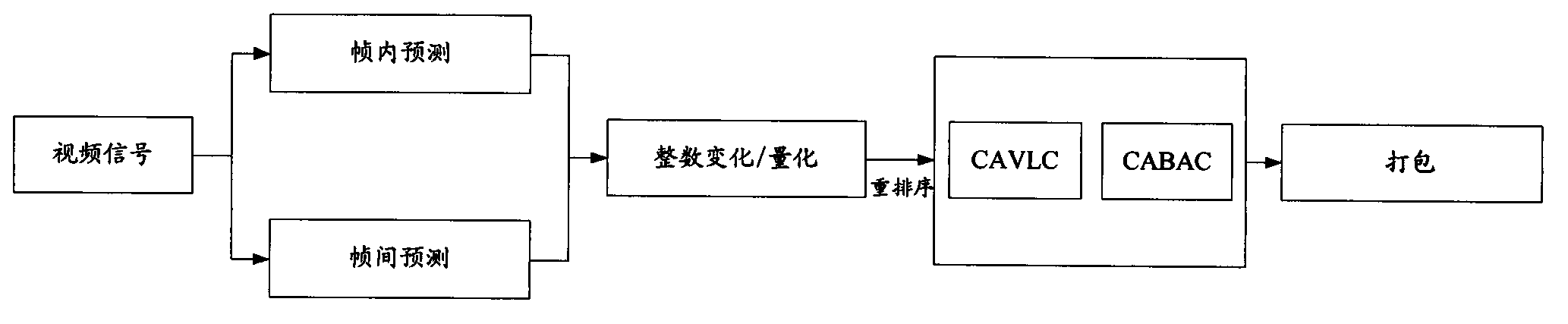
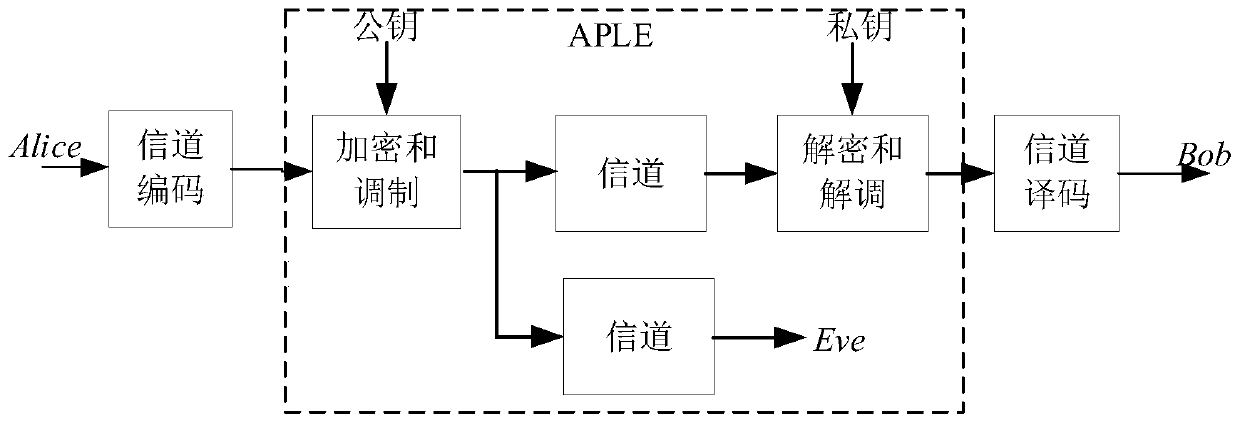
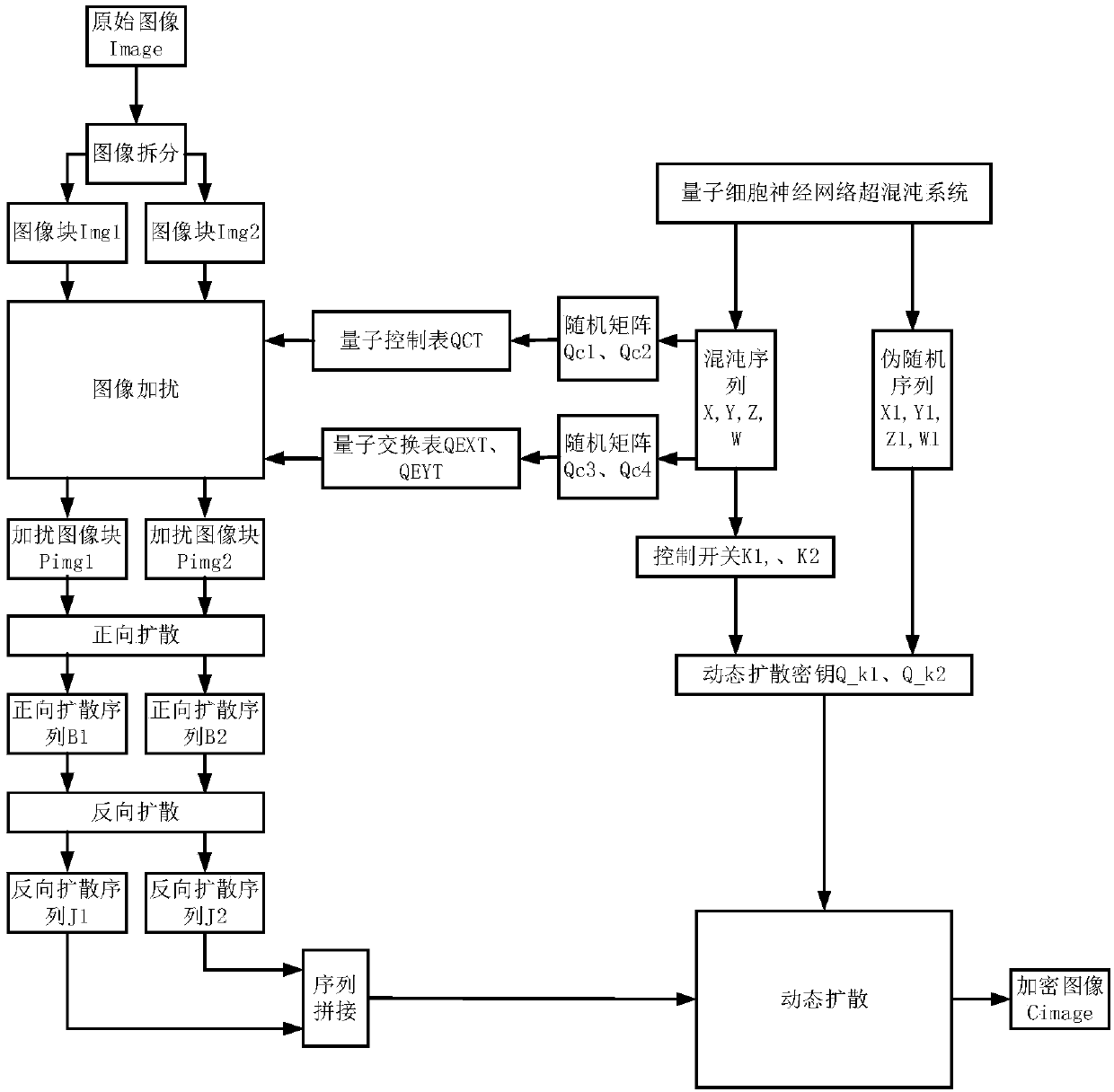
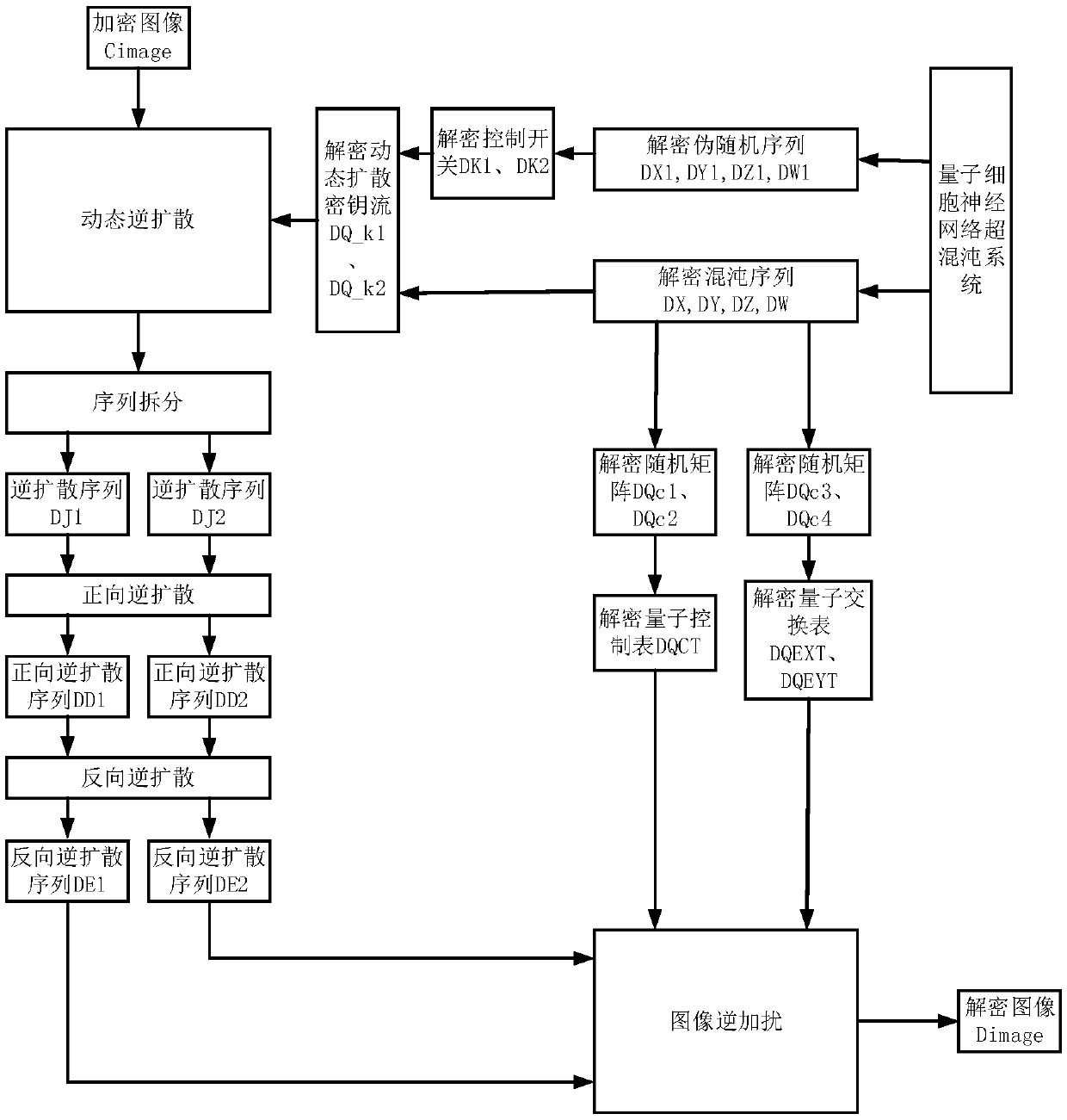
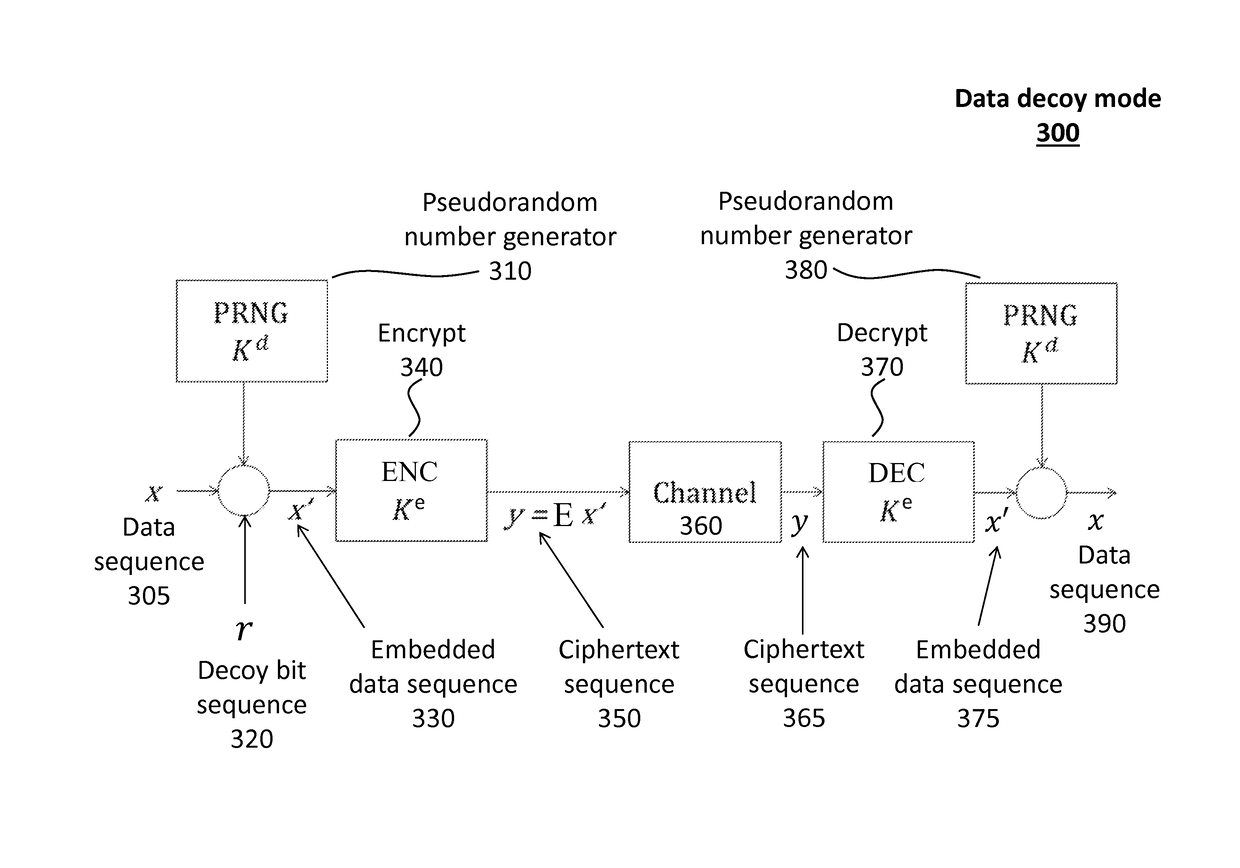
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
54 results about "Known-plaintext attack" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
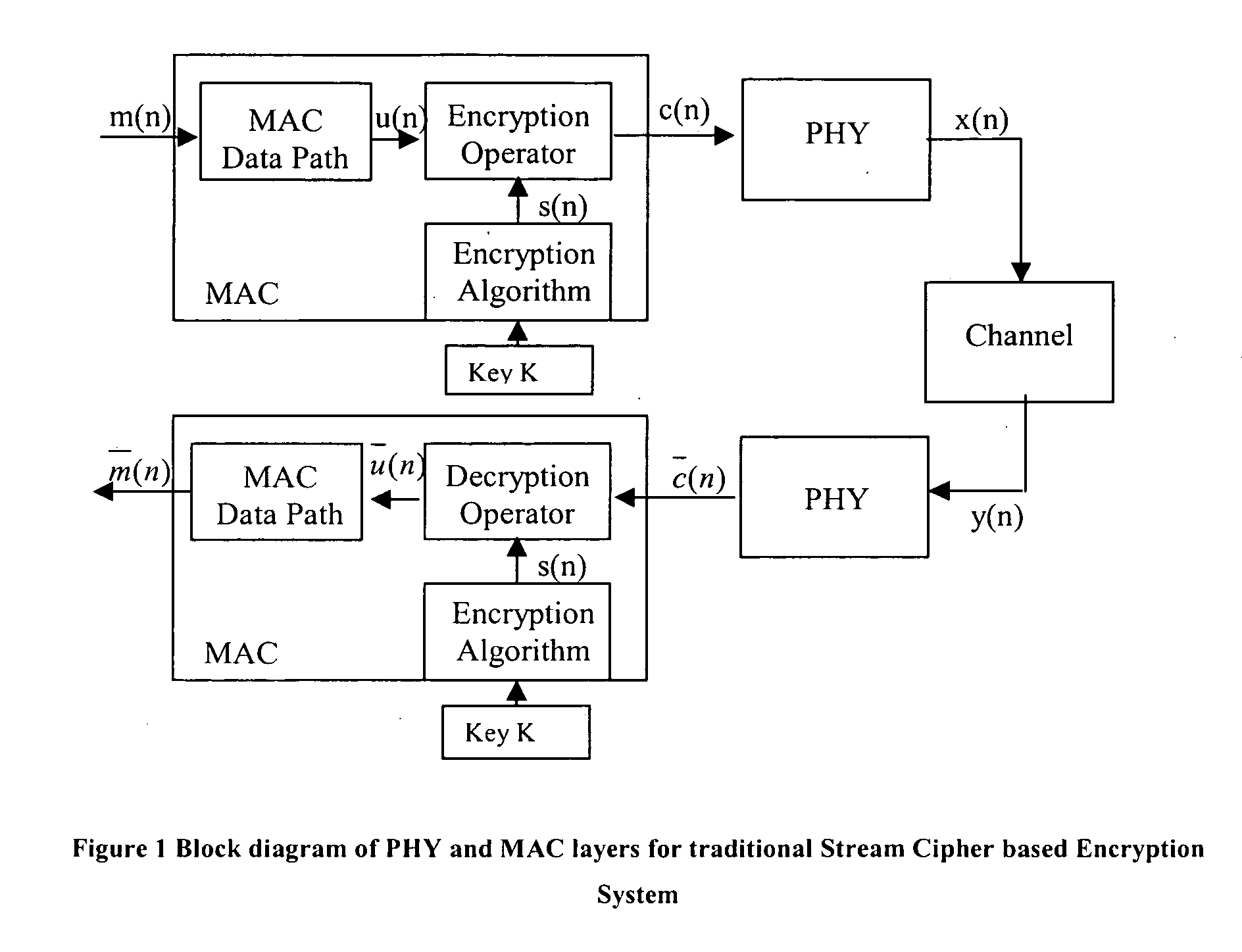
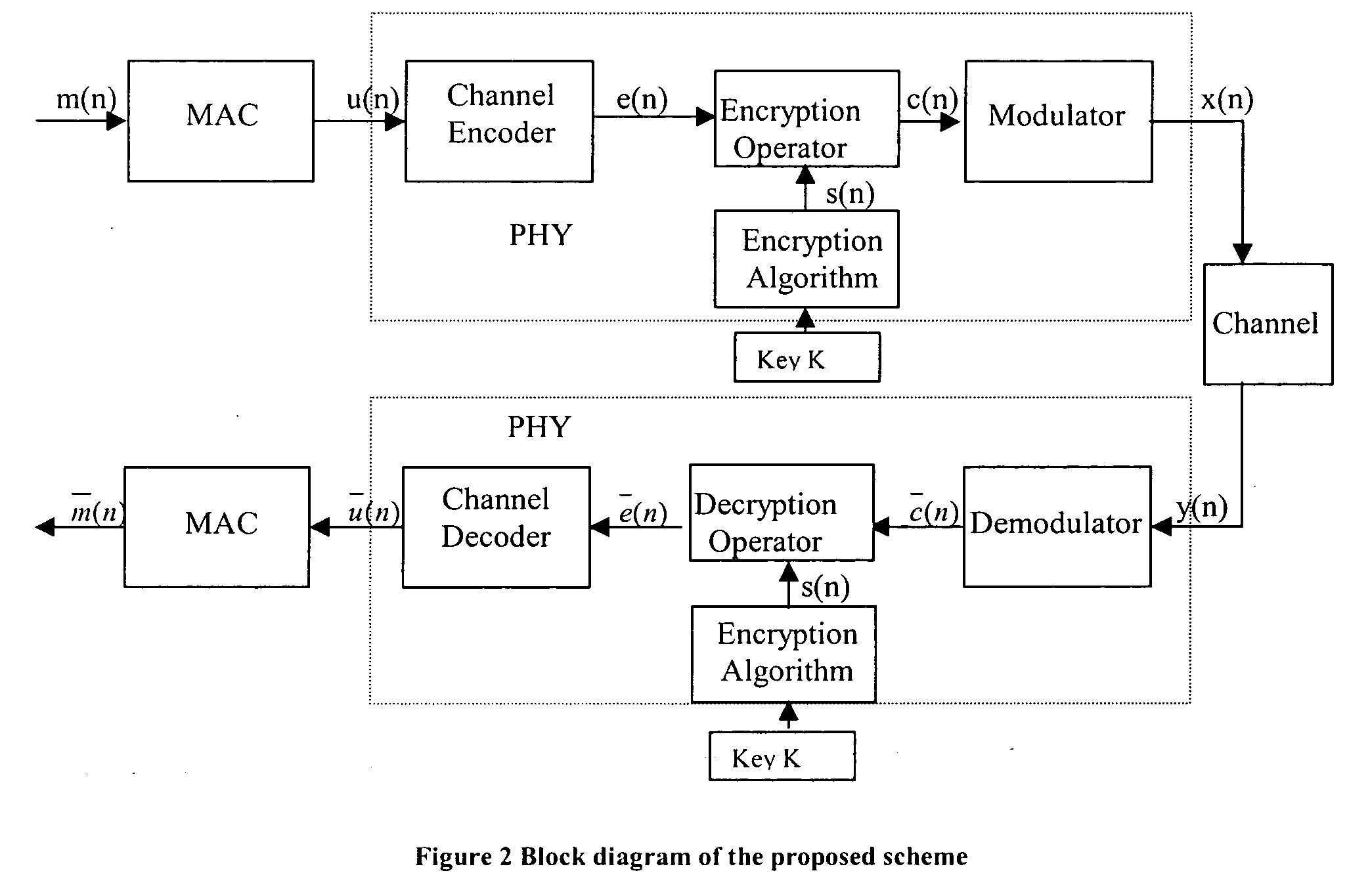
The known-plaintext attack (KPA) is an attack model for cryptanalysis where the attacker has access to both the plaintext (called a crib), and its encrypted version (ciphertext). These can be used to reveal further secret information such as secret keys and code books. The term "crib" originated at Bletchley Park, the British World War II decryption operation.
