Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
271 results about "Revocation list" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
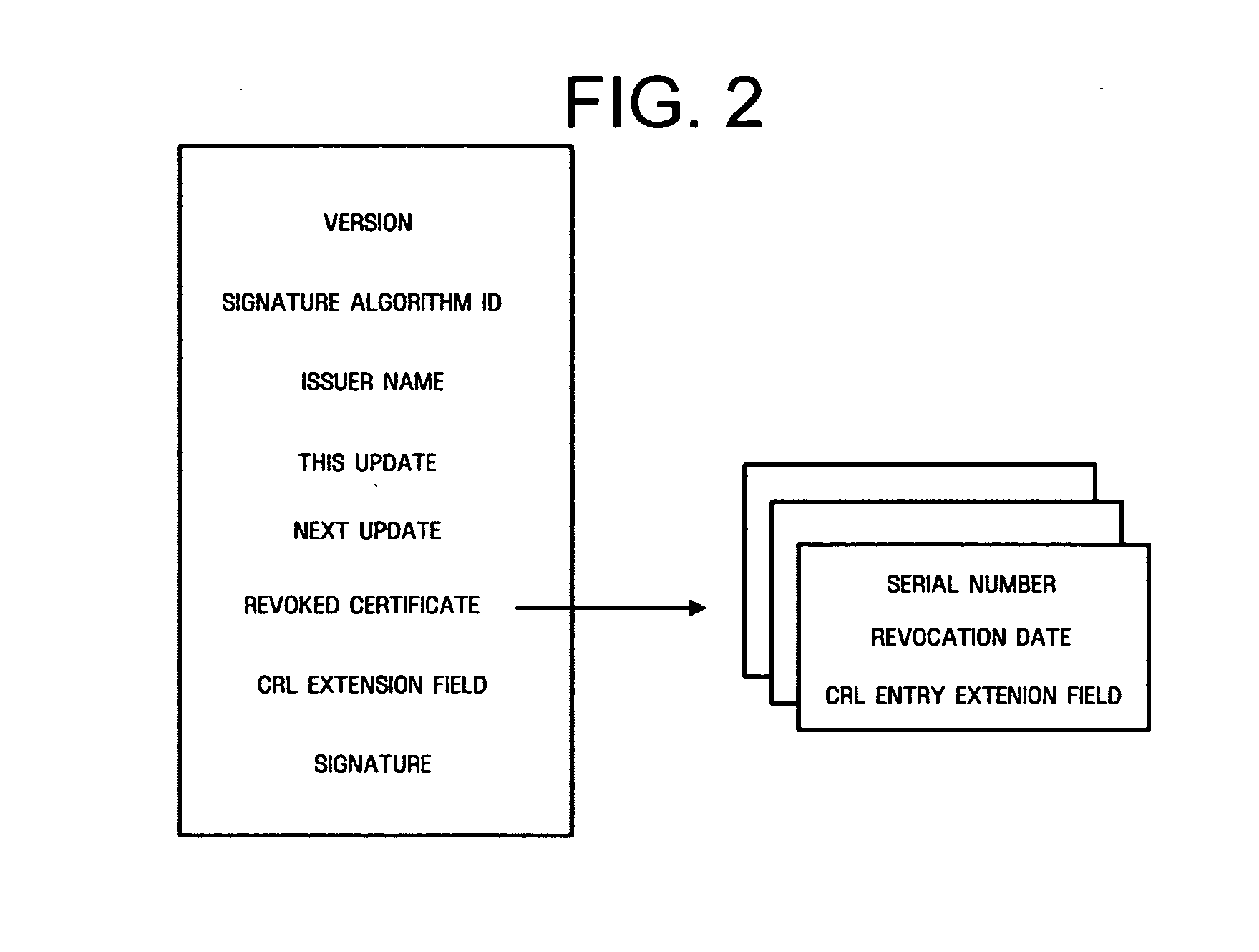
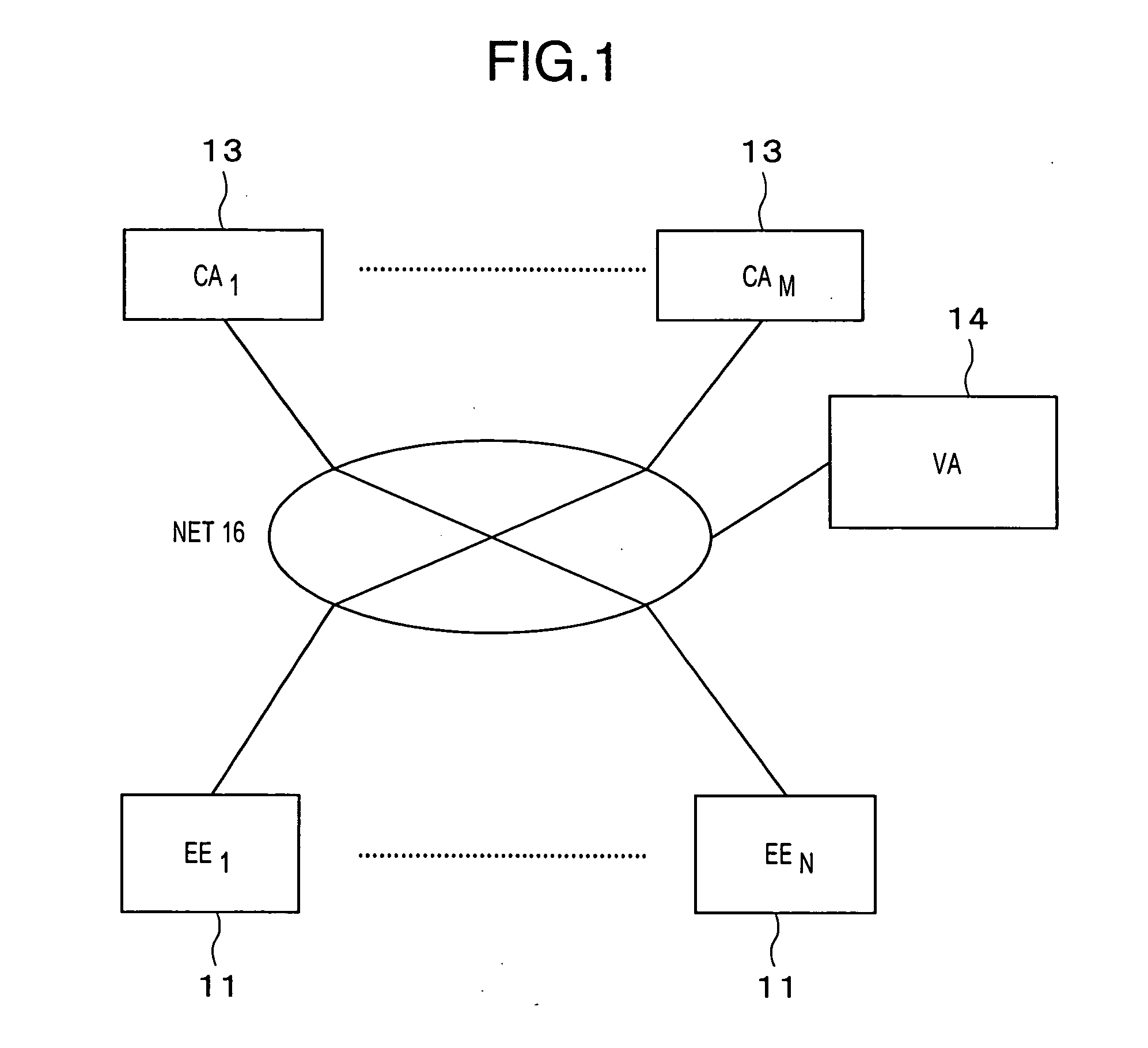
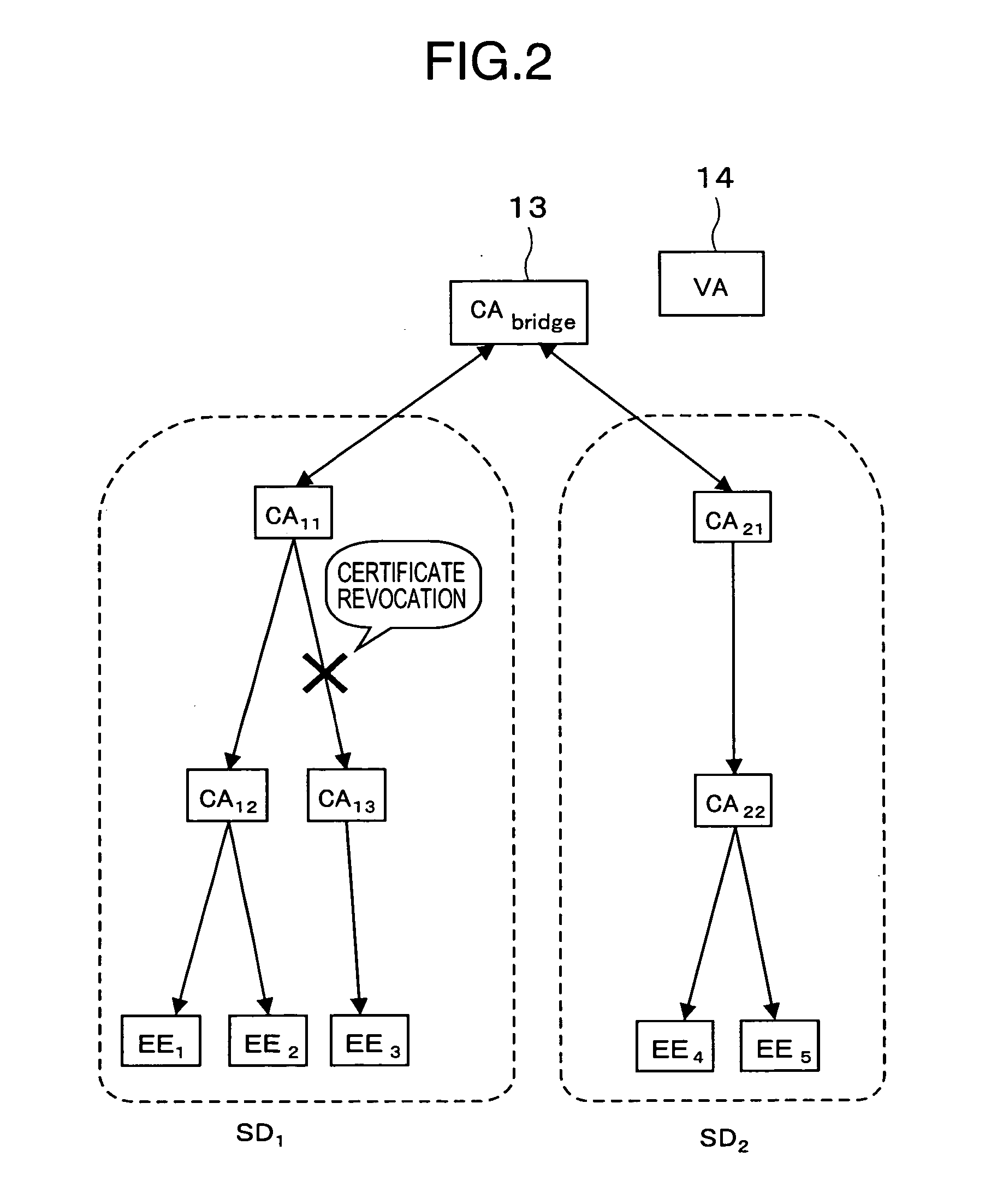
In cryptography, a certificate revocation list (or CRL) is "a list of digital certificates that have been revoked by the issuing certificate authority (CA) before their scheduled expiration date and should no longer be trusted".
Tokenization revocation list
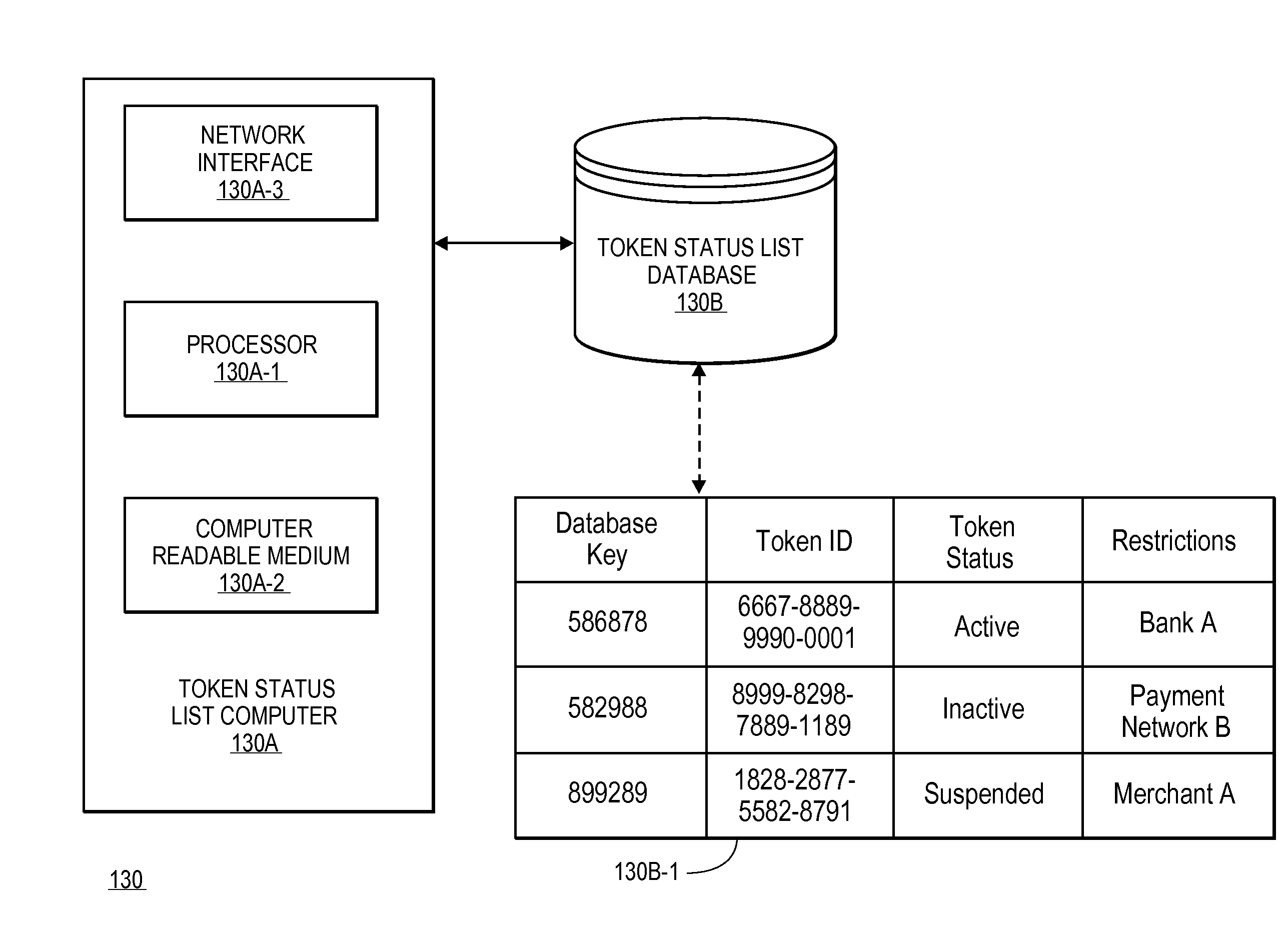
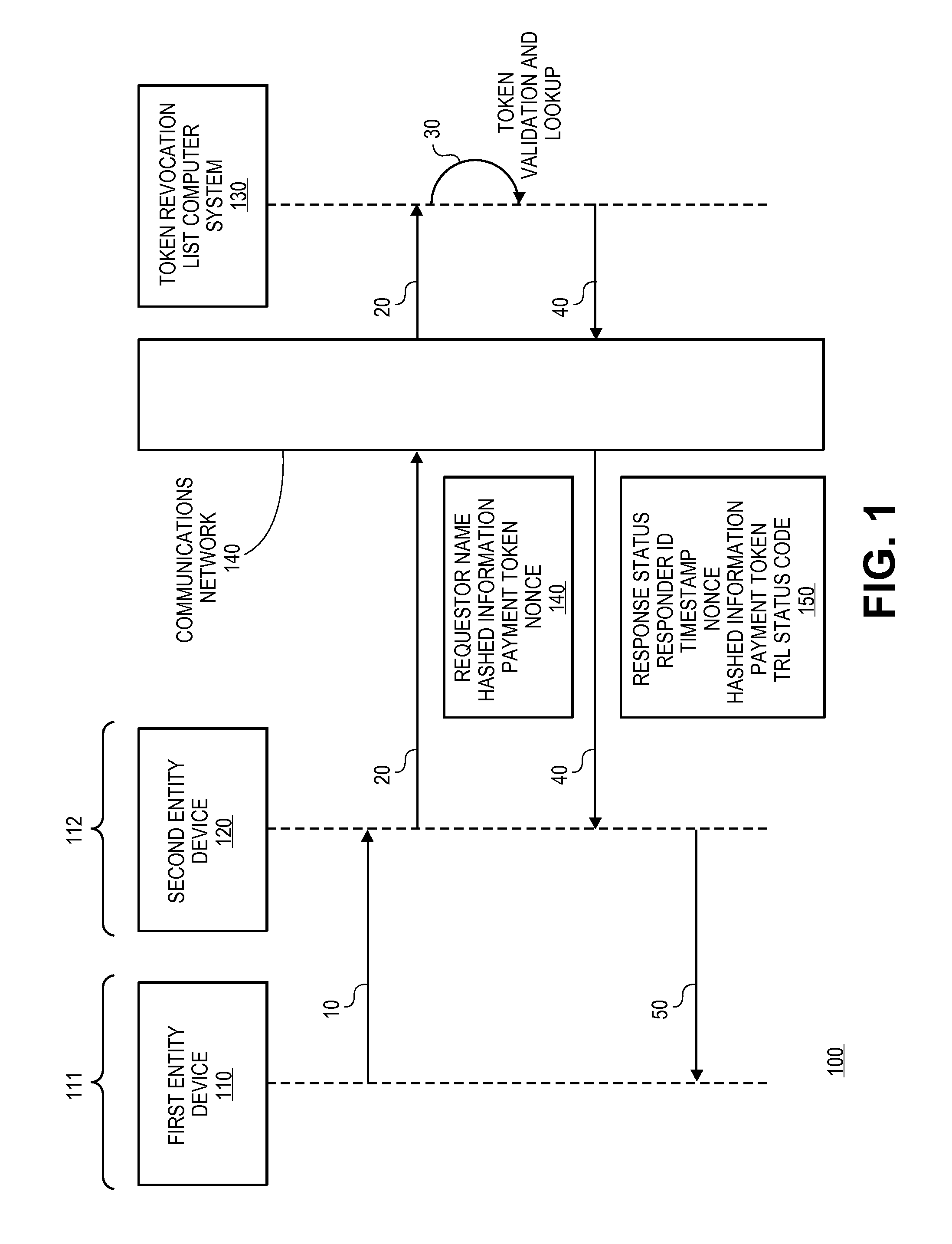
A method for providing a token revocation list is disclosed. The method includes maintaining a status for each of a plurality of tokens in a token revocation database. Token validation requests are received, and the statuses of payment tokens can be determined. Response messages with the statuses of the payment tokens are then sent to token status requesters so that they may make decisions on whether or not to use them to process transactions.
