Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
616results about How to "Prevent illegal use" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
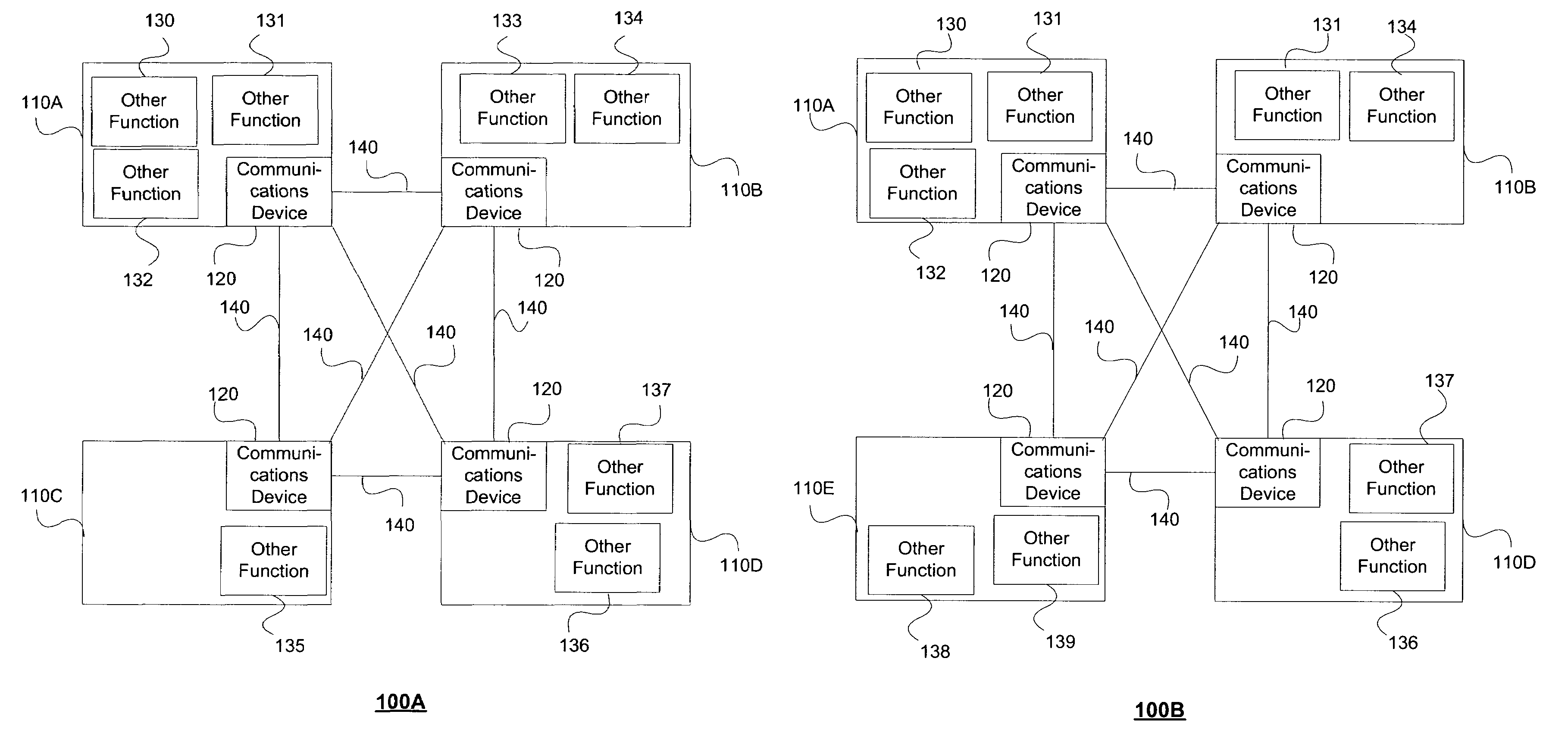
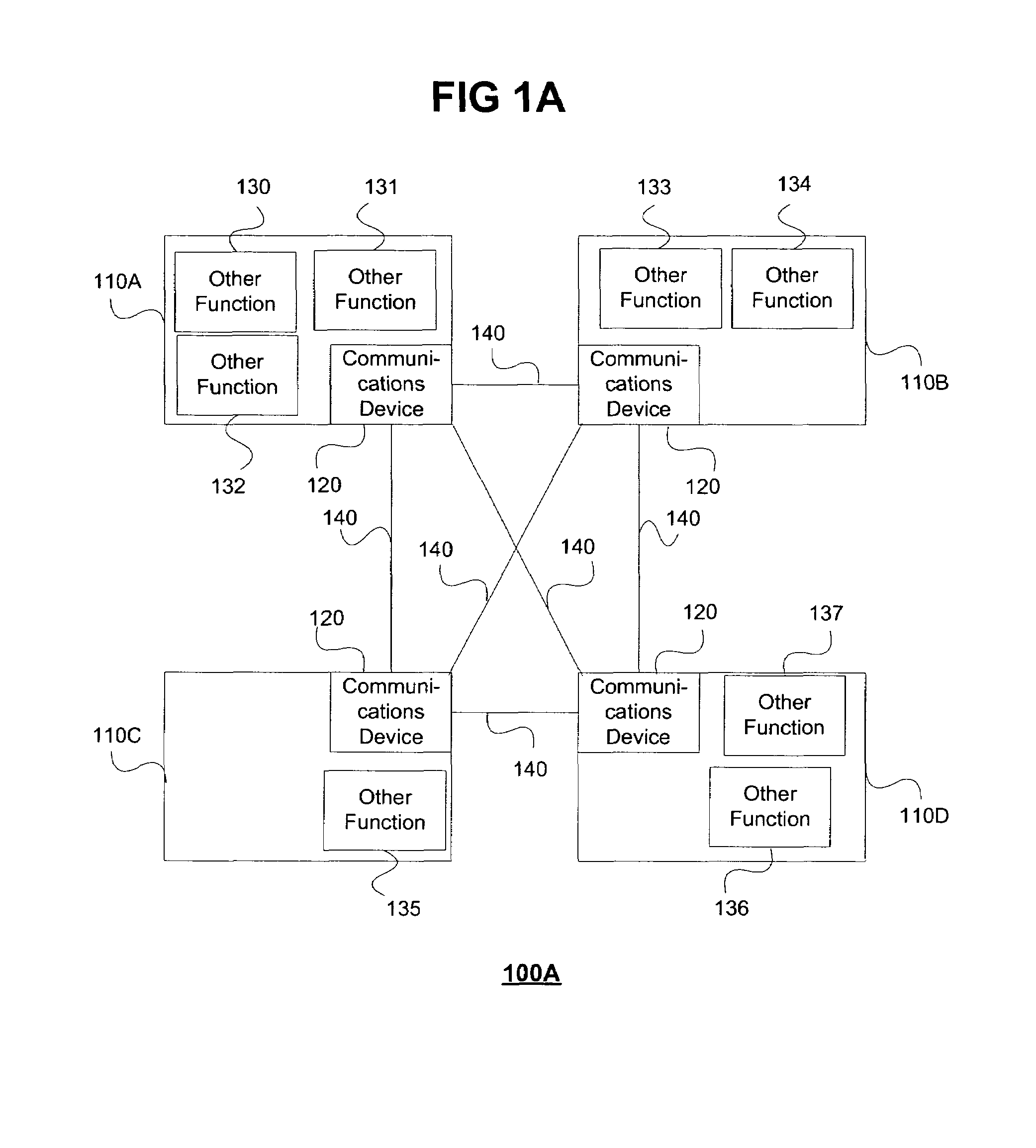
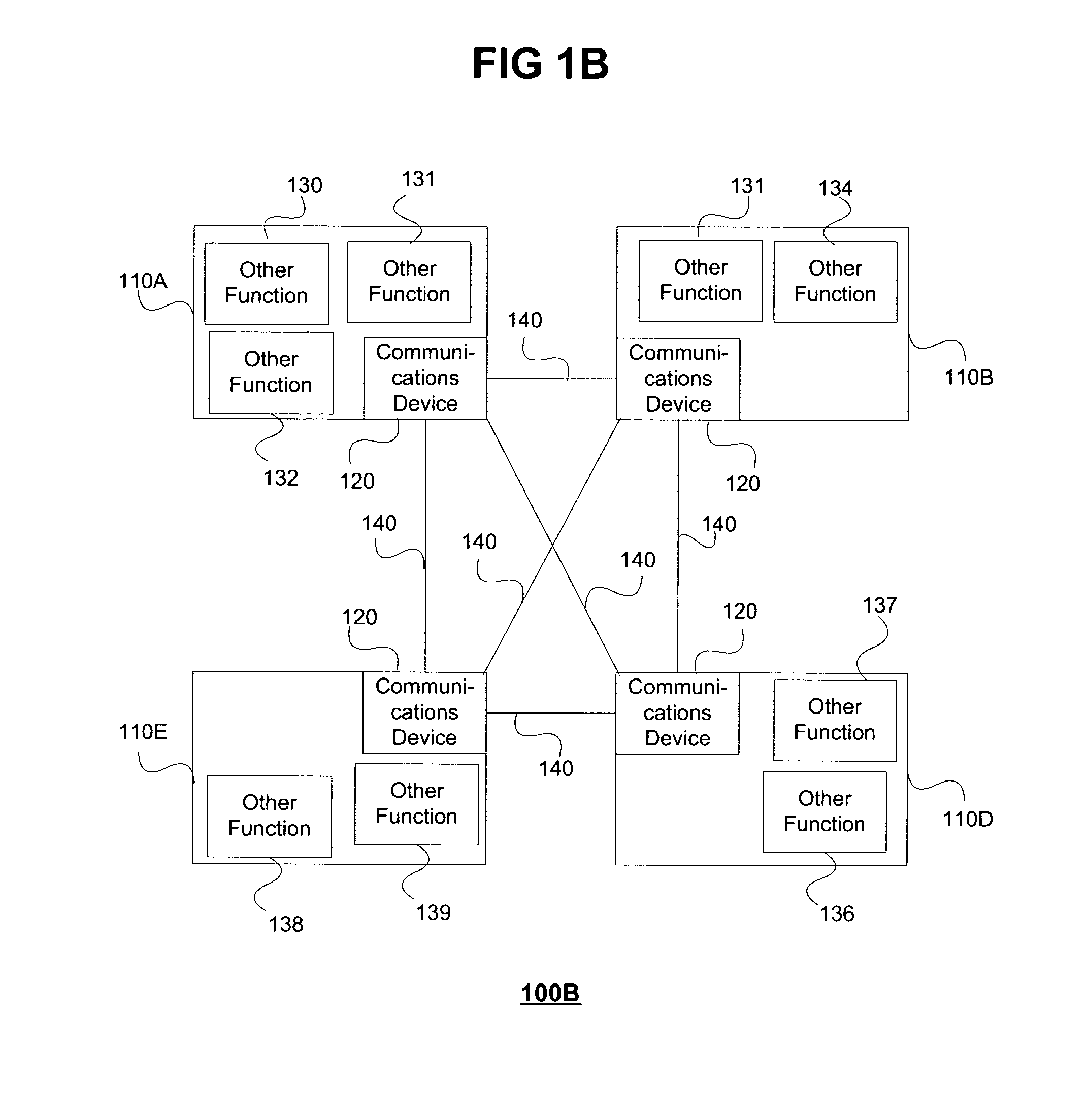
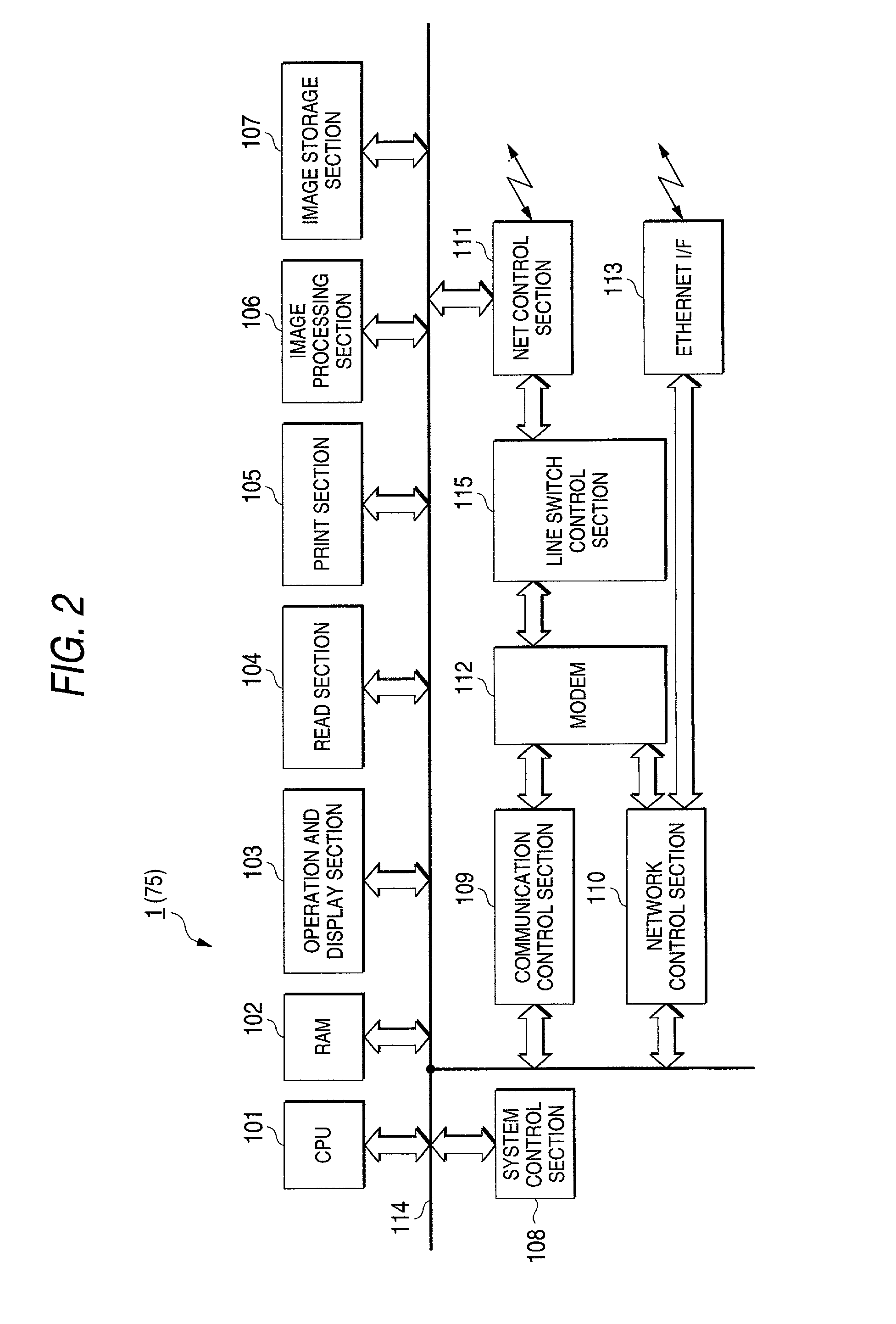
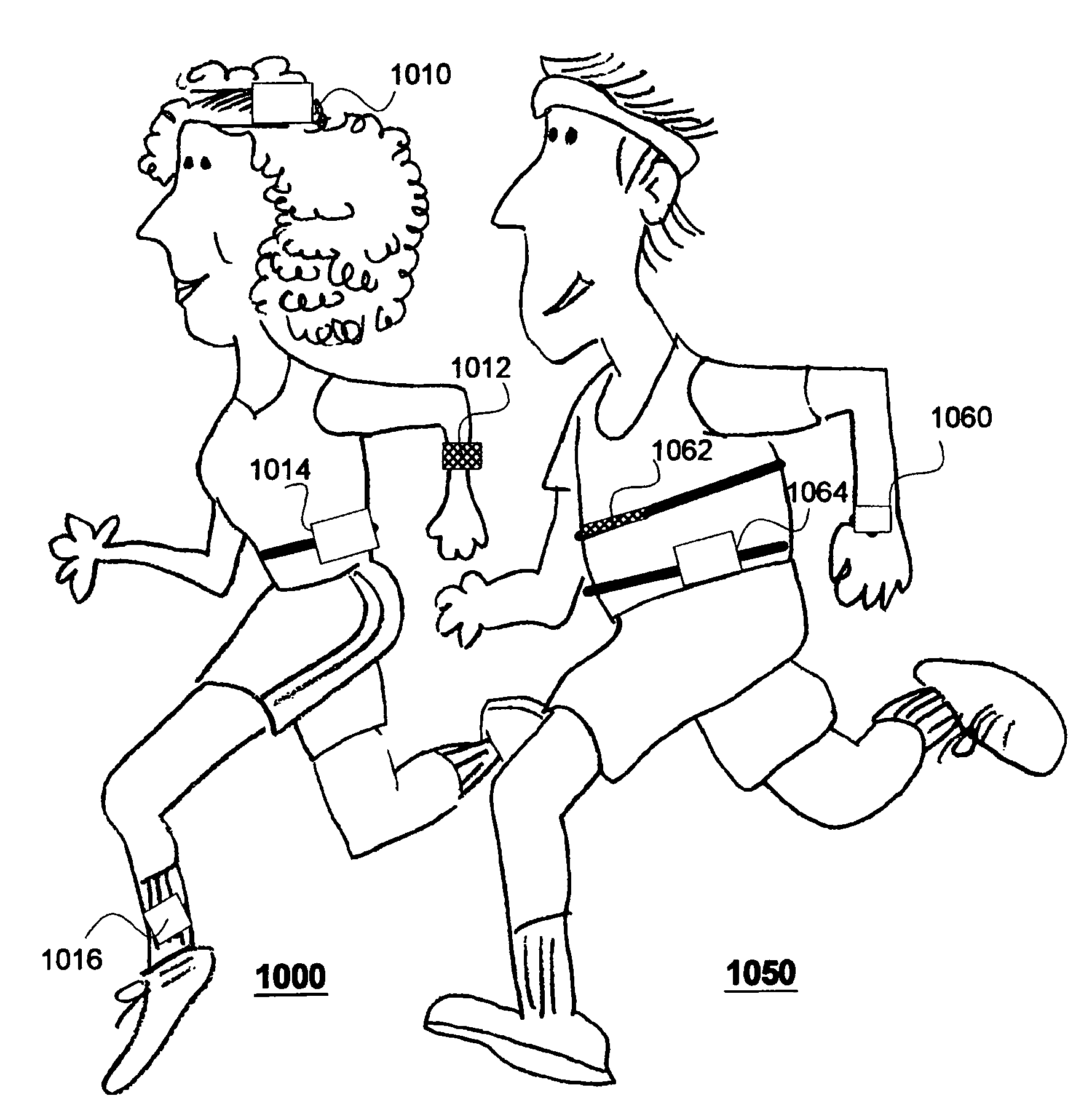
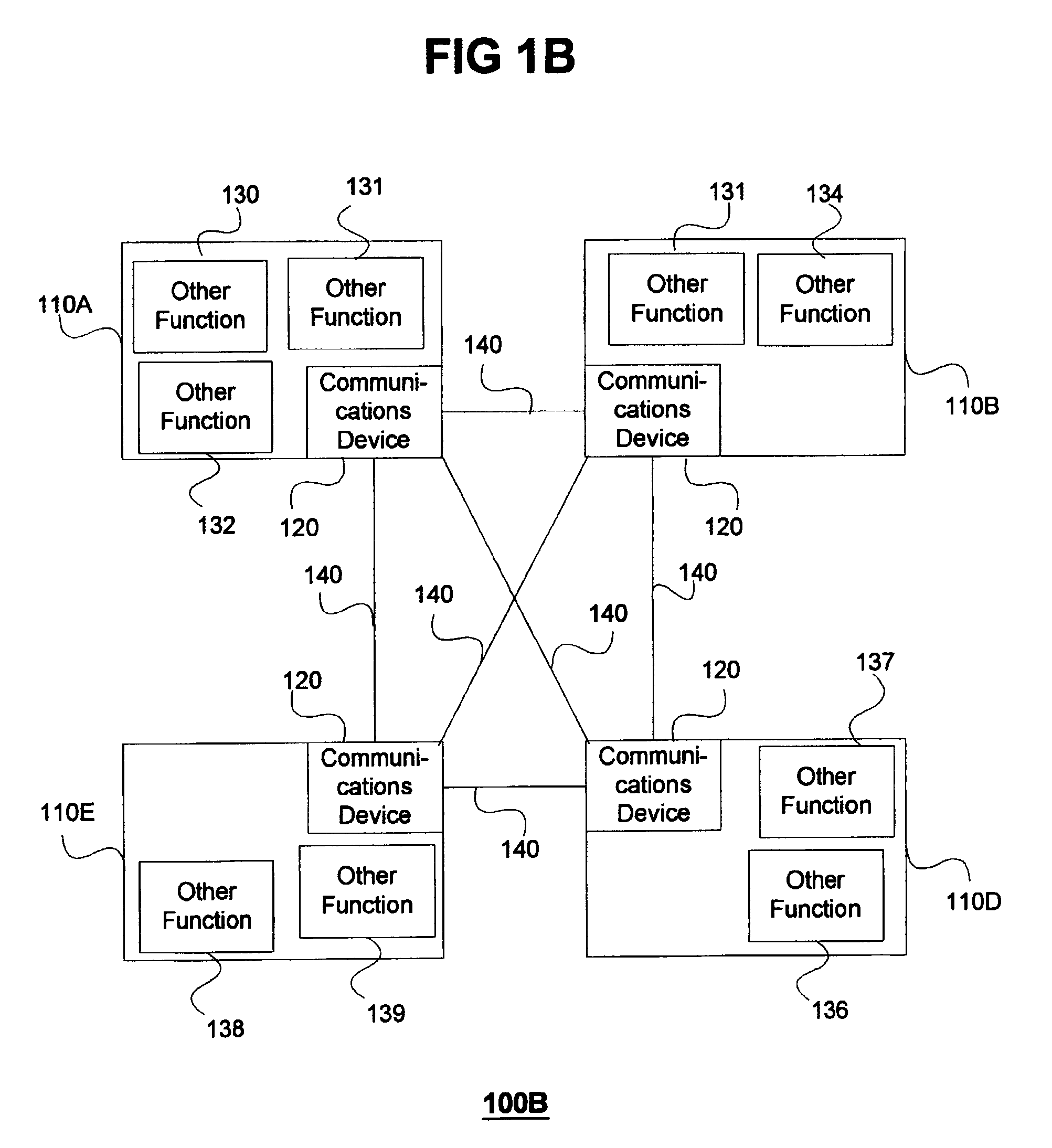
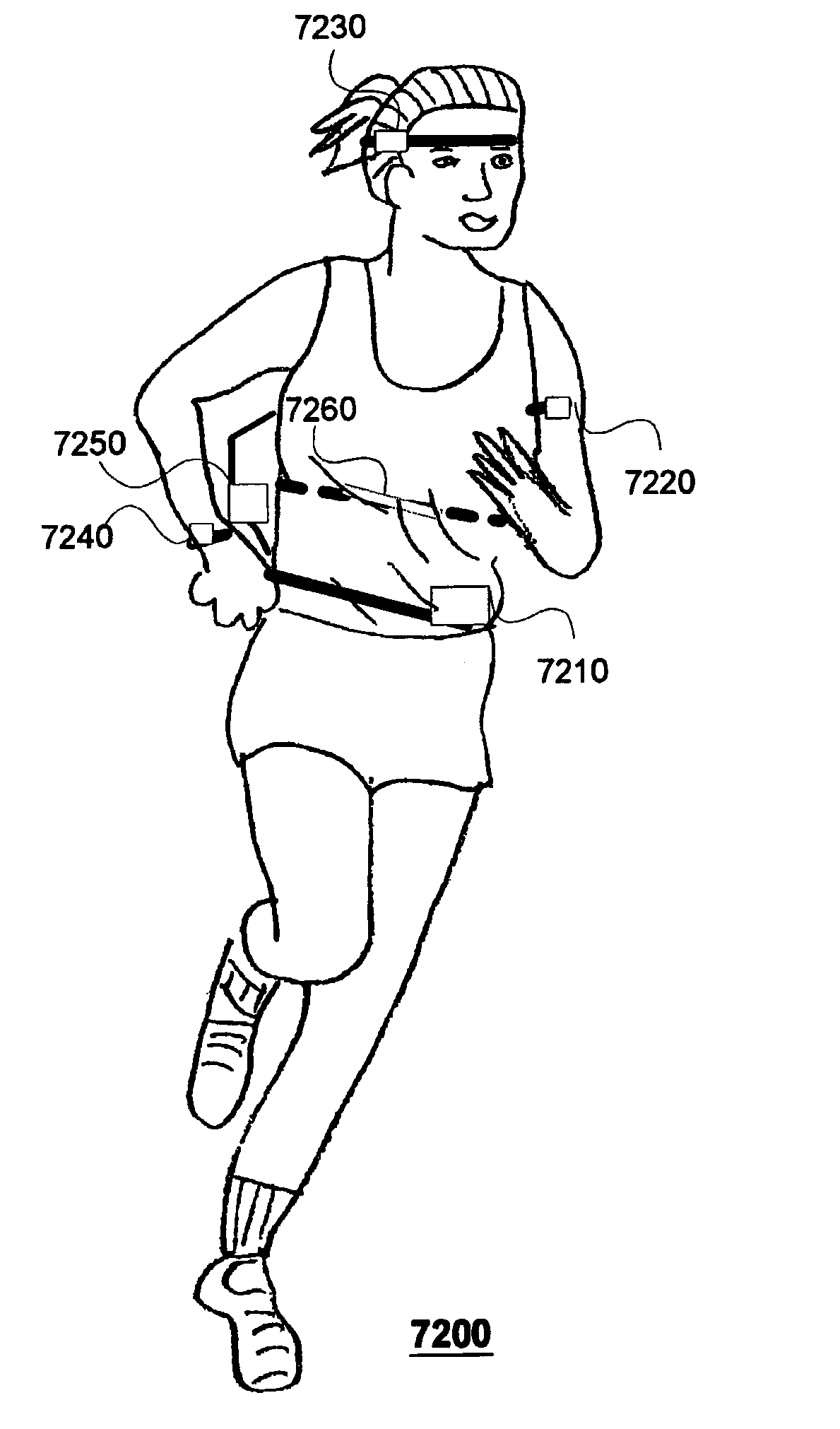
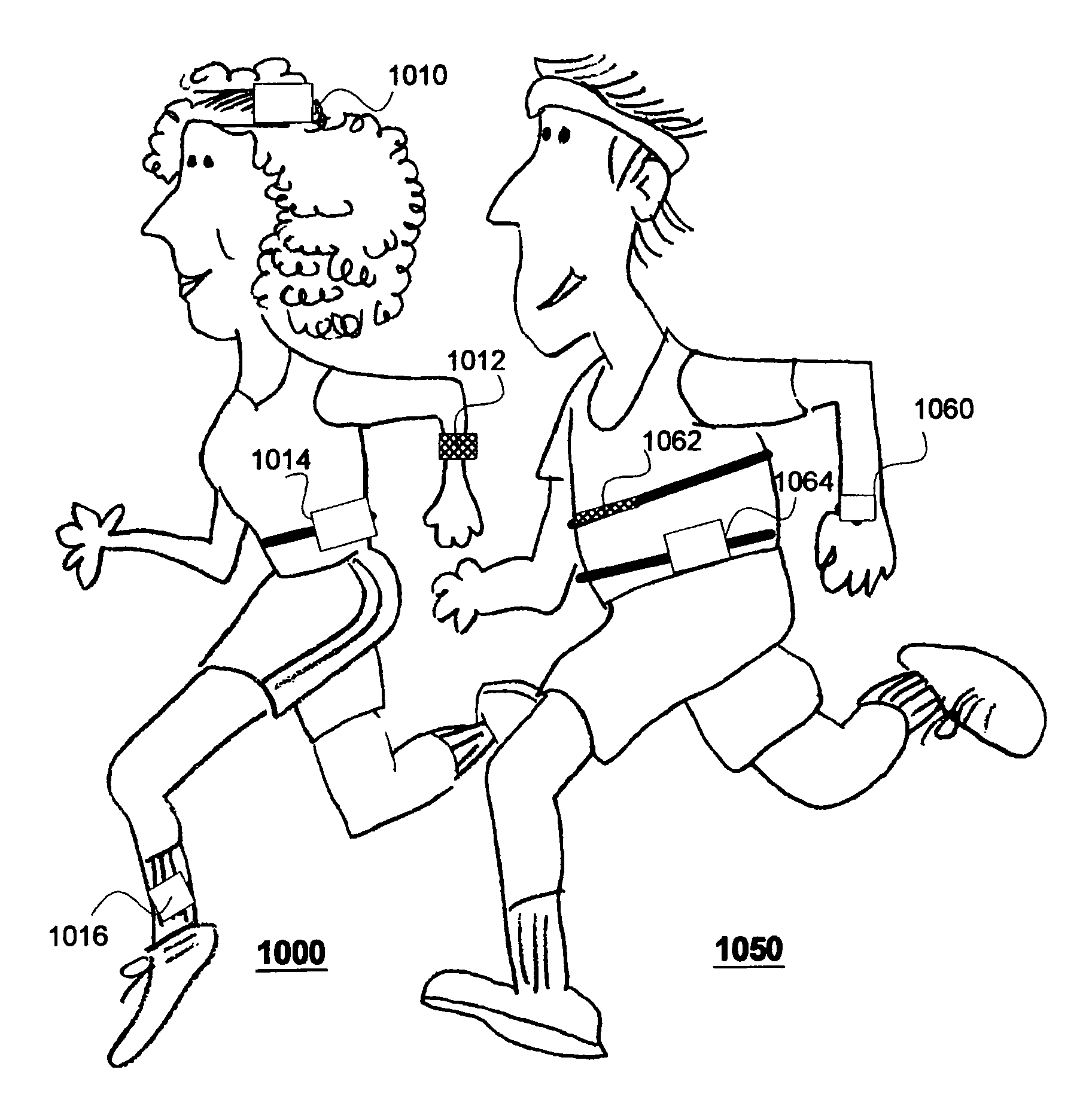
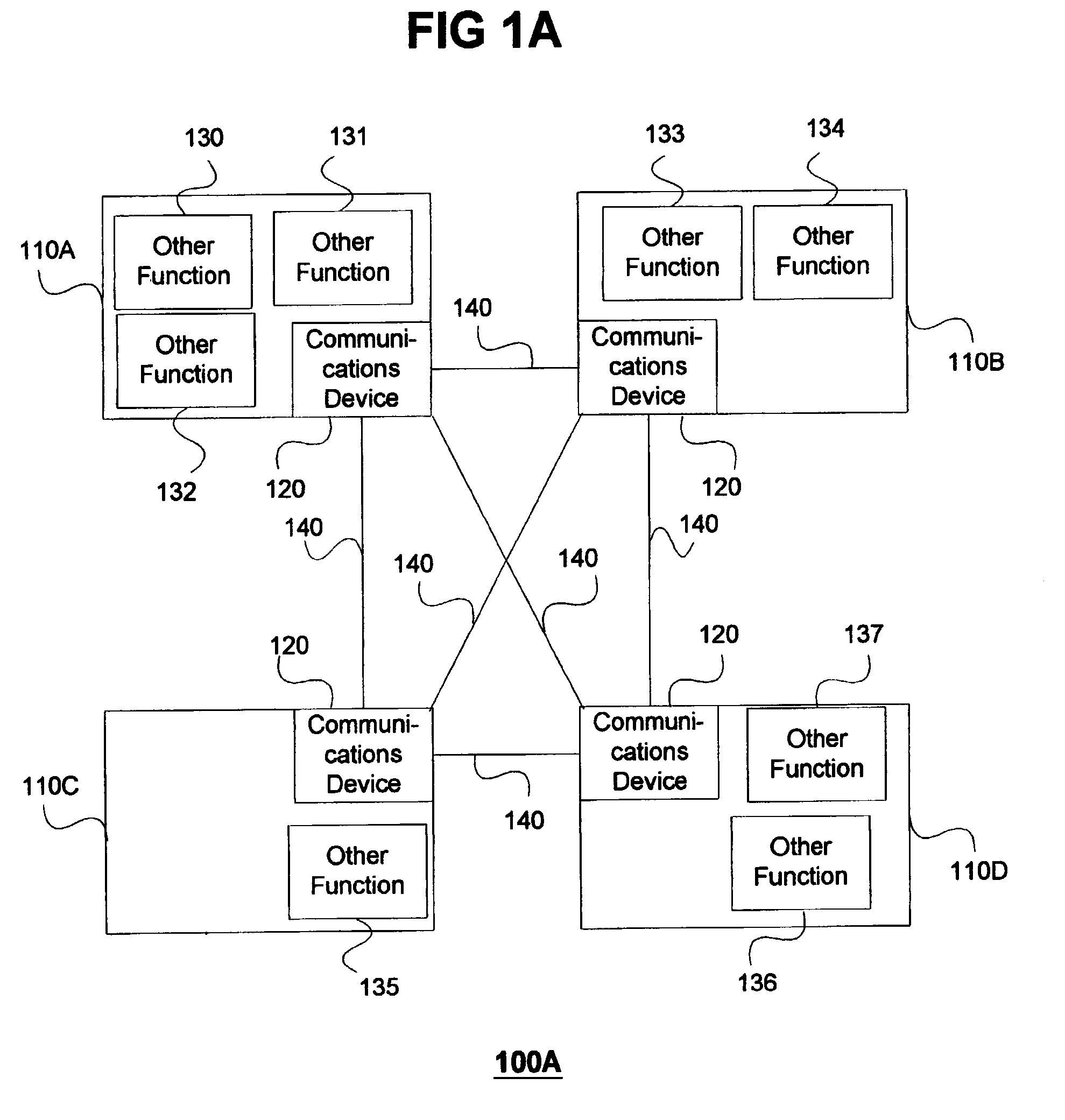
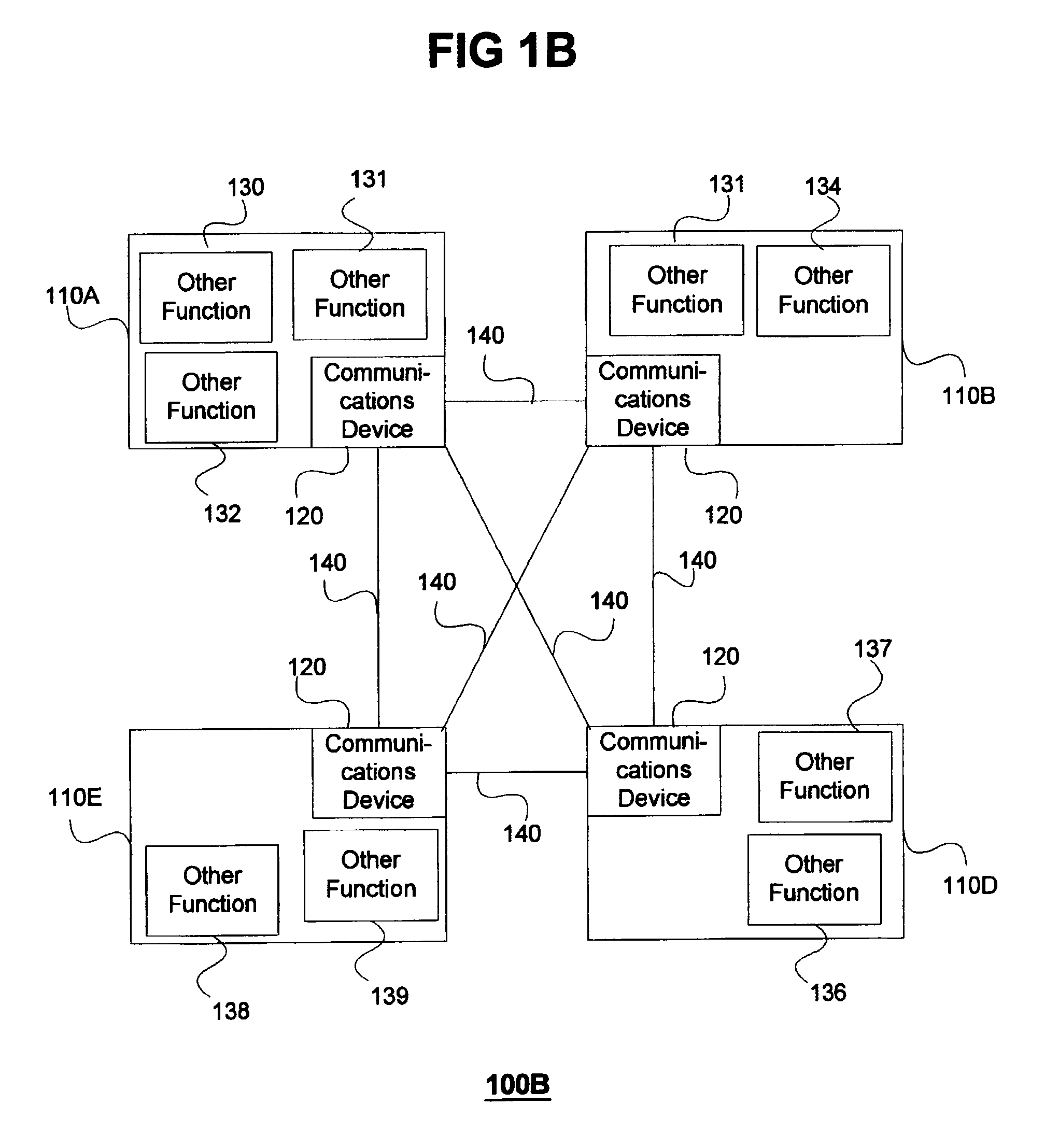
Modular personal network systems and methods
ActiveUS7670263B2Low costOptimizationPhysical therapies and activitiesMechanical/radiation/invasive therapiesGeneral purposeUser input
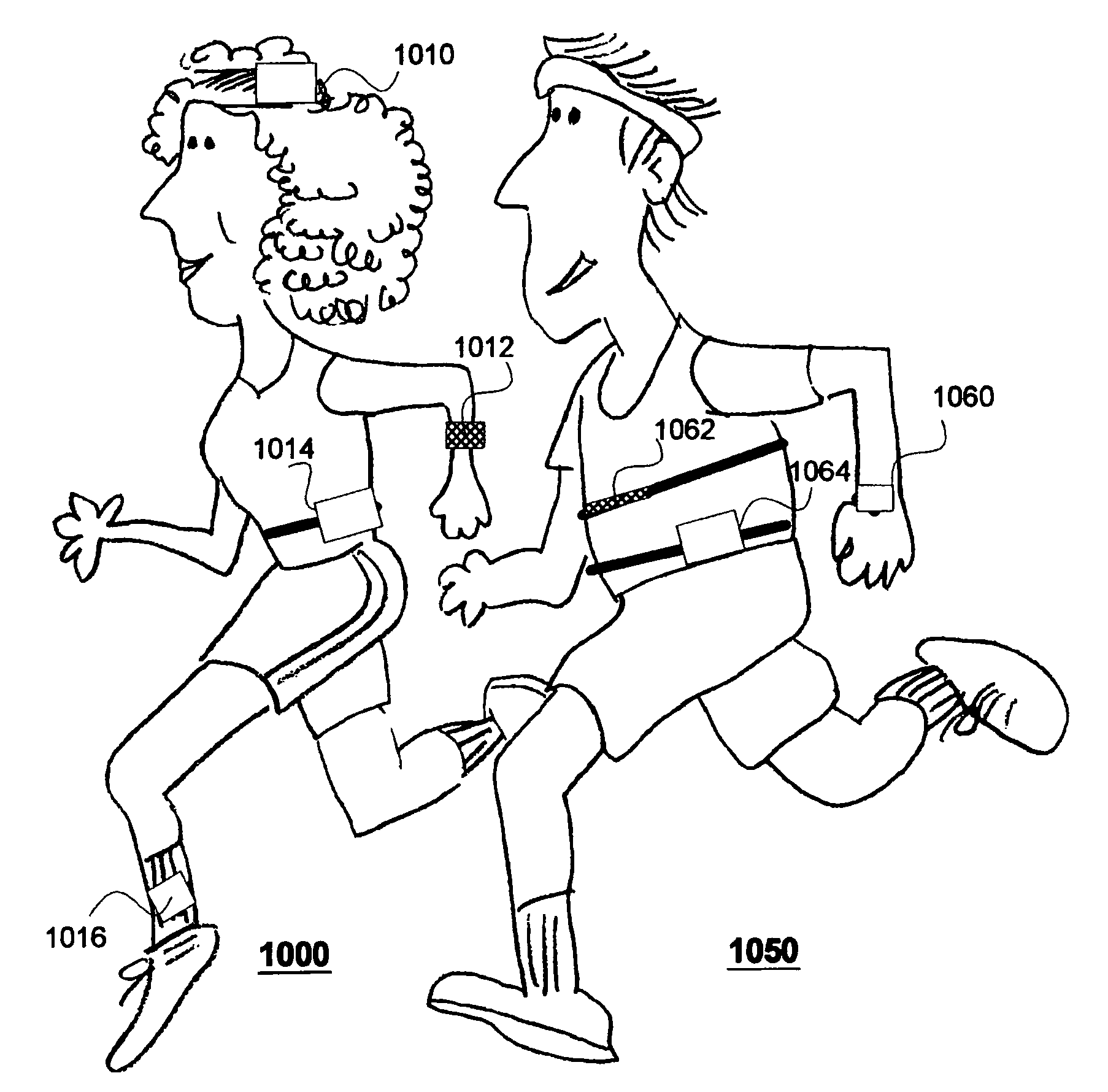
We have disclosed a modular personal network (MPN) that includes multiple devices that may be worn, carried, or used in close proximity to a user. The devices communicate wirelessly. Functions of the MPN may be modified by adding or removing components. The MPN may communicate with a personal computer. General purpose devices may include a control unit, a display, a user input, and an audio output. The MPN may provide a variety of functions, including time, communication, entertainment, organization, guidance, athletic, medical, travel, outdoors, identity, security, and military.
