Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
112 results about "Managing change" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
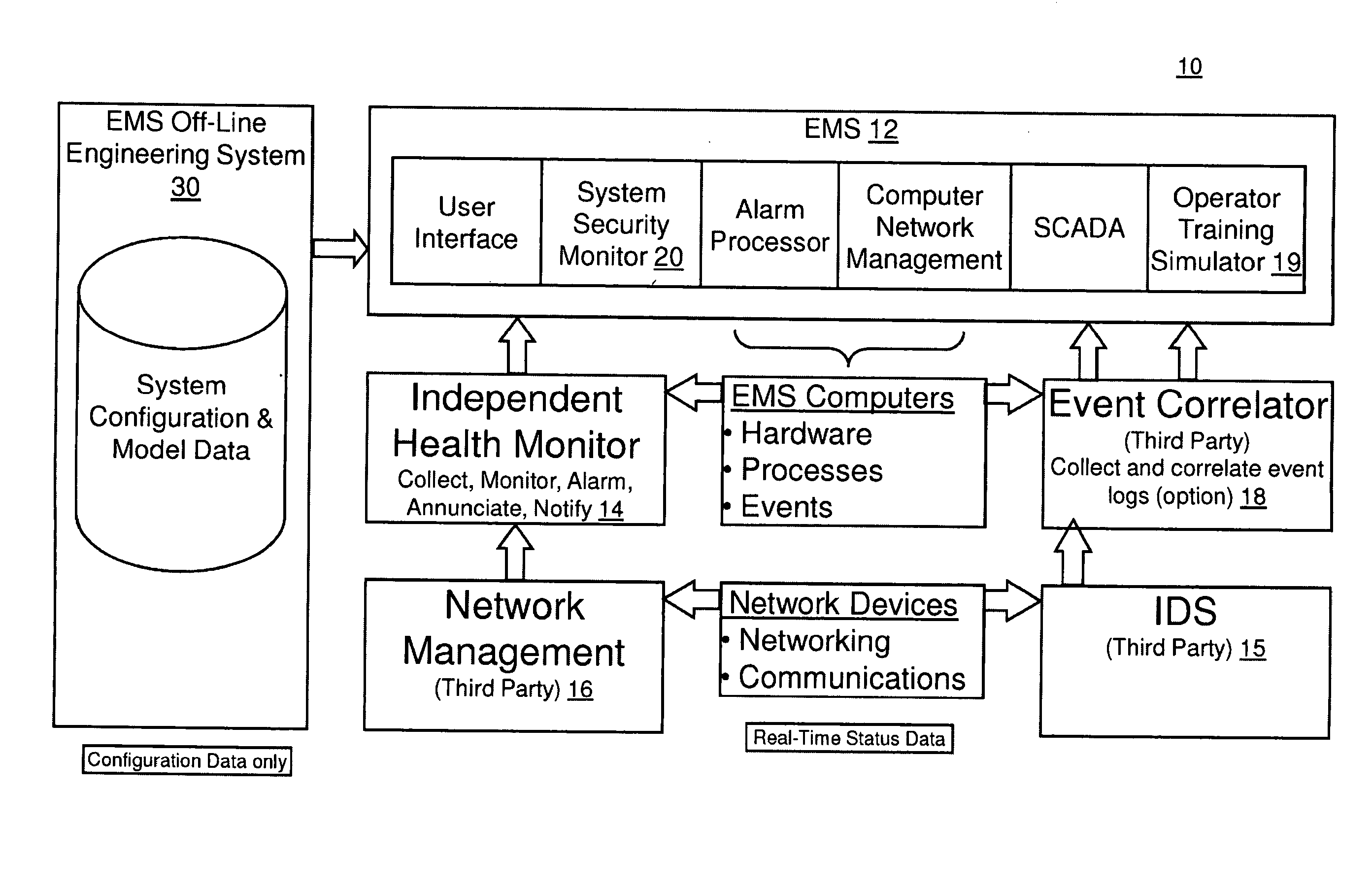
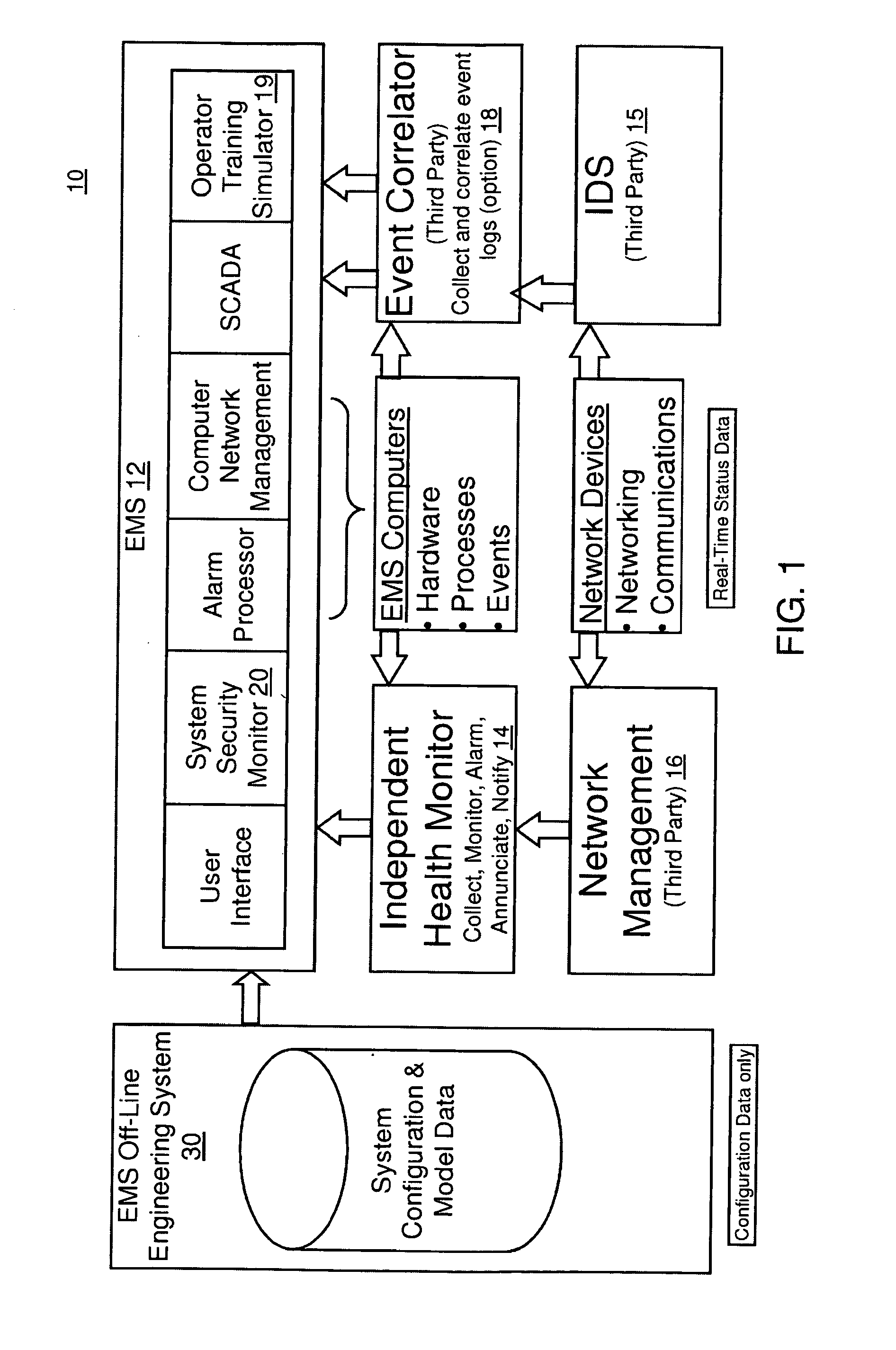
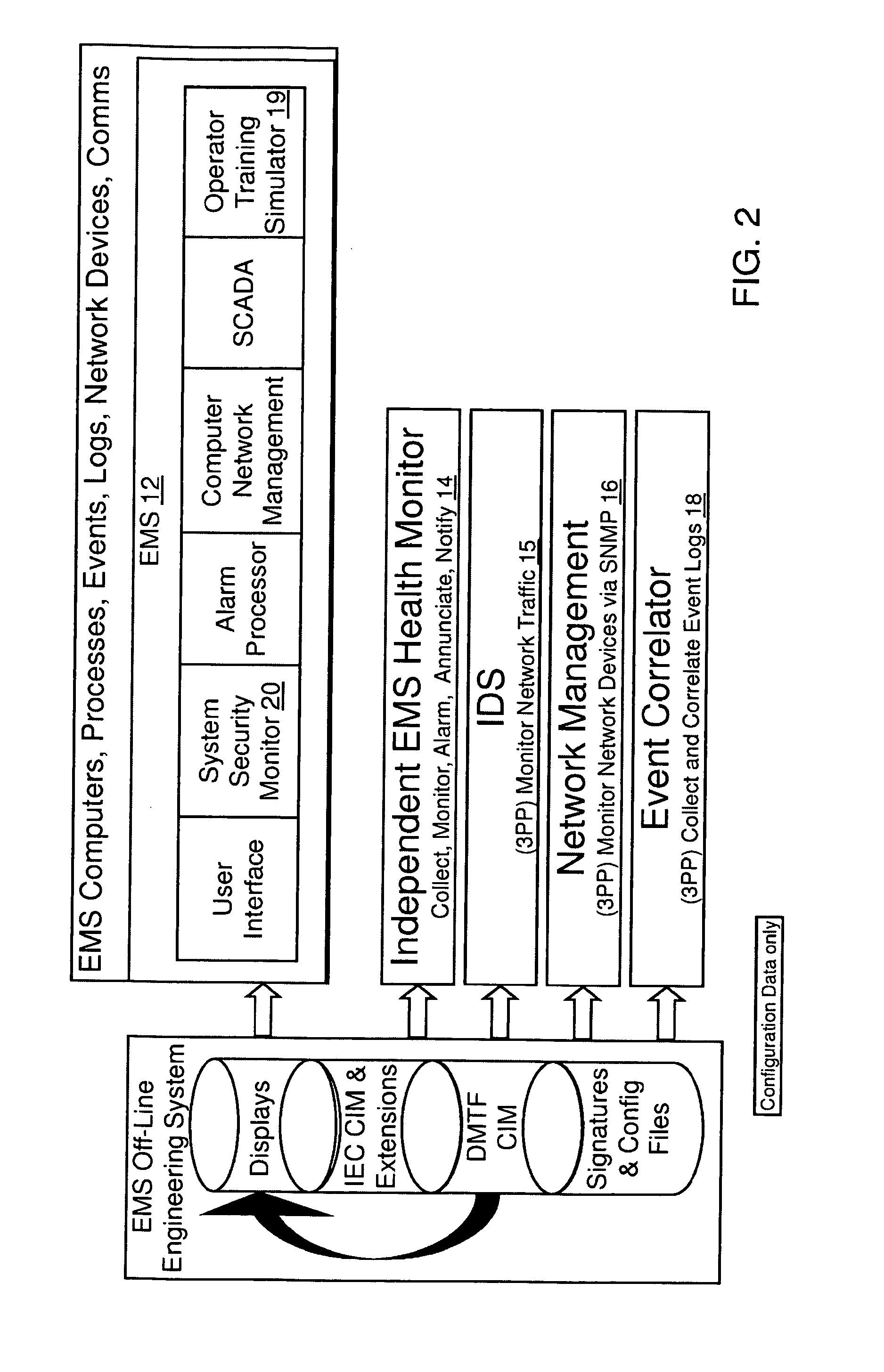
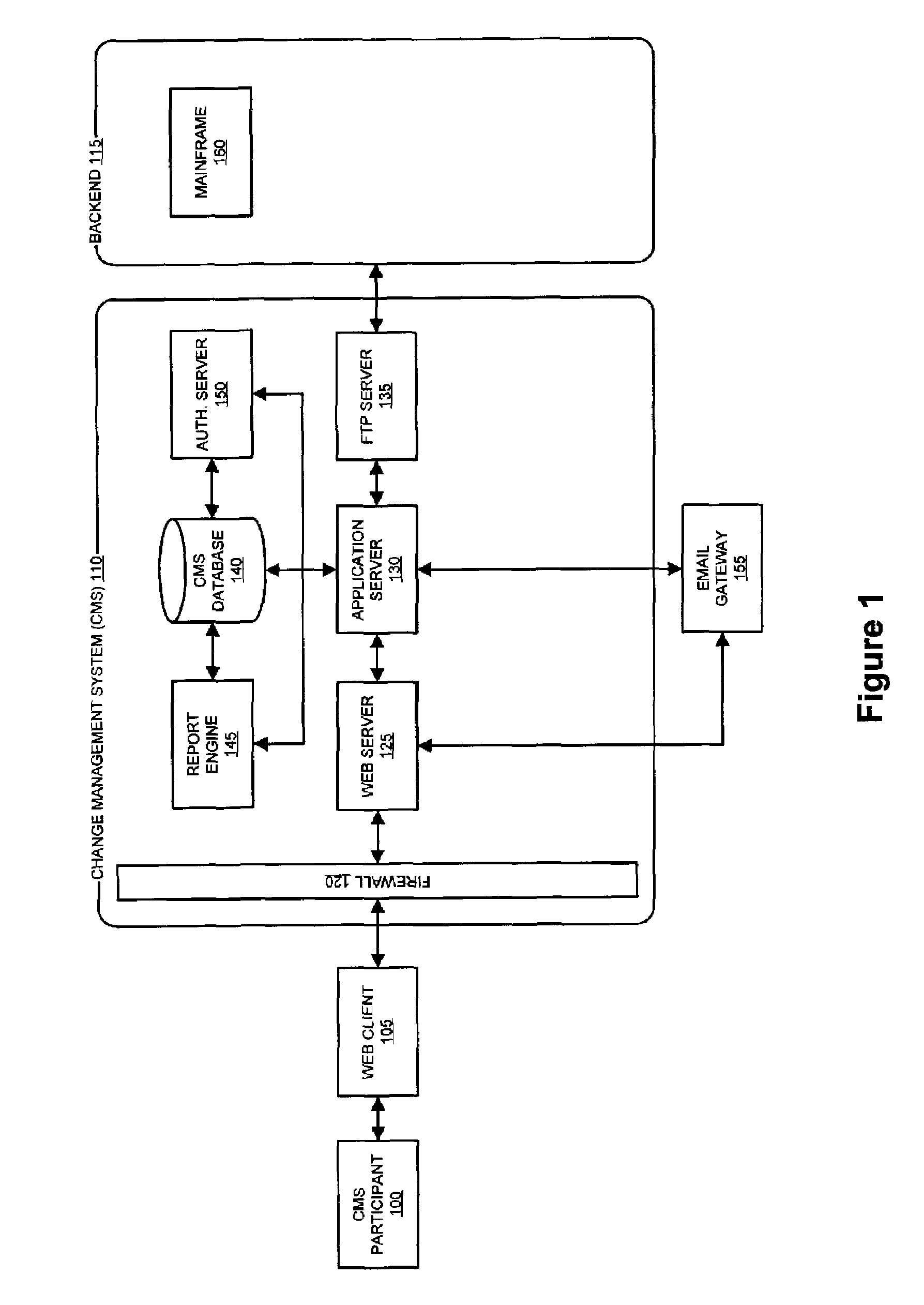
Method and system for cyber security management of industrial control systems
ActiveUS20110039237A1Low chanceFull accessMemory loss protectionError detection/correctionCommand and controlData acquisition
A method and system for cyber security management of Supervisory Control And Data Acquisition (SCADA) systems is provided to enhance situational awareness and cyber security management for industrial control systems. A centralized System Security Manager (SSM) is integrated into a SCADA to collect security related data for the industrial control system and an integrated command and control user interface displays security related data, a system security level, and interfaces with a user to allows for changing of system security settings for the industrial control system based on the security related data collected and manages changes in operational state of the SCADA based on the security level to restrict use of system interfaces and system accesses.
Owner:SIEMENS AG
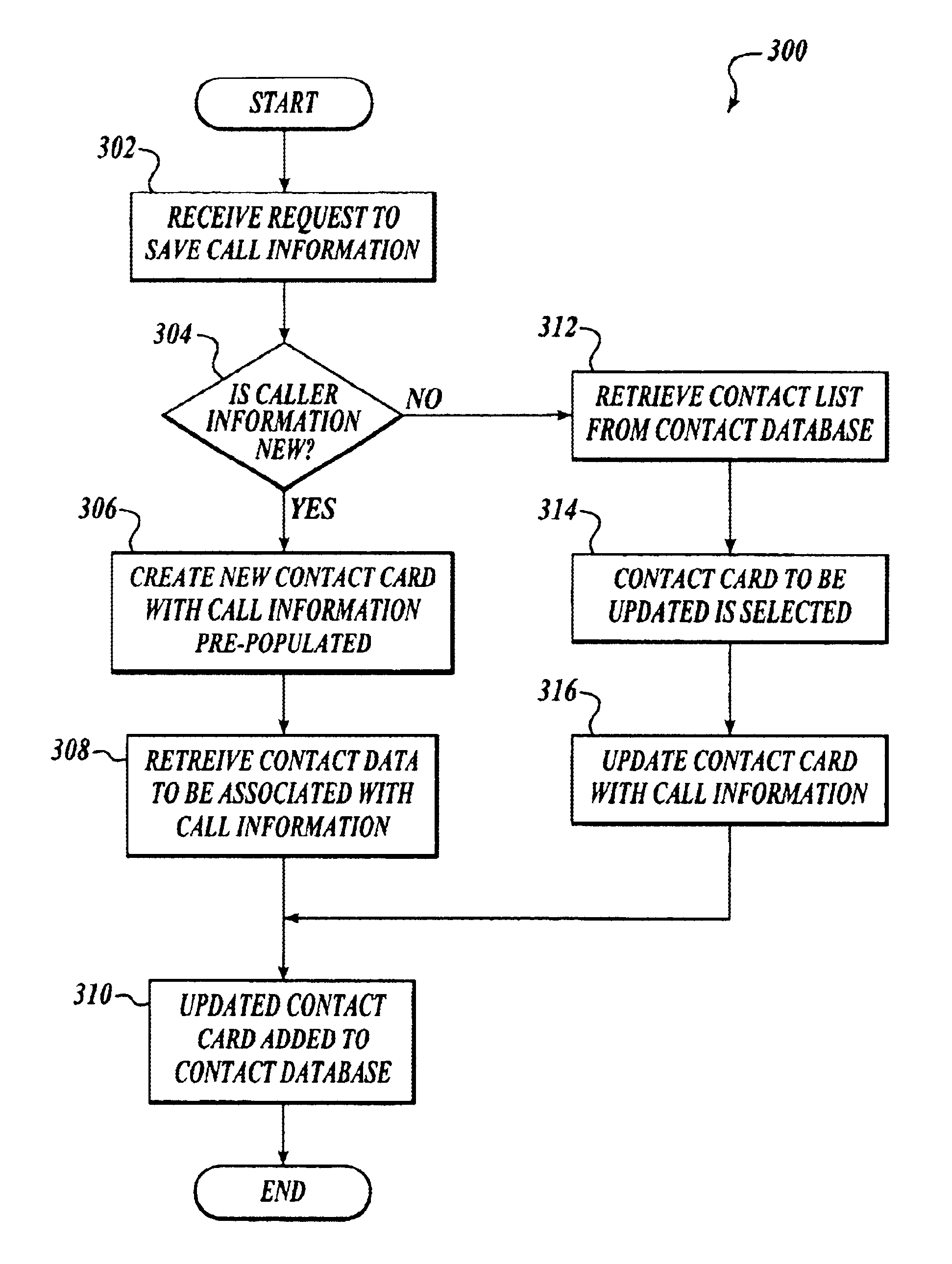
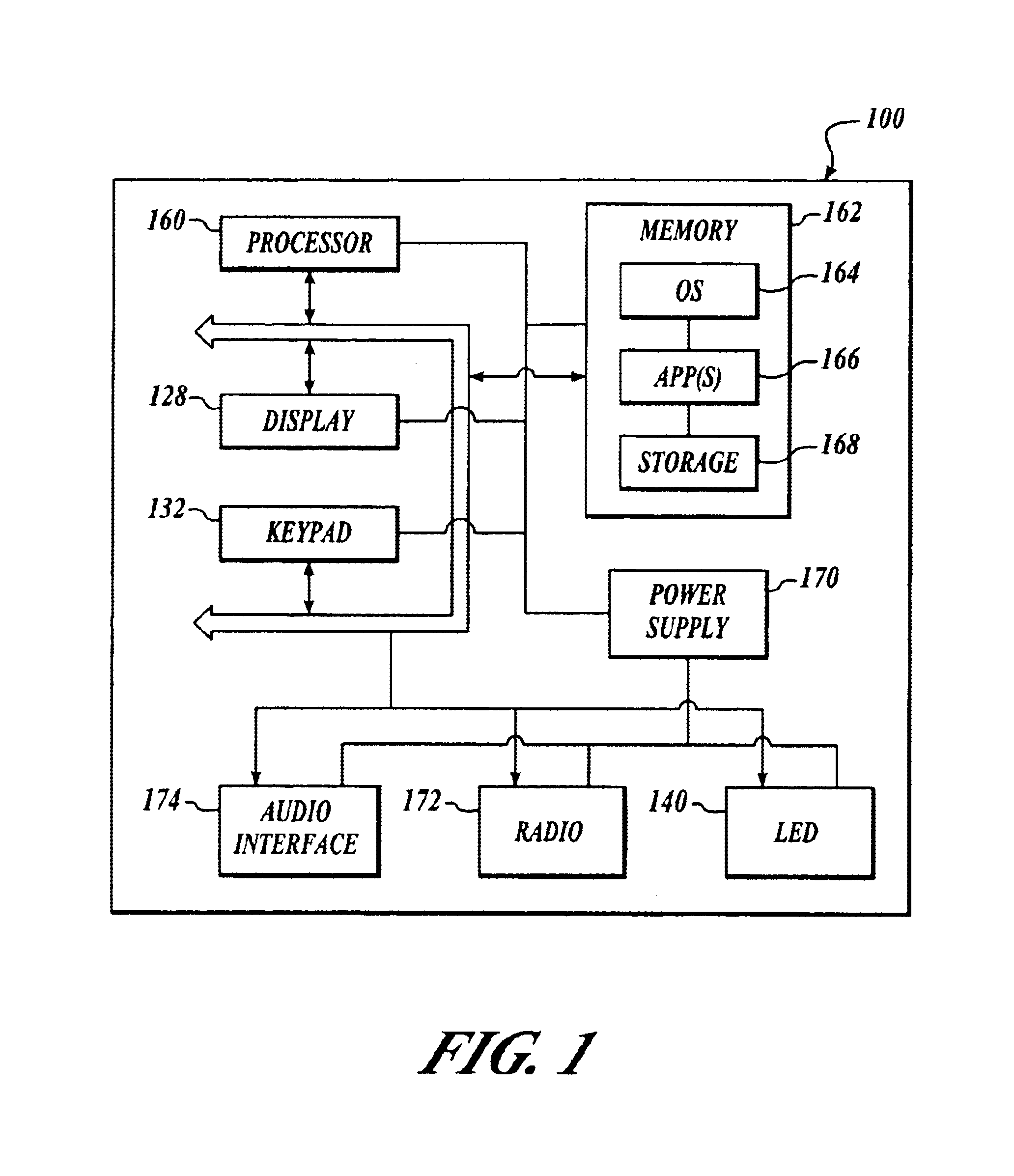
Method and system for managing changes to a contact database
InactiveUS6909910B2Reduce workloadData processing applicationsSpecial service for subscribersData fieldManaging change
Described is a system and method for updating a contact and adding a new contact from a call log in a communications device. The system includes a contact manager that is directed towards creating and updating call contact cards in a contact database with information retrieved from call logs of phone calls made to or from the communications device. In one embodiment, information is pre-populated into a predetermined data field of the contact card, thereby reducing workload to a user. The method includes determining if a request is for updating an existing contact card or for adding a new contact card to the contact database. The update or addition is made with information retrieved from call logs. Call information is pre-populated into a predetermined data field of the contact card, when it is determined that the request is to add a new contact card to the contact database.