Owner:VISA INT SERVICE ASSOC
Method and system for managing network identity
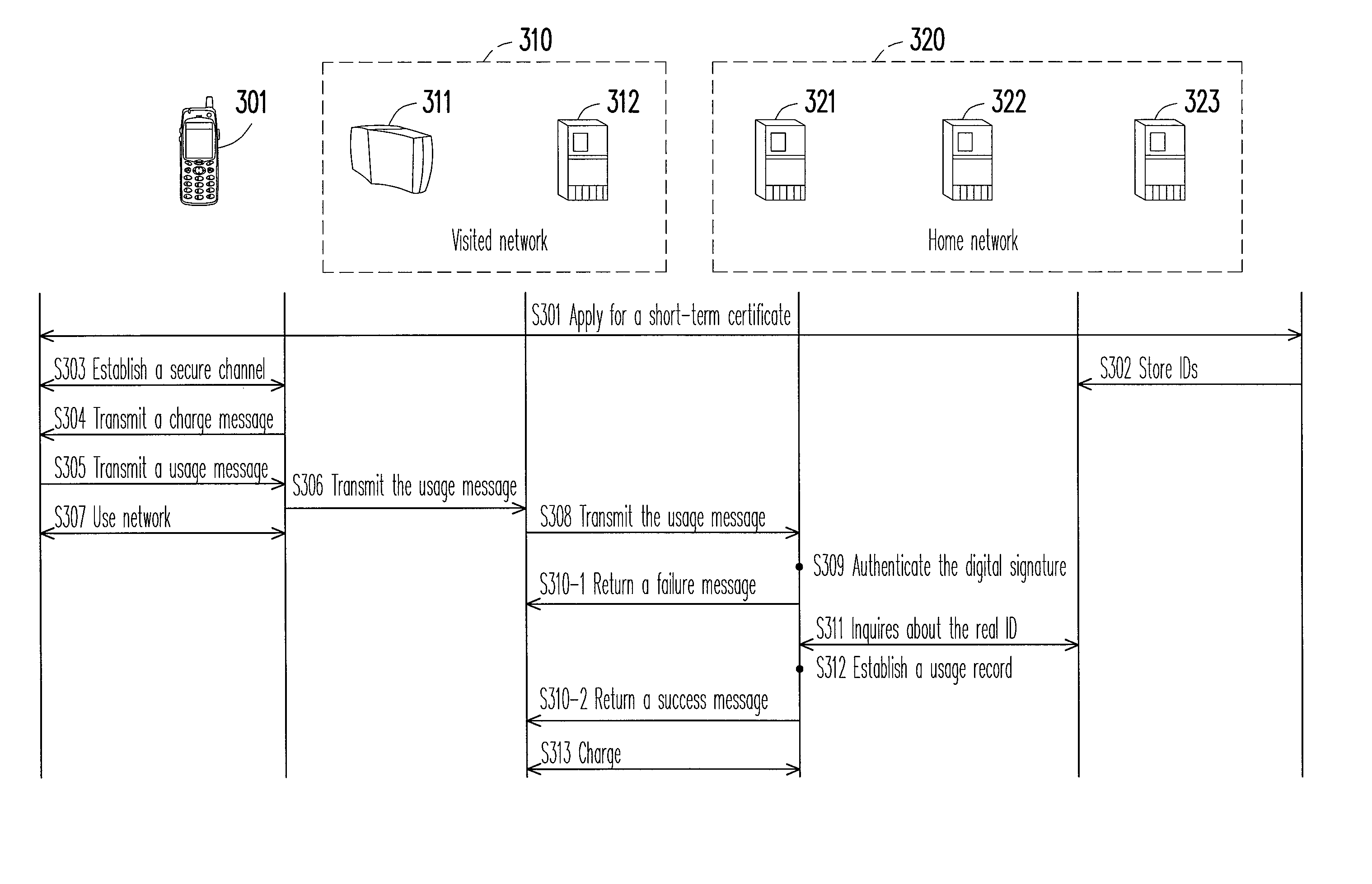
A method and a system for managing network identity are provided. The method and the system realize a management mechanism of temporary identification (ID) and real ID, which simultaneously achieves functionalities such as anonymity, accounting, and authorization. A short-term certificate and a corresponding public / private key pair are used to protect a temporary ID usable for accounting. This protection prevents the temporary ID from theft. The user generates a digital signature in the reply to a charge schedule statement from the visited network. This procedure is incorporated into an existing authentication framework based on Transport Layer Security (TLS) in order to provide an undeniable payment mechanism. The payment mechanism is applicable in an environment of multiple network operators and reduces the difficulty of integrating network operators. The method and the system do not have to consult a certificate revocation list (CRL) for authentication and thus are able to shorten authentication time.
Owner:IND TECH RES INST
Method for a public-key infrastructure for vehicular networks with limited number of infrastructure servers
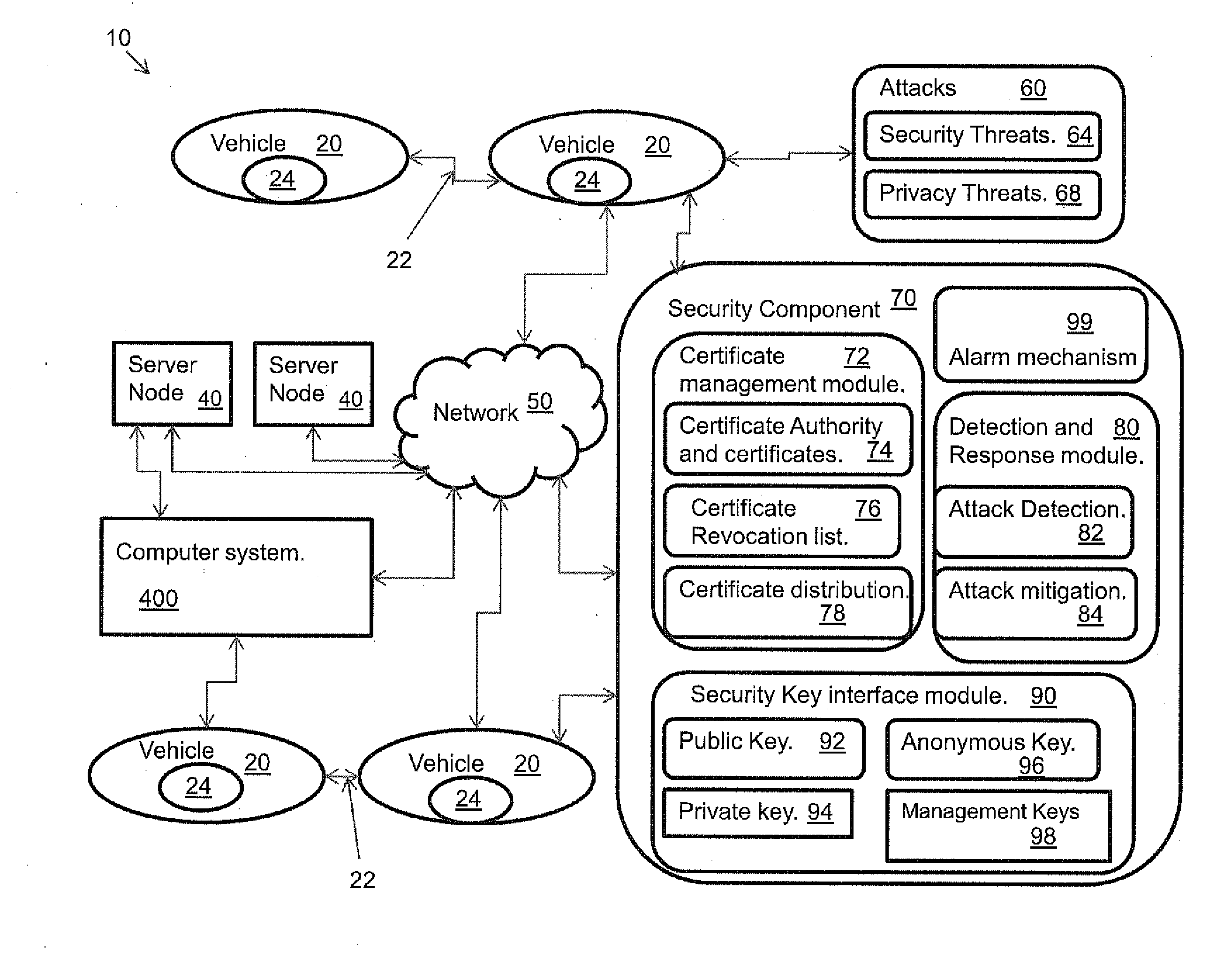
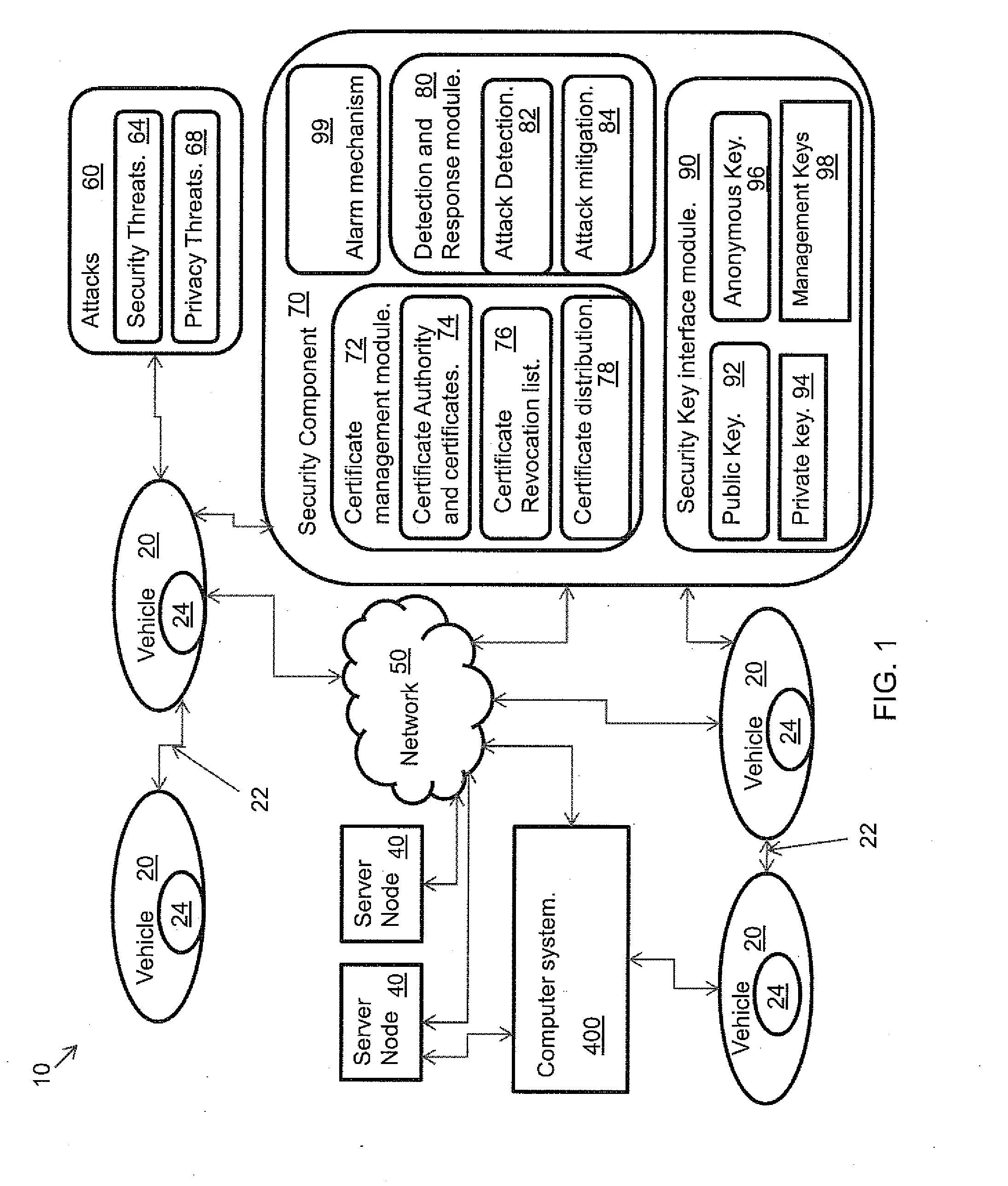
InactiveUS20110083011A1Provide securityCommunication securityDigital data processing detailsNetwork topologiesCommunications securitySecure communication
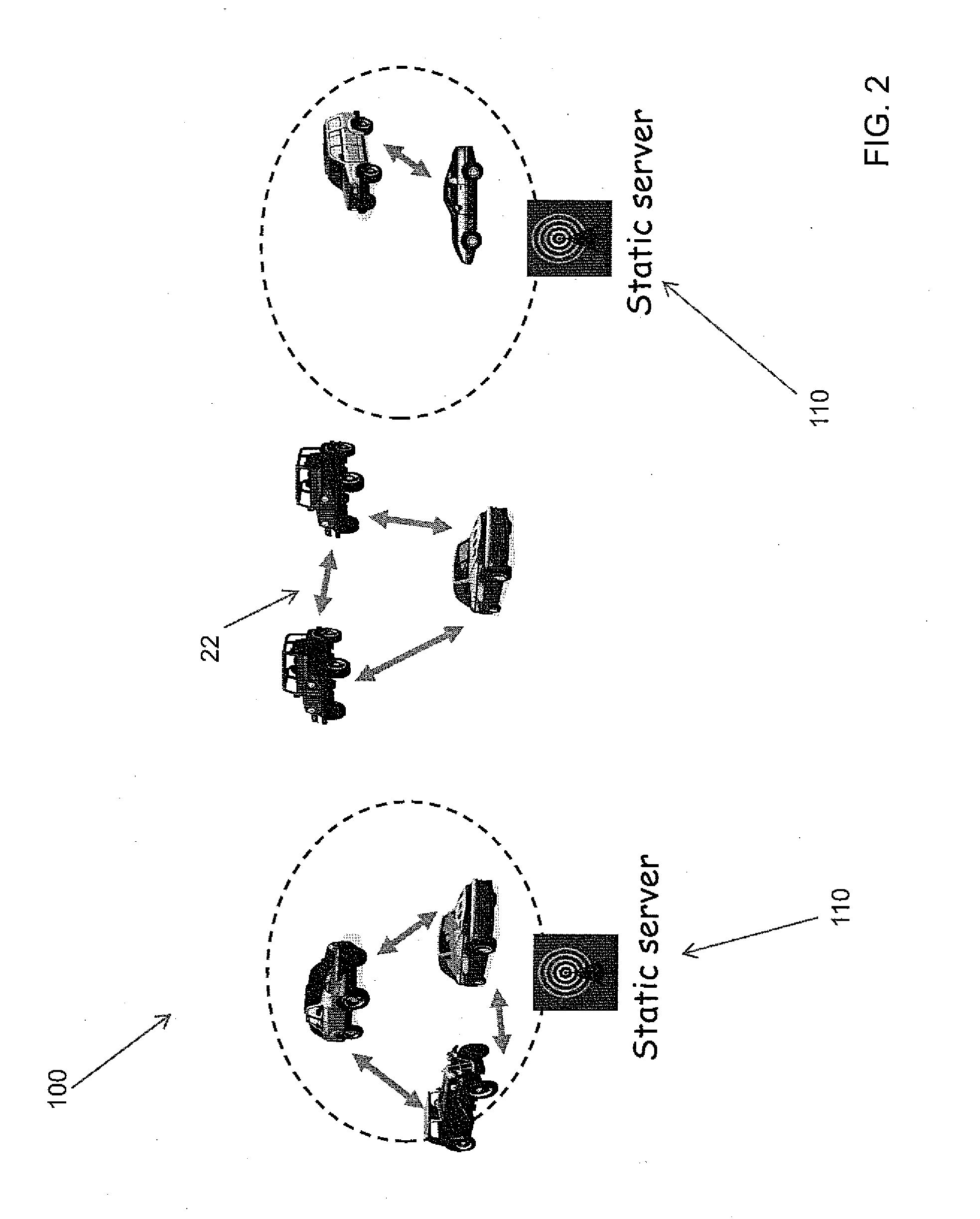
A system, and method related thereto, for providing a vehicular communications network public-key infrastructure. The system comprises a plurality of communications infrastructure nodes and a plurality of vehicles each having a communications component. The communications component provides vehicle to vehicle (V2V) communications, and communications via infrastructure nodes. A communications security component in each of the plurality of vehicles provides security for the communications between the plurality of vehicles using a plurality of security modules. The security modules include a certificate management module. A public key interface module may include a public key, a private key, an anonymous key and a management key. The system further includes a detection and response module for attack detection and attack mitigation. The communications security component assigns and installs at least one security key, a certificate of operation, and a current certificate revocation list. The communications component provides secure communications between the plurality of vehicles.
Owner:TELCORDIA TECHNOLOGIES INC
Method and apparatus for digital rights management using certificate revocation list
InactiveUS20050210241A1User identity/authority verificationProgram/content distribution protectionDigital rights managementRevocation list
A digital rights management method includes a stage for a device to update a Certificate Revocation List of the device through a connection to a portable storage, a stage to access to the updated Certificate Revocation List so as to judge the effectiveness of a certificate of the portable storage, and a stage to maintain communication with the portable storage, if the judgment proves the effectiveness of the portable storage.
Owner:SAMSUNG ELECTRONICS CO LTD
Threat mitigation in a vehicle-to-vehicle communication network
Owner:GM GLOBAL TECH OPERATIONS LLC
Certificate assignment strategies for efficient operation of the pki-based security architecture in a vehicular network
InactiveUS20090235071A1Small sizeReduce complexityTemperatue controlUser identity/authority verificationExpiration TimeCommunications system
A system and method for assigning certificates and reducing the size of the certificate revocation lists in a PKI based architecture for a vehicle wireless communications system that includes separating a country, or other area, into geographic regions and assigning region-specific certificates to the vehicles. Therefore, a vehicle need only process certificates and certificate revocation lists for the particular region that it is traveling in. Vehicles can be assigned multiple certificates corresponding to more than one region in the vehicles vicinity as advance preparation for possible travel or transmission into nearby regions. Further, the expiration time of certificates assigned to vehicles corresponding to a given geographic region can be tailored to be inversely proportional to the distance from a registered home region of the vehicle. A scalable design for a back-end certifying authority with region-based certificates can also be provided.
Owner:GM GLOBAL TECH OPERATIONS LLC
Public key infrastructure scalability certificate revocation status validation
InactiveUS20050228998A1Minimize network trafficReduce executionUser identity/authority verificationAuthentication serverCentral database
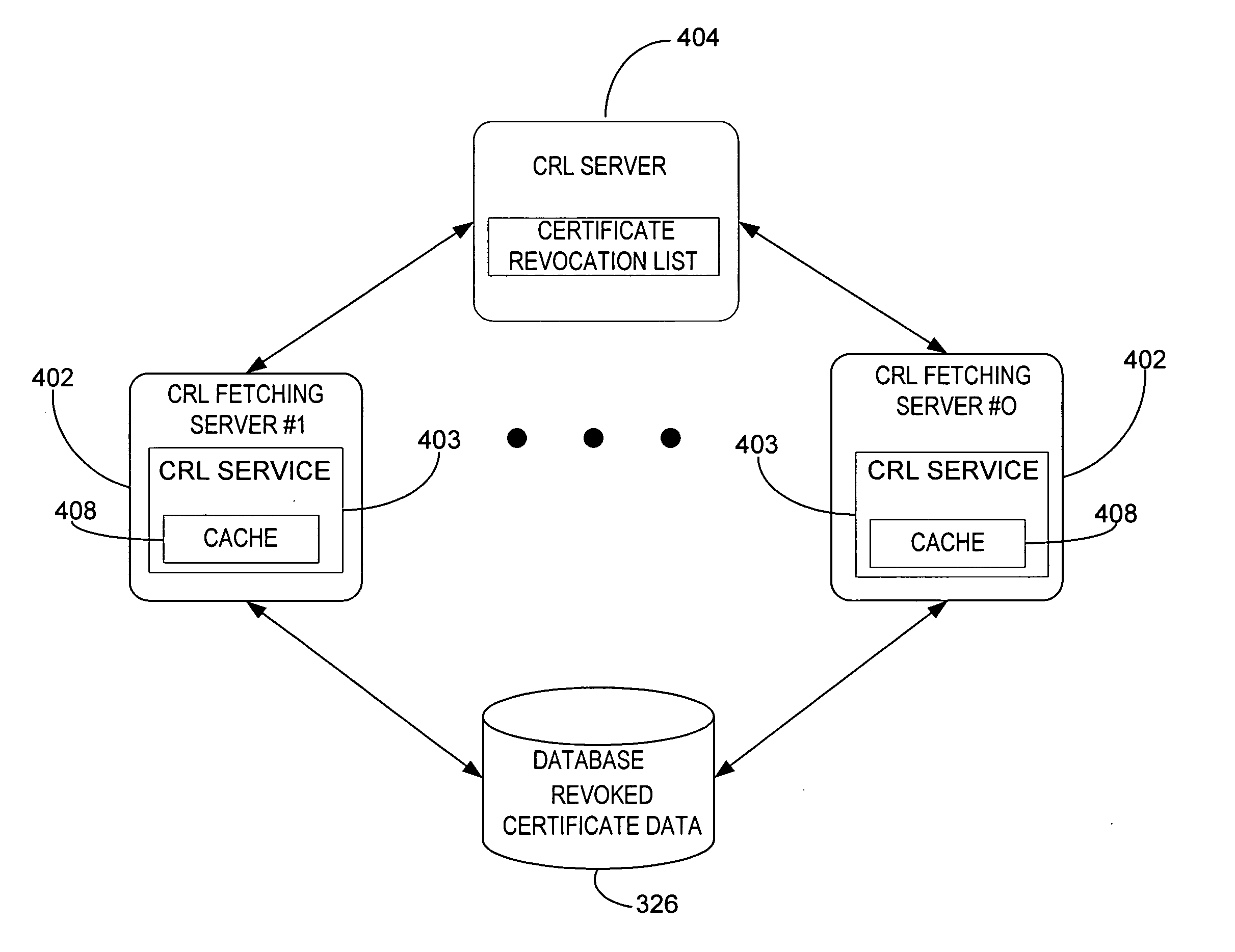
A system and method for retrieving certificate of trust information for a certificate validation process. Fetching servers periodically retrieve certificate revocation lists (CRLs) from servers maintained by various certificate issuers. The revoked certificate data included in the retrieved CRLs are stored in a central database. An authentication server receives a request from a client for access to a secure service and initiates a validation process. The authentication server retrieves revoked certificate data from the central database and compares the retrieved revoked certificate data to certificate of trust information received from the client along with the request. The authentication server denies access to the secure information if the certificate of trust information matches revoked certificate data from the central database, allows access if the certificate of trust information does not match revoked certificate data from the central database.