Owner:ADIDAS
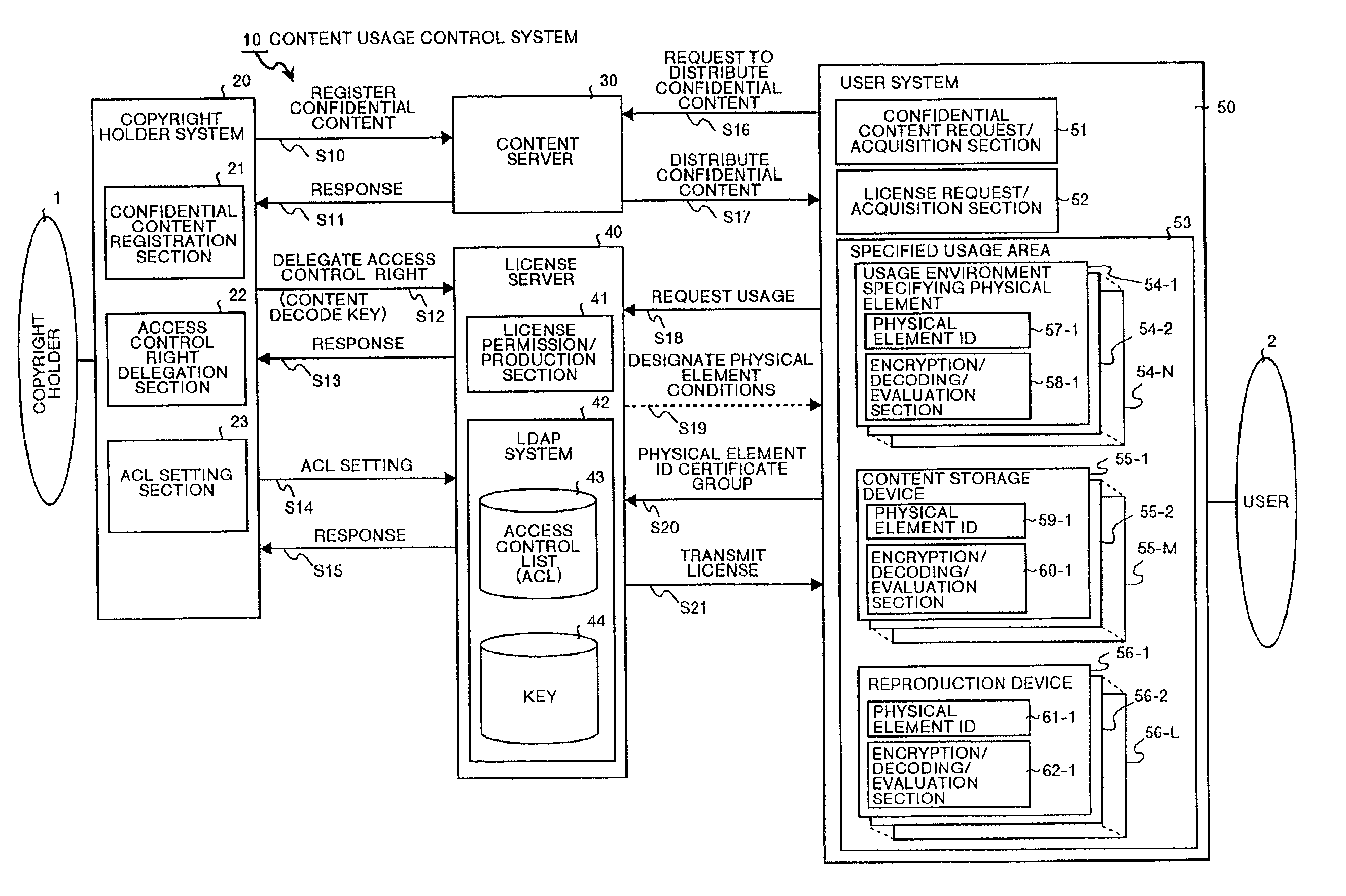
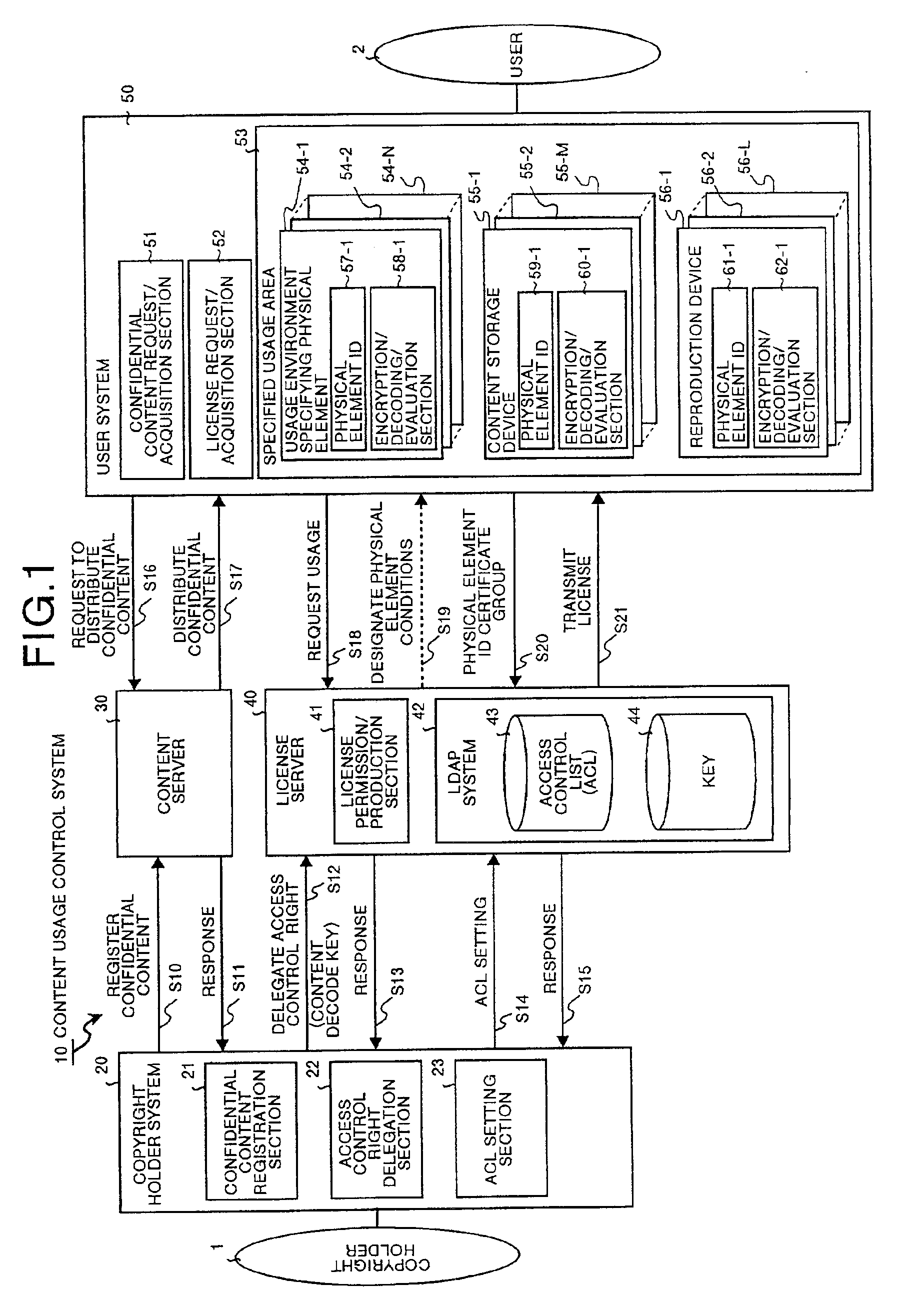
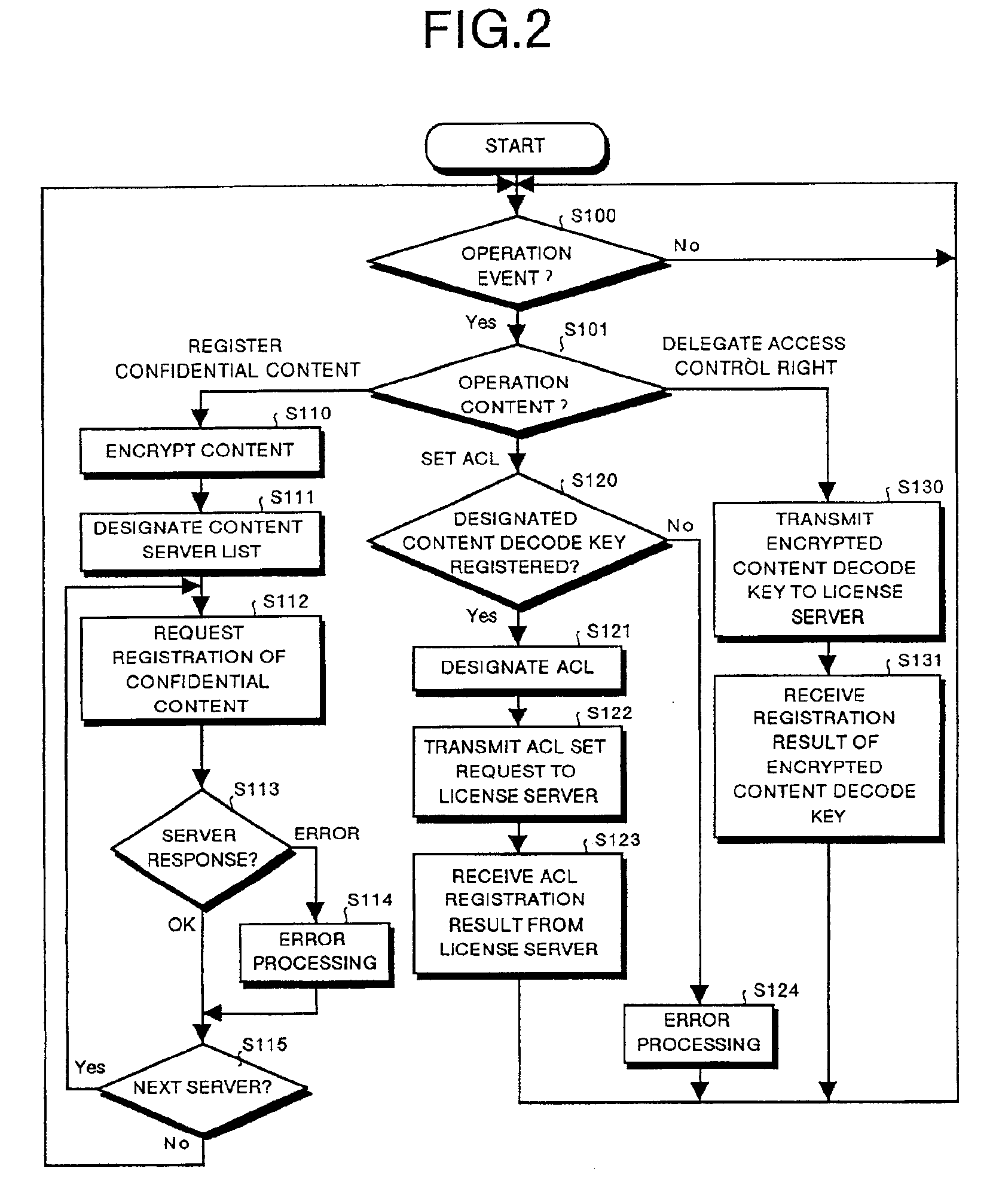
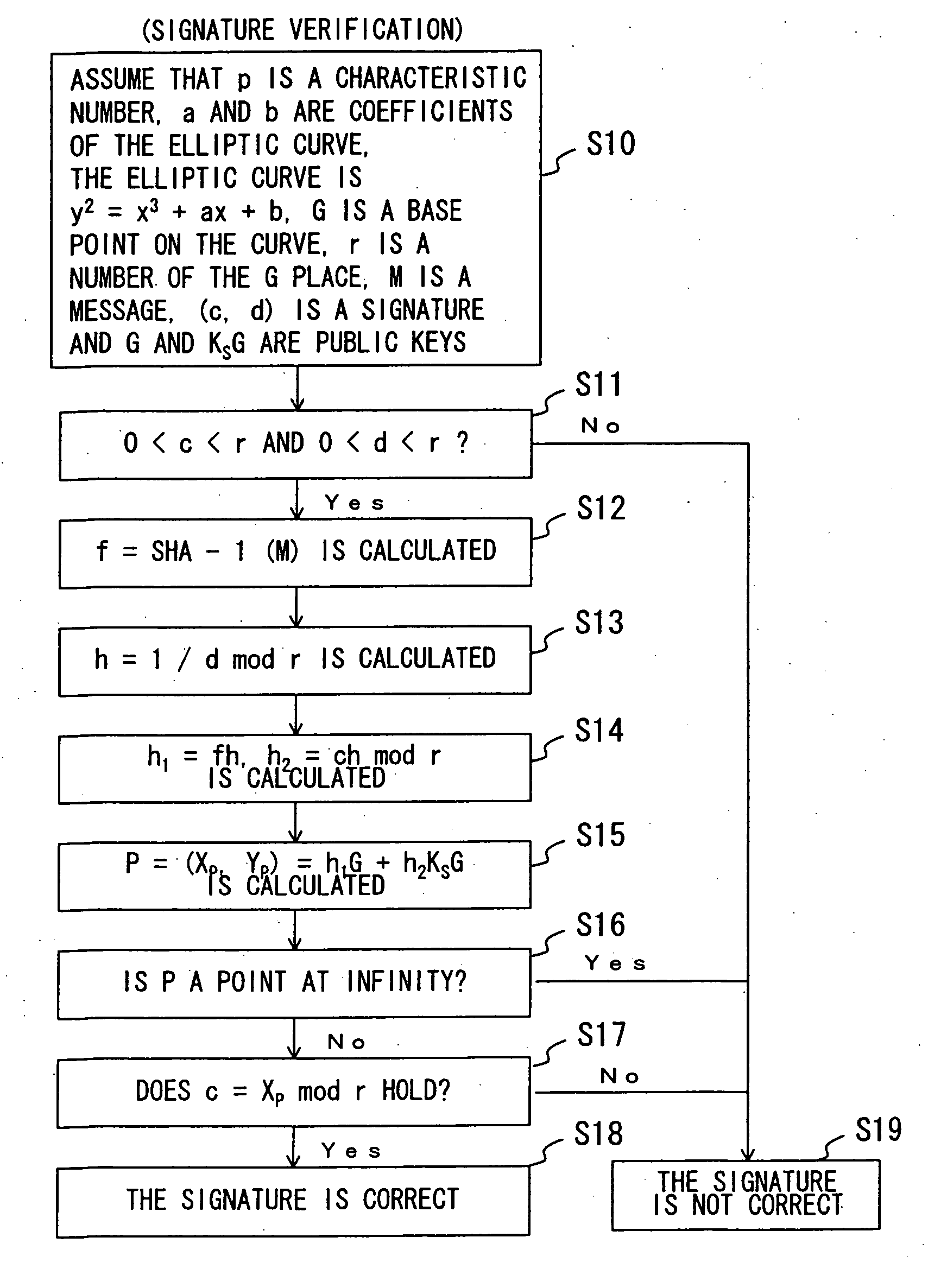
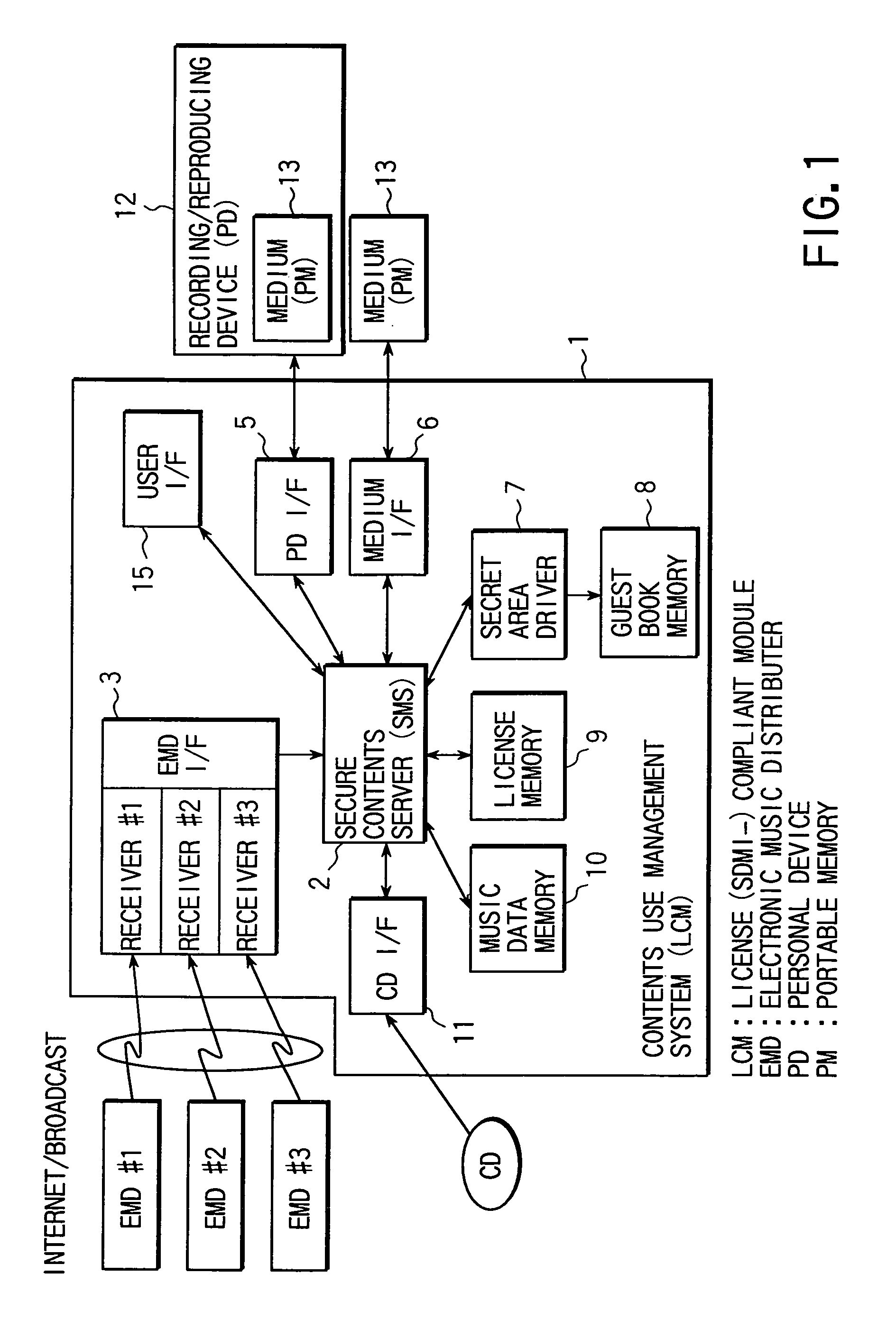
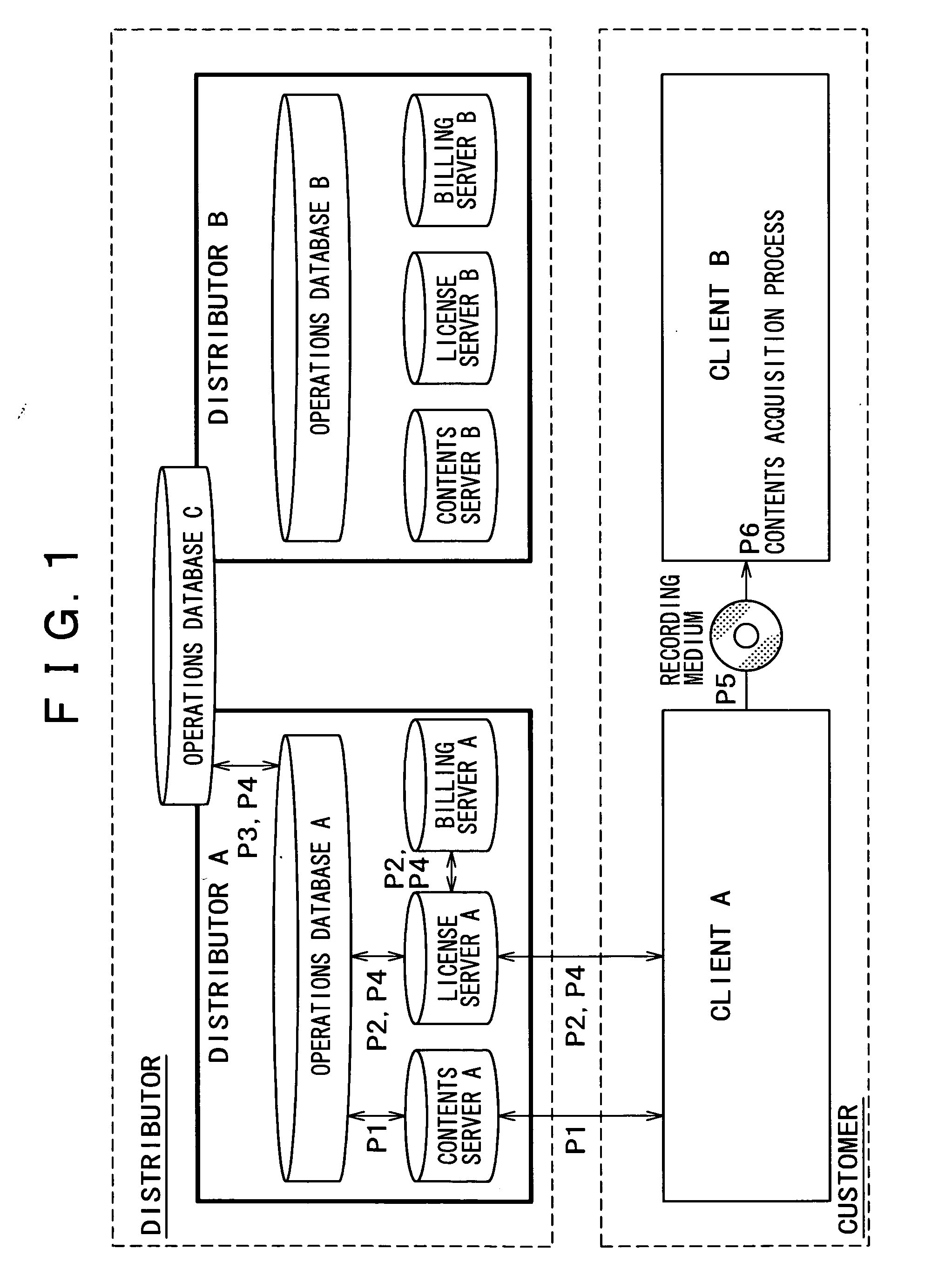
Content usage control system, content usage apparatus, computer readable recording medium with program recorded for computer to execute usage method
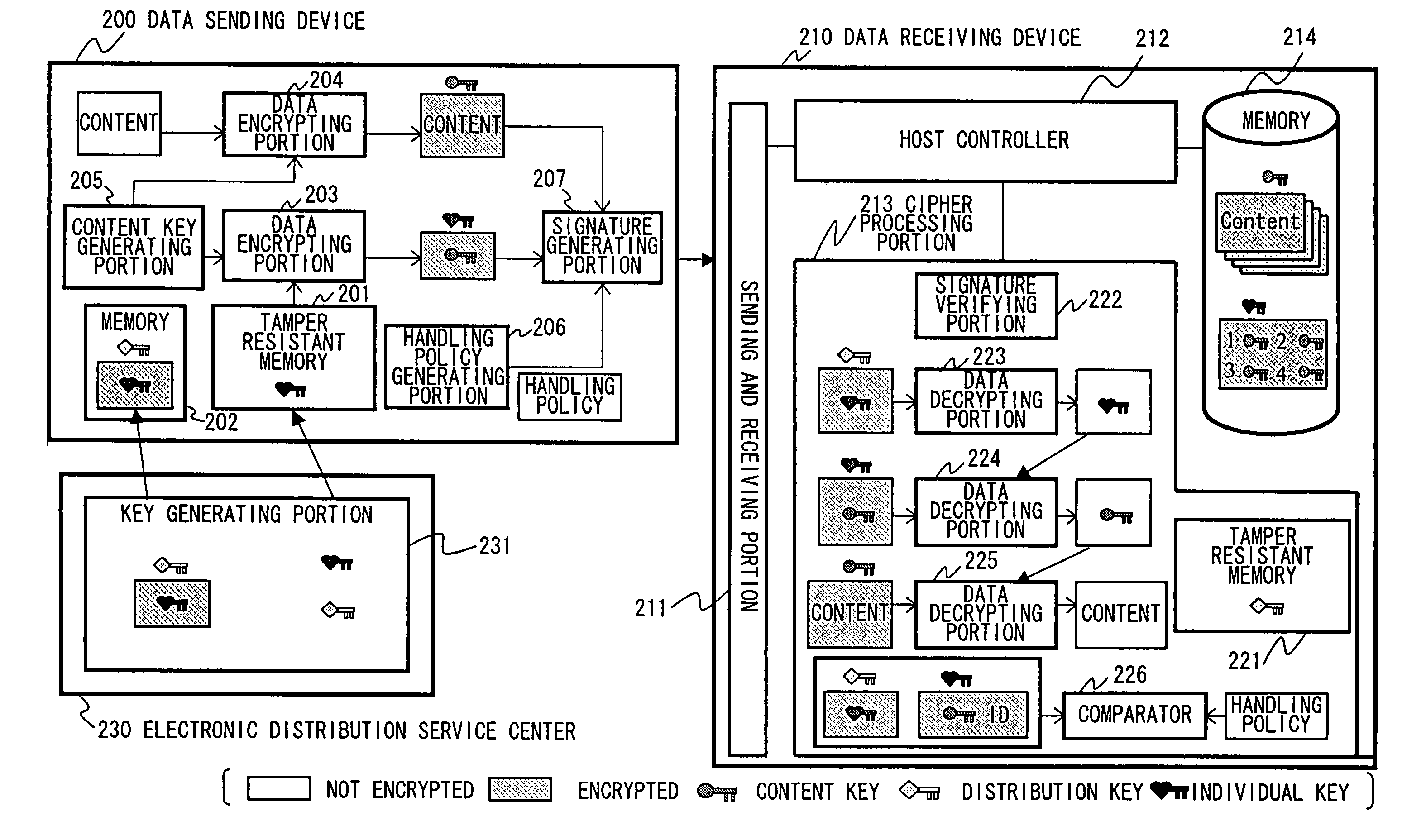
InactiveUS6873975B1Prevent illegal useImprove accuracyDigital data processing detailsAnalogue secracy/subscription systemsControl systemStructure of Management Information
A content usage control system comprises a copyright holder system, content server, license server and user system. The ACL setting section of the copyright holder system sets a license ACL expressed as a structure by a combination of logic sums and logic products of a plurality of partial licenses for the content, based on the user ID and a plurality of physical element IDs including media used in the user system, and stores the license ACL in an access control list. The license server controls the usage of the content by the user utilizing the access control list.
