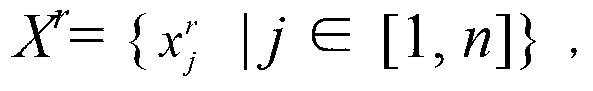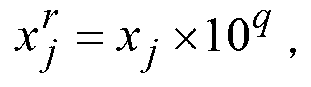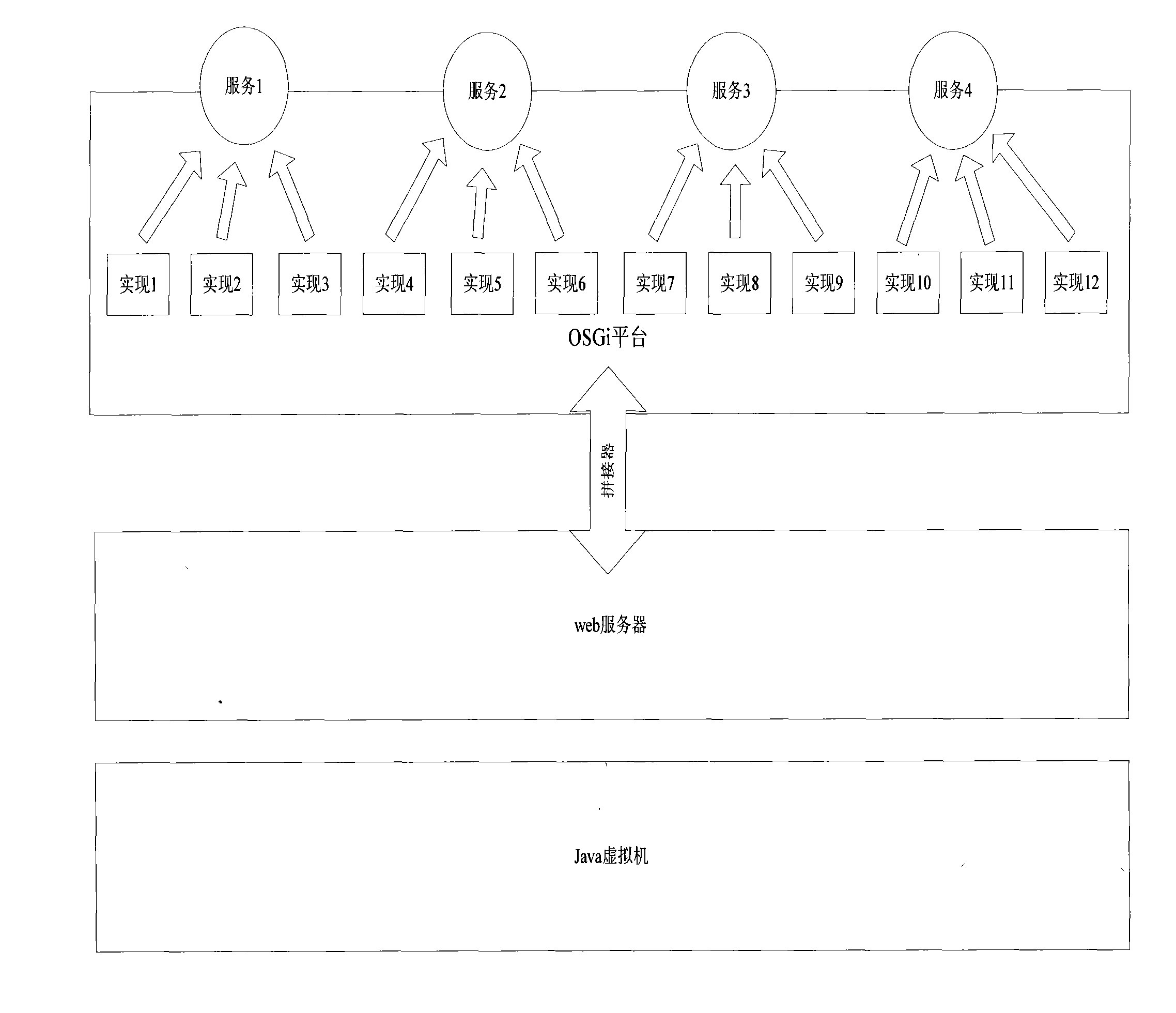Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
508results about How to "Achieve hidden" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
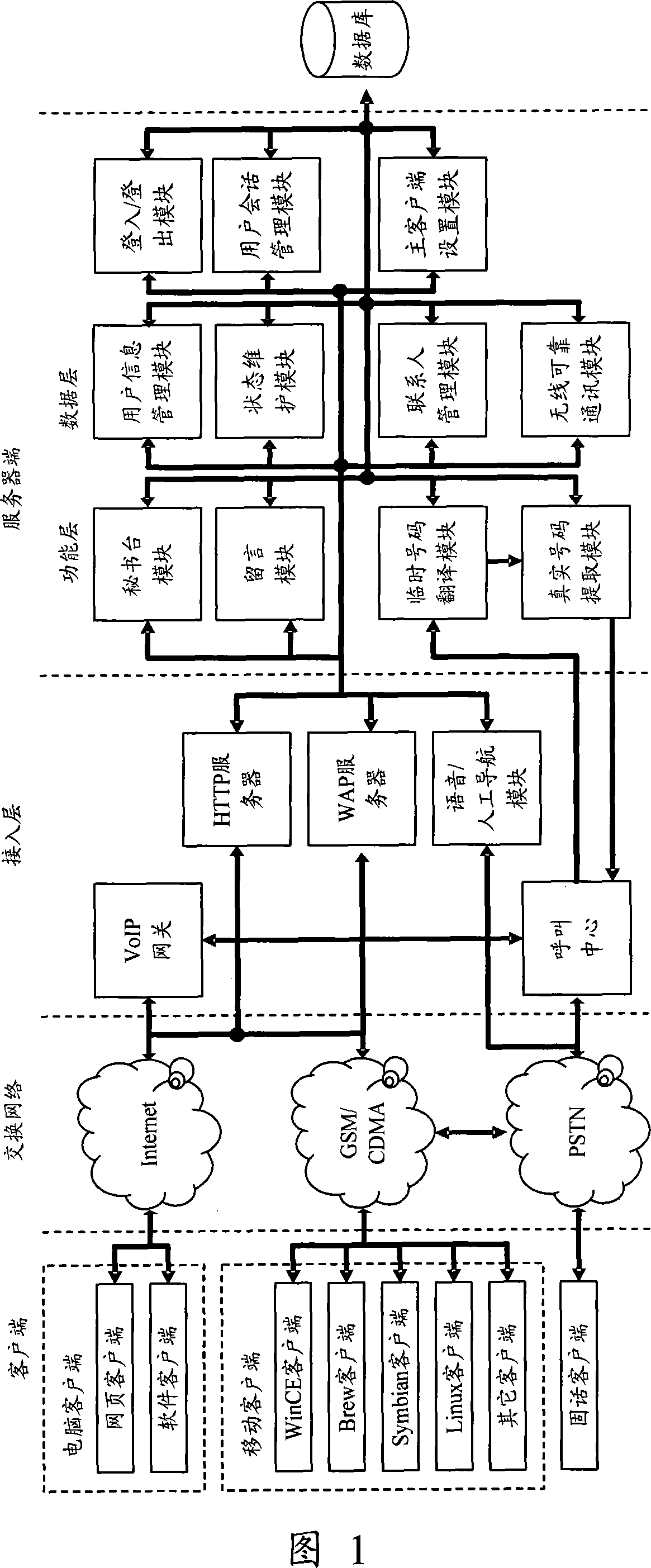
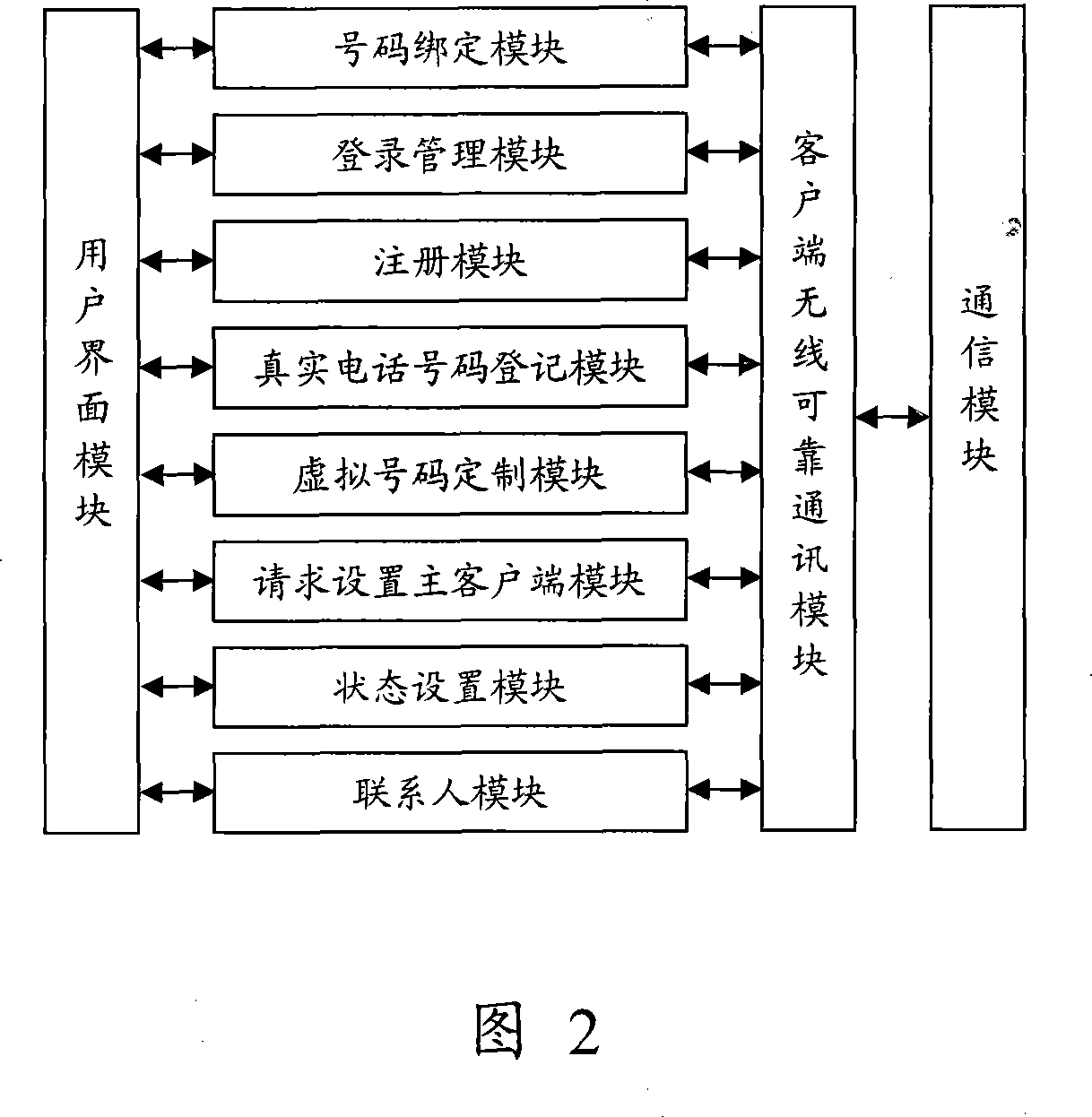
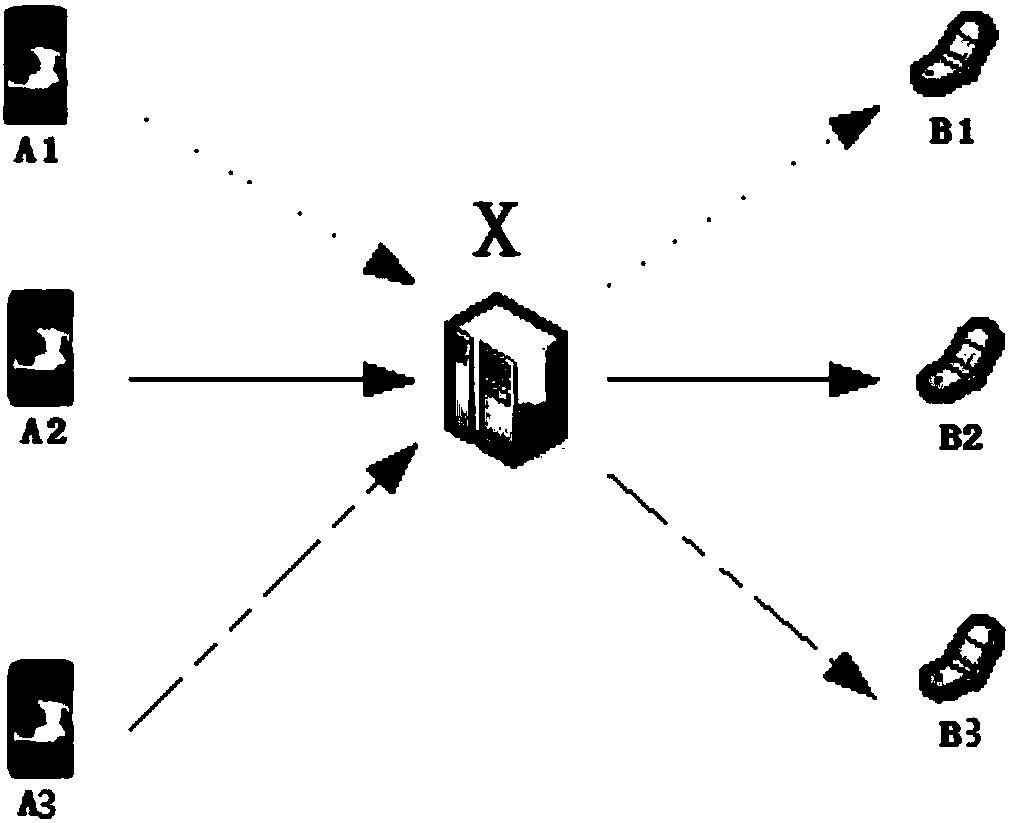
System for multimedia communication based on virtual number
InactiveCN101159778AAchieve hiddenSolve the shortageSpecial service for subscribersRadio/inductive link selection arrangementsCommunications systemClient-side
The invention discloses a multimedia communication system based on a virtual number. The system binds the virtual number for the real telephone number of user and transmits the contact person list from the client terminal to through a server, generates provisional numbers with certain service life, thereby providing the dual protection for the true telephone numbers of user, effective realizing the hidden of the true telephone numbers and solving the number resource shortage problem as well.
Owner:汤淼
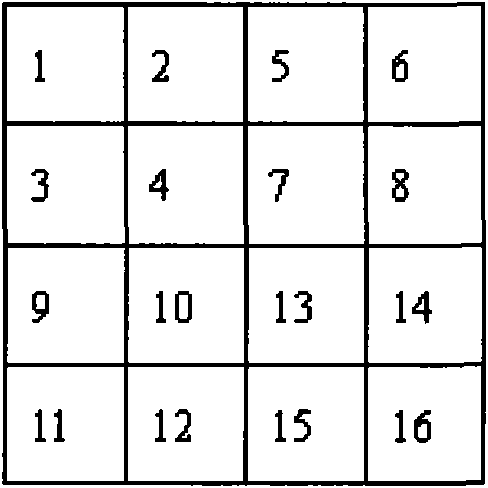
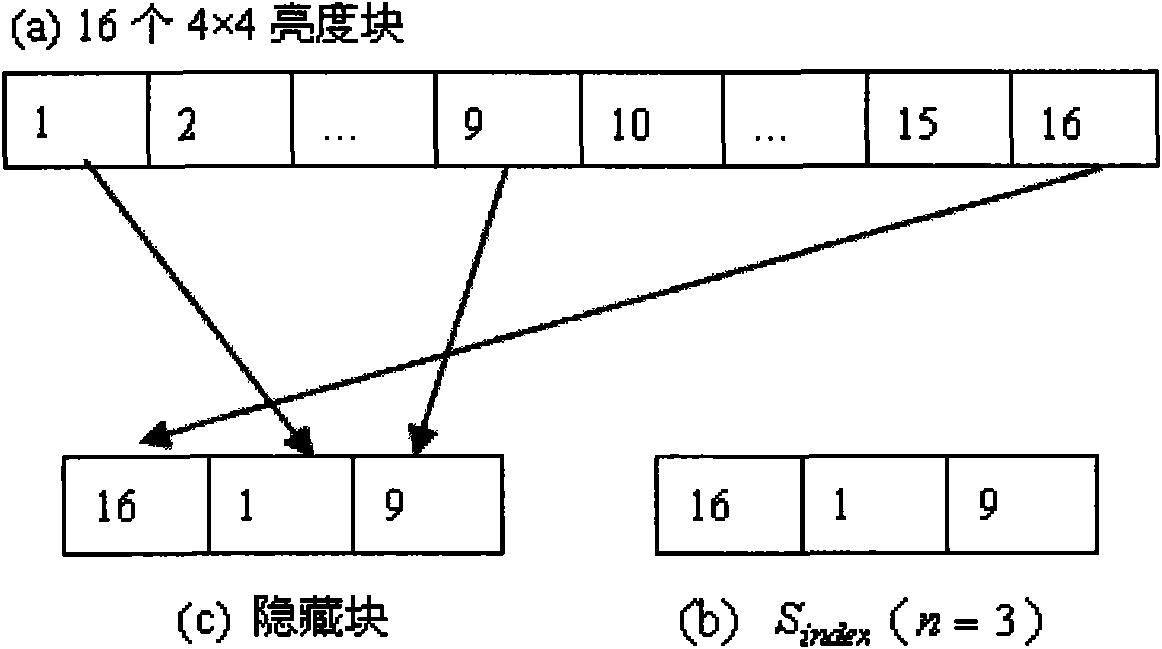
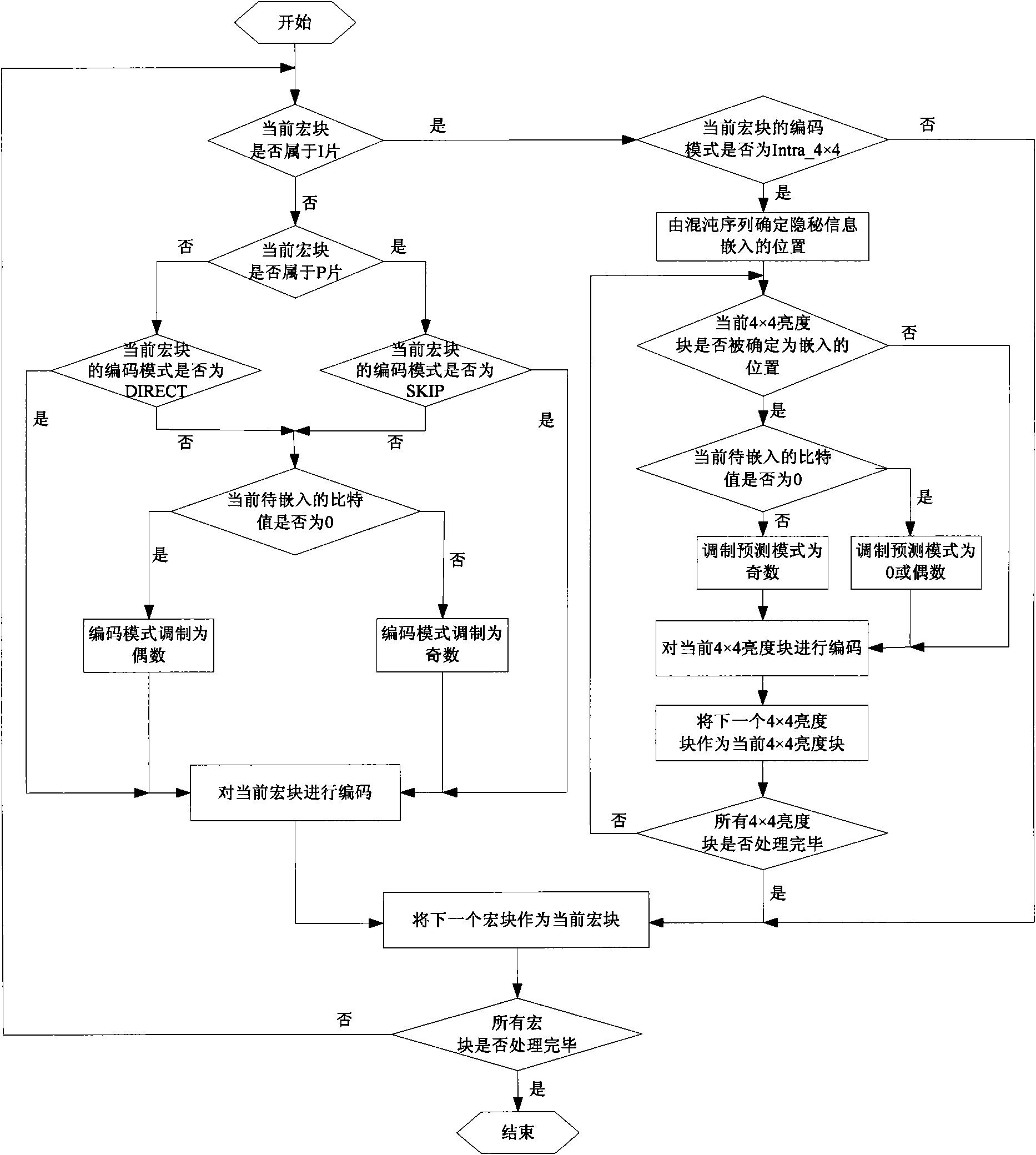
H.264/AVC video information hiding method based on predictive mode
InactiveCN101621692AAchieve hiddenReduce the impact of objective qualityTelevision systemsDigital video signal modificationObjective qualityComputer architecture
The invention discloses an H.264 / AVC video information hiding method based on a predictive mode. For a macro block whose coding mode is Intra_4*4 in an I chip, a predictive mode of a 4*4 luma block is modulated to a suboptimal predictive mode from an optimal predictive mode under the circumstance that the predictive mode of the 4*4 luma block needs to be changed, and for macro blocks whose coding modes are marked not by 0 in a P chip and a B chip, a coding mode of a macro block is modulated to a suboptimal predictive mode from an optimal predictive mode under the circumstance that the predictive mode of the macro block needs to be changed; the impact on the objective quality of a video, caused by the change of the predictive mode or the coding mode, can be reduced as much as possible under the circumstance of ensuring that the secret information can be effectively hidden at the same time; on the other hand, due to the fact that the secret information not only can be embedded in the macro block whose coding mode is Intra_4*4 in the I chip but also can be embedded in the macro blocks whose coding modes are marked not by 0 in the P chip and the B chip, the higher hiding capacity can be obtained.