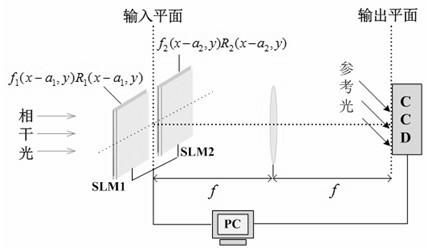
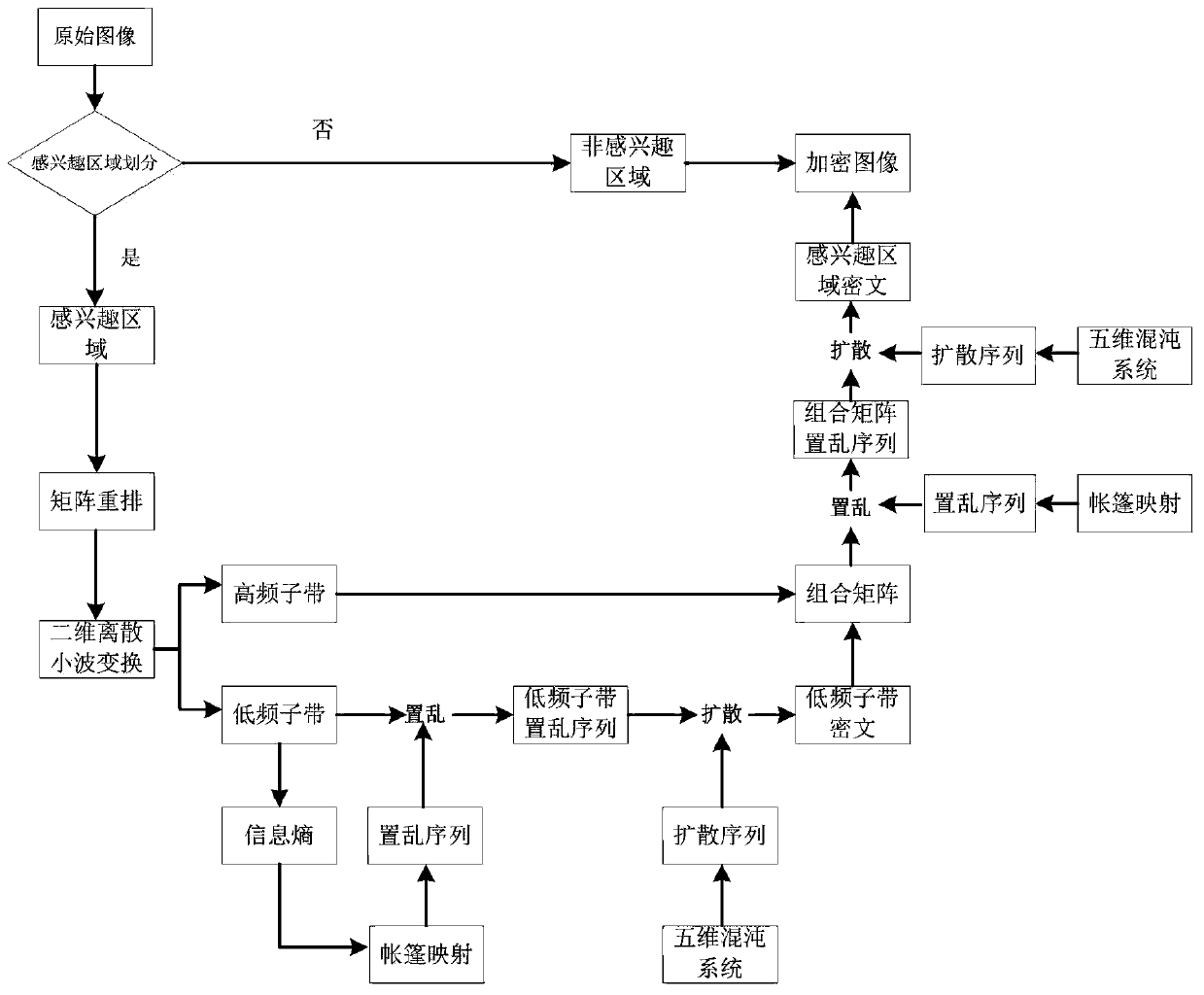
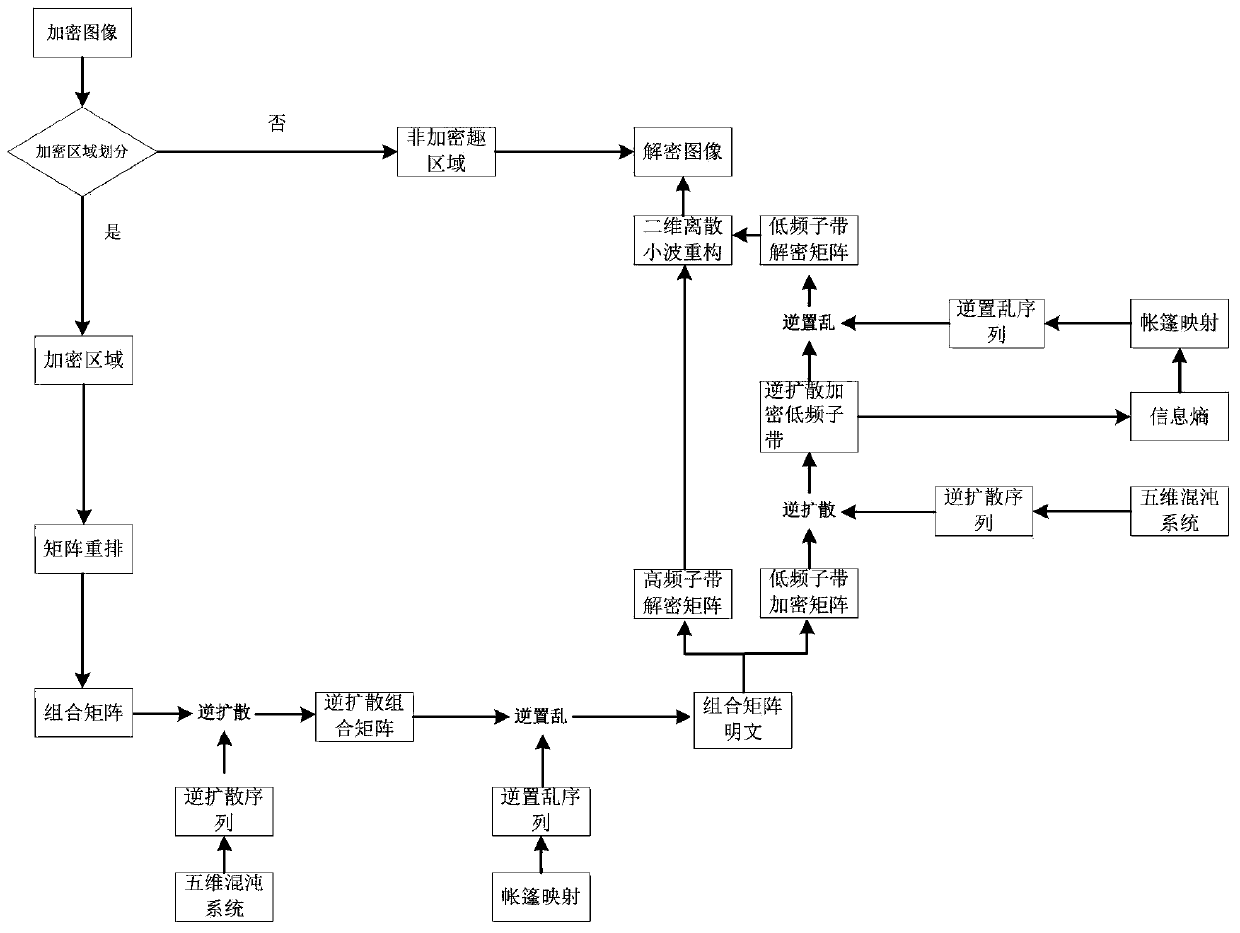
Image encryption method and image decryption method with visual security and data security based on compressed sensing
ActiveCN106600518AIncrease spaceEnhanced resistance to brute force attacksImage data processing detailsChosen-plaintext attackHash function
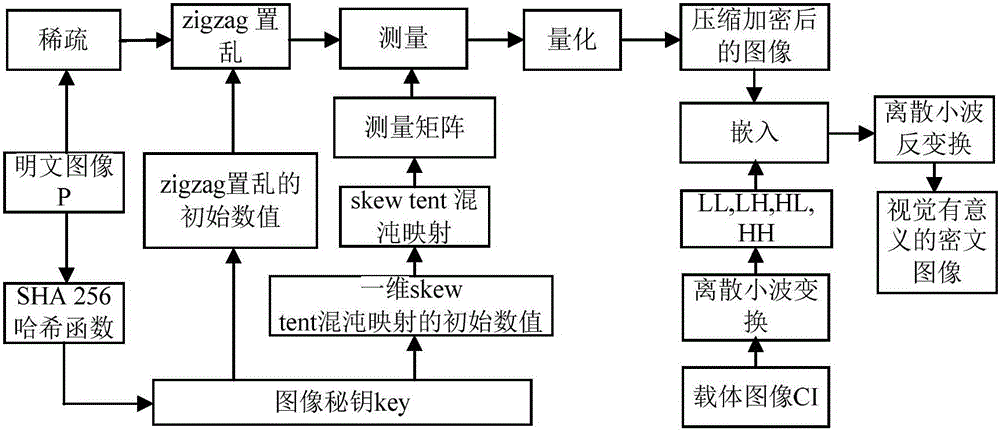
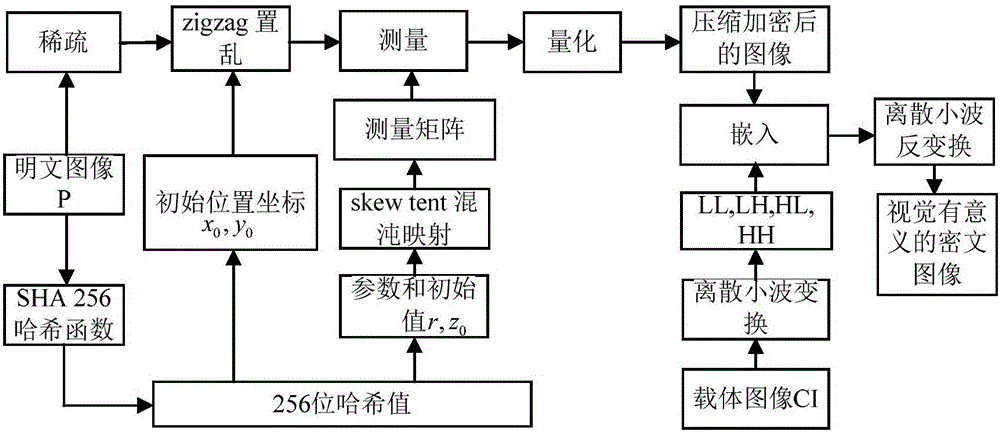
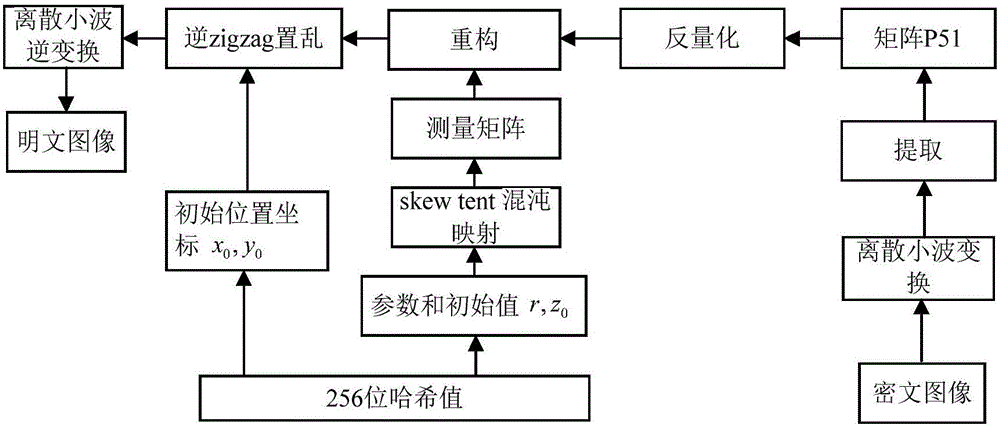
The invention relates to an image encryption method and an image decryption method with visual security and data security based on compressed sensing. The image encryption method comprises the steps of: firstly, utilizing an SHA 256 hash function to obtain a 256-bit hash value of a plaintext image as an image secret key, and calculating initial numerical values of one-dimensional skew tent chaotic mapping and zigzag scrambling; carrying out sparse processing on the plaintext image, and carrying out zigzag scrambling on a coefficient matrix; and then utilizing the one-dimensional skew tent chaotic mapping to generate a measurement matrix, measuring and quantifying a scrambling matrix to obtain a compressed and encrypted image, and embedding the image into a carrier image with visual significance to obtain a final ciphertext image with visual significance. The image encryption method realizes the visual security and data security of the plaintext image, has large secret key space, is highly sensitive to plaintext, has higher capacity of resisting brute-force attack, chosen-plaintext attack and known-plaintext attack, does not need an additional storage space, and can transmit and store the ciphertext image quickly and effectively.
