A construction method of electronic invoice security middleware based on cloud computing technology
An electronic invoice and cloud computing technology, applied in billing/billing, etc., can solve problems such as failure to meet business needs, affect system promotion and customer satisfaction, and lag in electronic invoices
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0024] The method of the present invention is described in detail below with reference to the accompanying drawings.
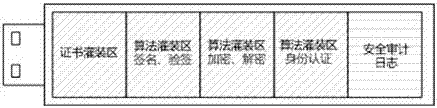
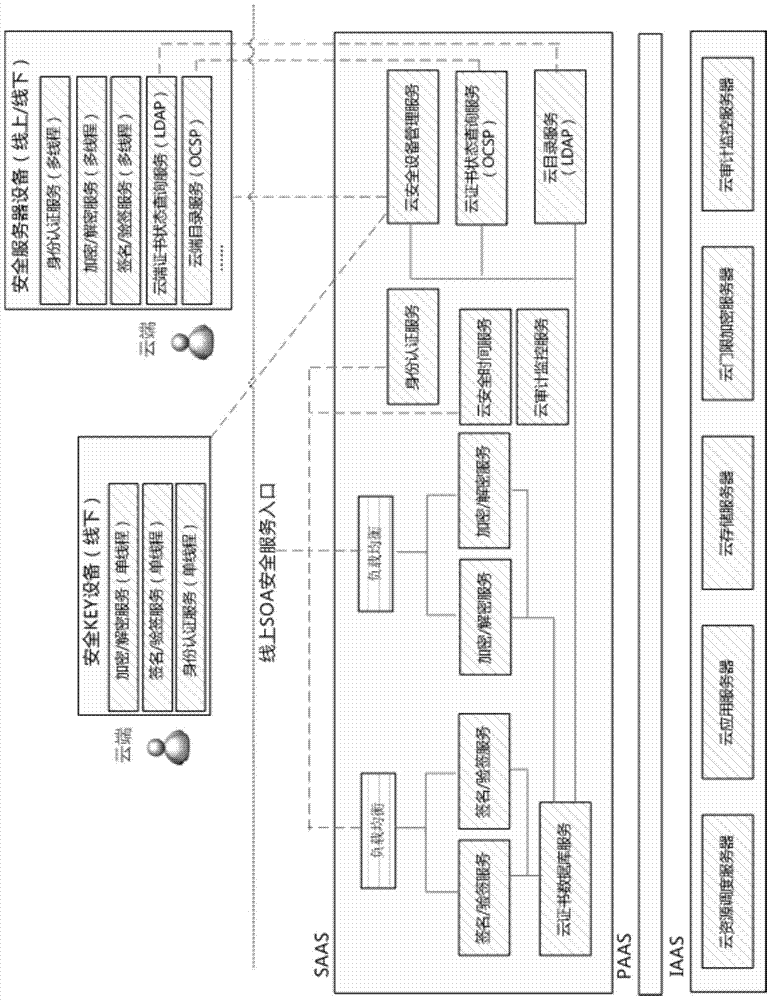
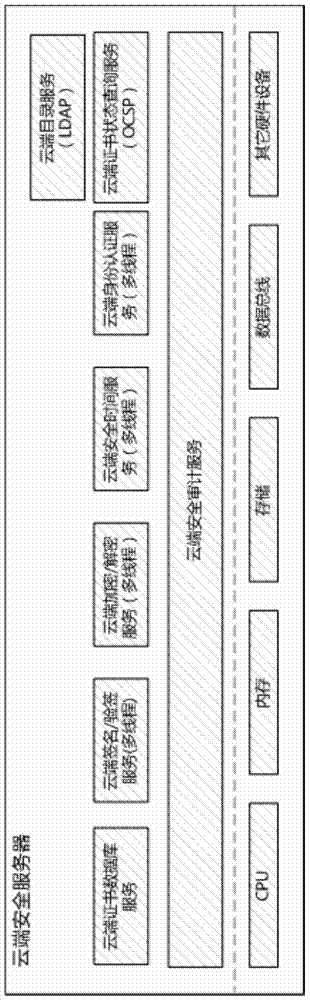
[0025] A method for constructing electronic invoice security middleware based on cloud computing technology is to use cloud computing technology to construct security middleware cloud security services, including cloud certificate database service, cloud directory service LDAP, cloud certificate status query service OCSP, cloud security equipment Management services, cloud signature and verification services, cloud encryption and decryption services, cloud identity authentication services, etc.; through resource scheduling services in cloud computing technology, signature and verification services, encryption and decryption services that have business peaks and valleys , identity authentication service to balance computing resources; through cloud security device management services, cloud security KEY devices and security server devices are issued and managed....
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com