Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
230 results about "Domain identification" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Dynamic current device status
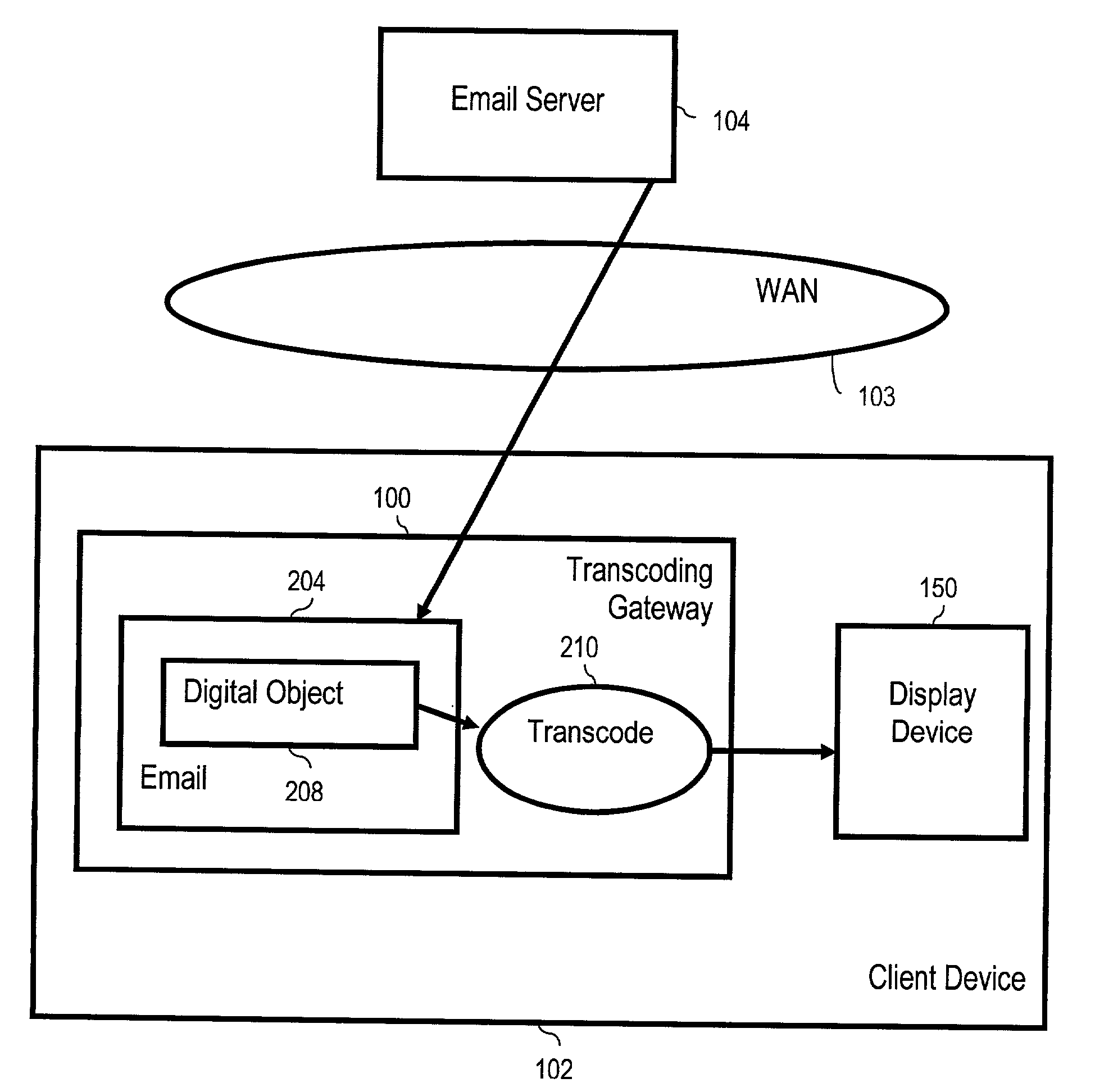
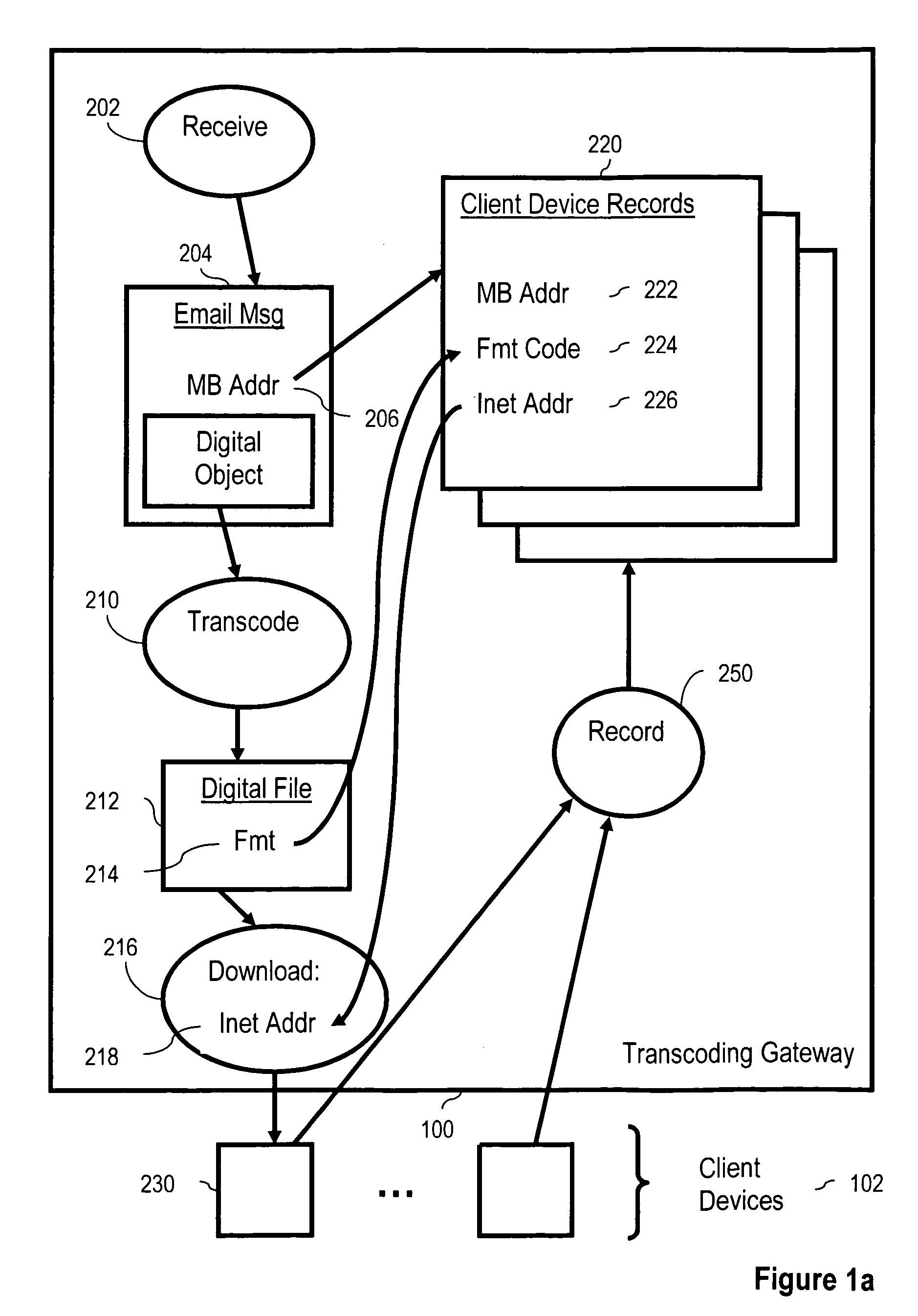
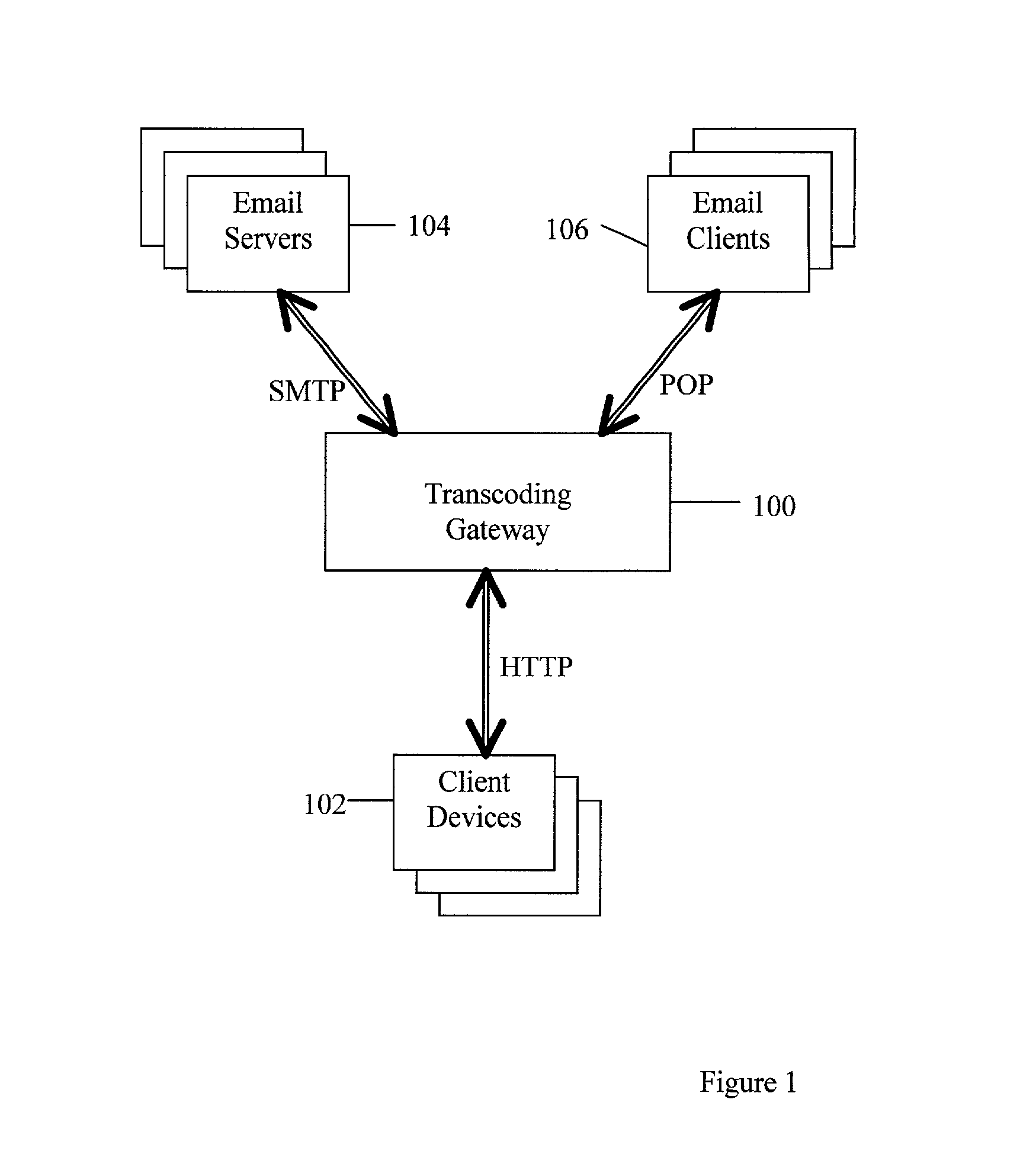
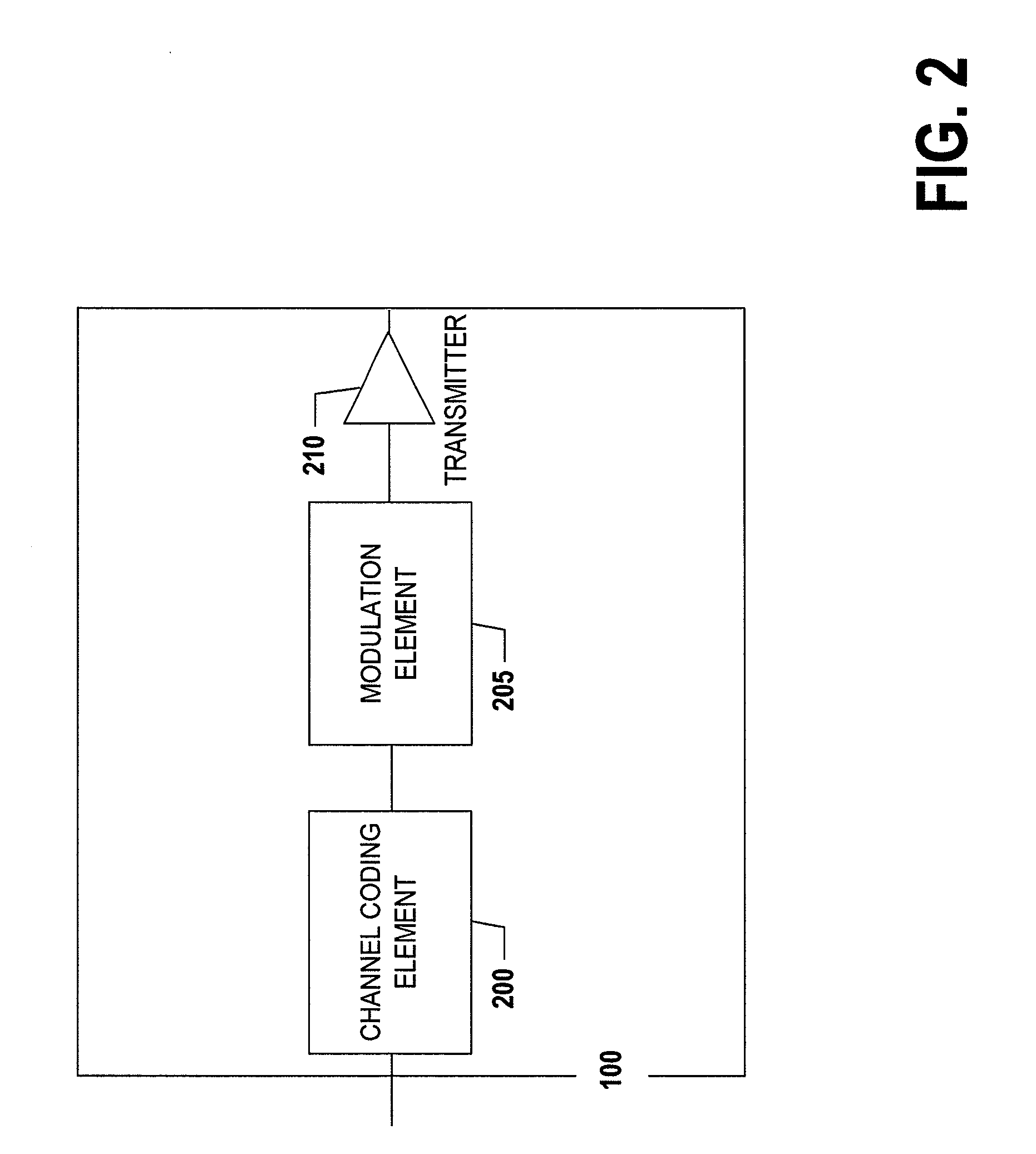
InactiveUS20030135563A1Multiple digital computer combinationsData switching networksInternet privacyTranscoding
A method of email administration including receiving in a transcoding gateway from a client device one or more email display status attributes describing one or more email display capability statuses for a domain, receiving in the transcoding gateway from a sender an email display capability status request for the domain, in which the capability status request includes a domain identification, finding, in dependence upon the domain identification, at least one email display capability status record for the domain, in which the email display capability status record for the domain includes at least one of the email display capability status attributes, and sending at least one of the email display capability status attributes to the sender.
