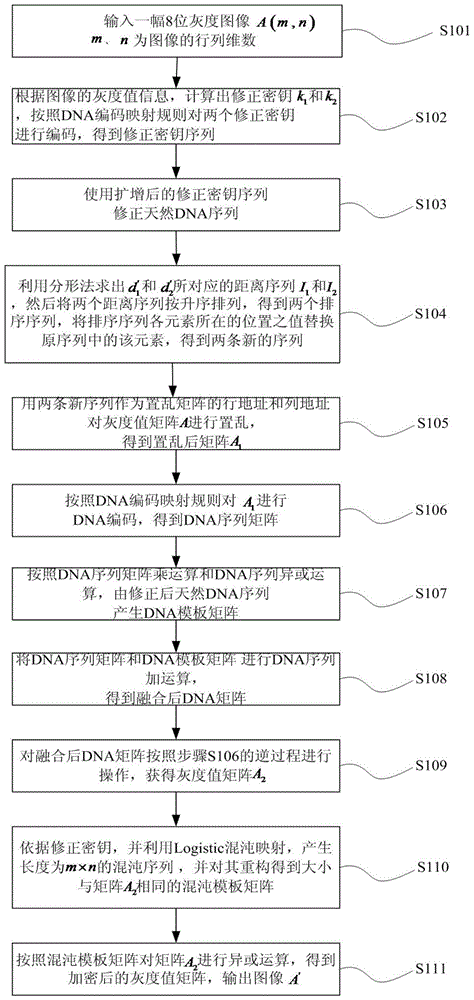
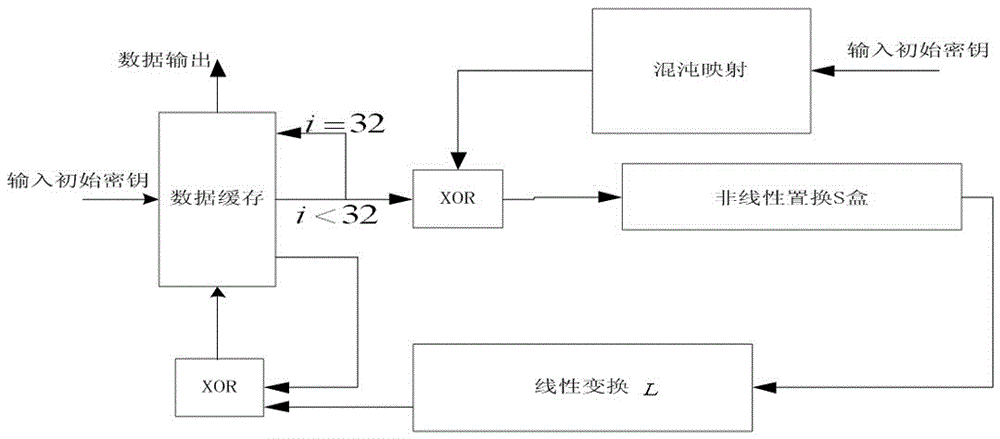
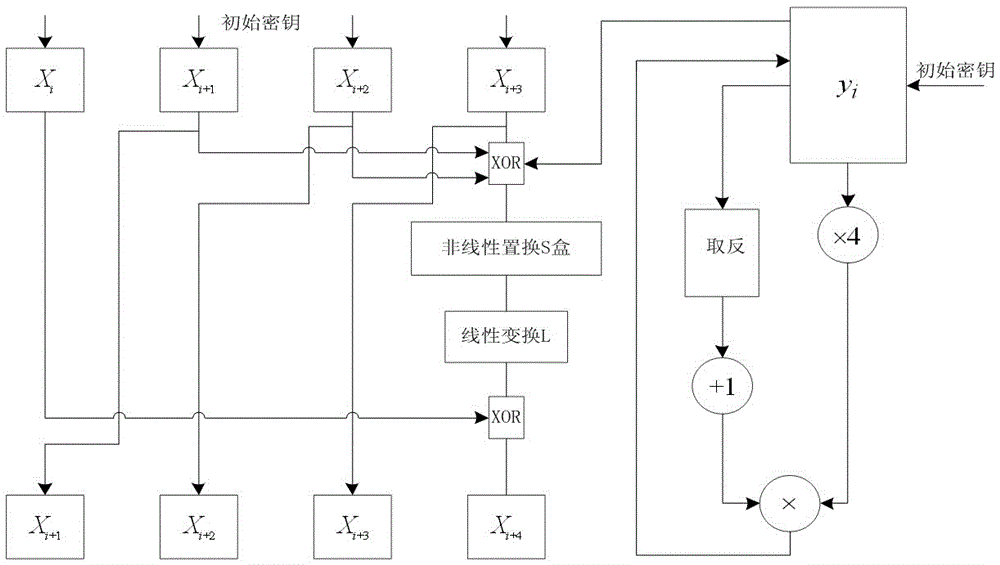
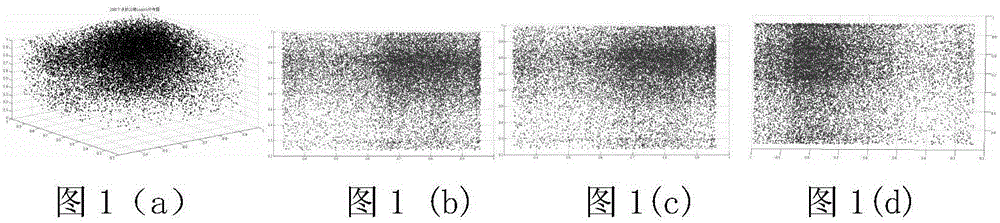
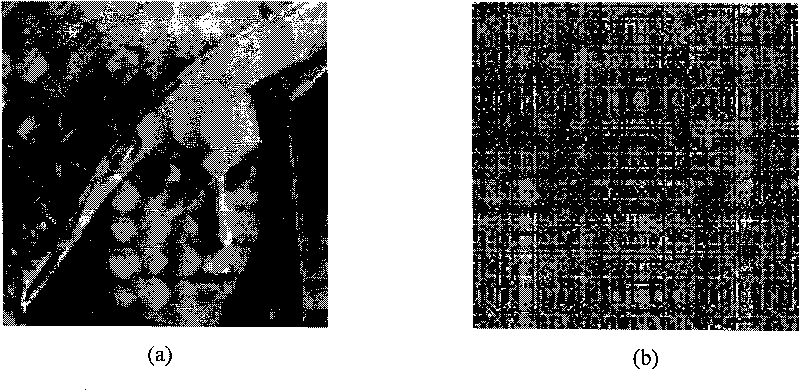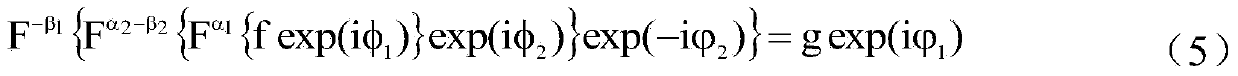Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
121 results about "Logistic map" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
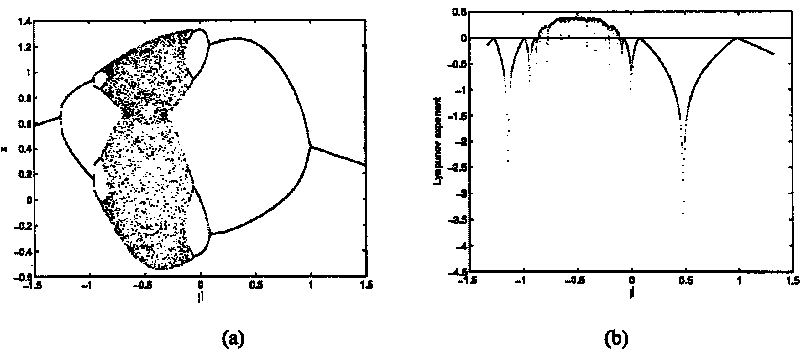
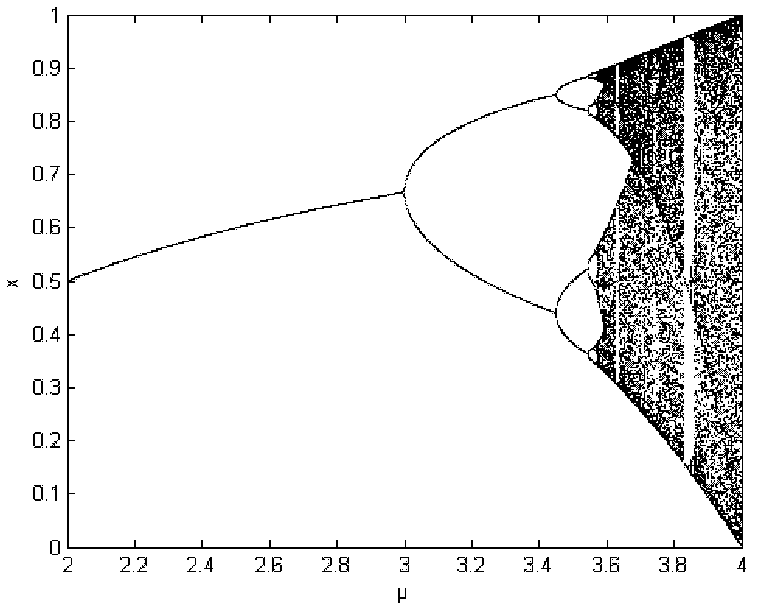
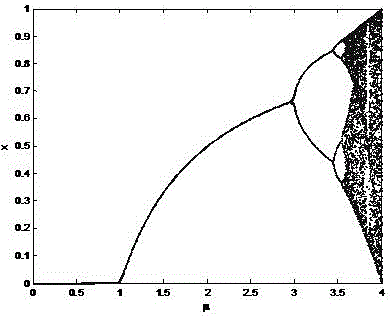
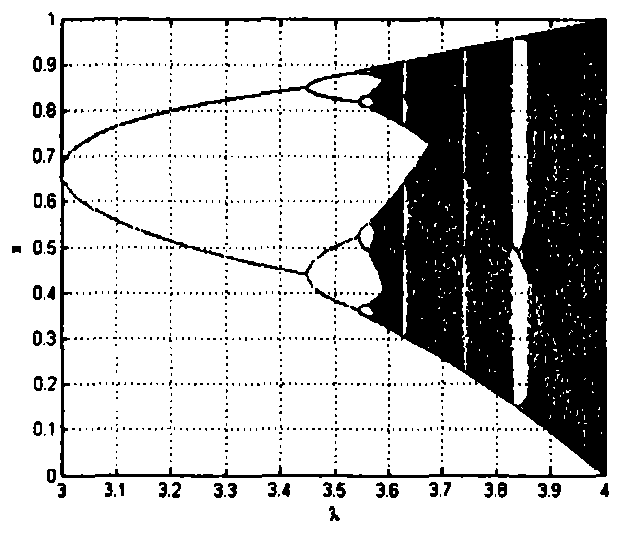
The logistic map is a polynomial mapping (equivalently, recurrence relation) of degree 2, often cited as an archetypal example of how complex, chaotic behaviour can arise from very simple non-linear dynamical equations. The map was popularized in a 1976 paper by the biologist Robert May, in part as a discrete-time demographic model analogous to the logistic equation first created by Pierre François Verhulst.
