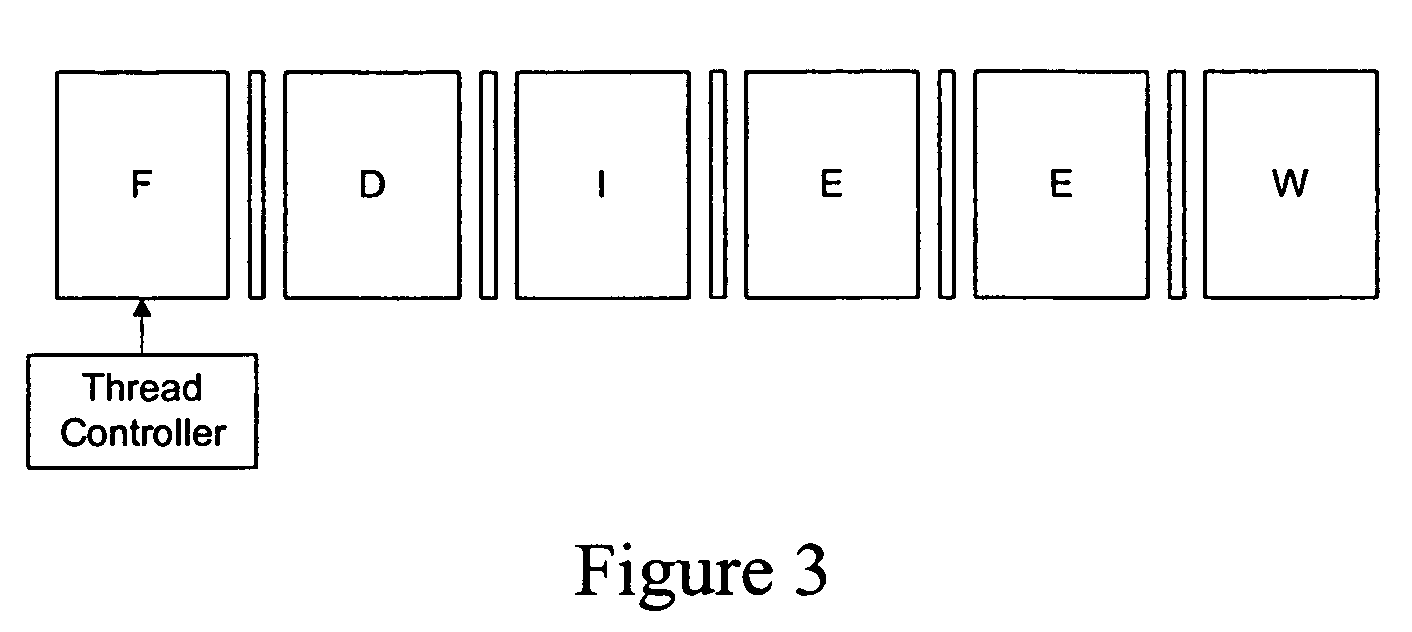
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
127 results about "Thread safety" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Thread safety is a computer programming concept applicable to multi-threaded code. Thread-safe code only manipulates shared data structures in a manner that ensures that all threads behave properly and fulfill their design specifications without unintended interaction. There are various strategies for making thread-safe data structures.
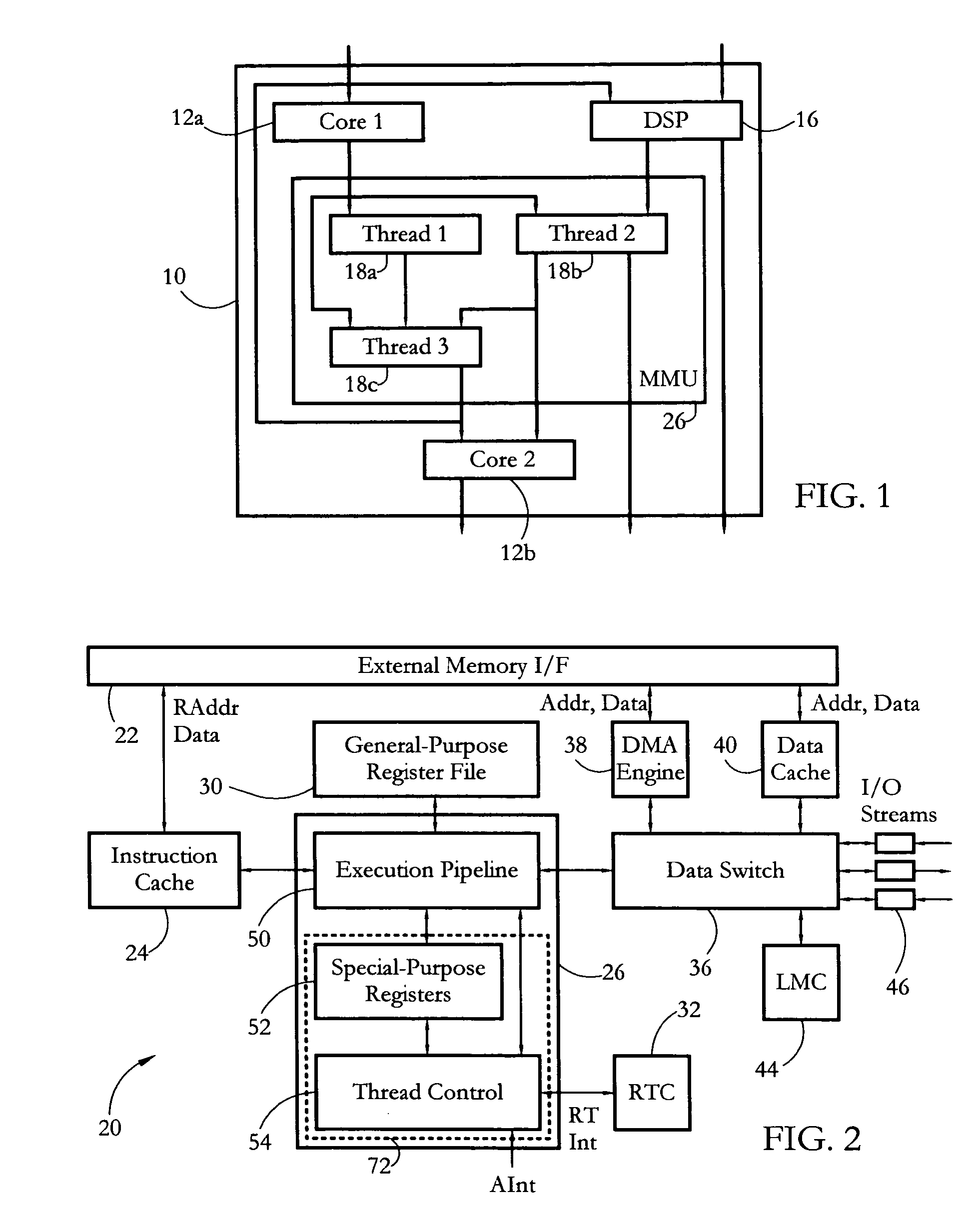
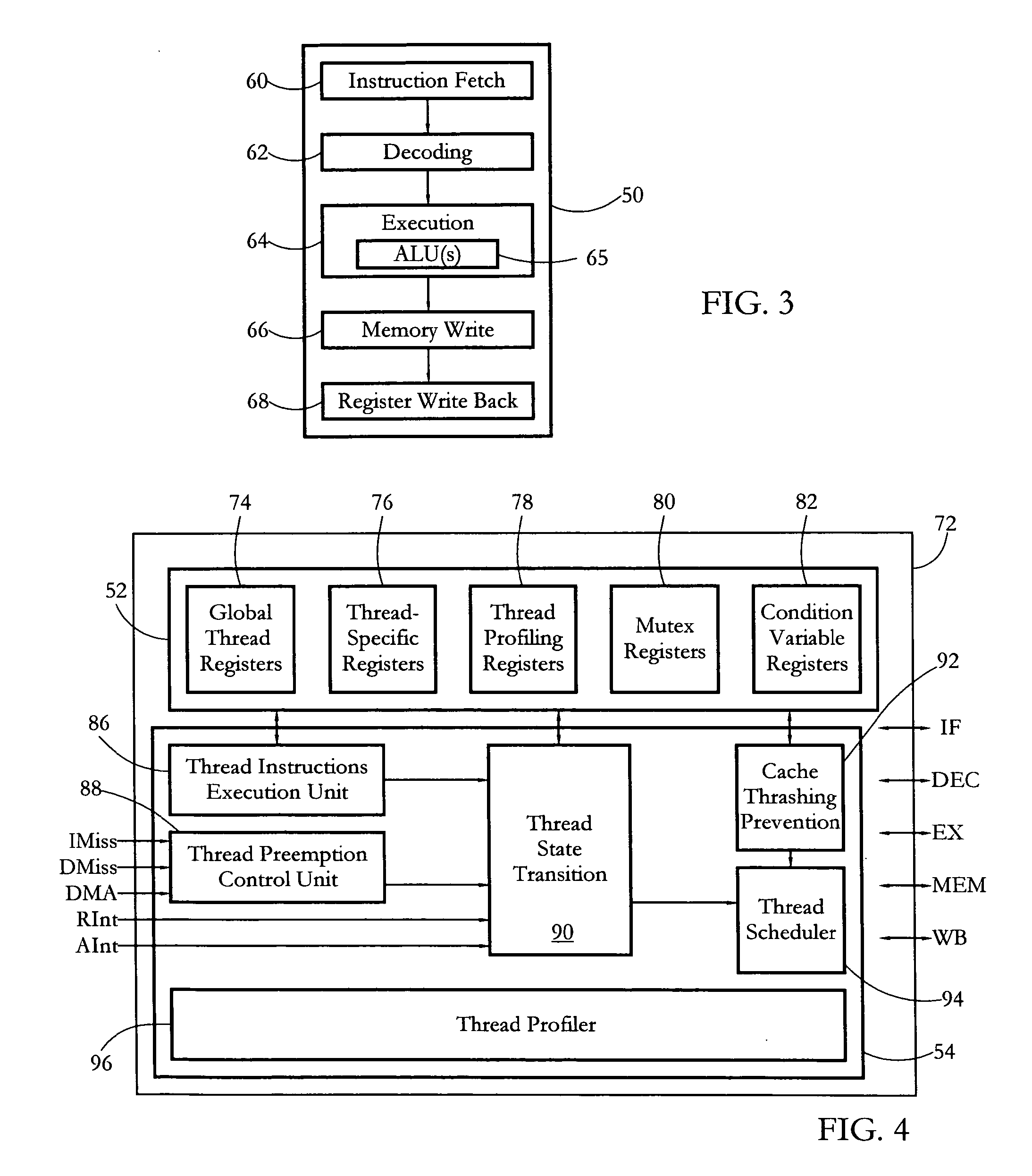
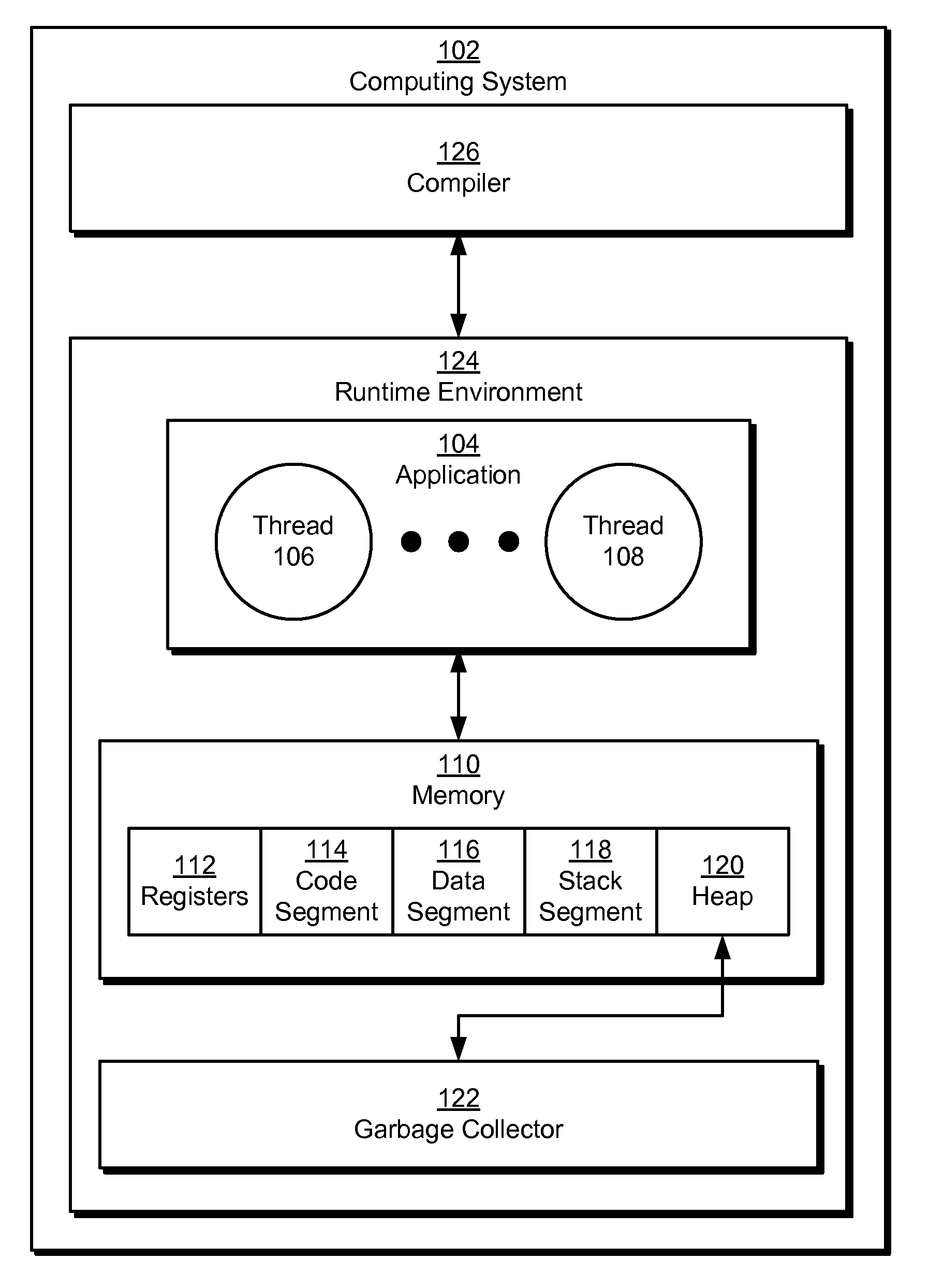
Hardware multithreading systems with state registers having thread profiling data
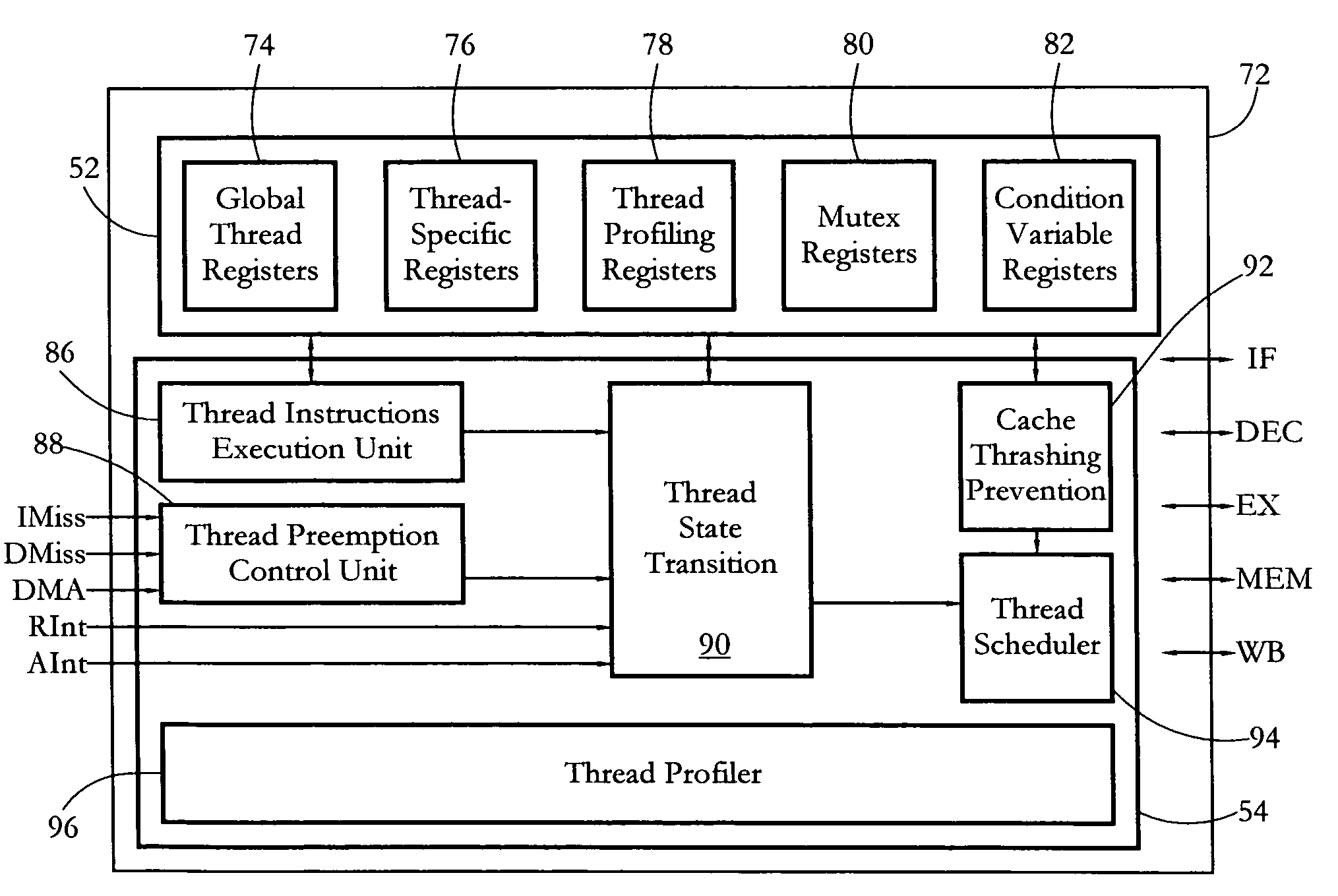
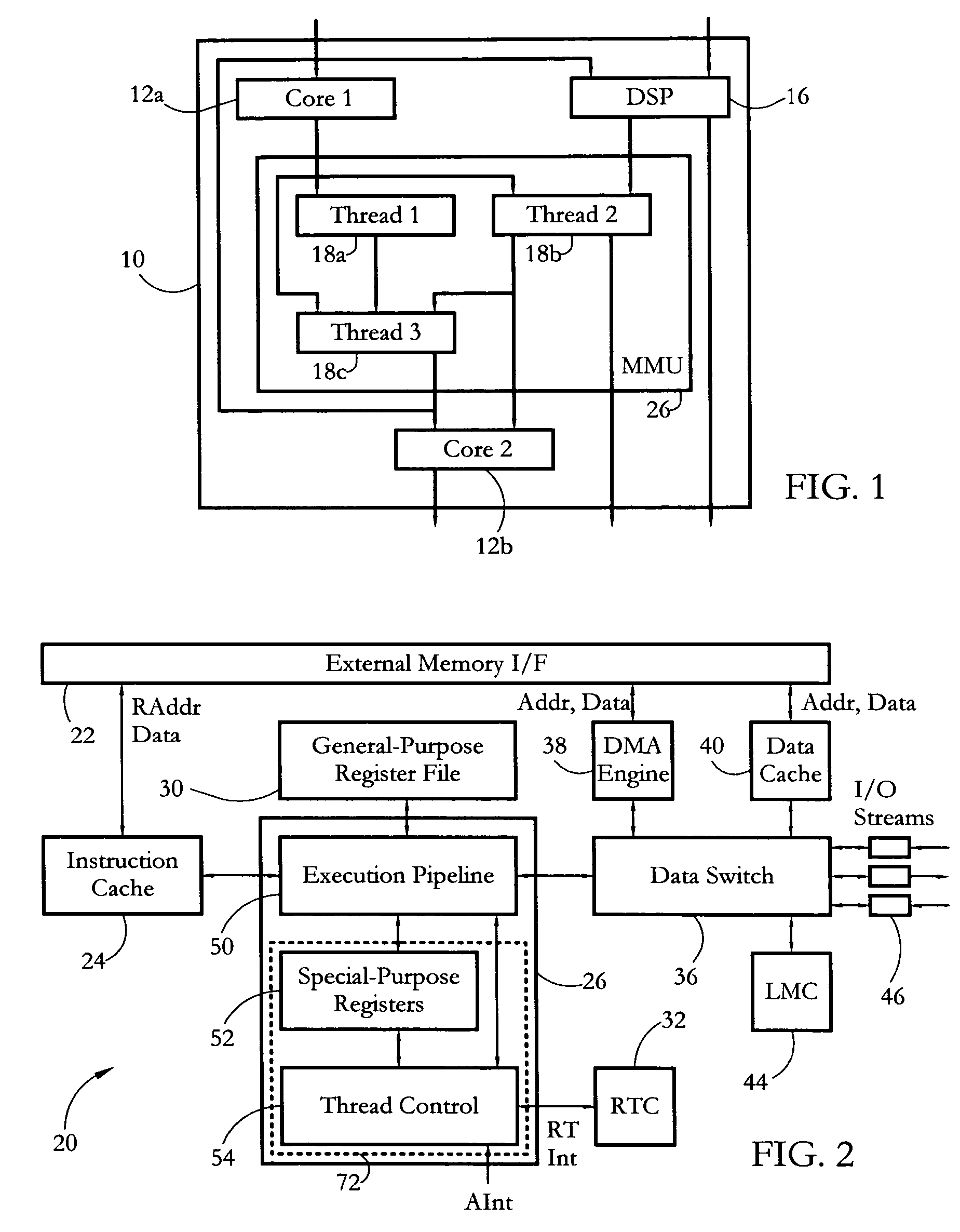
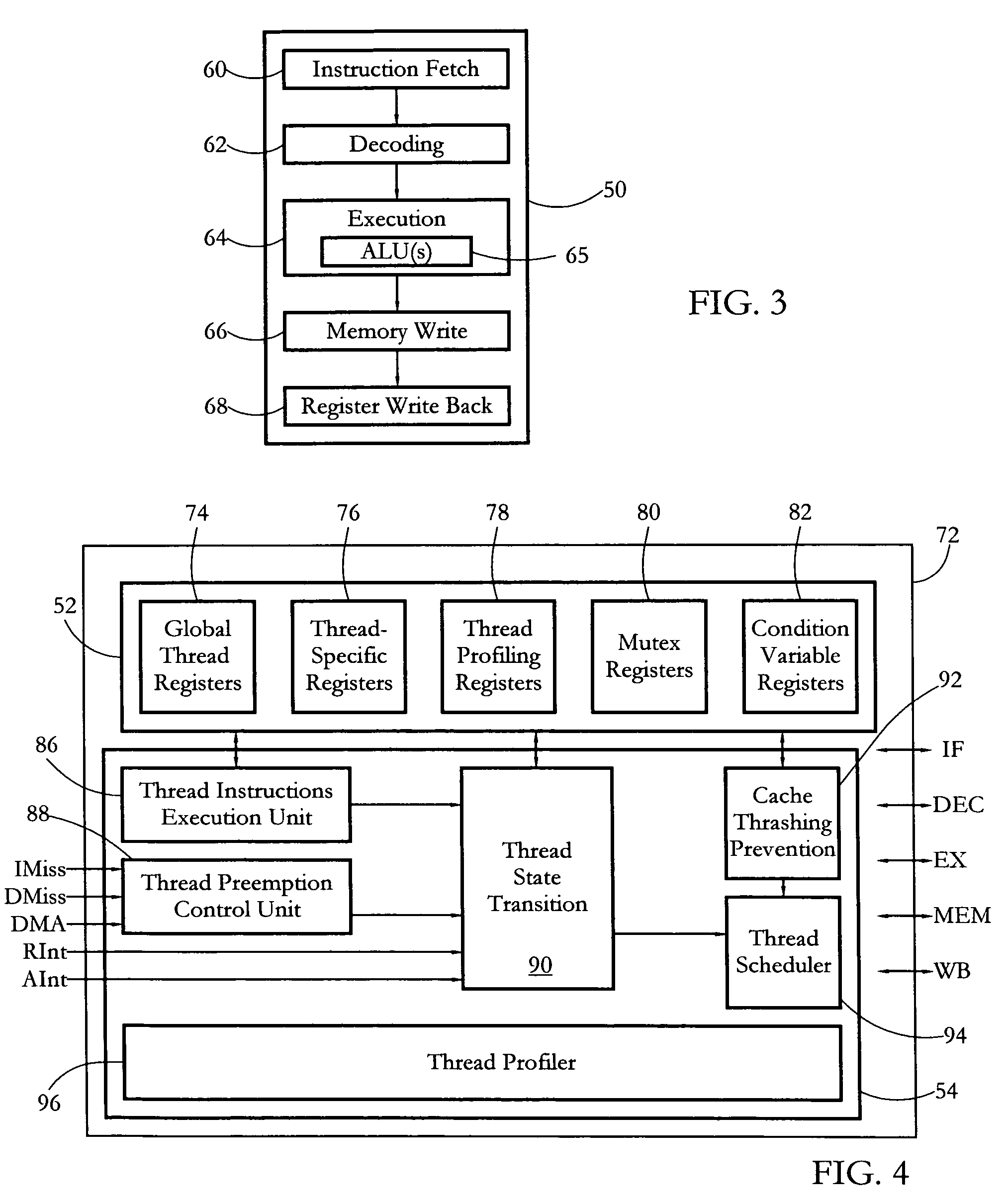
According to some embodiments, a multithreaded microcontroller includes a thread control unit comprising thread control hardware (logic) configured to perform a number of multithreading system calls essentially in real time, e.g. in one or a few clock cycles. System calls can include mutex lock, wait condition, and signal instructions. The thread controller includes a number of thread state, mutex, and condition variable registers used for executing the multithreading system calls. Threads can transition between several states including free, run, ready and wait. The wait state includes interrupt, condition, mutex, I-cache, and memory substates. A thread state transition controller controls thread states, while a thread instructions execution unit executes multithreading system calls and manages thread priorities to avoid priority inversion. A thread scheduler schedules threads according to their priorities. A hardware thread profiler including global, run and wait profiler registers is used to monitor thread performance to facilitate software development.