Owner:HENAN UNIVERSITY
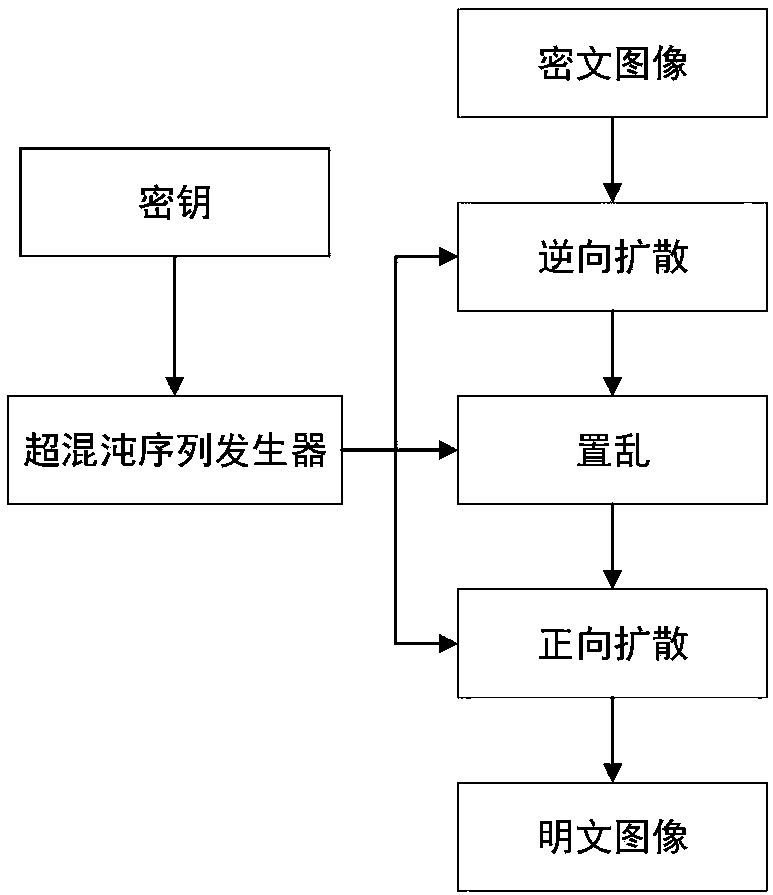
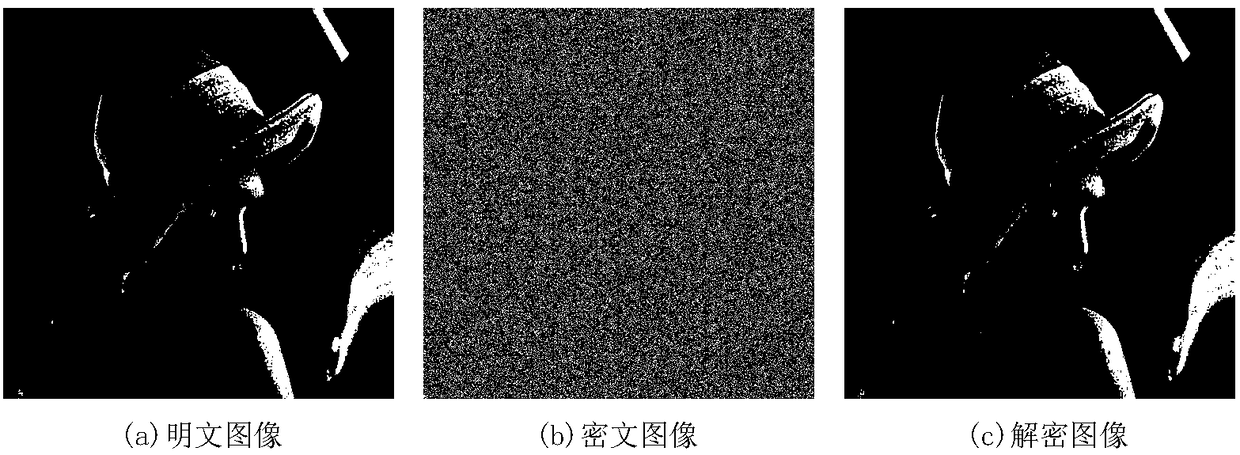
Plaintext associated image encryption algorithm based on hyperchaos Chen system
InactiveCN108234813AReduce the number of iterationsImprove the ability to resist known plaintext attacksKey distribution for secure communicationSecuring communication by chaotic signalsChosen-plaintext attackRelevant information
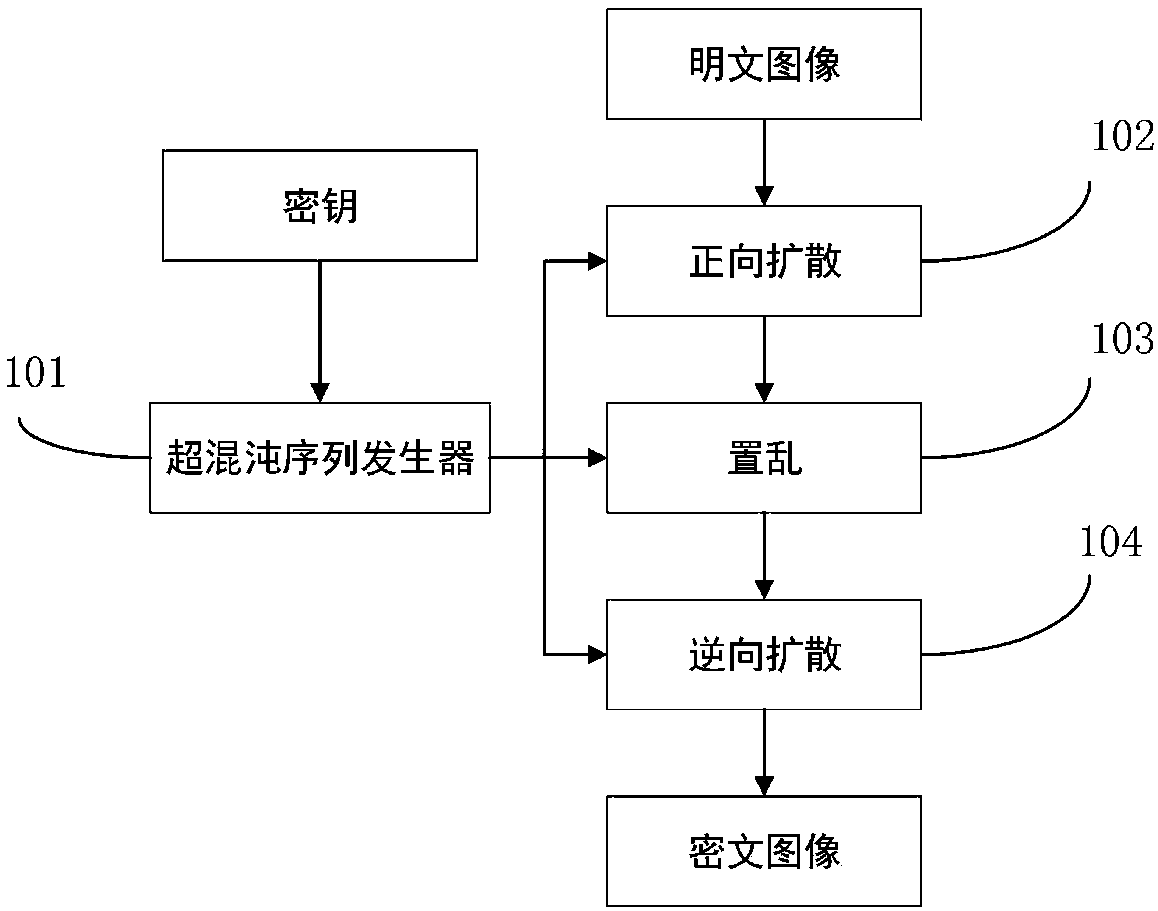
The invention relates to an image encryption algorithm based on a chaotic system, used for solving security problems that the image encryption algorithm is small in key space and poor in capacity of resisting to plaintext attacks. The algorithm comprises four modules such as a hyperchaos sequence generator, a forward diffusion module, a scrambling module and a reverse diffusion module. Firstly thehyperchaos Chen system is used for generating four chaotic pseudorandom sequences, a chaotic sequence and a plaintext image are used for performing forward diffusion operation to acquire a matrix A,then computation is performed in combination with the pseudorandom sequences and information related to the plaintext image to acquire a scrambled coordinate, the coordinate scrambling is performed onthe matrix A to acquire a matrix B, and at last the chaotic pseudorandom sequences and the matrix B are used for performing reverse diffusion operation to acquire a ciphertext image C. An experimentsimulation result expresses that the algorithm can improve the defect that the image encryption algorithm is small in key space, effectively resist to statistical attacks, differential attacks, and chosen-plaintext attacks, and achieve good encryption effect.
Owner:CHONGQING UNIV OF POSTS & TELECOMM
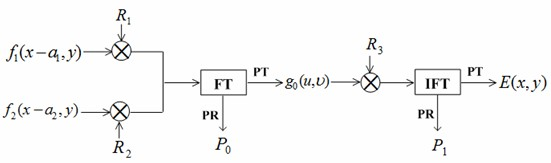
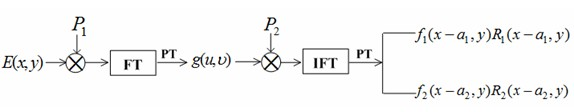
Asymmetric double image encryption method based on joint of fourier transformation and phase cutting
InactiveCN102567943AAchieve asymmetryResist attackImage data processing detailsFourier transform on finite groupsPhase mask
The invention discloses an asymmetric double-image encryption method based on a joint of a fourier transformation and a phase cutting. Under modulation of random phase masks, two plain texts are modulated by the joint of the fourier transformation and the phase cutting, so that symmetrical and linear characteristics of a traditional double random phase encryption method are eliminated, so that the anti-attack capability of the encryption system is greatly improved. An encryption process, a decryption process and the asymmetry of an encryption key and a decryption key are achieved, and an optical asymmetric encryption system based on the double random encryption method is established. The test shows that, compared with traditional double random encryption techniques which are easy to be attacked, the asymmetric double image encryption method can resist violent attacks, known plaintext attacks, direct public key attacks and iterative amplitude recovery algorithm attacks, so that high security is provided.
Owner:ZHEJIANG FORESTRY UNIVERSITY
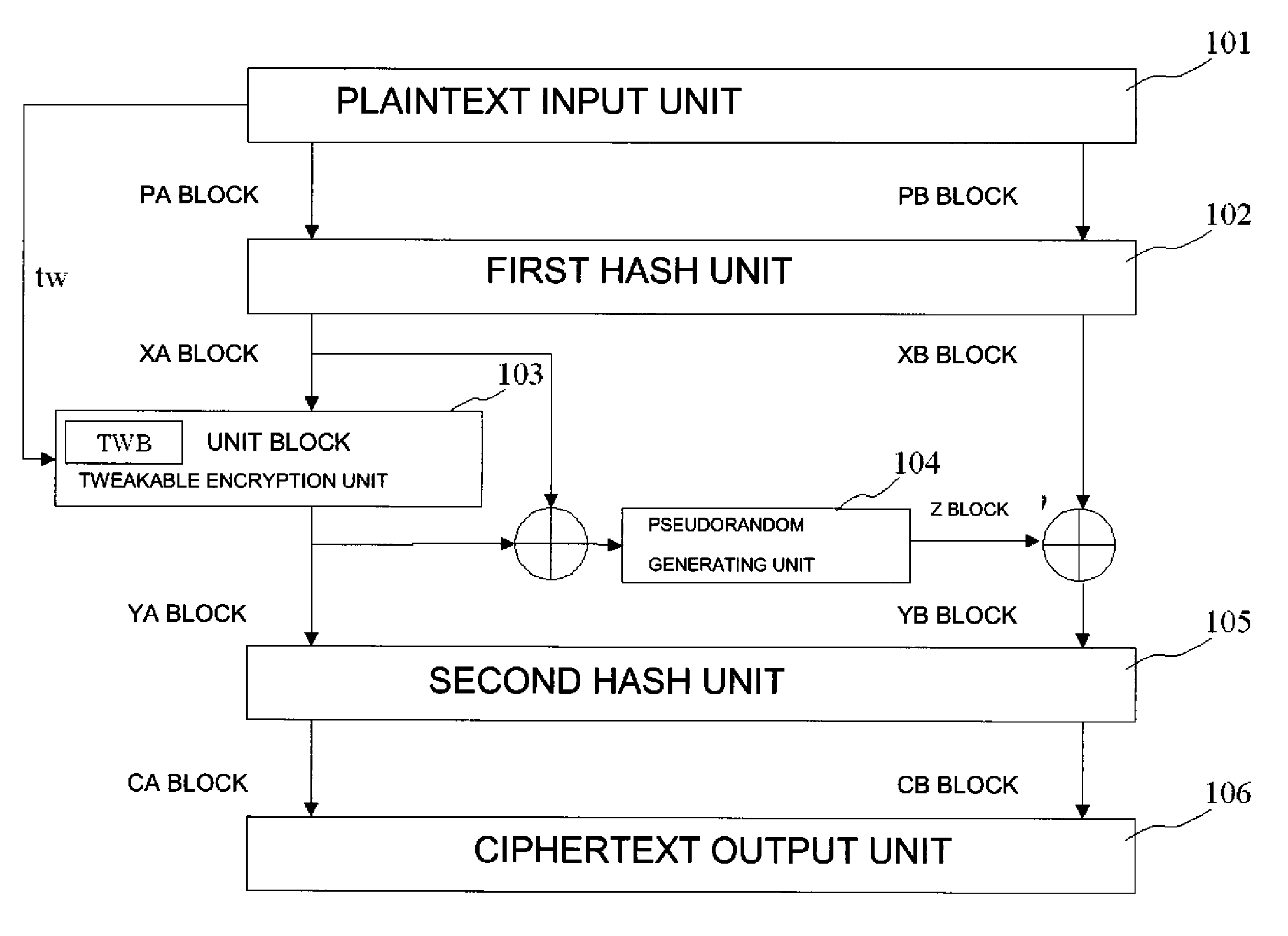
Common key block encryption device, common key block encryption method, and program
ActiveUS20110211691A1More processing timeSatisfies requirementEncryption apparatus with shift registers/memoriesPublic key for secure communicationComputer hardwareVariable length
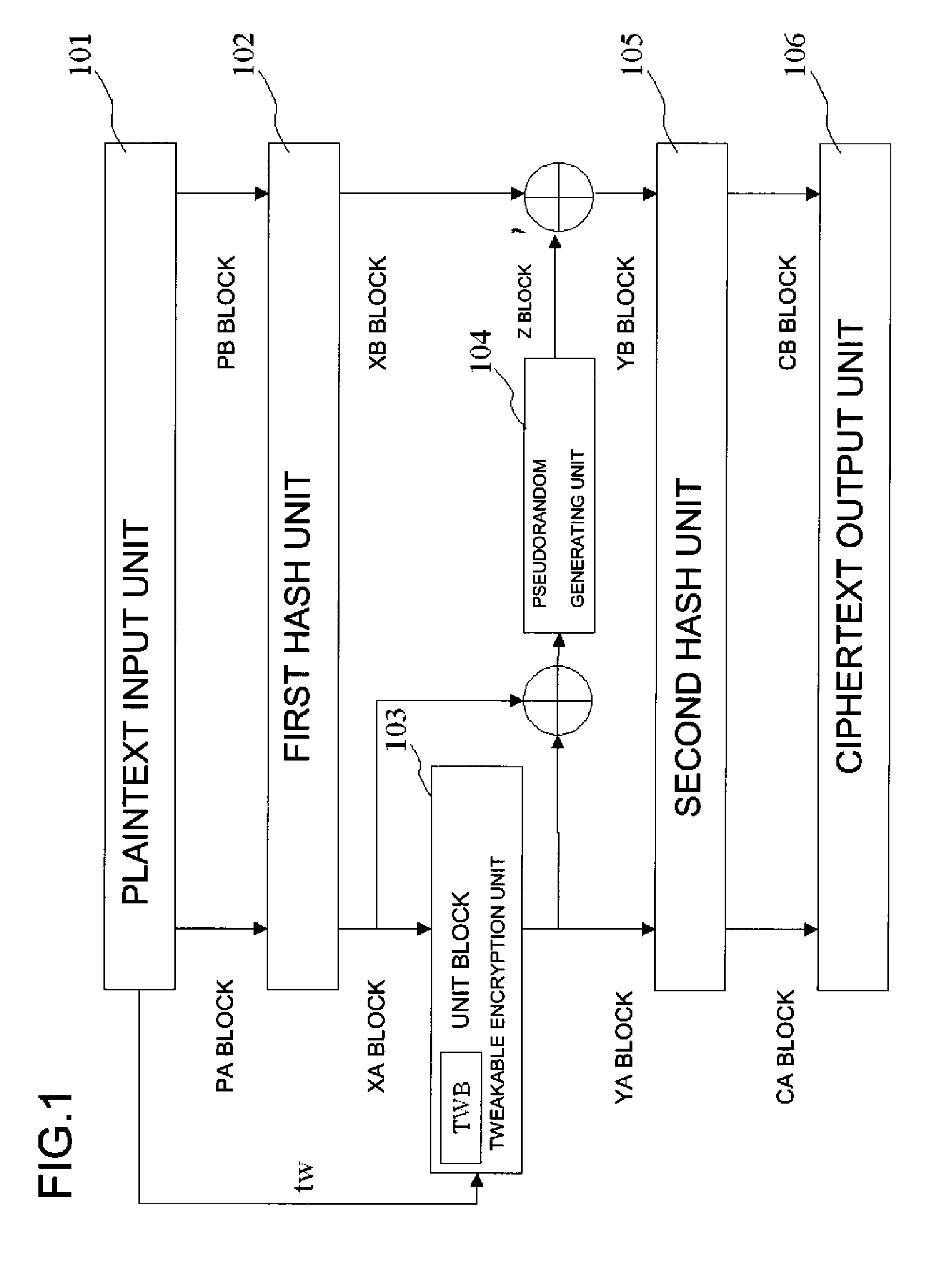
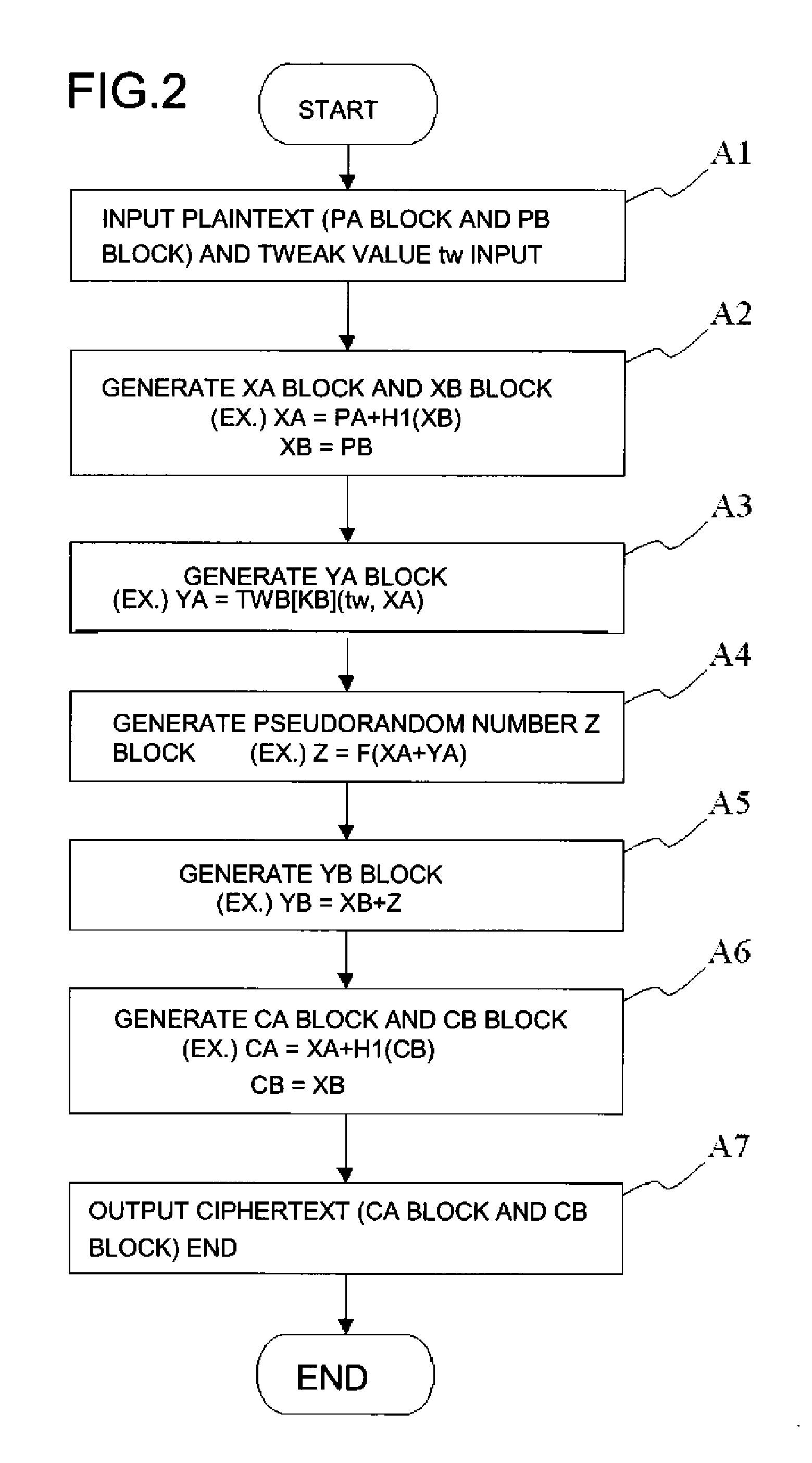
A common key block encryption device includes a first hash unit applying locked key permutation to a variable-length s-bit plaintext, and outputting a fixed-length n-bit first block and a second (s-n)-bit block; a first encryption processing unit outputting a third block encrypted by element of n-bit block tweakable block cipher using tweak, inputting the first block; a second encryption processing unit generating a random number (s-n)-bit block with a result of group computation of the third block and the first block as input by using an arbitrary cipher having theoretical security at least against a known-plaintext attack; and a second hash unit applying the locked key permutation to the result of the group computation of the random number block and the second block, and to the third block to output a fifth n-bit block and a sixth (s-n)-bit block. The fifth and sixth blocks are concatenated into an s-bit encryption.