Owner:FUJITSU LTD
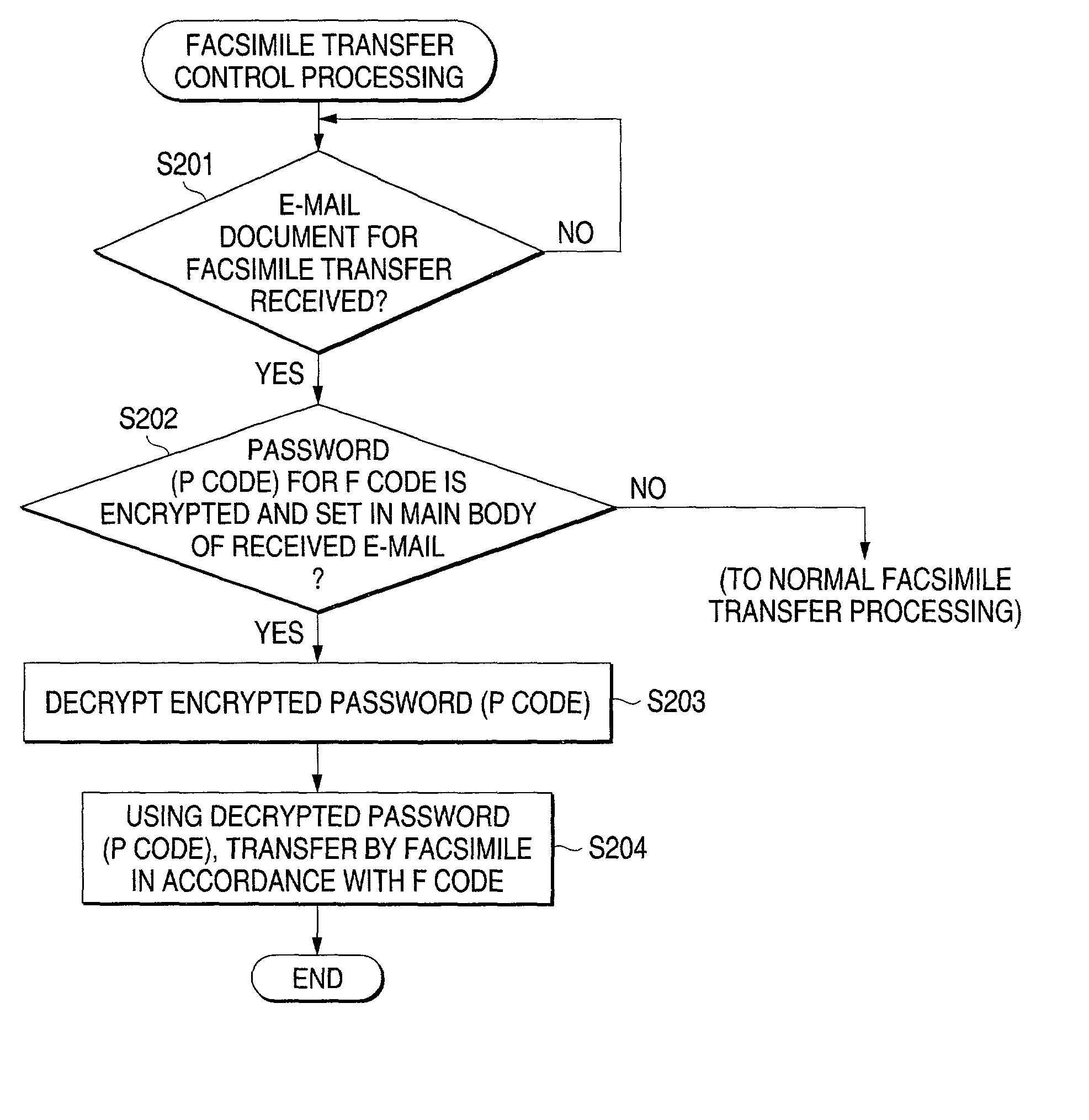
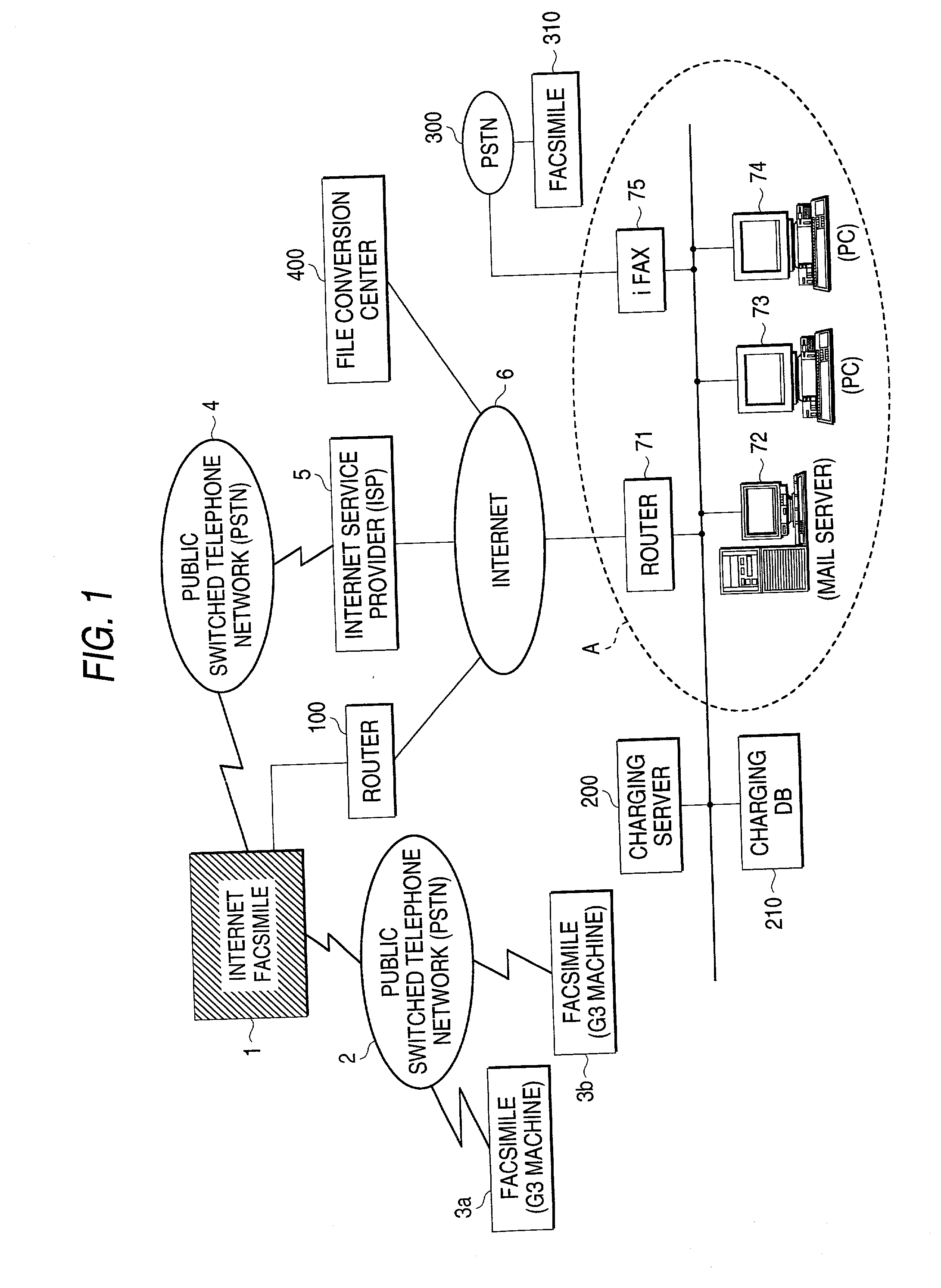
Internet facsimile and control method thereof and communication instruction terminal
InactiveUS20020157028A1Conducted safely and reliablyPrevent illegal useData processing applicationsDigital data processing detailsComputer hardwarePassword
In an Internet fax, to receive an electronic mail document for fax transfer, if a password related to a control command for indicating a facsimile communication function is encrypted and set in the destination field or the main body of the received electronic mail, the encrypted password is decrypted and using the decrypted password, facsimile transfer of the electronic mail document is executed following the control command.
Owner:FUJIFILM BUSINESS INNOVATION CORP
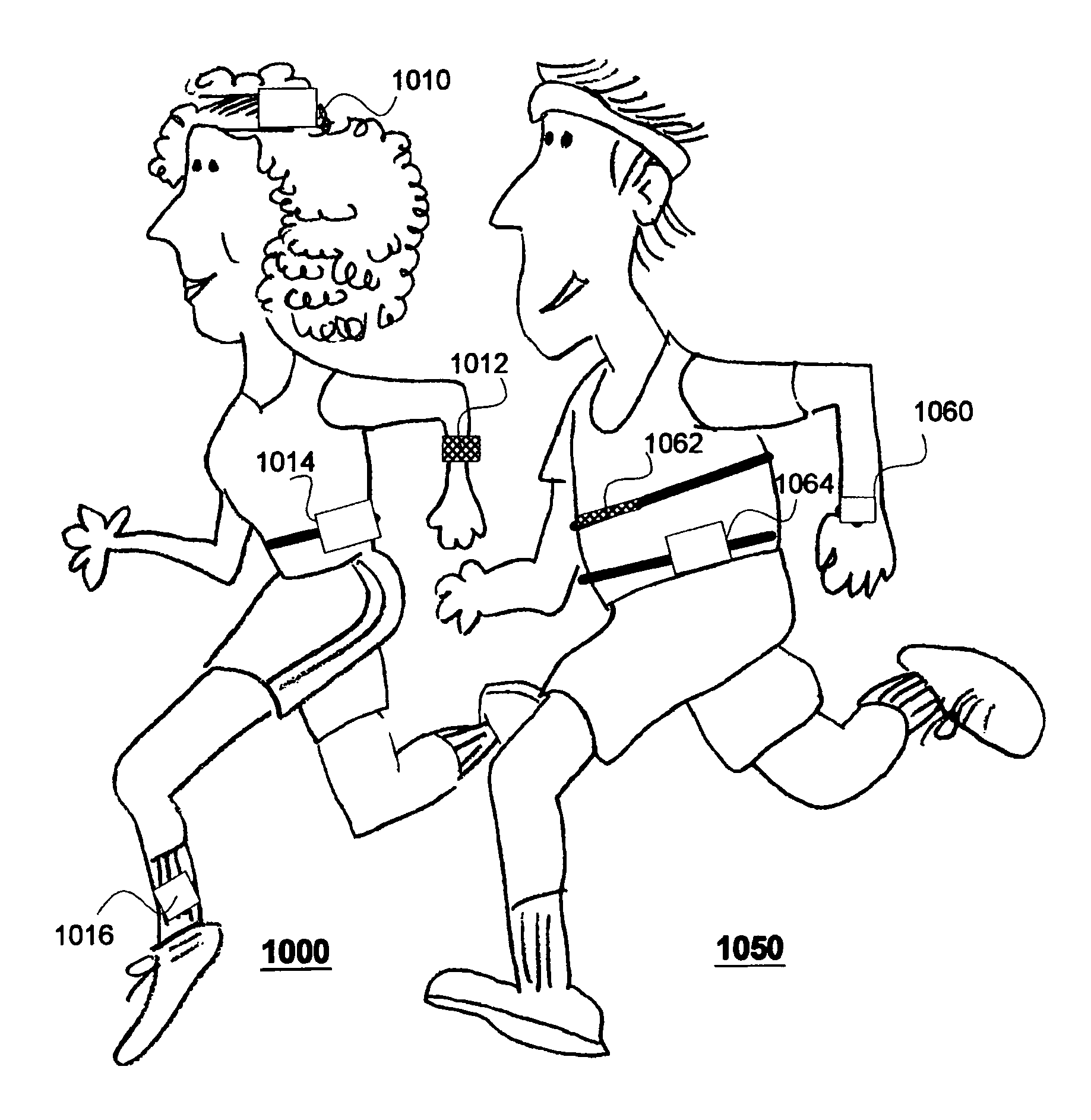
Position tracking and guidance methods
InactiveUS20100056340A1Prevent illegal useAvoid interferencePhysical therapies and activitiesMechanical/radiation/invasive therapiesGeneral purposeUser input
We have disclosed a modular personal network (MPN) that includes multiple devices that may be worn, carried, or used in close proximity to a user. The devices communicate wirelessly. Functions of the MPN may be modified by adding or removing components. The MPN may communicate with a personal computer. General purpose devices may include a control unit, a display, a user input, and an audio output. The MPN may provide a variety of functions, including time, communication, entertainment, organization, guidance, athletic, medical, travel, outdoors, identity, security, and military.
Owner:ADIDAS
Information transmission system, transmitter, and transmission method as well as information reception system, receiver and reception method
InactiveUS7099479B1Prevent piracySimple configurationKey distribution for secure communicationUnauthorized memory use protectionInformation transmissionInformation seeking
Owner:SONY CORP
Reconfigurable personal display system and method
InactiveUS20100059561A1Prevent illegal useAvoid interferencePhysical therapies and activitiesMechanical/radiation/invasive therapiesGeneral purposeComputer network
We have disclosed a modular personal network (MPN) that includes multiple devices that may be worn, carried, or used in close proximity to a user. The devices communicate wirelessly. Functions of the MPN may be modified by adding or removing components. The MPN may communicate with a personal computer. General purpose devices may include a control unit, a display, a user input, and an audio output. The MPN may provide a variety of functions, including time, communication, entertainment, organization, guidance, athletic, medical, travel, outdoors, identity, security, and military.
Owner:ADIDAS
Information sending system, information sending device, information receiving device, information distribution system, information receiving system, information sending method, information receiving method, information distribution method, apparatus, sending method of information receiving device, playback method of apparatus, method of using contents and program storing medium
InactiveUS20060168451A1Improve usabilityPrevent piracyKey distribution for secure communicationUser identity/authority verificationComputer hardwareDistribution method
Owner:SONY CORP
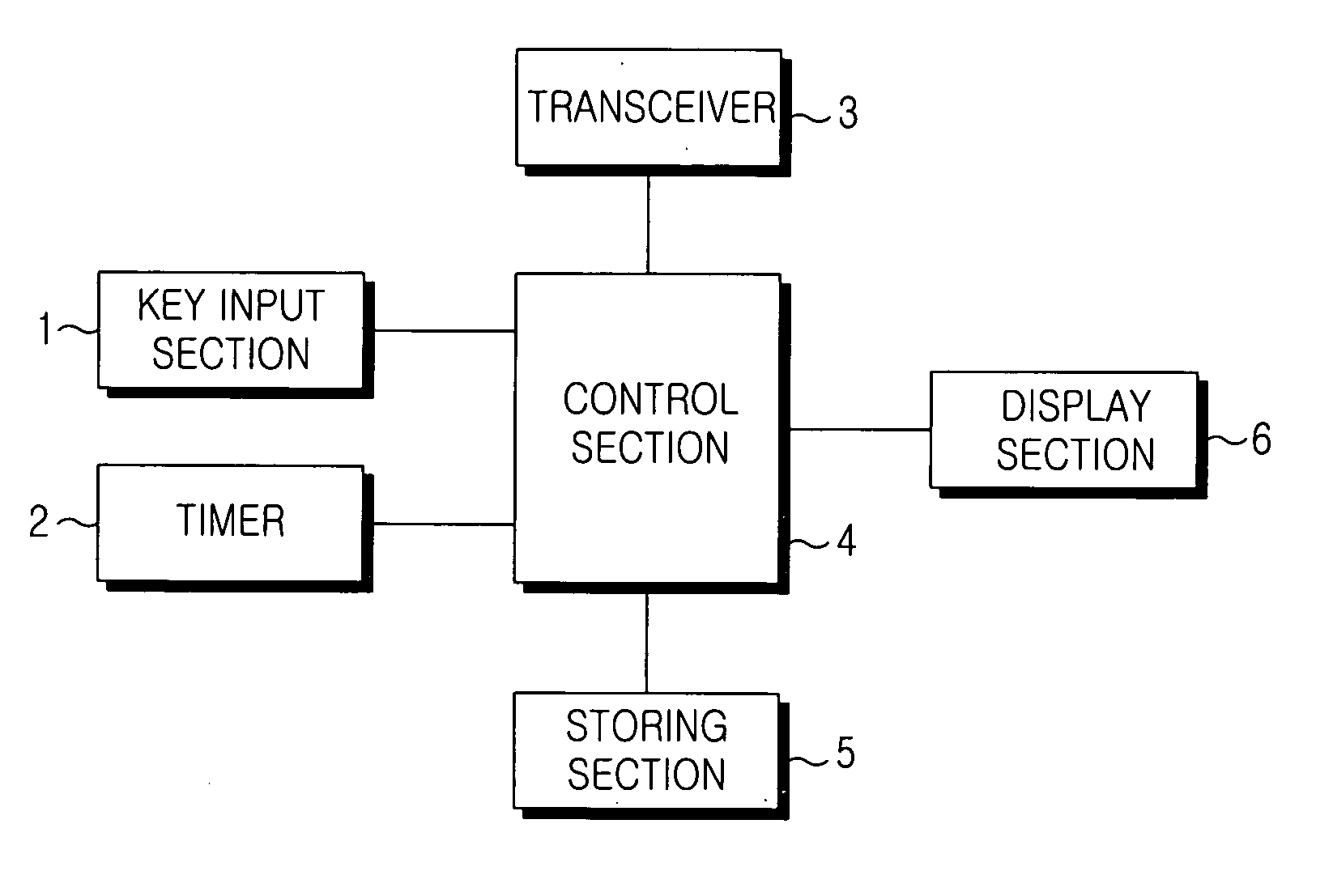
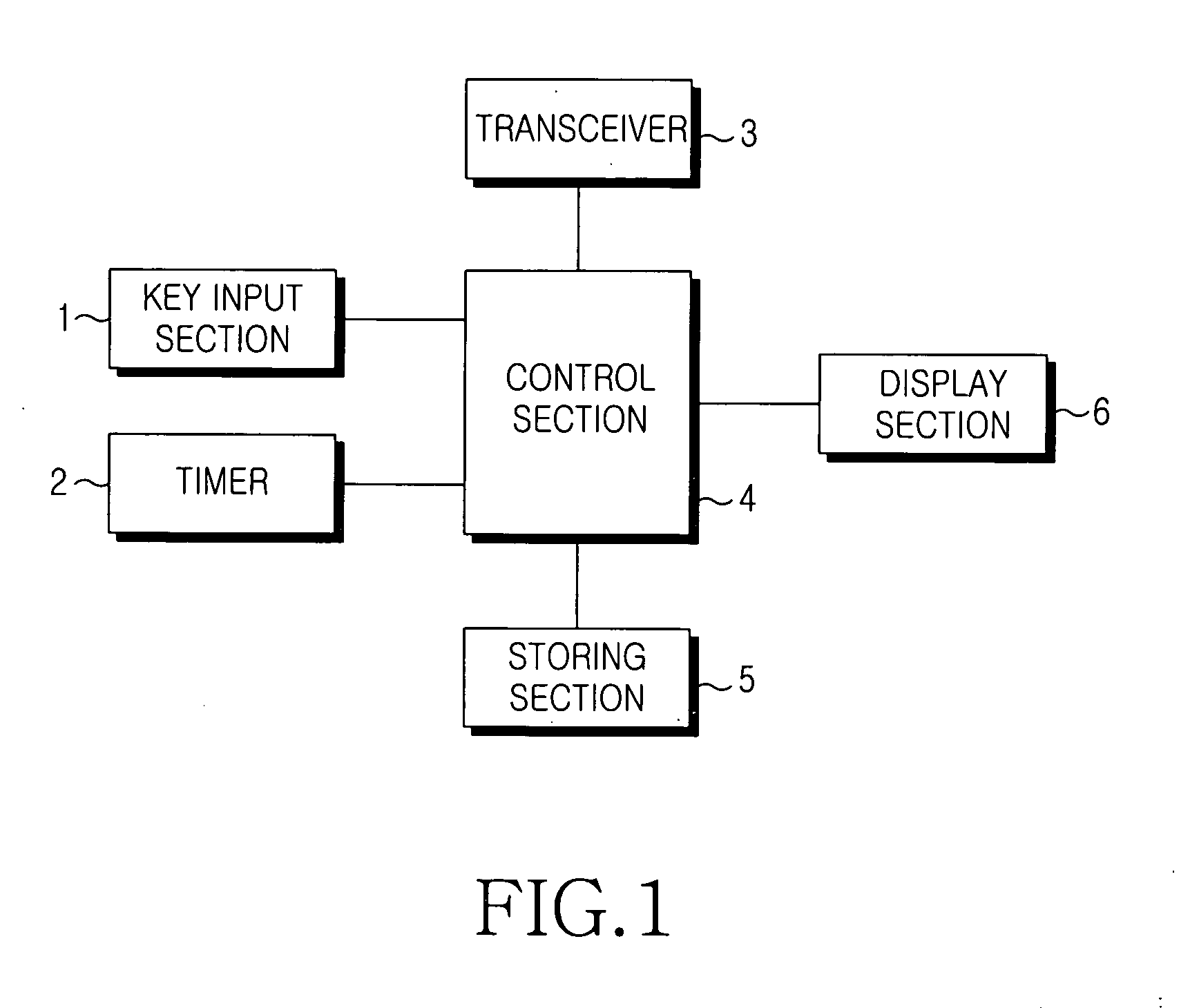
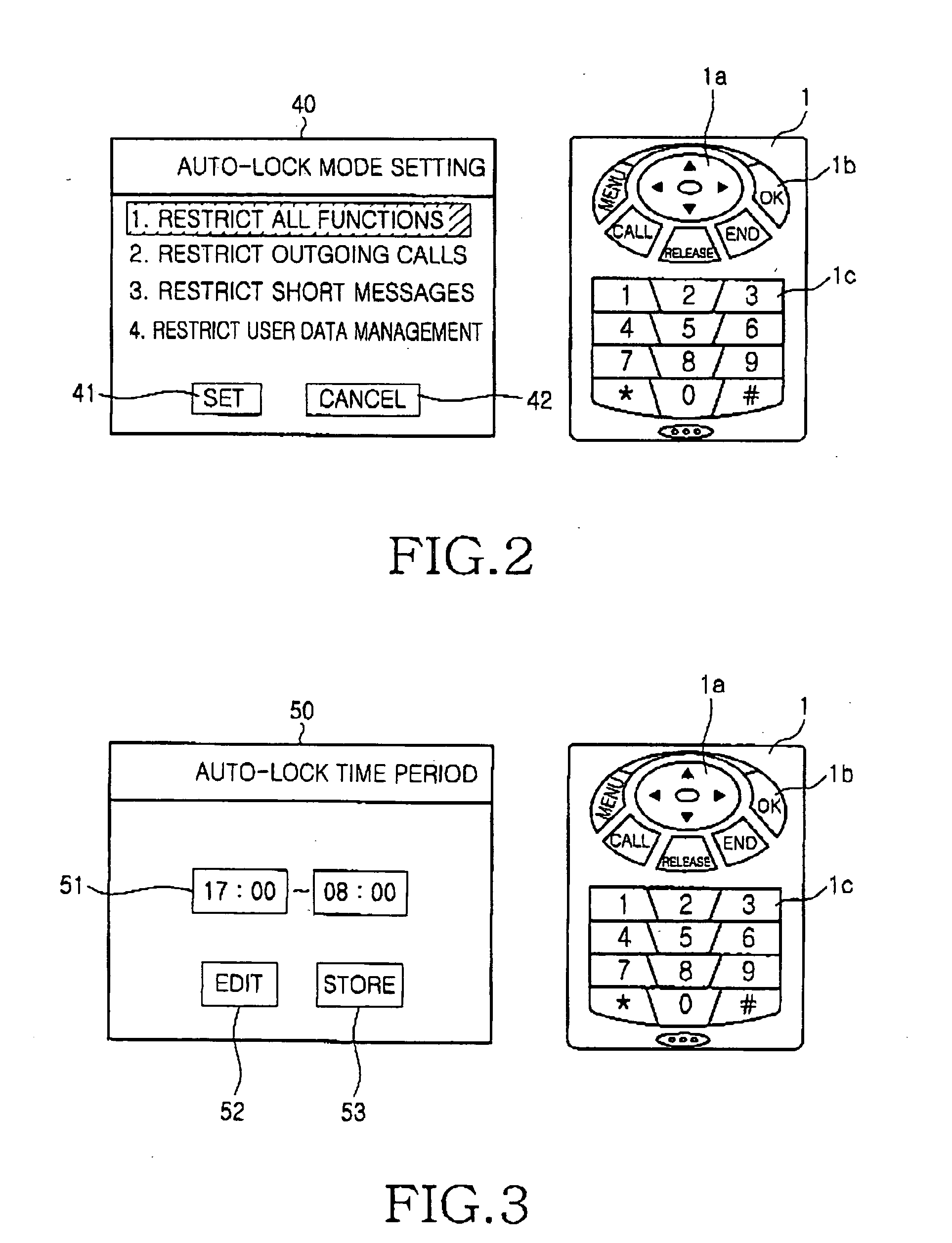
Mobile terminal and method for auto-locking thereof
InactiveUS20050154935A1Prevent illegal useAutomatically locking a mobile terminalUnauthorised/fraudulent call preventionDigital data processing detailsTime segmentComputer science
Disclosed is a method for automatically locking a mobile terminal having functions, such as incoming and outgoing calls. The method includes the steps of setting an auto-lock time period to restrict the use of one or more predetermined functions; activating an auto-lock mode to restrict the use of the predetermined functions during the auto-lock time period; and inactivating the auto-lock mode after the auto-lock time period. The auto-lock mode for automatically locking functions of the mobile terminal can be set to be activated only during specified time or during all other times of the day according to the spatial and temporal patterns of the user's daily routine.
