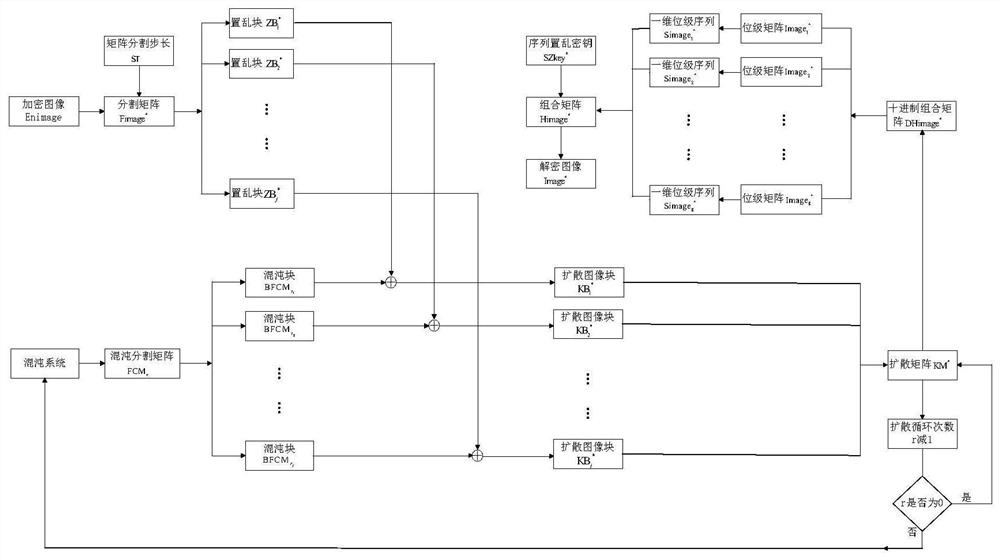
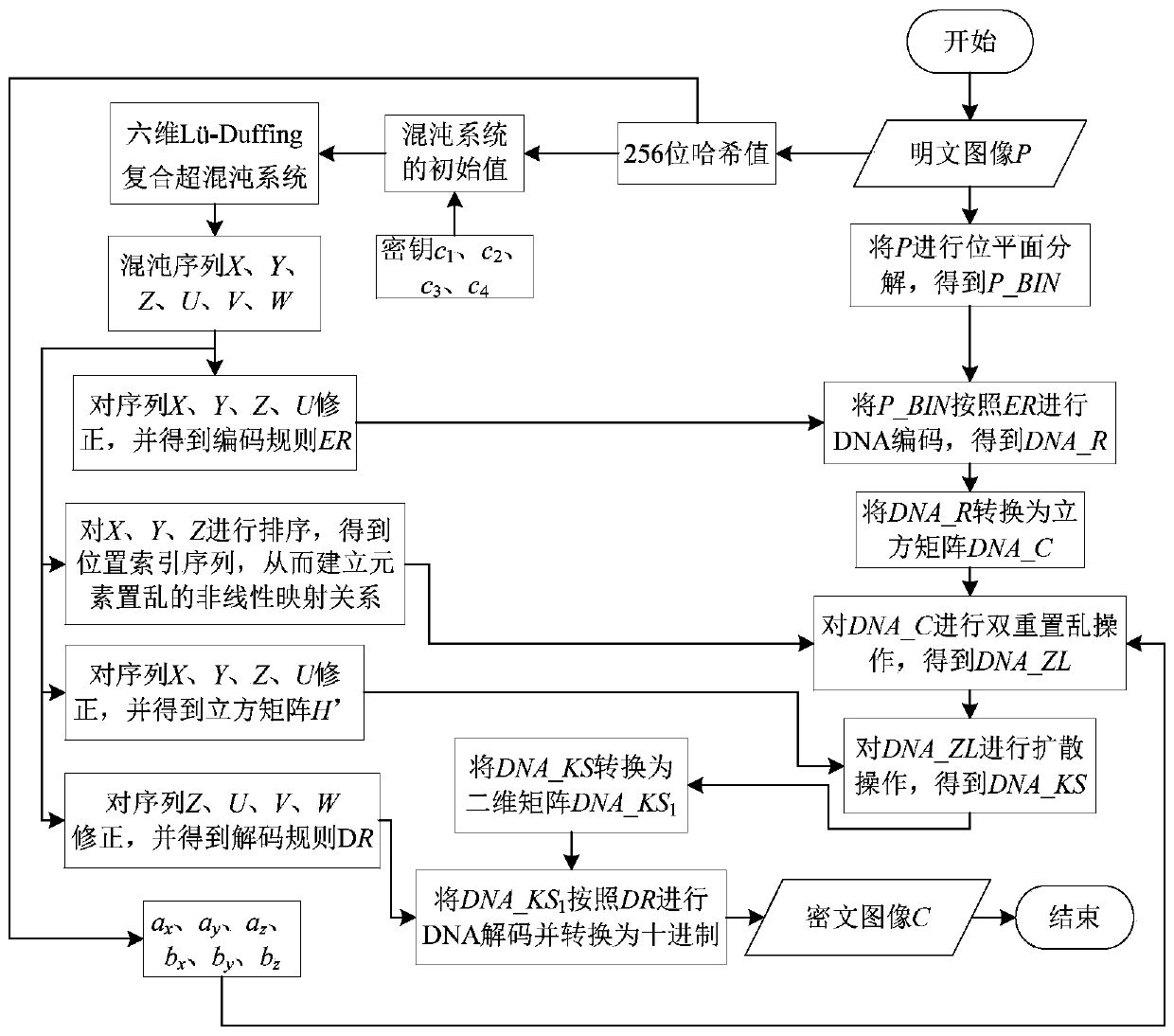
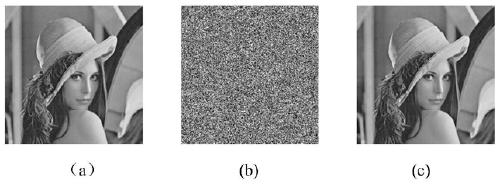
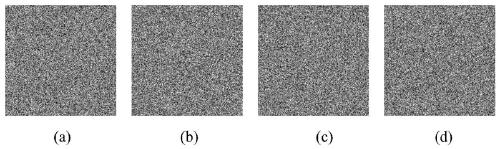
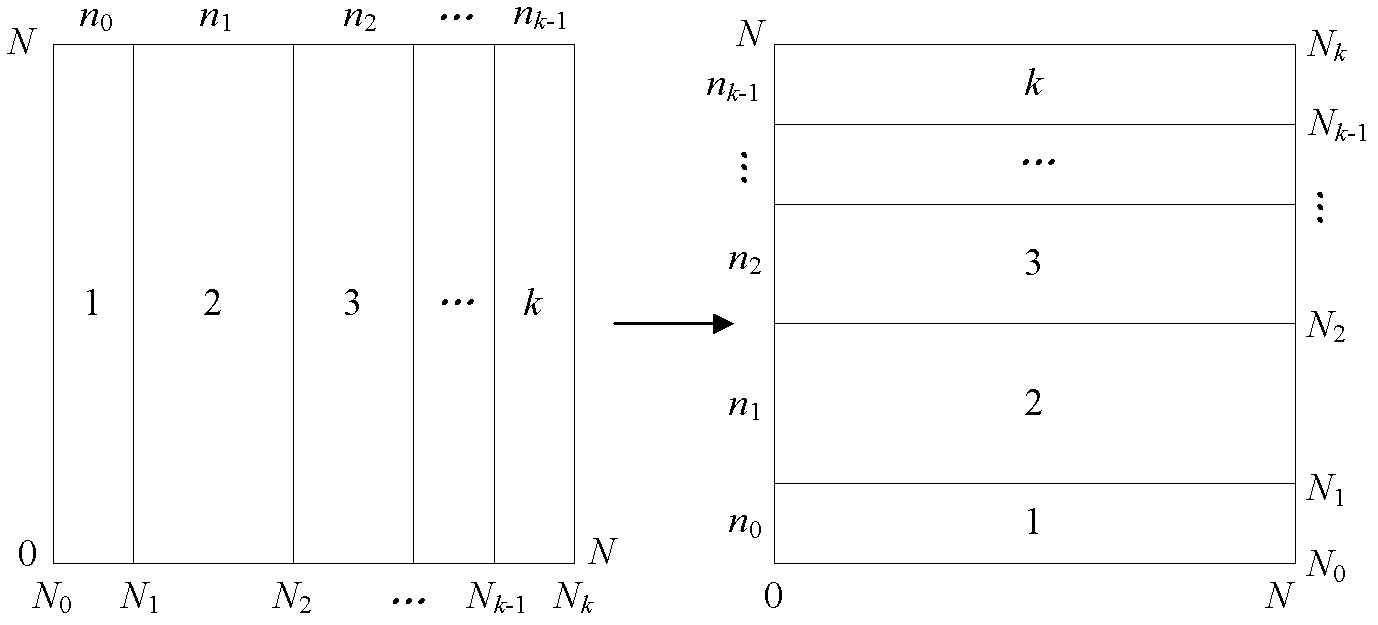Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
41results about How to "Reduce encryption time" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
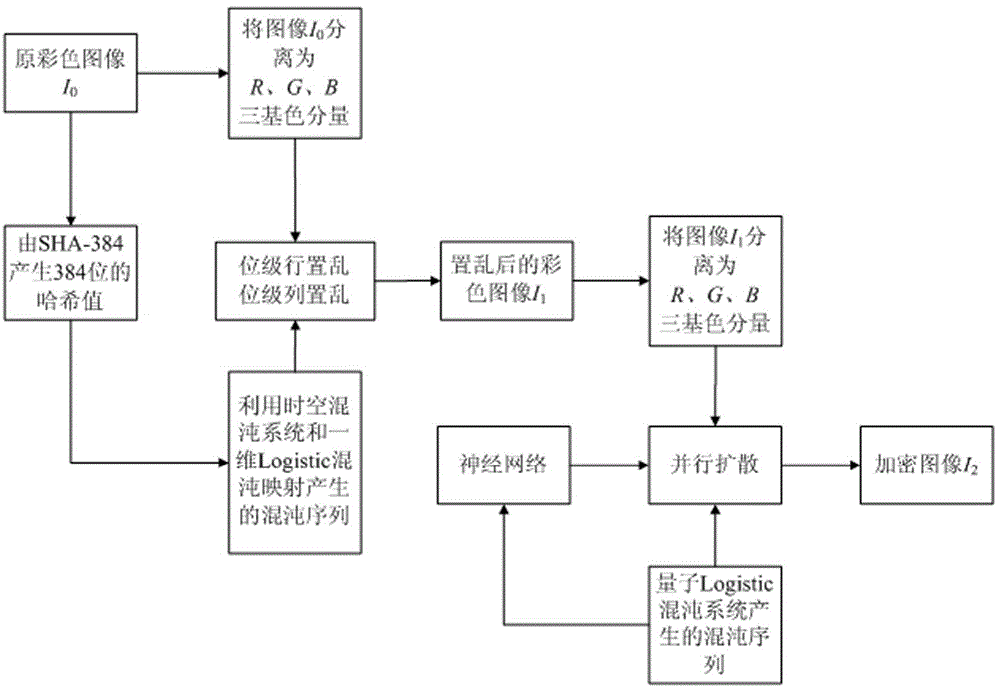
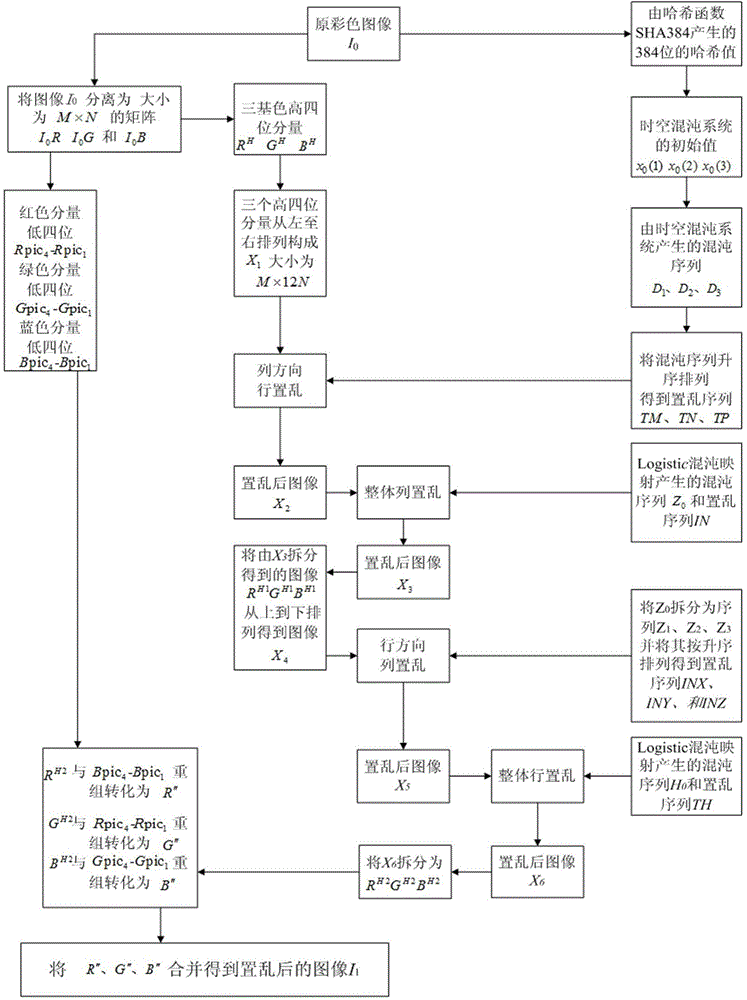
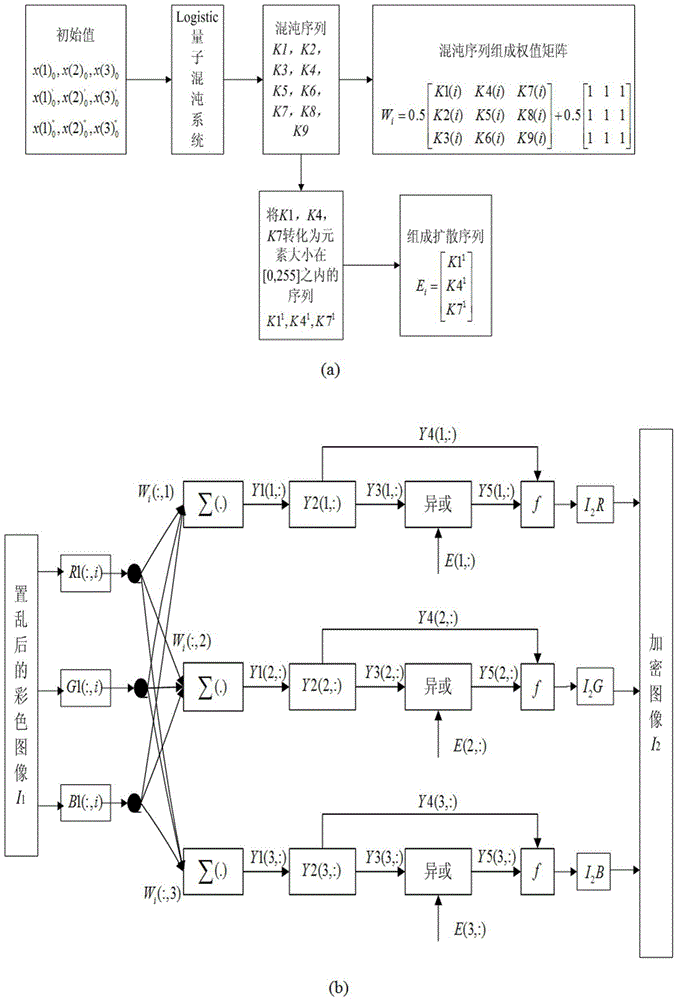
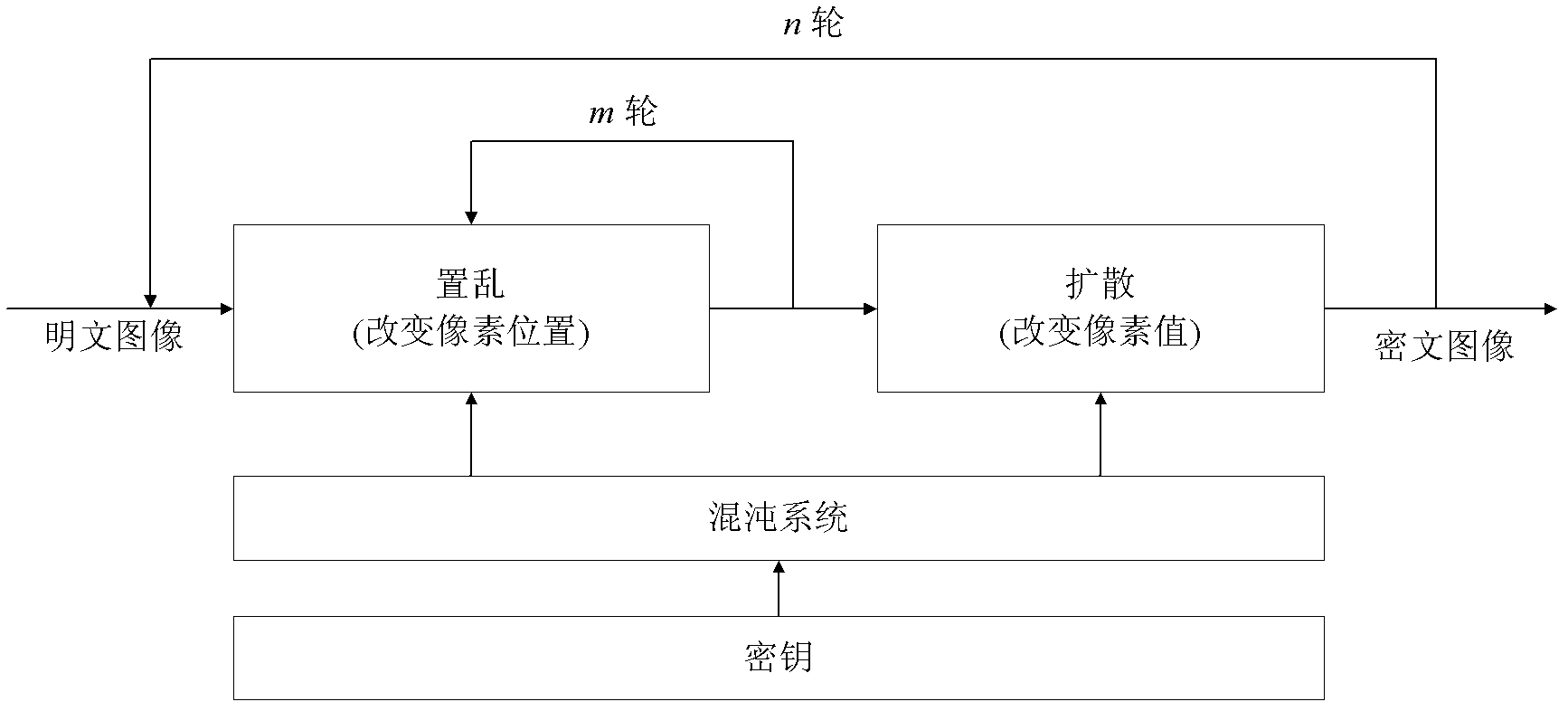
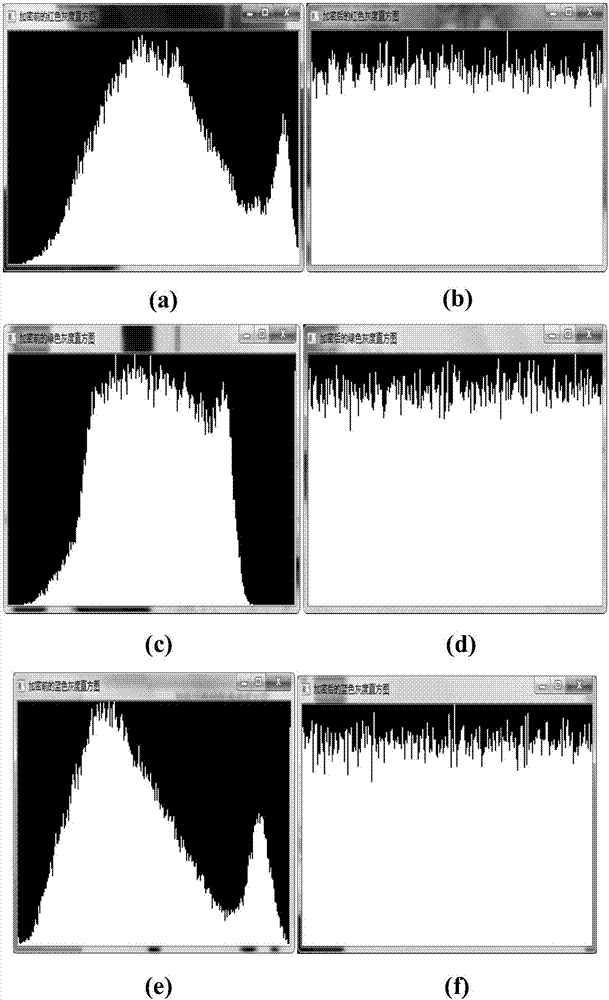
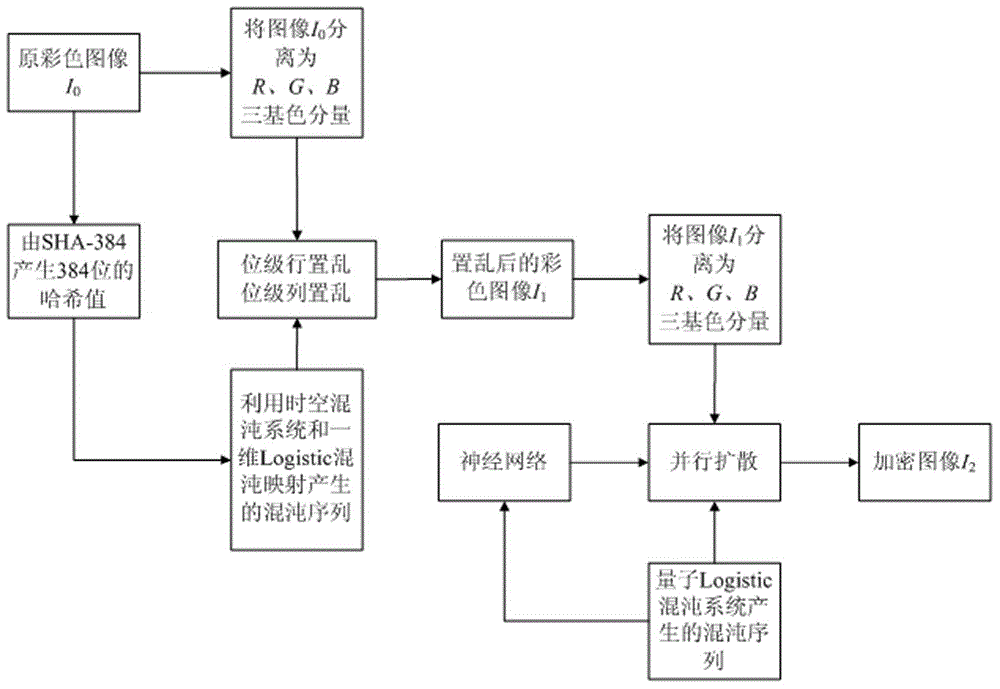
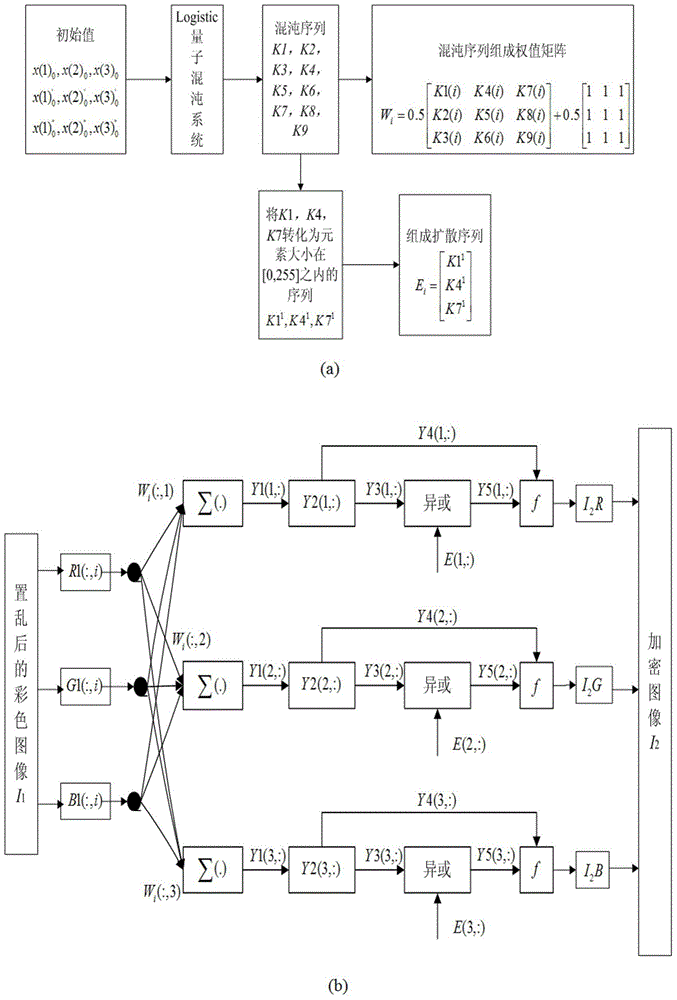
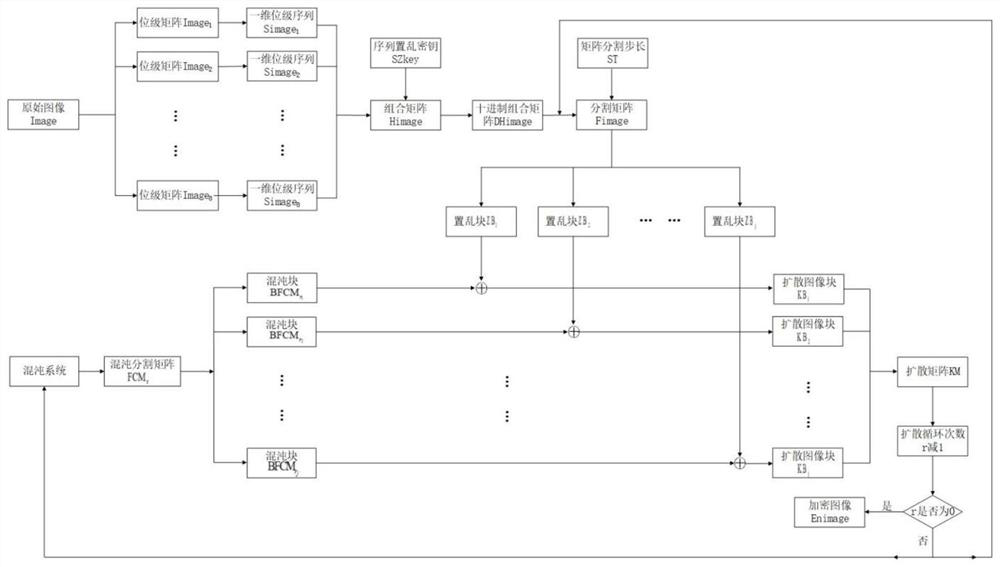
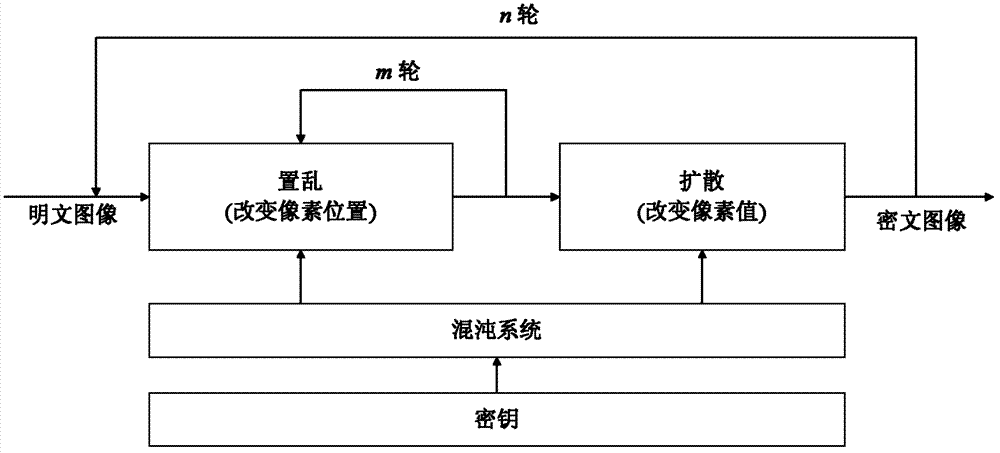
Color image encryption method based on SHA-384 function, spatiotemporal chaotic system, quantum chaotic system and neural network
ActiveCN104008520AImprove securityLarge key spaceImage data processing detailsComputer hardwareDiffusion
The invention relates to a color image encryption method based on an SHA-384 function, a spatiotemporal chaotic system, a quantum chaotic system and a neural network. The method includes the steps that an original color image I0 is calculated through the SHA-384 function, a Hash value is obtained as a secret key, the Hash value, a CML and one-dimension Logistic chaotic mapping are utilized for generating a chaos sequence, bit-level line-column scrambling is carried out on high four-digit images of components of three primary colors of the I0 through the chaos sequence, and a scrambled image I1 is obtained; the Logistic quantum chaotic system is utilized for generating a chaos sequence for encrypting the scrambled image, and is combined with the neural network to carry out parallel diffusion processing on all pixel values of components of three primary colors of the I1, and a final encrypted image I2 is obtained. By the method, the space of the secret key is greatly enlarged, the safety, encryption effect and secret key sensibility are higher, the attack resistance capacity is higher, the scrambling process and the encryption time are shorter, and hardware implementation is easier.