Owner:NEC CORP
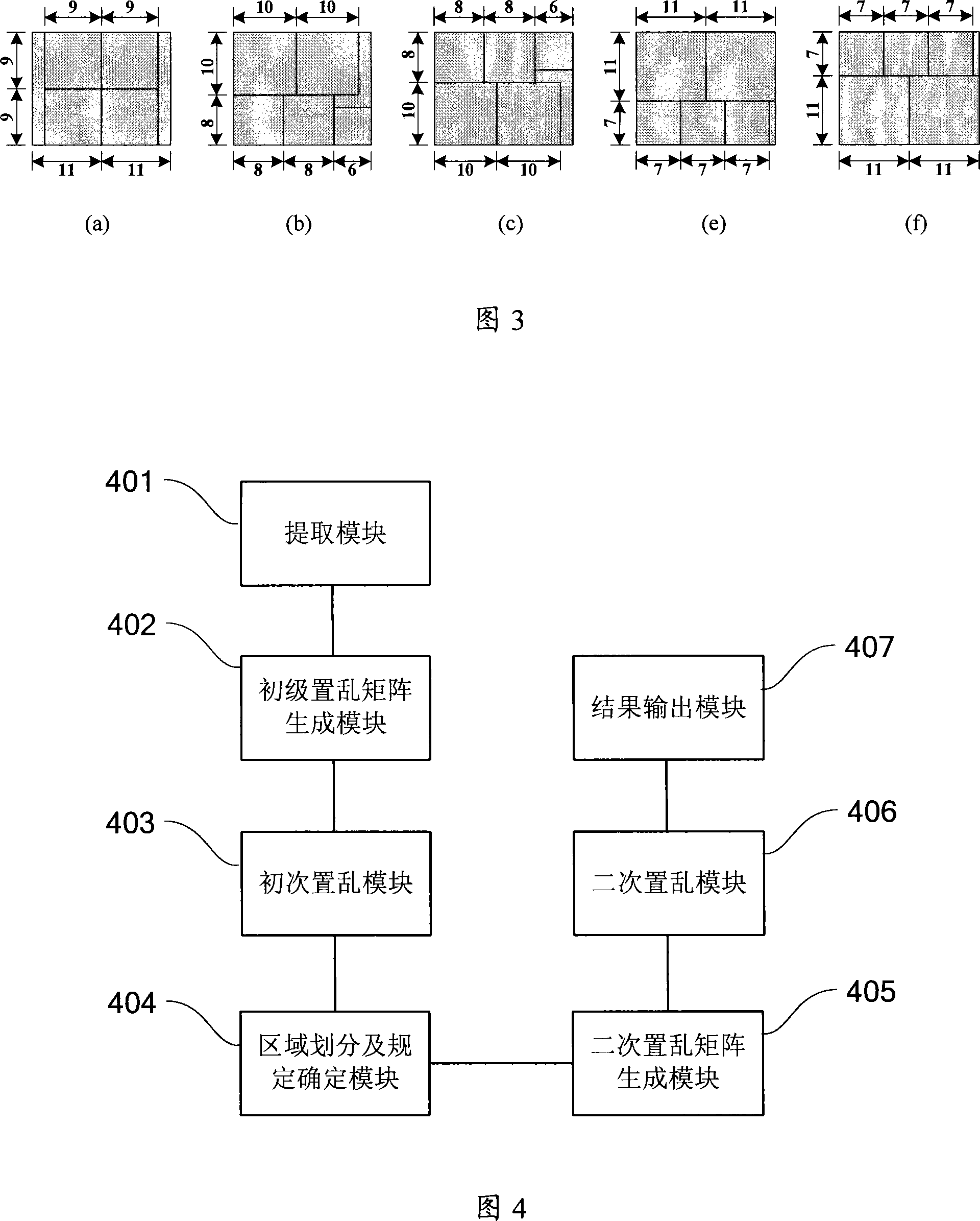
Method and apparatus for encrypting video data
InactiveCN101110944AReduce the likelihood of adjacentEncryption subjective effect is goodAnalogue secracy/subscription systemsStreaming dataCollocation
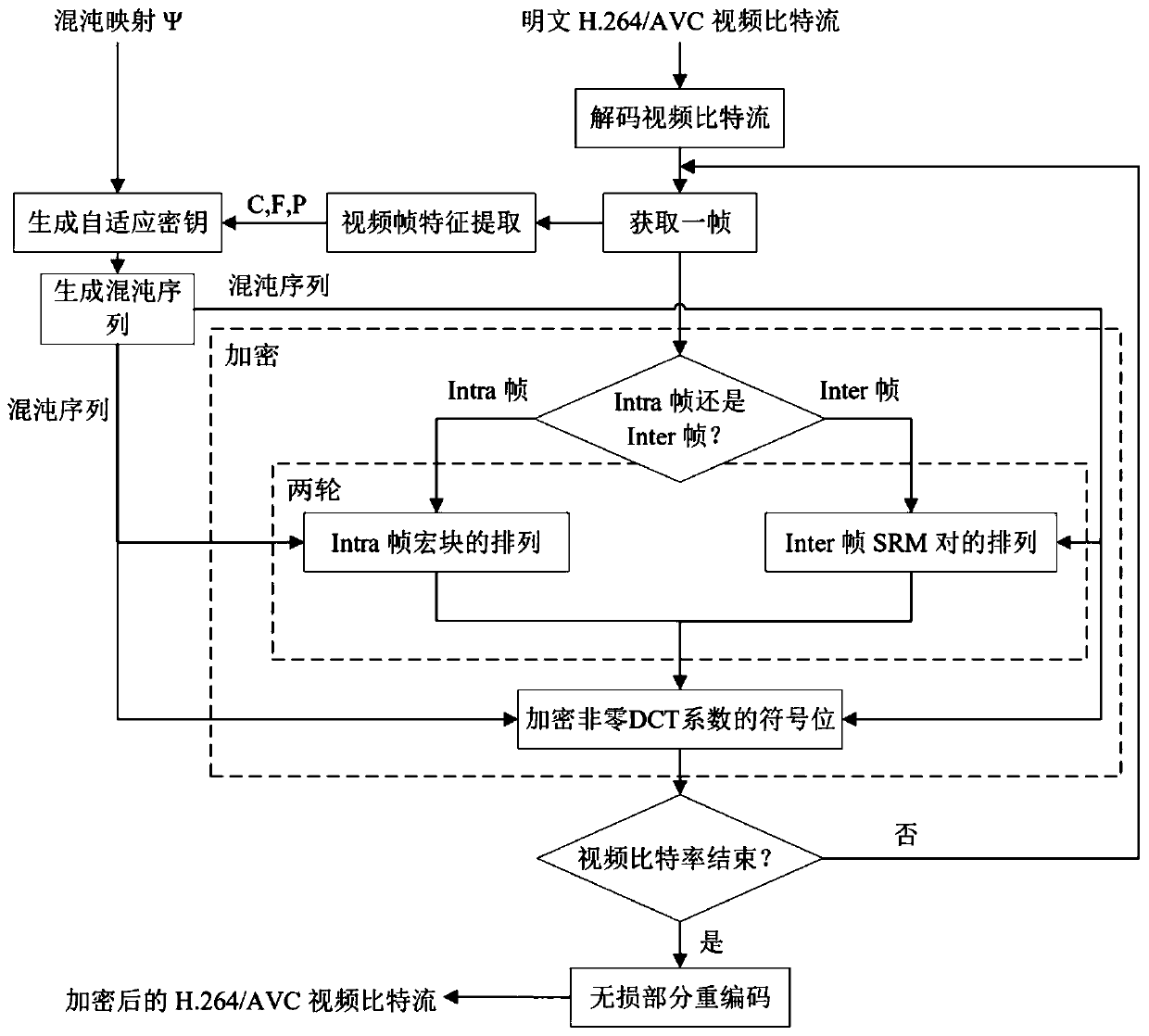
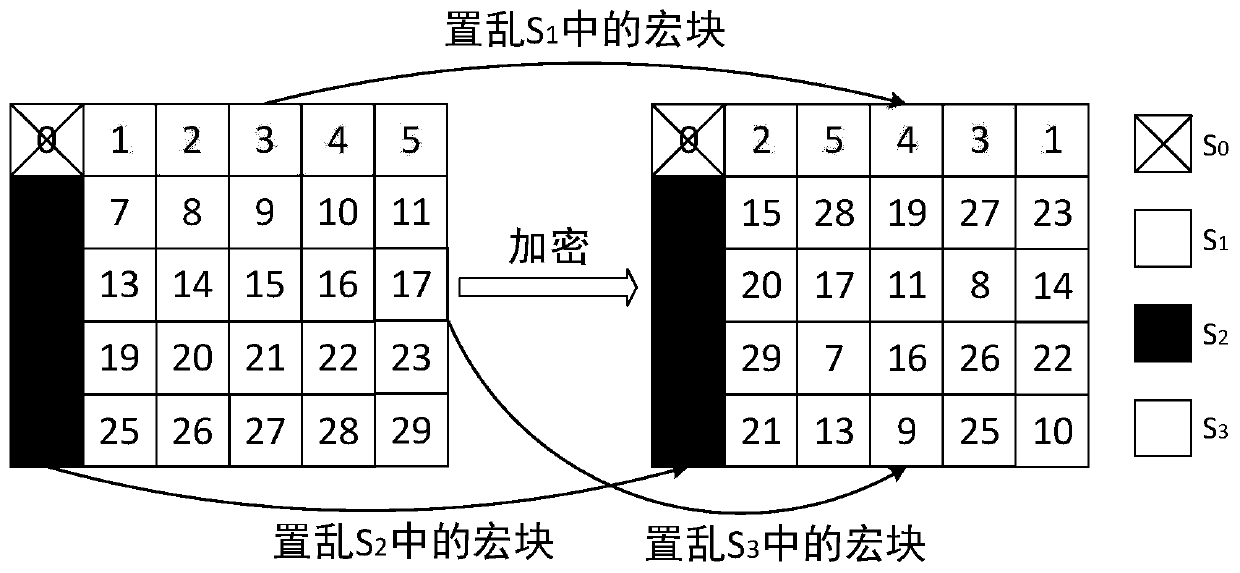
The present invention provides an encryption method for a video data, which comprises the following procedures: the macro block information of the video data is abstracted; a primary scrambling matrix is created; the macro block information is scrambled according to the primary scrambling matrix; the scrambling result of the primary scrambling matrix is divided into a plurality of areas, and a relative area scrambling rule for each area is determined; a secondary scrambling matrix for the entire video data is gained according to the collocation result by the coding information and the relative area scrambling rule of the macro block in each area; the scrambling result of the primary scrambling matrix is scrambled again according to the secondary scrambling matrix; a stream data is built and an encryption result is gained. The present invention solves the problem of the existing macro block scrambling algorithm that a partial encryption effect is inadequate, provides a better visual encryption effect, and the known plain text attack is ineffective. In conclusion, the present invention does not increase the stream, the speed is quick, the computing source occupation is low, the security is high, and the present invention is more suitable for the most real time application scene of the video encryption.
Owner:湖北鸿云科技股份有限公司
Method and apparatus for a security system for wireless networks
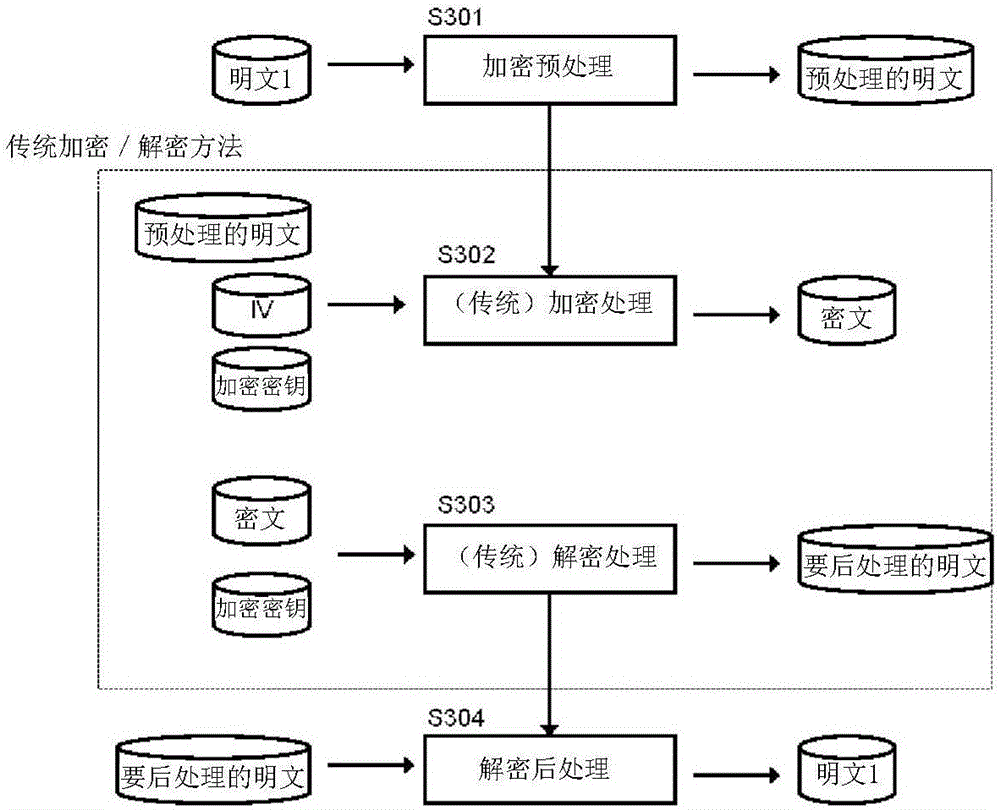
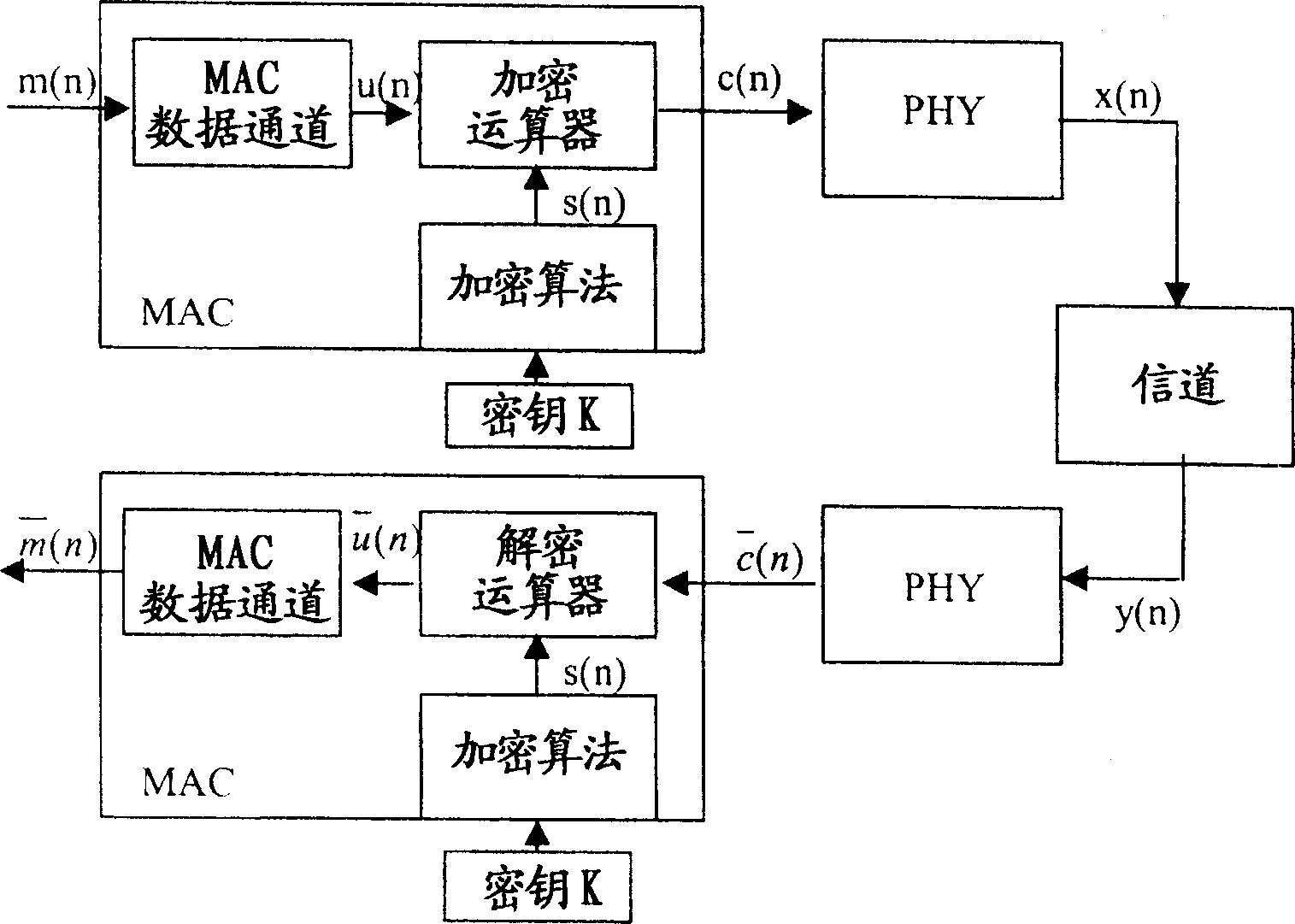
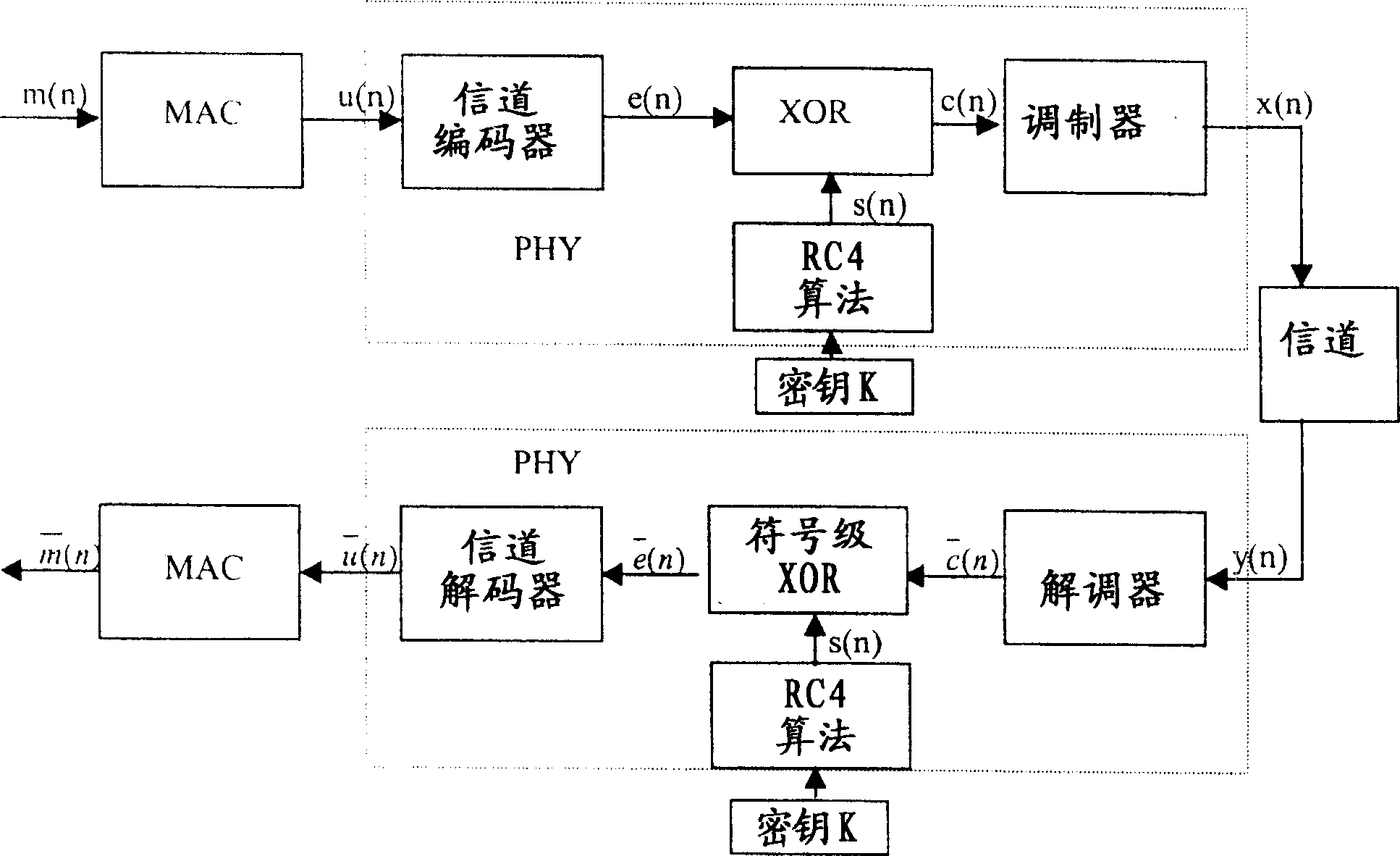
InactiveUS20060126841A1Avoid attackImprove communication performanceData stream serial/continuous modificationSecret communicationViterbi decoderCommunications system
A Method and Apparatus for a Security System for Wireless Networks is described. The technique involves encryption and decryption at the Physical layer. It also develops a criterion for choosing the encryption / decryption methodology for a particular embodiment for communication systems typically using a Viterbi Decoder and describes how the difficult-to-invert property of the Viterbi Decoder can be utilized to provide security against known-plaintext attacks. Some candidate encryption / decryption methodologies satisfying the developed criterion are also discussed.