Owner:GEO SEMICONDUCTOR INC
Safe language static variables initialization in a multitasking system
InactiveUS6901586B1Multiprogramming arrangementsProgram loading/initiatingVirtualizationStatic field
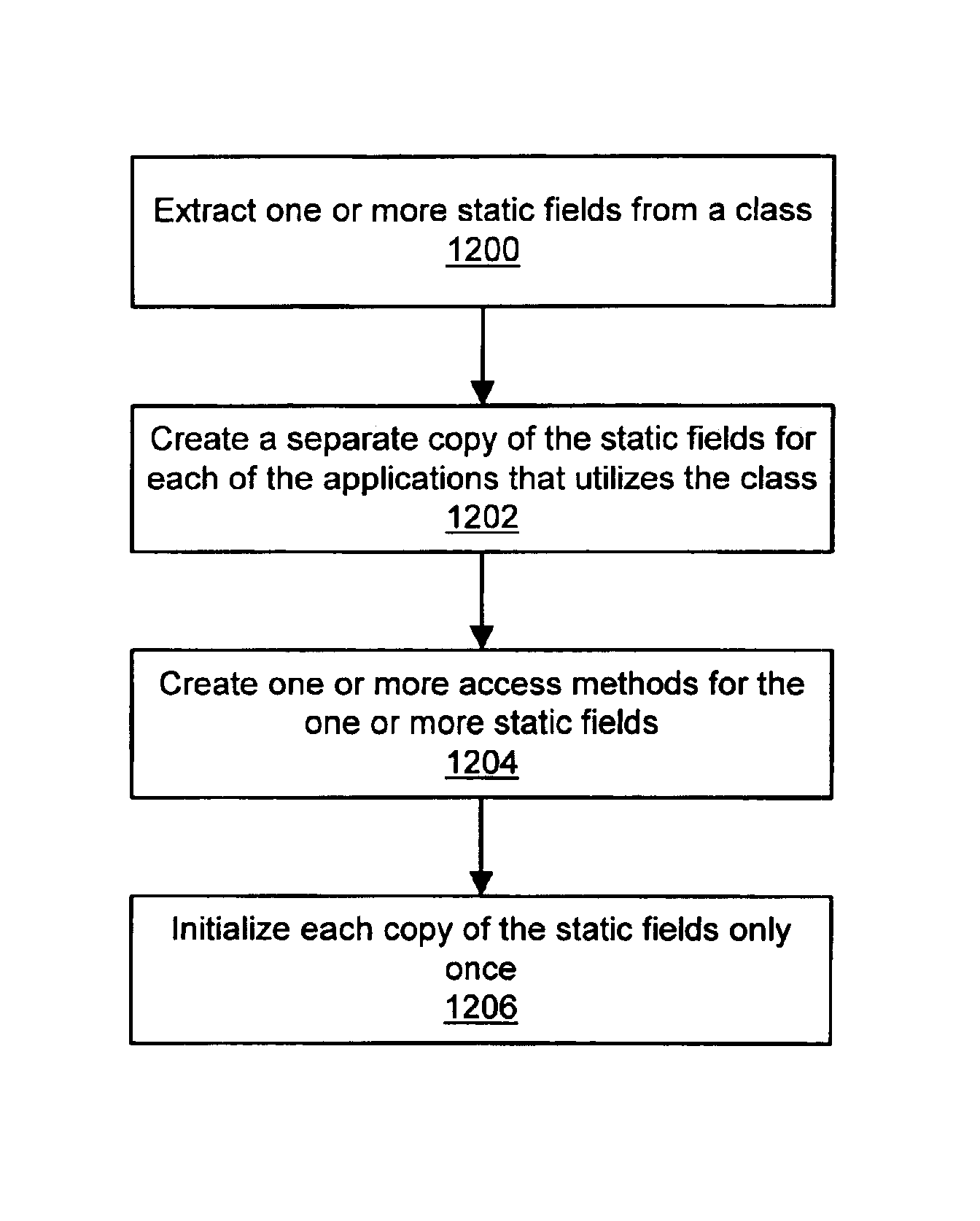
A system and method are provided for thread-safe initialization of static variables in a multitasking system. In one embodiment, the static fields of a class may be “virtualized” such that each application that utilizes the class has its own copy of static fields. Each separate copy of the static fields is initialized only once. Instructions for performing the initialization may be embedded in a class constructor. The class constructor may be executed only once for each separate copy of the static fields. A template class may be loaded for each separate copy of the static fields when a copy of the static fields is sought to be initialized. The template class may include a static initializer for one of the separate copies of the static fields. The static initializer may be executed once for each separate copy of the static fields.
Owner:ORACLE INT CORP
System and method for reading and writing a thread state in a multithreaded central processing unit
A system and method for enabling multithreading in a embedded processor, invoking zero-time context switching in a multithreading environment, scheduling multiple threads to permit numerous hard-real time and non-real time priority levels, fetching data and instructions from multiple memory blocks in a multithreading environment, and enabling a particular thread to modify the multiple states of the multiple threads in the processor core.
Owner:MAYFIELD XI +8
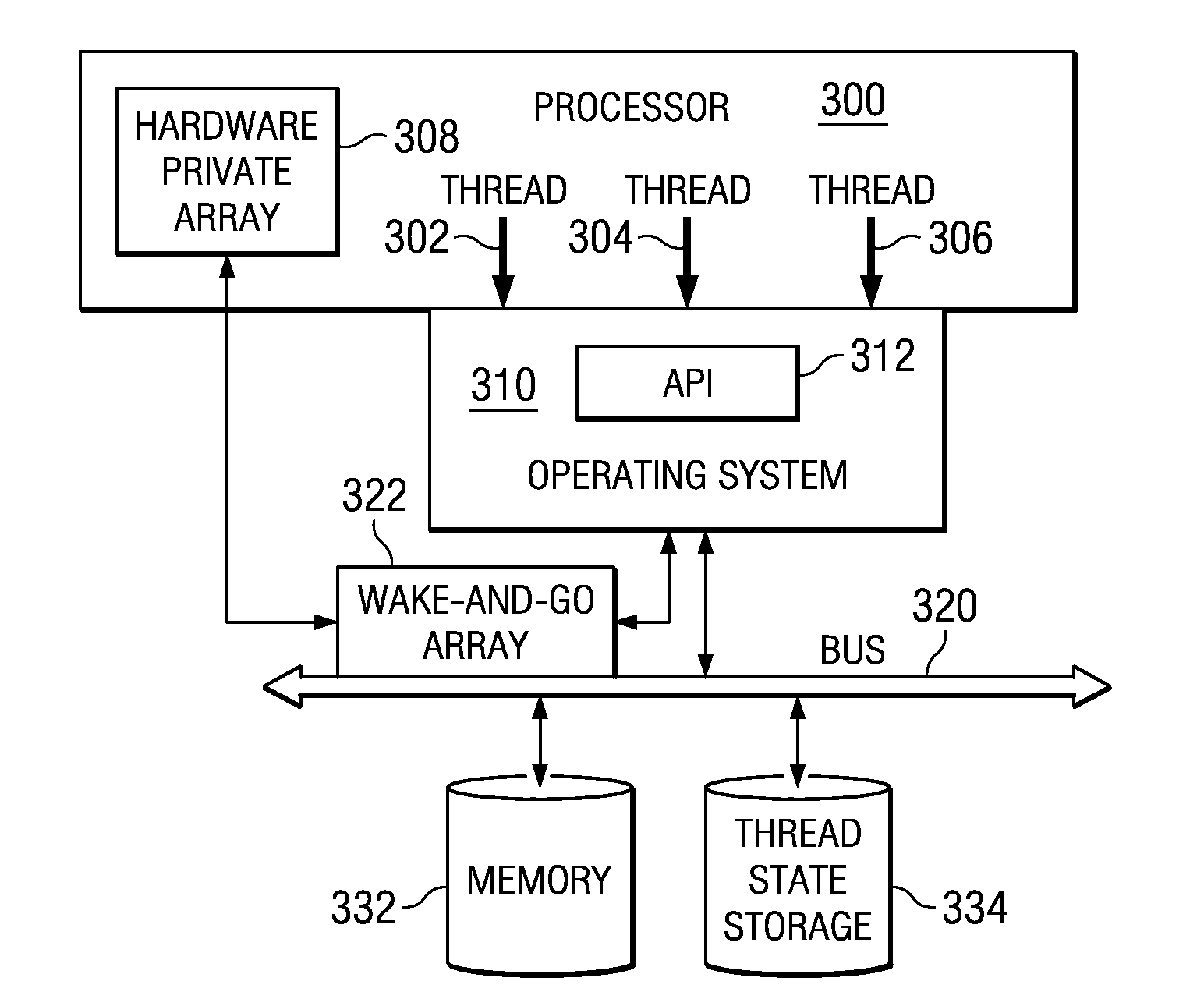
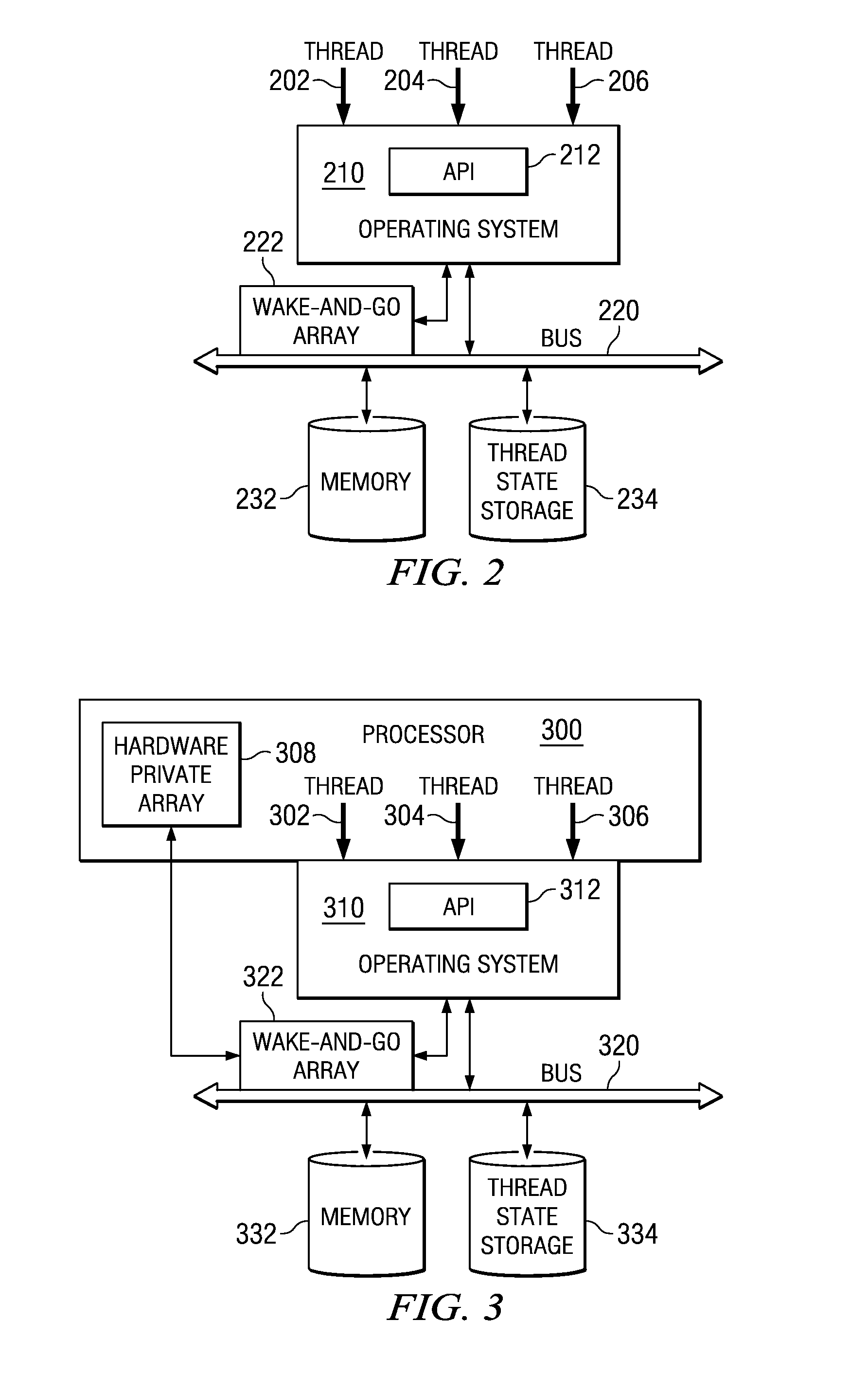
Wake-and-Go Mechanism With Software Save of Thread State
InactiveUS20090199184A1Program synchronisationMemory systemsData processing systemArray data structure
A wake-and-go mechanism is provided for a data processing system. When a thread is waiting for an event, rather than performing a series of get-and-compare sequences, the thread updates a wake-and-go array with a target address associated with the event. Software may save the state of the thread. The thread is then put to sleep. When the wake-and-go array snoops a kill at a given target address, logic associated with wake-and-go array may generate an exception, which may result in a switch to kernel mode, wherein the operating system performs some action before returning control to the originating process. In this case, the trap results in other software, such as the operating system or background sleeper thread, for example, to reload thread from thread state storage and to continue processing of the active threads on the processor.
Owner:IBM CORP
Security enhanced network device and method for secure operation of same
ActiveUS8402267B1Digital data processing detailsUnauthorized memory use protectionCommunication controlSecurity enhancement
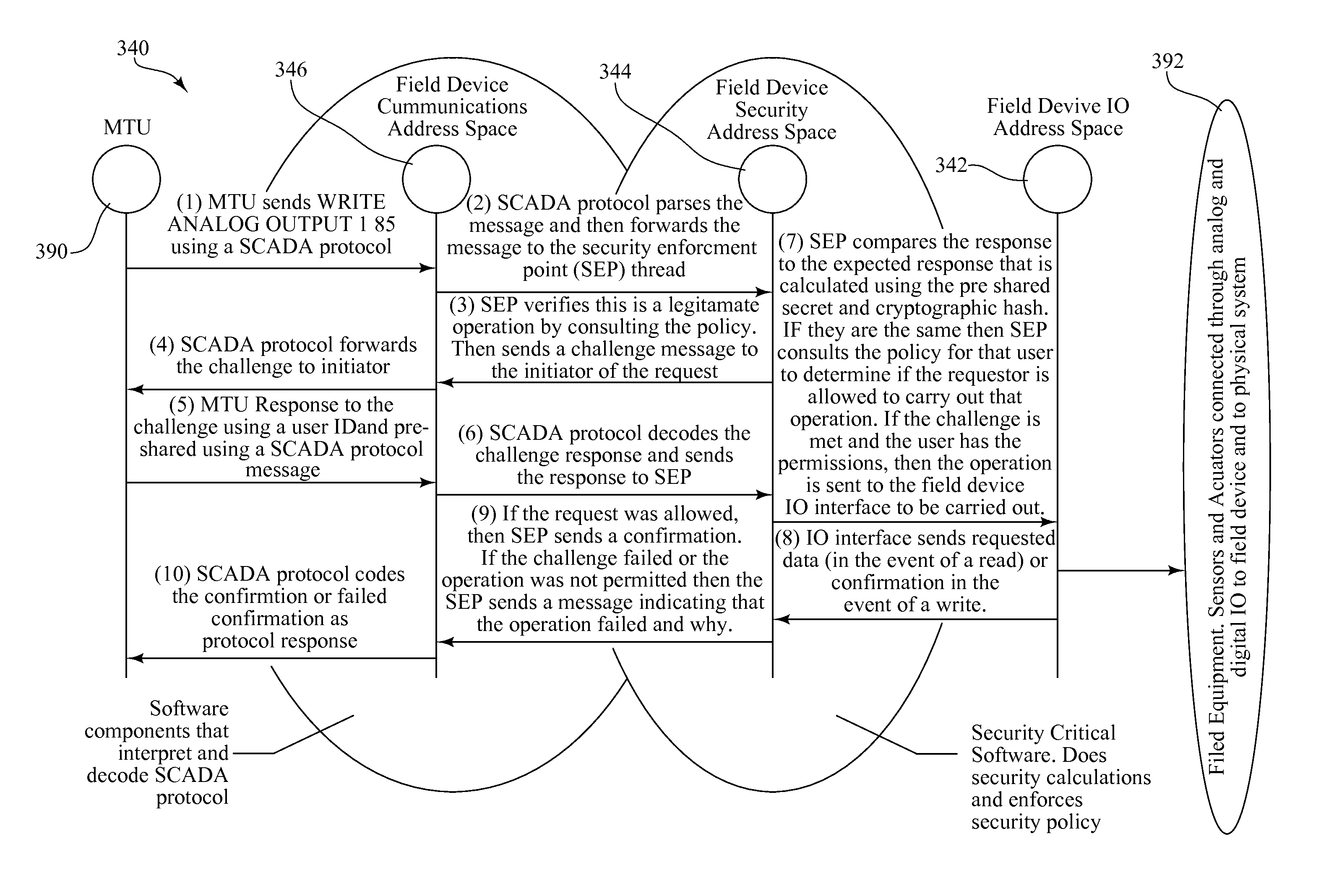
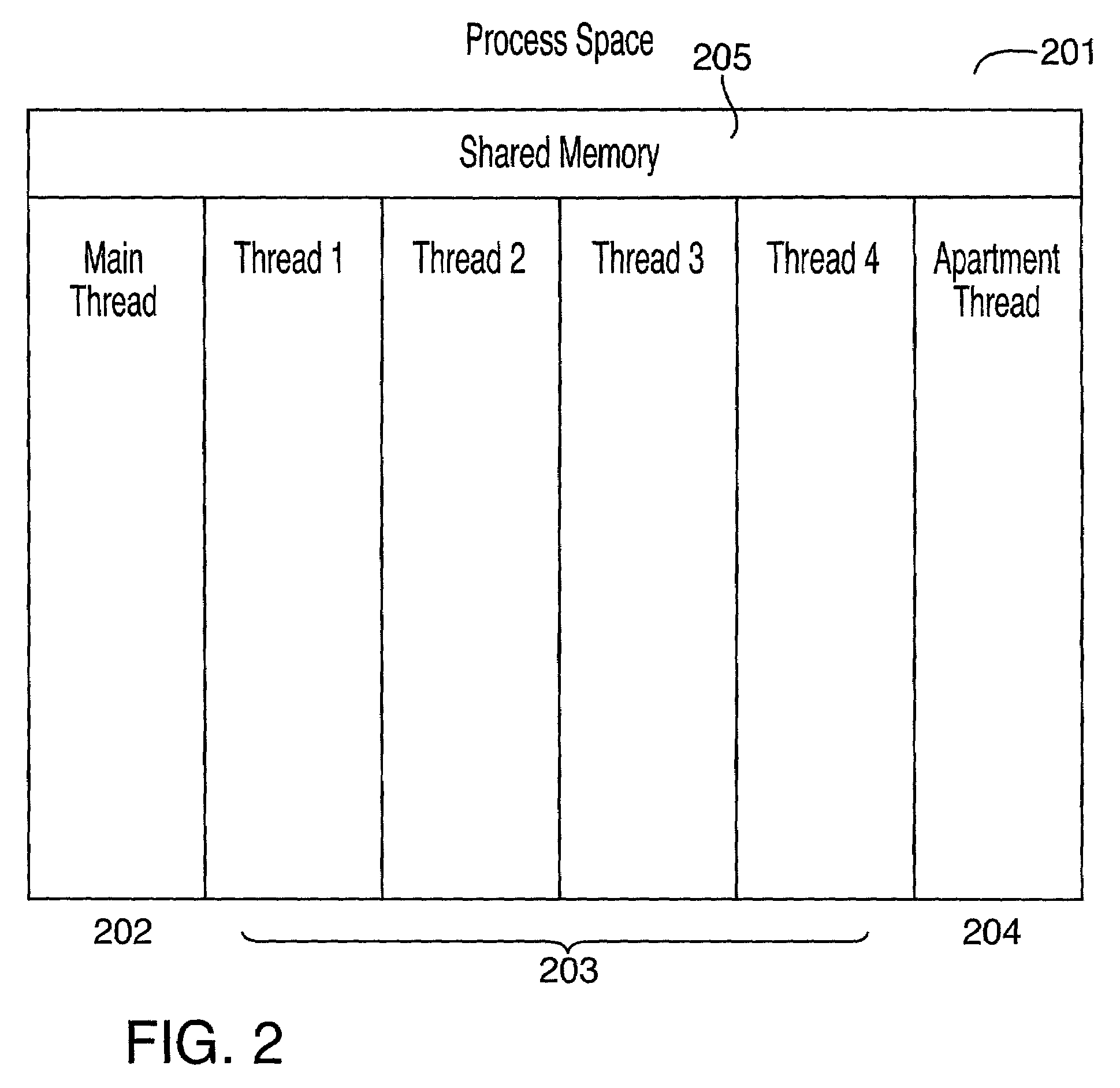
A security enhanced network device includes a processor, a memory, and a communication controller operably connected to form a processing device. A microkernel provides a partitioning between a communication address space, a security enforcement address space, and a protected operations address space. The communication address space contains communications threads for interacting with a network. The protected operations address space contains protected operations threads for performing protected operations. The security enforcement address space contains security threads for providing secure isolation of the protected operations address space from the communication address space. A method of secure operation of the network device includes: partitioning the network device into the communication address space, the security enforcement address space, and the protected operations address space; interacting with the network; providing secure isolation of the protected operations address space from the communication address space; and performing protected operations.
Owner:UNIV OF LOUISVILLE RES FOUND INC
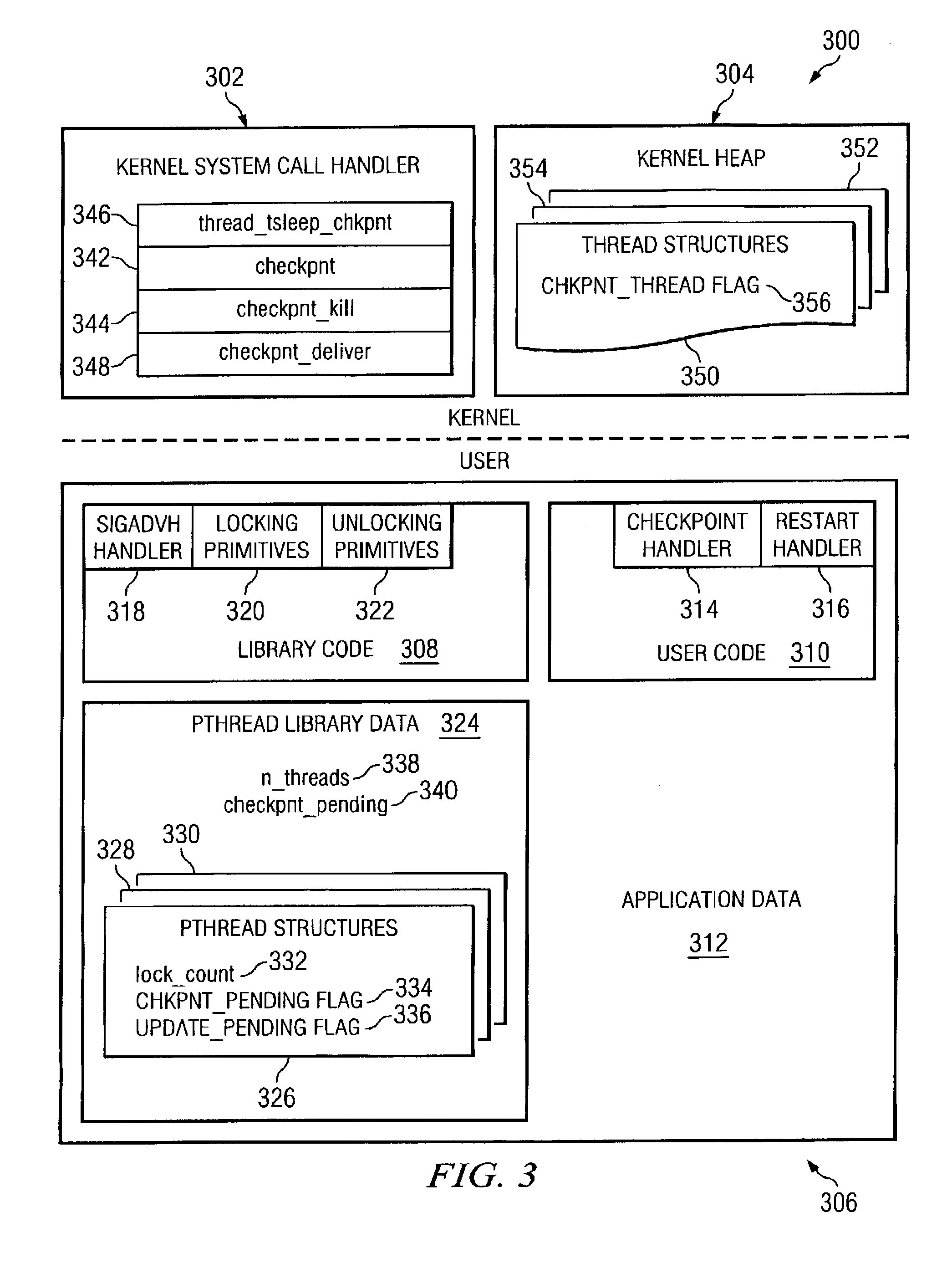
Method and apparatus for thread-safe handlers for checkpoints and restarts
InactiveUS20080077934A1Unauthorized memory use protectionMultiprogramming arrangementsData processing systemParallel computing
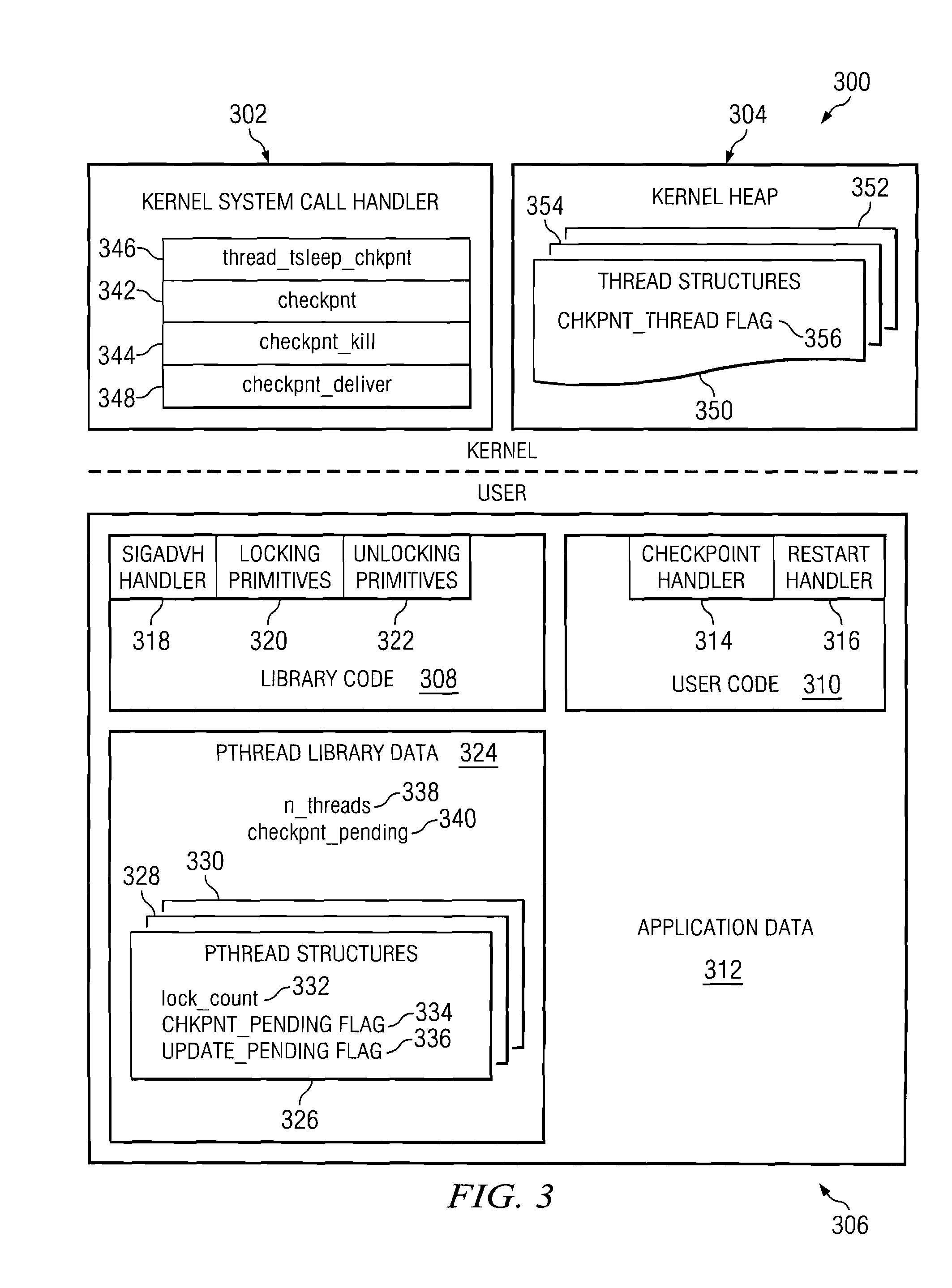
A method, apparatus, and computer instructions for executing a handler in a multi-threaded process handling a number of threads in a manner that avoids deadlocks. A value equal to the number of threads executing in the data processing system is set. The value is decremented each time a lock count for a thread within the number of threads is zero. A thread within the number of threads is suspended if the thread requests a lock and has a lock count of zero. A procedure, such as a handler, is executed in response to all of the threads within the number of threads having no locks.
