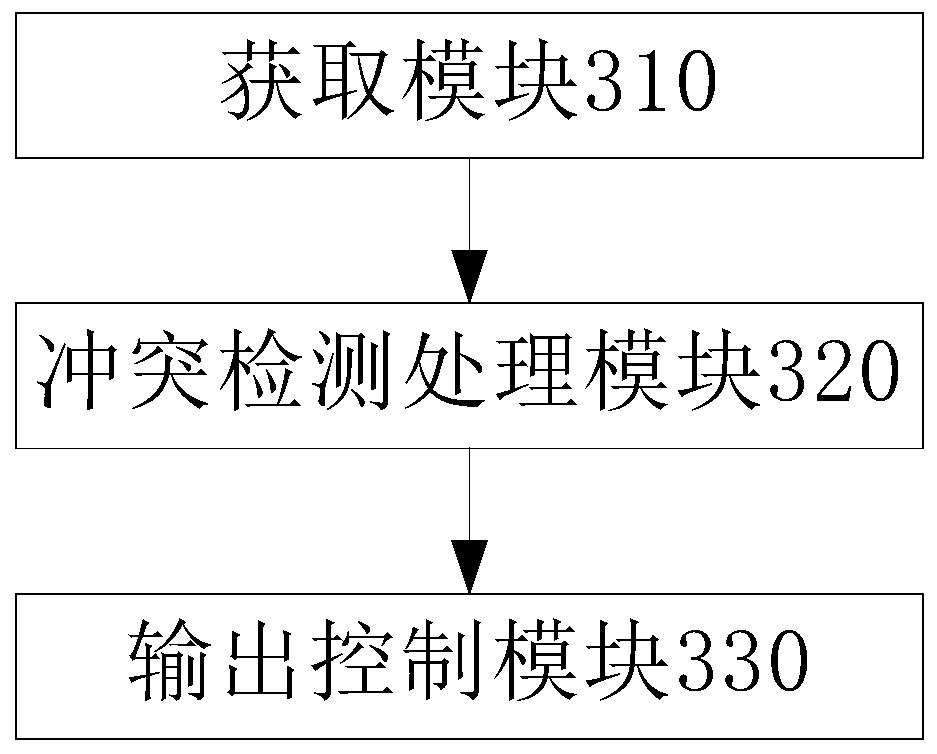
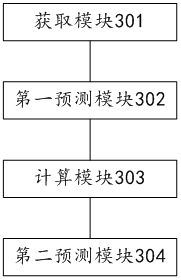
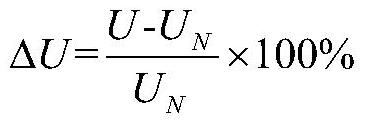Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
41results about How to "Disassociation" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
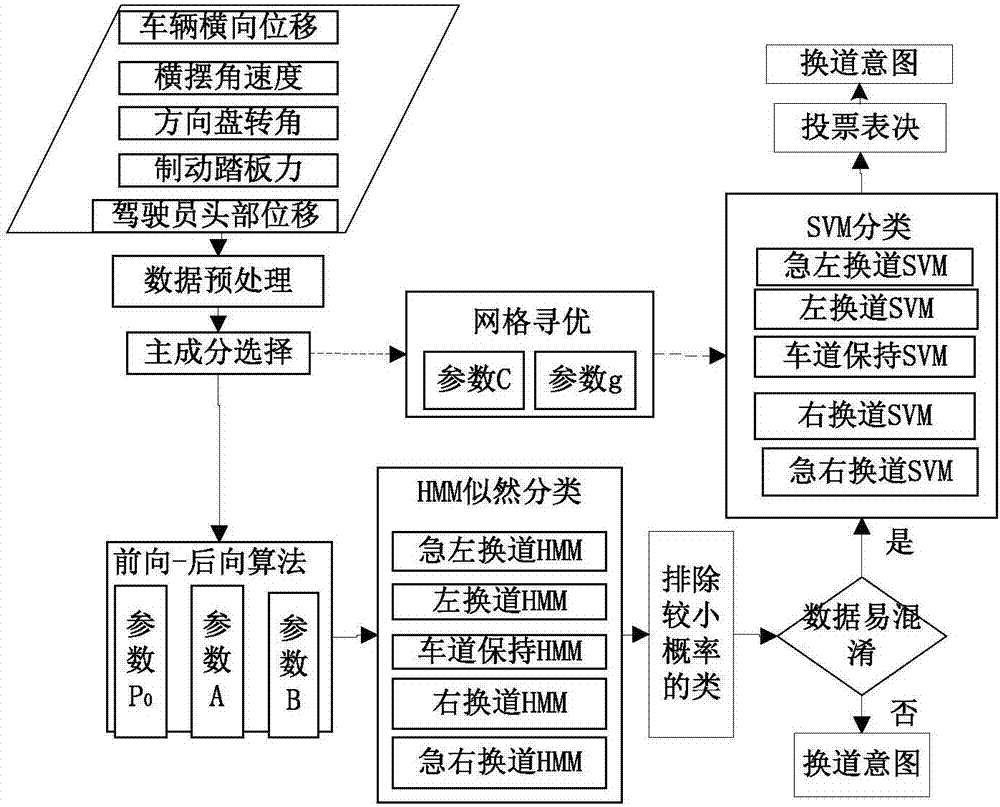
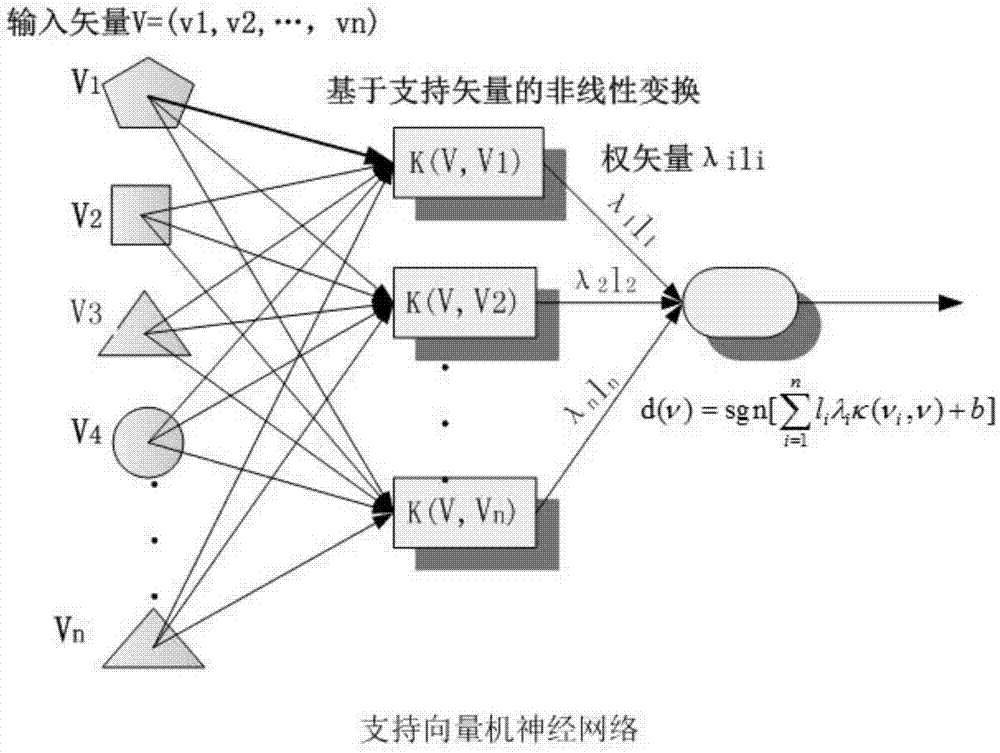
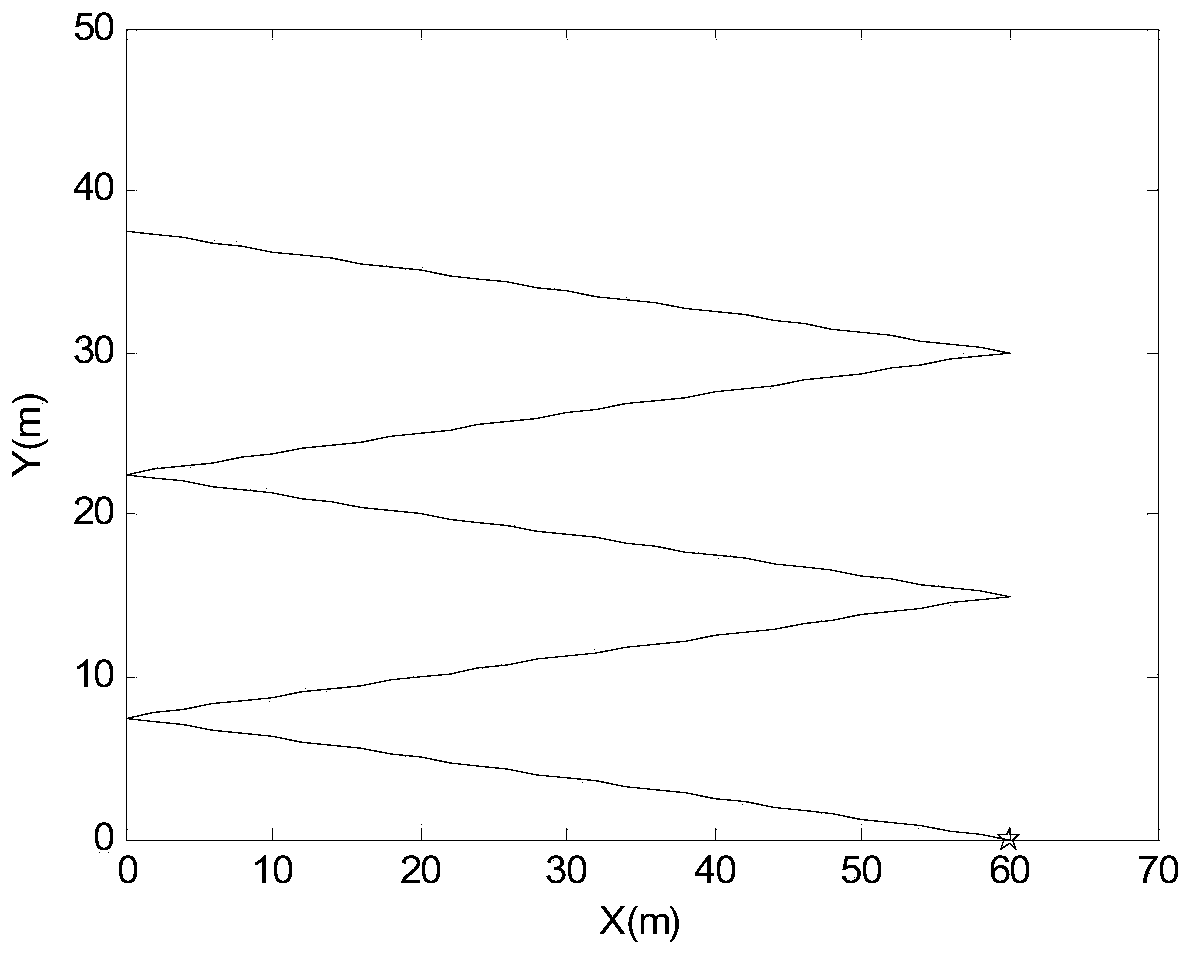
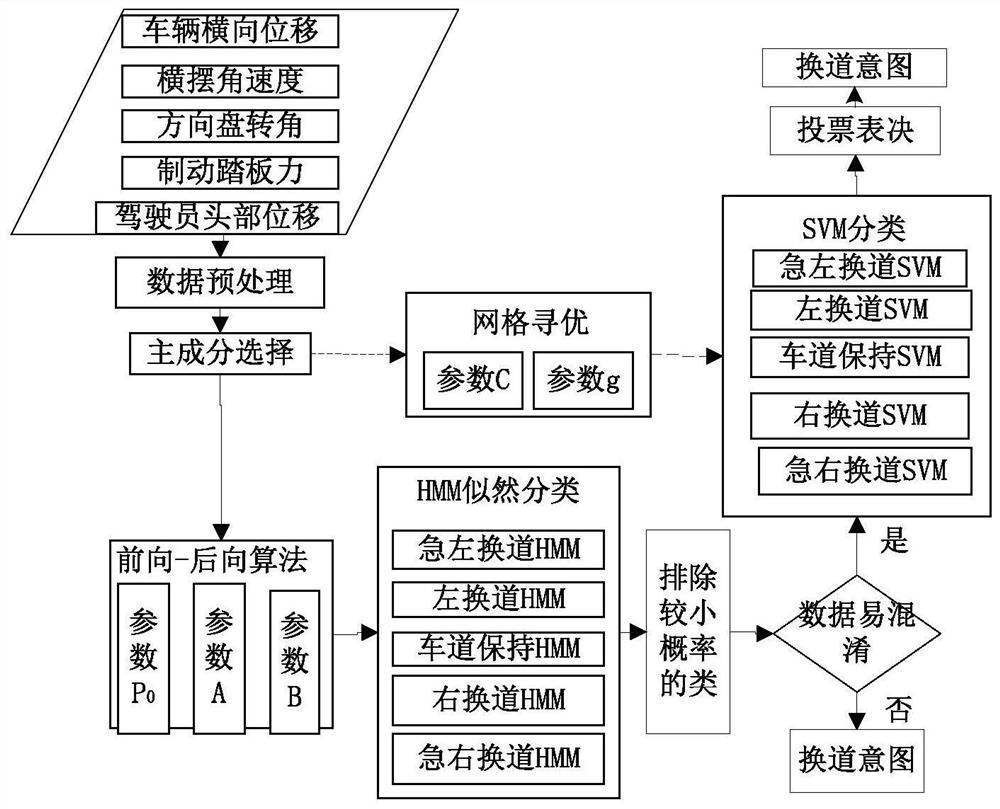
Driving intention identification method based on improved HMM and SVM double-layer algorithm
ActiveCN106971194ADriving Intent DeterminationFast operationCharacter and pattern recognitionAlgorithmData acquisition
The invention discloses a driving intention identification method based on an improved HMM and SVM double-layer algorithm. The method includes: step 1, classification of driving intentions of drivers: dividing the driving intentions of the drivers into five categories: emergent left lane-changing, normal left lane-changing, lane maintaining, normal right lane-changing, and emergent right lane-changing; step 2: experiment data acquisition and processing; step 3: offline training of the improved HMM and SVM double-layer algorithm; and step 4: identification of the driving intentions of the drivers. According to the method, a human-vehicle-road system is completely considered, information of vehicles, roads and drivers is acquired, the HMM and SVM double-layer learning model is employed, and the accuracy and the timeliness of a driver lane-changing intention identification model are improved.