Owner:TATA CONSULTANCY SERVICES LTD
Streaming media video encryption method and device based on H.264
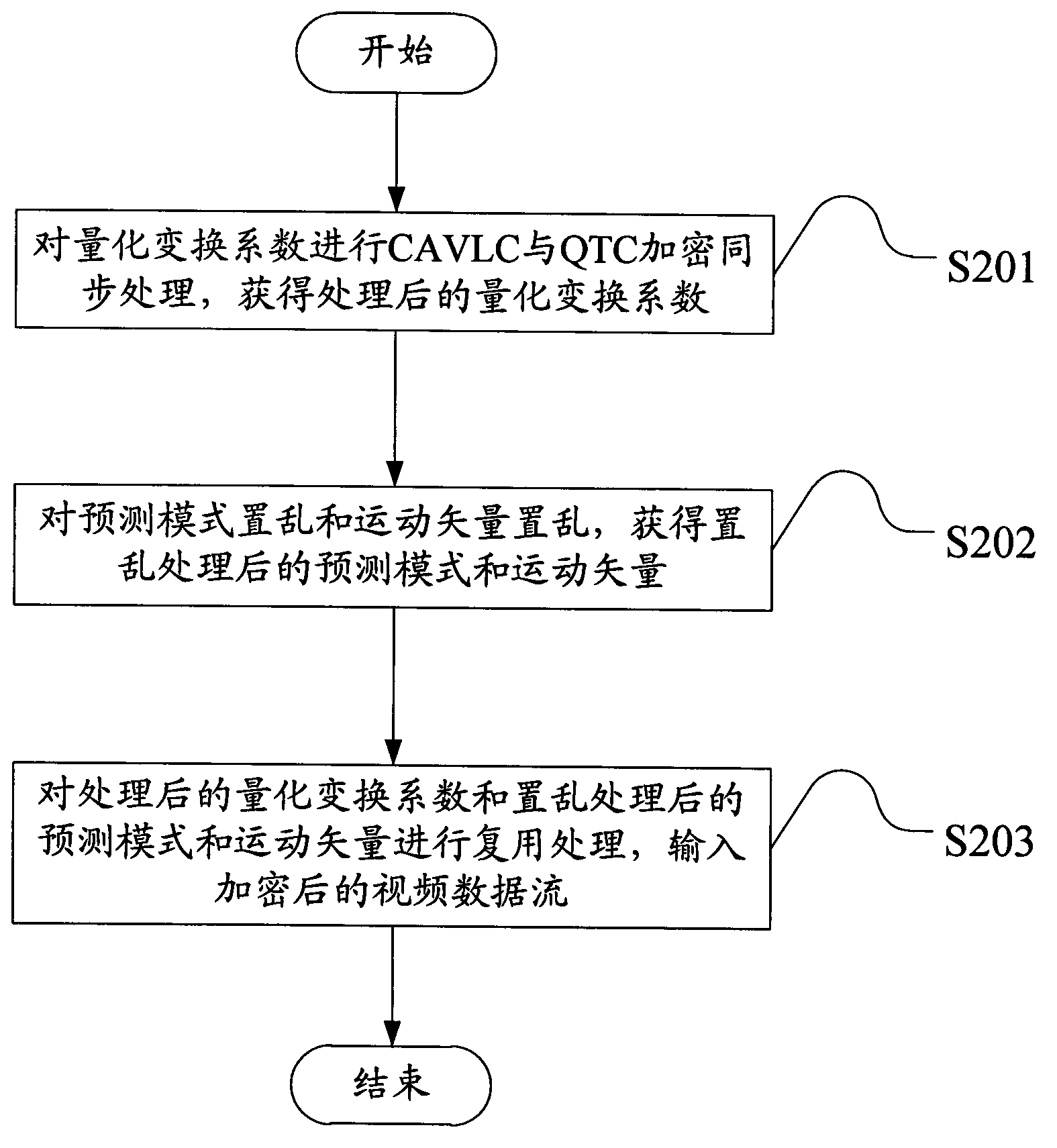
InactiveCN103856786APrevent guessingPrevent known plaintext attacksDigital video signal modificationSelective content distributionMultiplexingComputer hardware
The embodiment of the invention discloses a streaming media video encryption method and device based on H.264. The encryption method includes the steps that context-based adaptive variable length coding and QTC encryption are synchronously performed on the QTC, and the processed QTC is obtained; the prediction mode and motion vectors are scrambled, and the scrambled prediction mode and the scrambled motion vectors are obtained; multiplexing is performed on the processed QTC, the scrambled prediction mode and the scrambled motion vectors, and encrypted video data streams are input. Through the encryption method and device, the intra-frame prediction mode scrambling method in the prior art is improved, and Friedman key guessing and known plaintext attach can be prevented; safety of motion content is enhanced; the method is easy to achieve, real-time application complexity of data encryption in real-time application can be reduced, and the code error robustness of transmission of encrypted code streams is improved.
Owner:RES INST OF SUN YAT SEN UNIV & SHENZHEN
Image encryption method based on projection synchronization of hyperchaotic system
ActiveCN106997606AHas cryptographic propertiesIncreased complexityImage codingSecuring communication by chaotic signalsChosen-plaintext attackChaotic systems
The invention discloses an image encryption method based on the projection synchronization of a hyperchaotic system. The method comprises the steps of plaintext image quantifying and ciphertext image quantifying. The first step comprises generating of a hyperchaotic sequence of a hyperchaotic driving system, image row scrambling, image column scrambling, image diffusing, circulation image row scrambling, image column scrambling, multiple rounds of image diffusing, and a ciphertext image is acquired. The second step comprises ciphertext image quantifying, generating of a hyperchaotic sequence of a hyperchaotic response system, time acquiring, column scrambling index and line scrambling index valuing, image inverse diffusing, image inverse column scrambling, image inverse row scrambling, circulation image inverse diffusing, image inverse column scrambling, multiple rounds of image inverse row scrambling, and a decrypted image is acquired. According to the invention, a feedback mechanism with the current image is introduced; the row (column) scrambling address code and the key matrix are dynamically changed in each round of encryption; experiments show that the method has the advantages of good encryption effect, high security and large key space, can resist selected plaintext attacks, known plaintext attacks and various statistical attacks.
Owner:SHAANXI NORMAL UNIV
Homomorphic encryption algorithm based on modulo-like operation
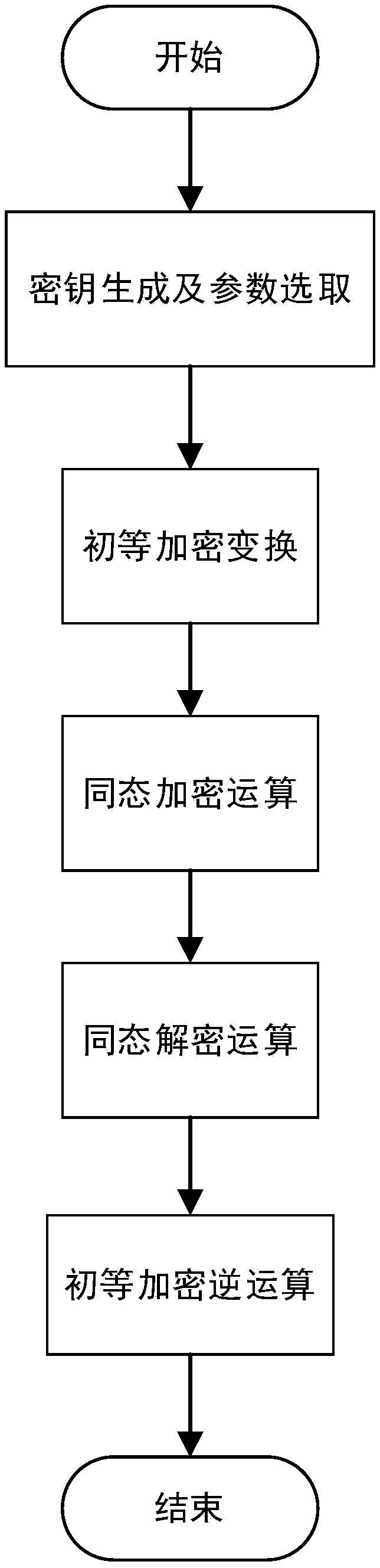
ActiveCN108111295AImprove execution efficiencyPrevent leakageCommunication with homomorphic encryptionKey generationKnown-plaintext attack
The invention discloses a homomorphic encryption algorithm based on modulo-like oepration. The homomorphic encryption algorithm comprises following steps: step 1, system initialization: key generationand parameter selection; step 2, encryption operation: primary encryption transform and homomorphic encryption operation; and step 3, decryption operation: homomorphic decryption operation and primary encryption inverse transform. According to the homomorphic encryption algorithm, known plaintext attacks can be resisted, and the leakage of plaintext information and an algorithm structure can be effectively avoided; and a conventional random function is replaced by an interference function so that the consumption of computing resources caused by generation of random numbers is avoided, and theexecution efficiency of the algorithm on a cloud computing platform is effectively improved.
Owner:HOHAI UNIV
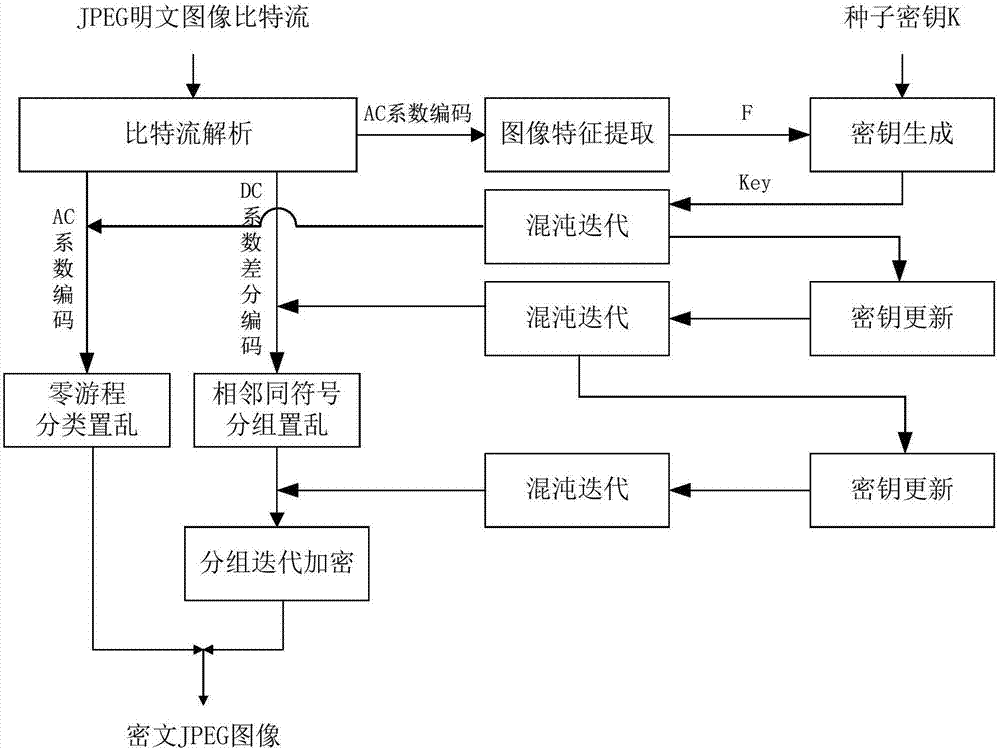
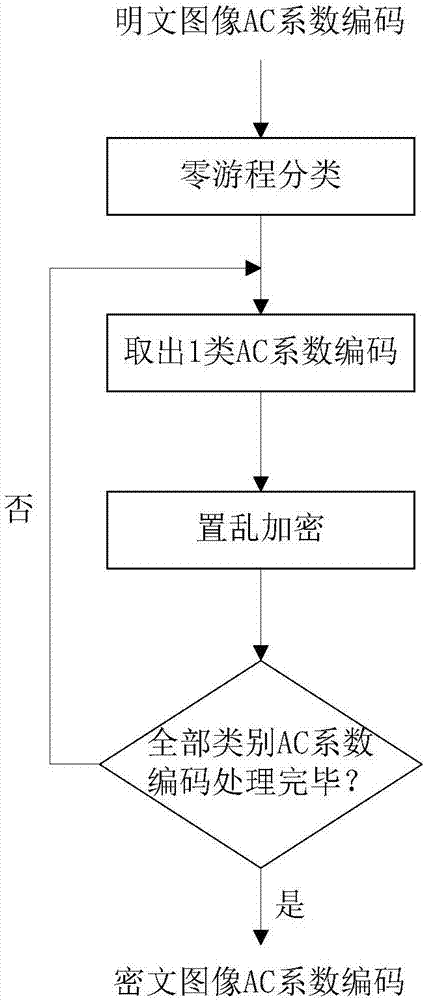
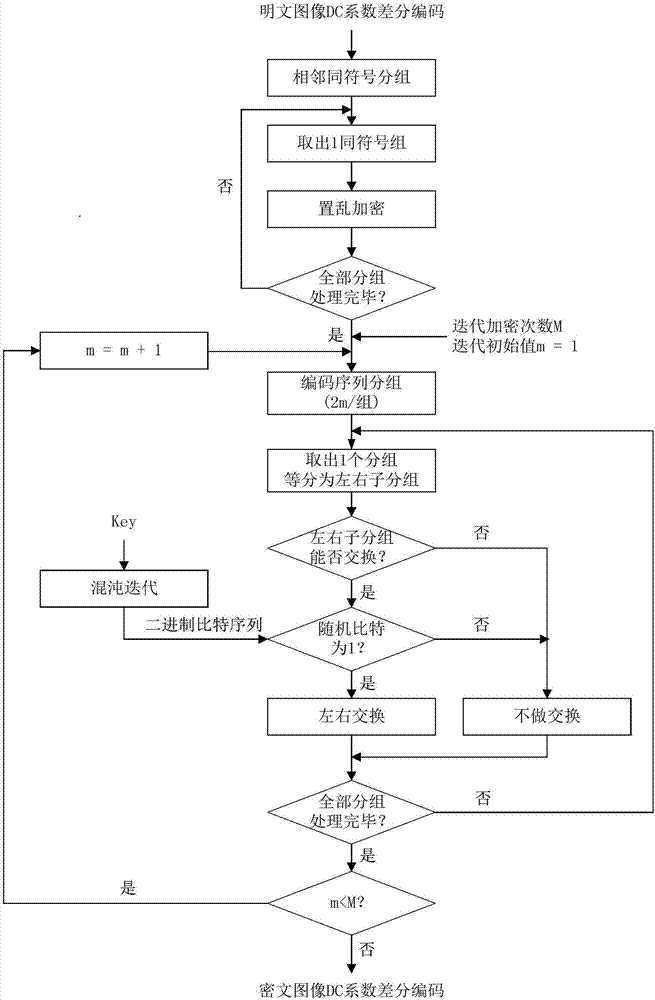
JPEG image encryption method compatible in format and invariant in size
ActiveCN107578452ABig spaceResist attackImage codingImage data processing detailsComputer hardwareAc coefficient
The present invention provides a JPEG image encryption method compatible in format and invariant in size, and belongs to the technical field of multimedia information safety. The method of the presentinvention includes three encryption steps: 1) classifying and scrambling AC coefficient-encoded zero runs; 2) grouping and scrambling DC coefficient-differentially encoded adjacent same symbols; 3) grouping and iteratively encrypting DC coefficient differential codes. According to the invention, the method can be used for protecting the safety and the privacy of military images, commercial images, medical images or personal images when the images are transmitted through a public channel or stored in the public cloud. The method aims to improve the ubiquitous defect that the size of a ciphertext image increases and the format compatibility of the image is not ideal based on existing JPEG image encryption methods. The above method can resist the known-plaintext attack, and substantially maintain the size of the ciphertext image to be unchanged. Meanwhile, the format compatibility is better and the encryption strength is adjustable.
Owner:SOUTH CHINA UNIV OF TECH
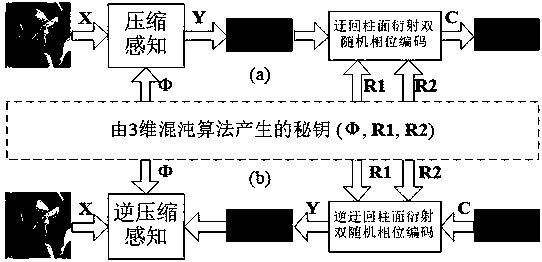
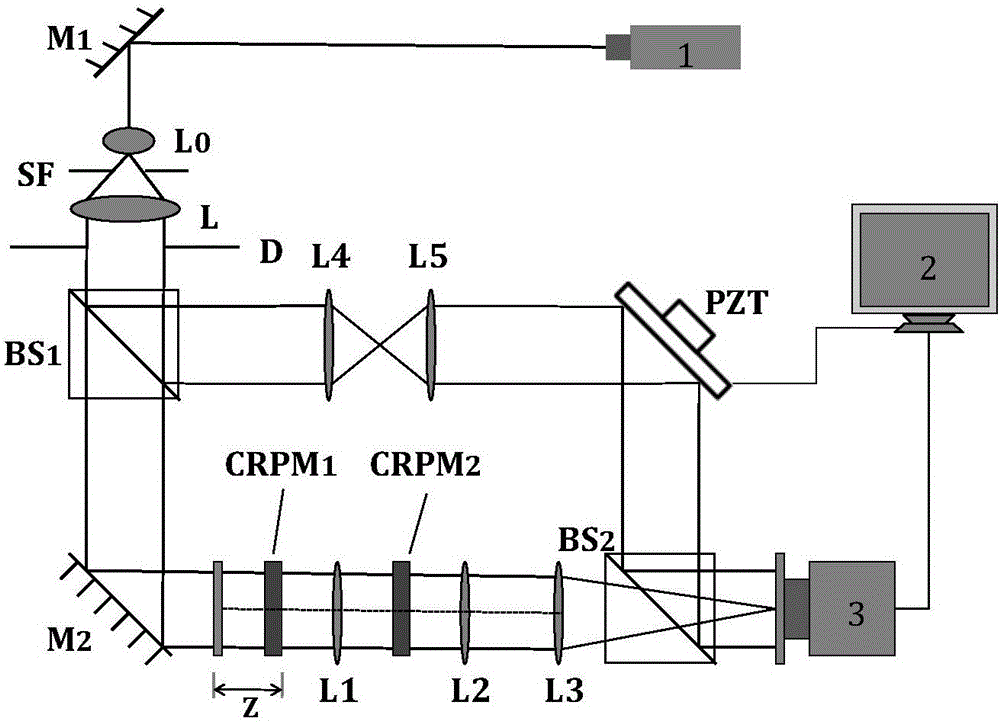
Optical image encryption method based on circuitous cylindrical diffraction and compressive sensing
ActiveCN108596989AStrong resistance to attackManyImage codingDigital data protectionComputer hardwareCiphertext-only attack
The invention provides an optical image encryption method based on circuitous cylindrical diffraction and compressive sensing. According to the method, a simple improvement on a classical first-compressive sensing and second-double random phase encoding encryption technique is performed, a cylindrical phase plate is used to replace a plane phase plate, and two reflection relay cylindrical diffraction processes are used to replace two continuous relay plane diffraction processes. By using the asymmetry between the two reflection relay cylindrical diffraction processes and a reverse process, thesecurity of the encryption method can be greatly improved, particularly, known plaintext attacks, ciphertext-only attacks and phase recovery attacks can be effectively resisted, keys are large in number and strong in sensitivity, a large key space can be realized, and good security can be ensured.
