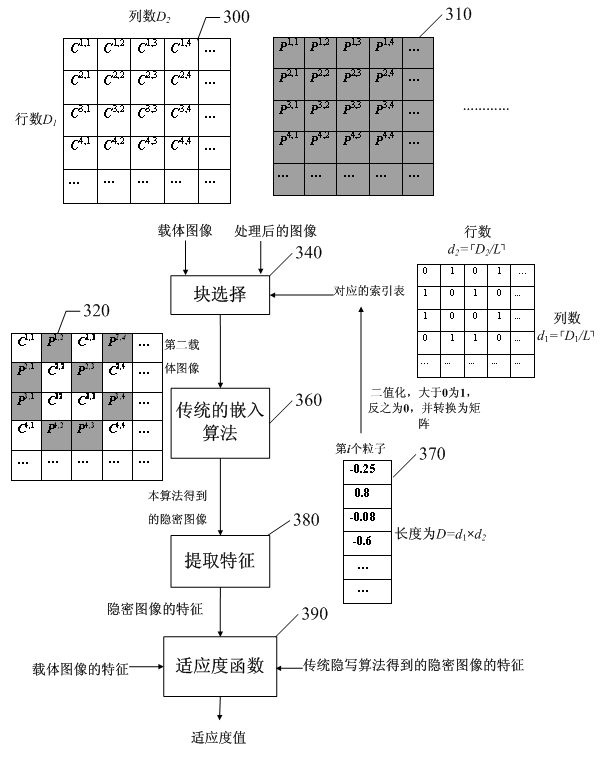
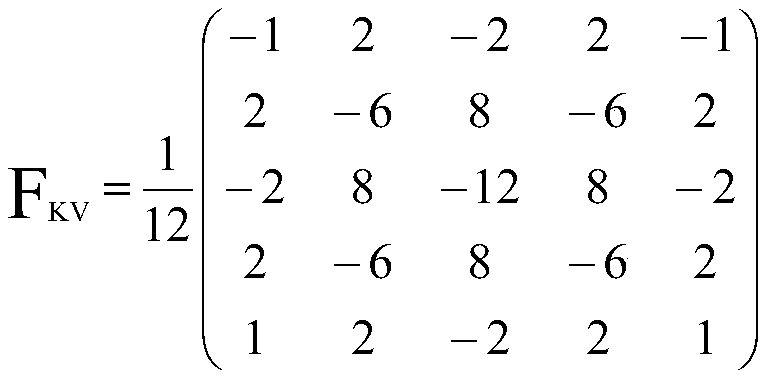Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
101 results about "Steganographic algorithm" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
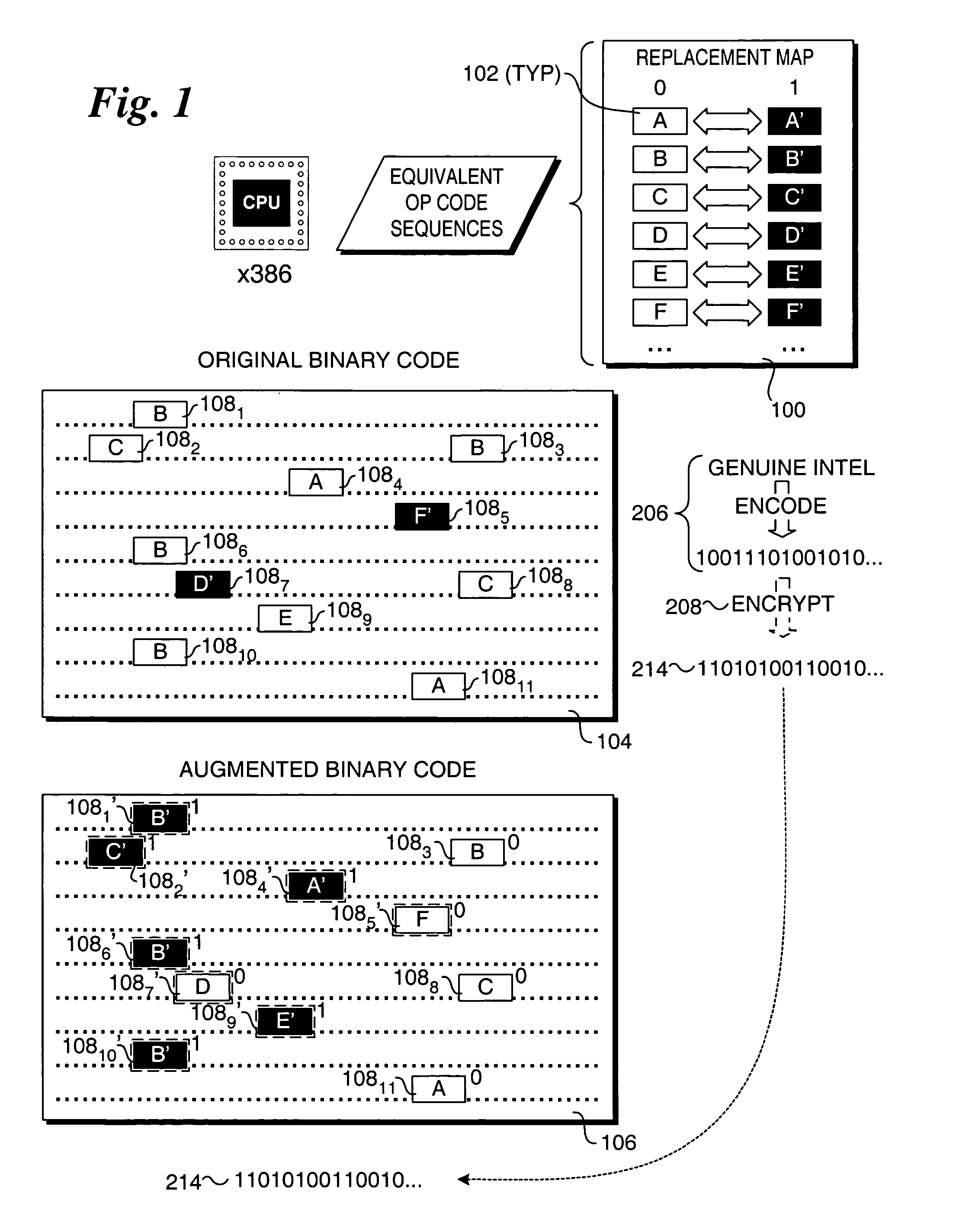
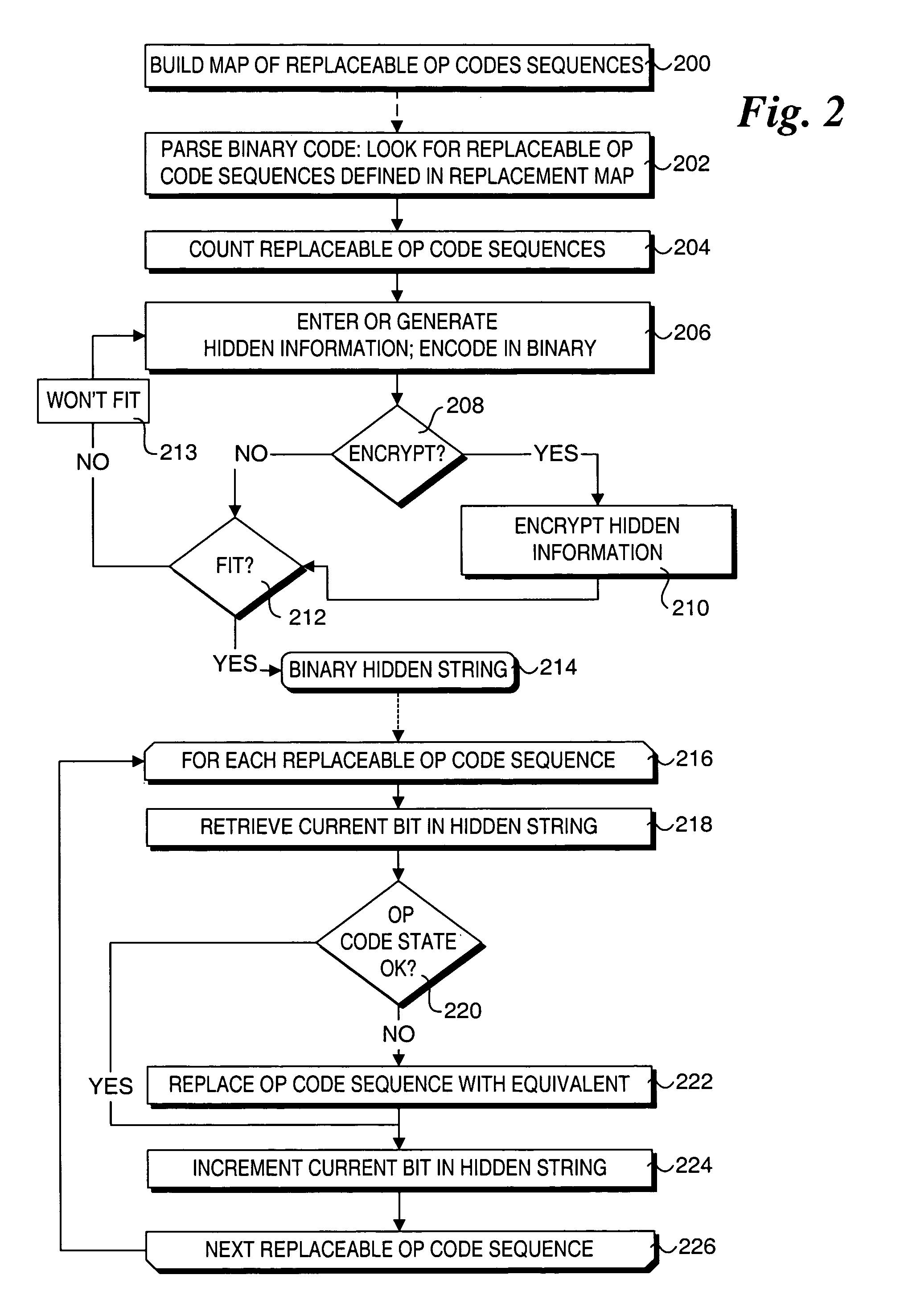
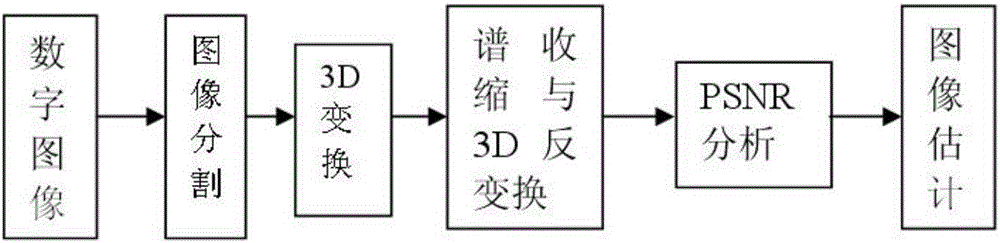
The steganography algorithm used for the development of the applications is using binary codes and pixels inside an image. The zipped file is used before it is converted to binary codes to maximize the storage of data inside the image.
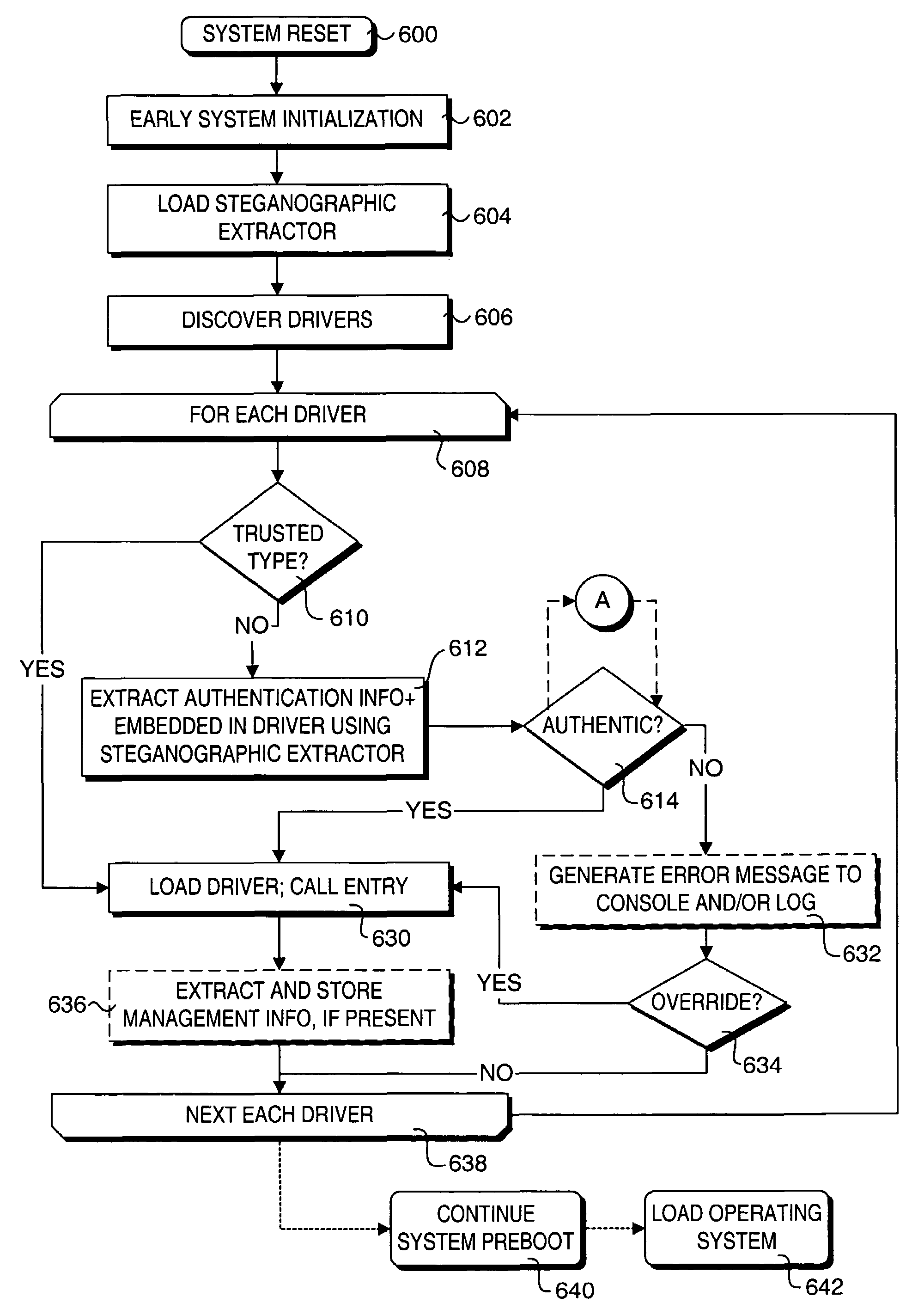
Method to provide transparent information in binary drivers via steganographic techniques
ActiveUS7751584B2User identity/authority verificationCharacter and pattern recognitionComputer hardwareHidden data
Methods for providing and extracting hidden information in firmware images using steganographic processes. Information is hidden in binary firmware images, such as drivers, using a steganographic process in which the functionality of the binaries do not change, and the size is not increased. During a pre-boot phase of a computer system, binary firmware drivers containing hidden steganographic data are identified, and a steganographic extraction process is performed to extract the hidden data. In one embodiment, a hash is employed on an authentic binary image to uniquely identify the op code content. The digest from the hash is stored in the steganographic data. In one embodiment, a vendor's private key and optional signature is used to encrypt the hash. A similar hash is performed on the binary image of a discovered binary firmware driver, and the authentic hash digest is extracted from the steganographic data. The hash digests are compared to authenticate the binary firmware driver.
Owner:INTEL CORP
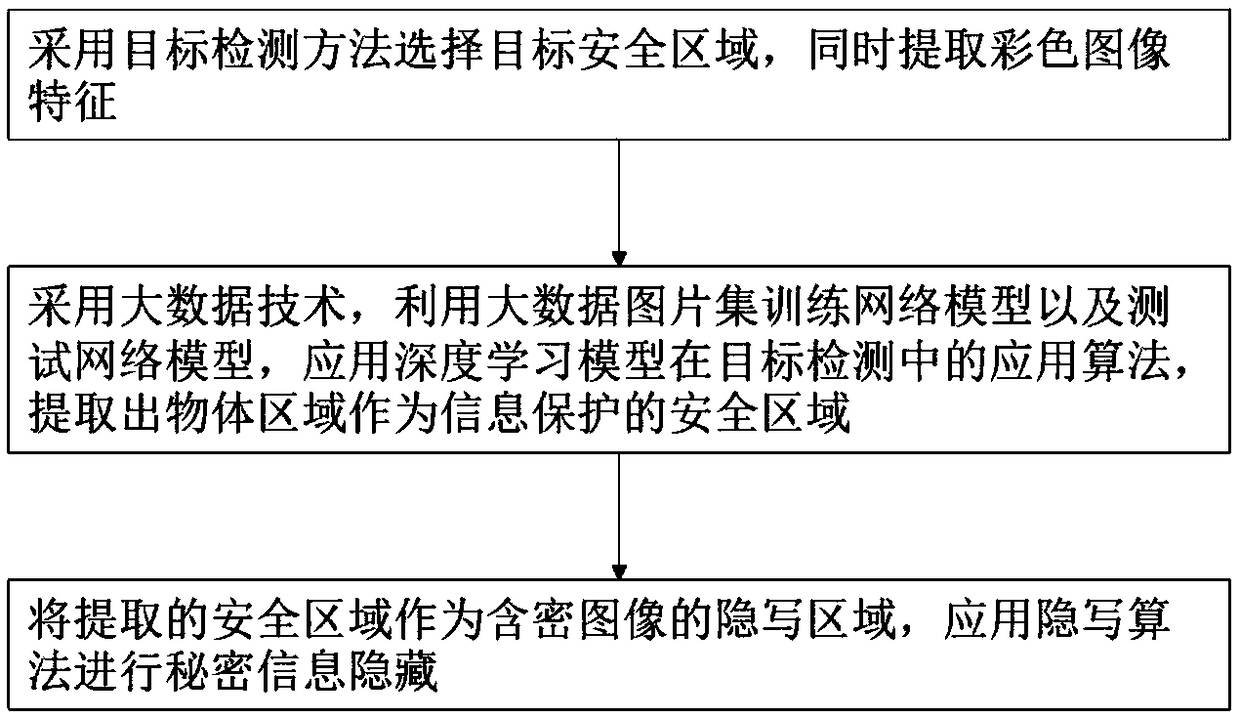
Big data image protection method and system based on a security area
ActiveCN109492416AAchieve hiddenImplement image protectionCharacter and pattern recognitionDigital data protectionColor imagePattern recognition
The invention provides a big data image protection method based on a security area, and the method comprises the steps: S1, selecting a target security area through employing a target detection method, and extracting color image features; s2, a big data technology is adopted, a big data picture set is utilized to train a network model and a test network model, an application algorithm of a deep learning model in target detection is applied, and an object area is extracted to serve as a safety area of information protection; and S3, taking the extracted security area as a steganography area ofthe encrypted image, and carrying out secret information hiding by applying a steganography algorithm. According to the invention, the application algorithm of the deep learning model is applied in the target detection, that is, the Mask R-CNN instance segmentation method, and select the region with complex texture noise in the image, an area with complex texture noise in the image, namely a foreground part, is selected, secret information is accurately hidden in a foreground object, and therefore the purpose of more secret image secret information hiding protection is achieved.