Owner:HENAN UNIVERSITY
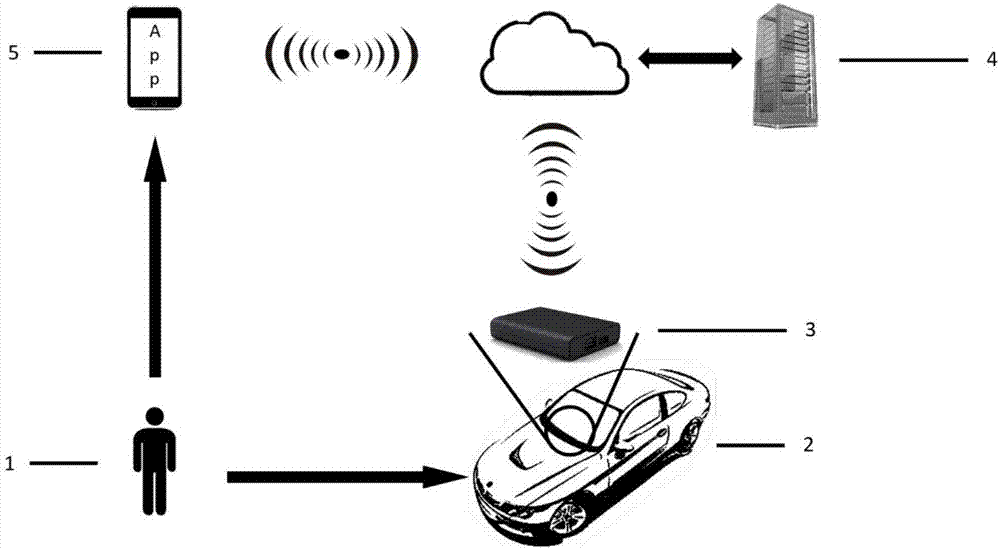
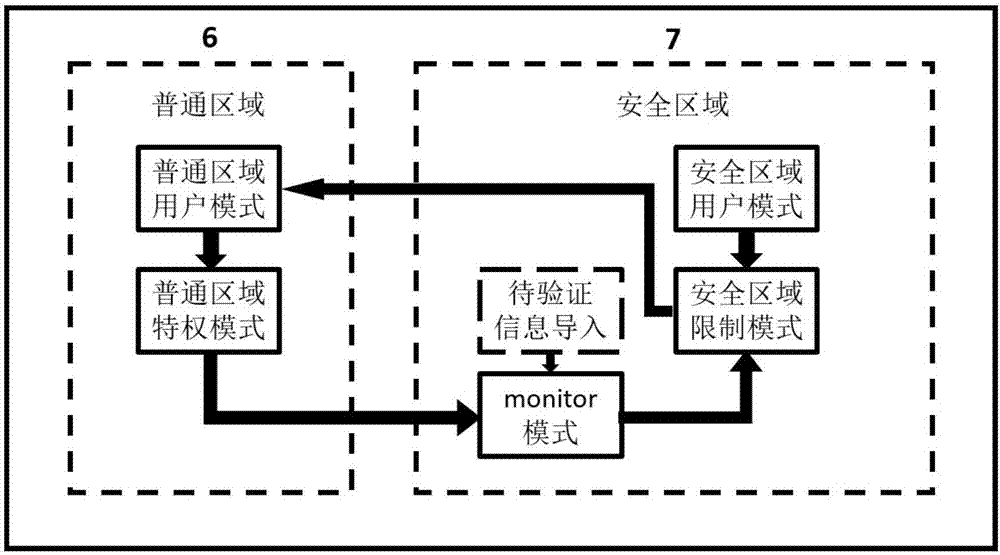
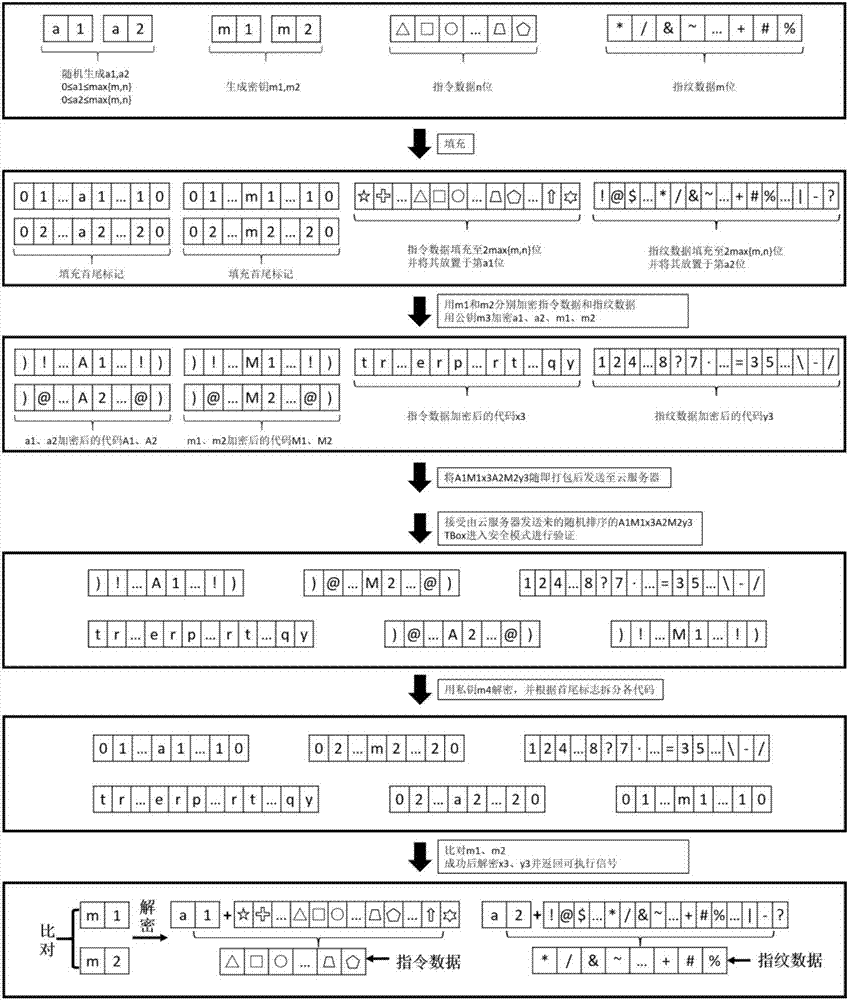
Safety certification system and method for information interaction between vehicle-mounted T-Box and user cellphone
ActiveCN106878008ASimple designProtection against intrusionKey distribution for secure communicationNormal modeSecure authentication
The invention discloses a safety certification system for information interaction between a vehicle-mounted T-Box and a user cellphone, and the system comprises a vehicle, the vehicle-mounted T-Box, a T-Box cloud server, and a mobile terminal. The invention also discloses a safety certification method for information interaction between the vehicle-mounted T-Box and the user cellphone, and the method comprises the following steps: 1, inputting the fingerprint of a user through the mobile terminal, enabling the mobile terminal to generate encryption data through the instruction data and fingerprint data and a downloaded APP, carrying out the random ordering of the encryption data, packaging the encryption data, and transmitting the packaged encryption data to a T-Box server; 2, enabling the T-Box server to search the corresponding vehicle-mounted T-Box according to a VIN code linked with an instruction source account, and then transmitting the information to the corresponding vehicle-mounted T-Box; 3, enabling the corresponding vehicle-mounted T-Box to carry out the authentication of the fingerprint information in the data in a safety mode: switching to a normal mode and carrying out the execution of the instruction if the authentication is successful, or else carrying out no operation.
Owner:BEIHANG UNIV
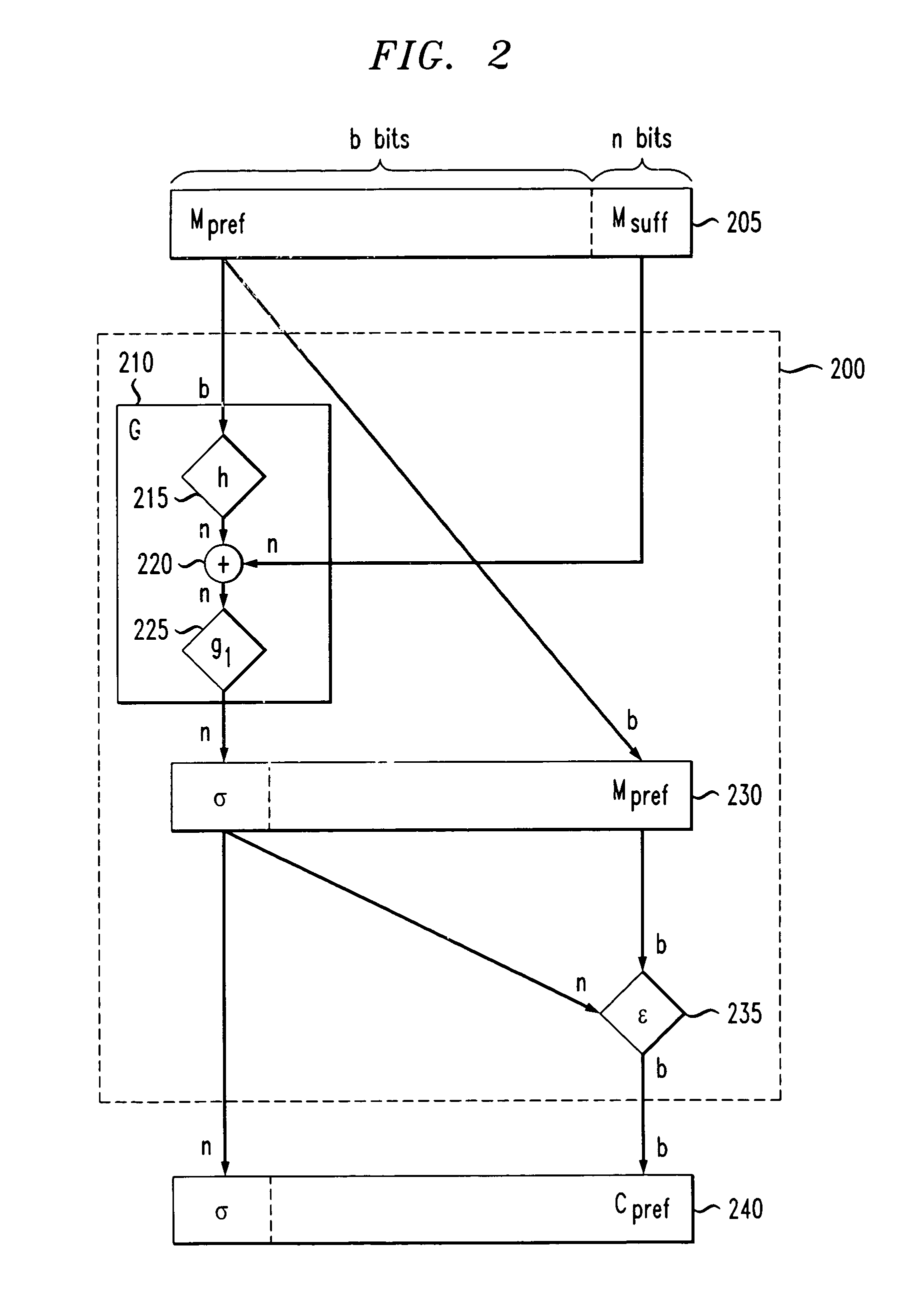
Constructions of variable input length cryptographic primitives for high efficiency and high security
ActiveUS7221756B2Improve securityEfficient constructionEncryption apparatus with shift registers/memoriesUser identity/authority verificationComputer hardwareHash function
A hash function is applied to a prefix of a VIL input. The output is added to a suffix of the input. A block cipher is applied to results of the addition. An encryption function is performed on the prefix. The final output is the output of the block cipher and the encryption function. In a second encryption technique, a hash function is applied to an input, and the output of the hash function has first and second portions. A block cipher is applied to the second portion. The output of the block cipher is added to the first portion, and a second function is applied to the result of this first addition. The output of the second function is added to the second portion. An inverse hash function is then applied to the output of the first and second additions, creating an encrypted output.
Owner:ALCATEL-LUCENT USA INC
Digital image encryption method based on chaotic orbit perturbation
InactiveCN102360488AImprove diffusion abilityImprove abilitiesImage data processing detailsMultiple encryptionPlaintext
The invention relates to a digital image encryption method based on chaotic orbit perturbation and relates to the field of encryption systems. The method comprises the following steps of: scrambling a plaintext image by adopting a generalized discrete Baker mapping-based method; diffusing the scrambled image by adopting a Logistic mapping-based method, and changing the pixel value of each point in the image; and performing multiple encryption according to the requirement on encryption strength. According to the method, a key flow is related to a key and a plaintext by introducing a chaotic orbit perturbation mechanism related to the plaintext, so that the diffusing effects of an encryption system are effectively improved, and the known plaintext resistance is obviously improved. Certain pixel value is changed in the diffusion process depending on the cumulative effect of all the encrypted pixel values before the pixel, so that the tiny change of one pixel value can be effectively diffused to all the subsequent pixels in the image. The method has short encryption time.
