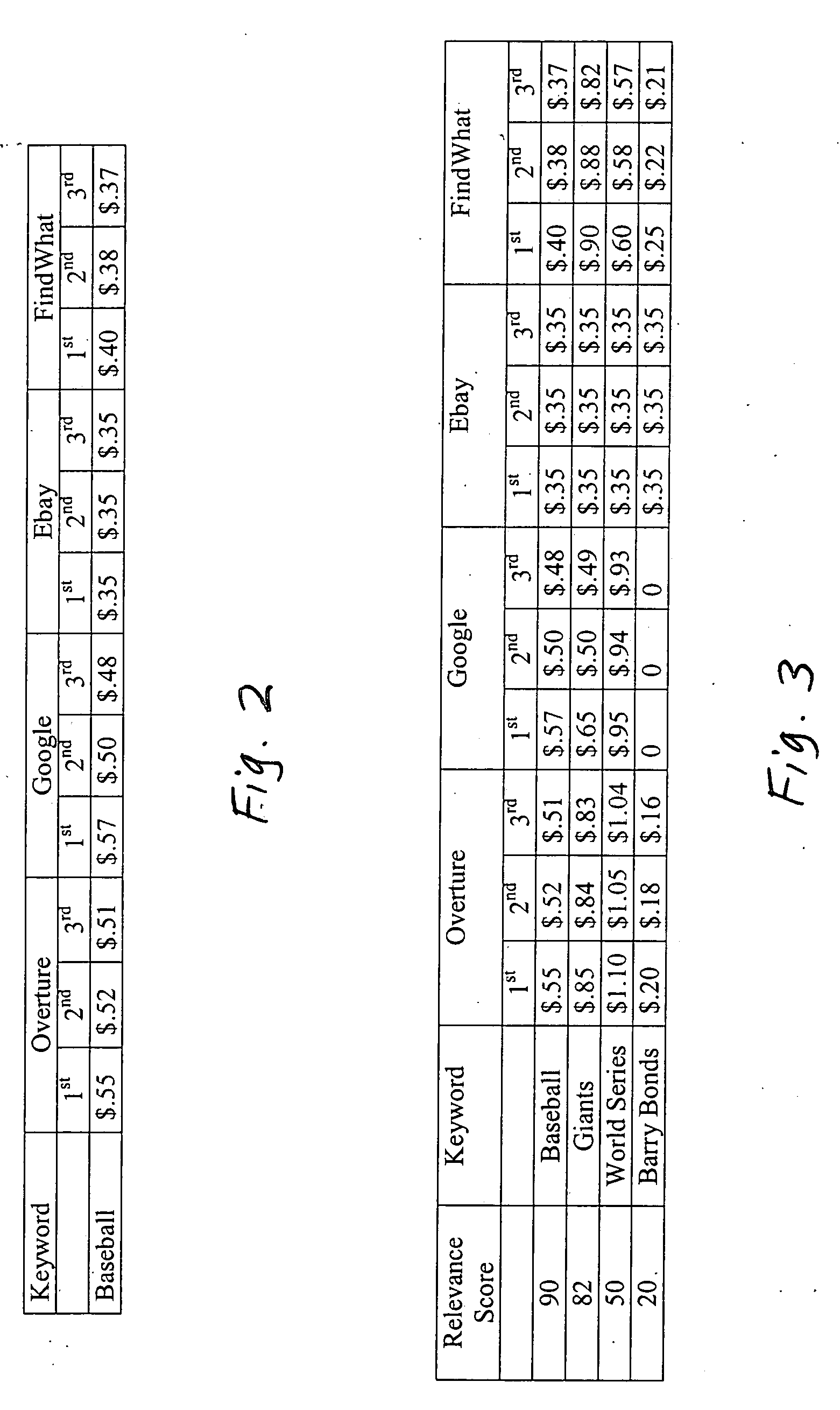
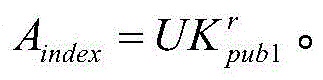Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
7393 results about "Index term" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
An index term, subject term, subject heading, or descriptor, in information retrieval, is a term that captures the essence of the topic of a document. Index terms make up a controlled vocabulary for use in bibliographic records. They are an integral part of bibliographic control, which is the function by which libraries collect, organize and disseminate documents. They are used as keywords to retrieve documents in an information system, for instance, a catalog or a search engine. A popular form of keywords on the web are tags which are directly visible and can be assigned by non-experts. Index terms can consist of a word, phrase, or alphanumerical term. They are created by analyzing the document either manually with subject indexing or automatically with automatic indexing or more sophisticated methods of keyword extraction. Index terms can either come from a controlled vocabulary or be freely assigned.
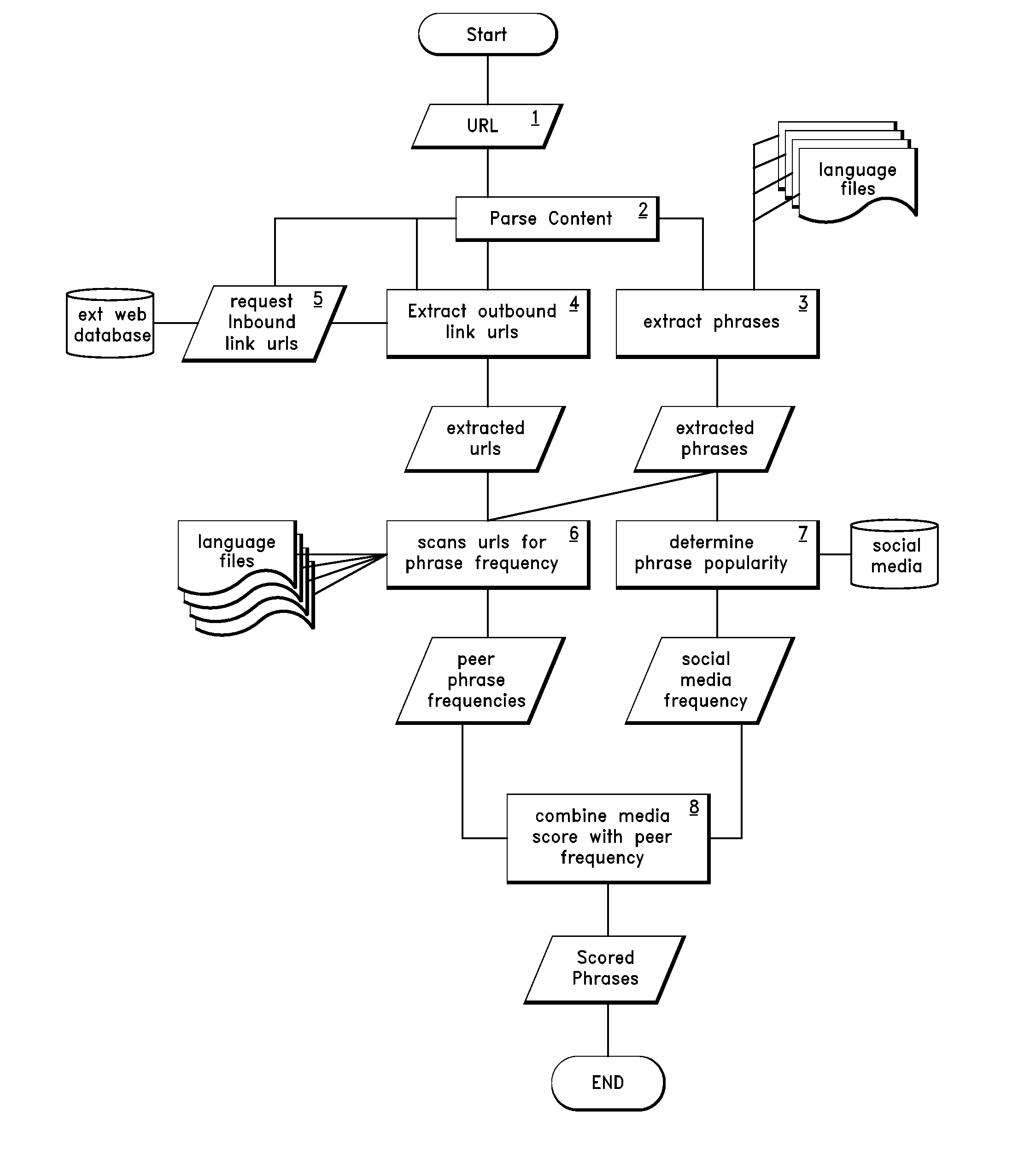
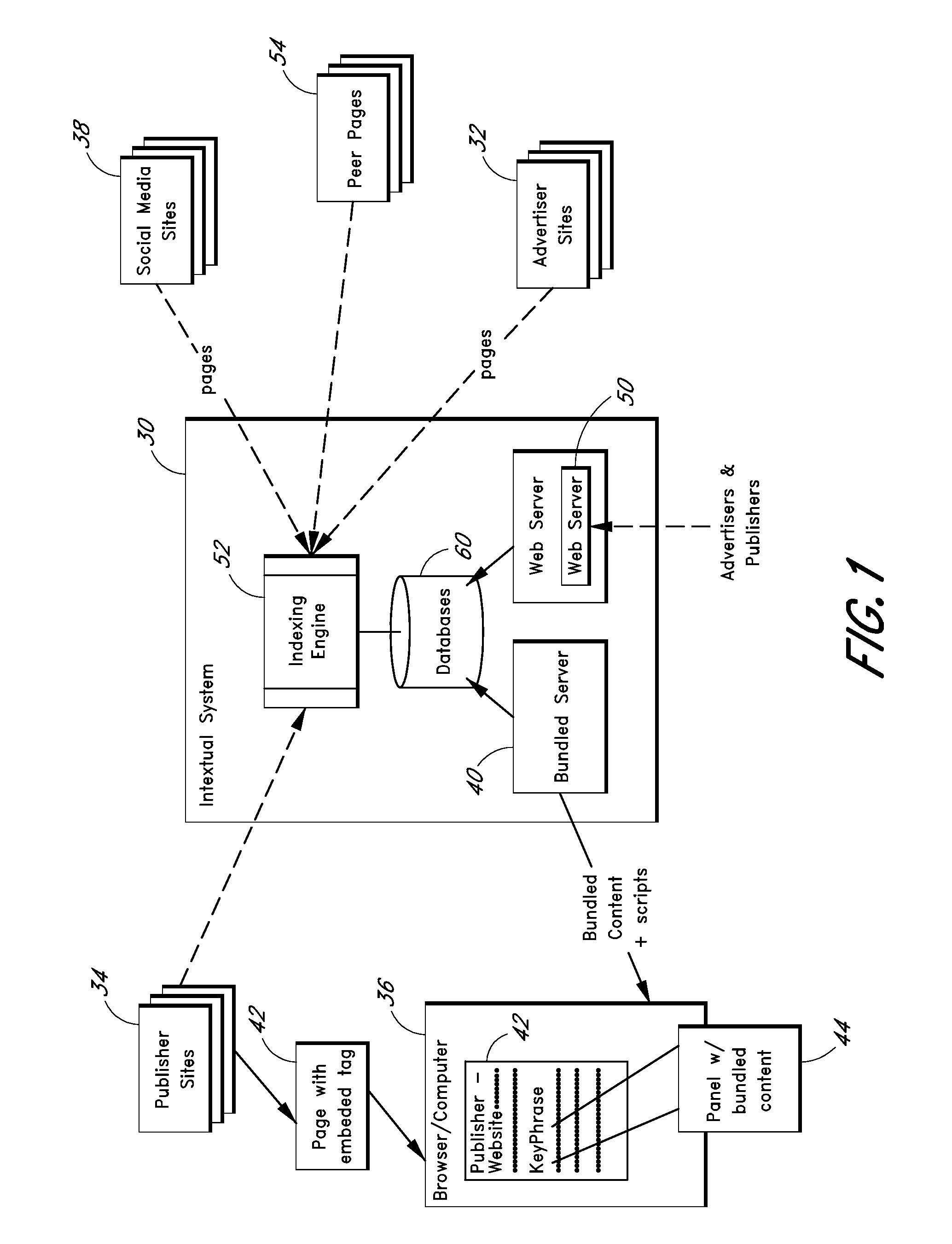
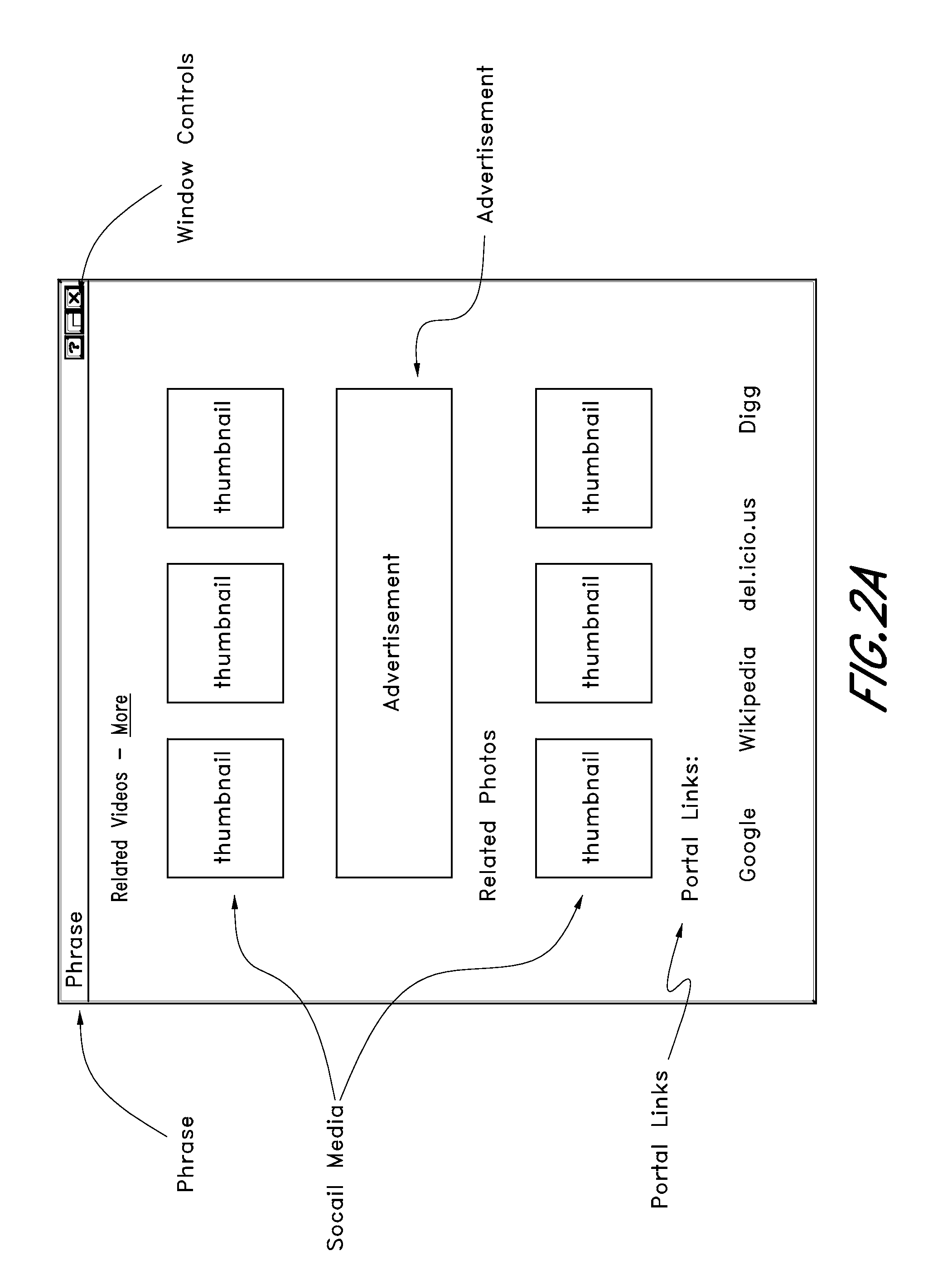
Selecting key phrases for serving contextually relevant content
A process is described for assessing the suitability of particular keyword phrases for use in serving contextually relevant content for display on particular web pages. In one embodiment, the process involves determining frequencies of occurrence of particular keyword phrases within a peer group of pages associated with a target URL. Popularity levels of the phrases, as assessed using other sources of information, may also be considered. A process is also disclosed in which selected keyword phrases on a web page are transformed into links that can be selected by a user to view bundled content that is related to such keyword phrases.
Owner:TAMIRAS PER PTE LTD LLC
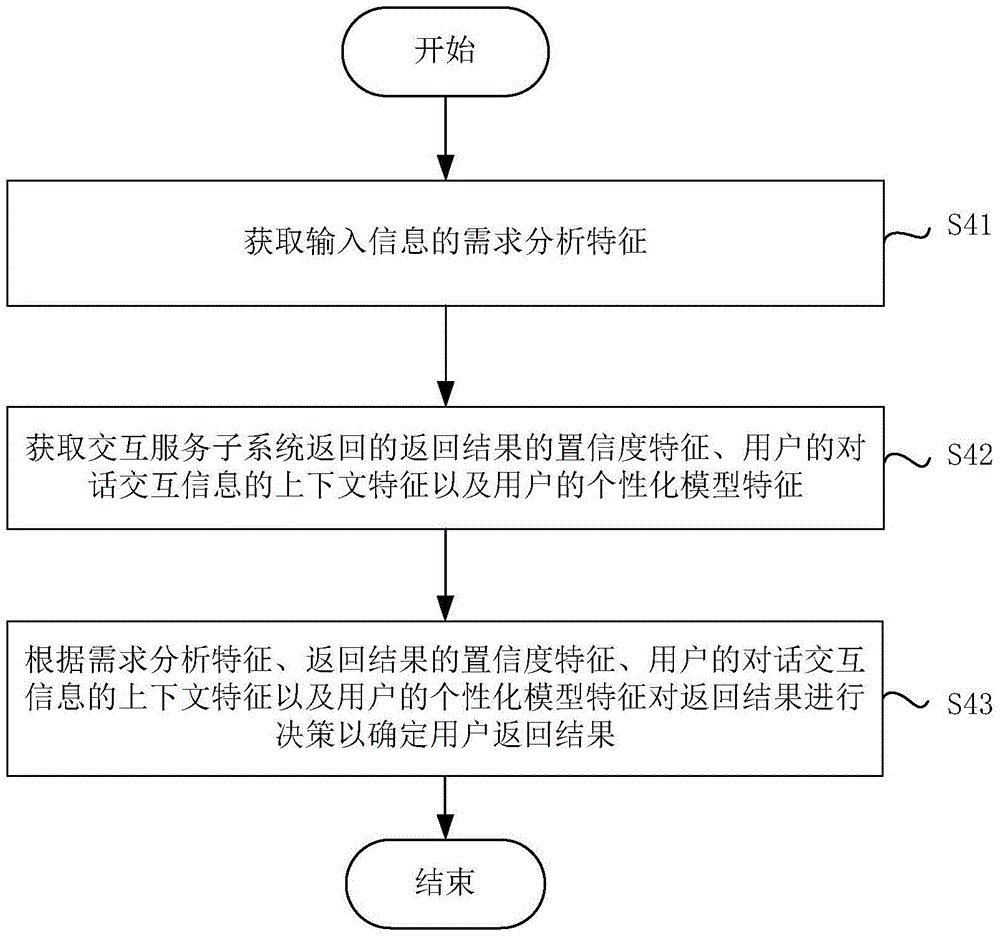
Man-machine interaction method and system based on artificial intelligence
ActiveCN105068661AEasy and pleasant interactive experienceInput/output for user-computer interactionGraph readingDecision strategyComputer terminal
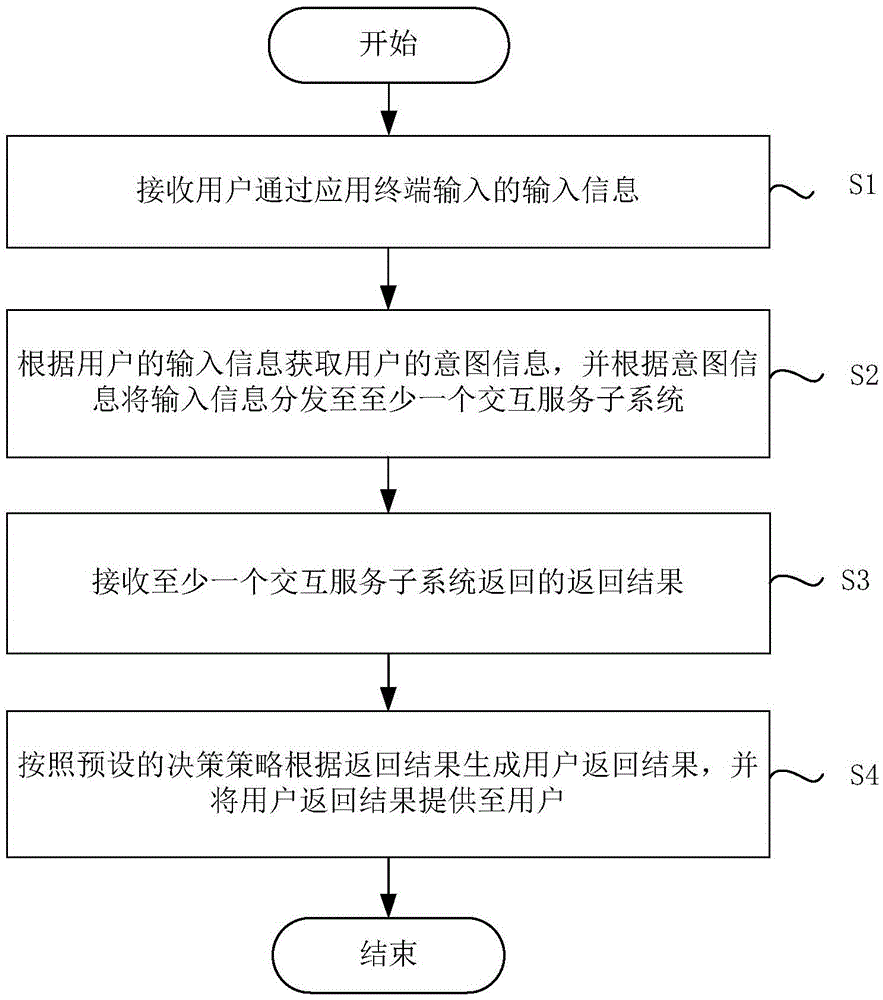
The invention discloses a man-machine interaction method and system based on artificial intelligence. The method includes the following steps of receiving input information input by a user through an application terminal, obtaining the intent information of the user according to the input information of the user, distributing the input information to at least one interaction service subsystem according to the intent information, receiving the return result returned by the interaction service subsystems, generating a user return result according to the return result through a preset decision strategy, and providing the user return result to the user. By means of the method and system, the man-machine interaction system is virtualized instead of being instrumentalized, and the user can obtain the relaxed and pleasure interaction experience in the intelligent interaction process through chat, research and other service. The search in the form of keywords is improved into the search based on natural languages, the user can express demands through flexible and free natural languages, and the multi-round interaction process is closer to the interaction experience among humans.