Owner:INT BUSINESS MASCH CORP
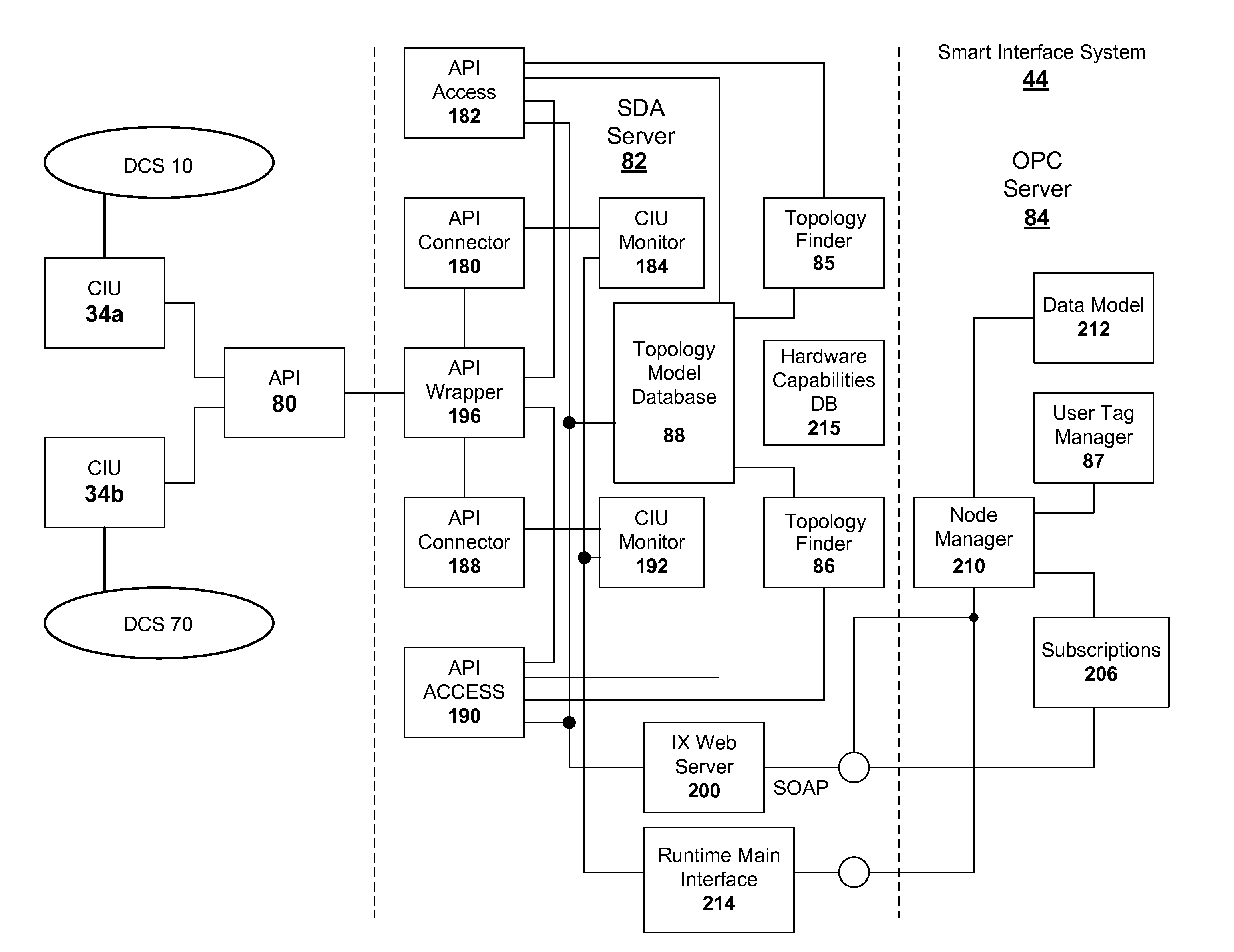
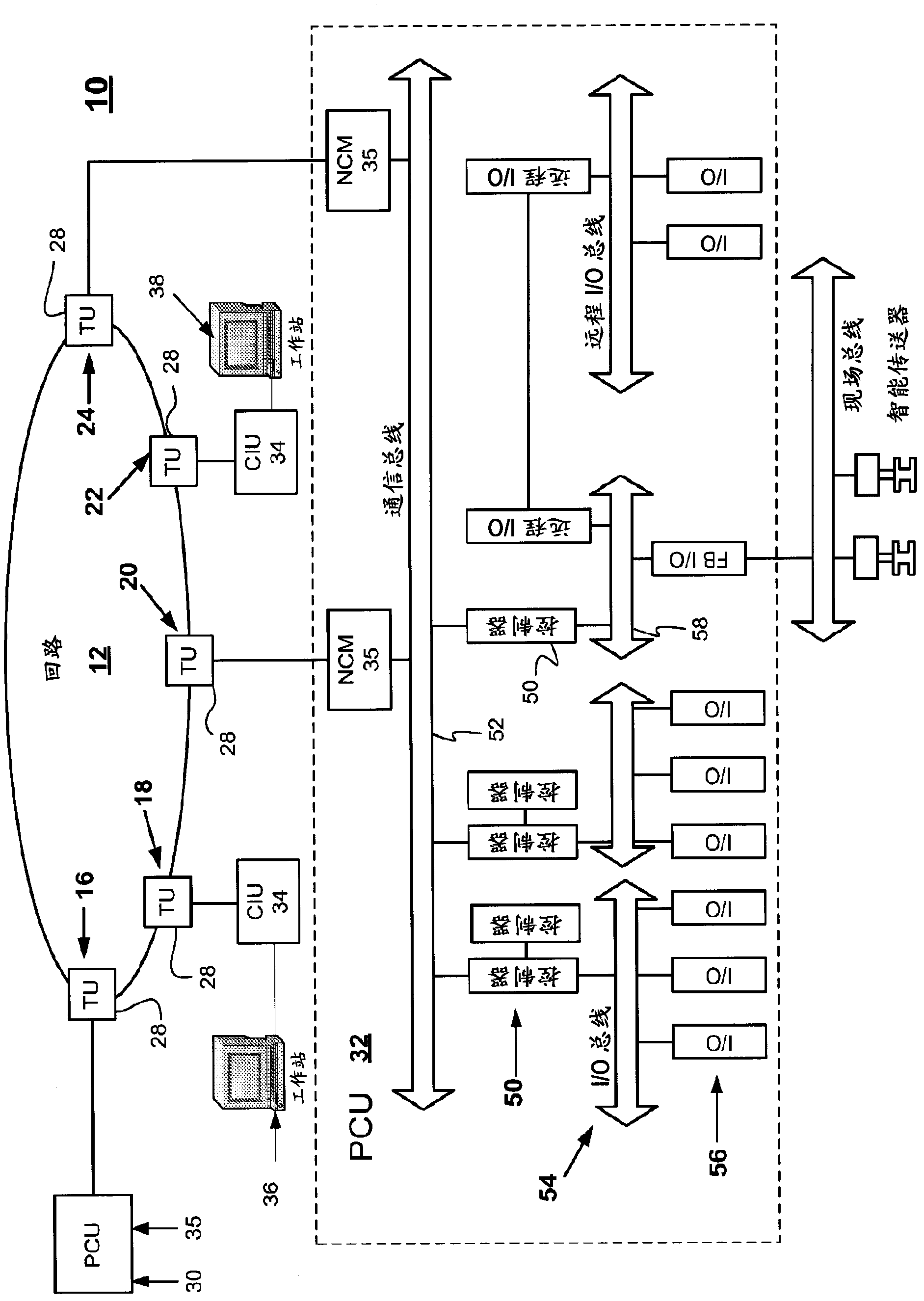
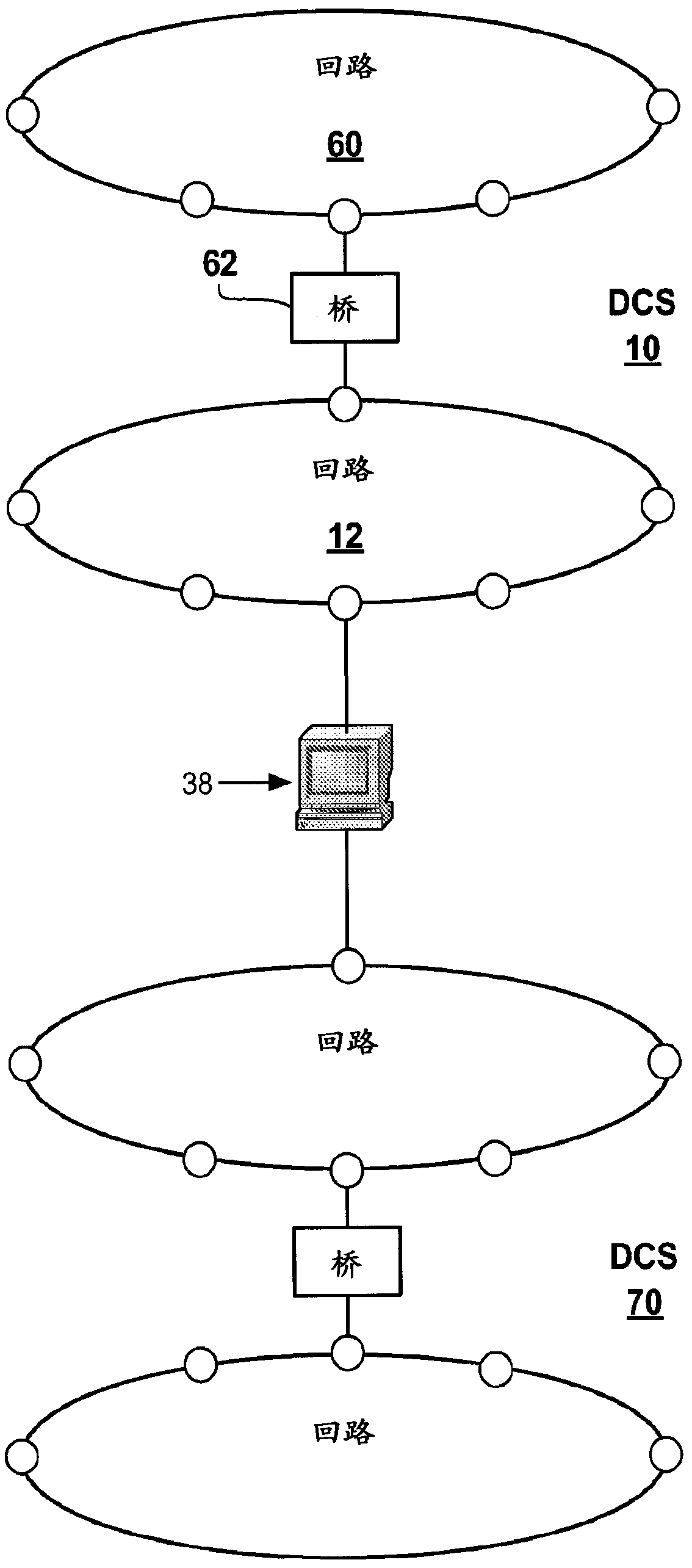
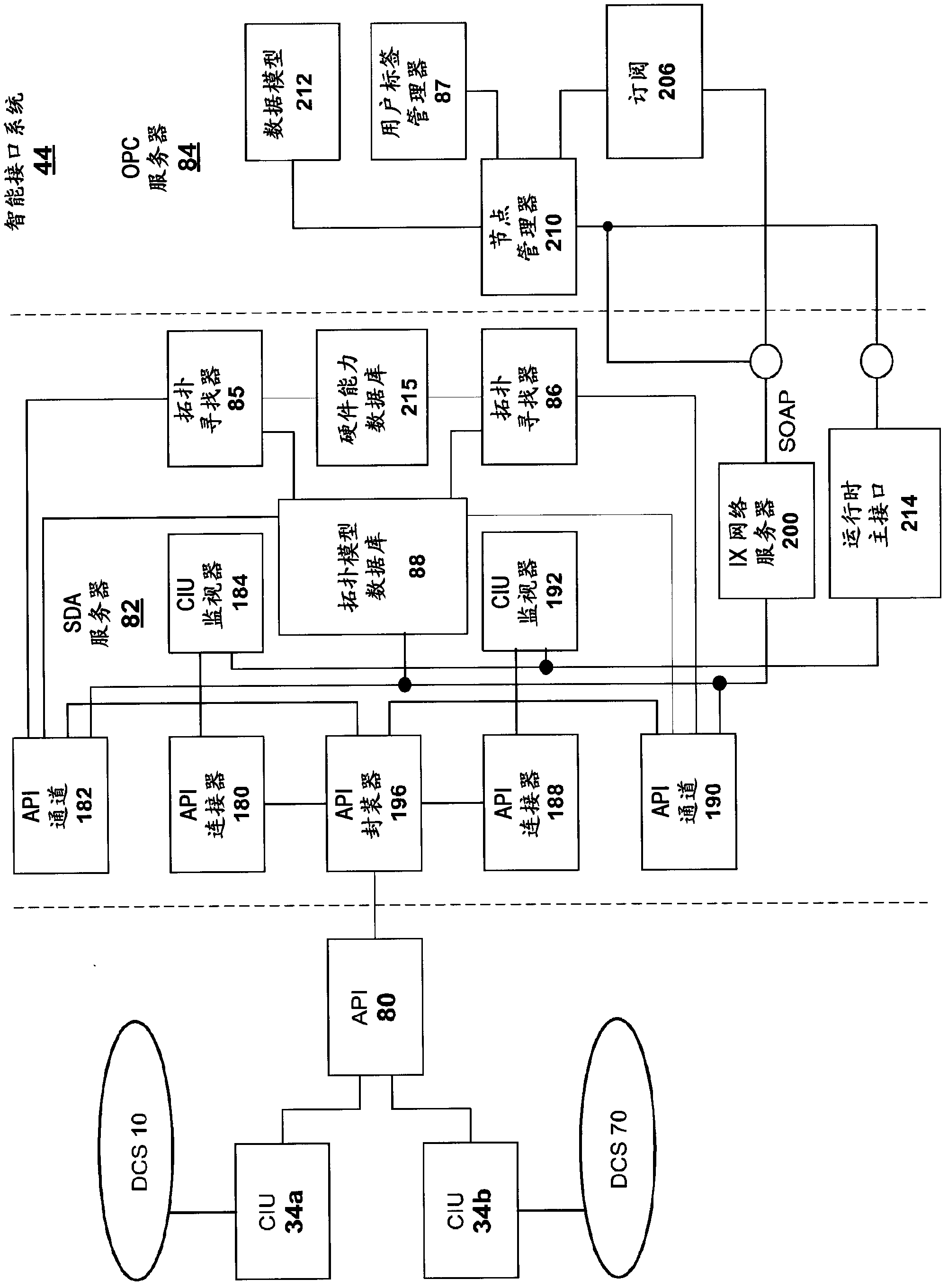
Intelligent interface for a distributed control system
InactiveUS20120089239A1Computer controlSimulator controlExternal applicationDistributed control system
An intelligent interface system is provided for connecting an external application to a distributed control system (DCS). The interface system is operable to automatically scan the DCS to determine its configuration and build a topology model of the DCS. The topology model is used to determine whether data requested from a module in the DCS can be provided by the module. The topology model is constructed to be thread-safe. A throttling mechanism in the interface system protects the DCS from being subjected to excessive data requests.
Owner:ABB INC
Hardware Multithreading Systems and Methods
Owner:GEO SEMICONDUCTOR INC
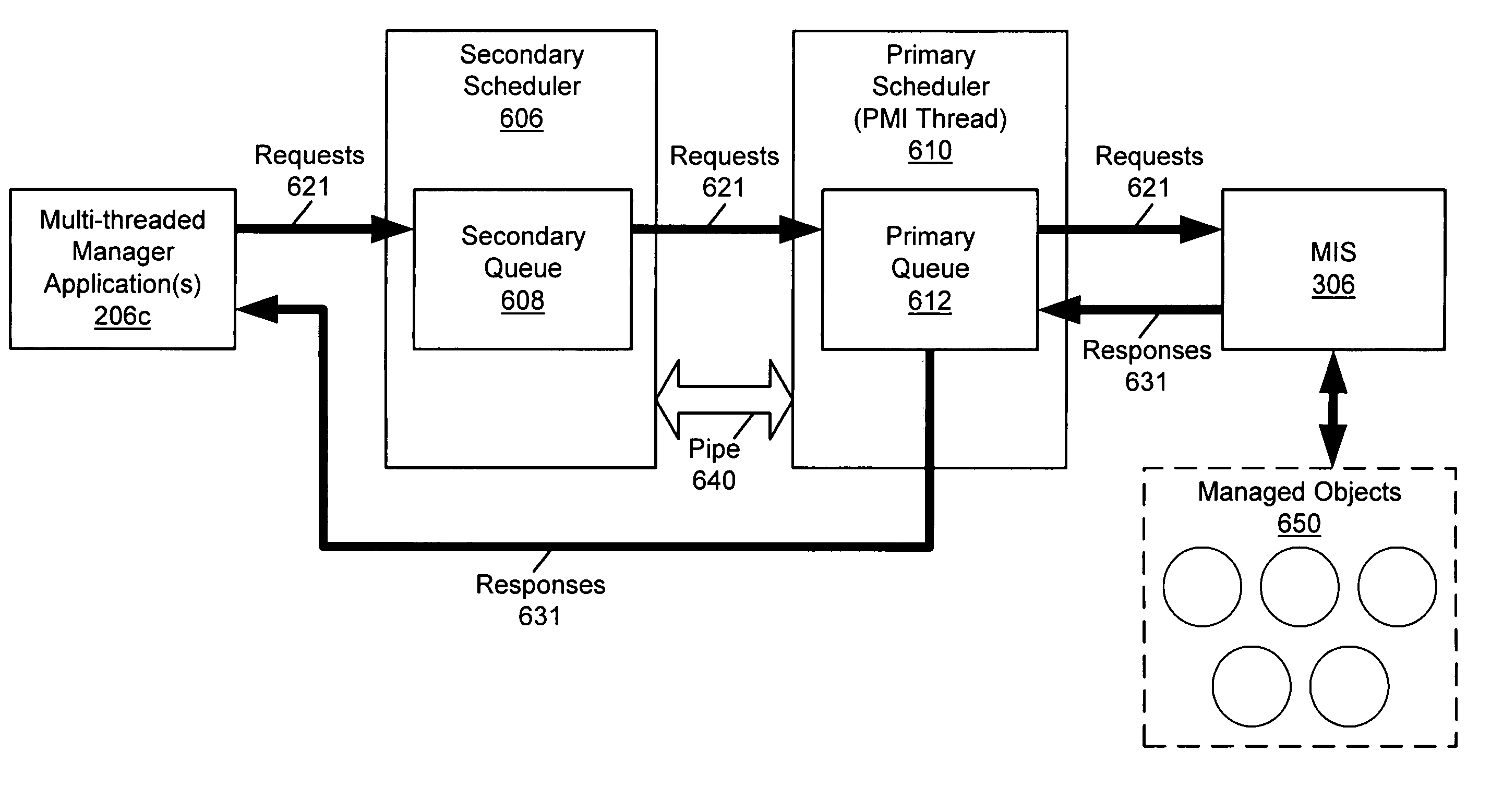
Thread-safe portable management interface
InactiveUS7206843B1Improve performanceImprove efficiencyResource allocationDigital computer detailsManaged objectMultithreading
A system and method for using a management interface such as Portable Management Interface (PMI) in a thread-safe and efficient manner. A secondary scheduler receives PMI management requests from multi-threaded manager applications in a thread-safe manner, such as through a lock. The secondary scheduler monitors the flow of PMI-related requests into PMI to ensure that, at any point in time, only one management request (e.g., callback function) is running on the PMI thread. When a request in the secondary queue is ready for scheduling with the primary scheduler, the secondary scheduler then accesses the primary scheduler in a thread-safe manner, such as through a lock, to send the request to the primary scheduler. The management requests are dispatched from the primary scheduler and executed on managed objects though a Management Information Server. The performance and efficiency of the manager applications is enhanced by increasing the responsiveness of interaction between the manager applications and the schedulers. The performance of the management interface is enhanced by eliminating the need for polling-based scheduling solutions.
