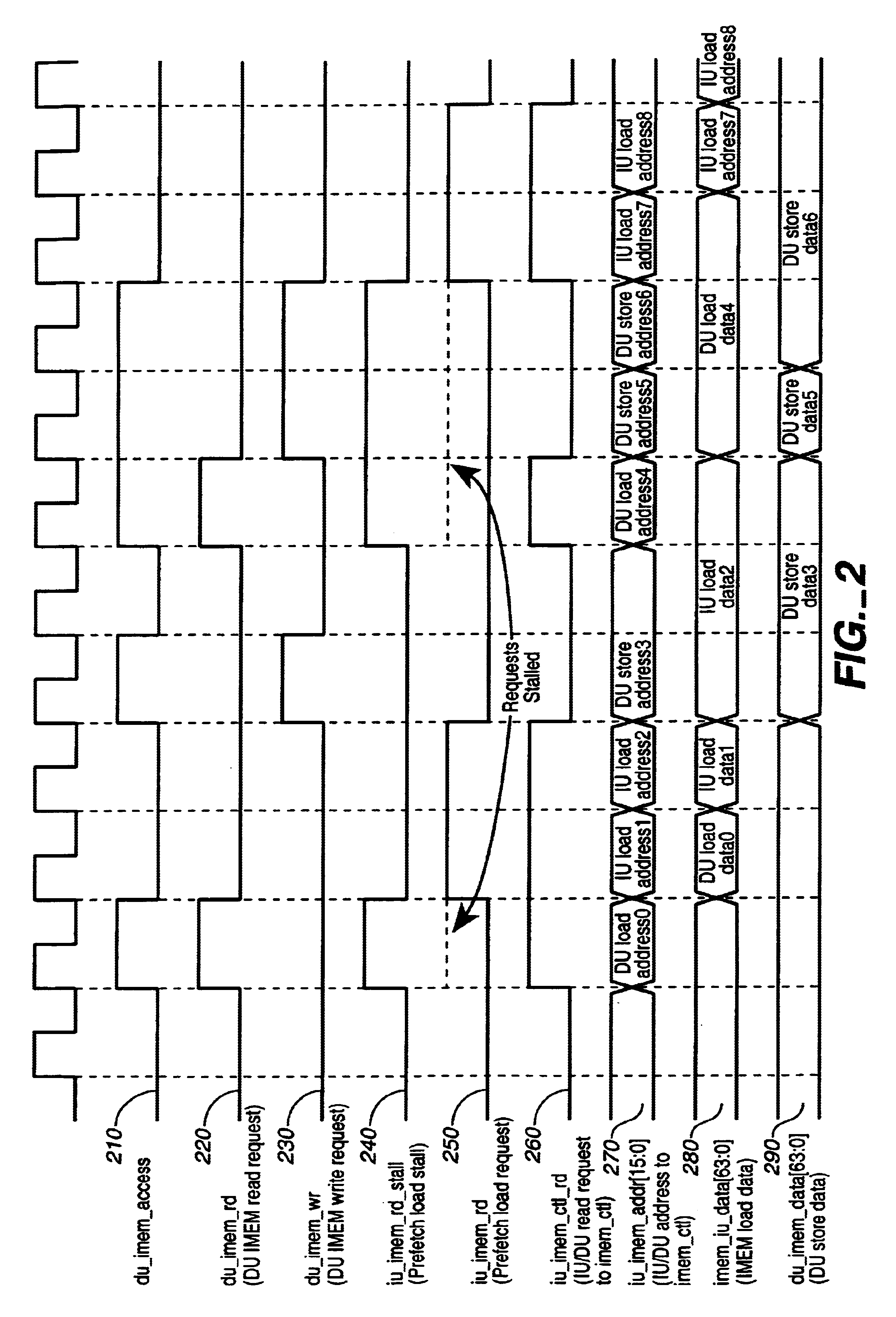
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
30 results about "Self-modifying code" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
In computer science, self-modifying code is code that alters its own instructions while it is executing – usually to reduce the instruction path length and improve performance or simply to reduce otherwise repetitively similar code, thus simplifying maintenance. Self-modification is an alternative to the method of "flag setting" and conditional program branching, used primarily to reduce the number of times a condition needs to be tested. The term is usually only applied to code where the self-modification is intentional, not in situations where code accidentally modifies itself due to an error such as a buffer overflow.
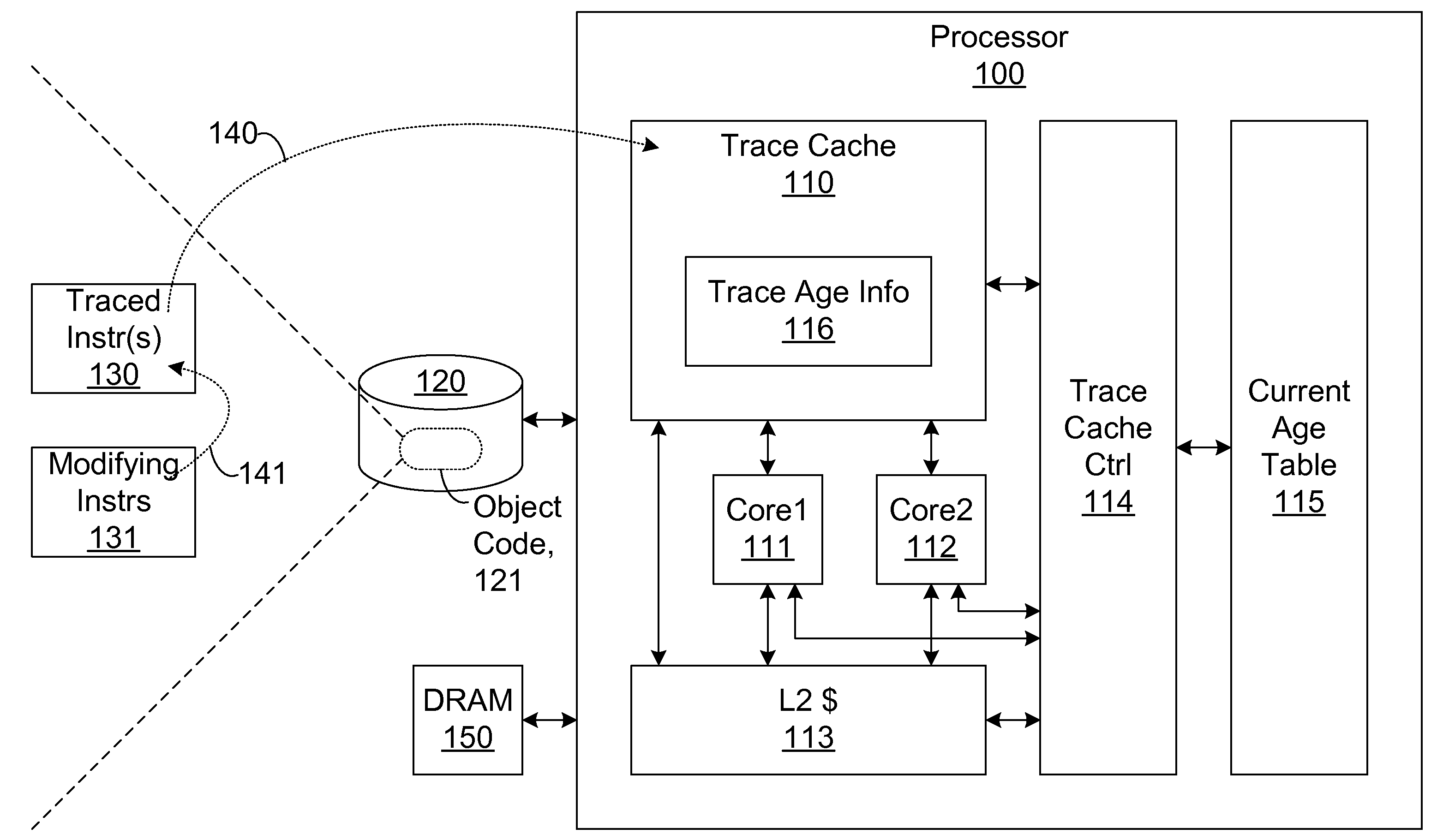
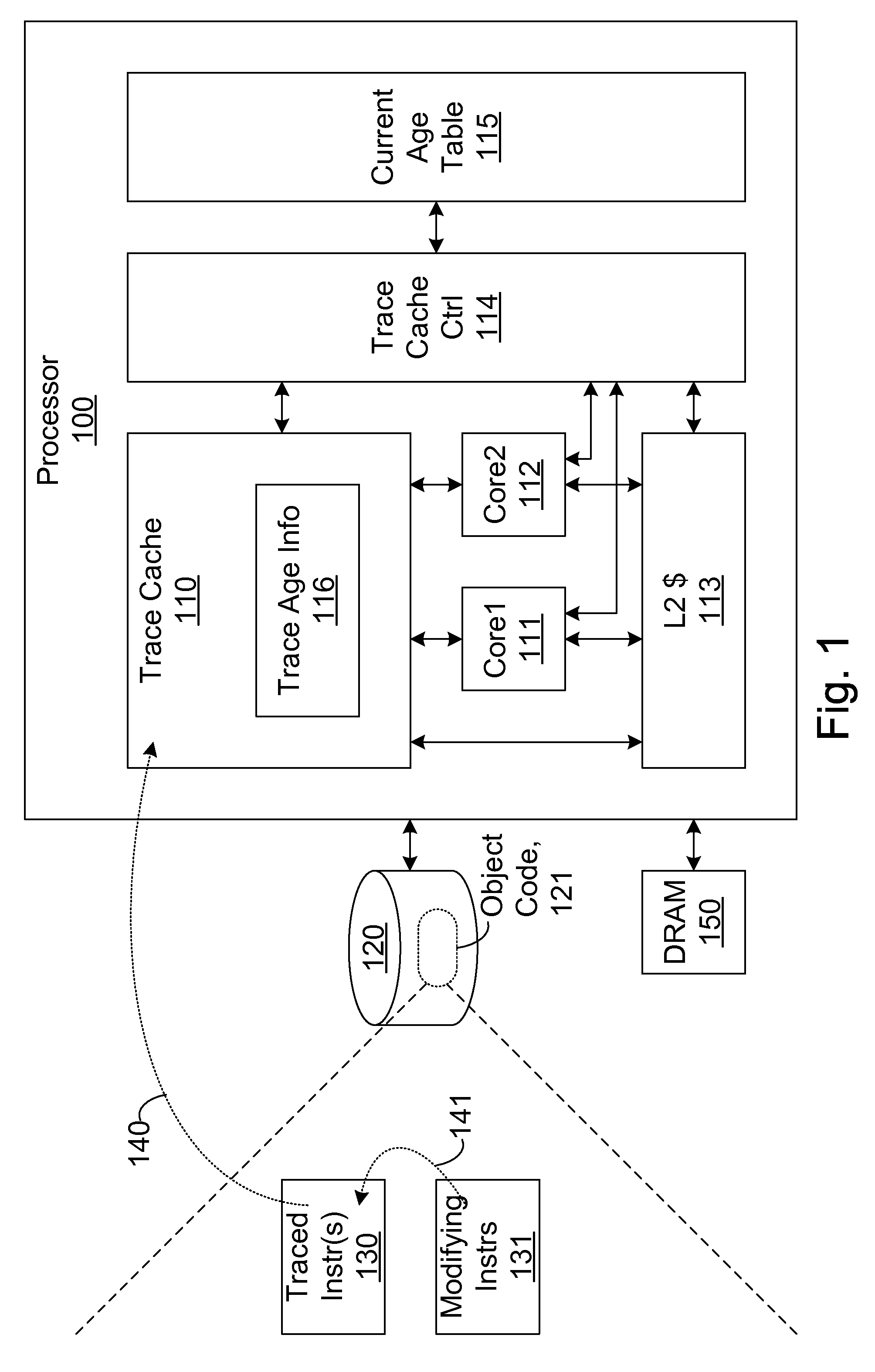
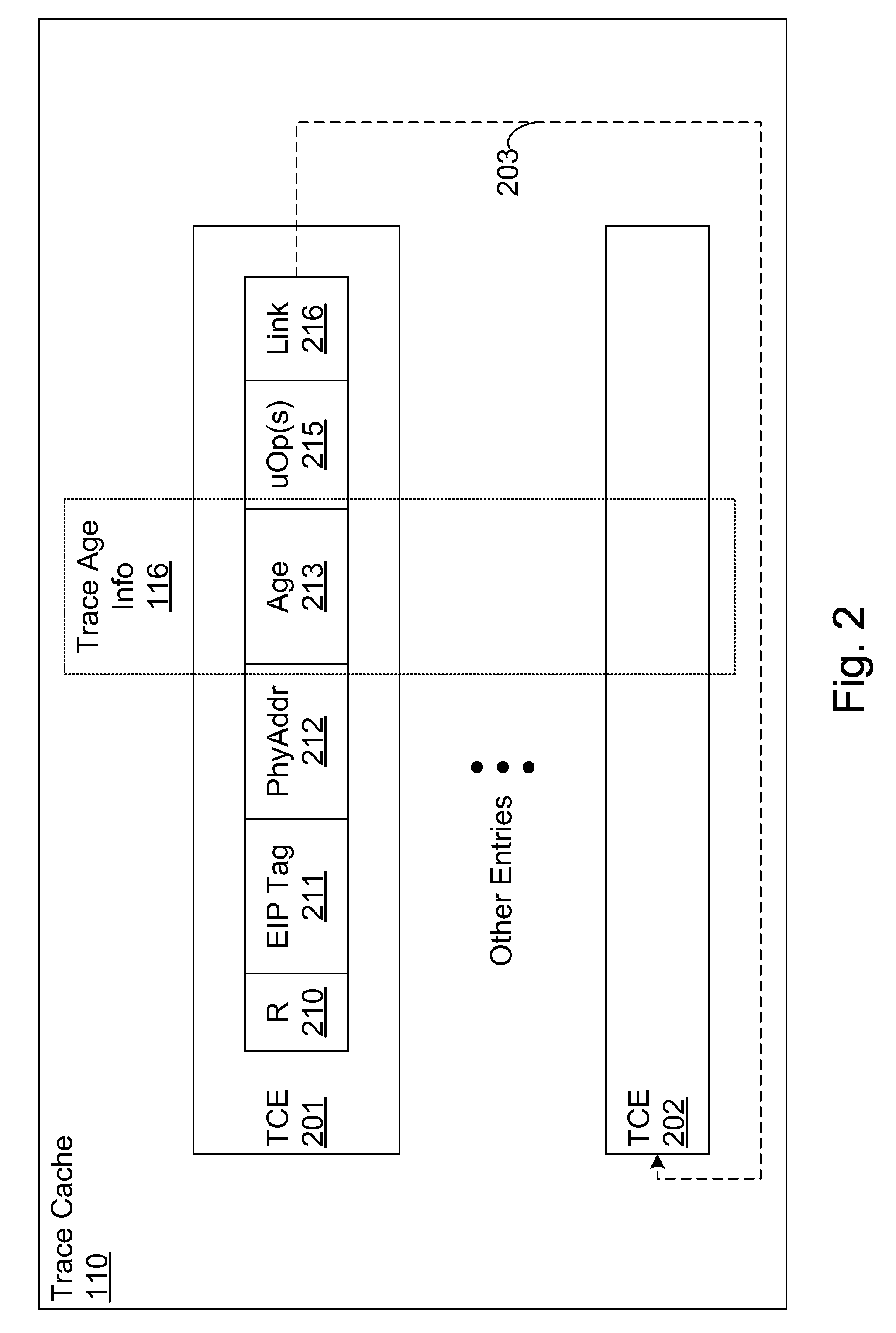
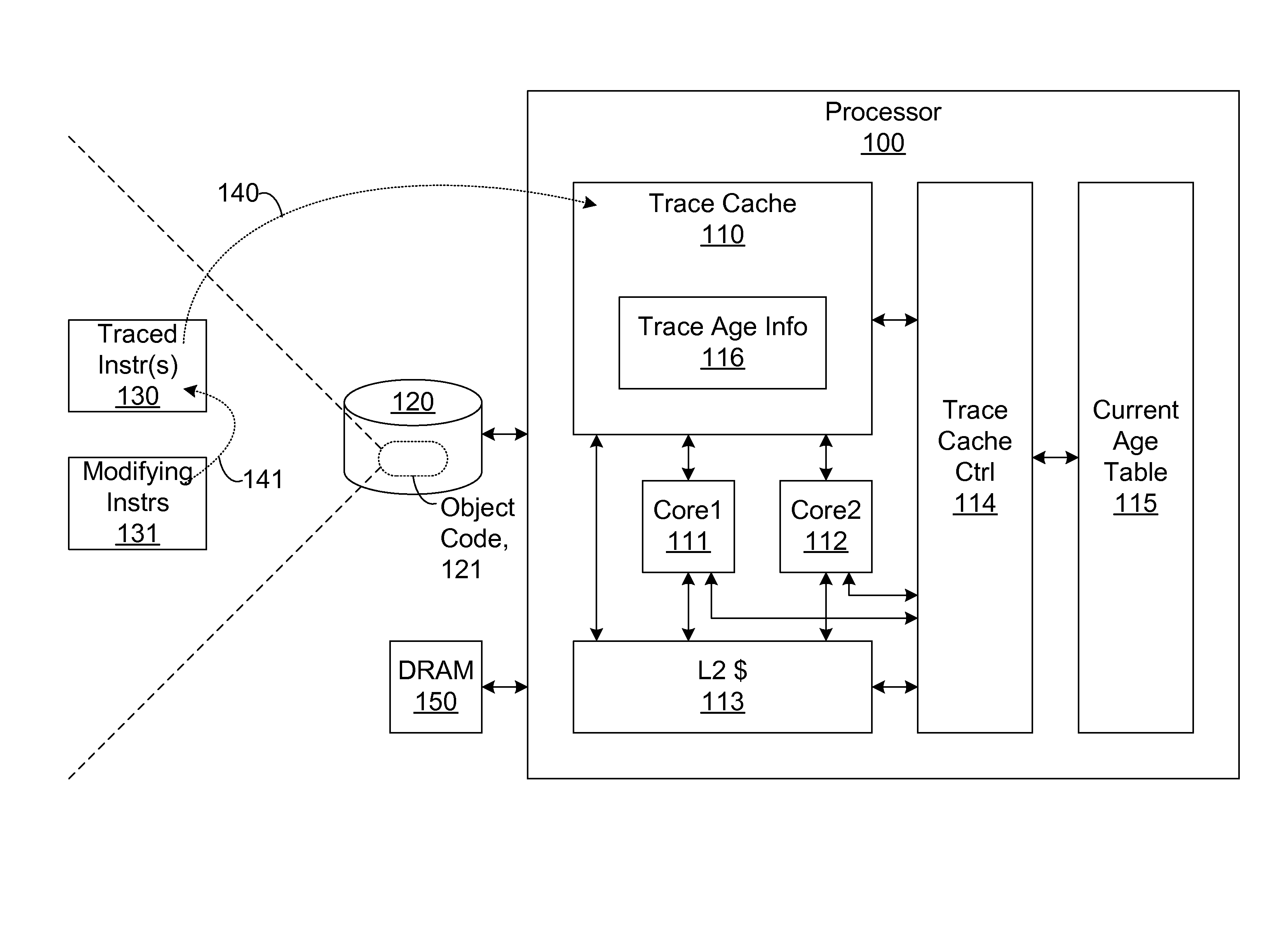
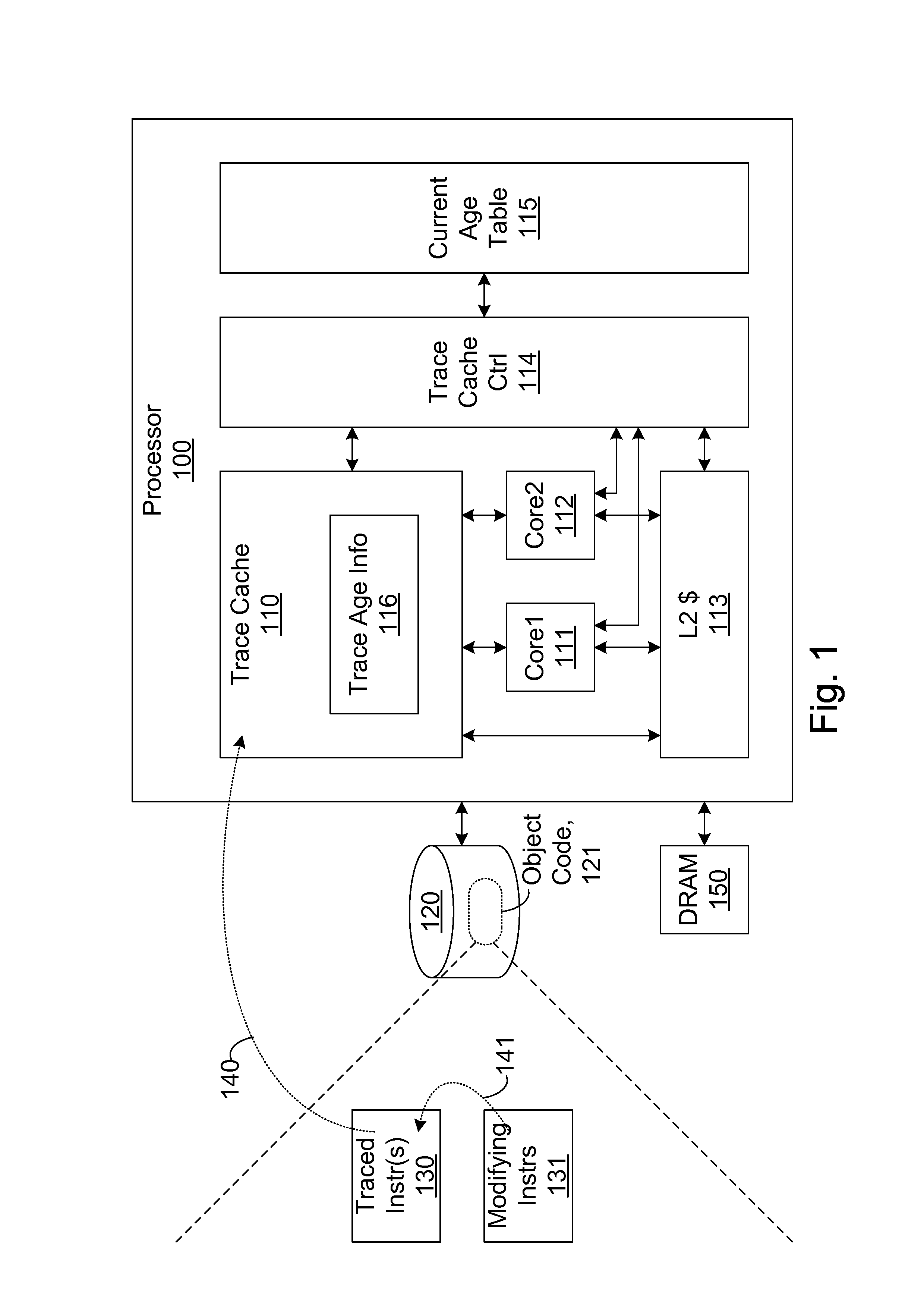
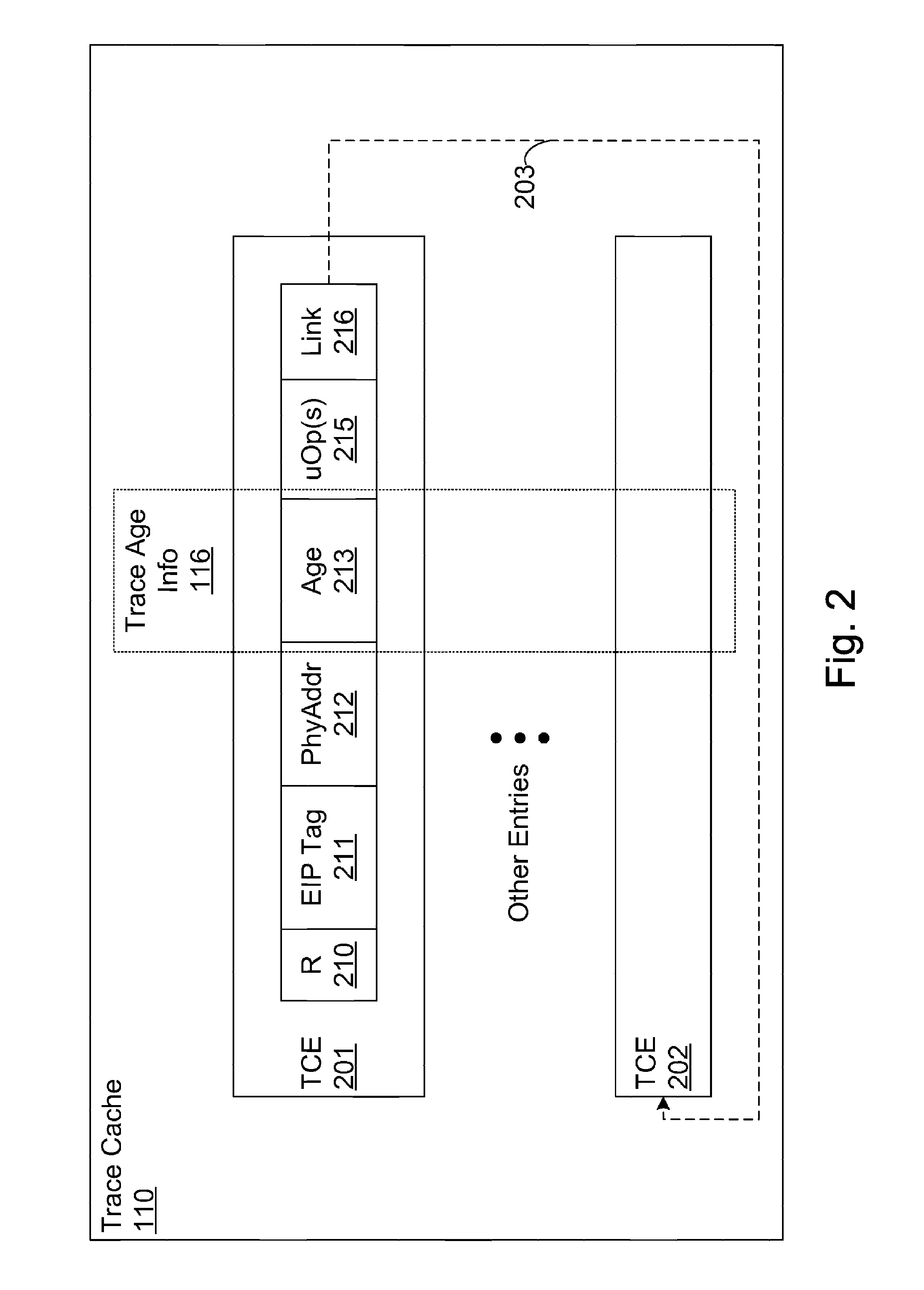
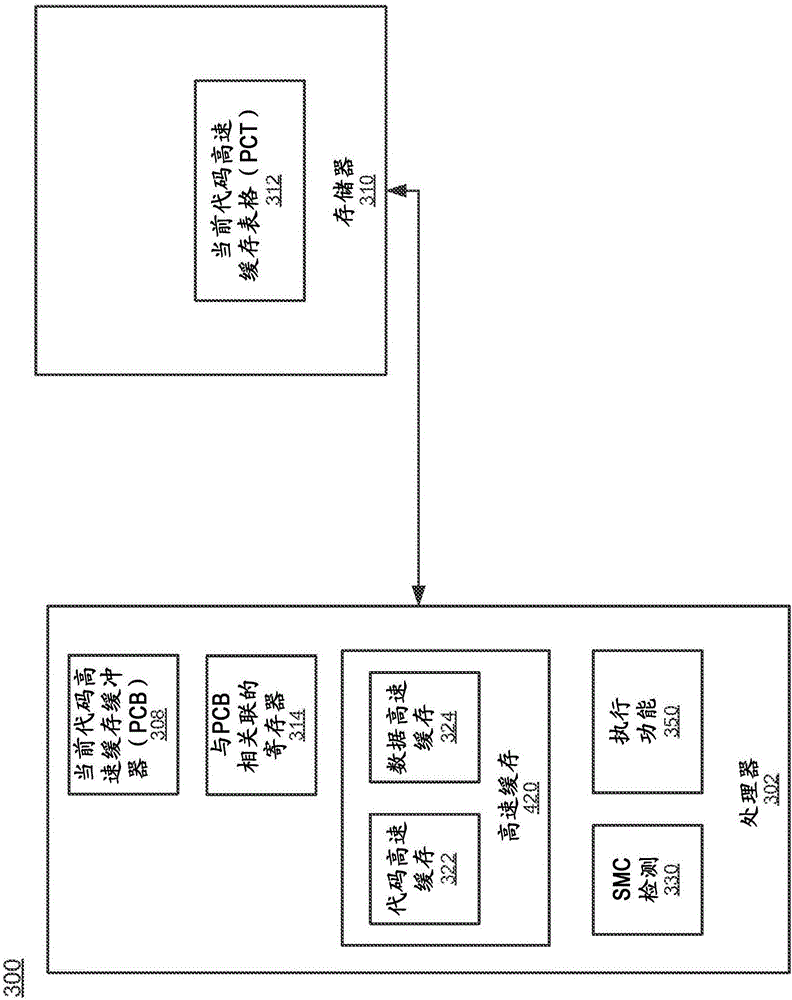
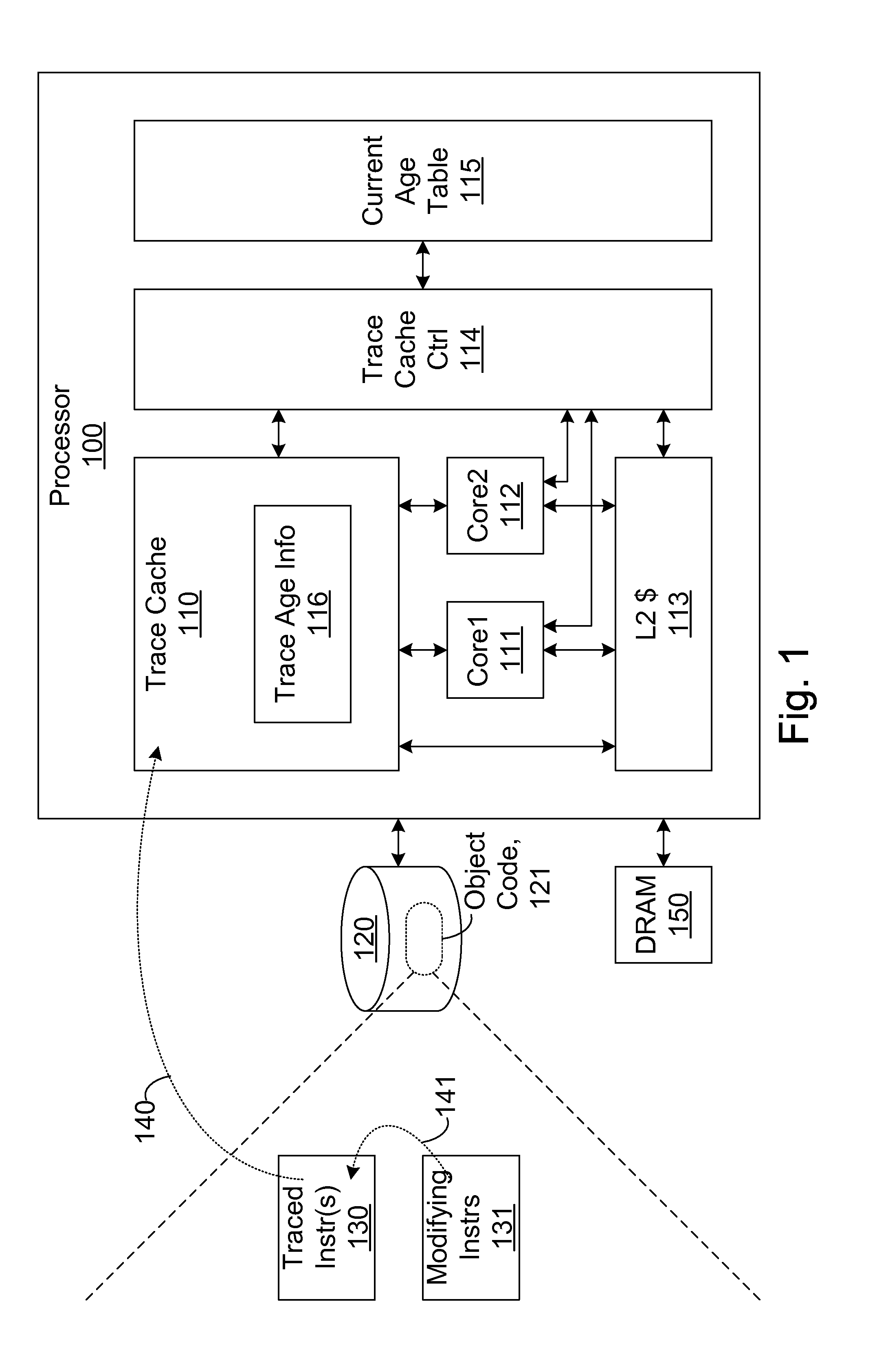
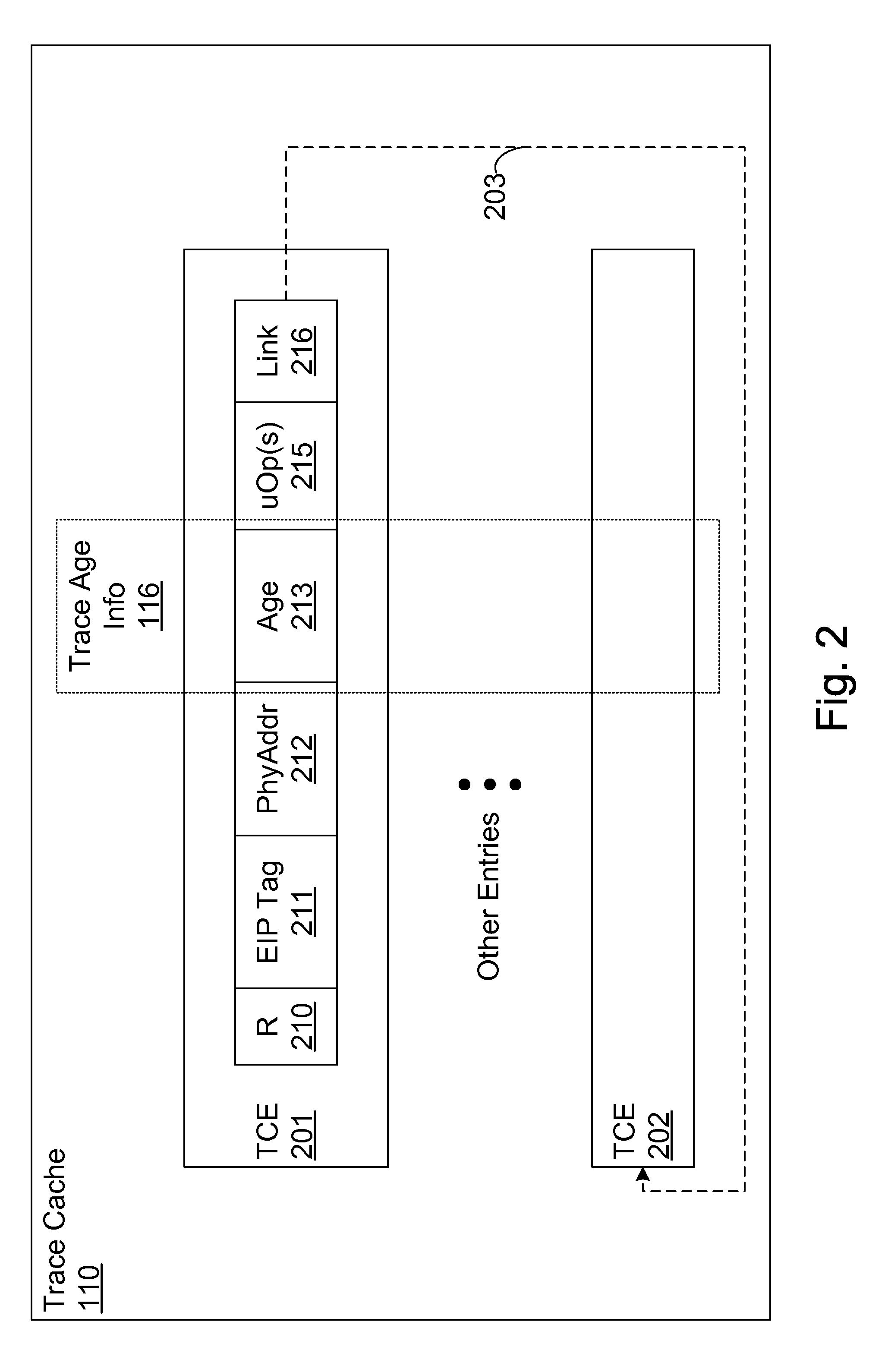
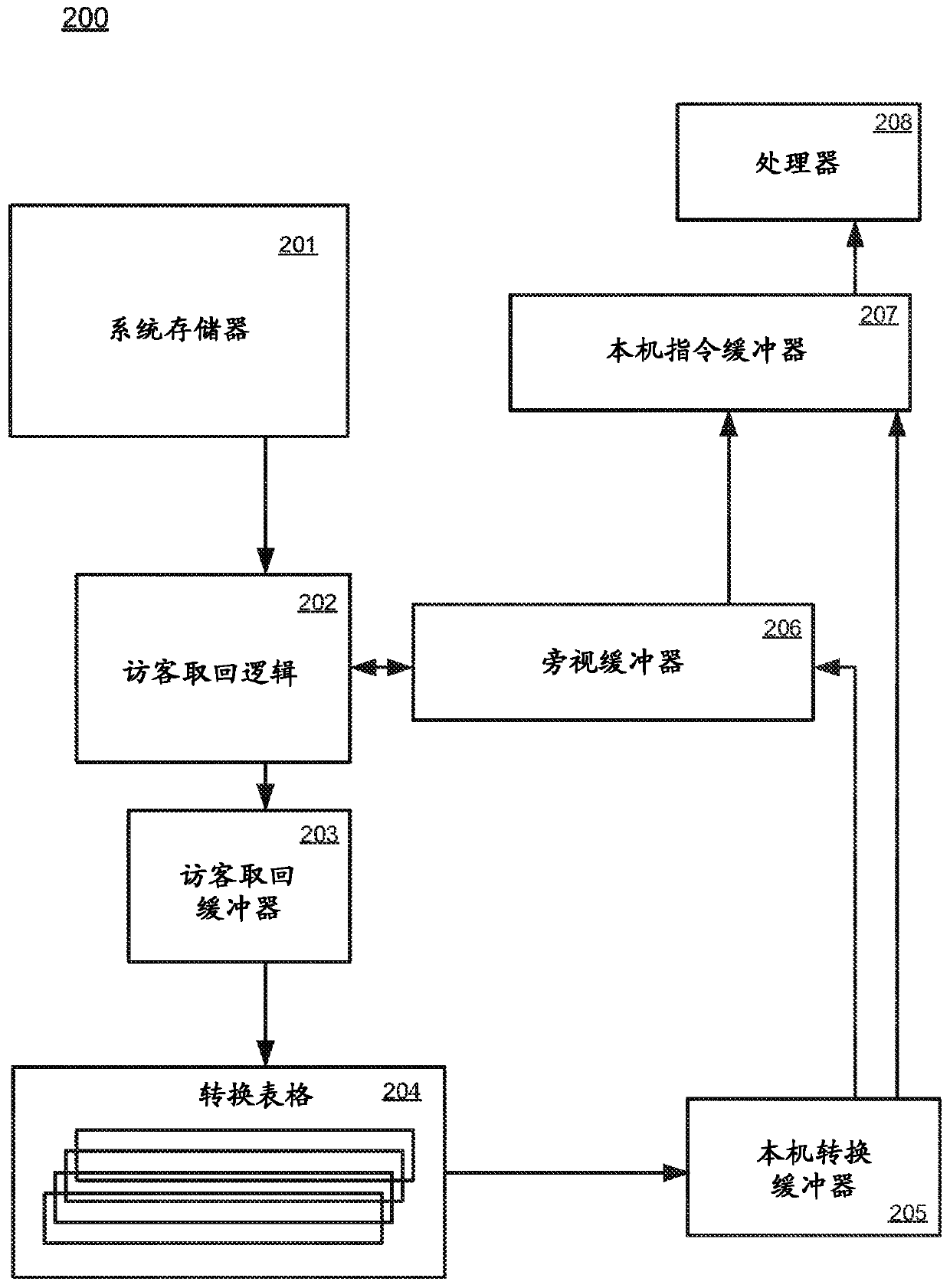
Efficient trace cache management during self-modifying code processing
ActiveUS7546420B1Process less-efficientMore hardwareEnergy efficient ICTProgram controlSelf-modifying codeMicro-operation
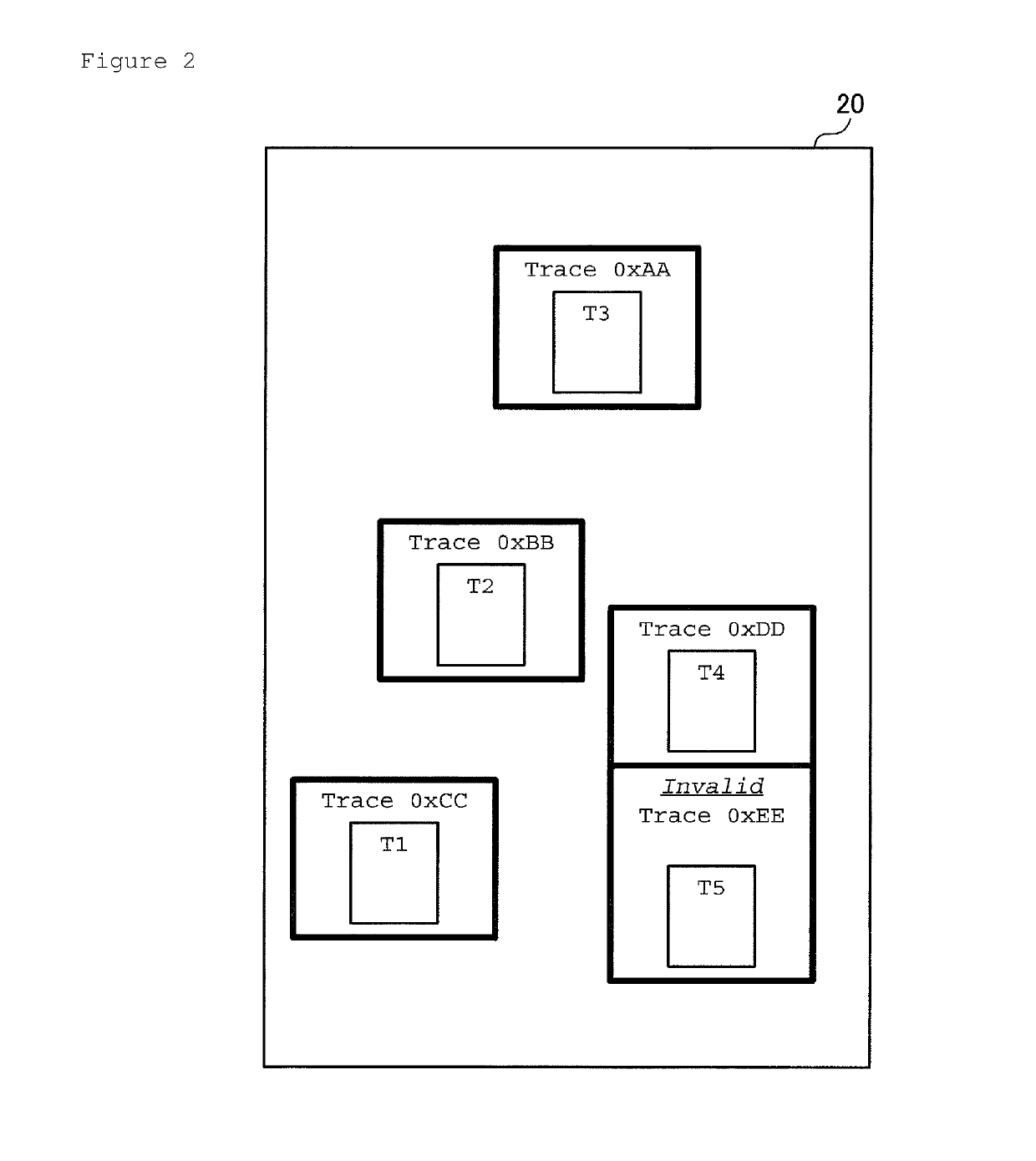
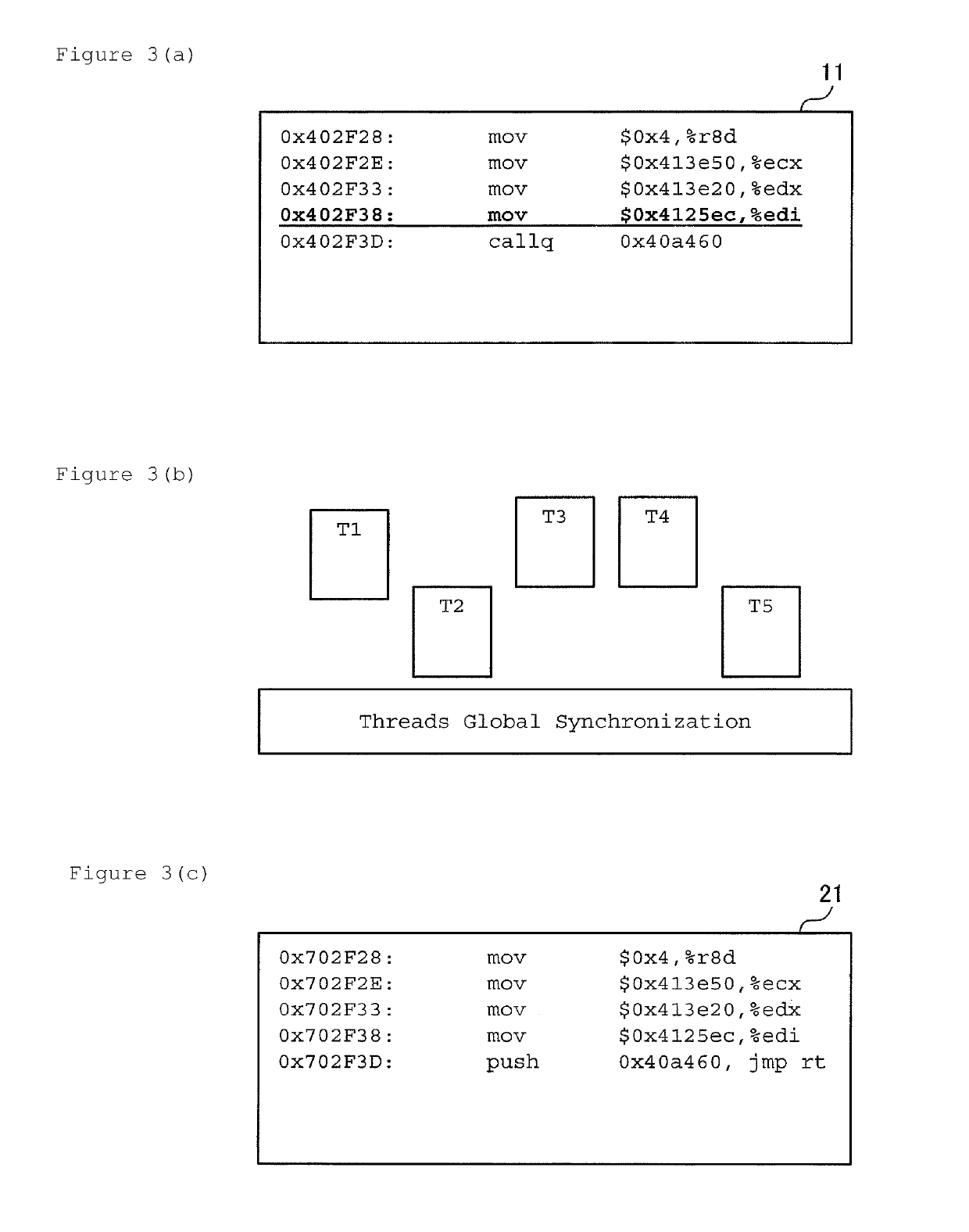
Efficient trace cache management during self-modifying code processing enables selective invalidation of entries of the trace cache, advantageously retaining some of the entries in the trace cache even during self-modifying code events. Instructions underlying trace cache entries are monitored for modification in groups, enabling advantageously reduced hardware. One or more translation ages are associated with each trace cache entry, and are determined when the entry is built by sampling current ages of memory blocks underlying the entry. When the entry is accessed and micro-operations therein are processed, the translation ages of the accessed entry are compared with the current ages of the memory blocks underlying the accessed entry. If any of the age comparisons fail, then the micro-operations are aborted and the entry is invalidated. When any portion of a memory block is modified, the current age of the modified memory block is incremented.