Owner:SICHUAN UNIV
Optical image encryption method based on Gyrator transform and coupled chaos
InactiveCN106651736AEnsure safetyEasy to manageImage data processing detailsInformation processingChosen-plaintext attack
The invention relates to the technical field of image information security and optical information processing, and aims to effectively resist known plaintext attack and chosen plaintext attack and make key management and transmission more convenient. The technical scheme adopted in the invention is as follows: an optical image encryption method based on Gyrator transform and coupled chaos comprises the following steps: (1) construction of a coupled Logistic chaos: two one-dimensional Logistic chaos maps are associated together by a coupling parameter; (2) generation of a chaotic key: two random phase masks serving as a master key are generated by coupled Logistic chaos systems controlled by different chaotic parameters; and (3) image encryption and decryption based on Gyrator transform: first, a to-be-encrypted image is modulated by the first chaos random phase mask in the process of encryption, and second, the image is modulated by the complex conjugate of the first chaos random phase mask. The method is mainly applied to an image information security occasion.
Owner:TIANJIN UNIV
Optical transmission device and reception device for yuen encryption, optical transmission method and reception method for yuen encryption, and encrypted communication system
ActiveUS20120328100A1Low costLow-cost implementationSecret communicationCryptographic attack countermeasuresInformation-theoretic securityDigitization
A configuration method of an optical signal, an encryption device, and an encryption system makes it possible for a legitimate communicating party to ensure information-theoretic security against a known plain text attack and to communicate long-distance. By adding a transmission information data sequence randomization device to the Yuen encrypted communications device according to the present information, which divides transmission information data into blocks, appends sequence numbers thereto, randomly switches the sequence of the blocks with a digitized signal of output of an electrical noise generator, and inputs same into a transmission data generator of a conventional Yuen encrypted optical transmitter, the relation between a known transmission information data sequence (plain text) and an optical signal which is outputted from the transmitter is randomized, allowing forcibly making even a circumstance wherein a known-plain text attack would be possible into a cipher-text-only attack, realizing information-theoretic security against a known-plain text attack.
Owner:TAMAGAWA ACADEMY & UNIV
Image encryption method based on filling curve and adjacent pixel bit scrambling
ActiveCN112714235ABreak high correlationImprove securityEncryption apparatus with shift registers/memoriesSecuring communication by chaotic signalsAlgorithmKnown-plaintext attack
The invention provides an image encryption method based on a filling curve and adjacent pixel bit scrambling. The method comprises the following steps: converting a gray level image into a two-dimensional image matrix; calculating a hash value of the image matrix, and calculating an initial value of a four-dimensional hyper-chaotic system; scrambling the image matrix by using the V-shaped filling curve, and transposing the image matrix for second scrambling; iterating the hyper-chaotic system according to the obtained initial value to respectively obtain four chaotic sequences; taking one chaotic sequence as a starting point and one chaotic sequence as a step length, and performing adjacent pixel bit scrambling by utilizing binary bits of adjacent pixels of a Josephf traversal image matrix; and performing forward diffusion and reverse diffusion on the image by using a sequence matrix obtained by the chaotic sequence to obtain a ciphertext image. According to the invention, the high correlation between the pixels is broken through dual replacement of the bit level and the pixel level, selection / known plaintext attacks and common image related statistical attacks are overcome, and the method has high key sensitivity and differential attack resistance.
Owner:ZHENGZHOU UNIVERSITY OF LIGHT INDUSTRY
Packet physical layer encryption method based on matrix transformation
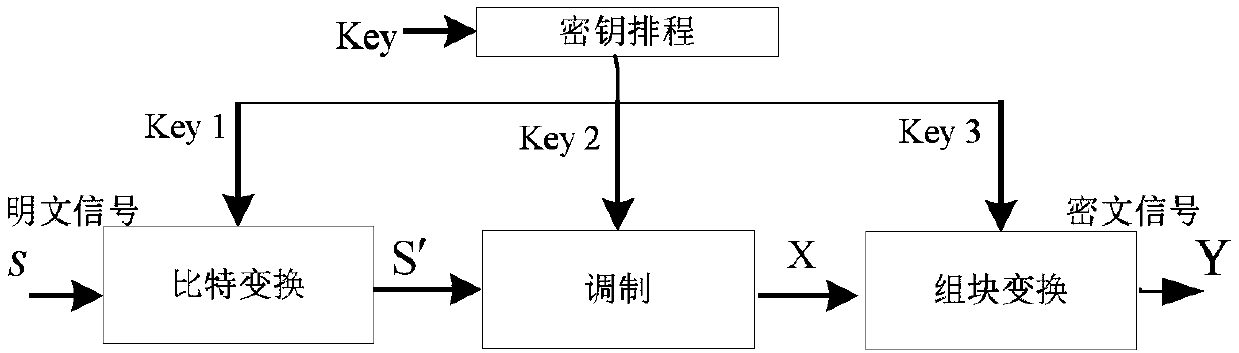
ActiveCN108833390AIncrease confusionImprove protectionKey distribution for secure communicationMulti-frequency code systemsComputer hardwarePhysical layer
The invention belongs to the field of communication signal encryption technology, and specifically designs a packet physical layer encryption method based on matrix transformation. The method comprises the following steps: (1) transforming plaintext signals S into an information sequence S' through bits; (2) modulating the information sequence S' to obtain modulation information X; and (3) performing block transformation on the modulation information X according to key information to output ciphertext signals Y. The invention also provides a packet physical layer encryption method of a block chaining mode, which adds a logical operation vector based on the matrix physical layer encryption method based on matrix transformation, so that each ciphertext block depends on all plaintext blocks in front. The method has larger ciphertext space and key space, increases the difficulty of deciphering, can resist known plaintext attacks and selective plaintext attacks, can protect training symbols, and has no loss on bit error rate performance but high constellation map chaos, and well protects constellation information.
Owner:NAT UNIV OF DEFENSE TECH
Image encryption method based on integer wavelet transform and compressed sensing
ActiveCN113115053AImprove securityStrong randomnessSecuring communication by chaotic signalsDigital video signal modificationPattern recognitionChosen-plaintext attack
The invention provides an image encryption method based on integer wavelet transform and compressed sensing, and solves the problem of insufficient encryption security of a mode of directly embedding a carrier after compressed sensing in a current spatial domain image encryption method based on compressed sensing. The method comprises the steps: preprocessing a plaintext image, and associating a random sequence generated by a chaotic system with plaintext image information, so that known plaintext attacks and selected plaintext attacks can be powerfully resisted; carrying out sparse processing on the preprocessed plaintext image, and sequentially carrying out scrambling operation; generating a measurement matrix, carrying out compressed sensing on a plaintext image after scrambling operation by using the measurement matrix, executing diffusion operation before embedding a carrier image to further improve the security of image encryption, finally obtaining a frequency coefficient by using integer wavelet transform, carrying out embedding operation on the carrier image, and then executing inverse integer wavelet transform. The data loss caused by frequency domain transformation is reduced, and the encryption security of the image information is improved.
Owner:GUANGDONG OCEAN UNIVERSITY
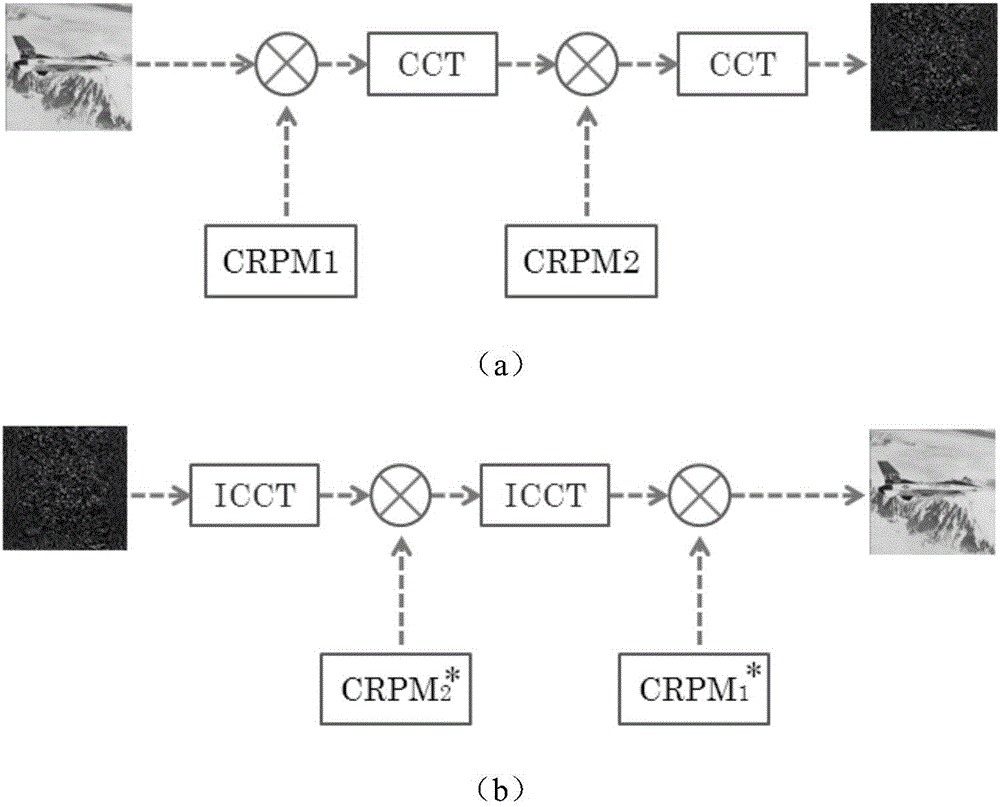
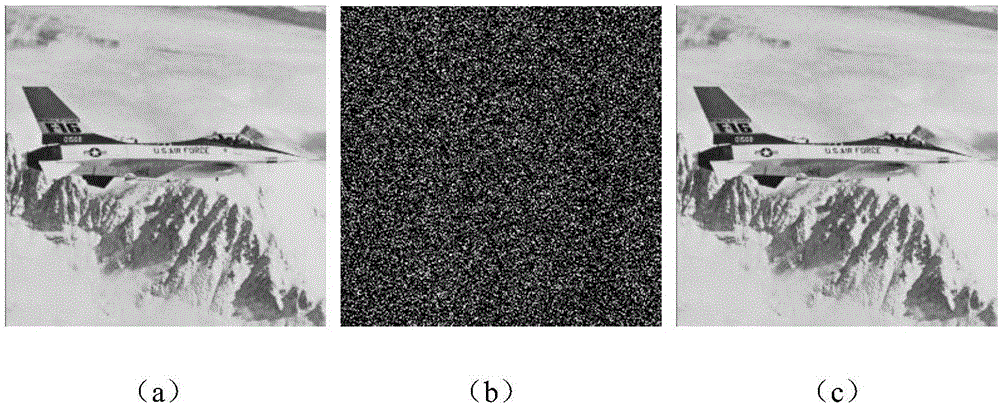
Regularized cosine transformation chaotic double-random phase encoding optical image encryption method
InactiveCN106503568ASmall amount of calculationEnsure safetyImage codingDigital data protectionInformation processingChosen-plaintext attack
The invention relates to the technical field of image information safety and light information processing and aims at effectively resisting known plaintext attack and selected plaintext attack, making key management and transmission convenient, further ensuring the safety and obtaining good violent attack, statistics attack, noise attack and shear attack resisting capability. According to the adopted technical scheme, a regularized cosine transformation chaotic double-random phase encoding optical image encryption method comprises the following steps that 1, a two-dimensional regularized cosine transformation CCT system is established; 2, a chaotic secret key is generated, wherein two random phase masks playing a main secret key effect are respectively generated by a one-dimensional sine chaotic system controlled by different chaotic parameters, and an initial value and control parameters of the sine chaotic system serve as main secret keys; 3, image encryption and decryption process is performed, wherein decrypted images are obtained. The method is mainly applied to image information safety and light information processing occasions.
Owner:TIANJIN UNIV
Region-of-interest medical image chaotic encryption method based on information entropy update key
ActiveCN110197077AImplement frequency domain encryptionAchieve protectionImage enhancementImage analysisChosen-plaintext attackChaotic systems
The invention discloses a region-of-interest medical image chaotic encryption method based on an information entropy update key, and relates to the technical field of image information security, whichcan overcome the security defects that an existing medical image encryption technology is low in encryption efficiency and cannot resist attacks of known plaintexts and selected plaintexts. Accordingto the information entropy updating key-based region-of-interest medical image chaotic encryption and decryption method provided by the invention, the region-of-interest of the medical image is processed by utilizing wavelet transform, so that the frequency domain encryption of the image is realized. Meanwhile, the hyperchaotic system is used for scrambling and diffusing the region of interest ofthe medical image, so that the protection of the image in a spatial domain is realized. Besides, according to the information entropy key updating method designed by the invention, the key is not only related to the parameters of the chaotic system, but also related to the plaintext image, so that known plaintext attacks or selected plaintext attacks can be resisted.
Owner:CHANGCHUN UNIV OF SCI & TECH
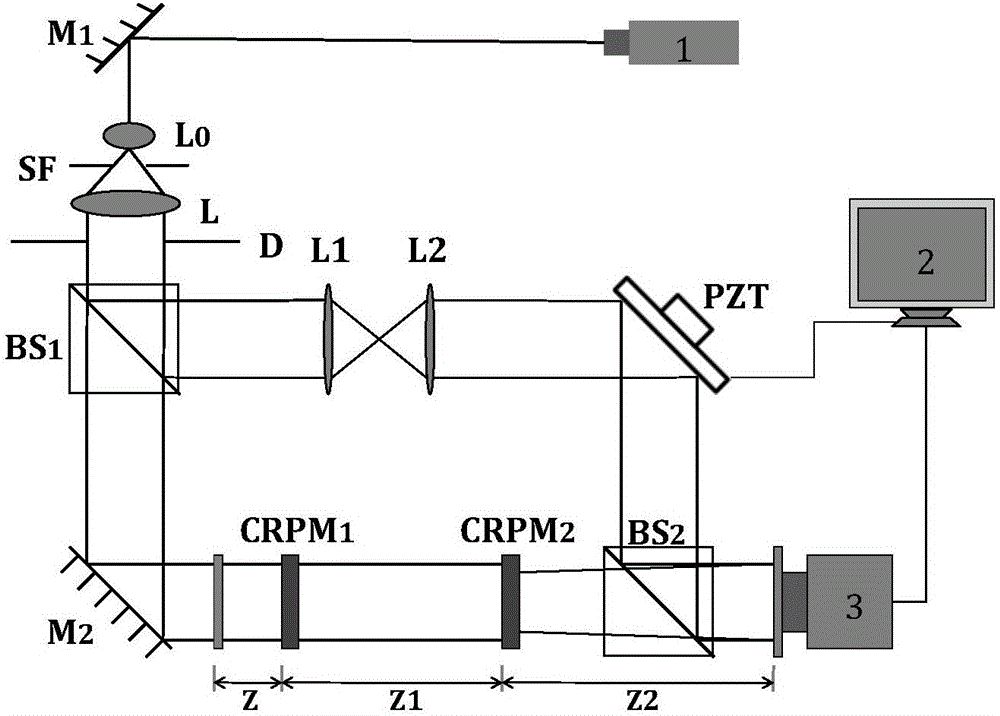
Three-step generalized phase-shifting and cascade fractional Fourier transform optical image encryption method
InactiveCN106529311AEnsure safetyAct as master keyKey distribution for secure communicationDigital data protectionInformation processingChosen-plaintext attack
The invention relates to the technical field of image information security and optical information processing, and provides an optical image encryption method capable of effectively resisting known plaintext attacks and selecting plaintext attacks. The problems of key management and transmission inconvenience are solved. A three-step generalized phase-shifting and cascade fractional Fourier transform optical image encryption method comprises the following concrete steps of (1) a key generation part: two random phase masks achieving the effect of main keys are respectively generated by Duffing chaotic systems controlled by different chaotic parameters; (2) an image encryption part: an image to be encrypted is subjected to Fresnel transform under the irradiation of incident light, and is then modulated by the first chaotic random phase mask; and the modulated image is subjected to fractional Fourier transform with the order being a1 and is then modulated by the second chaotic random phase mask; and (3) an image decryption part: the decrypted image is obtained. The optical image encryption method is mainly applied to image information security and optical information processing occasions.