Owner:NANJING UNIV OF INFORMATION SCI & TECH
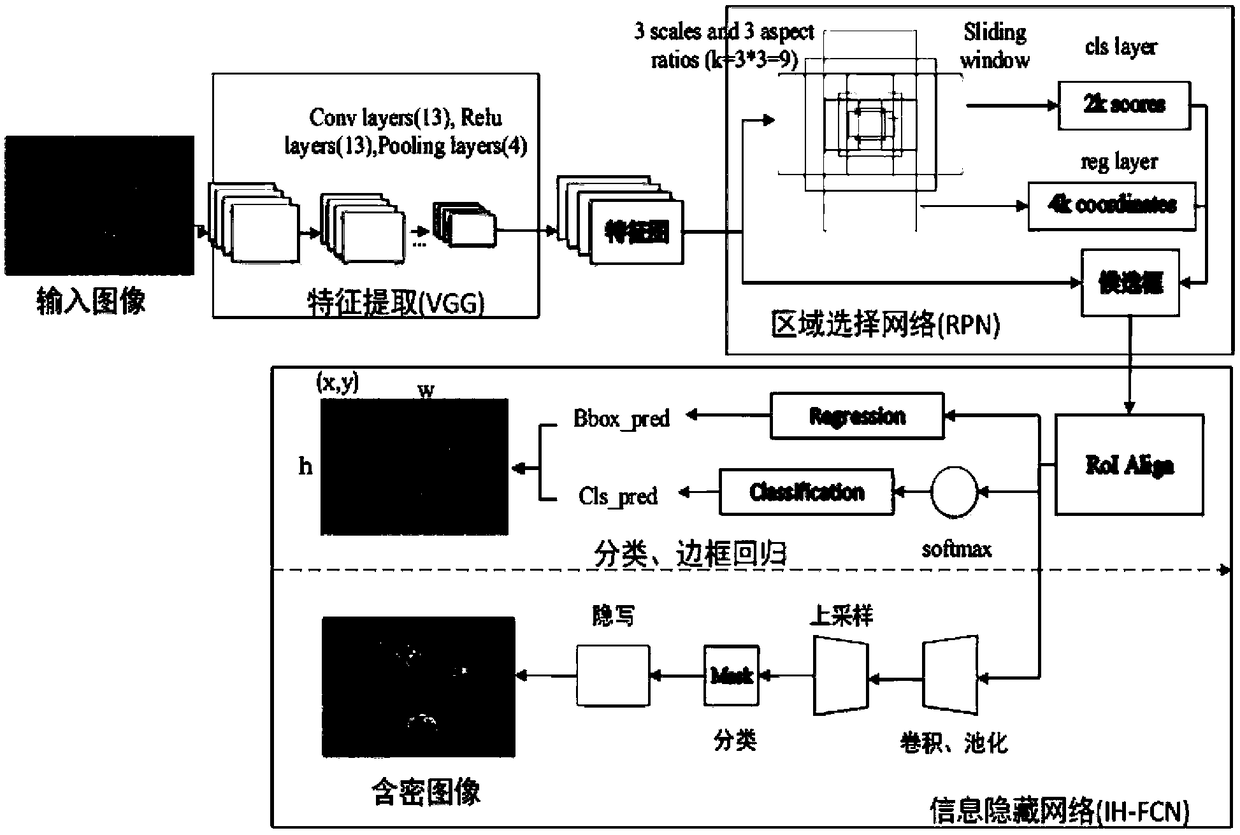
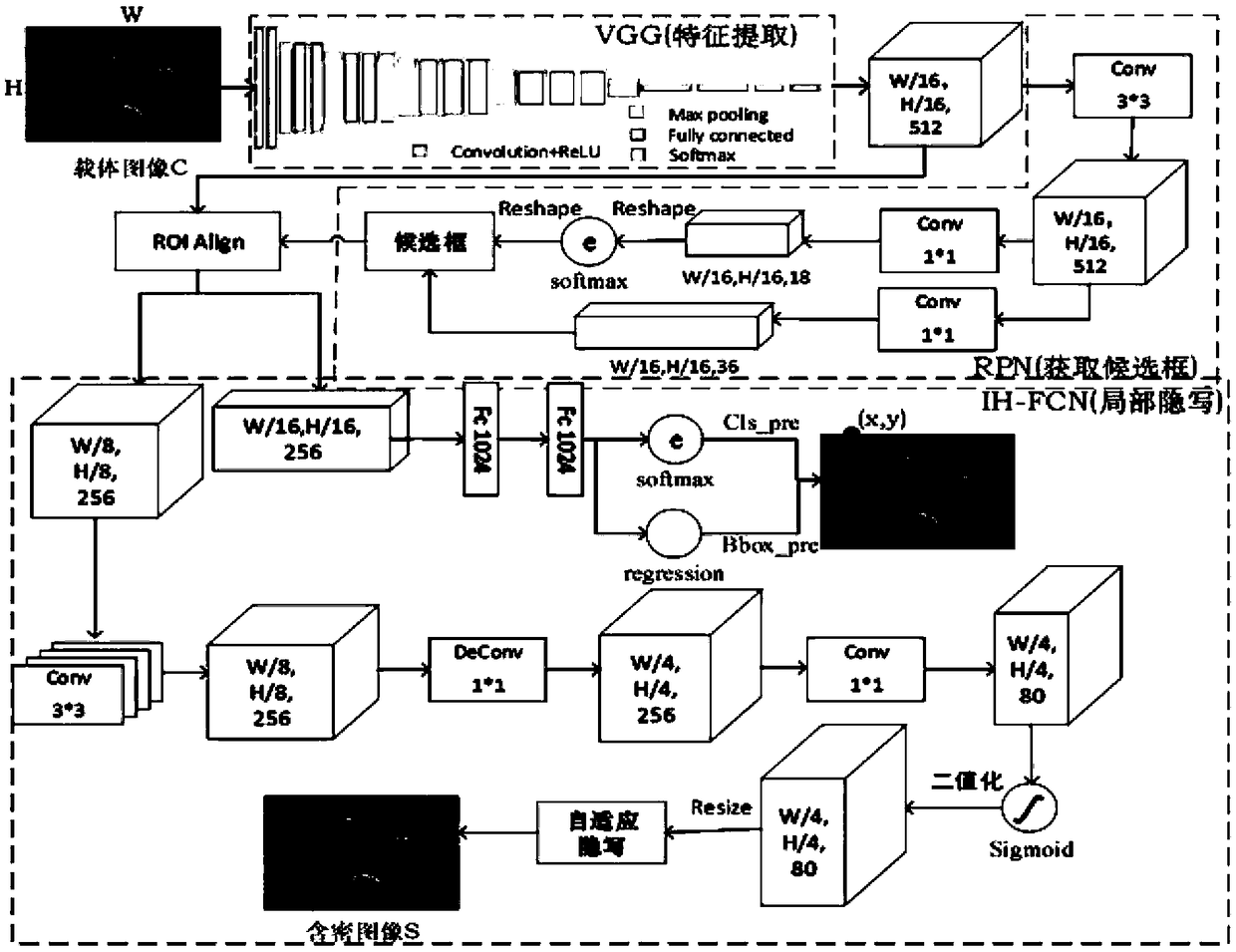
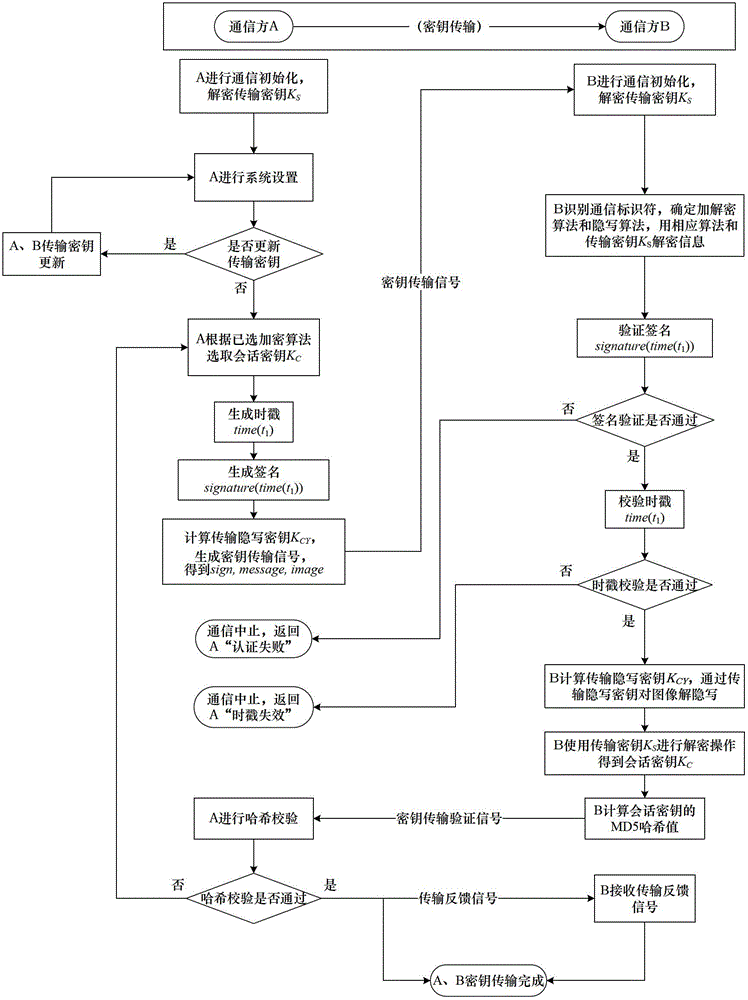
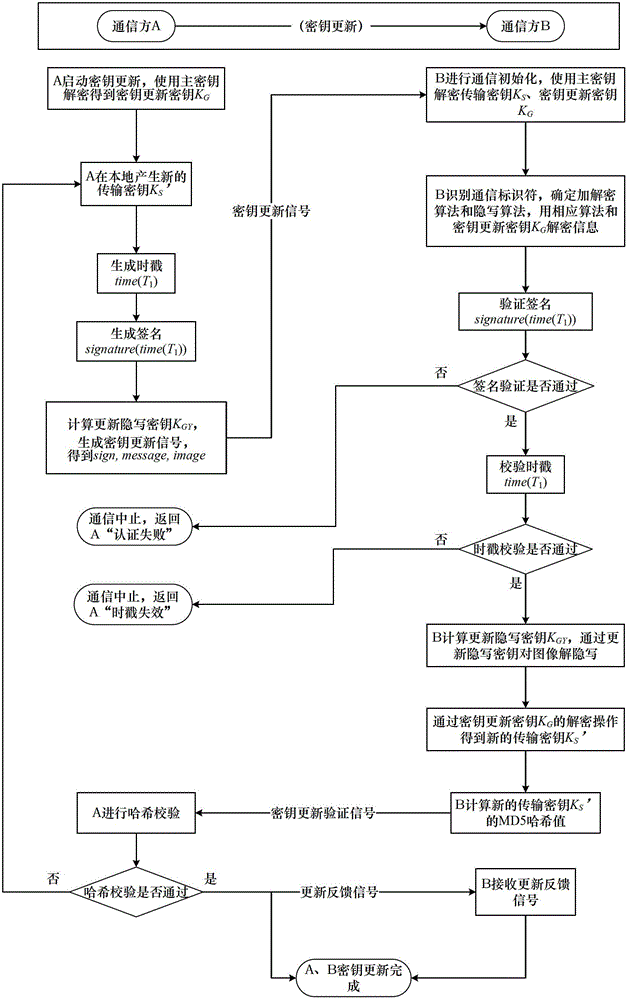
Steganography-based key transmission and key updating method
ActiveCN102724041AEffective verification of identity informationImprove authentication strengthEncryption apparatus with shift registers/memoriesUser identity/authority verificationMultiple encryptionCiphertext
The invention provides a steganography-based key transmission and key updating method, which is applied to the field of information safety. The method comprises the steps that a communication party A sets a communication type, an encryption algorithm an steganography algorithm, selects a steganography carrier and generates a communication identifier and then performs the updating of a transmission key or the transmission process of a conversion key; a new transmission key is selected when in updating, a time stamp and a signature are generated to encrypt and steganograph the transmission key, the key updating information is generated to be transmitted to a communication party B, and the communication party B performs the verification, de-staganography and deciphering to obtain the transmission key; and the conversion key is selected in transmission to generate a time stamp and a signature so as to encrypt and steganograph the conversion key, the key transmission information is generated to be transmitted to the communication party B, and the communication party B performs the verification, de-steganography and deciphering to obtain the conversation key. The key is concealed by utilizing the steganography, so that an encrypted data format in the key transmission process and the key updating process can be effectively protected, and the safety transmission of multiple encryption and decryption algorithm conversation keys can be realized.
Owner:BEIHANG UNIV
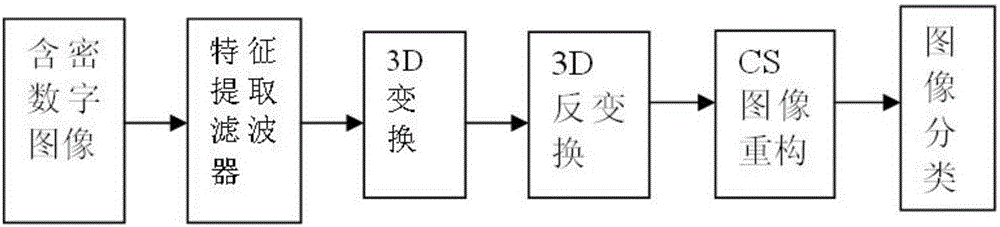
Image steganalysis method and system based on convolutional neural network
ActiveCN108961137ASimple designEasy to implementCharacter and pattern recognitionImage data processing detailsSteganographic algorithmSignal-to-noise ratio
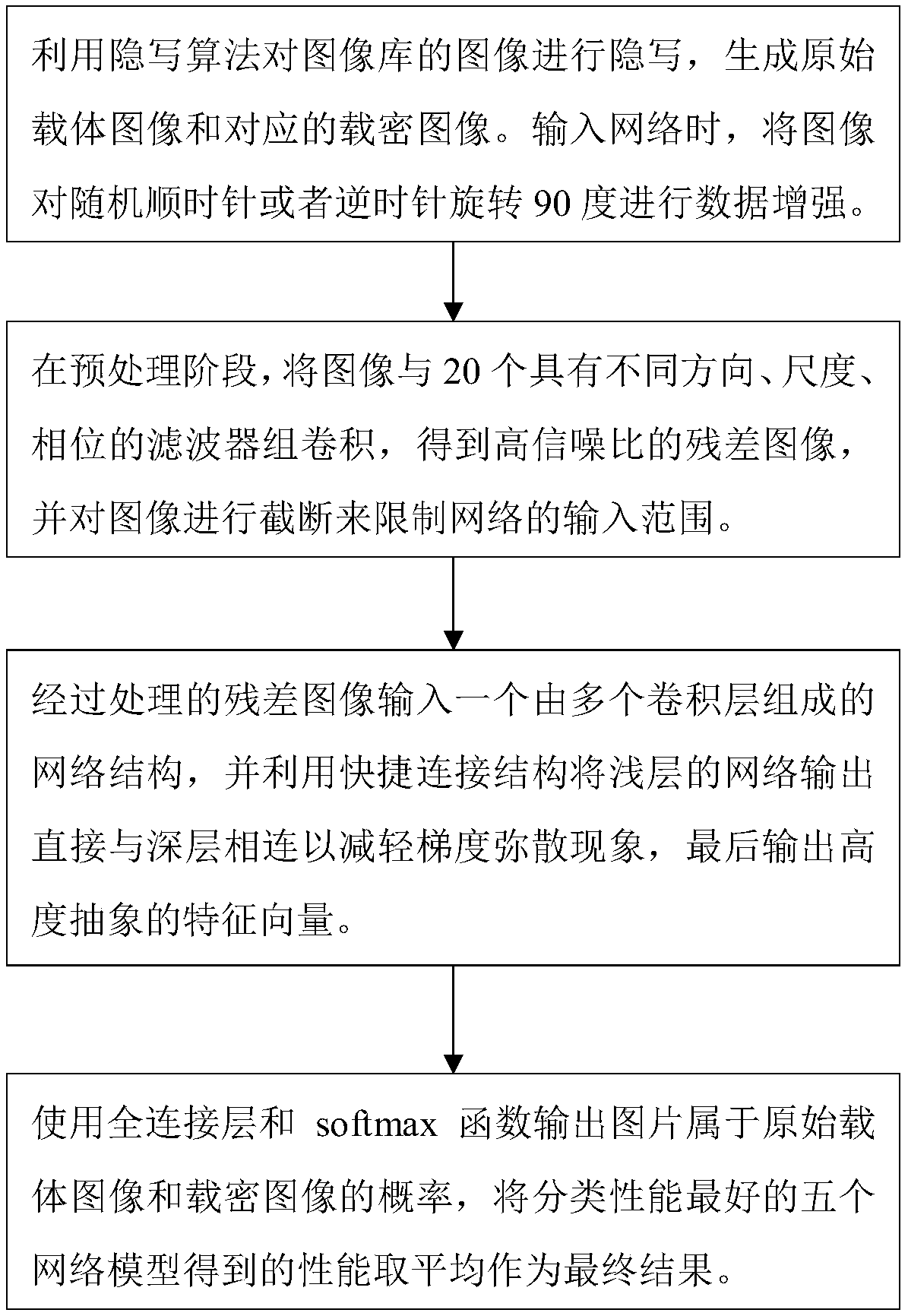
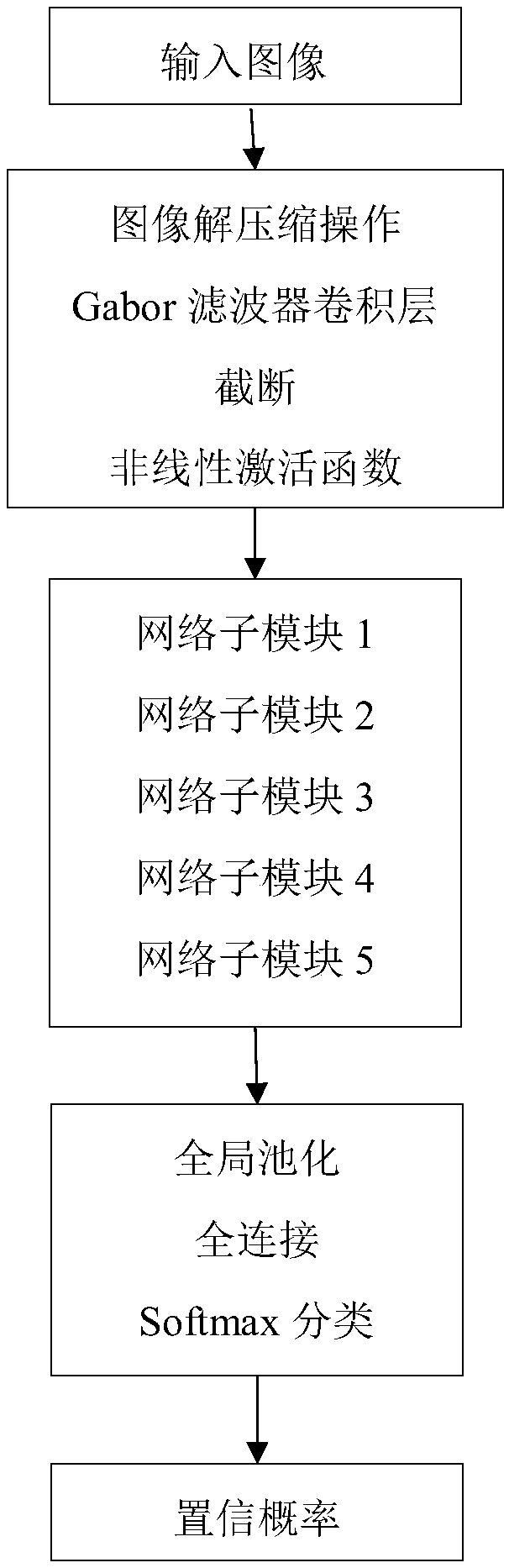
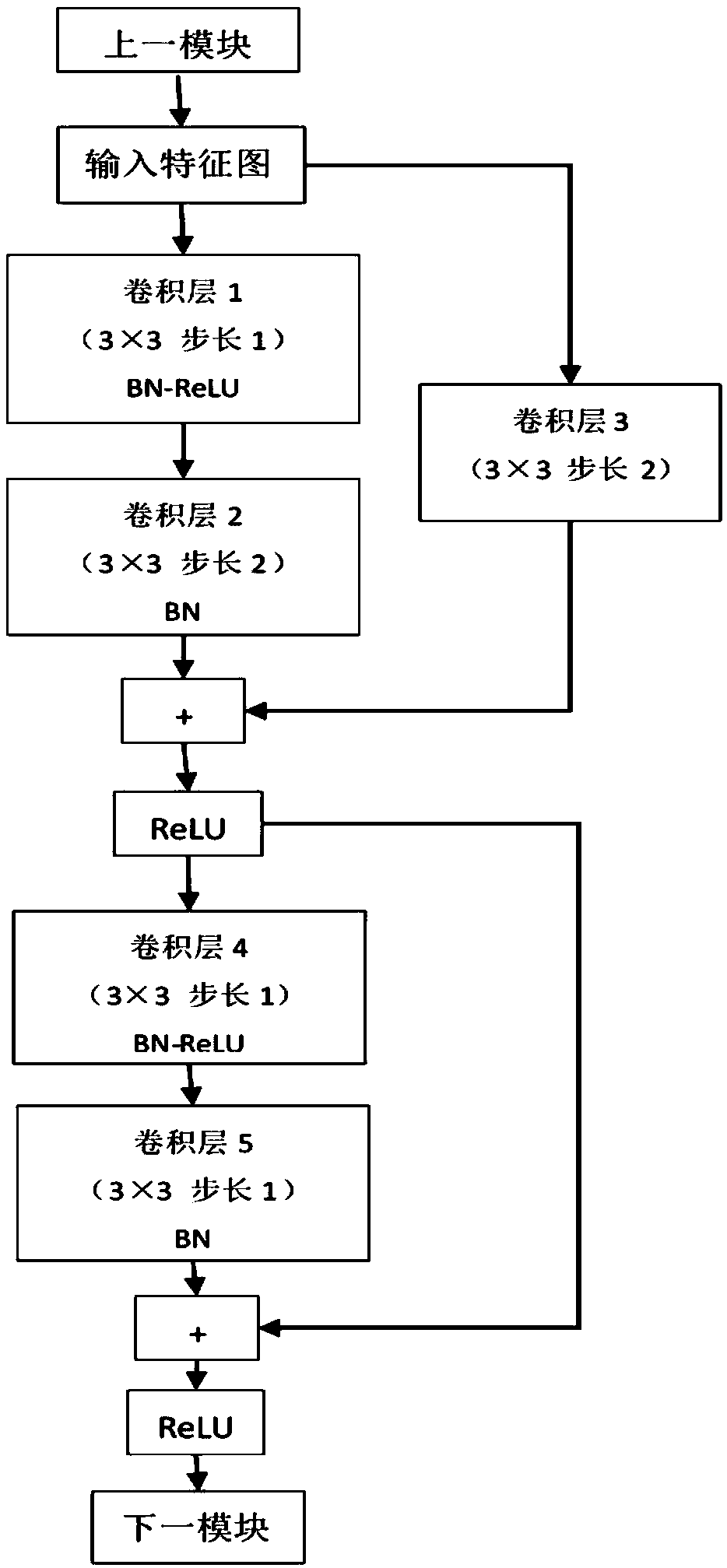
The invention discloses an image steganalysis method and system based on the convolutional neural network. The system comprises an image preprocessing part, a feature extraction part and a feature classification module. In the image preprocessing part, a group of Gabor filters with multiple directions and multi-dimension parameters is selected by experiments, and an image residual error with highsignal to noise ratio is obtained by input image convolution; and in the feature extraction part, a rapid connection structure is used to connect output of a shallow layer with a behind layer directlyto reduce a fitting phenomenon. The steganalysis method based on the convolutional neural network does not need a lot of knowledge in the fields of steganography and steganalysis, feature extractionand feature classification form a combined optimization process, design is simple, and enforcement is easy; the scale and direction properties of the Gabor filters can be used to help extract the image residual error from the network more effectively; and the method and system have better detection effects for adaptive steganography algorithms of J-UNIWARD and UED contents.