Owner:NINGBO UNIV
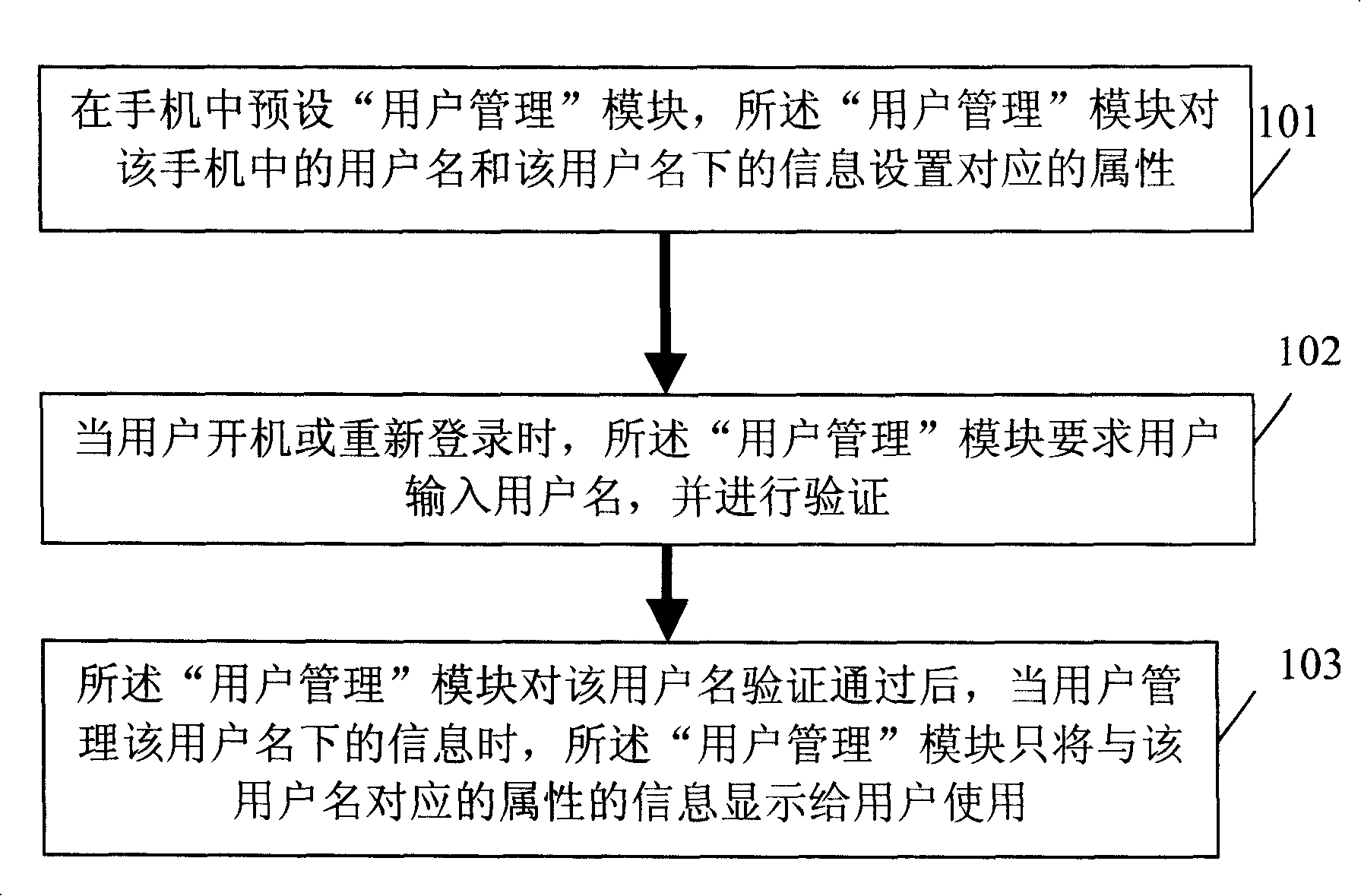
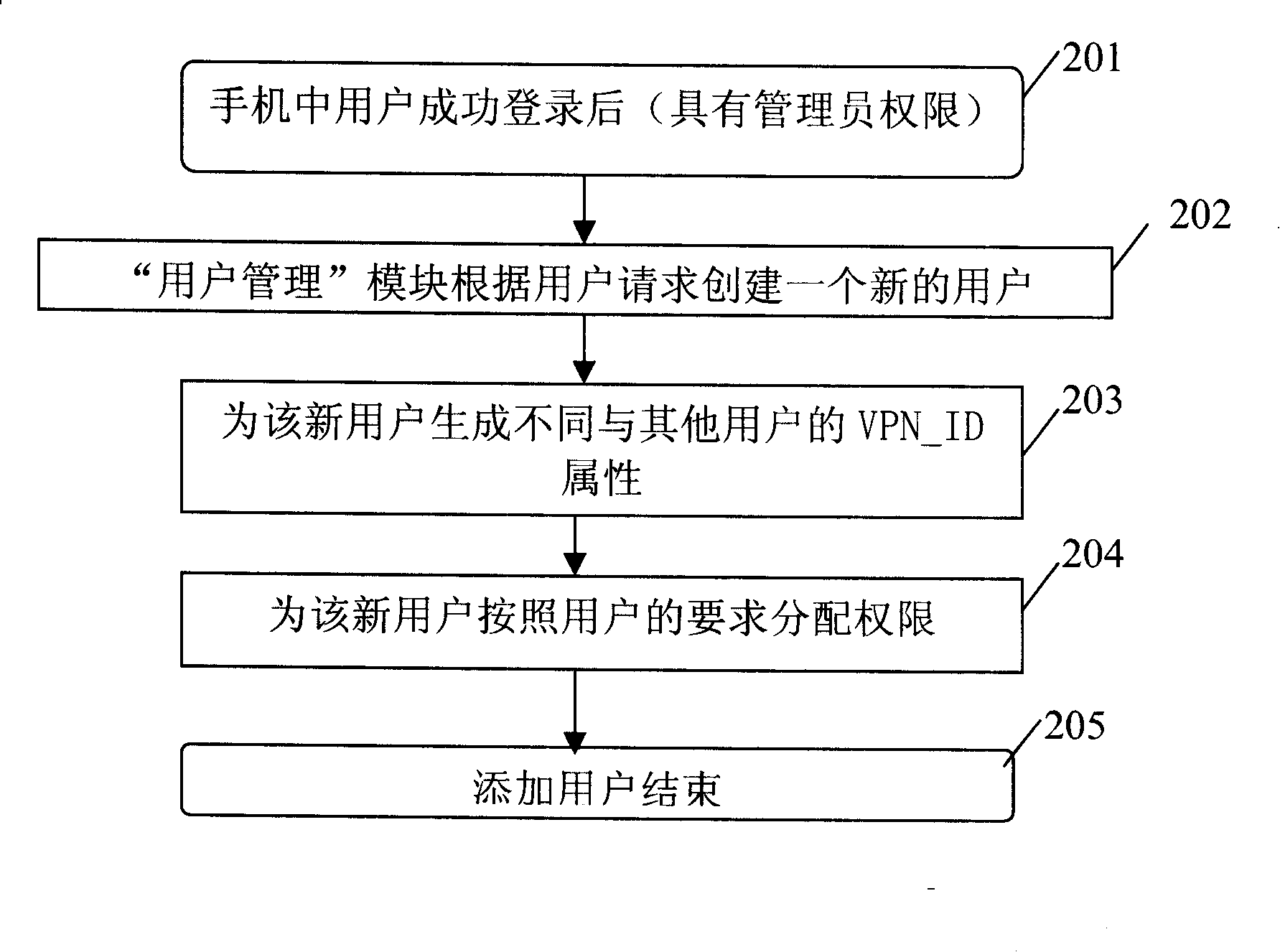
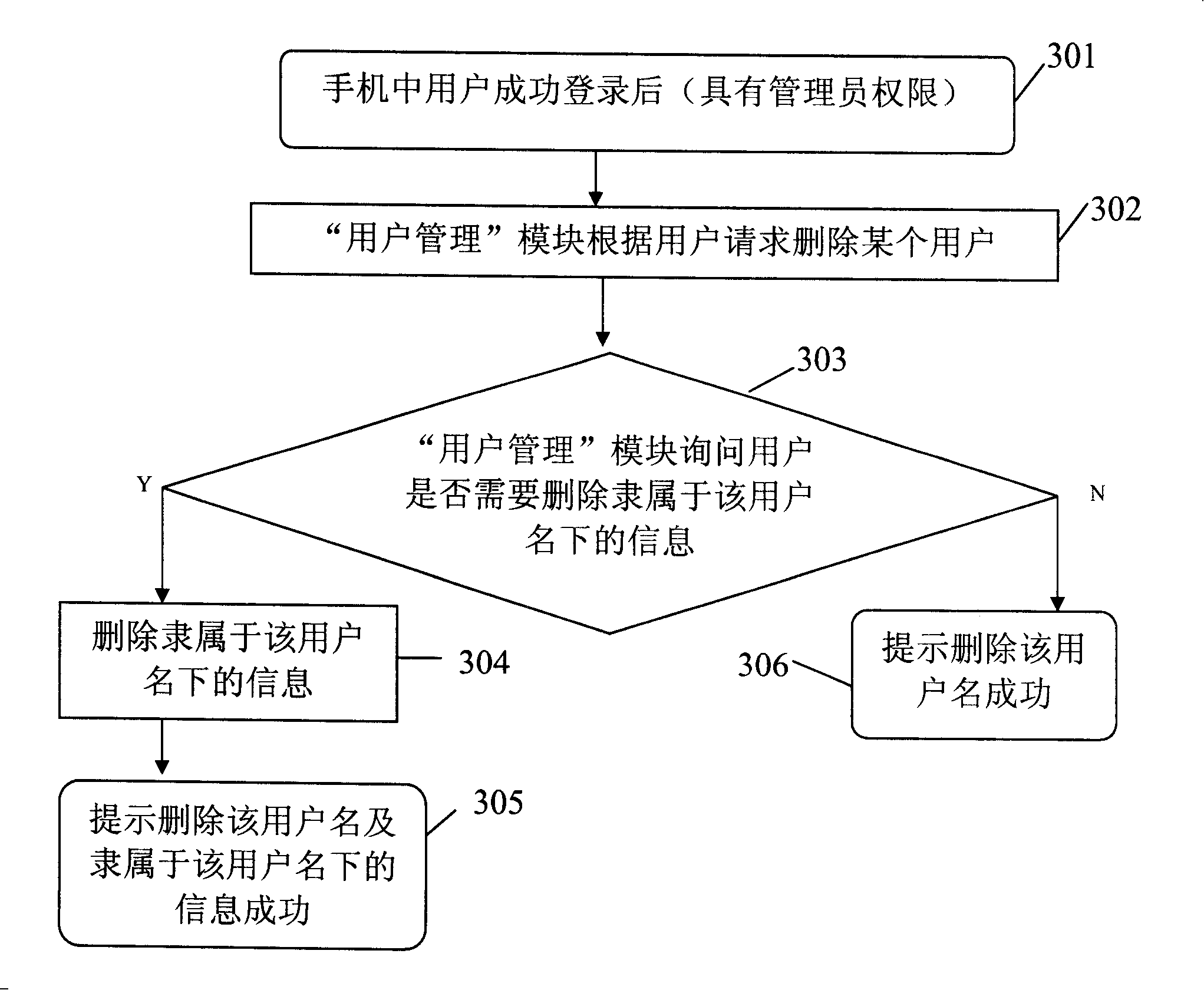
Method for implementing multi-user management and information hiding in mobile phone
InactiveCN101207864AAchieve hiddenUnauthorized memory use protectionRadio/inductive link selection arrangementsMulti user environmentMobile phone
The invention discloses a method of realizing multi-user management and information hiding on mobile phone, which is characterized in that, the method comprises the following steps: (1) presetting user management module in mobile phone, which configures corresponding attributes of the user name and the information under the user name; (2) when the user boots up or re-logins, the user management module requires the user to enter the user name, and verifies; (3) after the user management module completes the verification of user name, the user management module only provides the user the information of the attributes corresponding to the user name when the user manages the information under the user name. The invention solves the problem that the mobile phone cannot realize the multi-user management and information hiding in multi-user circumstance in existing technology.
Owner:ZTE CORP
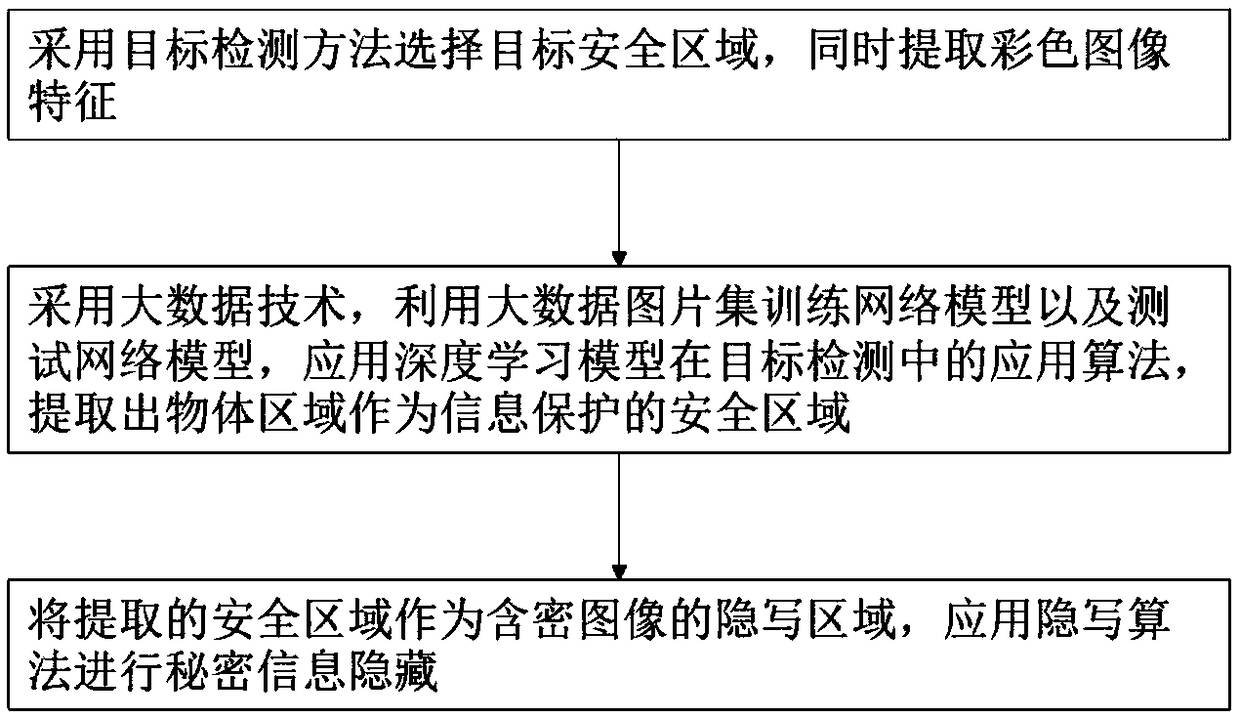
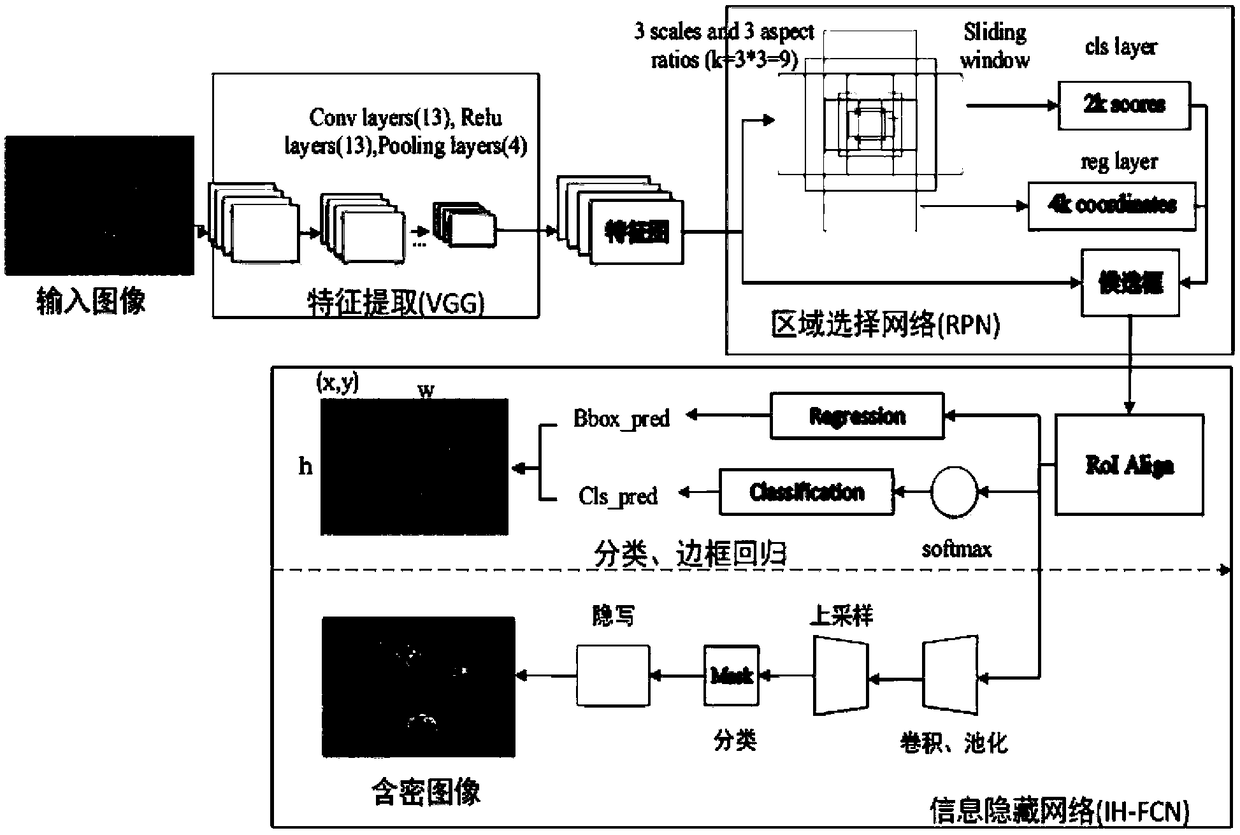
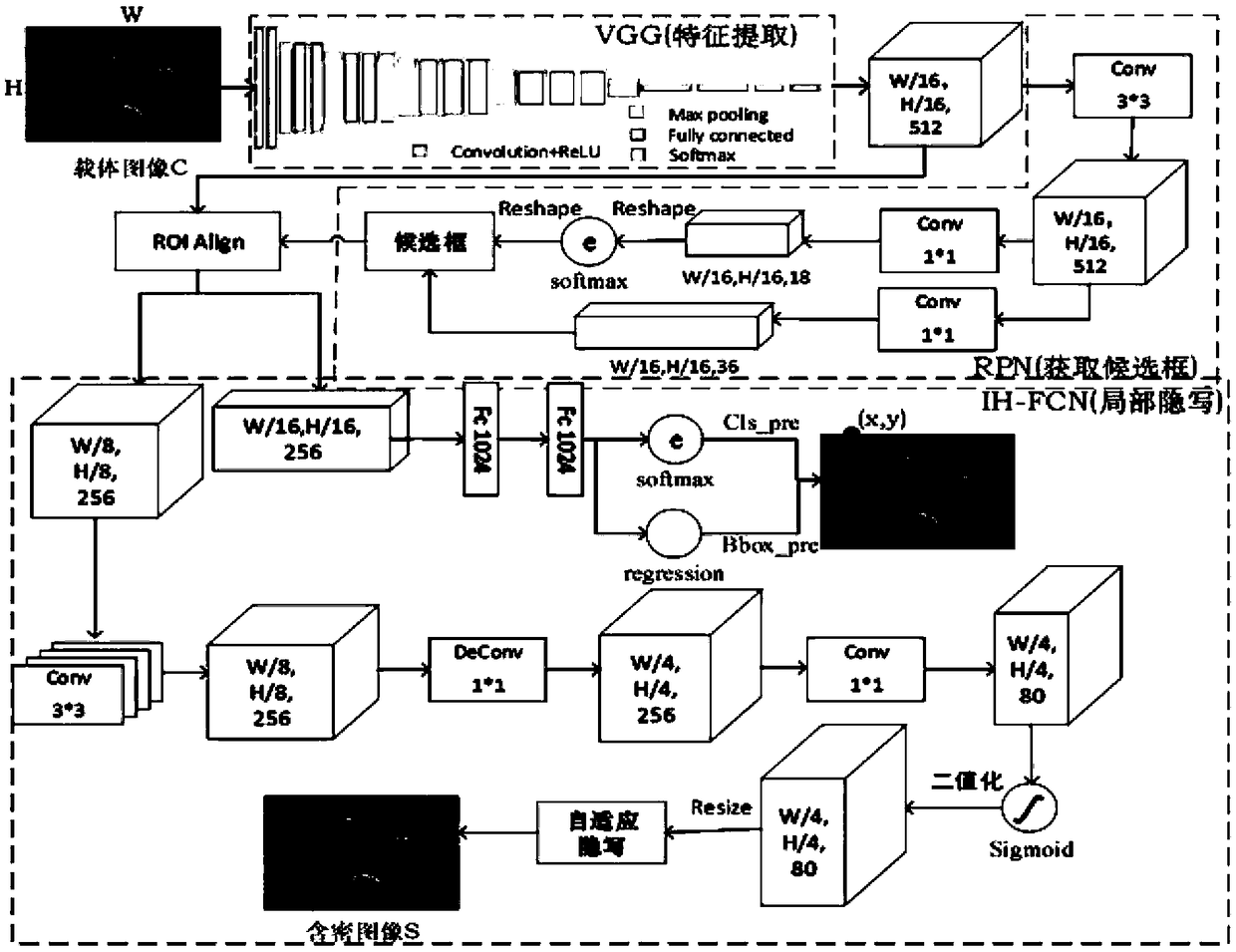
Big data image protection method and system based on a security area
ActiveCN109492416AAchieve hiddenImplement image protectionCharacter and pattern recognitionDigital data protectionColor imagePattern recognition
The invention provides a big data image protection method based on a security area, and the method comprises the steps: S1, selecting a target security area through employing a target detection method, and extracting color image features; s2, a big data technology is adopted, a big data picture set is utilized to train a network model and a test network model, an application algorithm of a deep learning model in target detection is applied, and an object area is extracted to serve as a safety area of information protection; and S3, taking the extracted security area as a steganography area ofthe encrypted image, and carrying out secret information hiding by applying a steganography algorithm. According to the invention, the application algorithm of the deep learning model is applied in the target detection, that is, the Mask R-CNN instance segmentation method, and select the region with complex texture noise in the image, an area with complex texture noise in the image, namely a foreground part, is selected, secret information is accurately hidden in a foreground object, and therefore the purpose of more secret image secret information hiding protection is achieved.
Owner:NANJING UNIV OF INFORMATION SCI & TECH
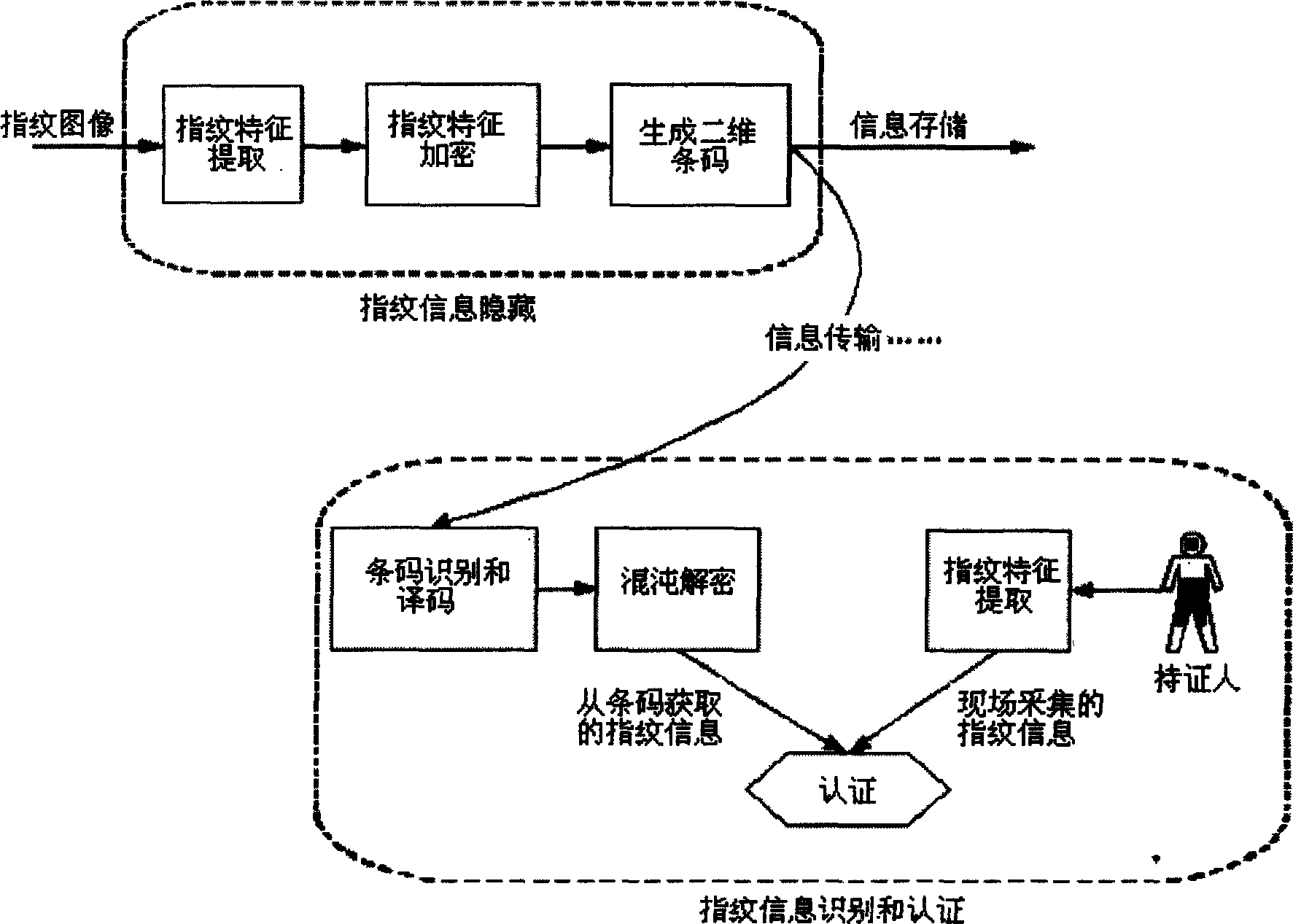
Fingerprint information hiding and verifying method based on two-dimensional bar code
InactiveCN1741043AWith automatic reading functionLarge capacityCo-operative working arrangementsCharacter and pattern recognitionComputer hardwareFeature extraction
The invented method includes the following steps: firstly, collecting fingerprint image, making characteristics extraction, encryption processing, printing it on the two-dimensional bar code, concealing the fingerprint information into two-dimensional bar code; collecting two-dimensional bar code image, making image segmentation, filtering, geometric correction and layered pretreatment, identifying and decoding said bar code image to obtain the loaded encrypted information, deciphering said encrypted information to obtain fingerprint characteristic information loaded in two-dimensional bar code, comparing said information with field fingerprint information, making detection so as to implement anti-false authentication of fingerprint.