Owner:SAMSUNG ELECTRONICS CO LTD
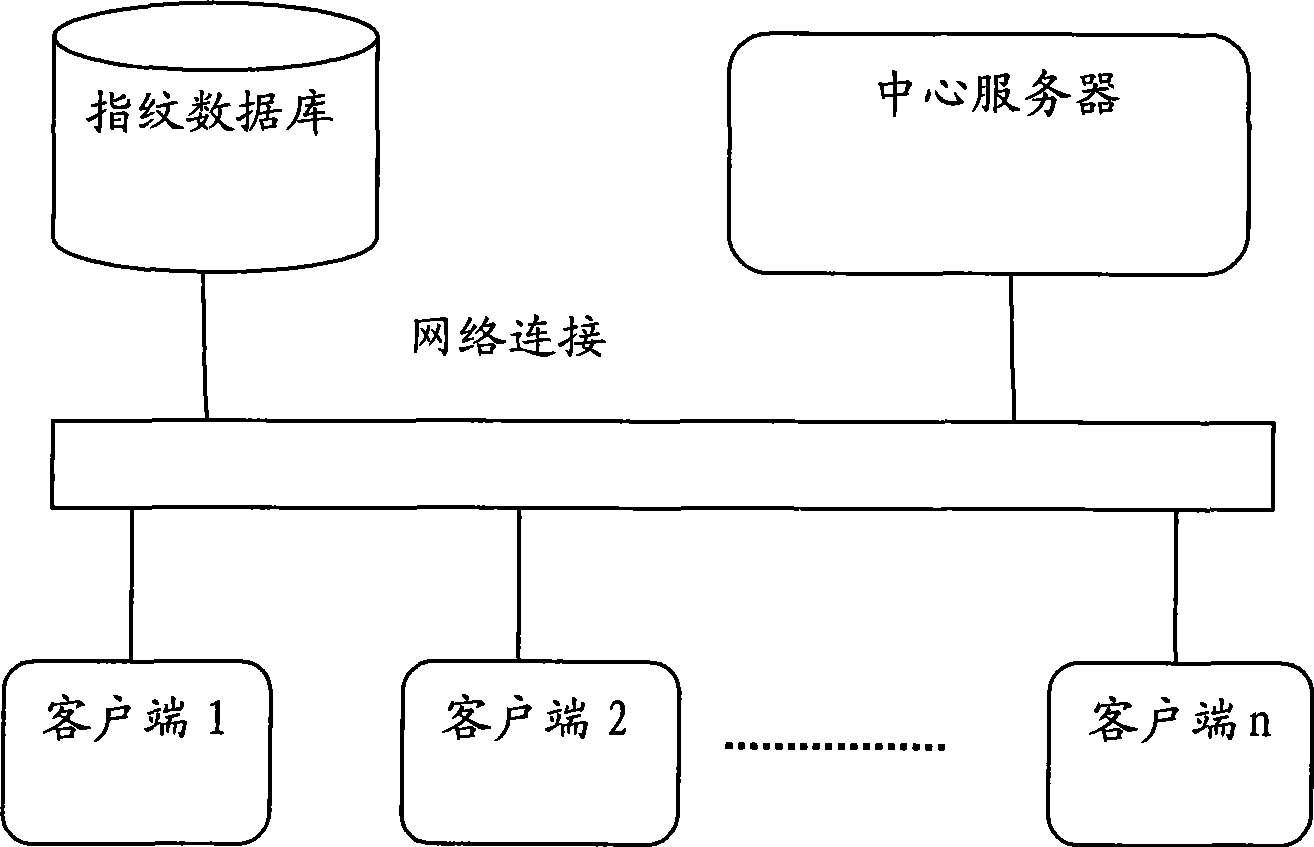
Fingerprint recognition system and control method
InactiveCN101414351AAvoid accessEasy constructionUser identity/authority verificationCharacter and pattern recognitionCapital investmentFingerprint database
The invention discloses a fingerprint identifying system which comprises three large parts of a fingerprint database, a central server and a client terminal; the fingerprint database is mainly used for memorizing the fingerprint characteristic information after digital coding; the central server is mainly responsible for validating the validity of the client terminal, receiving the fingerprint characteristic data, comparing the characteristics and returning the fingerprint identifying result; the client terminal is mainly responsible for collecting the fingerprint, extracting and uploading the fingerprint characteristic data. The system overcomes the defects of the prior art, can provide an online / offline fingerprint identifying system the basic algorithm library of which can be seamlessly expanded and the functions of which can be selected and matched. The fingerprint identifying system can lead a user to obtain the ID identification and authentication services with high quality under the situation of not needing a great amount of capital investment.
Owner:章毅 +2
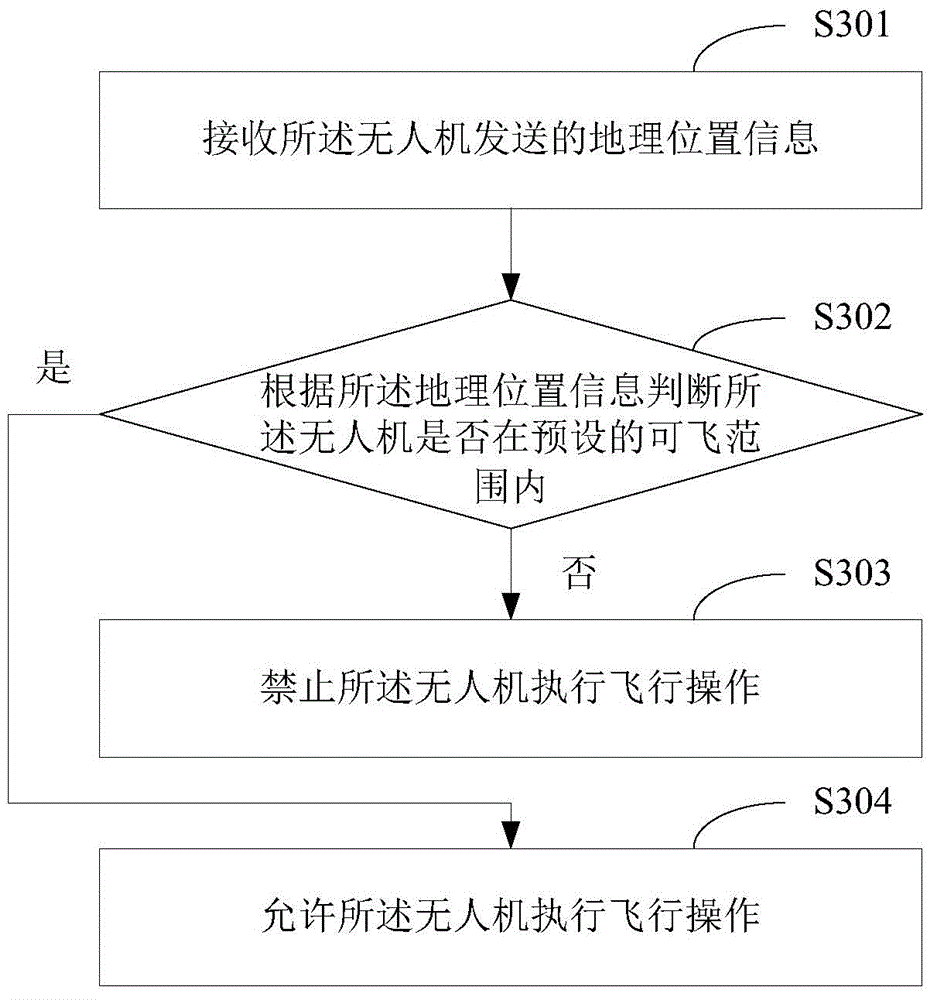
Unmanned aerial vehicle monitoring method and unmanned aerial vehicle management platform
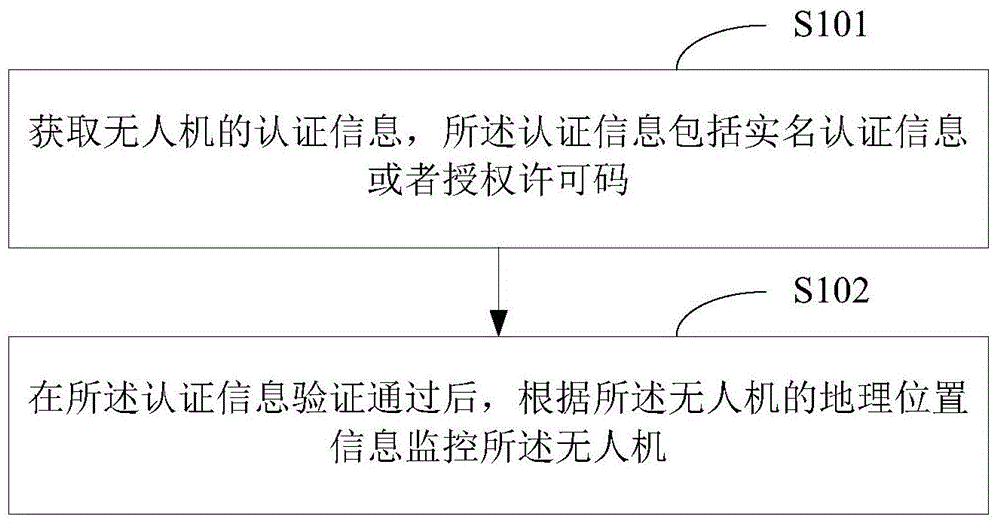
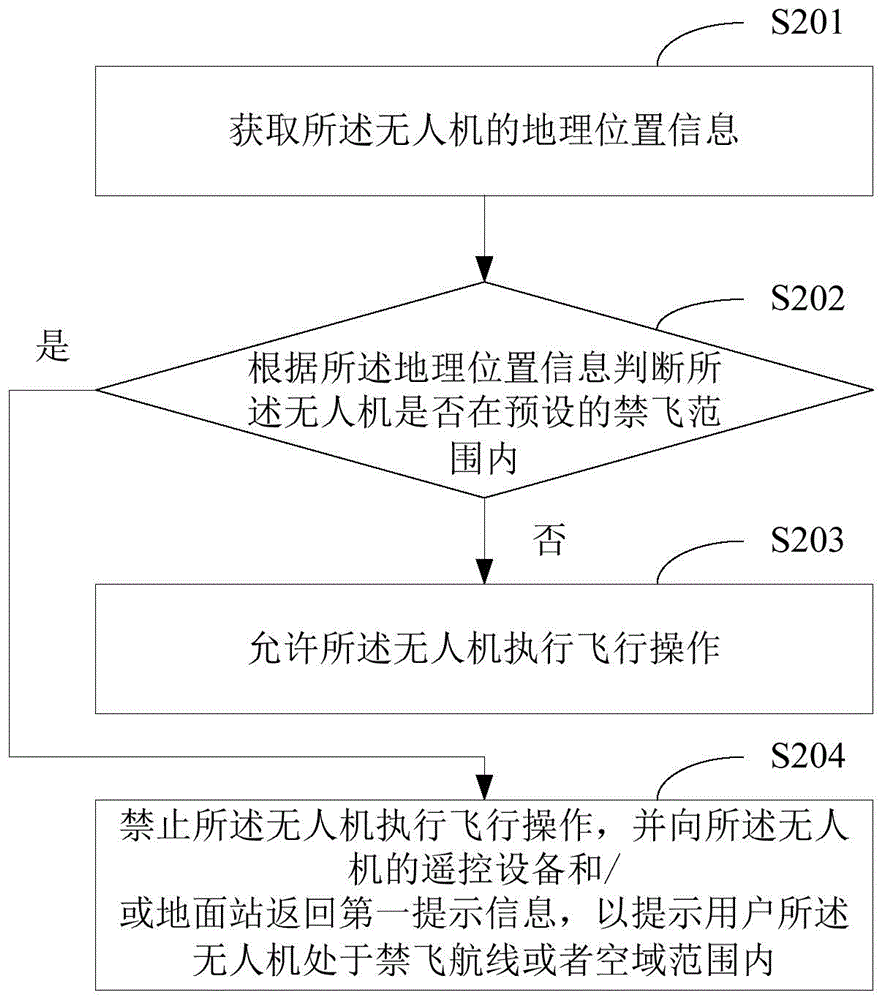
The invention is applicable to the technical field of unmanned aerial vehicles and provides an unmanned aerial vehicle monitoring method and an unmanned aerial vehicle management platform. The method comprises steps: authentication information of the unmanned aerial vehicle is acquired, the authentication information comprises real name authentication information or a license code, and after the authentication information passes verification, the unmanned aerial vehicle is monitored according to geological position information of the unmanned aerial vehicle. Use safety of the unmanned aerial vehicle is improved, the unmanned aerial vehicle can be prevented from being used by an illegal person, large additional influences can be ensured to be avoided when the unmanned aerial vehicle executes an application, and safety when the unmanned aerial vehicle flies can be improved.
Owner:SF TECH
Workout definition and tracking methods
InactiveUS20100056341A1Prevent illegal useAvoid interferencePhysical therapies and activitiesMechanical/radiation/invasive therapiesGeneral purposeUser input
We have disclosed a modular personal network (MPN) that includes multiple devices that may be worn, carried, or used in close proximity to a user. The devices communicate wirelessly. Functions of the MPN may be modified by adding or removing components. The MPN may communicate with a personal computer. General purpose devices may include a control unit, a display, a user input, and an audio output. The MPN may provide a variety of functions, including time, communication, entertainment, organization, guidance, athletic, medical, travel, outdoors, identity, security, and military.
Owner:ADIDAS
Network system, server device, unauthorized use detecting method, recording medium, and program
InactiveUS20090205031A1Increase flexibilityUnauthorized useDigital data processing detailsUser identity/authority verificationThird partyUser authentication
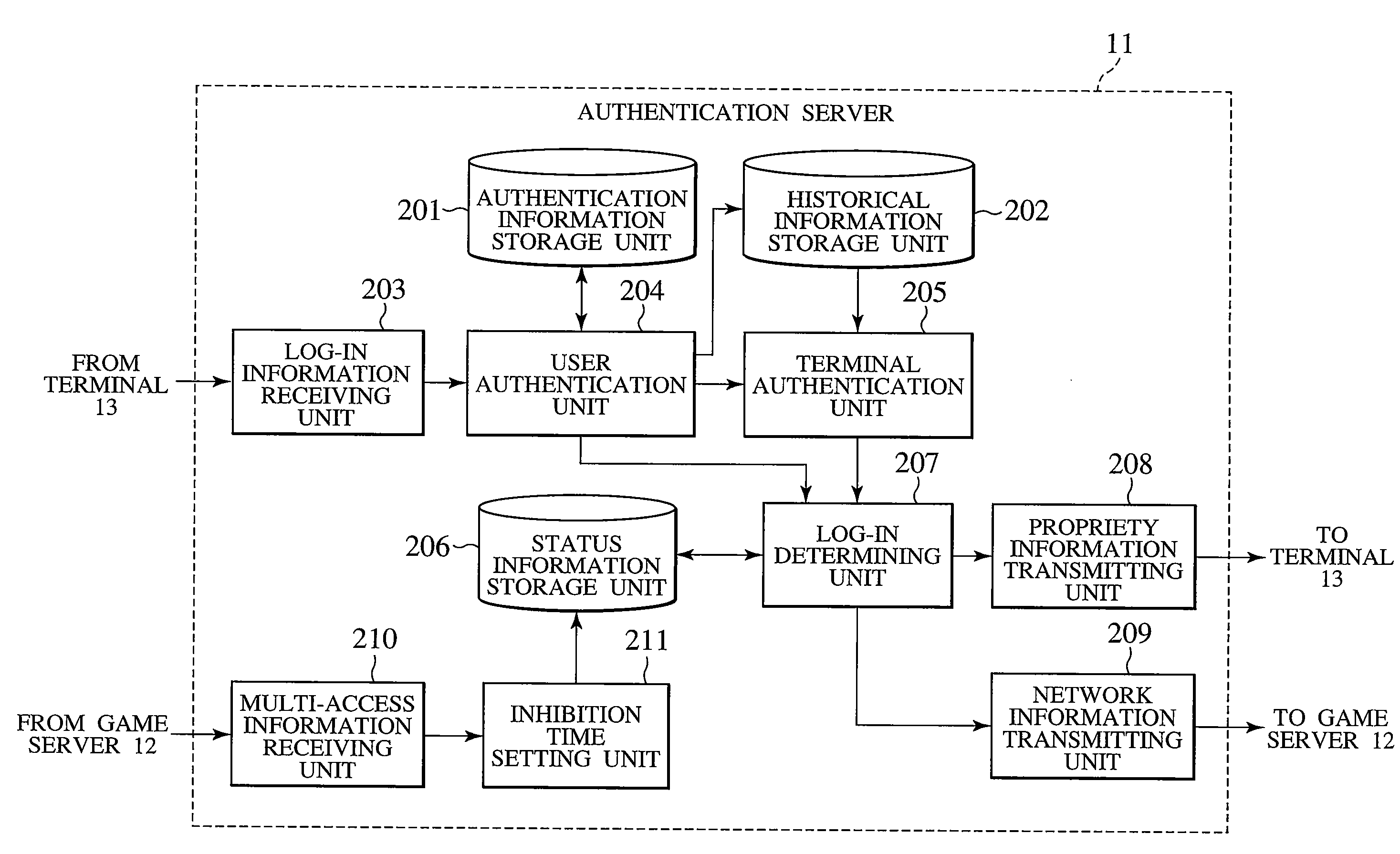
A log-in information receiving unit (203) receives log-in information sent from a terminal (13). A user authentication unit (204) authenticates a user based on the relationship between to-be-authenticated information included in the log-in information and authentication information stored in an authentication information storage unit (201). When the user is authenticated, unique information included in the log-in information is stored in a historical information storage unit (202). A terminal authentication unit (205) authenticates the terminal (13) based on the history of the unique information stored in the historical information storage unit (202). When different pieces of unique information have amounted to ten pieces then, for example, the terminal authentication unit (205) detects an unauthorized use by a third party.
Owner:KONAMI DIGITAL ENTERTAINMENT CO LTD
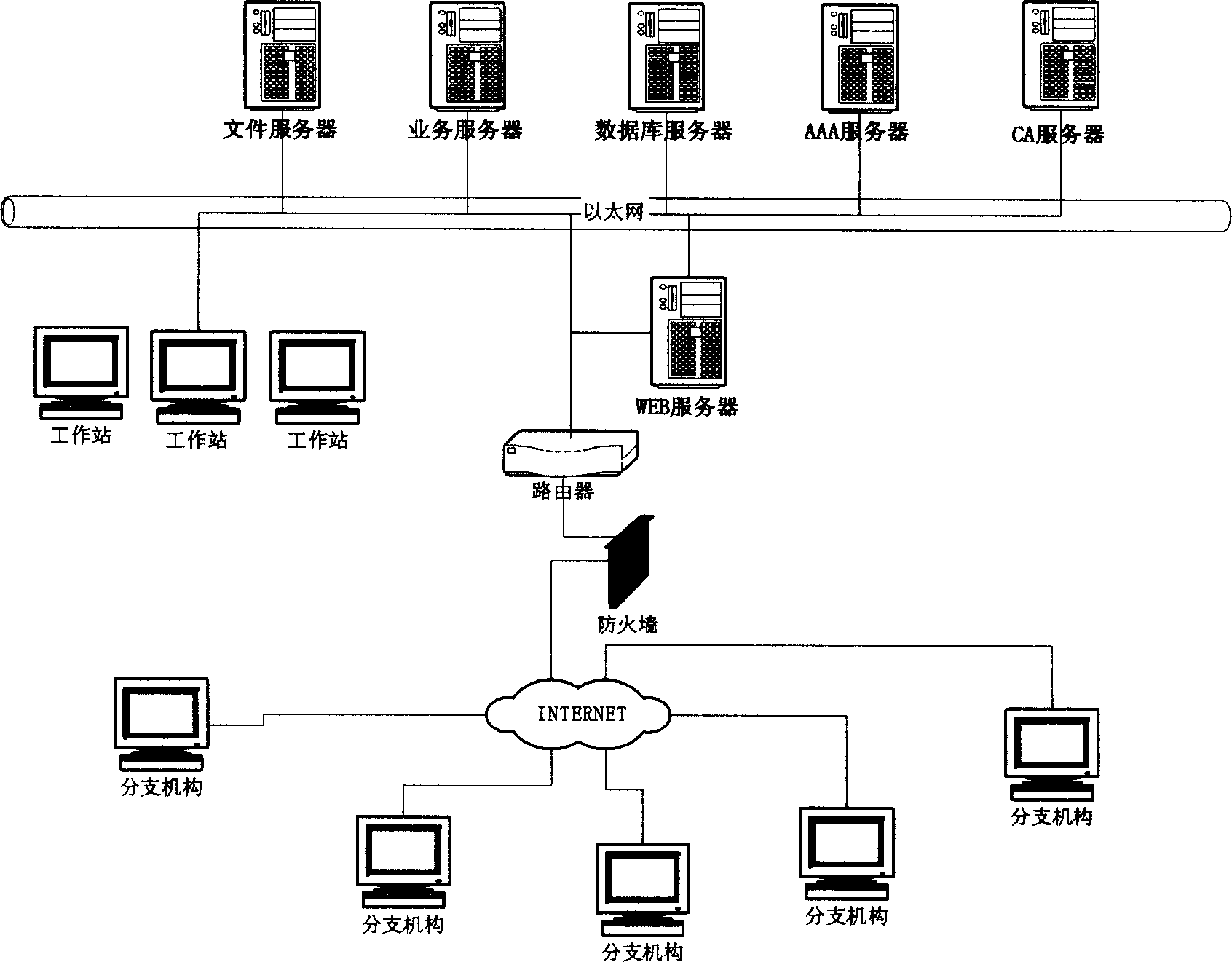
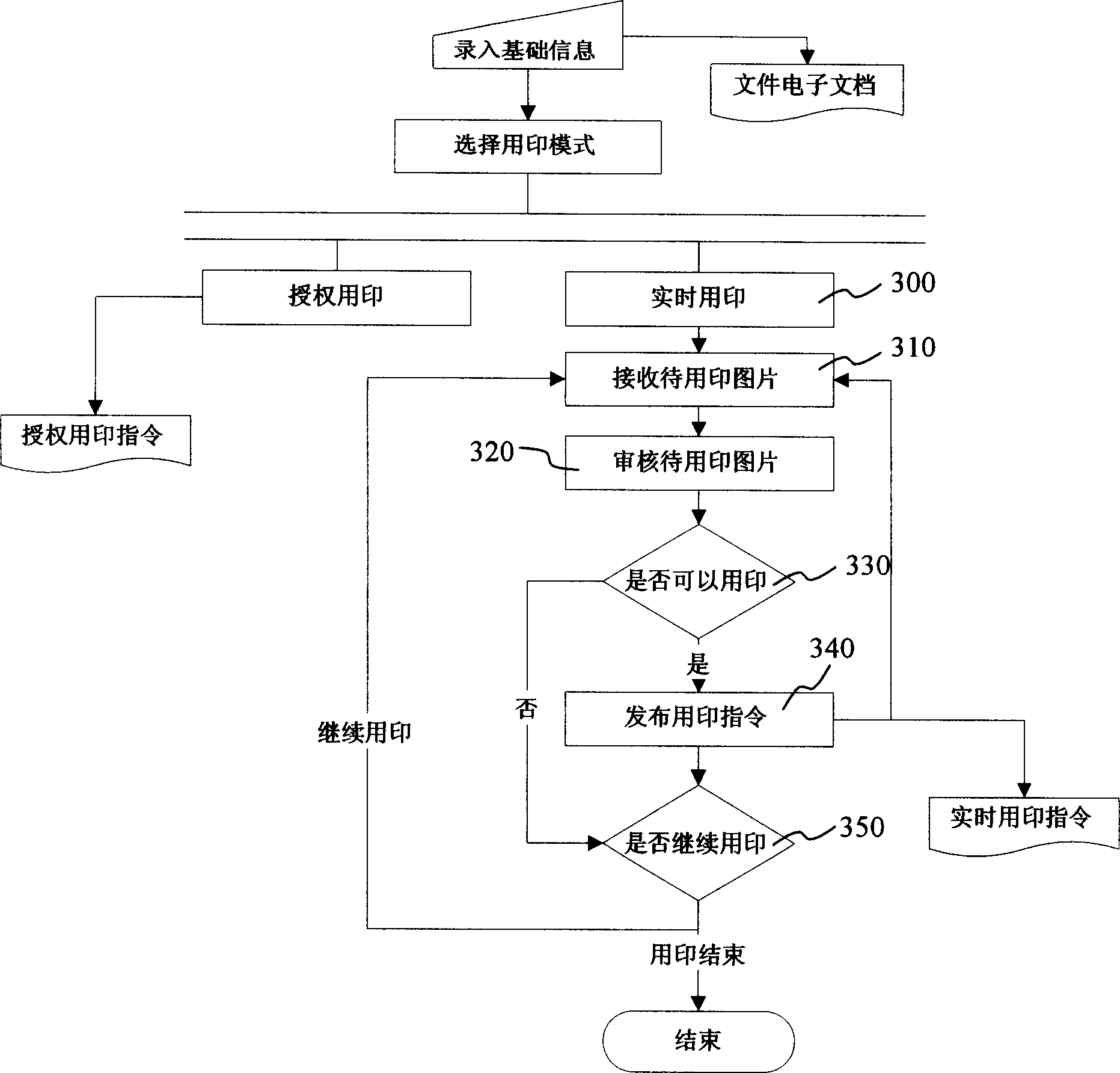
Sealing machine and method of controlling seal and its system
ActiveCN1623796ARealize automatic controlRealize managementProgram controlSpecial data processing applicationsGraphicsAutomatic control
The present invention provides a stamping machine, a stamping control method and a system thereof, wherein the method includes the following steps: opening the paper inlet and outlet door and moving in the stamping document to be used, and moving the stamping document to be used into a closed stamping machine , form the corresponding electronic text and / or graphic file of the document to be used, and display the picture of the document; automatically control the mobile seal, and control the seal to move to the corresponding printing position of the document to be printed according to the input printing command; complete stamping; remove the stamp After the file is removed, the sealed file is removed from the seal printing machine; the paper in and out door is closed. The printing machine and system adopting the above method realize the closed electronic control of the seal, and the whole printing process is carried out under the guarantee of safety, confidentiality and reliability, and has functions such as recording, verification and supervision.
Owner:BEIJING ORIENT JINYING INFORMATION TECH
Tamper respondent covering
ActiveUS8589703B2Operation is disabledPrevent illegal useDigital data processing detailsCasings/cabinets/drawers detailsPrinted circuit board
Disclosed is a tamper respondent covering. The tamper respondent covering has a cover-shaped structure to cover an electronic part which is exposed. This covering protects electronic parts embedded inside or exposed outside a product, such as ICs that contains data concerning security and certification, communication connectors that transmit data, etc. from a tempering operation or an alternating operation. The tamper respondent covering protects data from a tampering operation or an altering operation by erasing the data or disabling operation of the electronic part containing the data in response to an act of attempting to remove the covering from a printed circuit board of the electronic part or to drill a hole in the covering.