Owner:BAIDU ONLINE NETWORK TECH (BEIJIBG) CO LTD
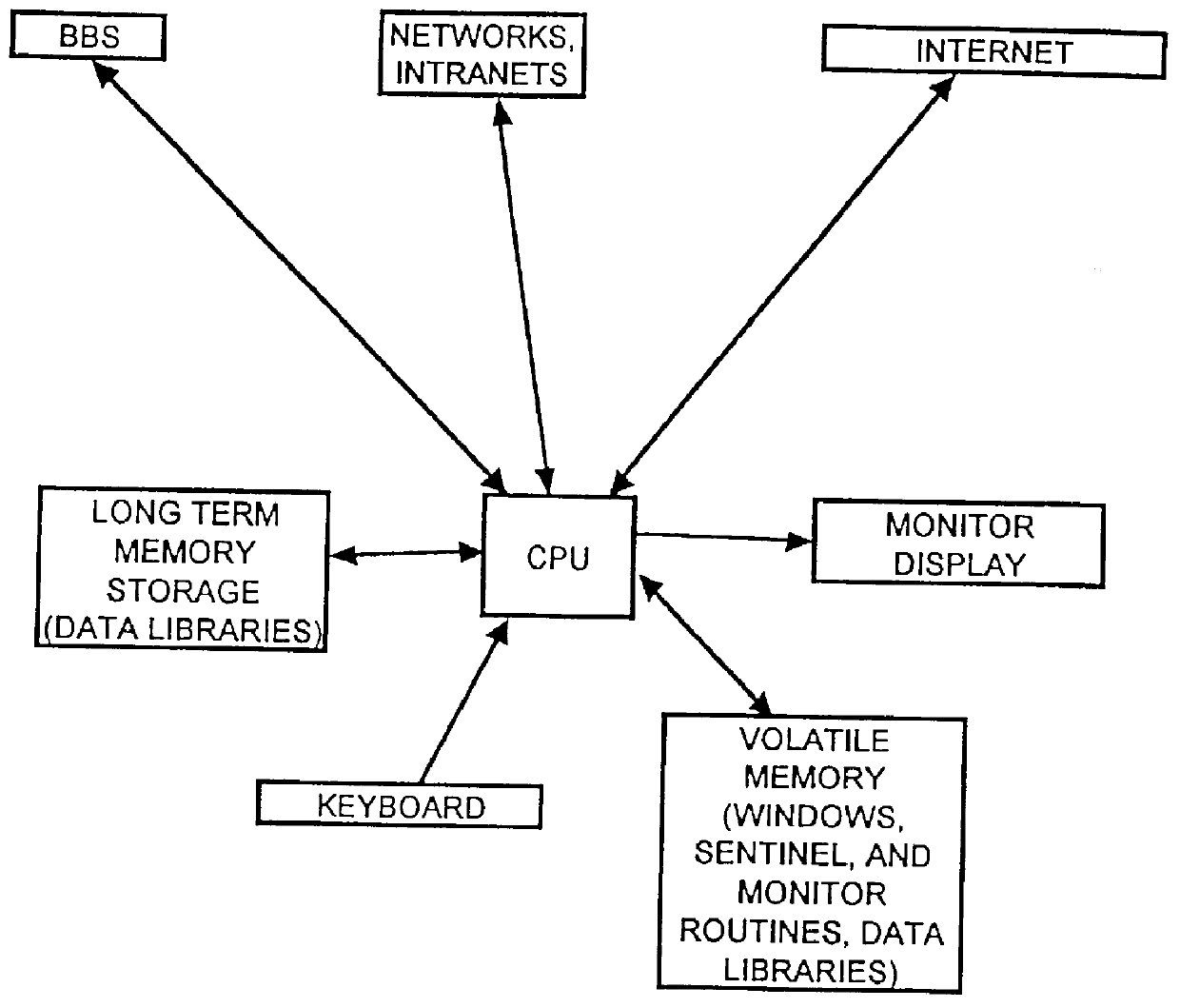
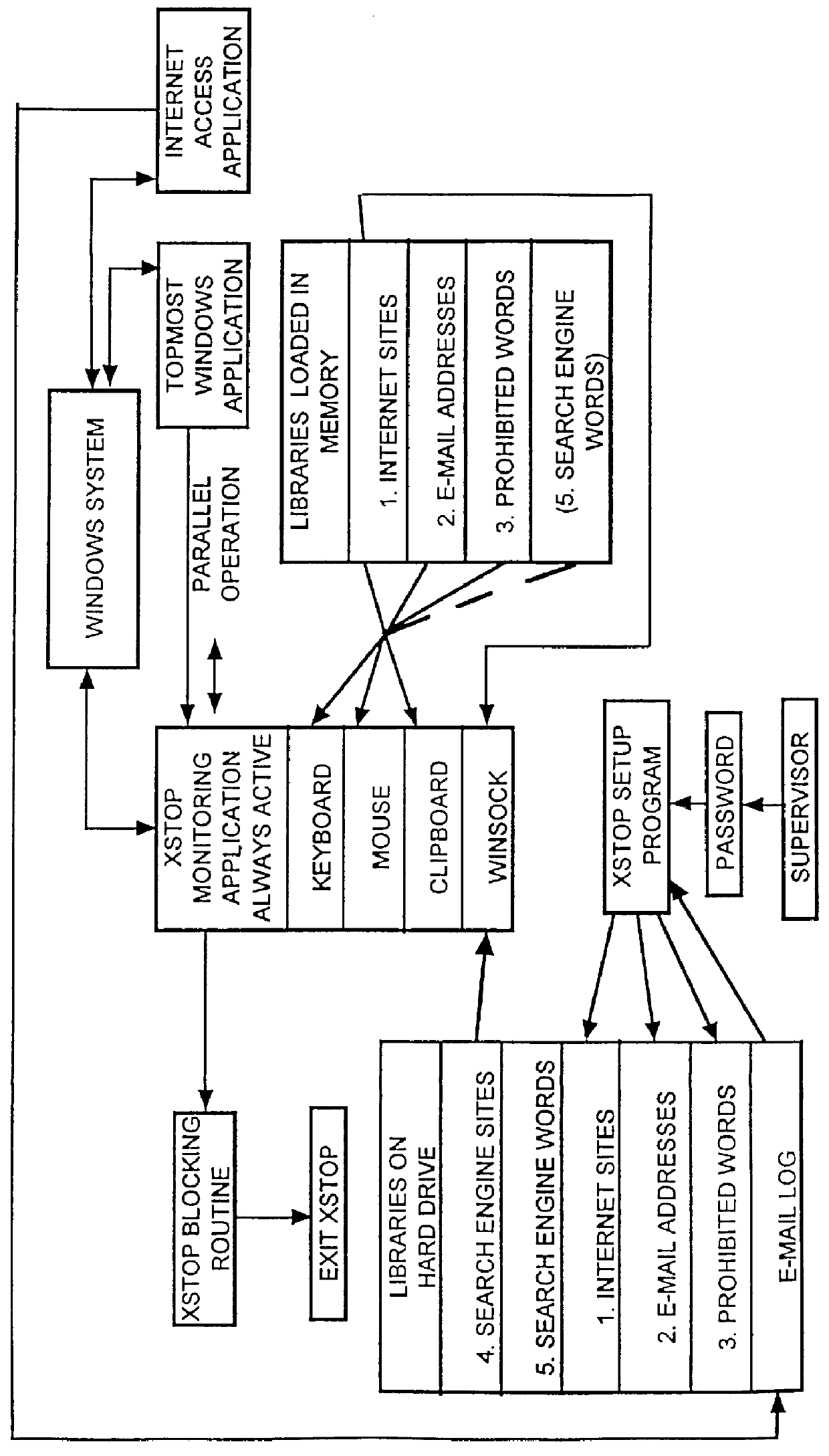
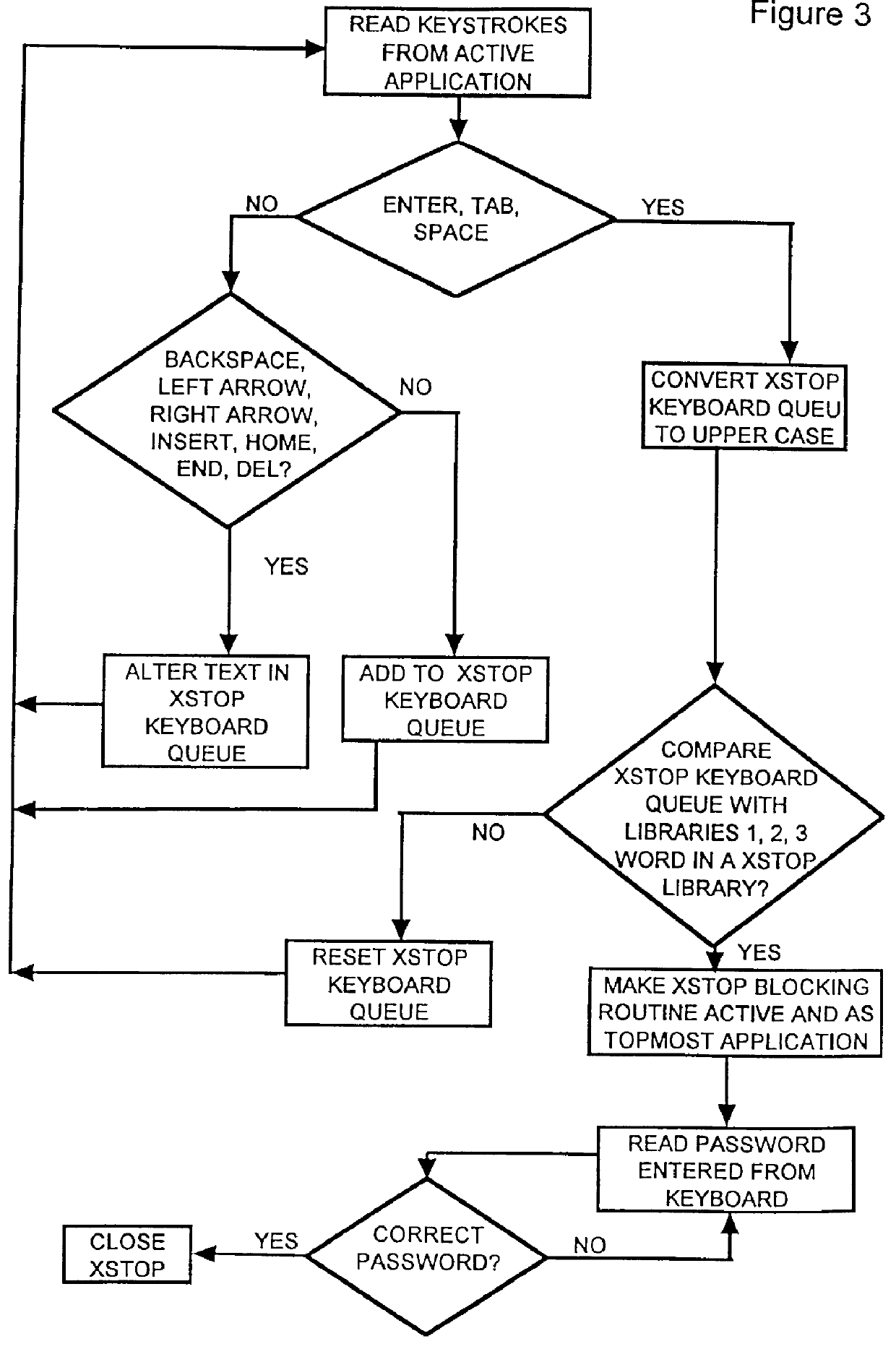
System to control content and prohibit certain interactive attempts by a person using a personal computer
InactiveUS6065056AReduce usageAvoid spreadingDigital data information retrievalMultiple digital computer combinationsPasswordWord search
A computer, terminal and a method for blocking the use and creating of vulgar and pornographic material in a responsive and interactive matter that comprehensively monitors computer operations for creation or transmission of vulgar and pornographic material. Data created by the keyboard, data passing through the clipboard, data selected by the mouse pointer, and data passing through the Internet interface are monitored for content and further operation of the computer terminal is blocked. The computer terminal may only be unblocked by a supervisory intervention, such as by entering of a password, or by restarting or resetting the terminal. Key word searches, such as those in Internet search engines, are also monitored, but the terminal adapts to monitor not only for words of a profane and vulgar nature, but also for words that are behaviorally tested to produce lists containing vulgar and profane items, e.g., Internet sites. The computer terminal and method can be modified to block other forms of communication or computer operation, such as blocking transmission of secret business data, blocking execution or opening of certain programs or files, and the like.
Owner:TW SECURITY CORP
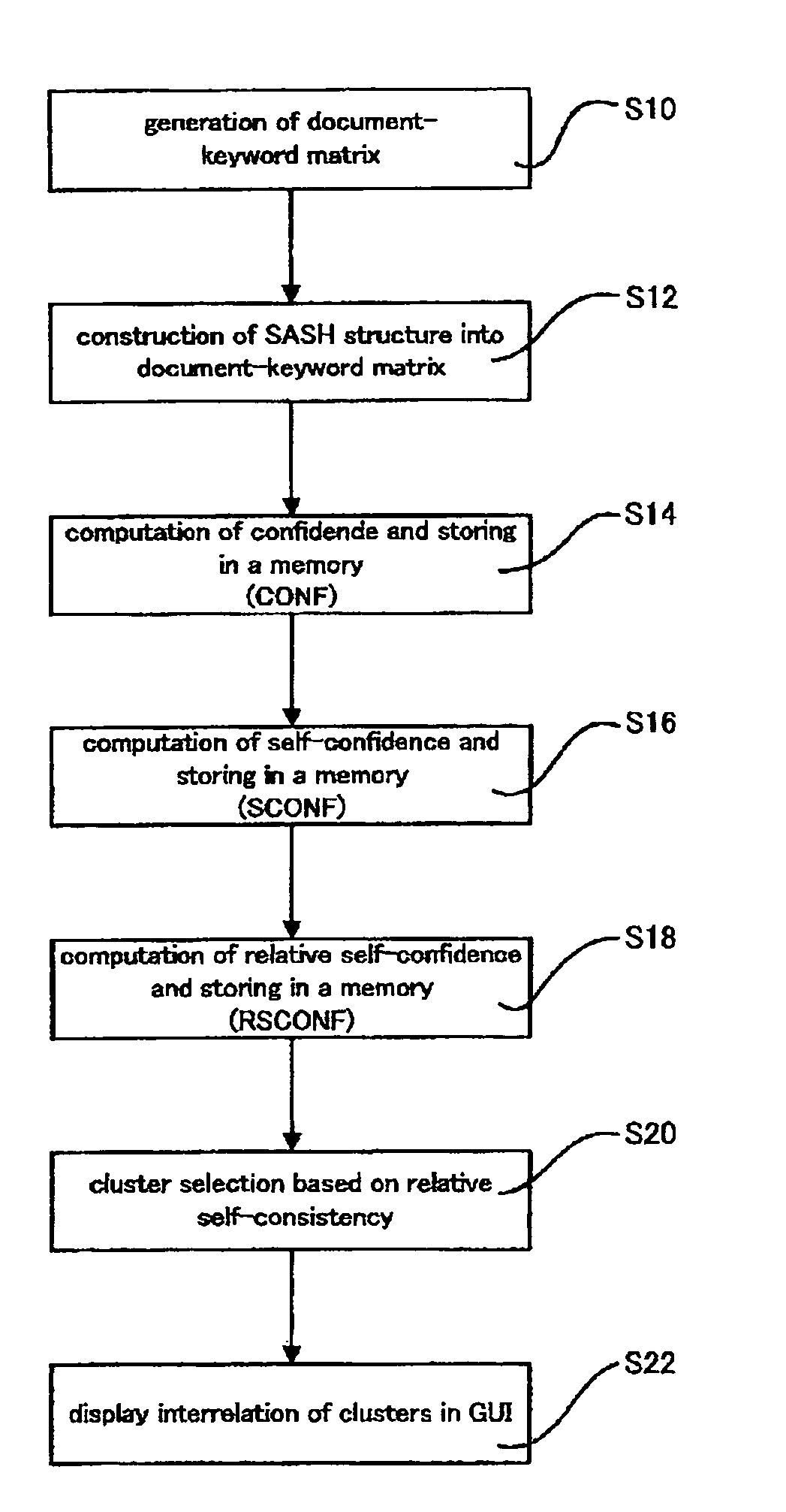
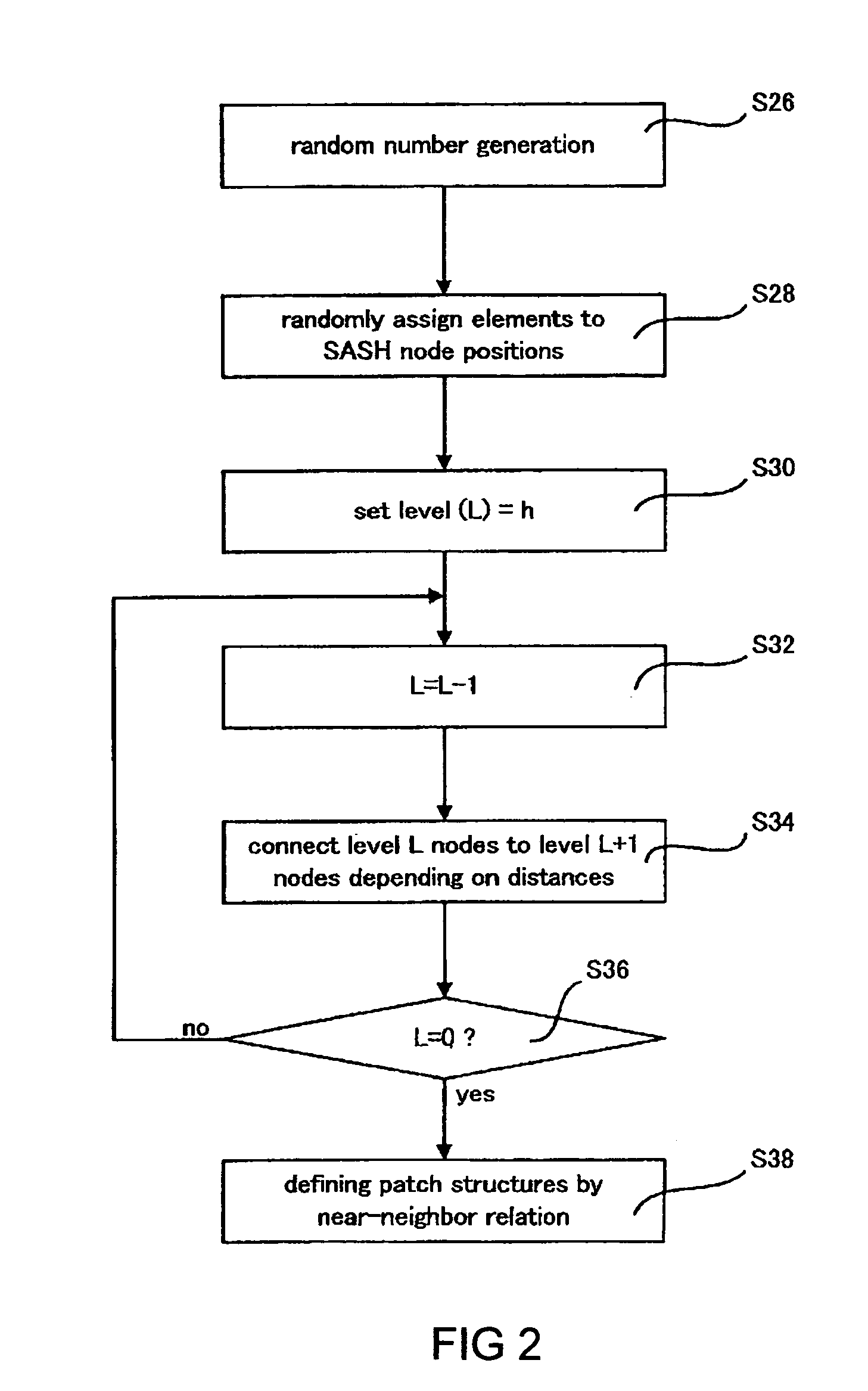
Computer system, method, and program product for generating a data structure for information retrieval, and an associated graphical user interface
InactiveUS7428541B2Improve scalabilityImprove detection efficiencyData processing applicationsSpeech recognitionClustered dataGraphics
A computer system for generating data structures for information retrieval of documents stored in a database. The computer system includes: a neighborhood patch generation system for defining patch of nodes having predetermined similarities in a hierarchy structure. The neighborhood patch generation subsystem includes a hierarchy generation subsystem for generating a hierarchy structure upon the document-keyword vectors and a patch definition subsystem. The computer system also comprises a cluster estimation subsystem for generating cluster data of the document-keyword vectors using the similarities of patches.
Owner:IBM CORP
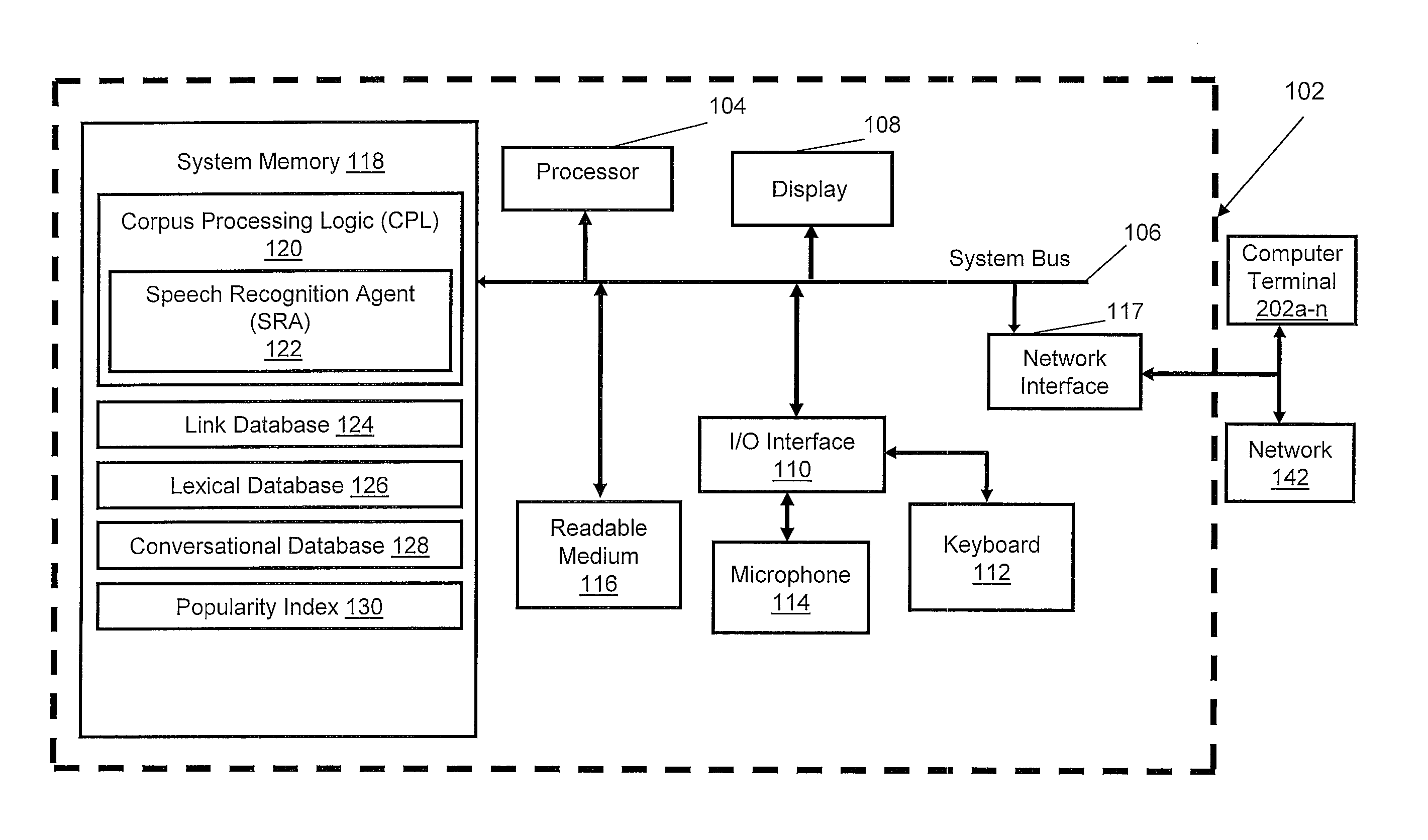
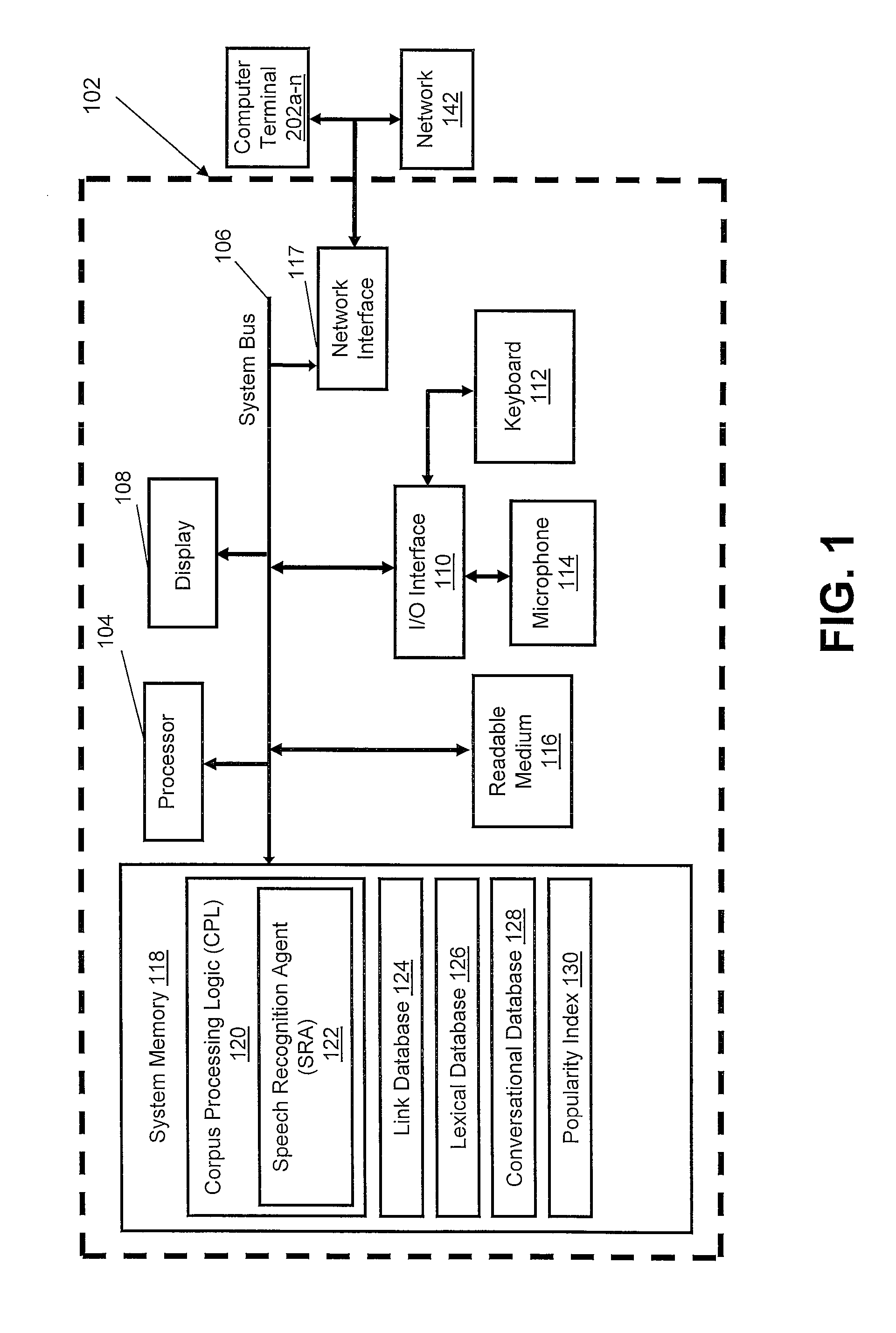
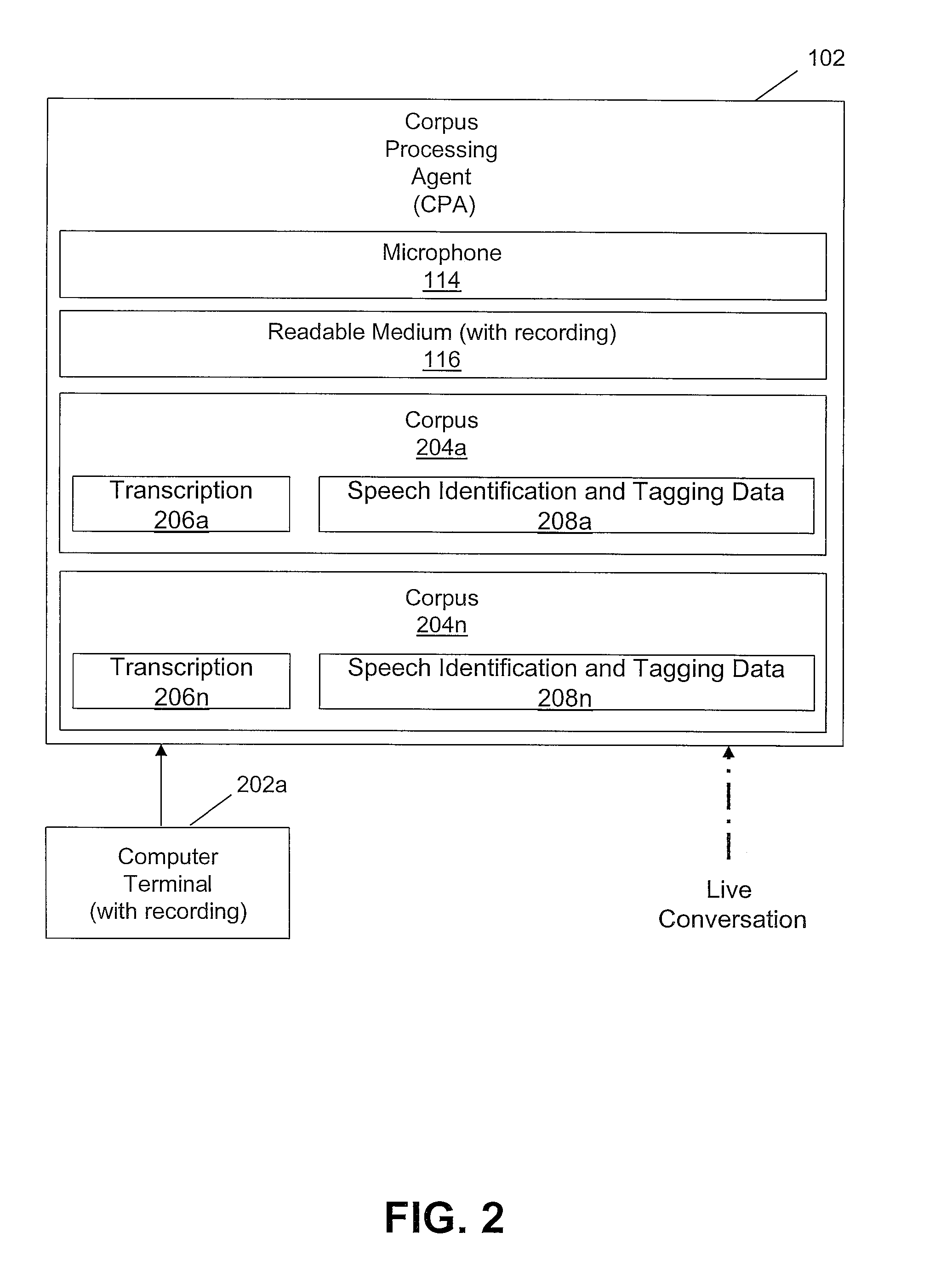
Data processing system for autonomously building speech identification and tagging data
ActiveUS20090306979A1Natural language data processingSpeech recognitionSpoken languageSpeech identification
A method, system, and computer program product for autonomously transcribing and building tagging data of a conversation. A corpus processing agent monitors a conversation and utilizes a speech recognition agent to identify the spoken languages, speakers, and emotional patterns of speakers of the conversation. While monitoring the conversation, the corpus processing agent determines emotional patterns by monitoring voice modulation of the speakers and evaluating the context of the conversation. When the conversation is complete, the corpus processing agent determines synonyms and paraphrases of spoken words and phrases of the conversation taking into consideration any localized dialect of the speakers. Additionally, metadata of the conversation is created and stored in a link database, for comparison with other processed conversations. A corpus, a transcription of the conversation containing metadata links, is then created. The corpus processing agent also determines the frequency of spoken keywords and phrases and compiles a popularity index.