Owner:ORACLE INT CORP
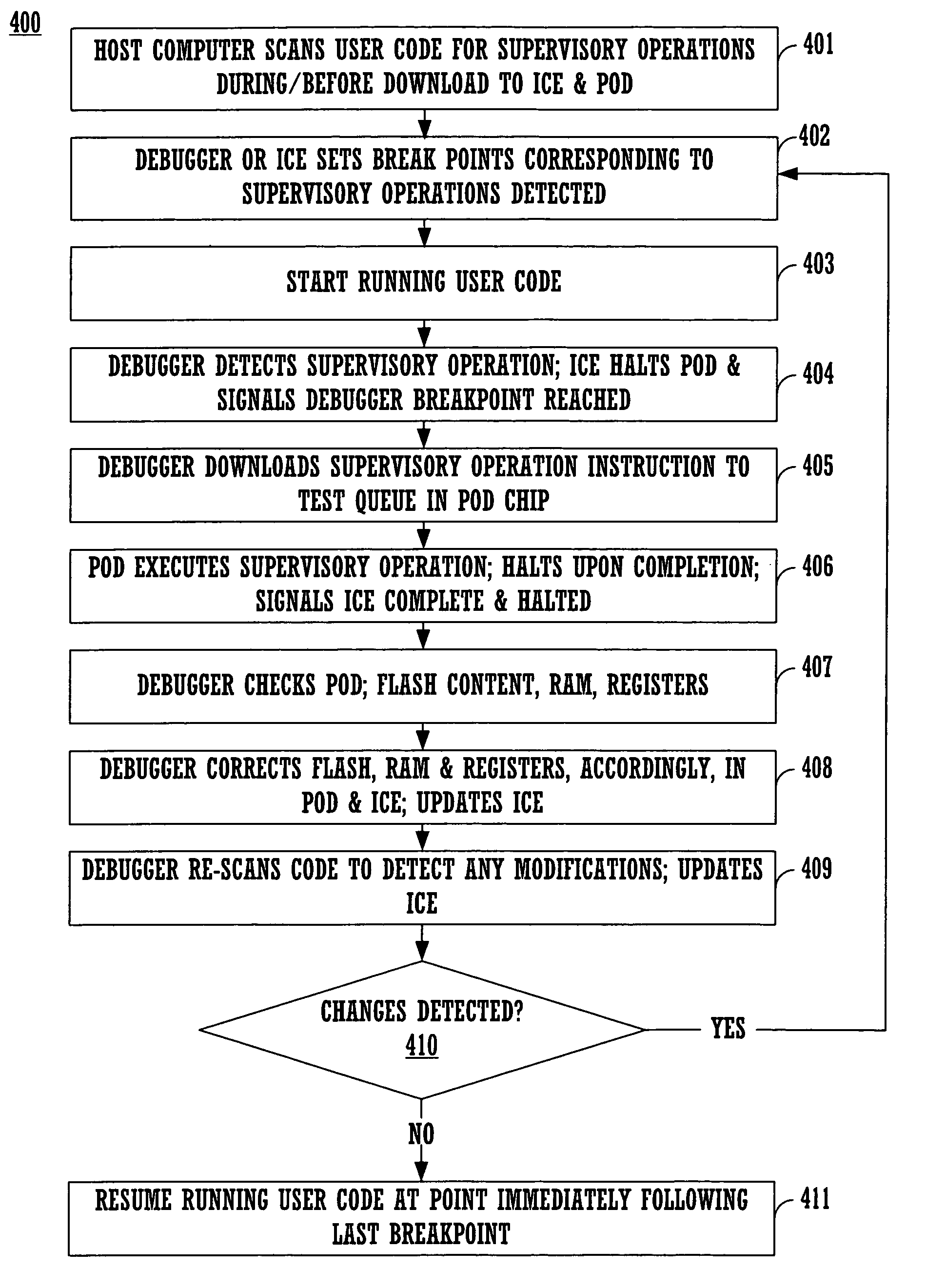
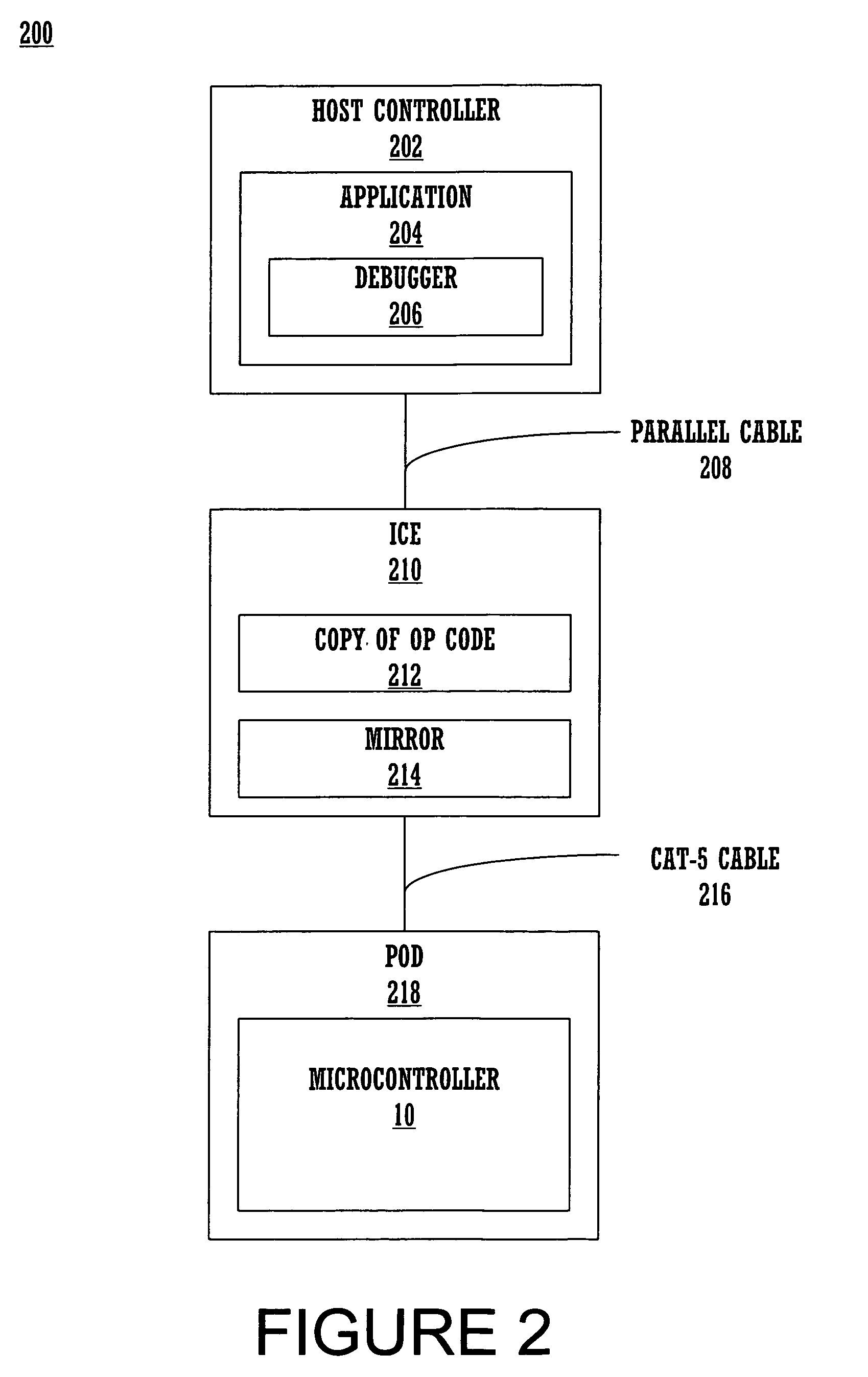
Method and system for debugging through supervisory operating codes and self modifying codes
ActiveUS7185321B1Easy to openEfficient use ofError detection/correctionDigital computer detailsMicrocontrollerSelf-modifying code
Embodiments of the present invention effectuate a method and system for debugging a device such as a microcontroller in a distributed architectural scheme, where the device may operate at speeds much faster than the debugger program is run, with limited debugging resources physically incorporated into the device itself, and with relatively limited computational capacity, vis-à-vis the platform deploying the debugging software. The embodiments place relatively modest, uncomplicated demands on the debugger software, and the ICE may also be relatively simple. Further, debugging methods and systems according to these embodiments are flexible and adaptable to a variety of different devices that must undergo debugging, yet remain effective, simple, and inexpensive.
Owner:MONTEREY RES LLC
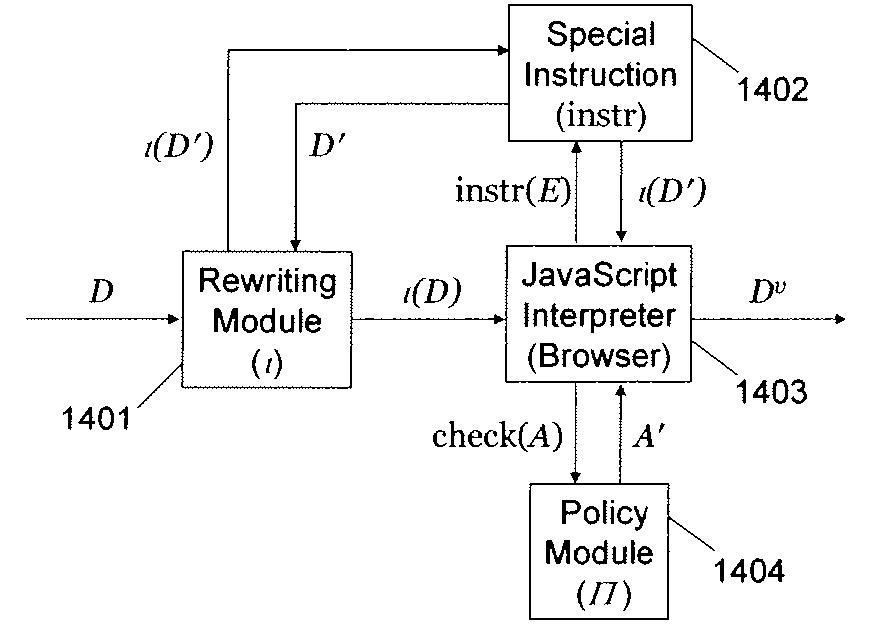
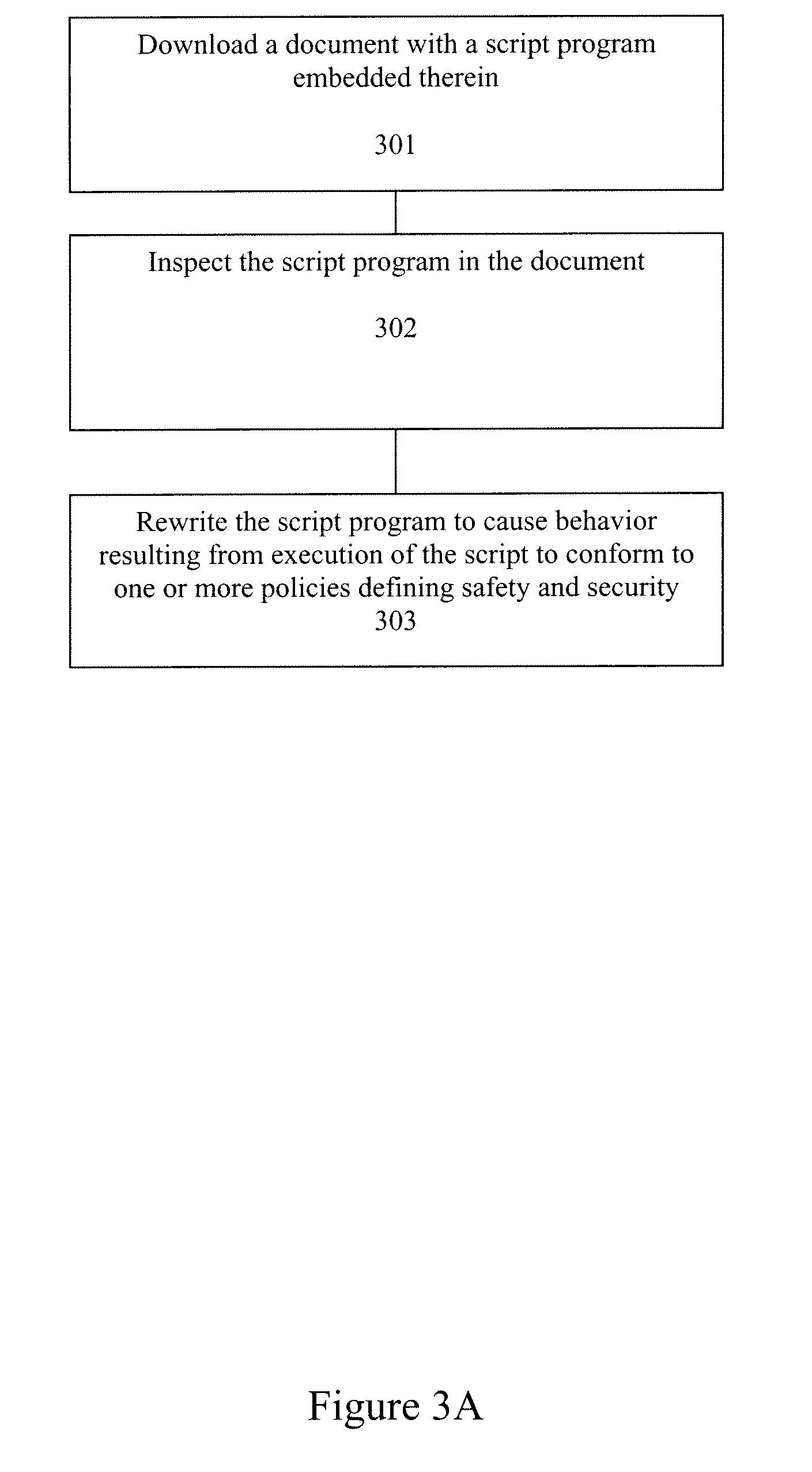
Program instrumentation method and apparatus for constraining the behavior of embedded script in documents
A method and apparatus is disclosed herein for constraining the behavior of embedded script in documents using program instrumentation. In one embodiment, the method comprises downloading a document with a script program embedded therein, inspecting the script program, and rewriting the script program to cause behavior resulting from execution of the script to conform to one or more policies defining safety and security. The script program comprises self-modifying code (e.g., dynamically generated script).
