Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
1592results about How to "Avoid detection" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
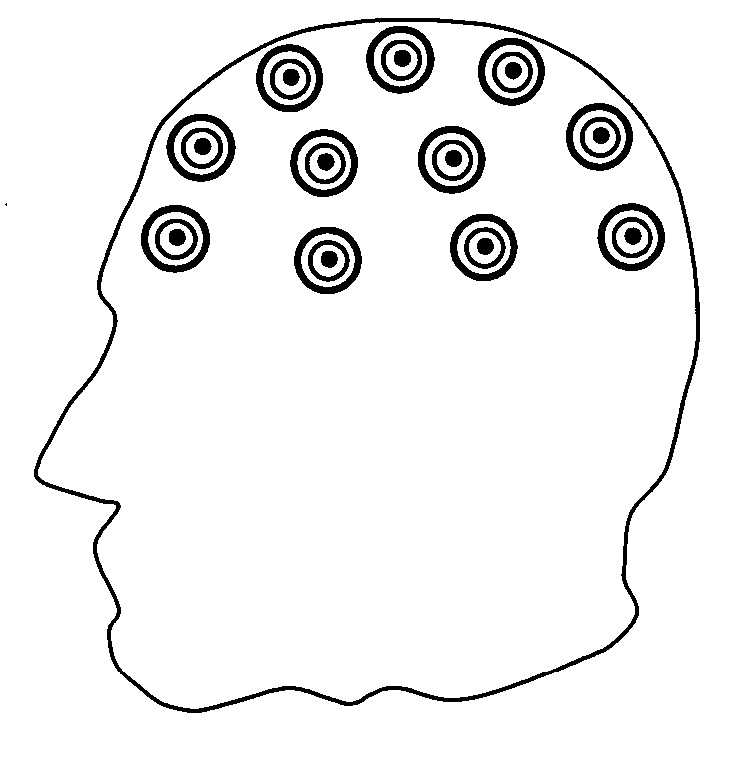
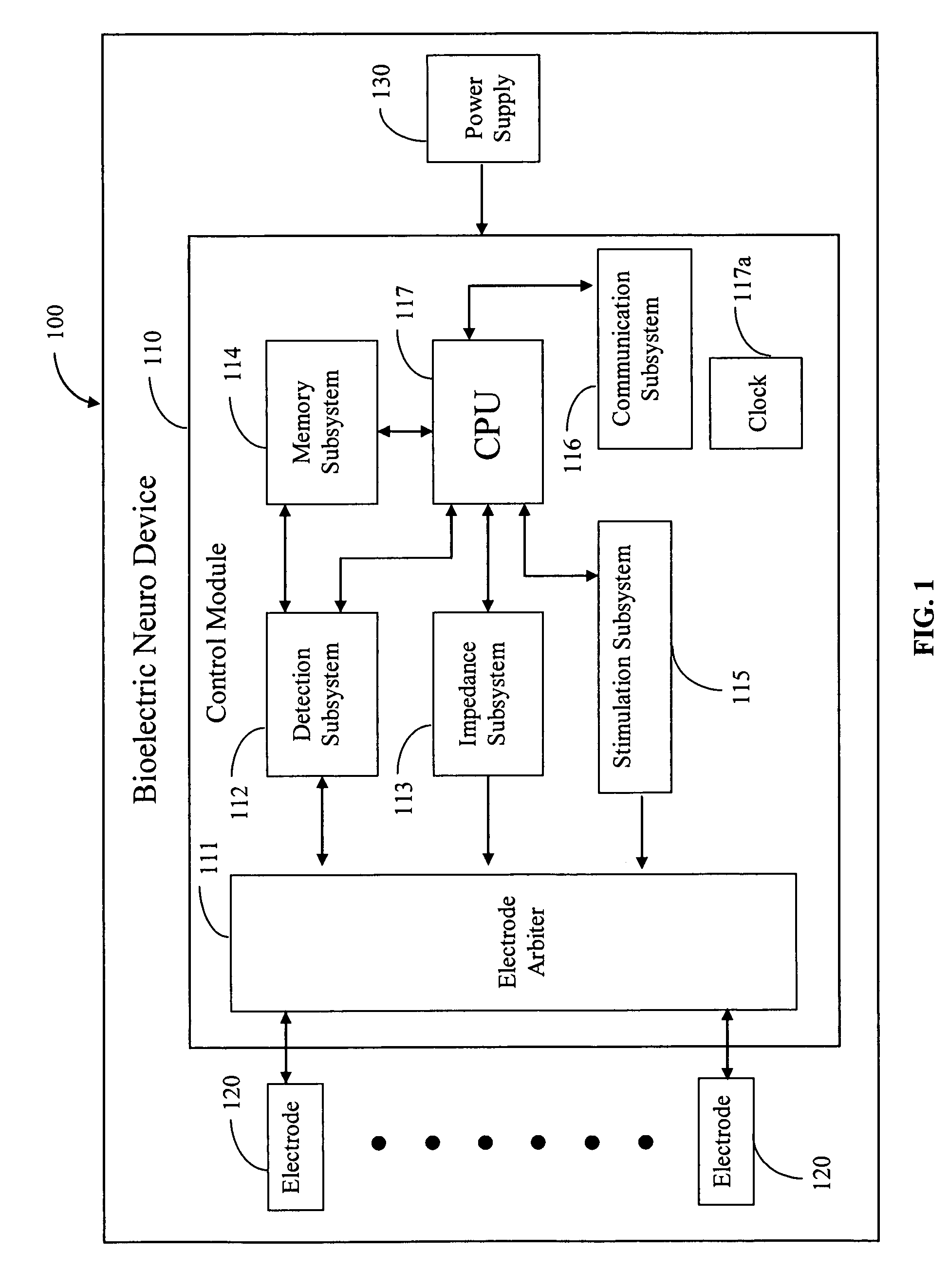
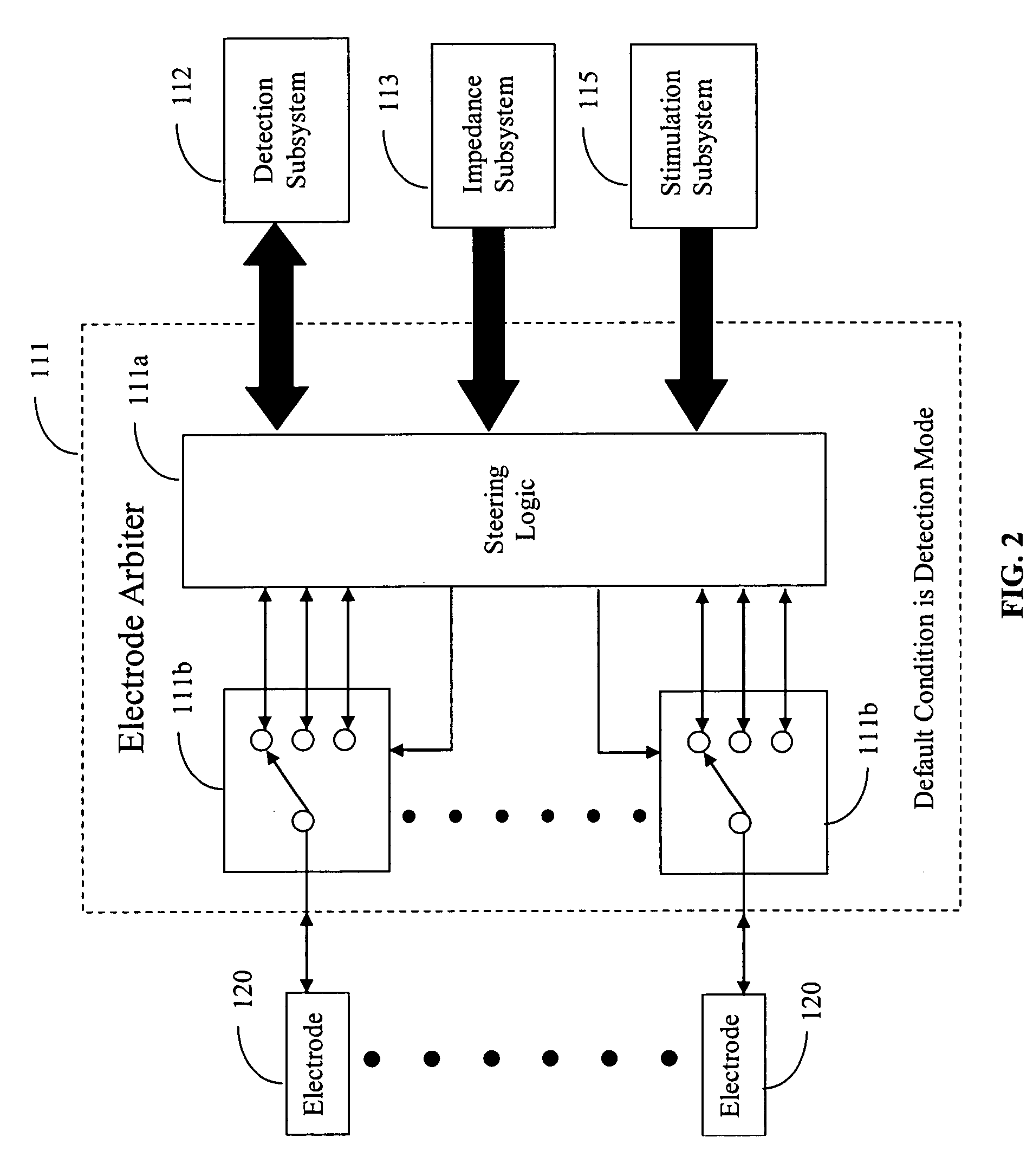
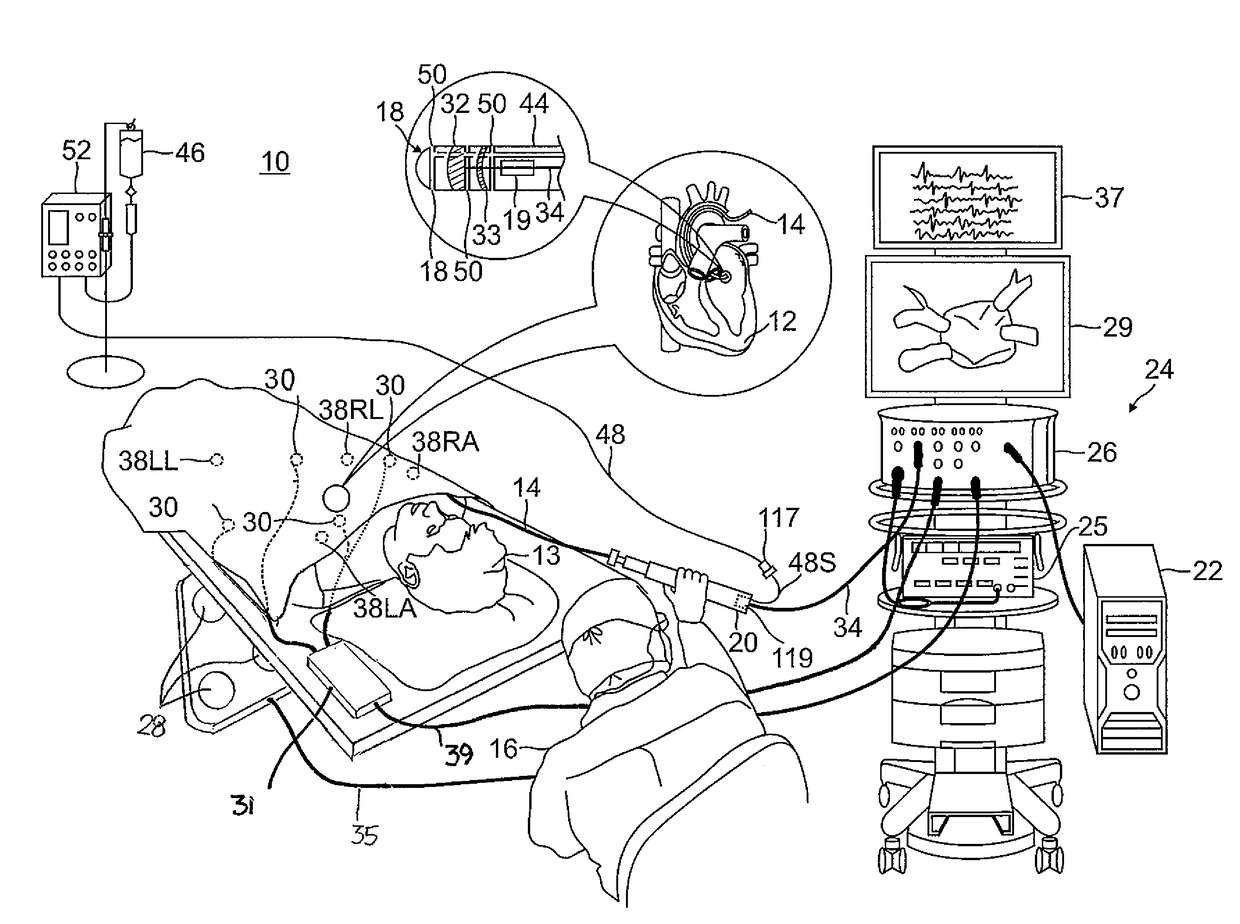
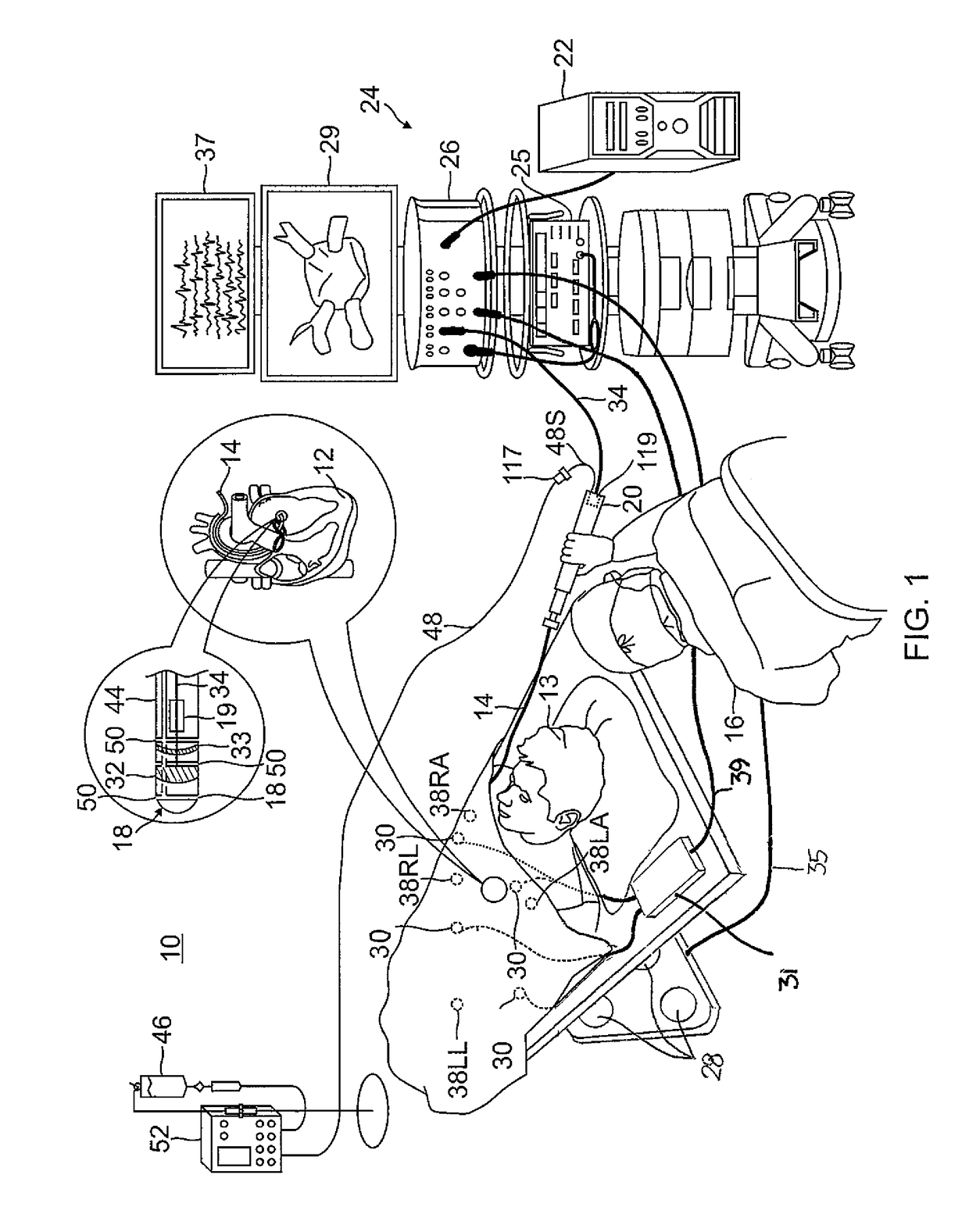
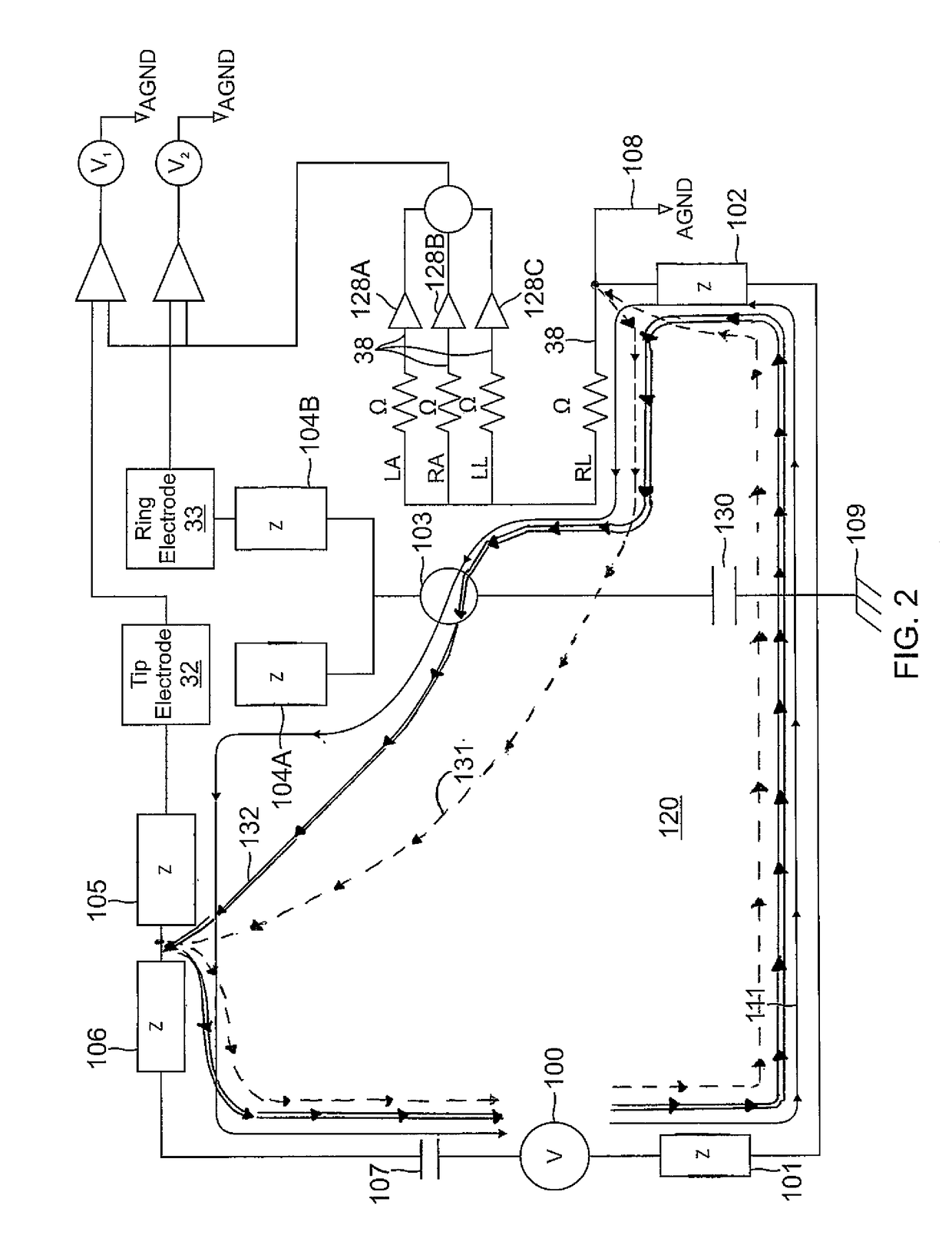
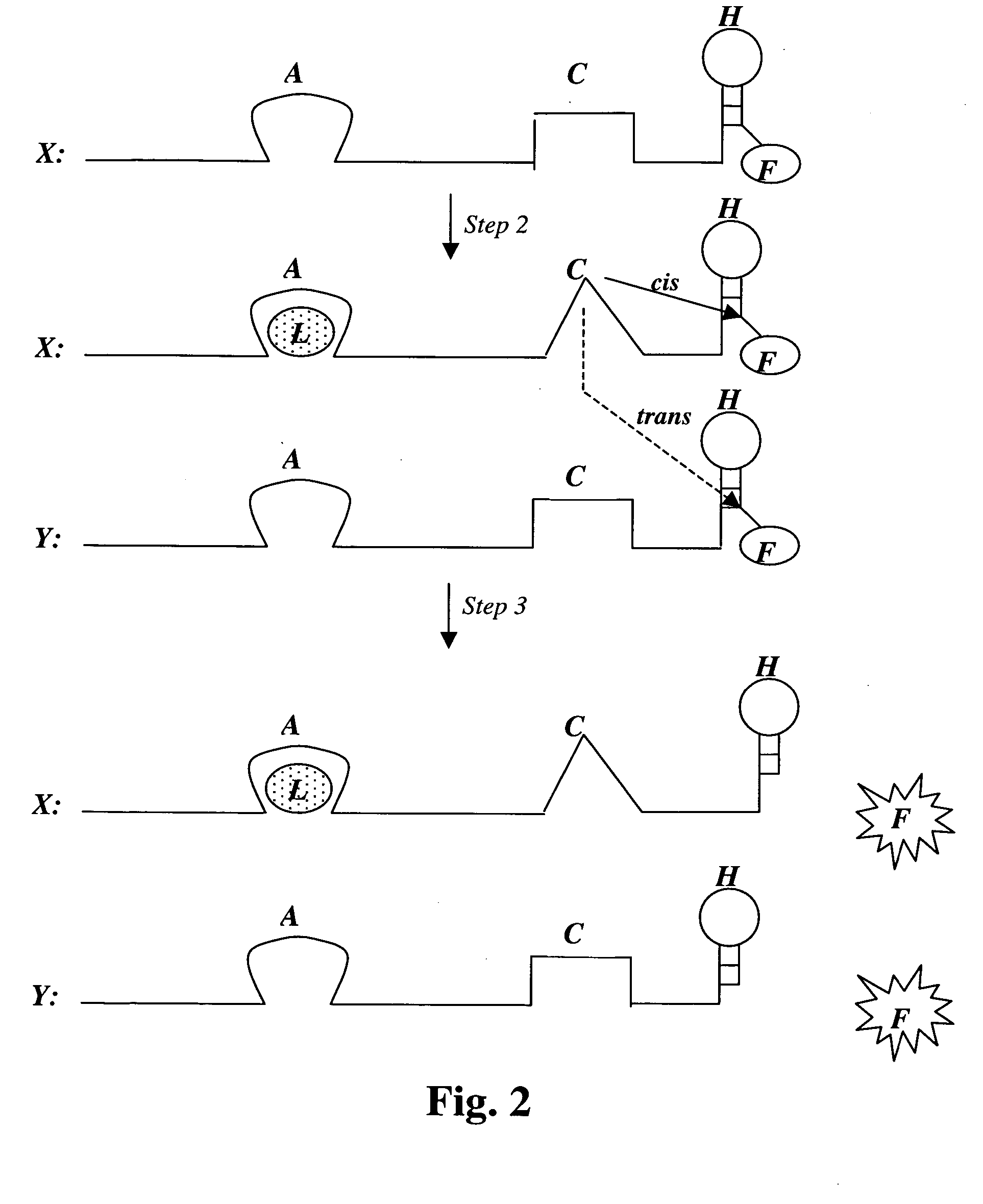
Medical devices for the detection, prevention and/or treatment of neurological disorders, and methods related thereto
ActiveUS20060173510A1Avoid detectionMinimal invasionElectroencephalographyHead electrodesSubstance abuserTranscranial Electrical Stimulations
Disclosed are devices and methods for detecting, preventing, and / or treating neurological disorders. These devices and methods utilize electrical stimulation, and comprise a unique concentric ring electrode component. The disclosed methods involve the positioning of multiple electrodes on the scalp of a mammal; monitoring the mammal's brain electrical patterns to identify the onset of a neurological event; identifying the location of the brain electrical patterns indicative of neurological event; and applying transcutaneous or transcranial electrical stimulation to the location of the neurological event to beneficially modify brain electrical patterns. The disclosed methods may be useful in the detection, prevention, and / or treatment of a variety of indications, such as epilepsy, Parkinson's Disease, Huntington's disease, Alzheimer's disease, depression, bipolar disorder, phobia, schizophrenia, multiple personality disorder, migraine or headache, concussion, attention deficit hyperactivity disorder, eating disorder, substance abuse, and anxiety. The disclosed methods may also be used in combination with other peripheral stimulation techniques.
Owner:LOUISIANA TECH UNIV RES FOUND A DIV OF LOUISIANA TECH UNIV FOUND +1
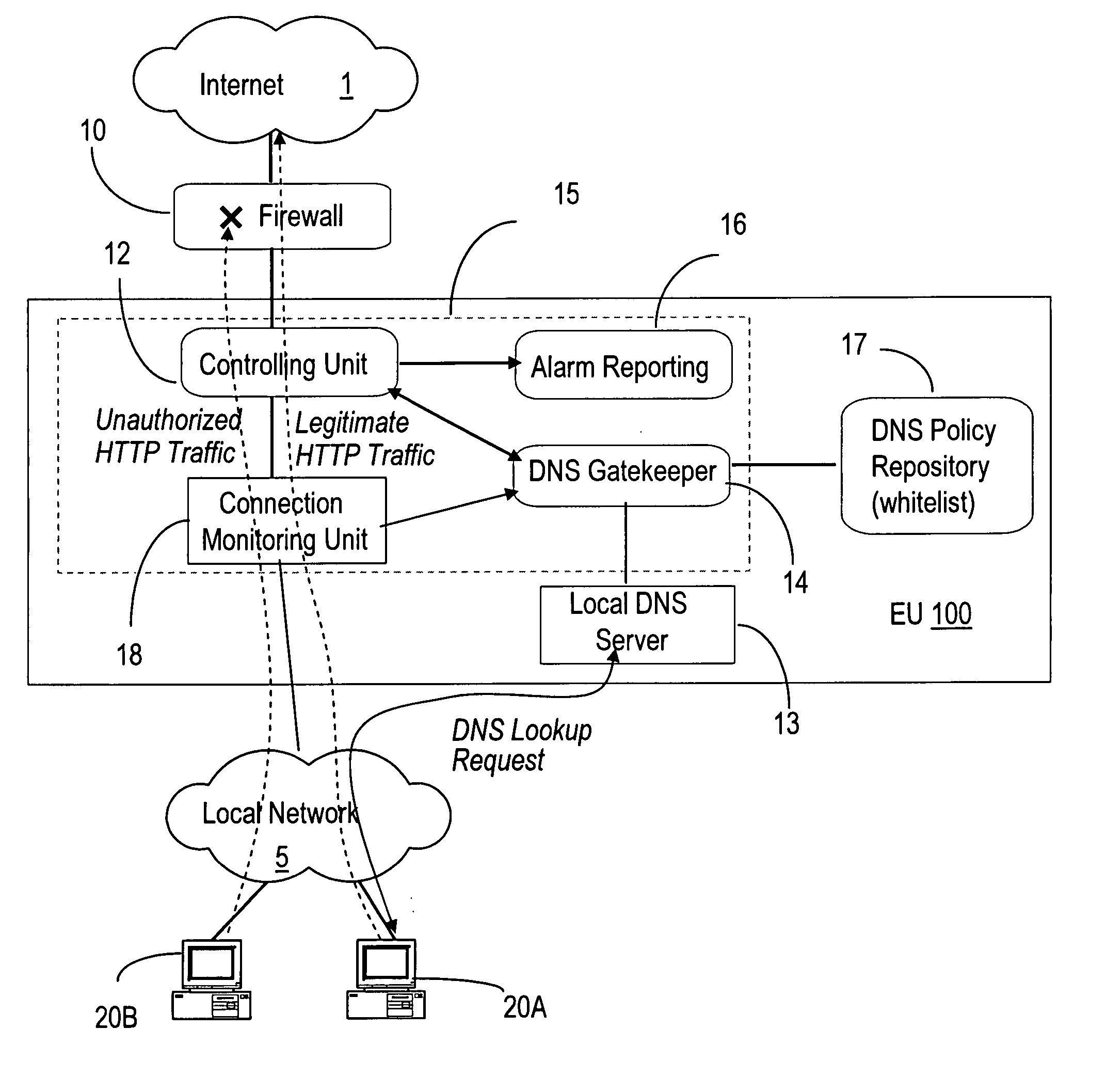
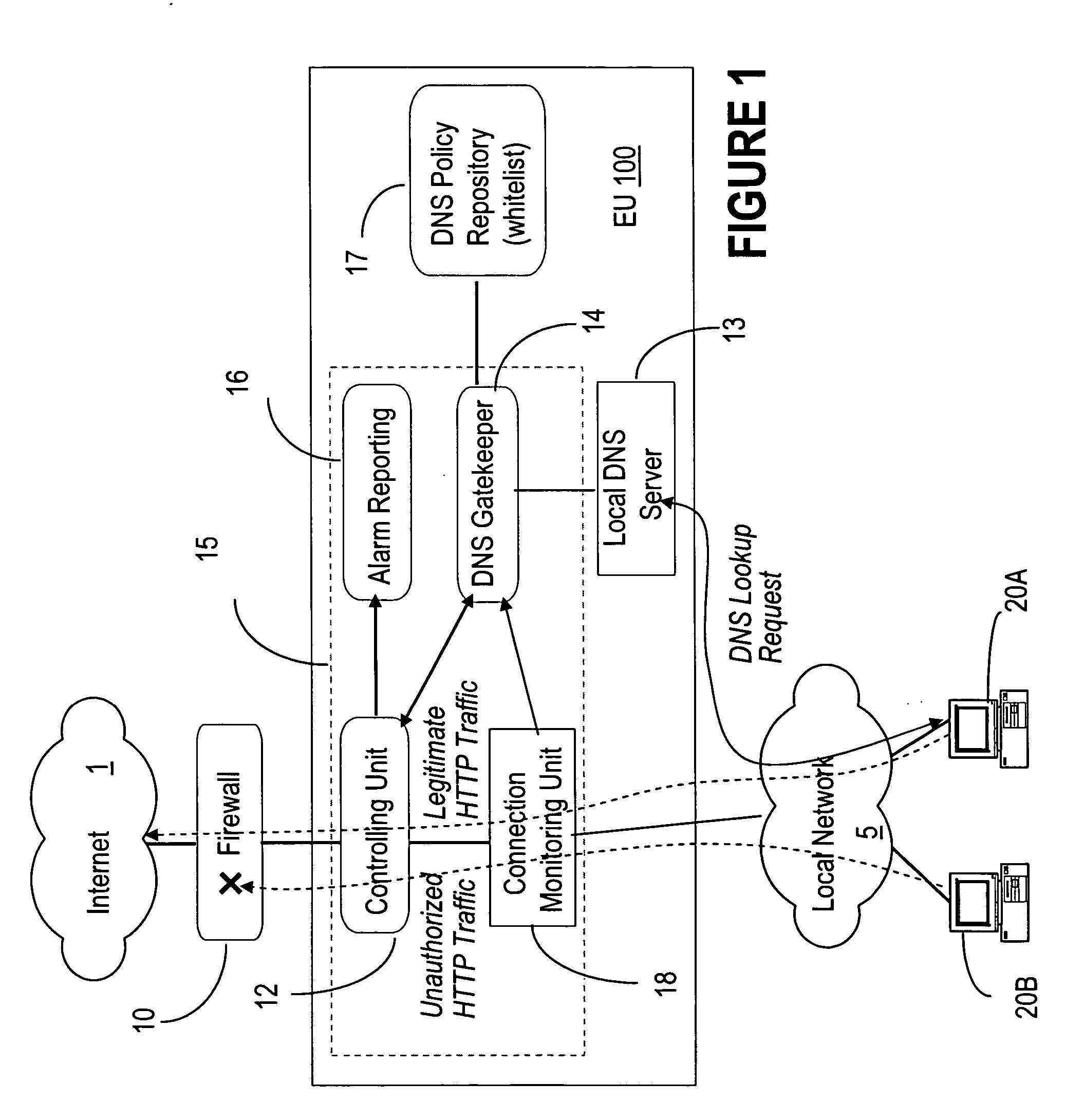
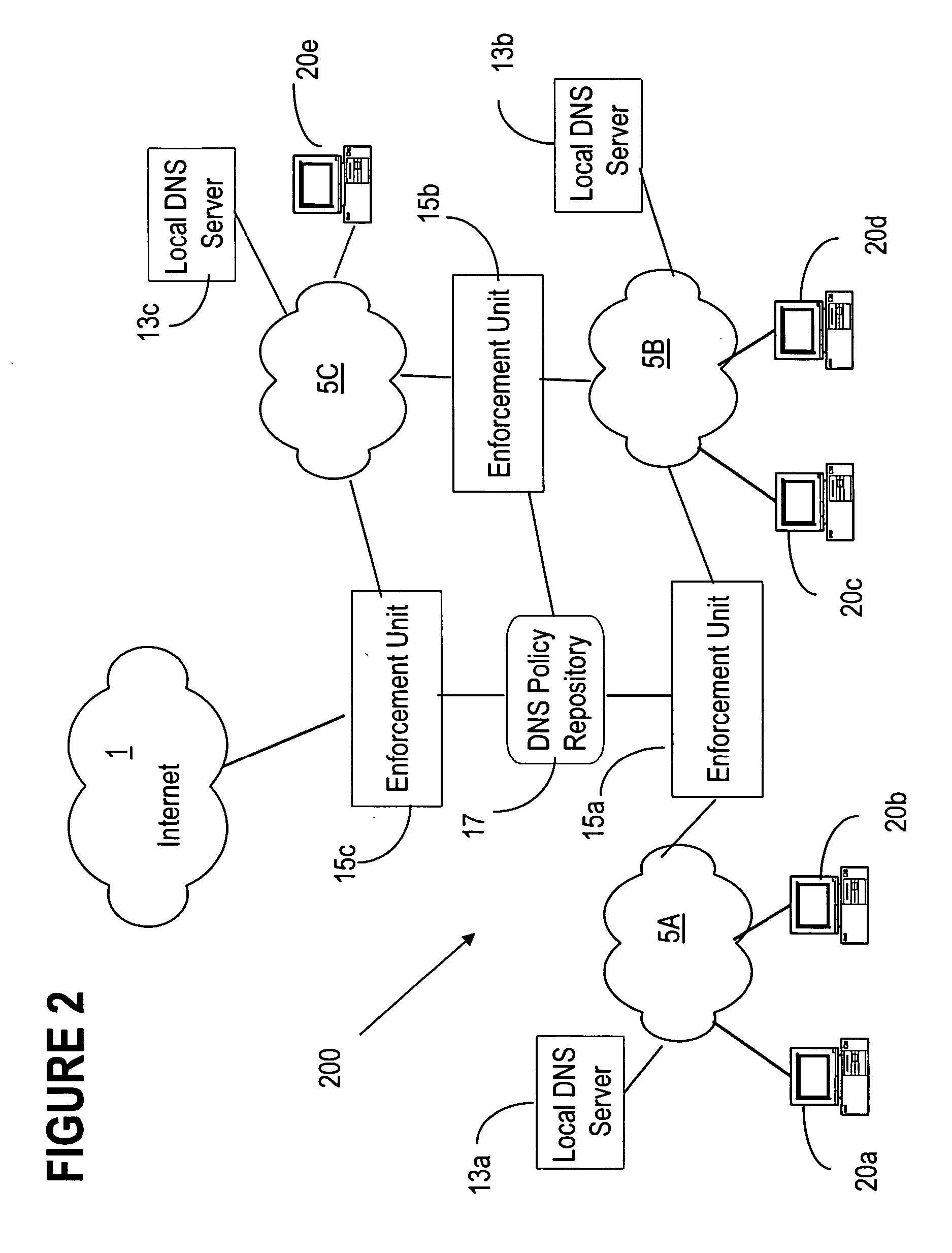
DNS based enforcement for confinement and detection of network malicious activities
InactiveUS20070033645A1Avoid detectionAvoid spreadingDigital data processing detailsUnauthorized memory use protectionDomain nameNetwork activity
Malicious network activities do not make use of the Domain Name System (DNS) protocol to reach remote targets outside a local network. This DNS-based enforcement system for confinement and detection of network malicious activities requires that every connection toward a resource located outside the local network is blocked by default by the local enforcement box, e.g. a firewall or a proxy. Outbound connections are allowed to leave the local network only when authorized directly by an entity called the DNS Gatekeeper.
