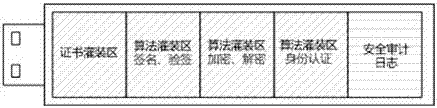
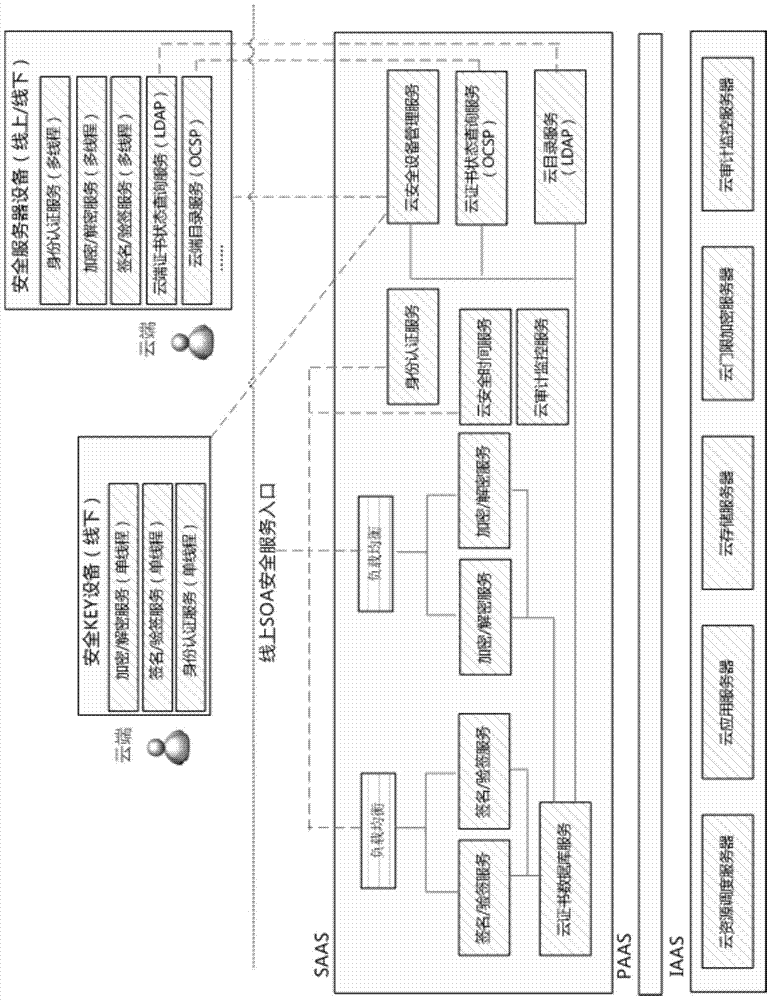
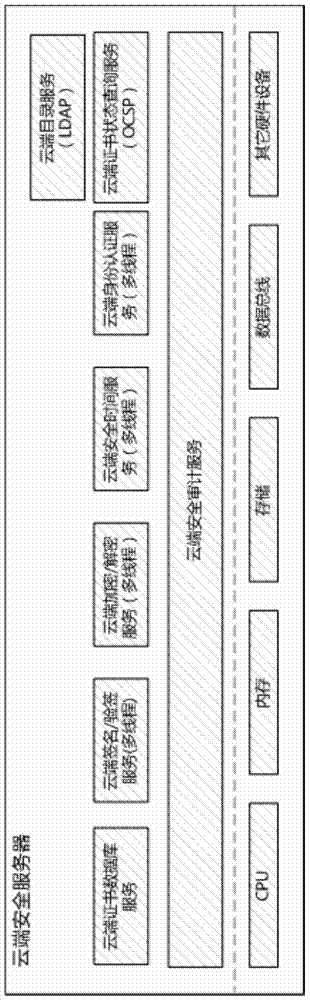
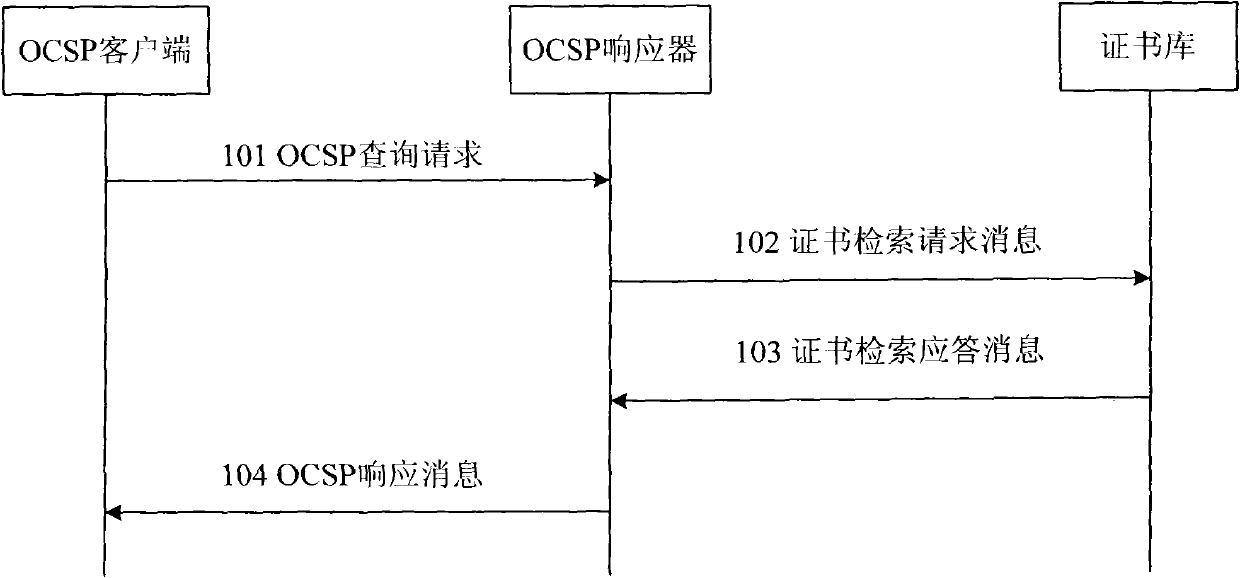
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
30 results about "Online Certificate Status Protocol" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
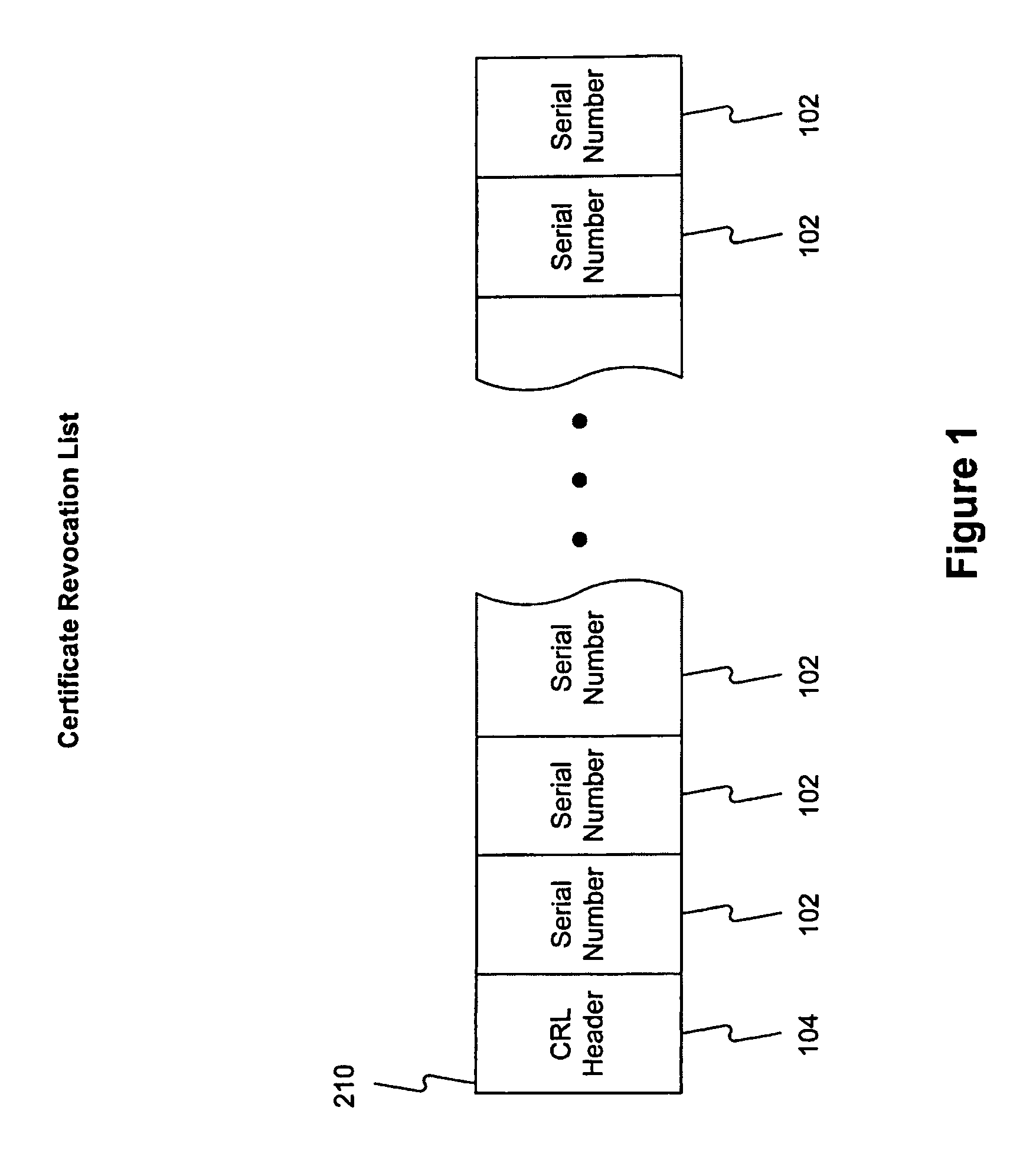
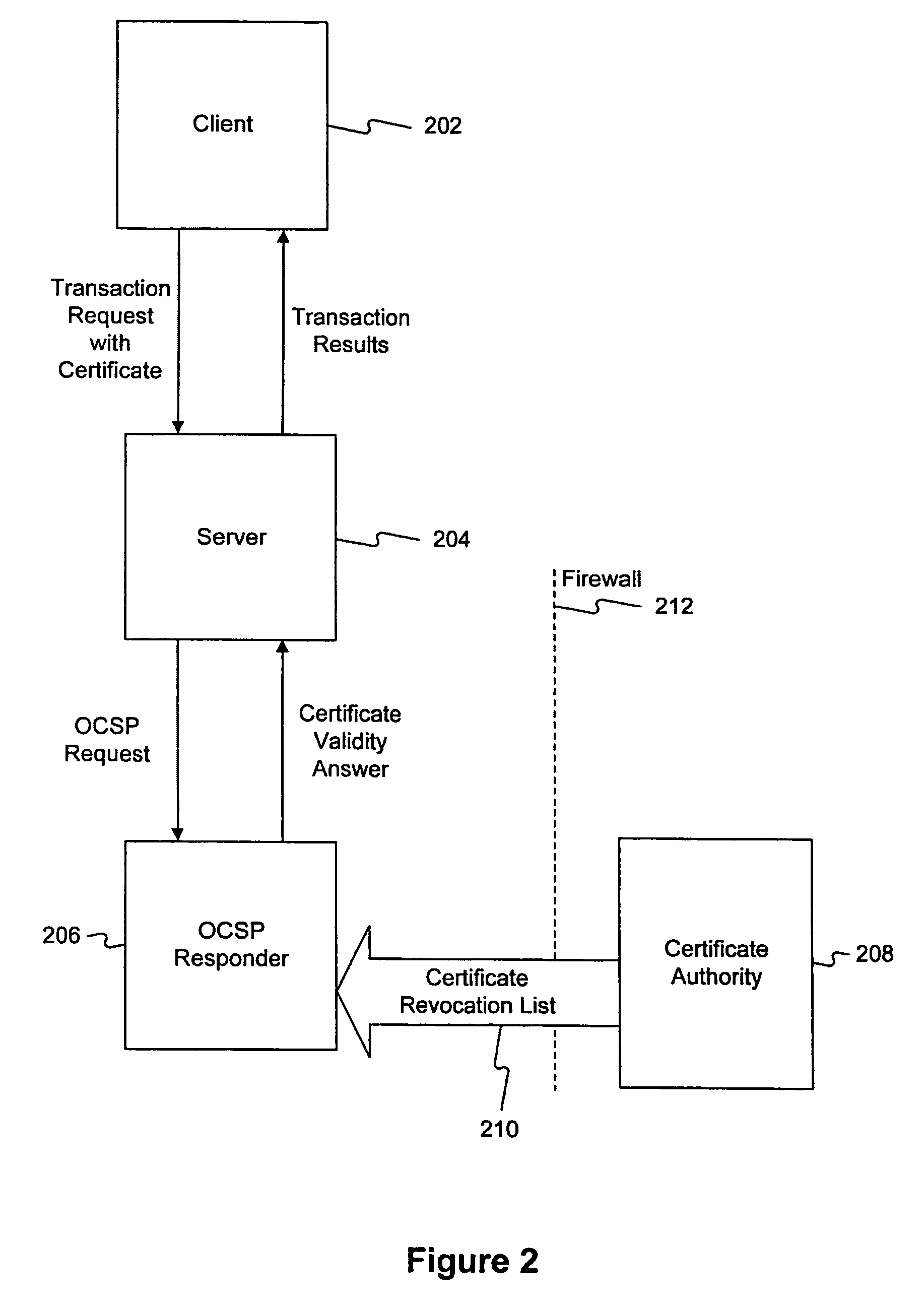
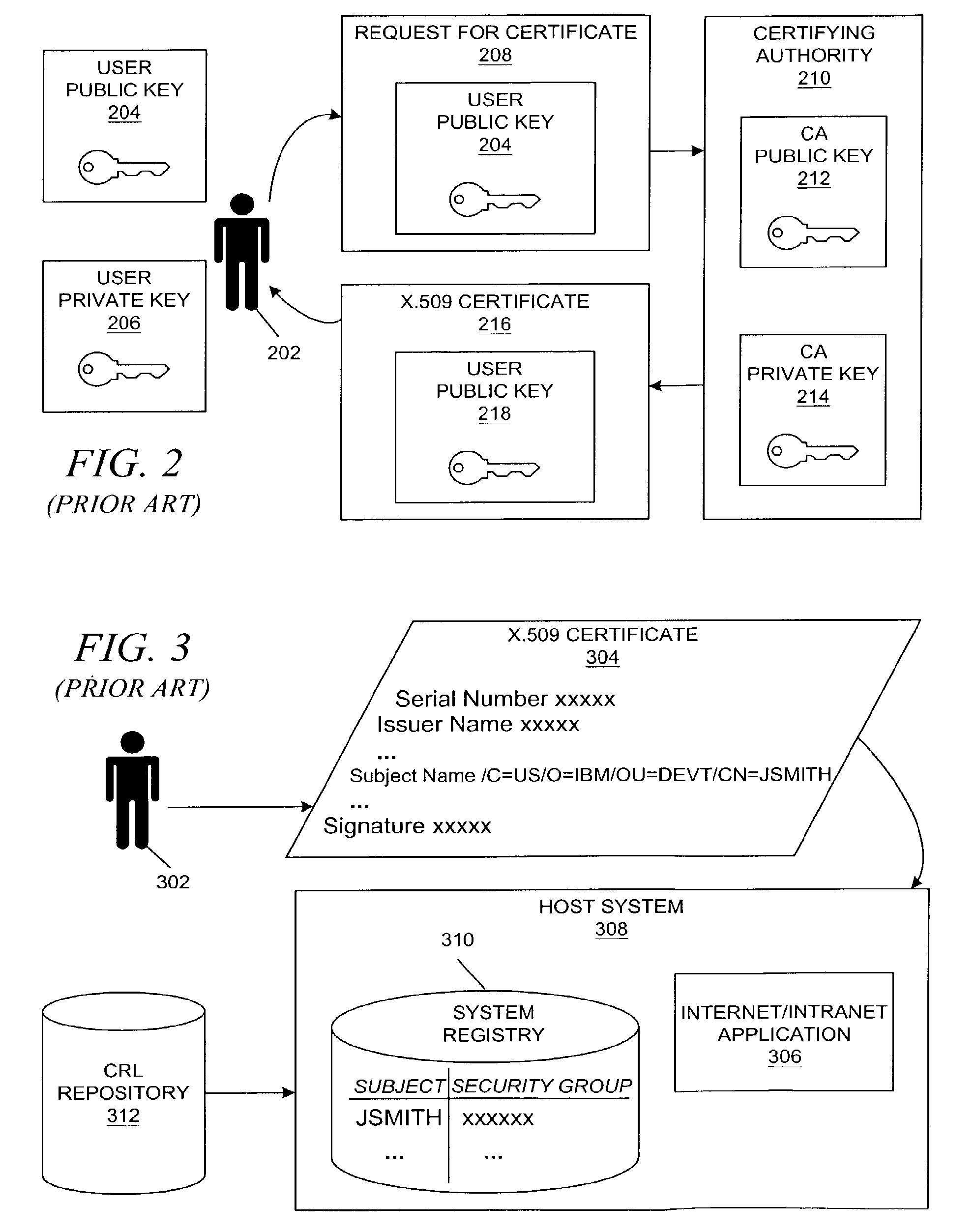
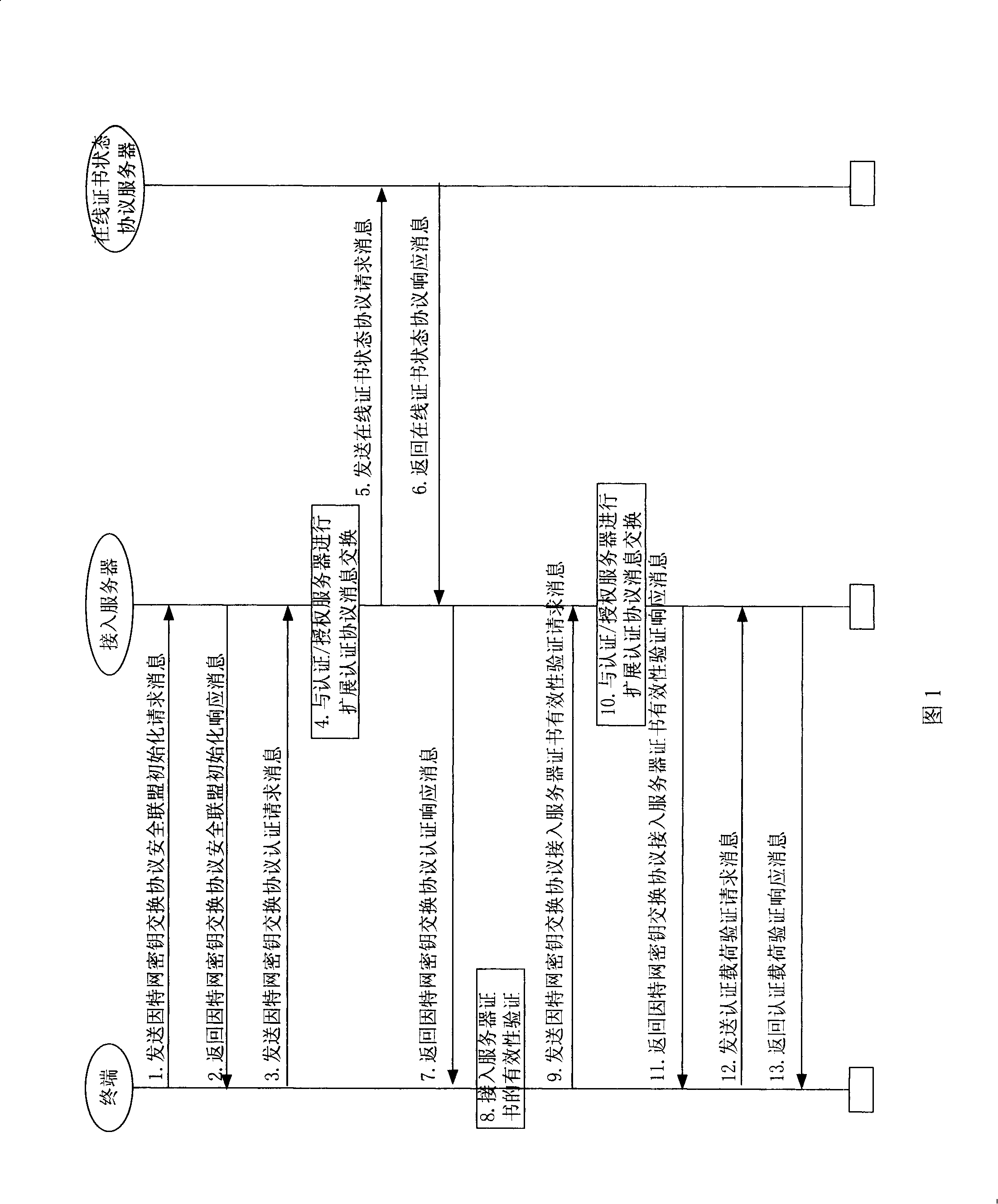
The Online Certificate Status Protocol (OCSP) is an Internet protocol used for obtaining the revocation status of an X.509 digital certificate. It is described in RFC 6960 and is on the Internet standards track. It was created as an alternative to certificate revocation lists (CRL), specifically addressing certain problems associated with using CRLs in a public key infrastructure (PKI). Messages communicated via OCSP are encoded in ASN.1 and are usually communicated over HTTP. The "request/response" nature of these messages leads to OCSP servers being termed OCSP responders.
Method and system for answering online certificate status protocol (OCSP) requests without certificate revocation lists (CRL)
InactiveUS6970862B2Digital data protectionElectronic credentialsDirectory Access ProtocolClient-side
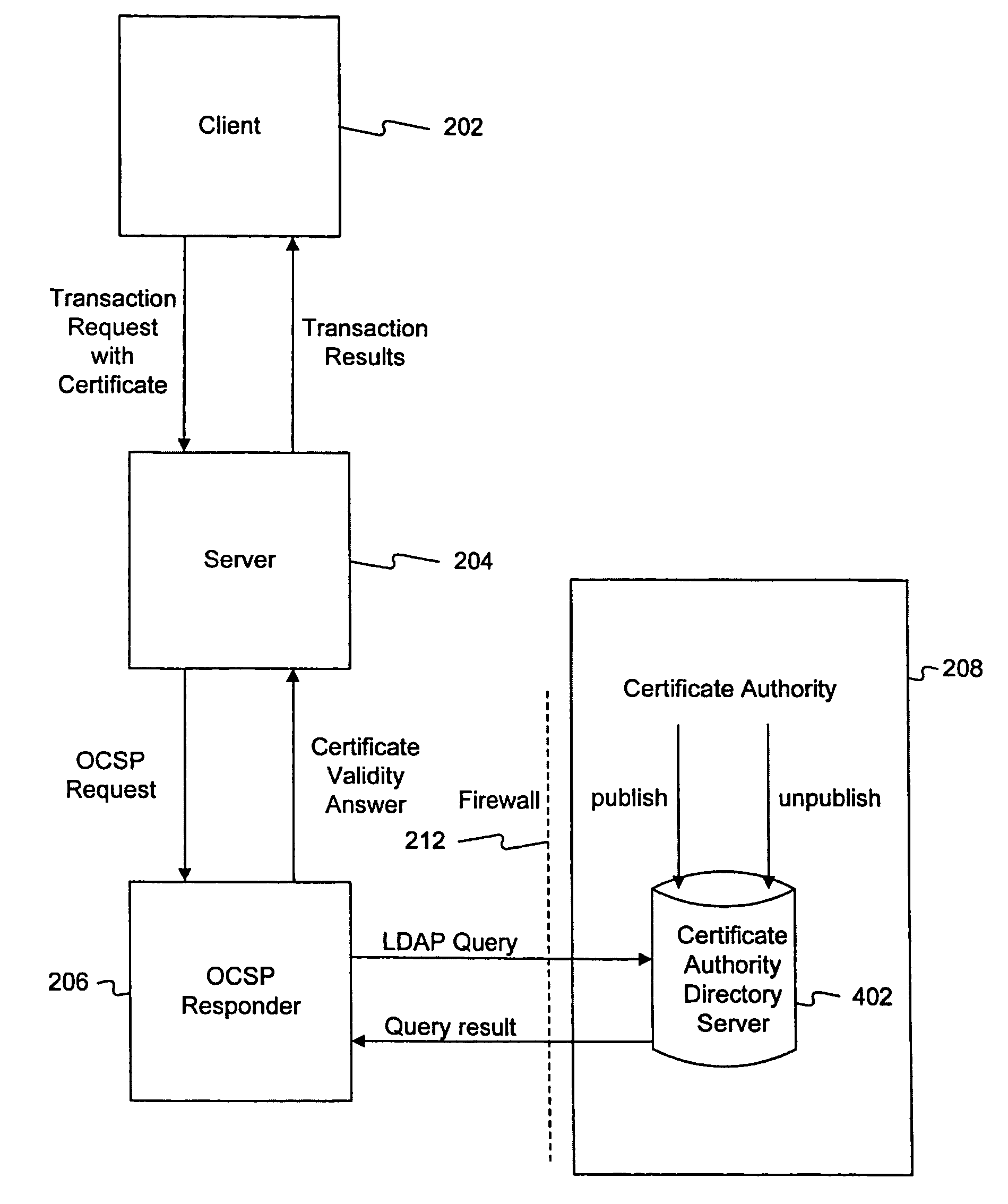
Methods and systems in accordance with the present invention efficiently validate digital certificates by answering Online Certificate Status Protocol (“OCSP”) requests without Certificate Revocation Lists (“CRL”). During validation of digital certificates, these methods and systems speed transmission, reduce required bandwidth and reduce required data storage by eliminating the need for the transmission of lengthy CRLs from a Certificate Authority (“CA”) when verifying a digital certificate from a client. In one implementation, they send a Lightweight Directory Access Protocol (“LDAP”) database query to a CA directory server to determine and pinpoint the existence of a valid digital certificate and check its validity without receiving a long list of data, such as a CRL, from a CA. The CA directory server returns the query result, and the database query in the CA directory server is performed faster than using an entire CRL, and furthermore, the transmission of the database query result is a small piece of information and does not require the large amounts of data transmission bandwidth and storage as required with transmitting CRL's.