Owner:ORACLE INT CORP
Recording medium, software verification apparatus and software verification method
InactiveUS20070220493A1Reduce verification costsSoftware engineeringSpecific program execution arrangementsSoftware engineeringParallel software
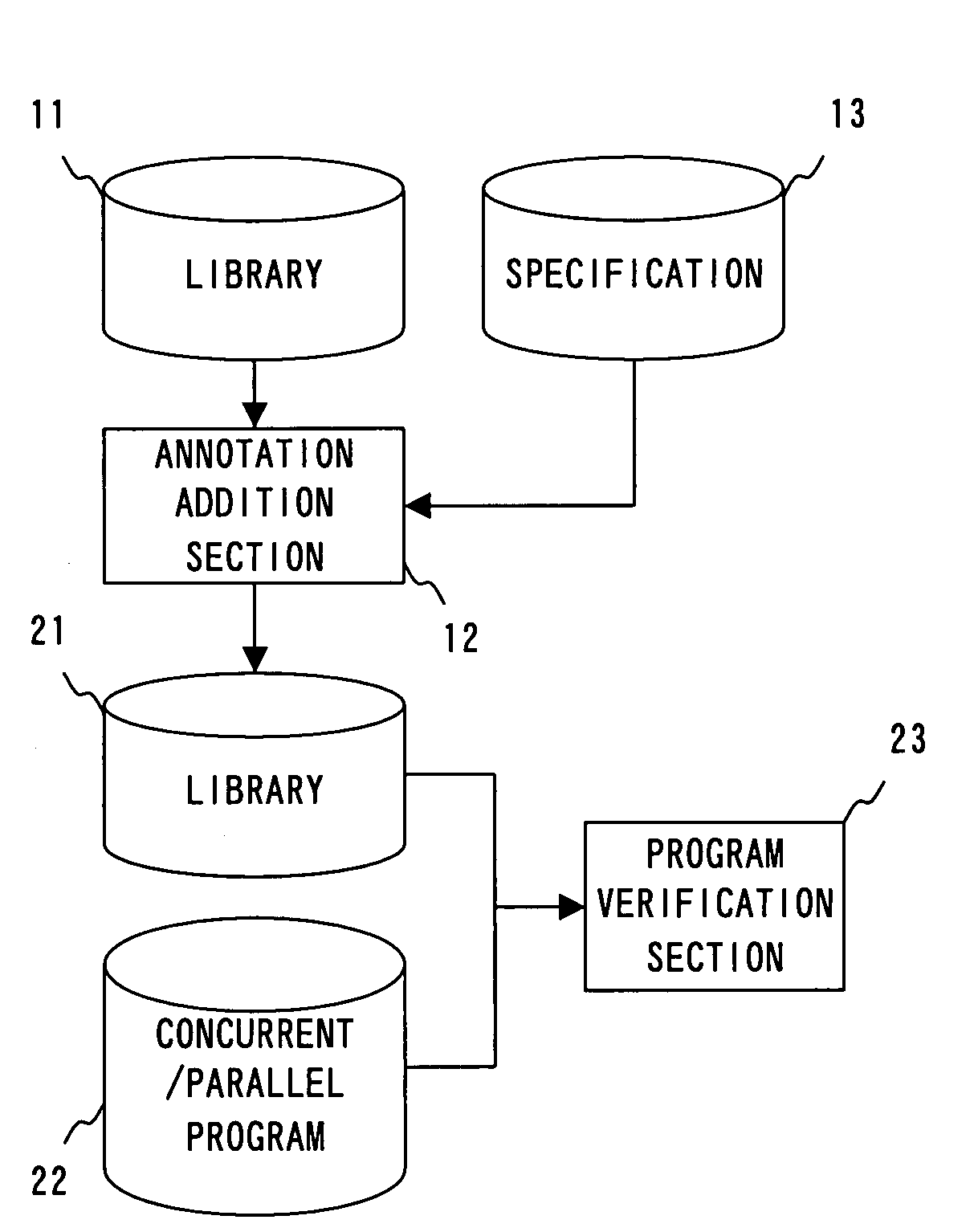
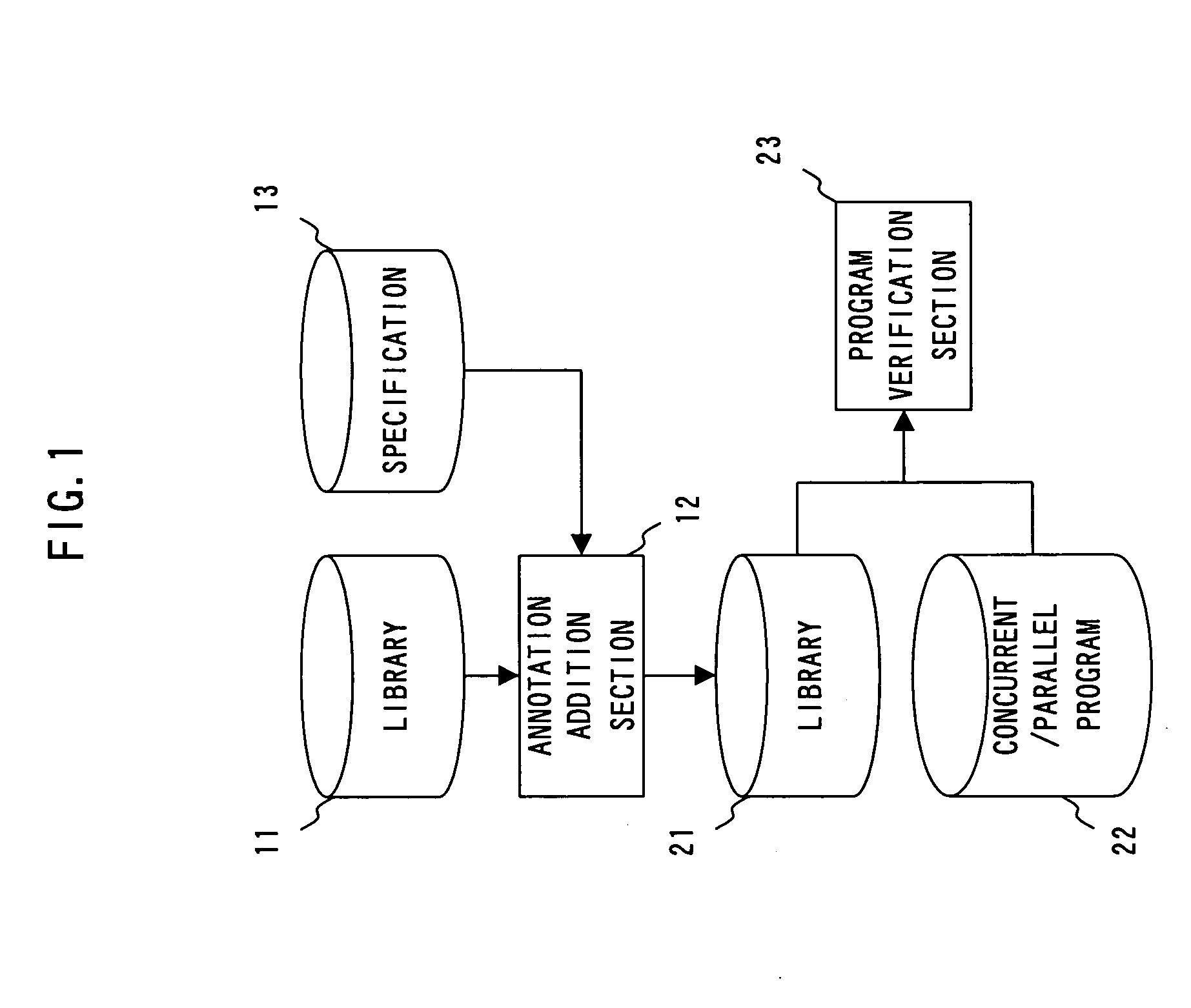
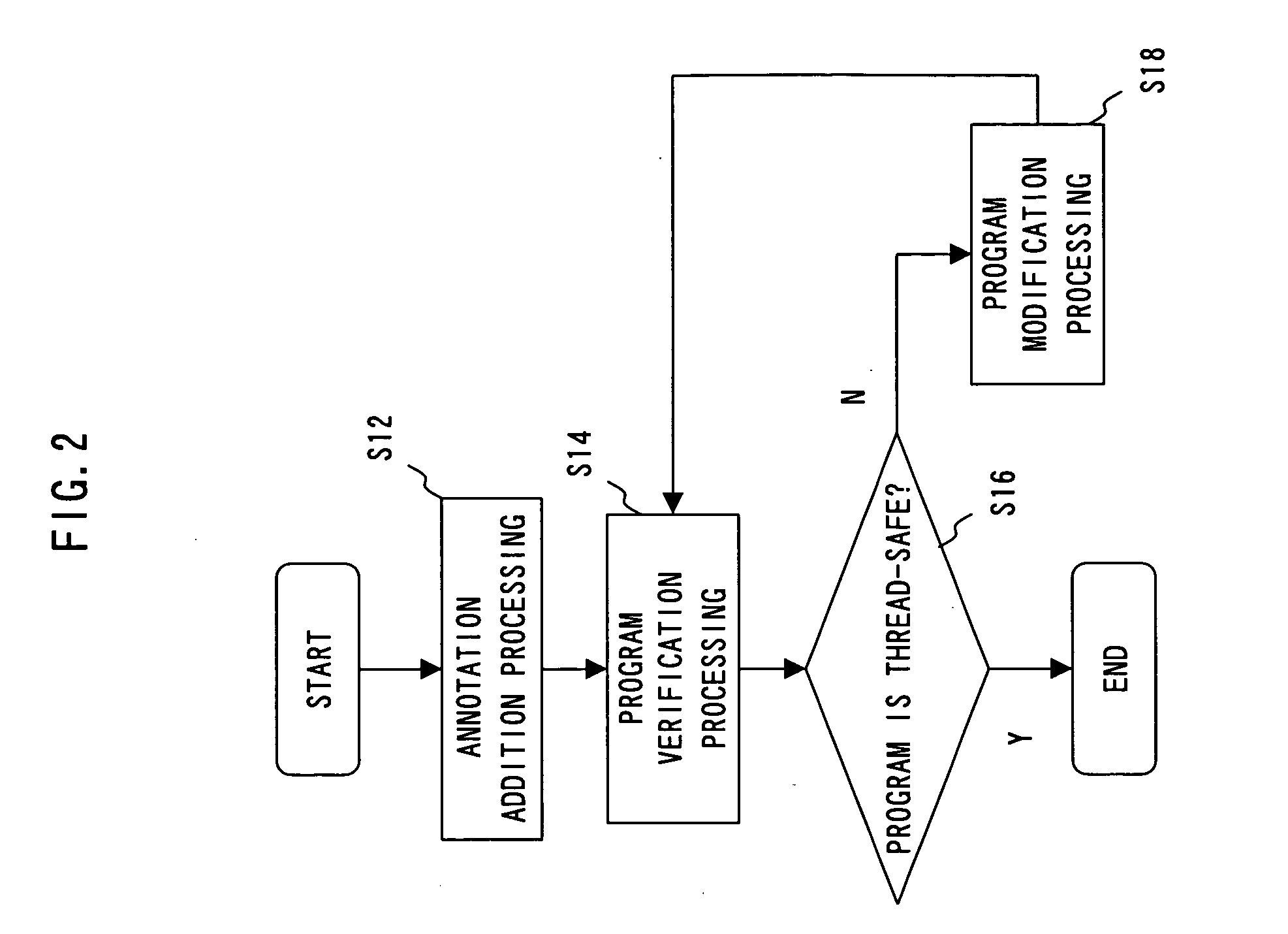
The present invention has been made to provide a software verification program, a software verification apparatus, and a software verification method capable of reducing verification cost of concurrent / parallel software.A software verification program allowing a computer to execute verification of software including a library 11 and a program that uses a library 21 to operate in a concurrent or parallel manner, comprises: a shared element utilizing part extraction step that extracts a part at which a shared element, which is an element that is defined in the library 21 and which can be used by the program 22, is used in the program 22; and a condition verification step that verifies based on a thread-safe condition defined in the library 21 for the each shared element whether a shared element in the shared element utilizing part extracted by the shared element utilizing part extraction step satisfies the thread-safe condition.
Owner:FUJITSU LTD
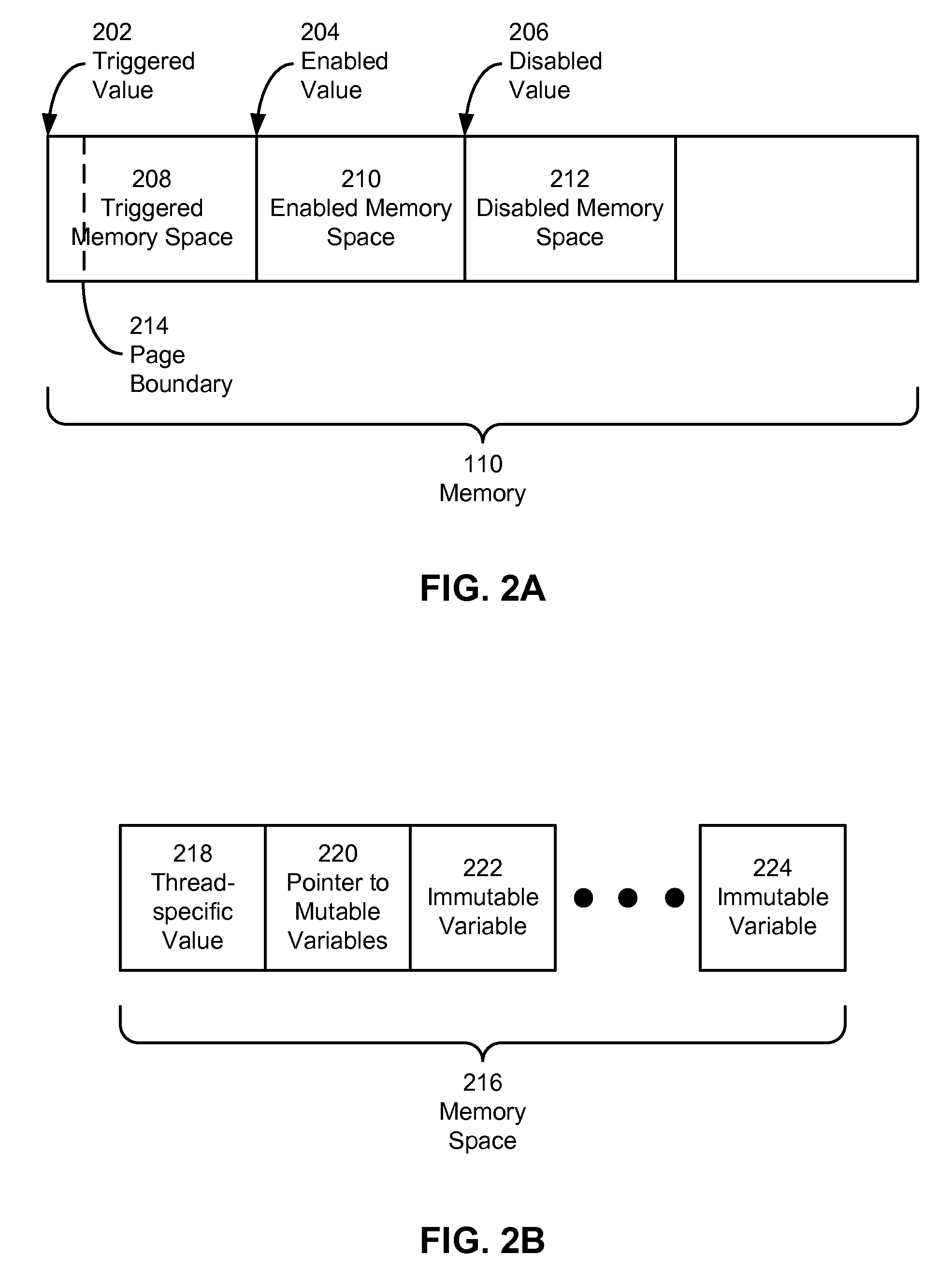
Efficient per-thread safepoints and local access
ActiveUS20100192139A1Program synchronisationError detection/correctionParallel computingThread safety
Some embodiments of the present invention provide a system that implements a safepoint for a thread, which includes a compiler and a runtime environment. During compilation of an application to be executed by the thread, the compiler obtains a register to be associated with the thread and inserts safepoint code into the application, wherein the safepoint code includes an indirect load from a memory location stored in the register to the register. During execution of the application by the thread, the runtime environment writes a thread-specific value for the thread to the register, wherein the thread-specific value corresponds to an enabled value, a triggered value, or a disabled value. In these embodiments, executing the indirect load by the thread causes the thread to trap if the thread-specific value corresponds to the triggered value.
Owner:SUN MICROSYSTEMS INC
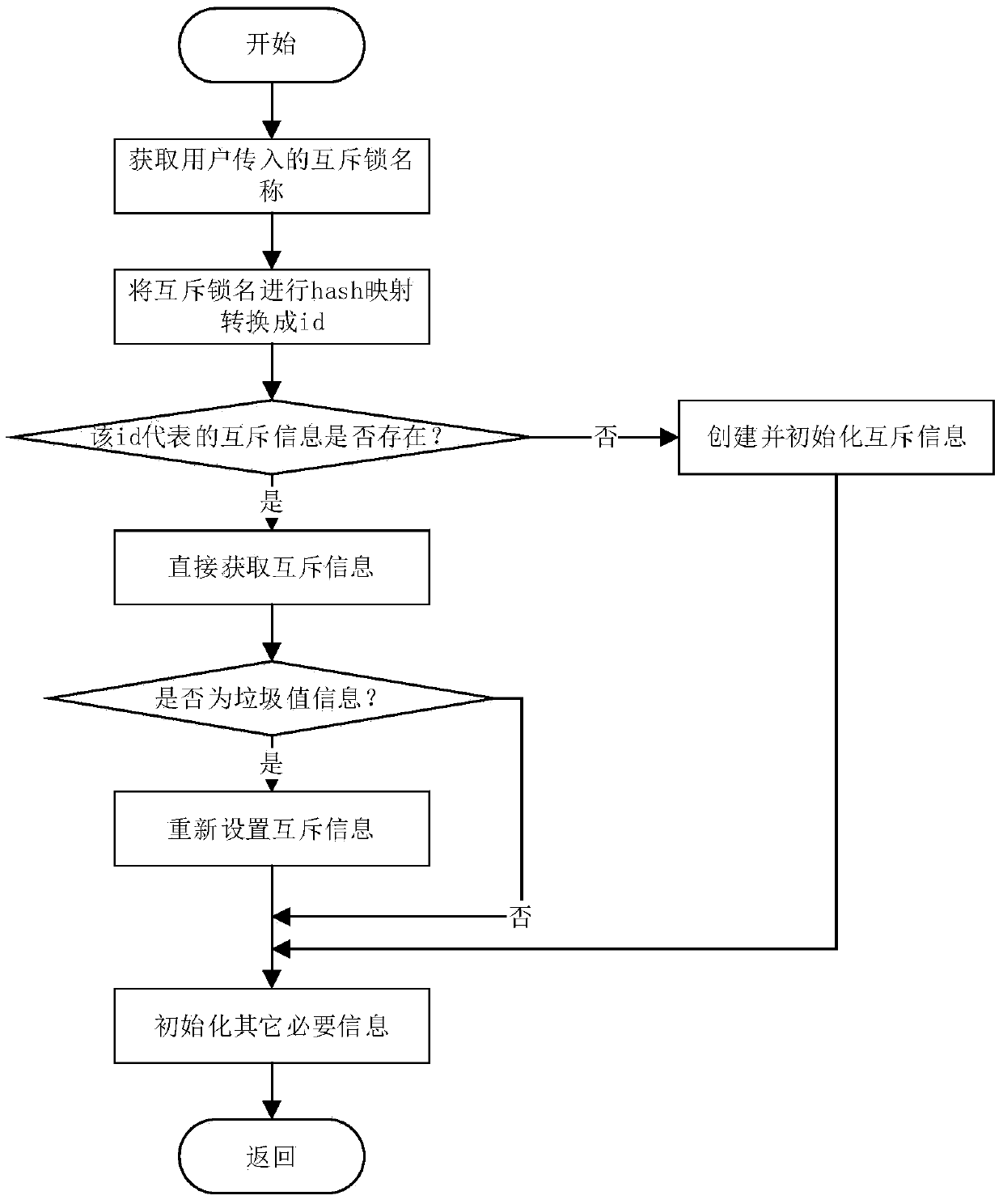
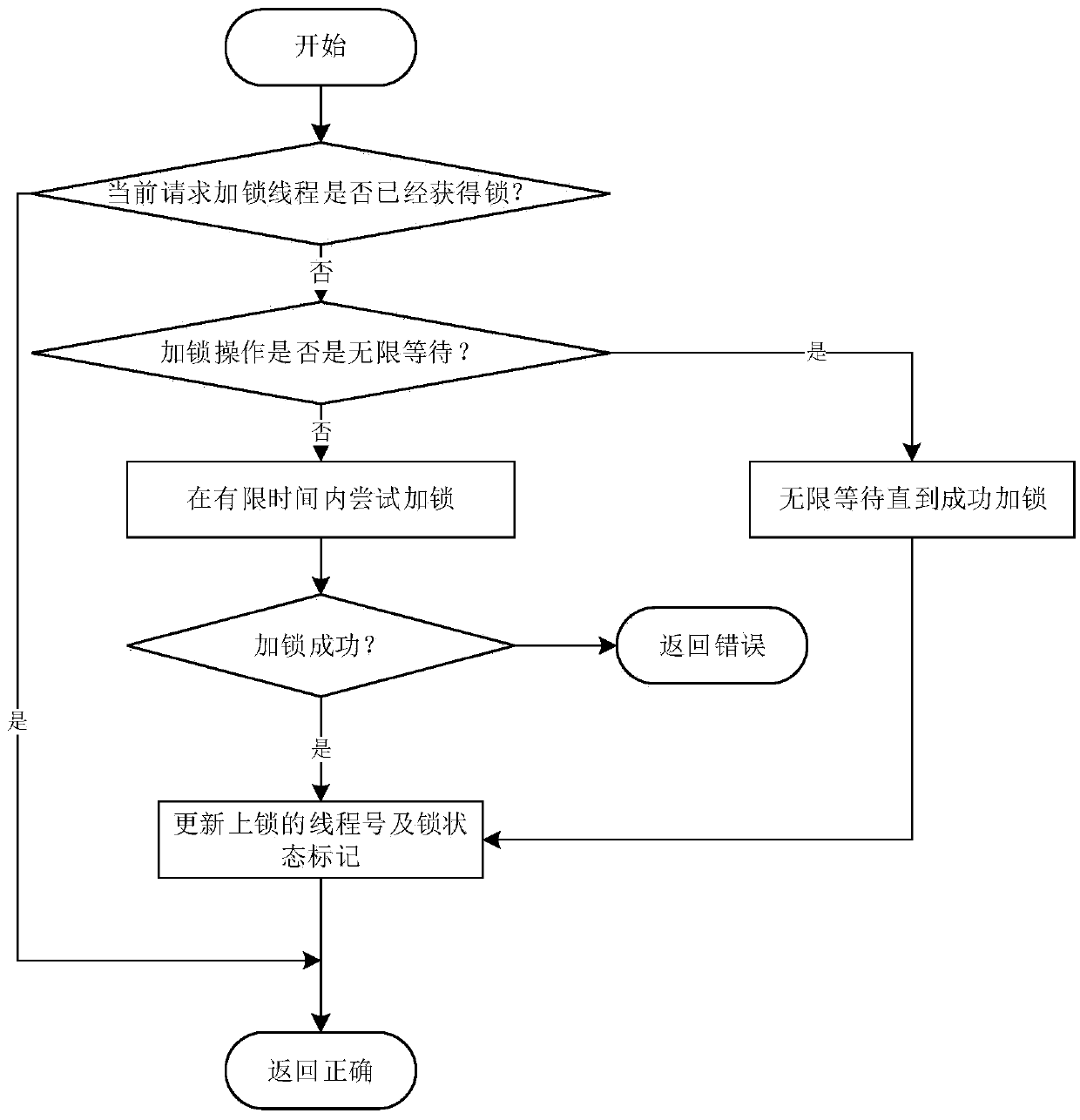
Inter-process thread mutex method
ActiveCN105511969AGuaranteed atomicityThread safetyProgram synchronisationCritical zoneShared resource
The invention relates to an inter-process thread mutex method. The inter-process thread mutex method comprises following steps: vying for mutex information by multiple threads and initializing mutex information by a successful thread; when obtaining mutex information by the successful thread and utilizing mutex information to lock a critical zone; obtaining a lock of mutex information by the thread after locking operation and visiting shared resources; waiting by other threads at the same time; parting the critical zone after the threads run out of shard resources; and continuing to compete for mutex information by other threads and repeating above steps. The inter-process thread mutex method has following beneficial effects: combined with a semaphore mechanism, atomicity of locking and unlocking is ensured; the method has thread safety and helps to effectively solve the problem of garbage value obtained by mutex information; abnormity is avoided when garbage value is obtained by using threads; the deadlocking problem is also overcome when the self body asks for a lock during locking; and the problem of unlocking out of limits of authority is avoided.
Owner:CSSC SYST ENG RES INST
Method and system for accessing objects of different thread types
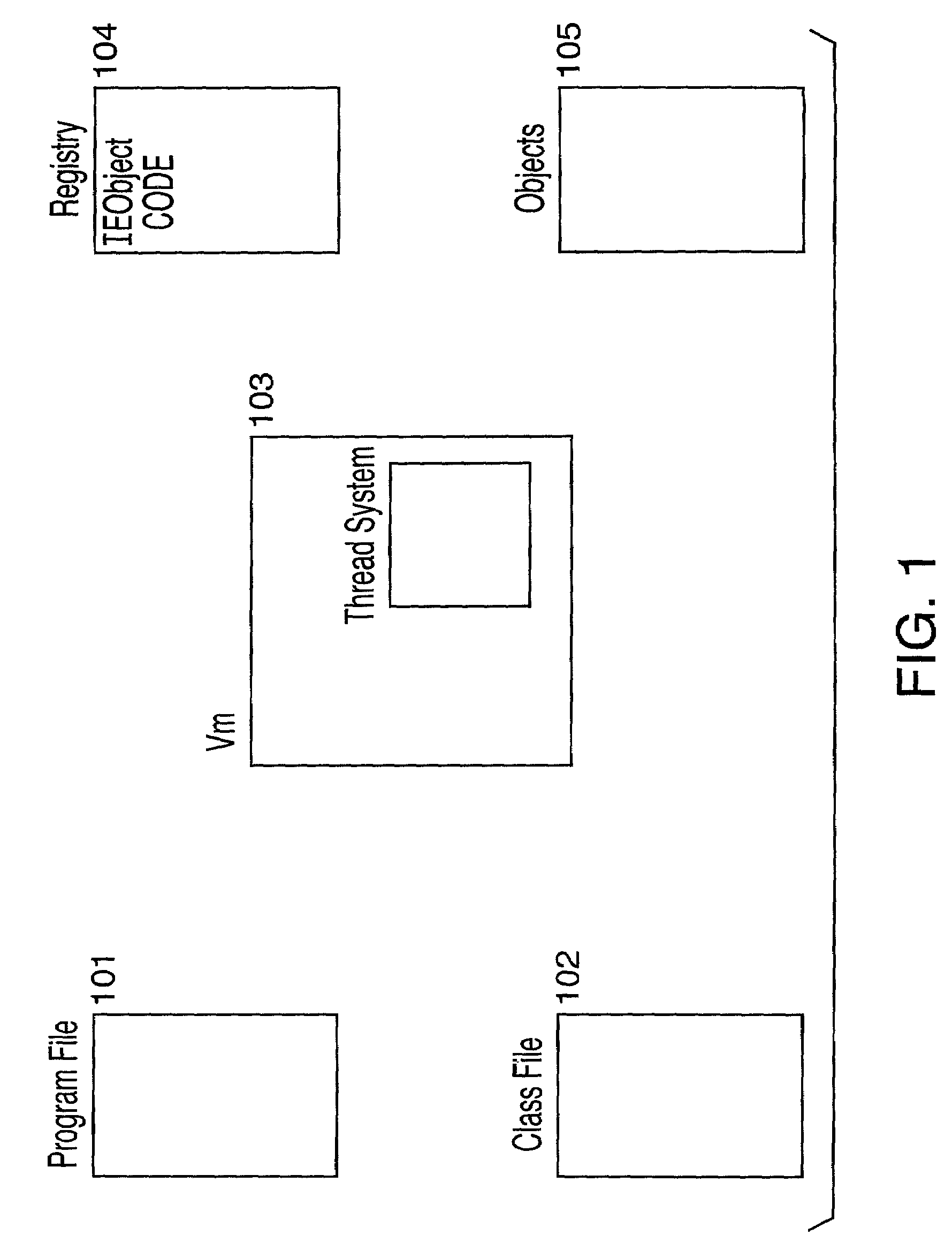
InactiveUS6981255B2Avoid overheadProgram initiation/switchingDigital data processing detailsComponent Object ModelComputerized system
A method in a computer system for accessing Microsoft Component Object Model (“COM”) objects of varying thread types from a Java-based program. The computer system has a Java virtual machine (“VM”) that executes statements of the Java program and that executes in a multithreaded process. When executing a statement of the Java-based program to instantiate a COM object, the system creates a wrapper object. When the COM object is not thread-safe, the system requests an appropriate thread to instantiate the COM object and stores an identifier of the thread in the wrapper object. When the COM object is thread-safe, the system instantiates the COM object from the current thread and stores an indication in the wrapper object that the COM object can be accessed from any thread. When executing a statement of the Java-based program to invoke a method of the COM object, the system requests the thread identified in the wrapper object to invoke the method of the COM object. When the wrapper object indicates that the COM object can be referenced from any thread, the system invokes the method of the COM object referenced by the wrapper object directly from the current thread.
