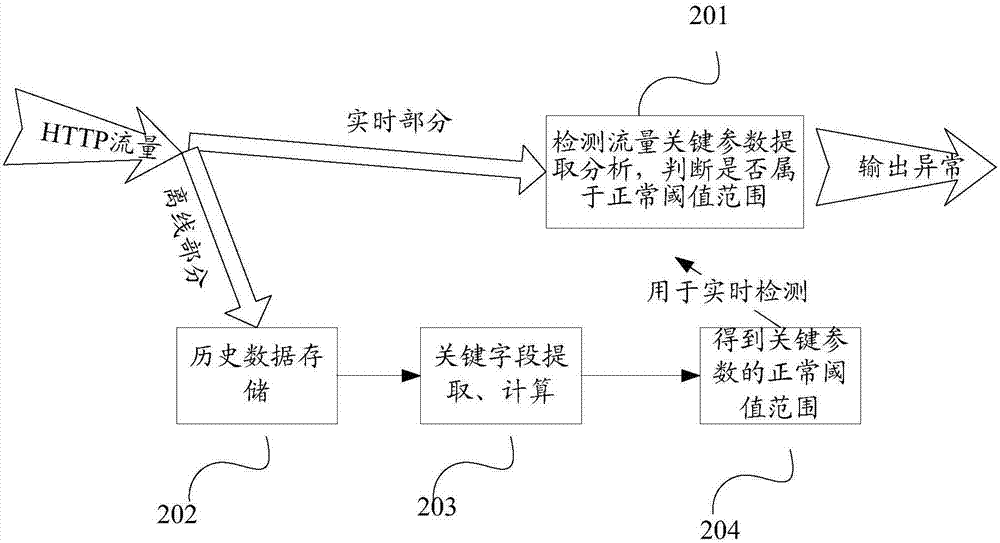
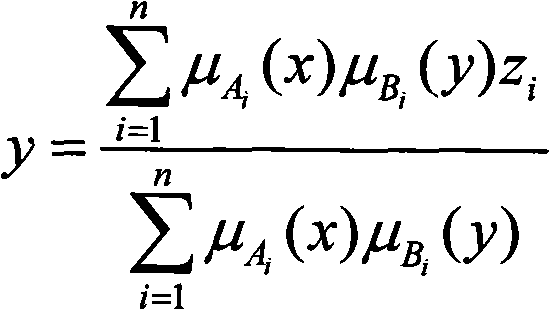Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
84 results about "Covert channel" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
In computer security, a covert channel is a type of attack that creates a capability to transfer information objects between processes that are not supposed to be allowed to communicate by the computer security policy. The term, originated in 1973 by Lampson, is defined as channels "not intended for information transfer at all, such as the service program's effect on system load," to distinguish it from legitimate channels that are subjected to access controls by COMPUSEC.
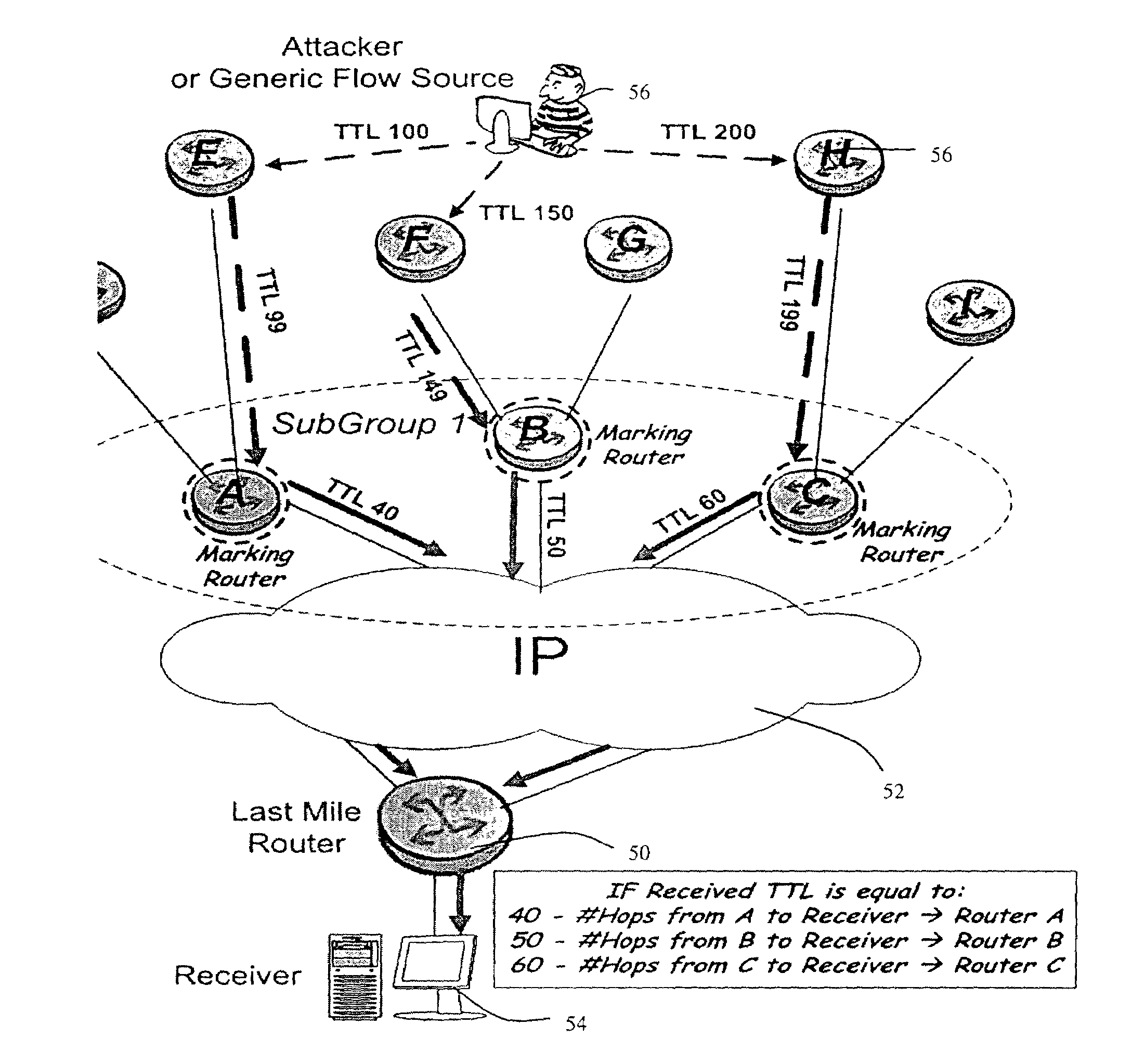
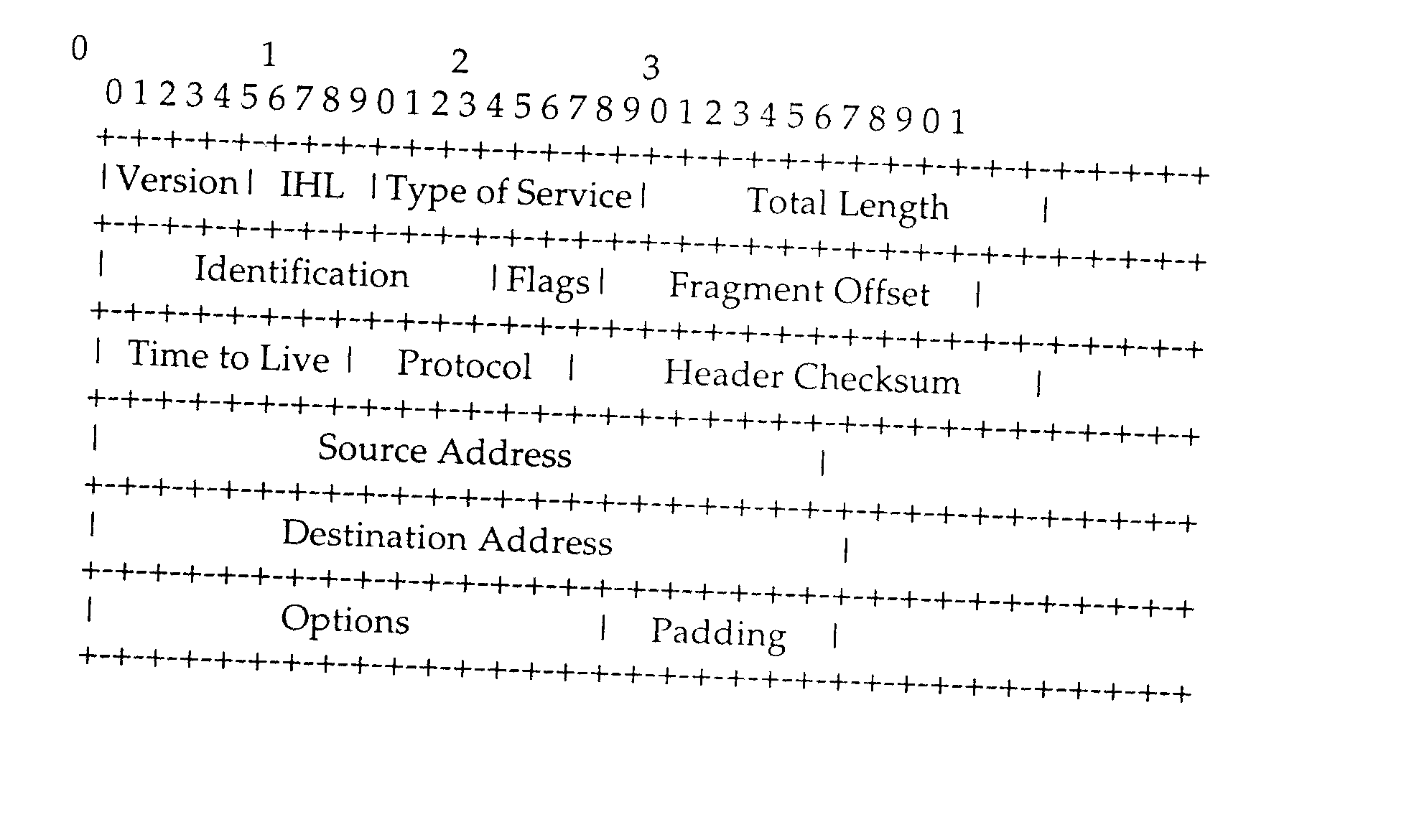
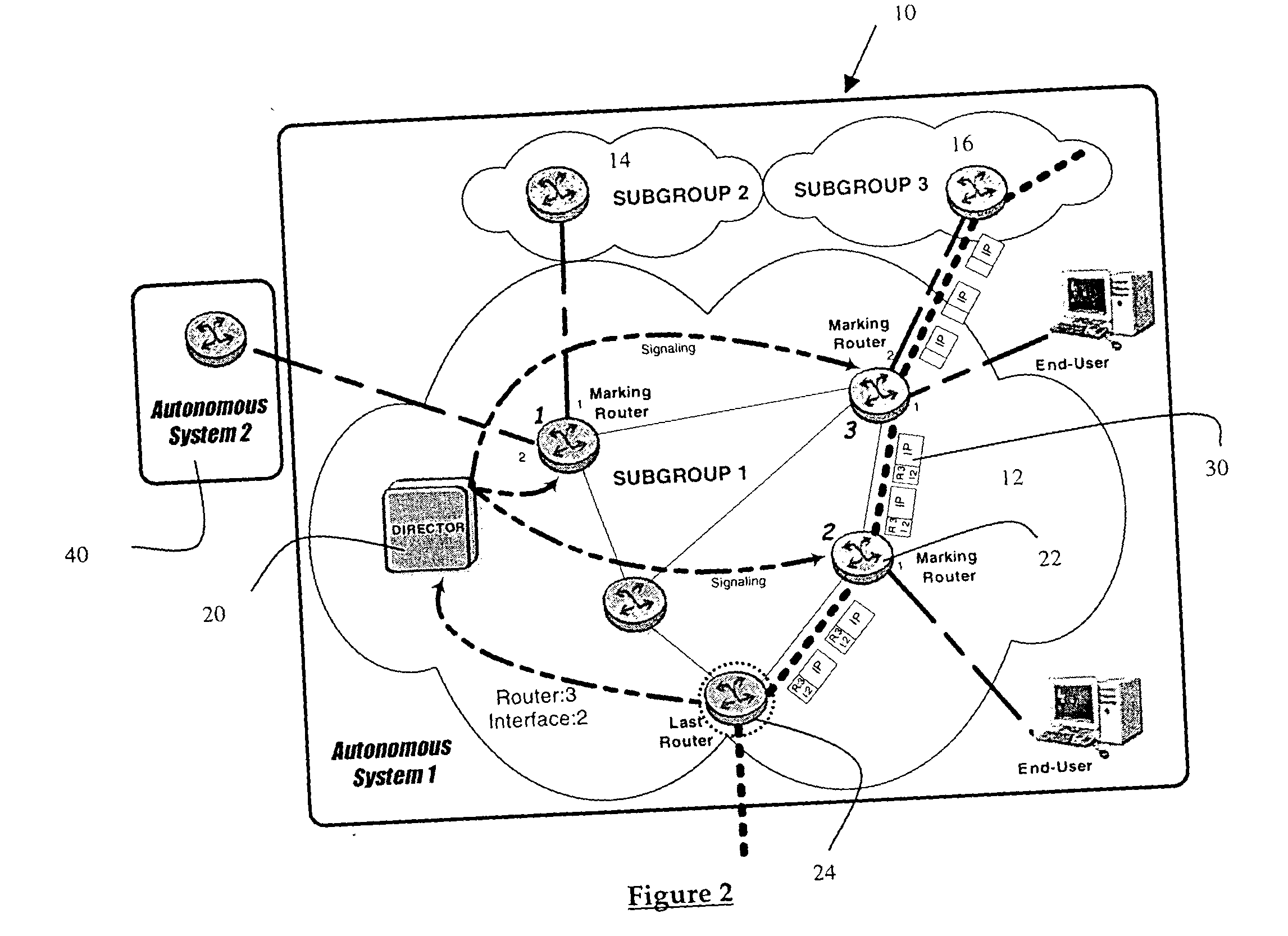
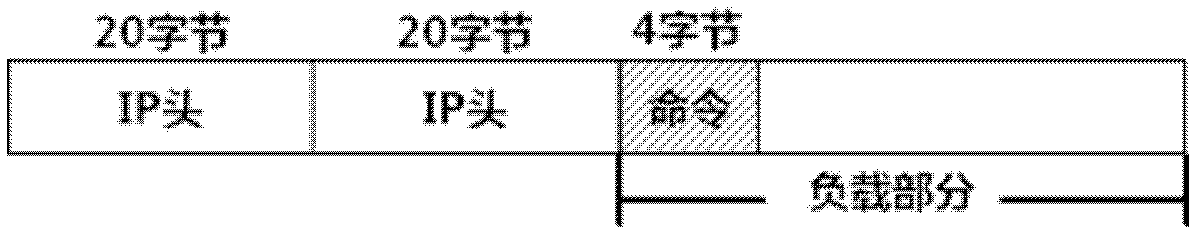
IP Time to Live (TTL) field used as a covert channel
The Time to Live (TTL) field in an IP header is used as a covert channel in a communication system. More particularly the TTL field can be used to selectively mark packets with unique identifiers as they pass through an upstream station on their way to a downstream station. In this way the source of a traffic flow at least within a particular domain can be absolutely identified. This method of performing a traceback operation doesn't utilize additional resources as it relies on functionality which already exists in the system.
Owner:RPX CORP
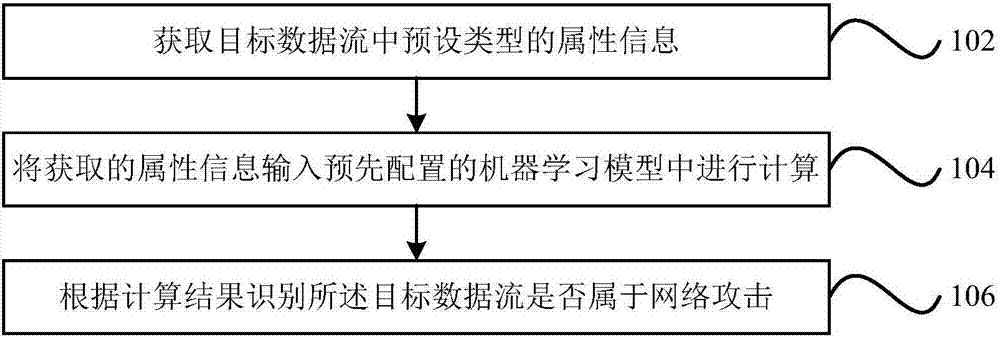
Network attack identification method and device as well as computer readable storage medium
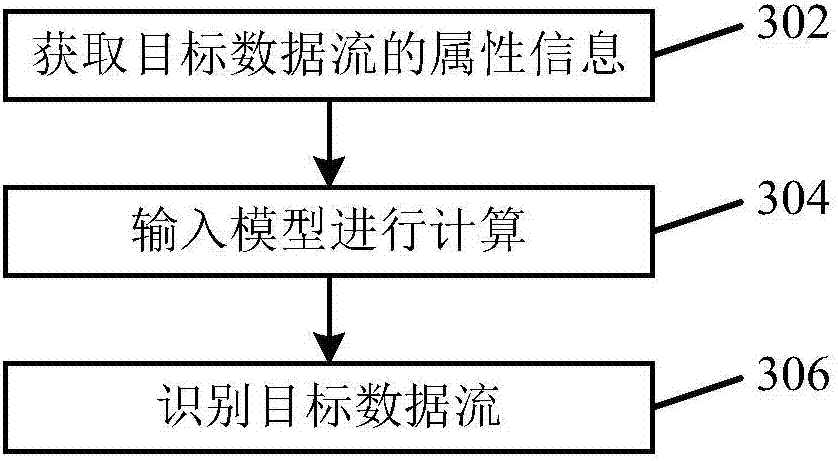
The application provides a network attack identification method and device as well as a computer readable storage medium. The method may include the following steps: acquiring a preset type of attribute information in a target data stream; inputting the acquired attribute information into a preconfigured machine learning model for calculation, wherein the machine learning model is obtained by training sample data through a supervised learning algorithm; and identifying whether the target data stream belongs to network attacks according to a calculation result. According to the technical scheme provided by the application, the data stream that belongs to the network attacks can be effectively identified; and meanwhile, the network attacks can be identified without extracting attack features, and messages that are transmitted through covert channels, encrypted channels and other modes and belong to the network attacks can be identified.