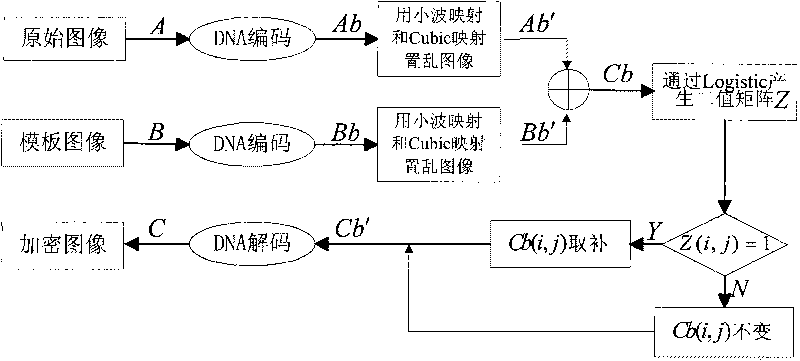
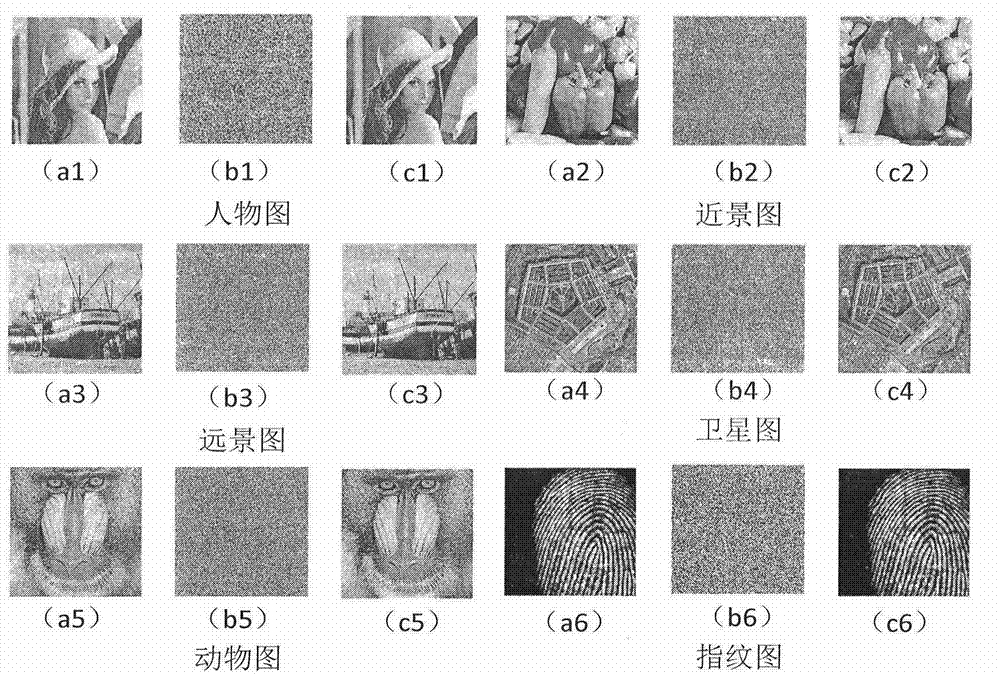
Digital image encryption method based on DNA sequence and multi-chaotic mapping
ActiveCN101706946AEasy to implementEasy to controlGenetic modelsImage data processing detailsChaotic systemsDigital image
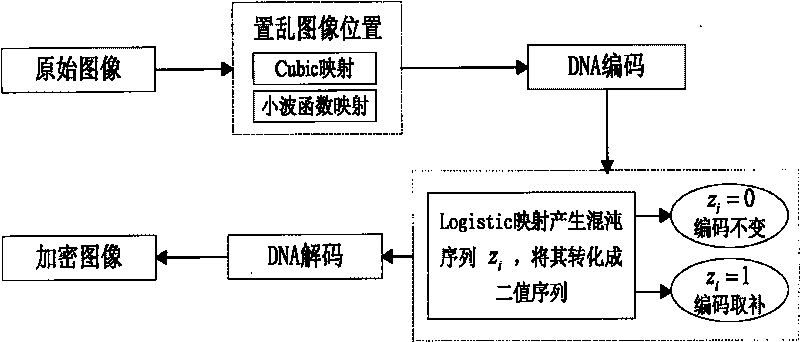
The invention discloses a novel digital image encryption method belonging to the field of DNA calculation and image encryption, and provides a digital image encryption method based on a DNA sequence and multi-chaotic mapping. The traditional encryption algorithm based on chaos has the defects that a key space is small, a chaos system is easy to analyze and forecast, and the like; and almost of the current encryption systems based on DNA need complex biological operation and are hard to realize. In order to overcome the defects, the invention provides the digital image encryption method based on a DNA sequence and multi-chaotic mapping, comprising the following steps of: firstly, scrambling the positions of pixels of images by utilizing a two-dimension chaotic sequence generated by Cubic mapping and Haar wavelet functions, and then disrobing the pixel values of the images under the action of a chaotic sequence generated by the DNA sequence and the Logistic mapping. The experimental result shows that the algorithm is easy to realize, has better encryption effect on images, large key space and high sensitivity to keys and can effectively resist exhaustive attack and statistical attack.
Owner:DALIAN UNIV
Multi-parameter multi-object chaotic particle swarm parameter optimization method
InactiveCN105631518ATroubleshooting Auto Equalization IssuesSolve the problem of difficult weight selectionChaos modelsNon-linear system modelsGlobal optimizationObject function
The present invention discloses a multi-parameter multi-object chaotic particle swarm parameter optimization method. The method comprises the steps of (1) determining a target function and a parameter to be optimized, (2) initializing an algorithm, (3) calculating the target function corresponding to each individual in a population, (4) updating an individual history optimal solution, (5) updating a particle velocity and position, (6) updating a global optimal solution set, (7) updating a global optimal solution, and (8) carrying out result judgment. Compared with a common random initialization method and an existing chaotic logistic mapping particle swarm initialization method, according to the method of the invention, the performance of global optimization is improved and the stability is good, compared with a common multi-object weighted optimization method, the Pareto optimal solution technology is employed by the method, and the problem of difficult weight selection in the multi-object method is solved.
Owner:XIAN UNIV OF TECH
Digital image encryption method based on chaotic orbit perturbation
InactiveCN102360488AImprove diffusion abilityImprove abilitiesImage data processing detailsMultiple encryptionPlaintext
The invention relates to a digital image encryption method based on chaotic orbit perturbation and relates to the field of encryption systems. The method comprises the following steps of: scrambling a plaintext image by adopting a generalized discrete Baker mapping-based method; diffusing the scrambled image by adopting a Logistic mapping-based method, and changing the pixel value of each point in the image; and performing multiple encryption according to the requirement on encryption strength. According to the method, a key flow is related to a key and a plaintext by introducing a chaotic orbit perturbation mechanism related to the plaintext, so that the diffusing effects of an encryption system are effectively improved, and the known plaintext resistance is obviously improved. Certain pixel value is changed in the diffusion process depending on the cumulative effect of all the encrypted pixel values before the pixel, so that the tiny change of one pixel value can be effectively diffused to all the subsequent pixels in the image. The method has short encryption time.
Owner:付冲 +1
Image fusion encryption method based on DNA sequences and multiple chaotic mappings
ActiveCN101706947AGood encryptionLarge key spaceGenetic modelsChaos modelsChaotic systemsImage fusion
The invention discloses an image fusion encryption algorithm based on DNA sequences and multiple chaotic mappings, belonging to the field of DNA computation and image encryption. The traditional chaos-based encryption algorithm has the defects that the key space is small, the chaotic system is easy to be analyzed and predicted, and the like, and the existing image fusion based encryption method features difficult control of fusion parameters and low safety. To overcome the above defects, the invention first utilizes the two-dimensional chaotic sequence based scrambled coded original image and the template image which are generated by the Cubic mapping and the wavelet function to obtain two DNA sequence matrices, then carries out addition operation on the two scrambled DNA sequence matrices and finally utilizes the chaotic sequence generated by Logistic mapping and the DNA sequence matrices obtained by addition operation to interact to obtain the encrypted image. The experimental results show that the algorithm can effectively encrypt the digital images and has higher safety.
Owner:DALIAN UNIV
DCT domain-based color image digital watermark embedding method and DCT domain-based color image digital watermark extracting method
InactiveCN101739657AImplement Adaptive EmbeddingImprove robustnessImage data processing detailsColor imageLogistic map
The invention discloses a DCT domain-based color image digital watermark embedding method and a DCT domain-based color image digital watermark extracting method. The DCT domain-based color image digital watermark embedding method comprises the following steps: before embedding a color watermark image, utilizing Logistic mapping to scramble the coordinates of components R, G and B of the color watermark image; embedding each component of the scrambled color watermark image as watermark sequences to a host image; and according to luminance, contrast and texture complexity, classifying image blocks of the host image. By utilizing human visual characteristics, the watermark components of different strengths can be embedded into image block DCT coefficients of different classes. The watermark image produced by the method has the characteristics of good perception effect and strong robustness and has good resistance to some conventional attacks.
