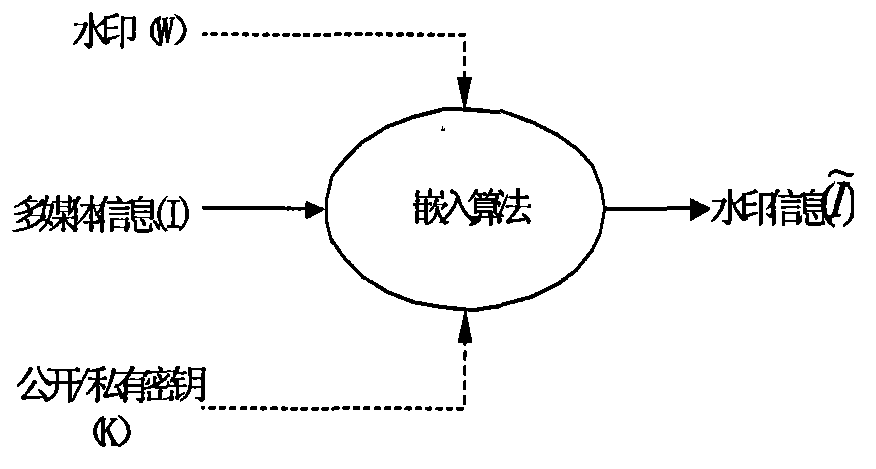
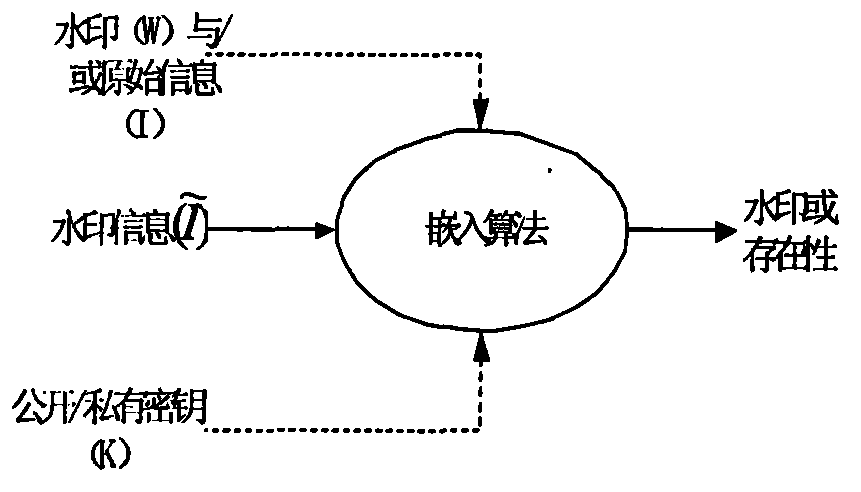
Digital watermark encryption realization method
An implementation method and technology of digital watermarking, applied in image data processing, image data processing, program/content distribution protection, etc., can solve problems such as inability to detect, and achieve the effects of good security, high sensitivity, and large key space.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0025] Select a Lena image with different texture features and a size of 512×512 as the simulation object, such as Figure 4 ;
[0026] The Logistic chaotic map is:
[0027] x n+1 =λx n (1-x n ) (5)
[0028] This chaotic map has the following properties:
[0029] ① When the system parameter 3.57<λ<4, the Logstic map is in a chaotic state.
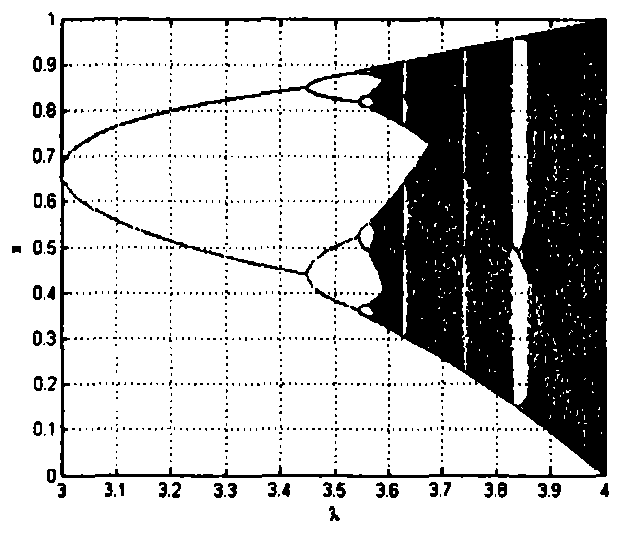
[0030] ②It is sensitive to the initial value. When x(1)=0.98, the chaotic sequence has regularity and ergodicity, and its mapping is as follows image 3 shown;
[0031] Using the above algorithm, watermark encryption is performed on the gray Lena image, and the watermark encrypted image is as follows Figure 5 As shown; you can clearly see the visual effect of the image after adding the chaotic sequence watermark
[0032] The digital watermark encryption algorithm completes the encryption of a gray image. It has the advantages of large key space, high sensitivity, good security, and strong anti-attack capability.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com