Owner:IBM CORP
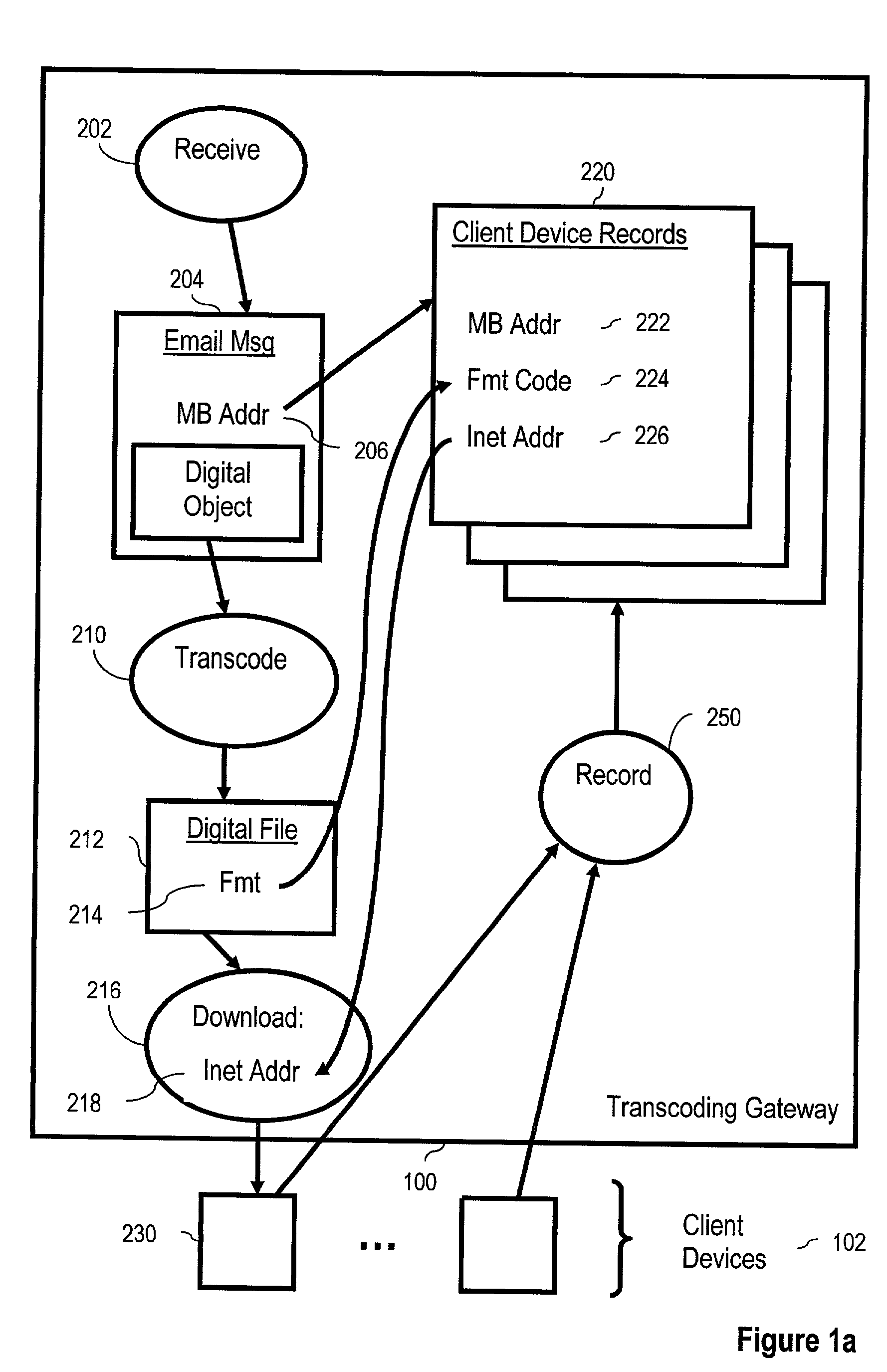
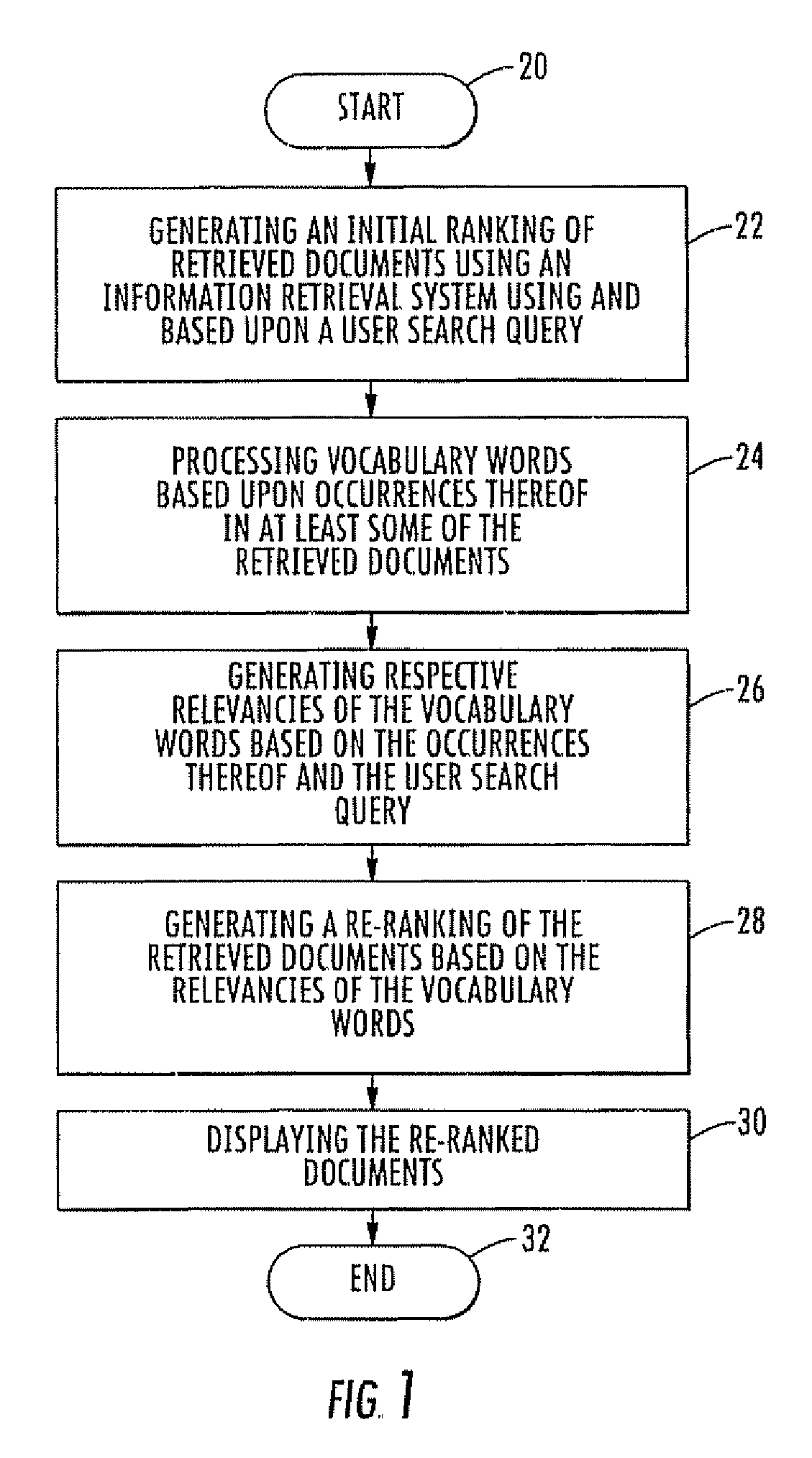
Method for domain identification of documents in a document database
InactiveUS20060206483A1Special data processing applicationsData selectionInformation retrievalDomain identification
A method for processing documents in a document database includes determining vocabulary words for each document, and determining a respective relevancy for each vocabulary word based upon occurrences thereof in all of the documents. Similarities are determined between the documents based upon the vocabulary words and their respective relevancies. At least one domain identification is determined for the documents based upon the determined similarities.
Owner:HARRIS CORP
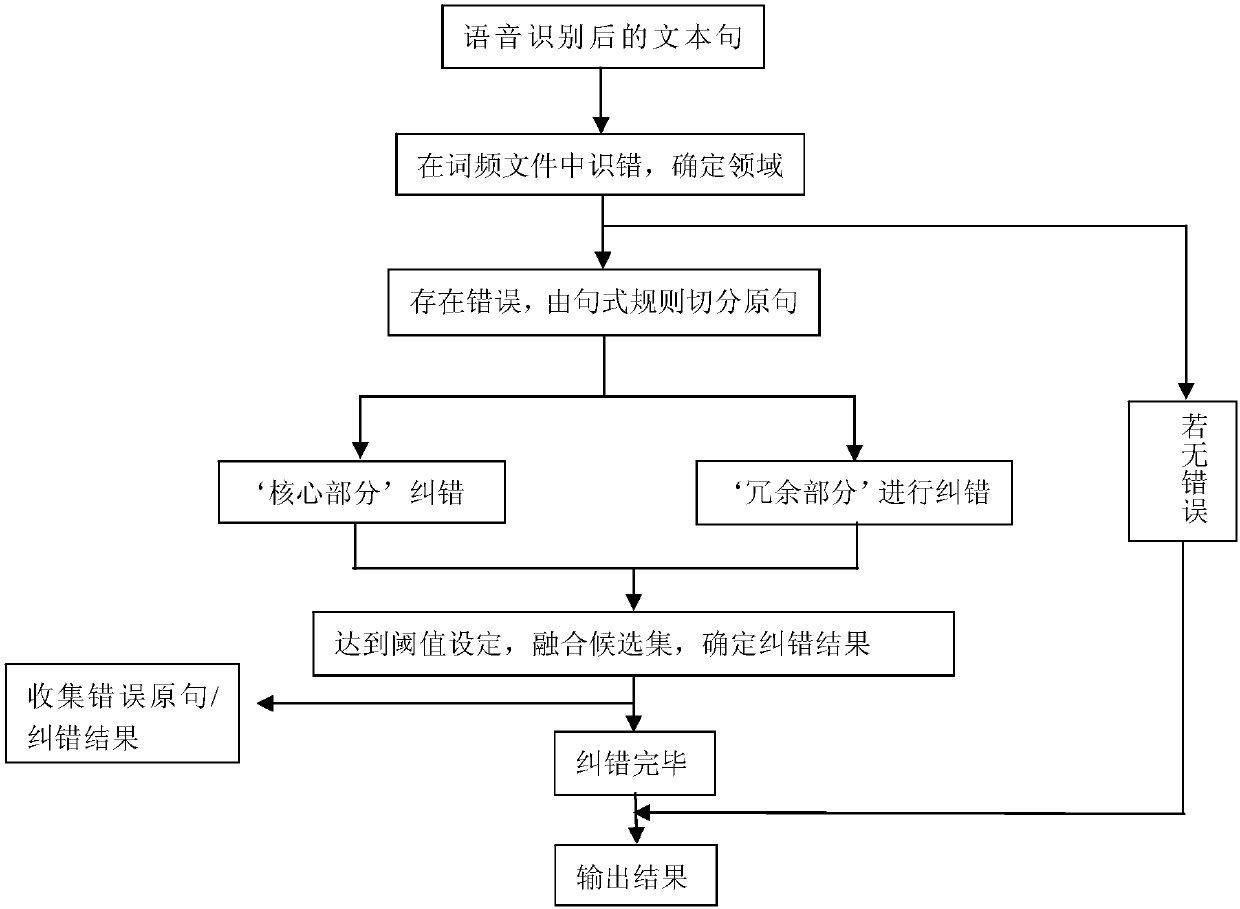
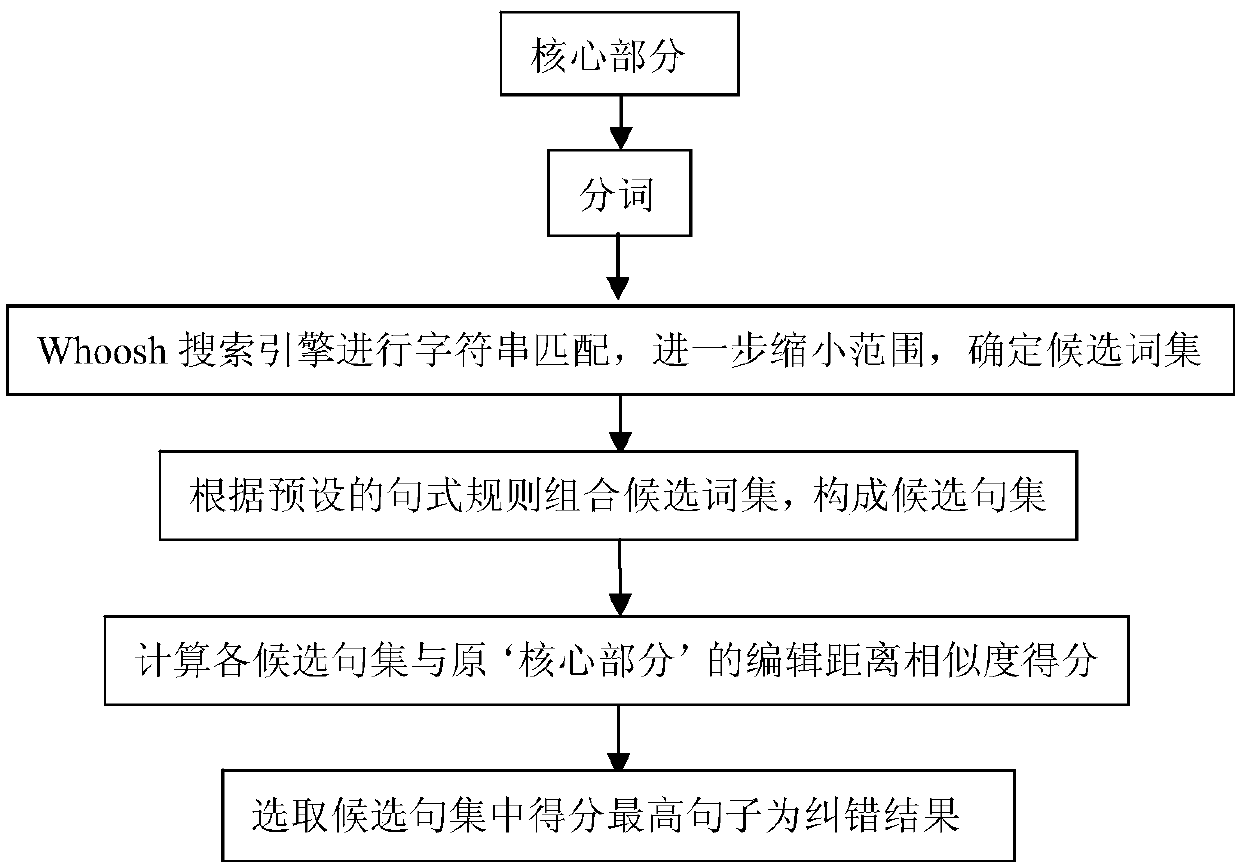
Method for text error correction after voice recognition based on domain identification
ActiveCN107741928ALess error-correcting processImprove the effect of practiceNatural language data processingSpeech recognitionSpeech identificationEdit distance
The invention belongs to the field of voice recognition text processing and discloses a method for text error correction after voice recognition based on domain identification and aims at solving theproblem that a processing method in the prior art needs lots of labor for intervention, is low in error correction efficiency and cannot conduct error correction on proper names. The method comprisesthe following steps that (a) error knowing and analysis are conducted on texts obtained after voice recognition, and the field which text sentences belong to are primarily determined; (b) sentences toundergo error correction are segmented according to predefined syntax rules and are divided into redundancy portions and core portions; (c) a search engine is utilized to perform character string fuzzy matching and determine candidate specific word bank sets of the core portions of the sentences; (d) similarity scores are calculated according editing distances, and error correction is conducted on the redundancy portions and the core portions; (e) the redundancy portions and core portions undergoing the error correction are fused, and then error correction results are output.
Owner:SICHUAN CHANGHONG ELECTRIC CO LTD
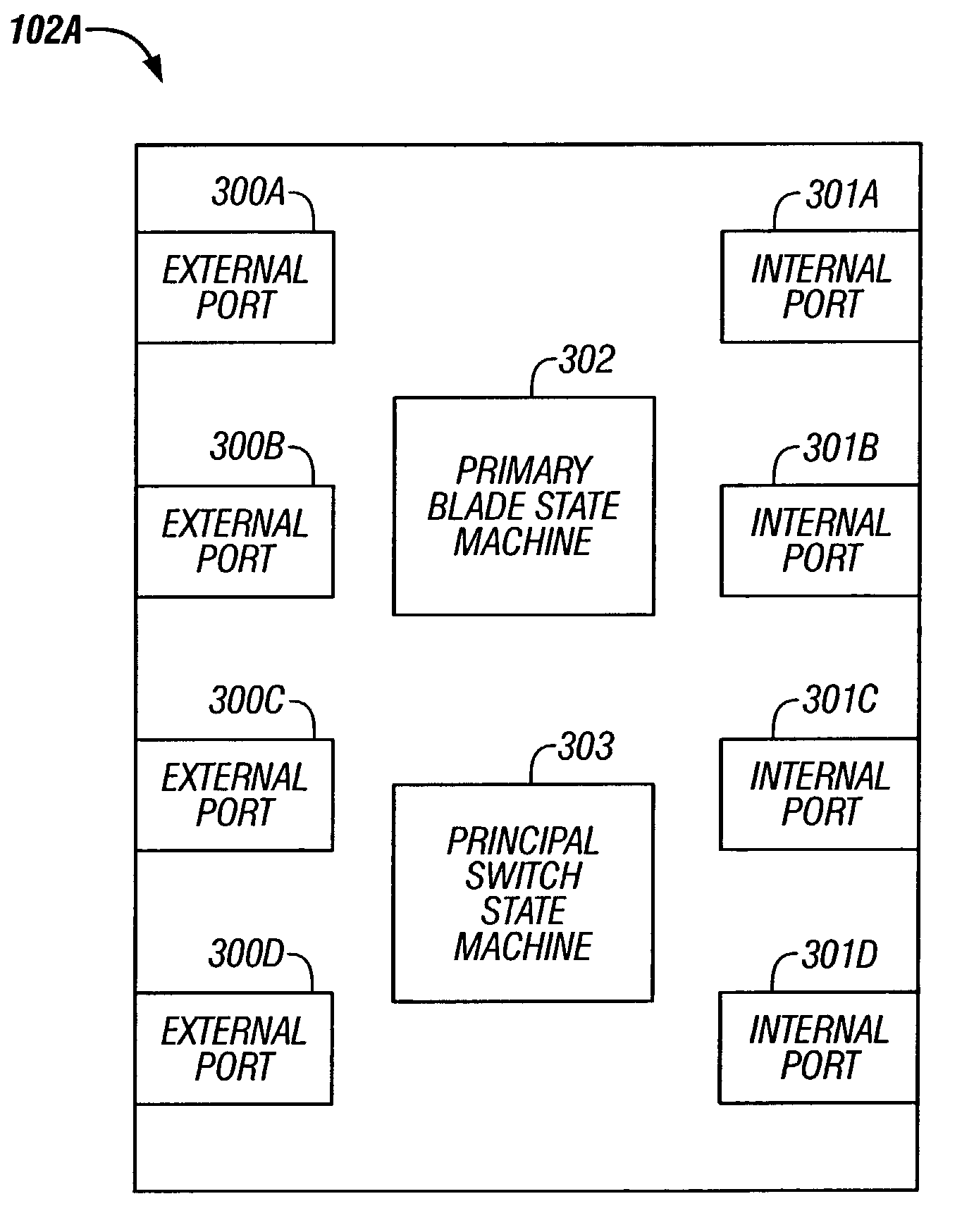
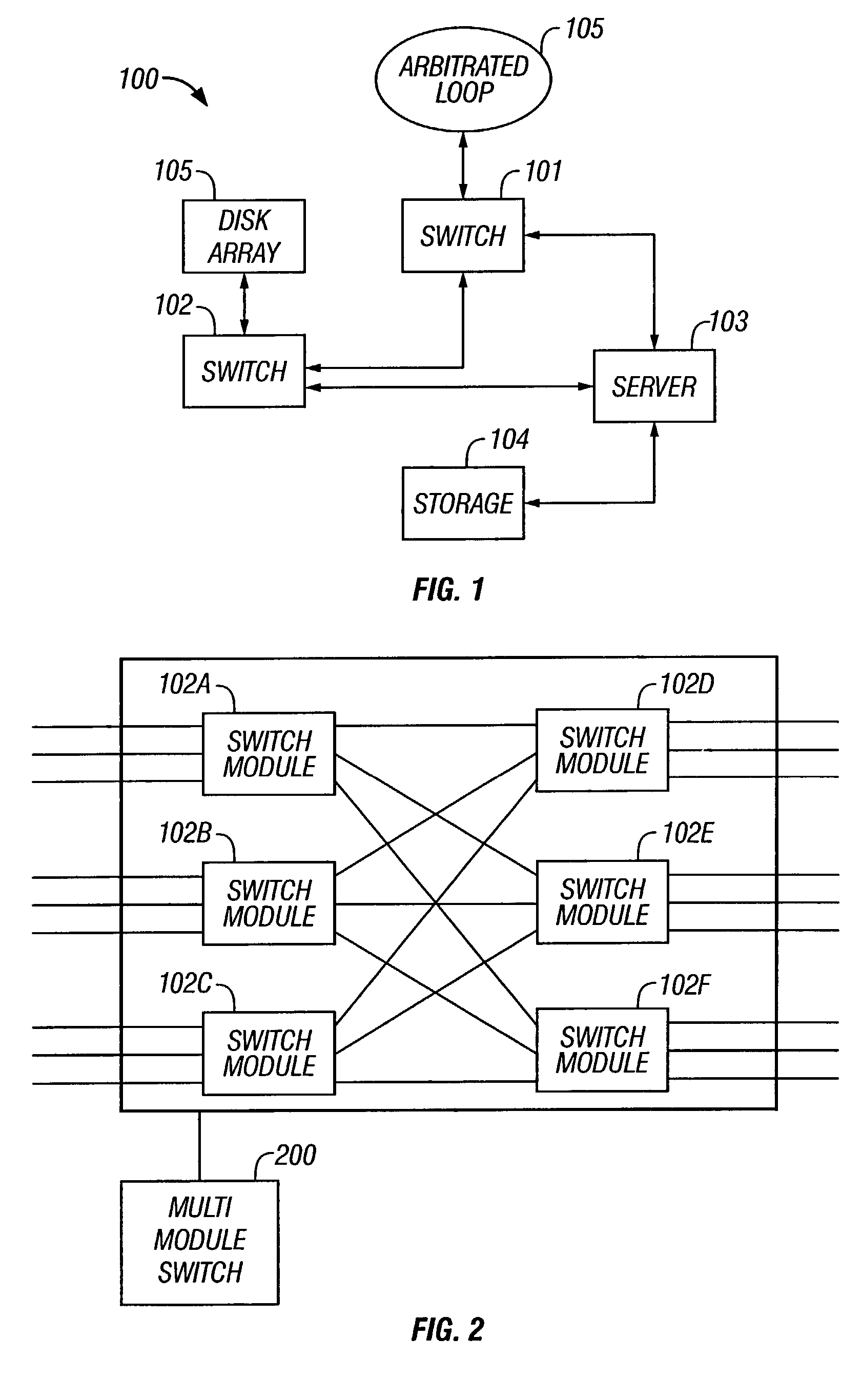
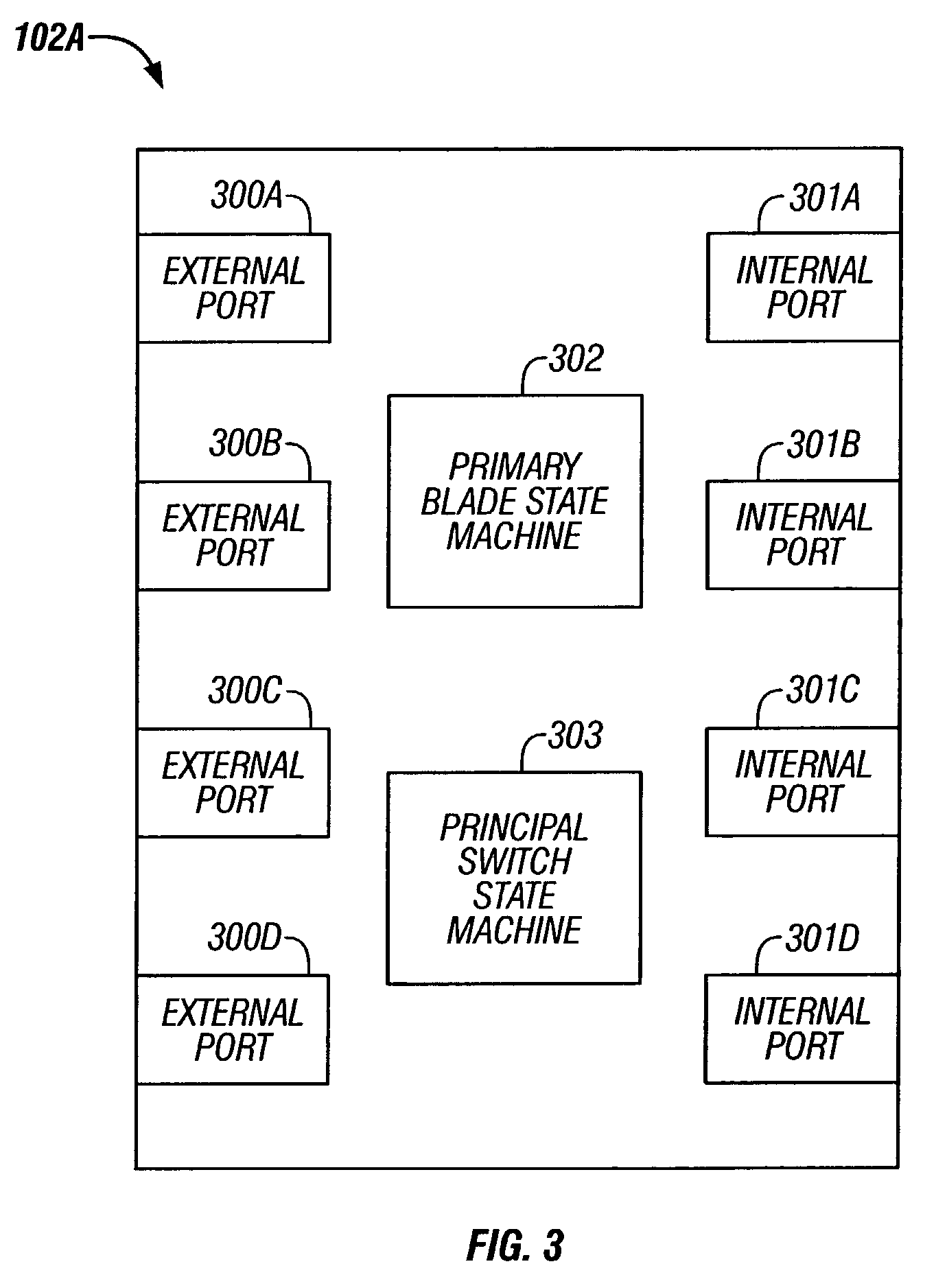
Method and system for dynamically assigning domain identification in a multi-module fibre channel switch
ActiveUS7230929B2Multiplex system selection arrangementsData switching by path configurationFiberStructure of Management Information
A method for entering fabric configuration in a fibre channel system for a multi-module fibre channel switch is provided. The method includes determining if a primary blade has been selected for the multi-module switch; sending exchange fabric parameters to internal ports of the multi-module switch; and processing principal switch selection events.
