Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
304results about How to "Copyright protection" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
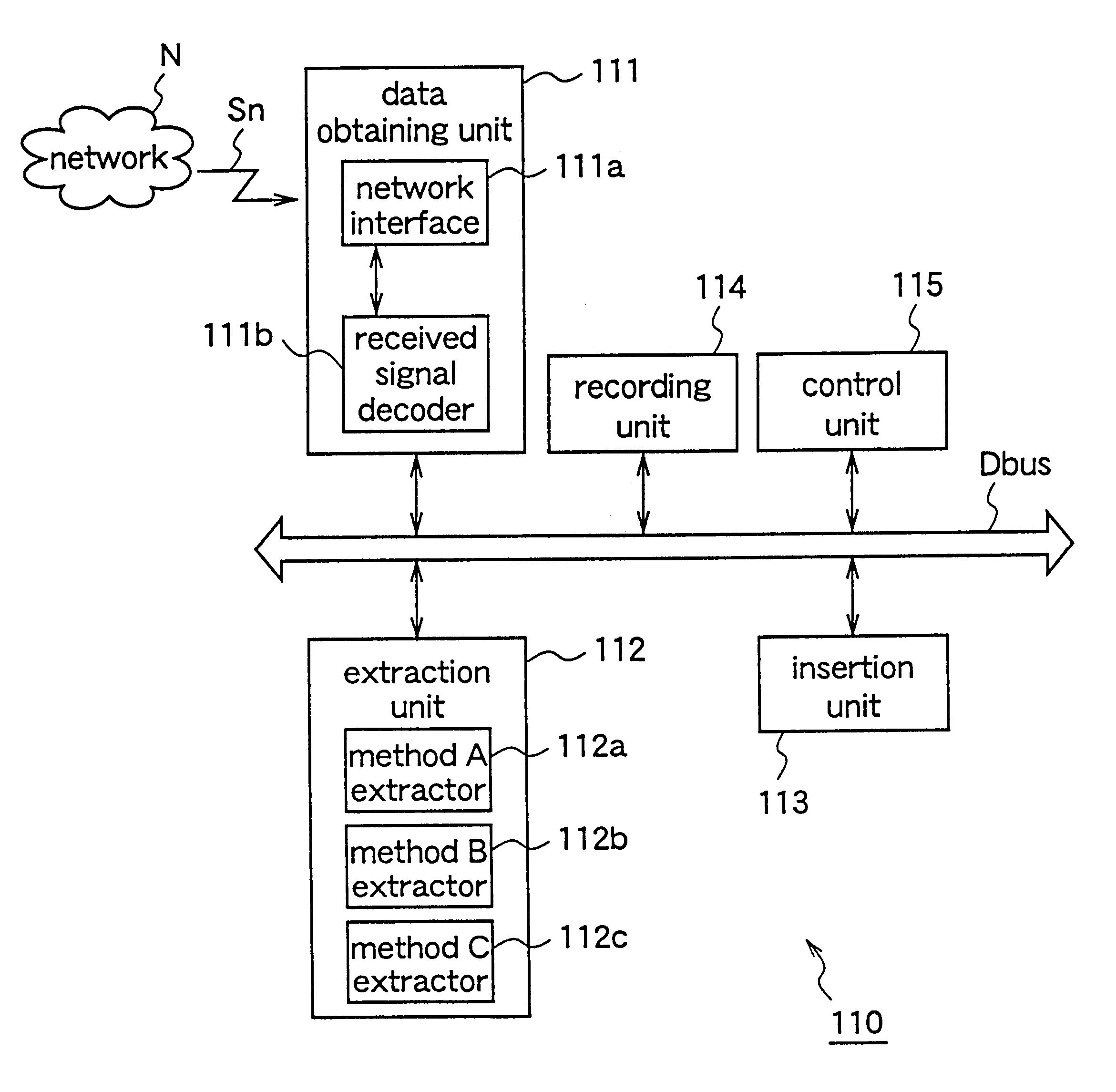
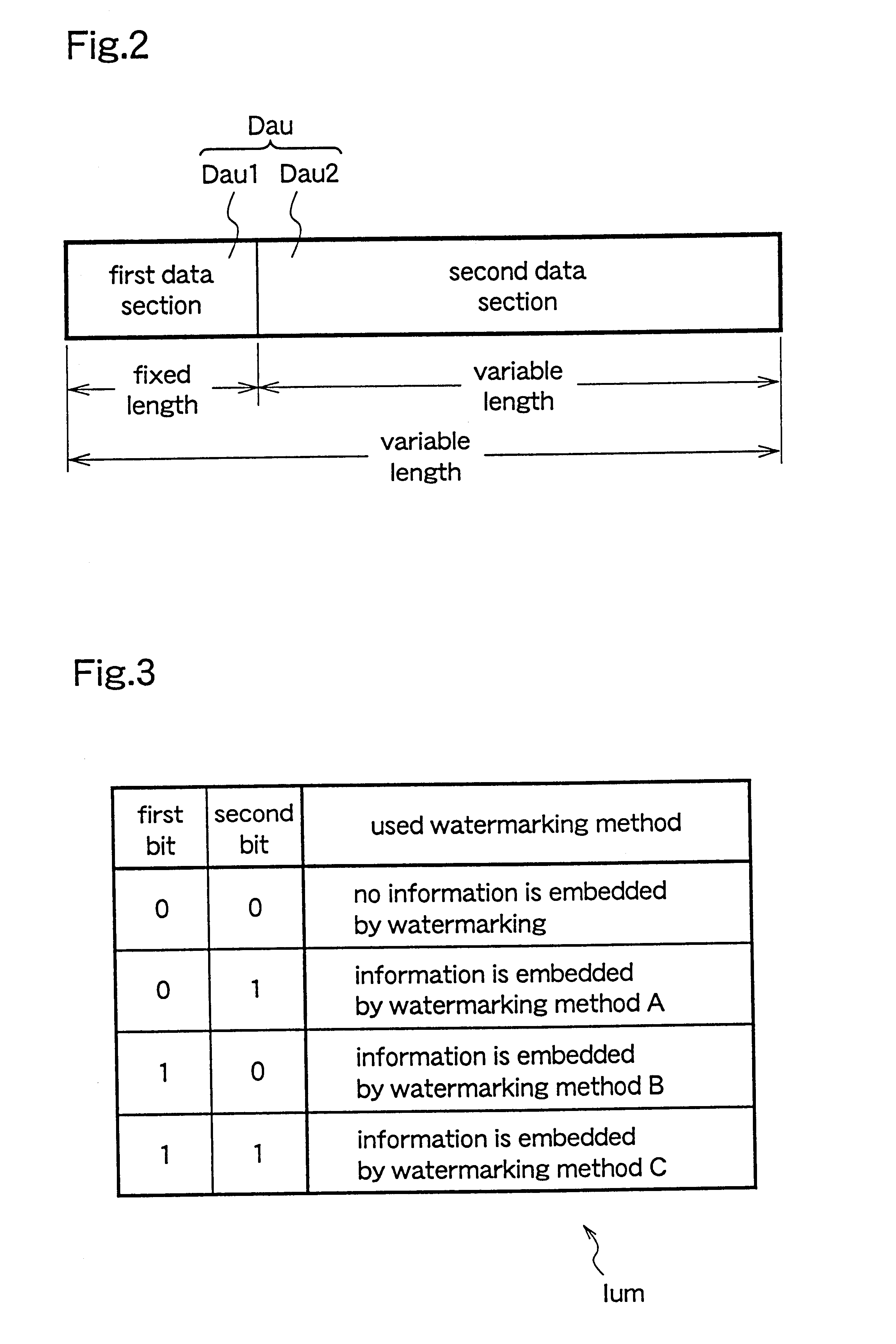
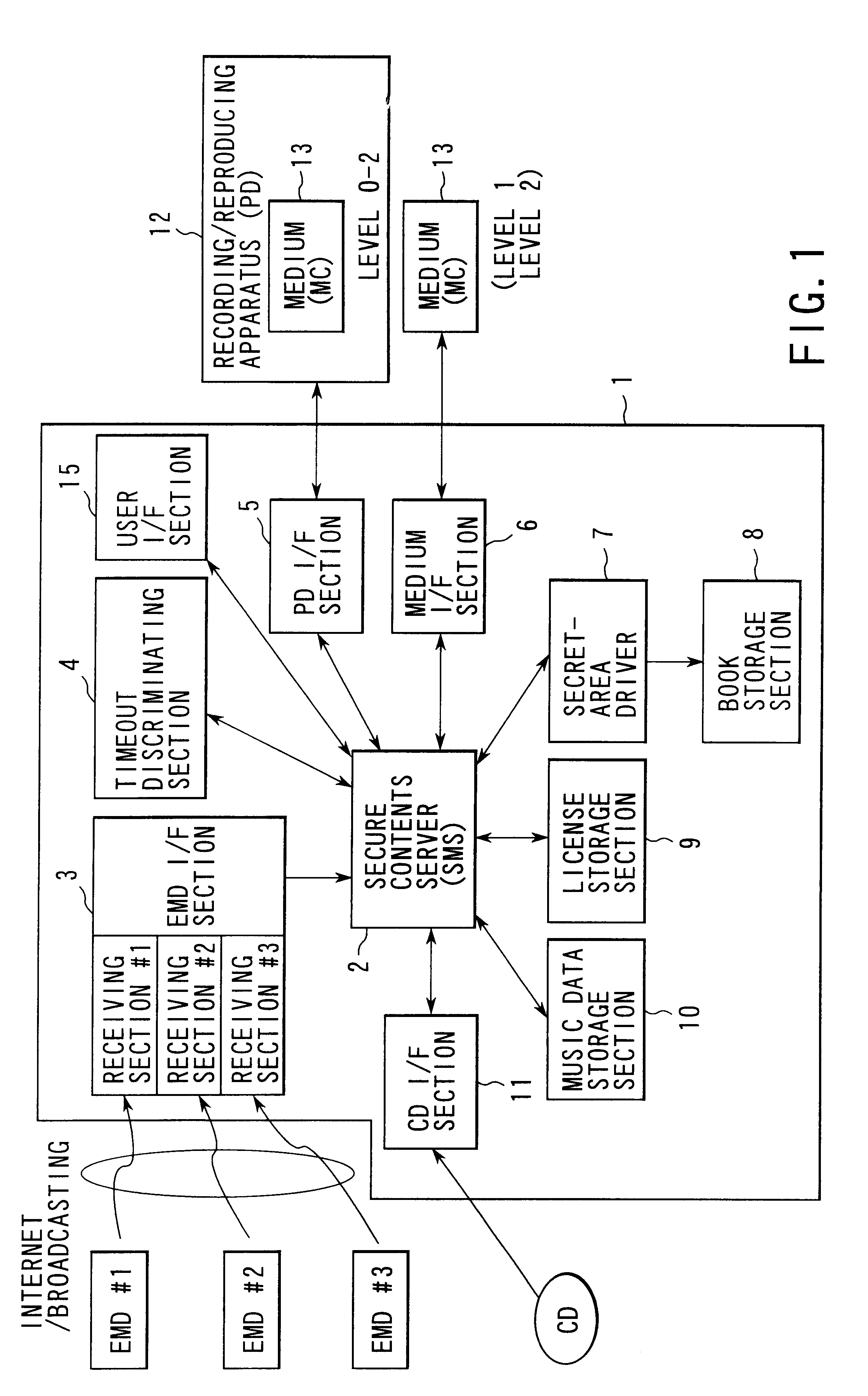
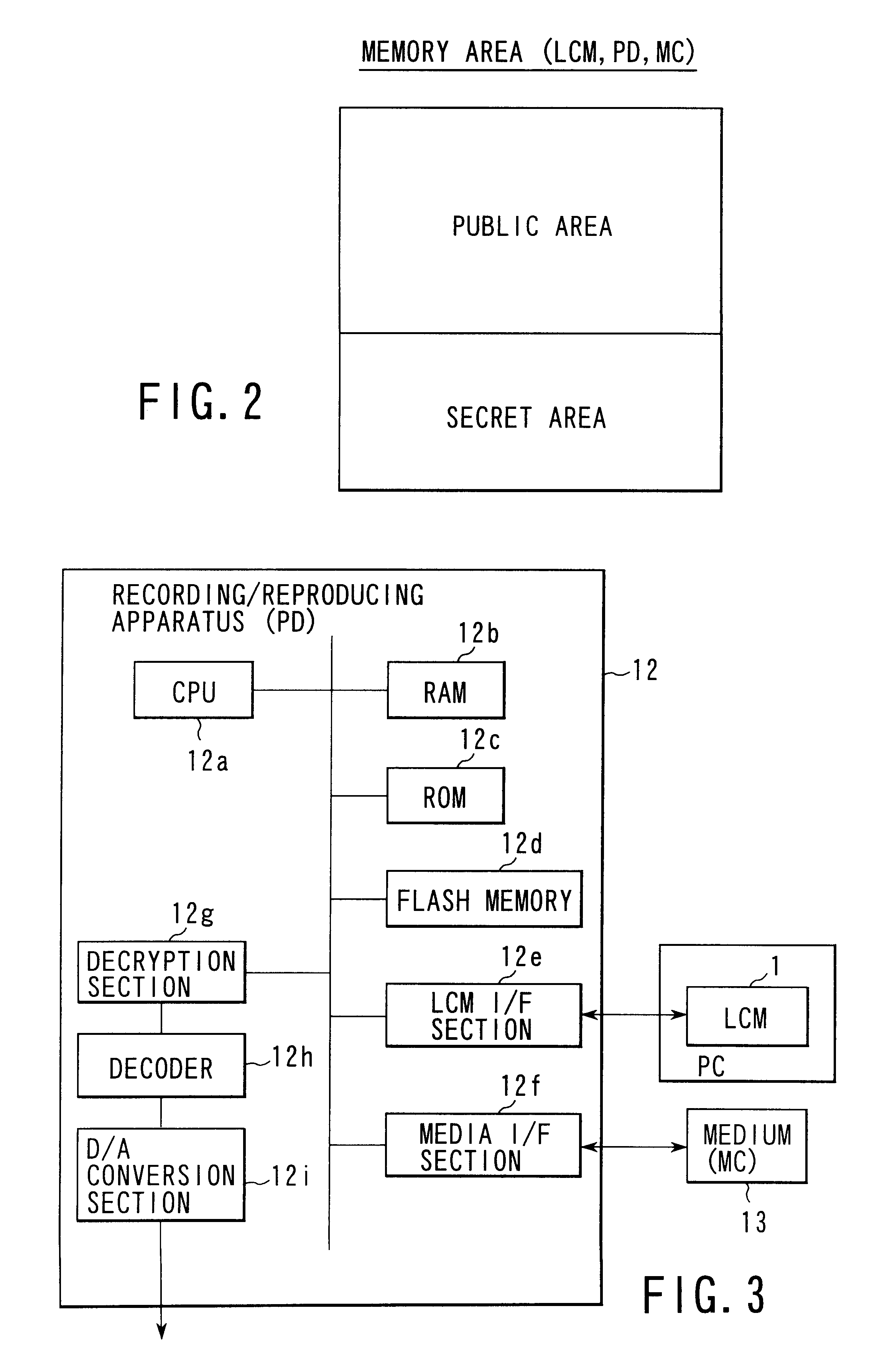
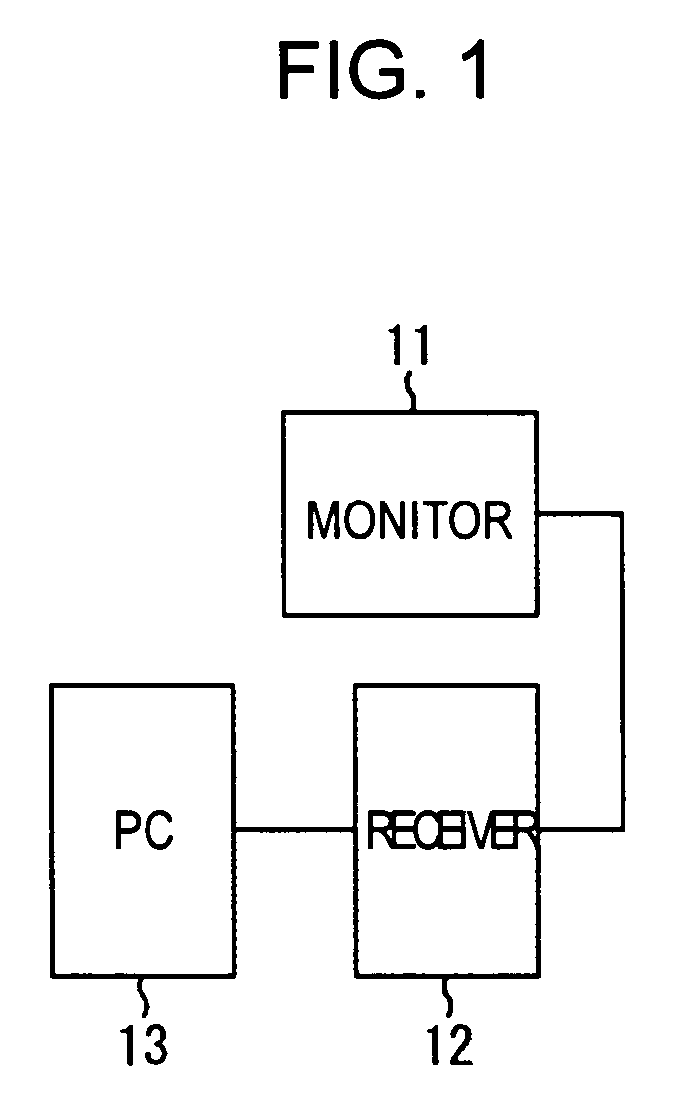
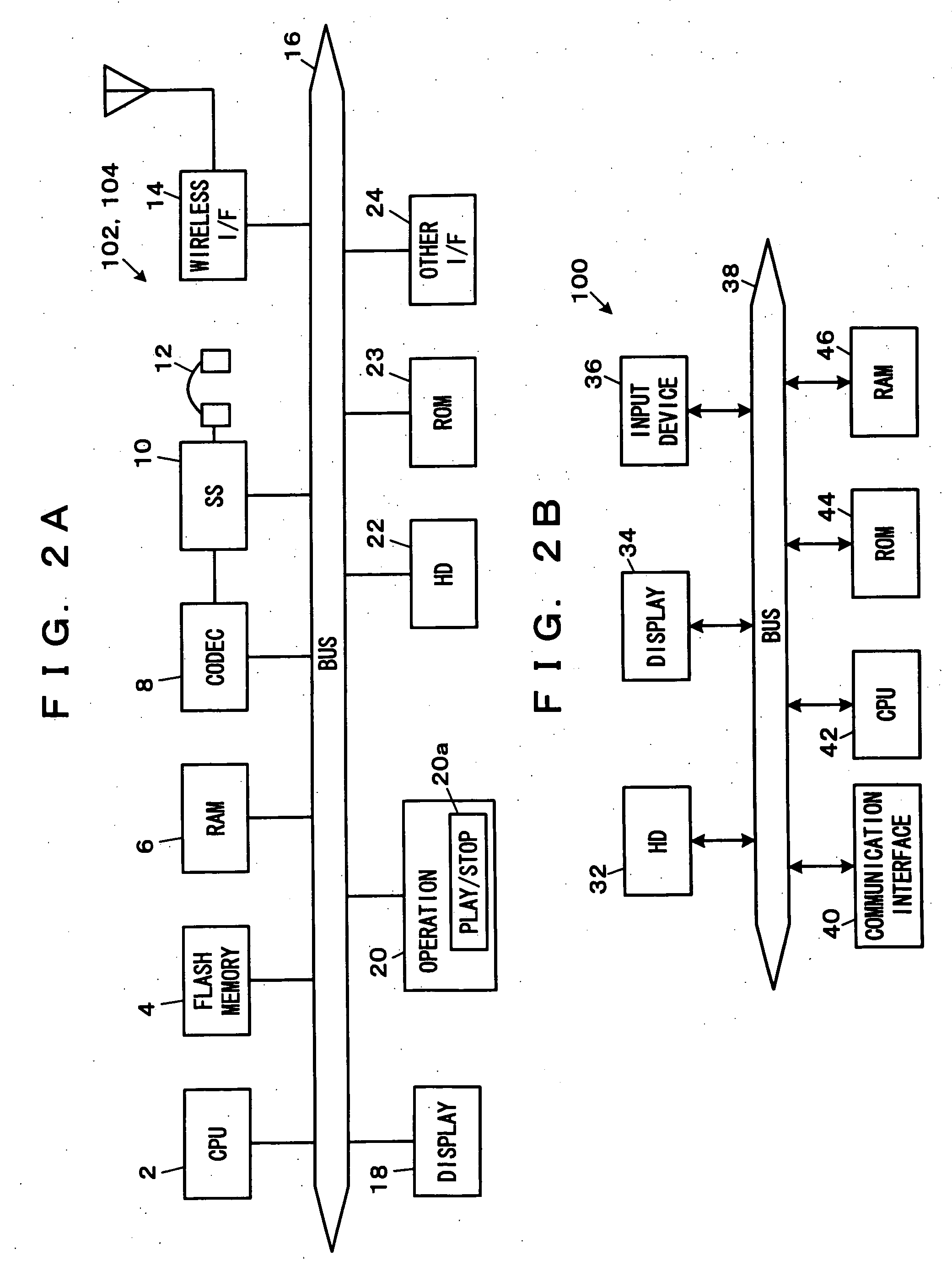
Data processing apparatus and data recording media
InactiveUS6529506B1Copyright protectionOptical discsUser identity/authority verificationData processingAudio frequency
A data processing apparatus is provided with a data obtaining unit which receives a network signal sn on a network N and obtains distributed audio data Dau in which copyright information or the like is embedded, and a control unit which obtains information indicating a watermarking method which has been used when embedding the copyright information or the like in the audio data. The embedded information is extracted by an appropriate watermarking method according to the obtained information indicating the used watermarking method. The extracted information is again embedded in the distributed audio data Dau by using a predetermined watermarking method, and thus obtained audio data is recorded on a recording medium. Therefore, regardless of the watermarking method used for embedding the copyright information or the like in the distributed audio data Dau, the distributed audio data Dau can be appropriately reproduced by reproduction apparatuses as domestic electrical equipment, according to the embedded information.
Owner:PANASONIC INTELLECTUAL PROPERTY CORP OF AMERICA
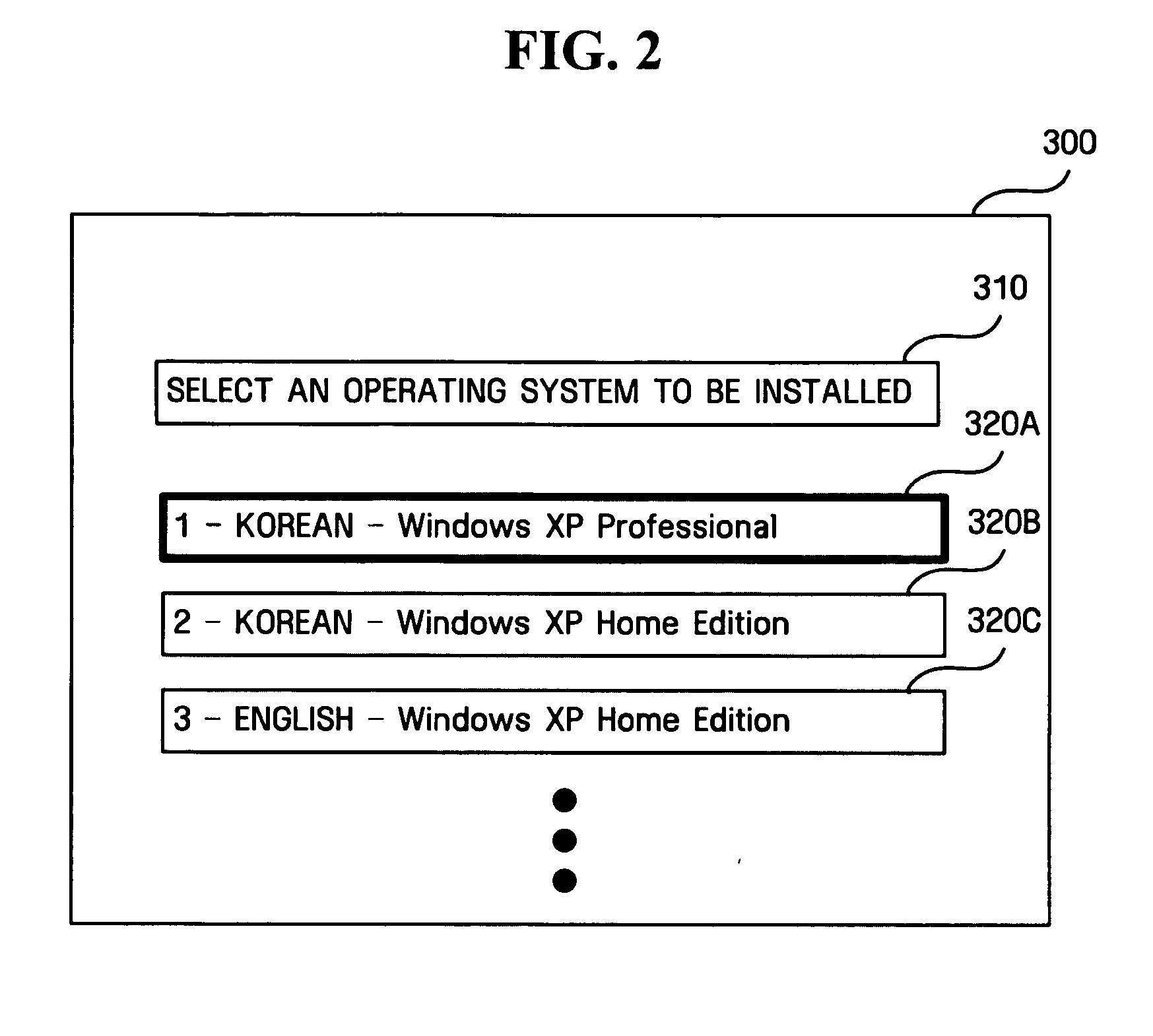
Computer system and method for selectively installing one operating system among a plurality of operating systems
InactiveUS20070011674A1Copyright protectionProviding user with convenienceBootstrappingProgram loading/initiatingOperational systemEngineering
A computer system for selectively installing an operating system from a plurality of operating systems is provided with an operating system storage unit for storing a plurality of operating systems; a selection / installation unit for selecting and installing a specified operating system from the stored operating systems; a deletion unit for disabling the operating systems not selected by the selection / installation unit among the stored operating systems; and an install information storage unit for storing information about the installed operating system.