Owner:NUANCE COMM INC
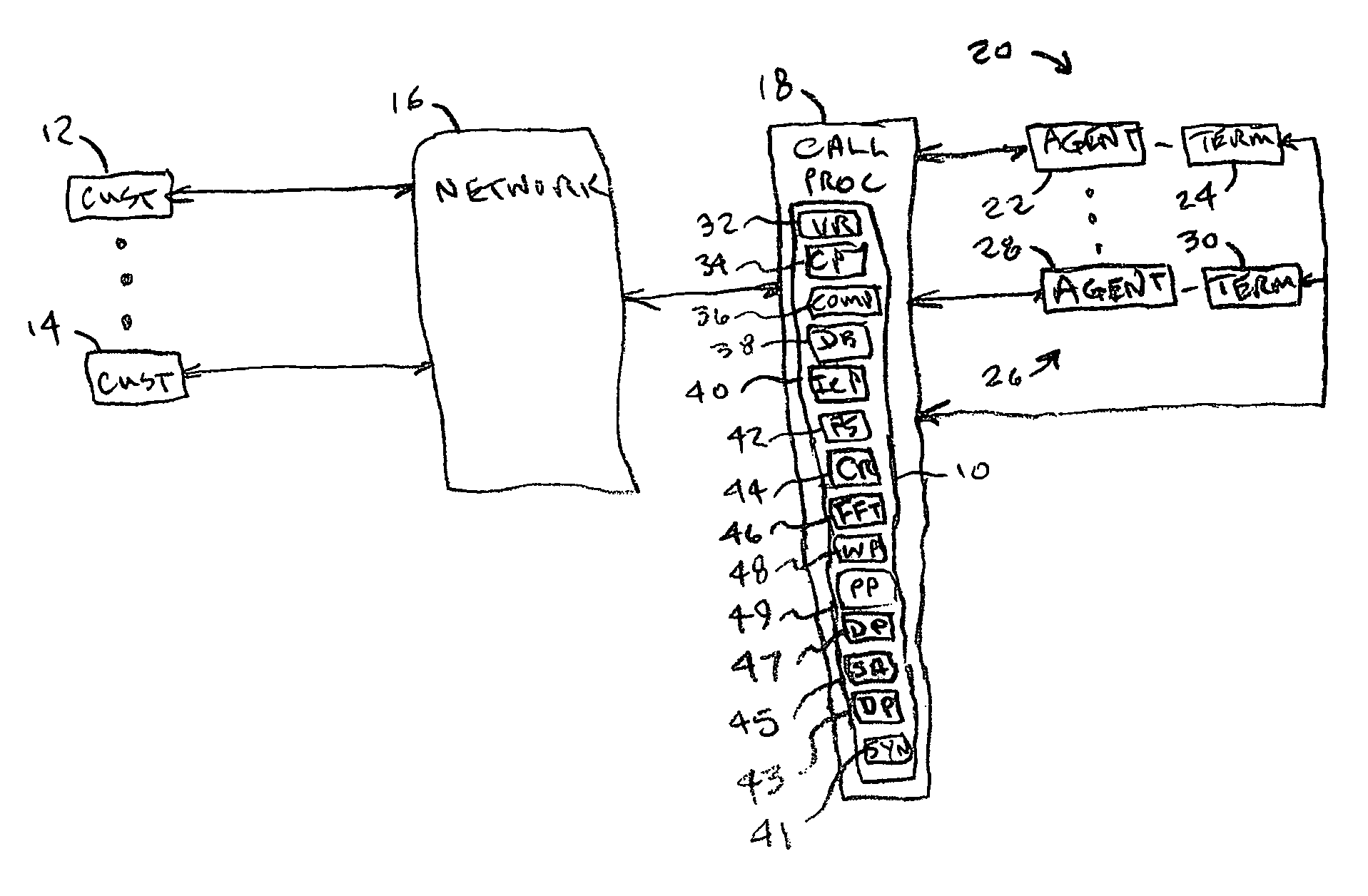
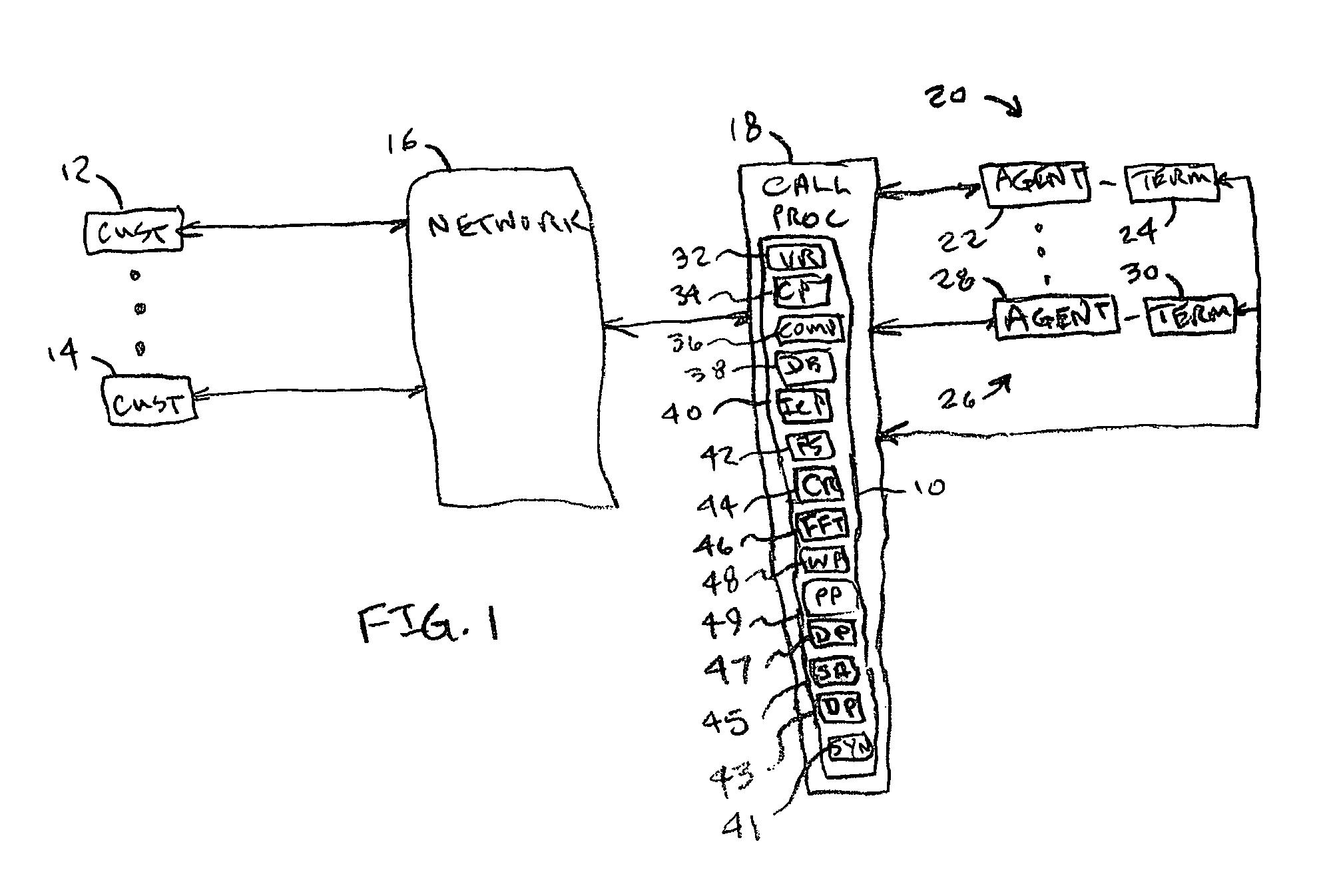
Method of creating scripts by translating agent/customer conversations
InactiveUS6970821B1Semantic analysisAutomatic call-answering/message-recording/conversation-recordingClose relativesKnowledge management
Owner:WILMINGTON TRUST NAT ASSOC AS ADMINISTATIVE AGENT +1
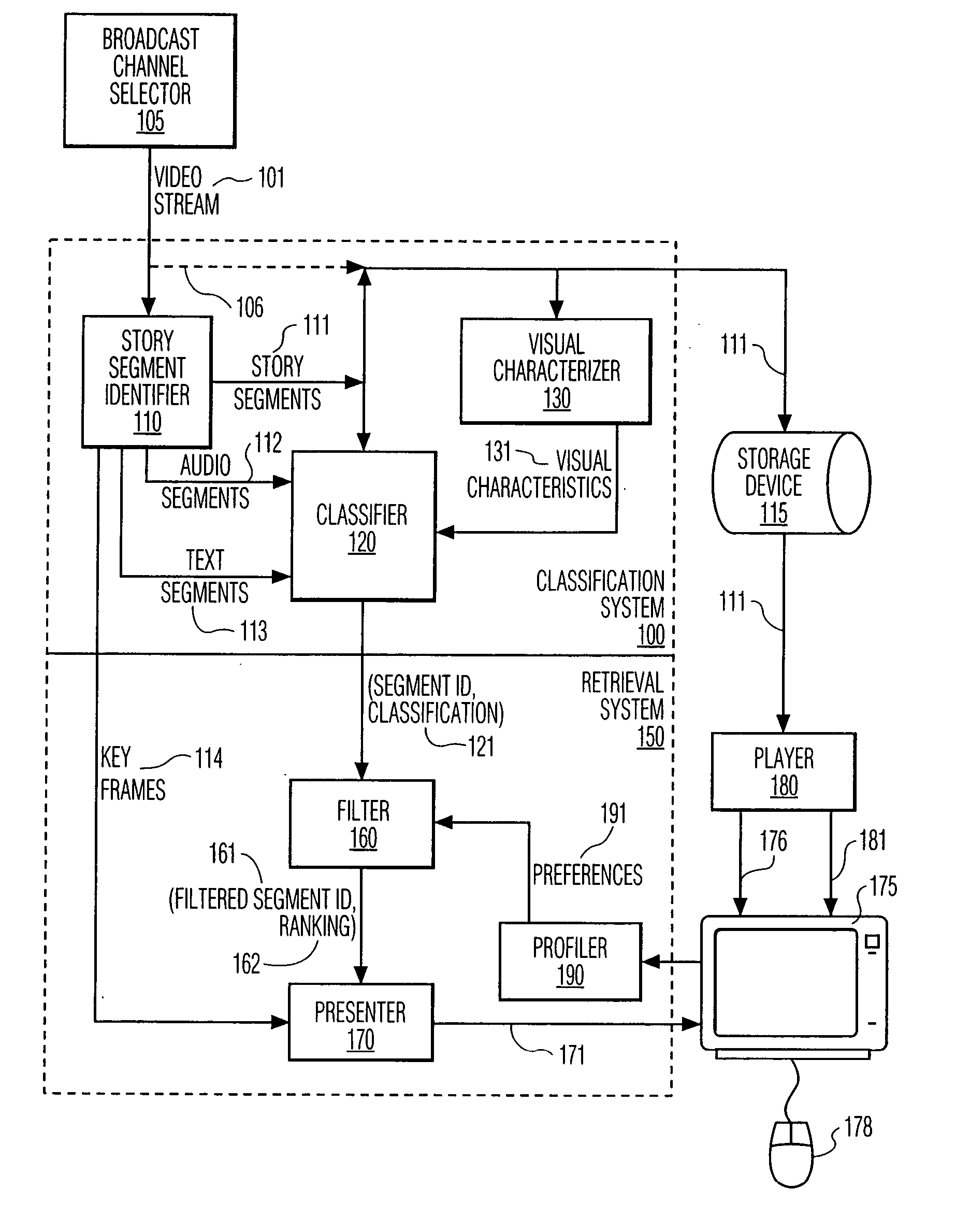
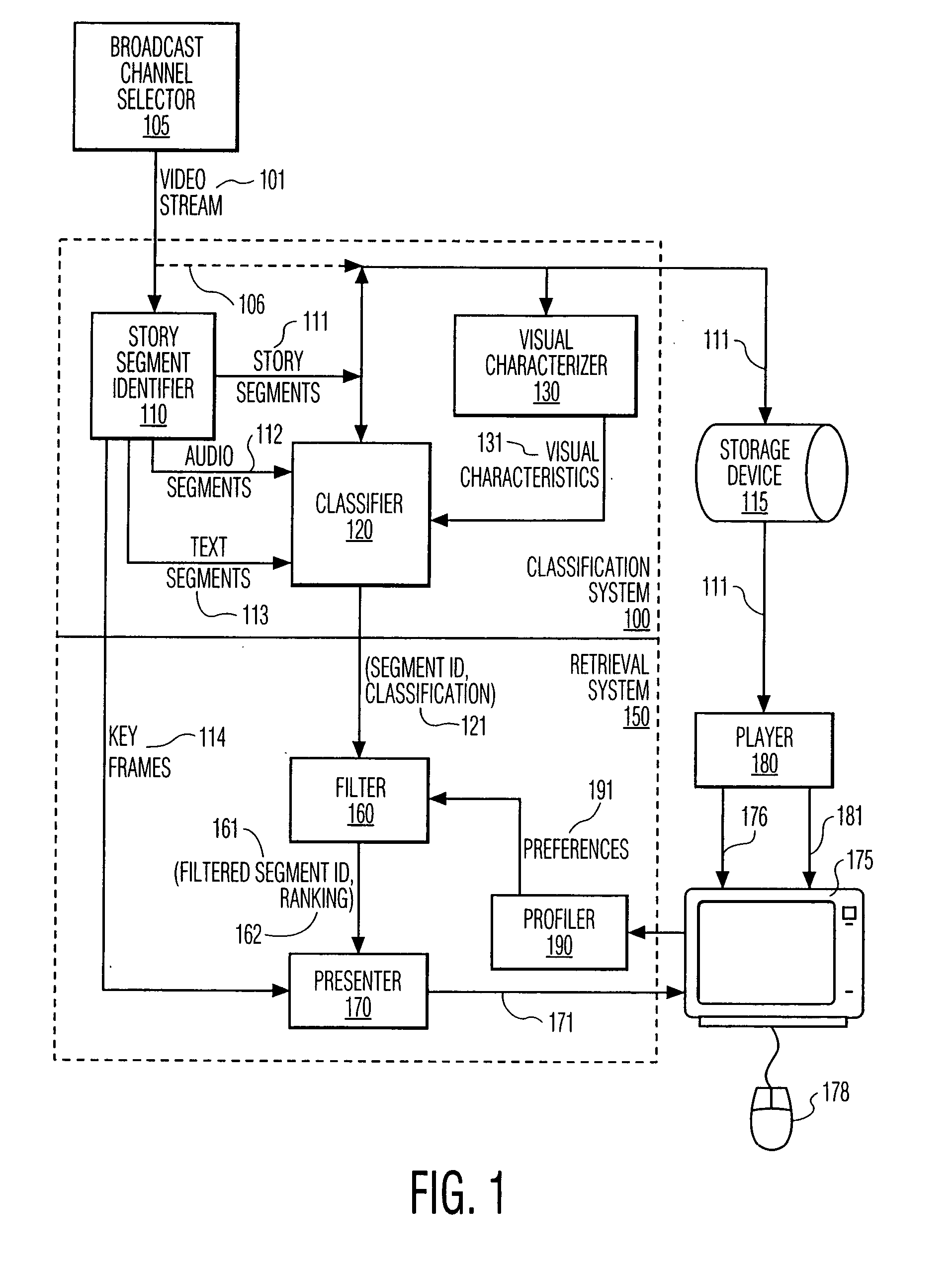
Personalized news retrieval system
InactiveUS20050028194A1Good suitQuickly and easily select and receiveTelevision system detailsDigital data processing detailsPersonalizationVideo retrieval
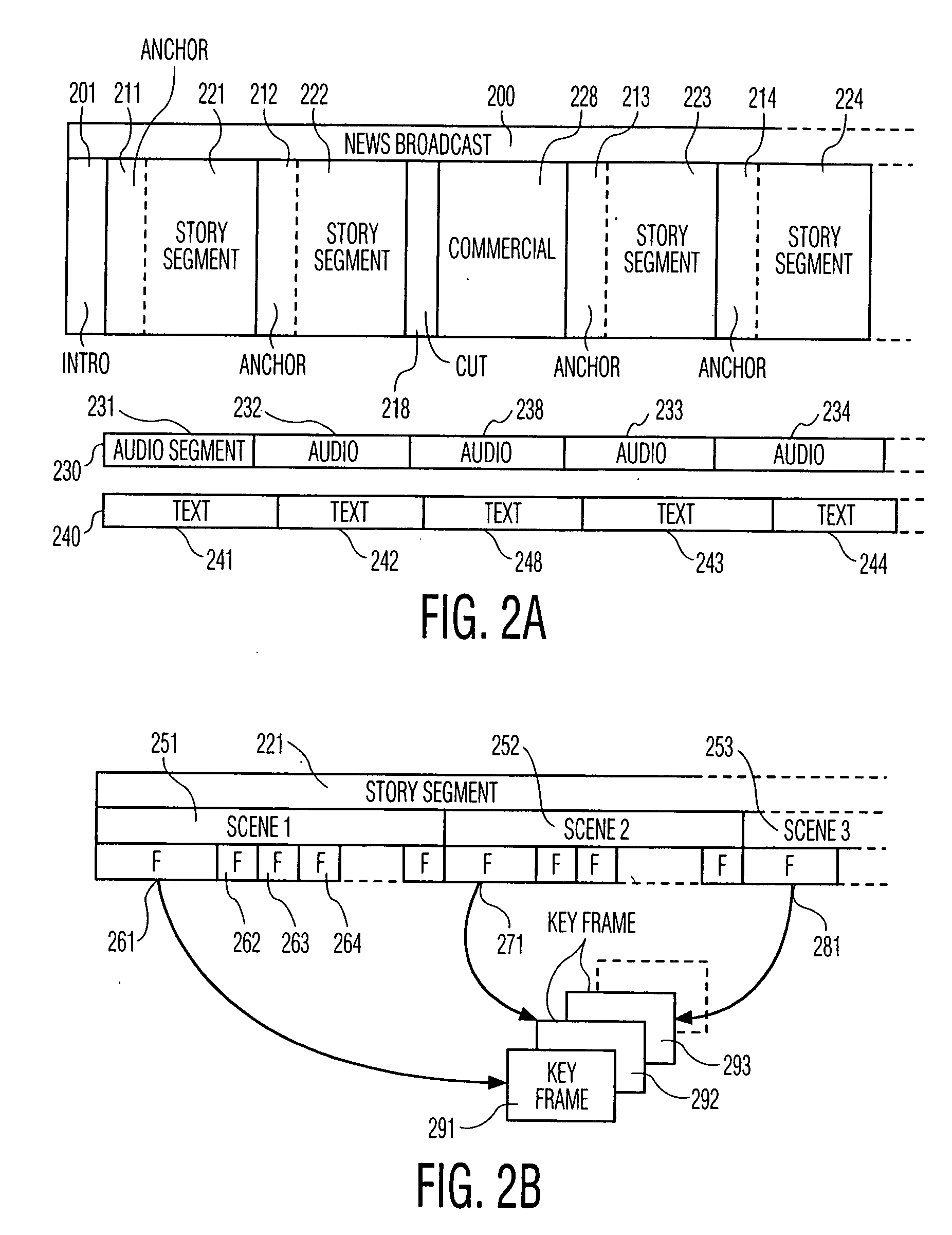
A video retrieval system is presented that allows a user to quickly and easily select and receive stories of interest from a video stream. The video retrieval system classifies stories and delivers samples of selected stories that match each user's current preference. The user's preferences may include particular broadcast networks, persons, story topics, keywords, and the like. Key frames of each selected story are sequentially displayed; when the user views a frame of interest, the user selects the story that is associated with the key frame for more detailed viewing. This invention is particularly well suited for targeted news retrieval. In a preferred embodiment, news stories are stored, and the selection of a news story for detailed viewing based on the associated key frames effects a playback of the selected news story. The principles of this invention also allows a user to effect a directed search of other types of broadcasts as well. For example, the user may initiate an automated scan that presents samples of broadcasts that conform to the user's current preferences, akin to directed channel-surfing.
Owner:ELENBAAS JAN HERMANUS +9
Methods and devices for analyzing user privacy based on a user's online presence
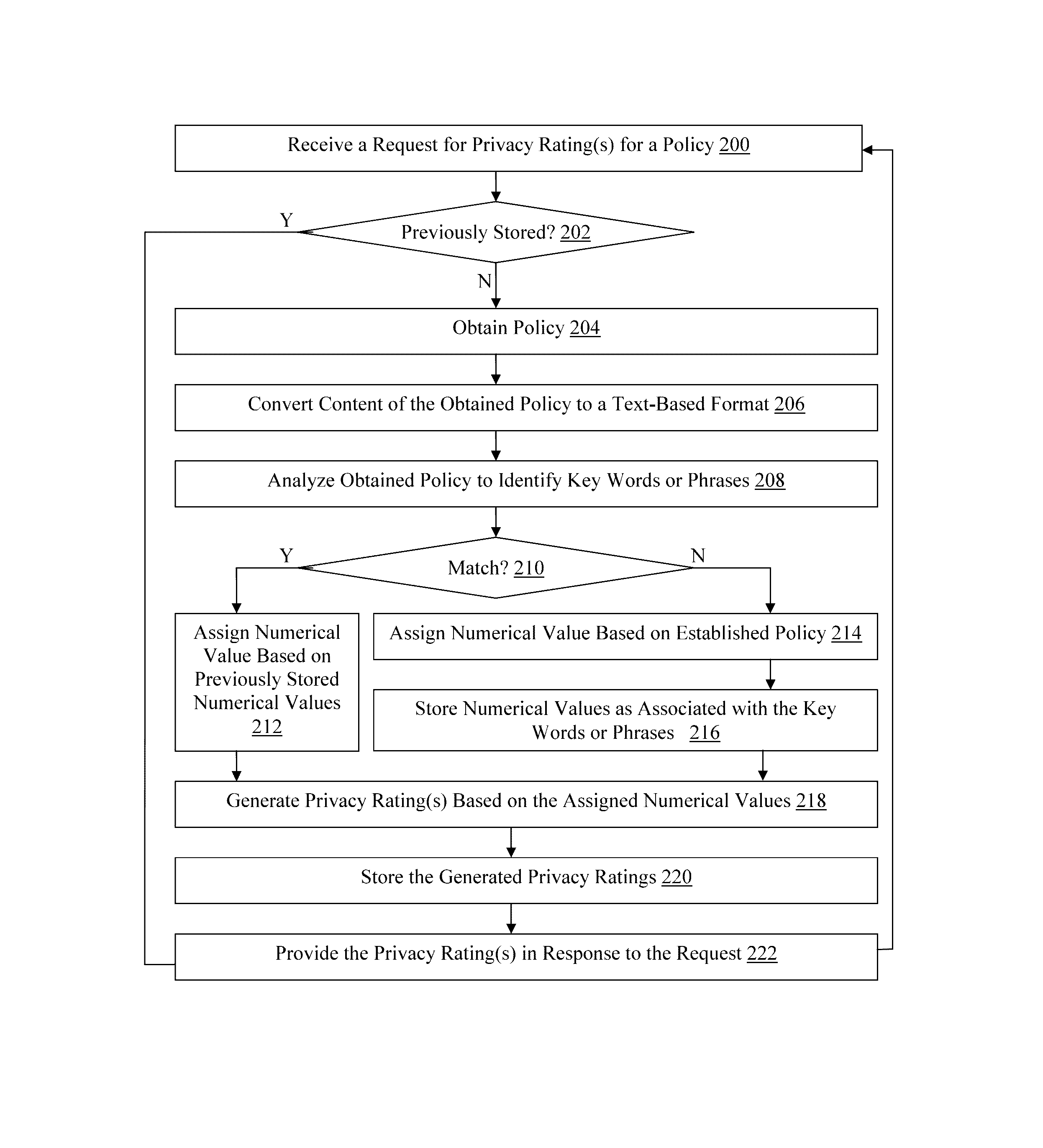
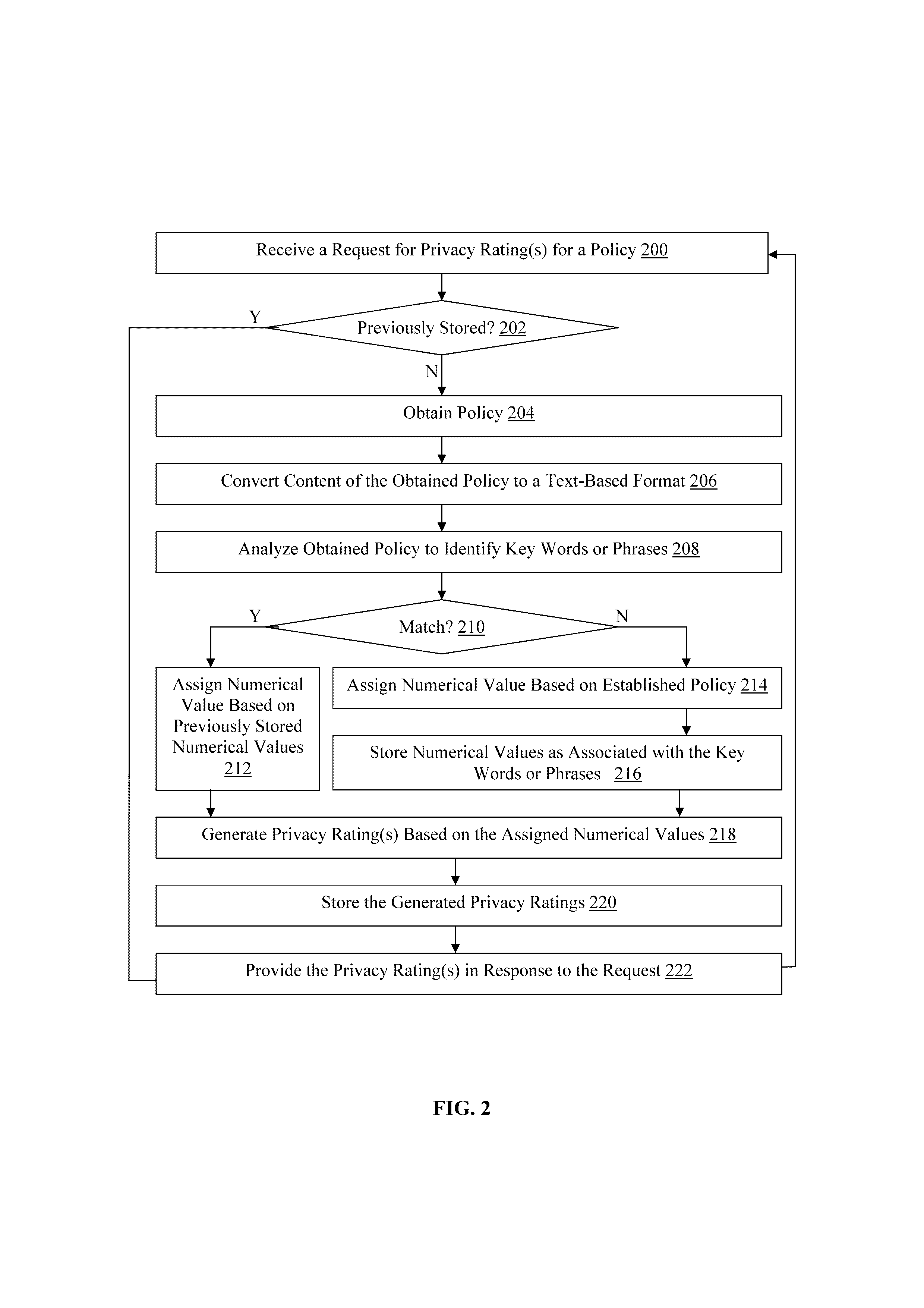
A method, non-transitory computer readable medium, and policy rating server device that receives a request from a client computing device for one or more privacy ratings. The request identifies at least one application, such as an application installed on the client computing device for example. A policy associated with the identified application is obtained. The obtained policy is analyzed to identify a plurality of key words or phrases associated with use by the at least one application of functionality of, or personal information stored on, the client computing device. One or more privacy ratings are generated based on numerical values assigned to each of the identified key words or phrases. The generated one or more privacy ratings are output to the client computing device in response to the request.
