Certificate authentication method and equipment
A technology of equipment and certificates, applied in the direction of electrical components, transmission systems, etc., to achieve the effect of realizing convenience and improving efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 example
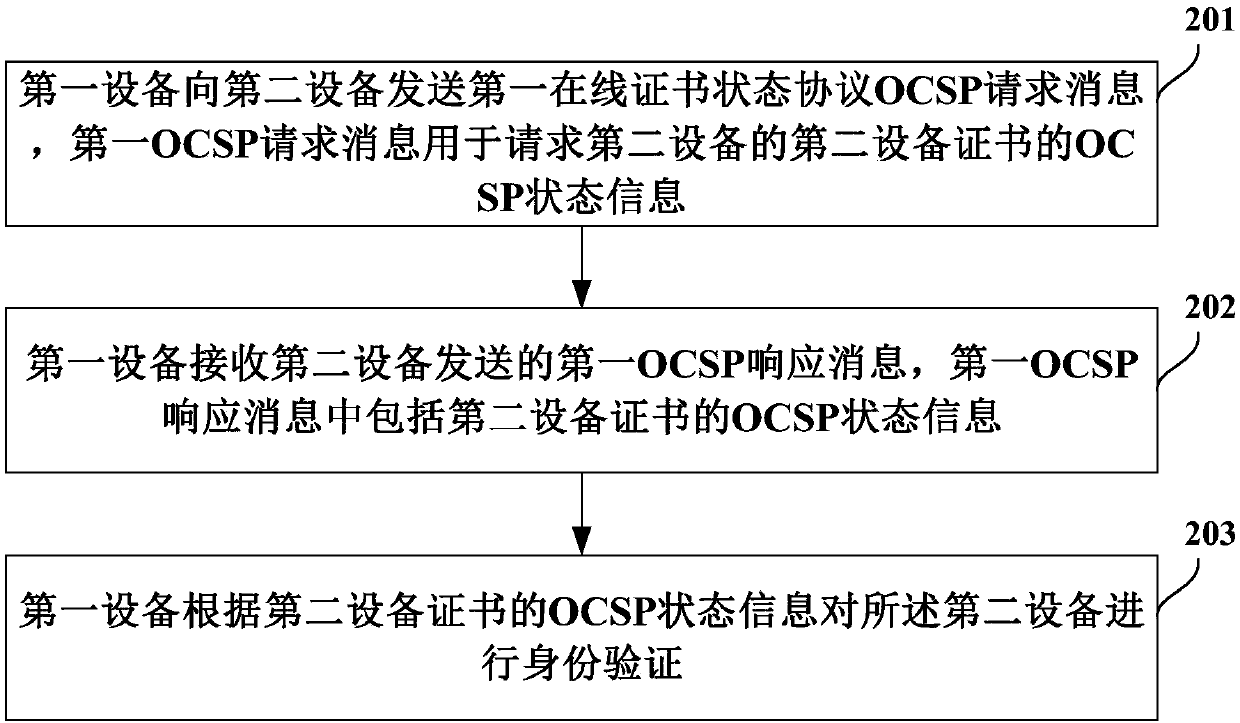
[0068] see figure 2 , the figure shows a certificate authentication method, which is applicable to the handshake process. The scenario is that the first device can send a request to the second device to query the certificate status of the second device certificate during the SSL / TLS handshake process. The second device After receiving the query request, return the certificate status of the second device to the first device as a response, the specific steps are as follows:
[0069] Step 201, the first device sends a first online certificate status protocol OCSP request message to the second device, and the first OCSP request message is used to request the OCSP status information of the second device certificate of the second device, and then enter step 202;
[0070] Optionally, the first device sends a first device handshake message and a first Online Certificate Status Protocol OCSP request message to the second device, and the first OCSP request message is used to request OC...