Owner:MARVELL ASIA PTE LTD
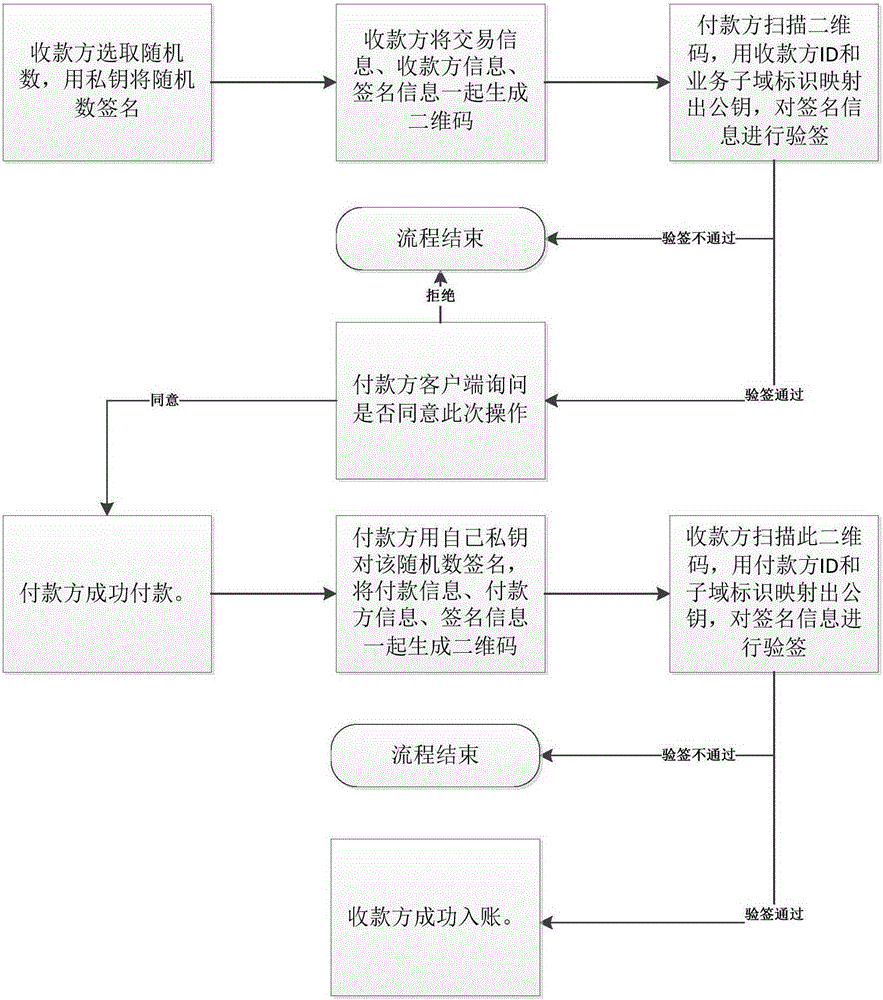
Novel offline payment method
InactiveCN105205664AConvenient paymentPrevent illegal tamperingPayment architecturePaymentMobile device
The invention discloses a novel offline payment method. The method comprises the steps that account numbers of an accountee party and a receiving party serve as IDs, and a corresponding public key and private key are mapped according to business sub-domain identifications; a random number is selected from the receiving party, signature is conducted on the random number through the private key, and a two-dimension code is generated; the two-dimension code is scanned through the accountee party, the public key is mapped by means of the receiving party ID and the service sub-domain identification, and attestation is conducted on a signing message; if attestation succeeds, the accountee party successfully pays according to transaction information; signature is conducted on the random number by the accountee party through the private key after payment to generate a two-dimension code; the receiving party scans the two-dimension code, the public key is mapped through the accountee party ID and the business sub-domain identification, and attestation is conducted on a signing message; if attestation succeeds, posting is successfully conducted on the receiving party. According to the novel offline payment method, payment does not rely on the support of a network any more, payment is achieved on various mobile equipment, and the payment process is greatly facilitated. The two-way authentication process based on the identifications is adopted by the two payment parties, the legality of transactions is fully guaranteed, and illegal manipulation of information and information disguising are prevented.
Owner:CHINA SMARTCITY TECH
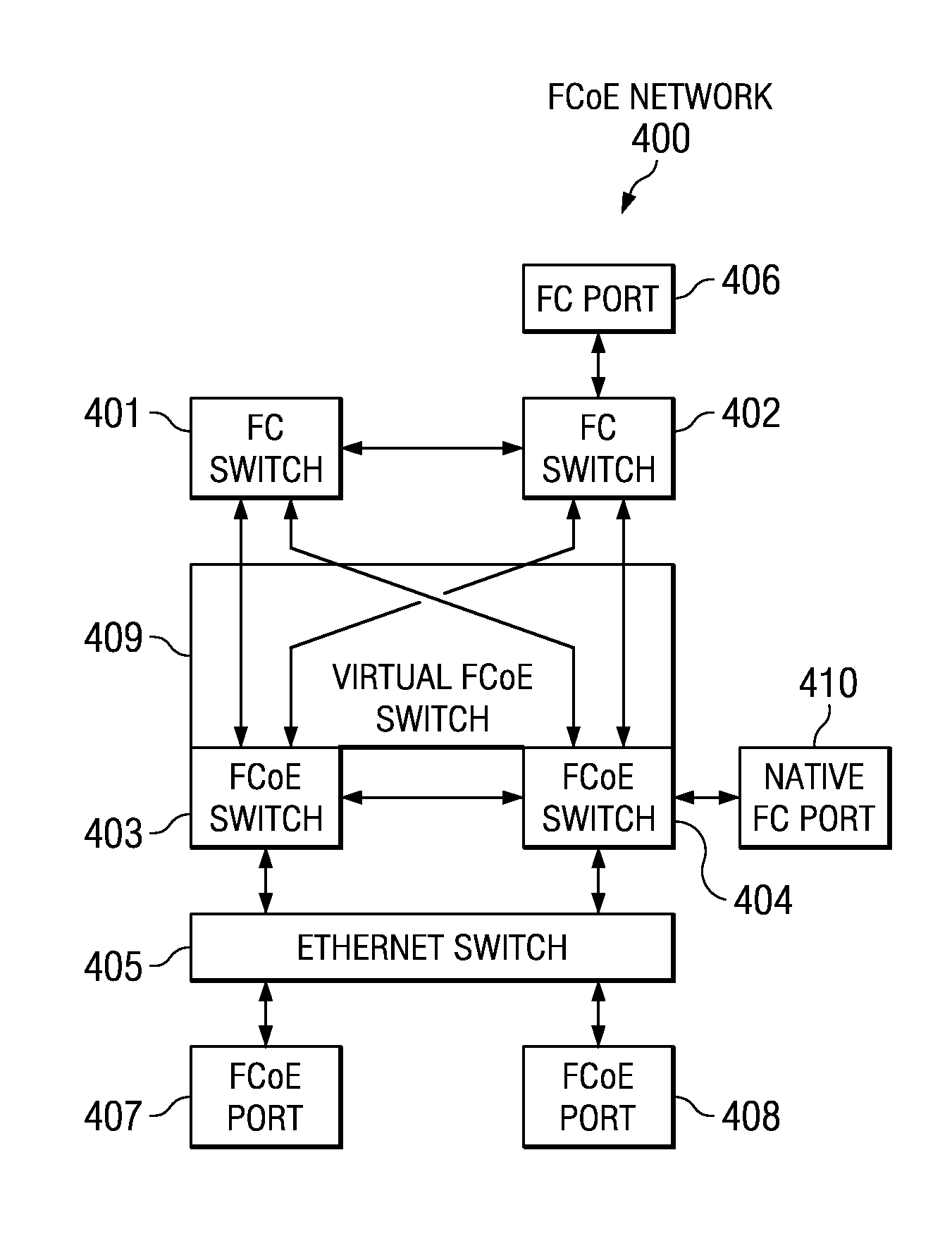
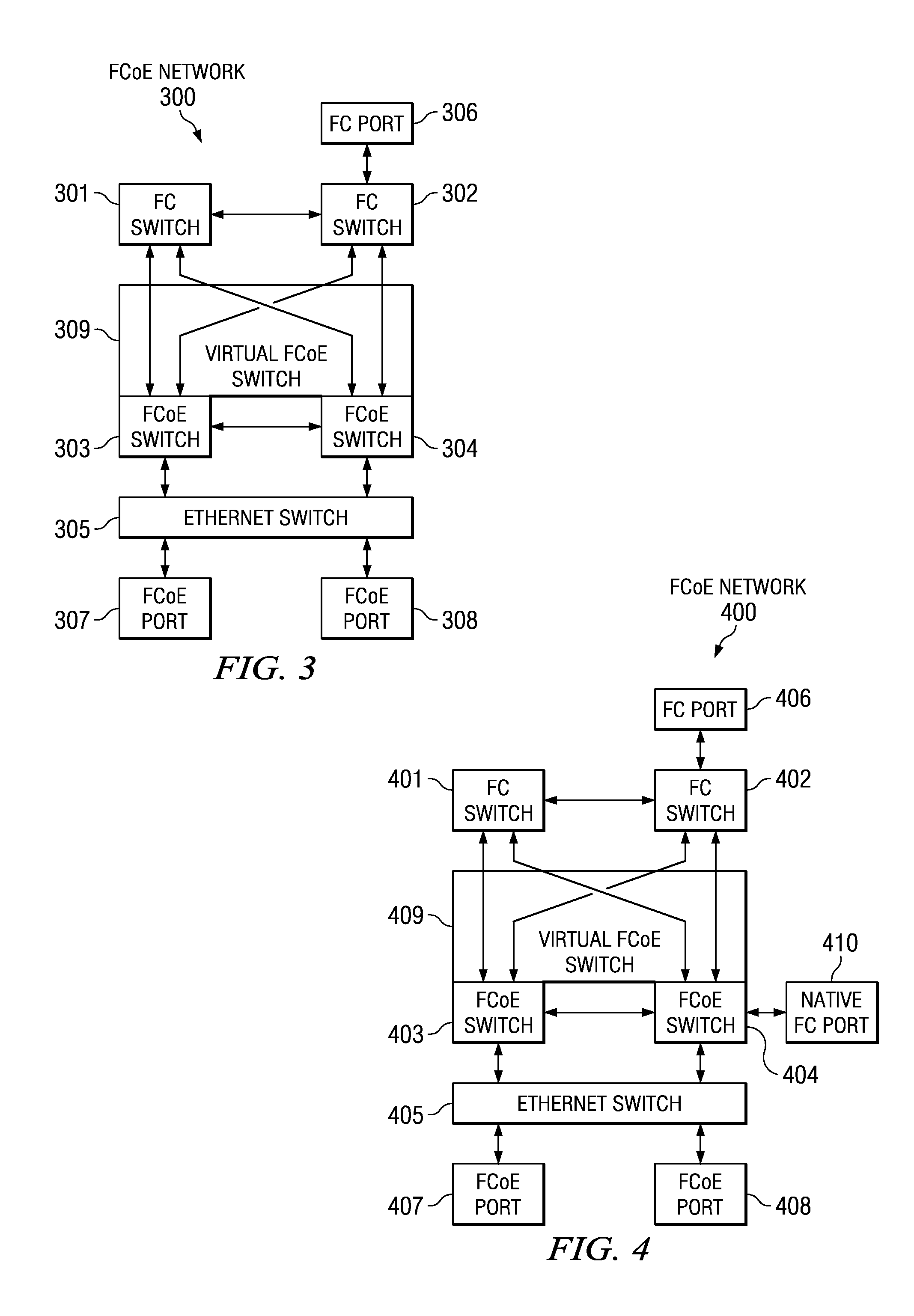
Virtual fibre channel over Ethernet switch
InactiveUS7792148B2Multiplex system selection arrangementsTime-division multiplexEngineeringFibre Channel over Ethernet
A system for using a virtual switch in a network. In response to a switch connecting to a network, network configuration data is read to determine whether the switch is part of a virtual switch. In response to determining that the switch is part of the virtual switch, a priority number for the switch is sent to other switches connected to the network. Priority numbers are received from the other switches. It is determined whether the switch has a highest priority number. In response to determining that the switch does have the highest priority number, the switch is selected to be a master switch for the virtual switch. Then, domain identification data for the virtual switch is sent to the other switches. Afterward, the switch and the other switches respond to requests over the network as one domain identified by the domain identification data.
Owner:IBM CORP
Data communication method and system
InactiveUS20070288754A1Easy to doDeterioration of performance can be preventedUser identity/authority verificationMultiple digital computer combinationsSession managementApplication server
An encrypted communication method, and a system for the method, can transfer a session control message designated by identification information inherent to an application to a connection destination through a session management server. When an application program of a client or encrypted communication software issues a connection request in the form designating an application server by identification information inherent to each application, the identification information is automatically changed to a desired address-of-record capable of domain identification and a transfer destination domain of a reception message is judged.