Owner:SHANGHAI SECOND POLYTECHNIC UNIVERSITY
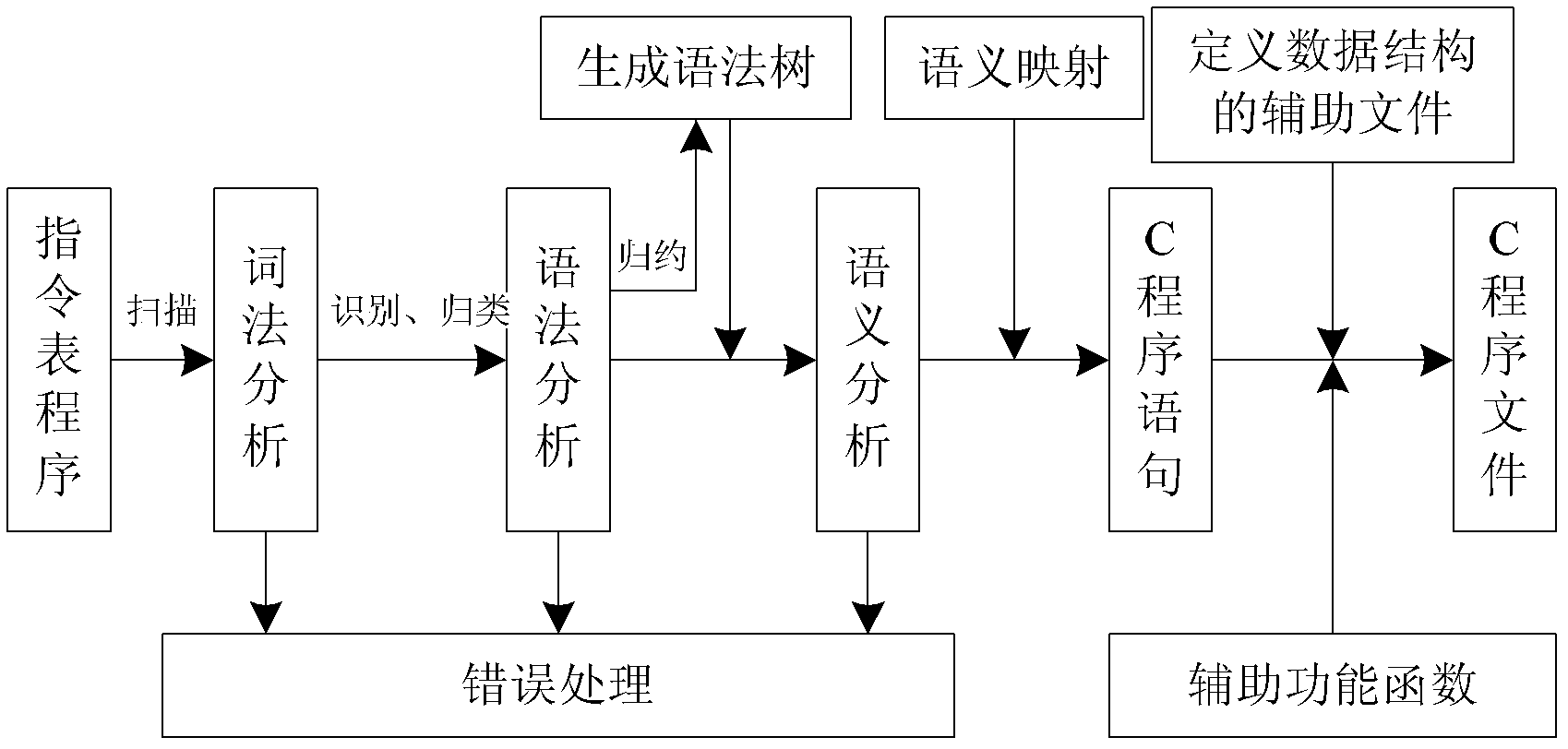
Compiling method from intermediate language (IL) program to C language program of instruction list
InactiveCN103123590AFeasible grammatical conventionFeasible semantic analysisProgram controlMemory systemsPerformance functionLexical analysis
The invention discloses a compiling method from an intermediate language (IL) program to a C language program of an instruction list. The method comprises the steps: building a middle storage structure syntax tree according to results of lexical analysis and grammatical analysis through logical analysis on a program of the instruction list and logistic mapping relation between semanteme of the instruction list and semanteme of the C language; combining an auxiliary performance function and an auxiliary data structure define file, and generating an integrated file of the C language program through program data of an original instruction list according to a C language programming method, wherein the program data of the original instruction list is stored in the structure of the syntax tree. The generated C language program completely corresponds to the logic program of the original instruction list and has the advantages of a high-level C language, wherein the advantages include strong transportability, strong compatibility and the like. Due to the structure of the syntax tree and an analytic method of semanteme mapping, compiling is standardized and mass-produced, complexity of the compiling is reduced through adoption of functions and modularization of an auxiliary function of a function block, compiling time is shortened, and speed of the whole compiling process is improved.
Owner:中国科学院沈阳计算技术研究所有限公司
Digital image encrypting and decrypting method
InactiveCN102609893AMaintain styleAchieving mean invarianceImage data processing detailsCiphertext48-bit
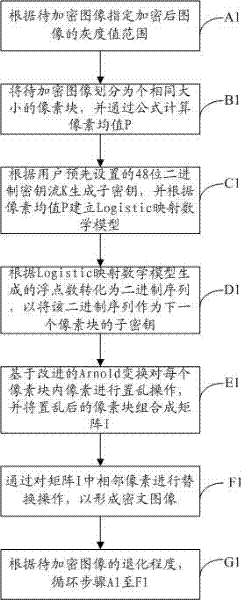
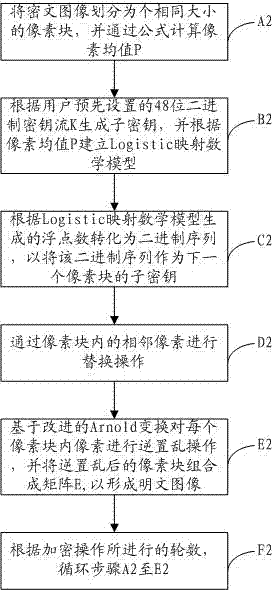
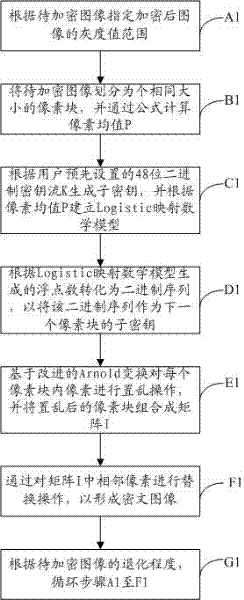
The invention discloses a digital image encrypting and decrypting method comprising the following steps of: appointing the gray value range of an encrypted image according to an image to be encrypted; dividing the image to be encrypted into pixel blocks with the same size, and computing a pixel mean value by virtue of a formula; generating a sub-secret key according a 48-bit binary system key stream preset by a user, and building Logistic mapping according to the pixel mean value; converting into a binary sequence according to the number of floating points generated by the Logistic mapping, and taking the binary sequence as the sub-secret key of the next pixel block; scrambling the pixel in each pixel block based on the improved Arnold conversion, and combining the scrambled pixel blocks into a matrix; and replacing the adjoining pixels in the matrix, so that a ciphertext image can be formed. According to the requirement of a user, the image can be encrypted by means of different numbers of sheaves, various filtering attacks can be resisted, and the invariability of the pixel mean value of the image can be realized, so that the whole style and feature of the original image can be maintained.
Owner:AEROSPACE SCI & IND SHENZHEN GROUP
High utilization universal logic array with variable circuit topology and logistic map circuit to realize a variety of logic gates with constant power signatures
ActiveUS20110085662A1Avoid detectionPower reduction in field effect transistorsLogic circuits characterised by logic functionMulti inputConstant power
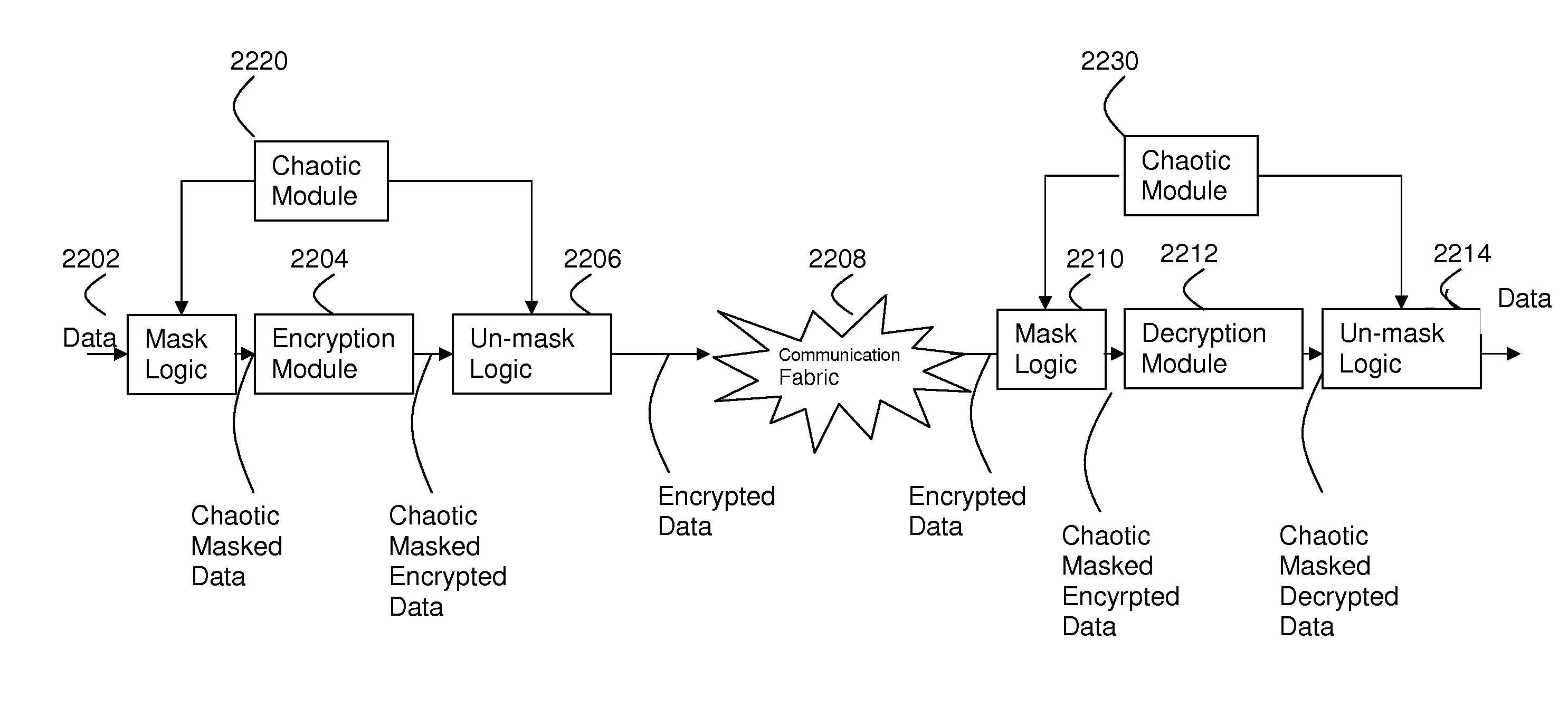
Disclosed is a novel circuit able to generate any logic combination possible as a function of the input logic signals. The circuit is described as a 2 input logistic map circuit but may be expanded to 3 or more inputs as required. Further disclosed is a universal logic array with variable circuit topology. A metallization layer and / or a via interconnection between cells in the array elements produce a circuit topology that implements a Boolean function and / or chaotic function and / or a logic function. The novel circuit provides a circuit topology for secure applications with no obvious physical correspondence between control signal values and input to output mapping. Further disclosed is a network which has a power signature independent of input signal state and output transition. This provides a very useful circuit to protect data from decryption from power signature analysis in secure applications.