Owner:HANGZHOU DPTECH TECH
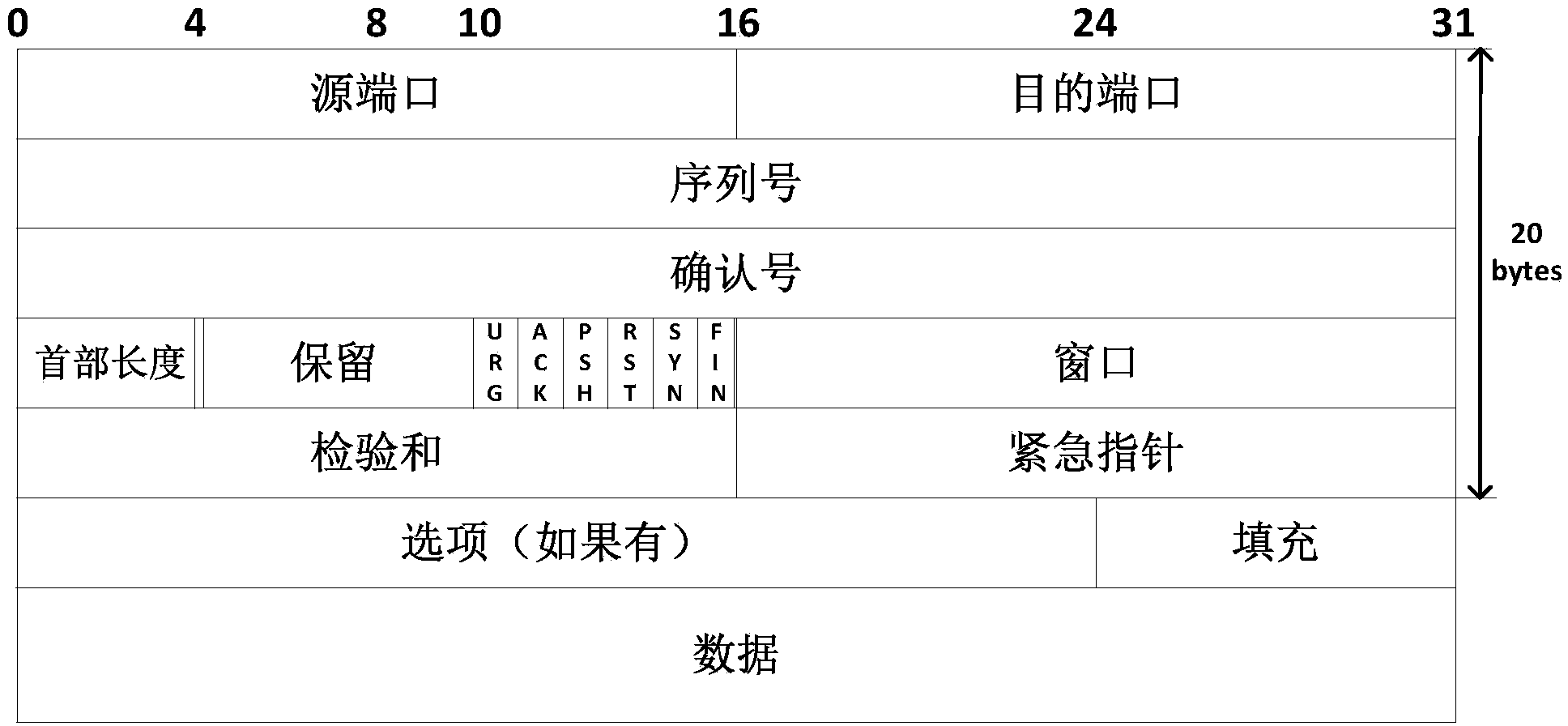
Method for detecting TCP/IP protocol concealed channel based on fuzzy neural network
InactiveCN101257417ARealize detectionEasy to detectData switching networksFeature vectorOperational system
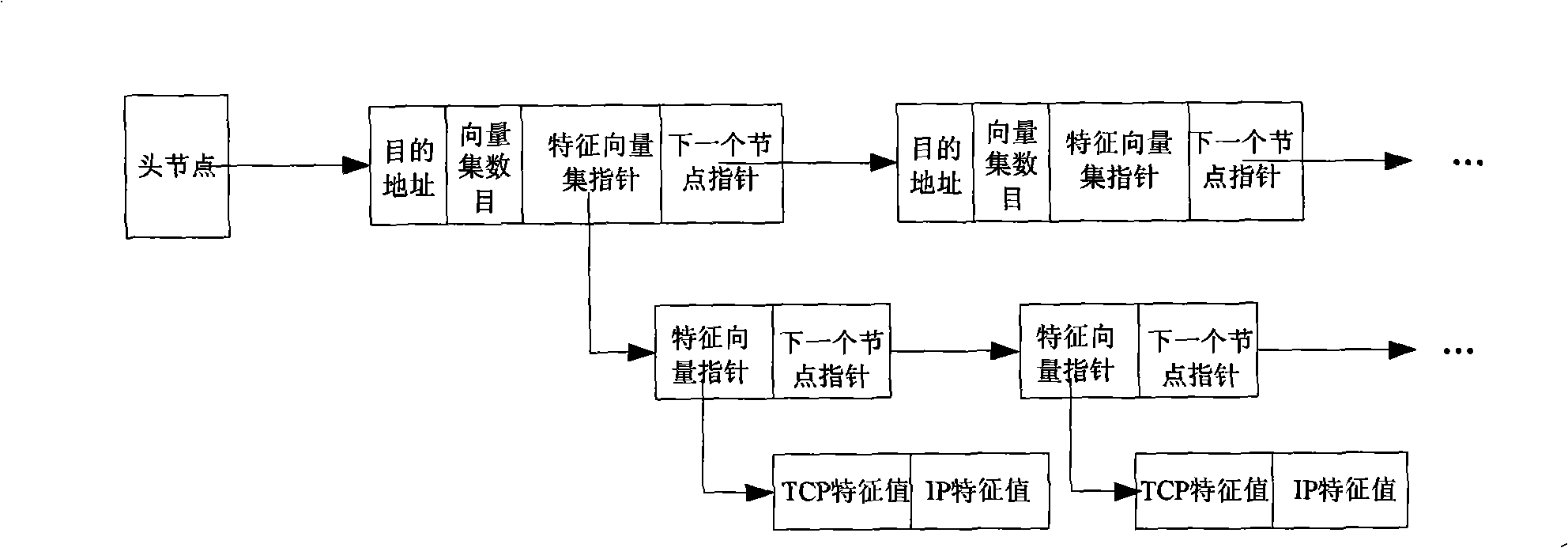
The invention discloses a method for detecting TCP / IP protocol covert channel based on fuzzy neural network. The method adopting the fuzzy neural network introduces a novel method for detecting the network covert channel by analyzing a domain in a TCP / IP data package head structure of a network interface. The method firstly obtains the TCP / IP data package from the network interface, analyzes the option domain in the data package head structure to obtain a network connection feature vector, sends the feature vector into the fuzzy neural network, trains the fuzzy neural network by a self-adapting fuzzy neural inference system to form a model of the fuzzy neural network, subsequently, sends the feature vector into the model of trained fuzzy neural network to get an output value, and finally performs fuzzy clustering onto the output value so as to distinguish whether the output data has covert channel. The invention is applicable for a mainstream operating system, has wide application range, can increase the security of the operating system and effectively prevents secret information leakage.
Owner:ZHEJIANG UNIV
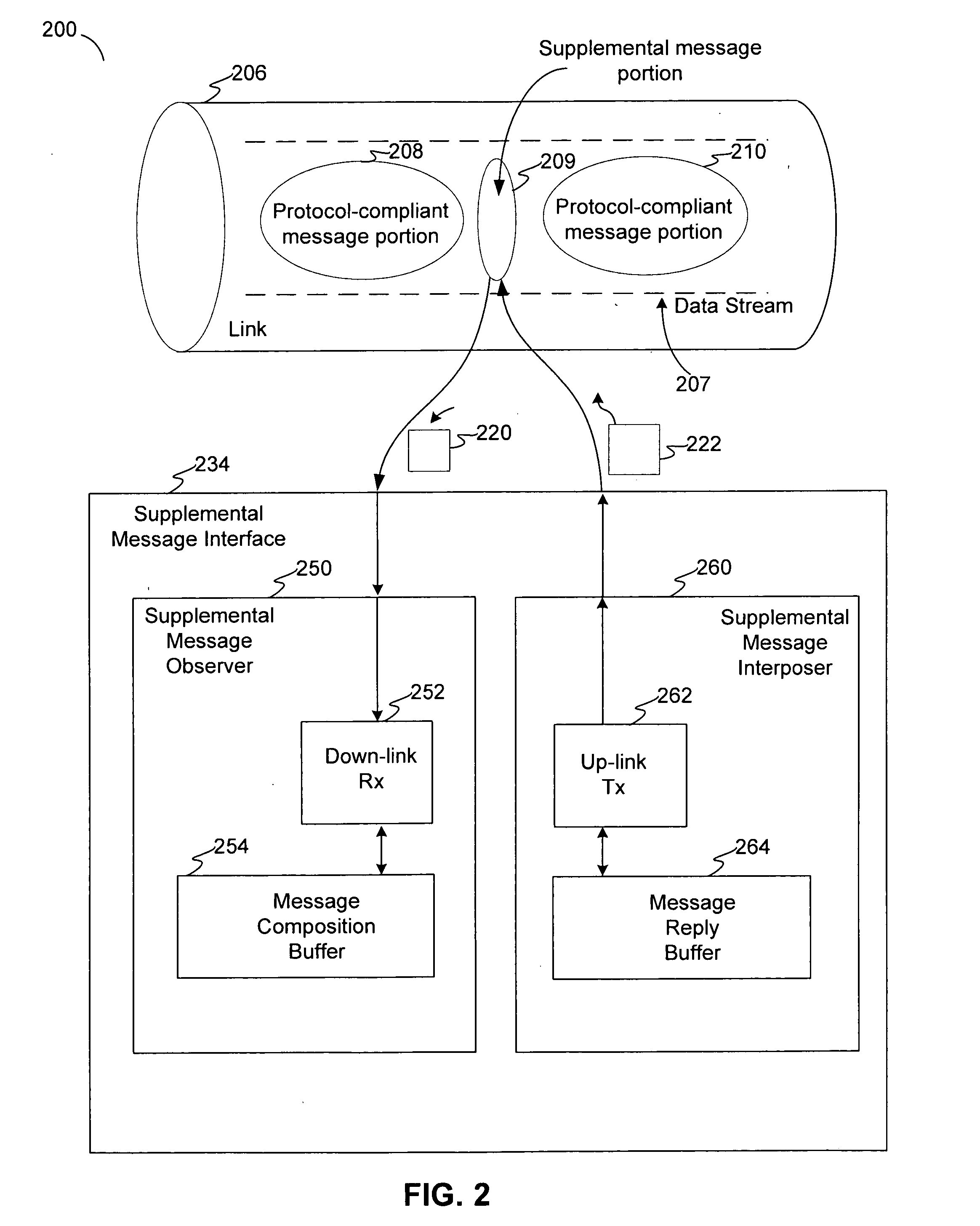
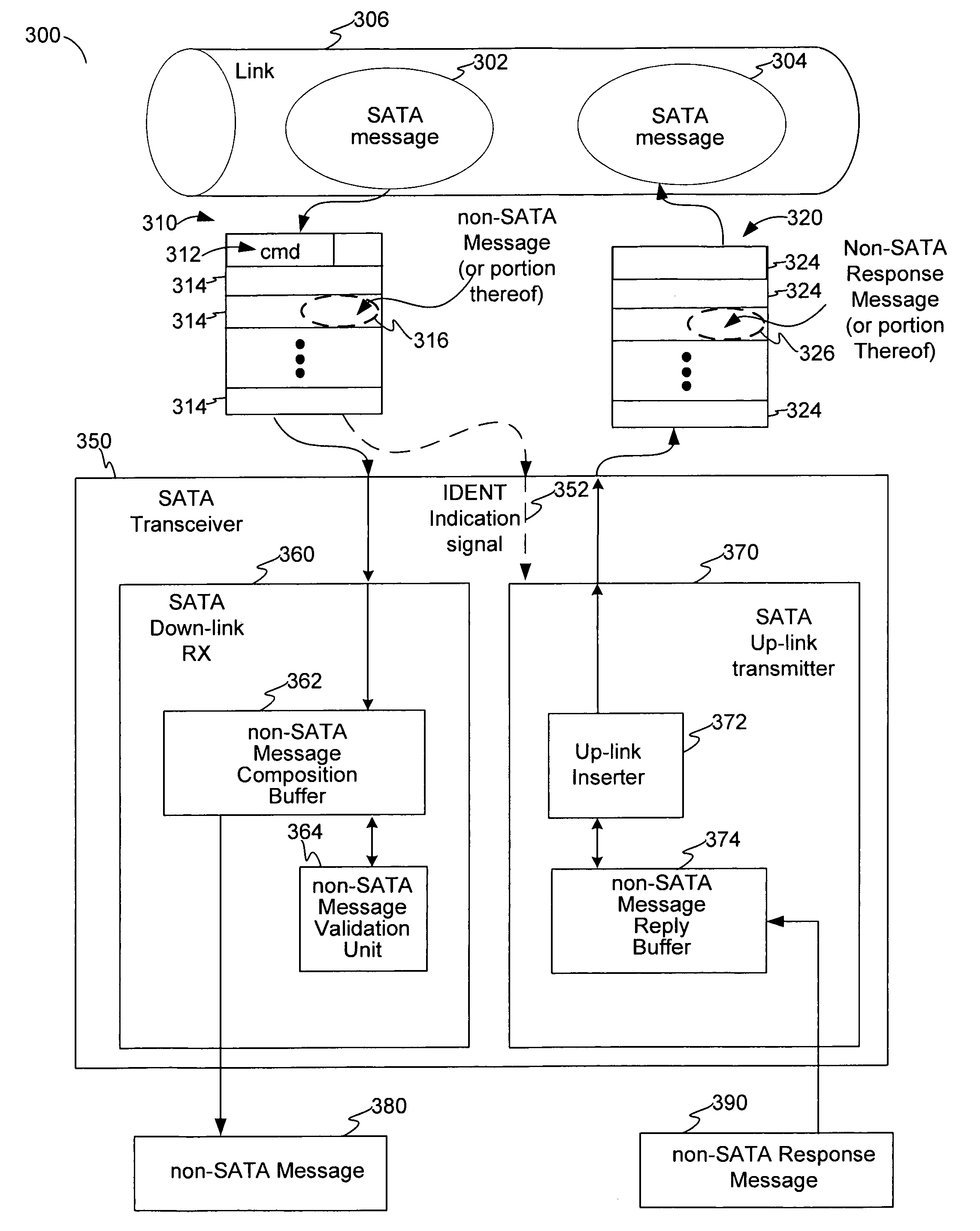
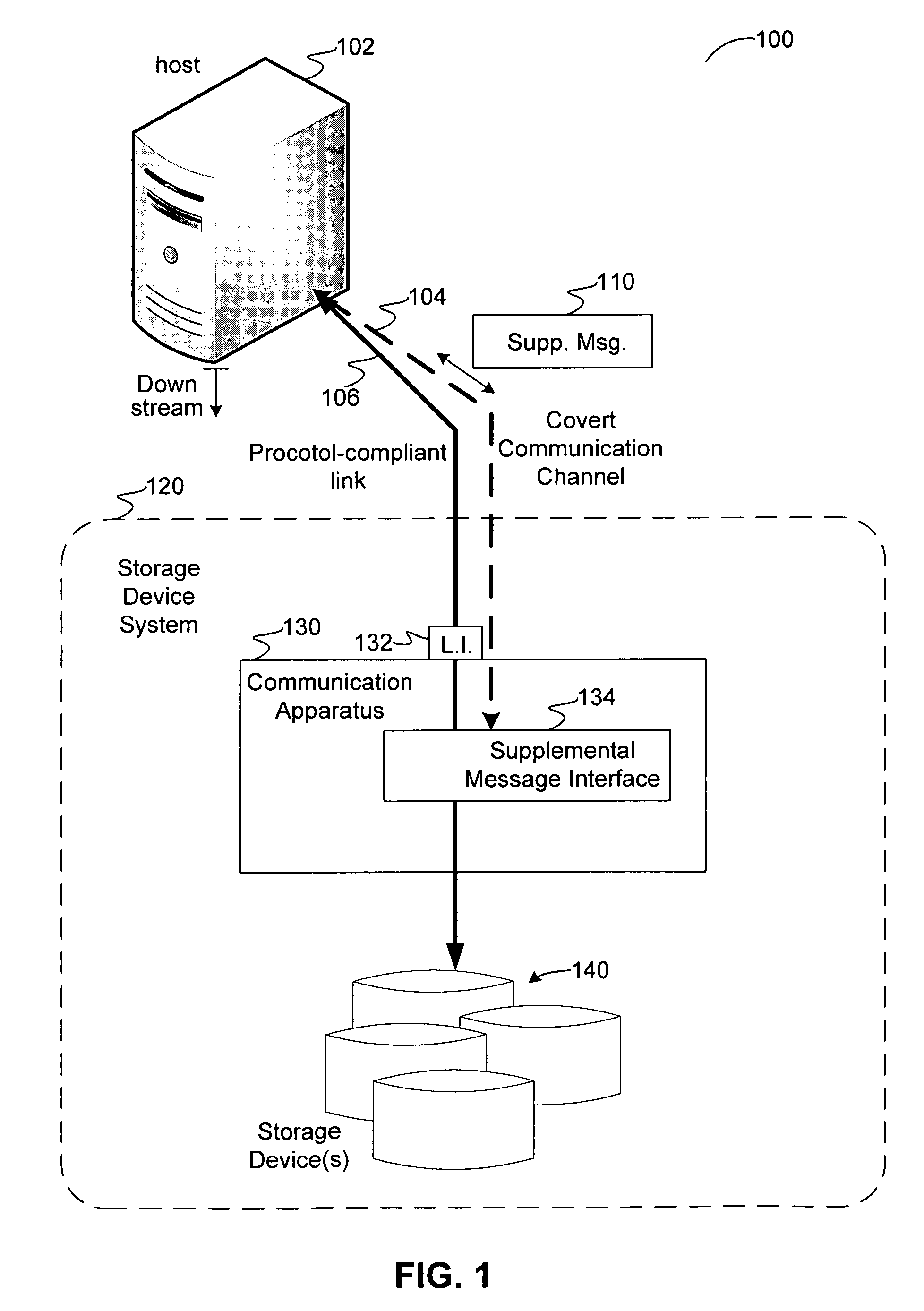
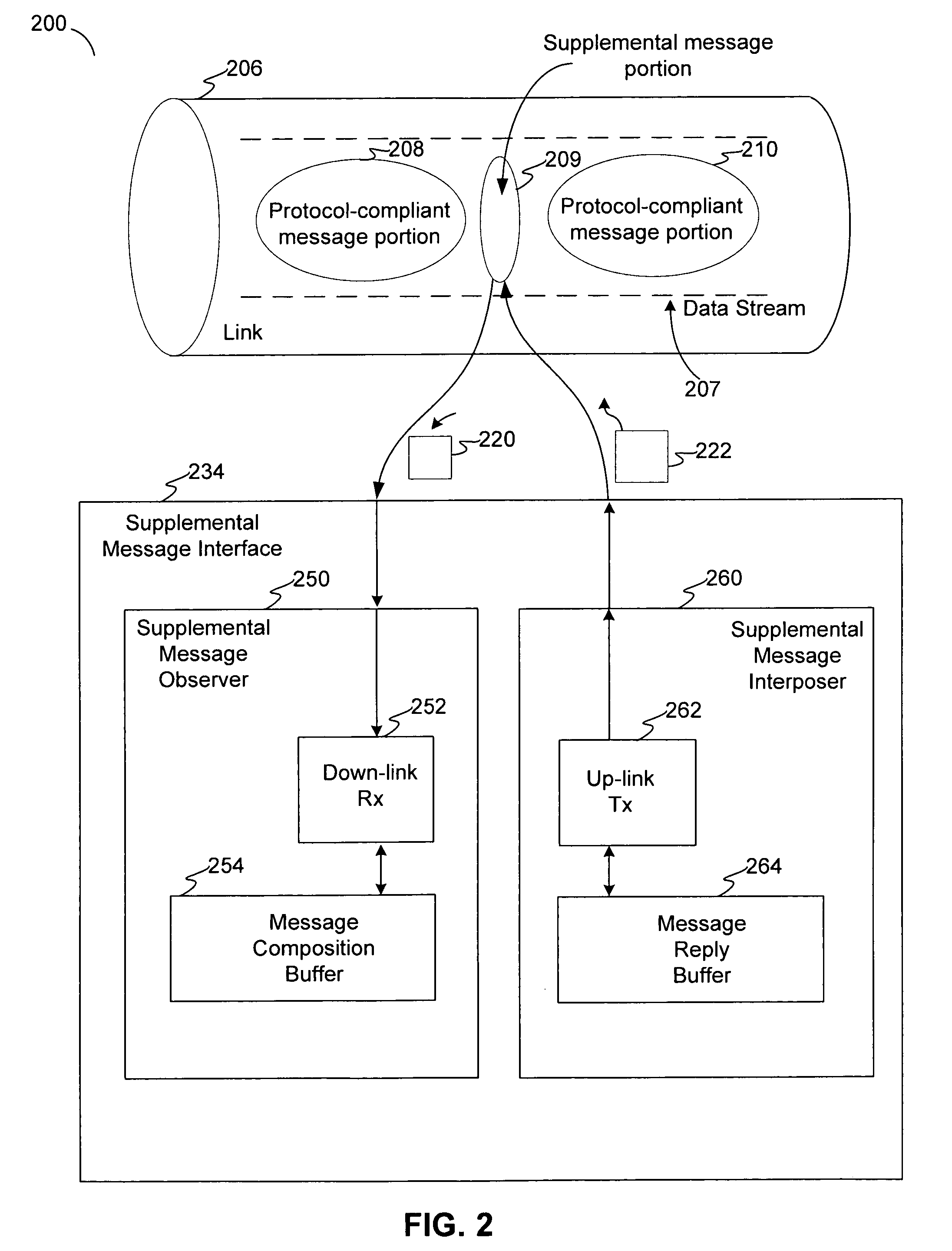
Covert channel for conveying supplemental messages in a protocol-defined link for a system of storage devices
ActiveUS20070180172A1Function increasePreserve computational resources of a host computing deviceCorrect operation testingData taking preventionPort multiplierData stream
Disclosed are communication apparatus, a SATA communication device, a system, an enhanced port multiplier and a method for, among other things, establishing a covert communication channel in a protocol-compliant link. In one embodiment, a communication apparatus includes a link interface and a supplemental message interface. The link interface is configured to communicatively couple the communication apparatus to the link for accessing a data stream passing through the link in accordance with a standardized protocol. The supplemental message interface is configured to exchange a supplemental message within the data stream to establish a covert communication channel in the link. The supplemental message supplements the standardized protocol without violating the protocol.