Owner:SUN YAT SEN UNIV
Adaptive spatial steganographic method based on adjacent pixel difference
InactiveCN101582157AImprove securityImplement embeddingImage data processing detailsPattern recognitionCovert communication
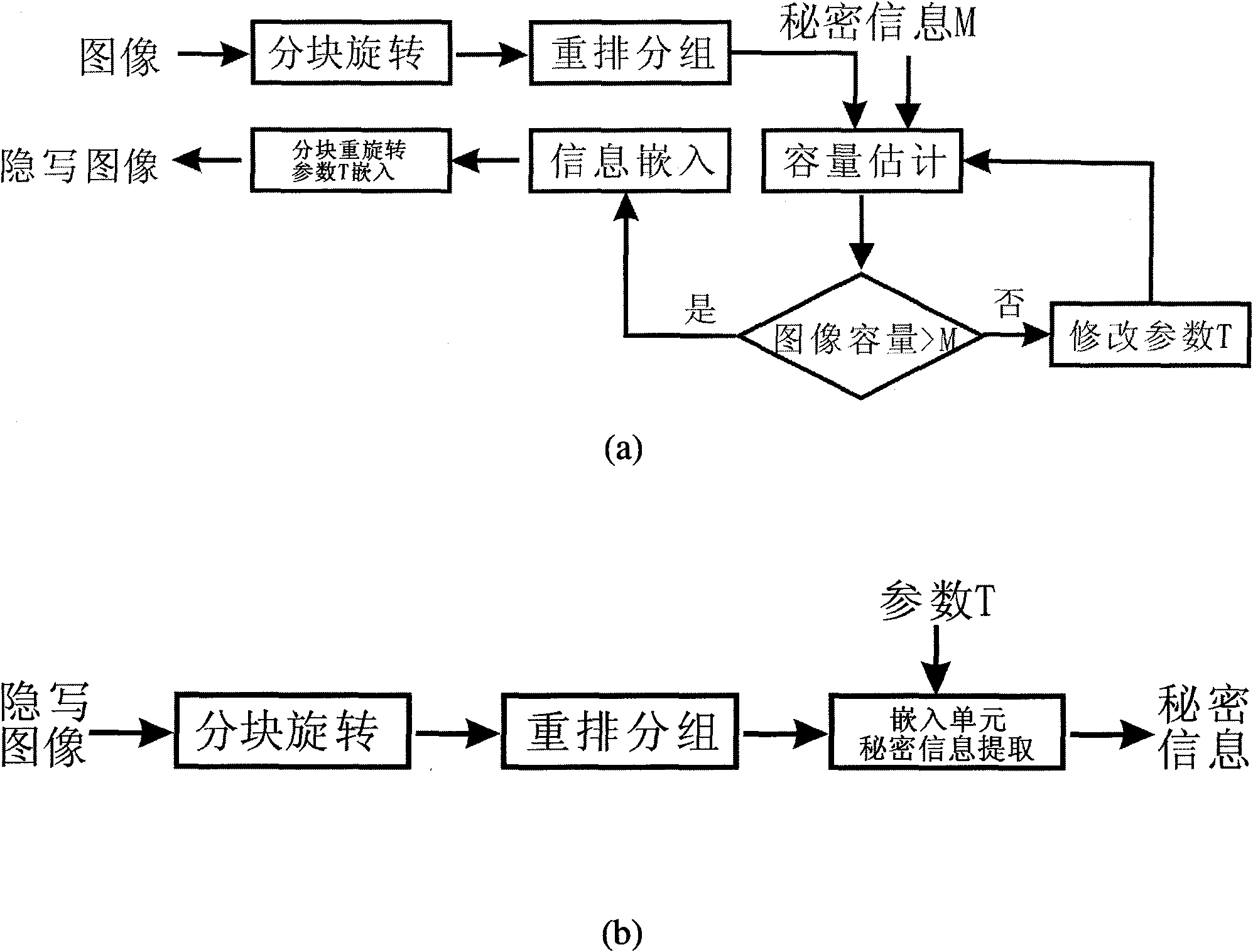
The invention provides an adaptive spatial steganographic method based on adjacent pixel difference. The method comprises the following two steps: embedding secret information and extracting the secret information. The method takes three continuous adjacent pixels in an image as an embedding unit and reaches the goal of hiding information by changing the value of the middle pixel in each unit. During information embedding, a steganographic algorithm always mains the size relationship of each pixel in the embedding unit, and adaptively adjusts the capacity of embedding information through a parameter according to the content of the image. Experiments show that the adaptive spatial steganographic method has higher safety and adaptive ability compared with the prior steganographic method based on pixel difference. Therefore, the adaptive spatial steganographic method has great practical significance to application fields such as covert communication and the like.
Owner:SUN YAT SEN UNIV
Digital image concealed information detecting and positioning method
The invention relates to a method for detecting and positioning hidden information in a digital image, which comprises the following steps: detecting a digital image containing hidden information by using a blocking effect computing method; if the digital image is in a JPEG image compressed format, extracting a quantization matrix of the JPEG; deducing a quantization DCT coefficient of an original image before the embedment of the hidden information according to a DCT coefficient of the digital image; and restoring the pixel value of the original image according to the DCT coefficient of the original image, determining the embedment position of the hidden information according to the difference between the pixel values of the original image and the digital image, and estimating the embedding quantity of the hidden information. The technical proposal of the invention overcomes the drawback that the prior hidden information detection technology cannot accurately position the embedment position of the hidden information, and can detect and position hidden information hidden by various steganography algorithms in the digital image.
Owner:SHANGHAI NORMAL UNIVERSITY
General video steganalysis method based on video pixel space-time relevance
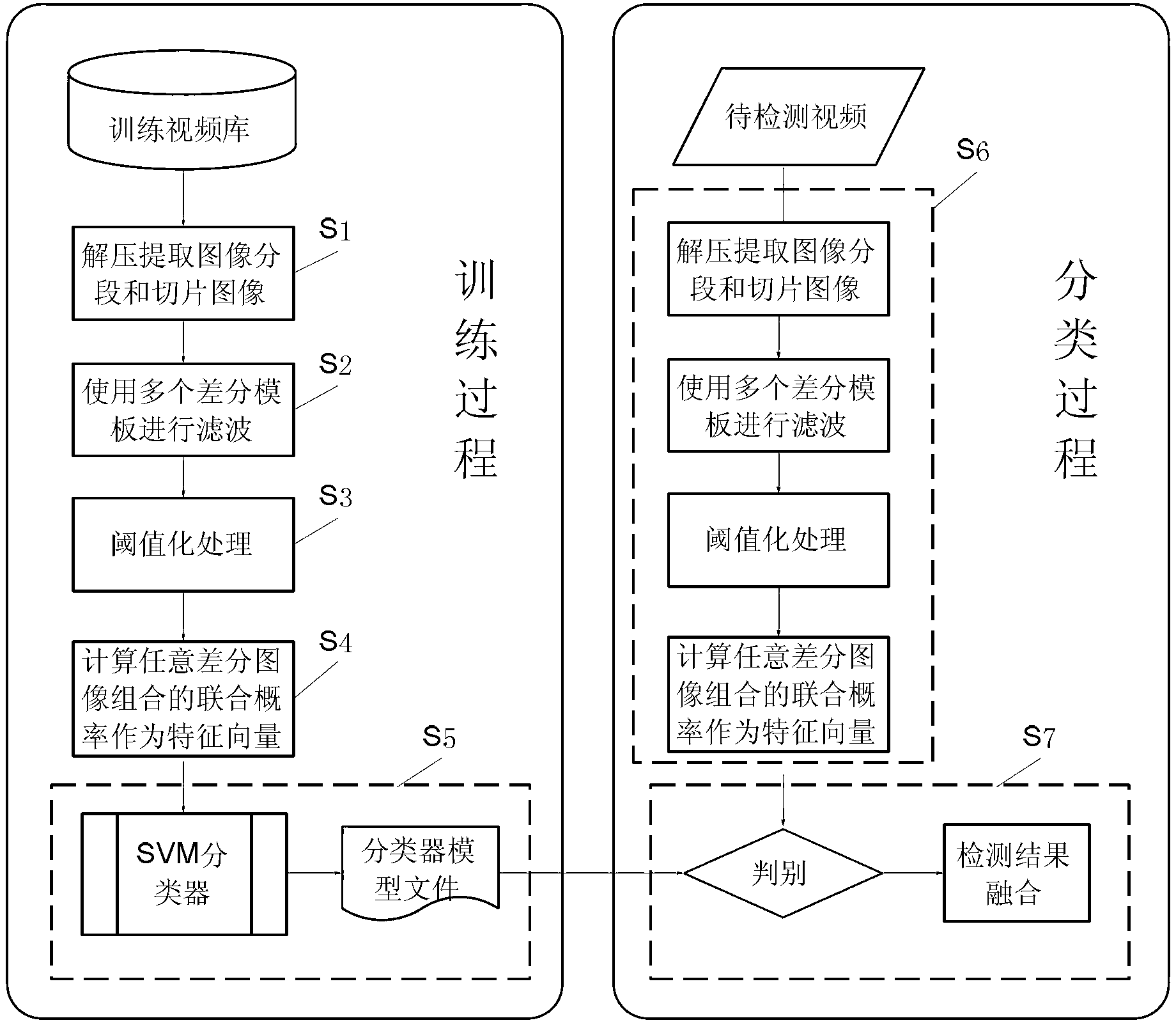
ActiveCN103281473AMonitor outflowImage data processing detailsPictoral communicationTime domainFeature vector
The invention discloses a general video steganalysis method based on video pixel space-time relevance. The method comprises the steps that a video in a training set is decompressed, a plurality of image sections are extracted, and each image section is sliced so that a plurality of spliced images can be obtained; difference filtering and threshold processing are conducted on each spliced image; two or more difference images are selected from all the difference images in each spliced image, a plurality of joint probability distribution matrixes corresponding to the spliced images are obtained through the description of a pixel neighborhood relation, and elements of each matrix are combined to be a one-dimensional vector which serves as a feature vector; the feature vectors are marked according to classes and input into a classifier, so that a classifier model is obtained; according to the steps, feature vectors of a video to be analyzed are extracted and input into the classifier model to be classified, so that a steganalysis result is obtained. According to the general video steganalysis method based on video pixel space-time relevance, the time domain relevance of the video is fully used, so that steganalysis effect is improved and the method can be used in analysis systems of various types of steganograph algorithms.
Owner:INST OF AUTOMATION CHINESE ACAD OF SCI
Ciphertext domain multi-bit reversible information hiding method
InactiveCN105634732AImplement encryptionEfficient extractionKey distribution for secure communicationImage data processing detailsLearning with errorsCiphertext
The invention provides a ciphertext domain multi-bit reversible information hiding method capable of effectively ensuring large volume embedment of data, reversible recovery of carrier data and undetectability of embedded information on the premise of meeting separable steganography. The method comprises the following steps: 1, parameter setting and data pre-processing; 2, encryption and information embedment; and 3, decryption and information extraction. By recoding ciphertext data based on an R-LWE (Ring Learning with Errors) public key cipher algorithm, a user can embed multi-ary information based on ciphertext domain operation to realize data encryption. After the information is embedded, the user can effectively extract the hidden information with a steganographic key and recover the data before encryption without errors by using a decryption key. Compared with the existing ciphertext domain steganography, the method has the advantages that error-free decryption of the embedded ciphertext and effective extraction of the hidden information can be realized, and the decryption and extraction processes are separable.
Owner:ENG UNIV OF THE CHINESE PEOPLES ARMED POLICE FORCE
Information hiding method based on SVD
ActiveCN106791872AAdd preprocessing mechanismHide hiddenDigital video signal modificationCiphertextSteganographic algorithm
The invention provides an information hiding method based on SVD, and the method comprises the steps: preprocessing, encrypting, and decrypting. The method specifically comprises the following steps: firstly carrying out the preprocessing of original secret information, carrying out the linear transformation of a secret information matrix, and obtaining compressed data, thereby achieving a purpose of reducing the embedding amount of the secret information; secondly achieving the further encryption of the data through an Arnold scrambling algorithm; finally enabling a JPEG image as a carrier, and enabling the encrypted information to be embedded into the carrier image. According to the invention, the DCT of the carrier image is carried out firstly, and a DCT coefficient matrix is obtained. Moreover, the SVD of the DCT coefficient matrix is carried out, and an optimal embedding position of the information is obtained, and then a ciphertext is embedded into the DCT matrix through an F5 steganographic algorithm. The method improves the information hiding amount through a compression factor, improves the hiding performance of an information hiding algorithm through employing the SVD technology, and achieves the safer data hiding.
Owner:NANJING UNIV OF POSTS & TELECOMM
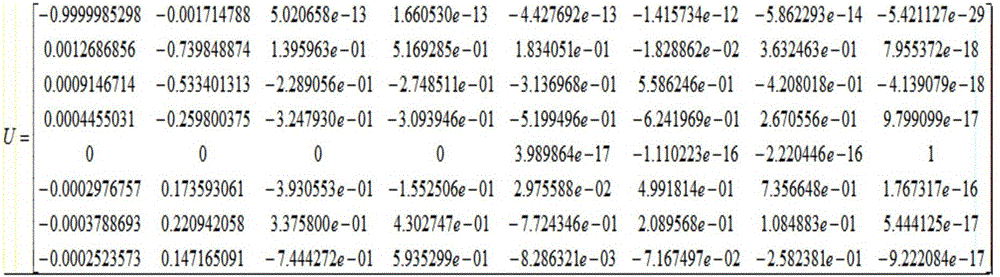
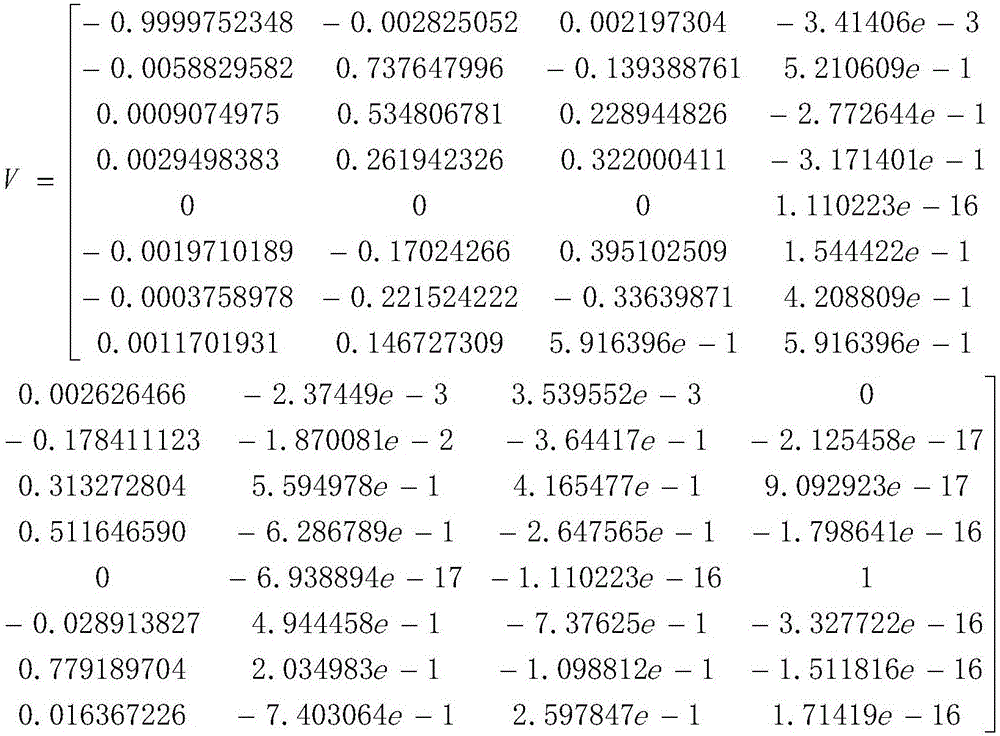
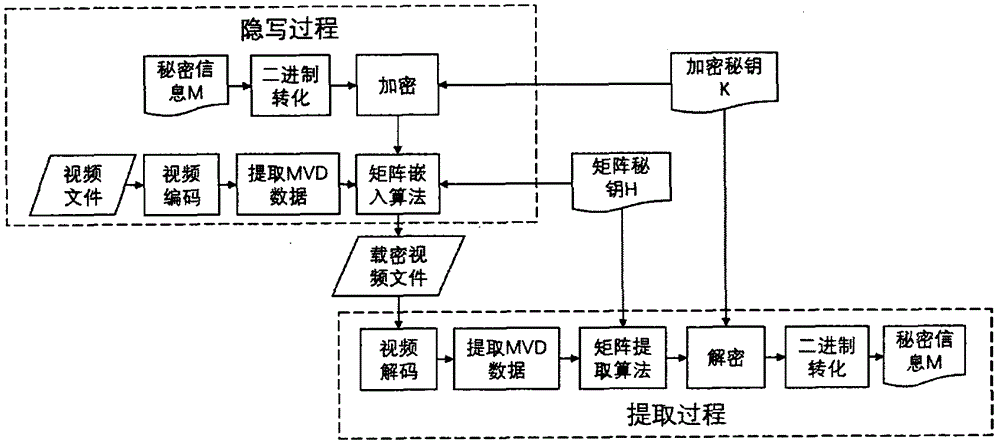
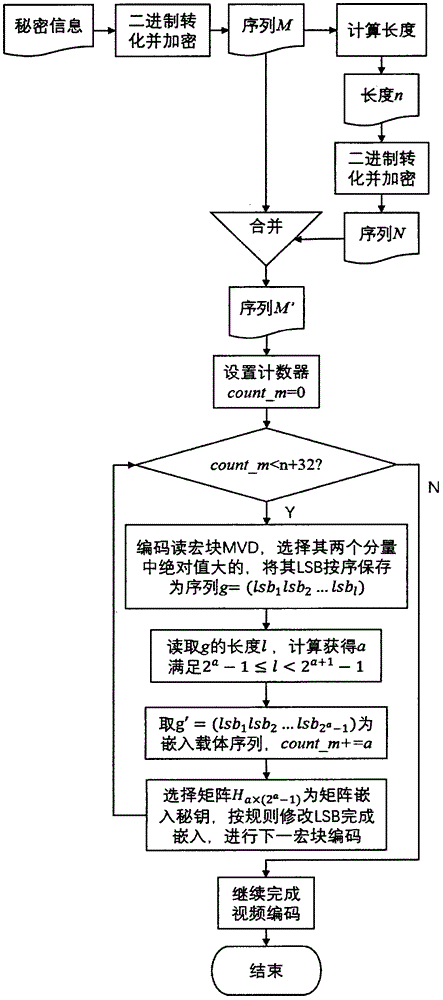
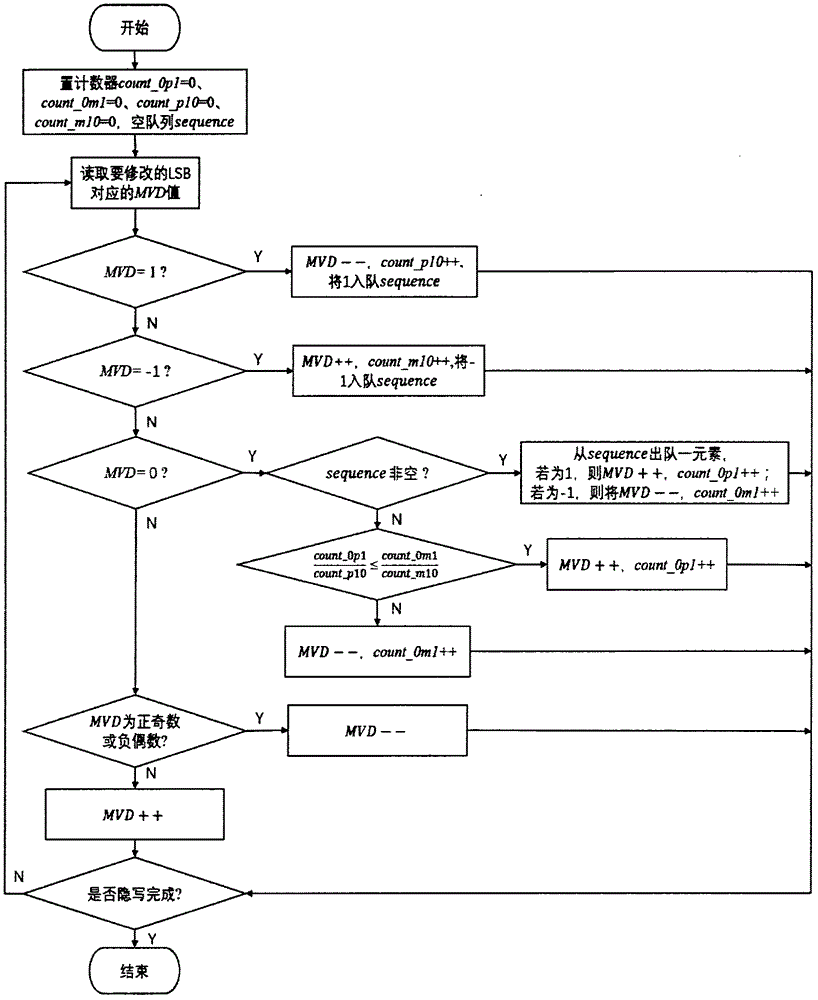
Video steganography algorithm based on motion vector difference
InactiveCN106713917ASpatio-temporal correlationSolve the problem of destroying the space-time correlation of motion vectorsDigital video signal modificationMotion vectorSteganographic algorithm
The invention provides a video steganography algorithm based on a motion vector difference MVD based on an H.264 / AVC video coding and decoding framework. Through proving connection between the motion vector difference and motion vector space-time correlation, a statistics characteristic of the motion vector difference is used to design an embedding rule. Through combining a matrix coding algorithm, a series of matrix embedding secret keys with different sizes are designed and secret information is adaptively embedded into a video compression process so that the motion vector difference can well maintain an original histogram characteristic before and after steganography. The algorithm possesses good visual invisibility and can well resist steganography analysis based on motion vector space-time correlation.
