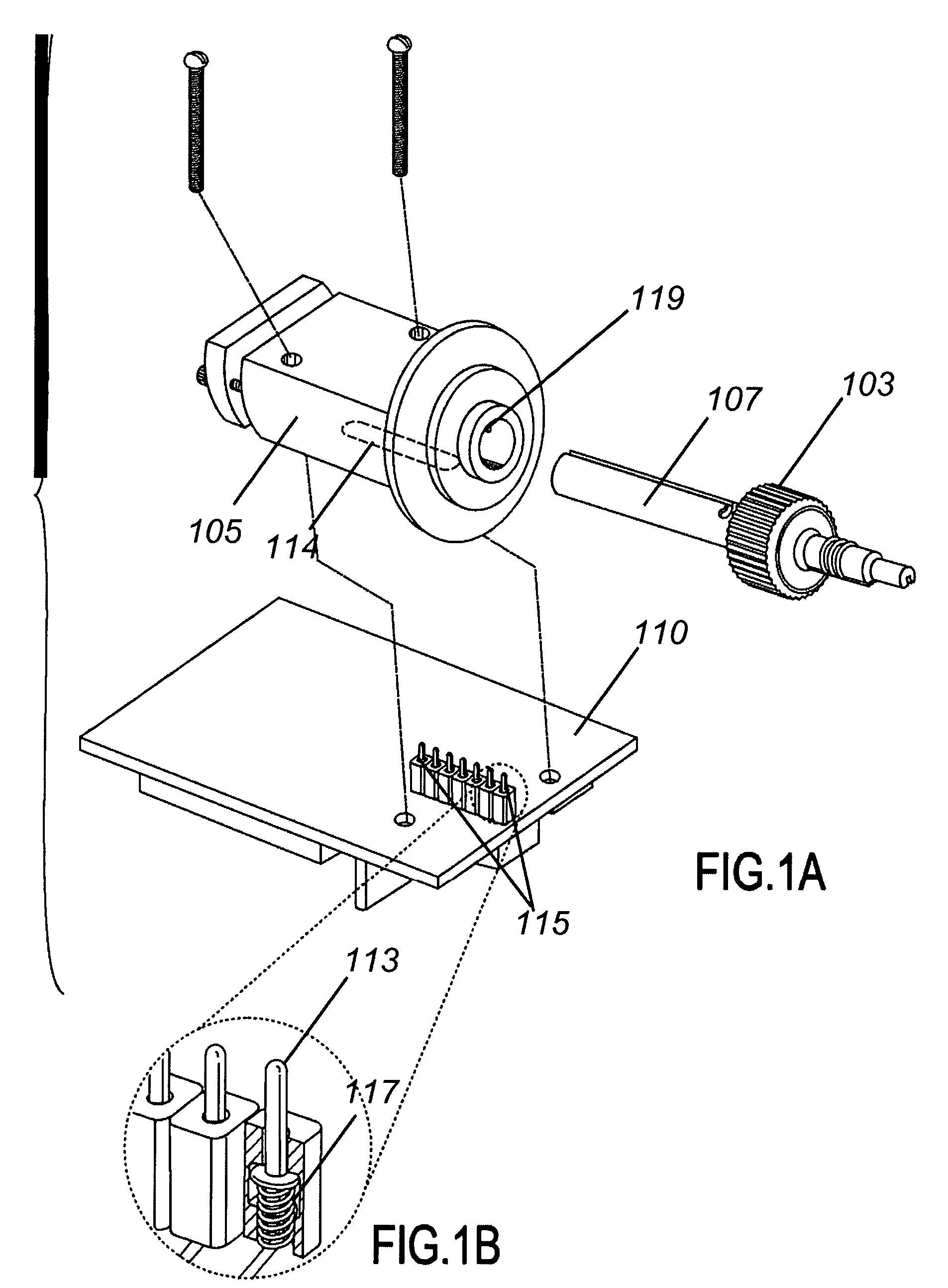
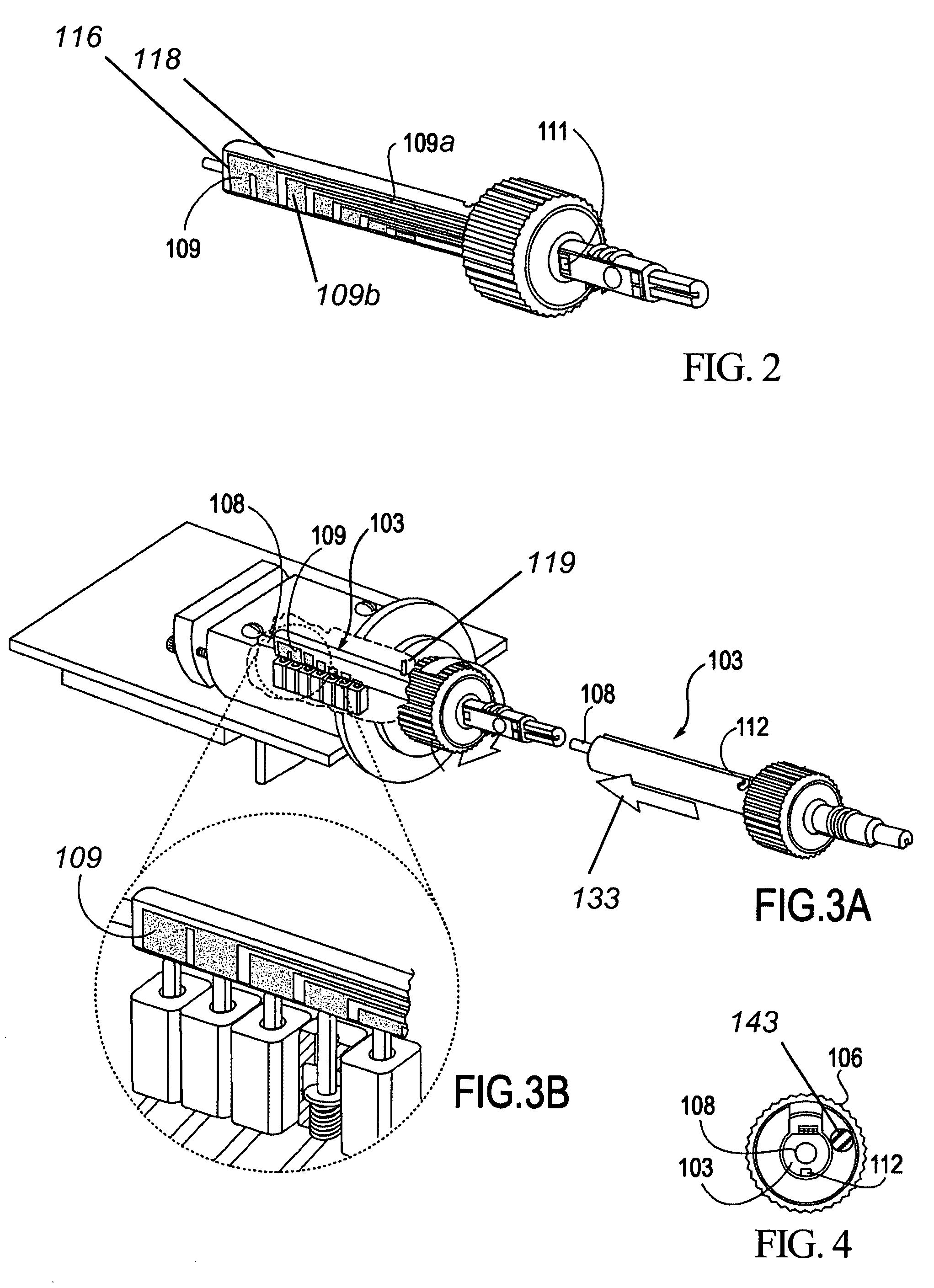
Apparatus and method for surgical suturing with thread management
InactiveUS6923819B2Efficient preparationExcellent ease of useSuture equipmentsDiagnosticsSuturing needleEngineering
An apparatus and a method for surgical suturing with thread management. An apparatus for tissue suturing comprising a cartridge having a suturing needle having a pointed end and a blunt end, the suturing needle capable of rotating about an axis; a pusher assembly comprising a cartridge holder having a needle rotation drive capable of releasably engaging the cartridge and rotating the suturing needle about the axis; and an actuator capable of releasably engaging the needle rotation drive to rotate the needle rotation drive. A method for suturing tissue comprising placing a suturing device having a cartridge containing a suturing needle to span separated tissue segments; activating an actuator to cause rotational movement of the suturing needle through the separated tissue segments; and deactivating the actuator to stop an advancing movement of the suturing needle to cause a suturing material to be pulled through the separated tissue segments forming a stitch.
Owner:INTUITIVE SURGICAL OPERATIONS INC
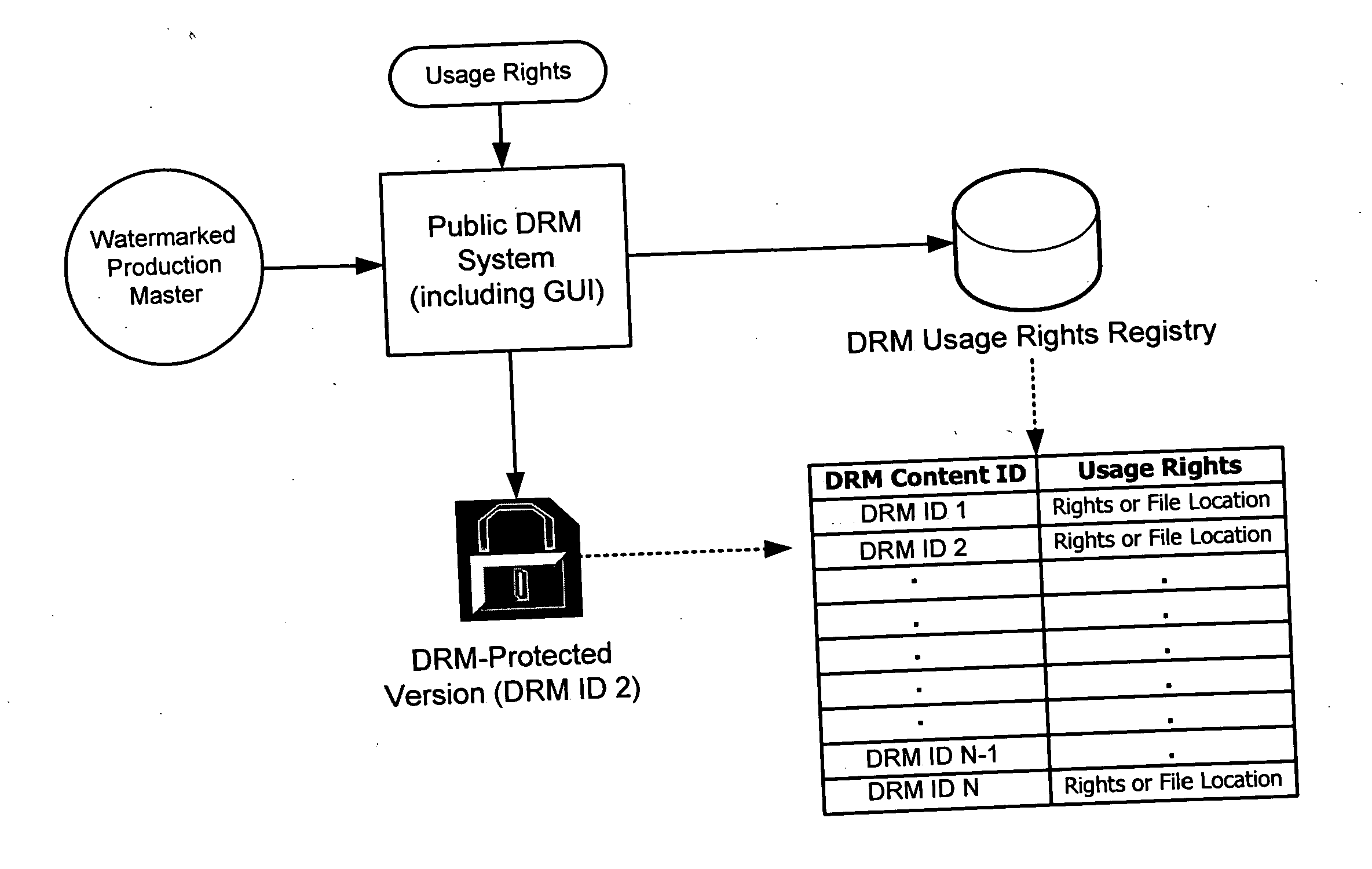
Rights management systems and methods using digital watermarking
ActiveUS20060062426A1Difficult to controlDifficult to trackUser identity/authority verificationAnalogue secracy/subscription systemsContent IdentifierRights management
A digital watermark (DWM) content identifier is steganographically embedded in content. The DWM content identifier provides a link to a rights registry storing usage rights associated with the content. In some implementations the rights registry provides an association between the DWM content identifier and a digital rights management (DRM) content identifier. The DRM content identifier is used to find associated usage rights. The DWM content identifier can also be used to transfer content from a first DRM system to a second DRM system.
Owner:DIGIMARC CORP (FORMERLY DMRC CORP)
Interconnection enclosure having a connector port and preterminated optical connector
InactiveUS6856748B1Maintaining bend radius controlReduce riskCoupling light guidesFibre mechanical structuresEngineeringInterconnection
An interconnection enclosure comprising at least one connector port operable for receiving a connector pair and a preterminated optical connector received in the at least one connector port, wherein the preterminated optical connector is adapted to be withdrawn from the exterior of the enclosure without entering the enclosure. The enclosure further comprising a tether means, a bend radius control means and a sealing means. An interconnection enclosure comprised of two halves held together by a fastening means, the enclosure defining an end wall and defining at least one connector port opening through the end wall for receiving a preterminated optical connector, the enclosure housing further defining an opening for receiving a distribution cable extending therethrough, wherein the preterminated optical connector is adapted to be withdrawn from the exterior of the enclosure without entering the enclosure.
Owner:CORNING OPTICAL COMM LLC
Method and system for custom-manufacturing footwear
A system and method for allowing a customer to custom-order footwear. The system and method may allow a retailer to control the selection of choices given to the customer for custom-manufacturing the footwear, including allowing a customer to order footwear with different sizes for their left and right feet.
Owner:NIKE INTERNATIONAL LTD
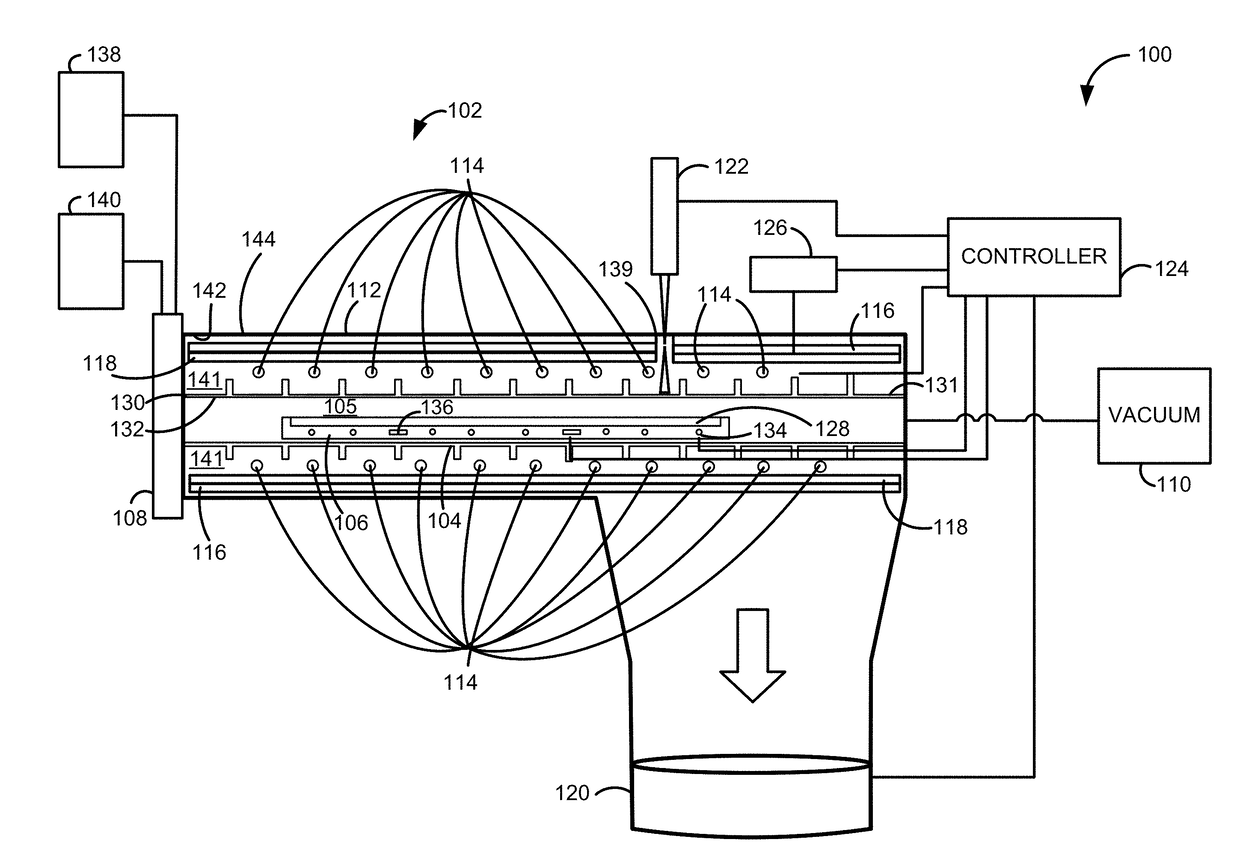
Reactor system and method to reduce residue buildup during a film deposition process
ActiveUS20180195174A1Mitigate formation of residueSubstrate throughput can be increasedSemiconductor/solid-state device testing/measurementSemiconductor/solid-state device manufacturingEtchingReactor system
A system and method for depositing a film within a reaction chamber are disclosed. An exemplary system includes a temperature measurement device, such as a pyrometer, to measure an exterior wall surface of the reaction chamber. A temperature of the exterior wall surface can be controlled to mitigate cleaning or etching of an interior wall surface of the reaction chamber.
Owner:ASM IP HLDG BV
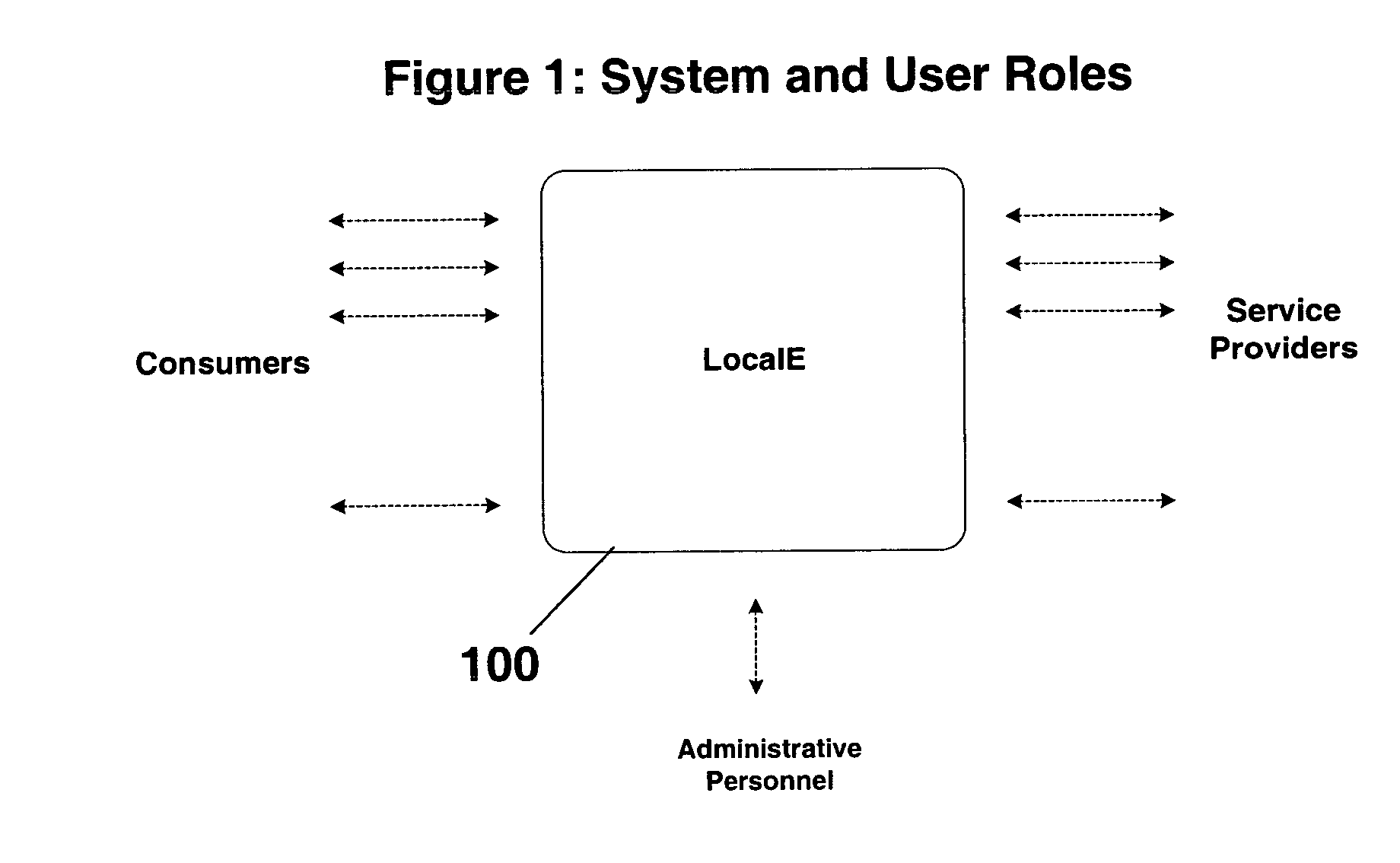
System and method for matching local buyers and sellers for the provision of community based services
A consumer-centric service for matching local consumers with local service providers. A matching is performed between consumer needs and local vendor capabilities and the results are presented back to the consumer so that the choice of which vendors to be contacted is left to the consumer. Mechanisms are provided for immediately and automatically contacting the chosen vendor in one or more of a plurality of communication media and offering the chosen vendor the details of the consumer's request, including the preferred method of contact information, for a fee. Also, the system immediately informs the consumer about the status of the vendor contacts, including whether or not the vendor has accepted the lead. Once a chosen vendor accepts the lead, the consumer is contacted by the vendor, in the manner requested by the consumer. Thus, the invention enables consumers to maintain control over the selection and contact process with matched vendors. The system of the invention is particularly advantageous for providing community based services such as babysitting, cleaning, painting, software support, typing, and in obtaining professional services from professionals such as electricians, carpenters, gardeners, accountants, lawyers, and the like.
Owner:ARKOSE TECH
Information collection in multi-participant online communities
InactiveUS20080091692A1Improve functionalityImprove user experienceDigital data processing detailsWebsite content managementSynthetic dataComputer science
A database of personal information is built and controlled by the individual users creating it. This database can then be used to enhance the functionality and user experience associated with multi-participant online communities. By collecting information from users themselves, and by allowing users to maintain such data, the data can have significant added value both to the users and to any commercial services that wish to use it. Appropriate precautions are taken to ensure that users maintain control over the data they choose to share. Data is owned by the user that provided it, and any application or release of such data is only performed at user direction and under user control. The users are also given incentives to provide such data, in the form of promised rewards. These mechanisms improve the amount and quality of collected data, so that comprehensive databases describing users can be built more easily and effectively.