Owner:XI AN JIAOTONG UNIV
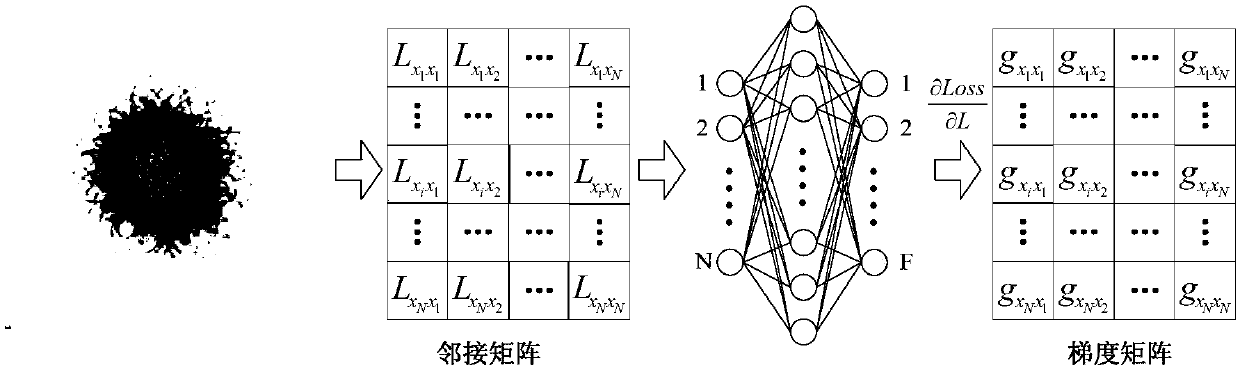
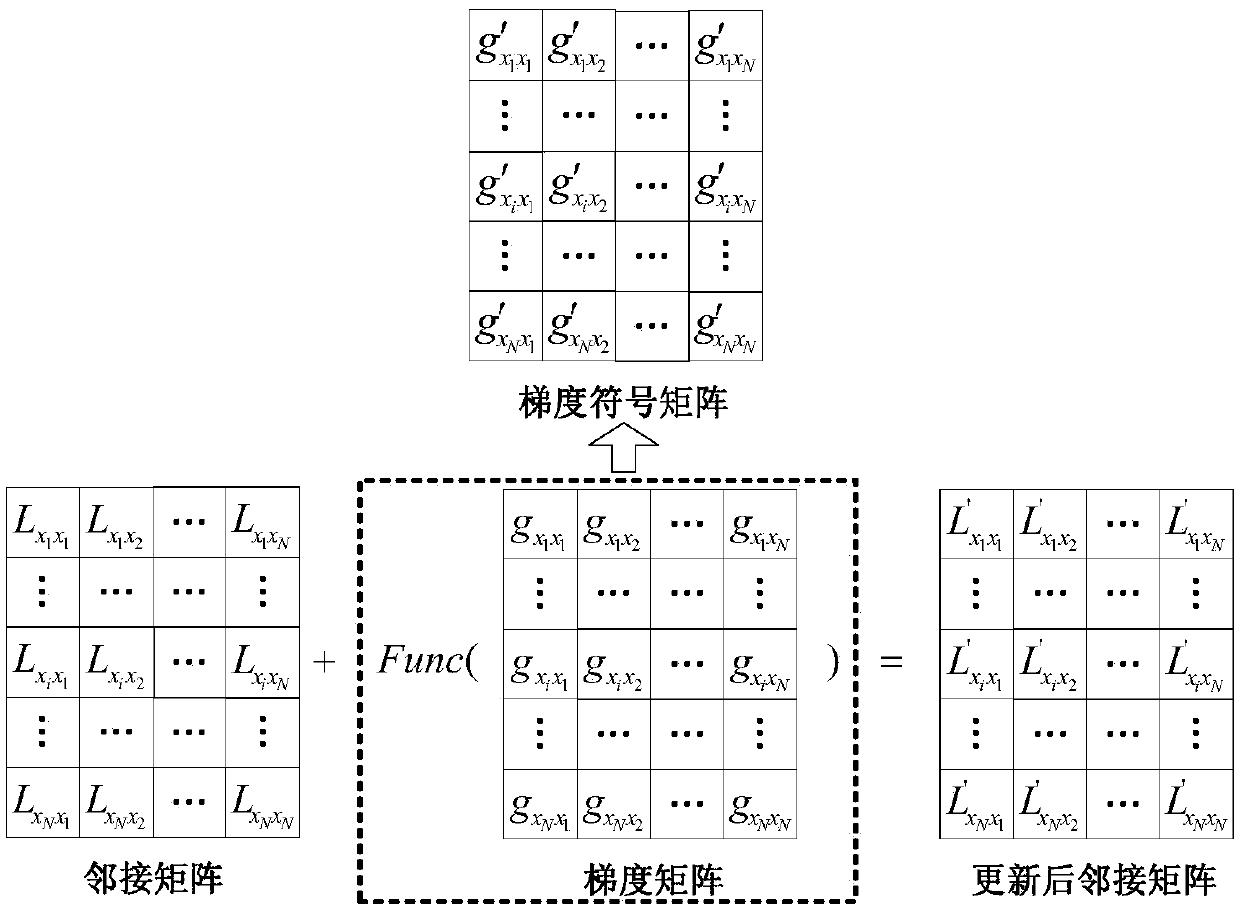
Graph convolutional network gradient-based node information hiding method
PendingCN108648095AAccurate classificationAchieve hiddenData processing applicationsCharacter and pattern recognitionNODALAlgorithm
The invention discloses a graph convolutional network gradient-based node information hiding method. The method comprises the steps of (1) constructing a network graph, constructing an adjacent matrixaccording to a connected edge set corresponding to the network graph, and preprocessing the adjacent matrix; (2) constructing and training a graph convolutional network model, and determining final weight information of the graph convolutional network model; (3) according to the final weight information, building an objective function based on a goal of ensuring non-target node classification tobe accurate as far as possible and enabling target node classification to be wrong, and calculating a connected edge gradient matrix corresponding to the adjacent matrix by utilizing the objective function; (4) according to a set gradient threshold, symbolizing the connected edge gradient matrix to obtain a connected edge gradient symbol matrix; and (5) updating the adjacent matrix by utilizing the connected edge gradient symbol matrix to hide node information. According to the method, the target node information of a network can be hidden under the condition of slightly changing the structureof the network as far as possible.
Owner:ZHEJIANG UNIV OF TECH
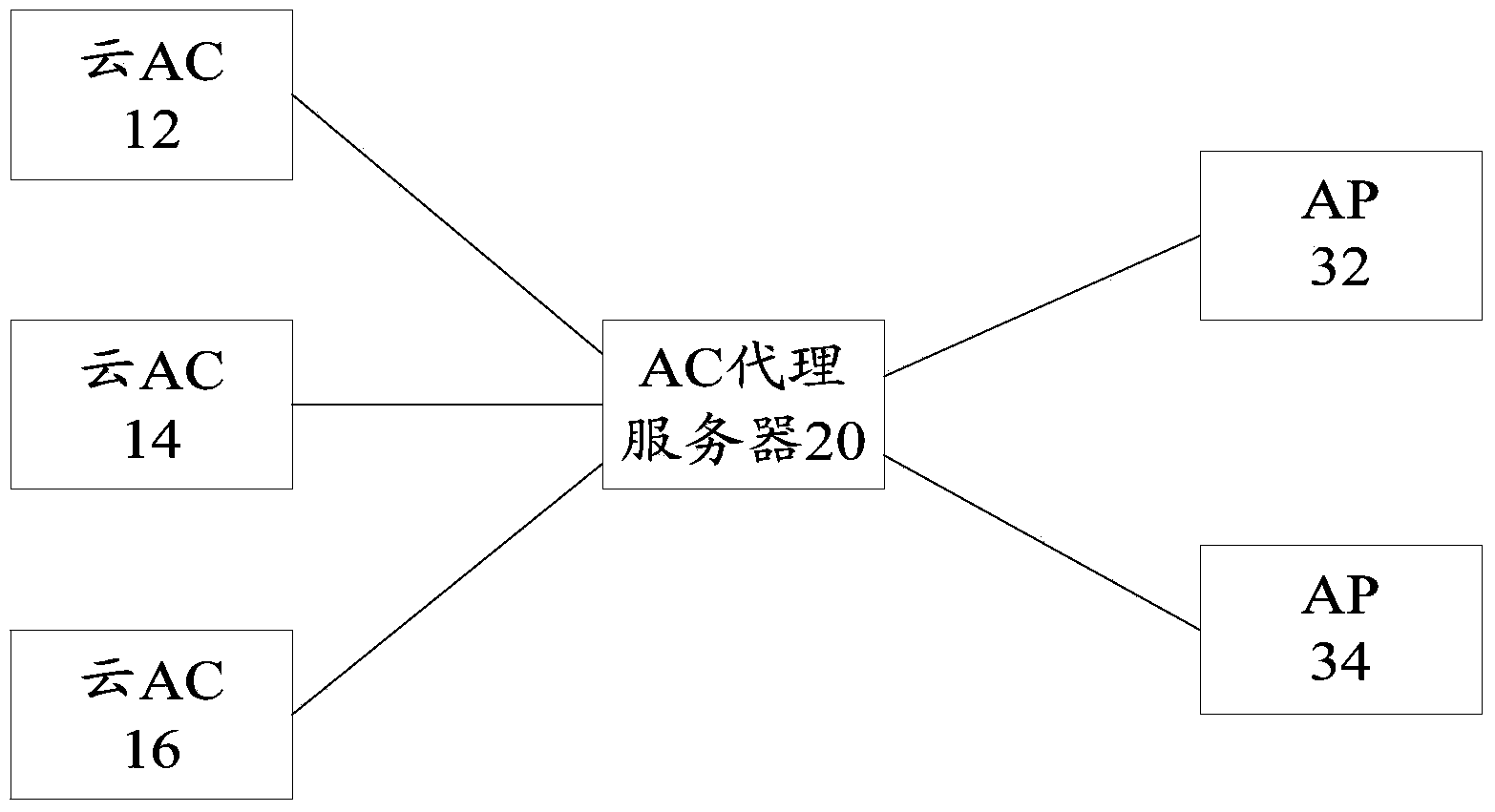
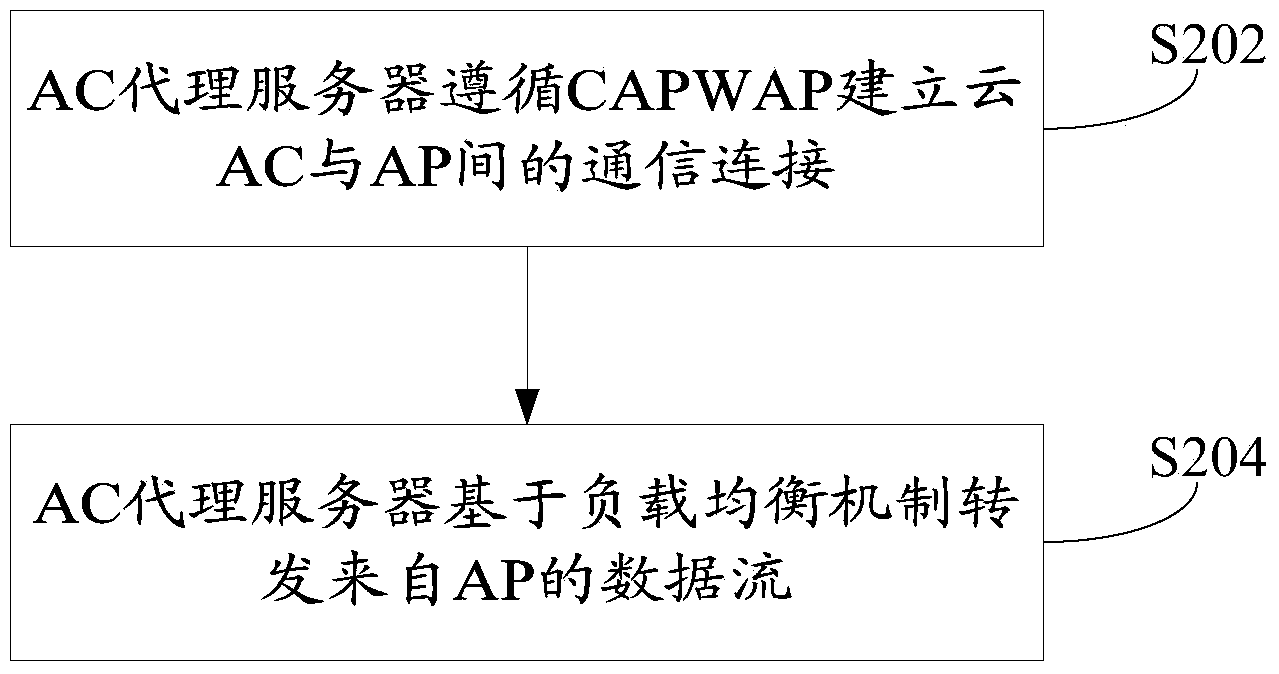
WiFi communication system deployed with cloud ACs (access controllers) and communication method adopting WiFi communication system deployed with cloud ACs
ActiveCN104113879AAchieve hiddenImprove securityNetwork traffic/resource managementTransmissionData streamCommunications system
The invention provides a WiFi communication system deployed with cloud ACs (access controllers) and a communication method adopting the WiFi communication system deployed with the cloud ACs (access controllers). The WiFi communication system comprises a plurality of cloud ACs, an AC proxy server used for performing load balancing treatment on data streams, and an AP (access point) communicated with the cloud ACs by the AC proxy server, wherein the CAPWAP (Control And Provisioning Of Wireless Access Points) follows between the AP and each AC proxy server, and the IP (internet protocol) address of the AC proxy server is opened to the AP, so that the AP can find the AC proxy server after being electrified. According to the system, other private protocols are not required to be expanded to the AP, so that the development cost is reduced on the basis of the cloud ACs, besides, the cloud ACs are not exposed to a client side, the ACs can be well hidden and the security of the ACs is improved.
Owner:CHENGDU SKSPRUCE TECH
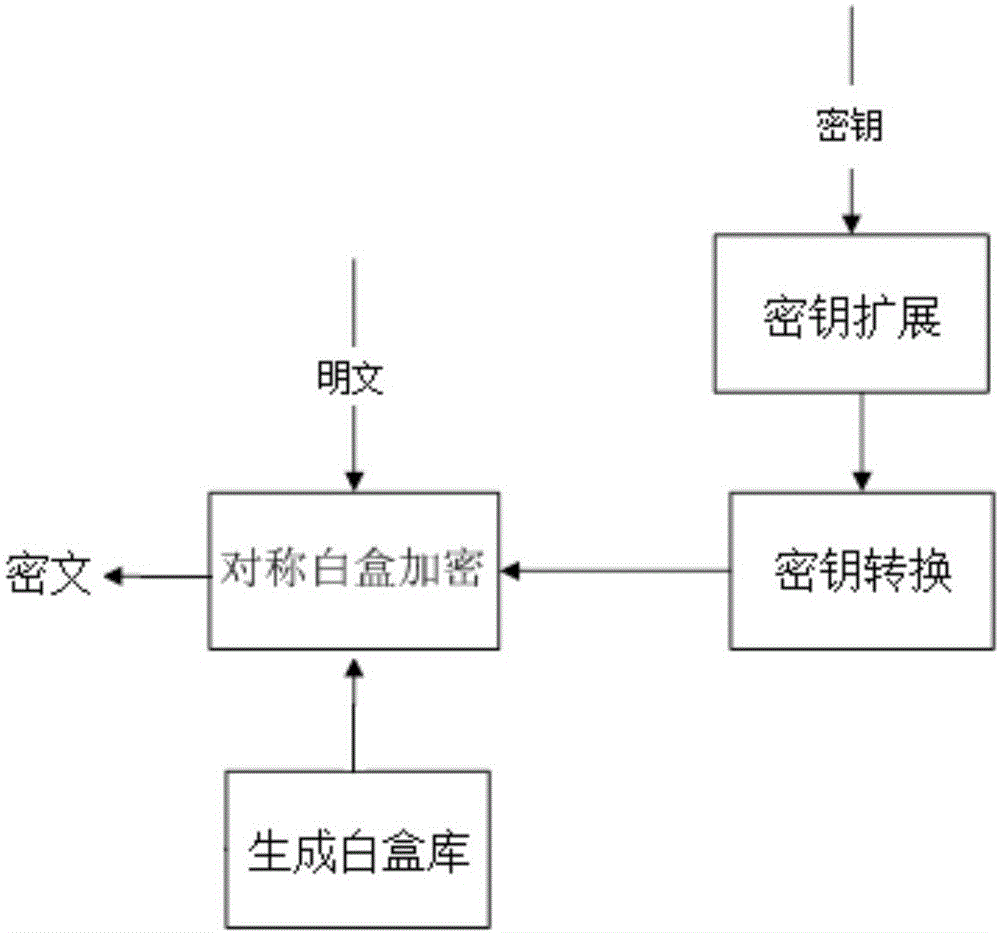
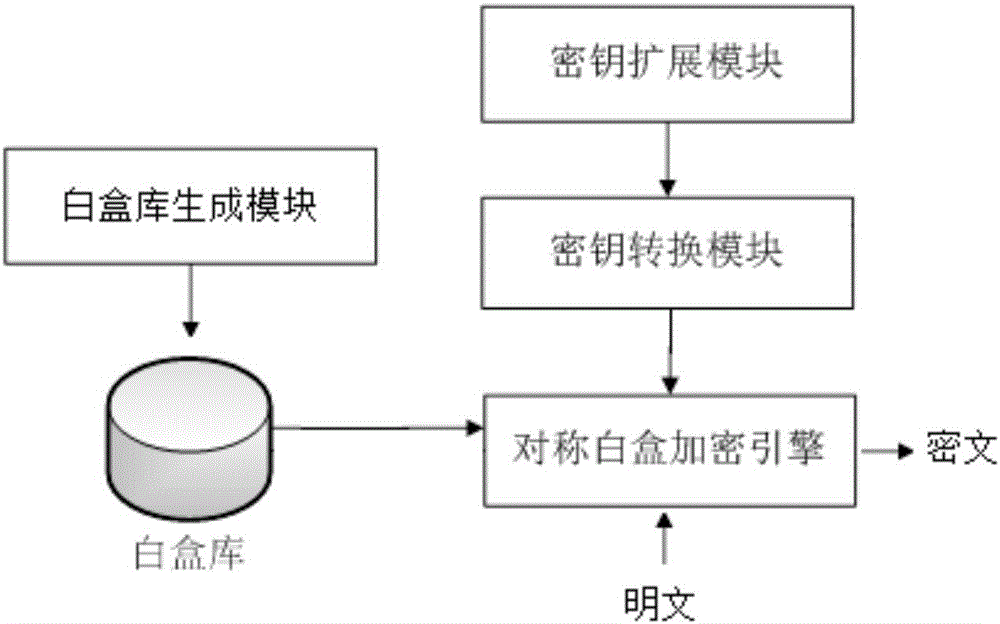
Symmetric white box encryption method with unfixed key and apparatus
ActiveCN106411518AIncrease diversityIncrease the difficultyMultiple keys/algorithms usageEncryption apparatus with shift registers/memoriesCiphertextAlgorithm
The invention provides a symmetric white box encryption method with an unfixed key. The method comprises the following steps: performing key expansion by using a symmetric encryption method to acquire multiple turns of encryption keys Kn; step 2, replacing the multiple turns of encryption keys Kn to acquire replaced keys Kn'; step 3, generating a white box library; step 4, transmitting the white box library and the replaced keys Kn' to a user; and step 5, performing white box encryption by a user on to-be-encrypted data by using the replaced keys Kn', and performing table lookup by using the white box library during the white box encryption to acquire ciphertext, wherein n represents the encryption turns of the symmetric encryption method. By adoption of the symmetric white box encryption method provided by the invention, the keys in the white box encryption are not only hidden, the white box library is separated from the keys, and users can set the keys by themselves, thereby being convenient and flexible.
Owner:BEIJING BANGCLE TECH CO LTD
Electronic equipment
ActiveCN108924299AImprove reliabilityAvoid damageTelevision system detailsDevices with sensorCamera moduleComputer science
The invention provides electronic equipment. The electronic equipment comprises a camera extension and contraction mechanism, a camera module and a controller which are mounted in the electronic equipment, wherein the controller determines whether the electronic equipment slips out of the hand and whether the camera module is in an extending state; and when determining that the electronic equipment slips out of the hand and whether the camera module is in the extending state, the controller controls the camera extension mechanism to operate to enable the camera module to contract into the electronic equipment. According to the electronic equipment provided by the invention, when the electronic equipment slips out of the hand, the camera module in the extending state is controlled to contract, so as to prevent damage to the camera module in the extending state after an electronic device slips out of the hand accidentally.