Owner:LEE CHEOL JAE
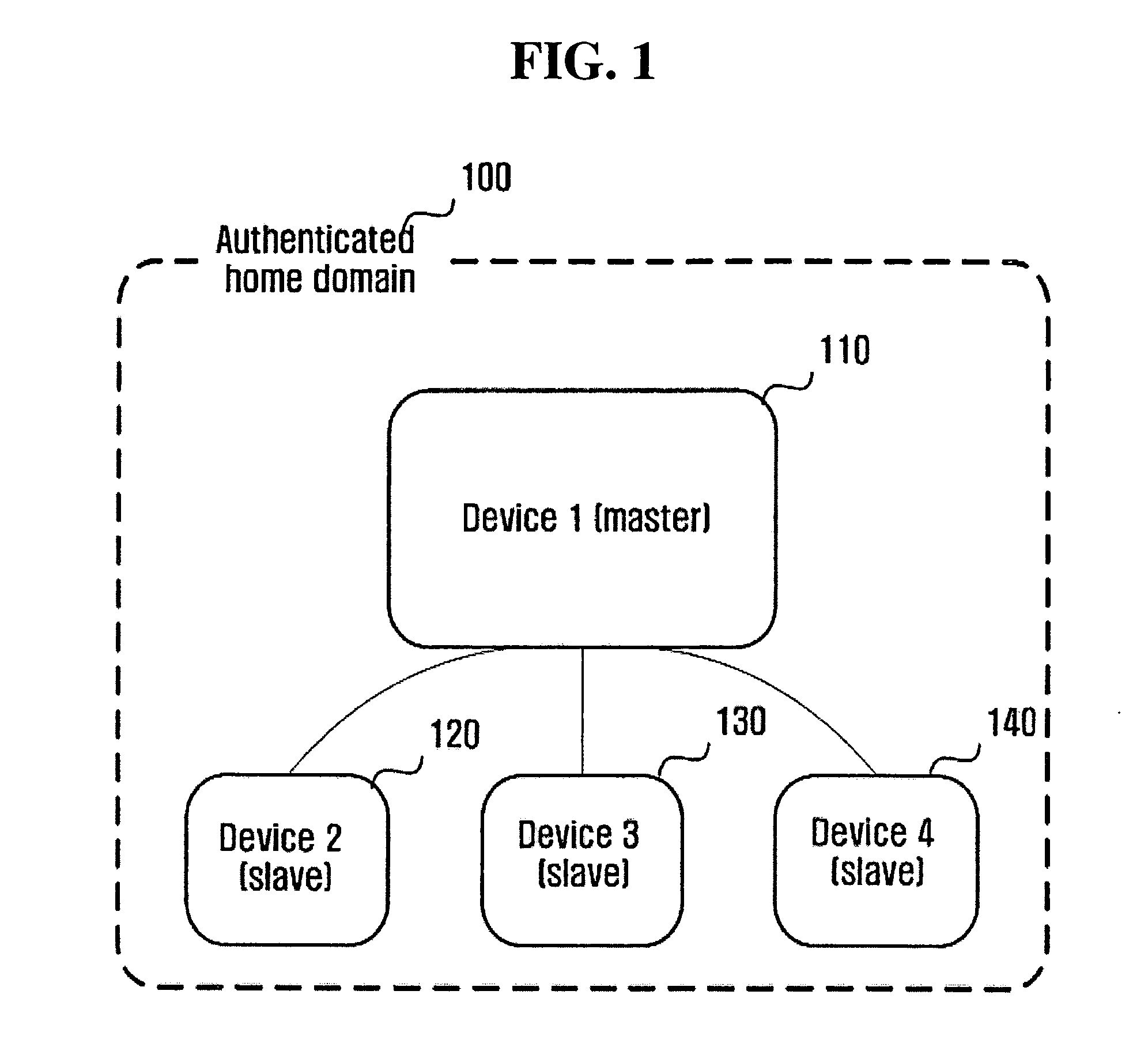
Method of constructing domain based on public key and implementing the domain through universal plug and play (UPnP)
InactiveUS20050086514A1Construction safetyPrevent illegal useDigital data processing detailsUser identity/authority verificationFamily networkNetsniff-ng
A method of constructing a unique domain for preventing content from being illegally used by an unauthorized third person in a public key-based architecture and applying the constructed domain to a home network using universal plug and play (UPnP). The method of the present invention includes selecting one of controlled devices that are operable as a master device and determining the selected device as the master device; performing device authentication in such a manner that other controlled devices receive a secret information block from the determined master device and create certificates; and determining slave devices by selecting one or more devices among the authenticated controlled devices.
Owner:SAMSUNG ELECTRONICS CO LTD
Smart terminal remote lock and format
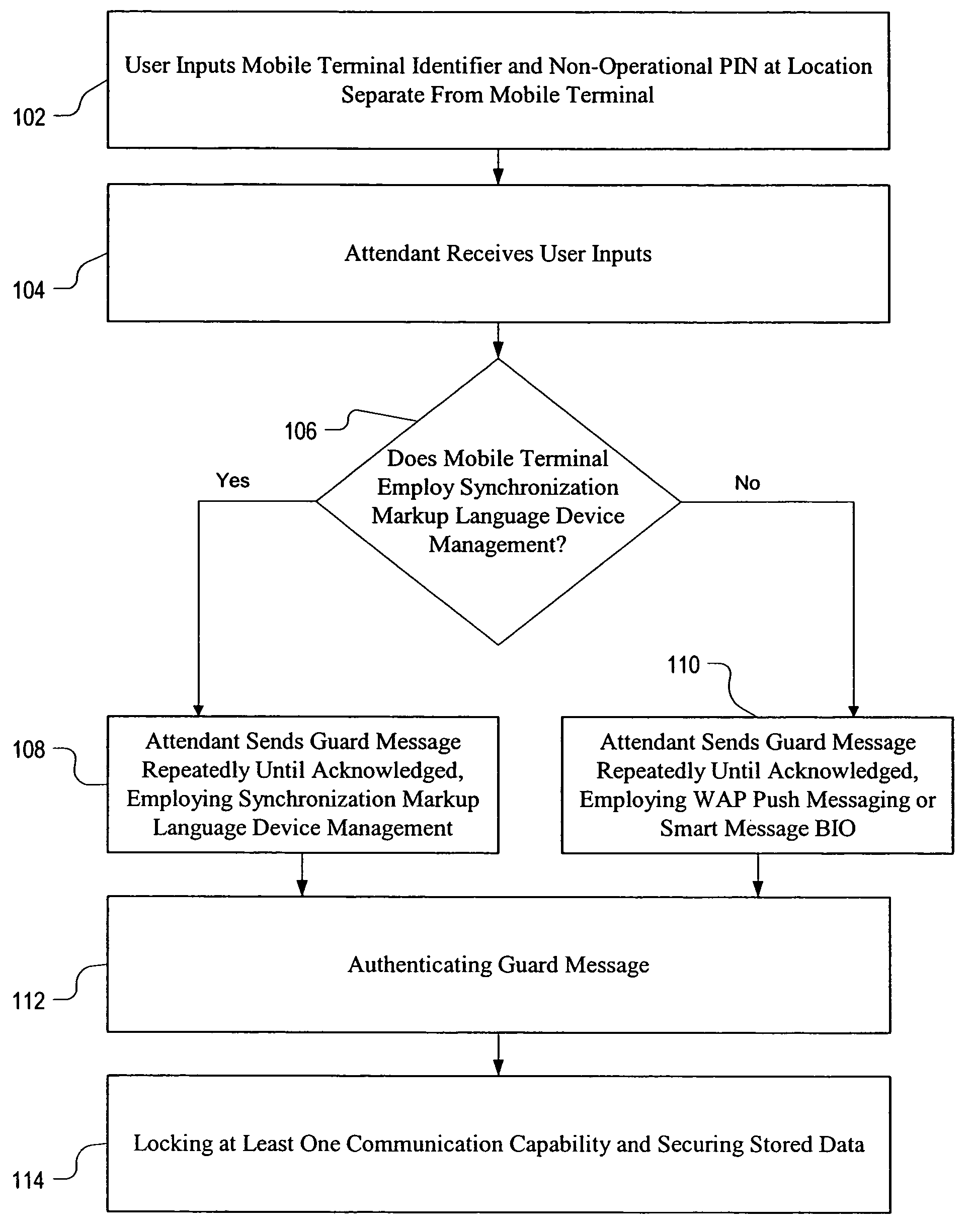
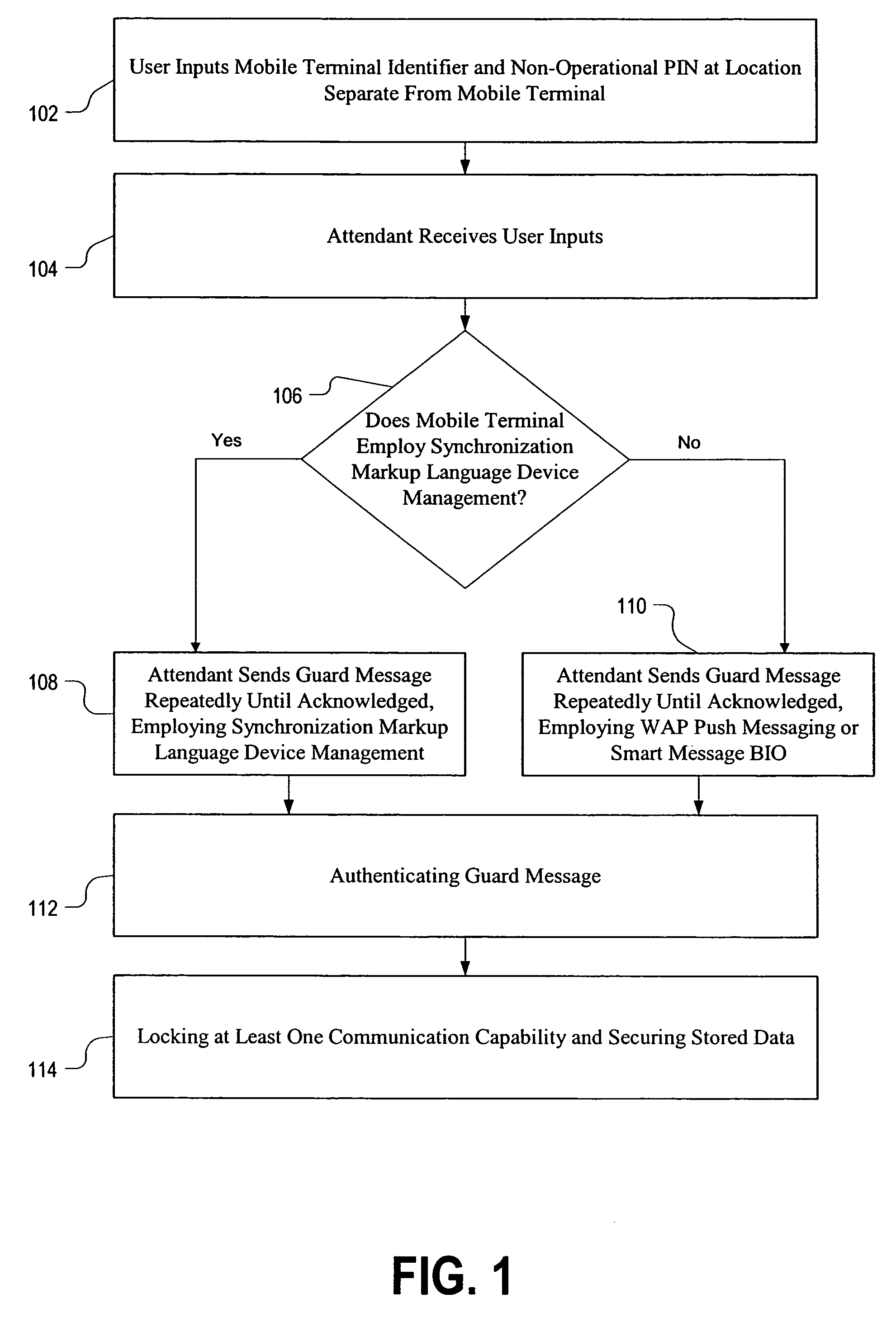
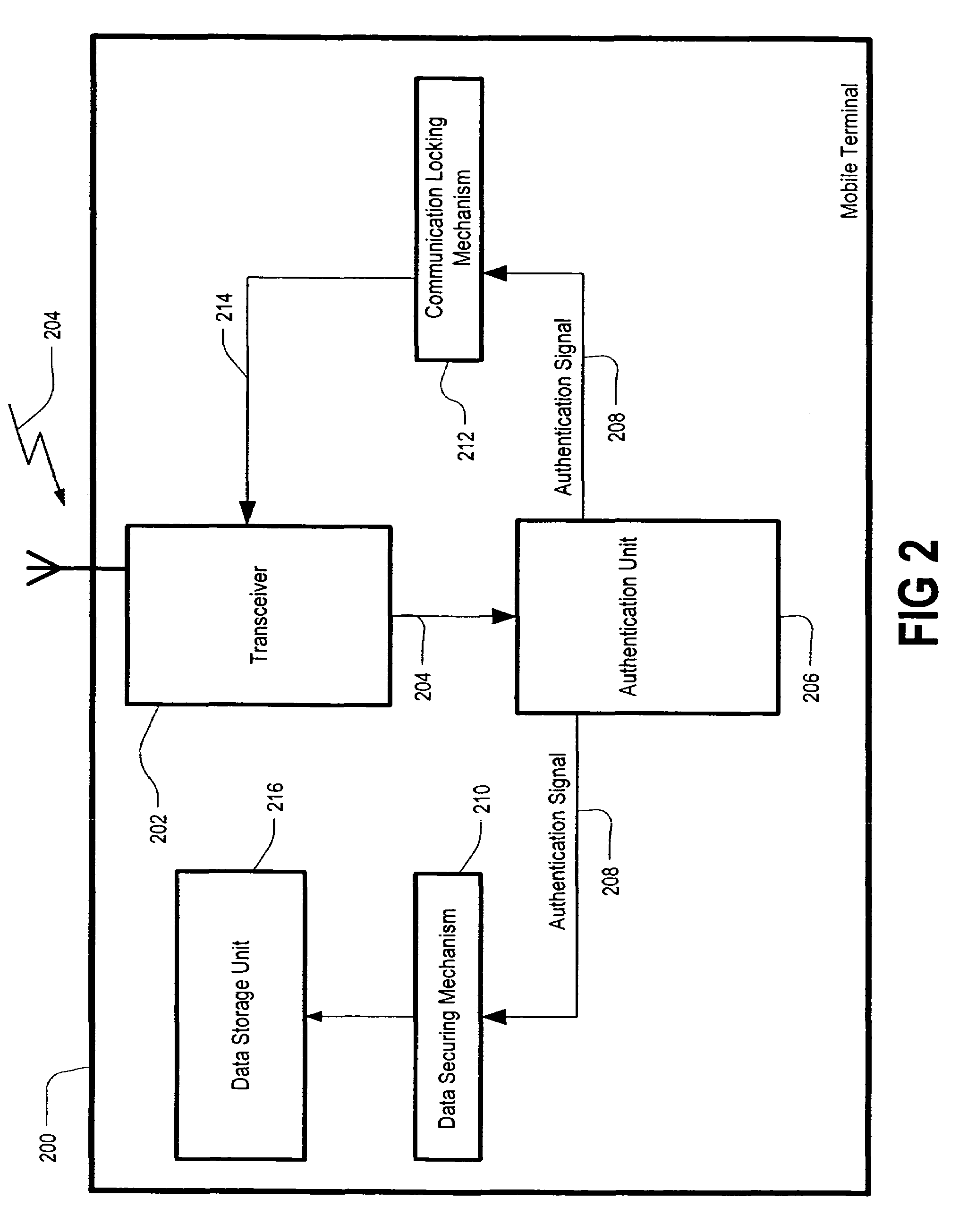
InactiveUS7184750B2Prevent illegal useUnauthorised/fraudulent call preventionEavesdropping prevention circuitsCommunications systemPersonal identification number
A method and mobile terminal are disclosed for use in a wireless communication system, in order to increase security of the mobile terminal when it is lost, stolen, or misplaced by a user. The method includes receiving a guard message at the mobile terminal, authenticating the guard message, locking at least one communication capability of the mobile terminal, and also securing at least some data that is stored in the mobile terminal. Initiation of the method requires inputting a personal identification code at a location separate from the mobile terminal.
Owner:III HLDG 3
Storage medium and contents protection method using the storage medium
InactiveUS7137012B1Reduce usagePrevent illegal useDigital data processing detailsUnauthorized memory use protectionComputer hardwareRevocation list
A revocation list is registered a public ROM area. The revocation list designates at least one electronic device in which use of the storage medium by the designated electronic device is to be revoked. A controller receives from the electronic device which attempts to access, identification information indicative of the electronic device, and checks whether identification information corresponding to the received identification information is contained in the revocation list, thereby determining whether or not use of the storage medium by the electronic device which attempts to access should be revoked.
Owner:KK TOSHIBA +1
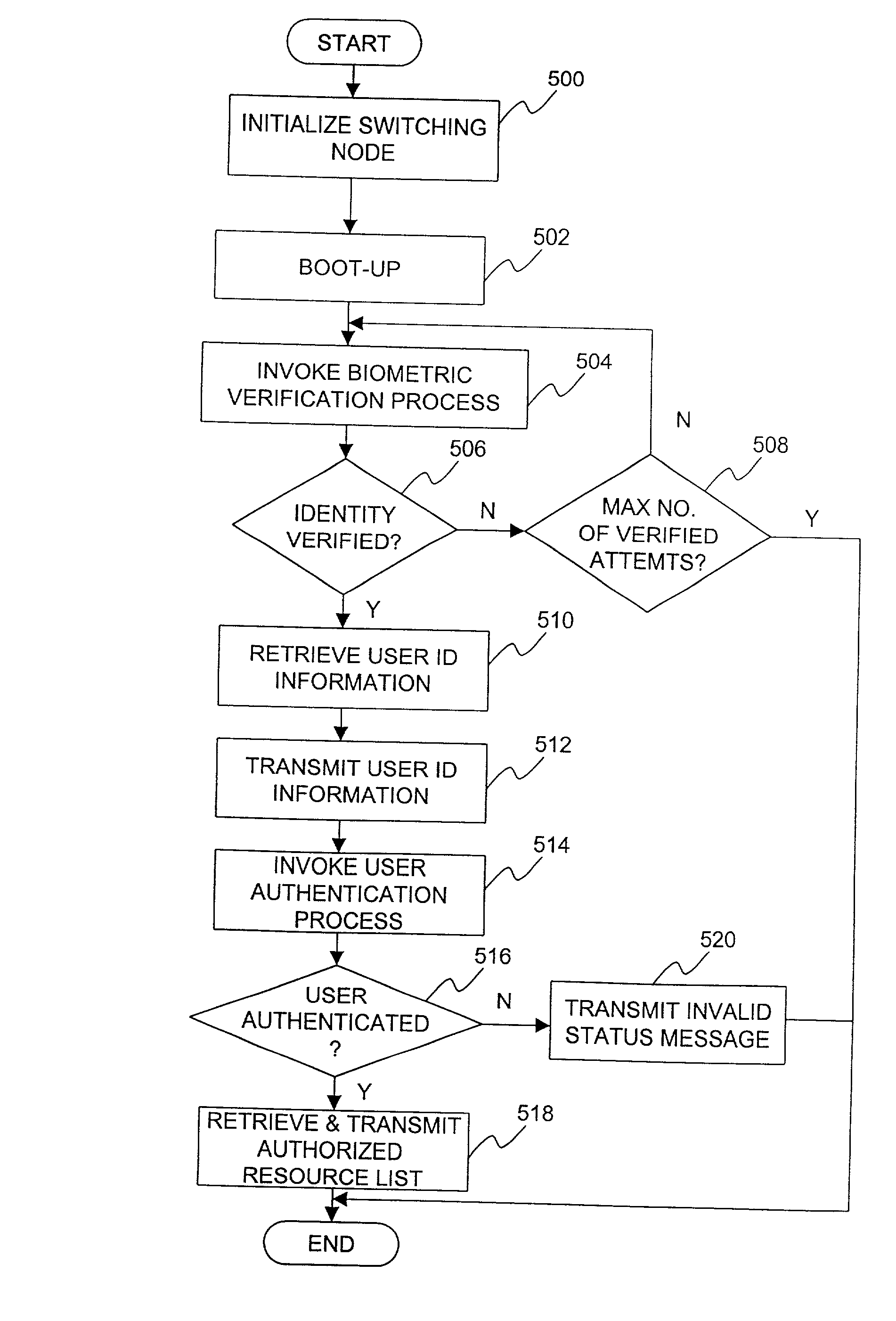
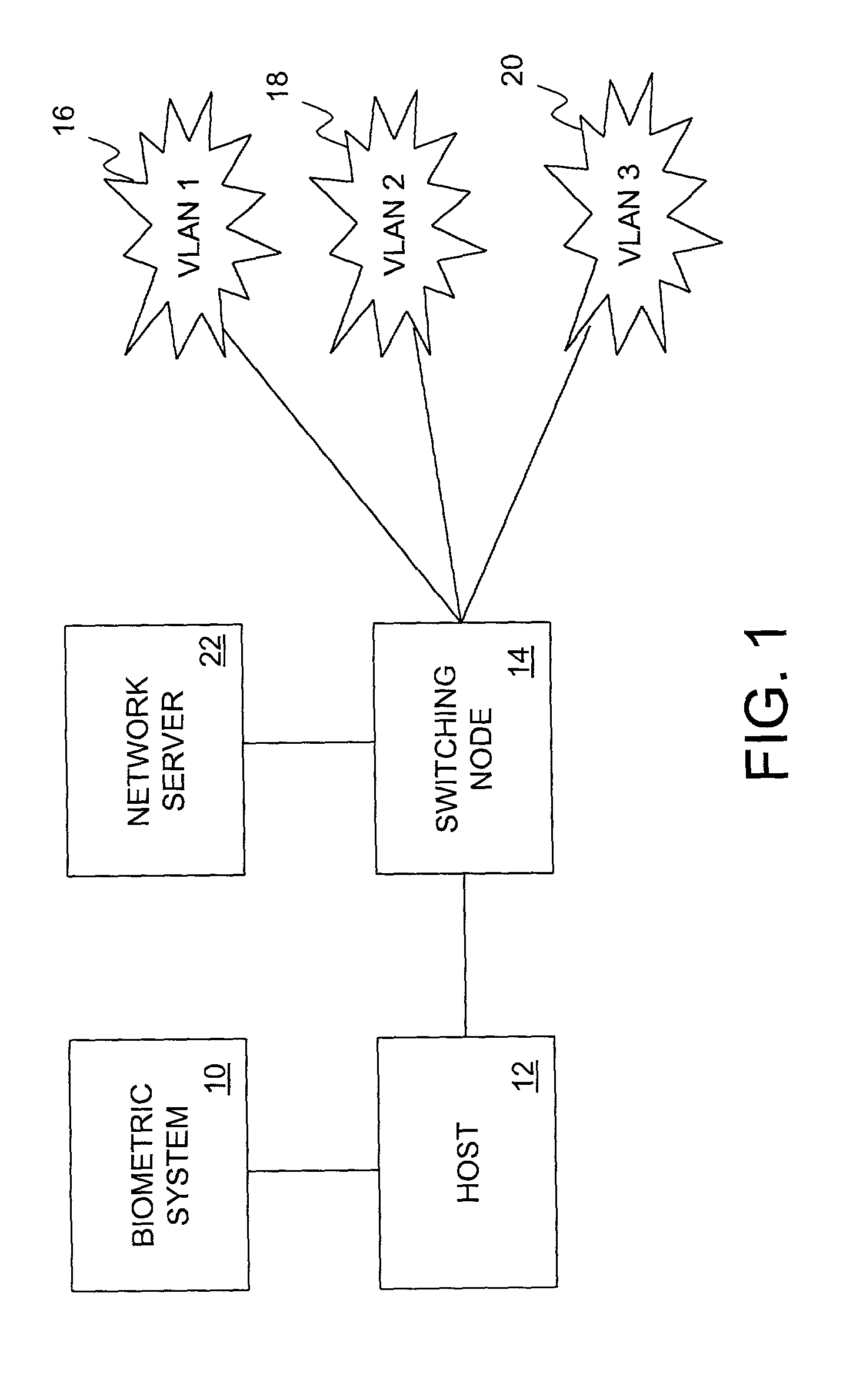
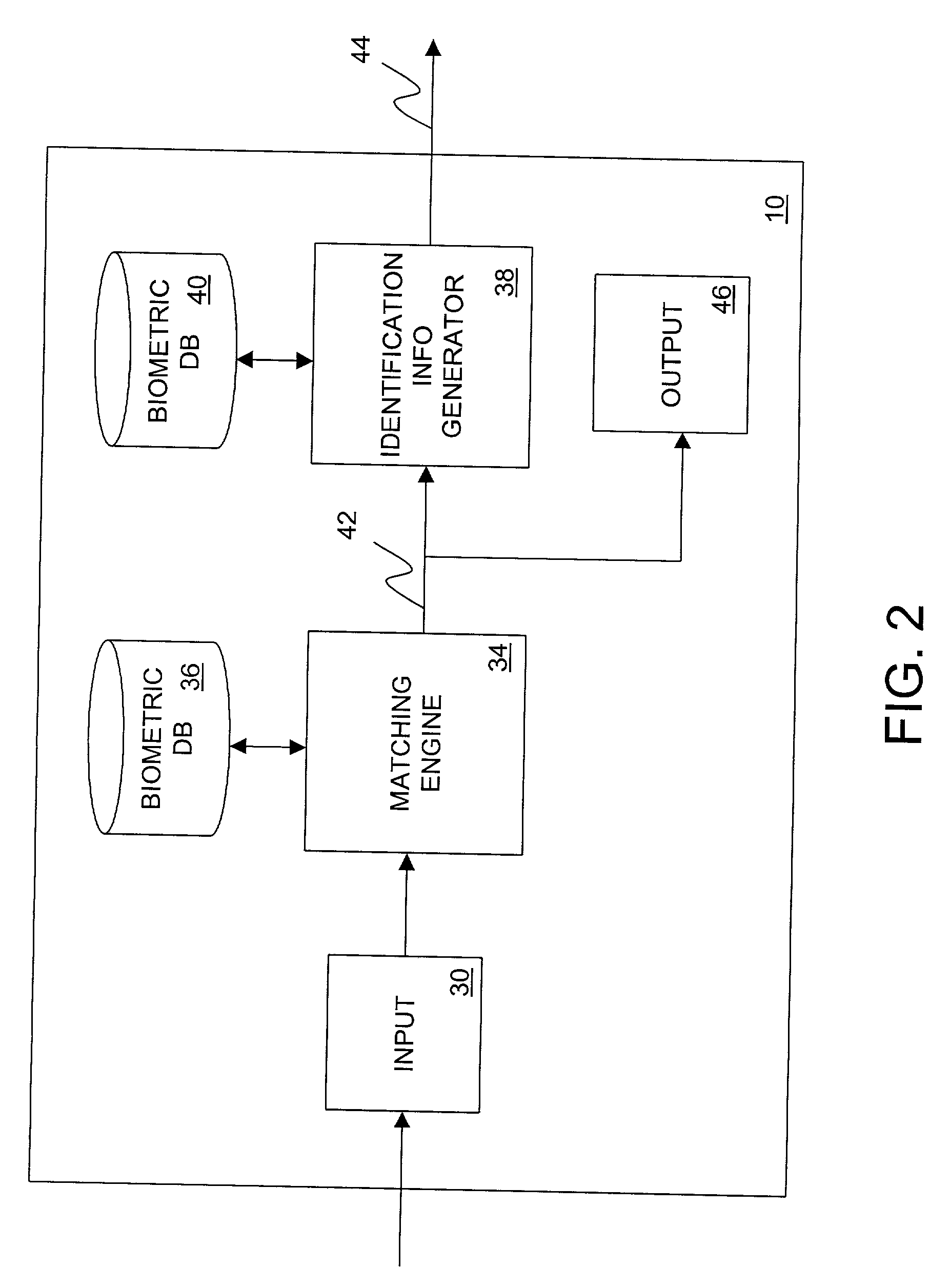
Biometric authenticated VLAN
InactiveUS20020129285A1Prevent illegal useUnauthorized useDigital data processing detailsUser identity/authority verificationInternet privacyUser authentication
A user authentication system and method for a data communication network that helps ensure that a user accessing the network resources is indeed the person having a claimed identity. The user's identity is verified by a biometric system by examining the user's physiological or behavioral characteristic. User identification information needed for accessing the network resources is stored in the biometric system and not released until the user's identity is verified. Upon verification of the user's identity, the user identification data is provided to a switching node for determining the VLANs that the user may access.