Owner:BRILIG
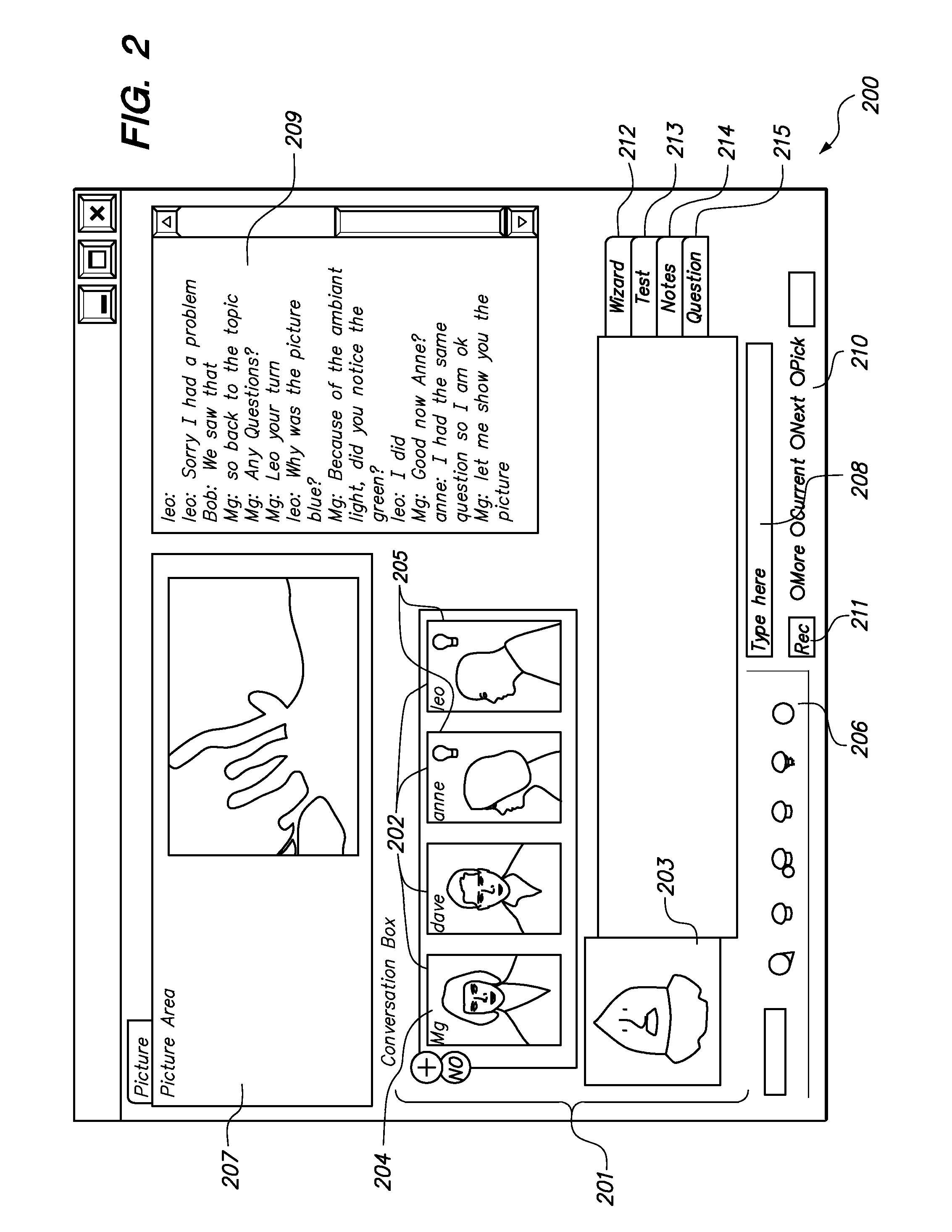
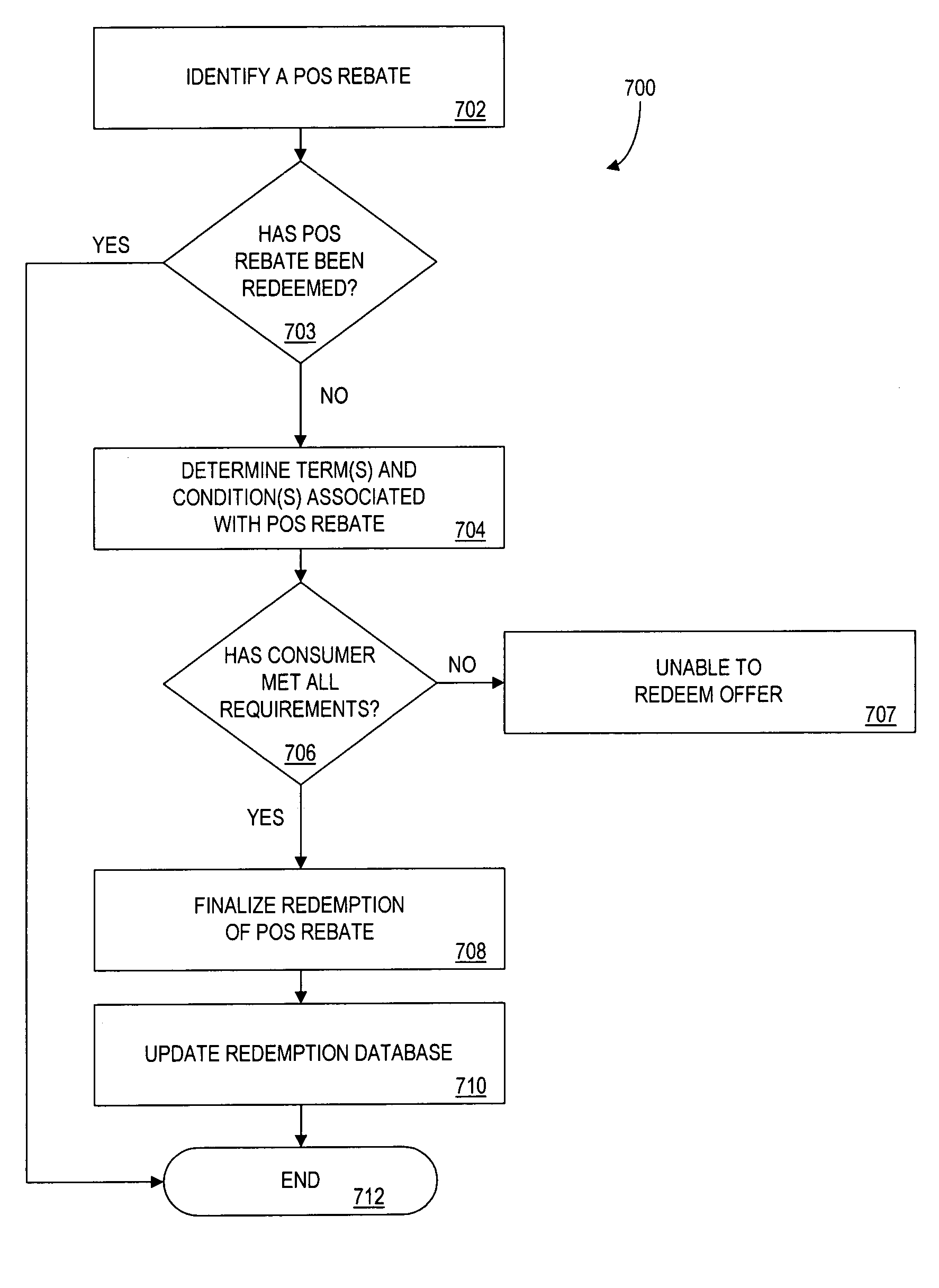
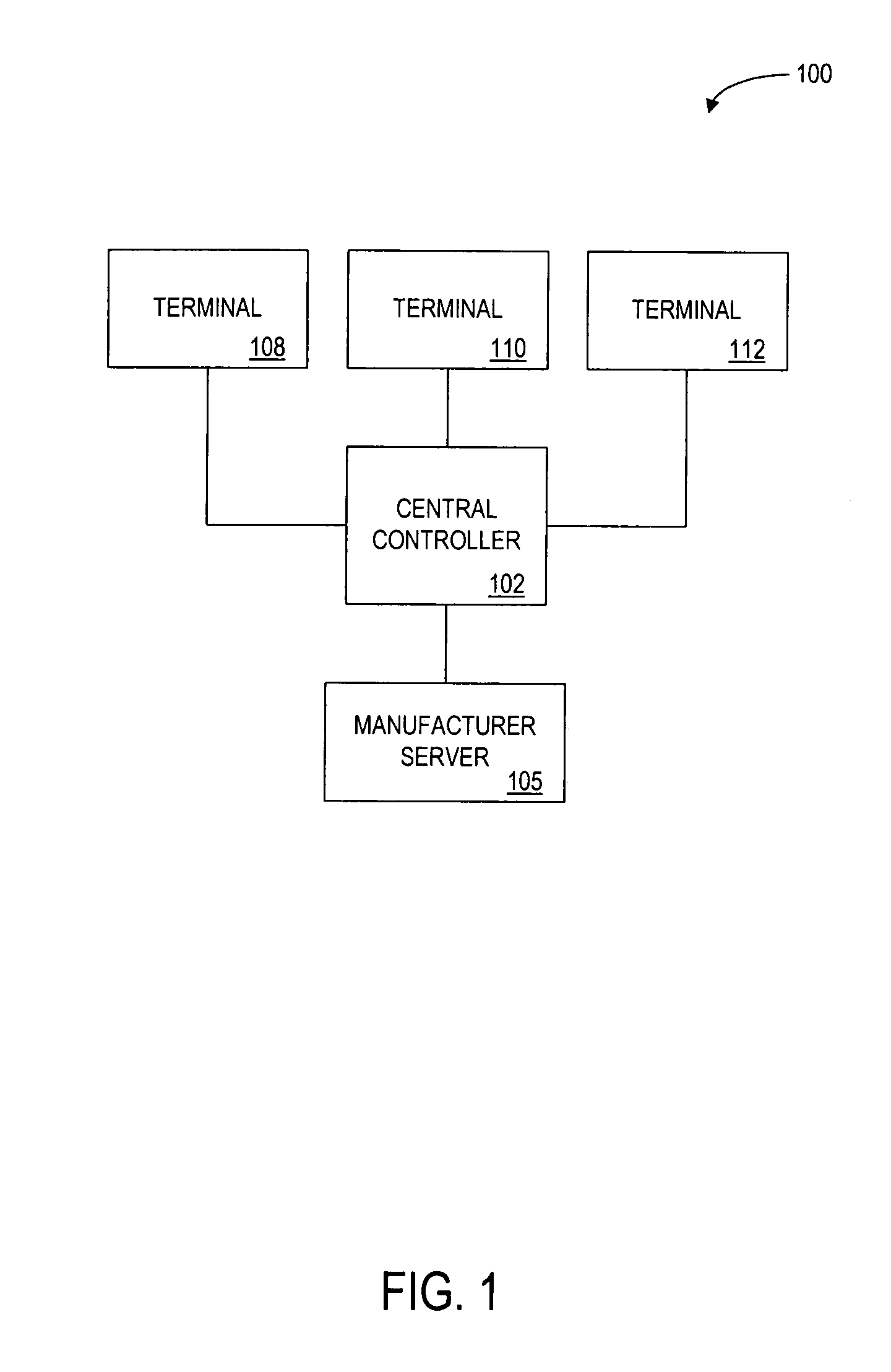
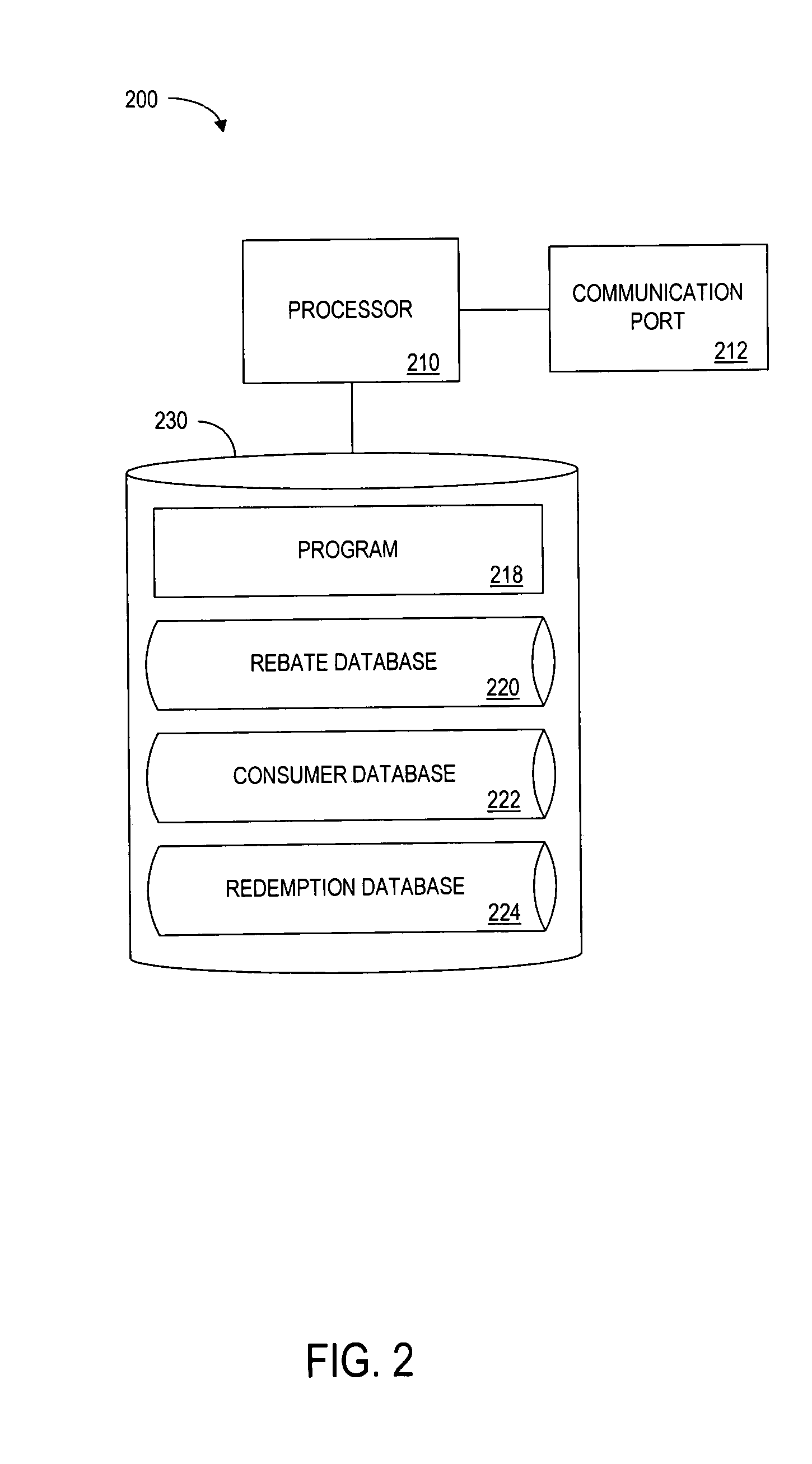
Method and system for processing a rebate
A point of sale (POS) rebate method and system allows a consumer purchasing a product having an associated manufacturer's mail-in rebate to redeem the rebate at the POS. Products that have associated manufacturer rebates are recognized when the products are purchased, e.g., based on information stored in a rebate database. When such products are identified, terms and conditions of a POS rebate are determined. The value of the POS rebate may be determined based on the value of the mail-in rebate offered by the manufacturer. The value of the POS rebate may be determined by querying a server containing rebate information, such as a server operated by or on behalf of the manufacturer or retailer. The consumer is then prompted to choose whether to keep the original manufacturer's mail-in rebate, or to accept the POS rebate, along with any terms and conditions associated with the POS rebate.
Owner:INVENTOR HLDG
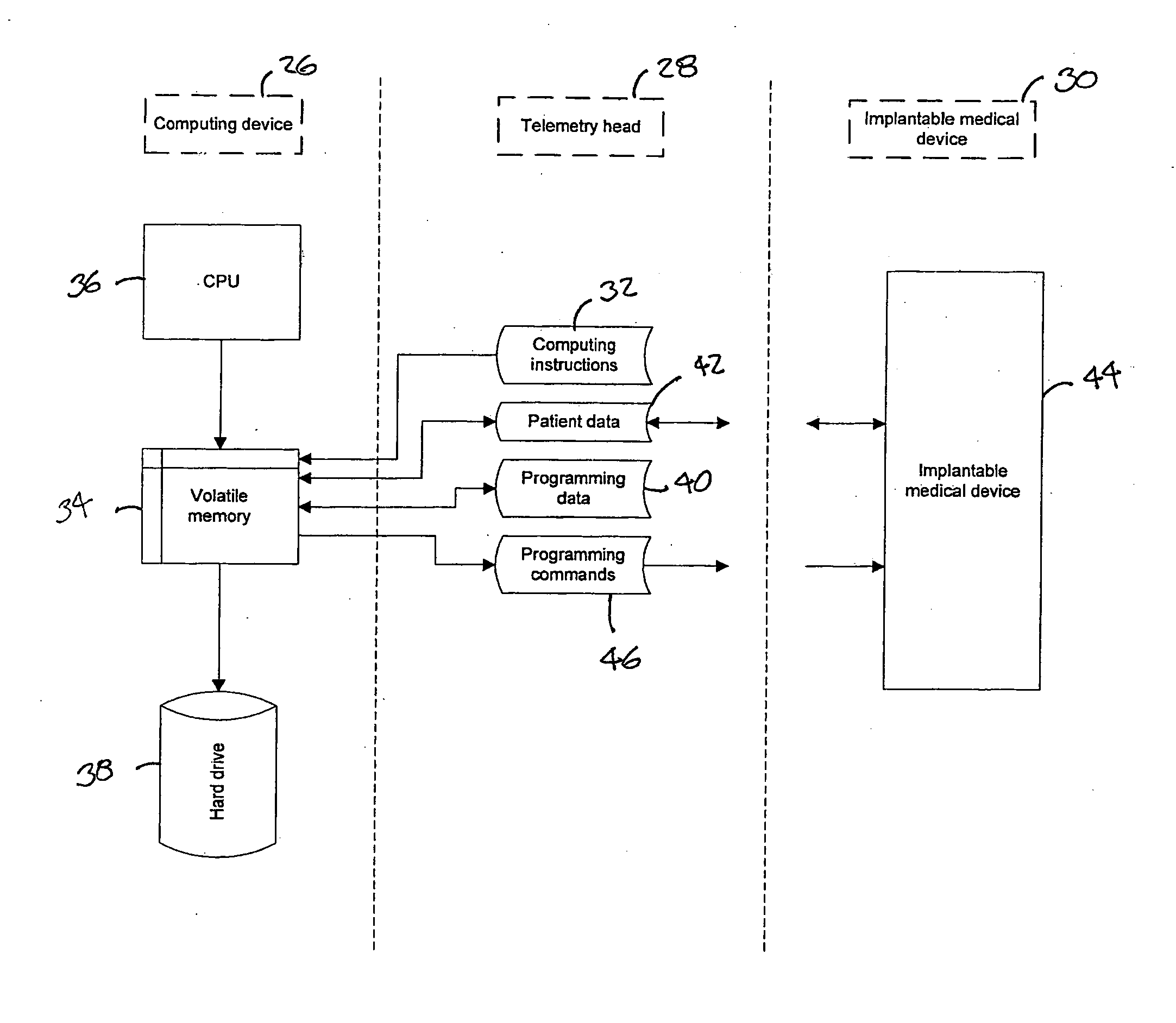
Telemetry head programmer for implantable medical device and system and method
System, telemetry head and method for programming an implantable medical device adapted to provide a therapeutic output to a patient, the implantable medical device being programmable through a telemetry interface. A telemetry head is adapted for transcutaneous communication with the implantable medical device through the telemetry interface when the telemetry head is positioned with respect to the implantable medical device. A computing device has computing processing power and a user interface linked with the telemetry head. The computing device processes the computing instructions associated with the implantable medical device. The computing device supplies the user interface based, at least in part, on the computing instructions associated with the implantable medical device. The telemetry head receives programming instructions from the computing device and provides the programming instructions to the implantable medical device using the transcutaneous telemetry interface.
Owner:MEDTRONIC INC
Method and apparatus for collaborative upload of content
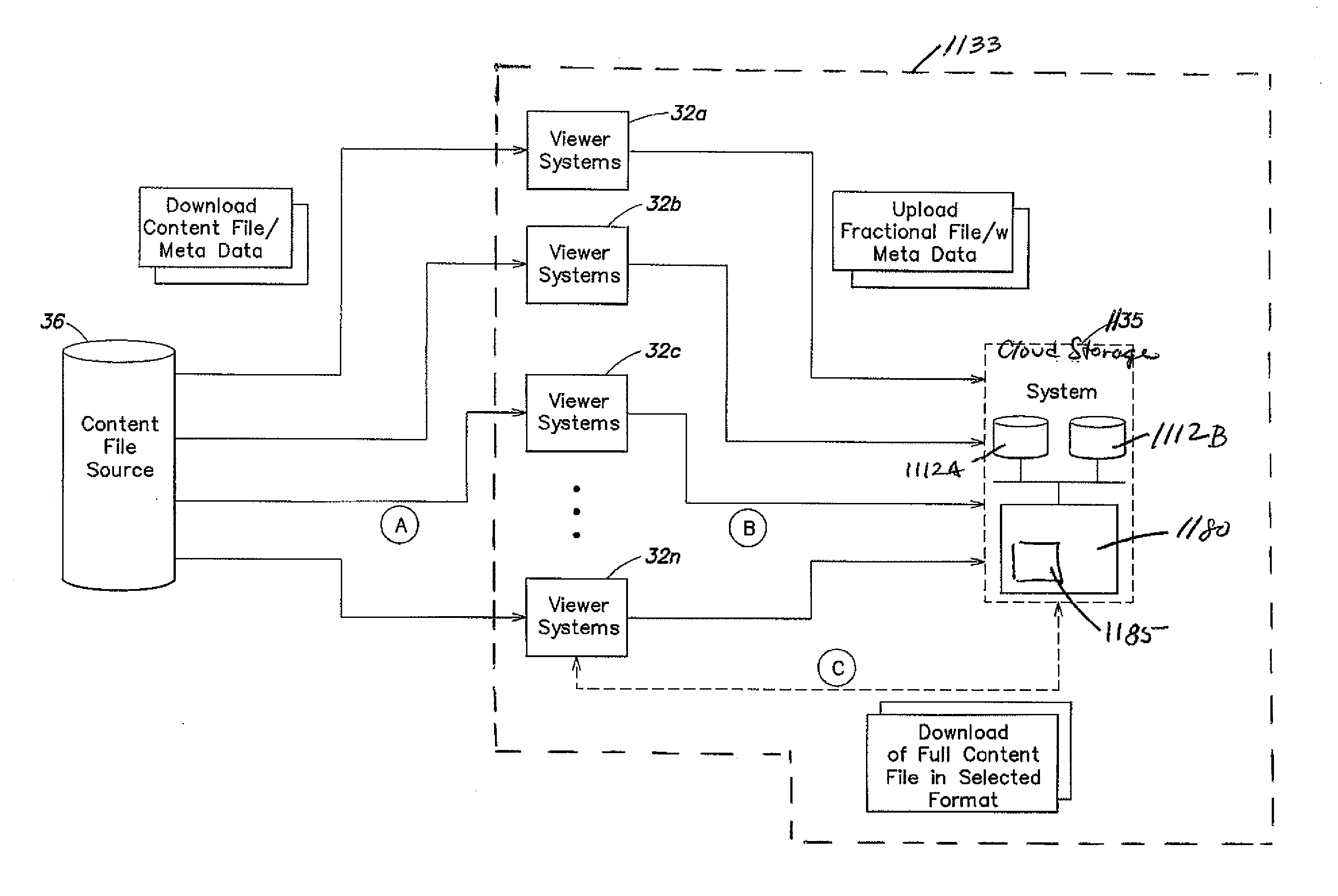
InactiveUS20120278831A1Accurate modelingEasy accessAnalogue secracy/subscription systemsBuying/selling/leasing transactionsCloud storage systemTime shifting
A collaborative cloud DVR system (ccDVR), which includes a cloud storage system and a plurality of participating DVR client devices, acts collaboratively as a single communal entity in which community members authorize each other to upload, remotely store and download licensed content for time shifted viewing, in a manner which rigorously protects legal rights of the content owners while overcoming the potential physical obstacles of limited bandwidth, power failures, incomplete uploads / downloads of content, limited cloud storage capacity, etc. The collaborative cloud DVR community collaboratively shares bandwidth and cloud storage capacity among DVR viewer / users with each owner / user of a DVR client device authorizing his or her individual DVR client device to be utilized by a cloud storage system server and any other owner / user of a DVR client device in the respective service community, and receiving similar permission in return to promote the convenience of cloud storage in an authorized manner.
Owner:RIGHT BRAIN INTERFACE
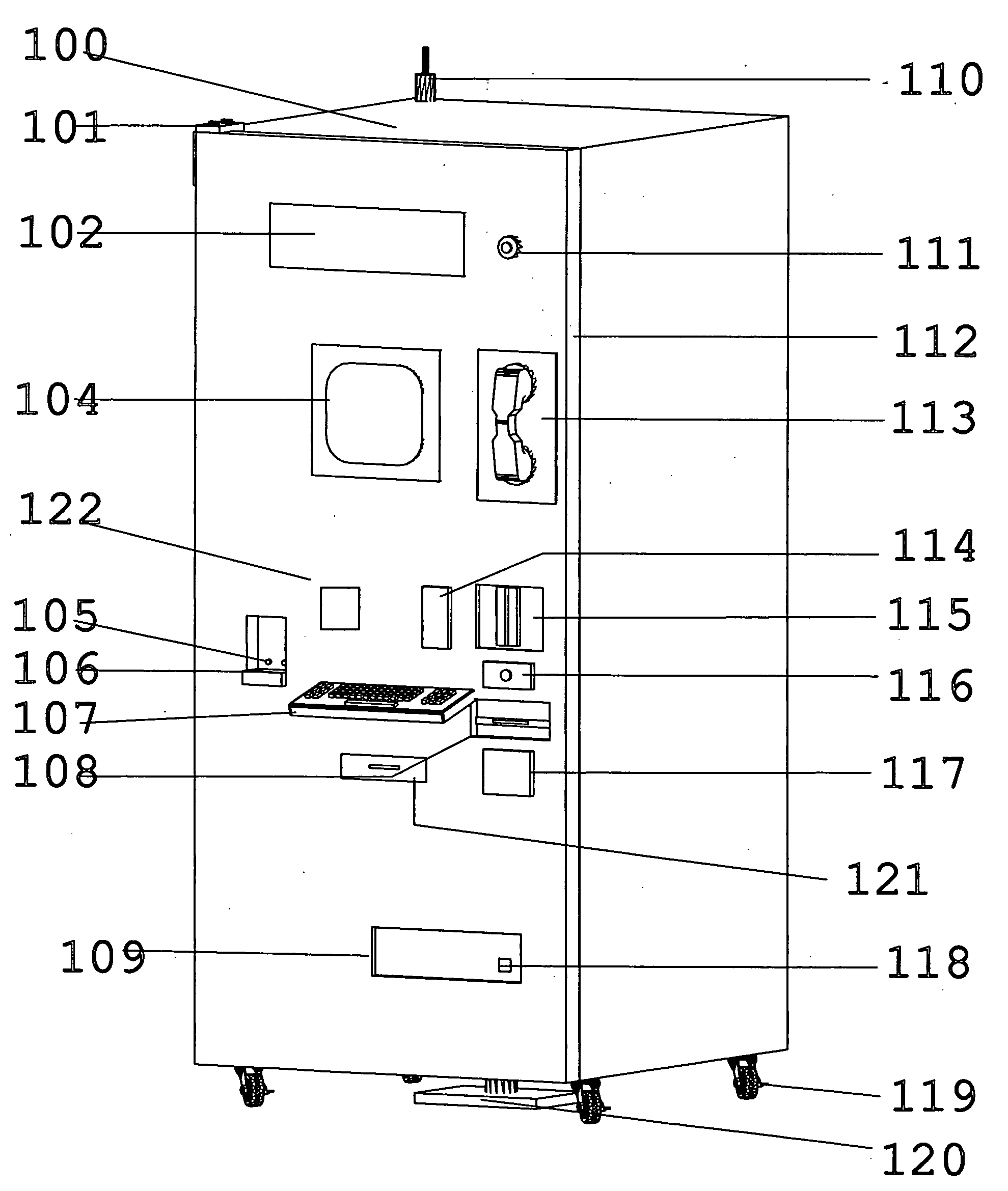
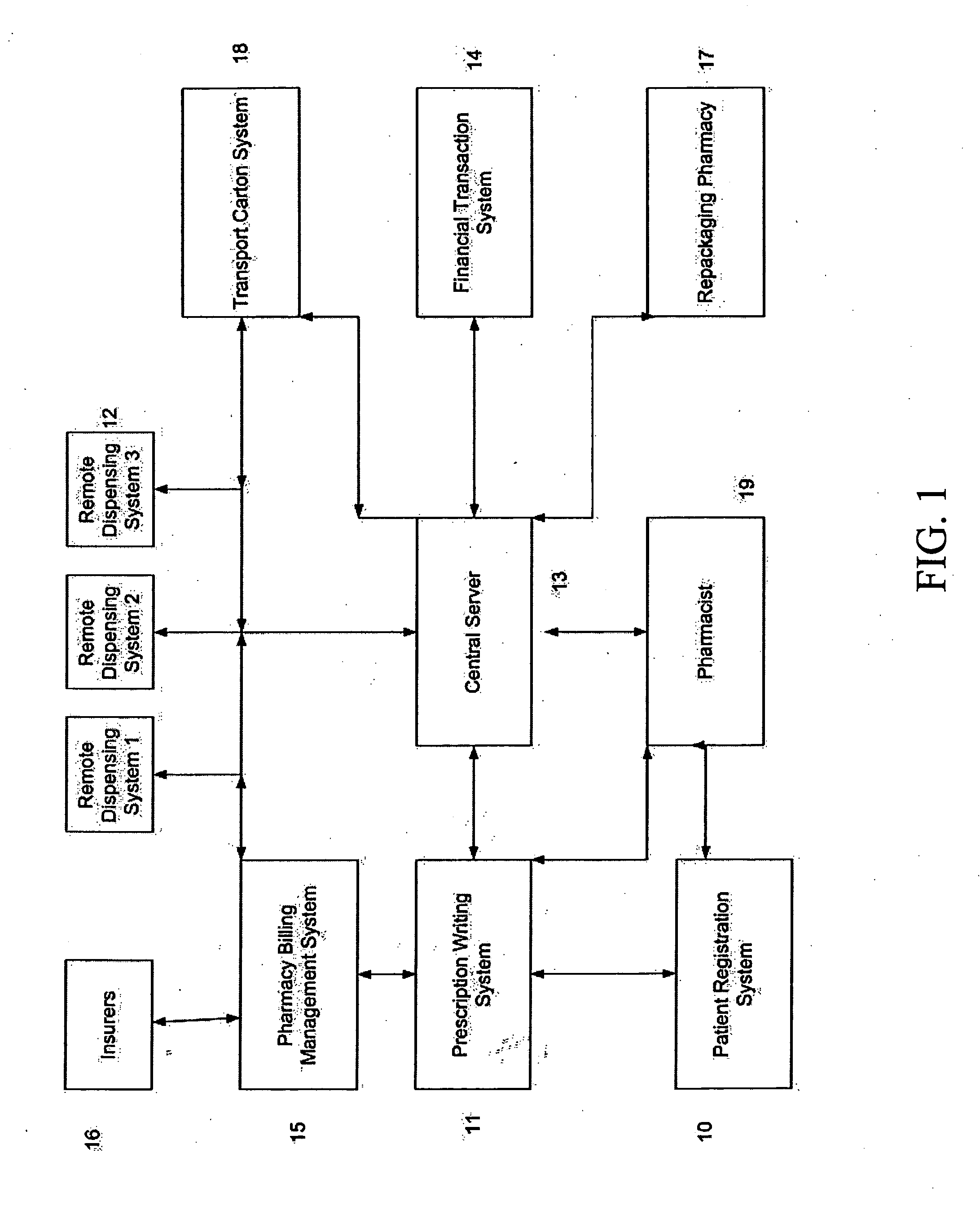
Inventory control and prescription dispensing system
ActiveUS20070043469A1Ensure integrityEnsure safetyDrug and medicationsCoin-freed apparatus detailsEngineeringPatient registration
An inventory control and prescription management and dispensing system including a dispensing vault for storing and dispensing prescriptions, the dispensing vault in communication with a central computer system that, in turn, communicates with prescription providers, insurance companies, and other third parties; the dispensing vault including robotic means for randomly accessing pre-filled prescriptions within the vault, with the vault further including RFID, bar code, and other means for verifying the content and internal location of pre-filled prescriptions; a customer interface that uses customer biometrics to ID a customer to ensure that prescriptions are only dispensed to the correct person; a patient registration system in communication with the central computer system for collecting insurance, doctor, biometric, and other information to facilitate transactions; a labeling system for labeling pre-filled prescriptions with customer specific information upon dispensing; transport container that integrate into the dispensing vault and provide secure transportation from a pharmaceutical manufacturer or repackager to the dispensing vault, security provided through RFID tags which communicate with the central computer to verify that the transport container contains the correct formulary and that the integrity of the container (temperature range, time in transit, tampering) has not been compromised; a payment system integral to the dispensing vault that is in communication with third party banks and pharmacy billing management systems, credit agencies and the central computer; a verification system for ensuring that pre-filled bottles received from the manufacturer (before they are placed into the storage locations inside the vault) have not had their integrity compromised, with this system evaluating each container's weight, size, moisture content, shape, velocity change, color, pattern, and physical integrity (all comparisons made against standards stored in the central computer).