Owner:SAMSUNG GUANGZHOU MOBILE R&D CENT +1
Virtual number-based communication method, system, server and storage medium
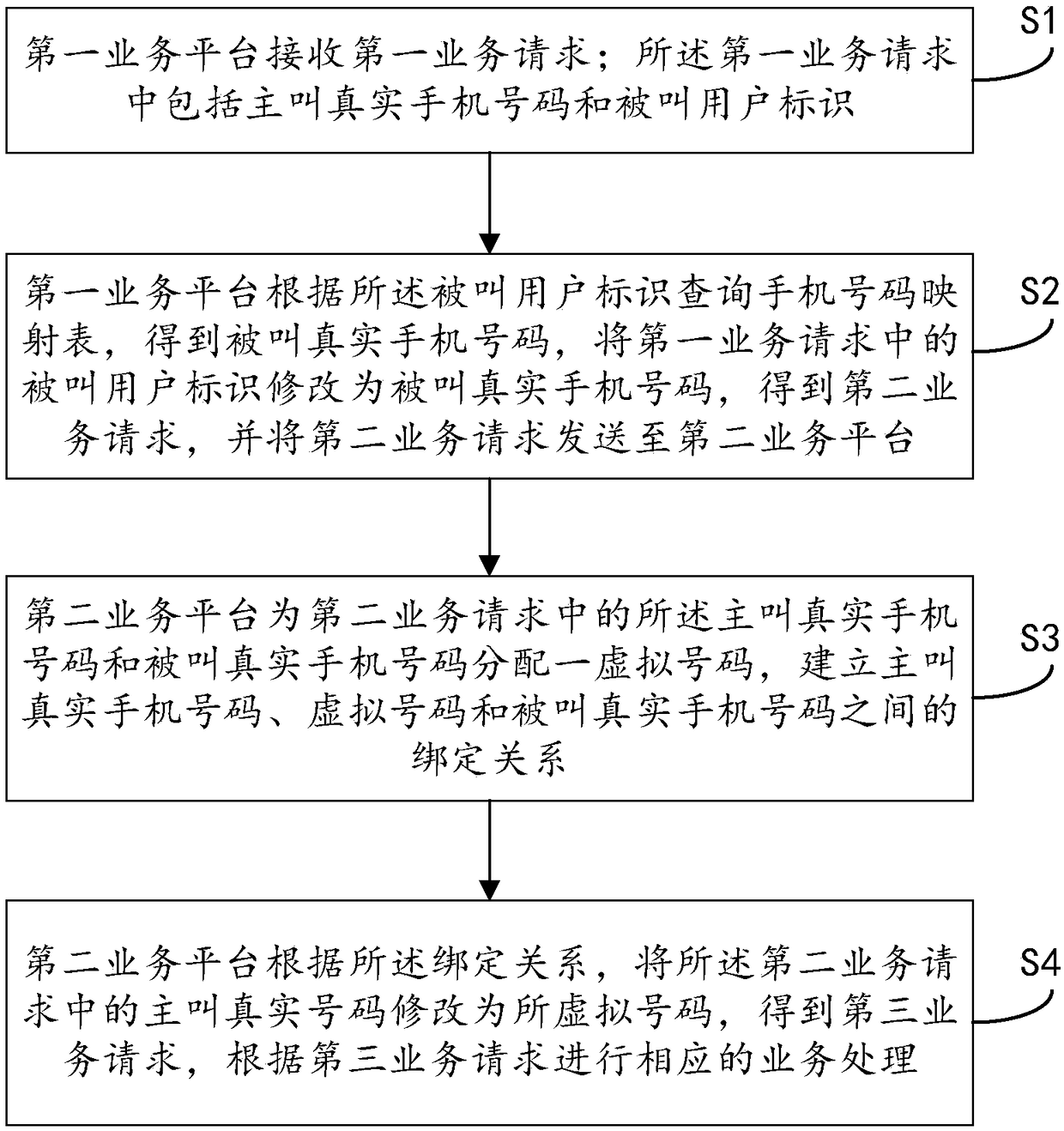
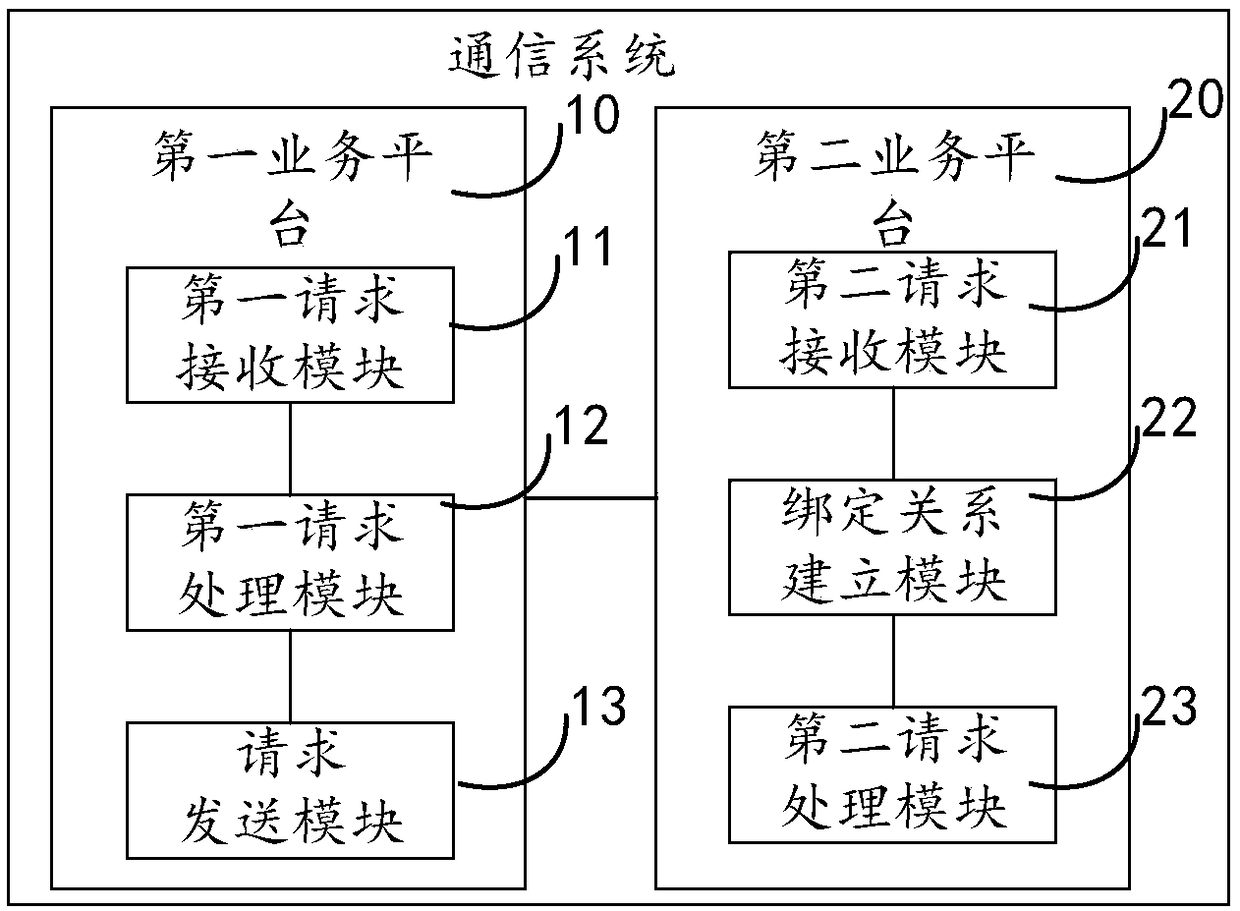
ActiveCN109257509AAchieve hiddenChange wasteSpecial service for subscribersNetwork data managementComputer scienceMobile phone
One embodiment of the invention provides a virtual number-based communication method, a system, a server and a storage medium. The method comprises: the first service platform receives the first service request, inquires the mobile phone number mapping table according to the called user identification in the first service request, obtains the called real mobile phone number, modifies the called user identification in the request to the called real mobile phone number, obtains the second service request, and sends the second service request to the second service platform. The second service platform assigns a virtual number to the calling real mobile phone number and the called real mobile phone number in the second service request. A binding relationship among a calling real mobile phone number, a virtual number and a called real mobile phone number is established, the calling real mobile phone number in the second service request is modified to a virtual number, a third service request is obtained, and corresponding service processing is carried out according to the third service request. The method solves the problem of code number resource waste caused by a user binding a virtual number in the prior art.
Owner:CHINA MOBILE GROUP ZHEJIANG +1
Real-name certification system and method capable of hiding identity information
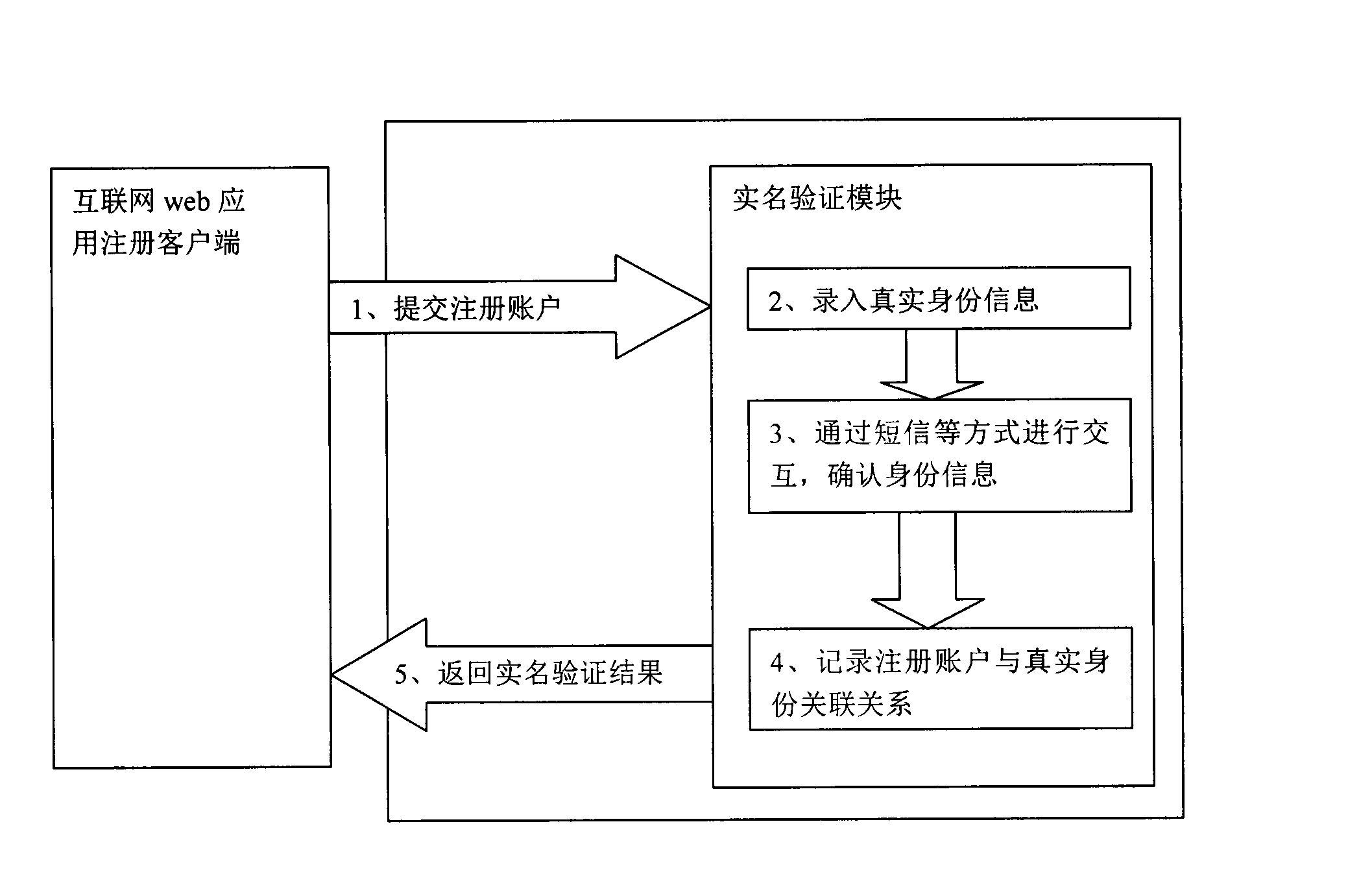
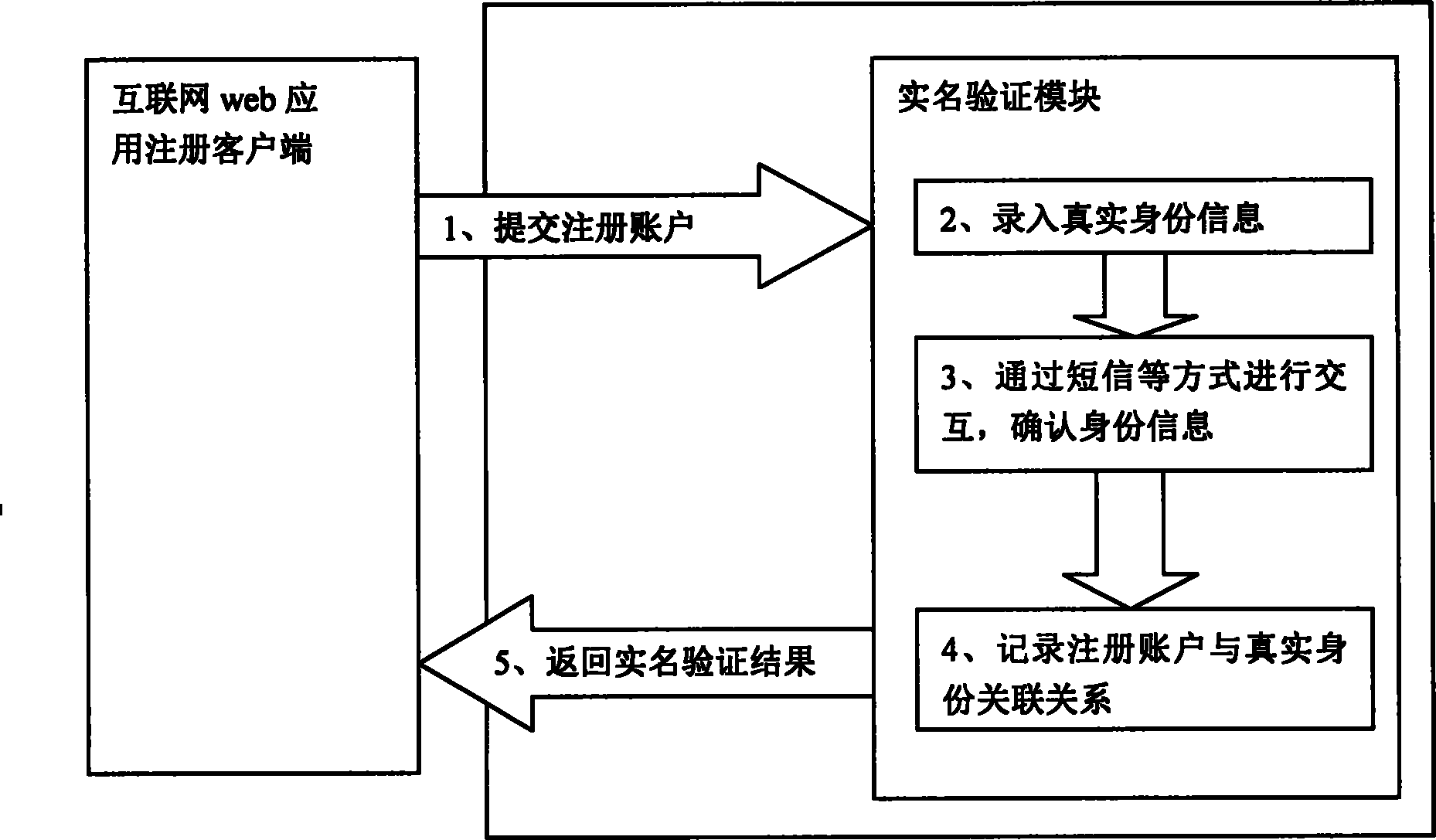
InactiveCN102647430APrevent leakageSimplify the registration processTransmissionWeb applicationThe Internet
The invention provides a real-name certification system and a method capable of hiding identity information. The system comprises an Internet web application registration user terminal and a real-name certification module. The method comprises that the real-name certification module is set, an Internet application which requires real-name certification calls the real-name certification module, and the real-name certification module filters information of a registered user and stores the association relationship between an Internet application registration account and the user, so that hiding of identity information and real-name certification are achieved. The method solves the problem of information disclosure caused by direct registration through a commercial website and provides a convenient and effective management method for management departments.
Owner:司文
Method for performing identity authentication on user node in block chain and related equipment
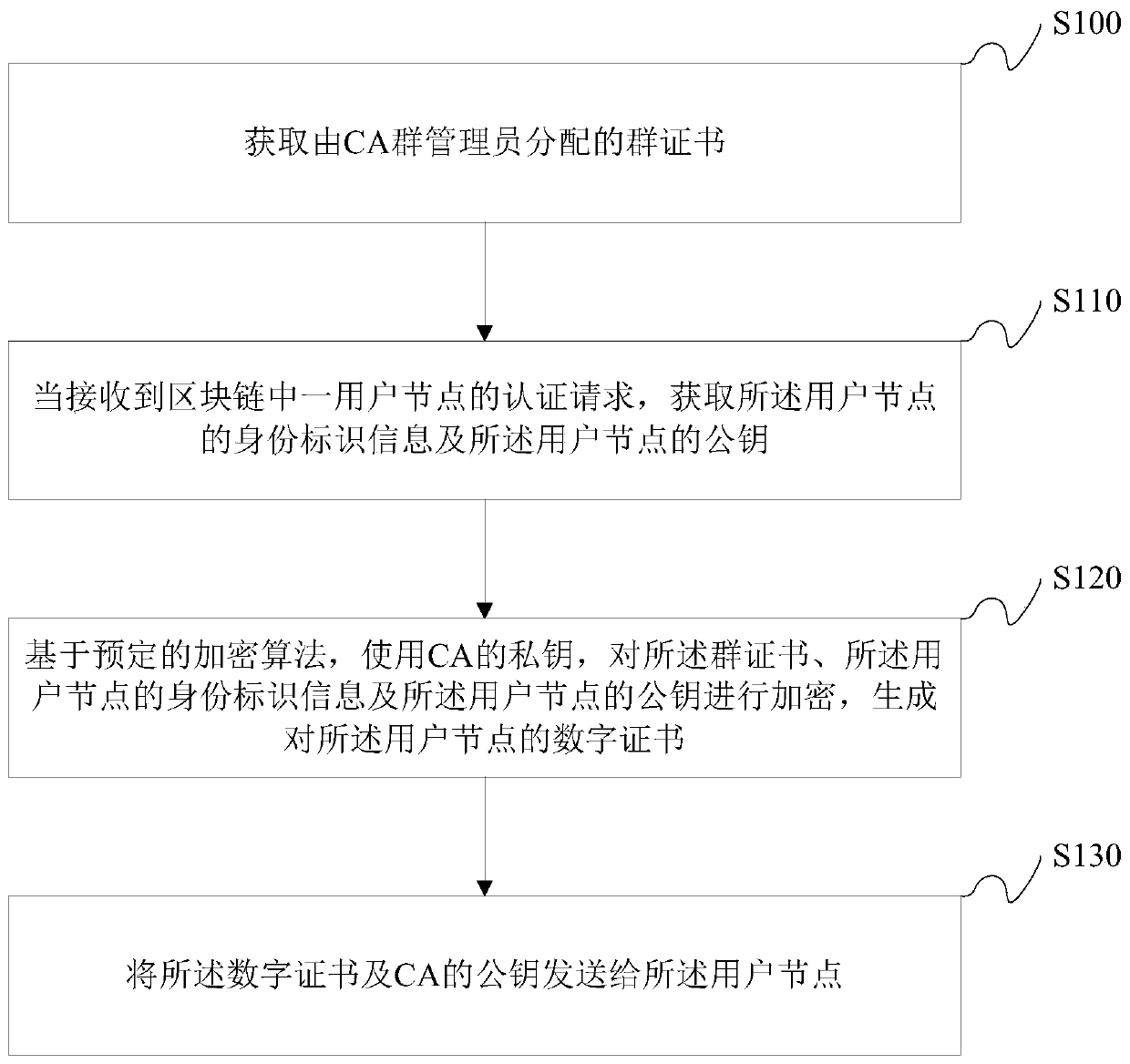
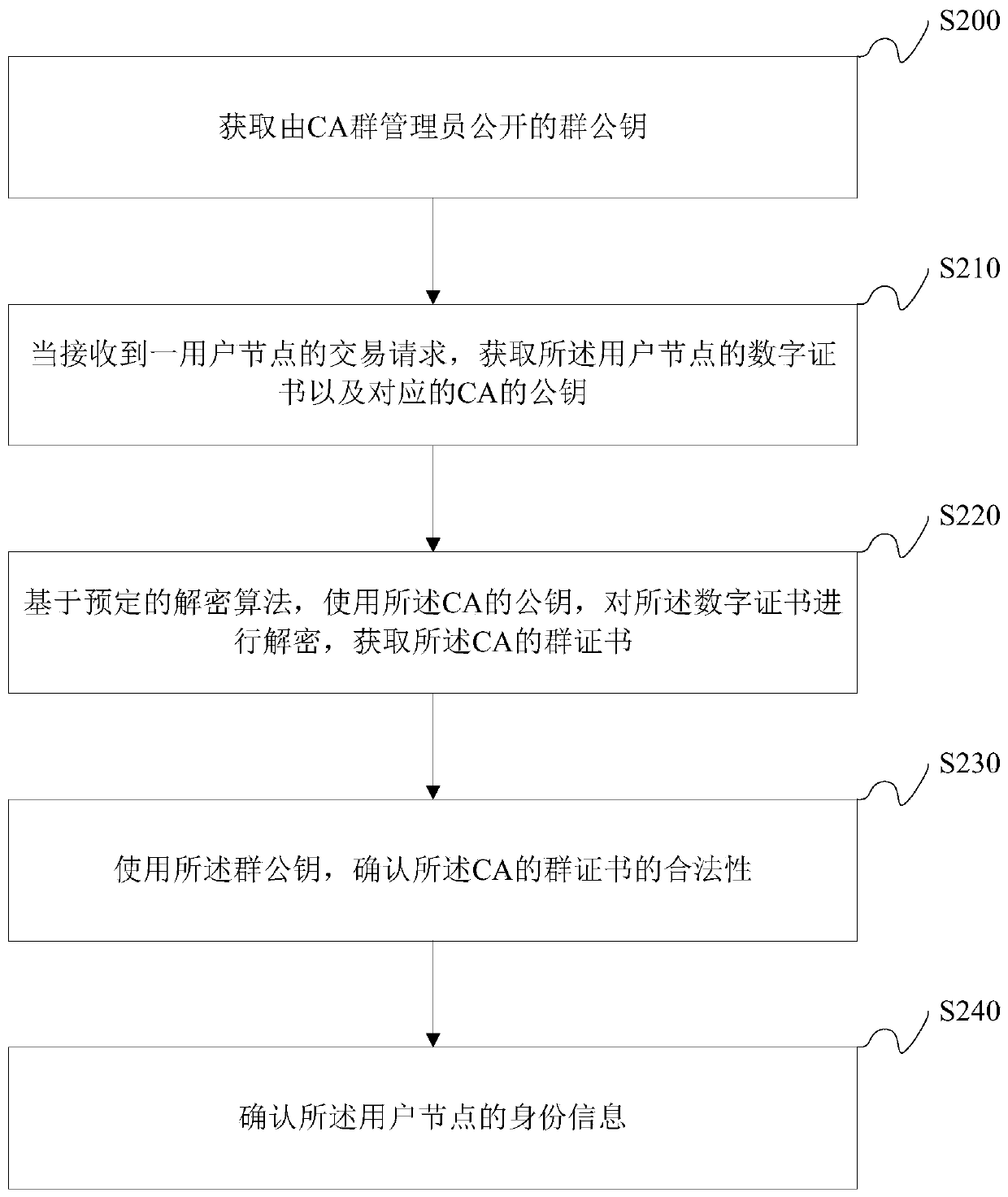
The invention discloses a method for performing identity authentication on user nodes in a block chain and related equipment, and relates to the field of transaction verification, and the method comprises the steps: obtaining a group certificate distributed by a CA group administrator; when an authentication request of a user node in the block chain is received, obtaining identity identification information of the user node and a public key of the user node; encrypting the group certificate, the identity identification information of the user node and the public key of the user node by using the private key of the CA based on a predetermined encryption algorithm to generate a digital certificate of the user node; and sending the digital certificate and the public key of the CA to the usernode. According to the method, hiding of CA identity information of the certificate authority is achieved, and protection of transaction privacy is enhanced.
Owner:ONE CONNECT SMART TECH CO LTD SHENZHEN
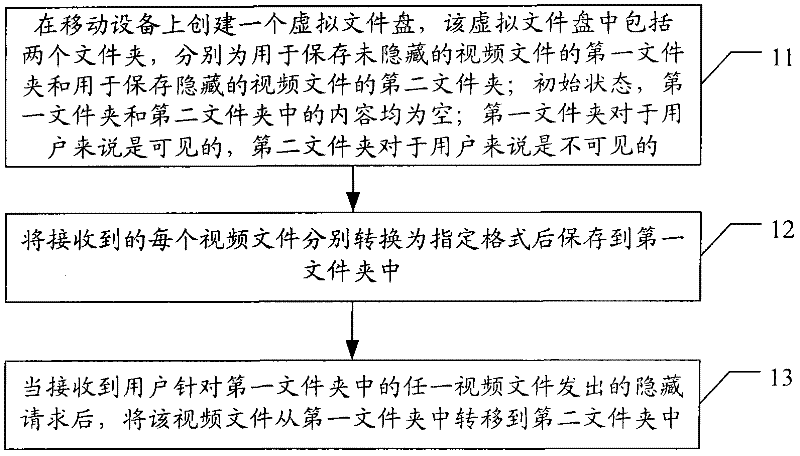
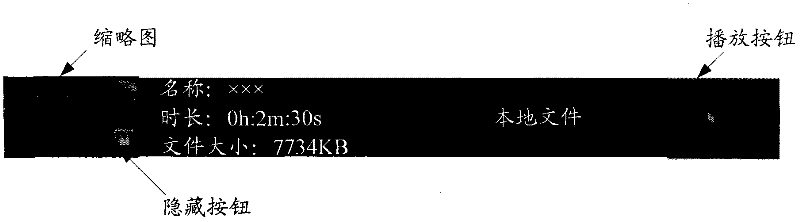
Mobile device and video file hiding method of mobile device
ActiveCN102479307AAchieve hiddenThe hiding process is simpleDigital data protectionSpecial data processing applicationsMobile deviceMultimedia
The invention discloses a video file hiding method of a mobile device. The method comprises the following steps of: creating a virtual file disk on the mobile device, wherein the virtual file disk comprises two folders, respectively, a first folder for storing the unhidden video files, and a second folder for storing the hidden video files, at initial state, the first folder and the second folder both are empty, the first folder is visible for users, and the second folder is invisible for the users; respectively converting each received video file into a specified format, and storing the converted files in the first folder; and after receiving a hiding request for any video file in the first folder from the user, transferring the video file from the first folder to the second folder. The invention also discloses the mobile device. The method and the device disclosed by the invention are convenient for a user to use.
Owner:TENCENT TECH (SHENZHEN) CO LTD
Air swinging structure and air conditioner
ActiveCN107806700AAchieve hiddenAvoid holesCondensate preventionLighting and heating apparatusMechanical engineeringDriven element
The invention discloses an air swinging structure and an air conditioner. The air swinging structure comprises a clamp plate assembly, a plurality of swinging blades, a transmission connecting rod anda driving element, wherein the clamp plate assembly and a casing are detachably connected; the clamp plate assembly forms an accommodating space and is provided with a plurality of installing holes communicating with the accommodating space; the plurality of swinging blades are positioned at an air outlet and are arranged at intervals in the length direction of the clamp plate assembly; each swinging blade comprises an air guide plate and a crank handle; the air guide plate is positioned in the air outlet; the crank handle is of an integral structure with the air guide plate; the crank handlecomprises a driving part and an installing shaft connected with one end of the driving part; the driving part is positioned in the accommodating space; the installing shaft passes through one corresponding installing hole and is connected with the air guide plate; the transmission connecting rod is accommodated in the accommodating space and is rotationally connected with the other end of the driving part; the driving element is connected with the transmission connecting rod; the driving element drives the transmission connecting rod to drive the swinging blades to rotate around the installing shaft. The air swinging structure provided by the invention is the air swinging structure with the advantages of low cost and high assembly efficiency.