Owner:江苏易齐物流有限公司
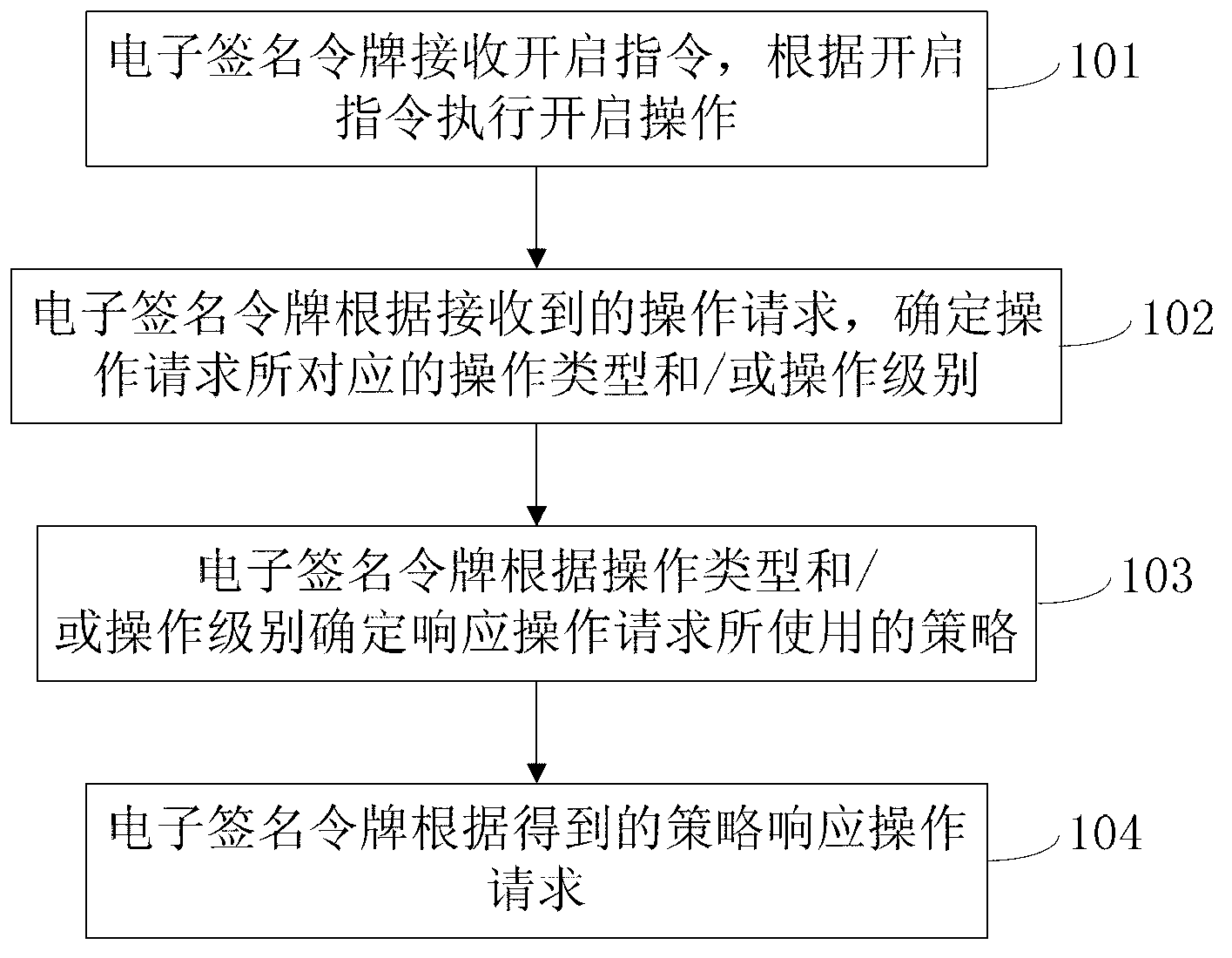
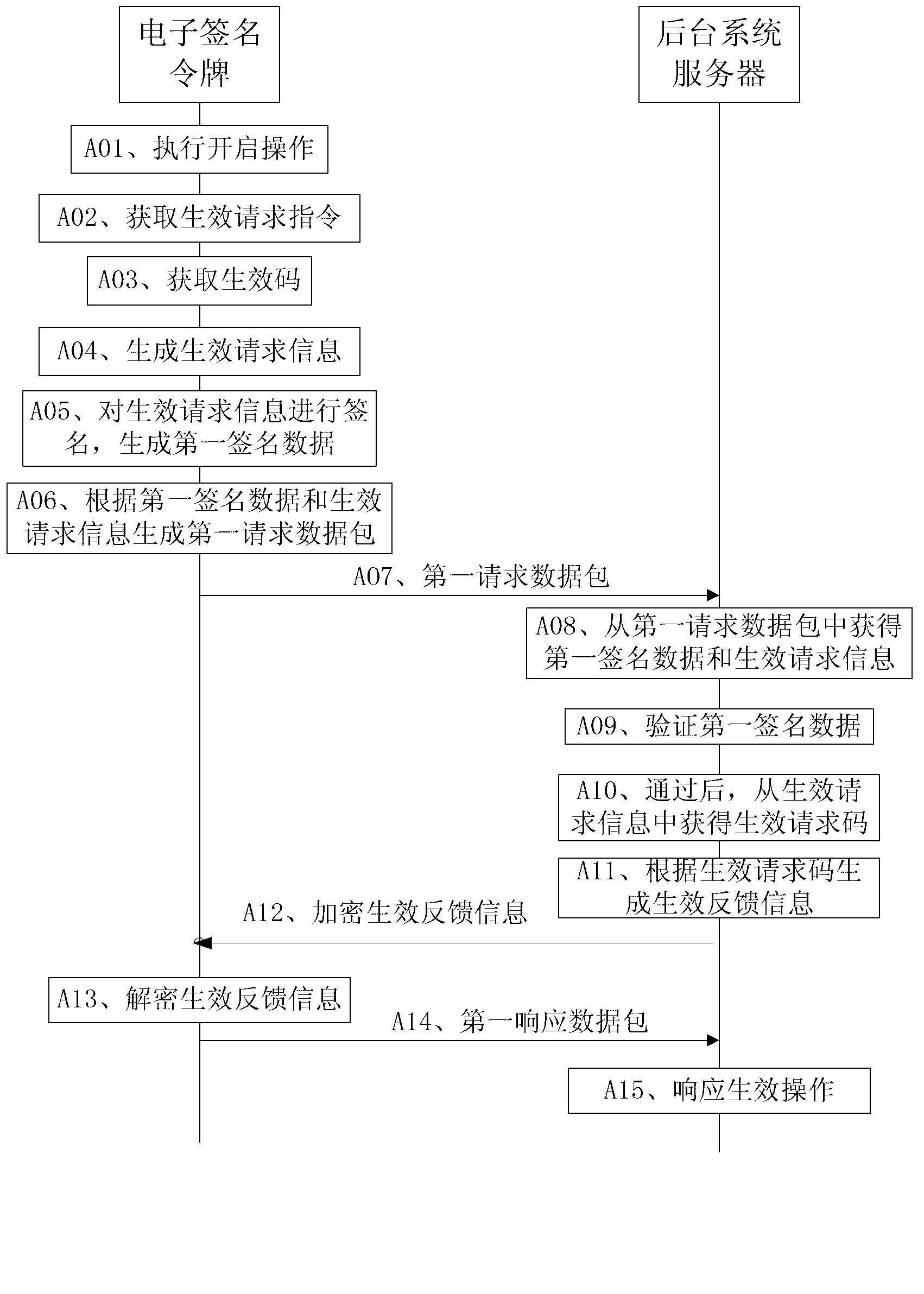
Method and system for electronic signature token to respond to operation request, and electronic signature token
ActiveCN103220145AEnsure safetyNo security riskUser identity/authority verificationComputer security arrangementsPasswordElectronic signature
The invention provides a method and a system for an electronic signature token to respond to an operation request, and the electronic signature token. The method comprises the following steps that the electronic signature token receives an enabling command and executes enabling operation according to the enabling command; the electronic signature token determines an operation type and / or operation level corresponding to the operation request according to the received operation request; and the electronic signature token determines a policy used for responding to the operation request according to the operation type and / or the operation level, and responds to the operation request according to the obtained policy, wherein the step of responding to the operation request according to the obtained policy comprises the following steps that the electronic signature token determines a key seed matched with the operation type according to the operation type, and at least generates a dynamic password value according to the key seed and a preset event factor; or the electronic signature token determines an event factor matched with the operation level according to the operation level, and at least generates a dynamic password value according to a preset key seed and the event factor.
Owner:TENDYRON CORP
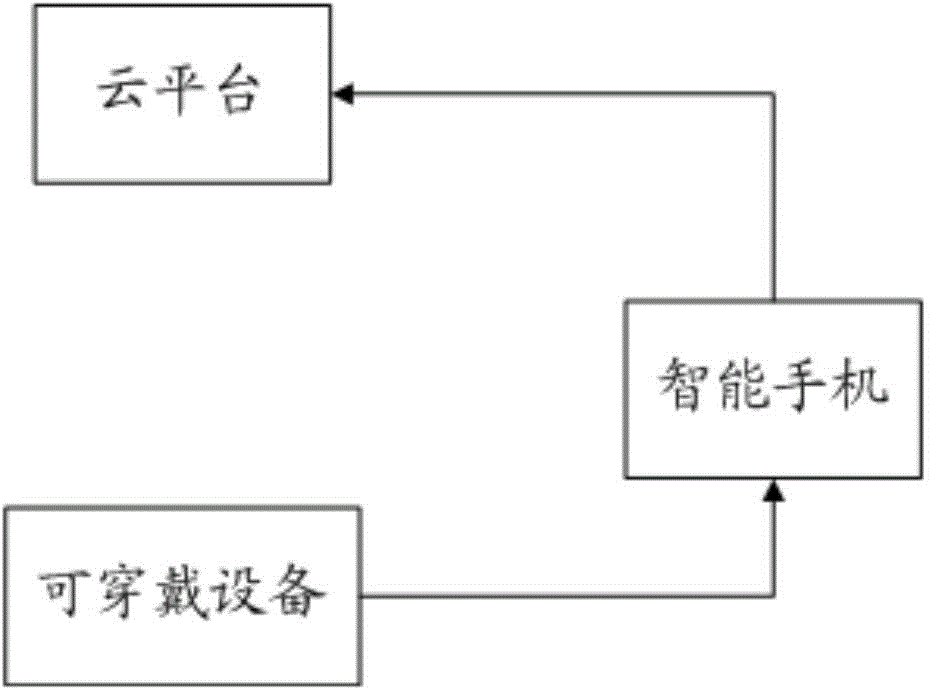
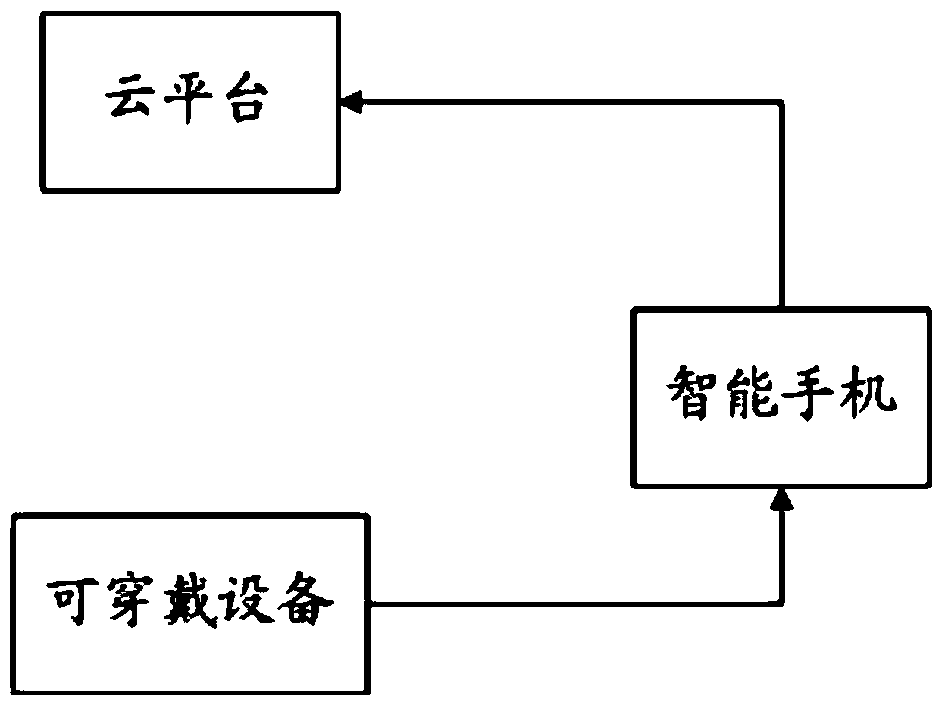
Pairing/un-pairing system and method for smart phone and wearable equipment
ActiveCN104994106ADisassociationConnection managementTransmissionElectronic communicationEmbedded system
The invention discloses a pairing / un-pairing system and a pairing / un-pairing method for a smart phone and wearable equipment, and relates to the technical field of electronic communication. The system comprises the smart phone, the wearable equipment and a cloud platform. The smart phone is communicated with the cloud platform via a first APP installed in the smart phone; the smart phone and the wearable equipment are communicated via Bluetooth, WIFI or NFC, and a second APP is fixed or loaded in the wearable equipment. The pairing / un-pairing method could be realized by using the mutual verification of the smart phone and the wearable equipment, and the cloud platform to verify the smart phone and the wearable equipment. The pairing / un-pairing system and the pairing / un-pairing method of the invention fill up the blank of mutual trust between devices and provide credible service basis for the cooperative work between the smart phone and the wearable equipment. The pairing / un-pairing system and the pairing / un-pairing method of the invention could remove the correlation of the two while one device is lost by a user or the user does not want to correlate with the device so as to un-pair the devices.
Owner:河南中盾云安全研究中心
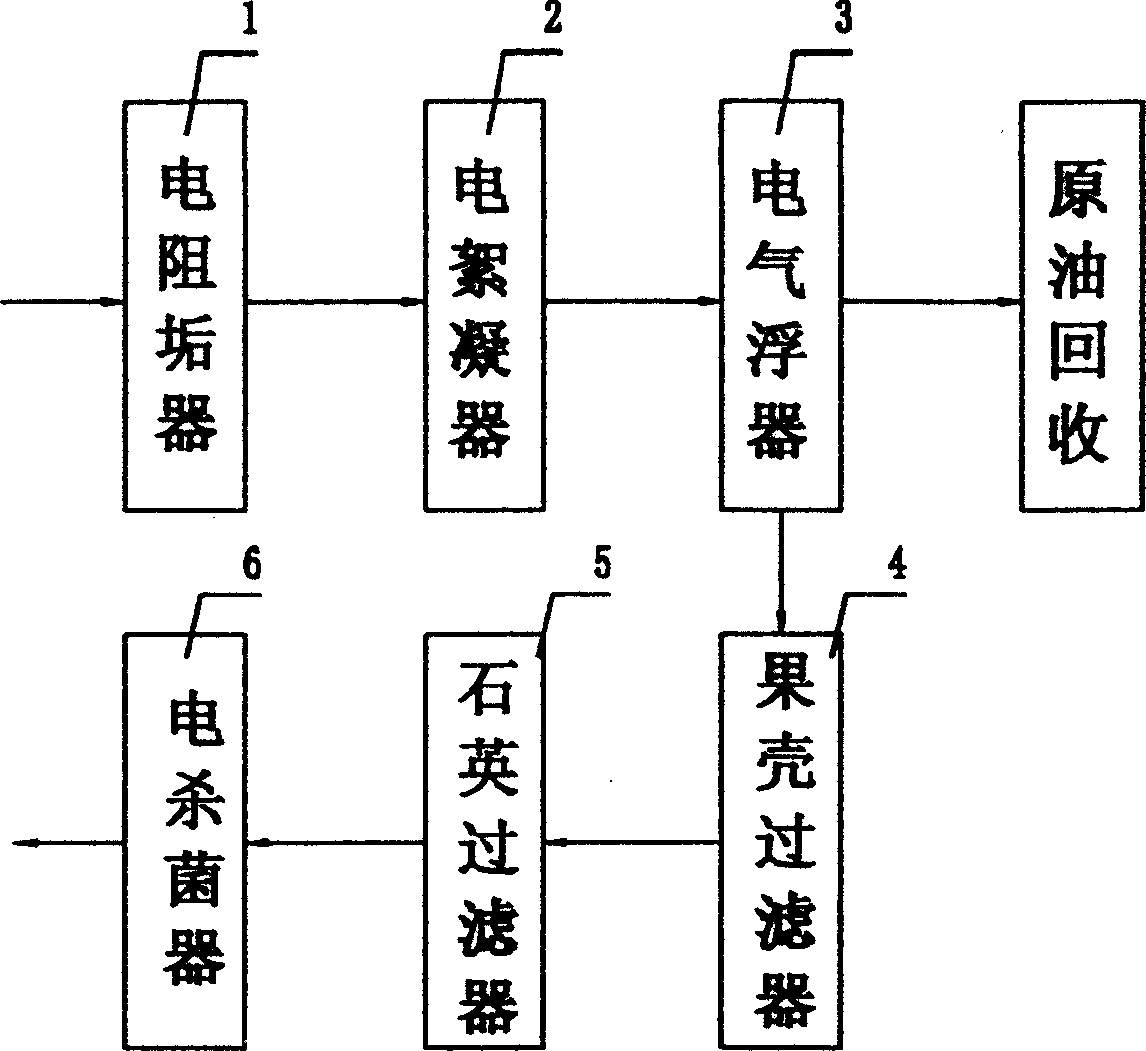
Oil field sewage treating equipment
InactiveCN1654350ADisassociationWon't breakWater/sewage treatment using germicide/oligodynamic-processWater/sewage treatment by flocculation/precipitationEcological environmentOil field
The oil field waste water treating apparatus includes electric antiscaling unit electric flocculating unit, electric air floating unit, fruit husk filter, quartz filter and electric disinfector connected successively with pipeline. In the upper opening part of the electric air floating unit, oil scraper is provided. The oil field waste water treating apparatus has simple operation and is automatic, and the treated water may be re-injected into stratum without damage on ecological environment. The present invention makes it possible to utilize raw oil in the oil bearing waste water, and this changes waste into useful matter while protecting environment.