Owner:NANJING UNIV OF AERONAUTICS & ASTRONAUTICS
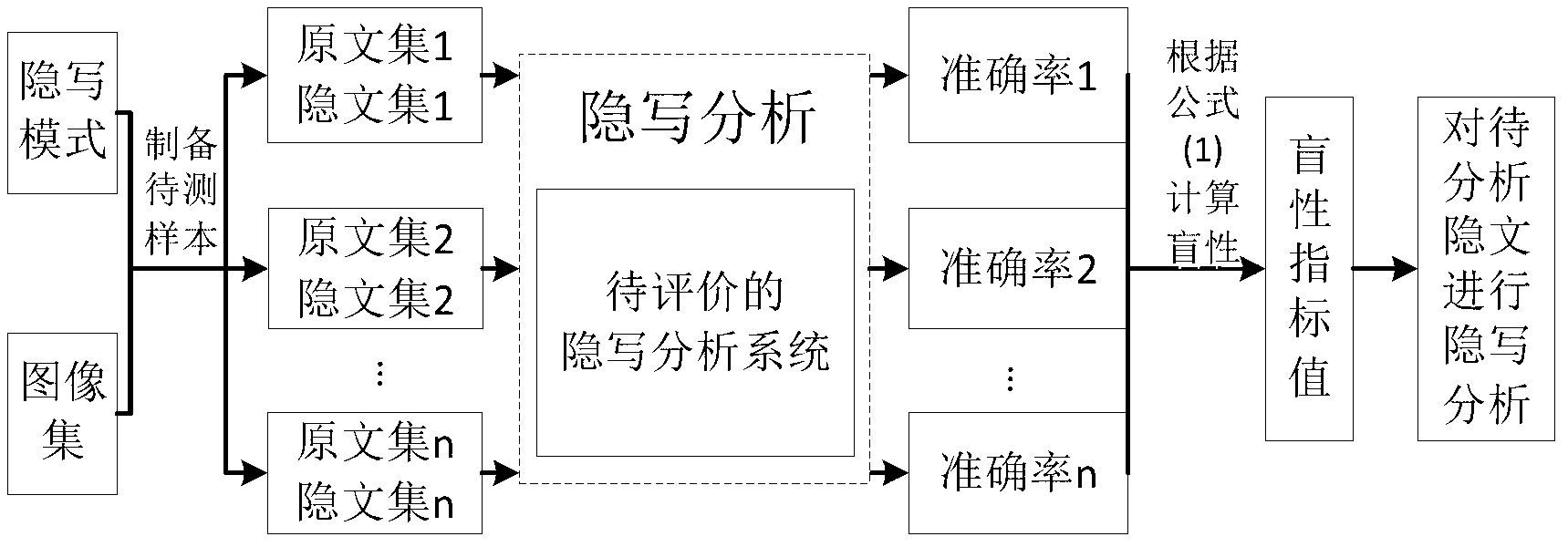
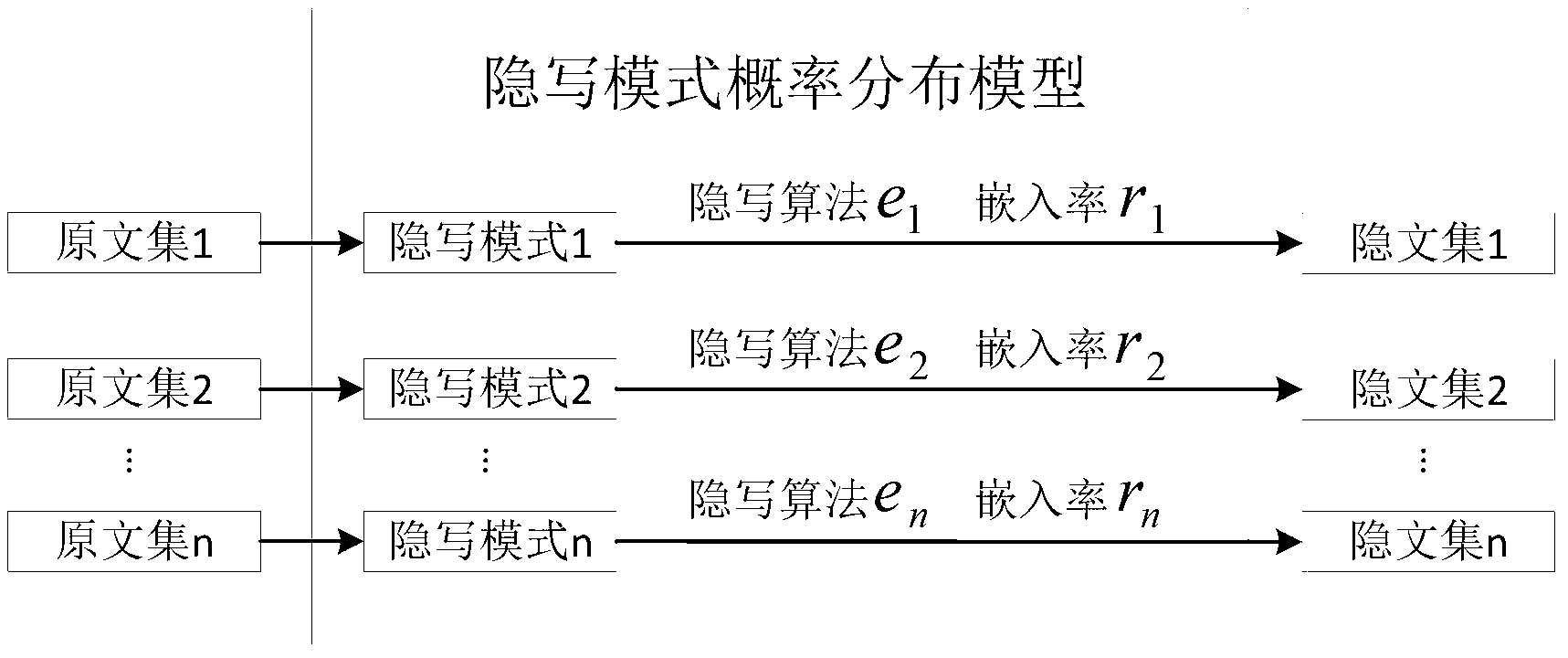
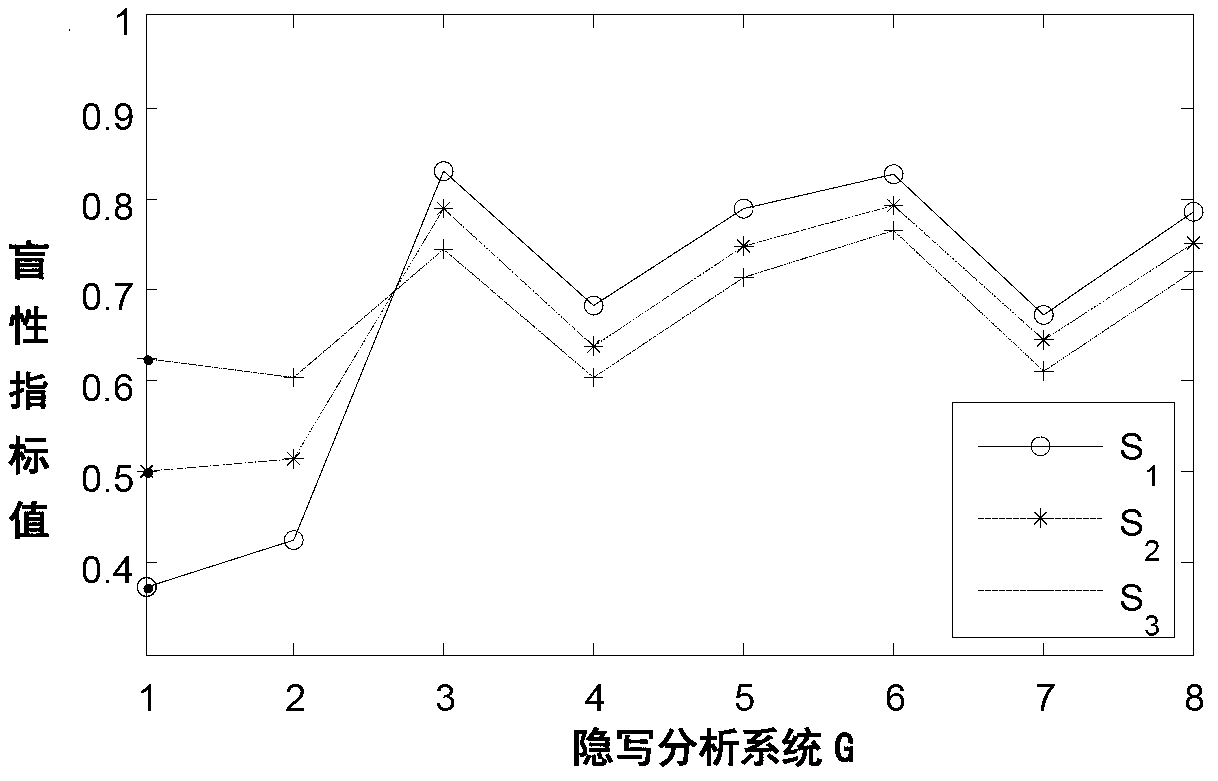
Steganalysis method based on blindness of steganalysis systems
InactiveCN103258123AQuick analysisCharacter and pattern recognitionSpecial data processing applicationsAlgorithmSteganographic algorithm
The invention discloses a steganalysis method based on blindness of steganalysis systems. The method includes the steps of (1) constructing a probability distribution model of a steganalysis mode, wherein the probability distribution model comprises various steganalysis modes and occurrence probabilities of the steganalysis modes, (2) choosing a group of original text sample sets and carrying out stegannaysis on one original text sample set by means of each steganalysis mode in the probability distribution model to produce a corresponding steganalysis sample set, (3) regarding the steganalysis systems to be tested, calculating the analysis accuracy of the steganalysis system for each corresponding steganalysis mode according to each steganalysis sample set and each corresponding original text sample set and carrying out weighted average on the analysis accuracy of each steganalysis mode according to the occurrence probabilities of the steganalysis modes to obtain the blindness value of the steganalysis system, and (4) carrying the steganalysis on a hidden text to be analyzed according to the steganalysis system with the highest blindness value. The steganalysis method can objectively evaluate practical analysis capacity of the steganalysis systems and improve analysis for unknown steganalysis arithmetic hidden texts.
Owner:INST OF INFORMATION ENG CHINESE ACAD OF SCI
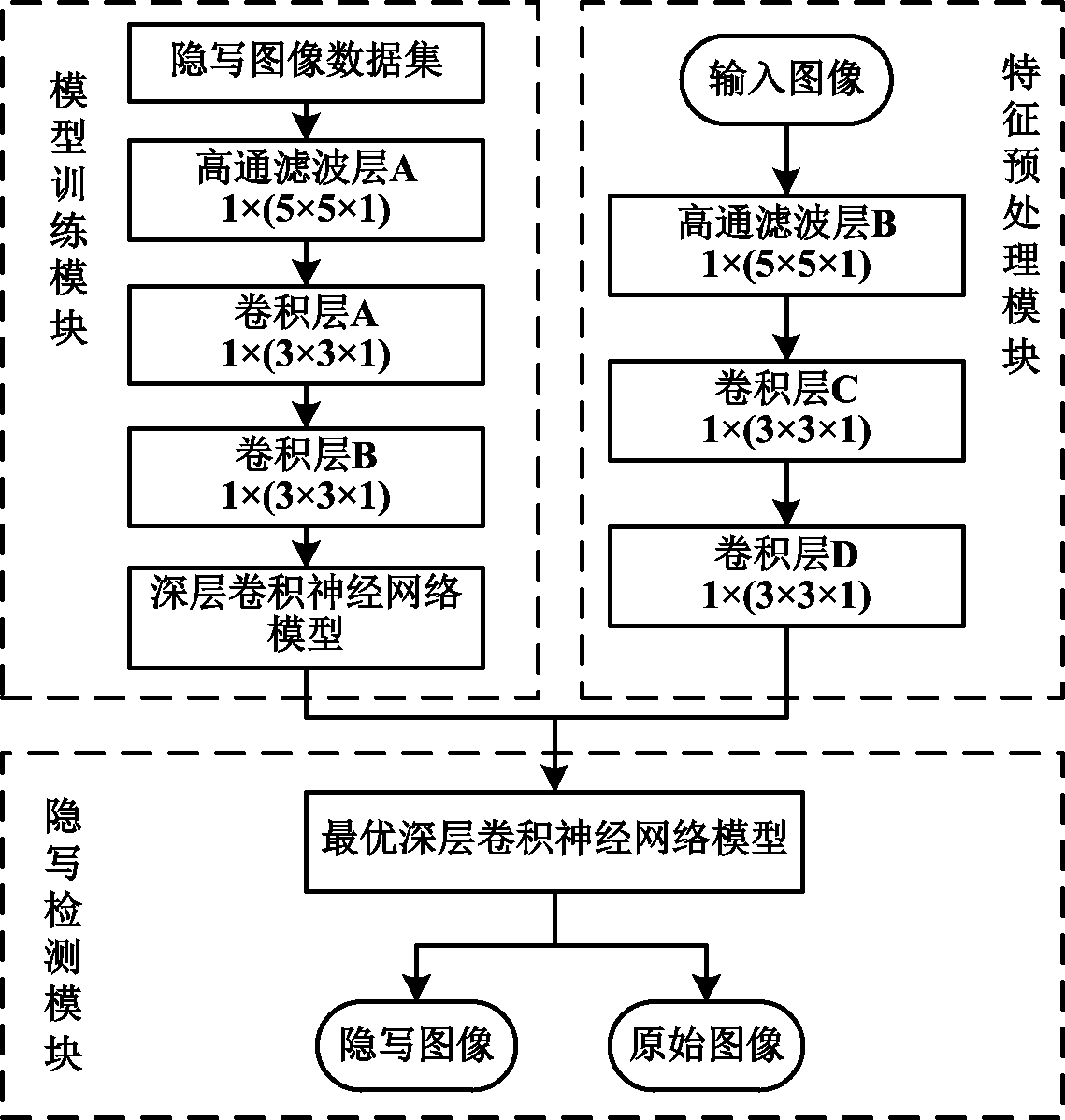
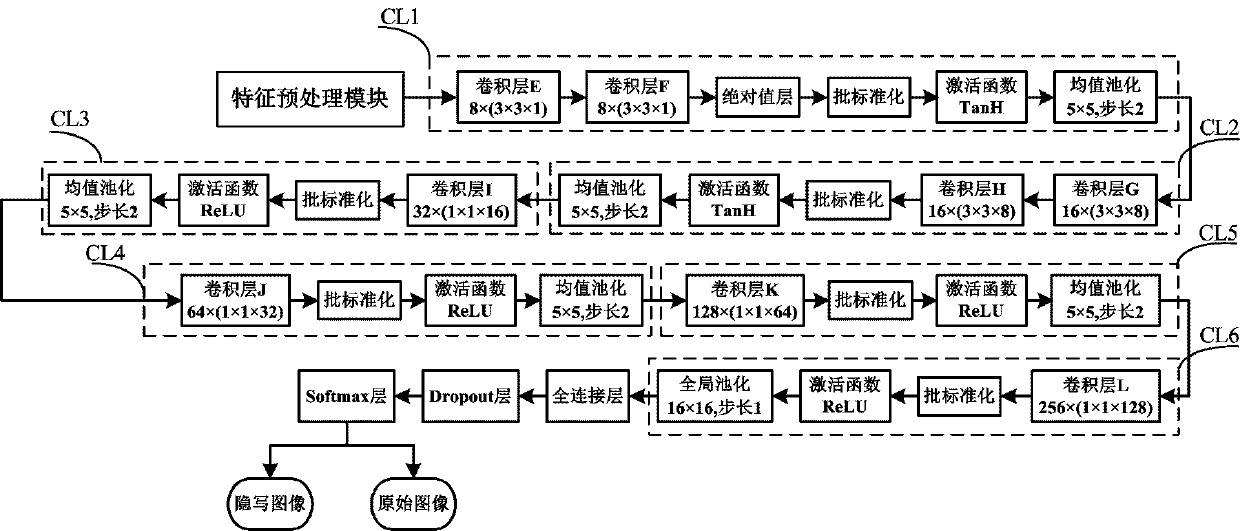
Adaptive image steganalysis method and system based on deep convolutional neural network
InactiveCN111507884AAvoid fit problemsImprove generalization abilityImage data processing detailsNeural architecturesData setFeature extraction
The invention relates to the technical field of image steganalysis, and discloses an adaptive image steganalysis method and system based on a deep convolutional neural network. The system comprises amodel training module, a feature preprocessing module and a steganalysis detection module. The method comprises the following steps: carrying out information embedding on a gray image through employing an adaptive image steganalysis algorithm, and manufacturing a steganalysis image data set; processing the gray image of the data set through a high-pass filtering layer and two cascaded 3 * 3 convolutional layers to obtain a residual image, and training the residual image on a deep convolutional neural network model; then continuously adjusting network parameters and structures, continuing training, and finally screening an optimal deep convolutional neural network model; selecting a gray image to be detected, and then performing high-frequency feature extraction on the image through the high-pass filtering layer and the two cascaded 3 * 3 convolutional layers; and inputting the extracted features into the optimal deep convolutional neural network model, carrying out steganography imagedetection, and outputting a detection result. The advantages of the deep convolutional neural network are utilized, so that the efficiency and accuracy of adaptive steganography image detection can beeffectively improved.