Owner:THE PRIVACY FACTOR
System and method for associating documents with contextual advertisements
InactiveUS20050080775A1Special service provision for substationDigital data processing detailsPaper documentDocument preparation
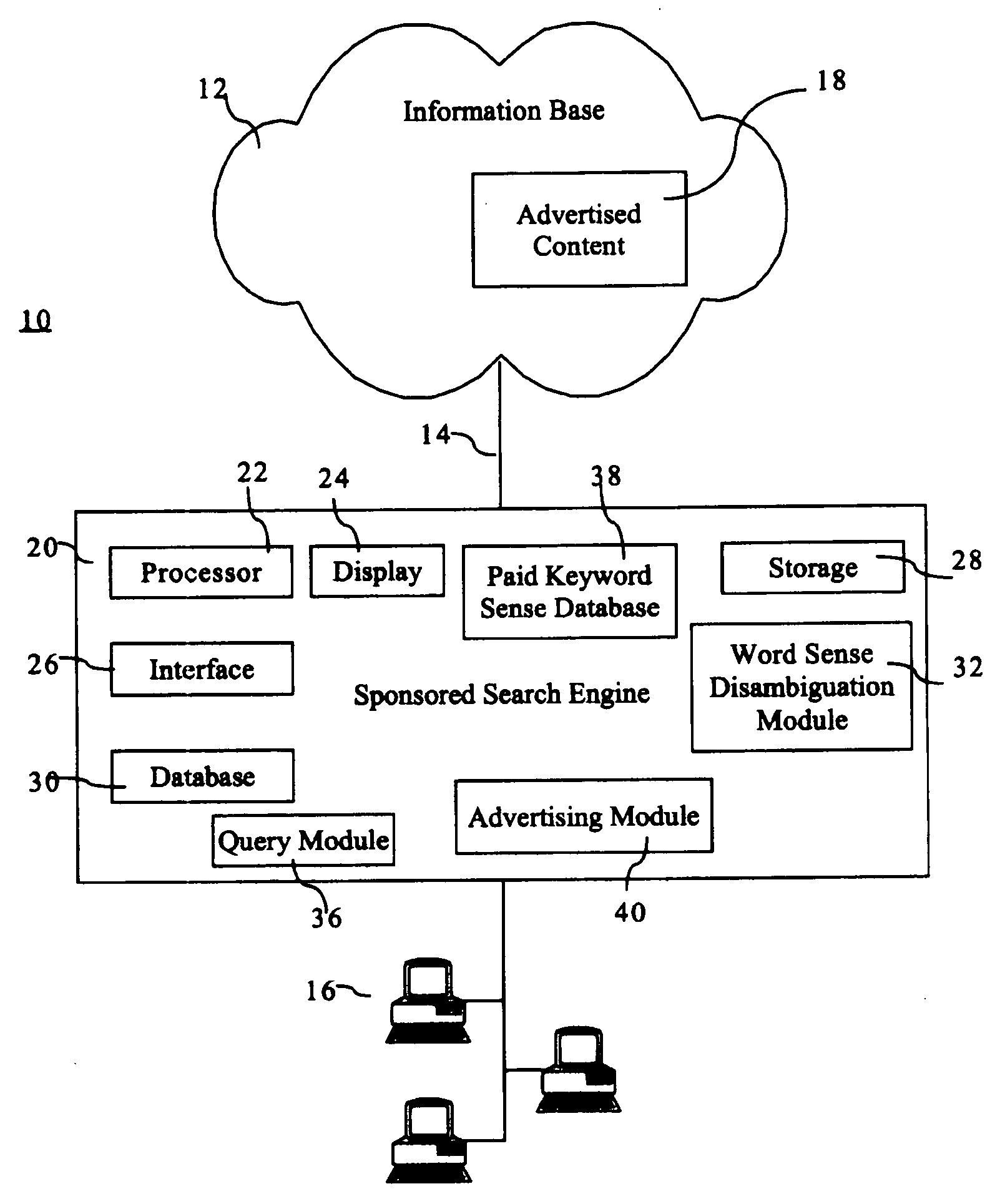
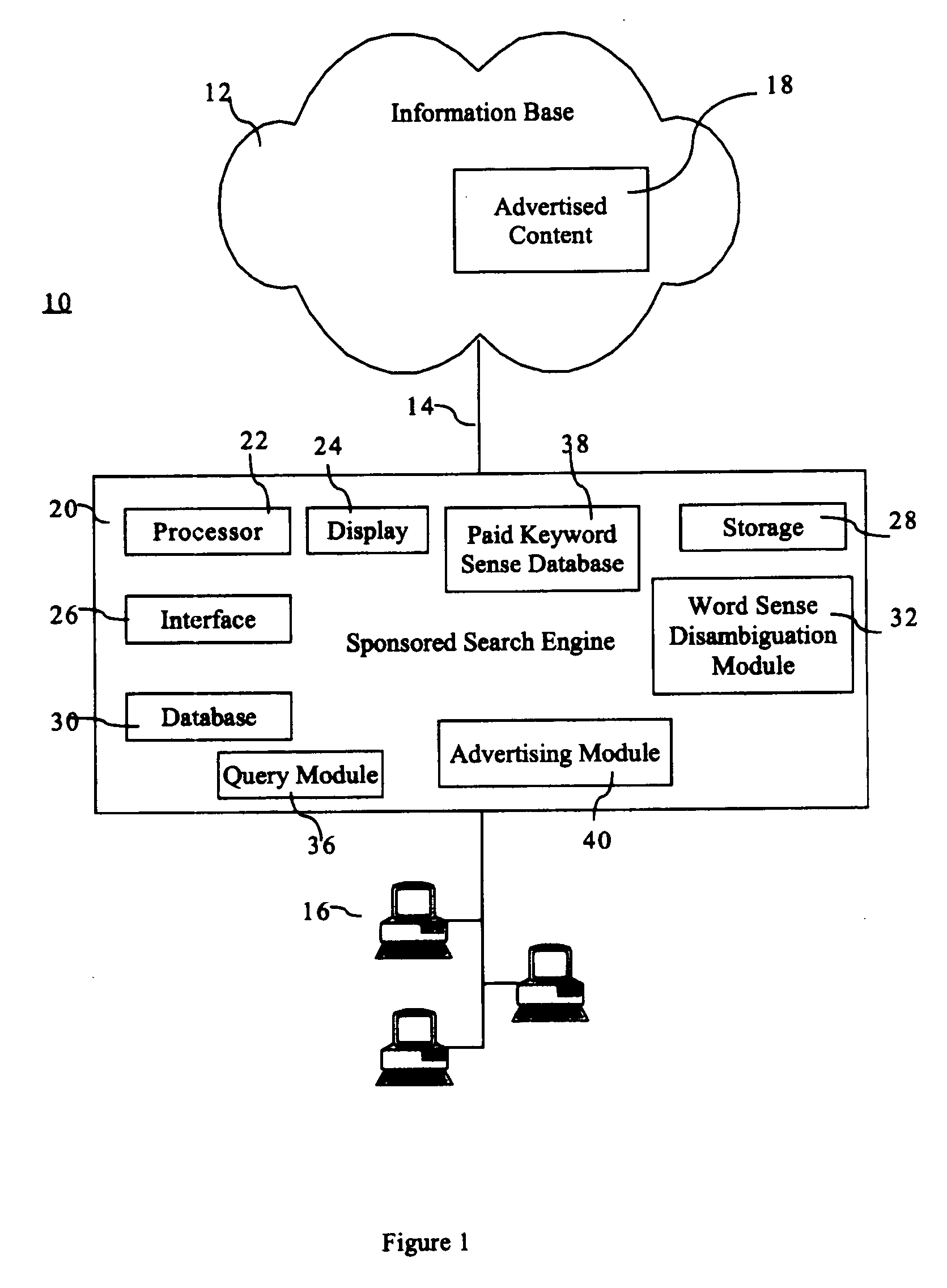
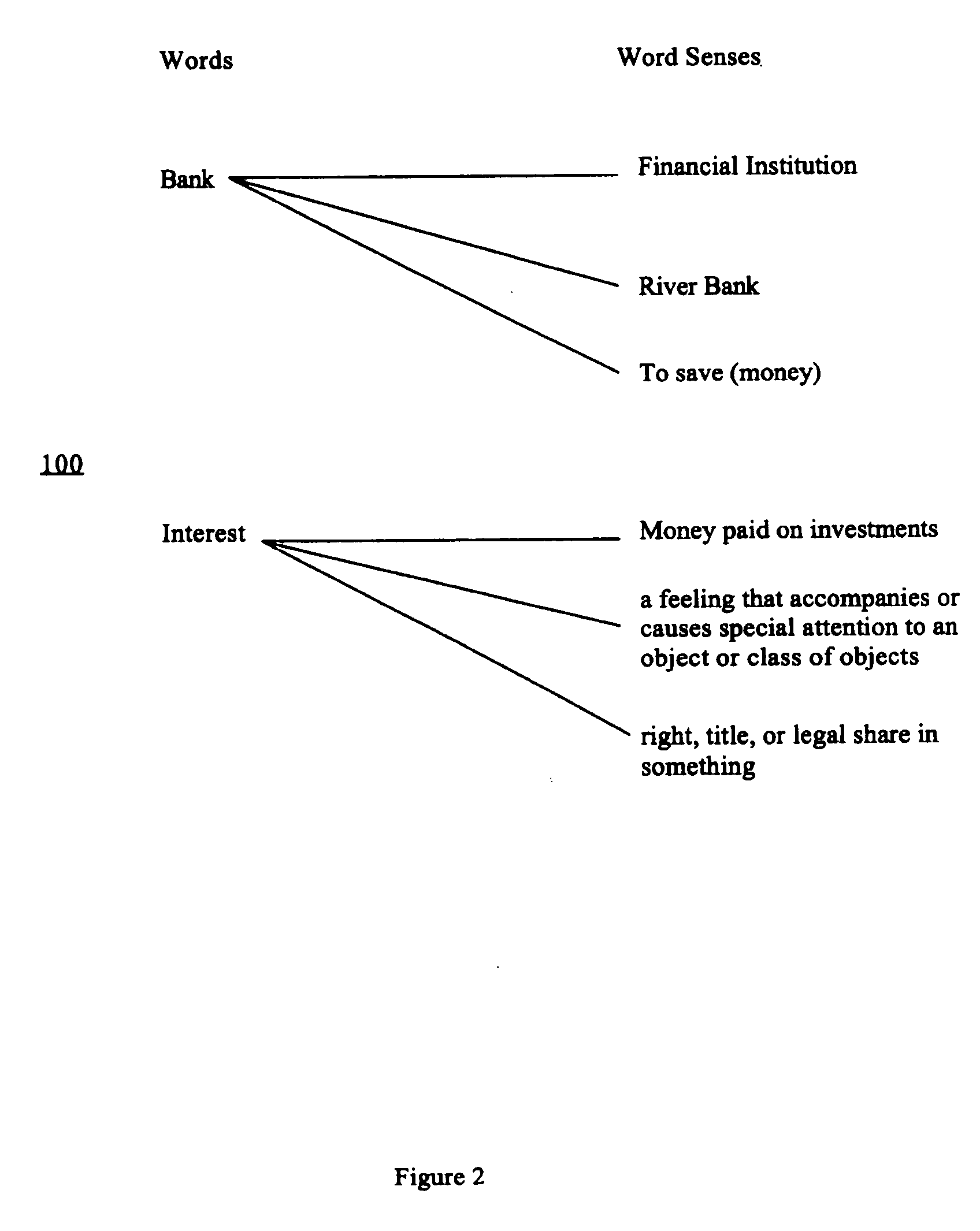
The invention provides a system and method of associating results from a query from a user directed to a search engine to advertisements associated with the search engine. In the method, there are the steps of: obtaining advertisement keyword senses associated with the advertisements; disambiguating the query to identify query keyword senses associated with the query; expanding the query keyword senses to include relevant semantic synonyms for the query keyword senses to create a list of expanded query keyword senses; using the expanded keyword senses to search the advertisement keyword senses to locate relevant advertisements correlating to the query; and providing the relevant advertisements to the user. The system incorporates modules conducting steps of the method.
Owner:IDILIA
Data security system and method adjunct to e-mail, browser or telecom program
InactiveUS7191252B2Ease overhead performanceHigh overhead performanceDigital data processing detailsUser identity/authority verificationCredit cardInternet privacy
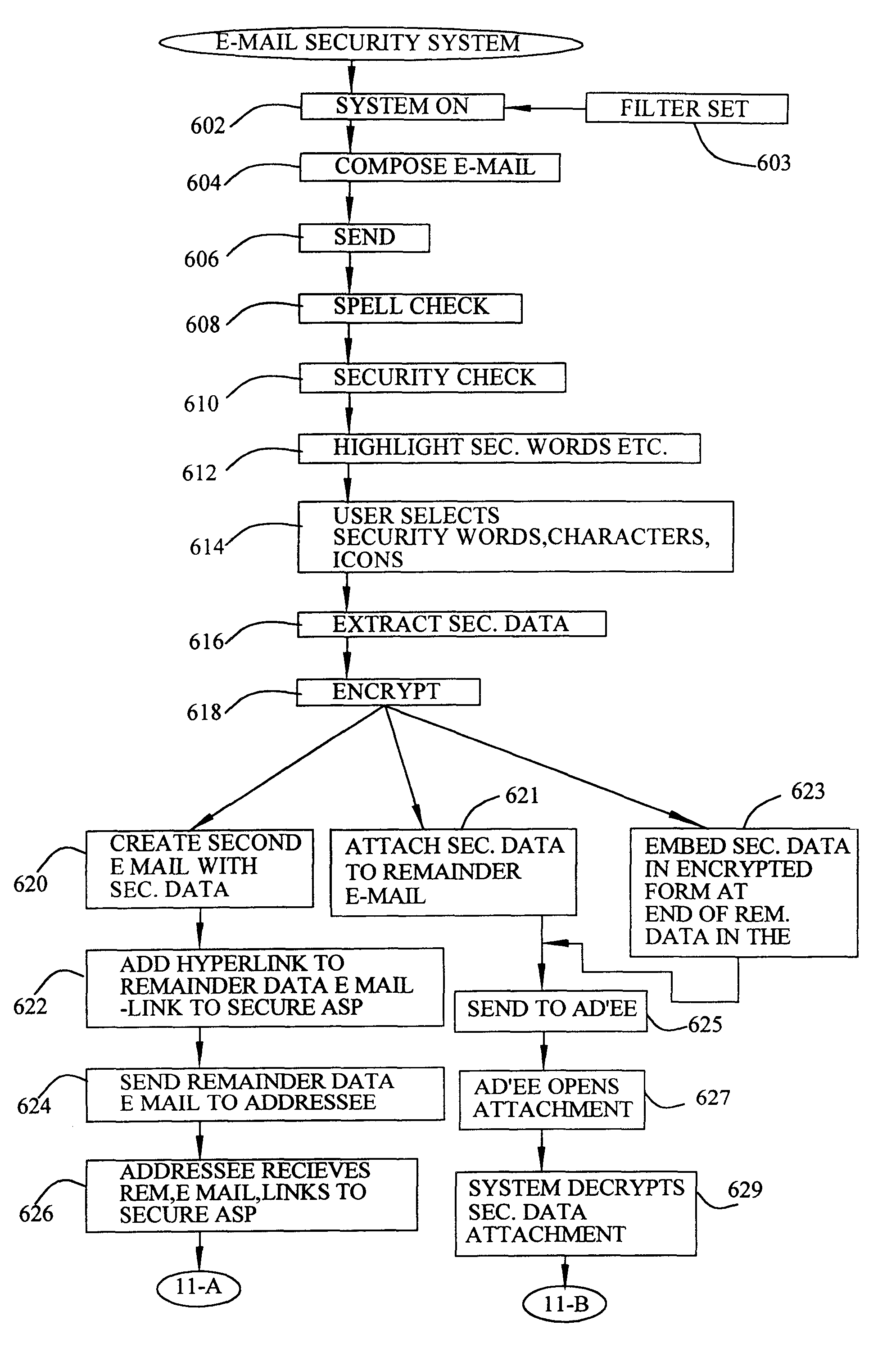
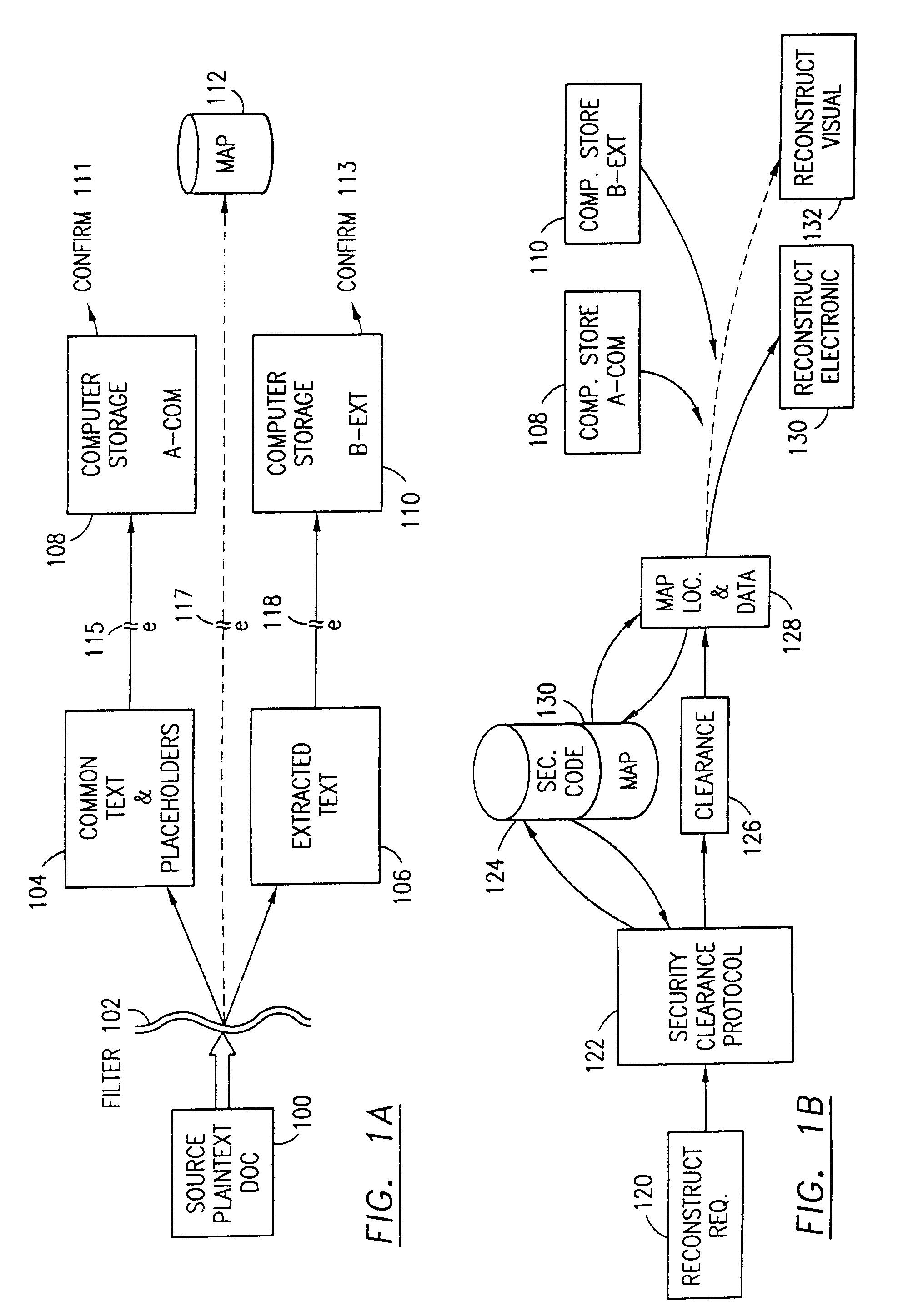
Data security for e-mail or browser-input data operates on identified security sensitive words, characters or icons which are extracted leaving remainder data. Extracted data, in one system, is stored in a remote, extract store in a distributed computer system. Other methods attach an encrypted version of the extract to the email. The browser system operates with an extract store. Remainder data is sent to the addressee or designated web server. The addressee is permitted to retrieve the extracted data from said extract store only in the presence of a security clearance and hence, reconstruct the source e-mail or browser-input data with the extract data. In other systems, the addressee reconstructs the email by decryption and integration. Parsing rather than identifying critical words is an option. The browser method extracts data, facilitates the storage in an extract store, forwards the remainder data to a targeted destination. The financial data or credit card scrubber may use a pop-up window to alert the user to enable the system.
Owner:DIGITAL DOORS
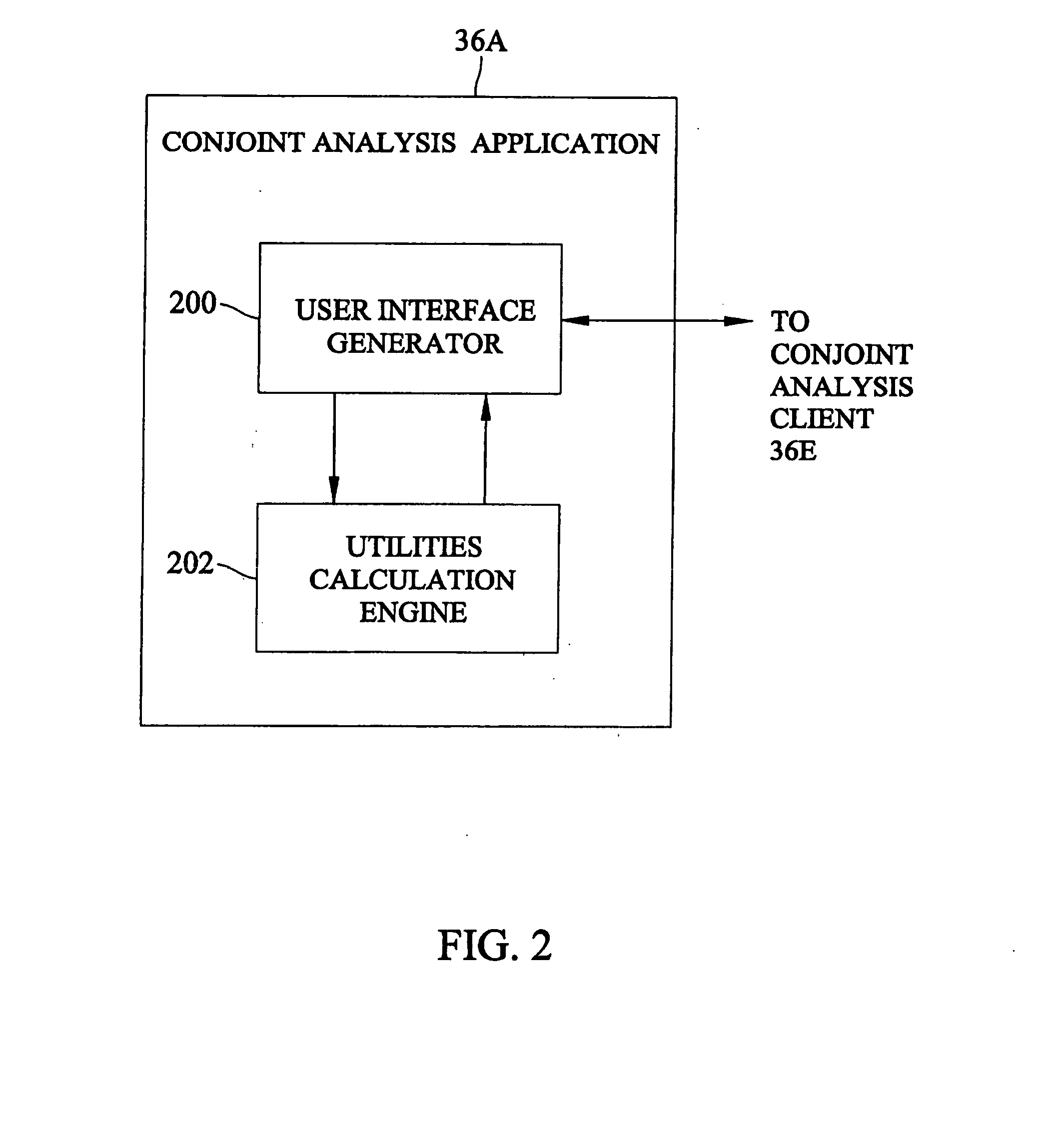
Methods, systems, and computer program products for facilitating user interaction with customer relationship management, auction, and search engine software using conjoint analysis
ActiveUS20070233730A1Facilitate user interactionDifficult to makeDigital data processing detailsMarketingConjoint analysisData mining
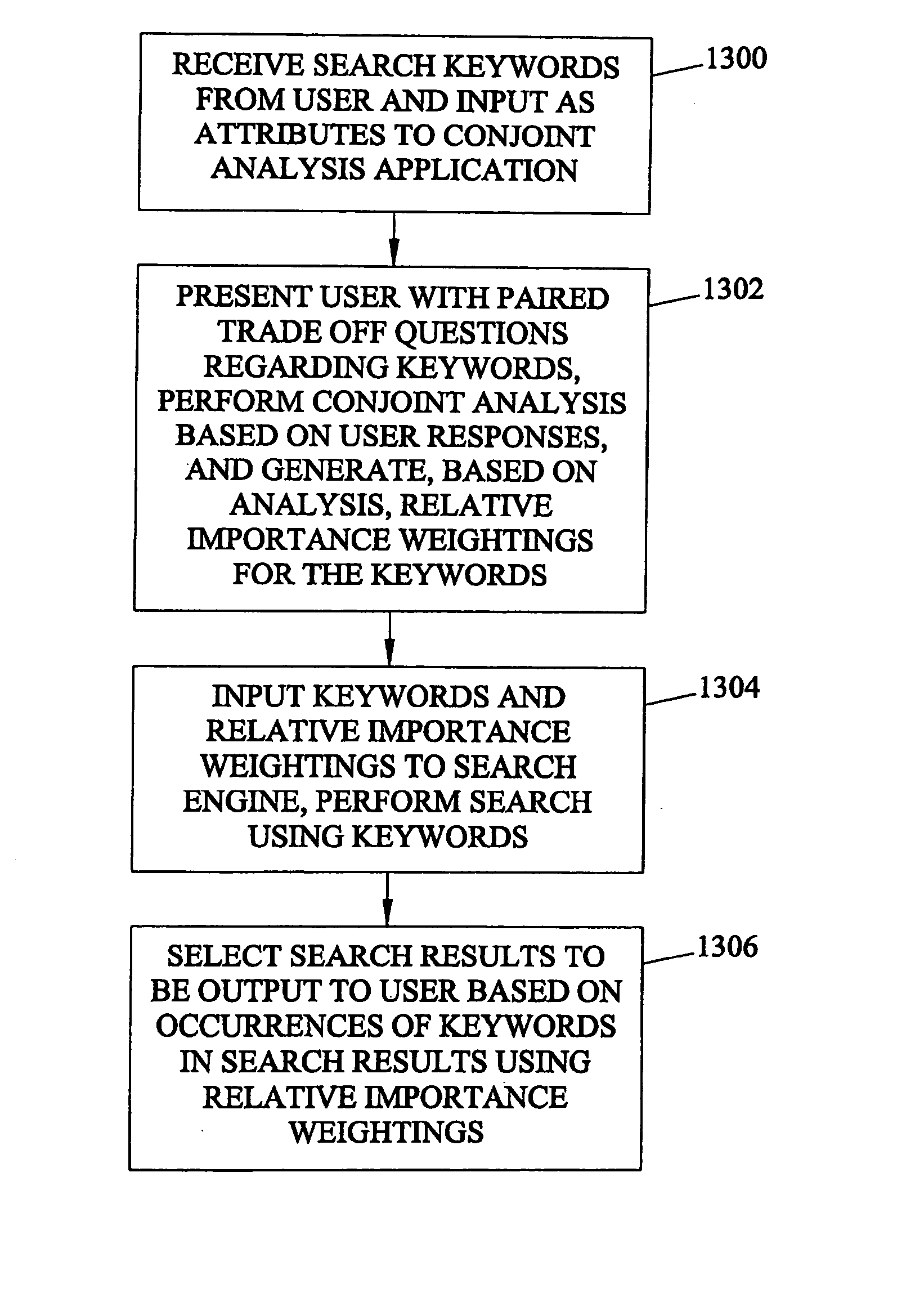
Methods, systems, and computer program products for combining conjoint analysis with customer relationship management software, search engine software, and auction software are disclosed. According to one method, conjoint analysis is used to facilitate user interaction with a search engine. According to the method, search keywords are received as a user and treated as attributes by a conjoint analysis application. The conjoint analysis application presents the user with paired trade-off questions regarding the search keywords. Conjoint analysis is performed based on user responses to the questions. Based on the user's responses to the questions, relative importance weightings are computed for keywords. The keywords and the relative importance weightings are input to a search engine. The search is performed using the keywords. Results to be output to the user are selected based on occurrences of the keywords in the search results and the relative importance weightings.