Owner:MICROSOFT TECH LICENSING LLC
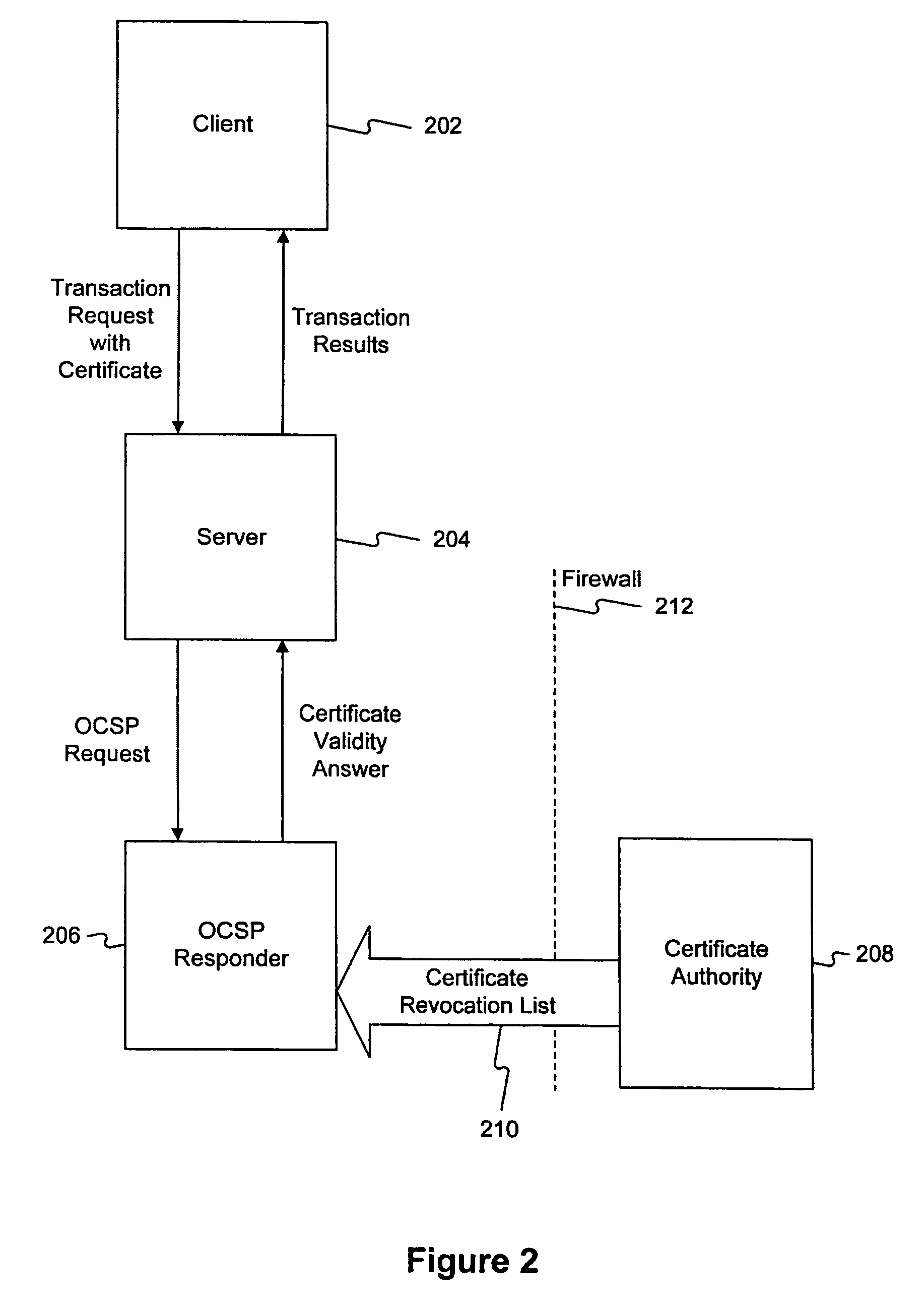
Method and system for answering online certificate status protocol (OCSP) requests without certificate revocation lists (CRL)
InactiveUS6970862B2Digital data protectionElectronic credentialsDirectory Access ProtocolClient-side
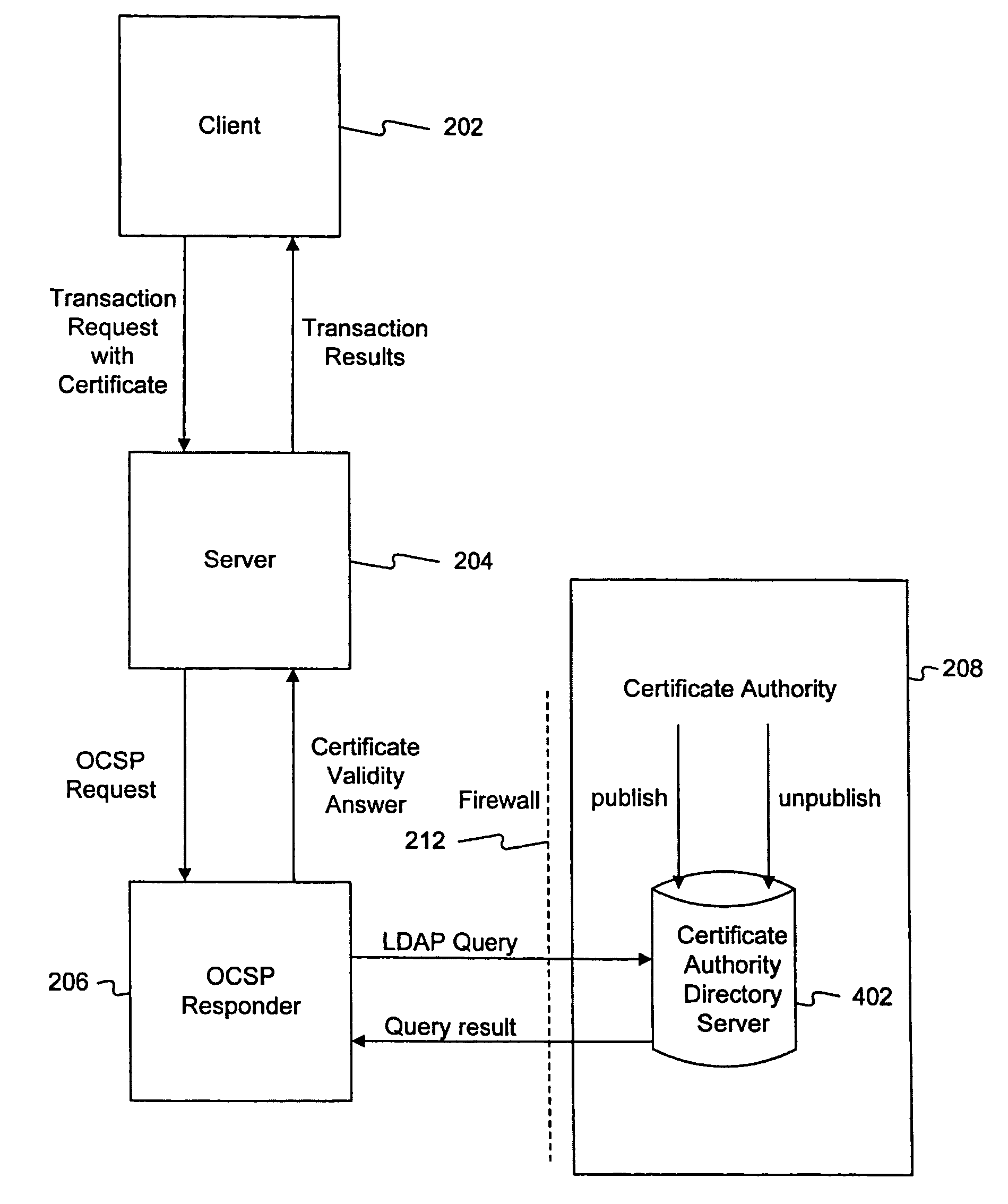
Methods and systems in accordance with the present invention efficiently validate digital certificates by answering Online Certificate Status Protocol (“OCSP”) requests without Certificate Revocation Lists (“CRL”). During validation of digital certificates, these methods and systems speed transmission, reduce required bandwidth and reduce required data storage by eliminating the need for the transmission of lengthy CRLs from a Certificate Authority (“CA”) when verifying a digital certificate from a client. In one implementation, they send a Lightweight Directory Access Protocol (“LDAP”) database query to a CA directory server to determine and pinpoint the existence of a valid digital certificate and check its validity without receiving a long list of data, such as a CRL, from a CA. The CA directory server returns the query result, and the database query in the CA directory server is performed faster than using an entire CRL, and furthermore, the transmission of the database query result is a small piece of information and does not require the large amounts of data transmission bandwidth and storage as required with transmitting CRL's.
Owner:ORACLE INT CORP
Processing system using internal digital signatures
InactiveUS20060015732A1User identity/authority verificationUnauthorized memory use protectionDigital signatureHandling system
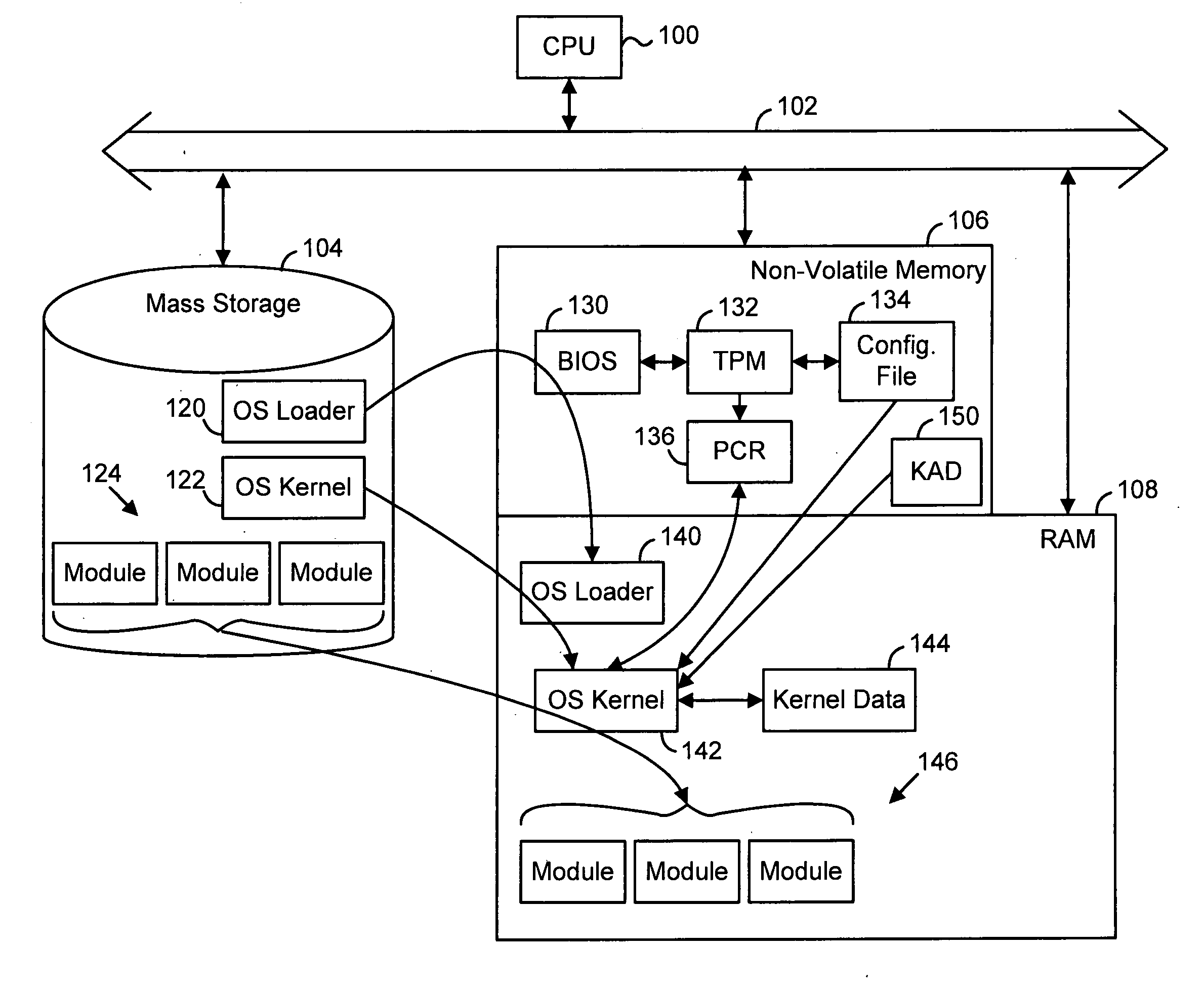
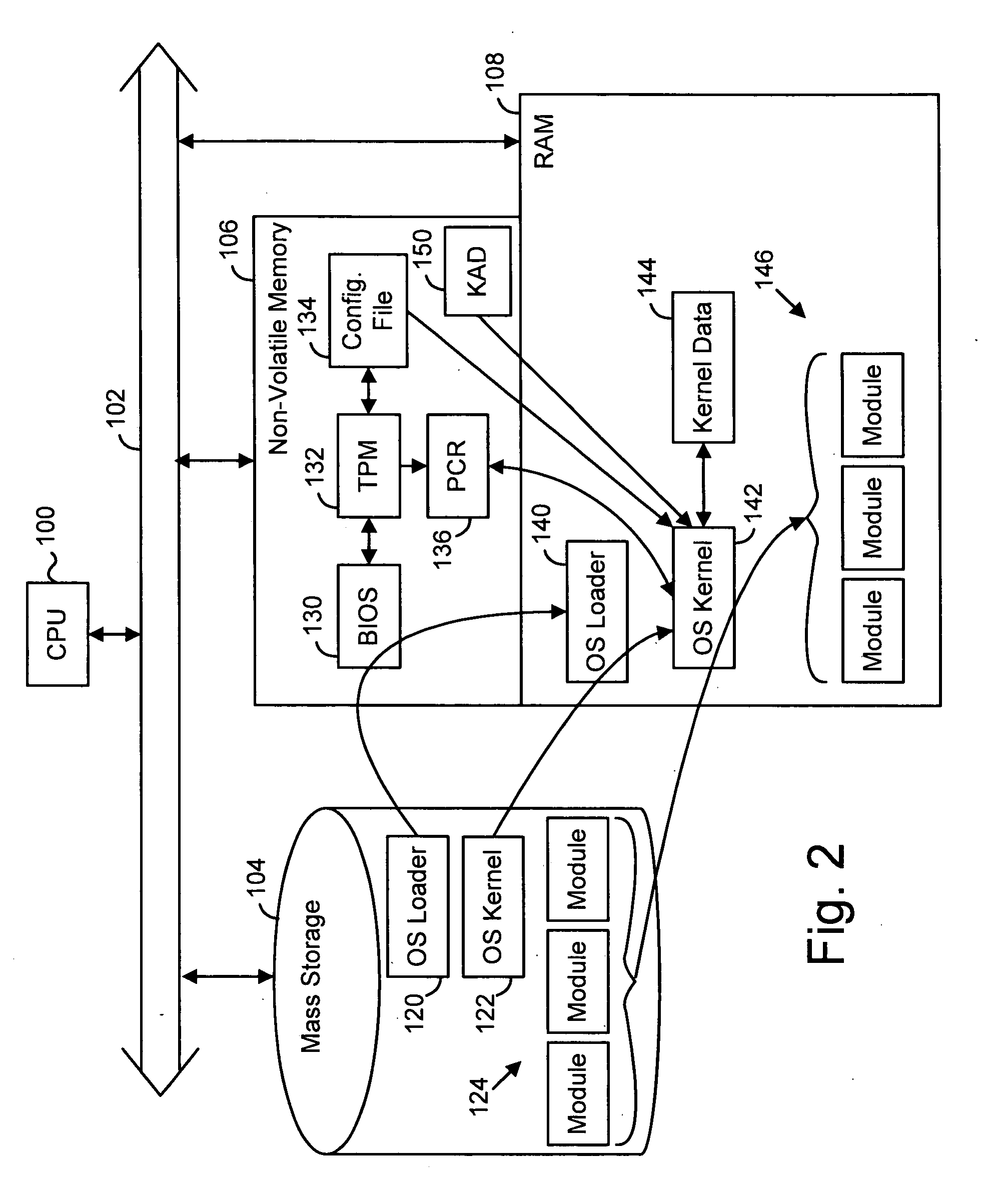
A preferred embodiment of the invention uses local or internal public and private keys for signatures. The keys are obtained and managed internally by a kernel process having access to a secure key storage area. The kernel process is booted within a trusted platform and is the only process that is allowed to access the key storage area. The internal keys can be used in addition to external keys for both internal key-based and external key-based signatures on a single digital item. In a preferred embodiment, the kernel process also maintains revocation lists and is synchronized with other entities by having the same criteria (e.g., time-based) for revoking or expiring known internal keys
Owner:SONY CORP +1
Storage medium and contents protection method using the storage medium
InactiveUS7137012B1Reduce usagePrevent illegal useDigital data processing detailsUnauthorized memory use protectionComputer hardwareRevocation list
A revocation list is registered a public ROM area. The revocation list designates at least one electronic device in which use of the storage medium by the designated electronic device is to be revoked. A controller receives from the electronic device which attempts to access, identification information indicative of the electronic device, and checks whether identification information corresponding to the received identification information is contained in the revocation list, thereby determining whether or not use of the storage medium by the electronic device which attempts to access should be revoked.