Owner:付冲 +1
Method of elliptic curve encryption
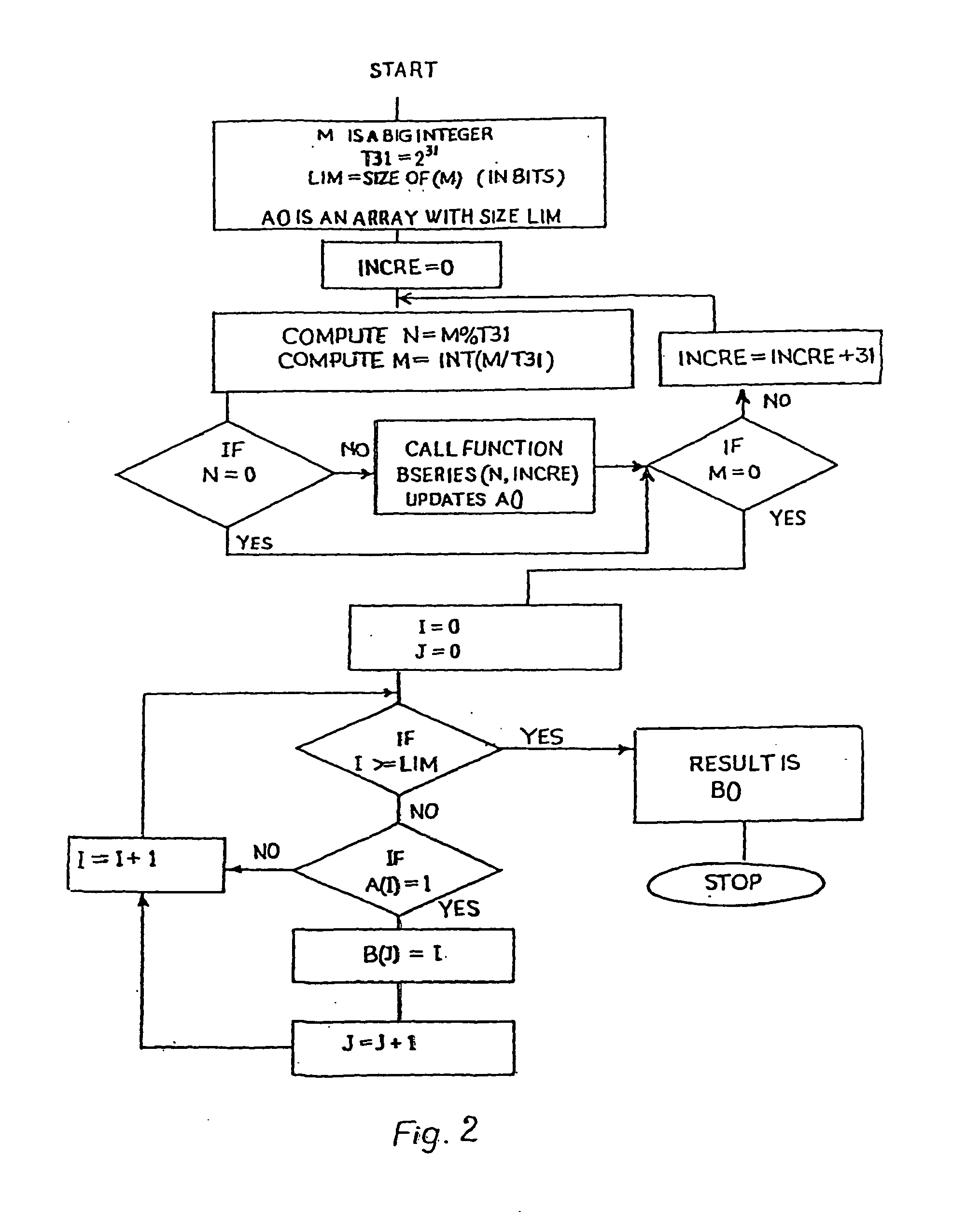
InactiveUS20060165231A1High level of securityOptimise multiplication timePublic key for secure communicationSecret communicationEllipseBit-length
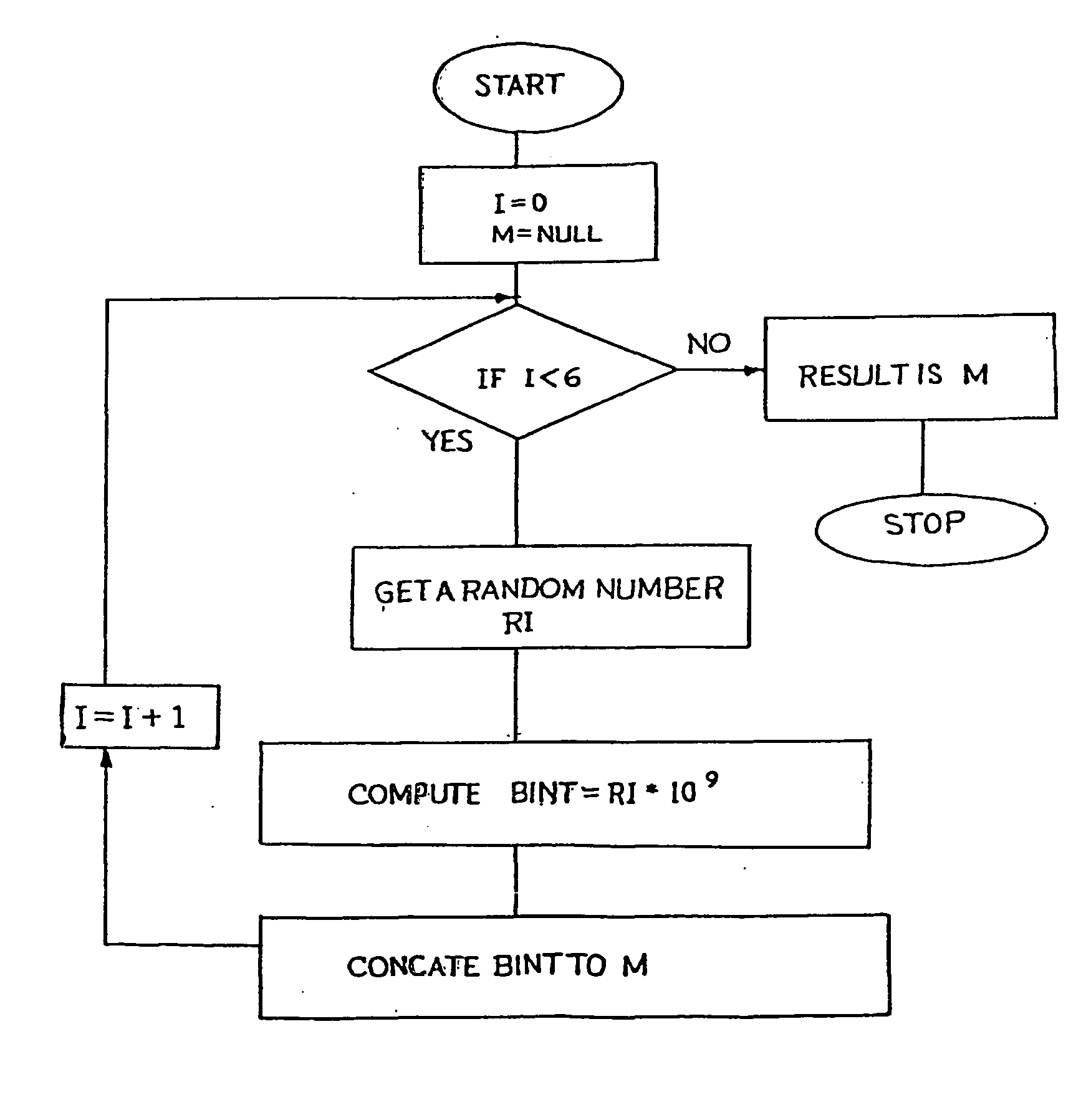
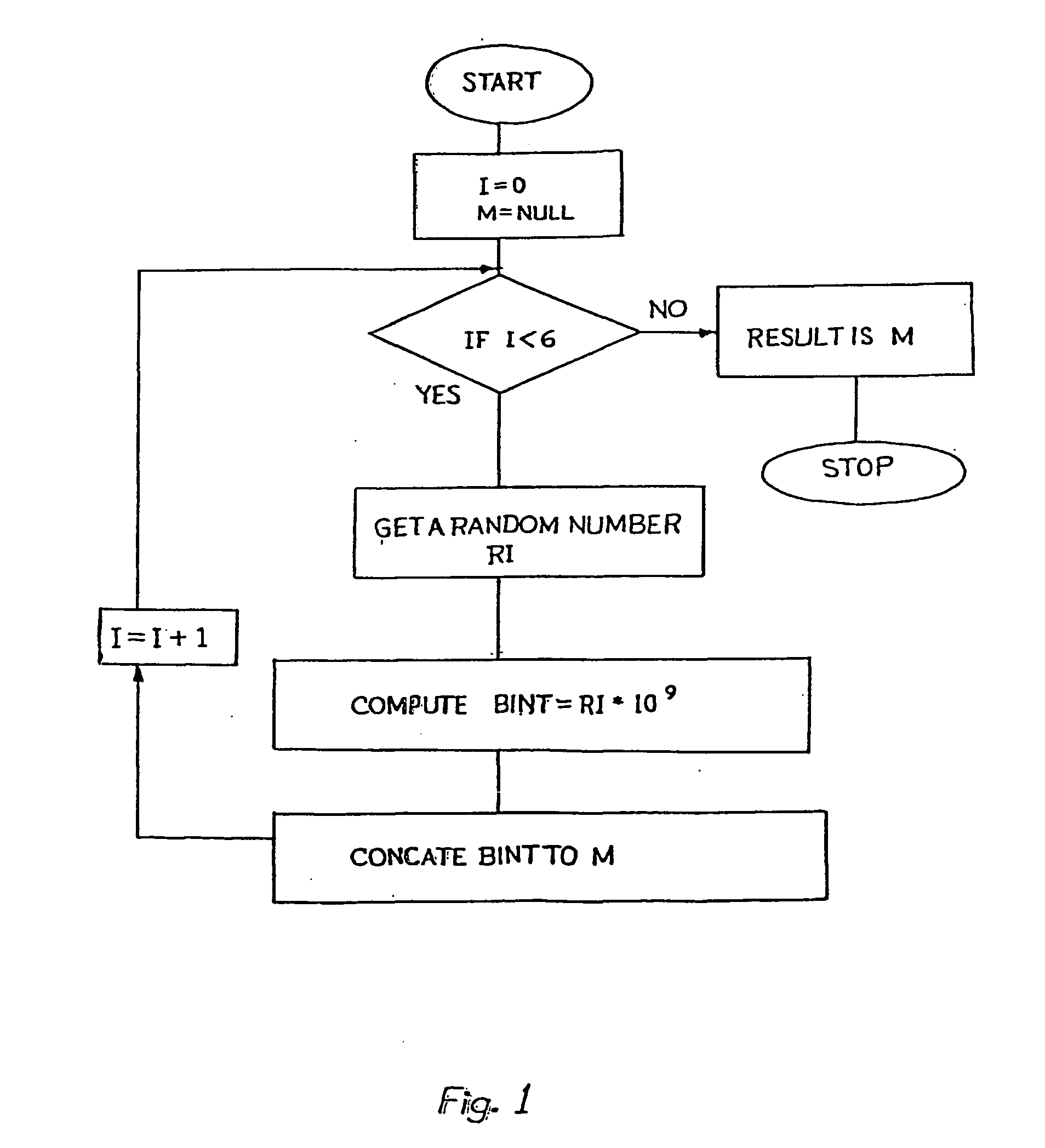
A method of elliptic curve encryption includes, (a) selecting an elliptic curve Ep (a,b) of the form y2=x3+ax+b mod (p) wherein a and b are non-negative integers less than p satisfying the formula 4 a3+27b2 mod (p) not equal to 0; (b) generating a large 160 bit random number by a method of concatenation of a number of smaller random numbers; (c) generating a well hidden point G (x,y) on the elliptic curve Ep (a,b) by scalar multiplication of a point B (x,y) on the elliptic curve with a large random integer which further includes the steps: (i) converting the large random integer into a series of powers of 231; (ii) converting each coefficient of 231 obtained from above step into a binary series; (iii) multiplication of binary series obtained from steps (i) and (ii) above with the point B (x,y) on the elliptic curve; (d) generating a private key nA (of about >=160 bit length); (e) generating a public key PA (x,y) given by the formula PA (x,y)=(nA-G (x,y)) mod (p); (f) encrypting the input message MSG; (g) decrypting the ciphered text.
Owner:THE ADDITIONAL DIRECTOR IPR
Encryption and decryption method and device applied to programmable device
InactiveCN105550570ADon't worry about being stolen anymoreReduce the number of rotationsEncryption apparatus with shift registers/memoriesDigital data authenticationComputer hardwareCiphertext
The invention discloses an encryption and decryption method and device applied to a programmable device. The encryption method comprises the following steps of according to the corresponding relationship of a preset character unit and a base unit and the corresponding relationship of the base unit and a multi-system data unit, coding data to be encrypted including the preset character unit into a multi-system sequence ciphertext, wherein the multi-system sequence ciphertext comprises at least one multi-system data unit; the character unit comprises at least one character; and the base unit comprises at least one DNA base; and storing or outputting the multi-system sequence ciphertext. The decryption method is matched with the encryption method. According to the invention, in combination with the DNA characteristics, the encryption and decryption technology extremely having the safety and the operability is provided; the method is free from constraint of a secret key; users don't have to worry about that the secret key is stolen any longer; the users can customize the two corresponding relationships; different requirements of the users to safety levels are really realized; the matrix row and column alternative time is reduced; and thus, the encryption time is shortened.
Owner:SHENZHEN PANGO MICROSYST CO LTD
System for elliptic curve encryption using multiple points on an elliptic curve derived from scalar multiplication
InactiveUS7680270B2Reduce encryption timeEfficient multiplicationPublic key for secure communicationSecret communicationEllipseMultiple point
Owner:DIRECTOR GENERAL DEFENCE RES & DEV ORG
Relational database encryption method and encrypted database query method
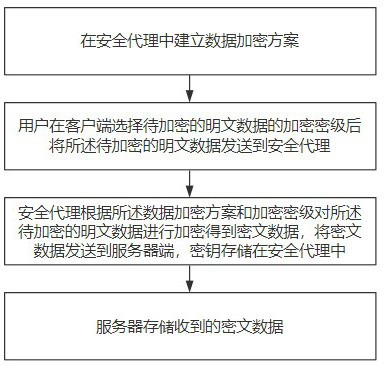
ActiveCN112380557AImprove encryption efficiencyImprove storage space utilizationRelational databasesDigital data protectionDatabase queryRelational database
The invention discloses a relational database encryption method and an encrypted database query method, and the method comprises the steps of building a data encryption scheme in a safety agent; enabling a user to select the encryption security level of to-be-encrypted plaintext data at a client and then to send the to-be-encrypted plaintext data to be transmitted to the safety agent; and enablingthe safety agent to encrypt the plaintext data to be encrypted according to the data encryption scheme and the encryption security level to obtain ciphertext data, sendiing the ciphertext data to a server, and storing a key in the security agent. By means of the mode, the encryption time can be greatly shortened, the data encryption efficiency and the storage space utilization rate are improved,the data safety is guaranteed, a safety agent mechanism is introduced, a safety agent only needs to decrypt a query result once during data query, decryption does not need to be conducted at a serverside, and the query efficiency and the data security are improved.