Owner:MICROSOFT TECH LICENSING LLC
Method and apparatus for thread-safe handlers for checkpoints and restarts
InactiveUS7337444B2Avoid deadlockUnauthorized memory use protectionMultiprogramming arrangementsData processing systemParallel computing
A method, apparatus, and computer instructions for executing a handler in a multi-threaded process handling a number of threads in a manner that avoids deadlocks. A value equal to the number of threads executing in the data processing system is set. The value is decremented each time a lock count for a thread within the number of threads is zero. A thread within the number of threads is suspended if the thread requests a lock and has a lock count of zero. A procedure, such as a handler, is executed in response to all of the threads within the number of threads having no locks.
Owner:IBM CORP
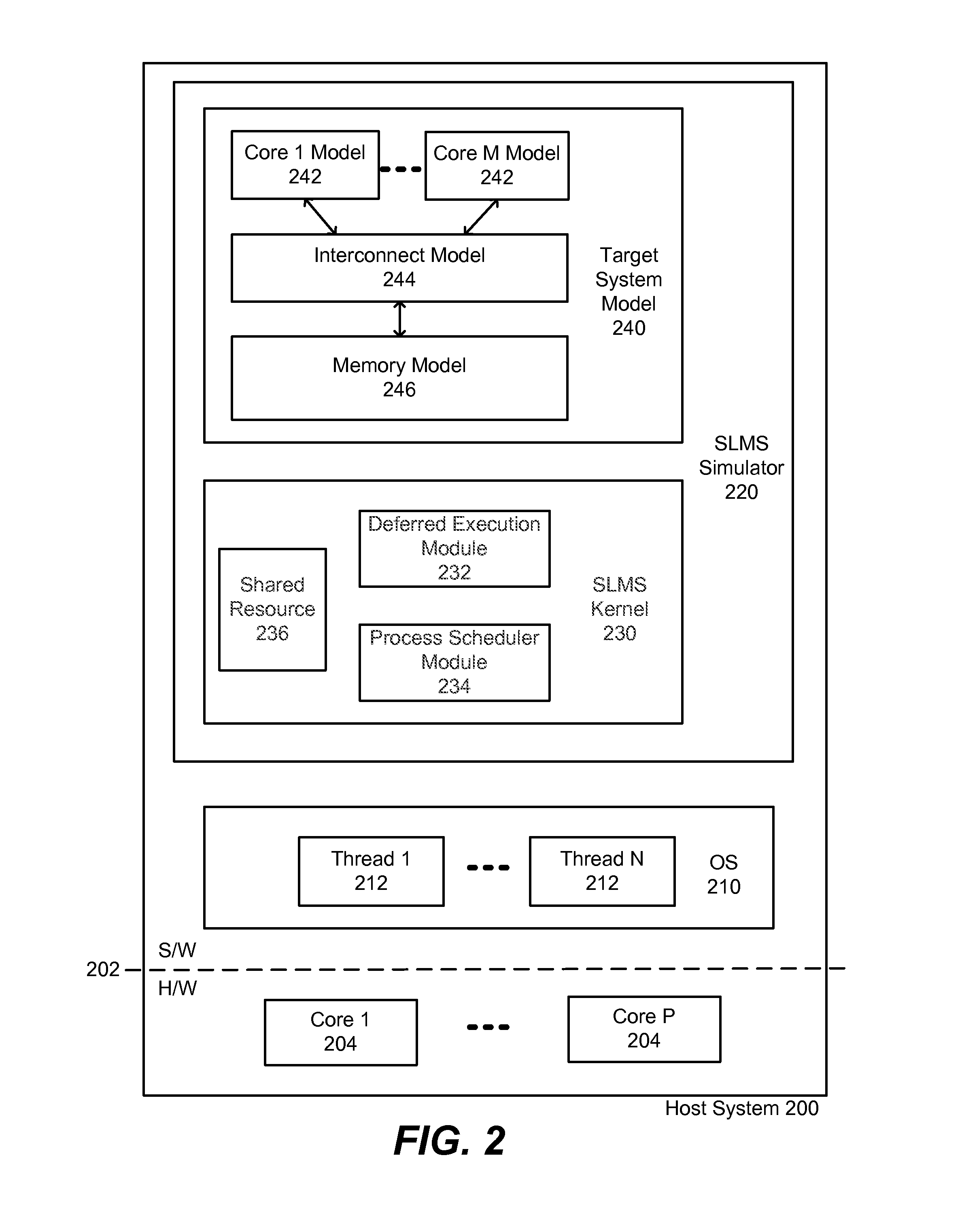
Deferred Execution in a Multi-thread Safe System Level Modeling Simulation
Methods, systems, and machine readable medium for multi-thread safe system level modeling simulation (SLMS) of a target system on a host system. An example of a SLMS is a SYSTEMC simulation. During the SLMS, SLMS processes are executed in parallel via a plurality of threads. SLMS processes represent functional behaviors of components within the target system, such as functional behaviors of processor cores. Deferred execution may be used to defer execution of operations of SLMS processes that access a shared resource. Multi-thread safe direct memory interface (DMI) access may be used by a SLMS process to access a region of the memory in a multi-thread safe manner. Access to regions of the memory may also be guarded if they are at risk of being in a transient state when being accessed by more than one SLMS process.
Owner:SYNOPSYS INC
Cross-environment communication framework
ActiveCN103262057AProgram control using stored programsCathode-ray tube indicatorsVirtualizationOperational system
Owner:Z124 MAPLES SERVICES
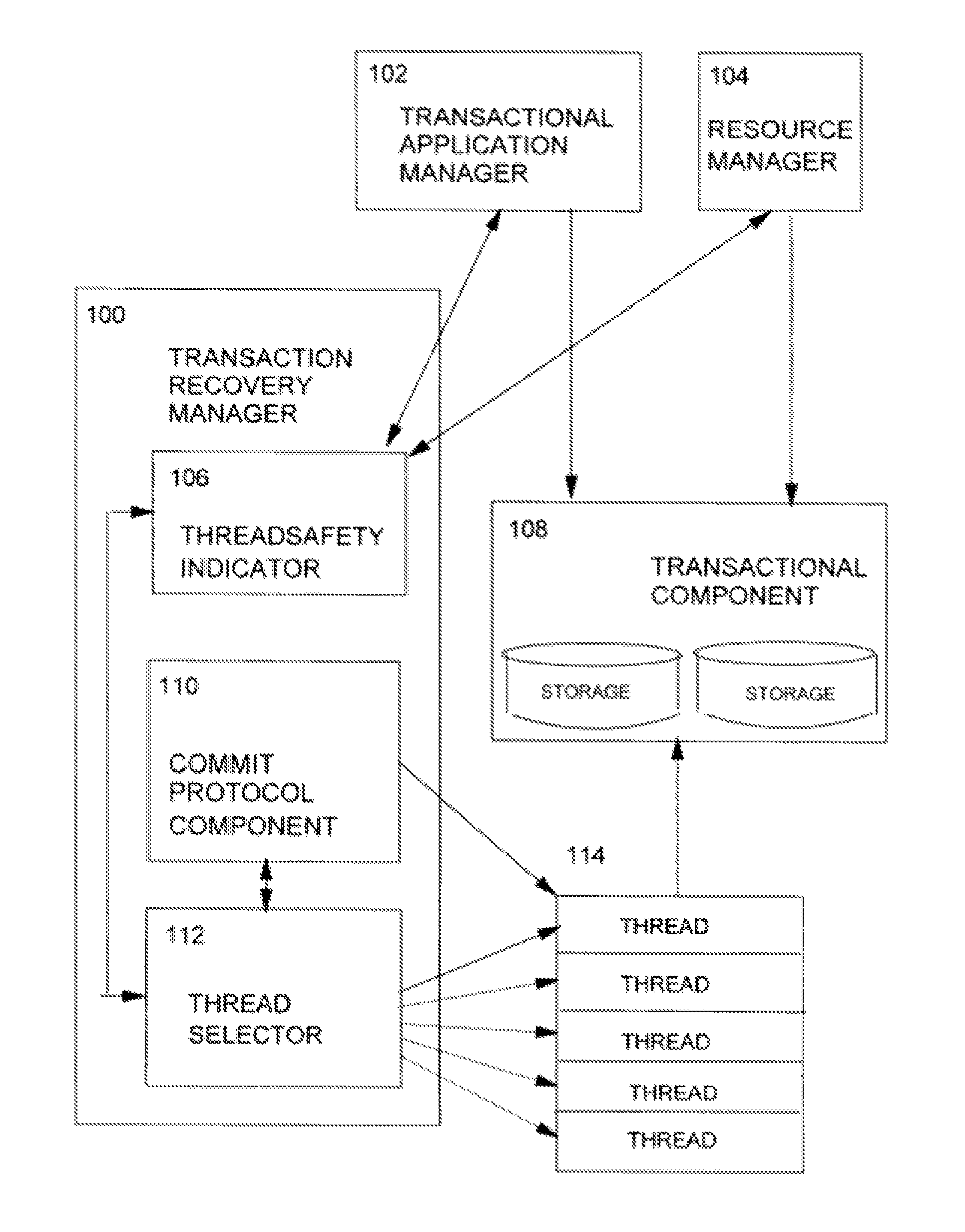
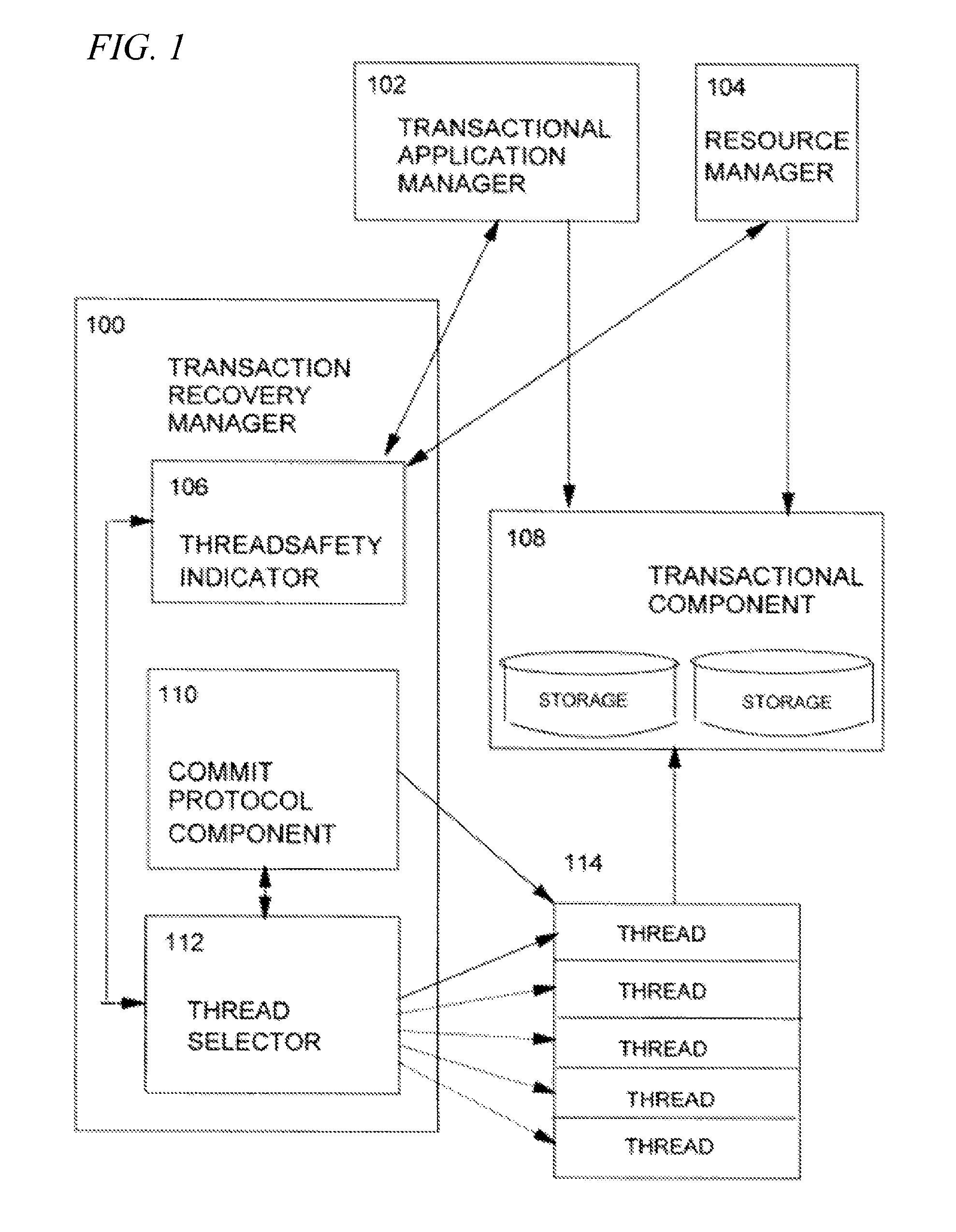
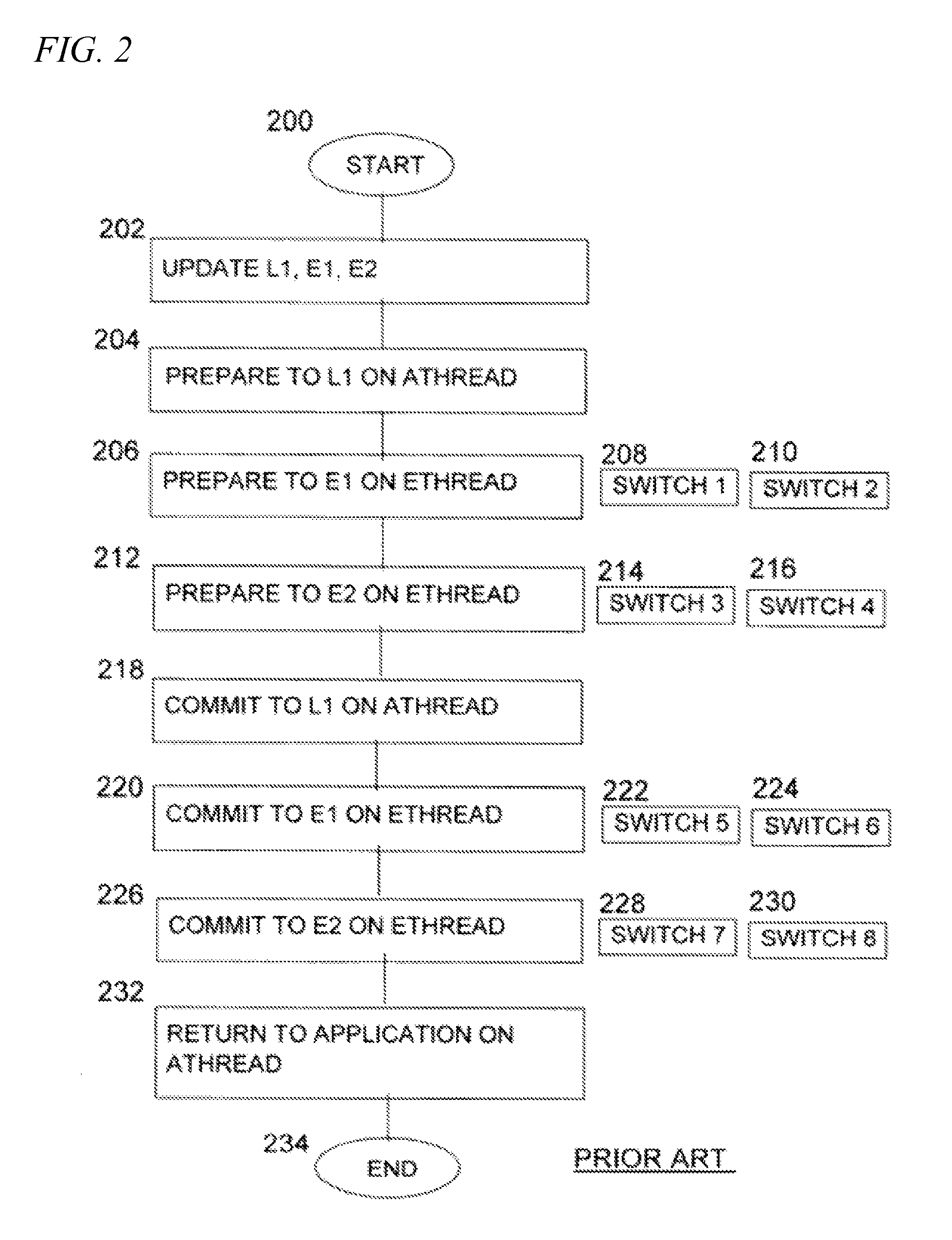
Multiprocessing transaction recovery manager
InactiveUS8499298B2Quantity minimizationMaximizes timeDigital data information retrievalSpecial data processing applicationsResource managementApplication software
Owner:INT BUSINESS MASCH CORP
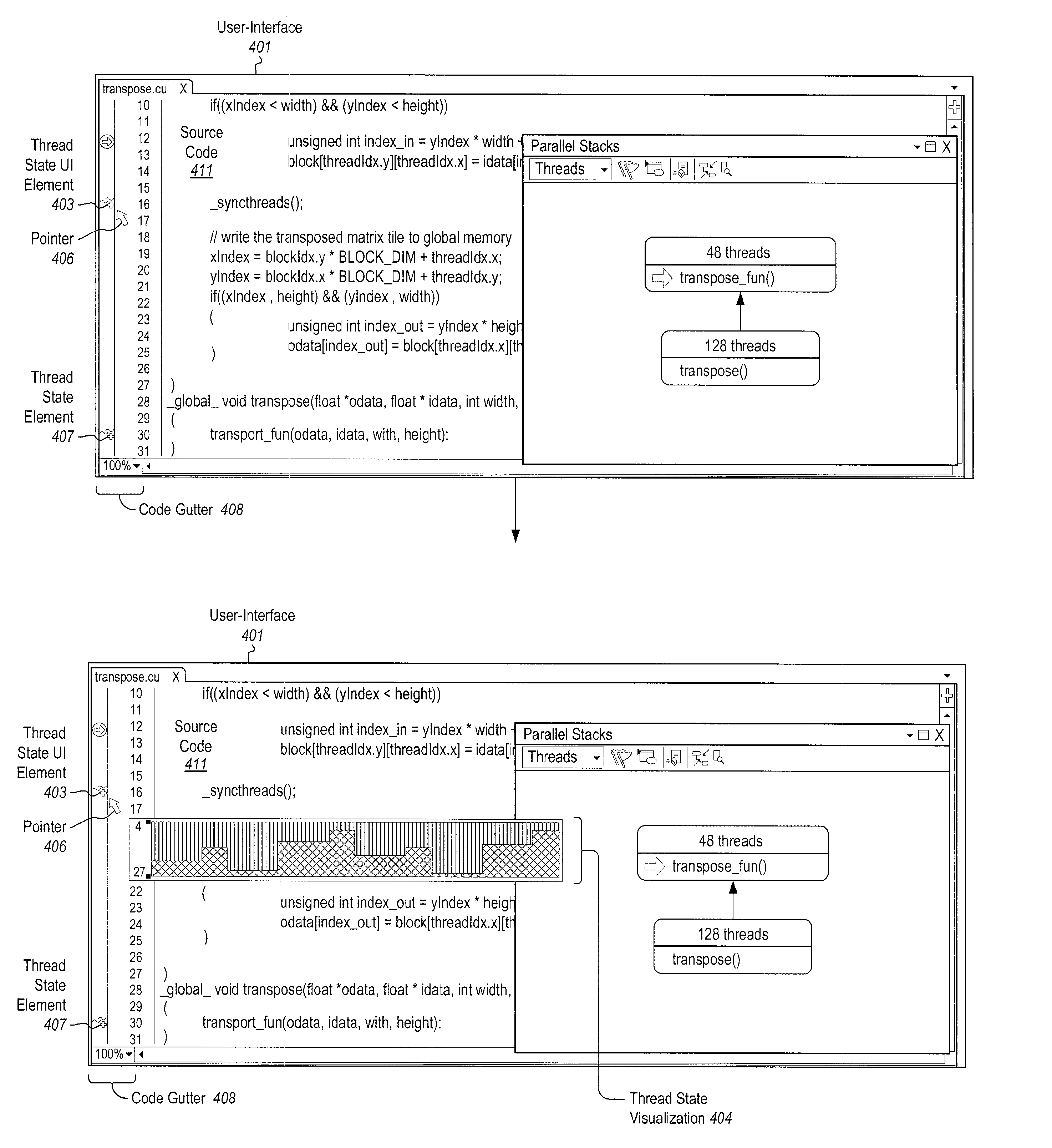
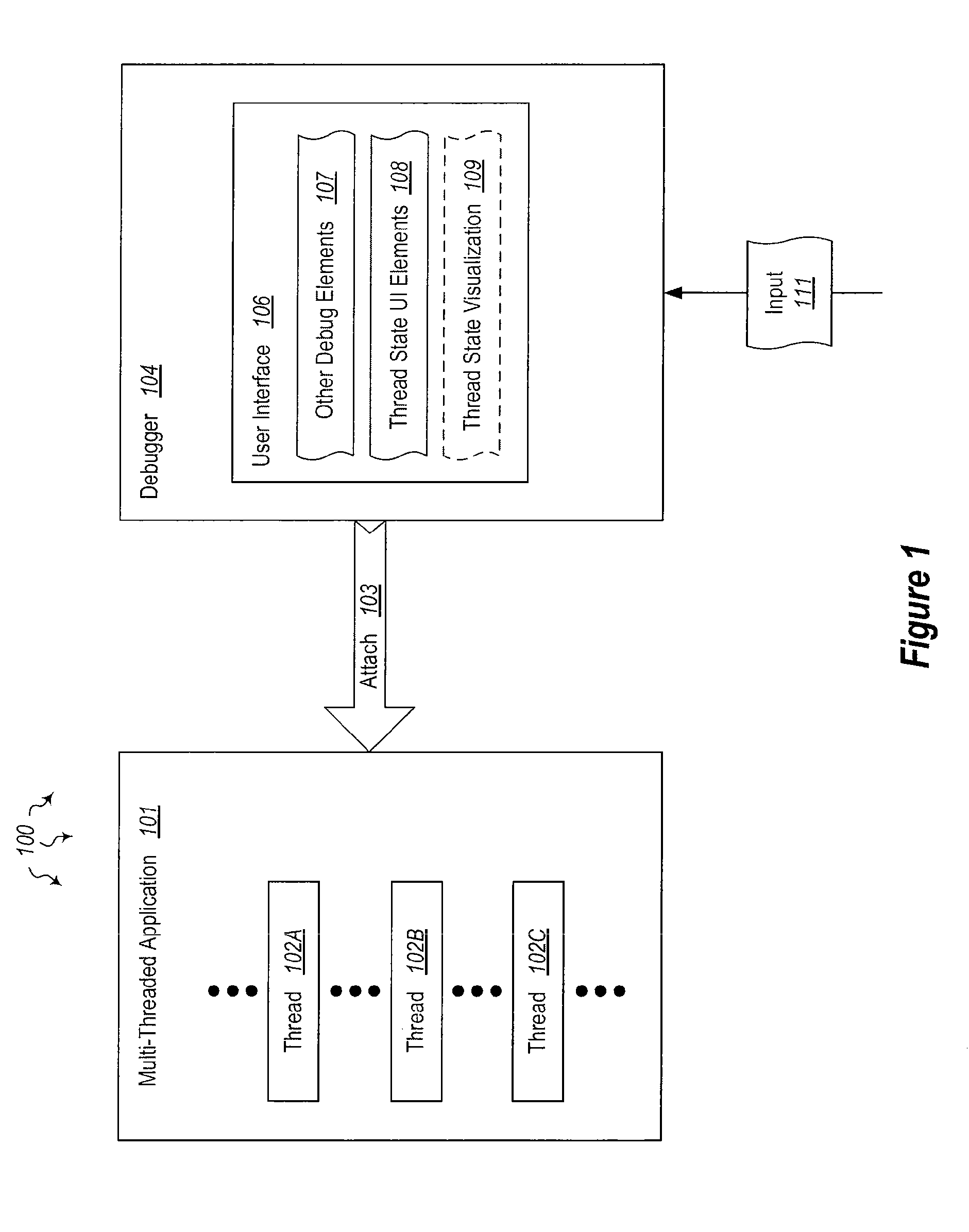
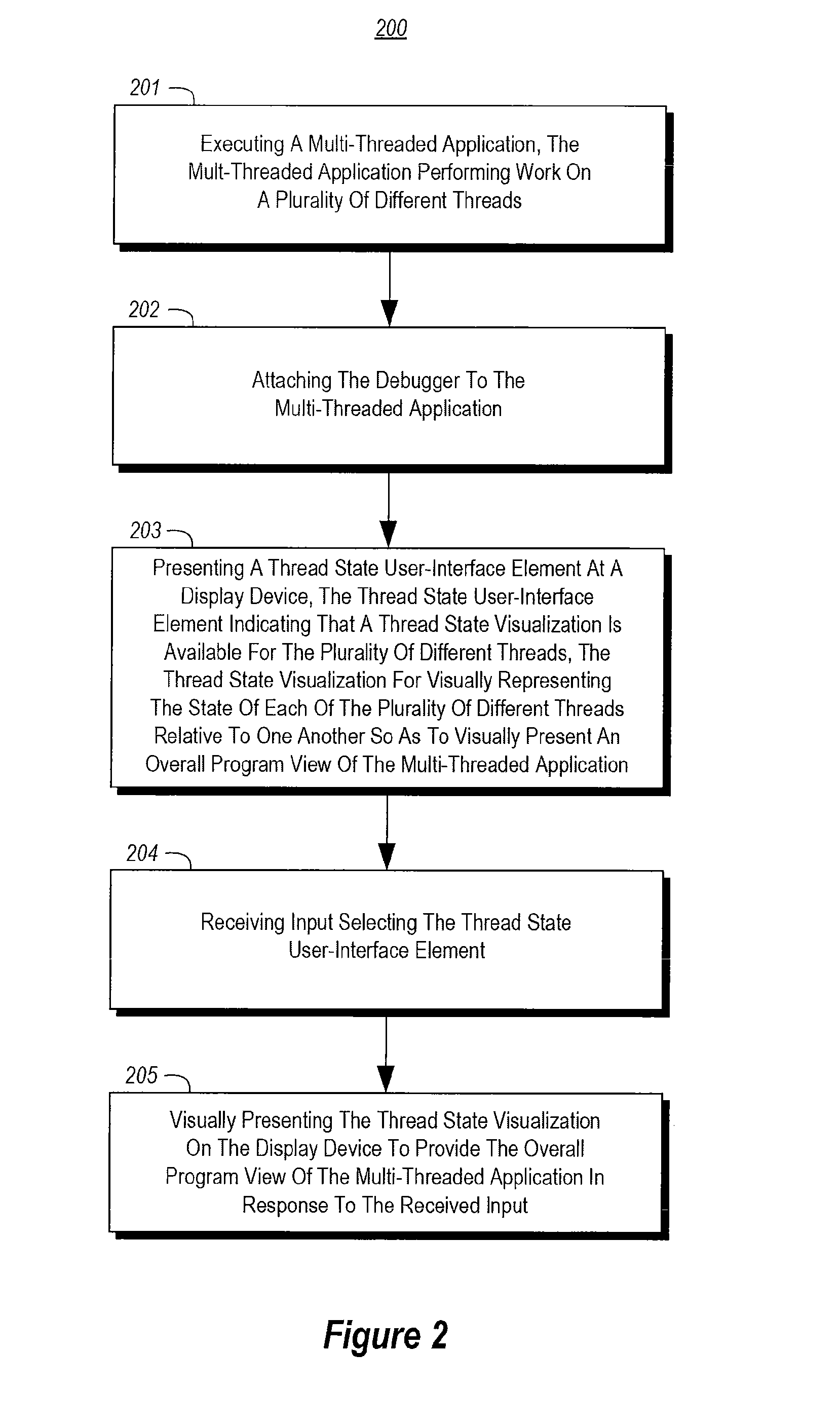
Visualizing thread state during program debugging
InactiveUS20130074042A1Error detection/correctionSpecific program execution arrangementsParallel computingApplication software
The present invention extends to methods, systems, and computer program products for visualizing thread state during program debugging. A tooltip can present a visual summary of the execution state of the application threads, what the values are, and patterns in the values, during debugging. As such, a developer debugging a parallel application can see the status of threads within a thread block. A visual tooltip (or other presentation mechanism) can be activated by hovering (e.g., placing a mouse pointer) over a user interface element. A visual tooltip can be presented by hovering over a status rollup visualization of the thread states or by hovering over an icon that appears in the code gutter for a code segment. Accordingly, developers can get a concise visual summary of thread states, variables, and values during debugging.