Owner:ADP
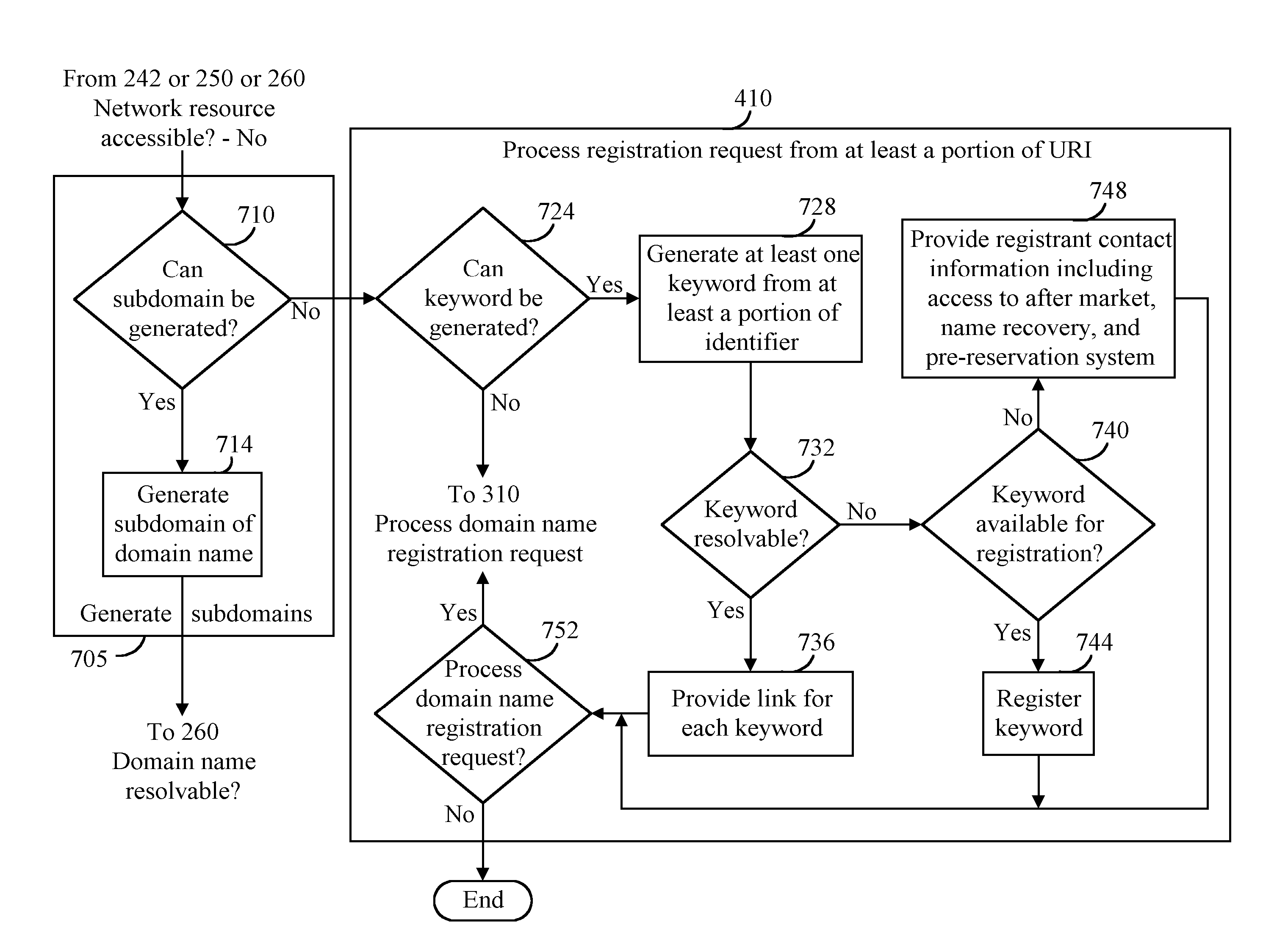
Method, product, and apparatus for requesting a network resource
InactiveUS8635340B1Easy to understandSaving distribution costMultiple digital computer combinationsTransmissionDomain nameIndex term
When a network resource request having a domain name is received, it is determined whether the network resource can be accessed from the domain name. Rather than displaying an error message or processing a search request in response to determining that a network resource can not be accessed, the domain name can instead be redirected to a registration service for domain names or keyword advertiser registration.
Owner:MEC MANAGEMENT LLC
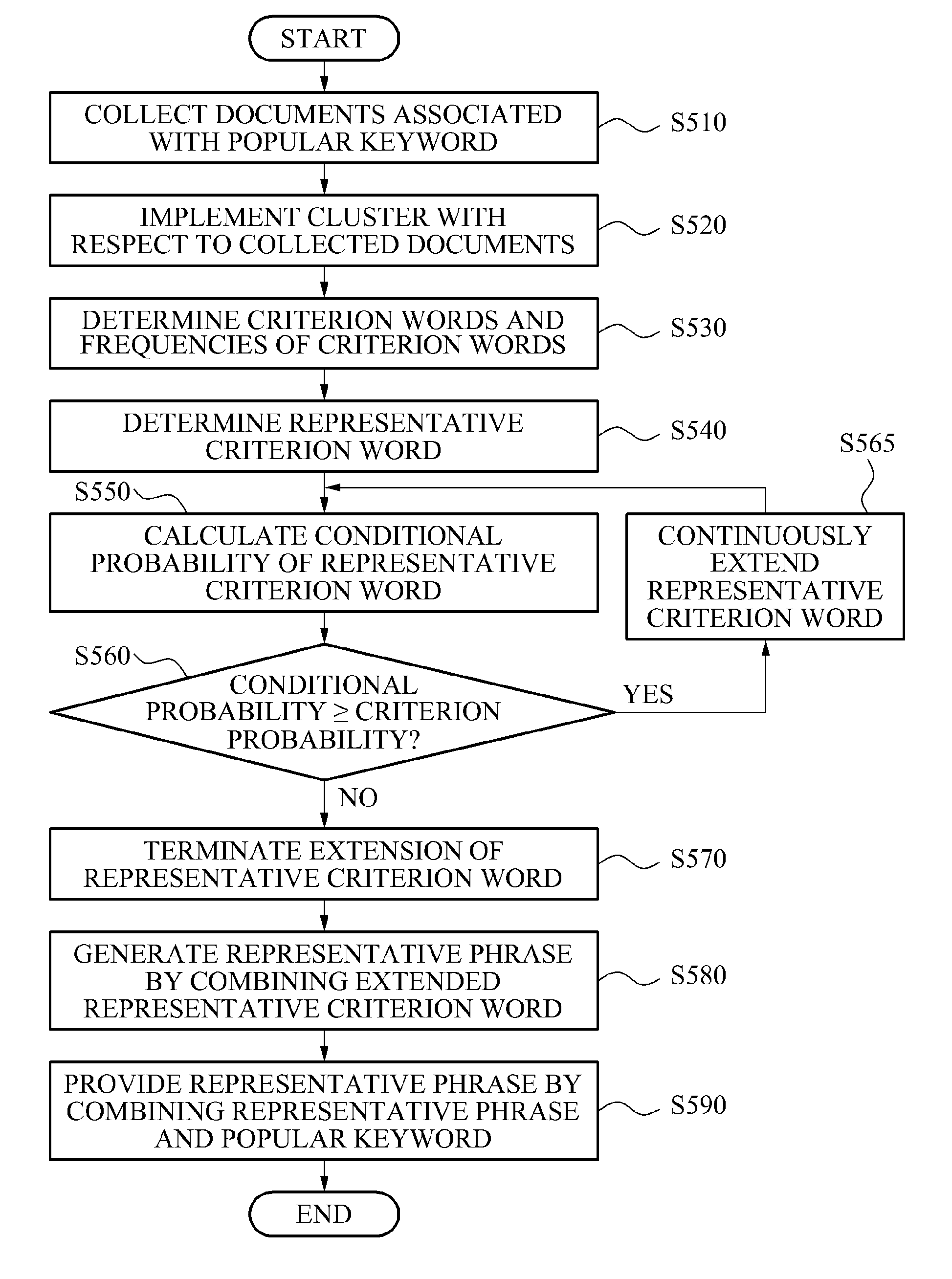
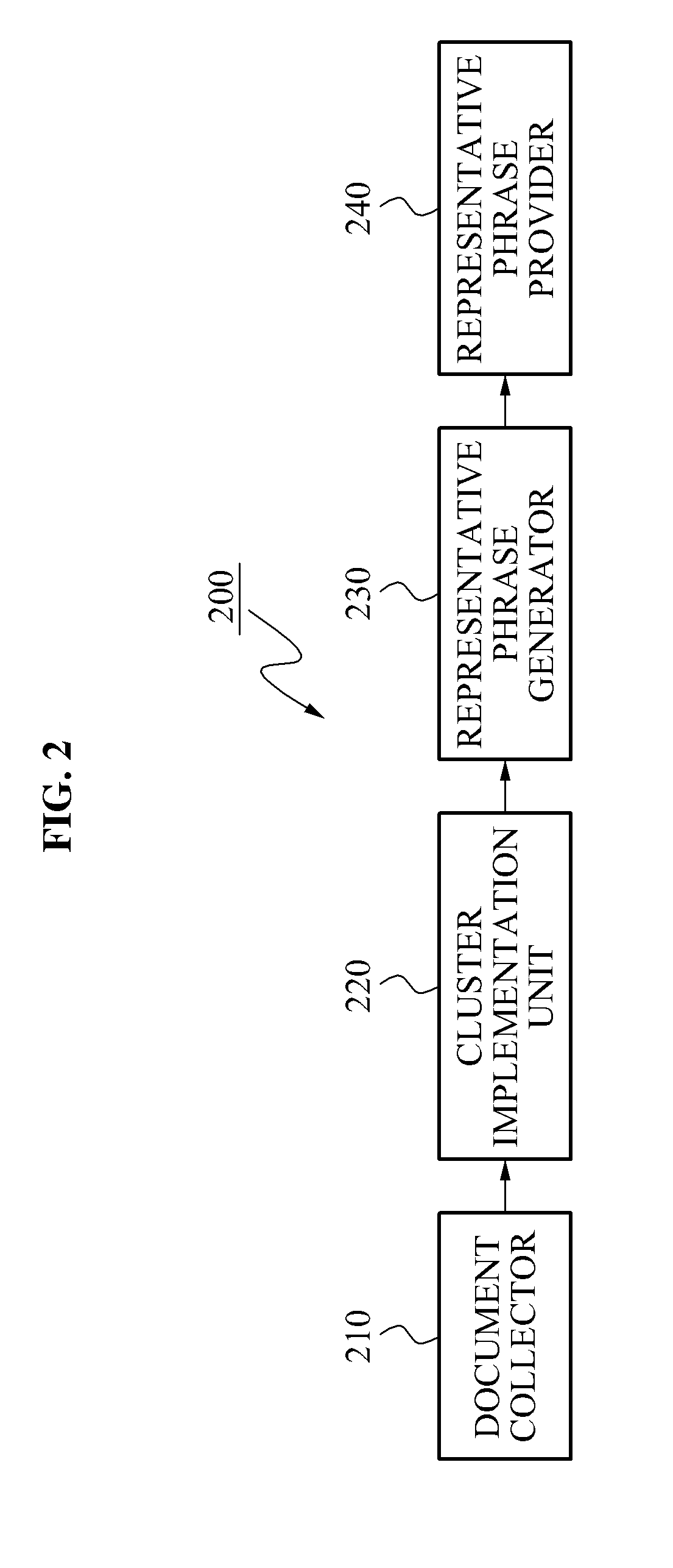
Method and system for providing representative phrase
ActiveUS20120004904A1Natural language data processingSpecial data processing applicationsMorphemeDocument preparation
A method and system for providing a representative phrase corresponding to a real time (current time) popular keyword. The method and system may extend a representative criterion word, determined by analyzing morphemes of words in documents grouped into a cluster, and may combine the extended representative criterion word and the popular keyword, thereby providing the representative phrases. The method and system may display the popular keyword and the representative phrases on a web page, or the like.
Owner:NHN CORP
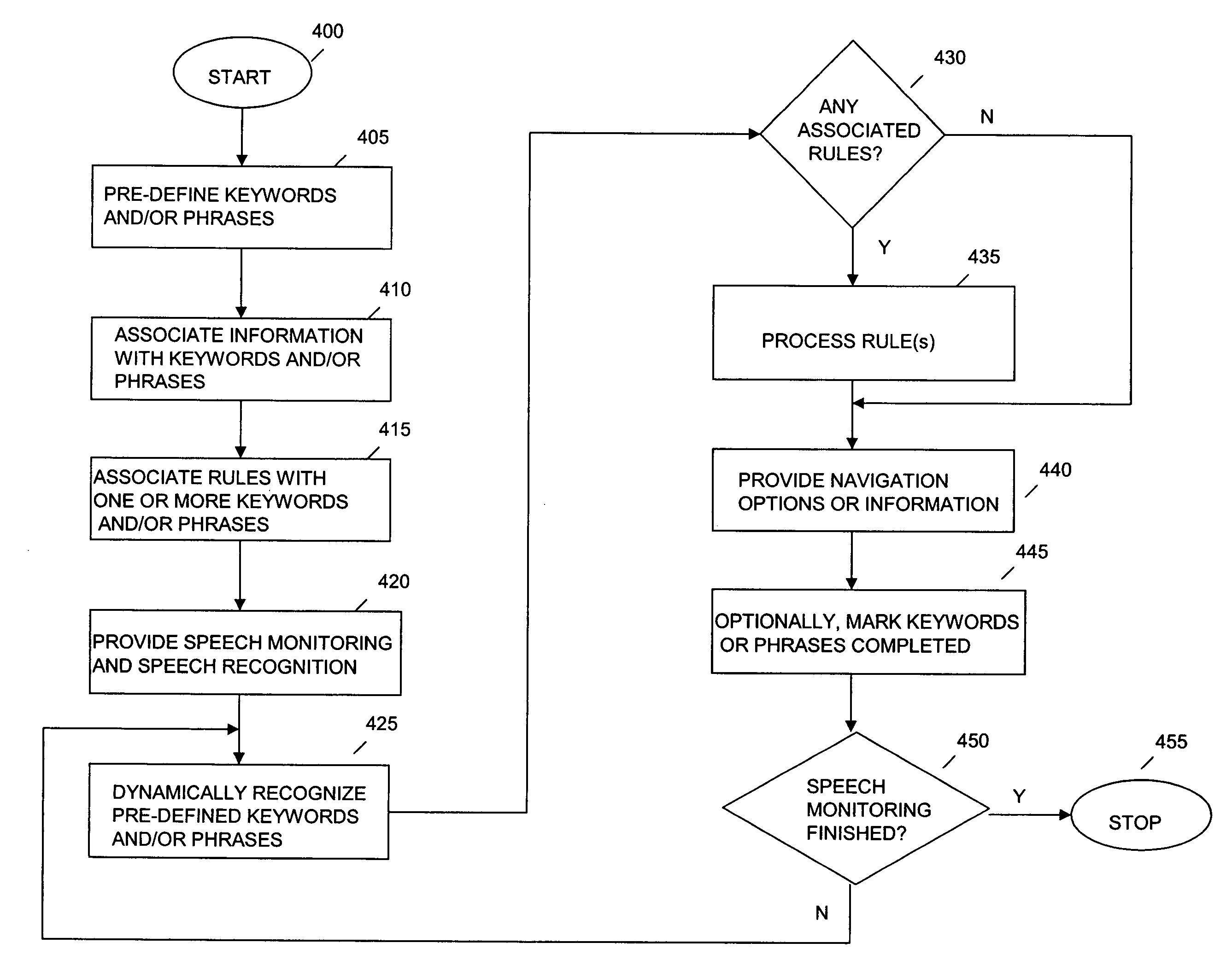
Method and system for keyword detection using voice-recognition
InactiveUS7672845B2Special service for subscribersAutomatic call-answering/message-recording/conversation-recordingDisplay deviceSpeech identification
A method and system is provided to monitor speech and detect keywords or phrases in the speech, such as for example, monitored calls in a call center or speakers / presenters using teleprompters, or the like. Upon detection of the keywords of phrases, information associated with the keywords or phrases may be presented to a display device so that a user may dynamically receive new information as context of the speech progresses. This provides dynamic information as the context of the conversation develops. The information may be presented as links, cues, text, or similar formats. The detected keywords or phrases may also be associated with rules that govern the conditions and criteria for processing the detected keyword and presentation of the information.
Owner:IBM CORP
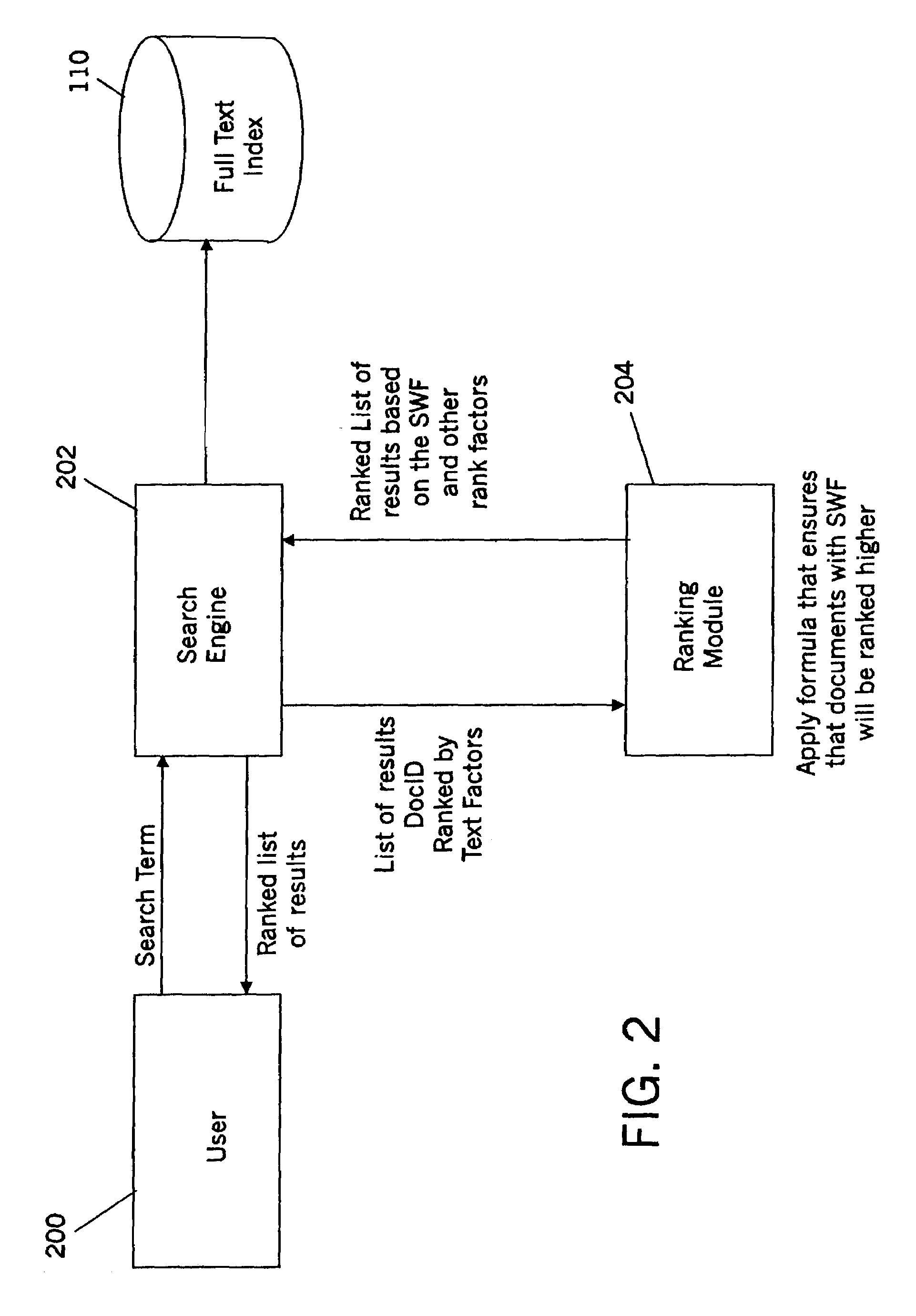
Method of promoting strategic documents by bias ranking of search results
InactiveUS7249058B2Remove information source biasIncrease probabilityMarketingWeb siteDocumentation procedure
A method, software and apparatus are provided which enable promotion of products and services in a deterministic manner free of conflicting actions modifying raw ranking data based on merchants interests. For this purpose, an information consolidator is provided to obtain search results for a plurality of sources including directly from merchants. When a shopper enters a set of key words in an entry field in an on-screen form for a web server to obtain a list of items (products and / or services) of interest to the shopper, the documents describing the items can be prioritized by the information provided by the information source based on the web sites owner's priorities. The information consolidator receives ranking information taking the highest ranked products and obtains the product information for the most highly ranked products. The information consolidator then reranks the products using a preferred ranking algorithm to remove information sources biases in this ranking of the products. The information consolidator can add weighting factors such as those covered in the copending applications by the merchant. The weighting factors are combined with the mentioned ranking mechanisms to the documents to increase the probability that certain items come to the top when the search results are presented to the shopper. These pages could be used to promote products or otherwise direct the selection shoppers. The weighting factors are configured so as to not decrease the shoppers confidence in the ranking process.
Owner:IBM CORP
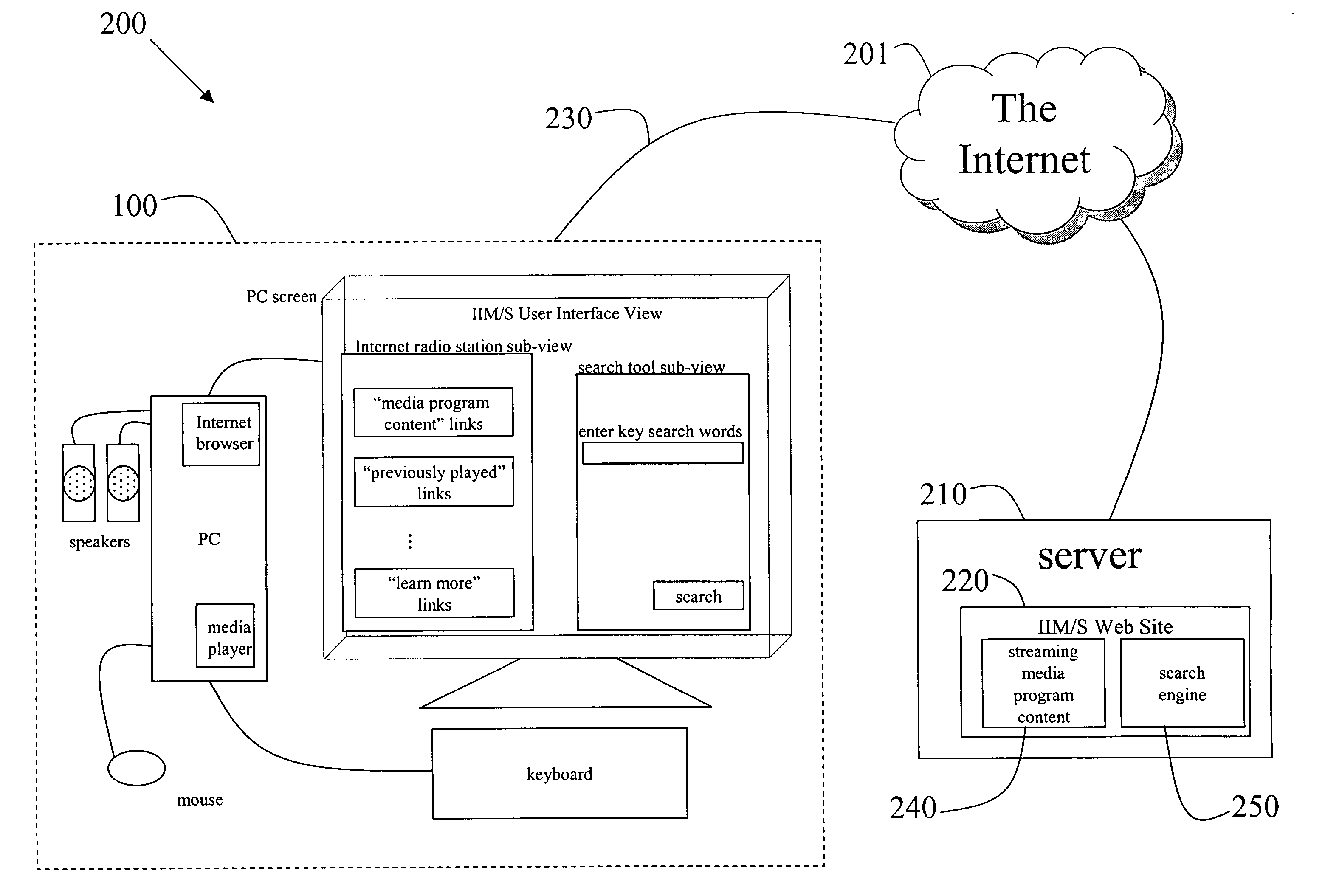
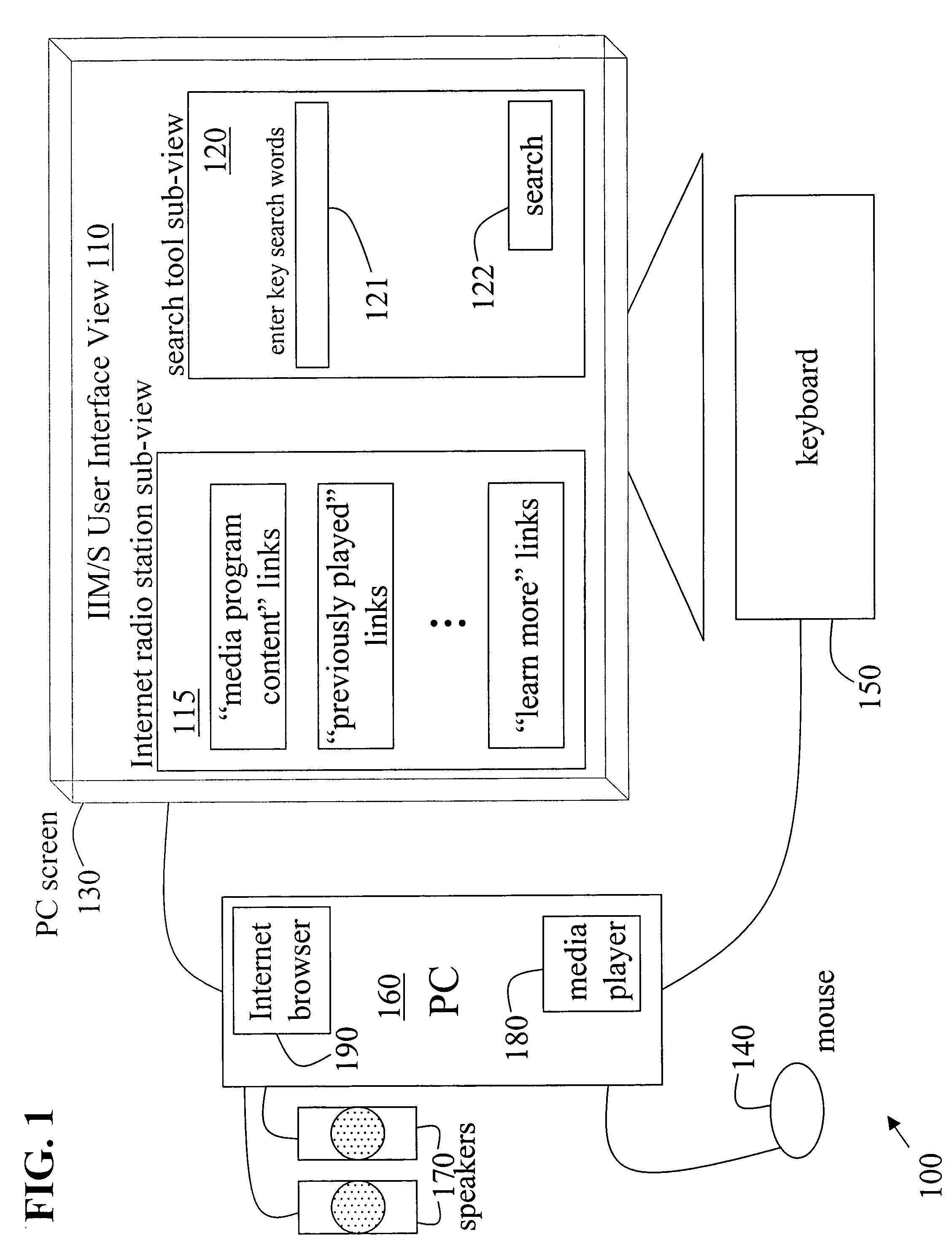
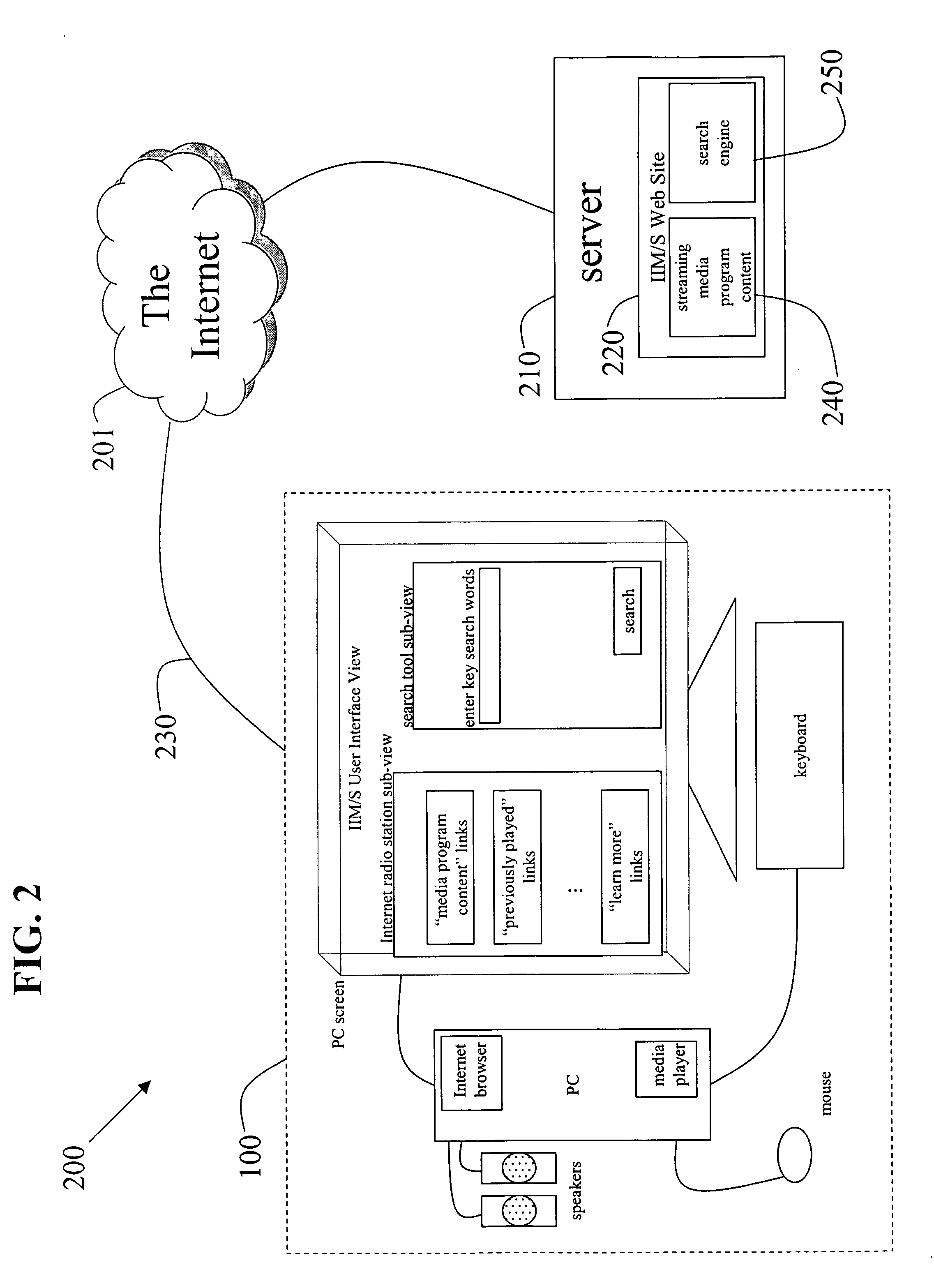
Methods to adapt search results provided by an integrated network-based media station/search engine based on user lifestyle
InactiveUS20060143674A1Television system detailsDigital data processing detailsWeb siteWeb search engine
Methods to adapt a user interface view, provided by an integrated media / search web site via a global informational network, based on a user's lifestyle are disclosed. The methods include populating a user interface view of the integrated web site with a first set of links to the global informational network, wherein the integrated web site integrates a streaming digital media provider station with a global search engine. A user selects a link from the first set of links or performs a key word search using the global search engine. The user interface view is then re-populated with an updated set of links to the global informational network based on demographic and psychographic associations made by the global search engine in response to at least the most recently selected link, the most recent key word search, or the most recent streaming media content. If a new link or a new key word search is performed, the user interface view is again re-populated with an updated set of links. Also, if the streaming media program content from the provider changes, the user interface view is again re-populated with an updated set of links.