Owner:JIANGXI NORMAL UNIV
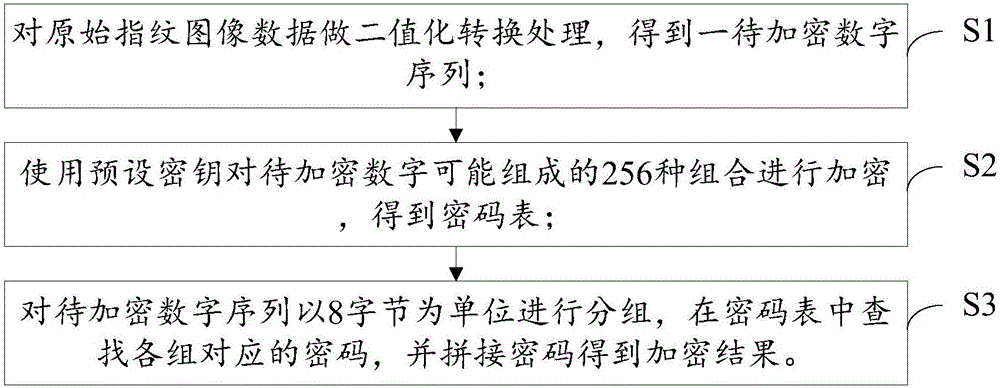
Encryption method and apparatus of fingerprint image data
InactiveCN106452779AImprove experienceReduce encryption timeEncryption apparatus with shift registers/memoriesUser identity/authority verificationPasswordByte
The invention provides an encryption method of fingerprint image data, for providing a novel scheme for performing rapid encryption on fingerprint image big data and a 3DES algorithm. The method comprises the following steps: obtaining a digital sequence to be encrypted by performing binary conversion processing on original fingerprint image data; obtaining a cipher table by encrypting 256 combinations which may be composed of digits to be encrypted by use of a preset secret key; and performing grouping on the digital sequence to be encrypted by taking eight bytes as a unit, searching the cipher table for a password corresponding to each group, and obtaining an encryption result by splicing the passwords. The invention also simultaneously provides an encryption apparatus of fingerprint image data, for realizing the method. According to the technical scheme, when a large volume of fingerprint image data is encrypted by use of 3DES, the encryption time can be greatly shortened, and user experience is improved.
Owner:FUJIAN LANDI COMML EQUIP CO LTD
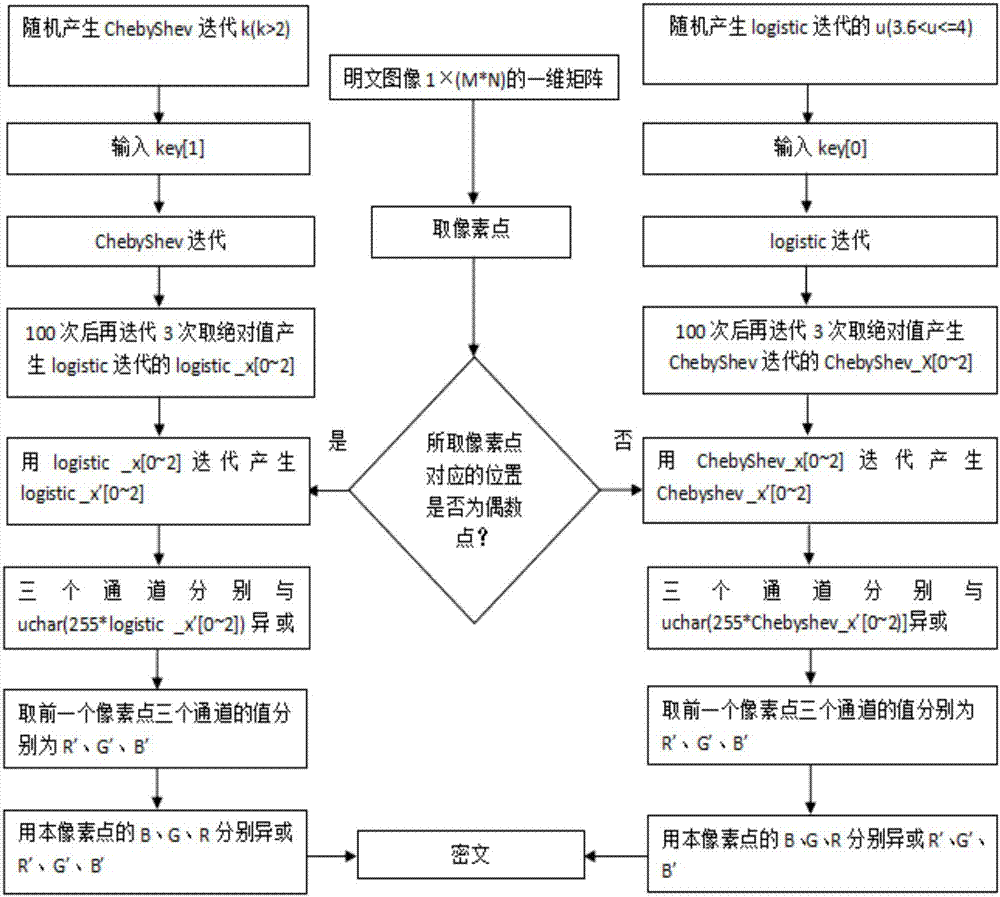
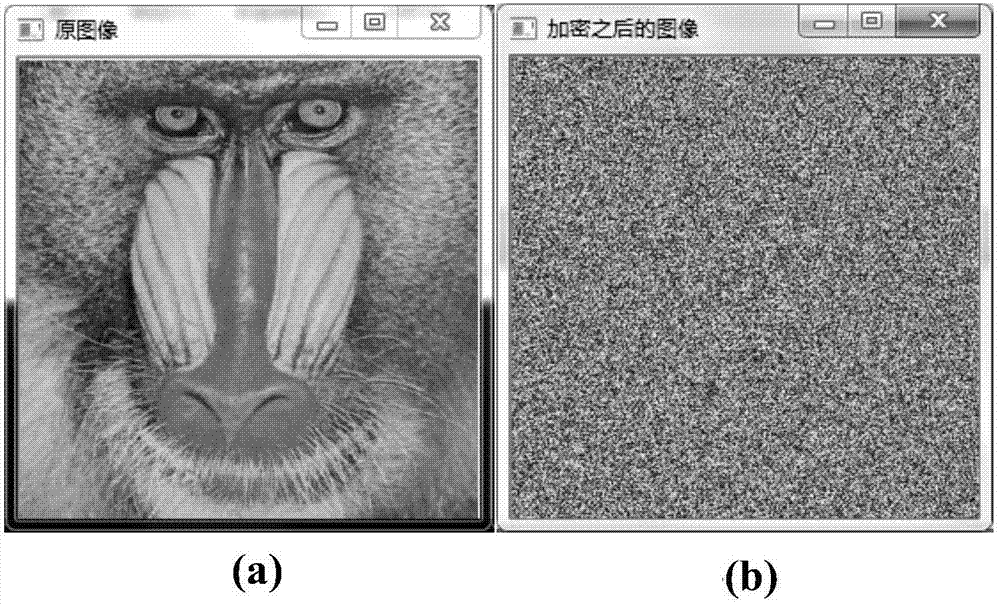
Color image encryption and decryption method and system based on double-chaos cross diffusion
PendingCN107330338AExpand the key spaceDestroy correlationDigital data protectionImage data processing detailsNumeric ValueTablet computer
The invention discloses a color image encryption and decryption method and system based on double-chaos cross diffusion. Firstly, parameters of Logistic and ChebyShev iteration are randomly generated, initial secret keys needed by Logistic and ChebyShev iteration are input, after a transit state is eliminated through multiple times of iteration, Logistic and ChebyShev are used for carrying out iteration three times respectively, iteration results serve as initial secret keys used during encryption respectively, and therefore secret key space is actually increased. Then a pixel point in an image is taken, if the value corresponding to the position of the pixel point is an odd number, an encryption key is obtained through ChebyShev iteration, or else the encryption key is obtained through Logistic iteration, and therefore the dependency between adjacent pixel points is reduced. Then R, G and B channels of the pixel point and R', G' and B' of the former encrypted pixel point are subjected to difference or operation for diffusion. The iteration frequency is reduced on the premise of guaranteeing safety, the encryption time can be shortened, efficiency is improved, and the method and system are especially suitable for image encryption of mobile equipment such as mobile phones and tablet computers with the high real-time performance requirement.
Owner:HENGYANG NORMAL UNIV
Upgrade package encryption and decryption method, electronic device and storage medium
ActiveCN110022558AReduce dependenceReduce the amount of encrypted dataSecurity arrangementComputer hardwareEncryption
The invention discloses an upgrade package encryption and decryption method, an electronic device and a storage medium, and the method comprises the steps: determining a target upgrade file based on an upgrade file of each to-be-upgraded partition in an original upgrade package; then, identifying a first upgrading sub-file and a second upgrading sub-file in the target upgrading file; encrypting afirst upgrading sub-file in the original upgrading package according to a first encryption algorithm, not encrypting the second upgrading subfile; obtaining encrypted upgrade package. Based on the description, a part of files in the target upgrade file are encrypted by adopting a partial encryption rule in the embodiment; therefore, the second upgrade subfile does not need to be encrypted, the encrypted data size is effectively reduced, the encryption time is shortened, when the upgrade package is decrypted, the data of the second upgrade subfile does not need to be decrypted into the memory according to the ratio of 1:1, the dependence of upgrade package decryption on the memory of the electronic device is reduced, the decryption time is shortened, and the upgrade efficiency is improved.
Owner:GUANGDONG OPPO MOBILE TELECOMM CORP LTD
Safe data storage and transmission method
ActiveCN104618355AReduce encryption timeImprove efficiencyUser identity/authority verificationData transmissionThird party
The invention discloses a safe data storage and transmission method. The safe data storage and transmission method comprises a data sender, a data receiver and a third party capable of communicating with the data sender and data receiver. The safe data storage and transmission method includes steps that A, the third party generates a symmetric key cache, encrypts and sends to the data sender; B, the data sender decodes the encrypted symmetric key, uses the decoded symmetric key to encrypt data to be transmitted, and transmits the encrypted data and a data receiver list to the third party; C, the third party uses a public key of each receiver to carry out conversion encryption treatment on the cached symmetric key according to the data receiver list and deletes the symmetric key; D, each data receiver receives the corresponding symmetric key performed with conversion encryption and the encrypted data from the third part, uses a private key thereof to decode the symmetric key performed with conversion encryption, and uses the decoded symmetric key to decode the encrypted data. The safe data storage and transmission method improves the data transmission efficiency and guarantees the data storage safety in the third party.
Owner:BEIJING HAITAI FANGYUAN HIGH TECH
Cloud-based image encryption method and device
InactiveCN104517059AReduce encryption timeDigital data protectionTerminal equipmentComputer terminal
The invention provides a cloud-based image encryption method and device, and relates to the technical field of data encryption. The method includes the steps: compressing image data and dividing the image data into first data and second data in the compressing process; storing the first data to a local terminal device; uploading the second data to a cloud server to store the second data by the cloud server. The method can solve the problems that encryption time of the current image encryption technology is long and private images are leaked as the current image encryption technology is easily cracked.
Owner:张凡
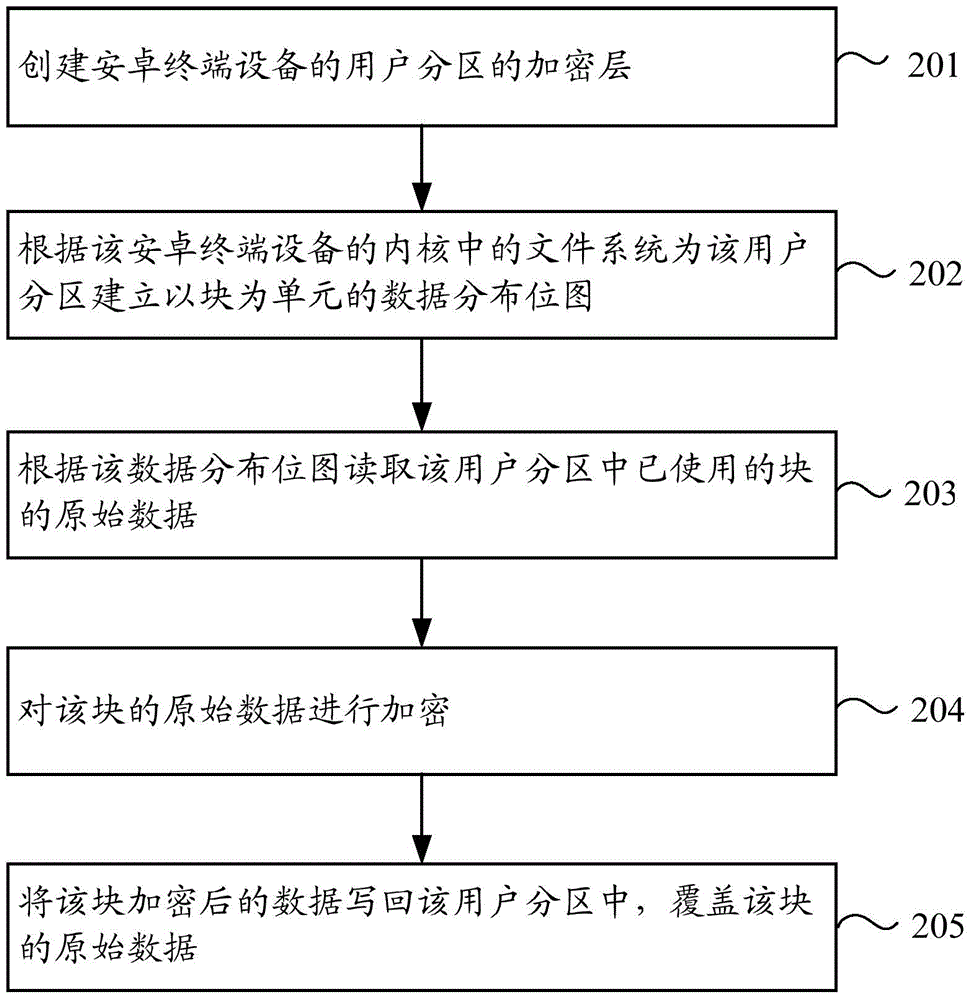
Fast encryption method and device for Android user partition and terminal equipment
InactiveCN104615941AReduce encryption timeEncryption avoidanceDigital data protectionOriginal dataFile system
The embodiment of the invention provides a fast encryption method and device for an Android user partition and terminal equipment. The method comprises the steps that an encryption layer of the user partition of the Android terminal equipment is set up; a data distribution bitmap with a Block as a unit is set up for the user partition according to a file system in an inner core of the Android terminal equipment, wherein the data distribution bitmap is used for showing the use state of the Blocks in the user partition; the original data of the used Blocks in the user partition are read according to the data distribution bitmap; the original data of the Blocks are encrypted; the encrypted data of the Blocks are written back to the user partition, and cover the original data of the Blocks. According to the fast encryption method and device for the Android user partition and the terminal equipment, the user partition of the Android terminal equipment is encrypted through information, recorded by the file system of the Android terminal equipment, of the used data blocks, invalid data are prevented from being encrypted when the user data are encrypted, and therefore the effect of shortening the time spent in encrypting the partition is achieved.