Owner:RPX CORP
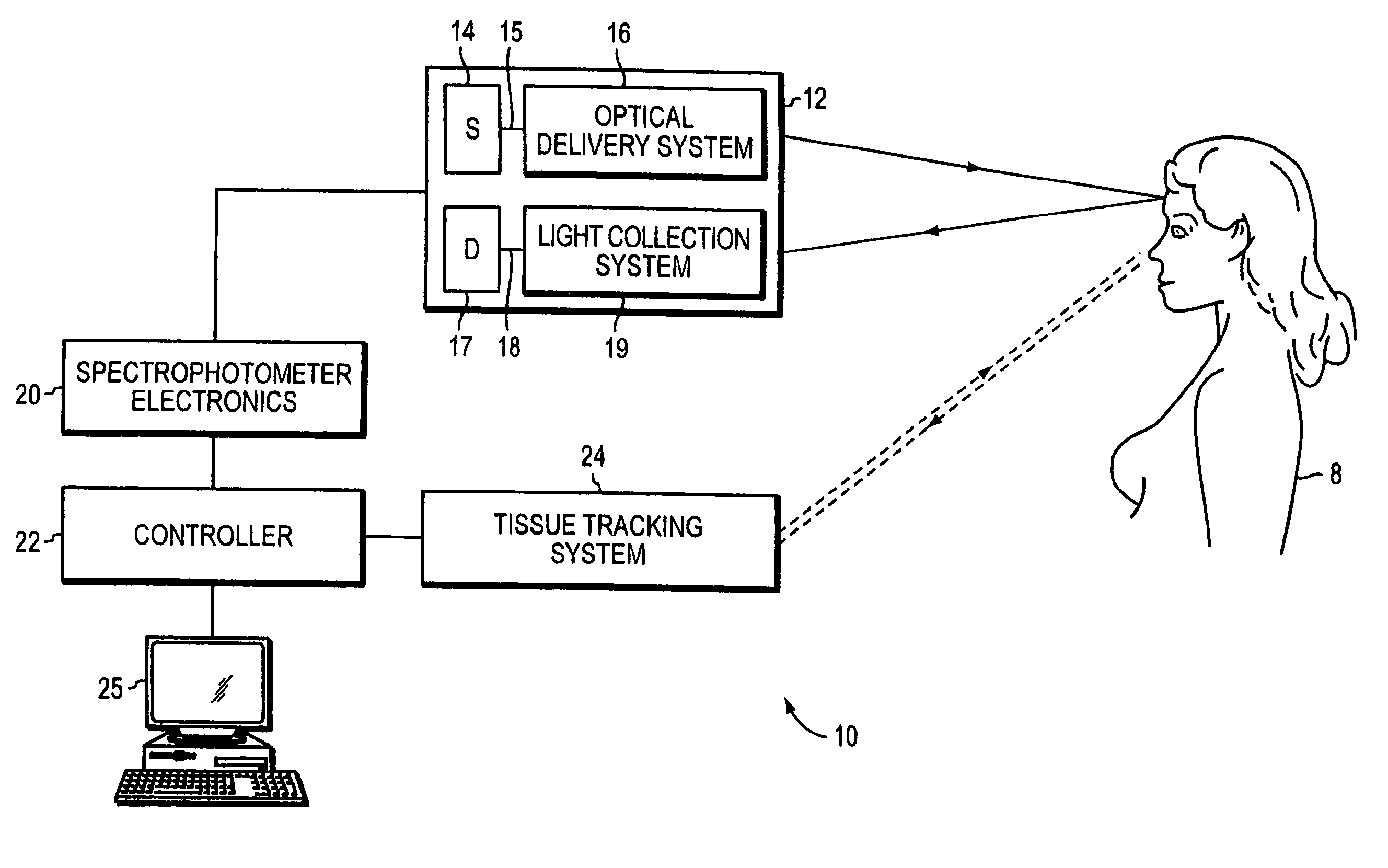
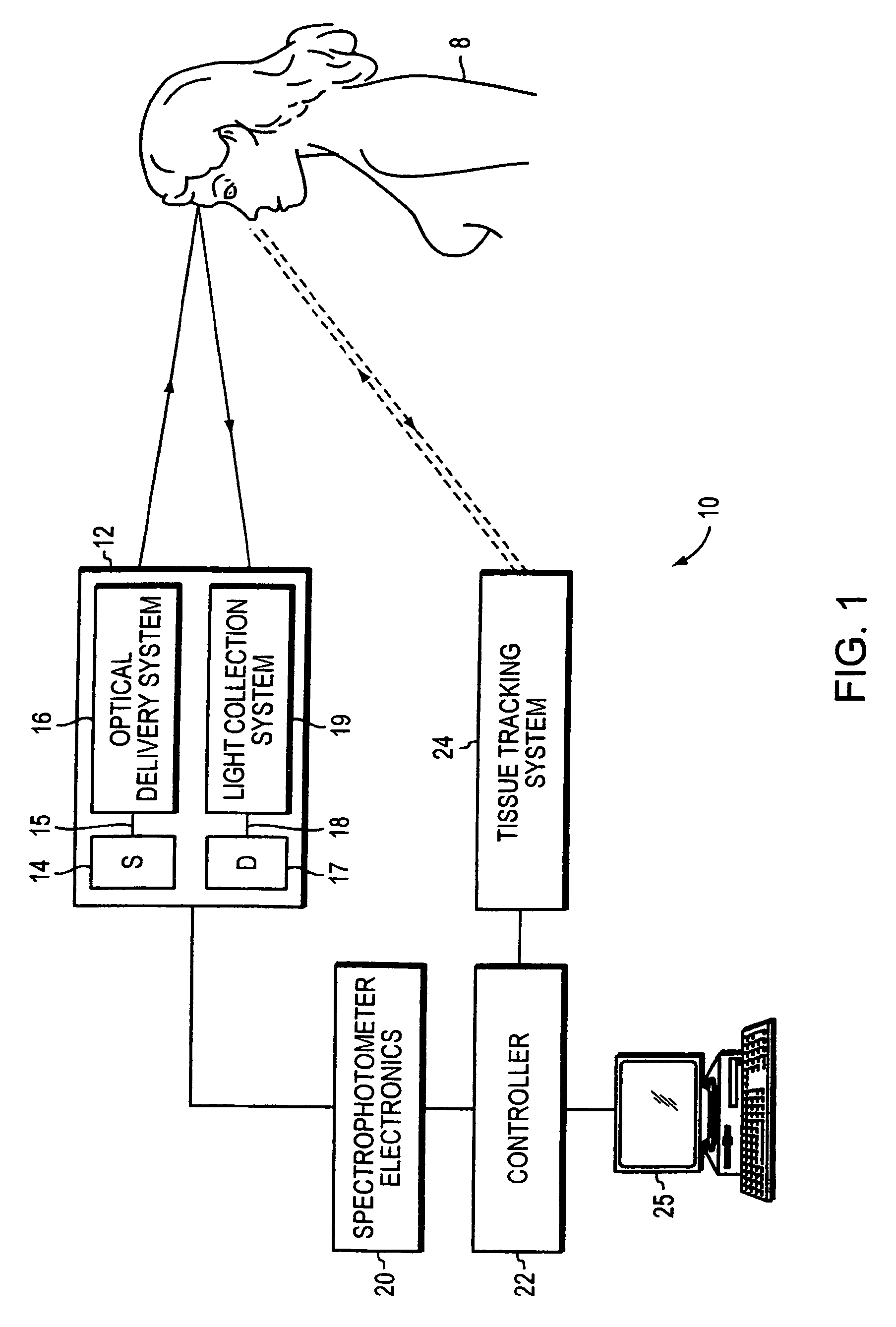
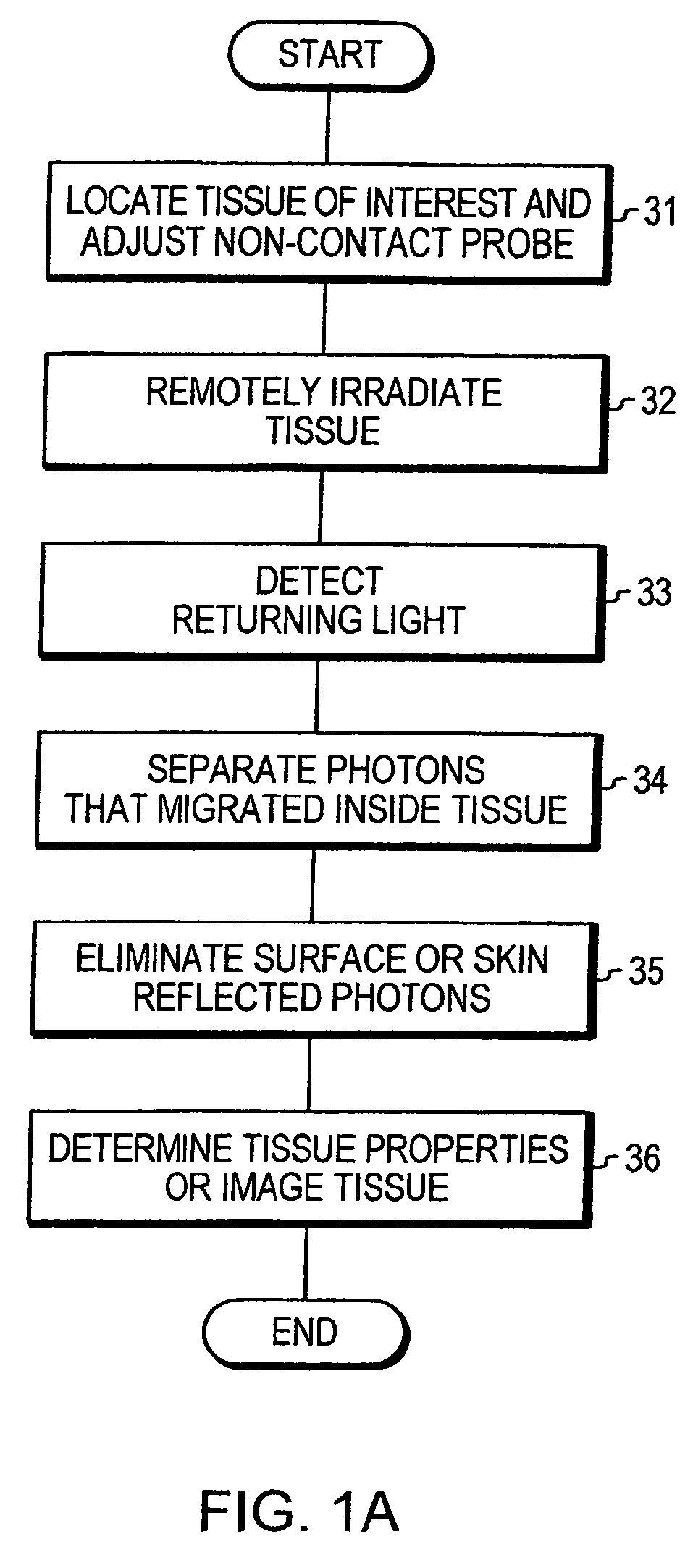
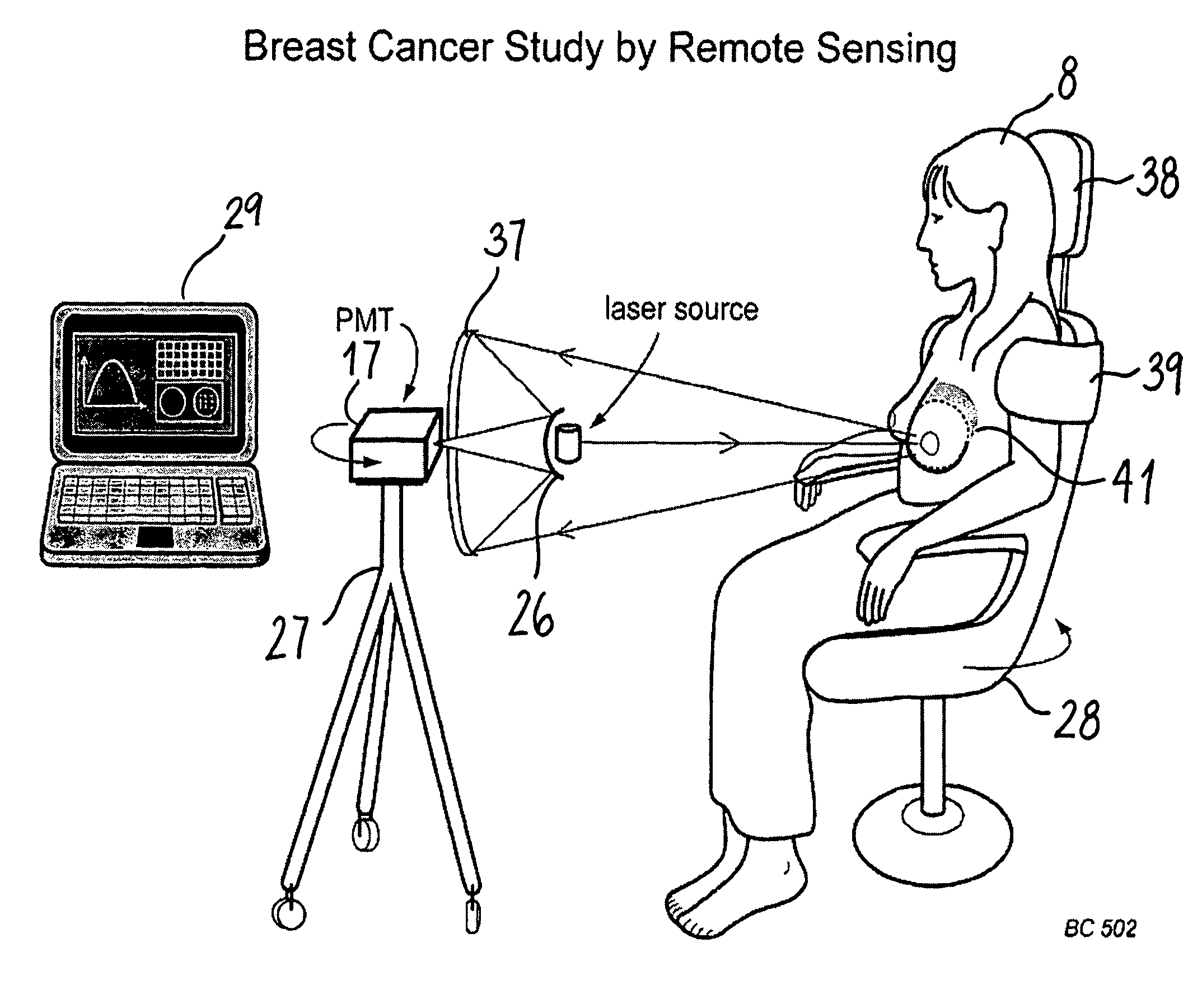
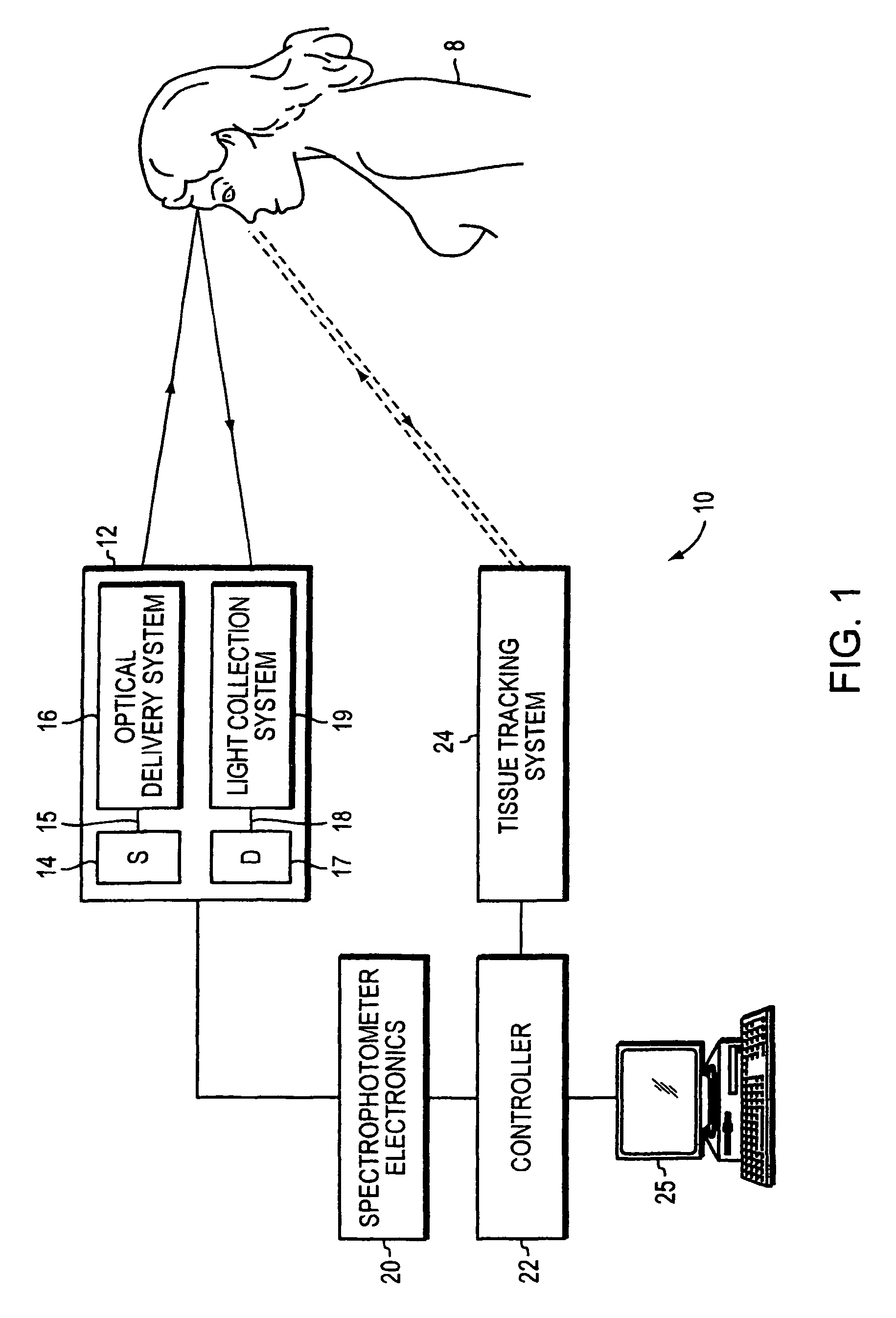
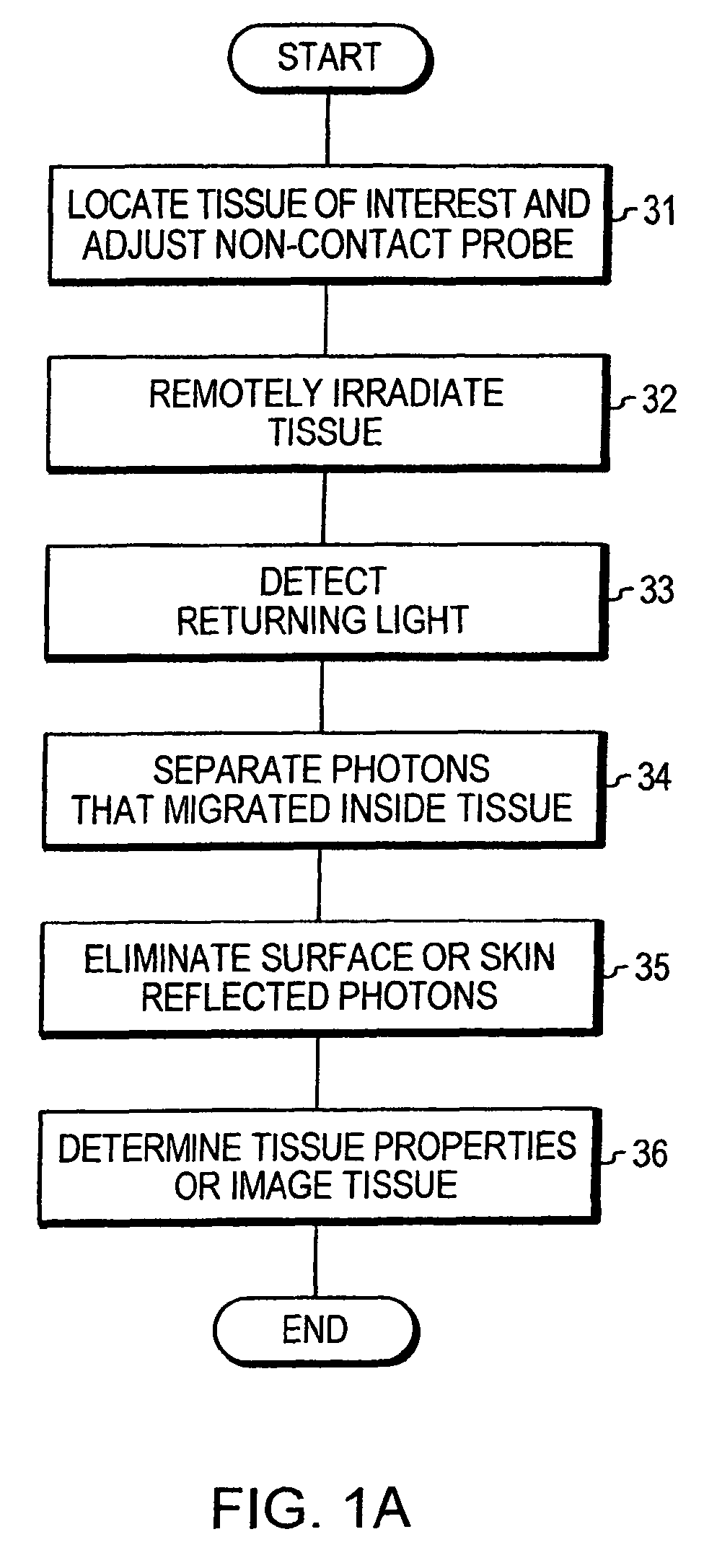
Optical examination of biological tissue using non-contact irradiation and detection
InactiveUS20060058683A1Avoid detectionCancel noiseDiagnostics using lightSensorsLight beamContact position
An optical system for examination of biological tissue includes a light source, a light detector, optics and electronics. The light source generates a light beam, transmitted to the biological tissue, spaced apart from the source. The light detector is located away (i.e., in a non-contact position) from the examined biological tissue and is constructed to detect light that has migrated in the examined tissue. The electronics controls the light source and the light detector, and a system separates the reflected photons (e.g., directly reflected or scattered from the surface or superficial photons) from the photons that have migrated in the examined tissue. The system prevents detection of the “noise” photons by the light detector or, after detection, eliminates the “noise” photons in the detected optical data used for tissue examination.