Owner:NTT DOCOMO INC
Method and system for safeguarding user access
ActiveCN101835156AImprove protectionNot vulnerableSecurity arrangementSelf-modifying codeNetwork-attached storage
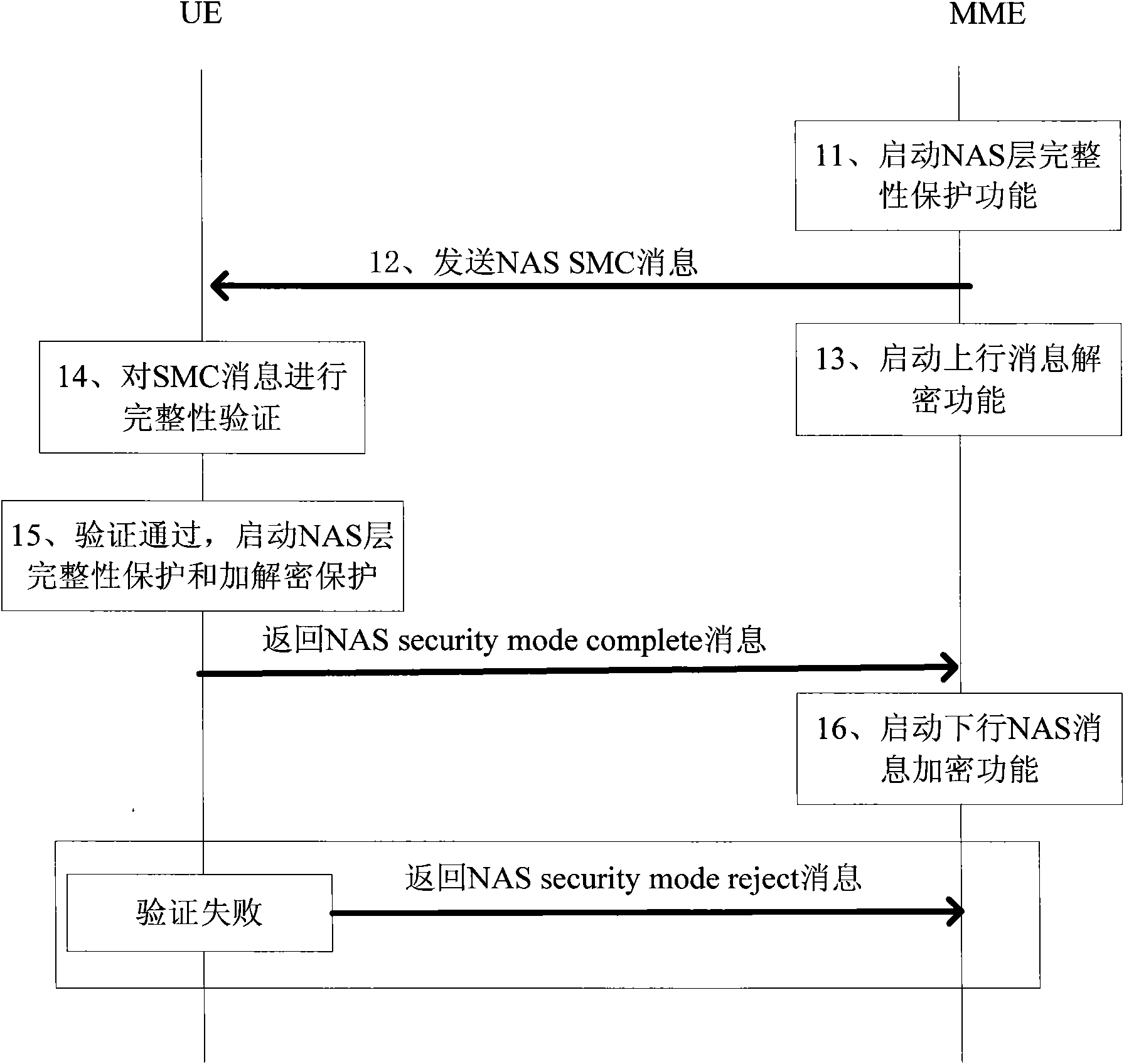
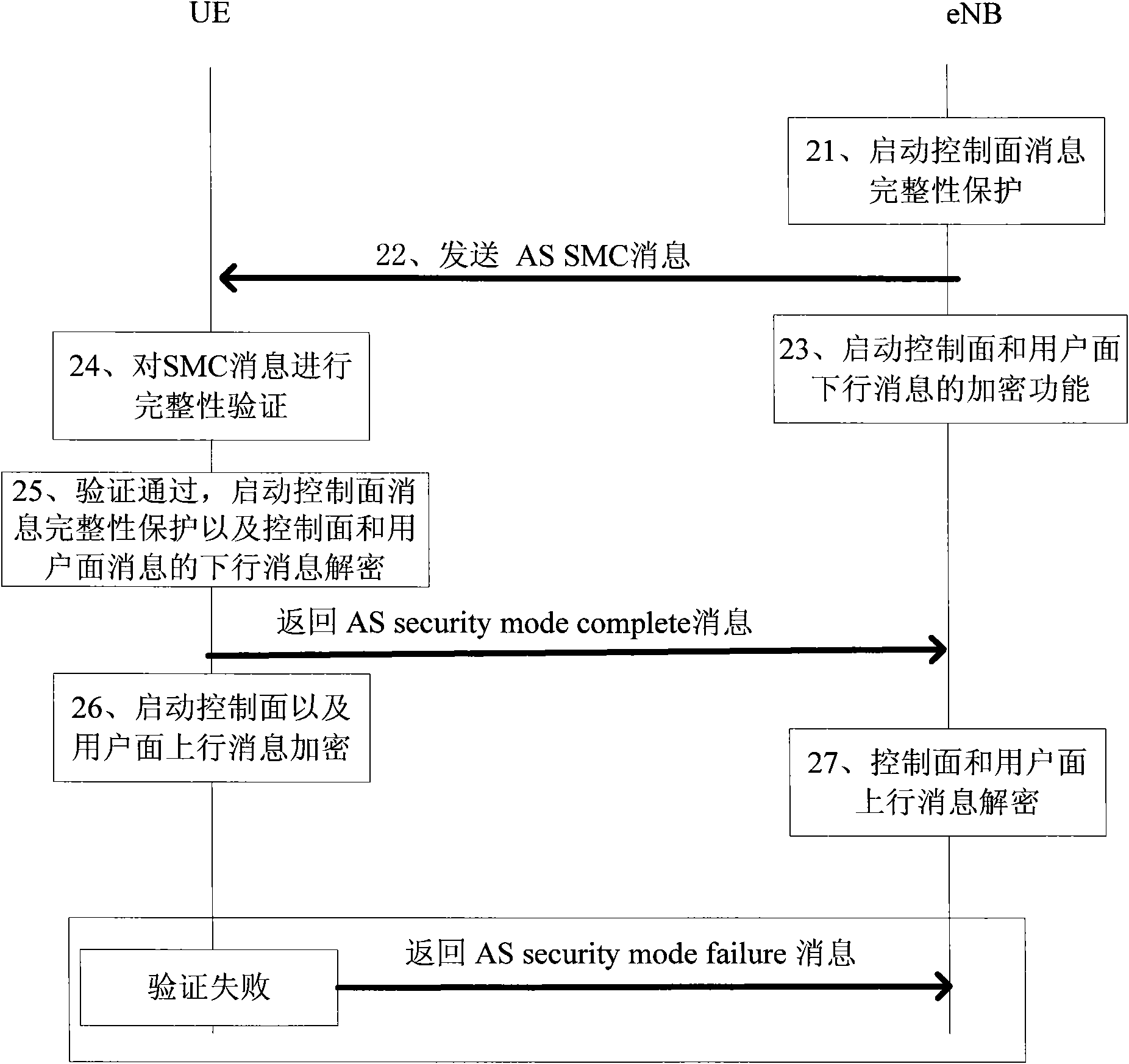
The invention provides a method and a system for safeguarding user access. The method is applied to an LTE (Long Term Evolution) system. UE accessing the LTE system issues an access safety activating command, verifies the integrity of a safe mode command message in an activating process and sends a verification failure message to a network side if verification fails, wherein preset discrimination information is added to the verification failure message, and the network side receives the verification failure message, detects whether the discrimination information is legal or not and restores the configuration before activation if the discrimination information is legal. In traditional NAS (Network Attached Storage) SMC (Self-Modifying Code) and AS SMC flows, the safeguarding of the verification failure message is enhanced so that the network side is hardly attacked by false messages.
Owner:ZTE CORP
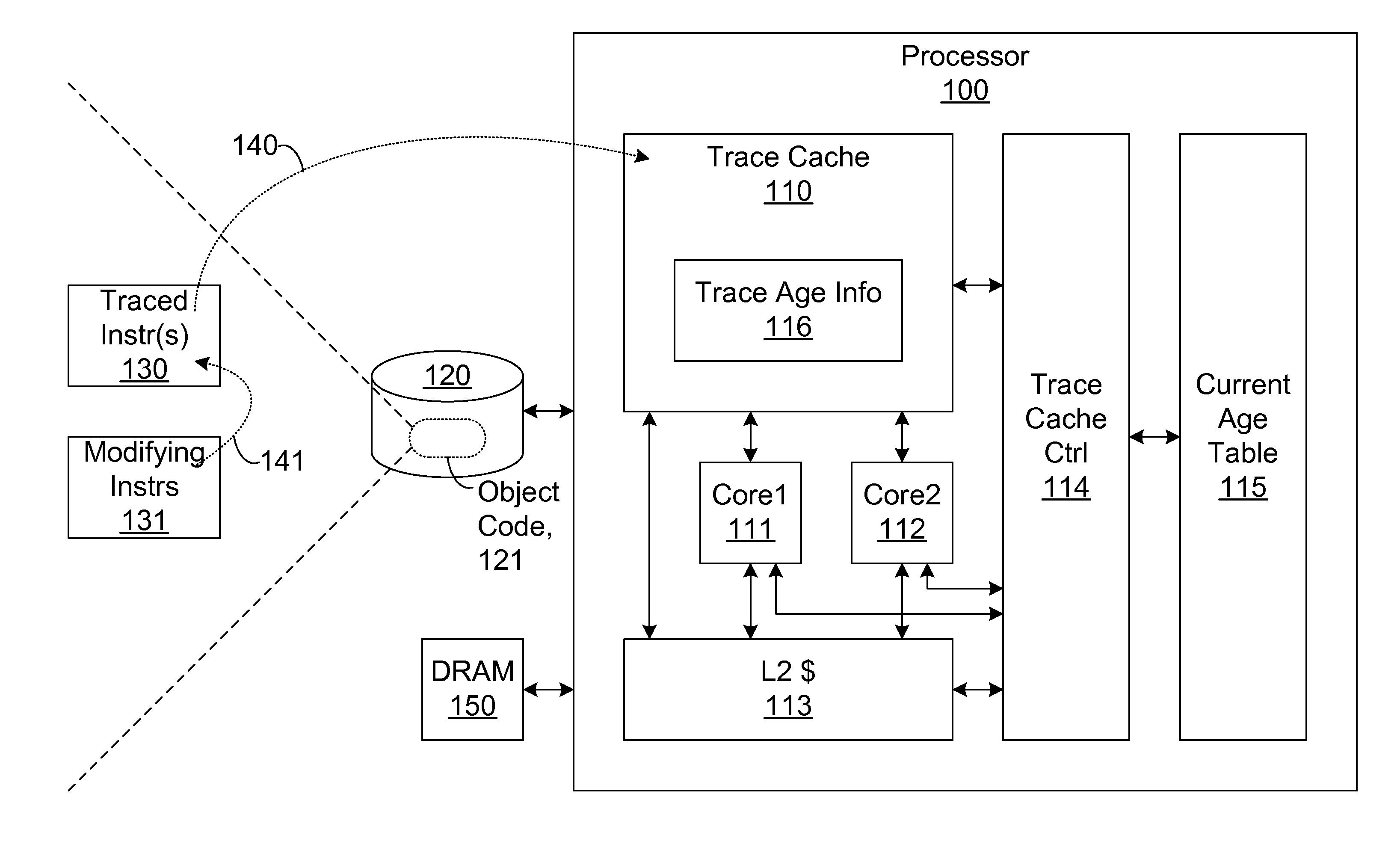
Trace cache for efficient self-modifying code processing
A trace cache for efficient self-modifying code processing enables selective invalidation of entries of the trace cache, advantageously retaining some of the entries in the trace cache even during self-modifying code events. Instructions underlying trace cache entries are monitored for modification in groups, enabling advantageously reduced hardware. Associated with trace cache entries are one or more translation ages, determined when the entry is built by sampling current ages of memory blocks underlying the entry. When the entry is accessed and micro-operations therein are processed, each of the translation ages of the accessed entry are compared with the current ages of the memory blocks underlying the accessed entry. If any of the age comparisons fail, then the micro-operations are aborted and the entry is invalidated. When any portion of a memory block is modified, the current age of the modified memory block is incremented.
Owner:SUN MICROSYSTEMS INC
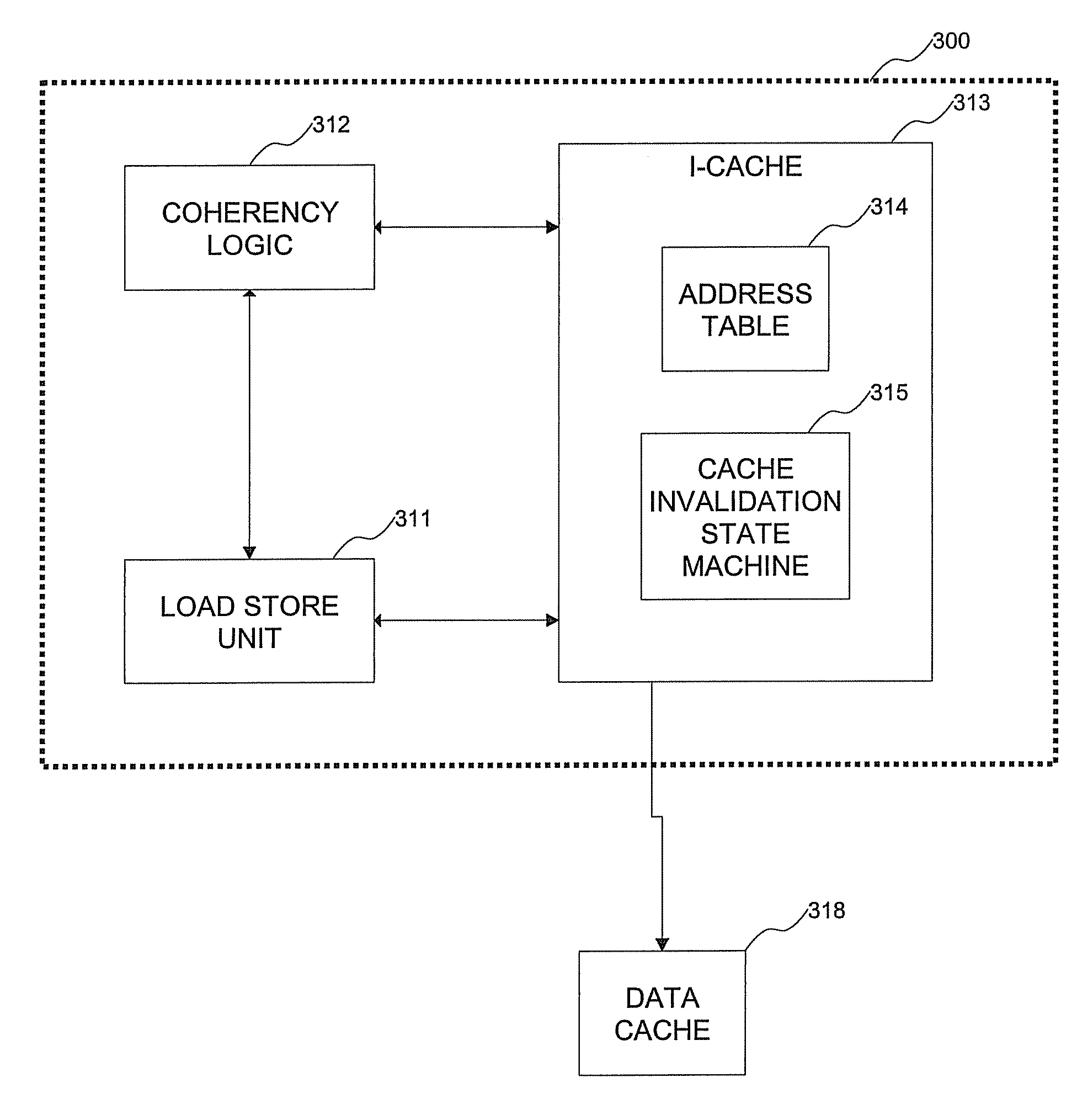
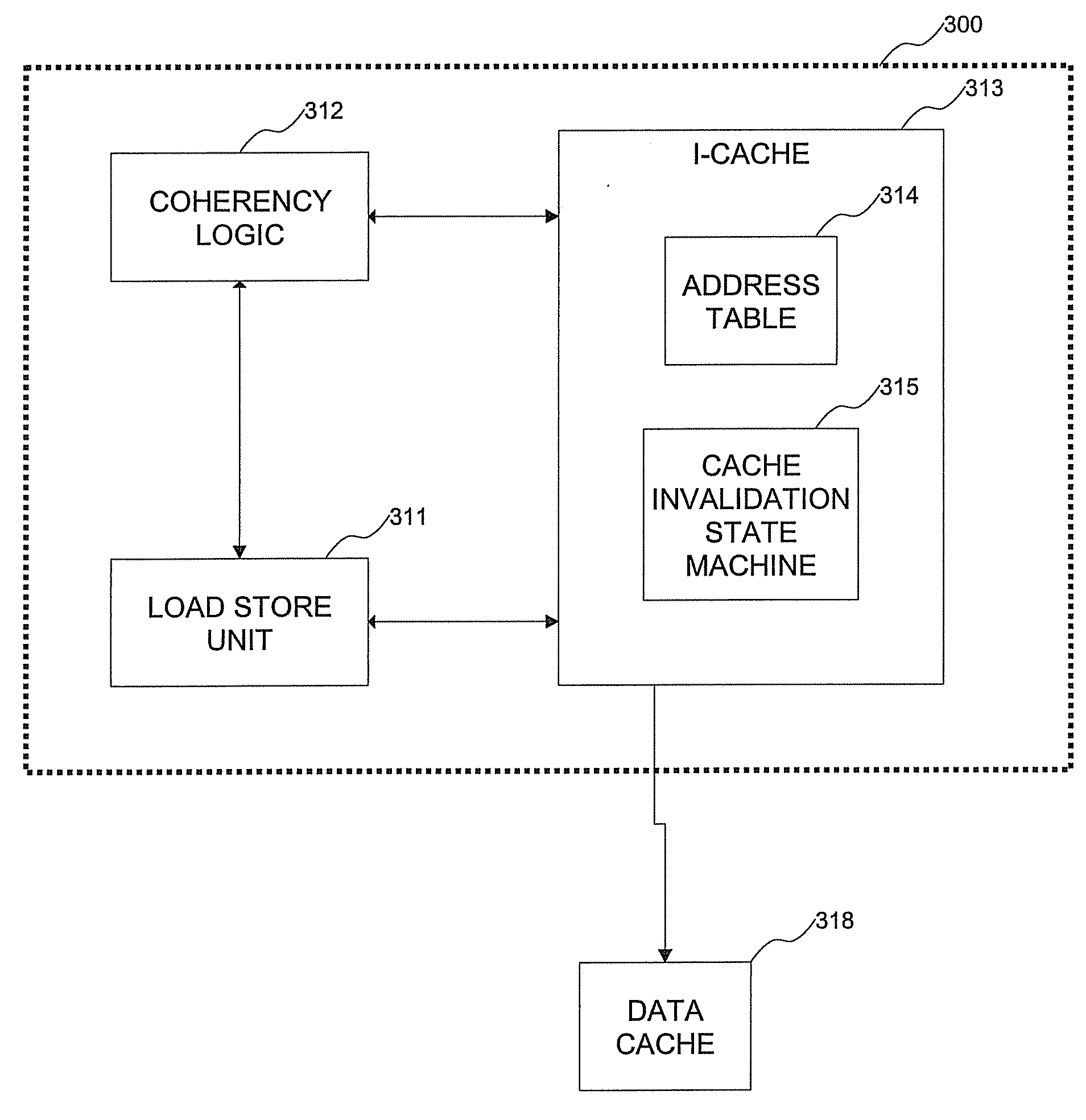
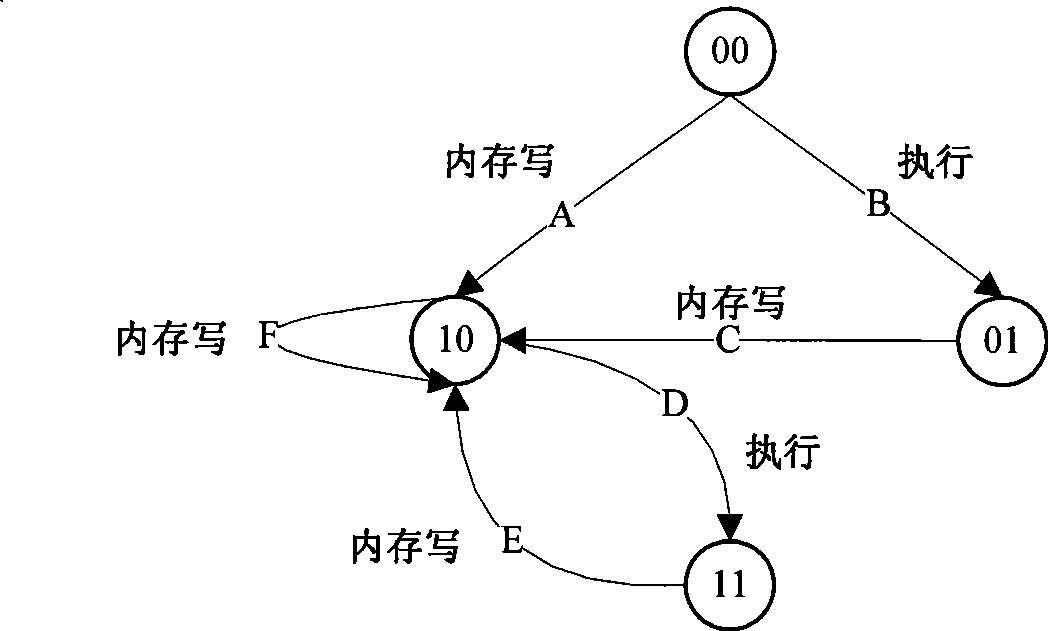
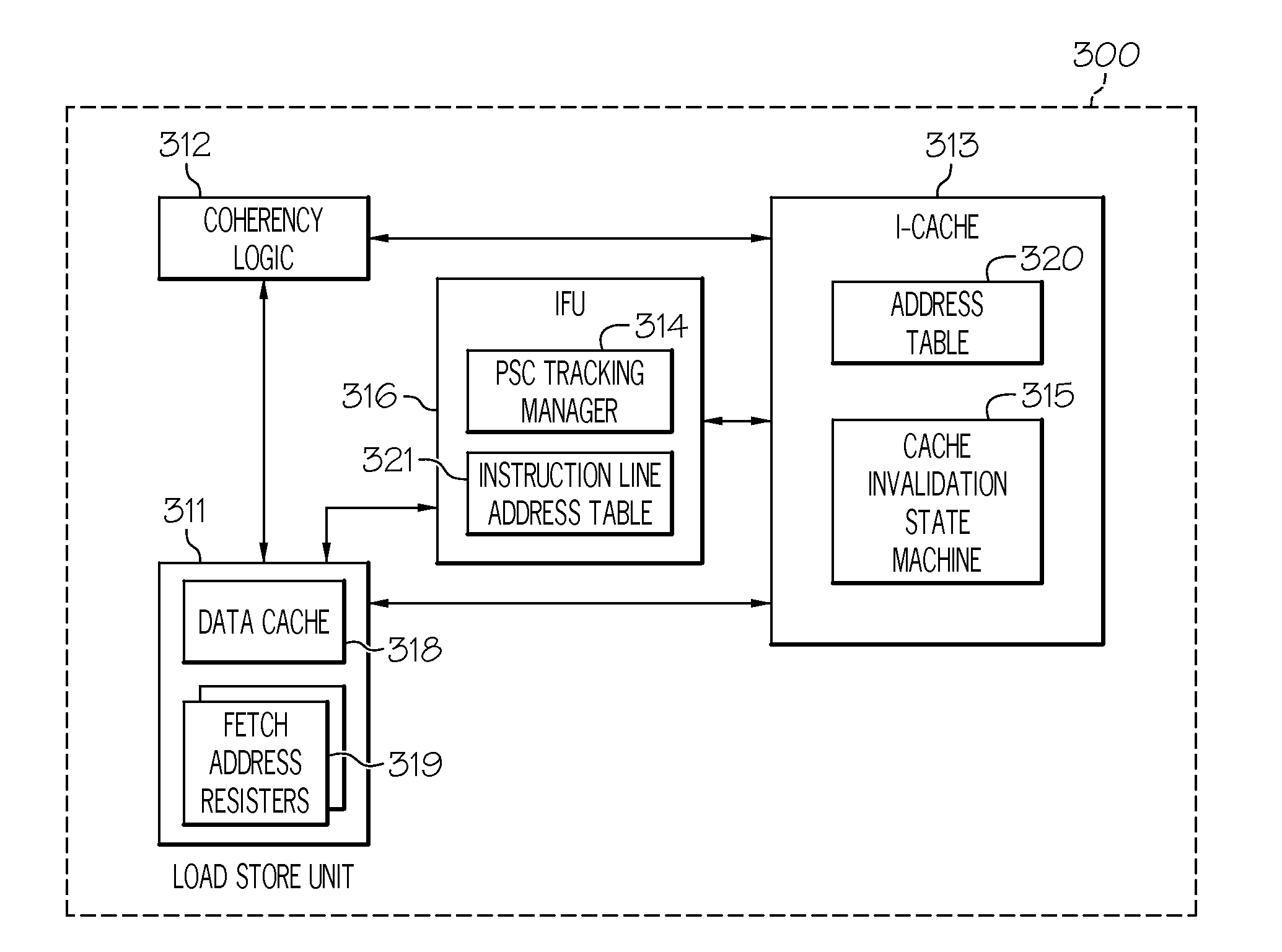
Method and system for handling cache coherency for self-modifying code
A method for handling cache coherency includes allocating a tag when a cache line is not exclusive in a data cache for a store operation, and sending the tag and an exclusive fetch for the line to coherency logic. An invalidation request is sent within a minimum amount of time to an I-cache, preferably only if it has fetched to the line and has not been invalidated since, which request includes an address to be invalidated, the tag, and an indicator specifying the line is for a PSC operation. The method further includes comparing the request address against stored addresses of prefetched instructions, and in response to a match, sending a match indicator and the tag to an LSU, within a maximum amount of time. The match indicator is timed, relative to exclusive data return, such that the LSU can discard prefetched instructions following execution of the store operation that stores to a line subject to an exclusive data return, and for which the match is indicated.