Owner:ALCATEL LUCENT SAS
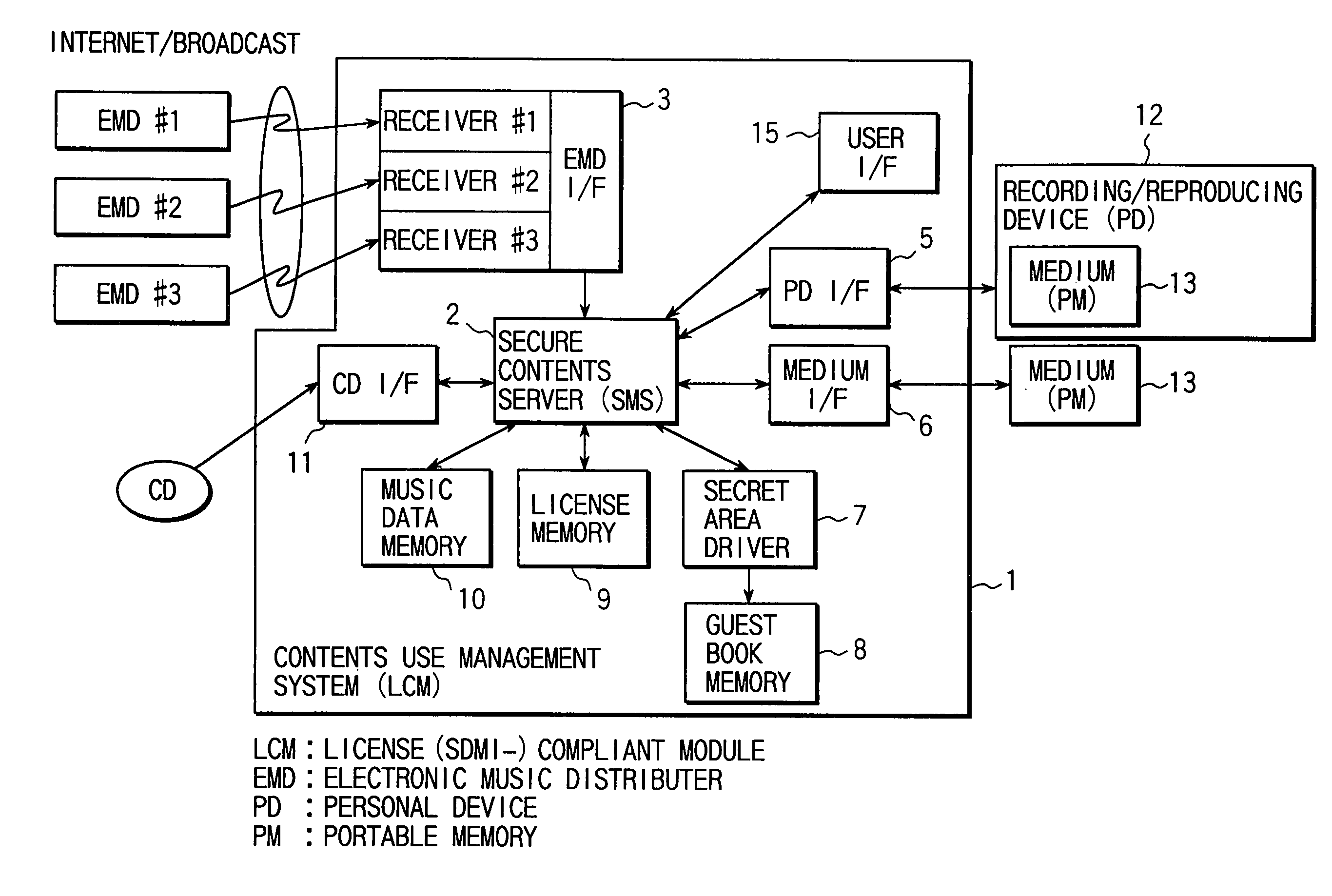
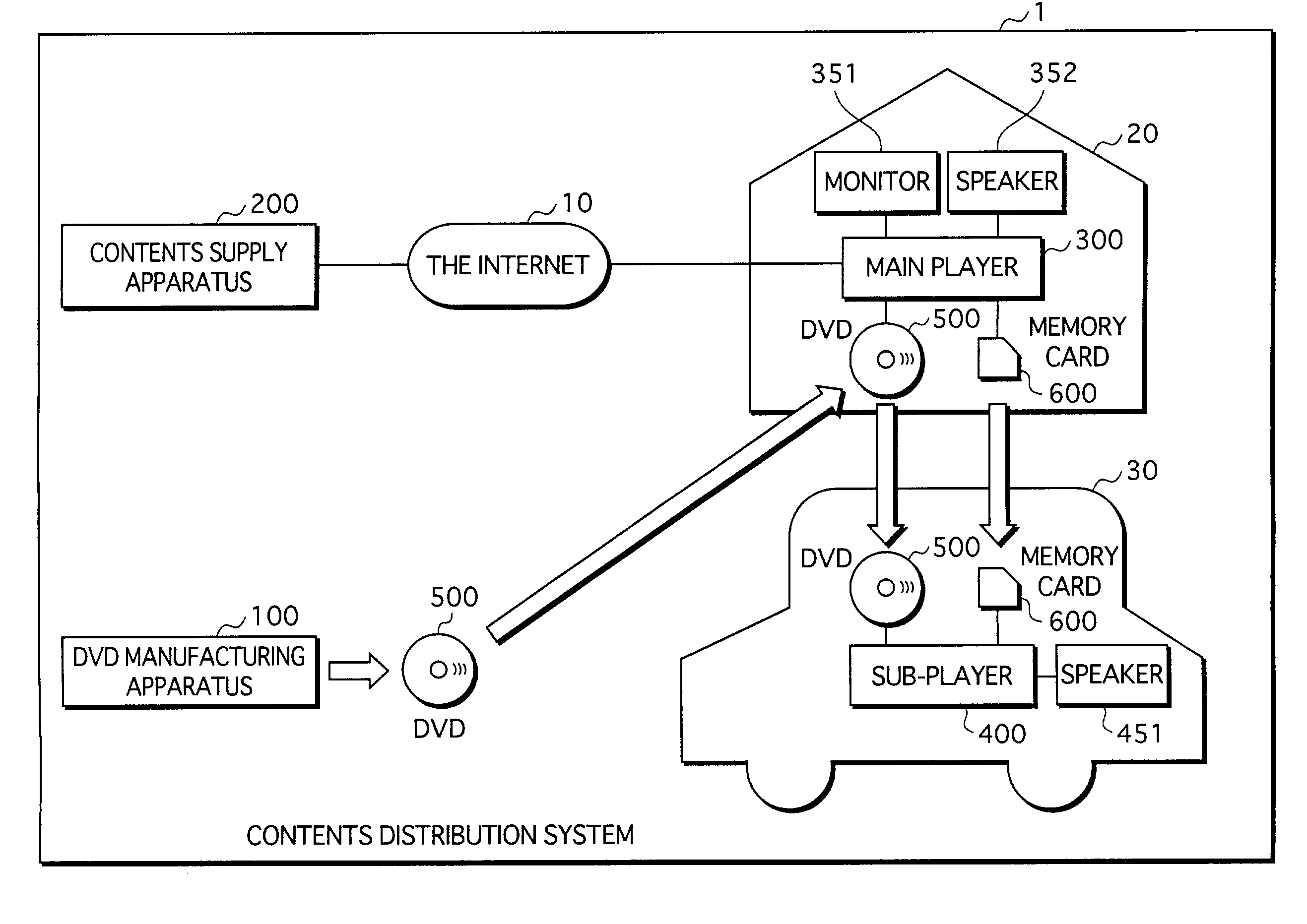
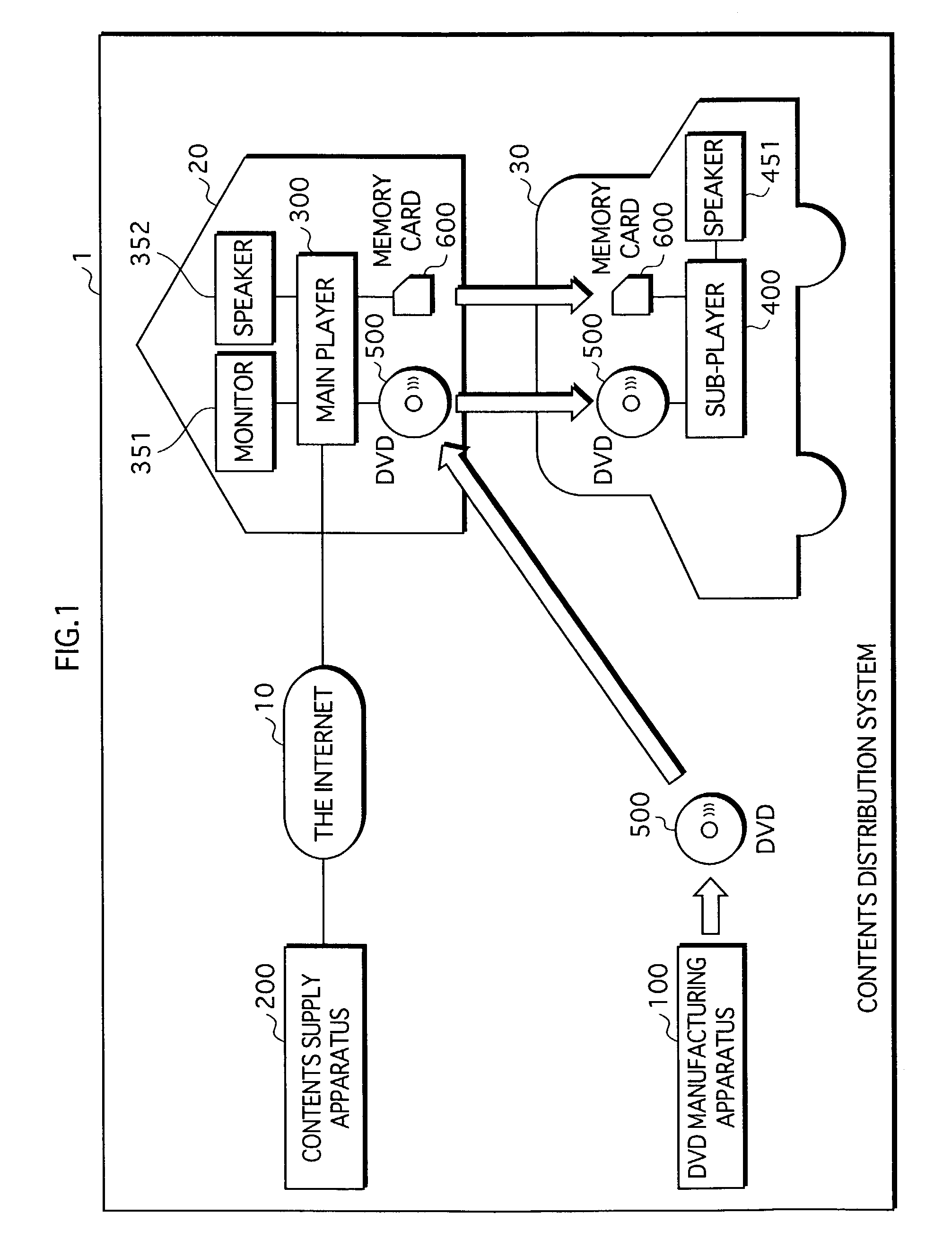
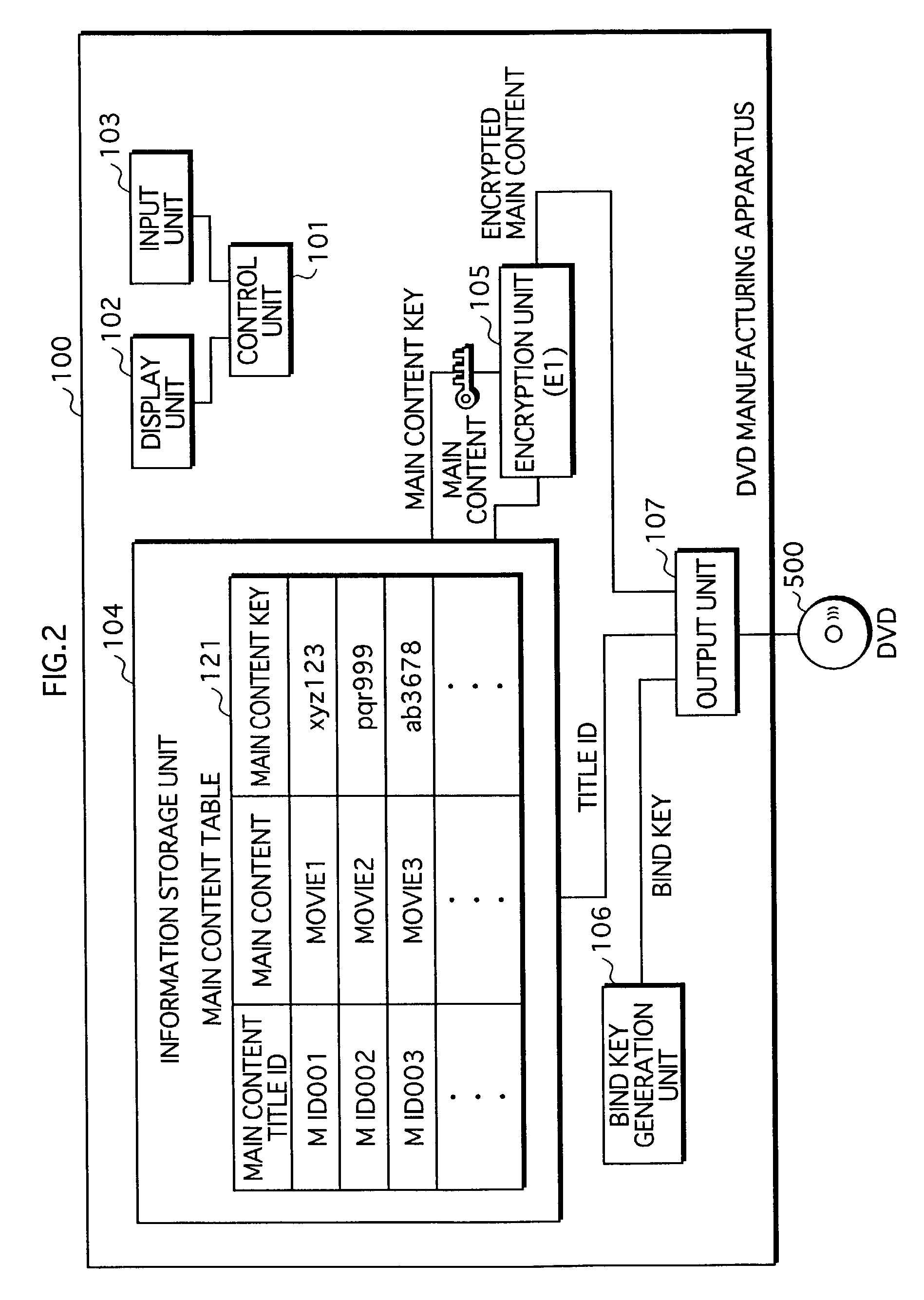
Contents distribution system
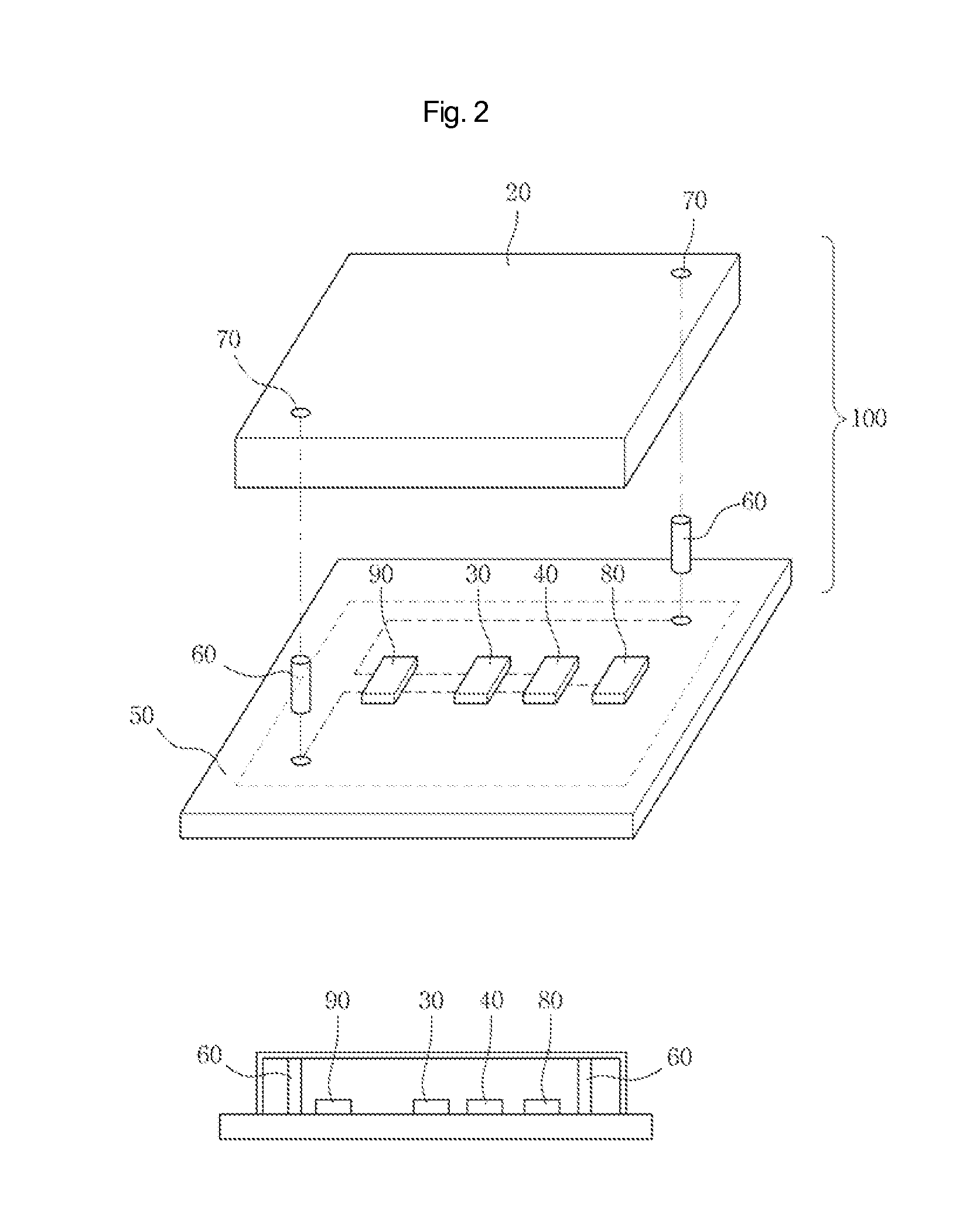
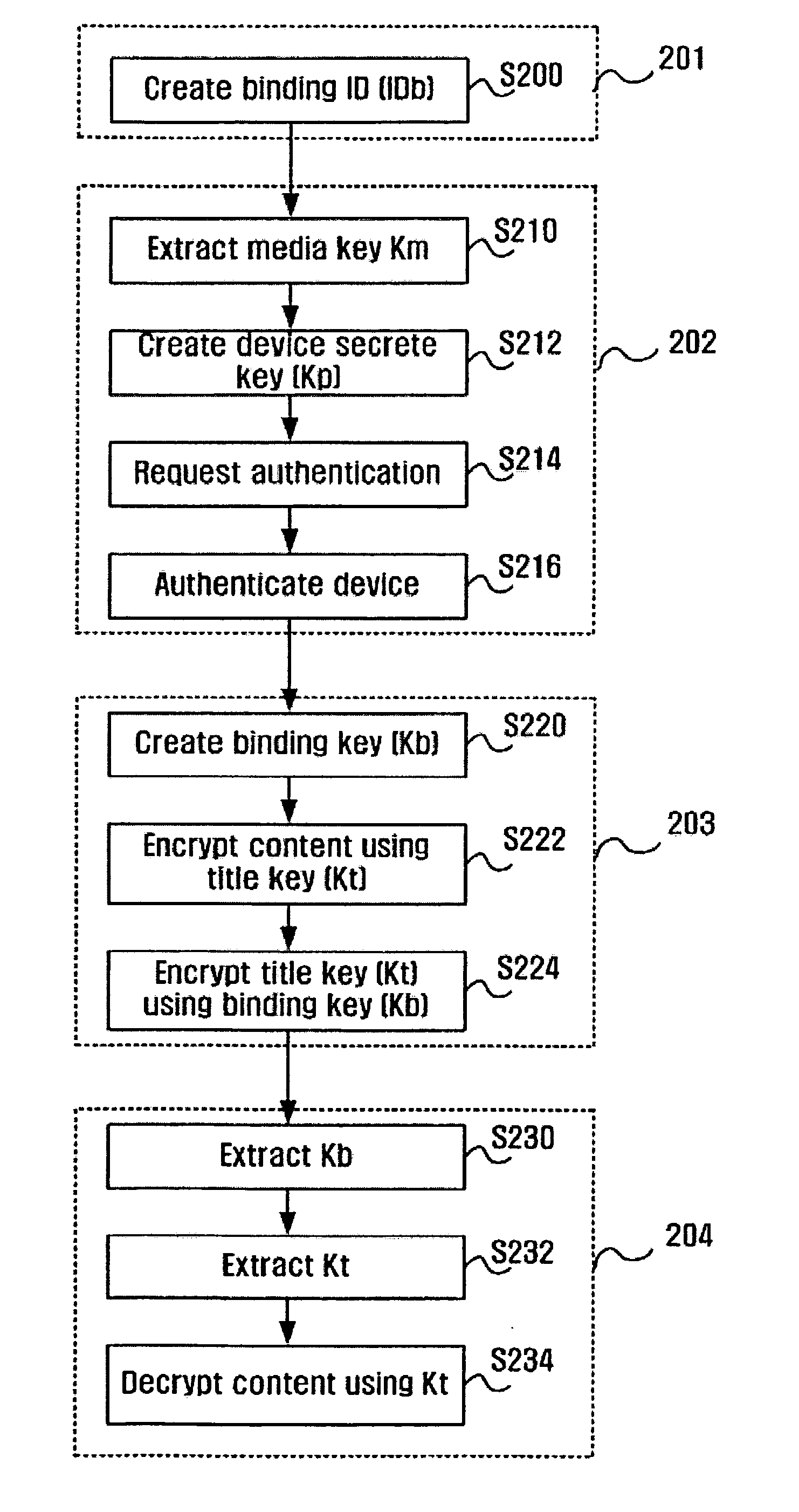
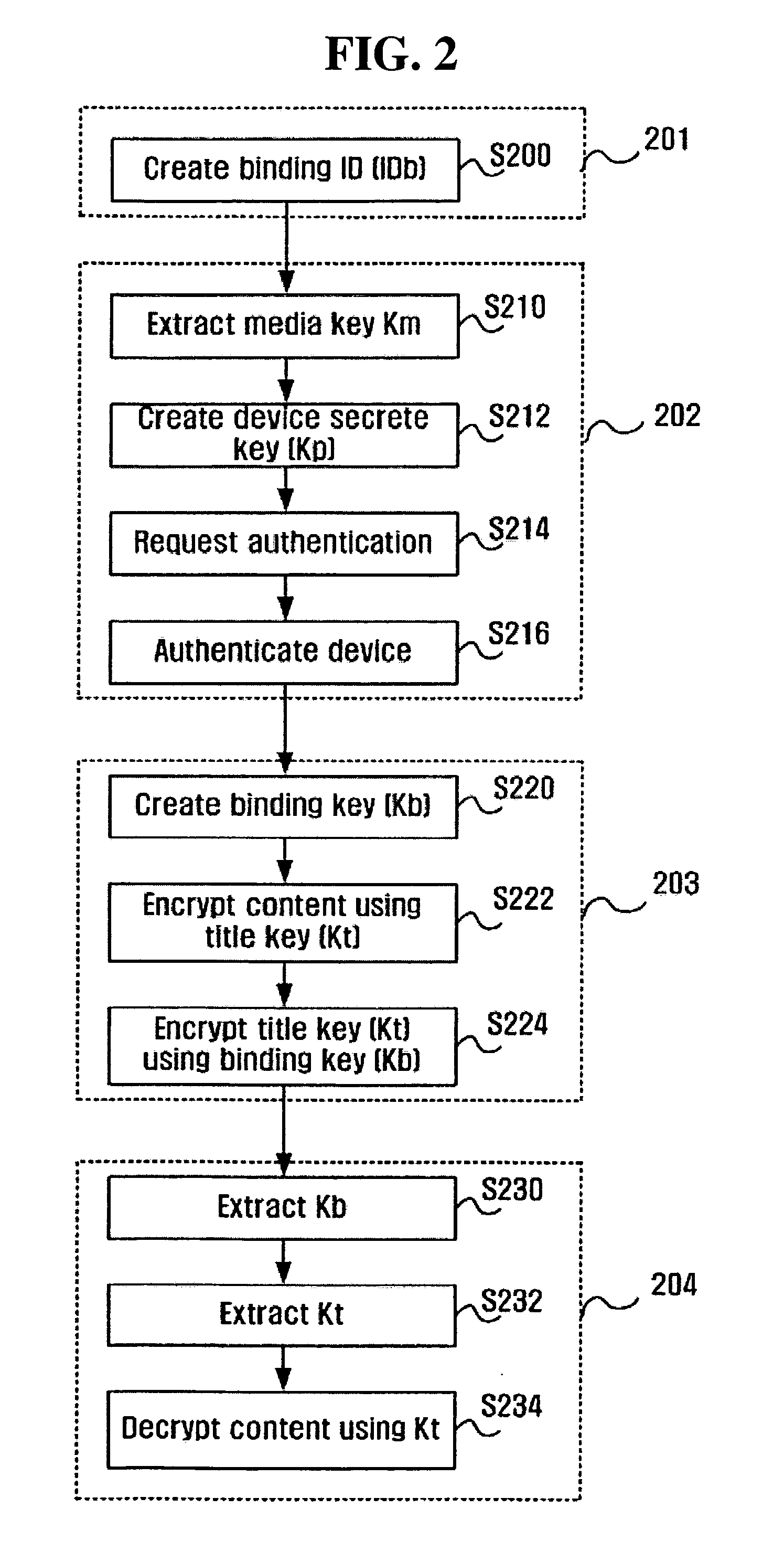
ActiveUS7353543B2Prevent illegal useImprove protectionTelevision system detailsKey distribution for secure communicationContent distributionDistribution system
A contents supply apparatus supplies sub-content that relates to main content. A DVD-ROM stores a bind key unique to the DVD-ROM and main content that is a digital work. A main player reads the bind key from the DVD-ROM, acquires sub-content that relates to the main content stored on the DVD-ROM, generates encrypted sub-content by encrypting the acquired sub-content based on the read bind key, and writes the generated encrypted content to an SD memory card. A sub-player reads the bind key from the DVD-ROM, reads the encrypted sub-content from the SD memory card, generates sub-content by decrypting the read encrypted sub-content based on the bind key, and plays back the generated sub-content.
Owner:PANASONIC CORP
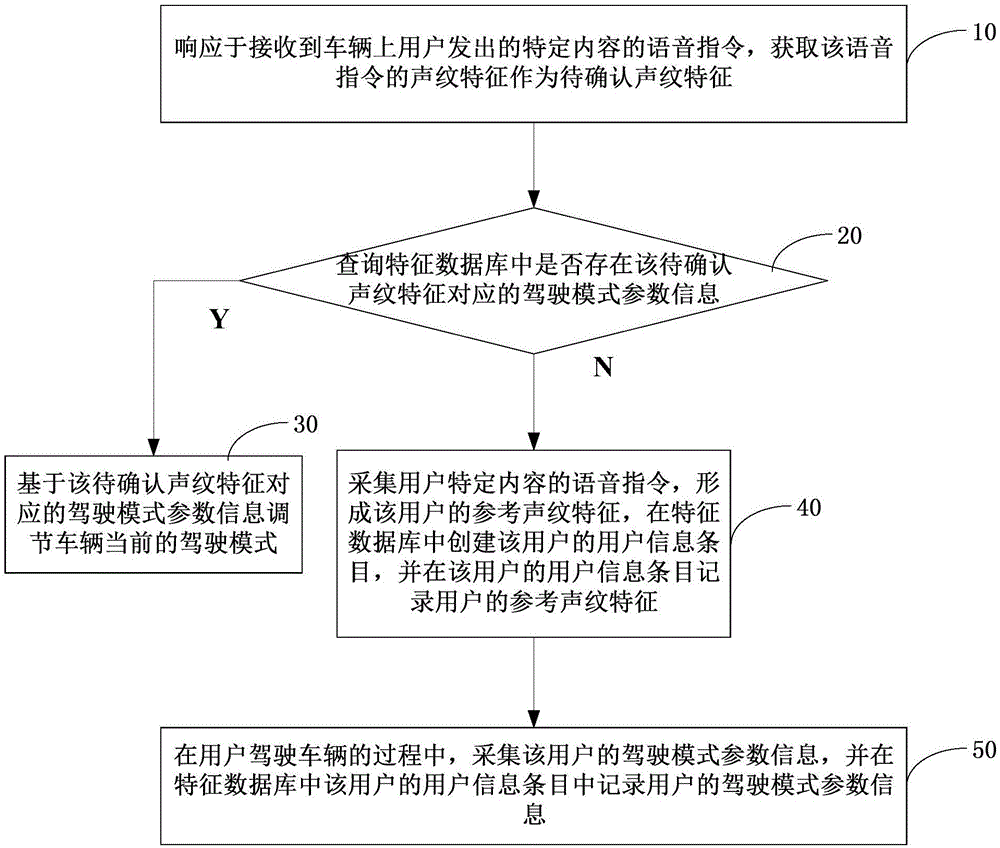
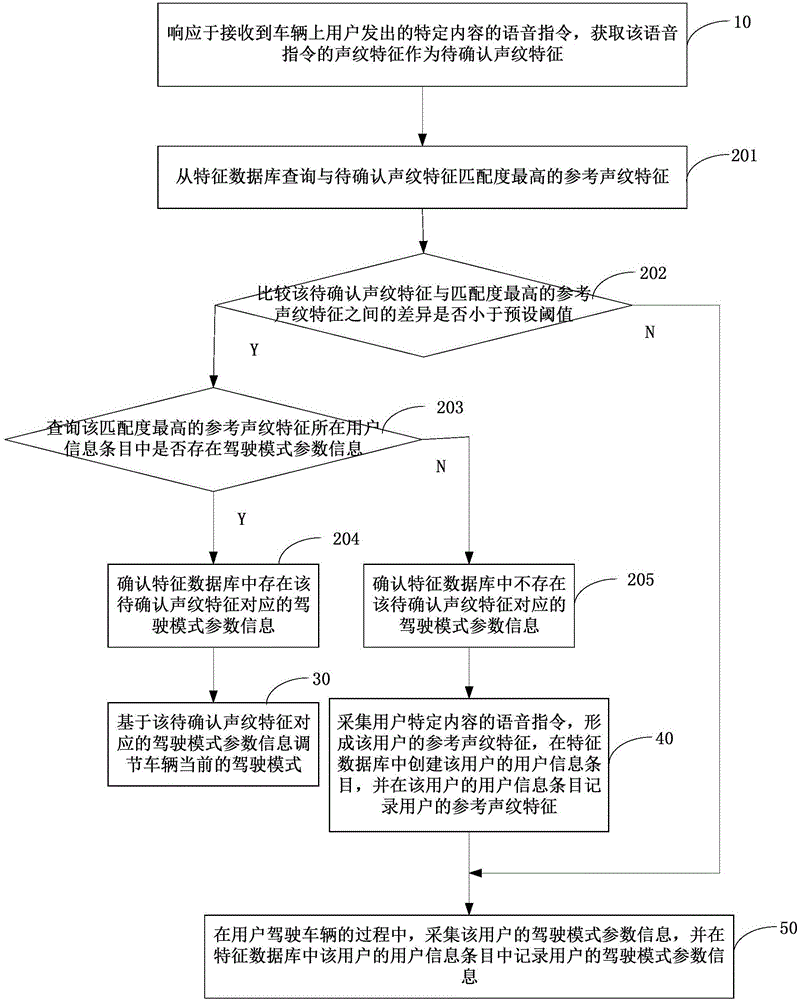
Method, device and system for adjusting driving modes and vehicle
ActiveCN106683673ARealize automatic adjustmentProtection securitySpeech recognitionPersonalizationVehicle driving
The invention discloses a method, a device and a system for adjusting driving modes and a vehicle. The method includes receiving a voice instruction; querying feature databases; determining parameter information of the driving modes on the basis of to-be-confirmed voiceprint features; acquiring the voice instruction and acquiring the parameter information of the driving modes in driving procedures. The method, the device, the system and the vehicle have the advantages that the vehicle can be adjusted to be in the most familiar and habitual driving modes by the aid of the single voice instruction, and accordingly users can be positioned in habitual driving environments without manually adjusting the parameter information of the driving modes; the parameter information of the driving modes of the users can be automatically acquired in the vehicle driving procedures of the users without being manually set by the users, the tedious properties of user operation can be prevented, specific physical buttons can be omitted, and influence on the aesthetics of internal environments of the vehicle can be prevented; the quantity of the parameter information of the driving modes of the users is unlimited for the same vehicle, and the personalized driving modes of the various users can be implemented.
Owner:ZHICHEAUTO TECH BEIJING
Conveniently viewable display device and method
InactiveUS20100053867A1Prevent illegal useAvoid interferencePhysical therapies and activitiesMechanical/radiation/invasive therapiesGeneral purposeUser input
We have disclosed a modular personal network (MPN) that includes multiple devices that may be worn, carried, or used in close proximity to a user. The devices communicate wirelessly. Functions of the MPN may be modified by adding or removing components. The MPN may communicate with a personal computer. General purpose devices may include a control unit, a display, a user input, and an audio output. The MPN may provide a variety of functions, including time, communication, entertainment, organization, guidance, athletic, medical, travel, outdoors, identity, security, and military.