Owner:NONINVASIVE TECH
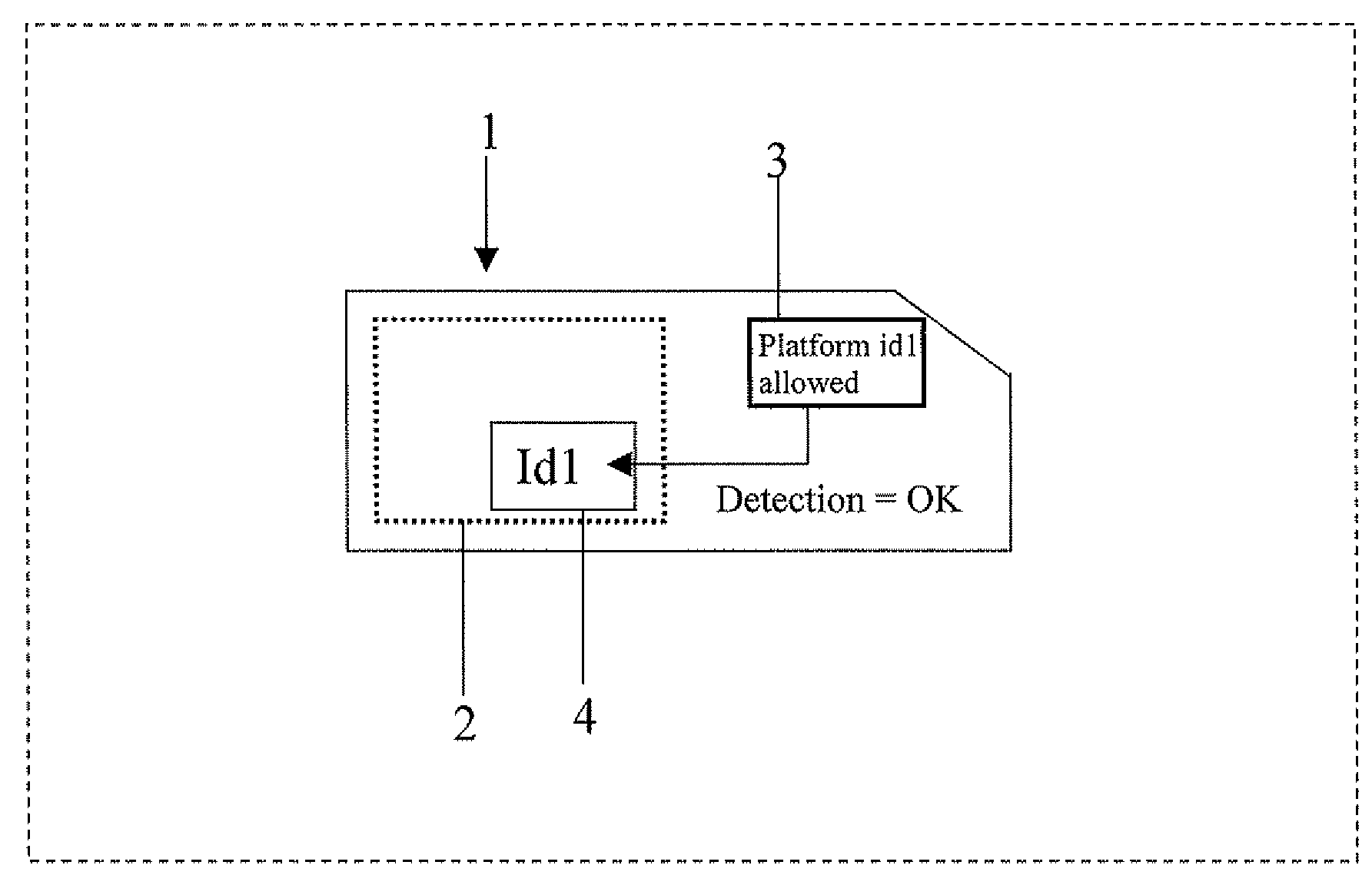
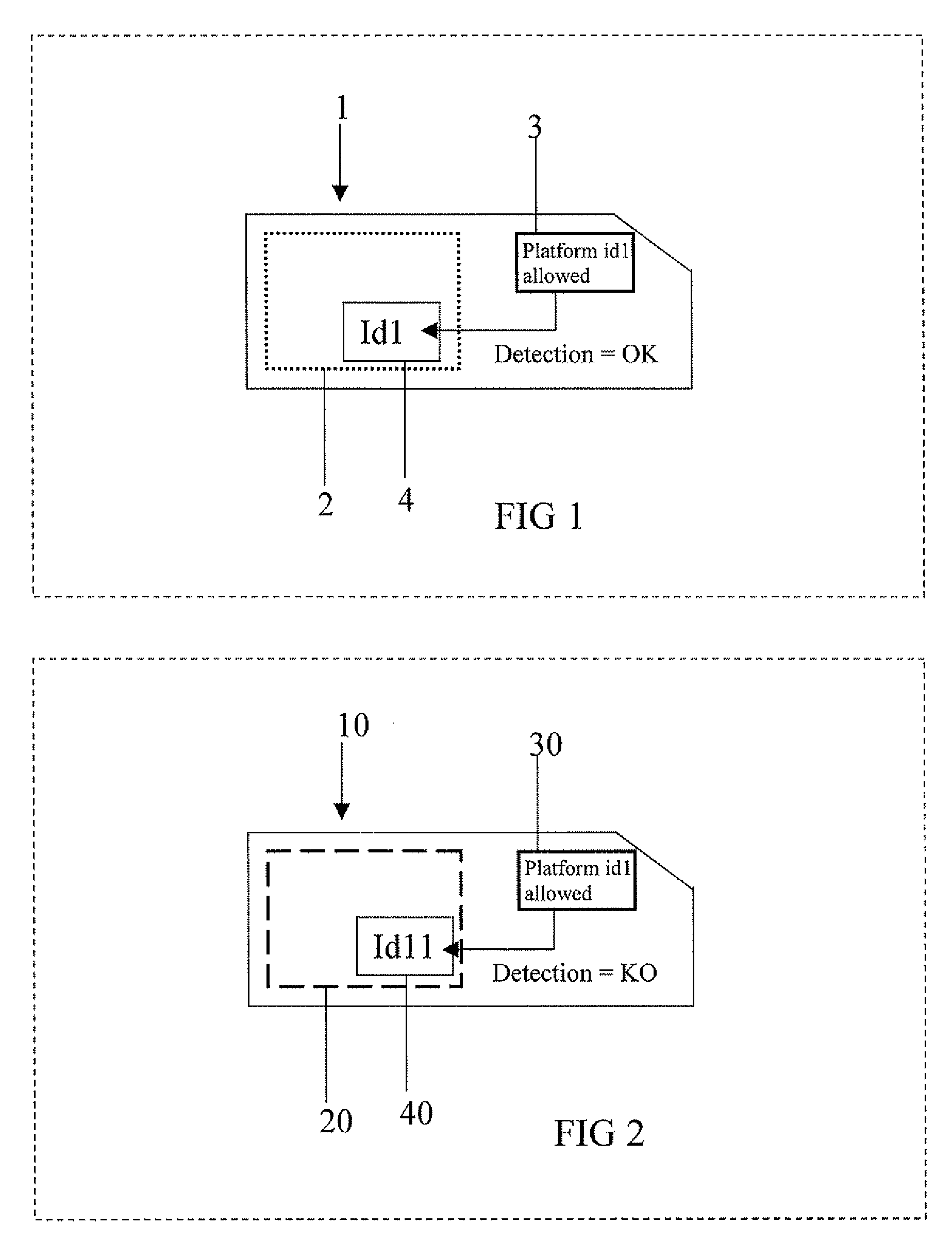
Method for controlling the execution of an applet for an IC card
ActiveUS20080288699A1Preventing executionAvoid business lossInternal/peripheral component protectionComponent plug-in assemblagesOperating systemJava Card
A method for controlling the execution of an applet for an IC Card including a java card platform, includes a phase for downloading the applet inside the IC Card, a phase for executing the applet through the java card platform and a phase for storing an identification platform number inside a memory portion of the IC Card. The phase for executing the applet has a first step for detecting the identification platform number to perform the phase for executing the applet with or without restrictions, respectively if the identification platform number is not or is detected by the step for detecting. The applet is a java card applet or a SIM toolkit applet.
Owner:STMICROELECTRONICS INT NV
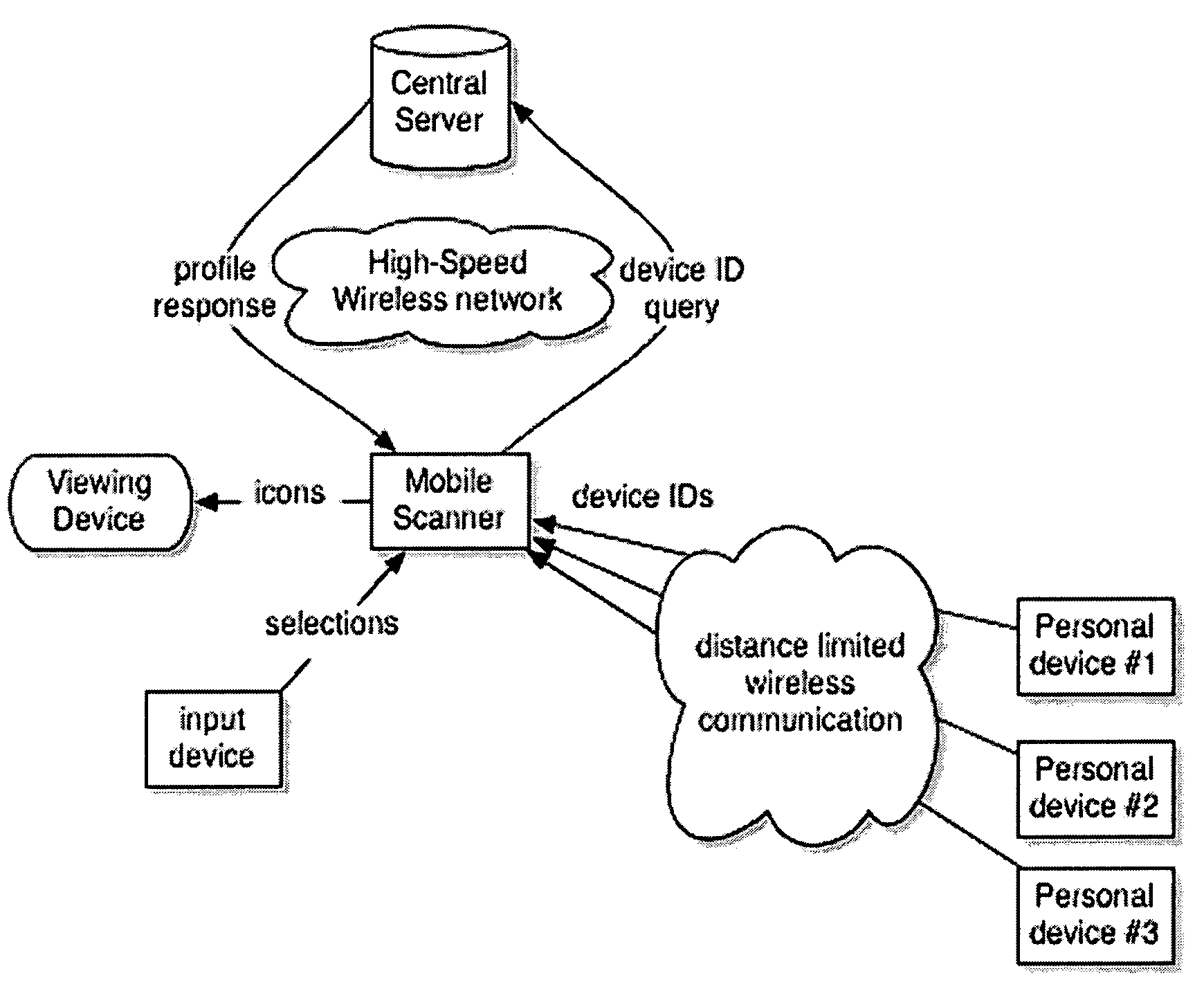
Virtual reality overlay
InactiveUS20090003662A1Avoiding detectionEnhanced information2D-image generationCharacter and pattern recognitionUser profileVirtual reality
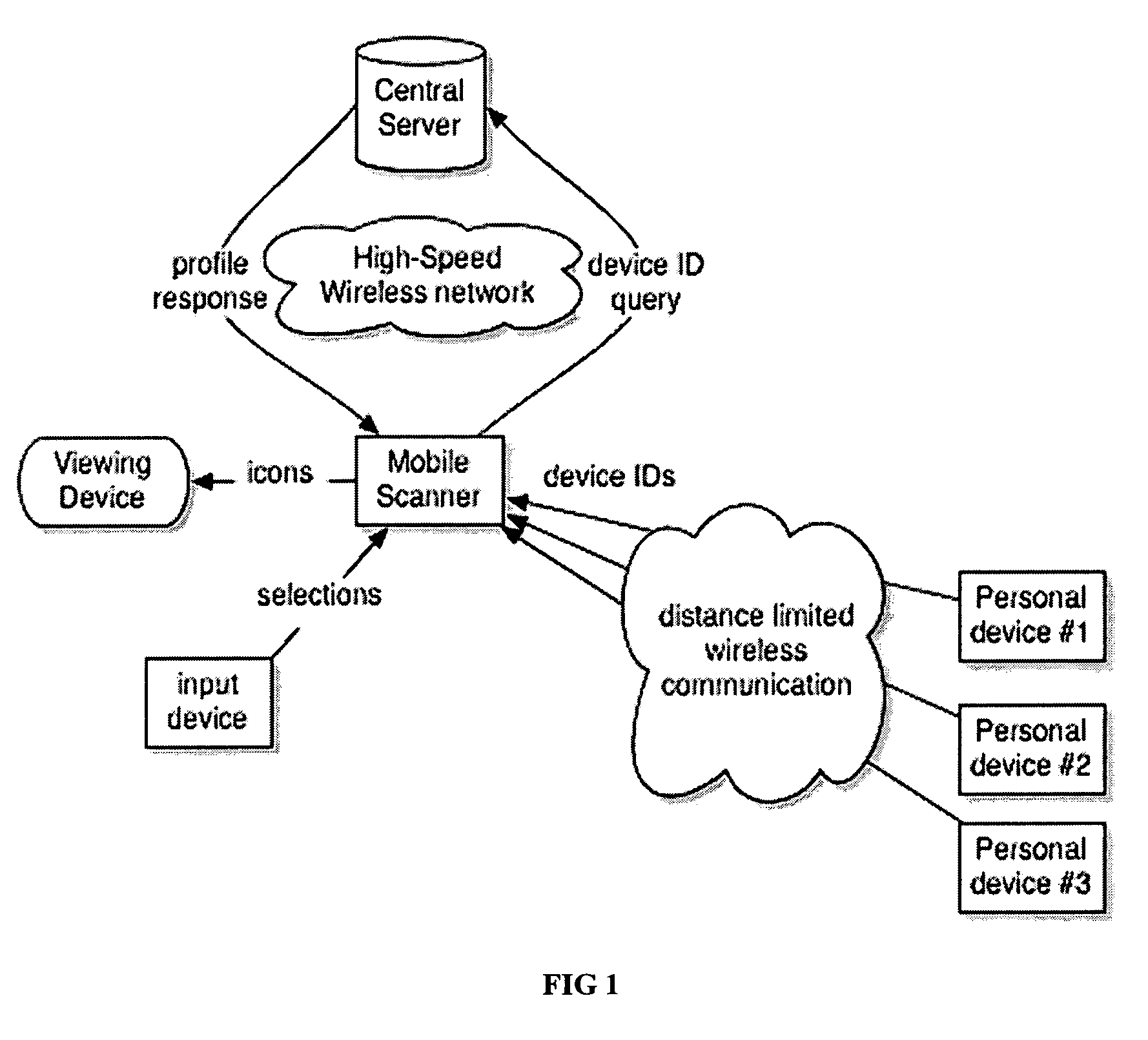
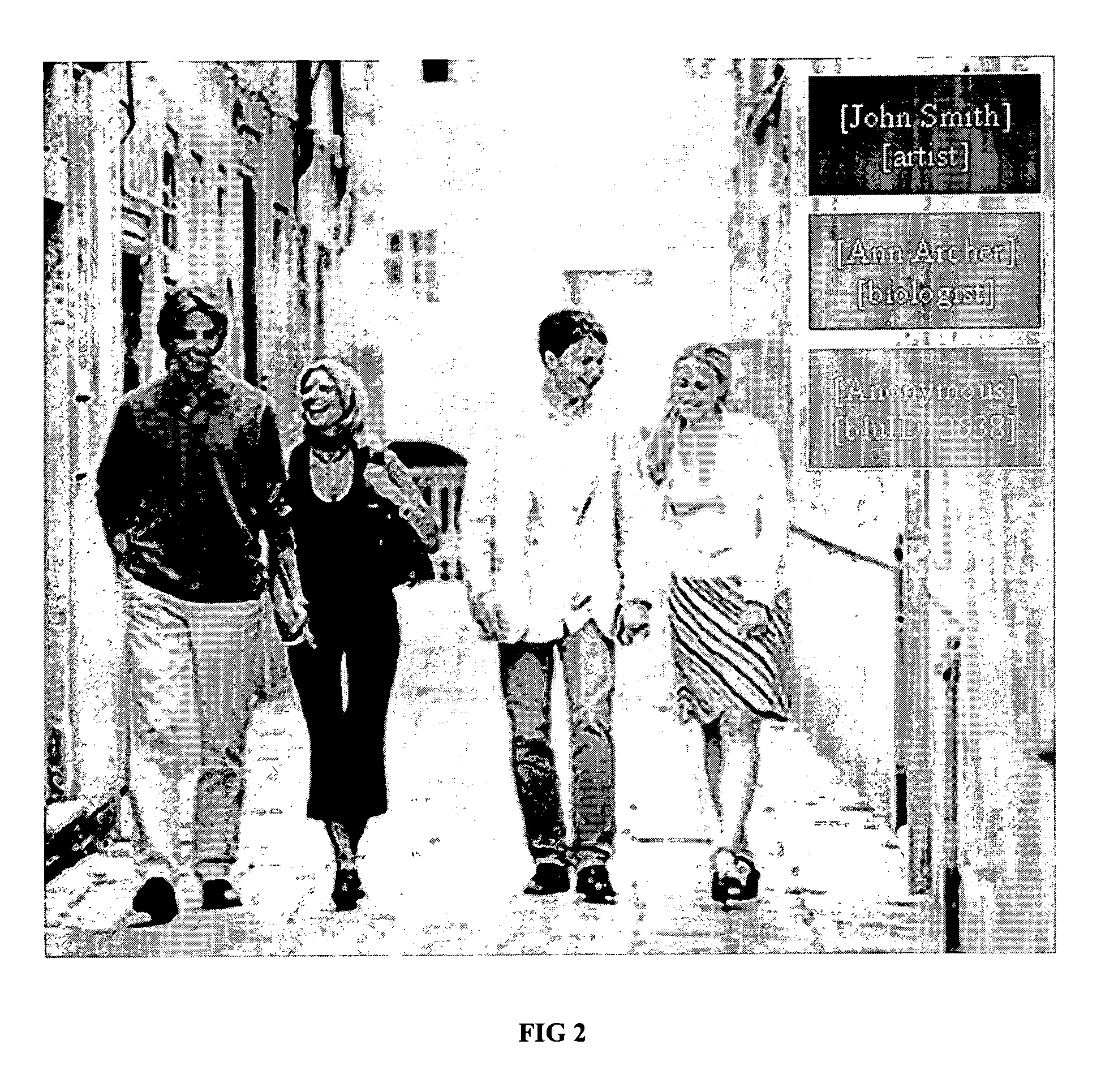
A mobile social networking system that provides aspects of an augmented reality experience comprising a wireless infrastructure; at least one central server having a at least one database of users; a mobile scanner that scans for other users through the use of an identification mechanism, queries the server, and downloads the user profiles and displays them on an inconspicuous viewing device. An unobtrusively manipulable input device is used to select and navigate through the profiles. The invention provides a system for obtaining additional social and other information about nearby users in an unobtrusive manner to avoid detection by others.
Owner:UNIV OF HAWAII
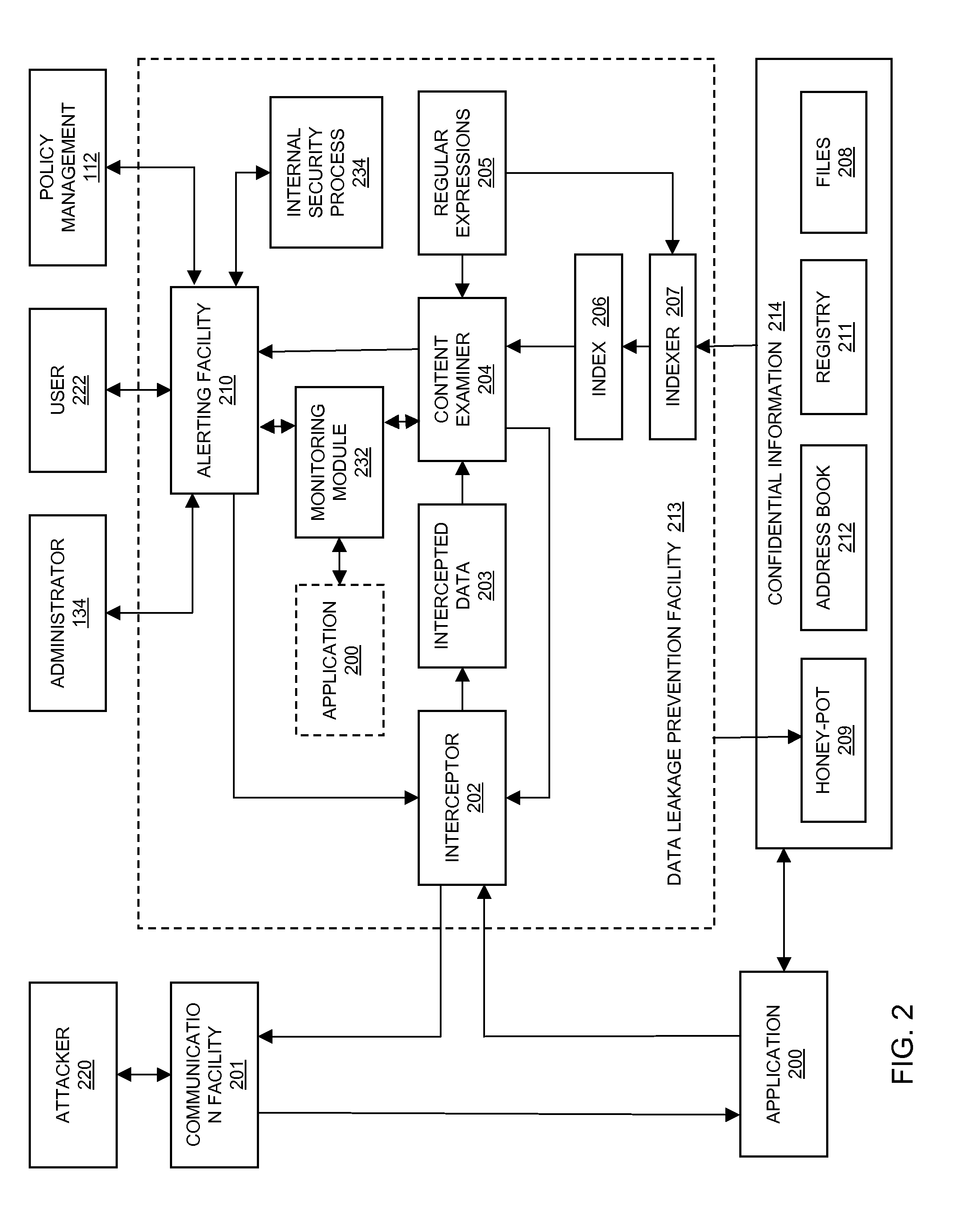
Method and system for preventing data leakage from a computer facilty
InactiveUS20100251369A1Avoid detectionAvoid runningMemory loss protectionError detection/correctionData ingestionSecurity software
In embodiments of the present invention improved capabilities are described for the steps of identifying, through a monitoring module of a security software component, a data extraction behavior of a software application attempting to extract data from an endpoint computing facility; and in response to a finding that the data extraction behavior is related to extracting sensitive information and that the behavior is a suspicious behavior, causing the endpoint to perform a remedial action. The security software component may be a computer security software program, a sensitive information compliance software program, and the like.
Owner:SOPHOS
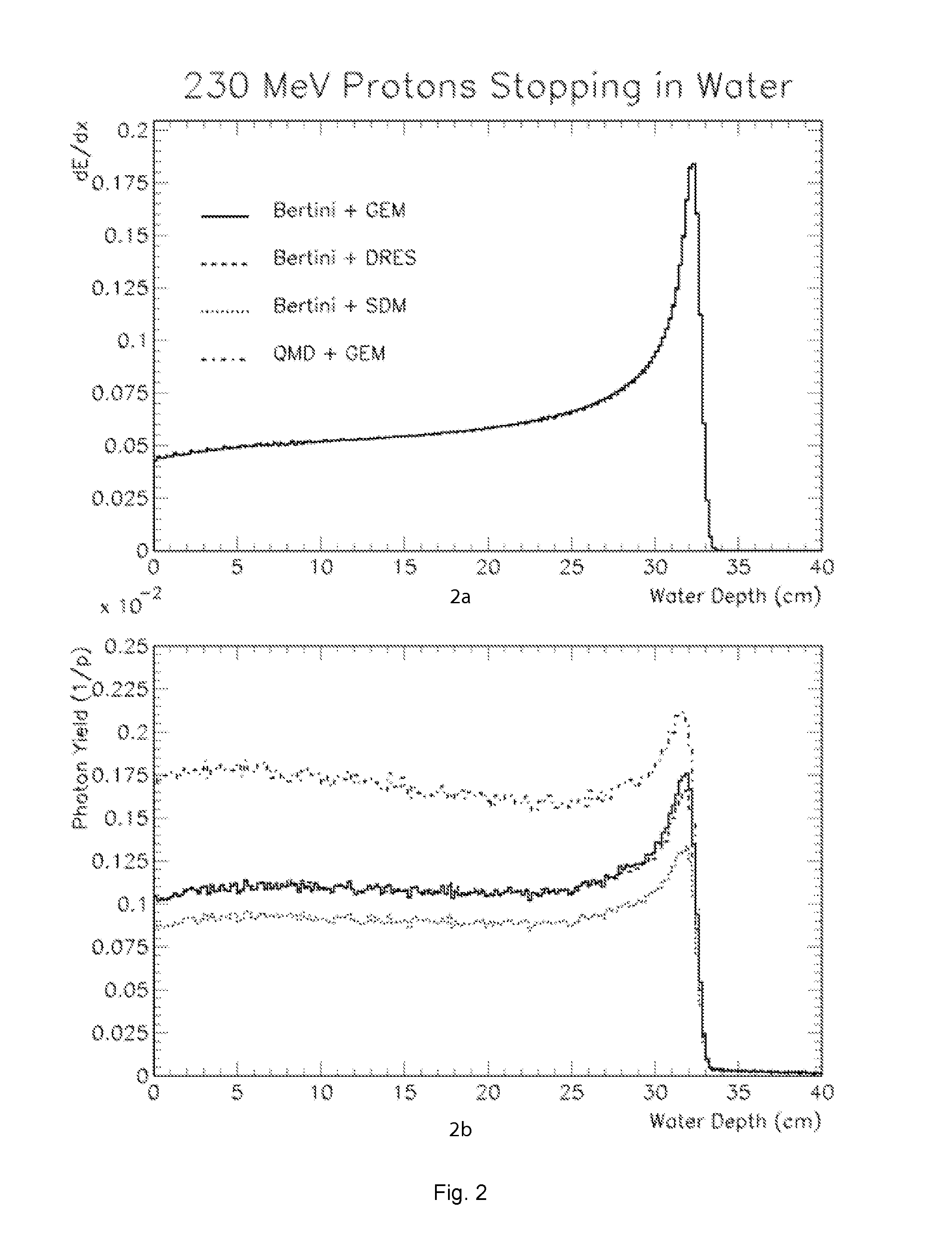
Device And Method For Particle Therapy Verification
InactiveUS20110186720A1Avoid detectionHandling using diaphragms/collimetersMaterial analysis by optical meansHadronDose distribution
The invention is related to the field of charged Hadron Therapy, i.e. radiation therapy using strongly interacting particles. More particularly, the invention relates to a detector and method for measuring the beam range of a charged hadron beam in a target object as well as the particle dose distribution in the target object.
Owner:ION BEAM APPL
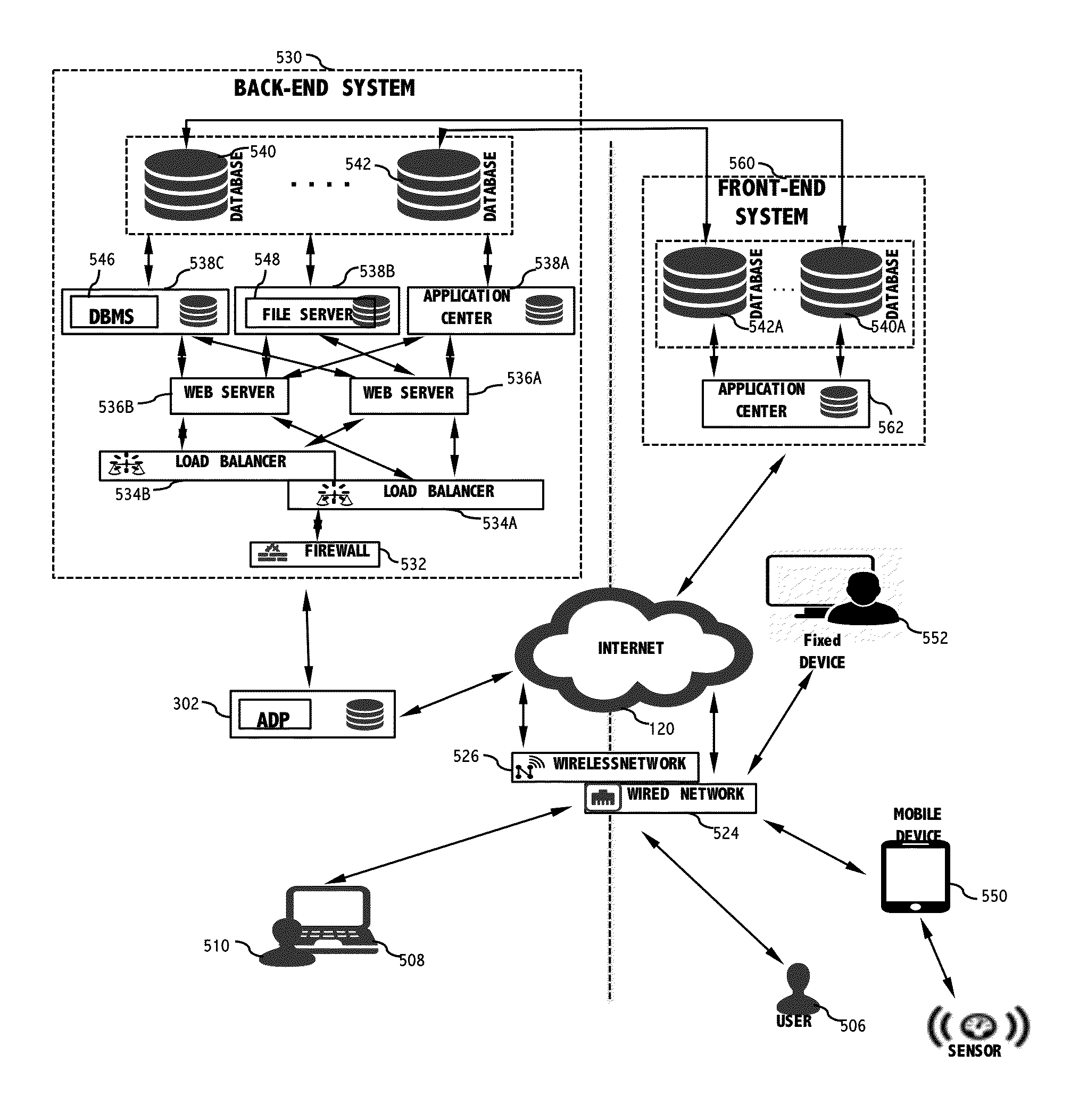
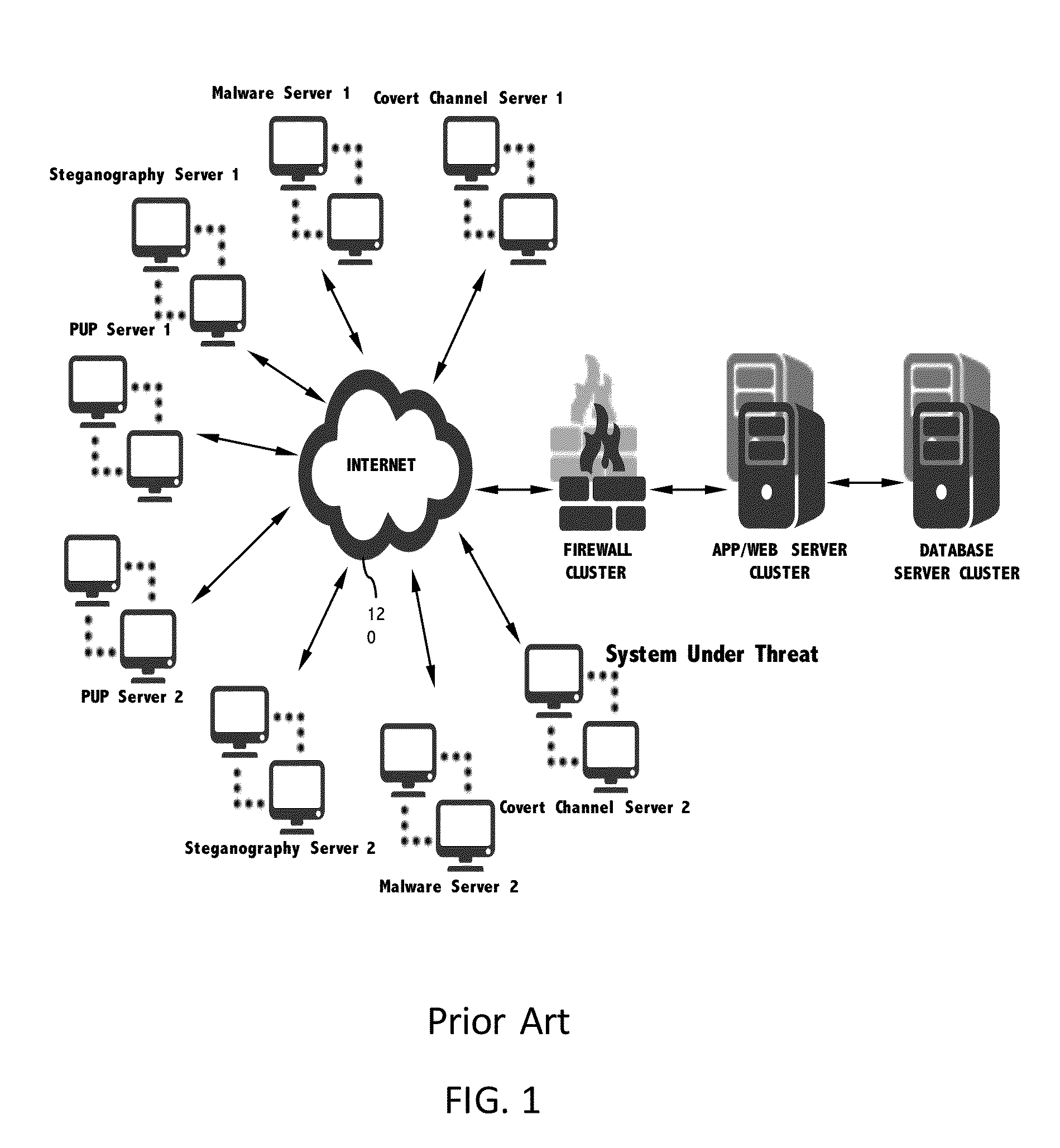
System and method for network intrusion detection of covert channels based on off-line network traffic
ActiveUS20160127395A1Avoid detectionMemory loss protectionError detection/correctionTraffic volumeTraffic capacity
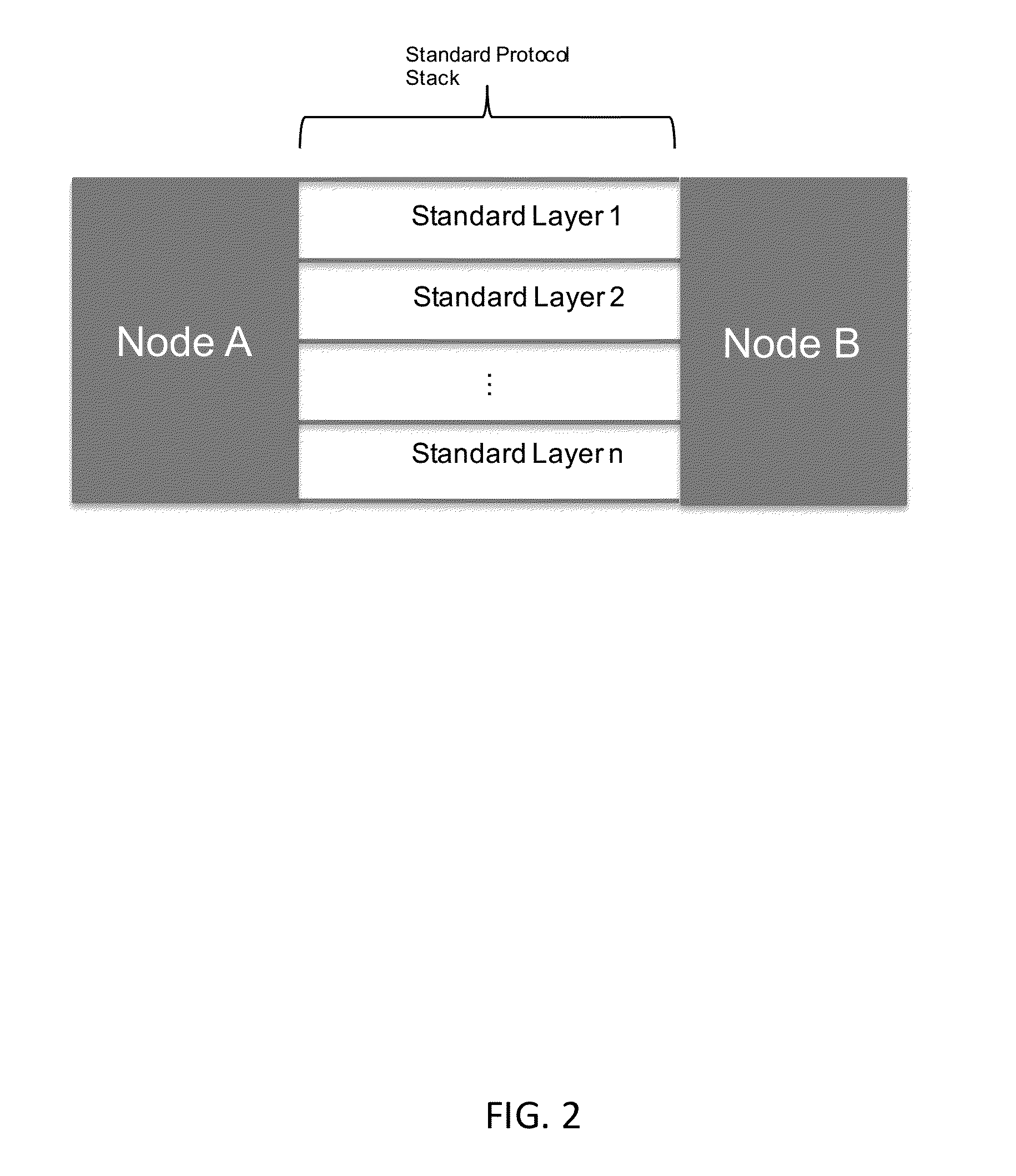
A network intrusion detection system and method is configured to receive off-line network traffic. The off-line network traffic with a predefined format, PCAP file, is capable of indicating existence of a plurality of covert channels associated with a corresponding plurality of covert channel signatures. Each covert channel comprises a tool that communicates messages by deviating from a standard protocol to avoid detection. A plurality of covert channel processors are configured to analyze off-line network traffic. The analysis determines whether the off-line network traffic deviates from the standard protocol based on one or more covert channel signatures. The covert channels are employed in at least one standard layer of the standard protocol stack and the off-line network data traffic comprises at least one standard protocol stack having multiple standard layers.
