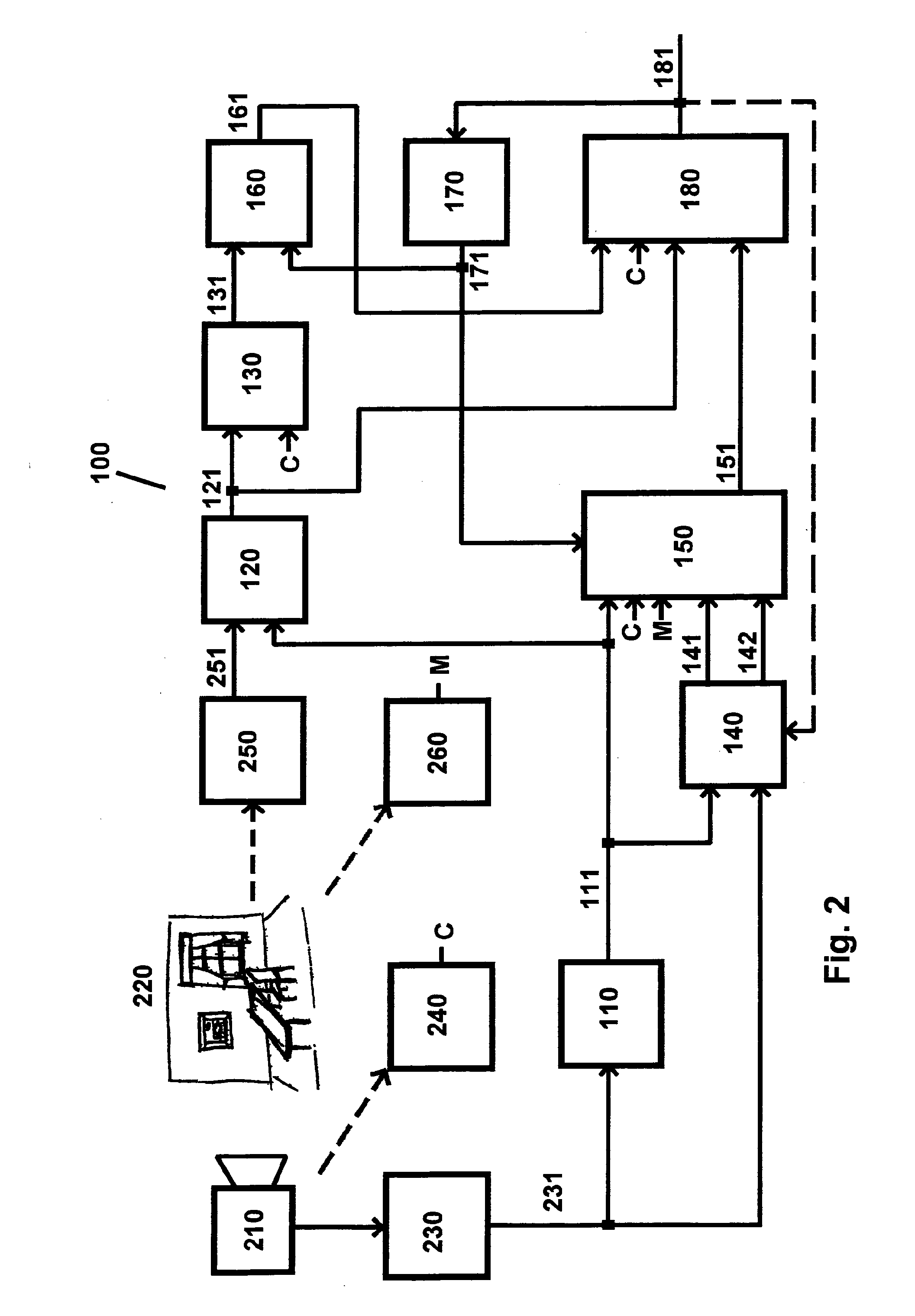
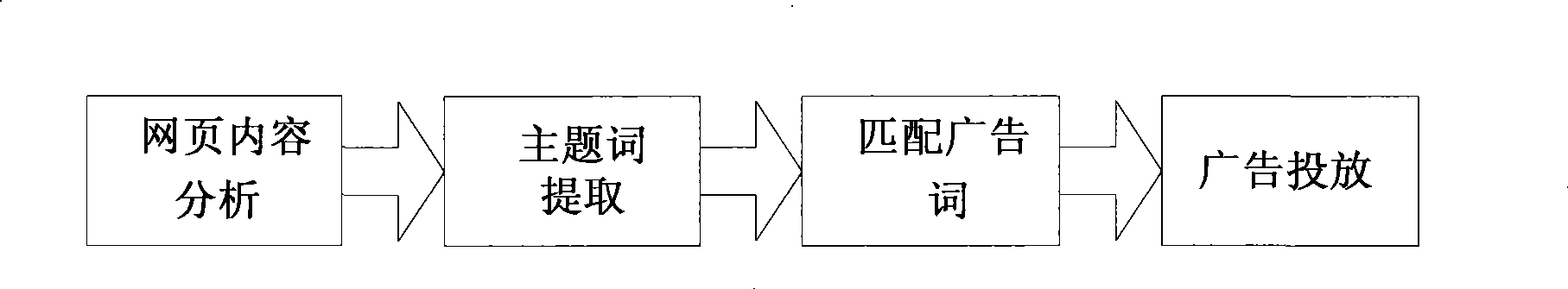
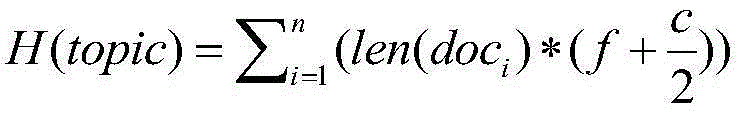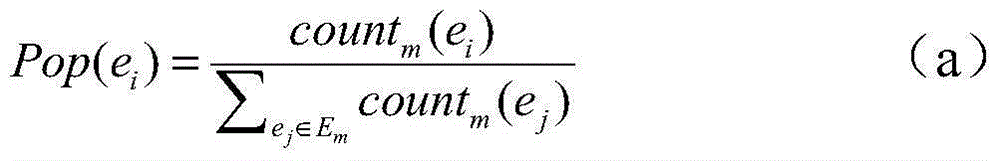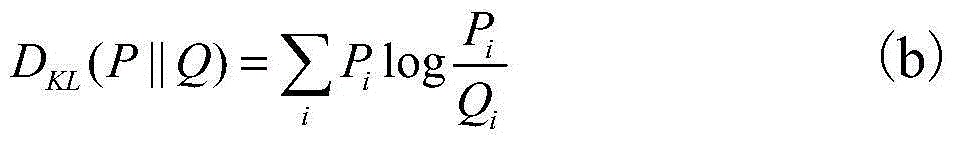Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
137 results about "Candidate key" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
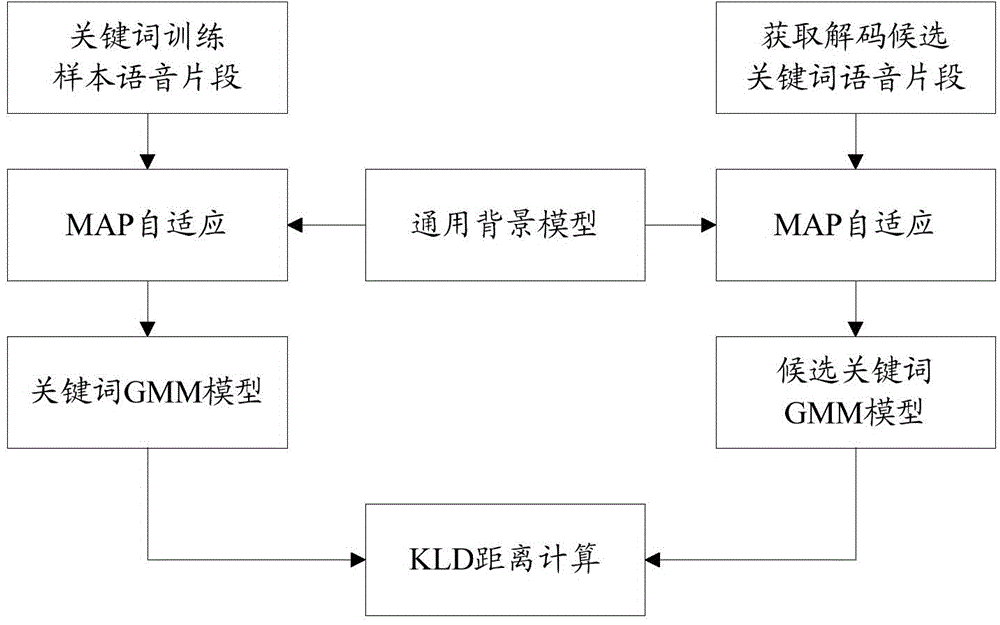
In the relational model of databases, a candidate key of a relation is a minimal superkey for that relation; that is, a set of attributes such that...
Intelligent key-frame extraction from a video
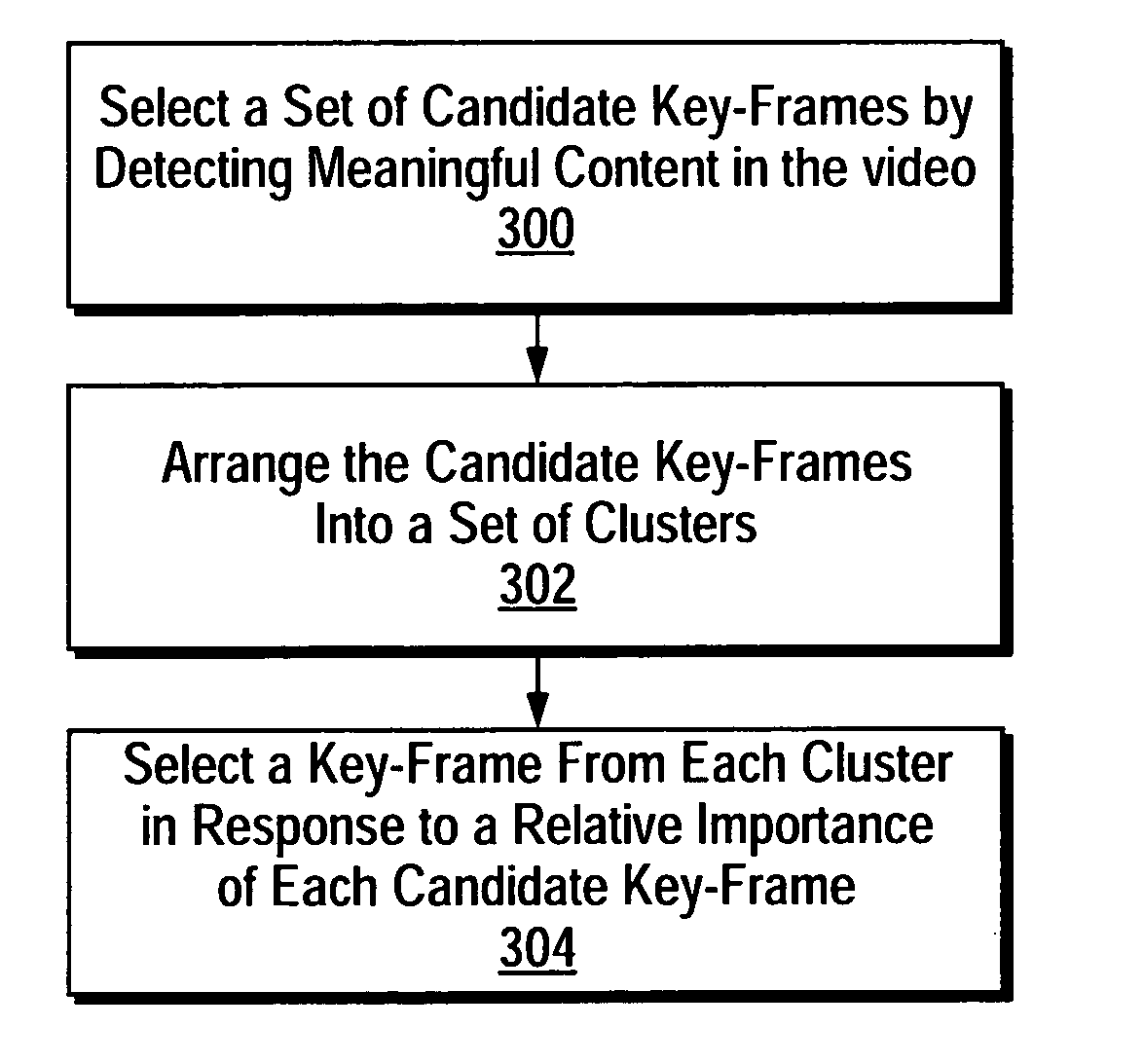
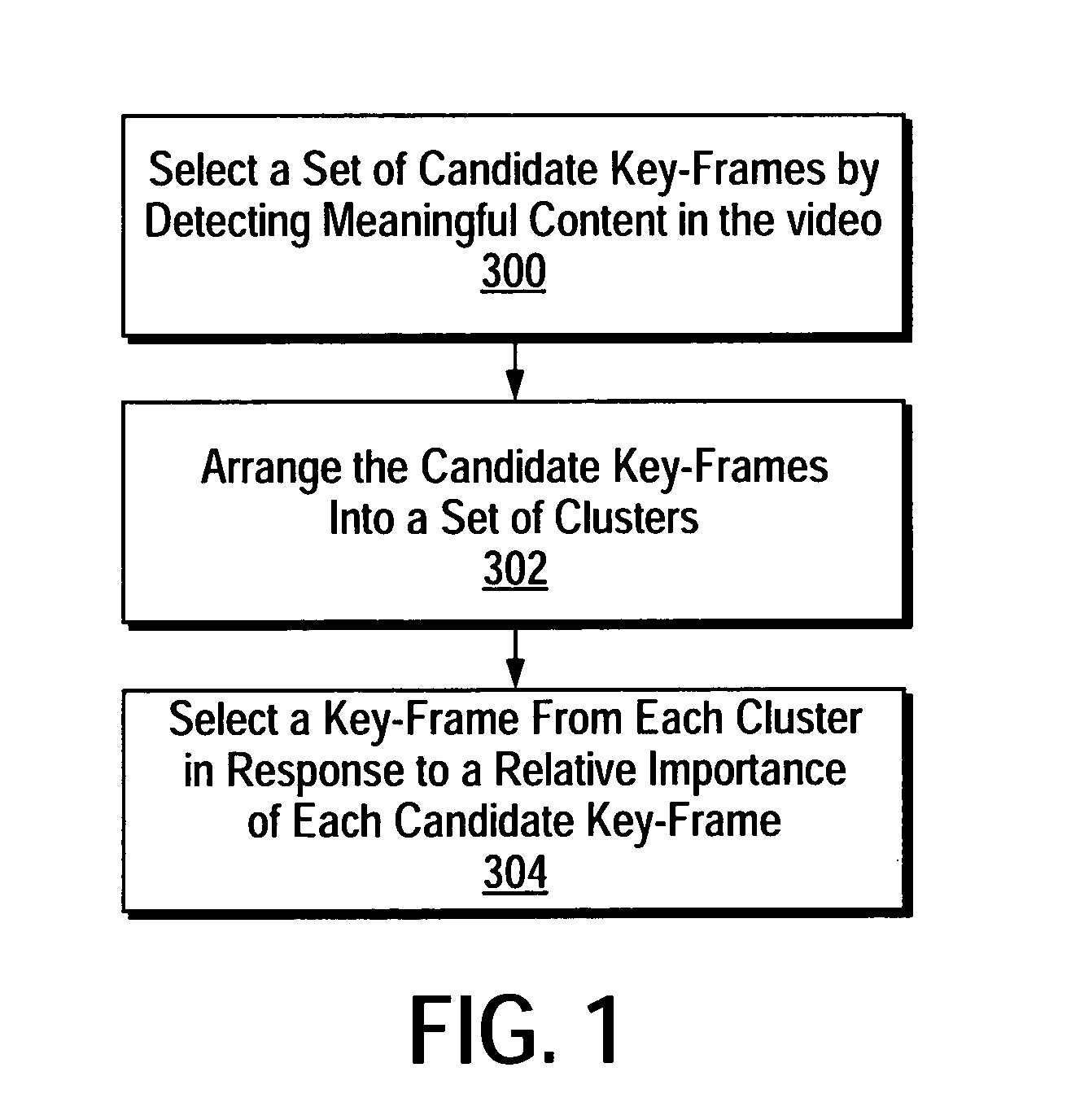
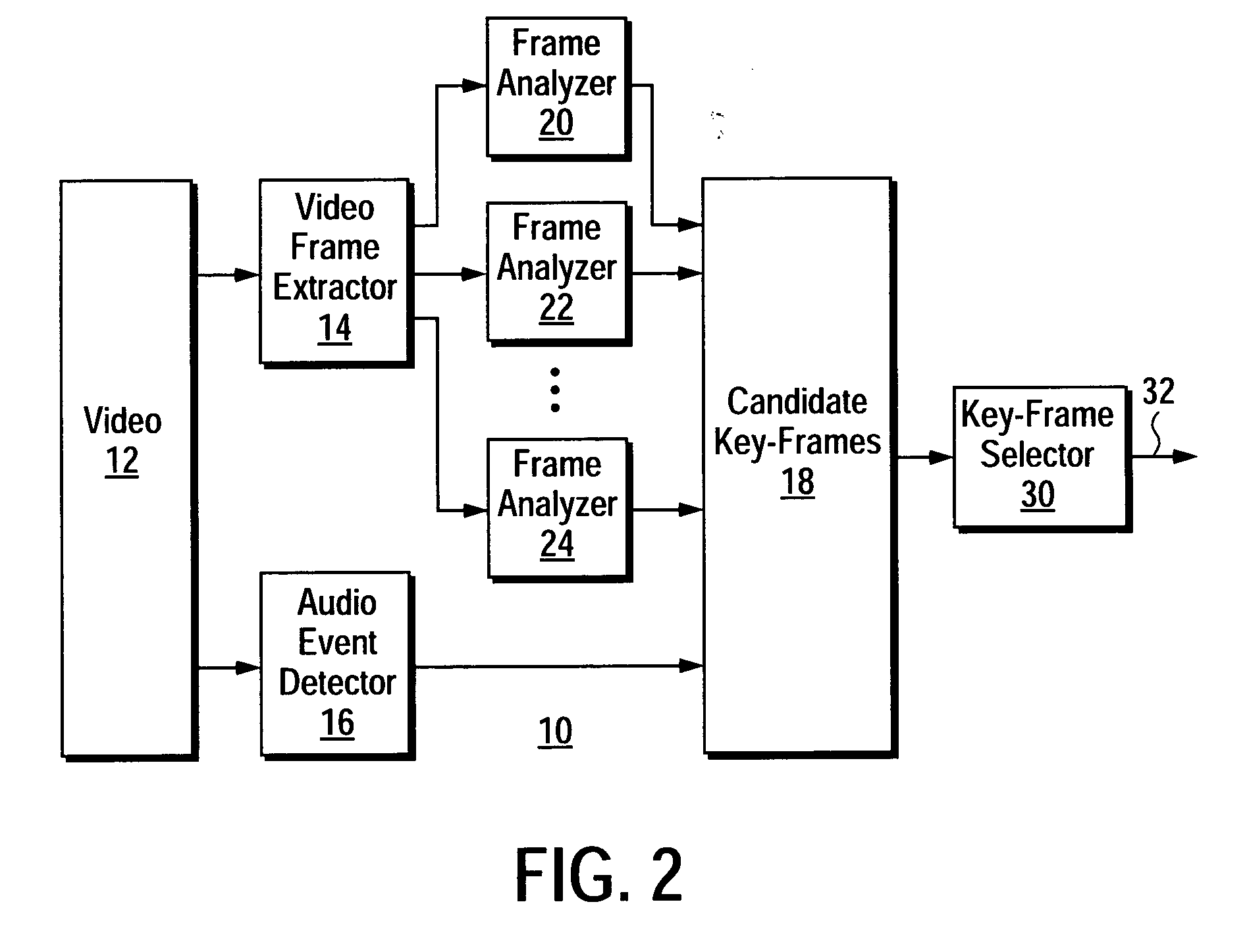
A method for intelligent extraction of key-frames from a video that yields key-frames that depict meaningful content in the video. A method according to the present techniques includes selecting a set of candidate key-frames from among a series of video frames in a video by performing a set of analyses on each video frame. Each analysis is selected to detect a corresponding type of meaningful content in the video. The candidate key-frames are then arranged into a set of clusters and a key-frame is then selected from each cluster in response to its relative importance in terms of depicting meaningful content in the video.