Owner:HUAWEI TECH CO LTD
Paillier encryption method based on cloud computing platform
ActiveCN107786580AReduce encryption timeEnsure safetyKey distribution for secure communicationModular exponentiationInformation security
The invention relates to a Paillier encryption method based on a cloud computing platform and belongs to the field of information security. The method is characterized in that Paillier encryption security is outsourced to a cloud server by adopting a security outsourcing algorithm based on modular exponentiation operation, so that a Paillier encryption person can protect encrypted information frombeing leaked, and Paillier encryption is efficiently carried out by utilizing computing power of the cloud server. The Paillier encryption method provided by the invention is applicable to security outsourcing and Paillier encryption in a cloud computing environment and is especially applicable to the situation that a user hopes to complete an encryption process by utilizing the cloud server andthe encrypted data cannot be leaked to the cloud server.
Owner:NANJING UNIV OF AERONAUTICS & ASTRONAUTICS
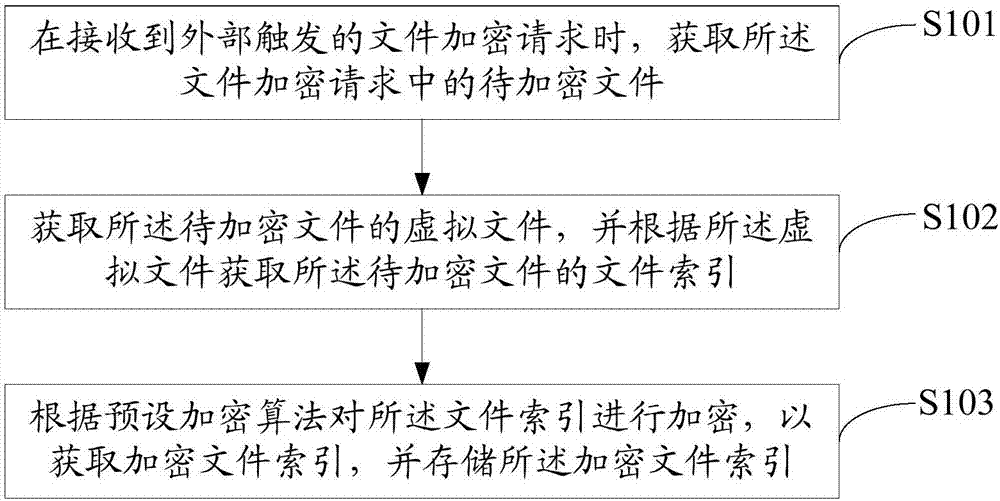
File encryption method, mobile terminal and computer readable storage medium
InactiveCN107256360AEncryption time is shortReduce encryption timeDigital data protectionComputer hardwareComputer terminal
The invention discloses a file encryption method, a mobile terminal and a computer readable storage medium. The file encryption method comprises the following steps of obtaining a to-be-encrypted file in a file encryption request when the file encryption request triggered by outside is received; obtaining a virtual file of the to-be-encrypted file, and obtaining a file index of the to-be-encrypted file according to the virtual file; and performing encryption on the file index according to the preset encryption algorithm to obtain an encrypted file index, and storing the encrypted file index. The file encryption time is effectively shortened and the file encryption efficiency is improved.
Owner:NUBIA TECHNOLOGY CO LTD
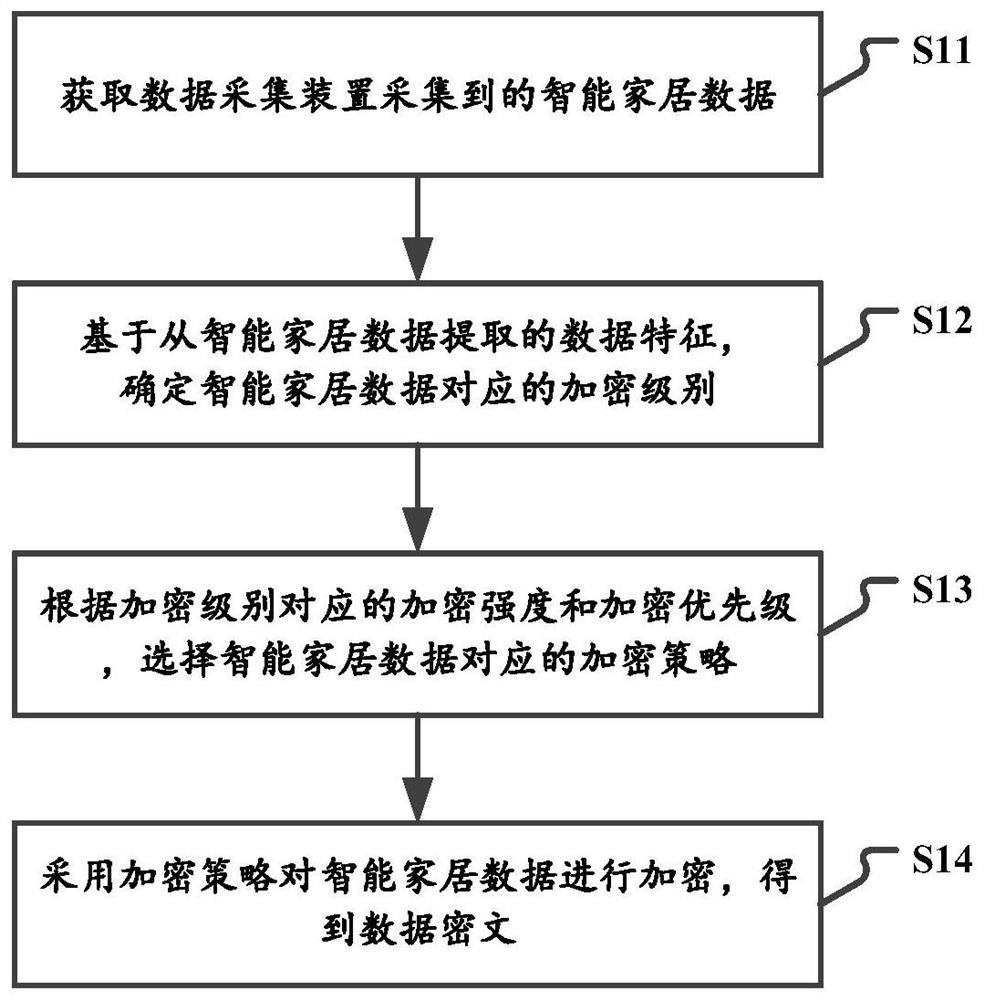
Data encryption processing method and device, electronic equipment and storage medium
InactiveCN112583833AEnsure safetyReduce encryption timeCharacter and pattern recognitionDigital data protectionData ingestionData class
The invention relates to a data encryption processing method and apparatus, an electronic device and a storage medium. The method comprises the steps of obtaining smart home data collected by a data collection apparatus; determining an encryption level corresponding to the smart home data based on data features extracted from the smart home data; selecting an encryption strategy corresponding to the smart home data according to the encryption strength and the encryption priority corresponding to the encryption level; and encrypting the smart home data by adopting the encryption strategy to obtain a data ciphertext. According to the technical scheme, based on the data type of the smart home data, the encryption strategy corresponding to the encryption strength and the encryption priority isselected for encryption. Thus, the security of important categories such as data related to user identity, privacy and other information is ensured, and for data with high real-time requirements, theencryption time of the data is shortened, and the transmission efficiency of the data is improved.
Owner:GREE ELECTRIC APPLIANCES INC +1
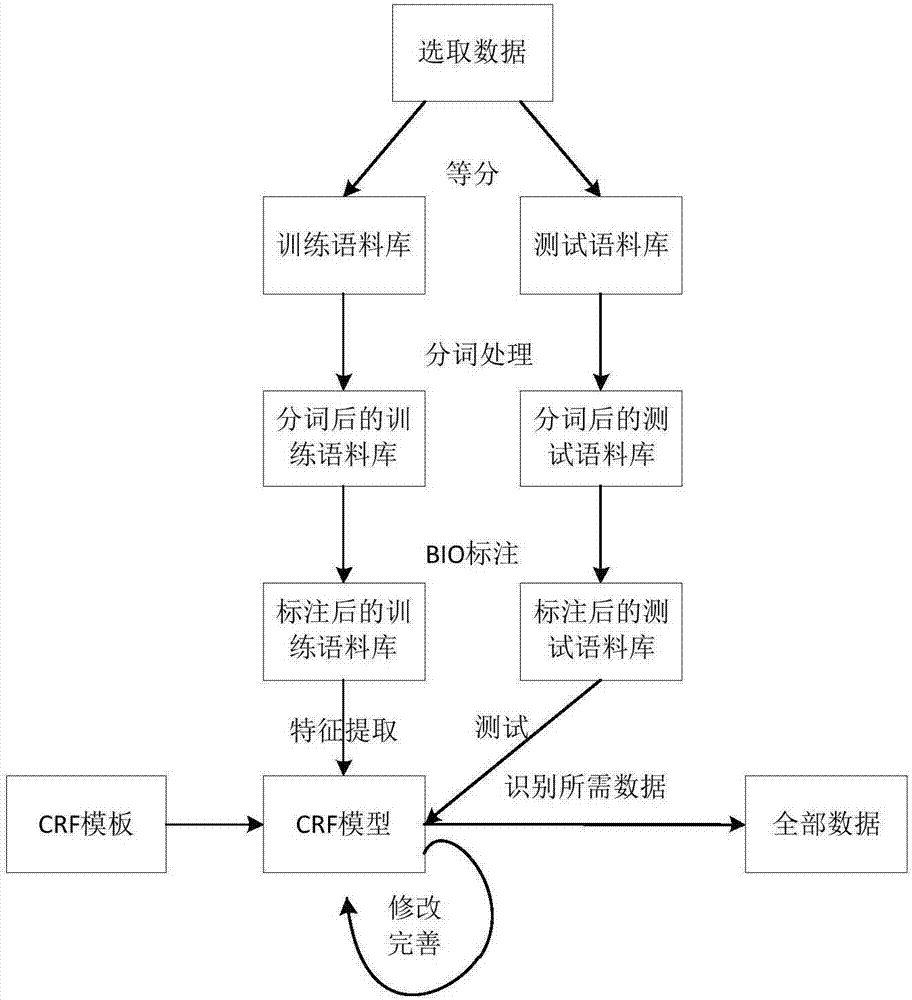
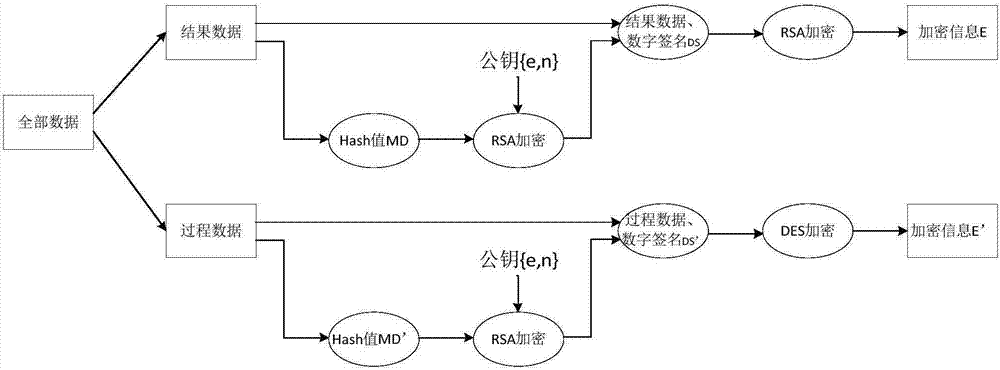
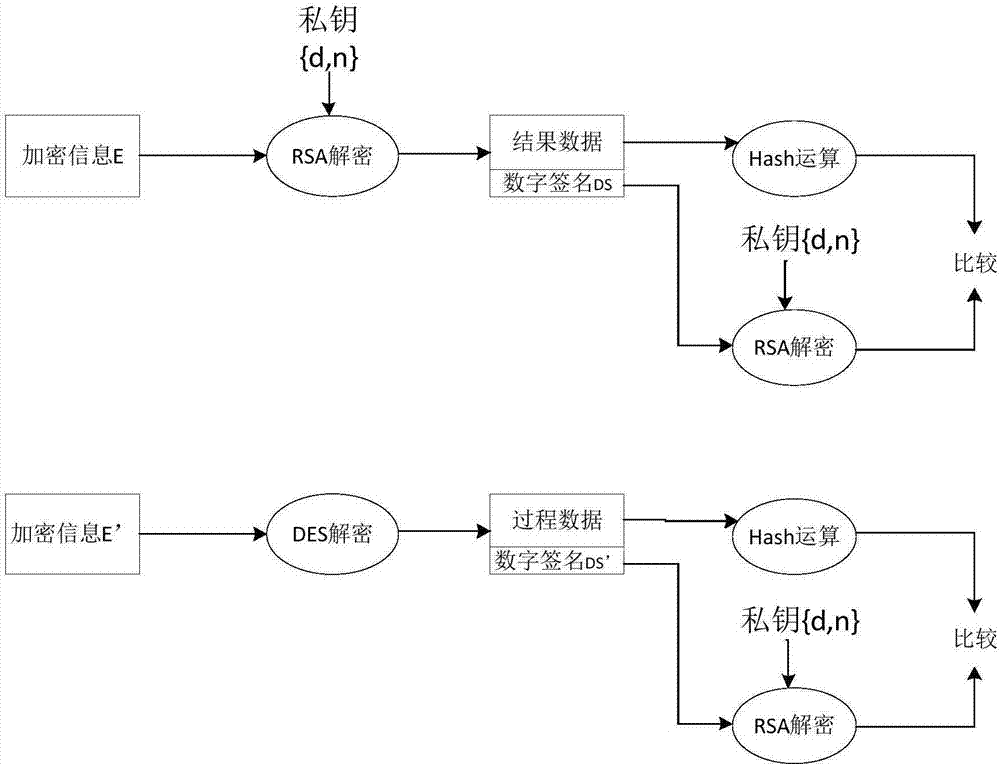
Sterility test data classification and encryption method based on conditional random field algorithm
InactiveCN106899572AWon't leakImprove securityMultiple keys/algorithms usageUser identity/authority verificationConditional random fieldDigital signature
Disclosed in the invention is a sterility test data classification and encryption method based on a conditional random field algorithm. The method comprises: first, marking important result data generated in a sterility test process, training a conditional random field model and recognizing the important result data; second, performing classification and encryption on the important result data recognized by the conditional random field model, and transmitting encrypted data to a receiver; and finally, recovering the data without loss by the receiver by virtue of a reversible decryption process. According to the method, the important result data generated in the sterility test process is recognized by using the conditional random field method, and the important result data is separated from process data for classification and encryption. At the same time, a digital signature technology utilized in the method can effectively prevent messages from being tampered so that the data cannot be leaked out. The sterility test data classification and encryption method can greatly reduce encryption time and improve the system efficiency while ensuring the security of the important data information.
