Application layer dynamic intrusion detection system and detection method based on artificial intelligence
An intrusion detection system, artificial intelligence technology, applied in the direction of biological neural network model, instrument, platform integrity maintenance, etc., can solve the problem of server being attacked by network, insufficient efficiency performance, inappropriate background, etc., to achieve good detection effect, The time consumption is short and the effect of reducing the false positive rate
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
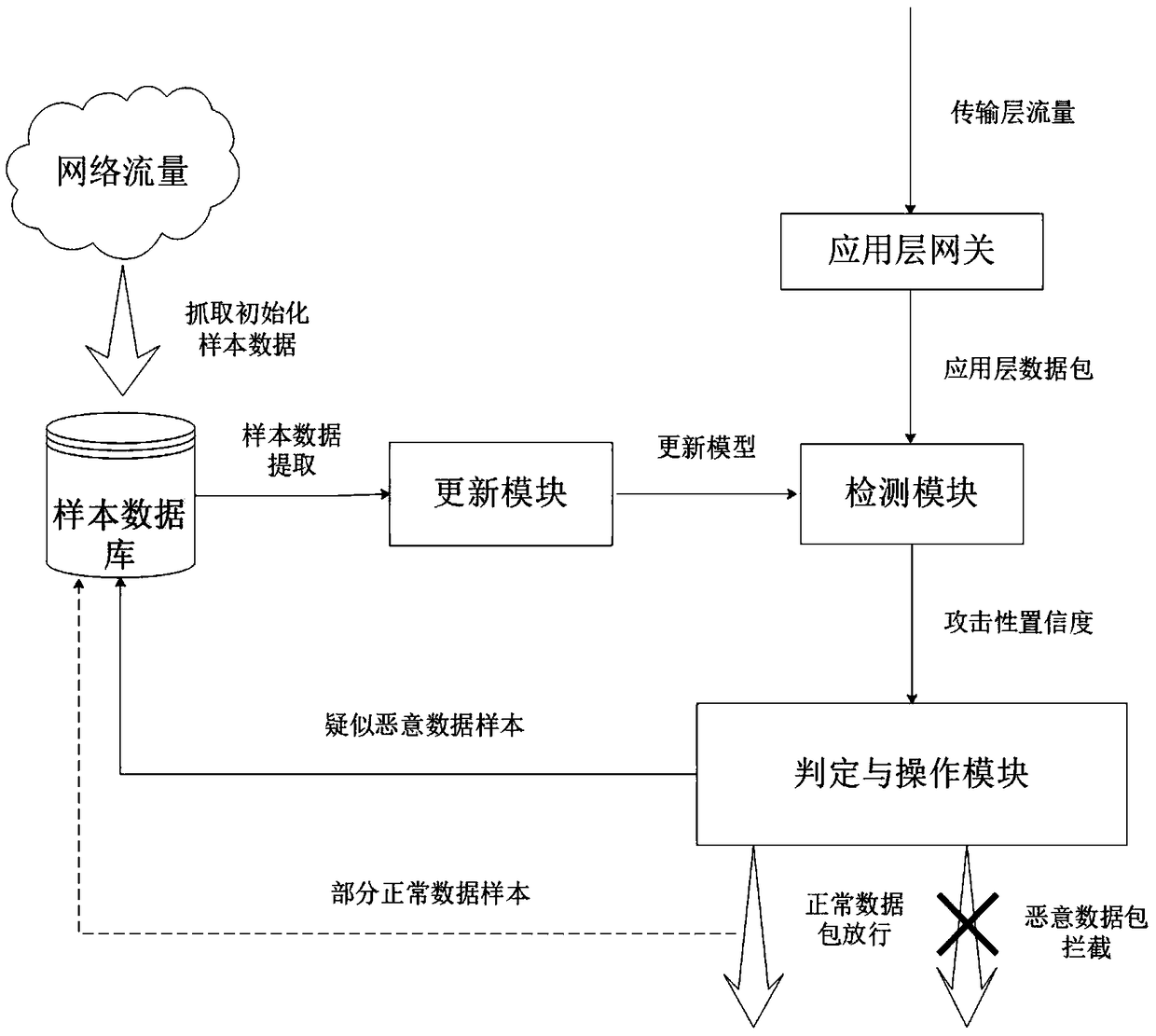
[0043] as attached figure 1 As shown, this embodiment discloses an application-layer dynamic intrusion detection system architecture based on artificial intelligence. The system includes the following modules: an application-layer gateway, a detection module, a judgment and operation module, a sample database, and an update module.