Owner:LATTICE SEMICON CORP
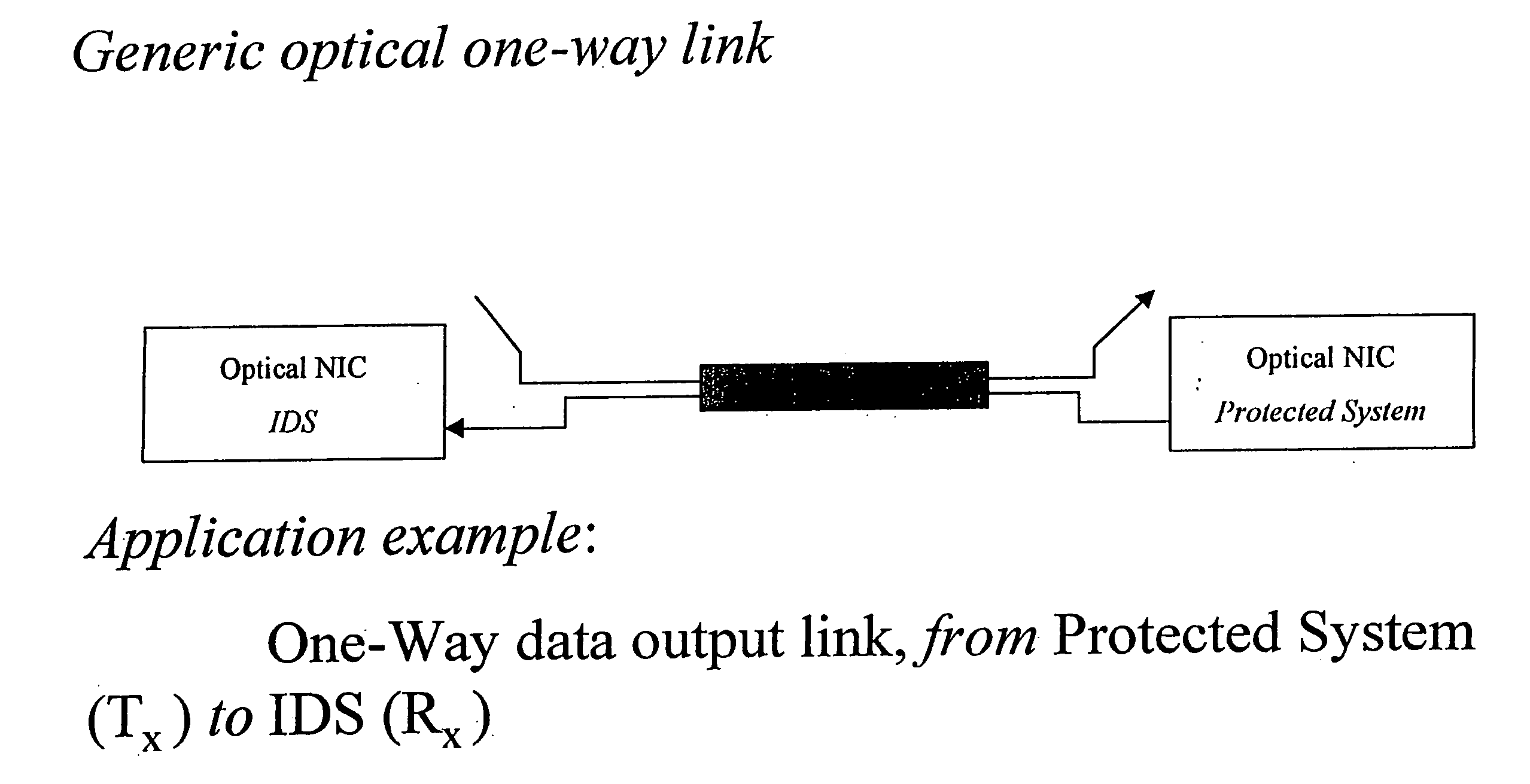
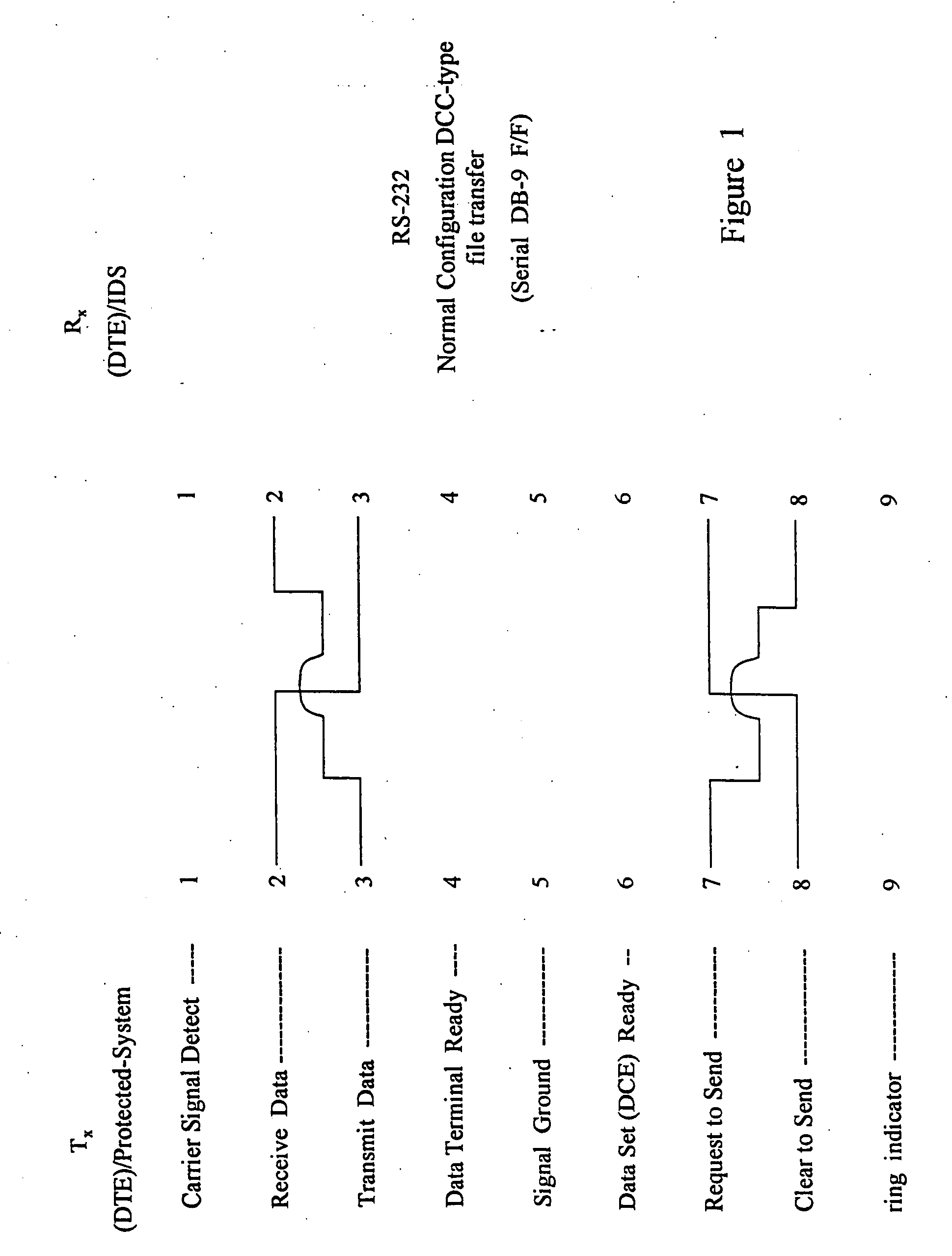
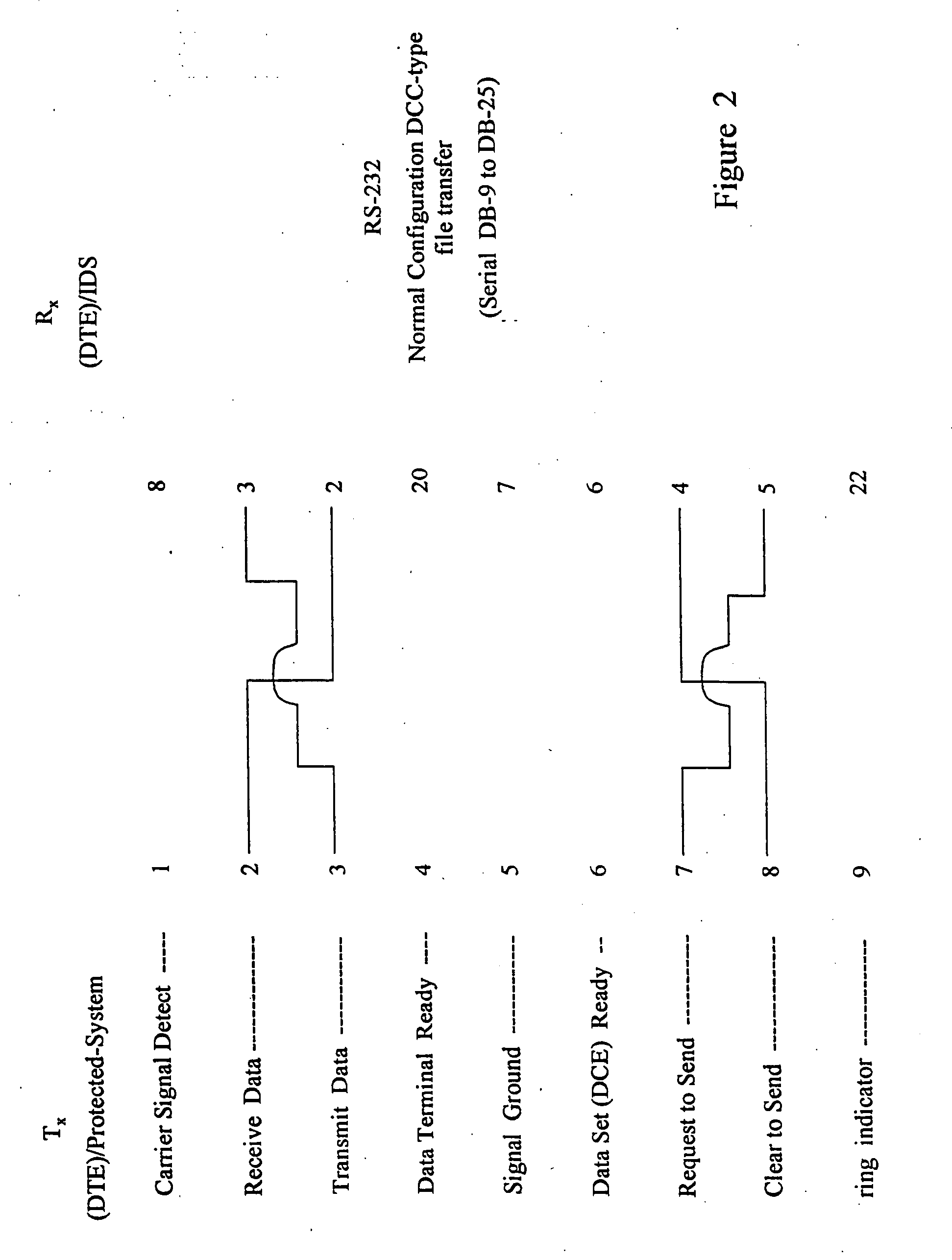
One-way data link for secure transfer of information
InactiveUS20080008207A1Time-division multiplexComputer security arrangementsTelecommunications linkSecure transmission
A one-way data communication link implementation method and system are presented. It is used to insure no covert channels exist between a transmitter system and receiver system. Covert channels can be used to pass information, for unauthorized purposes. Thus covert channels must be eliminated, if an information system or network is to be considered secure. The one-way link is an essential security tool for constructing secure information systems and networks. An example use of a one-way link is given for a system which acts as a communications front-end (CFE) module to a system it is protecting. The one-way link is use to transfer data in only a single direction from a protected system to the CFE-Module.
Owner:KELLUM CHARLES W
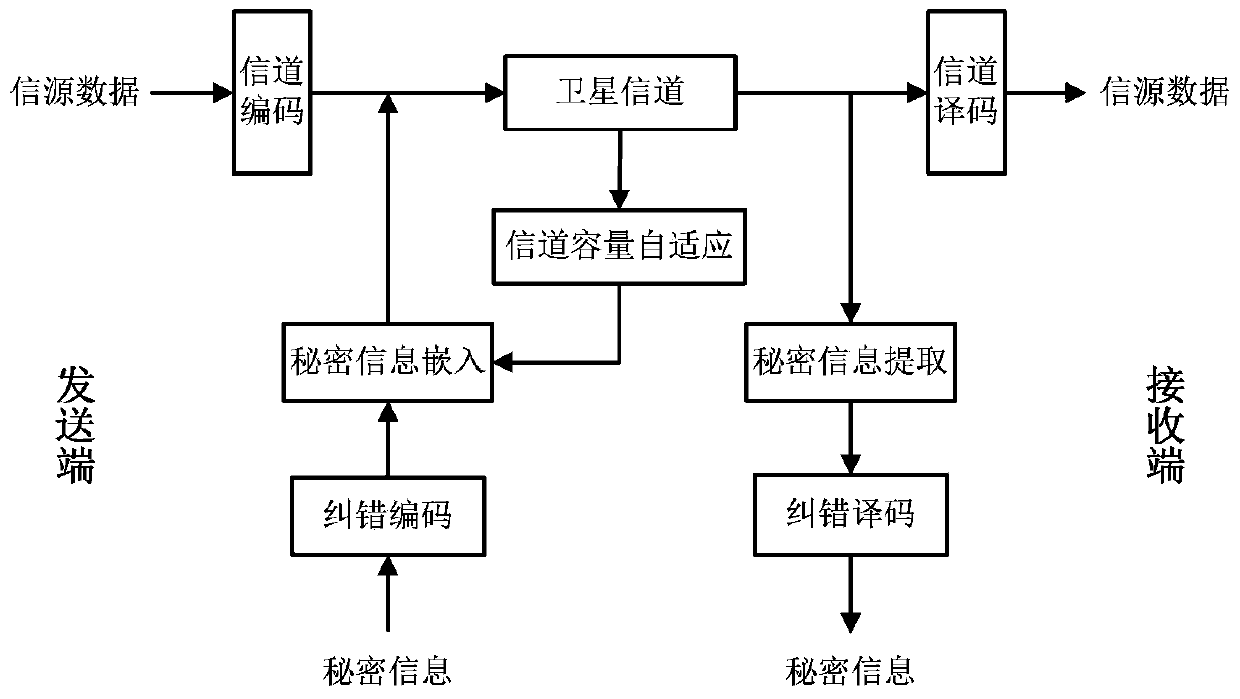
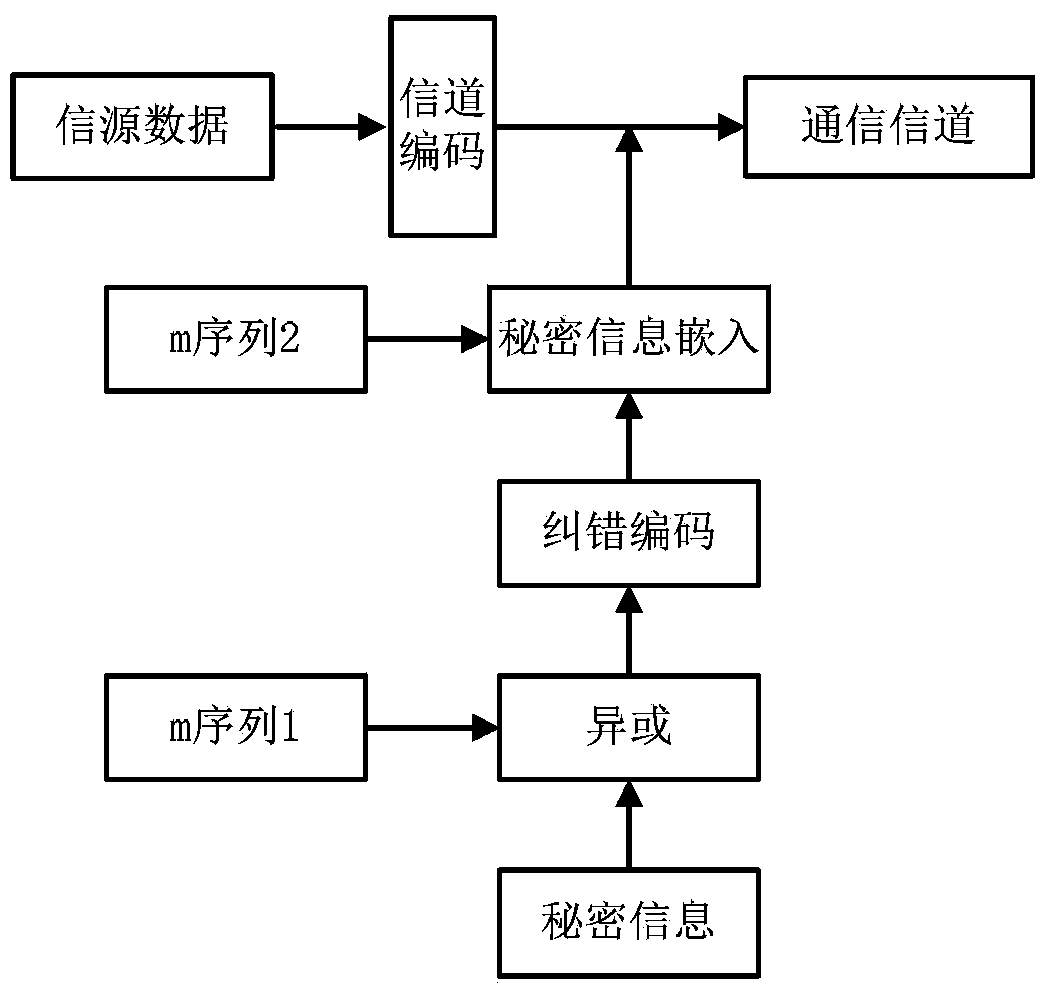
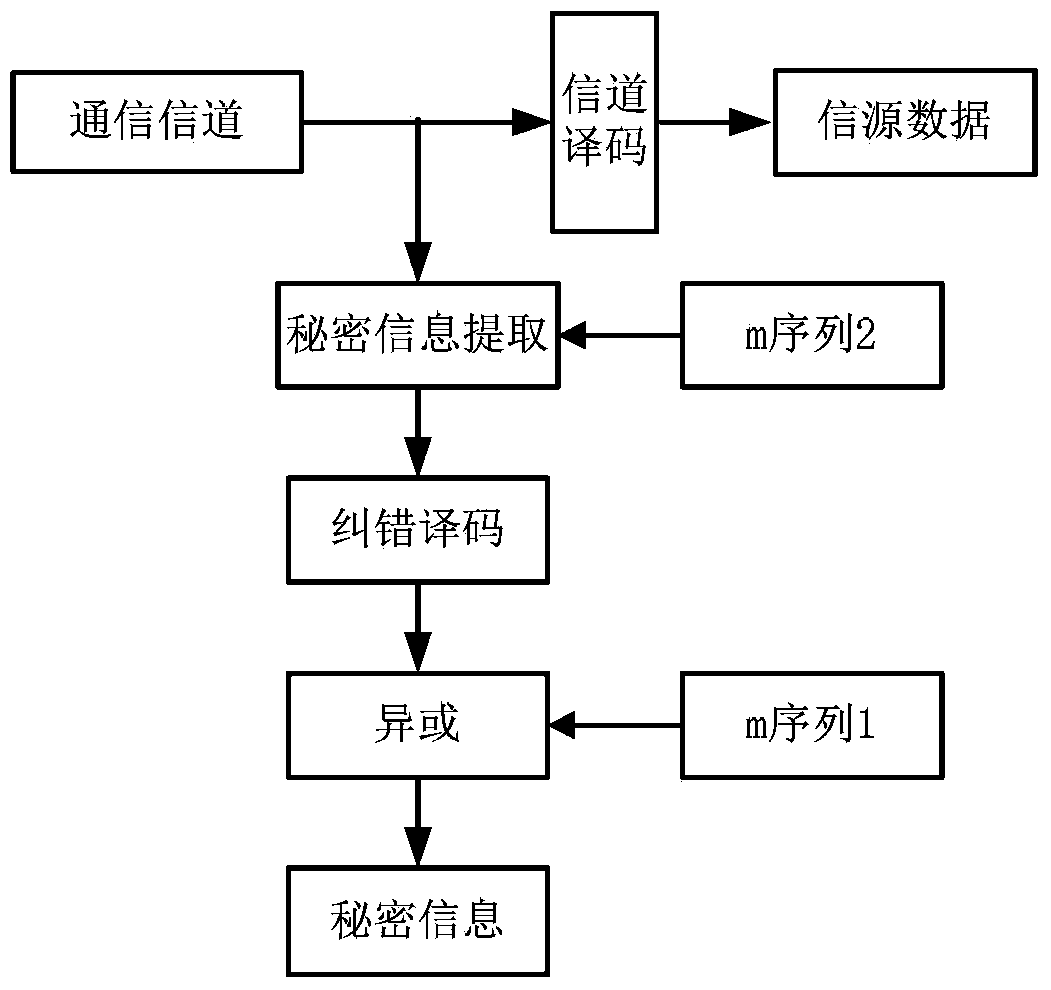
Self-adaption covert communication method based on satellite channel coding
InactiveCN103476026AAvoid bit errorsImprove securityError preventionSecurity arrangementBlock codeCovert communication
The invention provides a self-adaption covert communication method based on satellite channel coding, and directing at different channel encoding algorithms of block codes, RS codes, convolutional codes, serial concatenated code and the like, provides a capacity self-adaption method for secrete information embedding; further provides a channel encoding information embedding and extracting algorithm based on m sequences. By the utilization of the self-adaption covert communication method, the capacity of covert channels can be determined in a self-adaption mode according to different used channel encoding algorithms and different used communication environments; normal use of carriers containing secretes is not influenced, and main steganalysis attacks such as chi-square analysis attacks and RS analysis attacks can be resisted; under the condition that the satellite channel bit error rate is 10-3-10-5, quasi error-free transmission of secrete information can be realized.