Owner:ORACLE INT CORP
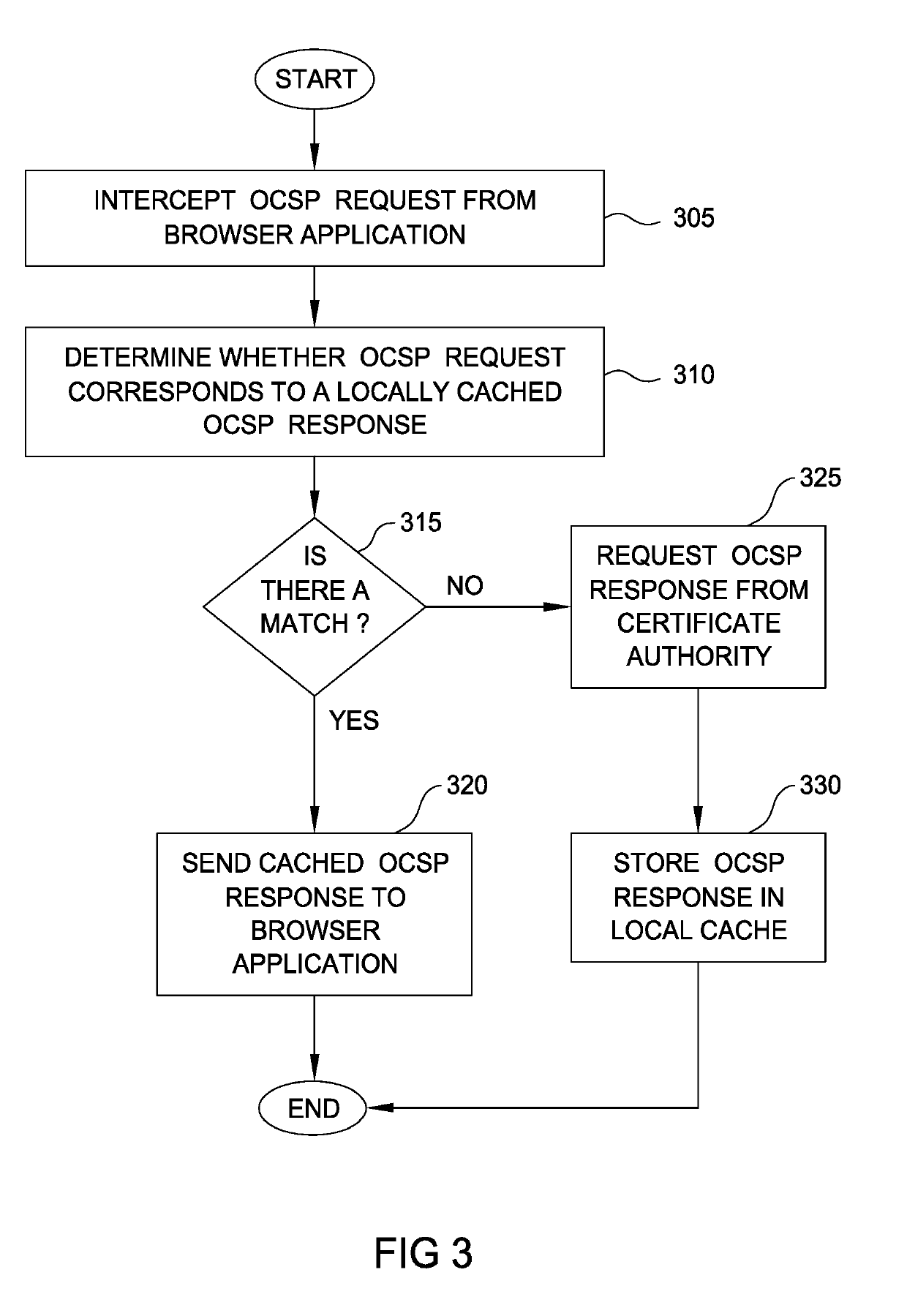
Certificate status delivery through a local endpoint
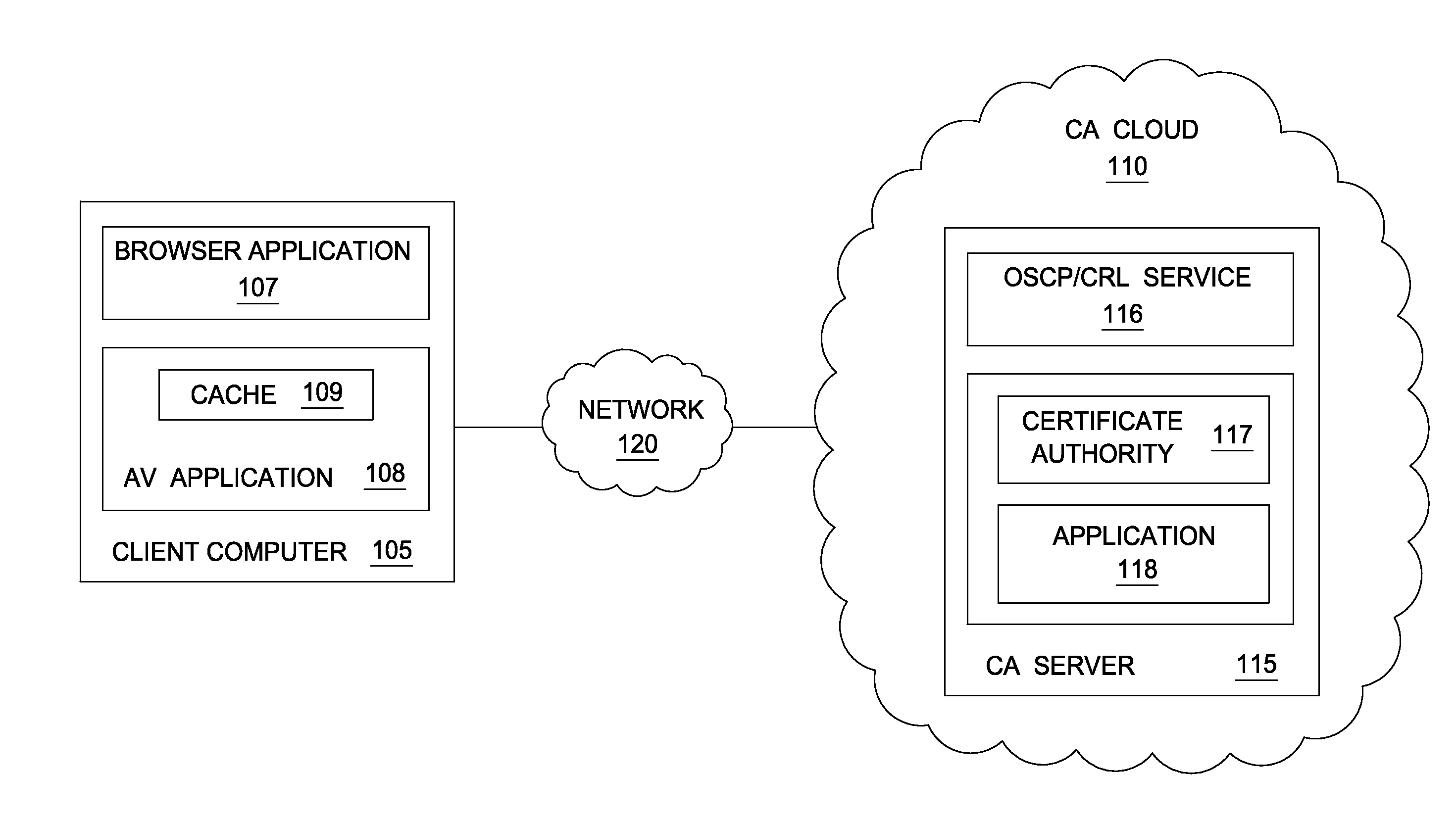
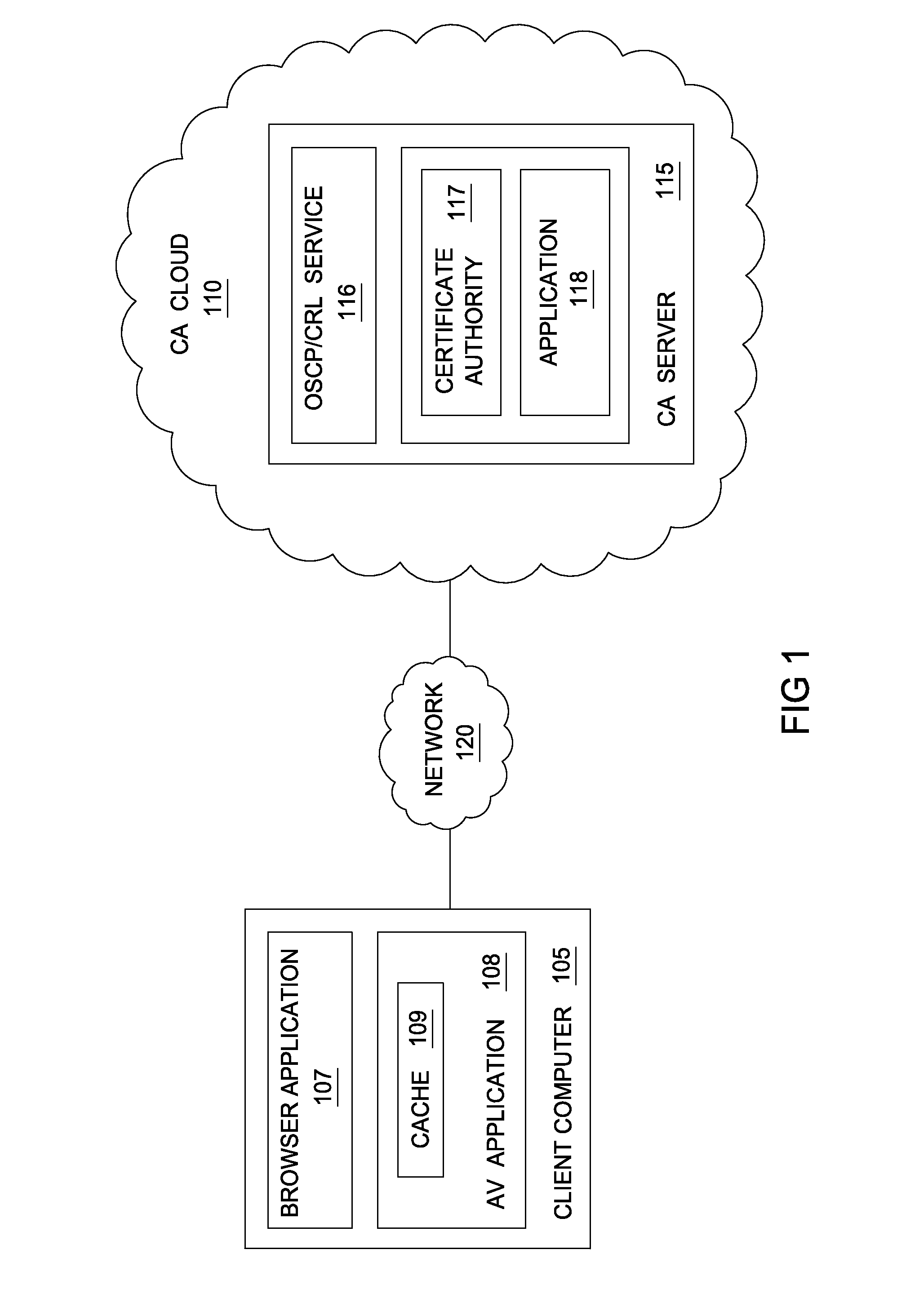
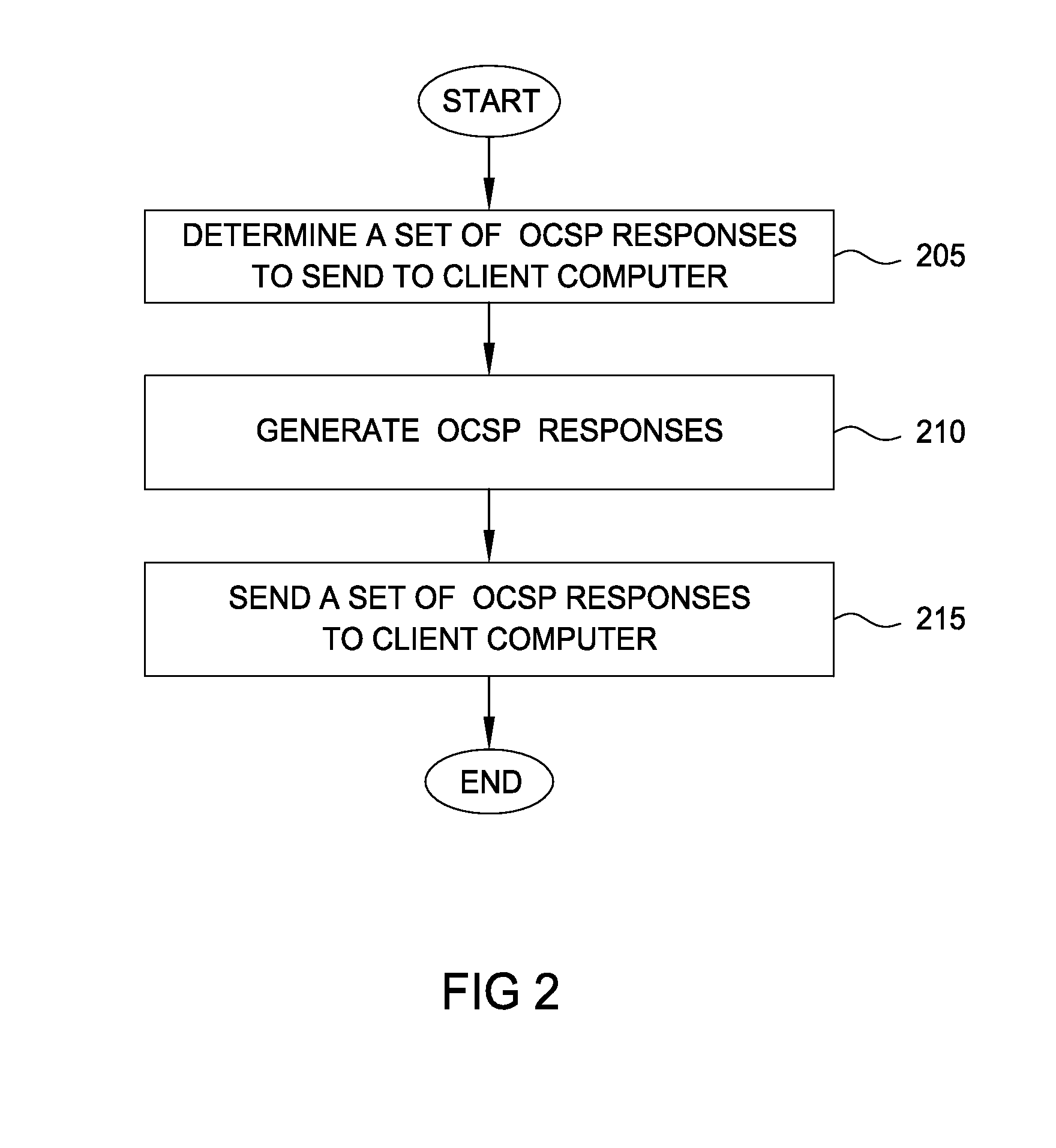
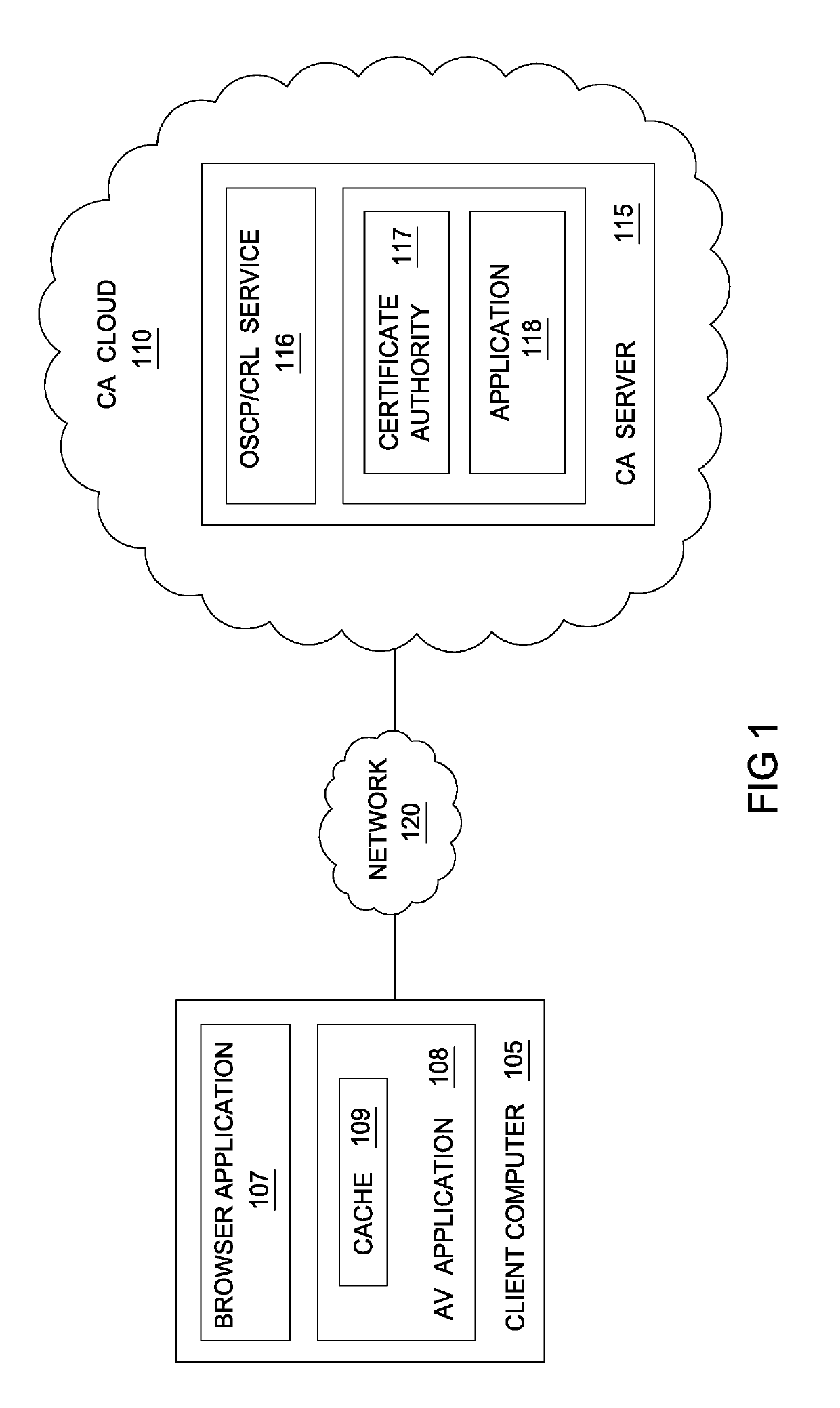
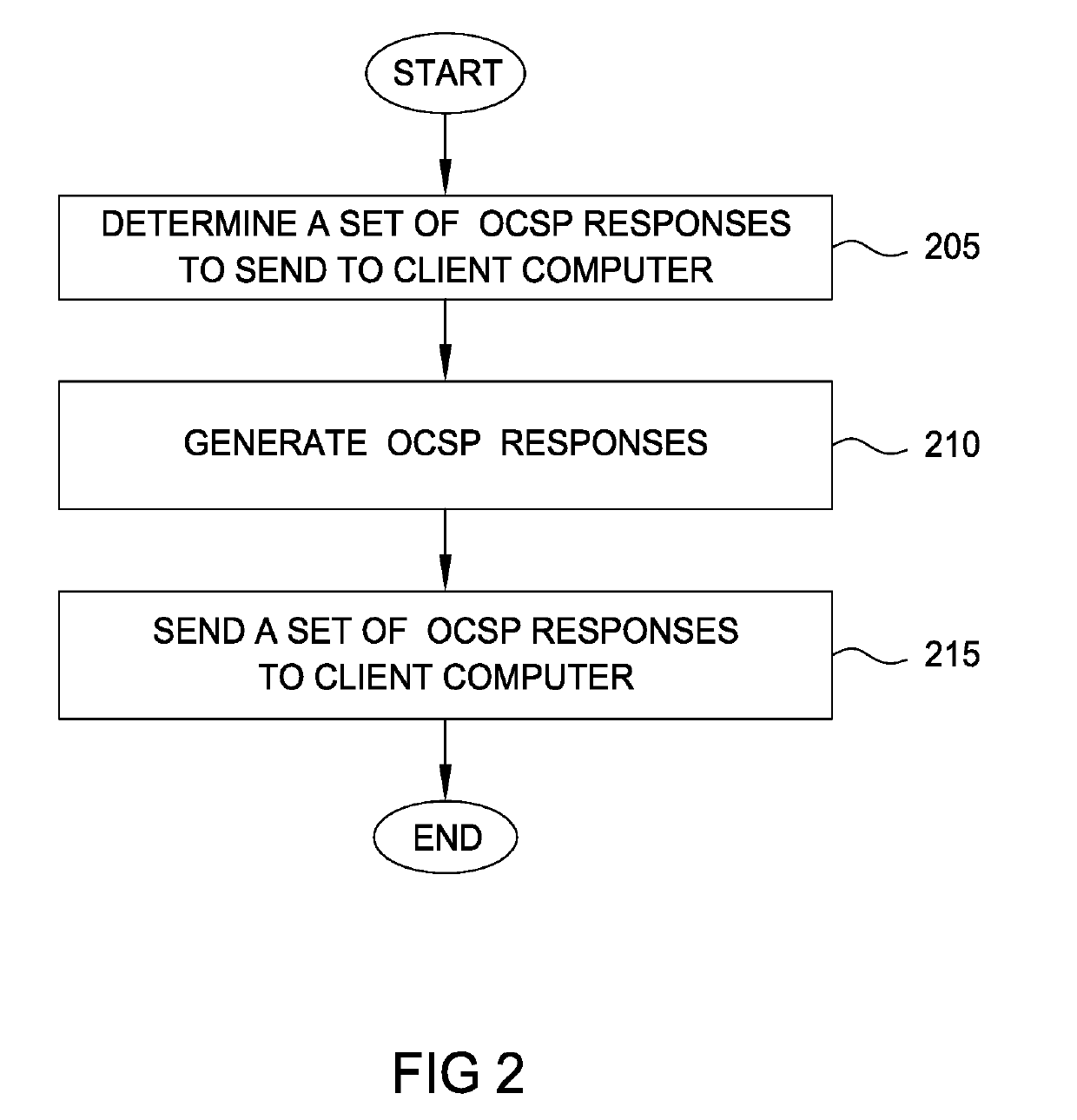
Techniques are disclosed for locally distributing online certificate status protocol (OCSP) responses to a client computer. A certificate authority (CA) proactively sends OCSP responses to an agent application (e.g., an antivirus application configured to handle OCSP responses) residing in the client computer. The agent application stores the OCSP responses in a cache. Thereafter, when a browser application sends an OCSP request to the CA, the agent application intercepts the request and determines whether a corresponding OCSP response is locally cached. If so, the agent application sends the cached OCSP response to the browser application. If not, the agent application retrieves the corresponding OCSP response from the CA and sends the response to the browser application.
Owner:DIGICERT
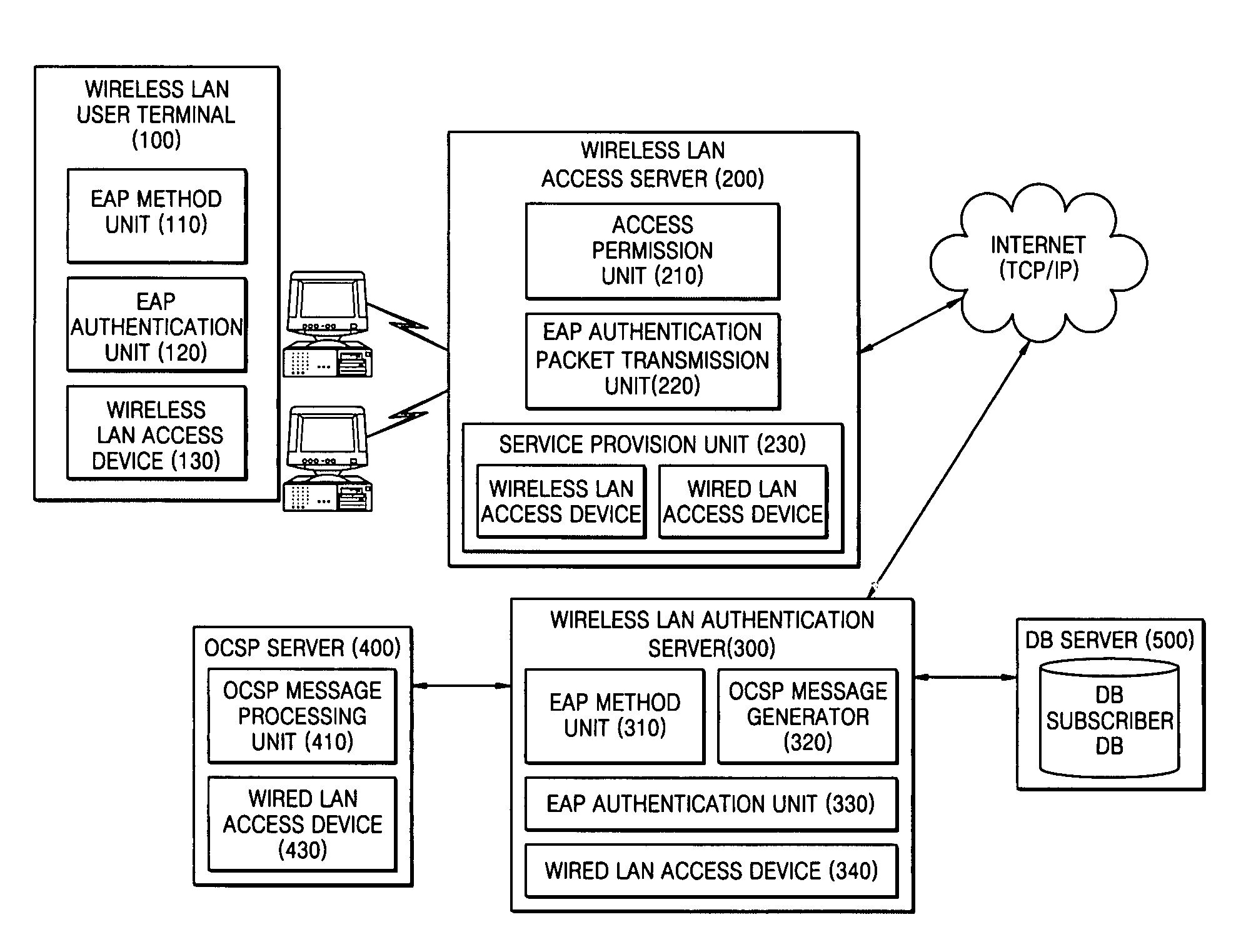
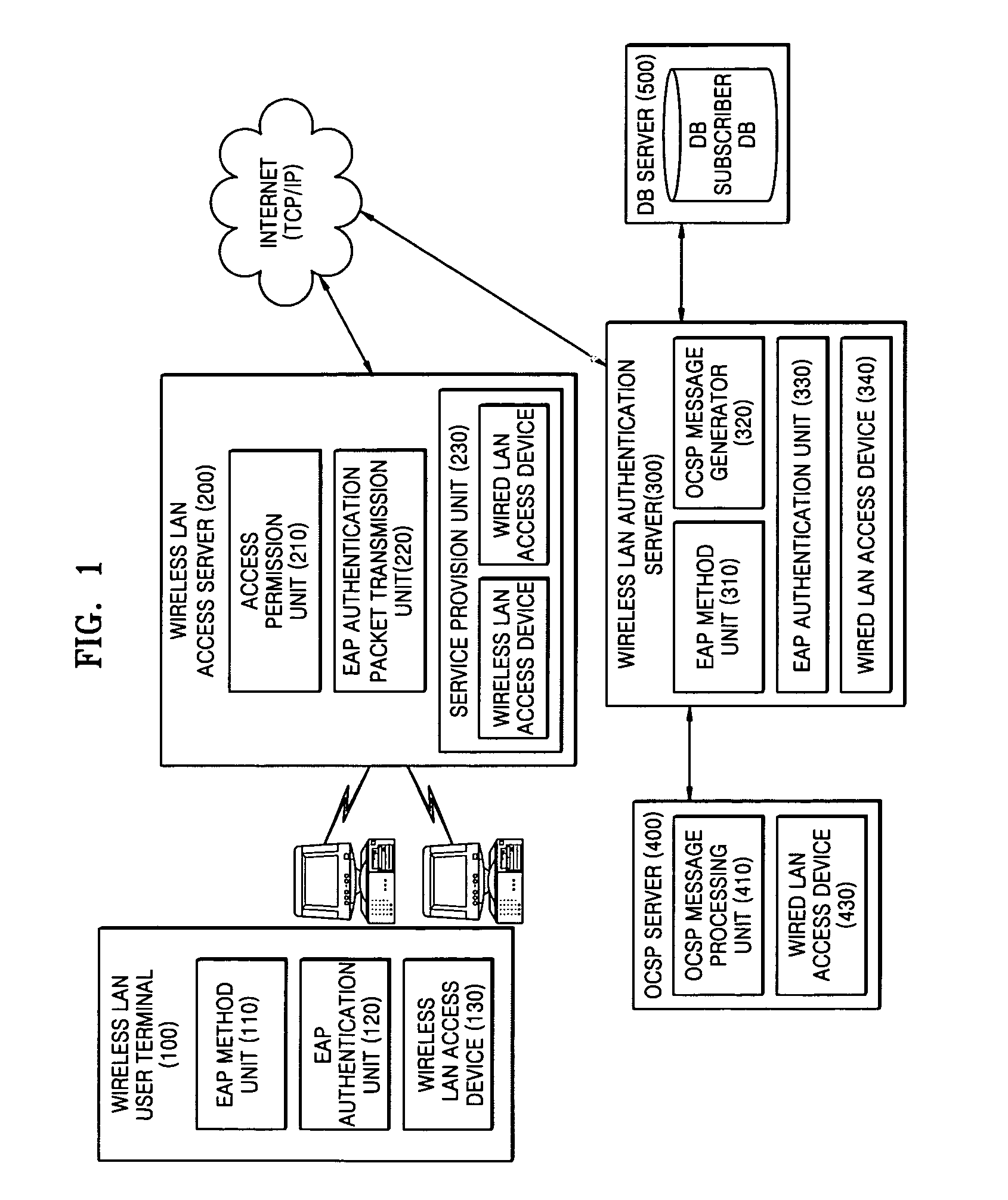
Server authentication verification method on user terminal at the time of extensible authentication protocol authentication for internet access
InactiveUS7533257B2Random number generatorsUser identity/authority verificationComputer terminalWireless lan
A server certificate verification method in a terminal during. Extensible Authentication Protocol authentication for Internet access is provided, the method including (a) receiving a server certificate from a wireless LAN authentication server, and transmitting a server certificate verification request message of the server certificate to a wireless LAN authentication server via a wireless LAN access server; (b) transmitting by the wireless LAN authentication server an On-line Certificate Status Protocol request message to an On-line Certificate Status Protocol server to verify the server certificate; (c) receiving a result of the server certificate verification performed by the OCSP server using an Extensible Authentication Protocol packet from the wireless LAN authentication server; and (d) determining whether the result of the server certificate verification is valid.
