Video steganography method based on motion vector local optimality preservation
A motion vector and local optimal technology, applied in the sub-field of information hiding, can solve the problems of distinguishing common carriers, being unable to resist attacks, destroying the local optimality of motion vectors, etc., to reduce the impact, improve the embedding efficiency and security, resist the effect of attack
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0069] Below through specific embodiment and in conjunction with appendix Figure 5-6 The present invention is further described.
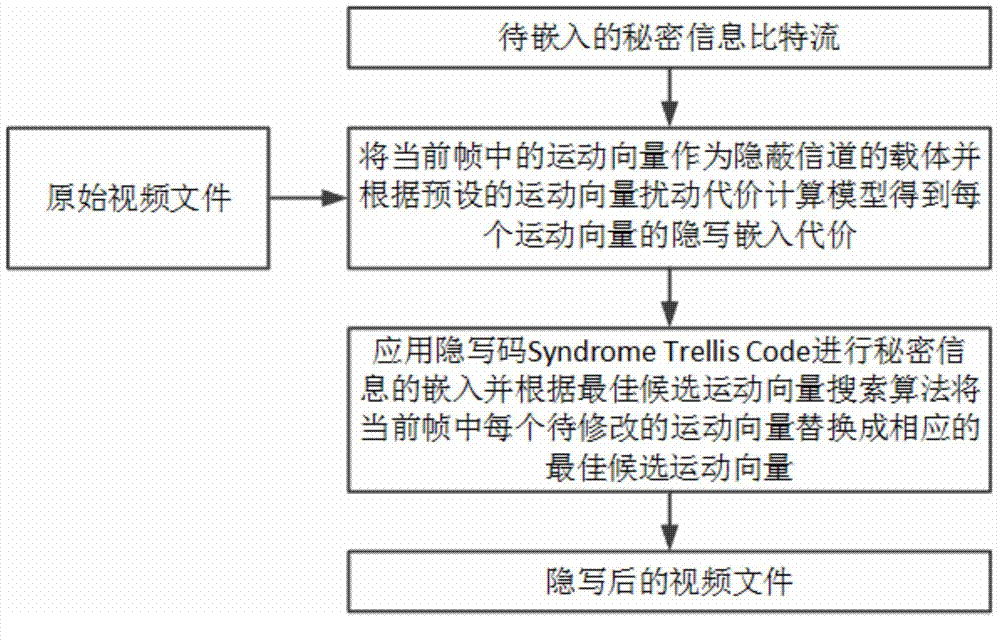
[0070] Before adopting the present invention to steganographically embed secret information, the data to be embedded can be encrypted first to obtain a random binary data stream. The secret information embedding process of the video steganography method based on the local optimality preservation of the motion vector proposed by the present invention is as follows: Figure 5 As shown, the specific operation details are as follows:
[0071] 1) Obtain the video frame that needs to be steganographically embedded, for each motion vector (mv x ,mv y ), get the lowest bit of the sum of its horizontal and vertical components, namely LSB (mv x +mv y ), and form all calculation results into a binary vector x;
[0072] 2) For each motion vector MV in the video frame 0,0 =(mv x ,mv y ), according to the preset motion vector perturbation cost calculat...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com