Owner:INST OF SOFTWARE - CHINESE ACAD OF SCI
IP time to live (TTL) field used as a covert channel
The Time to Live (TTL) field in an IP header is used as a covert channel in a communication system. More particularly the TTL field can be used to selectively mark packets with unique identifiers as they pass through an upstream station on their way to a downstream station. In this way the source of a traffic flow at least within a particular domain can be absolutely identified. This method of performing a traceback operation doesn't utilize additional resources as it relies on functionality which already exists in the system.
Owner:RPX CORP
Covert channel for conveying supplemental messages in a protocol-defined link for a system of storage devices
ActiveUS7571269B2Function increasePreserve computational resources of a host computing deviceCorrect operation testingData taking preventionPort multiplierData stream
Disclosed are communication apparatus, a SATA communication device, a system, an enhanced port multiplier and a method for, among other things, establishing a covert communication channel in a protocol-compliant link. In one embodiment, a communication apparatus includes a link interface and a supplemental message interface. The link interface is configured to communicatively couple the communication apparatus to the link for accessing a data stream passing through the link in accordance with a standardized protocol. The supplemental message interface is configured to exchange a supplemental message within the data stream to establish a covert communication channel in the link. The supplemental message supplements the standardized protocol without violating the protocol.
Owner:LATTICE SEMICON CORP
Two-way reliable covert channel based on TCP effective loads
InactiveCN103841118AReduce embedding rateIncreased resistance to detectionError prevention/detection by using return channelDecoding methodsNetwork packet
The invention discloses a secret information coding and sending method based on TCP effective loads and a corresponding secret information receiving and decoding method. On a sender, an encoder encodes secret information according to a coding schedule consulted in advance; then, the secret information is sent to a receiver. On the receiver, after the receiver monitors and captures a data packet of a fixed port, a decoder carries out TCP effective load extraction on the data packet monitored and captured at the fixed port, and the secret information is obtained through decoding according to the coding schedule. The methods are designed based on a TCP, and the quality and safety of covert channel communication are guaranteed through the reliability of the TCP. High practicality is achieved, the methods can be applied to the actual communication process well, the proportion of coding to non-coding of effective length can be adjusted in a balanced mode, and the controllability of the detection resisting performance of a covert channel is achieved.
Owner:SUZHOU INST FOR ADVANCED STUDY USTC
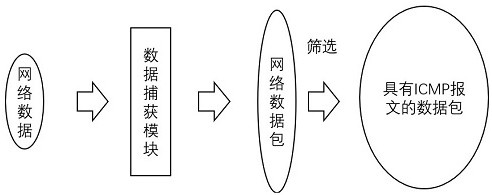
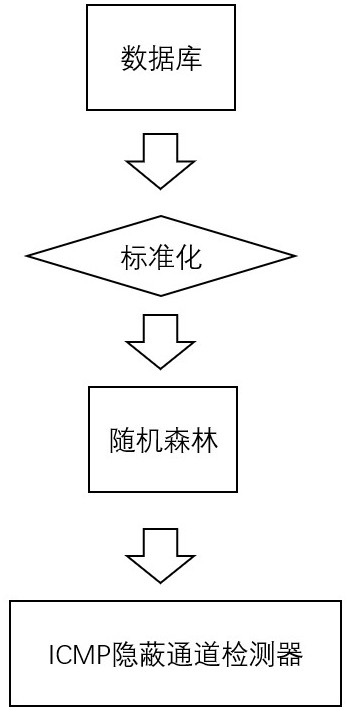
ICMP covert channel detection method based on random forest
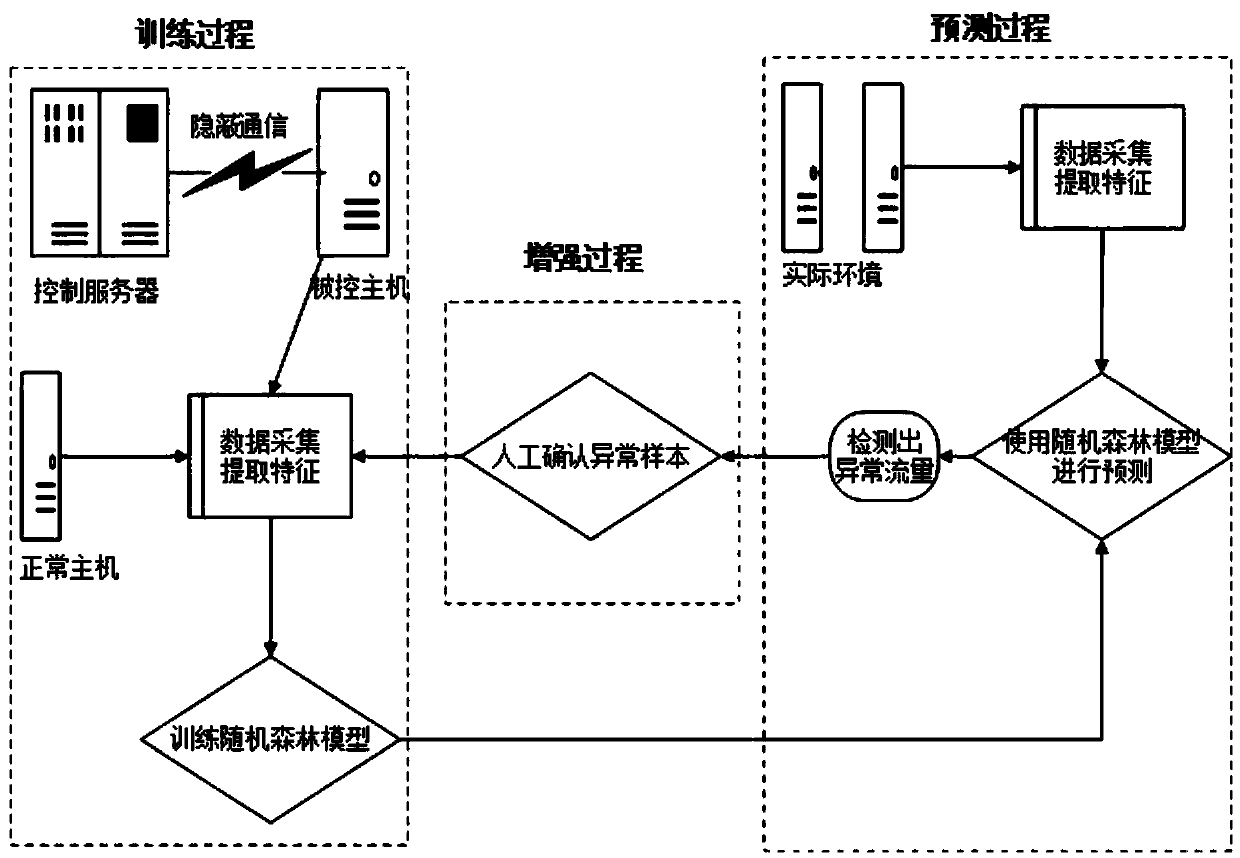
ActiveCN112085039AEfficient detectionImprove accuracyCharacter and pattern recognitionMachine learningPattern recognitionData pack
The invention relates to the field of machine learning algorithms and covert channel detection, and aims to provide an ICMP covert channel detection method based on a random forest machine learning algorithm. According to the technology, firstly, data packets of inter-network communication are captured, basic information (a source IP address, a destination IP address and the like) related to the data packets in the data packets is extracted, the information is classified, an ICMP message flow is formed according to the information, and characteristics are extracted from the corresponding ICMPmessage flow by utilizing a specific rule of the method; the method comprises the following steps: obtaining the characteristics of the ICMP message communication data flow between a source IP addressand a destination IP address, training the characteristics by using a random forest-based machine learning method, and finally obtaining a classifier for detecting an ICMP covert channel. When the method is used for ICMP covert channel detection, the calculation cost and the time cost are low, the generated ICMP flow features are strong in pertinence and high in reliability, and the ICMP covert channel can be effectively detected.
Owner:SICHUAN UNIV
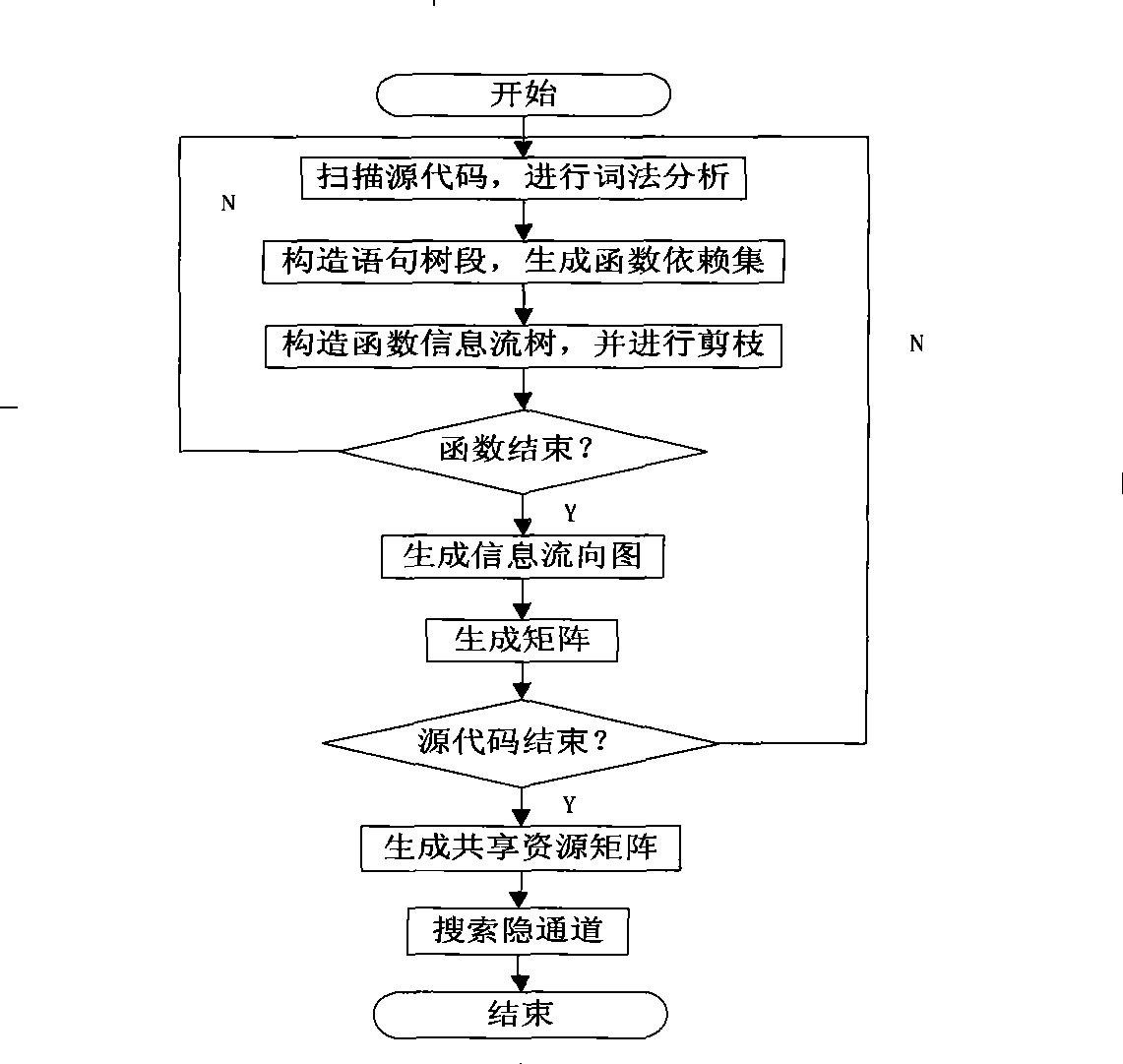
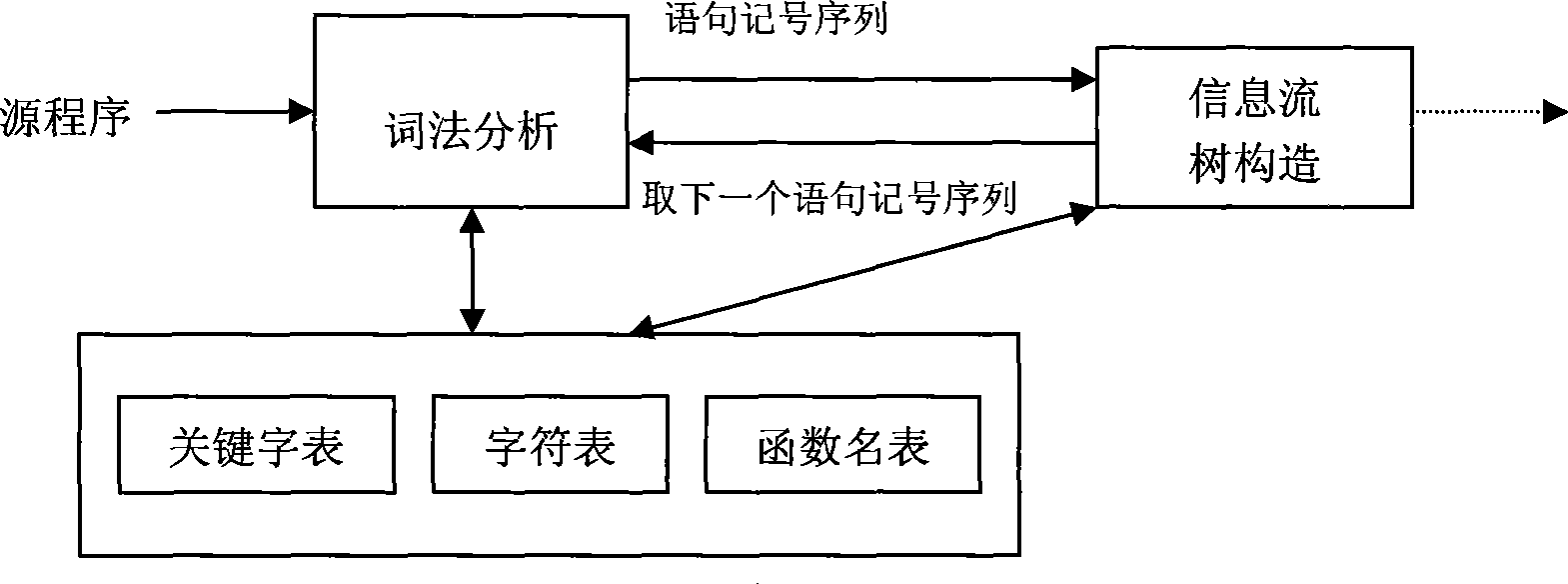
Information flow analysis method based on system source code searching concealed channel
InactiveCN101377806AHigh precisionAvoid introducingPlatform integrity maintainanceTransmissionVisibilitySource code
The invention provides an information flow analytic method based on the searched convert channels of system source codes, which comprises the following steps: functions in the source codes and the statements and the variables in the functions are identified by dint of lexical analyzers and scanning system source codes; the call relations of the functions are determined, statement tree fields are constructed and functional dependence gathers of each function are given according to the functions and the function call statements identified by scanners; function information flow trees are constructed and are lopped with the statements and the variables which can generate information flow and are identified by the scanners as the input for information flow analysis; the function information flow trees are traversed, and the information flow graphs of each function are output; the shared variable visibility between dependence concentration functions and the modifiability information are acquired in functional dependence gathers according to the functional dependence gathers and the information flow graphs, thus generating shared resource matrices; covert channels are searched with the shared resource matrices as the input, and the covert channel sequences in the system are output. By adopting the information flow analytic method, the search work precision of the covert channels is improved.