Owner:SAMSUNG ELECTRONICS CO LTD
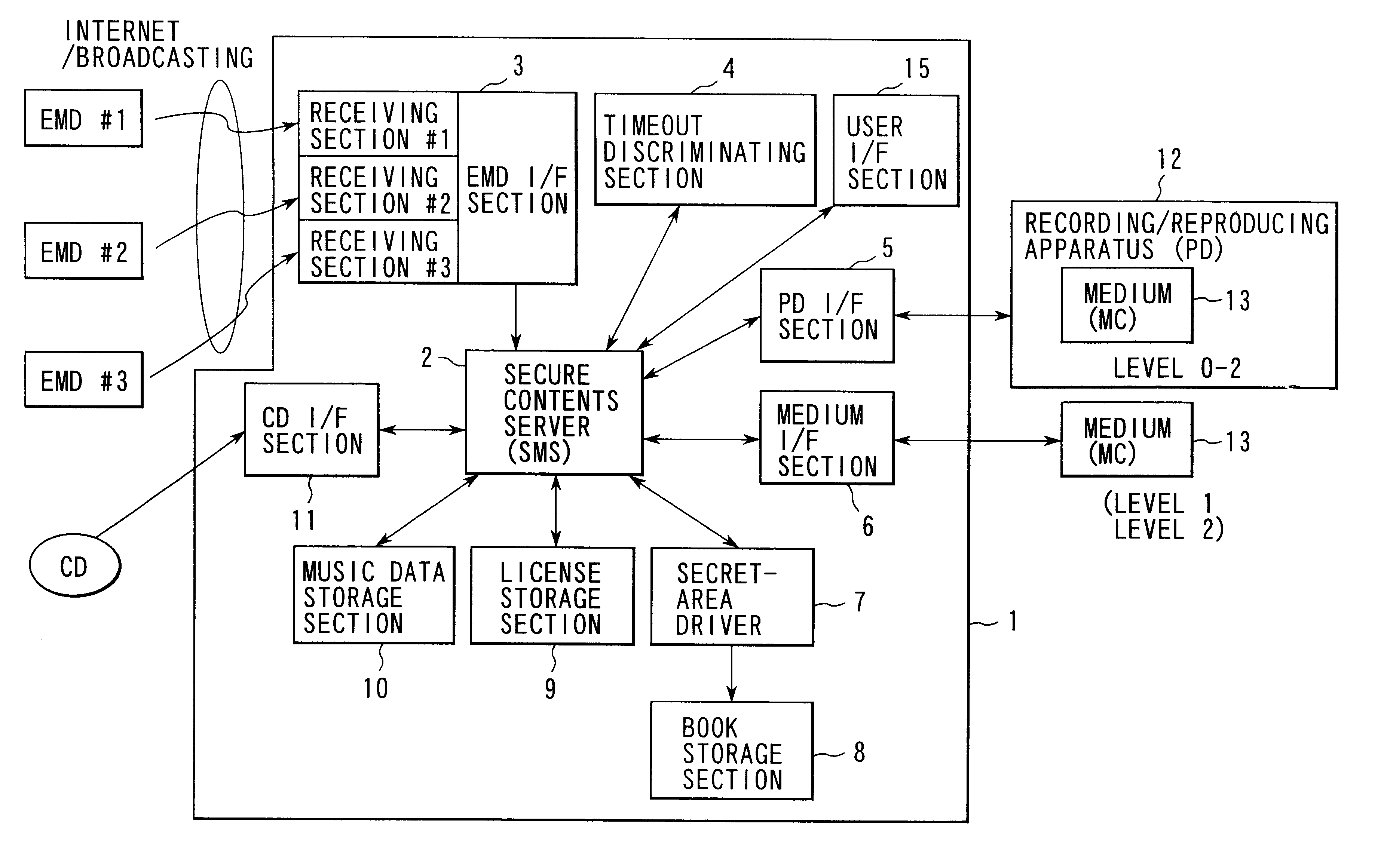
Contents managing method and contents managing apparatus
InactiveUS6847950B1Copyright protectionTelevision system detailsMemory loss protectionComputer hardwareContent management
Owner:KK TOSHIBA
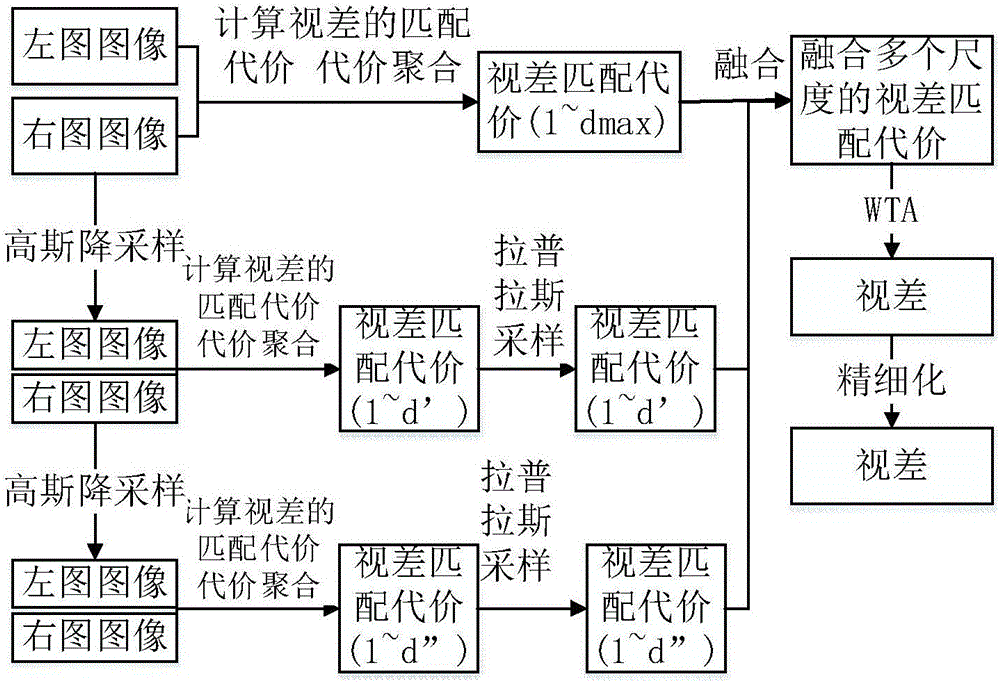
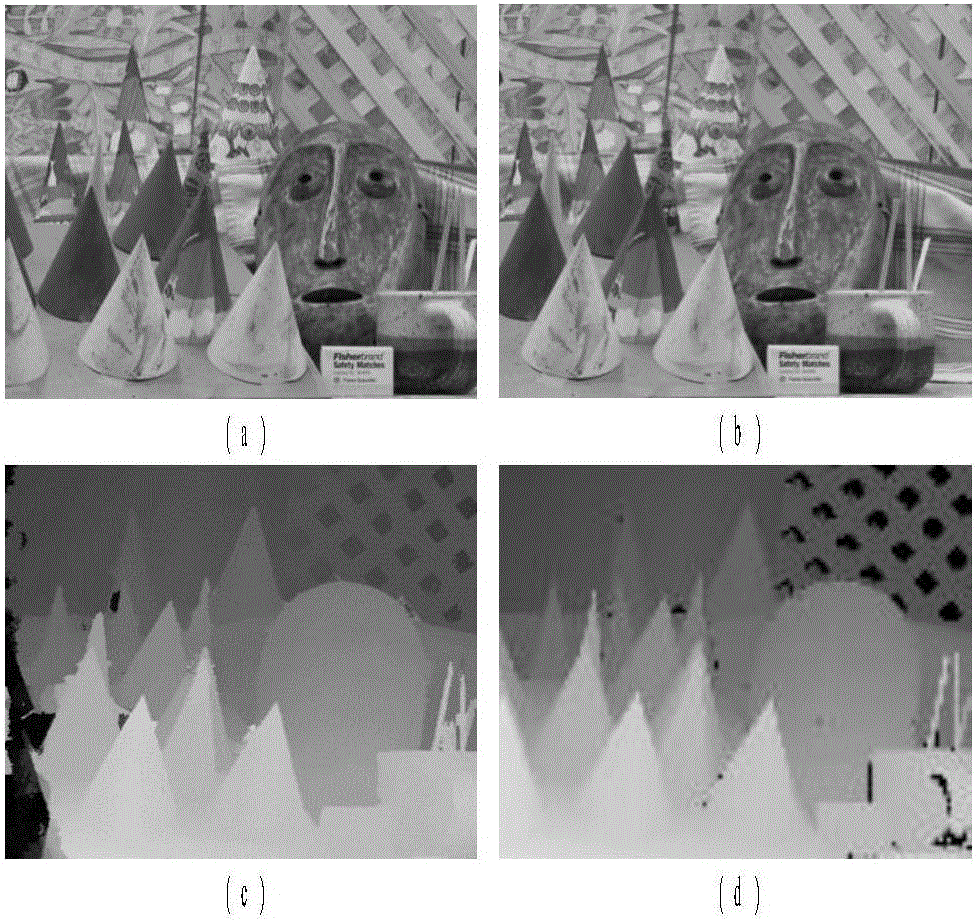
Binocular stereoscopic vision-based stereo matching method
InactiveCN106340036AHigh precisionAlleviate weak and repetitive texturesImage enhancementImage analysisGaussian pyramidA-weighting
The invention relates to a binocular stereoscopic vision-based stereo matching method. The method includes the following six stages: Gaussian pyramid construction; cost calculation matching and cost aggregation; cost fusion matching; disparity computation; disparity map repair and void filling; and disparity refinement. Laplacian pyramid transformation is additionally adopted in the cost aggregation stage. An edge-protection-based interpolation algorithm is used in the disparity map repair and hole filling stage. A weighting and bilateral filtering combination-based disparity refinement method is additionally adopted in the disparity refinement stage, so that a high-accuracy disparity map can be obtained. The calculation amount of the method of the invention is moderate; matching results at different scales are fused, improvement is made in the cost aggregation stage and the disparity refinement stage, and therefore, a better disparity map can be obtained; and the method has certain robustness to illumination, external noises and the like.
Owner:SOUTHEAST UNIV
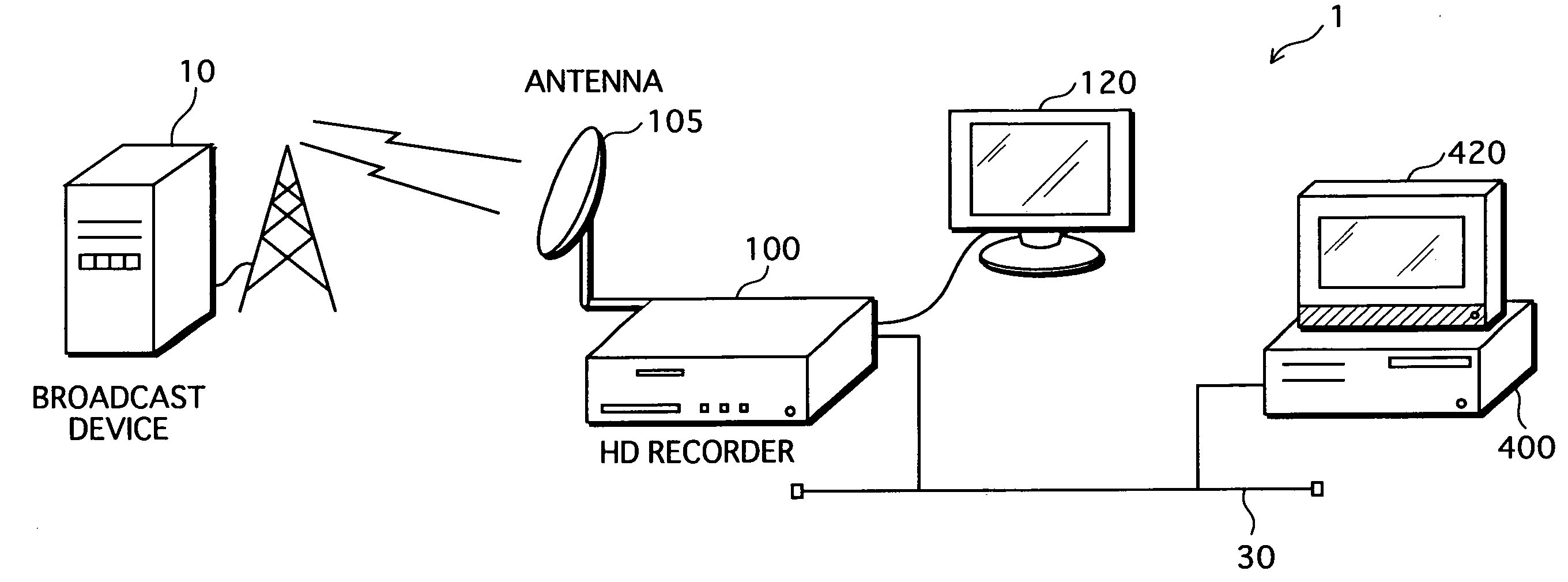
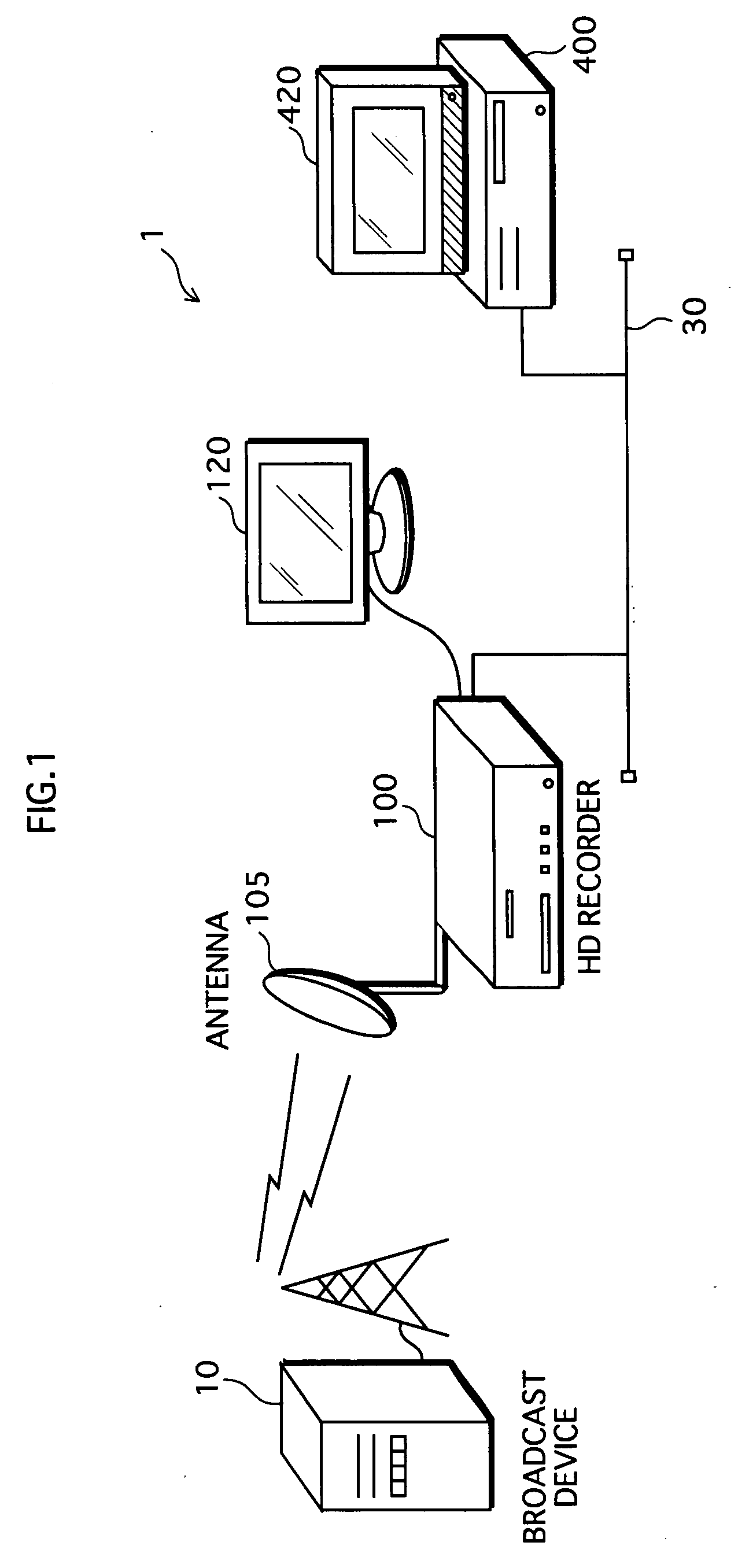
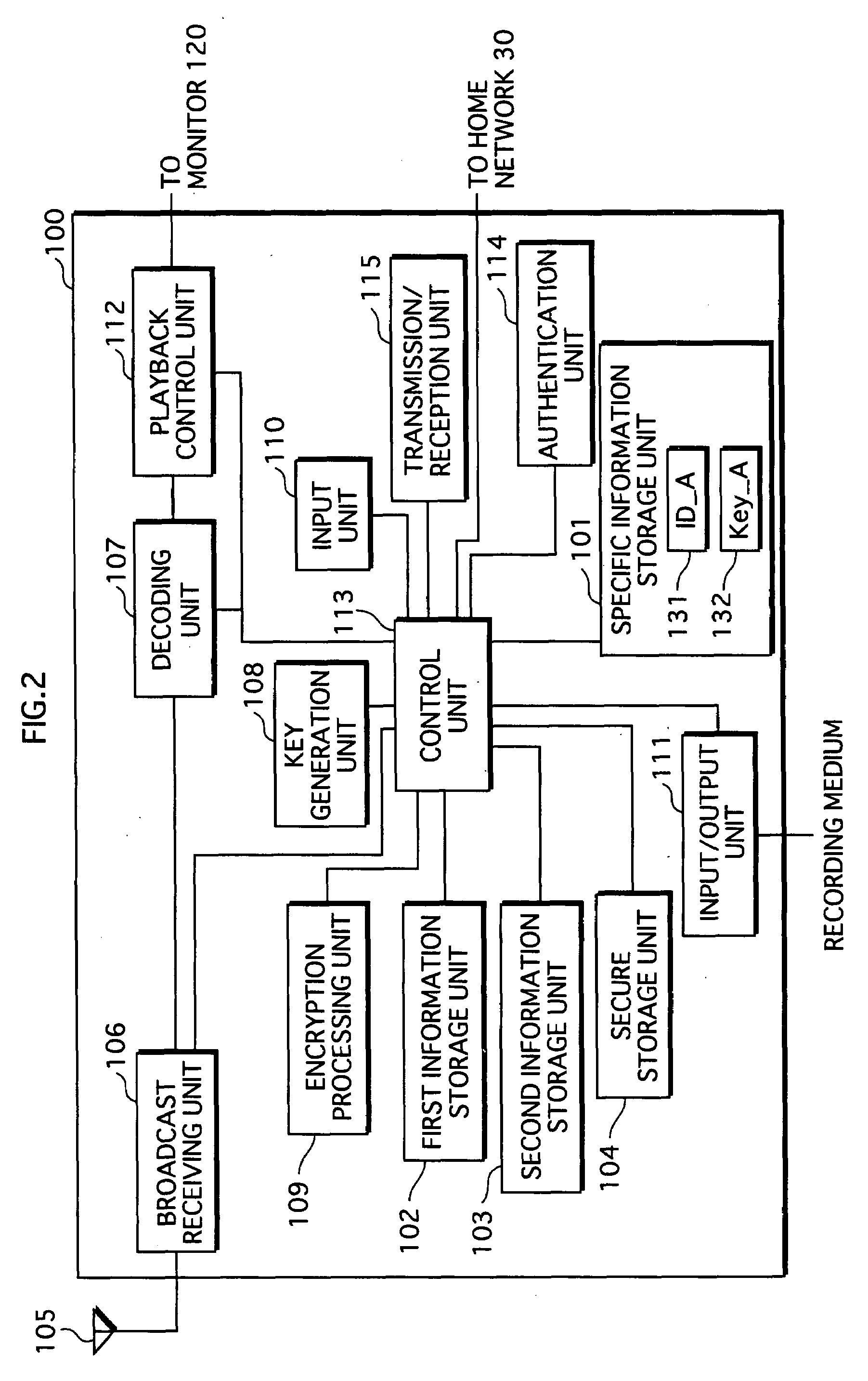
Backup Management Device, Backup Management Method, Computer Program, Recording Medium, Integrated Circuit, and Backup System
InactiveUS20080310628A1Copyright protectionKey distribution for secure communicationOptical re-recordingComputer hardwareEncryption
To provide a backup management device that deletes a content so as to be restorable in the future while protecting a copyright of the content, in a case where there exists a backup of the content. In an HD recorder 100, a first information storage unit 102 stores a content, a second information storage unit 103 stores a backup of the content, a secure storage unit 104 stores a hash value of the content. If receiving an instruction to delete the content so as to be restorable, a control unit 113 deletes the content from the first information storage unit 102. When the content is played back, an encryption processing unit 109 applies a calculation to the content to generate detection information, and the control unit 113 compares the hash value with the detection information to judge whether the content has been tampered.