Owner:HENGYANG NORMAL UNIV
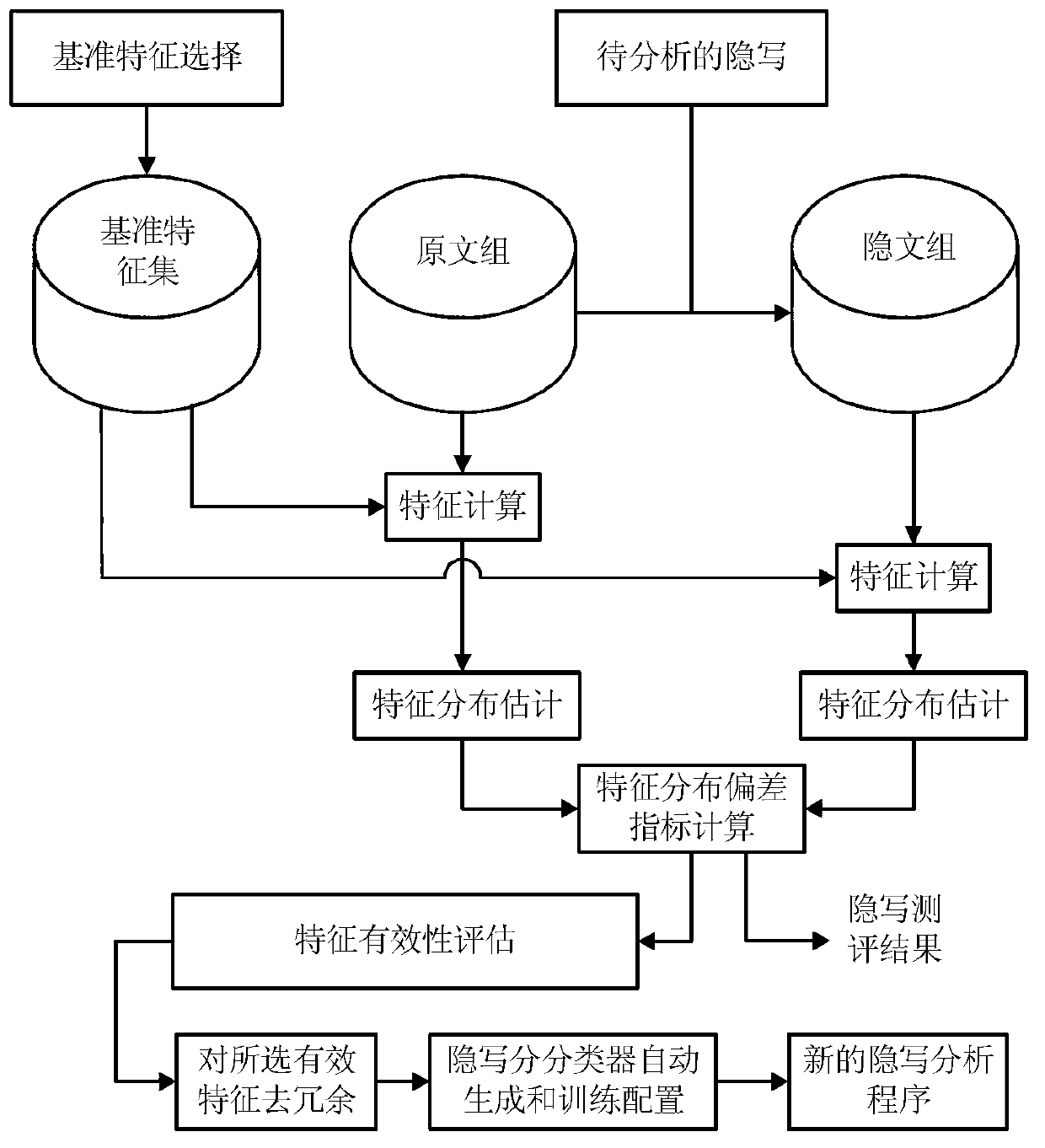
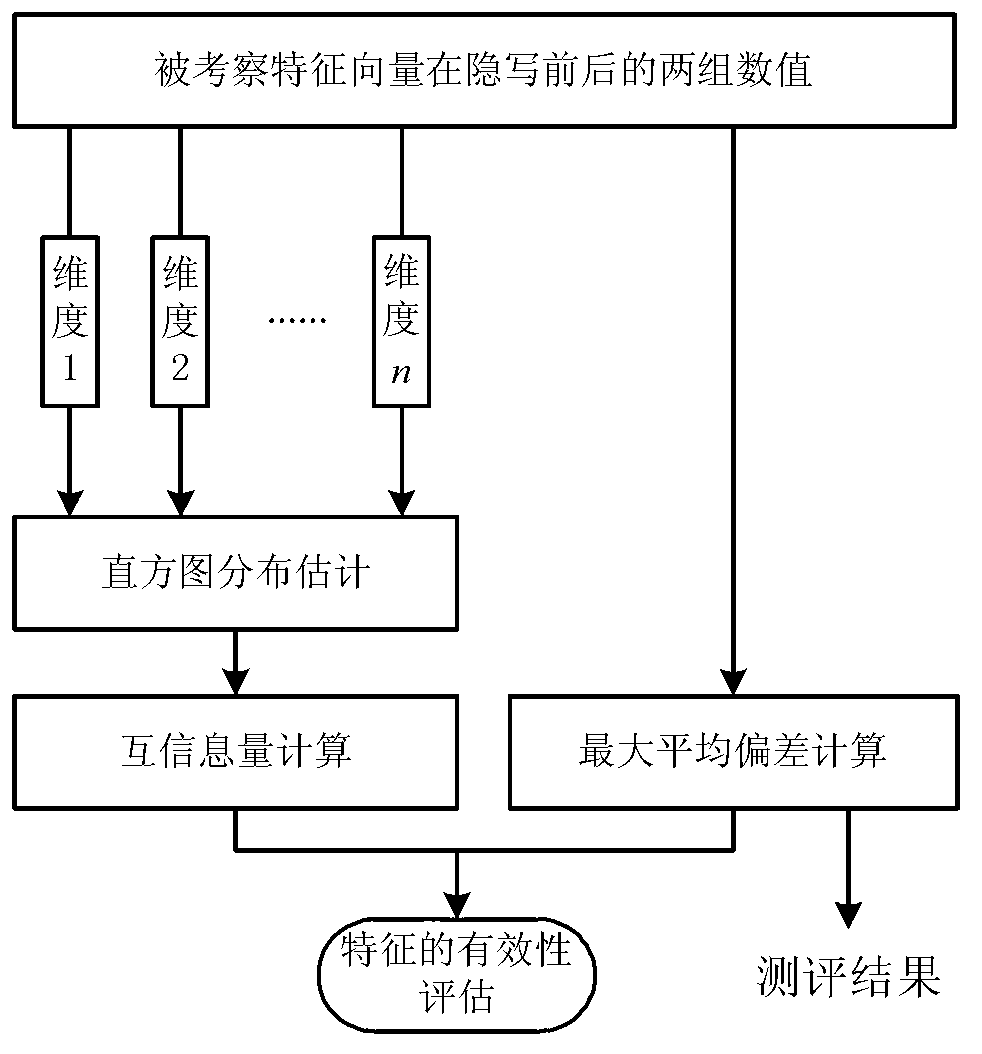
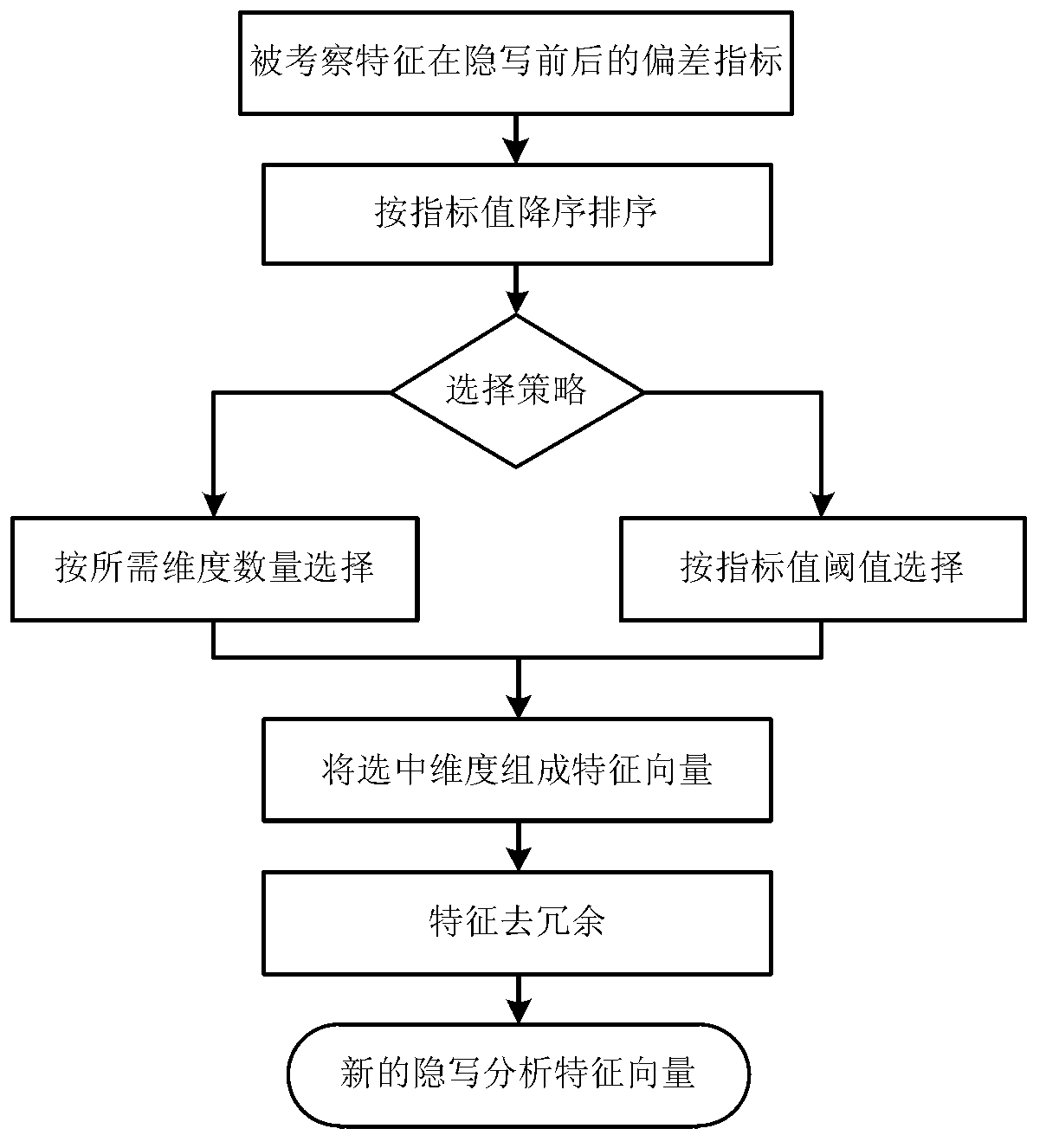
Steganography evaluation based steganalysis method
InactiveCN102930495AImprove efficiencyImproving the efficiency of steganalysis implementationImage data processing detailsFeature vectorEvaluation result
The invention discloses a steganography evaluation based steganalysis method. The steganography evaluation based steganalysis method comprises the steps of: (1) establishing a reference feature set containing a plurality of steganographic features; (2) performing steganography on a group of original text {Xi} by adopting a to-be-analyzed steganographic algorithm to generate a corresponding group of hidden text {Yi}; (3) selecting partial features in the reference feature set as inspecting features, calculating a inspecting feature vector of each sample in both the original text set and the hidden text set to respectively obtain feature vector sets {xi} and {yi} of both the original text set and the hidden text set; (4) evaluating effectiveness of each component of each inspecting feature vector serving as each hidden writing feature based on {xi} and {yi}; (5) repeating steps (3) and (4) for multiple times to obtain an effectiveness evaluation result of a group of feature vector components; and (6) selecting a plurality of components from an effectiveness evaluation result to build a new feature vector, performing redundancy elimination to obtain feature vectors of the steganographic algorithm for the steganalysis on the to-be-analyzed steganographic algorithm, and detecting if the to-be-analyzed steganographic algorithm contains hidden information. The steganography evaluation based steganalysis method, disclosed by the invention, has the advantage of greatly improving realization efficiency of steganalysis.
Owner:INST OF INFORMATION ENG CHINESE ACAD OF SCI
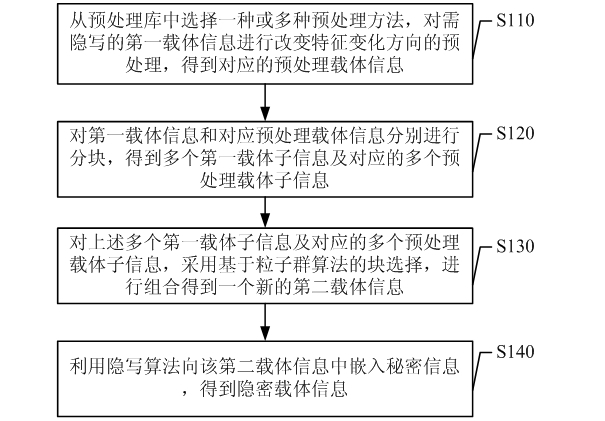
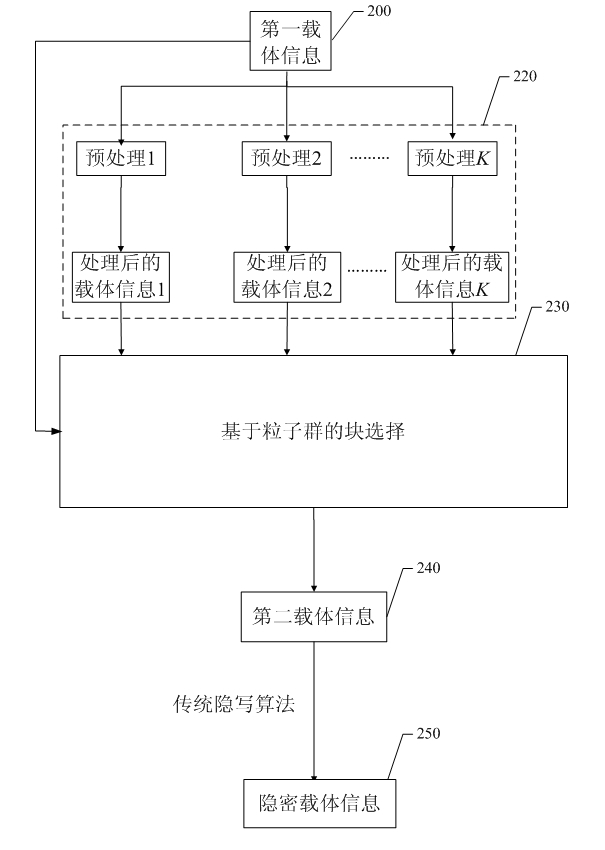
Information steganography method and device
InactiveCN102075283ARandomImprove securitySecret communicationImage data processing detailsEngineeringSteganographic algorithm
The invention relates to the field of information hiding in information security, and discloses an information steganography method and device. The method comprises the following steps: firstly pre-processing a first carrier message in need of steganography by changing feature change direction for a plurality of times to obtain a plurality of corresponding preprocessed carrier message; respectively partitioning the first carrier message and the plurality of corresponding preprocessed carrier message to obtain a plurality of first carrier sub-messages and a plurality of corresponding preprocessed carrier sub-messages; combining the plurality of first carrier sub-messages and the plurality of corresponding preprocessed carrier sub-message to obtain a new second carrier message by utilizing a block selection mode based on particle swarm optimization (PSO); and finally embedding a secret message into the new second carrier message by utilizing a steganographic algorithm. By utilizing the method and the device, a plurality of pre-processing methods are selected for pre-processing the first carrier sub-message by changing the feature change direction so that feature change has randomness, thus steganalysis can not be carried out according to laws, and blind steganalysis can be resisted.
Owner:SHENZHEN UNIV
Singular value modification video steganographic algorithm based on combination with improved matrix coding
ActiveCN105791854AImprove impactSmall modification rateDigital video signal modificationSingular value decompositionPattern recognition
The invention provides a singular value modification video steganographic algorithm based on combination with improved matrix coding. A maximum singular value of all blocks after block division of each frame is used as a steganographic embedding carrier and modification is carried out by combining matrix coding to achieve an objective of secret information embedding. 8*8 blocking division is carried out on a video frame of a compressed video sequence; singular value decomposition is carried out on each divided block; a maximum singular value after singular value decomposition of all divided blocks is extracted; and information hiding is carried out on the secret information after pretreatment. Lowest three significance bits after singular value binary system processing are used as to-be-modified values; modification operation with no carrying bit is carried out on a carrier bit ay; a code stream is reformed to carry out transmission to a receiving terminal; and the receiving terminal receives secret information again to obtain original secrete information, thereby completing video steganography and extraction. The provided algorithm has the following beneficial effects: the imperceptibility is high and the bit rate increment is low; the algorithm robustness is good; the noise and filter attacks can be resisted; and the carrier modification rate is low on the premise that the embedding capacity is identical.
Owner:ENG UNIV OF THE CHINESE PEOPLES ARMED POLICE FORCE
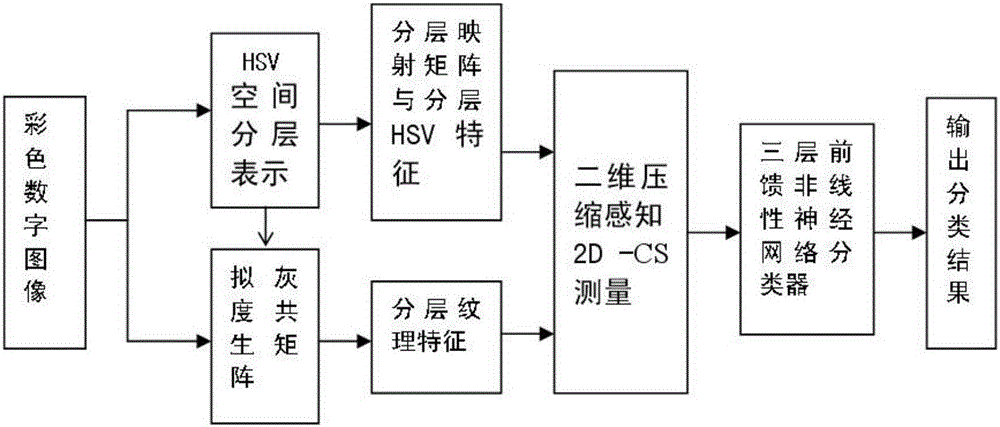
Low embedding rate compressive sensing universal steganalysis method for color image
InactiveCN106504177ASolve the problem of blind detection in general steganalysisSolve the problem of steganalysis detection accuracyImage data processing detailsPattern recognitionColor image
The invention aims to provide a low embedding rate compressive sensing universal steganalysis method for a color image. The method comprises the following steps of (1) establishing two-dimensional compressive sensing (2d-CS) measurement model; (2) establishing a two-dimensional image HSV layered expression model; and (3) carrying out quasi-gray-level co-occurrence matrix and layered texture feature analysis. By the data statistic technology in the compressive sensing (CS) domain, the problem of the universal steganalysis blind detection of the digital image steganographic algorithm is solved. By researching current CS steganalysis based on LSB and DCT domains, the low embedding rate steganalysis detection precision problem of JPEG and BMP image formats in the traditional F5, Outguess, MB1, MB2, Jsteg and other different steganographic algorithms is solved.
Owner:GUANGDONG POLYTECHNIC NORMAL UNIV
Universal digital image invisible information detecting method
InactiveCN1737819ARich varietySimple way of judgingCharacter and pattern recognitionSteganographic algorithmDigital image
This invention discloses one general digital image invisible information testing method, wherein, the original images without invisible information is different to the one with images through quantities attack of varying degrees of statistics variable. The method uses the wavelet analysis system statistic variable as training sample and uses one kind of vector as divider to identify the multiple invisible images.
Owner:SHANGHAI NORMAL UNIVERSITY
Information hiding detection method under unknown steganographic algorithm situation
ActiveCN107273916ATroubleshoot unbalanced datasetsCharacter and pattern recognitionImage data processing detailsDiscriminantData set
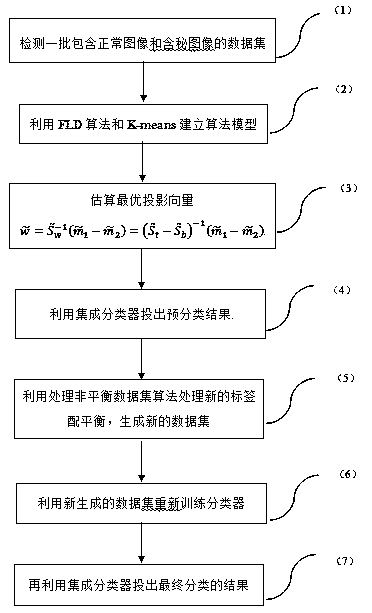
The invention relates to an information hiding detection method under an unknown steganographic algorithm situation. The method comprises the following specific operation steps that: 1) judging which images in one bath of images contain secret information; 2) utilizing an FLD (Fisher Linear Discriminant) algorithm and a K-means clustering algorithm to establish an algorithm model; 3) estimating an optimal projection vector, and detecting the batch of images; 4) utilizing an ensemble classifier to output a pre-classification result; 5) utilizing an unbalanced algorithm to carry out balance coordination; 6) utilizing a new dataset to train the ensemble classifier again; and 7) reusing the ensemble classifier to output a final classification result. By use of the method, the practical problem of situations of no labels and unbalanced datasets can be effectively solved.
Owner:SHANGHAI UNIV
Secret document steganography and extraction method suitable for wireless communication environment
InactiveCN102938888ABreak through the shackles of thoughtAvoid detectionSecurity arrangementCommunications systemSteganographic algorithm
The invention provides a secret document steganography and extraction method suitable for a wireless communication environment. A steganography method comprises the steps of secretly writing a secret document into a real-time speech data which are streams with a plurality of bytes, and rewriting the last bit of pseudo-random S bytes in every R-byte speech data into a binary coding of the secret document, wherein every R-byte speech data can be embedded into S-bit data, the speech data totally have S / 8 bytes, and S / 8 bytes of secrete information is transmitted to the other person involved when every R-byte speech data are transmitted through a communication system. An extraction method comprises the step of extracting the binary coding embedded into the secret document by receiving the sent speech data and using an improved least significant bite (LSB) algorithm to obtain the secrete information sent by a sender. Due to the fact that the confidential information is hidden by means of a steganographic algorithm, even through lawless persons intercept communication information during communication, the lawless persons cannot obtain the secrete document secretly written in the communication information.
Owner:SOUTH CHINA UNIV OF TECH
A method for embedding secret information in an image based on texture synthesis
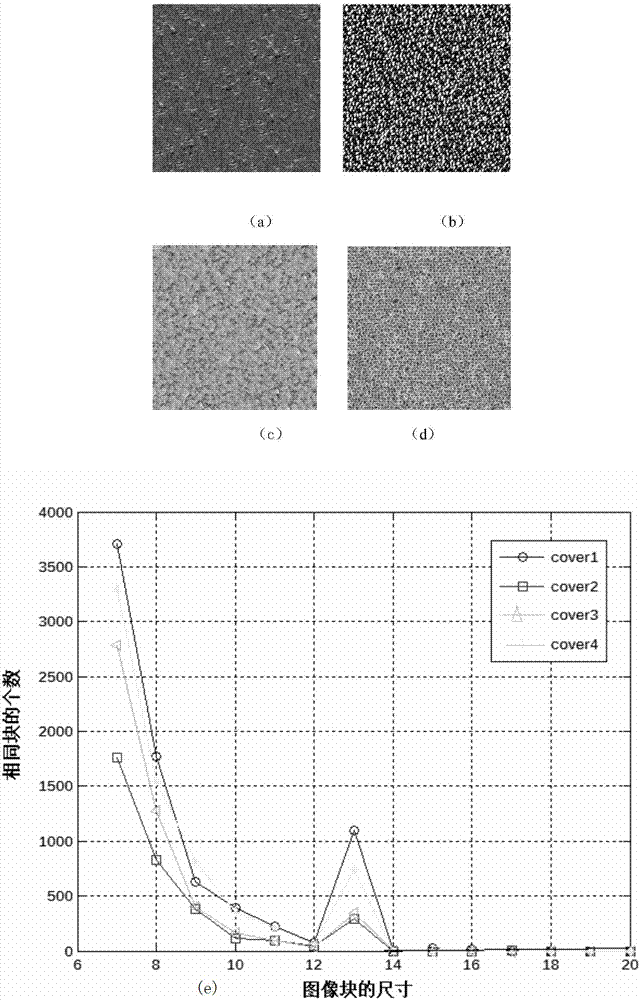
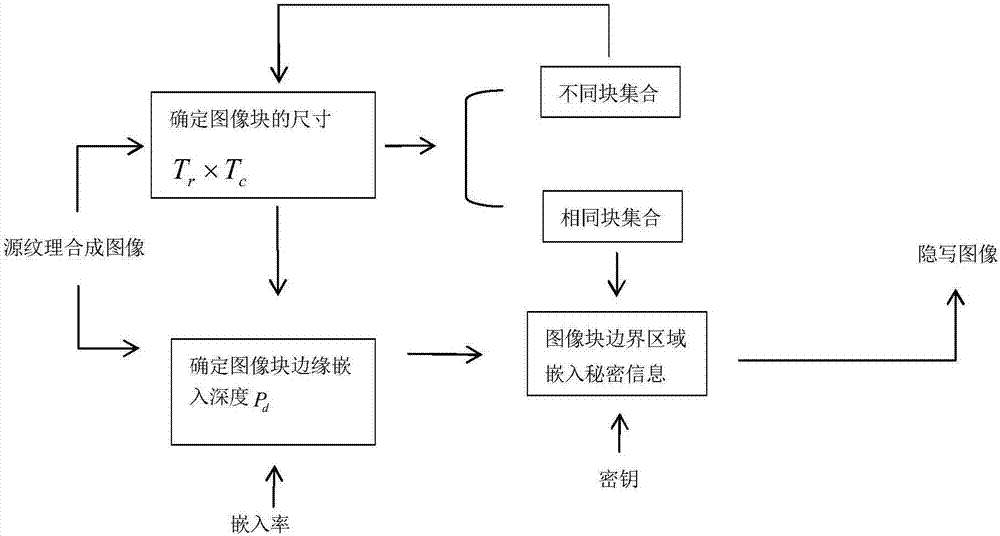
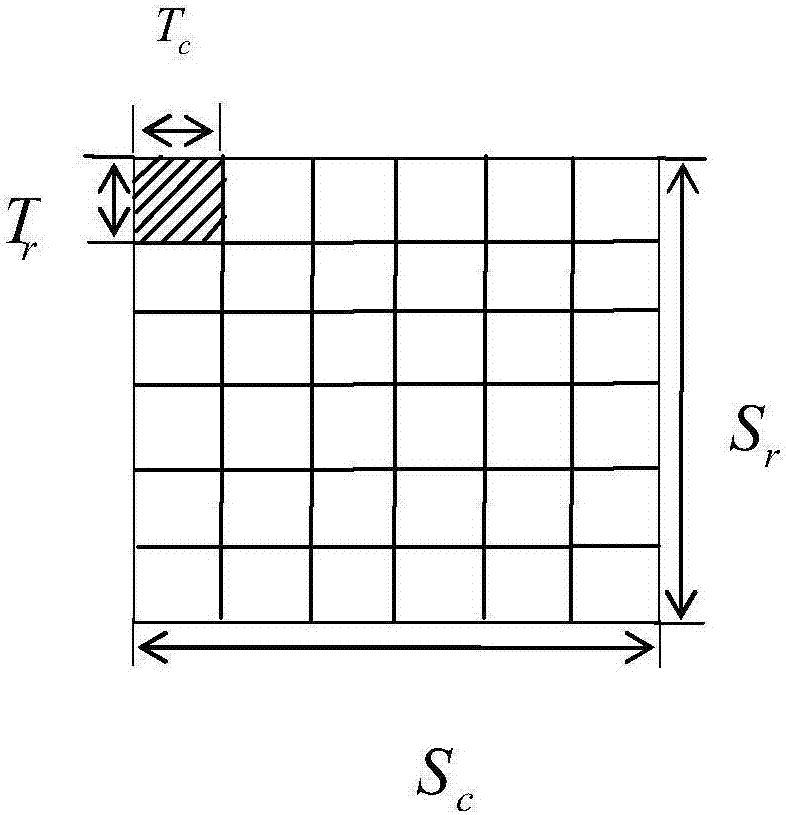
ActiveCN107578362AStrong ability to hide modification tracesImprove robustnessImage data processing detailsPattern recognitionLsb steganography
The invention discloses a method for embedding secret information in an image based on texture synthesis. According to the method, by setting different sizes, an image is divided to generate multipleimage blocks with the same size, and the number of the same blocks corresponding to the different sizes is recorded; when the secret information is embedded in the synthesized texture image, the sizewhen the number of same blocks is the largest is selected and determined to be the size of the sub-block of the synthesized texture image; a steganographic algorithm embeds the secret information in the image block boundary region using the LSB steganography, and the same blocks are embedded with the same information; and then the size of the image block is reduced stage by stage to re-divide theareas of the remaining different blocks, and then the secret information is embedded again according to the method that the same blocks are embedded with the same information until the embedding of the secret information is completed. The method proposed by the invention can resist the LSB steganalysis, so that the method of the invention can improve the robustness of the steganographic image; andthe embedding rate of the secret information can be adjusted according to the embedded depth of the texture image block so as to ensure the relatively high embedding rate.