Owner:HEWLETT PACKARD DEV CO LP
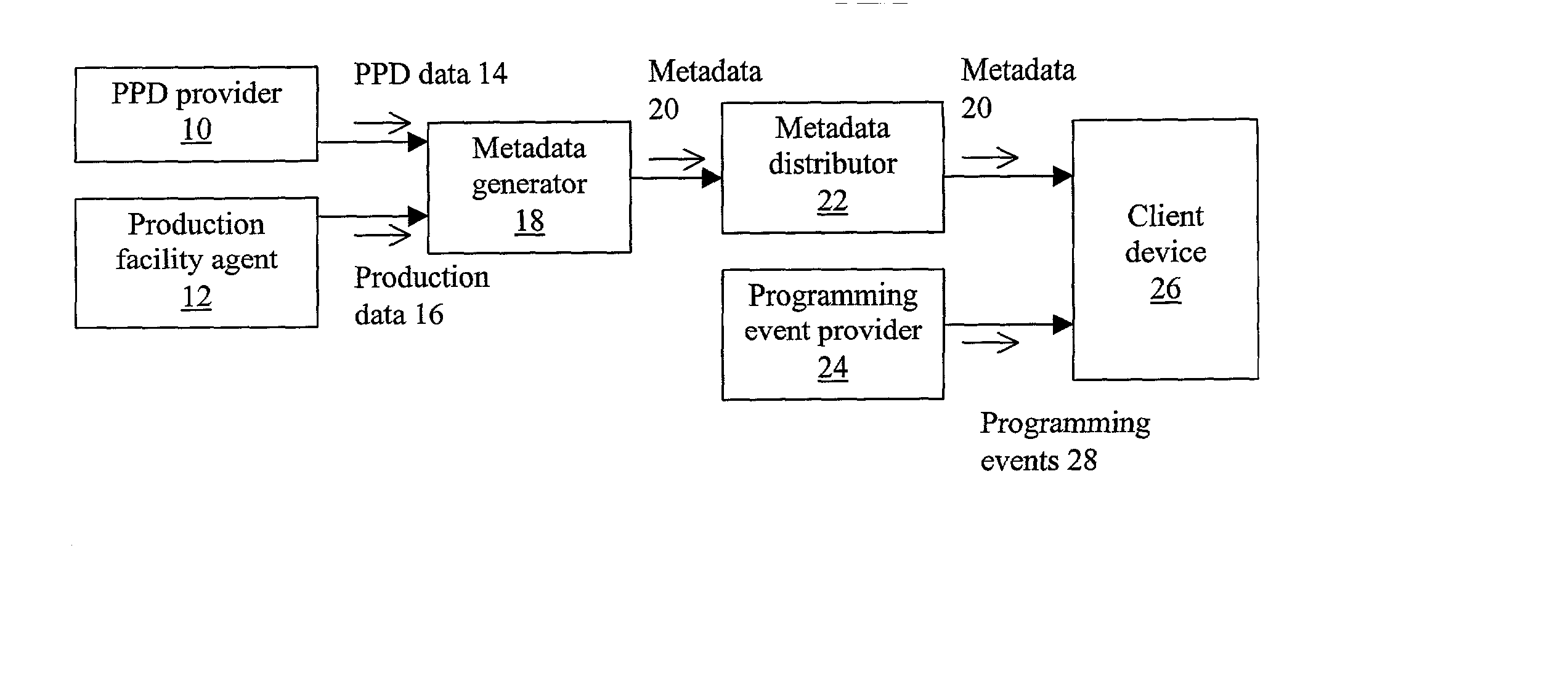
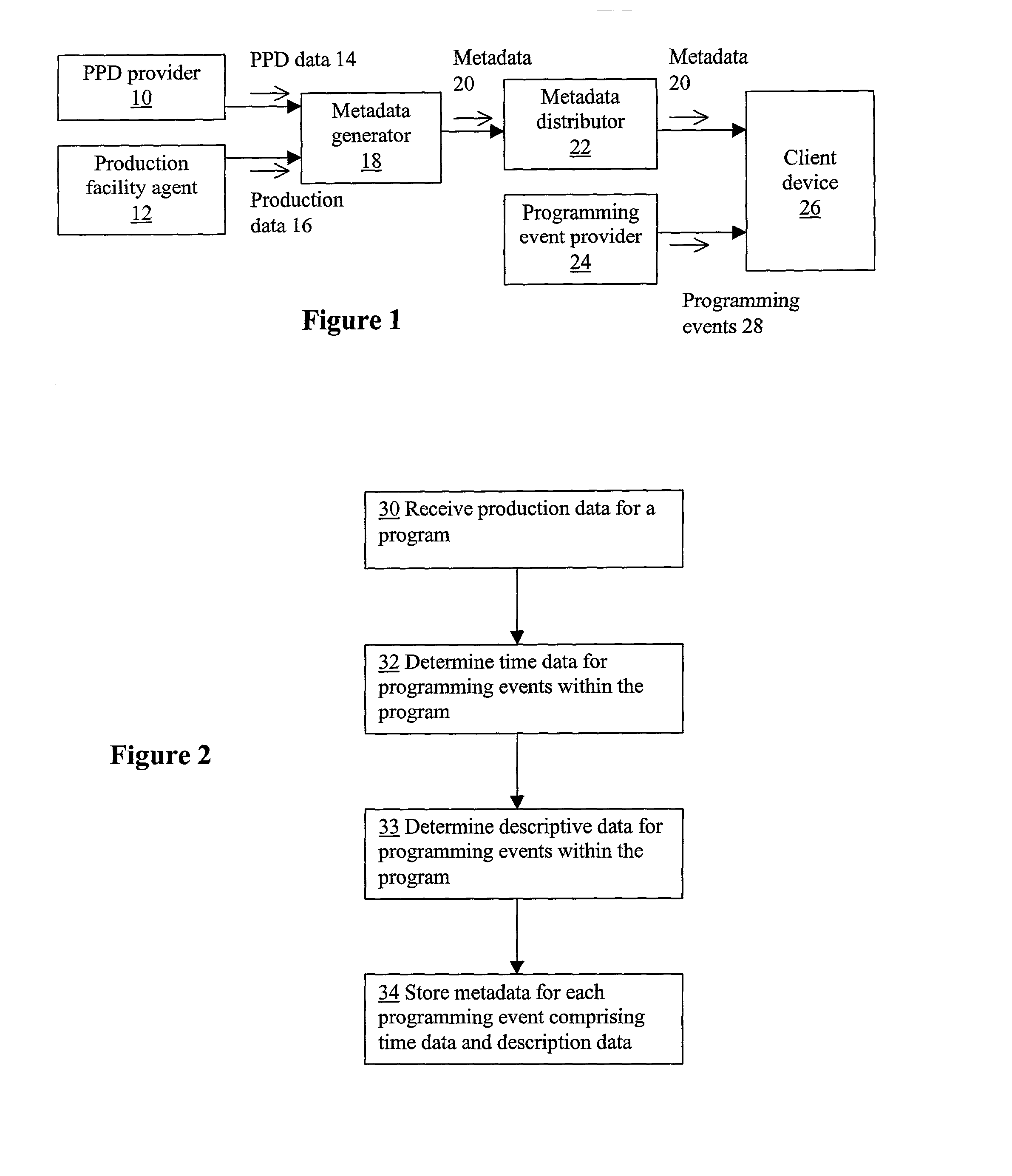
System and method for generating metadata for programming events
InactiveUS20020092031A1Television system detailsData processing applicationsGoodness of fitTime data
Metadata for a programming event may be generated by receiving descriptive information and timing information for the programming event and analyzing this information to determine category goodness of fit scores for the programming event corresponding to categories of a classification hierarchy. The information is further analyzed to determine keywords associated with the programming event. The category goodness of fit scores and keywords may be stored along with time data and descriptive data for the programming event as metadata for the programming event. Goodness of fit scores may also be generated for the keywords. Related embodiments may pertain to a device implementing such processing. Keyword metadata may be generated using candidate keywords taken from descriptive data associated with the programming event. The candidate key words may be provided individually as inputs to a classification tool configured to generate goodness of fit scores for categories of a classification hierarchy. Keywords may then be selected from among the candidates based on their individual scores, and stored as part of the metadata for the programming event. The scores of the keywords may be stored in association with the keywords.
Owner:MEEVEE
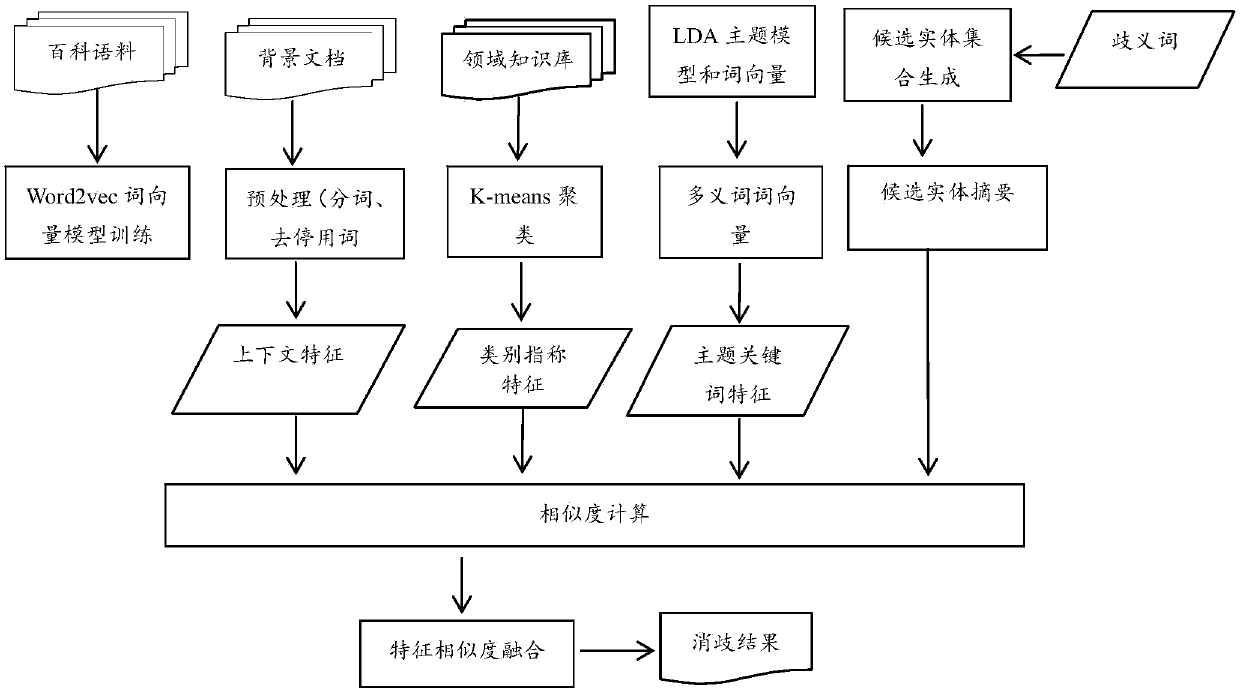
Domain entity disambiguation method for fusing word vectors and topic model
ActiveCN107861939AImprove accuracyGood effectWeb data indexingSemantic analysisAlgorithmDocument preparation
The invention relates to a domain entity disambiguation method for fusing word vectors and a topic model, and belongs to the technical field of natural language processing and deep learning. The method comprises the steps of obtaining candidate entity sets of to-be-disambiguated entities; obtaining vector forms of the to-be-disambiguated entities and candidate entities, obtaining categorical referents of the to-be-disambiguated entities in combination with a hyponymy relation domain knowledge base, and performing context similarity and categorical referent similarity calculation; performing word vector training on documents in different topic classifications by utilizing the LDA topic model and a Skip-gram word vector model, obtaining word vector representations of different meanings of apolysemous word, extracting a topic domain keyword of a text by using a K-Means algorithm, and performing domain topic keyword similarity calculation; and finally, fusing three feature similarities, and taking the candidate entity with the highest similarity as a final target entity. The method is superior to a conventional disambiguation method and can well meet the demands of actual applications.
Owner:KUNMING UNIV OF SCI & TECH
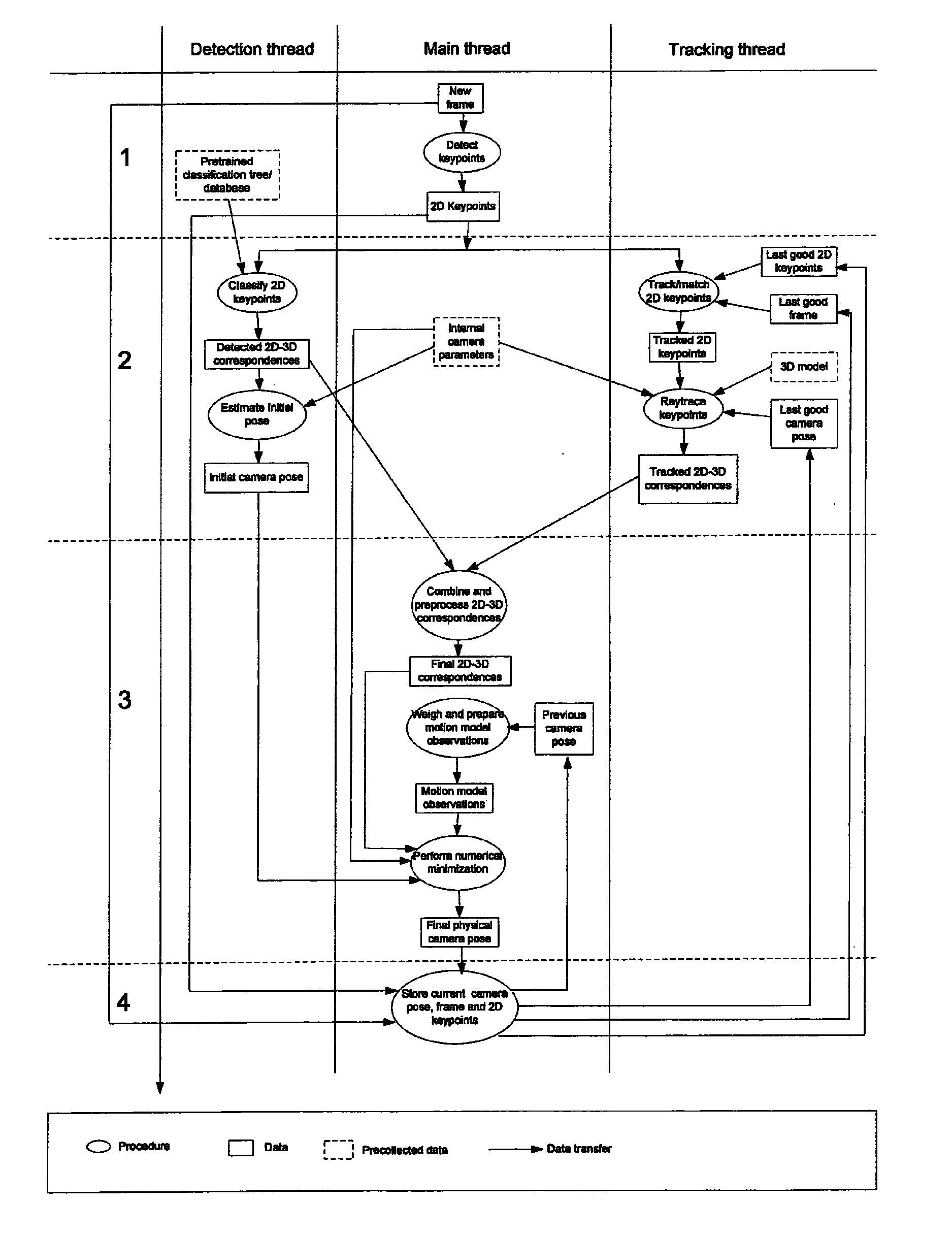
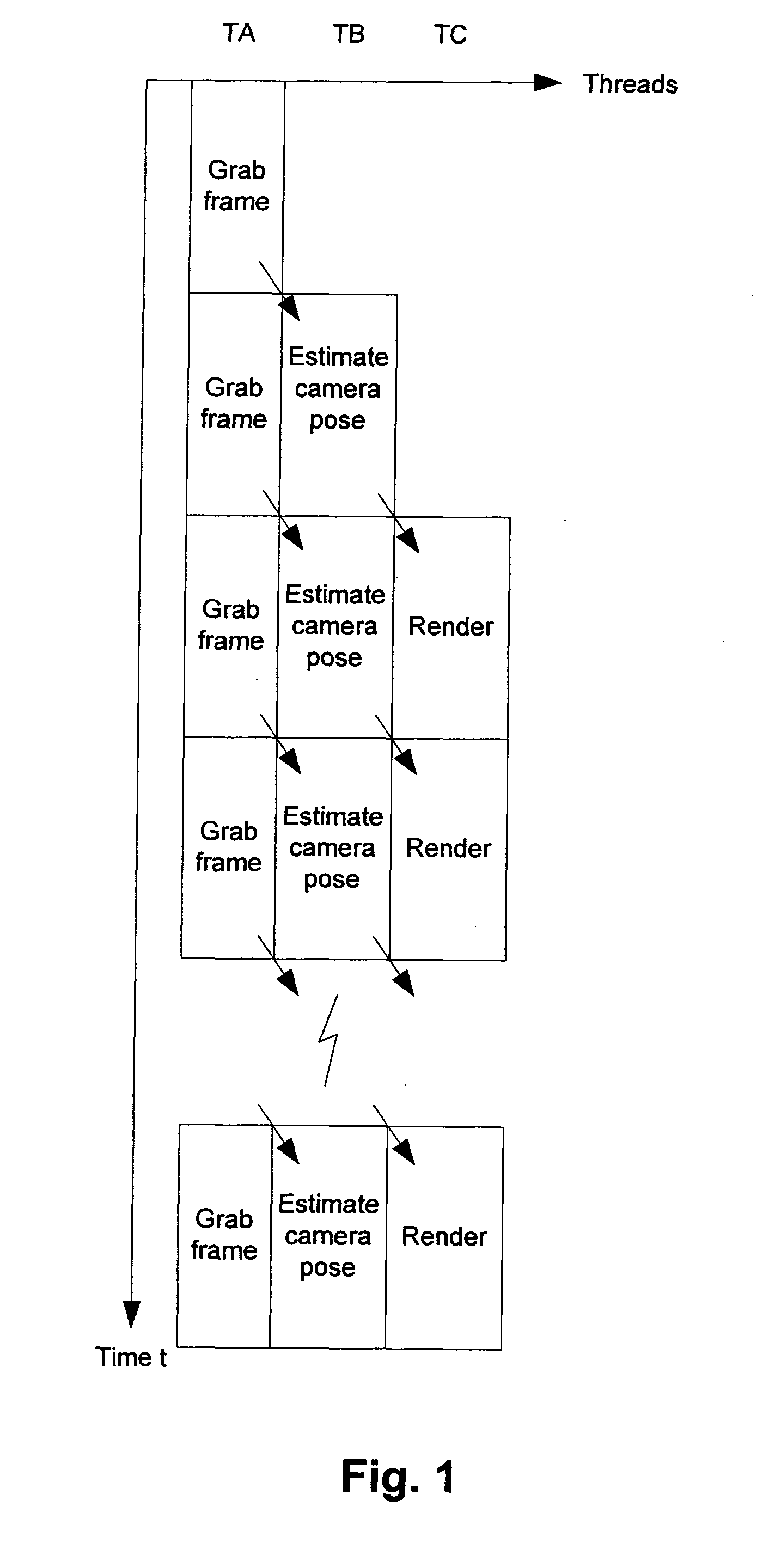
Camera pose estimation apparatus and method for augmented reality imaging
ActiveUS20100232727A1Satisfactory accuracyFast and efficient implementationImage enhancementImage analysis3d cameraCandidate key
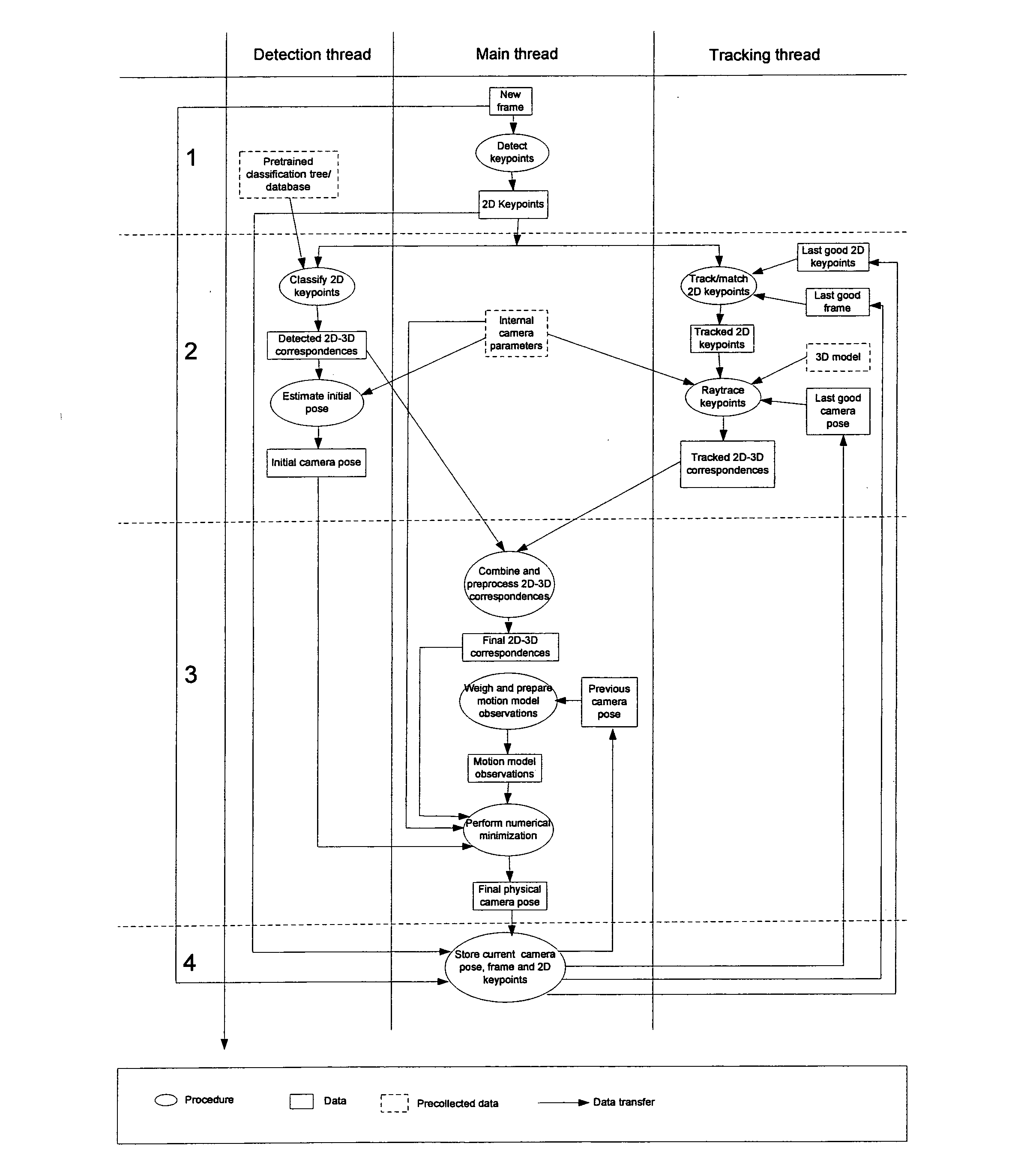
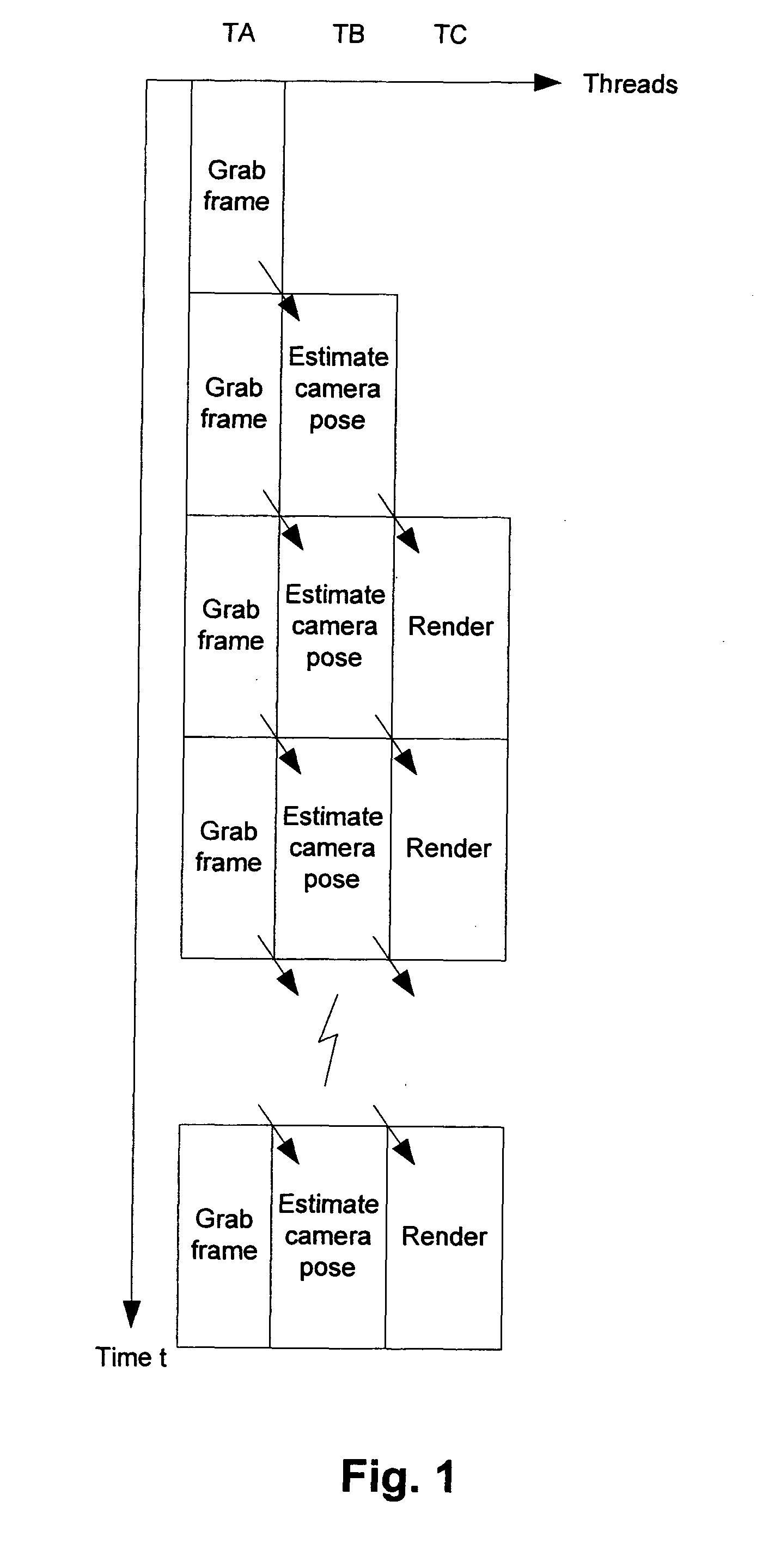
An apparatus for providing an estimate for a 3D camera pose relative to a scene from 2D image data of 2D image frame provided by said camera. A candidate 2D key points detector determines candidate 2D key points from the 2D image frame. A detected 3D observations detector determines detected 3D observations from pre-recorded scene data and the candidate 2D key points. A detected 3D camera pose estimator determines a detected 3D camera pose estimate from the camera data, the detected 3D observations and the candidate 2D key points. A first storage stores the detected 2D candidate key points and the 2D image data, and outputs in response to a 3D camera pose estimate output previous 2D image data and candidate 2D key points related to a previous 3D camera pose estimate output. A second storage stores and outputs a previous 3D camera pose estimate. A tracked 3D observations detector determines tracked 3D observations from the 2D image data, the candidate 2D key points, the camera data, the previous 2D image data and candidate 2D key points, the previous 3D camera pose estimate and 3D scene model data. A pose estimate selector outputs a selected one of the detected camera pose estimate and the previous 3D camera pose estimate. A 3D camera pose estimator computes and outputs the 3D camera pose estimate from the camera data, the detected 3D observations, the tracked 3D observations and the selected 3D camera pose estimate.