Owner:PANASONIC CORP
Digital Copyright Management Using Secure Device
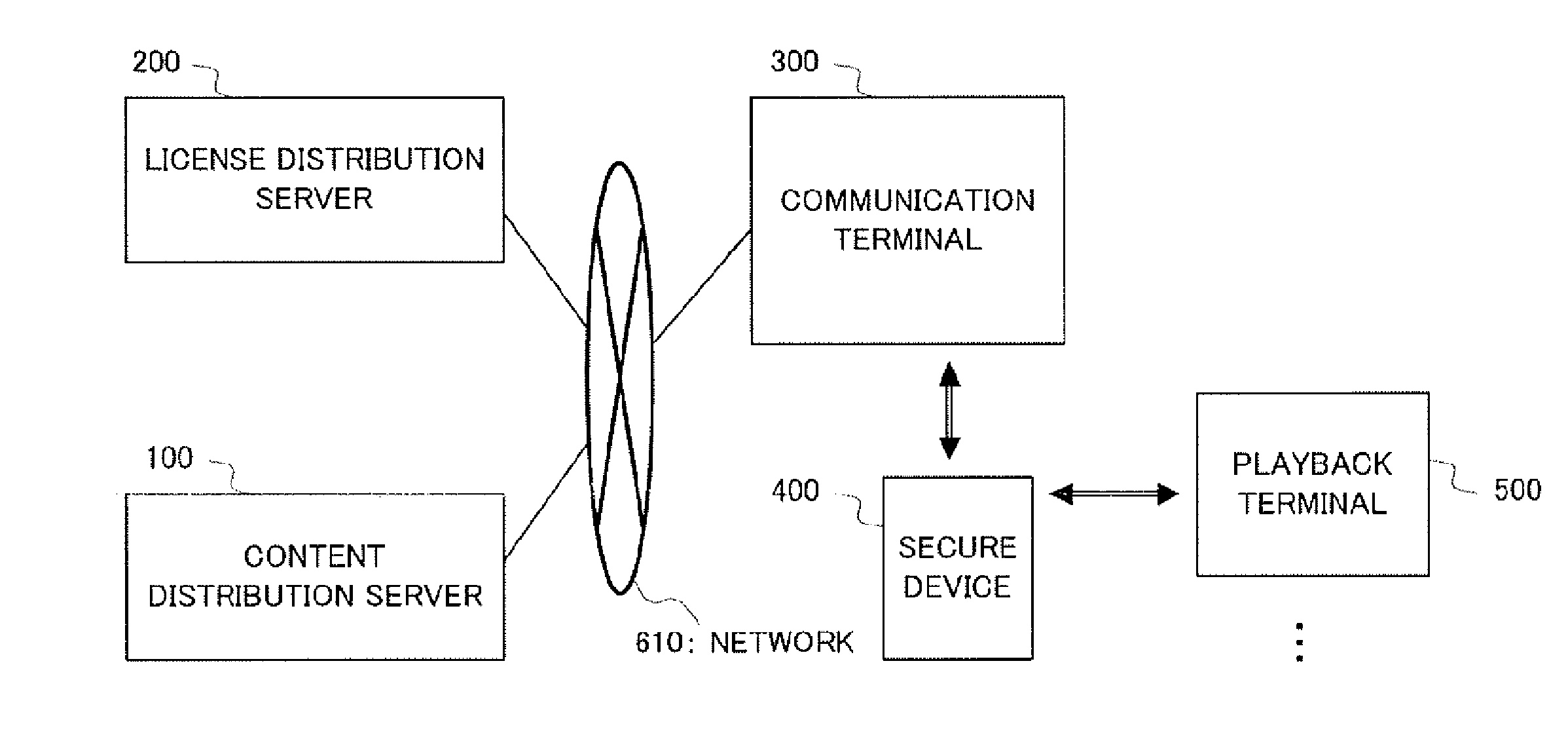
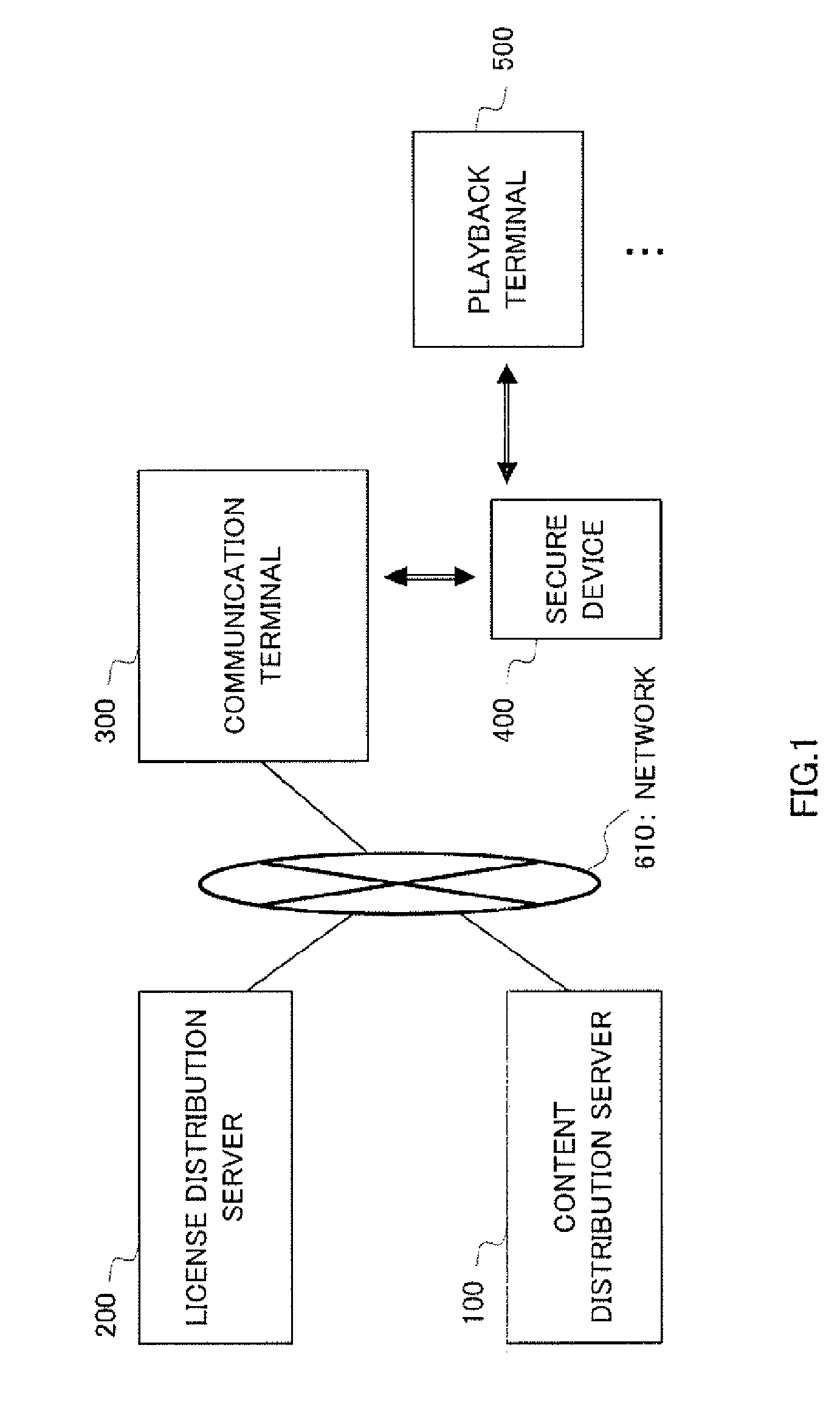
InactiveUS20070276760A1Copyright protectionUnnecessary operationTelevision system detailsKey distribution for secure communicationDigital rights managementLicense
There is provided a content use management method capable of preventing unauthorized distribution of a content and improving user-friendliness. In this method, the same group key is stored in a secure device (400) and a playback terminal (500). Moreover, a license issuing application is received from a license distribution server (200) and stored in the secure device (400). After this, a license encrypted by the group key is sent to the playback terminal (500) and the license encrypted by the group key is stored in the playback terminal (500). Upon playback of the encrypted content, the playback terminal (500) decrypts the license by using the group key and acquires the content decryption key, thereby decrypting the encrypted content. Even when the encrypted license flows into the network, it cannot be decrypted by a playback terminal not having the same group key and the copyright is protected. Moreover, the playback terminal (500) which already holds the group key and the license encrypted by the group key does not need the secure device when reproducing the encrypted content.
Owner:PANASONIC CORP
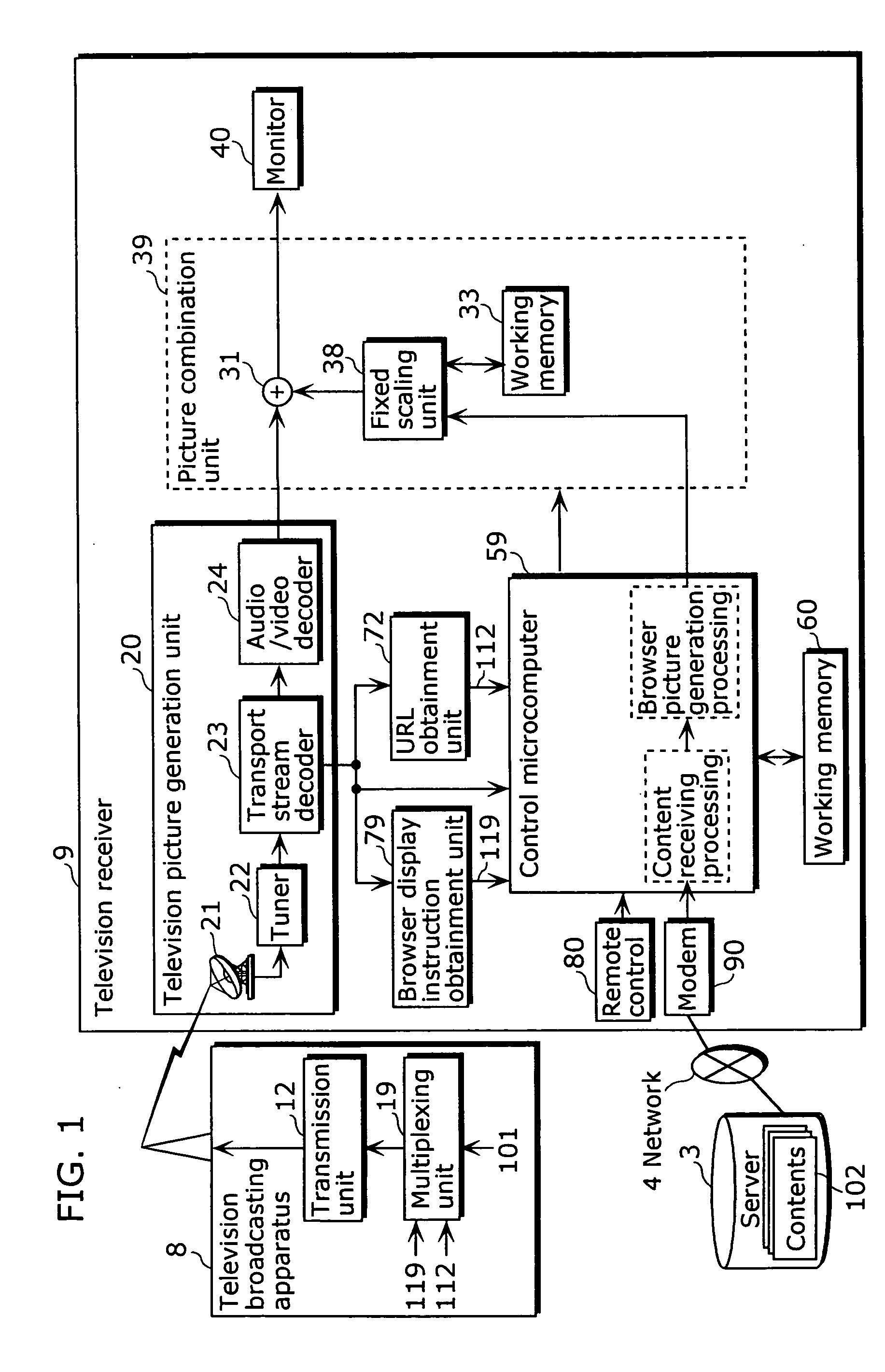
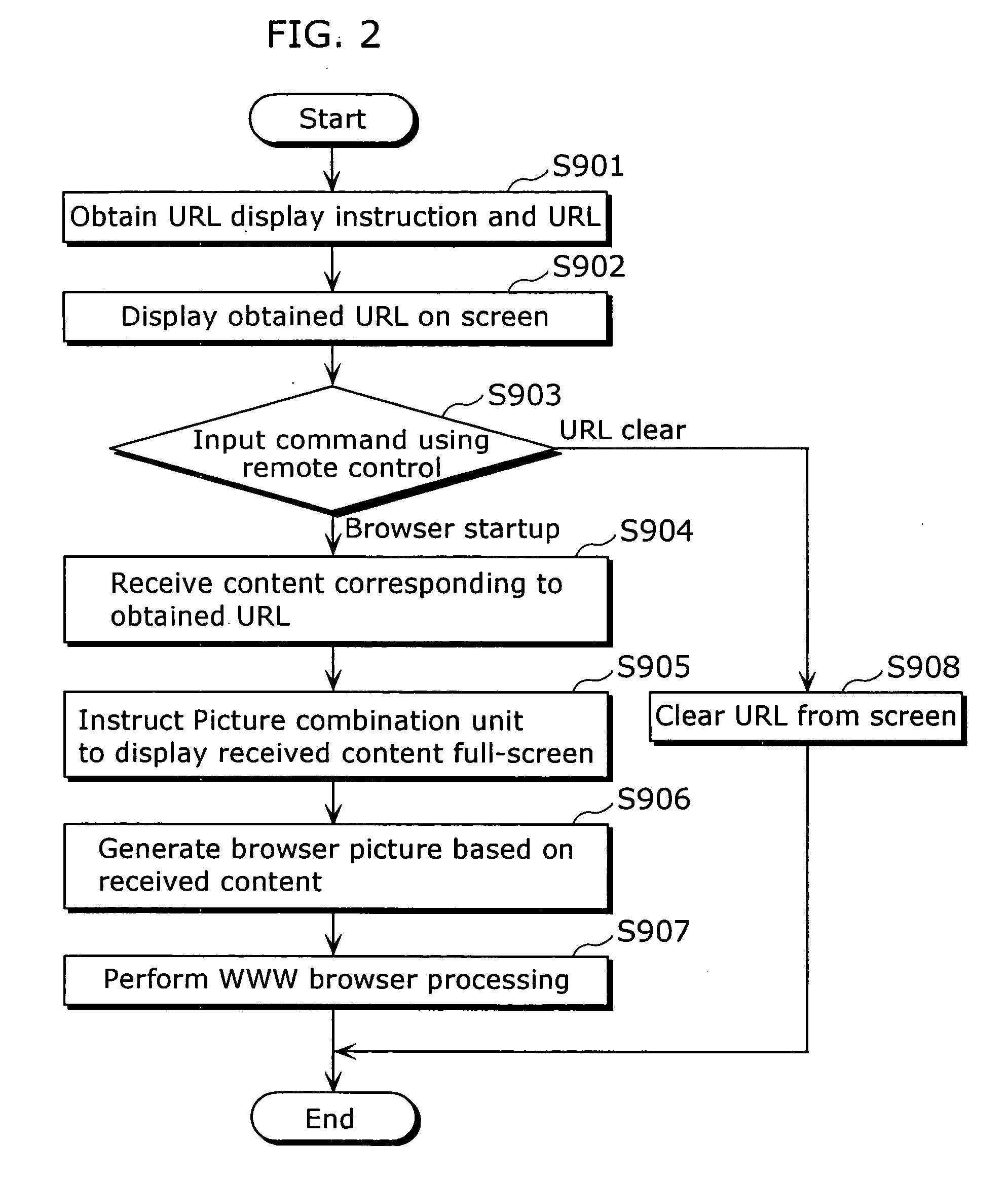
Receiving apparatus, method for displaying in conjunction with television program, and printing control method
InactiveUS20050066366A1Effective maintenancePrinting is restrictedTelevision system detailsPulse modulation television signal transmissionMicrocomputerTelevision receivers
A television receiver 2 includes: a television picture generation unit 200 that receives at least one television program broadcast including a URL which indicates a server 3 where a content 301 related to the television program broadcast is stored; a picture combination unit 300 that displays the received television program on a single screen; a modem 900 that receives the content 301 from the server 3 indicated by the URL included in the television program; and a control microcomputer 500 that changes the size of the picture of the television program to a predetermined size, and controls the picture combination unit 300 so as to continue displaying the television program picture, as a window on the screen, in front of the picture of the received content 301.
Owner:PANASONIC CORP
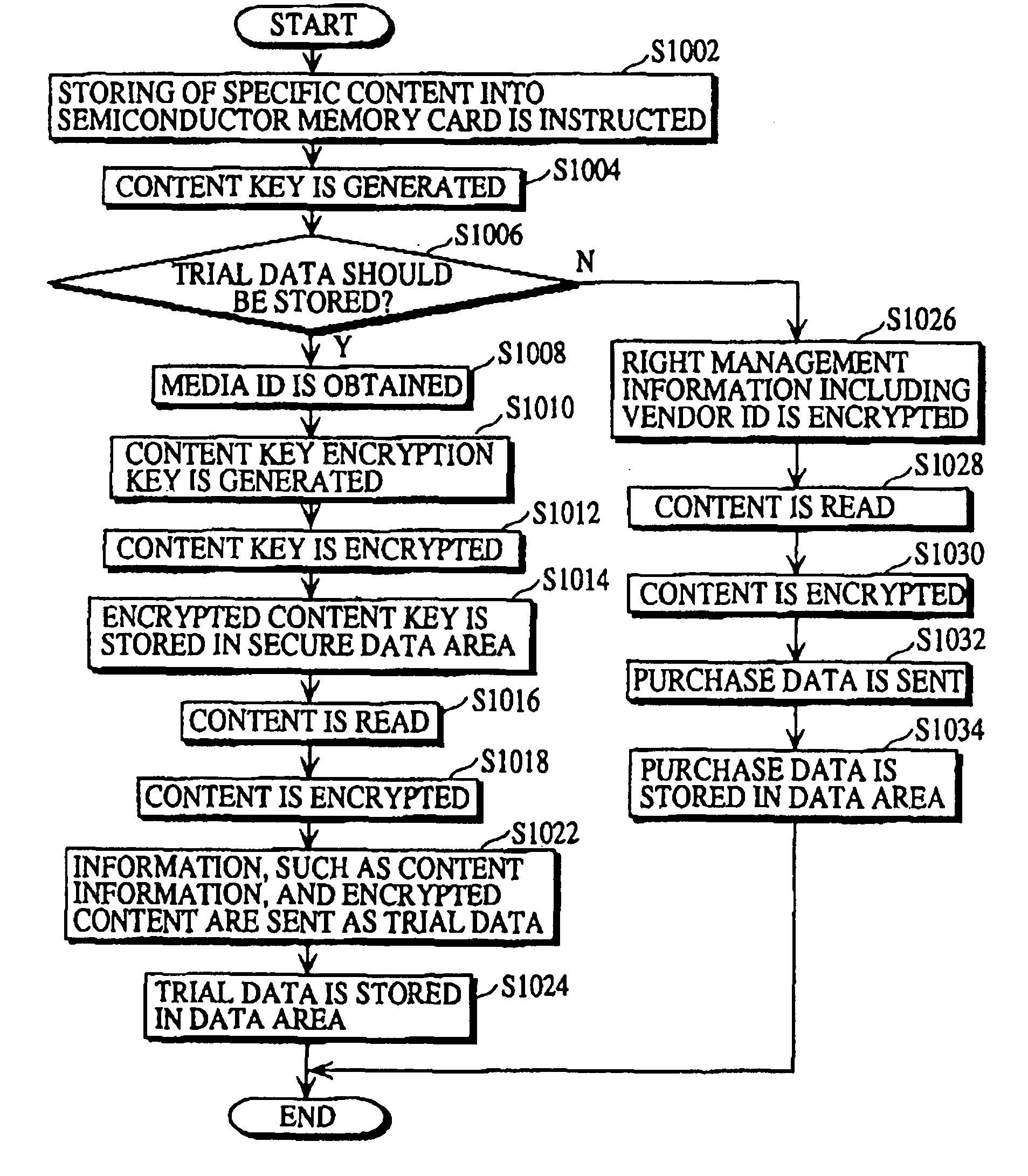
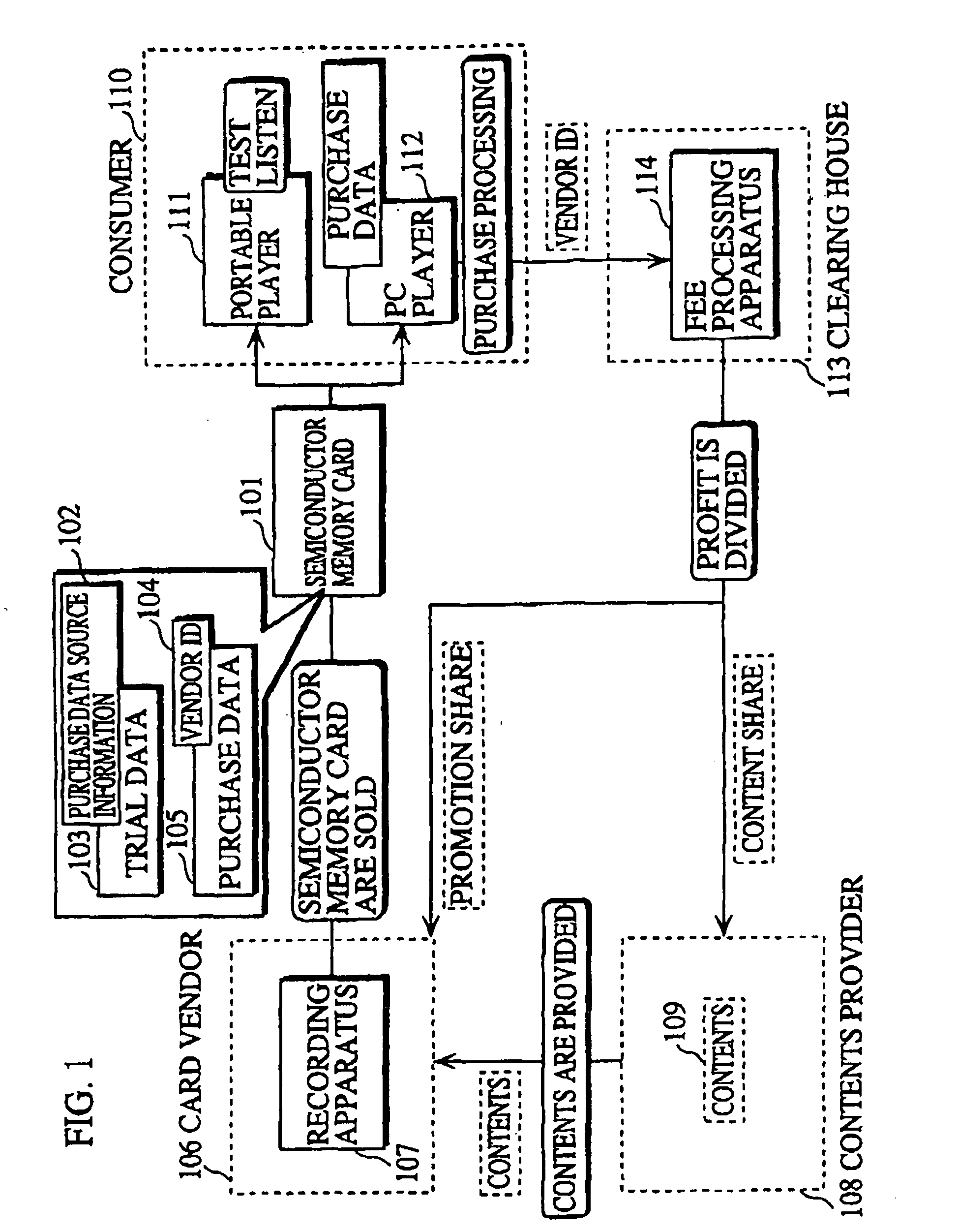
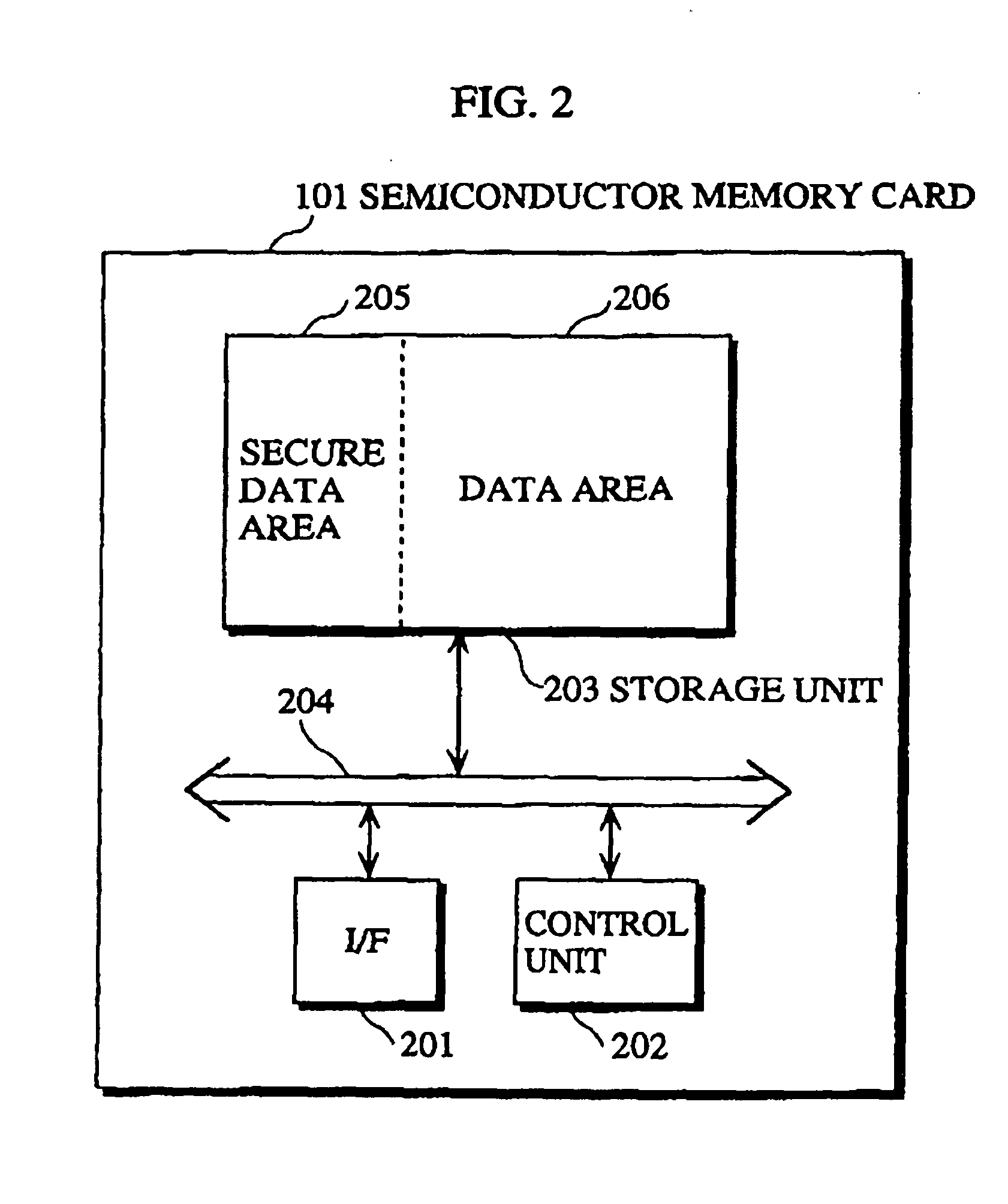
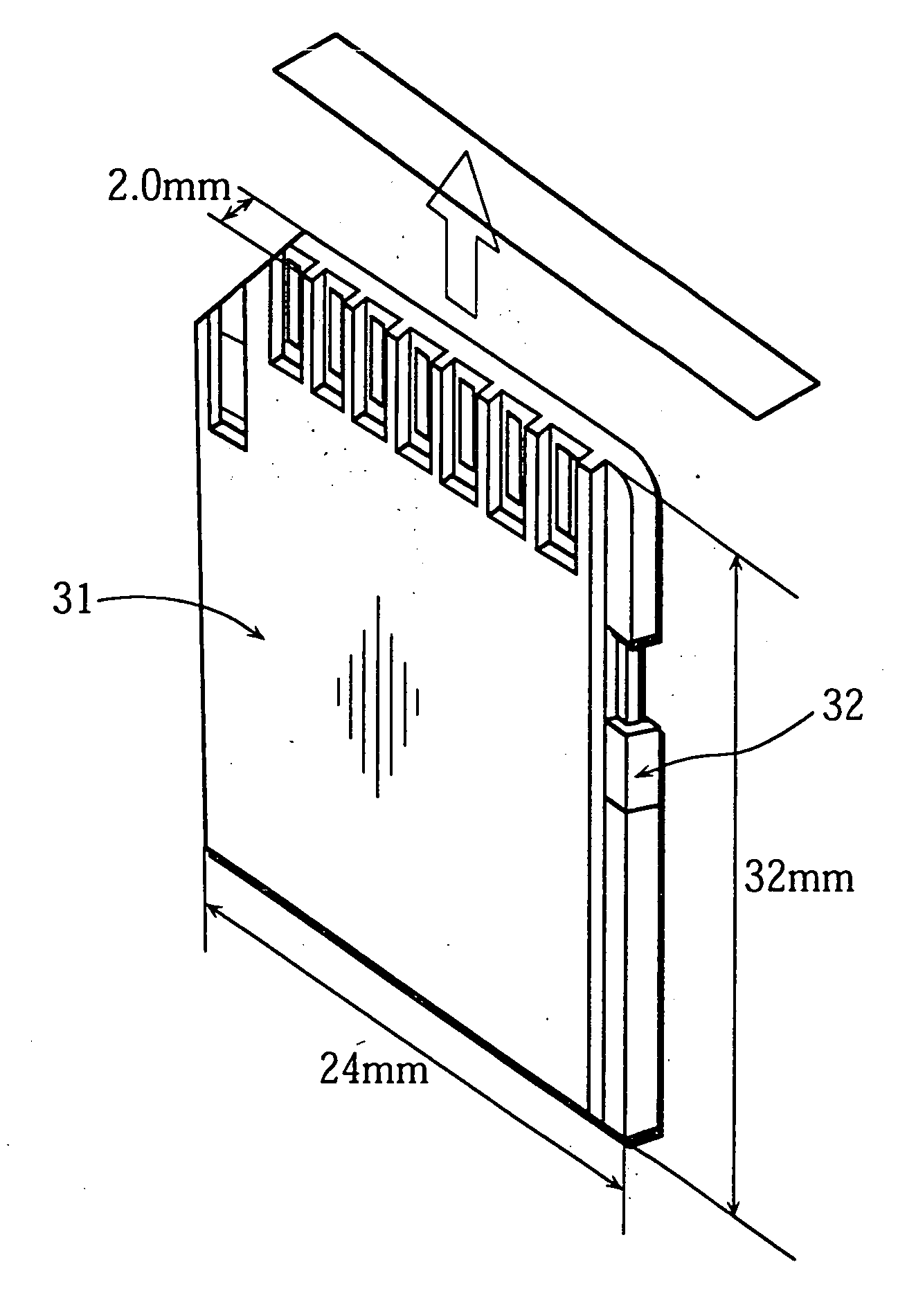
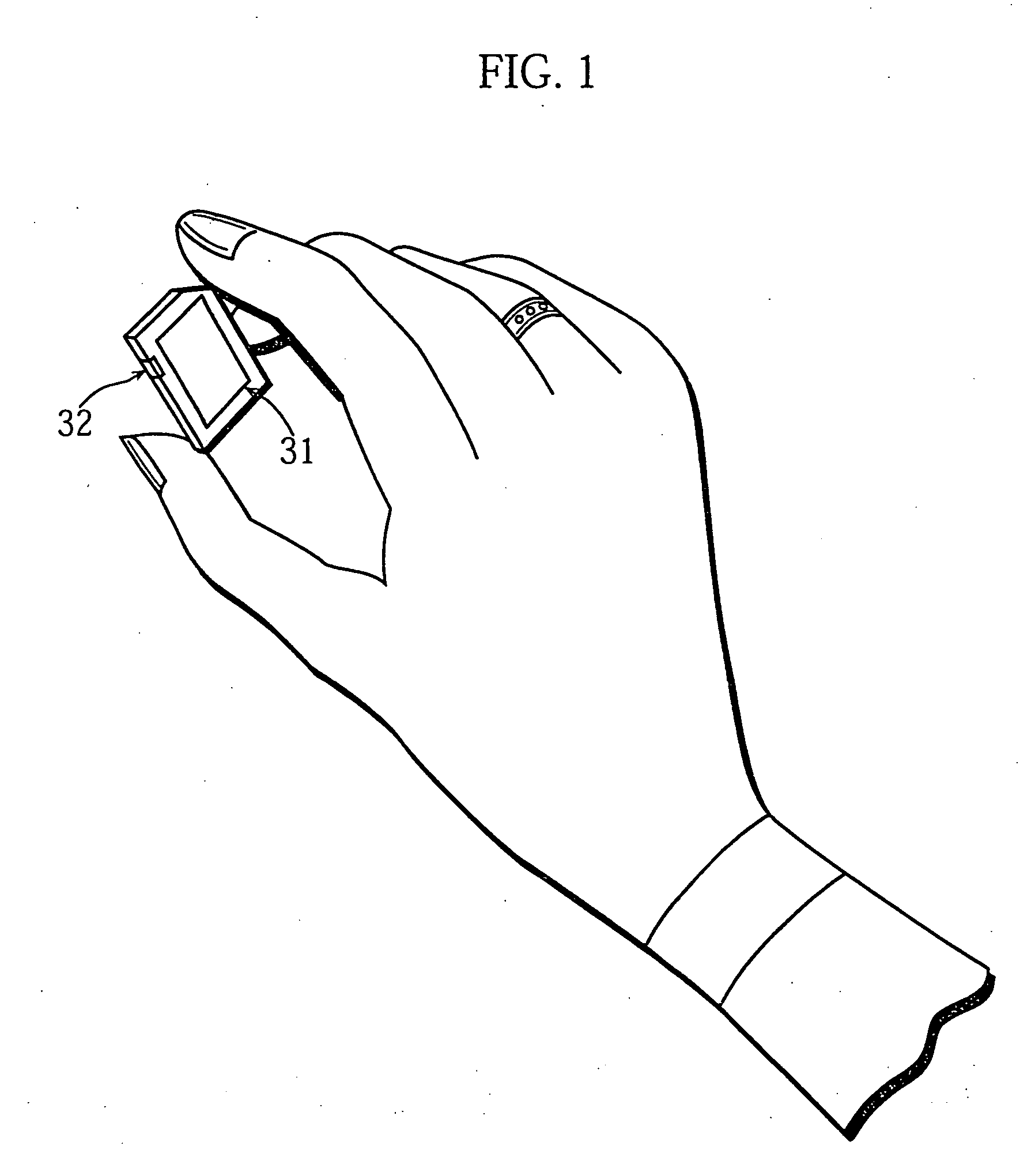
Semiconductor memory card that records contents for trial and purchase, and recording apparatus, recording and reproducing apparatus, and sales method for the same
InactiveUS20050160053A1Easy accessCopyright protectionKey distribution for secure communicationUser identity/authority verificationSemiconductorRecording media
A recording medium which allows consumers to access and purchase content while protecting the copyright of the content. The recording medium includes a secure data area and a non-secure data area. The secure data area is accessible by an apparatus whose authenticity is verified, and the non-secure area is accessible by the apparatus regardless of such verification. The secure data area stores a first content key. The non-secure data area stores first data and second data which can be decrypted. The first data includes a first encrypted content which is generated by encrypting a first content with the first content key, and the second data includes a second encrypted content which is generated by encrypting a second content with a second content key, where the first and second contents are related to each other.
Owner:OKAMOTO RYUICHI +3
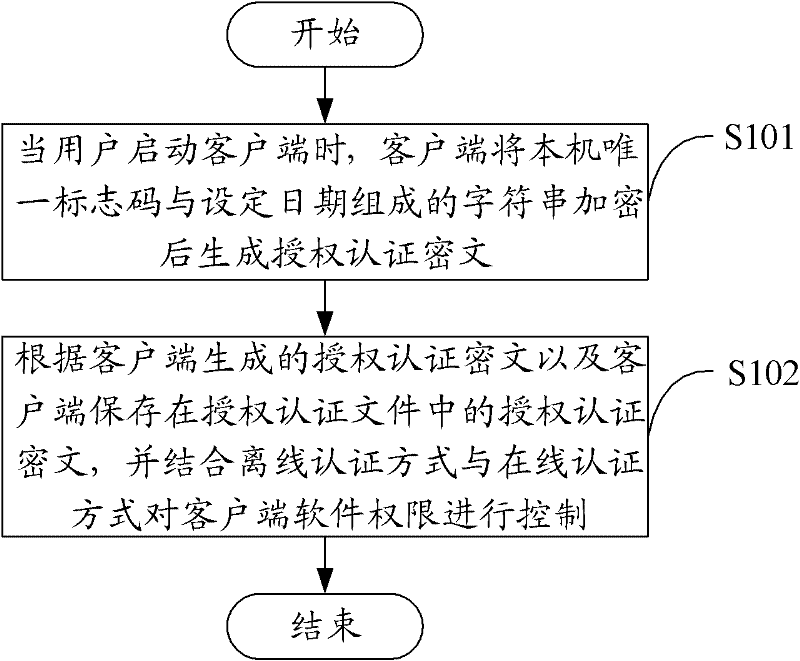
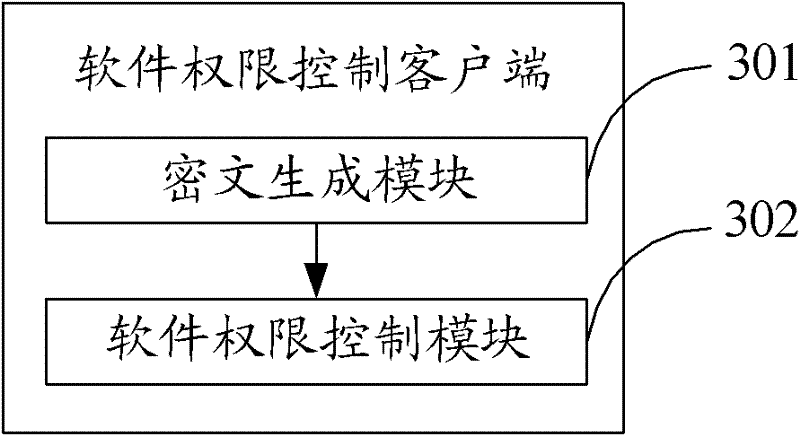
Method, client and system for software access control
ActiveCN102479304ACopyright protectionEasy to useDigital data authenticationTransmissionCiphertextNetwork Access Control