Owner:JIANGSU UNIV
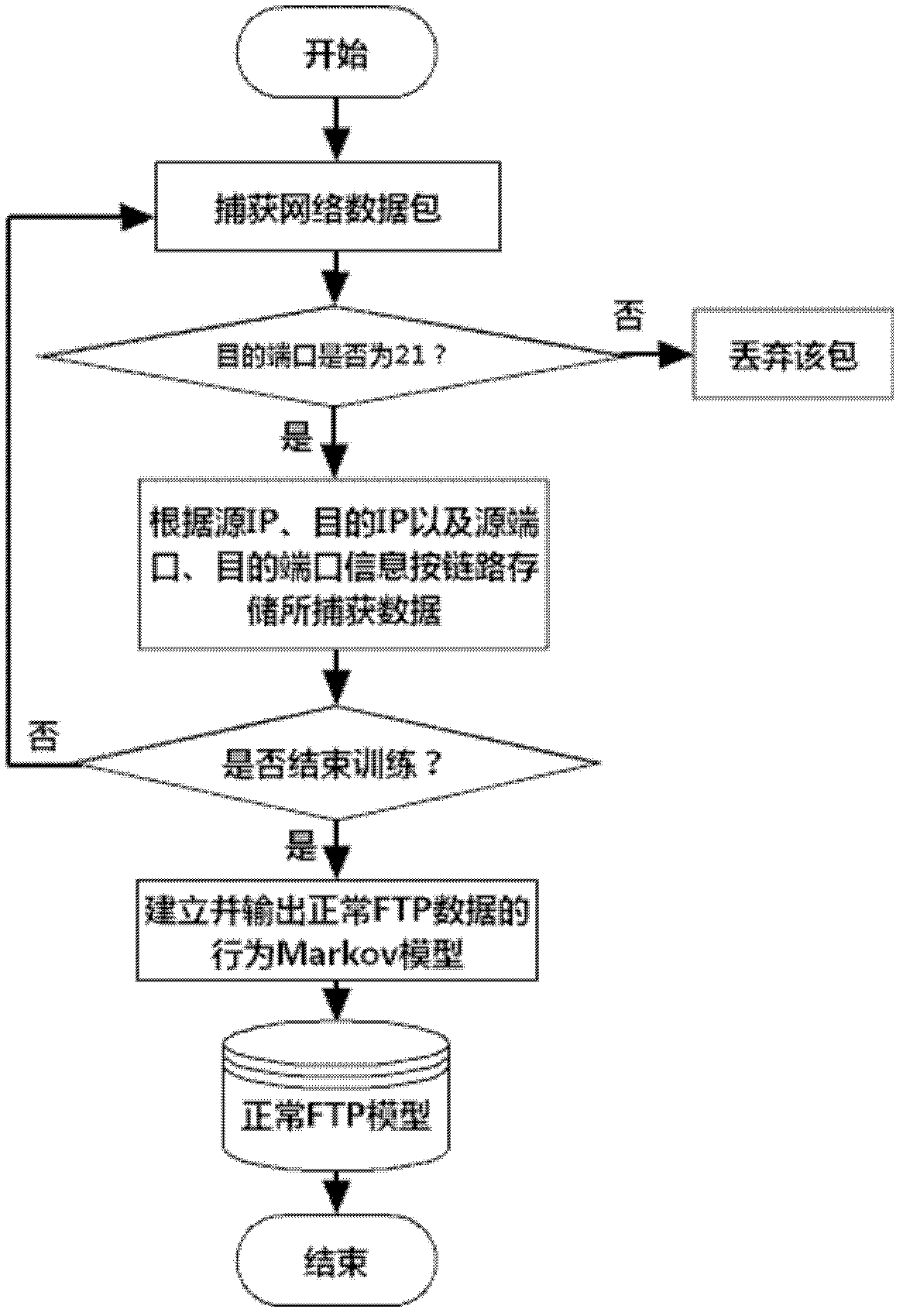
Network covert channel detecting method
InactiveCN102594619AReliable detectionOvercome the disadvantages of only targeting specific covert channelsData switching networksData streamCovert communication
An FTP (File Transfer Protocol) command-sequence-coding network covert channel (FTP-NCC) is a covert communication mode that a transmitting end embeds covert information into a normal FTP application by a certain coding mode. The invention discloses a network covert channel detecting method for the FTP command sequence coding on the basis of a Markov model. The network covert channel detecting method comprises two steps of training and detection, wherein the training step is used for acquiring the Markov model of a normal FTP communication command data stream; the detection step is used for performing FTP-NCC detection by using a maximum posterior probability method according to the model obtained by the training step. The method can realize reliable detection for the FTP-NCC.
Owner:CHANGSHU RES INSTITUE OF NANJING UNIV OF SCI & TECH
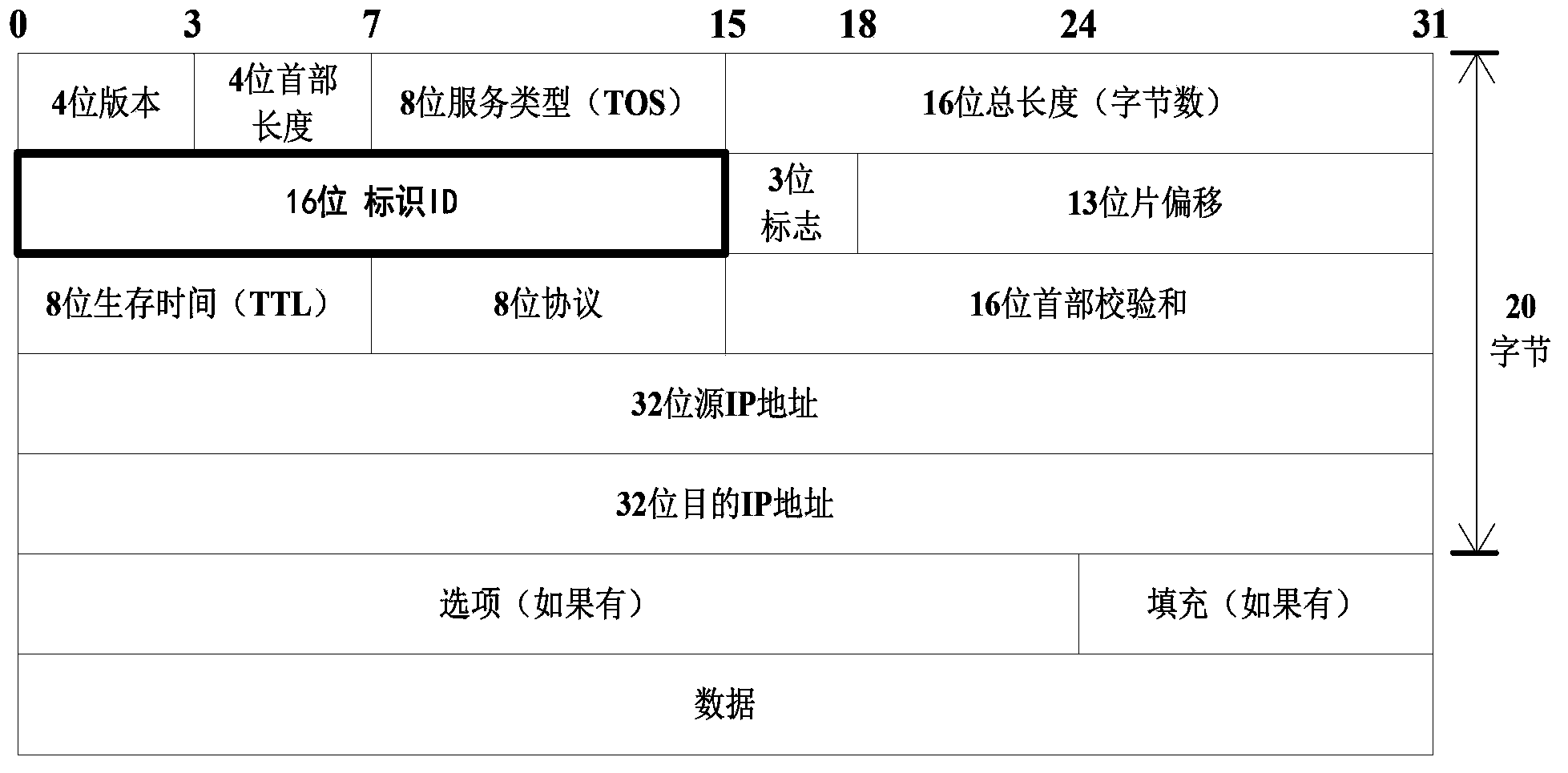
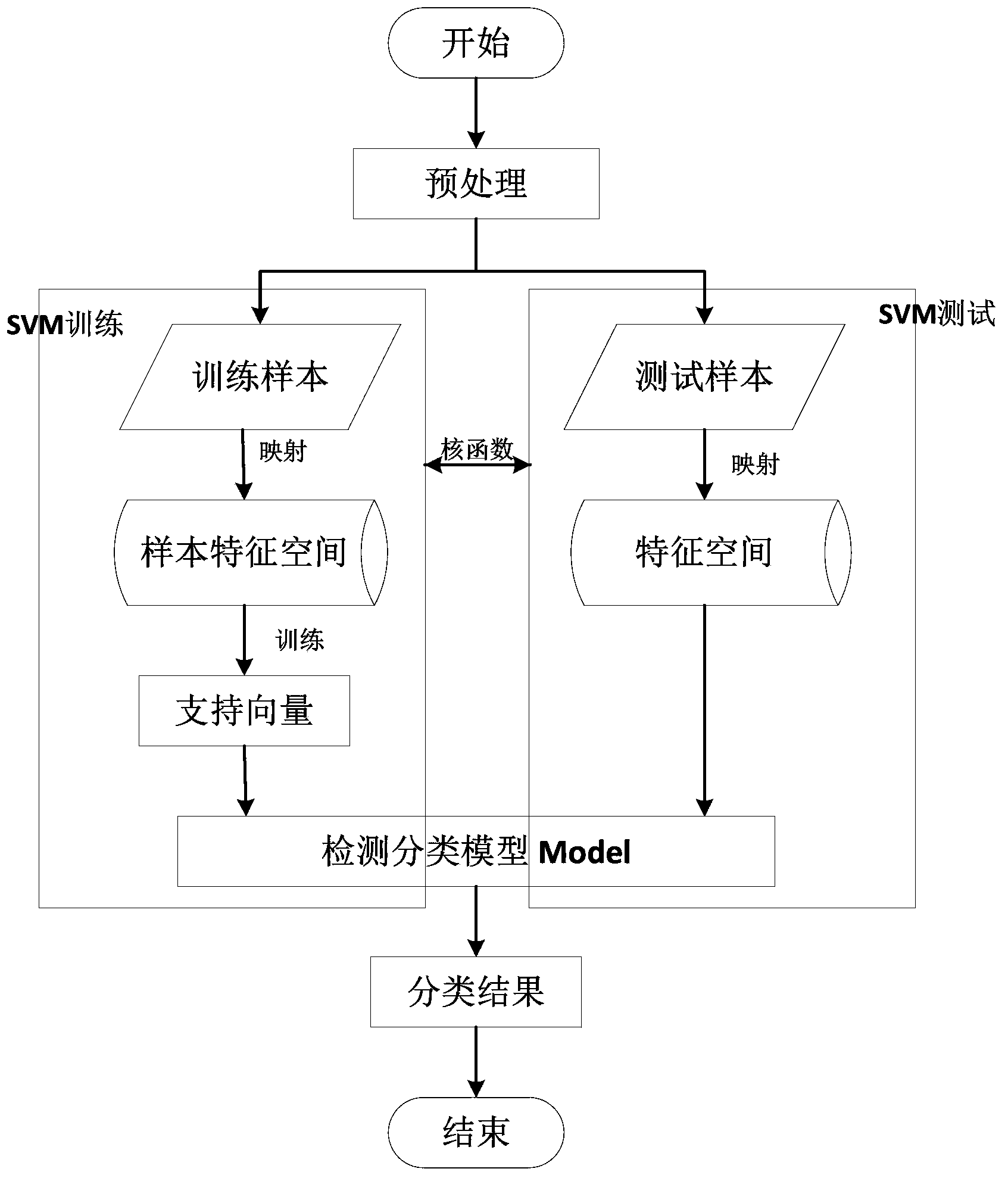
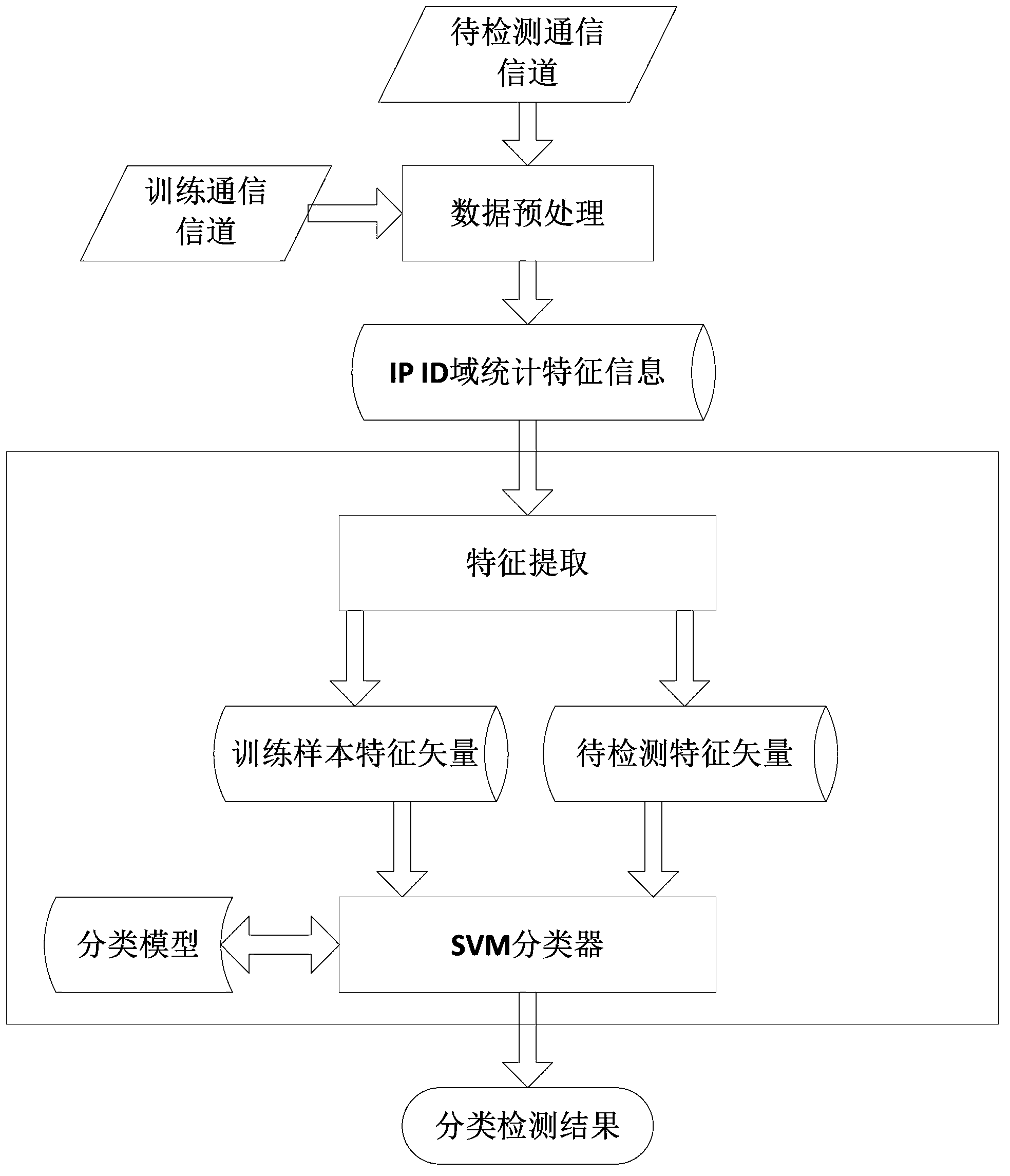
Method using multi-dimensional feature vectors to detect IP ID covert channel
InactiveCN103577835AImprove applicabilityImprove detection efficiencyCharacter and pattern recognitionFeature vectorNetwork packet
The invention discloses a method using multi-dimensional feature vectors to detect an IP ID covert channel. The method comprises the following steps of the feature extracting step 1 of respectively and continuously capturing N IP data packets for normal and abnormal training samples, extracting information of an ID domain of the head of an IP, acquiring the ID difference value of delta id1, delta id2,..., delta idn-1 between adjacent data packets, and carrying out statistics on a mean value E, a standard deviation D and an entropy of the id1, delta id2,..., delta idn-1 to obtain three-dimensional feature vectors, the step 2 of carrying out training on an SVM classifier, repeating the step 1 to obtain a three-dimensional feature vector set of the normal training samples and a three-dimensional feature vector set of the abnormal training samples, and carrying out training on the SVM classifier to obtain a classifying detecting model, and the step 3 of classifying the feature vectors of a channel to be detected through the SVM classifier according to the trained and obtained classifying model. The method is high in detecting efficiency, uses multi-dimensional statistic features as classifying data and improves the detection accuracy.
Owner:SUZHOU INST FOR ADVANCED STUDY USTC
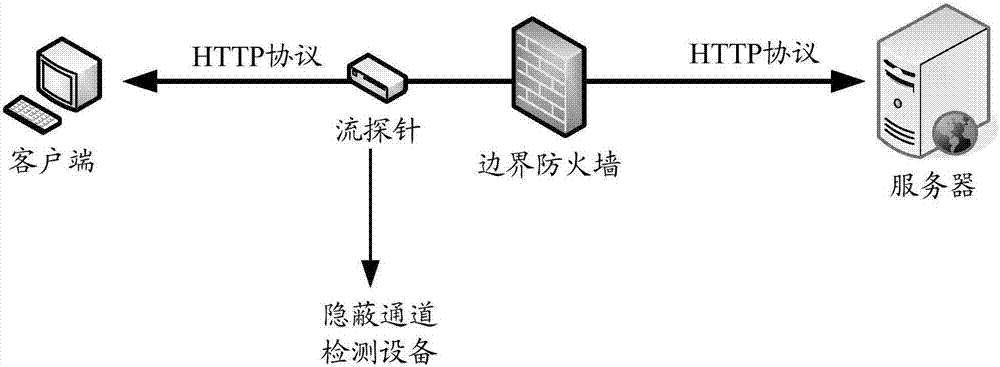
Detection method and detection equipment of hidden channel
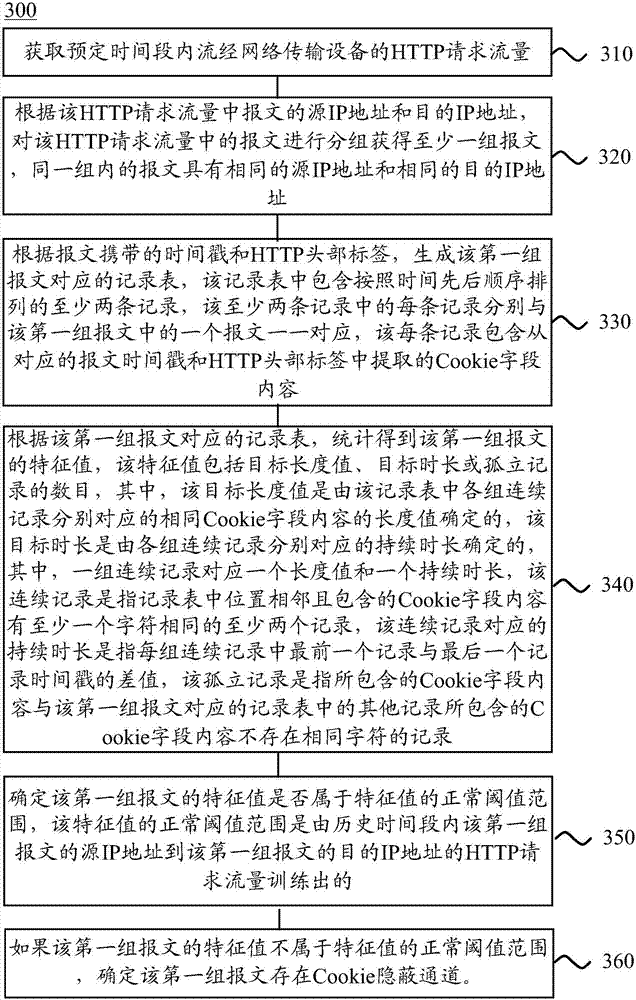
ActiveCN107332723AEasy to detectImprove the detection rateData switching networksTimestampIp address
The embodiment of the application provides a detection method and detection equipment of a hidden channel. The detection method comprises the following steps: grouping HTTP (Hyper Text Transport Protocol) request flow according to source IP (Internet Protocol) addresses and target IP addresses of messages in the HTTP request flow to obtain at least one group of messages, and executing subsequent steps for a first group of messages: generating a record table corresponding to the first group of messages according to timestamps and HTTP head tags carried by the messages; performing statistics to obtain a feature value of the first group of messages according to the record table corresponding to the first group of messages; and if the feature value of the first group of messages does not belongs to a normal threshold range of the feature value, determining that a Cookie hidden channel exists in the first group of messages, wherein the normal threshold range of the feature value is trained by HTTP request flow in a history time interval. In the embodiment of the application, whether the hidden channel exists in the HTTP request flow within predetermined time or not is judged through normal ranges of feature values of normal messages, so that the detection effectiveness of the HTTP hidden channel is improved.