Owner:MICROSOFT TECH LICENSING LLC
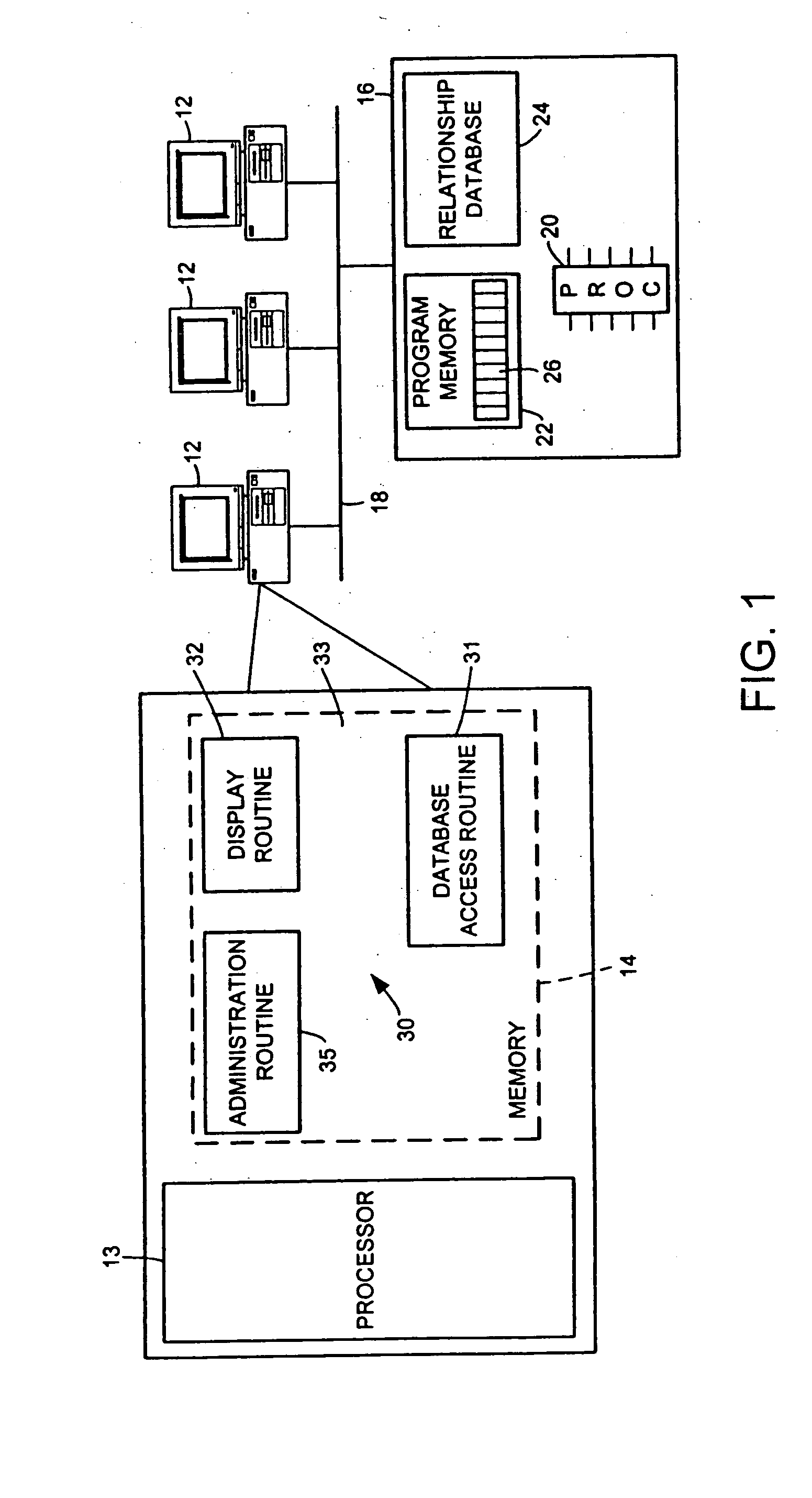
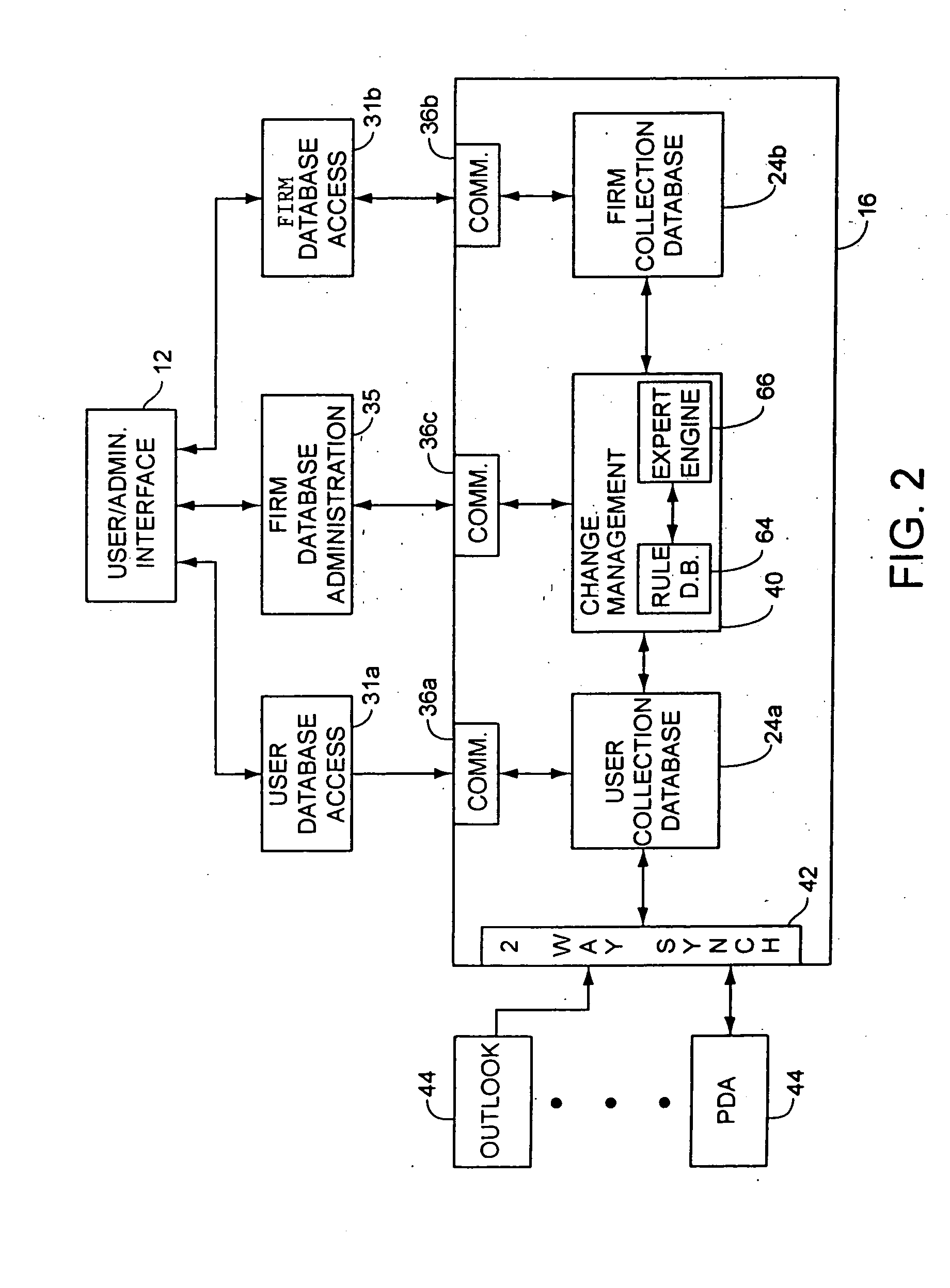
Managing changes in a relationship management system
A relationship management system stores multiple versions of contact information for a particular contact by storing the contact information that is available to all of the users of system that know a particular contact in a firm collection and by storing information about the particular contact that is available to a limited number of users that know the particular contact in one or more user collections. When changes are made to the user collection for a particular contact, the system detects the change, and based upon a number of administrative rules determines whether the change should be contributed to the firm collection. The system may automatically make the corresponding changes to each of the contact files within the firm collection or may recommend to the user whether the change should be promoted, allowing the users to accept or reject the recommendation. Preferably, each user will be provided with a default number of days to accept or reject the recommendation, after which the system may promote the contact information automatically.
Owner:REED ELSEVIER INC
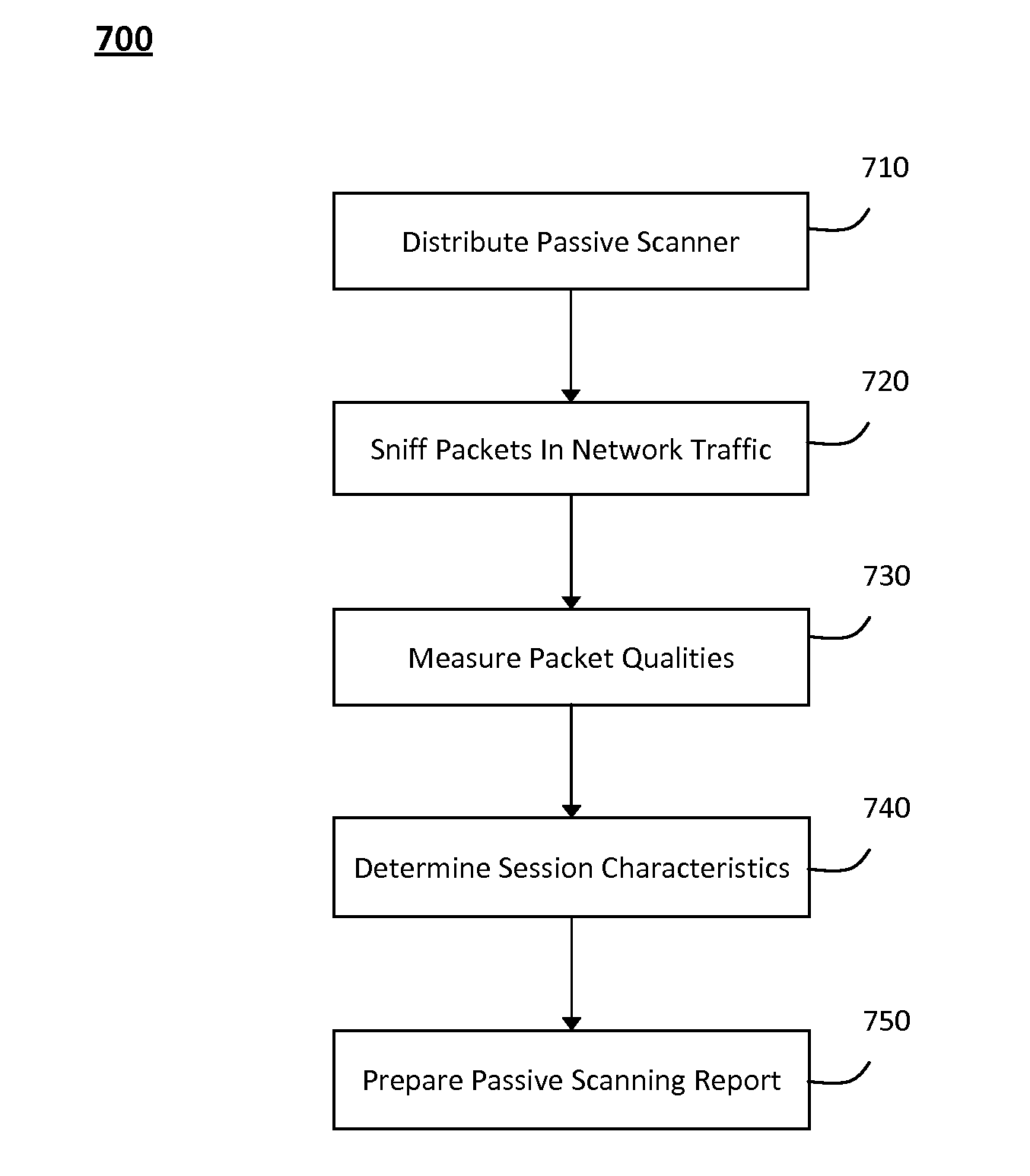
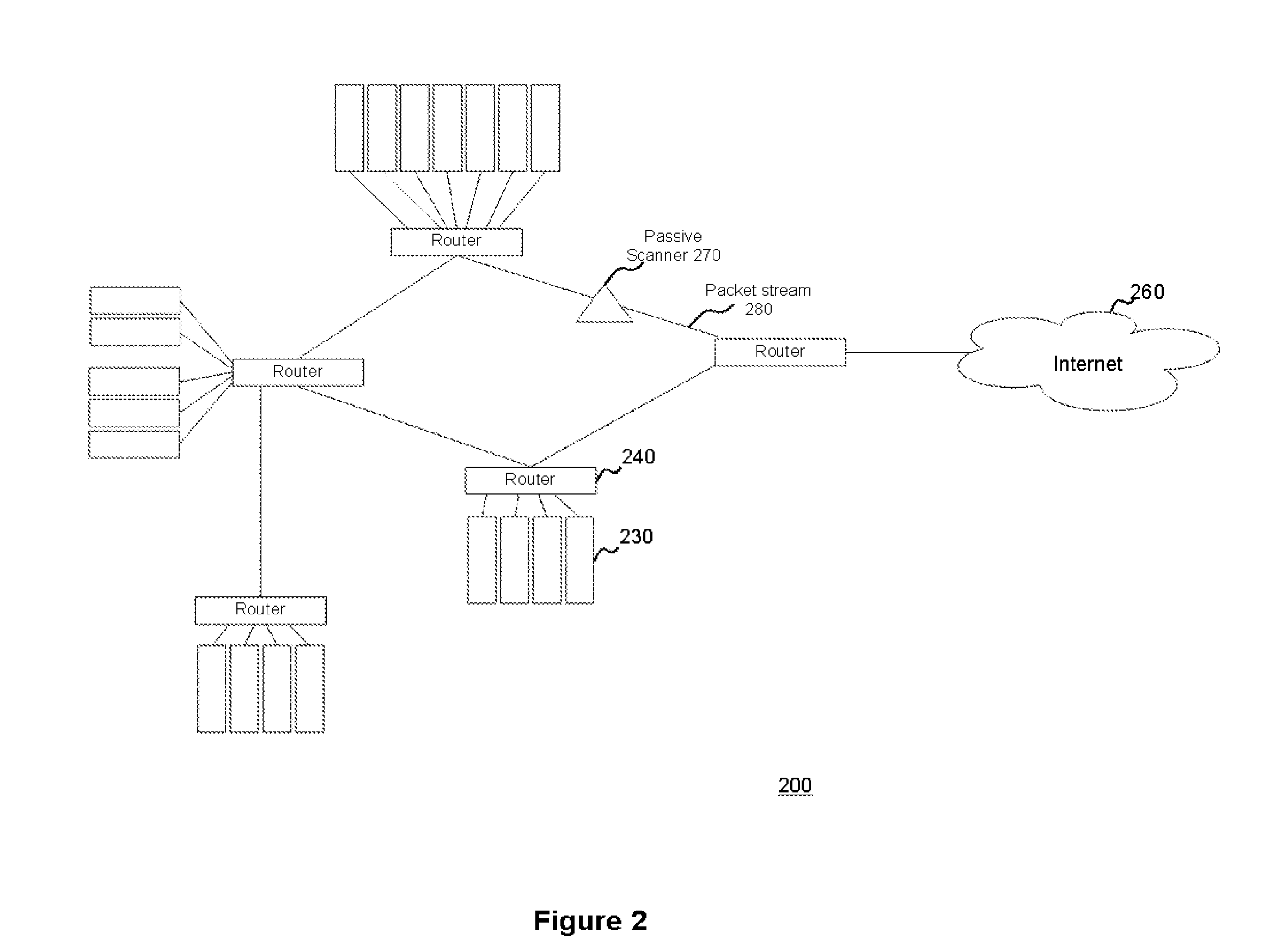
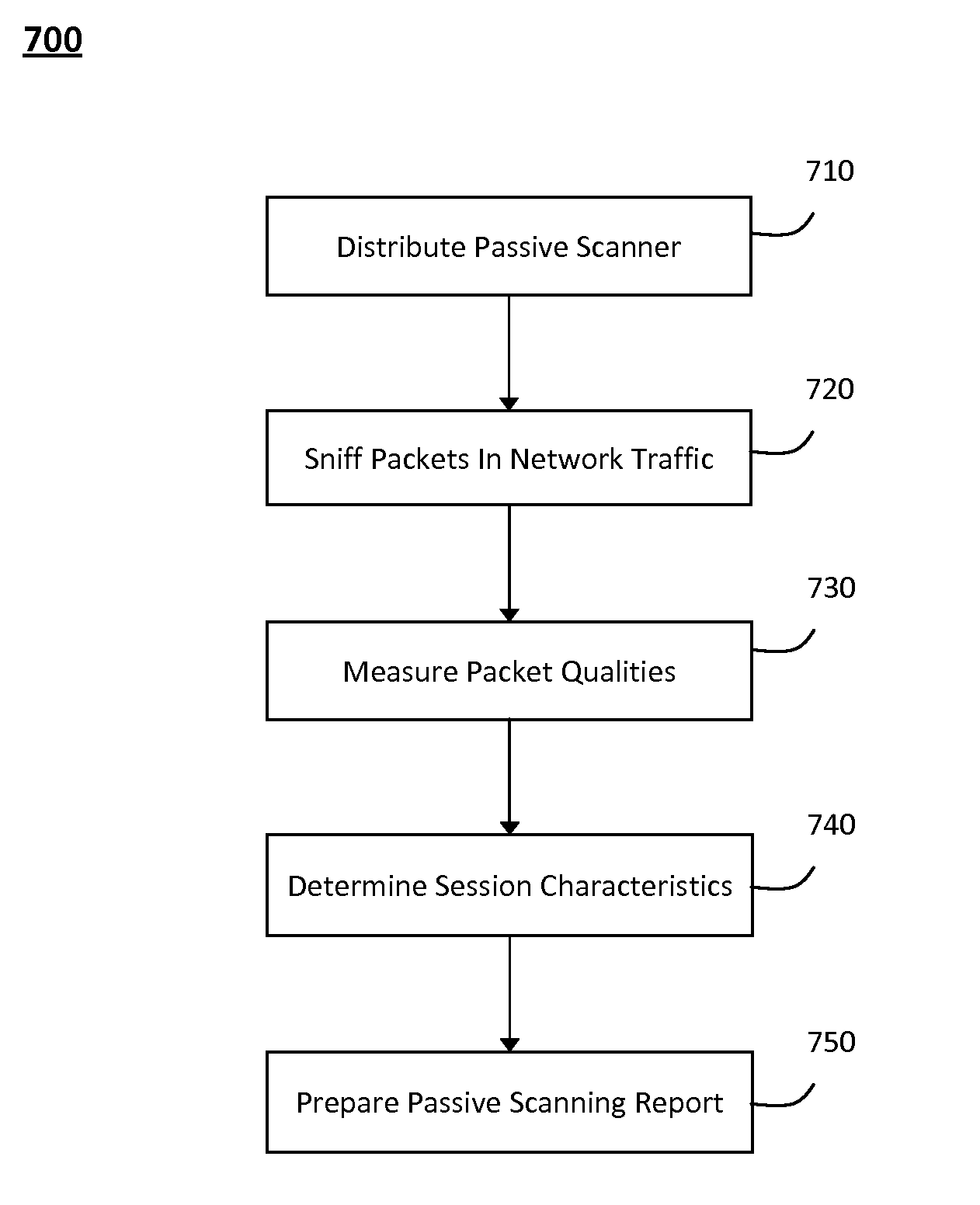
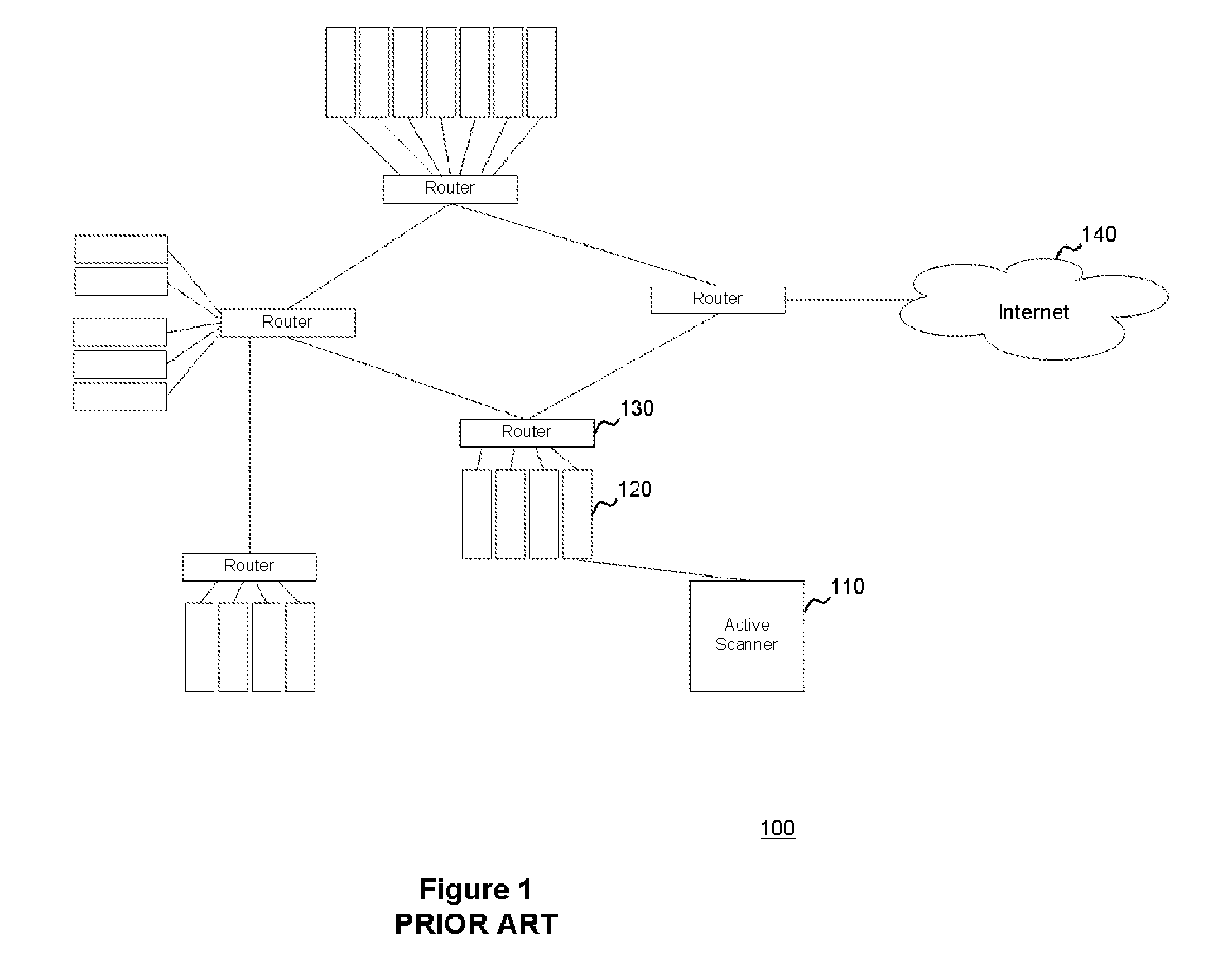
System and method for passively identifying encrypted and interactive network sessions
The system and method for passively identifying encrypted and interactive network sessions described herein may distribute a passive vulnerability scanner in a network, wherein the passive vulnerability scanner may observe traffic travelling across the network and reconstruct a network session from the observed traffic. The passive vulnerability scanner may then analyze the reconstructed network session to determine whether the session was encrypted or interactive (e.g., based on randomization, packet timing characteristics, or other qualities measured for the session). Thus, the passive vulnerability scanner may monitor the network in real-time to detect any devices in the network that run encrypted or interactive services or otherwise participate in encrypted or interactive sessions, wherein detecting encrypted and interactive sessions in the network may be used to manage changes and potential vulnerabilities in the network.
Owner:TENABLE INC
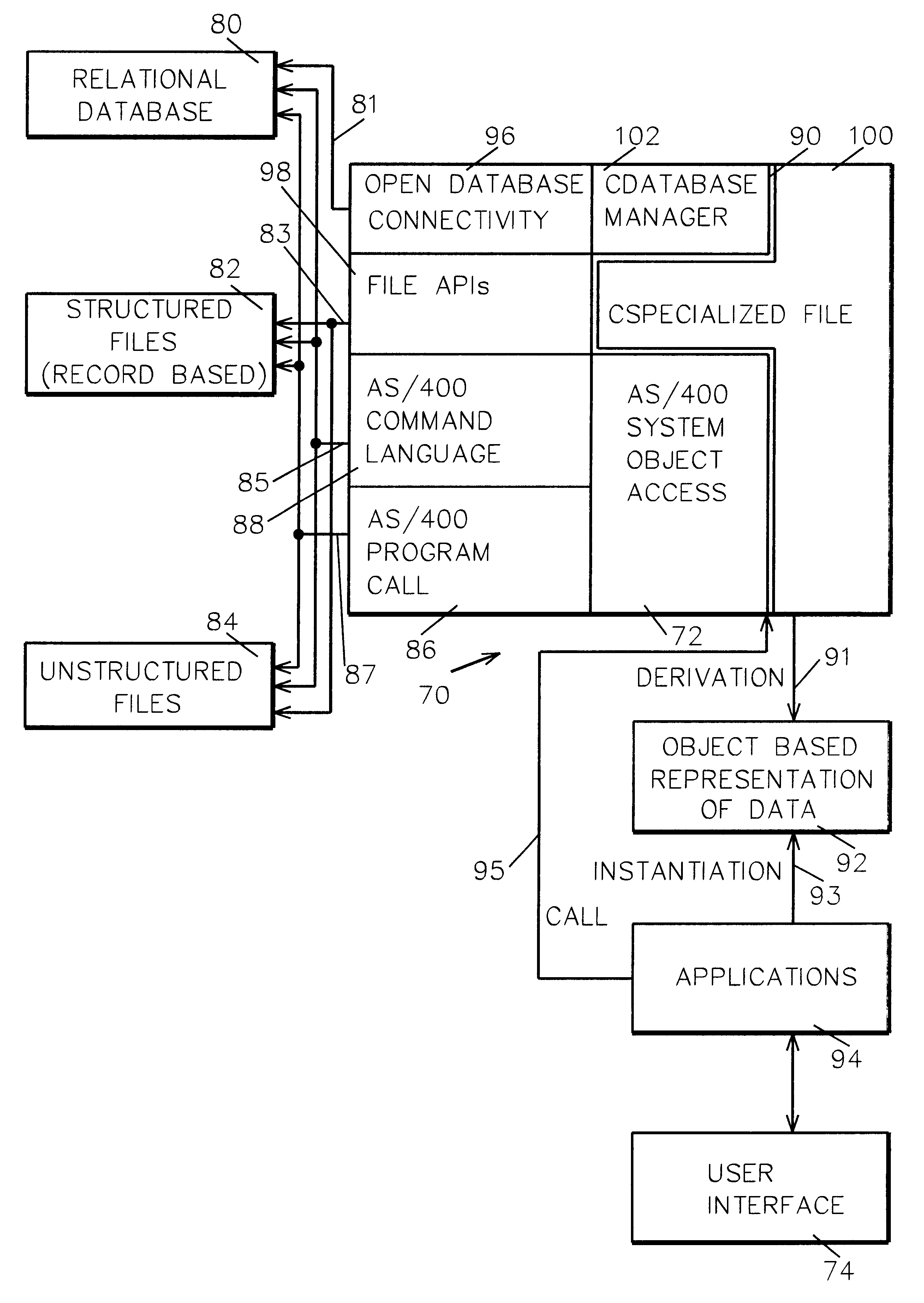
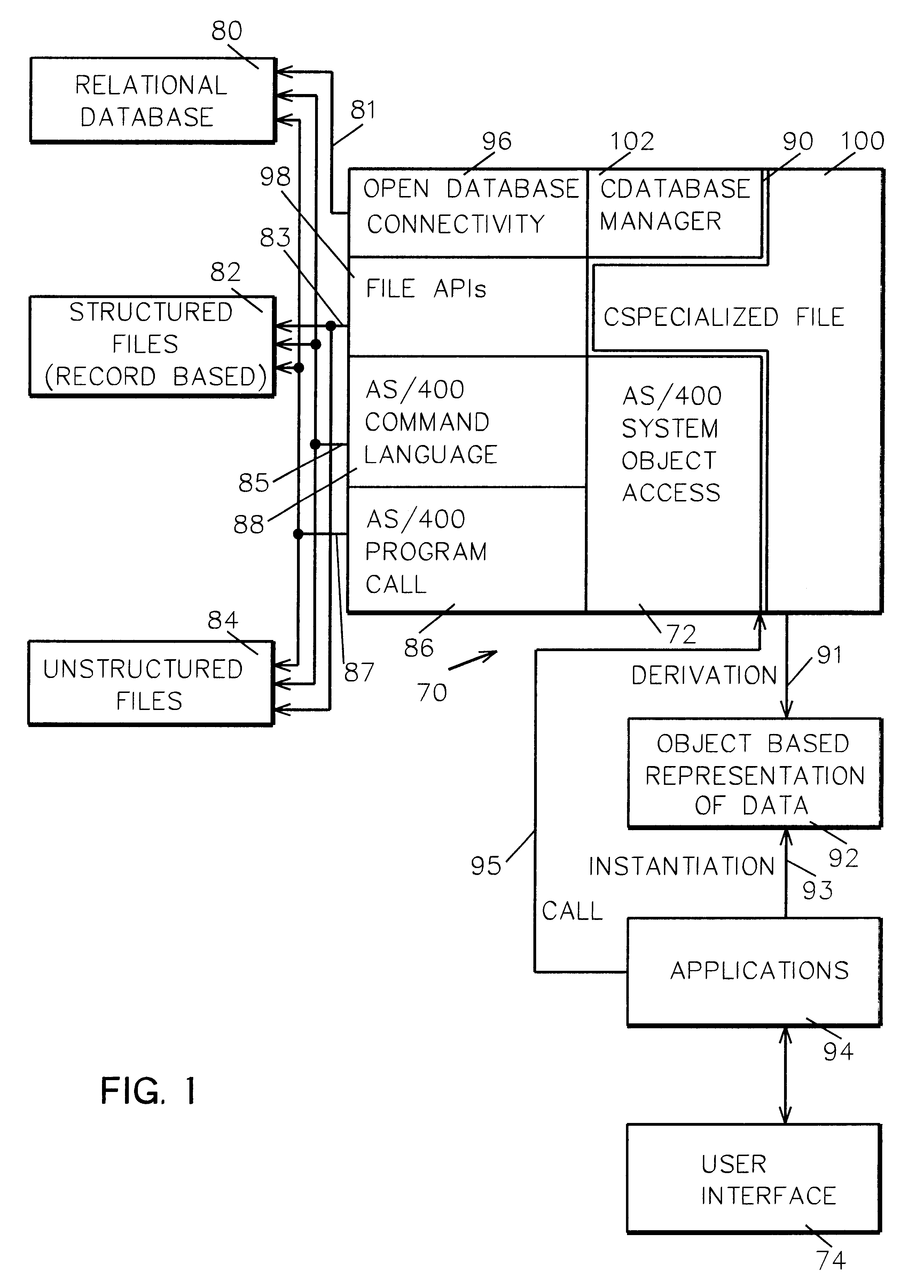
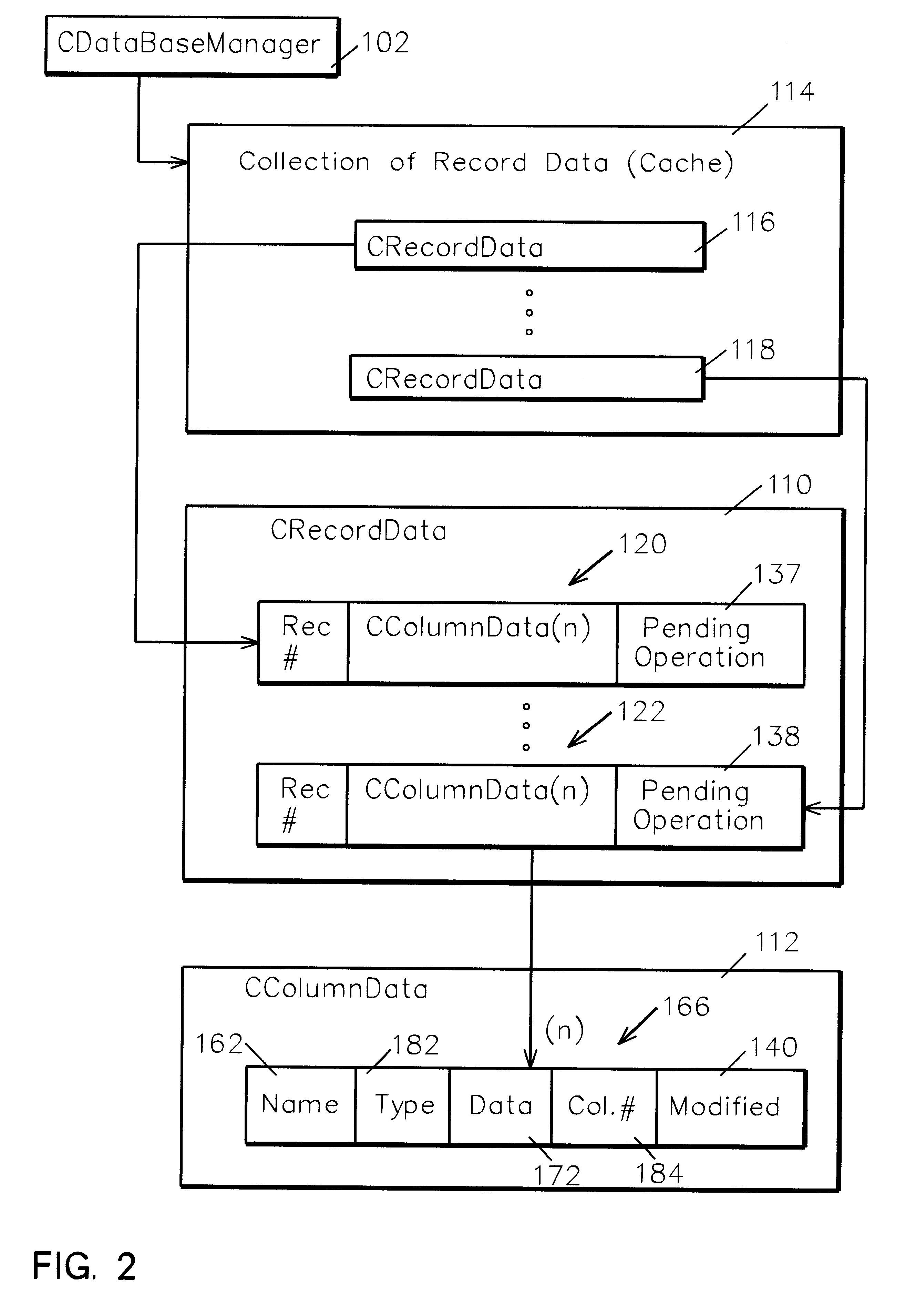
System and method for data manipulation in a dynamic object-based format
An extensible framework provides a unified interface for data manipulation in a dynamic object-based format. A data access layer of the Transmission Control Protocol / Internet Protocol (TCP / IP) Graphical User Interface (GUI) component uses ODBC to read and write files. Four abstractions implement the framework. These are (1) a CDatabaseManager class that provides access to data stored in a database; (2) a CSpecializedFile class which composes a CDatabaseManager that abstracts the management of reading and writing to database files and provides a unified interface for use by accessors. If the base class functionality of the CSpecializedFile class is not sufficient then derived specialized file classes are implemented to override the CSpecializedFile commit method and update the file in a different-fashion and / or implement specialized get / set methods by column data item and data type; (3) a CRecordArray class which manages vectored access to information stored as objects in a CColumnData class; and (4) a CColumnData object which manages changes made to the information and saves it when requested.