Owner:MICROSOFT TECH LICENSING LLC
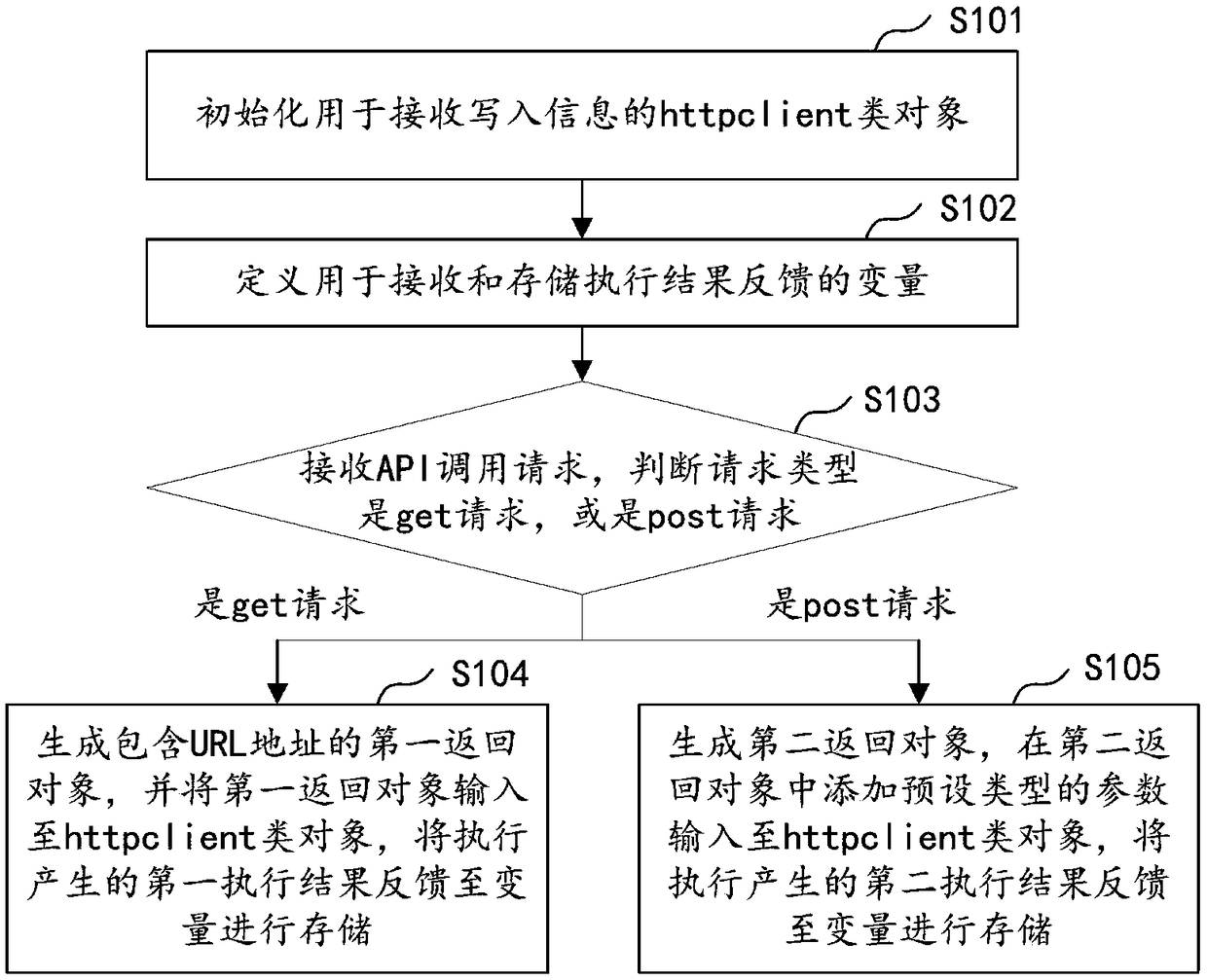
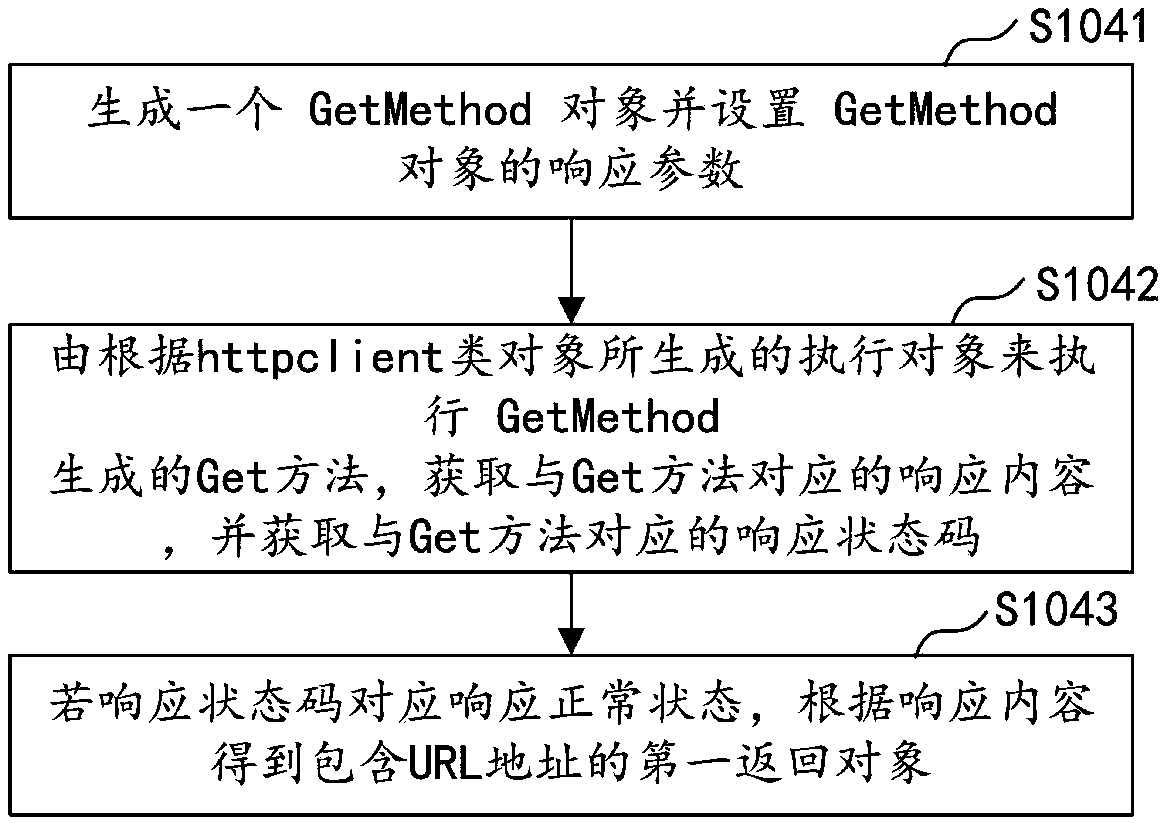
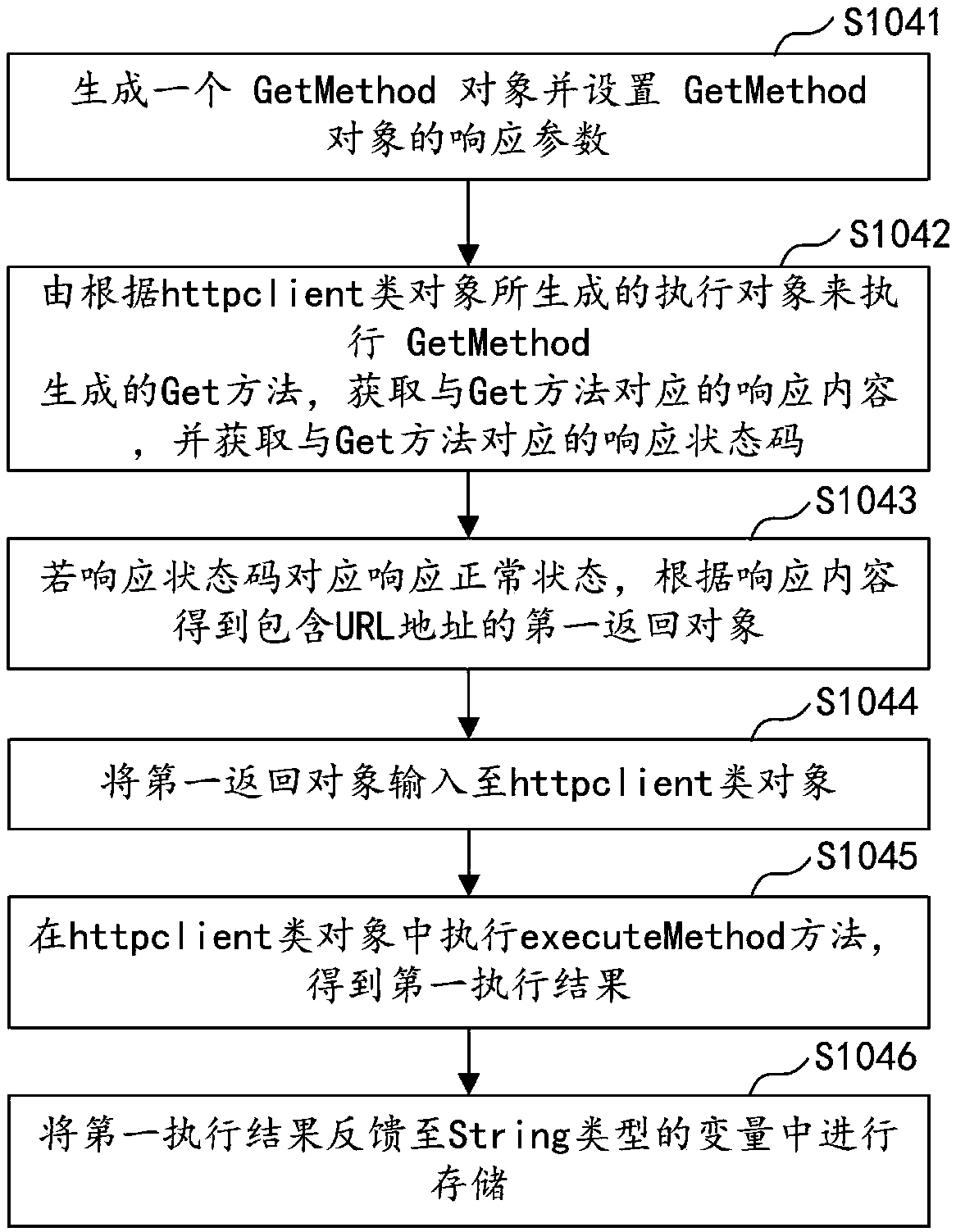
Interface calling method and device, computer equipment, and storage medium
PendingCN108762955ARich typeImprove securityInterprogram communicationSoftware testing/debuggingProgramming languageUniform resource locator
The embodiment of the invention discloses an interface calling method and device, computer equipment, and a storage medium. The method comprises the following steps: initializing an httpclient type object used for receiving written information; defining a variable used for receiving and storing execution result feedbacks; receiving an API calling request, and judging whether a request type is a get request or a post request; if the request type is the get request, generating a first returned object comprising a URL, inputting the first returned object into the httpclient type object, and feeding a first execution result, which is generated by execution, back to the variable for storage; and if the request type is the post request, generating a second returned object, adding parameters of apreset type into the second returned object, inputting the second returned object with the added parameters into the httpclient type object, and feeding a second execution result, which is generatedby execution, back to the variable for storage. The method has the advantages that interface calling during testing is extremely simple, abundant types of parameters can be supported, and the thread safety during calling is improved.
Owner:PINGAN PUHUI ENTERPRISE MANAGEMENT CO LTD
Dynamic atomic arrays
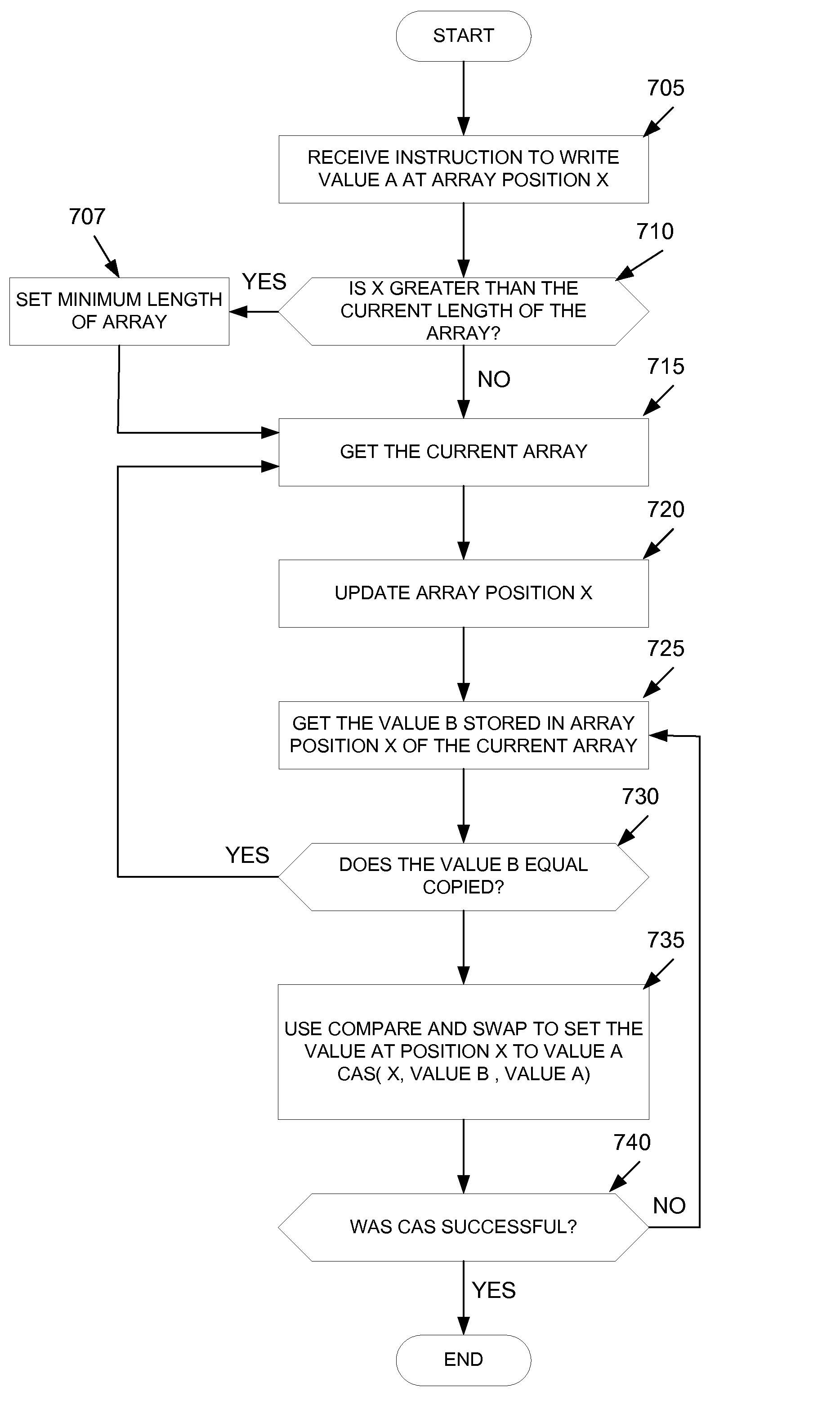
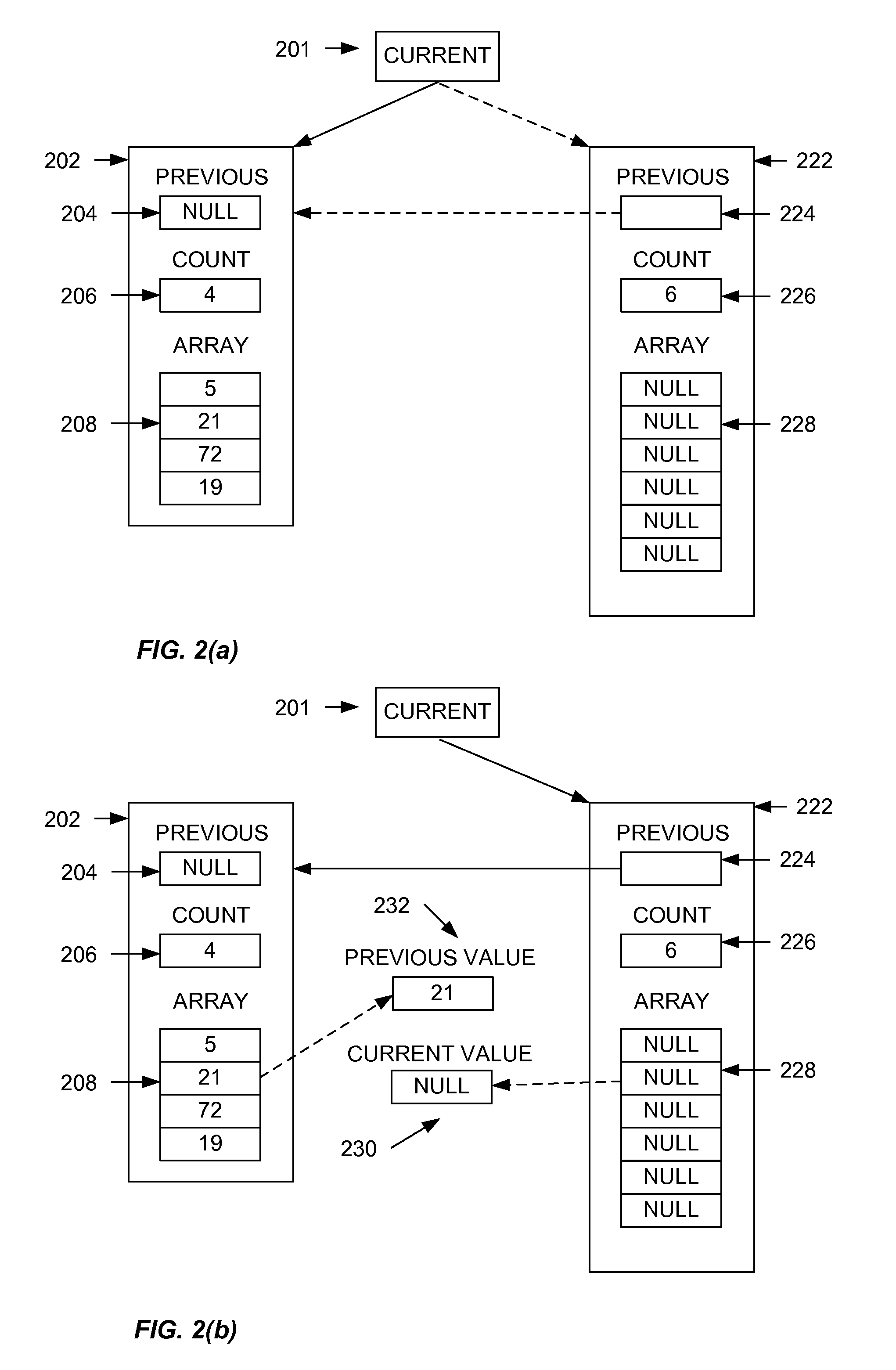
ActiveUS20110066885A1Digital data processing detailsMemory adressing/allocation/relocationComplex typeArray data structure
Embodiments of the present invention provide techniques, including systems, methods, and computer readable medium, for dynamic atomic arrays. A dynamic atomic array is a data structure that provides an array that can grow or shrink in size as required. The dynamic atomic array is non-blocking, wait-free, and thread-safe. The dynamic atomic array may be used to provide arrays of any primitive data type as well as complex types, such as objects.
Owner:ORACLE INT CORP
Methods and Systems for Automatic Generation of Multithread-Safe Software Code
InactiveUS20120030649A1Software engineeringSpecific program execution arrangementsThread safetySoftware
An exemplary method of automatic generation of multithread-safe software code includes a multithread-safe code generator subsystem analyzing data representative of non-multithread-safe software code and automatically generating data representative of multithread-safe software code based on the analyzing of the data representative of the non-multithread-safe software code. Corresponding methods and systems are also described.