Owner:CYBER CRUCIBLE
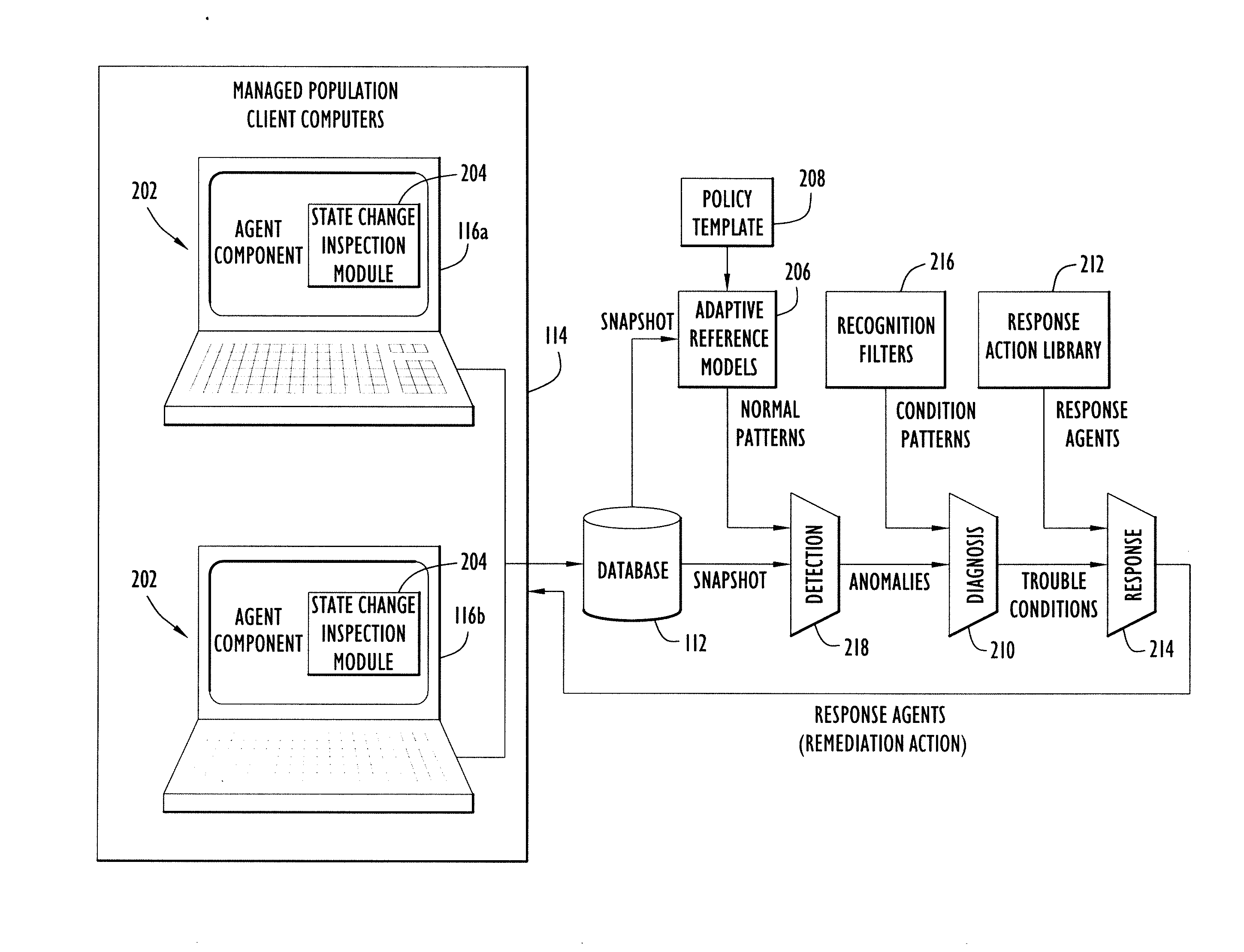
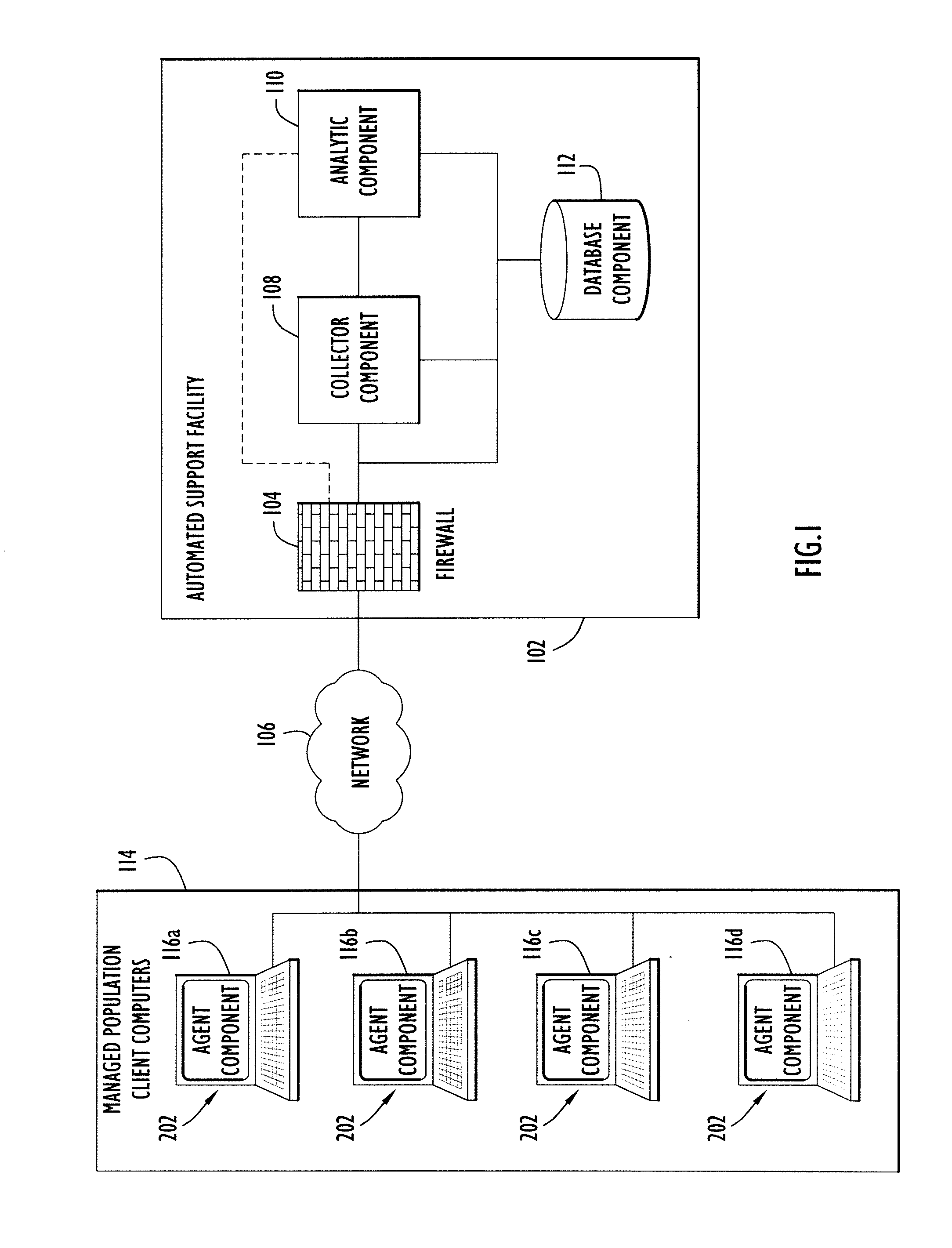
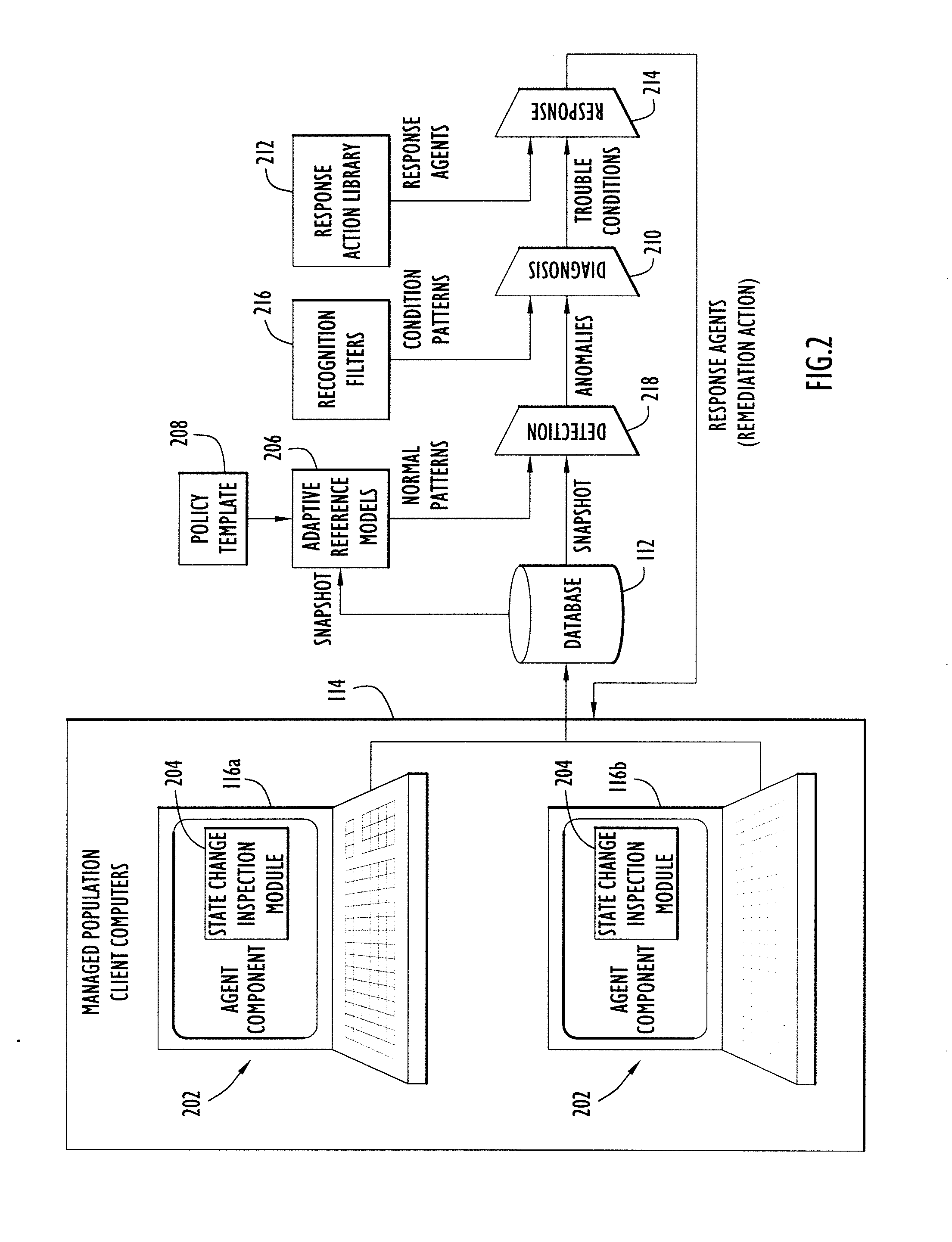
Automated Malware Detection and Remediation
ActiveUS20110247071A1Avoid detectionMemory loss protectionError detection/correctionState variationRemedial action
Systems and methods for detecting malware in a selected computer that is part of a network of computers. The approach includes inspecting a predetermined set of operational attributes of the selected computer to detect a change in a state of the selected computer. In response to a detected change in state, the selected computer is scanned to create a snapshot of the overall state of the selected computer. The snapshot is transmitted to an analytic system wherein it is compared with an aggregated collection of snapshots previously respectively received from a plurality of computers in the computer network. Based on the comparison, anomalous state of the selected computer can be identified. In turn, a probe of the selected computer is launched to gather additional information related to the anomalous state of the selected computer so that a remediation action for the anomalous state of the selected computer can be generated.
Owner:RPX CORP
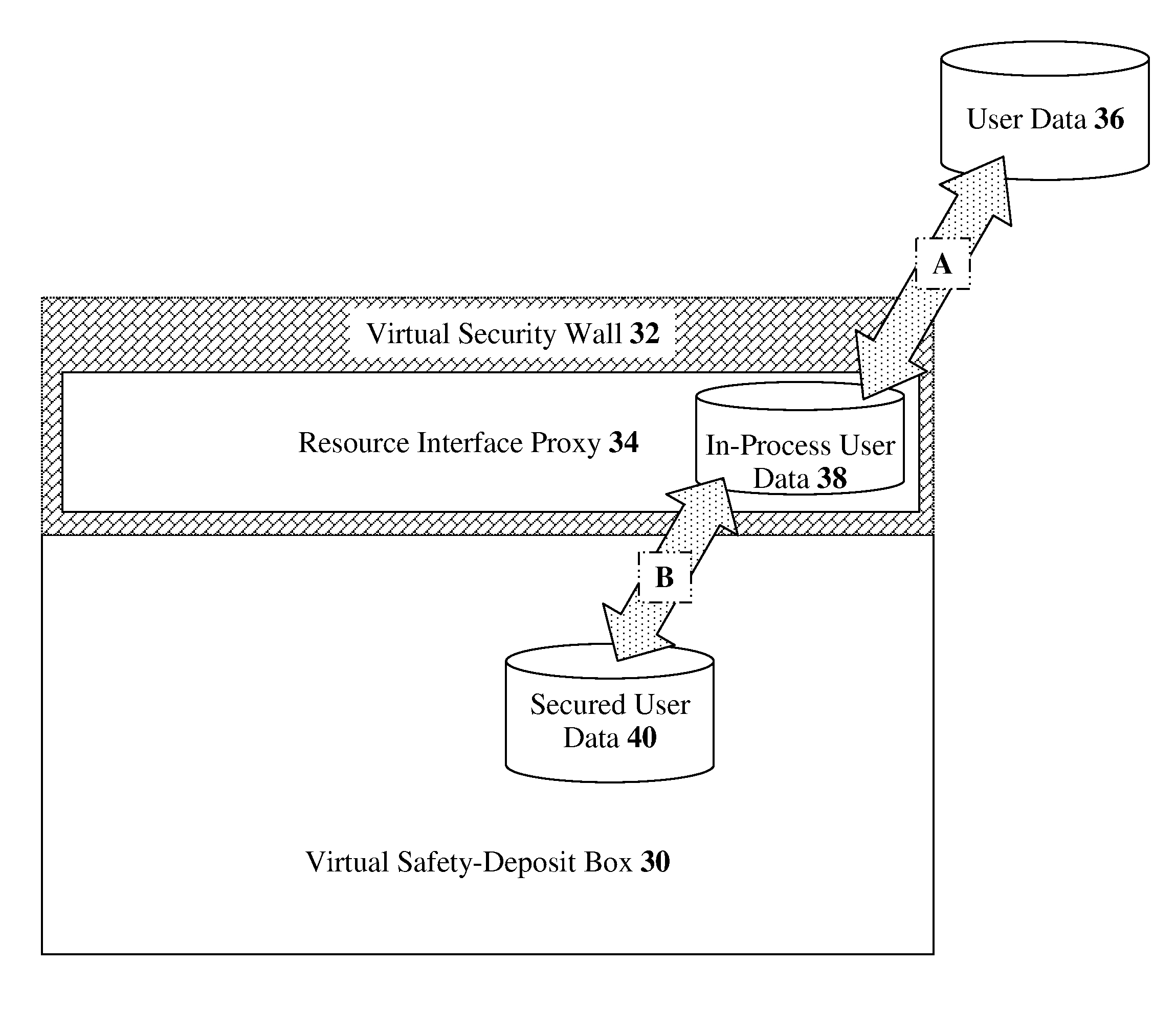
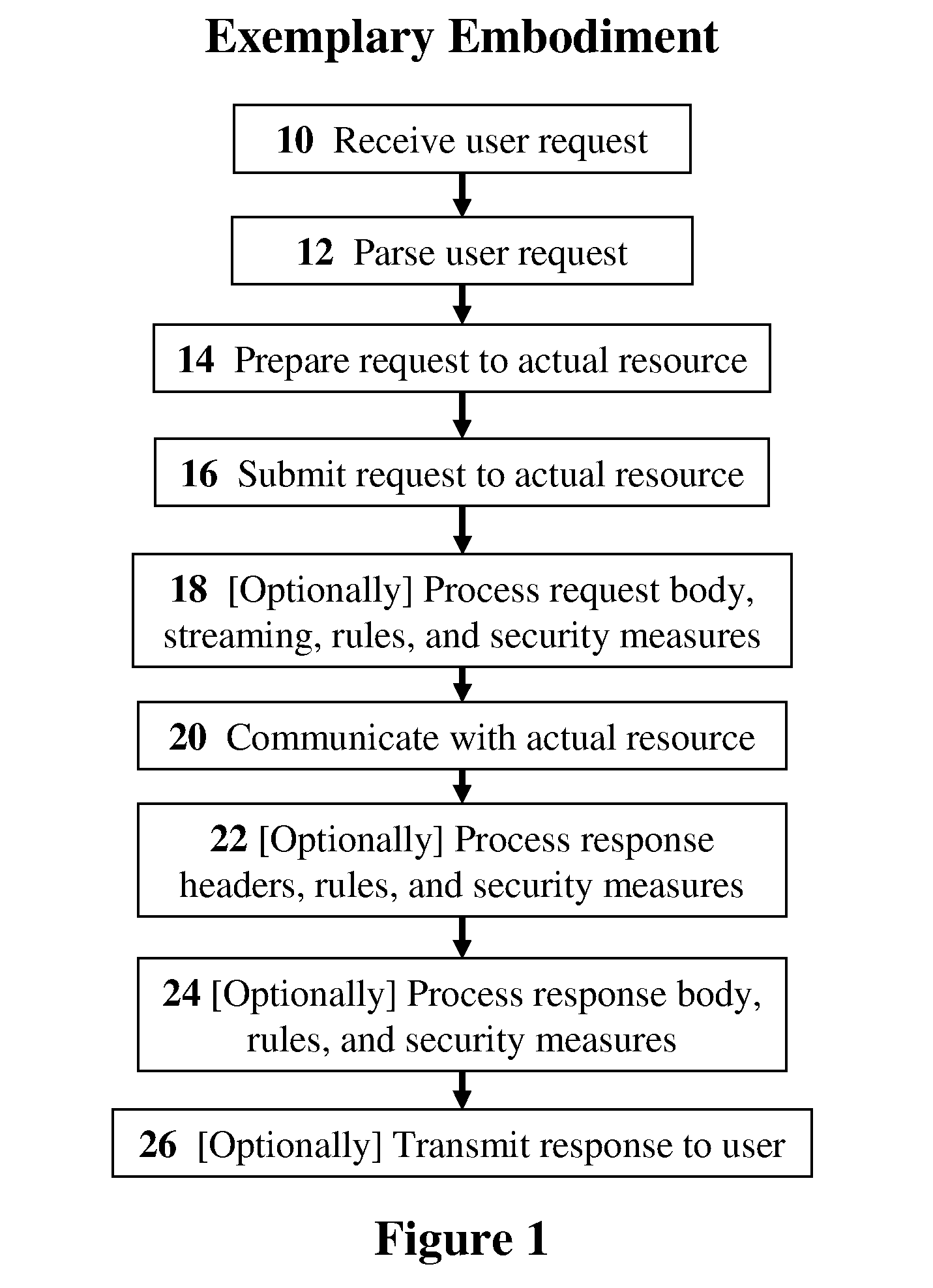
Methods, devices, and media for securely utilizing a non-secured, distributed, virtualized network resource with applications to cloud-computing security and management
InactiveUS20110072489A1Full securityFull controlDigital data protectionMultiple digital computer combinationsVirtualizationData stream
The present invention discloses methods, devices, and media for securely utilizing a non-secured, distributed, virtualized network resource with applications to cloud-computing security and management. Methods including the steps of: receiving, by a deployed security mechanism, a user request over a network; parsing the user request by the deployed security mechanism; preparing, including applying security measures, the user request to transmit to a computing-service resource; and submitting, by the deployed security mechanism, the user request to the computing-service resource. Methods further including the steps of: dividing an original data stream into a set of split data streams; applying a first invertible transformation function to the split data streams, which produces an intermediate set of data streams; and extracting a final set of data streams from the intermediate set by applying a selection rule which produces the final set, thereby transforming the original data stream into individually-unintelligible parts.