Owner:HITACHI LTD
System and method for grid fault identification based on random point distribution PMU
ActiveCN103323742AReduce dependencyMeet the needs of backup protection applicationsEmergency protective circuit arrangementsFault locationGrid faultElectric power system
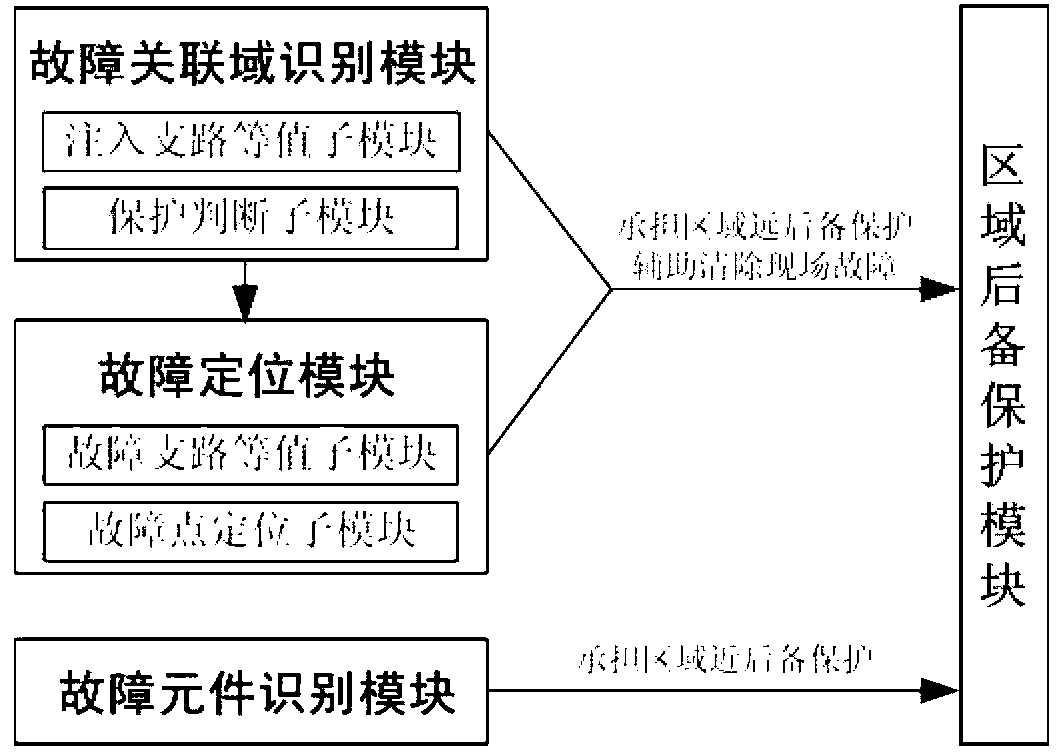
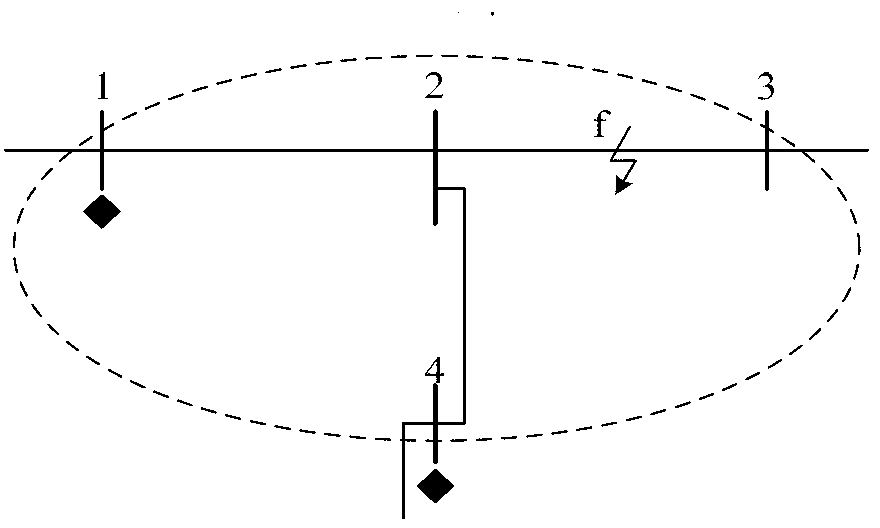
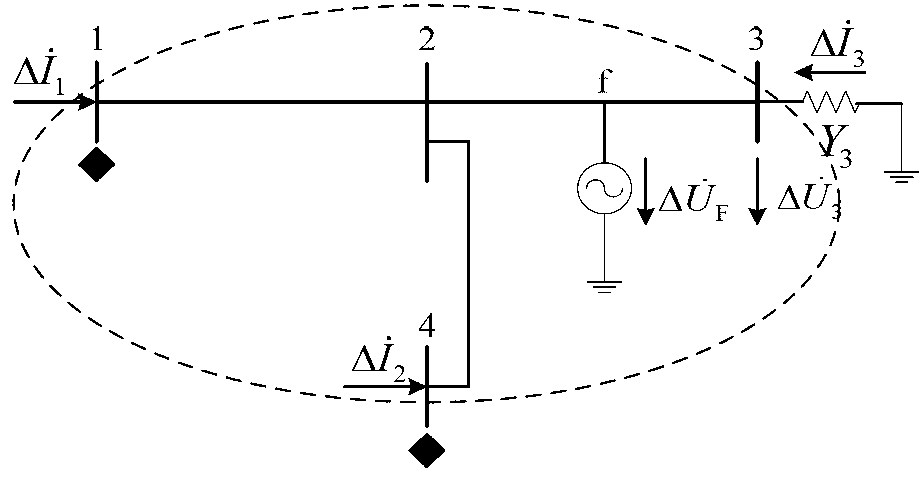
The invention discloses a system and method for grid fault identification based on a random point distribution PMU and belongs to the technical field of power system fault identification. The system comprises a fault relative domain identification module, a fault locating module, a fault component identification module and a domain backup protection module. A grid structure changing characteristic is evolved to a branch current difference by the fault relative domain identification module, so that fault relative domain identification is achieved; overall traversal is conducted on a relative domain by the fault locating module, so that accurate location of a fault point is achieved based on a node voltage matching condition; based on virtual current differential, protecting criteria are constructed through an opposite terminal calculated current and a home terminal actually detected current by the fault component identification module, so that fault component identification is achieved; according to domain backup protection operation logic, the near backup tripping function and the far backup tripping function are achieved by the domain backup protection module. Complete domain backup protection under the environment of random PMU point distribution is achieved and the dependence degree on synchronous data of protection is reduced to a great extent.
Owner:NORTH CHINA ELECTRIC POWER UNIV (BAODING)
Method and device for real-time detection of webpage cross-domain requests
ActiveCN103001817AImprove real-time performanceCutting costsData switching networksDomain nameClient-side
The invention discloses a method for real-time detection of webpage cross-domain requests. The method includes: monitoring page elements marking webpage page resources in a webpage and behavior of the page elements so as to capture an address and a domain name of the page resources and / or capture a new domain name generated by the behavior of the page elements; performing abnormal domain identification according to the extracted domain; and if the domain name is an abnormal domain name, acquiring page information of the abnormal domain name and blocking application programs to access to the domain name. The method judges whether malicious codes exist or not on the basis of detecting whether a client side browser crosses domains to reference unknown resources or not instead of detecting injected codes by a server, so that a vulnerability detection base and keyword filtering are not needed. In addition, the method is high in timeliness, low in cost, less prone to perceiving and bypassing and capable of achieving timely acquisition, prevention and analysis.
Owner:XIAMEN MEIYA PICO INFORMATION
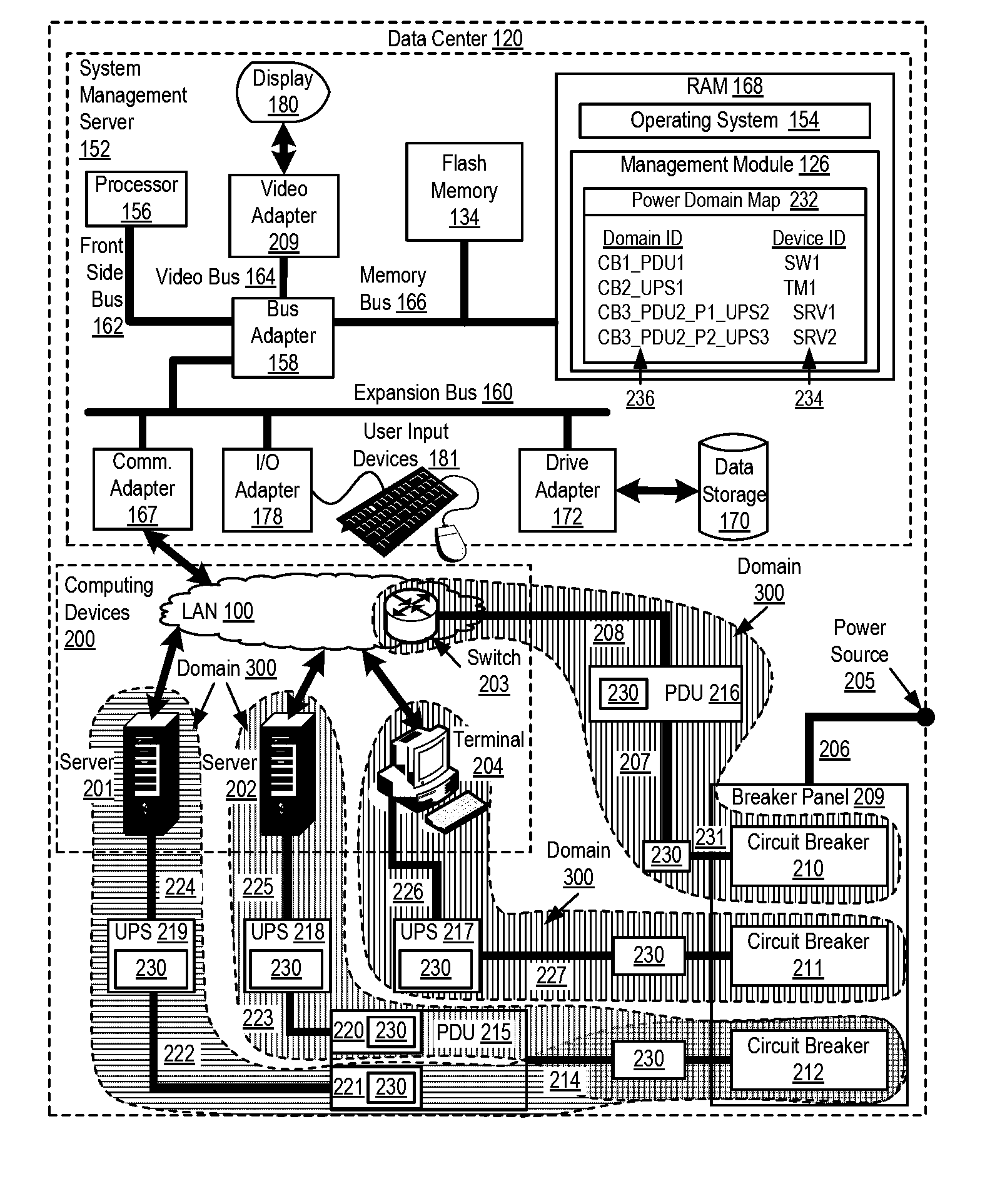
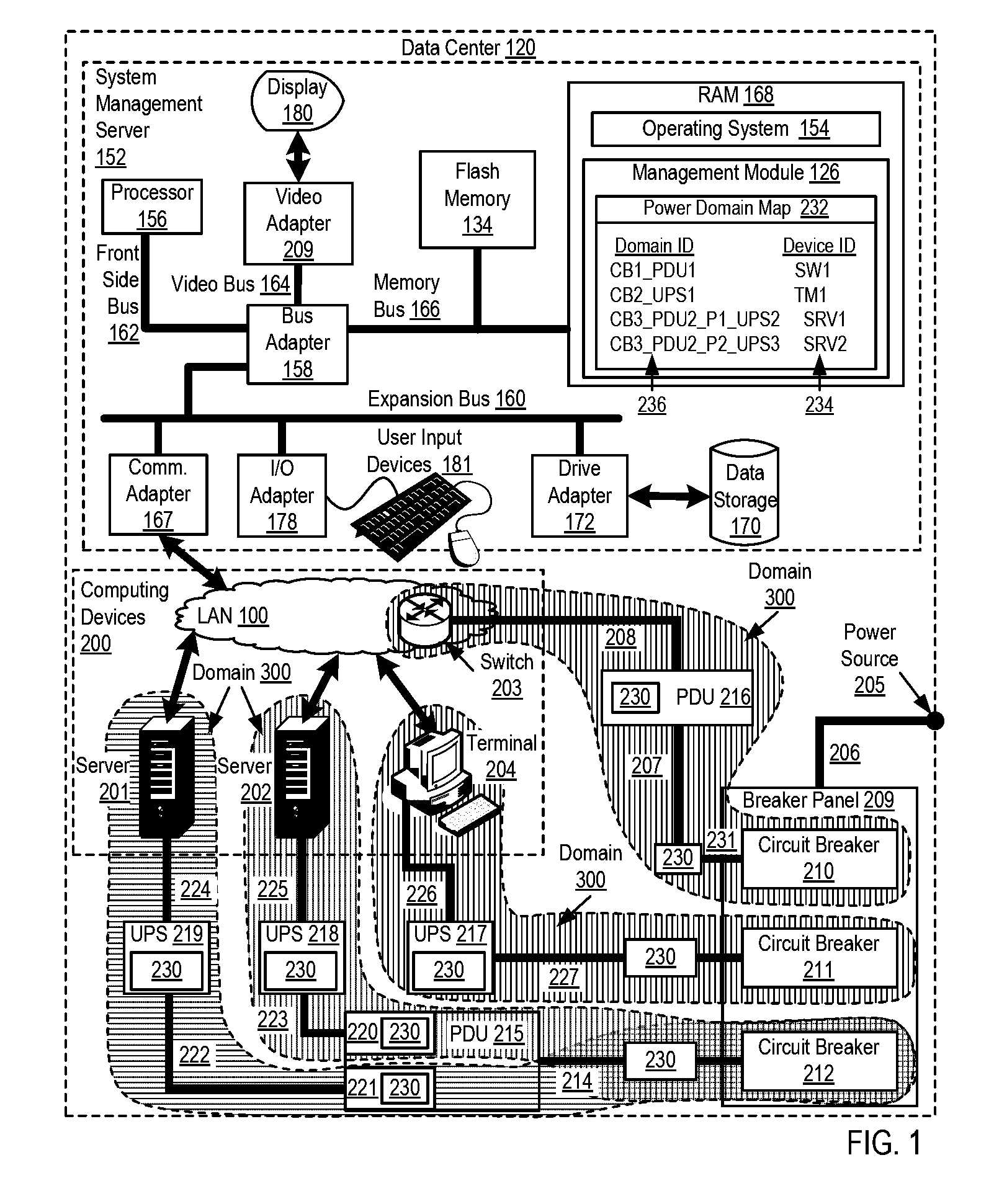
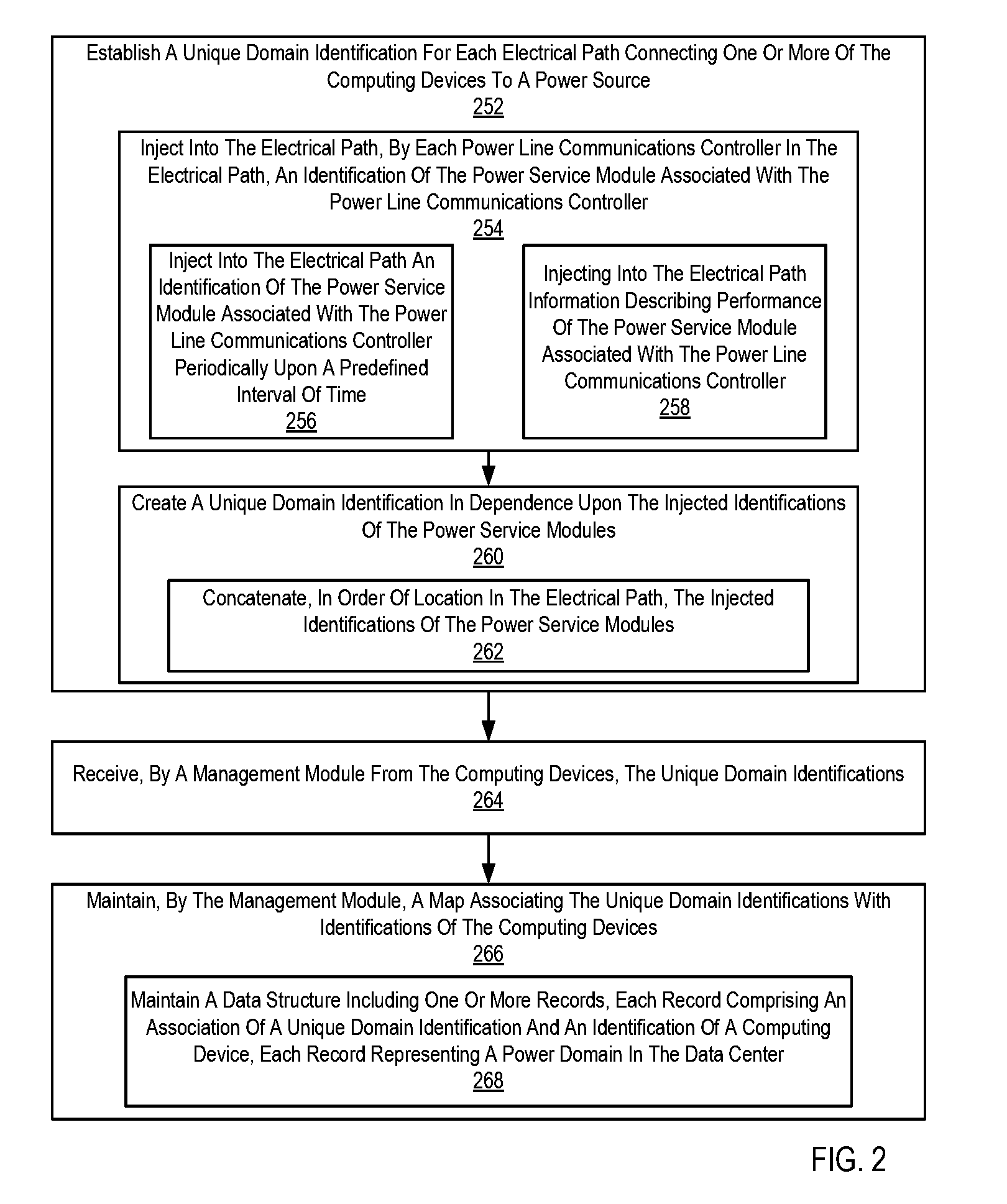
Mapping power domains in a data center
Mapping power domains in a data center, the data center including one or more power consuming computing devices, the computing devices managed by a management module, each power domain in the data center including one or more power service modules located in an electrical path connecting one or more of the computing devices to a power source, each power service module associated with a power line communications controller, where the mapping includes establishing a unique domain identification for each electrical path connecting one or more of the computing devices to a power source; receiving, by the management module from the computing devices, the unique domain identifications; and maintaining, by the management module, a map associating the unique domain identifications with identifications of the computing devices.