Owner:ADVANCED BIONICS AG
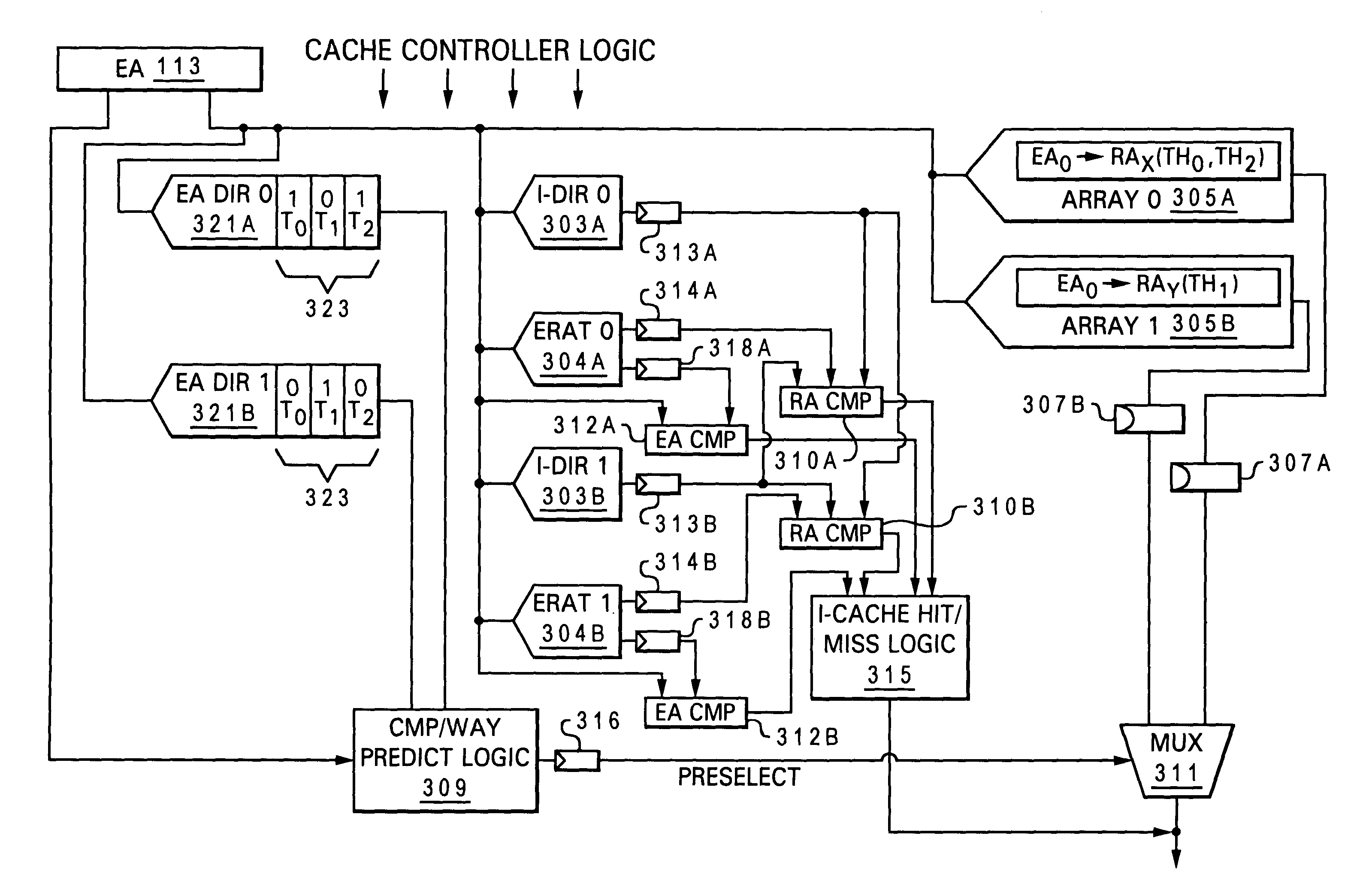
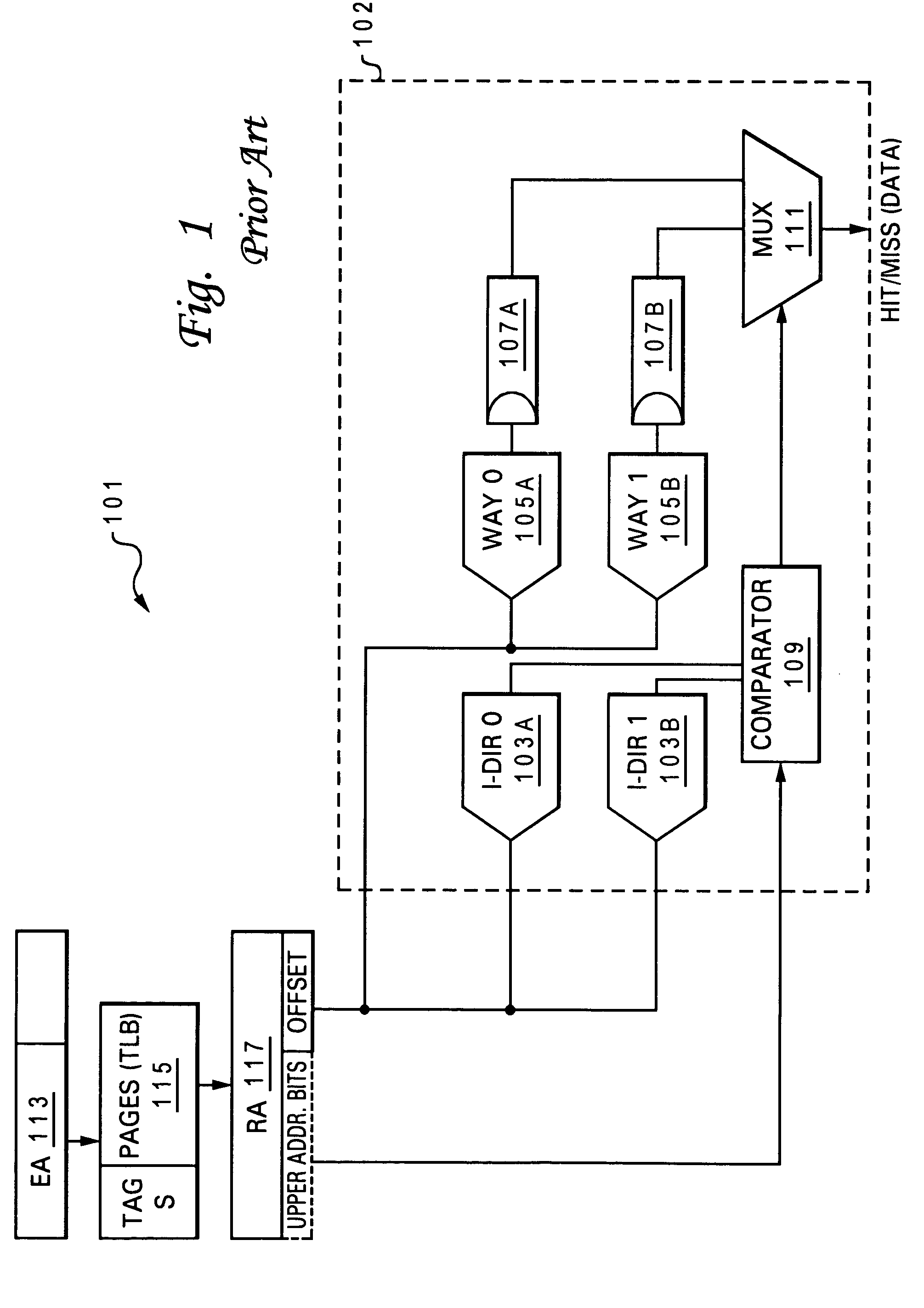
Cache predictor for simultaneous multi-threaded processor system supporting multiple transactions
ActiveUS7039768B2Avoid choiceEarly selectionMemory architecture accessing/allocationMemory adressing/allocation/relocationThread safetySimultaneous multithreading
A set-associative I-cache that enables early cache hit prediction and correct way selection when the processor is executing instructions of multiple threads having similar EAs. Each way of the I-cache comprises an EA Directory (EA Dir), which includes a series of thread valid bits that are individually assigned to one of the multiple threads. Particular ones of the thread valid bits are set in each EA Dir to indicate when an instruction block the thread is cached within the particular way with which the EA Dir is associated. When a cache line request for a particular thread is received, a cache hit is predicted when the EA of the request matches the EA in the EA Dir and the cache line is selected from the way associated with the EA Dir who has the thread valid bit for that thread set. Early way selection is thus achieved since the way selection only requires a check of the thread valid bits.
Owner:TWITTER INC
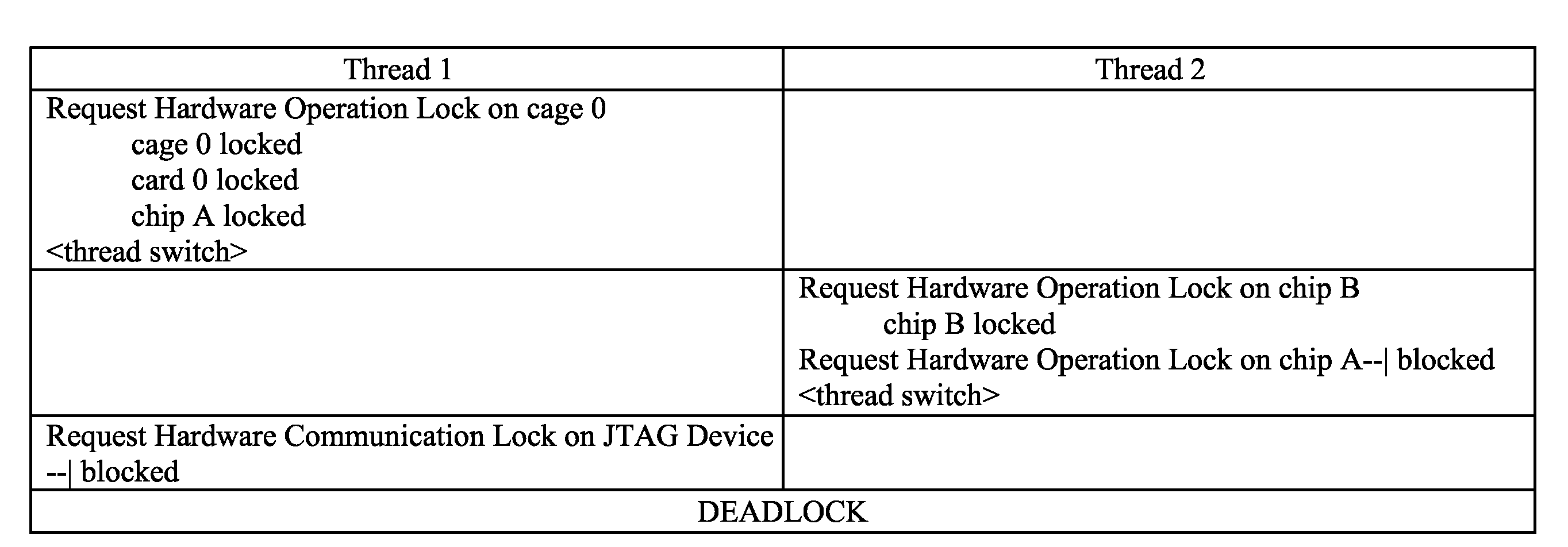
Making Hardware Objects and Operations Thread-Safe
ActiveUS20100275216A1Improve performancePrevent hangingMultiprogramming arrangementsMemory systemsComputer hardwareData Corruption
Performance in object-oriented systems may be improved by allowing multiple concurrent hardware control and diagnostic operations to run concurrently on the system while preventing race conditions, state / data corruption, and hangs due to deadlock conditions. Deadlock prevention rules may be employed to grant or deny request for hardware operation locks, hardware communication locks, and / or data locks.
Owner:IBM CORP
Partitioning code in program code conversion
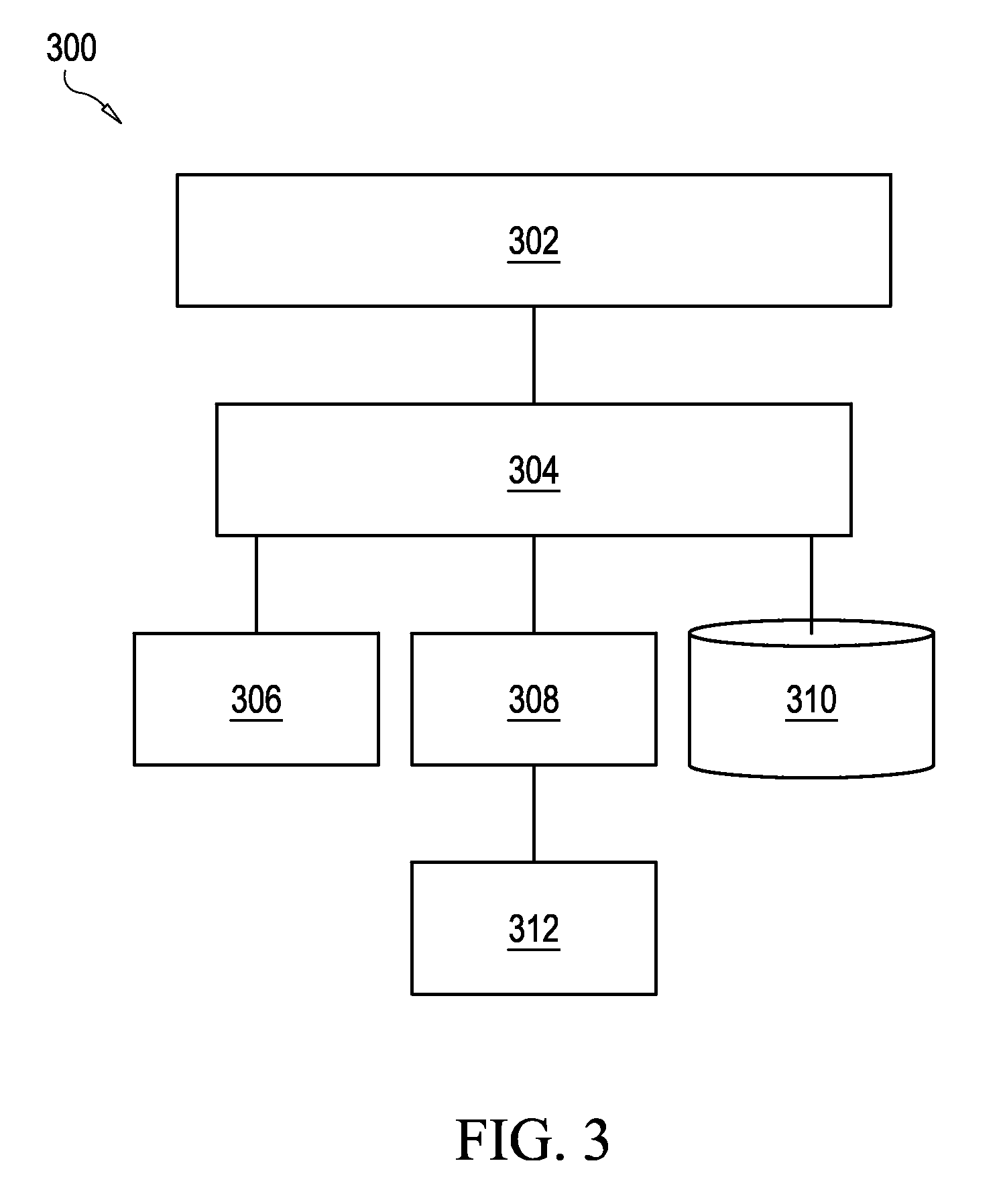
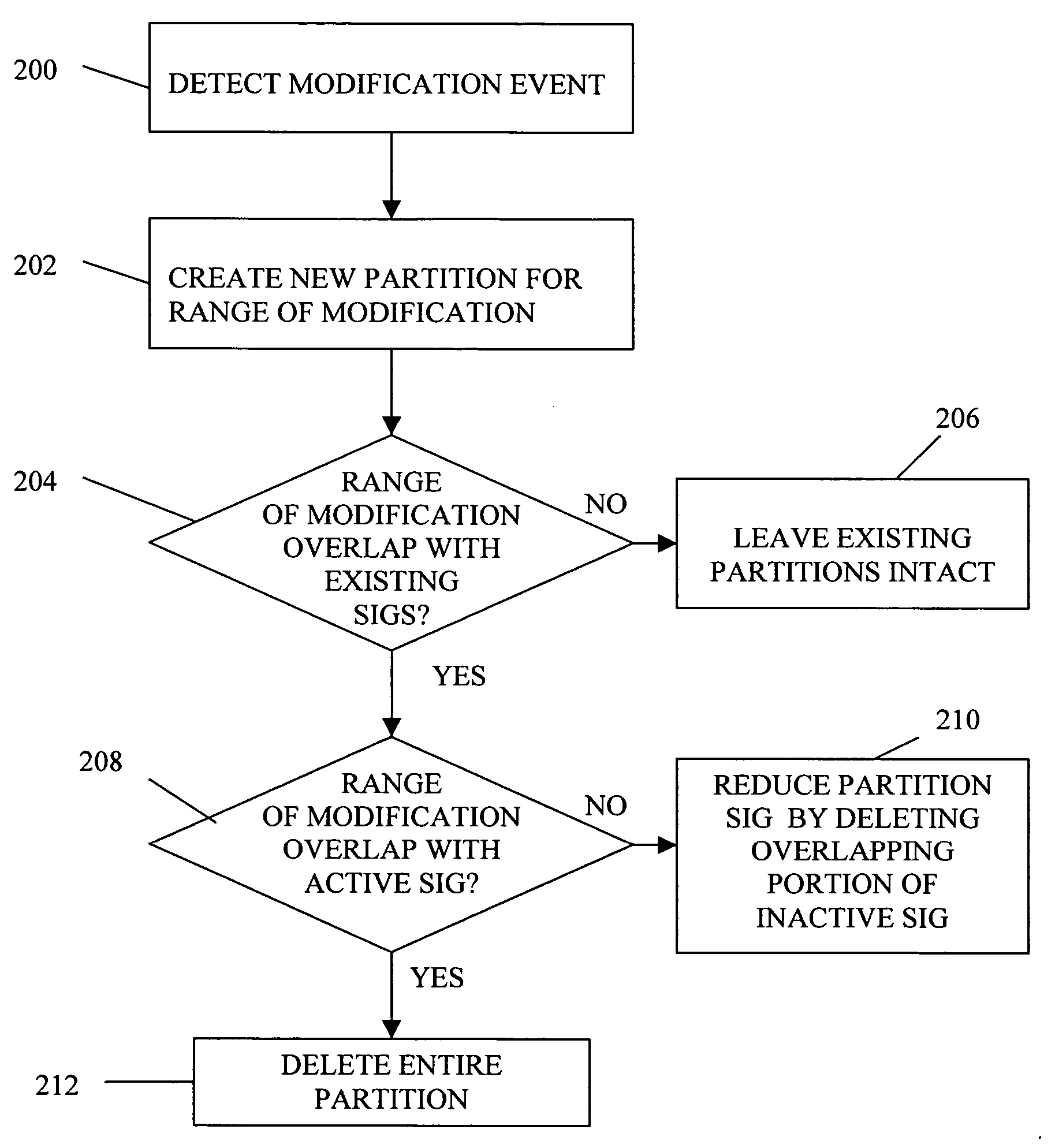
ActiveUS7934204B2Limited amountProgram loading/initiatingSoftware reuseSelf-modifying codeCode Translation
A partitioning technique utilized by a translator to divide the subject code space into regions, referred to hereafter as partitions, where each partition contains a distinct set of basic blocks of subject code and corresponding target code. The partitioning technique divides the translator's representation of subject code and subject code translations into non-overlapping regions of subject memory. In this manner, when the subject program modifies subject code, only those partitions actually affected by the self-modifying code need be discarded and all translations in unaffected partitions can be kept. This partitioning technique is advantageous in limiting the amount of target code that must be retranslated in response to self-modifying code operation. In another process, the partitioning technique allows multithreaded subject programs that also involve self-modifying code to perform code modification in a thread-safe manner.
Owner:INT BUSINESS MASCH CORP
Configurable plug-in type data service method
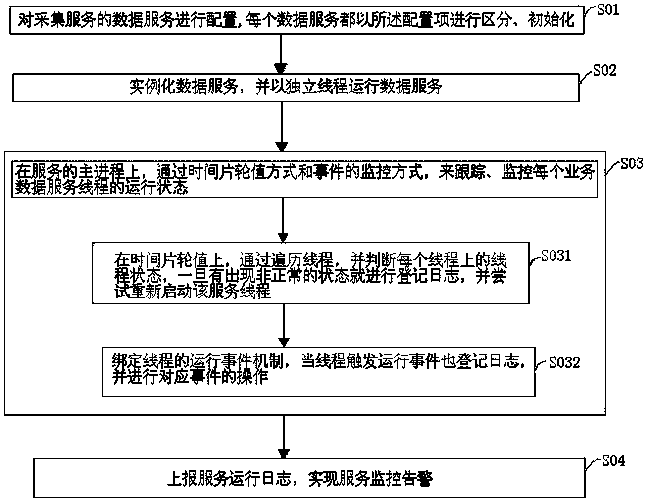
ActiveCN103632331ASolve many problems such as management troubles and unstable data servicesData processing applicationsData switching networksConfiguration itemData service unit
The invention relates to a configurable plug-in type data service method which is characterized by comprising the following steps of step S01, configuring data services of a collecting service, wherein each data service is partitioned and initialized by a configuration item; step S02, instantiating the data services and operating the data services with an independent thread; step S03, on the host process of the service, tracing and monitoring the operation state of the thread of each data service by a time slice shift mode and an event monitoring mode, wherein the step S03 comprises the following steps of step S031, passing and traversing the thread on the time slice shift, judging the thread state on each thread, registering a log once an abnormal state occurs and trying to restart the service thread, and step S032, binding the operation event mechanism of the thread, registering the log when the thread triggers the operation event and performing operation on the corresponding event; step S04, reporting the service operation log and realizing the service monitoring and alarming.
Owner:SICHUANG TECH CO LTD
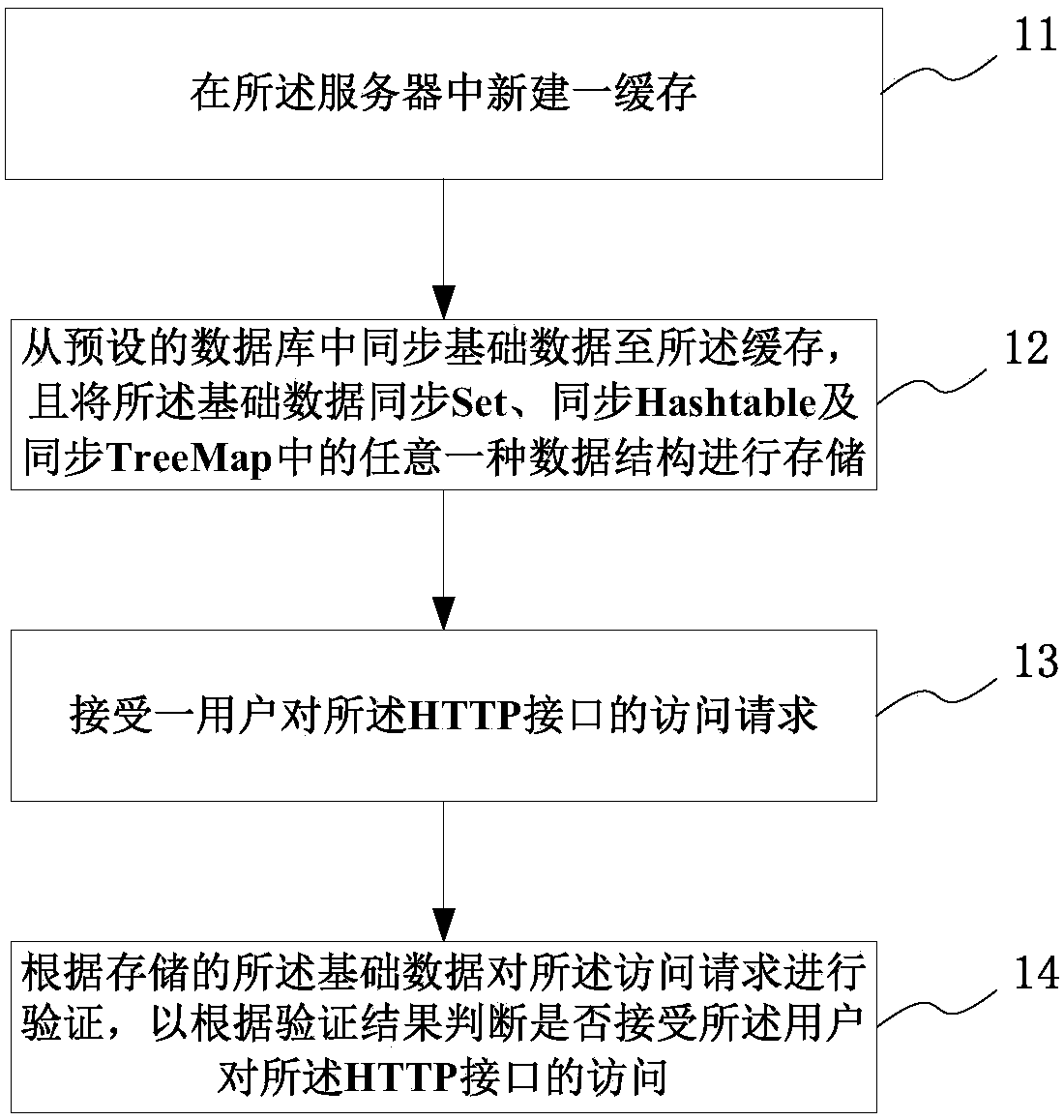
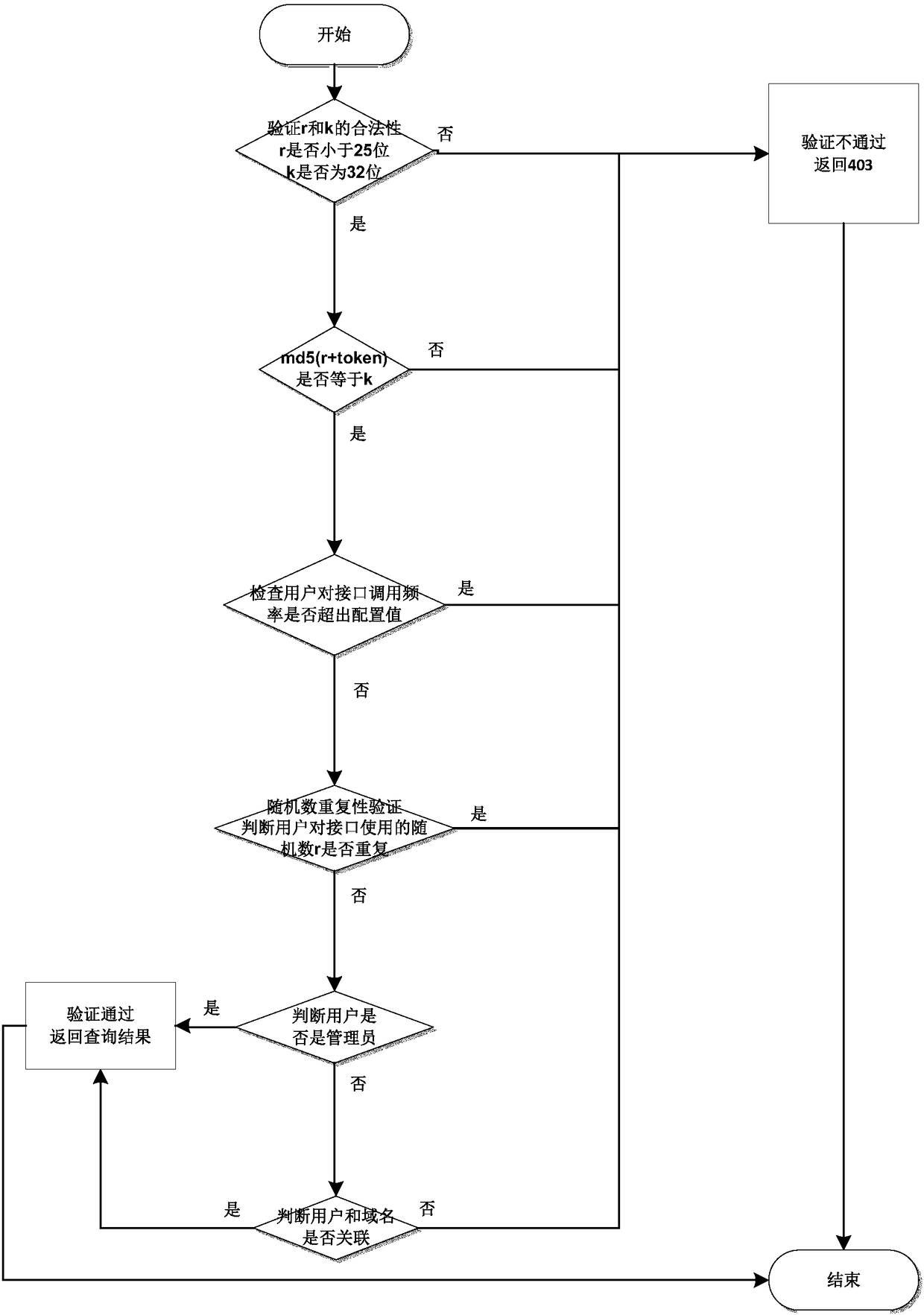
HTTP interface access authority verification method, system and server
The invention provides an HTTP interface access authority verification method, a system and a server. The method comprises a step of creating a new cache in the server, a step of synchronizing basic data from a preset database to the cache and storing the basic data according to a synchronous TreeMap data structure, a step of receiving a user's access request to an HTTP interface, and a step of verifying the access request according to the stored basic data to determine whether to accept the user's access to the HTTP interface according to a verification result. The basic data is stored in thenewly created cache in the server, the reading rate of the basic data can be improved, the basic data is stored according to any data structure of a synchronous Set, a synchronous Hashtable and a synchronous TreeMap, the bottleneck of cross-table query and a lock table problem of reading and writing conflicts are solved, and the thread safety is ensured. The operating efficiency and safety performance of the invention are high, and the stability of the interface can be improved.