Owner:CHAOLOGIX INC
Composite chaotic secondary scrambling image encryption algorithm
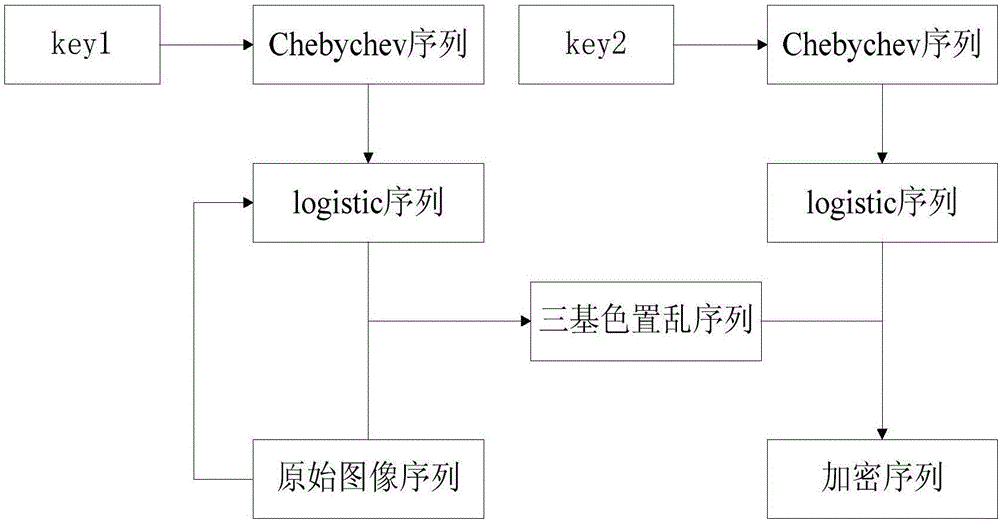
InactiveCN108133446AAvoid failureSmall amount of calculationImage data processing detailsChebyshev mapLogistic map
The invention provides a composite chaotic secondary scrambling image encryption algorithm and belongs to the technical field of encryption. The algorithm is characterized by, to begin with, generating an initial value of Logistic mapping through Chebyshev mapping; then, forming a two-dimensional chaotic matrix through the Logistic mapping; and carrying out position and grayscale secondary scrambling on images needing encryption through the matrix. The algorithm utilizes Chebyshev mapping and Logistic mapping to alternately generate mixed chaotic sequences, thereby not only inheriting characteristics of the single Logistic mapping chaotic sequence, but also improving the phenomenon of stable window of the single chaotic sequence; in comparison, random performance of the sequence is higher;and in particular, the system is very sensitive to encryption keys, and subtle changes in the keys will directly lead to changes in the location and grayscale matrix, so that decryption fails, and the system has higher safety.
Owner:QINZHOU JINGTONG TECH CO LTD
Partitioning double-layer self-adaptation diffusion image encryption method
InactiveCN104766264AEnhanced scrambling randomnessIncreased sensitivityImage data processing detailsPlaintextCiphertext
The invention provides a partitioning double-layer self-adaptation diffusion image encryption method. The partitioning double-layer self-adaptation diffusion image encryption method includes the steps that every two kinds of Logistic mapping, Tent mapping and Sine mapping are combined to build three kinds of new one-dimensional chaotic mapping, and initial chaotic sequences are extracted, so that the new one-dimensional chaotic mapping has wide chaotic ranges and good chaotic behaviors; then scrambling and diffusion are synchronously carried out by combining Arnold forward mapping and Arnold backward mapping. The opportunities of accessing sequences of pixels and the opportunities of storage sequences of positions can be equal, the scrambling randomness can be improved, and the defects in the rules and random accessing of conventional Arnold mapping can be overcome; in addition, partitioning double-layer self-adaptation diffusion is adopted in the scrambling process, the interaction between the ciphertext pixels, the interaction between the ciphertext pixels and the plaintext pixels and the interaction between the ciphertext pixels and chaotic random sequences are used, influences of the pixels are nonlinearly diffused into a whole image array, a chaotic system is continuously disturbed in the diffusion process, a self-adaptation diffusion process is formed, and the sensitivity of an encryption image to a secret key, a ciphertext and a plaintext is improved.
Owner:NORTHWESTERN POLYTECHNICAL UNIV
Hyper-spectral image compression and encryption method
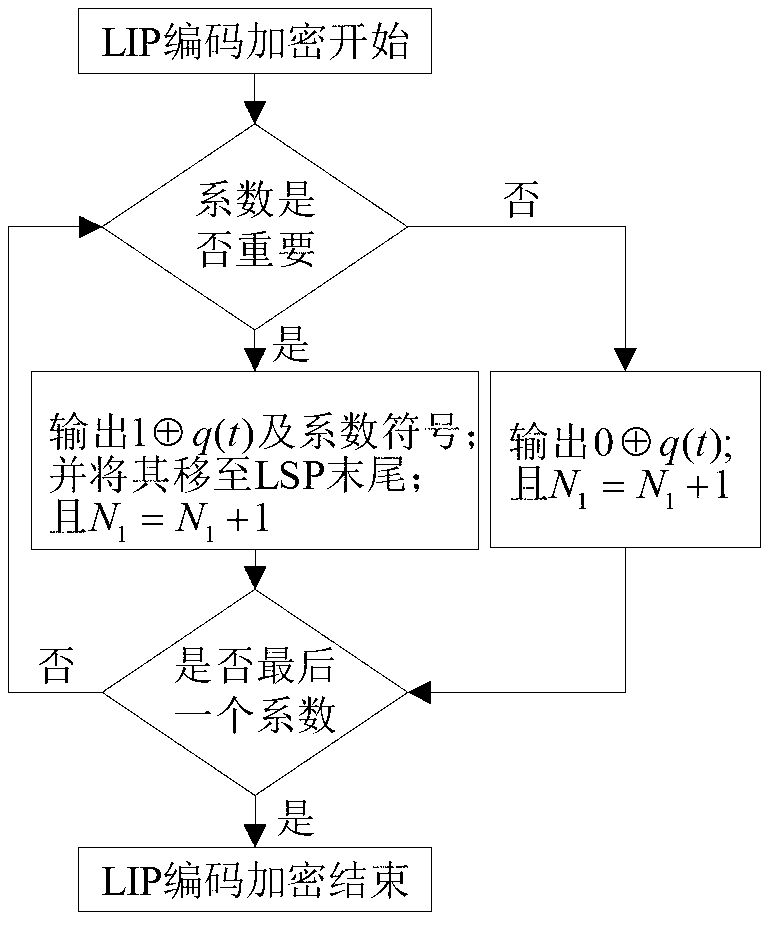
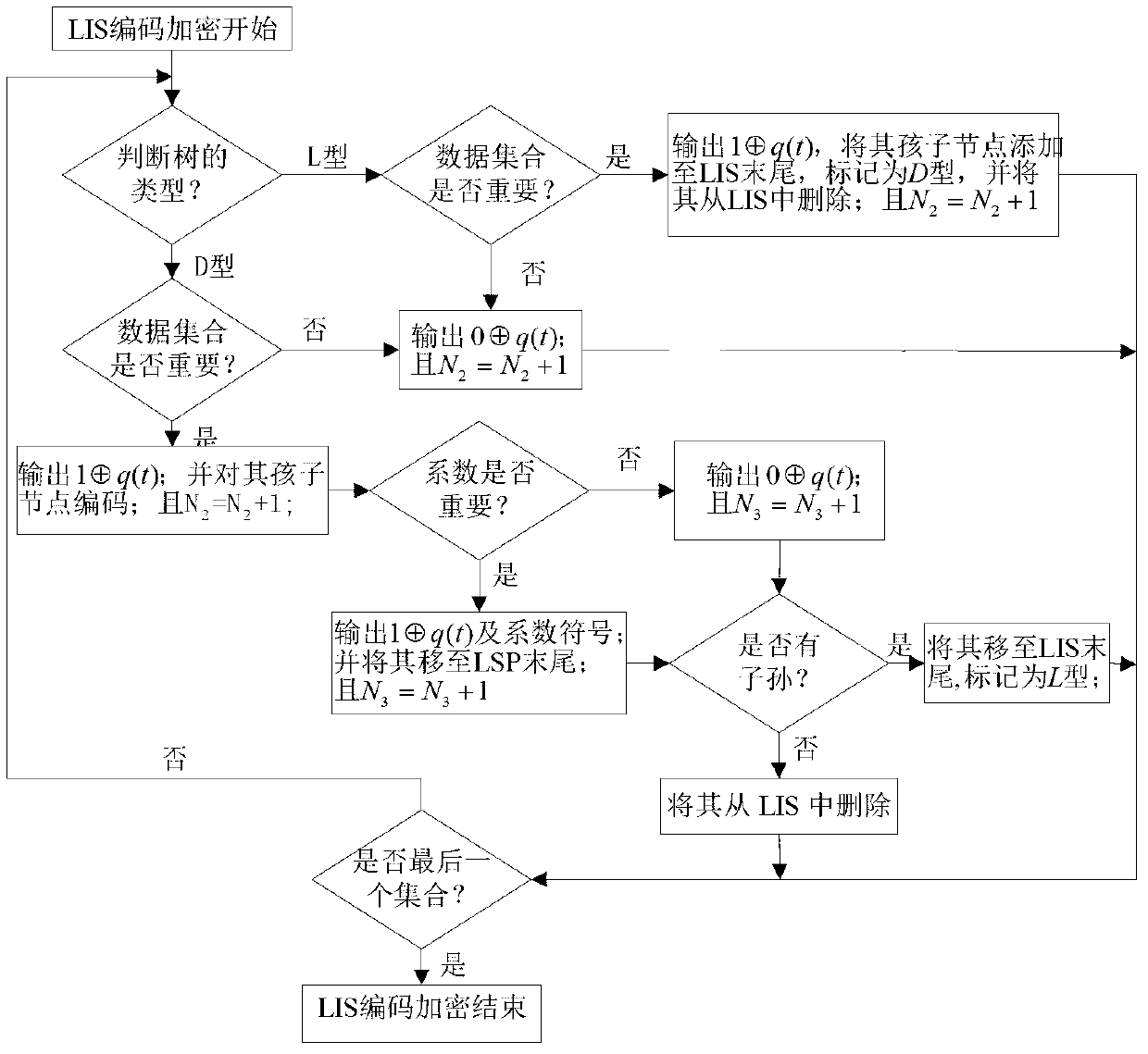
InactiveCN103281534AReduce the amount of encrypted dataImprove transmission efficiencyTelevision systemsComputer hardwarePlaintext
The invention provides a hyper-spectral image compression and encryption method. The method comprises the following steps of performing coding in a wavelet transform three-dimensional set partitioning in hierarchical trees (3DSPIHT) coding way, simultaneously performing encryption, constructing a scrambling table in a Logistic mapping way to scramble an initial list of insignificant pixels (LIP), continuously iterating a Chen's model until all bits of data of significant types are encrypted, and in a decryption process which is the inverse operation of encryption, continuously updating an initial value of the Chen's model to decrypt the data of the significant types to make the decrypted data gradually approximate to an original image and finally reproduce the original image. According to the method, forward dependence of a 3DSPIHT coding method is utilized, and the data of the significant types is selectively encrypted in real time in a compression process, so that the encrypted data volume of the image is reduced, and the image transmission and encryption efficiency is improved; and the encrypted data volume of each significant type in a bit plane is calculated, and an initial key is scrambled after preprocessing, so that the sensitivity of the coding method to a plaintext is improved.