Owner:LENOVO ENTERPRISE SOLUTIONS SINGAPORE
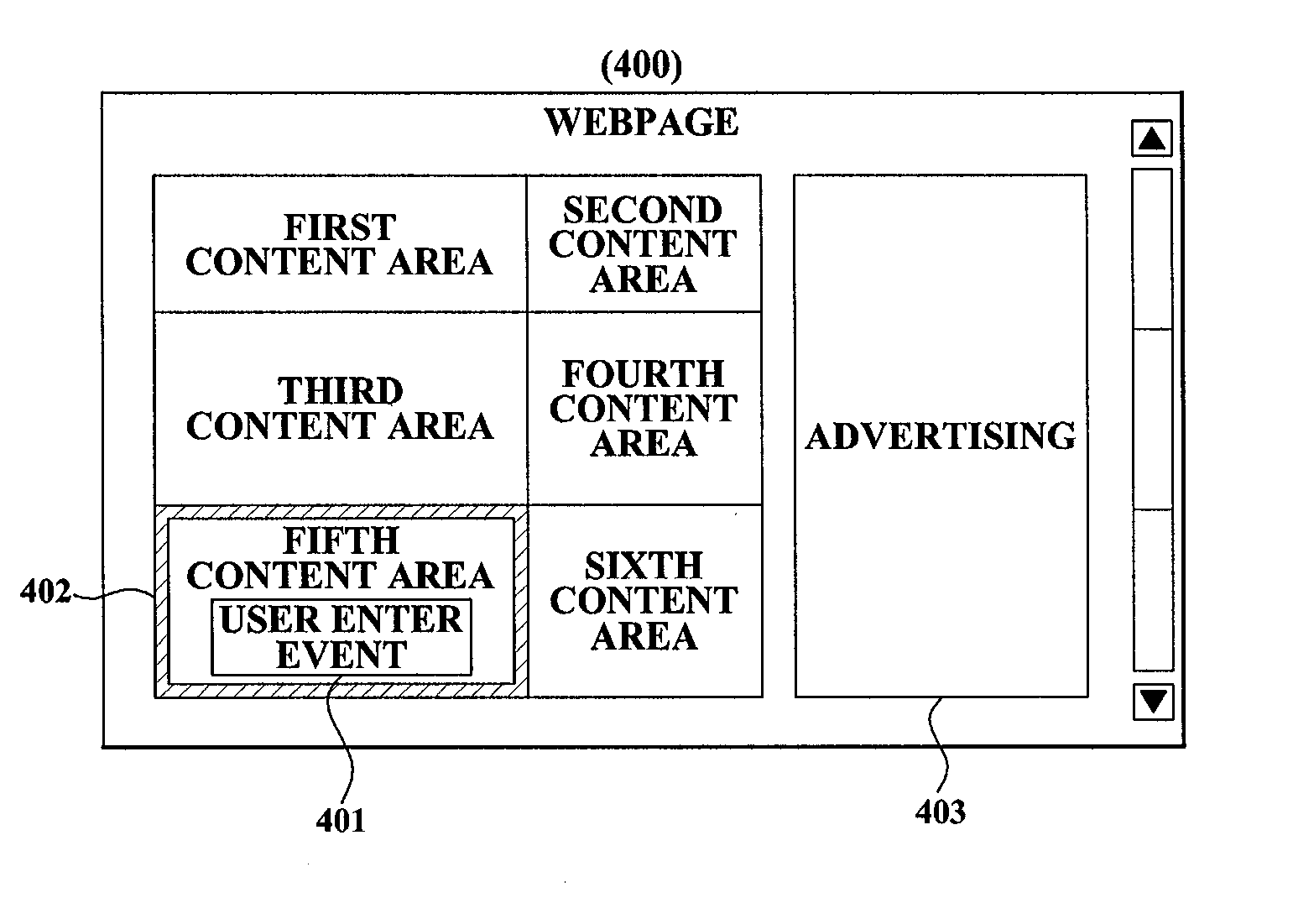
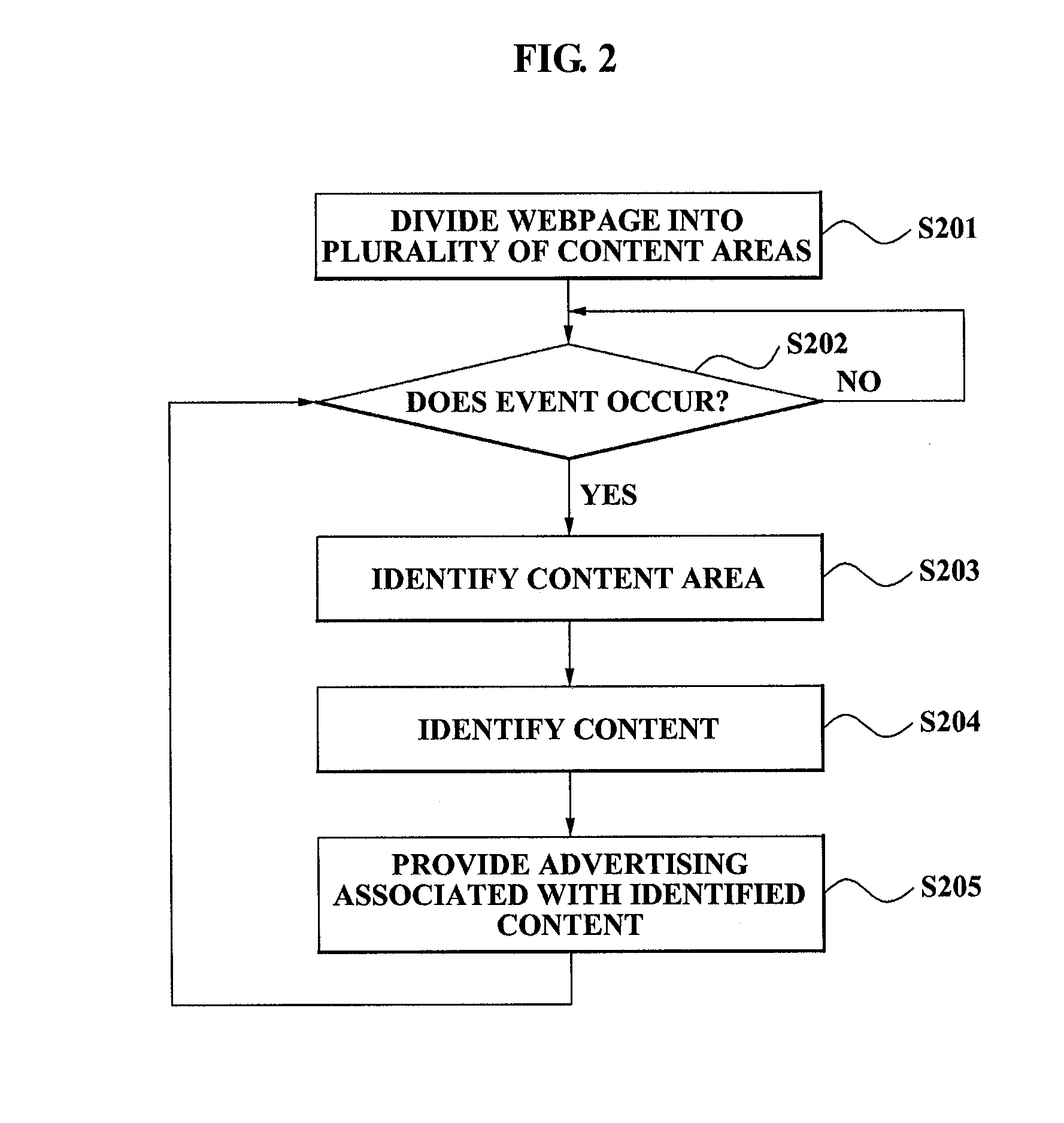
Method for offering advertisement in association with contents in view and system for executing the method
A method of providing advertising associated with a content in a visible area, and a system for executing the method are provided. A method of providing advertising associated with a content includes the steps of: dividing a webpage into a plurality of content areas using a predetermined area division scheme; identifying a content area where a predetermined event occurs, when the event occurs on the webpage; identifying a content included in the identified content area; and providing advertising associated with the identified content.
Owner:NAVER CORP
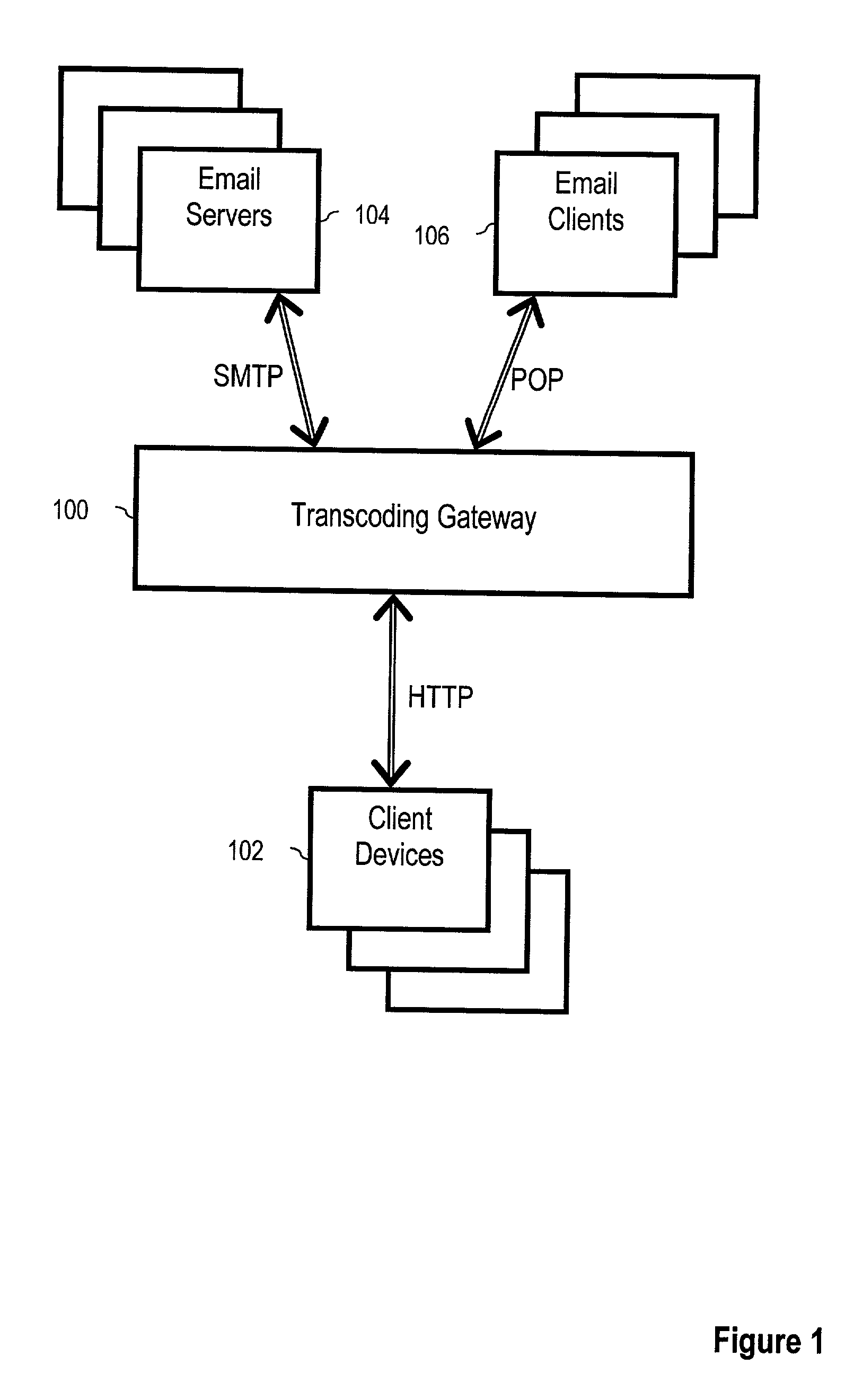
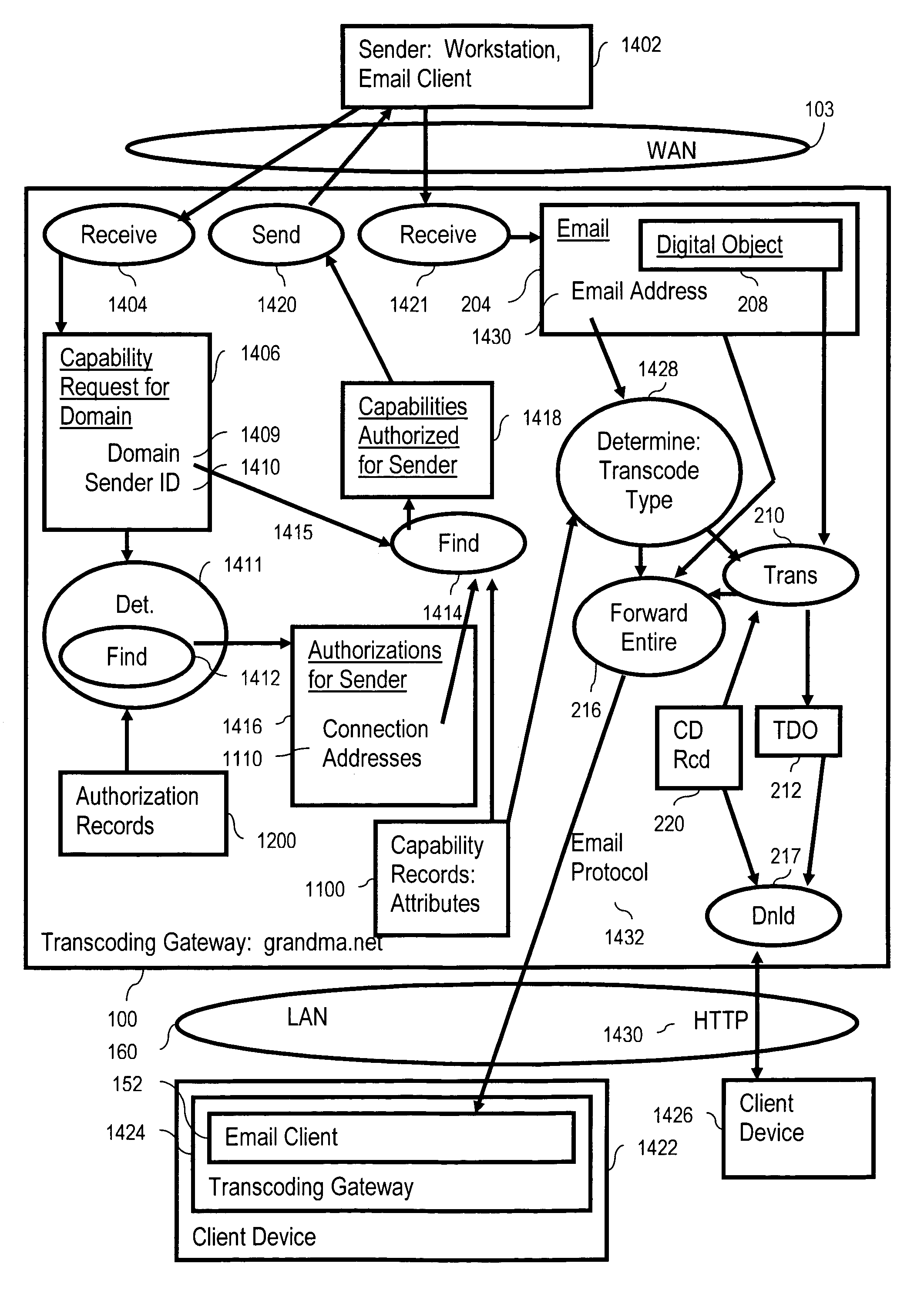
Dynamic indication of email capabilities
InactiveUS7213076B2Multiple digital computer combinationsSubstation equipmentInternet privacyEmail management
A method of email administration including receiving in a transcoding gateway from a sender an email display capability request for a domain, wherein the capability request comprises a domain identification, finding in dependence upon the domain identification, at least one email display capability record for the domain, wherein the email display capability record for the domain comprises display capability attributes describing an email display capability for the domain, and sending at least one of the email display capability attributes to the sender.
Owner:INT BUSINESS MASCH CORP
System for and method of re-using public domain identifications
ActiveUS20110158396A1Intelligent networksInterconnection arrangementsTelecommunicationsComputer science
A system for and method of re-using telephone number is presented. The system and method may include receiving, via an input / output module, a public call invite request message to establish a communication session between a calling party and a called party, establishing, via the input / output module, a first communication session with the calling party based at least in part on the public call invite request message, transmitting, via a telephone number re-use module, a plurality of private call invite request messages to a plurality of communication devices associated with the called party, establishing, via the telephone number re-use module, a second communication session with the called party based at least in part on the plurality of private call invite request messages, and coupling, via a processing module, the first communication session and the second communication session to establish the communication session between the calling party and the called party.
Owner:VERIZON PATENT & LICENSING INC
Dynamic indication of email capabilities
InactiveUS20030135561A1Telephonic communicationMultiple digital computer combinationsInternet privacyEmail management
A method of email administration including receiving in a transcoding gateway from a sender an email display capability request for a domain, wherein the capability request comprises a domain identification, finding in dependence upon the domain identification, at least one email display capability record for the domain, wherein the email display capability record for the domain comprises display capability attributes describing an email display capability for the domain, and sending at least one of the email display capability attributes to the sender.
Owner:IBM CORP
Identification distribution and separate-storage method, identification replacing transmission method and system
InactiveCN101754219AImprove the protective effectSupport mobilitySecurity arrangementTelecommunicationsService domain
The invention discloses an identification distribution and separate-storage method, an identification replacing transmission method and system, relating to the field of network safety. The identification distribution and separate-storage method comprises the following steps of: dividing a heterogeneous wireless network by function into a user domain, an access domain, a service domain and an attribution domain, wherein the service domain comprises at least one access domain, the access domain comprises at least one user domain, and the attribution domain and the service domain are the same network when in local service; and after the successful authentication of a terminal, allocating the attribution domain, the service domain and the access domain with domain identifications domain by domain. Based on the access authentication of the heterogeneous wireless network, the invention provides a mechanism of the identification distribution, the separate storage and the replacing transmission of the identification. In the transmission process of the domain identification in the user domain, the access domain, the service domain and the attribution domain, the real identity and the location information of a terminal can be effectively concealed through the retrieval and the replacement among domains and the dynamic update at different identification mapping servers, thereby enhancing the credible access of the heterogeneous wireless network and the safety protection capacity on mobility problems.
Owner:THE PLA INFORMATION ENG UNIV
Method for establishing machine learning model to check webpage hidden links through domain identification and theme identification
ActiveCN107566391AImprove the problem of poor recognition effectSolve the problem of tamperingComputing modelsTransmissionFeature extractionDomain analysis
The invention provides a method for establishing a machine learning model to check webpage hidden links through domain identification and theme identification. The method comprises the steps of collecting a great number of webpage source codes which are marked as the webpage source codes comprising hidden links and the webpage source codes marked as the normal webpage source codes, and forming a training set based on the webpage source codes; extracting a risk text, risk degree, theme difference degree, a theme, a risk text vector, a risk text abnormal probability and the risk text length in each web page source code through suspicious domain identification, sensitive domain identification, secure domain identification, all-domain analysis and theme identification; carrying out model training on characteristic data of all web page source codes in the training set through utilization of a machine learning algorithm, thereby obtaining a classification distinguishing model; and importingthe characteristic data of to-be-predicted web page source codes into the classification distinguishing model, thereby obtaining a result of whether the to-be-predicted web page source codes comprisethe hidden links or not. According to the method, the highly mixed hidden link code identification effect is good, the feature extraction is relatively complete and the problem that a traditional method cannot accurately distinguish the hidden links and page tampering can be solved well.
Owner:上海斗象信息科技有限公司
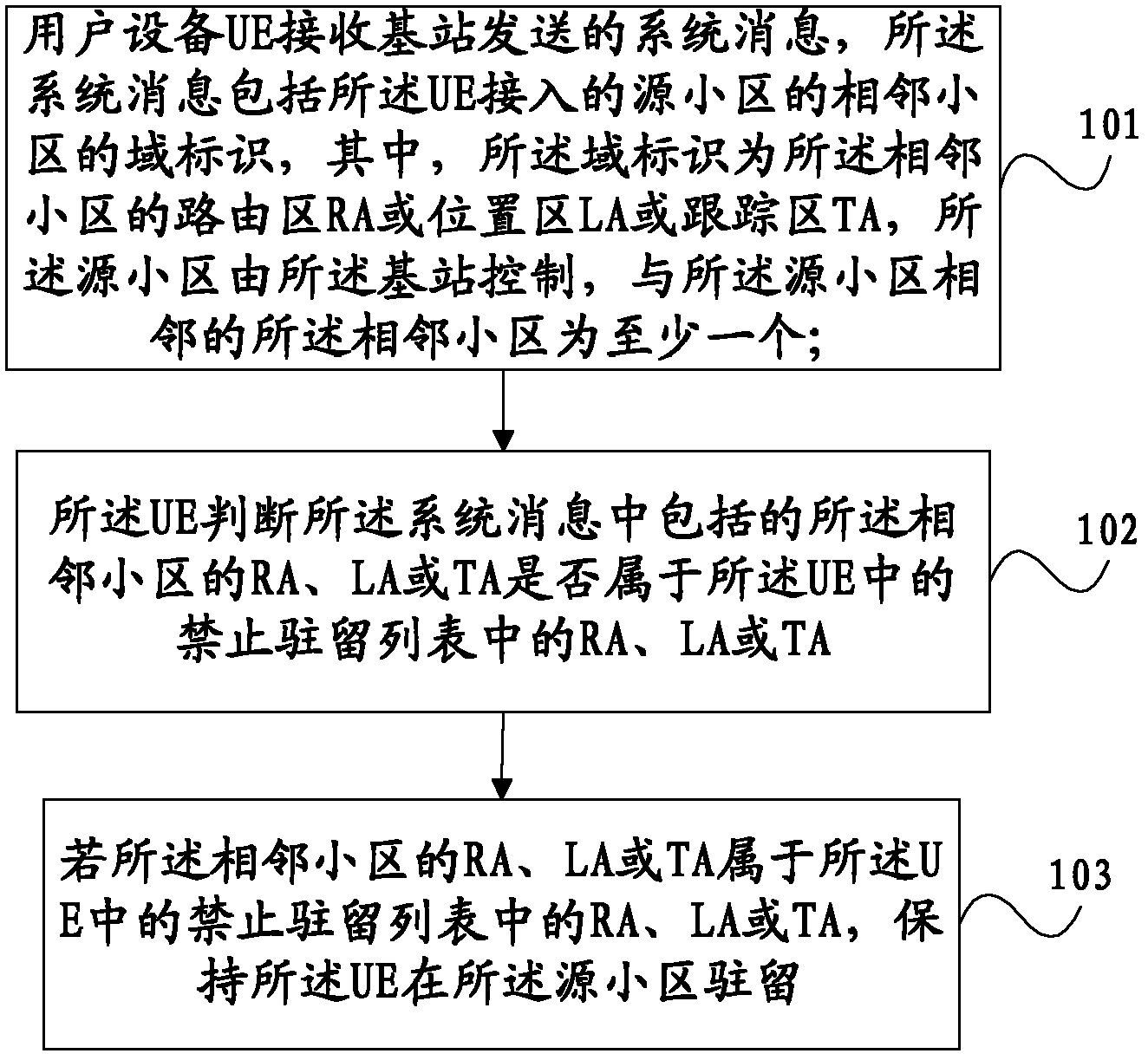
Cell reselection method and user equipment
ActiveCN103220655AImprove reselection efficiencySave wireless resourcesNetwork data managementA domainLocation area
The invention discloses a cell reselection method and user equipment (UE). The method includes the steps of receiving system information through the UE; judging through the UE whether a domain identification of an adjacent cell belongs to an routing area (RA) or a location area (LA) or a tracing area (TA) in a prohibition resident list in the UE or not; and keeping the UE to reside in a source cell if the domain identification of the adjacent cell belongs to the RA or the LA or the TA in the prohibition resent list in the UE, wherein the system information is sent by a base station and includes the domain identification of the adjacent cell of the source cell which is accessed by the UE, the domain identification is the RA or the LA or the TA, the source cell is controlled by the base station, and the number of the adjacent cell is at least one. The cell reselection method and the UE are suitable for conducting reselection between cells through the UE.