Owner:IBM CORP
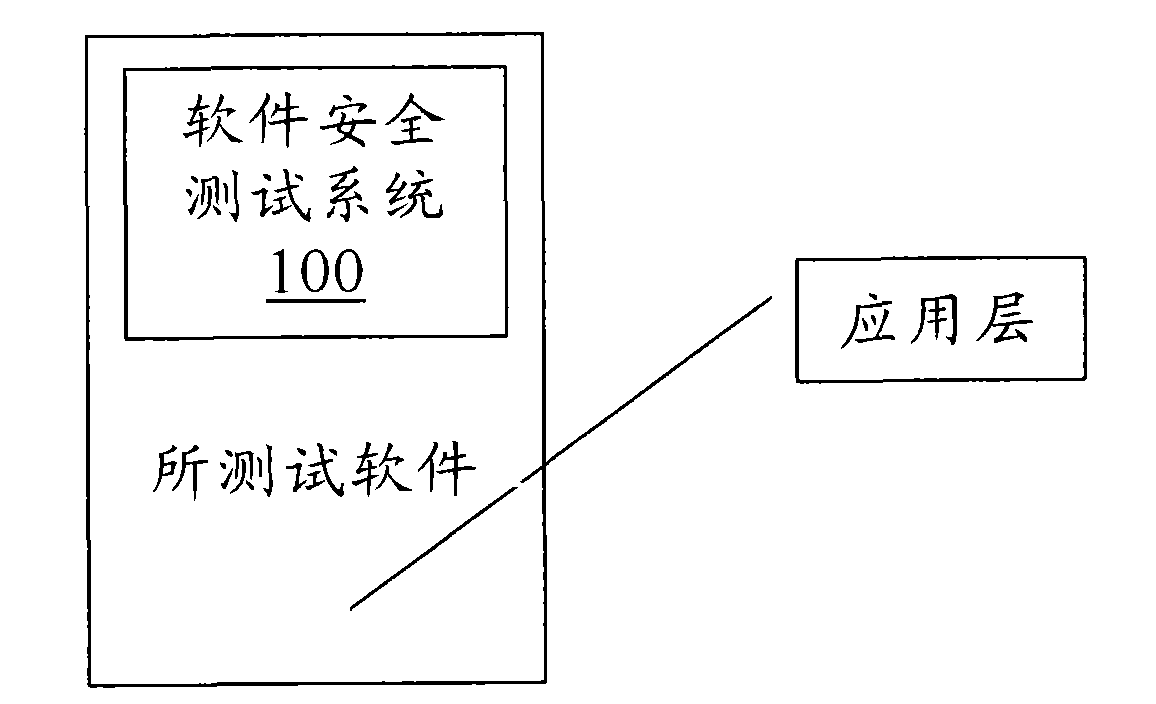
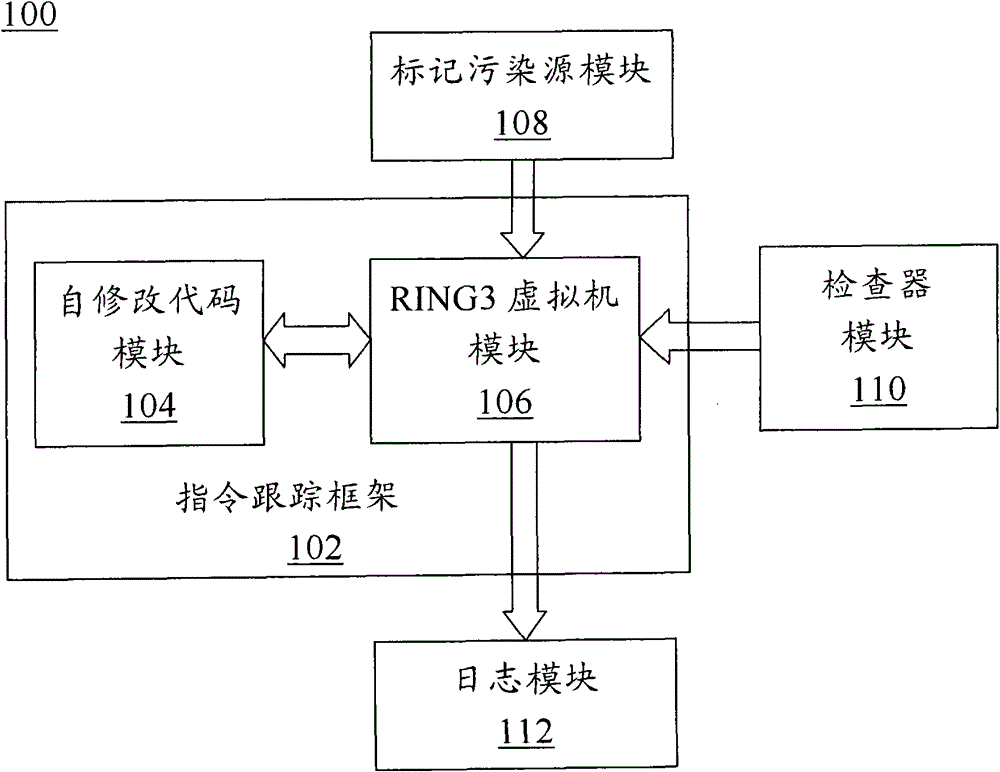
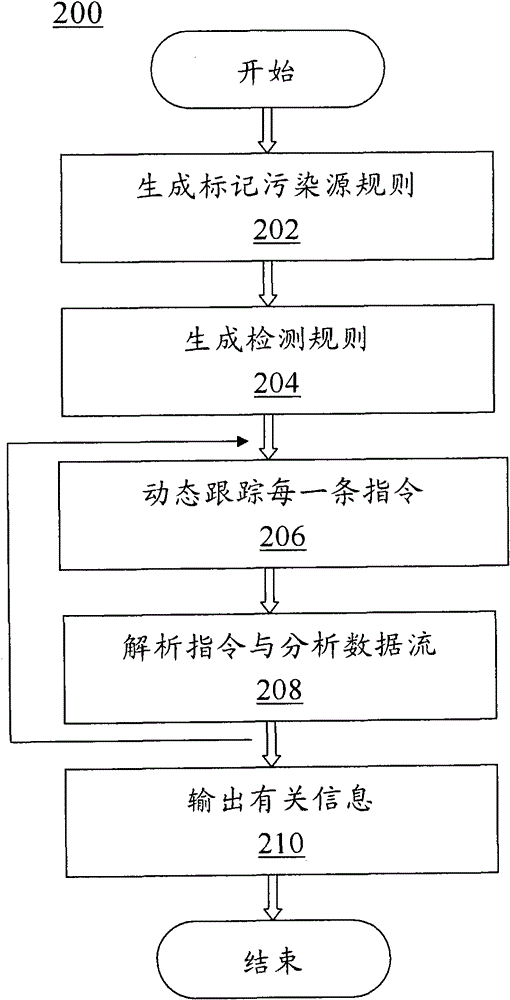
Software security testing system and method based on dynamic taint propagation
ActiveCN102081719ARealize real-time dynamic trackingSoftware testing/debuggingPlatform integrity maintainanceSelf-modifying codeCode module
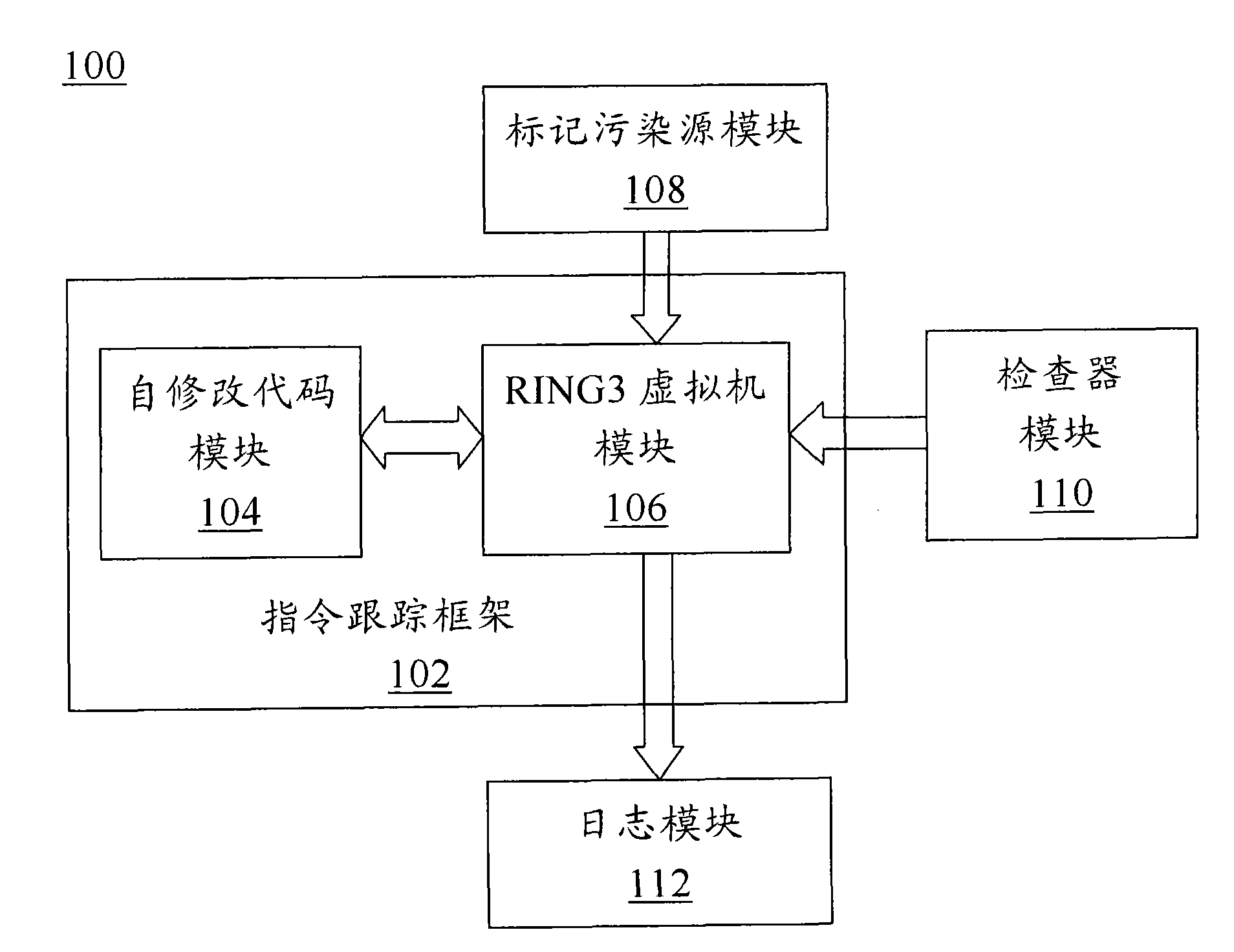
The invention discloses a software security testing system and method based on dynamic taint propagation. The system comprises a taint source marking module (108) used for generating a taint source marking rule, a detector module (110) used for generating a detection rule, a self-correction code module (104) used for dynamically tracing each binary command of software to be tested by using a self-correction code technology, an RING3 virtual machine module (106) used for analyzing each binary command of the software to be tested by using an RING3 virtual machine and analyzing the flowing direction of the data carried by the command so as to realize taint propagation, as well as calling the taint source marking rule to mark a taint source and calling the detection rule to detect each binary command of the software to be tested, and a log module (112) used for outputting related information violating the detection rule. The software security testing system and method provided by the invention can be used for improving the detection rate of software and reducing false alarm rate and missed alarm rate.
Owner:阿里巴巴华北技术有限公司
Method and system for handling cache coherency for self-modifying code
A method for handling cache coherency includes allocating a tag when a cache line is not exclusive in a data cache for a store operation, and sending the tag and an exclusive fetch for the line to coherency logic. An invalidation request is sent within a minimum amount of time to an I-cache, preferably only if it has fetched to the line and has not been invalidated since, which request includes an address to be invalidated, the tag, and an indicator specifying the line is for a PSC operation. The method further includes comparing the request address against stored addresses of prefetched instructions, and in response to a match, sending a match indicator and the tag to an LSU, within a maximum amount of time. The match indicator is timed, relative to exclusive data return, such that the LSU can discard prefetched instructions following execution of the store operation that stores to a line subject to an exclusive data return, and for which the match is indicated.
Owner:IBM CORP
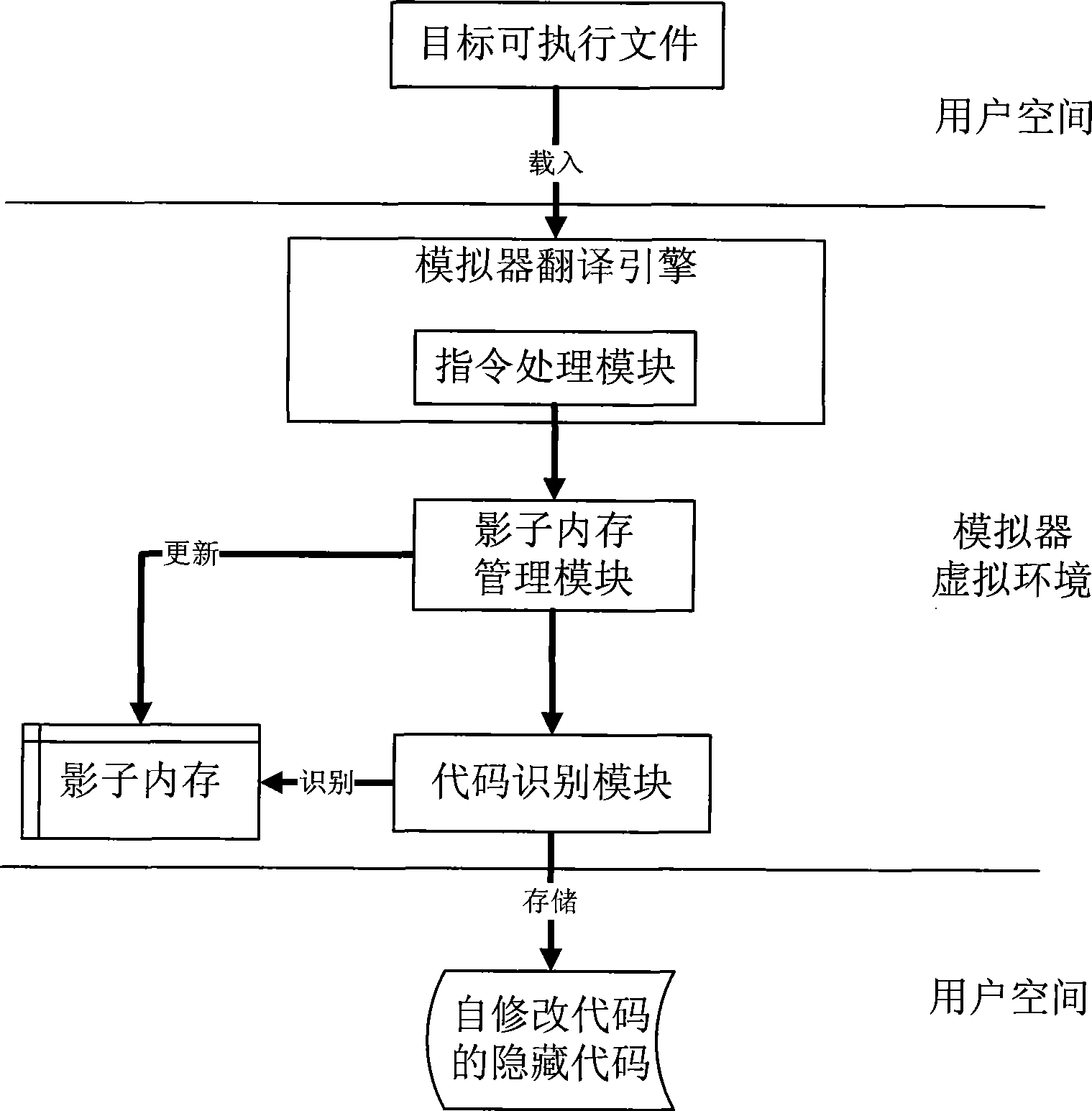
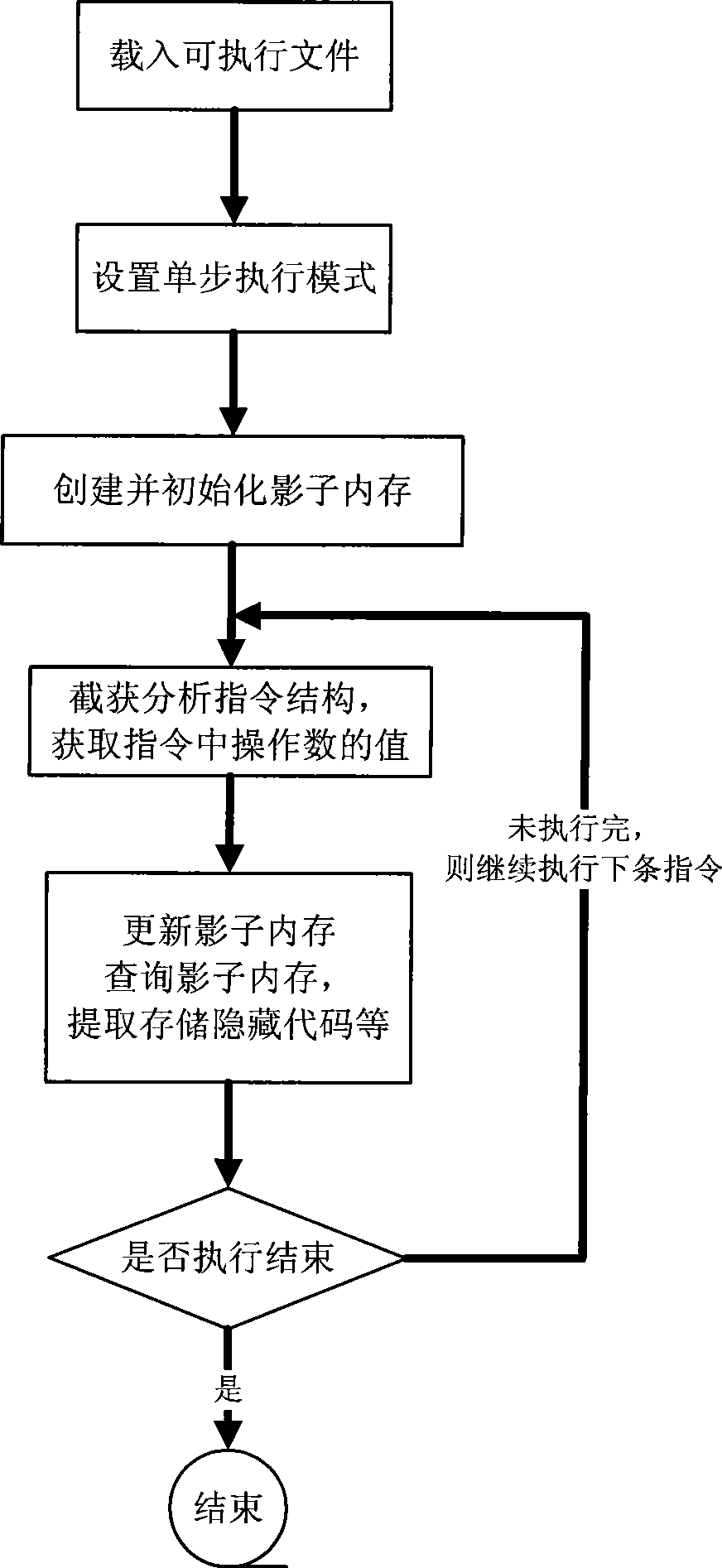
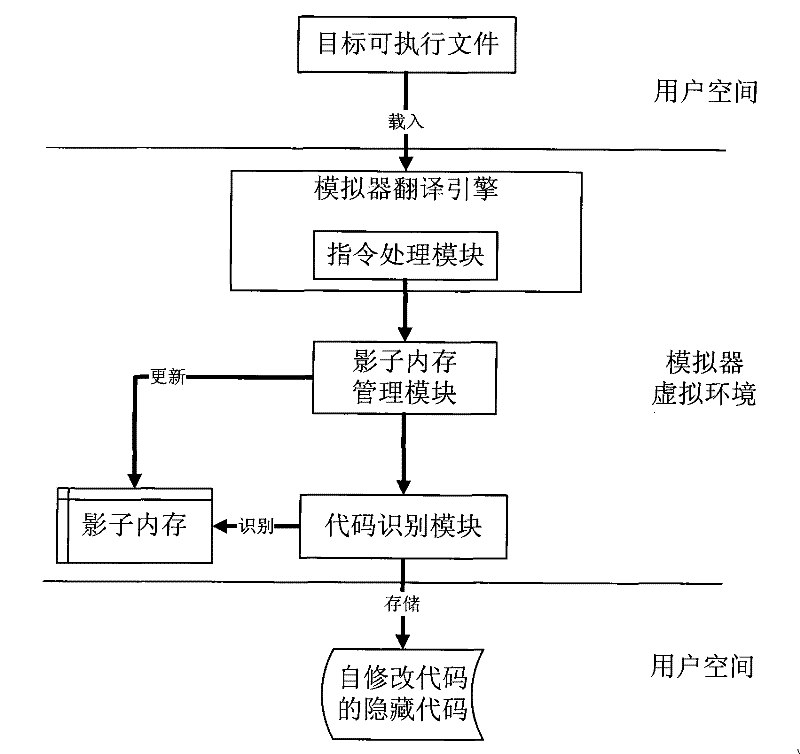
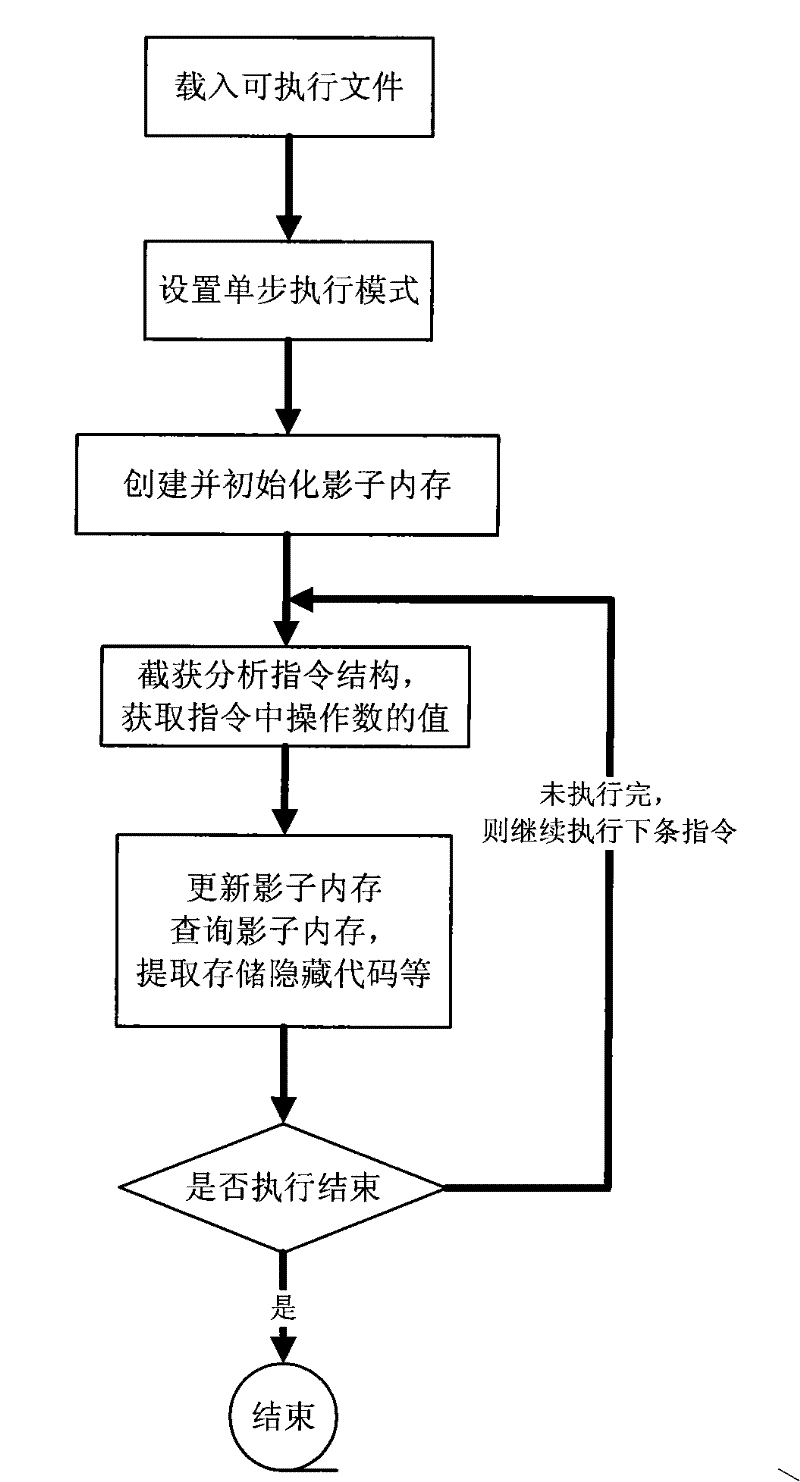
Self-modifying code identification method based on hardware emulator
ActiveCN101458630AImprove analysis efficiencyHigh transparencyProgram controlProgram/content distribution protectionSelf-modifying codeSecurity measurement
The invention belongs to the technical field of software security measurement and evaluation, especially relates to a self-modifying code recognition method based on a hardware simulator. The invention is provided with a marker in the hardware simulator in order to only execute a target executable file by one step and capture a virtual system execute instruction, the information in the process can be executed by using a shadow memory monitoring program, the code which is dynamically released into the memory and is executed can be recognized and executed in the course of program execution, so that data information of the analysis target can be acquired. The data acquisition of the invention is implemented by the simulation hardware, is not executed by placing the malevolence code on a true CPU, so the actual system can not be affected. The invention adopts the hardware simulator as a dynamic analysis platform, which can improve the transparency between the analysis platform and the code and can effectively defend against the detection of the code.
Owner:INST OF SOFTWARE - CHINESE ACAD OF SCI
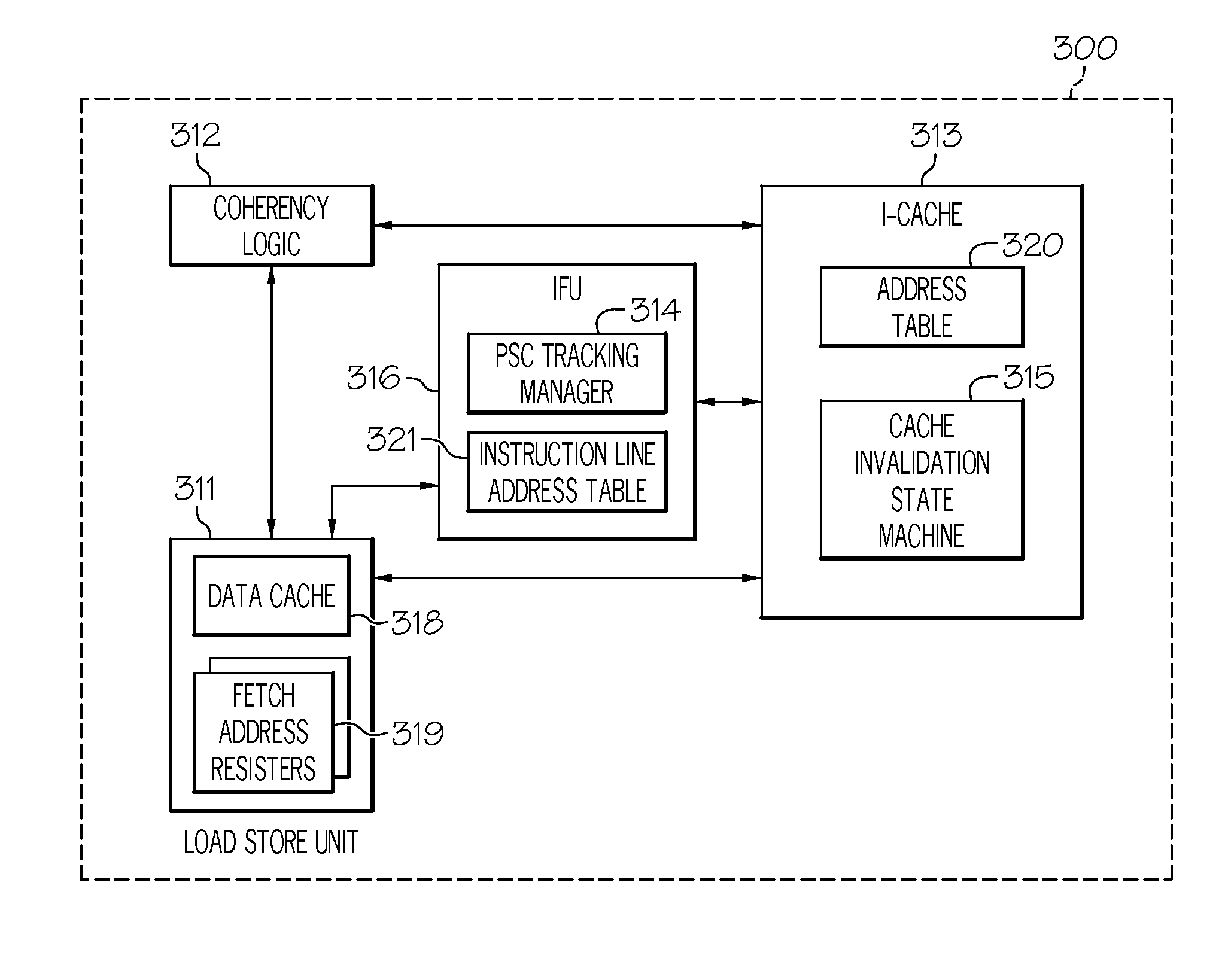
Managing cache coherency for self-modifying code in an out-of-order execution system
InactiveUS8417890B2Memory architecture accessing/allocationDigital computer detailsSelf-modifying codeCache invalidation
A method, system, and computer program product for managing cache coherency for self-modifying code in an out-of-order execution system are disclosed. A program-store-compare (PSC) tracking manager identifies a set of addresses of pending instructions in an address table that match an address requested to be invalidated by a cache invalidation request. The PSC tracking manager receives a fetch address register identifier associated with a fetch address register for the cache invalidation request. The fetch address register is associated with the set of addresses and is a PSC tracking resource reserved by a load store unit (LSU) to monitor an exclusive fetch for a cache line in a high level cache. The PSC tracking manager determines that the set of entries in an instruction line address table associated with the set of addresses is invalid and instructs the LSU to free the fetch address register.