Owner:TCL AIR CONDITIONER ZHONGSHAN CO LTD
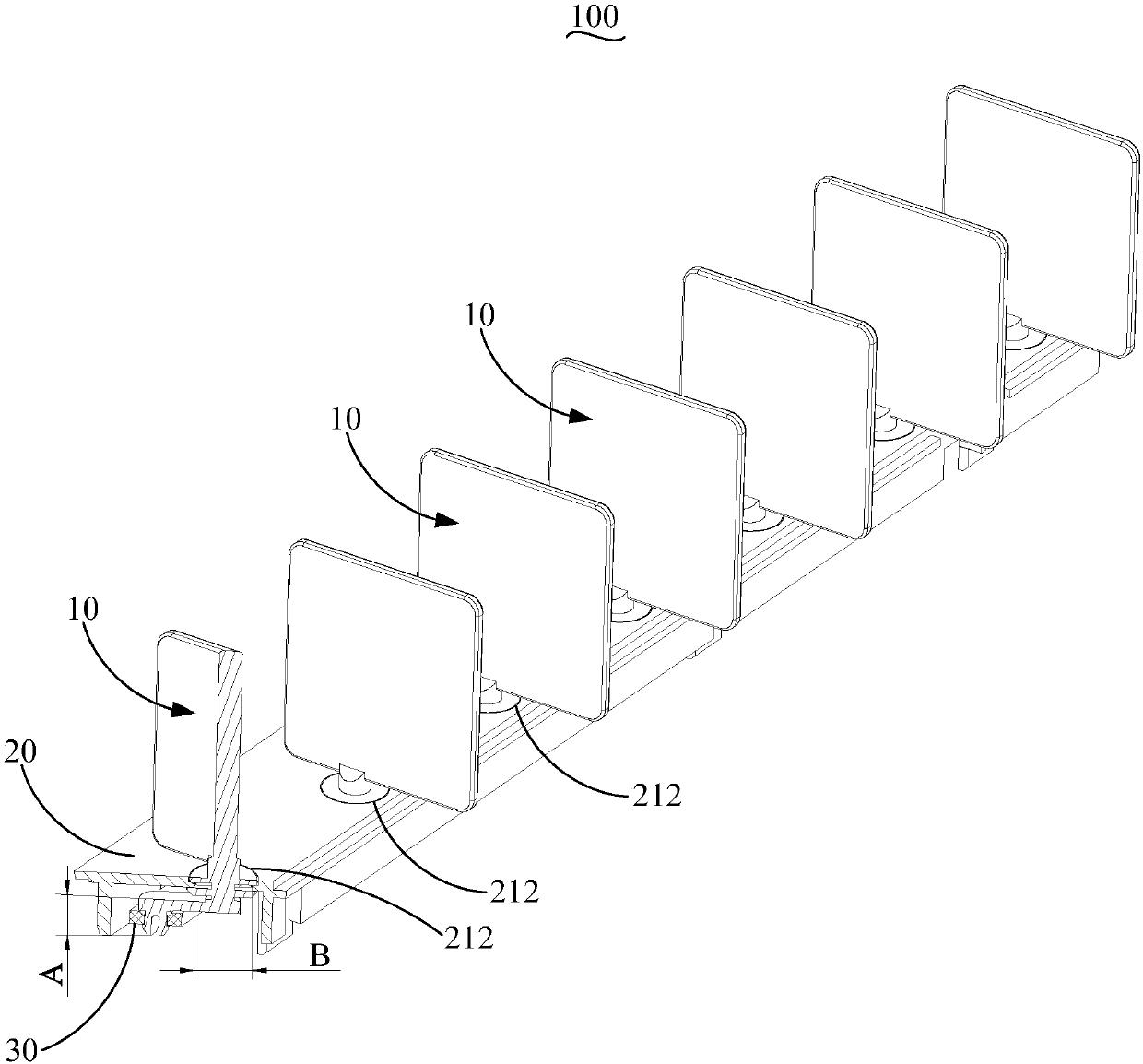
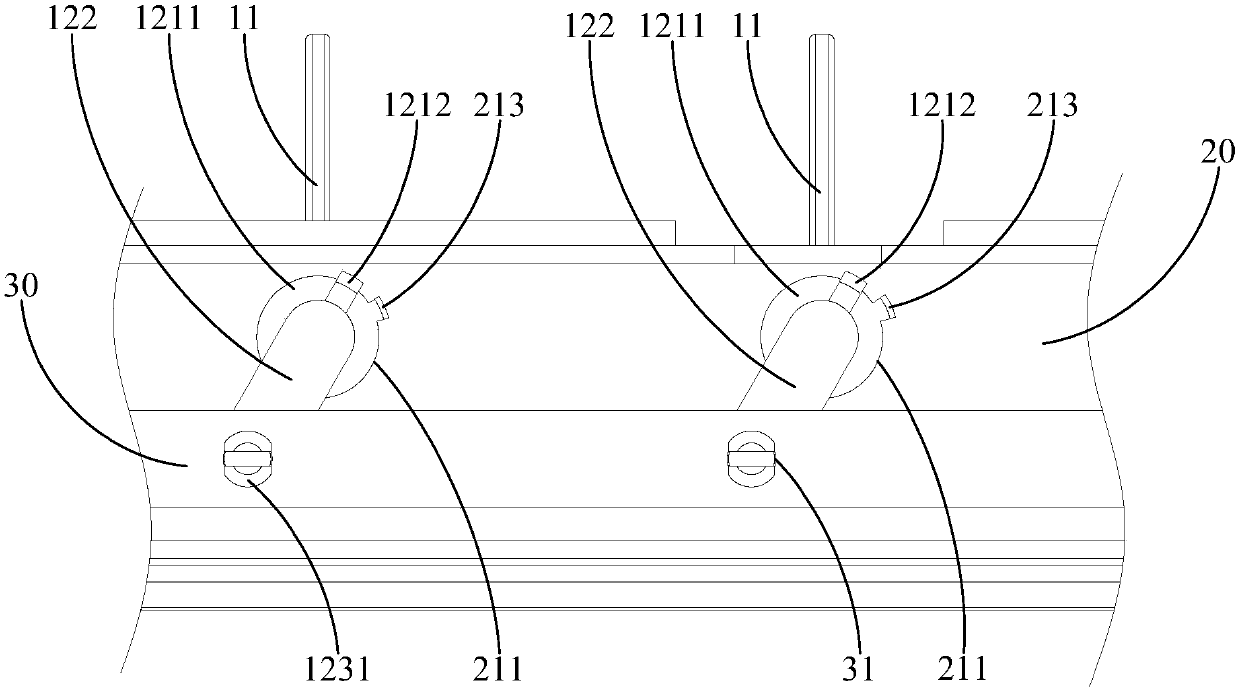
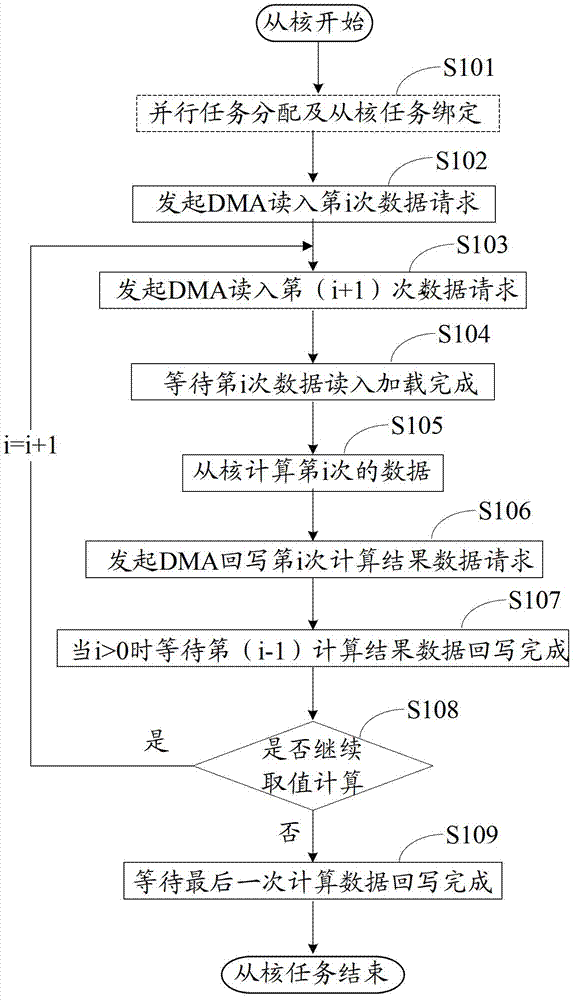
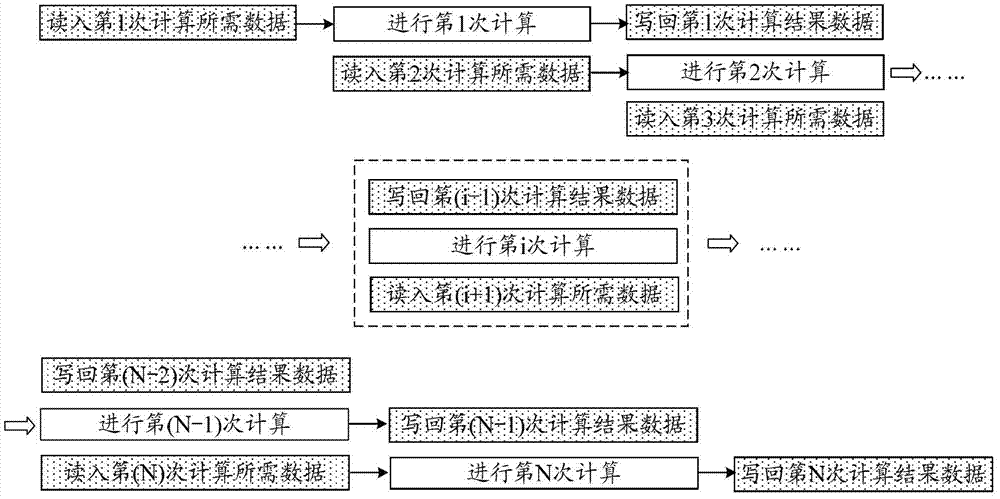
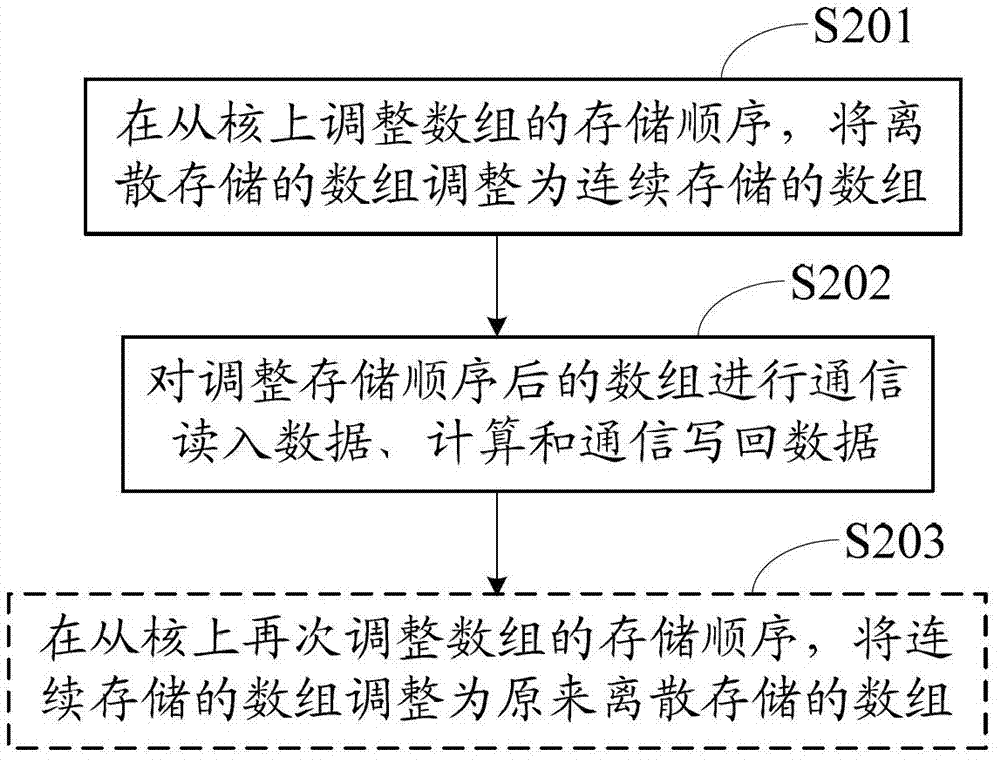
Multistage memory access method and discrete memory access method based on heterogeneous multi-core processor
ActiveCN102929724AMaximize performance efficiencyAchieve hiddenResource allocationFully developedAccess method
The invention discloses a multistage memory access method and a discrete memory access method based on a heterogeneous multi-core processor. The multistage memory access method comprises that an auxiliary core reads in data needed by a first time calculation; besides the first time, the auxiliary core reads in data needed by a next time calculation while performing the data calculation; besides the last time, the auxiliary core writes back result data of the last calculation while performing the data calculation; and the auxiliary core writes back result data of the last time calculation. The discrete memory access method includes that storage orders of digit groups are adjusted on the auxiliary core, and discretely-stored digit groups are adjusted into continuously stored digit groups; and communication read-in data, calculation and communication write-back data are performed on the digit groups through the auxiliary core by the multistage memory access method. According to the multistage memory access method and the discrete memory access method based on the heterogeneous multi-core processor, maximum hides between expenditures and multistage storage resource access expenditures are effectively calculated, the multistage memory access efficiency is improved, the performance efficiency of the auxiliary core is fully developed, and accordingly, the calculation efficiency of a scientific calculation subject is enhanced.
Owner:JIANGNAN INST OF COMPUTING TECH
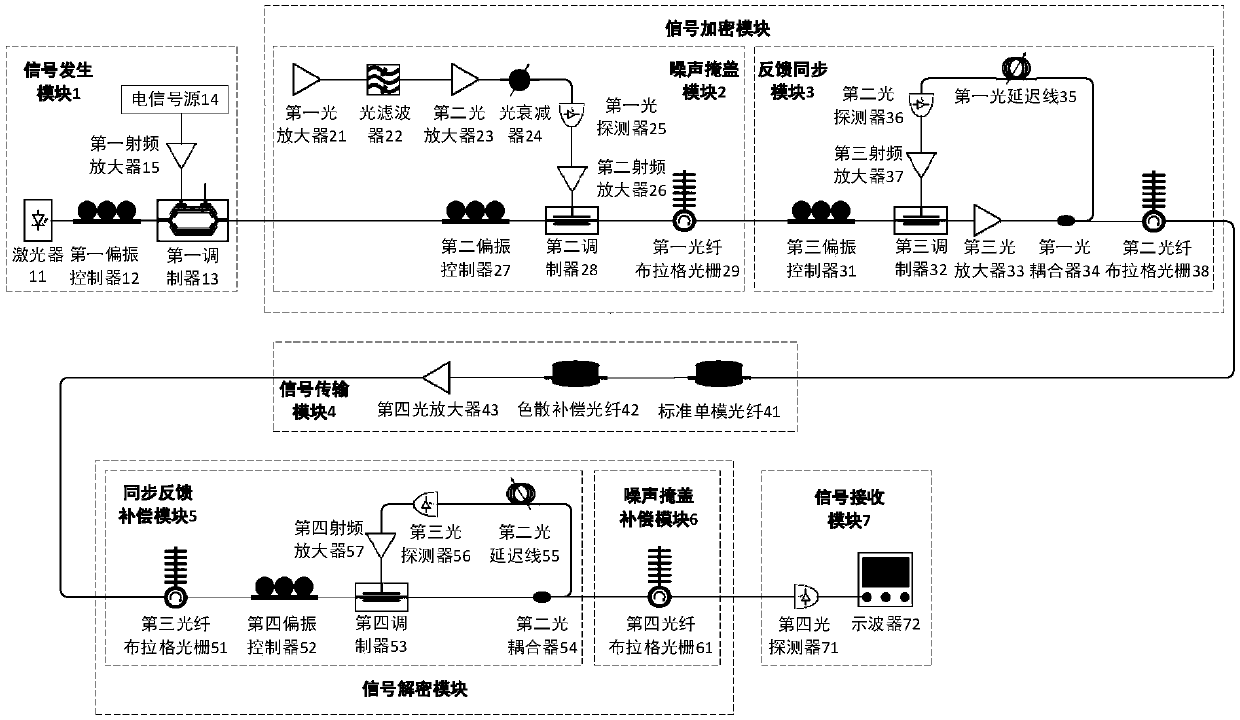
Phase-amplitude conversion based secure optical communication system
ActiveCN107769859AAchieve hiddenIncreased complexityDistortion/dispersion eliminationElectromagnetic transmission optical aspectsSecure communicationTime delays
The invention discloses a phase-amplitude conversion based secure optical communication system, and belongs to the technical field of secure communication. The phase-amplitude conversion based secureoptical communication system is to convert a noise signal at a phase to an amplitude so as to realize masking encryption for the data signal at the amplitude through the phase-amplitude conversion; compared with the traditional noise secure optical communication system, the phase-amplitude conversion based secure optical communication system can decrypt through the phase-amplitude conversion, is not required to filter a masking signal, has an unlimited signal rate, has the masking signal not required to be transmitted in a link and can greatly improves the security of the encryption system; meanwhile, the system is subjected to secondary encryption through the photoelectric feedback circuit, increases the key space by introducing time delay, increases the key space dimension by a dispersion element in the system and realizes time delay masking. Compared with the traditional chaotic secure optical communication system, the system has higher key dimension and bigger key space.
Owner:HUAZHONG UNIV OF SCI & TECH
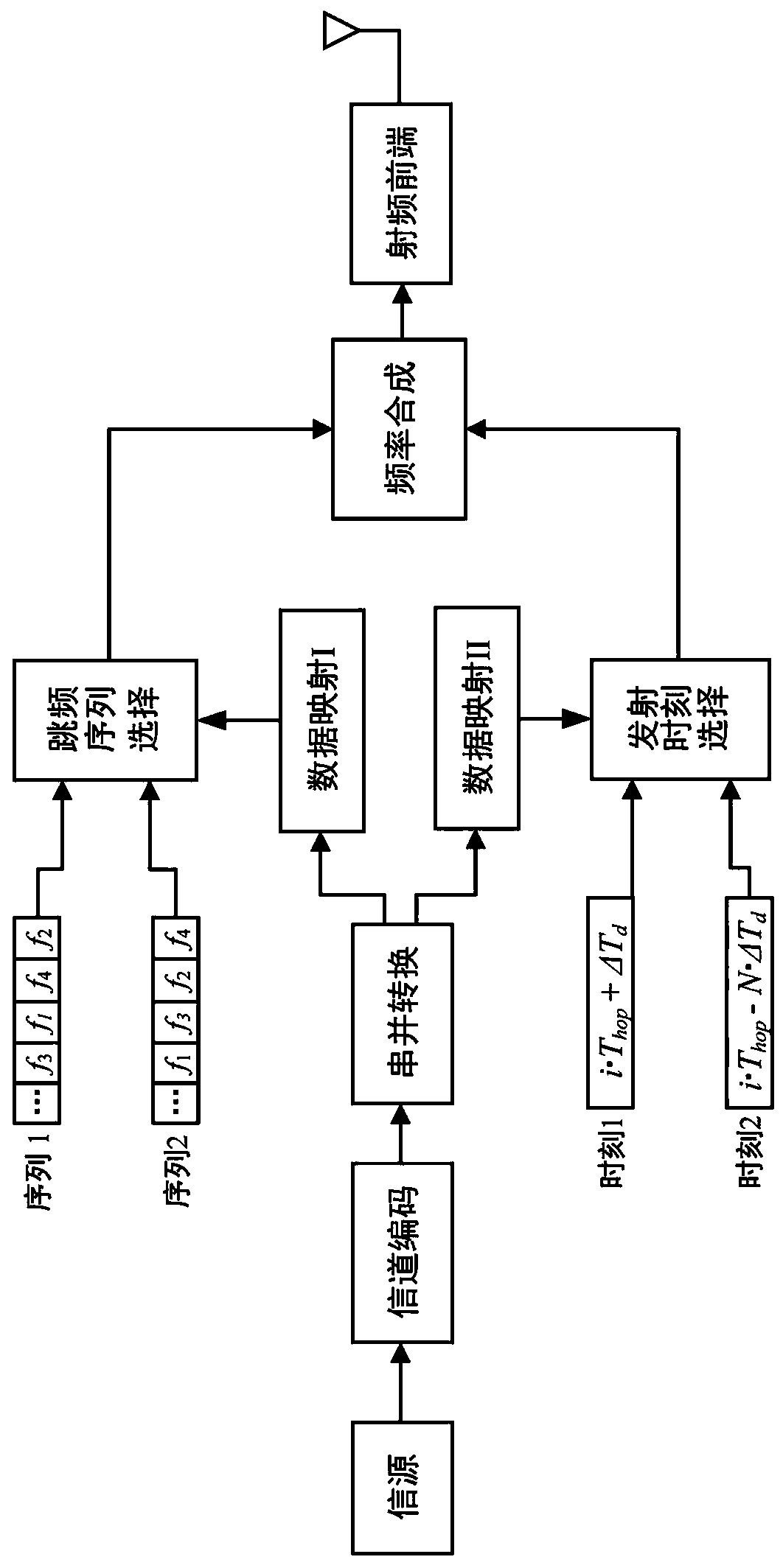
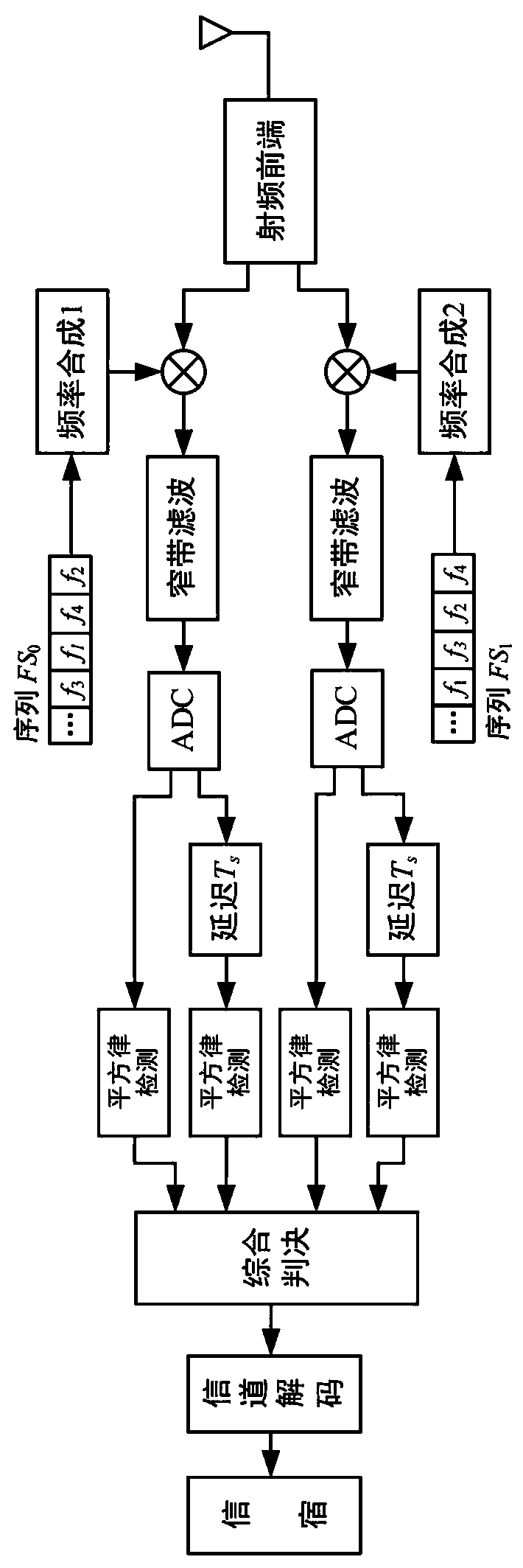
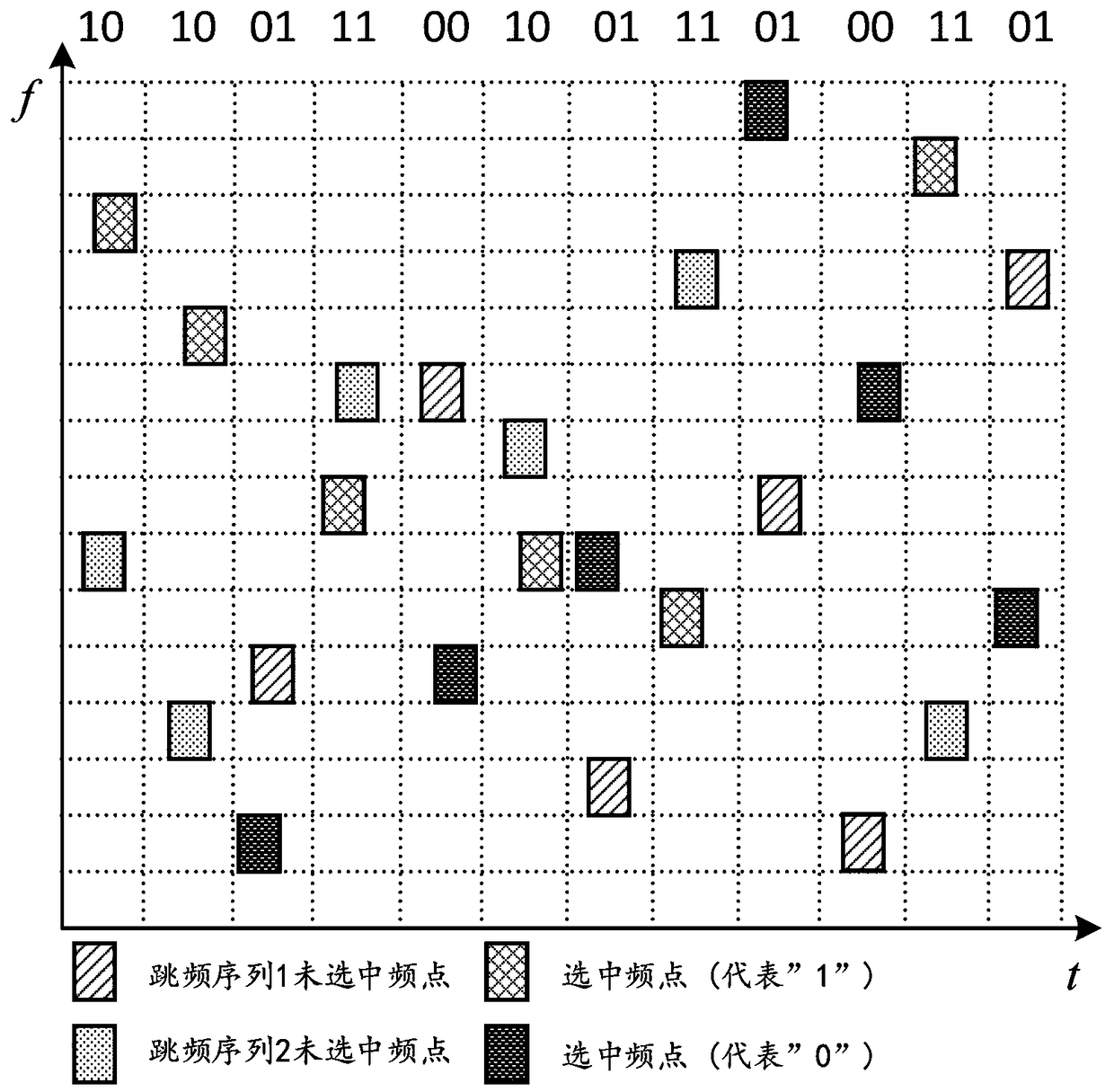
Two-dimensional pattern modulation frequency hopping communication method
ActiveCN109194365AAchieve hiddenReduce the probability of being tracked and interferedTransmissionTime domainInformation transmission
The present invention relates to a two-dimensional pattern modulation frequency hopping communication method. The method comprises the steps of: in a frequency hopping communication process, mapping sent information bits to two information carrier units consisting of a symbol of a frequency hopping sequence and a symbol of a frequency hopping take-off moment, and employing the frequency domain change and the time domain change of the frequency hopping patterns to represent information so as to achieve time frequency two-dimensional frequency hopping pattern modulation. The two-dimensional pattern modulation frequency hopping communication method can effectively inhibit the frequency hopping modes of tracking interference and part of frequency band interference, has an unequal interval frequency hopping period and is easy to improve the information transmission rate.