Owner:KK TOSHIBA +1
Method and system for use in managing vehicle digital certificates
InactiveUS20110191581A1Effectively enables vehicle certificate managementLevel of security and privacyTransmissionSecure communicationTransceiver
Owner:TELCORDIA TECHNOLOGIES INC
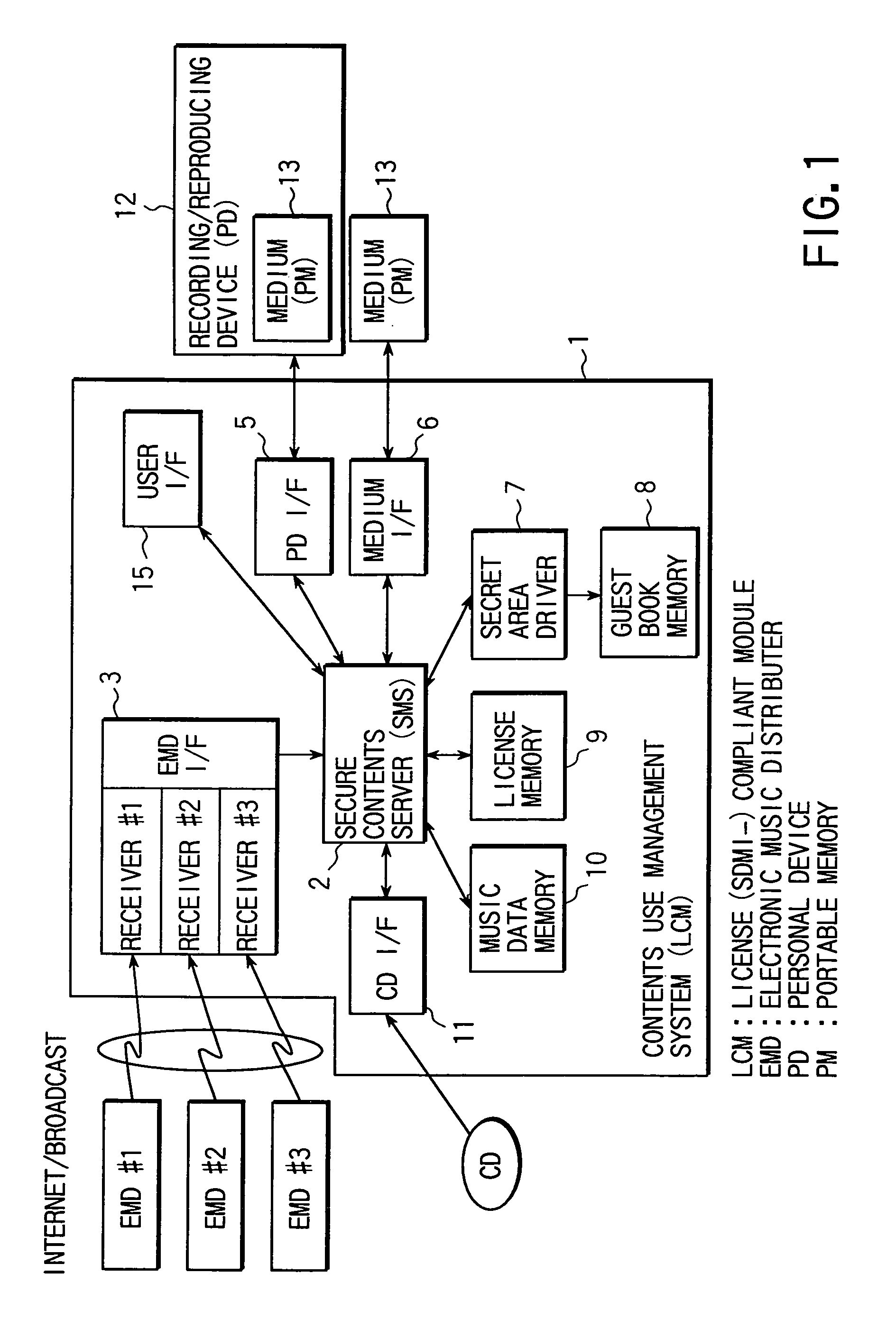
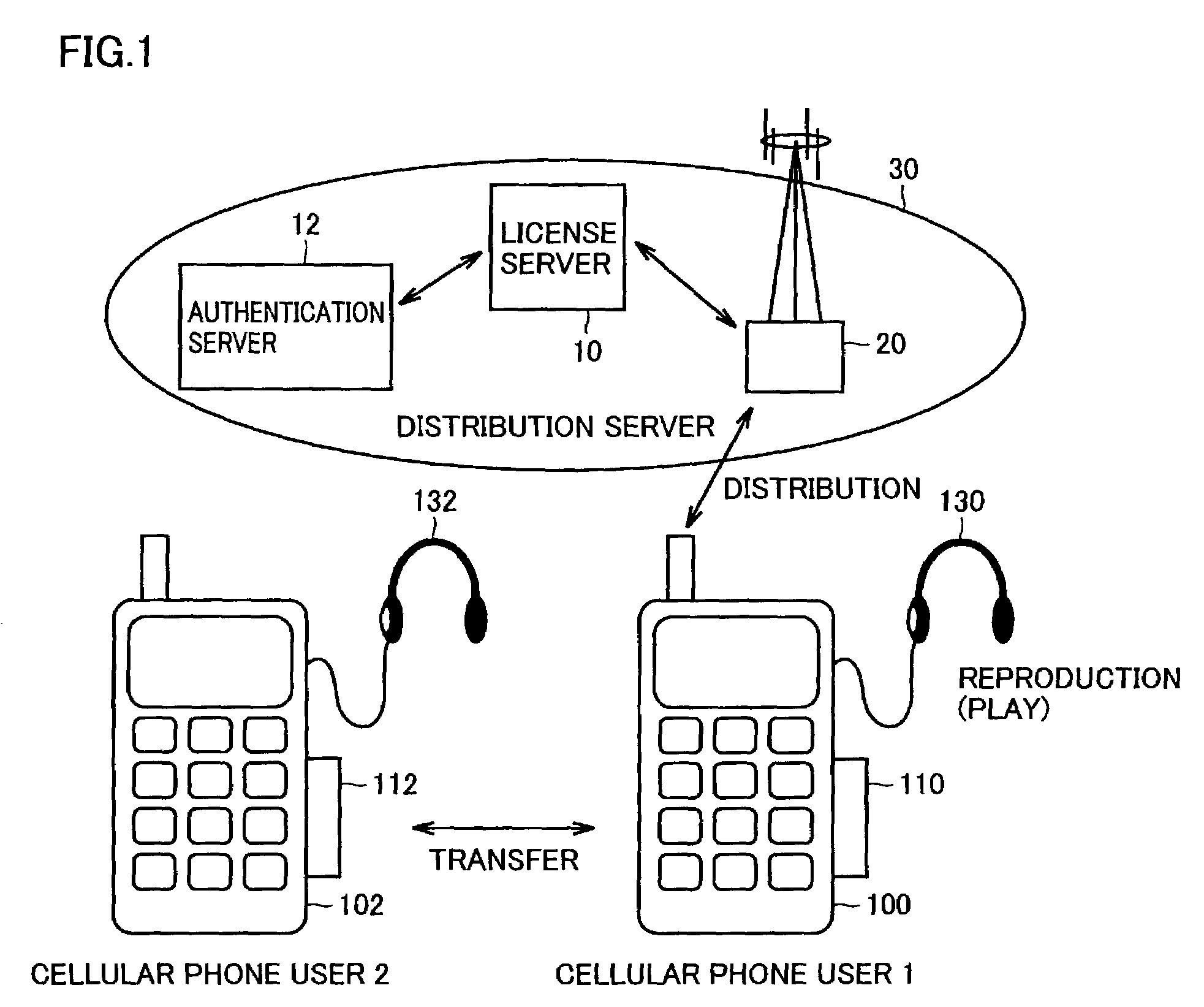
Data distribution system and recording device and data provision device used therefor
InactiveUS7219227B2Avoid dataCopyright protectionDigital data processing detailsUnauthorized memory use protectionDistribution controlDistribution system
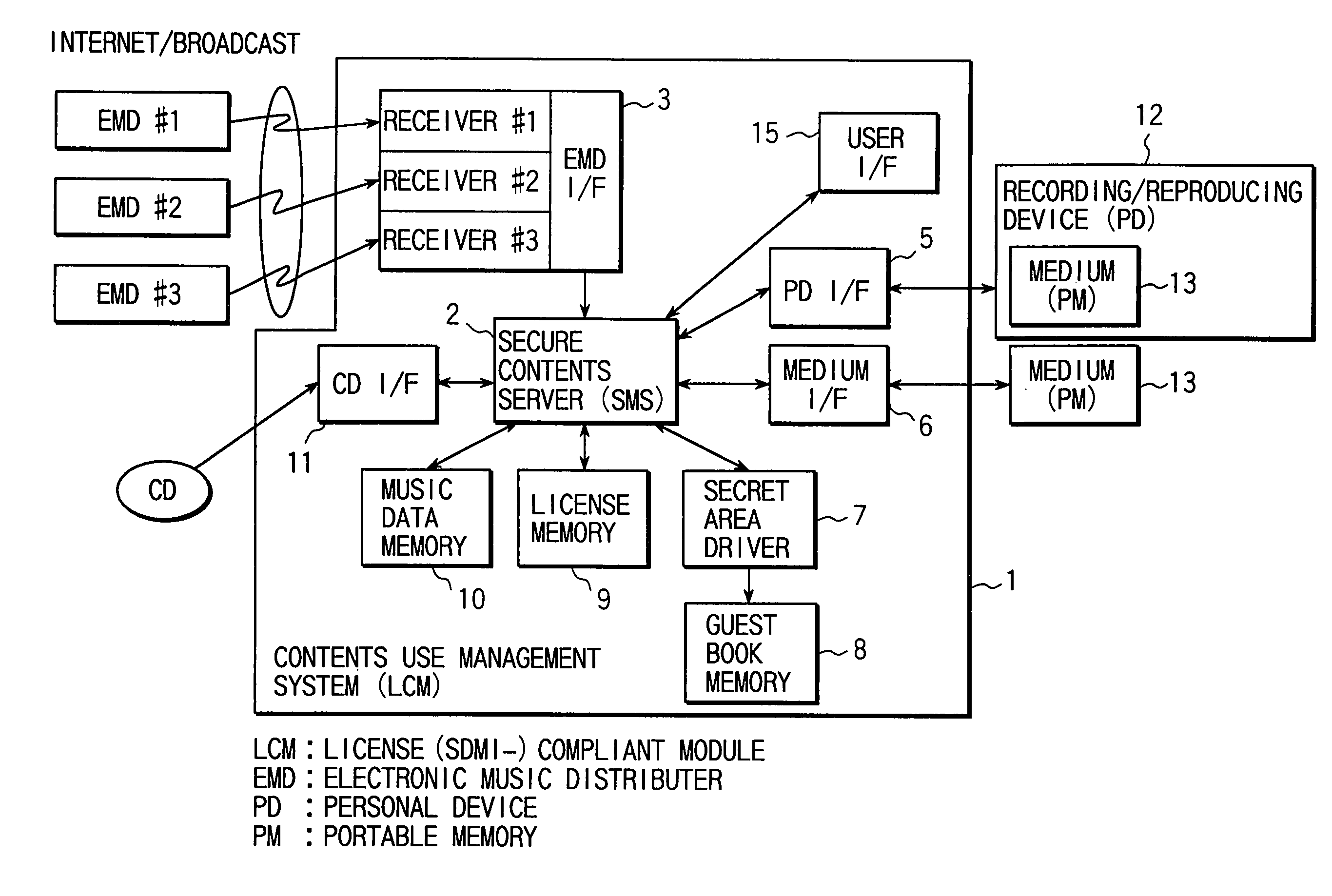
A license server (10) includes a CRL database (306) holding a revocation list recording therein classes predetermined corresponding respectively to a memory device, such as a memory card, and a content reproduction circuit, such as a cellular phone, that are subjected to revocation of distributing, reproducing and transferring content data. A distribution control unit (315) suspends an operation distributing content data if the distribution is addressed to a class listed on the revocation list. The revocation list is also held in the memory card and distribution control unit (315) in distributing content also transmits information for updating the revocation list in the memory card.
Owner:SANYO ELECTRIC CO LTD +2
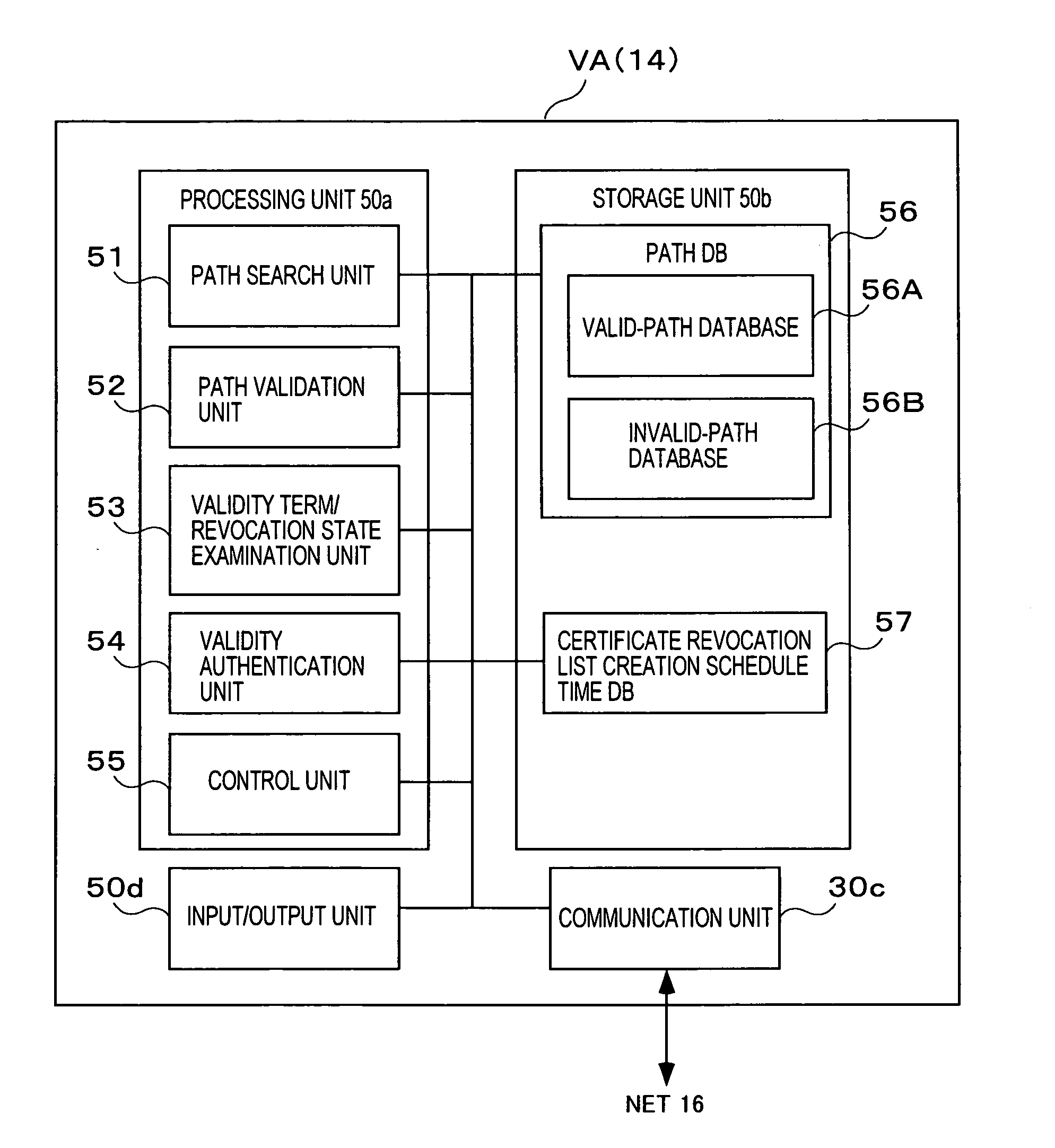
Method and apparatus for accelerating public-key certificate validation
InactiveUS20050081037A1Shorten the time periodKey distribution for secure communicationUser identity/authority verificationDatabaseRevocation list
A validation authority for certificates searches for and verifies paths and certificate revocation lists periodically, and classifies the paths into valid paths and invalid paths in accordance with the results of the validations, so as to register the paths in databases beforehand. Besides, in a case where a request for authenticating the validity of a certificate has been received from an end entity, the validation authority judges the validity of the public key certificate by checking in which of the valid-path database and the invalid-path database a path corresponding to the request is registered. On the other hand, in a case where the path corresponding to the validity authentication request is not registered in either of the databases, the validity of the public key certificate is authenticated by performing path search and validation anew.
Owner:HITACHI LTD
Mobile certificate distribution in a PKI
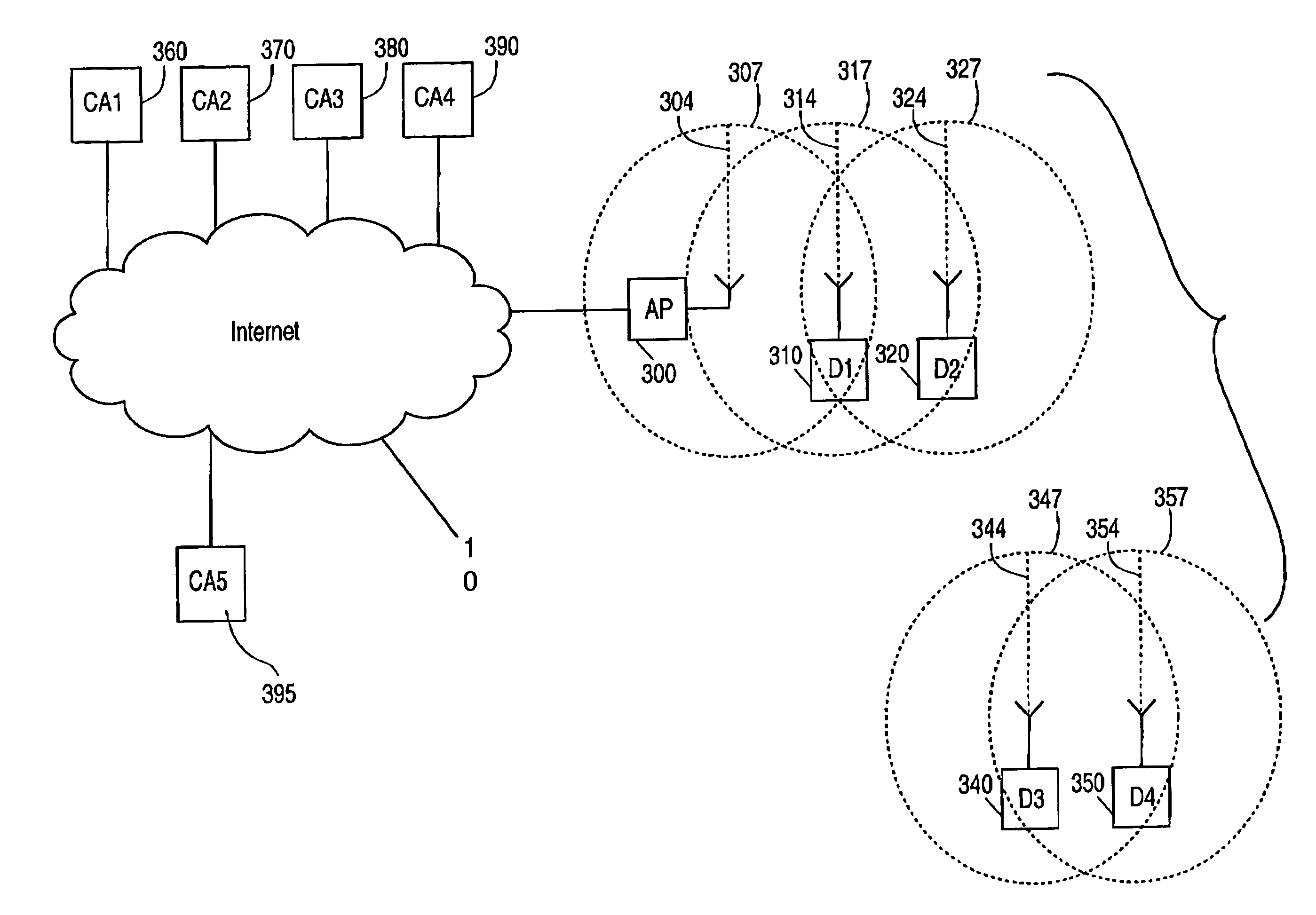
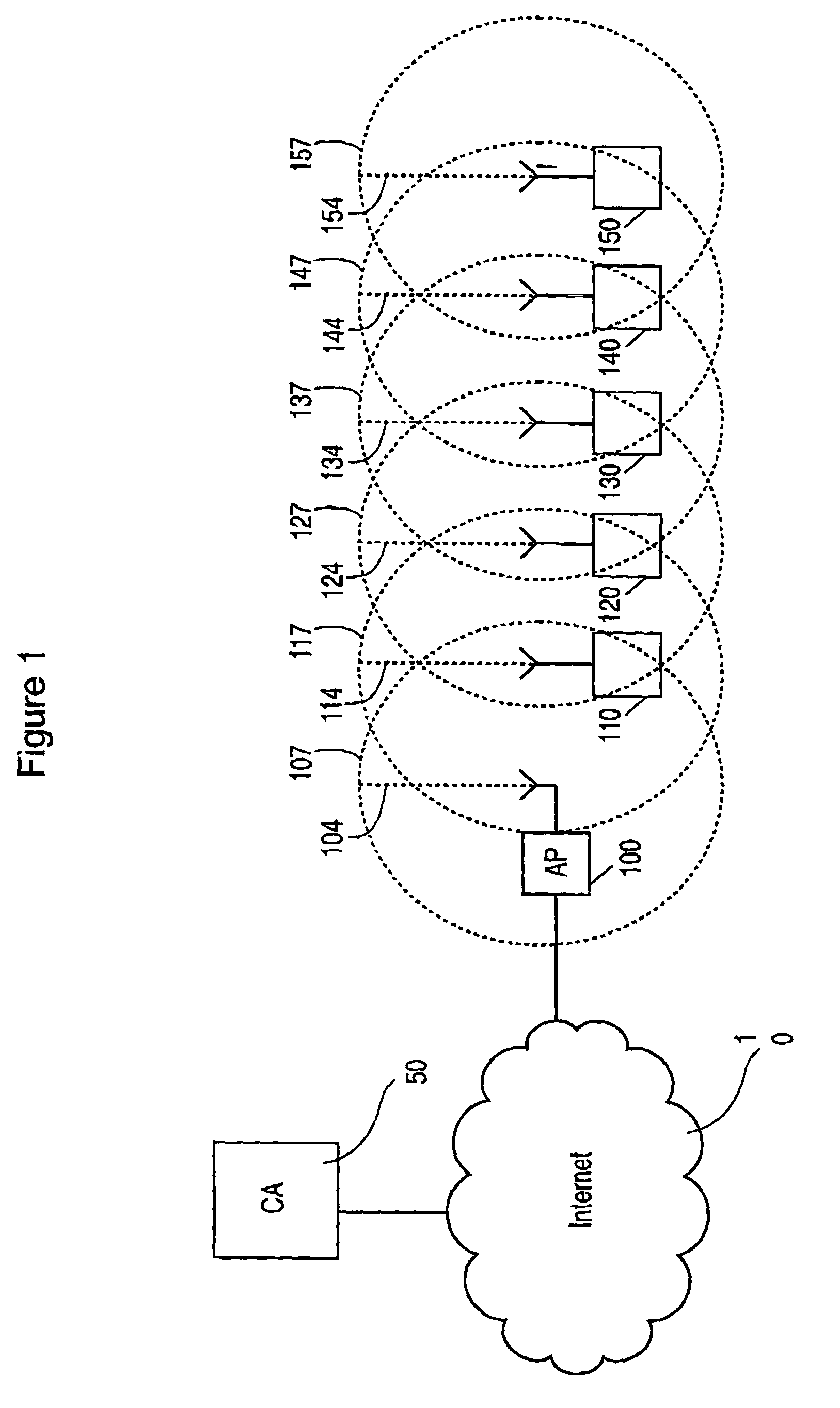
ActiveUS20050191990A1Unauthorised/fraudulent call preventionEavesdropping prevention circuitsThe InternetBluetooth
A method of providing certificate issuance and revocation checks involving mobile devices in a mobile ad hoc network (MANET). The wireless devices communicate with each other via Bluetooth wireless technology in the MANET with an access point (AP) to provide connectivity to the Internet. A Certificate authority (CA) distributes certificates and certification revocation lists (CRLs) to the devices via the access point (AP). Each group of devices has the name of the group associated with the certificate and signed by the CA. A device that is out of the radio range of the access point may still connect to the CA to validate a certificate or download the appropriate CRL by having all the devices participate in the MANET.