Owner:NORTHWESTERN POLYTECHNICAL UNIV
Medical image robust watermarking method based on SIFT-DCT
The invention discloses a medical image robust watermarking method based on SIFT-DCT, and belongs to the field of multimedia signal processing. The method comprises the steps of firstly, carrying outsymbol encryption on a watermark in a frequency domain by utilizing the properties of a Logistic Map; secondly, extracting an eigenvector by performing SIFT-DCT on a medical image to perform watermarkembedding, associating the eigenvector with a binary watermark to obtain a binary logic sequence, and storing the binary sequence in a third party; and thirdly, extracting an eigenvector by performing the SIFT-DCT on the to-be-tested medical image again, and associating the eigenvector with the binary sequence stored in the third party to carry out watermark extraction. The method is a medical image digital watermarking technology based on the SIFT-DCT, has relatively good robustness, and is especially outstanding for geometric attacks such as rotation, translation, shearing and the like; and watermark embedding does not change contents of original encrypted volume data, so that the method is a zero watermarking technology.
Owner:HAINAN UNIVERSITY
An image encryption method based on Duffing mapping and genetic operation
ActiveCN109376540AIncreased sensitivityIncrease the difficulty of decipheringDigital data protectionPlaintextExclusive or
The invention provides an image encryption method based on Duffing mapping and genetic operation. The hash value of a plaintext image is calculated by using a Keccak algorithm as an initial value input key of a chaotic system; the sensitivity and pseudo-randomness of the chaotic map to the initial conditions are used, the pseudo-random sequence is obtained by iterating the Logistic map and the Hill encryption matrix is generated to scramble and replace the image matrix. Combined with Duffing map and DNA coding technology, pixel selection, crossover and mutation are realized by genetic operation to achieve pixel diffusion and scrambling, and bidirectional exclusive OR operation with chaotic sequence to enhance its confusion and diffusion characteristics. The invention utilizes the pseudo-randomness of Duffing mapping and Logistic mapping, ergodicity and the crossover mutation operation of genetic algorithm, has strong sensitivity to key, can effectively resist statistical attack and differential attack, etc., has good security and application potential, and the image encryption effect and performance are remarkably improved.
Owner:ZHENGZHOU UNIVERSITY OF LIGHT INDUSTRY
Plaintext feature-based double-chaos image encryption method
The invention discloses a plaintext feature-based double-chaos image encryption method. According to the method, Logistic mapping and Chebyshev mapping are combined; a key is generated by means of the balance of the Chebyshev mapping; the parameters of the Logistic mapping are controlled, so that a plurality of different Logistic sequences can be generated to carry out overall scrambling on color components in an image; and diffusion operation is performed scrambled image pixels, so that plaintext information can be better hidden. As indicated by an experimental simulation result, the method can not only resist statistical characteristic analysis and differential attack, but also can resist selective plaintext (ciphertext) attack, and has the advantages of good encryption effect, large key space and the like.
Owner:GUANGDONG UNIV OF TECH
Logistic chaotic mapping-based digital image encryption method
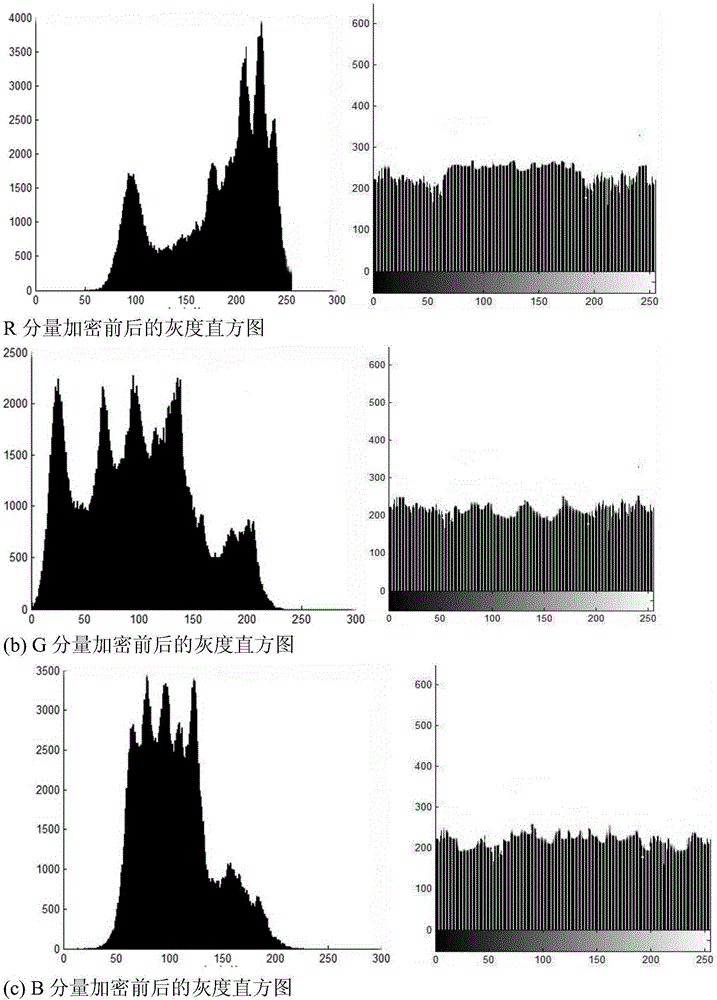
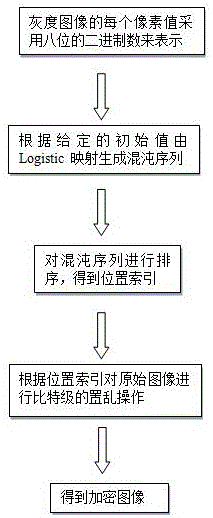
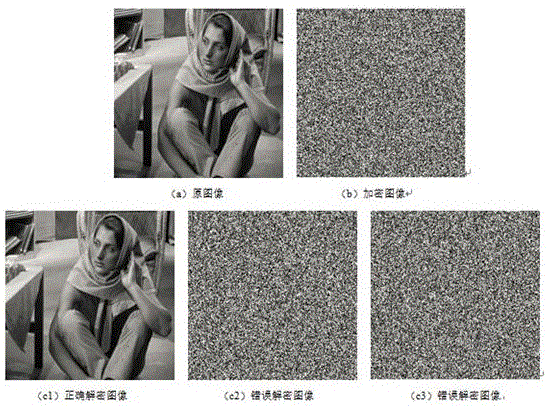
InactiveCN106530207AAchieved image encryption resultsImage data processing detailsComputer visionDigital image
The present invention discloses a logistic chaotic mapping-based digital image encryption method. Each pixel value of a gray-scale image is represented in the form of eight-bit binary numbers, so that the two-dimensional gray-scale image is converted into a one-dimensional code digital string of 0 and 1 for further treatment. According to given initial values, a chaotic sequence is generated based on the logistic mapping method. The chaotic sequence is then sorted, so that a position index is obtained. According to the position index, the original image is subjected to bit-level scrambling operation. In this way, an image encryption result, which integrates pixel fusion and pixel scrambling as a hole, is obtained.