Owner:ARMY ENG UNIV OF PLA
Transmitting end and receiving end of secure communication system
InactiveCN105978679AImprove securityImprove security levelSecuring communication by chaotic signalsCommunications systemTime delays
The invention discloses a transmitting end and a receiving end of a secret communication system. The transmitting end includes a main laser, an external cavity of the main laser and an information encryption module. The external cavity of the main laser has a feedback cavity, and the laser emitted by the main laser passes through the feedback cavity to form a feedback loop, so that the main laser works in a chaotic state. A phase modulator is arranged in the feedback loop of the laser, and the phase modulator performs phase modulation on the light in the feedback loop according to the phase key, and the phase key is a pseudo-random sequence. The chaotic laser signal sent by the main laser working in the chaotic state is sent out through the information encryption module. Only when the laser at the receiving end has the same feedback structure and phase modulation as the main laser can it correctly demodulate the information. At the same time, the multi-feedback external cavity with high-speed phase modulation can also hide the time-delay tag of the chaotic laser, improving the security of the communication system.
Owner:江宁 +1
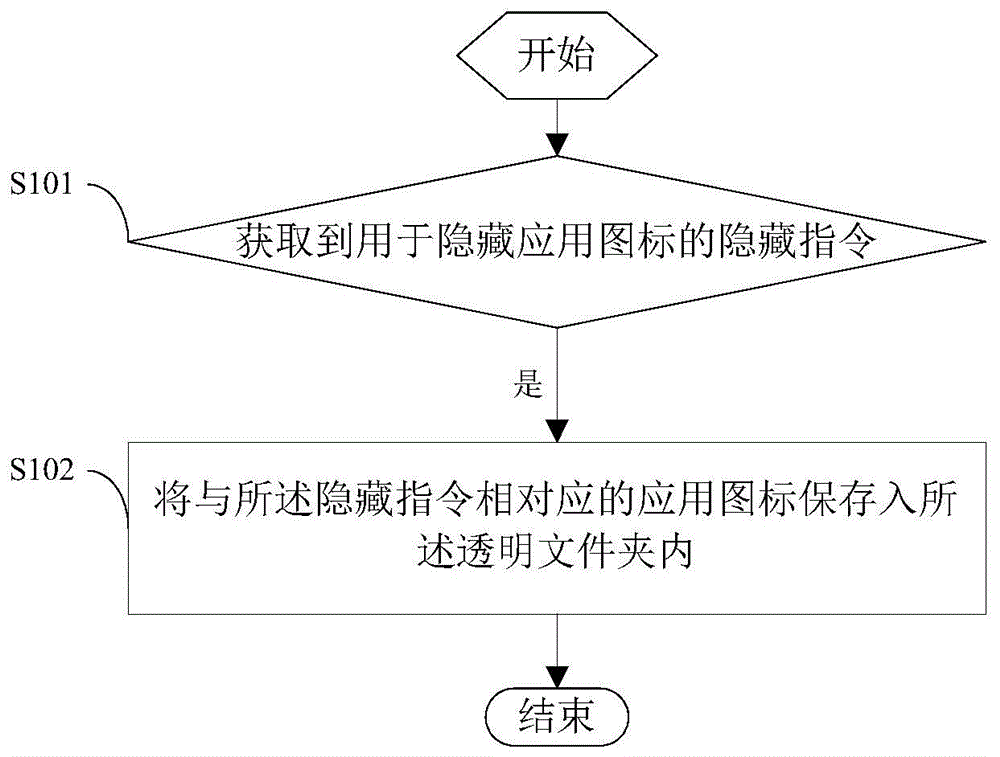
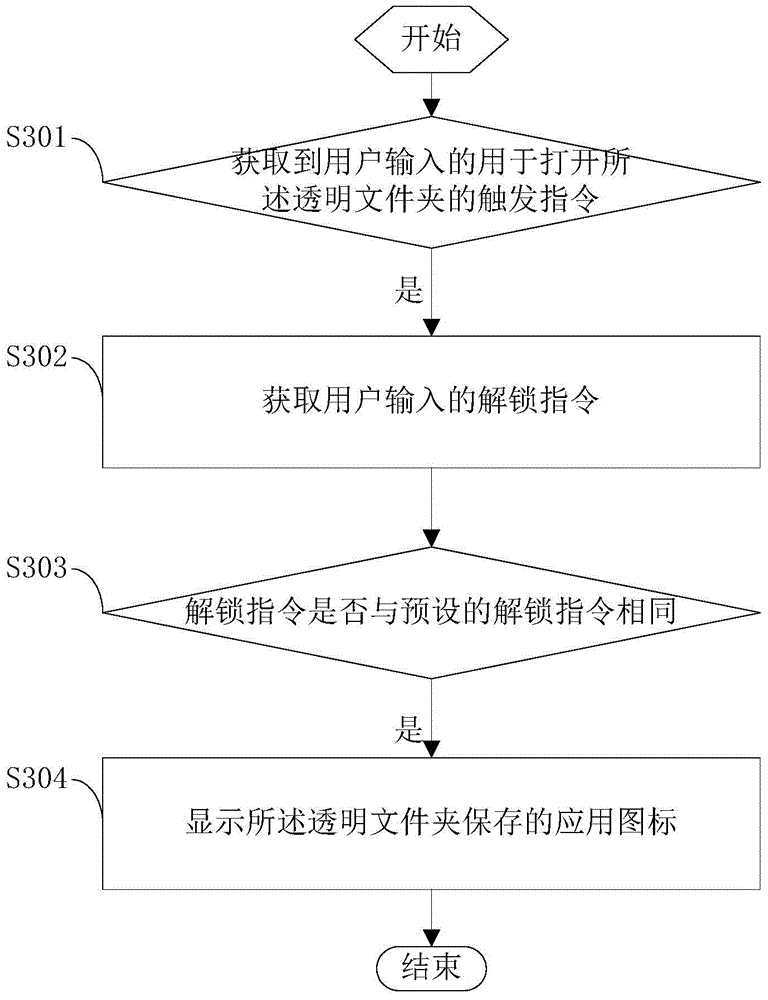
Application icon hiding method and system, and intelligent terminal
InactiveCN105700884AAchieve hiddenDigital data authenticationExecution for user interfacesUser needsUser input
The present application provides a method and system for hiding application icons, and an intelligent terminal. When detecting a user-input hiding instruction, it is determined that the user needs to hide the application icon at this time, and the application icon corresponding to the hiding instruction is determined. Drag the application icon corresponding to the hiding instruction into the transparent folder to hide the application. It can be seen that compared with the application hiding method in the prior art, it is more convenient and quicker.
Owner:THUNDER SOFTWARE TECH
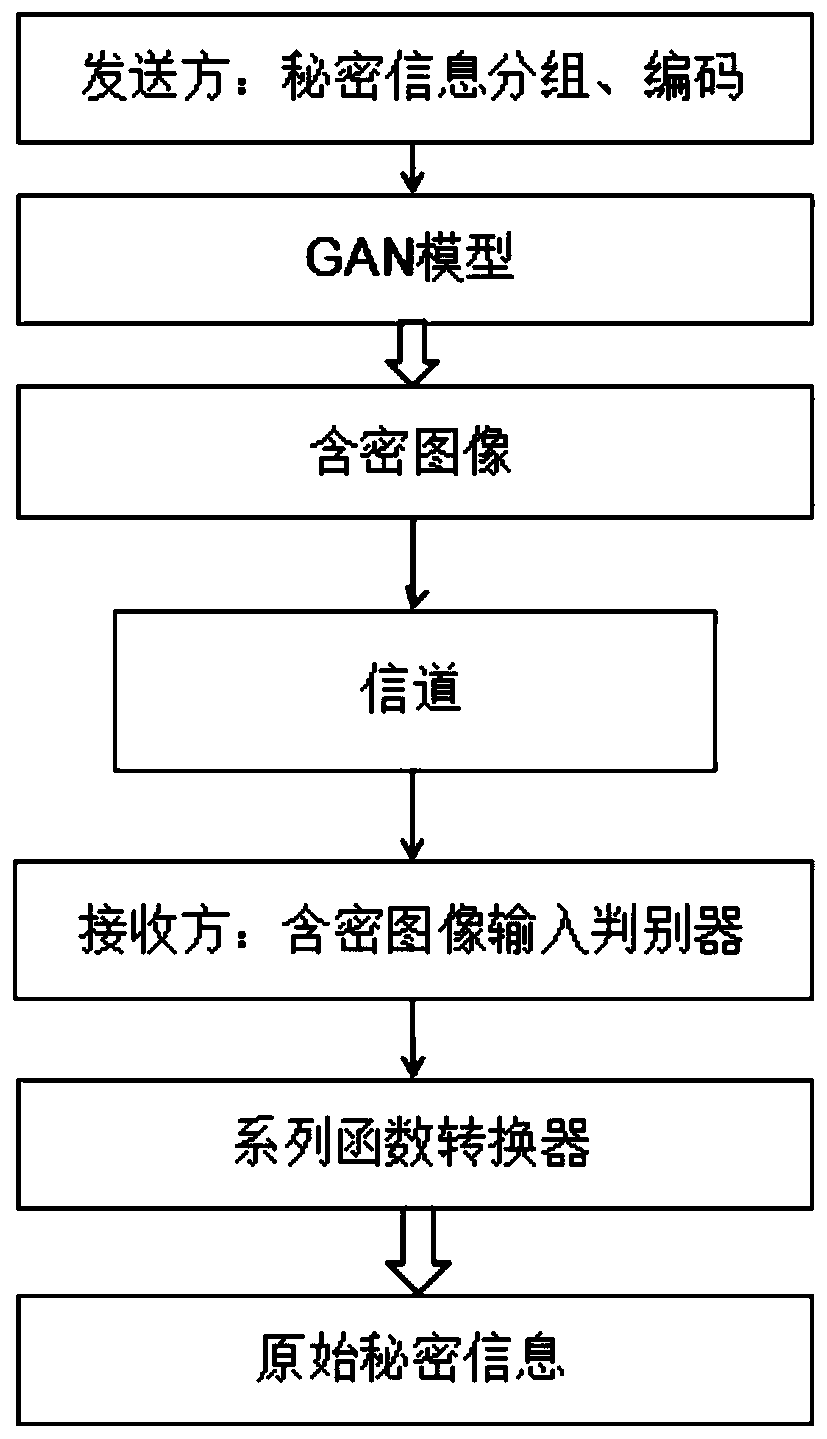
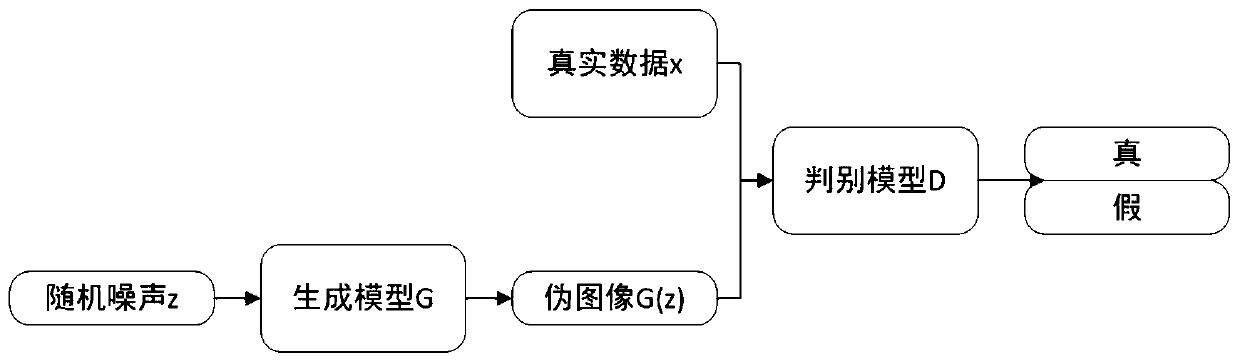
Universal steganography method based on deep learning
PendingCN110533570ACannot be resolved completelyResolve accuracyCharacter and pattern recognitionImage data processing detailsPattern recognitionDiscriminator
The invention discloses a general steganography method based on deep learning. The method comprises the following steps: S1, carrying out hiding processing on a sender; dividing secret information tobe hidden into n groups of information fragments, wherein each group of information fragments correspond to one category label, a deep learning model is adopted, the category label and random noise are used as drive, a pseudo-natural image of a specified category is generated, and the pseudo-natural image is used as a secret-containing image input channel after hiding processing; and S2, carryingout extraction processing at a receiver: inputting the secret-containing image into a discriminator by the receiver to carry out image authenticity identification and image category judgment, then sending the image category information into a function converter to be processed to obtain a secret information fragment, and decoding the secret information fragment to obtain original secret information. According to the invention, the security and confidentiality of information transmission can be greatly improved.
Owner:NANJING INST OF TECH
Transmitting terminal and receiving terminal of secure communication system
InactiveCN106712890AImprove securityImprove security levelSecret communicationSecuring communication by chaotic signalsCommunications systemEngineering
The invention discloses a transmitting terminal and a receiving terminal of a secure communication system. The transmitting terminal comprises a main laser, an external cavity of the main laser and an information encryption module, the external cavity of the main laser is provided with a feedback cavity, and the laser emitted by the main laser forms a feedback loop after passing through the feedback cavity, so that the main laser works in a chaotic state. A phase modulator is arranged in the feedback loop of the laser, the phase modulator performs phase modulation on the light in the feedback loop according to a phase key, and the phase key is a pseudo-random sequence. A chaotic laser signal emitted by the main laser working in the chaotic state is transmitted by the information encryption module. Only when the laser of the receiving terminal has the same feedback structure and phase modulation as the main laser, the information can be correctly demodulated. Meanwhile, a plurality of feedback external cavities of high-speed phase modulation can also hide a delay tag of chaotic laser, and thus the security of the communication system is improved.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
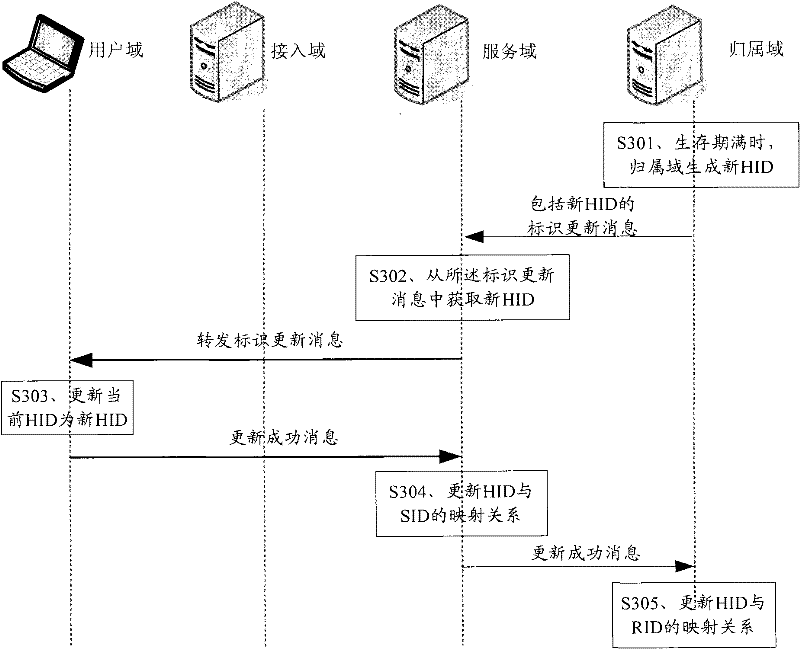
Identification distribution and separate-storage method, identification replacing transmission method and system
InactiveCN101754219AImprove the protective effectSupport mobilitySecurity arrangementTelecommunicationsService domain
The invention discloses an identification distribution and separate-storage method, an identification replacing transmission method and system, relating to the field of network safety. The identification distribution and separate-storage method comprises the following steps of: dividing a heterogeneous wireless network by function into a user domain, an access domain, a service domain and an attribution domain, wherein the service domain comprises at least one access domain, the access domain comprises at least one user domain, and the attribution domain and the service domain are the same network when in local service; and after the successful authentication of a terminal, allocating the attribution domain, the service domain and the access domain with domain identifications domain by domain. Based on the access authentication of the heterogeneous wireless network, the invention provides a mechanism of the identification distribution, the separate storage and the replacing transmission of the identification. In the transmission process of the domain identification in the user domain, the access domain, the service domain and the attribution domain, the real identity and the location information of a terminal can be effectively concealed through the retrieval and the replacement among domains and the dynamic update at different identification mapping servers, thereby enhancing the credible access of the heterogeneous wireless network and the safety protection capacity on mobility problems.
Owner:THE PLA INFORMATION ENG UNIV
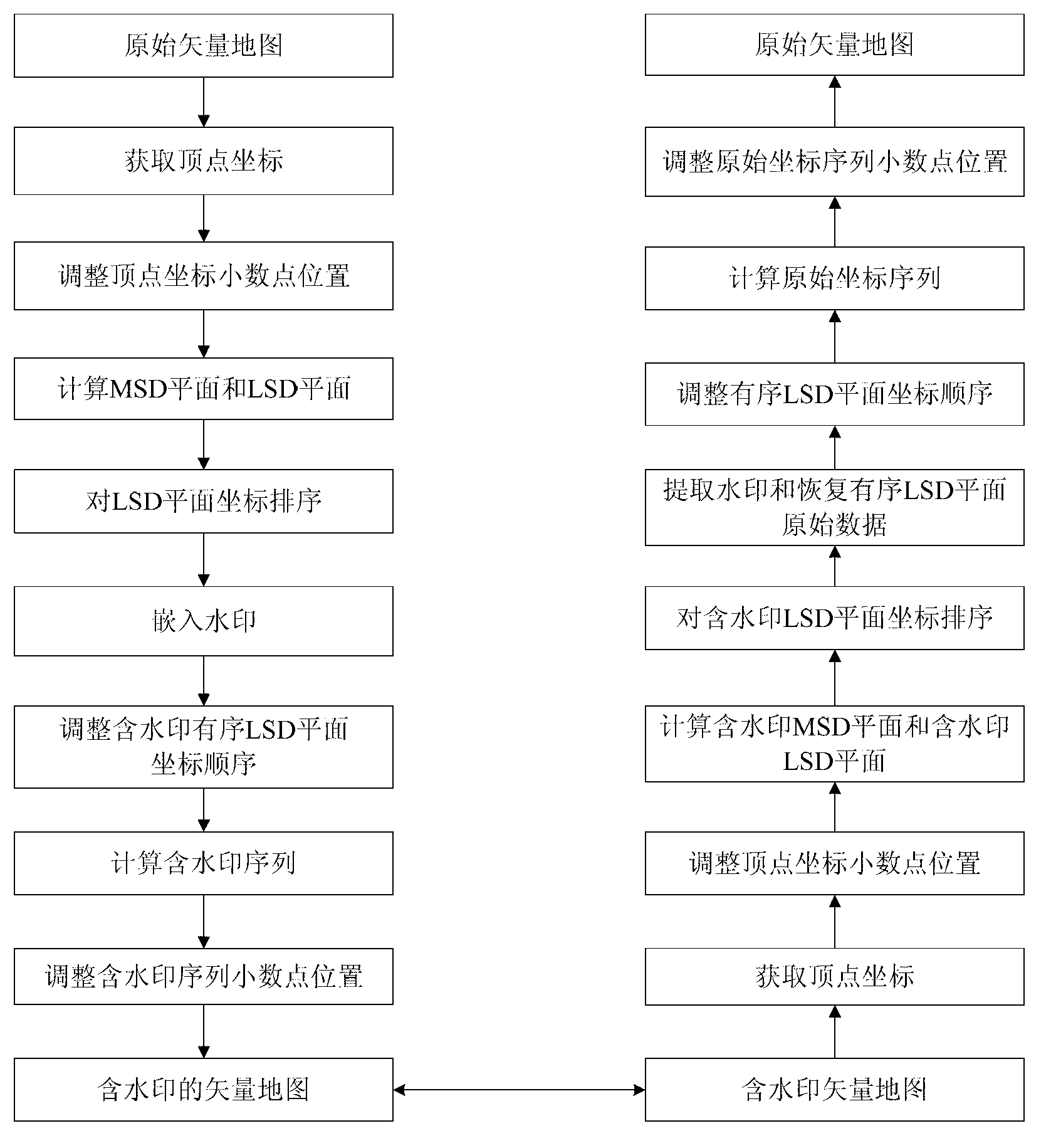
Vector map reversible information hiding method based on LSD planes
InactiveCN103325082AEasy to useGain invisibilityMaps/plans/chartsImage data processing detailsInformation hidingVector map
The invention relates to a vector map reversible information hiding method based on LSD planes. Top points of a vector map are sequentially scanned to obtain x-coordinate sequences and y-coordinate sequences of the top points; scaling positions of the coordinates are moved towards the right side to obtain new coordinate sequences; MSD planes and the LSD planes are calculated; the LSD planes are sequenced according to the ascending sequence to obtain orderly LSD planes; watermarks are embedded in the orderly LSD planes; the coordinate sequences of the orderly LSD planes containing the watermarks are adjusted to obtain LSD planes containing the watermarks; the coordinate sequences containing the watermarks are obtained through calculating; scaling positions of the coordinates in the coordinate sequences containing the watermarks are adjusted; a vector map containing the watermarks is obtained.