Owner:IBM CORP
Methods that provide dispatchers in power grid control centers with a capability to manage changes
InactiveUS20110071690A1Easy to manageMechanical power/torque controlLevel controlProgram planningPower grid
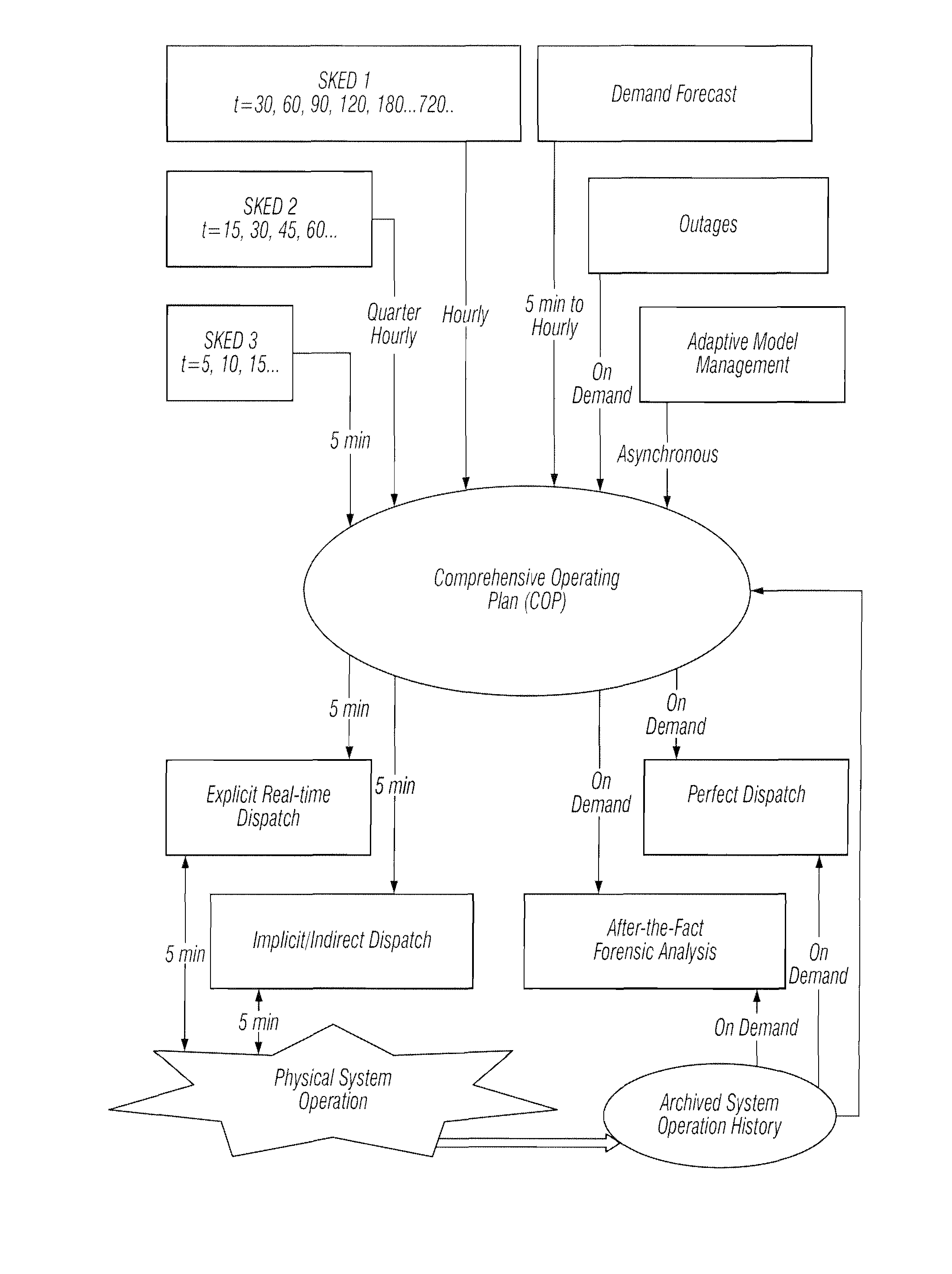
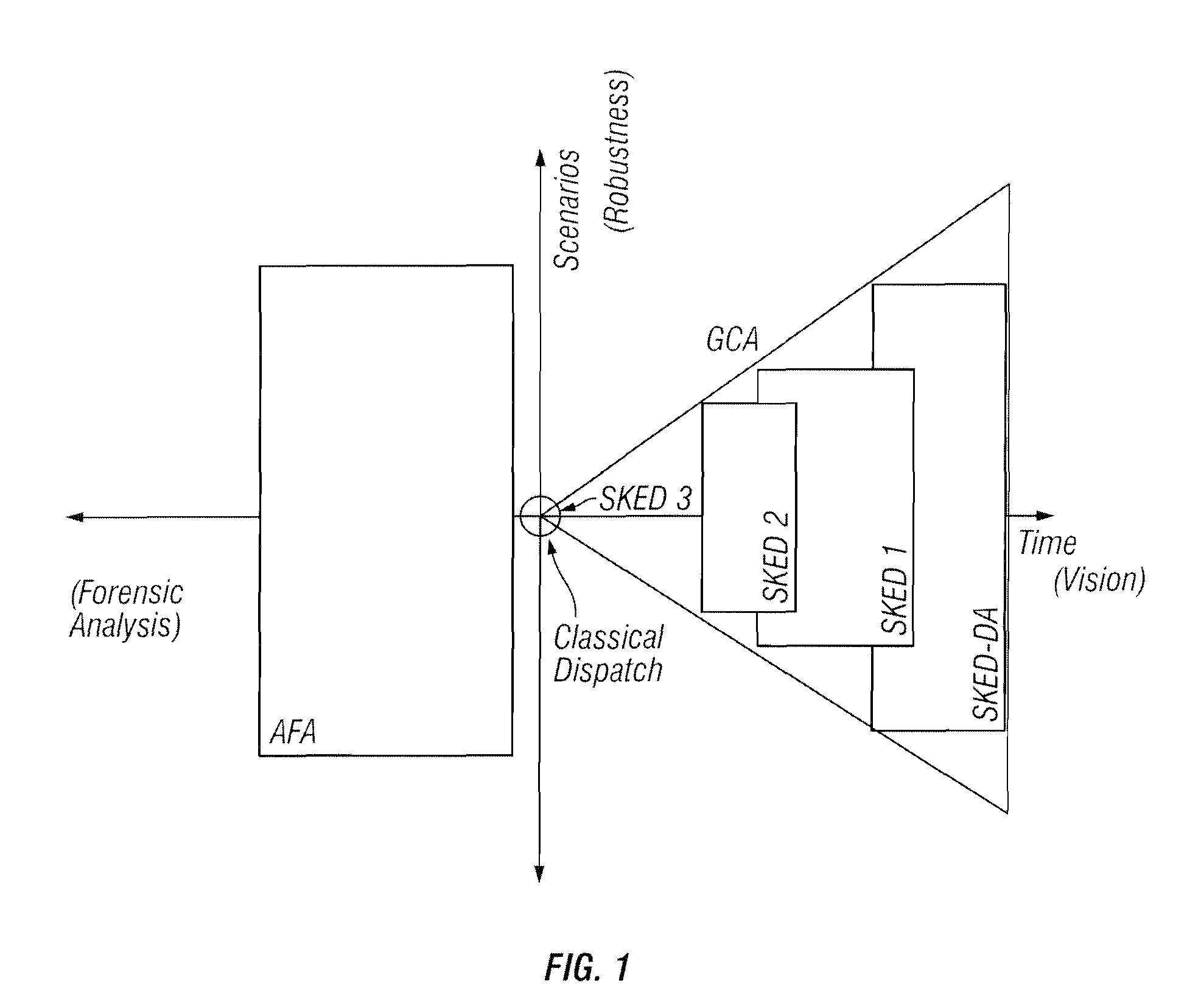
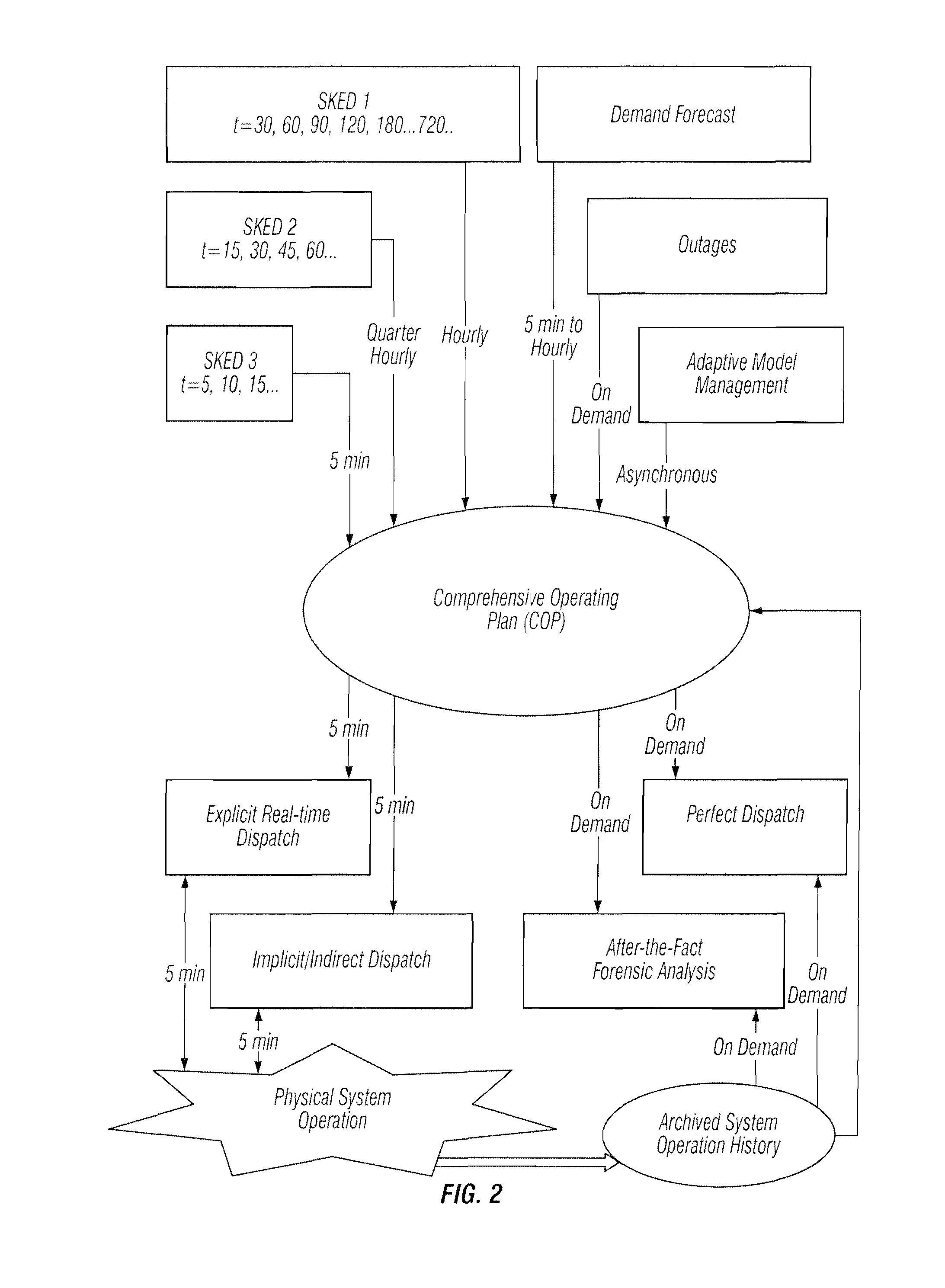
Methods are provided that enable dispatchers in power grid control centers to manage changes. A comprehensive operating plan is provided with multiple, security constrained economic dispatch engines 1, 2 and 3. The scheduler engines are security constrained unit commitments and economic dispatch sequences with different look-ahead periods. The comprehensive operation plan is configured to integrate scheduler engines into a unified scheduling system. The comprehensive operating plan includes a repository of all operating plans in a multi-stage decision process.
Owner:ALSTOM TECH LTD
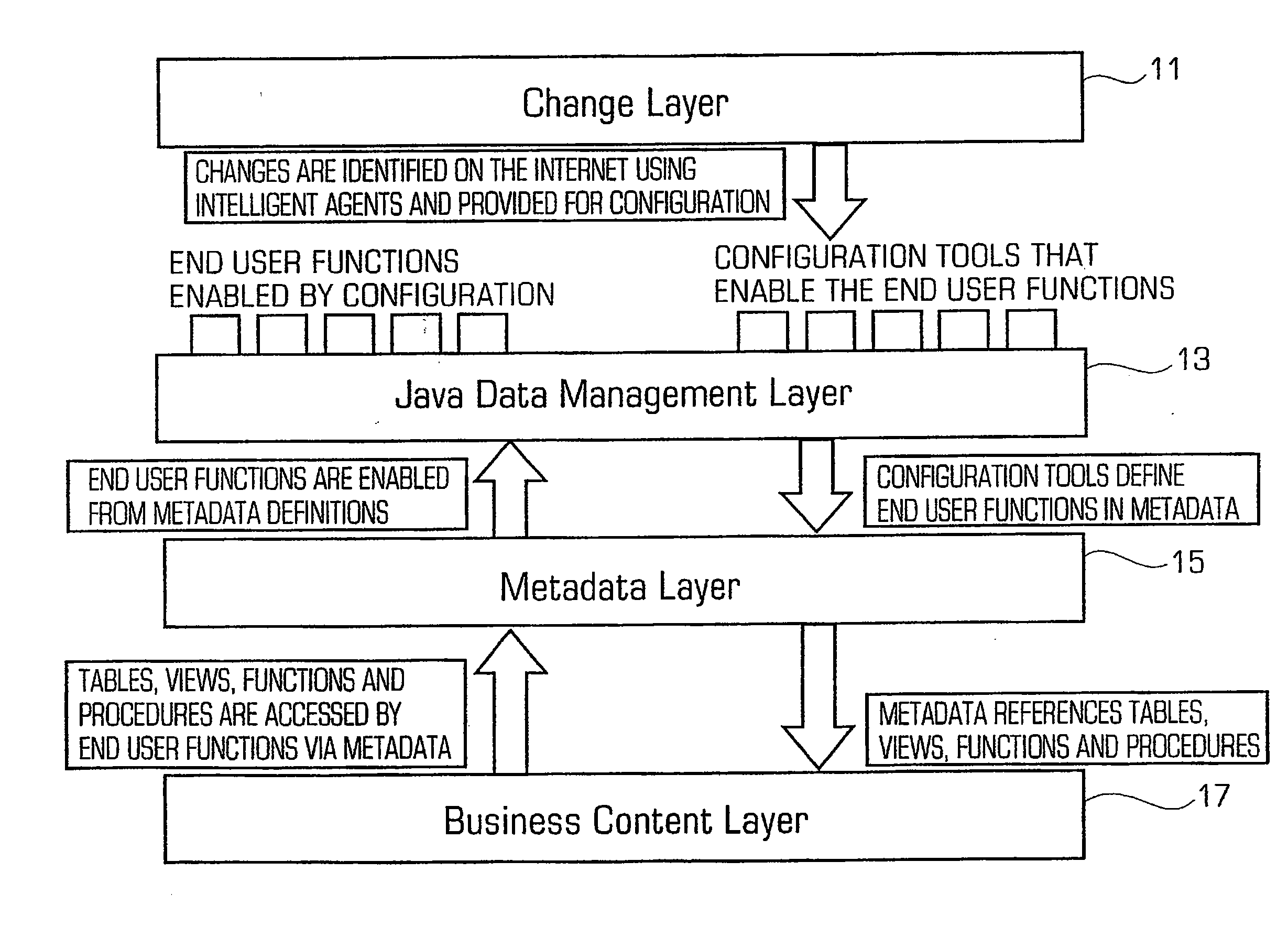
System and methodology for developing, integrating and monitoring computer applications and programs
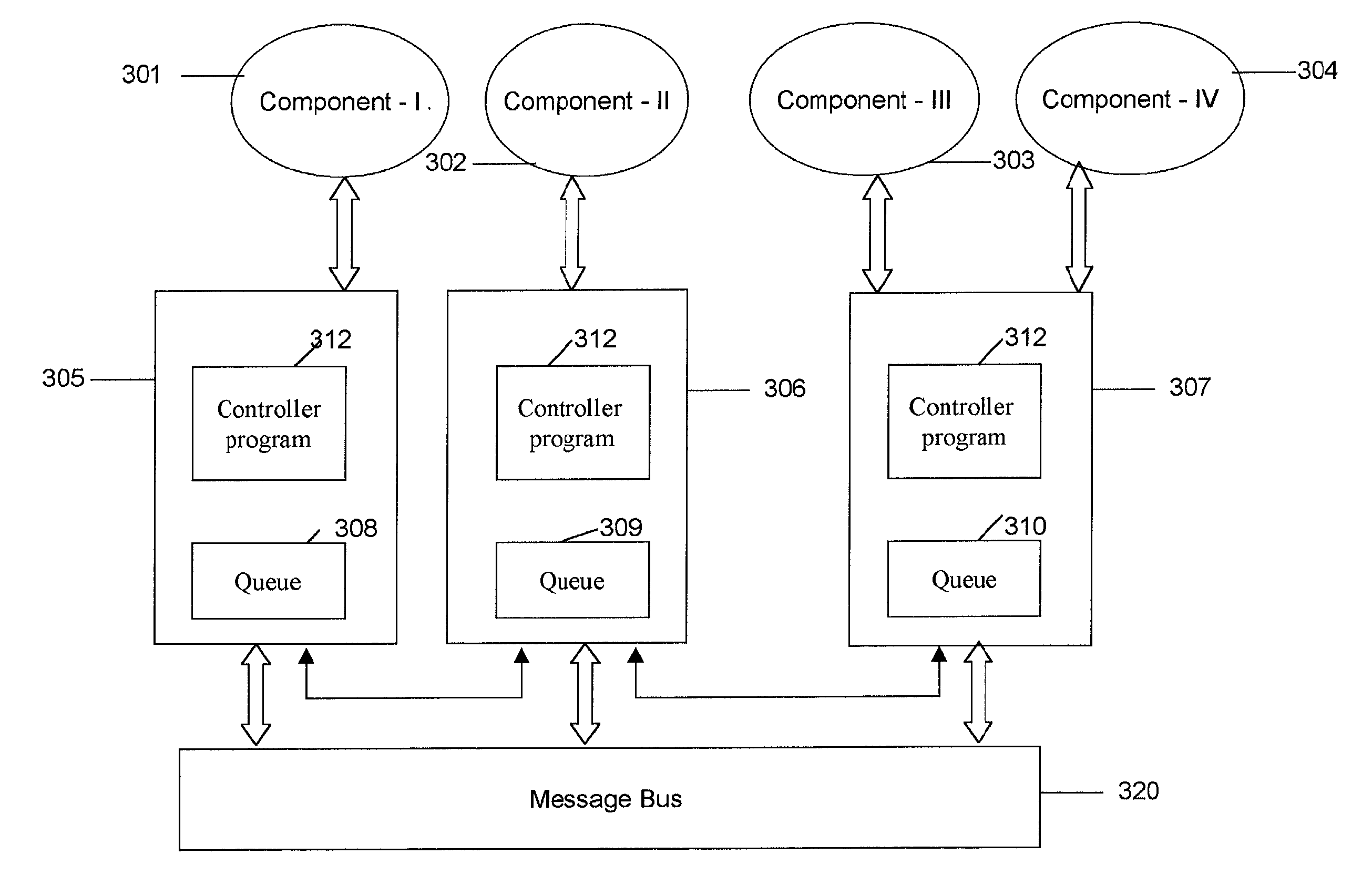
ActiveUS7174370B1Facilitates composingDigital computer detailsTransmissionComputational logicApplication software
The present invention provides a system, method and computer program product for developing distributed applications, integrating component programs, integrating enterprise applications and managing change. The invention provides for an infrastructure where component programs that are the computational logic of the distributed application are installed over a network of computing units having controller programs running on each of these computing units. The invention provides for separating the concerns of computation, installation, execution and monitoring of the distributed application in terms of time, space and people involved. This is accomplished as the component programs simply perform the computation task and the communication between the component programs and their monitoring is handled by the controller programs.