Owner:NANJING UNIV OF SCI & TECH
Asymmetric double-image encryption and decryption method based on chaos and cascade DFrRT
InactiveCN104050623AAdd nonlinearityIncrease disorderImage data processing detailsPlaintextCiphertext
The invention discloses an asymmetric double-image encryption method based on chaos and cascade DFrRT. The encryption method comprises the steps that two original gray level images are normalized and connected into an extension image in the horizontal direction; next, the extension image is scrambled by i times of cat mapping, and then the extension image is decomposed into two new images; two phase masks are generated through the image f'1, and the image f'2 and one phase mask are subjected to convolution; Logistic mapping is conducted on an obtained complex matrix, and a conversion result is obtained through DFrRT conversion with the order of alpha; the amplitude of the complex matrix is extracted, and the amplitude and the other phase mask are subjected to convolution; Logistic mapping is conducted on an obtained second complex matrix, and a conversion result is obtained through DFrRT conversion with the order of beta; the amplitude of the second complex matrix is extracted, and then a final ciphertext image is obtained. The invention further discloses a corresponding decryption method. By means of the asymmetric double-image encryption and decryption method, the nonlinearity and disorder of a plaintext image in a spatial domain and a transformation domain are enhanced, and conventional attacks can be well resisted.
Owner:XIAN UNIV OF TECH
Image encryption method based on fractal and DNA sequence operation
ActiveCN105701755AImprove securityGood encryptionImage data processing detailsThe InternetLogistic map
The invention discloses an image encryption method based on fractal and DNA sequence operation, which mainly comprises the steps of: scrambling an original image by utilizing a scrambling sequence generated by adopting a fractal method; then acquiring a DNA template matrix by utilizing a corrected natural DNA sequence; then encoding the scrambled image, and carrying out DNA sequence add operation on a result and the DNA template matrix; and finally utilizing a chaos template matrix generated by Logistic mapping and a matrix obtained after DNA decoding to interact to obtain an encrypted image. The image encryption method has the advantages of high security, good encryption effect and large secret key space, and can effectively resist exhaustive attacks, statistical attacks and differential attacks. And the algorithm is easy to implement, the cost is low, and the encryption results can be transmitted through the Internet.
Owner:DALIAN UNIV
Long key-based realization system and method for SM4 key extending algorithm
ActiveCN106209358AIncrease randomnessLarge key spaceKey distribution for secure communicationSecuring communication by chaotic signalsS-boxTheoretical computer science
The invention discloses a long key-based realization system and method for an SM4 key extending algorithm. The system comprises a chaotic mapping module, a data caching module, an xor module, a nonlinear permutation S box module and a linear transformation L module, wherein an input of the chaotic mapping module is a partial initial key, a pseudorandom sequence with good randomness is generated as an input of an original SM4 key extending algorithm by utilizing multi-time iterations of chaotic mapping, and the chaotic mapping module selects Logistic mapping through considering chaotic performance and hardware implementation resource consumption; and the chaotic mapping is fused in the SM4 key extending algorithm. By optimizing the SM4 key extending algorithm, the key space of the SM4 algorithm is expanded and the randomness of sub-keys in each round is enhanced.
Owner:HEILONGJIANG UNIV
Image duel scrambling method based on three-dimensional Logistic mapping
InactiveCN103606126ADouble reset implementationSimple methodImage data processing detailsDigital signal processingLogistic map
An image duel scrambling method based on three-dimensional Logistic mapping belongs to the field of digital image processing. The image positive scrambling process comprises the steps that firstly an IMAGE to be scrambled with the size of M*N is obtained, 5*M*N three-dimensional Logistic mapping function values are respectively obtained according to a three-dimensional Logistic mapping formula, the Logistic function values of last M first dimensions, last N second dimensions, and last M*N third dimensions of the 5*M*N three-dimensional Logistic mapping function values are obtained and sorted in an ascending mode respectively, and position sequences of an index 1, an index 2 and an index 3 are obtained; pixel position scrambling is conducted on the IMAGE by utilizing the sequences of the index 1 and the index 2, and an Image is obtained and converted into a single-dimensional image; an xor operation is conducted on the image and a result obtained through a reminder operation of the index 3 and 255, an image pixel value is changed to obtain an image fig, and the size of the fig is converted into the size of the IMAGE to obtain an image FIG which is a scrambling image. According to the image duel scrambling method based on three-dimensional Logistic mapping, the function value sequences of the three-dimensional Logistic mapping are utilized to respectively change the pixel position and the pixel value of the scrambling image, dual scrambling to the image is achieved, and the image duel scrambling method has the advantages of being high in generality and good in safety.
Owner:LIAONING UNIVERSITY
Multi-image encryption method based on chaos and FrFT domain phase retrieval process
InactiveCN103903215AAdd nonlinearityIncrease disorderImage data processing detailsCiphertextPhase retrieval
A multi-image encryption method based on the chaos and FrFT domain phase retrieval process includes the chaos scrambling step, the pure phase extraction step, the phase modulation step and the chaos diffusion step. The method includes the steps of firstly, scrambling multiple original gray level images to be encrypted through paired logistic mapping to obtain scrambled images; secondly, conducting the iterated phase retrieval process on each scrambled image to extract a pure phase function of the scrambled image; thirdly, conducting phase modulation on the pure phase functions on the multiple original gray level images to be encrypted; fourthly, conducting chaos diffusion on the amplitudes of the results obtained through modulation to obtain the final cipher text. According to the multi-image encryption method, nonlinearity and randomness of plaintext images in the spatial domain and the conversion domain are enhanced, the convergence speed of an encryption system is increased, and security of the encryption system is enhanced.
Owner:XIAN UNIV OF TECH
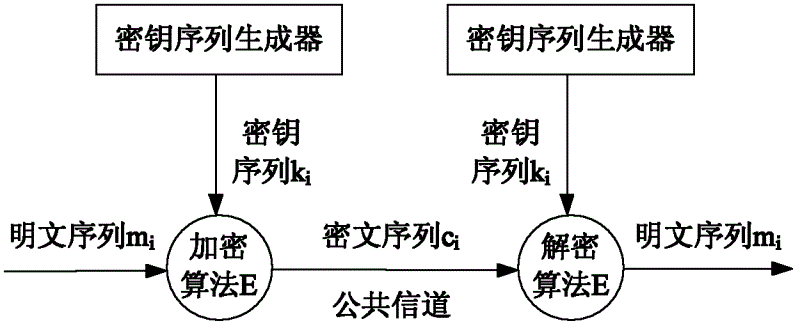
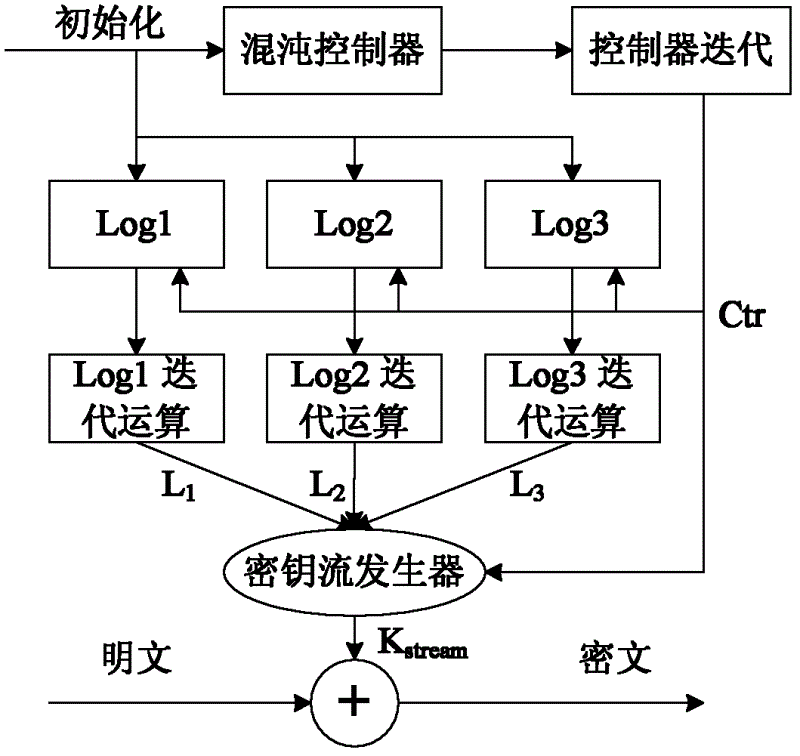
Wireless sensor network-oriented mutual interference compound chaos stream cipher implementation method
ActiveCN102624519AImprove safety and practicalitySolve the degradation problemSecurity arrangementSecuring communicationWireless mesh networkWireless sensor networking
The invention relates to a wireless sensor network-oriented mutual inference compound chaos stream cipher implementation method, which comprises the following steps of: (1) converting typical Logistic mappings and Tent mapping into a discrete function on an integer field and enabling a chaos sequence integer model to be implemented on a sensing node of a wireless sensor network which supports integer computation; (2) on the basis of an integer chaos function, establishing three Logistic chaos mappings with different initial values as a main chaos system, and then establishing a Tent chaos mapping as a chaos controller; and (3) enabling the chaos controller to mutually interfere with the three Logistic mappings, and simultaneously, enabling the Tent chaos controller to be compounded with the three Logistic chaos mappings to form a safer random cipher stream with longer period to further form a complete chaos stream cipher. The wireless sensor network-oriented mutual interference compound chaos stream cipher implementation method has favorable chaos characteristic and enhanced safety and practicability.
Owner:ZHEJIANG UNIV OF TECH
Test case set generation method based on combination chaotic sequence
InactiveCN105117326AImprove global search performanceImprove computing efficiencySoftware testing/debuggingChebyshev mapChaotic systems
The invention discloses a test case set generation method based on a combination chaotic sequence; the method comprises the following steps in sequence: a, using Chebyshev mapping and Logistic mapping to combine, thus forming the chaotic sequence; b, using the chaotic sequence to initialize population; c, setting an individual fitness function; d, defining a heredity operator; e, adding chaotic disturbance. The method uses the combination chaotic mapping to generate the initial population, each population individual comprises n genes, the population individual is a possible test case selection scheme, the combination chaotic sequence with uniform distribution characteristic is introduced to heredity algorithmic selection, intersect and variation operation, thus effectively preventing immature convergence, improving algorithmic global search capability, and calculating efficiency chaotic system generation initial population genes, adding chaotic small disturbance to each chaotic variable so as to carry out population optimization, and restraining to a proper individual through continuously evolution; test case minimization is converted into a method in which the individual with least genes is searched in the population, thus covering all test needs.