Owner:SHANGHAI UNIV
JPEG asymmetric digital image steganography method
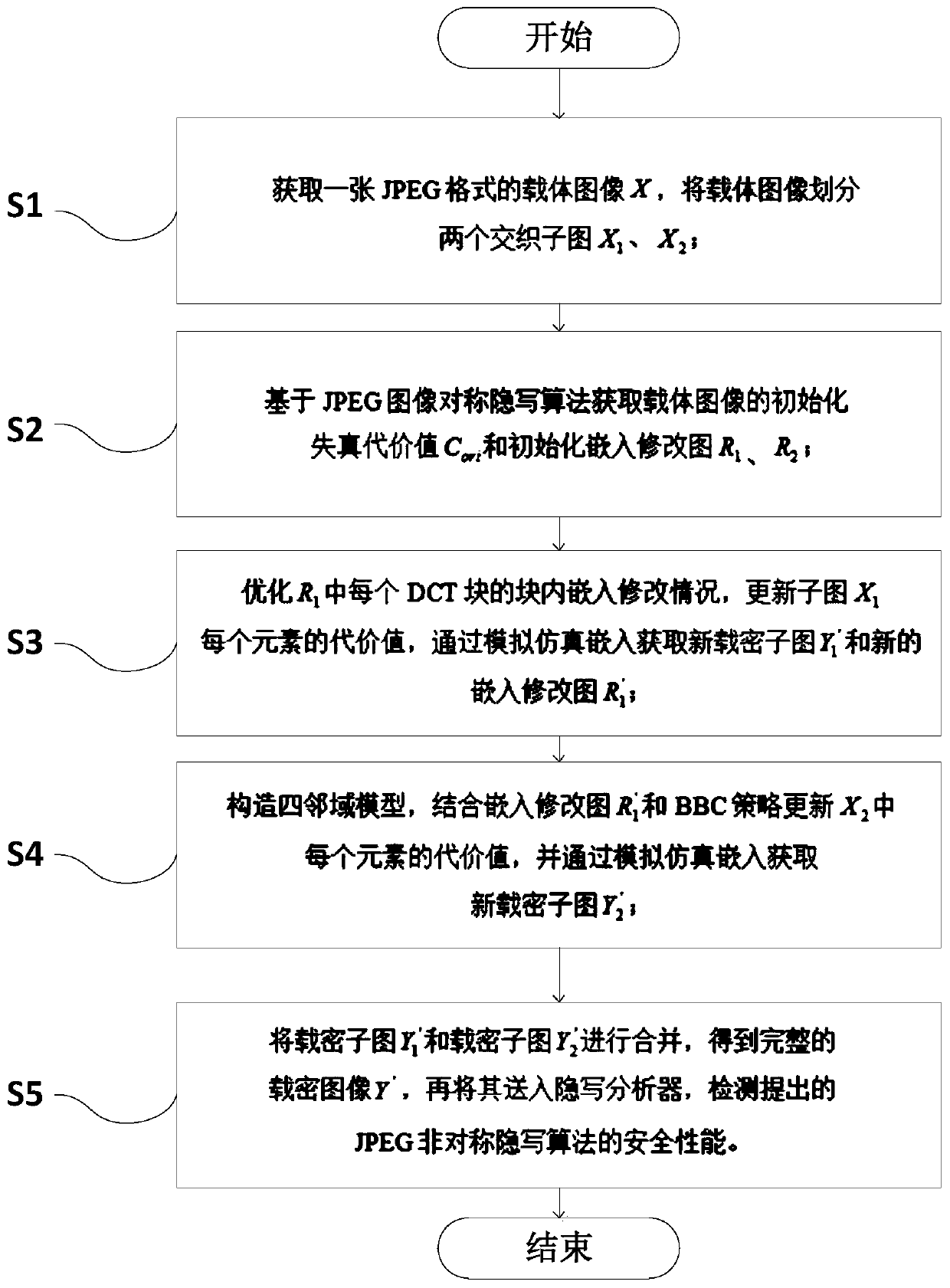
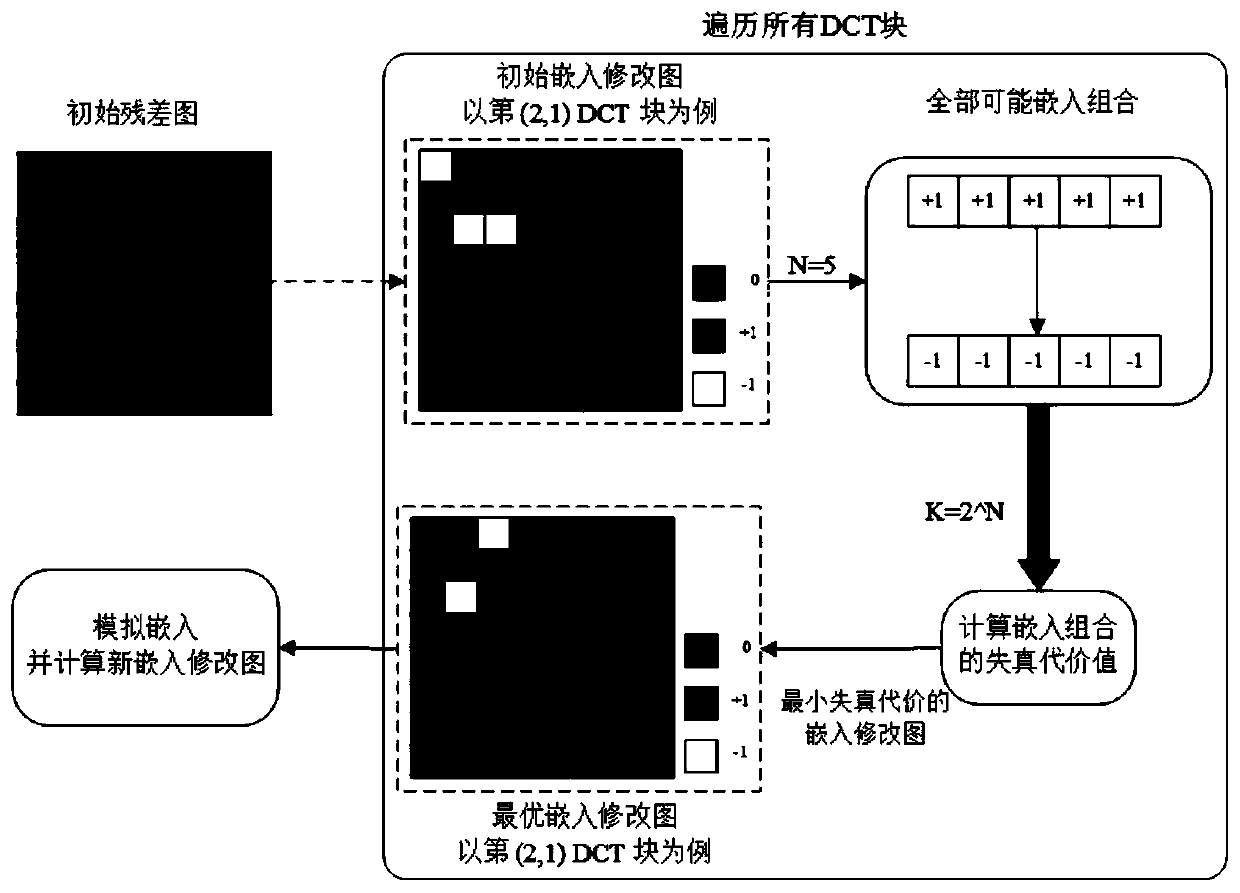
ActiveCN110009547ALow complexity involvedImprove securityImage data processing detailsJPEGSteganographic algorithm
The invention relates to a JPEG asymmetric digital image steganography method, which comprises the following steps of: obtaining a carrier image, and dividing the carrier image into two interleaved sub-images X1X2; calculating an initialization distortion cost value of the carrier image and initializing embedded modification graphs R1 and R2; optimizing the in-block embedding modification condition of each DCT block in the R1, updating the cost value of each element of the sub-image X1, and obtaining a new secret-carrying sub-image Y'1 and a new embedded modification graph R'1; constructing afour-neighborhood model, updating the cost value of each element in the X2 by combining an embedded modification image R'1 and a BBC strategy, and obtaining a new secret-carrying sub-image Y'2; and merging the secret-carrying sub-image Y'1 and the secret-carrying sub-image Y'2 to obtain a complete secret-carrying image Y', and sending the complete secret-carrying image Y' into a steganography analyzer to detect the safety performance of the JPEG asymmetric steganography algorithm. According to the JPEG asymmetric digital image steganography method provided by the invention, a new cost value updating method is constructed, the safety performance of the algorithm is effectively improved, and through establishment of a four-neighborhood model, simultaneous updating of + 1 / -1 distortion cost values in the horizontal direction and the vertical direction is realized, and the convergence speed is high.
Owner:SUN YAT SEN UNIV
Information steganography algorithm of binary image double disturbance scoring based on STC coding
ActiveCN109963159ALow embedding distortionGood visual quality of imagesDigital video signal modificationAlgorithmImaging quality
The invention provides a binary image double disturbance scoring information steganography algorithm based on STC coding. According to the algorithm, disturbance scoring is conducted on an image through an improved crmiLTP distortion measurement method, the influence of pixel point overturning before steganography and pixel point overturning after steganography on a disturbance mapping graph is considered, secret information is embedded through efficient STC coding on the basis of block hiding, and finally the steganography algorithm small in visual distortion and high in safety is designed. According to the invention, the carrier image property is considered; a double disturbance scoring criterion is set, bidirectional evaluation analysis is carried out on reversible points of an image edge area, and STC coding is combined, so that the algorithm has high image quality, small visual distortion and certain anti-steganography analysis and detection performance, and has a very large effect on secure secret communication.
Owner:SUN YAT SEN UNIV
Intelligent imaging implicit writting analytical system based on three-layer frame
InactiveCN1818925AReduce computational complexityShort response timeCharacter and pattern recognitionSecuring communicationFeature extractionIntegrated database
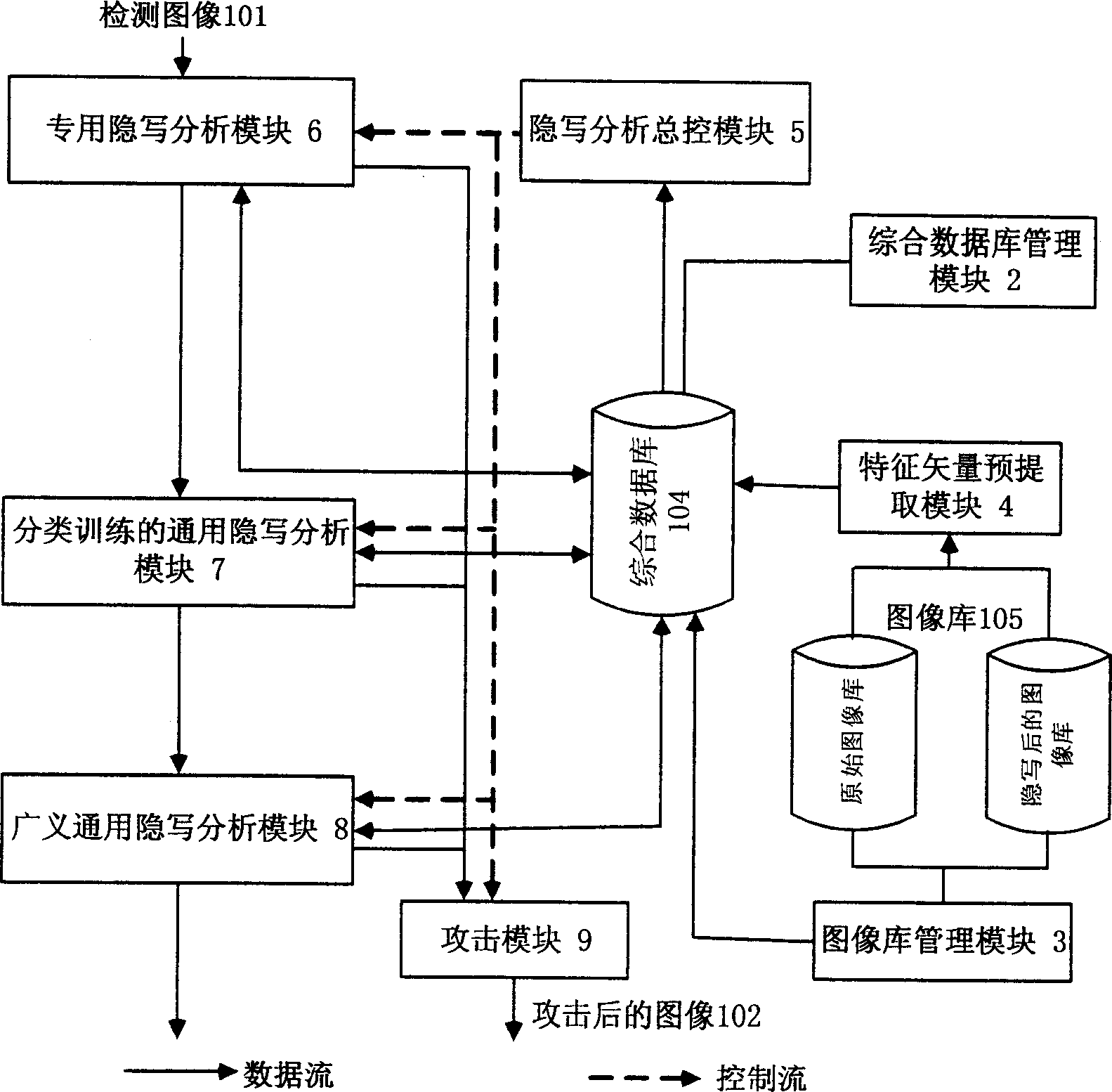
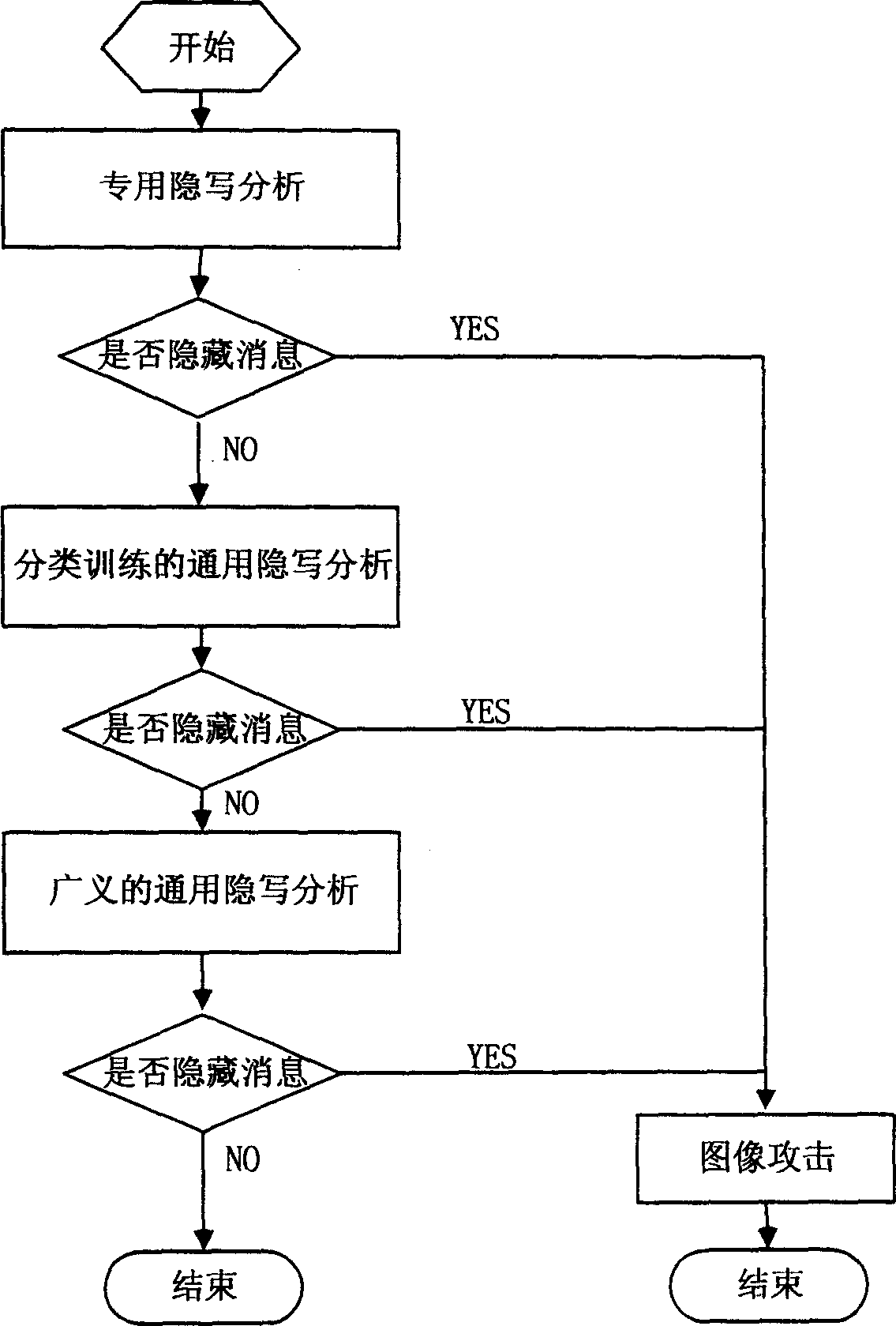
An intelligent image hidden-writing analysis system based on three-layer construction, that includes the integrated database, the image-base, the managing module of the integrated database, the managing module of the image-base, the pre-pickup module of the character vector, the main-control module of the hidden-writing analysis, the attacking module, the special hidden-writing analysis module that contrapose the hidden-writing arithmetic promulgated and has corresponding special hidden-writing analysis arithmetic, the current hidden-writing analysis module that contrapose the hidden-writing arithmetic promulgated without corresponding special hidden-writing analysis arithmetic classified training, and the unpromulgating generalized current hidden-writing analysis module that contrapose the hidden-writing analysis module. The invention adopts three-layer construction, constructing special hidden-writing analysis subsystem that contrapose the belonging type of the hidden-writing arithmetic, that has veracity and applicability; use the special hidden-writing method to setup the module-base and rule-base by the professional system, renewing the hidden-writing analysis rule-base constantly by the operator-computer interaction, that has capacity; combining the character distill of the main element and classified training of the swatch image-base, to improve the efficiency and veracity of calculation.