Owner:APPLE INC
Method used by an access point of a wireless LAN and related apparatus
InactiveUS20060107050A1Increasing internet securityKey distribution for secure communicationMultiple keys/algorithms usageComputer networkWireless lan
The present invention discloses a method used by an Authenticator of a wireless LAN. The Authenticator is capable of communicating wirelessly with a Supplicant of the wireless LAN. The Authenticator holds a plurality of candidate keys whereas the Supplicant holds one key. The key held by the Supplicant is included in the plurality of candidate keys held by the Authenticator. The method includes determining which one of the plurality of candidate keys is the key held by the Supplicant and communicating with the Supplicant wirelessly according to the determined key held by the Supplicant.
Owner:DRAYTEK
Human body posture identification method based on multi-characteristic fusion of key frame
ActiveCN102682302ADescribe wellEfficient analysisImage analysisCharacter and pattern recognitionHuman bodyFeature vector
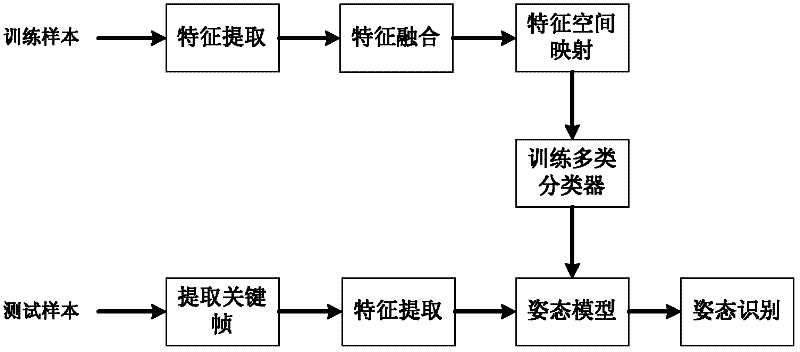
The invention provides a human body posture identification method based on multi-characteristic fusion of a key frame, comprising the following steps of: (1) extracting Hu invariant moment characteristics from a video image; calculating a covering rate of an image sequence; extracting the highest covering percentage of the covering rate as a candidate key frame; then calculating a distortion rate of the candidate key frame and extracting the minimum distortion percentage as the key frame; (2) carrying out extraction of a foreground image on the key frame to obtain the foreground image of a moving human body; (3) extracting characteristic information of the key frame, wherein the characteristic information comprises a six-planet model, a six-planet angle and eccentricity; obtaining a multi-characteristic fused image characteristic vector; and (4) utilizing a one-to-one trained classification model, wherein the classification model is a posture classifier based on an SVM (Secure Virtual Machine); and identifying a posture. The human body posture identification method has the advantages of simplified calculation, good stability and good robustness.
Owner:ZHEJIANG UNIV OF TECH
Computer readable medium having a private key encryption program
InactiveUS6956950B2No Undue Burden on UserEasy accessKey distribution for secure communicationAcutation objectsComputer hardwareKey generation
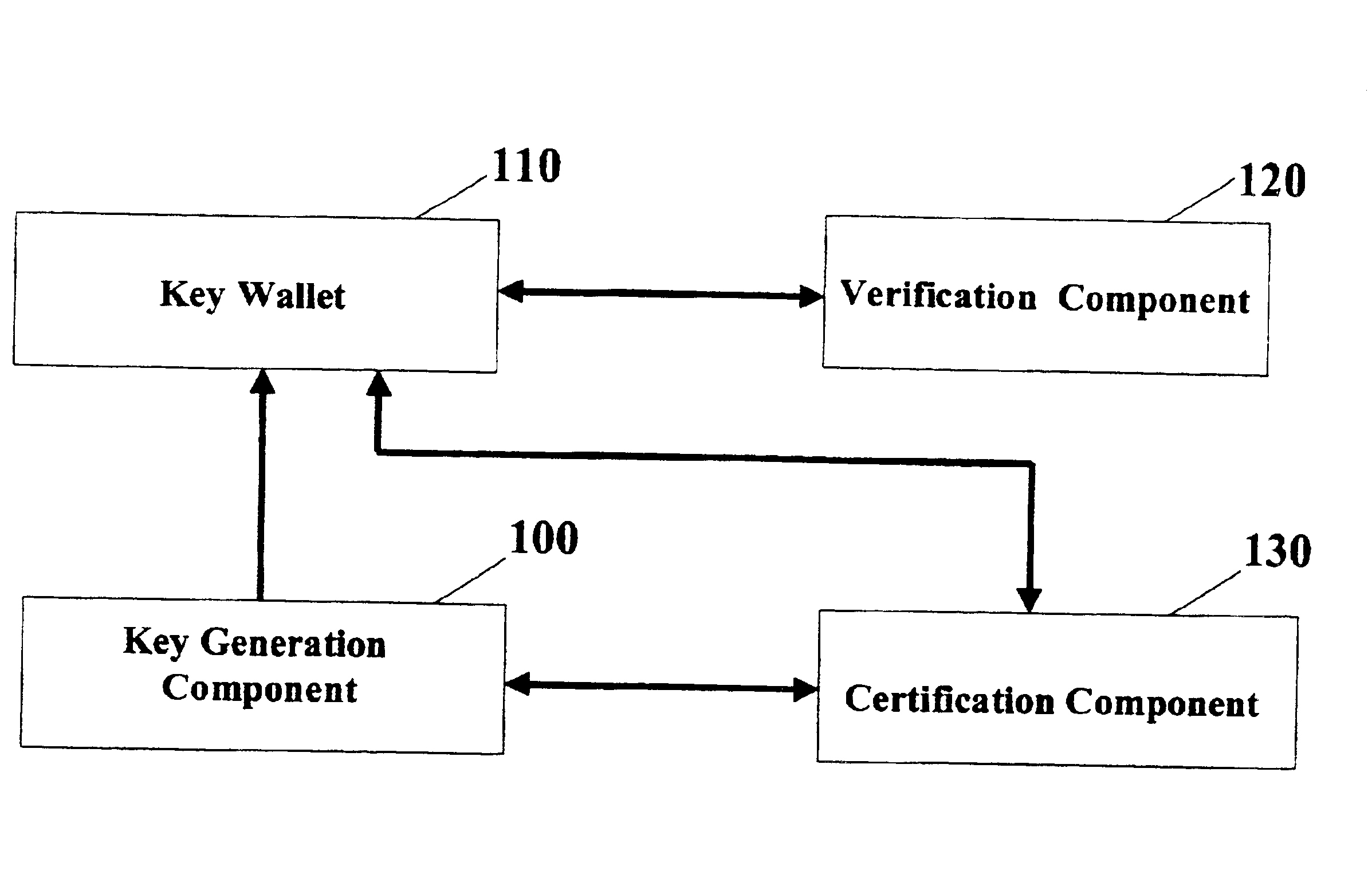
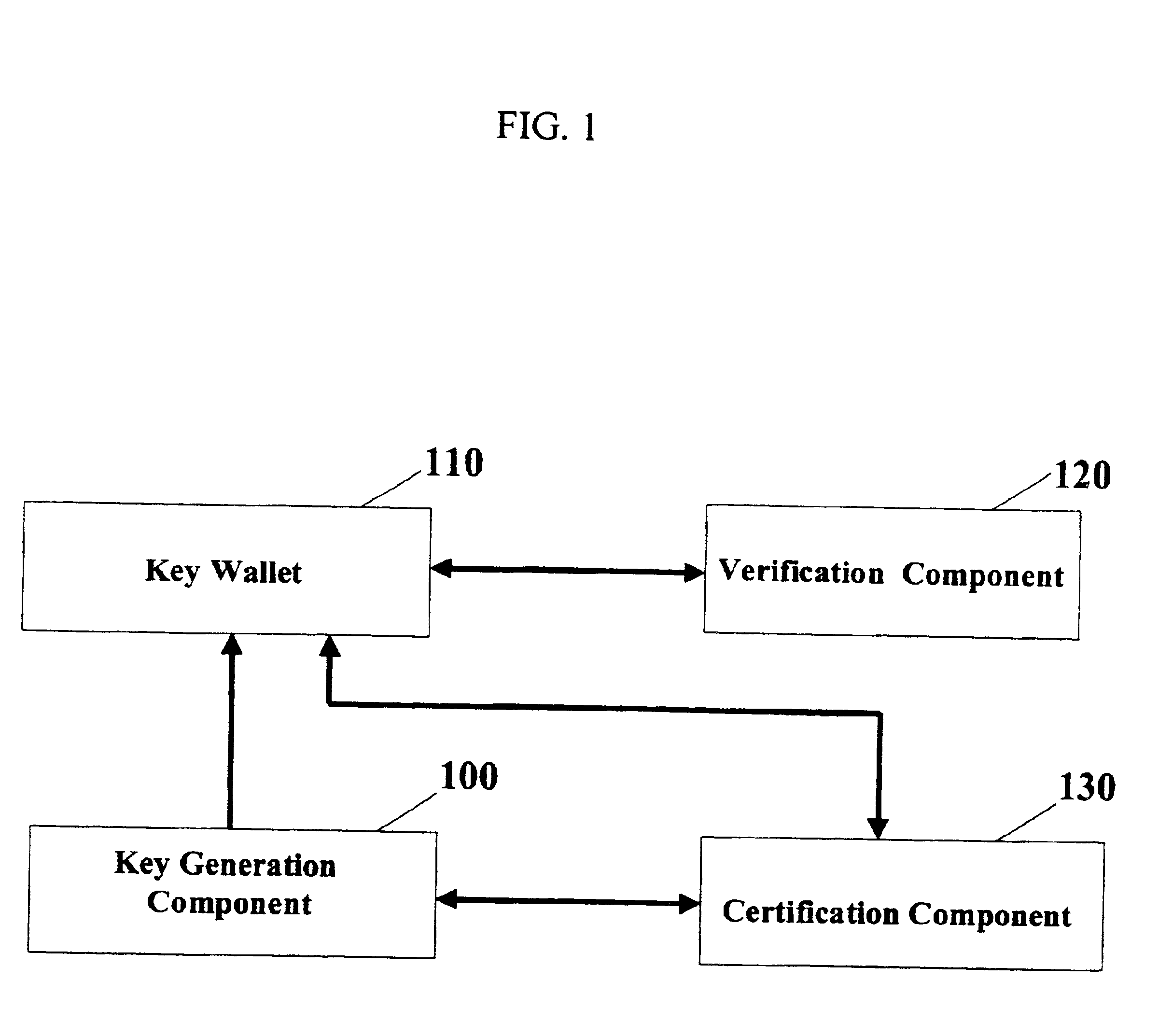
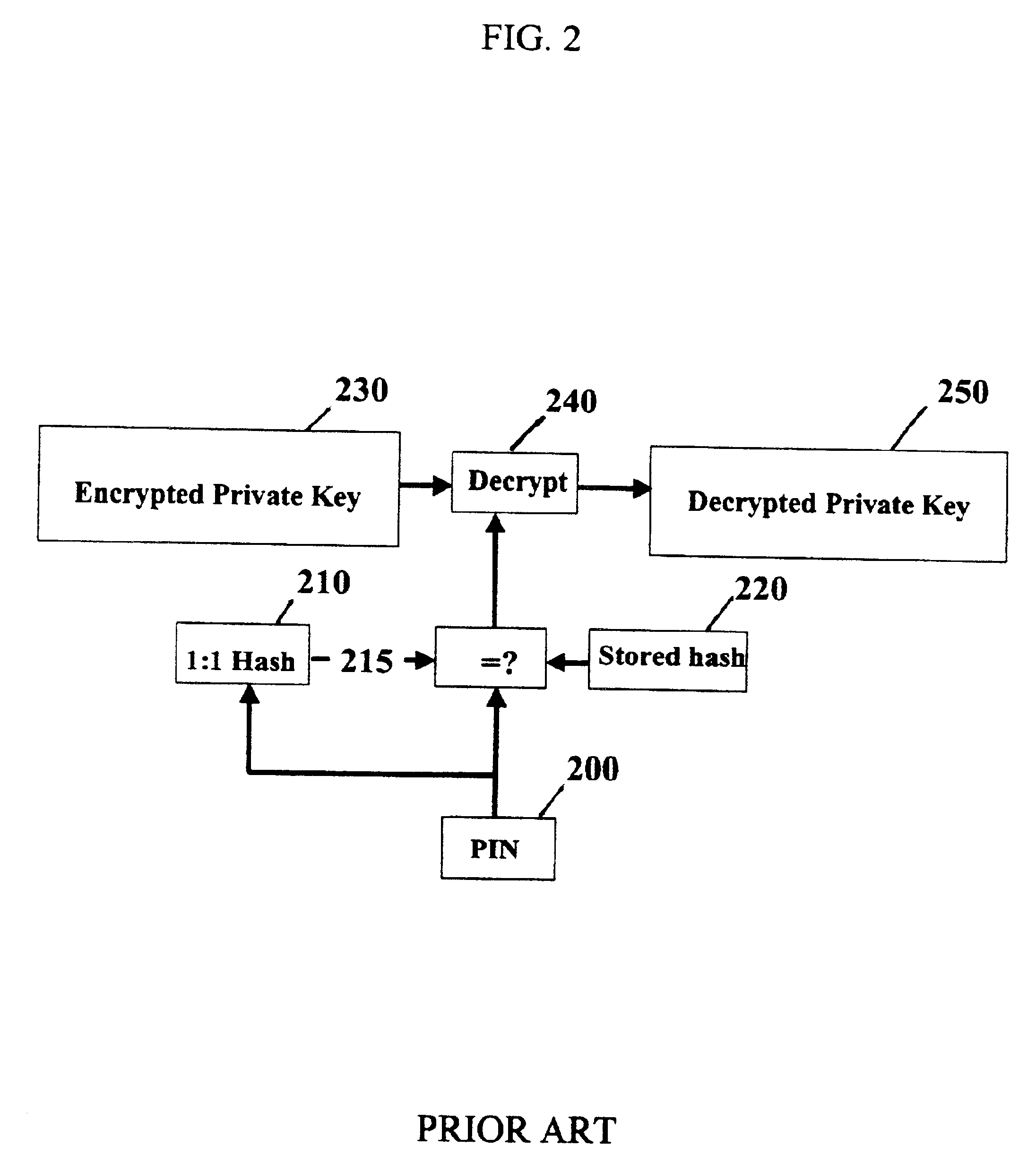
A digital wallet stores an cryptographically camouflaged access-controlled datum, e.g., a private key encrypted under the user's PIN. Entry of the correct PIN will correctly decrypt the stored key. Entry of certain pseudo-valid PINs will also decrypt the stored key, but improperly so, resulting in a candidate key indistinguishable from the correct key. Such pseudo-valid PINs are spread thinly over the space of PINs, so that the user is unlikely to realize a pseudo-valid PIN via a typographical error in entering the correct PIN. In existing wallet technologies, which lack pseudo-valid PINs, only the correct PIN produces a decrypted key; thus, hackers can find the correct PIN by entering all possible PINs until a key is produced. The present invention's plurality of candidate keys prevent a hacker from knowing when he has found the correct key. In addition, hacker detection may be moved off-line into devices accepting messages signed with candidate keys, and / or the lockout threshold may be increased. Thus, the wallet can be forgiving of typographic or transposition errors, yet a hacker trying large numbers of PINs will eventually guess a pseudo-valid (but still incorrect) PIN and recover a candidate private key whose fraudulent use will be detected. The wallet may be used with associated key generation, certification, and verification technologies. Such technologies may include pseudo-public keys embedded in pseudo-public certificates, i.e., public keys that are not generally known and which are contained in certificates that are verifiable only by entities so authorized by the certifying authority.