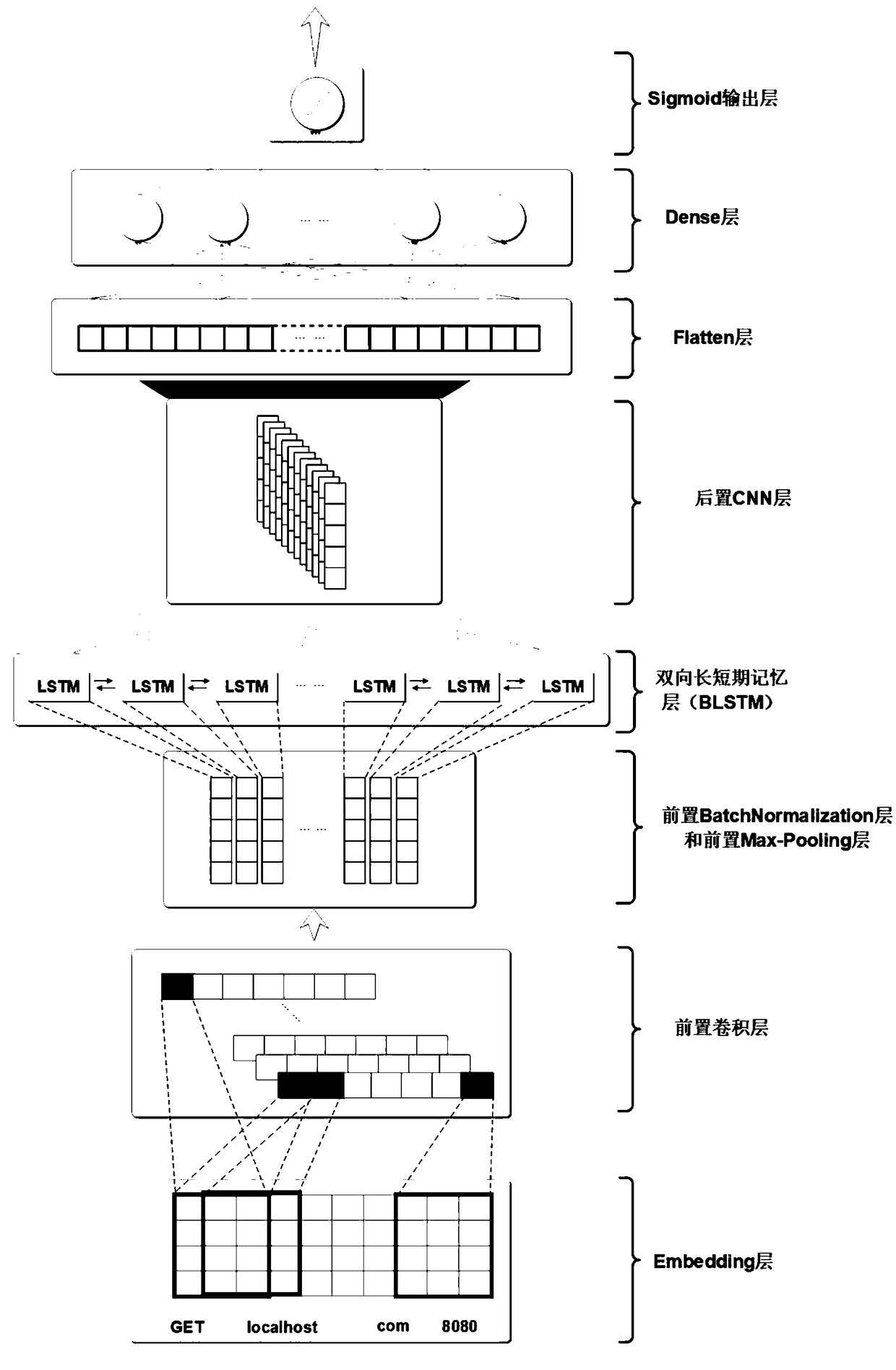
[0044] The detection module in the present invention is mainly based on two kinds of deep learning models—convolutional neural network (CNN) and bidirectional long-short memory neural (BLSTM) network, and these two kinds of deep learning models are briefly introduced below:
[0045] CNNs perform well in image recognition and classification problems. Usually, a typical CNN model consists of an input layer, multiple convolutional layers, pooling layers, and a fully connected output layer. The convolution layer is the core part of CNN, which is used to deeply extract the features of the input image, where the convolution kernel and receptive field i...
Embodiment 2
[0071] This embodiment describes the detection method of the application layer dynamic intrusion detection system based on artificial intelligence. Firstly, the detection system is initialized, and the system is applied to detect and filter / release the application layer data packets. The specific process is as follows:
[0072] Step 1, the initialization phase of the sample database. Suppose, the initialization of the detection model requires a training set of 20,000 data samples. The database extracts 10,000 malicious data samples and 10,000 normal data samples from Internet traffic; or, using a public dataset, stores the above-mentioned number of data samples into the sample database.
[0073] Step 2, the initialization phase of the detection module. The update module extracts 10,000 malicious data samples and 10,000 normal data samples from the sample database, and trains the detection model for the first time. When the accuracy of the model is greater than 99% or remain...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com