The invention relates to a method, a client and a system for software access control. The method comprises the following steps: when a user starts the client, the client encrypts a character string consisting of a local unique identification code and a set date and generates an authorization and authentication ciphertext; and the software access of the client is controlled by combining an offline authentication mode and an online authentication mode according to the authorization and authentication ciphertext generated by the client and an authorization and authentication ciphertext which is stored in an authorization and authentication file by the client. According to the method, the client and the system, the copyright of software is effective protected in a mode that the online authentication is combined with the offline authentication, and the authorized user can conveniently use the software. In the network environment specified by the user, registration and login are not required, and the software can be used without limit; in the environment besides the specified environment, the software is conditionally limited; and the software which is allowed to normally operated in the specified environment can be operated for a preset time in the same computer off the specified network operating environment, and the software is effectively limited to be copied and used among computers.
Owner:SLICONGO MICROELECTRONICS INC
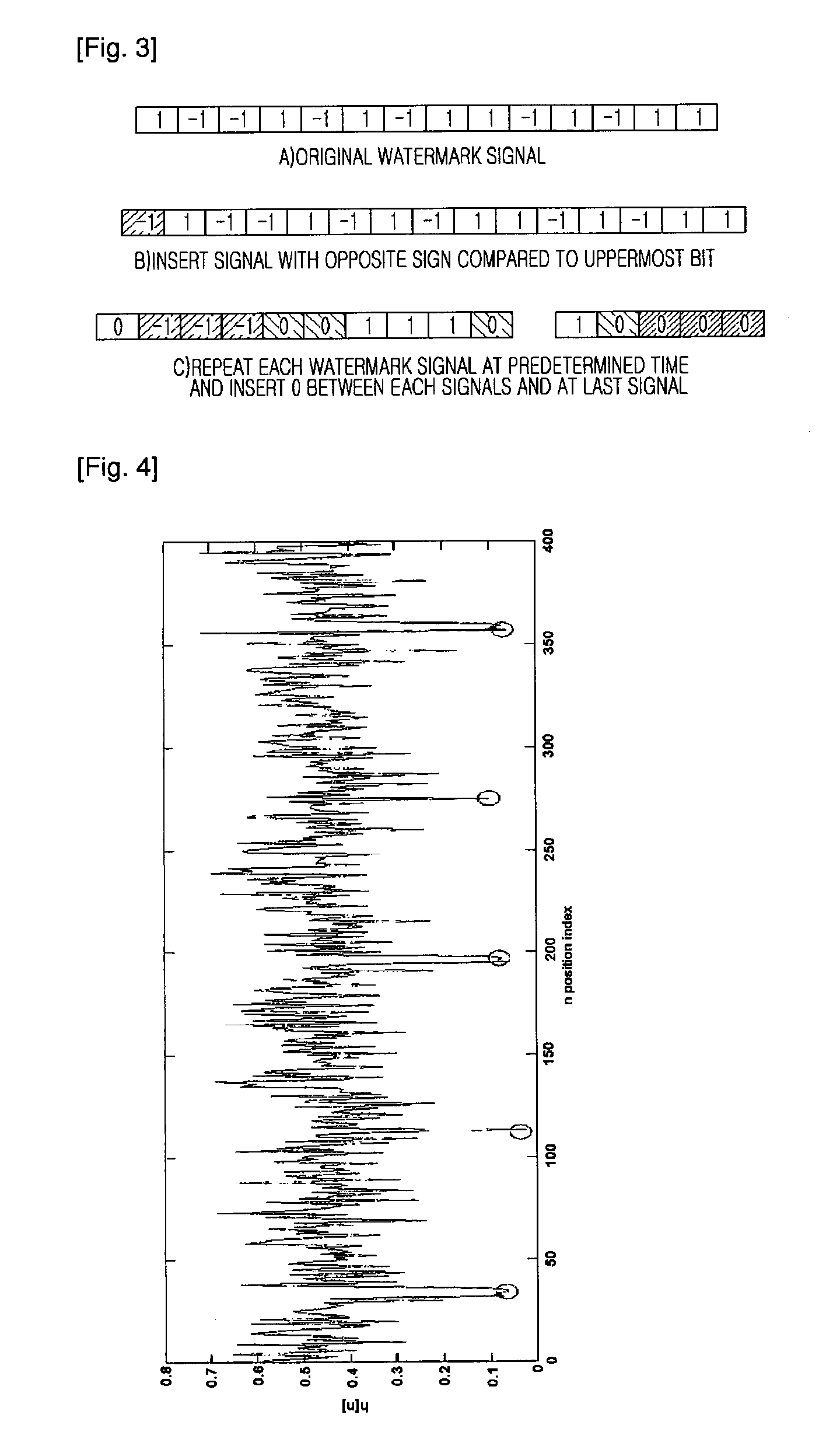
Apparatus and method for inserting/extracting capturing resistant audio watermark based on discrete wavelet transform, audio rights protection system using the same
InactiveUS20090125310A1Easy to detectVarious distortionTelevision system detailsBroadcast systems characterised by watermarksAudio watermarkProtection system
An apparatus and method for embedding and extracting a capturing-resistant audio watermark based on discrete wavelet transform, and a copyright management system using the same are provided. The apparatus for embedding a wavelet based audio watermark includes: a framing unit for dividing an input audio signal into small signals with a regular length; a discrete wavelet transform unit for calculating an mean value of wavelet coefficients by transforming the small signals based on a discrete wavelet transform; and an embedding unit for changing the calculated mean value according to a watermark where a synchronization signal is inserted and inserting the watermark into the audio signal.
Owner:ELECTRONICS & TELECOMM RES INST
Semiconductor memory card, playback apparatus, recording apparatus, playback method, recording method, and computer-readable recording medium
InactiveUS20050192686A1Copyright protectionMinimizing damageKey distribution for secure communicationInput/output to record carriersEngineeringAudio frequency
An audio stream is divided into a plurality of audio object (AOB) files that are recorded having each been encrypted using a different encryption key. At least one piece of track management information (TKI) is provided corresponding to each track. Playlist information (PLI) assigns a playback position in a playback order to each track when a plurality of tracks are to be played back one after the other.
Owner:PANASONIC CORP
Data processor
InactiveUS20070239948A1Copyright protectionMemory loss protectionError detection/correctionData memoryAccess control
A data processor includes: a first medium on which a content's data has been bound-recorded; a memory having stored thereon the content's access control information; and a read / write section for reading and writing data from / on a second medium. In response to a request to back up the content, the read / write section writes the content's data on the second medium and the memory retains the access control information without modifying the information. If a request to restore the content has been received and if the access control information that makes the content accessible is stored in the memory and if the content's data has been written on the second medium, then the read / write section reads the content's data from the second medium and writes the data on the first medium.