Owner:CA TECH INC
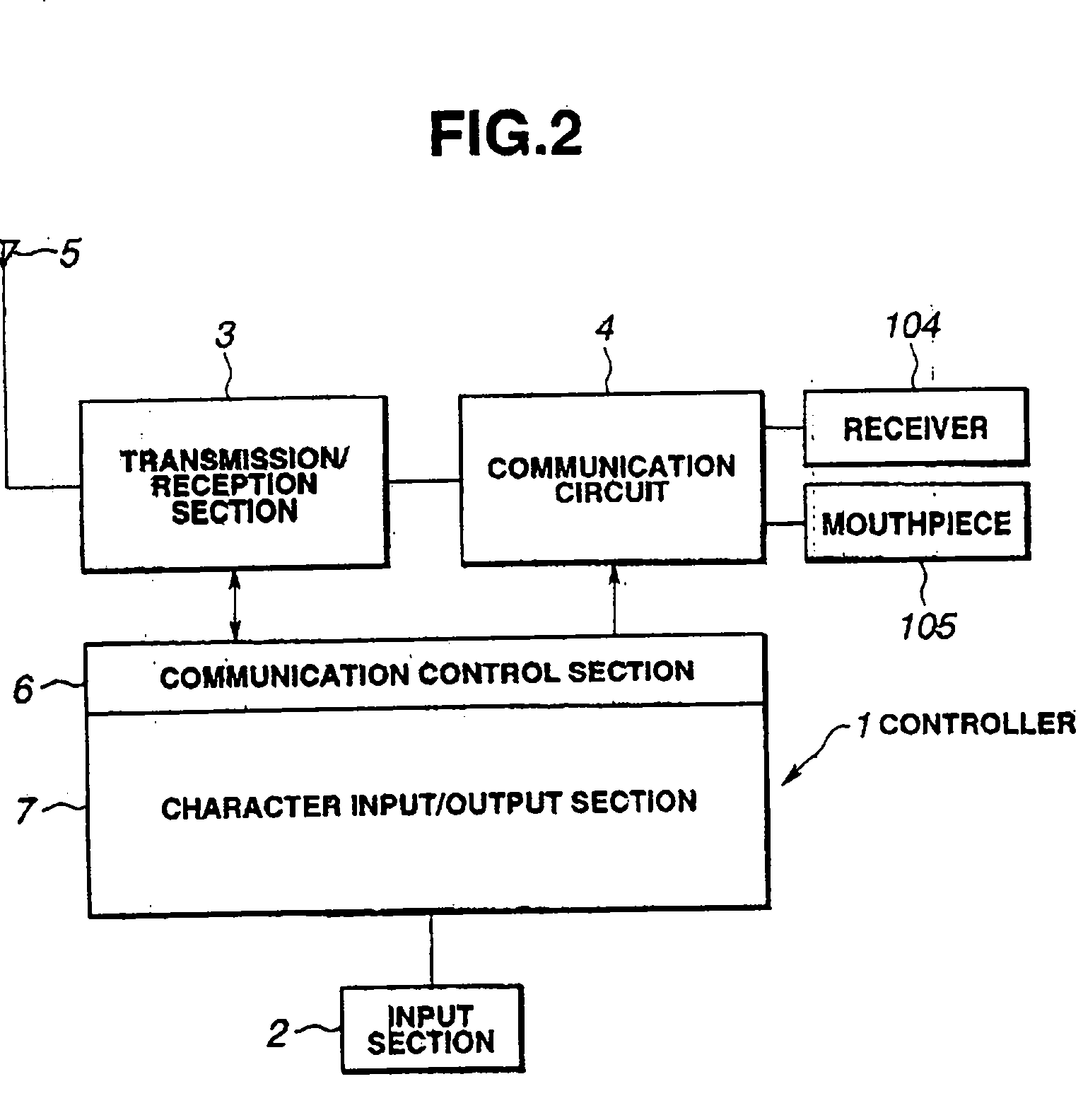
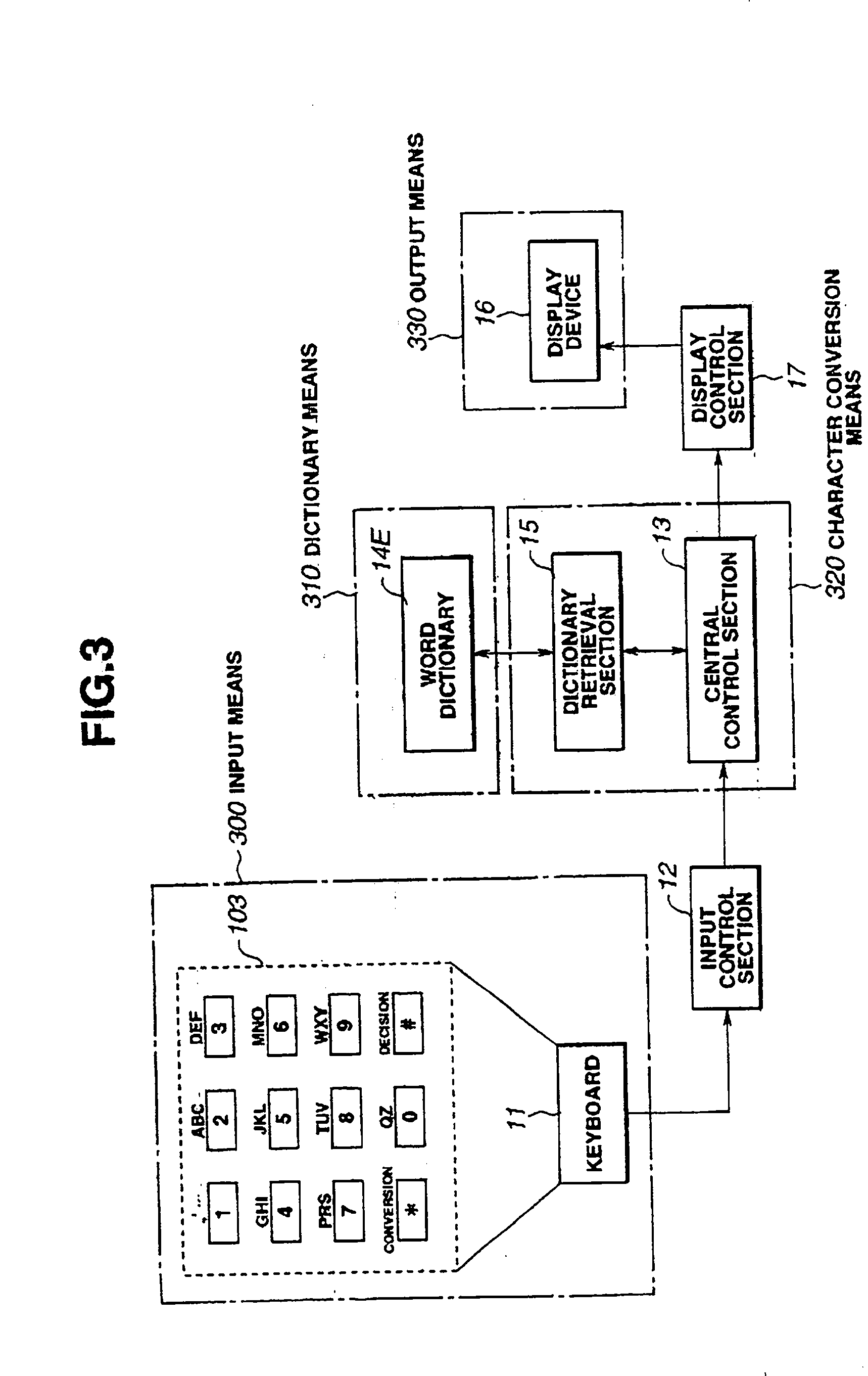
Character input device and method
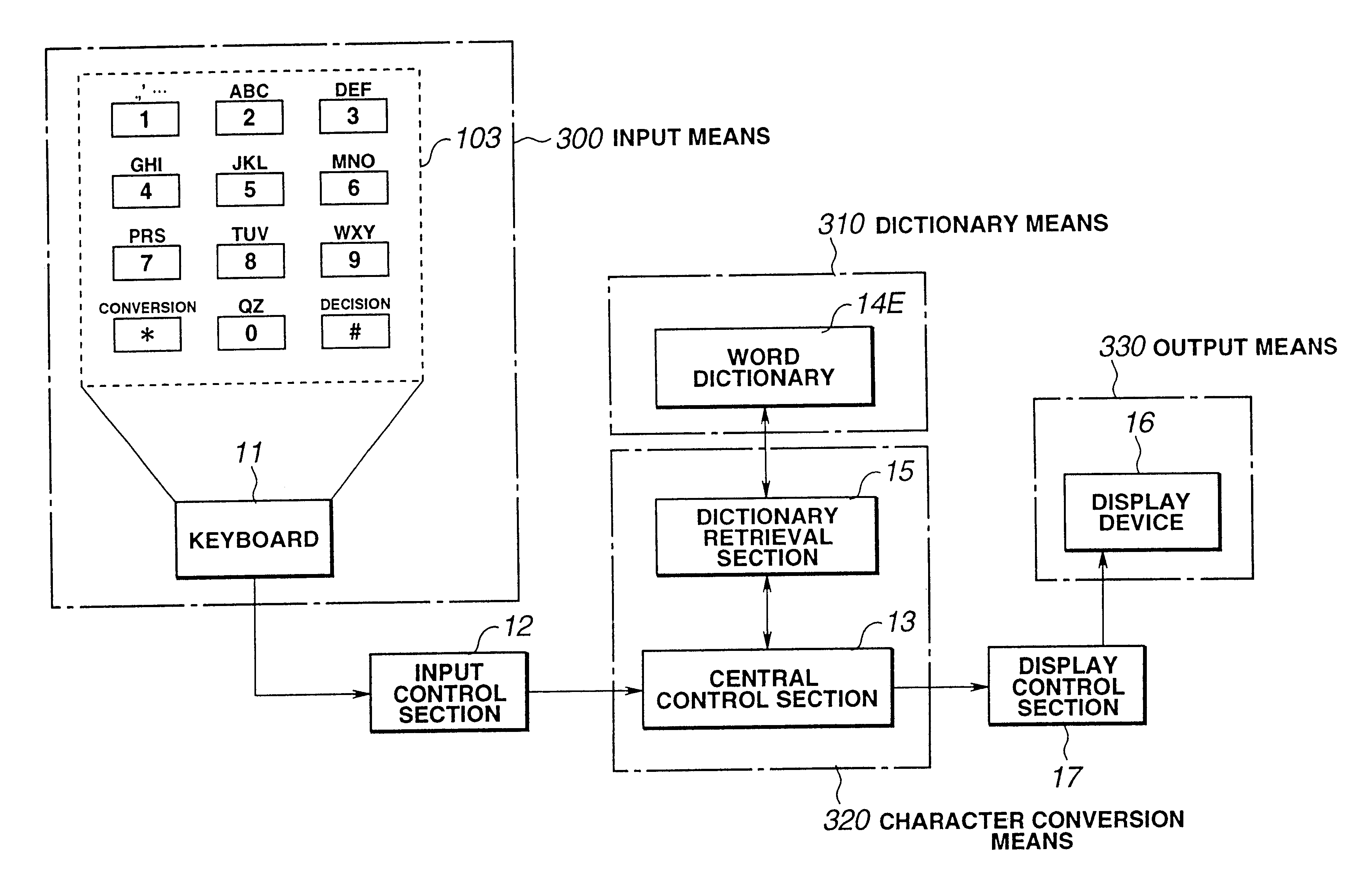
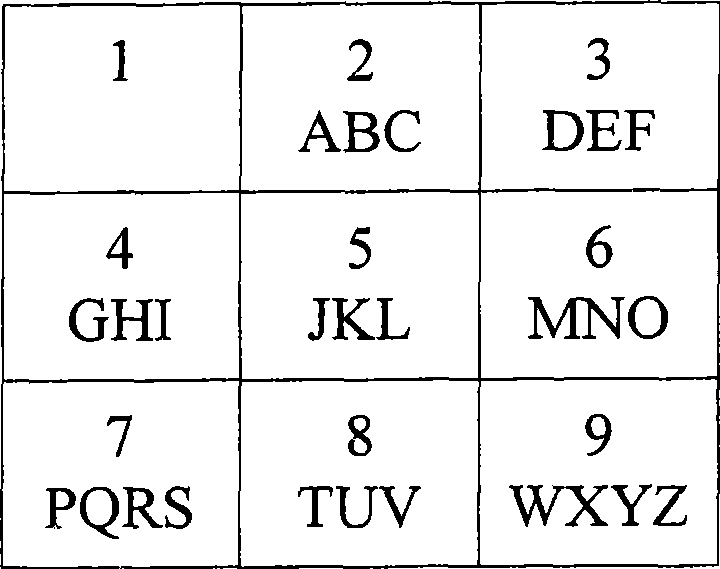
Texts including required message are entered with a small number of keys such as those of a cellular telephone. In this case, a conversion table is unnecessary and the number of key operations is reduced. The number of input characters or input character strings composed by sequentially selecting one from a plurality of alphabets distributed to sequentially entered keys is relevant to the number of operation keys (N) raised to the number of distributed character (M) power (=NM) including meaningless characters or character strings and, with respect to these, character conversion is executed by referring to a dictionary means, through the operation of the conversion / next candidate key. The dictionary means stores numeric strings and words of meaningful characters or character strings among the said characters and character strings.
Owner:FUJITSU TOSHIBA MOBILE COMM LTD
Character input method for all-purpose keyboard and processing device thereof
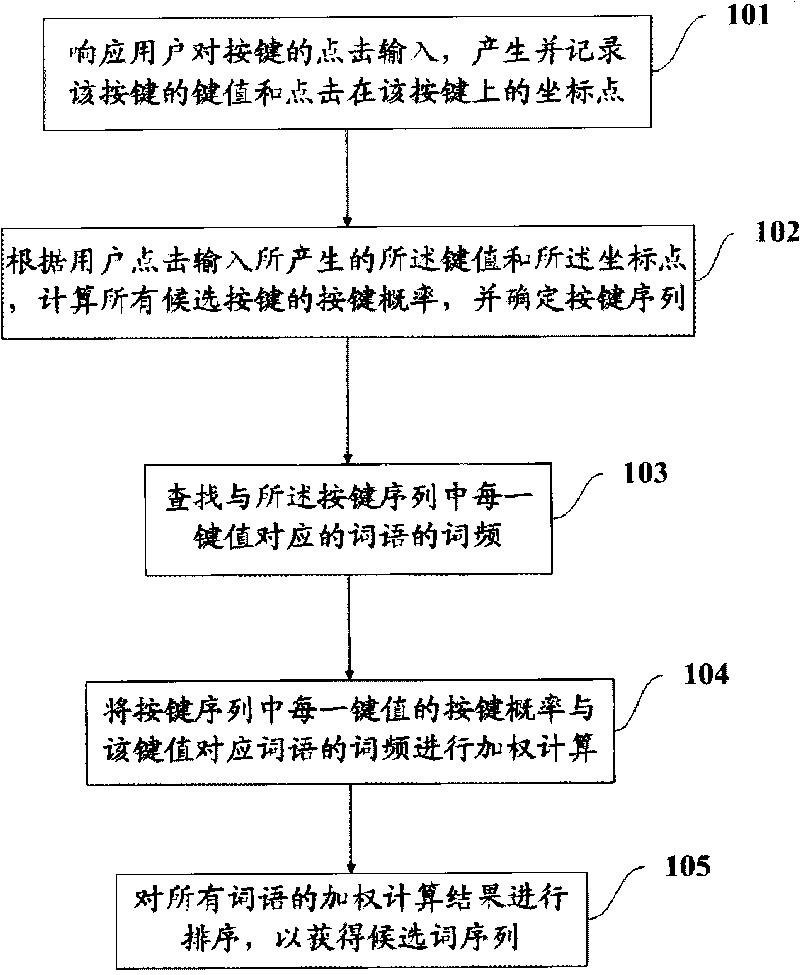
InactiveCN101719022AAvoid Manual CalibrationIncrease typing speedInput/output processes for data processingAlgorithmCandidate key
The invention discloses a character input method for an all-purpose keyboard, which comprises the following steps of: responding the clicking input for a key by a user, and generating and recording the key value of the key and the coordinate of a clicking point; computing the keying probability of all candidate keys according to the key value and the coordinate, and determining a keying sequence, wherein the candidate keys comprise a clicked key and a plurality of character or number keys adjacent to the clicked key; searching the word frequency of a word corresponding to each key value in the keying sequence; carrying out weighing computation for the keying probability of each key value and the word frequency of the word corresponding to the key value in the keying sequence; and sequencing the weighing computation results of all words so as to obtain a candidate word sequence. The invention also discloses a character input processing device which comprises a receiving unit, a probability computing unit, a word frequency inquiry unit and a weighing computation unit. The invention comprehensively considers the word frequencies of the words and further improves the input speed.