Owner:PORTICOR
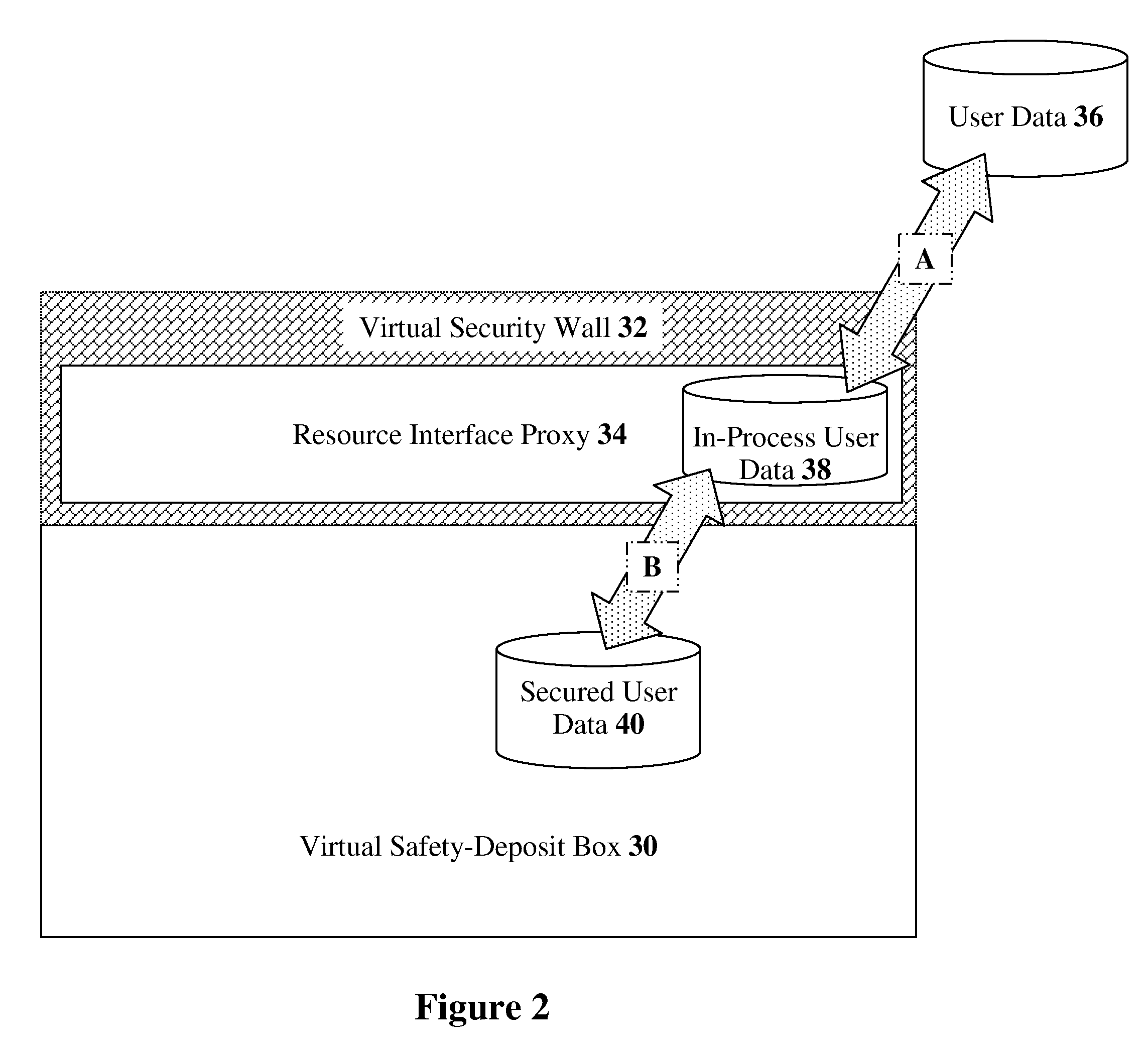
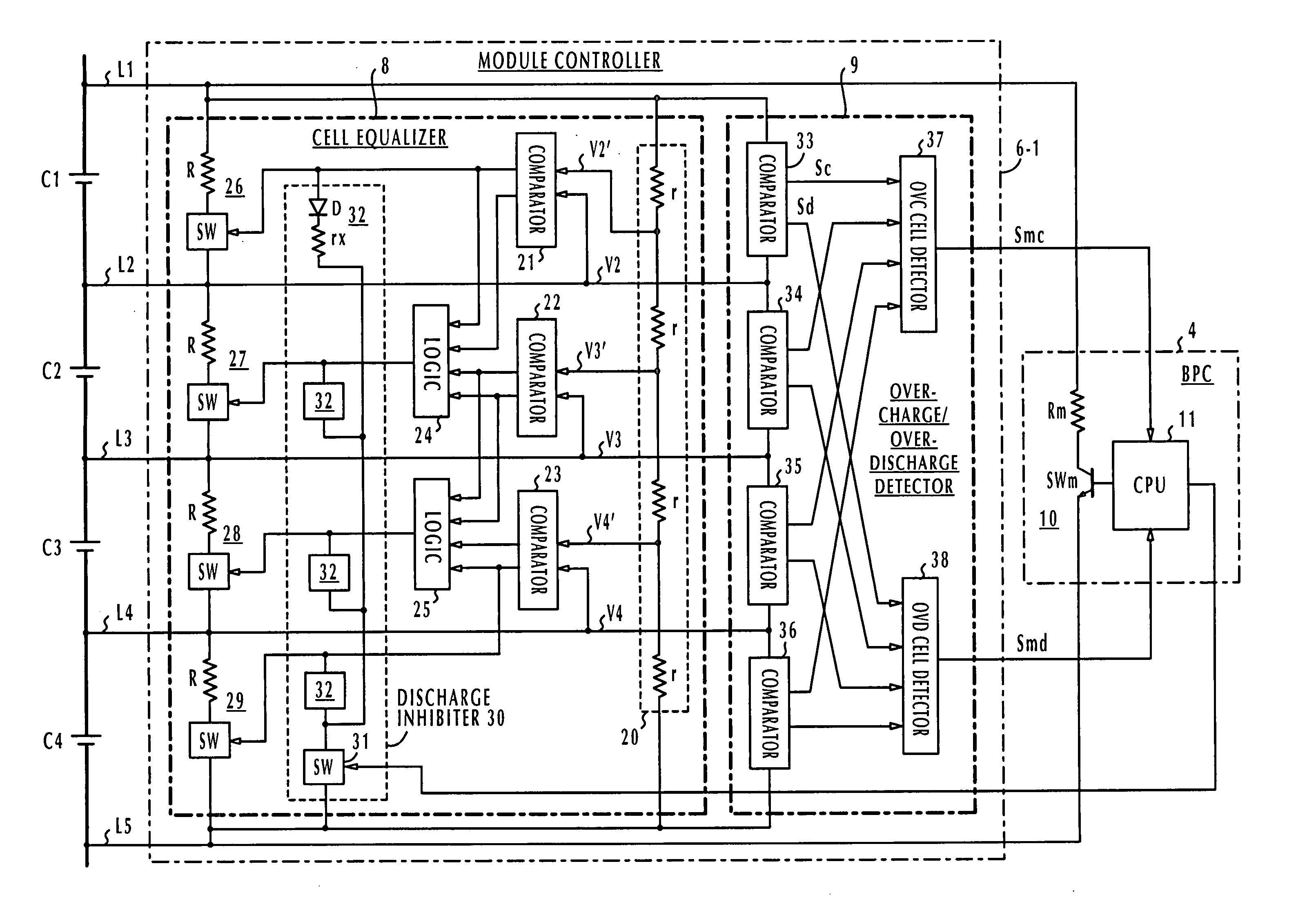
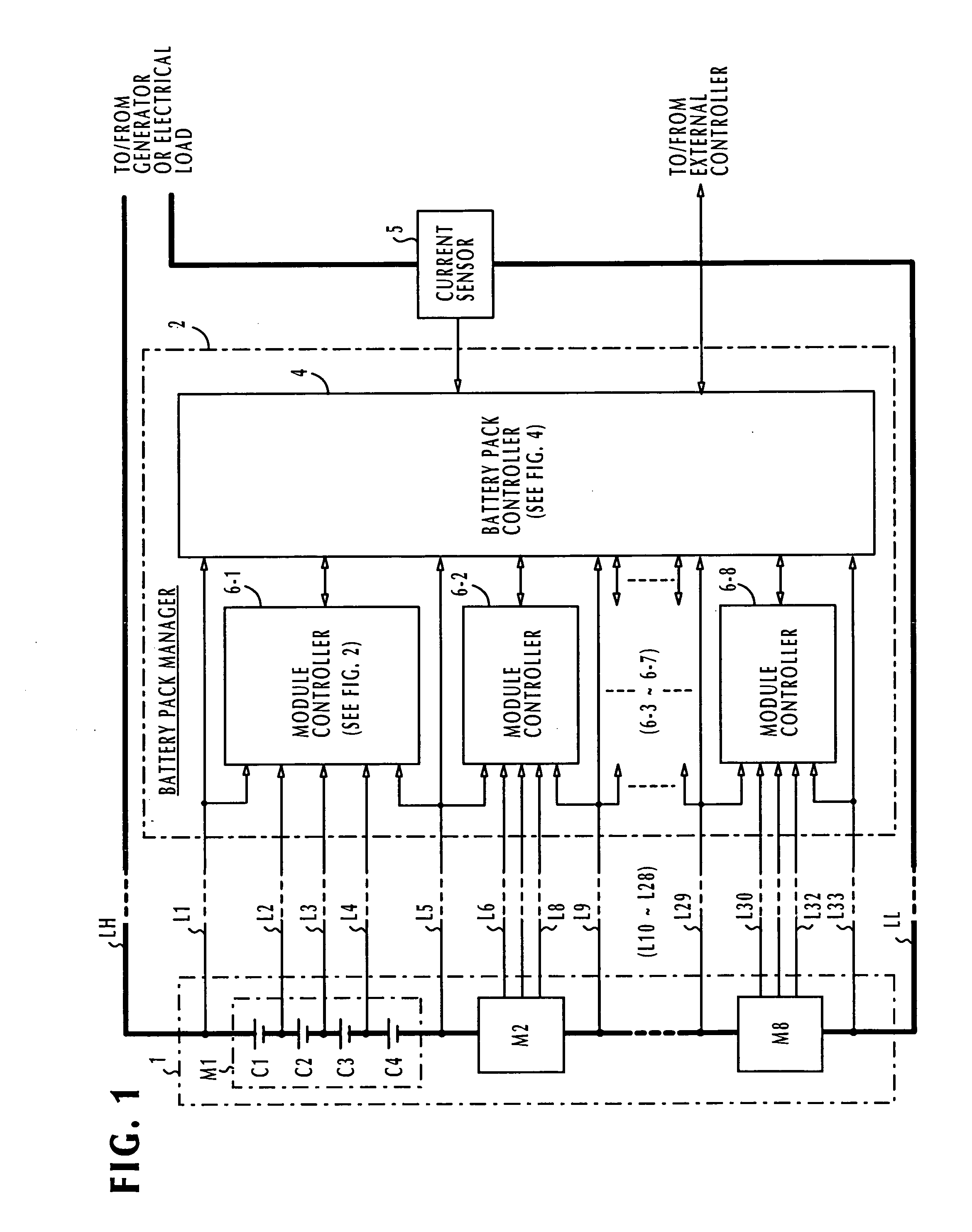
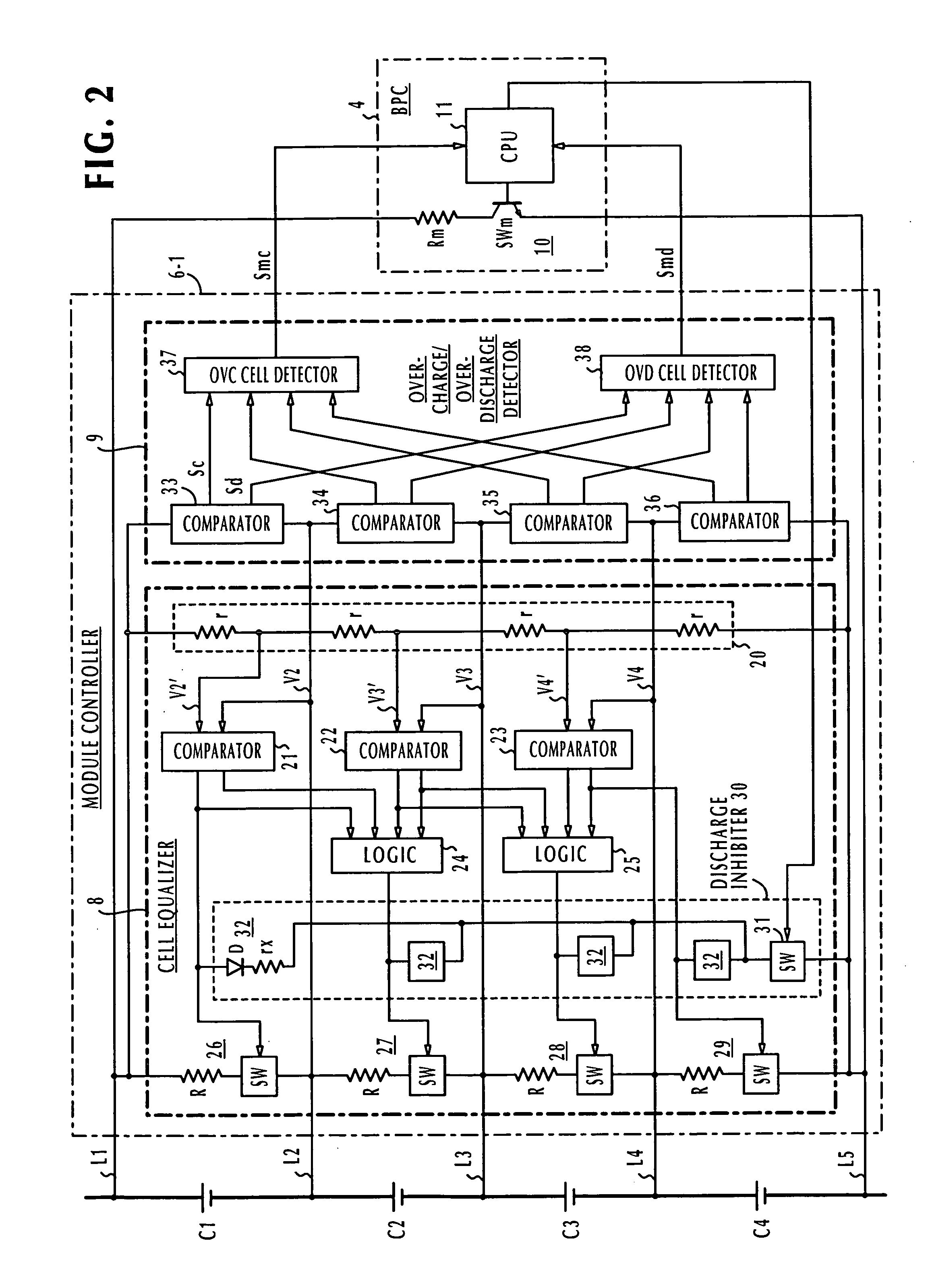
Battery pack manager
ActiveUS20060103351A1Without introducing complexityIncrease power consumptionCharge equalisation circuitMaterial analysis by electric/magnetic meansEngineeringVoltage reference
In a battery pack manager that manages series-connected rechargeable unit cells, a cell equalizer equalizes the cell voltages by individually discharging the unit cells according to deviations from reference voltages. An overcharge / overdischarge detector detects an overcharge and an overdischarge state of each unit cell. An inhibit circuit prevents the cell equalizer from discharging the unit cells when the overcharge / overdischarge detector is activated to reduce the cell voltage variability, which would otherwise occur as a result of interference from the overcharge / overdischarge detector, so that the overcharge / overdischarge states of all unit cells can be determined with precision. Connecting lines of the unit cells are monitored to detect a line-cut. The inhibit circuit further inhibits the cell equalizer when the connecting lines are being monitored to reduce the cell voltage variability, which would otherwise occur as a result of interference from the line-cut detection, so that false line-cut detection is avoided.
Owner:DENSO CORP
Radio communications receiver and method of receiving radio signals
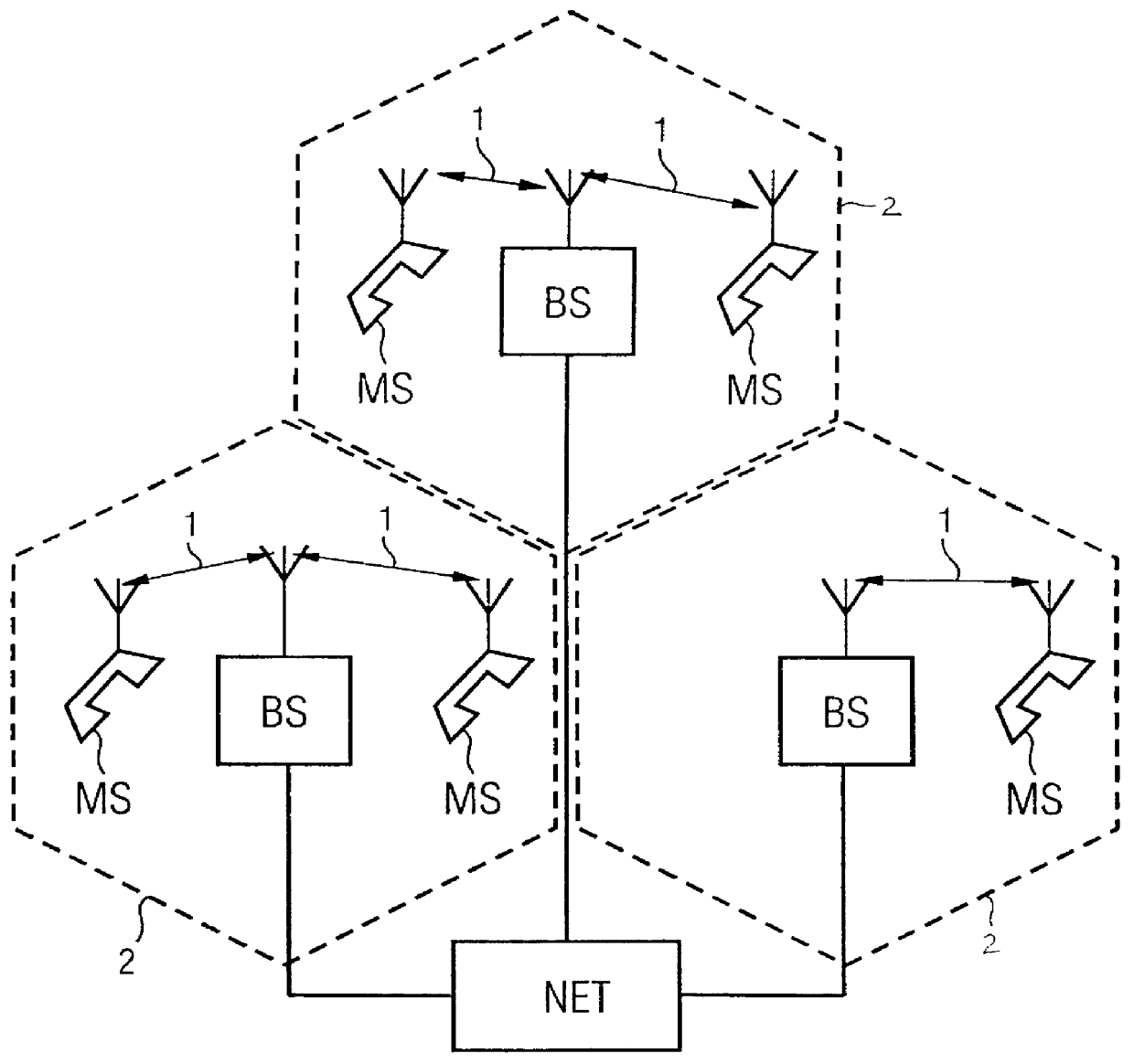
InactiveUS6064689AImprove abilitiesAvoid detectionError preventionLine-faulsts/interference reductionRadio communicationsRadio signal
A radio communications receiver which detects radio signals and recovers data representative of the radio signals in a presence of contemporaneously detected interfering signals, the radio communications receiver having a detector that detects said radio signals and generates digital base band signals representative of the radio signals, a matrix former that forms a correlation matrix having rows and columns from the base band signals, and a data processor that generates a factor matrix of the correlation matrix, the factor matrix having rows and columns, and recovers data from the factor matrix. The data processor generates the factor matrix by calculating first elements of the factor matrix from the correlation matrix using a factorization algorithm in accordance with a pre-determined structure of the factor matrix, and forming second elements of the factor matrix by selectively copying first elements in accordance with the pre-determined structure.
Owner:NOKIA SIEMENS NETWORKS GMBH & CO KG
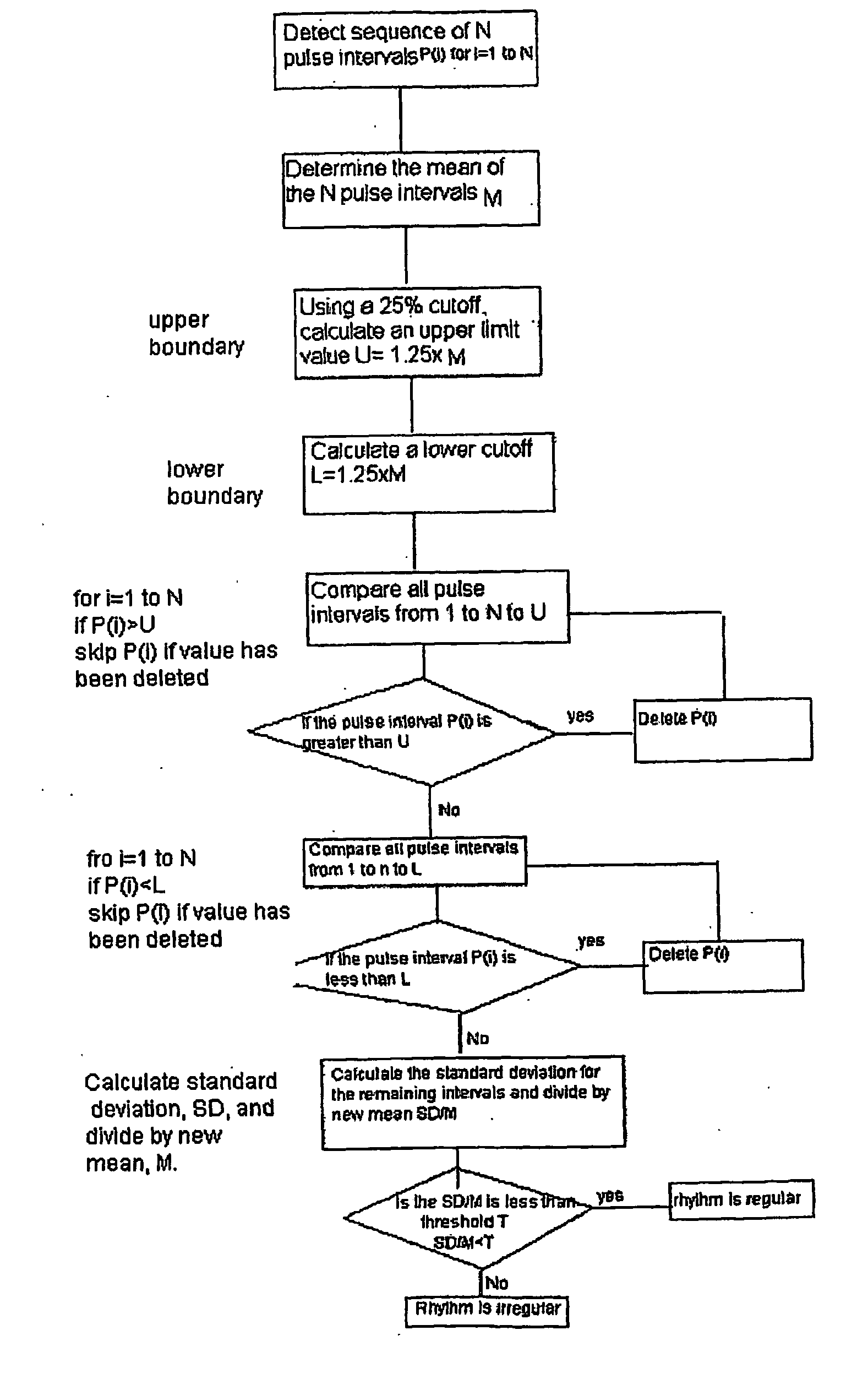
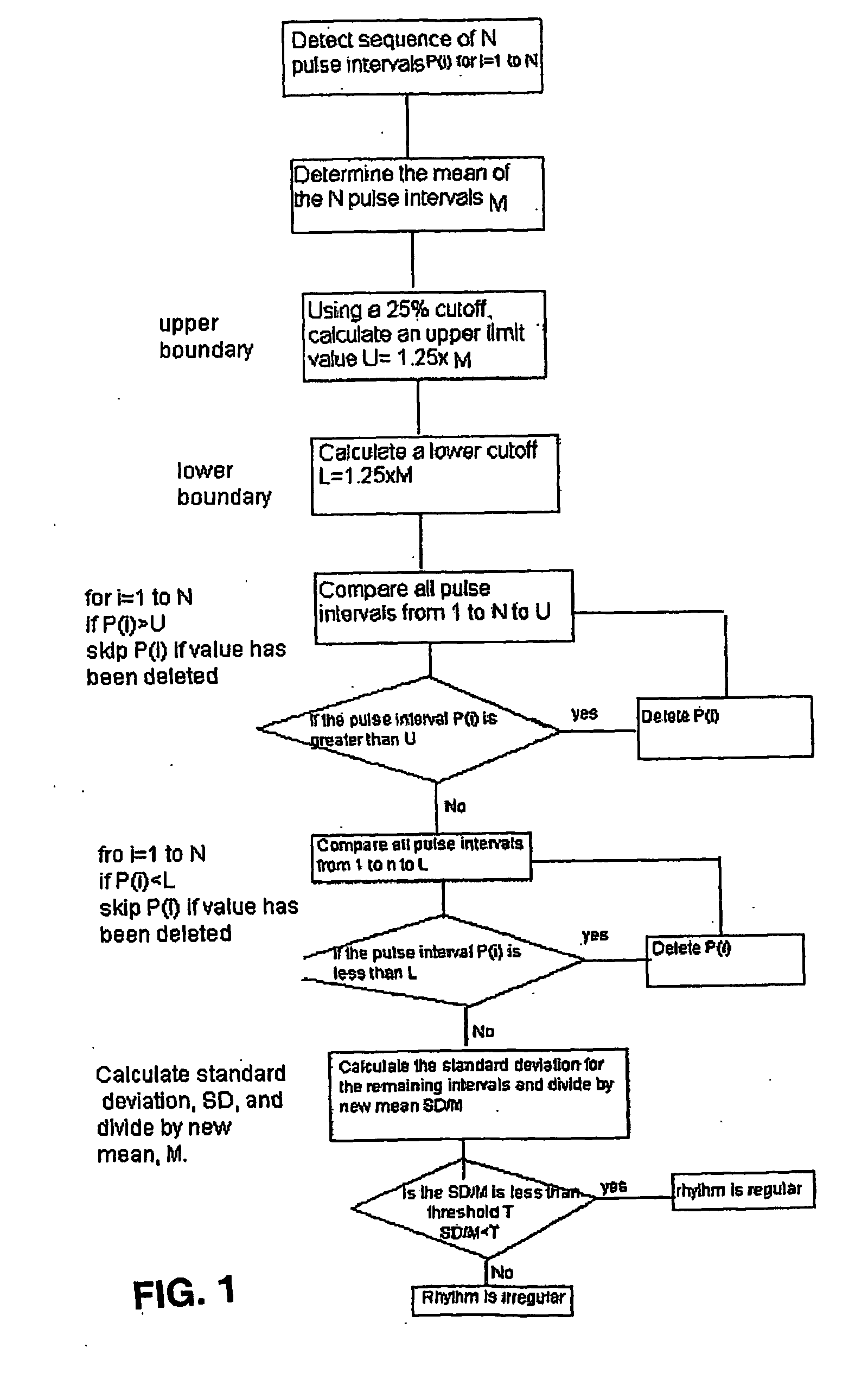
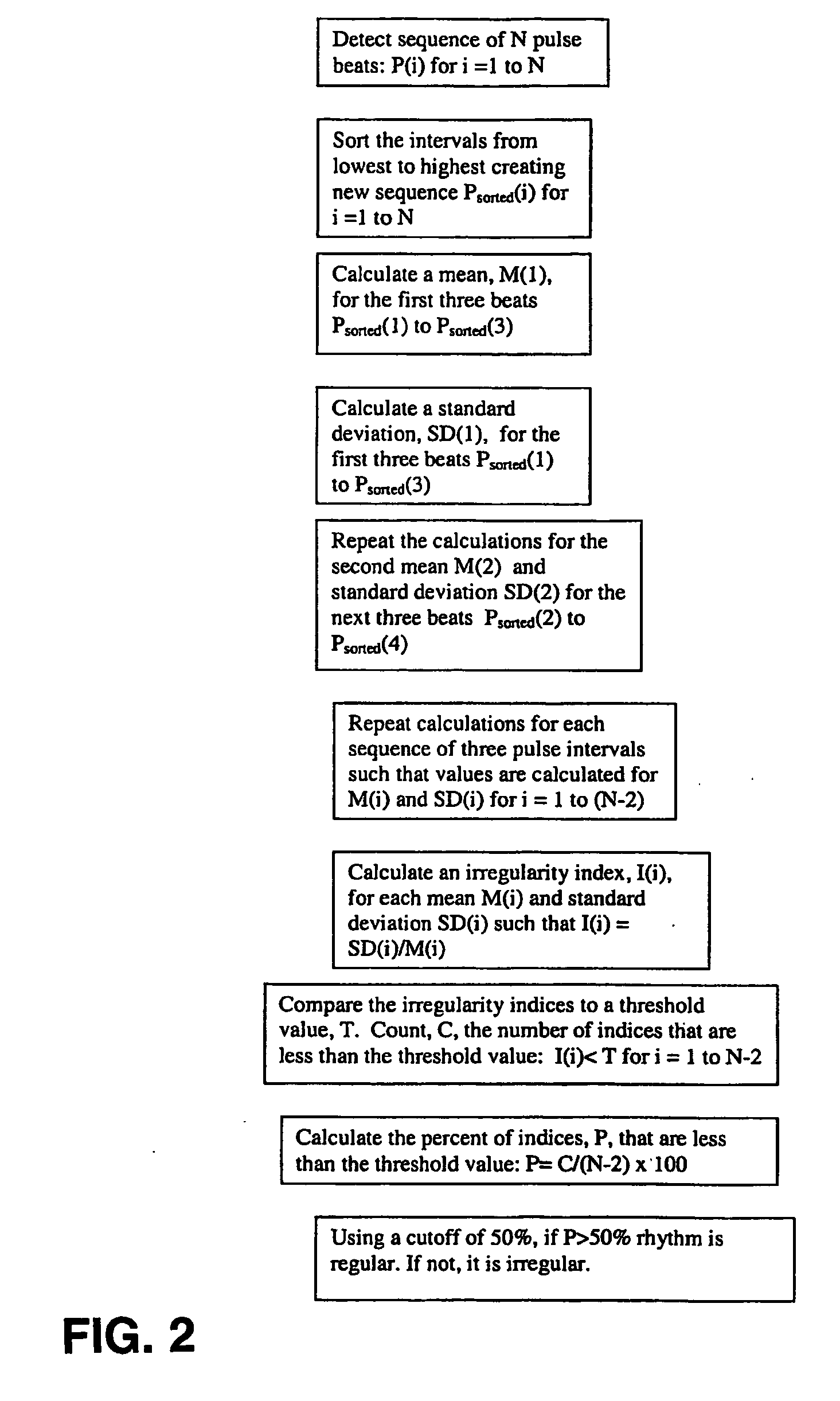
Detecting Atrial Fibrillation, Method of and Apparatus for
ActiveUS20090012412A1Avoid detectionReduce false alarm rateElectrotherapyElectrocardiographyAtrial fibrillationPulse rhythm
A method and apparatus to determine possible atrial fibrillation or absence of atrial fibrillation that includes detecting pulse rhythms from a succession of time intervals each corresponding to a respective interval of time between successive pulse beats; analyzing the detected pulse rhythms to make a determination of possible atrial fibrillation; indicating the possible atrial fibrillation from the determination; or making a determination of the absence of atrial fibrillation.
Owner:WIESEL JOSEPH
Optical examination of biological tissue using non-contact irradiation and detection
InactiveUS7904139B2Avoid detectionCancel noiseDiagnostics using lightSensorsLight beamContact position
An optical system for examination of biological tissue includes a light source, a light detector, optics and electronics. The light source generates a light beam, transmitted to the biological tissue, spaced apart from the source. The light detector is located away (i.e., in a non-contact position) from the examined biological tissue and is constructed to detect light that has migrated in the examined tissue. The electronics controls the light source and the light detector, and a system separates the reflected photons (e.g., directly reflected or scattered from the surface or superficial photons) from the photons that have migrated in the examined tissue. The system prevents detection of the “noise” photons by the light detector or, after detection, eliminates the “noise” photons in the detected optical data used for tissue examination.