Owner:ZHEJIANG UNIV
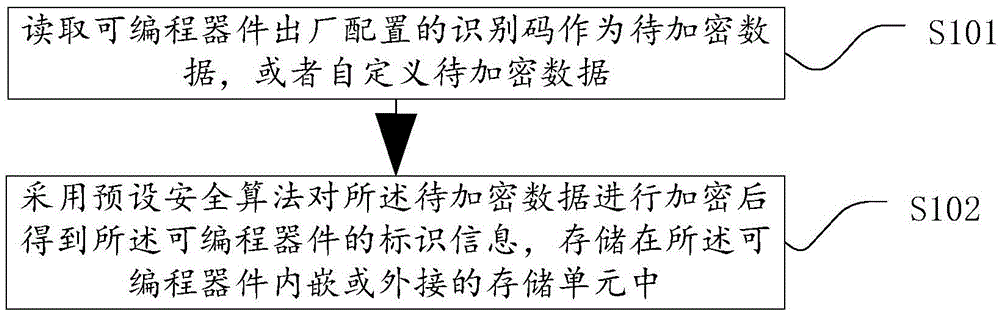
Configuration methods and devices for programmable device, identification information and programming data flow
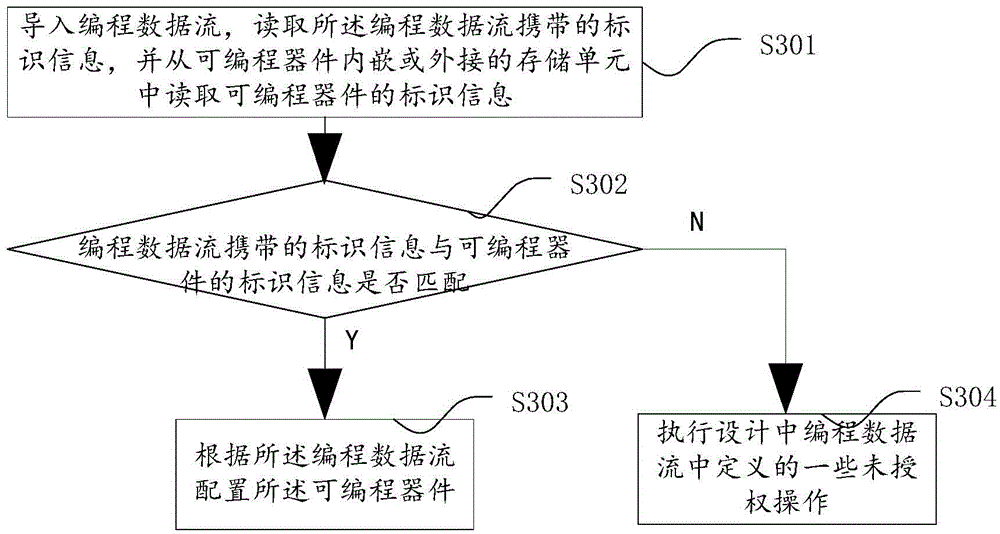
ActiveCN105550541AEnsure safetyProperly design the functionKey distribution for secure communicationGenetic modelsData streamProgrammable logic device
The invention discloses configuration methods and devices for a programmable device, identification information and programming data flow. A configuration method for the programmable device comprises the steps: inputting the programming data flow; reading identification information, which the programming data flow carries; reading identification information of the programmable device from a storage unit which is embedded in or externally connected with the programmable device; comparing the identification information, which the programming data flow carries, with the identification information of the programmable device; if the identification information, which the programming data flow carries, matches the identification information of the programmable device, configuring the programmable device according to the programming data flow. According to the configuration methods and devices for the programmable device, the identification information and the programming data flow, a problem that correspondence between the programming data flow and the programmable device cannot be achieved in the prior art is solved.
Owner:SHENZHEN STATE MICROELECTRONICS CO LTD
Image encryption method based on bit level scrambling and dynamic superposition diffusion
ActiveCN111131656AImprove diffusion efficiencyReduce encryption timePictoral communicationAlgorithmEngineering
The invention discloses an image encryption method based on bit level scrambling and dynamic superposition diffusion and relates to the technical field of image encryption. The problem of contradiction between the existing image encryption efficiency and security is solved; the invention provides an image encryption method based on bit level scrambling and dynamic superposition diffusion. The method comprises an encryption process and a decryption process. In the scrambling process, a pixel plane is converted into a bit level plane; bit-level pixel scrambling is carried out on the basis of a bit-level plane, a dynamic superposition diffusion method is adopted for a diffusion part, superposition diffusion operation is carried out on pixels, diffusion efficiency is improved, encryption timeis greatly shortened, and a safe encryption effect is achieved under the condition that the operation speed is guaranteed.
Owner:CHANGCHUN UNIV OF SCI & TECH
Method and device for configuring programmable device, identification information and programming data flow
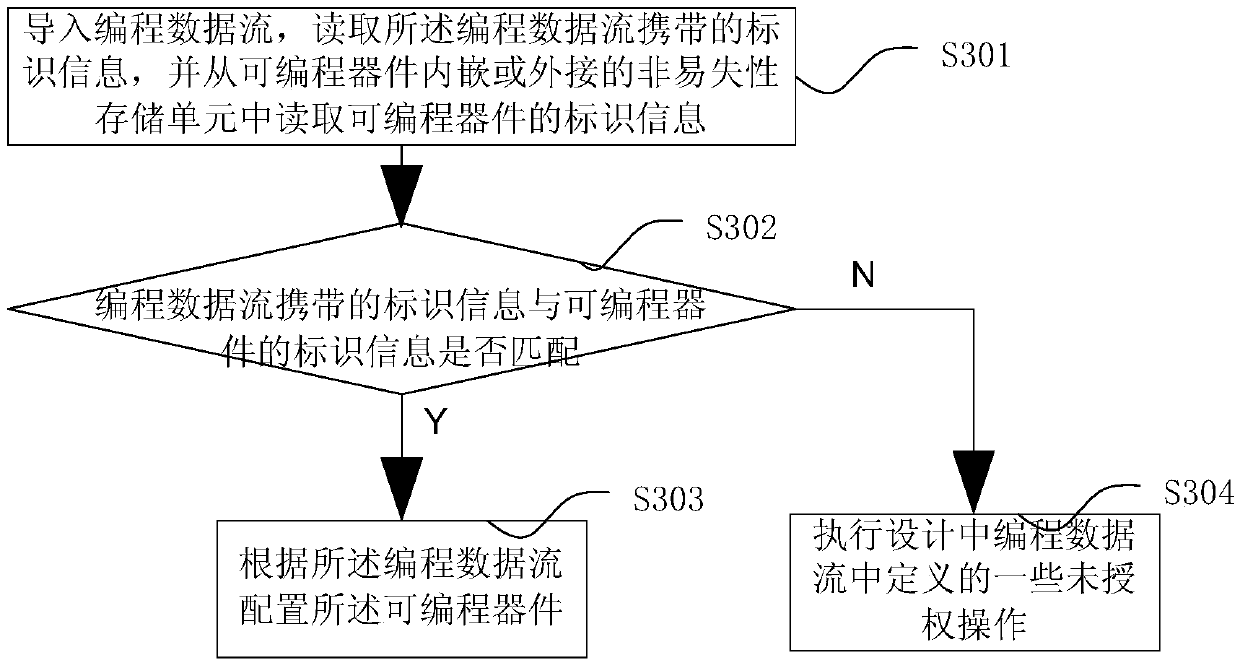
ActiveCN105515849AEnsure safetyProperly design the functionKey distribution for secure communicationGenetic modelsData streamProgrammable logic device
The invention discloses a method and a device for configuring a programmable device, identification information and programming data flow. The method for configuring the programmable device comprises the following steps: importing programming data flow, reading identification information carried by the programming data flow, and reading the identification information of the programmable device from a nonvolatile storage unit embedded in or externally connected with the programmable device; comparing the identification information carried by the programming data flow with the identification information of the programmable device; and if the two is matched, configuring the programmable device according to the programming data flow. The method disclosed by the invention is used for solving the problem in the prior art that the programming data flow cannot correspond to the programmable device.
Owner:SHENZHEN PANGO MICROSYST CO LTD
Color image encryption method based on SHA-384 function, spatiotemporal chaotic system, quantum chaotic system and neural network
ActiveCN104008520BImprove securityLarge key spaceImage data processing detailsComputer hardwareDiffusion
The invention relates to a color image encryption method based on an SHA-384 function, a spatiotemporal chaotic system, a quantum chaotic system and a neural network. The method includes the steps that an original color image I0 is calculated through the SHA-384 function, a Hash value is obtained as a secret key, the Hash value, a CML and one-dimension Logistic chaotic mapping are utilized for generating a chaos sequence, bit-level line-column scrambling is carried out on high four-digit images of components of three primary colors of the I0 through the chaos sequence, and a scrambled image I1 is obtained; the Logistic quantum chaotic system is utilized for generating a chaos sequence for encrypting the scrambled image, and is combined with the neural network to carry out parallel diffusion processing on all pixel values of components of three primary colors of the I1, and a final encrypted image I2 is obtained. By the method, the space of the secret key is greatly enlarged, the safety, encryption effect and secret key sensibility are higher, the attack resistance capacity is higher, the scrambling process and the encryption time are shorter, and hardware implementation is easier.
Owner:HENAN UNIVERSITY
An efficient privacy-preserving indoor positioning method based on wi-fi fingerprints
ActiveCN105530609BReduce encryption timeReduce space complexityParticular environment based servicesLocation information based serviceWi-FiArray data structure
The invention provides an indoor positioning method for efficient privacy protection based on Wi-Fi fingerprint. The indoor positioning method comprises the following steps: at first, collecting the fingerprint of each position indoors and generating an index set; and then, transmitting the index set to a client through a wireless network, for enabling a user to look up the position information per se, wherein the fingerprint refers to a RSS signal of each position corresponding to each Wi-Fi access point, and the index set comprises multiple hash tables, parameters of a corresponding function group of each hash table and a position coordinate of each fingerprint marked by a fingerprint serial number. According to the indoor positioning method provided by the invention, a method of using a position sensitive hash function to encrypt position privacy is adopted to achieve high efficiency and privacy protection properties. The positioning is redesigned to achieve the purposes of reducing the computing time and space, improving the positioning precision and protecting the privacy of the position information of a user and a server.
Owner:广州高新兴机器人有限公司
Image encryption method based on bit-level scrambling and network diffusion
ActiveCN112887506BImprove diffusion efficiencyReduce encryption timeSecuring communication by chaotic signalsPictoral communicationEncryptionElectrical and Electronics engineering
The image encryption method based on bit-level scrambling and network diffusion relates to the field of image encryption technology and solves the problem of conflicting existing image encryption efficiency and security. The image encryption method based on bit-level scrambling and network diffusion proposed by the present invention, The scrambling process converts the pixel plane into a bit-level plane, and performs bit-level pixel scrambling on the basis of the bit-level plane. The diffusion part uses the "simplified Feistel network" diffusion method to perform diffusion operations on pixels, which improves the diffusion efficiency and greatly The encryption time is reduced, and the safe encryption effect is achieved while ensuring the operation speed.
Owner:CHANGCHUN UNIV OF SCI & TECH
A Neural Network-Based Face Recognition and Local Encryption Method on Intelligent Cloud Platform
ActiveCN109872279BEncryption accelerationReduce encryption timeImage enhancementCharacter and pattern recognitionAlgorithmPassword
The invention discloses an intelligent cloud platform face recognition and local encryption method based on a neural network. The method comprises the steps of processing an original image through animage pyramid; establishing a face / non-face classifier, and outputting a large number of results which may be face classification, boundary frame regression and face position; carrying out bounding box regression, refining the candidate windows, and discarding a large number of overlapped windows; carrying out landmark positioning, removing a candidate window and displaying five face key point positioning at the same time; and encrypting the data through a chaotic logic diagram and an RC4 stream password. A local encryption mode is adopted, so that the picture encryption time is shortened, andthe encryption efficiency is greatly improved.