Owner:ELECTRONICS & TELECOMM RES INST
Apparatus and method of verifying online certificate for offline device
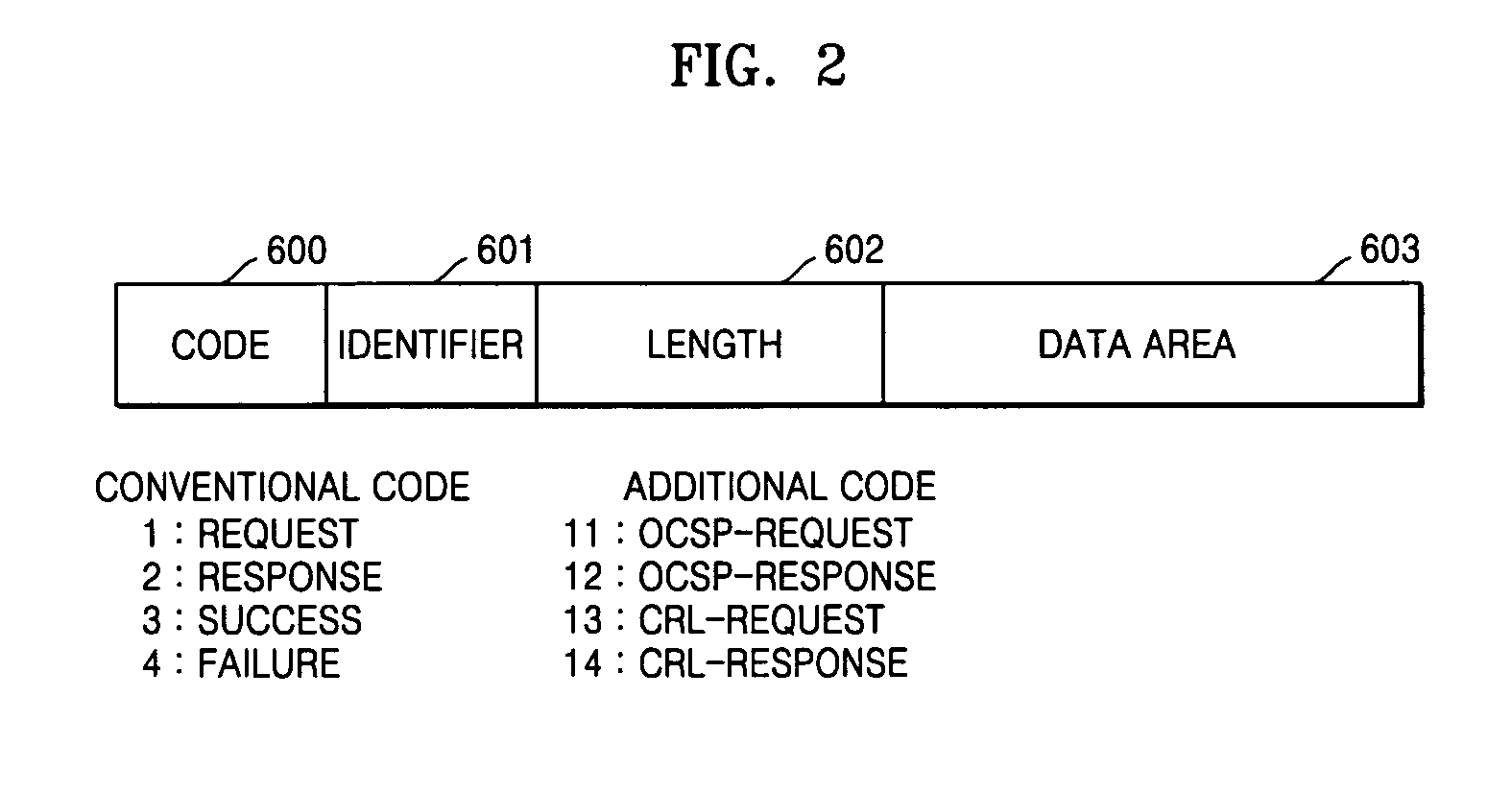
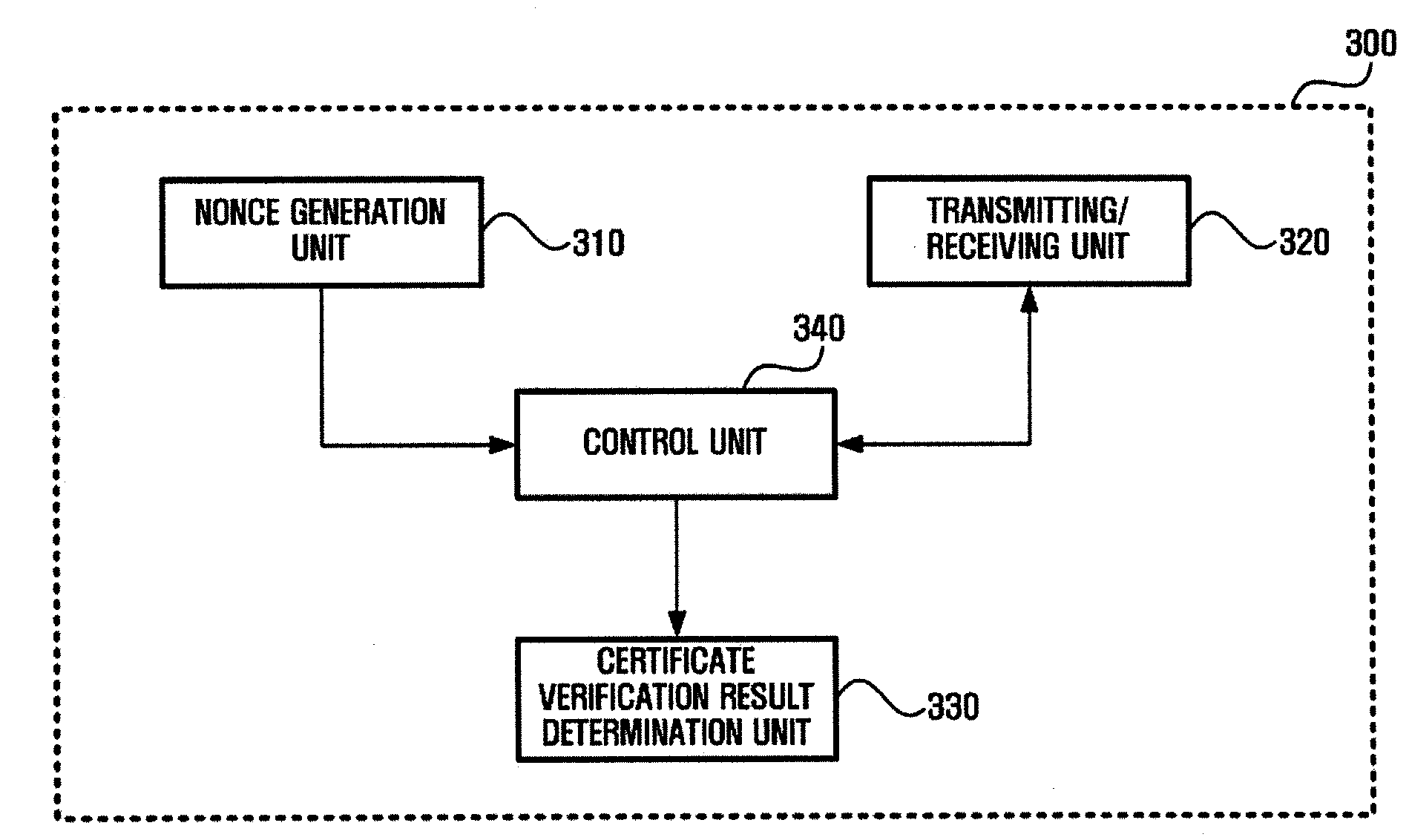
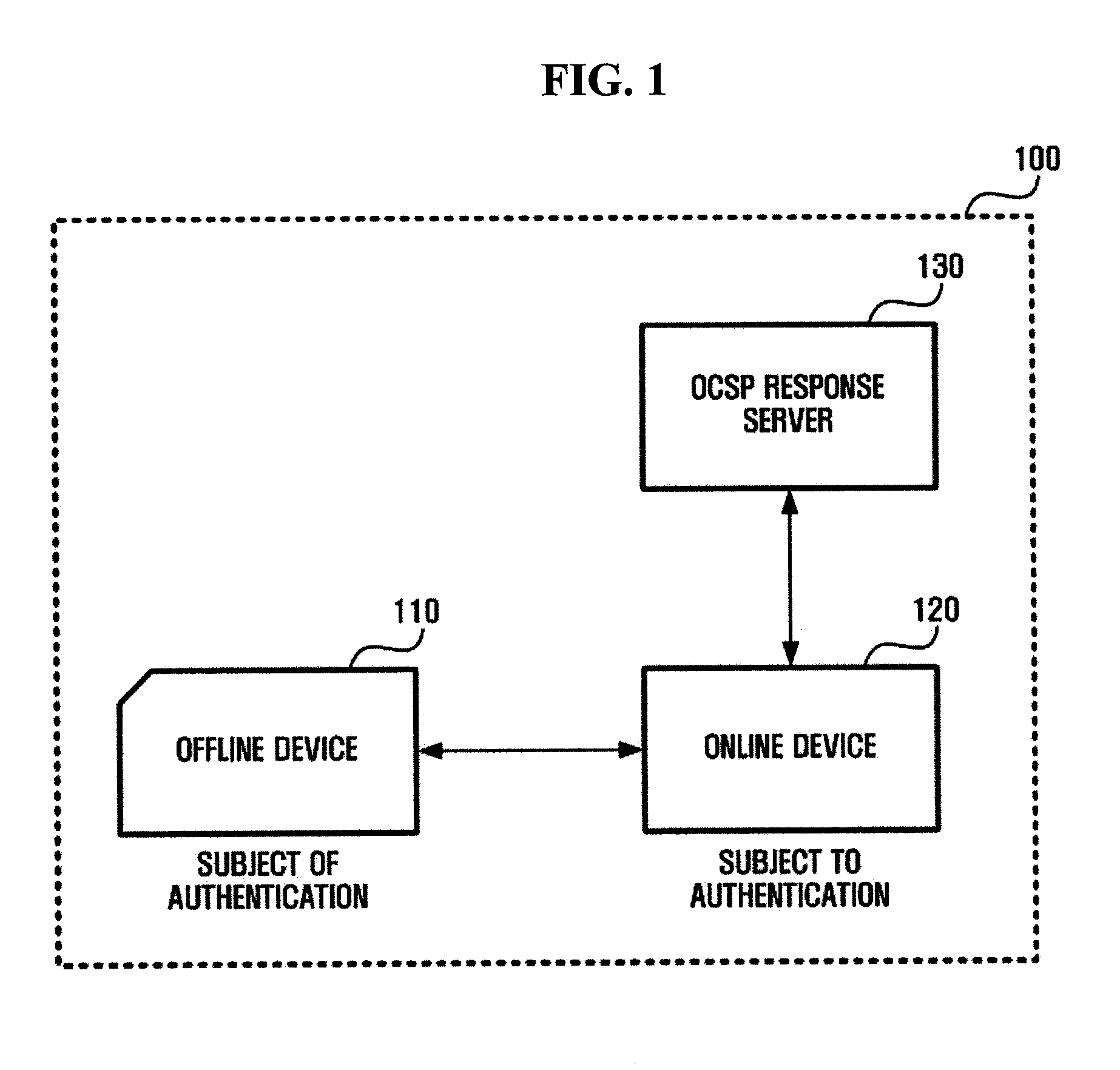
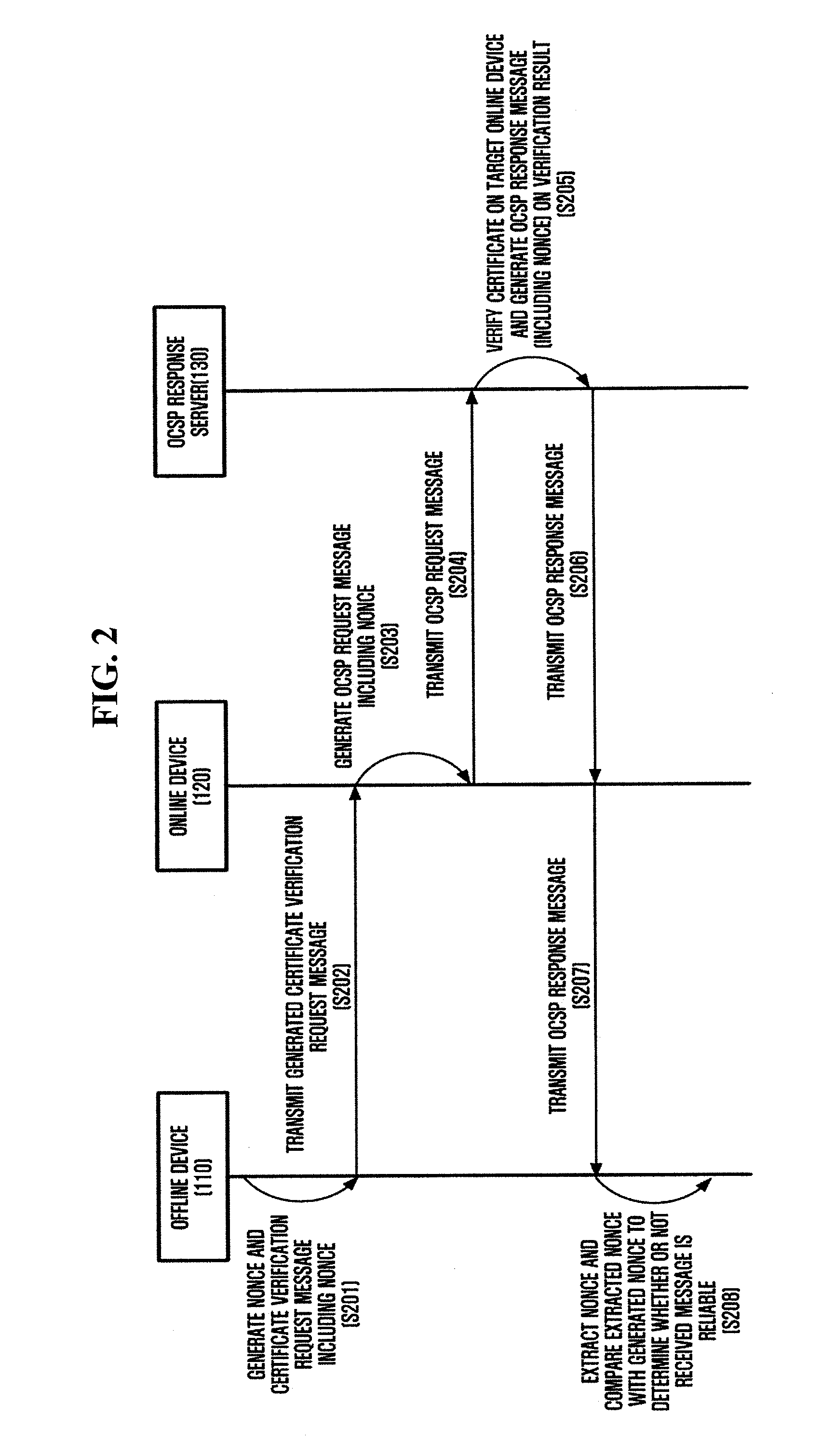
InactiveUS20080301793A1Reliable resultsDigital data processing detailsUser identity/authority verificationRandom number generationOnline Certificate Status Protocol
An apparatus and a method are provided for verifying an online certificate for an offline device. The apparatus includes a nonce generation unit which generates a nonce and a certificate verification request message that requests verification of a certificate on a target online device subject to authentication, wherein the certificate verification request message includes the generated nonce; a transmitting and receiving unit which transmits the certificate verification request to an online device and receives an online certificate status protocol (OCSP) response message from the online device; and a certificate verification result determination unit which extracts a nonce from the OCSP response and compares the extracted nonce with the nonce generated by the nonce generation unit to determine whether the OCSP response is reliable.
Owner:SAMSUNG ELECTRONICS CO LTD
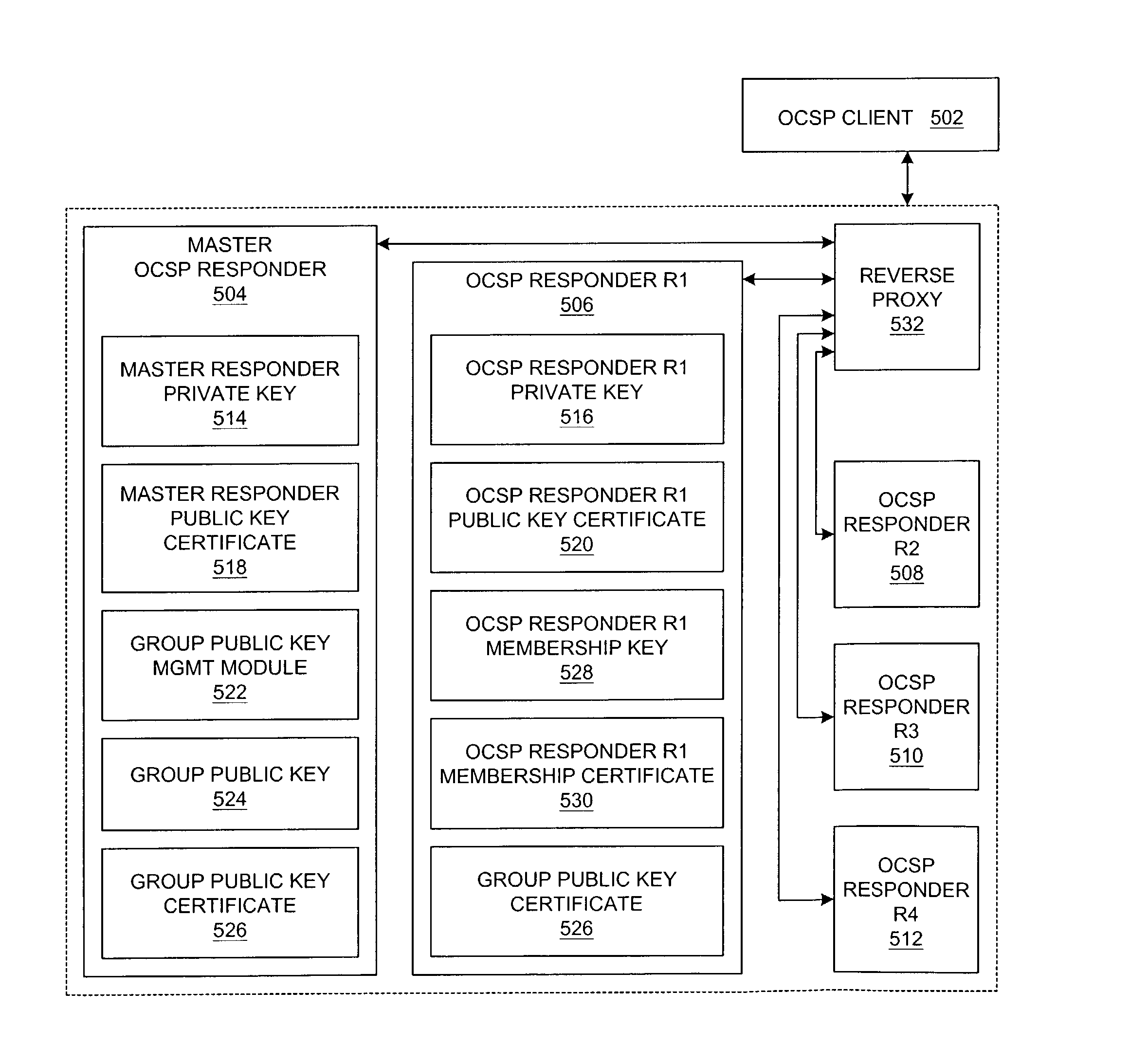
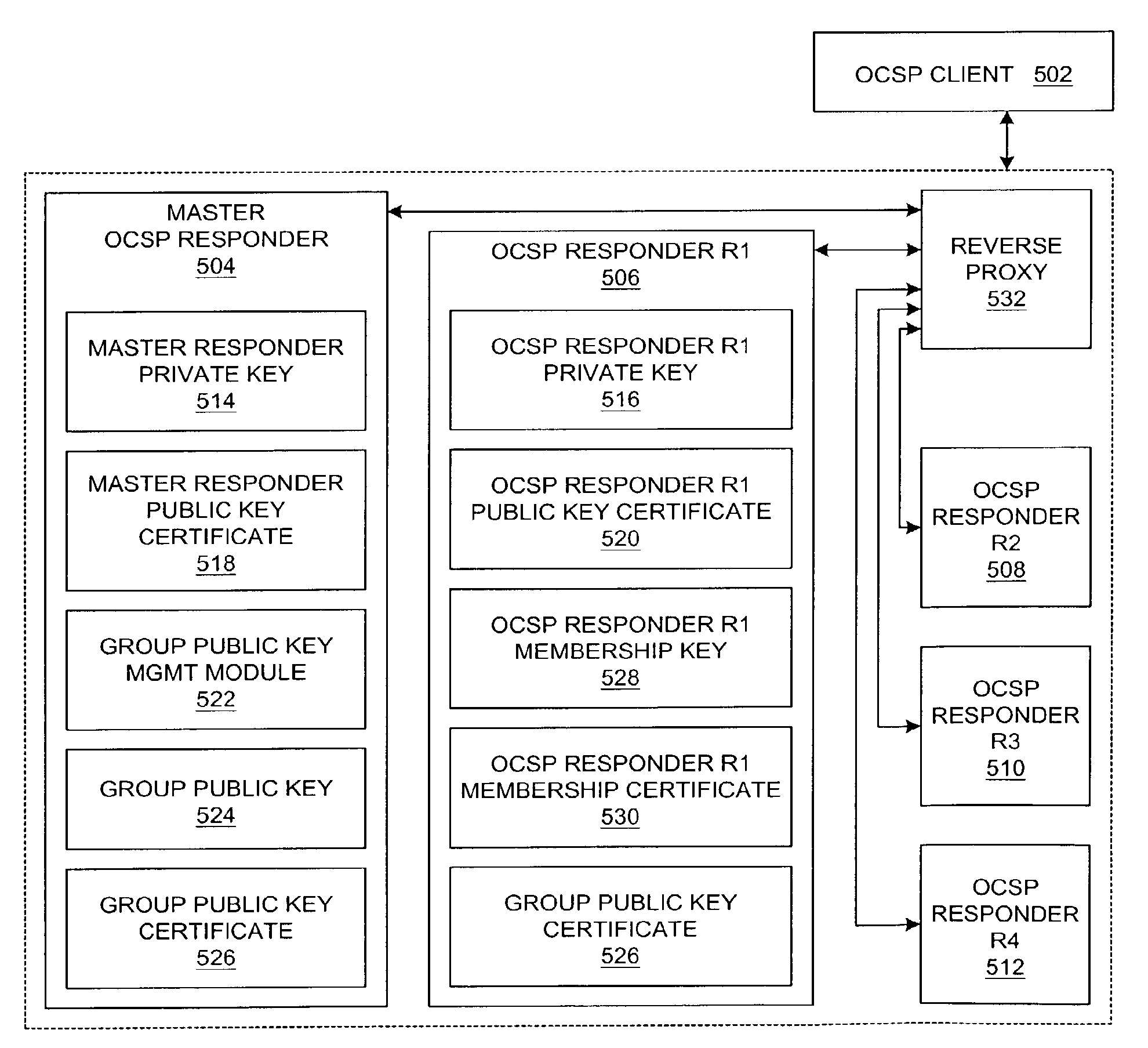
Method and system for configuring highly available online certificate status protocol responders
ActiveUS7318155B2Improve usabilityReduce loadUser identity/authority verificationDigital signatureHigh availability
A method and system is presented for configuring a group of OCSP (Online Certificate Status Protocol) responders so that they are highly available. Each of the grouped OCSP responders share a common public key. When responding to an OCSP request, an OCSP responder generates an OCSP response that is signed with a group digital signature; the certificate for the common or group public key can be attached to the OCSP response. An OCSP client uses the group public key to verify the group digital signature on an OCSP response from any of the OCSP responders. For an OCSP client, the availability of this group of responders is greater than the availability of any one member of the group.
Owner:SERVICENOW INC
Method and system for configuring highly available online certificate status protocol
InactiveUS7865721B2Improve availabilityImprove usabilityUser identity/authority verificationDigital signatureHigh availability
A method and system is presented for configuring a group of OCSP (Online Certificate Status Protocol) responders so that they are highly available. Each of the grouped OCSP responders share a common public key. When responding to an OCSP request, an OCSP responder generates an OCSP response that is signed with a group digital signature; the certificate for the common or group public key can be attached to the OCSP response. An OCSP client uses the group public key to verify the group digital signature on an OCSP response from any of the OCSP responders. For an OCSP client, the availability of this group of responders is greater than the availability of any one member of the group.