Owner:HANVON CORP
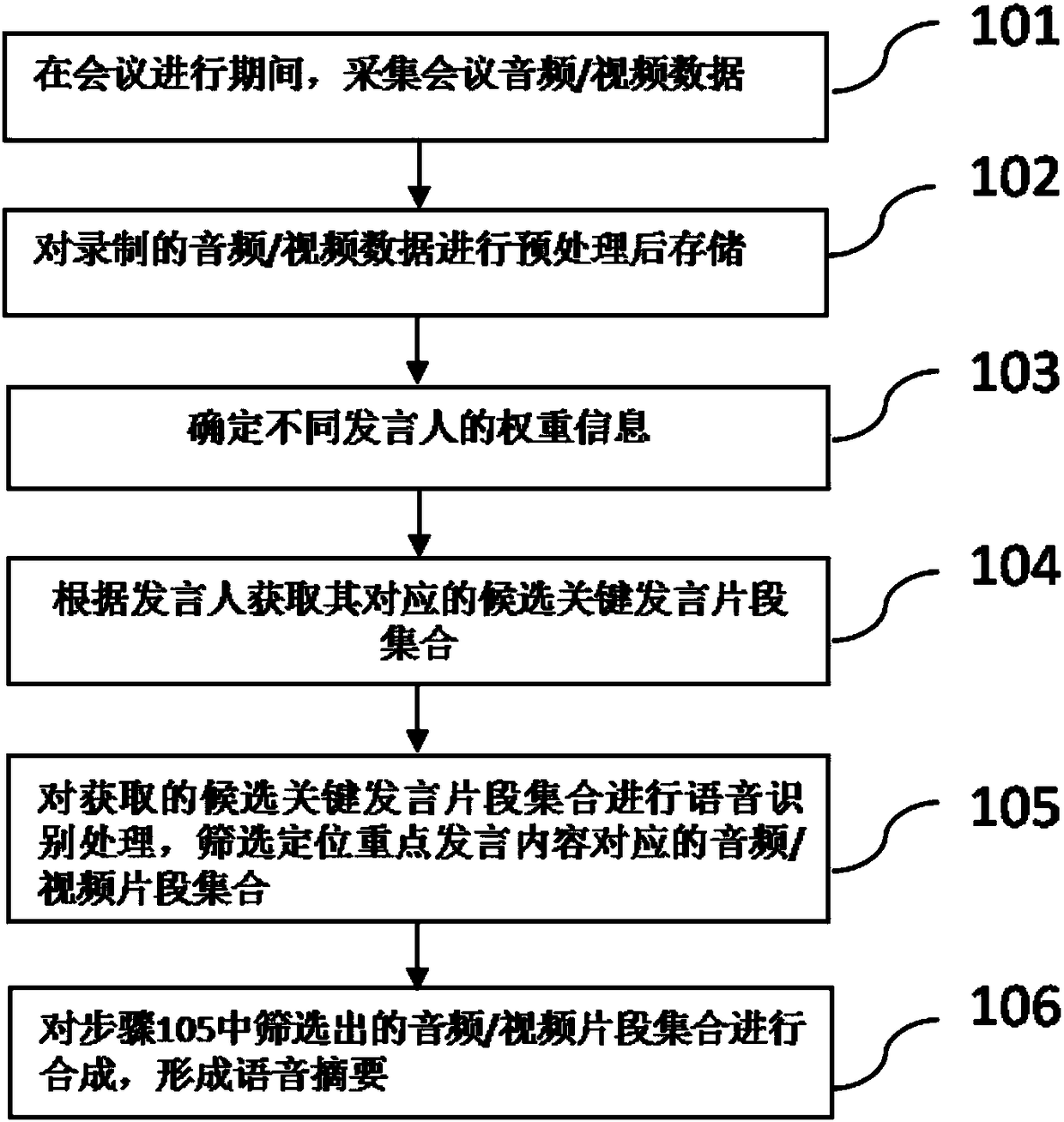
Voice abstract forming method and voice abstract forming system for conference
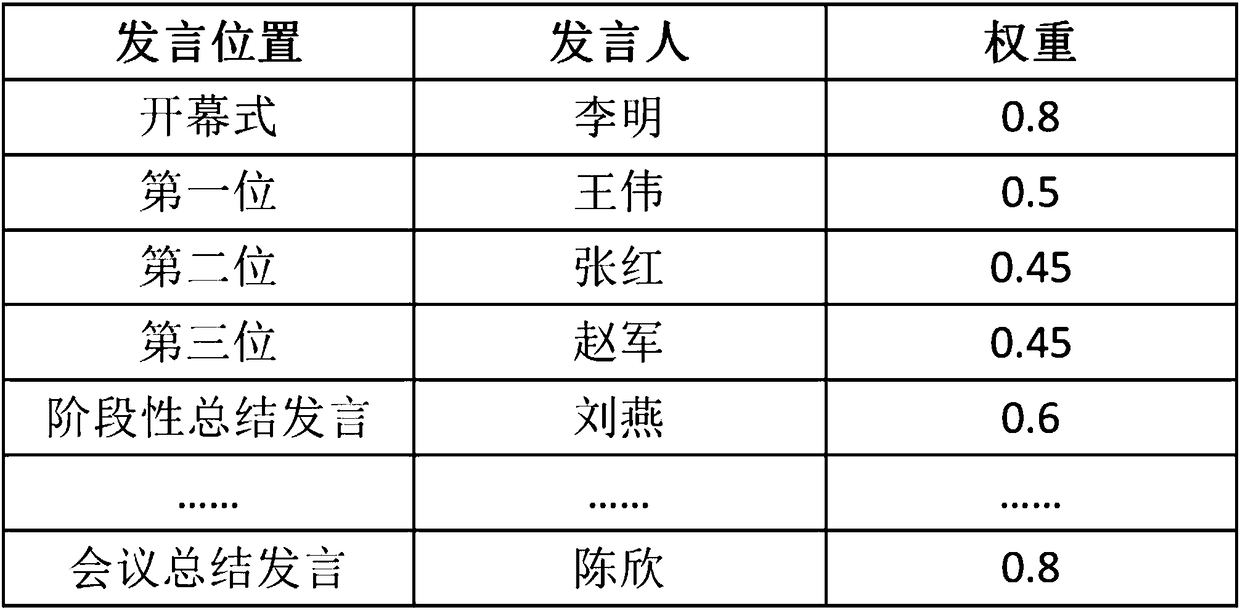
ActiveCN108305632AImprove effectivenessReduce recordsTelevision system detailsTelevision conference systemsWeight coefficientSpeech sound
The invention discloses a voice abstract forming method and a voice abstract forming system for a conference, and relates to the field of voice recognition. According to the invention, the speaking position, the identity information, the personnel data and other information of a speaker in a conference are analyzed, and then the weight coefficient of the speaker is determined. As a result, candidate key speaking segments corresponding to different speakers can be obtained by using different preset strategies according to the weight coefficients of speakers. Furthermore, according to the characteristics of the speaking content, for example, the large-probability interval of the important content of the utterance on a speaking time axis, key transitional words and key connection words in theimportant content of statements, and the like, a set of candidate key speaking segments is intercepted. The intercepted set of candidate key speaking segments is processed and then a set of audio / video segments for forming a voice abstract is obtained. As a result, more content is extracted from important statements, while less content is extracted from non-important statements. The content of afinally formed abstract is more reasonable. The more effective help is provided for users.
Owner:SHENZHEN EAGLESOUL TECH CO LTD
Input method for inputting content by keyboard and terminal equipment
InactiveCN101424977AFix typosMeet usage habitsInput/output processes for data processingInput languageCandidate key
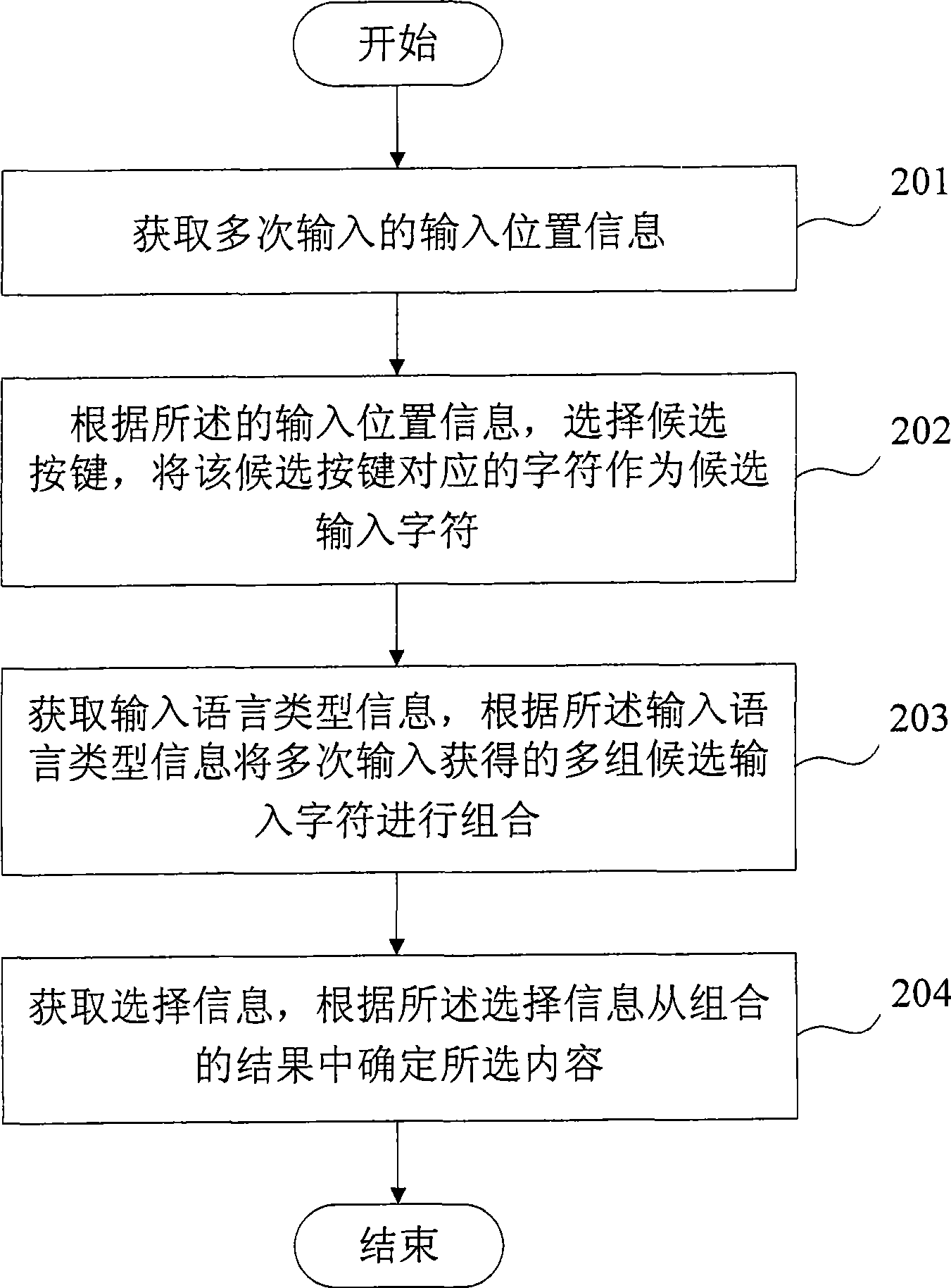
The embodiment of the invention provides an input method adopting a keyboard to input content and an input device. The input method comprises the following steps: input position information input for several times are obtained; candidate keys are selected according to the input position information, and characters corresponding to the candidate keys are used as input characters; input language type information can be obtained, several groups of input characters obtained by several input are combined according to the input language type information; selective information is obtained, and the selected content is determined in the combined result according to the selective information. The input method and the input device solve the misinput problem of the input manner of the prior touch keyboard and the prior mechanical keyboard, and improve the input efficiency and the input accuracy on the premise of more according with the use habit of a user.
Owner:HUAWEI DEVICE (SHENZHEN) CO LTD
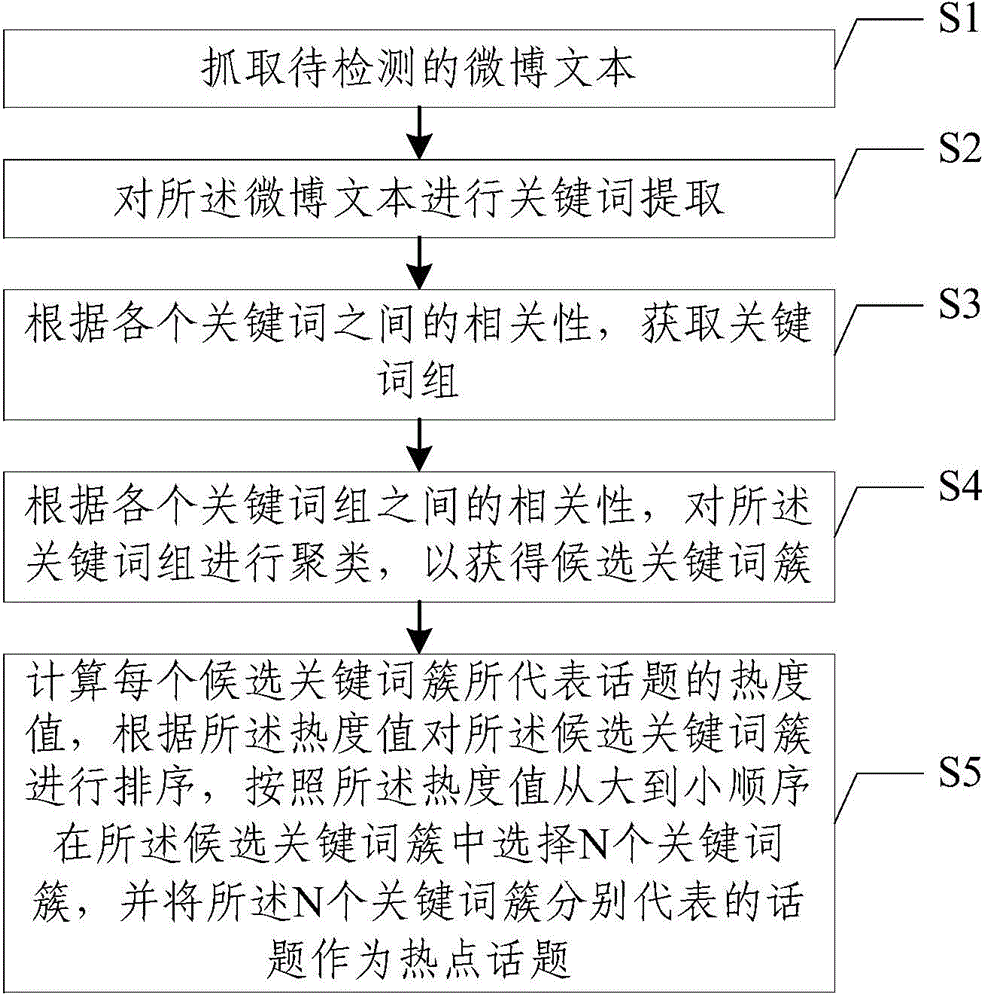
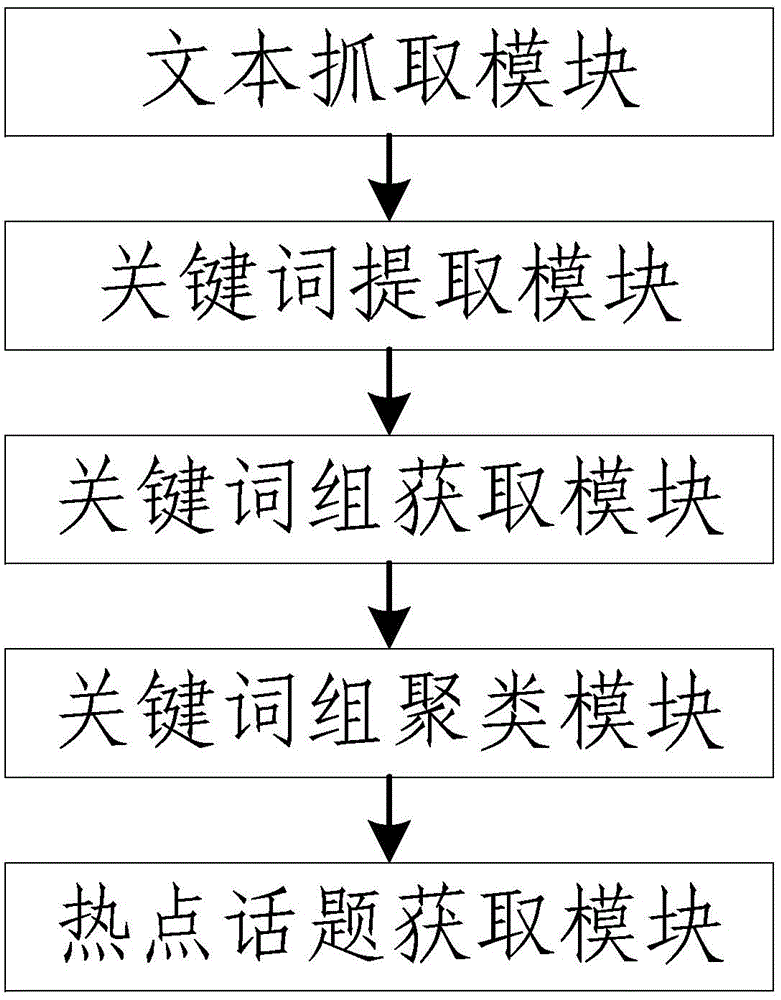
Method and device for automatic detection of microblog hot topics
ActiveCN104615593AEfficient detectionReduce complexitySpecial data processing applicationsKey termsMicroblogging
The invention discloses a method and device for automatic detection of microblog hot topics, relating to the technical field of internet. According to the invention, key words are extracted from a to-be-detected microblog text, then key terms are acquired, next, the key terms are clustered, so that candidate key word clusters are obtained; finally, the concern degree of the topic corresponding to each candidate key word cluster is computed, and the hot topics are selected according to the concern degrees. Through adoption of the method and device, hot topic detection becomes simple and the hot topics can be detected effectively.