Owner:FIORANO TECH INC
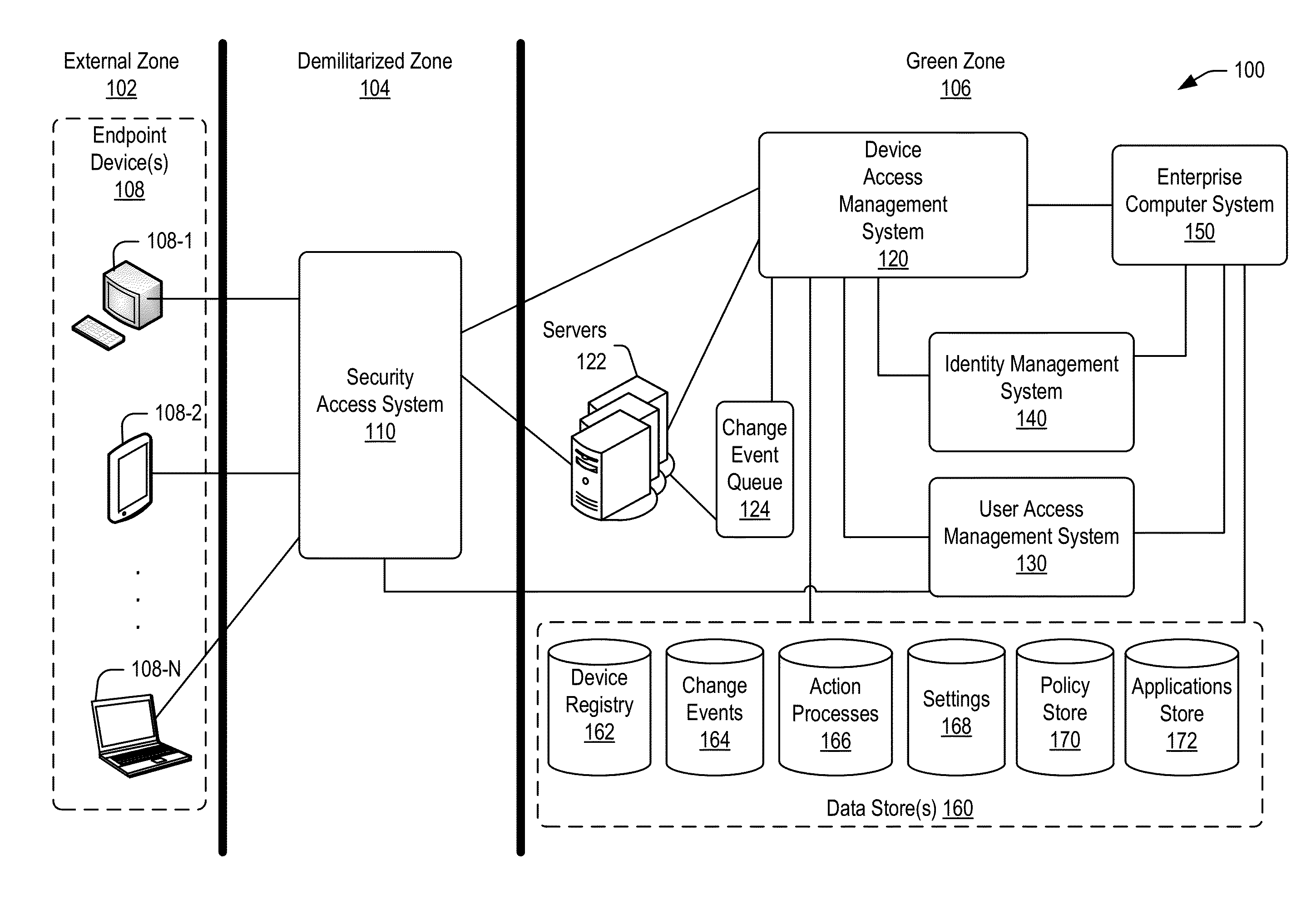
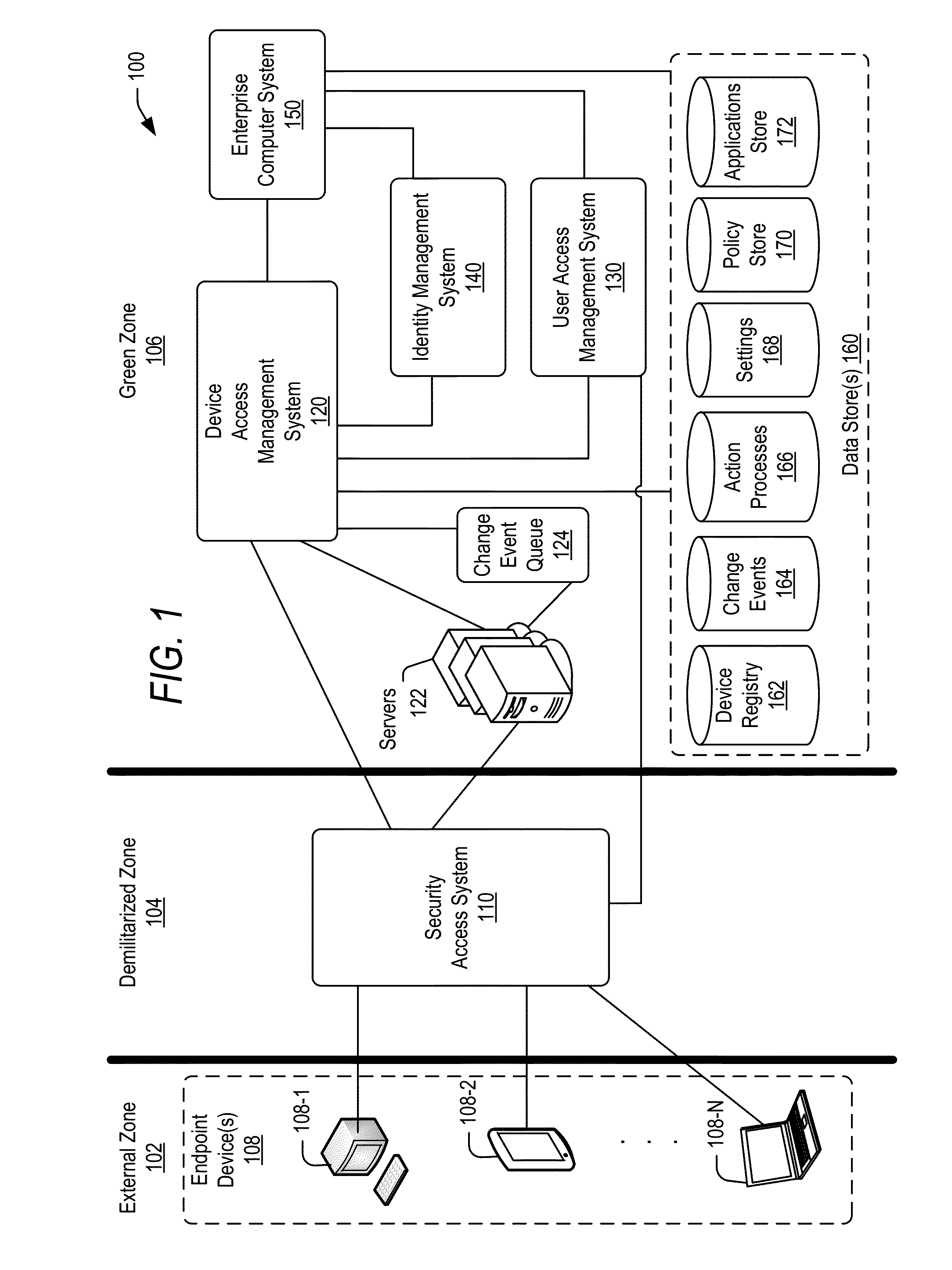
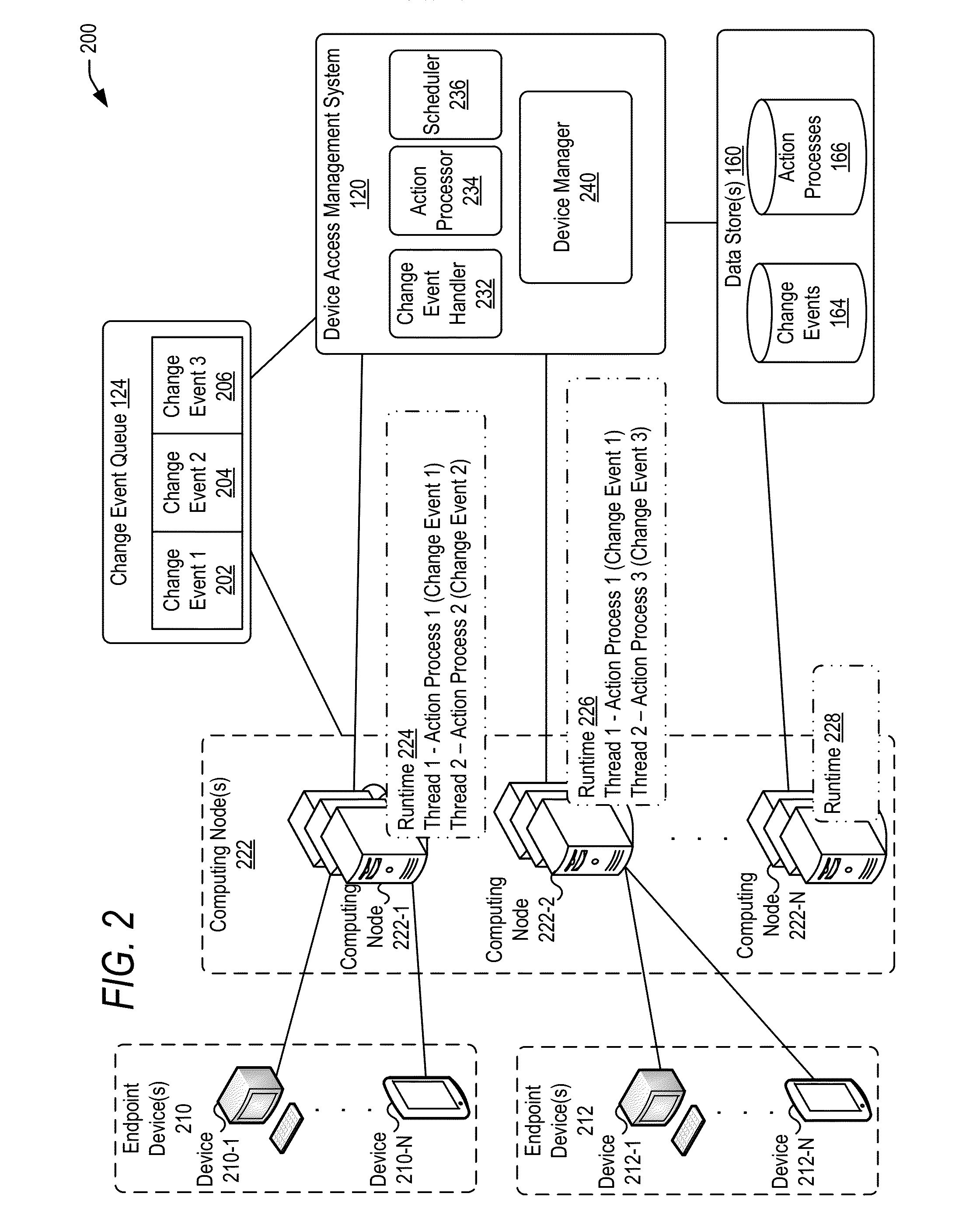
Managing change events for devices in an enterprise system
ActiveUS20160087854A1Load balancingChange performanceVersion controlDigital data authenticationManaging changeAccess management
Techniques are disclosed for communicating to remote devices information about change events related to changes in access to an enterprise system. A device access management system may facilitate communication about a change event to the remote devices. Information about a change event may be stored in a change event object based on the type of change event (e.g., a policy change, an application change, and a settings change). A change event queue may persistently store information corresponding to change events. One or more computing nodes may be scheduled to execute an action process for each change event based on the type of the change event. A computing node may communicate information (e.g., an instruction to implement adjust access) about a change event to remote devices. A change event may persist on the queue until all remote devices are notified about the change event.
Owner:ORACLE INT CORP
Dynamic partitioning of a reusable resource
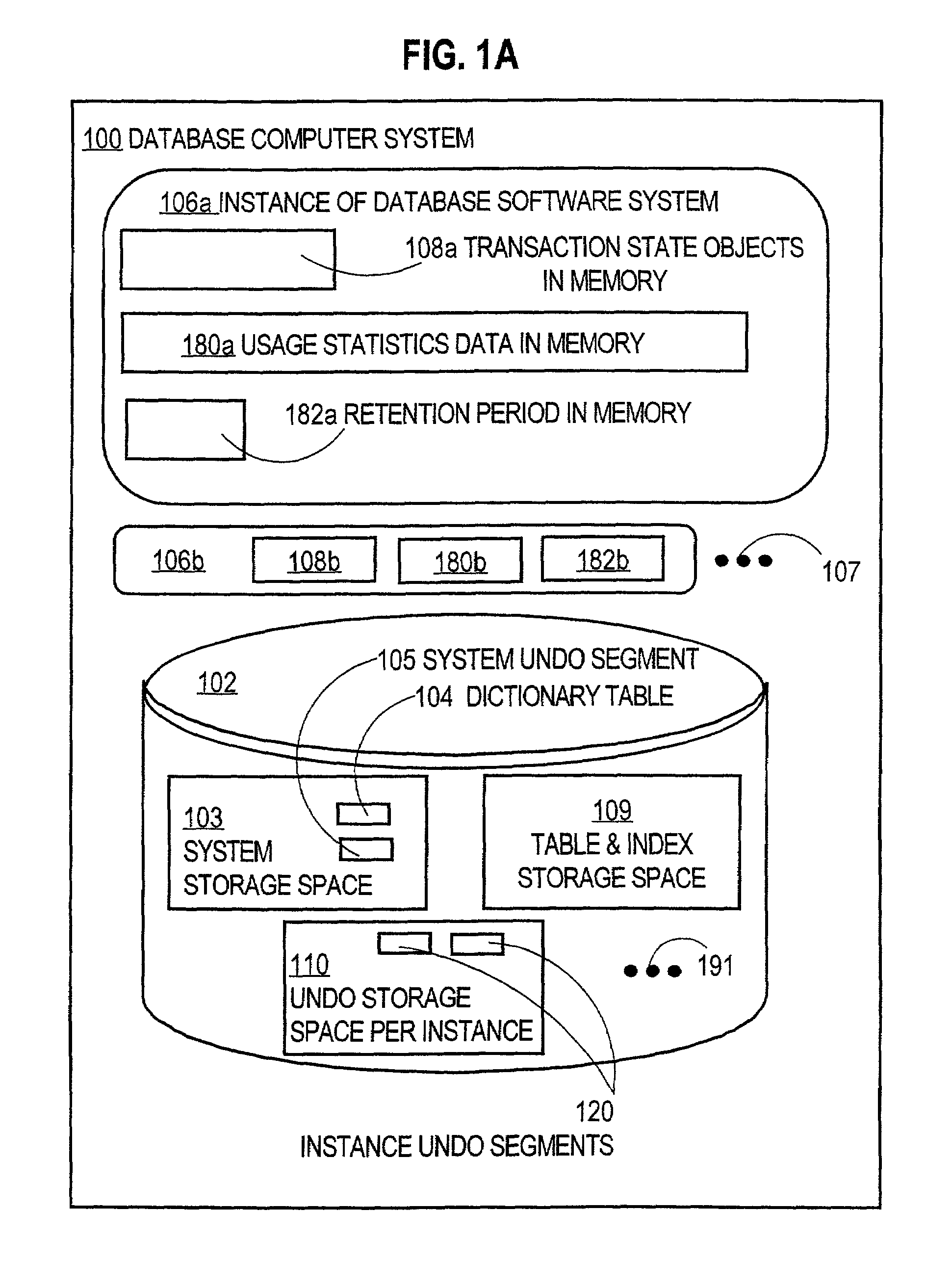
InactiveUS7047386B1Data processing applicationsDigital data information retrievalComputerized systemManaging change
Techniques for managing changes in a computer system include storing, in a storage space, undo information for removing changes that are being made by entities. The undo information for each entity is stored in a segment of multiple segments within the storage space. Usage of the storage space by the entities is monitored. The number of segments in the plurality of segments or the sizes of the plurality of segments or both are adjusted automatically based on the usage. These techniques allow a resource to be recycled and allocated for new uses by other entities in a computer system dynamically based on usage. These techniques do not burden a human administrator with partitioning the resource and then penalize the administrator and users by generating errors when the partitions do not match usage.
Owner:ORACLE INT CORP
Process for managing change within an enterprise
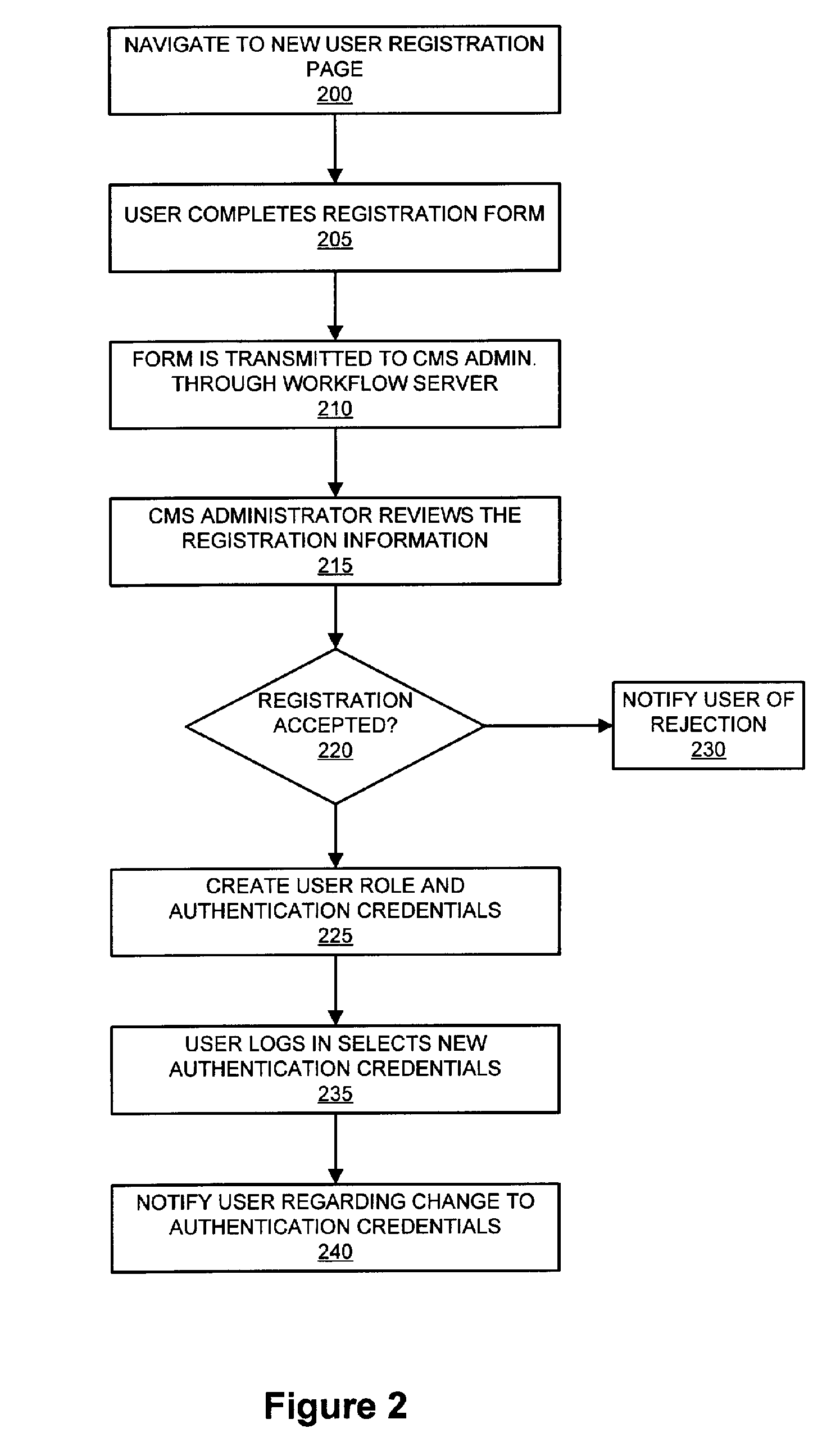
InactiveUS6996601B1Effectively manage and record and communicateMultiple digital computer combinationsResourcesChange managementProgram management
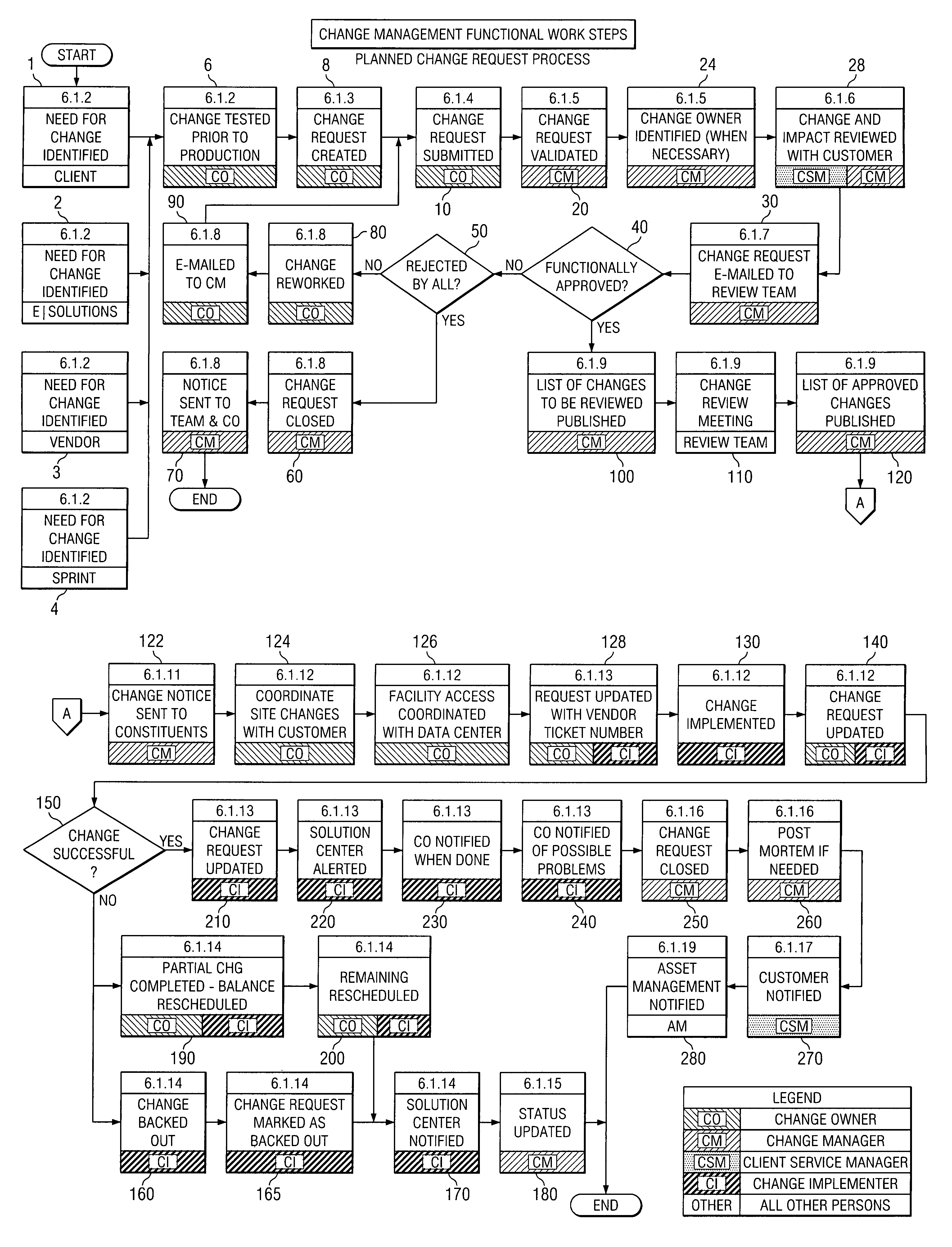
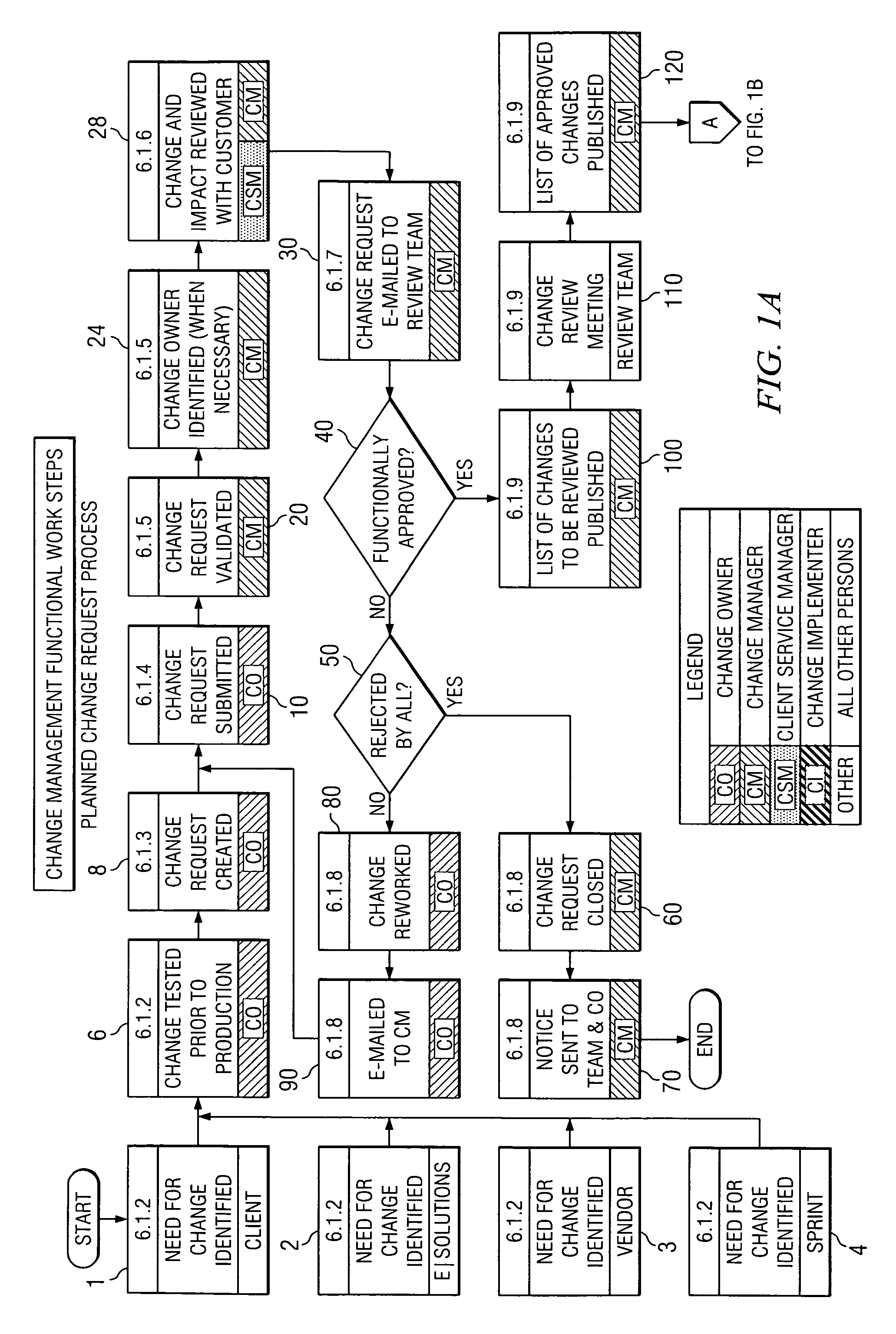
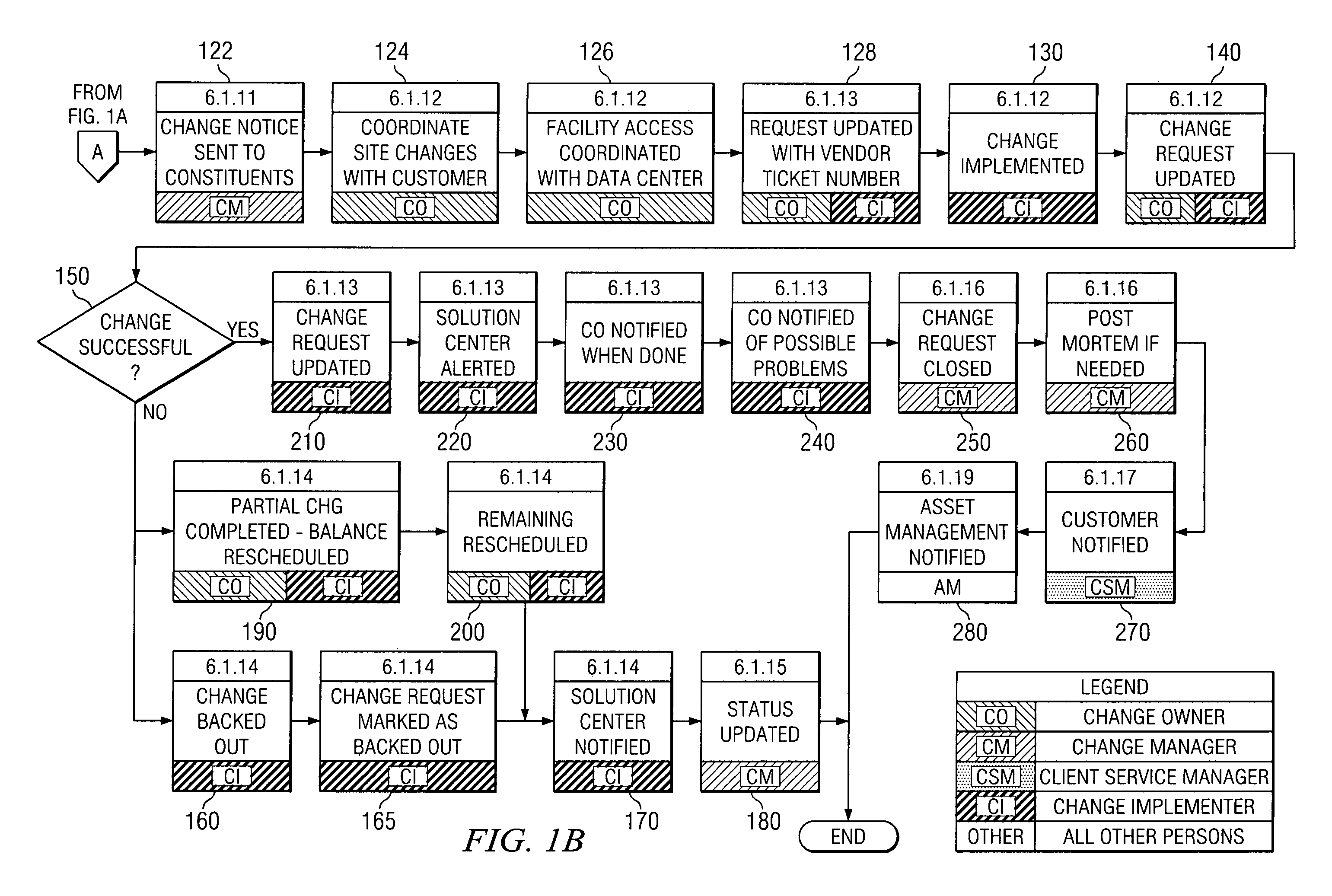
The present invention is a Change Management Procedure that enables businesses and other enterprises to effectively manage, record, and communicate changes by employing a centralized control agency to review, approve, document, and communicate changes taking place within an enterprise. While the Change Management Procedure is applicable to any type of change, in the preferred embodiment the procedure manages changes in electronic computer systems including but not limited to architecture changes, outages (e.g., hardware, software or facility), replacement of hardware, upgrading of software, and rebooting of devices. By requiring that all changes be formally requested and approved, the Change Management Procedure prevents unauthorized changes. The Change Management Procedure also creates an audit trail that keeps a record of all changes for future reference. Another advantage of the Change Management Procedure is the communication of changes to operating units within the enterprise that are potentially interested in the change. At any step within the Change Management Procedure, entities that might be affected by a change may be notified of the change. Thus, potentially interested operating units can be aware of changes before they occur and can be informed of all changes that have occurred.
