Digital certificate authentication method, system, usb Key device and server
A technology of digital certificates and authentication methods, which is applied in the field of information security and can solve problems such as the illegal use of digital certificates
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
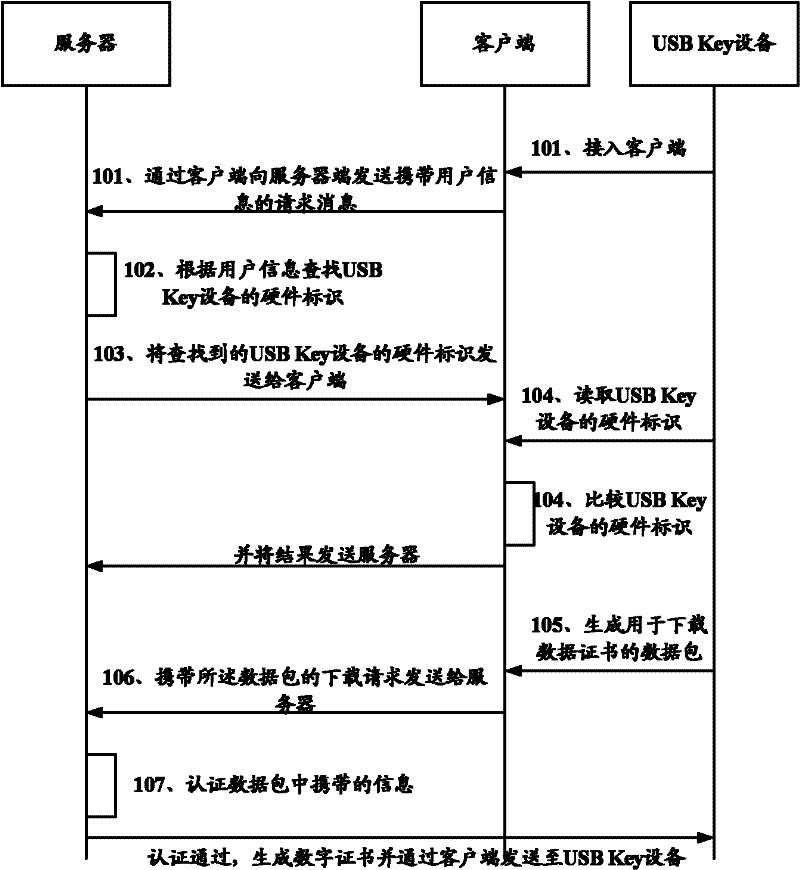
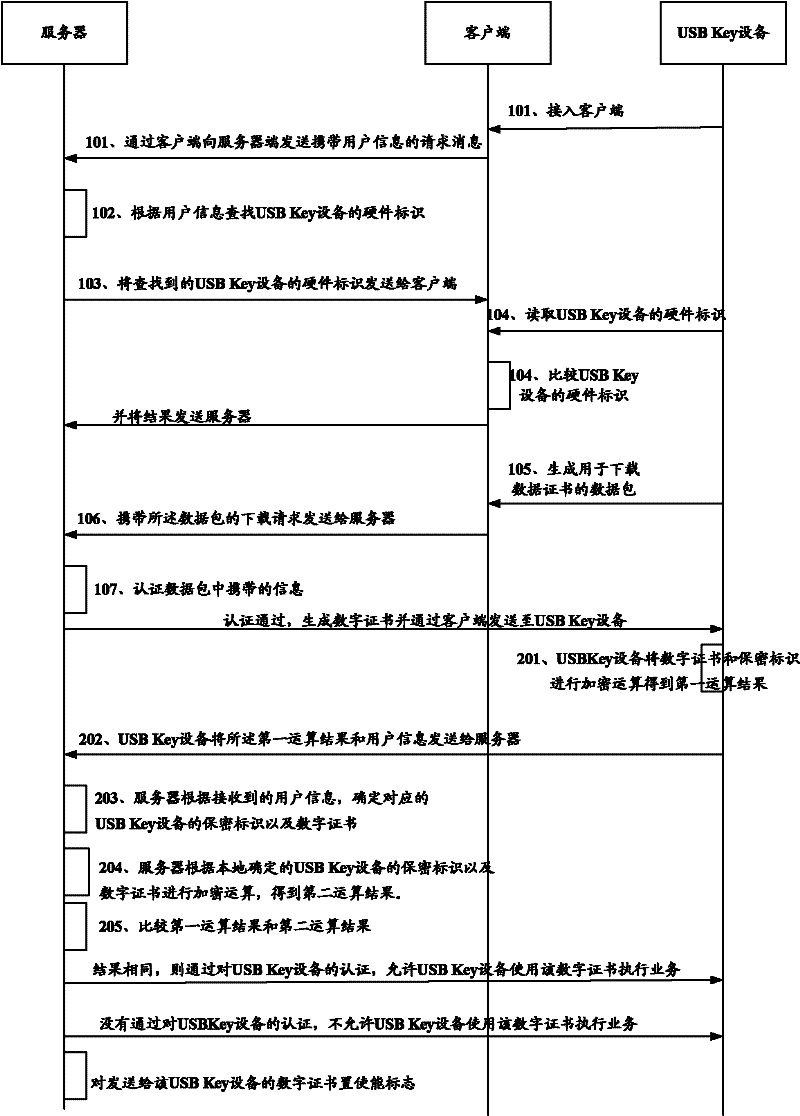
[0048] Such as figure 2 As shown, it is a schematic flow chart of the digital certificate authentication method in Embodiment 1 of the present invention, and the specific content includes the following steps:
[0049] undertake figure 1 In the shown method, step 107: the server sends the digital certificate to the USB Key device.