Owner:BLU VENTURES +1
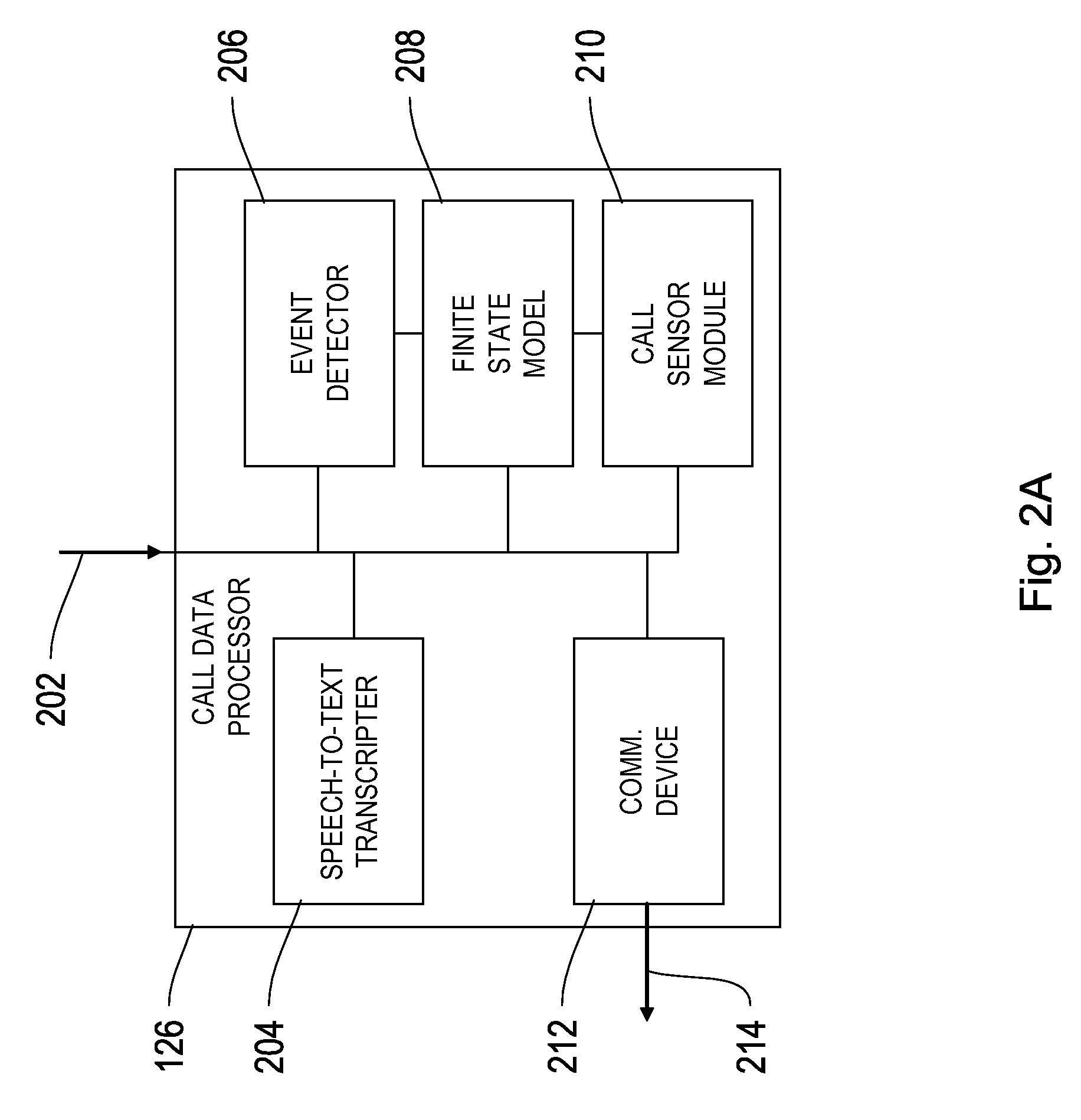
System and method for removing sensitive data from a recording
InactiveUS20130266127A1Easy to integrateElectronic editing digitised analogue information signalsAutomatic call-answering/message-recording/conversation-recordingStart timePhrase
Systems and methods for, among other things, removing sensitive data from an recording. The method, in certain embodiments, includes receiving an audio recording of a call and a text transcription of the audio recording, identifying events which occur during the call by detecting characteristic audio patterns in the audio recording and selected keywords and phrases in the text transcription, determining, from the identified events, a first event which precedes sensitive data in the call and a second event which occurs after sensitive data in the call, determining a portion of the call containing sensitive data with a start time at the first event and an end time at the second event, and removing the portion of the call between the start time and end time from the audio recording.
Owner:RAYTHEON BBN TECH CORP
Selecting ads for a web page based on keywords located on the web page
InactiveUS20050091106A1Generate revenueSpecial data processing applicationsMarketingPaper documentDocument preparation
A system for use on computer servers on a network serving client computers for selecting an advertisement to be presented among a plurality of possible advertisement candidates based on key words. When a client computer requests a document from a server on the network, the system considers words contained within the document and compares them to a set of key words for each possible advertisement of a plurality of possible advertisements. The system selects an advertisement to be presented with the information where a key word associated with the advertisement matches one or more words in the document. If more than one advertisement qualifies, the system considers a price value of each advertisement and a relevance score for each word, which is a function of proximity to the start of the document, to determine which advertisement will be presented.
Owner:HERE GLOBAL BV
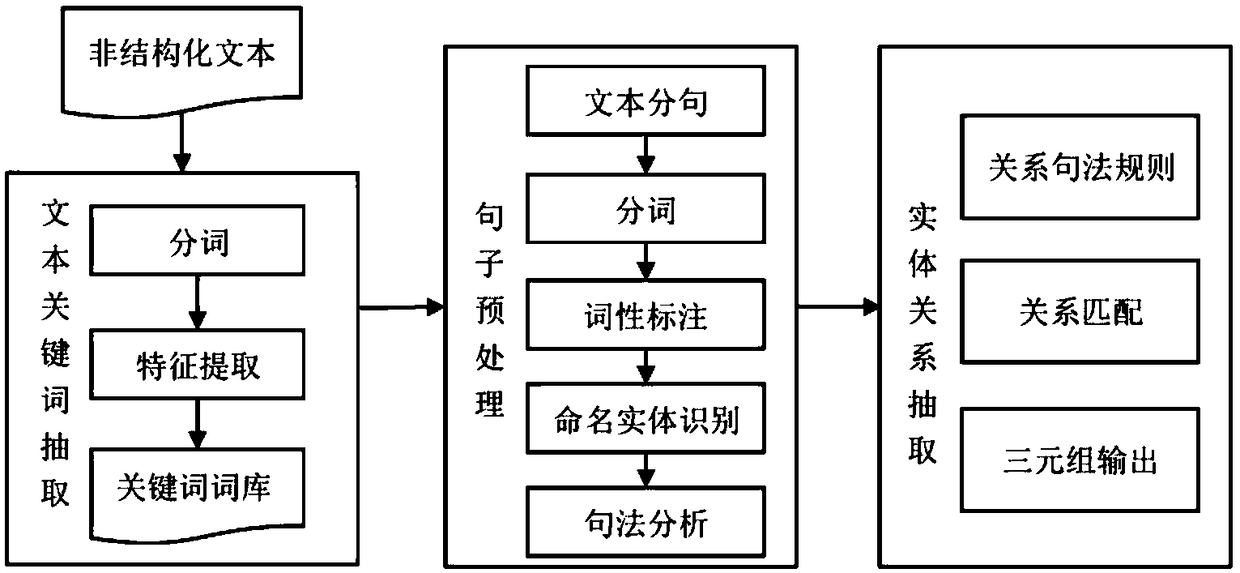
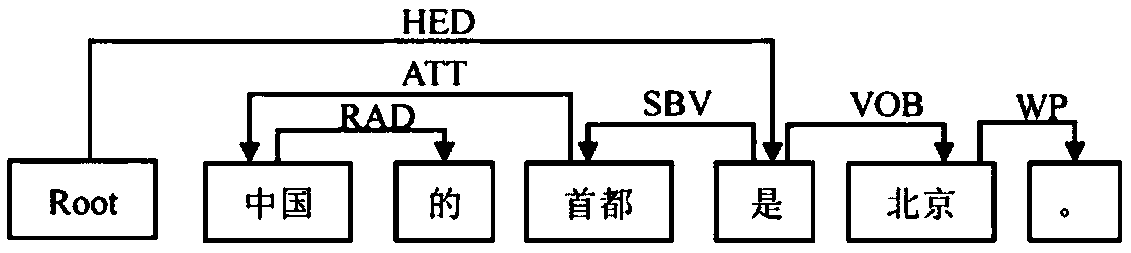
Chinese entity relation extraction method based on keyword and verb dependency
ActiveCN109241538AAdd semantic relationSemantic analysisSpecial data processing applicationsSentence segmentationNamed-entity recognition
The invention discloses a Chinese entity relation extraction method based on keyword and verb dependency. Taking large-scale unstructured free text as target text, firstly, the text is segmented and keywords are extracted to form a text keyword thesaurus. Then the text is subjected to sentence segmentation, word segmentation, part-of-speech tagging, named entity recognition, dependency parsing, and entity corpus is constructed by combining named entity thesaurus and keyword thesaurus. According to the characteristics of Chinese sentence structure, syntactic structure and the dependency betweenwords, the entity-relation syntactic rules are constructed from verbs, and then each sentence in the text is matched with the relation syntactic rules. Finally, the relation triple is output and theset of text relation triple is obtained. The invention can make the entity relation extraction of the large-scale Chinese text more effective and more accurate.
Owner:SHANGHAI DATATOM INFORMATION TECH CO LTD
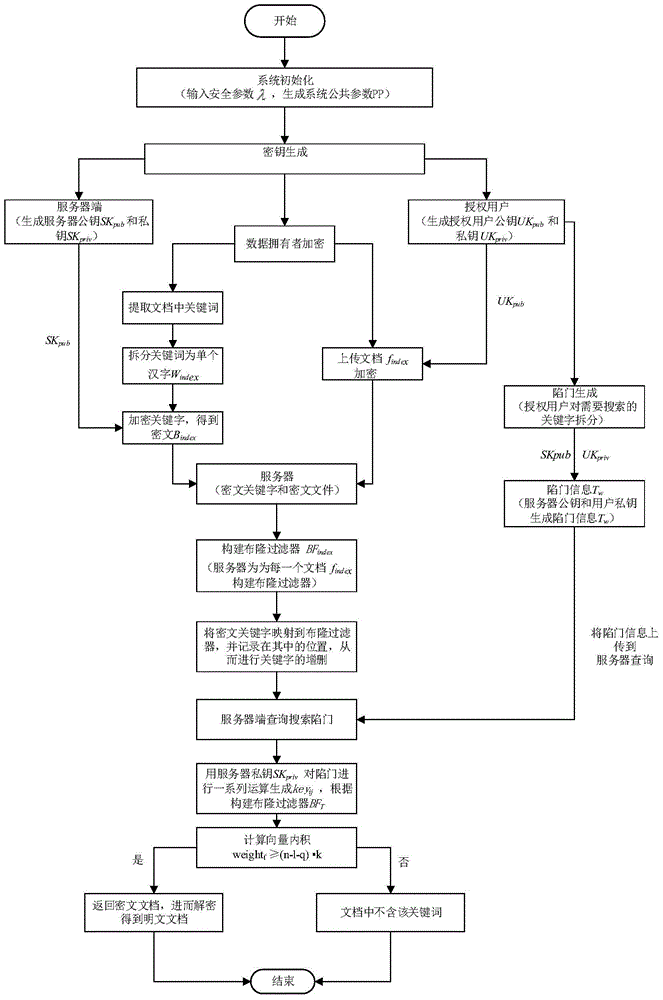
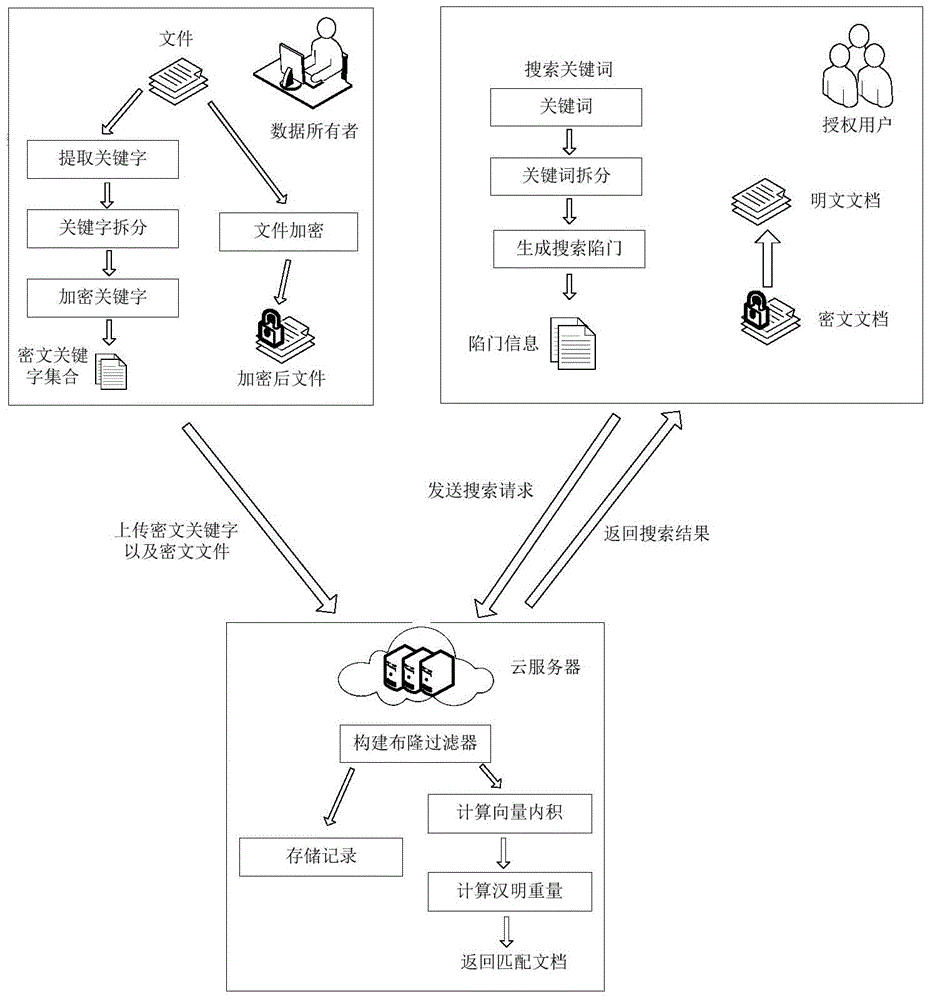
Searchable encryption method based on Chinese in cloud environment
ActiveCN105681280ASearchable implementationSearchable encryption implementationTransmissionSpecial data processing applicationsDocument preparationSearch function
The invention discloses a searchable encryption method based on Chinese in a cloud environment. A dynamic searchable encryption scheme is finished based on the features of a PEKS scheme and a Bloom filter; a ciphertext search function is finished in an insecure channel; fuzzy keyword search based on a public key searchable encryption scheme is supported; multi-keyword search of the Chinese is supported; the keywords in a document are dynamically added or deleted; according to the method provided by the invention, an inner product operation is carried out through constructing a search vector and a file vector so as to finish a fuzzy search matching function; the similarity weight of the keywords in the document and the keywords of a search trap door is calculated through importing the vectors; the ciphertext search function and the fuzzy keyword search function are realized; the ciphertext keywords can be securely transmitted on a public channel in adoption of a server and user double-key pair mode; in application of a hash function and a pseudo-random function, through the scheme, the keyword selection attack can be resisted effectively; and the ciphertext is searched under a condition that the cloud server is semi-trusted.
Owner:XIDIAN UNIV
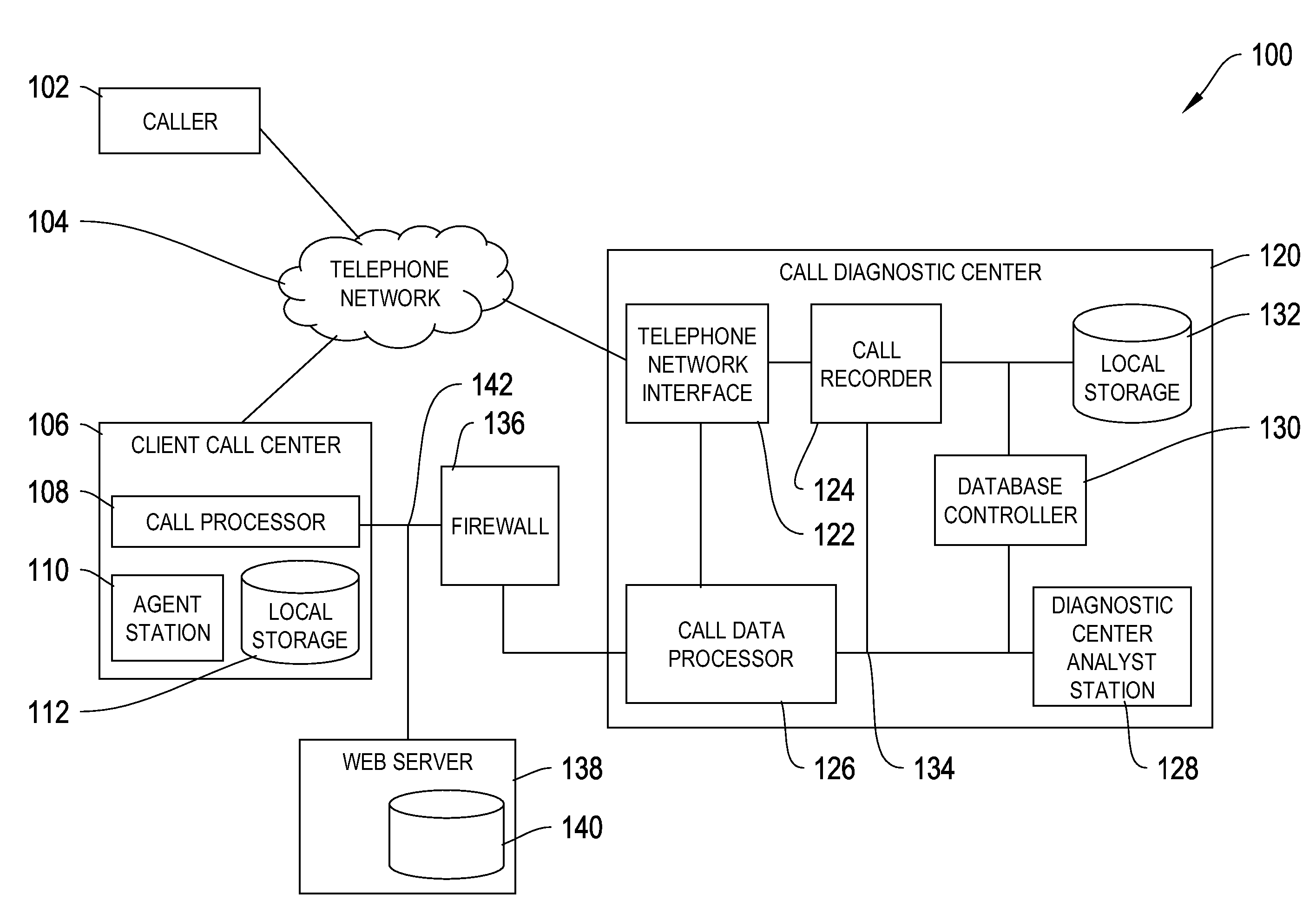
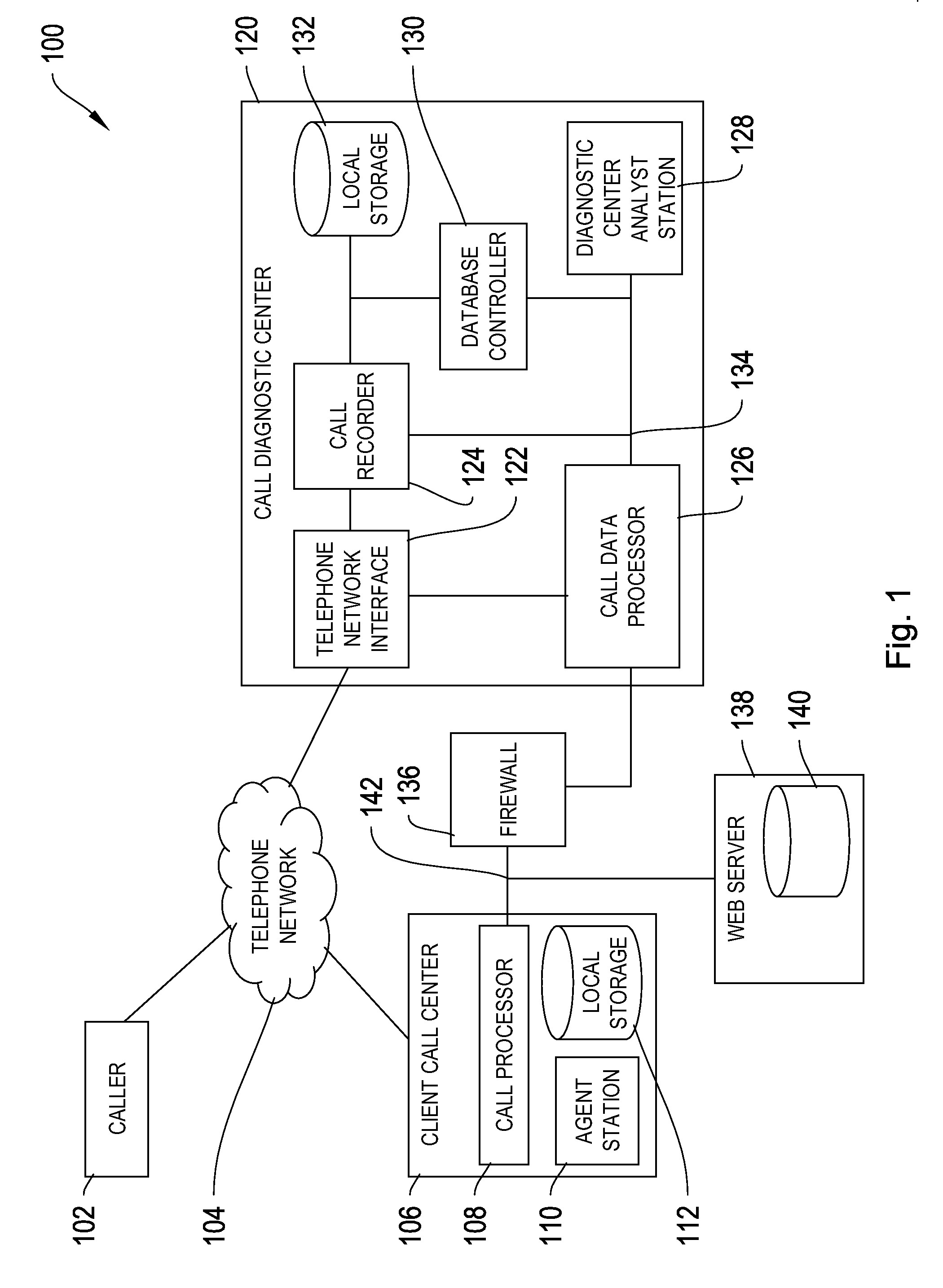
Information provision for call centres
ActiveUS7542902B2Improving technological and economic efficiencyOvercome problemsDigital data information retrievalSpecial service for subscribersSpeech soundManagement system
A voice platform monitors a conversation between a call center agent and a caller to identify any predetermined keywords or phrases used in the conversation therebetween. These keywords or phrases can then be used to interface into an existing knowledge management system in order to allow information from the system to be pushed to the agent, thus improving agent efficiency. In a preferred embodiment additional processing is provided which generates an information item score based in the detected keywords or phrases, and those information items with the highest scores are then pushed to the agent, by displaying shortcuts to the information to the agent in the form of a shortcut tree.