Owner:CHINANETCENT TECH
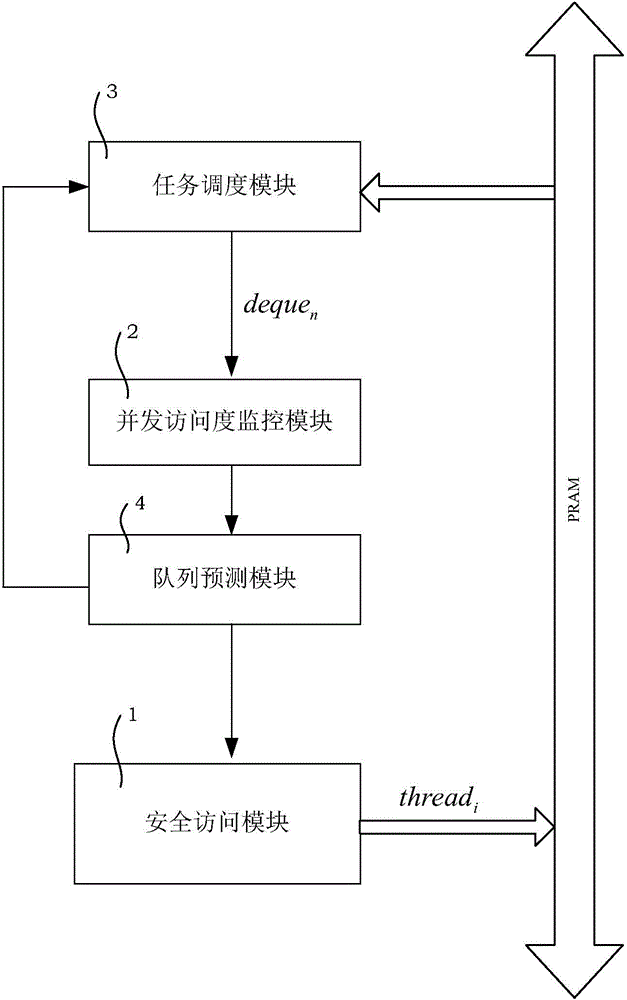
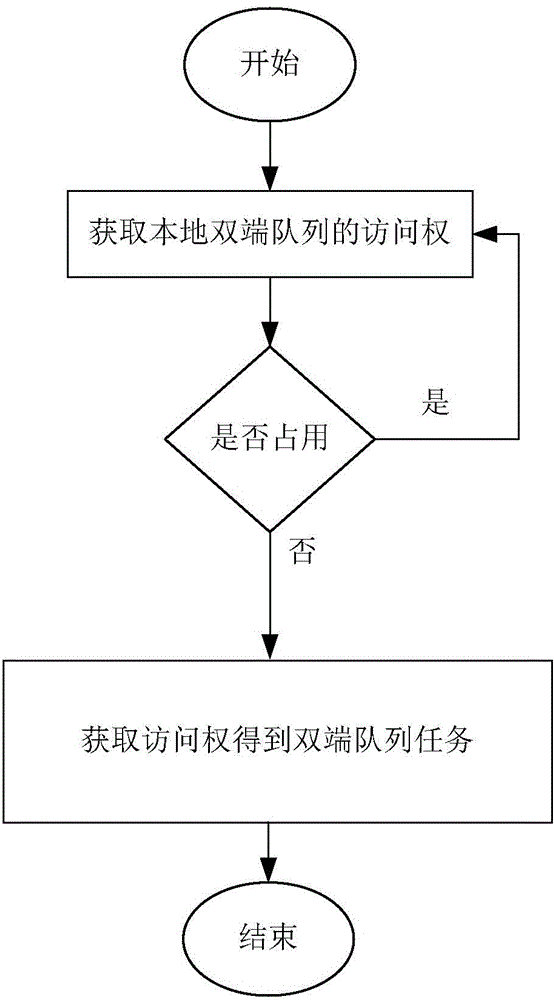
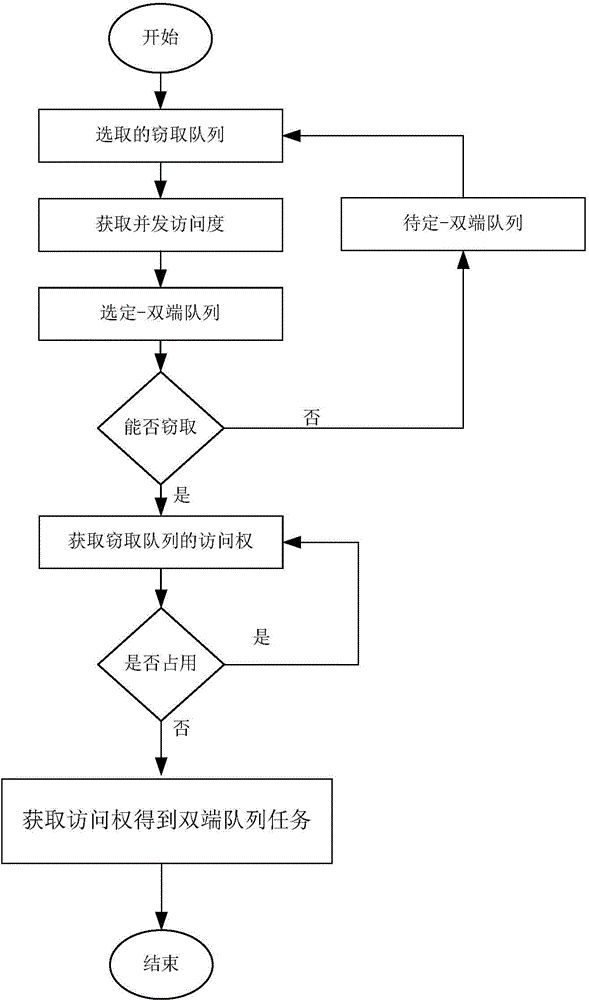
Concurrent queue access control method and system based on task eavesdropping
InactiveCN104156260AFlexible operationImprove performanceMultiprogramming arrangementsRandom-access machineControl system
The invention discloses a concurrent queue access control method and system based on task eavesdropping. The concurrent queue access control system based on task eavesdropping comprises a safe access module (1), a concurrent access degree monitoring module (2), a task scheduling module (3) and a prediction module (4). By means of the method, operations of double-end queues are separated from access control, a queue concurrent access degree monitoring mechanism is built, in the task eavesdropping process, the queues are dynamically selected in a self-adaptation mode for operation according to the queue concurrent access degree, accordingly concurrent access of the double-end queues is evenly distributed to the double-end queues, and thread safety of execution operations of the double-end queues is guaranteed in a blocking mode in terms of access of each double-end queue. The method supports different task eavesdropping strategies, and as for applications using task eavesdropping and operating on a concurrent random access machine, a higher throughput rate and the acceleration effect are achieved.
Owner:凯习(北京)信息科技有限公司
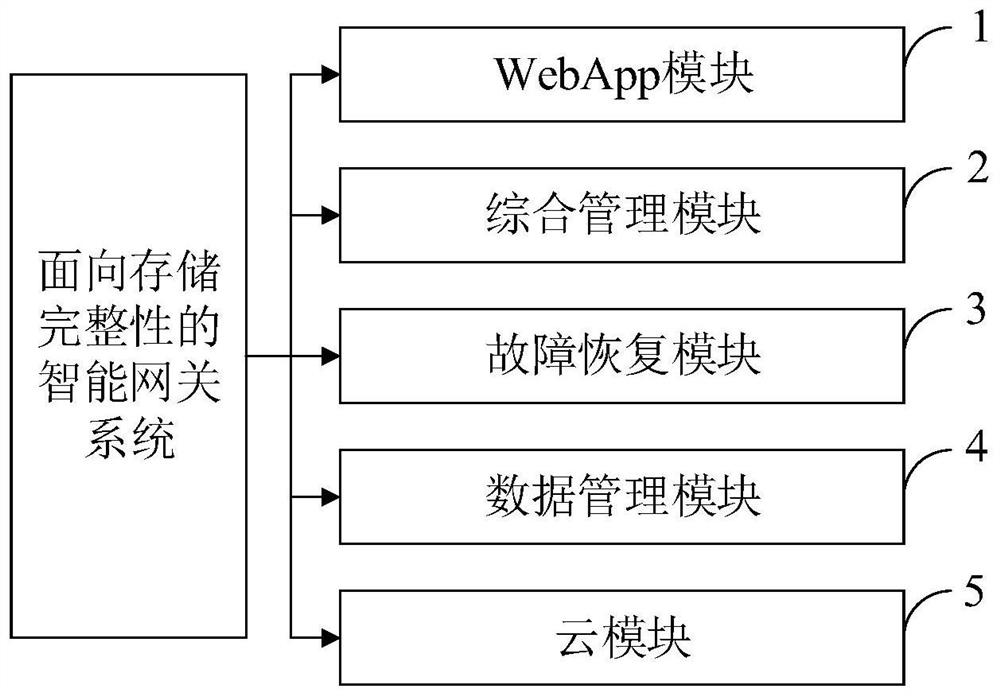
Storage integrity-oriented intelligent gateway system, device and control method thereof
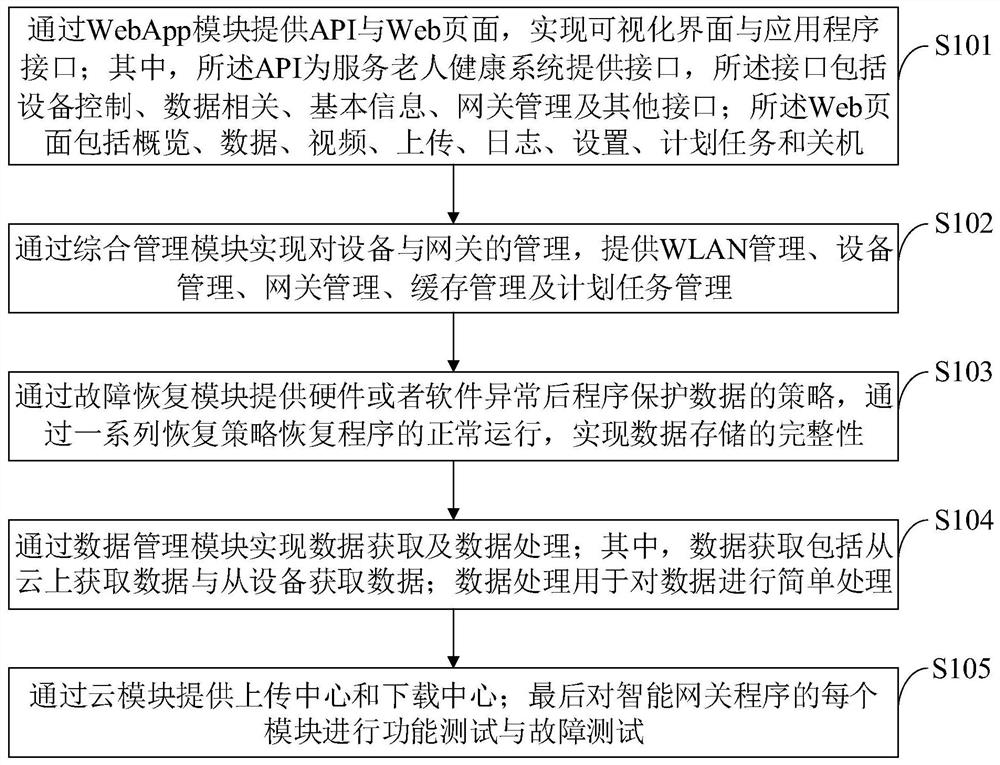
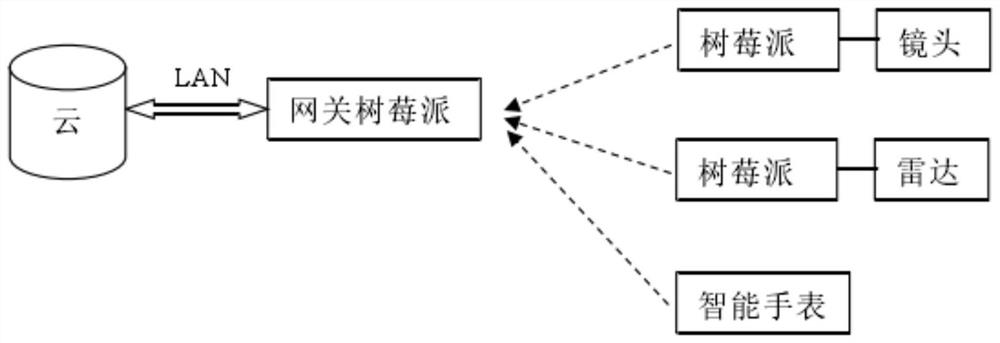
ActiveCN112637318AThe test results are in line with expectationsData switching networksData integrityElderly health
The invention belongs to the technical field of intelligent gateways, and discloses a storage integrity-oriented intelligent gateway system, a storage integrity-oriented intelligent gateway device and a storage integrity-oriented intelligent gateway control method. The storage integrity-oriented intelligent gateway system comprises a WebApp module, an integrated management module, a fault recovery module, a data management module and a cloud module; the storage integrity-oriented intelligent gateway device comprises a gateway Raspberry Pi, an equipment Raspberry Pi, sensors such as a lens and a radar, a intelligent watch and a cloud storage. According to the invention, Java is used as a main development language, and an intelligent gateway system is realized and is used for data management and equipment management in an elderly health information system. According to the method, the data integrity is realized by virtue of thread safety queue design and a plurality of fault recovery mechanisms; for multi-thread performance optimization, the stability of the system is also improved, and the safety of data is guaranteed; through environmental simulation and field application, the intelligent gateway system is subjected to system test, and the test result meets the expectation.
Owner:HARBIN INST OF TECH AT WEIHAI
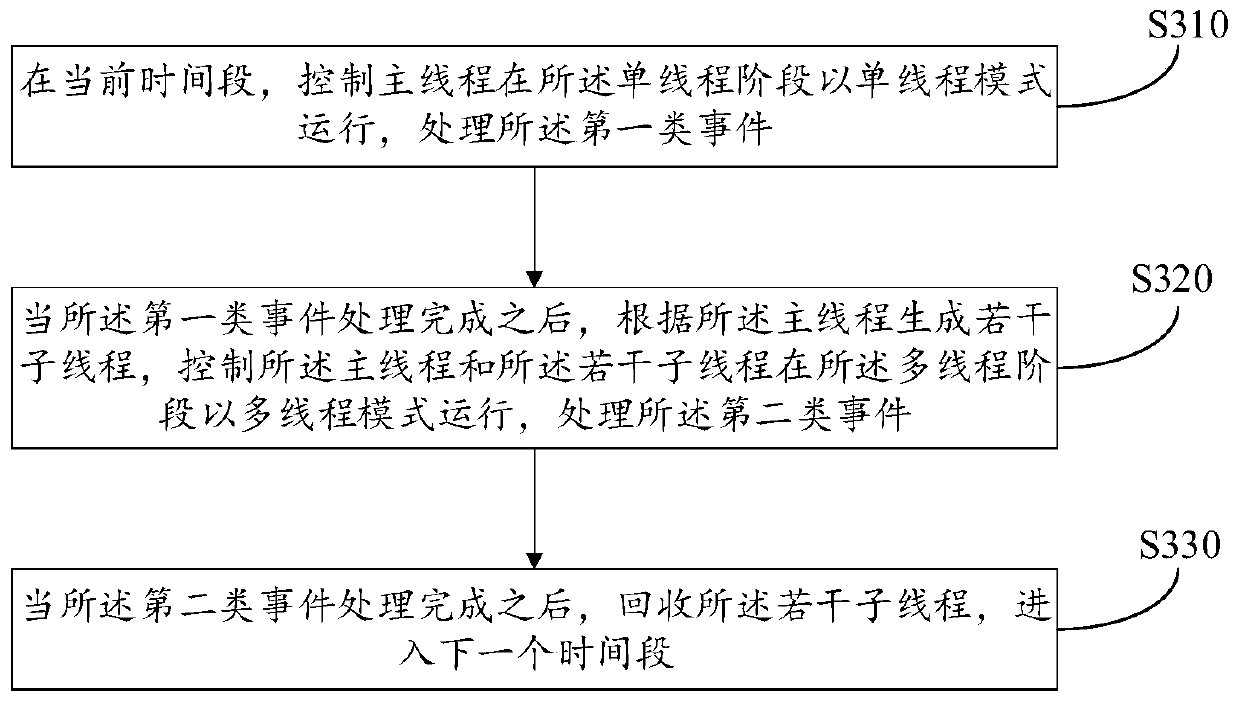
Event processing method and device, equipment and storage medium
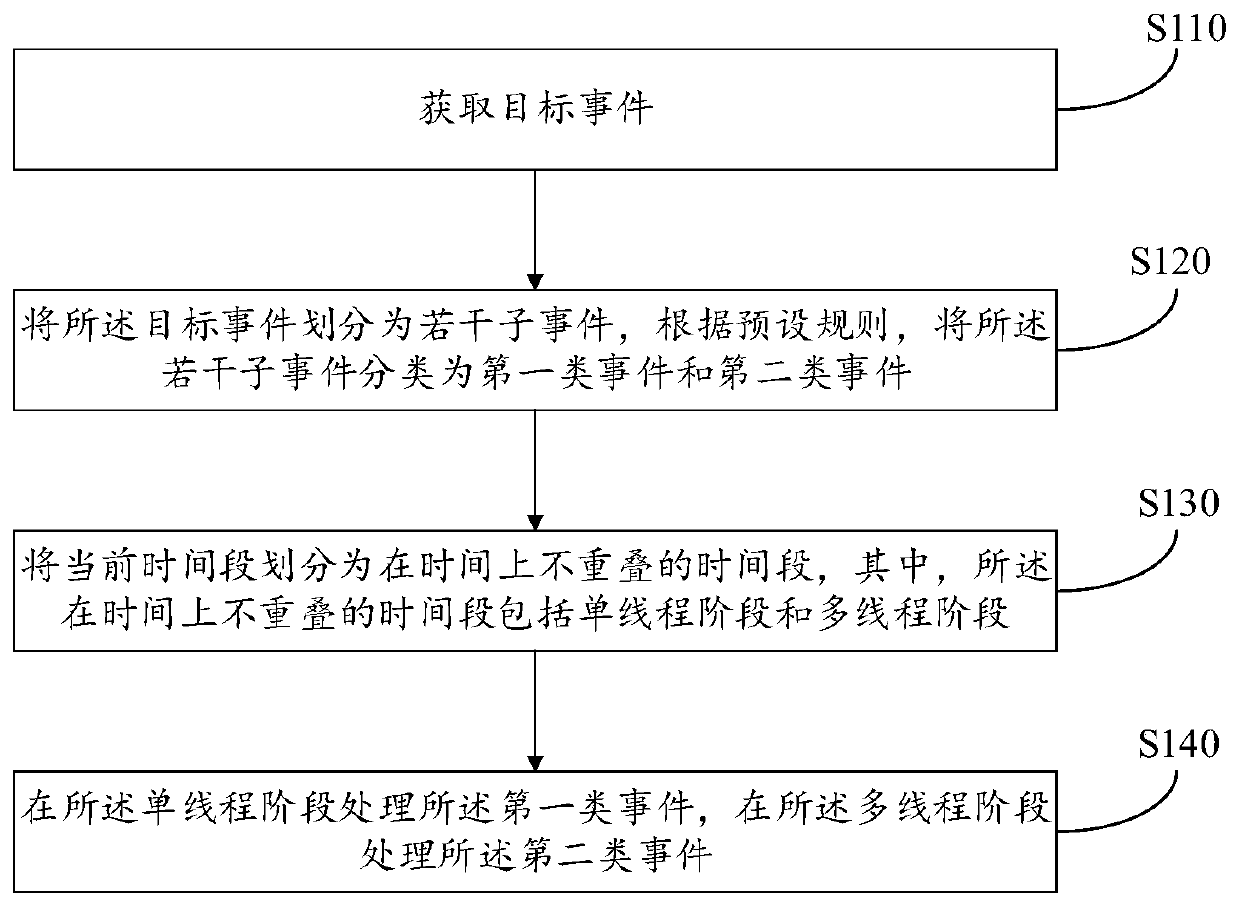
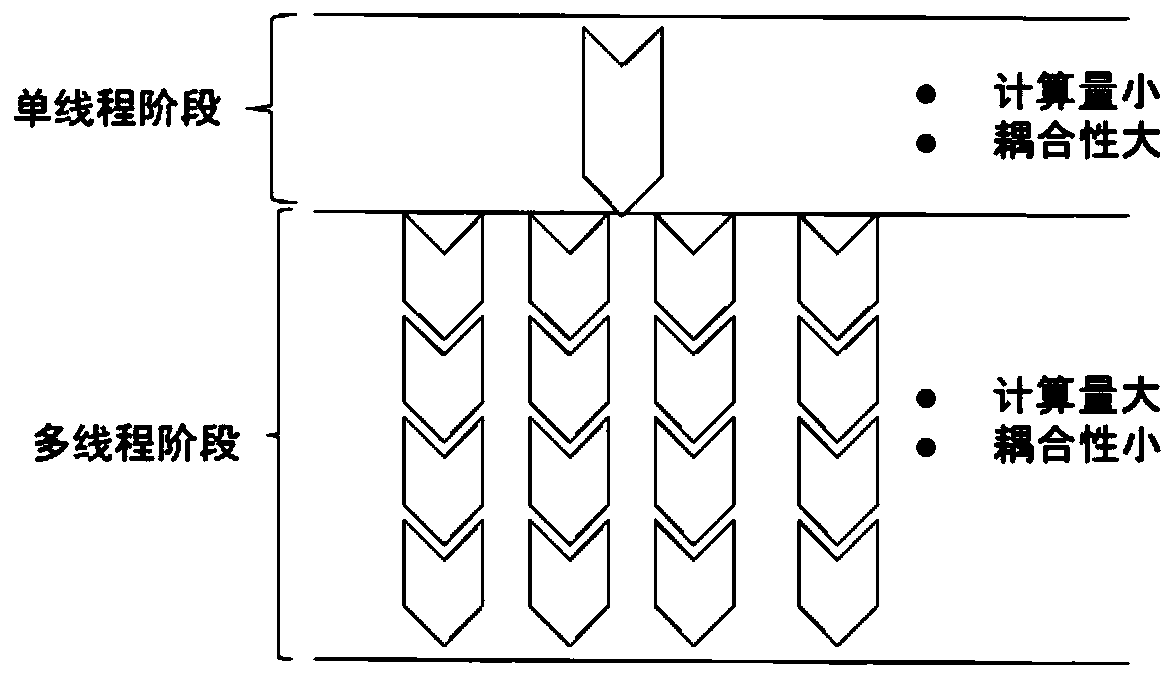
ActiveCN110147269AImprove development efficiencyImprove system performanceEnergy efficient computingTransaction processingComputer scienceThread safety
The invention relates to an event processing method and device, equipment and a storage medium. The method comprises: acquiring a target event; dividing the target event into a plurality of sub-events, and classifying the plurality of sub-events into a first type of events and a second type of events according to a preset rule; dividing the current time period into time periods which are not overlapped in time, the time periods which are not overlapped in time comprising a single-thread stage and a multi-thread stage; and processing the first type of events in the single thread stage, and processing the second type of events in the multi-thread stage. According to the processing characteristics of different threads, different types of events are put in different thread stages to be processed, so that the development efficiency and the system performance are improved; and meanwhile, a single thread is combined with multiple threads, so that the development cost and the performance are balanced.
Owner:TENCENT TECH SHANGHAI
Intelligent interface for a distributed control system
InactiveCN103221891AData switching networksTotal factory controlExternal applicationDistributed control system
An intelligent interface system is provided for connecting an external application to a distributed control system (DCS). The interface system is operable to automatically scan the DCS to determine its configuration and build a topology model of the DCS. The topology model is used to determine whether data requested from a module in the DCS can be provided by the module. The topology model is constructed to be thread-safe. A throttling mechanism in the interface system protects the DCS from being subjected to excessive data requests.
Owner:ABB (SCHWEIZ) AG
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com