Owner:ADIDAS
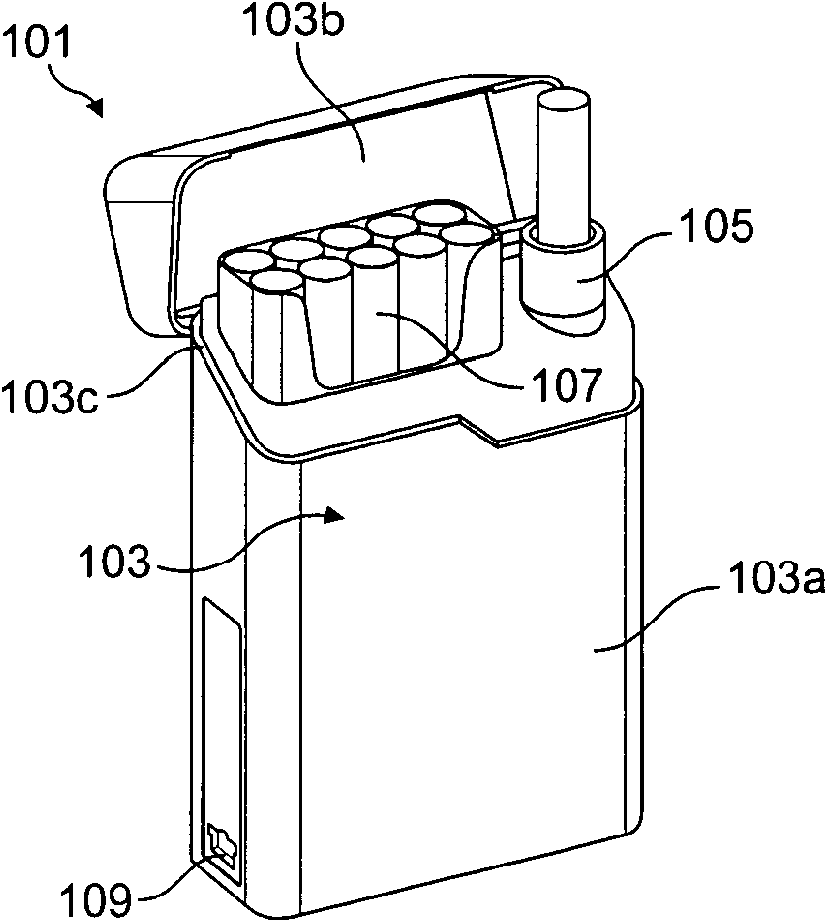
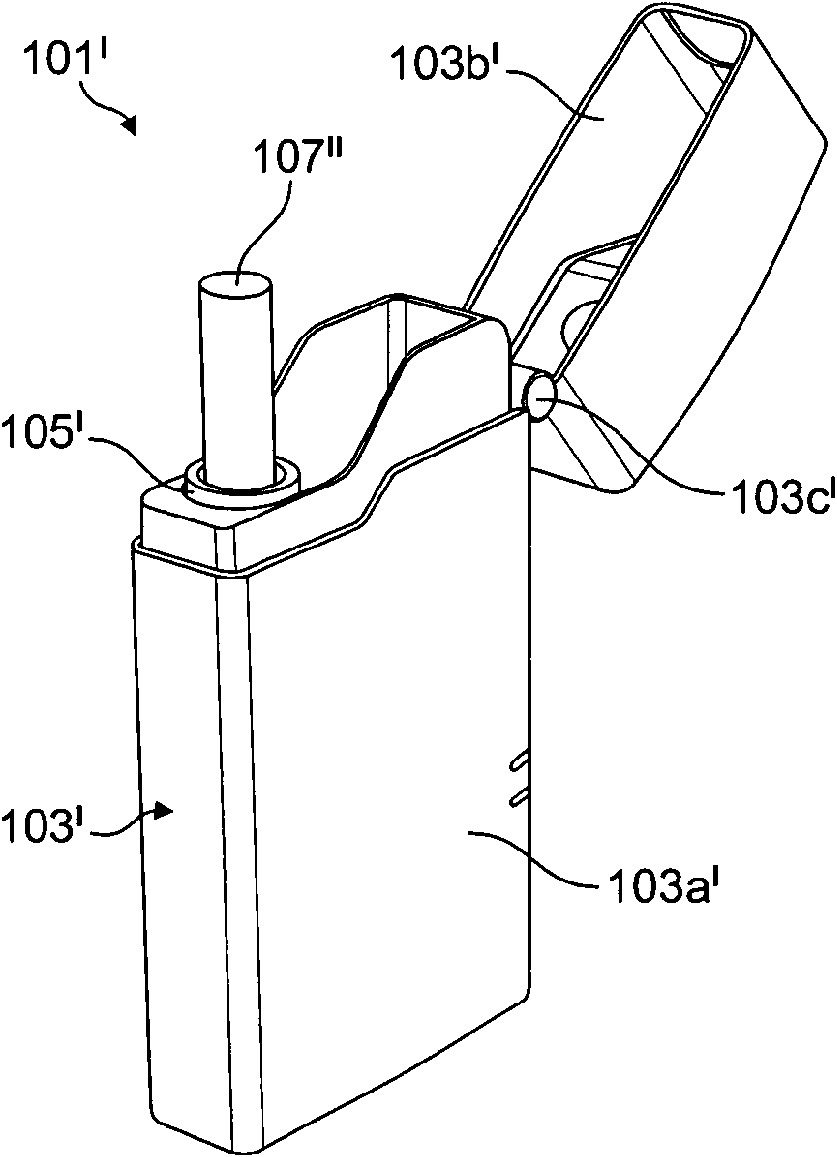
An electrically heated smoking system comprising at least two units
ActiveCN103281920ASmall sizeAids in suctionCircuit monitoring/indicationTobacco treatmentElectricityEngineering
There is provided an electrically heated smoking system comprising a secondary unit capable of receiving a smoking article having an aerosol-forming substrate. The secondary unit comprises at least one heating element and an interface for connection to a primary power supply. The secondary unit further comprises a secondary power supply and secondary circuitry.; The secondary circuitry is arranged to control supply of electrical power from the secondary power supply to the at least one heating element in a pre-heating mode during which the temperature of the aerosol-forming substrate is increased to an operating temperature, to control supply of electrical power from the secondary power supply to the at least one heating element in a smoking mode, during which the temperature of the aerosol-forming substrate is maintained at substantially the operating temperature, and to control charging of the secondary power supply by the primary power supply, in a charging mode,; so that the secondary power supply has sufficient charge to increase the temperature of the aerosol-forming substrate to the operating temperature in the pre-heating mode and to maintain the temperature of the aerosol-forming substrate at substantially the operating temperature during the smoking mode. The electrically heated smoking system may optionally include a primary unit comprising the primary power supply and primary circuitry. By dividing the power supply between the primary unit and the secondary unit, the secondary unit can be made smaller and more convenient for the user.
Owner:PHILIP MORRIS PROD SA
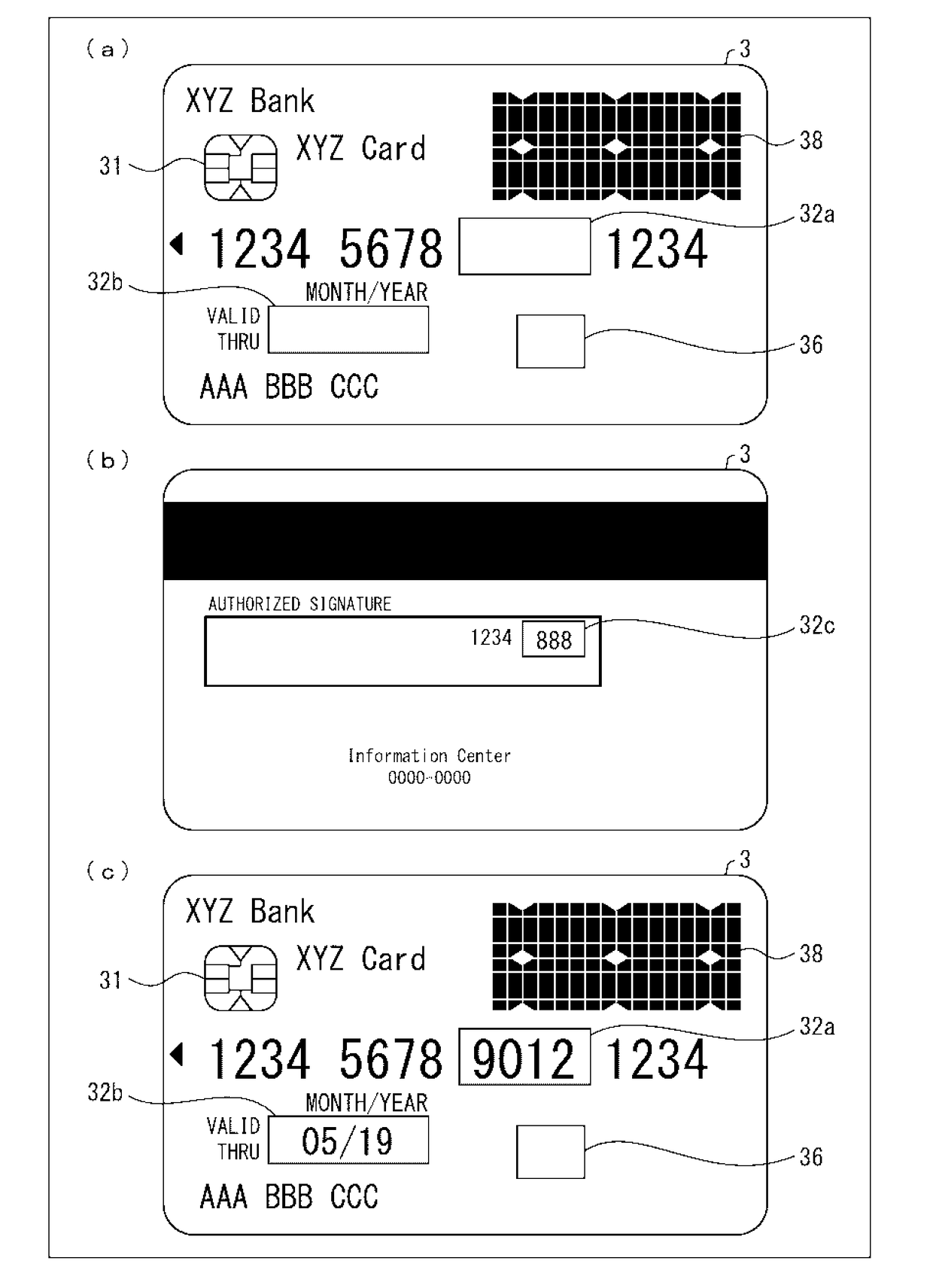
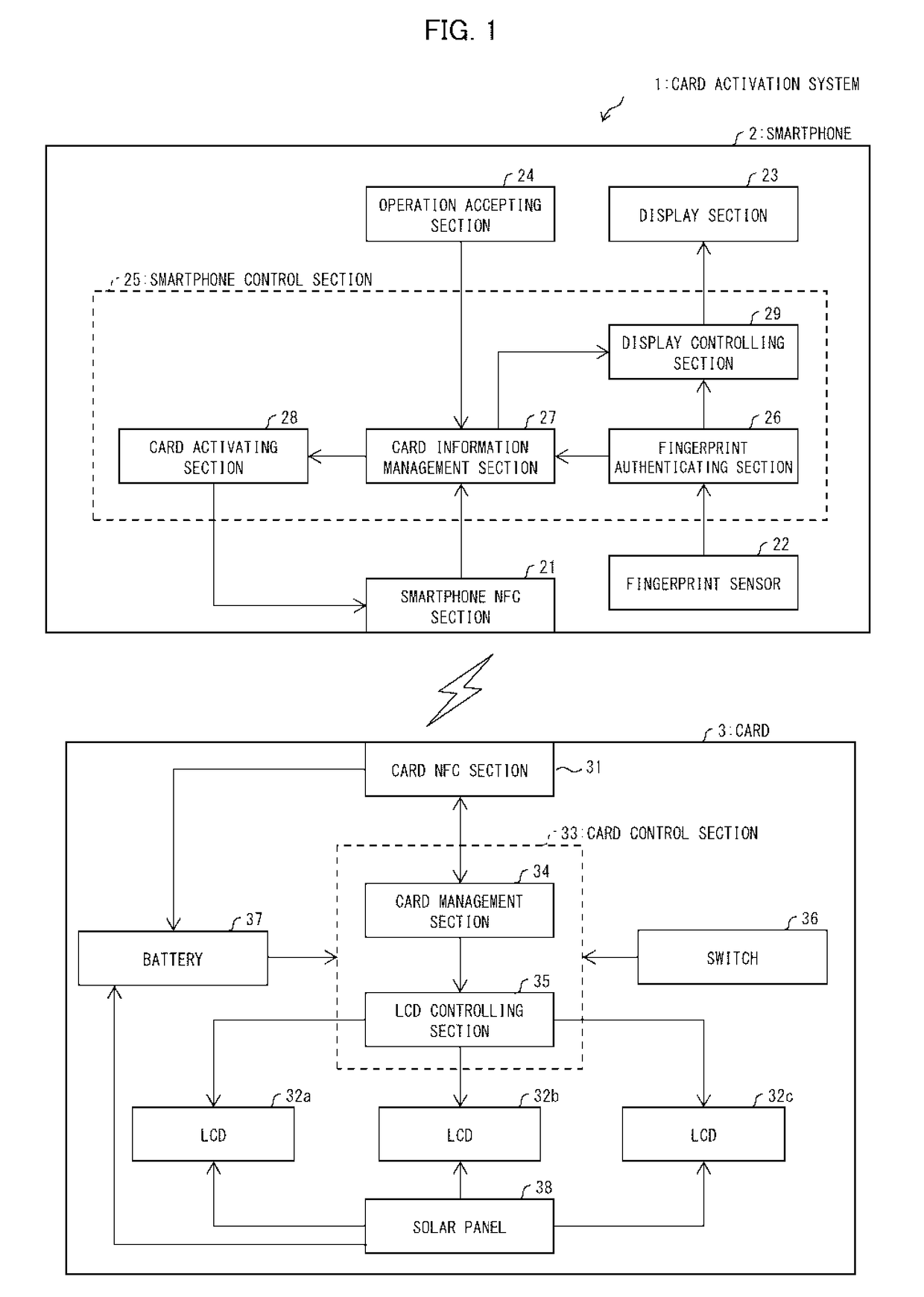
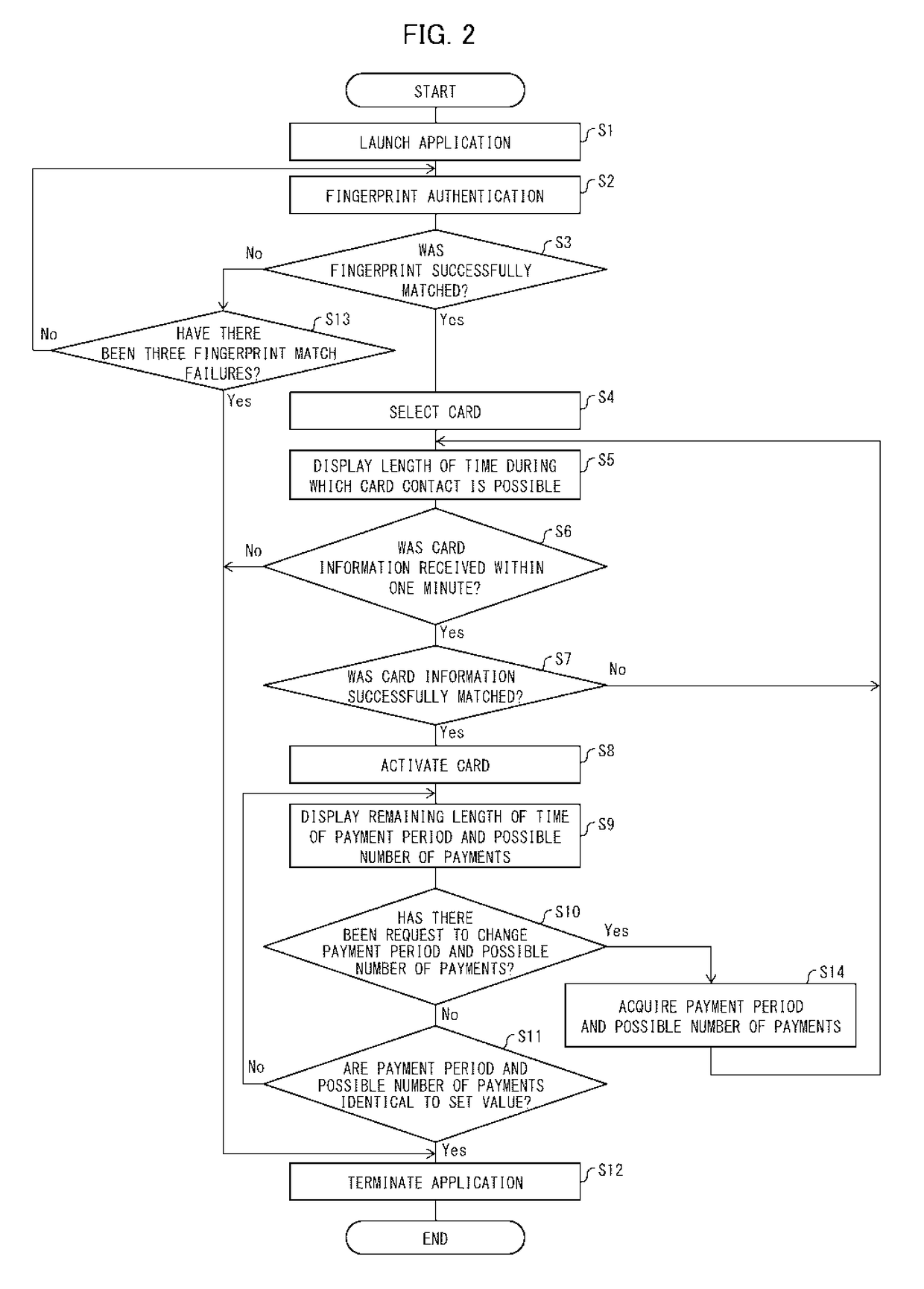
Card and application program
InactiveUS20180117944A1Prevent illegal useAvoid power consumptionDigital data protectionPayment architectureCredit cardComputer hardware
A card functions as a credit card or a cash card, the card including: a card management section configured to (i) transmit card information to a smartphone, (ii) accept from the smartphone an instruction for activating the card, and (iii) activate the card in accordance with the instruction thus accepted; and a battery which is rechargeable and is configured to supply electric power used in the card.
Owner:APS SA
Contents delivery system, information processing apparatus or information processing method and computer program
InactiveUS20050144019A1Easy to managePrevent illegal useKey distribution for secure communicationUser identity/authority verificationInformation processingClient-side
An environment in which copyright management is exercised is supplied so that encrypted contents and the license for decrypting the encrypted contents can be handled independently. Further, each client legally uses the contents. When contents acquired by client A are to be moved to client B, the information about client B is attached to the contents so that client B can be identified. In this manner, the contents can be shared between clients A and B, while the contents are protected. A licensed user can use contents from a plurality of devices, while preventing an illegal use of the contents.
Owner:SONY CORP
An electrically heated smoking system
ActiveCN102438470ASmall sizeAids in suctionTobacco treatmentTobacco pipesOperating temperatureElectricity
There is provided an electrically heated smoking system comprising a secondary unit capable of receiving a smoking article having an aerosol-forming substrate. The secondary unit comprises at least one heating element and an interface for connection to a primary power supply for supplying electrical power to the at least one heating element during a pre-heating mode, to increase the temperature of the aerosol-forming substrate to an operating temperature. The secondary unit further comprises a secondary power supply arranged to supply electrical power to the at least one heating element during a smoking mode, to maintain the temperature of the aerosol-forming substrate at substantially the operating temperature. The secondary unit further comprises secondary circuitry. The electrically heated smoking system may optionally include a primary unit comprising the primary power supply and primary circuitry. By dividing the power supply between the primary unit and the secondary unit, the secondary unit can be made smaller and more convenient for the user.
Owner:PHILIP MORRIS PROD SA
Vehicle and program for vehicle
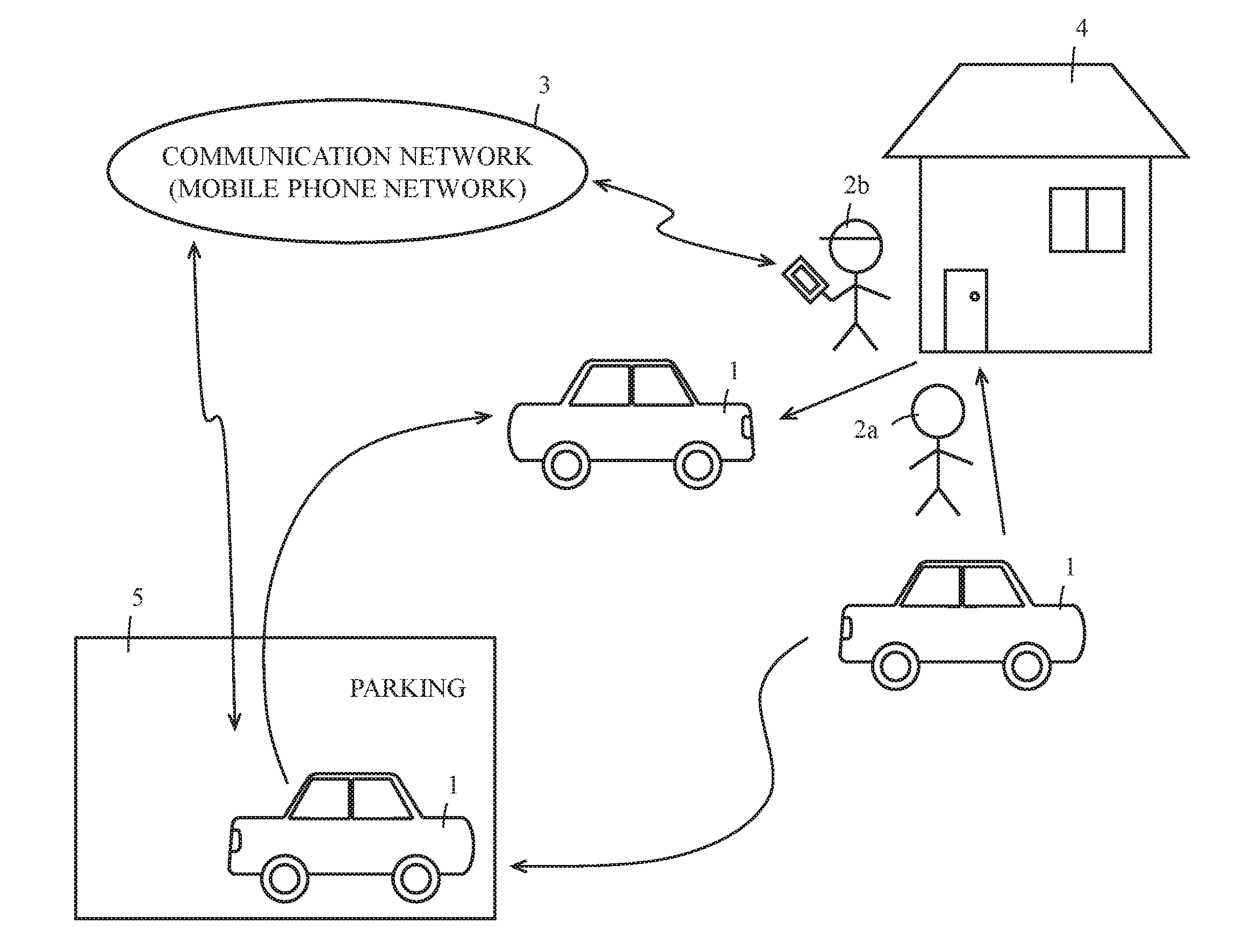
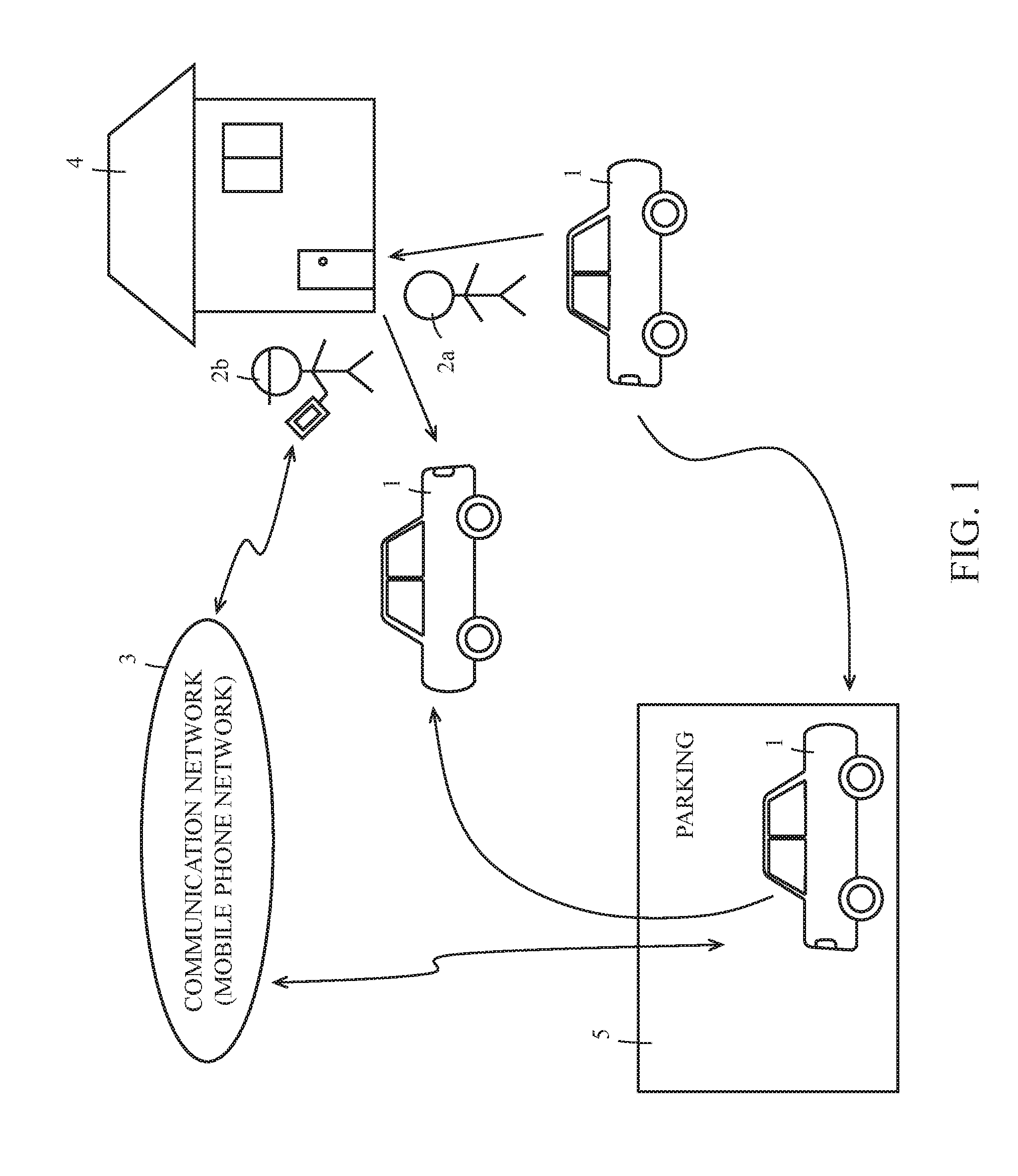
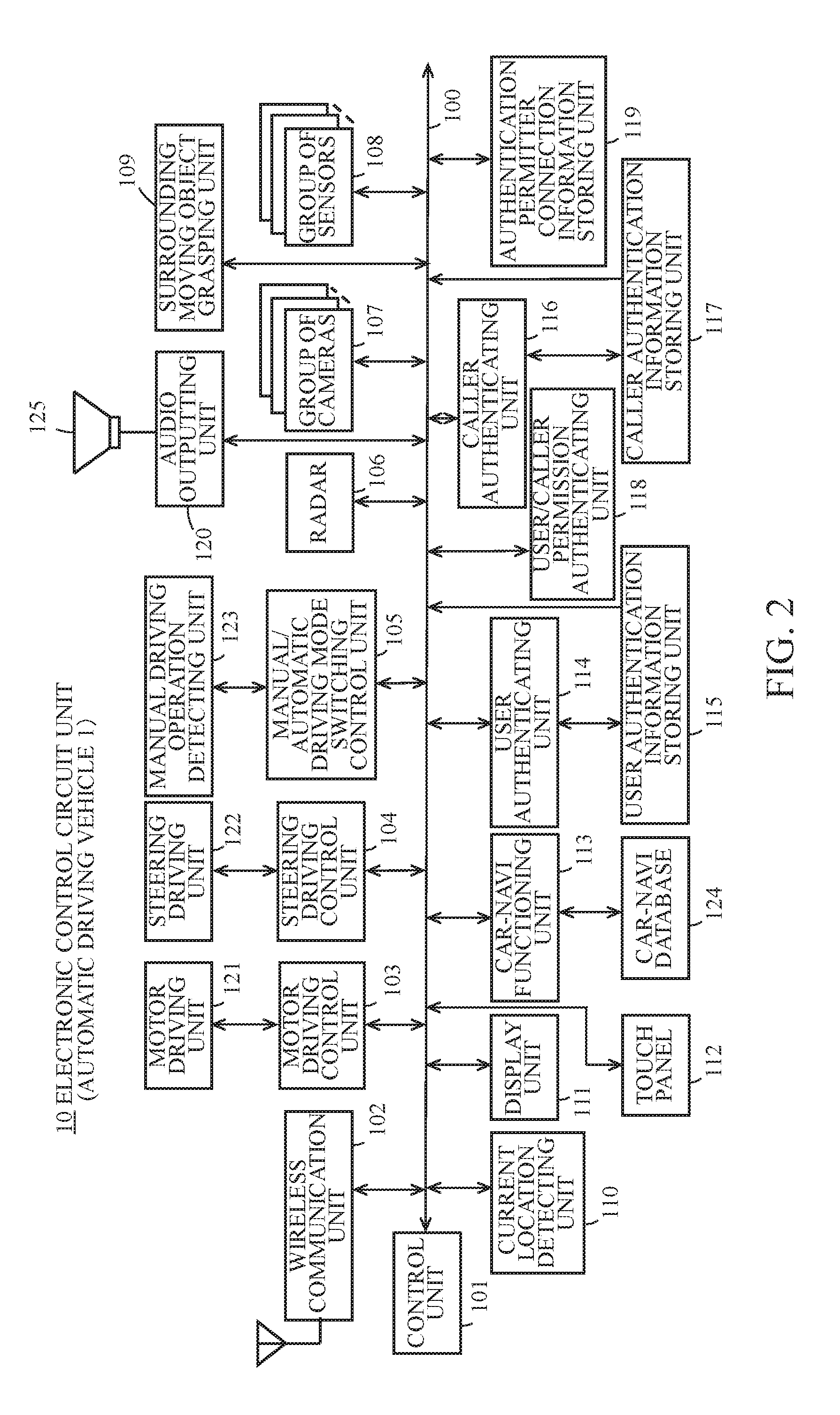
ActiveUS20170008490A1Prevent illegal useAutonomous decision making processAnti-theft devicesEmbedded systemTelecommunications equipment
A vehicle that even a person whose information for authentication is not registered can use includes: a first storing means for storing information for authentication of a passenger; a first authenticating means for carrying out authentication for a user who tries to use own vehicle using the information for authentication stored in the first storing means; a communicating means for carrying out communication with a destination; a second storing means for storing information for communication with a registered destination through the communicating means; a second authenticating means for carrying out authentication for the user by connecting to the registered destination using the information stored in the second storing means by means of the communicating means; and a determining means for determining whether the user is allowed to use the own vehicle in accordance with an authentication result of the first authenticating means and / or the second authenticating means.