Owner:NONINVASIVE TECH
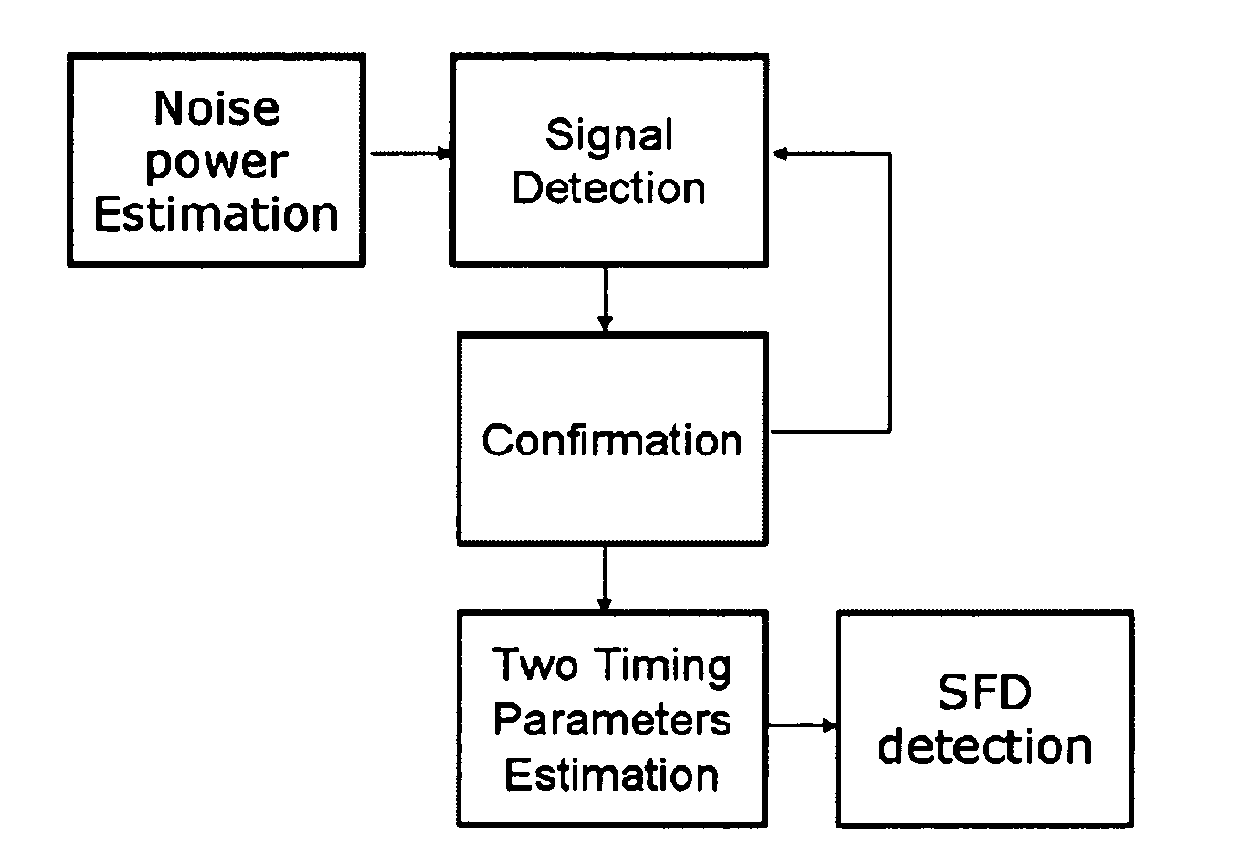
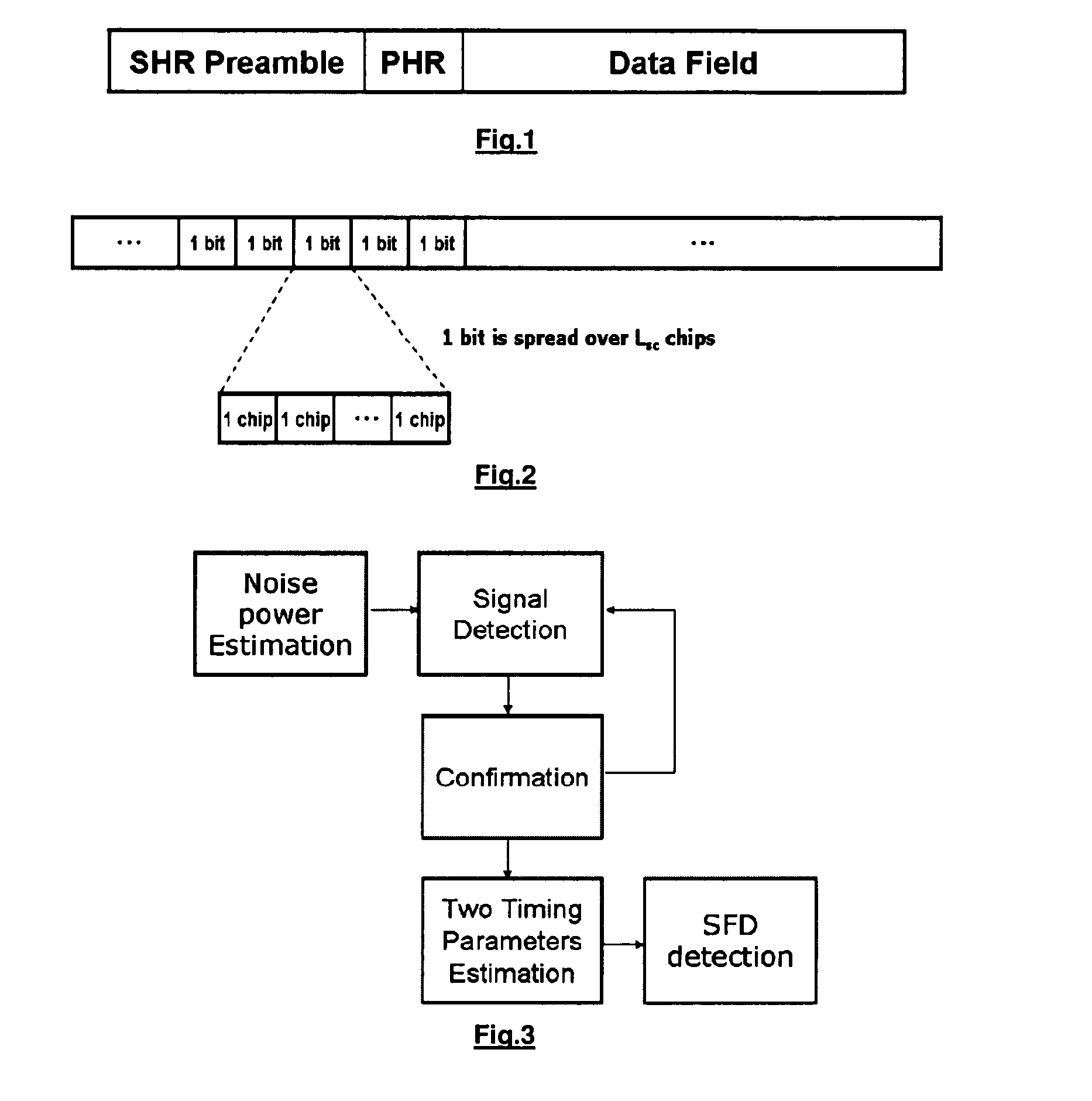
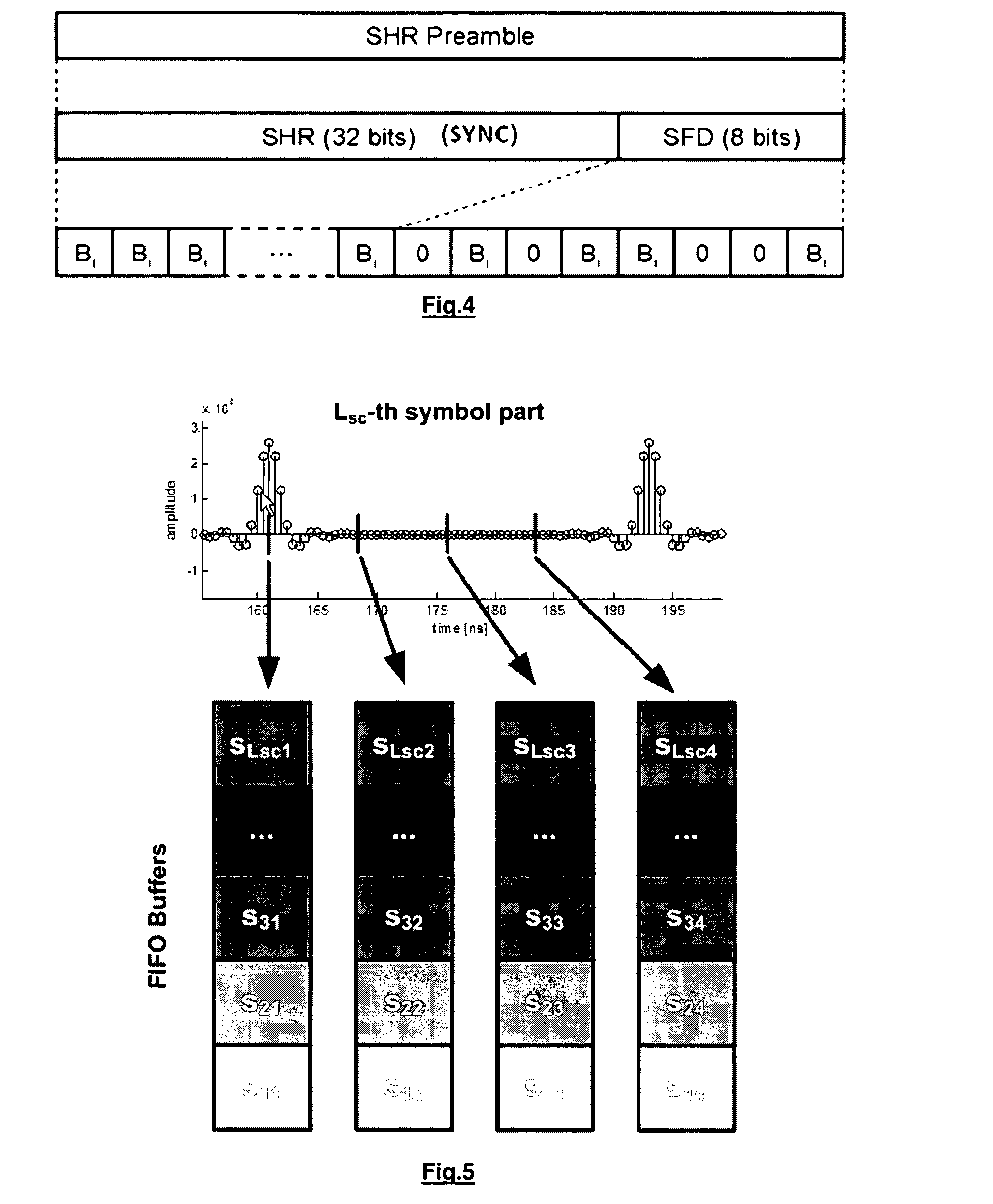
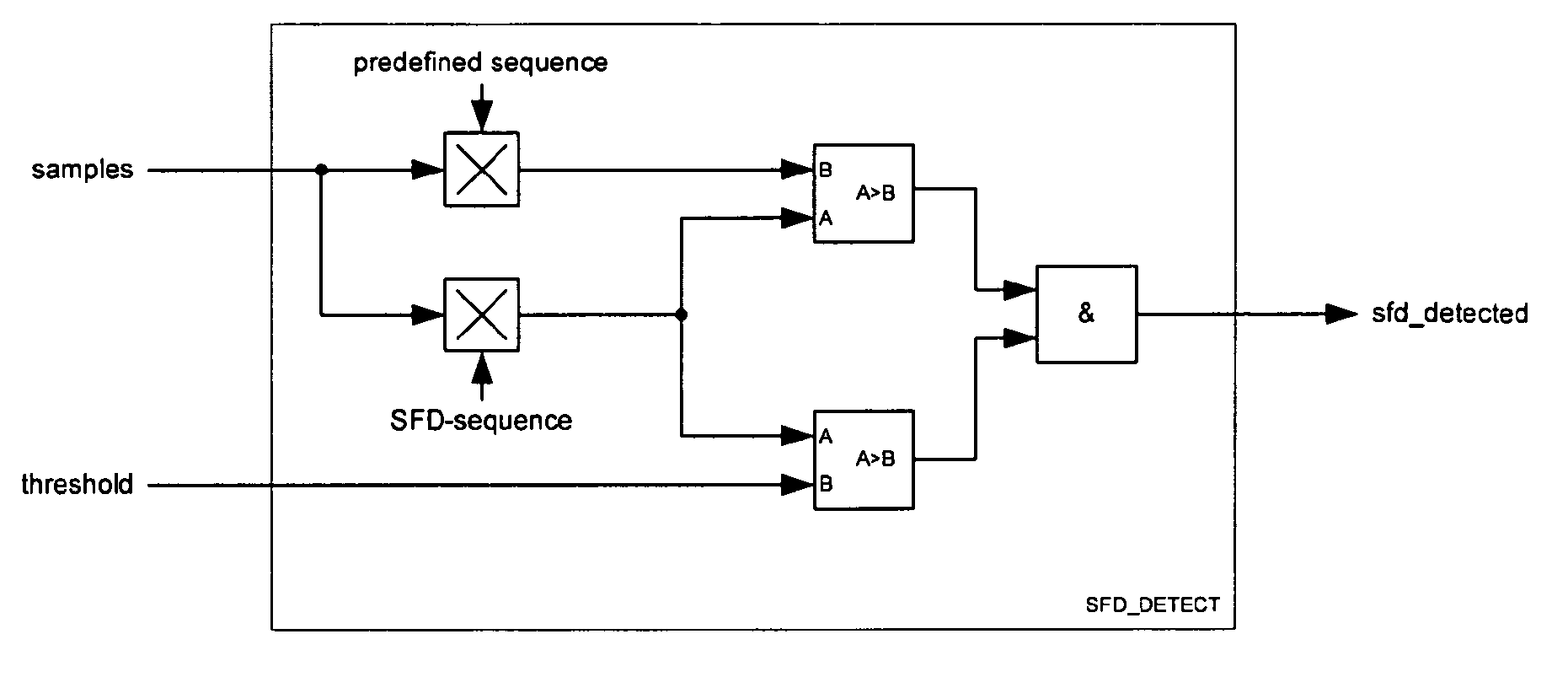
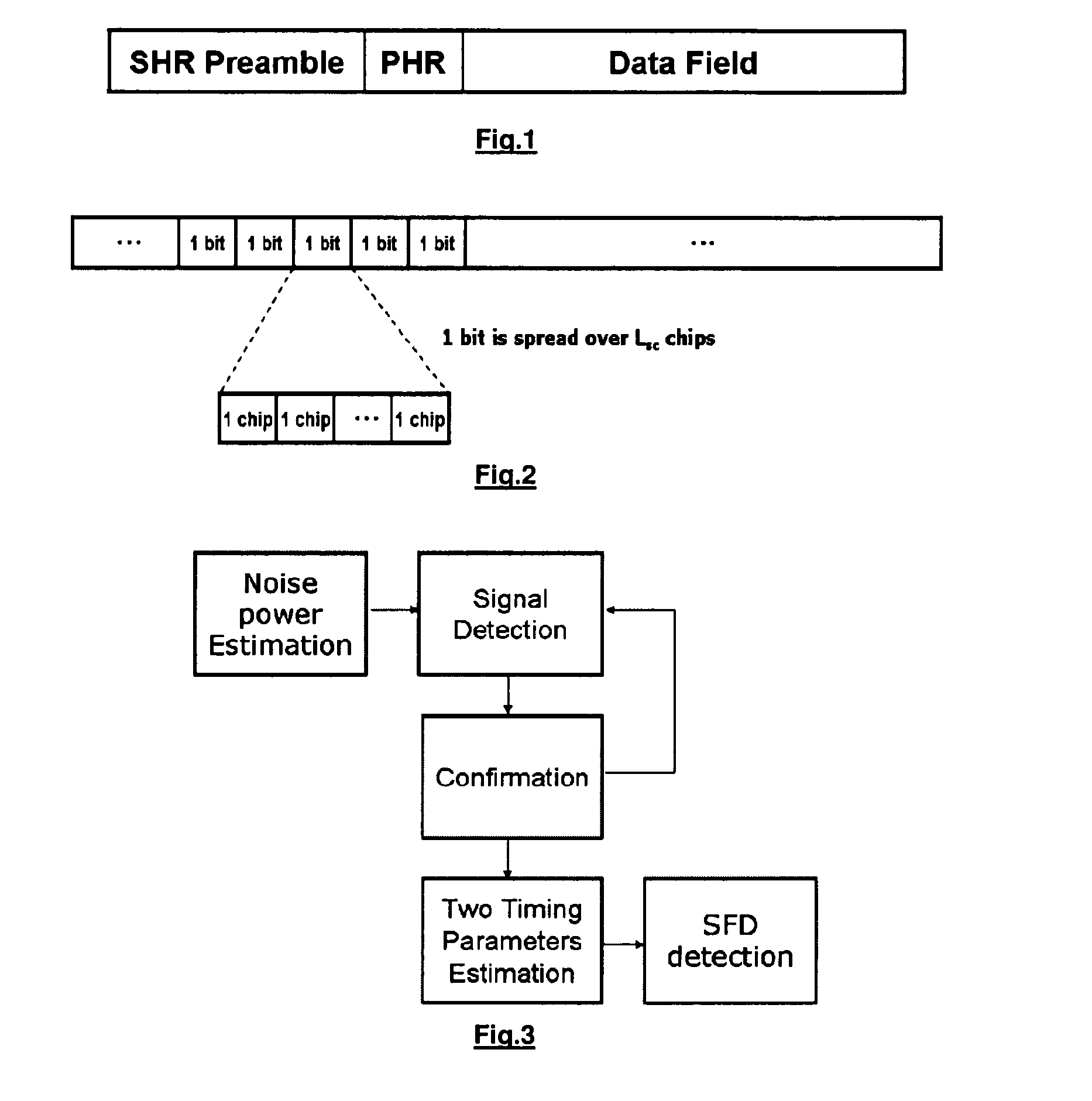
Method and Apparatus for Start of Frame Delimiter Detection
ActiveUS20130114645A1Easy to startReduce data rateData switching by path configurationSynchronising arrangementNetwork packetReal-time computing
The present disclosure is related to detecting a start frame delimiter. A received data packet is correlated with a known sequence, which provides a first correlation result. The received data packet is correlated with a predefined sequence, which yields at least a second correlation result. The data packet comprises at least a preamble portion and a header portion, whereby the preamble portion comprises the start frame delimiter. The predefined sequence is determined according to the preamble pattern. The method further comprises of comparing the first correlation result with the second correlation result and comparing the first correlation result with a given threshold. The process of correlating will be continued until two criteria are met: the first correlation result is larger than the threshold and larger than the at least second correlation result. Only then it is decided that the start of frame delimiter pattern has been detected.
Owner:STICHTING IMEC NEDERLAND
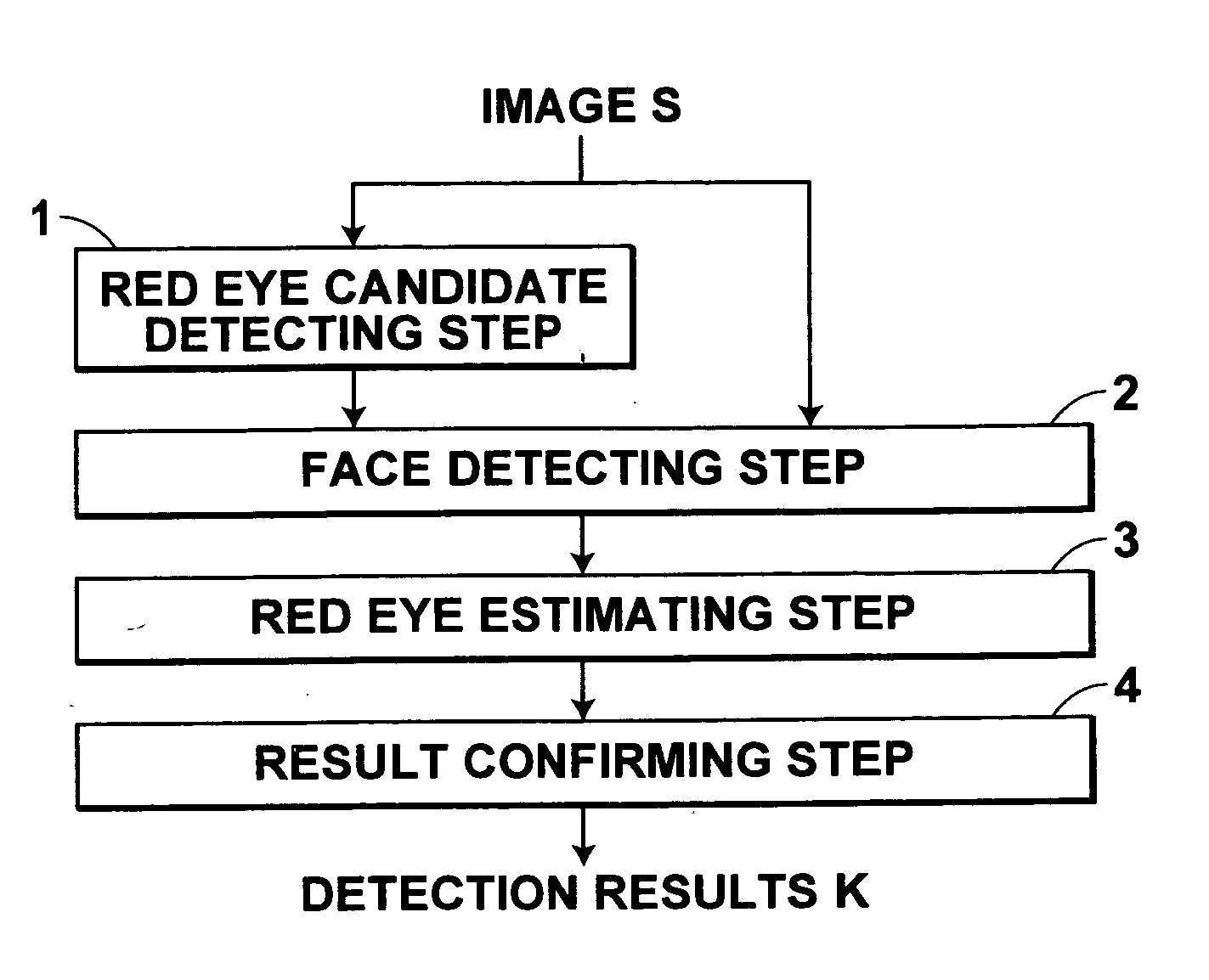
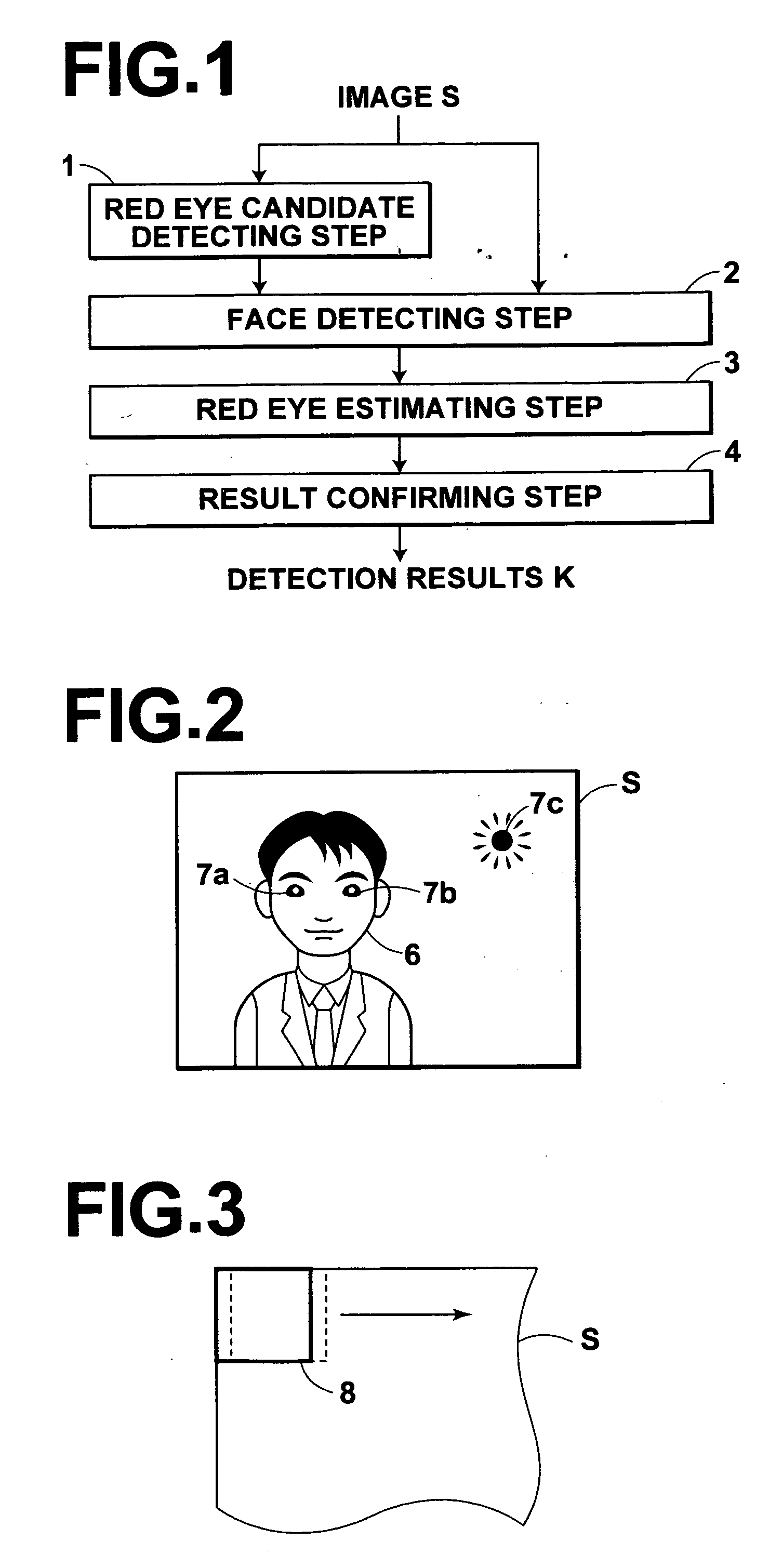
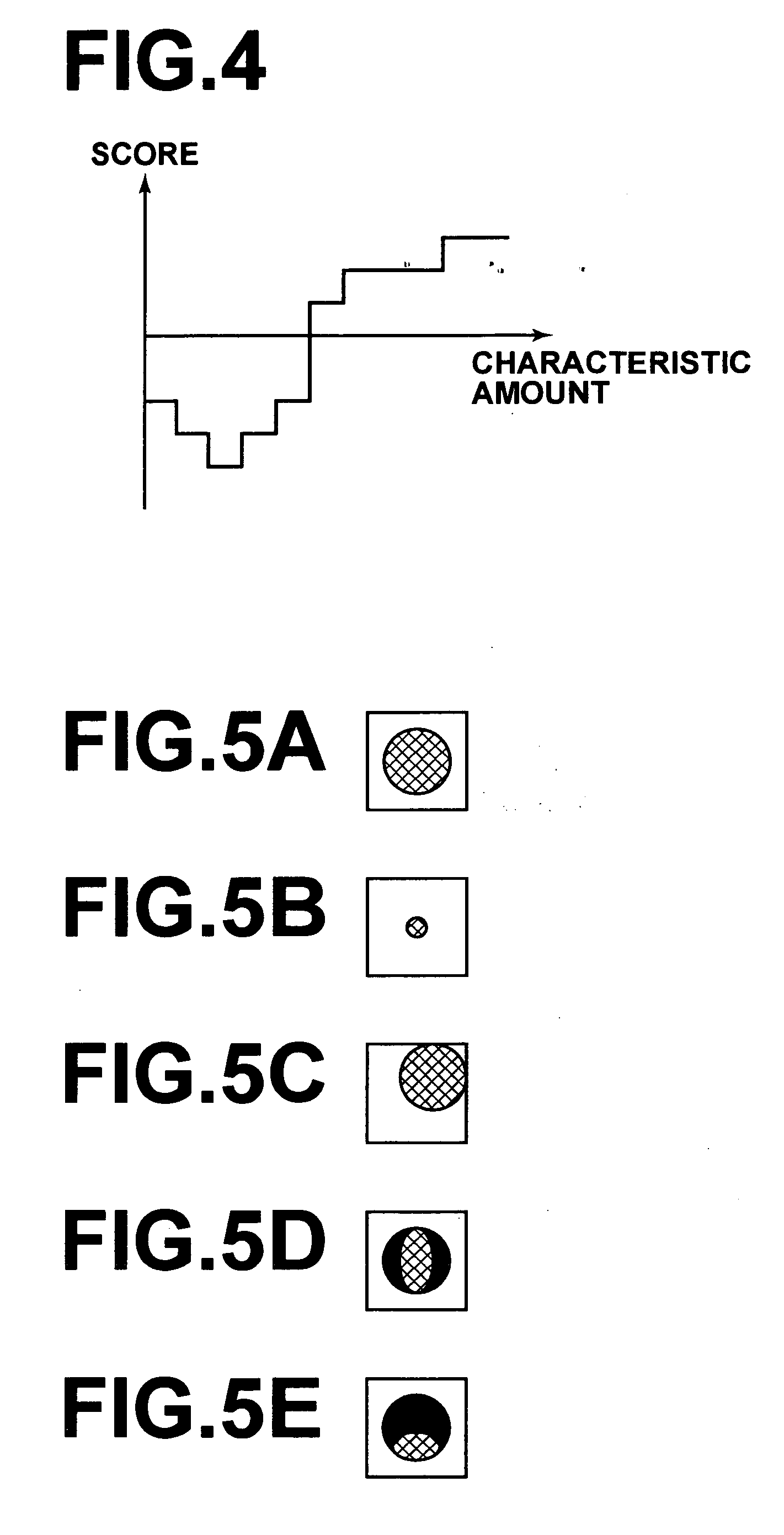
Method, apparatus, and program for detecting red eye
InactiveUS20060204052A1False positive detection can be preventedAvoid detectionImage enhancementImage analysisComputer science
Owner:FUJIFILM CORP +1
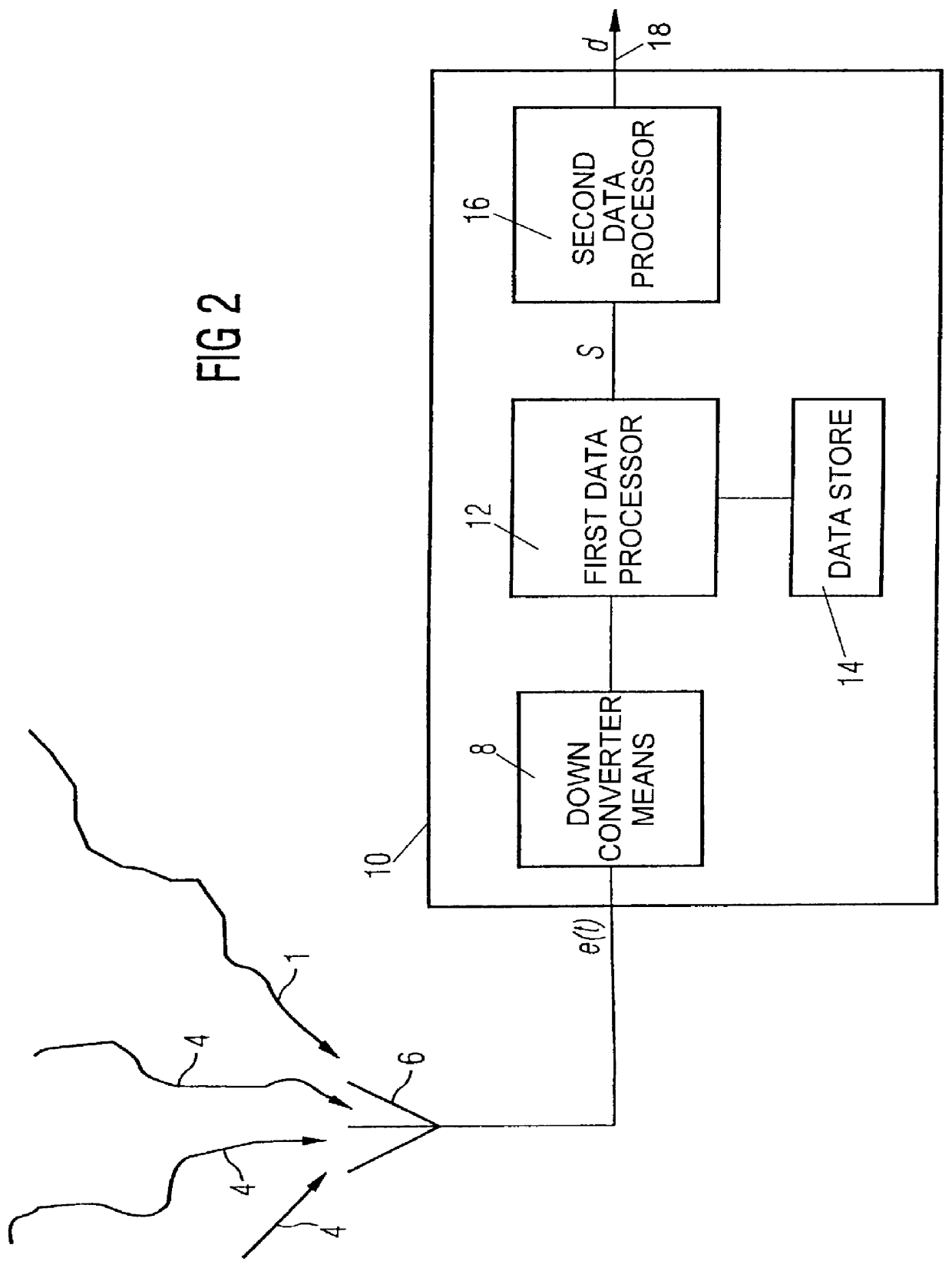
Noise reduction for analyte detection systems
InactiveUS20070258083A1Improve accuracyReduce contentCatheterDiagnostic recording/measuringPhysicsMicrophonics
Methods and apparatus are provided for determining the concentration of an analyte in a sample, such as an analyte in a sample of bodily fluid. Some embodiments use a synchronous demodulator and digital filter to reduce microphonic signal content. Some embodiments monitor the microphonic signal content and “hold off” on making a measurement until vibrations subside. Monitoring can be performed using an accelerometer or other vibration sensor. An algorithm can be used to examine the detector output signal and detect excessive microphonic components, making an accelerometer unnecessary.
Owner:OPTISCAN BIOMEDICAL
Systems and methods for fault-based power signal interruption
InactiveUS20050018371A1Reducing and eliminating chanceEasily damagedProvisions for user interfaceArrangements responsive to excess currentAnalog signal processingSystems approaches
Systems, methods, and apparatus for fault detection and interruption in power lines are provided. Circuitry is implemented via software and hardware that is configured to sense an operational aspect of a power line and apply signal processing to the sensed operational aspect to detect faults including different types of faults such as transient and steady state faults and can also be configured to identify the type of fault. Information on the fault and the identification of the type of fault can be displayed, stored, or some other output operation can be implemented. Circuitry can be implemented to provide digital signal processing and analog signal processing to, for example, independently and in parallel (e.g., redundant operation) detect faults and respond to faults as they occur (i.e., in real time). The types of faults can include transient type faults that can include ground, arc, line-to-line, and imbalance type faults and can also include steady state type faults (e.g., those showing wear in the machinery of a load).