Owner:PANASONIC CORP
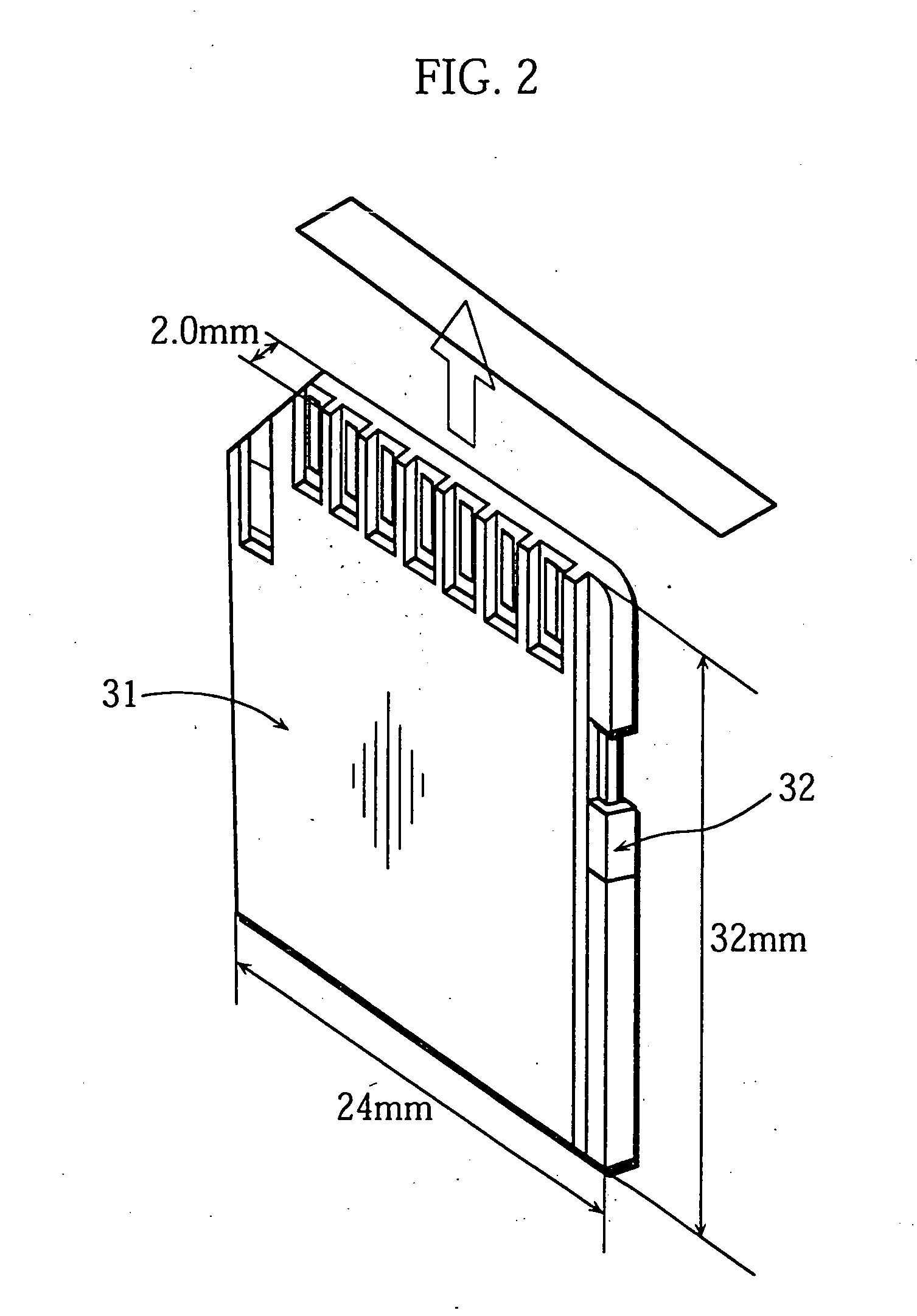
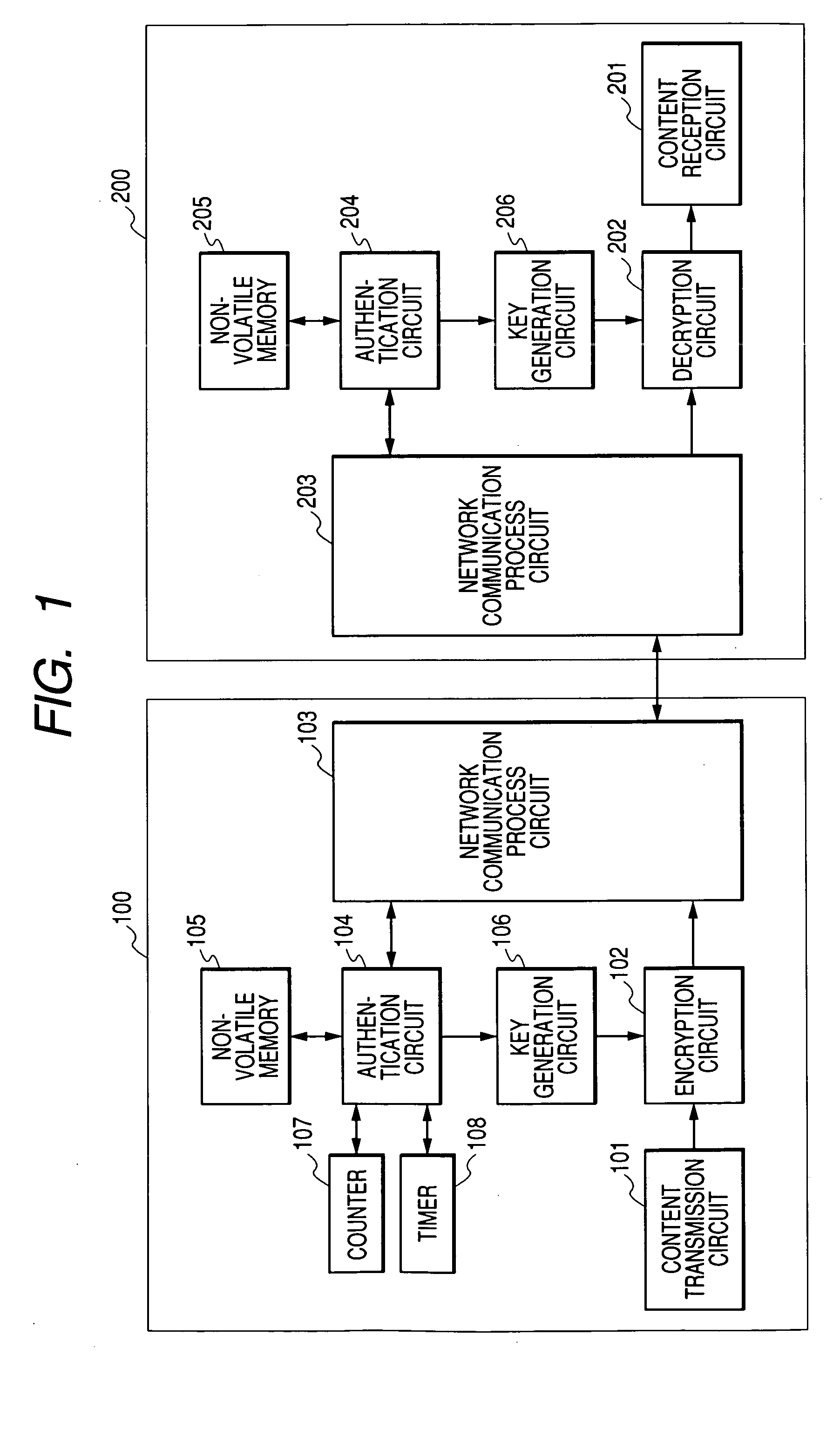
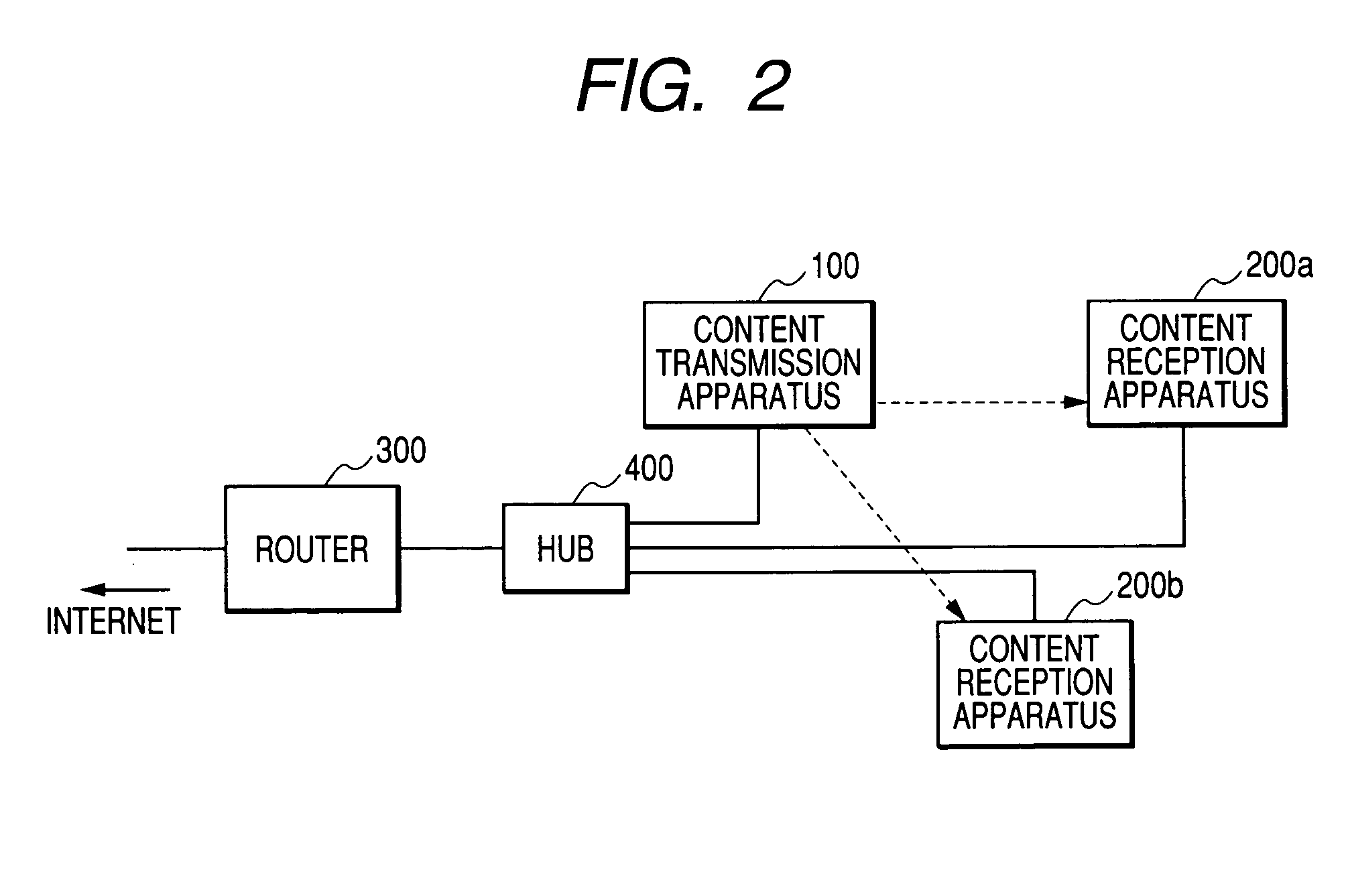
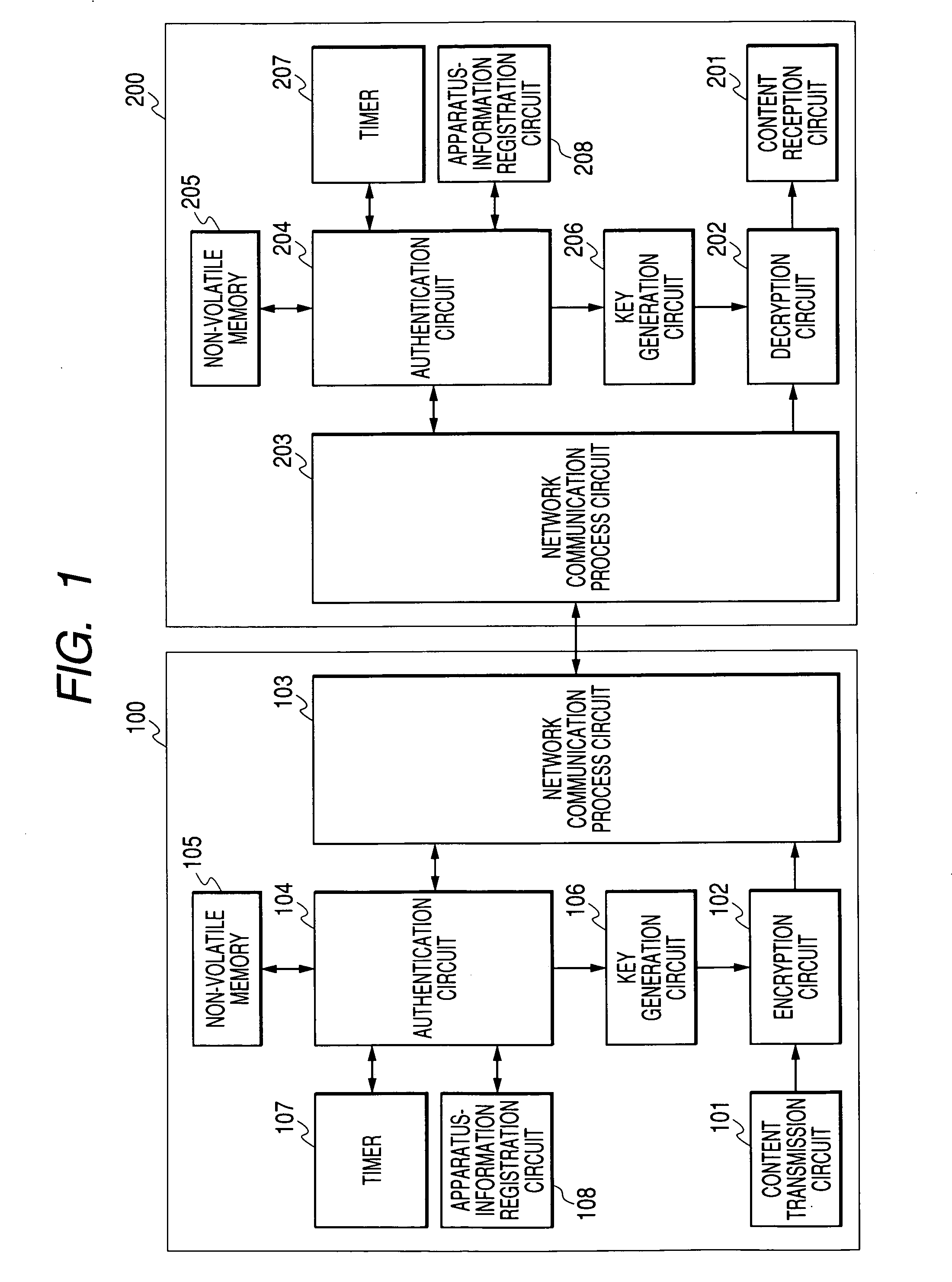
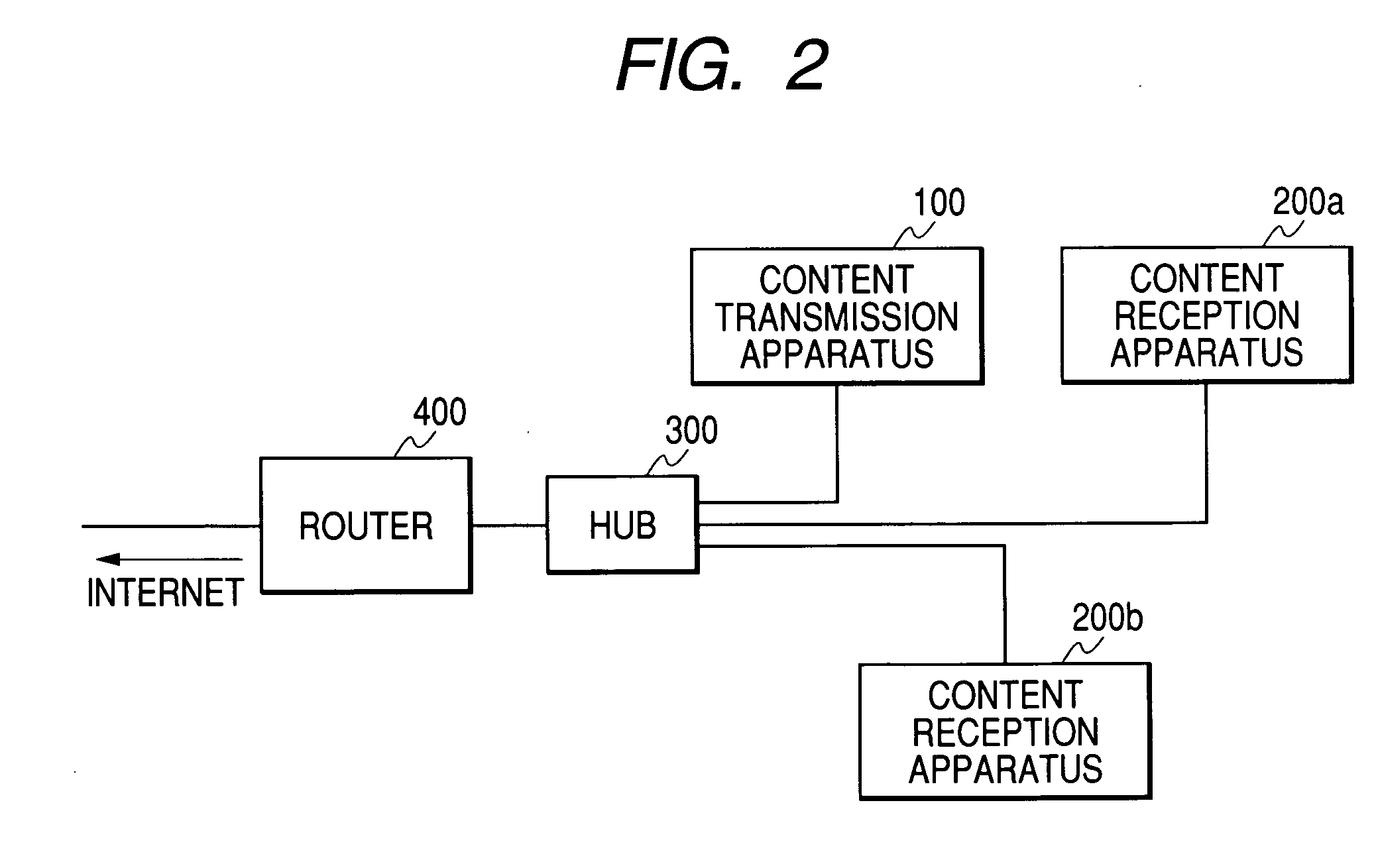
Content transmission apparatus, content reception apparatus and content transmission method
ActiveUS20050160265A1Limit legal operationIncrease heightKey distribution for secure communicationUser identity/authority verificationAuthentication information
A copyright of a content is protected by preventing creation of illegal copies of the content and the content is prevented from being transmitted beyond a range of personal use in a process to transmit the content through a LAN. Before transmission of a content, a content transmission apparatus and a content reception apparatus perform a determination of authentication information available in a predetermined command accompanying authentication information, or an authentication determination based on a time until reception of a response to a predetermined command request accompanying predetermined authentication information. If the authentication is unsuccessful, the requested content is not transmitted to the content reception apparatus. With such arrangement, it is possible to effectively protect a copyright when a content is transmitted by way of a network.
Owner:MAXELL HLDG LTD
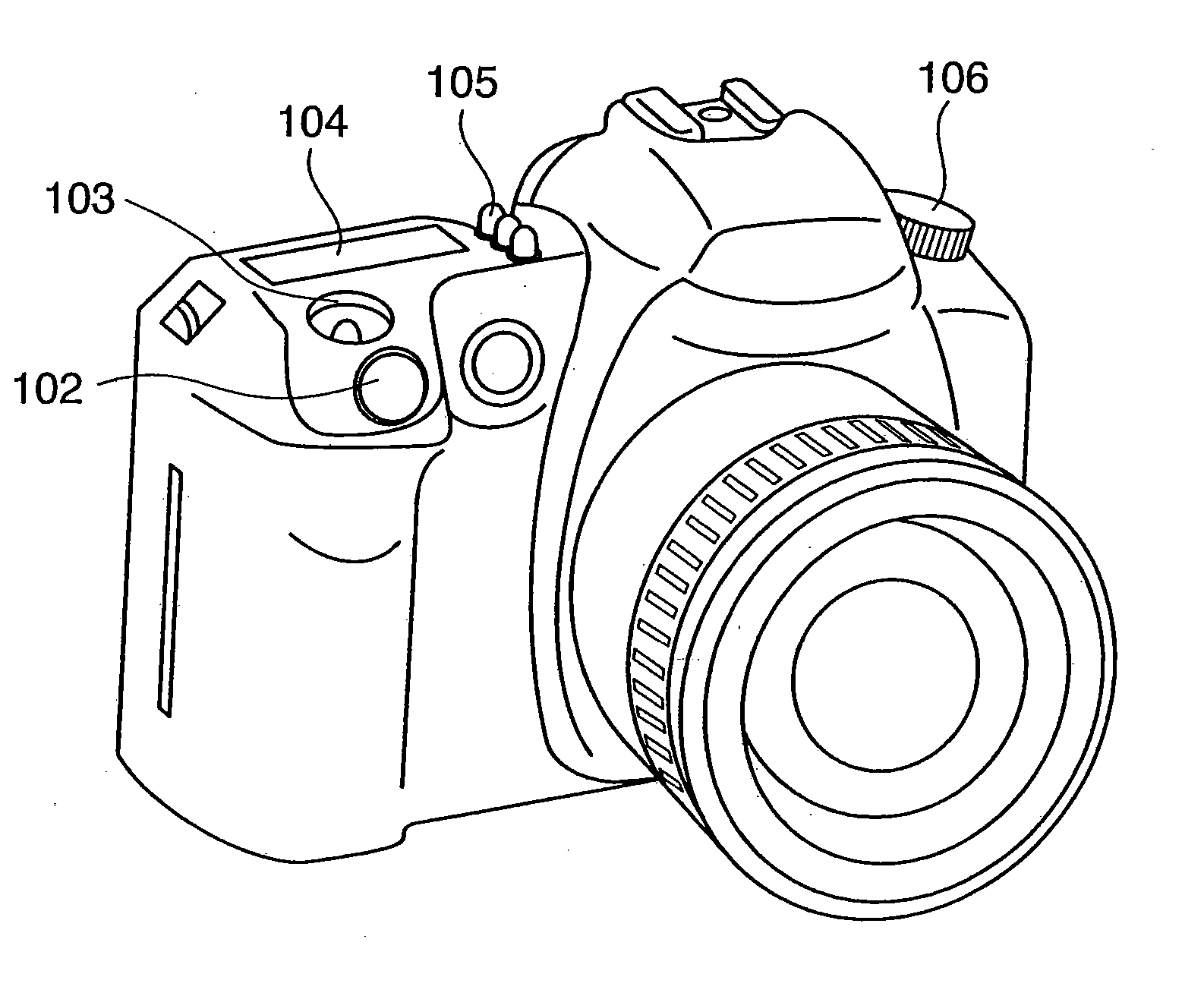
Picture taking apparatus and method of controlling same
InactiveUS20080025574A1Copyright protectionTelevision system detailsUser identity/authority verificationIris imageComputer science
The camera includes a sensor for sensing the photographer's iris image and registering the image in advance. The iris image is recorded in the image of a subject by a digital MCU at a timing different from that at which the image of the subject is captured. The recording timing is that at which the camera power supply is turned off, that at which a recording medium is ejected from the camera or that at which the iris image to be recorded is changed to changed to the registered iris image of another photographer. The recording of the iris image is achieved by embedding it as a watermark or by appending it to metadata.
Owner:CANON KK
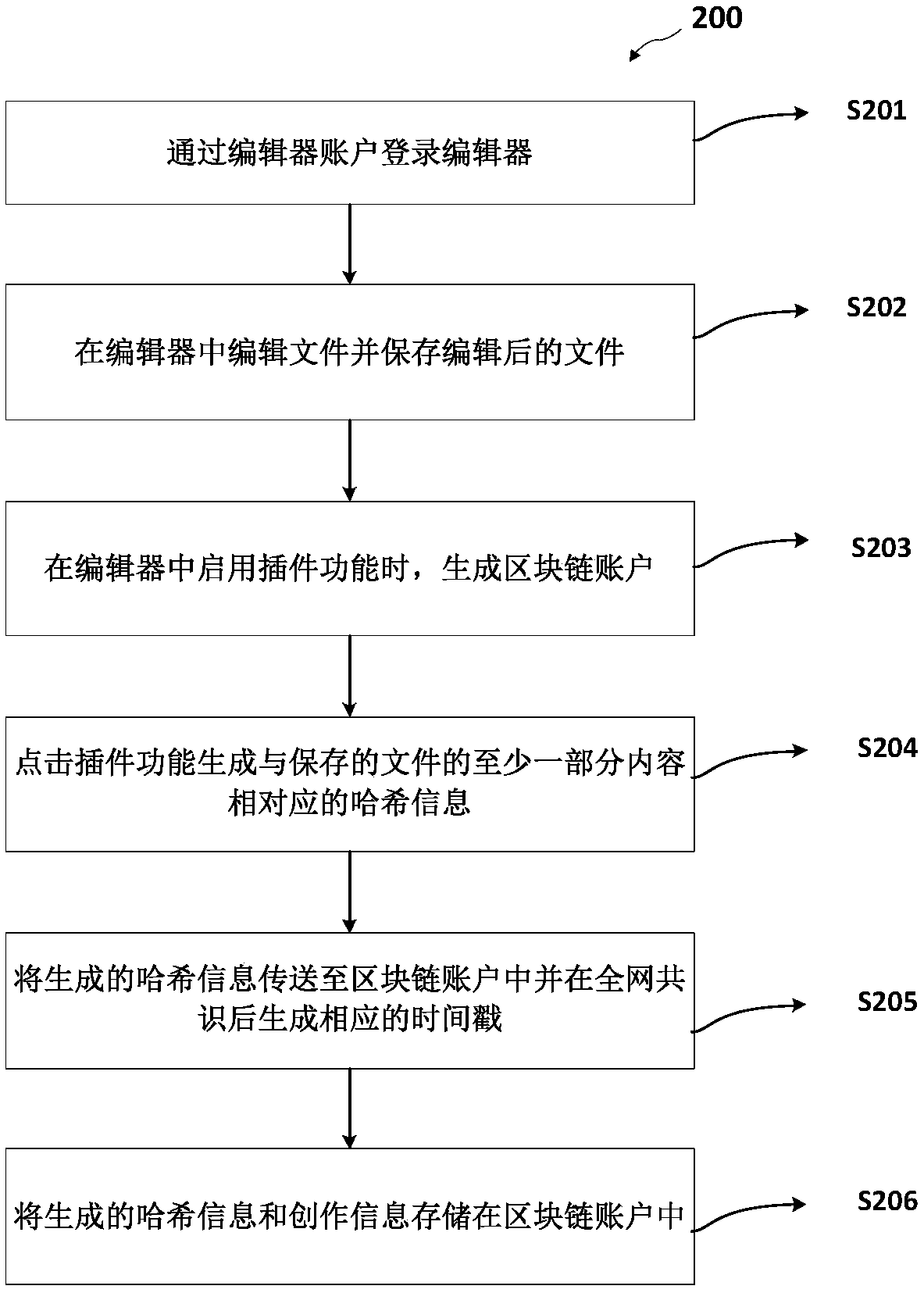
File processing method and device based on block chain
InactiveCN109344568ACopyright protectionDigital data protectionProgram/content distribution protectionBlockchainOperating system
The invention provides a file processing method based on a block chain. The method comprises the following steps: editing a file in an editor; Enabling the specified plug-in in the editor to generatea chunk chain account; hash-calculating At least a portion of that content of the file by a specified plug-in to generate corresponding hash information. The invention utilizes the plug-in of the associated block technology to obtain the hash information related to the file in real time, and utilizes the characteristic of block chain anti-tampering to confirm the right of the file edited by the editor, thereby effectively protecting the copyright of the creator.