Owner:DRAPER LONNIE
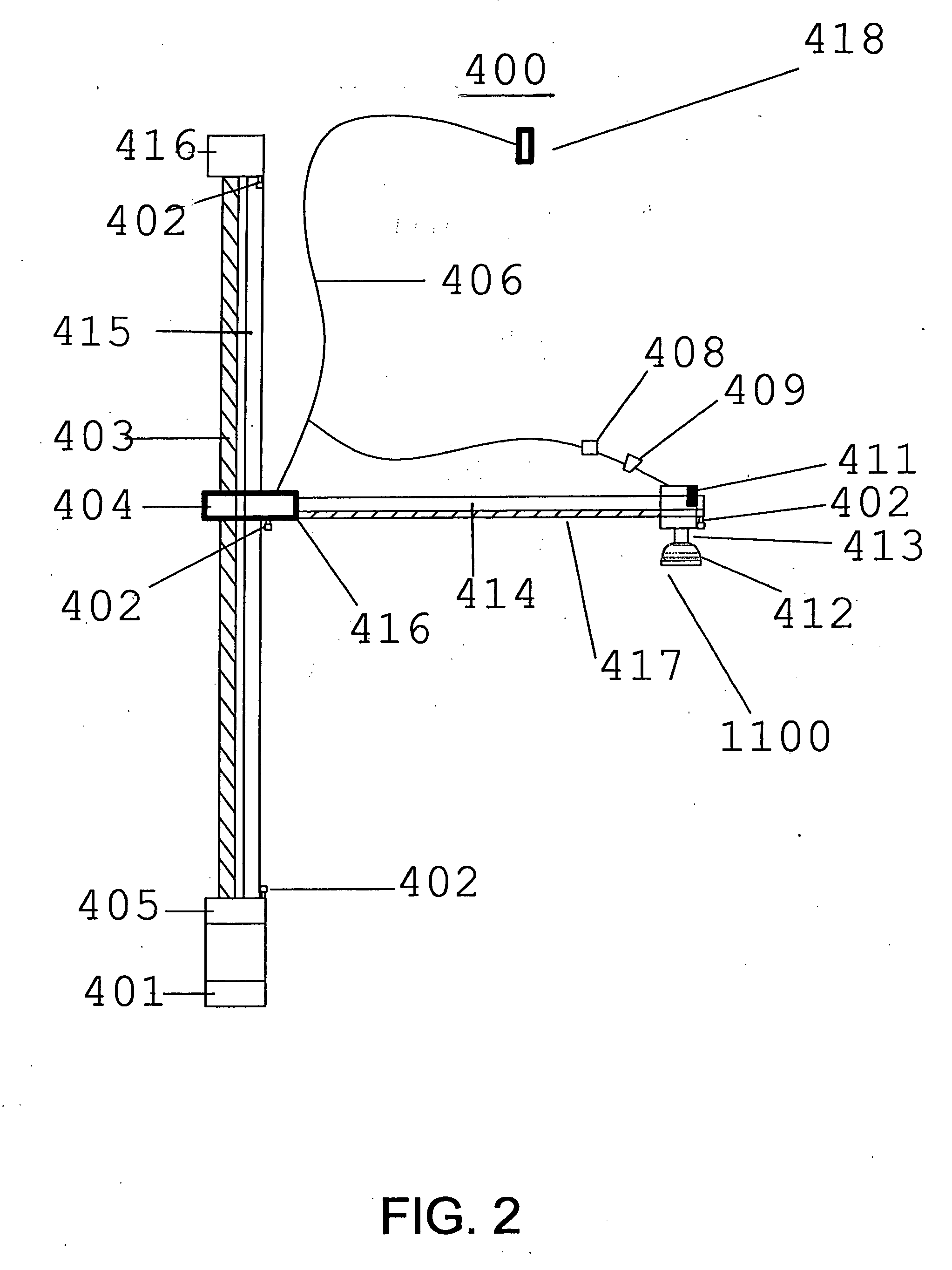
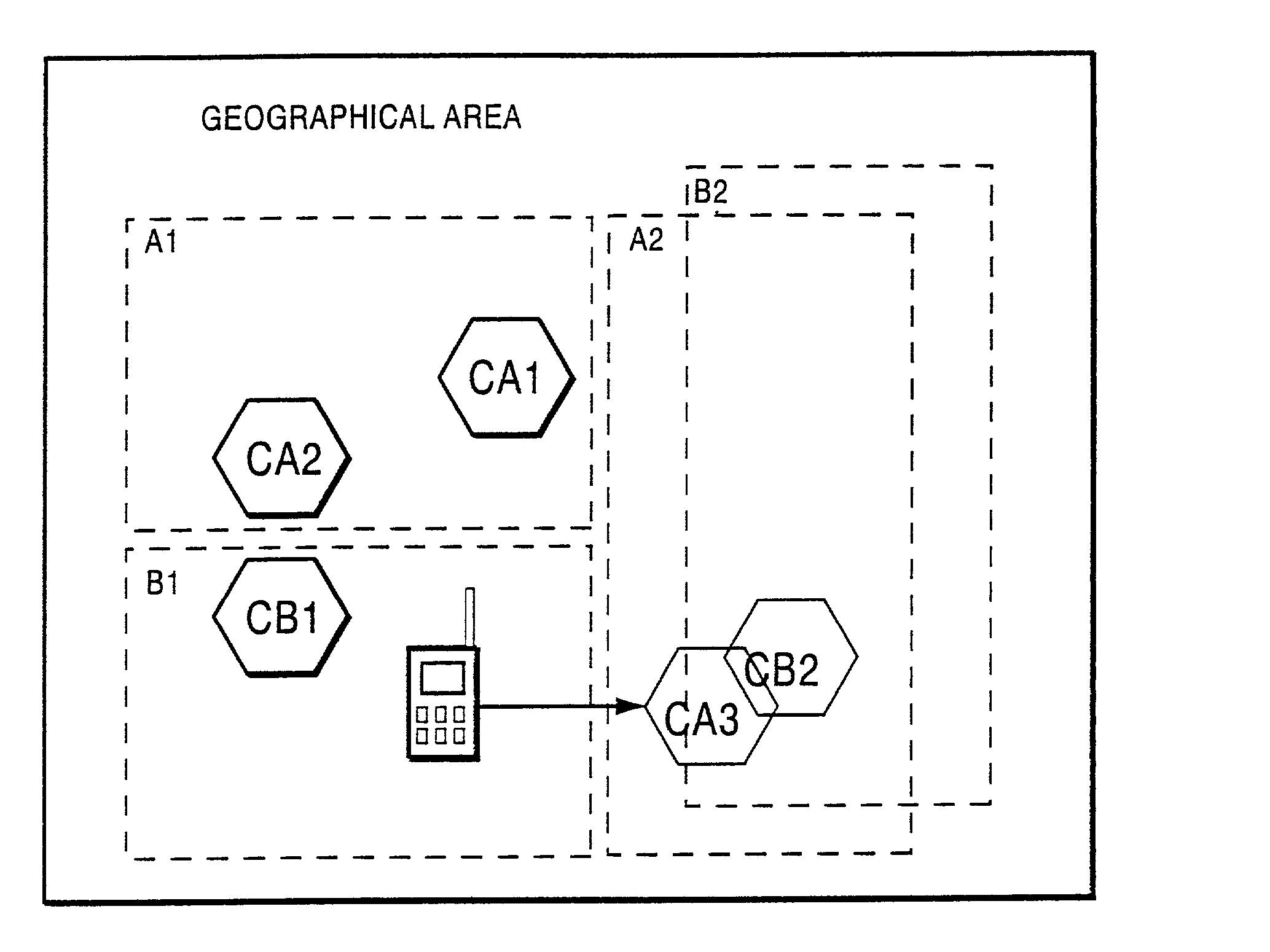
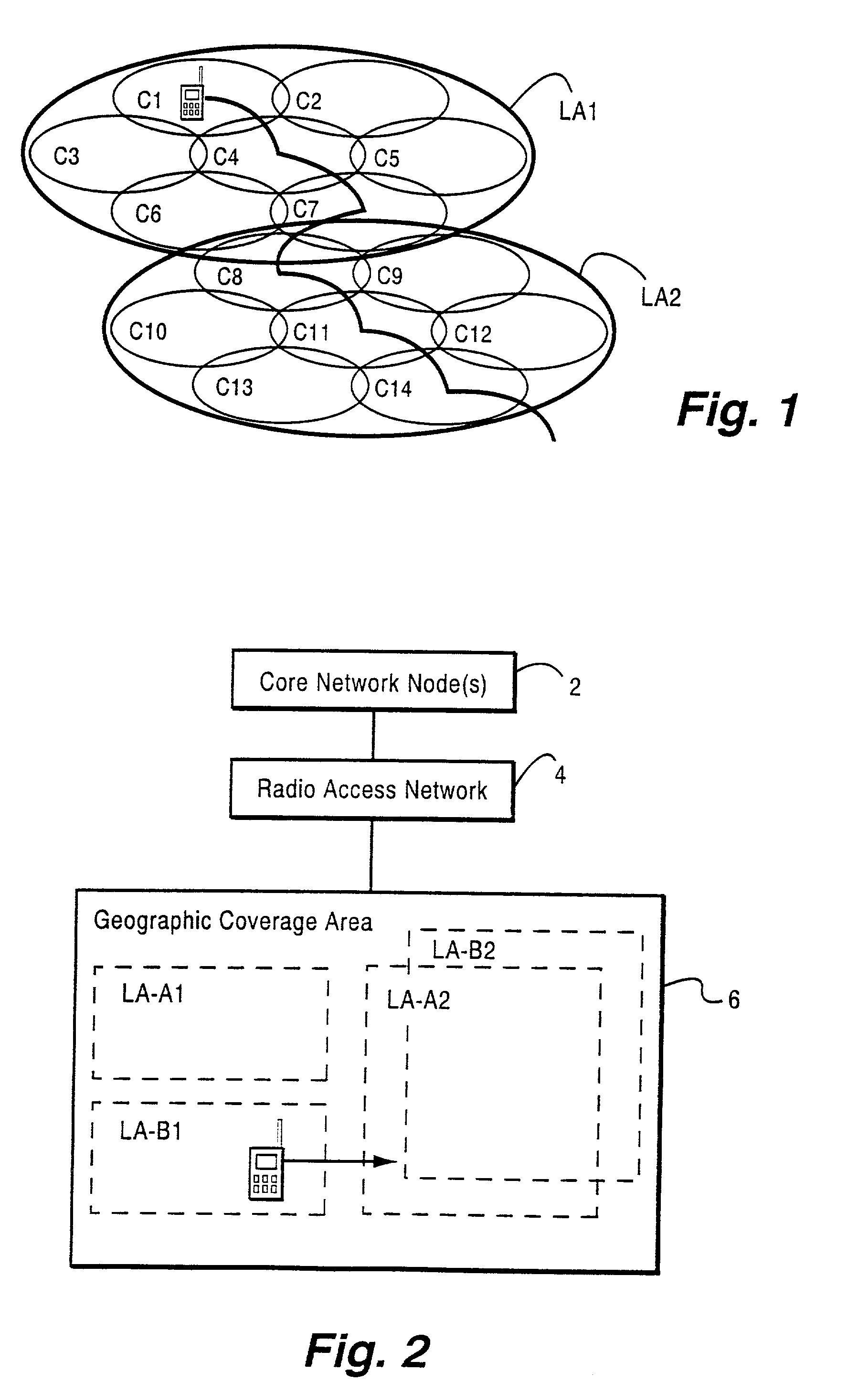
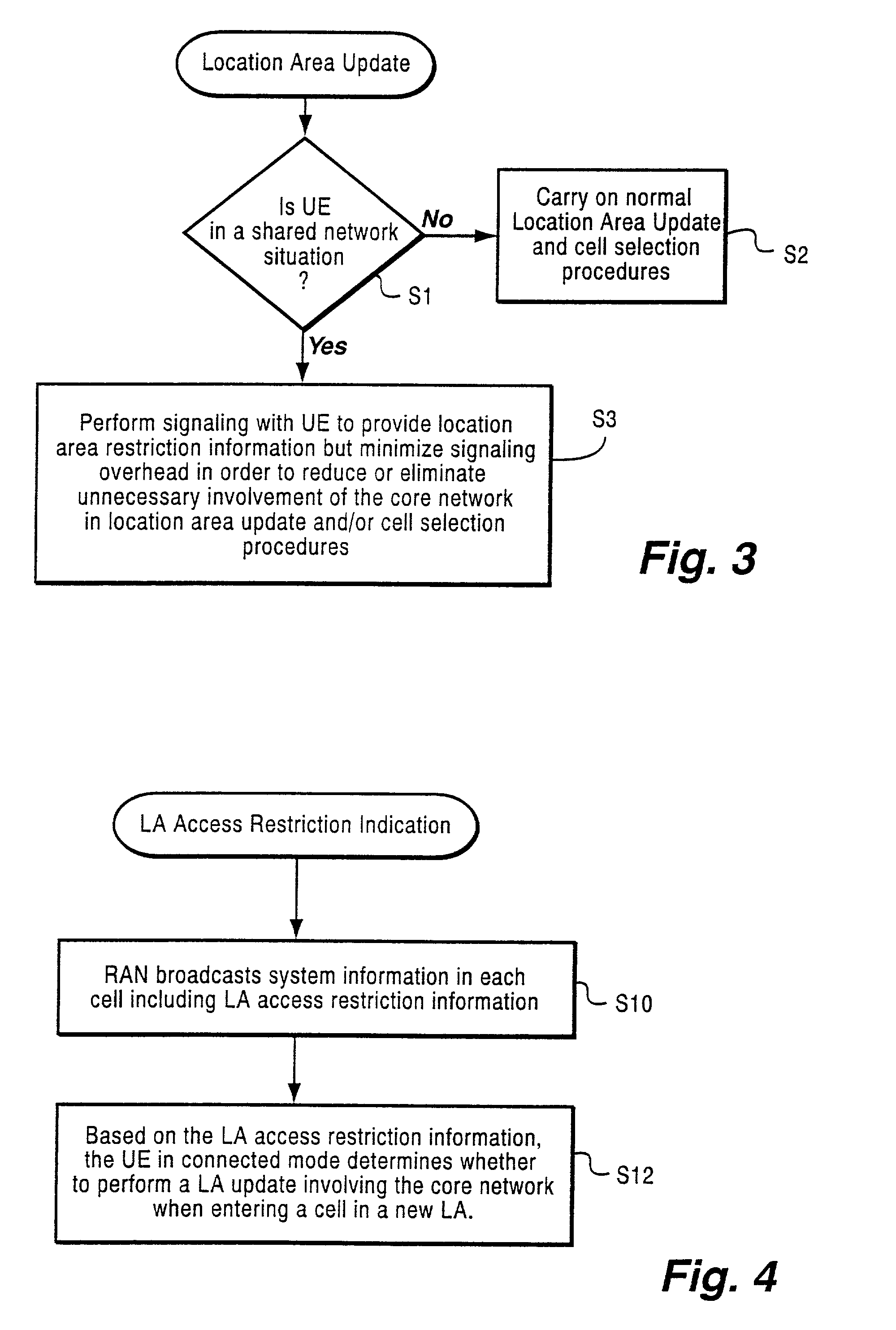
Method and apparatus for location area updating in cellular communications
InactiveUS20030040314A1No disruption to callIncrease speedAssess restrictionRadio/inductive link selection arrangementsRadio access networkMobile radio
A connection is established between a mobile radio terminal and a radio access network serving plural geographic coverage areas. The radio access network transmits information associated with one of the geographic coverage areas indicating whether the one geographic coverage area requires a geographic coverage area update procedure. During the connection, when the mobile radio terminal considers selecting the one geographic coverage area, it determines whether to perform a geographic coverage area update procedure depending on the transmitted information associated with the one geographic coverage area. In a preferred, non-limiting application, the radio access network is shared by two operators, and the transmitted information indicates that the geographic coverage area update procedure should be performed for geographic coverage areas that are shared by the two operators and that the geographic coverage area update procedure need not be performed for geographic coverage areas that are not shared by the two operators.
Owner:TELEFON AB LM ERICSSON (PUBL)
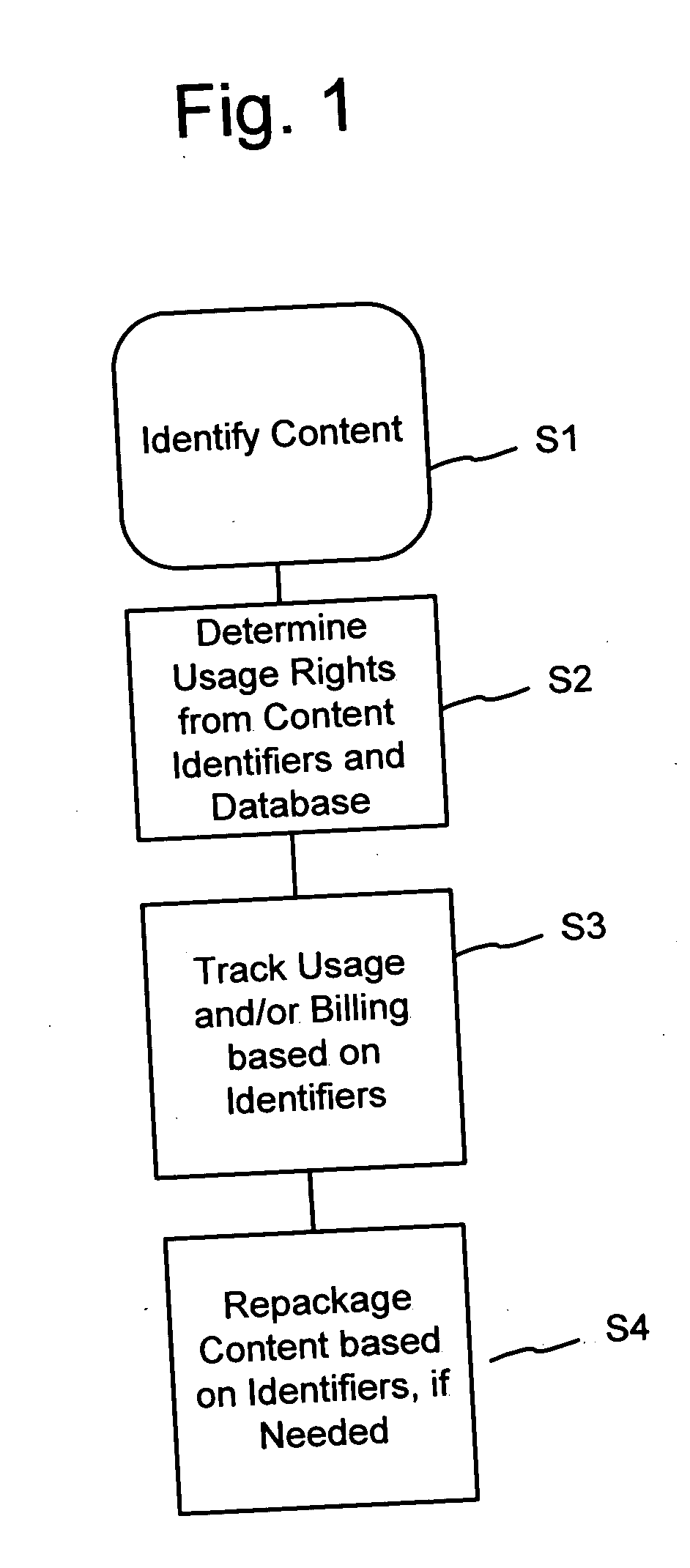
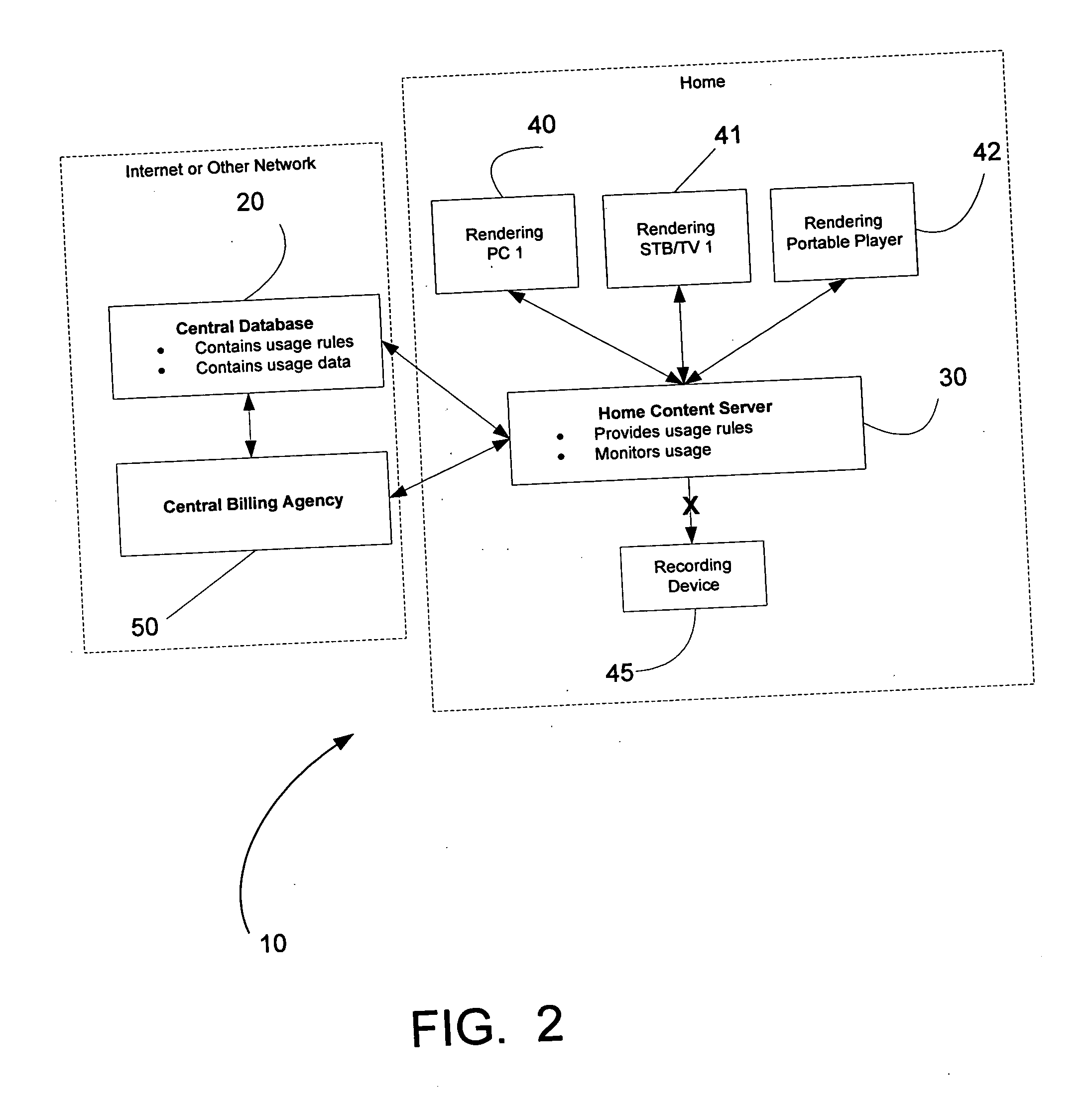
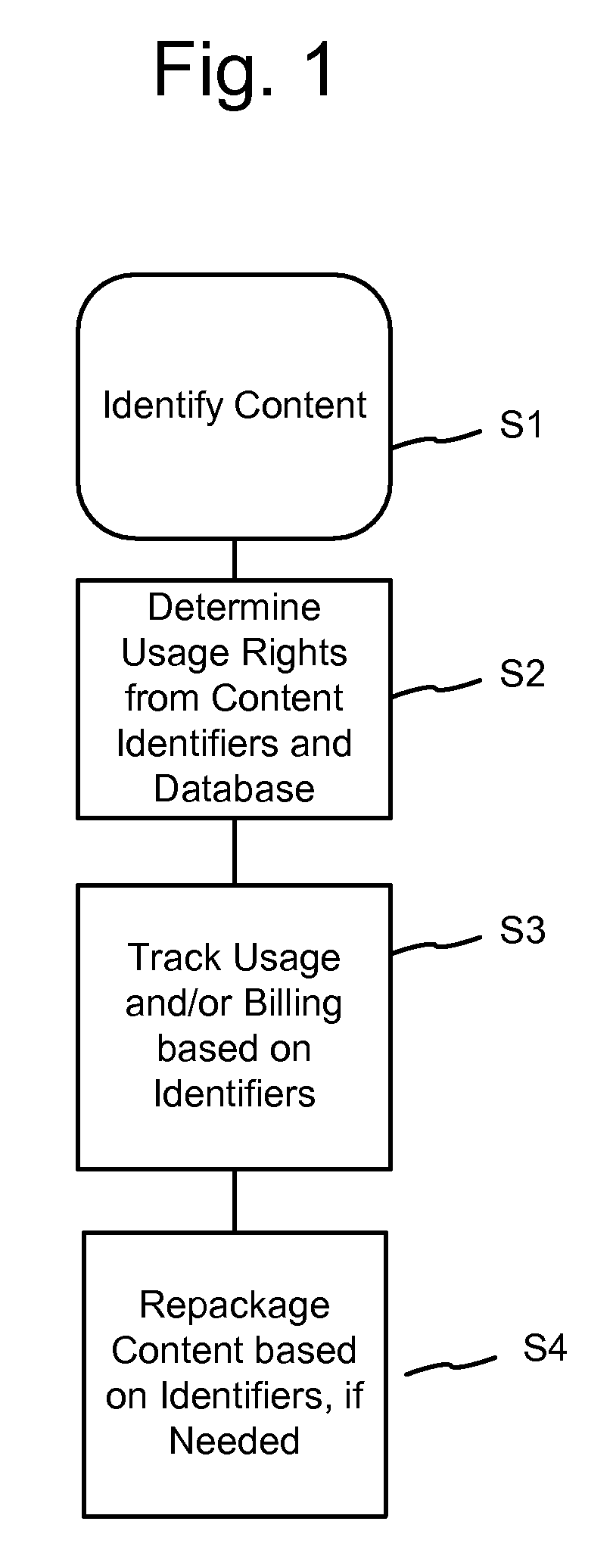
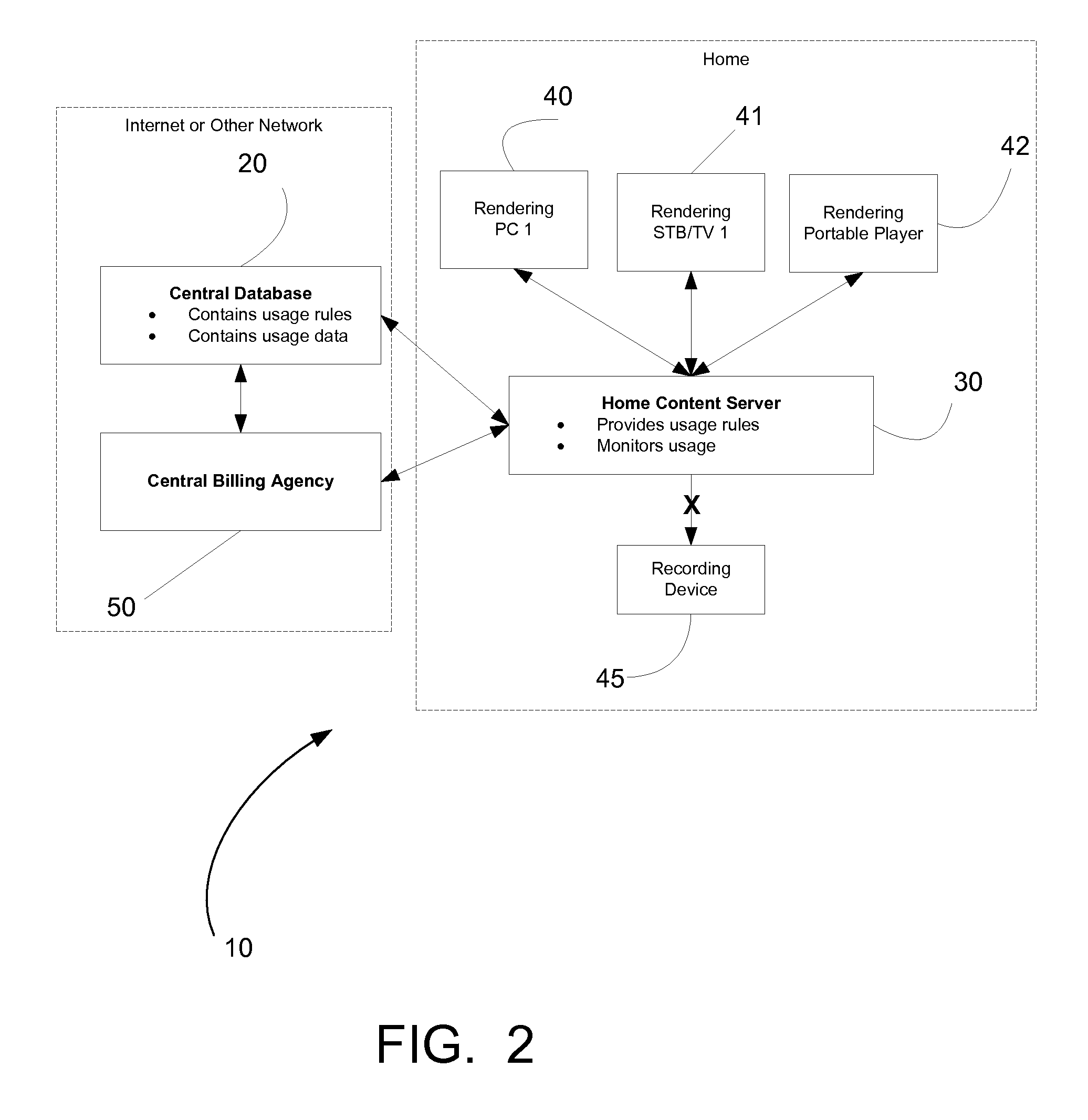
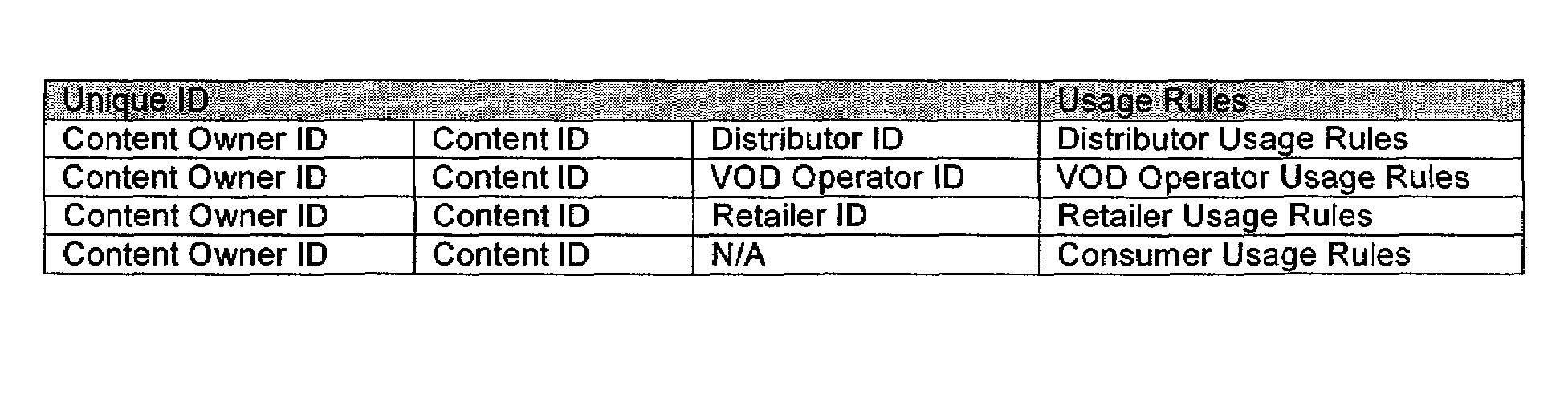
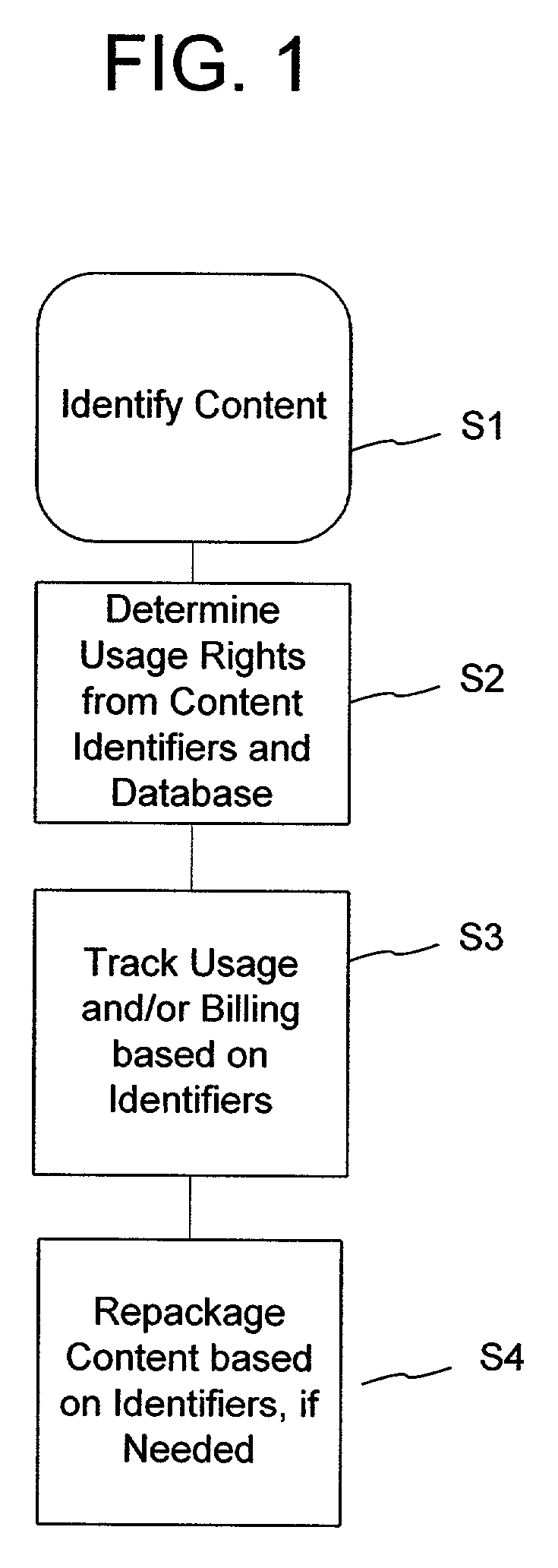
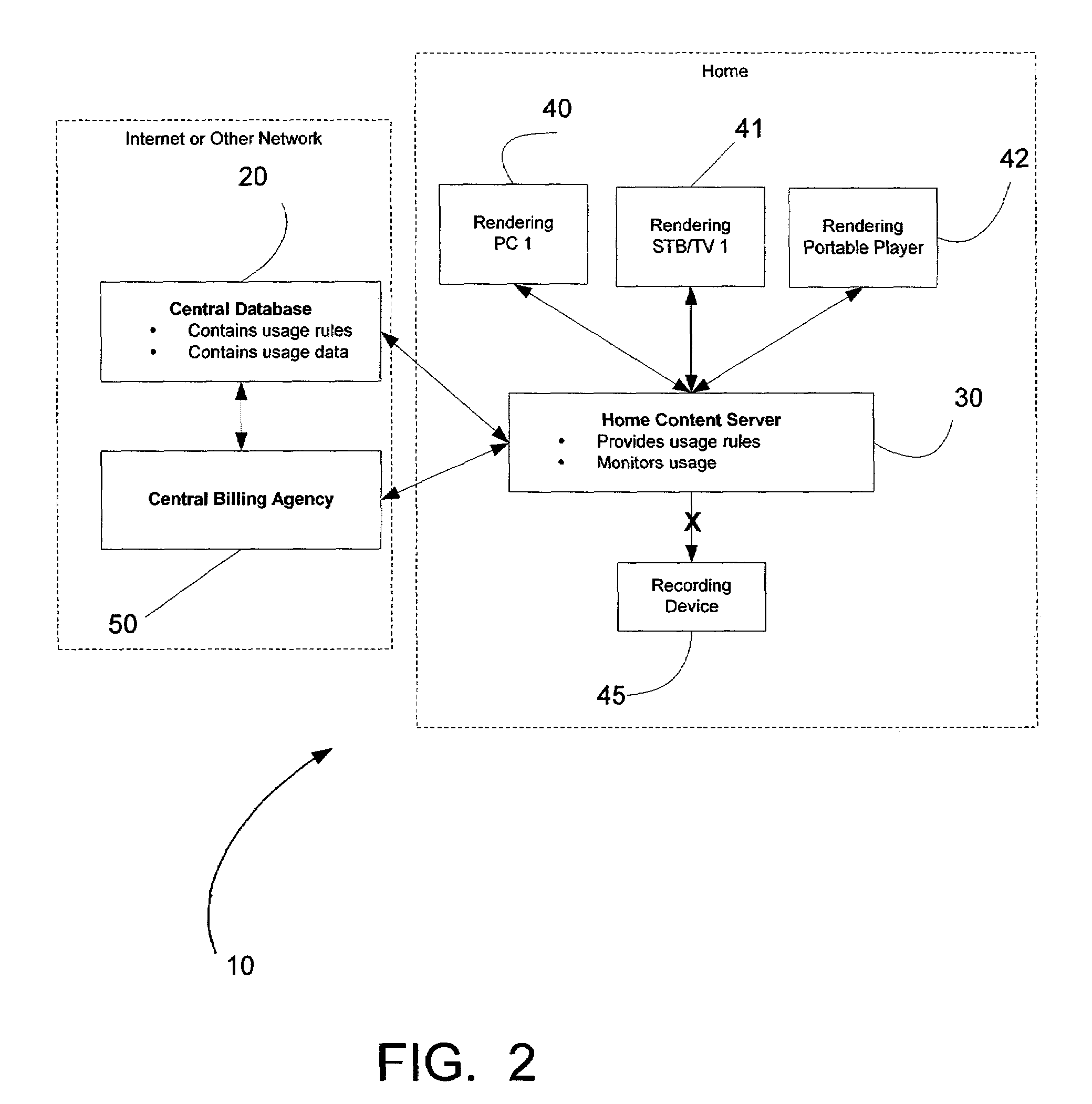
Rights Management Systems and Methods Using Content Identifiers