Owner:NEW FOUNDER HLDG DEV LLC +2
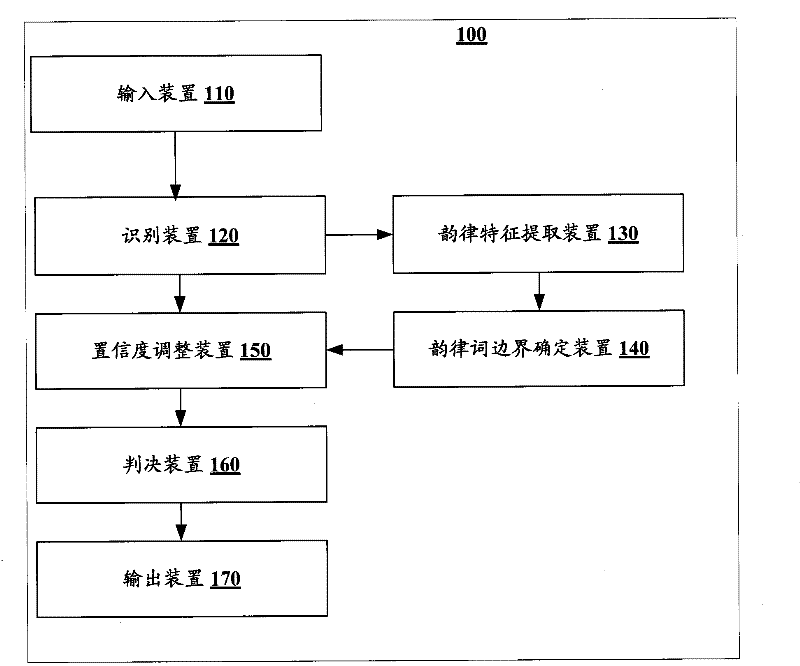
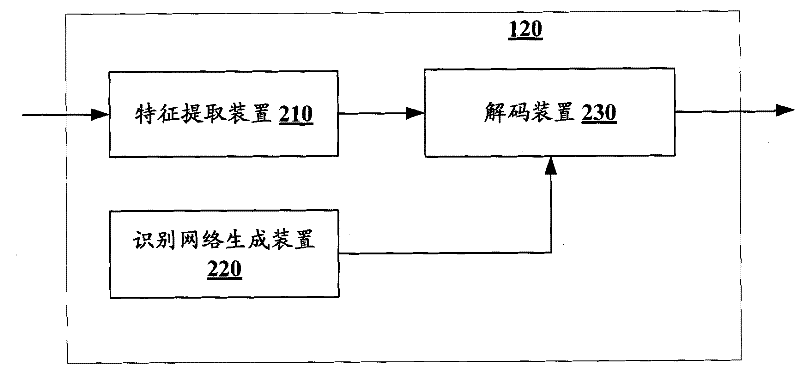
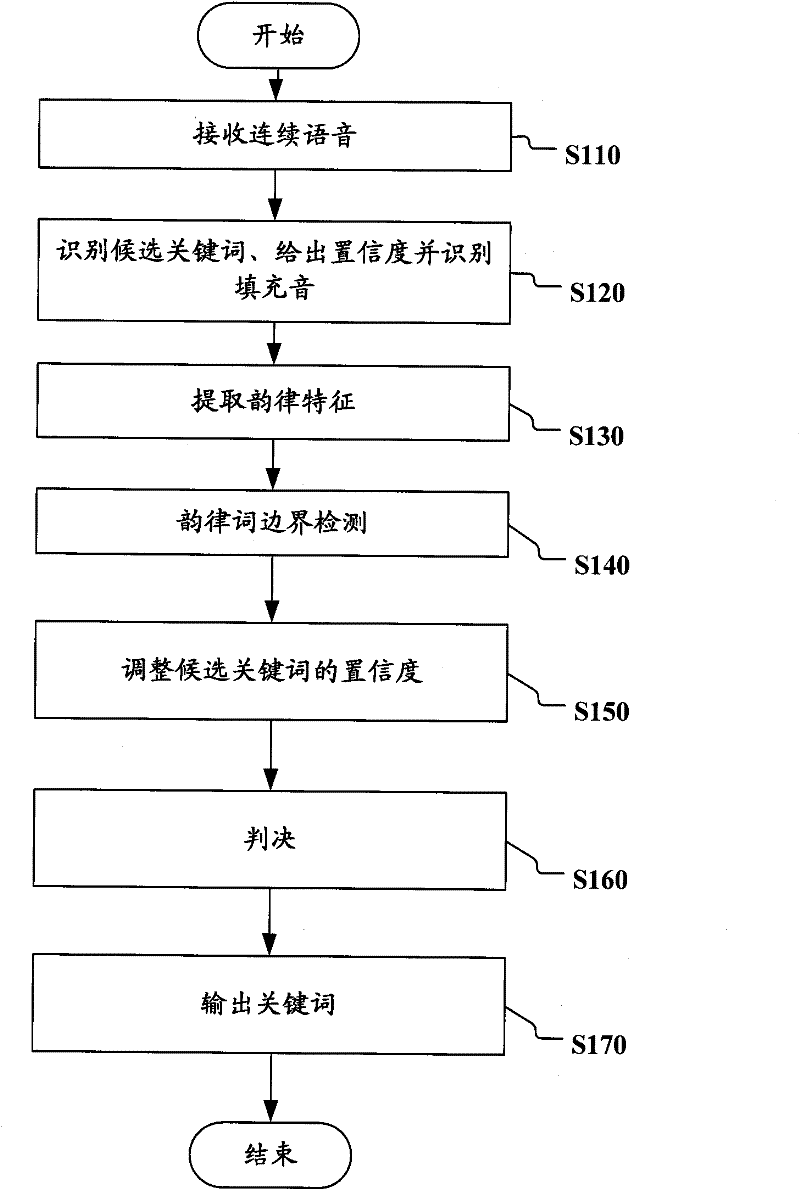
Equipment and method for detecting key word in continuous speech
The invention discloses equipment and a method for detecting a key word in continuous speech. The equipment comprises an input device, an identification device, a prosodic feature extraction device, a prosodic word boundary determination device, a confidence adjustment device, a judgment device and an output device, wherein the input device is used for inputting the continuous speech; the identification device is used for identifying a candidate key word from the continuous speech, giving out corresponding confidence, and identifying filling sounds included in the continuous speech; the prosodic feature extraction device is used for extracting prosodic features related with adjacent specific filling sounds; the prosodic word boundary determination device is used for determining the boundary between the adjacent specific filling sounds to be the probability of the prosodic word boundary according the prosodic features; the confidence adjustment device is used for adjusting the confidence of the candidate key word according to the boundary which is between the adjacent specific filling sounds included in a speech segment corresponding to the candidate key word and serves as the probability of the prosodic word boundary; the judgment device is used for judging whether the adjusted confidence of the candidate key word is higher than a preset threshold value; and the output device is used for outputting the candidate key word which has the adjusted confidence higher than the preset threshold value and serves as the key words.
Owner:FUJITSU LTD
Language-irrelevant key word recognition method and system
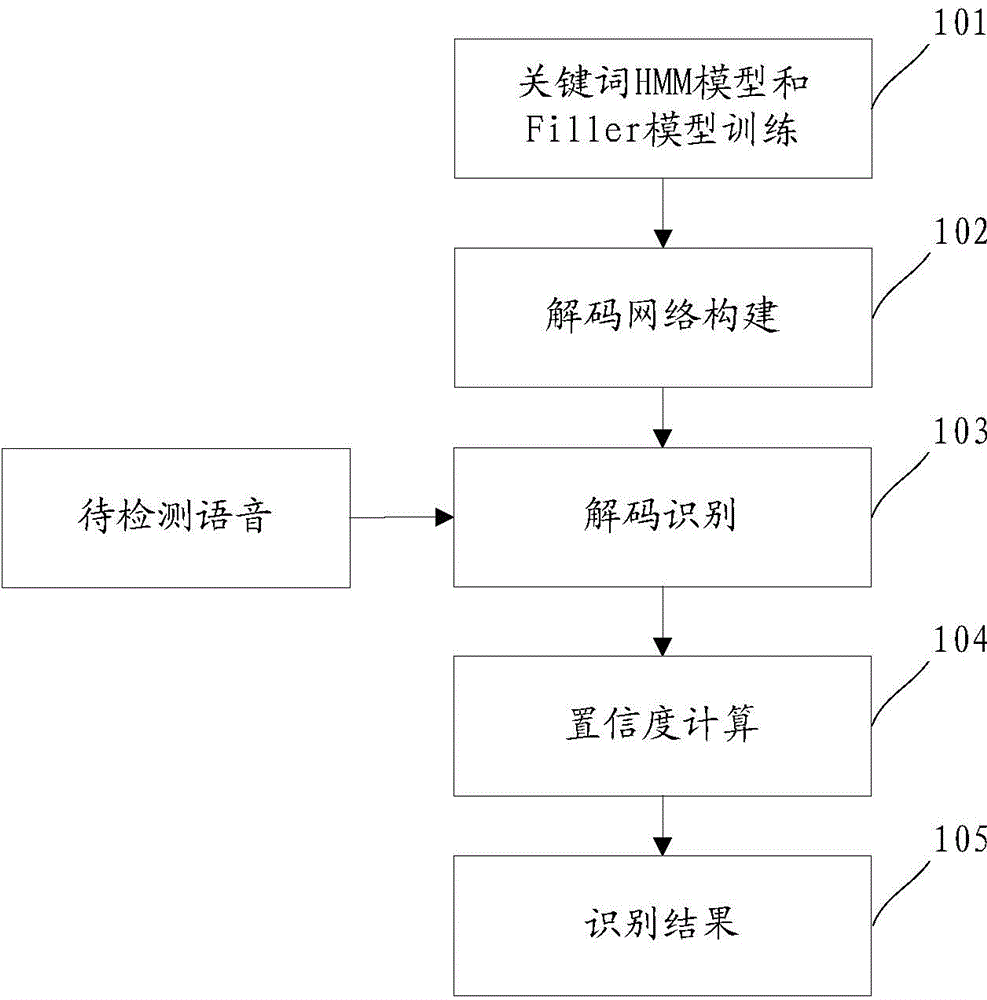
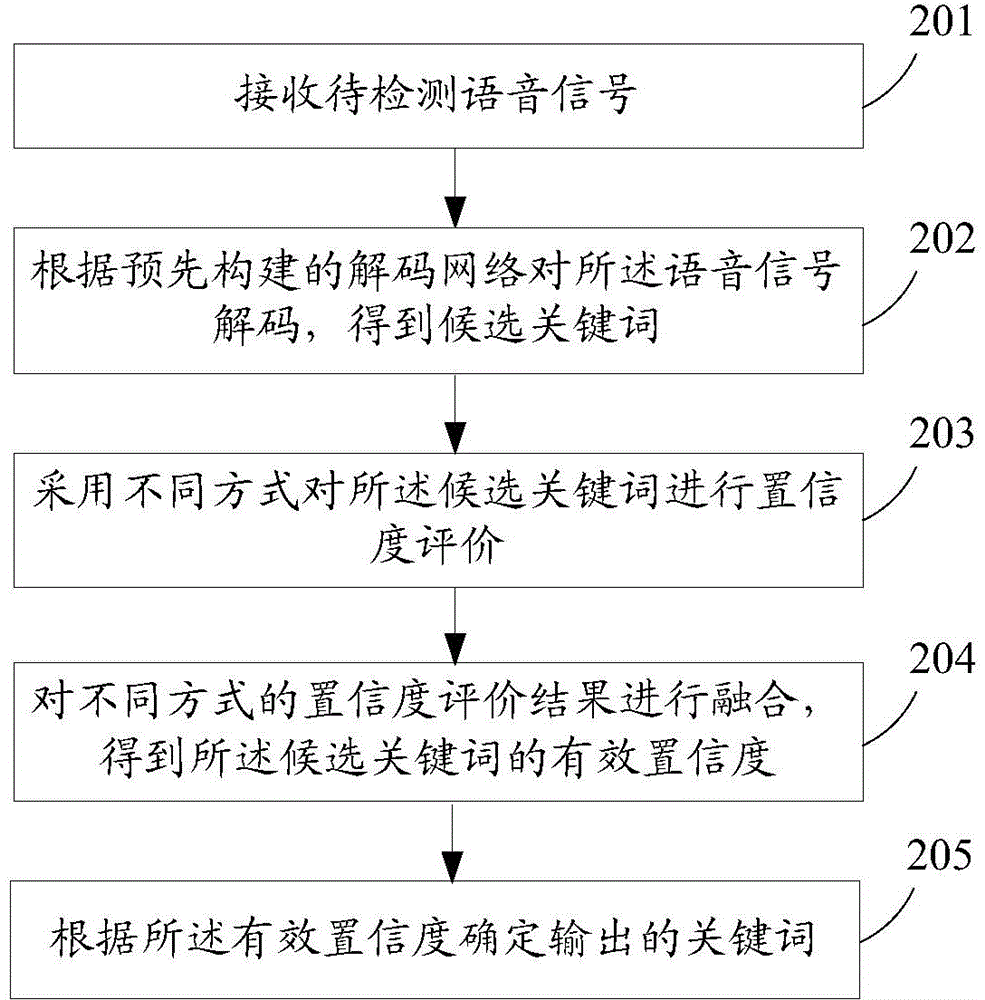
ActiveCN103559881AFiltration is accurate and reasonableImprove performanceSpeech recognitionEvaluation resultSpeech sound
The invention discloses a language-irrelevant key word recognition method and system. The method includes the steps of receiving a voice signal to be detected, decoding the voice signal according to a pre-constructed decoding network to obtain candidate key words, evaluating confidence coefficients of the candidate key words in different modes, fusing the confidence coefficient evaluation results in different modes to obtain the effective confidence coefficients of the candidate key words, and determining the output key words according to the effective confidence coefficients.
Owner:科大讯飞河北科技有限公司
Large scale key word matching method
InactiveCN101398820AReduce the problem of high false alarm rateImprove retrieval efficiencySpecial data processing applicationsExact matchPattern matching
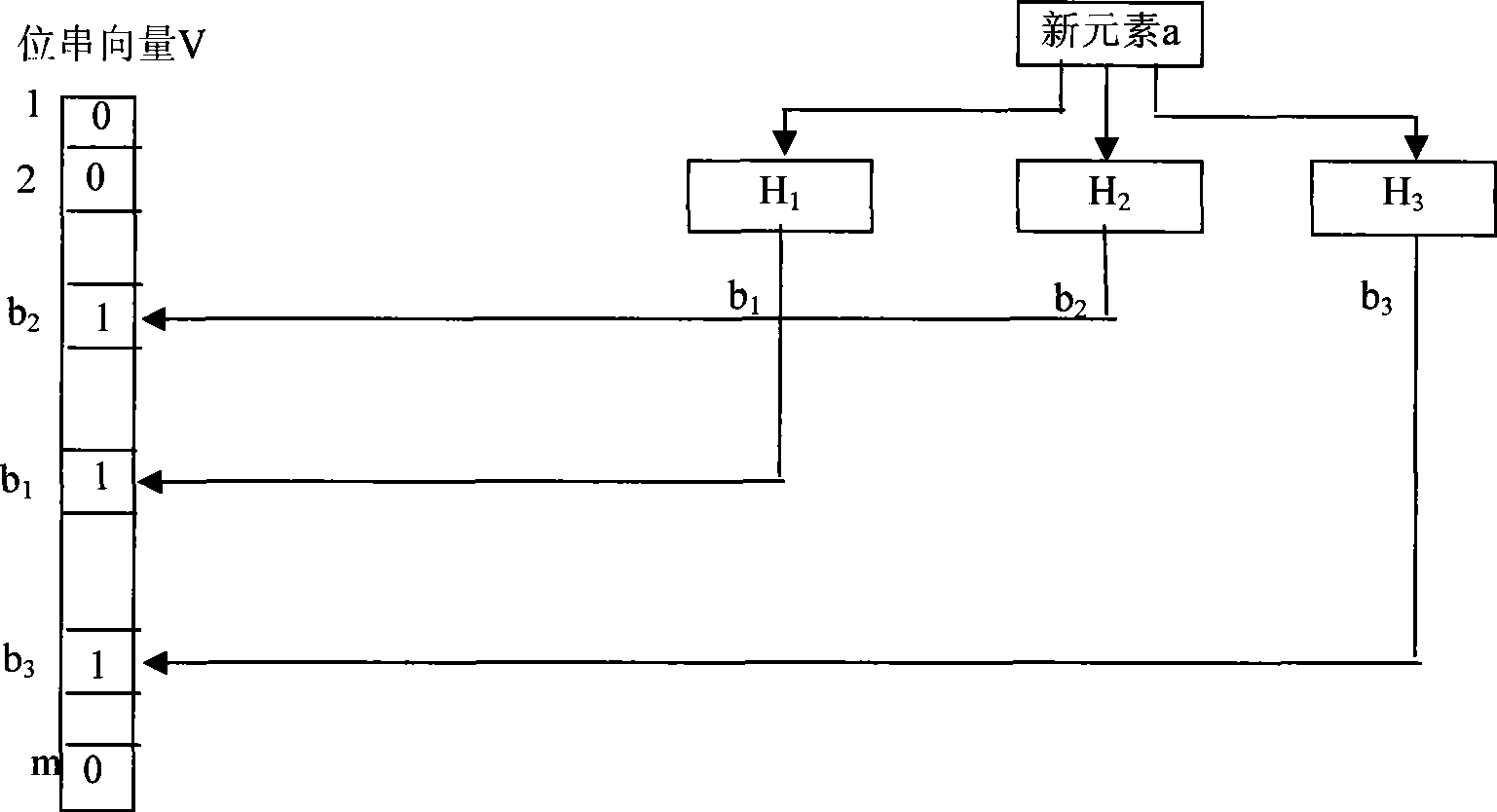
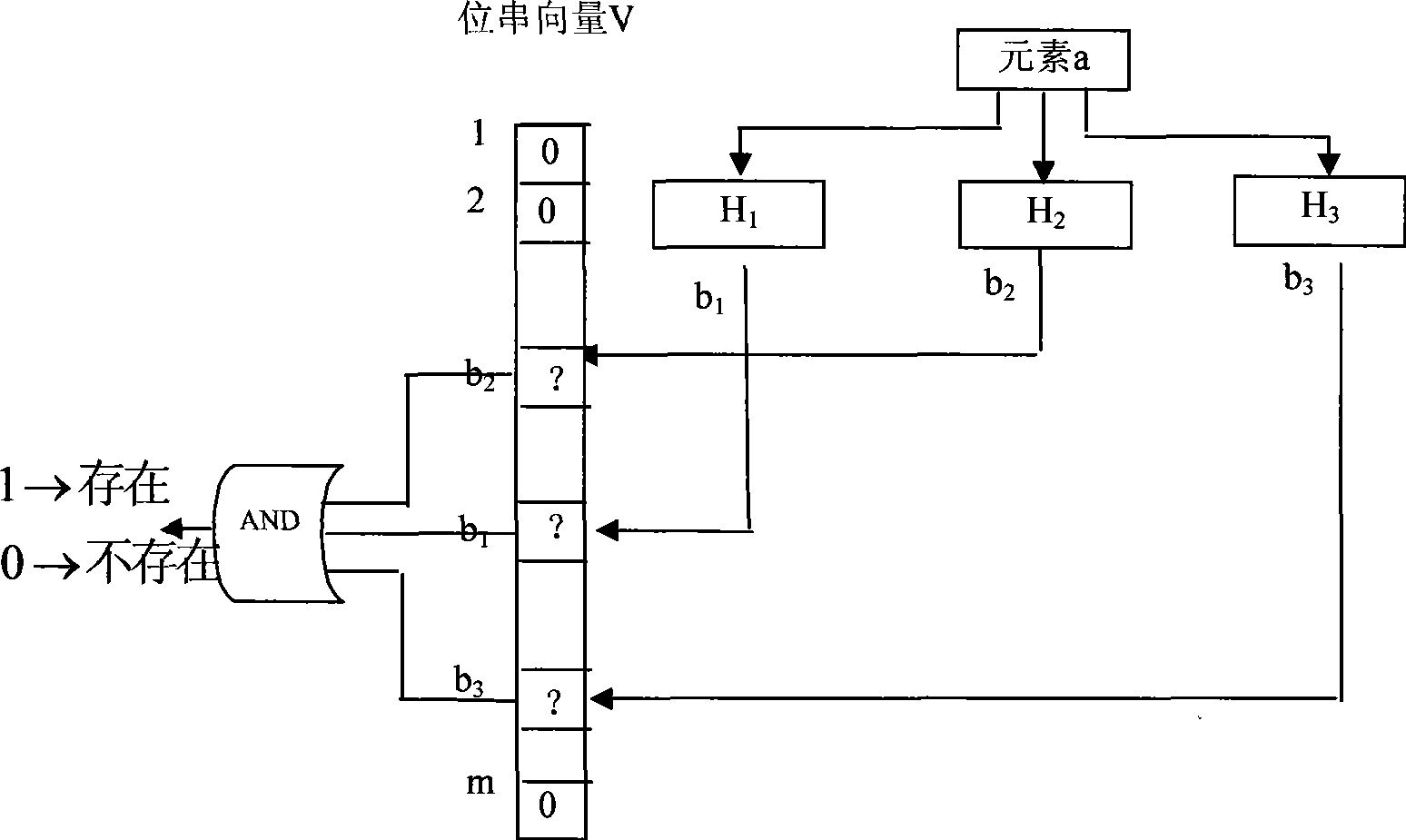
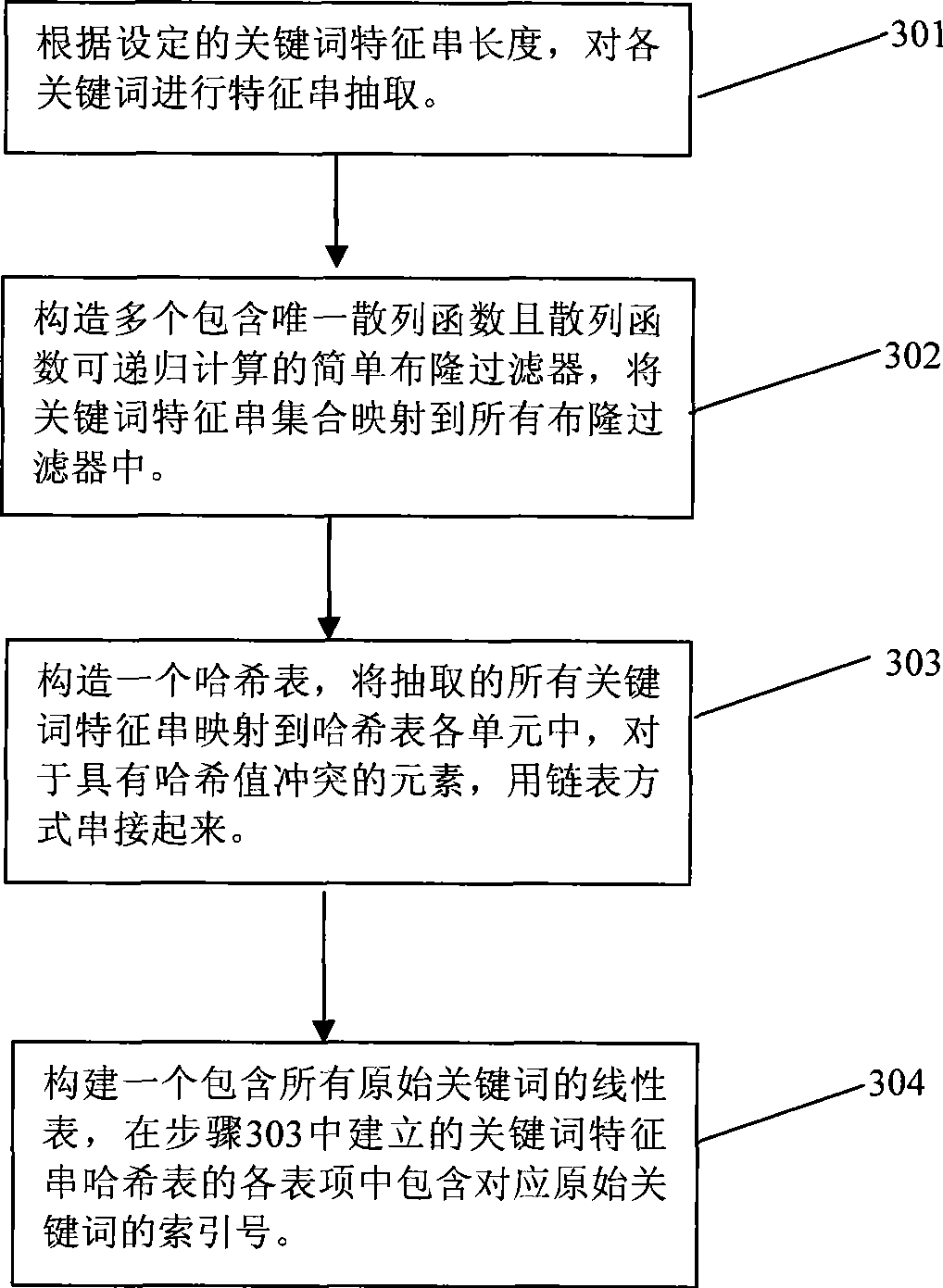
The invention provides a matching method used for large-scale key words, comprising a pre-processing stage and a mode matching stage; the pre-processing stage comprises a key word characteristic string cutter, the structure of a plurality of simple bloom filter based on key word characteristic string sets, and a Hash table structure based on the key word characteristic string sets; the mode matching stage comprises the steps as follows: quick judgment that the text string in the current window is not matched with any key word characteristic string is achieved by the simple bloom filter series of previous structure; the precise match with candidate key words is executed under a failed judgment condition; during the text scanning process, current hash values of the current text corresponding to all simple bloom filters are quickly calculated by a recursive algorithm. The matching method sufficiently uses the characteristics that the match success rate of the text to be matched and the key words is extremely low and the recursive hash arithmetic has high efficiency, can realize the high-speed match under the condition of large-scale key words, and is extremely suitable for online virus scanning application such as virus detection and the like.
