Method of preoenting software non-authorized use by using network card physical address
A physical address and network card technology, applied in digital data processing parts, electrical components, electrical digital data processing, etc., can solve the problems of computer hardware damage, high failure rate of floppy disk, low security, etc., and achieve simple and convenient use, encryption The effect of low cost and guaranteed safety
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
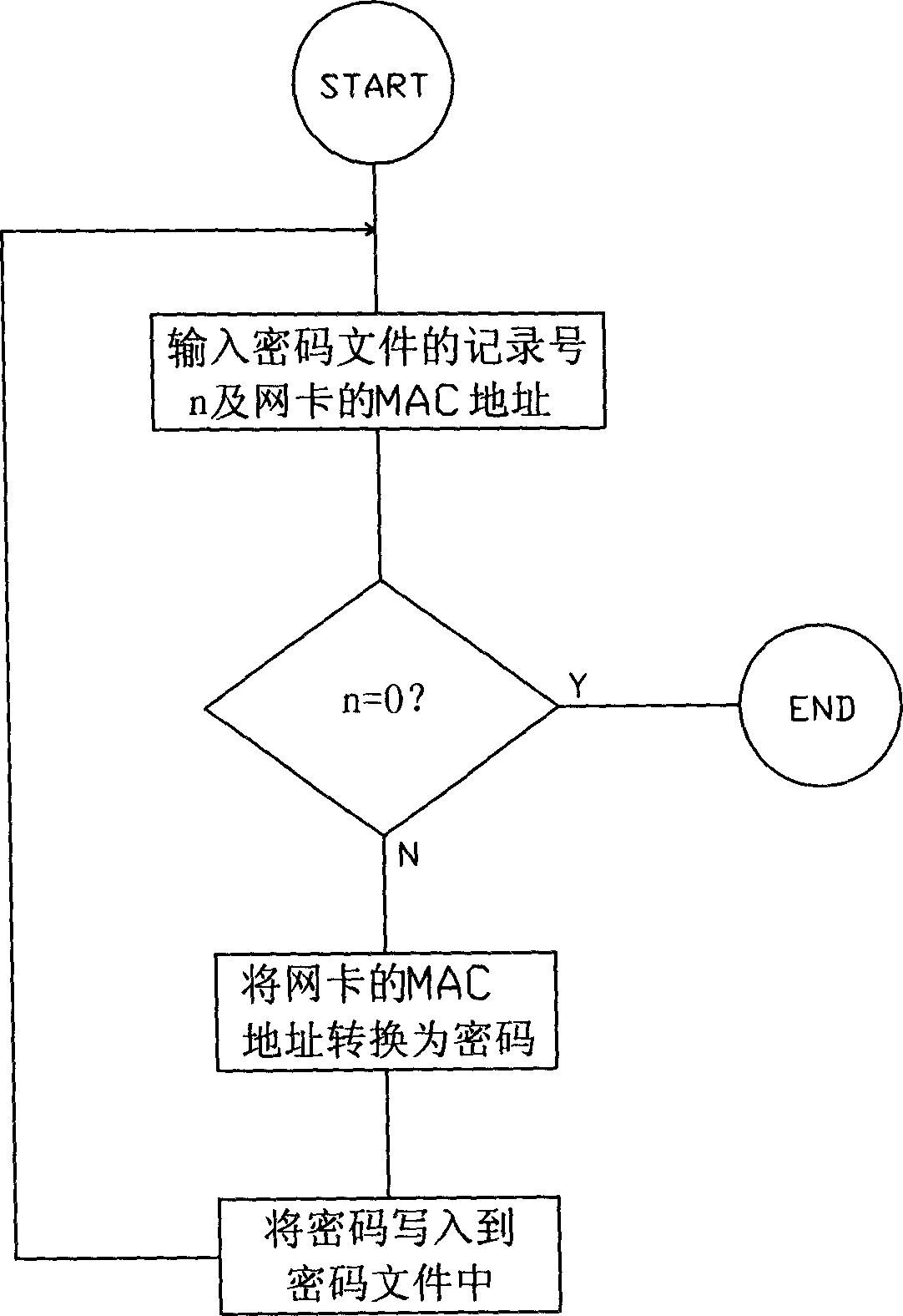
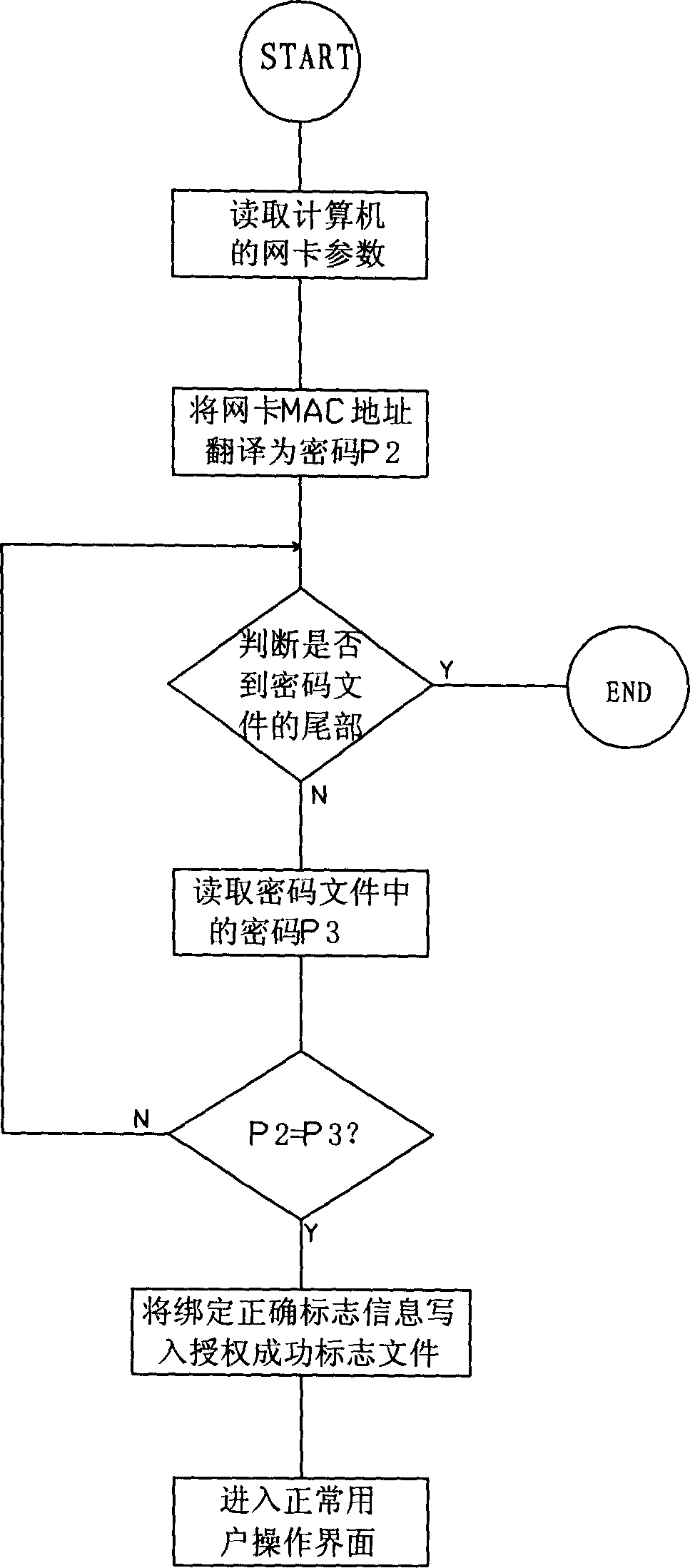
[0013] The invention utilizes the network card and the encryption software to realize the encryption of the software and prevent the software from being copied and installed illegally. The encryption software consists of two parts, one is the encryption software management program, and the other is the encryption software application program. A unified encryption algorithm and password file are used between the two. The management program provides the application program with a password file of the same system after encryption. The application program can be placed in front of the application software (that is, the software to be encrypted and protected) by batch processing commands, or added to the application software by an external call method, or added to the application software by a library function call method. The management program is used by the software developer. Its main function is to pre-authorize and register the client computer, generate a password file accordi...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com