Owner:INT BUSINESS MASCH CORP
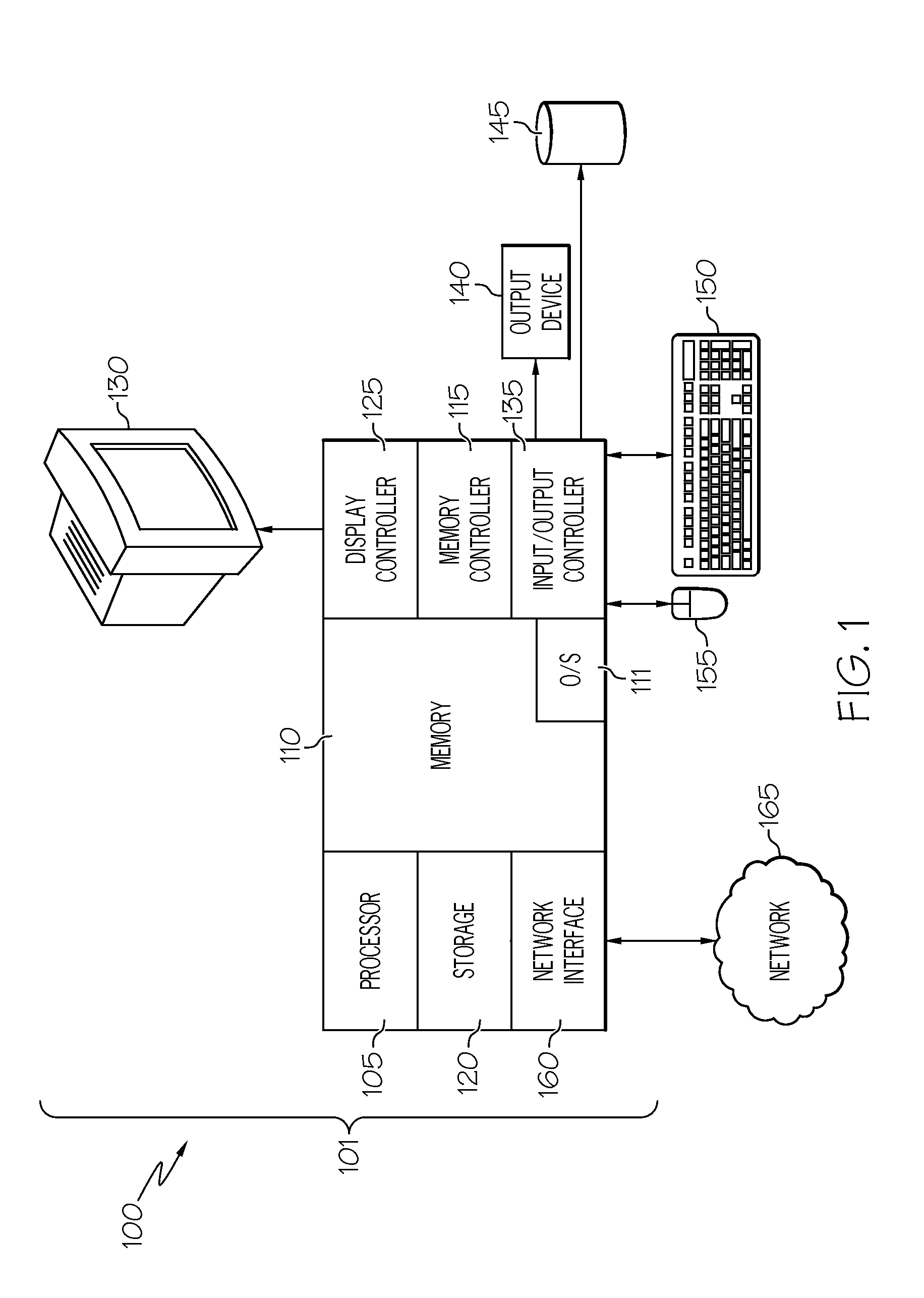
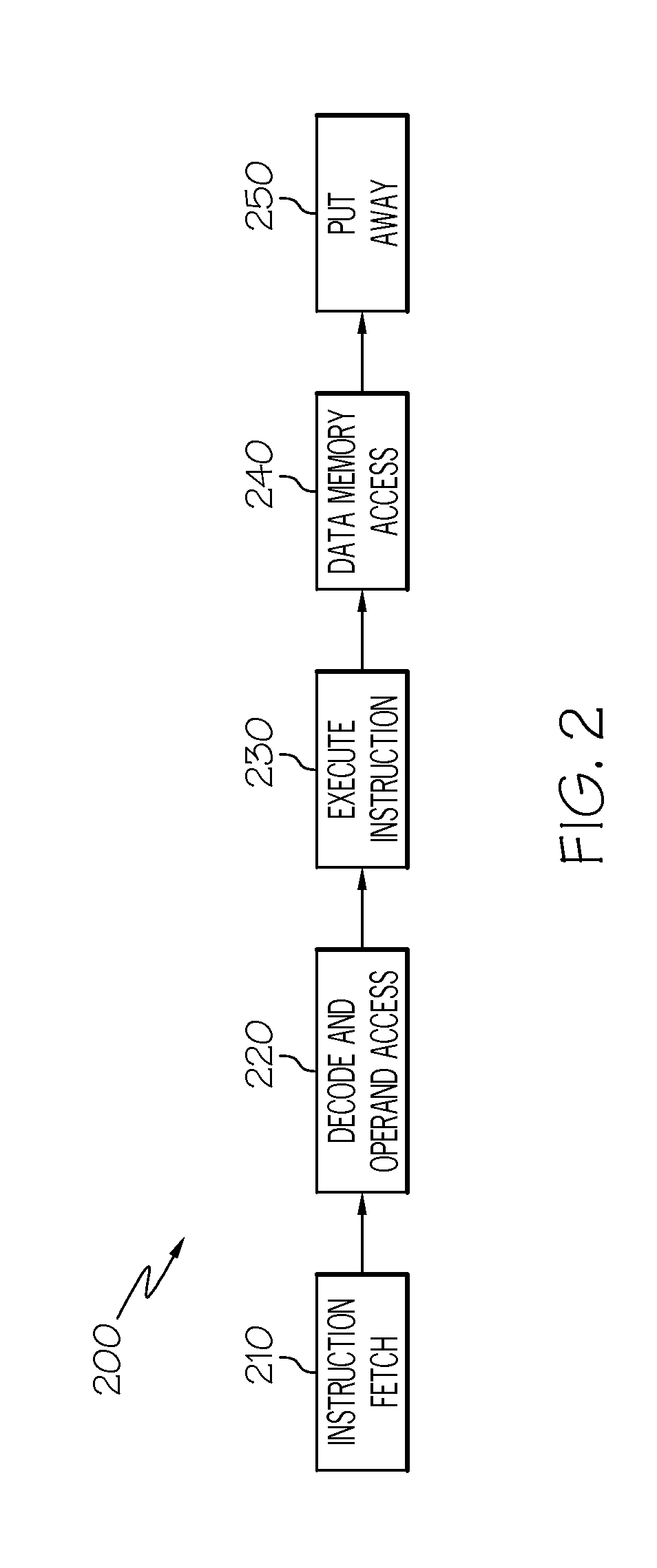
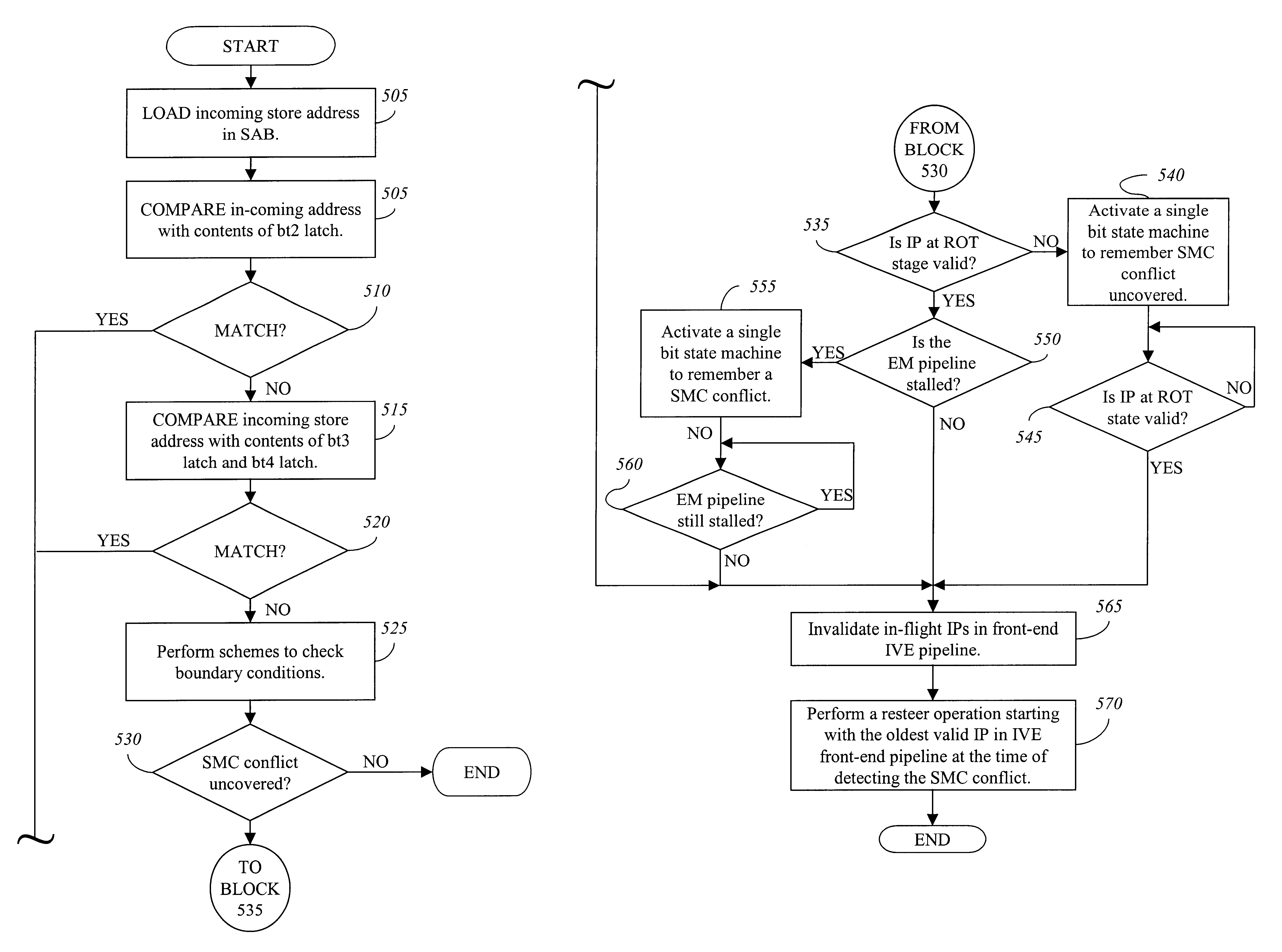
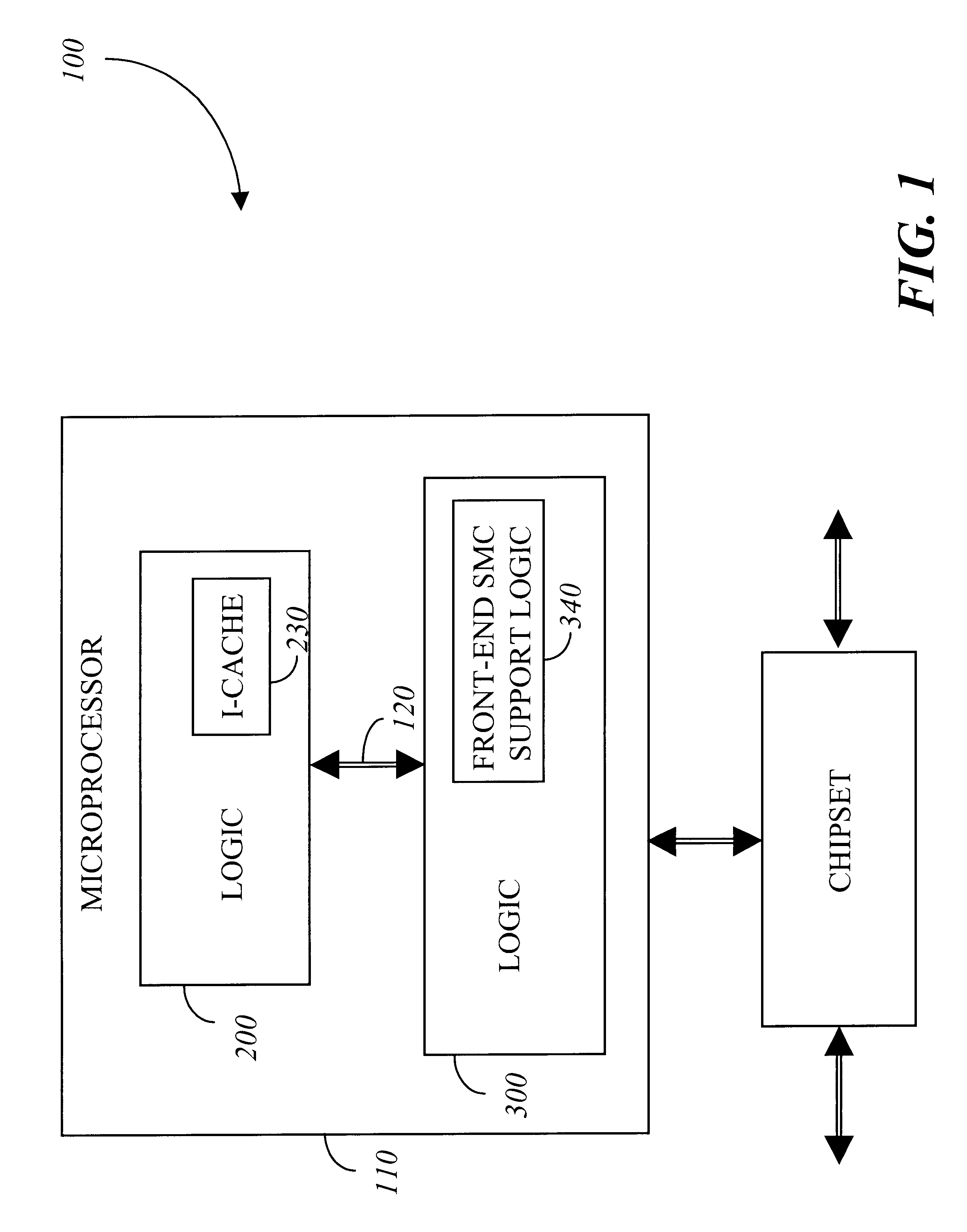
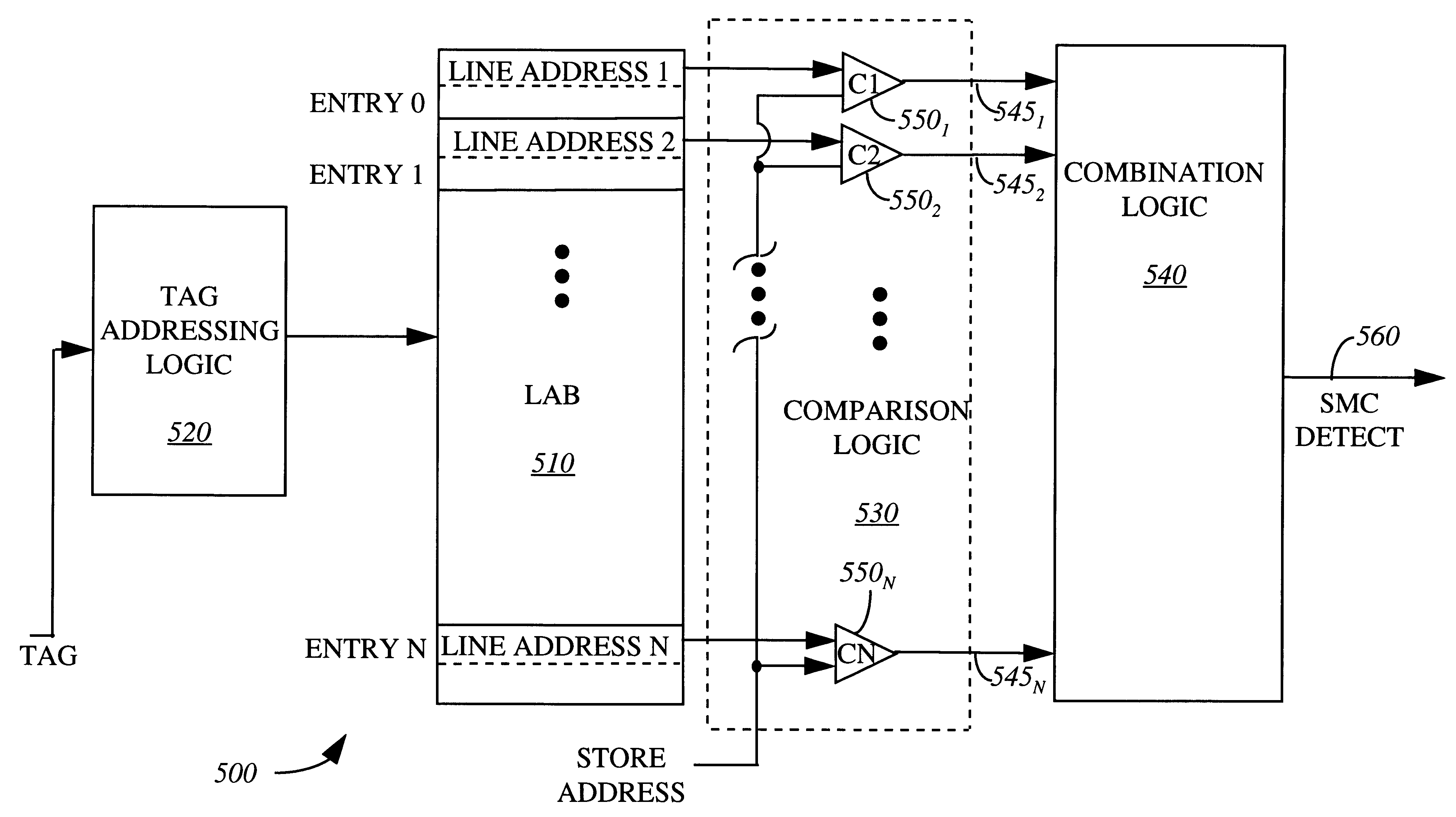
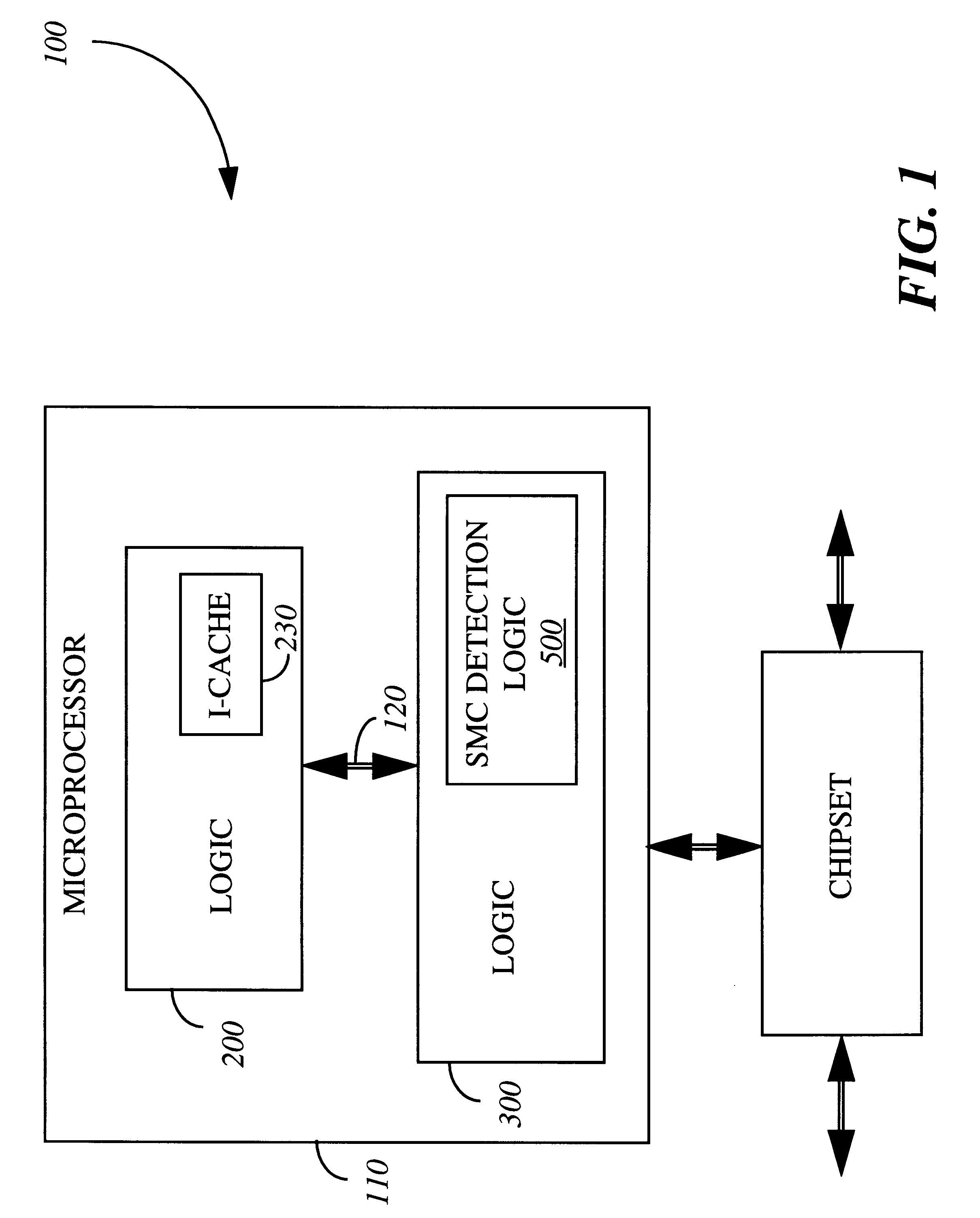
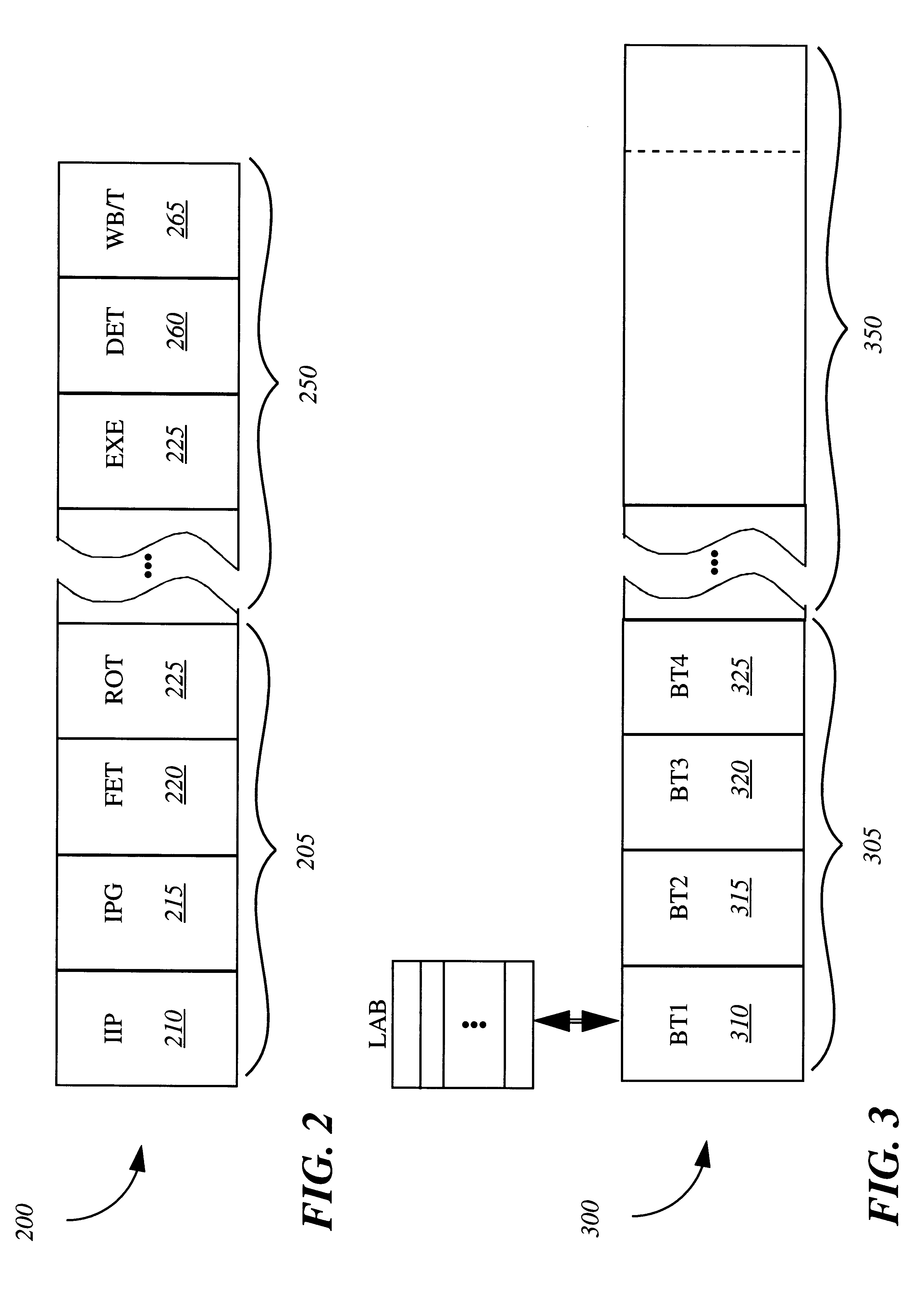
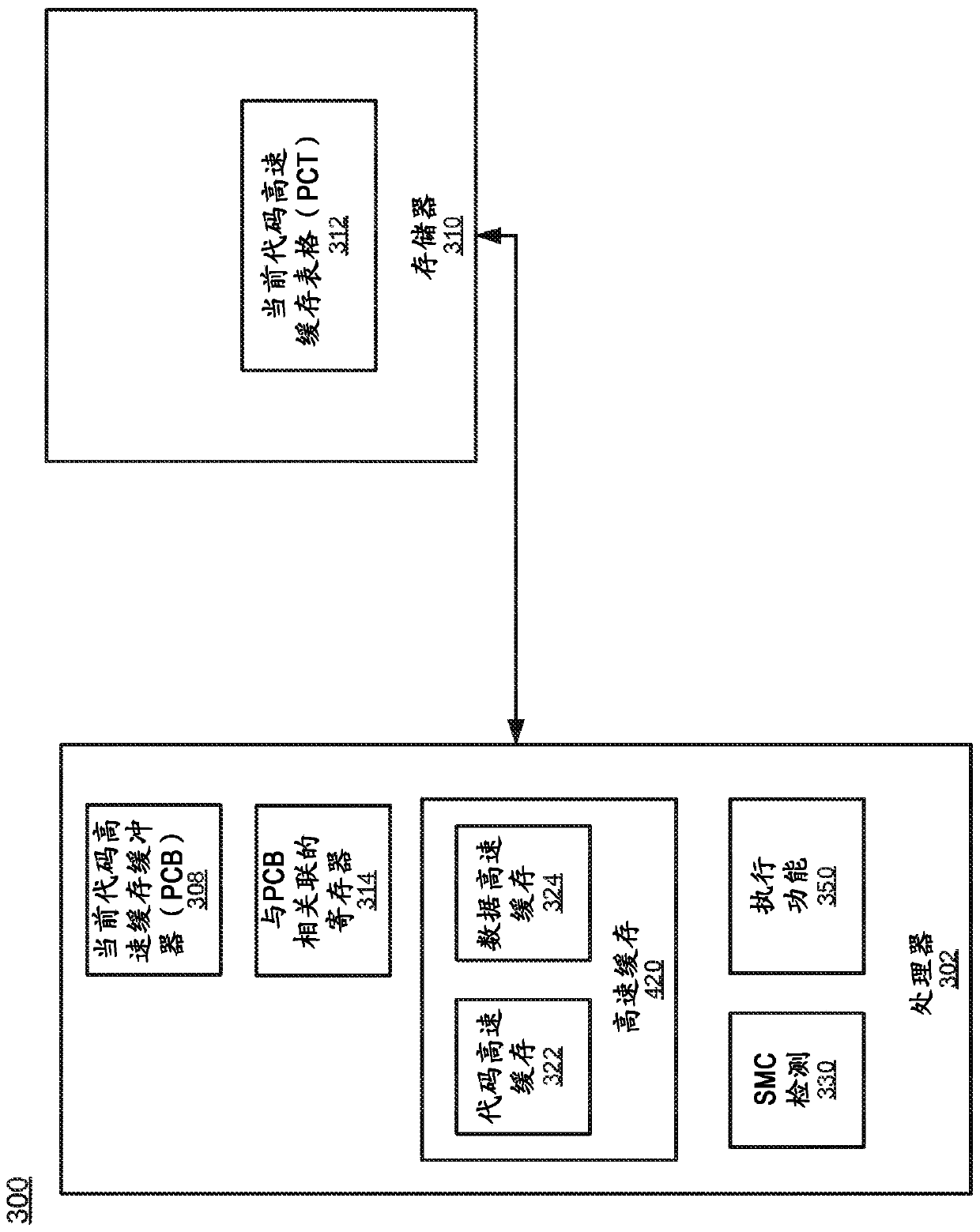
Apparatus and method for detecting and handling self-modifying code conflicts in an instruction fetch pipeline
InactiveUS6405307B1Digital computer detailsConcurrent instruction executionSelf-modifying codeInstruction pipeline
A system and method are described for detecting and recovering from self-modifying code (SMC) conflicts. In one embodiment, detection is accomplished by accessing the contents of a memory, configured to contain a number of recently executed instructions, to obtain an address. This address is compared to information propagating through a front-end pipeline of an instruction pipeline. The instruction pipeline includes the front-end pipeline to support loading and propagation of information through the instruction pipeline and a back-end pipeline to support execution of instructions along with writeback to the memory. If the address matches the information propagating through the front-end pipeline, a SMC conflict has occurred and at least some of the pipelined information is invalidated.
Owner:INTEL CORP
Partitioning code in program code conversion
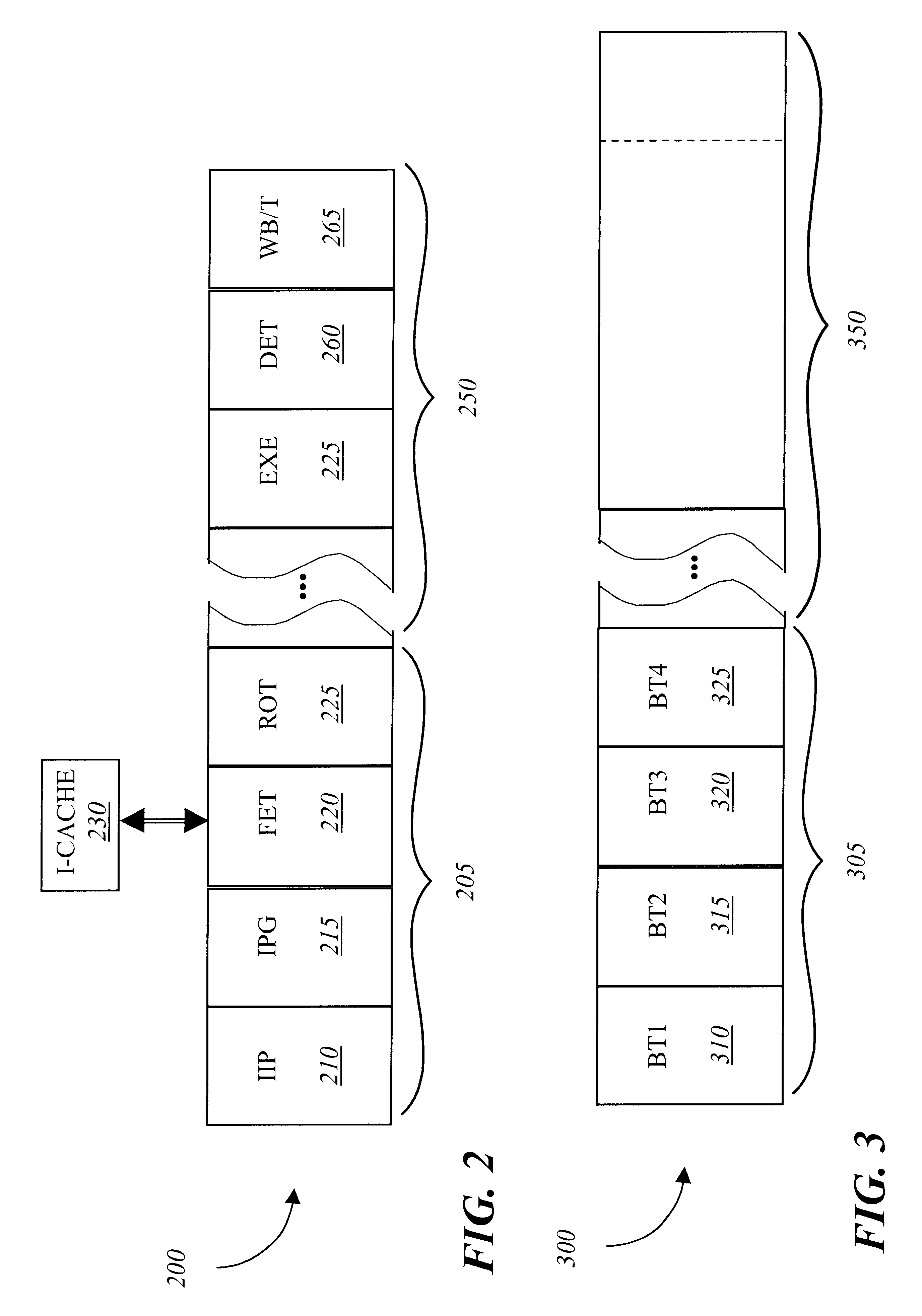
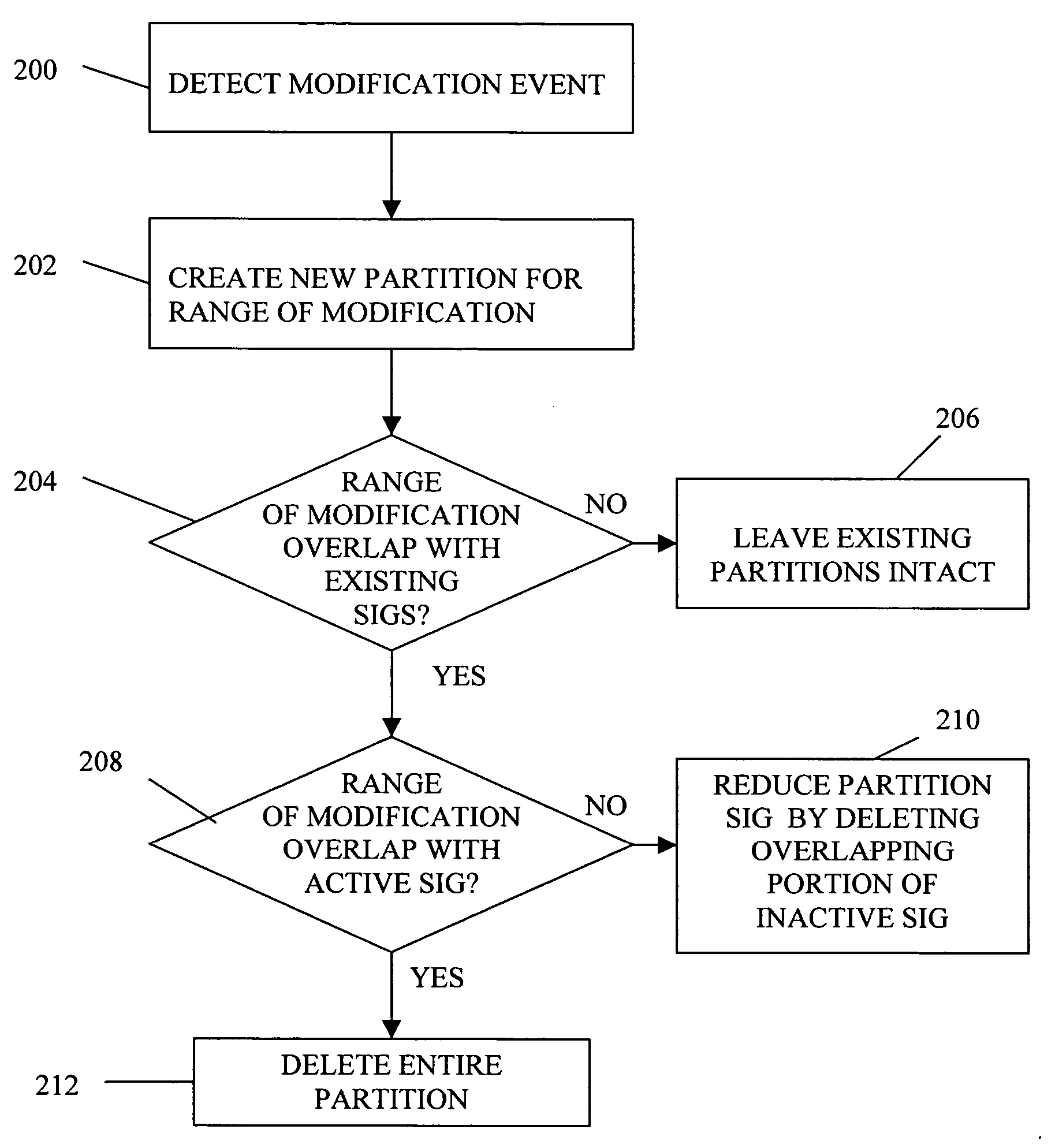
ActiveUS7934204B2Limited amountProgram loading/initiatingSoftware reuseSelf-modifying codeCode Translation
A partitioning technique utilized by a translator to divide the subject code space into regions, referred to hereafter as partitions, where each partition contains a distinct set of basic blocks of subject code and corresponding target code. The partitioning technique divides the translator's representation of subject code and subject code translations into non-overlapping regions of subject memory. In this manner, when the subject program modifies subject code, only those partitions actually affected by the self-modifying code need be discarded and all translations in unaffected partitions can be kept. This partitioning technique is advantageous in limiting the amount of target code that must be retranslated in response to self-modifying code operation. In another process, the partitioning technique allows multithreaded subject programs that also involve self-modifying code to perform code modification in a thread-safe manner.