Owner:SERVICENOW INC
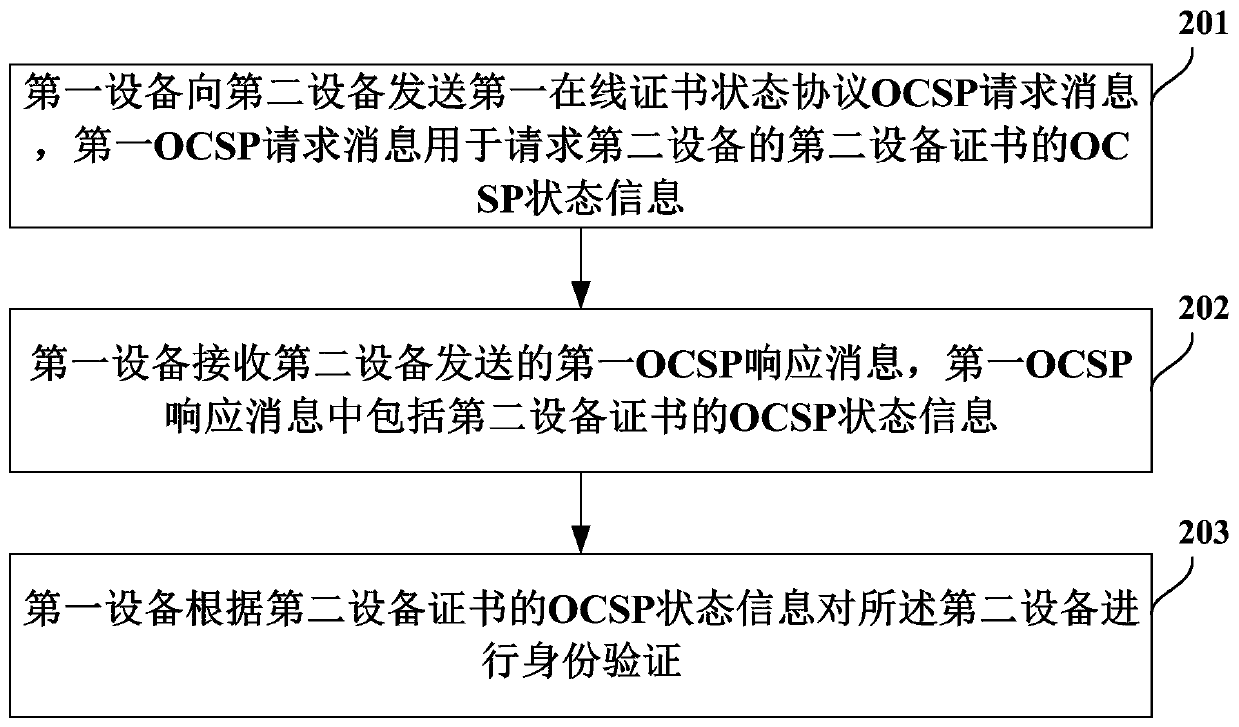
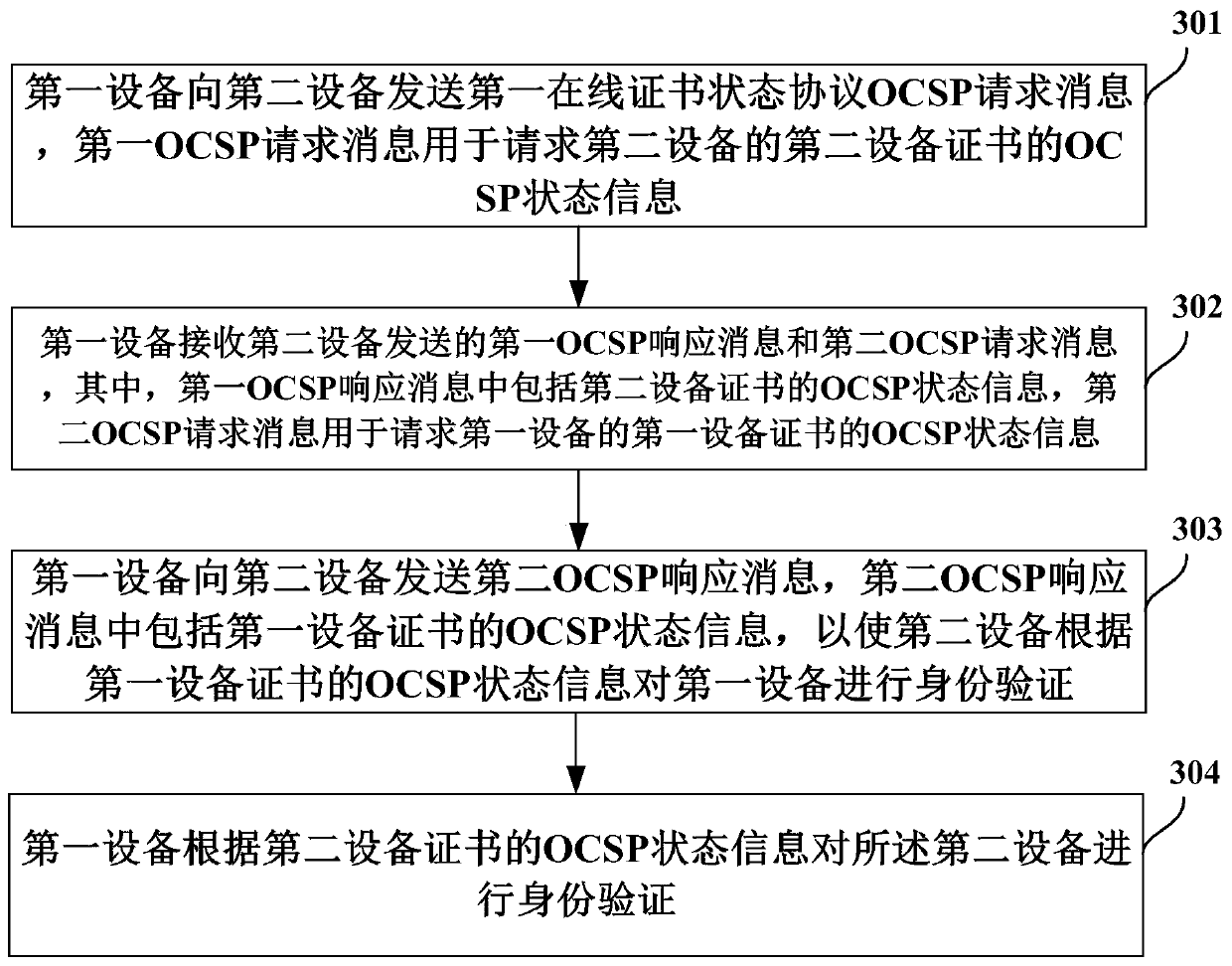
Certificate authentication method and equipment
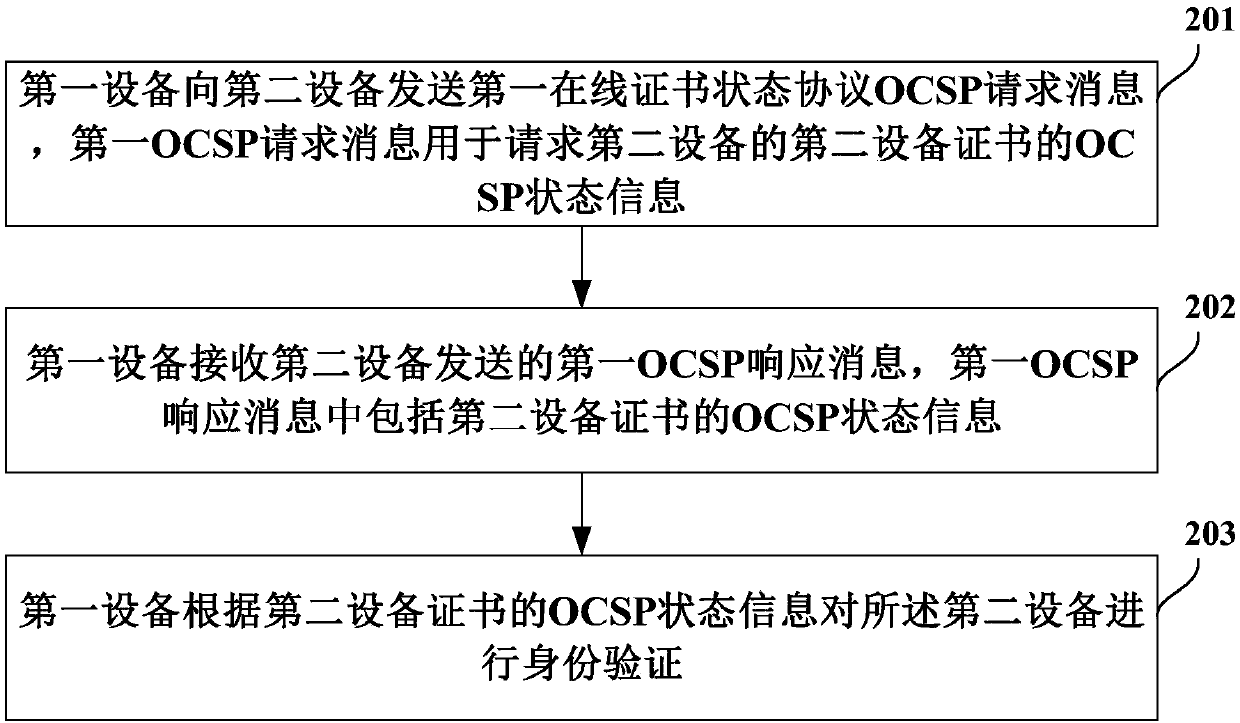
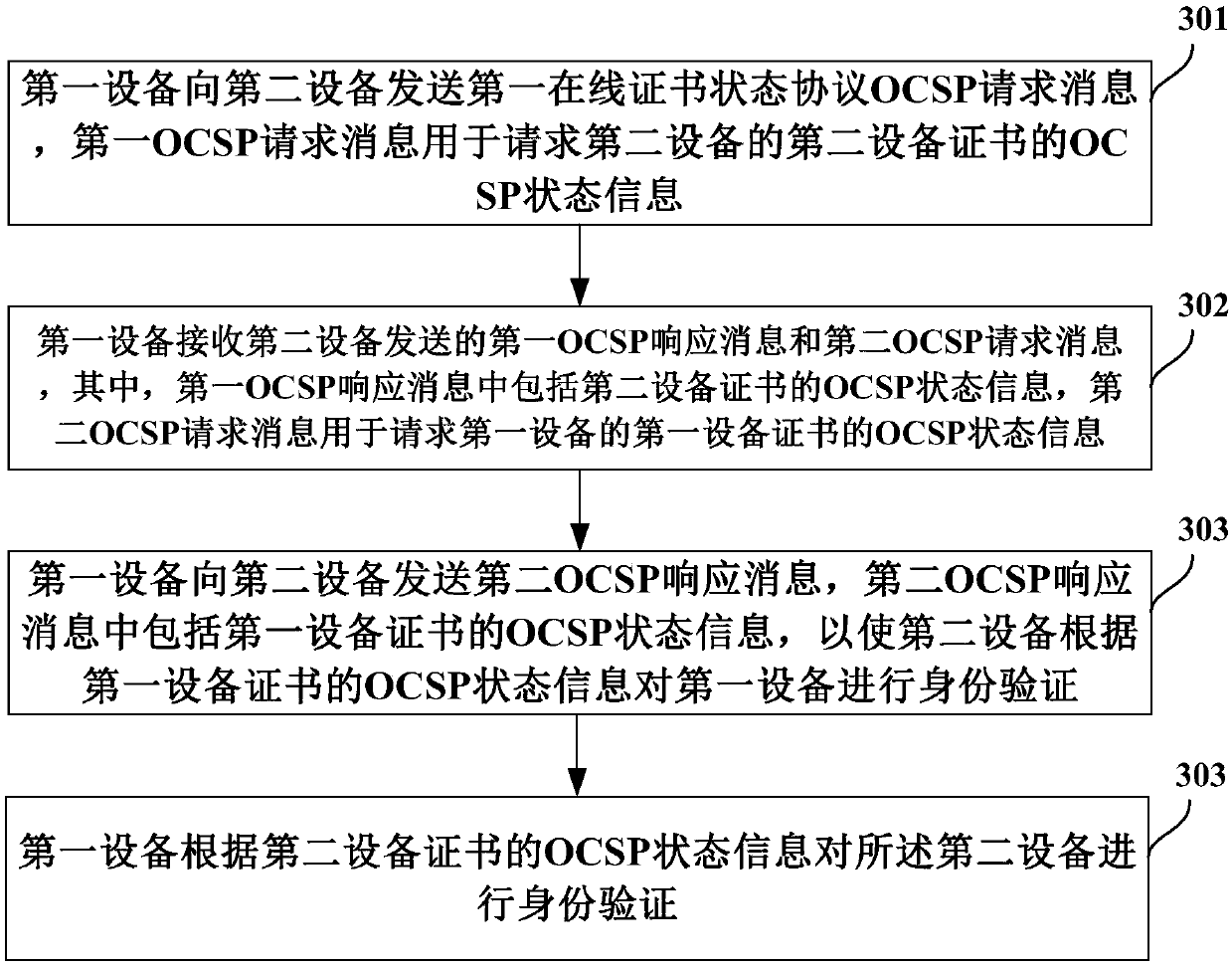
ActiveCN107786515AValid inspectionEasy accessTransmissionProtocol for Carrying Authentication for Network AccessAuthentication
Embodiments of the invention provide a certificate authentication method and equipment. The method comprises the following steps that first equipment sends a first online certificate status protocol (OCSP) request message to second equipment, wherein the first OCSP request message is used for requesting OCSP status information of a second equipment certificate of the second equipment; the first equipment receives a first OCSP response message sent by the second equipment, wherein the first OCSP response message includes OCSP status information of the second equipment certificate; and the firstequipment carries out identity verification on the second equipment according to the OCSP status information of the second equipment certificate. According to the certificate authentication method and equipment, a problem that a client does not need to access a CRL or OCSP server to carry out validity verification on the certificate of the server in a handshaking process is solved.
Owner:CHINA MOBILE COMM LTD RES INST +1
Method for authenticating validity of IKE V2 certificate
The invention discloses a validation verification method of a second edition certification of an internet key exchange protocol. The present validation verification method of an accessing server certification is not only with low efficiency, but also lacks of safety guarantee. For solving the problems, the validation verification method of the second edition certification of the internet key exchange protocol of the invention, which comprises the following steps: (1) the validity of the accessing server certification is verified by a terminal through the protocol server in an online certification status. If the accessing server certification is effective, a next step is carried out; if the accessing server certification is not effective, the steps are ended; (2) the validity of the terminal identification is approved by the accessing server. If the terminal identification is legal, communication is established by the both side; if the terminal identification is illegal, the steps are ended. The invention is applicable to a safety verification field of the second edition in the internet key exchange protocol.
Owner:ZTE CORP
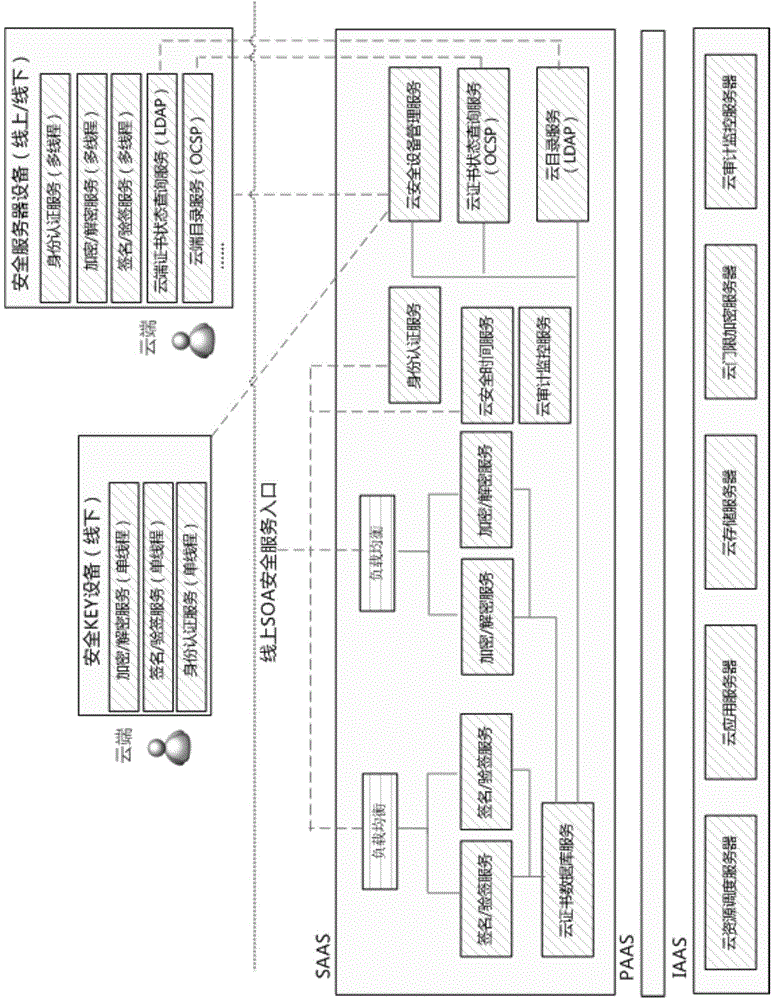
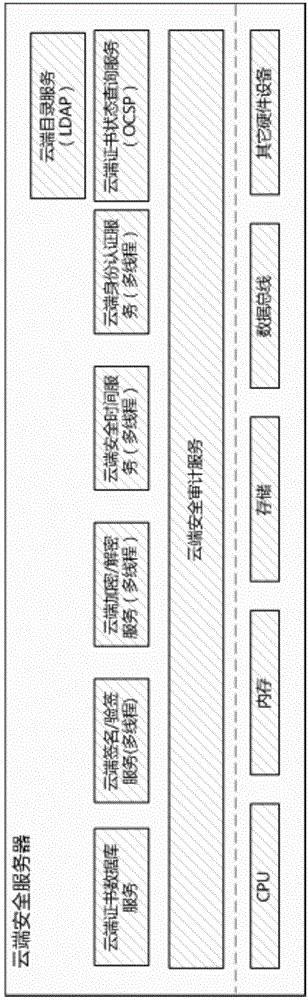