Owner:SPRINT CORPORATION
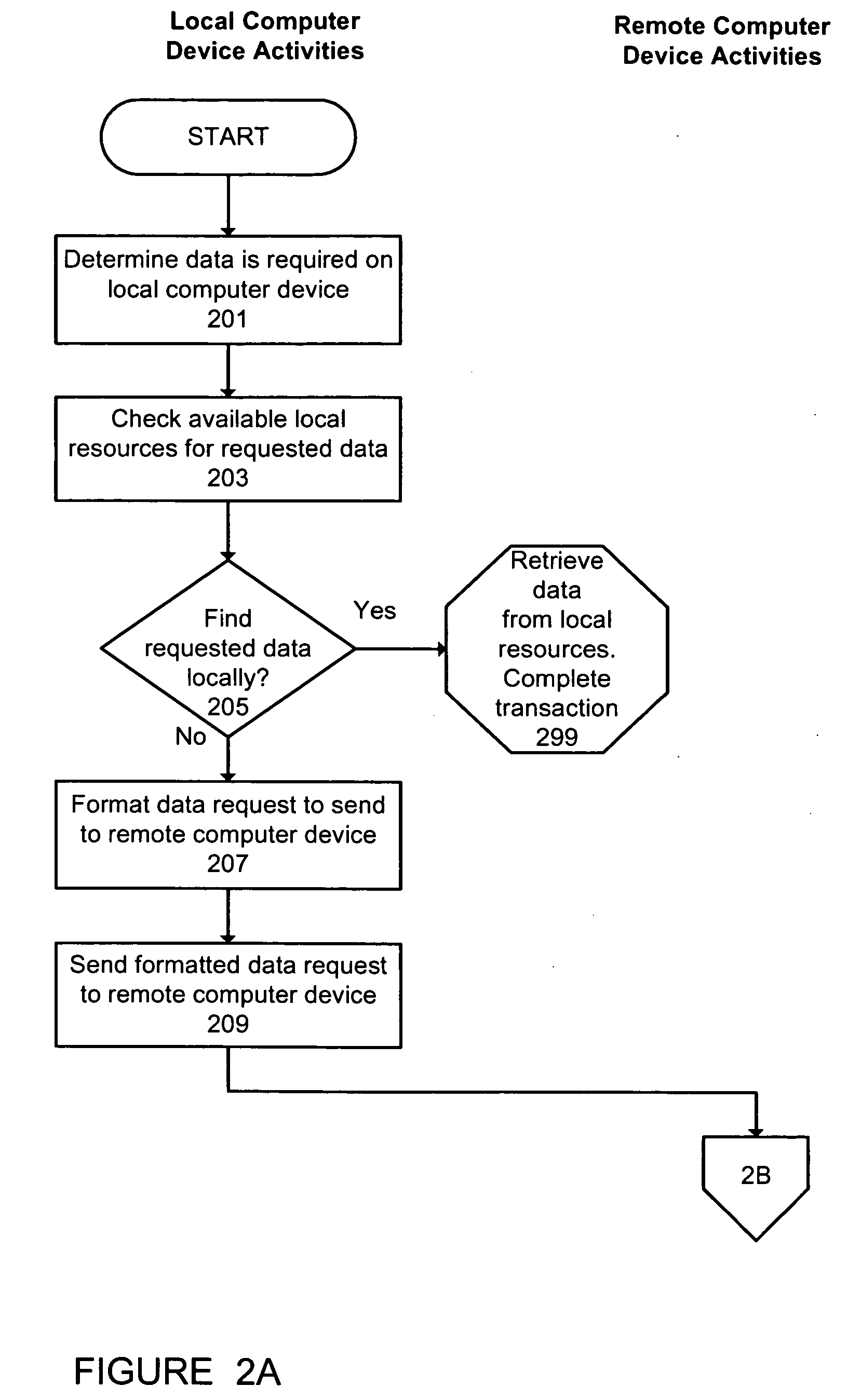
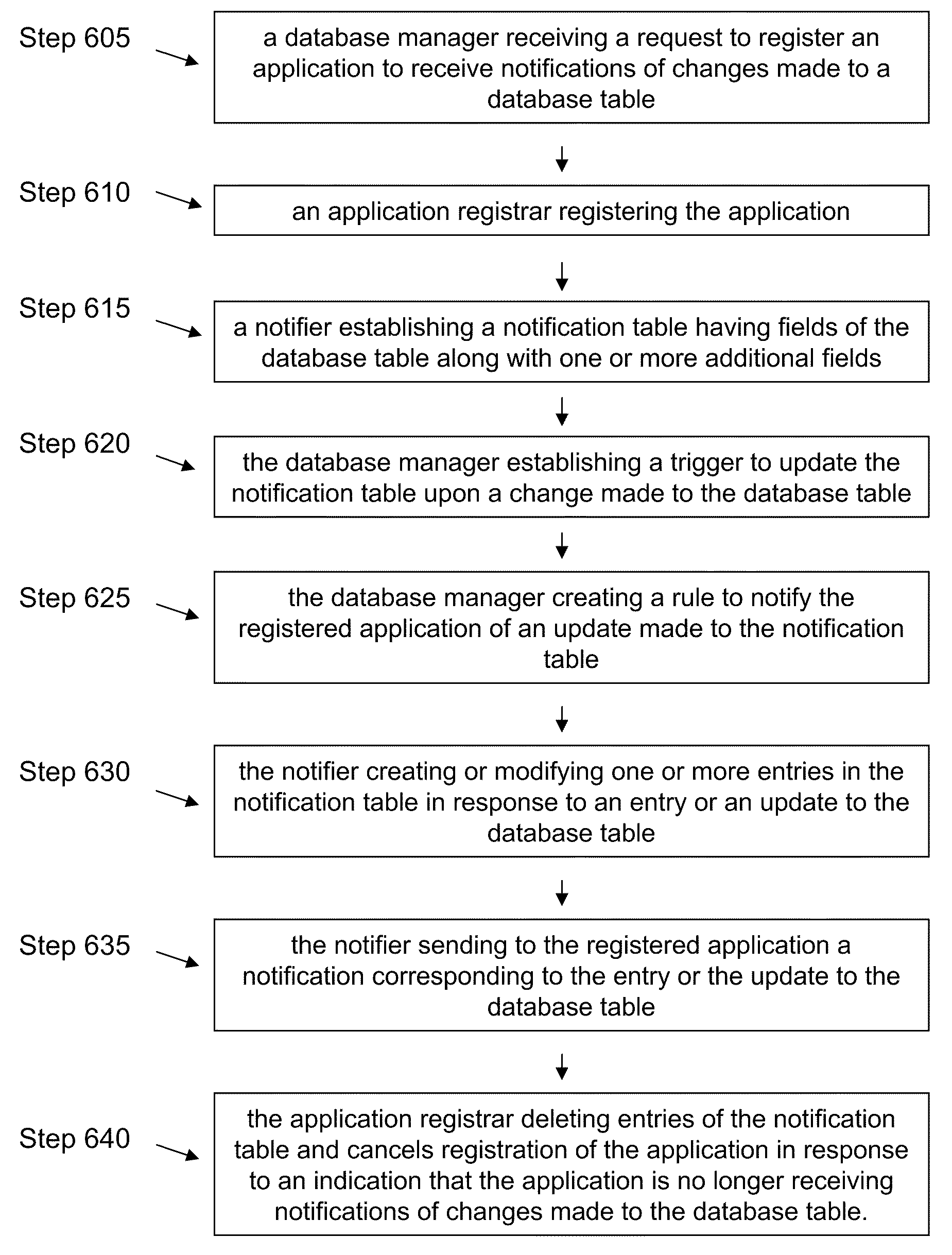
Systems and methods for database notification interface to efficiently identify events and changed data
ActiveUS20120023077A1Digital data information retrievalDigital data processing detailsDatabase managerManaging change
Systems and methods for providing notifications of changes made in a database table to a remote application is presented. The system and methods manage change notification of a table in a database by notifying an application registered to receive notifications of changes made to a database table. A database manager executing on a device may receive a request to register an application to be notified when a first table of a plurality of tables in a database is changed. The database manager may establish a notification table comprising fields of the first table and one or more additional fields for managing notification. The database manager may establish a trigger on the first table to invoke a trigger procedure to copy a changed row of the first table to the notification table. The database manager may create a rule for the notification table to notify registered applications when a new row is inserted into the notification table
Owner:CITRIX SYST INC
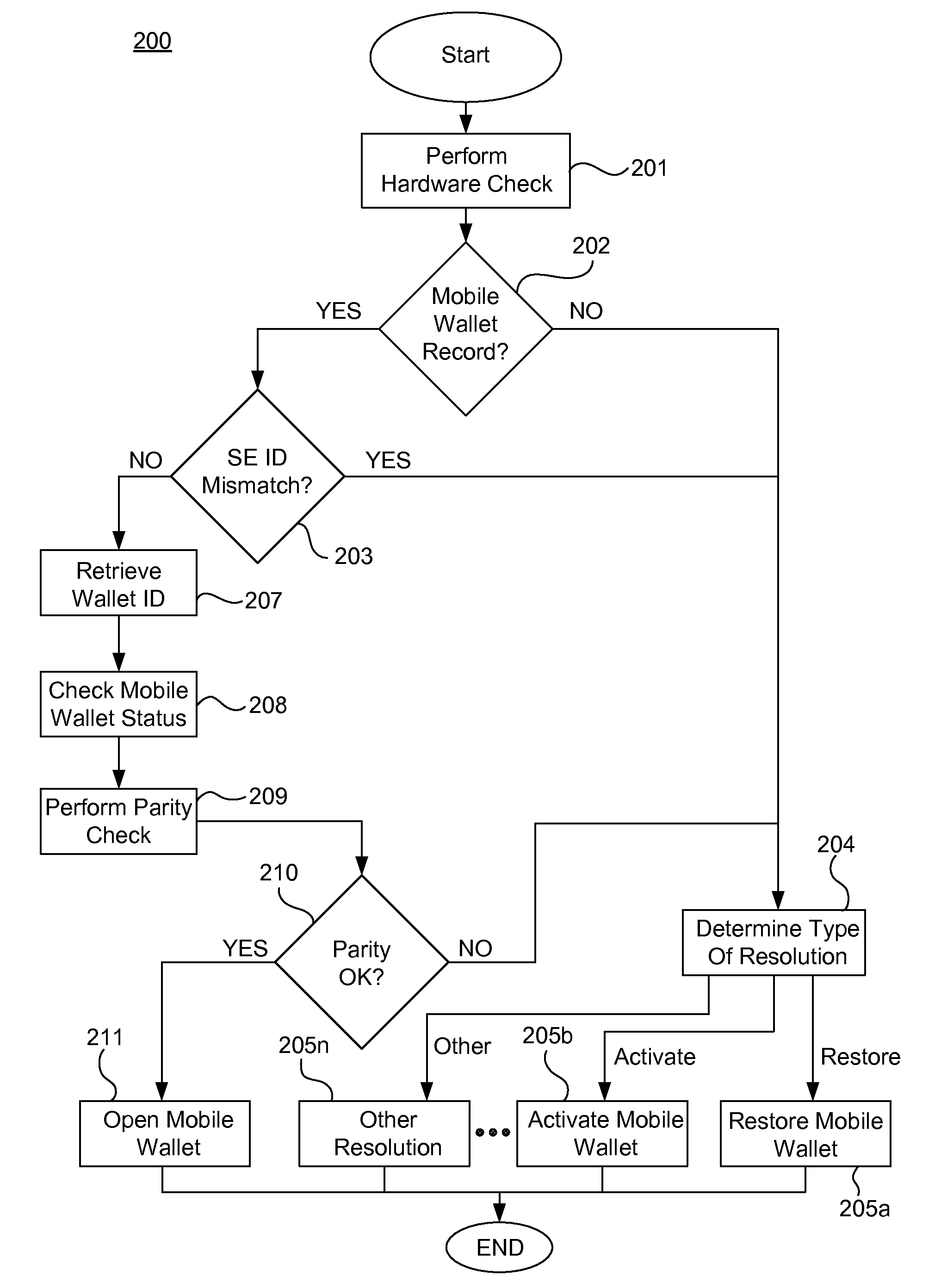
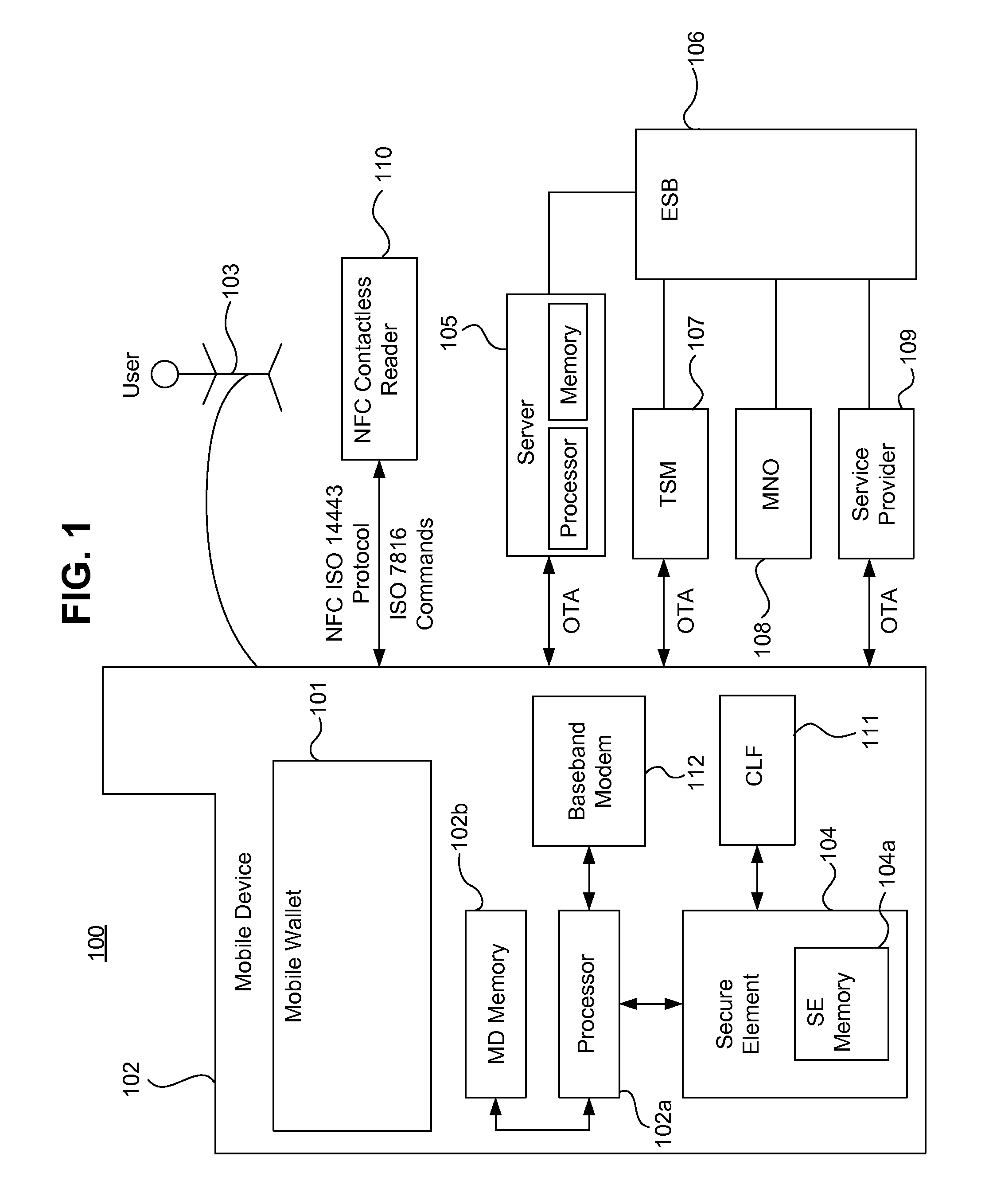
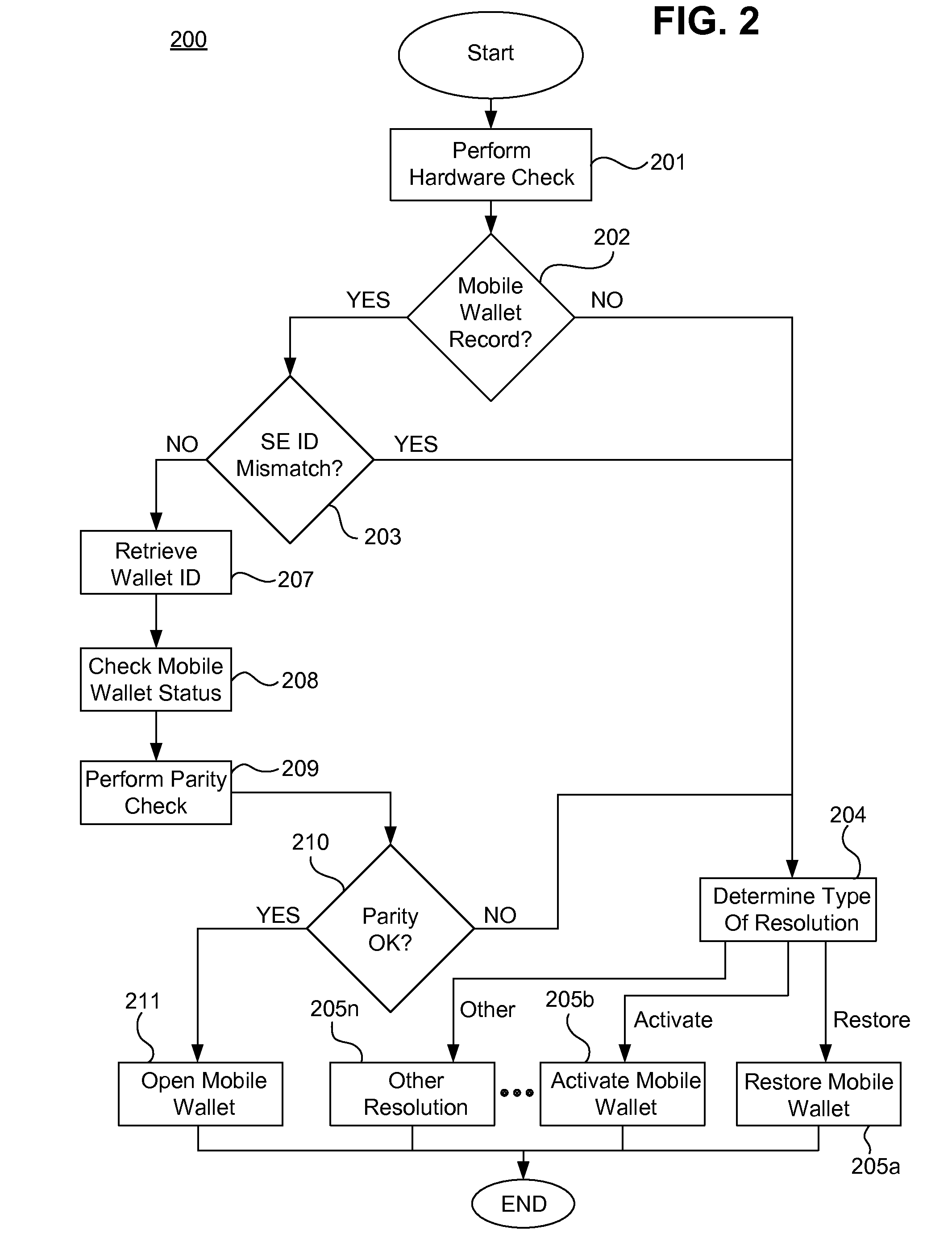
Systems, methods, and computer program products for detecting and managing changes associated with mobile wallets
System, methods, and computer program products are provided for detecting and managing changes associated with a mobile wallet. Current mobile wallet data is retrieved from at least one memory, and new mobile device attributes are retrieved. It is determined whether a change has occurred based on a comparison of the current mobile wallet data and the new mobile device attributes. A request to process a change is transmitted to a server on a communications network. Update data is received over the communications network, and the current mobile wallet data is updated in the at least one memory with the update data.
Owner:CELLO PARTNERSHIP DBA VERIZON WIRELESS
System and method for evaluating a requirements process and project risk-requirements management methodology
InactiveUS20070162316A1Advance the development processSimple processFinanceResourcesRequirements processRequirements management
A system, method and computer program product for requirements management. Particularly, a requirements management scheme performs at least the following functions: 1) it guides a team through the requirements process and provides a structure for collecting “requests”. By using the scheme, team members are prompted to think about and record relevant information that will help clarify and complete requests; and, 2) the scheme allows users to use the attributes throughout the development process to identify risk and make improvements to their process. Many of these attributes can be refined during the development phase or even later. Besides helping team members achieve continuous improvement in their requirements process by providing a set of data and metrics for collection and assessment, the scheme enables an organization to effectively manage their requirements as well as manage changes to those requirements.