Owner:山东正源电气有限公司
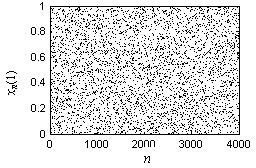
Quick parallel generating method for multidimensional pseudo-random sequence with uniform distribution characteristics
InactiveCN102684871ADisassociationSuppression of short-period phenomenaSecuring communicationTent mapTheoretical computer science
The invention discloses a quick parallel generating method for a multidimensional pseudo-random sequence with uniform distribution characteristics, wherein the quick parallel generating method improves a classic coupled map lattice (CML) model according to the security requirement of the cryptography, cancels diffusion coefficients thereof, increases constant terms, limits the grid value to be within [0, 1] through modular operation, and achieves a novel coupled tent map lattice system with the uniform distribution characteristics; and in addition, the pseudo-random sequence is generated through user key conversion and initial vector conversion by utilizing a coupled tent map lattice system model with the uniform distribution characteristics. The quick parallel generating method inherits the coupling diffusion mechanism and the parallel iteration characteristics of the CML model, leads system state tendency to achieve ergodicity through the stretching and folding of the local grid tent map as well as the double nonlinear action of the modular operation, overcomes the defect of the CML model on security, and can generate the multidimensional pseudo-random sequence with the uniform distribution characteristics in a parallel and quick manner.
Owner:BEIJING INSTITUTE OF PETROCHEMICAL TECHNOLOGY
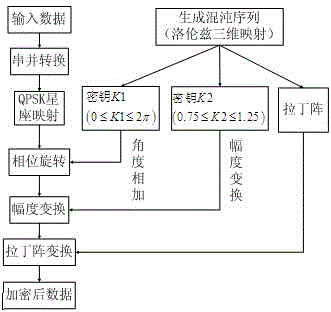
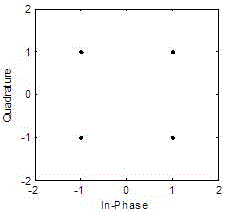
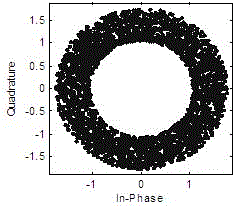
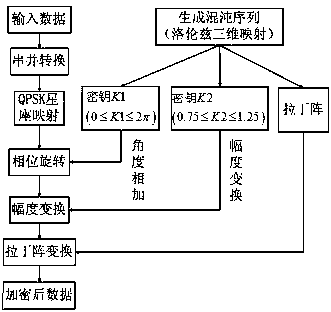
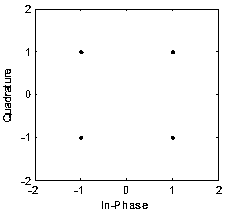
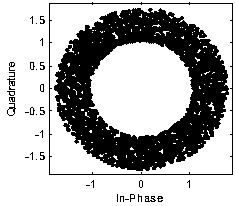
Physical layer encryption method introducing Latin array
ActiveCN105846947AImprove securityDisassociationSecret communicationSecuring communication by chaotic signalsPhysical layerChaotic systems
The invention relates to a physical layer encryption method introducing a Latin array, comprising steps of using a chaotic system and a Latin array to generate a key which is good in performance, using the key to scramble a constellation graph, making distribution of constellation points of various modulation modes on a complex plane toward uniformity, making individual characteristic parameters of various modulation modes toward consistency, achieving a goal of protecting the modulation mode and the modulation information from the physical layer, and fully utilizing the mapped complex plane information to achieve a goal of maximally expanding the key space. The physical layer encryption method introduces an Extract function, fully eliminates the relevance between the chaotic sequences, does not need to generate massive keys on the premise that the key space is guaranteed, greatly reduces the complexity of realizing hardware, performs an NIST random test on a generated key and verifies the unpredictability.
Owner:NAT UNIV OF DEFENSE TECH
Intelligent eyeglasses and control method and control device thereof
InactiveCN106502422AEasy to manageImprove convenienceInput/output for user-computer interactionSound input/outputEmbedded system
Owner:SHANGHAI QINGGAN INTELLIGENT TECH CO LTD
Memory access mode protection method based on data redundancy
The invention discloses a memory access mode protection method based on data redundancy, which can efficiently and safely confuse the memory access mode, and the confused memory access sequence is difficult to be correlated by an attacker, thereby achieving the goal of safety. The invention adopts the data redundancy technology, dynamically converts each request address and encrypts each data block. At the same time, combined with the position map optimization technology, the invention makes the optimize position map hundreds of times smaller than the traditional position map, and can effectively protect the 4GB memory only require a few megabytes of on-chip cache. The invention has the advantages of high safety, high speed, hardware compatibility and the like, which are not possessed by the prior methods, and is helpful for popularizing in practice.
Owner:ZHEJIANG UNIV
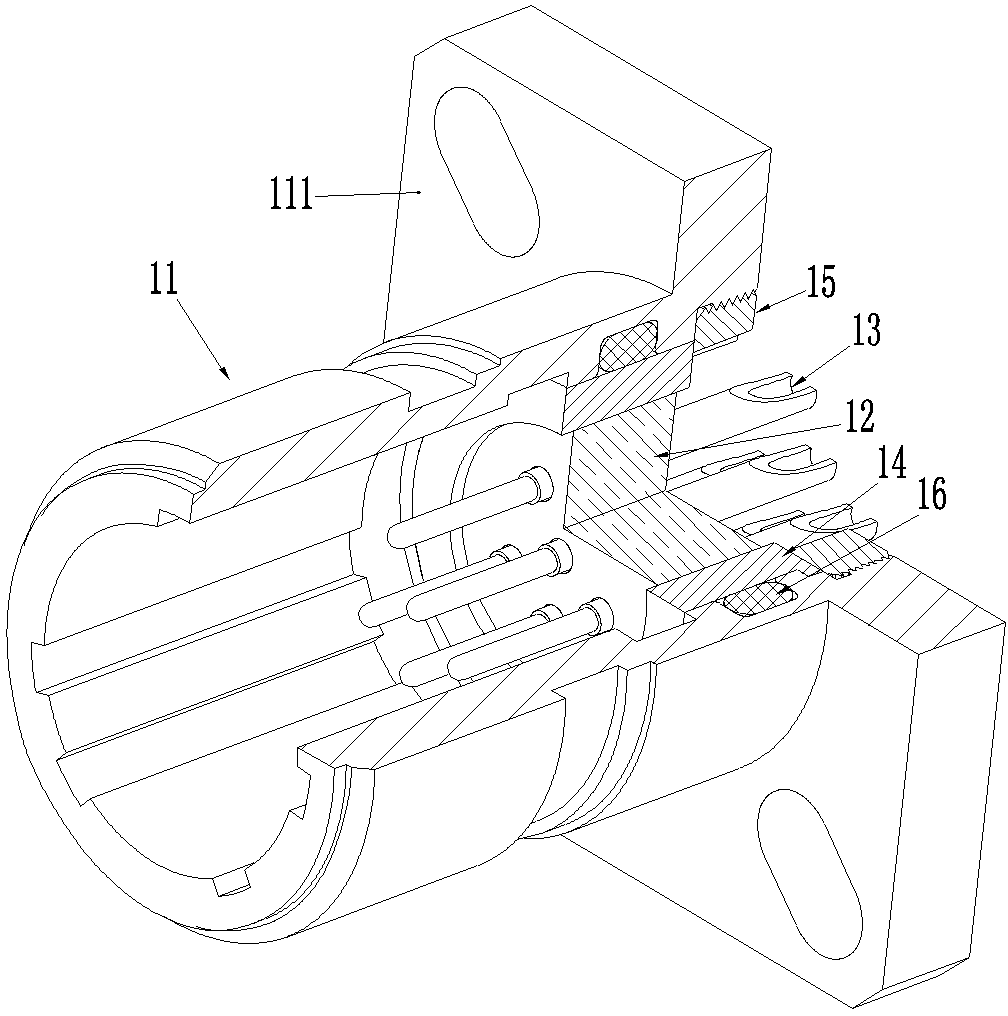
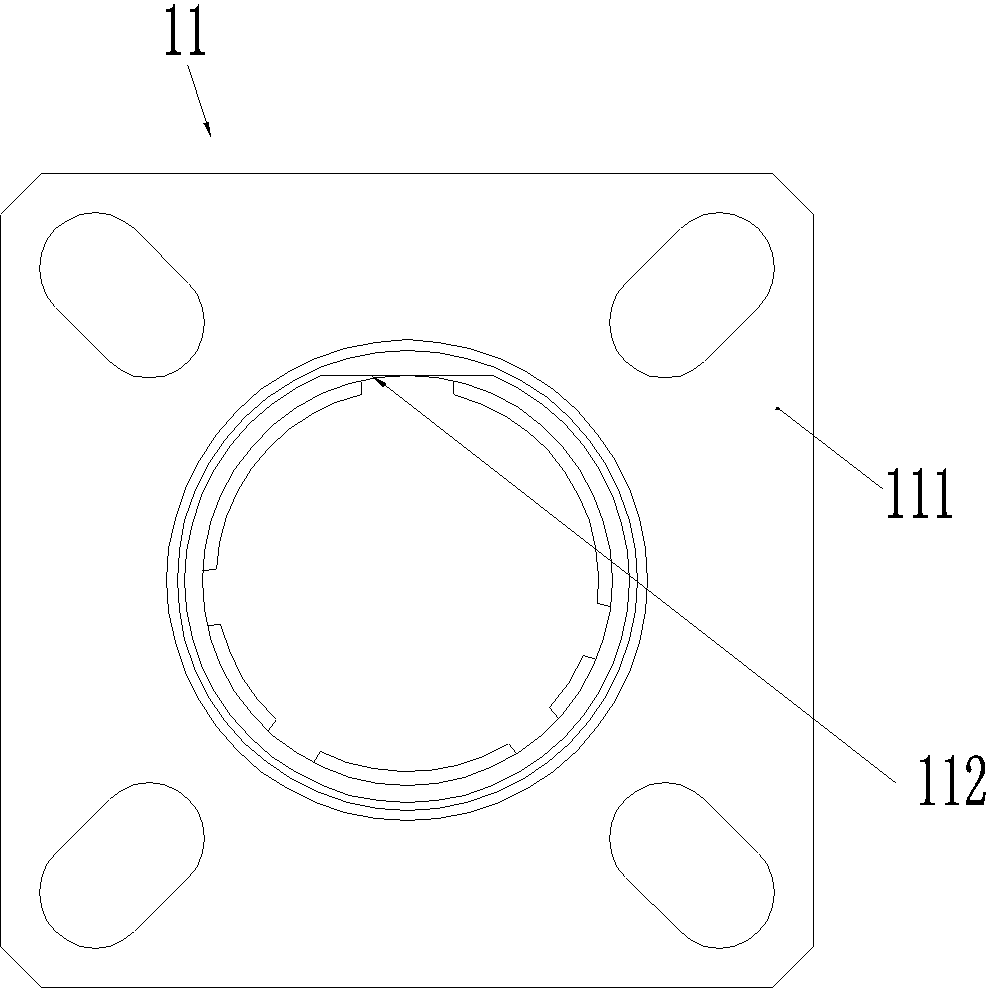
Contact element component and hermetic seal connector using component
The invention relates to the field of an electric connector, in particular to a contact element component and a hermetic seal connector using the component. The electric connector comprises a housing and the contact element component assembled in the housing; the contact element component comprises a glass insulator, at least one contact element assembled in the glass insulator and a metallic sheath arranged outside the glass insulator; the contact element and the metallic sheath are sintered together through the glass insulator; the contact element component is fixedly assembled in the housing through the metallic sheath; and the metallic sheath is matched with the housing in a sealing manner. The electric connector is capable of preventing the housing from withstanding high temperature when the contact element is assembled, and simultaneously the glass insulator and the housing are not required to be sintered and the requirement of binding ability of housing material and glass is also reduced, so that the limitation to the heat resistance of the housing material of the electric connector and the binding property of glass is solved, a user can select a lighter material as the housing material according to requirements, and the problem that the existing electric connector is heavy in weight is solved.
Owner:CHINA AVIATION OPTICAL-ELECTRICAL TECH CO LTD
Crypto-currency transaction privacy protection method and system based on block chain
ActiveCN108737068AProtect transaction privacyDisassociationKey distribution for secure communicationEncryption apparatus with shift registers/memoriesPrivacy protectionCryptocurrency
The invention provides a crypto-transaction privacy protection method and system based on a block chain. The method comprises the following steps: forming a currency mixing group, creating a currencymixer wallet, summarizing currency, sending a currency mixing demand, receiving the currency mixing demand, creating the currency mixing transaction, performing currency mixing transaction signature,sending transaction information and verifying the currency mixing information. The method provided by the invention can be used for protecting the block chain transaction privacy information, the designed currency mixing method based on the random node can split the direct contact between both transaction parties, the association between a sender and a receiver in the transaction information is eliminated, and the aim of protecting the crypto-currency transaction privacy is achieved.