Owner:INT BUSINESS MASCH CORP
Managing cache coherency for self-modifying code in an out-of-order execution system
InactiveUS20110307662A1Memory architecture accessing/allocationMemory adressing/allocation/relocationSelf-modifying codeCache invalidation
A method, system, and computer program product for managing cache coherency for self-modifying code in an out-of-order execution system are disclosed. A program-store-compare (PSC) tracking manager identifies a set of addresses of pending instructions in an address table that match an address requested to be invalidated by a cache invalidation request. The PSC tracking manager receives a fetch address register identifier associated with a fetch address register for the cache invalidation request. The fetch address register is associated with the set of addresses and is a PSC tracking resource reserved by a load store unit (LSU) to monitor an exclusive fetch for a cache line in a high level cache. The PSC tracking manager determines that the set of entries in an instruction line address table associated with the set of addresses is invalid and instructs the LSU to free the fetch address register.
Owner:IBM CORP
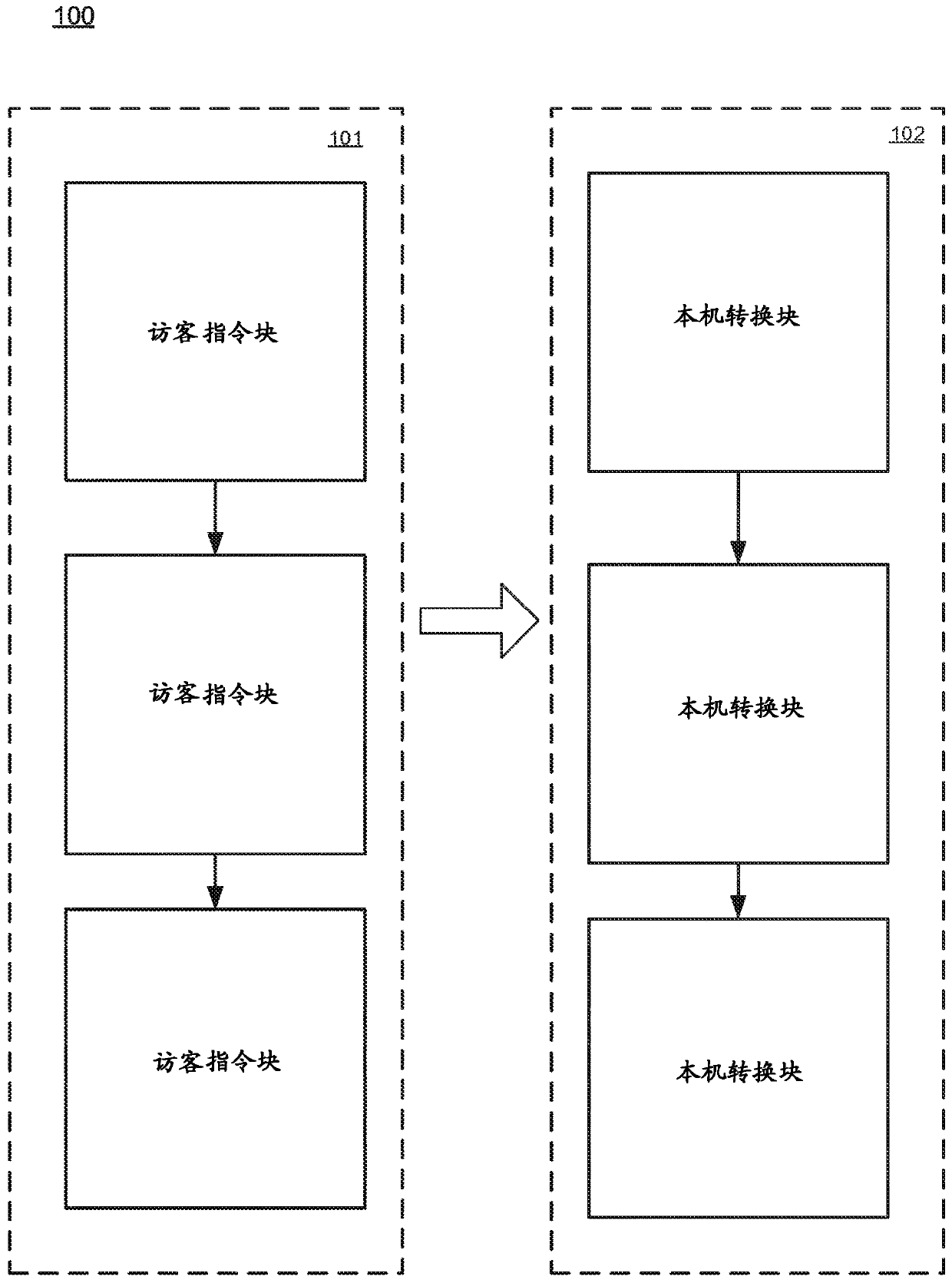
Method and apparatus for providing hardware support for self-modifying code
InactiveCN106796506ARuntime instruction translationConcurrent instruction executionSelf-modifying codeComputer hardware
A method and apparatus for providing support for self modifying guest code. The apparatus includes a memory, a hardware buffer, and a processor. The processor is configured to convert guest code to native code and store converted native code equivalent of the guest code into a code cache portion of the processor. The processor is further configured to maintain the hardware buffer configured for tracking respective locations of converted code in a code cache. The hardware buffer is updated based a respective access to a respective location in the memory associated with a respective location of converted code in the code cache. The processor is further configured to perform a request to modify a memory location after accessing the hardware buffer.
Owner:INTEL CORP
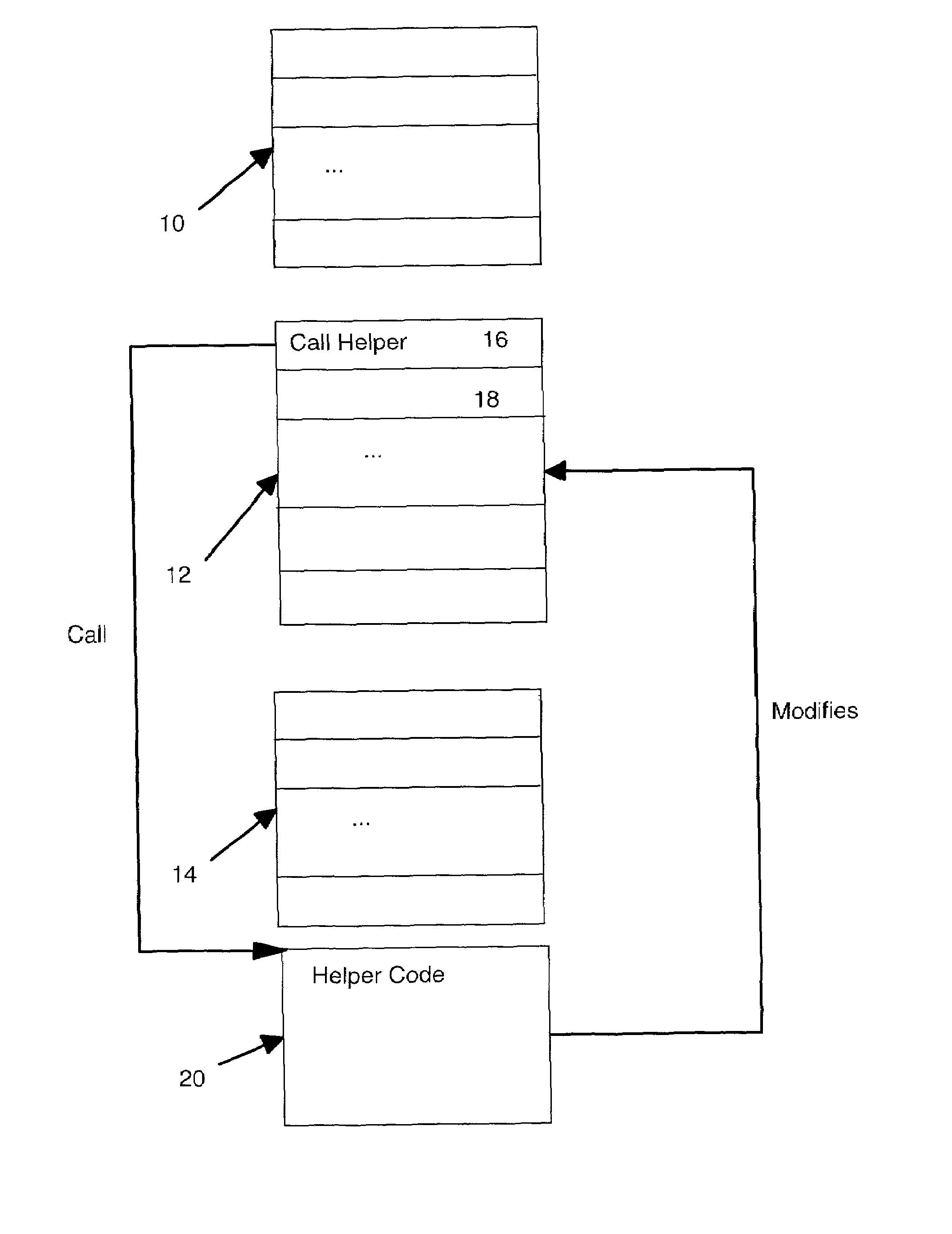
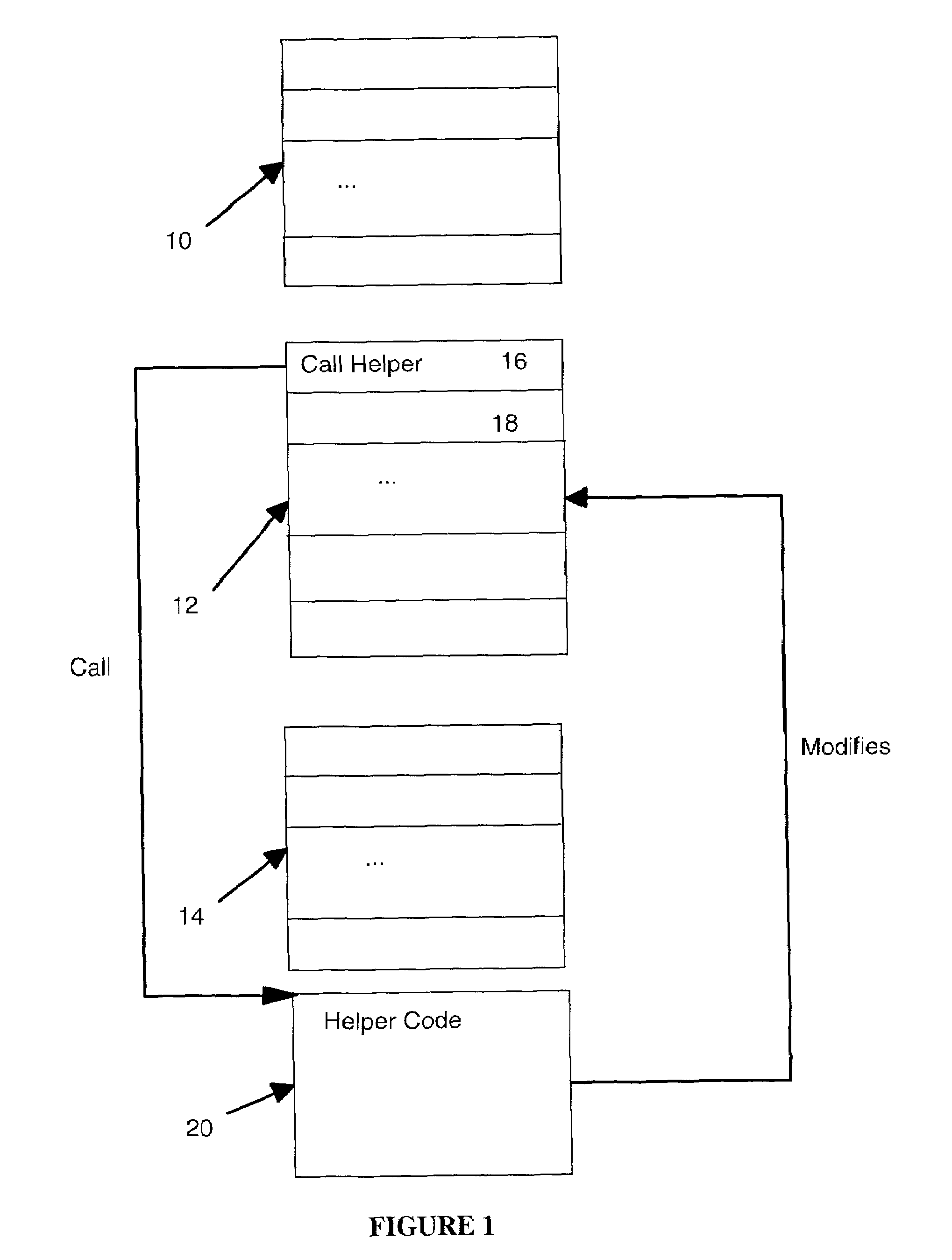
Efficient locking for thread-safe self-modifying code
InactiveUS7185337B2Data processing applicationsProgram synchronisationCoding blockSelf-modifying code
A locking mechanism for use in a multi-thread environment supporting self-modifying code in which modifications to the code are made at runtime. The locking mechanism having associated helper code accessed by a call from the first instruction address in the code block. The helper code calculating the binary encoding for the call instruction and using an atomic compare and exchange instruction to compare the calculated binary encoding with the actual contents of the first instruction address. Where there is a match, a self loop instruction is written to the first instruction address to lock the specified code block for subsequent threads. The helper code contains instructions to resolve the references in the specified block. The last such instruction is an atomic store operation to replace the self loop instruction at the first instruction address with the appropriate modified instruction.
Owner:IBM CORP
Selective trace cache invalidation for self-modifying code via memory aging
Selective trace cache invalidation for self-modifying code via memory aging advantageously retains some of the entries in a trace cache even during self-modifying code events. Instructions underlying trace cache entries are monitored for modification in groups, enabling advantageously reduced hardware. Associated with each trace cache entry are translation ages that are determined when the entry is built by sampling current ages of memory blocks underlying the entry. When the entry is accessed and micro-operations therein processed, the translation ages of the accessed entry are compared with the current ages of the memory blocks underlying the accessed entry. If any of the age comparisons fail, then the micro-operations are aborted and the entry is invalidated. When any portion of a memory block is modified, the current age of the modified memory block is incremented. If one of the current ages overflows, then the entire trace cache is flushed.
Owner:ORACLE AMERICAN INC
Partitioning code in program code conversion to account for self-modifying code
ActiveCN1836210AImprove understandingConcurrent instruction executionProgram loading/initiatingSelf-modifying codeCode Translation
A partitioning technique utilized by a translator to divide subject code space into partitions, where each partition contains a distinct set of basic blocks of subject code and corresponding target code. Thus the translator's representation of subject code and subject code translations is divided into non-overlapping regions of subject memory. In this manner, when the subject program modifies subject code, only those partitions actually affected by the self-modifying code need be discarded and all translations in unaffected partitions can be kept. This partitioning technique is advantageous in limiting the amount of target code that must be retranslated in response to self-modifying code operation. In another process, the partitioning technique allows multithreaded subject programs that also involve self-modifying code to perform code modification in a thread-safe manner.
Owner:INT BUSINESS MASCH CORP
System and method for tracking in-flight instructions in a pipeline
InactiveUS6237088B1Digital computer detailsConcurrent instruction executionSelf-modifying codeOperating system
An apparatus, system and method are described for tracking in-flight line addresses. Such tracking enables a determination of a self-modifying code (SMC) conflict. In one embodiment, the apparatus comprises a line address buffer and companion logic. The line address buffer contains a first plurality of line addresses. Each line address is associated with a fetched instruction pointer. The comparison logic compares a second plurality of line addresses with an address of an instruction being executed in order to detect an event.
Owner:INTEL CORP
Method and apparatus for providing hardware support to self-modifying code
InactiveCN106796506BRuntime instruction translationConcurrent instruction executionSelf-modifying codeComputer hardware
Methods and apparatus for providing support for self-modifying visitor code. The device includes memory, hardware buffers and a processor. The processor is configured to convert the guest code to native code and store the converted native code equivalent to the guest code in a code cache portion of the processor. The processor is also configured to maintain a hardware buffer configured to track a corresponding location of the translated code in the code cache. The hardware buffer is updated based on respective accesses to corresponding locations in memory associated with corresponding locations of the translated code in the code cache. The processor is also configured to execute the request to modify the memory location after accessing the hardware buffer.
Owner:INTEL CORP
Self-modifying code identification method based on hardware emulator
ActiveCN101458630BImprove analysis efficiencyHigh transparencyProgram controlProgram/content distribution protectionSelf-modifying codeSecurity measurement
The invention belongs to the technical field of software security measurement and evaluation, especially relates to a self-modifying code recognition method based on a hardware simulator. The invention is provided with a marker in the hardware simulator in order to only execute a target executable file by one step and capture a virtual system execute instruction, the information in the process can be executed by using a shadow memory monitoring program, the code which is dynamically released into the memory and is executed can be recognized and executed in the course of program execution, so that data information of the analysis target can be acquired. The data acquisition of the invention is implemented by the simulation hardware, is not executed by placing the malevolence code on a trueCPU, so the actual system can not be affected. The invention adopts the hardware simulator as a dynamic analysis platform, which can improve the transparency between the analysis platform and the code and can effectively defend against the detection of the code.
Owner:INST OF SOFTWARE - CHINESE ACAD OF SCI
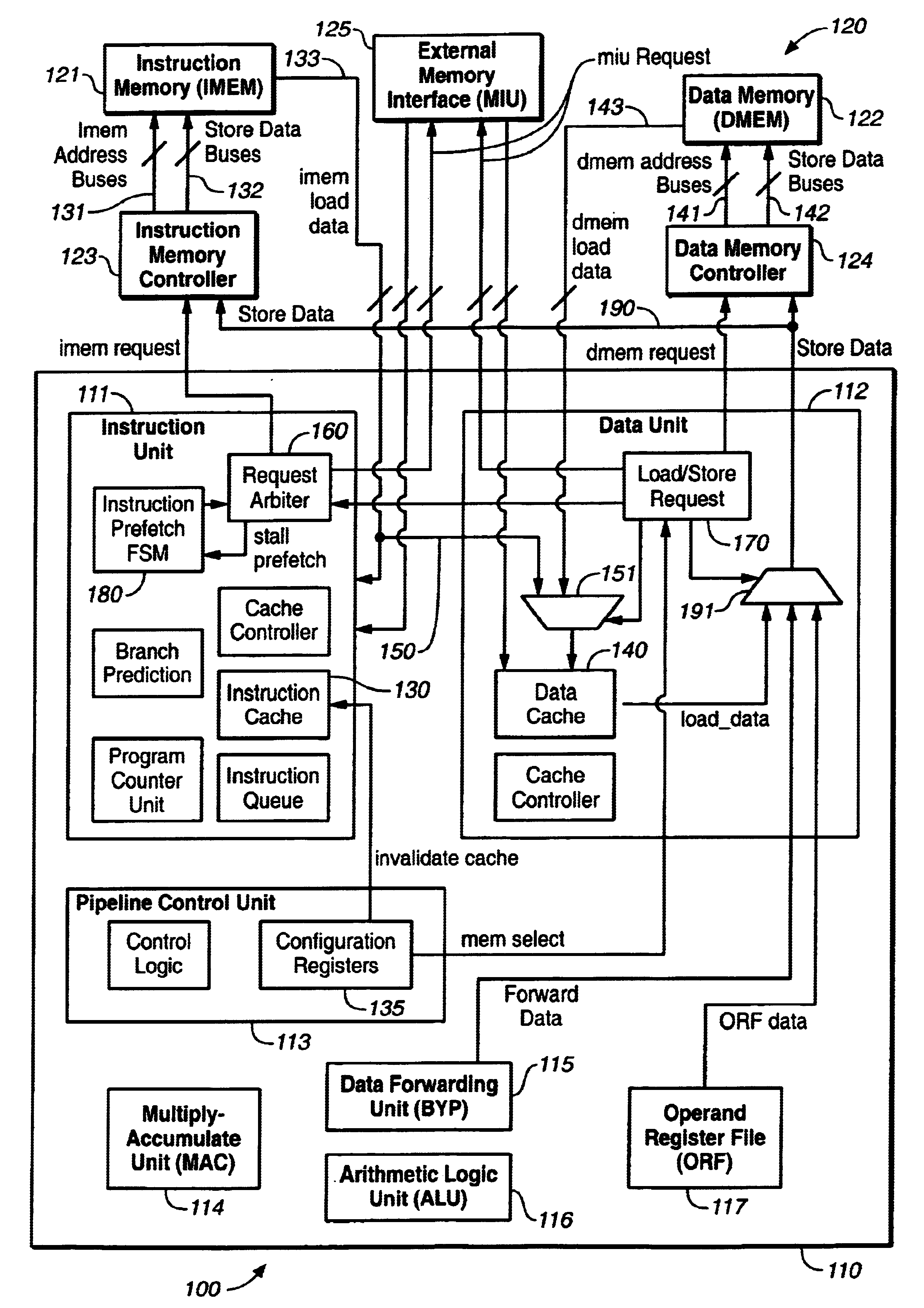
Mechanism for supporting self-modifying code in a harvard architecture digital signal processor and method of operation thereof
InactiveUS6871247B1Impact processor performanceRaise priorityGeneral purpose stored program computerConcurrent instruction executionInstruction memorySelf-modifying code
For use in a processor having separate instruction and data buses, separate instruction and data memories and separate instruction and data units, a mechanism for, and method of, supporting self-modifying code and a digital signal processor incorporating the mechanism or the method. In one embodiment, the mechanism includes: (1) a crosstie bus coupling the instruction bus and the data unit and (2) a request arbiter, coupled between the instruction and data units, that arbitrates requests therefrom for access to the instruction memory.
Owner:VERISILICON HLDGCO LTD
Self-modifying code detection method and device based on binary translation
ActiveCN109710267BEasy to detectImprove efficiencyBinary to binaryMemory systemsSelf-modifying codePhysical address
Owner:康烁
Method and apparatus for processing self-modifying codes
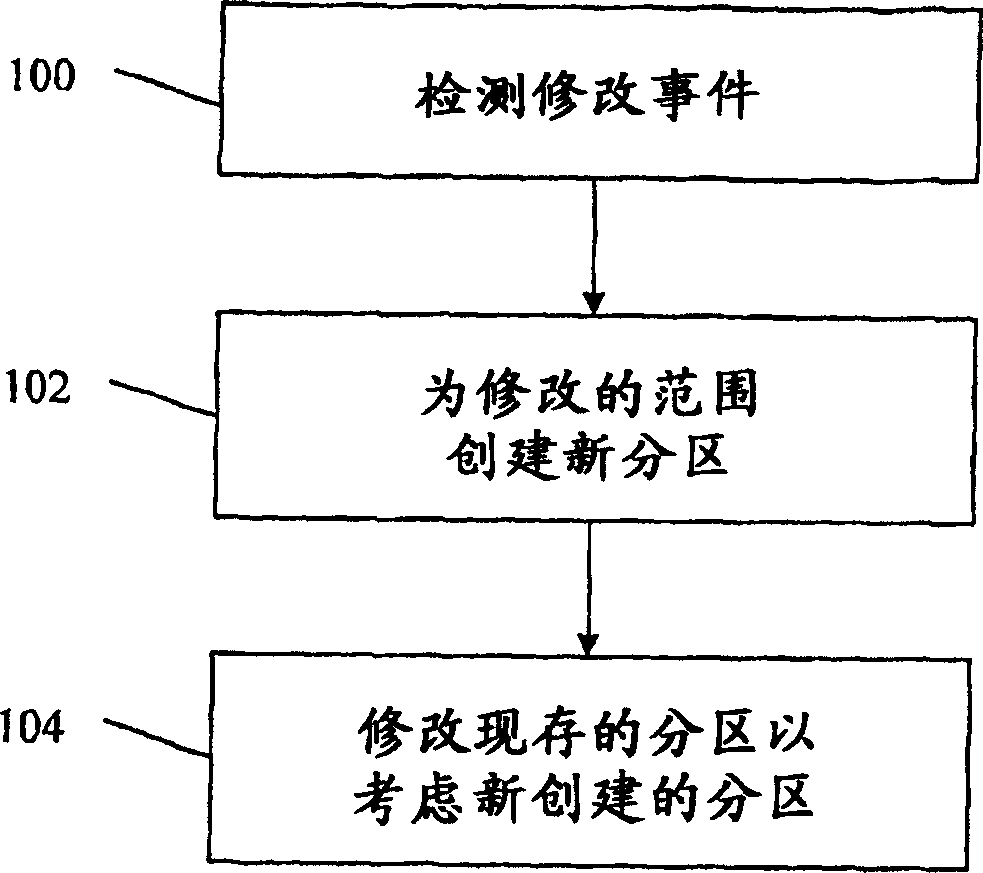
PendingCN110178115AInstruction analysisConcurrent instruction executionEngineeringSelf-modifying code
A method of handling self-modifying codes is presented. The method is performed by computer processor and comprises: receiving a fetch block of instruction data from an instruction fetch buffer; before transmitting the fetch block of instruction data to a decoding unit of the computer processor, determining whether the fetch block includes instruction data of self-modifying codes; responsive to determining that the fetch block includes instruction data of self-modifying codes, transmitting a flush signal to reset one or more internal buffers of the computer processor.
