Optical image encryption method based on four-step generalized phase shifting and multi-step Fresnel transform
A technology of transformation optics and encryption methods, which is applied in the field of optical image encryption based on four-step generalized phase-shift digital holography and multi-step Fresnel transform, can solve the problems of key management and transmission inconvenience, and achieve the effect of security assurance
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
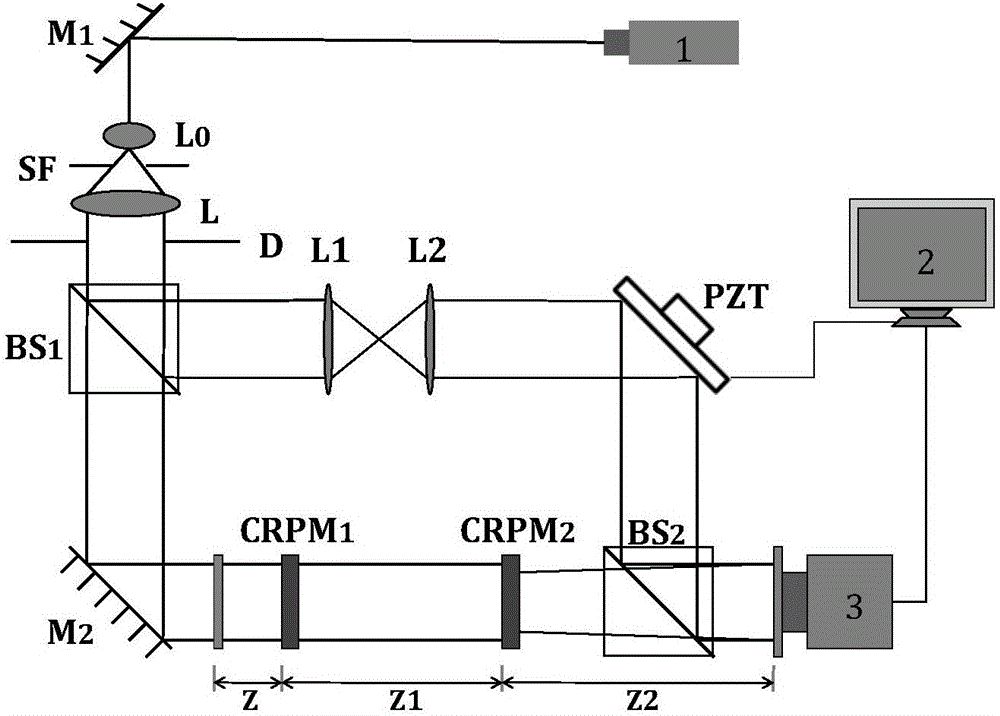
[0103] An optical image encryption method based on four-step generalized phase-shift digital holography and multi-step Fresnel transform, the optical path diagram is as follows figure 1 As shown, the encryption method consists of three parts: the key generation part, the image encryption part and the image decryption part.
[0104] see figure 1 , where the key generation part consists of two pieces of chaotic random phase mask CRPM generated by the Tinkerbell chaotic system 1 and CRPM 2 ; The image encryption part and the image decryption part include: lens (L, L 0 , L 1 , L 2 ), mirror (M 1 ,M 2 ), spatial filter (SF), beam splitter (BS 1 , BS 2 ), phase shifter (PZT), laser, CCD camera, computer, etc.
[0105] (1) Key generation part:
[0106] In the encryption method provided by the present invention, two random phase mask keys are respectively generated by Tinkerbell chaotic systems controlled by different chaotic parameters. The initial value and control parame...
Embodiment 2
[0113] Combine below figure 1 1. The design principle introduces the scheme in embodiment 1 in detail, see the following description for details:
[0114] An optical image encryption method based on four-step generalized phase-shift digital holography and multi-step Fresnel transform. The corresponding optical path of the encryption and decryption process is as follows: figure 1 As shown, the encryption method consists of three parts: the key generation part, the image encryption part and the image decryption part. The specific implementation manners of these three parts will be described in detail below.
[0115] (1) Key generation part:
[0116] In the encryption method, two chaotic random phase masks act as the master key, and the wavelength of the object light wave and the Fresnel transform distance act as the auxiliary key. The following is a detailed introduction on how to use the Tinkerbell chaotic system to generate these two chaotic random phase masks.
[0117] Th...
Embodiment 3
[0150] Below in conjunction with specific accompanying drawing, the scheme in embodiment 1 and 2 is carried out feasibility verification, see the following description for details:
[0151] Adopt the encryption method provided by the implementation of the present invention to an image (such as figure 2 As shown in (a), after encryption, the obtained encrypted image is as follows figure 2 (b) shown.
[0152] Depend on figure 2 (b) It can be seen that any information of the original image is hidden. When all the keys are correct, the decrypted image is as follows figure 2 (c) shown. Depend on figure 2 (c) It can be seen that the original image can be well restored. It shows that the encryption and decryption of grayscale images using this system is successful.
[0153] In addition, when one key is wrong and other keys are correct, the decryption result is as follows: image 3 (a)-3(j). It can be seen that the security of the system can be guaranteed.
[0154] Fi...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com