Owner:BEIJING VENUS INFORMATION TECH
Relation extension method based on entity links
InactiveCN107506486AGuaranteed accuracyImprove performanceRelational databasesSpecial data processing applicationsEntity linkingEntity type
The invention provides a relation extension method based on entity links. The method is characterized in that the technological means of entity links are used, text in natural language is linked to the corresponding entities in knowledge bases, unlabeled entities in message box attributes are identified, using the labeling systems of encyclopedic entries to serve as the types of the entities according to the matching degree between candidate entity types and entity types at two ends of a relation; meanwhile, a model fusion method is used to sort the candidate entities, and the advantages of a nonlinear boosting integrated model are fused into a linear model so as to increase model performance and guarantee relation accuracy. By the method, unlinked entities in the message box can be identified effectively, the problems of entities with identical names and entities with aliases are solved, a relation with the target entity is built, and relation extension is achieved.
Owner:BEIHANG UNIV
Method and system for authentication, data communication, storage and retrieval in a distributed key cryptography system
InactiveUS20050033963A1Improve securityUser identity/authority verificationPassphraseData processing system
A method for protecting the transfer and storage of data by encryption using a private key encrypted with a first key encrypting key, which is encrypted using a second key encrypting key. This latter key is encrypted using a hashed passphrase value, obtained by hashing a passphrase known only to the authorized user. Upon receipt of a request initiated by the user by entering a passphrase, a first hashed passphrase is transferred to a first data processing system, where it is compared with a predefined hash string. If they match, the first data processing system transfers to a second data processing system the encrypted second key encrypting key. A candidate key is obtained by decrypting the encrypted second key encrypting key using a second hashed passphrase. Upon successful validation of the candidate key, the passphrase is verified and the user is authenticated. After the user has been authenticated, the first data processing system transmits to the second data processing system the encrypted private key and the encrypted data. The second processing system then decrypts the encrypted first key encrypting key using the second key encrypting key, decrypts the encrypted private key using the first key encrypting key and finally decrypts the data using the private key.
Owner:EISST
Machine learning-based patent quality metric
InactiveUS20150206069A1Digital computer detailsCharacter and pattern recognitionLearning basedReceiver operating characteristic
A machine-learning based artificial intelligence device for finding an estimate of patent quality, such as patent lifetime or term is disclosed. Such a device may receive a first set of patent data and generate a list of binary classifiers. A candidate set of binary classifiers may be selected and using a heuristic search, for example an artificial neural network (ANN), a genetic algorithm, a final set of binary classifiers is found by maximizing iteratively a yield according to a cost function, such an area under a curve (AUC) of a receiver operating characteristic (ROC). The device may then receive patent information for a target patent and report an estimate of patent quality according to the final set of binary classifiers.
Owner:BEERS MATTHEW +1
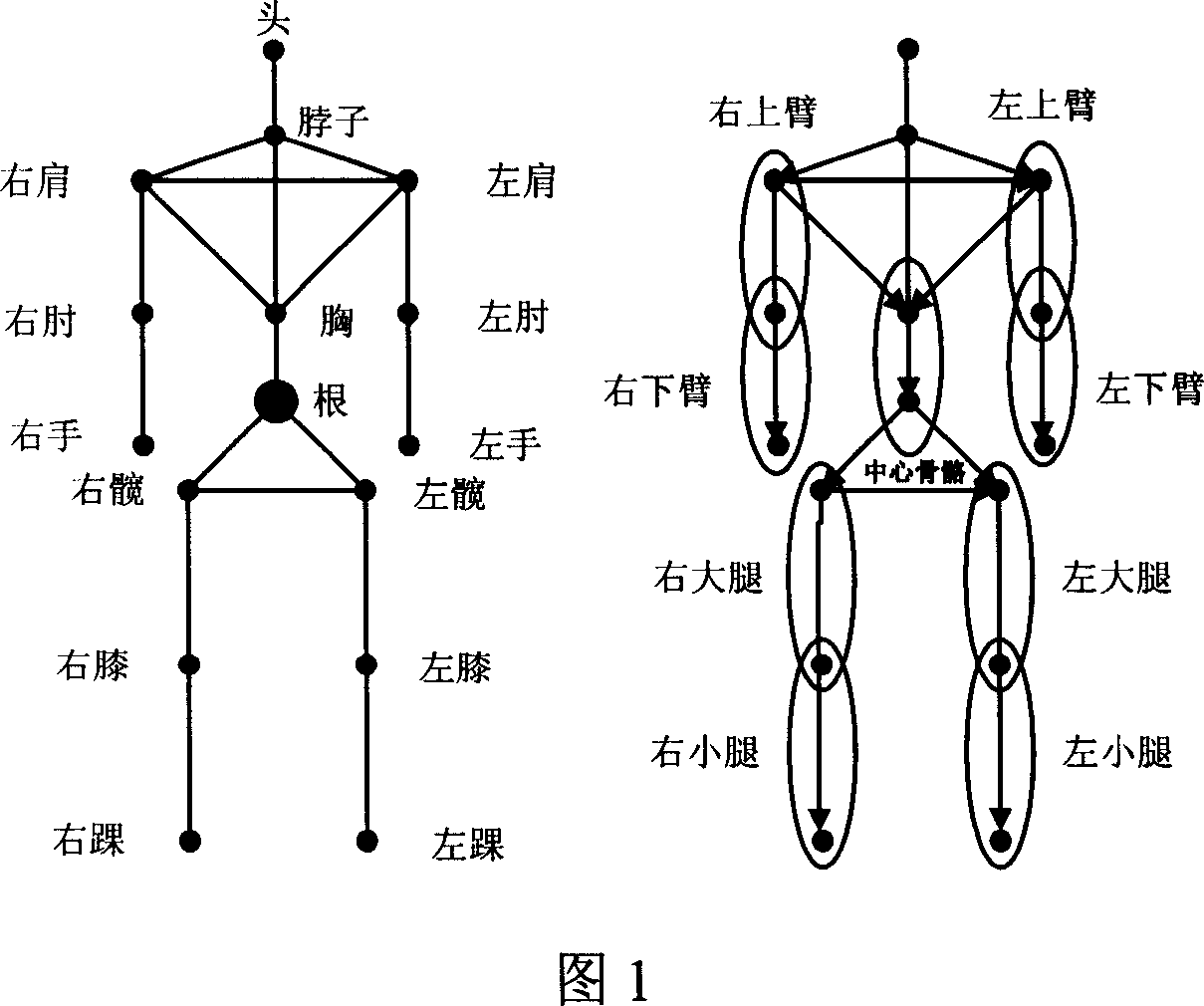
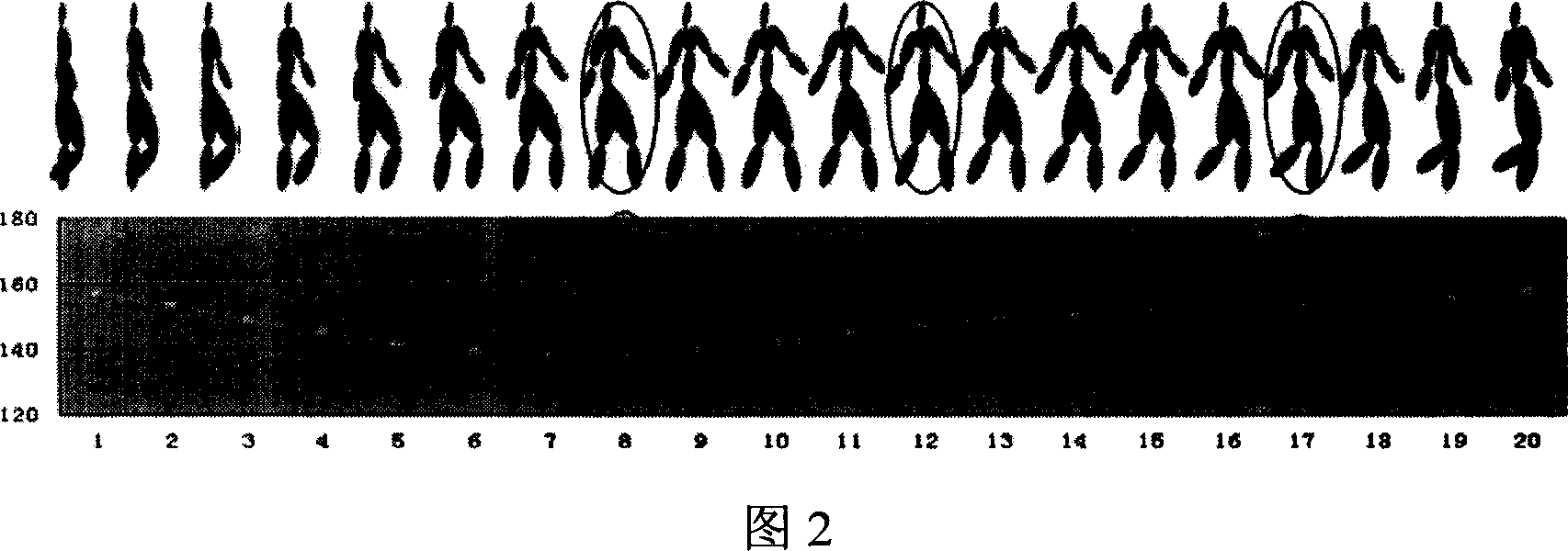
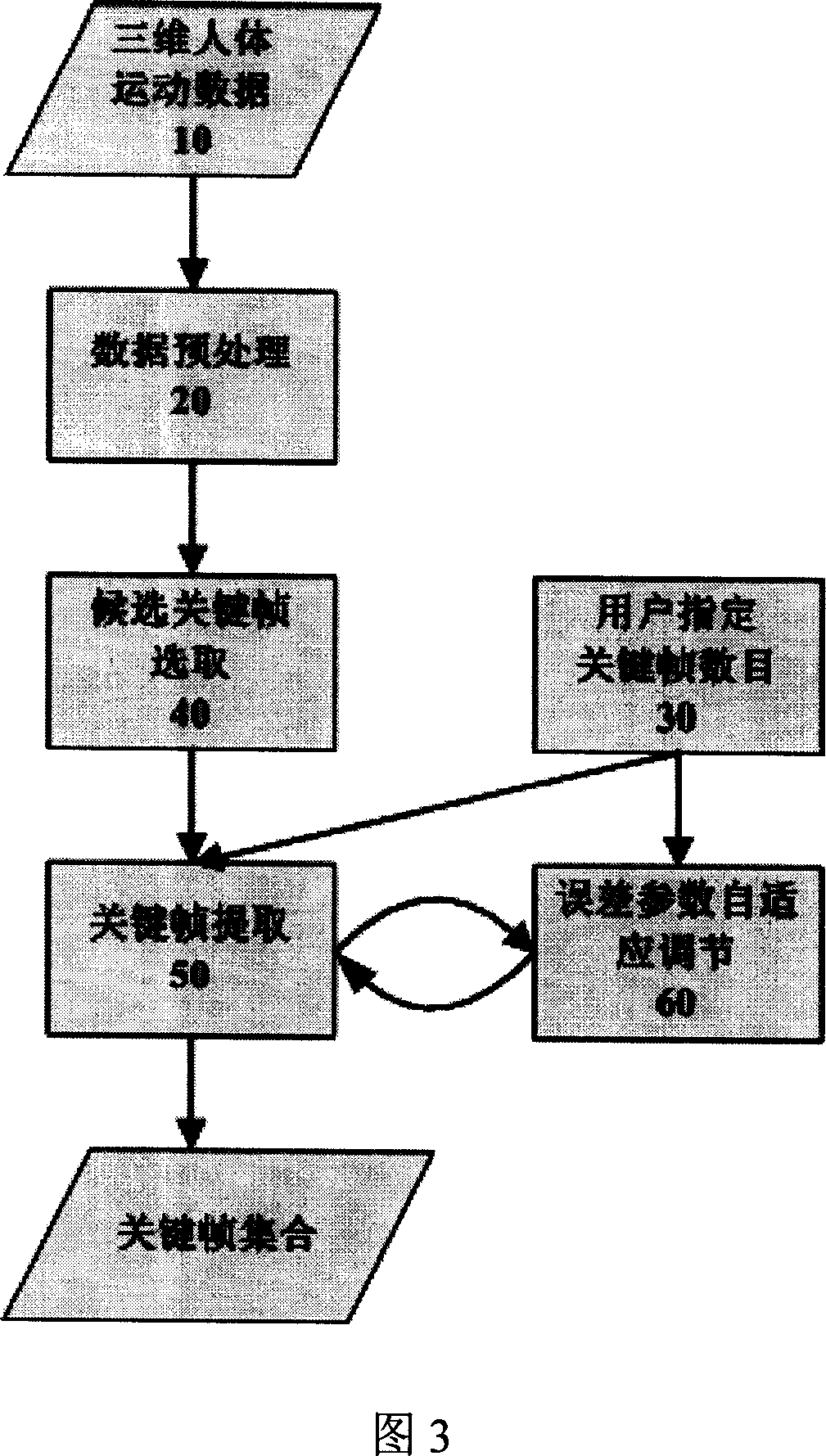
Extraction method of key frame of 3d human motion data
InactiveCN1967525AEfficient extractionReduce computational complexityImage analysisSpecial data processing applicationsHuman motionKey frame
The invention discloses an automatic key frame extraction method of the human sport data. On the data representation, it uses the separation angle of the human limbs bones and central bones as the sports characterization, and tokens the three-dimensional human sport data. Then, it makes the possible existing ''border'' posture to be a candidate key frame set when determining the movement according to the sport track of the angle between bones. Finally, it selects the candidate key frame to get the final key frame set by layered curve reduced algorithm. Meanwhile, the invention also proposed an adaptive mistake parameter adjustment method to meet the requirements of different compression rate. The method has good effects of key frame extraction and compression to human sport data, and guarantees the consistency in the similar sport key frame set to some extent.