Owner:SHENZHEN LETEER TECH CO LTD
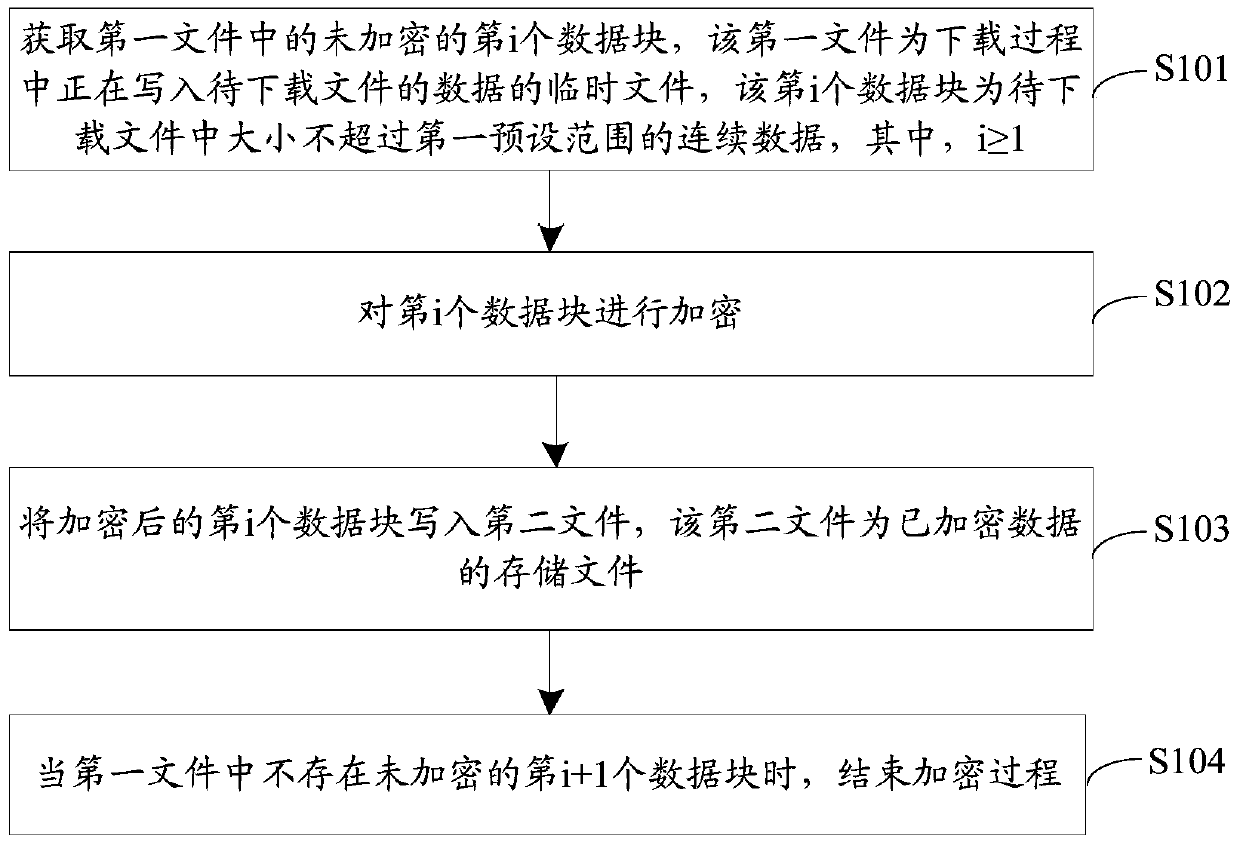
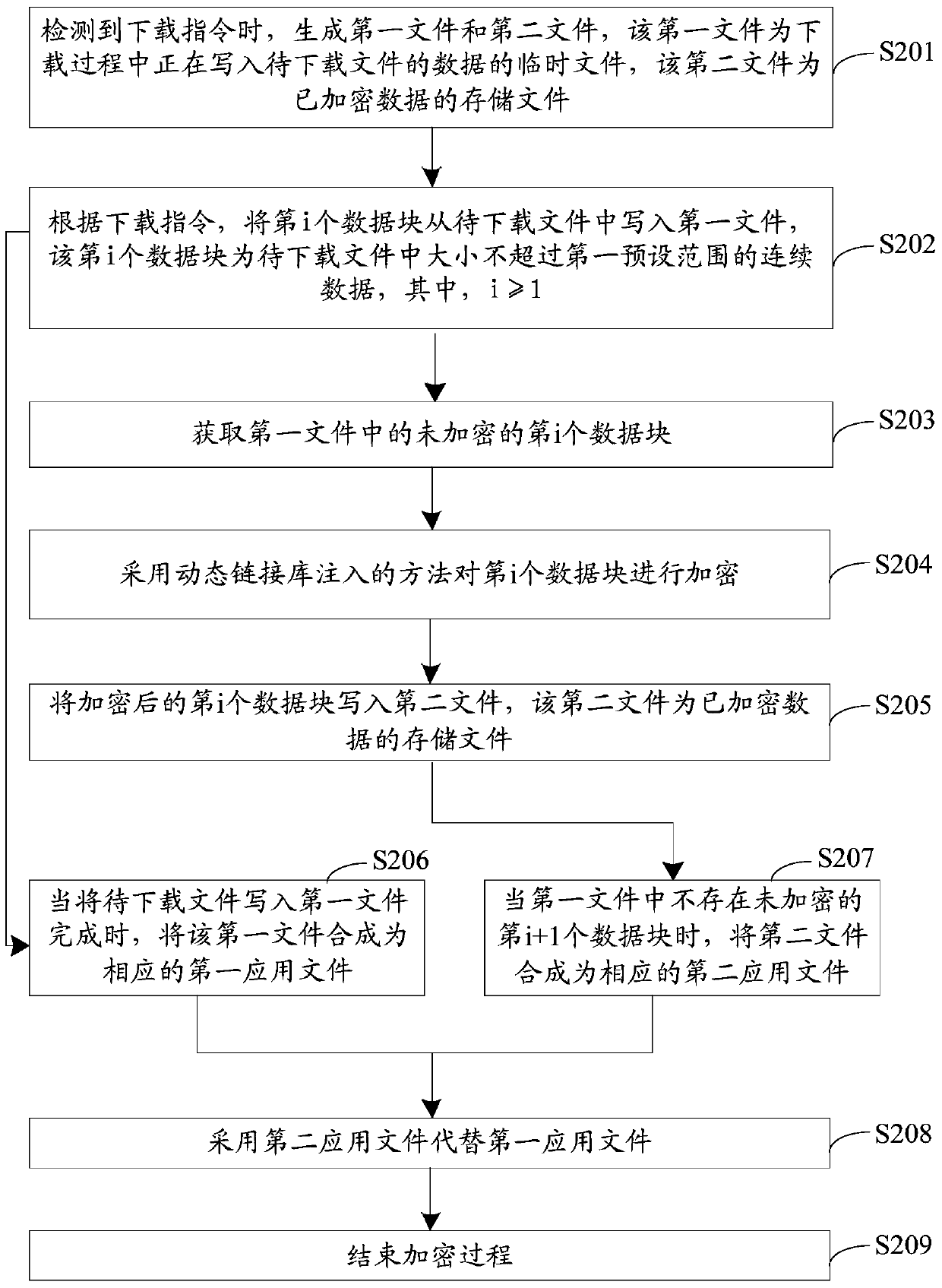
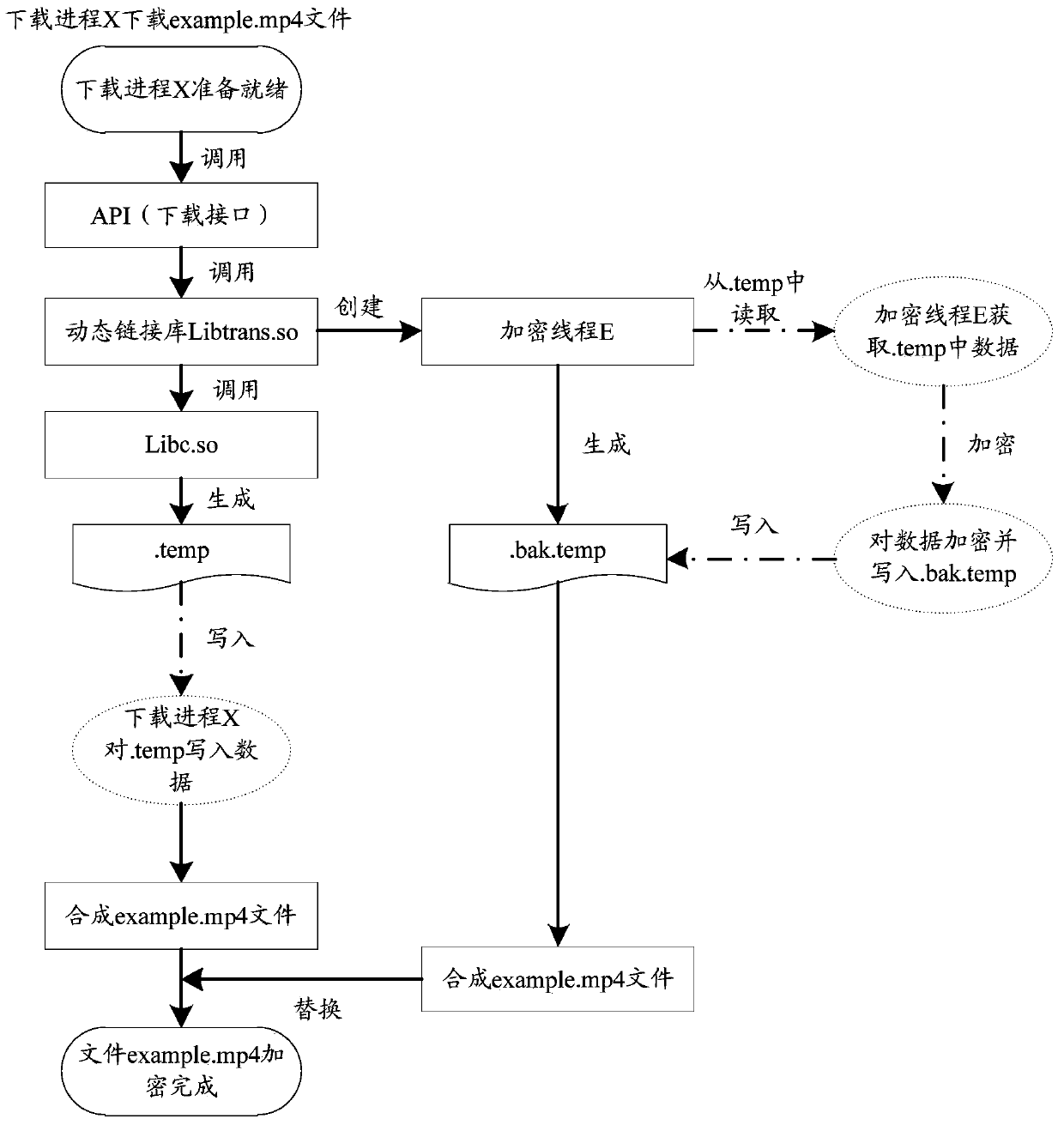
An encryption method and device
The embodiment of the invention discloses an encryption method comprising steps of: obtaining the unencrypted ith data block in a first file, wherein the first file is a temporary file into which the data of a file to be downloaded is being written during a downloading process, the ith data block is continuous data not beyond a first preset range in the file to be downloaded, and i is greater than or equal to 1; encrypting the i-th data block; writing the encrypted ith data block into a second file; and ending the encryption process when the first file does not have unencrypted (i+1)th data block. The embodiment of the present invention also discloses an encryption apparatus.
Owner:CHINA MOBILE COMM GRP CO LTD
Image encryption method based on bit-level scrambling and dynamic superposition and diffusion
ActiveCN111131656BImprove diffusion efficiencyReduce encryption timePictoral communicationComputer hardwareEngineering
Owner:CHANGCHUN UNIV OF SCI & TECH
Chaotic Image Encryption Method Based on Double Reset Scrambling and DNA Coding
ActiveCN108898025BAvoid multiple iterationsImprove securityDigital data protectionHash functionAlgorithm
The invention relates to a chaos image encryption method based on dual scrambling and DNA coding, firstly, carrying out bit plane decomposition on a plaintext image and carrying out DNA coding and transformation on the image to turn the image into a three-dimensional DNA matrix; then, scrambling the three-dimensional DNA matrix through the dual scrambling operation, wherein the sequence of the chaotic sequences is scrambled and the DNA sequence is scrambled in a bit level through combining the three-dimensional cat mapping; next, performing diffusion operation on the scrambled three-dimensional DNA matrix, and converting the diffused matrix into a two-dimensional DNA matrix; finally, performing decoding operation on the two-dimensional DNA matrix to obtain a ciphertext image. According tothe invention, the SHA256 hash function of the plaintext image is used to calculate the initial value of the chaotic system, and the parameters of three-dimensional cat mapping are also related to theplaintext image, which enhances the ability of the algorithm to resist the selection of plaintext attack. Experimental results and safety analysis show that the encryption scheme can resist various known attacks, and can effectively protect the security of images and also can improve the security level.
Owner:HENAN UNIVERSITY
A cloud storage encryption, decryption and verification method and system
ActiveCN110460604BReduce the amount of calculationReduce energy consumptionDigital data protectionSecurity arrangementAccess structureCiphertext
This application discloses a cloud storage encryption, decryption and verification method and system, which is applied to a data upload terminal, including: generating temporary ciphertext in advance using the encryption parameters used for encryption in the system public parameters; using the system public parameters for verification Complete data verification parameters, temporary ciphertext, plaintext data, and access structure to generate outsourced ciphertext; send outsourced ciphertext to the cloud server; this application pre-uses system public parameters for encryption when the data upload terminal has sufficient energy The encryption parameters are used to generate temporary ciphertext, and the part of the encryption process that consumes too much energy in the encryption process using the system public parameters for encryption is preprocessed in advance, so that even in the case of insufficient energy, the amount of calculation when encrypting data is reduced. And energy consumption, you can directly use the temporary ciphertext, verification parameters, plaintext data and access structure to generate outsourced ciphertext, shorten the encryption time, and reduce the amount of calculation and energy consumption.
Owner:GUANGDONG UNIV OF TECH
Digital image encryption method based on chaotic orbit perturbation
InactiveCN102360488BImprove diffusion abilityImprove abilitiesImage data processing detailsMultiple encryptionPlaintext
The invention relates to a digital image encryption method based on chaotic orbit perturbation and relates to the field of encryption systems. The method comprises the following steps of: scrambling a plaintext image by adopting a generalized discrete Baker mapping-based method; diffusing the scrambled image by adopting a Logistic mapping-based method, and changing the pixel value of each point in the image; and performing multiple encryption according to the requirement on encryption strength. According to the method, a key flow is related to a key and a plaintext by introducing a chaotic orbit perturbation mechanism related to the plaintext, so that the diffusing effects of an encryption system are effectively improved, and the known plaintext resistance is obviously improved. Certain pixel value is changed in the diffusion process depending on the cumulative effect of all the encrypted pixel values before the pixel, so that the tiny change of one pixel value can be effectively diffused to all the subsequent pixels in the image. The method has short encryption time.
Owner:付冲 +1
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com