Owner:深圳市有芯电子有限公司
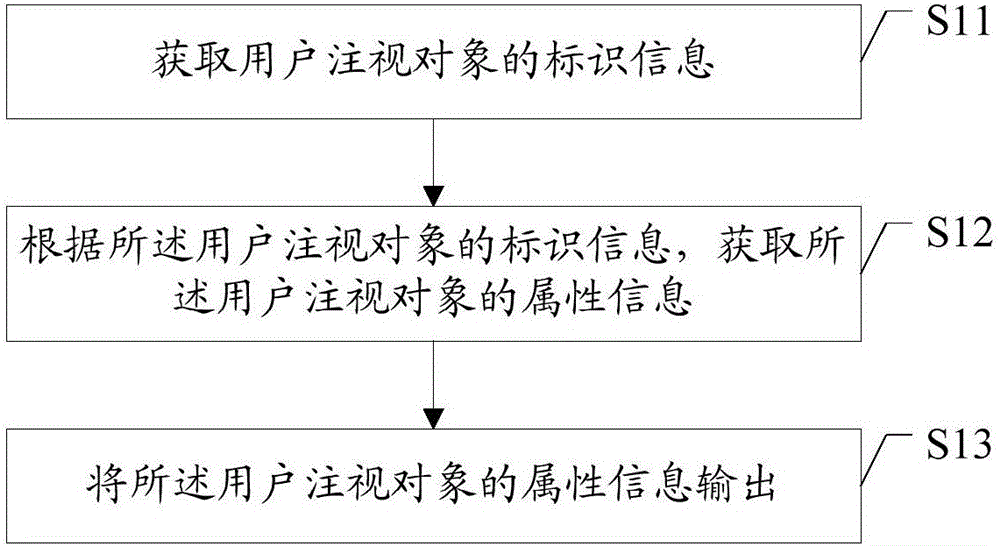
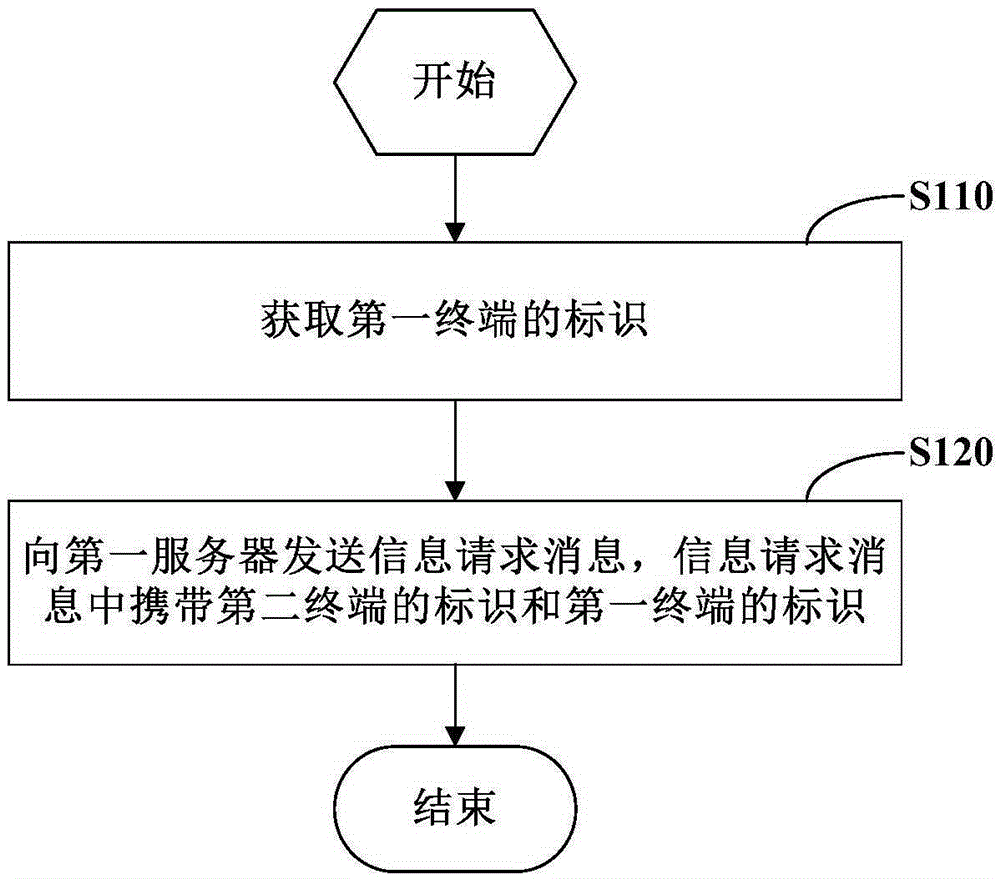
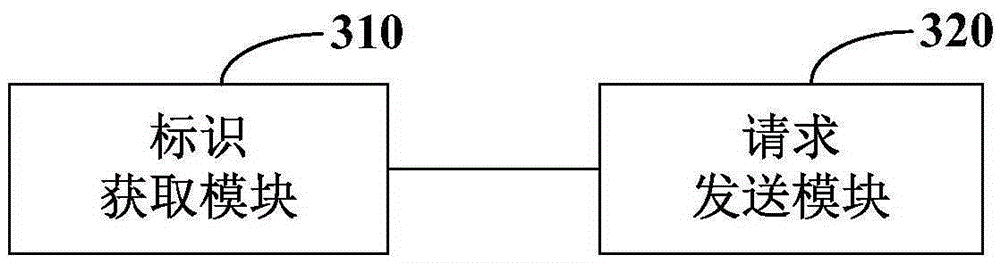
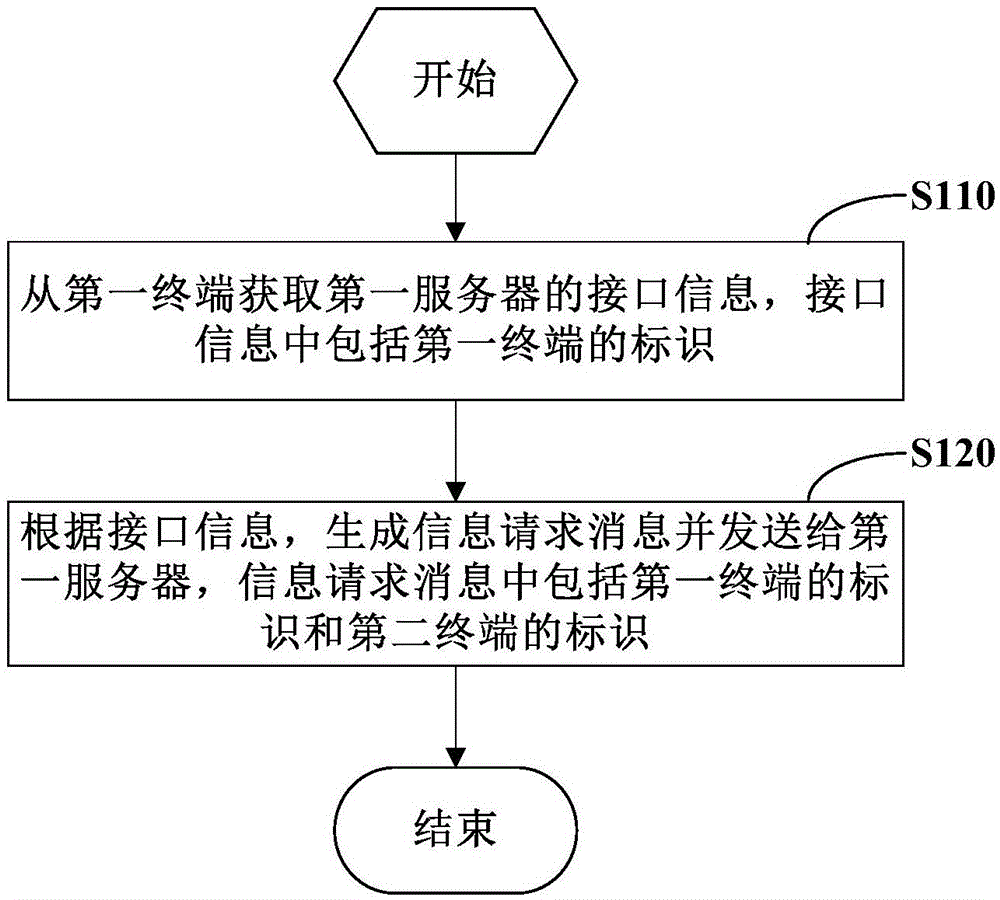
Information processing method, information pushing method and device
InactiveCN105897547ADisassociationImprove accuracyData switching networksInformation processingComputer terminal
The invention provides an information processing method, an information pushing method and a device. The information processing method comprises the steps that the mark of a first terminal is acquired; and an information request message is transmitted to a first server, wherein the information request message carries the mark of a second terminal and the mark of the first terminal. According to the information processing method, the information pushing method and the device, the information request message which carries the marks of two associated terminals is sent to the server; a basis is provided for across device user tracking and continuous user serving; and the accuracy of information pushing is improved.
Owner:LETV INFORMATION TECH BEIJING
Verifiable ciphertext data range query method
ActiveCN108197499AHigh query securityImprove efficiencyEncryption apparatus with shift registers/memoriesDigital data protectionCiphertextComputer science
The invention discloses a verifiable ciphertext data range query method. The method comprises the steps that sorting is conducted aiming at each local data to obtain triple data and prefix sets of each local data, and the prefix sets of each local data are stored in a PBtree; encryption is conducted aiming at each triple data and each prefix set, and each encrypted local data is stored in leaf nodes in the PBtree; the above processed data is transmitted to a cloud server; a trap door is generated through the query range, searching is conducted by the cloud server in the PBtree by using the trap door, finally the ciphertext data in the corresponding searched leaf nodes is returned, decryption is conducted on the ciphertext data by a data user, and whether or not the size of the obtained data is constant is determined according to the decrypted data to determine whether or not the results returned by the cloud server are complete. According to the method, by storing additional information in the PBtree leaf nodes, user queries are verifiable to prevent incompleteness of the queried results of the cloud server.
Owner:JINAN UNIVERSITY
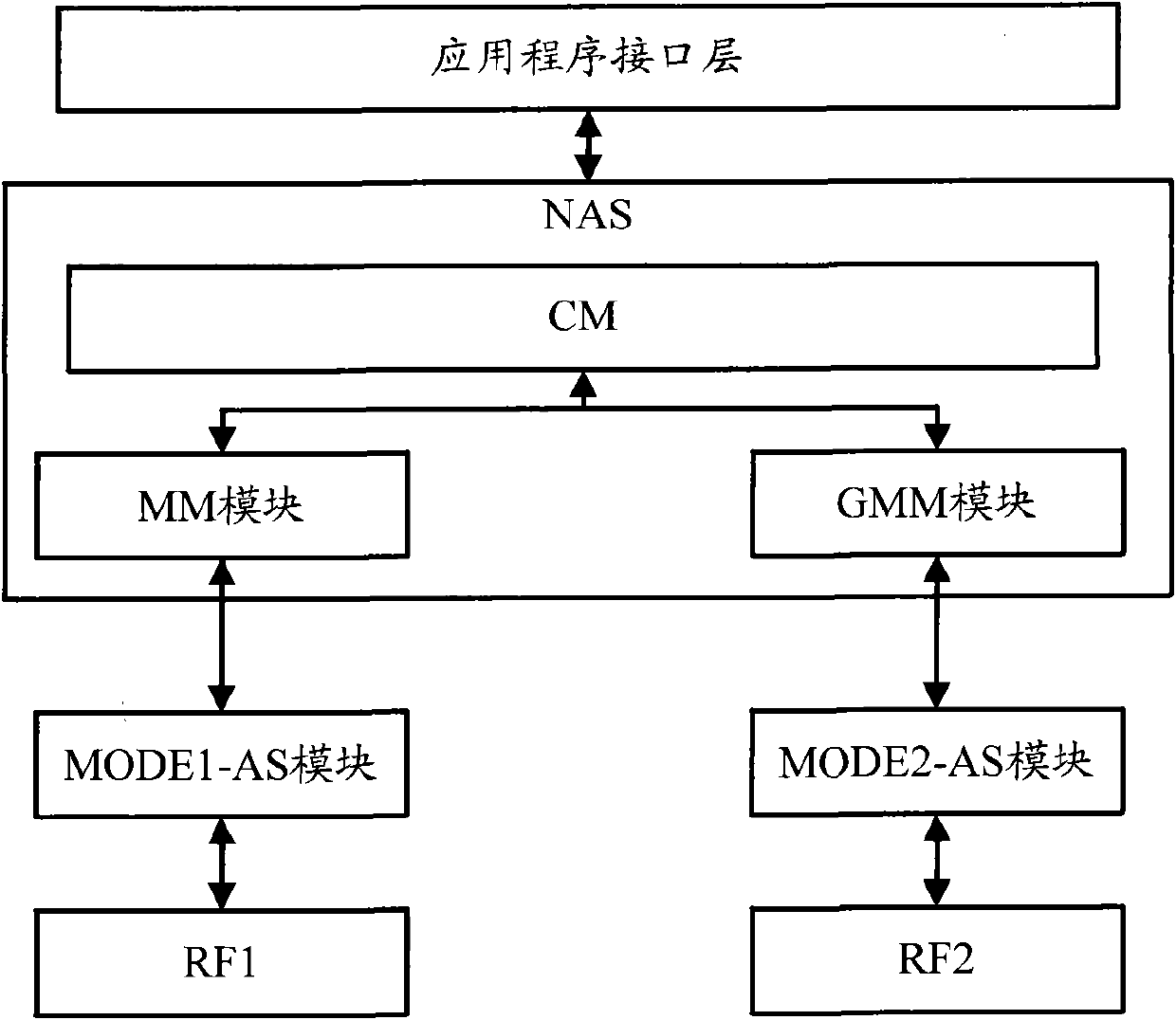
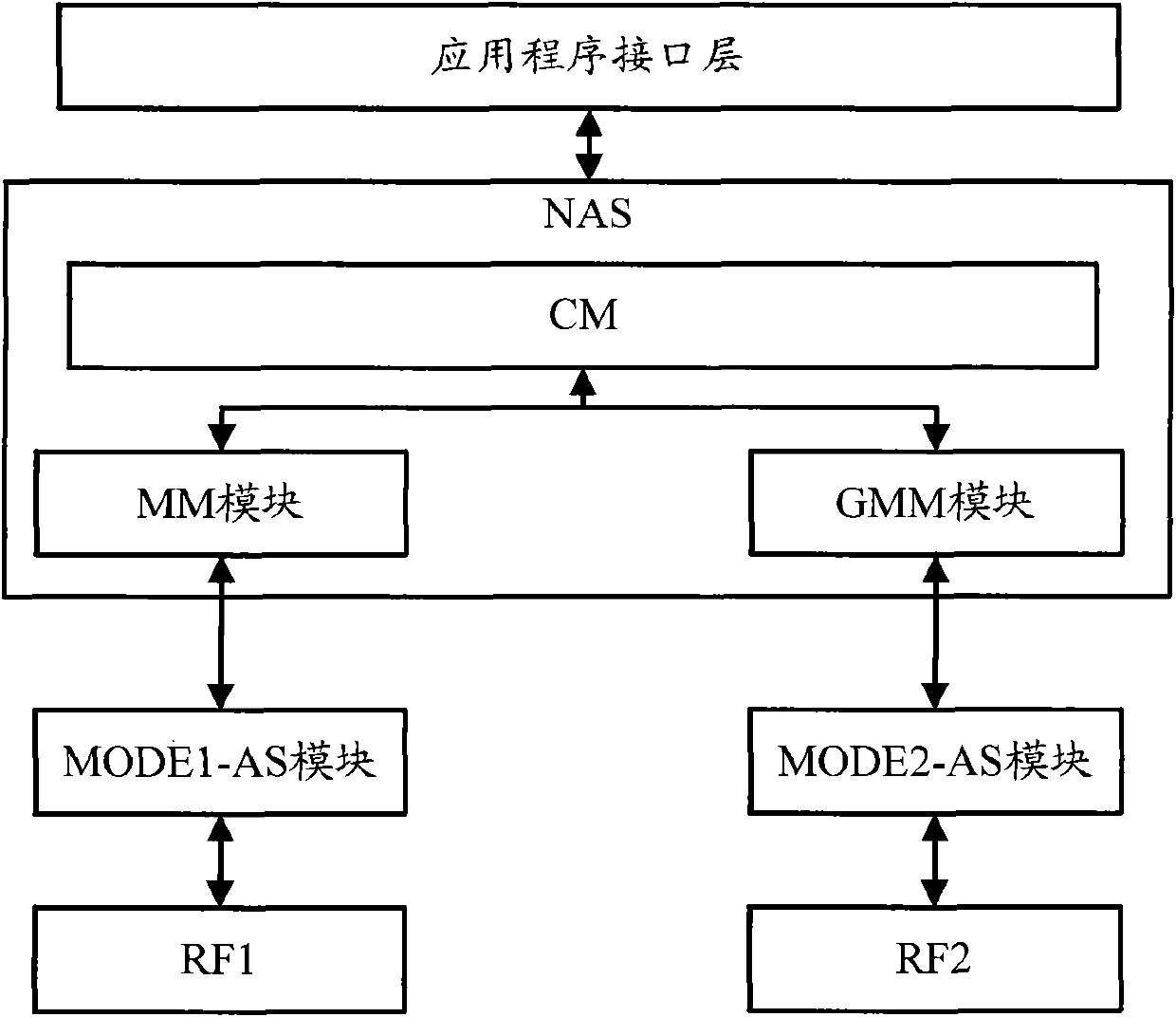
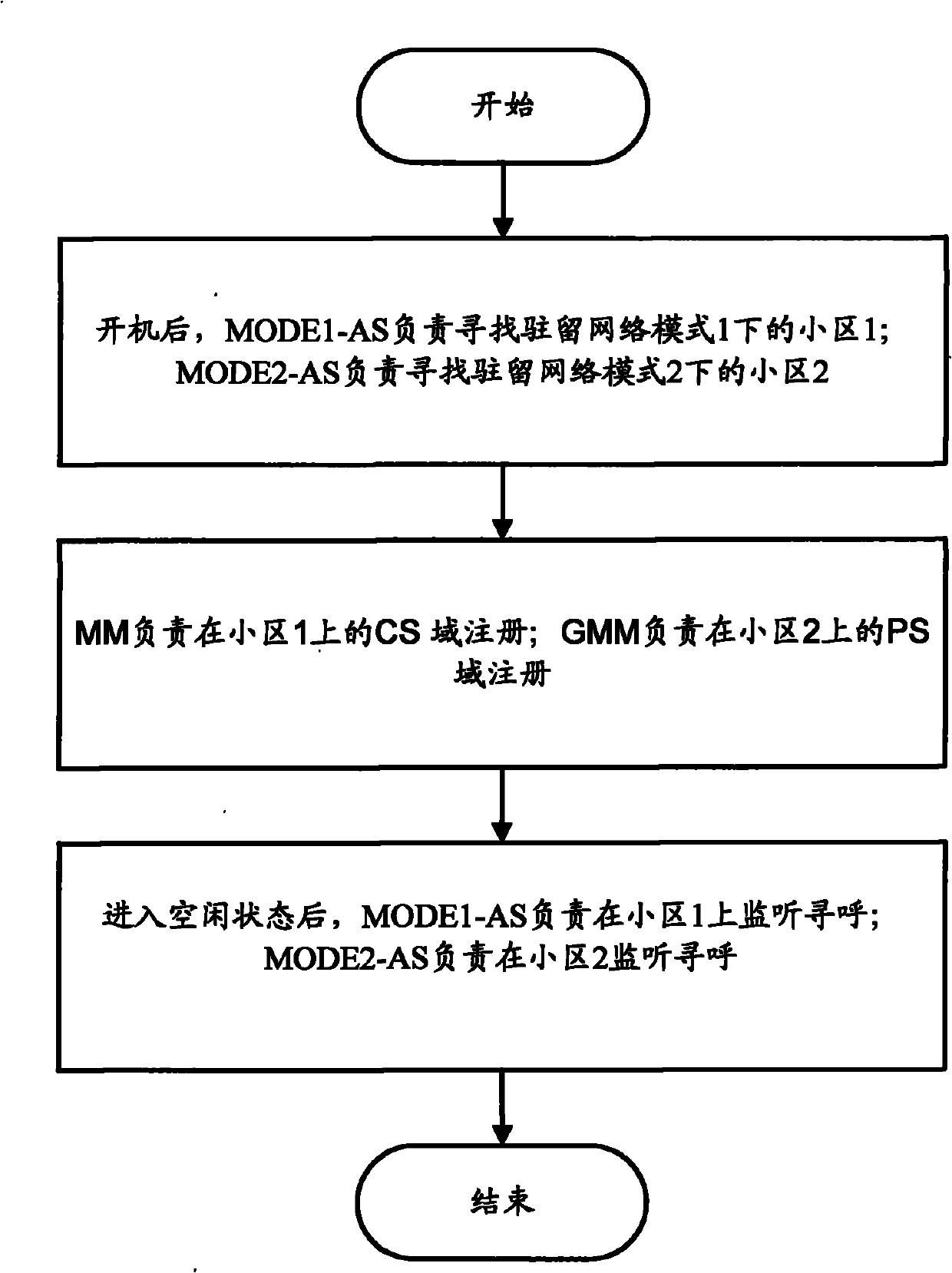
Terminal equipment and communication method for terminal
ActiveCN101951669ANo changes involvedDisassociationAssess restrictionQuality of servicePhysical layer
The invention relates to the field of communication, and discloses terminal equipment and a communication method for a terminal. In the terminal equipment, the functions of CS and PS services are mutually independent by reforming an MM and a GMM in a non-access layer and removing the correlation between the MM and the GMM on the premise of keeping the implementation mode of an access layer (comprising a physical layer). Therefore, the terminal equipment can perform the operations of residing, receiving broadcast information, initiating services and the like in two different service cells at the same time so as to comprehensively provide good quality of service, and is simple to implement.