Owner:MICO LATTA
Government affair data storage and query method and system based on block chain double-chain structure
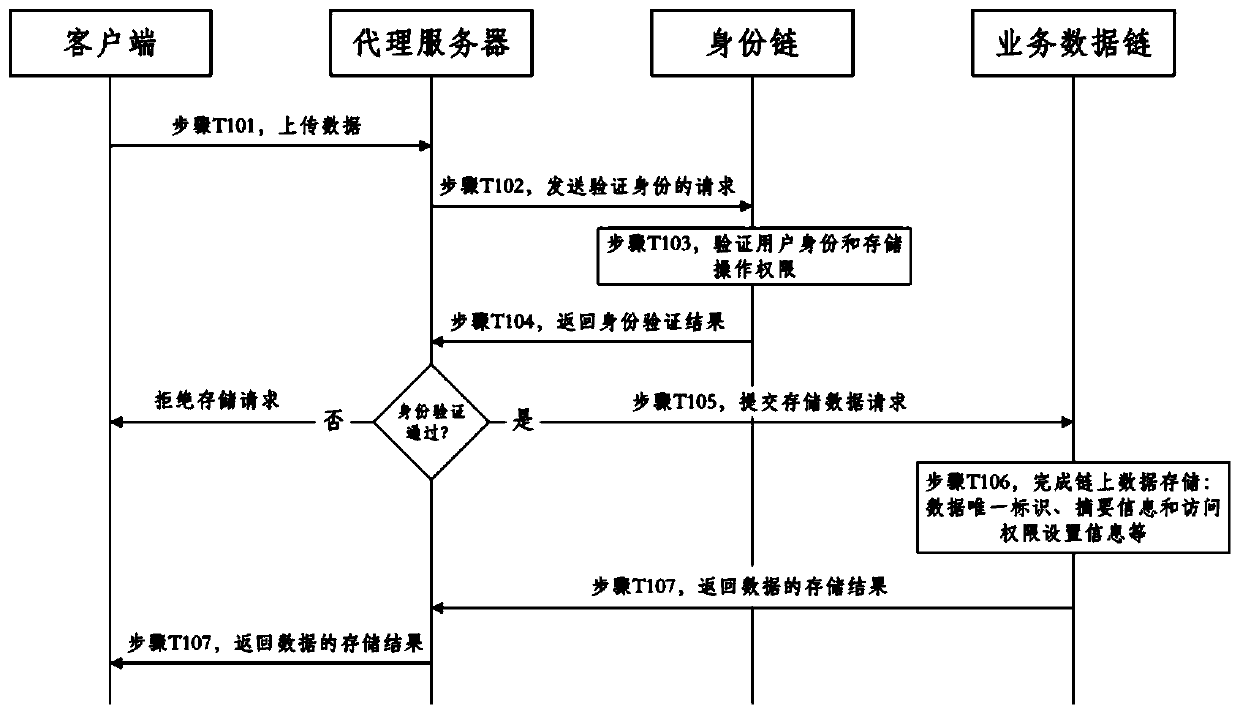
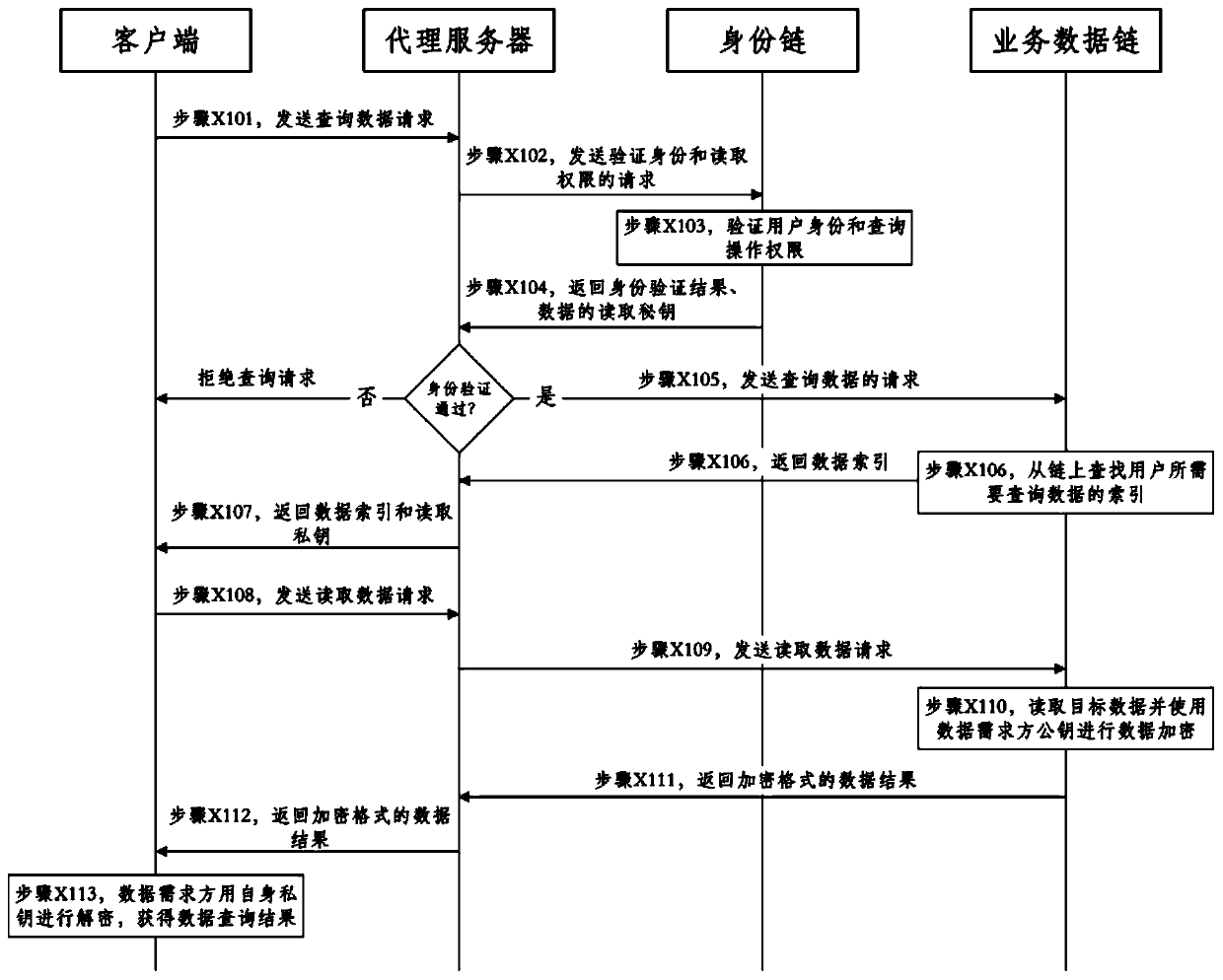
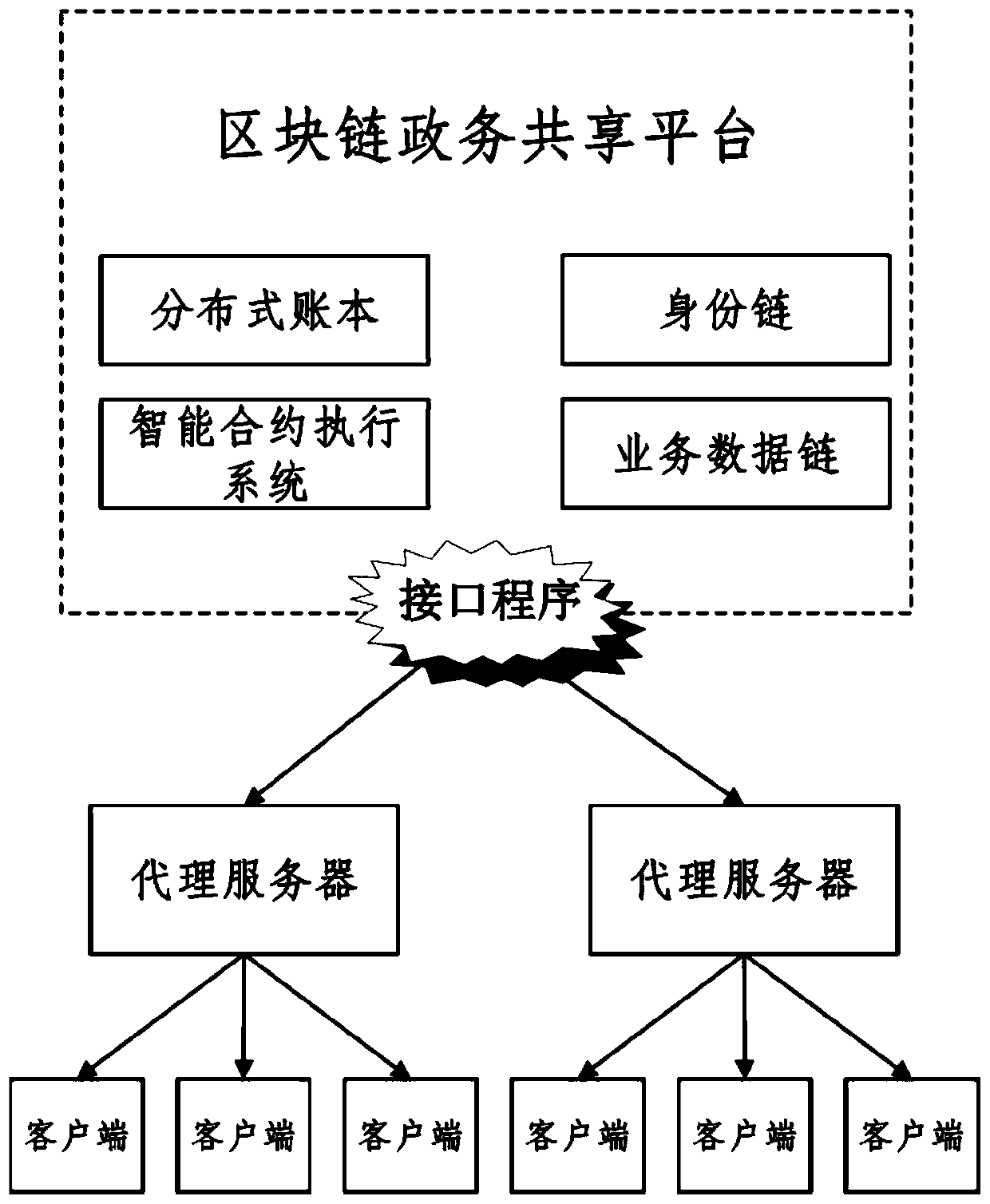
ActiveCN110109930AEnsure safetyGuaranteed controllableData processing applicationsDigital data protectionStructure of Management InformationClient-side
The invention provides a government affair data storage and query method and system based on a block chain double-chain structure. The government affair data storage method based on the block chain double-chain structure comprises the steps that a client uploads the data to a proxy server; the proxy server sends a data storage request to the identity chain and verifies the user identity and the data storage request; the identity chain verifies the identity of the user who makes the request and the storage operation authority, and returns a verification result to the proxy server; if the verification does not pass, the proxy server sends a data storage rejection request to the client; if the verification passes, the proxy server submits a data storage request to a service data chain, and the service data chain completes a consensus process according to the data storage request of the client and stores the data related information in a block chain system state database; and the service data chain feeds back a storage result to the client through the proxy server.
Owner:SHANDONG COMP SCI CENTNAT SUPERCOMP CENT IN JINAN
Personal data collection systems and methods
InactiveUS20100056876A1Prevent illegal useAvoid interferencePhysical therapies and activitiesMechanical/radiation/invasive therapiesGeneral purposeUser input
We have disclosed a modular personal network (MPN) that includes multiple devices that may be worn, carried, or used in close proximity to a user. The devices communicate wirelessly. Functions of the MPN may be modified by adding or removing components. The MPN may communicate with a personal computer. General purpose devices may include a control unit, a display, a user input, and an audio output. The MPN may provide a variety of functions, including time, communication, entertainment, organization, guidance, athletic, medical, travel, outdoors, identity, security, and military.
Owner:ADIDAS
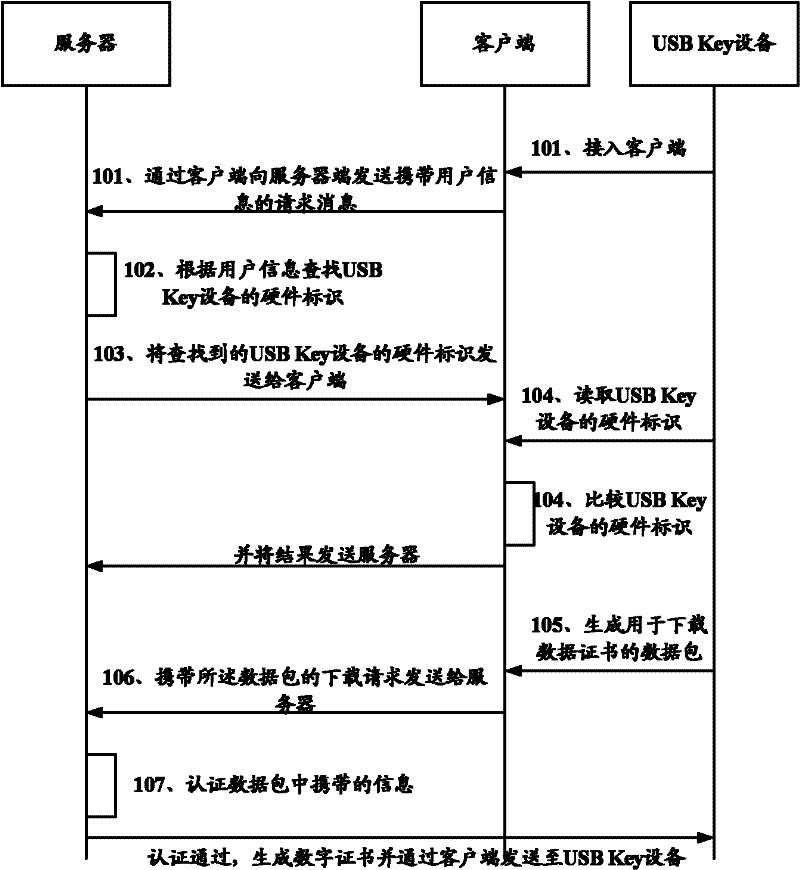
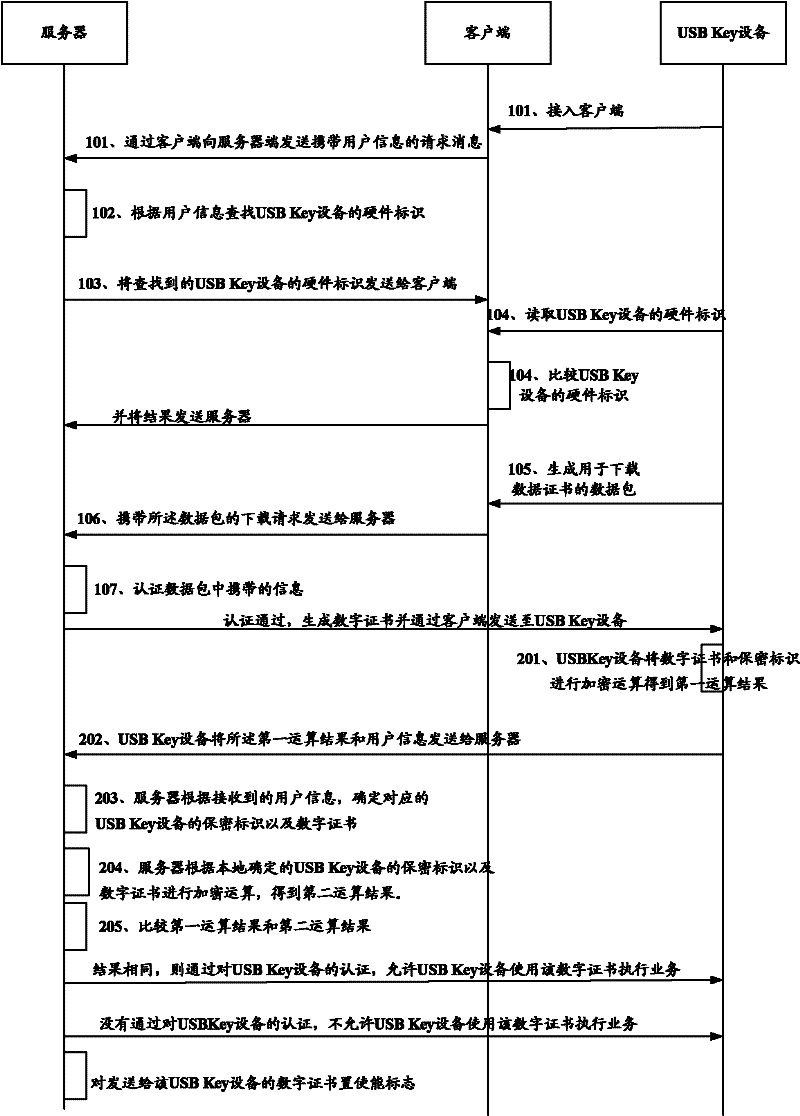
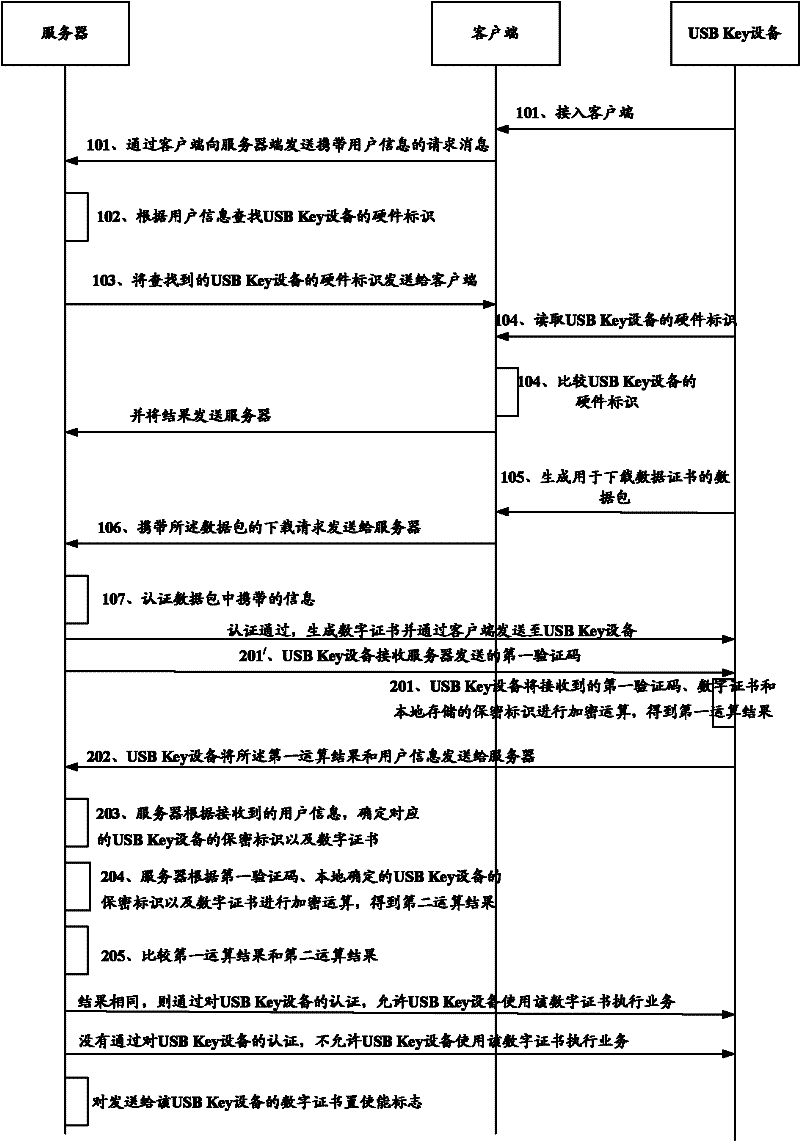
Digital certificate authentication method, system, usb Key device and server
ActiveCN102271042APrevent illegal useImprove business securityUser identity/authority verificationClient-sideUSB
The invention discloses a certificate authorization method, a certificate authorization system, universal serial bus (USB) Key equipment and a server. A secure storage area in the USB Key equipment additionally stores a security identifier with uniqueness, correspondence between a hardware identifier of the USB Key equipment and the security identifier is established in the server, an operationalresult of an encryption operation performed by utilizing the security identifier and a received digital certificate is transmitted to the server, and the server authenticates the received operationalresult by utilizing a locally stored security identifier and allows the USB Key equipment to use the received digital certificate only when the received operational result passes the authentication. A client cannot read information in the secure storage area in the USB Key equipment, so illegal USB Key equipment cannot pass the authentication of the server even after acquiring the digital certificate to avoid the illegal usage of the digital certificate and improve the service security of a legal user.
Owner:NSFOCUS INFORMATION TECHNOLOGY CO LTD +1
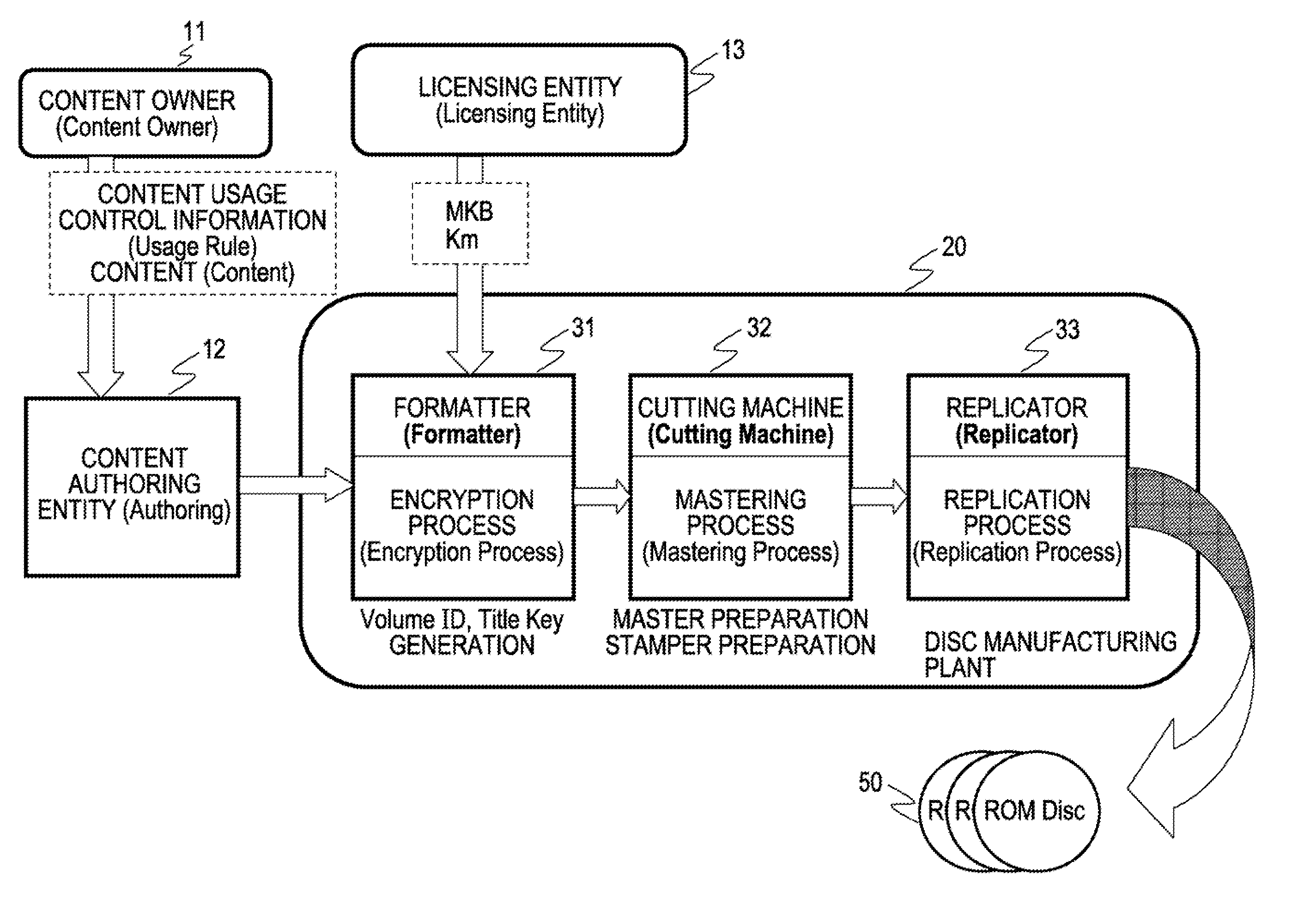
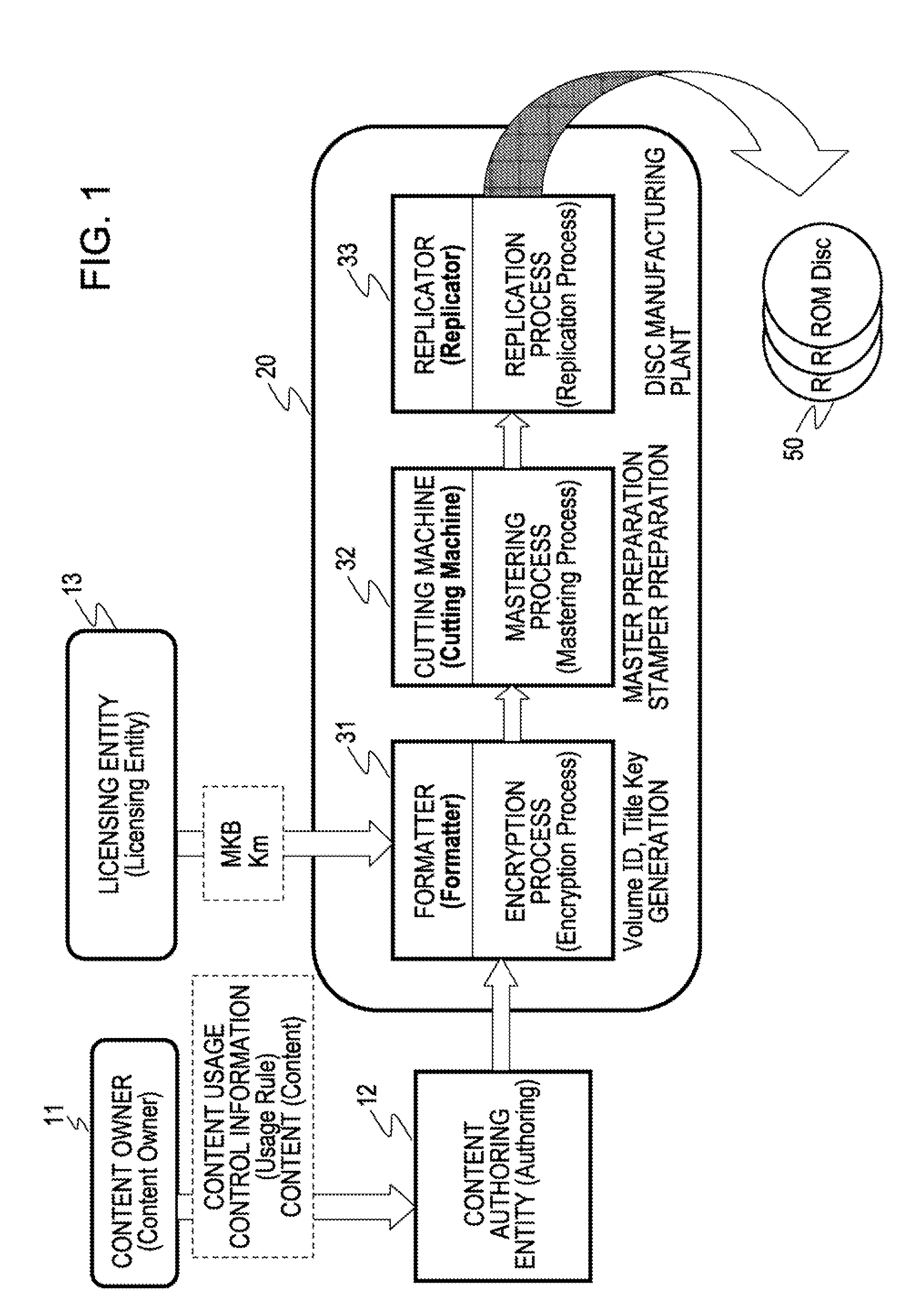
Disc manufacturing method, data recording apparatus, information recording medium, information processing apparatus and method, and computer program
InactiveUS20090238362A1Prevent illegal usePrevent unauthorized reproduction and useDigital data processing detailsRecord information storageInformation processingPublic key certificate
A product mark including a public key certificate issued with respect to an information-recording-medium manufacturing entity or information-recording-medium manufacturing equipment, and an encrypted volume ID calculated by computation based on a product-mark-associated value such as a hash value generated on the basis of the product mark, and a volume ID as an identifier set with respect to a given set of discs to be manufactured, are generated. The product mark and the encrypted volume ID are set as information for generating a key used for decryption of encrypted content, and recorded onto a disc by a reflective-film-removal recording method. Due to this configuration, the product mark and the encrypted volume ID as key generating information cannot be read from a pirated disc produced by physically copying a pit pattern on the basis of a legitimate commercial disc, thereby making it possible to prevent unauthorized reproduction or use of content.
Owner:SONY CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com