Owner:IBM CORP
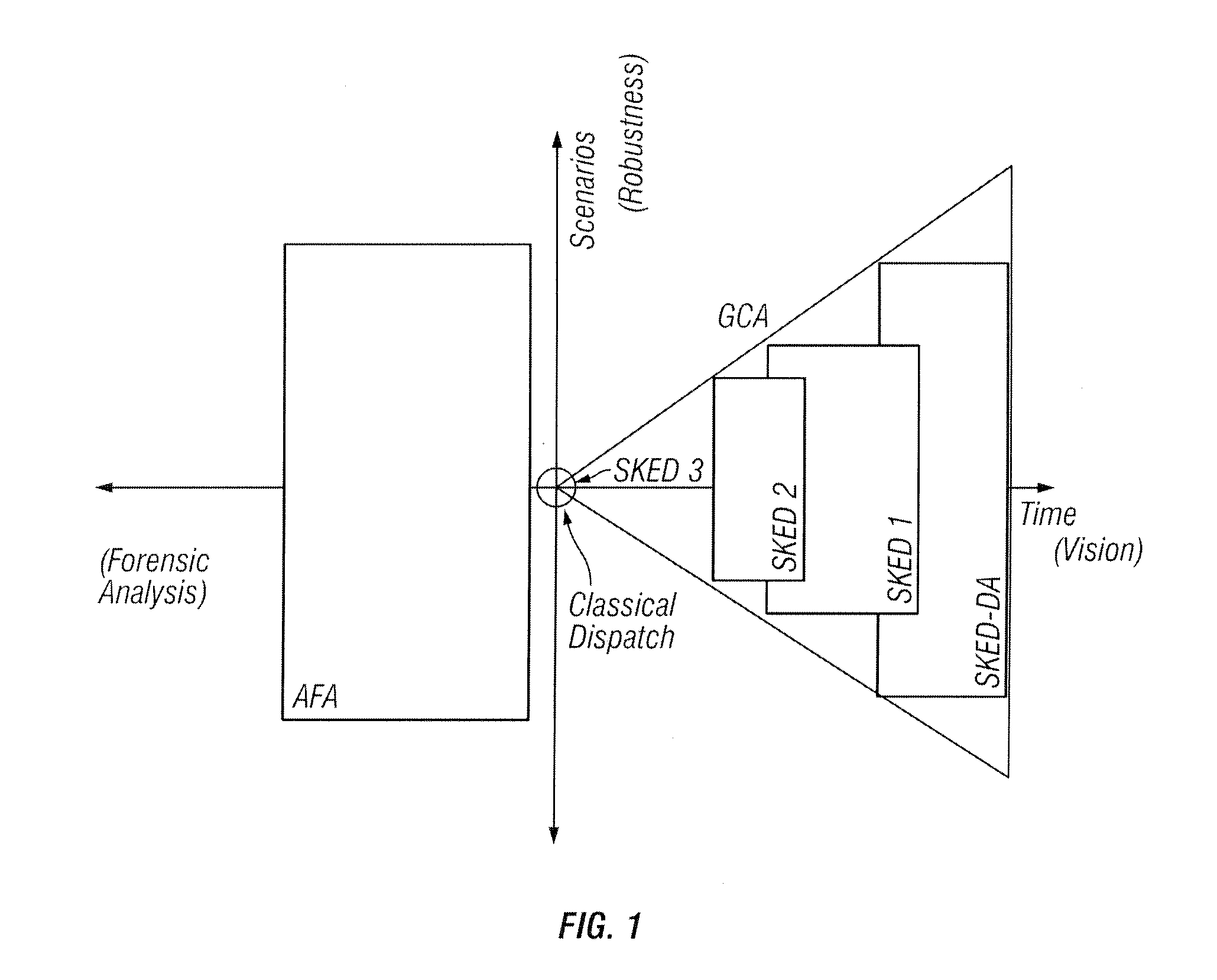
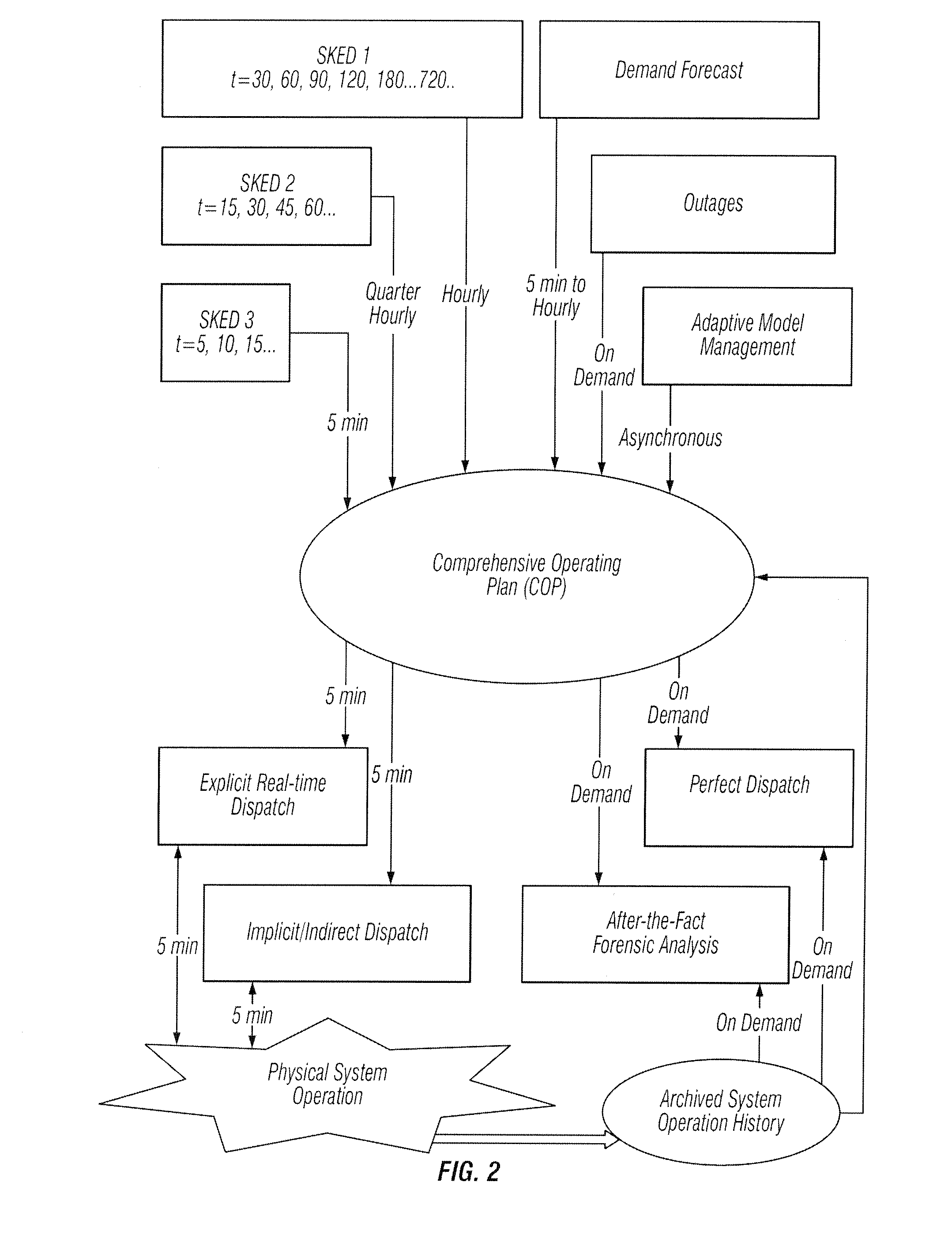
Multi-interval dispatch method for enabling dispatchers in power grid control centers to manage changes
A method is provided that enables dispatchers in power grid control centers to manage changes by applying multi-interval dispatch. A multi-stage resource scheduling engine and a comprehensive operating plan are used. Multiple system parameter scenarios are coordinated.
Owner:ALSTOM TECH LTD
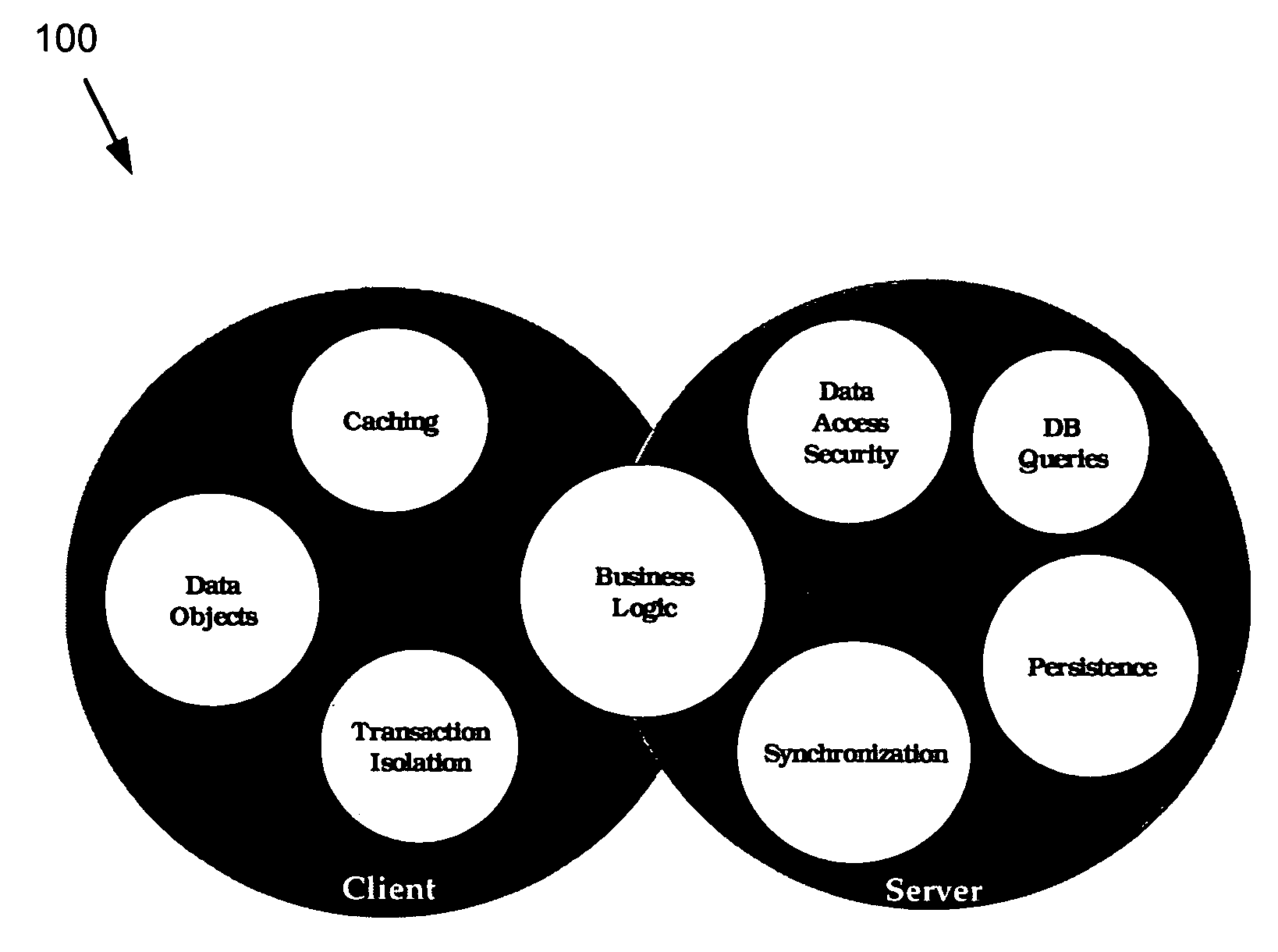
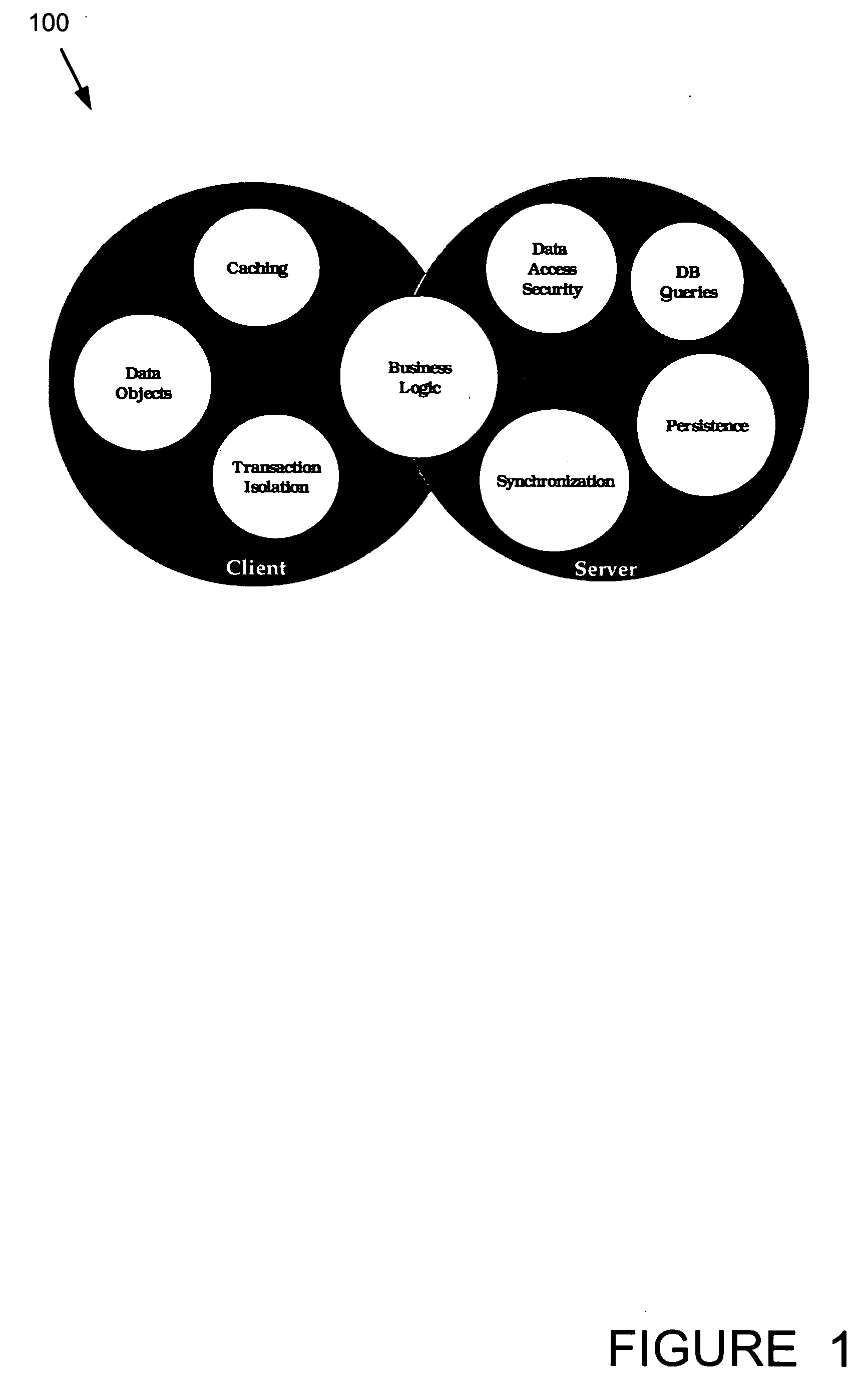
Intelligent client architecture computer system and method
ActiveUS20050235018A1Quickly and easily and developedUser interfaceData processing applicationsDatabase distribution/replicationData synchronizationDistributed object
A collision detection and data synchronization mechanism operates to expand the speed and capability of distributed applications. The execution environment employs collision detection and data synchronization to distribute data objects to appropriate network nodes to support local processing. The collision detection and data synchronization mechanism defines the set of processes and algorithms used to track distributed data objects and to manage changes to the distributed objects throughout a network of intelligent computing devices. Data and code are distributed to local computing devices necessitating tracking and synchronizing updates. The system and method ensures that data updates received during the course of a local transaction do not unwillingly affect the results of other transactions by notifying the local computing devices of changes to the data that are subject of the transaction. These conflicts are then resolved in the applications, and notification of the resolution is sent to the remaining intelligent computing devices.
Owner:LANDMARK TECH PARTNERS
Systems and methods for database notification interface to efficiently identify events and changed data
ActiveUS9292587B2Digital data information retrievalDigital data processing detailsDatabase managerApplication software
Owner:CITRIX SYST INC
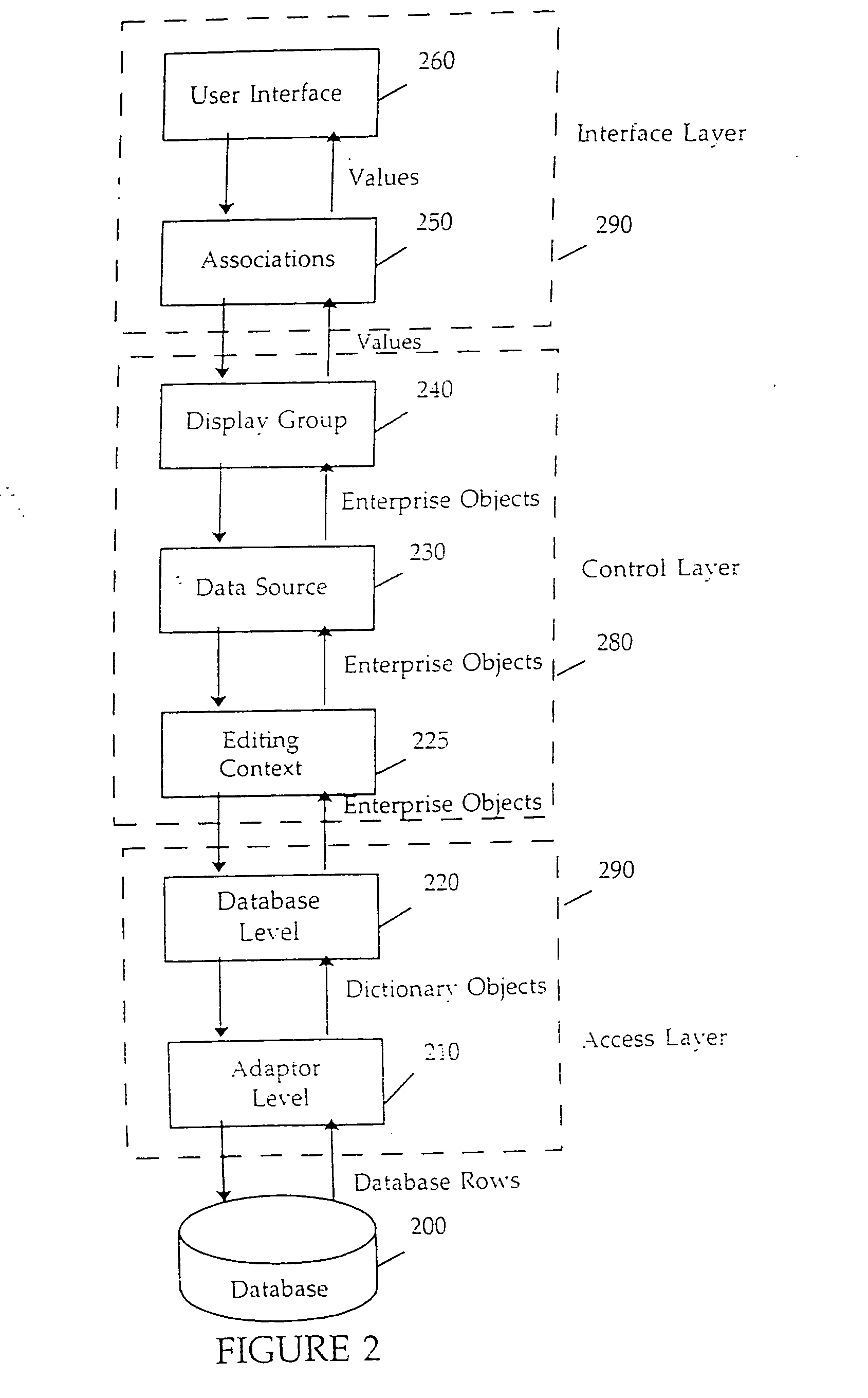
Object graph editing context and methods of use
InactiveUS20060271586A1Data processing applicationsDigital data processing detailsGraphicsManaging change
The present invention comprises a novel system for managing changes to a graph of data bearing objects. In one embodiment, an object graph manager object referred to as an editing context is used to identify changes made to data bearing enterprise objects and to notify other interested objects when changes occur. As a result, data bearing objects need not themselves contain code necessary for monitoring changes. In another embodiment of the invention, the editing context is used to provide event-based “undo” capabilities. In another embodiment of the invention, each enterprise object has a primary key that is used to maintain the identification between an enterprise object instance and a corresponding database row. In another embodiment of the invention, multiple levels of editing contexts are used to provide multiple isolated object graphs, each of which allows independent manipulation of the underlying data bearing objects.
Owner:NEXT
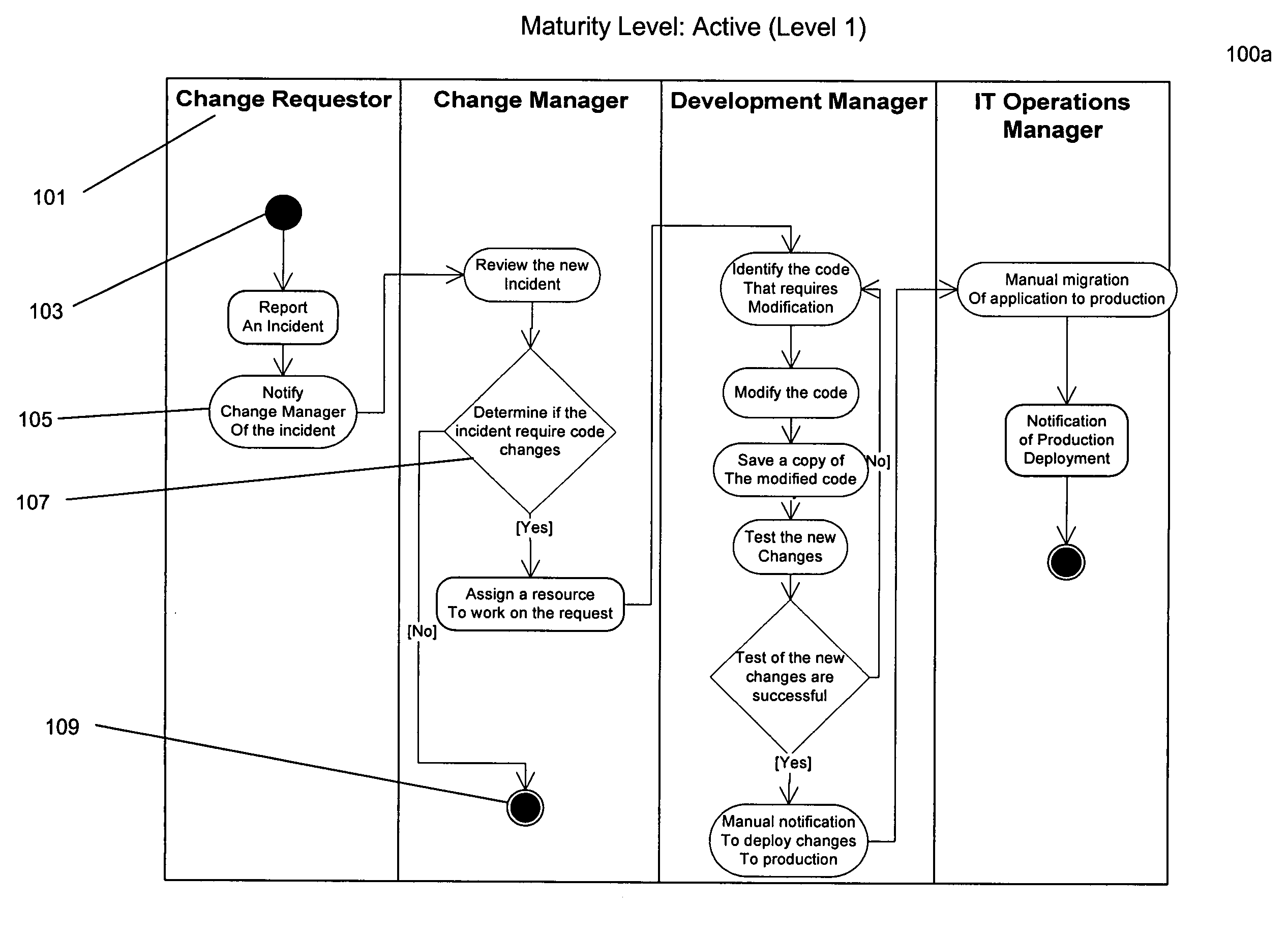
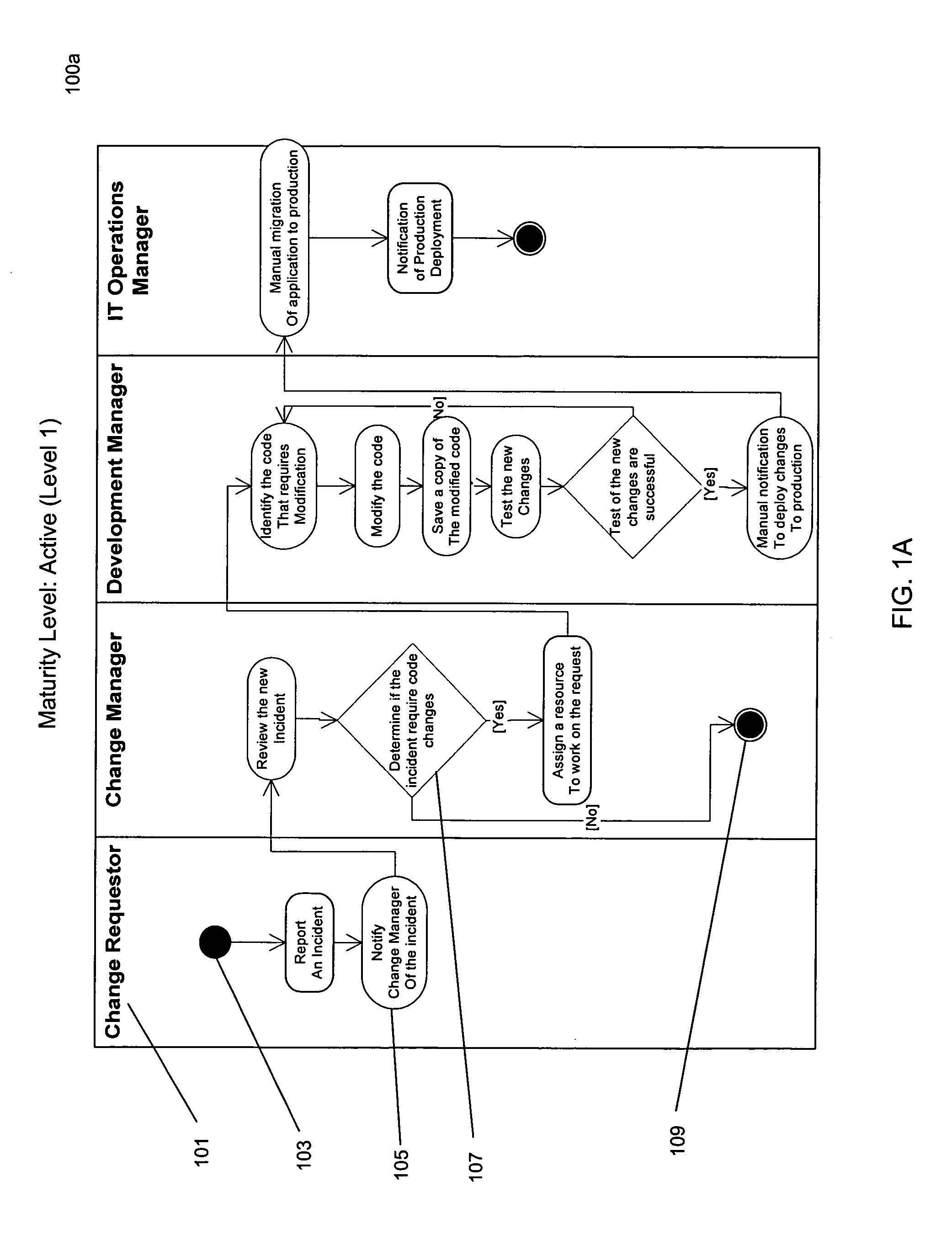
Application change request to deployment maturity model
InactiveUS20070061191A1Change managementImprove performanceHardware monitoringResourcesChange managementManaging change
The invention provides a system and method of improving change management structure of an organization, wherein change management structure includes process definitions for managing change requests to software applications. In one embodiment, the invention may include receiving current change management information regarding an organization. A current maturity level for the organization may then be determined from a hierarchy of predefined change management maturity levels. A target change management maturity level may then be determined from the hierarchy. One or more improvement operations may then be defined that, when performed, shift the organization to the target change management process maturity level. The one or more improvement operations may then be performed.