InactiveUS20080140433A1Difficult to controlDifficult to trackRecord information storageAnalogue secracy/subscription systemsContent IdentifierRights management
Owner:DIGIMARC CORP
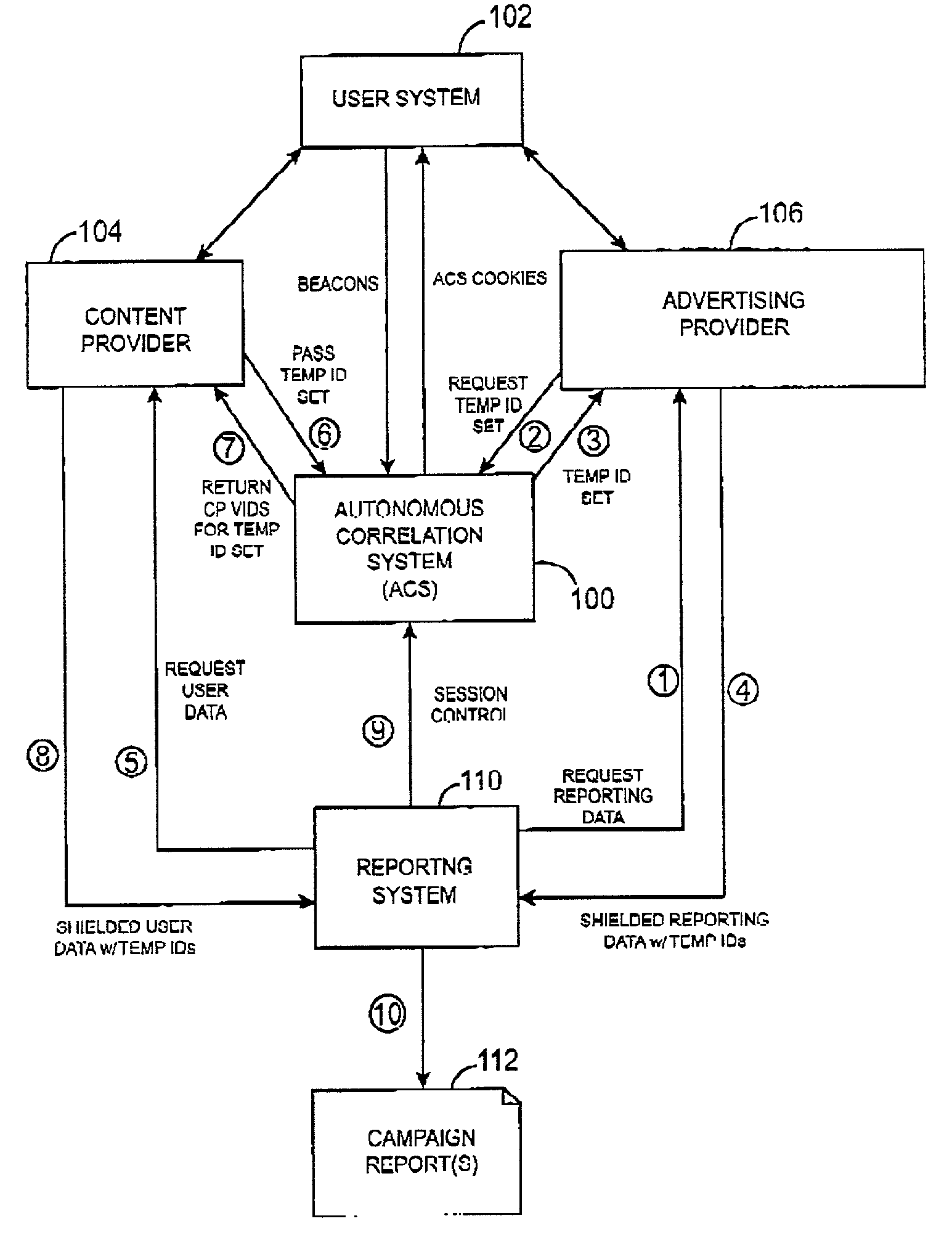
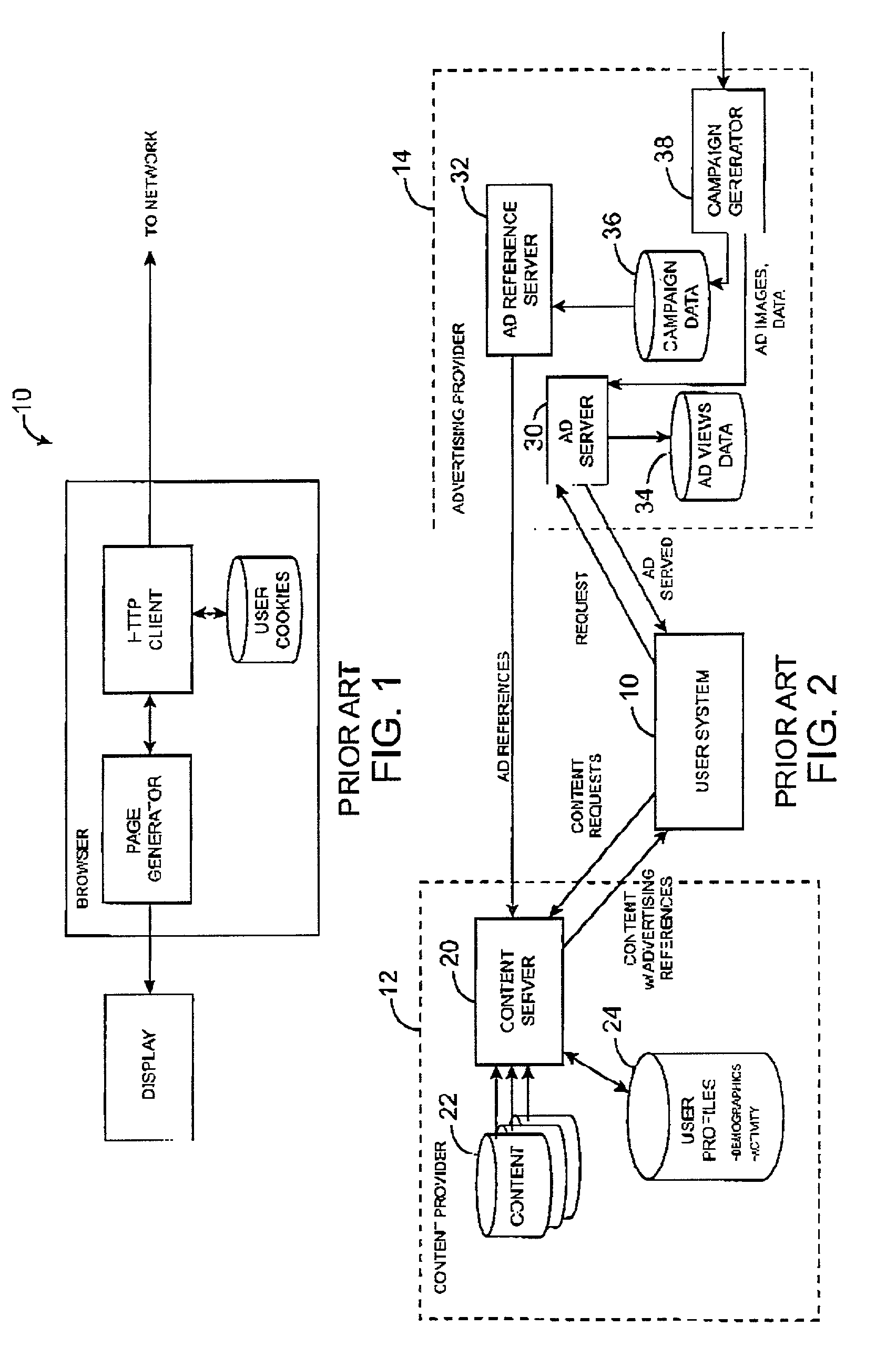
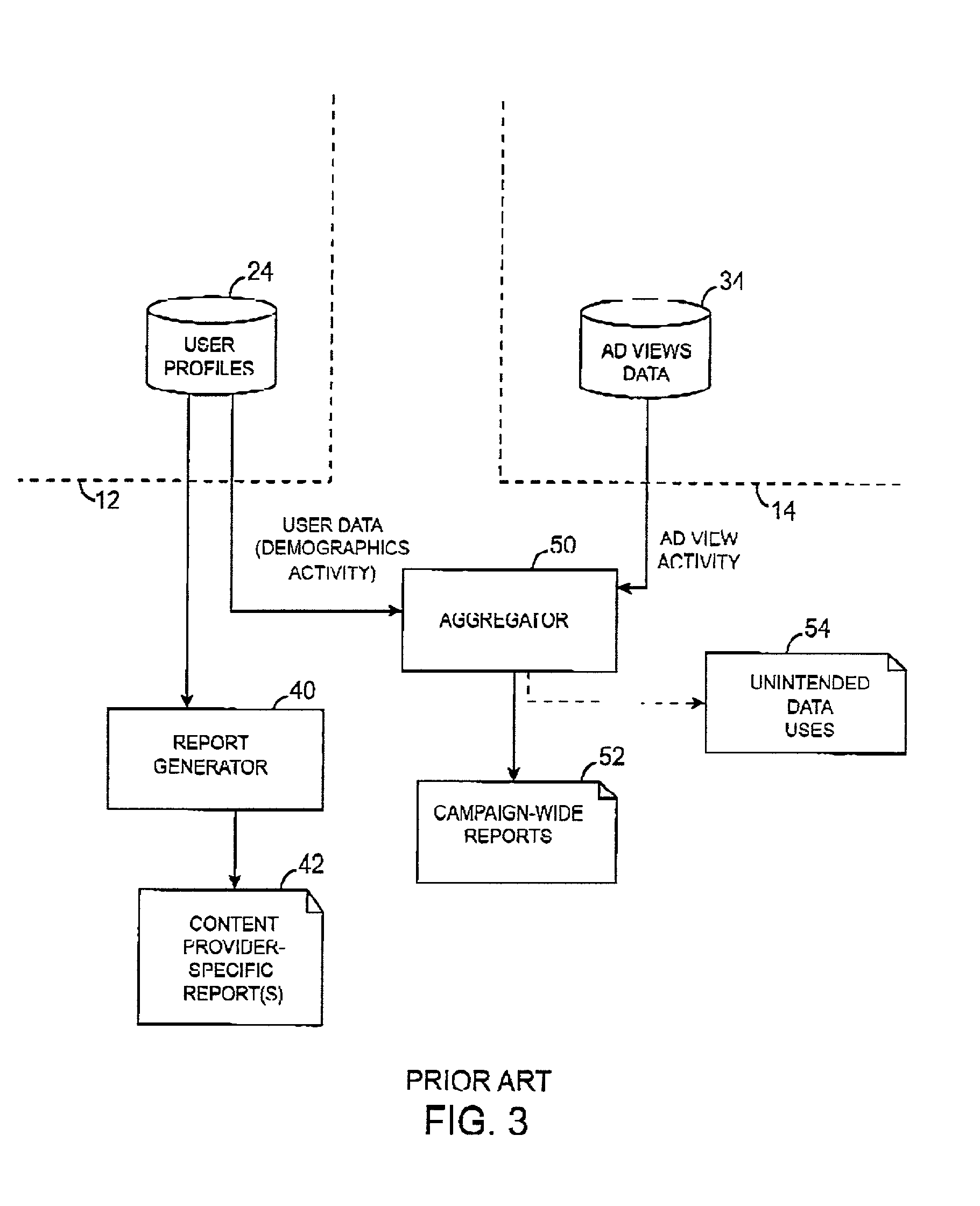
System and method for correlating user data from a content provider and user data from an advertising provider that is stored on autonomous systems
ActiveUS7257546B2Increase valueProtect user privacyAdvertisementsAnalogue secracy/subscription systemsReference databaseUser identifier
An autonomous correlation system correlates user data from a content provider and advertising view data from an advertising provider, wherein the user data is present on one autonomous system and the advertising view data is present on another autonomous system distinct from the one autonomous system, the systems being autonomous in that each is normally secured against unconstrained access by another. The autonomous correlation system comprises logic to accept a first message from a user, wherein the first message contains an indication of an object being presented to the user, the object being at least one of a content page and an advertisement, a first user identifier associated with the user by a presenter of the object; a reference database for storing an association between the first user identifier and the user; logic to accept a second message from the user, wherein the second message contains an indication of an object being presented to the user, the object being at least one of a content page and an advertisement, a second user identifier associated with the user by a presenter of the object; wherein the reference database stores an association between the second user identifier and the user.