Owner:ZHONGAN INFORMATION TECH SERVICES CO LTD
Playing on demand system for video
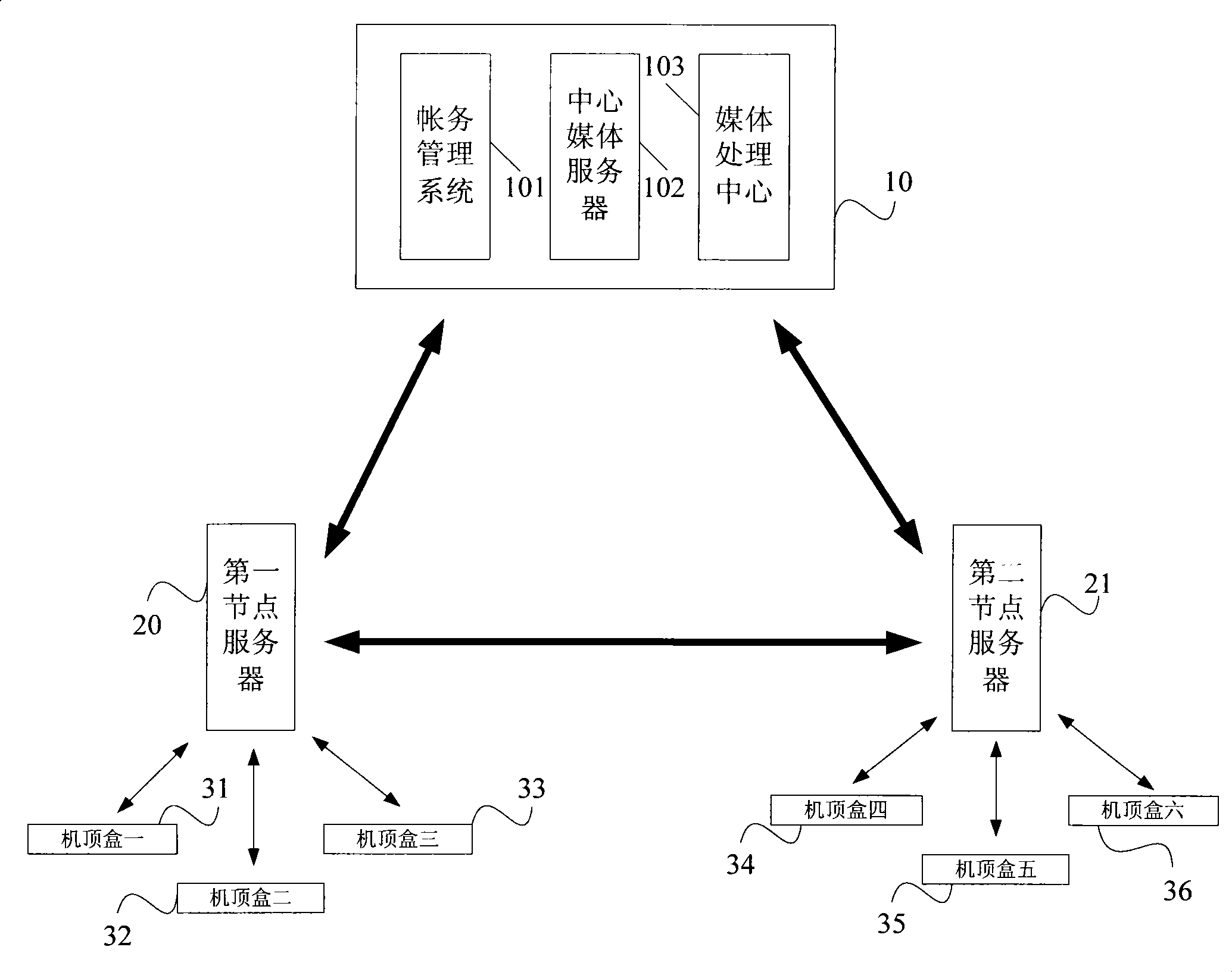
ActiveCN101453624ARealize network operationEasy to distributeTwo-way working systemsCommunity orComputer science
The invention discloses a (hotel, community or family) video-on-demand system. The video-on-demand system comprises a center server, a node server and a user terminal, wherein the center server is used for storing video information; the node server is used for establishing communication with the center server through a network so as to obtain at least one part of the video information and generating a programme list according to the video information; the user terminal is used for reading the programme list and displaying the programme list through display equipment; and when a user orders a corresponding programme, the user sends a video-on-demand request to the node server, reads corresponding decoded video information and plays the information through the display equipment. In the video-on-demand system, as each (hotel, community or family) node server is connected with the center server through the wide area network, thereby realizing network operation of the whole video-on-demand system. The video-on-demand system can carry out programme distribution and management through the network, thereby making the distribution and management operation simple and feasible and also improving efficiency.
Owner:QINGDAO TONGXIN INNOVATION LAB TECH CO LTD
Content transmission apparatus and content reception apparatus
InactiveUS20050160274A1Avoid creatingData quality of the content hardly deterioratesKey distribution for secure communicationMultiple keys/algorithms usageWireless lanTimer
It is an object of the present invention to protect a copyright of a content by suppressing creation of illegal copies of the content and prevent a content from being transmitted beyond a range of personal use in a process to transmit the content through a wire or wireless LAN. Before transmitting a content from a content transmission apparatus to a content reception apparatus, the content transmission apparatus and the content reception apparatus authenticate each other. In the authentication, a timer measures a time interval between a transmission of an authentication request and a reception of an acknowledgement of a reception of the request or between a transmission of a response to a received authentication request and a reception of an acknowledgement of a reception of the response. If the time interval does not exceed an upper limit, a content encrypted by using a shared key is transmitted from the content transmission apparatus to the content reception apparatus, and the address of the content reception apparatus as well as apparatus information unique to the content reception apparatus are cataloged in the content transmission apparatus. Thus, in order to transmit another content, the content is merely encrypted prior to the transmission without measuring a time interval.
Owner:HITACHI LTD
Signal processing system, recording method, program, recording medium, reproduction device and information processing device
InactiveUS20050089165A1Enhanced informationSecuring safety of a copyright protection technologySpeech analysisRecord information storageInformation processingNumber generator
A recorder is composed of a drive 102 and a host 103 that mutually authenticate each other. A C2_G 141 of the drive 102 calculates a medium ID and a medium key and obtains a medium unique key. The medium unique key is encrypted using a session key Ks generated by the mutual authentication and transferred to the host 103. A title key generated by a random number generator 143 of the drive 102 is transferred to the host 103. A content key calculated by a C2_G 145 of the drive 102 using the title key and the CCI 232 is encrypted using the session key Ks and then transferred to the host 103. A content is encrypted using a content key decrypted by the host 103. The drive 102 records the encrypted content, the encrypted title key, and the CCI 232 to the medium 101.
Owner:SONY CORP
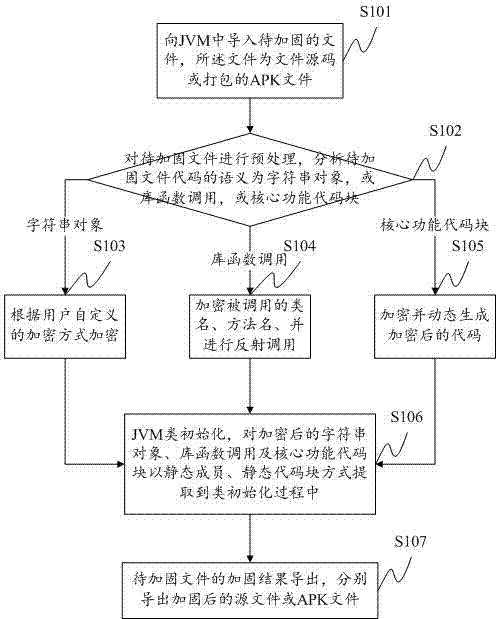
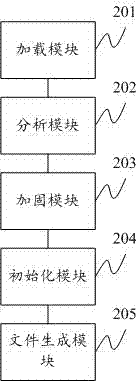
APK application reinforcing method and system
InactiveCN103902858ACopyright protectionReduce the possibility of reverse engineeringProgram/content distribution protectionCoding blockReverse analysis
The invention provides an APK application reinforcing method and system. The method comprises the steps of inputting the source code of files to be reinforced or APK files, preprocessing the files to be reinforced, analyzing the semantics, using different encryption ways according to different objects, conducting JVM class initialization processing on the encrypted objects, extracting the encrypted objects to the class initialization process in the modes of static members, static code blocks and the like, and at last outputting a reinforcing result. Through the APK application reinforcing method, APK application programs under the Android can be reinforced, displaying and calling of any cleartext character string or library functions can not occur to a decompilation result, a core code function is hidden, the difficulty of reverse analysis of the APK files is greatly increased, and therefore the effect of protecting the application codes of a developer is achieved.
Owner:WUHAN ANTIY MOBILE SECURITY
Pirated video monitoring method and system
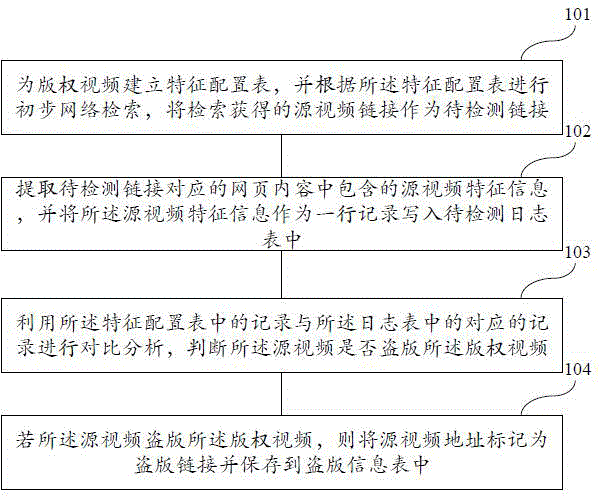
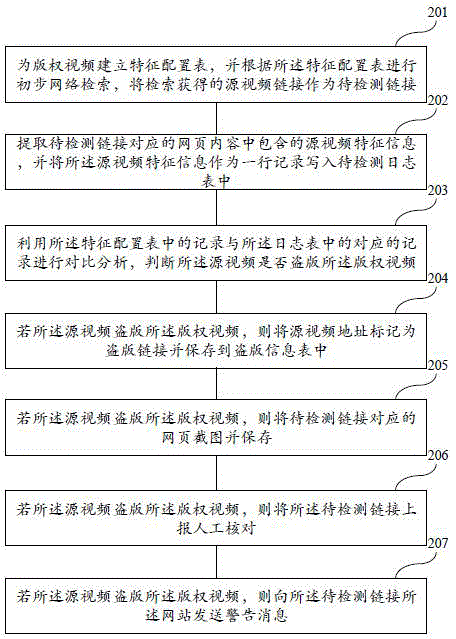
ActiveCN104143055AImprove accuracyProtect video copyrightWeb data retrievalVideo data retrievalWeb pageVideo monitoring
The invention discloses a pirated video monitoring method and system. The method comprises the following steps of constructing a characteristic configuration table for a copyrighted video, performing preliminary network retrieval according to the characteristic configuration table, and taking a source video link obtained by the retrieval as a link to be detected; extracting source video characteristic information in a webpage content corresponding to the link to be detected, and writing the source video characteristic information as a line record into a log table to be detected; comparing a record in the characteristic configuration table with a corresponding record in the log table and analyzing, and judging whether the source video pirates the copyrighted video or not; and if the source video pirates the copyrighted video, marking an address of the source video as a pirated link, and storing the address into a pirate information table. According to the pirated video monitoring method and system, relevant data of network videos is regularly acquired from a network for comparison analysis, so that the existence of the pirated video in the network can be judged.
Owner:ALIBABA (CHINA) CO LTD
Methods and systems of watermarking multimedia data using mobile communication terminals
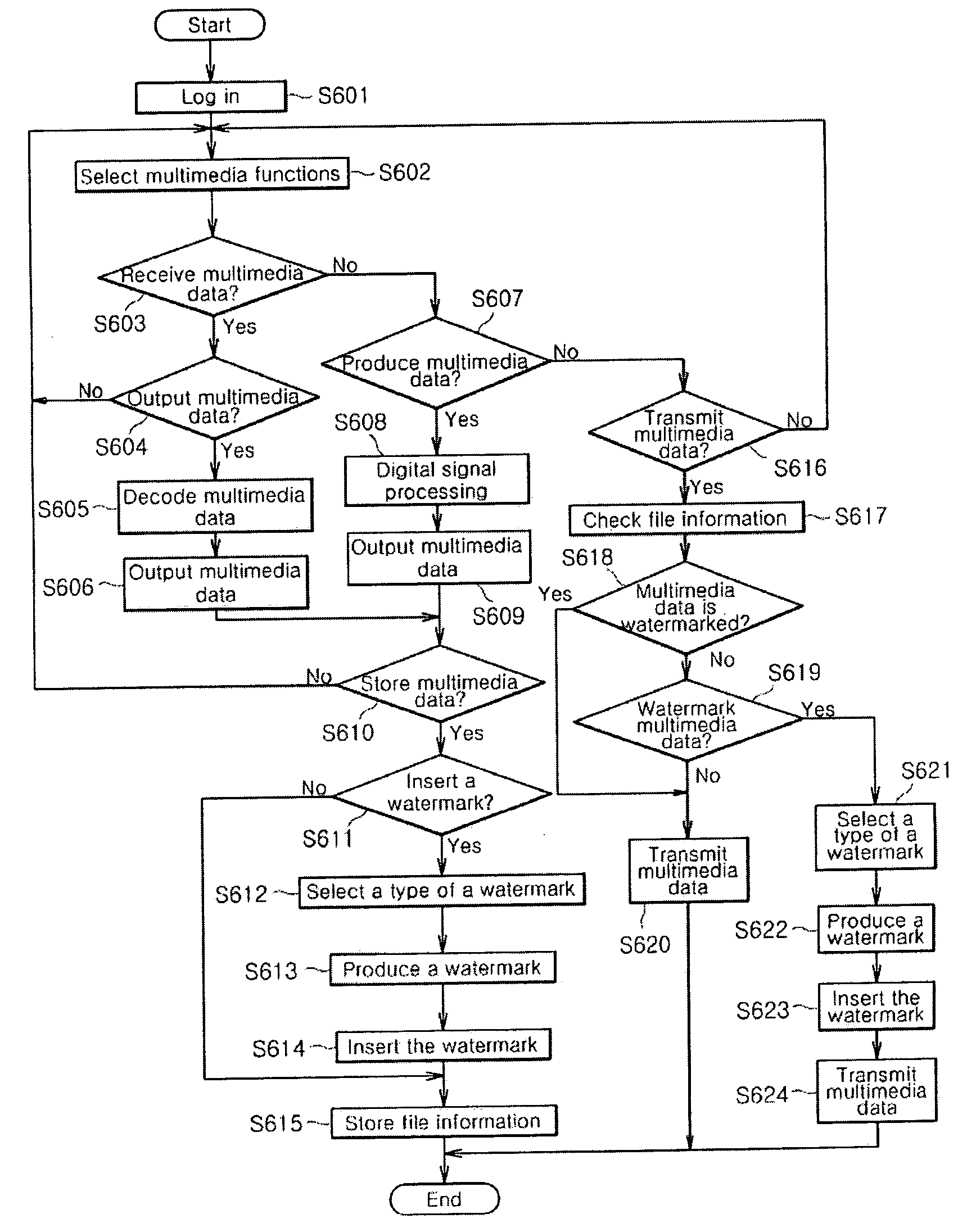
InactiveUS20050018843A1Reduce economic lossProcessing speed blockSubstation equipmentTelevision systemsComputer networkCertificate authority
Disclosed are methods and systems of watermarking multimedia data using mobile communication terminals. More particularly, methods and systems of selectively watermarking the multimedia data are disclosed. According to the present invention, it is made possible to trace and check author or provider of multimedia data without intervention of a certificate authority, thereby protecting copyright of multimedia data and resolving problems misusing and abusing multimedia data relating to other person's privacy. Further, it is made possible to minimize economic loss and to prevent processing speed of mobile communication terminals from being reduced.
Owner:PANTECH CO LTD
Information-processing apparatus, information-processing method, program, and storage medium
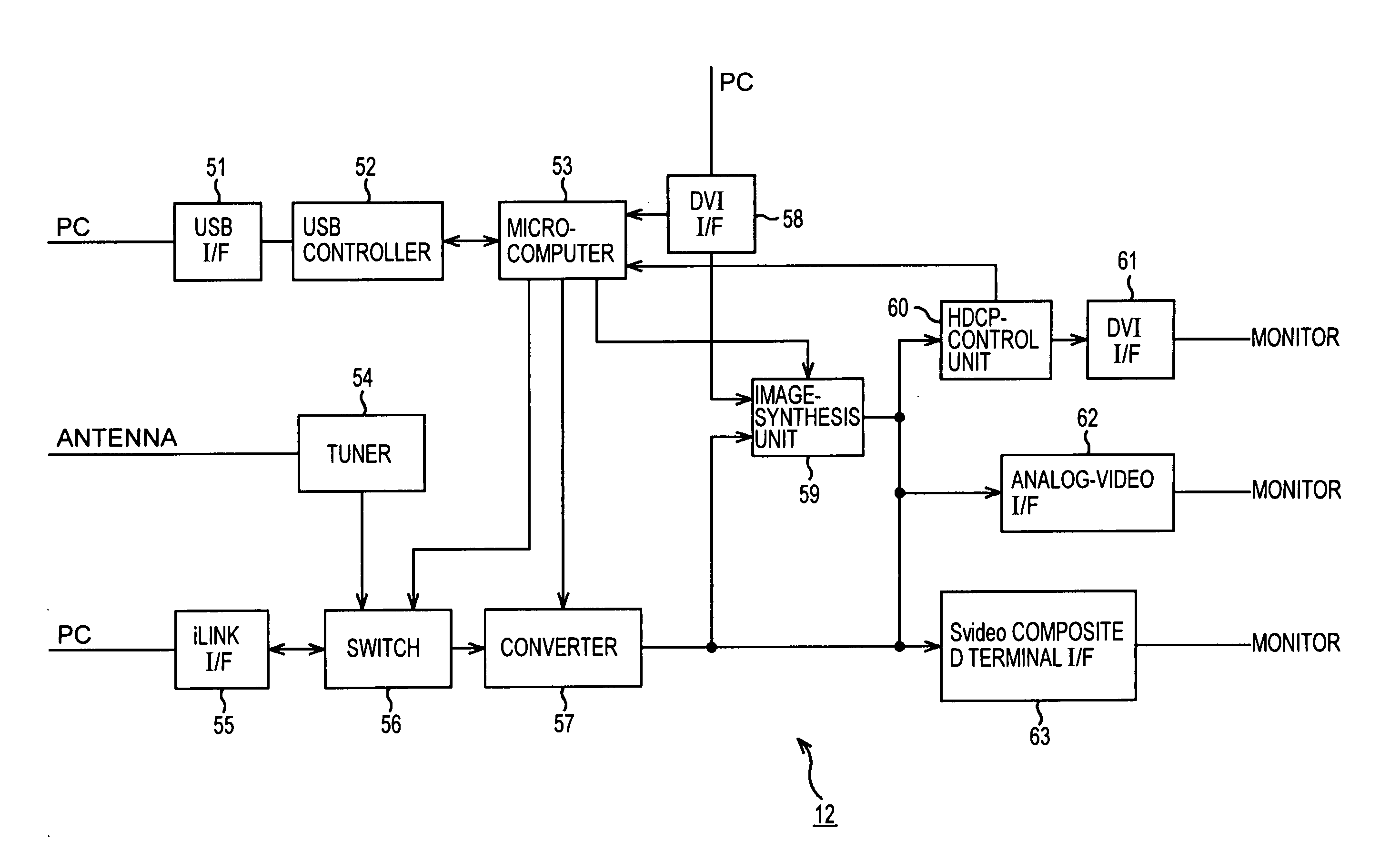
ActiveUS20060071920A1Copyright protectionTelevision system detailsDigital data processing detailsInformation processingDigital data
An information-processing apparatus comprises an acquisition unit configured to acquire information about a communication-method type from a display device connected to the information-processing apparatus, a determination unit configured to determine whether or not the display device is adapted to receive data on digital contents by using a predetermined copyright-protection technology based on the communication-method-type information, a conversion unit configured to convert an image quality of the digital contents based on the determination result, and an output unit configured to transmit the converted digital contents to the display device.
Owner:SONY CORP
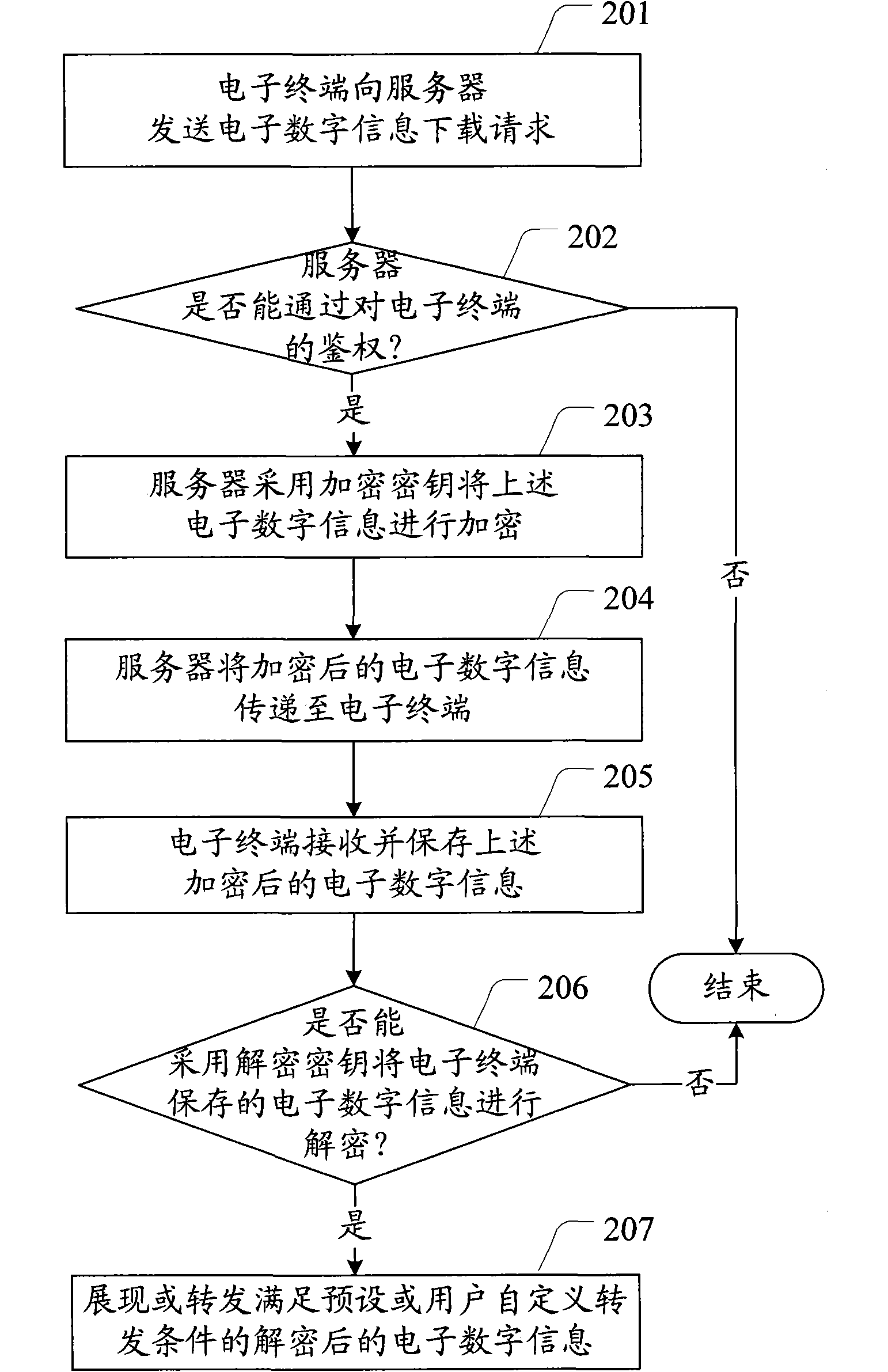
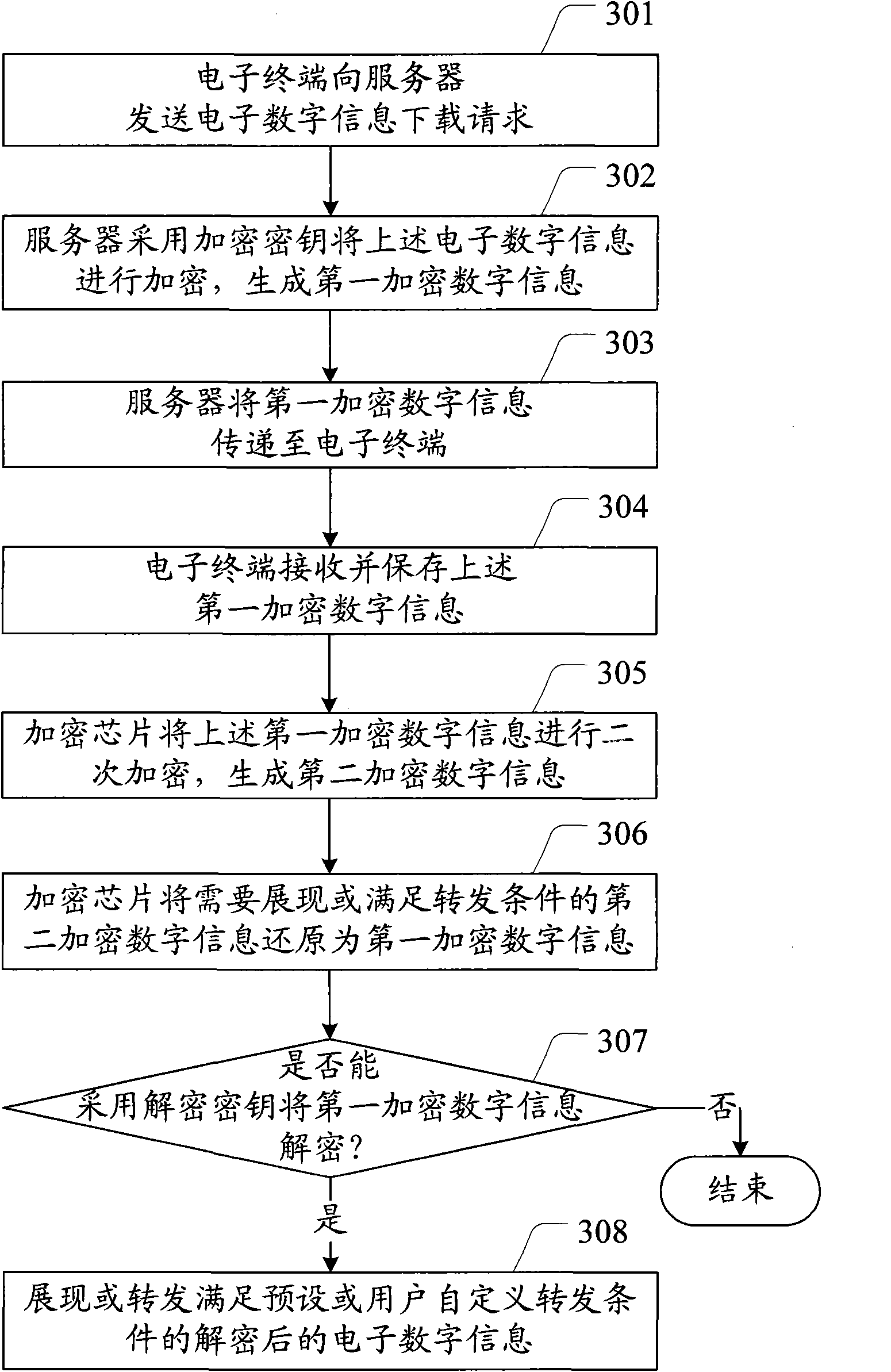
Electronic digital information copyright protection method and system as well as electronic terminal
InactiveCN102117395ACopyright protectionEnsure transmission securityDigital data protectionStore-and-forward switching systemsInformation transmissionForward conditioning
The invention provides an electronic digital information copyright protection method and system as well as an electronic terminal. The method comprises: the electronic terminal transmits an electronic digital information downloading request to a server; the server encrypts the electronic digital information by use of an encryption key to obtain encrypted digital information; the server transmits the encrypted digital information to the electronic terminal; the electronic terminal receives and stores the encrypted digital information; and the electronic terminal determines whether to decrypt the encrypted digital information by use of a decryption key, and if yes, displaying the decrypted electronic digital information or forwarding the decrypted electronic digital information meeting a preset forwarding condition or a user-defined forwarding condition. Because the electronic digital information to be distributed or stored is encrypted by the encryption key, the encrypted electronic digital information has to be decrypted before being displayed for forwarded by a user, so that only the authorized user can process the electronic digital information, thereby protecting the copyright of the electronic digital information occupier.