[0050] Step 201: The USB Key device encrypts the received digital certificate and the locally stored confidentiality identifier to obtain a first calculation result.
[0051] In the scheme of this step, the USB Key device can encrypt the digital certificate and the confidentiality mark according to the MD5 algorithm. Even if the first calculation result is obtained illegally by other devices, the confidential identification cannot be analyzed therefrom. The algorithm used in the first embodiment is not limited to other algorithms with irreversible properties.
[0052] Step 202: The USB Key device sends the first calculation result and user info...
Embodiment 2
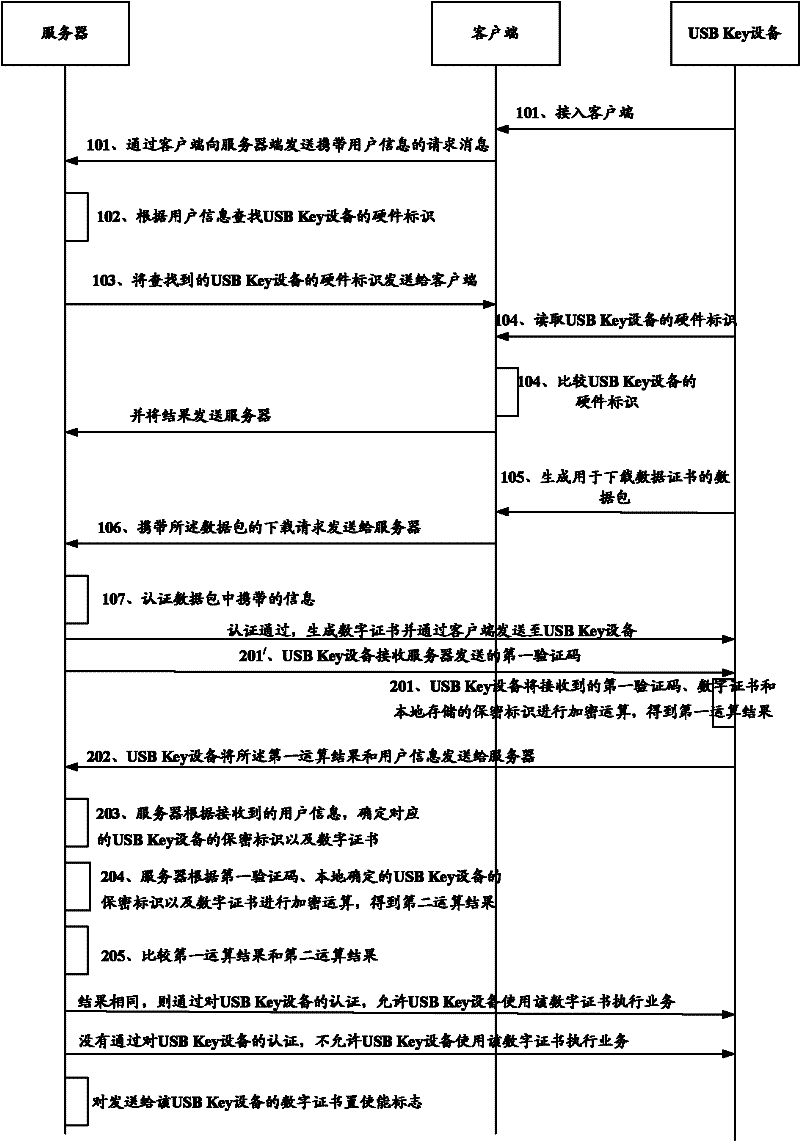
[0067] Such as image 3 As shown, it is a schematic flow chart of a digital certificate authentication method in Embodiment 2 of the present invention. The solution in Embodiment 2 is basically the same as the solution in Embodiment 1. The difference is that the solution in Embodiment 1 does not need to use additional verification codes. To authenticate the USB Key device, in the solution of the second embodiment, the server can authenticate the USB Key device by sending a verification code to the USB Key device on the basis of the solution of the first embodiment, specifically, in In the solution of the second embodiment, after step 107 and before step 201, the following steps are also included:
[0068] Step 201 / : The USB Key device receives the first verification code sent by the server.
[0069] The first verification code may be a random number.
[0070] In the scheme of this step 201 / , the server may send the first verification code to the USB Key device while sending ...
Embodiment 3
[0076] Embodiment 3 is based on Embodiment 1 or Embodiment 2, and realizes that the USB Key device authenticates the validity of the digital certificate received. The specific authentication process is: the USB Key device authenticates the server that sends the digital certificate, If the authentication is passed, it is determined that the digital certificate sent by the server is legal; otherwise, it is determined that the digital certificate sent by the server is illegal.
[0077] In the solution of the third embodiment, the USB Key device authenticates the server by sending a verification code to the server.
[0078] Such as Figure 4 As shown, it is a schematic flow chart of the digital certificate authentication method in the third embodiment. In the solution of the third embodiment, after the USB Key device receives the digital certificate, and the USB Key device uses the received digital certificate to perform business At any point before, do the following:
[0079] S...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com