Owner:PINTEREST
Rights Management System and Methods
ActiveUS20070294173A1Difficult to controlDifficult to trackDigital data processing detailsRecord information storageContent IdentifierRights management
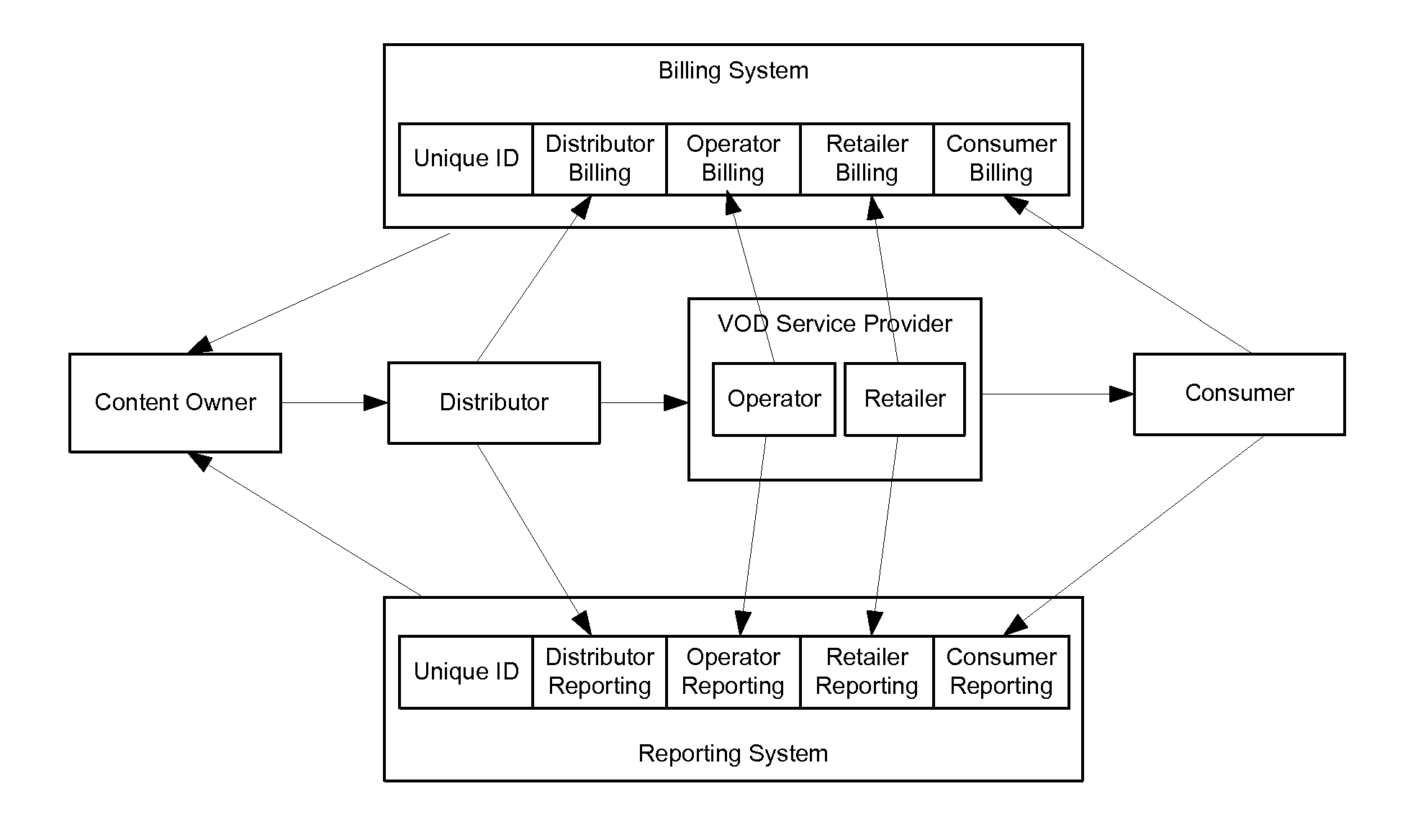
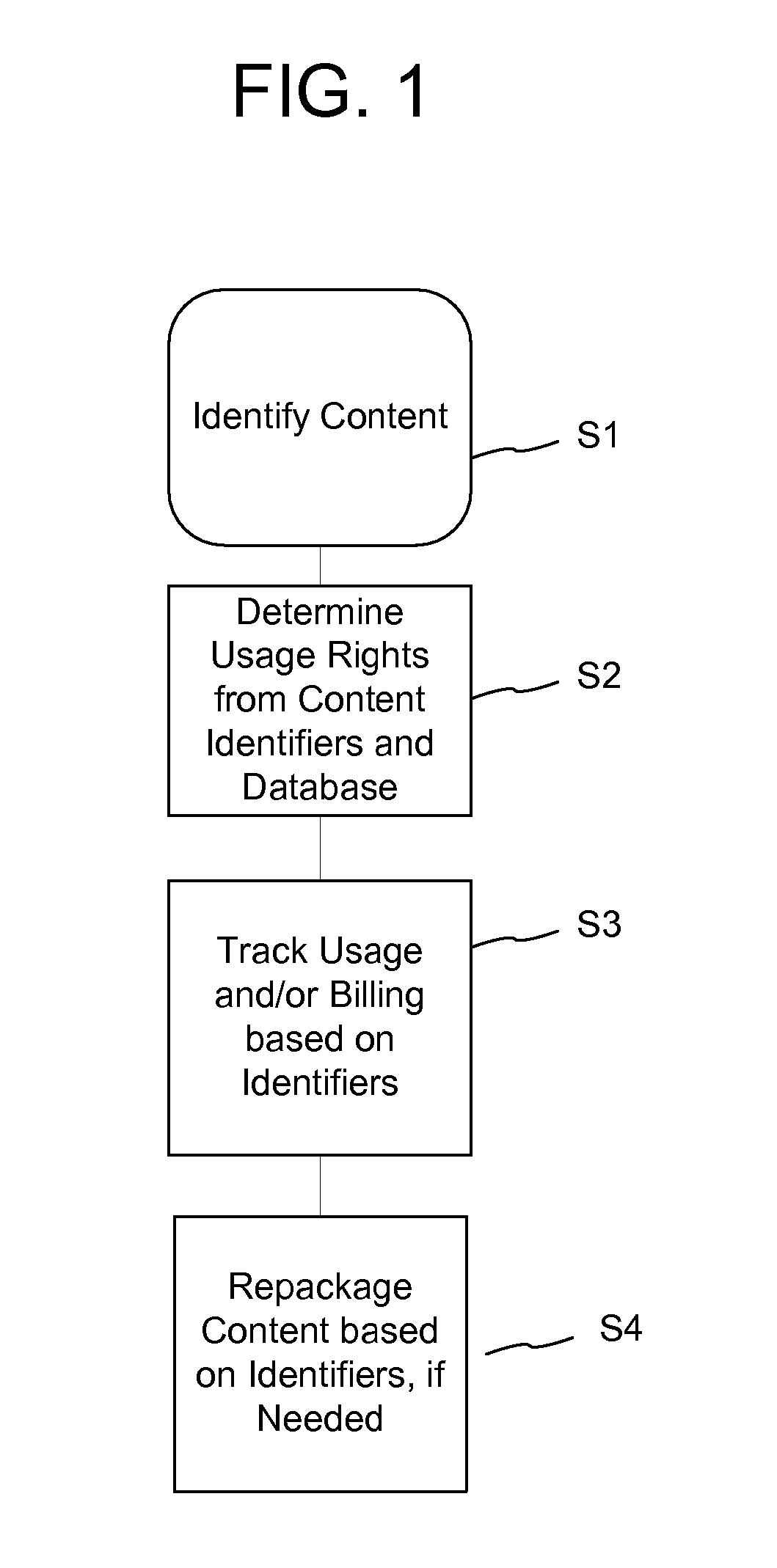
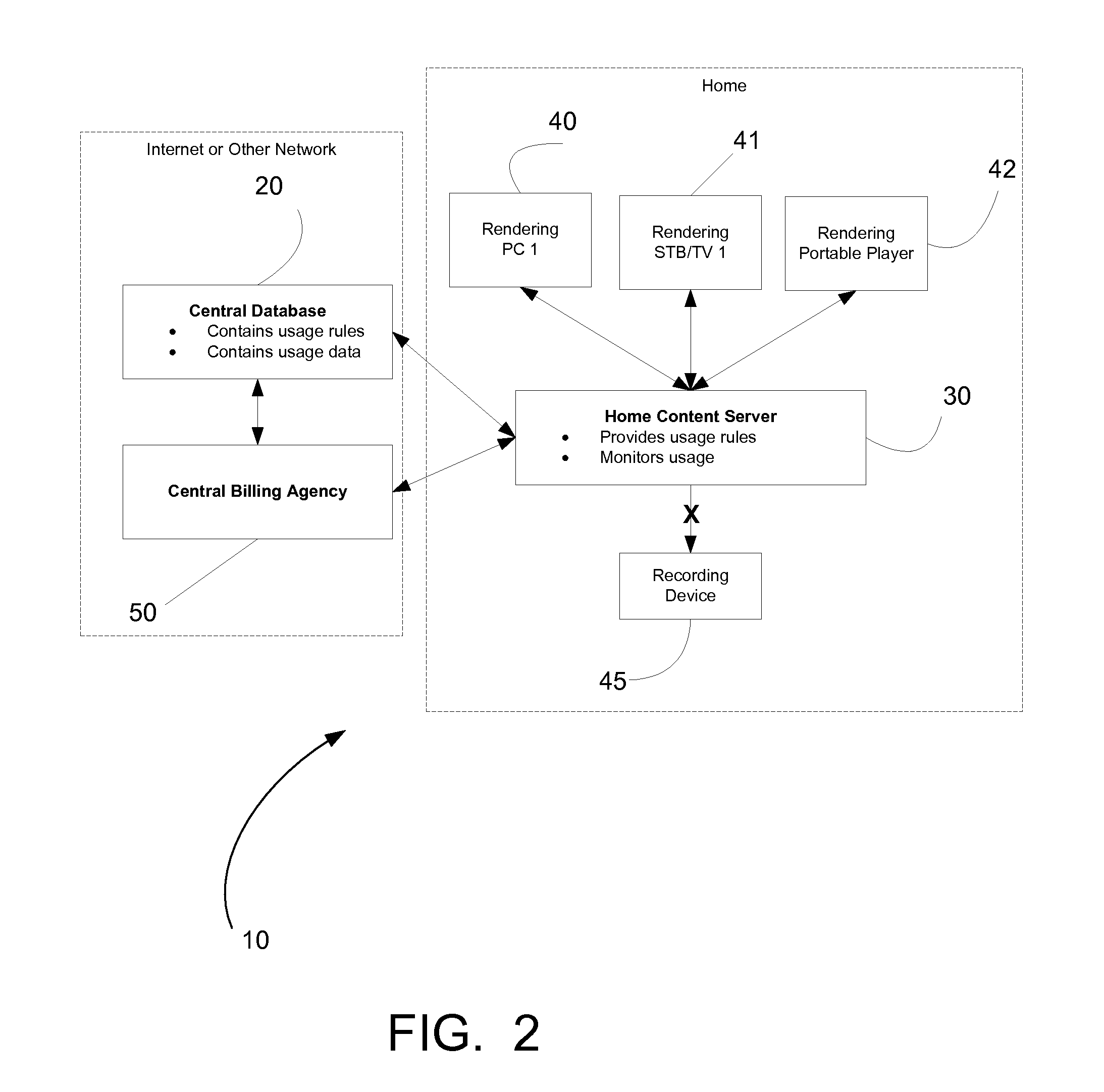
A method of performing digital asset management of content is provided. The content is identified with an identifier. The identifier can be identified with a digital watermark, header file, or both. The identifier is linked to usage rules to regulate usage and protect the content. The usage rules can be maintained on a remote or local database or server. Once extracted, an identifier is used to index the database to locate a corresponding usage rule, and can be used to override copy control information with proper purchase and subsequent protection. Content can be managed from such. In another embodiment, an identifier is used to track usage, such as amount of content viewed, time played, and copies made. In yet another embodiment, a content identifier is used to regulate content throughout a distribution chain, and a distributed set of databases with information relevant only to the owner of the database act as one database due to a central router.
Owner:DIGIMARC CORP
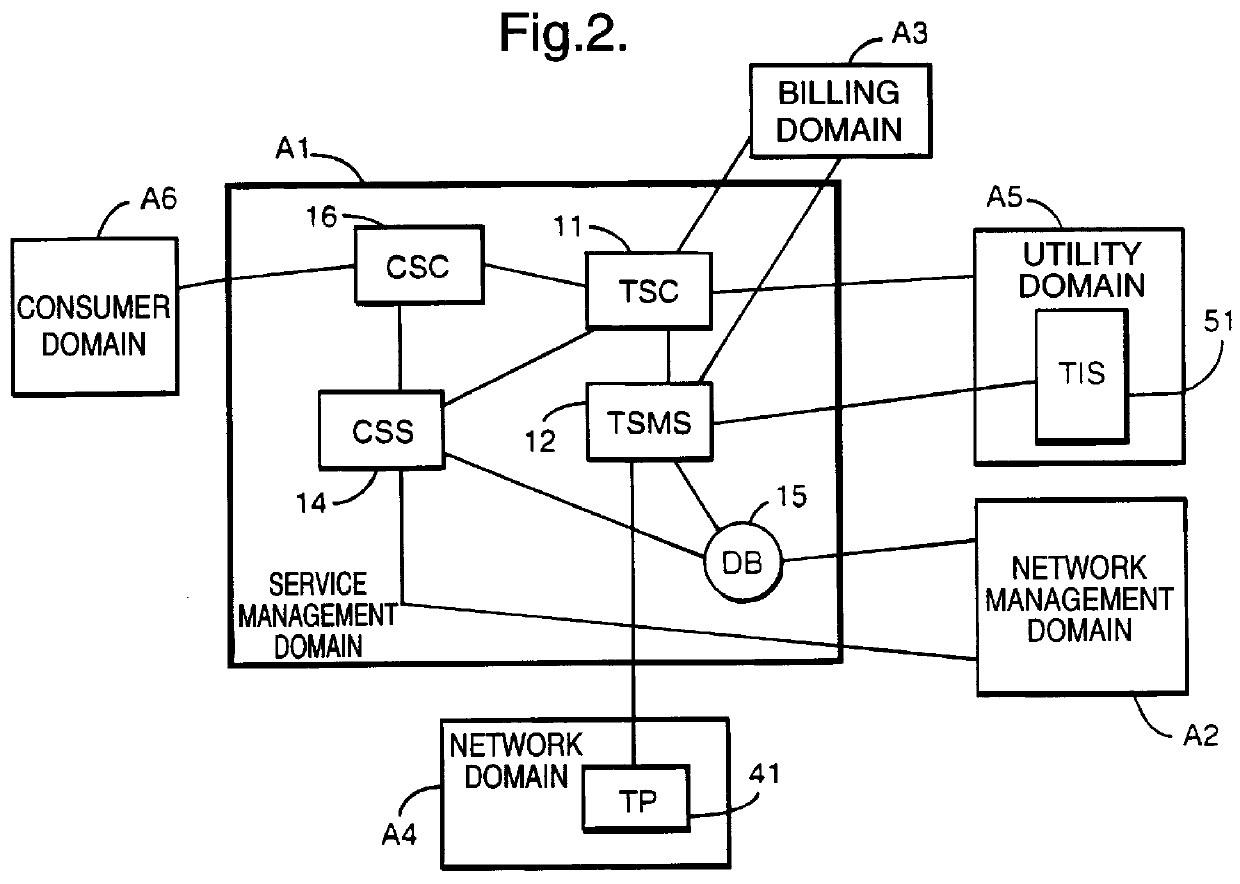
Remote access systems
InactiveUS6073174AImprove the level ofKeep full controlTelephonic communicationMultiple digital computer combinationsTraffic capacityTelecommunications
A management system provides a remote access service to units of equipment at distributed locations of a communications network. For instance, it can provide automatic meter reading over a PSTN for utility companies. The management system initiates calls over the network to selected units, usually pre-determined, in response to call requests, and can provide considerable functionality such as authentication and batch processing of the request. Conflict with ordinary traffic on the network can be avoided by monitoring for ordinary traffic calls and clearing down any existing conflicting remote access calls or blocking any requested potentially conflicting remote access calls. Uncompleted or blocked remote access calls are automatically re-scheduled by the management system.
Owner:BRITISH TELECOMM PLC
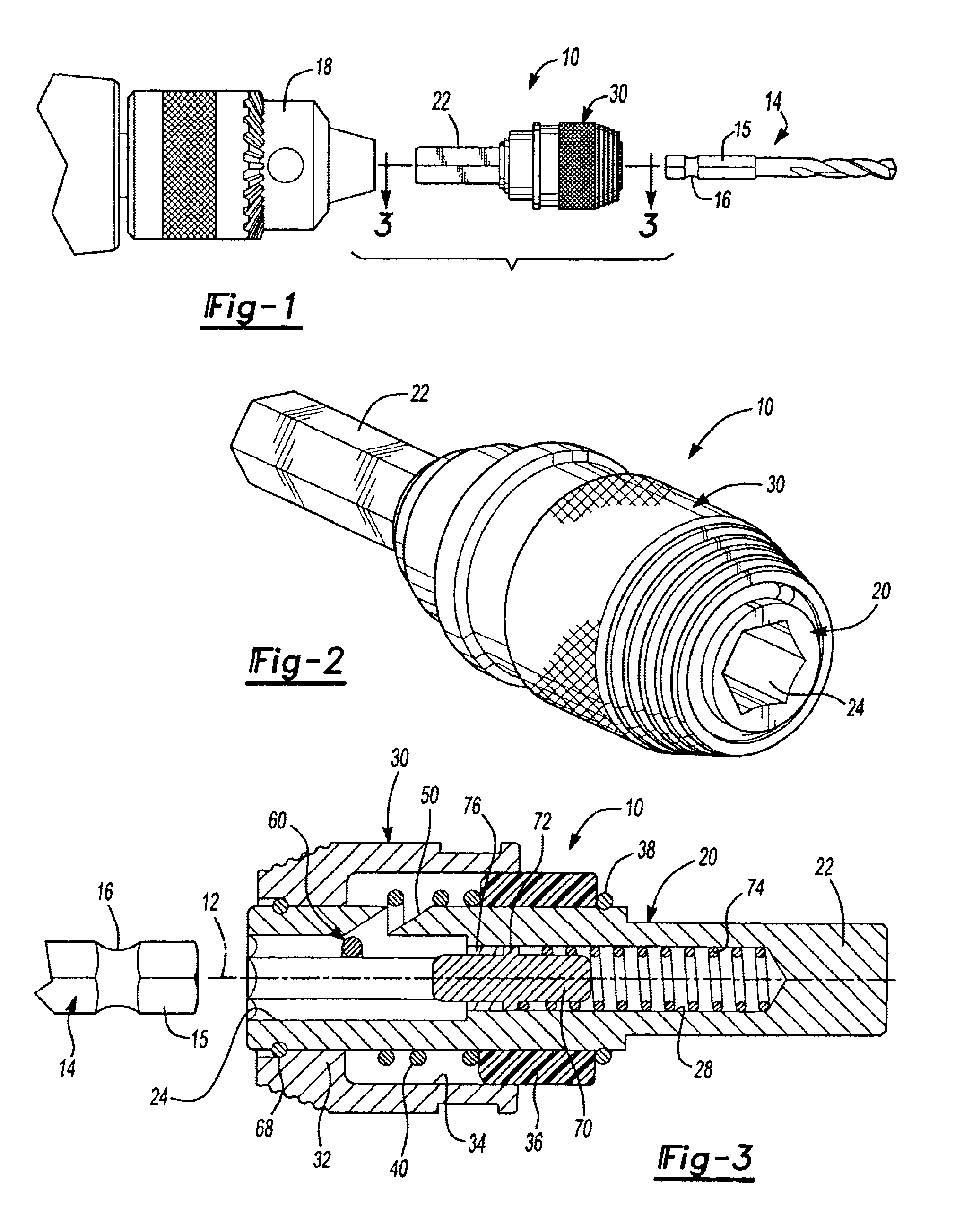
Bit holder
InactiveUS6929266B2Increase speedImprove convenienceSleeve/socket jointsSpannersCoil springEngineering
A “snap-in” bit chuck assembly for a rotary hand or powered tool, includes a body having a hex shank at its rearward end and a retraction collar slidably disposed on the body. The body has a coaxial hex socket formed therein to allow a tool bit to be inserted thereinto. A coil spring biases the retraction collar forwardly and biases a retaining clip toward the bottom of an angular slot formed in the body. The bit is removed by sliding the retraction collar rearwardly, to compress the coil spring and allow the retaining clip to retract back up the slot. The bit is biased out of a locked position by a plunger that ensures that the bit remains disengaged when the retraction collar is released.
Owner:BLACK & DECKER INC
User-friendly rights management systems and methods
ActiveUS7266704B2Difficult to controlDifficult to trackDigital data processing detailsMultimedia data retrievalRights managementDigital watermarking
This application describes methods and systems of performing digital asset management. In one implementation a method of determining whether content should be encrypted when the content is found in an unencrypted form is provided. The unencrypted form of the content includes a digital watermark embedded therein including a message. The method recites: decoding the digital watermark from the encrypted form of the content to obtain the message; based at least in part on the message, determining whether the unencrypted form of the content should be encrypted; and if so decided by the determination, encrypting the unencrypted form of the content. Other implementations and embodiments are provided as well.
Owner:DIGIMARC CORP +1
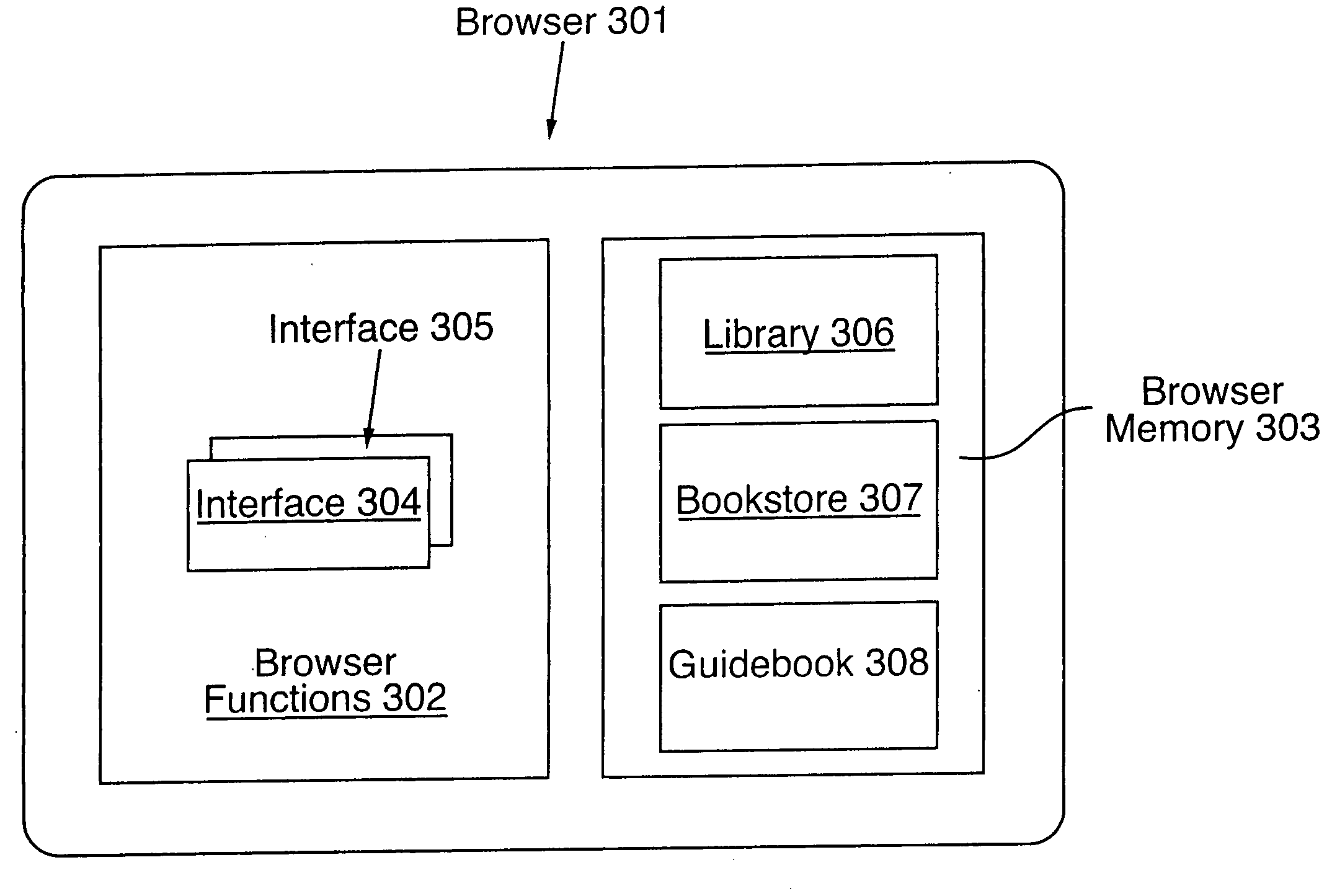
Client portal
InactiveUS20050097007A1Easy to useKeep full controlBuying/selling/leasing transactionsSpecial data processing applicationsSpecific functionElectronic book
A client portal that is optimized to fulfill a specific function. The portal can include a browser that is dedicated to performing a particular task, such as reviewing and purchasing electronic books. For example, to better perform the specific function, the browser may only be able to directly access sites designated by an authorized party, e.g., the browser's publisher. Because the browser is dedicated to performing a single task, the user interface for operating the dedicated browser may be simplified to include only those controls useful for performing the assigned task. Also, the content available for access by the client portal can be controlled by a single authorized party, such as the portal's publisher or distributor.
Owner:MICROSOFT TECH LICENSING LLC
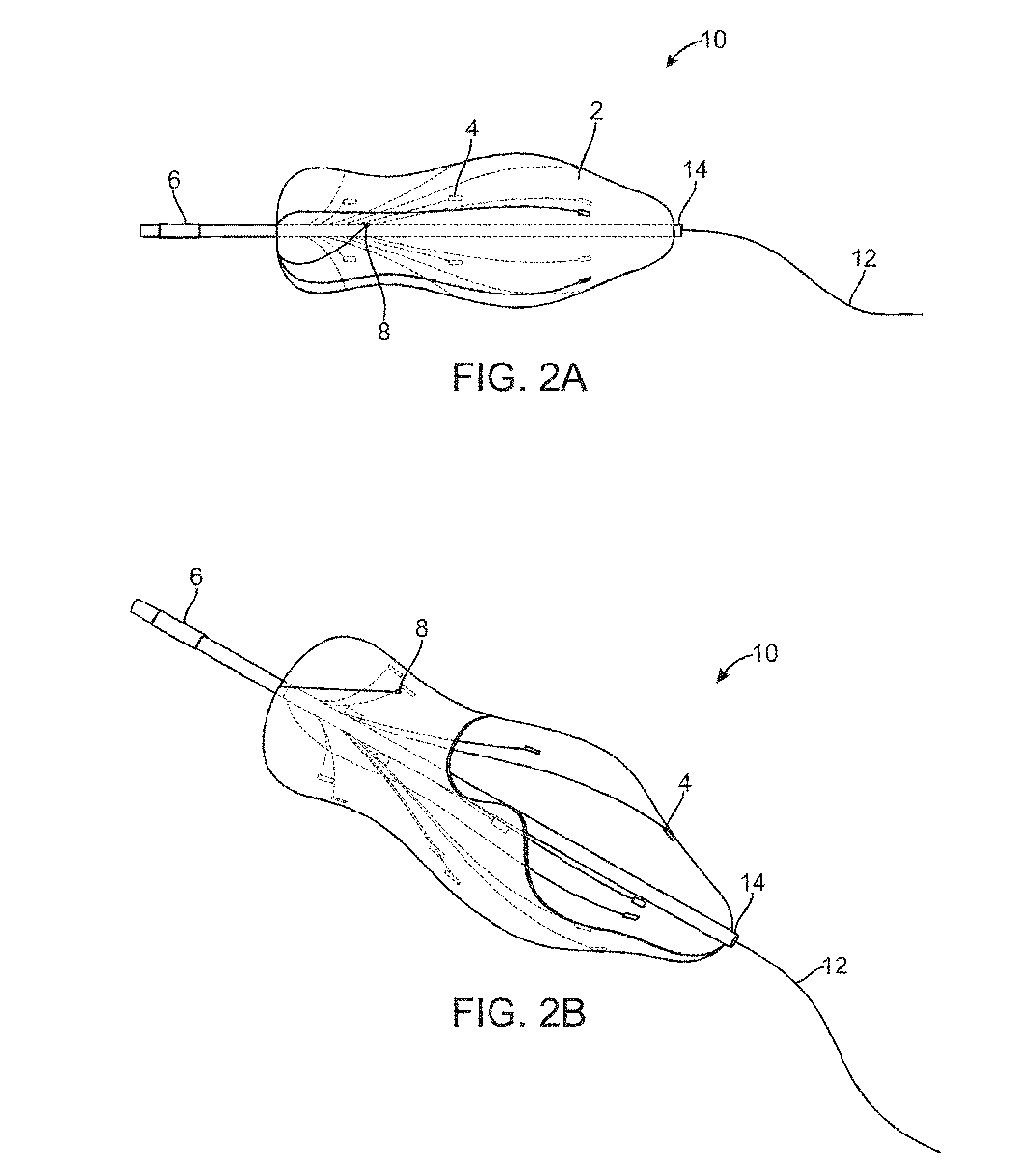
Shape-sensing expandable member
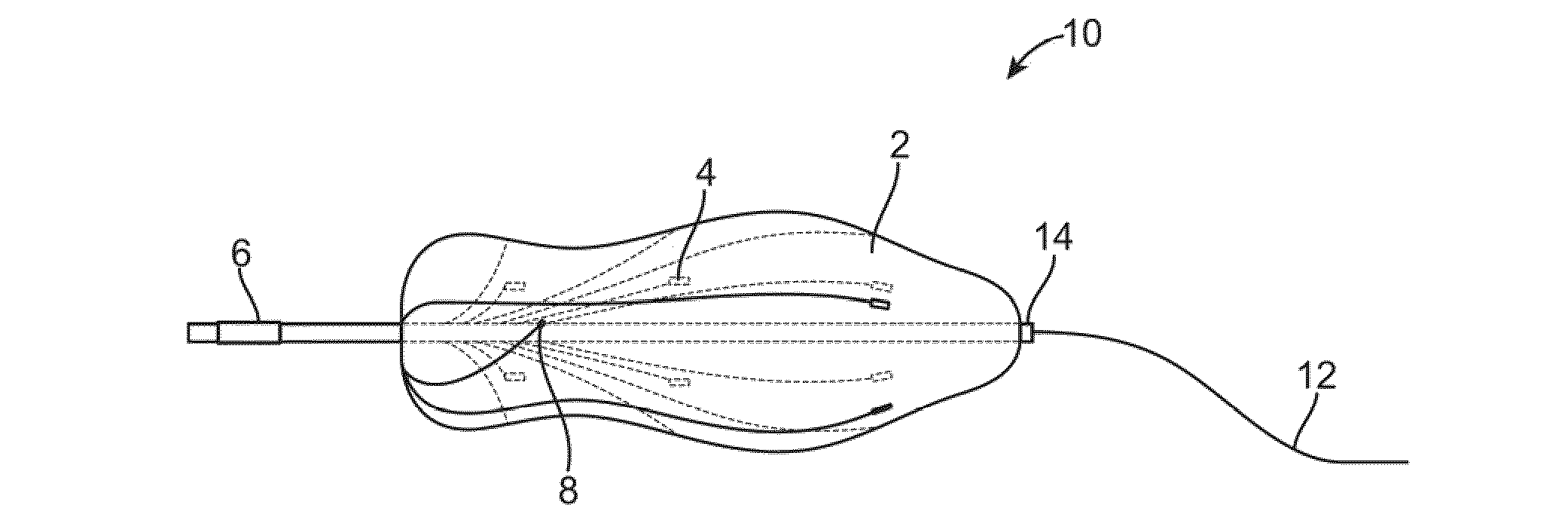
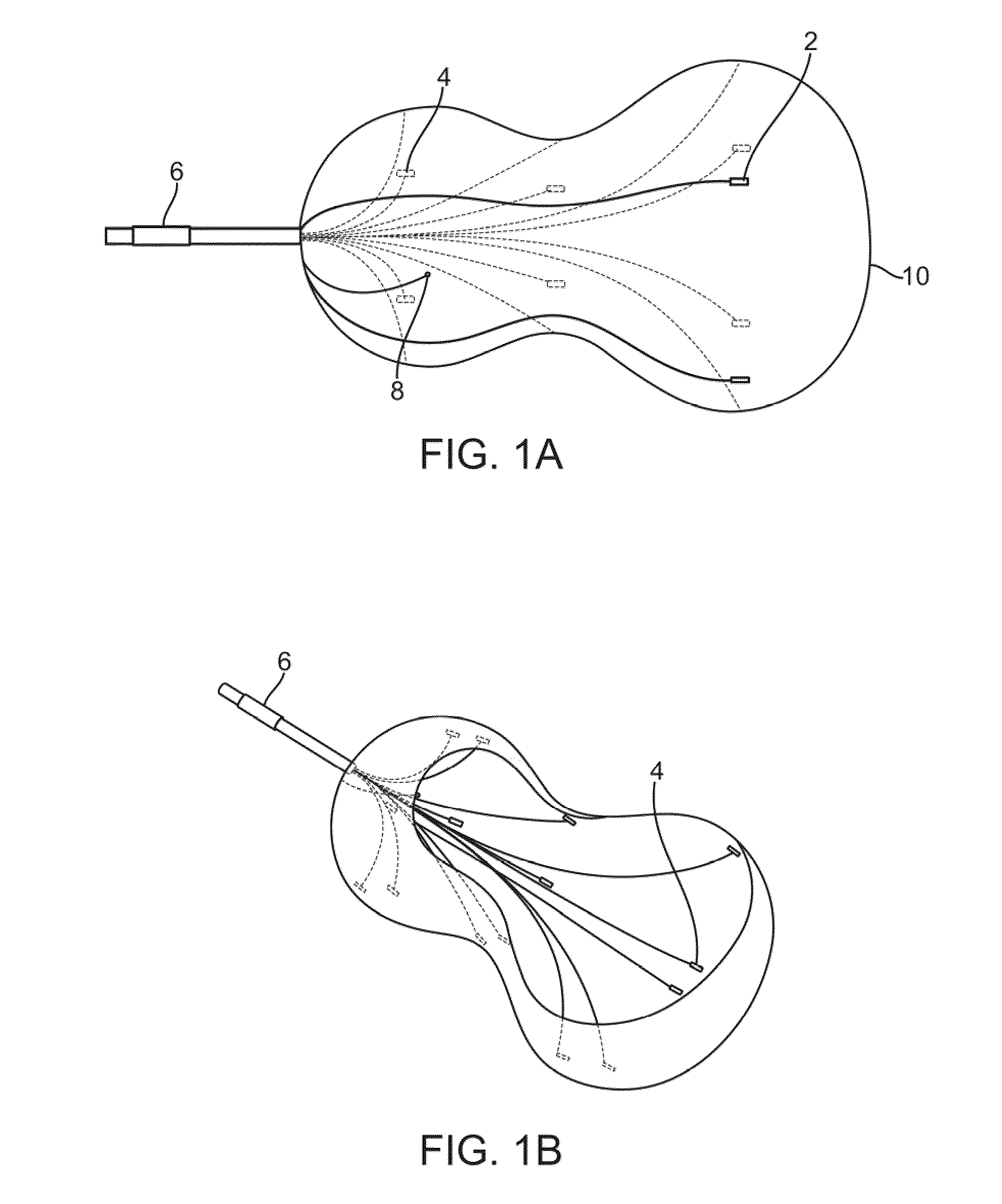
ActiveUS20090005674A1Easy procedureSufficient informationUltrasonic/sonic/infrasonic diagnosticsCatheterThree-dimensional spaceTransducer
An expandable member for characterizing a three-dimensional space within a mammalian body is described. The expandable member is delivered to a target region in a deflated state where it is expanded by inflation of the member. Sensory transducers that contact the member relay sensory information generated when the member is in an expanded state to a microprocessor located outside the body. Using the sensory information, a data-driven picture that characterizes the three-dimensional space within the body is created with a microprocessor. The apparatus is useful in preparation for minimally invasive surgical therapy.