Electronic invoice safety middleware configuring method based on cloud computing technology
ActiveCN104636960AAvoid duplication of investment in constructionBilling/invoicingInvoiceEngineering
The invention provides an electronic invoice safety middleware configuring method based on the cloud computing technology. The electronic invoice safety middleware configuring method includes steps of using the cloud computing technology to configure cloud safety services of safety middleware, issuing and managing cloud safety KEY devices and safety server devices, and balancing computing resources of service modules with service peaks and valleys via resource dispatching services in the cloud computing technology; filling certificates and algorithms to the cloud safety KEY devices by the special communication protocol, issuing API (application program interface) ports to the outside through the devices and providing offline, movable and single-thread safety services for electronic invoice users; synchronizing certificates for the cloud safety server devices by standard directory services LDAP and certificate status query services (OCSP online certificate status protocol) and providing multithread safety services based on the local area network for the electronic invoice users. Cloud safety services, cloud KEY devices and cloud safety server devices can jointly form a cloud safety middleware configuring method.
Owner:SHANDONG LANGCHAO YUNTOU INFORMATION TECH CO LTD
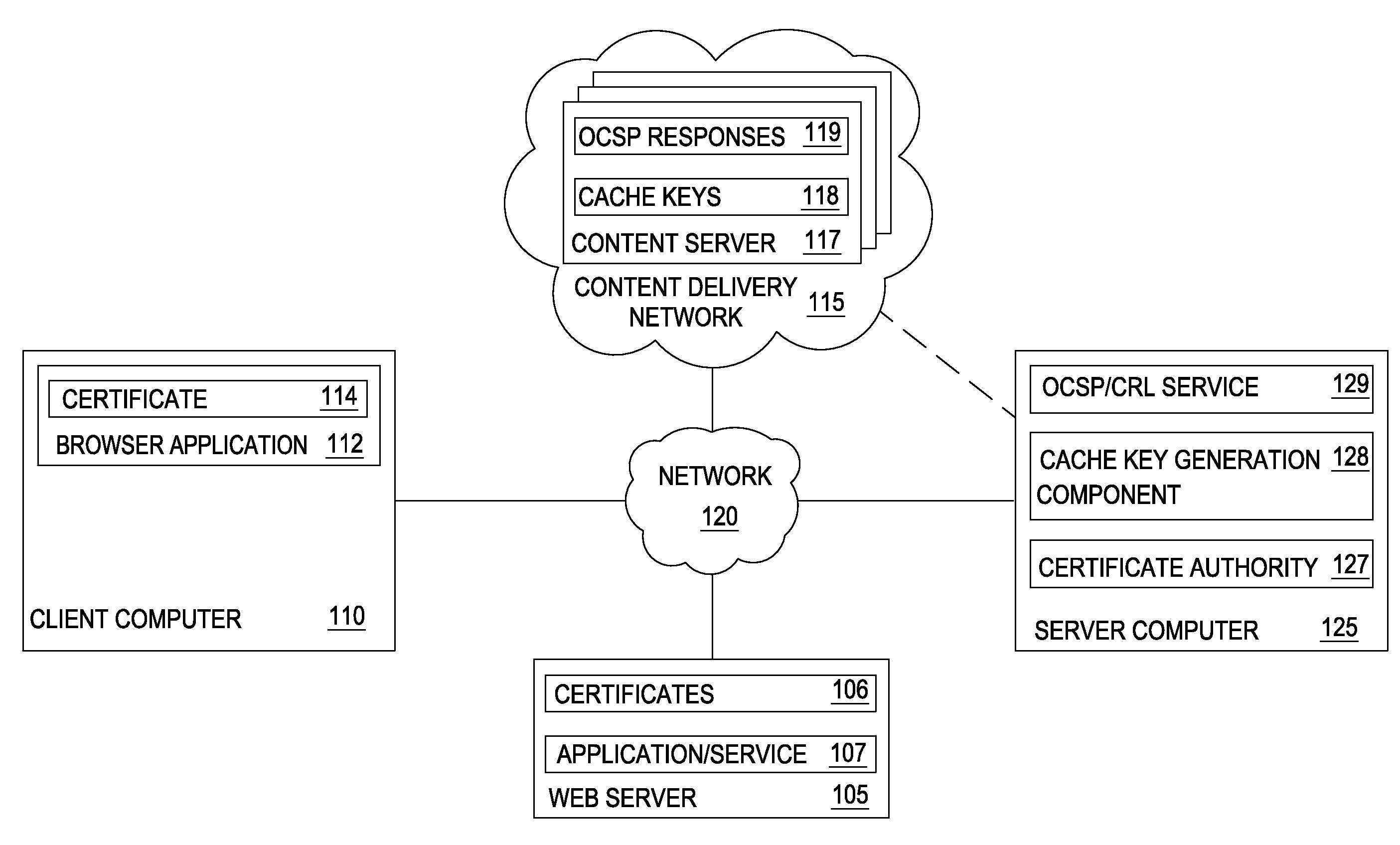
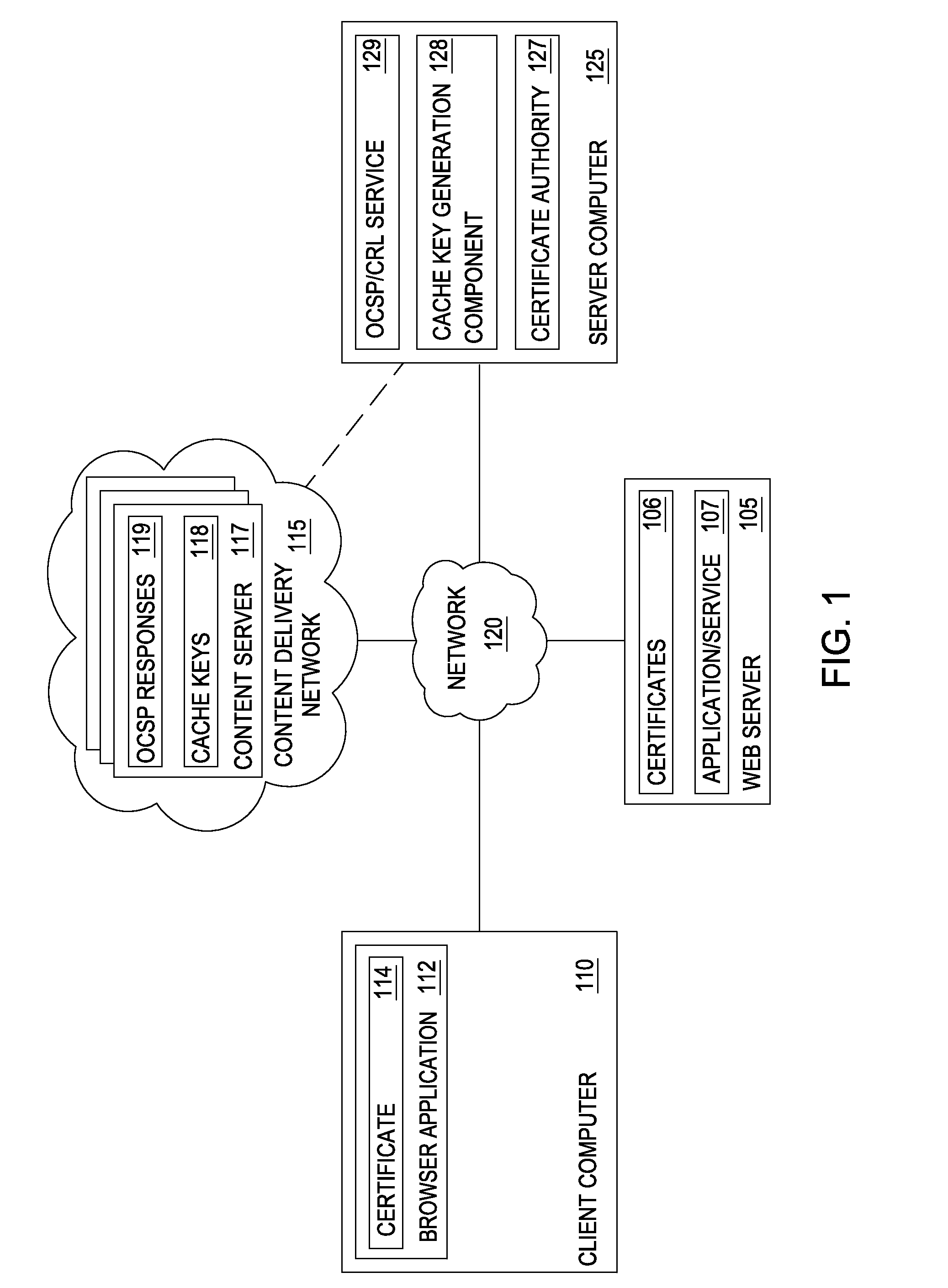
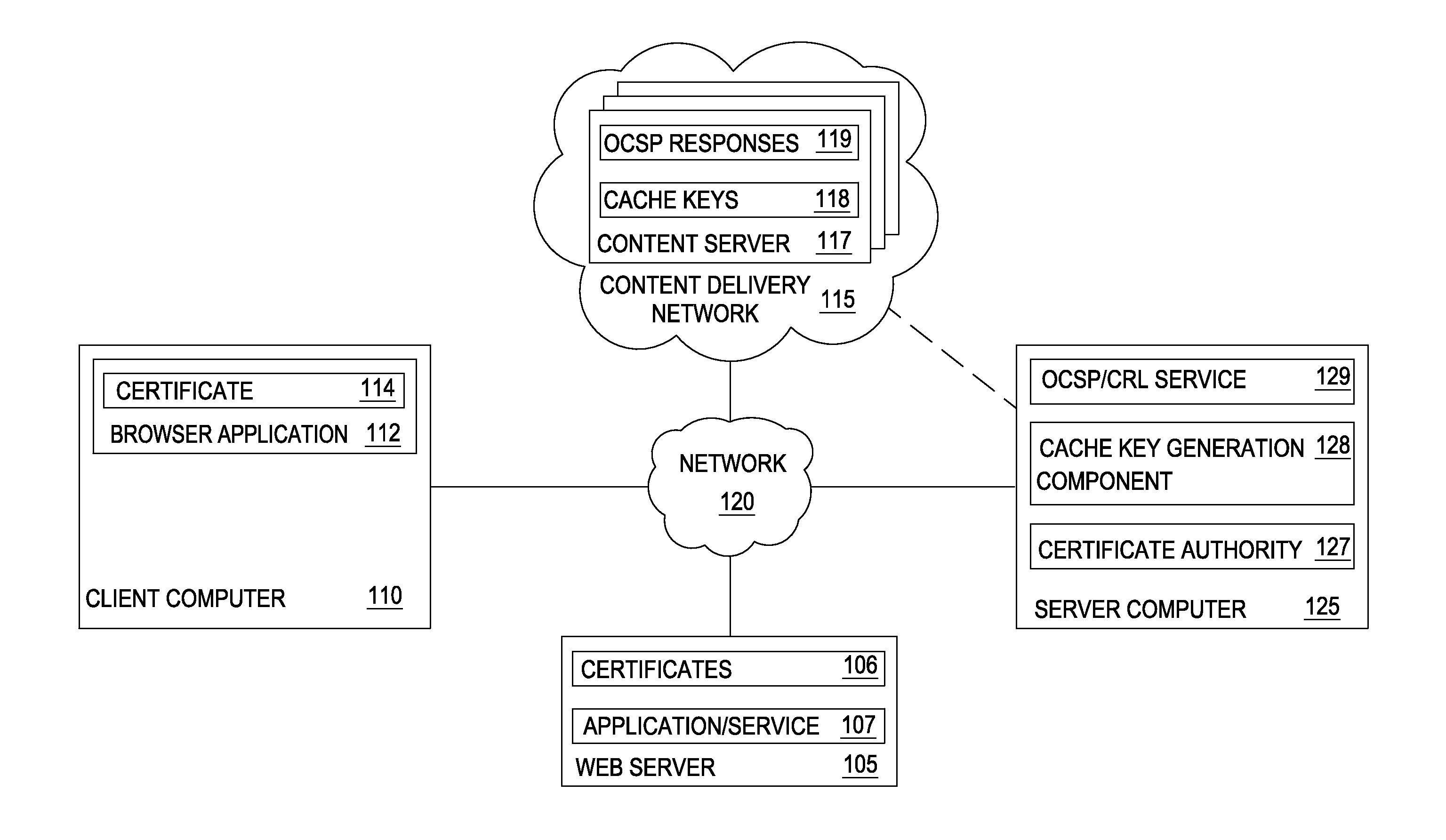
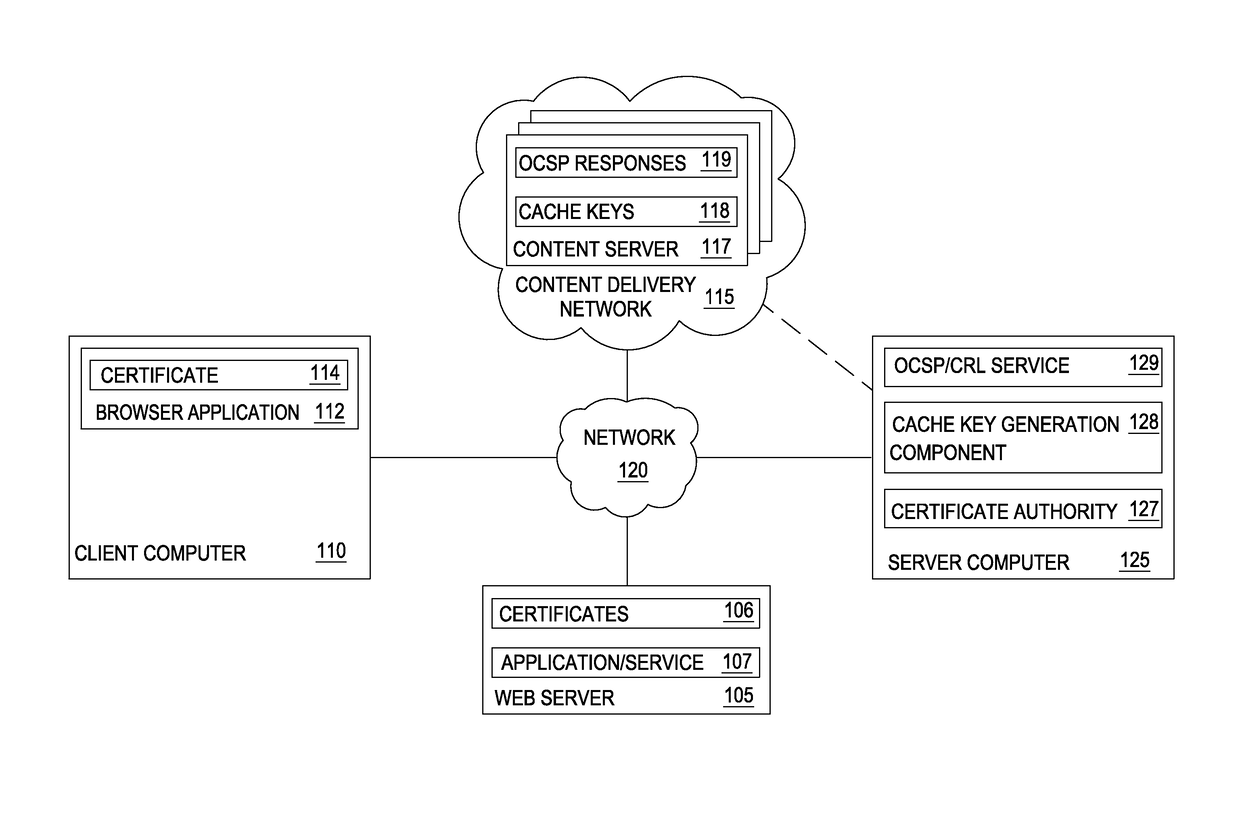
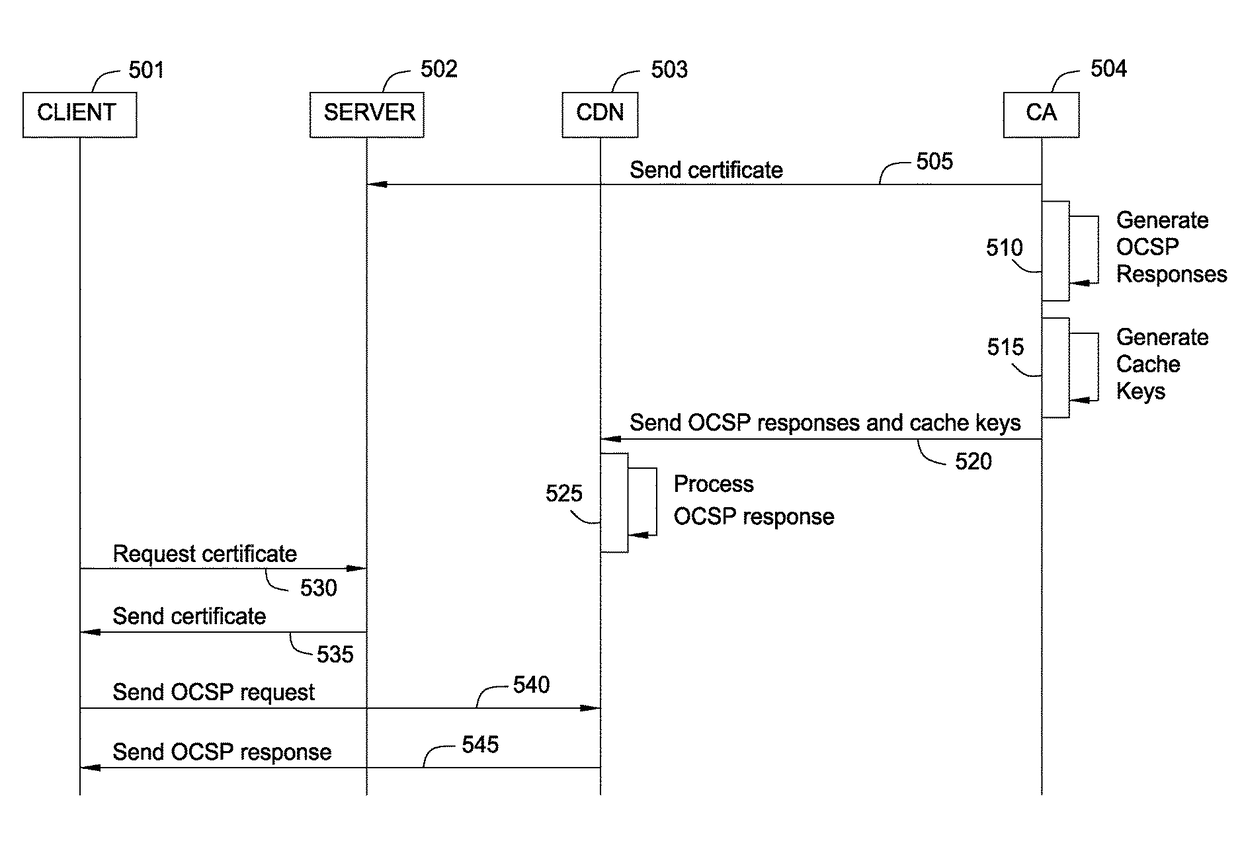
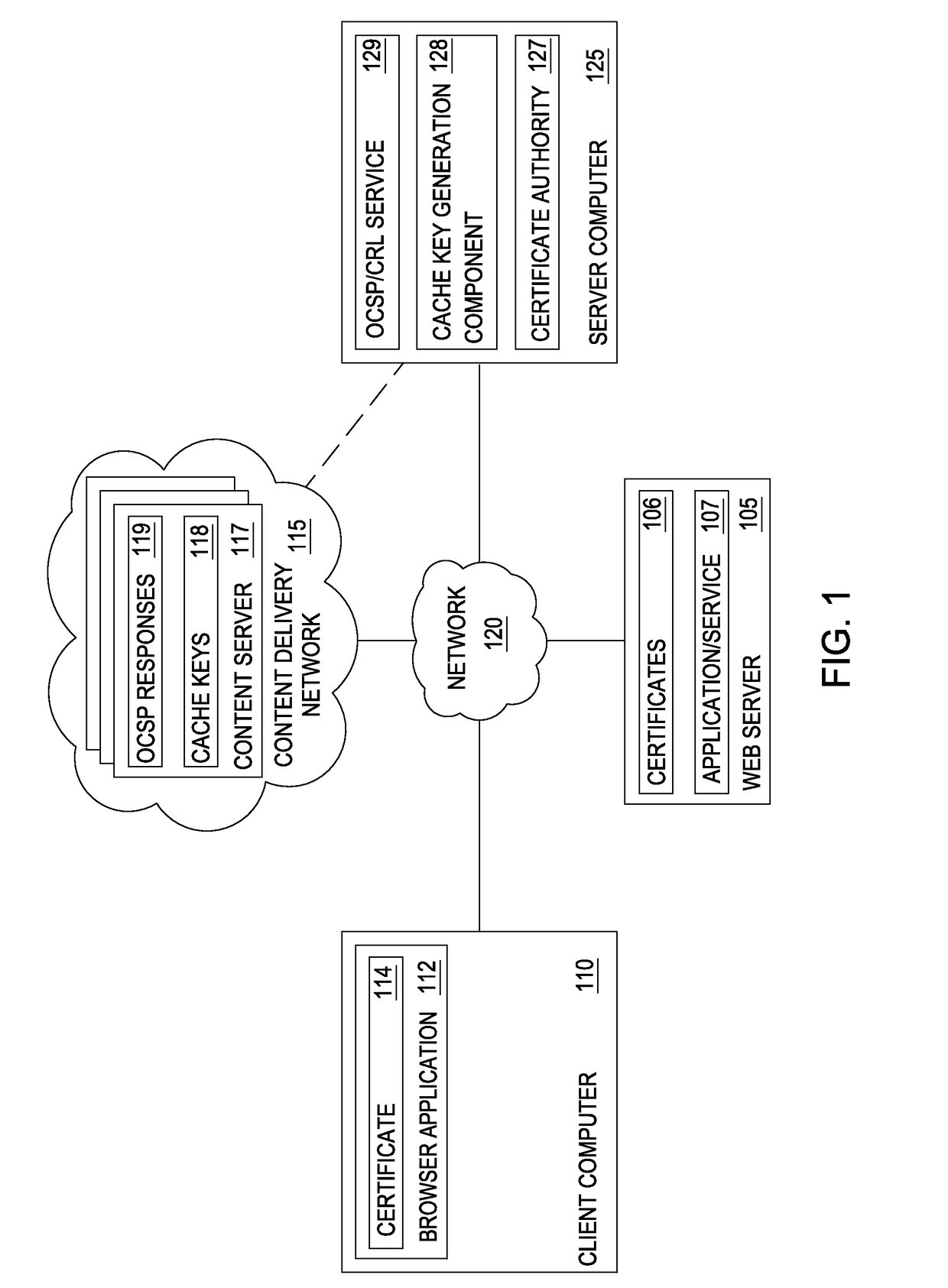
Accelerating ocsp responses via content delivery network collaboration
ActiveUS20150100778A1Securing communicationComputer networkProtocol for Carrying Authentication for Network Access
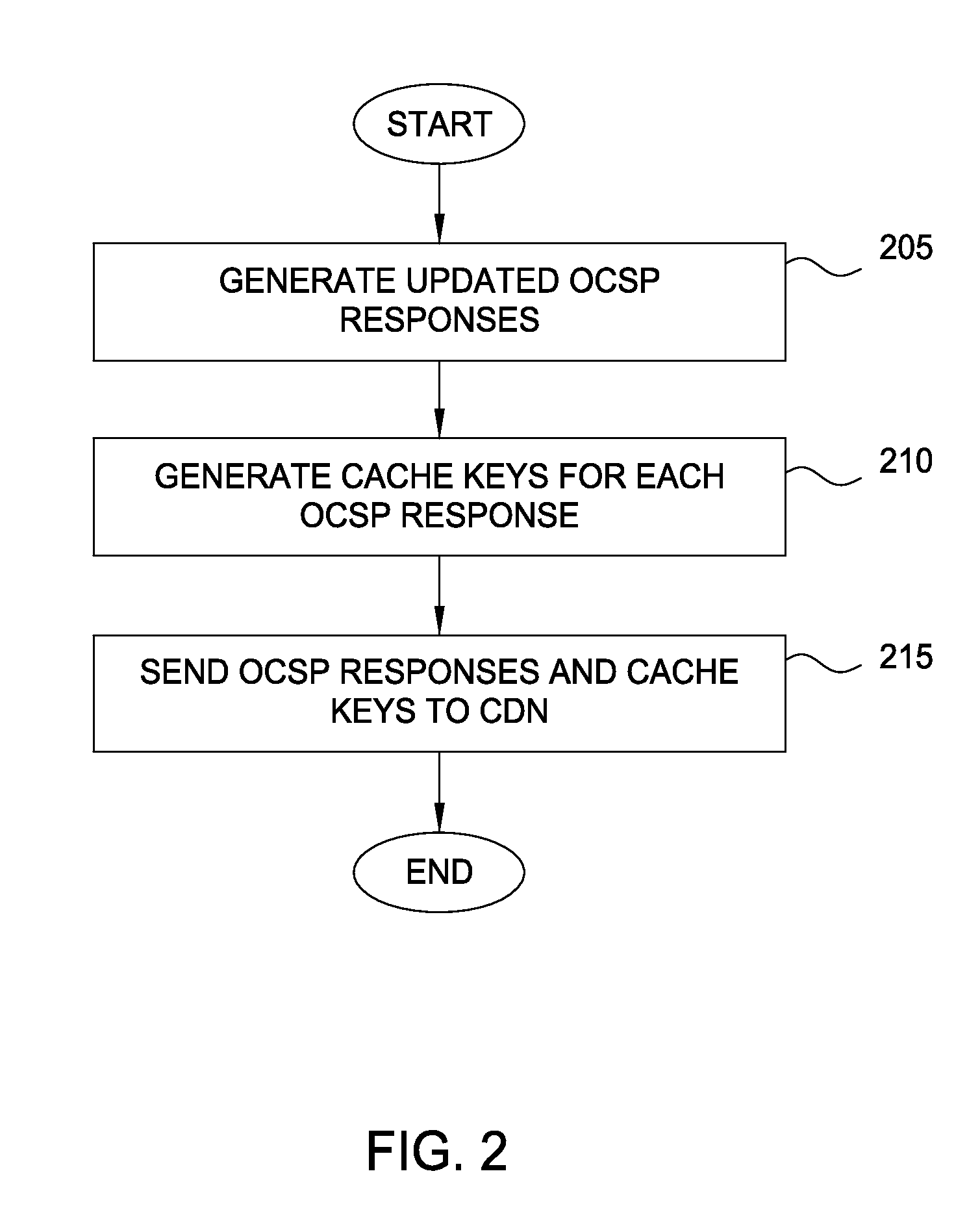
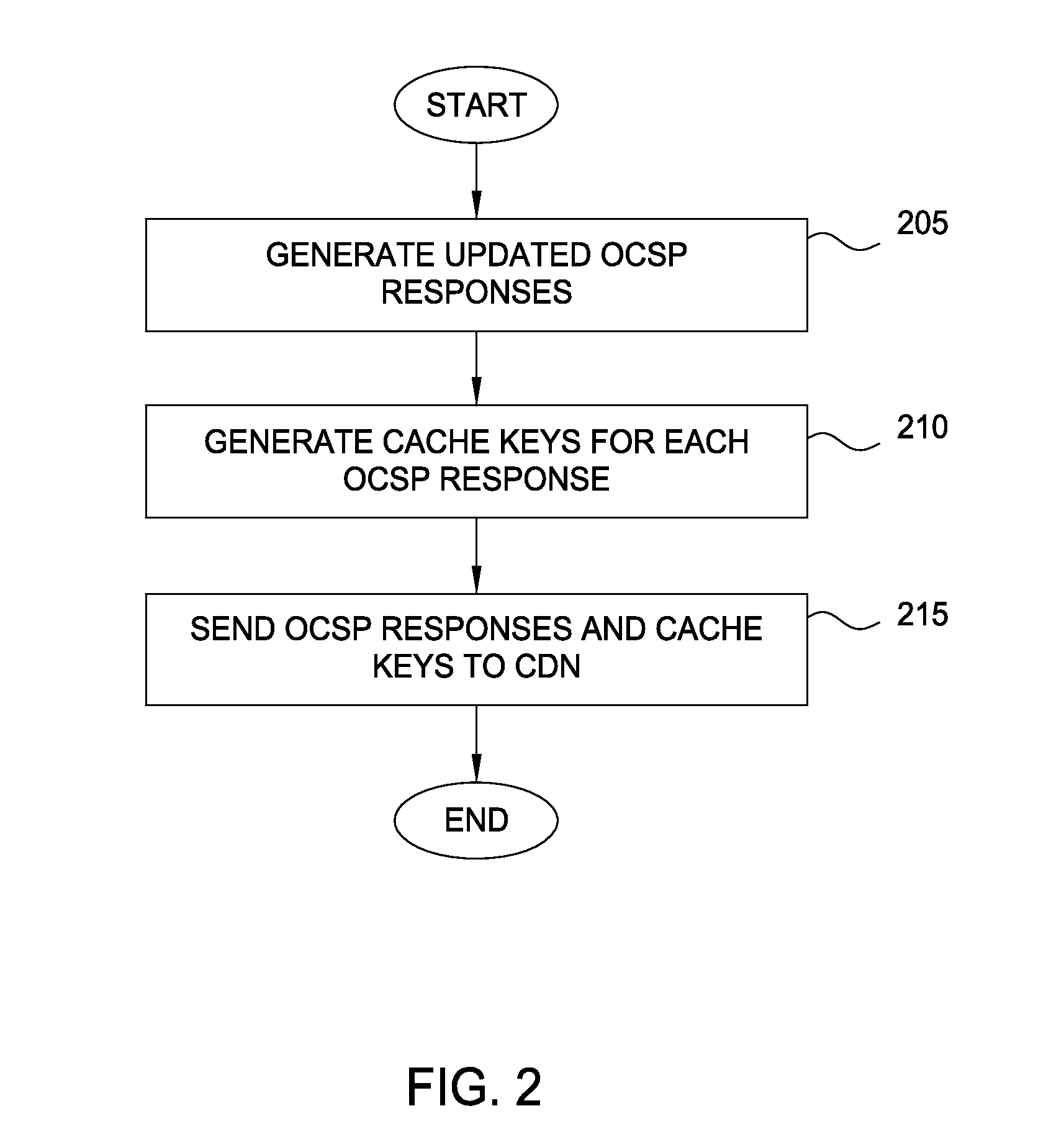
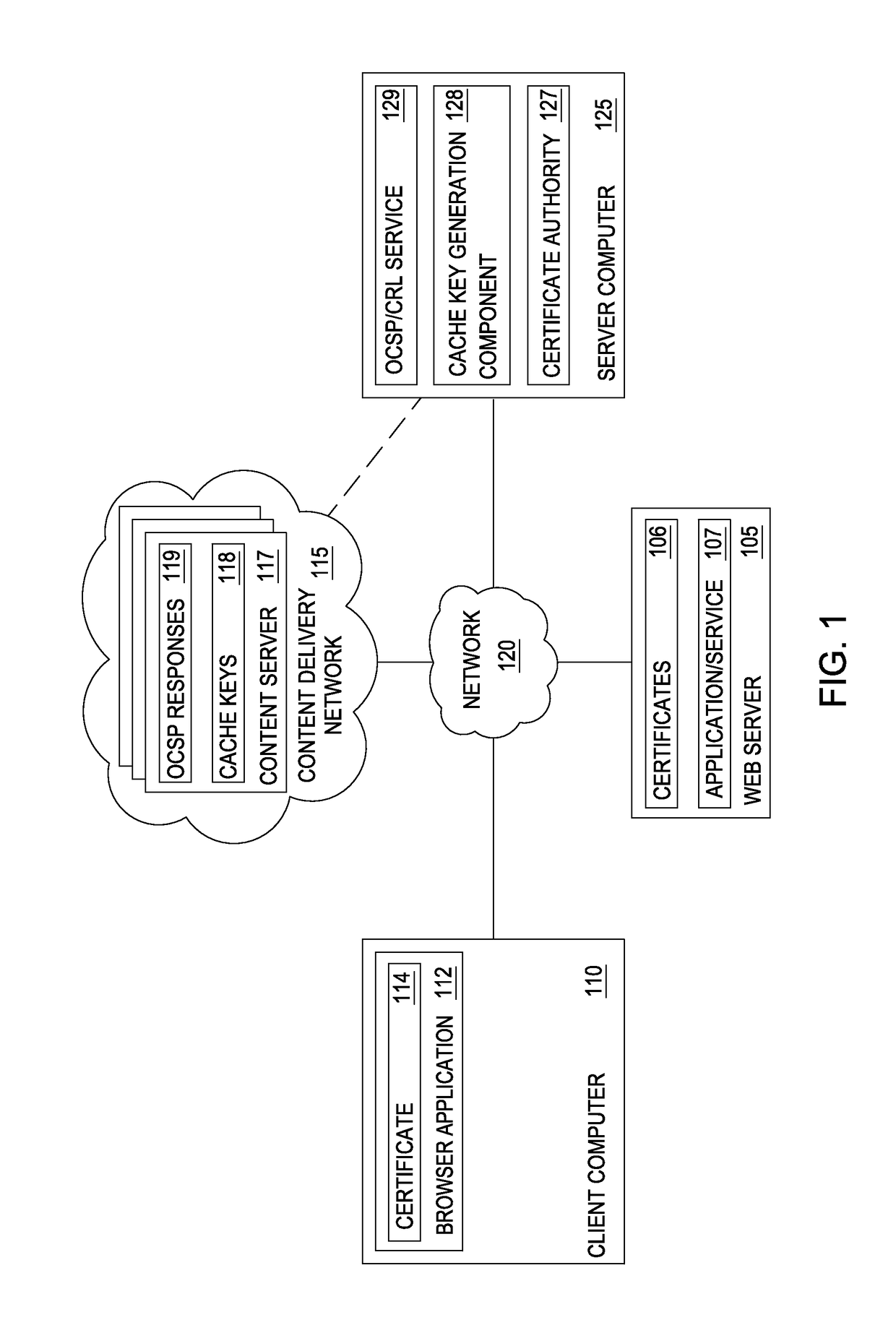
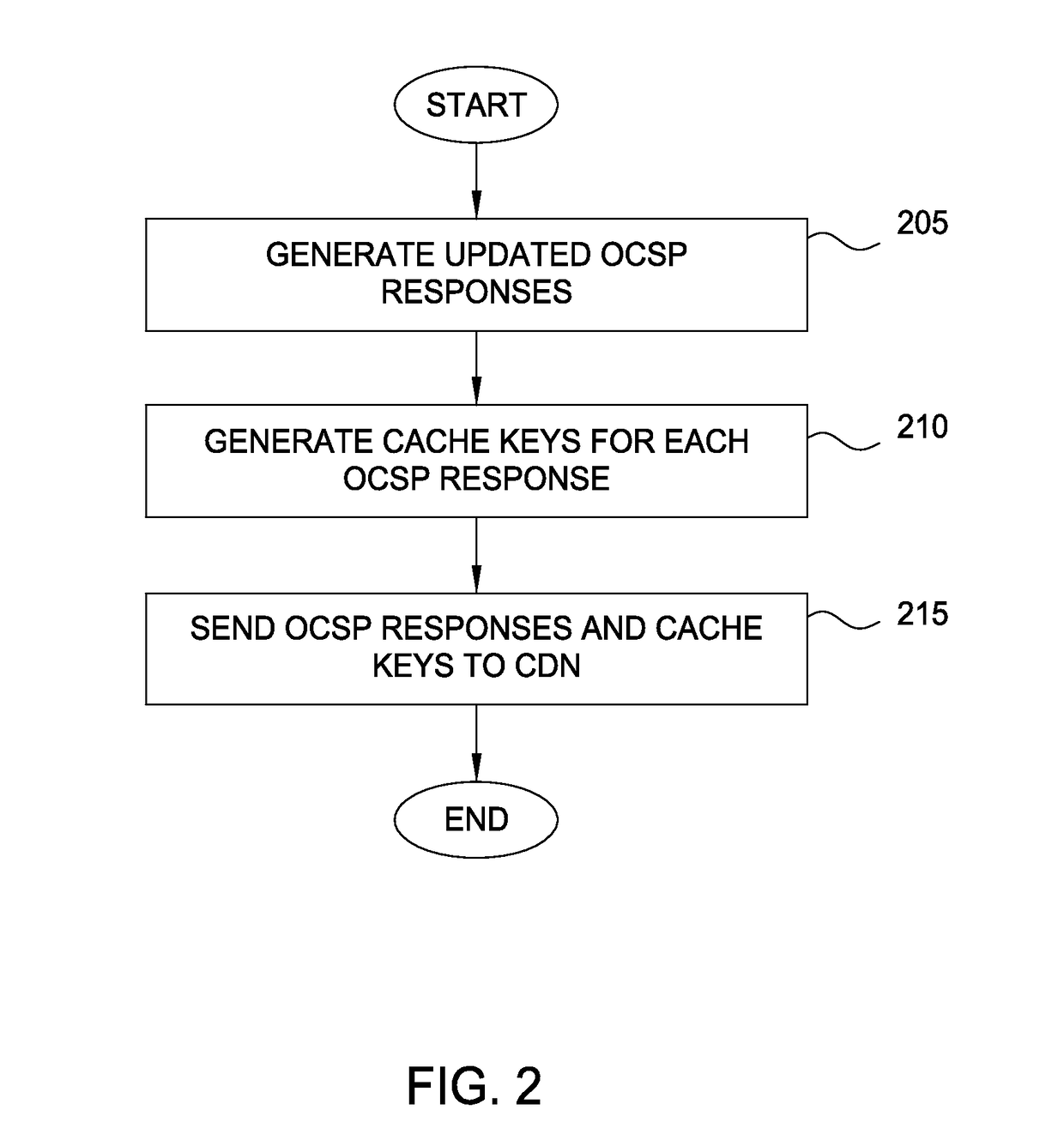
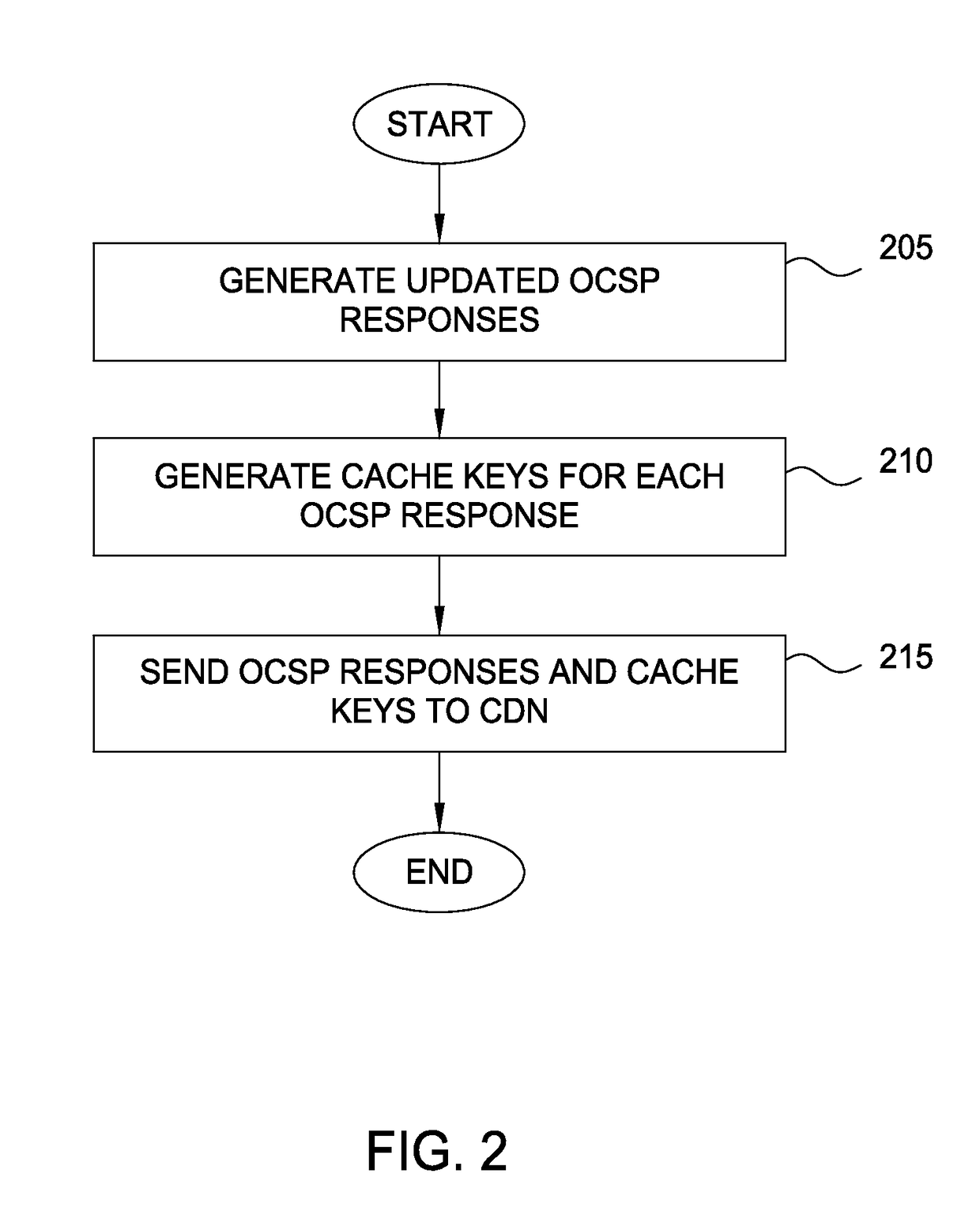
Techniques are disclosed for accelerating online certificate status protocol (OCSP) response distribution to relying parties using a content delivery network (CDN). A certificate authority generates updated OCSP responses for OCSP responses cached in the CDN that are about to expire. In addition, the certificate authority pre-generates cache keys in place of CDNs generating the keys. The certificate authority sends the OCSP responses and the cache keys in one transaction, and the CDN, in turn, consumes the new OCSP responses using the cache keys.