Owner:SPREADTRUM COMM (SHANGHAI) CO LTD
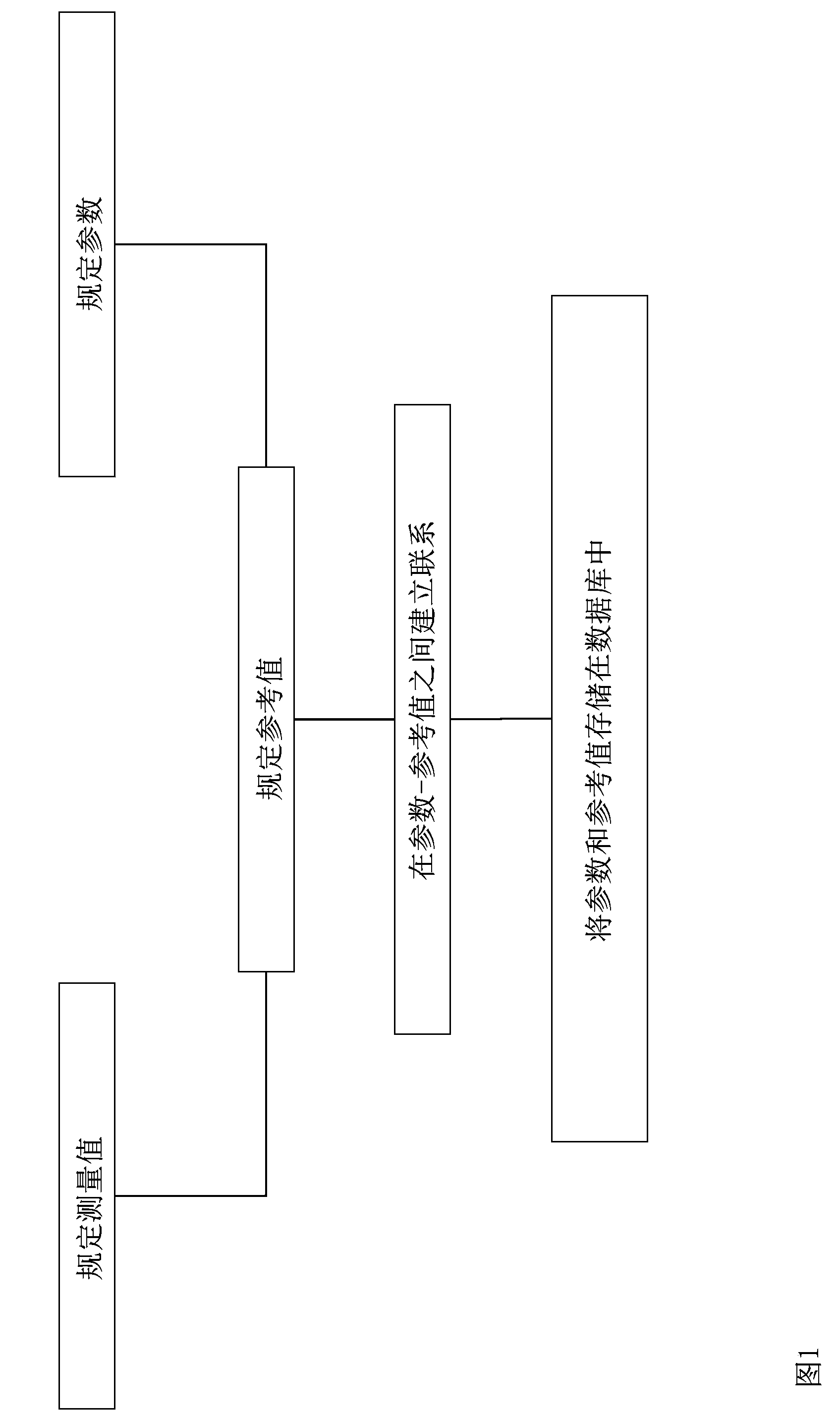
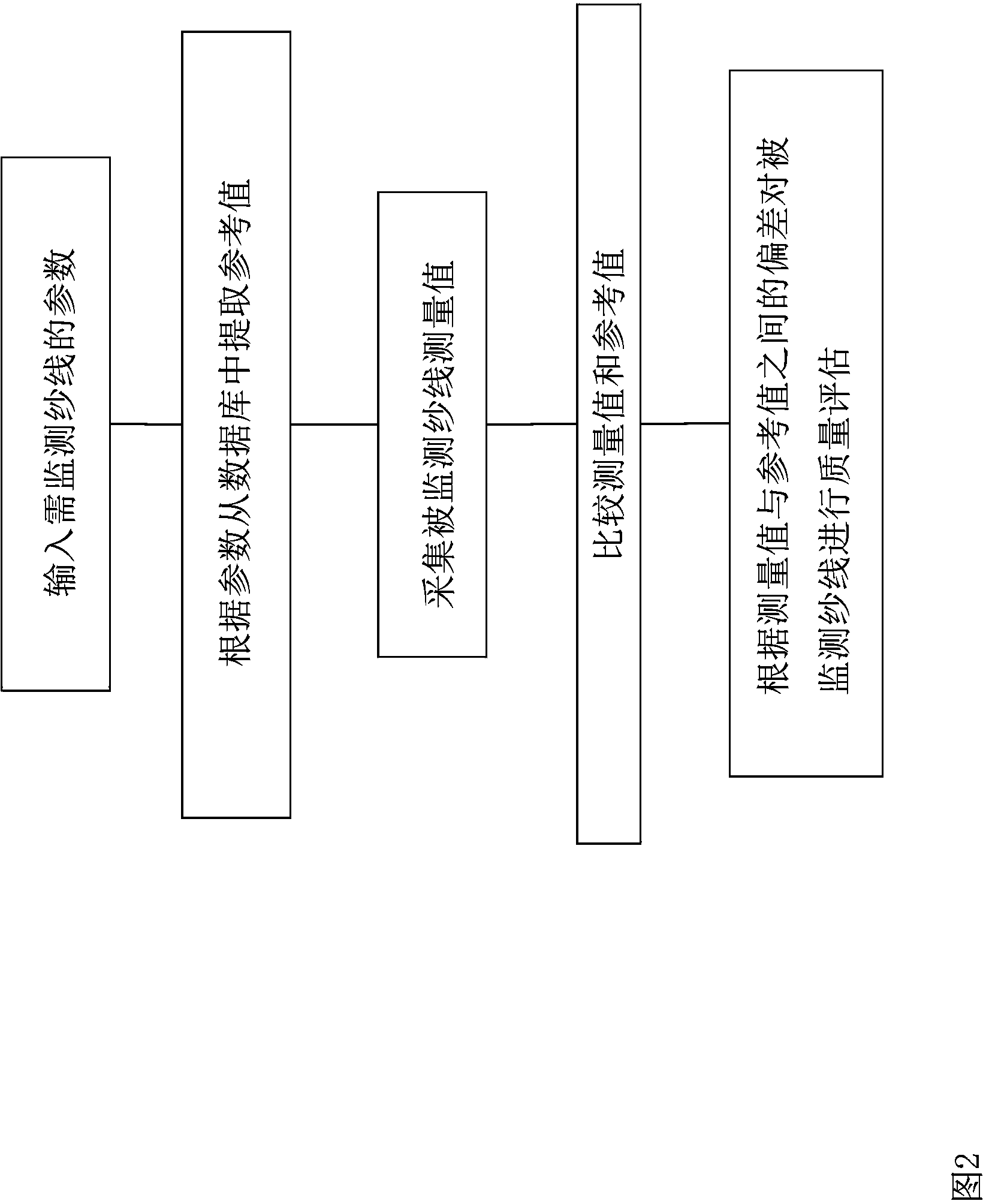
Yarn monitoring method
InactiveCN104203788ADisassociationNarrow or increase the intervalFilament handlingTextile testingYarnControl system
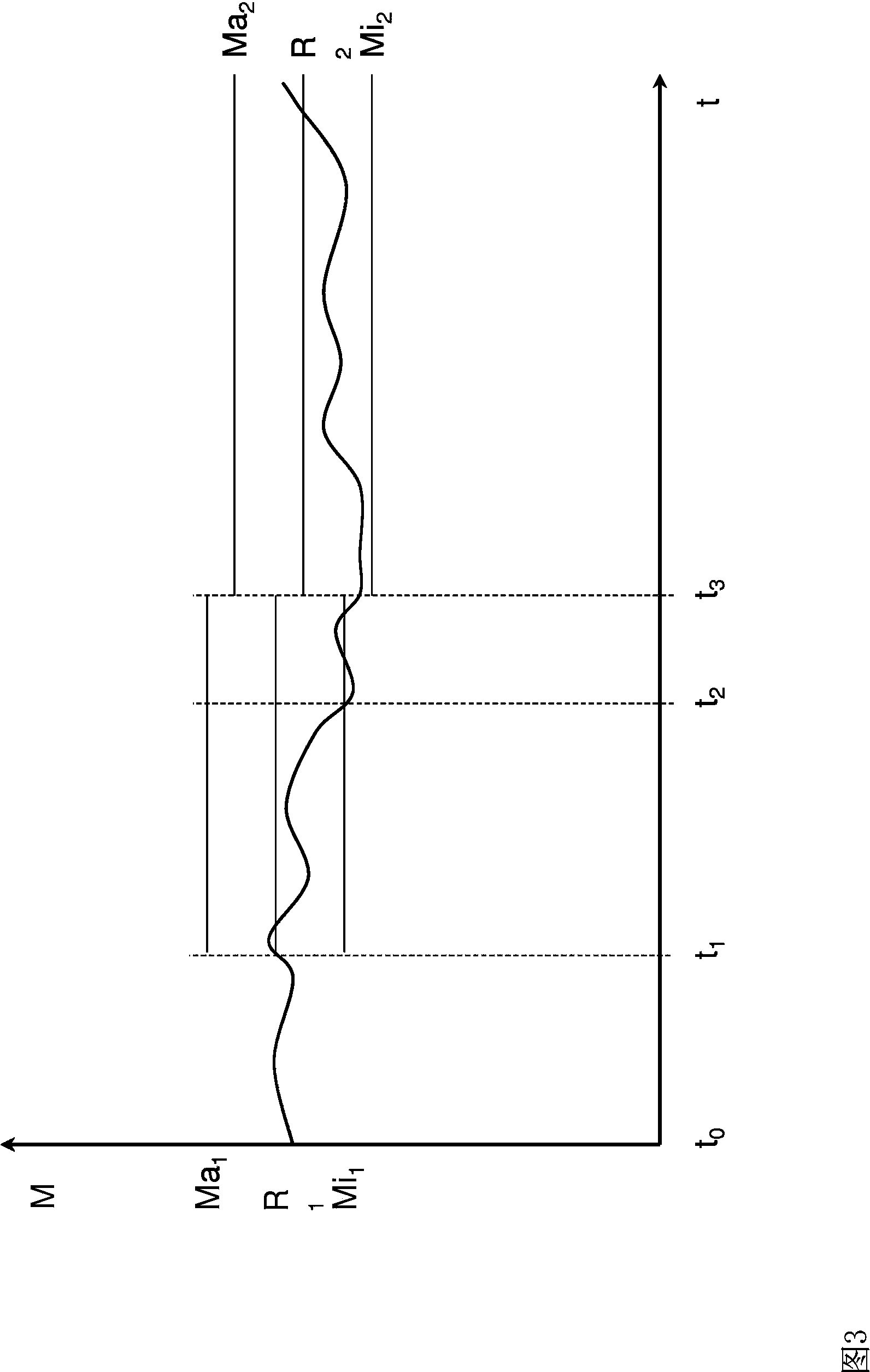
The invention relates to a method for monitoring the quality of a yarn on a textile machine, wherein the yarn passes a monitoring unit of the textile machine, with the aid of which at least one measured variable (M) which is dependent on a physical parameter of the yarn is determined, and wherein the measured variable (M), or a variable derived therefrom, is evaluated with respect to the position thereof with regard to at least one reference value (R). According to the invention, it is proposed that the selection of the reference value(s) (R) takes place taking into account one or more characteristic variables of the yarn, said characteristic variables being yarn-specific and defined prior to evaluating the measured variable (M). Furthermore, a textile machine is proposed which comprises at least one monitoring unit for monitoring at least one physical parameter of the yarn, and at least one controller which is operatively connected to the monitoring unit. The textile machine is characterized in that the controller is configured to monitor the yarn quality according to one or more of the preceding claims.
Owner:MASCHINENFABRIK RIETER AG
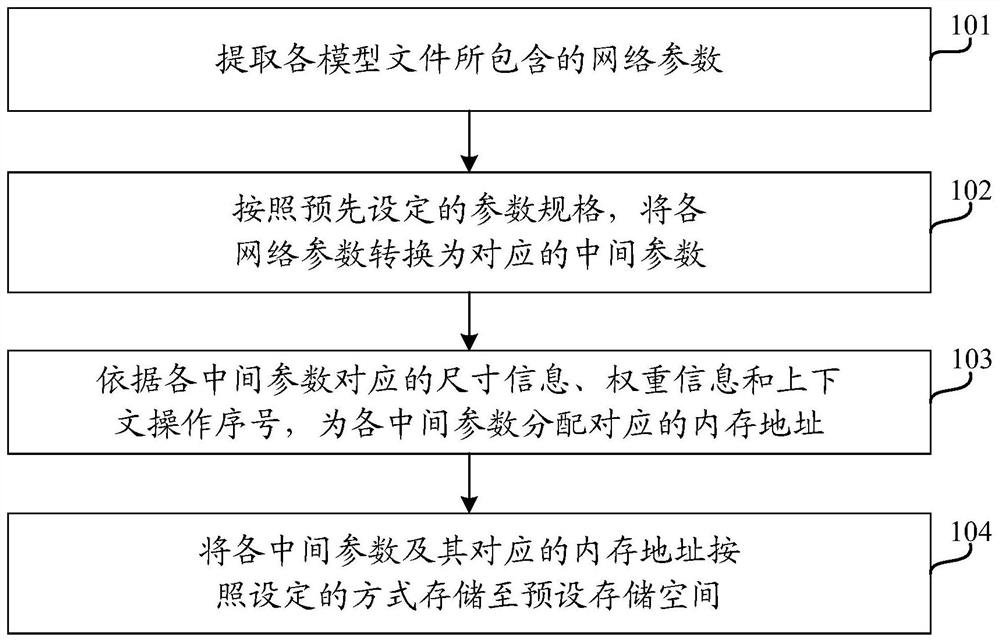
Parameter compiling method and device and computer readable storage medium
The embodiment of the invention discloses a parameter compiling method and device and a medium. The method comprises the following steps: extracting network parameters contained in each model file; converting each network parameter into a corresponding intermediate parameter according to a preset parameter specification; allocating a corresponding memory address to each intermediate parameter according to the size information, the weight information and the context operation sequence number corresponding to each intermediate parameter; and storing the intermediate parameters and the memory addresses corresponding to the intermediate parameters into a preset storage space according to a set mode. By converting the network parameters of the model files, the model files of different frameworks can be converted into unified and hardware-friendly intermediate parameters, the correlation between various operation operations of the network parameters and hardware is relieved, and the problemsof software code redundancy, dependency library conflicts and the like caused by supporting various frameworks are well solved. The data is written into hardware in the FPGA preprocessing stage, so that communication between the host and the FPGA is not needed any more, and the communication pressure between the host and the FPGA does not exist.