Owner:YINGHUADA (SHANGHAI) ELECTRONIC CO LTD
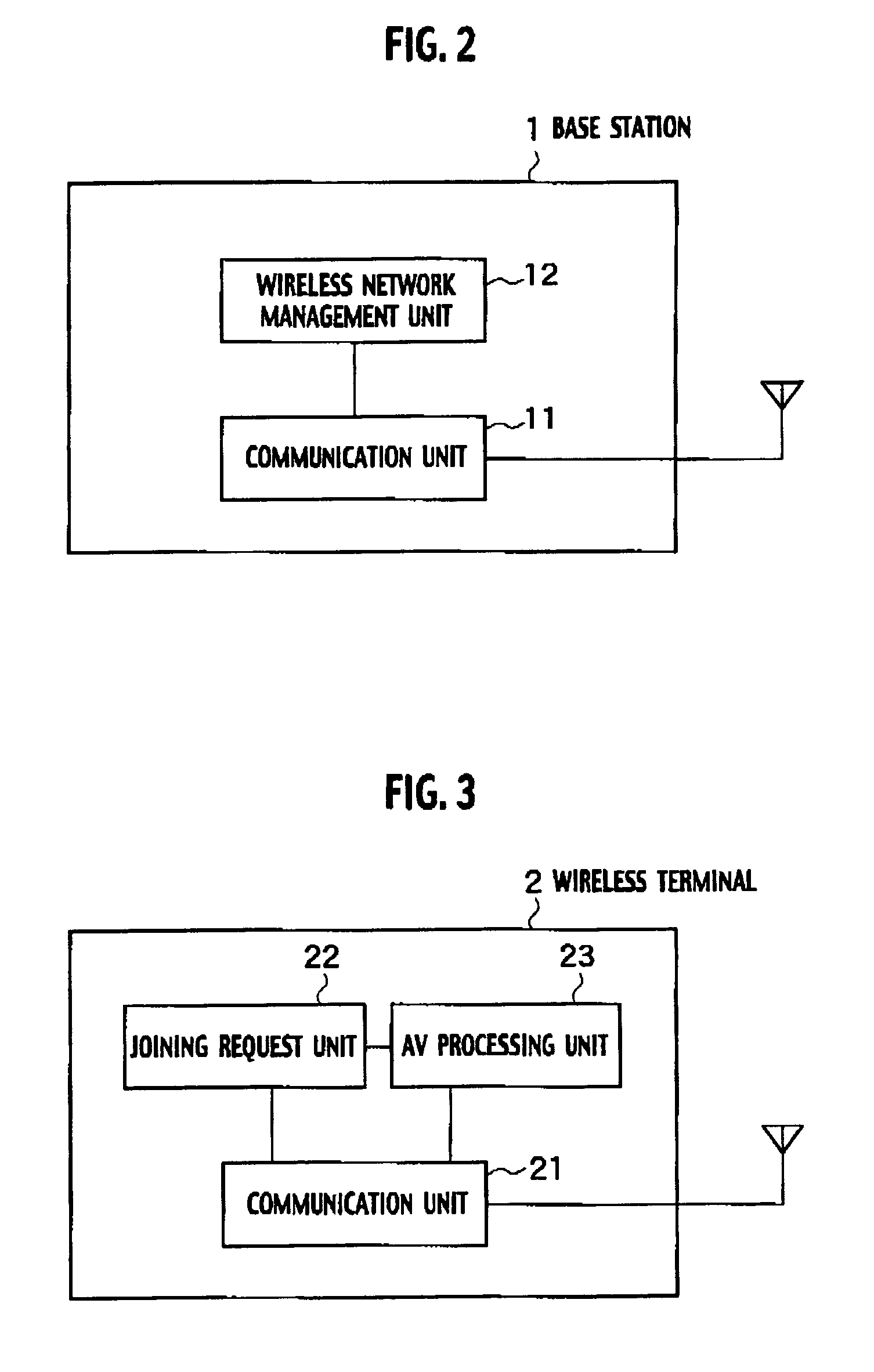
Wireless communication scheme with communication quality guarantee and copyright protection
InactiveUS7024204B2Guaranteed communication qualityAdversely affecting convenience of userNetwork traffic/resource managementAssess restrictionCommunication qualityWireless sensor network
A wireless base station which controls joining of a plurality of wireless terminals to a wireless network, stores a maximum joining possible terminal number which indicates a maximum number of the wireless terminals of each terminal type that can join the wireless network simultaneously, and which is set in advance for each one of a plurality of terminal types that classify the wireless terminals, and a currently joining terminal number which indicates a number of the wireless terminals of each terminal type that are currently joining the wireless network, for each one of the plurality of the terminal types. Then, the wireless base station judges whether the joining of one wireless terminal of one terminal type which sent a request message to the wireless network is permitted or not, according to the maximum joining possible terminal number for the one terminal type and the currently joining terminal number stored for the one terminal type.
Owner:KK TOSHIBA
P2P (Point-to-Point) streaming media system, P2P user equipment and streaming media data transmitting method
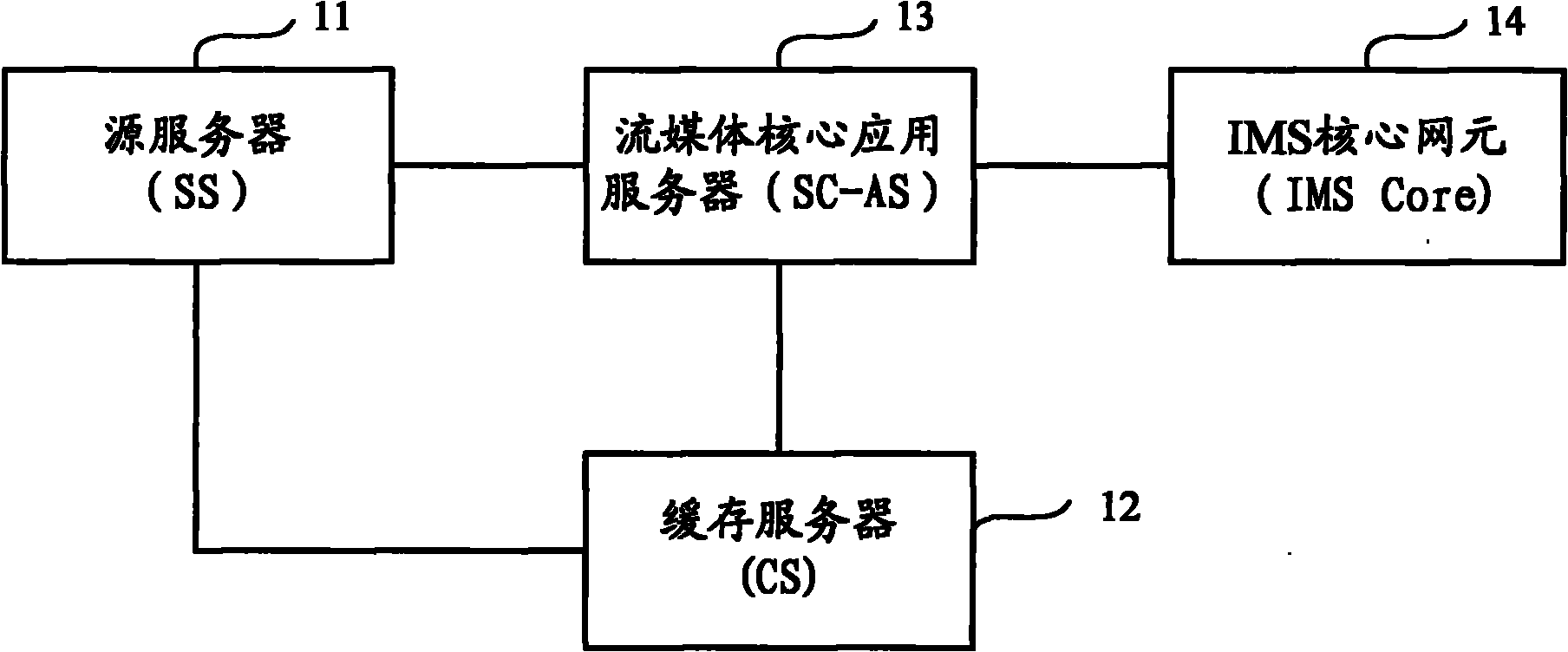
InactiveCN101924778ACopyright protectionRealize managementData switching networksApplication serverData information
The invention discloses a P2P (Point-to-Point) streaming media system which comprises a source server, a caching server, a streaming media key application server and an IMS (IP Multimedia Subsystem) key network element, wherein the source server stores streaming media contents; the caching server caches streaming media data and sends to P2P user equipment; the streaming media key application server is interacted with the caching server to generate program information, obtains owned streaming media data information and current state information reported by the P2P user equipment through the IMS key network element, and provides corresponding program information and resource information for the P2P user equipment requesting streaming media service; and the IMS key network element accesses the P2P user equipment into an IMS network and controls the connection negotiation among the P2P user equipment, the caching server providing the downloading of the corresponding streaming media data and other P2P user equipment. The invention also provides the P2P user equipment and a streaming media data transmitting method. The invention realizes that the P2P user equipment is accessed into the IMS network through the IMS key network element for controlling the streaming media service.
Owner:CHINA MOBILE COMM GRP CO LTD
Encrypted Correction Code to protect the integrity and originality of electronic documentation and secure online payment and online wallet
InactiveUS20150019440A1Prevent fraudCopyright protectionPayment protocolsCoding/ciphering apparatusComputer hardwareDocumentation procedure
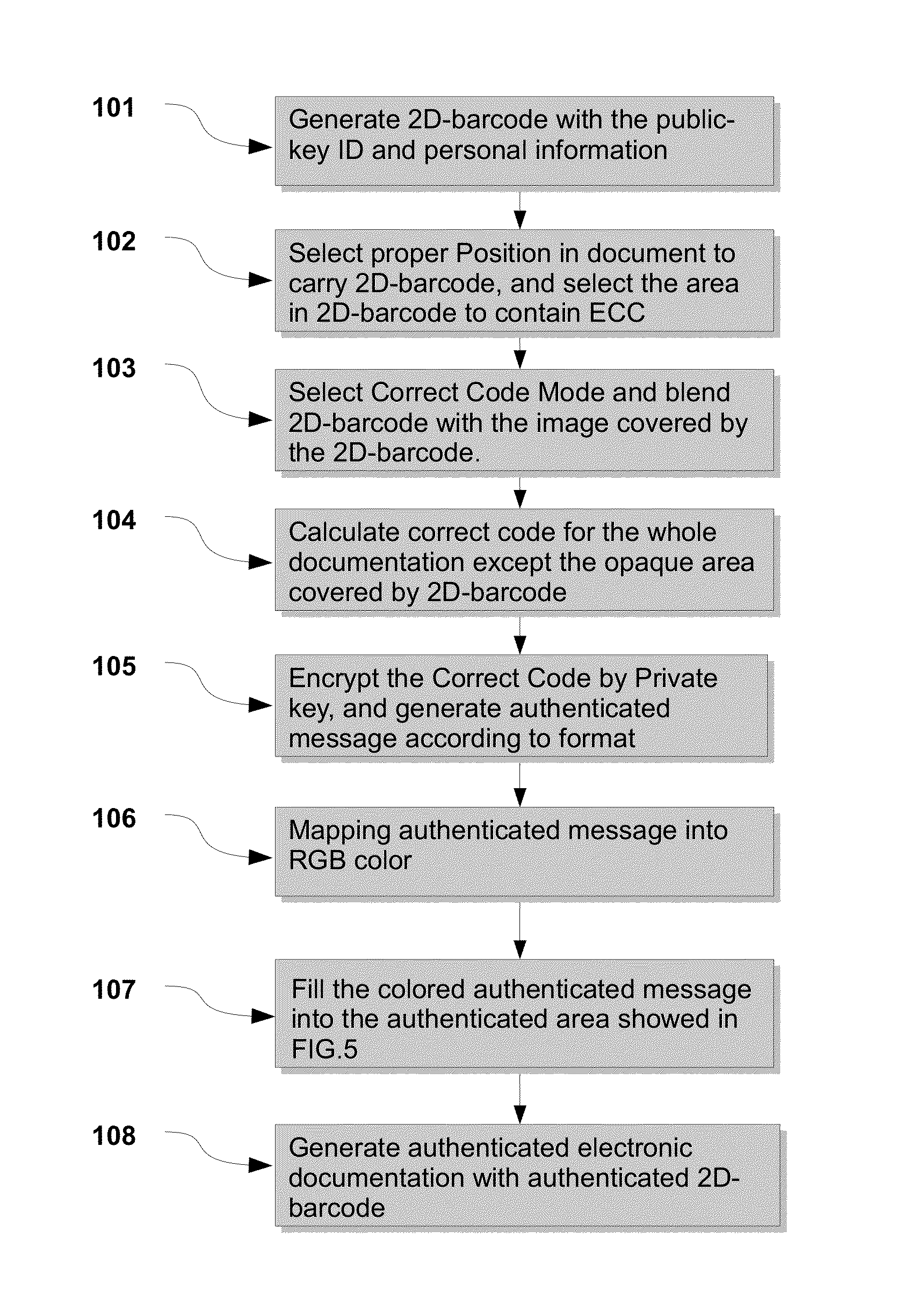
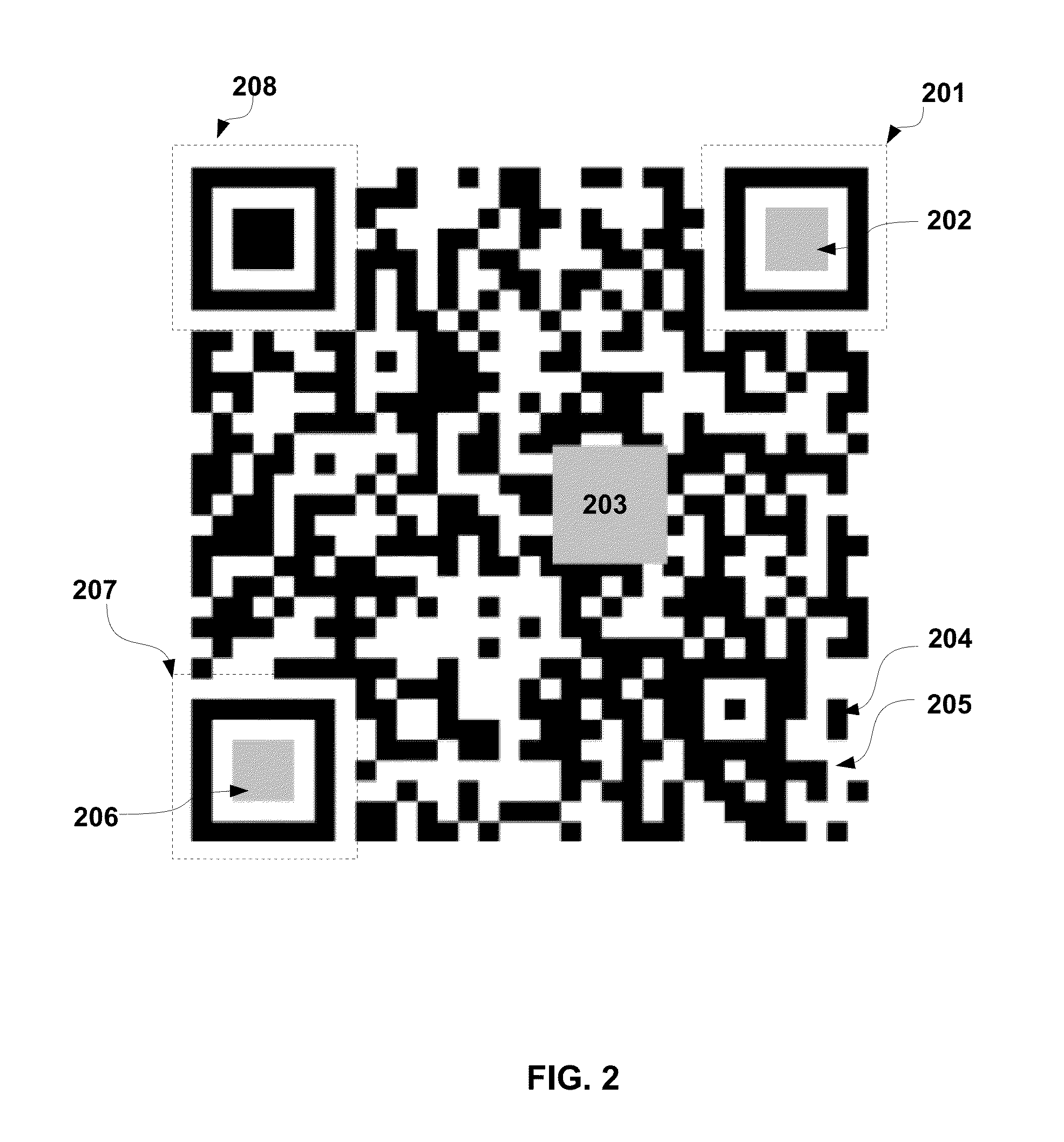
A method is provided for protecting the integrity and originality of electronic documentation and supporting securer and easier online payment using the Encrypted Correction Code which is correction code of the whole documentation and encrypted by the private key of RSA. The code is imbedded into 2D-barcode as RGB color value of pixels. First, 2D-barcode is generated with public-key ID, and then blend and imbedded into electronic documentation. Then the Correction Code is calculated and is encrypted by RSA private key. After that, the Encrypted Correction is mapped into color in the image of 2D-barcode. When the file is received, the integrity and originality is checked by comparing Correction Code decrypted from 2D-barcode with the Correction Code of the documentation. The present invention can be applicable to support more secure and easier online wallet using three-layer encryption and free from any personal information.