Owner:HUAZHONG UNIV OF SCI & TECH
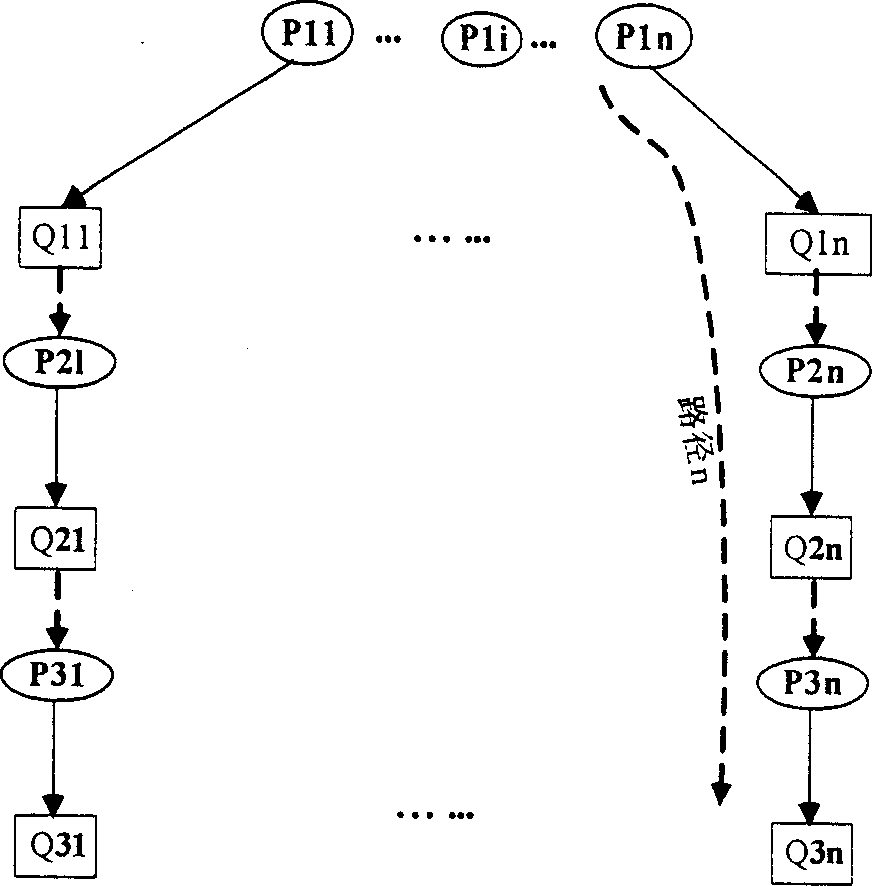
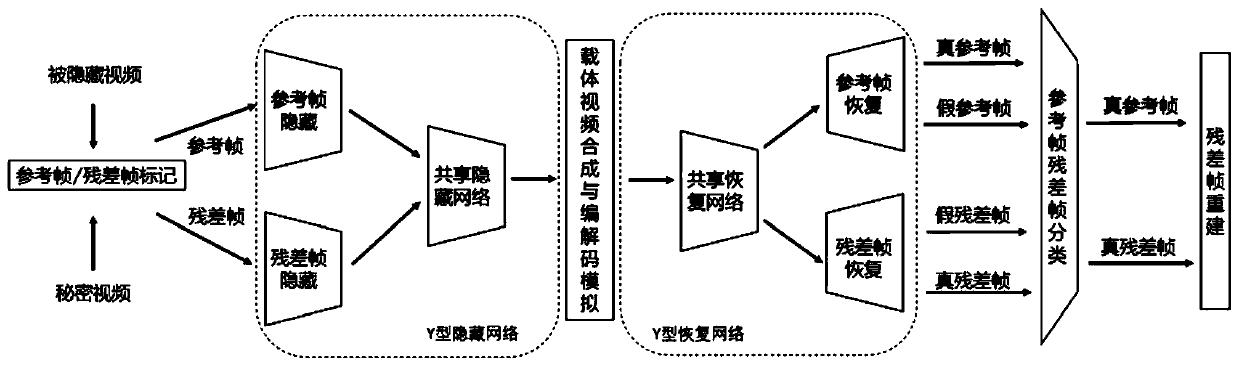
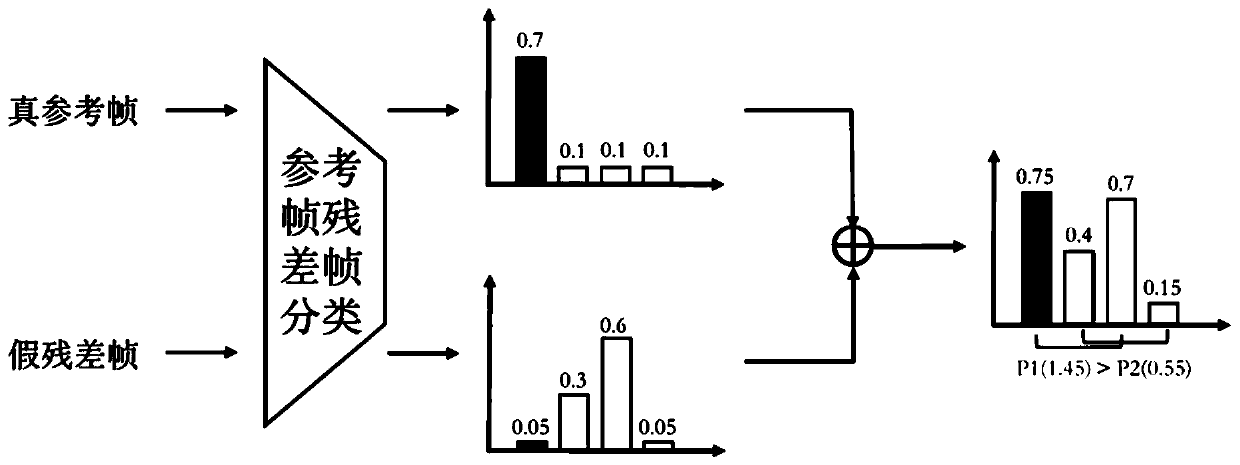
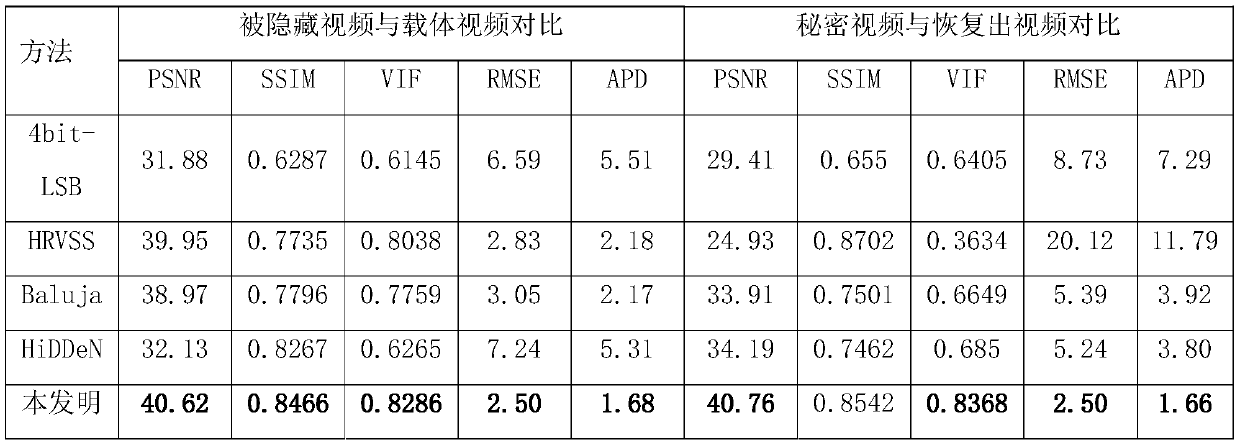
High-embedding-capacity video steganography method and system based on time sequence residual convolution modeling
ActiveCN110312138AGuaranteed imperceptibleEasy to embedDigital video signal modificationNeural architecturesConsecutive frameSteganographic algorithm
The invention relates to a high-embedding-capacity video steganography method and system based on time sequence residual convolution modeling. The method comprises the following steps: marking a reference frame and a residual frame of a secret video, simultaneously processing the reference frame and the residual frame by adopting a Y-shaped convolutional neural network to hide secret information and output a carrier video frame, and synthesizing the carrier video frame into a carrier video; and recovering secret information in the carrier video by adopting a Y-type convolutional neural network. Compared with a convolutional neural network-based image steganography algorithm which is directly applied to video steganography, the video steganography method has the advantages that the sparsityof a residual error between continuous frames is explored, two Y-type convolutional neural network structures are adopted, different endpoint processing is adopted for video frames with different properties, and part of convolutional layer parameters are shared at the same time. One video can be hidden in the other video with the same length, the hidden information amount can reach 24 bpp and ismuch larger than that of a traditional method, and the problem that the traditional method cannot be applied to high-embedding-capacity video steganography is solved to a great extent.
Owner:PEKING UNIV +1
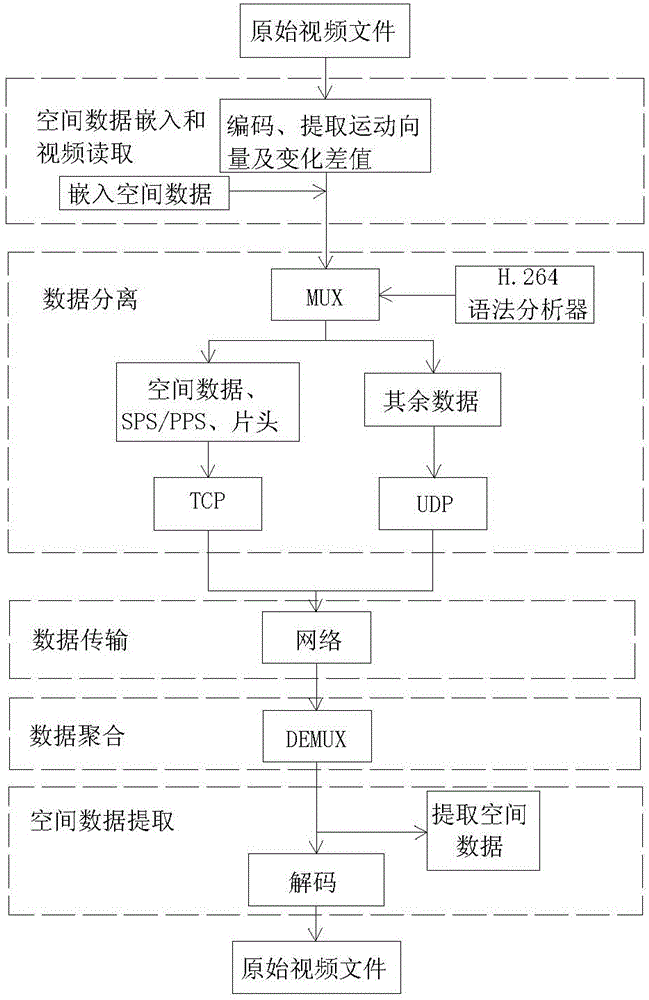
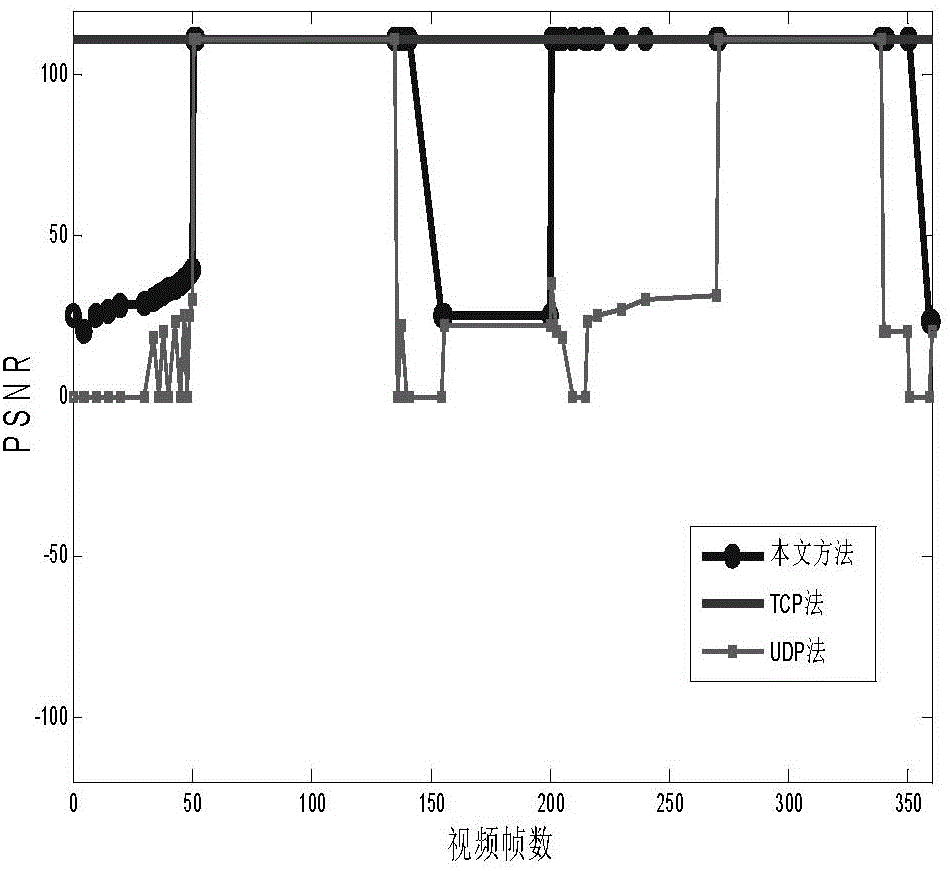
Spatial data double-protocol transmission method based on video steganography
InactiveCN105141961AEasy to useSolve the lossDigital video signal modificationTransmissionMultiplexerSteganographic algorithm
The invention relates to a spatial data double-protocol transmission method based on video steganography, used for effectively ensuring the integrity of spatial data hidden in a video and preventing the spatial data from being lost. The spatial data double-protocol transmission method is as follows: a H.264 video having good network adaptation ability is used as a carrier for hiding the spatial data; the security of the spatial data in a network environment is increased by adopting a H.264 video steganographic algorithm based on DCT (Discrete Cosine Transform) coefficients; a macro block containing the spatial data and a macro block not containing the spatial data are separated by utilizing a grammar analyzer and a multiplexer; transmission is carried out by adopting a TCP (Transmission Control Protocol) and a UDP (User Datagram Protocol) respectively; loss of the spatial data is avoided; the network security transmission efficiency of the spatial data is increased; the double-protocol transmission in the invention is carried out through combination of the TCP and the UDP; the security is high; the capacity is high; the security and the integrity of the spatial data are ensured; loss of the spatial data in transmission is prevented; and thus, the spatial data double-protocol transmission method has high practical value.
Owner:THE PLA INFORMATION ENG UNIV
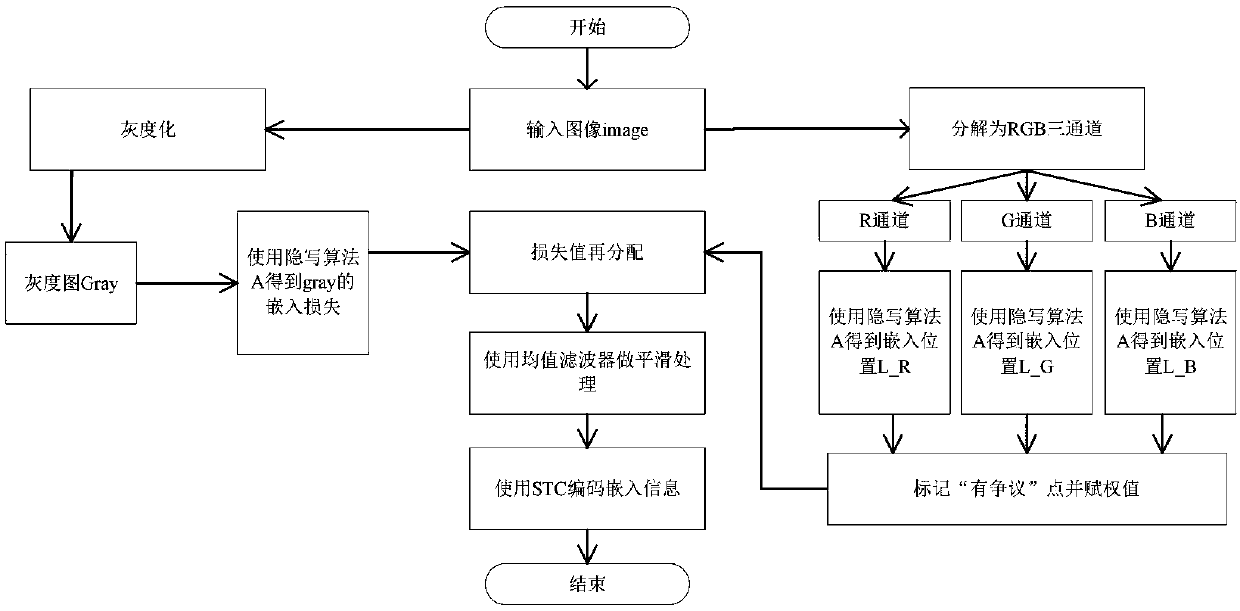
Image steganography algorithm using "controversial" pixels in RGB (Red, Green, Blue) color space
InactiveCN109547664AEmbedding Position OptimizationImprove anti-steganalysis performancePictoral communicationColor imageInformation embedding
The invention discloses an image steganography algorithm using "controversial" pixels in a RGB (Red, Green, Blue) color space, comprising the following steps: respectively extracting three color channels of red, green and blue of a color image in the RGB color space; using the steganography algorithm for respectively perform information embedding on the three color channels of red, green and blueto respectively obtain information embedding positions; formulating a "controversy" rule, giving the pixel points with different degrees of controversy different weights; performing grey scale processing on the color image to obtain a grayscale image, calculating the embedding loss values of each pixel in the grayscale image to obtain an initial grayscale loss value; using a mean filter to smooththe grayscale image loss value; selecting STC encoding to embed the secret information in the carrier image according to the grayscale image loss value to obtain a steganographic image. The algorithmimproves the anti-steganography analysis performance, thereby realizing the secure transmission of secret information in the image.
Owner:TIANJIN UNIV
Information embedding system and information extracting system using 2D/3D videos
ActiveCN103731654AGood camouflage environmentGuaranteed real-timeSelective content distributionSteroscopic systemsComputer hardwareCommunications system
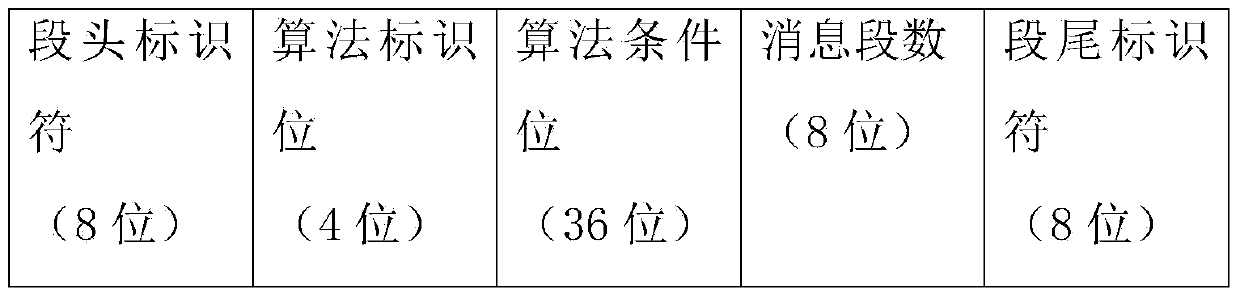
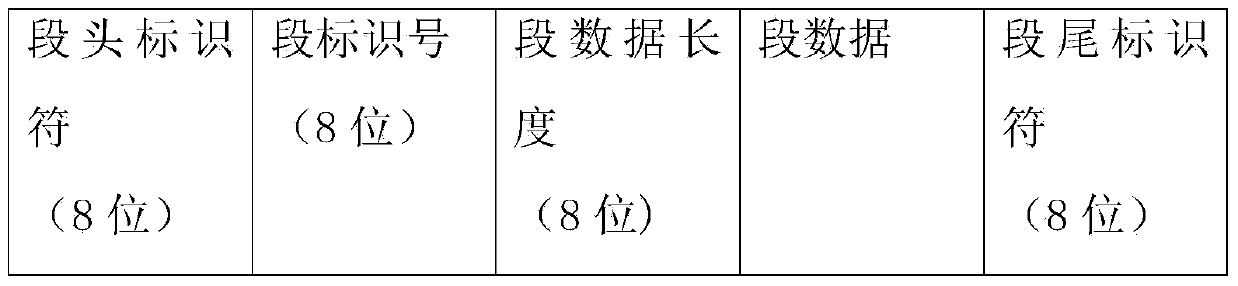
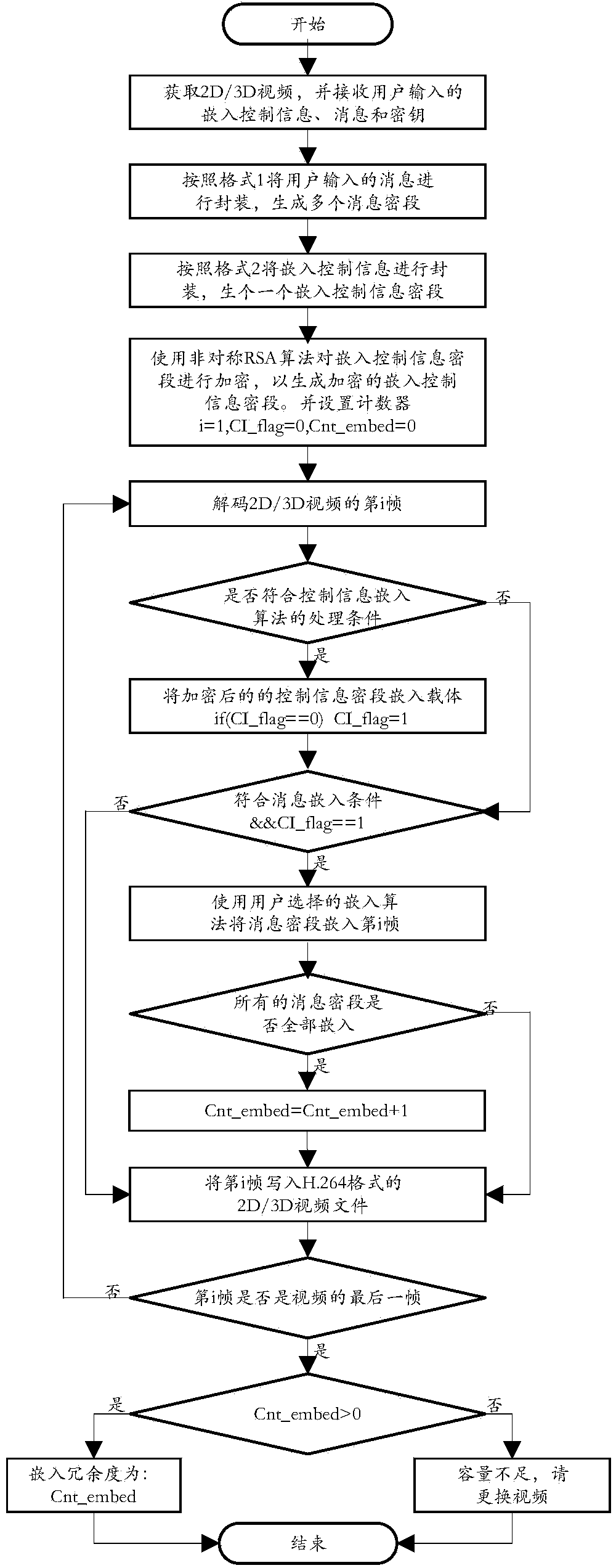
The invention discloses an information embedding method using 2D / 3D videos. The method includes the steps that the 2D / 3D videos are obtained, embedding control information, a message and a secret key are received, wherein the embedding control information, the message and the secret key are input by a user, the message input by the user is packaged to generate a plurality of bit strings serving as dense segments, the embedding control information is packaged to generate a bit string, the bit strings generated in the step (3) are encrypted by using an encryption algorithm to generate encrypted and embedded control information dense segments, a counter is set with i=1, the mark CI_flag used for marking first-time complete embedment of the embedding control information is set to be zero, the mark Cnt_embed used for marking the number of times for repeated embedment of the information is set to be zero, the i frame of the 2D / 3D videos is decoded, and whether the decoded i frame meets the processing condition of a control information embedding algorithm or not is judged. The technical problems that in the prior art, a steganography algorithm can not directly provide support for a covert communication system and can not be directly applied to the 2D / 3D videos are solved.