Owner:MALIKIE INNOVATIONS LTD
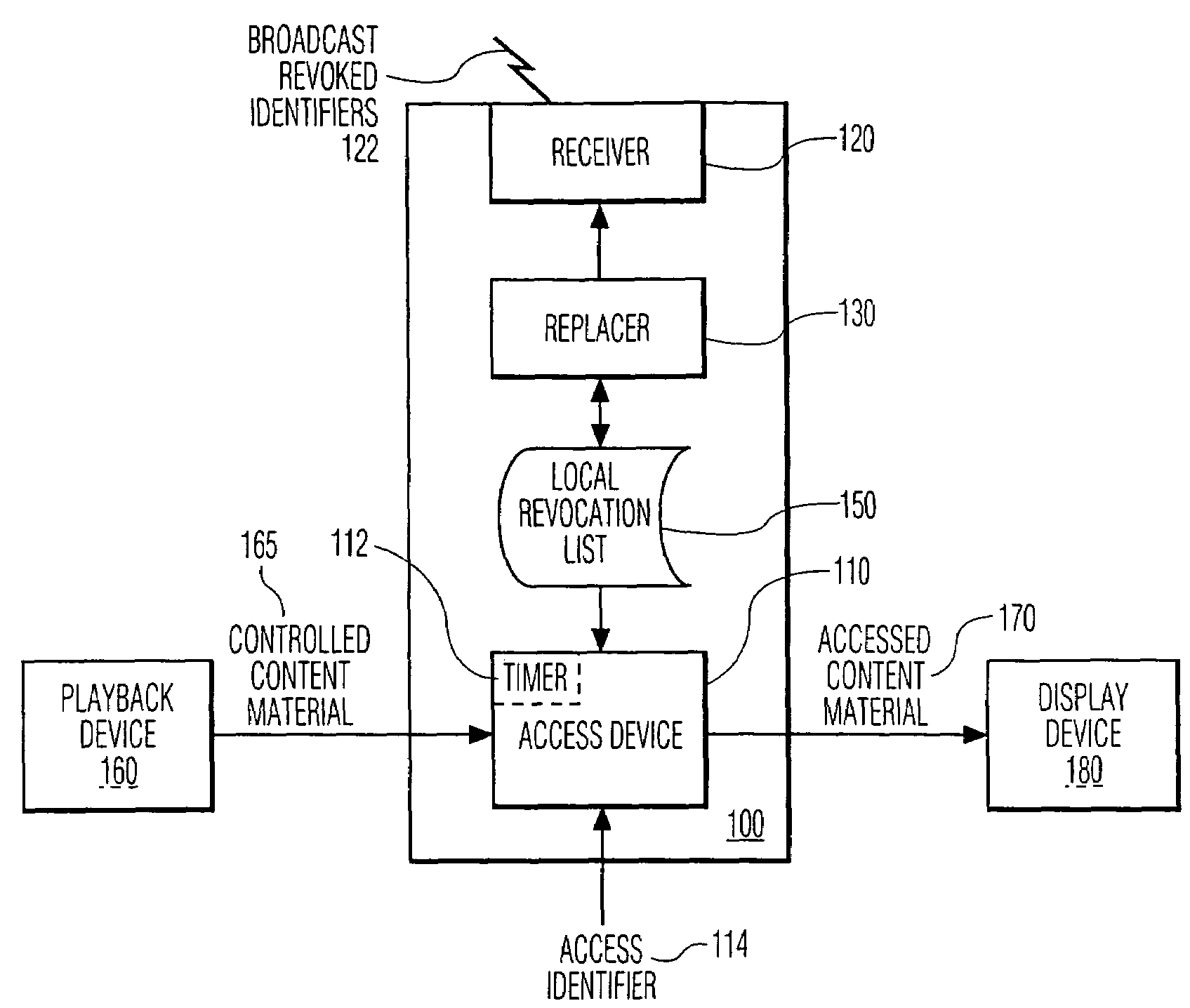
Method and apparatus for implementing revocation in broadcast networks
InactiveUS7225164B1Analogue secracy/subscription systemsRecord information storageComputer moduleConditional access
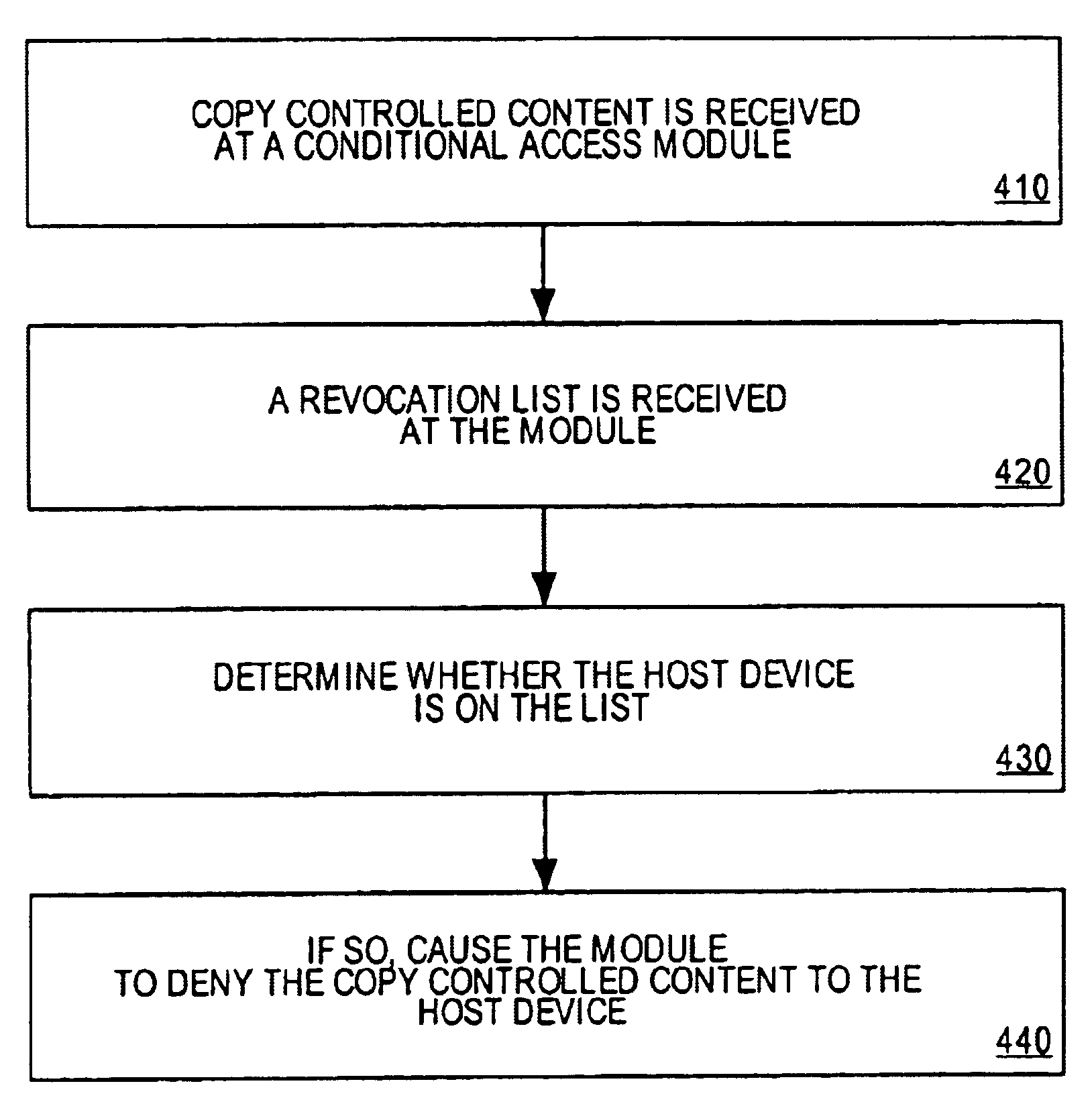
A method of revoking a descrambling privilege for copy controlled content to a host device is provided. The method includes receiving copy controlled content at a conditional access module. A revocation list is also received at the module. The method includes determining whether the host device associated with the module is on the list. If so, the conditional access module will not descramble the content.
Owner:SONY CORP +1
Method and apparatus for revocation list management
InactiveUS7260715B1Improve efficiencyReduces of other system resource consumedDigital data processing detailsUser identity/authority verificationComputer scienceContact list
Access to information is controlled by maintaining, for a given device or other entity through which information may be accessed, a contact list that includes information identifying one or more other entities which have attempted to communicate with the given entity. In accordance with the invention, the contact list is utilized in conjunction with a revocation list stored in a memory associated with the given entity in order to determine which of the other entities are authorized to communicate with the given entity. The contact list includes a number of entries, each entry having at least an identifier of a particular one of the other entities and a corresponding revocation flag indicating whether the particular entity has been revoked. The contact list is updated after a modification of the revocation list, or if a new entity not already included in the contact list attempts to communicate with the given entity.
Owner:KONINKLIJKE PHILIPS ELECTRONICS NV
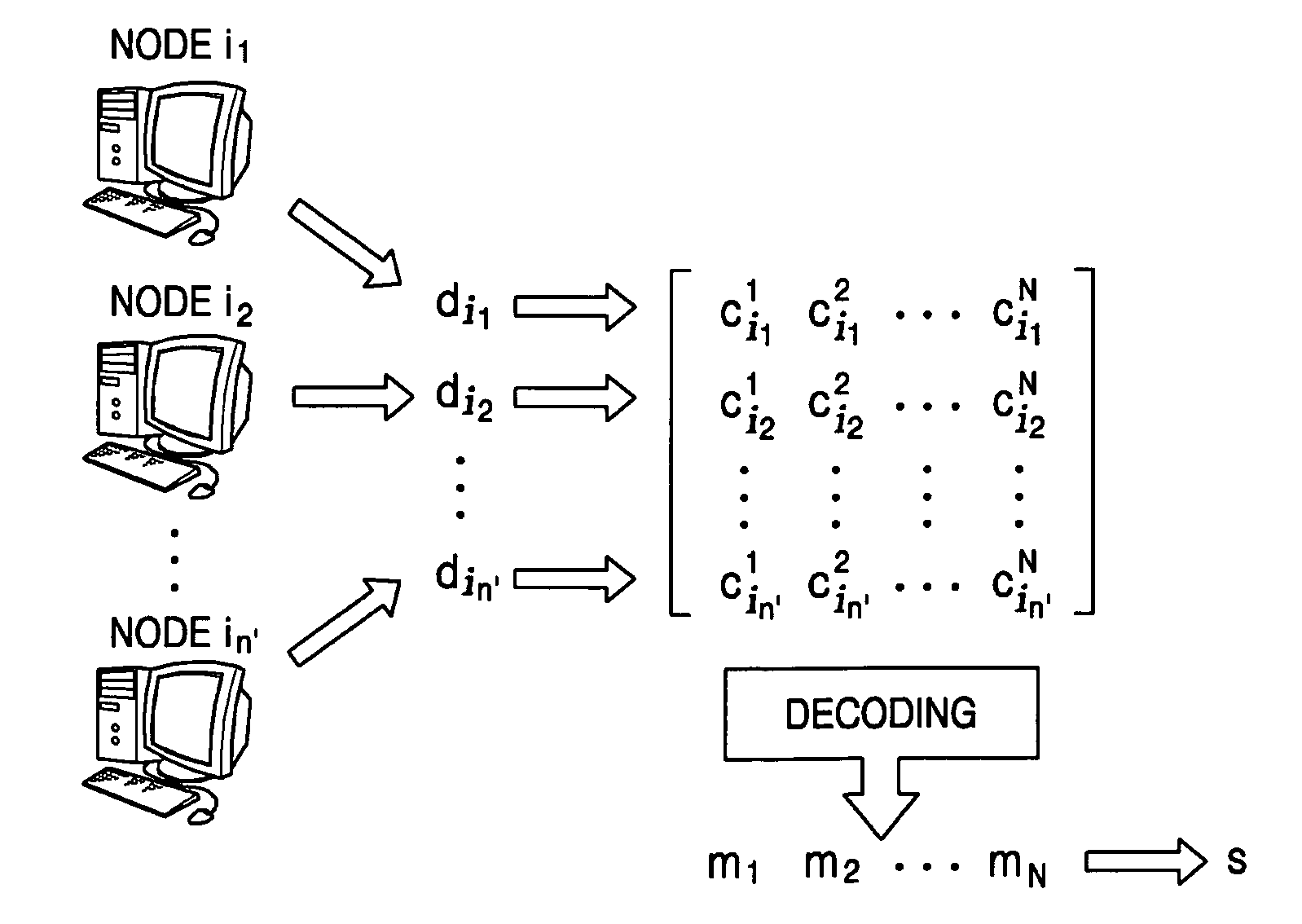
Method and system for distributed certificate management in ad-hoc networks
InactiveUS20050053045A1User identity/authority verificationNetwork topologiesSelf-organizing networkDistributed computing
A method and system for distributed certificate management in an ad-hoc network including a plurality of nodes, the method includes making a certificate revocation list (CRL), distributing the CRL among the plurality of nodes, receiving portions of the distributed CRL from a predetermined number of nodes, and reconstructing the CRL by combining the portions of the distributed CRL.
Owner:SAMSUNG ELECTRONICS CO LTD
Revocation of a certificate and exclusion of other principals in a digital rights management (DRM) system based on a revocation list from a delegated revocation authority
InactiveUS7543140B2User identity/authority verificationDigital computer detailsDigital rights managementRevocation list
A digital certificate identifies an entity as having authority over the certificate to revoke same as delegated by the issuer. The certificate also has at least one revocation condition relating to possible revocation of the certificate. To authenticate the certificate, the identification of the delegated revocation authority, a location from which a revocation list is to be obtained, and any freshness requirement to be applied to the revocation list are determined from the certificate. It is then ensured that the revocation list from the location is present and that the present revocation list satisfies the freshness requirement, that the revocation list is promulgated by the delegated revocation authority identified in the certificate, and that the certificate is not identified in the revocation list as being revoked.
Owner:MICROSOFT TECH LICENSING LLC
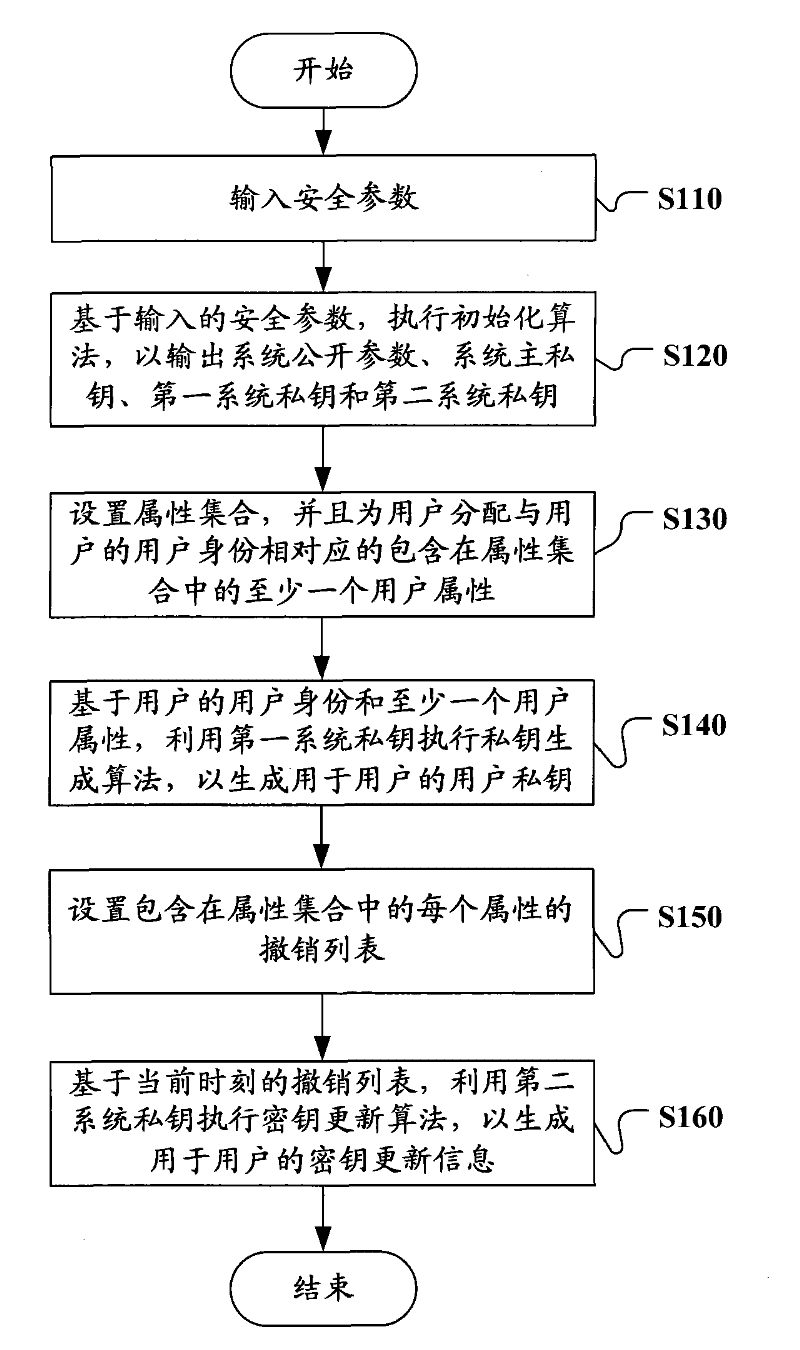
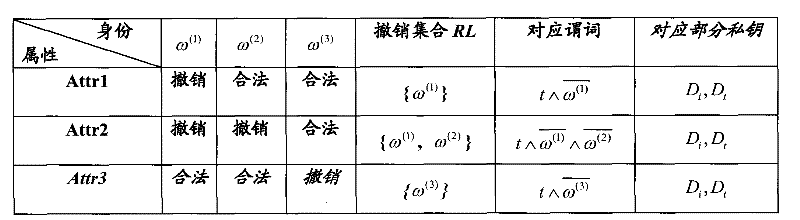
Ciphertext policy based revocable attribute-based encryption method and equipment and system utilizing same
InactiveCN102546161AThe ability to undo is not affectedPublic key for secure communicationUser identity/authority verificationAttribute-based encryptionCiphertext
The invention discloses a ciphertext policy based revocable attribute-based encryption method and equipment and a system utilizing same. A key generation method includes of inputting safety parameters; executing the initializing algorithm according to the input safety parameters to output system public parameters, a main system private key, a first system private key and a second private key by an output system; setting an attribute set, distributing at least one user attribute, which corresponds to the user identity and belongs to the attribute set, for users; executing the private key generation algorithm according to the user identity and the at least one user attribute to generate a user private key; setting a revocation list of each attribute belonging to the attribute set to reflect corresponding relation between each attribute and the user identity of the user, of the attribute, revoked at the current moment; and executing the private key updating algorithm by the second system private key on the basis of the current revocation list so as to generate private key updated information.
Owner:SONY CORP
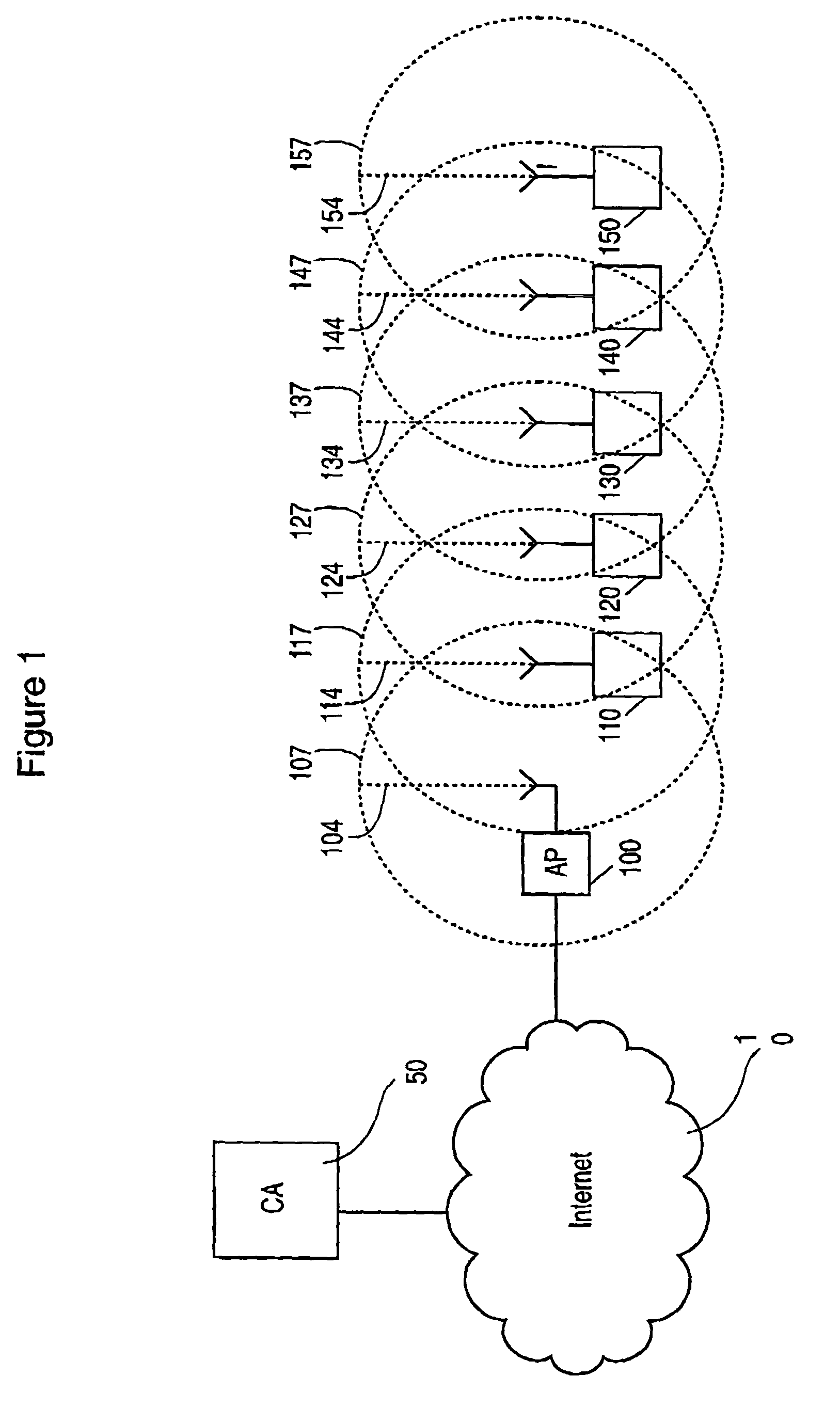
Certificate revocation system
InactiveUS20050055548A1Easy to manageReduce the numberUser identity/authority verificationPayments involving neutral partyCommunications systemDigital signature
A method of managing certificates in a communication system having a certifying authority and a directory. Preferably, the method begins by having the certifying authority generate certificates by digitally signing a given piece of data. At a later point time, the certifying authority may produce a string that proves whether a particular certificate is currently valid without also proving the validity of at least some other certificates. The technique obviates use of certification revocation lists communicated between the certifying authority and the directory.