Owner:NIDUS MEDICAL
Non-slip glove
A non-slip glove for all types of weather is disclosed where emory cloth is employed as an exterior friction material to prevent and substantially eliminate slipping from the surface of a moving object as well as handles of golf clubs and baseball bats. The glove has applications to other environments such as construction workers using high-speed drills, drum hammers and the like. Further a finer grit emory cloth has been employed in the interior surface of the glove so as to not irritate the skin but maintain friction contact with the hand so that moisture that may enter inside the glove will not cause the glove to slip on the hand.
Owner:CASS NORMAN ALVIN
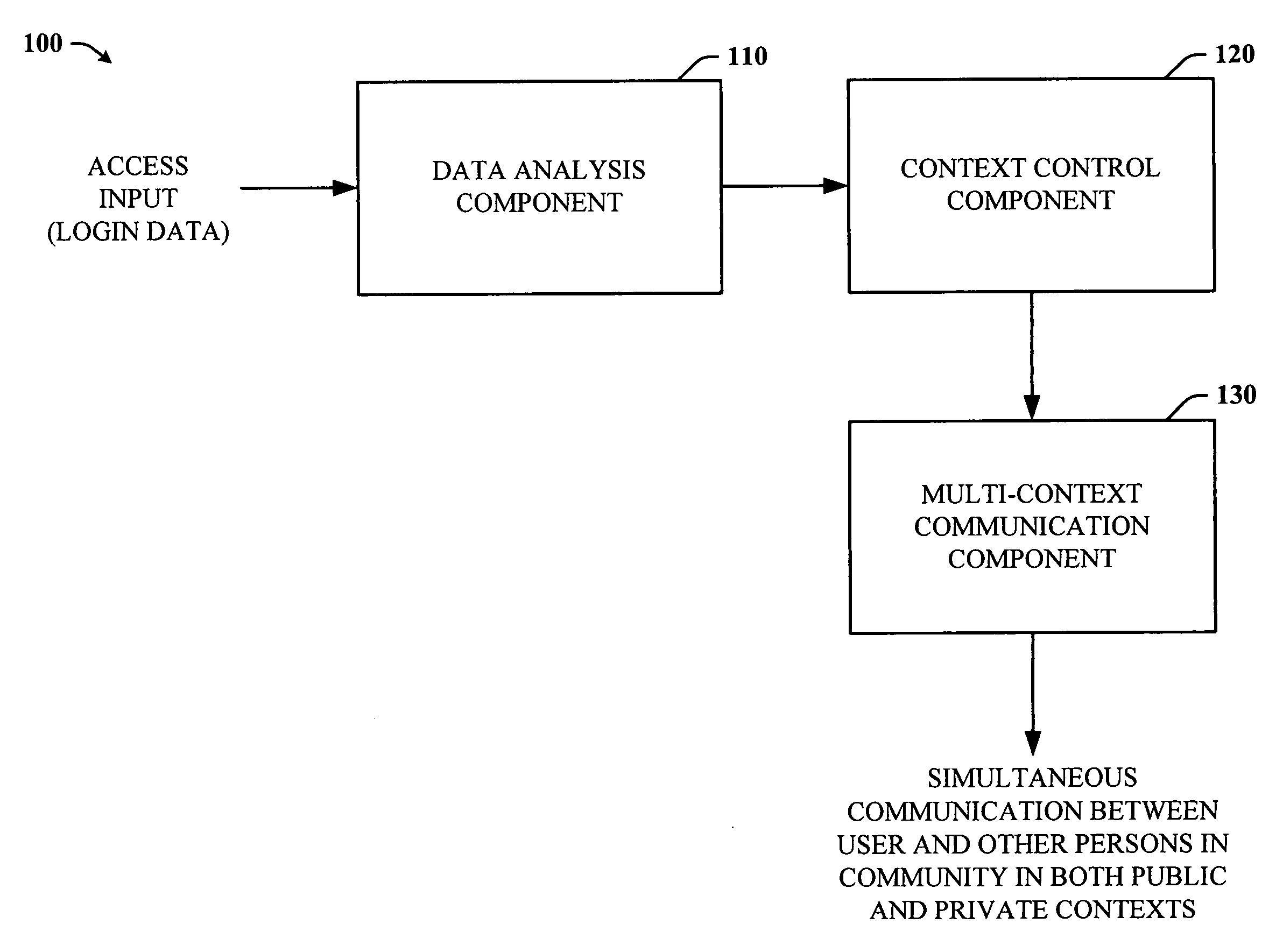
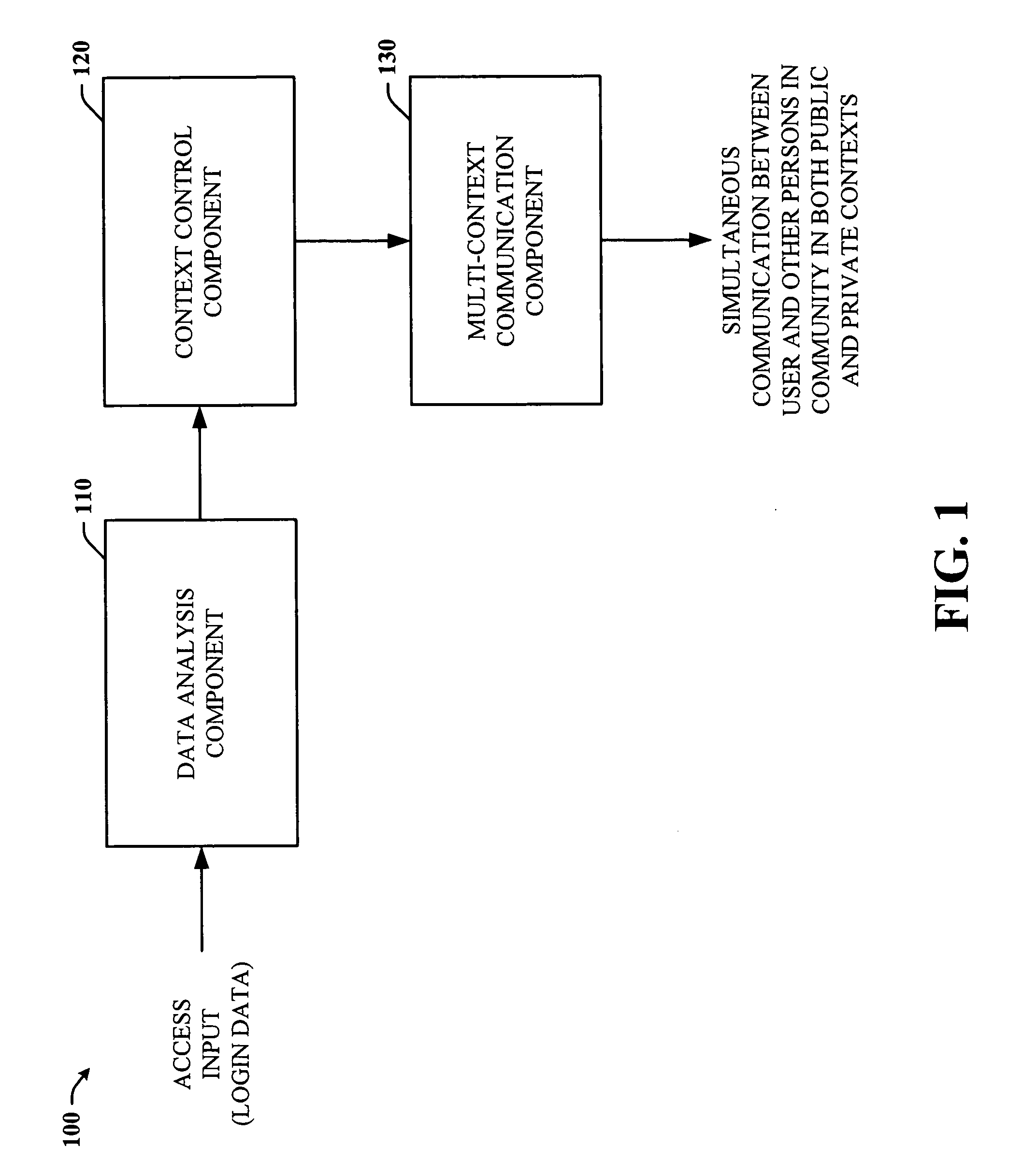
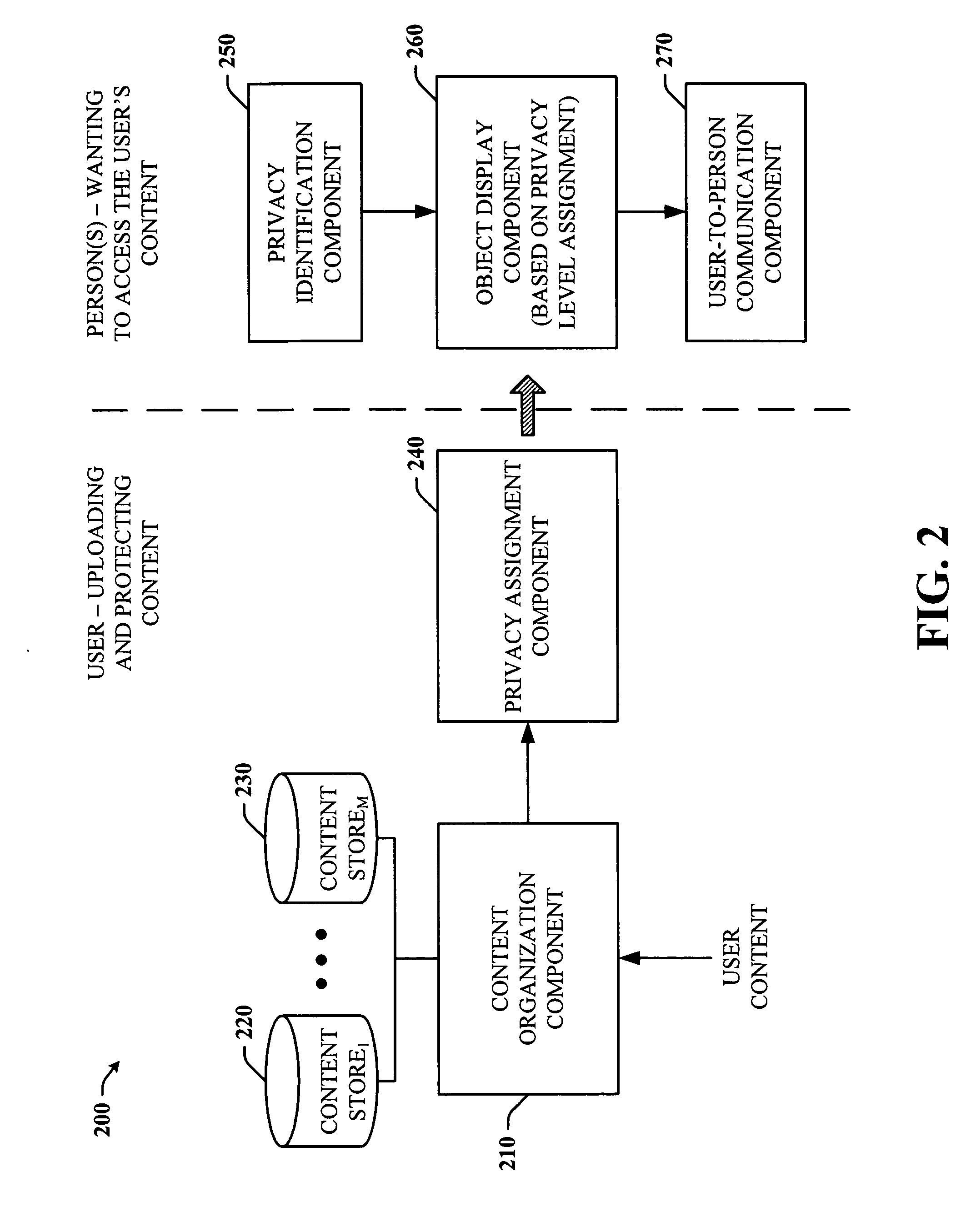
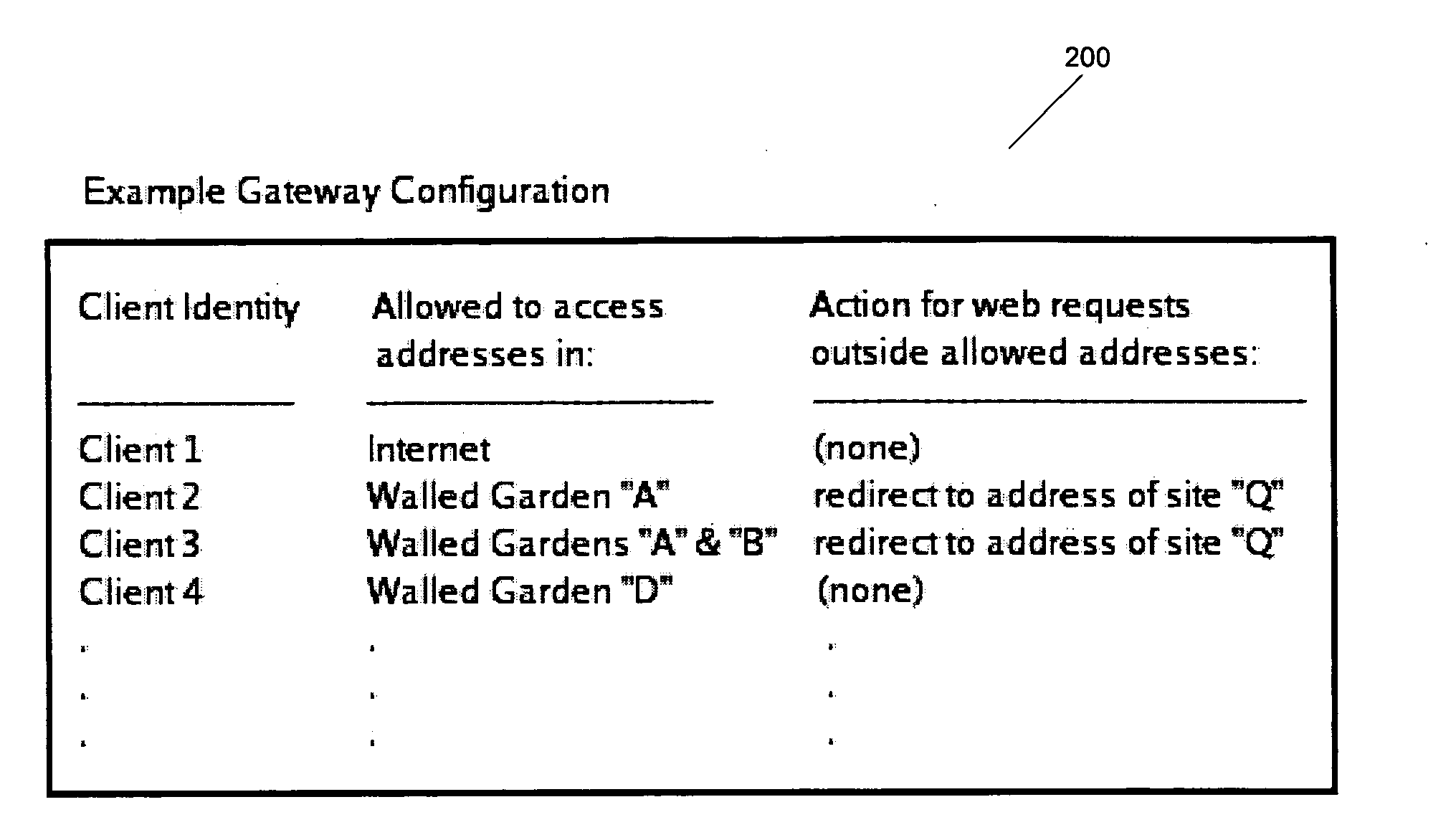
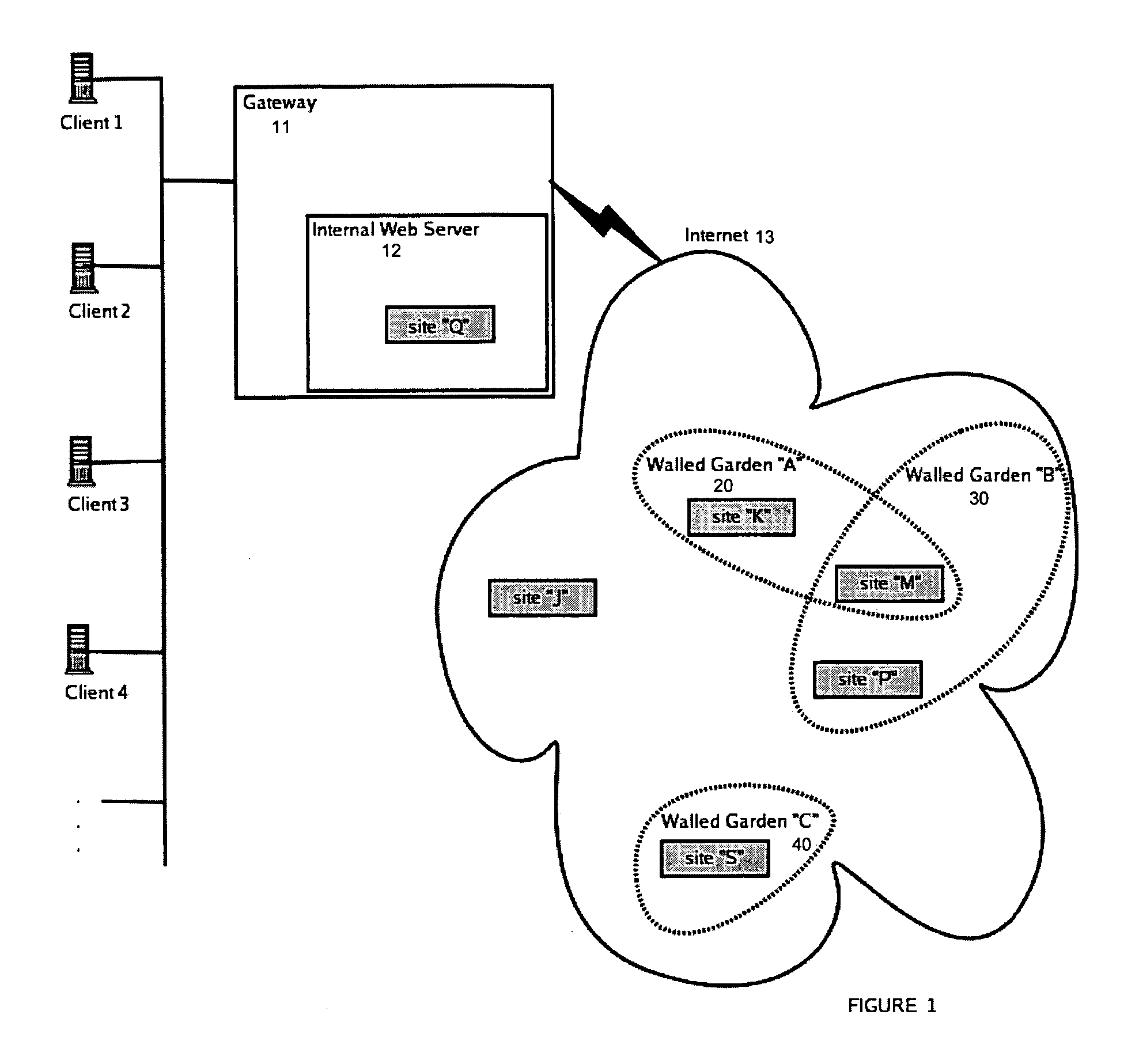
Walled gardens
ActiveUS20060248584A1Facilitates simultaneous communicationEffectively transparentDigital data processing detailsUnauthorized memory use protectionVisibilityInternet privacy
The subject invention provides a unique system and method that facilitates a controlled communication environment which allows a user to participate in a plurality of privacy contexts with other people in a simultaneous manner in an online community. A user can assign or define varying levels of privacy to his / her information or content to control the visibility of such information by others. In particular, a first user can maintain one or more “gardens” or stores of content which may be accessible to at least a subset of the online community. Access to the contents of any one garden can be based on the privacy level of the garden and the privacy level (e.g., access parameters) granted to the person. The privacy levels and arrangement of content can be hierarchal and / or non-overlapping. Thus, a user can seamlessly communicate with multiple users at the same time regardless of their context or privacy level while maintaining the privacy boundaries of each garden.