no. 2 example
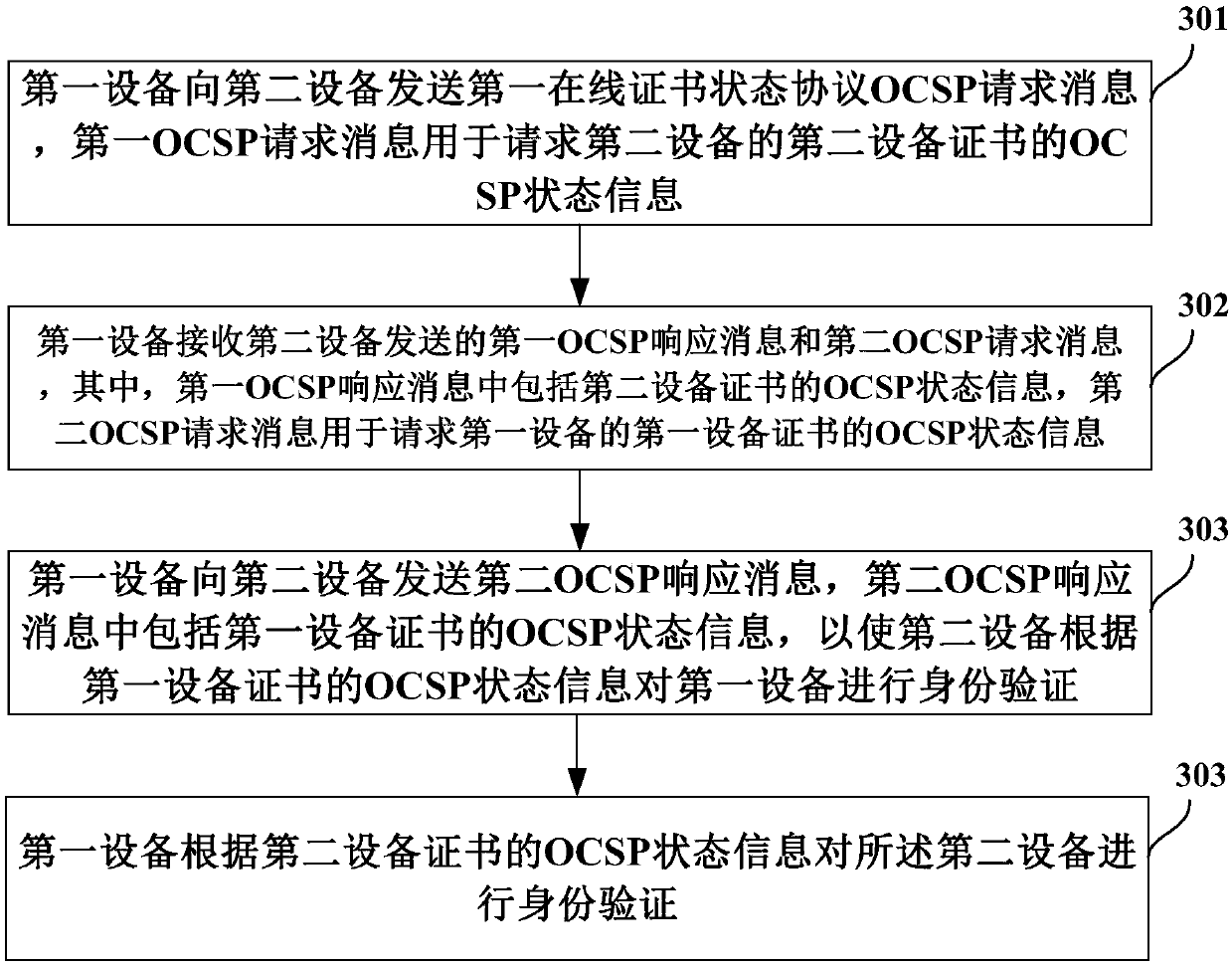
[0083] see image 3 , the figure shows a certificate authentication method, which is suitable for the handshake process. In this embodiment, the first device and the second device can carry OCSP status information during the handshake process. This method can reduce the first During the handshake process, the device and the second device actively query the CRL and OCSP to the CA to improve the handshake efficiency. The specific steps are as follows:
[0084] Step 301, the first device sends a first online certificate status protocol OCSP request message to the second device, and the first OCSP request message is used to request the OCSP status information of the second device certificate of the second device, and then enter step 302;
[0085] Optionally, the first device sends a first device handshake message and a first Online Certificate Status Protocol OCSP request message to the second device, and the first OCSP request message is used to request the second device certificat...
no. 3 example
[0100] see Figure 4 , the figure shows a certificate authentication method, which is suitable for the handshake process, and the specific steps are as follows:
[0101] Step 401, the second device receives the first online certificate status protocol OCSP request message sent by the first device, the first OCSP request message is used to request the OCSP status information of the second device certificate of the second device, and then enters step 402;
[0102] Optionally, the second device receives the first device handshake message and the first Online Certificate Status Protocol OCSP request message sent by the first device, and the first OCSP request message is used to request the second device certificate of the second device OCSP status information.
[0103] Of course, it can be understood that the above-mentioned first device may be a client and the second device may be a server, or the first device may be a server and the second device may be a client.
[0104] Step...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com