Owner:TIANJIN UNIV
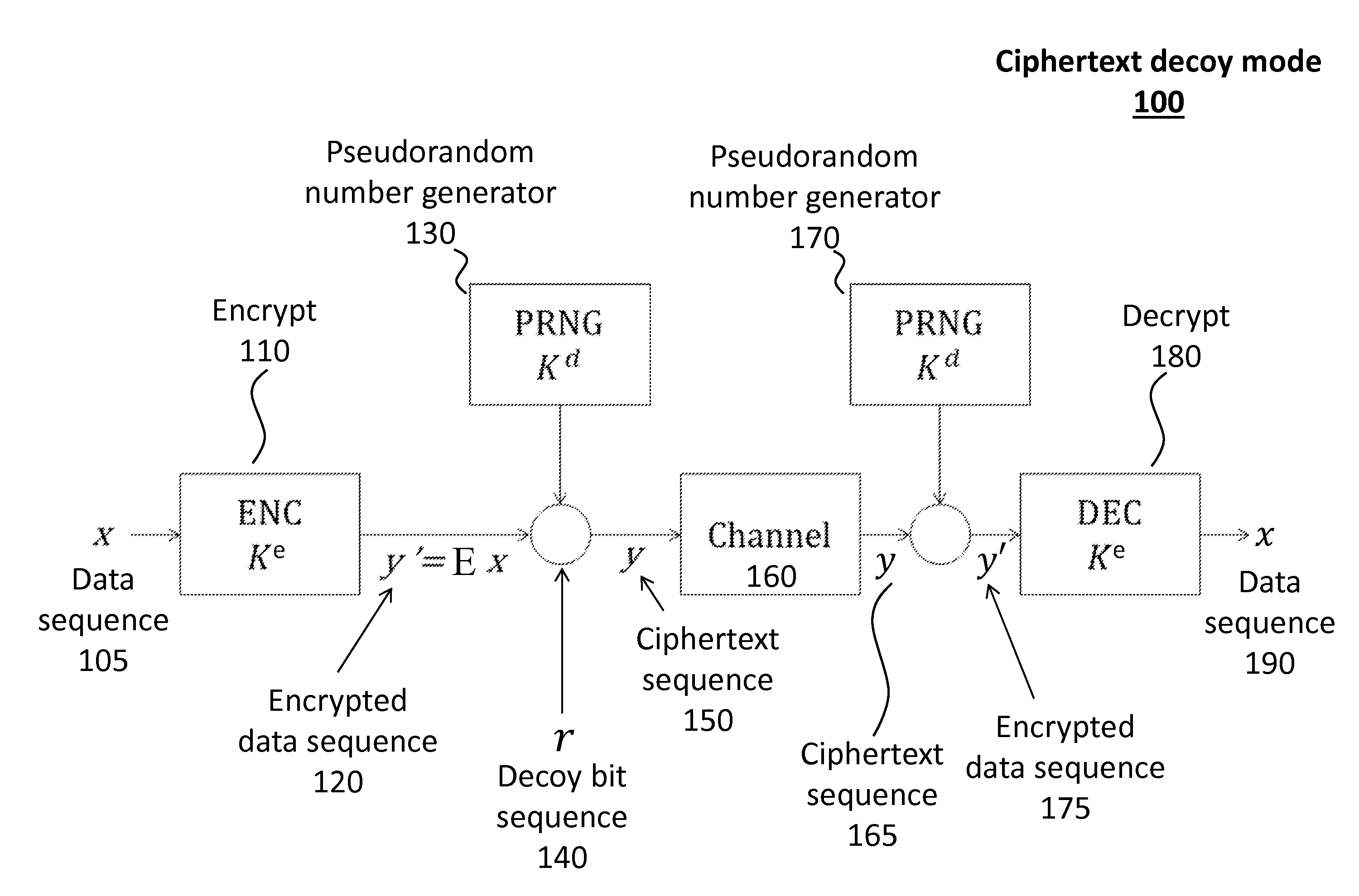
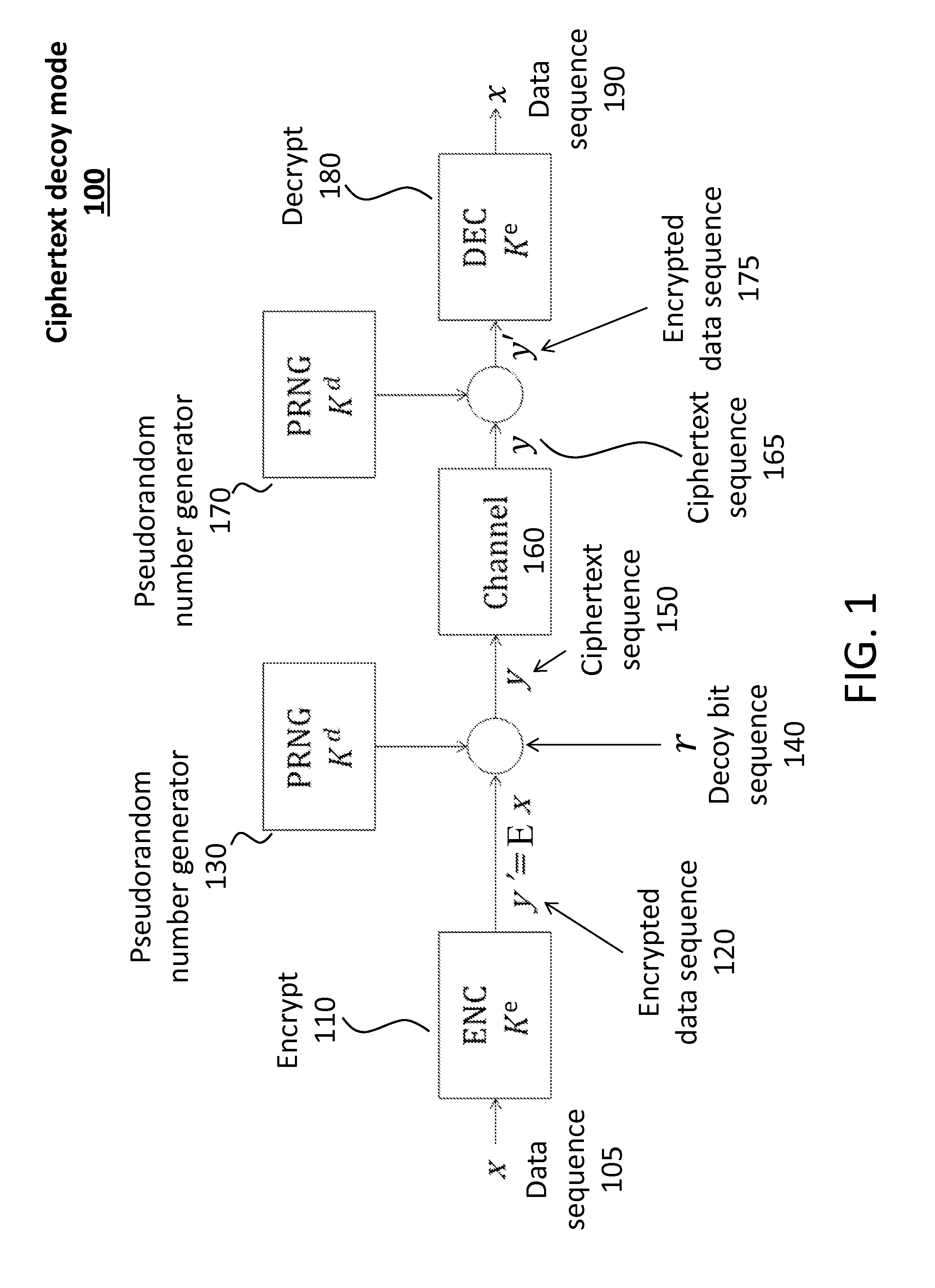
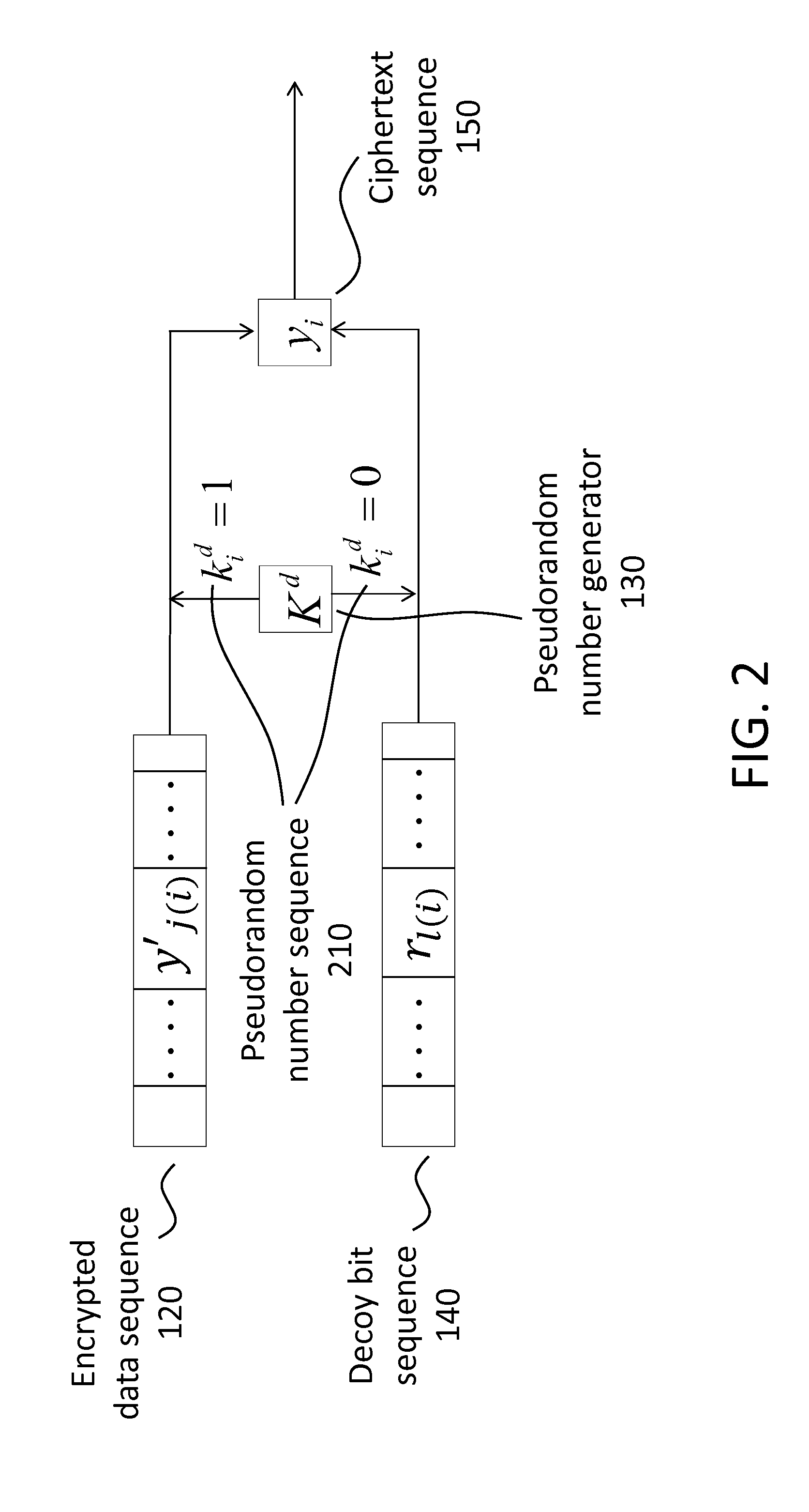
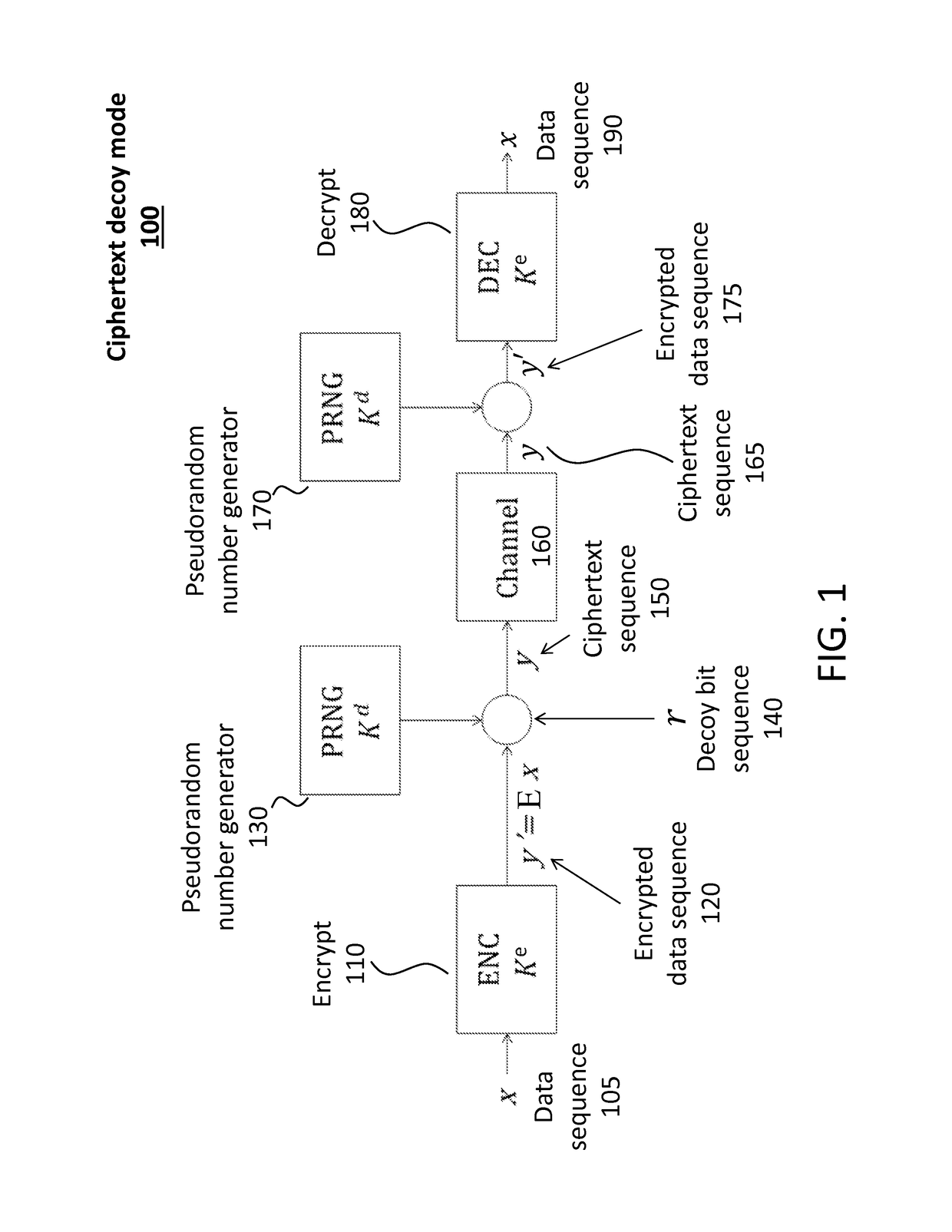
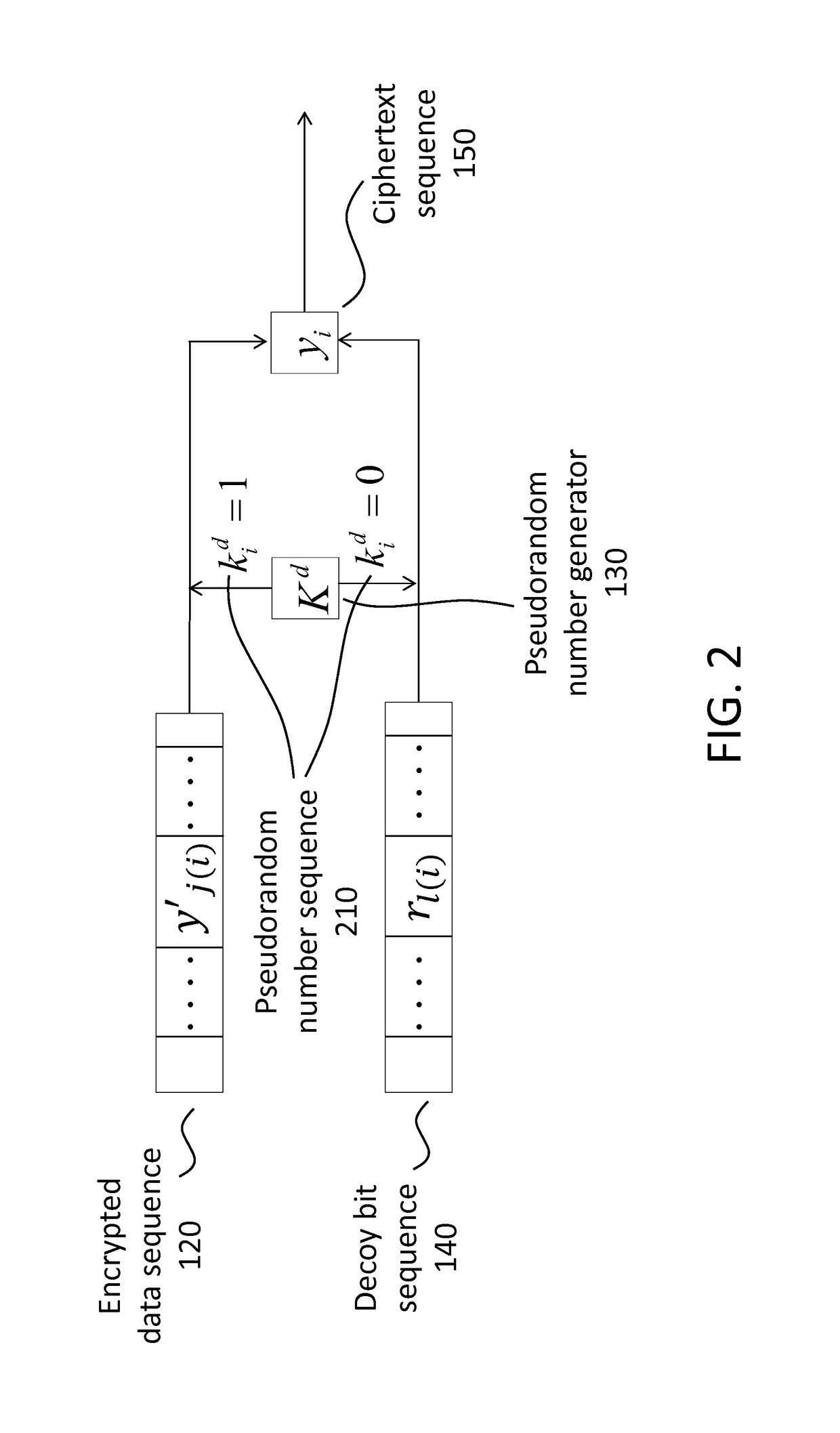
Decoy bits method for direct encryption and key generation
InactiveUS20160285621A1Overcome limitationsData stream serial/continuous modificationCryptographic attack countermeasuresDecoyCombined use
A new cryptographic technique is disclosed, called decoy bits method, which can be used to obtain near ideal information theoretic security in both quantum and classical key generation and data encryption, not only for raw security but also under known-plaintext attacks. The technique relates to a method of data encryption by insertion of random bits, called decoy bits, into a data sequence whereby the decoy bits are discarded upon decryption. The positions of the decoy bits are determined by a decoy position determining mechanism. This method can be used in conjunction with other standards of encryption to increase security.
Owner:QUANTUM ADVANCE TECH
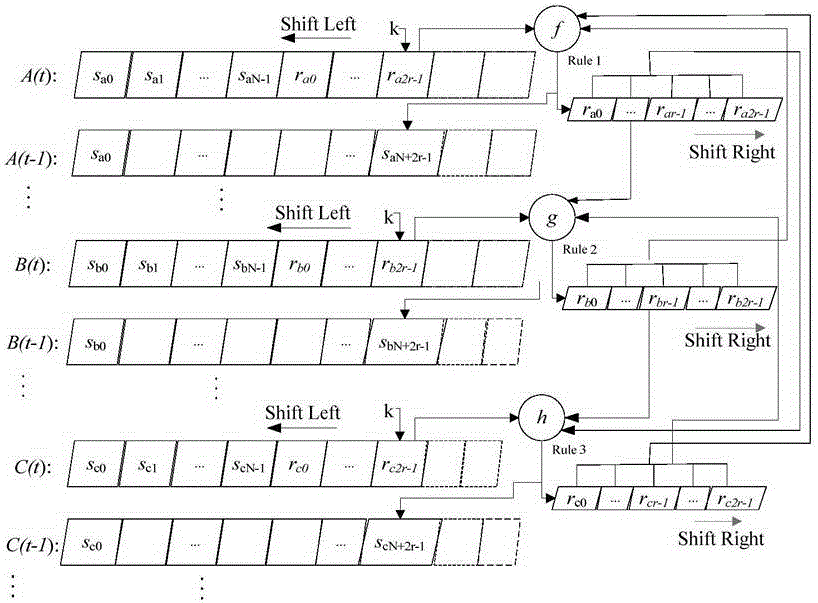
Encryption and decryption method based on coupling and self-triggering cellular automata
InactiveCN105099654ASimple local actionIntrinsic parallelismComputing modelsSecuring communicationCellular automationCoupling
The invention discloses an encryption and decryption method based on coupling and self-triggering cellular automata. The encryption and decryption method comprises: according to the properties of the coupling and self-triggering cellular automata, adopting n interactional cellular automata as an entirety, and constructing an encryption and decryption system of coupling and self-triggering cellular automata. A simulation experiment result indicates that the algorithm greatly improves the key space and effectively prevents brute force attack; and meanwhile, when a random number is introduced in an encryption process to prevent an attacker from obtaining an exclusive plaintext and ciphertext pair, so that known plaintext attach and selective ciphertext attach are effectively prevented.