Owner:LANGCHAO ELECTRONIC INFORMATION IND CO LTD
Dynamic data processing method applied to Oracle database
InactiveCN102819588ADisassociationReduce couplingSpecial data processing applicationsData operationsTheoretical computer science
The invention relates to a dynamic data processing method applied to an Oracle database, which comprises the following steps of: creating data access objects, i.e. DAO (Data Access Object) objects, which comprise data insertion, updating and deletion; setting the connected database Oracle; setting structured query languages, i.e. SQL languages, corresponding to the DAO objects; setting corresponding bound parameters corresponding to each SQL languages; executing the dynamic data processing, receiving data operation commands and storing the data operation commands into caches of the corresponding DAO objects; judging whether the DAO objects to be processed need to be subjected to data insertion and if yes, continuously inserting data into the caches distributed for the data by the DAO objects; or, executing the data processing and finishing. According to the invention, by a dynamic DAO technology, the reconstruction upgrading cost is greatly reduced, the investment of manpower resources is reduced and the stability of a system is improved.
Owner:WHALE CLOUD TECH CO LTD
A three-dimensional grating and naked-eye 3D display device
The invention discloses a three-dimensional raster and a naked eye three-dimensional display device. The three-dimensional raster comprises a substrate and a raster graphic film fixed to the substrate, wherein the raster graphic film is provided with light-proof shielding parts and light transmitting slit parts, and the light-proof shielding parts and the light transmitting slit parts are arranged in a repeatedly alternated mode; the light transmitting slit parts are used for eliminating the relevance between the light transmitting slit parts and a sub-pixel structure of a plane display device so as to avoid generation of moire fringes. The light transmitting slit parts can eliminate the relevance between the light transmitting slit parts and the sub-pixel structure of the plane display device by modifying the shape of the light transmitting slit parts on the three-dimensional raster, the generation of the moire fringes is avoided, the naked eye three-dimensional display device has the advantages of being high in brightness, free of moire fringes and obvious in three-dimensional effect and the like, and accordingly comfortable sensation of people to watch three-dimensional display images is improved greatly.
Owner:TCL CORPORATION
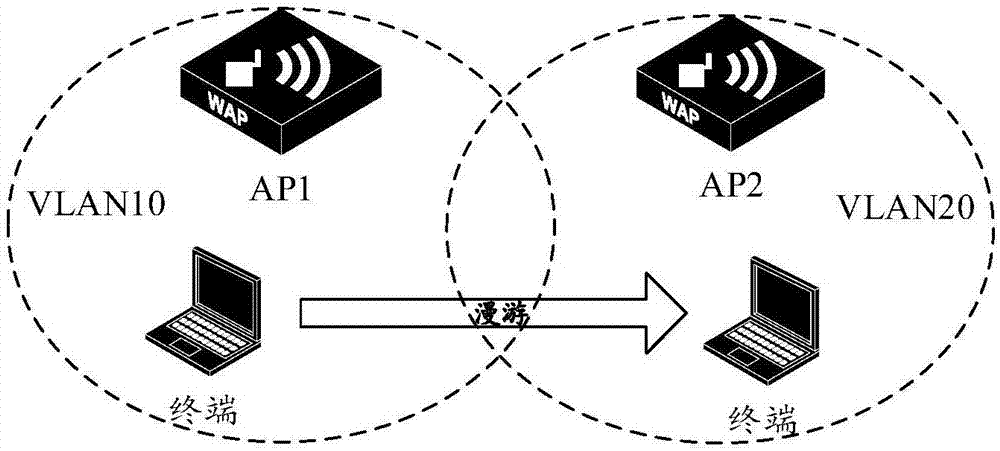
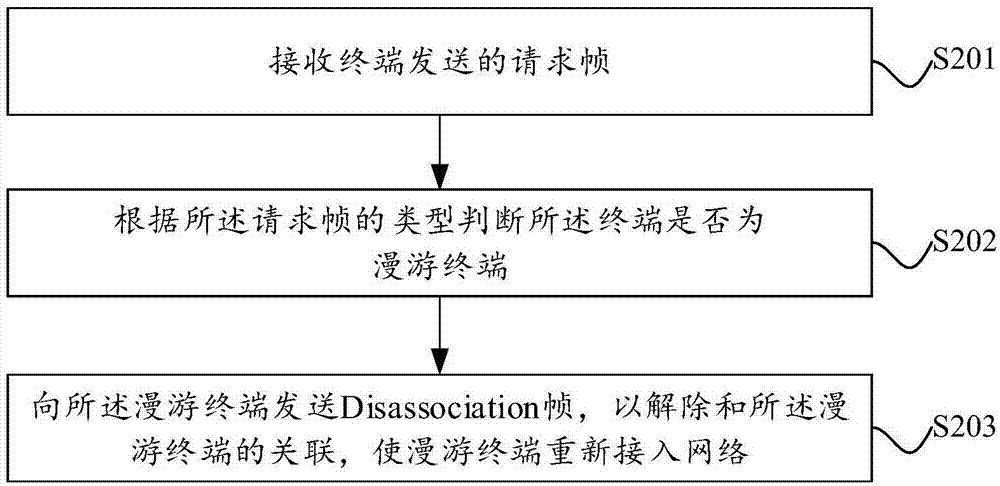
Terminal roaming switching method and device
ActiveCN107484223ARealize roaming switchingDisassociationAssess restrictionNetwork topologiesTelecommunications
The present invention provides a terminal roaming switching method and device. The terminal roaming switching method is applied to an AP. The terminal roaming switching method is characterized in that the method comprises the following steps that: a request frame sent by a terminal is received; whether the terminal is a roaming terminal is judged according to the type of the request frame; and if the terminal is a roaming terminal, a disassembly frame is sent so as to disassemble an association with the roaming terminal, so that the roaming terminal re-accesses a network. With the terminal roaming switching method and device of the invention adopted, roaming switching unsensible to the terminal can be realized, and the services of the terminal are not interrupted in a roaming process.
Owner:杭州迪普信息技术有限公司
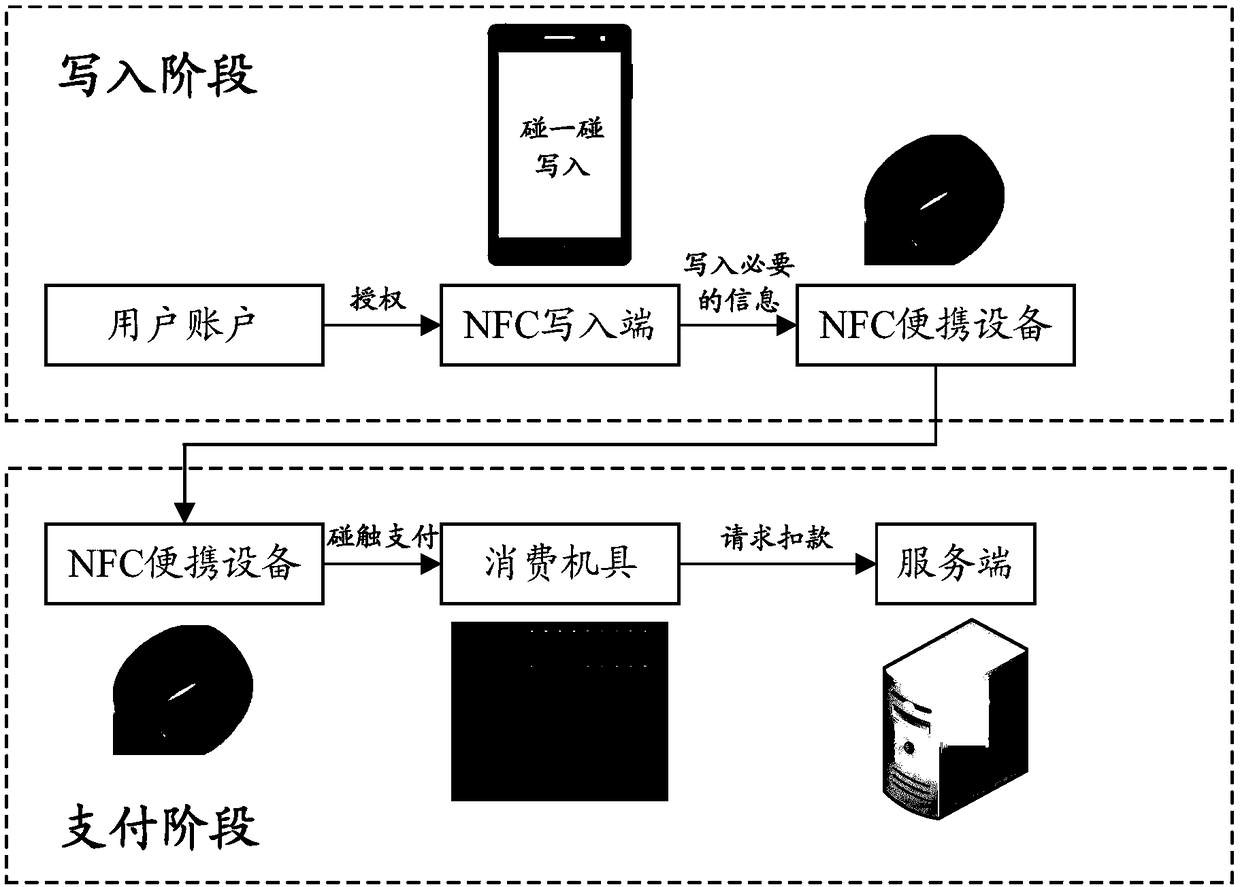
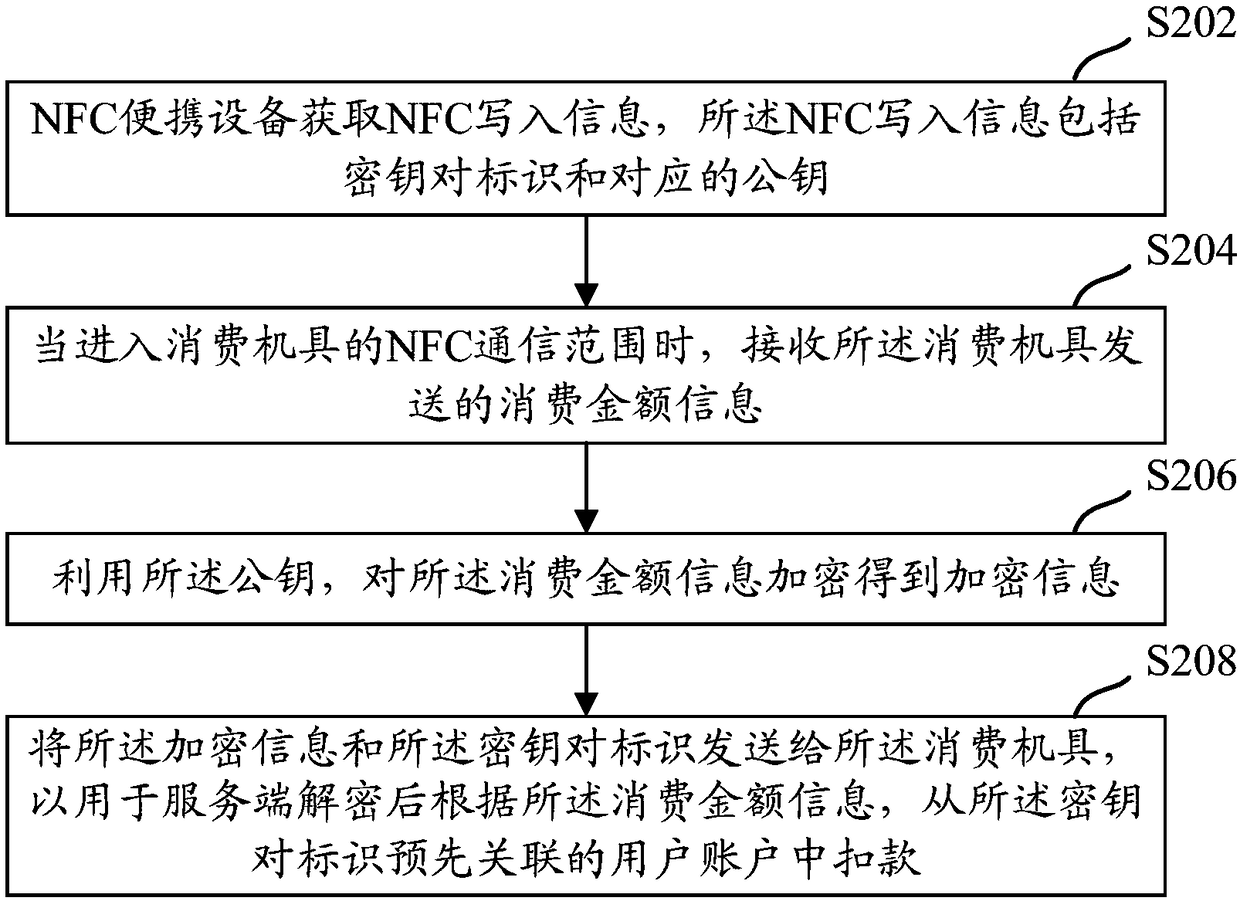
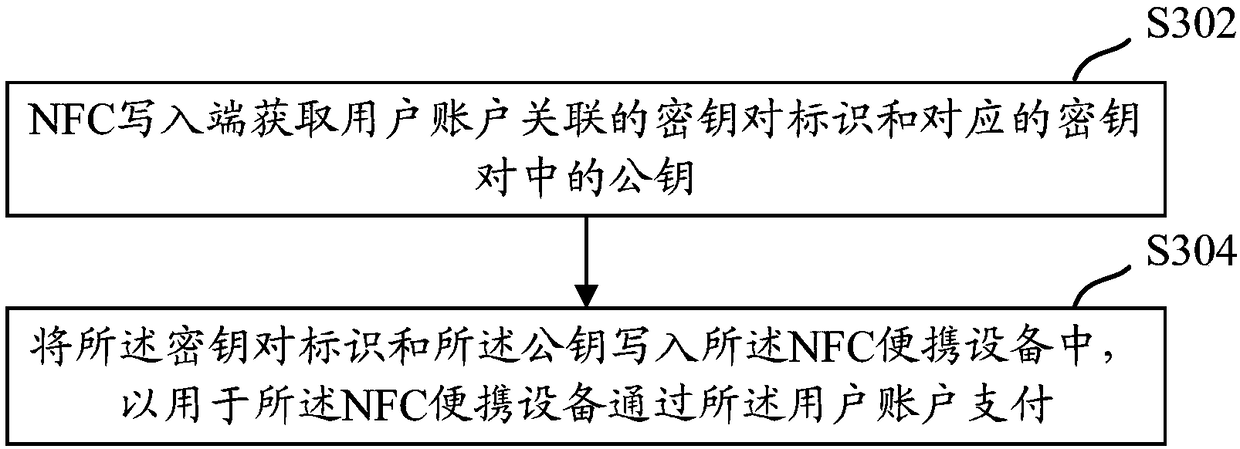
Writing method, payment method, device and equipment for NFC portable equipment
ActiveCN108241974ADisassociationEnsure safetyFinancePublic key for secure communicationComputer hardwarePayment
The embodiment of the present invention discloses a writing method for NFC portable equipment, a payment method, a device and equipment based on the NFC portable equipment. The solution comprises thesteps that: a server generates a key pair identifier associated with a user account and a corresponding key pair in advance, the NFC writing end writes the key pair identifier and a corresponding public key into the NFC portable equipment, then the NFC portable equipment can carry out payment based on the communication with a consumption machine, and server carries out deduction from a user account, wherein the NFC portable equipment is, for example, wearable equipment or card with the support of NFC.