Owner:HARBIN ENG UNIV
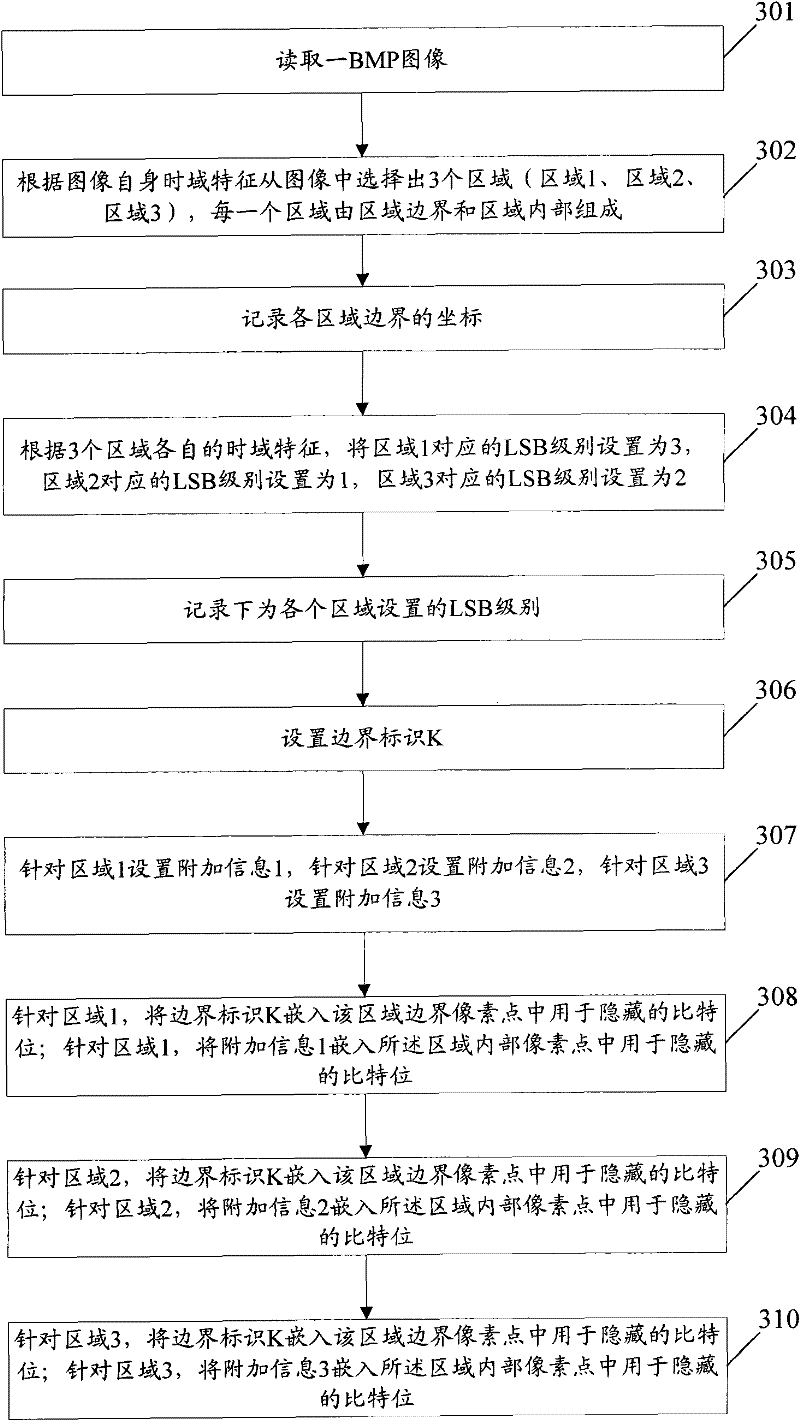
A method and device for embedding additional information in an image
InactiveCN102270335AEmbedded flexibleAchieve hiddenImage data processing detailsTime domainLeast significant bit
The present invention provides a method and device for embedding additional information in an image, including: selecting at least one area from the image according to the temporal characteristics of the image itself, and the area is composed of the area boundary and the area inside; The time-domain features are respectively set with the corresponding least significant bit LSB level; for each region, according to the corresponding LSB level and the LSB hiding method is used to embed the pre-set boundary mark into the region boundary, according to the corresponding LSB level and adopt the LSB hiding method to Additional information is embedded inside the area. The application of the solution of the present invention not only realizes the hiding of additional information, but also embeds additional information more flexibly under the condition of ensuring that the image is not perceived.
Owner:SAMSUNG ELECTRONICS CHINA R&D CENT +1
Electronic device
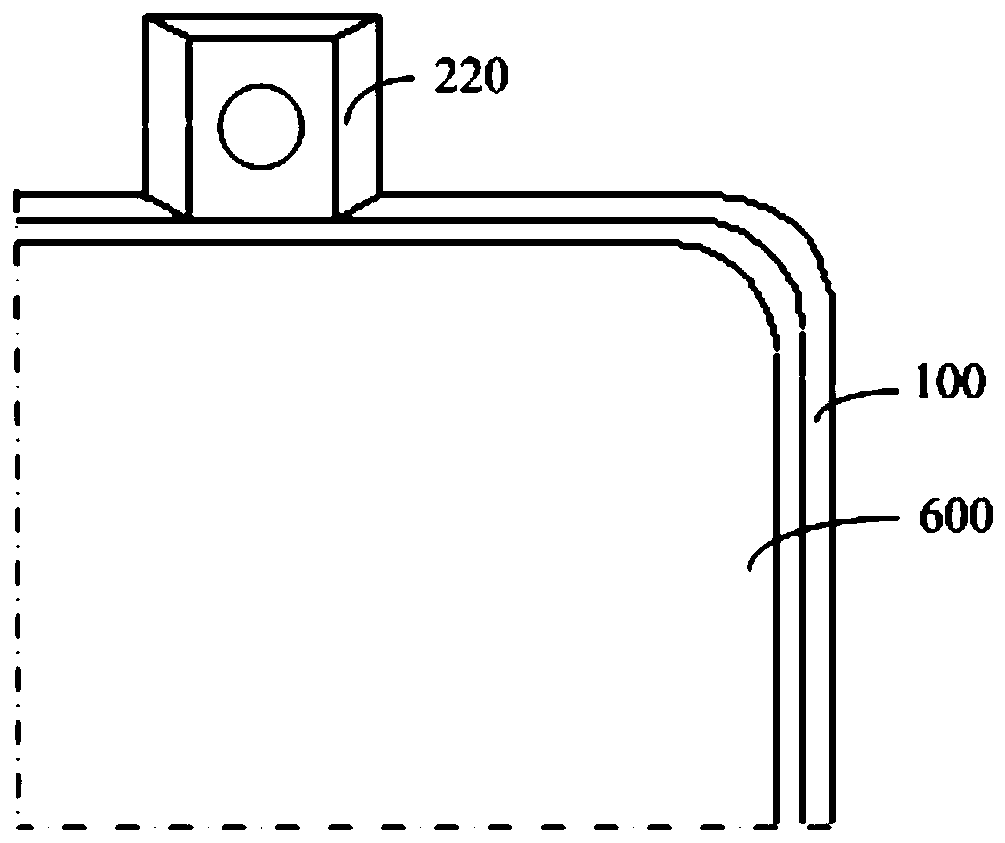
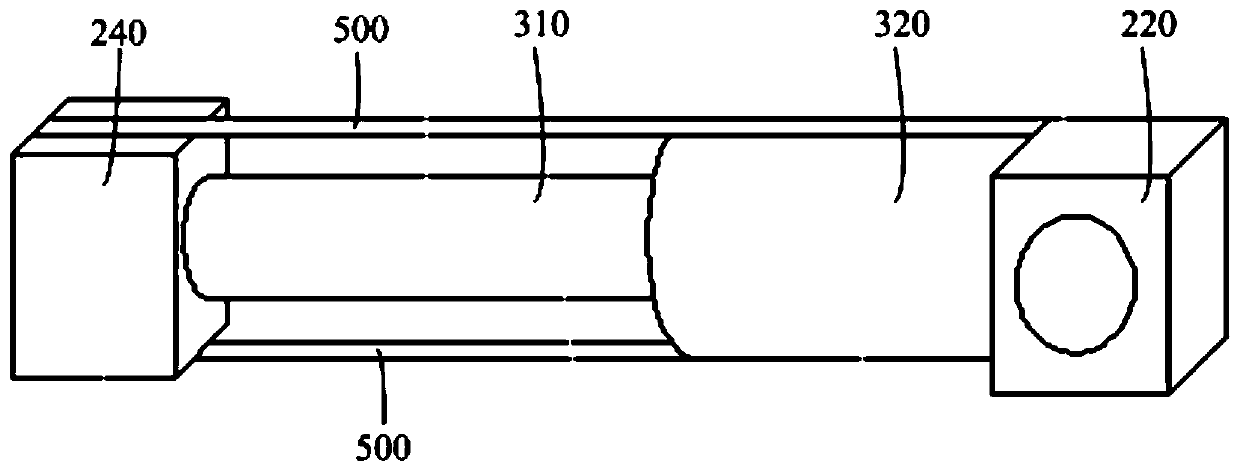
ActiveCN111050047AMitigate the impactStick out to avoidTelevision system detailsColor television detailsPhysicsAmbilight
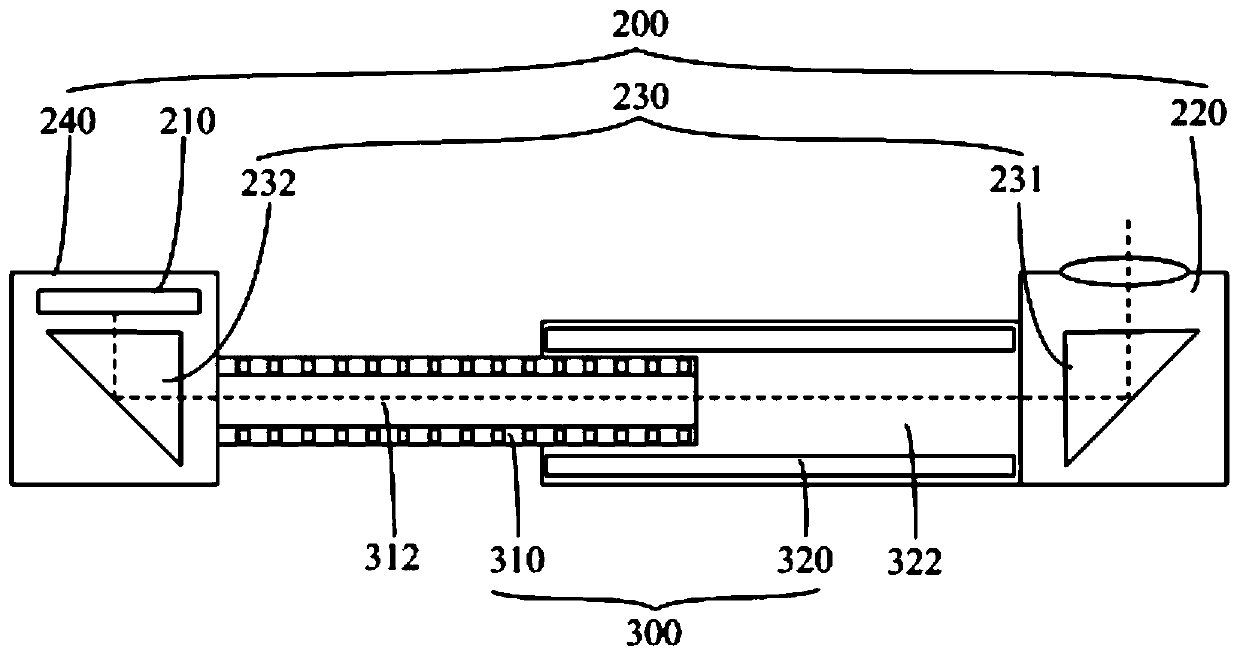
The invention discloses an electronic device which comprises a device shell (100) and a camera module (200), wherein the device shell (100) is provided with an inner cavity and an opening. The openingcommunicates with the inner cavity. , The camera module (200) comprises a photosensitive chip (210), a lens (220) and a reflector (230). The photosensitive chip (210) is arranged in the inner cavity;wherein the lens (220) is movably arranged in the equipment shell (100); the lens (220) can extend out of the equipment shell (100) or retract into the equipment shell (100) through the opening, andunder the condition that the lens (220) is located outside the equipment shell (100), the reflection piece (230) can reflect ambient light emitted into the lens (220) to the photosensitive chip (210).According to the scheme, the problem that an antenna of the electronic equipment is greatly influenced in the shooting process due to the fact that the existing electronic equipment is provided witha lifting type camera can be solved.
Owner:VIVO MOBILE COMM CO LTD
Generation method of RFID member
InactiveCN101634946ARealize the operationRealize hot swapSpecific program execution arrangementsBusiness process managementService oriented
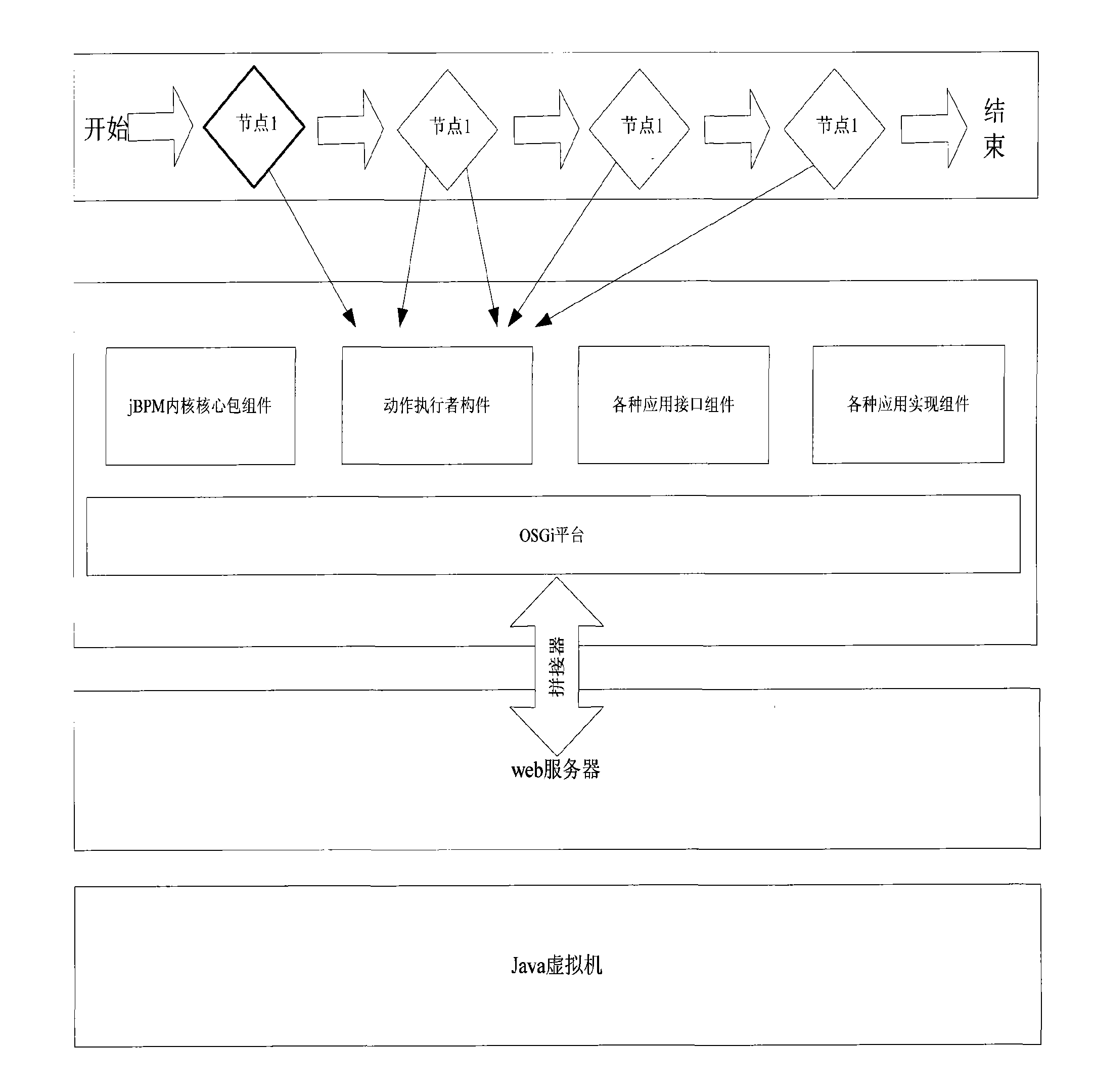
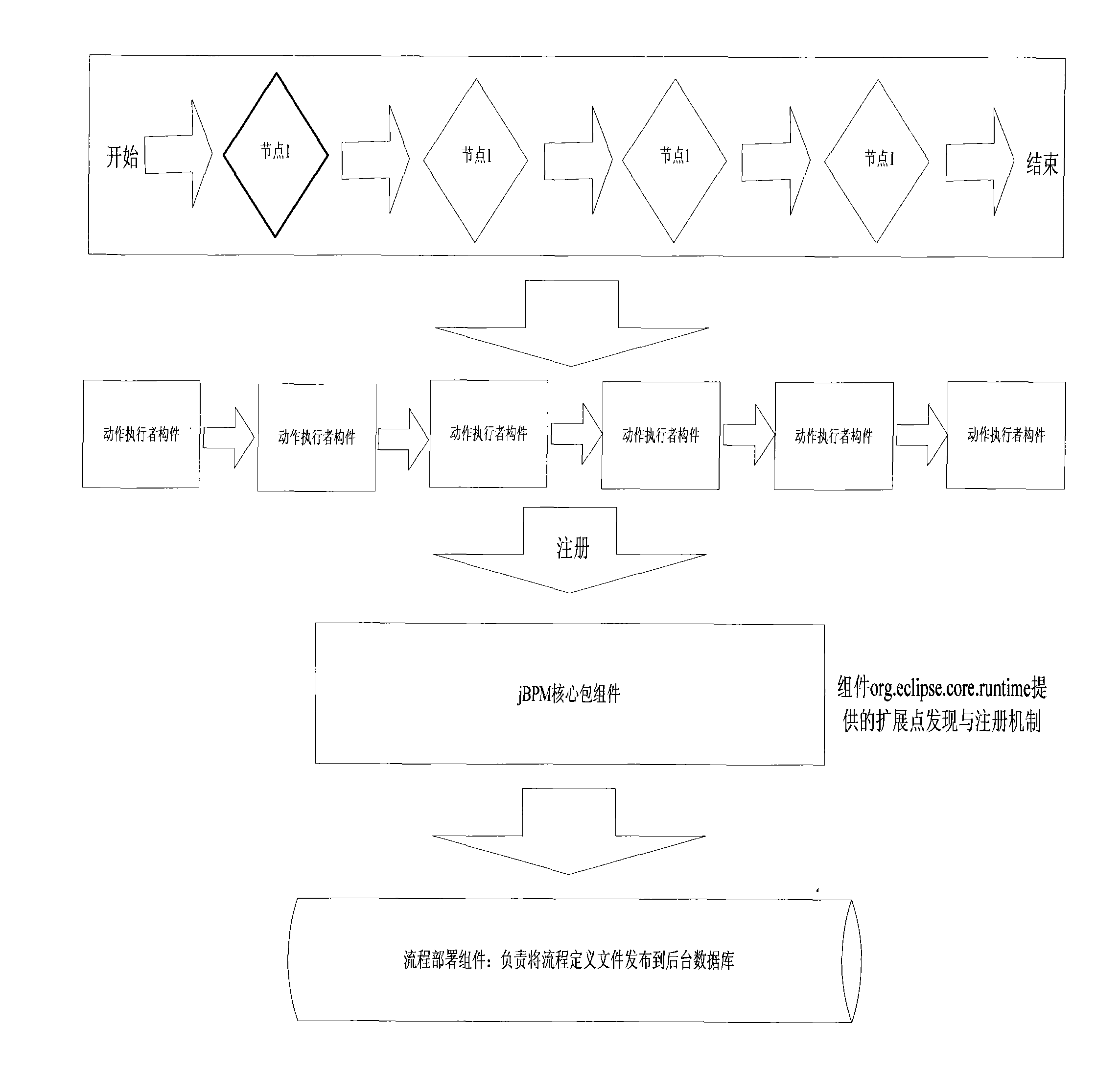
The invention provides a generation method of an RFID member. The method comprises the following steps: integrating a computer service platform OSGi with workflow of Java business process management (JBPM), setting an RFID middleware application system as an independent application member, and operating on an engine of the workflow of the JBPM as a workflow node to realize business process of the RFID application system. The generation method is characterized by combining the JBPM with the OSGi, and managing change and business recombination of the business process by the workflow technology and the service-oriented member technology, and relative independence of the JBPM and the OSGi bundle causes correspondence of the bundle and the JBPM node; management of the OSGi on the bundle causes separation of service from realization, hot plug of the bundle is realized without restarting the platform; service is clear, realization is hidden, and service-oriented operation is really realized.
Owner:SOUTH CHINA UNIV OF TECH
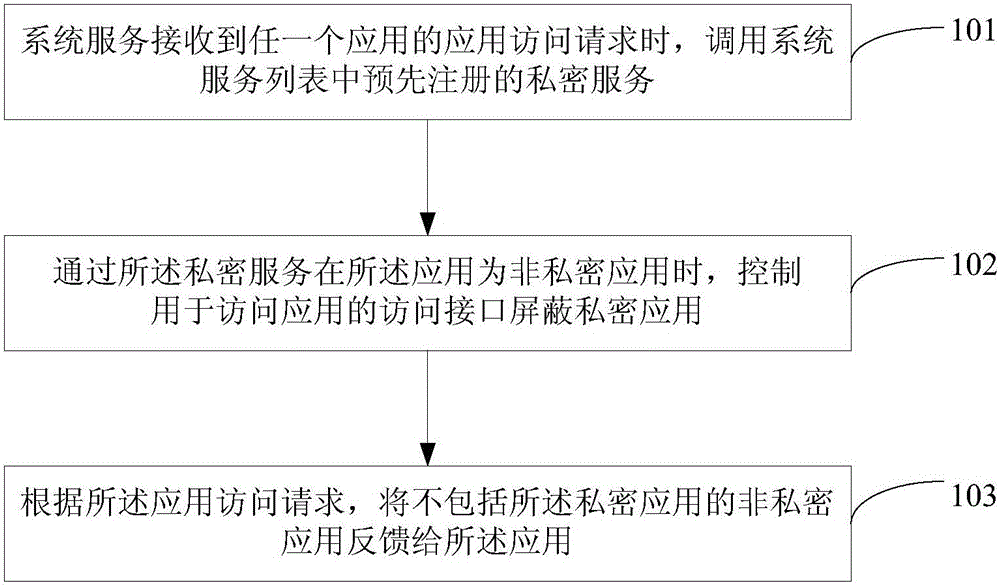
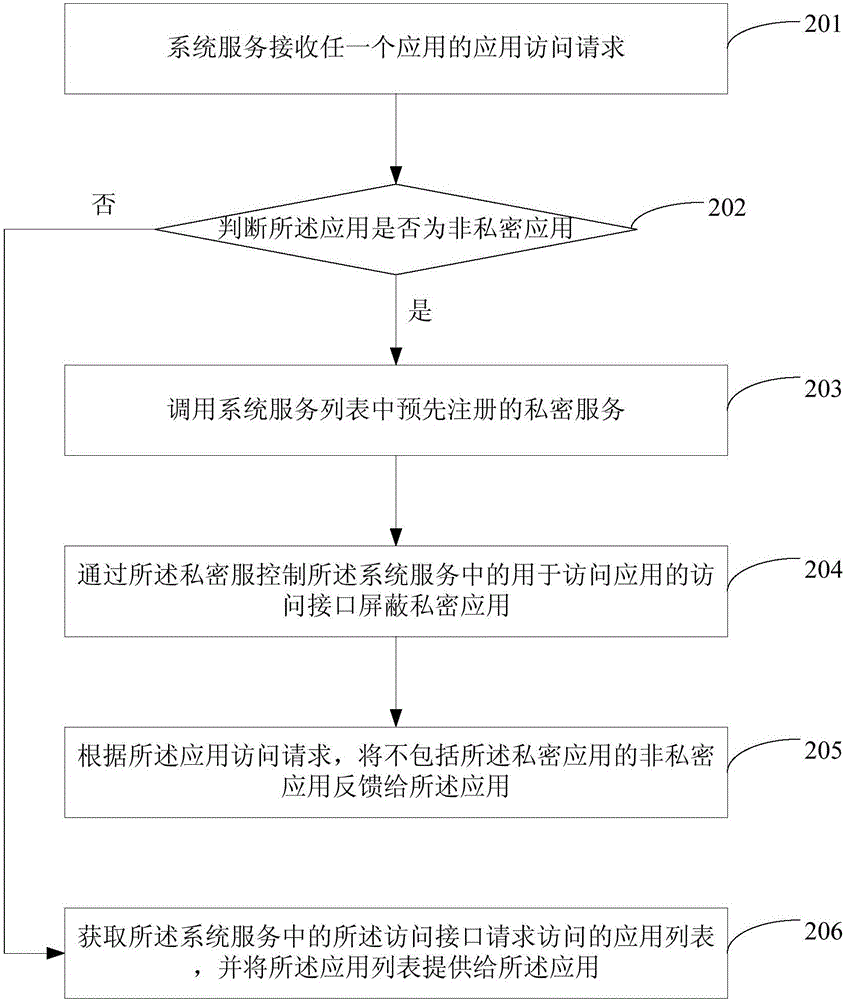
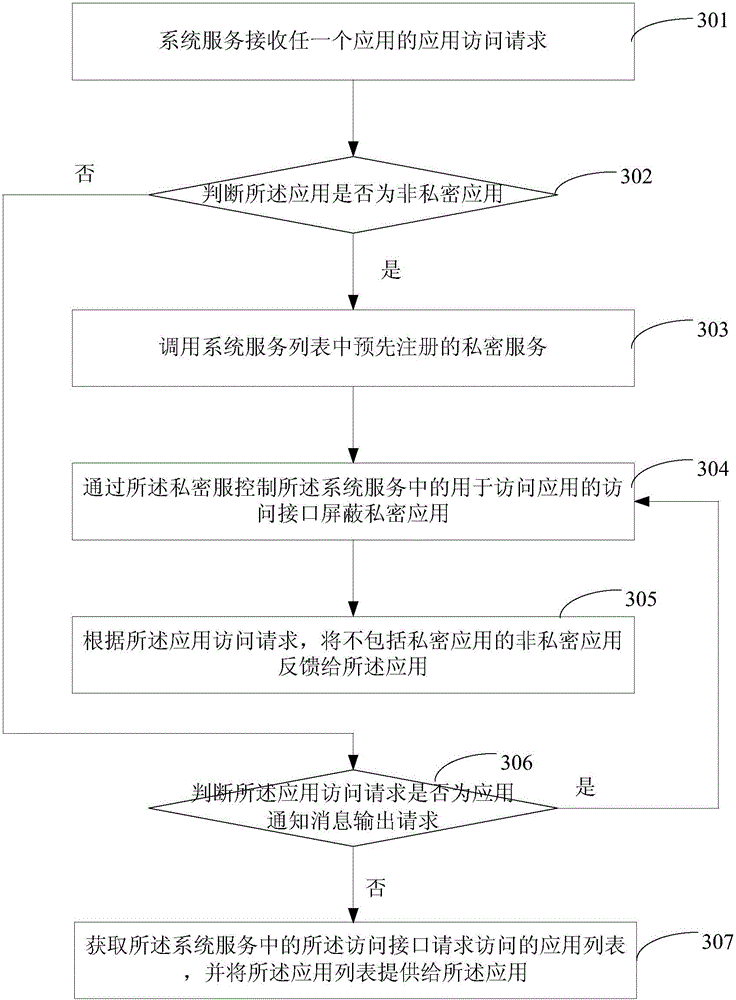
Application access control method and device
The embodiment of the invention provides an application access control method and an application access control device. The method comprises the steps of when a system service receives an application access request of any application, calling a pre-registered private service in a system service list; when the application where the private service is located is the non-private application, controlling an access interface, used for accessing the application, in the system service to shield the private application, wherein the private application is the application, requested by a user to be hidden according to a hiding request of the user, determined by the private service; and feeding the non-private application not including the private application back to the application according to the application access request. According to the method provided by the embodiment of the invention, the non-private application cannot access the private application in any case, thus the user privacy is effectively protected, and the security is improved.