Owner:HUAWEI TECH CO LTD
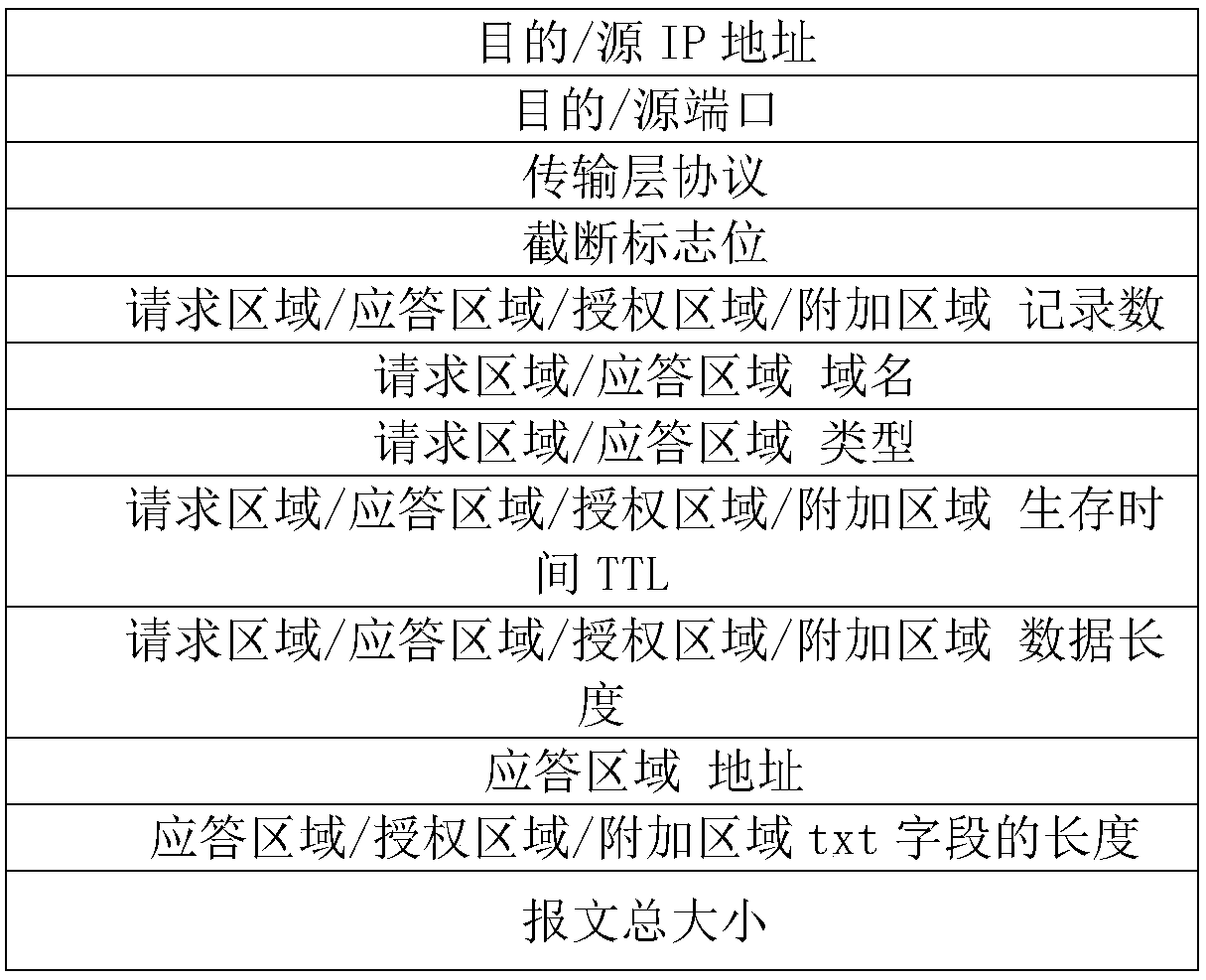
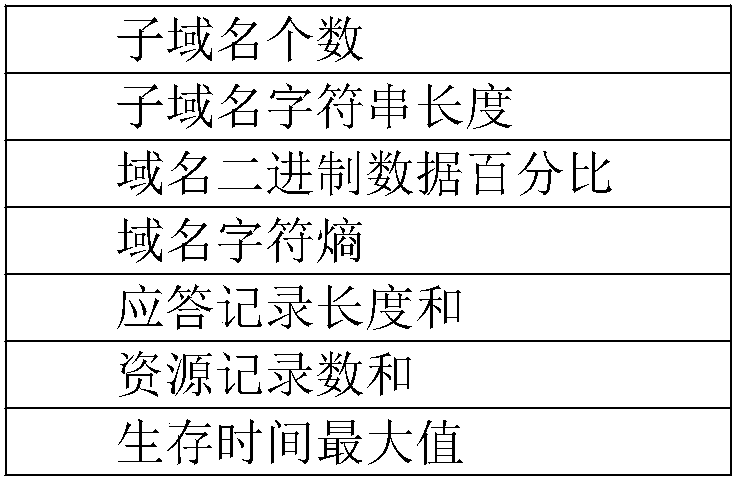
DNS covert tunnel detection method based on deep learning
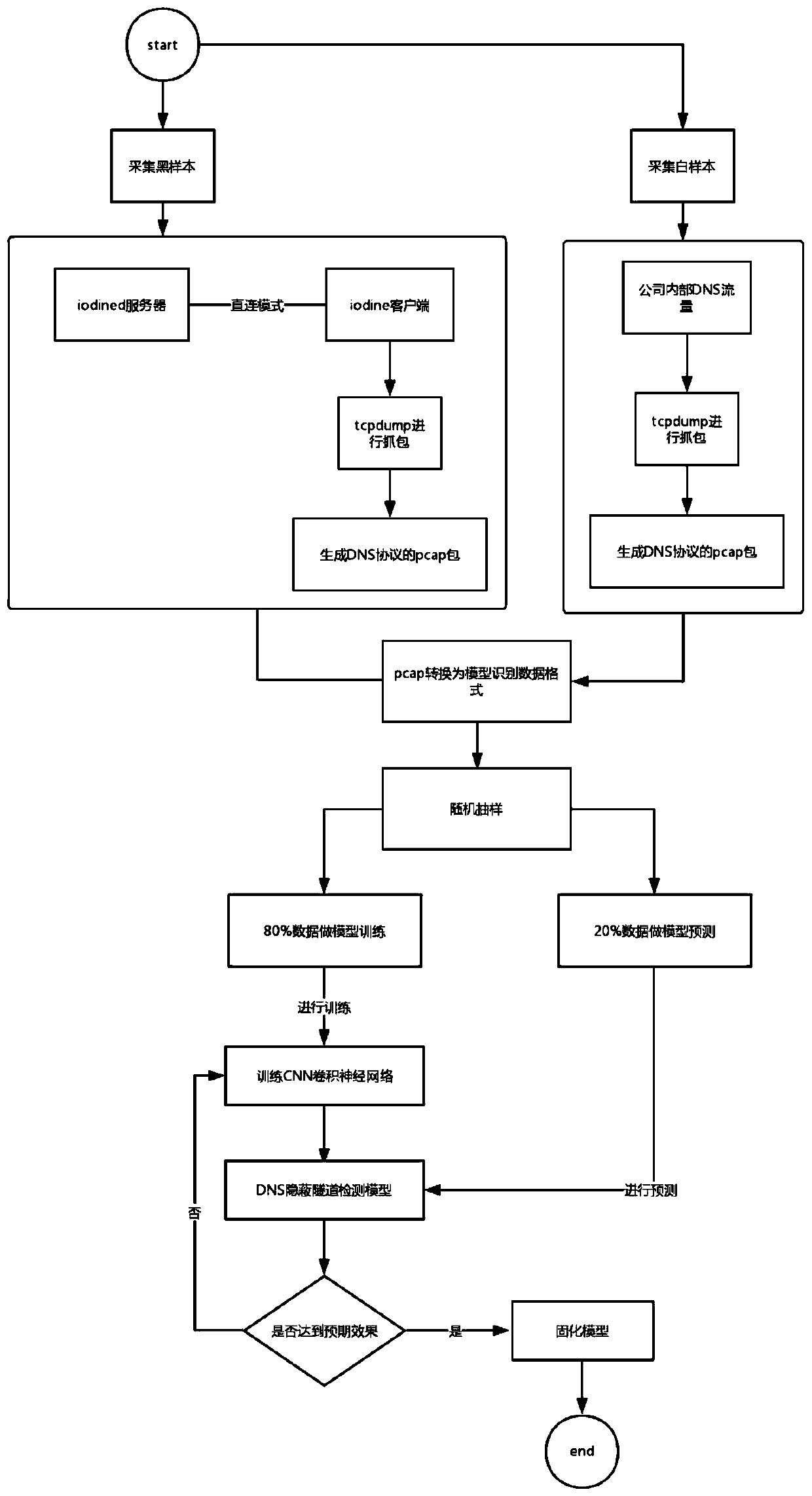
InactiveCN110149418AImprove detection efficiencyReduce labor costsNeural architecturesData switching networksModel validationConvolution
The invention discloses a DNS covert tunnel detection method based on deep learning, and the method is characterized in that the method comprises the steps: employing a tcpdump to capture DNS messagestransmitted and received by a DNS covert channel tool iodine, and obtaining a black sample; capturing the internal DNS flow by using tcpdump to obtain a white sample; converting the black sample andthe white sample into files which can be identified by a deep learning detection algorithm; performing random sampling on the recognizable file to obtain sampling data; training a convolutional neuralnetwork by using 80% of the sampling data, and carrying out model verification on the convolutional neural network by using the remaining 20% of the sampling data to generate a preliminary model; testing the preliminary model by using a DNS sample with a hidden channel attack, and generating a stable detection model after an expected effect is achieved; and detecting the DNS covert tunnel by using the detection model.
Owner:STATE GRID INFORMATION & TELECOMM GRP +2
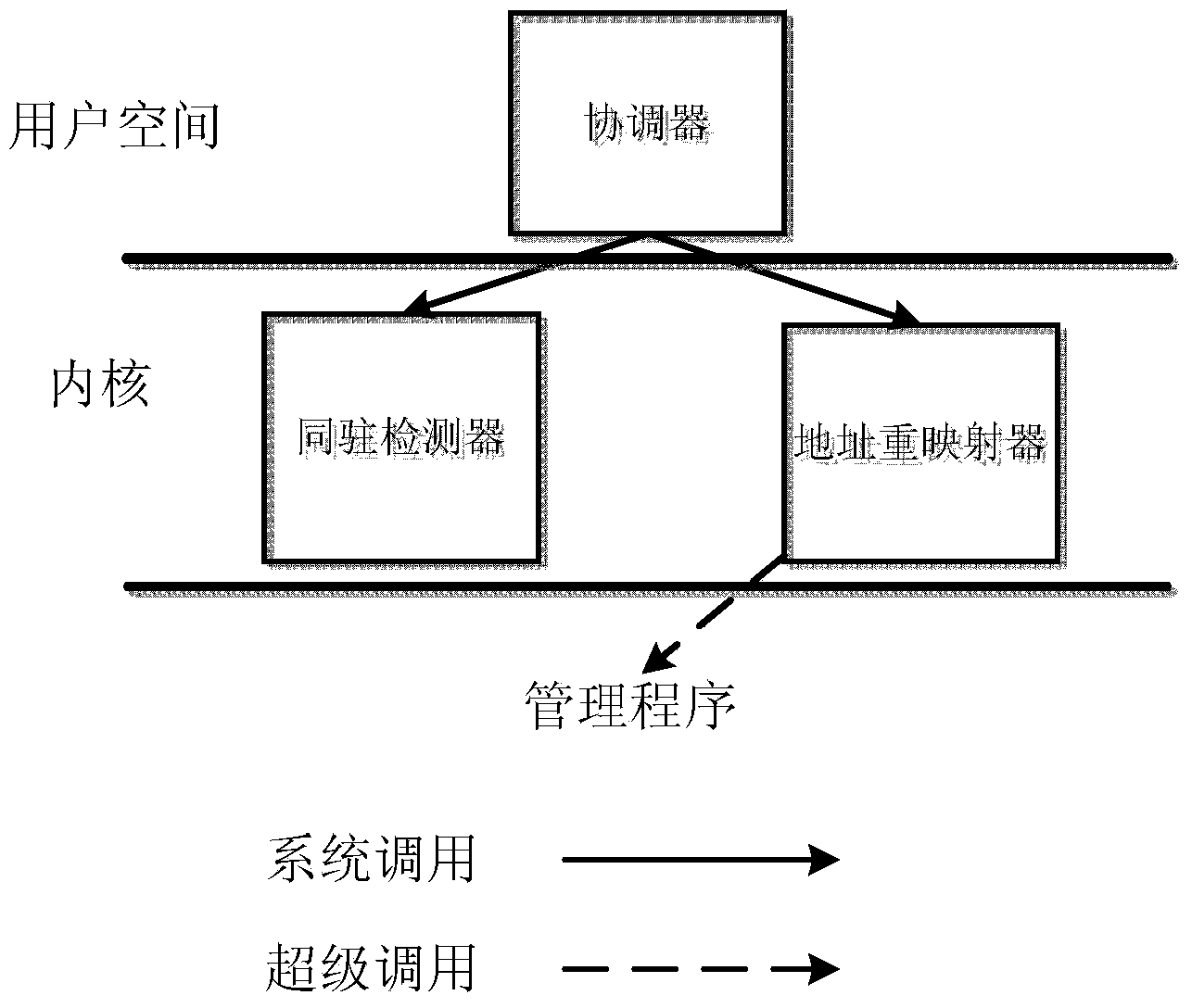
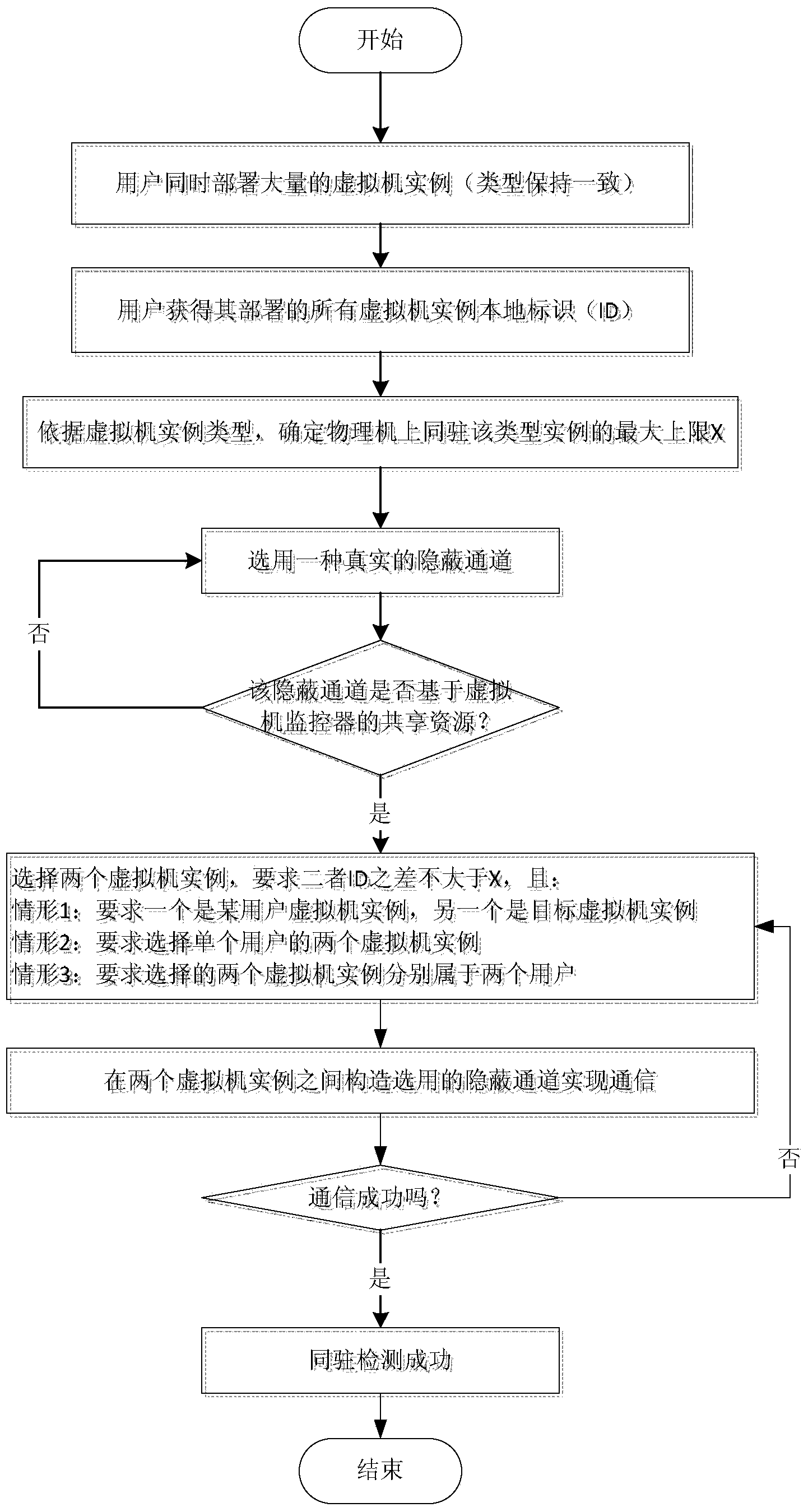
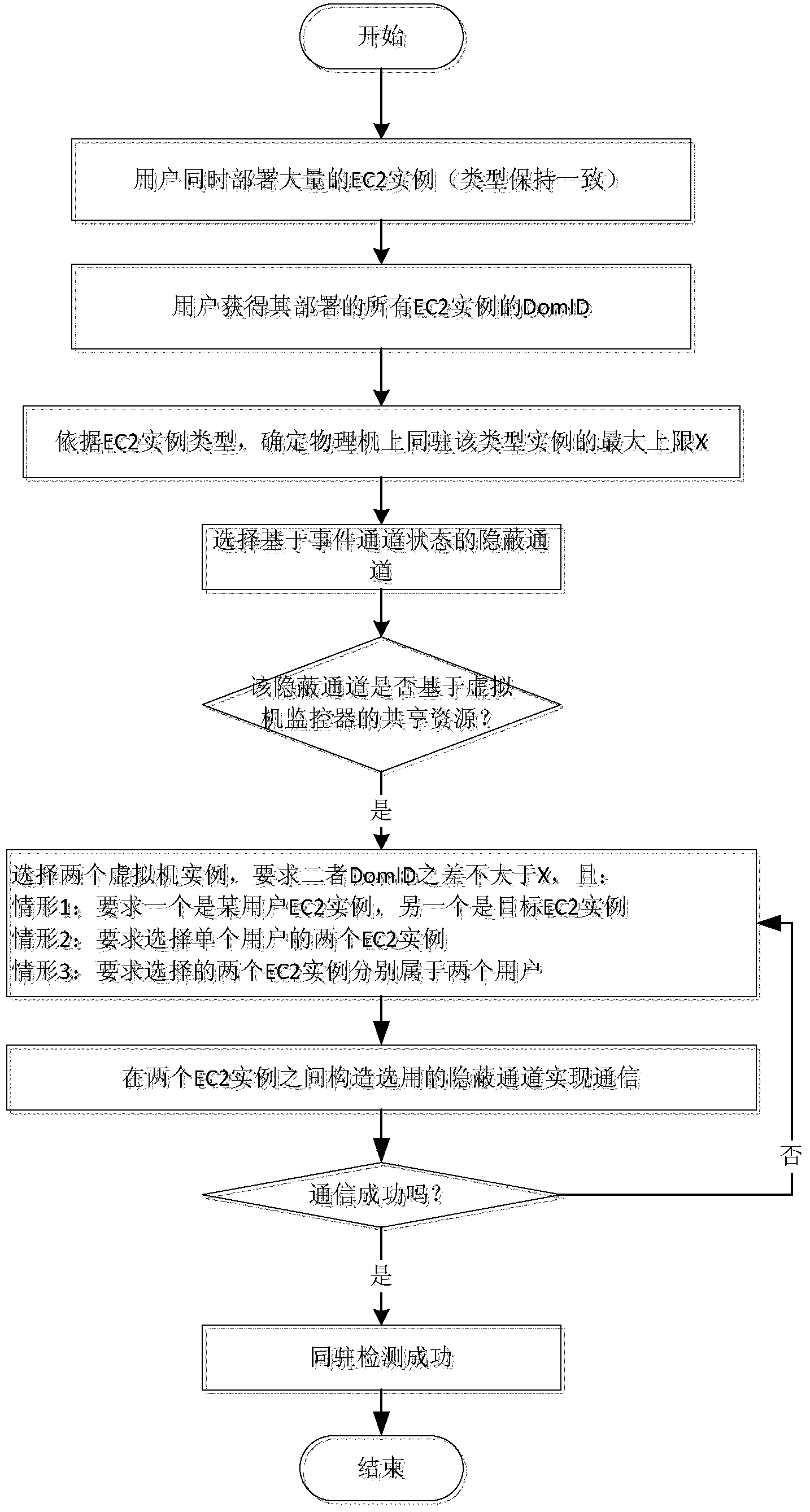
Virtual machine simultaneous-locating detection method based on hidden channel under cloud environment
ActiveCN104009885AImprove performanceReliable test resultsData switching networksSoftware simulation/interpretation/emulationShared resourceVirtual machine
The invention discloses a virtual machine simultaneous-locating detection method based on a hidden channel under a cloud environment. The method includes the steps that (1) a plurality of virtual machine embodiments of the same type are deployed on a cloud platform; (2) the real hidden channel, based on the cloud platform, of virtual machine monitor share resources is selected; (3) two virtual machine embodiments are selected from the virtual machine embodiments and recorded as the virtual machine embodiment A and the virtual machine embodiment B respectively; (4) the virtual machine embodiment A and the virtual machine embodiment B serve as a sender and a receiver of the hidden channel respectively, the hidden channel is used for communication, if the communication succeeds, the virtual machine embodiment A and the virtual machine embodiment B are simultaneously located on a physical machine, and if not, the virtual machine embodiment A and the virtual machine embodiment B are not simultaneously located on the physical machine. By means of the virtual machine simultaneous-locating detection method based on the hidden channel under the cloud environment, efficiency and reliability of the simultaneous-locating detection are improved, excessive dependence on the network is avoided through the hidden channel, and the problem of simultaneous-locating detection is solved on the premise that the performance is not lowered.