Owner:COMP ASSOC THINK INC
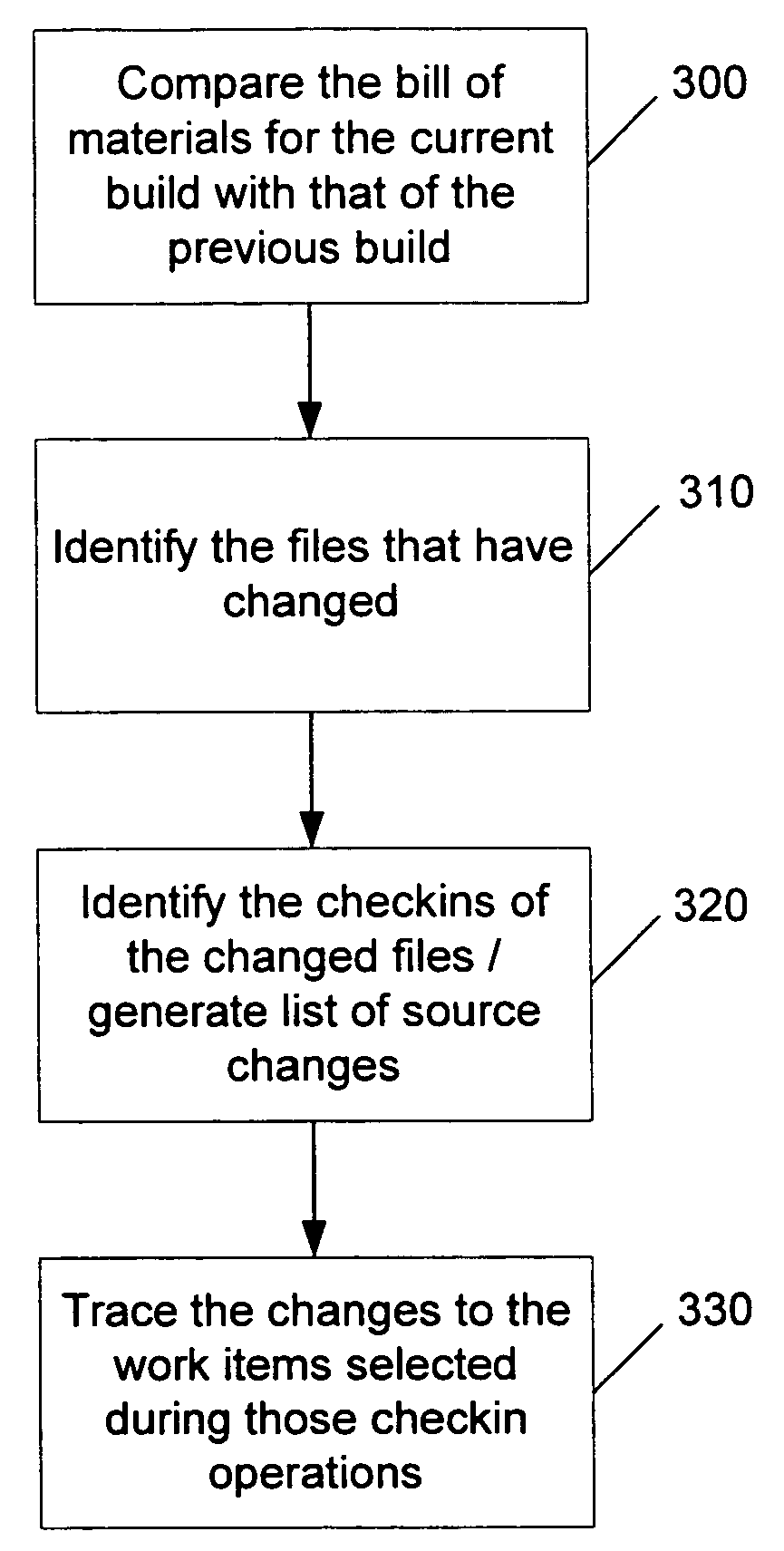
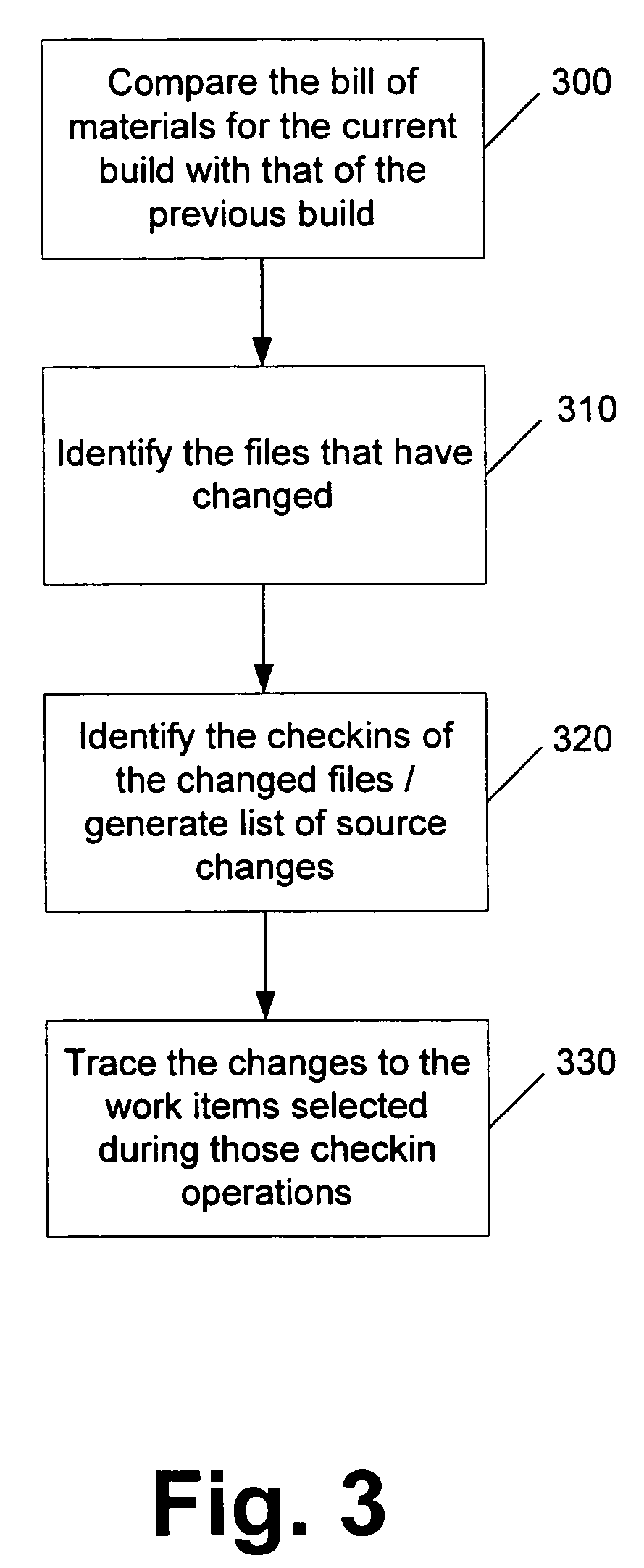
Task aware source checkin and build
ActiveUS20060236301A1Easy to specifyVersion controlSpecific program execution arrangementsSoftware engineeringManaging change
An integrated source code control and work item tracking tool is capable of establishing a relationship between work definition and work implementation. Once established, a more holistic view of the development process can be attained, and specific tasks can be easily accomplished. Tasks that be may accomplished using an integrated source code control and work item tracking tool include: automated generation of a list of work items that are completed in a new build of the system; automated updates of work items that are included in a build so that the work item details reflect the build in which it became available; automated transitioning of work items through a workflow when their implementation is complete and when their implementation is available in a new build; validation that source code changes represent the implementation of work items that have been approved; and managing change in the source code system with a focus on what work items it represents rather than a focus on what files are affected.
Owner:MICROSOFT TECH LICENSING LLC
Method and system for cyber security management of industrial control systems
ActiveUS8595831B2Low chanceFull accessMemory loss protectionError detection/correctionCommand and controlData acquisition
A method and system for cyber security management of Supervisory Control And Data Acquisition (SCADA) systems is provided to enhance situational awareness and cyber security management for industrial control systems. A centralized System Security Manager (SSM) is integrated into a SCADA to collect security related data for the industrial control system and an integrated command and control user interface displays security related data, a system security level, and interfaces with a user to allows for changing of system security settings for the industrial control system based on the security related data collected and manages changes in operational state of the SCADA based on the security level to restrict use of system interfaces and system accesses.
Owner:SIEMENS AG
System tools that provides dispatchers in power grid control centers with a capability to make changes
InactiveUS20110029142A1Mechanical power/torque controlData processing applicationsEngineeringUser interface
A system tool provides dispatchers in power grid control centers with a capability to manage changes. A user interface and a plurality of scheduler engines are provided. A comprehensive operating plan has multiple dispatch engines that are security constrained unit commitments and economic dispatch sequences with different look-ahead periods. The comprehensive operating plan is configured to integrate the dispatch engines into a unified scheduling system. The comprehensive operating plan has a data structure for capturing scheduling data, transaction scheduling, load forecast and time series data. The comprehensive operating plan is configured to coordinate scheduling data to and from power grid system applications and present a comprehensive, synchronized and harmonized view of scheduling data to at least one of, applications, power grid system operators and other stakeholders for power grid system operations.
Owner:ALSTOM TECH LTD
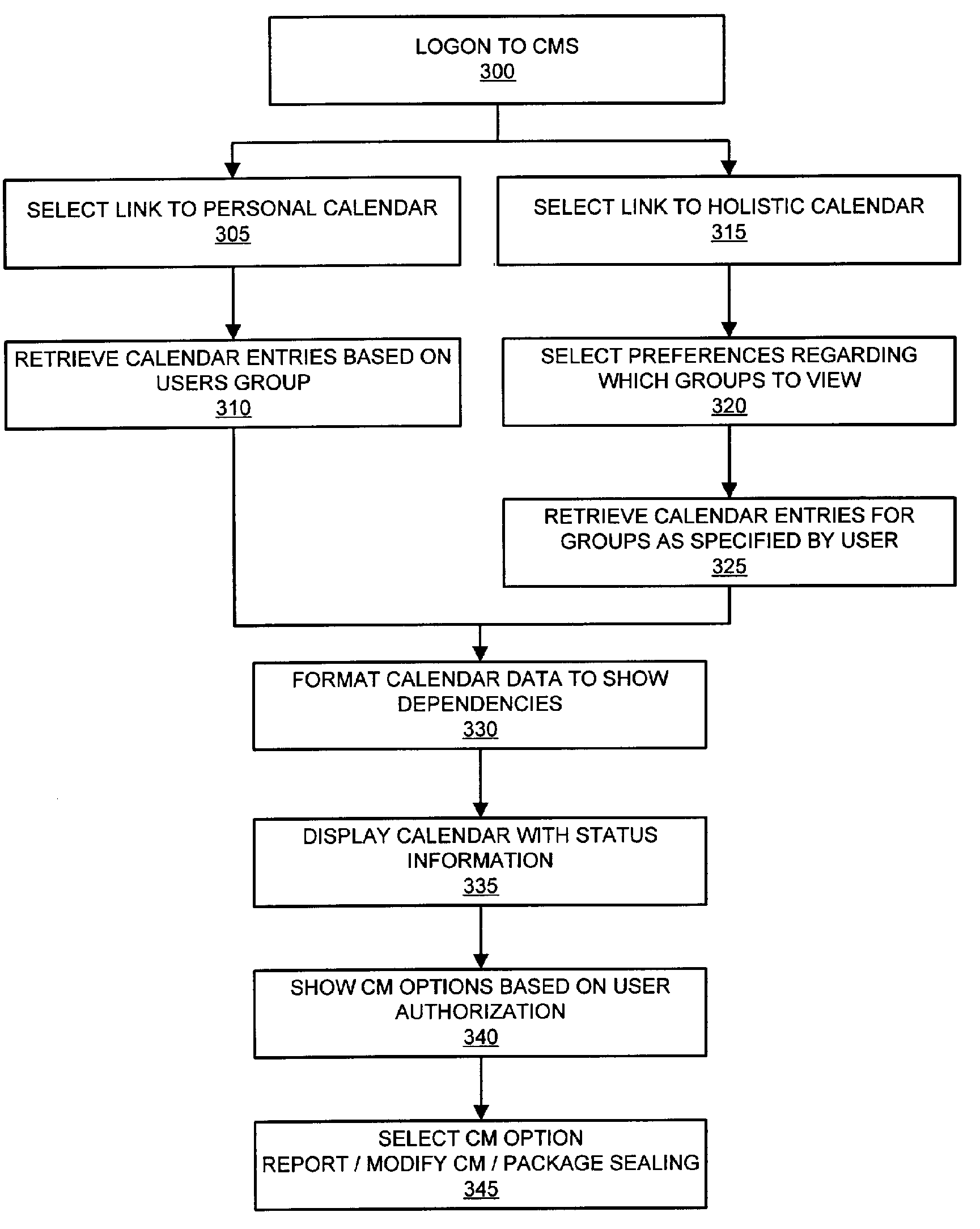
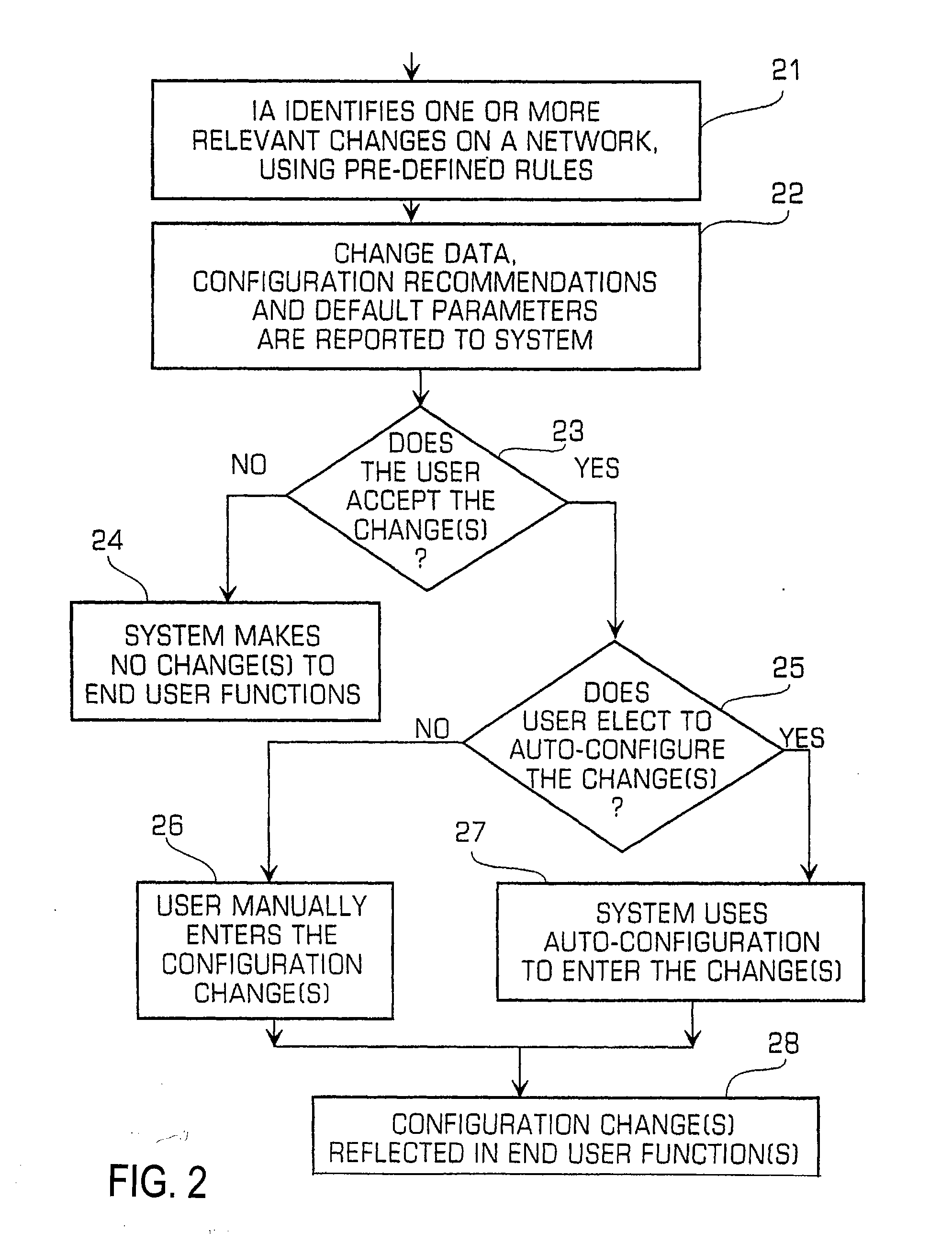
System and method for change management process automation
InactiveUS7574483B1Facilitates planning implementationReduce riskMultiple digital computer combinationsResourcesChange managementManaging change
The invention enables an enterprise to manage changes to computing infrastructure through an online change management system. The invention enables authorized users to logon to the system, view a personal and holistic calendar, create reports, modify change management records, attach files or other artifacts to change management records. The invention also provides business rules which can be employed online for service which then invokes various system components to create a workgroup and workflow according to predefined business rules.
Owner:LIBERTY PEAK VENTURES LLC
System and method for passively identifying encrypted and interactive network sessions
The system and method for passively identifying encrypted and interactive network sessions described herein may distribute a passive vulnerability scanner in a network, wherein the passive vulnerability scanner may observe traffic travelling across the network and reconstruct a network session from the observed traffic. The passive vulnerability scanner may then analyze the reconstructed network session to determine whether the session was encrypted or interactive (e.g., based on randomization, packet timing characteristics, or other qualities measured for the session). Thus, the passive vulnerability scanner may monitor the network in real-time to detect any devices in the network that run encrypted or interactive services or otherwise participate in encrypted or interactive sessions, wherein detecting encrypted and interactive sessions in the network may be used to manage changes and potential vulnerabilities in the network.
Owner:TENABLE INC
Integrated Change Management Unit
InactiveUS20080256133A1Web data indexingDigital data processing detailsChange managementThe Internet
An integrated system for managing changes in regulatory and non-regulatory requirements for business activities at an industrial or commercial facility. Application of this system to environmental, health and safety activities, and to food, drug, cosmetic, and medical treatment and device activities, are discussed as examples. The system: provides one or more databases that contain information on operations and requirements concerning an activity or area of business; receives information on regulatory and non-regulatory changes that affect operations of the business; converts these changes into changes in data entry forms, data processing and analysis procedures, and presentation (by printing, electronic display and / or distribution) of data processing and analysis results to selected recipients, without requiring the services of one or more programmers to re-key and / or reformat the items affected by the change; and implements receipt of change information and dissemination of data processing and analysis results using the facilities of the Internet.