Owner:BEIJING ANYUNSHIJI TECH CO LTD
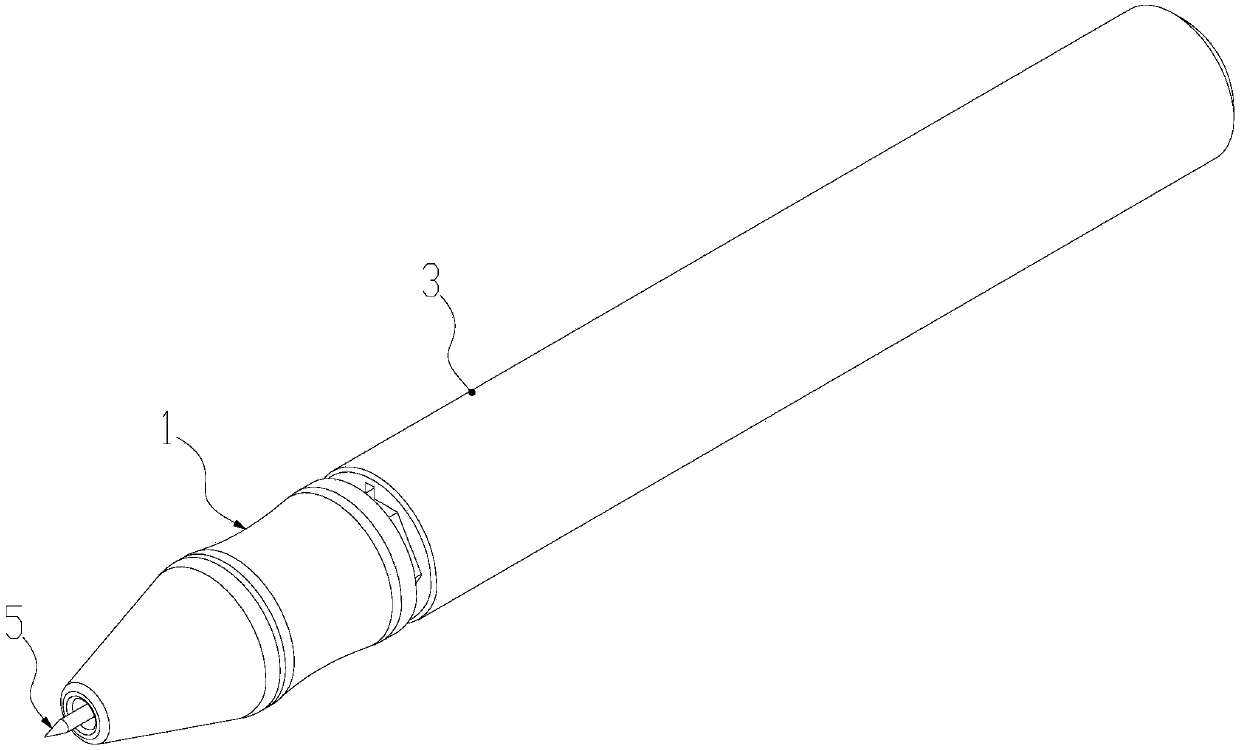
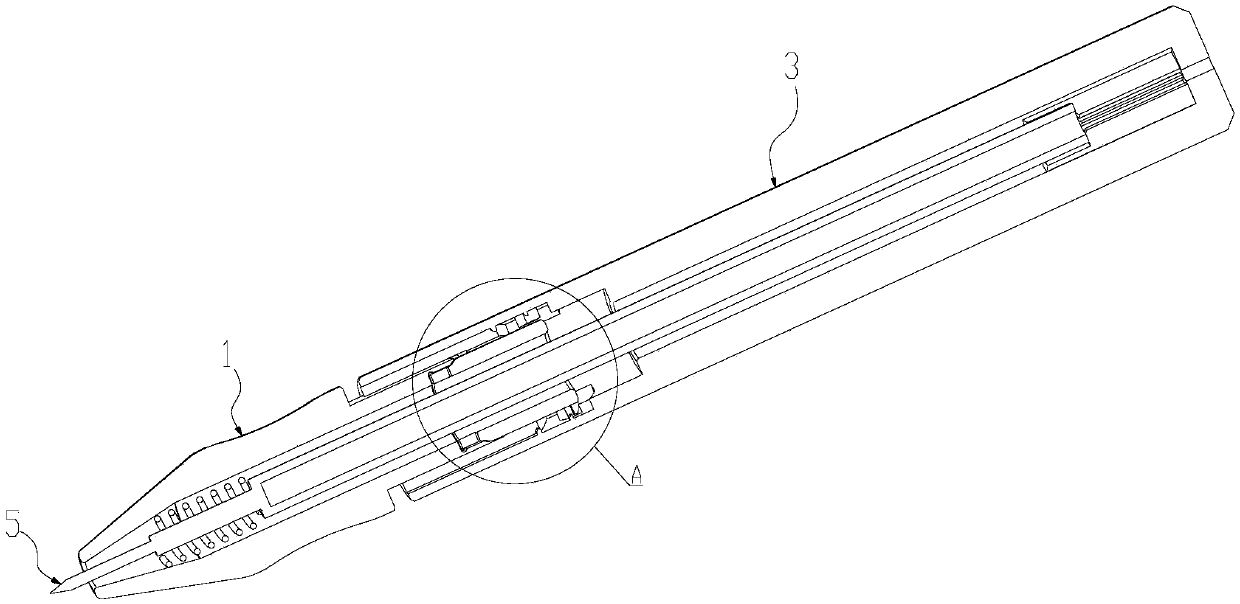
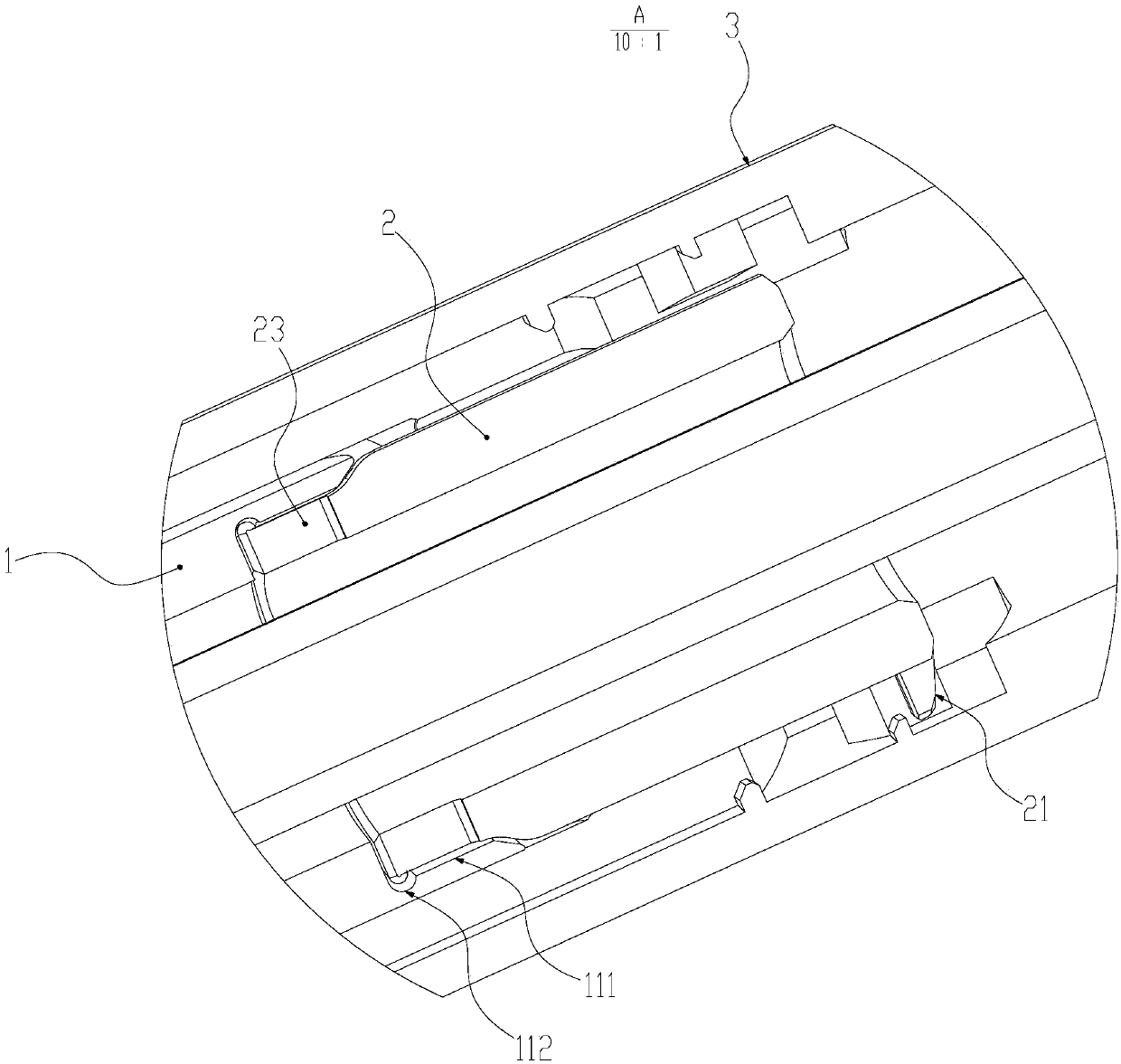
Novel gesture pressing pen
The invention provides a novel gesture pressing pen. During writing, a single-hand gesture can be used for quickly operating and hiding or extending out of the pen core. The novel gesture pressing pencomprises a pen core, a spring, a connecting body with a buckle, a front pen holder and a rear pen holder, and a pen point of the pen core can extend out of a front end part of the front pen holder;a polygonal inserting connection part is arranged at the rear part of the front pen holder, a clamping groove is formed in the inner surface of the polygonal inserting connection part, and a clampingring corresponding to the clamping groove is arranged at the front part of the connecting body with the buckle; the connecting body with the buckle is connected with the front pen holder through the clamping ring and can rotate in the rear pen holder along with the clamping groove; a clamping piece which protrudes outwards is arranged at the rear part of the connecting body with the buckle, and alocking groove capable of axially compressing a certain stroke along with the front pen holder and the rear pen holder is arranged in the rear pen holder; the connecting body with the buckle is rotated to enable the clamping piece to be locked or unlocked in the locking groove, so that the pen point of the pen core is in an exposed state or a hidden state, so that the single-hand rapid operation pen core can extend out or be hidden.
Owner:温州市简系文具有限公司
Control flow hiding method for remote computing
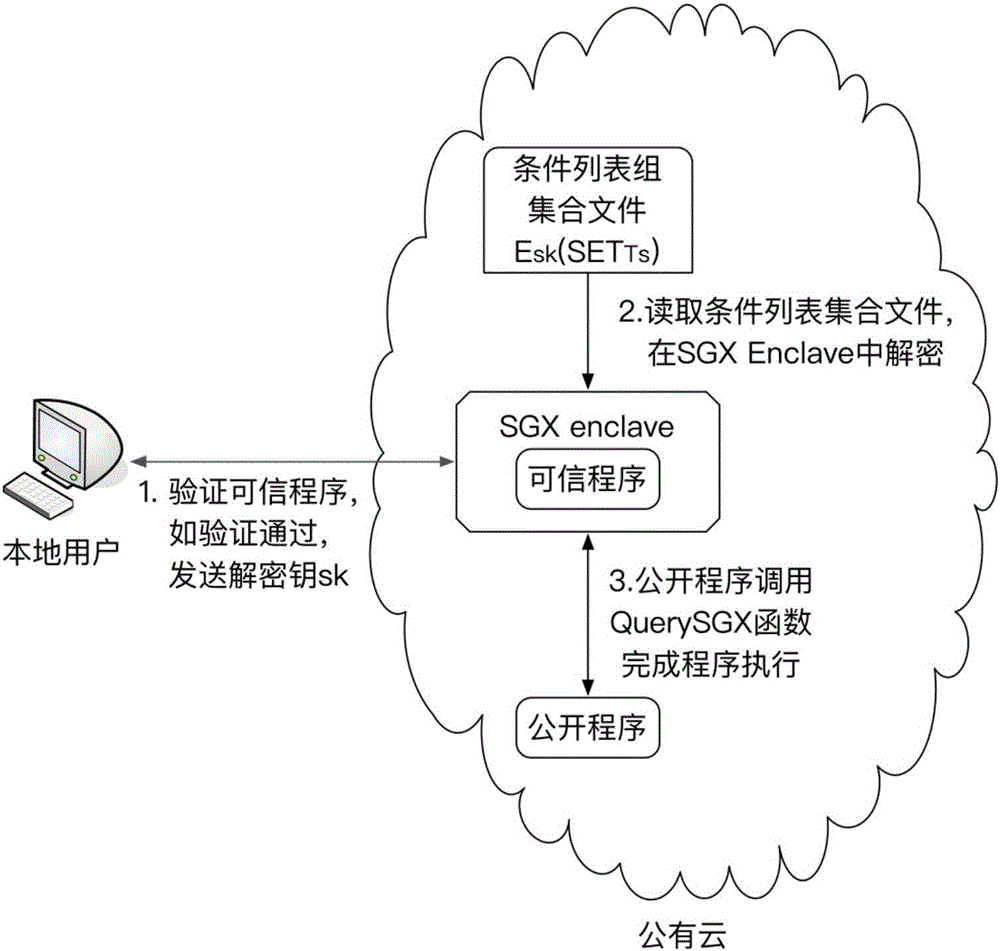
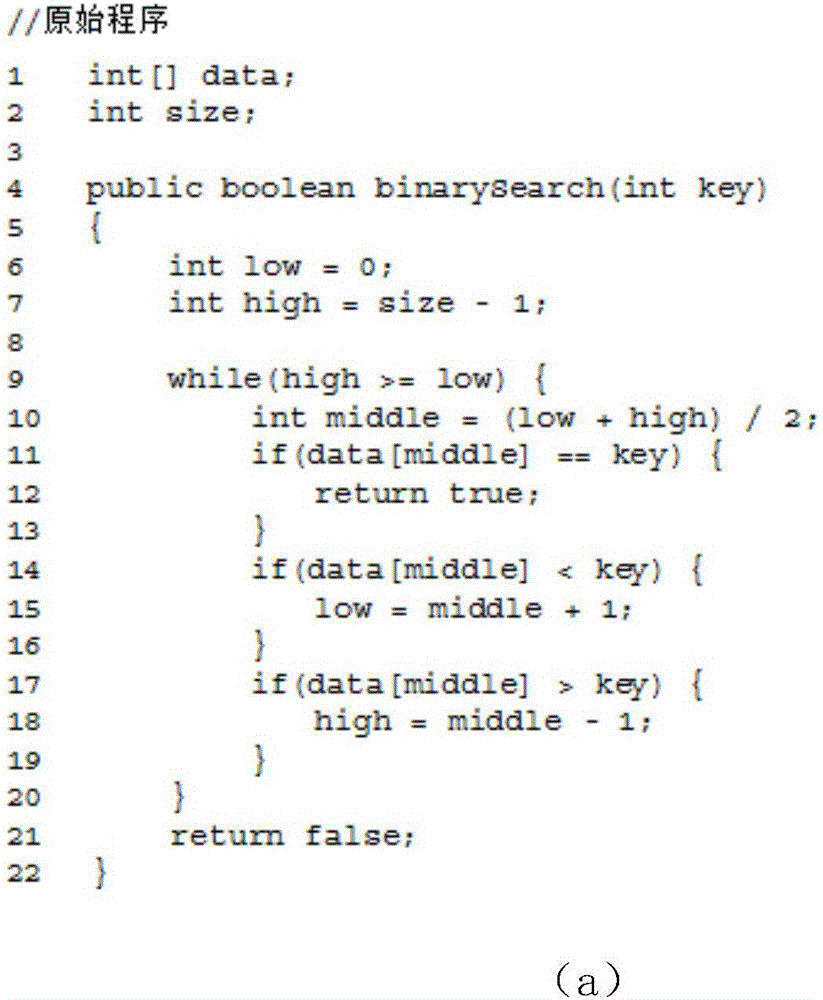
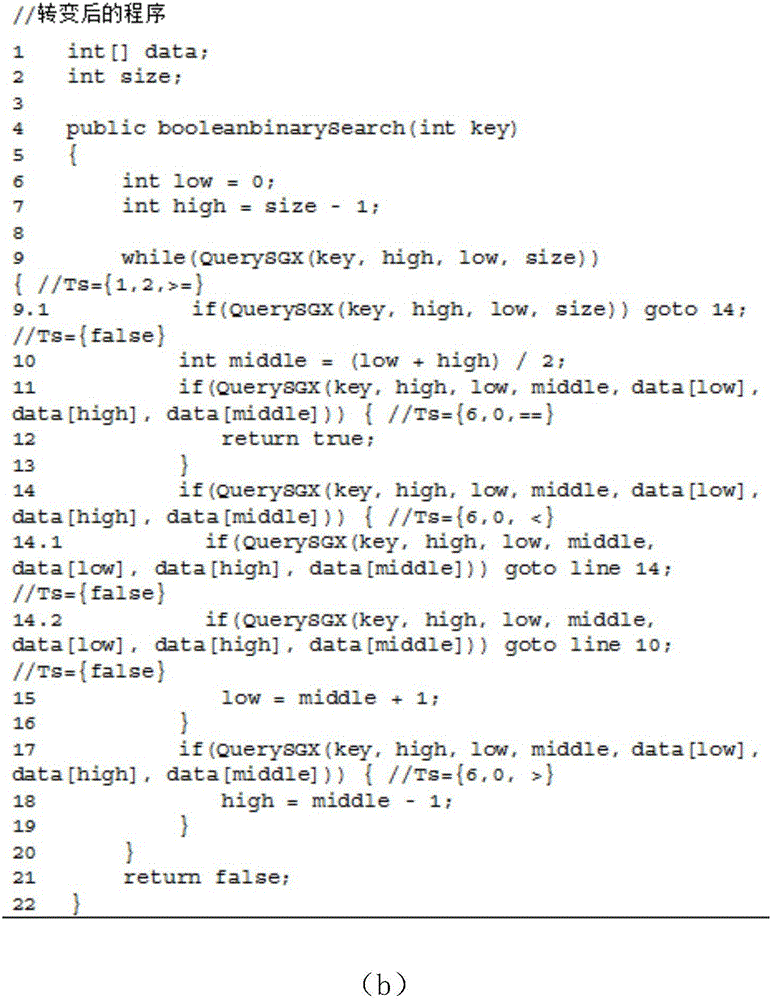
ActiveCN106845168AReduce operating overheadAchieve real hiddenSoftware designTransmissionControl flowIntel processor
The invention discloses a control flow hiding method for remote computing. The method includes the following steps that original programs are divided into the open programs, the confidence programs and condition list group set files, the SGX function of the safe execution environment of a sixth-generation Intel processor is used for performing program branching statement condition judging in a confidence region with the hardware protection function, and therefore real hiding of program branching statement conditions is achieved.
Owner:XIDIAN UNIV
Synthetic method for mosaic image and device thereof
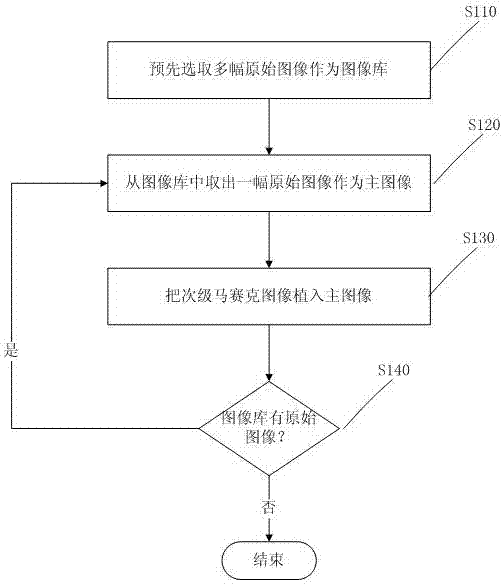
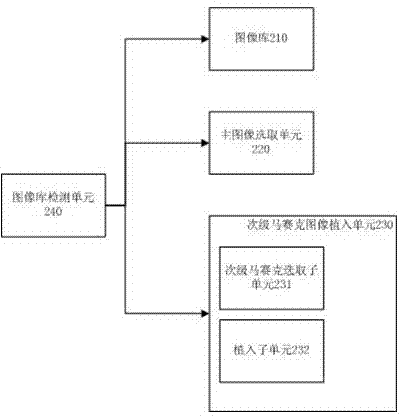
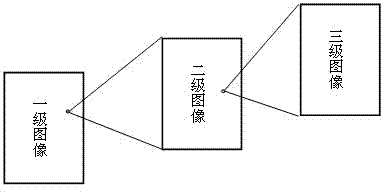
InactiveCN102609894ASolve hidden problemsAchieve hiddenImage enhancementImage data processing detailsImage retrievalInformation hiding
The invention relates to the technical field related to the field of information safety and signal treatment and particularly relates to a synthetic method for a mosaic image and a device thereof. The synthetic method comprises the following steps: selecting a plurality of original images as an image library in advance; selecting one original image from the image library as a main image; if no secondary mosaic image exists, selecting one original image from the image library as the secondary mosaic image and embedding the secondary mosaic image into the main image so as to obtain the main image after being embedded; and otherwise, replacing the main image after being planted by the secondary mosaic image and embedding the secondary mosaic image into the main image. According to the synthetic method provided by the invention, the problem of hiding and transferring of more information is solved. A multilayer mosaic image can be utilized to realize the hiding of multilayer information as well as the hiding and transferring of more information. The multilayer mosaic image has a potential application value in a series of applications, such as information hiding, image retrieval, computer art, philosophy, computer simulation, scene conversion, image transferring, and the like.
Owner:JINAN UNIVERSITY
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com