Owner:NANJING UNIV OF SCI & TECH
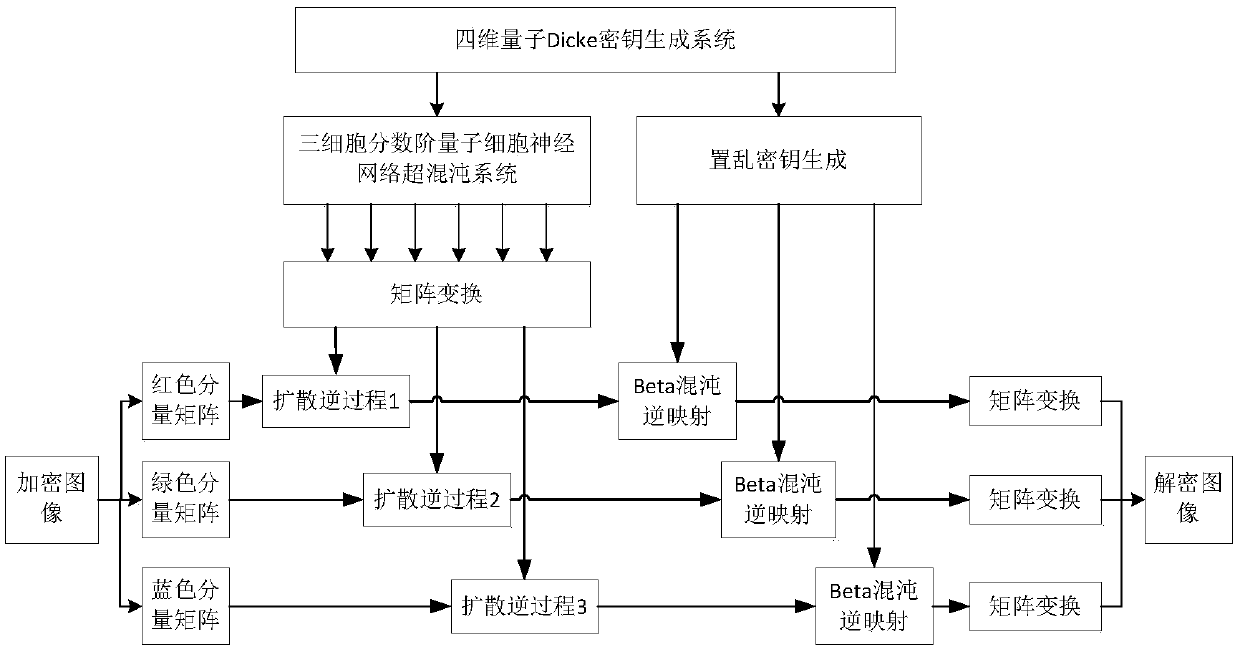
Image encryption and decryption method based on four-dimensional quantum Dicke mapping
ActiveCN109003314AShorten the lengthSecurity SensitivityImage enhancementImage analysisChosen-plaintext attackNeural network system
The invention provides an image encryption and decryption method based on four-dimensional quantum Dicke mapping and relates to the field of image encryption technology. The invention aims to solve the shortage of key space and insufficient randomness, as well as inability to effectively resist known plaintext attacks and security flaws in selective plaintext attacks in the existing image encryption methods. The invention uses a quantum Dicke chaotic system as a key generator to generate a plurality of sets of scrambling keys and diffusion keys, which are randomly selected by a user. The invention ensures the key space and the key sensitivity, shortens the length of the key and reduces the cost of storing and transmitting the key by the user. The invention applies the hyperchaotic system of the fractional-order quantum cellular neural network to the image diffusion stage, The hyperchaotic characteristic of the fractional-order quantum cellular neural network system guarantees the randomness and ergodicity of image diffusion, and the encryption method of the invention can effectively resist the known plaintext attack and the selected plaintext attack because the diffusion key streamis related to plaintext.
Owner:CHANGCHUN UNIV OF SCI & TECH
Common key block encryption device, common key block encryption method, and program
ActiveUS8577032B2Many timesFulfil requirementsPublic key for secure communicationMechanically effected encryptionComputer hardwareVariable length
A common key block encryption device includes a first hash unit applying locked key permutation to a variable-length s-bit plaintext, and outputting a fixed-length n-bit first block and a second (s-n)-bit block; a first encryption processing unit outputting a third block encrypted by element of n-bit block tweakable block cipher using tweak, inputting the first block; a second encryption processing unit generating a random number (s-n)-bit block with a result of group computation of the third block and the first block as input by using an arbitrary cipher having theoretical security at least against a known-plaintext attack; and a second hash unit applying the locked key permutation to the result of the group computation of the random number block and the second block, and to the third block to output a fifth n-bit block and a sixth (s-n)-bit block. The fifth and sixth blocks are concatenated into an s-bit encryption.
Owner:NEC CORP
Physical layer secure transmission method based on an asymmetric key
ActiveCN109768990ABig spaceLarge key spaceKey distribution for secure communicationPublic key for secure communicationCommunications securityNon symmetric
The invention belongs to the technical field of communication security, and particularly relates to a physical layer secure transmission method and system based on an asymmetric key. The method comprises the following steps that a sender maps and converts binary information Sb into a complex vector signal X, the complex vector signal X is encrypted through a security matrix U, the complex vector signal X is converted into a complex vector signal Y, Y = UX, and the complex vector signal Y is sequentially processed through an IFFT module, a cyclic prefix adding module and a DAC module and then sent out through a radio frequency module; a receiver receives a signal through the radio frequency module, the signal is processed through the ADC module, the cyclic prefix removal module and the FFTconversion module to obtain a complex vector signal Y ', the complex vector signal Y' is decrypted through the security matrix to obtain a complex vector signal X ', and binary information is furtherrecovered through demapping. The physical layer secure transmission system comprises a sending end, a transmission channel and a receiving end. According to the invention, ciphertext attacks, known plaintext attacks and selective plaintext attacks can be resisted, and a stronger security effect is achieved.
Owner:NAT UNIV OF DEFENSE TECH
Multi-diffusion image encryption and decryption method based on quantum cellular neural network chaos
ActiveCN108932691AHigh key dimensionLarge key spaceBiological neural network modelsBiomolecular computersKnown-plaintext attackControl table
The invention relates to a multi-diffusion image encryption and decryption method based on cellular neural network chaos, which relates to the technical field of image encryption and solves the problems that the existing image encryption method is insufficient in key space and insufficient in randomness and solves the safety defects that known plaintext attacks and selected plaintext attacks can not be effectively resisted. A chaos control table and a quantum exchange table are generated by a quantum cellular neural network, intra-block and inter-block scrambling for plaintext images is carried out, and the correlation between image pixels is removed through multiple chaotic diffusion steps with positive and negative diffusion and dynamic diffusion included. A quantum cellular neural network hyperchaotic system has a higher key dimension, larger key space, stronger sensitivity and stronger ability to resist various safety attacks, and as a quantum chaotic system is a novel nano-scale device which mutually transmits information under Coulomb interaction between quantum dots and a quantum cellular automata, the quantum cellular neural network hyperchaotic system has the advantages ofultra-high integration, low power consumption, lead-free integration and the like.
Owner:CHANGCHUN UNIV OF SCI & TECH
Decoy bits method for direct encryption and key generation
InactiveUS9608802B2Data stream serial/continuous modificationUnauthorized memory use protectionDecoyXML Encryption
A new cryptographic technique is disclosed, called decoy bits method, which can be used to obtain near ideal information theoretic security in both quantum and classical key generation and data encryption, not only for raw security but also under known-plaintext attacks. The technique relates to a method of data encryption by insertion of random bits, called decoy bits, into a data sequence whereby the decoy bits are discarded upon decryption. The positions of the decoy bits are determined by a decoy position determining mechanism. This method can be used in conjunction with other standards of encryption to increase security.
Owner:QUANTUM ADVANCE TECH
Optical image encryption method based on four-step generalized phase shifting and multi-step Fresnel transform
InactiveCN106548042AEnsure safetySolve management problemsDigital data protectionImage data processing detailsInformation processingChosen-plaintext attack
The invention relates to the technical field of image information security and optical information processing, can effectively resist known-plaintext attack and chosen-plaintext attack, and solves the problem of being inconvenient in key management and transmission on an aspect of key generation so as to further guarantee security. The optical image encryption method based on four-step generalized phase shifting and multi-step Fresnel transform comprises the following steps of: 1) a key generation part: two random phase masks which perform a main key function are independently generated by Tinkerbell chaotic systems controlled by different chaotic parameters; 2) an image encryption part: four holograms are used for obtaining an encrypted image; and 3) an image decryption part: after an input image is subjected to Fresnel inverse transform of which the distance is Z2, the input image is subjected to complex conjugation modulation by a second chaotic random phase mask and is subjected to the complex conjugation modulation by a first chaotic random phase mask, and then, the obtained input image is subjected to the Fresnel inverse transform of which the distance is Z to obtain a decrypted image. The method is mainly applied to the field of image information security.
Owner:TIANJIN UNIV
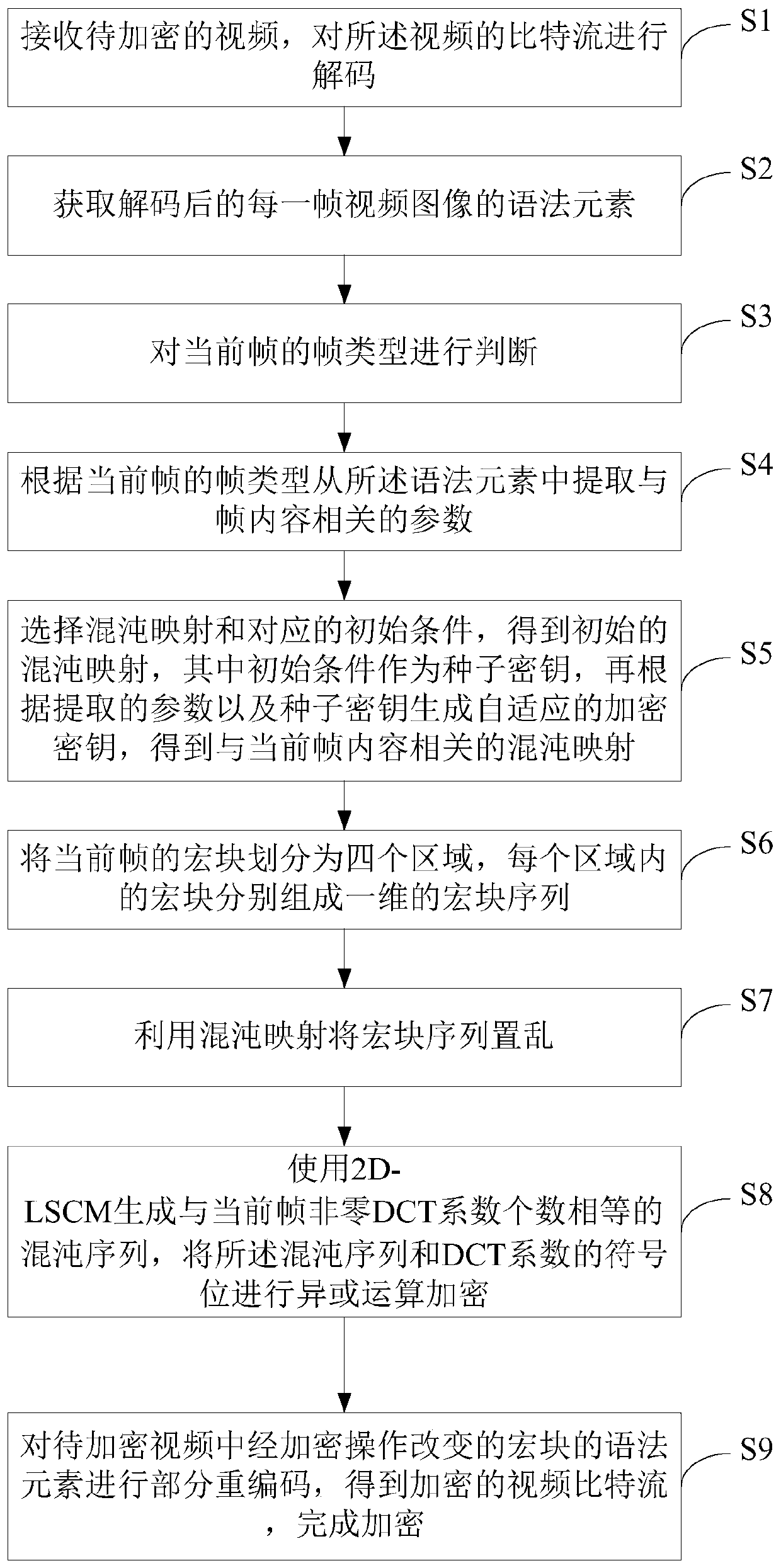
Video encryption method for resisting contour attacks
ActiveCN110677694AEffective against contour attacksResistant to Contour AttacksDigital video signal modificationSelective content distributionVideo bitstreamNonzero coefficients
The invention discloses a video encryption method for resisting contour attacks, which comprises the following steps of receiving a video to be encrypted, and decoding a bit stream of the video; dividing the macro block of the current frame into four regions, wherein the macro blocks in each region respectively form a one-dimensional macro block sequence; scrambling the macro block sequence by using chaotic mapping; using a 2D-LSCM for generating chaotic sequences with the number equal to that of non-zero DCT coefficients of the current frame, and conducting exclusive-OR operation encryption on the chaotic sequences and sign bits of the DCT coefficients; and performing partial recoding on syntax elements of the macro block changed by the encryption operation in the to-be-encrypted video toobtain an encrypted video bit stream, thereby finishing encryption. According to the invention, encryption is realized by using optimally designed macro block scrambling, so that various types of existing contour attacks can be effectively resisted. Meanwhile, the encryption key of the method is related to the non-zero DCT coefficient quantity histogram of the video frame to be encrypted, so thatthe known plaintext attack can be effectively resisted.
Owner:SOUTH CHINA UNIV OF TECH
Encryption method, program, and system
ActiveCN106165340AGood encoding rateData stream serial/continuous modificationMultiple keys/algorithms usageMutual correlationTheoretical computer science
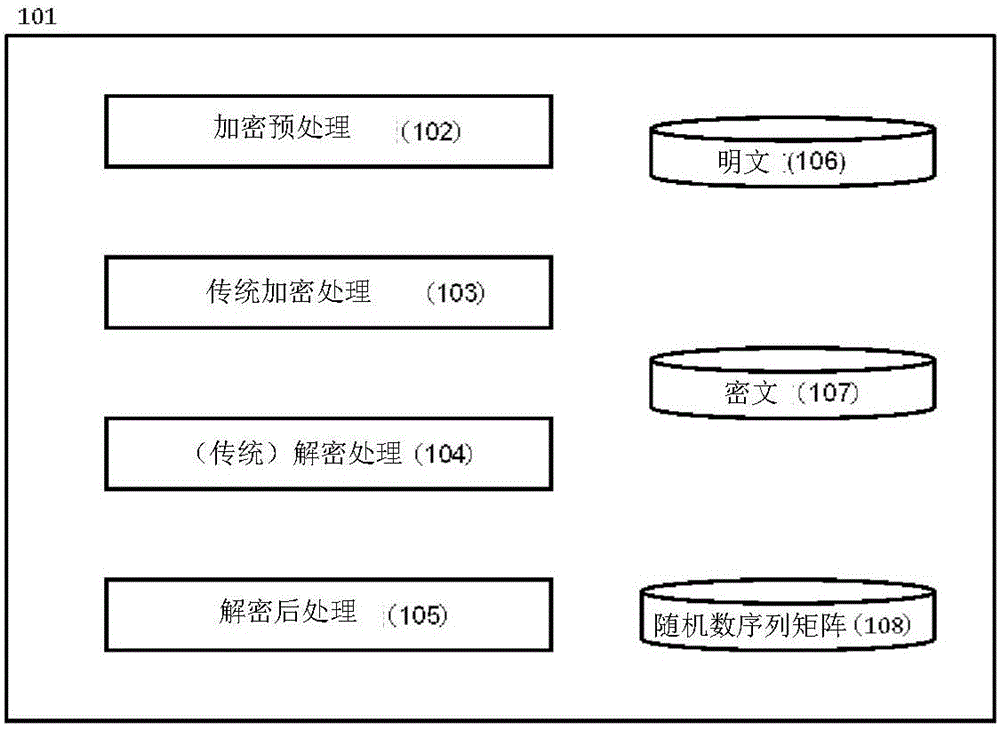
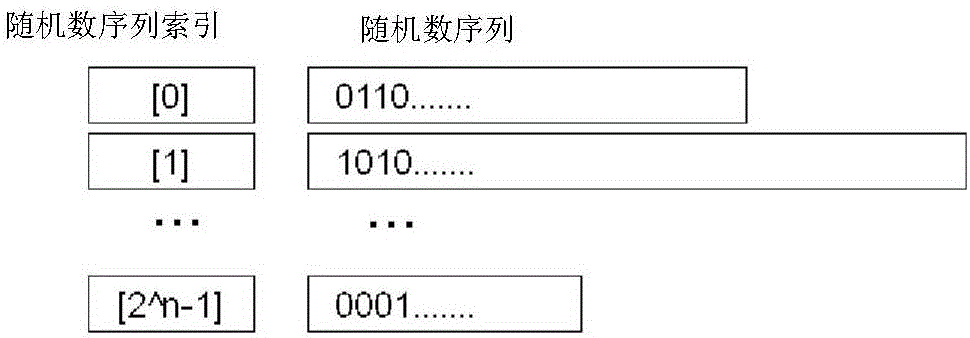
[Problem] To perform, by use of an existing encryption scheme, an encryption that is excellent in encoding rate and suitable for stream encryption and that exhibits a high security against known plain text attacks. [Solution] From a random number sequence matrix consisting of random number sequences having no mutual correlations and having different lengths, a random number sequence is selected by using, as an index, a random number that is independently generated by means of a physical random number or the like. A plain text to be encrypted is then camouflaged on the basis of the selected random number sequence, further coupled to the aforementioned random number and thereafter subjected to application of a conventional type of encryption algorithm.
Owner:加泽一郎
Method and device for security system
InactiveCN1798022AHigh costCryptographic equivalentEncryption apparatus with shift registers/memoriesViterbi decoderGuideline
The invention discloses technique includes encrpytion and decrpytion at physical layer. The invention also develops guidelines for specific implement case to select method of encrpytion / decrpytion. The said implement case is in use for communication system of using typical viterbi decoder. The invention also discloses how to implement characteristic of viterbi decoder difficult to be reversed in order to provide security for preventing known-plain text attack. The invention also discusses candidate method of encrpytion / decrpytion of satisfying the said guidelines of development.
Owner:TATA CONSULTANCY SERVICES LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com