Owner:ALTERNATIVE SYST
Database and data access layer
InactiveUS20100268705A1Efficient constructionEasy to buildDigital data processing detailsResourcesManaging changeBusiness intelligence
The system of the present invention facilitates the collection, processing, optimization and communication of data. Project data is accessed through an architecture, comprising an access layer, with programs for retrieving, processing and communicating data from a database, and a Customer User Interface (CUI) presentation layer. The CUI provides individual users with interaction throughout the project life-cycle, for example, for recording and processing information, completing project tasks, producing and managing documents, managing changes, issues and risks and producing reports and business intelligence, including individual project and projects portfolio status indicators.
Owner:PROJECT MANAGEMENT SOFTWARE
Method and system for capturing and reusing intellectual capital in IT management
A method and system for generating a graph-based model of an IT system that experiences certain undesirable events. The graphical representation of the IT system and its events is used to resolve other undesirable events occurring on the same system or a similar system and is also used to manage changes within the IT system.
Owner:IBM CORP
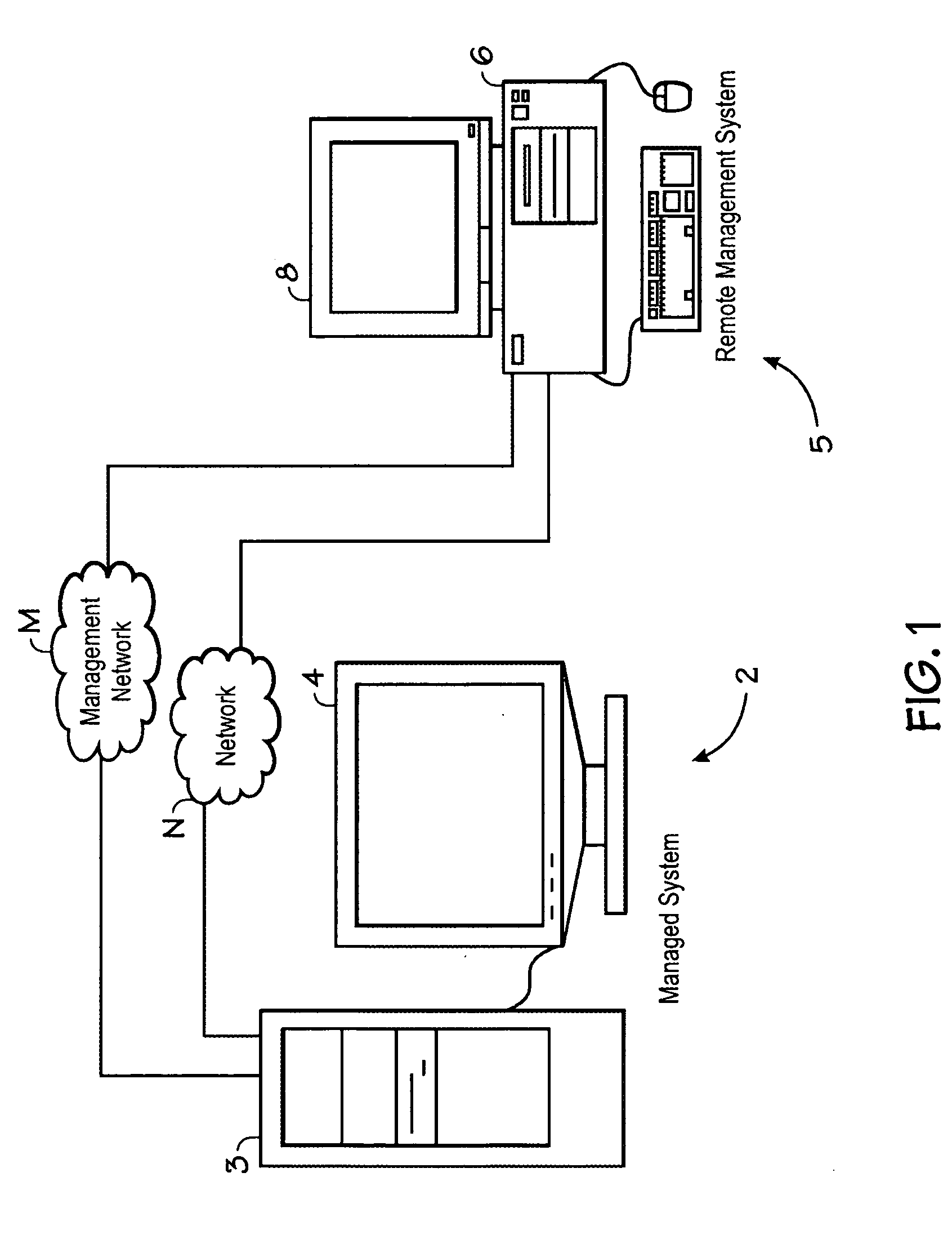
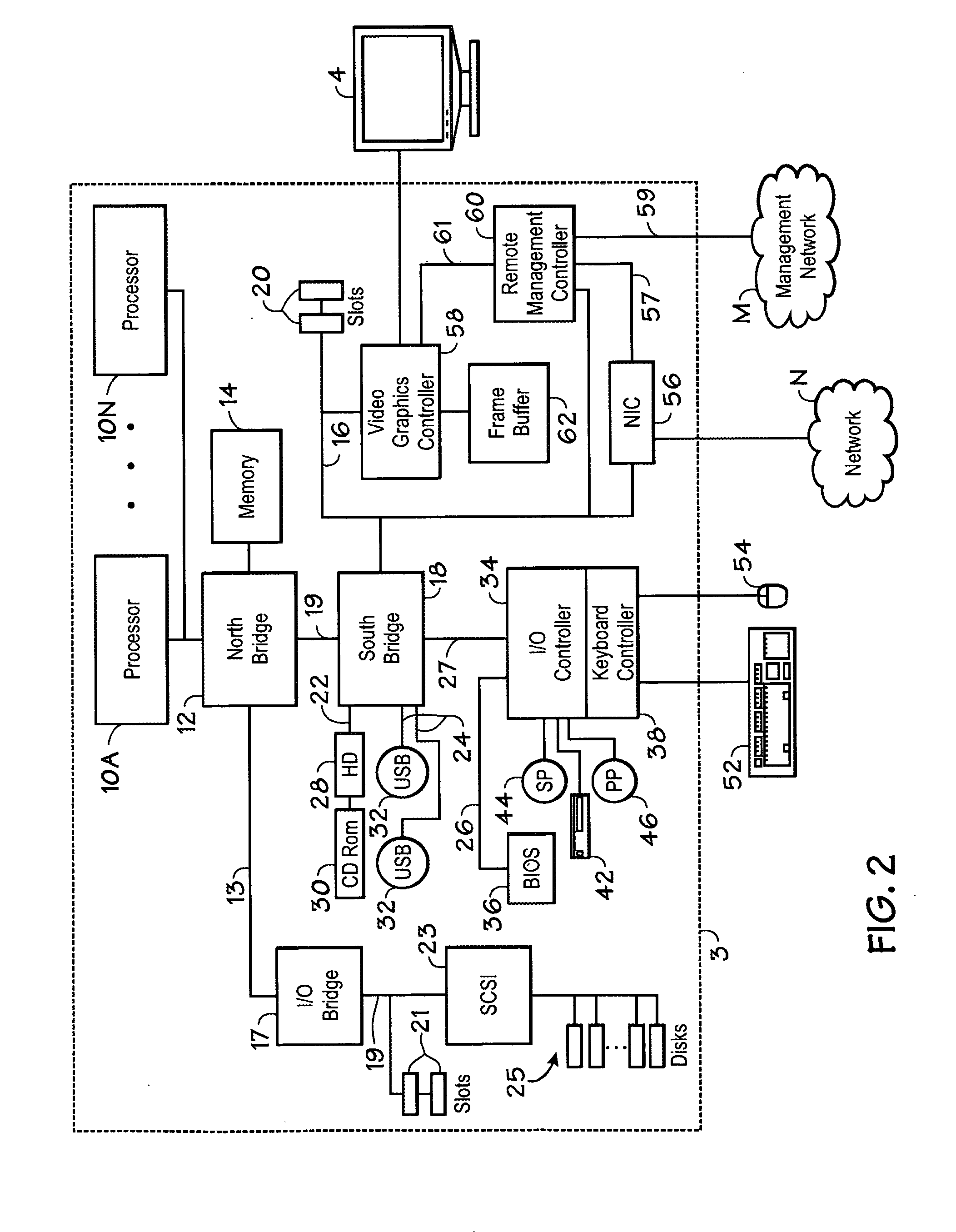
Method and apparatus for managing changes in a virtual screen buffer
ActiveUS20060039466A1Picture reproducers using cathode ray tubesPicture reproducers with optical-mechanical scanningGraphicsVirtual screen
A remote management controller may include a capture engine and a processor. The capture engine may be configured to: obtain a slice of video data output from a video graphics controller; calculate at least one value correlative to the slice of video data; determine whether any portion of the slice has been locked; and if any portion has not been locked and if the calculated value for such portion of the slice differs from a value for a previously obtained corresponding portion, move the portion to a virtual screen buffer, update a table associated with the virtual screen buffer with the calculated value, and modify a change table to indicate that the portion has changed. The processor may be configured to: read the change table to determine whether any portion of video data in the virtual screen buffer has changed; and if any portion has changed, lock any changed portion from being accessed by the capture engine, access the changed portion from the virtual screen buffer, and process the changed portion in the virtual screen buffer for transmission to a remote system.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
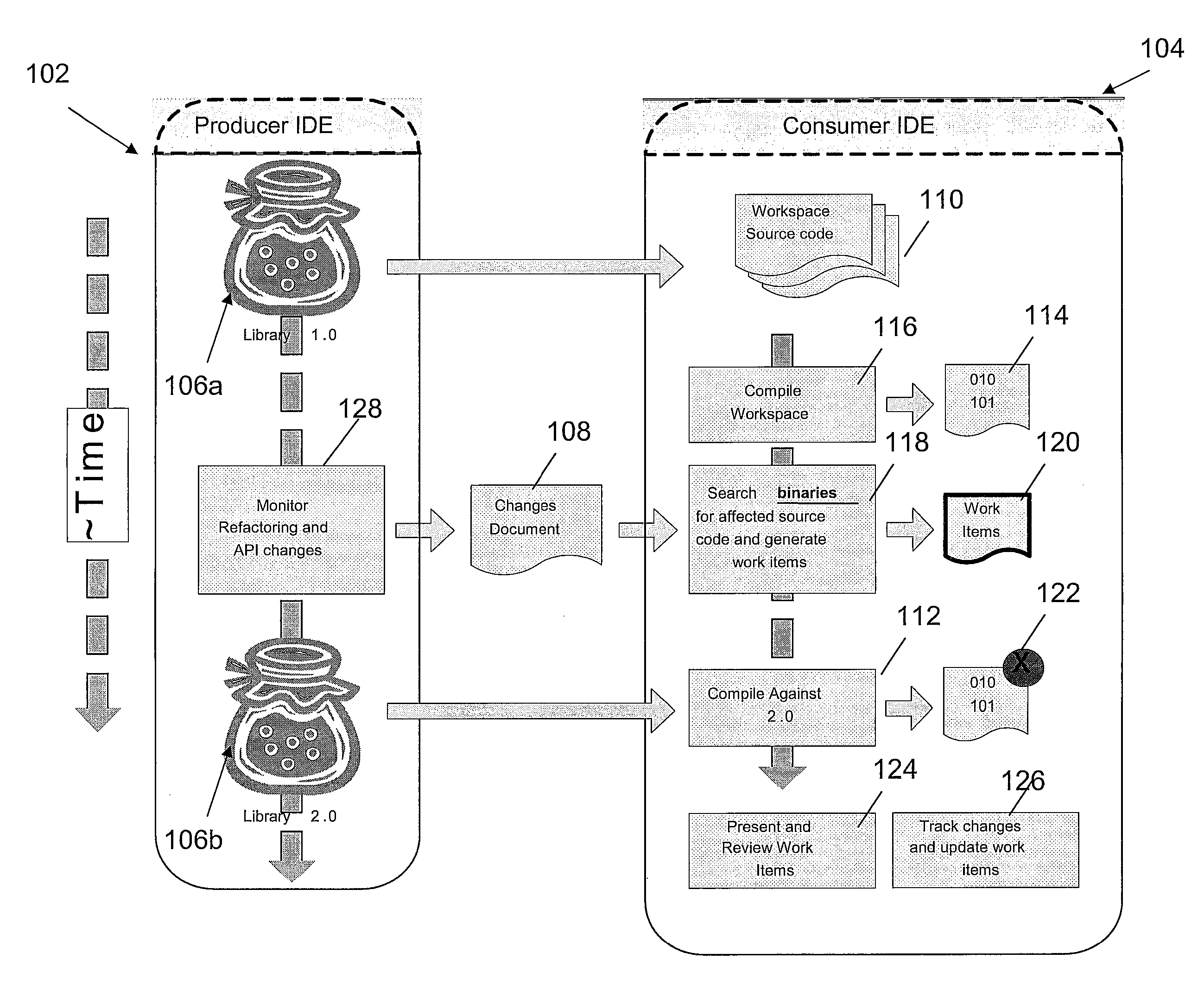
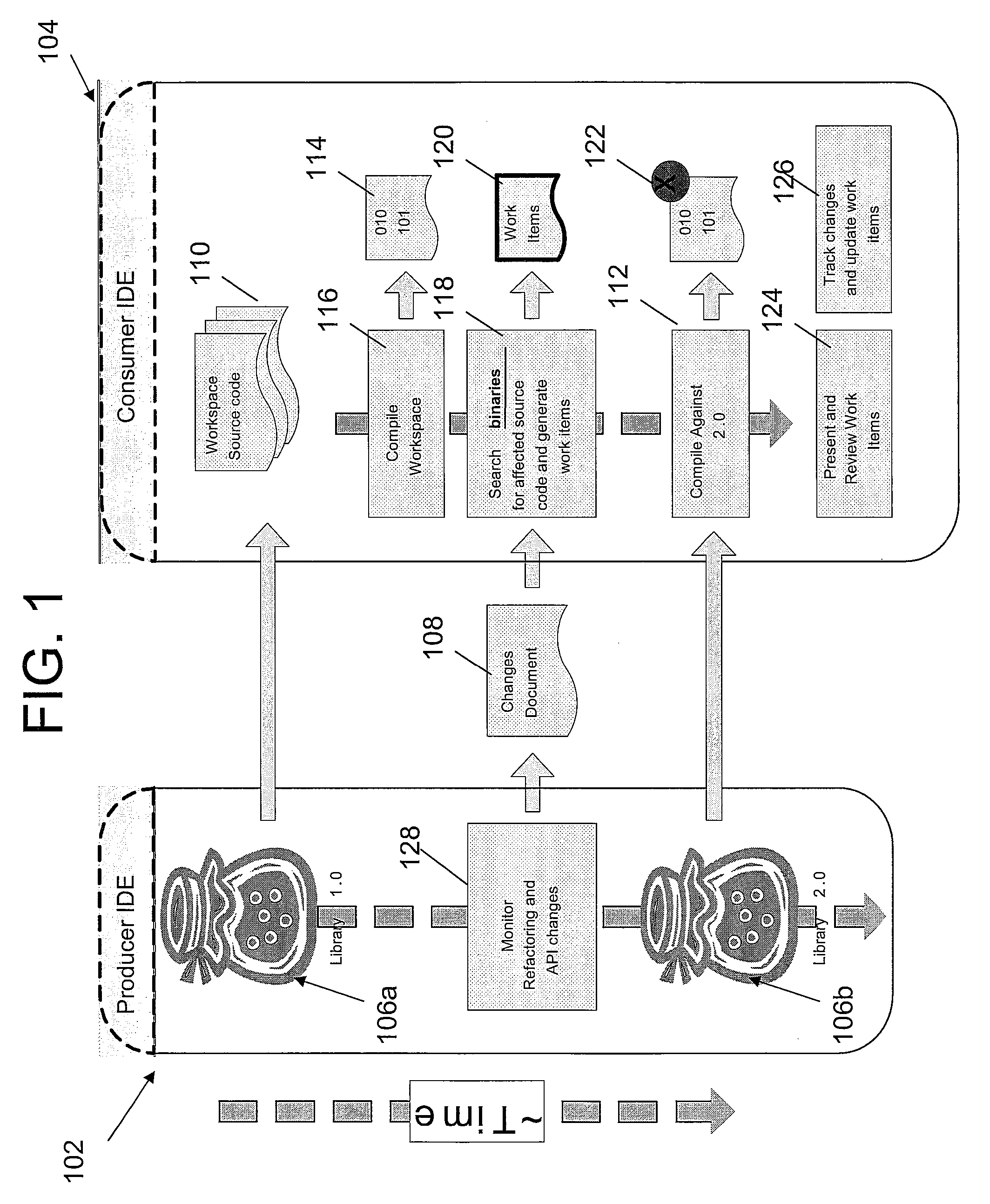
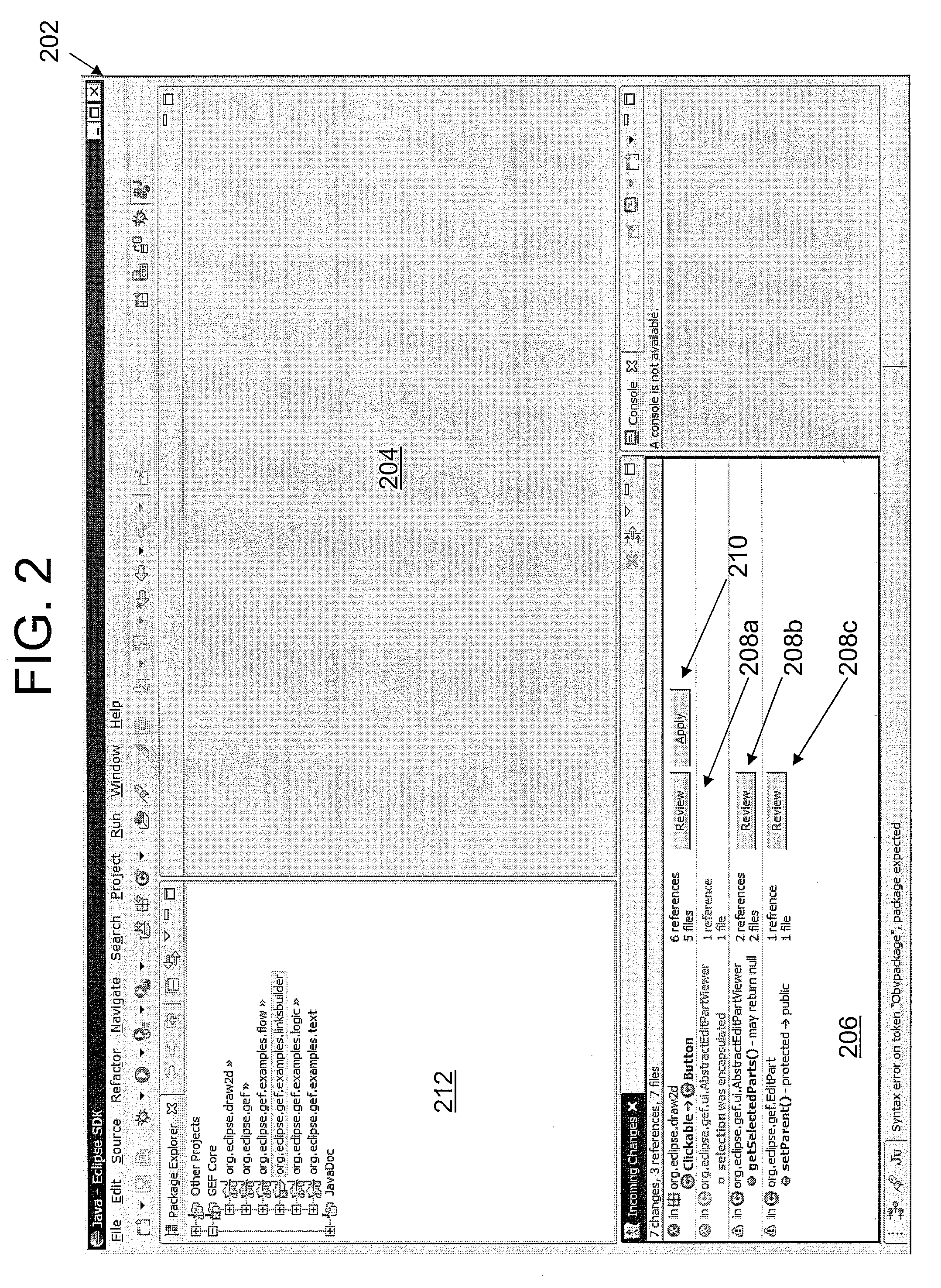
Applying deferred refactoring and API changes in an IDE
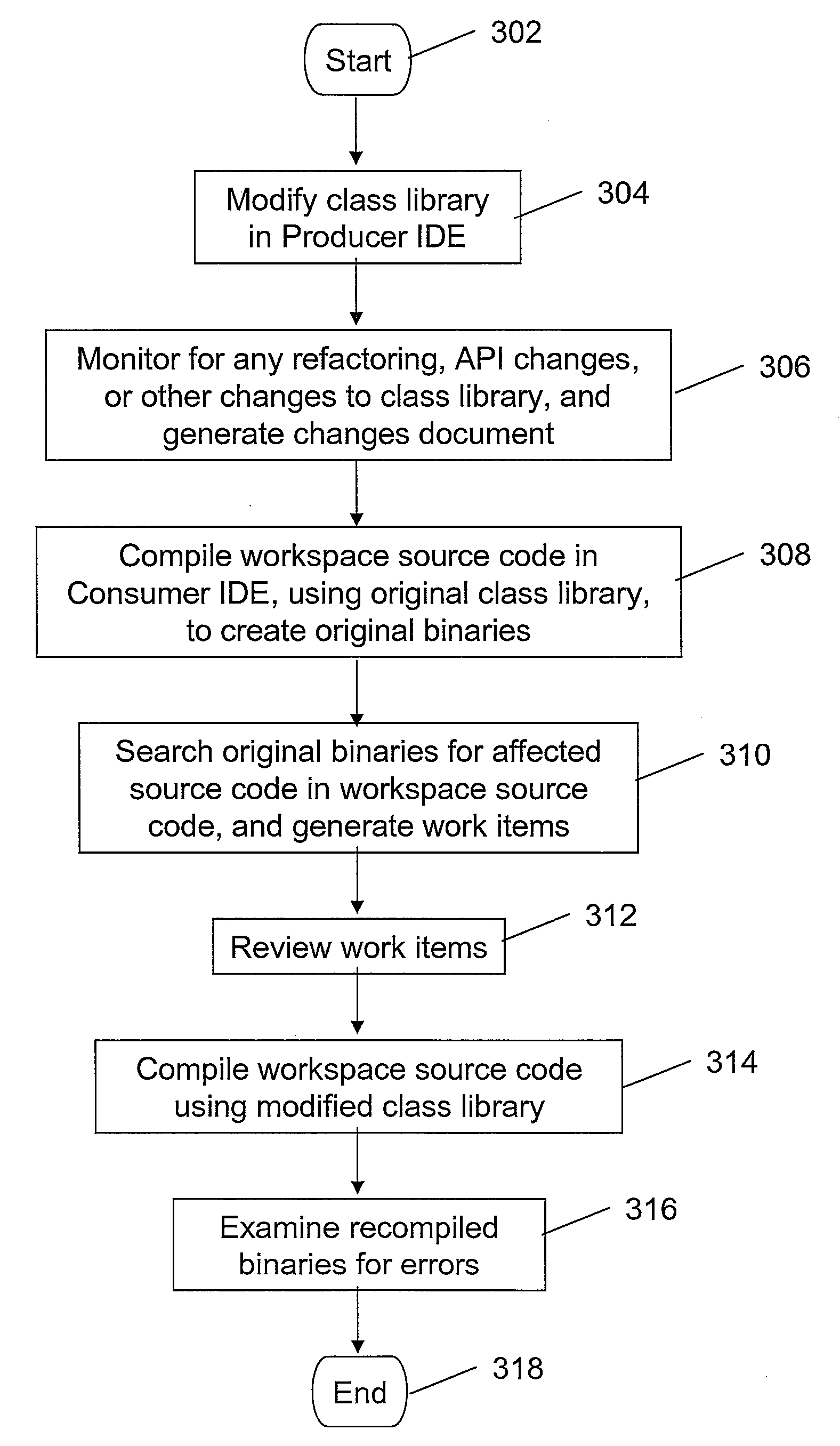
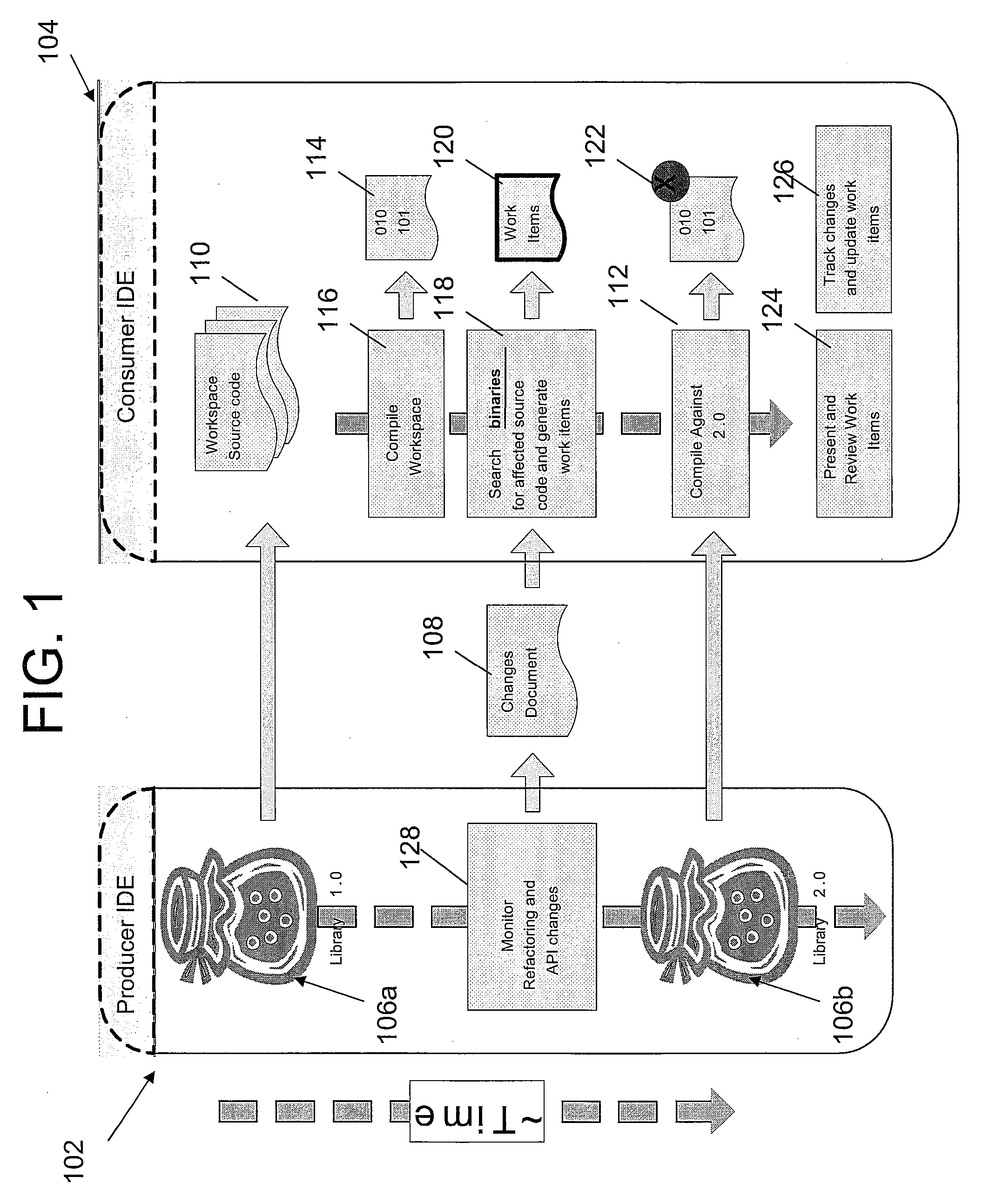
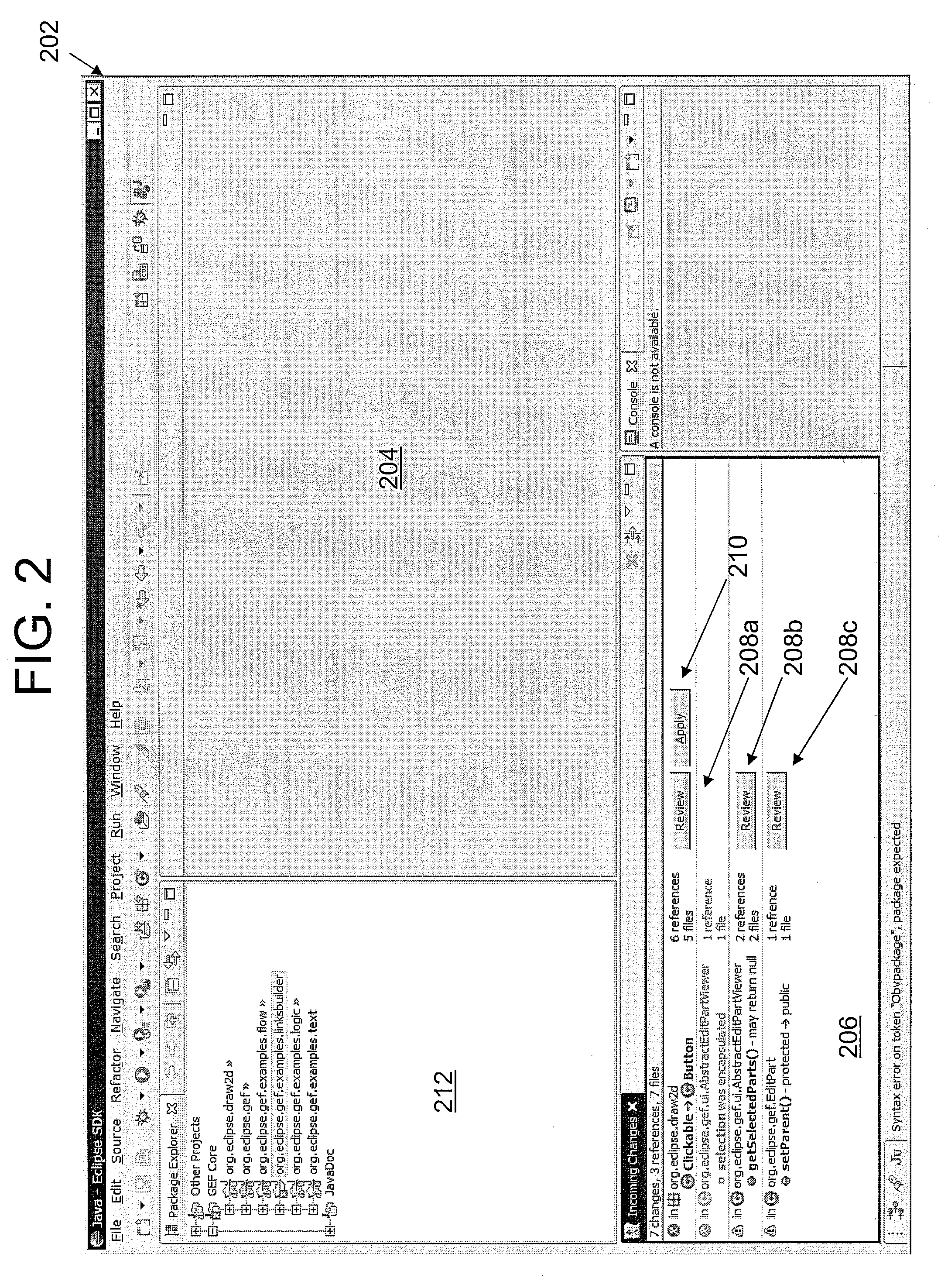
A method, apparatus and computer-readable medium for managing changes to a library in a Producer IDE is presented. In one embodiment, the method includes the steps of compiling user source code in a consumer's workspace using at least one class from an original class library to produce a user's executable binary files; searching the executable binary files for references to Application Program Interface (API) changes that occurred when the original class library was updated; and generating at least one work item for each of the API changes that is referred to by the user's executable binary files.
Owner:IBM CORP
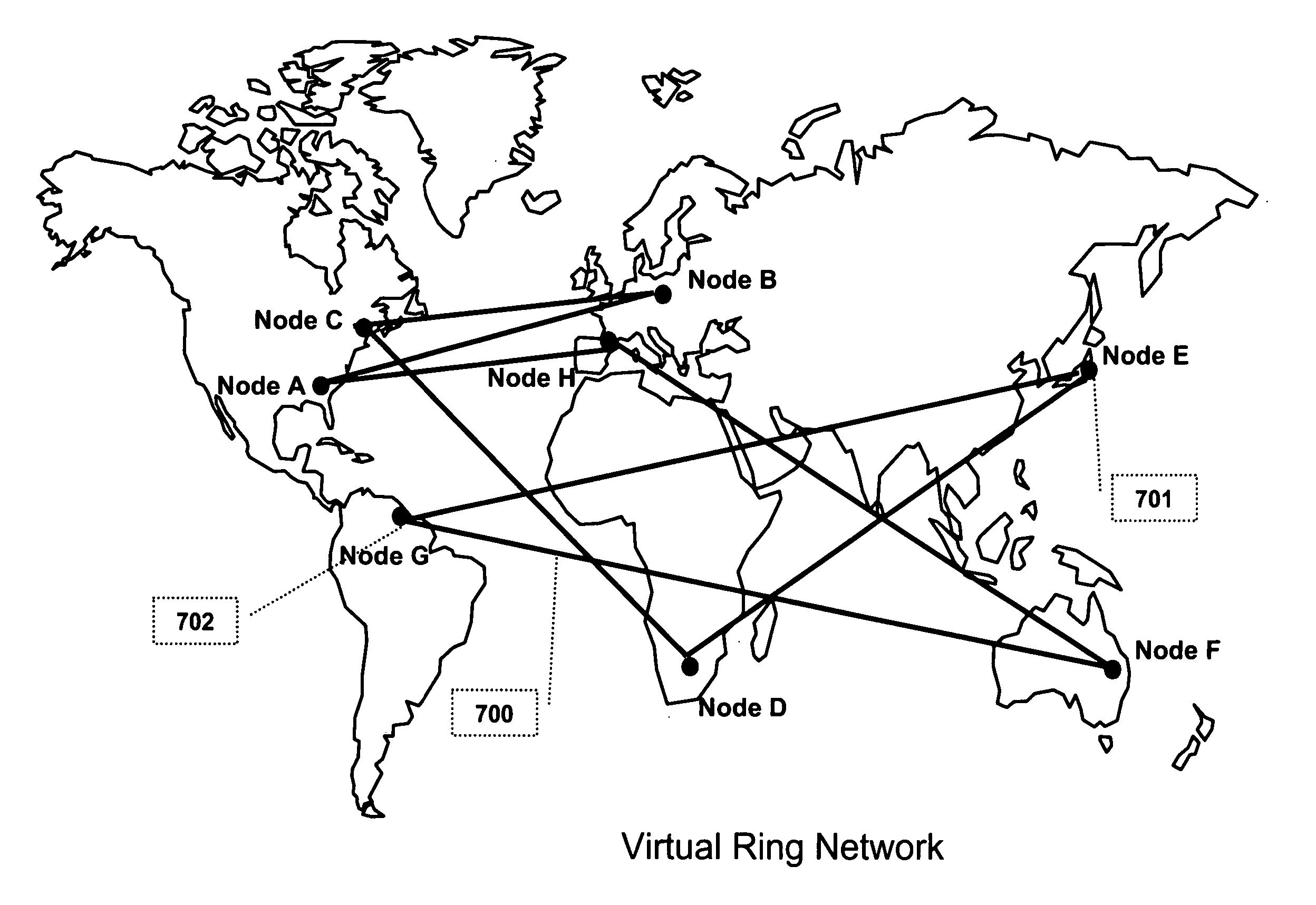
System and method for optimizing the topology of a virtual ring based upon a TCP/IP network
InactiveUS20070081461A1Reduce resource consumptionError preventionTransmission systemsManaging changeMulticast communication
In a network having nodes, N nodes are members of a virtual communications ring for multicast communication among the N nodes, each of the N nodes being associated with only an upstream and a downstream one of the other N nodes. One of the N nodes manages changes in ring membership, including requesting the others of the N nodes to participate in measuring distances to a N+1th, node responsive to receiving an insertion request message. The manager node inserts the N+1th node in the communications ring responsive to receiving replies, which includes inserting the N+1th node in a selected location between two selected ones of the N nodes, such that the N nodes and the N+1th node are enabled to multicast messages around the ring. Due to the selected location of the N+1th node, communication distances for muticasted messages tend to be shorter than such distances that would otherwise occur.
Owner:IBM CORP
Applying Deferred Refactoring and API Changes in an Ide
InactiveUS20080022266A1Simple methodCode refactoringSpecific program execution arrangementsWorkspaceManaging change
A method, apparatus and computer-readable medium for managing changes to a library in a Producer IDE is presented. In one embodiment, the method includes the steps of compiling user source code in a consumer's workspace using at least one class from an original class library to produce a user's executable binary files; searching the executable binary files for references to Application Program Interface (API) changes that occurred when the original class library was updated; and generating at least one work item for each of the API changes that is referred to by the user's executable binary files.
Owner:IBM CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com