Owner:TDG AEROSPACE
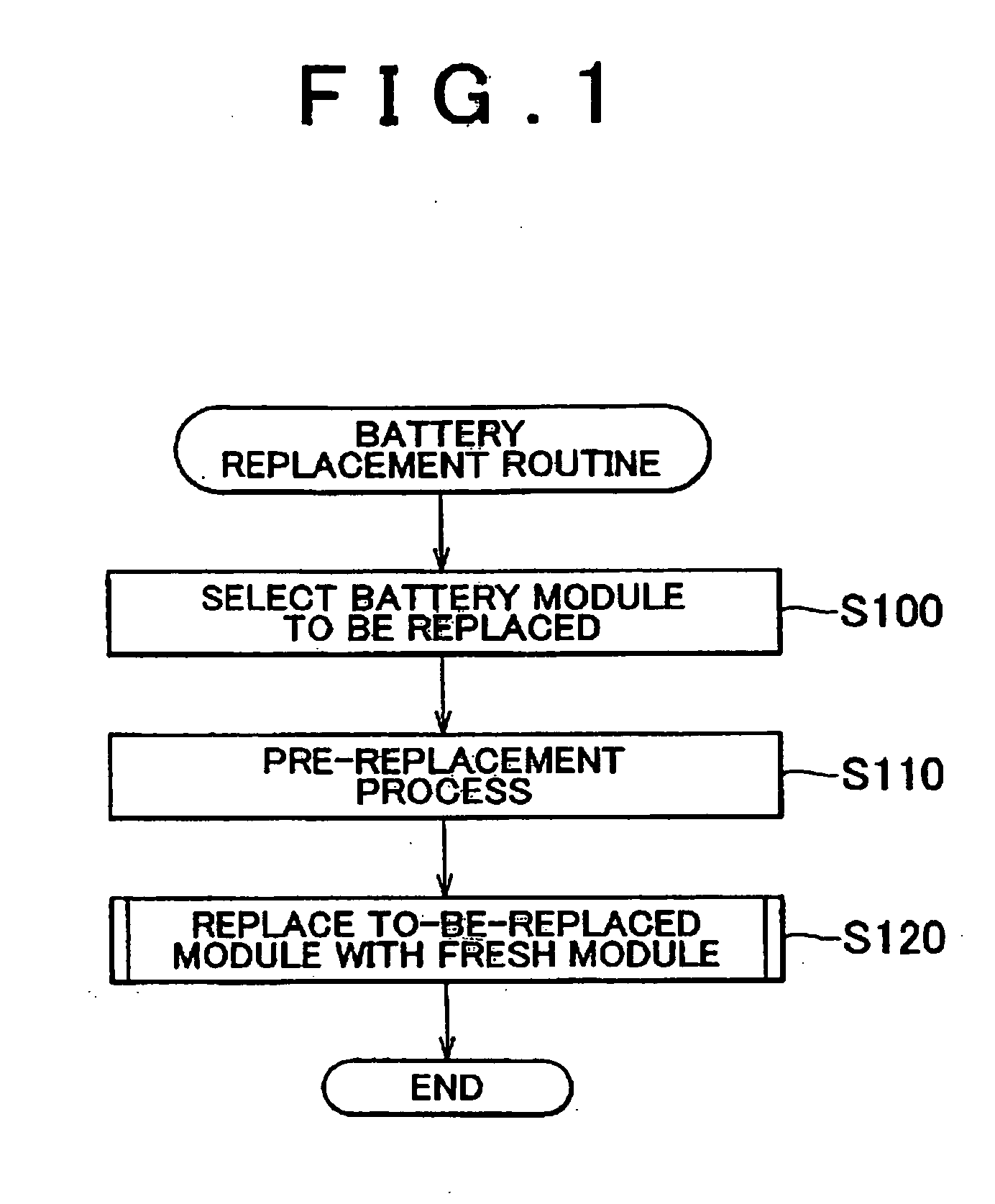
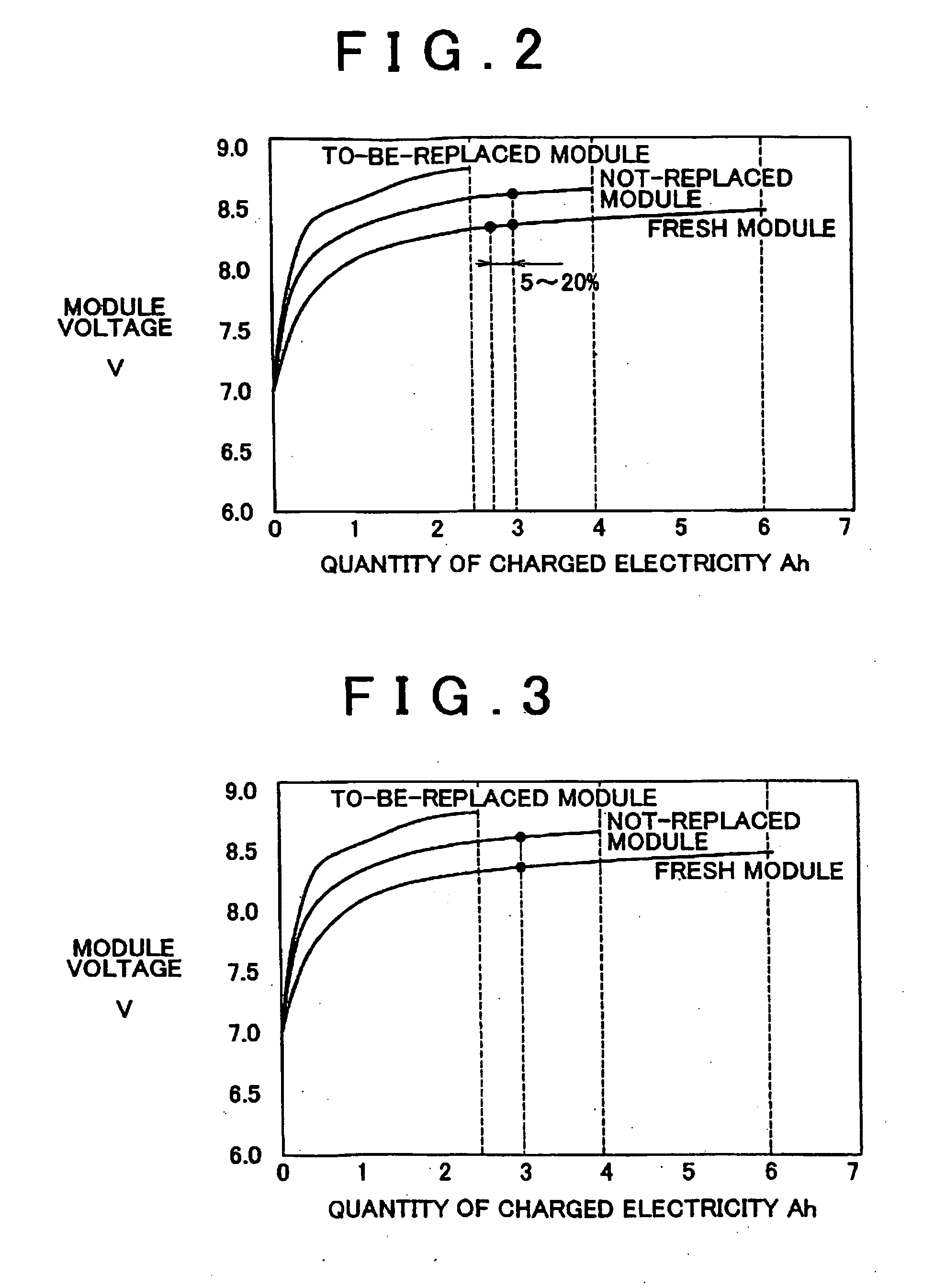
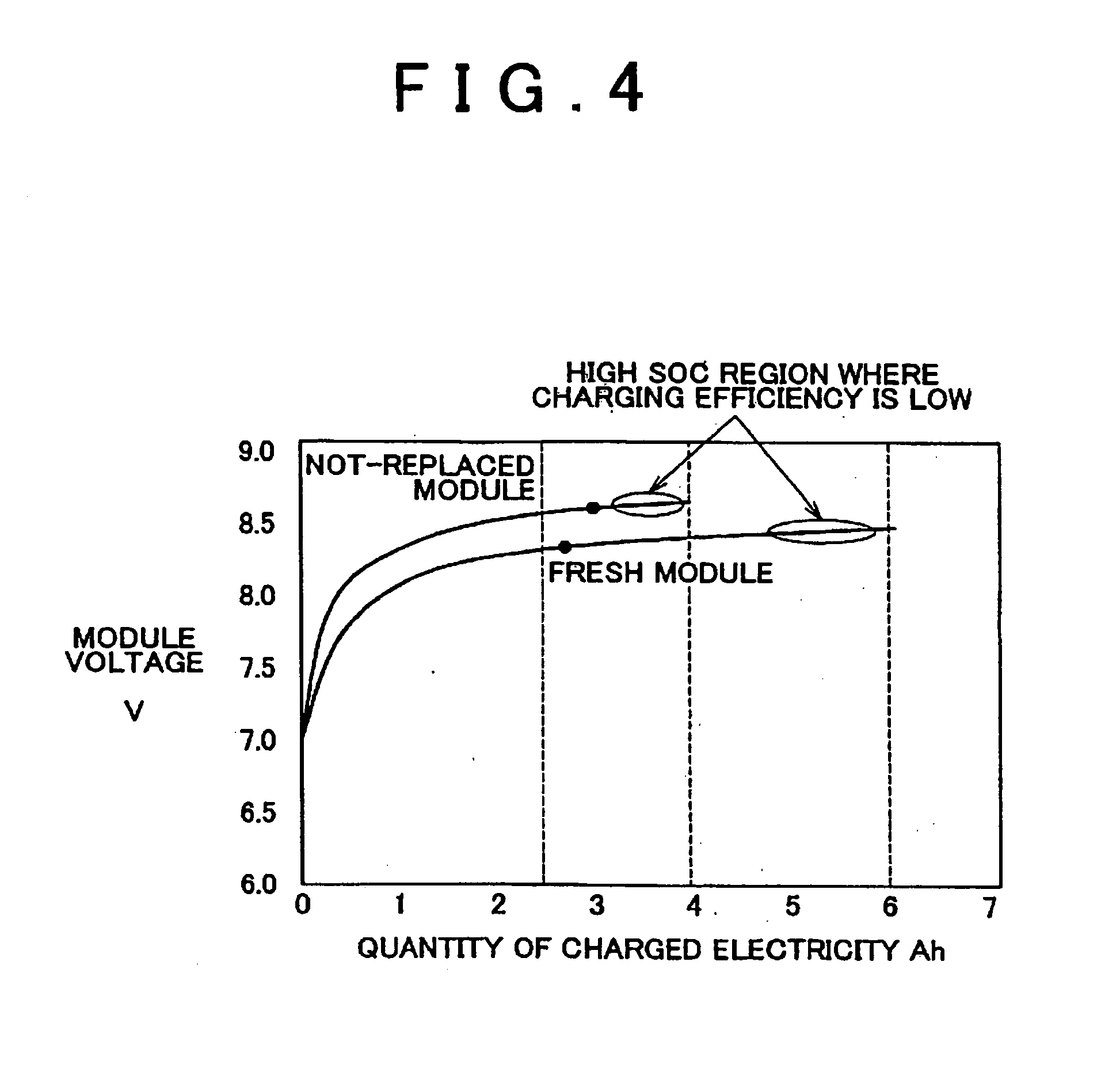
Secondary battery replacement method
ActiveUS20060012330A1Maximum performance of batteryPrevent false detectionParallel/serial switchingElectrical testingElectricityEngineering
A replacement method is provided for replacing a to-be-replaced battery module with a replacing fresh battery module in a battery assembly formed by electrically connecting a plurality of battery modules in series or parallel. The method includes the step (S110) of charging the fresh battery module so that the quantity of charged electricity of the fresh battery module is 5 to 20% less than the quantity of charged electricity of a battery module other than the to-be-replaced battery module, and the step (S120) of replacing the to-be-replaced battery module with the charged fresh battery module.
Owner:TOYOTA JIDOSHA KK
Event monitoring and collection
ActiveUS8122122B1PowerfulAvoid detectionDigital computer detailsComputer security arrangementsApplication softwareEvent monitoring
Embodiments of the invention provide systems, software and methods for monitoring events on a computer. In a set of embodiments, a monitoring application monitors events on a monitored computer. Each of the monitored events may be analyzed, and based on the analysis, some or all of the monitored events may be collected. A variety of rules may be used in analyzing events. In some cases, collected events can be queued, for example, by storing a representation of each collected event in an event cache. When connectivity with a monitoring computer is available, a connection with the monitoring computer may be established, and / or the queued events may be transmitted to the monitoring computer. In a particular set of embodiments, the monitoring application is designed to avoid detection by a user of the monitored computer.
Owner:SILICON VALLEY BANK
Coupling method
ActiveUS20140262784A1Avoid detectionOptimization orderSludge treatmentVolume/mass flow measurementAnalyteNucleic acid sequencing
The invention relates to a new method of determining the presence, absence or characteristics of an analyte. The analyte is coupled to a membrane. The invention also relates to nucleic acid sequencing.
Owner:OXFORD NANOPORE TECH LTD
Electrocardiogram noise reduction
ActiveUS9801585B2Without compromising safetyRemove noiseElectrocardiographyCatheterPeristaltic pumpEcg signal
Owner:BIOSENSE WEBSTER (ISRAEL) LTD
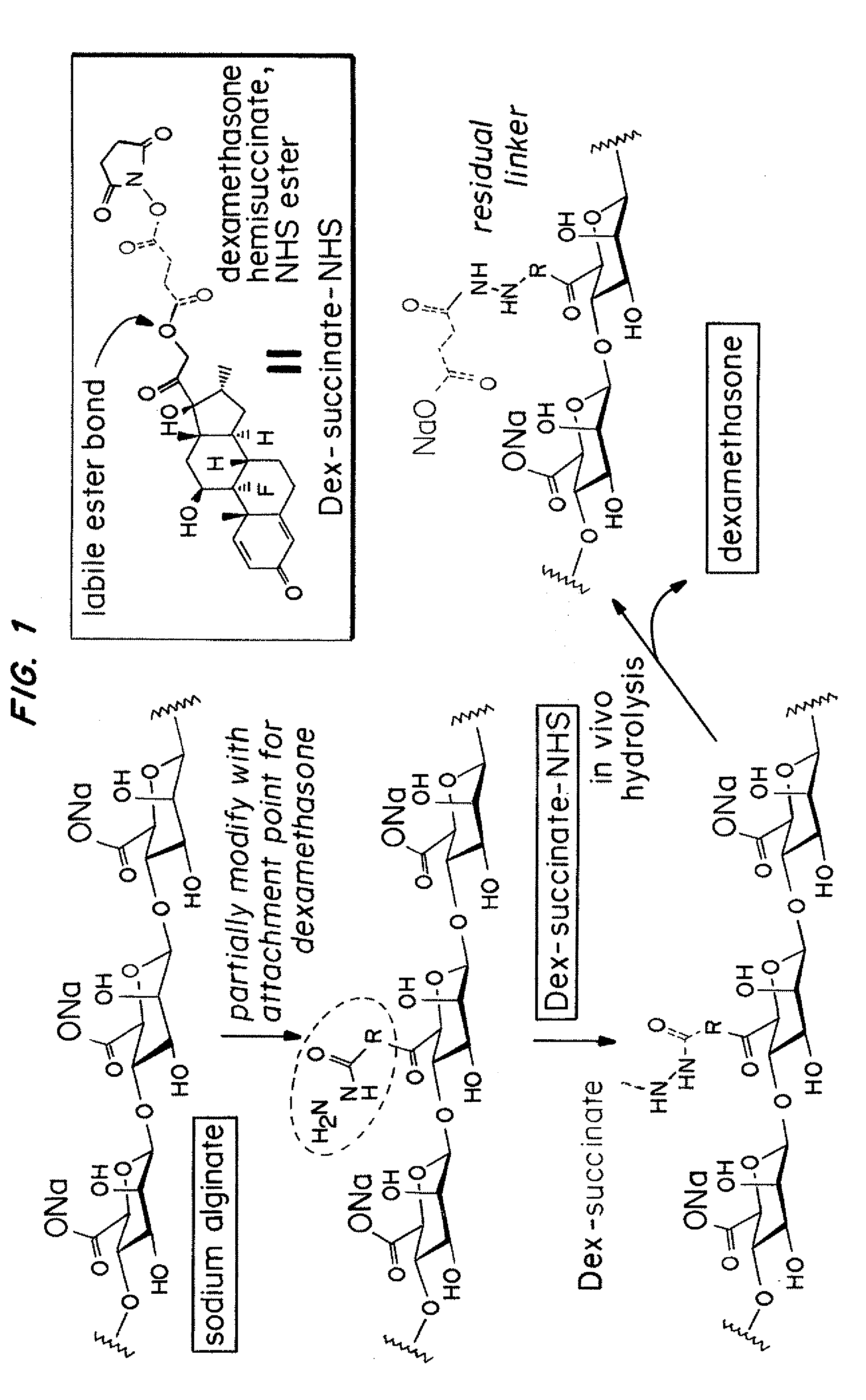
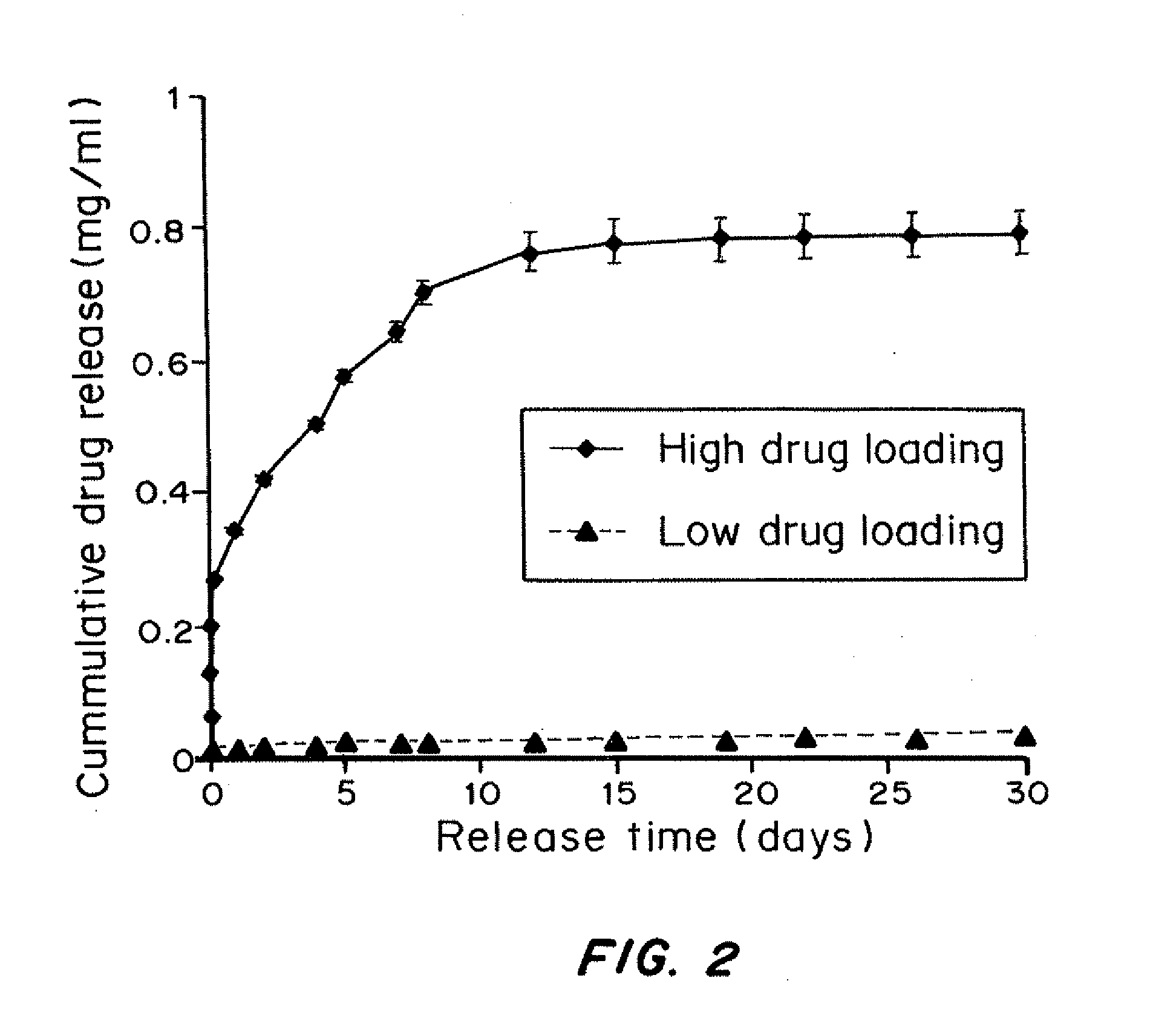
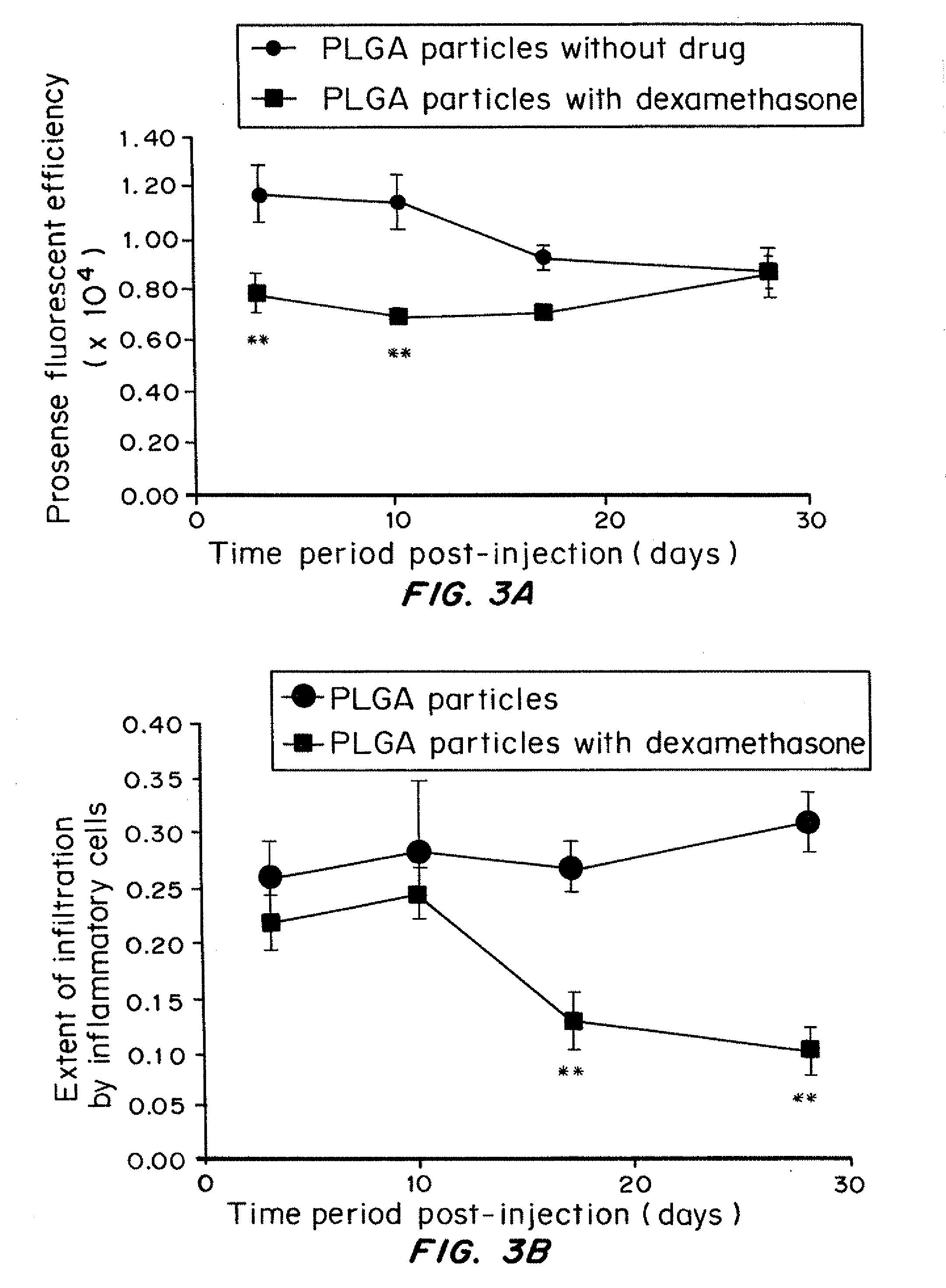
Hydrogel encapsulated cells and Anti-inflammatory drugs
ActiveUS20120213708A1Maximizes drug interactionMinimize interferenceOrganic active ingredientsBiocideDiseaseMedicine
A composition containing biocompatible hydrogel encapsulating mammalian cells and anti-inflammatory drugs is disclosed. The encapsulated cells have reduced fibrotic overgrowth after implantation in a subject. The compositions contain a biocompatible hydrogel having encapsulated therein mammalian cells and anti-inflammatory drugs or polymeric particles loaded with anti-inflammatory drugs. The anti-inflammatory drugs are released from the composition after transplantation in an amount effective to inhibit fibrosis of the composition for at least ten days. Methods for identifying and selecting suitable anti-inflammatory drug-loaded particles to prevent fibrosis of encapsulated cells are also described. Methods of treating a disease in a subject are also disclosed that involve administering a therapeutically effective amount of the disclosed encapsulated cells to the subject.
Owner:MASSACHUSETTS INST OF TECH +1
Method and apparatus for start of frame delimiter detection
ActiveUS8831070B2Easy to startReduce dataData switching by path configurationAmplitude-modulated carrier systemsNetwork packetComputer science
Owner:STICHTING IMEC NEDERLAND
Method and system for web integrity validator
ActiveUS20150256556A1Avoid detectionMemory loss protectionError detection/correctionClient-sideValidator
A computer-implemented method and system for the validation of a true browsing user on a website is disclosed. The invention allows for the collection of data regarding the evolving threat landscape created by online attackers. The system and method fingerprint user behavior to detect differences between a local user, a remote / foreign user, and an automated script. The system then covertly transmits that information back to a financial institution client without giving online attackers the opportunity to notice such transmittal. Certain embodiments of the invention also correspond with the browsing user to validate their identity. The claimed system and method proactively reveal attackers and attack ploys, additionally enabling institutions and security consultants to adapt to attacks in an automated fashion.
Owner:HUMAN SECURITY INC
Nucleic acid aptamer-based compositions and methods
InactiveUS20070111222A1Improve responseReduce detectionAntibacterial agentsBioreactor/fermenter combinationsFluorescenceBiology
The present invention relates to compositions that can detect the presence of specific entities or substances in an environment, and provide an amplified response to the detection as manifested by release of enzymes, reporter signals or drugs. The detection and response is based on nucleic acid functionalities, such as aptamer regions that are designed to specifically bind almost any entity or ligand, and enzymatic regions that can cleave nucleic acids at specific sequences. The response can be amplified on a first order through creating an allosteric relationship between the different nucleic acid functionalities present on the same nucleic acid molecule and on a second order through the release of active cargo molecules capable of generating molecules detectable by their color, fluorescence, luminescence, or ability to modulate an electric signal.