Owner:ALIBABA GRP HLDG LTD
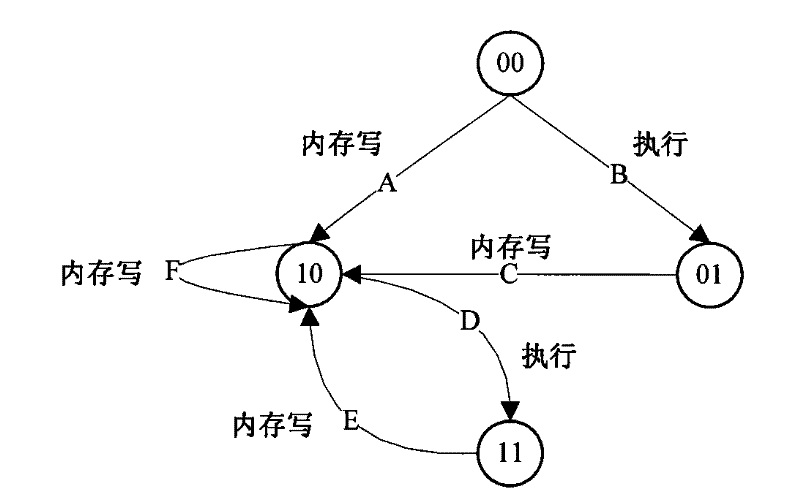
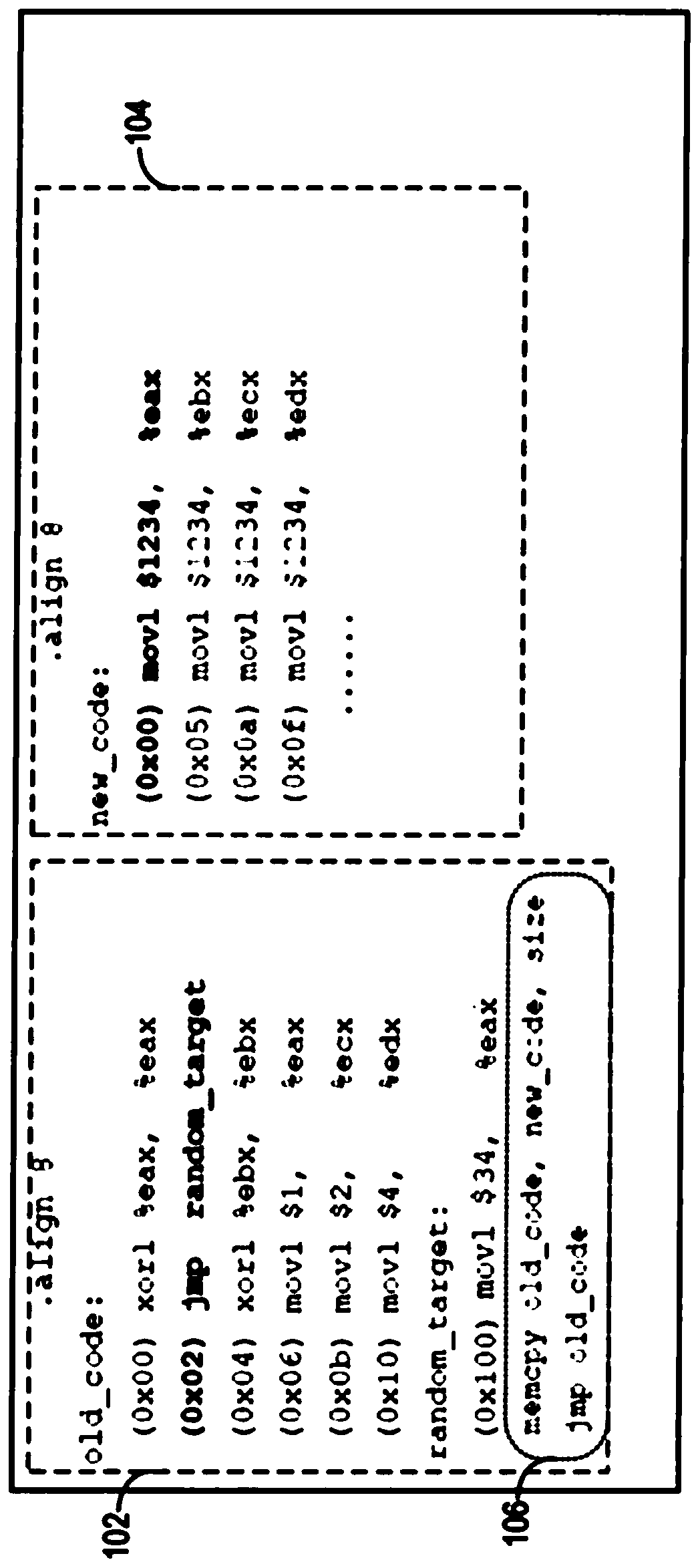
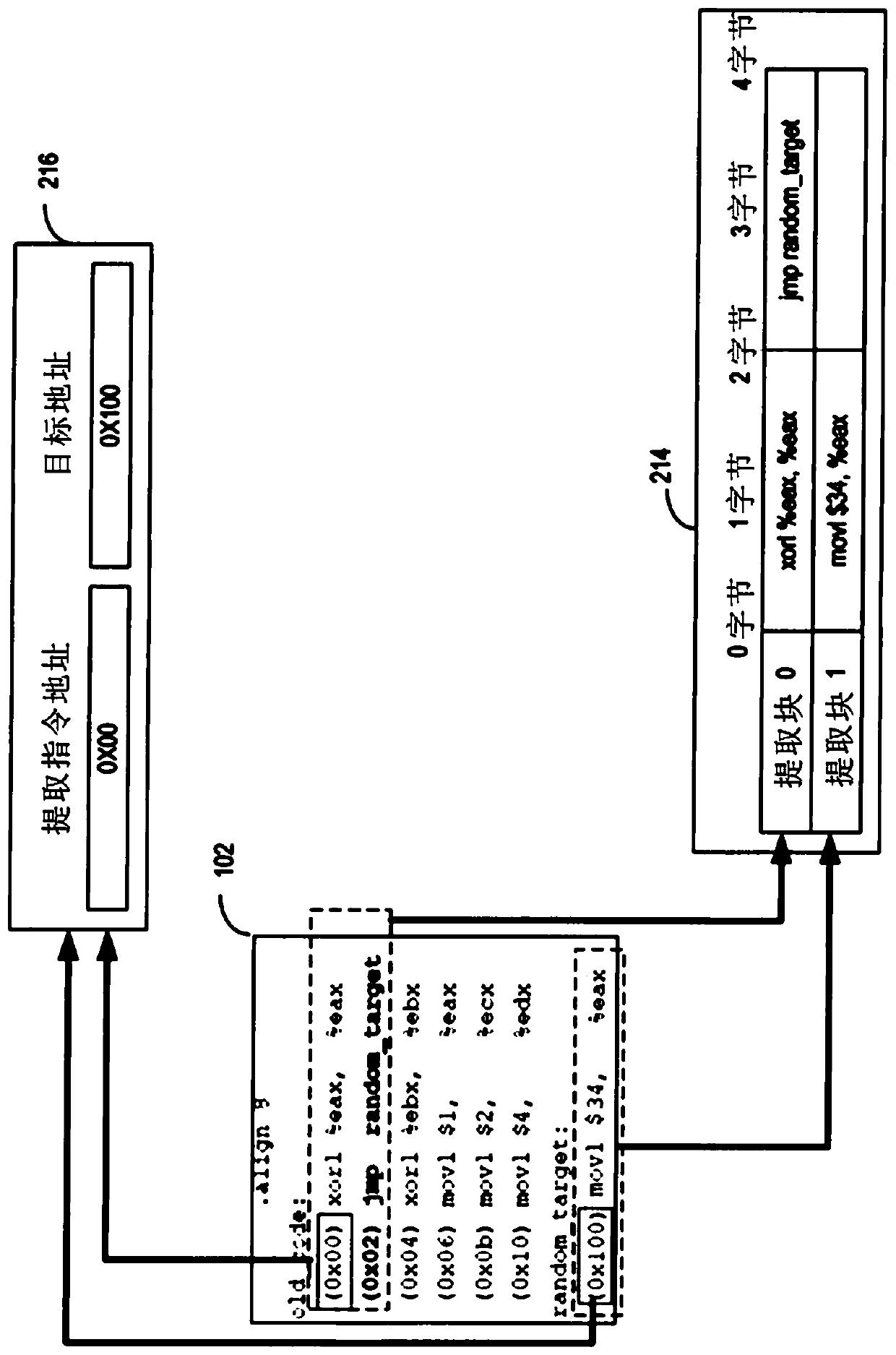
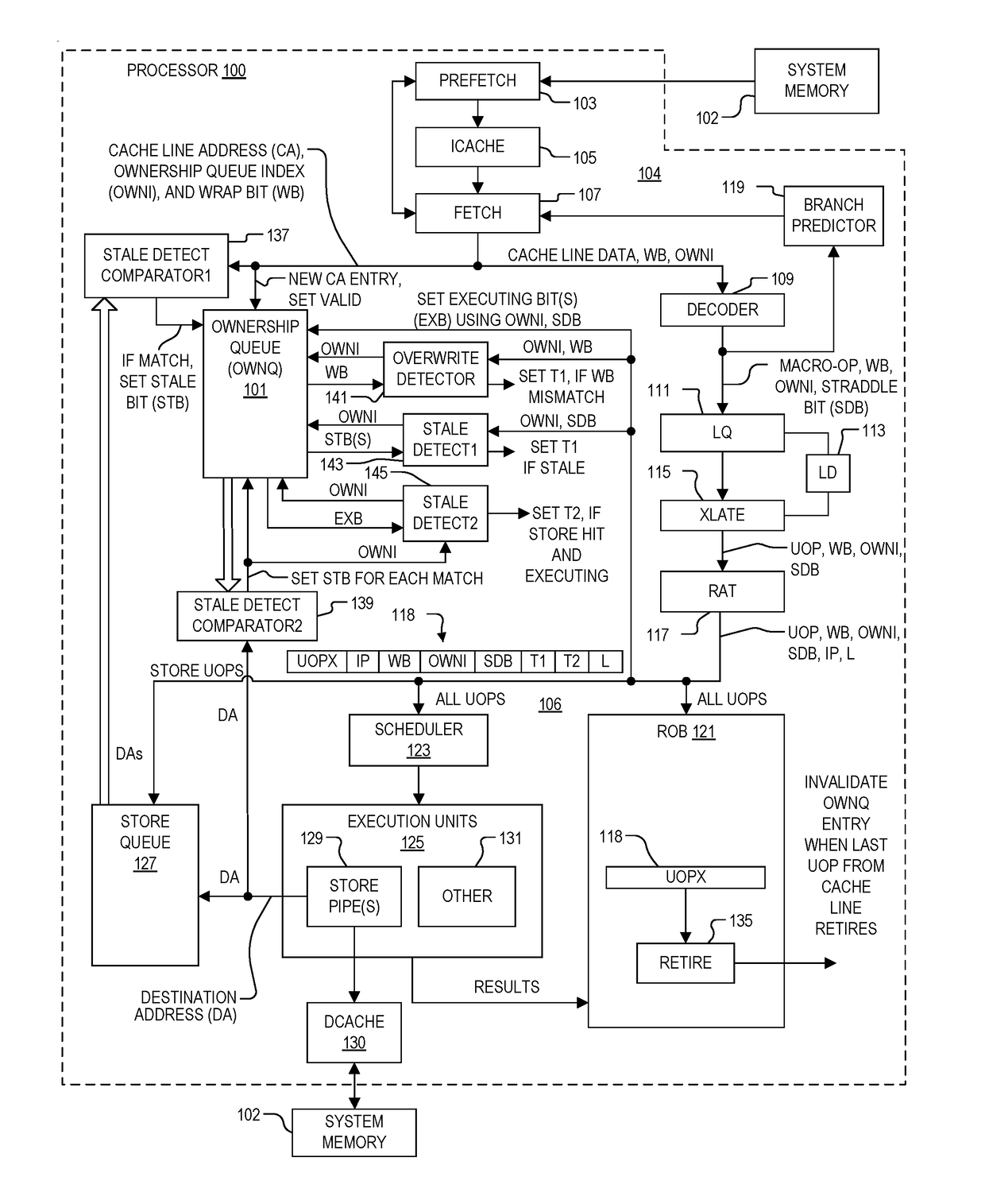
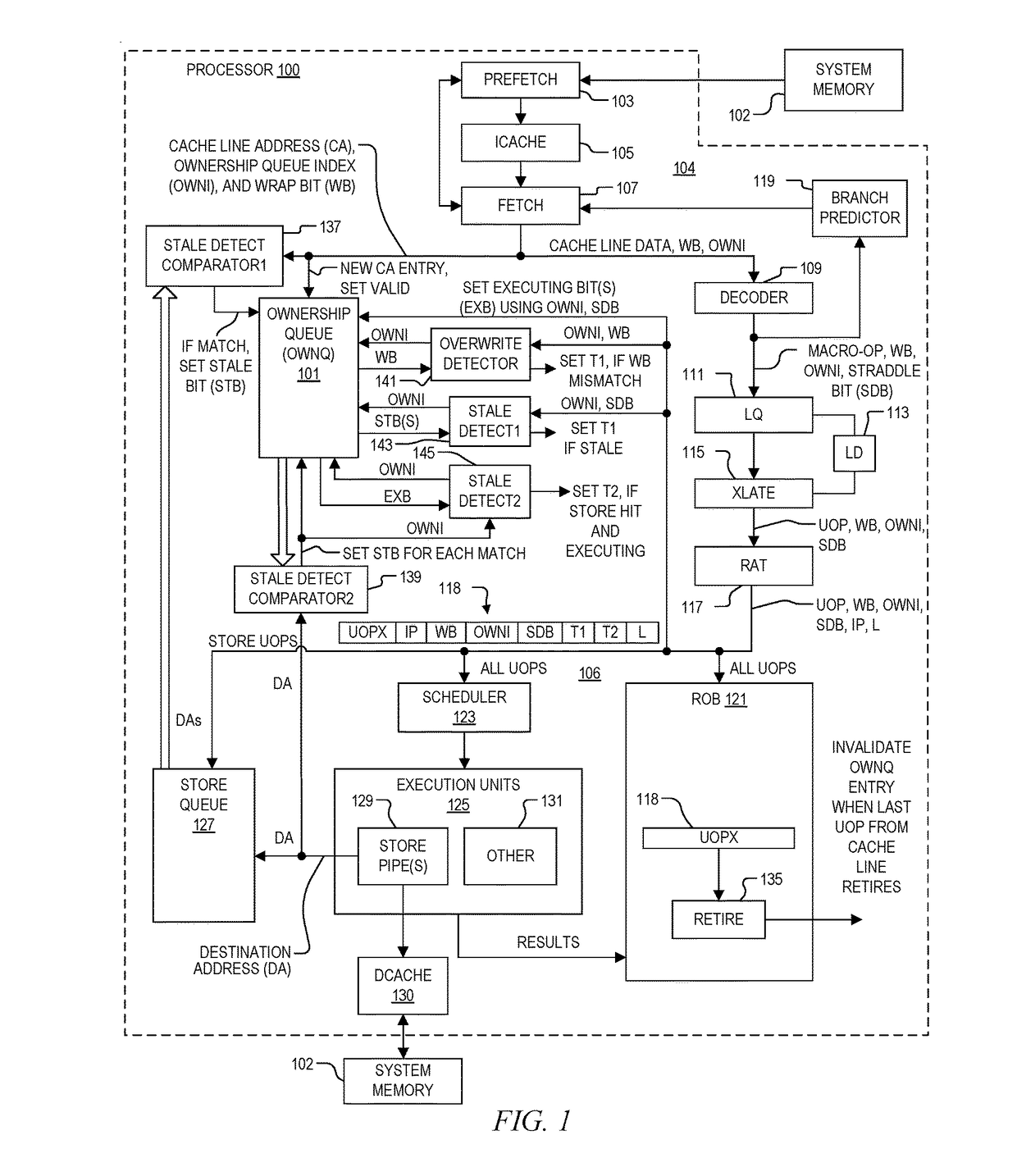
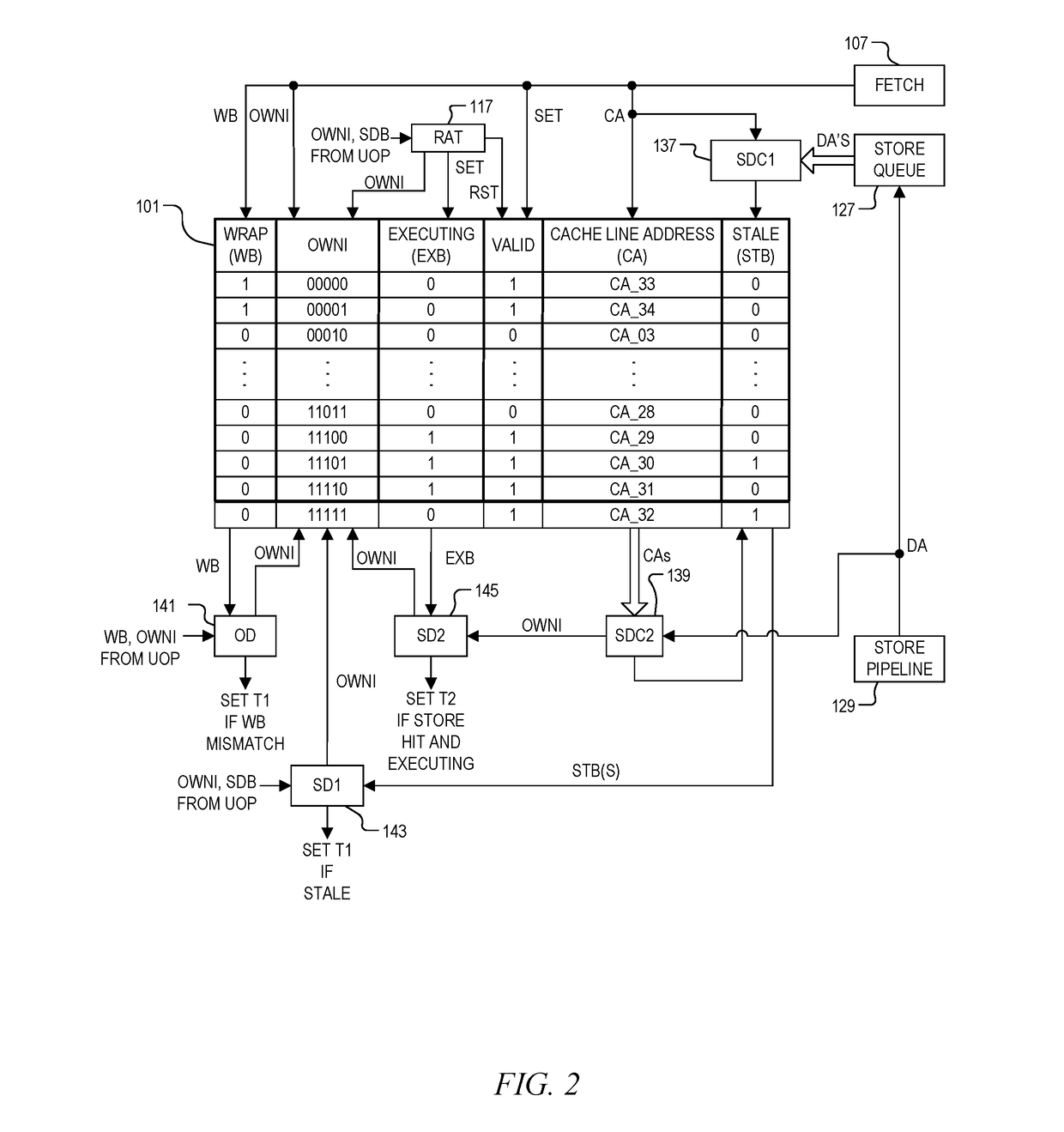
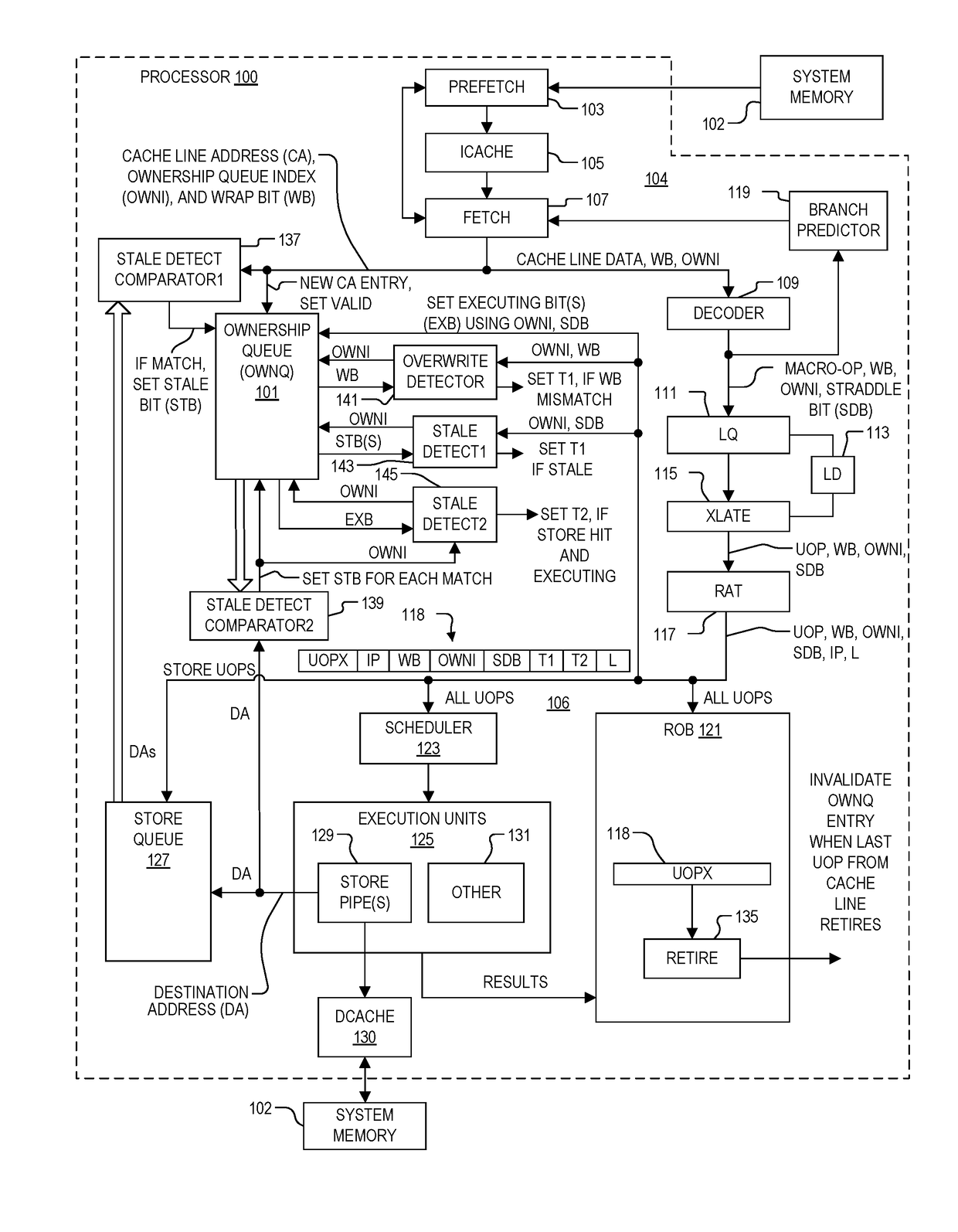
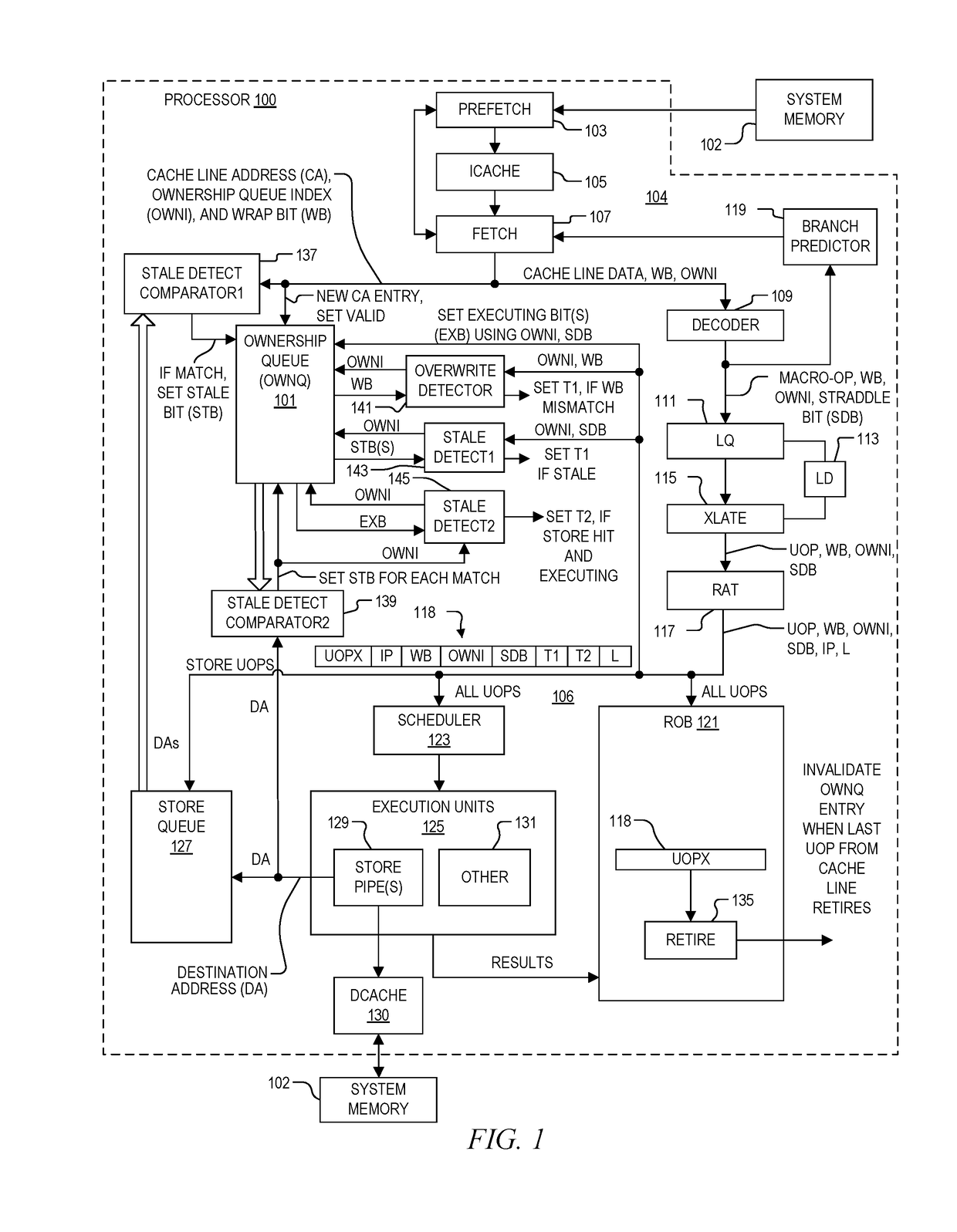
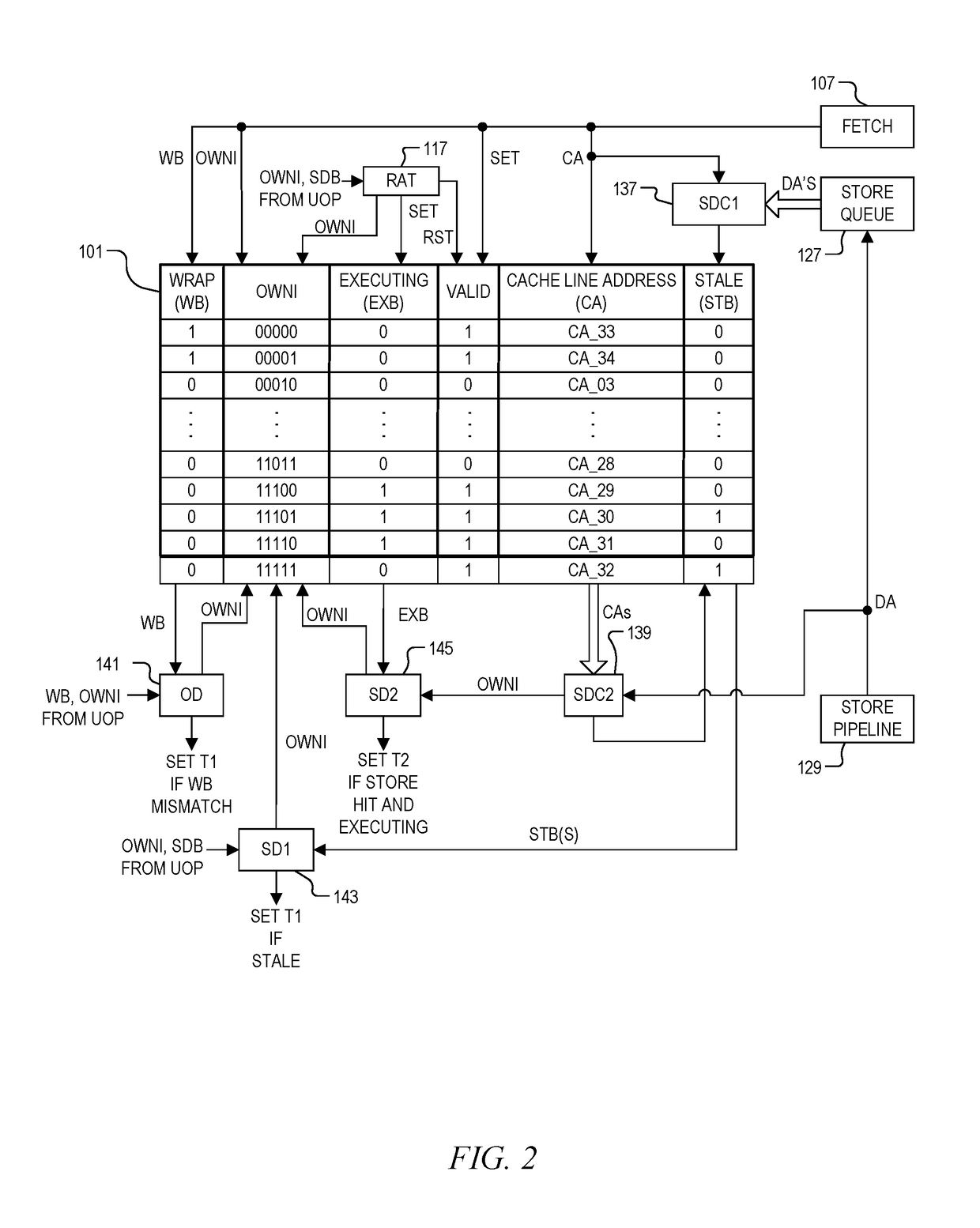
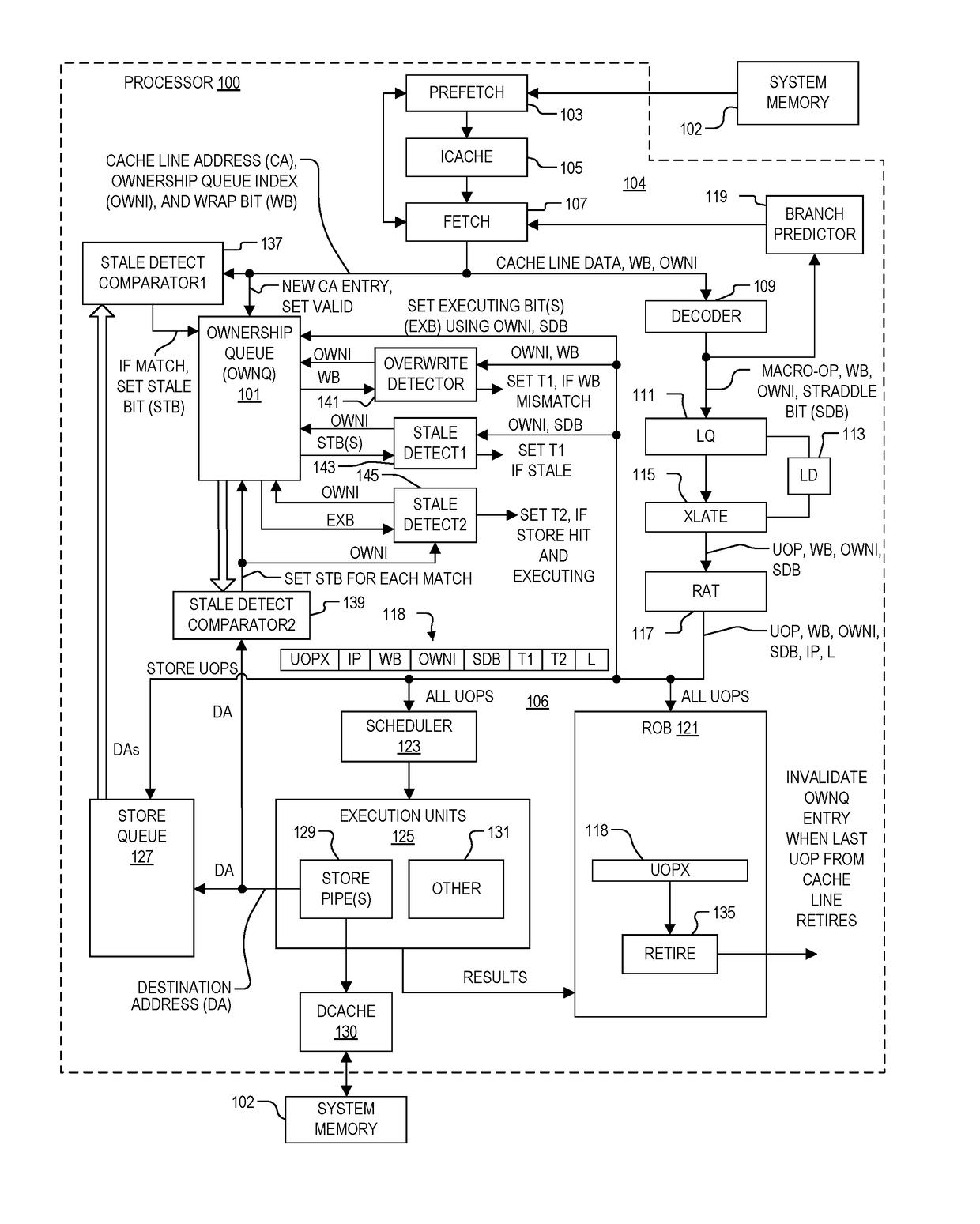
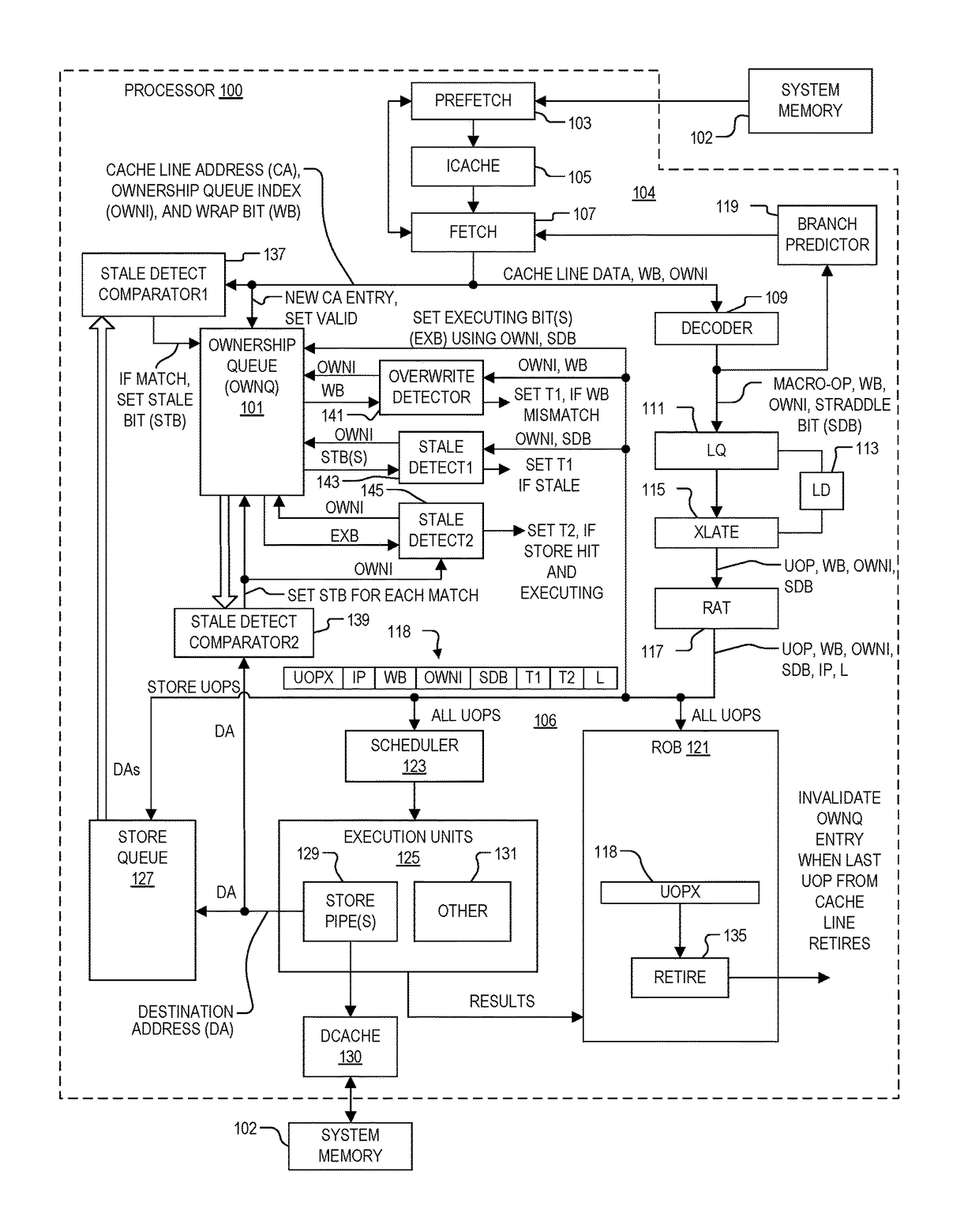
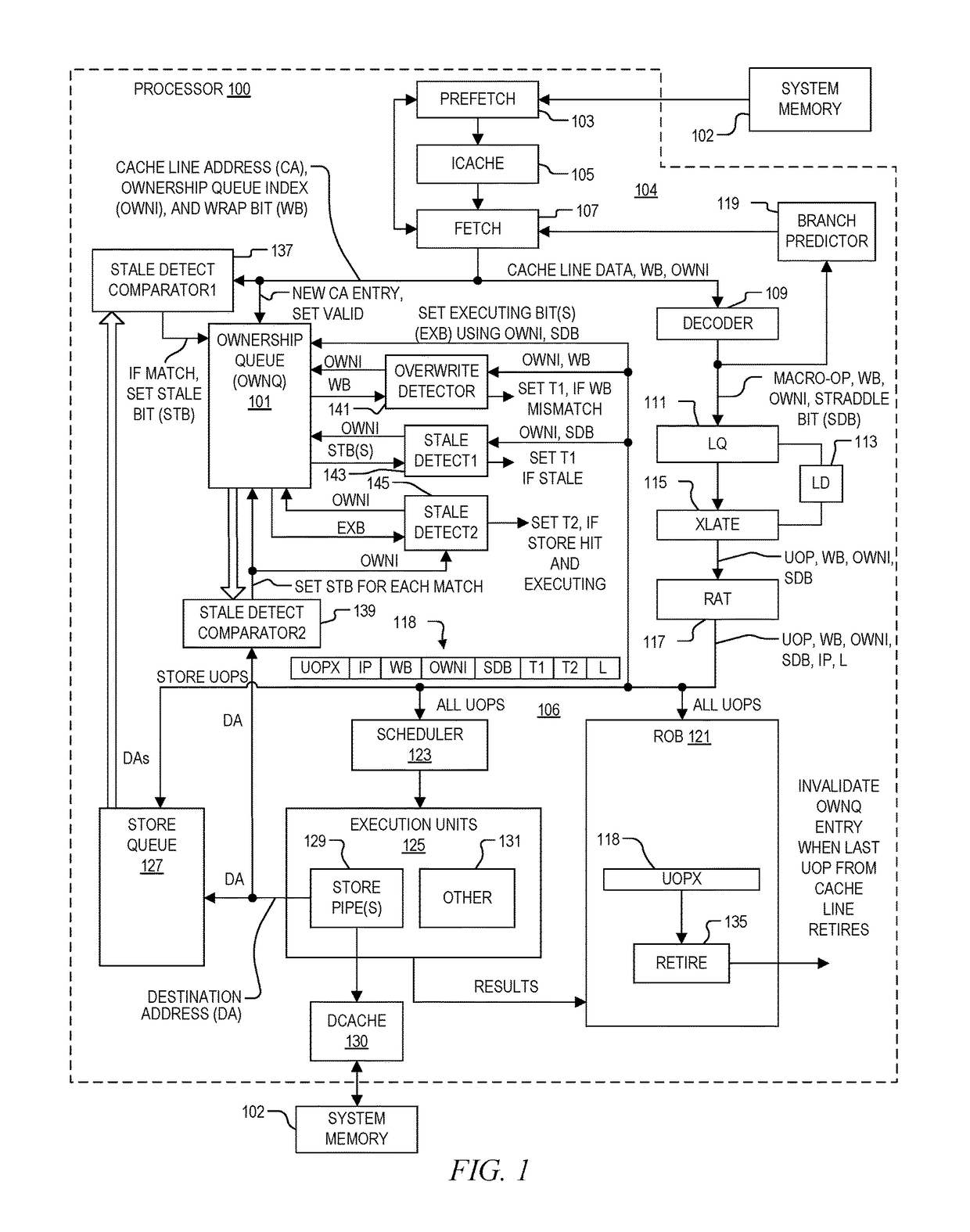
System and method of determining memory ownership on cache line basis for detecting self-modifying code including code with looping instructions
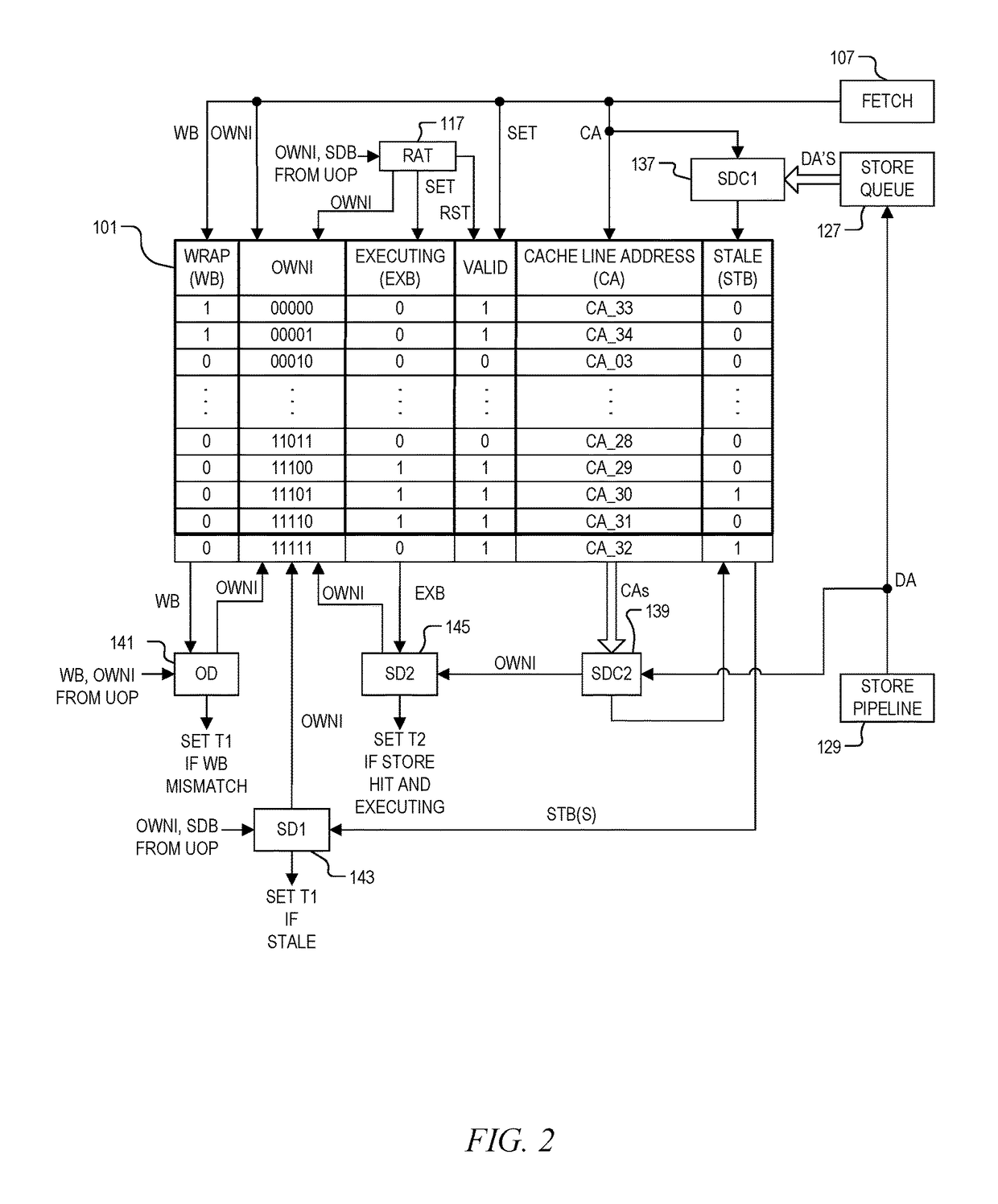
ActiveUS9798675B1Memory architecture accessing/allocationMemory systemsSelf-modifying codeParallel computing
A system and method of determining memory ownership on a cache line basis for detecting self-modifying code including code with looping instructions. An ownership queue includes multiple entries for determining memory ownership on a cache line basis. An ownership index and a wrap bit are determined for each cache line in the ownership queue, which are provided with each instruction derived from the same cache line. When an instruction is issued for execution, the ownership index provided with the instruction is used to access the corresponding entry in the ownership queue. If the instruction and entry wrap bits do not match, then an overwrite of the cache line is detected. The instruction is marked to invoke a first exception, which is performed when the instruction is ready to retire. The first exception flushes the processor, prevents the instruction from being retired, and re-fetches the instruction to continue processing.
Owner:VIA ALLIANCE SEMICON CO LTD
System and method of determining memory ownership on cache line basis for detecting self-modifying code including code with instruction that overlaps cache line boundaries
ActiveUS9792216B1Memory architecture accessing/allocationMemory systemsSelf-modifying codeParallel computing
A system and method for determining memory ownership on a cache line basis for detecting self-modifying code with instructions that overlap cache line boundaries. An ownership index and a cache line address are entered into the ownership queue for each cache line. The cache lines are translated into instructions, and a straddle bit is set for each instruction that was derived from cache line data that overlapped two cache lines. A stale bit is set for any entry of the ownership queue that collides with a store instruction. Each instruction issued for execution is marked with a first exception when the stale bit of the corresponding ownership queue entry is set, or when the straddle bit of the issued instruction and a stale bit of a next sequential entry are both set. A first exception is performed for each instruction ready to retire that is marked with the first exception.
Owner:VIA ALLIANCE SEMICON CO LTD
System and method of determining memory ownership on cache line basis for detecting self-modifying code
ActiveUS9798669B1Memory architecture accessing/allocationMemory systemsSelf-modifying codeParallel computing
System and method of determining memory ownership on cache line basis for detecting self-modifying code. An ownership queue stores cache line addresses and corresponding ownership indexes. The cache line data is translated into instructions, and each instruction is provided with an ownership index of an associated entry in the ownership queue. Each new cache line address is compared with the destination address of each store instruction, and each destination address, when determined, is compared with each cache line address in the ownership queue. Matching entries are marked as stale, and each instruction derived from a stale entry causes an exception when ready to retire. In this manner, a hit between a cache line and a corresponding store instruction causes an exception. An exception flushes the processor to resolve the potential modified code condition.
Owner:VIA ALLIANCE SEMICON CO LTD
System and method of determining memory ownership on cache line basis for detecting self-modifying code including modification of a cache line with an executing instruction