Owner:ASSA ABLOY AB
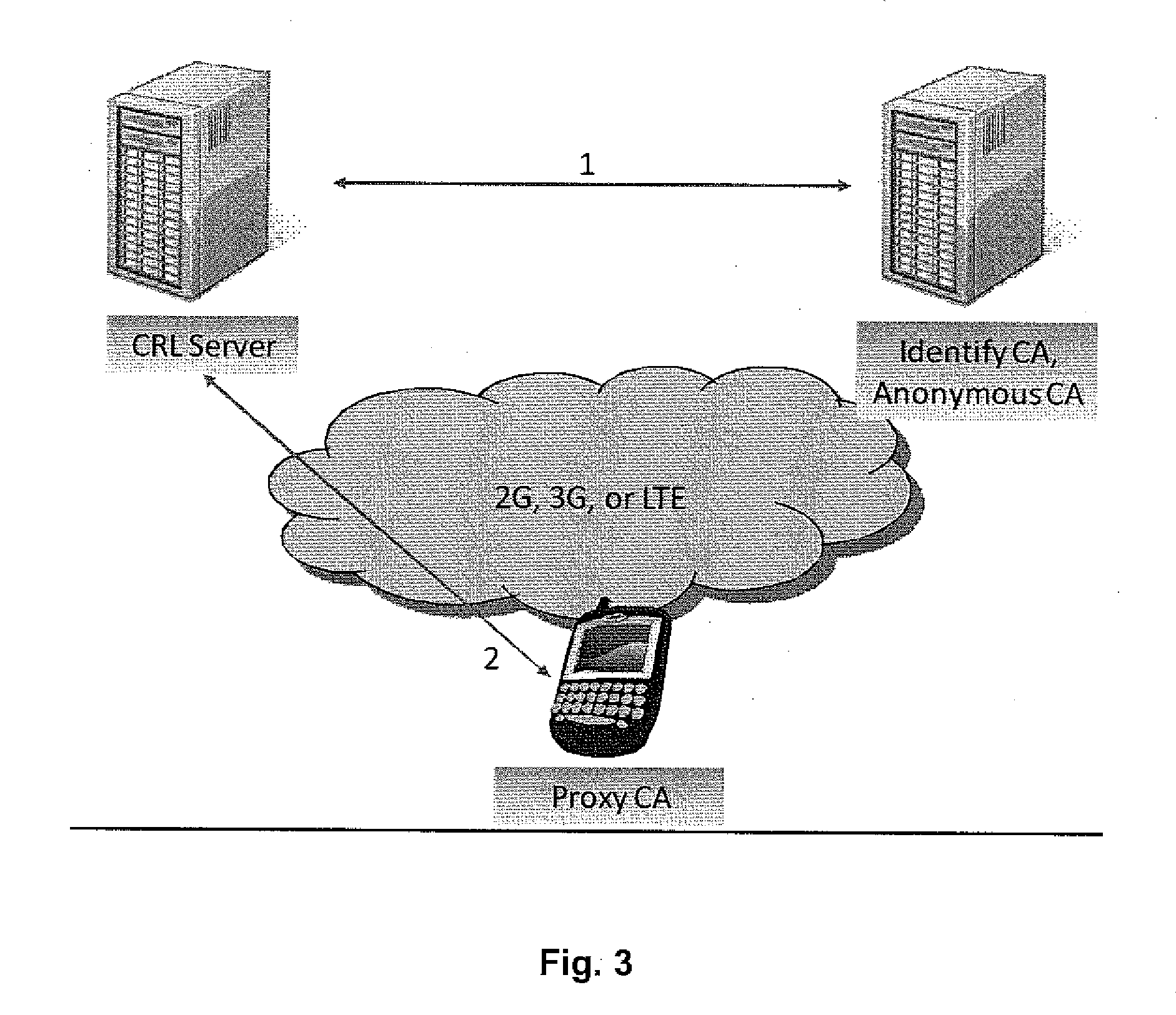
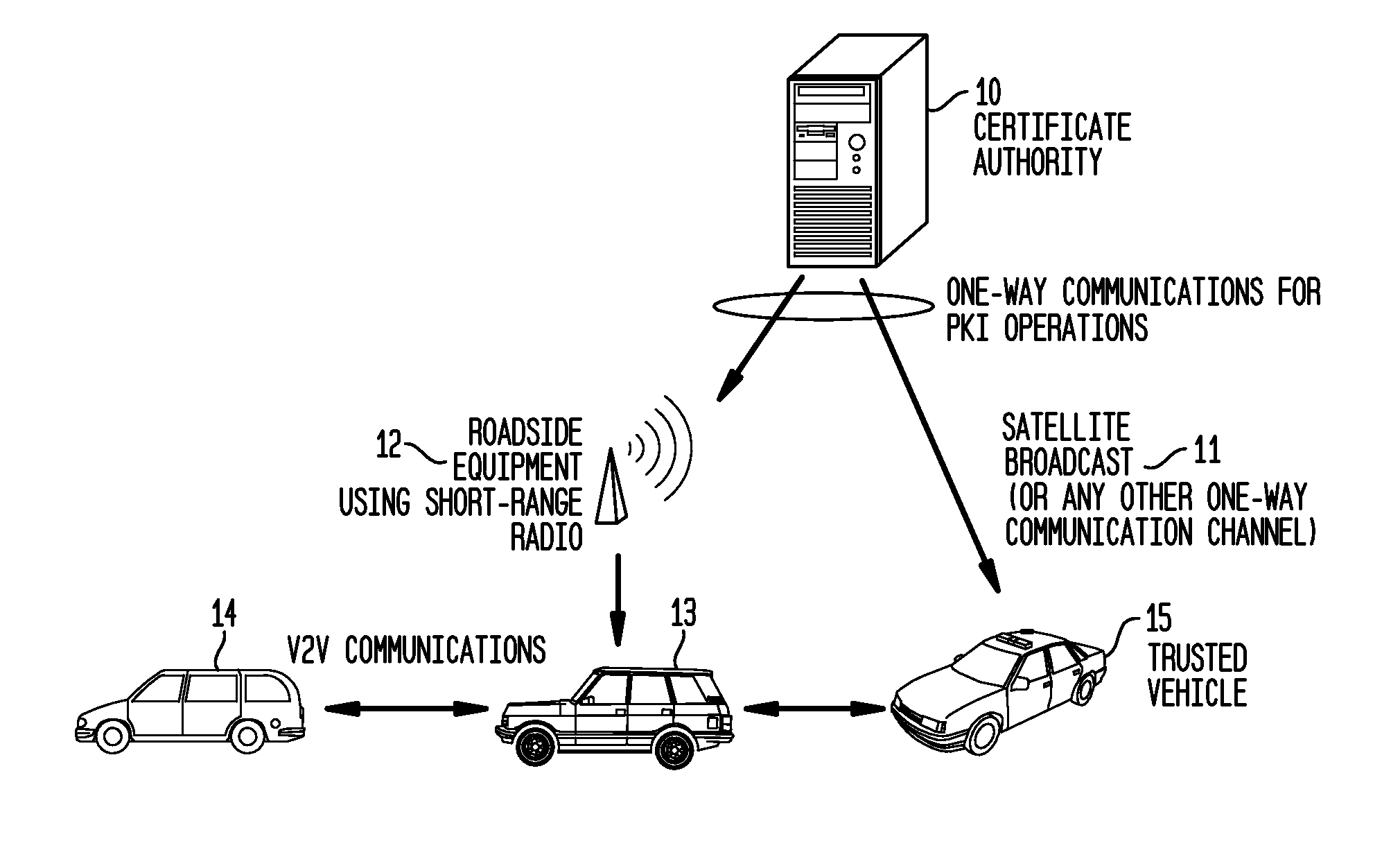
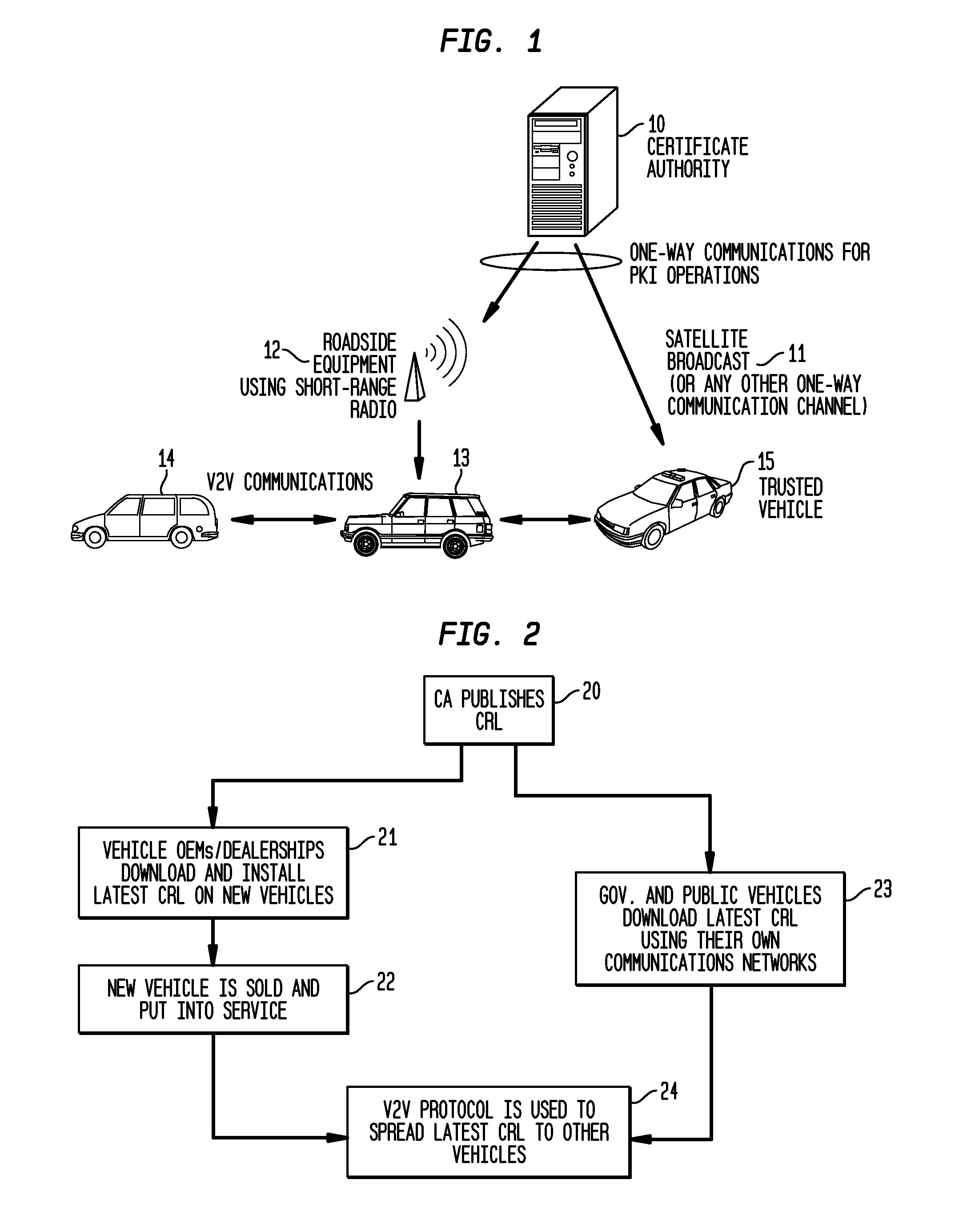
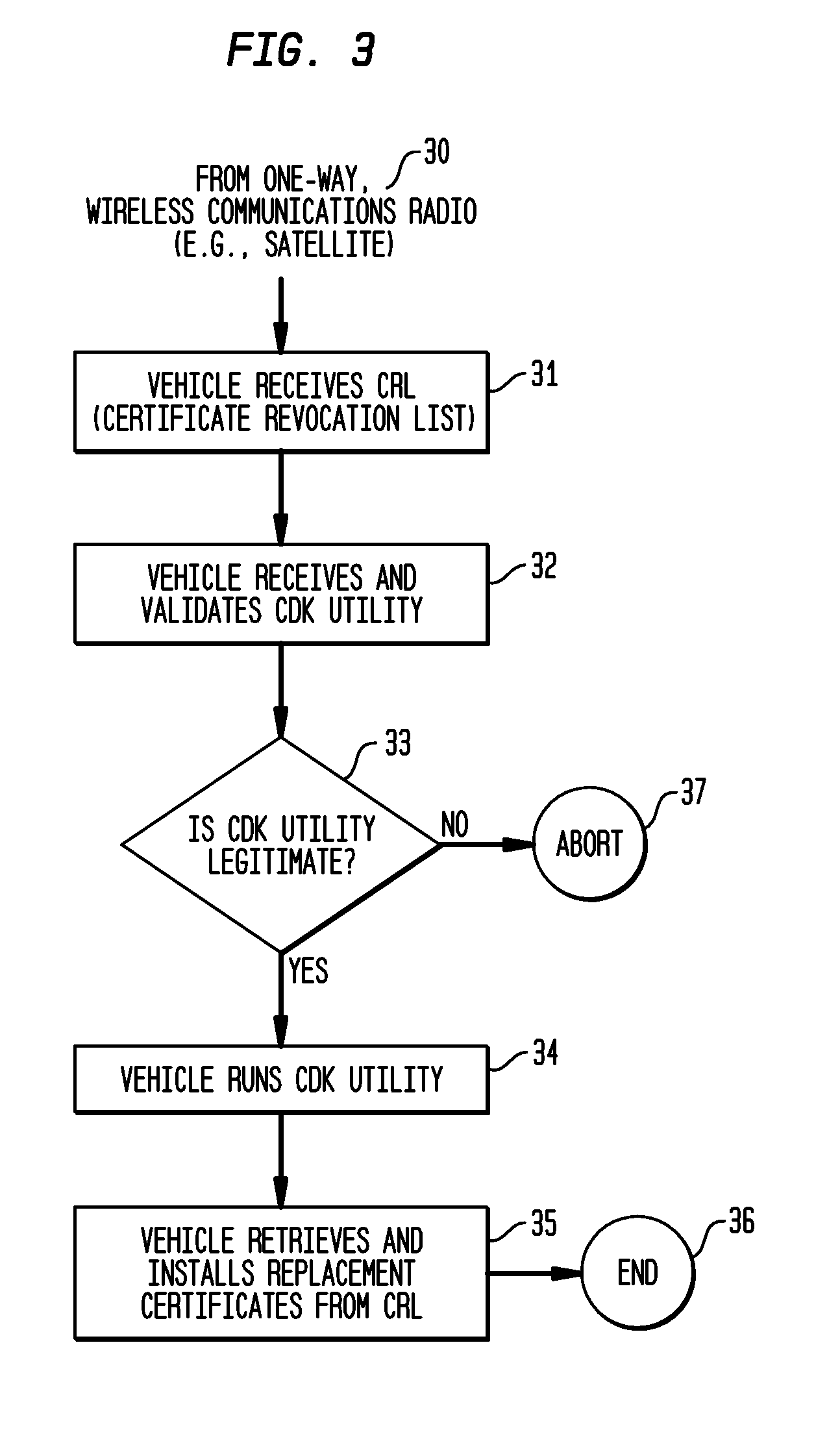
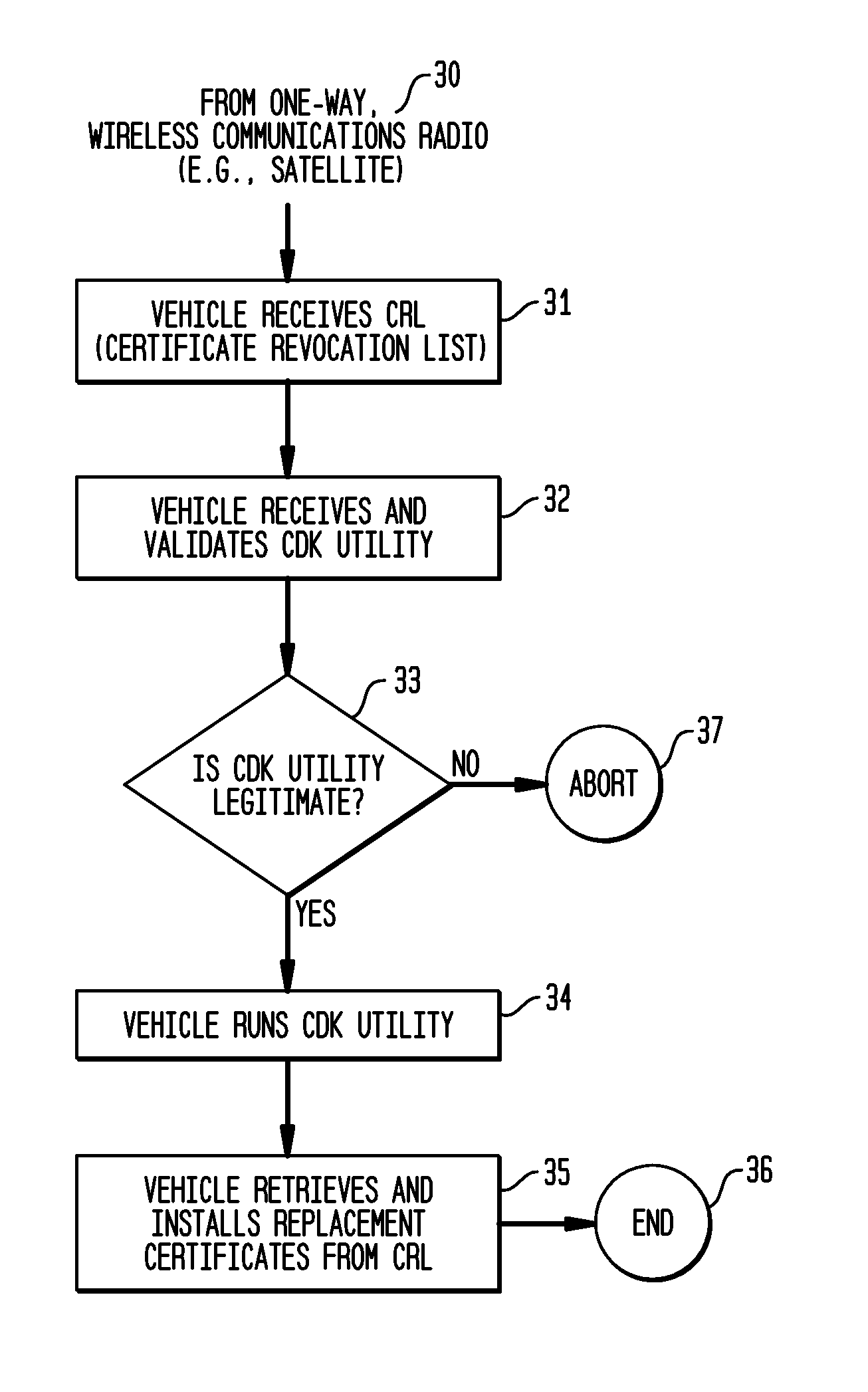
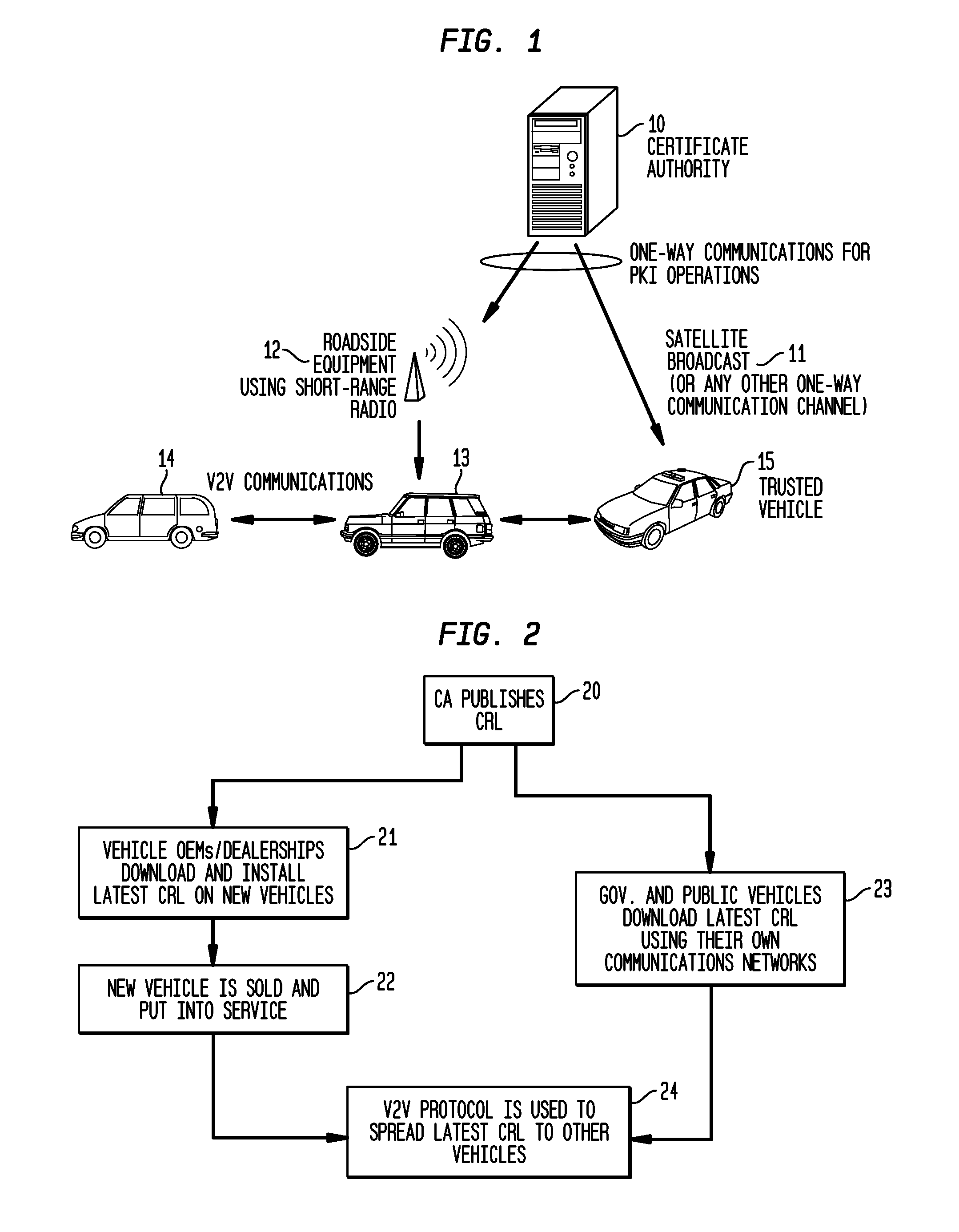
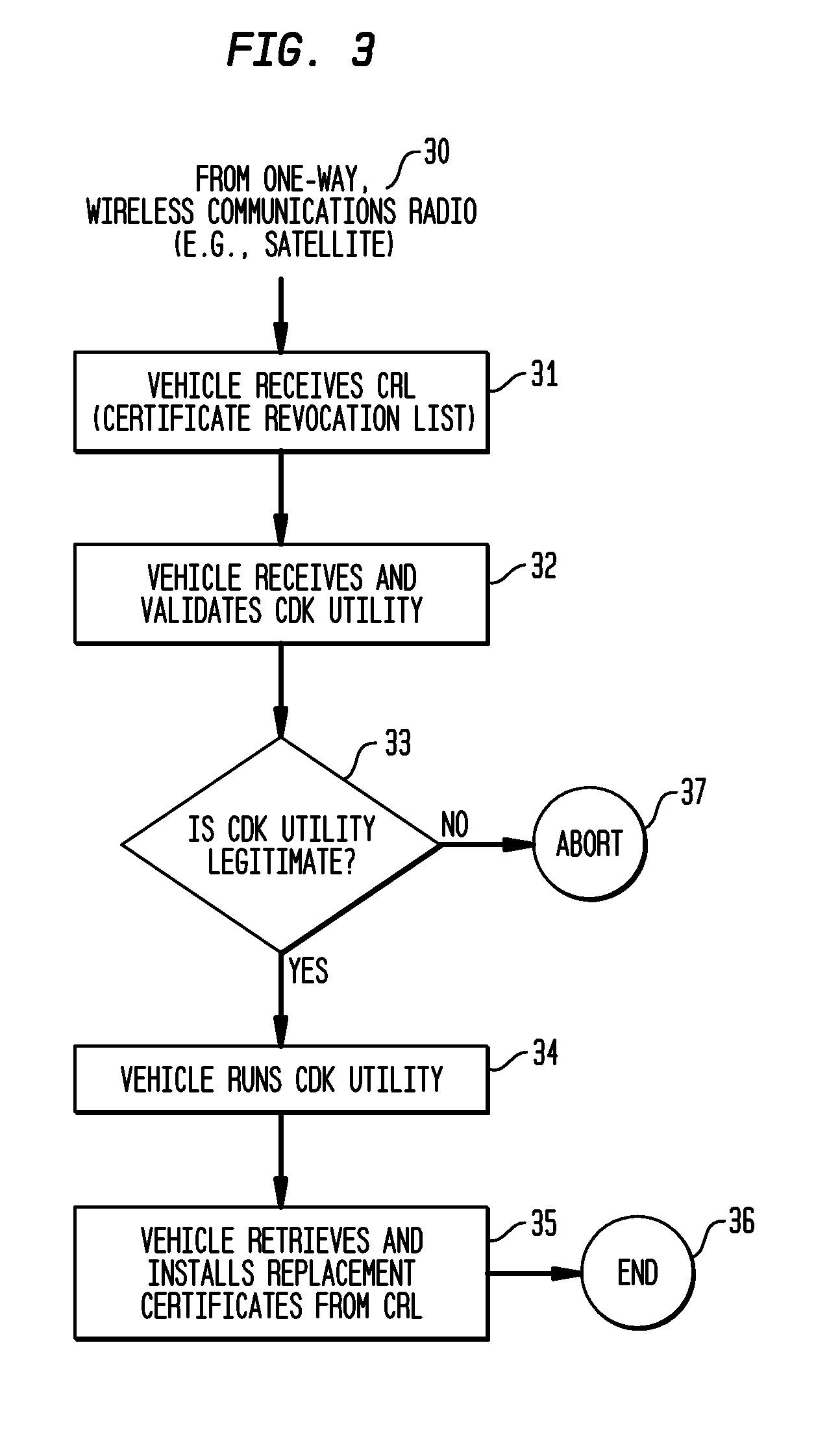
System and Methods to Perform Public Key Infrastructure (PKI) Operations in Vehicle Networks using One-Way Communications Infrastructure
ActiveUS20110213968A1Reduces and eliminates relianceParticular environment based servicesUser identity/authority verificationIn vehicleRevocation list
A set of certificate management methods designed to significantly reduce or eliminate reliance on infrastructure network connectivity after vehicles are sold uses techniques to support certificate management operations in order to reduce the frequency which vehicles need to communicate with the Certificate Authorities (CAs) and the amount of data that needs to be exchanged between vehicles and the CA. These methods include, for example, approaches to use one-way communications and vehicle-to-vehicle (V2V) communications to replace expired certificates, approaches to use one-way communications and V2V communications to replace revoked certificates, and use of a small subset of vehicles as proxies to help retrieve and distribute Certificate Revocation Lists (CRLs) and replacement certificates. The combination of these techniques leads to solutions that can eliminate the need for roadside infrastructure networks completely.