Owner:HUAWEI TECH CO LTD
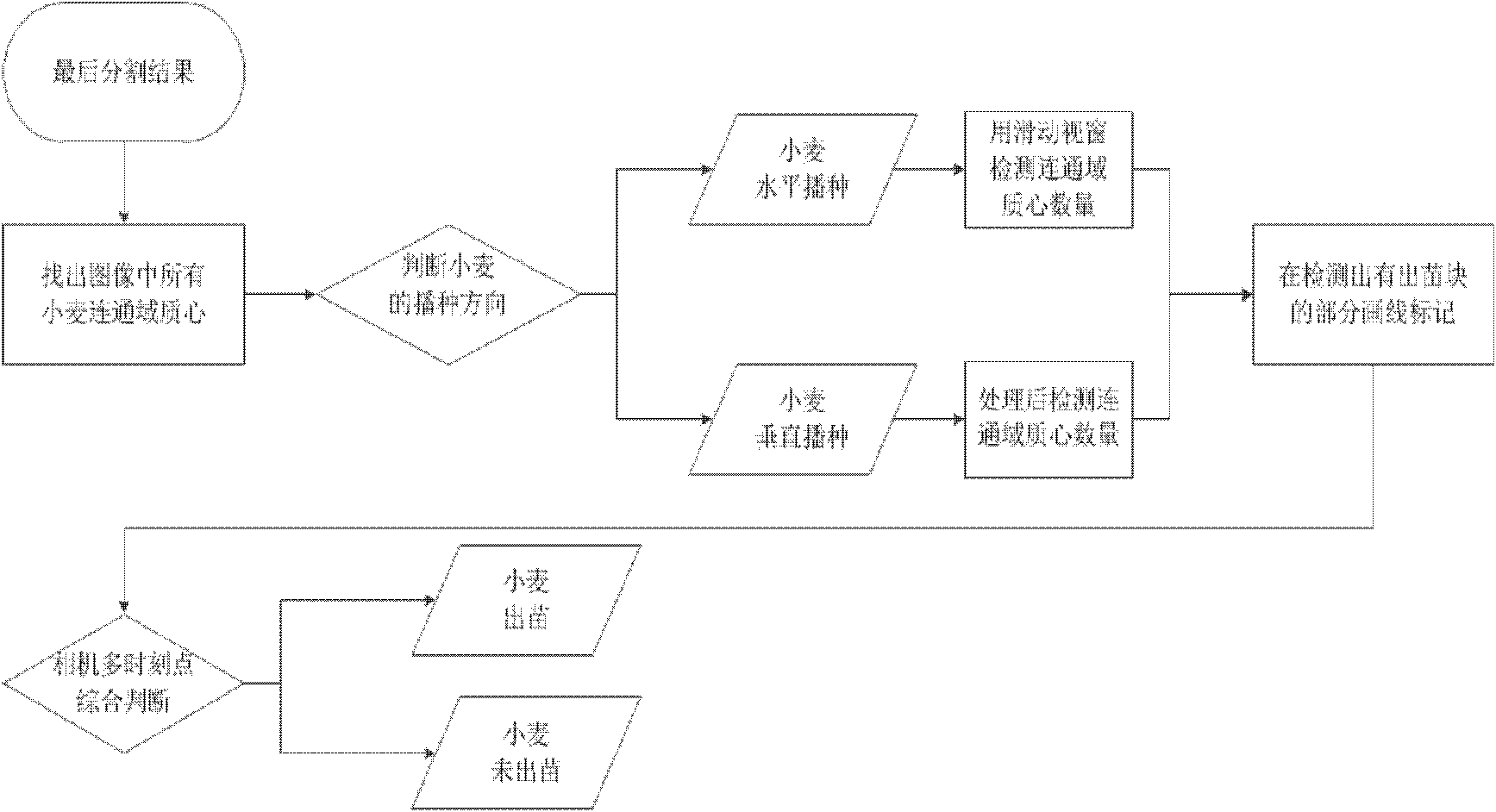
Automatic detection method of wheat seedling emergence
The invention provides an automatic detection method of wheat seedling emergence, comprising the following steps: a wheat image is acquired through segmenting a wheat field image acquired by using a camera in real time; connected domain identification is performed on the wheat image, and centers of mass of connected domains are marked; the seeding direction of the wheat is identified according to the wheat image, if the seeding direction is a horizontal direction, the wheat image is divided into a plurality of subsections in a vertical direction, and if being a vertical direction, the wheat image is divided into a plurality of subsections from a horizontal direction; and the number of the center of mass of the connected domains in each subsections is counted. If the number of the center of mass of the connected domains is greater than a predetermined subsection seedling emergence determining threshold value then the corresponding subsection is determined to be a seedling emergence subsection. If the number of the seedling emergence subsections is greater than an image seedling emergence determining threshold value then the wheat in the wheat image are in a period of seedling emergence. The method can determine the growth period of the wheat in real time with high accuracy of detection results, and has important guiding significance for all kinds of farming activities of the wheat.
Owner:HUAZHONG UNIV OF SCI & TECH
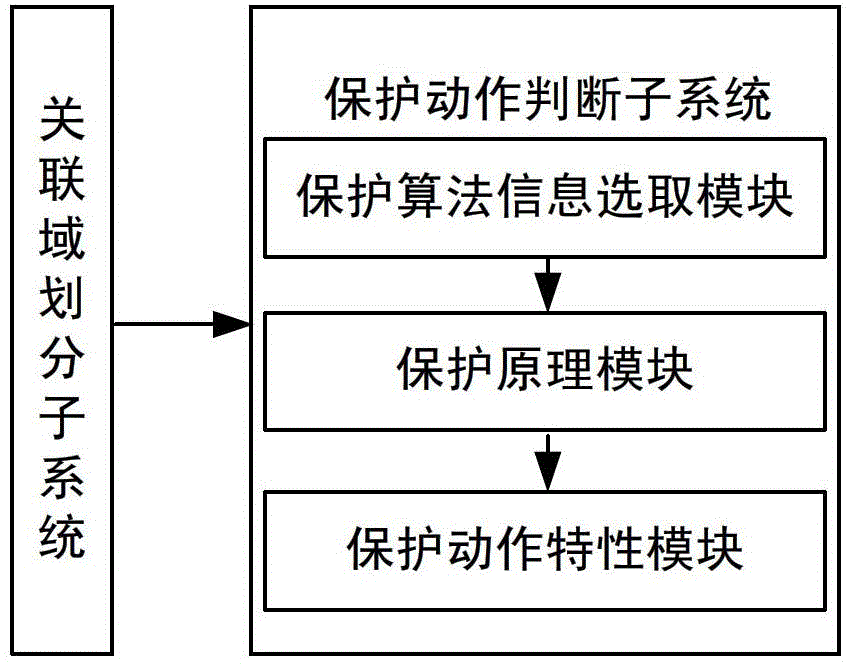
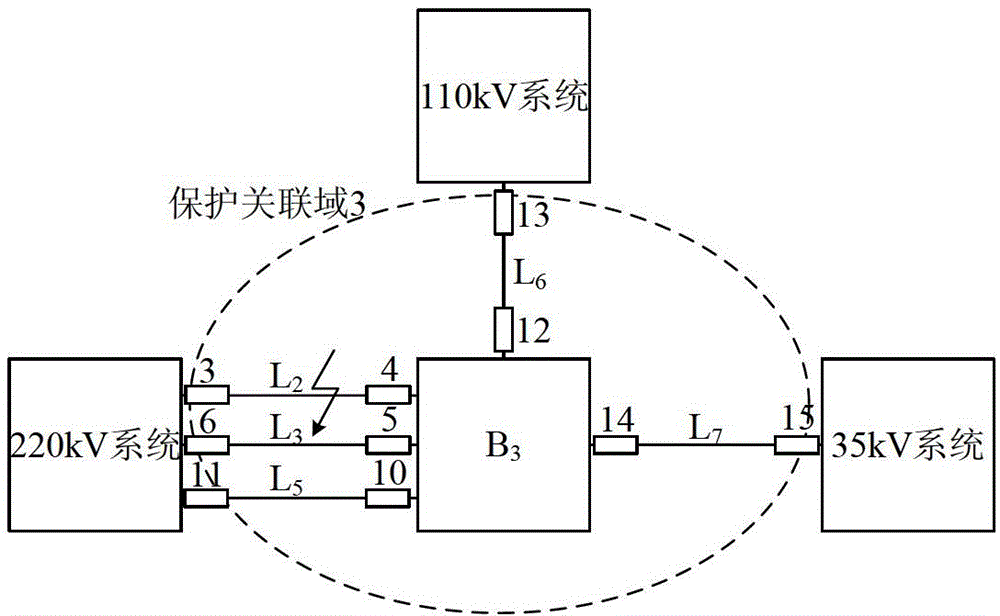
Fault correlation domain identification system based on fault component reactive power and method thereof
ActiveCN103336191ARealize the remote backup protection functionImprove securityElectrical testingSpecial data processing applicationsTransformerElectric power system
The invention relates to a fault correlation domain identification system based on fault component reactive power and a method thereof and belongs to the electric power system fault identification technology field. The fault correlation domain identification system comprises a correlation domain division subsystem and a protection motion determination subsystem, wherein the correlation domain division subsystem takes each start protection station as a center and takes a same voltage grade outgoing line pair end station as a boundary division protection correlation domain, the protection motion determination subsystem realizes establishment of a protection algorithm model, a protection algorithm information selection module extracts fault component reactive power in a fault association domain, a protection principle module realizes construction of protection action quantity and braking quantity based on the fault component reactive power, a protection motion characteristic module determines and identifies the fault association domain according to protection action. The fault correlation domain identification system can respectively acquire accurate determination results during occurrence of each types of faults in and out of the fault correlation domain, has sensitive and reliable protection performance, not only realizes an electrical network remote backup protection function under a common condition, but also successively solves a problem of protection difficulty under a condition of direct current disappearance of a transformer station and further improves electrical network security.
Owner:NORTH CHINA ELECTRIC POWER UNIV (BAODING)
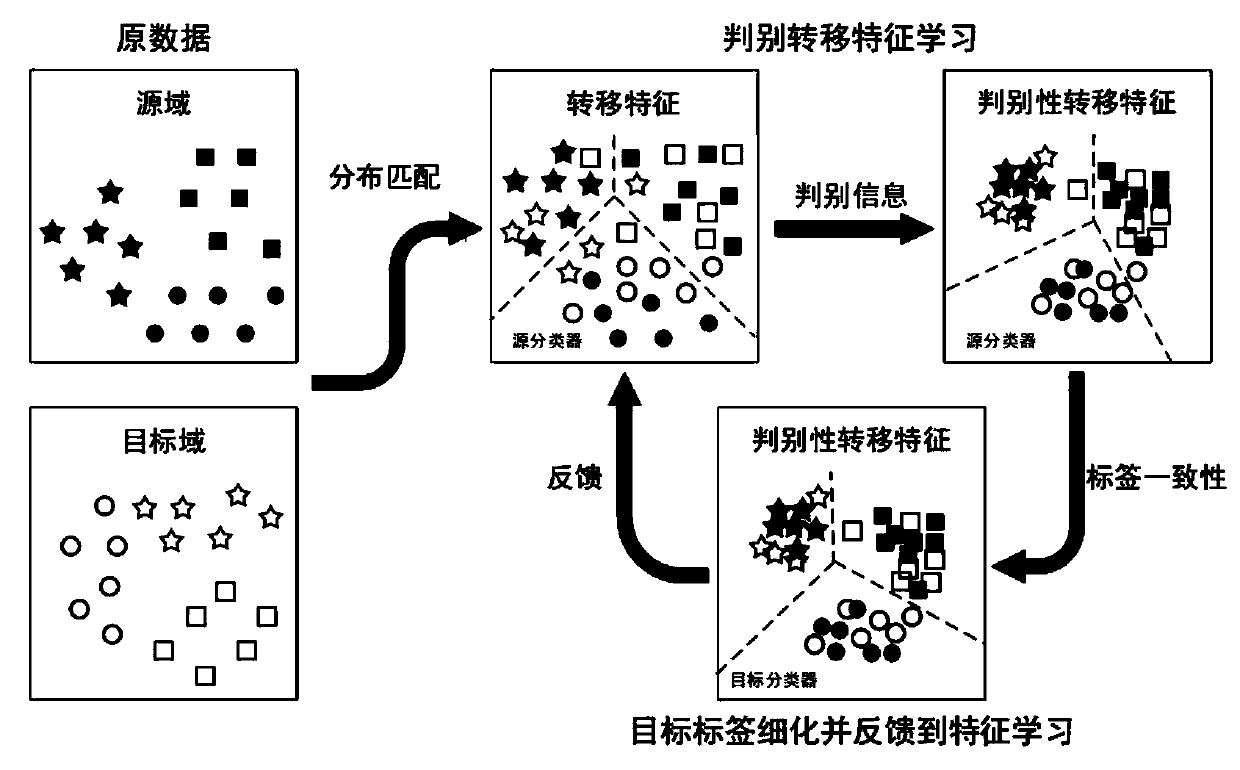
Domain adaptive migration feature method and system
ActiveCN110348579AImprove accuracyImprove performanceCharacter and pattern recognitionMachine learningAlgorithmA domain
The invention provides a domain adaptive migration feature method and system, and the method comprises the steps: S1, setting an initial value for an MMD matrix and intra-class / inter-class dispersionbased on a source domain and a target domain, and setting the maximum number of iterations; s2, optimizing a source classifier based on the MMD matrix and the intra-class / inter-class dispersion, and determining a pseudo label corresponding to the target data based on the optimized source classifier; s3, obtaining a target classifier based on the source domain, the target domain and the pseudo tagscorresponding to the target data, and refining the pseudo tags corresponding to the target data based on the target classifier; and S4, updating the MMD matrix and the intra-class / inter-class dispersion according to the refined pseudo tags, repeatedly executing the step S2 and the step S3 until the maximum number of iterations is reached, and setting the pseudo tags corresponding to the target data as the tags corresponding to the target data. According to the method provided by the invention, the accuracy of target domain identification is improved.
Owner:BEIJING INSTITUTE OF TECHNOLOGYGY
Method and apparatus for synchronizing a data communications network
InactiveUS7366099B2Error preventionTransmission systemsDistributed computingBroadcast communication network
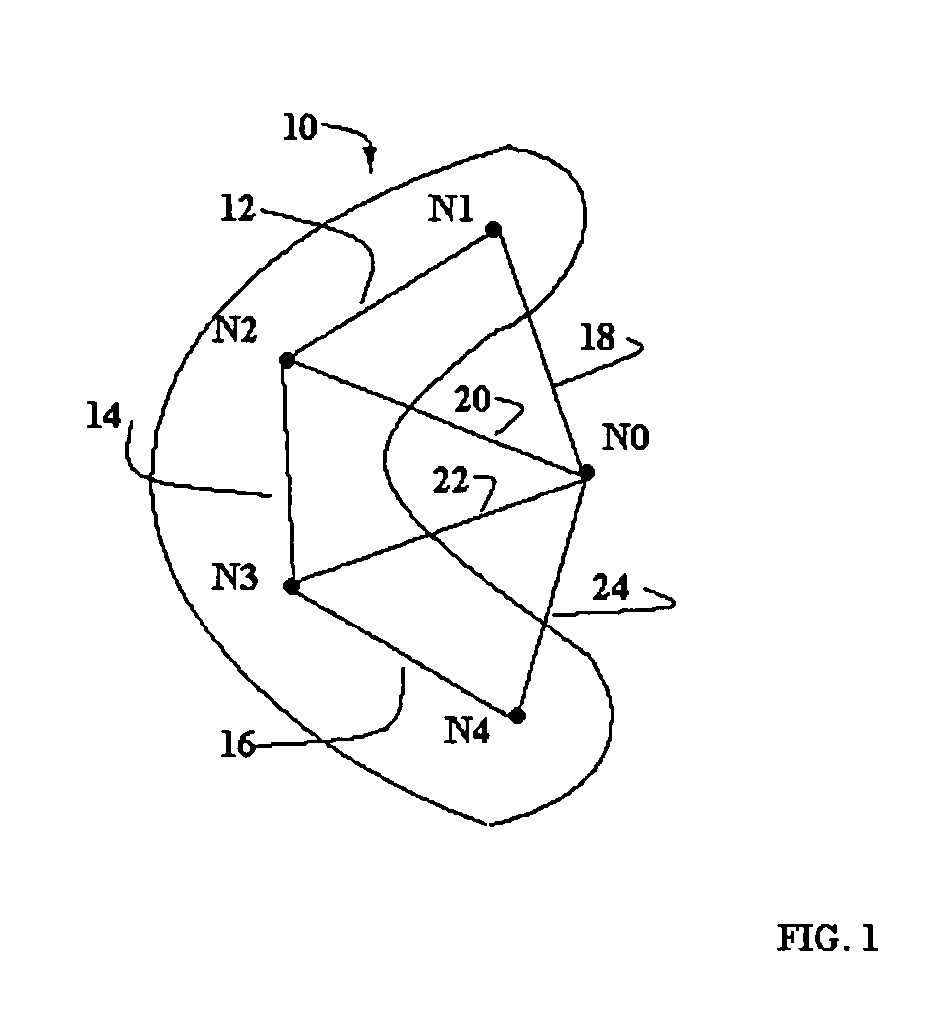
A method is disclosed for synchronizing a data communications network. The data communications network comprises a plurality of existing nodes forming one or more synchronization domains and a node entering the network. Each existing node in a synchronization domain stores a common representation of the synchronization domain and is configured to flood the synchronization domain with domain representation information. In a synchronization domain identification step formed at the entering node, the entering node exchanges entering node domain representation information with a first neighboring existing node. The entering node identifies as a first synchronization domain common with the first neighboring existing node all neighboring existing nodes from which the entering node domain representation information is flooded back the entering node.