Owner:DIGICERT
Pre-signed response generation and verification method and generation and verification device
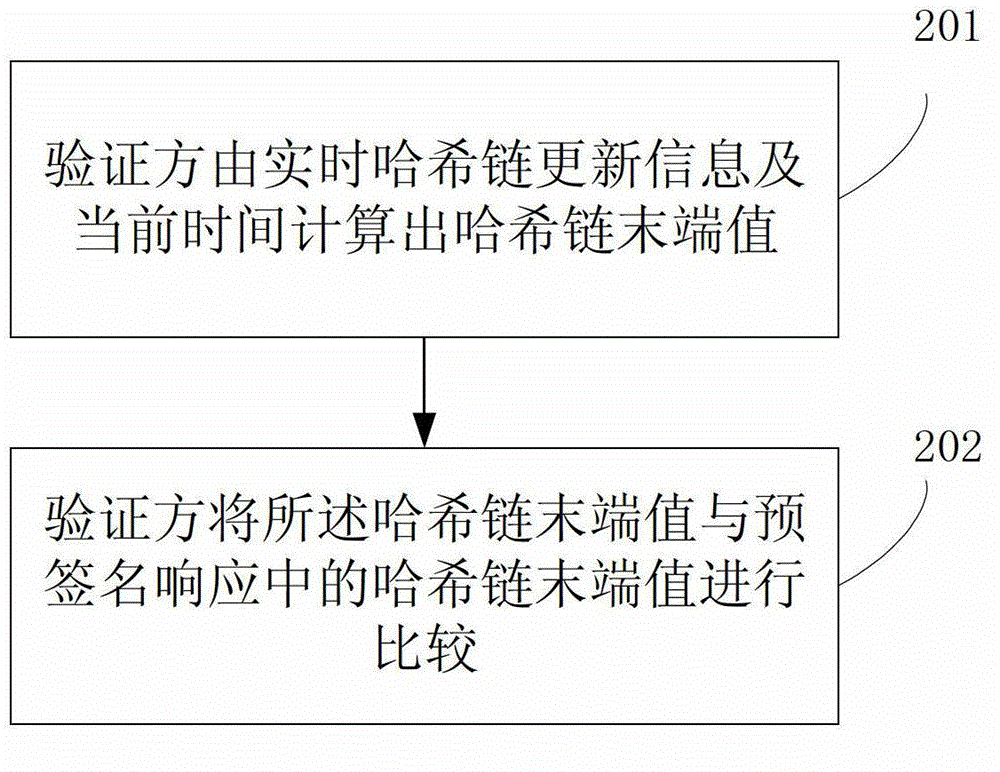
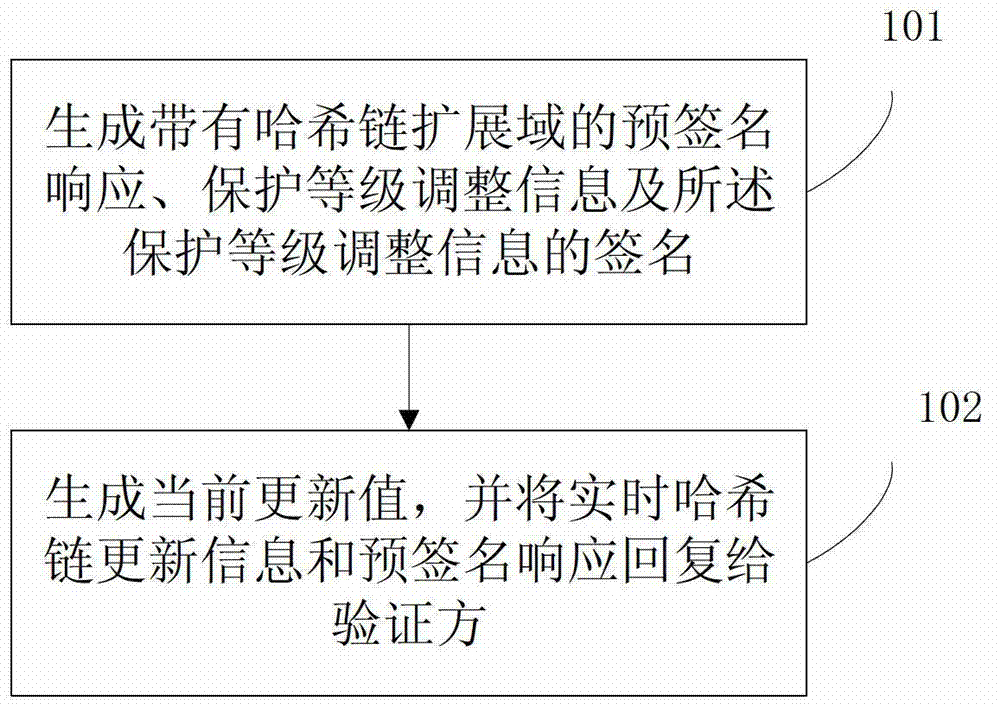
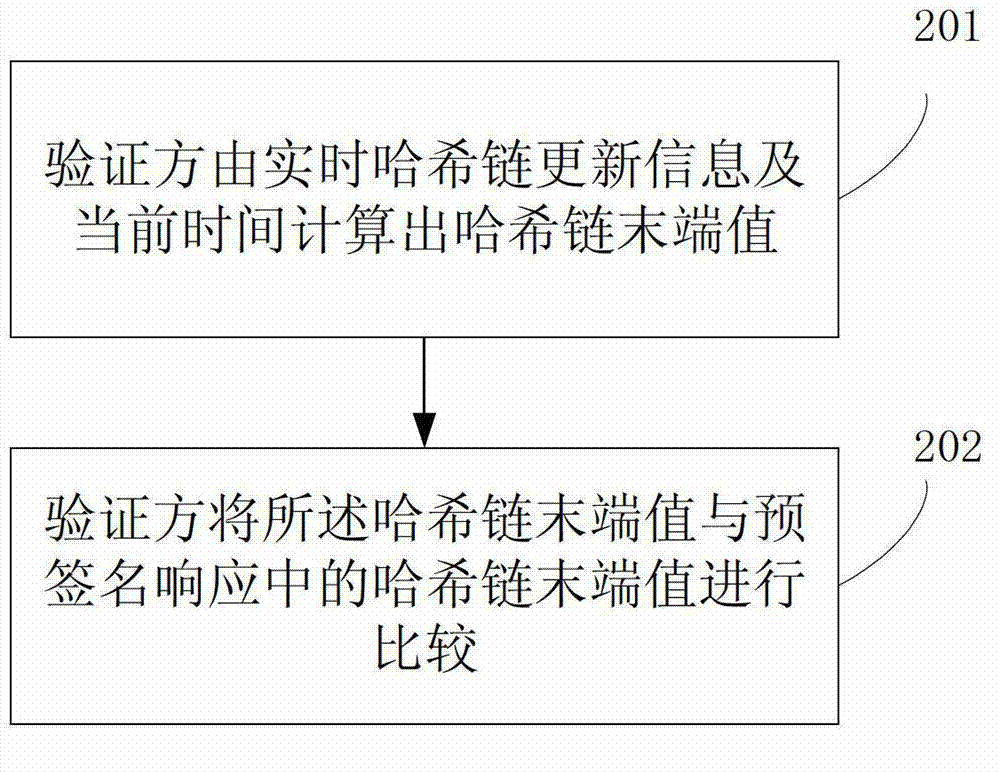
ActiveCN102724198AImprove the ability to resist replay attacksTransmissionResponse generationValidation methods
The invention relates to a pre-signed response generation and verification method and a pre-signed response generation and verification device. An online certificate status protocol (OCSP) responder generates protection level adjustment information and a signature thereof as well as the pre-signed response of a Hash chain extension field, and can dynamically adjust the protection level adjustment information; when receiving an on-line certificate verification request from a verifier, the OCSP responder calculates a current update value to form the real-time Hash chain update information, and sends the real-time Hash chain update information and the pre-signed response to the verifier. After receiving the pre-signed response and the real-time Hash chain update information, the verifier can instantaneously play back and calibrate according to the real-time Hash chain update information, so that the anti-playback attack capability is improved.
Owner:ZHENGZHOU SEANET TECH CO LTD
Reducing latency for certificate validity messages using private content delivery networks
ActiveUS20150100779A1Reduce response delaySecuring communicationSchema for Object-Oriented XMLOnline Certificate Status Protocol
Techniques are disclosed for accelerating online certificate status protocol (OCSP) response distribution to relying parties using a content delivery network (CDN). A certificate authority generates updated OCSP responses for OCSP responses cached in the CDN that are about to expire. In addition, the certificate authority pre-generates cache keys in place of CDNs generating the keys. The certificate authority sends the OCSP responses and the cache keys in one transaction, and the CDN, in turn, serves requests for the OCSP responses using the cache keys. For new certificates, a private CDN is pre-populated with an OCSP response for a certificate concurrent with that certificate being issued. Doing so effectively uses the PCDN as an origin server for OCSP responses, reducing CA infrastructure needs.
Owner:DIGICERT
System and method for validity verification of certificate in mobile backhaul net
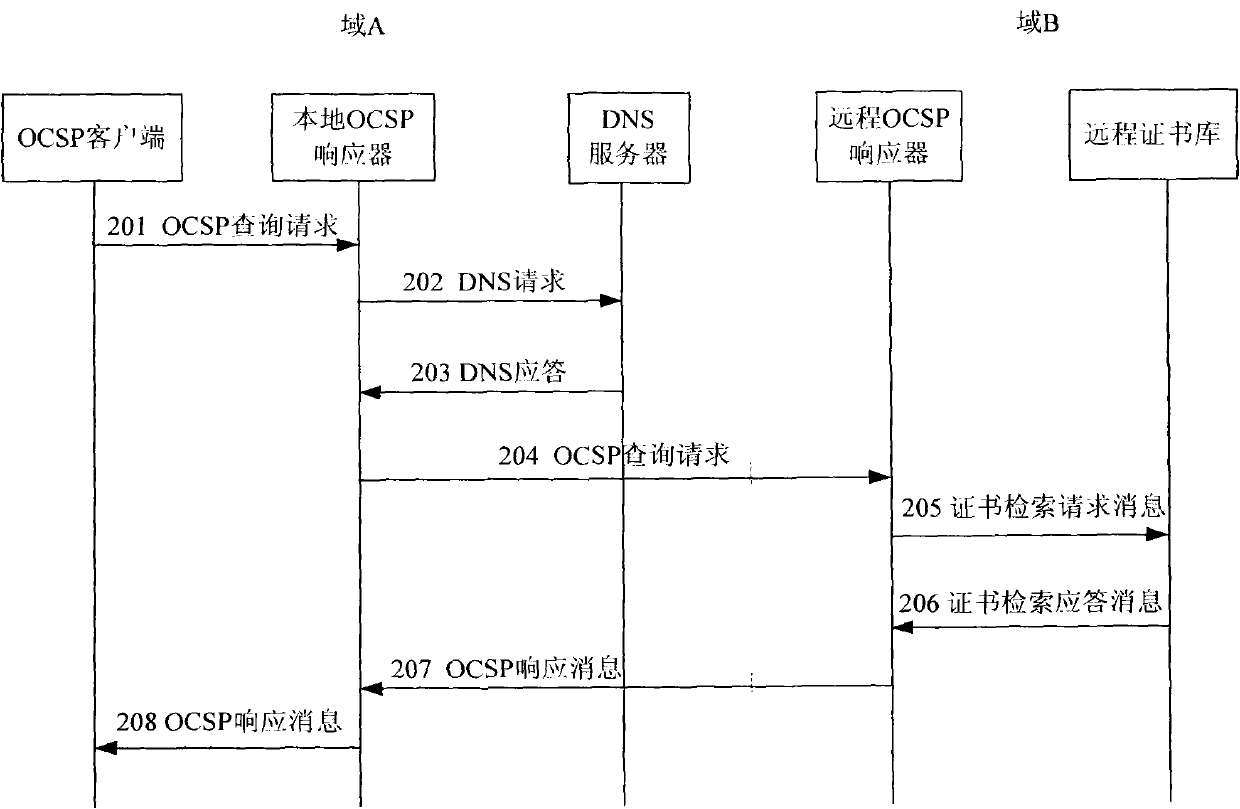
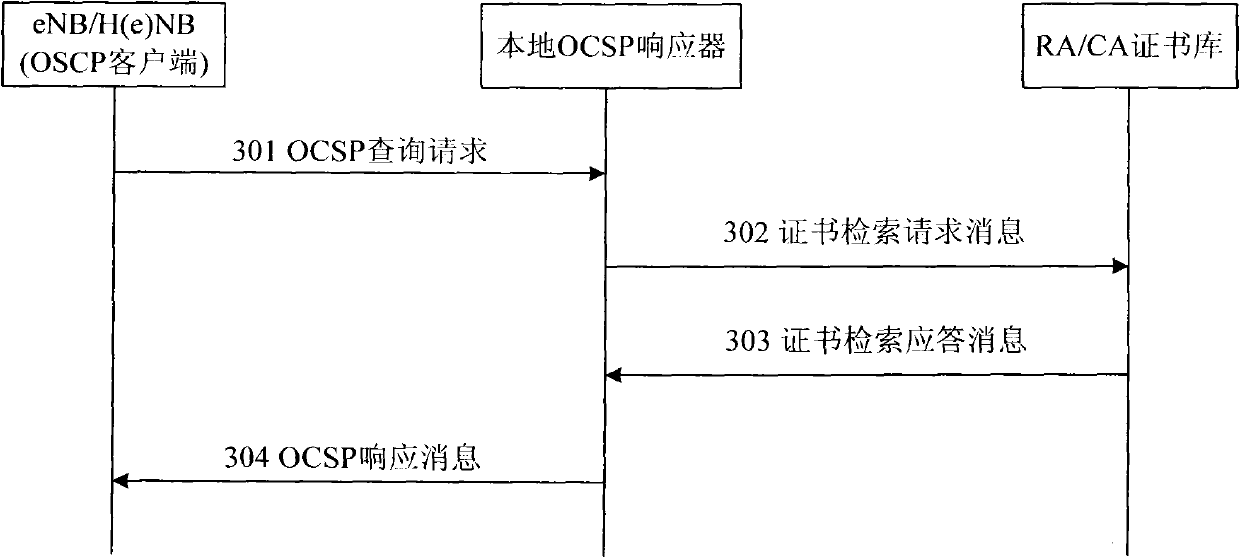
InactiveCN102026161AValidity verification is efficientEfficient verificationTransmissionSecurity arrangementClient-sideA domain
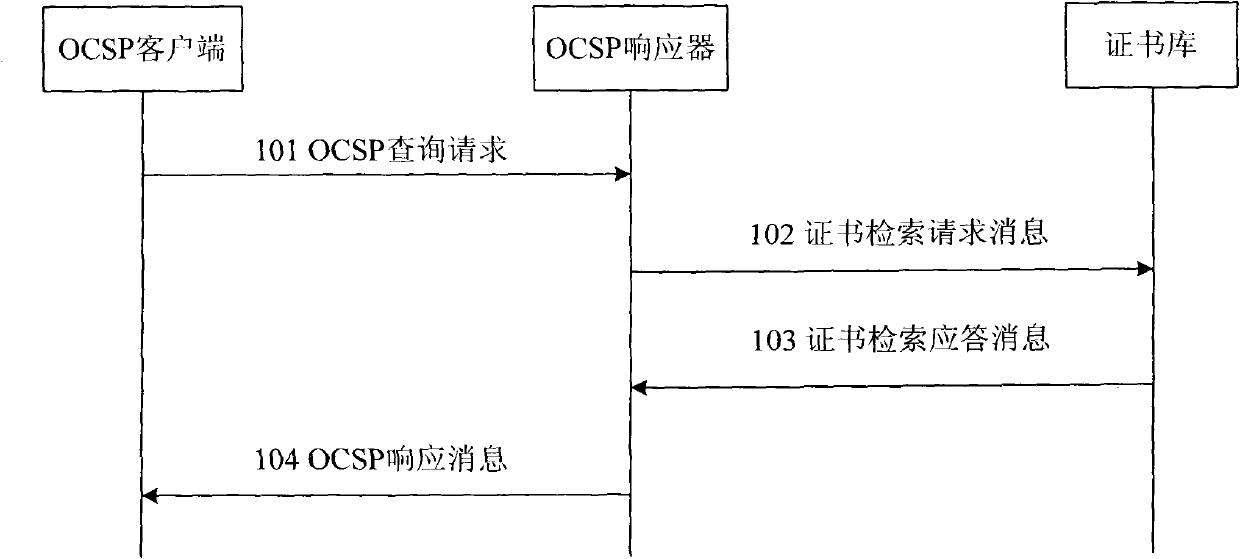
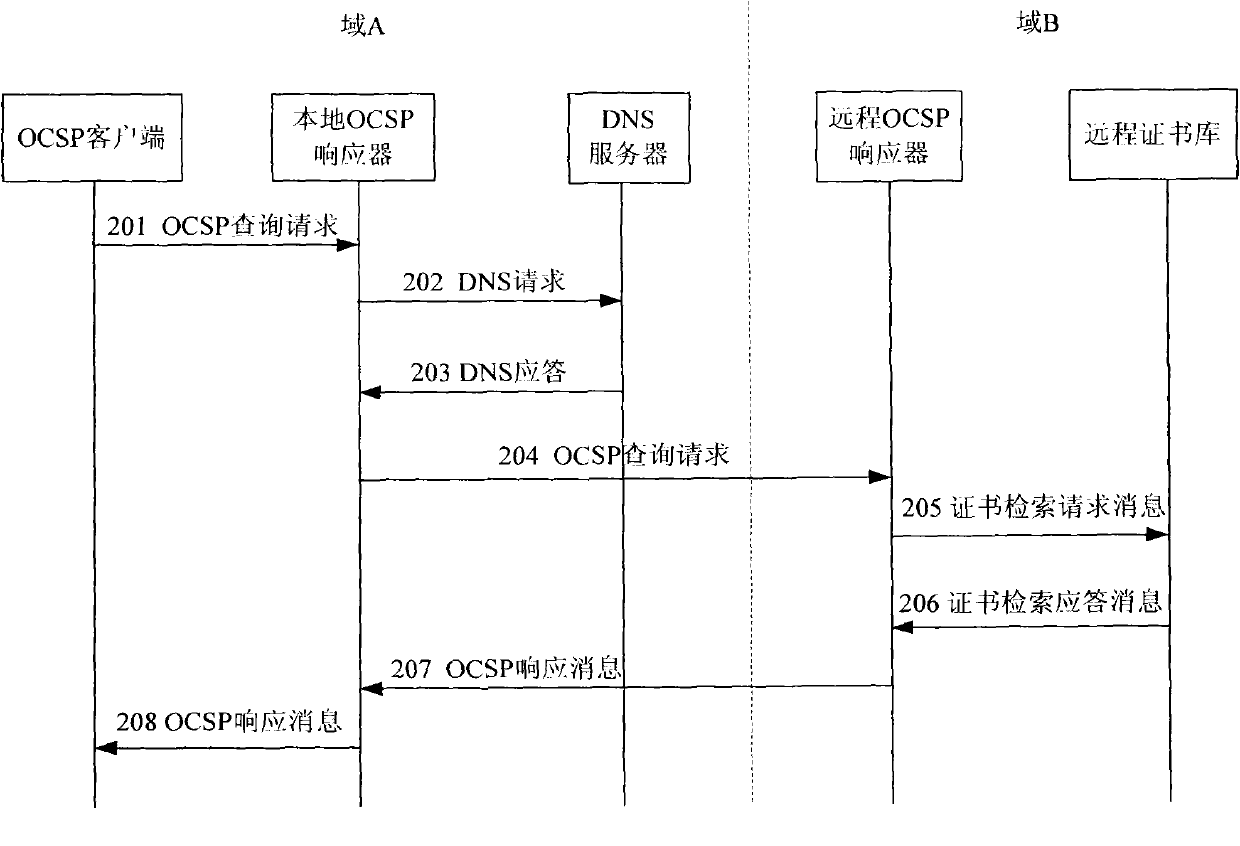
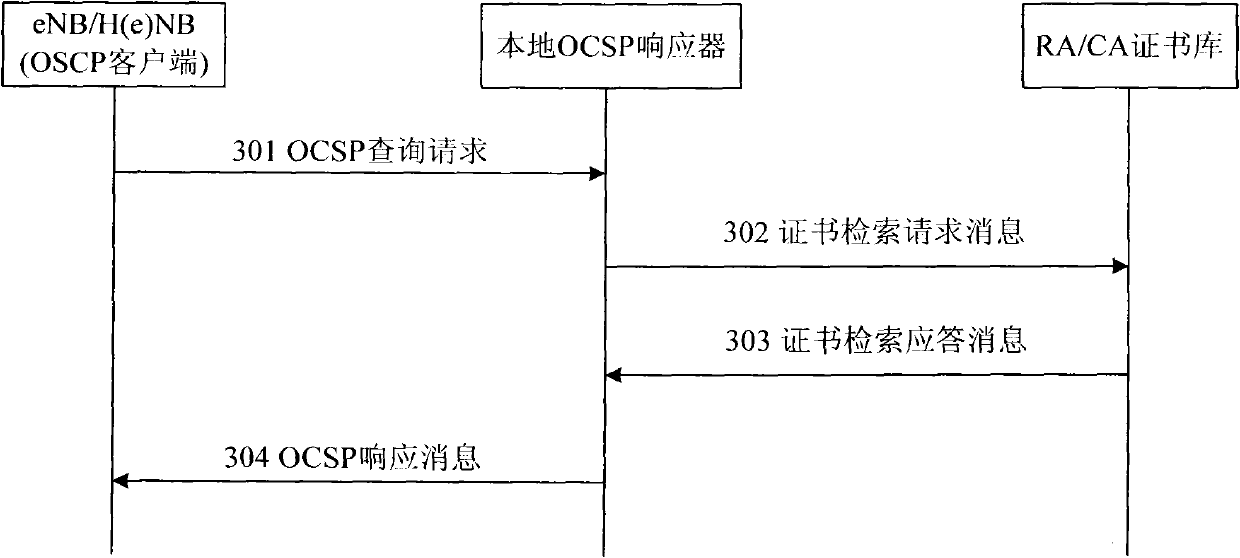
The invention provides system and method for validity verification of a certificate in a mobile backhaul net. The method comprises the following steps of: when the validity of a domain certificate is verified, the client side of an online certificate status protocol (OCSP) sends an OCSP search request to an OCSP responser, and a request certificate table is carried; after the OCSP responser receives the OCSP search request, a certificate library is requested to verify the validity of the certificate in the request certificate table, and the certificate library searches the validity of the certificate in the request certificate table and transmits the search results of the validity of the certificate to the OCSP client side by the OCSP responser. The invention can efficiently verify the validity of the certificate in the mobile backhaul net in real time.
