Encryption method, program, and system
A computing system and computer program technology, applied in the field of security against known plaintext attacks, can solve problems such as increasing memory space, and achieve a good encoding rate.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0026] Hereinafter, an embodiment of the present invention will be described with reference to the accompanying drawings.
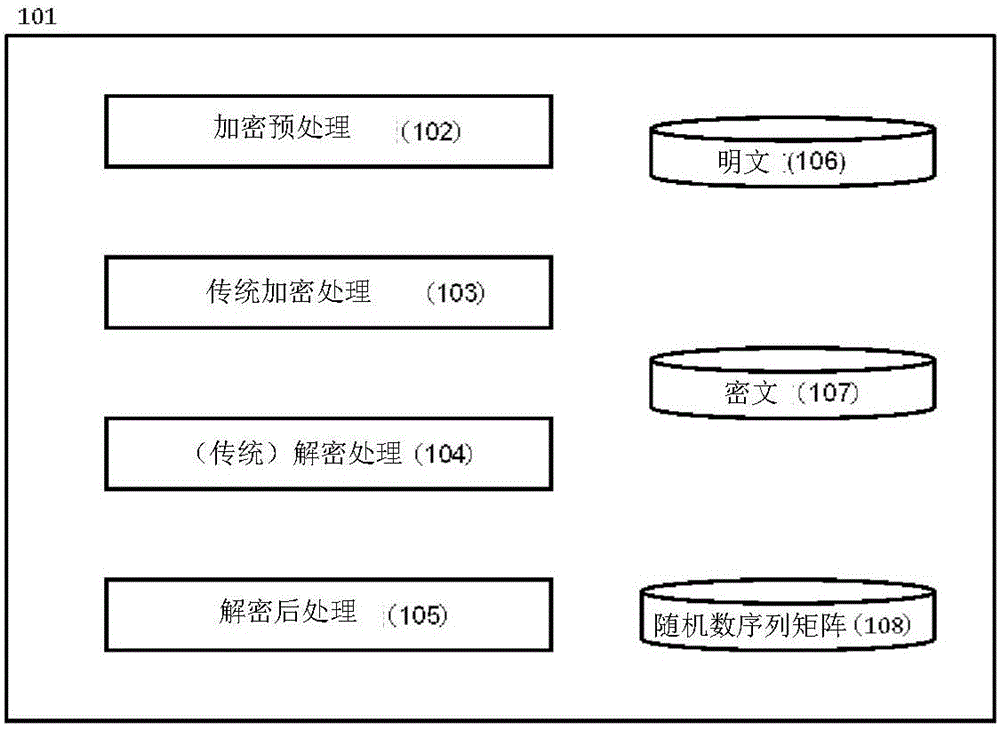
[0027] figure 1 is a functional overview diagram of an exemplary information system 101 used in one embodiment of the invention. The information system 101 may be composed of physical computers, or virtual computing resources provided by, for example, cloud infrastructure services.
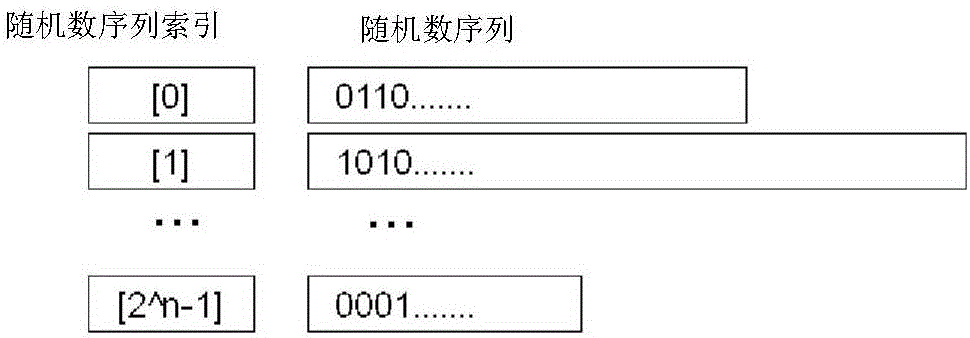
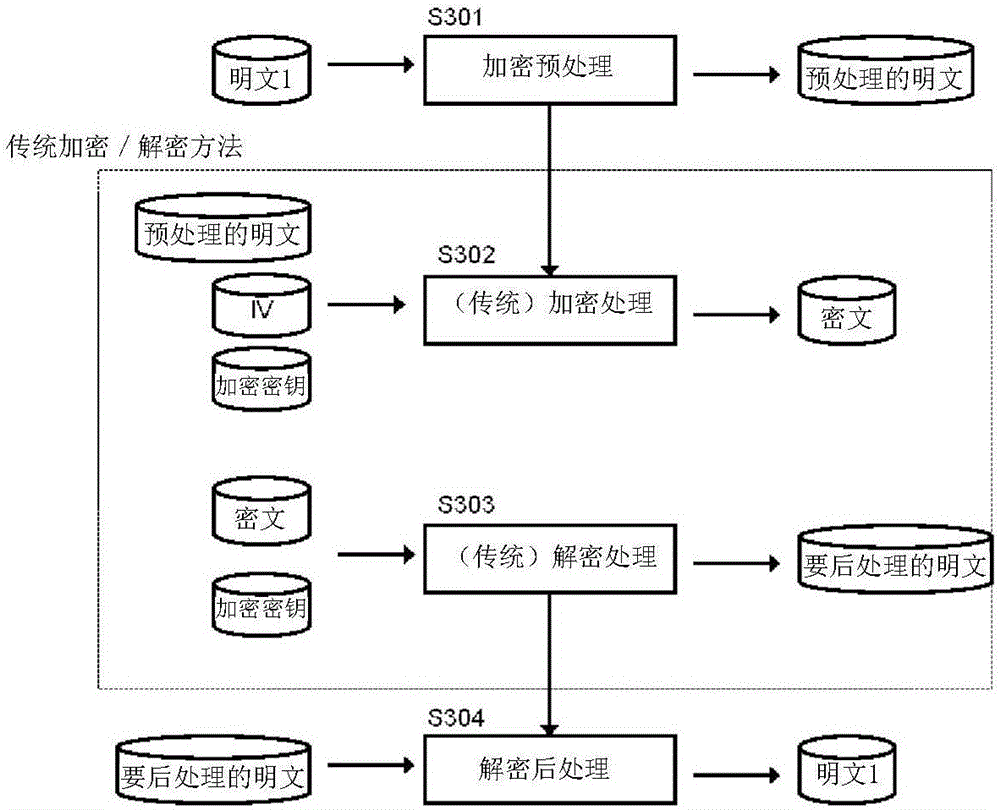
[0028] Encryption preprocessing 102 is the function of transforming plaintext prior to conventional encryption 103 . Its details are in Figure 4 shown in and described below.
[0029] Conventional encryption 103 is a function of performing encryption (converting plaintext into ciphertext) using a well-known encryption method such as Data Encryption Standard (DES). It is well known and self-explanatory, so it will not be discussed further.
[0030] Conventional decryption 104 is the function of performing decryption (transforming ciphertext to plaintext) using a well-kno...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com