Owner:CISCO TECH INC
Method for distributing intelligent terminal service attribute in broad network service processing system
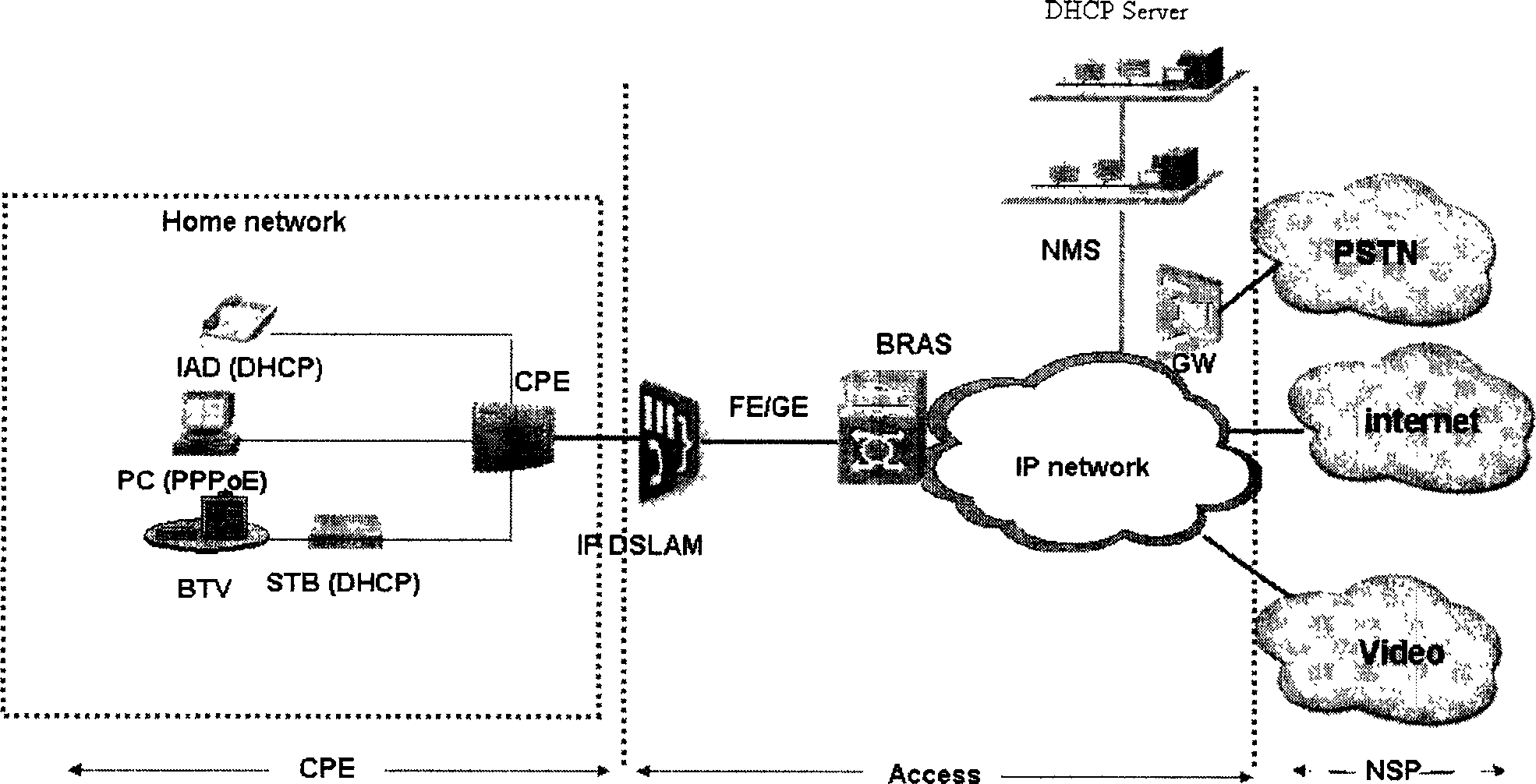
ActiveCN1859172AEase of doing businessReduce management costsData switching networksDistribution methodNetwork service
The present invention discloses an intelligent terminal service attributive distribution method in broadband network service treatment system, suitable for Triple Play service treatment system. Said method includes A, setting different domain identification for different type intelligent terminal; B, intelligent terminal transmitting self domain identification carried message to broadband access server BRAS; C, BRAS receiving message and according to predetermined domain identification and service attributive corresponded relation querying said message carried domain identification corresponded service attribute; D, BRAS distributing queried service attribute to said intelligent terminal. The present invention can low cost expeditiously realize Triple Play service treatment system management to intelligent terminal.
Owner:HUAWEI TECH CO LTD
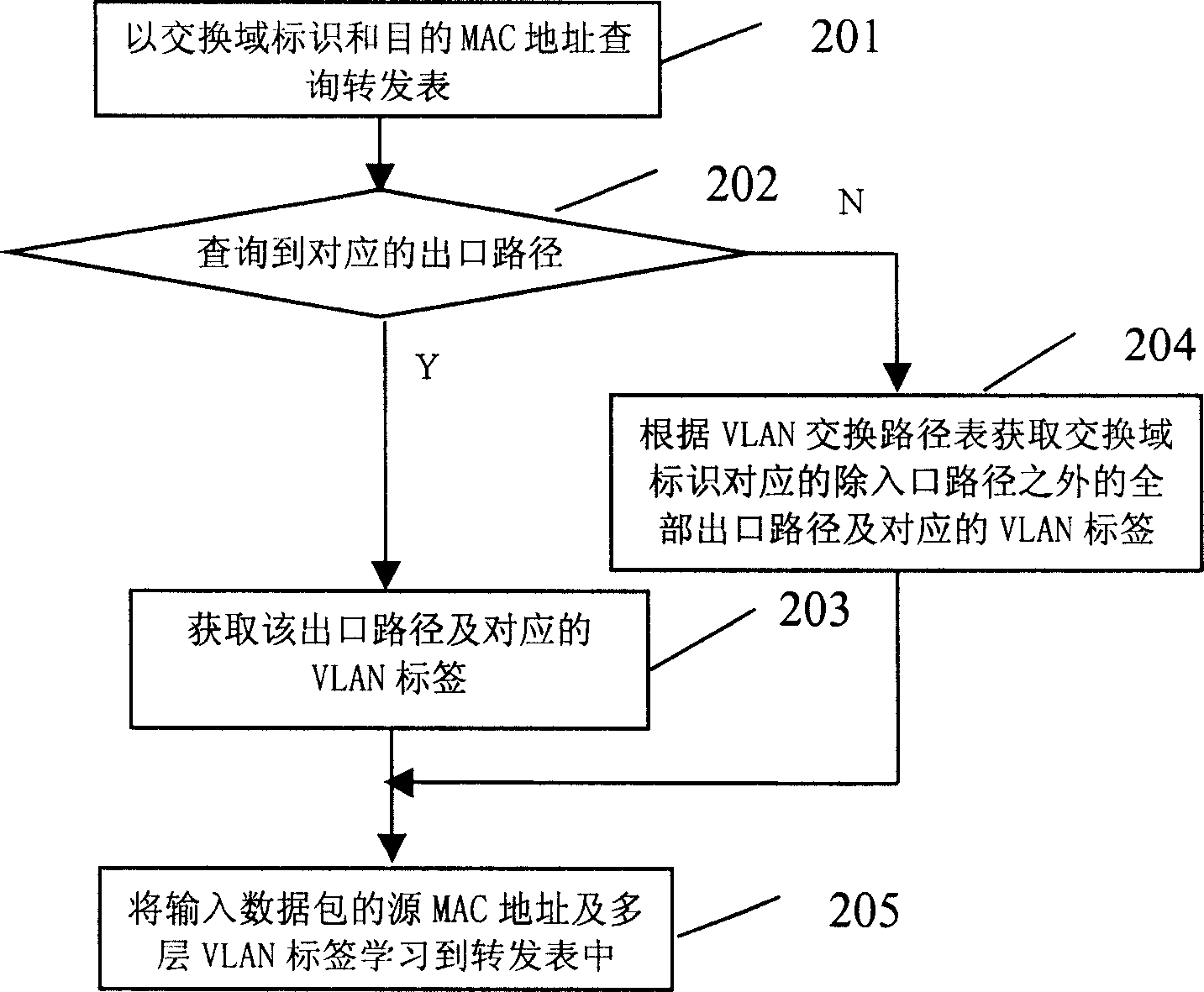
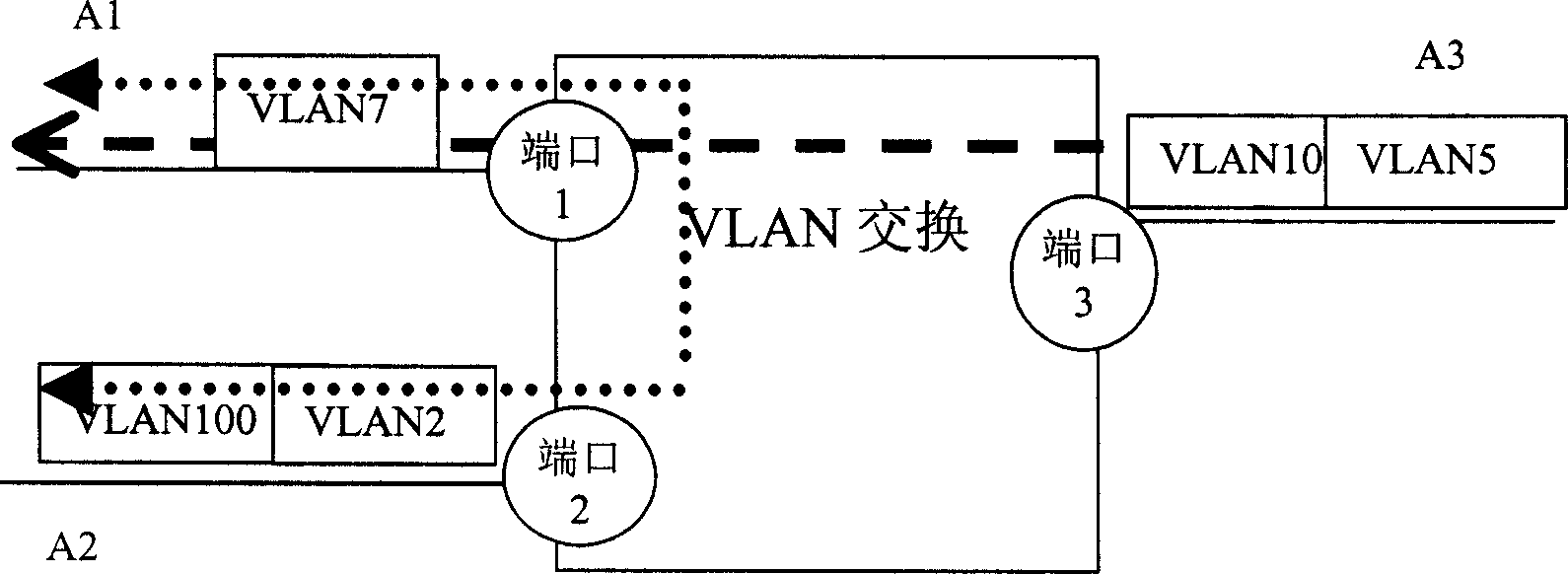
Method of multilayer VLAN switching
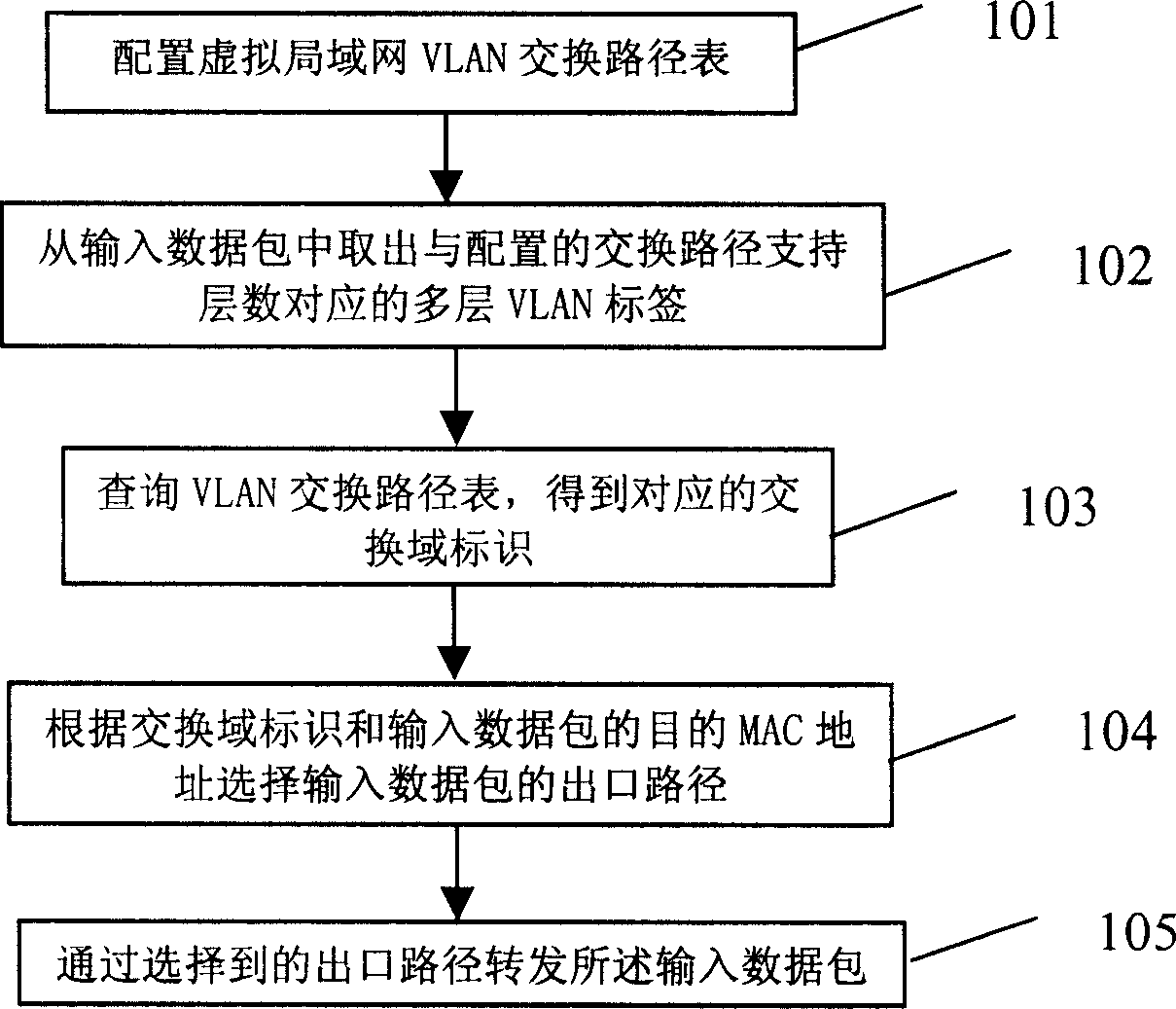
ActiveCN1725730AImprove connection efficiencyEasy to operateNetworks interconnectionVirtual LANNetwork packet
A method for switching virtual local network with multi-layer includes setting up virtual local network VLAN switching path table having VLAN data participated switch under all switch domains, obtaining the corresponding switch domain identification as per VLAN switching path table, selecting outlet path of input data packet according to said identification and destination MAC address of input data packet and using said outlet path to retransmit the input data packet.
Owner:NEW H3C TECH CO LTD
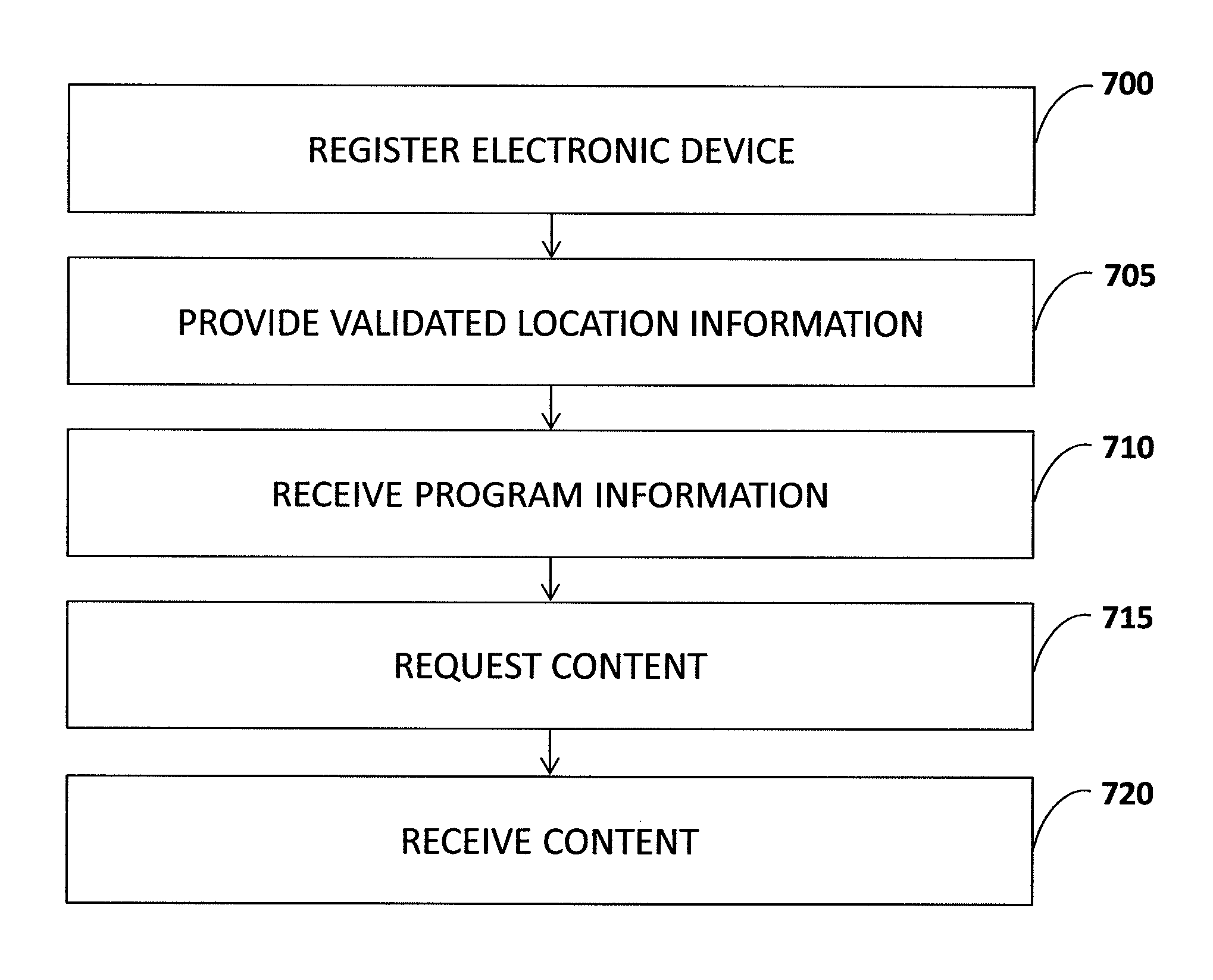
Secure broadcast area identification
InactiveUS20130117775A1Special service provision for substationBroadcast with distributionComputer networkComputer program
Systems, methods, apparatus, and computer program products are provided for receiving content available for consumption. For example, in one embodiment, an electronic device can provide location information to a management server that can be validated as originating from a trusted source of the electronic device. The management server can then validate the location information and determine the appropriate broadcast area for the electronic device based at least in part on the location information.