Owner:TELCORDIA TECHNOLOGIES INC
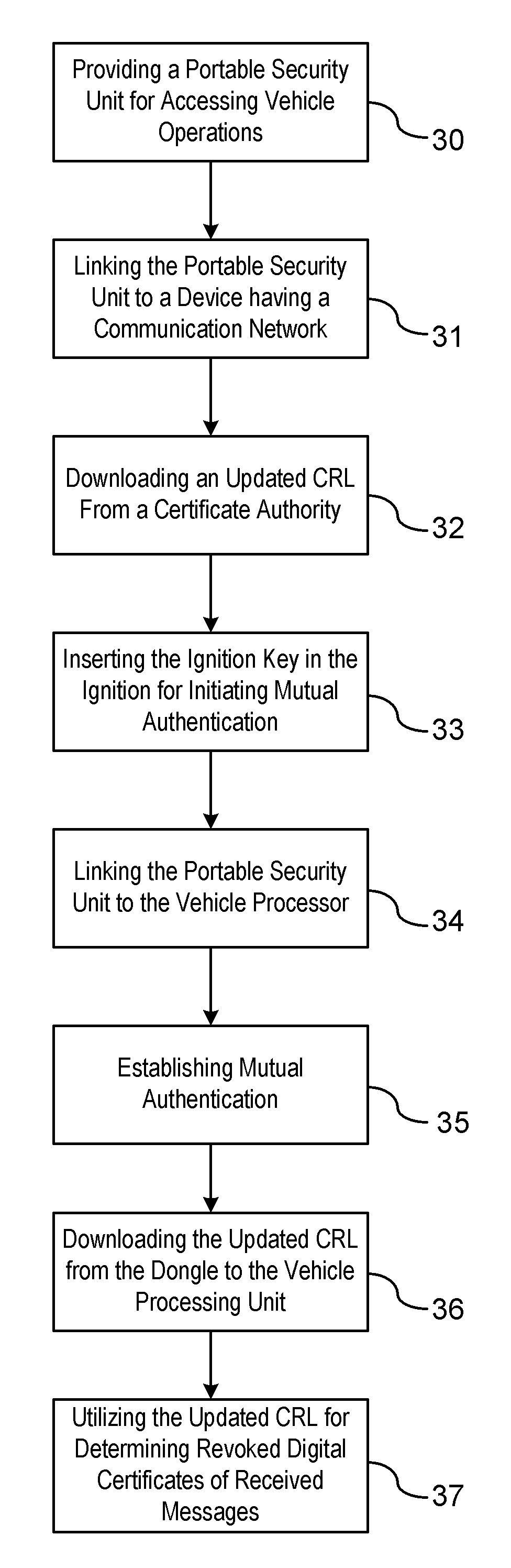
Threat Mitigation in a Vehicle-to-Vehicle Communication Network
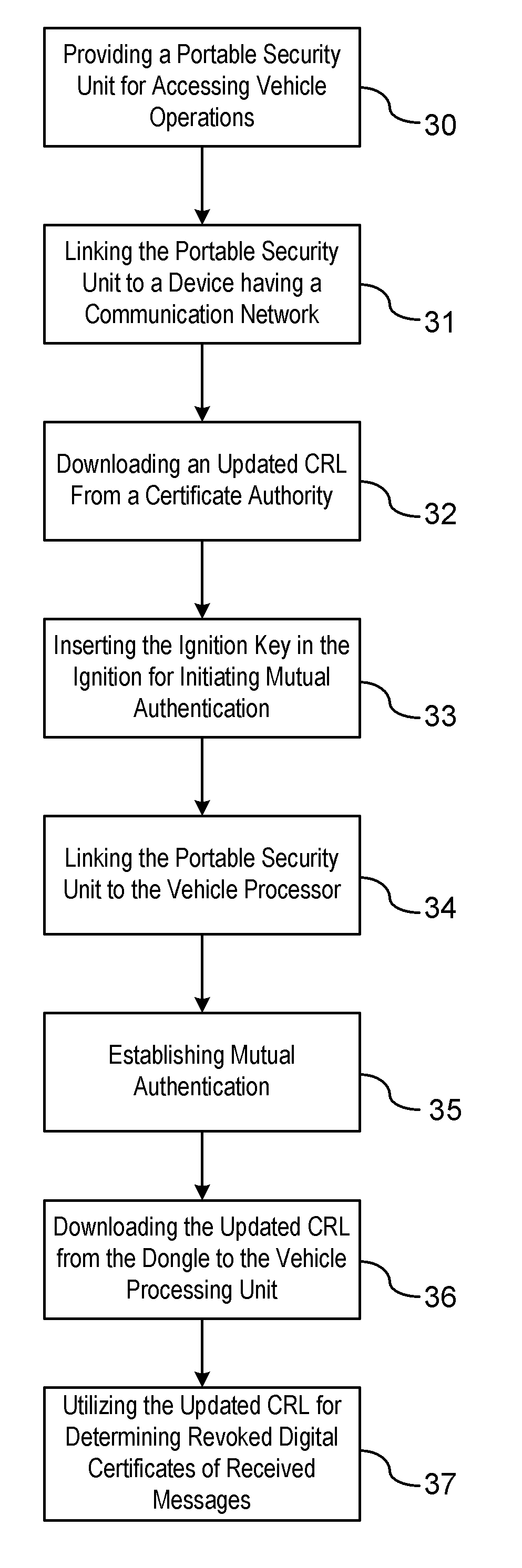
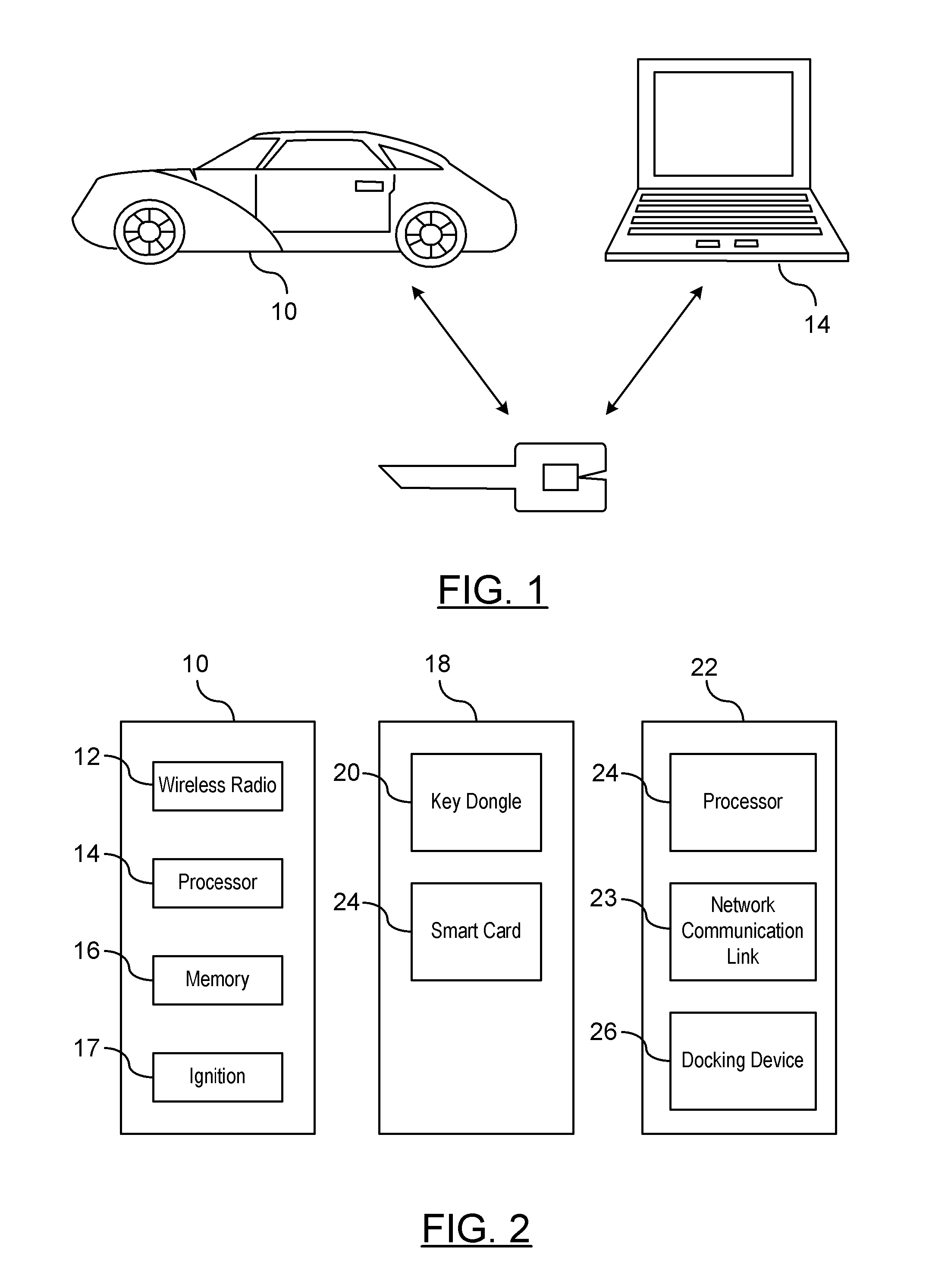
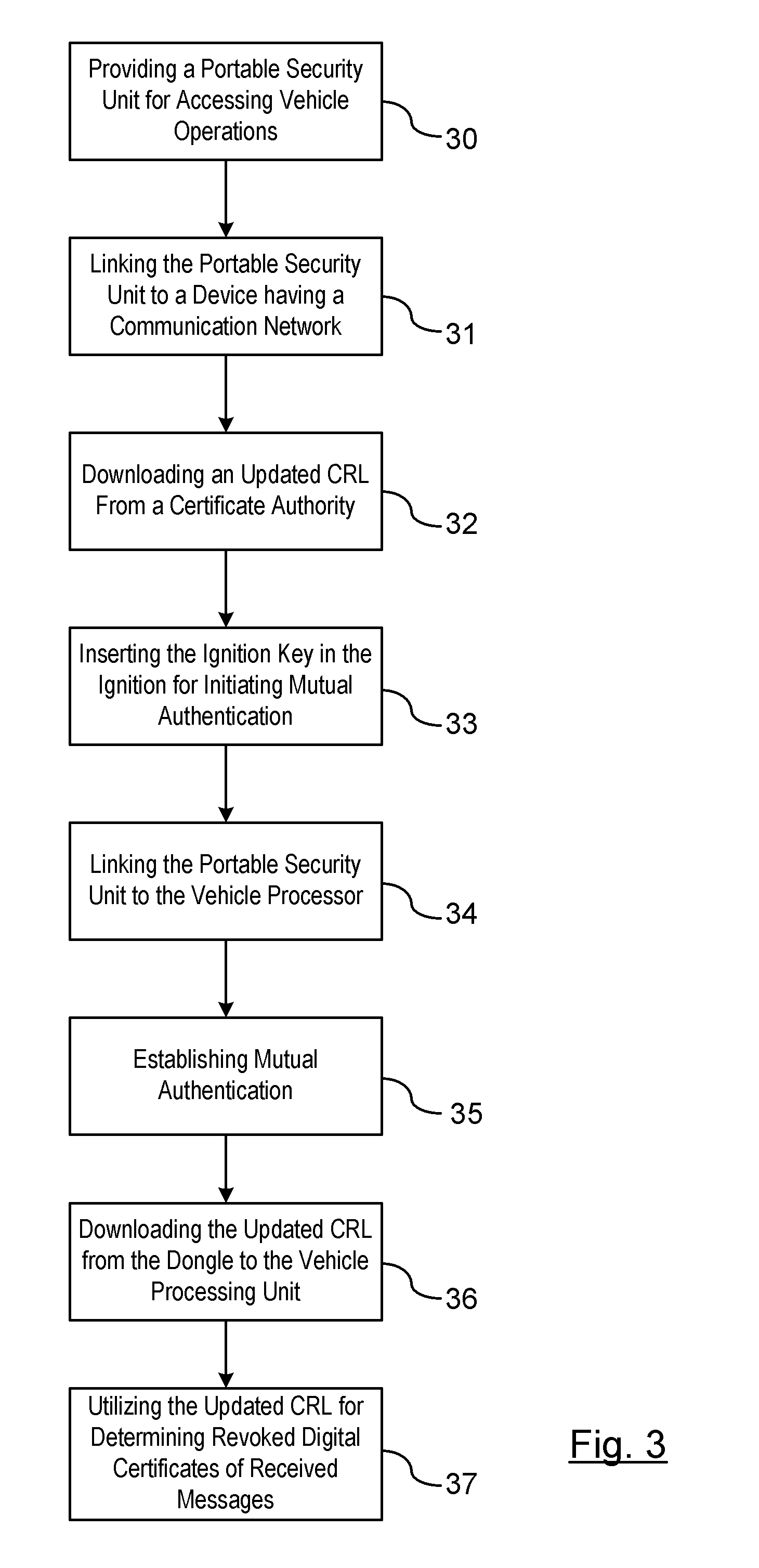
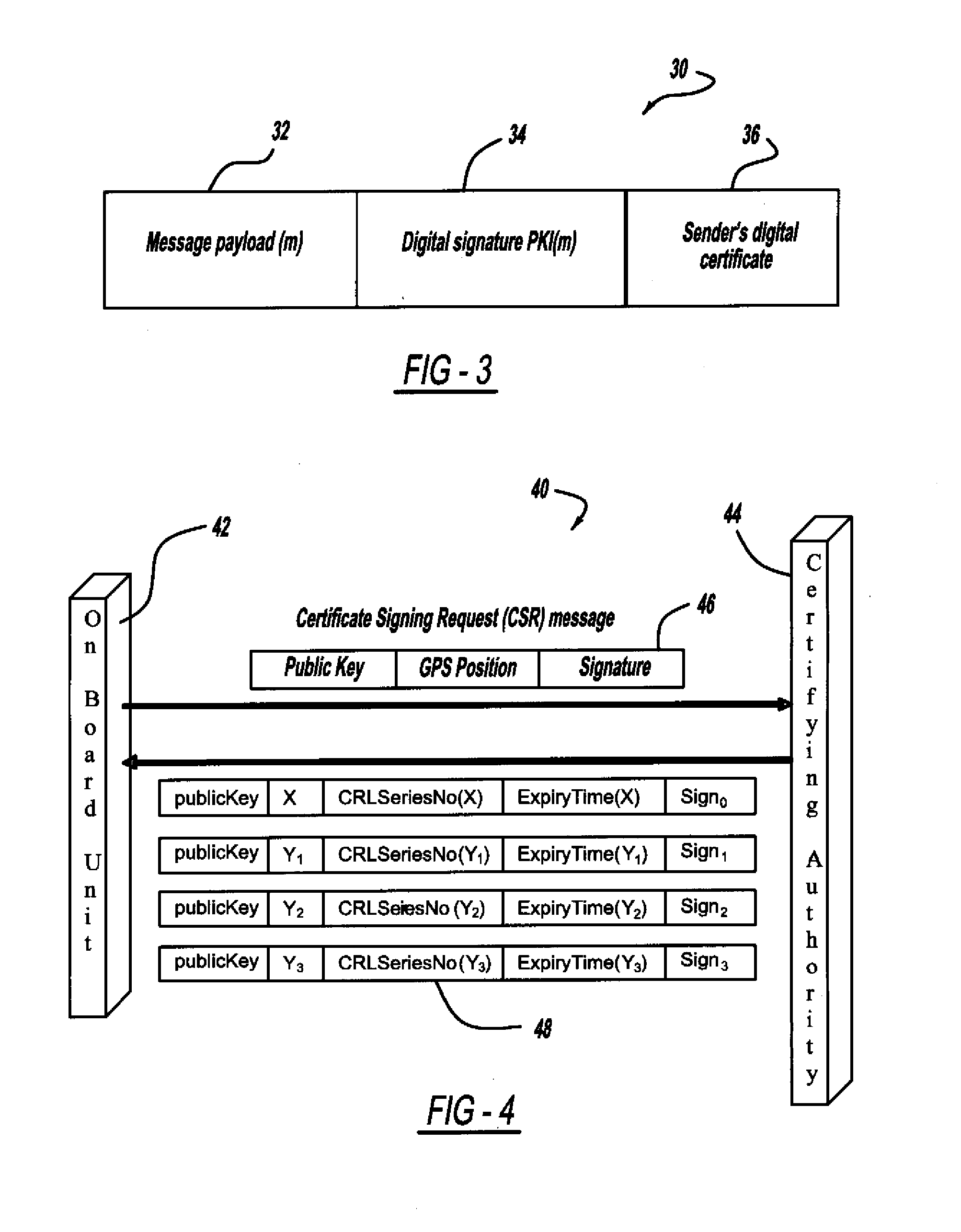
ActiveUS20110258435A1User identity/authority verificationTelecommunications linkCommunications system
A method is provided for obtaining a certificate revocation list (CRL) for a vehicle in a vehicle-to-vehicle communication system. A portable security unit is provided to access secured operations for the vehicle. The portable security unit is linked to a device having access to a communication network. The communication network is in communication with a certificate authority for issuing an updated CRL. The updated CRL is downloaded from the certificate authority to the portable security unit. At a later time, when a user enters the vehicle, a communication link is established between the portable security unit and a vehicle processor unit. Mutual authentication is exchanged between the portable security unit and the vehicle processing unit. The updated CRL stored in the portable security unit is downloaded to a memory of the vehicle communication system in response to a successful mutual authentication.