Owner:BRITISH TELECOMM PLC
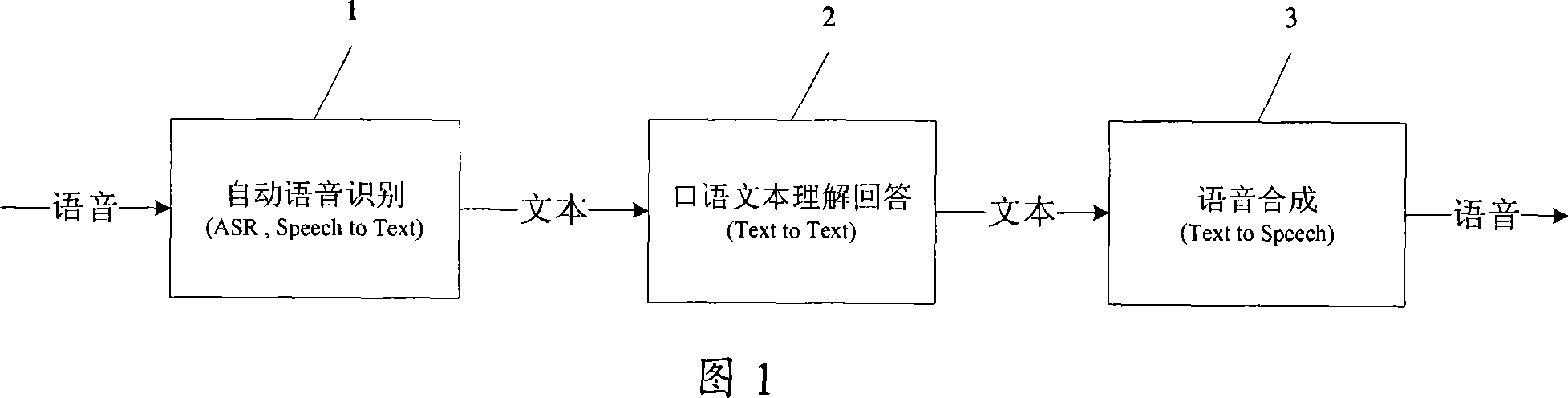
Intelligent chatting system and its realizing method
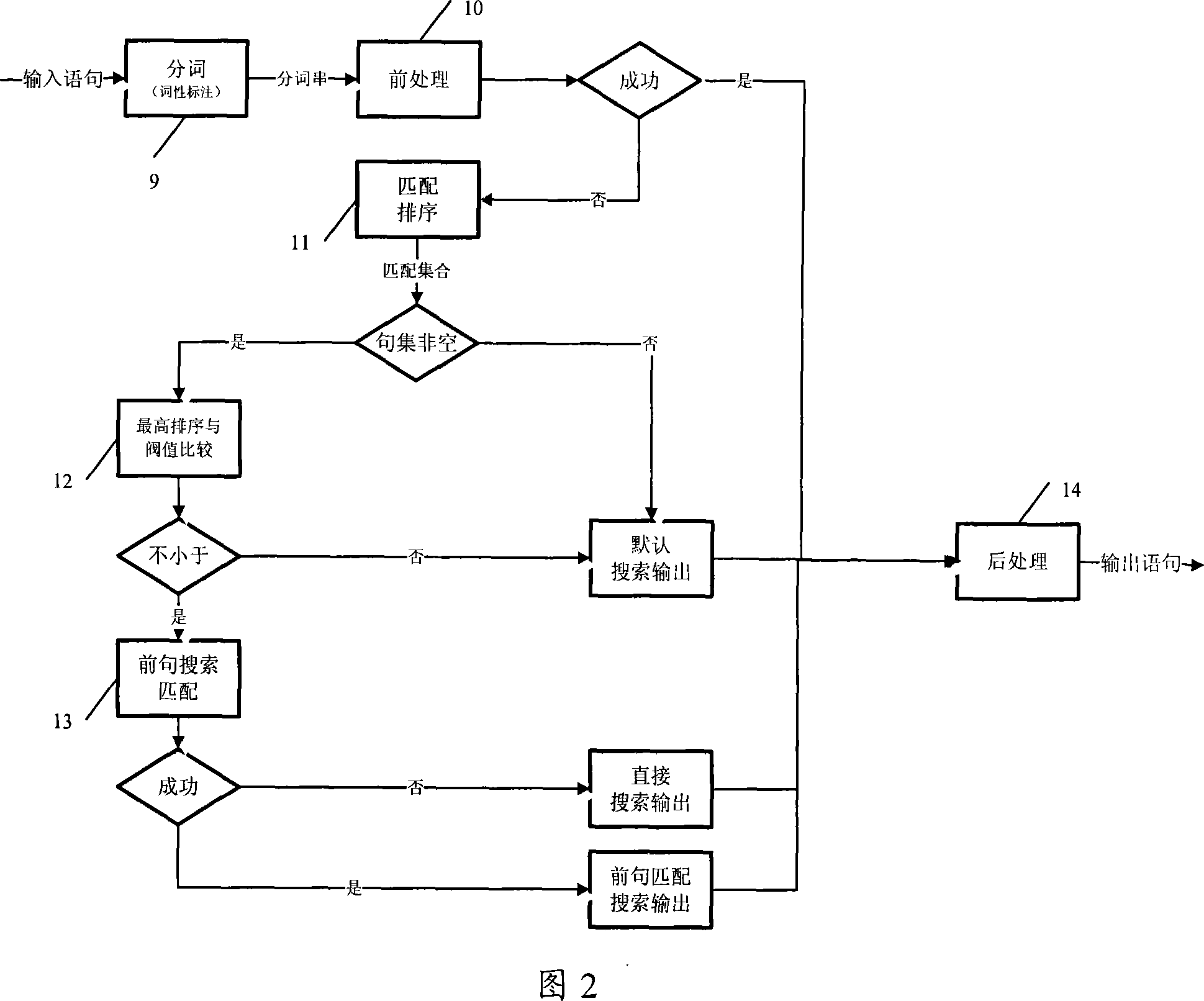
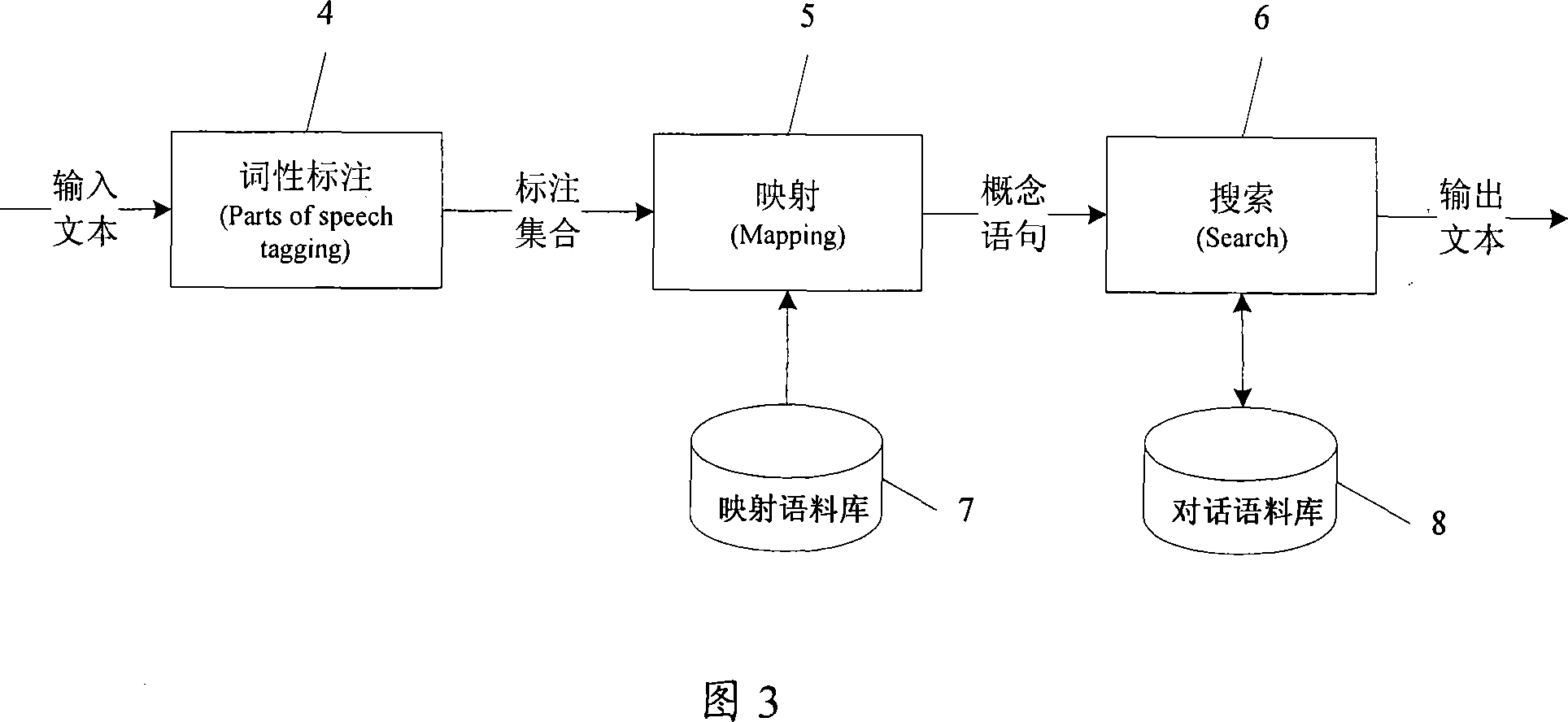
ActiveCN101075435AEnable real language dialogueImprove accuracySpeech recognitionSpeech synthesisHuman languageIndex term
An intelligent chatting system comprises participle unit for carrying out word property label on input text to obtain terms set with word property label, mapping word bank for storing mapping relation of key word to concept statement, mapping unit for searching said mapping word bank according to said terms set in order to obtain concept statement, conversation word bank for setting up and storing the mapping relation of concept statement to output text, and searching unit for searching said conversation word bank according to concept statement in order to obtain output text by mapping.
Owner:SHENZHEN INST OF ADVANCED TECH
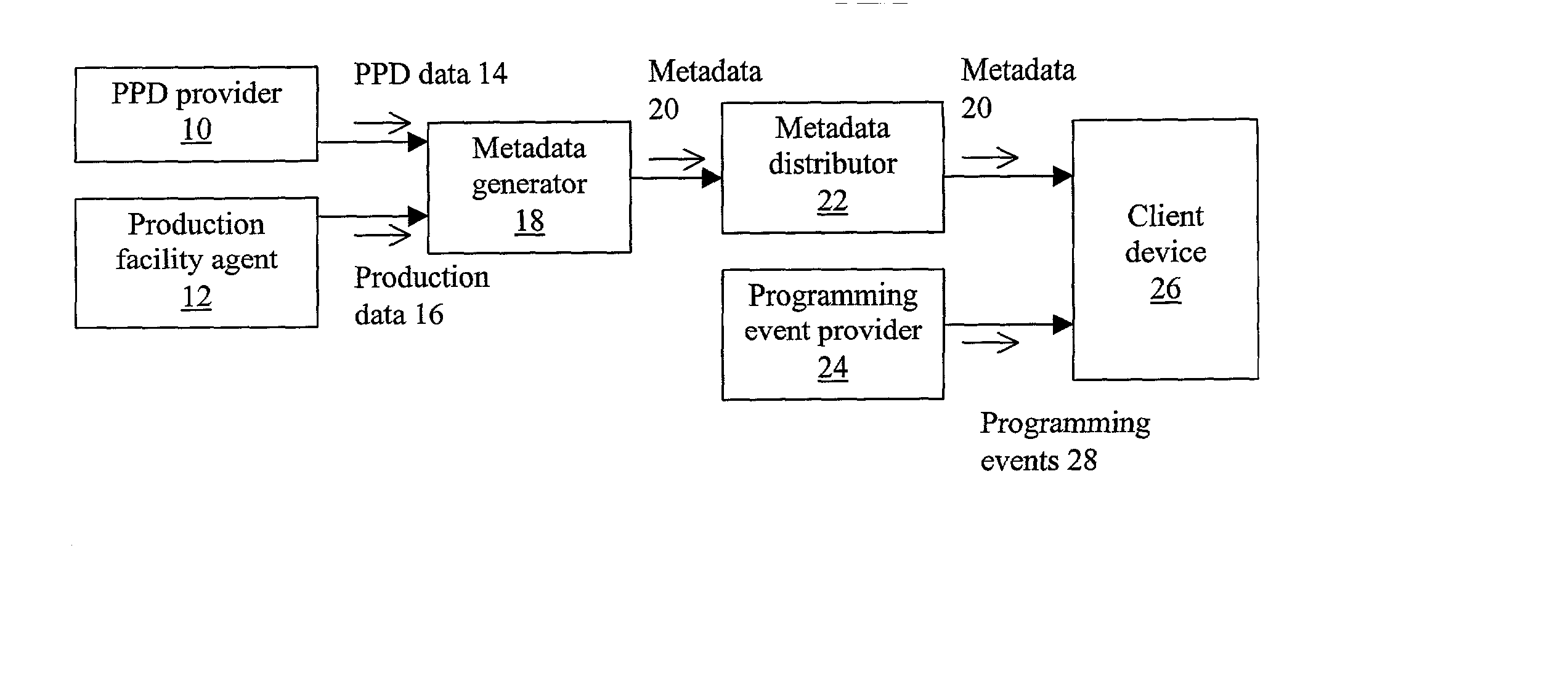
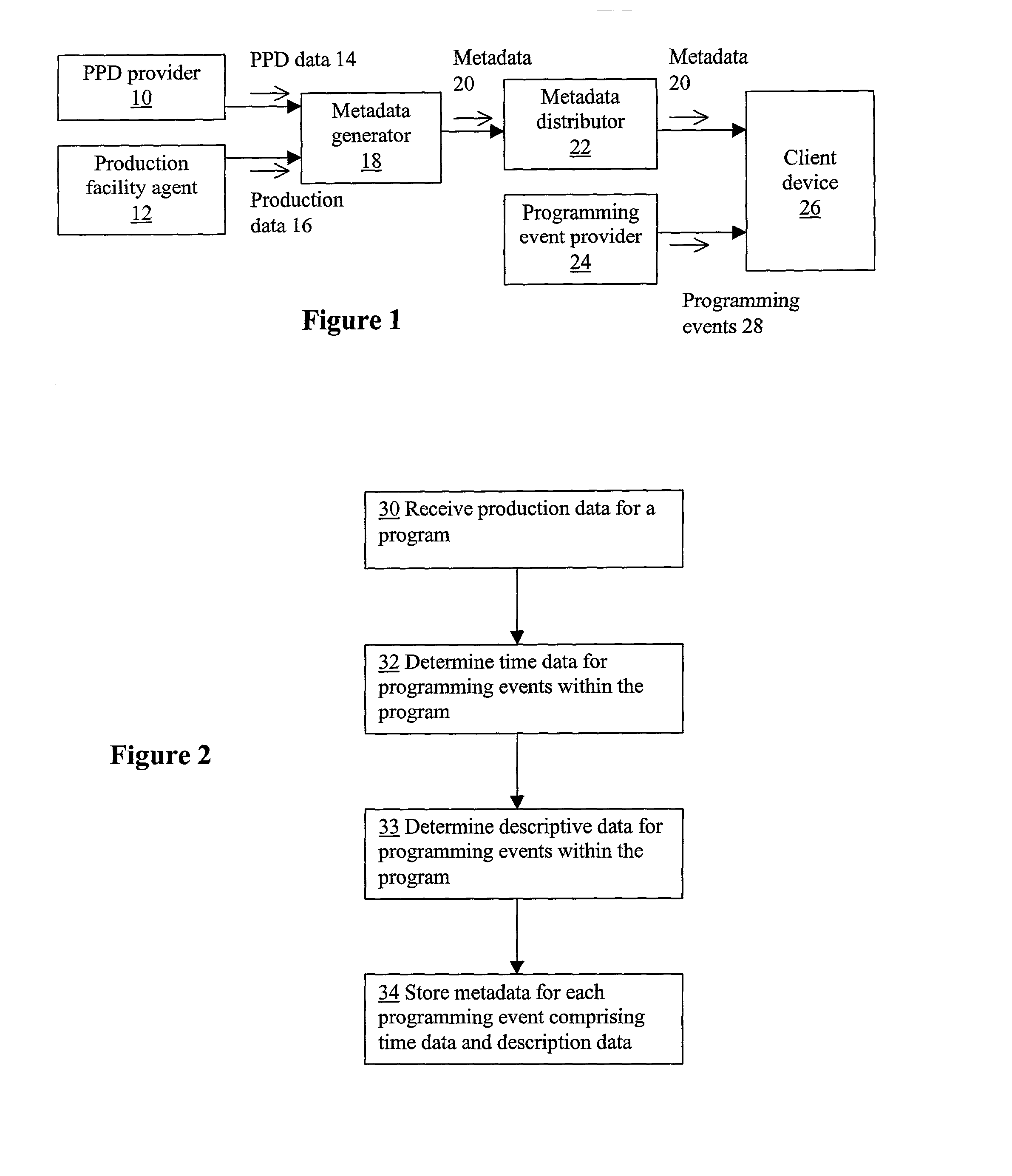
System and method for generating metadata for programming events
InactiveUS20020092031A1Television system detailsData processing applicationsGoodness of fitTime data
Metadata for a programming event may be generated by receiving descriptive information and timing information for the programming event and analyzing this information to determine category goodness of fit scores for the programming event corresponding to categories of a classification hierarchy. The information is further analyzed to determine keywords associated with the programming event. The category goodness of fit scores and keywords may be stored along with time data and descriptive data for the programming event as metadata for the programming event. Goodness of fit scores may also be generated for the keywords. Related embodiments may pertain to a device implementing such processing. Keyword metadata may be generated using candidate keywords taken from descriptive data associated with the programming event. The candidate key words may be provided individually as inputs to a classification tool configured to generate goodness of fit scores for categories of a classification hierarchy. Keywords may then be selected from among the candidates based on their individual scores, and stored as part of the metadata for the programming event. The scores of the keywords may be stored in association with the keywords.
Owner:MEEVEE
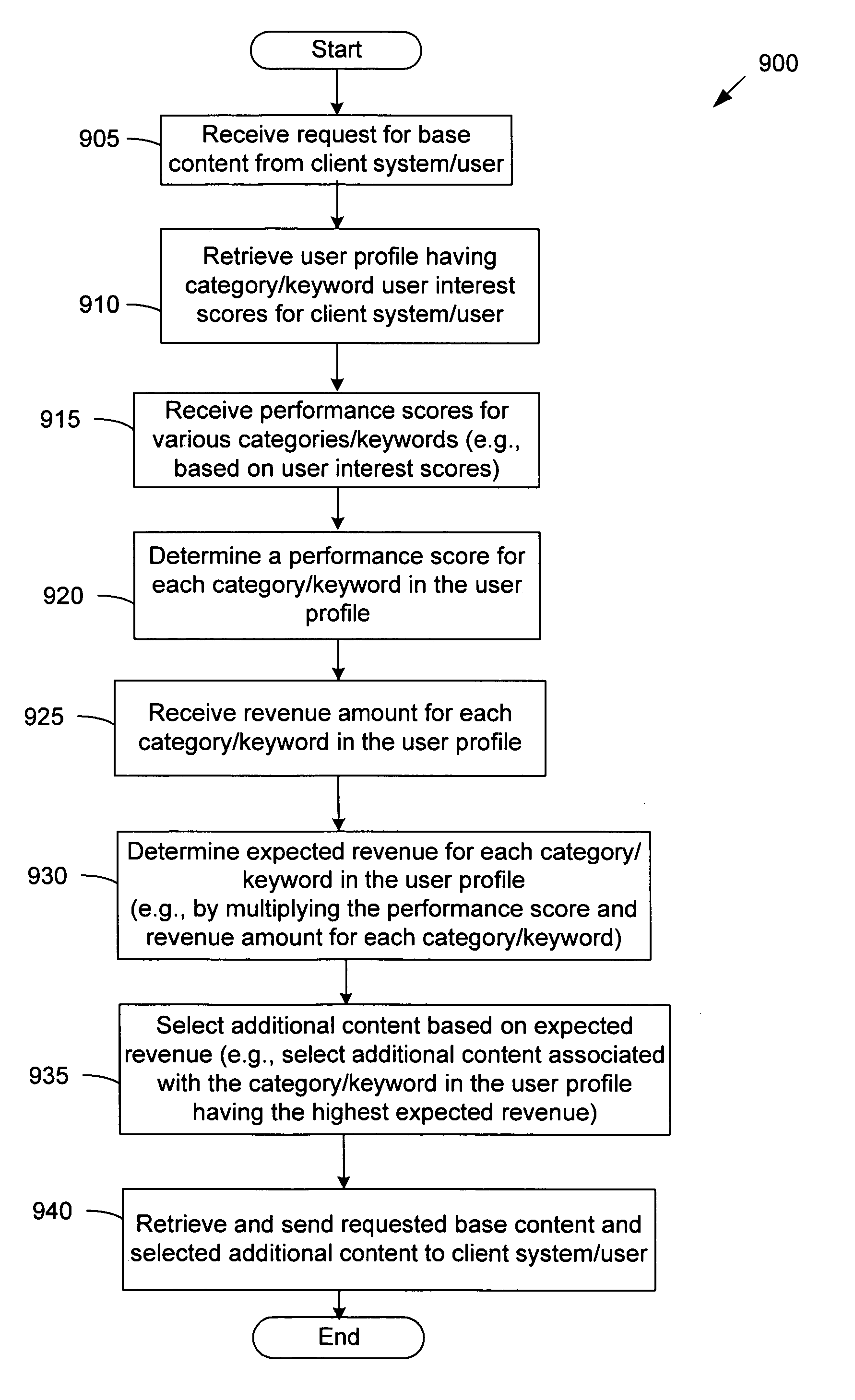
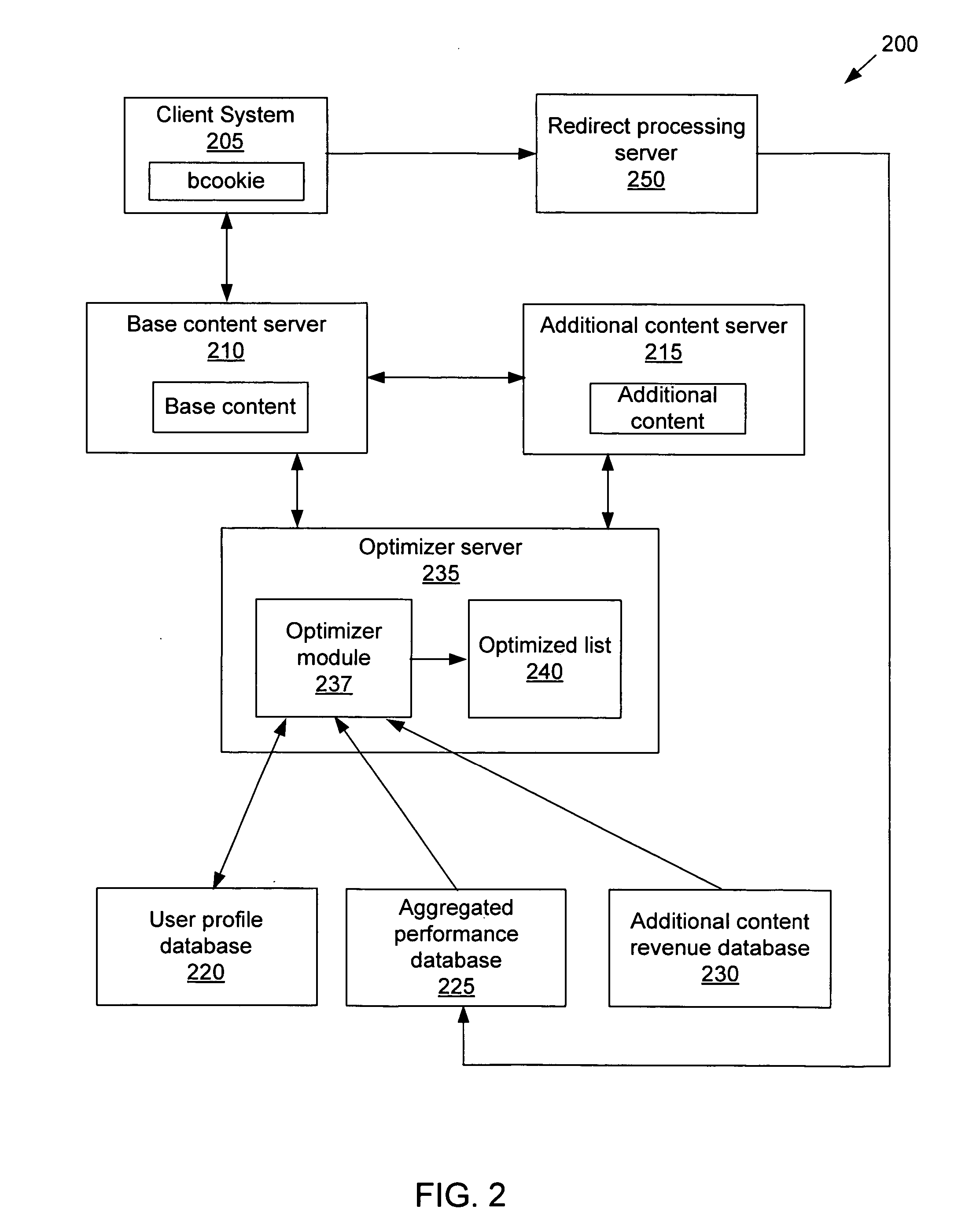
Method and apparatus for selecting advertisements to serve using user profiles, performance scores, and advertisement revenue information
A method and apparatus for selecting additional content to display to a user when the user requests base content is provided. A user profile of the user having user interest scores of categories or keywords is received, each user interest score reflecting the degree of interest the user has in the category or keyword. Performance scores reflecting the probability that a user having particular user interest scores will select additional content associated with particular categories or keywords is also received. In addition, revenue amounts associated with each category or keyword of the user profile is received. The user interest scores, performance scores, and revenue amounts are used to produce an expected revenue amount for each category or keyword in the user profile. Additional content to be sent to the user is then selected using the determined expected revenue amounts.