Owner:ZTE CORP
Digital authentication system based data switching
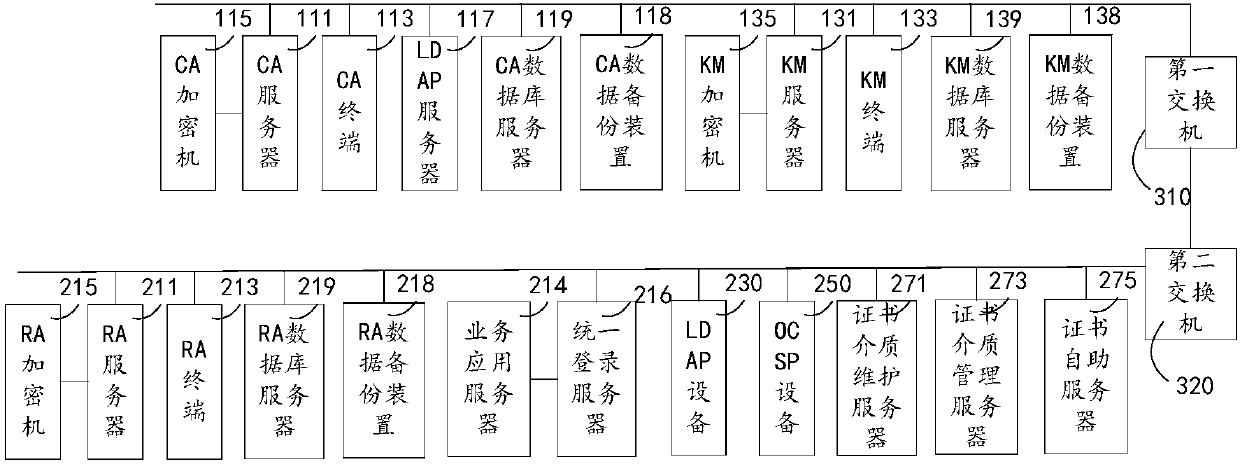
InactiveCN107733881AImprove securityPublic key for secure communicationNetwork connectionData exchange
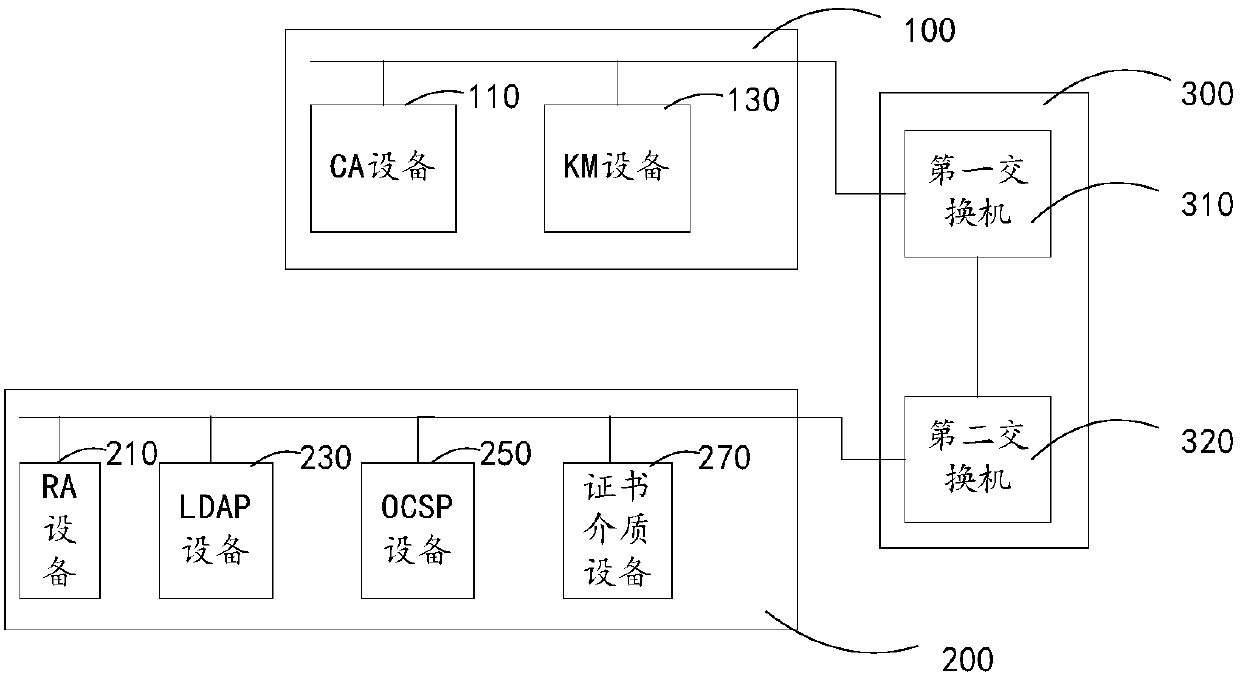
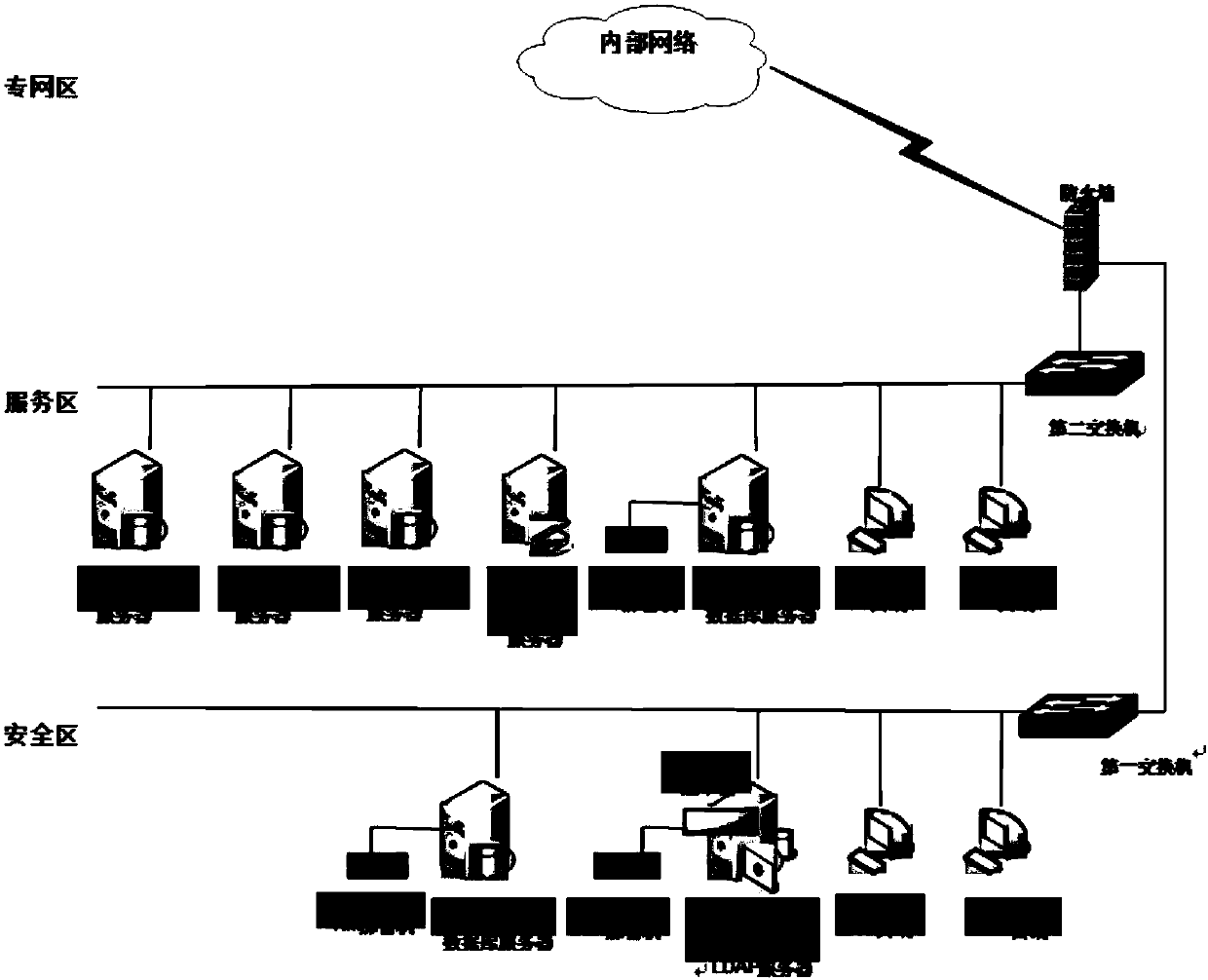
The invention relates to a digital authentication system based data switching. The digital authentication system comprises safe area devices, service area devices, and a network connection device connected with the safe area devices with the service area devices. The network connection device comprises a first switch connected with the safe area devices and a second switch connected with the service area devices. A firewall is set between the first switch and the second switch. The safe area devices comprise a CA (Certificate Authority) device and a KM (Key Management) device. The CA device and the KM device are in mutual communication connection and are connected with the first switch. The service area devices comprise an RA device, and an LDAP (Lightweight Directory Access Protocol) device, an OCSP (Online Certificate Status Protocol) device and a certificate media device which are in communication connection with the RA device. The RA device, the LDAP device, the OCSP device and thecertificate media device are connected with the second switch. The CA device realizes digital certificate authentication comprising an SM2 algorithm. The KM device realizes key management comprisingthe SM2 algorithm. According to the digital authentication system based on data switching, the system security can be improved.
Owner:ELECTRIC POWER RESEARCH INSTITUTE, CHINA SOUTHERN POWER GRID CO LTD
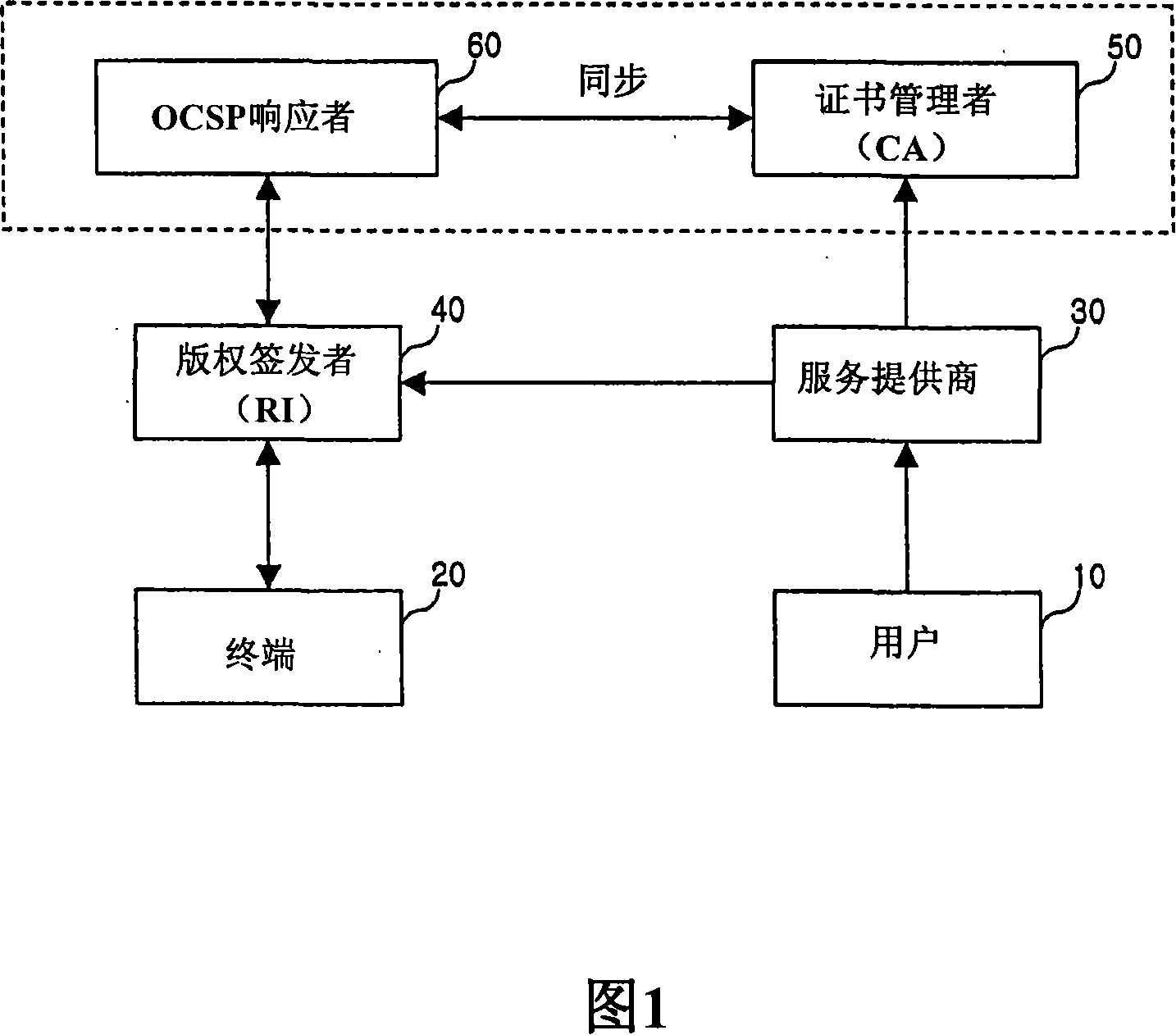
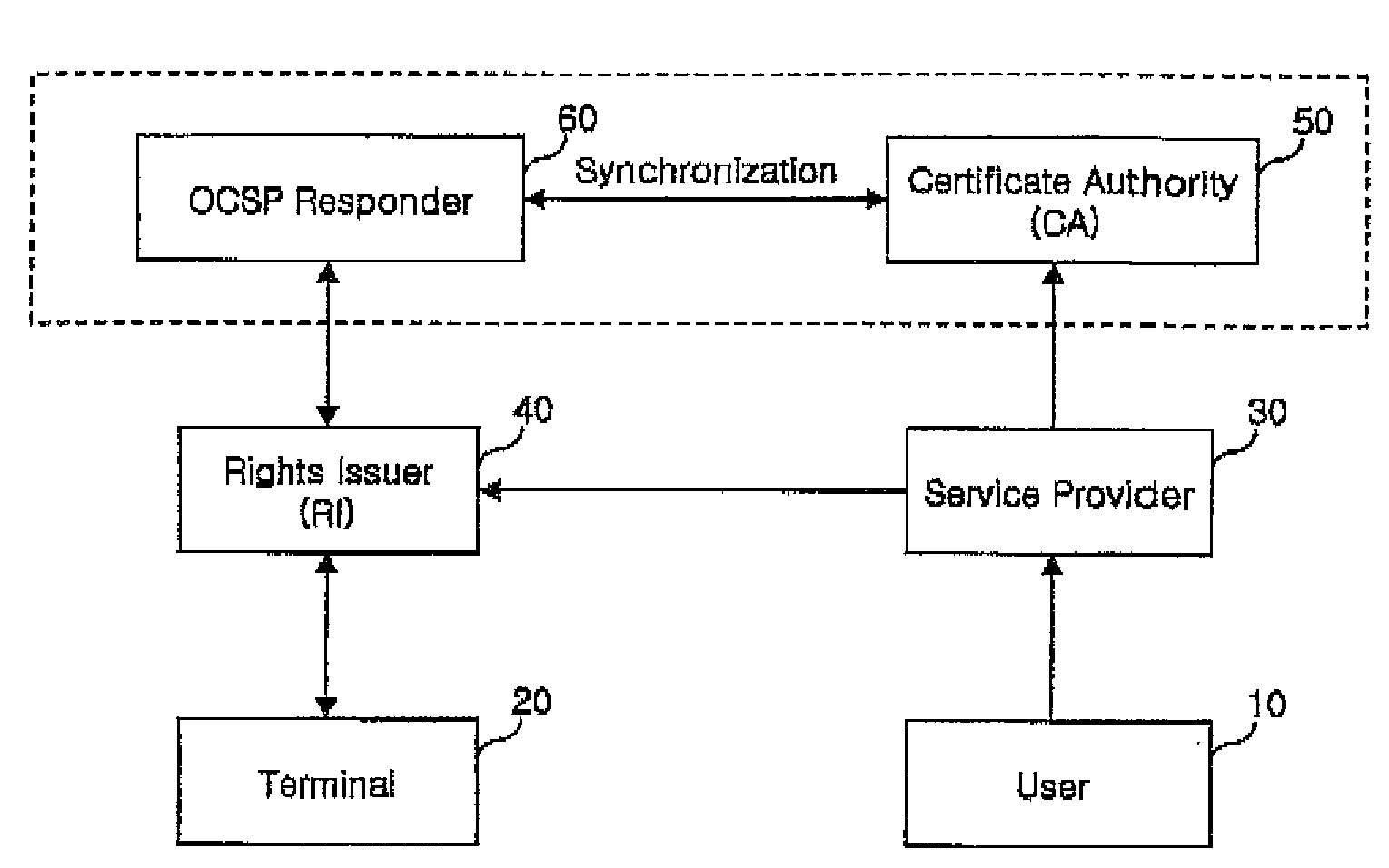
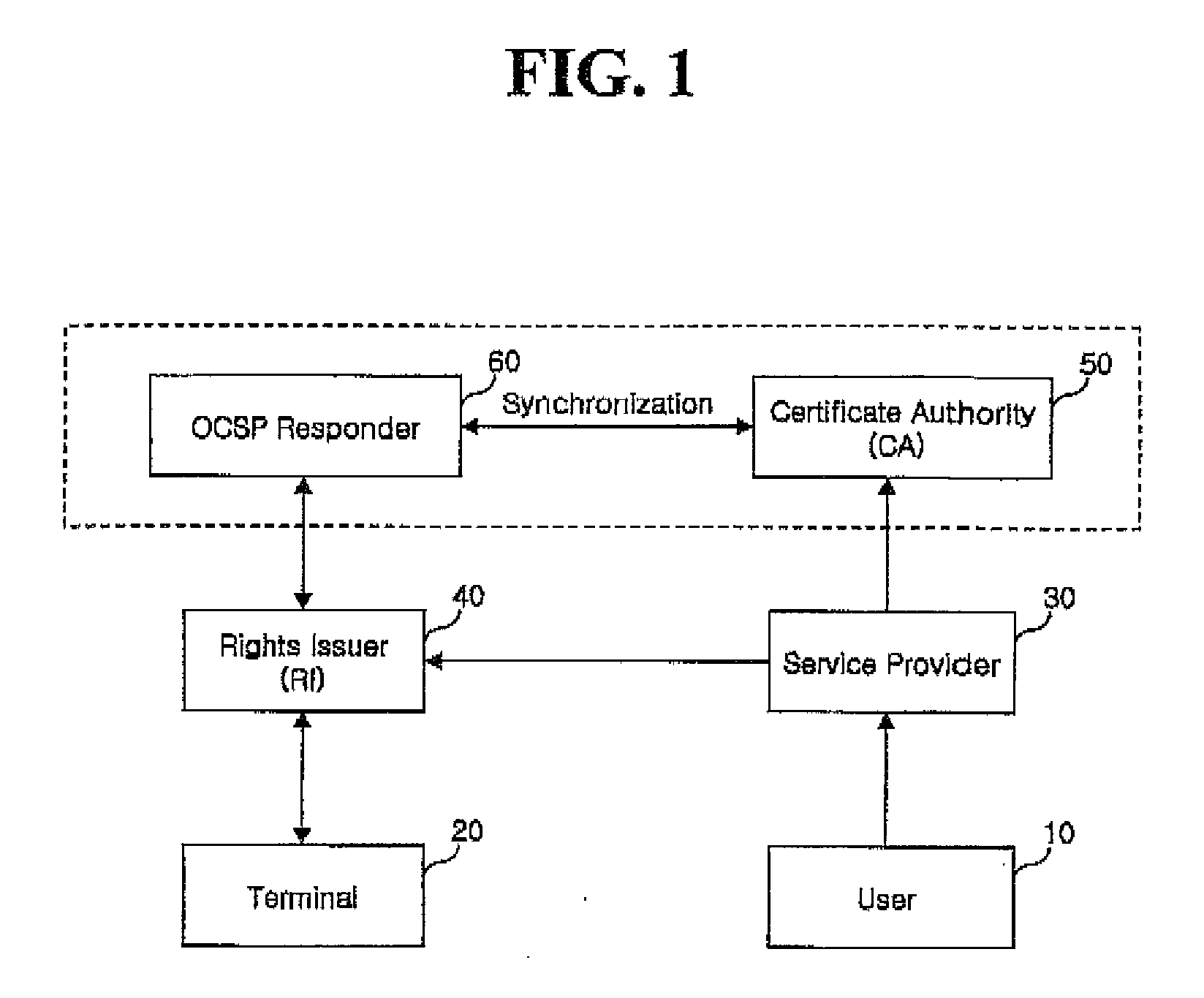
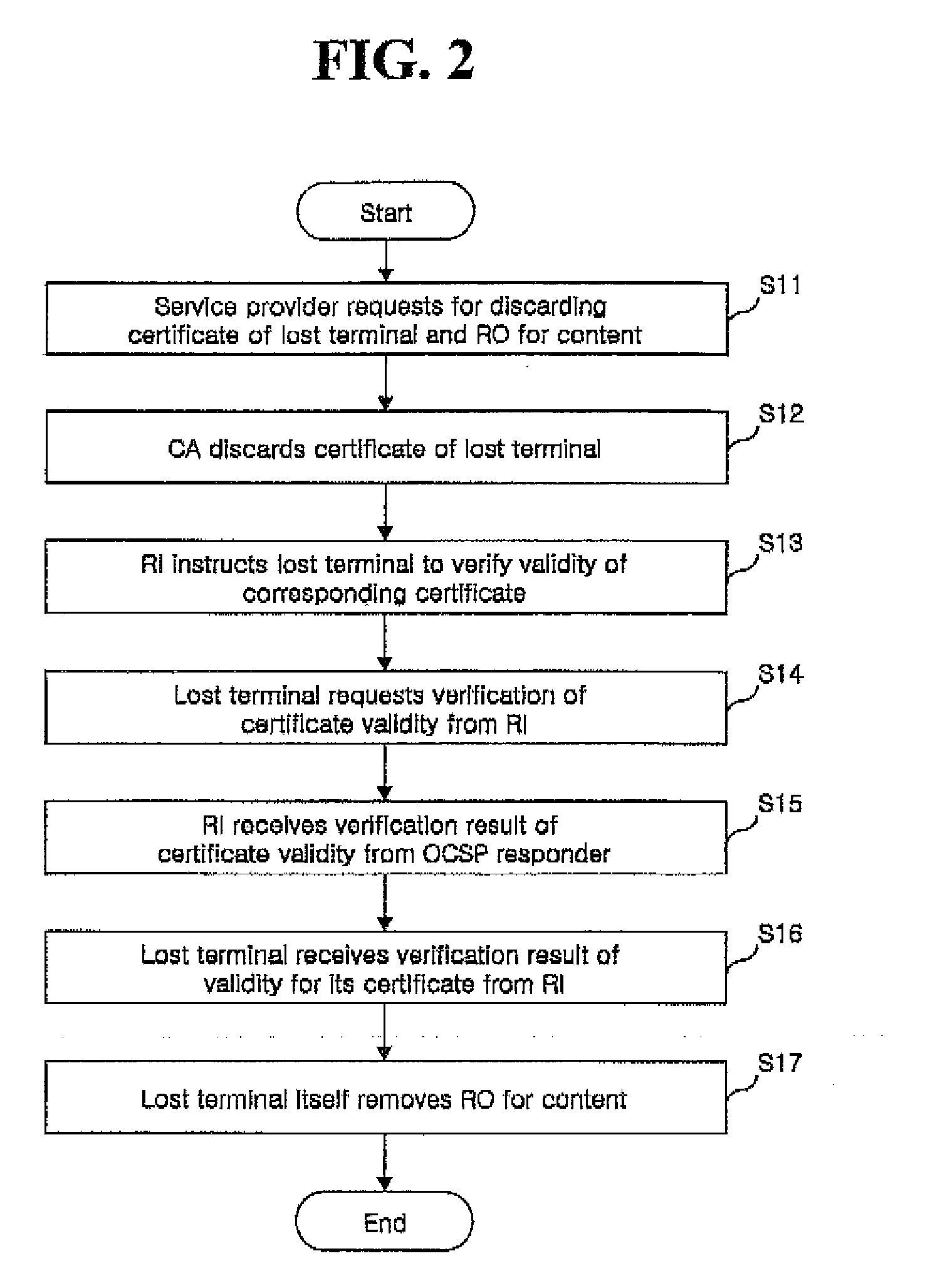
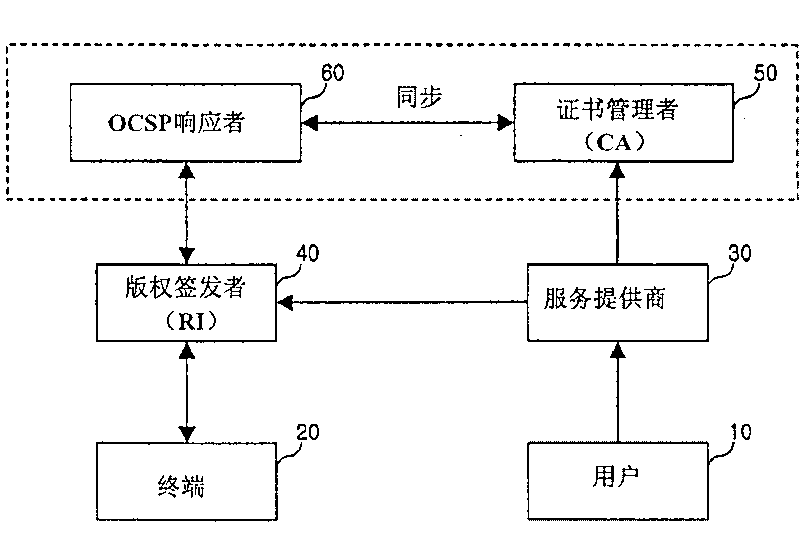
Contents rights protecting method
InactiveCN101133410AReduce usageCrankshaftsMachines/enginesOnline Certificate Status ProtocolComputer security
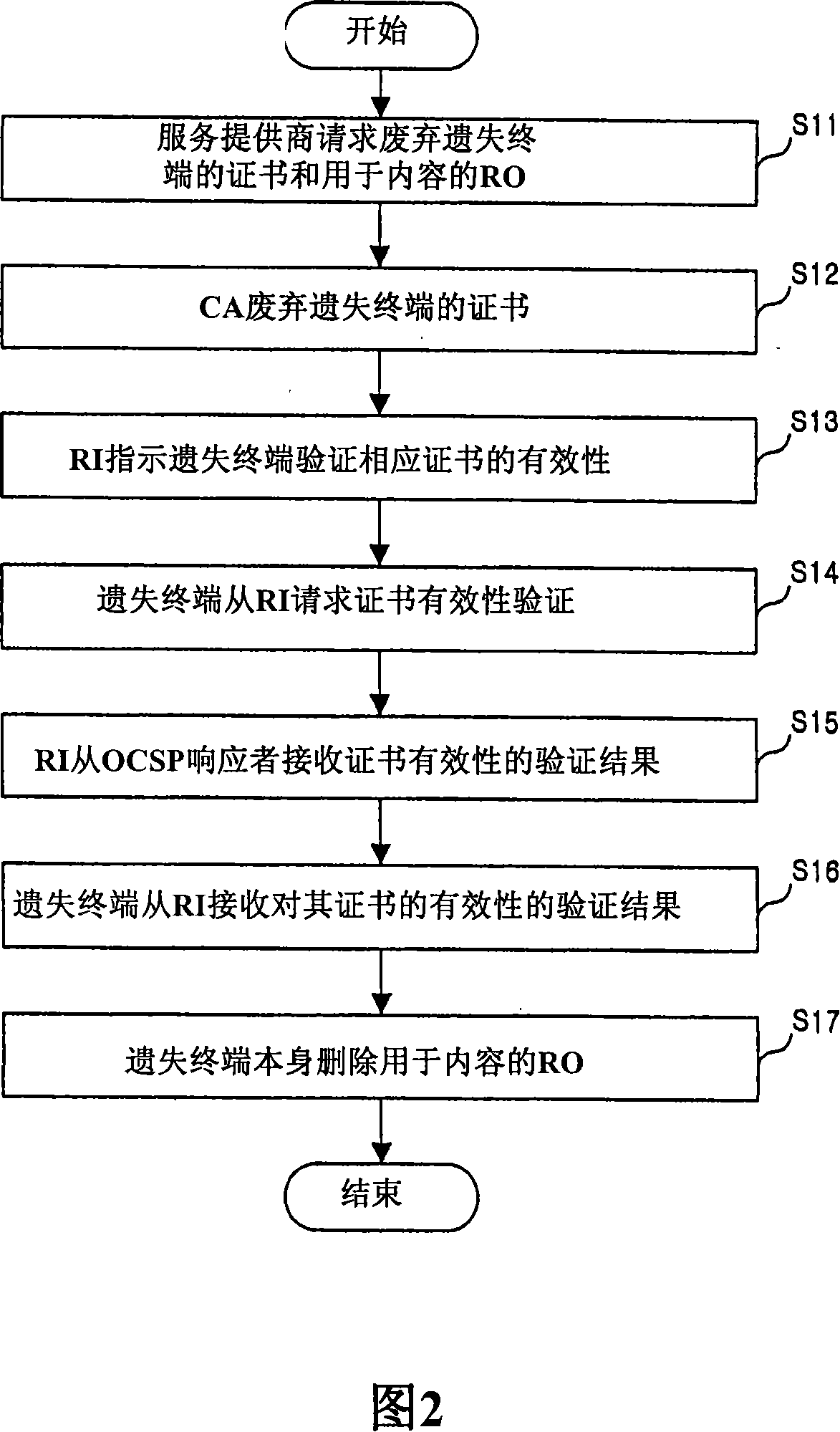
A method for protecting a rights object for a content, wherein when a discard of a rights object with respect to a certain content is requested due to a missing of a terminal which stores the rights object with respect to the content, a rights issuer (Rl) receives a confirmation request for whether a certificate has been discarded from the terminal, confirms the certificate discard through an Online Certificate Status Protocol (OCSP) responder, and then notifies the terminal of the certificate discard, and accordingly the terminal confirms the discard of the certificate of the terminal and removes the rights object with respect thereto. In addition, a user who has removed the rights object with respect to the content can continuously use the corresponding content by entirely or partially re-obtaining the rights object with respect to the content from which the rights object has been discarded.
Owner:LG ELECTRONICS INC
Method for governing the ability of computing devices to communicate
InactiveUS20110202771A1Improve clarityProblem can be addressedDigital data processing detailsUser identity/authority verificationIPsecNetwork Access Control
A method is provided to perform network access control. A computing device utilising Online Certificate Status Protocol responder functionality determines whether attempted communication should be allowed between other computing devices appropriately configured with Internet Protocol Security (IPsec), digital certificates and OCSP client software. This determination is based on a set of rules considering the role or roles of the computing devices attempting to communicate, and whether the computing devices attempting to communicate have previously exhibited suspicious or undesirable behaviour.