Owner:GM GLOBAL TECH OPERATIONS LLC
System and methods to perform public key infrastructure (PKI) operations in vehicle networks using one-way communications infrastructure
ActiveUS8522013B2Reduces and eliminates relianceParticular environment based servicesServices signallingIn vehicleRevocation list
A set of certificate management methods designed to significantly reduce or eliminate reliance on infrastructure network connectivity after vehicles are sold uses techniques to support certificate management operations in order to reduce the frequency which vehicles need to communicate with the Certificate Authorities (CAs) and the amount of data that needs to be exchanged between vehicles and the CA. These methods include, for example, approaches to use one-way communications and vehicle-to-vehicle (V2V) communications to replace expired certificates, approaches to use one-way communications and V2V communications to replace revoked certificates, and use of a small subset of vehicles as proxies to help retrieve and distribute Certificate Revocation Lists (CRLs) and replacement certificates. The combination of these techniques leads to solutions that can eliminate the need for roadside infrastructure networks completely.
Owner:TELCORDIA TECHNOLOGIES INC
Method and system for distributed certificate management in ad-hoc networks
InactiveUS7382762B2User identity/authority verificationNetwork topologiesDistributed computingRevocation list
A method and system for distributed certificate management in an ad-hoc network including a plurality of nodes, the method includes making a certificate revocation list (CRL), distributing the CRL among the plurality of nodes, receiving portions of the distributed CRL from a predetermined number of nodes, and reconstructing the CRL by combining the portions of the distributed CRL.
Owner:SAMSUNG ELECTRONICS CO LTD
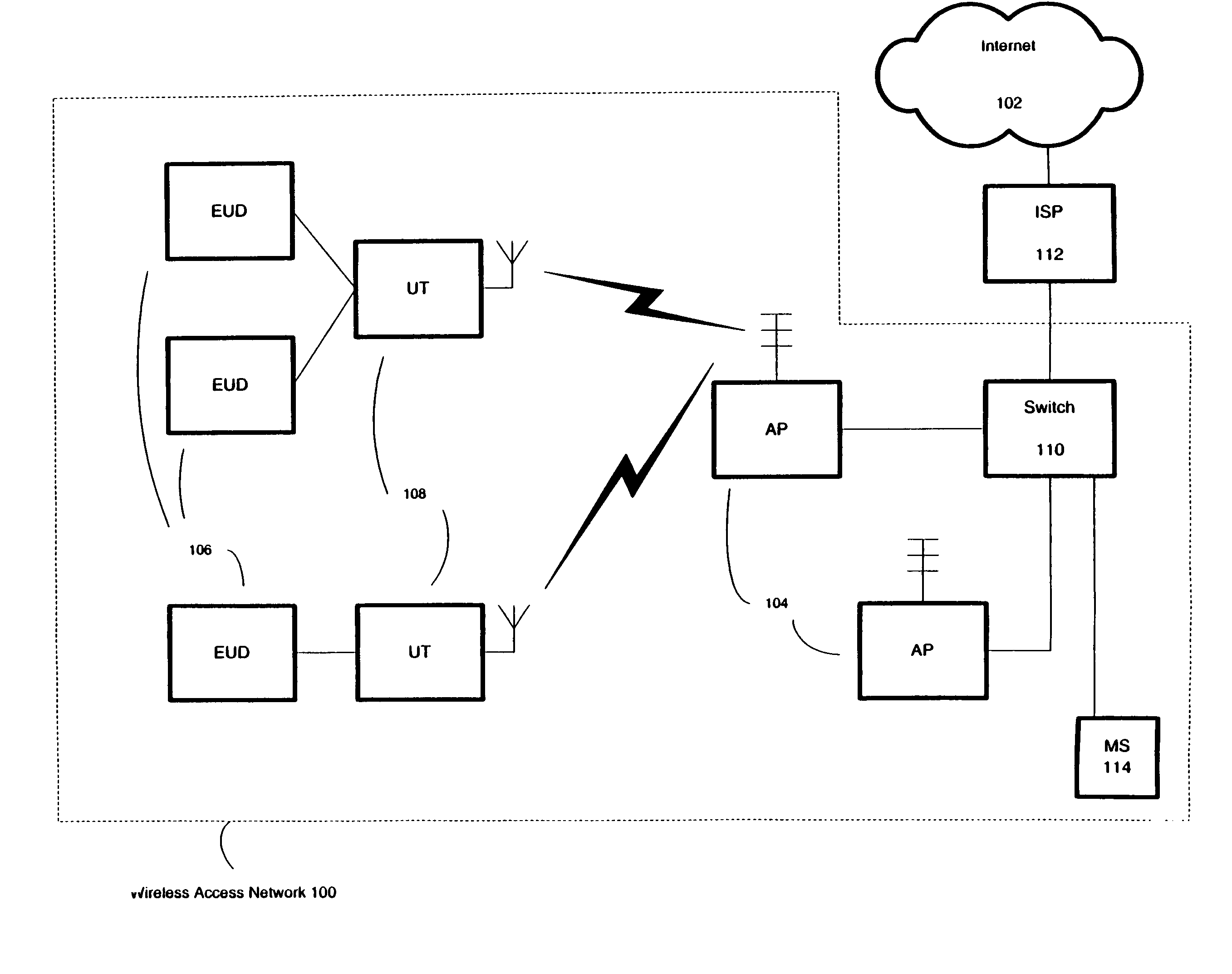
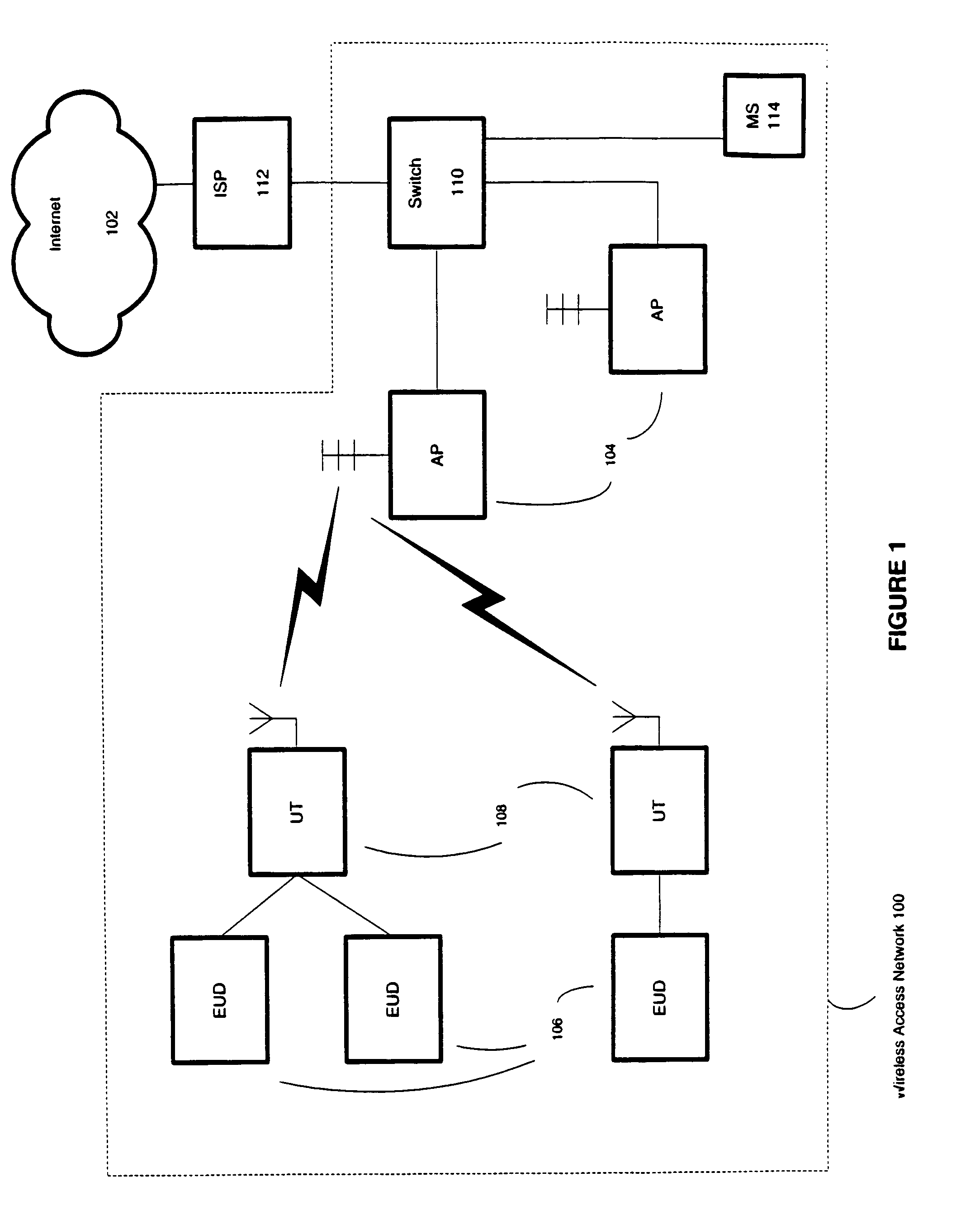
Reducing certificate revocation lists at access points in a wireless access network
InactiveUS7430606B1Reduce accessShort maintenance periodMultiple digital computer combinationsSecurity arrangementAccess networkWireless mesh network
The certificate revocation lists at access points of a wireless access network can be reduced. In one embodiment, an Internet Service Provider (“ISP”) connected to the wireless access network can receive a subscription request from a user terminal capable of accessing the ISP using the wireless access network. When the ISP assigns a subscription identifier to the user terminal, it also provides a service certificate signed by a certificate authority including the subscription identifier. In addition, the ISP also provides the user terminal one or more session certificates to be used to access the wireless access network, where the session certificates having a shorter validity period than the service certificate.
Owner:INTEL CORP
Apparatus and method for enhanced revocation of direct proof and direct anonymous attestation
InactiveUS20080270790A1Digital data processing detailsPublic key for secure communicationTrusted hardwareDigital signature
In some embodiments, a method and apparatus for enhanced revocation of direct proof and direct anonymous attestation are described. In one embodiment a trusted hardware device verifies that membership of the device within a trusted membership group is not revoked according to a revocation list received with a challenge request from a verifier. Once such verification is performed, the device convinces the verifier of possessing cryptographic information without revealing unique, device identification information of the trusted hardware device or the cryptographic information. In one embodiment, the trusted hardware device computes a digital signature on a message received with the challenge request to the verifier if membership of the anonymous hardware device within a trusted membership group is verified. In one embodiment, the verifier authenticates the digital signature according to a public key of the trusted membership group to enable a trusted member device to remain anonymous to the verifier. Other embodiments are described and claimed.
Owner:INTEL CORP
Mobile certificate distribution in a PKI
ActiveUS7356329B2Unauthorised/fraudulent call preventionEavesdropping prevention circuitsThe InternetBluetooth
A method of providing certificate issuance and revocation checks involving mobile devices in a mobile ad hoc network (MANET). The wireless devices communicate with each other via Bluetooth wireless technology in the MANET, with an access point (AP) to provide connectivity to the Internet. A Certificate authority (CA) distributes certificates and certification revocation lists (CRLs) to the devices via the access point (AP). Each group of devices has the name of the group associated with the certificate and signed by the CA. A device that is out of the radio range of the access point may still connect to the CA to validate a certificate or download the appropriate CRL by having all the devices participate in the MANET.
Owner:MALIKIE INNOVATIONS LTD
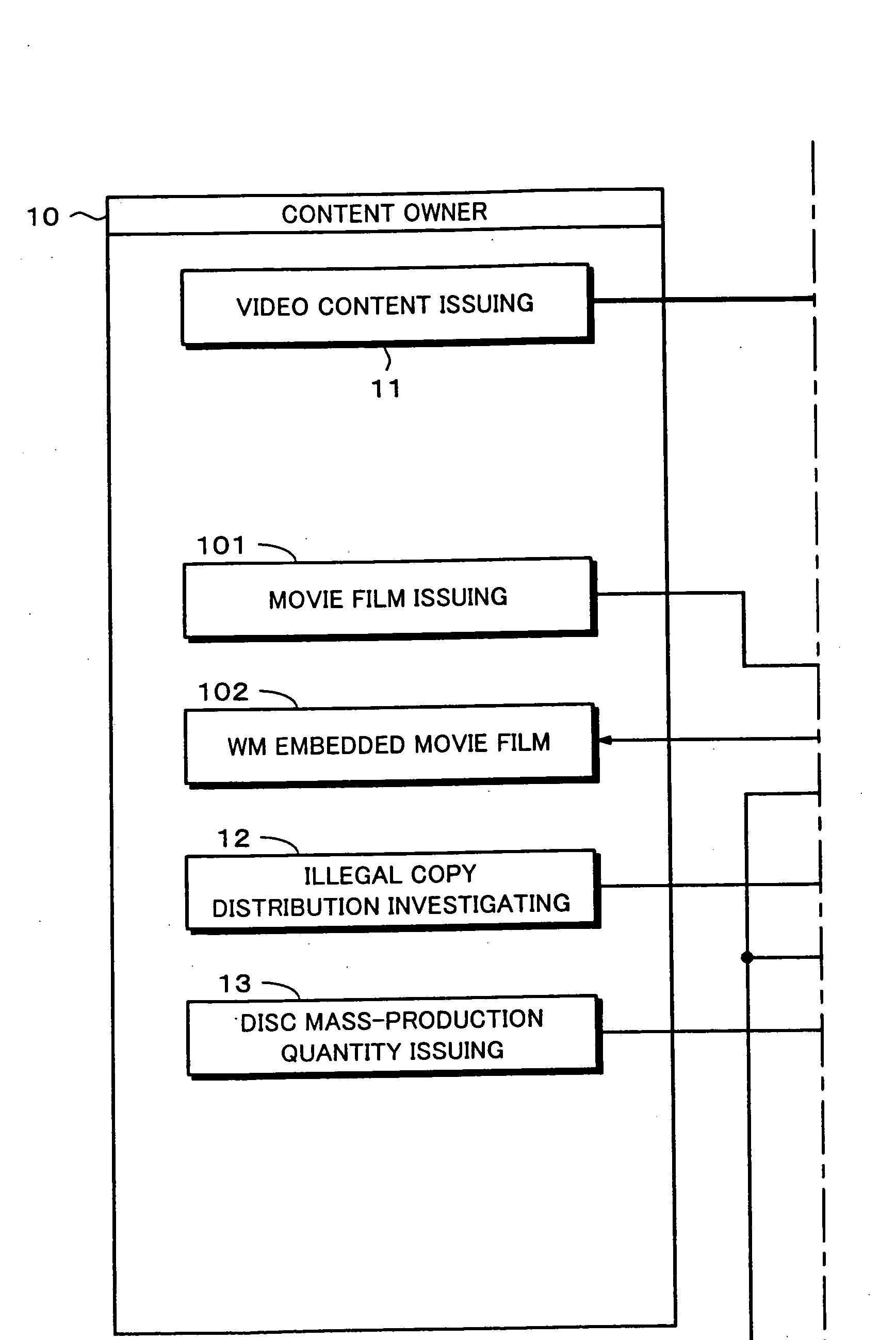
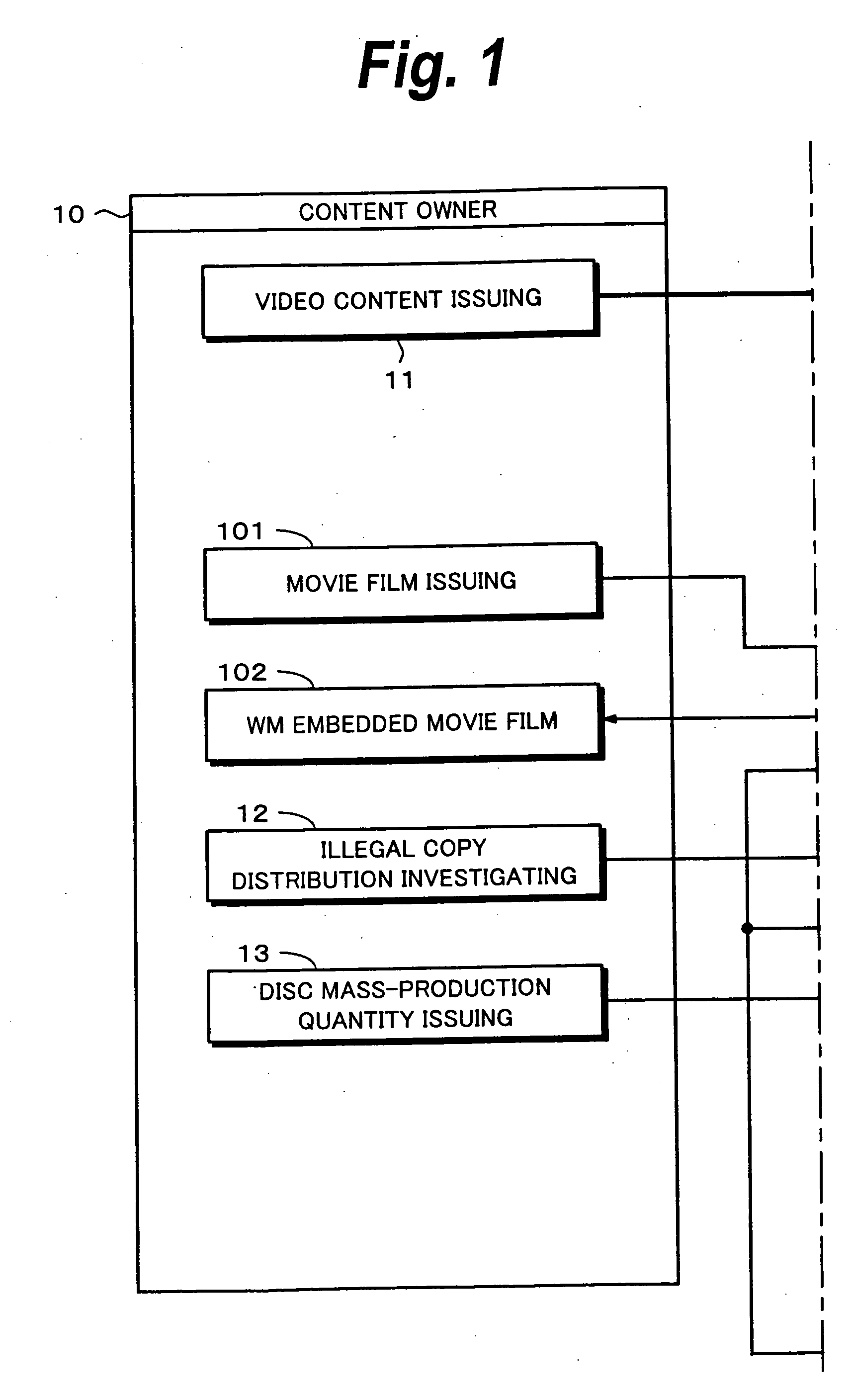
Recording medium and producing method thereof, reproducing method and reproducing apparatus, and copyright managing method
InactiveUS20060062073A1Controlled reproductionTelevision system detailsDisc-shaped record carriersDigital videoSerial code
A GUID as title information and a global serial number are recorded in a BCA of a digital video disc 60. A hash value of the GUID is embedded as an electronic watermark in a data area 64. When content data is reproduced from the digital video disc 60, a match of information of the two GUIDs is checked so as to prevent the digital video disc 60 from being illegally copied. A lead-in area 63 and a managing organization 20 provide disc revocation lists. With a global serial number and a disc revocation list, content data can be prevented from being reproduced from an illegally distributed disc. A film WM detector 84 detects data embedded in a movie shown in a theater so as to prevent content data from being reproduced from a disc on which the embedded data is recorded. Thus, content data can be prevented from being reproduced from an illegally distributed disc before a copyright supervisor of the content authorizes the disc to be distributed.
Owner:SONY CORP +1
Group Signature System, Member Status Judging Device, Group Signature Method And Member Status Judging Program
InactiveUS20080091941A1User identity/authority verificationSpecial data processing applicationsManagement unitAnonymity
For group signature data capable of keeping anonymity, it is possible to efficiently determine whether the user having created the group signature data is a valid member of the group. When a message and group signature data are received, the verification unit 3 authenticates the data and inquires, of the member status response unit 4, whether the user of the signature unit 2 having created the group signature data is a valid member of the group. In response to the inquiry, the response unit 4 determines the member status of the user having created the group signature data, according to a member revocation list notified from the group management unit 1. The response unit 4 then transmits a judge result of the member status to the verification unit 3.
Owner:NEC CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com