Owner:PEKING UNIV
High-security combined covert channel synchronization method
InactiveCN103281164AGuaranteed correctnessGuaranteed accuracyError prevention/detection by using return channelNetwork packetData transmission
The invention discloses a high-security combined covert channel synchronization method. The secrete data transmission accuracy of dual combined covert channel communication parties can be ensured. In a combined covert channel communication process, the dual communication parties modulate synchronization information into a channel under the condition of no changes in normal communication Internet protocol identification (IPID) bit rules. When transmitting secrete information, a transmitting end modulates the synchronization information into an ID bit difference value of an adjacent IP data packet according to a preset modulation method. After receiving a data packet from the transmitting end, a receiving end first extracts values of adjacent IPID bits, then calculates a difference value of the values of the adjacent IPID bits, and solves the secrete information according to a corresponding combined covert channel synchronization mode. According to the synchronization method, own redundancy characteristic of a protocol is fully utilized, and the secrete data transmission and receiving accuracy of a combined covert channel is ensured under the condition of no additionally introduced channels.
Owner:JIANGSU UNIV OF SCI & TECH
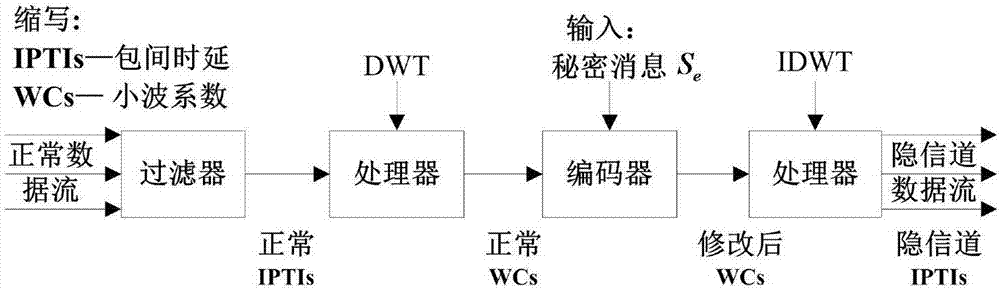
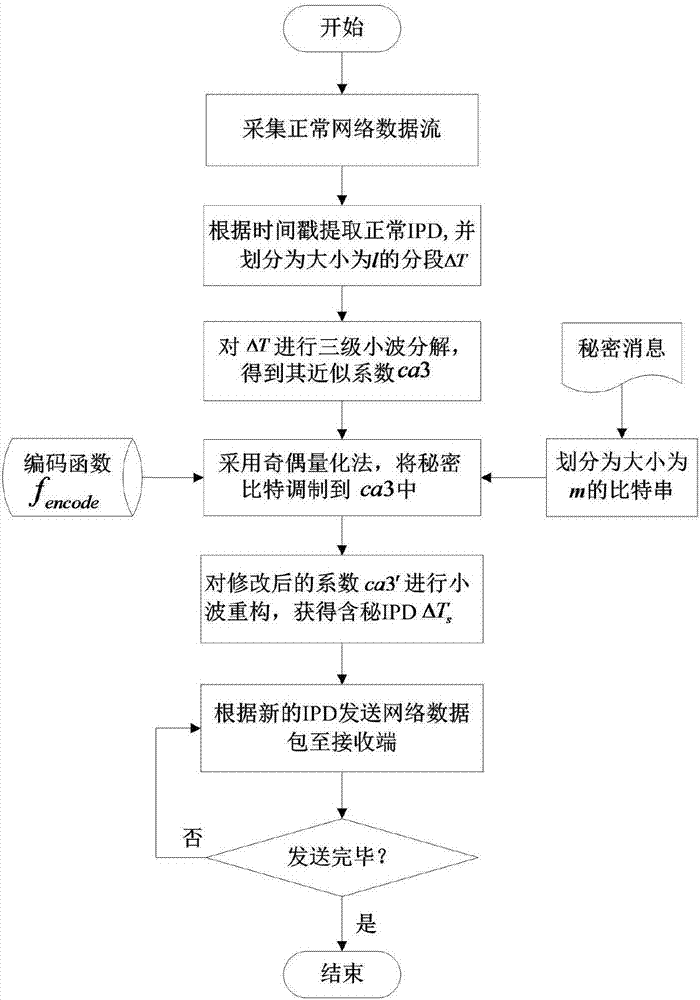
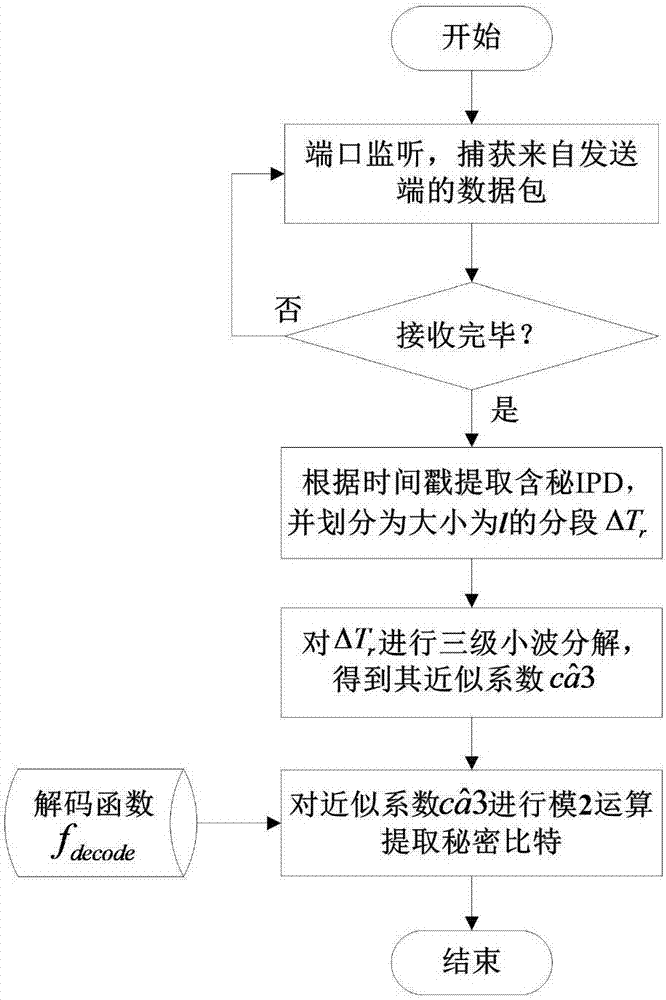
Time type network covert channel construction method based on discrete wavelet transform
ActiveCN107222309ANormal lawNormal characteristicsKey distribution for secure communicationDigital video signal modificationTime domainData stream
The invention discloses a time type network covert channel construction method based on discrete wavelet transform, and belongs to the technical field of network information security. According to the time type network covert channel construction method disclosed by the invention, a secret message is embedded in a wavelet domain coefficient of a normal IPD sequence, and the embedding position and intensity are controlled to reduce the time domain changes to the original carrier and the properties of the original carrier as much as possible; and the generated covert communication data streams have normal rules and features and better anti-detection property. Meanwhile, the secret message bits are embedded in a part of approximation coefficients of wavelet decomposition by adopting the odd-even quantification method, and the network noise interference can be resisted to a certain extent without importing additional synchronization cost, and the robustness is relatively good.
Owner:CHANGZHOU INST OF MECHATRONIC TECH
Systems analysis and dividing method orienting covert channel analysis
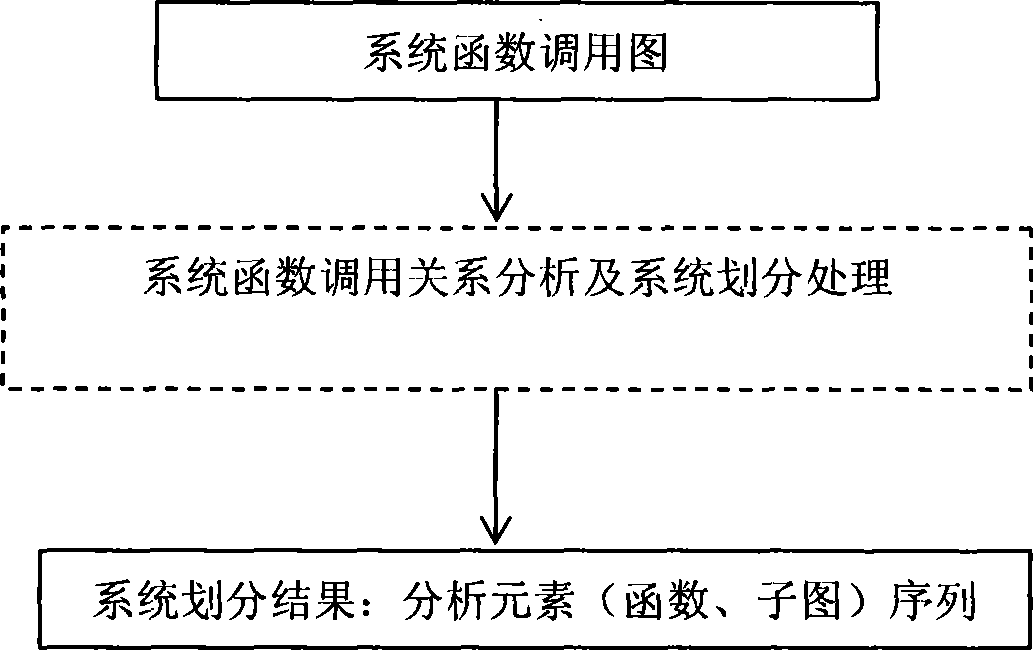
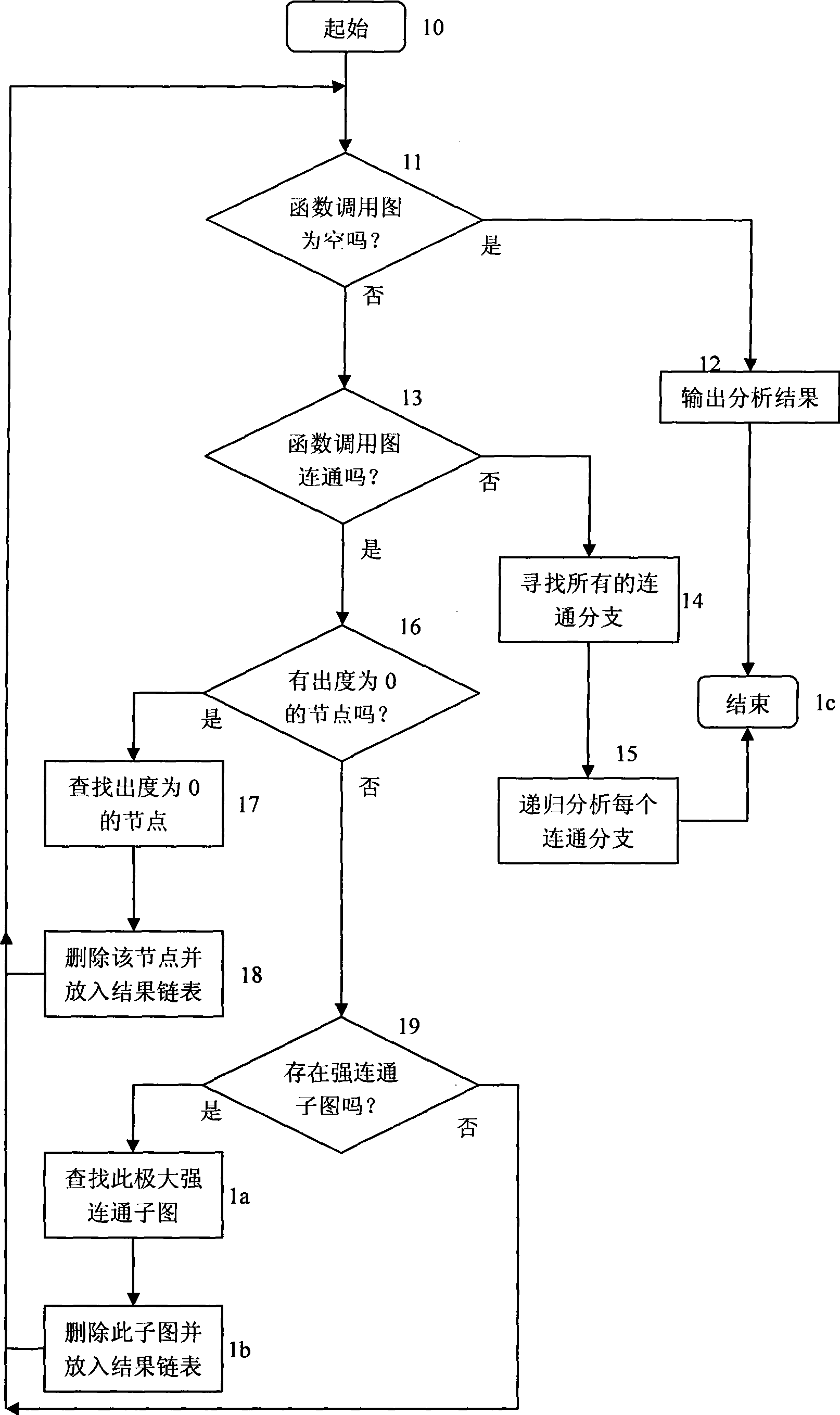
InactiveCN101364203ASolving large scaleSolve complexitySoftware testing/debuggingSystems analysisCircular analysis
A systematic method for analyzing and dividing a covert channel comprises the following steps: Step 10: initializing operation; Step 11: determining whether function call graph is null, turning to Step 12 and indicating that the analytical partitioning algorithm is ended if the function call graph is null, otherwise turning to Step 13; Step 12: outputting the analytical results; Step 13: determining whether the function call graph is connected; Step 14: finding out all disconnected branches of the function call graph; Step 15: circularly analyzing each connected branch of the function call graph; Step 16: determining whether nodes which are independent of other nodes exist in the function call graph; Step 18: deleting the nodes the outdegree of which is zero from the function call graph and adding the nodes at the end of a result linked list; Step 19: determining whether a maximum strongly connected subgraph exists in the function call graph, if so, turning to Step 1a, otherwise turning to Step 11; Step 1a: finding the maximum strongly connected subgraph from the function call graph; Step 1b: deleting the maximum strongly connected subgraph; Step 1c: ending operation.
Owner:NANJING UNIV
Method and system for actively cutting off hidden channels to cope with cache side channel attacks
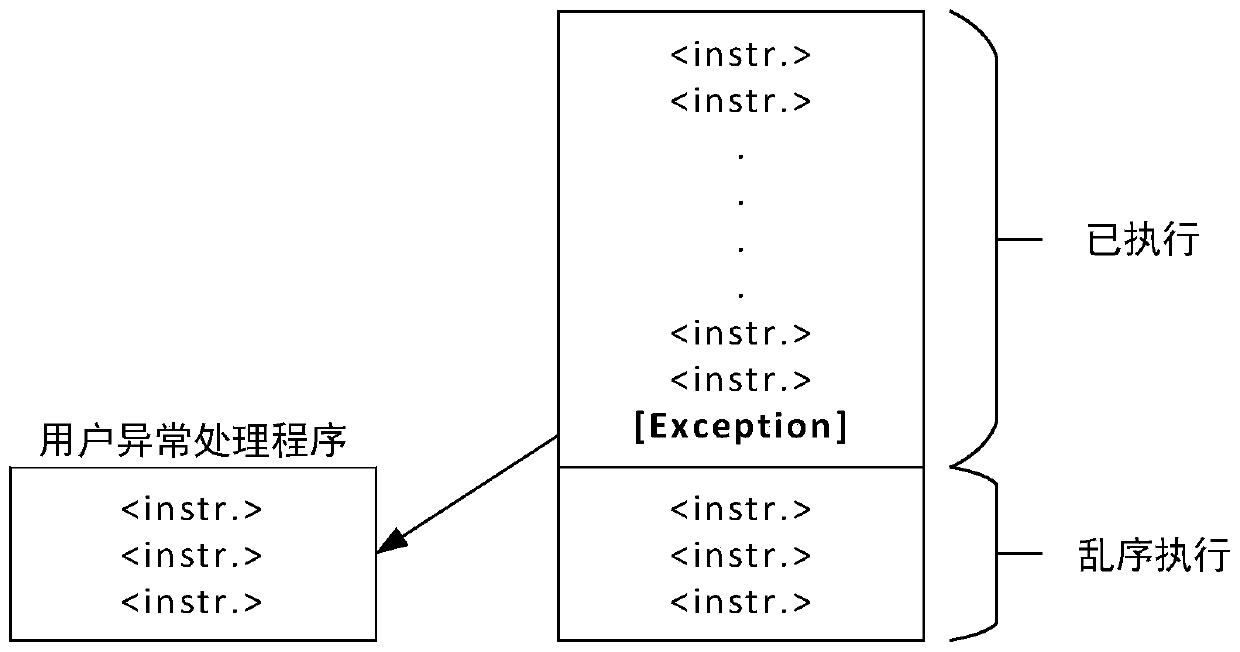
ActiveCN110032867APrevent leakagePerformance is not affectedInterprogram communicationPlatform integrity maintainanceCountermeasureProcessor register
The invention discloses a method and system for actively cutting off a hidden channel to cope with a cache side channel attack. The method comprises the following implementation steps of interceptingexceptions caused by program operation; and if the exception caused by the program operation is intercepted, judging whether the current exception is the cache side channel attack or not, if the current exception is the cache side channel attack, injecting the noise data into the cache by clearing the cache data, resetting a micro-architecture state, and finally calling a user exception processingprogram to continue to process the current exception. According to the method disclosed by the invention, the cache side channel attack including a Meltdown attack is defended from a software countermeasure level; the method can achieve the purpose of giving consideration to the performance, can effectively prevent the leakage of the sensitive information, hardly affects the performance of a normal application program, does not need to modify CPU hardware, can resist the variants read by the maliciously system registers, and has the advantages of being low in defense cost and flexible to implement.