Owner:ADVANCED NEW TECH CO LTD
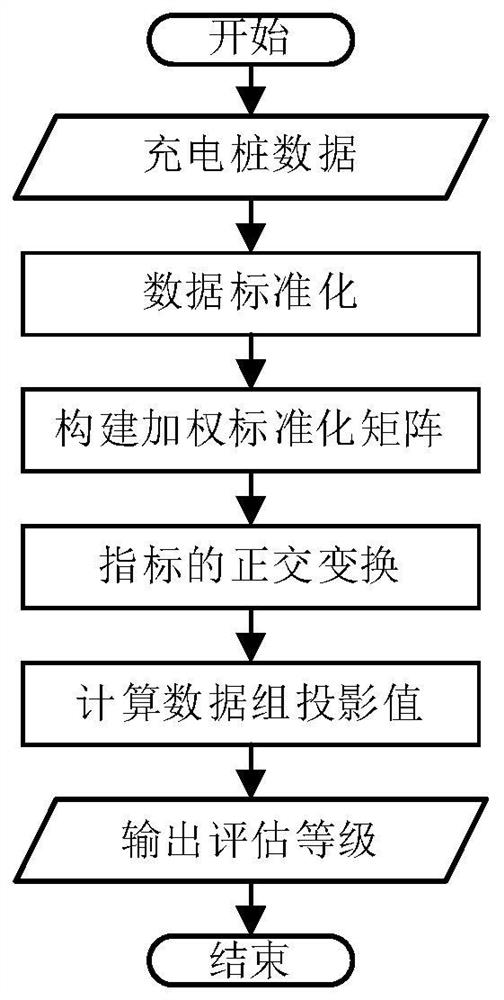
Large-scale charging station electric energy quality comprehensive evaluation method
PendingCN112288293ADisassociationEase of evaluationTechnology managementResourcesPower qualityComputer science
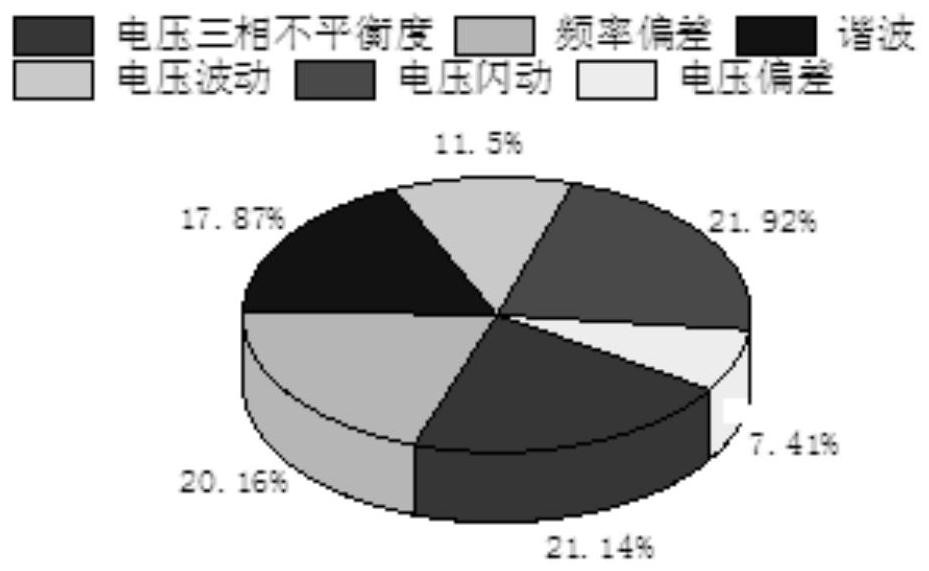
The invention relates to the field of charging stations, and aims to provide a large-scale charging station electric energy quality comprehensive evaluation method which evaluates the electric energyquality of a distribution network by connecting large-scale charging piles in a charging station through a method of combining example analysis and actual data, and specifically comprises the following steps: step 1, constructing a power distribution network electric energy quality index system of the charging station, wherein the electric energy quality indexes comprise a voltage deviation value,a frequency deviation value and a three-phase voltage unbalance degree; executing the step 2; step 2, taking the power quality indexes as input, inputting the power quality indexes into a trained power quality comprehensive evaluation model, outputting evaluation levels of the power quality indexes, and executing the step 3; and step 3, determining the distribution of the charging piles in the charging station according to the evaluation level of the power quality indexes.
Owner:ZHEJIANG HUADIAN EQUIP TESTING INST +1
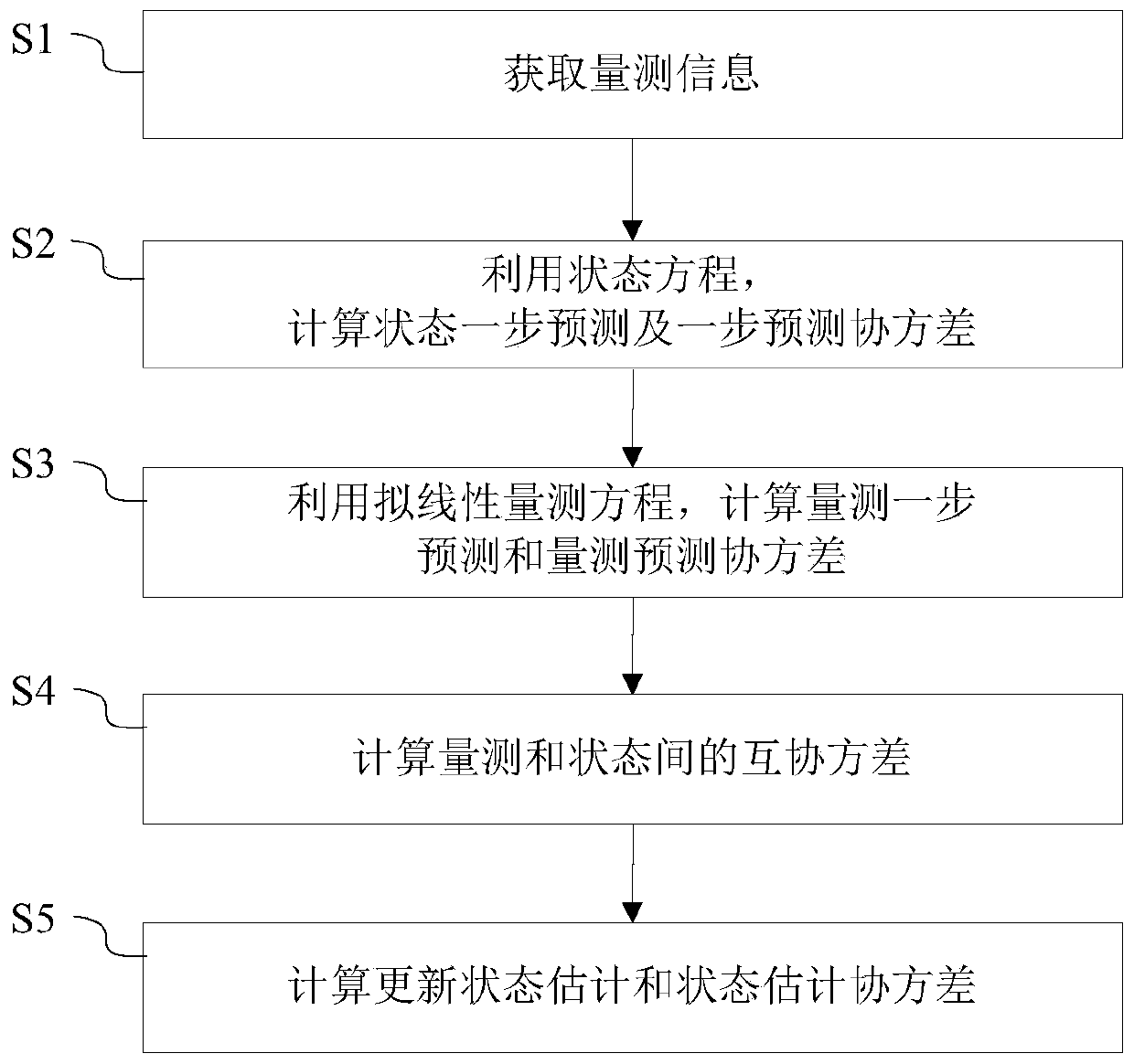
Bearing-only-tracking pseudo-linear filtering method
ActiveCN110208791AImprove accuracyImprove consistencyRadio wave reradiation/reflectionState predictionRadar
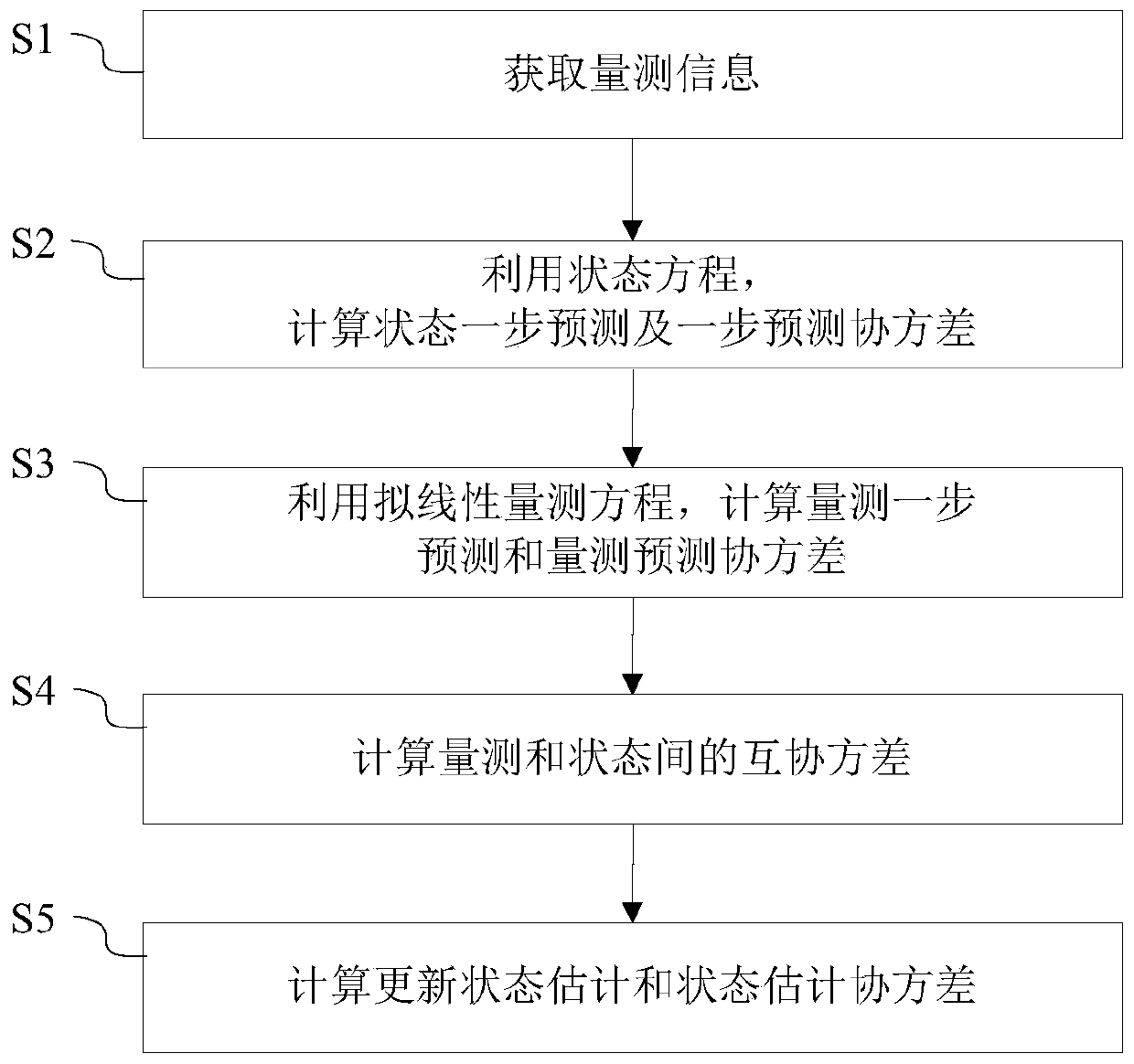
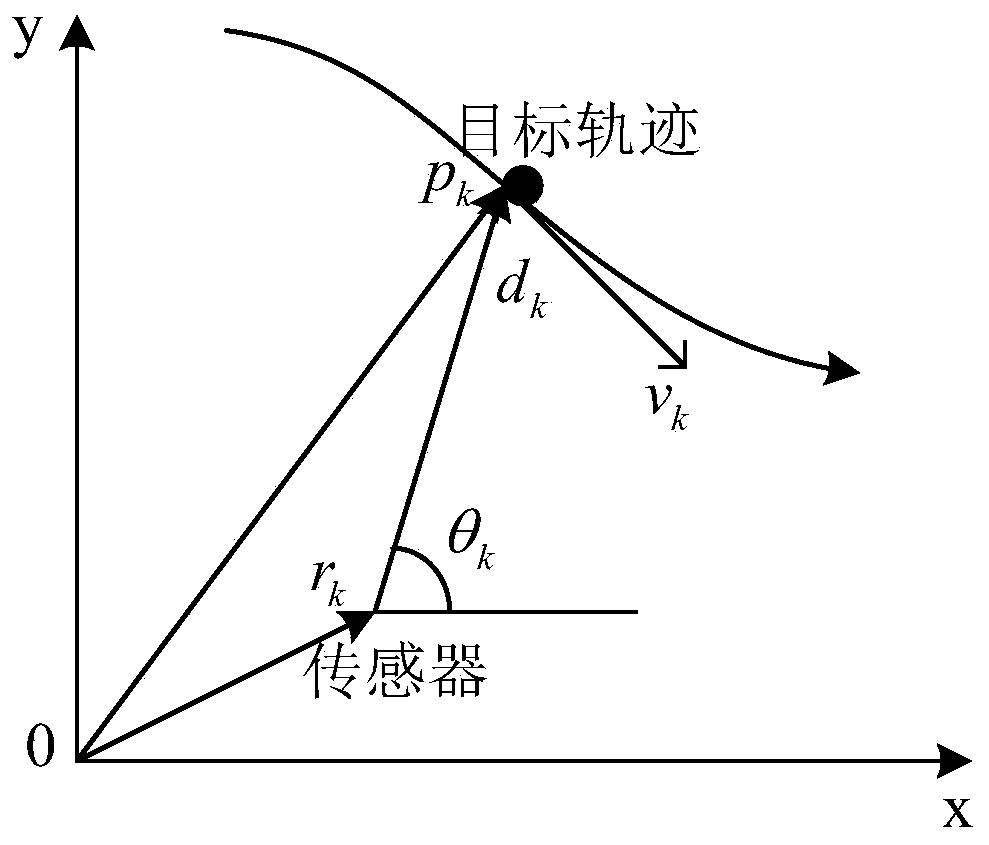
The invention relates to a bearing-only-tracking pseudo-linear filtering method. The method is performed as follows in each tracking period: acquiring measurement information from an observation radar, forming Gaussian distribution around a real target state and generating target state estimation under the condition of determining the current period to be an initial period; on the basis of the obtained measurement information, calculating state one-step prediction and a state prediction covariance by using a state equation; on the basis a quasi-linear measurement equation, calculating measurement one-step prediction and a measurement prediction covariance; acquiring an azimuth prediction value and a prediction measurement matrix based on the one-step prediction of the state and thus calculating a cross-covariance between the estimated state and the measurement; and calculating an updated state estimation and state estimation covariance to complete the target tracking of the current period. Therefore, the target tracking performance is improved effectively.
Owner:HARBIN INST OF TECH
Information sharing and information pushing method and device
InactiveCN105897829AAchieve sharingImprove effectivenessData switching networksInformation sharingComputer terminal
The invention provides an information sharing and information pushing method and device. The information sharing method comprises the steps that the interface information of a first server is acquired from a first terminal, wherein the interface information comprises the mark of the first terminal; and according to the interface information, an information request message is generated and sent to the first server, wherein the information request message comprises the mark of the first terminal and the mark of a second terminal. According to the information sharing and information pushing method and device, across device information sharing is realized; a user can be tracked; the effectiveness of information pushing is improved; and the method and the device are conducive to information expansion and effective information dissemination.
Owner:LETV INFORMATION TECH BEIJING
A driving intention recognition method based on improved hmm and svm double-layer algorithm
ActiveCN106971194BDriving Intent DeterminationFast operationCharacter and pattern recognitionPattern recognitionDriver/operator
The invention discloses a driving intention recognition method based on an improved HMM and SVM double-layer algorithm. Step 1: Classify the driver's driving intention: classify the driver's driving intention into sudden left lane change, normal left lane change, lane keeping, Five categories of normal right lane change and emergency right lane change; Step 2: Experimental data collection and processing; Step 3: Offline training of the improved HMM and SVM two-layer algorithm; Step 4: Driver's driving intention recognition. The present invention completely considers the people-vehicle-road system, collects the information of the vehicle, the road and the driver, adopts the HMM and SVM double-layer learning model, and improves the accuracy and timeliness of the driver's lane-changing intention identification model.