Owner:MICROSOFT TECH LICENSING LLC
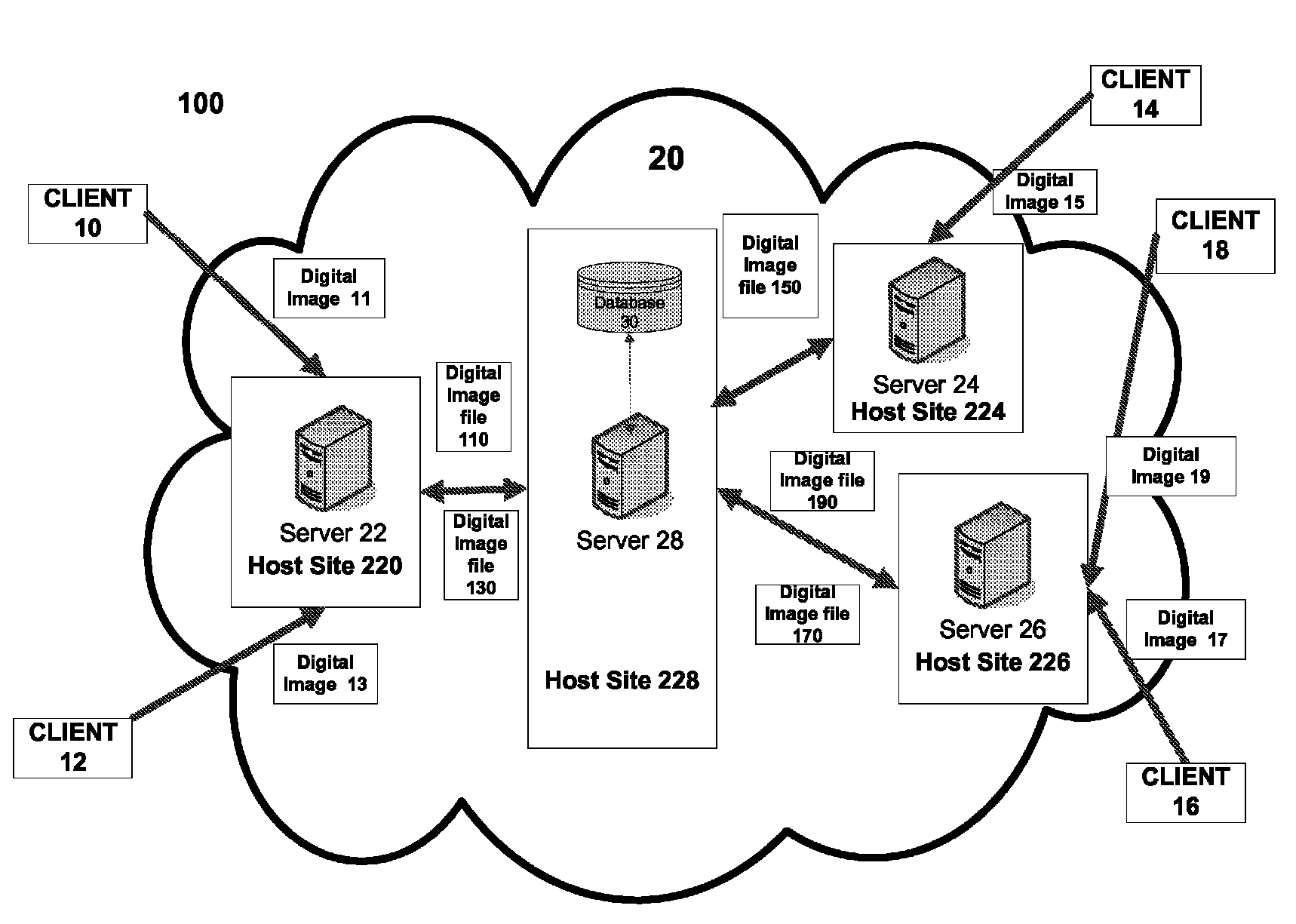
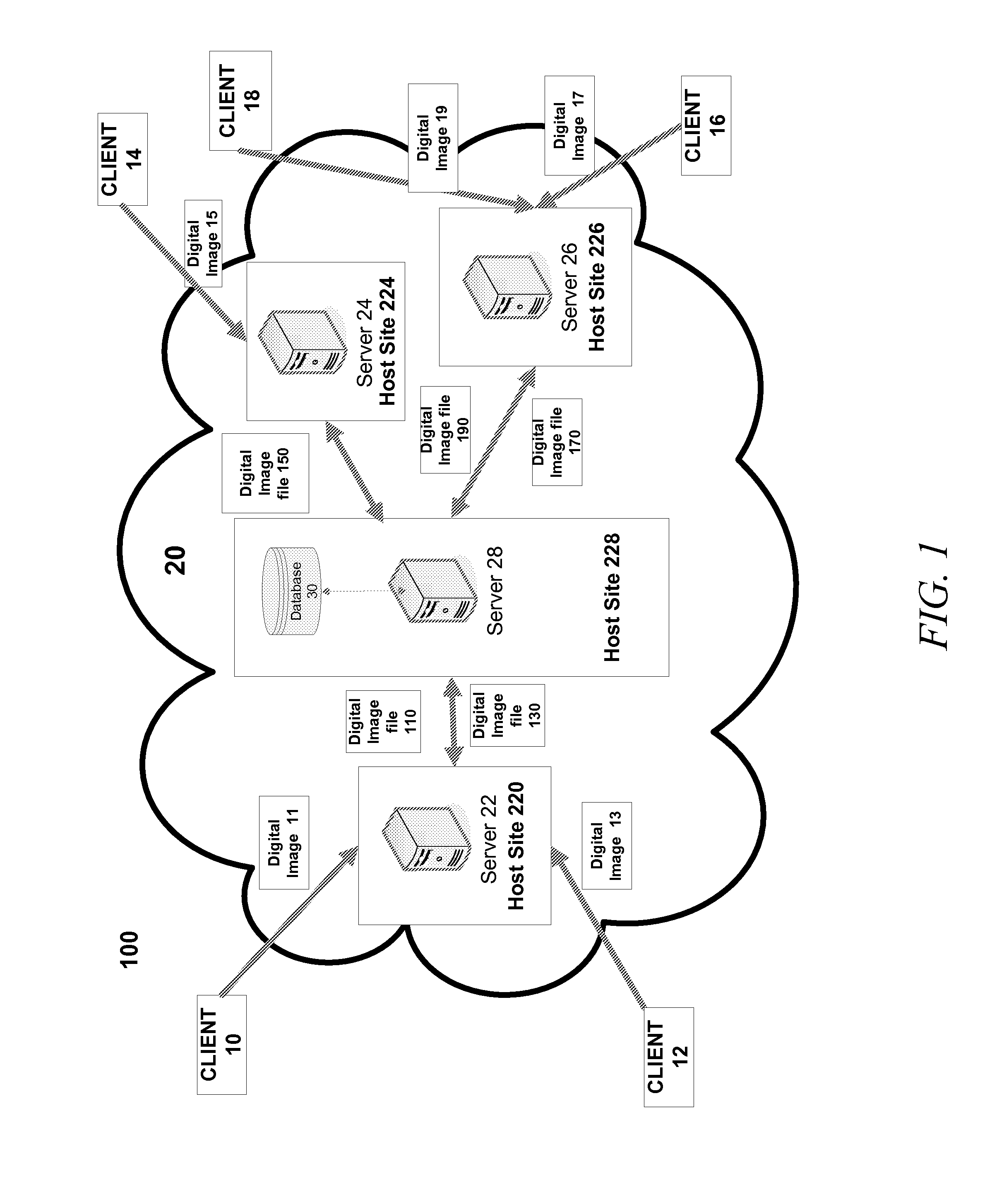
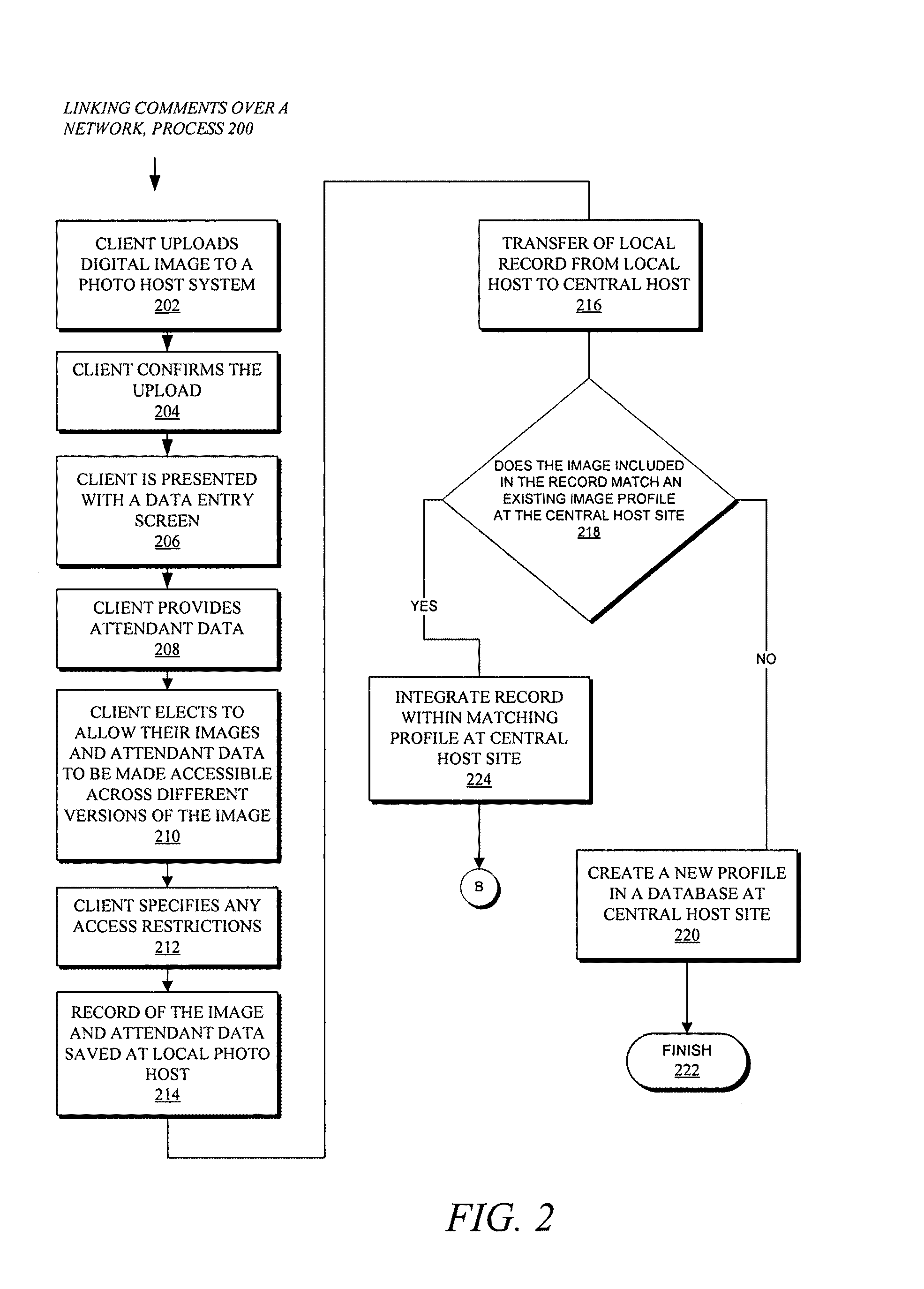
System and method for linking data related to a set of similar images
ActiveUS7903904B1Easy to shareReliable informationCharacter and pattern recognitionStill image data indexingData sharingLinked data
There are provided methods and systems for linking data related to a set of similar images in a manner that both facilitates collaborative data sharing and commenting to generate a more robust set of information about the collective set of images while concurrently allowing users to maintain control over their particular images. A useful and collaborative development of content is achieved between many users interacting with similar versions of the same image. The interacting users may, for example, be friends who may have shared the image through other means, perhaps many years before, or may otherwise be unknown to one another.
Owner:LOEB ENTERPRISES
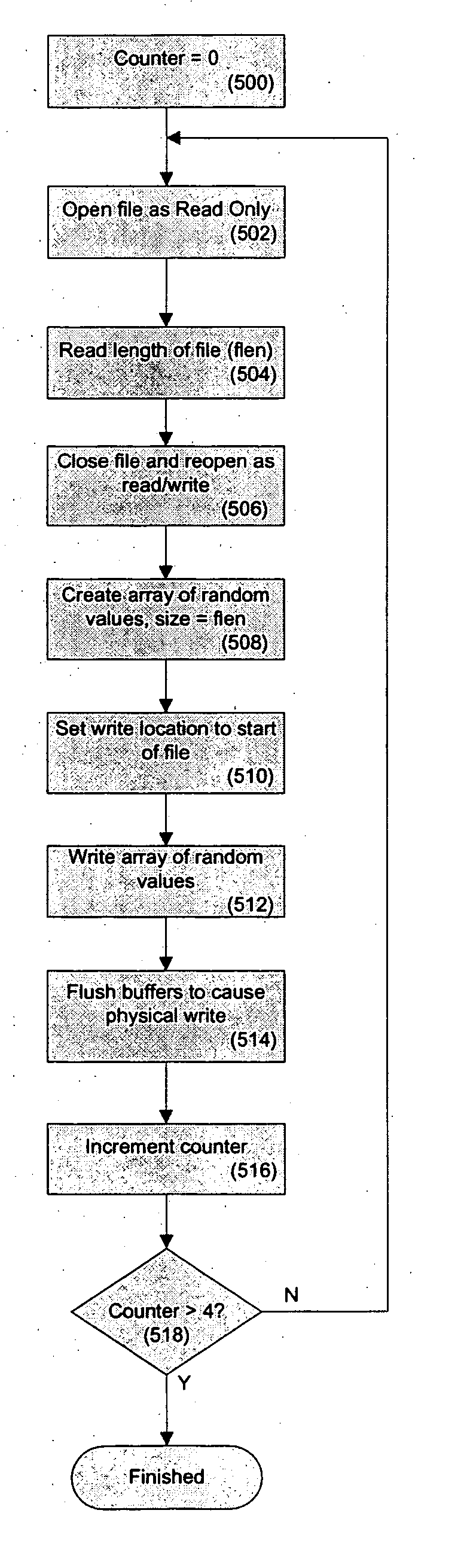
System and method for lost data destruction of electronic data stored on a portable electronic device which communicates with servers that are inside of and outside of a firewall
ActiveUS20060021006A1Reduces and eliminates riskReduce riskDigital data processing detailsUser identity/authority verificationBiological activationData loss
A data security system and method protects stored data from unauthorized access. According to one aspect of the invention, a client computing device communicates periodically with a server. If communications is note established between the client and the server for a selected activation interval and a subsequent grace period, the data is determined to be lost, and programmed security rules are automatically executed. The server with which the client computer device communicates includes one server located inside the firewall of a particular organization, or a mirror server located outside the firewall, and thereby allow for the re-setting of the activation interval when the client is properly outside of the firewall through communication with the mirror server, as well as the to provide command an control over a lost or stolen client by pushing updated rules if communication is subsequently attempted with the mirror server.
Owner:BEACHHEAD SOLUTIONS
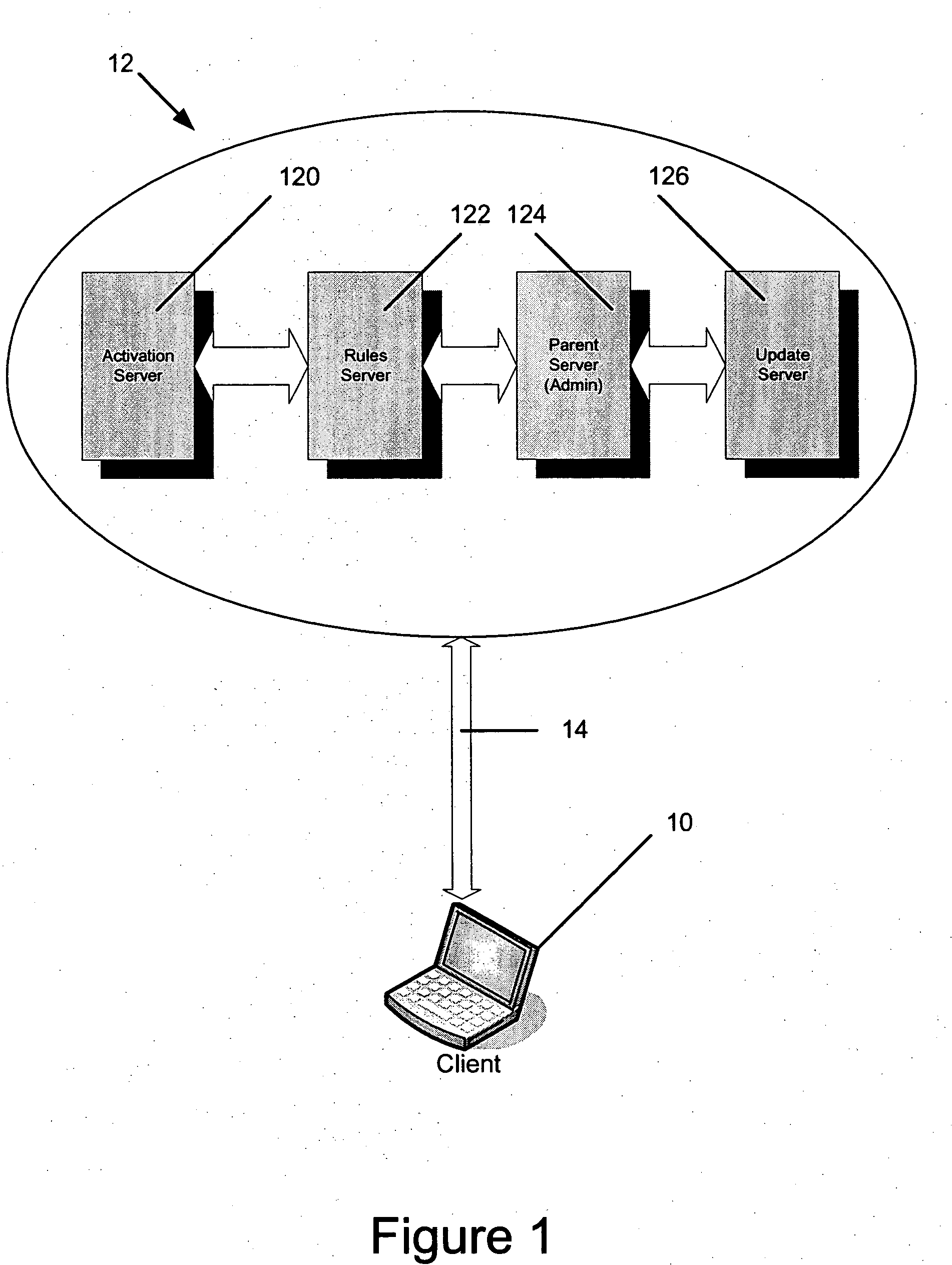
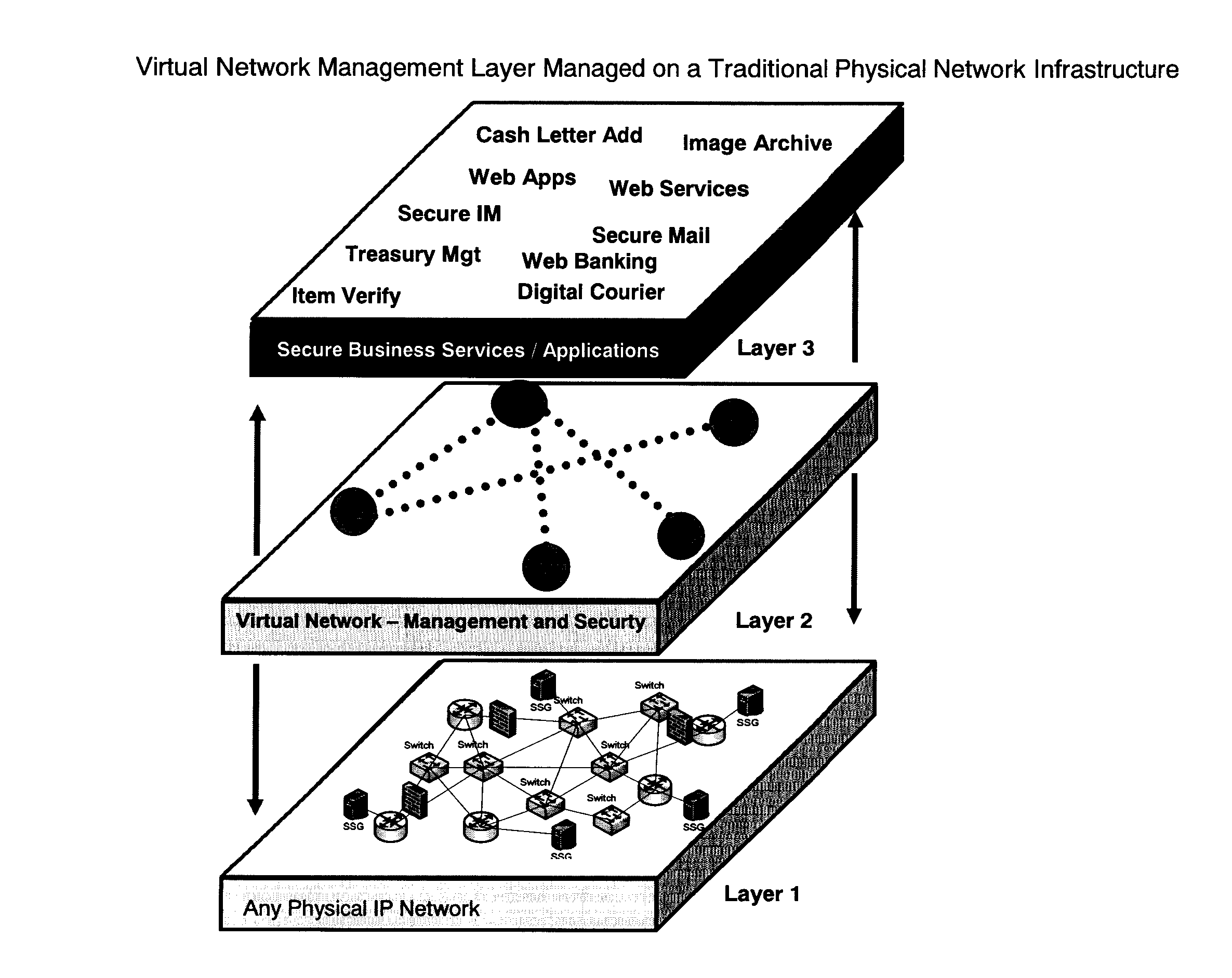
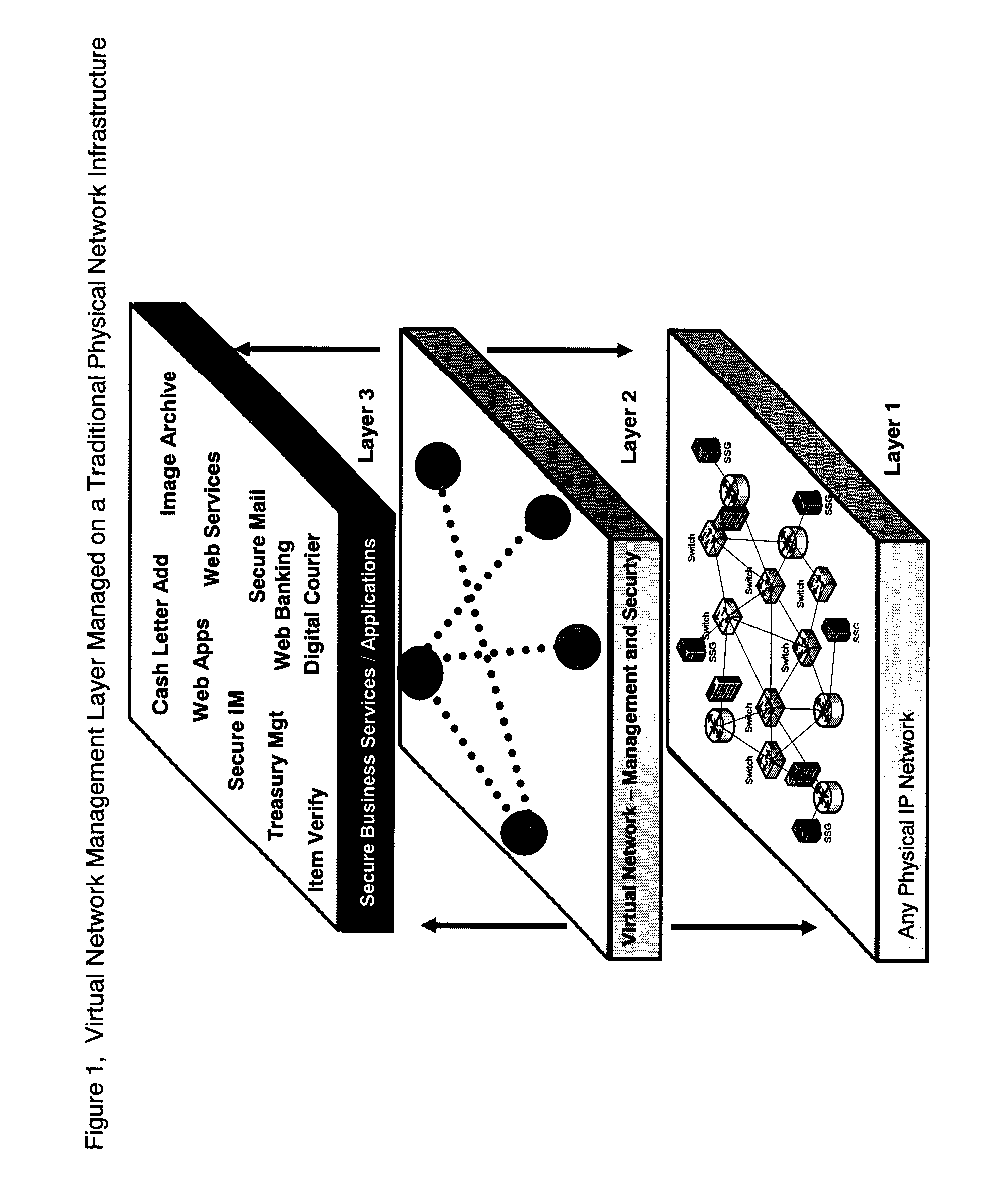
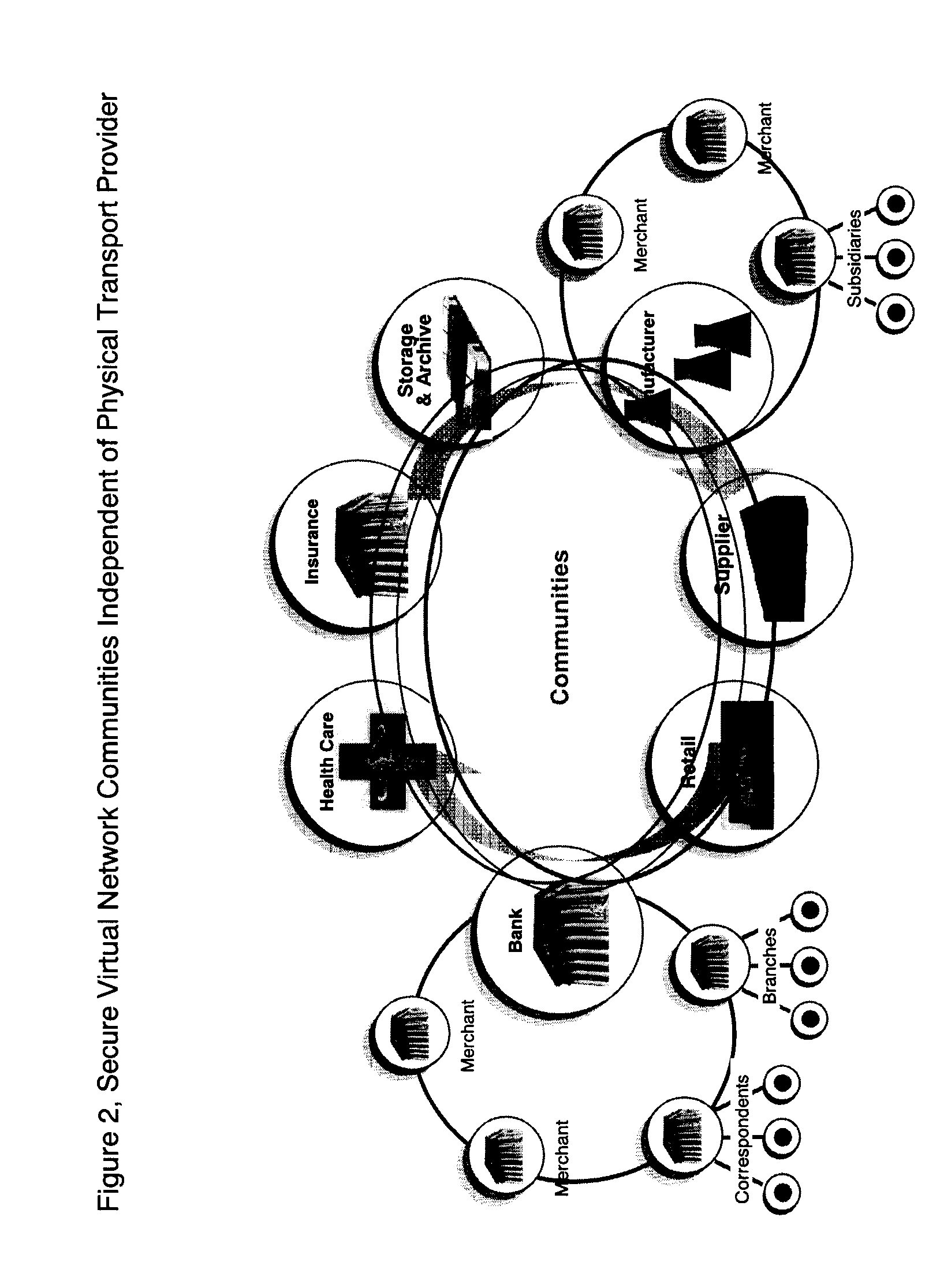
Infrastructure Architecture for Secure Network Management with Peer to Peer Functionality
ActiveUS20070112578A1Maintain security and privacyReduction of it valueData processing applicationsDigital data processing detailsNetwork managementNetwork architecture
Architecture defining a secure virtual network of communities of two or more participants where security and business management reporting is a result of a network architecture and where participants can maintain absolute security and control over their services independent of any other participant according to implemented selection rules of the network architecture administration.