Owner:NAT UNIV OF DEFENSE TECH
Information flow enforcement for risc-style assembly code in the presence of timing-related covert channels and multi-threading
InactiveUS20080072323A1Program control using stored programsMemory loss protectionTraffic capacitySecurity policy
A method and apparatus is disclosed for performing information flow enforcement for assembly code. In one embodiment, the method comprises receiving assembly code having timing annotations with type information that enforce information flow with respect to one or more of timing-related covert and concurrent channels when statically checked as to whether the code is in violation of a security policy and performing verification with respect to information flow for the assembly code based on a security policy.
Owner:NTT DOCOMO INC
Cryptographic method protected against covert channel type attacks
InactiveUS7742595B2Facilitate the breaking down of each blockSecret communicationPlatform integrity maintainanceComputer hardwareCovert channel
The invention relates to a cryptographic method secured against a covert channel attack. According to the invention, in order to carry out a selected block of instructions as a function of an input variable amongst N predefined instruction blocks, a common block is carried out on the predefined N instruction blocks, a predefined number of times, the predefined number being associated with the selected instruction block.
Owner:GEMPLU
DNS protocol covert channel detection method based on random forest
The invention discloses a DNS protocol covert channel detection method based on a random forest. According to the method, a random forest algorithm in machine learning is used to learn features; according to the method, malicious traffic of a DNS hidden channel can be quickly identified, the DNS hidden channel can be effectively detected, DNS requests and response traffic are analyzed by analyzingthe DNS traffic, feature extraction is performed on common fields for transmitting hidden information, and statistics of normal threshold ranges is performed on features; and then learning normal andabnormal DNS traffic characteristics by using a random forest model, establishing a model, and identifying whether the traffic is abnormal traffic, thereby realizing detection of a hidden channel.
Owner:成都蓝盾网信科技有限公司
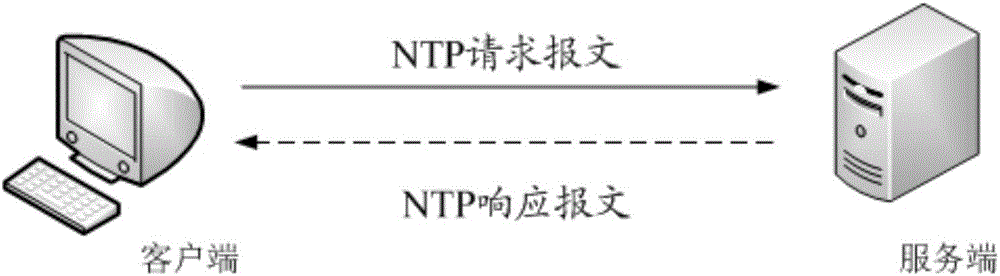
Method and client for realizing covert communication, and server
ActiveCN106453225AImprove concealmentImprove securityTime-division multiplexTransmissionCovert communicationUplink transmission
The invention discloses a method and a client for realizing covert communication, and a server. The method comprises steps that agreement of design rules of an NTP protocol packet with the server is carried out; the uplink transmission data is added to an NTP request message according to the design rules of the NTP protocol packet, the NTP request message is sent to the server, so the server is enabled to analyze the NTP request message according to the design rules of the NTP protocol packet to acquire the uplink transmission data. The method is advantaged in that strong penetrating power, good crypticity and high availability are realized, communication crypticity and security are improved, and preventive bases for malicious utilization of a covert channel are provided.
Owner:北龙中网(北京)科技有限责任公司
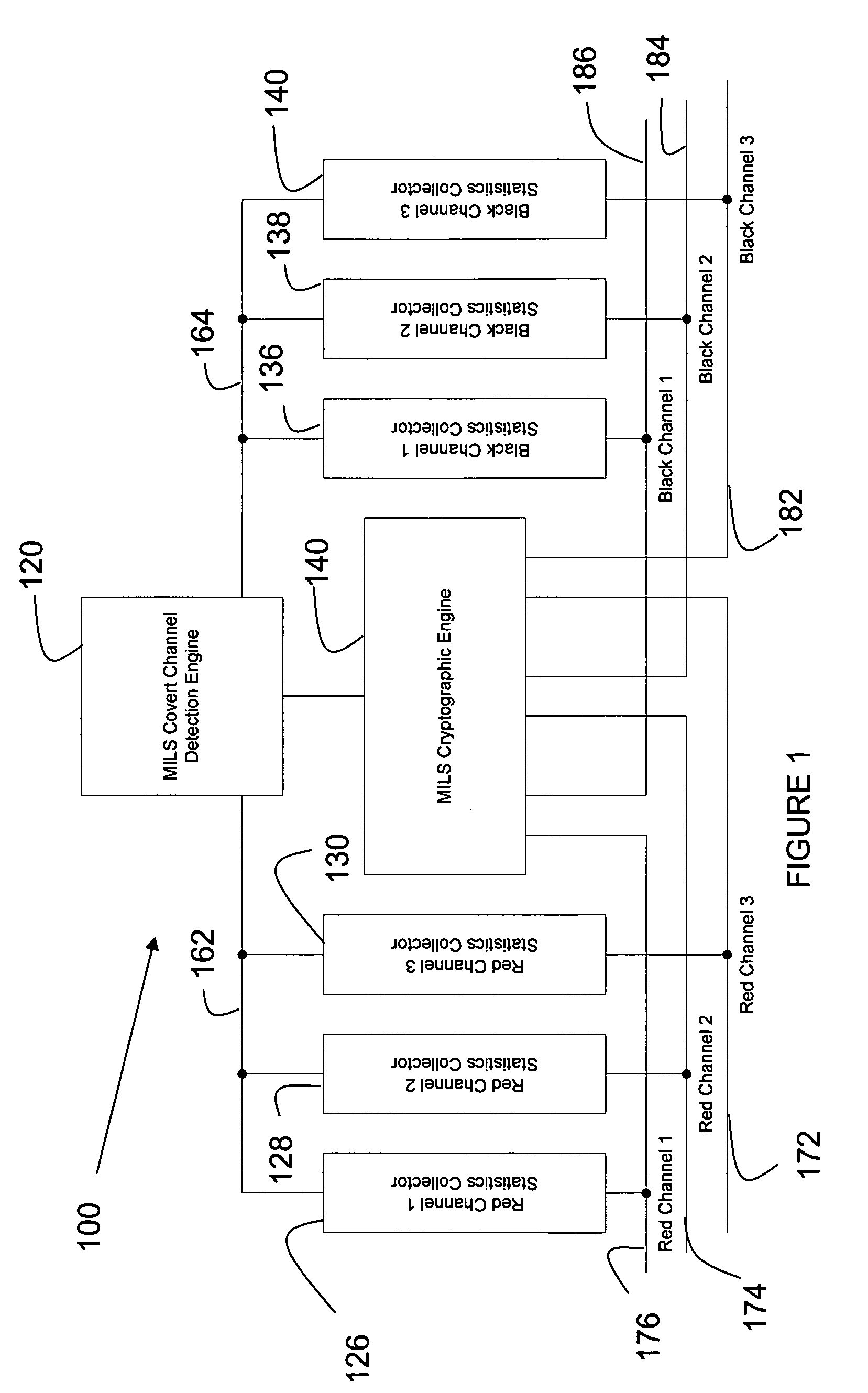
System and method for convert channel detection
ActiveUS7920705B1Programme controlUnauthorised/fraudulent call preventionCommunications systemMultiple single-level
A communication system comprises a covert channel detector. The covert channel detector can be used in a multi-level security system (MLS) or multiple single levels of security (MSLS). The covert channel detector detects covert channels in a cryptographic system. The cryptographic system can be used in a military radio system.
Owner:ROCKWELL COLLINS INC
Video information hiding method and device based on inter-block decoupling
InactiveCN108965887AAvoid cost driftFacilitates adaptive embeddingDigital video signal modificationComputer architectureChannel parameter
The invention relates to a video information hiding method and device based on inter-block decoupling. The method includes the following steps: (1) inputting a carrier video to be embedded and obtaining the channel parameters thereof, wherein the channel parameters include whether each block is a non-reference block, the values of non-zero DCT coefficients in each non-reference block and the embedding cost of each non-reference block; (2) carrying out steganographic coding by taking the non-zero DCT coefficients in all the non-reference blocks as the carrier of a covert channel; and (3) compressing the carrier video to be embedded, and using the lowest bit to replace and modify the non-zero DCT coefficients in all the non-reference blocks according to the channel parameters acquired in step (1) and the coding result obtained in step (2) in the process of compression to obtain a steganographic video file. The generation of the cost drift phenomenon is avoided by using the technology ofdecoupling between carrier blocks. The method and the device are especially suitable for a covert communication scenario requiring low real-time performance and high security performance.
Owner:INST OF INFORMATION ENG CAS
Method and apparatus for cross-core covert channel
InactiveUS20160117246A1Memory architecture accessing/allocationMemory adressing/allocation/relocationAccess timeVirtual machine
Passing messages between two virtual machines that use a single multicore processor having inclusive cache includes using a cache-based covert channel. A message bit in a first machine is interpreted as a lowest level cache flush. The cache flush in the first machine clears a L1 level cache in the second machine because of the inclusiveness property of the multicore processor cache. The second machine reads its cache and records access time. If the access time is long, then the cache was previously cleared and a logical 1 was sent by the first machine. A short access time is interpreted as a logical 0 by the second machine. By sending many bits, a message can be sent from the first virtual machine to the second virtual machine via the cache-based covert channel without using non-cache memory as a covert channel.
Owner:THOMSON LICENSING SA
Method for building covert channel with network flow watermarking of forward error correction code and interleaved code
ActiveCN108650054ATroubleshoot transmission correctness issuesVerify reliabilityForward error control useComputer hardwareInformation transmission
The invention discloses a method for building a covert channel with network flow watermarking of a forward error correction code and an interleaved code, and relates to a covert channel for information secure transmission in the field of communication. The method comprises the following steps: firstly, encoding original secret information to be transmitted by an error correction code encoder, andprocessing an obtained codeword signal according to a network flow watermarking method; in a decoding stage, making a secret information receiver acquire a watermark signal from target network stream,and transmit the watermark signal to an interleaved code decoder for processing to obtain a de-transposed watermark signal; if the watermark signal is subjected to PN code spread spectrum processing,processing the watermark signal with a PN decoder; and finally, transmitting the de-transposed watermark signal or the PN decoded watermark signal to an error correction code decoder for processing to recover the original secret information. Through adoption of the method for building the covert channel with network flow watermarking of the forward error correction code and the interleaved code,the automatic error correction capability specific to the secret information is realized, and the reliability of information transmission is enhanced.
Owner:XIAMEN UNIV
Detection method of time-sequence type covert channel based on neural network
InactiveCN104753617AImprove accuracyImprove versatilityPropogation channels monitoringFeature vectorNerve network
The invention discloses a detection method of a time-sequence type covert channel based on a neural network. The method comprises the steps of obtaining three feature values of a time interval sequence including a variable coefficient, similarity and an entropy value according to a time interval between data packages; taking a four-dimensional feature vector consisting of the variable coefficient, the similarity, the entropy value and a channel type is a training sample of the neural network to train; detecting by the neural network to judge whether the communication channel has the convert channel and the belonged type after the neural network is astringed.
Owner:SUZHOU INST FOR ADVANCED STUDY USTC
Video steganography method based on motion vector local optimality preservation
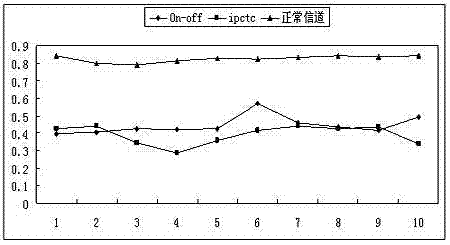
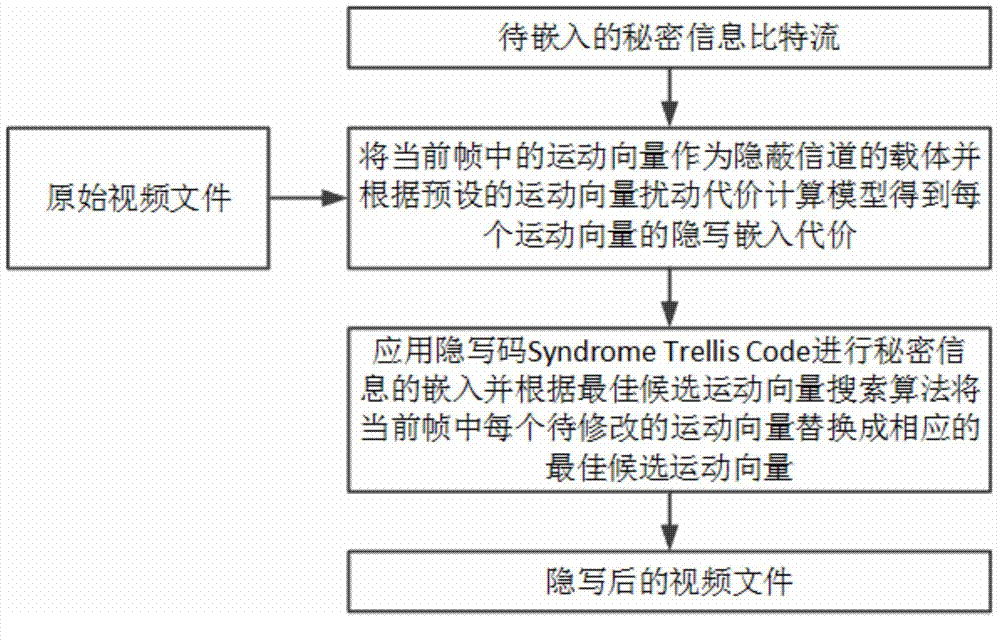
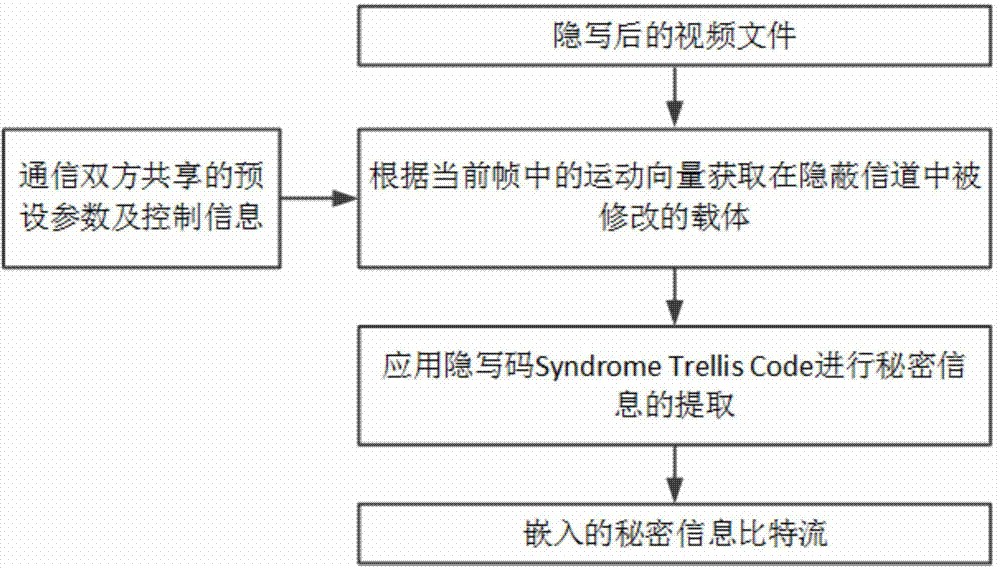
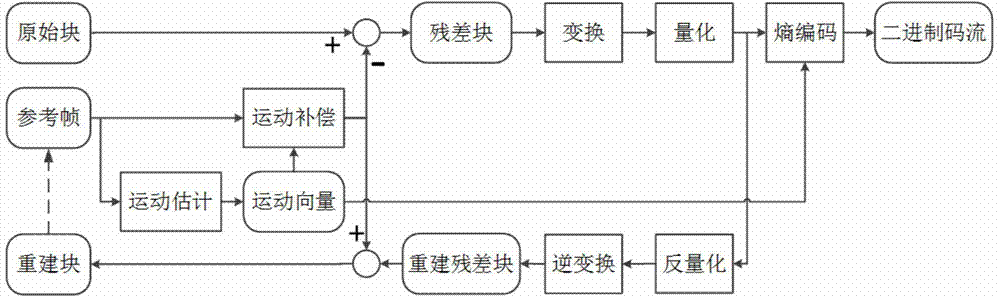
InactiveCN104853215AEncoding Performance ImpactReduce video encoding performance impactDigital video signal modificationSteganalysisLocal optimum
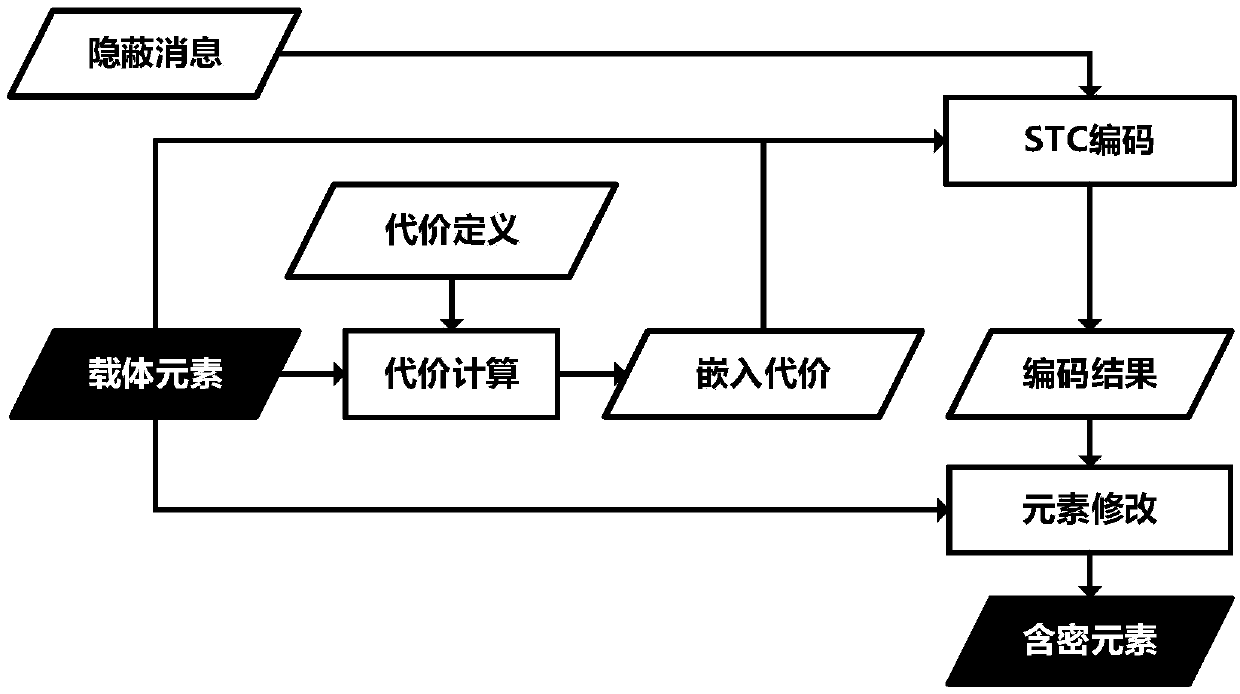
The present invention relates to a video steganography method based on motion vector local optimality preservation. Criteria for motion vector local optimality and a search algorithm for optimal candidate motion vectors are established. On this basis, by constructing a reasonable motion vector disturbance cost calculation model and selecting the most efficient steganographic codes, covert channels are established to complete steganographic insertion of secret information, and an extraction process of the secrete information is thus completed. Syndrome trellis code (STC) steganographic codes are preferably adopted. The method provided by the present invention is a motion vector field video steganography method which is based on motion vector local optimality preservation, has a high insertion efficiency and can effectively resist conventional steganalysis attacks, and is especially applicable to covert communication situations with high safety requirements.
Owner:INST OF INFORMATION ENG CHINESE ACAD OF SCI
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com