ActiveUS9798670B1Memory architecture accessing/allocationMemory systemsSelf-modifying codeParallel computing
A processor that determines memory ownership on a cache line basis for detecting self-modifying code including modification of a cache line with an executing instruction. An ownership index and corresponding cache line address are entered for each cache line into an ownership queue. The ownership index is provided with each instruction derived from the cache line. When the instruction is issued, an executing bit is set in the corresponding entry. When a destination address of a store instruction matches an entry in the ownership queue, the store instruction is marked to invoke an executing exception if the executing bit of the entry is set. When a store instruction that is ready to retire is marked to invoke the executing exception, the store instruction is allowed to retire, the processor is flushed, and the next instruction after the store instruction is re-fetched to continue processing.
Owner:VIA ALLIANCE SEMICON CO LTD
A binary translation-based self-modification code detection method and device
ActiveCN109710267AEasy to detectImprove efficiencyBinary to binaryMemory systemsSelf-modifying codeParallel computing
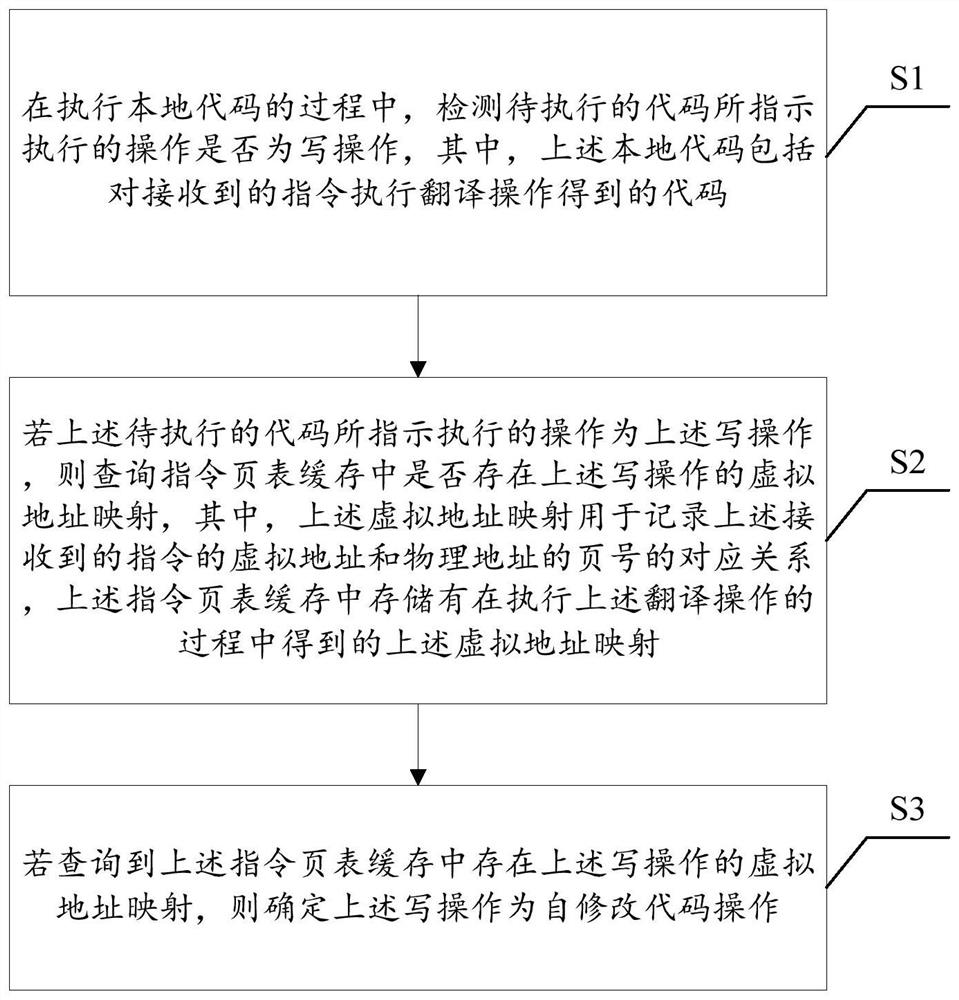
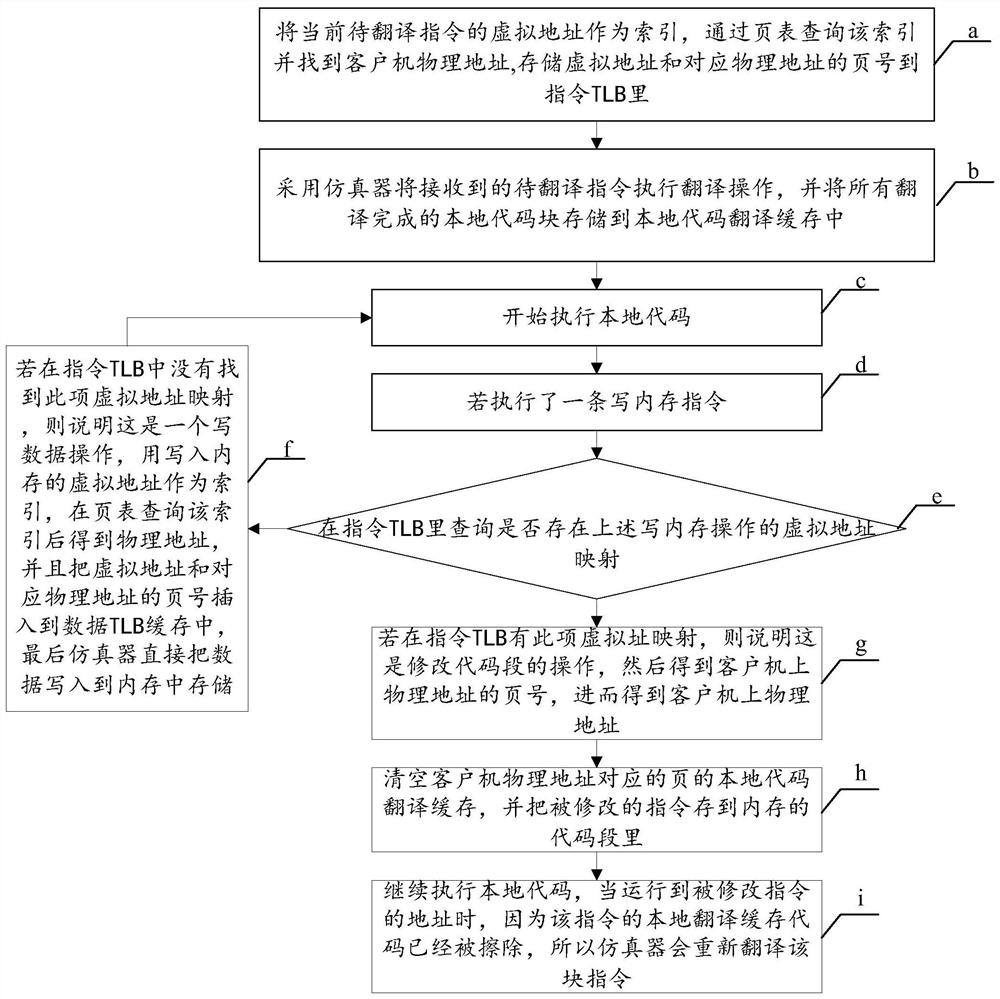
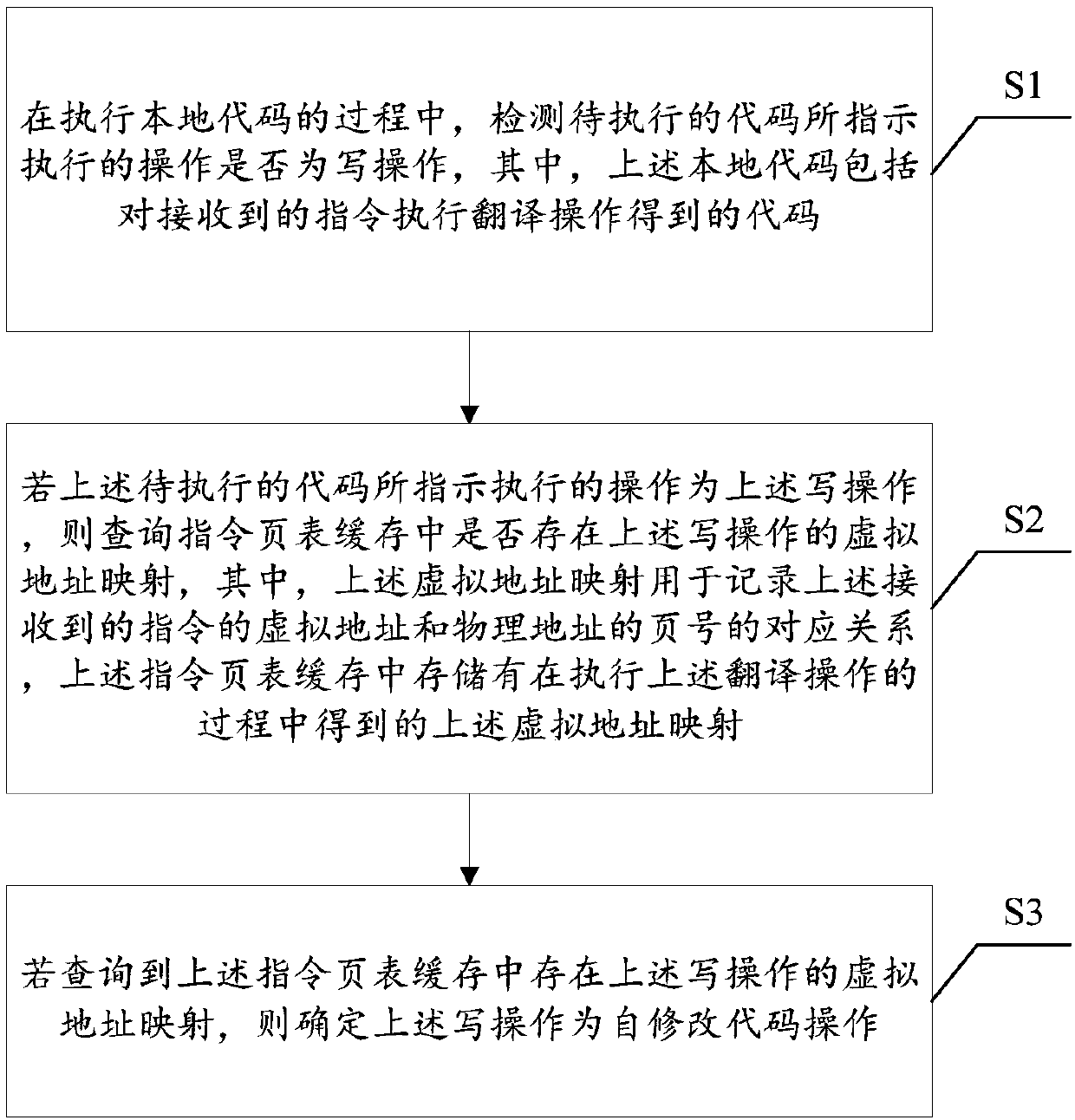
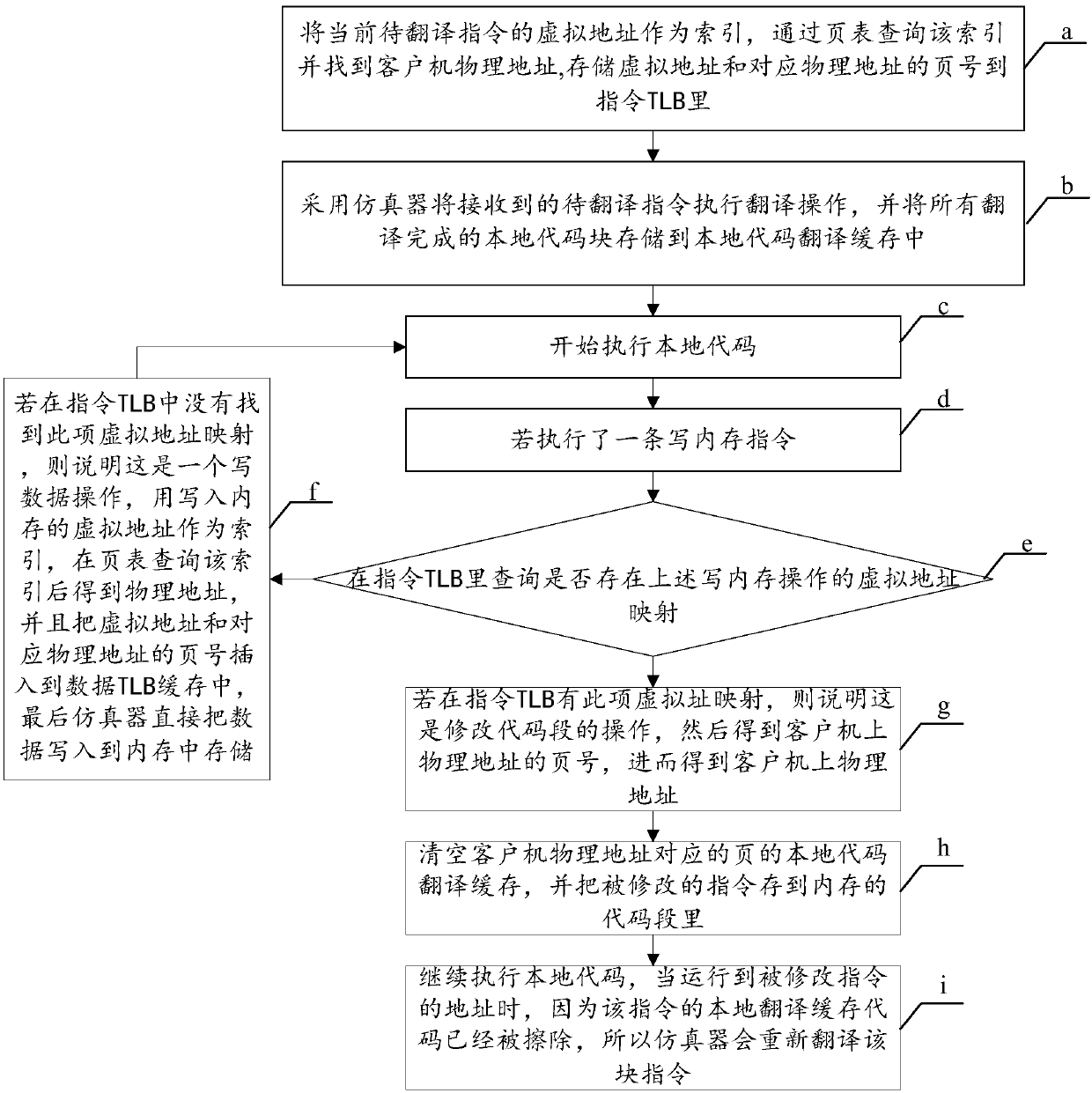
The invention discloses a binary translation-based self-modification code detection method and device. The method comprises the steps that in the process of executing a local code, whether an operation indicated to be executed by a to-be-executed code is a write operation or not is detected, and the local code comprises a code obtained by executing a translation operation on a received instruction; if the operation indicated to be executed by the to-be-executed code is the write operation, inquiring whether virtual address mapping of the write operation exists in an instruction page table cache or not is inquired, wherein the virtual address mapping is used for recording the corresponding relation between the virtual address of the received instruction and the page number of the physical address, and the virtual address mapping obtained in the process of executing the translation operation is stored in the instruction page table cache; and if it is queried that the virtual address mapping of the write operation exists in the instruction page table cache, determining the write operation as a self-modification code operation. Through the method and the device, the detection and re-translation efficiency of the self-modified code can be improved.
Owner:康烁
Software security testing system and method based on dynamic taint propagation
ActiveCN102081719BRealize real-time dynamic trackingSoftware testing/debuggingPlatform integrity maintainanceCode moduleSelf-modifying code
The invention discloses a software security testing system and method based on dynamic taint propagation. The system comprises a taint source marking module (108) used for generating a taint source marking rule, a detector module (110) used for generating a detection rule, a self-correction code module (104) used for dynamically tracing each binary command of software to be tested by using a self-correction code technology, an RING3 virtual machine module (106) used for analyzing each binary command of the software to be tested by using an RING3 virtual machine and analyzing the flowing direction of the data carried by the command so as to realize taint propagation, as well as calling the taint source marking rule to mark a taint source and calling the detection rule to detect each binary command of the software to be tested, and a log module (112) used for outputting related information violating the detection rule. The software security testing system and method provided by the invention can be used for improving the detection rate of software and reducing false alarm rate and missed alarm rate.
Owner:阿里巴巴华北技术有限公司
Controlling execution of binary code
Owner:IBM CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com