Owner:THE TRUSTEES OF COLUMBIA UNIV IN THE CITY OF NEW YORK
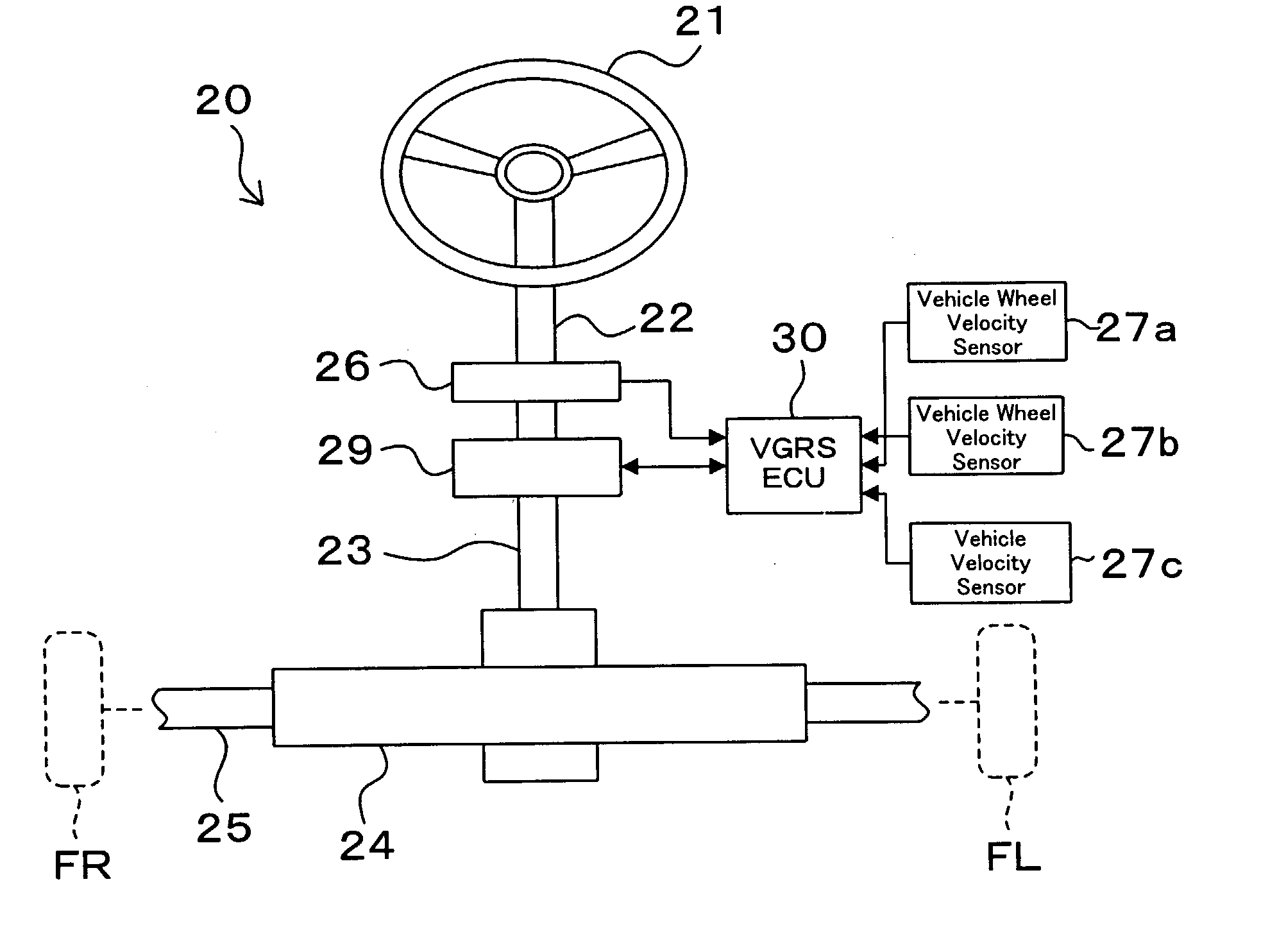
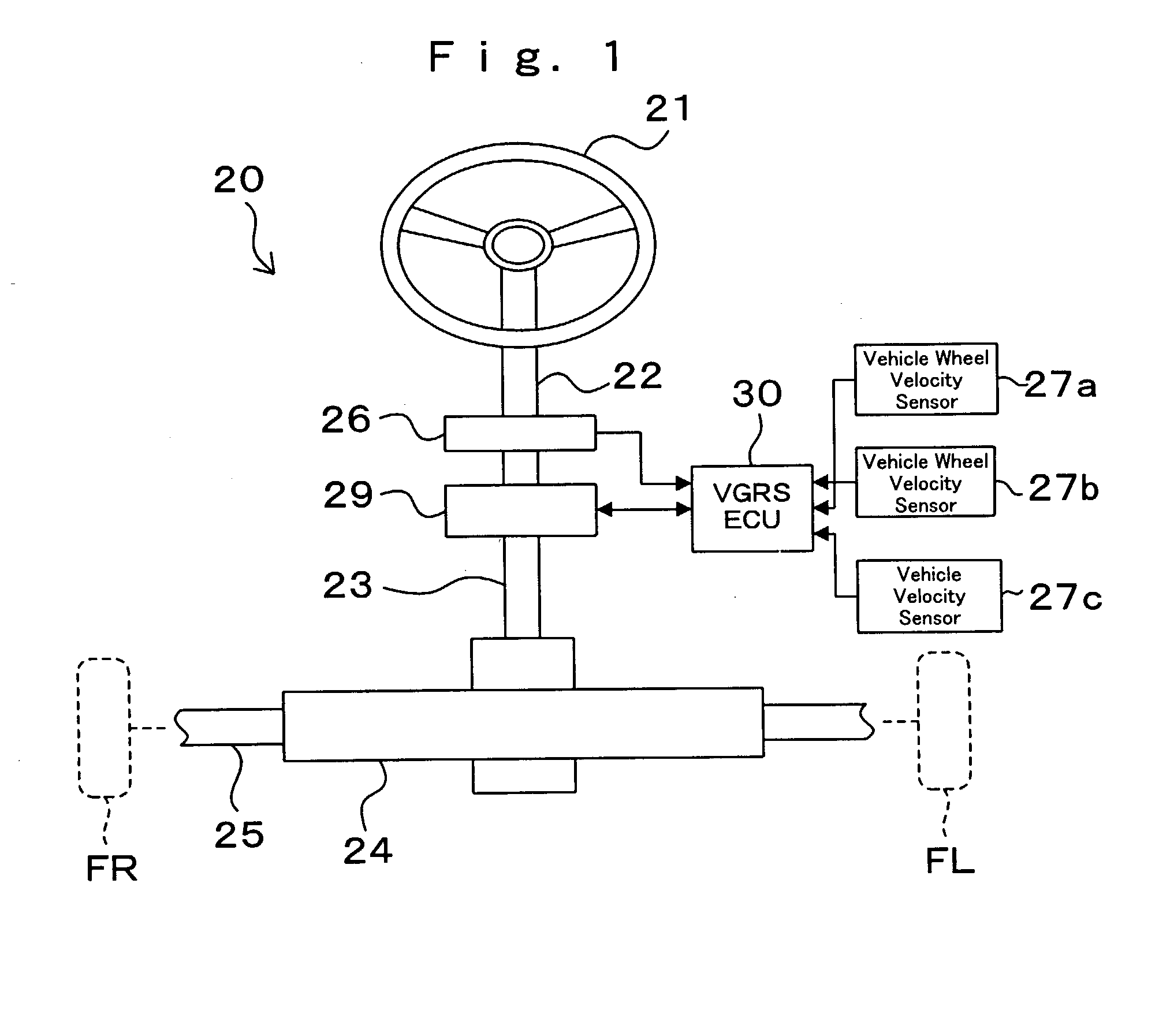
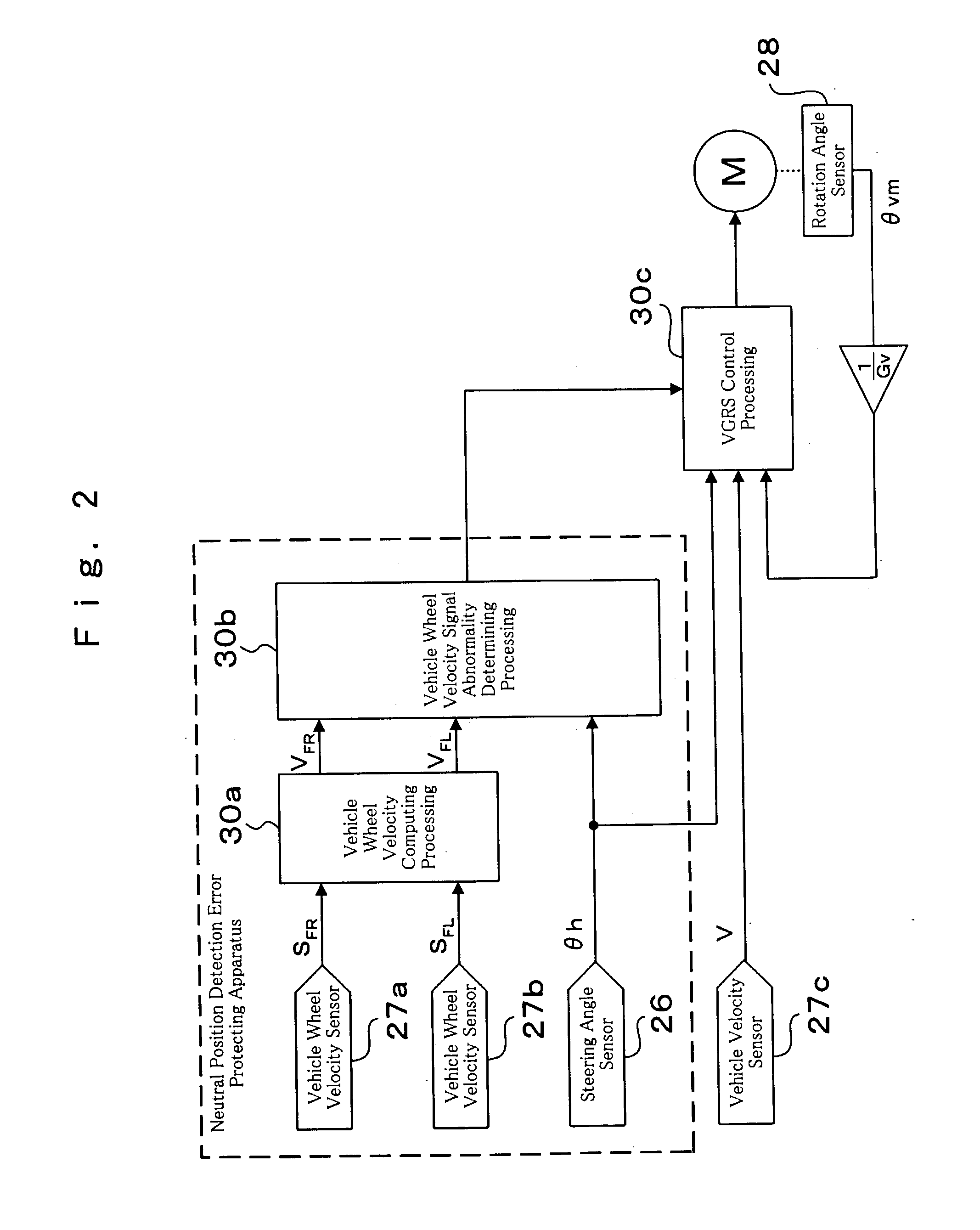
Steering angle neutral position detection error protecting method and detection error protecting apparatus
InactiveUS20040046346A1Detection errorAvoid detectionVehicle testingRegistering/indicating working of vehiclesLocation detectionDrive wheel
In a neutral position detection error protecting apparatus, vehicle wheel velocities SFR, SFL of right / left driven wheels FR, FL are detected by vehicle wheel sensors 27a, 27b and a right / left wheel velocity difference VFD is obtained from vehicle wheel velocities VFR, VFL of the driven wheels FR, FL through vehicle wheel velocity signal abnormality determining processing 30b so as to detect steering angle information thetah from the steering wheel 21. Then, when a condition that a right / left wheel velocity difference VFD is less than a predetermined velocity V1, a condition that a rotation angle of steering angle information thetah is more than a predetermined value thetak and a condition that a vehicle wheel velocity is more than a predetermined velocity V2 according to vehicle wheel velocities VFR, VFL of the driven wheels FR, FL are all satisfied in a predetermined period T, it is determined that there is any abnormality in the vehicle wheel velocities SFR, SFL (VFR, VFL) of the driven wheels FR, FL through vehicle wheel velocity signal abnormality determining processing 30b.
Owner:TOYODA MASCH WORKS LTD
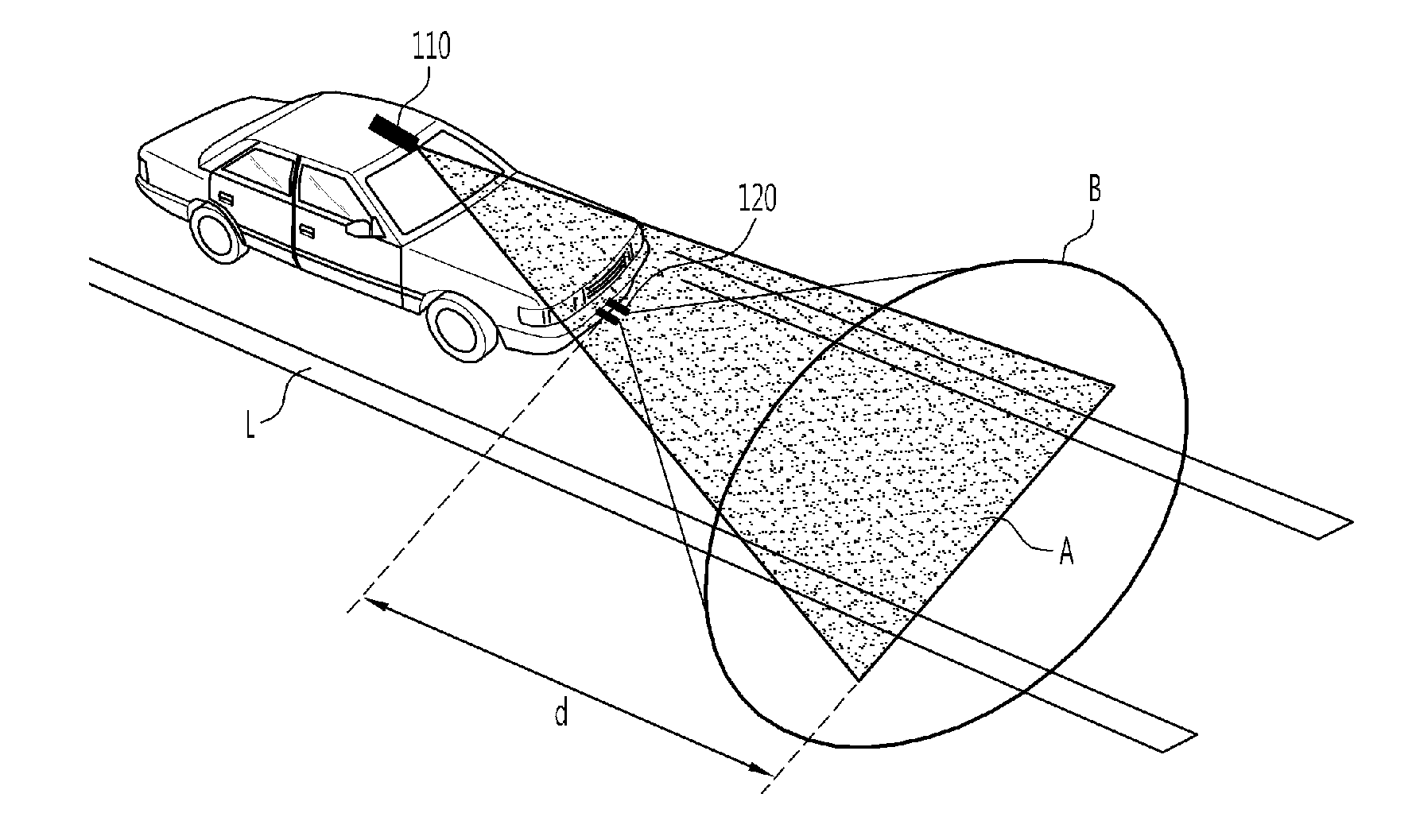
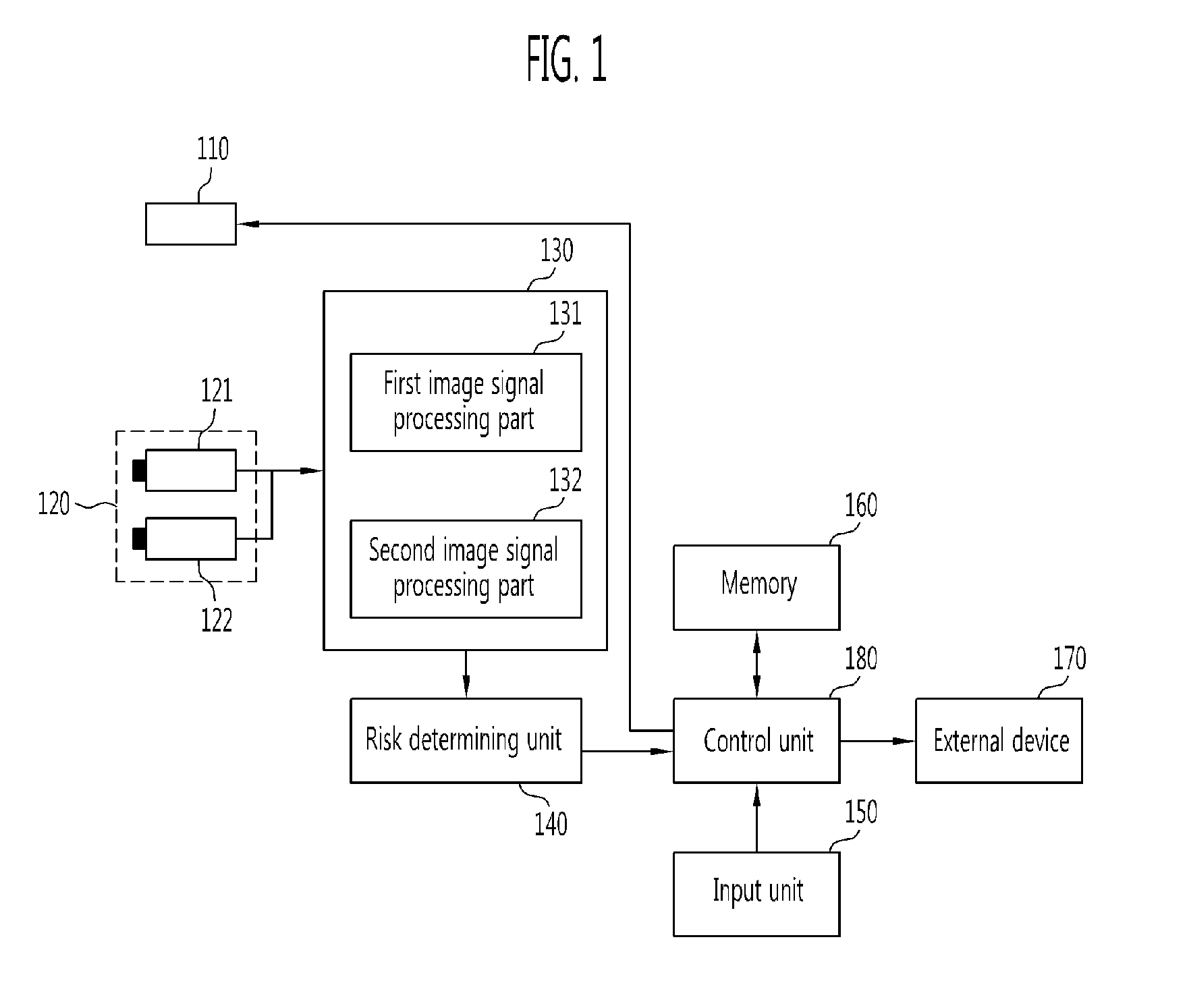
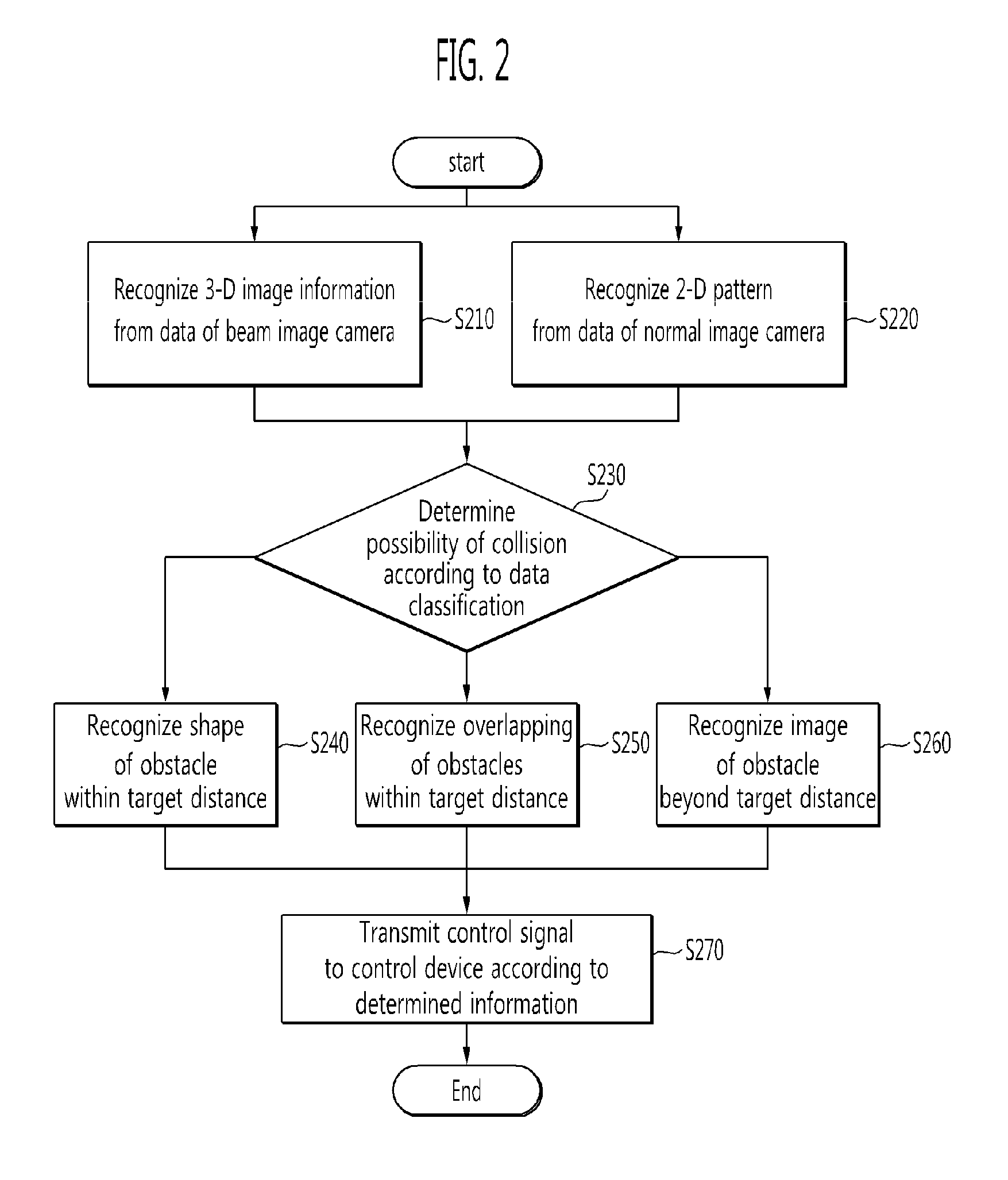
Obstacle detecting system and method
InactiveUS20120081542A1Quick fixAvoid detectionColor television detailsScene recognitionRoad surfaceComputer science
The obstacle detecting system includes a first image acquiring unit which acquires first image information by selectively receiving a laser beam emitted from at least one laser source toward a road surface at a target distance; a second image acquiring unit which acquires an image of actual surroundings as second image information; an image recognizing unit which recognizes an image of an obstacle by performing 3-D image recognition signal processing on line information of the laser beam using the first image information, and recognizes a pattern of the obstacle by performing pattern recognition signal processing on the second image information; and a risk determining unit which determines a possibility of collision due to presence of the obstacle within the target distance by classifying the recognized obstacles according to whether or not the image-recognized obstacle is matched with the pattern-recognized obstacle.
Owner:ELECTRONICS & TELECOMM RES INST +1
Touch control liquid crystal display device
ActiveUS20140168540A1Low detection sensitivityControl loadNon-linear opticsInput/output processes for data processingMetal gridLiquid-crystal display
One inventive aspect is a touch control liquid crystal display device. The device includes a color film substrate, a thin film transistor array substrate, and a liquid crystal layer between the color film substrate and the thin film transistor array substrate. The color film substrate includes a grid-shaped black matrix layer, a touch control layer, and a color film layer. The touch control layer includes metal grid electrodes in a rectangle, where the metal grid electrodes include metal lines intersecting transversely and vertically. In addition, the metal grid electrodes include drive electrodes and sense electrodes. The drive electrodes are connected together through first metal connection lines in a first direction, and the sense electrodes are connected together through second metal connection lines in a second direction. In addition, the projection of the metal grid electrodes falls into the projection of the black matrix layer in the light transmission direction.
Owner:SHANGHAI TIANMA MICRO ELECTRONICS CO LTD
Presentation video control system
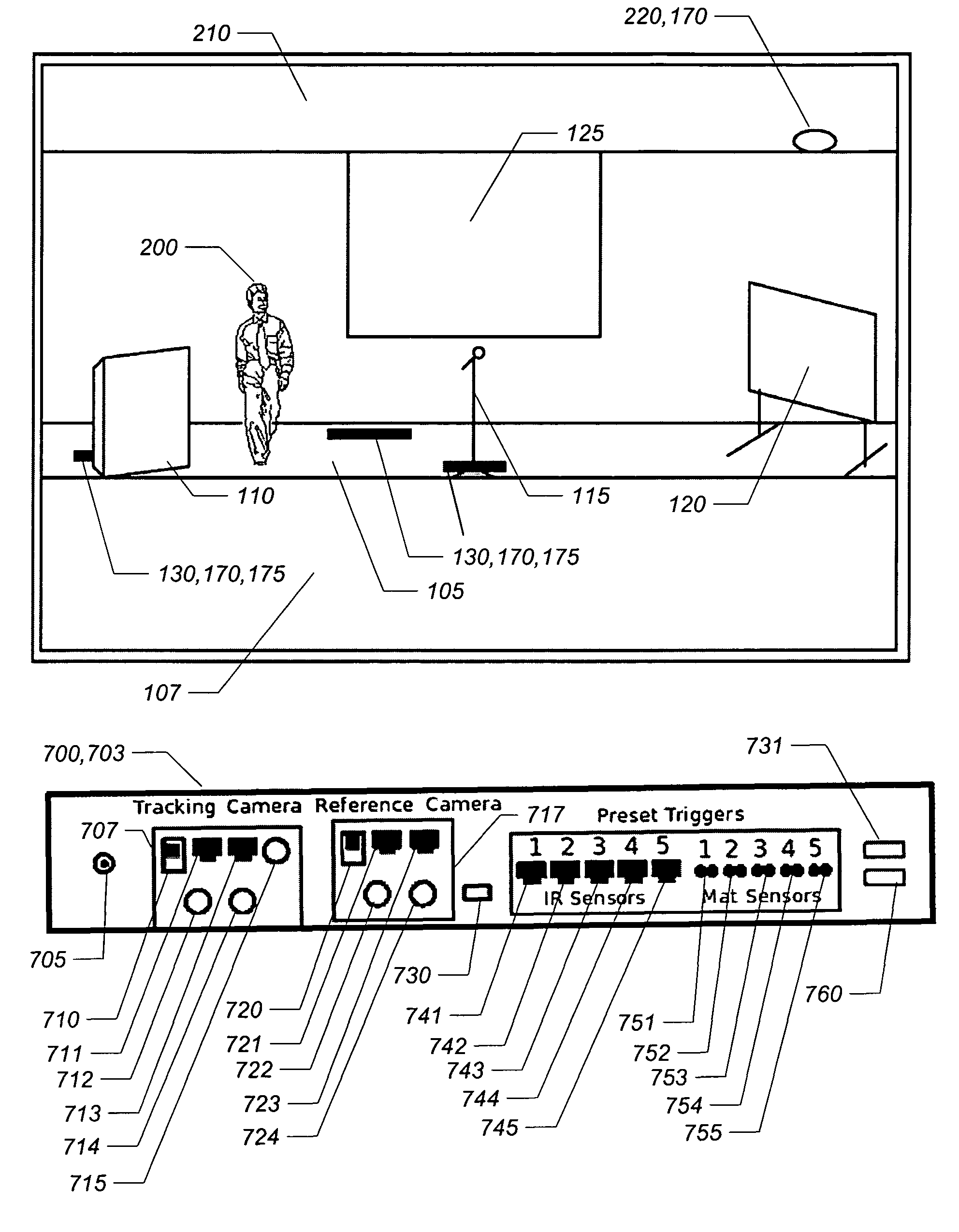
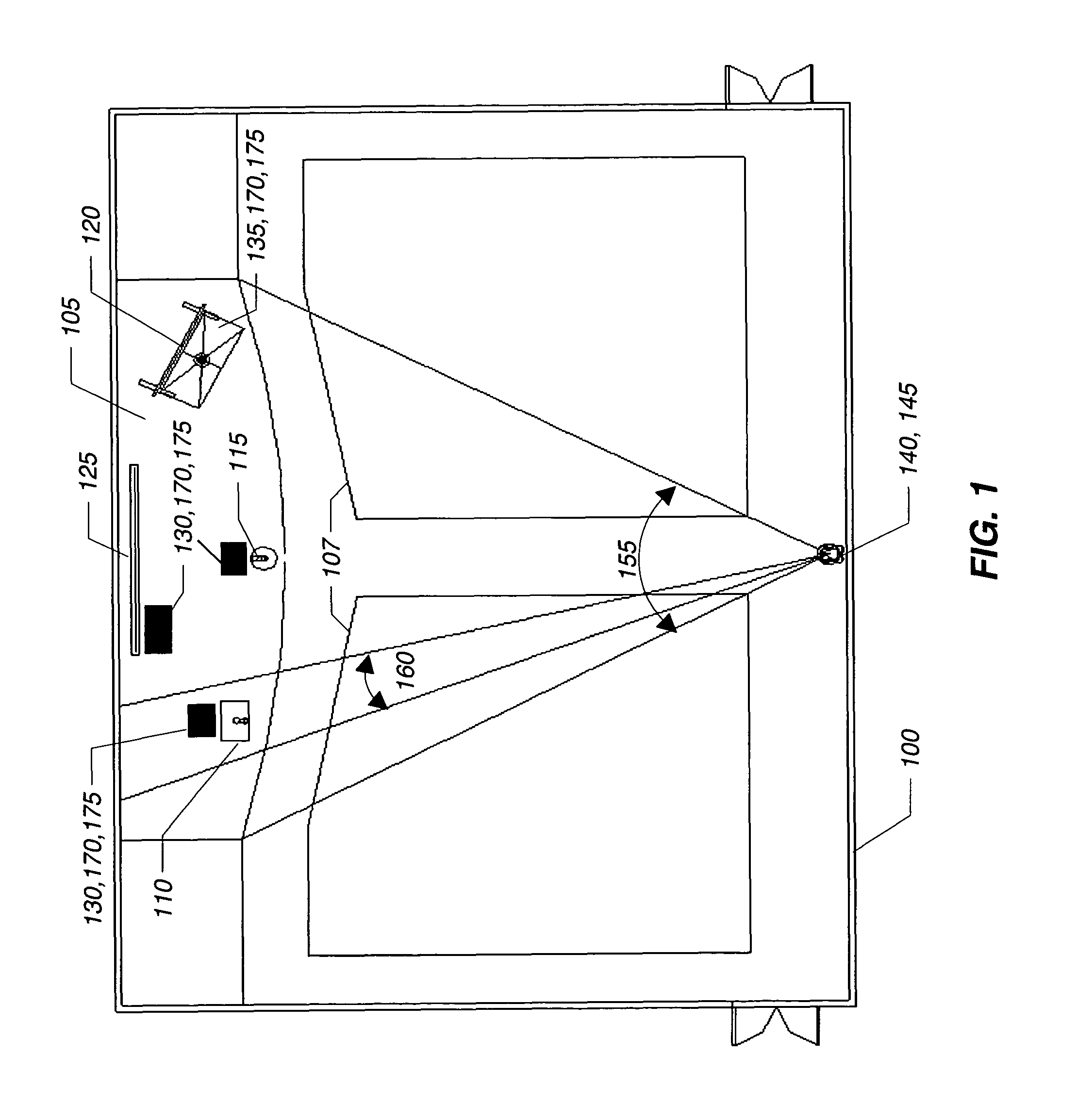
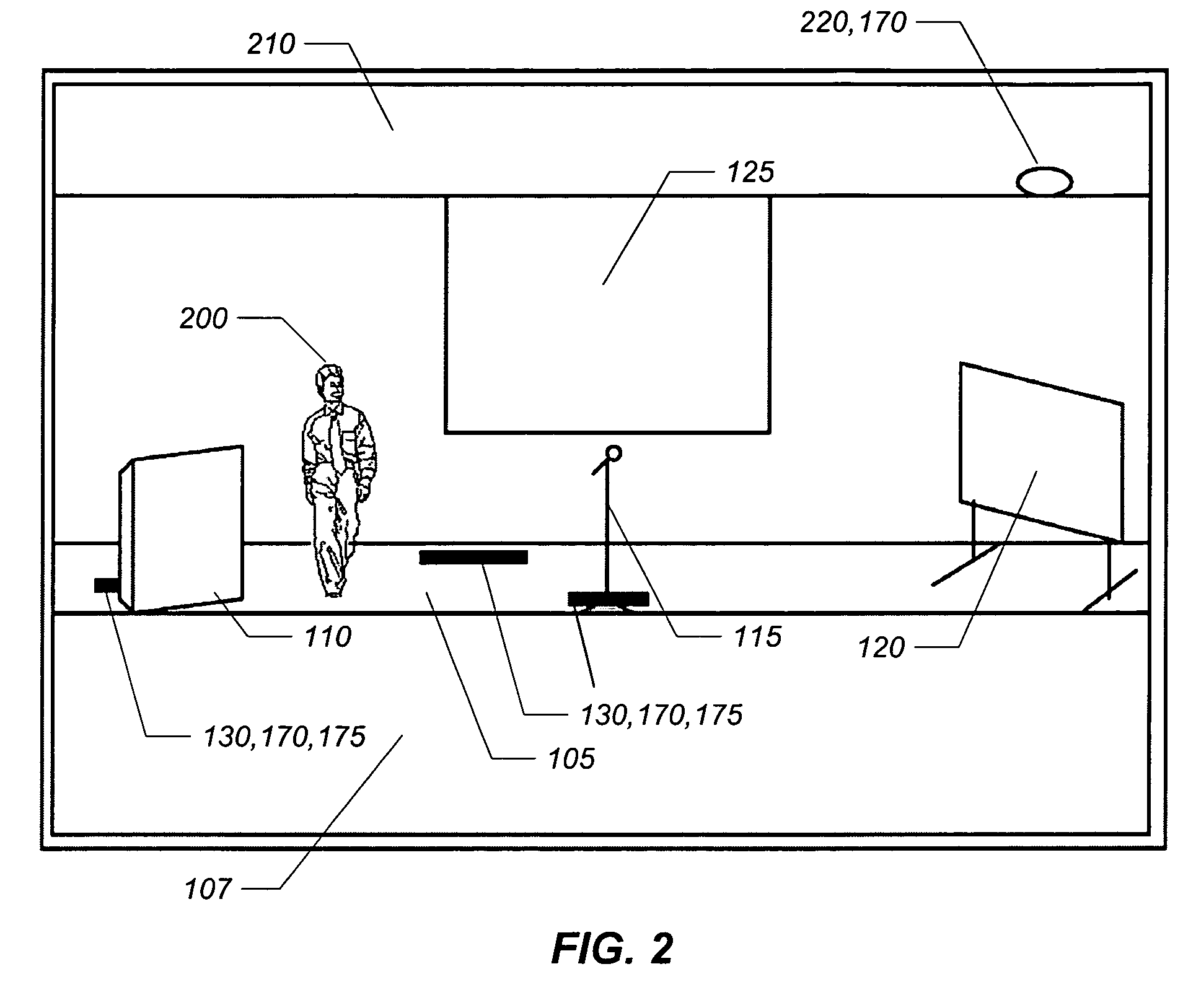
ActiveUS8094193B2Avoid detectionConfigure operationTelevision system detailsColor television detailsCamera controlSystems design
The present invention is a camera control system designed for video capture of a presentation made in a lecture hall or similar place. The system combines preset views triggered by presence-sensing devices at fixed locations with views tracking the motion of the presenter elsewhere. A tracking camera displays a preset view when the presenter steps on a switch mat or enters into the region of detection of some other presence sensor such as an infrared sensor. At other times, the tracking camera is guided by motion detection logic that uses a wide field of vision provided by a reference camera. The reference camera, the tracking camera, and the presence-sensing devices are integrated by a controller. Various parameters can be configured by a user through a graphical user interface on a computer, manual controls on the box housing the controller, or a hand-held remote control device.
Owner:NATURE VISION
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com