Owner:HUZHOU TEACHERS COLLEGE
Watermarking method for medical images on basis of DFT (discrete Fourier transform) and LogisticMap
InactiveCN102938132ASolve the quickness problemImprove securityImage data processing detailsFeature vectorHash function
The invention relates to a robust watermarking method on the basis of DFT (discrete Fourier transform) and a Logistic Map, and belongs to the field of multimedia signal processing. The robust watermarking method includes preprocessing and embedding watermarks and then extracting and reducing the watermarks, and particularly includes steps of (1), generating a binary encrypted matrix by the aid of the Logistic Map; (2), obtaining encrypted watermarks; (3), performing DFT for an original image and extracting feature vectors; (4), generating a binary logic sequence by the aid of the feature vectors and the chaotically encrypted watermarks to complete the process for preprocessing and embedding the watermarks; (5), performing DFT for an image to be measured to extract vectors of a feature; (6), extracting watermarks by the aid of a Hash function and the binary logic sequence generated when the watermarks are embedded; (7), generating a binary encrypted matrix by the Logistic Map; and (8), solving the reduced watermarks so as to complete the process for extracting and reducing the watermarks. The robust watermarking technology has a high practical value in the aspect of protecting personal information of patients during remote medical treatment.
Owner:HAINAN UNIVERSITY
Encrypted face recognition method based on ciphertext domain
InactiveCN107045627APrevent leakagePrevent tamperingCharacter and pattern recognitionImage watermarkingFeature vectorMultimedia signal processing
The invention discloses an encrypted face recognition method based on a ciphertext domain. The encrypted face recognition method belongs to the field of multimedia signal processing. The encrypted face recognition method comprises the steps of: firstly, encrypting face images in a frequency domain by using nature of a Logistic Map; extracting face eigenvectors through performing DTF transform on encrypted images; and performing encryption on a face to be detected in a transform domain, extracting encrypted feature eigenvectors in a DFT transform domain, and carrying out face recognition through calculating similarities among the eigenvectors. The encrypted face recognition method is an encrypted face recognition technology based on the ciphertext domain, and has good resistance to conventional attack, geometric attack, occlusion, lighting and the like attacks.
Owner:HAINAN UNIVERSITY
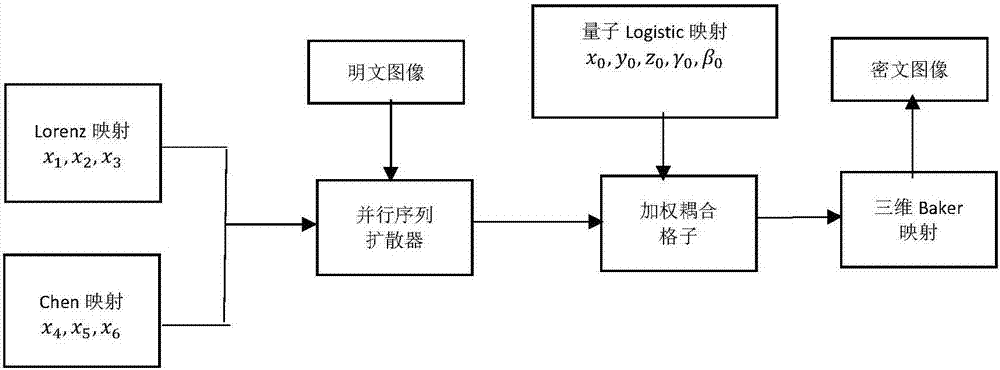
Quantum chaos-based parallel image encryption method
InactiveCN107292802ASmooth connectionResist Differential AttacksImage data processing detailsPlaintextComputer hardware
The invention relates to a quantum chaos-based parallel image encryption method. The invention aims to solve the defects of a current traditional serial chaotic encryption algorithm. According to the method of the invention, a sequence generated by hyperchaotic Lorenz mapping and Chen mapping is used as an input sequence for parallel encryption; a generated intermediate ciphertext is adopted as the input of quantum logistic mapping; three-dimensional Baker scrambling operation is performed; and therefore, plaintext information can be hidden. As indicated by experimental simulation, the encryption speed of the algorithm of the invention is higher than that of the traditional serial encryption algorithm, the algorithm of the invention can effectively resist statistical attacks and differential attacks to achieve a very good encryption effect.
Owner:GUANGDONG UNIV OF TECH
Color picture encryption algorithm and device
ActiveCN108199828AImprove performanceImprove robustnessEncryption apparatus with shift registers/memoriesSecuring communication by chaotic signalsPlaintextCiphertext
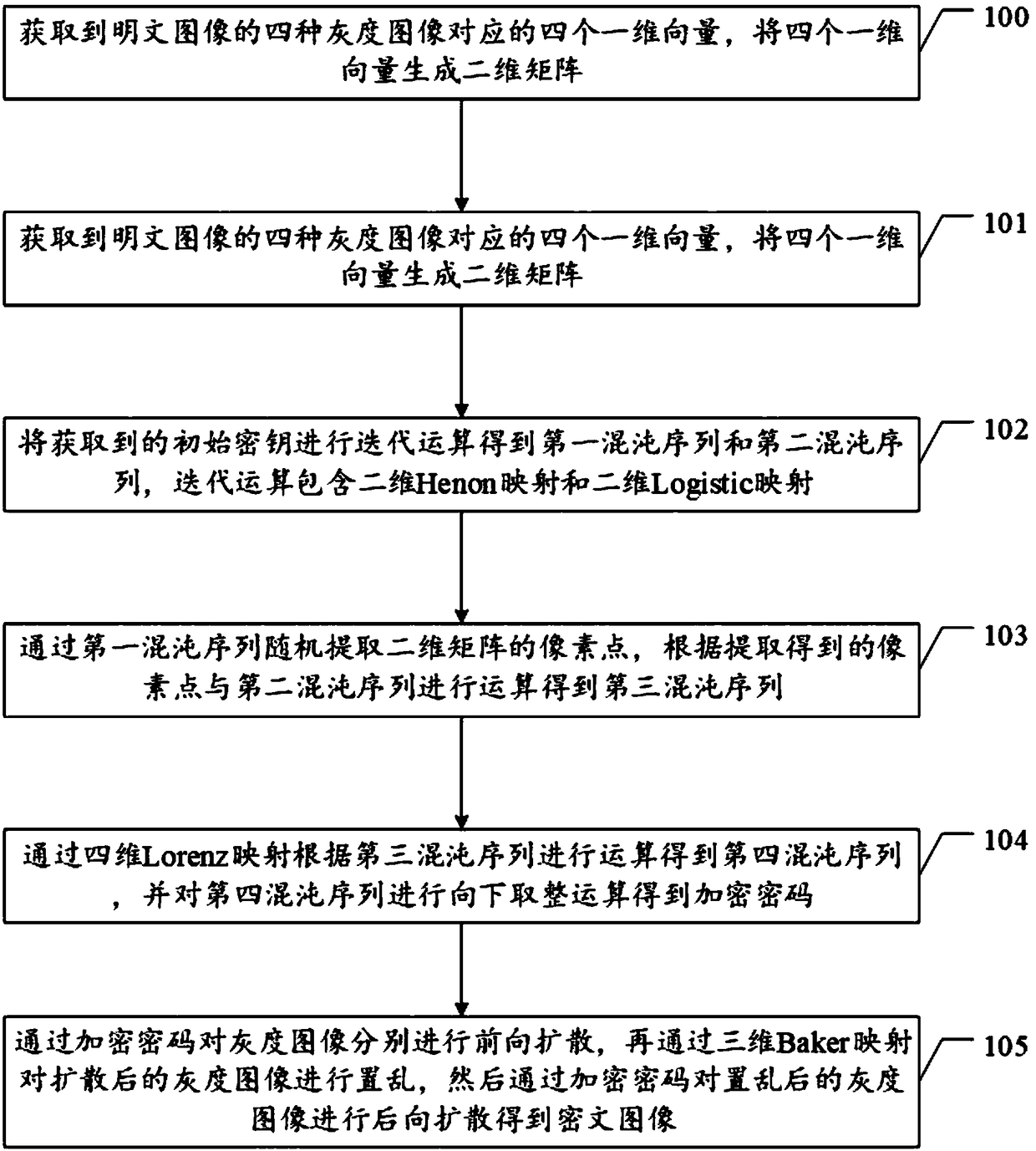
The embodiments of the invention provide a color picture encryption algorithm and device. The method comprises the steps of: acquiring four one-dimensional vectors corresponding to four gray images ofa plain text image, and generating a two-dimensional matrix from the four one-dimensional vectors; performing iterative operation on the acquired initial key to obtain a first chaotic sequence and asecond chaotic sequence, the iterative operation comprising two-dimensional Henon mapping and two-dimensional Logistic mapping; randomly extracting pixels of the two-dimensional matrix through the first chaotic sequence, and performing operation on the extracted pixels and the second chaotic sequence to obtain a third chaotic sequence; performing operation on the third chaotic sequence through four-dimensional Lorenz mapping to obtain a fourth chaotic sequence, and rounding down the fourth chaotic sequence to obtain an encrypted password; forwardly diffusing the gray images respectively through the encrypted password, then scrambling the diffused gray images through three-dimensional Baker mapping, and backwardly diffusing the scrambled gray images through the encrypted password to obtaina cipher text image.