Owner:HUAZHONG UNIV OF SCI & TECH
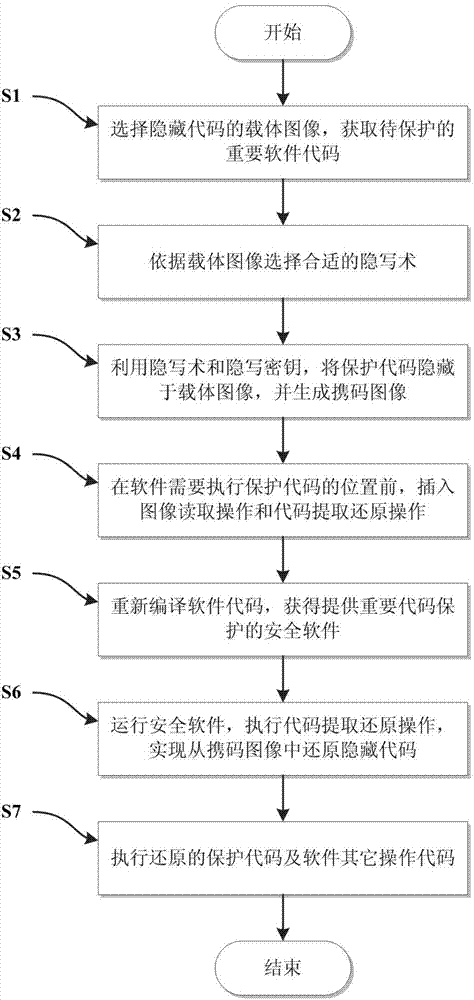
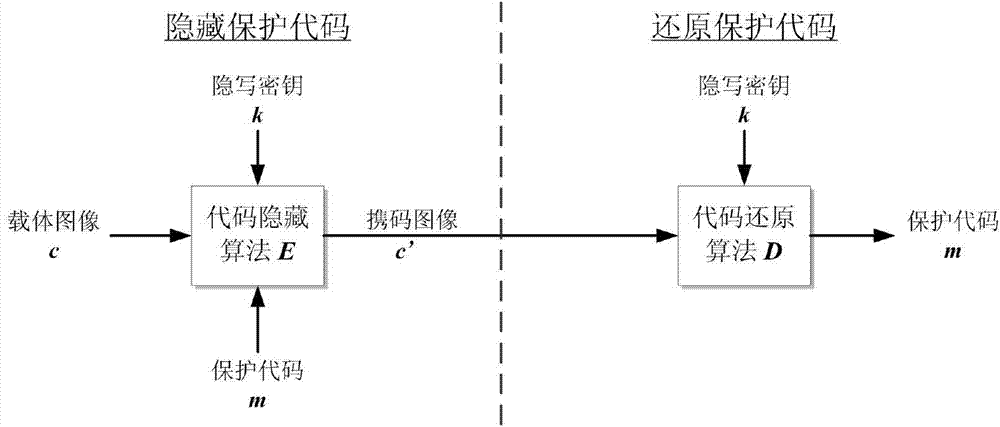
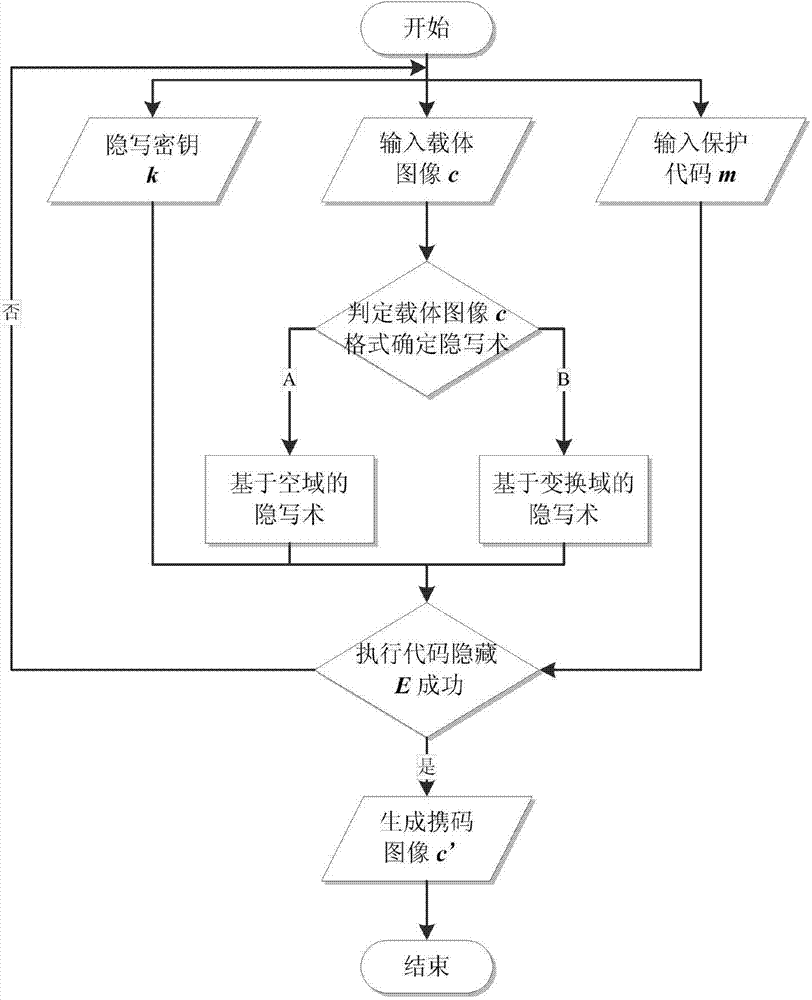
Steganography-based code protecting and restoring method
InactiveCN104765986AImprove concealmentImprove securityProgram/content distribution protectionBase codeSteganographic algorithm
The invention discloses a steganography-based code protecting and restoring method. The method comprises the following steps: 1) embedding a procedure to be protected in the important software to an image carrier by using a selected steganography algorithm, and generating a code carrying image; 2) searching the position of every embedded procedure code in the important software, and then inserting an image reading operation and a code extracting and restoring operation at the corresponding position; 3) re-coding the processed code in step 2) and writing a steganography secrete key of the selected steganography algorithm, and obtaining a safety software which provides the procedure code protection; running the safety software at a restoring terminal, and extracting the steganography secrete key; when the image reading operation and a code extracting and restoring operation are executed, restoring the hidden procedure code from the code carrying mage by using the code extracting method and the steganography secrete key corresponding to the steganography algorithm. According to the steganography-based code protecting and restoring method, the safety of the important software is improved.
Owner:INST OF INFORMATION ENG CAS
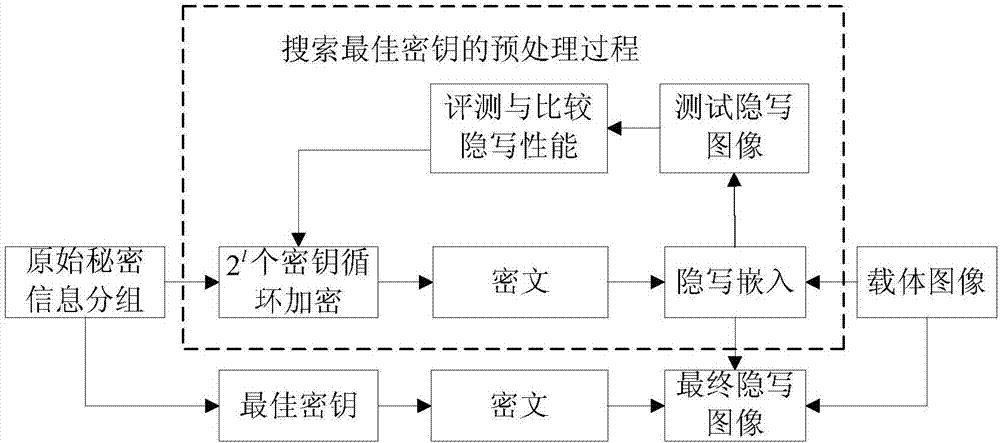
Digital image steganography method based on best key searching
ActiveCN107169913AImprove universalityImprove steganographic performanceKey distribution for secure communicationEncryption apparatus with shift registers/memoriesCiphertextSteganographic algorithm
The invention relates to a digital image steganography method based on best key searching. The original secret information is encrypted; and the encrypted ciphertext information is embedded to a carrier image through a steganography algorithm, and a final steganography image is formed. The method is characterized in that the original secret information is encrypted in a ciphertext information generation method, and the final to-be-embedded ciphertext information is acquired. Compared with the prior art, the method has the advantages that the steganography system by using the best key to encrypt the secret information has good performance, the decryption calculation complexity of the steganography system is low, and the method is applicable to a mobile communication terminal.
Owner:湖州优研知识产权服务有限公司
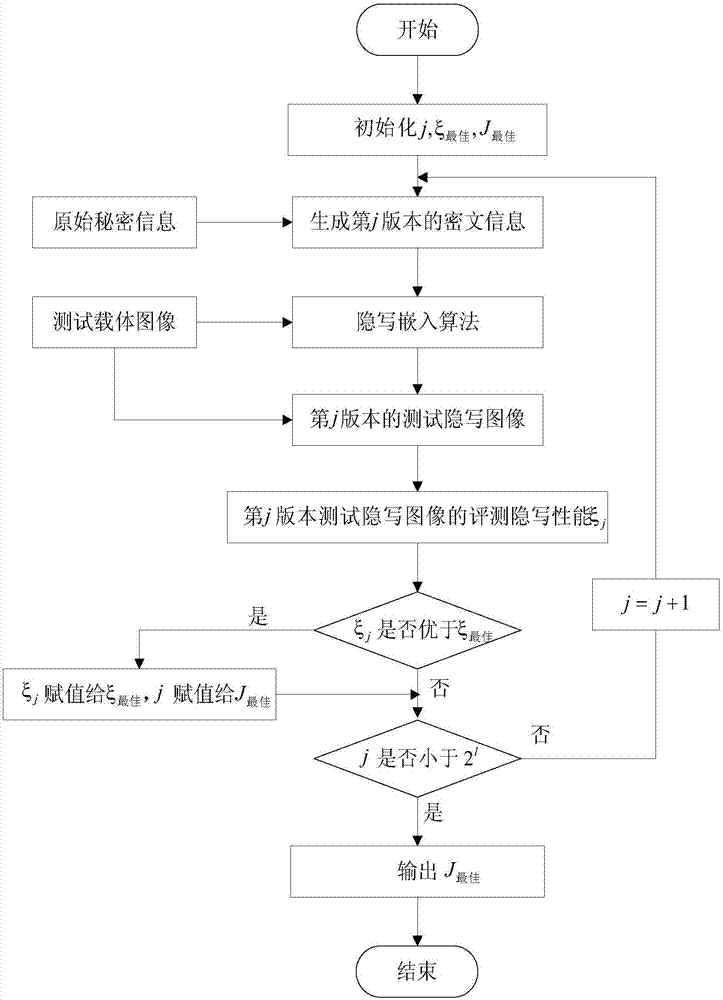
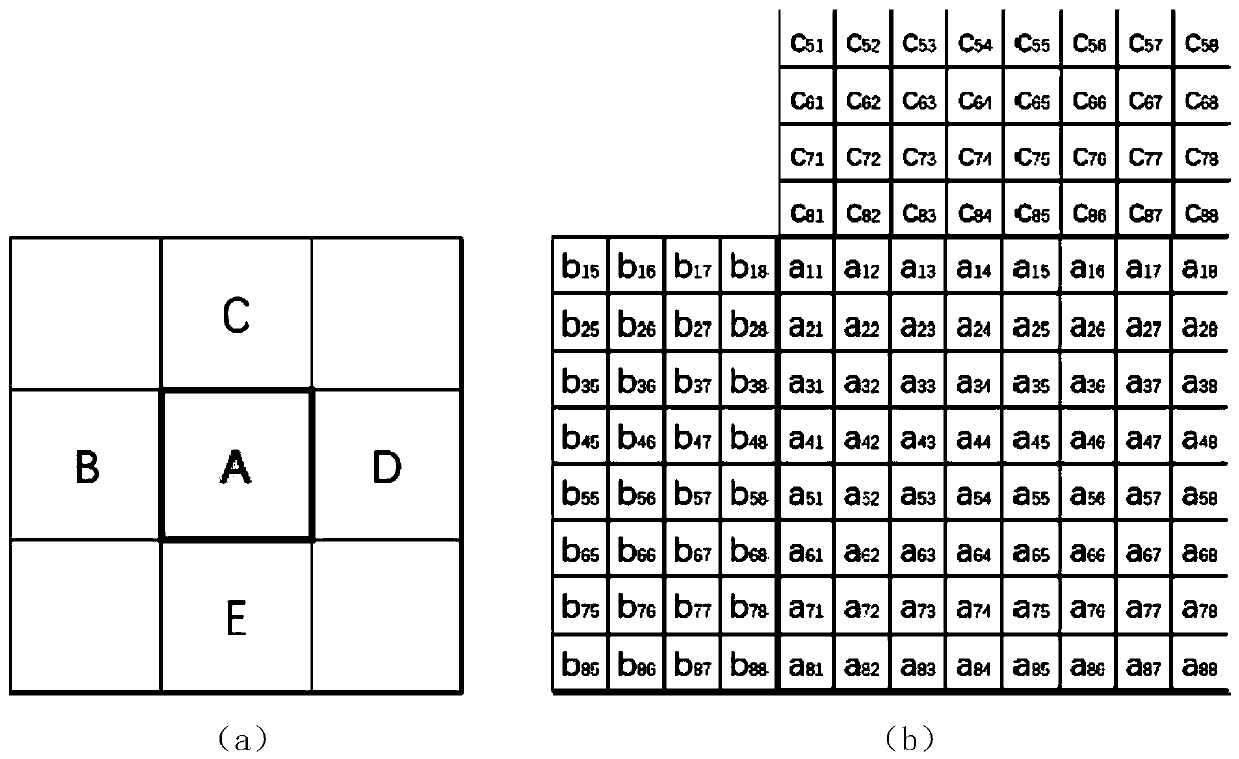
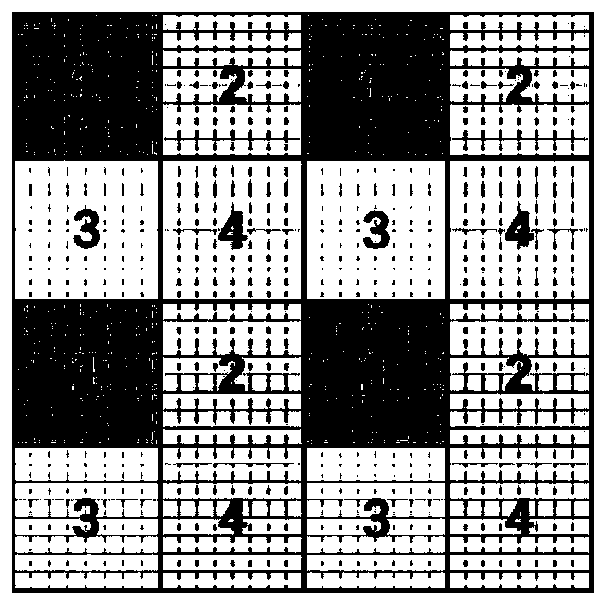
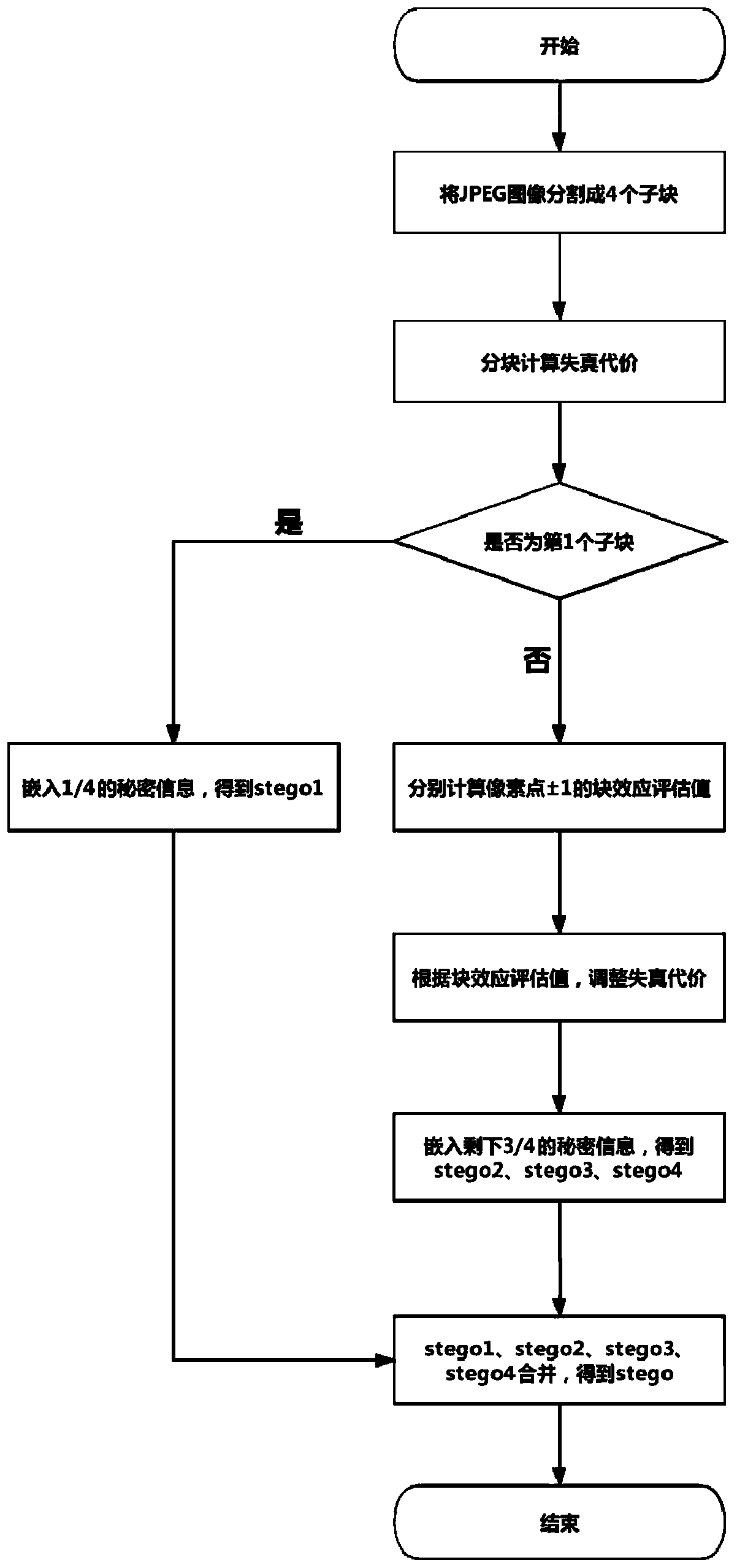
Non-additive distortion JPEG image steganography method based on block effect
ActiveCN110728613AEnhanced ability to resist detectionImprove securityImage data processing detailsPattern recognitionJpeg steganography
The invention discloses a non-additive distortion JPEG image steganography method based on a block effect. Based on the blocking effect of a JPEG image, the invention provides a method for guiding thedistortion cost to be adjusted towards the direction of reducing the blocking effect. Through combination of blocking effect evaluation and local distortion cost adjustment, improvement of an existing mainstream JPEG steganography algorithm is realized, and detection of current most advanced high-dimensional steganography analysis features is resisted. The method has the advantages that the current mainstream JPEG steganography algorithm is based on steganography of additive distortion cost and is easily detected by high-dimensional steganography analysis features, and the correlation betweenimage elements is kept based on the blocking effect from the perspective of non-additive distortion cost, so that the steganography concealment and safety are improved. The method has high universality and is beneficial to improving the safety of the JPEG steganography algorithm.
Owner:WUHAN UNIV
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com