Owner:SYNCBAK
System and methods for spoofed domain identification and user training
Systems and methods are disclosed that minimize ongoing risk to an organization from user behaviors which magnify the severity of a spoofed domain. Systems and method are provided which enable an entity and users of an entity to identify potential harmful domains, combining search, discovery, reporting, the generation of risk indicators, end-user risk assessments, and training into a security awareness system.
Owner:KNOWBE4 INC
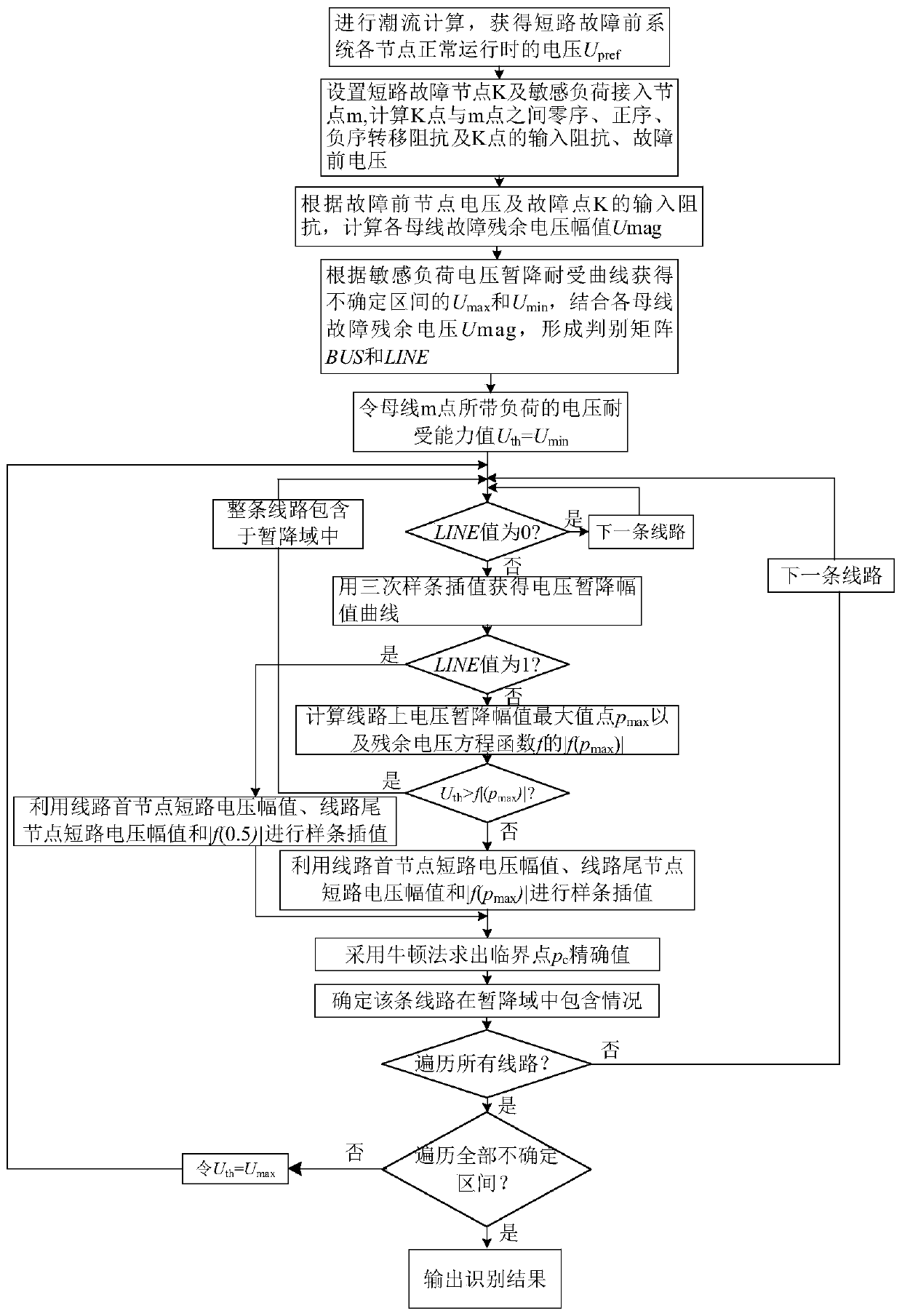
Sag domain identification method considering load sensitivity uncertainty
The invention discloses a sag domain identification method considering load sensitivity uncertainty. The method comprises the following steps of carrying out power flow calculation to obtain a systemnode voltage amplitude before failure; calculating each sequence impedance; calculating a residual voltage of each bus fault; obtaining upper and lower limits of a uncertainty interval of a sensitiveload according to an existing voltage tolerance curve and forming a discriminant matrix; calculate a line critical point according to the discriminant matrix and a lower limit and an upper limit of the uncertainty interval of the sensitive load; and traversing all lines and all uncertain spaces, and outputting two sag domain identification results corresponding to the upper and lower limits of theuncertainty interval of the sensitive load. In the invention, the uncertainty interval of load sensitivity is considered, a sag domain which is close to an actual project is described, and disadvantages that an existing sag domain identification method does not consider different tolerance capacities of the sensitive load to a voltage sag, the sag domain is fixed by a clear boundary, and all sagdomain critical points can not be considered are overcome.
Owner:GUANGDONG POWER GRID CO LTD +1
Method for domain identification of documents in a document database
InactiveUS7814105B2Special data processing applicationsData selectionDocument preparationDocumentation
A method for processing documents in a document database includes determining vocabulary words for each document, and determining a respective relevancy for each vocabulary word based upon occurrences thereof in all of the documents. Similarities are determined between the documents based upon the vocabulary words and their respective relevancies. At least one domain identification is determined for the documents based upon the determined similarities.
Owner:HARRIS CORP
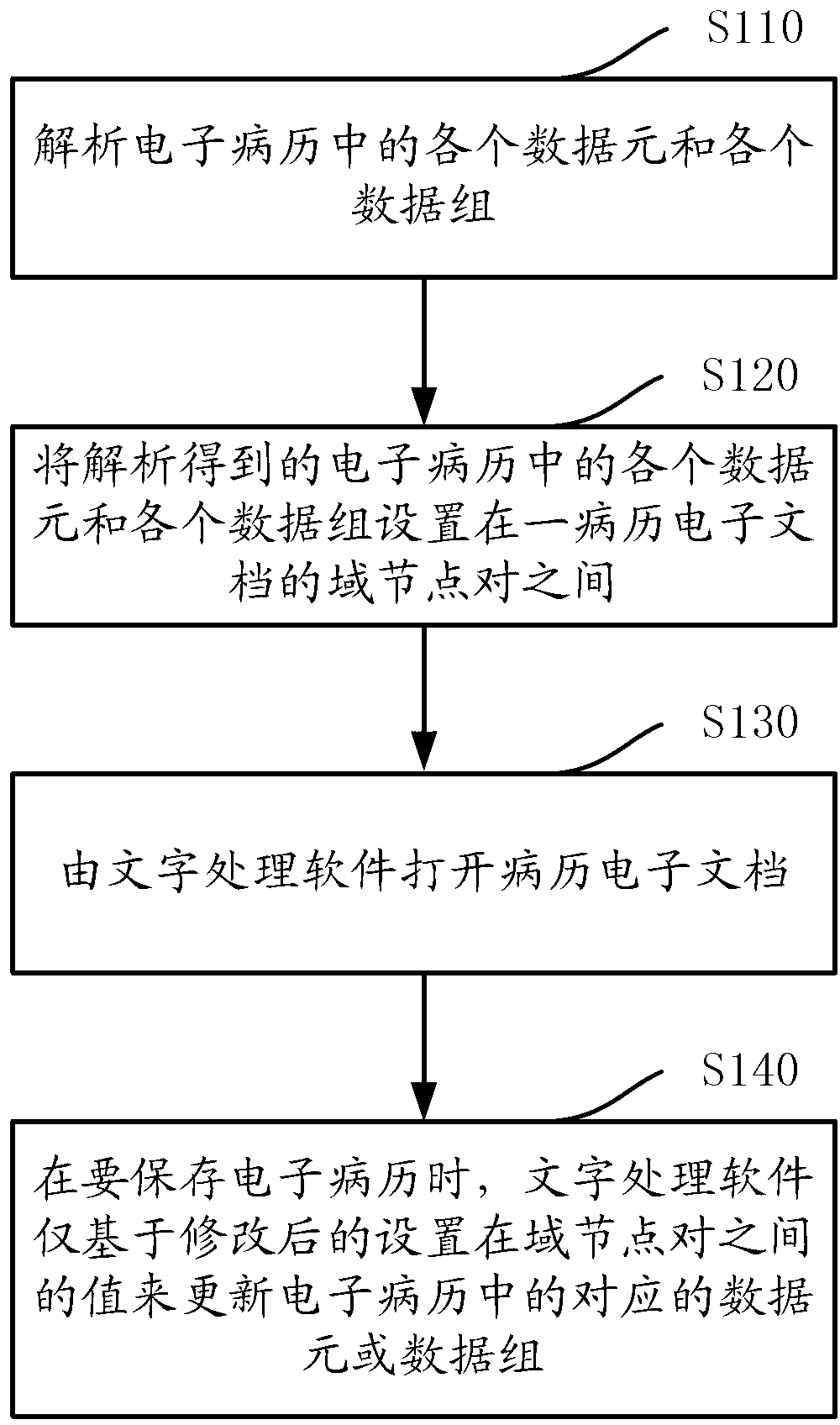
Electronic medical record editing method and system
InactiveCN103295176AFlexible editingImprove visual effectsData processing applicationsPatient-specific dataMedical recordData element
The invention discloses an electronic medical record editing method and system. The electronic medical record editing method includes: analyzing various data elements and various data arrays in an electronic medical record; setting the various data elements and data arrays of the electronic medical record into an electronic medical record file, setting each data element and array allowing to be edited between each domain node pair of the electronic medical record file, and setting various domain identifications for each data element and array allowing to be edited; opening the electronic medical record file by word processor software; updating the corresponding data elements or arrays in the electronic medical record by the word processor software on the basis of values between the domain node pairs when to store the electronic medical record. By the electronic medical record editing system, the electronic medical record can be endowed with stronger editing function and better vision effect.
Owner:CHINA STANDARD SOFTWARE
Online classroom video knowledge point identification method and device
InactiveCN111462554AAccurate identificationNarrow down the range of recognitionMultimedia data indexingElectrical appliancesData scienceVideo based
The invention relates to the field of teaching, and discloses an online classroom video knowledge point identification method and device, which can accurately identify all knowledge points contained in a classroom video. The method comprises the following steps: determining a knowledge point domain of a classroom video; acquiring a classroom video, which comprises a teaching courseware part and ablackboard writing part; for the teaching courseware part, dividing the teaching courseware part into multiple sections of videos according to courseware page switching time points, and identifying afirst set of knowledge points contained in each section of video based on the knowledge point domain; for the blackboard writing part, dividing the blackboard writing part into multiple sections of videos according to blackboard writing updating time points, and identifying a second set of knowledge points contained in each section of video based on the knowledge point domain; dividing the audio corresponding to each section of video into a plurality of audio clips according to audio pause points, and identifying a third set of knowledge points contained in each audio clip based on the knowledge point domain; and calculating a set of the knowledge points contained in the classroom video according to the first set, the second set and the third set.
Owner:浙江蓝鸽科技有限公司
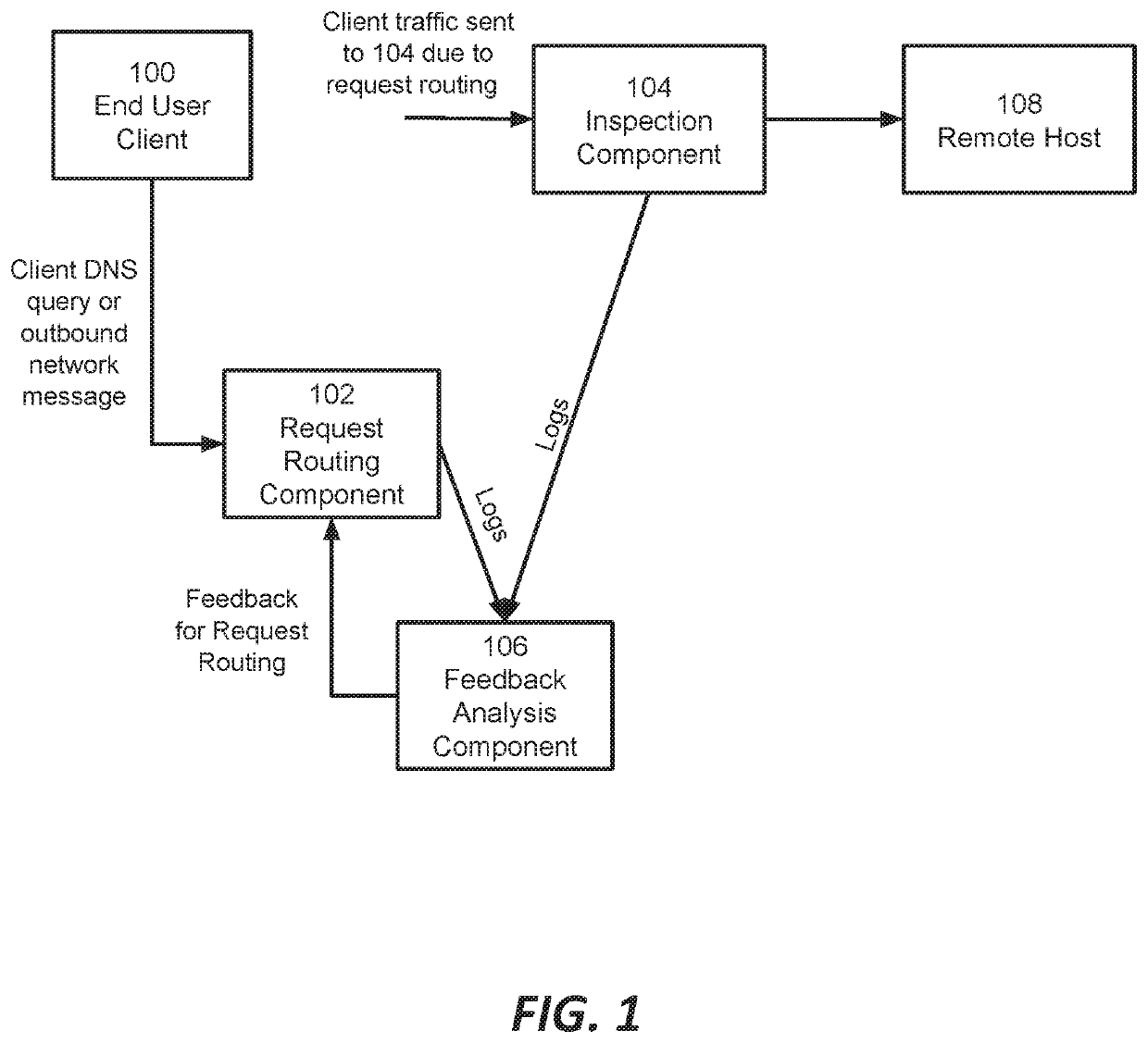
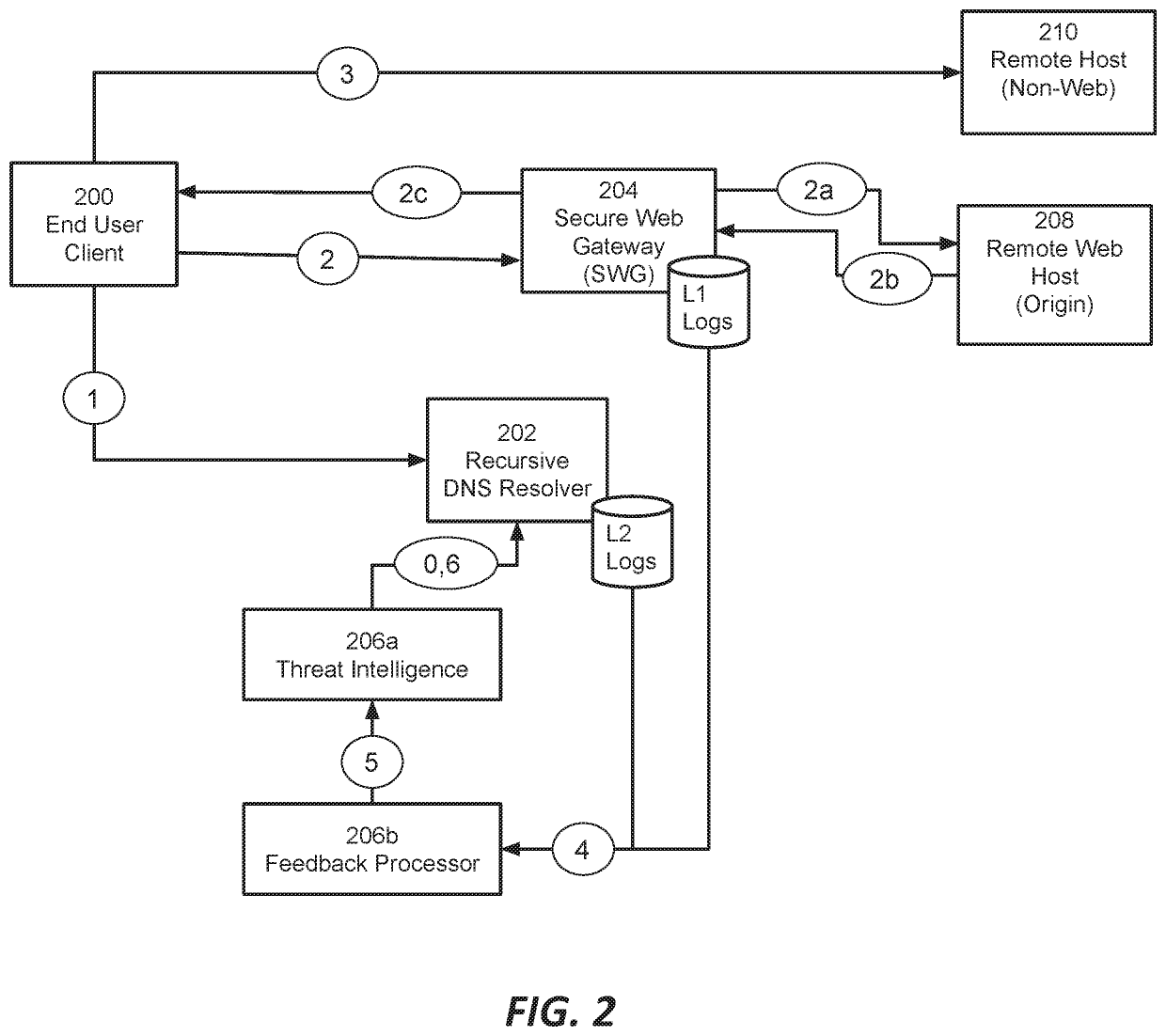
Network security system with enhanced traffic analysis based on feedback loop and low-risk domain identification
This document describes among other things, network security systems that incorporate a feedback loop so as to automatically and dynamically adjust the scope of network traffic that is subject to inspection. Risky traffic can be sent for inspection; risky traffic that is demonstrated to have high rate of threats can be outright blocked without further inspection; traffic that is causing errors due to protocol incompatibility or should not be inspected for regulatory or other reasons can be flagged so it bypasses the security inspection system. The system can operate on a domain by domain basis, IP address basis, or otherwise.
Owner:AKAMAI TECH INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com