Owner:RANDLE WILLIAM M +1
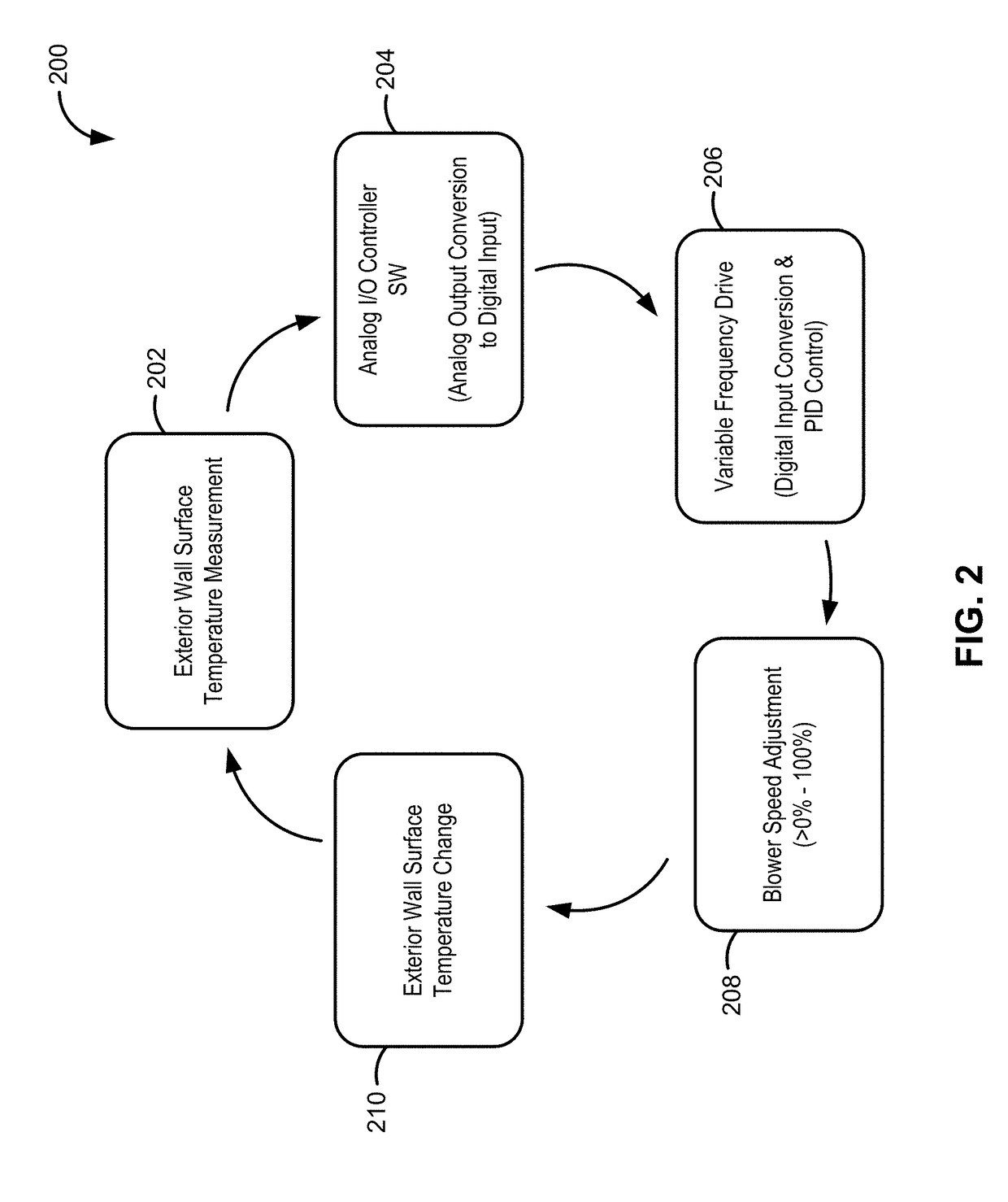
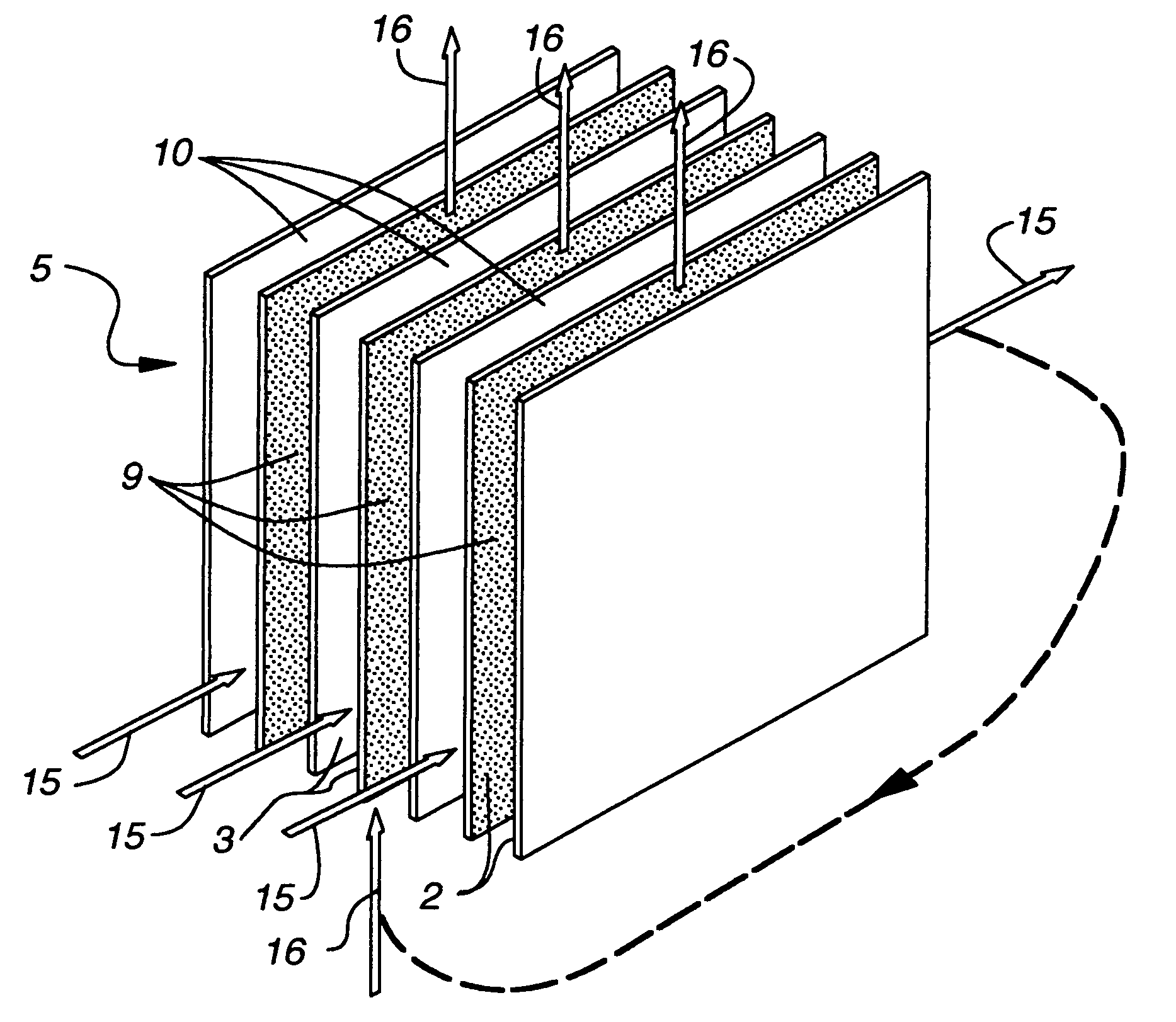
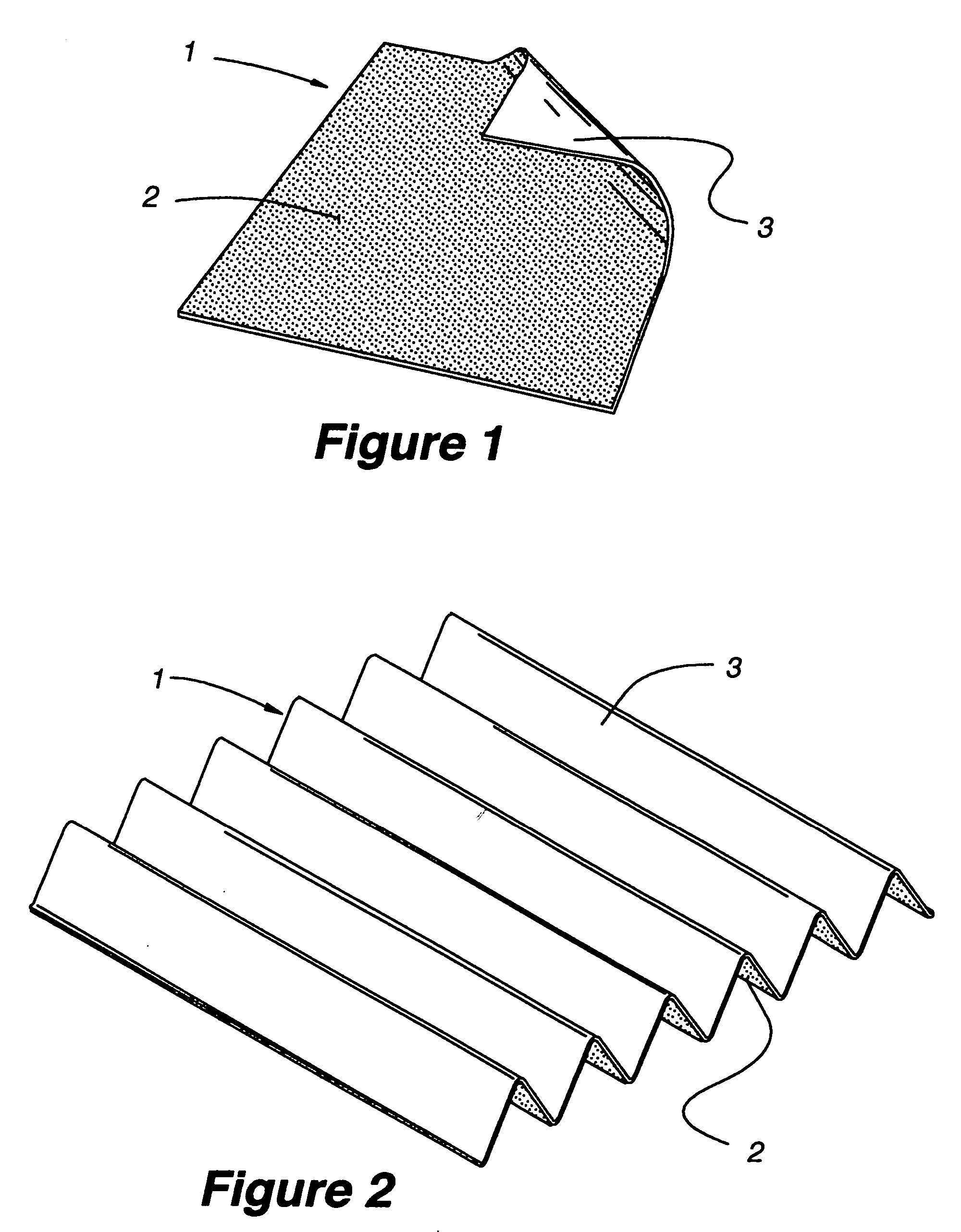
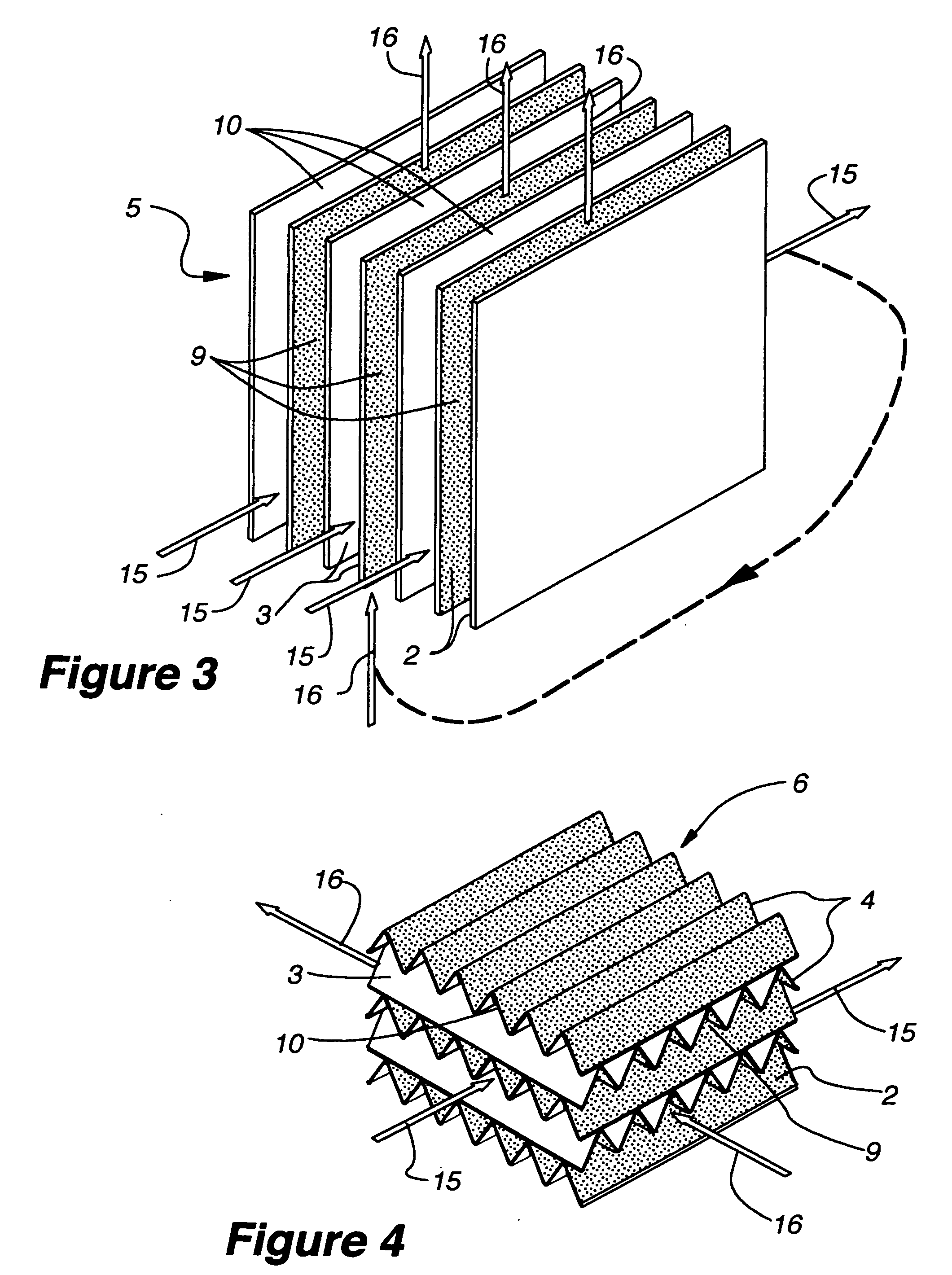
Indirect evaporative cooling mechanism
InactiveUS20050218535A1Improve economyImprove efficiencyInternal combustion piston enginesFree-cooling systemsDesiccantPlastic materials
The present invention relates to methods for indirect evaporative air-cooling with the use of plates, heat exchangers and feeder wicks—of the indirect evaporative type. Several components for an indirect evaporative heat exchanger described as follows: A plate for an indirect evaporative heat exchanger where the plate is made of laminate material having one sheet of wicking material for wet zone(s) and the other of a water proof plastic material for the dry zone(s). An evaporative heat exchanger is created by assembling the plates forming spacing for wet channels, (they are created by the wet zone of the plates,) and dry channels, (they are created by the dry zone of the plates,) with channel guides or corrugated plates. The spacing between the plates is defined to reduce pressure drop for increased airflow. A feeder wick system creates the wetting of the wet channels without excess water. Sometimes the wet zone of the plate can be made of a membrane material where the opposite side of this membrane material is covered by a solid desiccant creating the wet zone of this desiccant plate. An indirect evaporative heat exchanger that is created by assembling both wick coated with plastic plates and desiccant plates, can realize not only the evaporative cooling but also the dehumidification of air.
Owner:MAISOTSENKO VALERIY +3
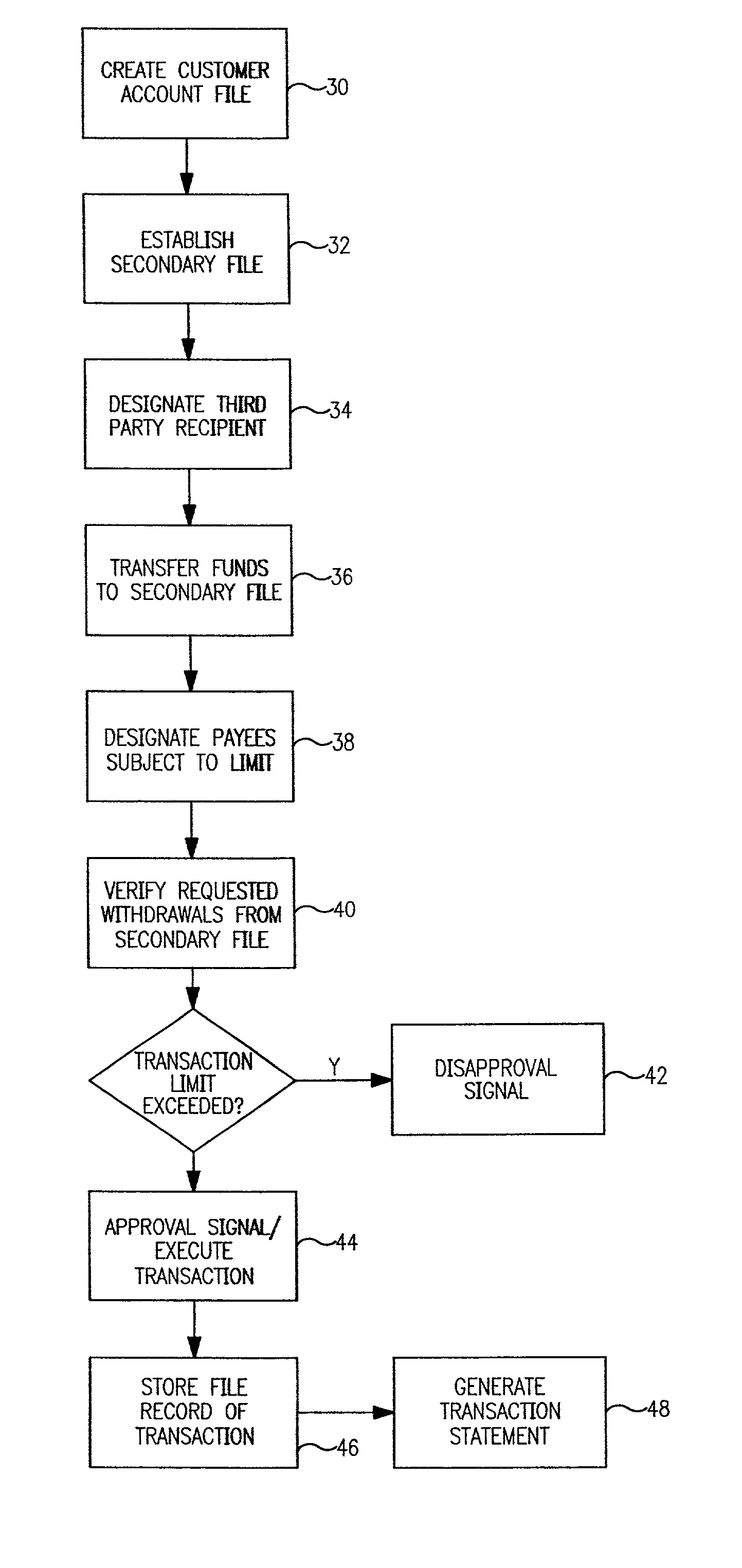
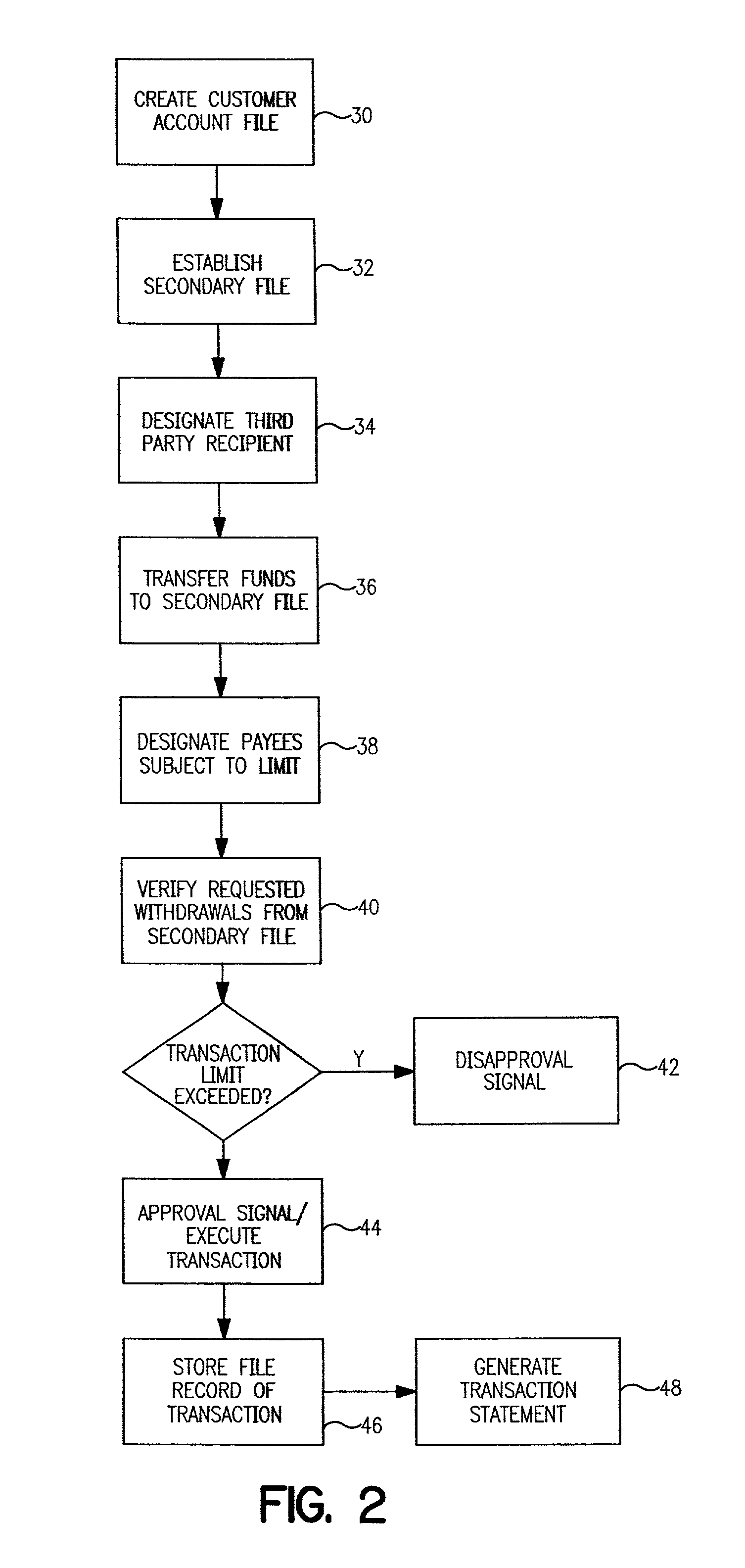
Controlled entertainment spending account
InactiveUS7143064B2Some control over how the money is spentControl habitFinancePayment circuitsComputer basedMultimedia
A computer-based method for allocating funds in pre-established accounts for use by customers, by creating for each customer a customer account file containing a record of funds deposited for the customer, and limiting how the funds in each customer account file may be spent on audio and video entertainment in the form of goods and services in response to command instructions from the fund depositor, wherein the limit on the funds is a limit on transaction amount or a limit according to content on the audio or video entertainment on which the funds may be spent. Computer-based systems implementing the inventive method are also disclosed.
Owner:RESTRICTED SPENDING SOLUTIONS +1
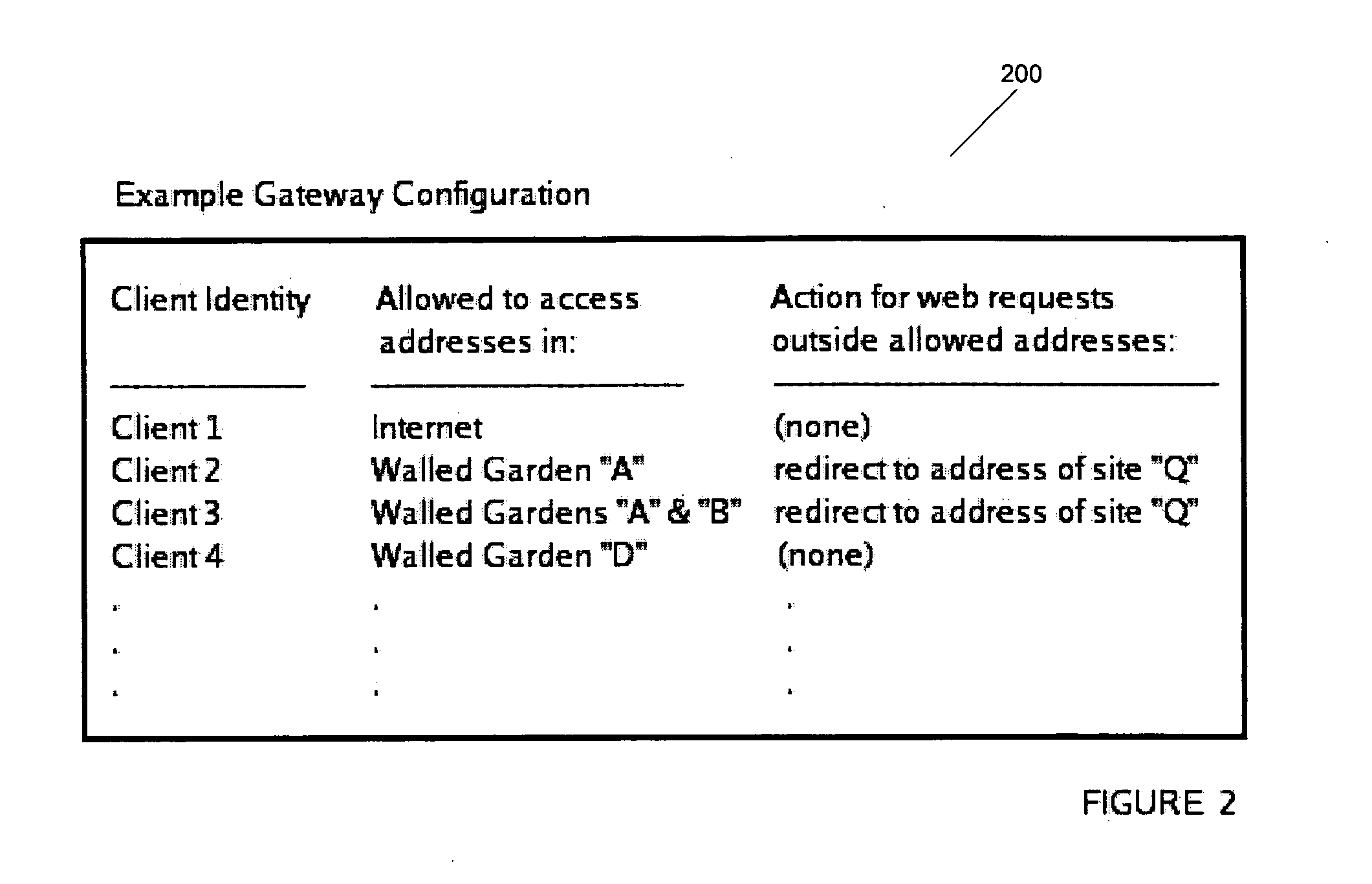
Method and system for controlling network access
ActiveUS20050204050A1Reduce negative impactKeep full controlMemory loss protectionDigital data processing detailsNetwork communicationClient-side
Systems and methods intended to control a network devices access to a network are disclosed. Embodiments of the current invention expose a method for confining a network client's network access to a specific logical region of the network. A network communication may be received and the client that originated this communication determined. This client is associated with a set of rules or walled garden that specifies the access allowed by that client. The destination of the communication may also be determined and if the destination is allowed by the set of rules associated with the client and access to the destination allowed if access to the destination is allowed by the set of rules.
Owner:RPX CORP
Optical and electrical hybrid connector
InactiveUS7427165B2Smooth connectionQuick connectionCoupling contact membersTwo-part coupling devicesElectricityFiber
Owner:J FITNESS LLC
Retainer ring for wire package
InactiveUS7178755B2Reduce amount of tangleKeep full controlFilament handlingArc welding apparatusEngineeringElectric wire
A welding wire package comprising a cylindrical drum with a central axis, multiple layers of looped welding wire defining a wire stack to be paid out, said body having an upper ring shaped surface with an outer cylindrical surface generally covering or overhanging the wire stack and an inner cylindrical surface defining a central bore concentric with the drum axis and a flexible permanent magnet retainer ring on top of the upper ring shaped surface wherein the retainer ring allows welding wire to be paid from under the ring upwardly from the central bore.
Owner:LINCOLN GLOBAL INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com