Owner:MCLEOD STEVEN CHARLES
Reducing latency for certificate validity messages using private content delivery networks
ActiveUS10110592B2Reduce response delayMosaic printer telegraph systemUser identity/authority verificationSchema for Object-Oriented XMLOnline Certificate Status Protocol
Techniques are disclosed for accelerating online certificate status protocol (OCSP) response distribution to relying parties using a content delivery network (CDN). A certificate authority generates updated OCSP responses for OCSP responses cached in the CDN that are about to expire. In addition, the certificate authority pre-generates cache keys in place of CDNs generating the keys. The certificate authority sends the OCSP responses and the cache keys in one transaction, and the CDN, in turn, serves requests for the OCSP responses using the cache keys. For new certificates, a private CDN is pre-populated with an OCSP response for a certificate concurrent with that certificate being issued. Doing so effectively uses the PCDN as an origin server for OCSP responses, reducing CA infrastructure needs.
Owner:DIGICERT
Contents Rights Protecting Method
InactiveUS20090013411A1Reduce usageCrankshaftsDigital data processing detailsOnline Certificate Status ProtocolComputer security
A method for protecting a rights object for a content, wherein when a discard of a rights object with respect to a certain content is requested due to a missing of a terminal which stores the rights object with respect to the content, a rights issuer (RI) receives a confirmation request for whether a certificate has been discarded from the terminal, confirms the certificate discard through an Online Certificate Status Protocol (OCSP) responder, and then notifies the terminal of the certificate discard, and accordingly the terminal confirms the discard of the certificate of the terminal and removes the rights object with respect thereto. In addition, a user who has removed the rights object with respect to the content can continuously use the corresponding content by entirely or partially re-obtaining the rights object with respect to the content from which the rights object has been discarded.
Owner:LG ELECTRONICS INC
Accelerating OCSP responses via content delivery network collaboration
ActiveUS9887982B2User identity/authority verificationComputer networkOnline Certificate Status Protocol
Techniques are disclosed for accelerating online certificate status protocol (OCSP) response distribution to relying parties using a content delivery network (CDN). A certificate authority generates updated OCSP responses for OCSP responses cached in the CDN that are about to expire. In addition, the certificate authority pre-generates cache keys in place of CDNs generating the keys. The certificate authority sends the OCSP responses and the cache keys in one transaction, and the CDN, in turn, consumes the new OCSP responses using the cache keys.
Owner:DIGICERT
Method for governing the ability of computing devices to communicate
InactiveUS8261081B2Improve clarityProblem can be addressedDigital data processing detailsUser identity/authority verificationIPsecNetwork Access Control
Owner:MCLEOD STEVEN CHARLES
Secure Ids Certificate Verification for a Primary Platform
PendingUS20220014389A1Key distribution for secure communicationUser identity/authority verificationKey exchangeTamper resistance
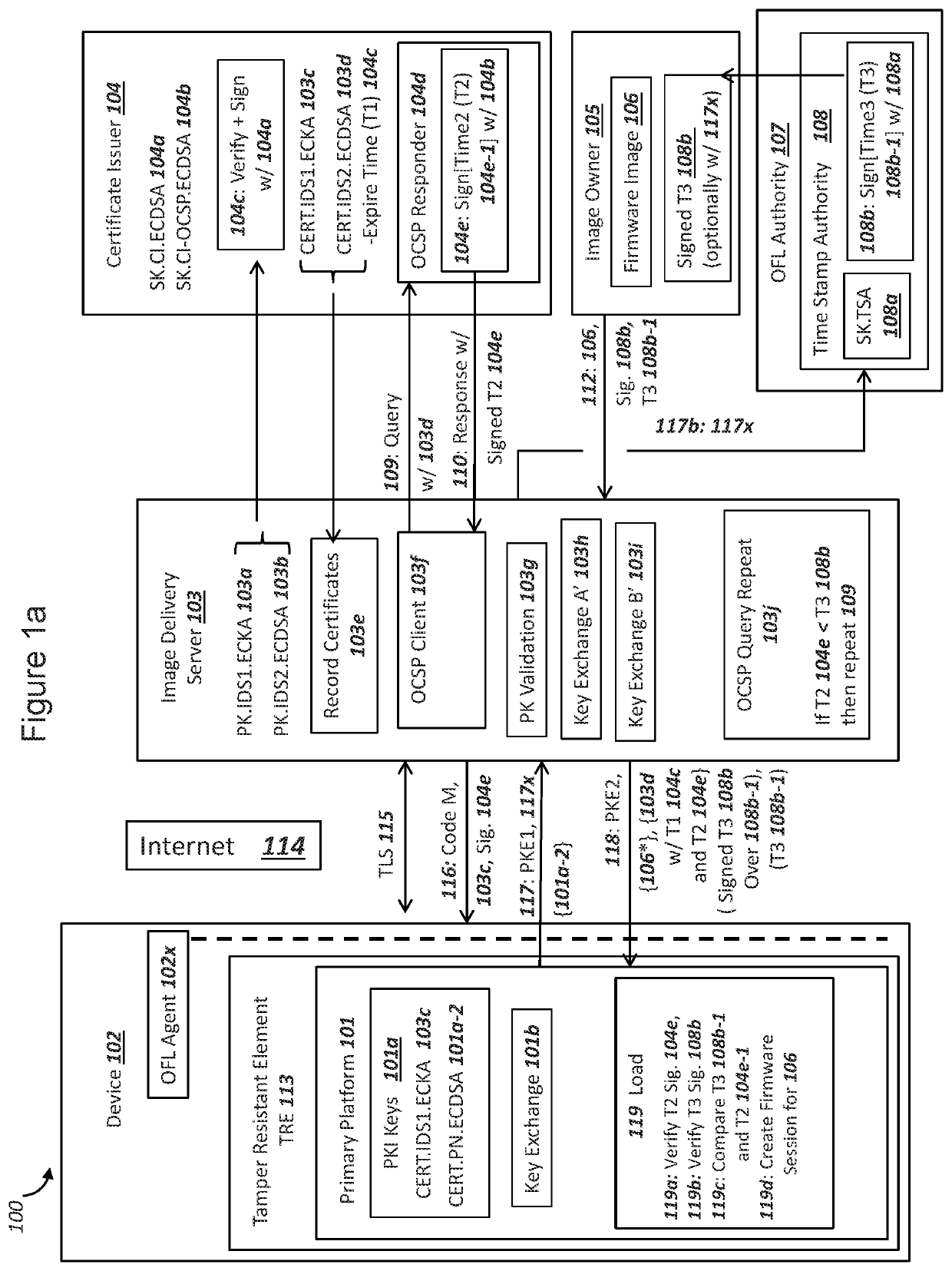
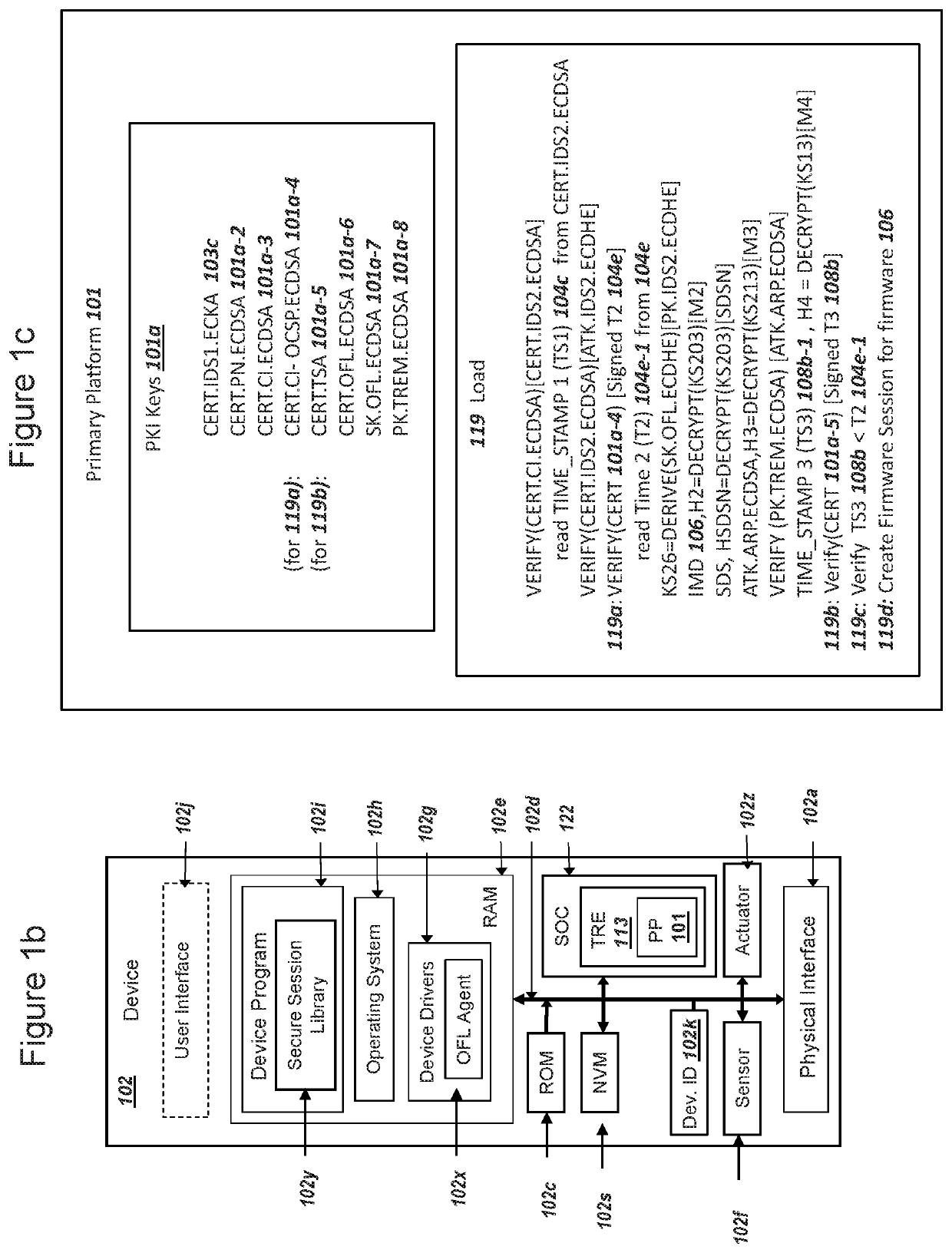
A tamper resistant element (TRE) in a device can operate a primary platform and support a “Smart Secure Platform”. The TRE may not keep time when electrical power is removed from the TRE. The device can receive (i) a certificate for an image delivery server (IDS) with a first timestamp and (ii) a signed second timestamp from a certificate authority, comprising a signature according to the Online Certificate Status Protocol (OCSP) with stapling. The device can forward the certificate and second timestamp to the TRE. The device can receive a ciphertext and an encrypted image from the IDS, where the ciphertext includes a third timestamp from a Time Stamp Authority (TSA), and forward the data to the TRE. The TRE can conduct a key exchange to decrypt the ciphertext. The TRE can compare the second and third timestamps to verify the certificate has not been revoked.
Owner:IOT & M2M TECH LLC
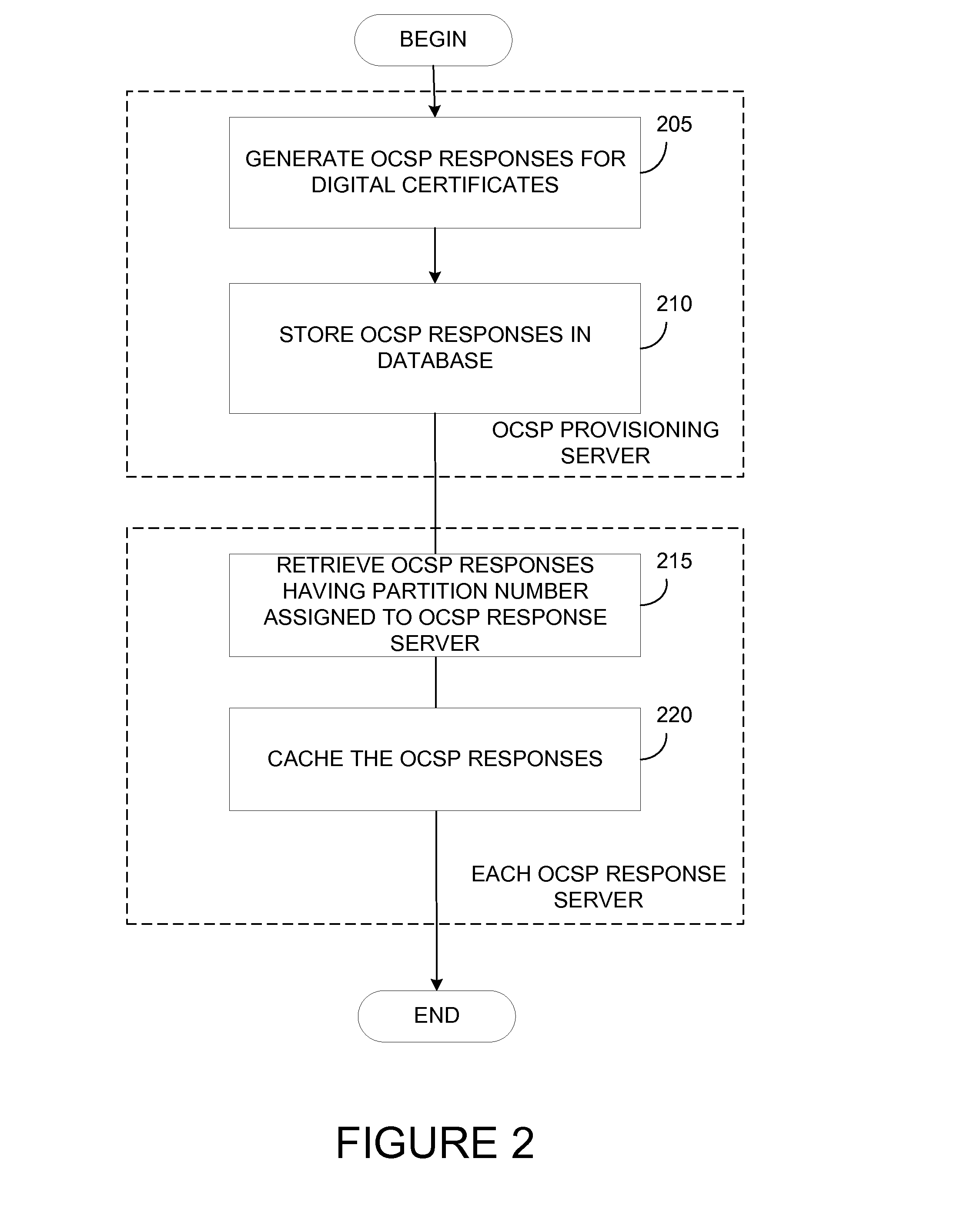
Splitting certificate status responses evenly across multiple distributed certificate status responders
ActiveUS20150244533A1User identity/authority verificationDigital data authenticationDistributed computingModulo operation
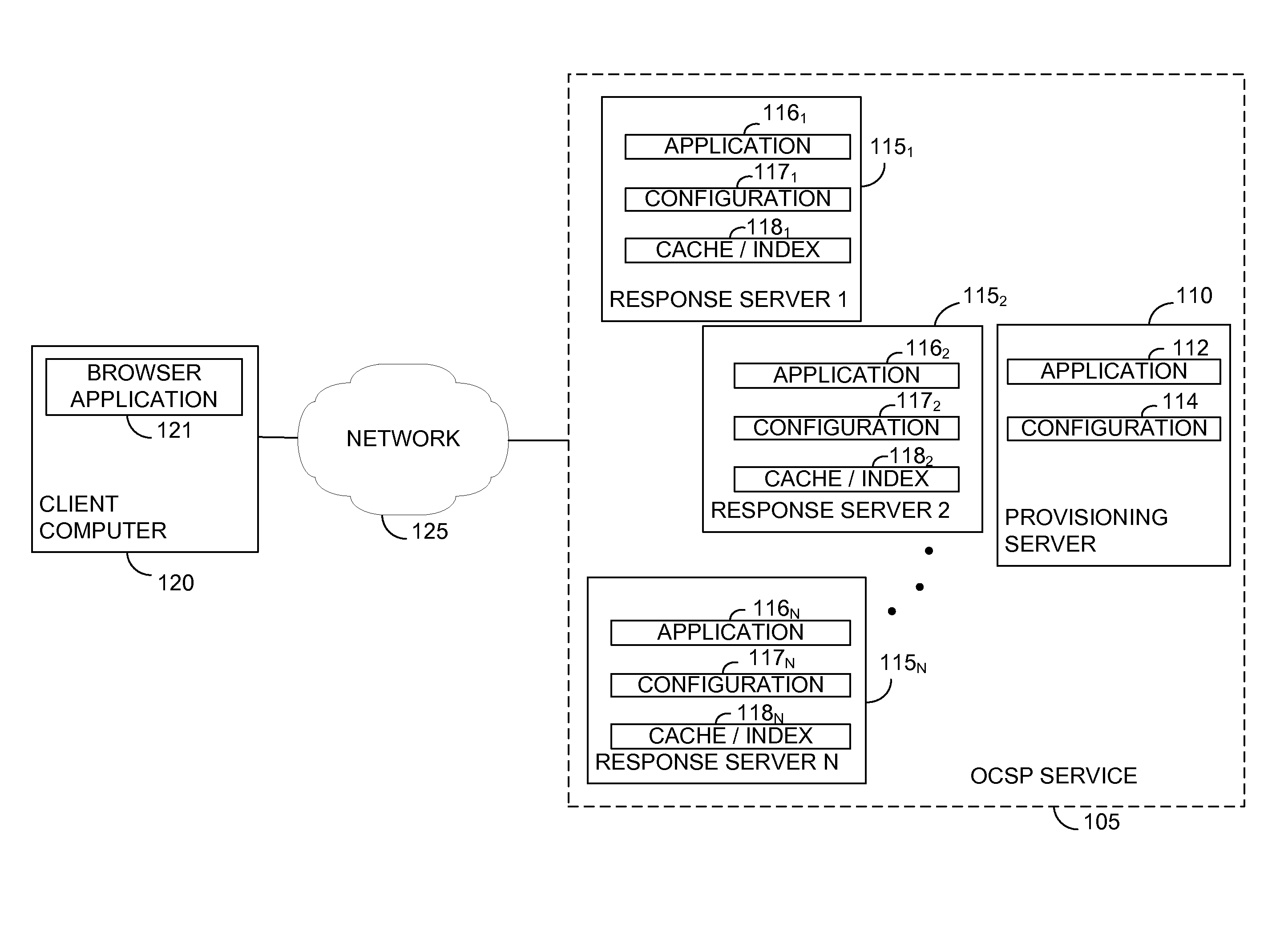
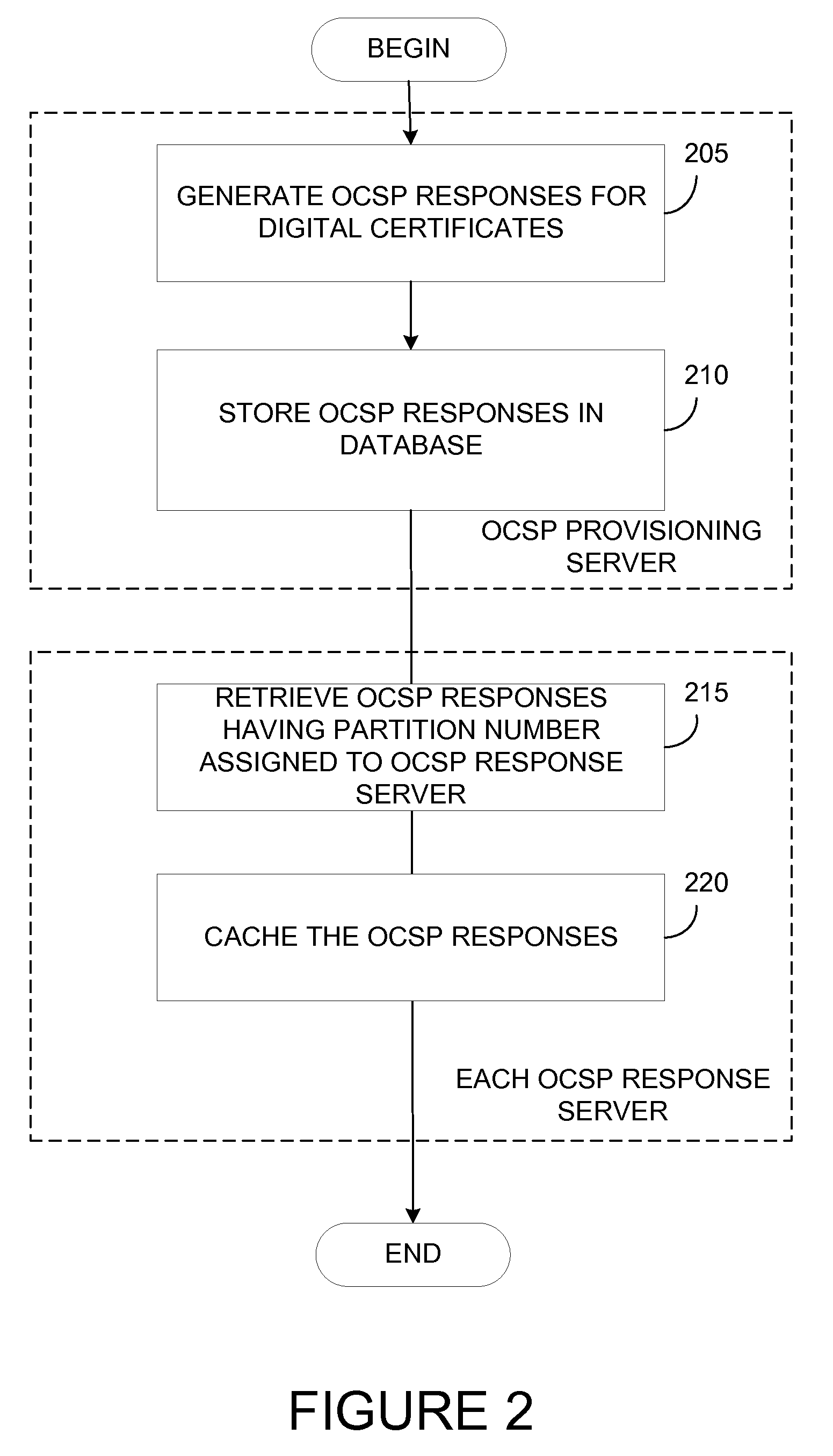
Techniques are disclosed for evenly distributing certificate status validity messages across multiple response servers. A certificate authority (CA) may partition subsets of online certificate status protocol (OCSP) responses to each be handled by OCSP response servers. The partitions are based on serial numbers of the underlying digital certificates of the OCSP responses. For example, to determine which OCSP response server is assigned to distribute a particular OCSP response, a modulo operation may be performed between the last octet value of the underlying certificate serial number and the total number of available OCSP response servers of the CA. The result yields a partition number that may be used to identify the corresponding OCSP response server.
Owner:DIGICERT
Method and device for certificate authentication
ActiveCN107786515BValid inspectionEasy accessTransmissionEngineeringProtocol for Carrying Authentication for Network Access
Embodiments of the invention provide a certificate authentication method and equipment. The method comprises the following steps that first equipment sends a first online certificate status protocol (OCSP) request message to second equipment, wherein the first OCSP request message is used for requesting OCSP status information of a second equipment certificate of the second equipment; the first equipment receives a first OCSP response message sent by the second equipment, wherein the first OCSP response message includes OCSP status information of the second equipment certificate; and the firstequipment carries out identity verification on the second equipment according to the OCSP status information of the second equipment certificate. According to the certificate authentication method and equipment, a problem that a client does not need to access a CRL or OCSP server to carry out validity verification on the certificate of the server in a handshaking process is solved.
Owner:CHINA MOBILE COMM LTD RES INST +1
Contents rights protecting method
InactiveCN101133410BReduce usageCrankshaftsMachines/enginesOnline Certificate Status ProtocolComputer security
A method for protecting a rights object for a content, wherein when a discard of a rights object with respect to a certain content is requested due to a missing of a terminal which stores the rights object with respect to the content, a rights issuer (Rl) receives a confirmation request for whether a certificate has been discarded from the terminal, confirms the certificate discard through an Online Certificate Status Protocol (OCSP) responder, and then notifies the terminal of the certificate discard, and accordingly the terminal confirms the discard of the certificate of the terminal and removes the rights object with respect thereto. In addition, a user who has removed the rights object with respect to the content can continuously use the corresponding content by entirely or partially re-obtaining the rights object with respect to the content from which the rights object has been discarded.
Owner:LG ELECTRONICS INC
Splitting certificate status responses evenly across multiple distributed certificate status responders
ActiveUS9300478B2User identity/authority verificationDigital data authenticationProtocol for Carrying Authentication for Network AccessDistributed computing
Techniques are disclosed for evenly distributing certificate status validity messages across multiple response servers. A certificate authority (CA) may partition subsets of online certificate status protocol (OCSP) responses to each be handled by OCSP response servers. The partitions are based on serial numbers of the underlying digital certificates of the OCSP responses. For example, to determine which OCSP response server is assigned to distribute a particular OCSP response, a modulo operation may be performed between the last octet value of the underlying certificate serial number and the total number of available OCSP response servers of the CA. The result yields a partition number that may be used to identify the corresponding OCSP response server.
Owner:DIGICERT
Pre-signed response generation and verification method and generation and verification device
ActiveCN102724198BImprove the ability to resist replay attacksTransmissionResponse generationValidation methods
The invention relates to a pre-signed response generation and verification method and a pre-signed response generation and verification device. An online certificate status protocol (OCSP) responder generates protection level adjustment information and a signature thereof as well as the pre-signed response of a Hash chain extension field, and can dynamically adjust the protection level adjustment information; when receiving an on-line certificate verification request from a verifier, the OCSP responder calculates a current update value to form the real-time Hash chain update information, and sends the real-time Hash chain update information and the pre-signed response to the verifier. After receiving the pre-signed response and the real-time Hash chain update information, the verifier can instantaneously play back and calibrate according to the real-time Hash chain update information, so that the anti-playback attack capability is improved.
Owner:ZHENGZHOU SEANET TECH CO LTD
A construction method of electronic invoice security middleware based on cloud computing technology
The invention provides an electronic invoice safety middleware configuring method based on the cloud computing technology. The electronic invoice safety middleware configuring method includes steps of using the cloud computing technology to configure cloud safety services of safety middleware, issuing and managing cloud safety KEY devices and safety server devices, and balancing computing resources of service modules with service peaks and valleys via resource dispatching services in the cloud computing technology; filling certificates and algorithms to the cloud safety KEY devices by the special communication protocol, issuing API (application program interface) ports to the outside through the devices and providing offline, movable and single-thread safety services for electronic invoice users; synchronizing certificates for the cloud safety server devices by standard directory services LDAP and certificate status query services (OCSP online certificate status protocol) and providing multithread safety services based on the local area network for the electronic invoice users. Cloud safety services, cloud KEY devices and cloud safety server devices can jointly form a cloud safety middleware configuring method.
Owner:SHANDONG LANGCHAO YUNTOU INFORMATION TECH CO LTD
System and method for validity verification of certificate in mobile backhaul net
InactiveCN102026161BValidity verification is efficientEfficient verificationTransmissionSecurity arrangementA domainClient-side
The invention provides system and method for validity verification of a certificate in a mobile backhaul net. The method comprises the following steps of: when the validity of a domain certificate is verified, the client side of an online certificate status protocol (OCSP) sends an OCSP search request to an OCSP responser, and a request certificate table is carried; after the OCSP responser receives the OCSP search request, a certificate library is requested to verify the validity of the certificate in the request certificate table, and the certificate library searches the validity of the certificate in the request certificate table and transmits the search results of the validity of the certificate to the OCSP client side by the OCSP responser. The invention can efficiently verify the validity of the certificate in the mobile backhaul net in real time.
Owner:ZTE CORP
Certificate status delivery through a local endpoint
Techniques are disclosed for locally distributing online certificate status protocol (OCSP) responses to a client computer. A certificate authority (CA) proactively sends OCSP responses to an agent application (e.g., an antivirus application configured to handle OCSP responses) residing in the client computer. The agent application stores the OCSP responses in a cache. Thereafter, when a browser application sends an OCSP request to the CA, the agent application intercepts the request and determines whether a corresponding OCSP response is locally cached. If so, the agent application sends the cached OCSP response to the browser application. If not, the agent application retrieves the corresponding OCSP response from the CA and sends the response to the browser application.
Owner:DIGICERT
Method for authenticating validity of IKE V2 certificate
Owner:ZTE CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com