Owner:YAHOO INC
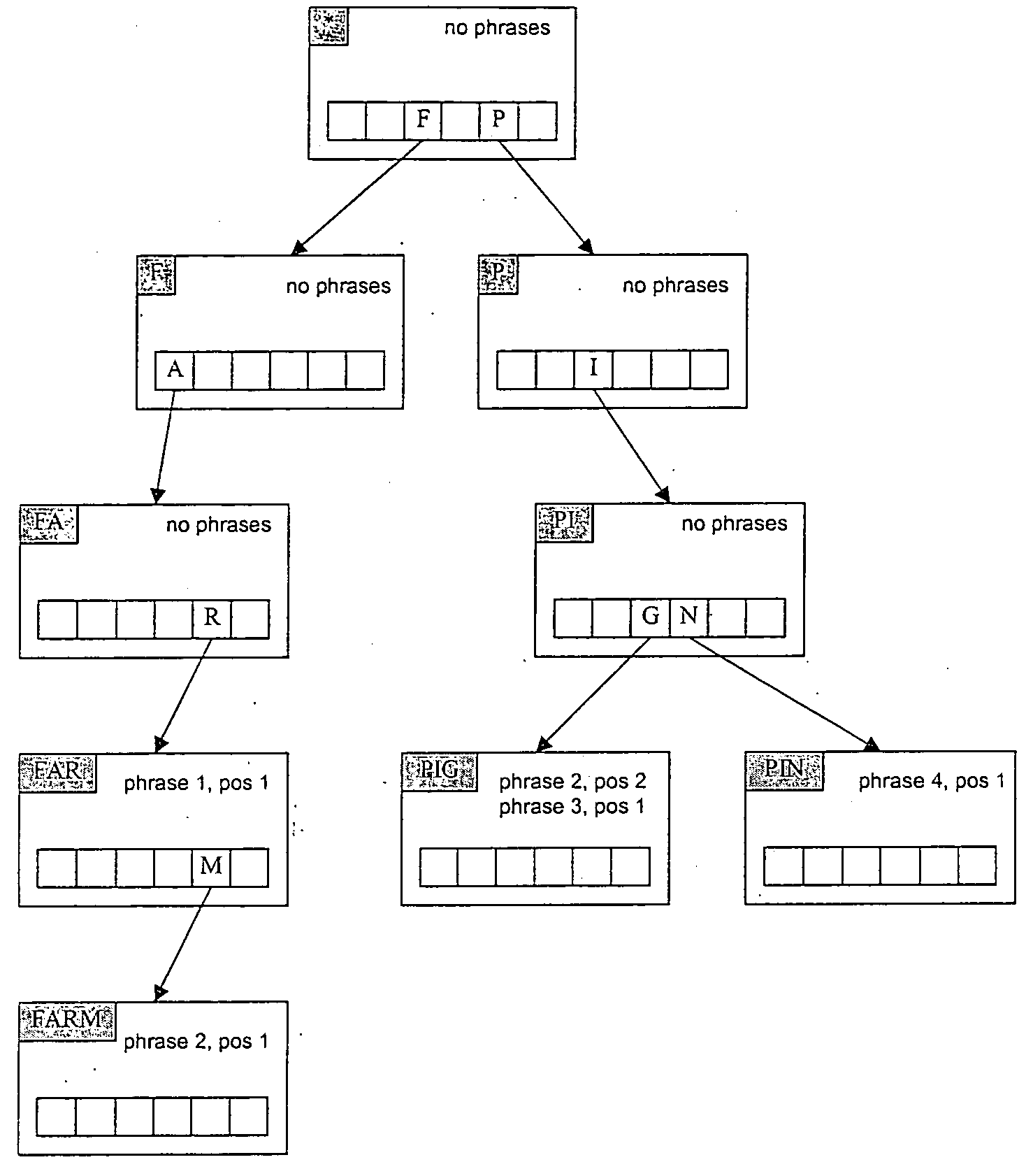
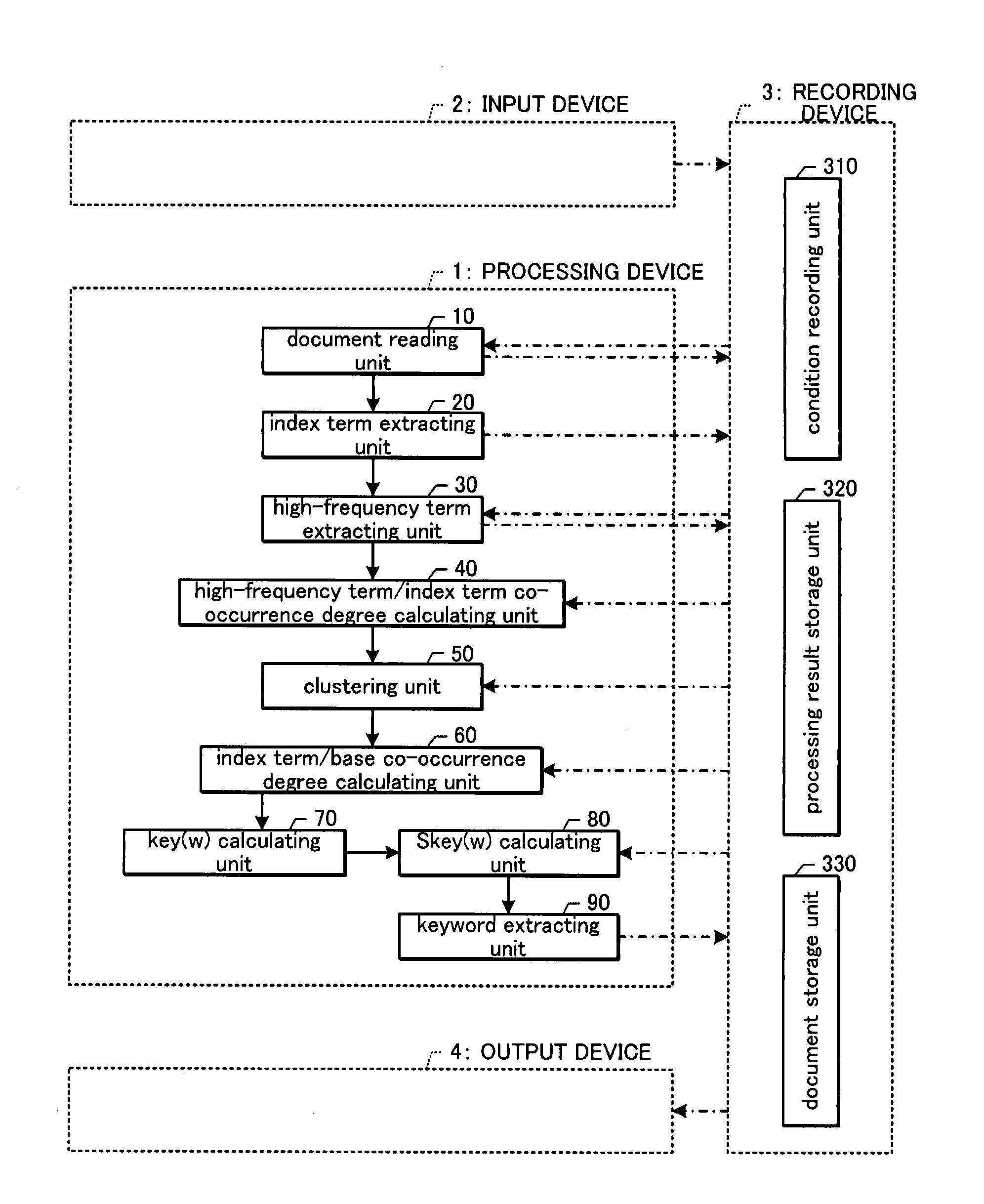
Keyword Extracting Device
InactiveUS20080195595A1Accurate representationAccurate featuresDigital data information retrievalSpecial data processing applicationsFrequency levelCo-occurrence
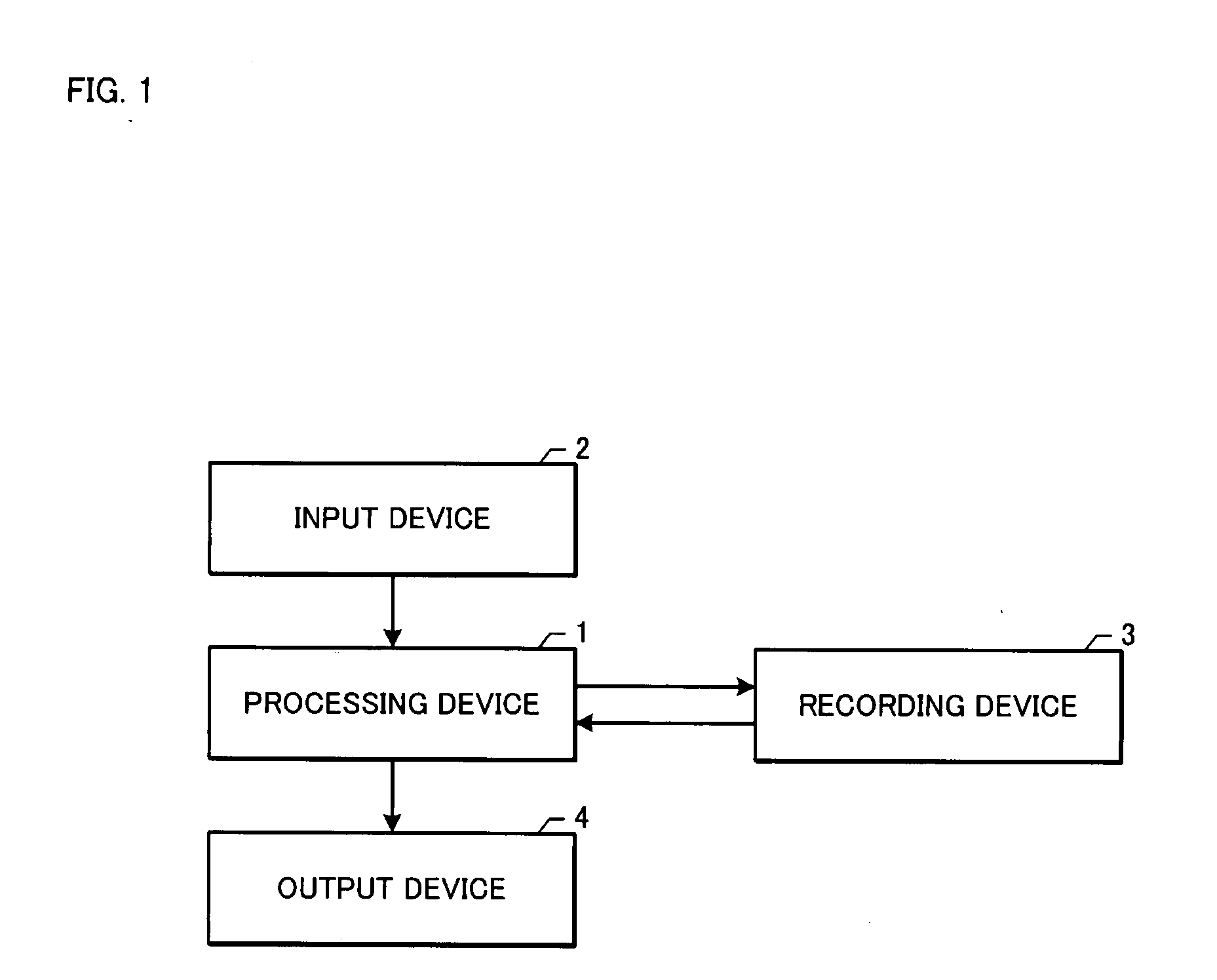
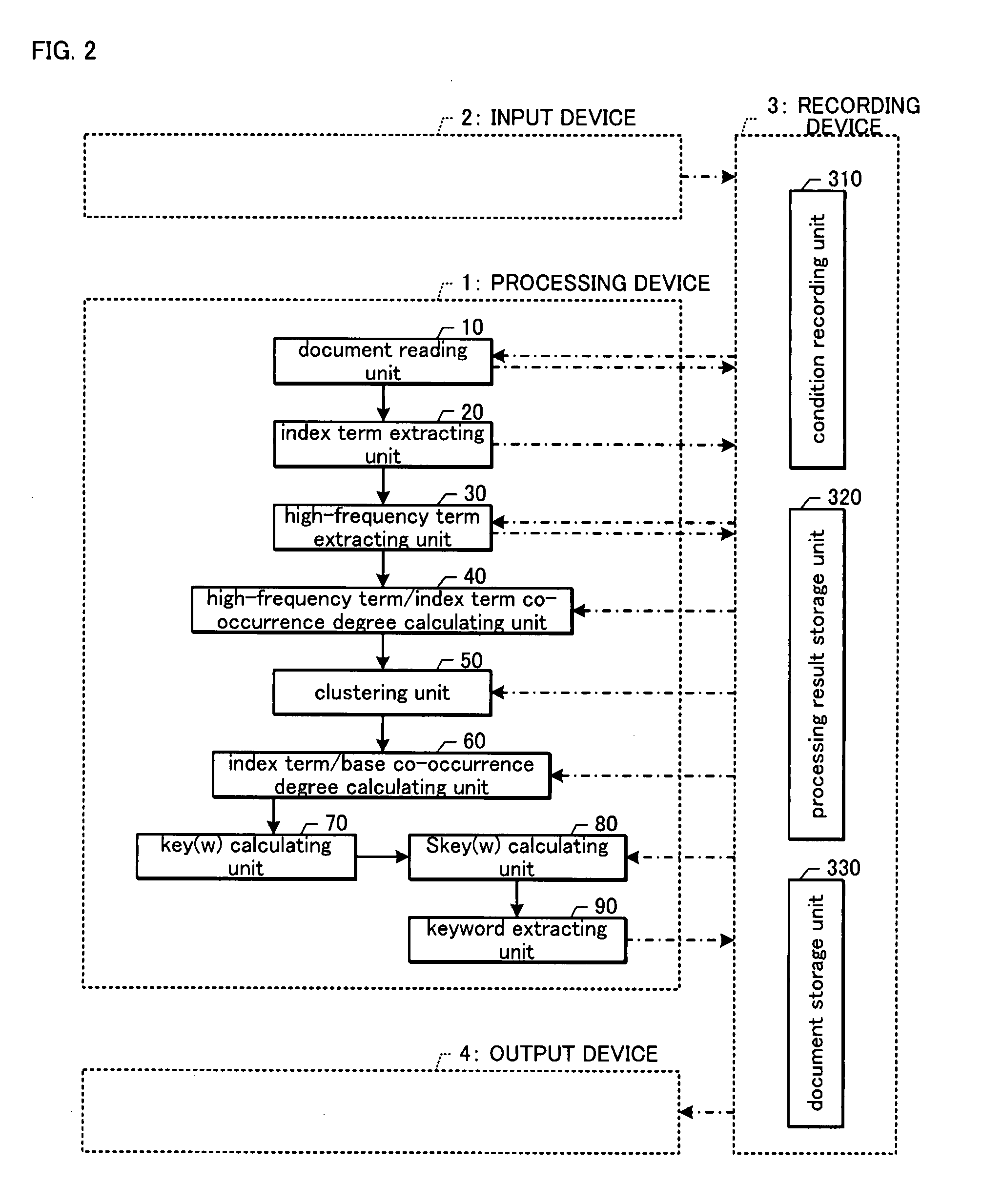
A keyword extracting device includes high-frequency term extracting means (30) for extracting high-frequency terms which are index terms having a great weight among the index terms in a document group (E) including a plurality of documents (D), the weight including evaluation on the level of an appearance frequency of each index term, clustering means (50) for clustering the high-frequency terms on the basis of a co-occurrence degree C. which is based on the presence / absence of the co-occurrence of each document with the index terms (w) in the document group (E) in each document, score calculating means (70) for calculating a score key(w) of each index term (w) such that a high score is given to the index term among the index terms (w) that co-occurs with the high-frequency term belonging to more clusters (g) and that co-occurs with the high-frequency term in more documents (D), and keyword extracting means (90) for extracting keywords on the basis of the scores. Accordingly, the keywords indicating a feature of a document group including a plurality of documents can be automatically extracted.
Owner:INTPROP BANK CORP (JP)
Domain entity disambiguation method for fusing word vectors and topic model
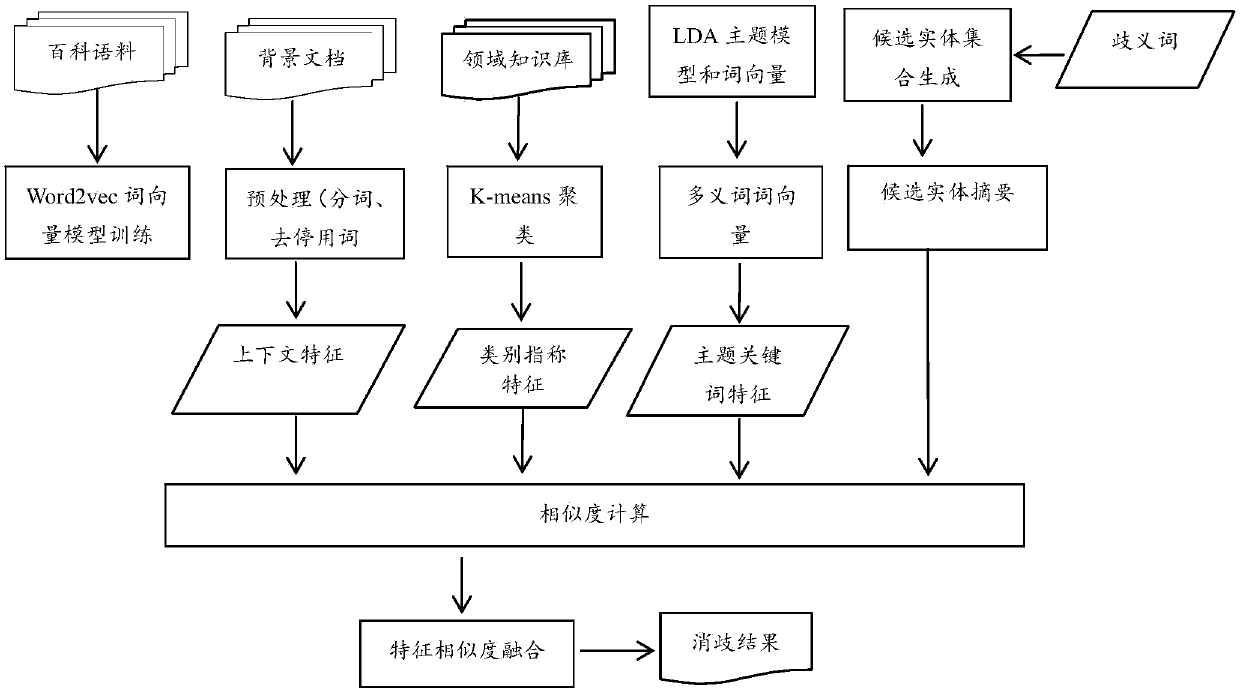
ActiveCN107861939AImprove accuracyGood effectWeb data indexingSemantic analysisAlgorithmDocument preparation
The invention relates to a domain entity disambiguation method for fusing word vectors and a topic model, and belongs to the technical field of natural language processing and deep learning. The method comprises the steps of obtaining candidate entity sets of to-be-disambiguated entities; obtaining vector forms of the to-be-disambiguated entities and candidate entities, obtaining categorical referents of the to-be-disambiguated entities in combination with a hyponymy relation domain knowledge base, and performing context similarity and categorical referent similarity calculation; performing word vector training on documents in different topic classifications by utilizing the LDA topic model and a Skip-gram word vector model, obtaining word vector representations of different meanings of apolysemous word, extracting a topic domain keyword of a text by using a K-Means algorithm, and performing domain topic keyword similarity calculation; and finally, fusing three feature similarities, and taking the candidate entity with the highest similarity as a final target entity. The method is superior to a conventional disambiguation method and can well meet the demands of actual applications.
Owner:KUNMING UNIV OF SCI & TECH
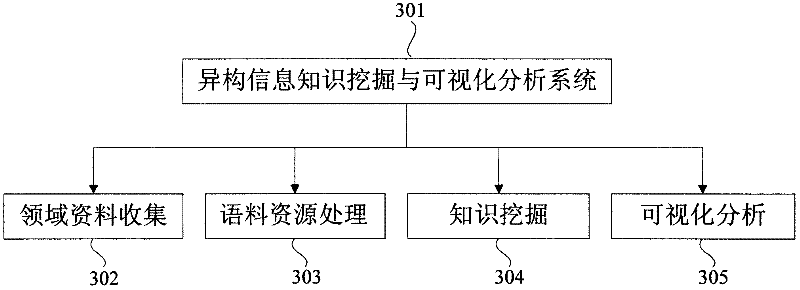
System and method for heterogeneous information mining and visual analysis
InactiveCN102609512ARealize dynamic displayCorrect understanding of requirementsSpecial data processing applicationsInformation miningStatistical analysis
The invention relates to the field of heterogeneous information retrieval, in particular to an intelligent retrieval and analyzing method based on domain ontology and information mining and a visual analyzing system comprising the method. The system mainly comprises a field data acquisition subsystem, a corpus resource processing subsystem, an information mining subsystem and a visual analyzing subsystem, wherein the field data acquisition subsystem is used for acquiring data by network capturing and local uploading, the field data acquisition subsystem is used for pre-processing field related data, the field data acquisition subsystem is used for analyzing and mining related information in corpus, and the visual analyzing subsystem is used for dynamically displaying and counting and analyzing retrieval results. Concepts in a domain ontology base and mutual relations of the concepts are fully used by the system for heterogeneous information mining and visual analysis, requirements of users can be correctly understood to automatically cluster hierarchical structural information of a certain field so as to support the users to inquire key words, phrases and simple sentences and optimize retrieval results, relevant concepts and extension concepts can be found by ontological reasoning to support graphic display preview of each information meaning in the inquiry results, and the professional-field information retrieval performance can be remarkably improved to realize dynamic information display.
Owner:BEIJING ZHONGJIKEHAI TECH & DEV
Query-based document composition
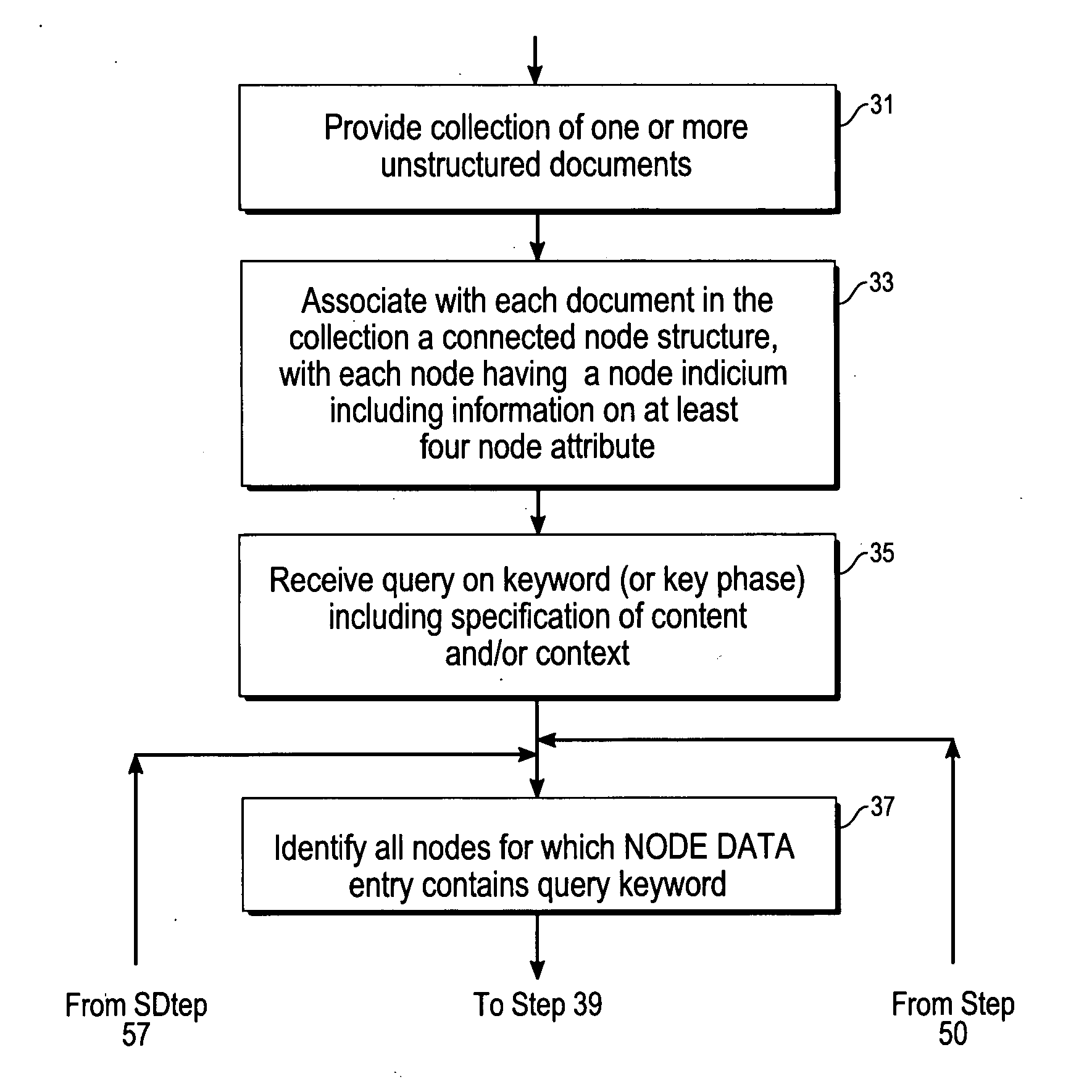
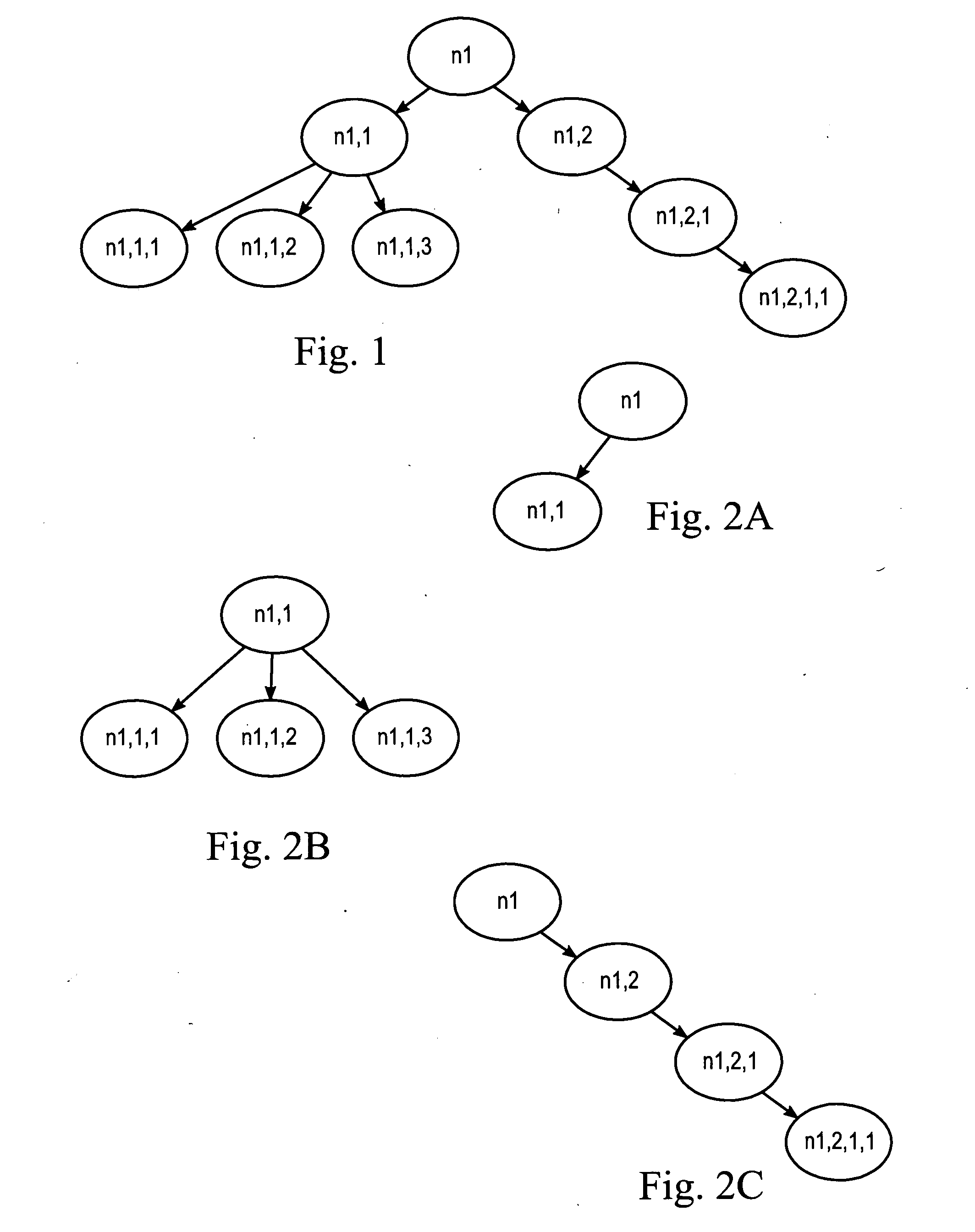
InactiveUS20060047646A1Digital data information retrievalDigital data processing detailsPaper documentDocument preparation
Method and system for querying a collection of unstructured and semi-structured documents in a specified database to identify presence of, and provide context and / or content for, keywords and / or keyphrases. The documents are analyzed and assigned a node structure, including an ordered sequence of mutually exclusive node segments or strings. Each node has an associated set of at least four, five or six attributes with node information and can represent a format marker or text, with the last node in any node segment usually being a text node. A keyword (or keyphrase) query is specified, the query is converted to a statement that is recognized and respondeed to by the specified database, and the last node in each node segment is searched for a match with the keyword. When a match is found at a query node, or at a node determined with reference to a query node, the system displays the context and / or the content of the query node.
Owner:NASA +2
Text content auditing method and system based on sensitive word
ActiveCN106445998AReduce false positive rateImprove audit accuracyWeb data indexingNatural language data processingCo-occurrenceDatabase
The invention discloses a text content auditing method based on a sensitive word. The text content auditing method comprises the following steps of: receiving a text to be audited, carrying out parsing and word segmentation on the text to be audited, and obtaining all keywords in the text to be audited; according to all keywords, inquiring a preset sensitive word database, and obtaining the sensitive word in the text to be audited, wherein the sensitive word database comprises sensitive words and the synonyms or the homoionyms of the sensitive words; obtaining the co-occurrence keyword of the sensitive word in a preset text length, calculating the violation weight of the sensitive word and the co-occurrence keyword of the sensitive word, and judging whether the violation weight is greater than a preset violation threshold value or not; and if the violation weight is greater than the preset violation threshold value, proving that the text to be audited is a violation text, and otherwise, proving that the text to be audited is a normal text. By use of the text content auditing method, a misjudgment probability is effectively lowered, auditing accuracy is improved, and the text content auditing method has quick reaction capacity for anagrams and net neologisms.
Owner:DATAGRAND TECH INC
System, method and apparatus for selecting, displaying, managing, tracking and transferring access to content of web pages and other sources
ActiveUS7278092B2Easy searchAdjustable sizeRecording carrier detailsRecord information storageAnimationMouseover
A method, system and apparatus for selecting, displaying, managing, tracking and transferring access to content of Internet web pages and other sources along with custom text messages has programming permitting a user to create custom selections of selected image, animation, movie and text content items, and other types of content items from web pages or other sources from the same or different network sources containing multiple content items, along with user-supplied text messages, in an independent, resizable, rescalable browser window; permitting the user to transfer access to the custom selection of content items to a recipient; permitting the user or recipient to navigate quickly to a source of a content item in the custom selection; and permitting the user to define search keywords for performing searches related to content items in a custom selection; and other features. A method of tracking viewing and sharing activities of content items and custom selections of content items by users and recipients is also disclosed. A method of assisted content selection provides temporary borders around content items on mouseover.
Owner:SALESFORCE COM INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com