Owner:YANG GONGMING
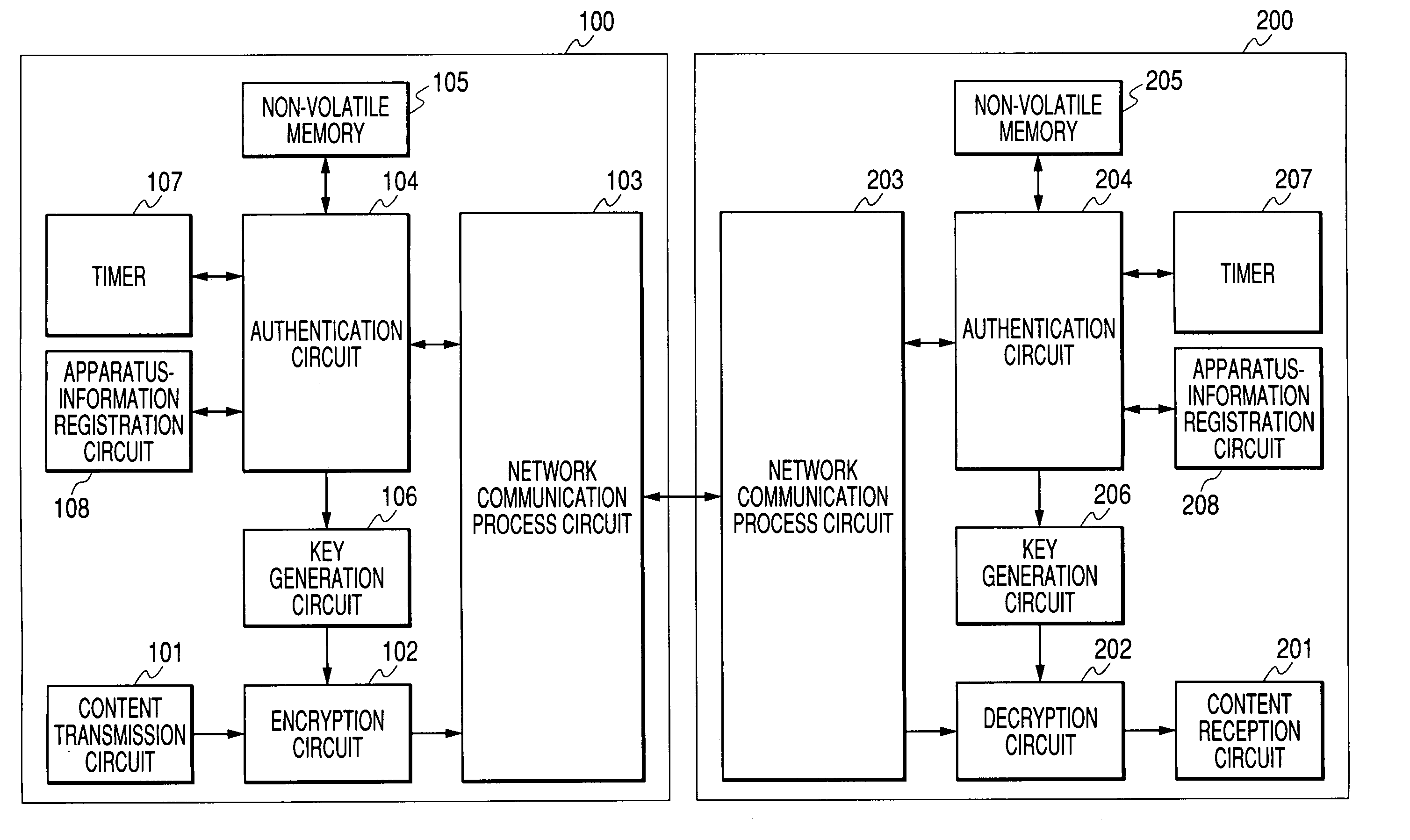
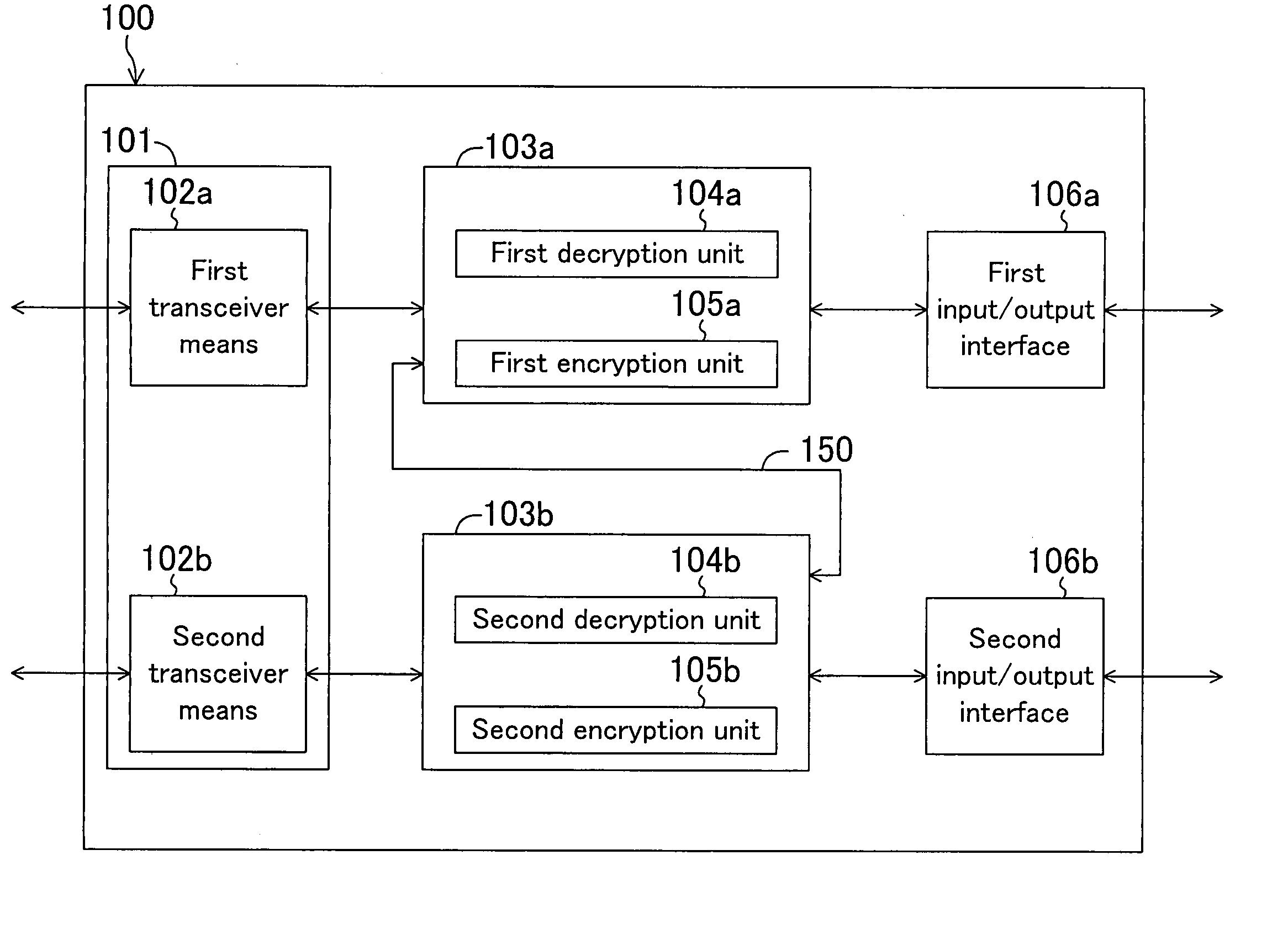
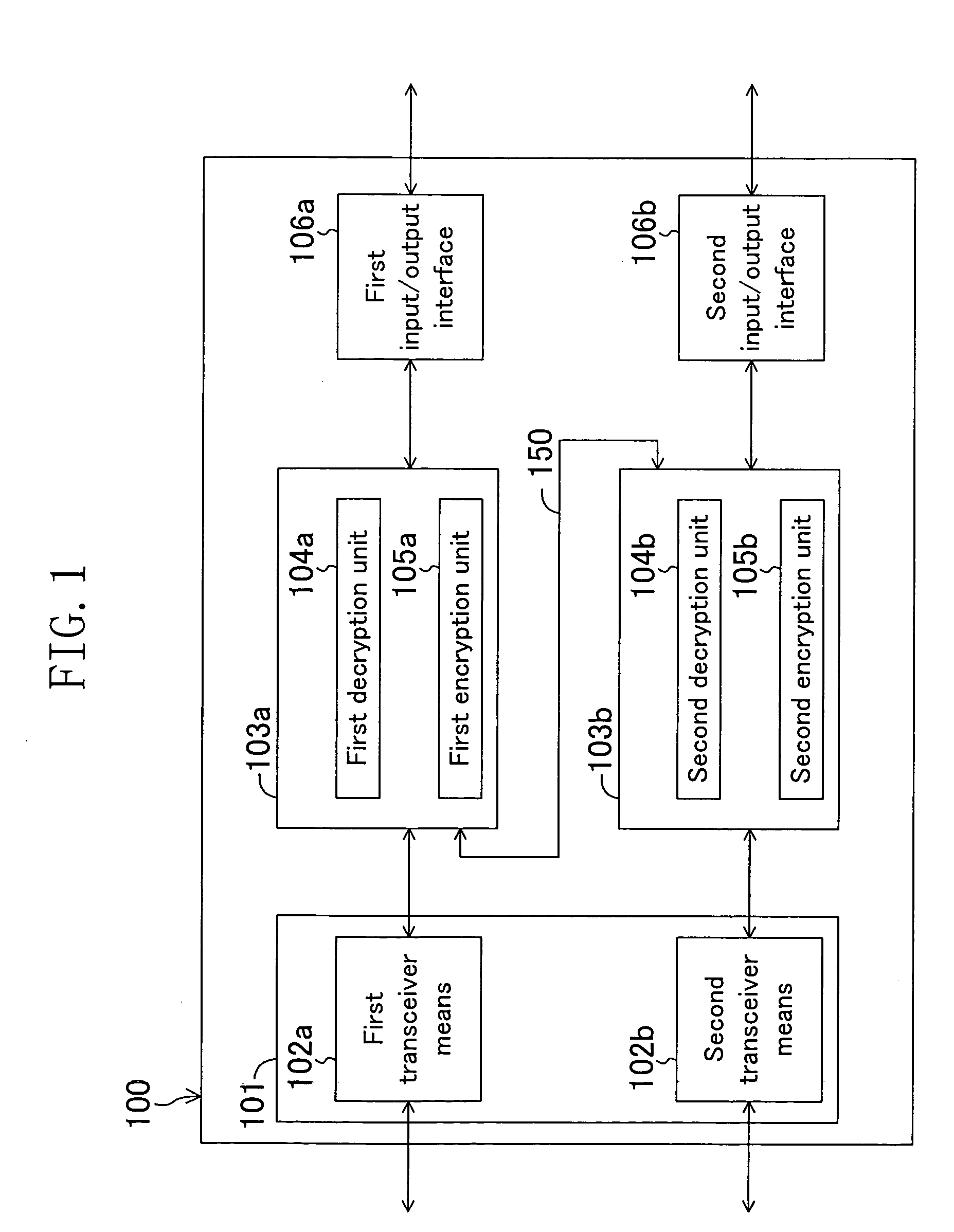
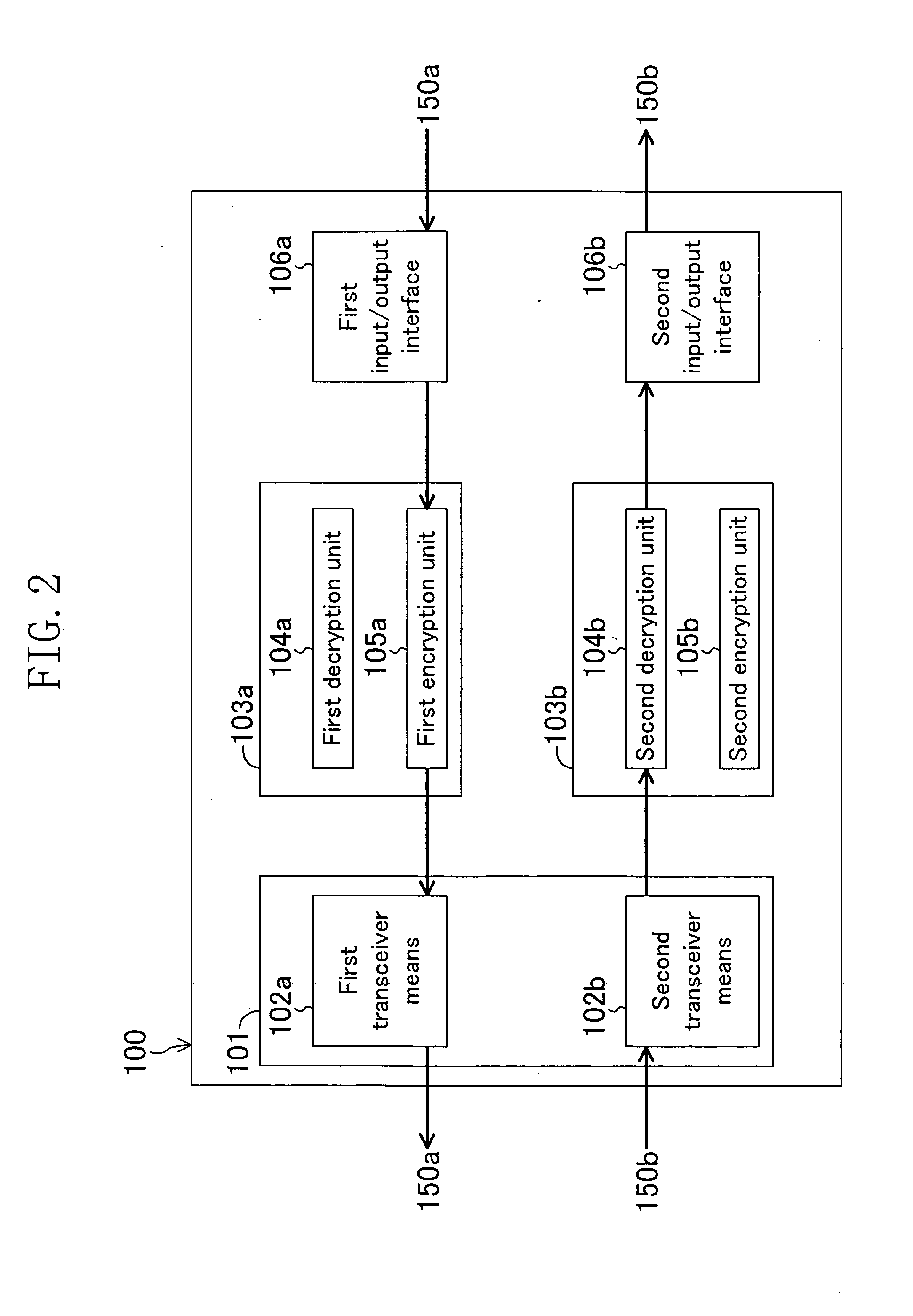
Data transceiver and data transceiver system
InactiveUS20050010763A1Increase in circuit sizeCopyright protectionAnalogue secracy/subscription systemsCoding/ciphering apparatusTransceiverComputer science
A data transceiver includes: at least first and second encrypting / decrypting means each for encrypting and decrypting data; and transceiver means for transmitting and receiving data. In a first transmission mode, first transmission data encrypted by the first or second encrypting / decrypting means is transmitted by the transceiver means. In a first reception mode, first received data received by the transceiver means is decrypted by the first or second encrypting / decrypting means. In a second transmission mode, second transmission data decrypted by the first encrypting / decrypting means is encrypted by the second encrypting / decrypting means and then is transmitted by the transceiver means. In a second reception mode, second received data received by the transceiver means is decrypted by the second encrypting / decrypting means and then is encrypted by the first encrypting / decrypting means.
Owner:PANASONIC CORP
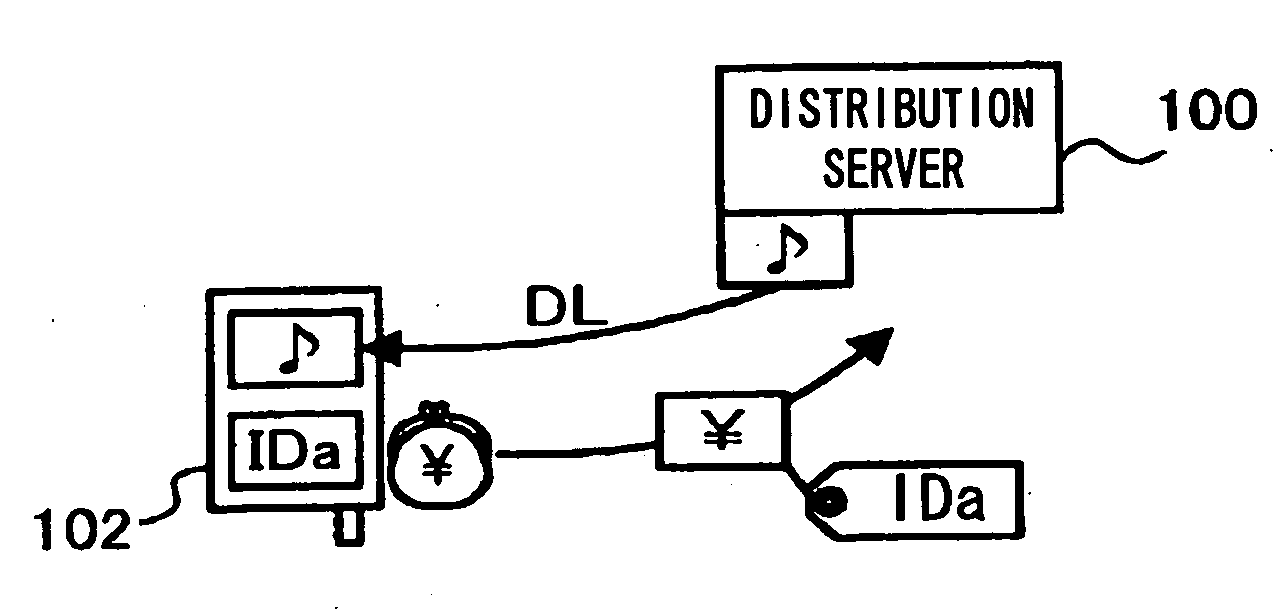
Music player
InactiveUS20060217829A1Large facilitySimple configurationRecord information storageMultiple digital computer combinationsMusic playerComputer science
A portable music player downloads a musical composition data from a distribution server. When this musical composition data is played back, a sample musical composition data composing a part of the musical composition data is distributed to a surrounding player by wireless. At this time, a terminal identification number IDa of the supplier player is included in tag information of the sample musical composition data, and the user of the surrounding player can download the musical composition data related to the sample musical composition data for value from the distribution server. A part of its sold price is refunded to the user of the supplier player.
Owner:YAMAHA CORP
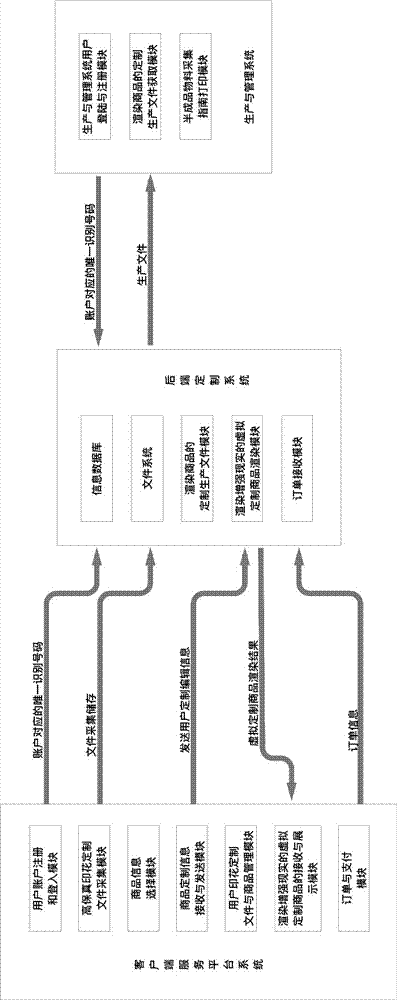
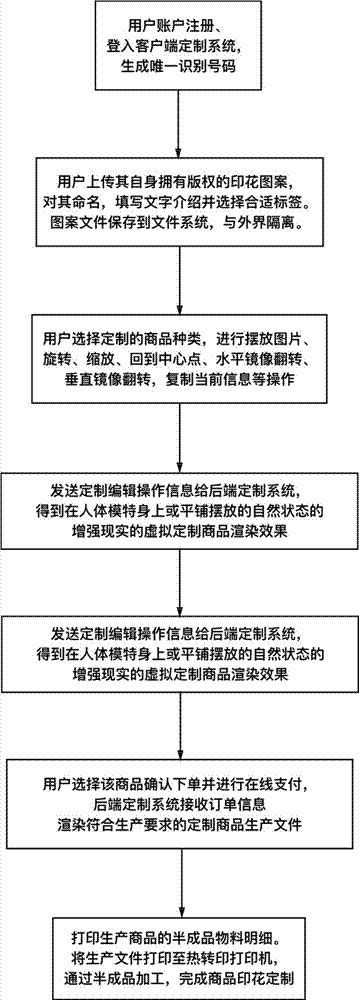
Commodity printing customization method and platform thereof
InactiveCN107016596AUnlimited editingLess difficult to reuseBuying/selling/leasing transactionsWork in processClient-side
The invention discloses a commodity printing customization method and a platform thereof. The commodity printing customization platform comprises a client service platform system, a production and management system and a rear-end customization system, the client service platform system comprises a high-fidelity printing customization file acquisition module, a commodity information selection module and a user printing customization file and commodity management module, the rear-end customization system comprises a virtual customization commodity rendering module for rendering the augmented reality, and the production and management system comprises a semi-finished product material acquisition guide printing module. The commodity information selection module can provide two-dimensional editing areas corresponding to different composition parts of a commodity, users can edit the printing without limitation, and the printing customization is more flexible.
Owner:SHENZHEN QIANHAI YICHUANGYILE TECH LTD
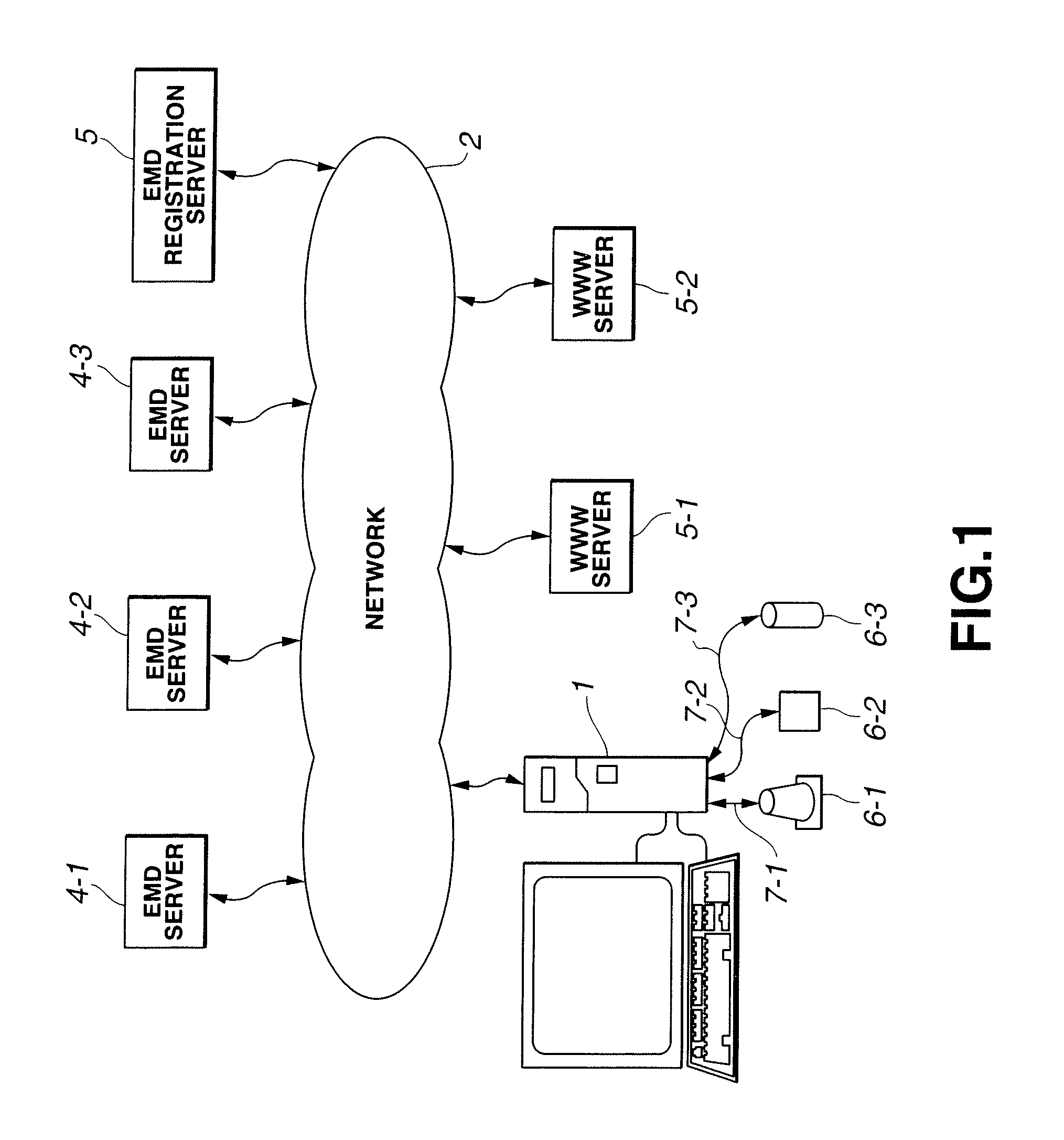
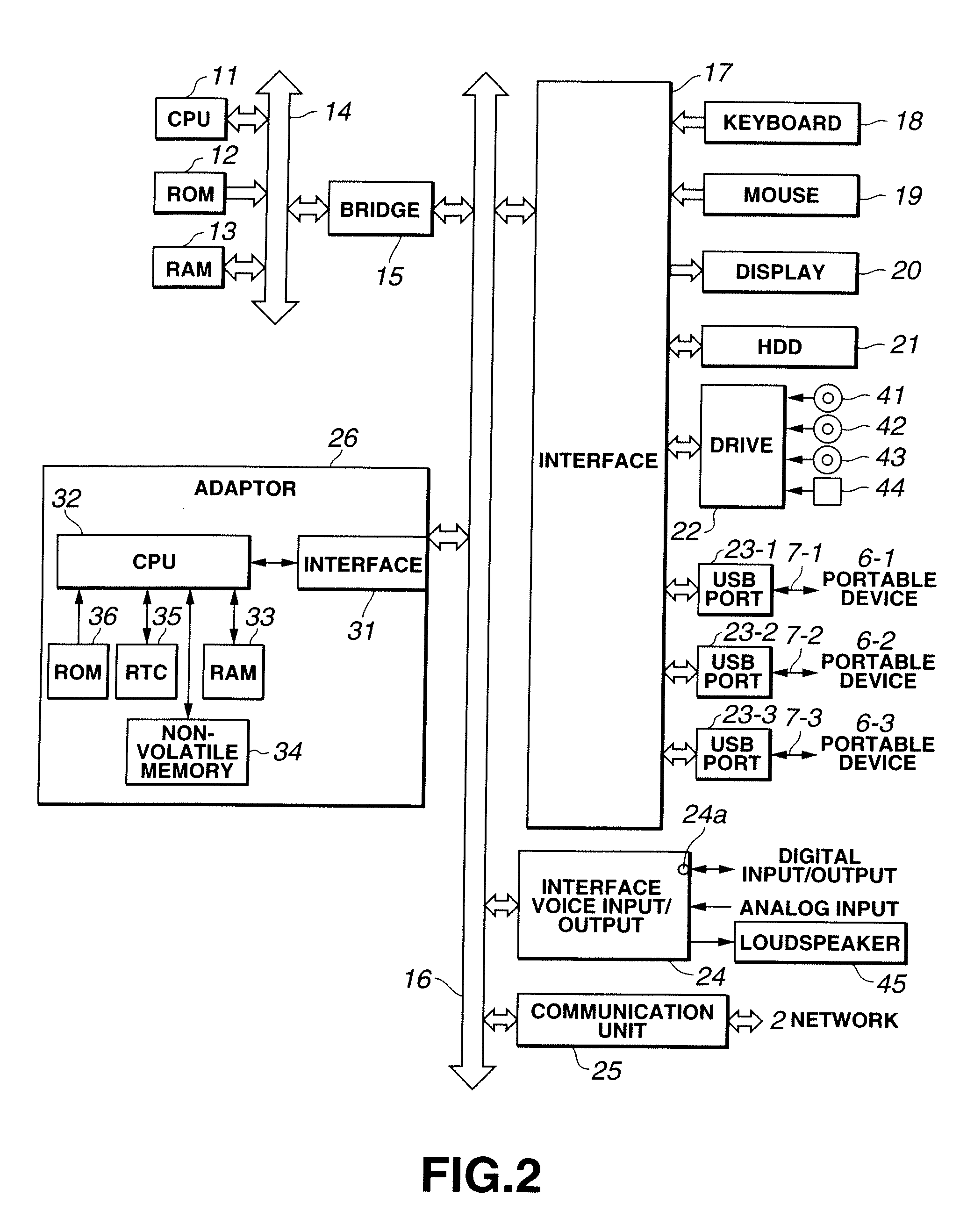
Contents furnishing system
InactiveUS20070174302A1Copyright protectionMetadata audio data retrievalDigital data processing detailsComputer hardwareComputer science
Even if contents data distributed over a network are once destroyed, the contents data are restored, as the copyright protection is maintained. A PC memorizes backup of distributed music contents on a hard disc, at the same time as it transmits the using log information of the music contents stored in the hard disc to an EMD server. If the music contents in the hard disc are destroyed, the PC acquires the using log information from the EMD server to reproduce the backup data memorized in the hard disc depending on the using log information.
Owner:SONY CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com