Multi-image encryption and decryption method based on Walsh transform and ghost imaging calculation
A multi-image, ghost imaging technology, applied in the field of information security, can solve the problems of large measurement times and data, limitations, etc., to achieve the effect of increasing security, high security, and simple process
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
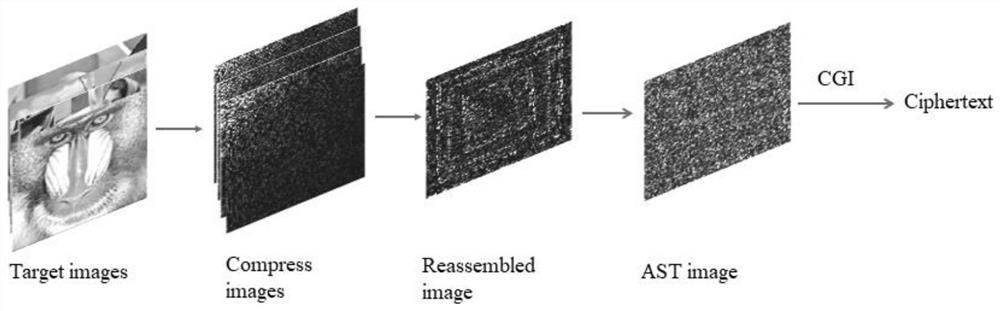
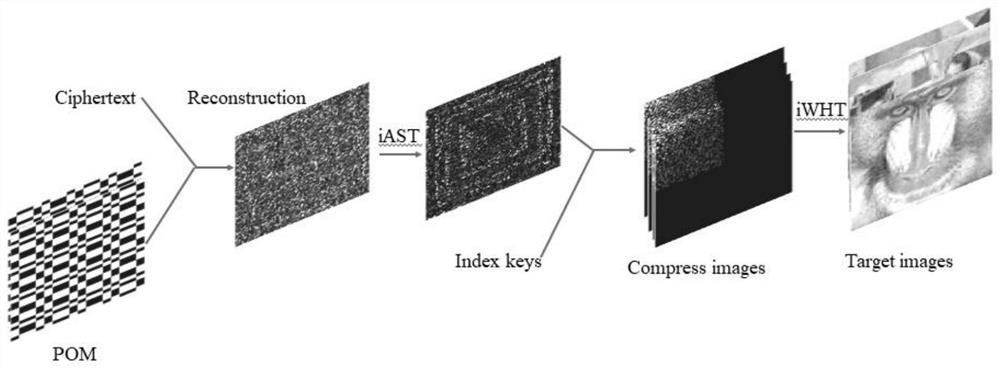
[0044] Embodiment: multi-image encryption and decryption methods based on Walsh transform and computational ghost imaging, including as figure 1 Encryption steps shown:
[0045] S1, to many images f i (i=1,2,3...N) (ie figure 1 Target images) to perform Walsh-Hadamard transform to obtain the compressed sparse image g i ( figure 1 Compress images in), ie g i (x 0 ,y 0 ) = WHT[f i (m,n)], where WHT[] represents the Walsh-Hadamard transform, extracting all sparse images g i The pixels in the energy concentrated part of the middle form the pixel set Pix(x, y), and the pixel set is reorganized according to the index sequence of the back shape to obtain the reorganized image B(x, y)( figure 1 in Reassembledimage); namely B(x, y)=RA{Pix(x, y)}, wherein RA{} represents the extraction operation of the back font, that is, scans and extracts the pixels in the matrix sequence according to the back font;
[0046] S2. After performing the sign-taking operation on the restructured i...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com