Owner:GUANGDONG UNIV OF TECH
DWT-DCT (Discrete Wavelet Transform-Discrete Cosine Transform) and Logistic Map-based medical image robust watermarking method
InactiveCN102945543AStrong resistance to conventional attacksStrong ability to resist geometric attacksImage data processing detailsThird partyFeature vector
The invention relates to a DWT-DCT (Discrete Wavelet Transform-Discrete Cosine Transform) and Logistic Map-based medical image robust watermarking method, which belongs to the field of multimedia signal processing. The method comprises preprocessing of a watermark and embedding of the watermark, wherein the preprocessing of the watermark and embedding of the watermark comprise the following steps of: (1) obtaining an encryption matrix by using a Logistic Map; (2) obtaining an encrypted watermark; (3) performing DWT on an original image, performing DCT on an approximation sub-image and extracting the vector of a characteristic; (4) obtaining a corresponding two-valued logic sequence by using the characteristic vector and chaotically encrypted watermark, storing the two-valued sequence at a third party, and then extracting and reducing the watermark, wherein the extraction and the reduction of the watermark comprise the following steps of: (5) performing operation similar to the step (3) on an image to be tested to solve one characteristic vector; (6) extracting the encrypted watermark; (7) generating a two-valued encryption matrix by using the Logistic Map; and (8) solving the reduced watermark. According to the method, the secrecy of information of a patient can be protected.
Owner:HAINAN UNIVERSITY
Digital watermark encryption realization method
InactiveCN103020496ALarge key spaceIncreased sensitivityImage data processing detailsProgram/content distribution protectionChaos theoryPredictability
The invention provides a digital watermark encryption realization method. On the basis of the research of a digital watermark embedding algorithm in a wavelet domain, the chaos theory is introduced into the establishment of the digital watermark; the algorithm that a chaos sequence which is generated by Logistic mapping is embedded into a wavelet domain digital watermark is proposed and realized; and the algorithm has the characteristics of secret key uniqueness, irreversibility, invisibility and robustness according to the specific unpredictability of the chaos sequence. An experiment proves that the algorithm has a good visual effect and is a practical and feasible digital watermark encryption algorithm.
Owner:王少夫
Noise auxiliary encryption and signal recovery method of broadband access network
The present invention discloses a noise auxiliary encryption and signal recovery method of a broadband access network. The method is characterized in that noise signals of pilot frequency subcarriers and preambles, namely M+1 noise QAM symbols n1 to n(M+1), and the distribution of the pilot frequency subcarriers are obtained by the one-dimensional logistic mapping (chaotic mapping), and an N*N switching matrix Msw is obtained according to the distribution of the pilot frequency subcarriers. During the encryption process, an original signal and the noise signal are switched by the switching matrix Msw, so that not only the noise signal is inserted in the original signal, but also the distribution of the original signals is changed. At a receiving terminal, the pilot frequency subcarriers and the preambles loaded with the noise signals recover the original signals by a method reverse with a sending terminal. According to the present invention, and during the encryption process, the noise signal used for signal recovery is added in a useful signal randomly, and the original useful signal itself is disturbed and reconstructed, so that an invalid intruder can not obtain all useful information from an encryption signal if not having a secret key.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
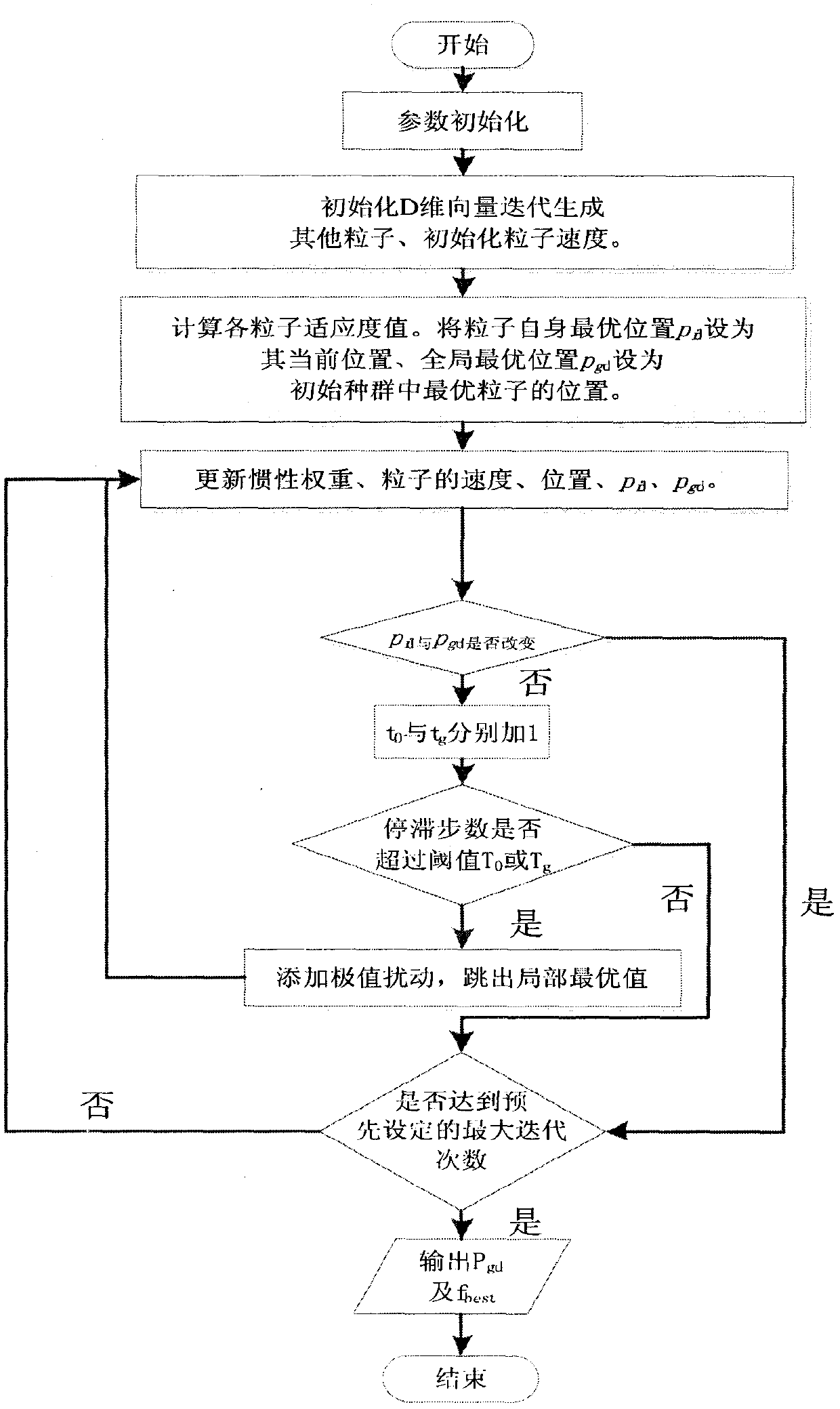
A self-adaptive inertia weight chaotic particle swarm algorithm
PendingCN109697299AFast trackImprove search accuracyForecastingDesign optimisation/simulationLocal optimumChaotic particle swarm optimization
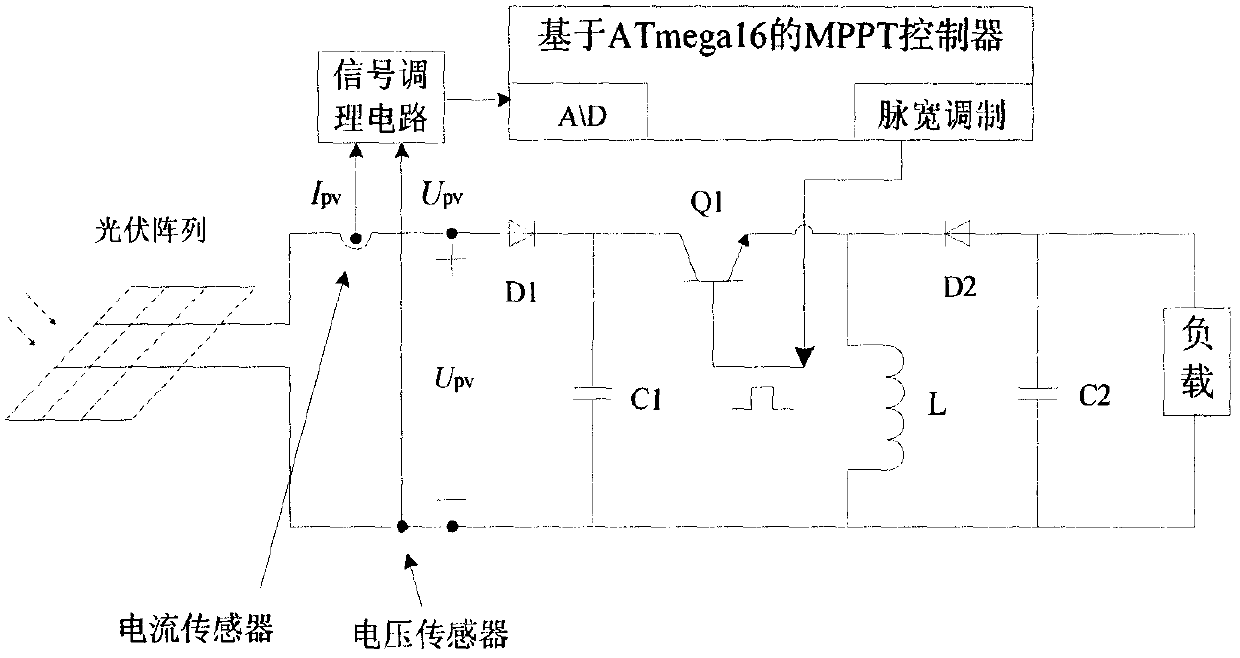
The invention relates to the field of photovoltaic power generation, in particular to an adaptive inertial weight chaotic particle swarm optimization (ACPSO) algorithm. The algorithm utilizes segmented Logistic mapping with higher efficiency than general Logistic mapping to generate a chaotic sequence to initialize the positions of particles, so that the diversity of global search is ensured; then, a particle swarm algorithm is optimized by adopting an adaptive inertia weight, so that the tracking speed of the maximum power is increased; and finally, if the judgment algorithm falls into precocity, performing extreme value disturbance on the particle optimal position and the global optimal position at the same time. Compared with single extreme value disturbance, the method can enable the algorithm to jump out of local optimum faster. According to the algorithm, the maximum power point can be tracked more quickly and effectively in real time according to sunlight changes, the system works near the maximum power point, meanwhile, the oscillation phenomenon of the system at the maximum power point is reduced, and the utilization rate of a photovoltaic array is increased.
Owner:TIANJIN UNIVERSITY OF SCIENCE AND TECHNOLOGY
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com