Owner:江苏易齐物流有限公司
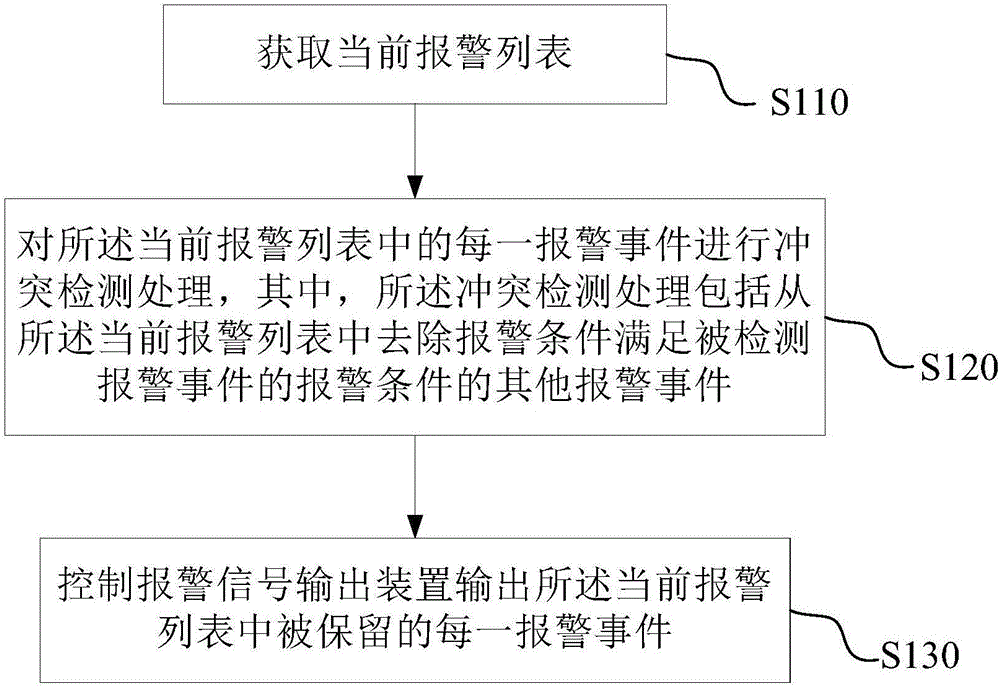
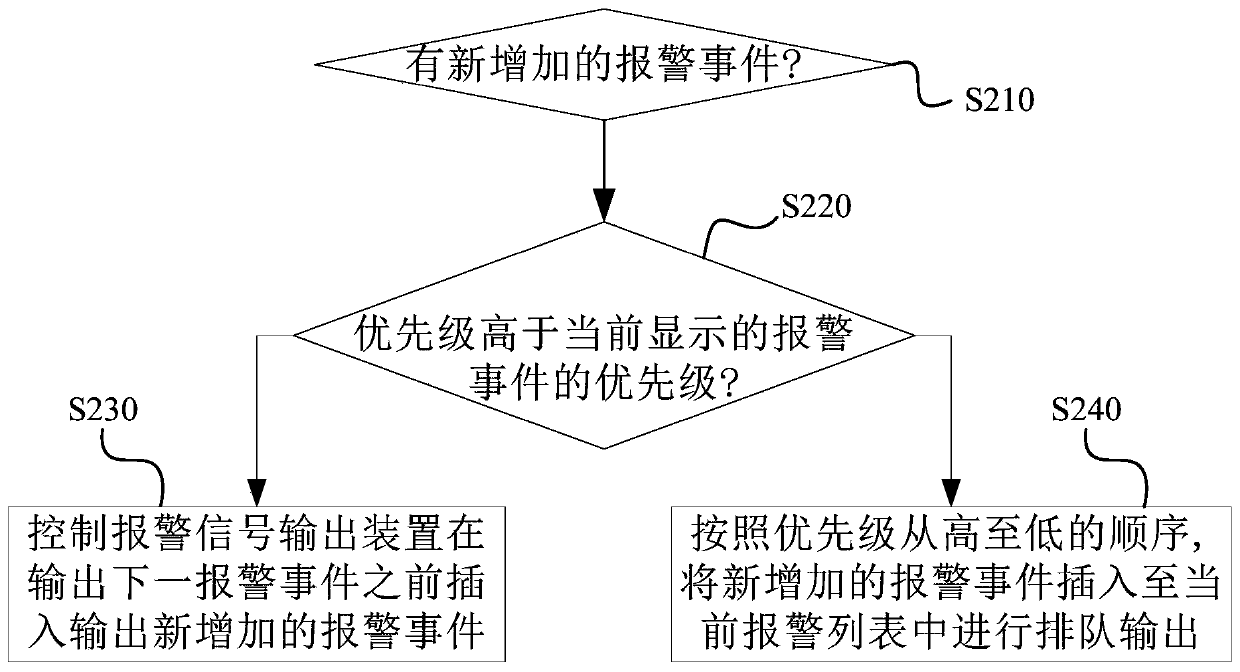
Alarming method and device and breathing machine
ActiveCN106730196AImprove usabilityReduce in quantityRespiratorsMedical devicesCollision detectionOutput device
The invention discloses an alarming method and device and a breathing machine. The alarming method comprises the steps that a current alarming list is obtained; collision detection processing is conducted on each alarming event in the current alarming list, wherein the collision detection processing includes the operation that other alarming events with alarming conditions including the alarming conditions of detected alarming events are removed from the current alarming list; an alarm signal output device is controlled to output each alarming event retained in the current alarming list.
Owner:BMC MEDICAL
A Physical Layer Encryption Method Introducing Latin Matrix
ActiveCN105846947BImprove securityDisassociationSecret communicationSecuring communication by chaotic signalsKey spaceAlgorithm
Owner:NAT UNIV OF DEFENSE TECH
A kind of alarm method, device and ventilator
ActiveCN106730196BImprove usabilityReduce in quantityRespiratorsMedical devicesCollision detectionOutput device
The invention discloses an alarming method and device and a breathing machine. The alarming method comprises the steps that a current alarming list is obtained; collision detection processing is conducted on each alarming event in the current alarming list, wherein the collision detection processing includes the operation that other alarming events with alarming conditions including the alarming conditions of detected alarming events are removed from the current alarming list; an alarm signal output device is controlled to output each alarming event retained in the current alarming list.
Owner:BMC MEDICAL
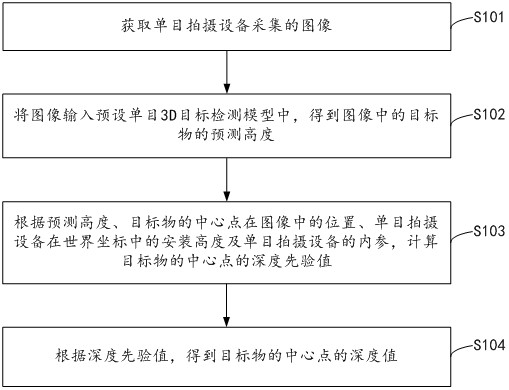
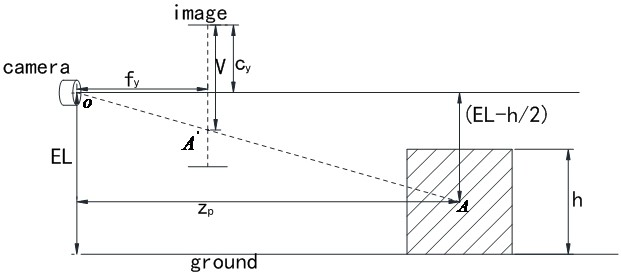
Target detection method and device for automatic driving, and equipment
ActiveCN113538546AImprove generalization abilityImprove reliabilityImage analysisComputer graphics (images)Radiology
The invention relates to a target detection method and device for automatic driving, and equipment. The method comprises the following steps: acquiring an image acquired by monocular shooting equipment; inputting the image into a preset monocular 3D target detection model to obtain a predicted height of a target object in the image; calculating a depth priori value of the central point of the target object according to the predicted height, the position of the central point of the target object in the image, the installation height of the monocular shooting equipment in world coordinates and the internal reference of the monocular shooting equipment; and obtaining the depth value of the central point of the target object according to the depth priori value. According to the scheme provided by the invention, the coupling between the model and the monocular camera can be removed in the process of predicting the depth value z, so that the generalization of the model is improved, and the reliability of a target detection result is improved.
Owner:ZHIDAO NETWORK TECH (BEIJING) CO LTD
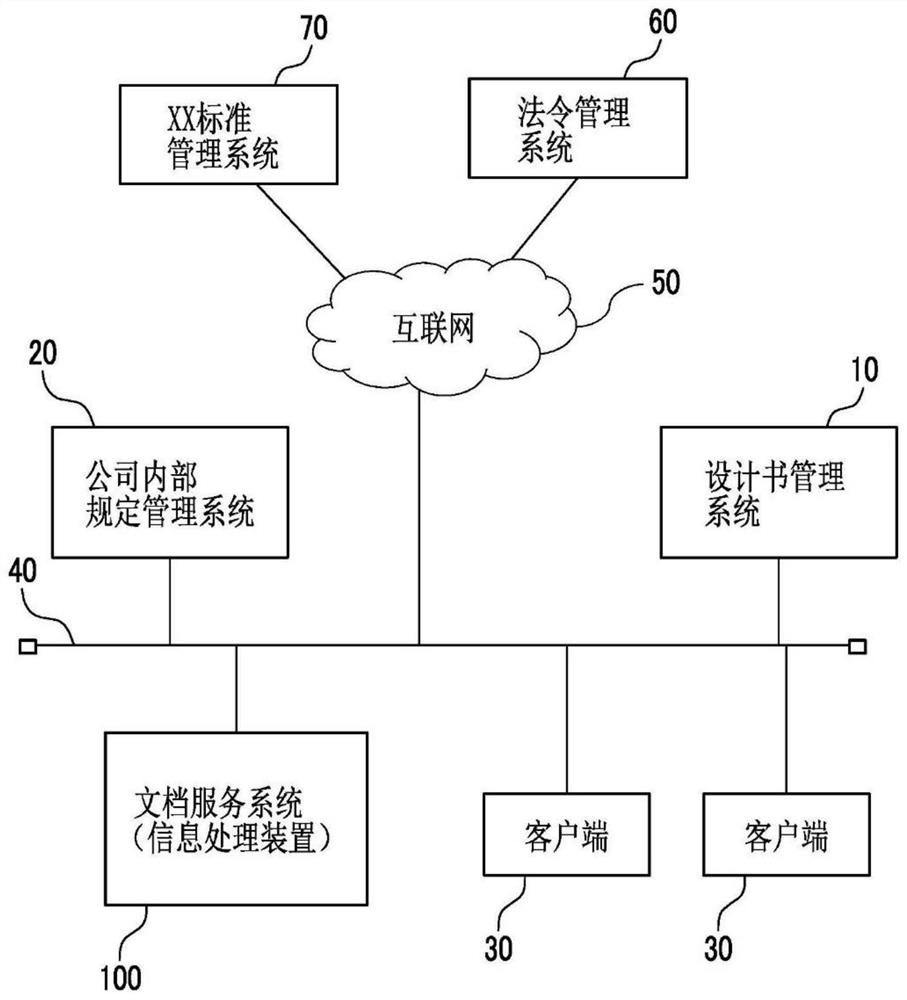
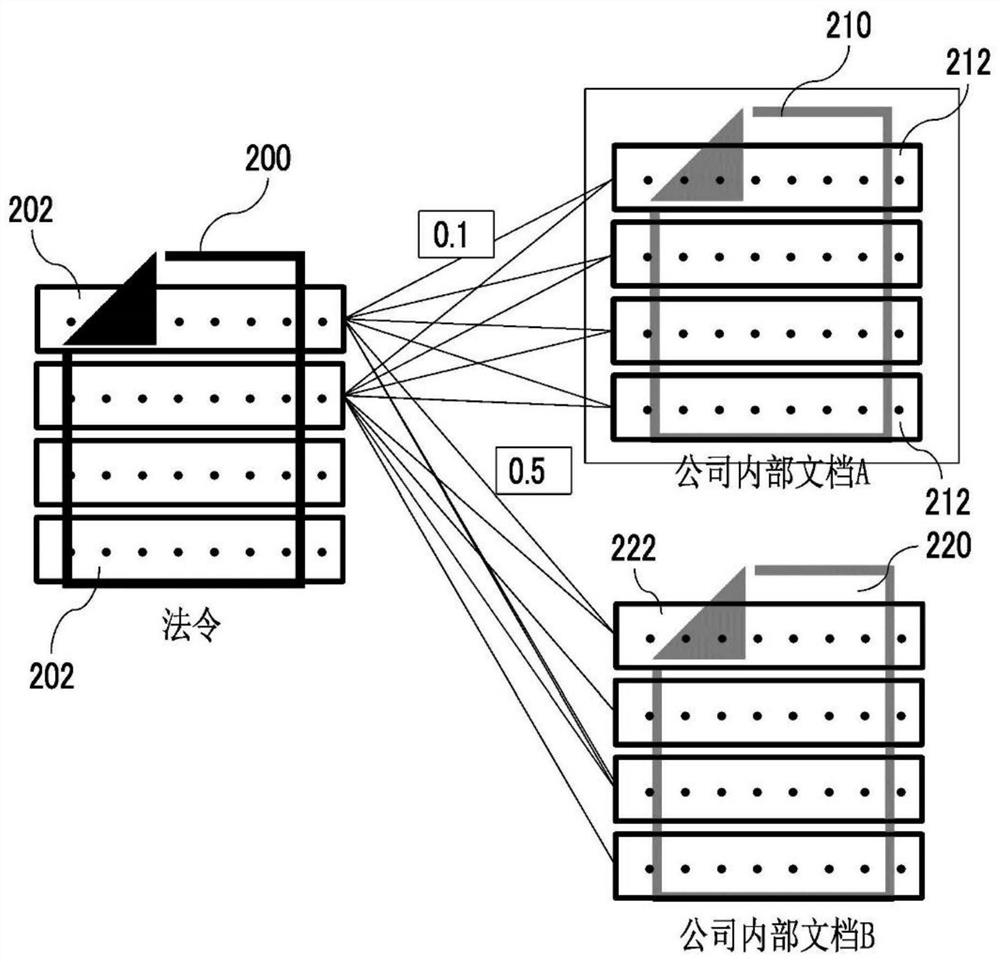
Information processing apparatus, storing program and information processing method
PendingCN113139046AReduce computing loadDisassociationCharacter and pattern recognitionNatural language data processingInformation processingEngineering
The invention provides an information processing apparatus, a storing program and an information processing method. The information processing apparatus is characterized in that the information processing apparatus includes a storage device, and a processor configured to execute calculation of degrees of similarity between an interest document element and document elements associated with the interest document element for each associated document element, and execute display control for the associated document elements based on the degrees of similarity between the associated document elements and the interest document element obtained by the calculation and past degrees of similarity stored in the storage device.
Owner:FUJIFILM BUSINESS INNOVATION CORP
Pairing/unpairing system and method for smartphone and wearable device
ActiveCN104994106BDisassociationConnection managementTransmissionElectronic communicationHuman–computer interaction
The invention discloses a pairing / unpairing system and method for a smart phone and a wearable device, and relates to the technical field of electronic communication. The system includes: a smart phone, a wearable device, and a cloud platform; through the first APP installed in the smart phone, the smart phone communicates with the cloud platform; the smart phone communicates with the wearable device through Bluetooth, WIFI or NFC; Solidify or load the second APP in the wearable device. Both the pairing / disassembly methods require the mutual verification of the smart phone and the wearable device and the verification of the two by the cloud platform to be realized. The invention fills the gap of mutual trust between devices, provides a credible service basis for the collaborative work between smartphones and wearable devices, and realizes that when a user loses one of the devices or does not want to associate the device, the relationship between the two devices can be released. to unpair the device.
Owner:河南中盾云安全研究中心
A Pure Angle Tracking Pseudolinear Filtering Method
ActiveCN110208791BImprove accuracyImprove consistencyRadio wave reradiation/reflectionState predictionRadar
Owner:HARBIN INST OF TECH
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com