Owner:ZHEJIANG UNIV
Keyboard error reduction method and apparatus
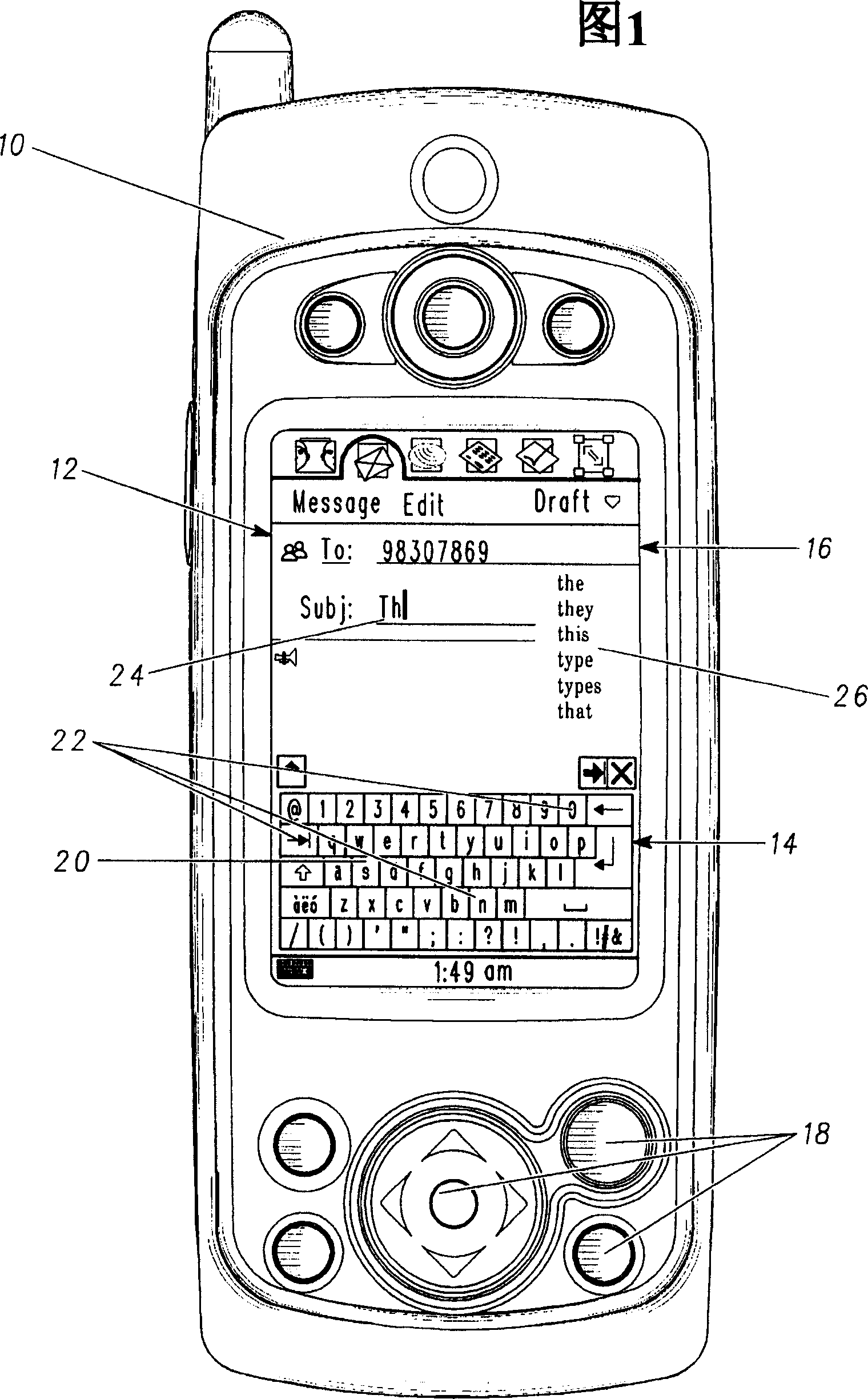
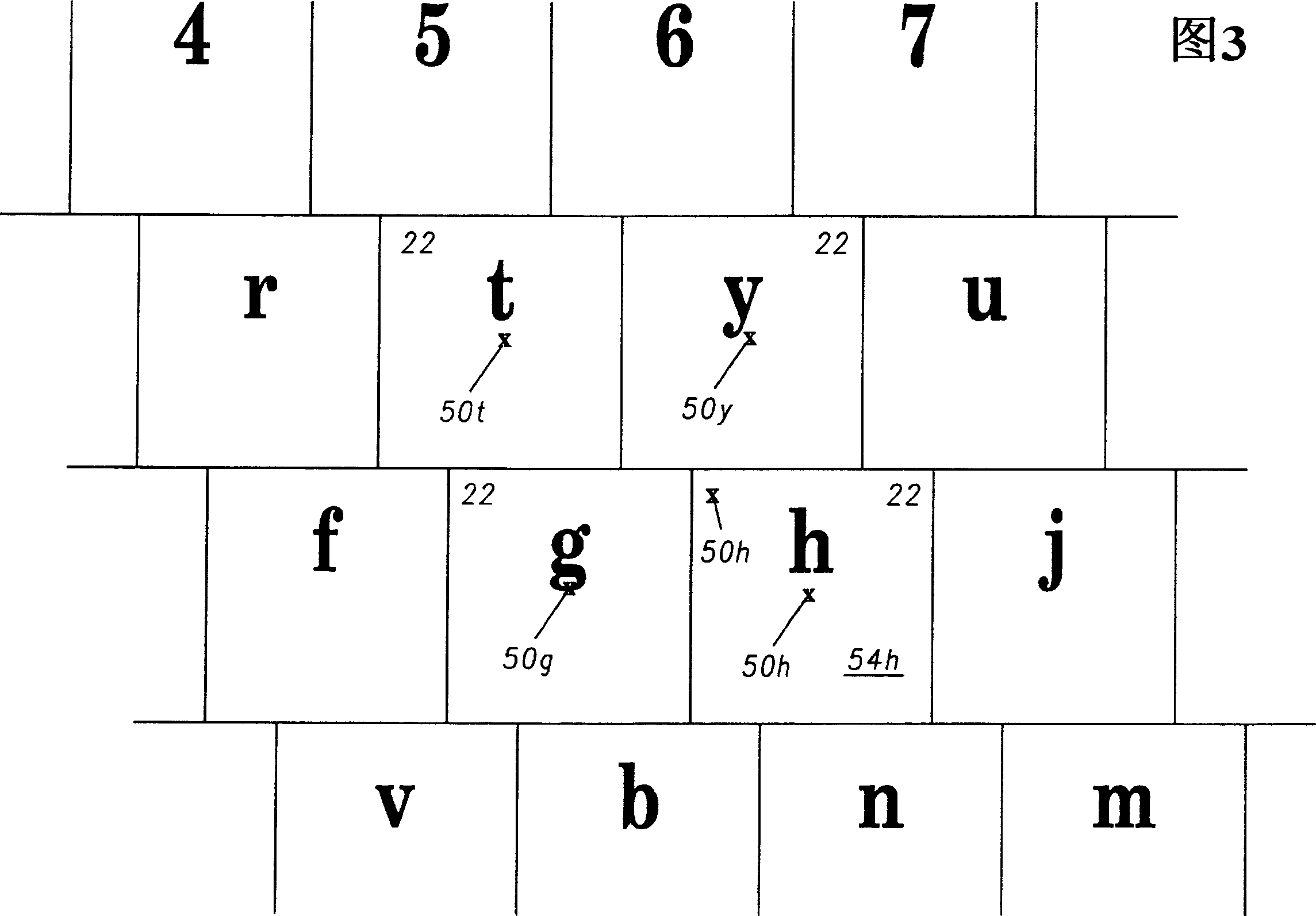
In a mobile telephone (10) with a virtual keyboard and a touch screen (12), with individual virtual keys (22) having their own representative positions. During a selection operation to select a key (22), where the touch screen is touched becomes the selected position. The distance between the selected position and adjacent representative positions is used to decide a first set of candidate keys. These candidate keys are then used to provide a set of potential words that would result from the input of any one of those keys. A list of candidate words is then produced and displayed on a display area (26) based on the frequency of use of the words in the set of potential words and the distances between the selected position and the representative position of the keys (22). Once a key (22) is confirmed as having been selected, the offset between the selected position and the representative position of that key is used to re-calibrate that representative position.
Owner:MOTOROLA INC
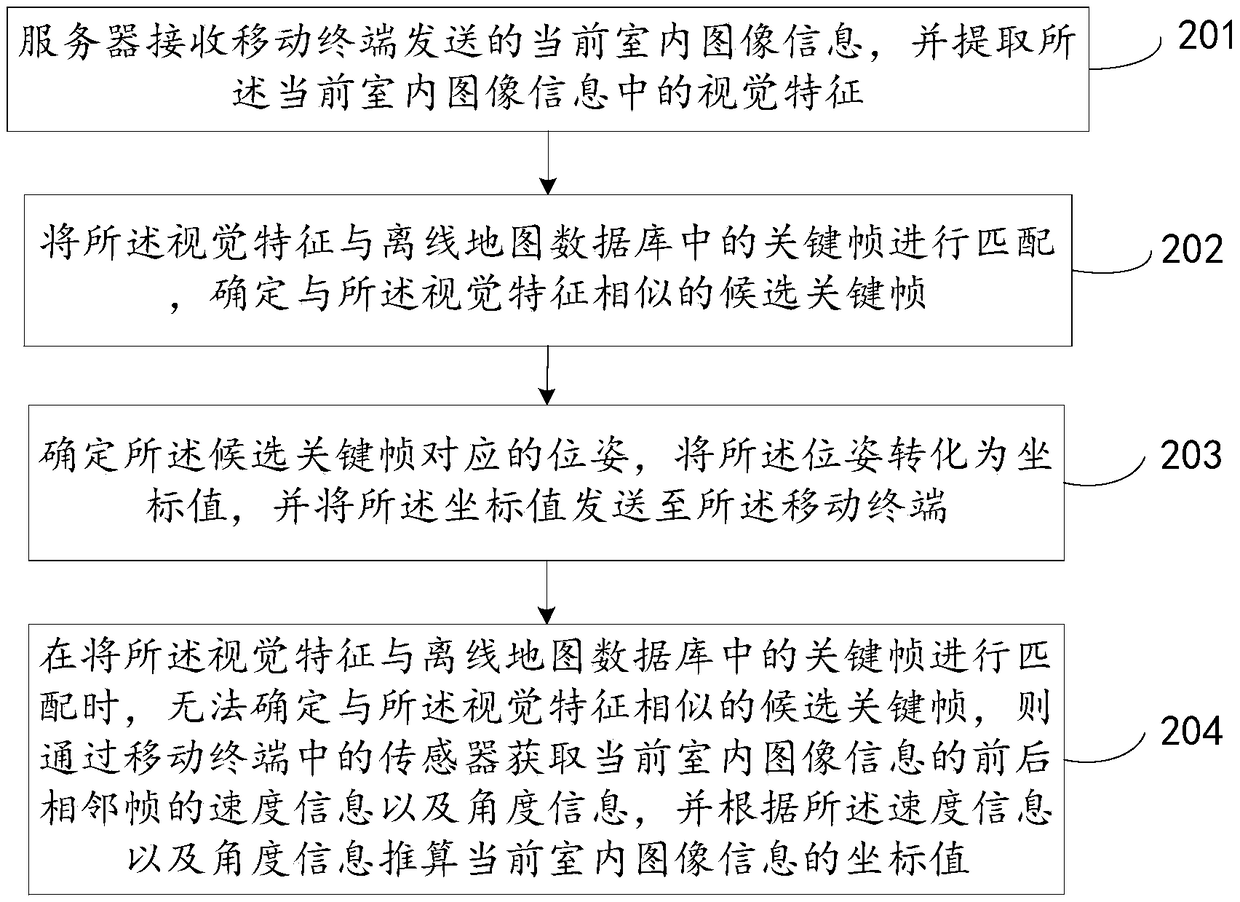
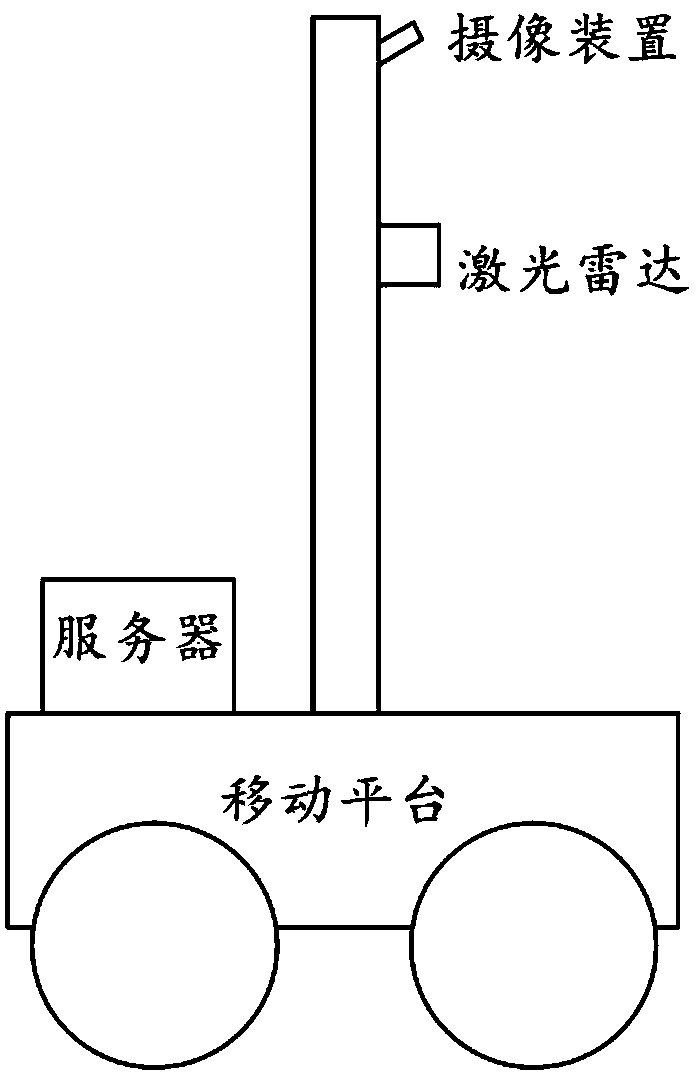
Positioning method, device and system in indoor environment
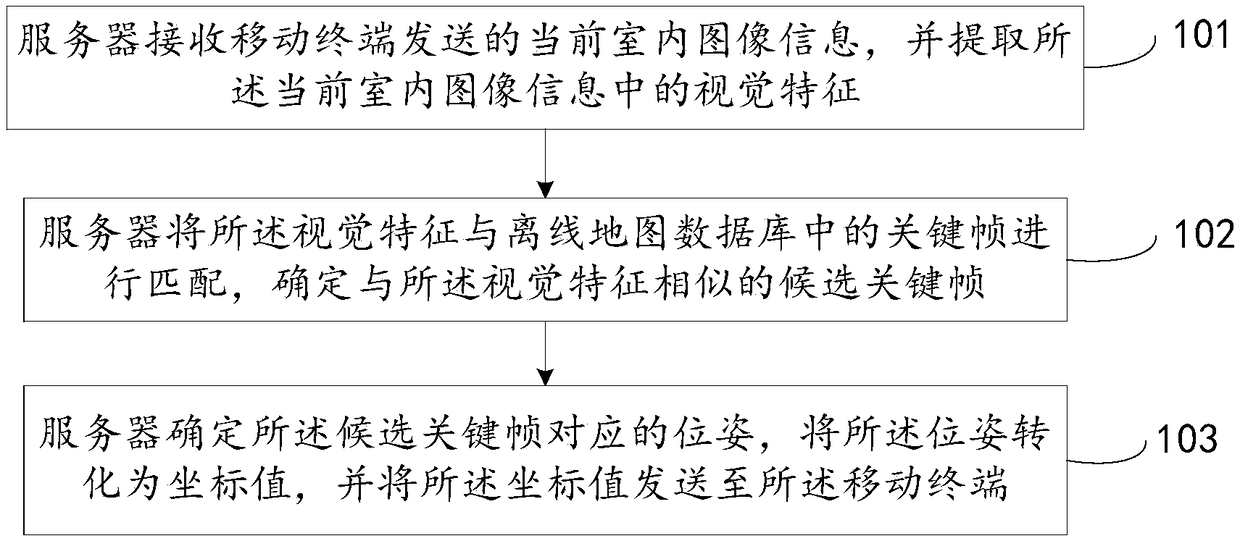
ActiveCN108717710APrecise positioningImage enhancementImage analysisComputer terminalComputer vision
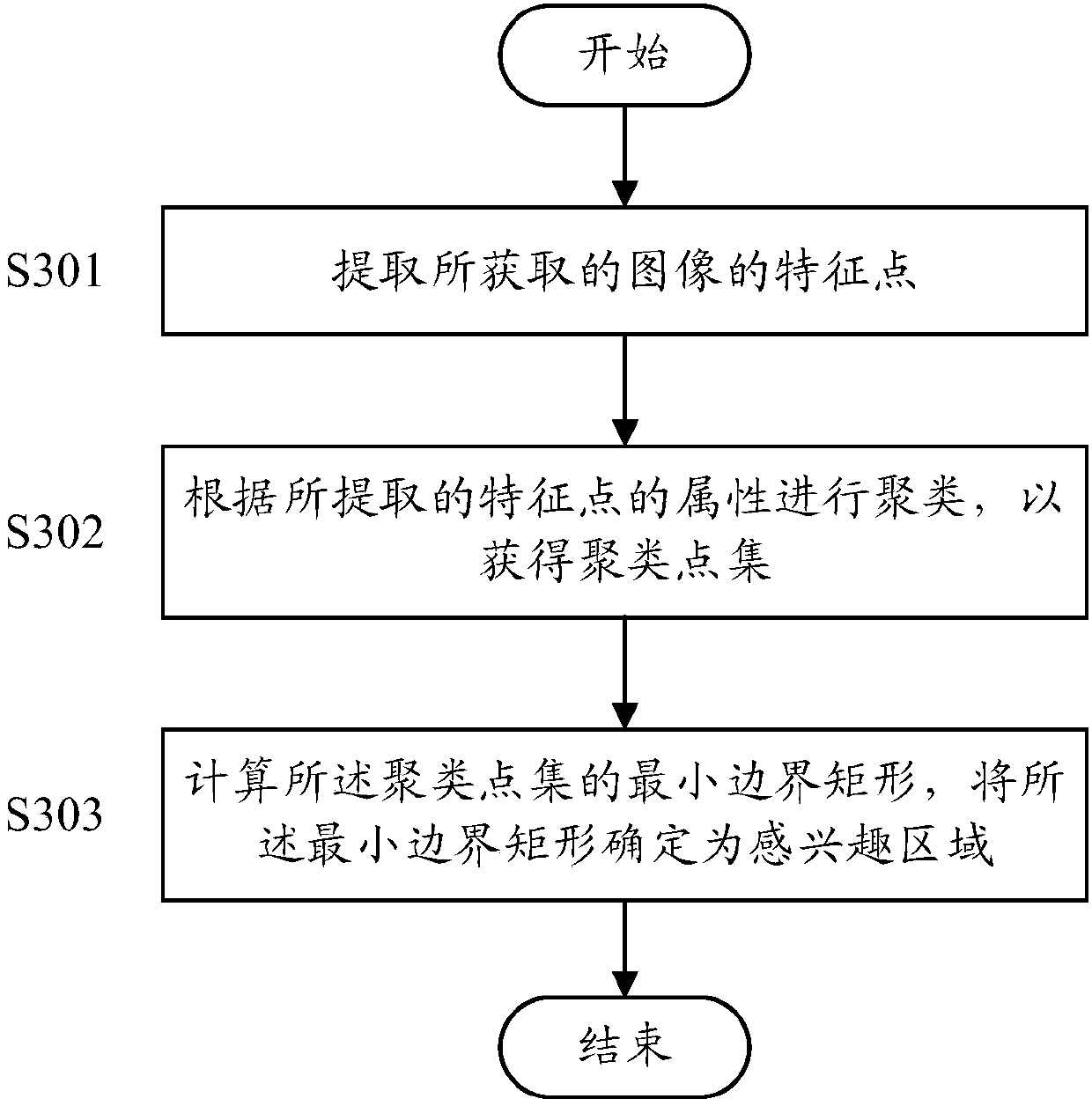
The invention discloses a positioning method, device and system in an indoor environment, relates to the technical field of positioning and has the main purpose of realizing the precise positioning inthe indoor environment. The main technical scheme provided by the invention comprises the steps of receiving current indoor image information sent by a mobile terminal and extracting visual featuresin the current indoor image information; matching the visual features with key frames in an offline map database, and determining candidate key frames similar to the visual features; and determining poses corresponding to the candidate key frames, converting the poses into coordinate values, and sending the coordinate values to the mobile terminal.
Owner:BOE TECH GRP CO LTD
Camera pose estimation apparatus and method for augmented reality imaging
ActiveUS8452080B2Satisfactory accuracyFast and efficient implementationImage enhancementImage analysis3d cameraCandidate key
Owner:APPLE INC
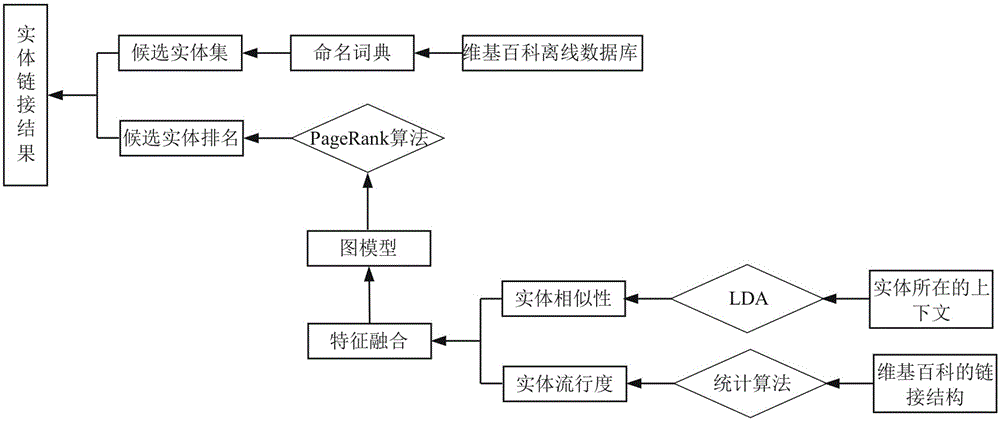
Entity linkage algorithm based on graph model
InactiveCN105045826AImprove reliabilityEntity features are well integratedSpecial data processing applicationsEntity linkingData set
The present invention discloses an entity linkage algorithm based on a graph model. The entity linkage algorithm based on a graph model is characterized by comprising: forming a candidate entity by using the Wikipedia knowledge base; constructing a semantic feature between the entities by using LDA; constructing relationships between entities based on linkage structures of Wikipedia to form a graph model; and integrating related semantic features into the graph model; and ranking the entities by using the PageRank algorithm to obtain an entity linkage result, which specifically comprises steps of calculation and integration of a naming dictionary, a candidate entity set, related features, construction of the graph model, and ranking of candidate entities. Compared with the prior art, the entity linkage algorithm based on a graph model has the advantages of being good in entity feature integration and high in reliability of the entity linkage result; data is downloaded by using Wikipedia, so that no additional costs are needed, and especially data sets do not need to be noted manually; and the method is simple, convenient in usage, and saves time and efforts.
Owner:EAST CHINA NORMAL UNIV
Method and apparatus used for putting candidate key words advertisement
InactiveCN101477566AMake sure to match the resultOvercoming Problems That Are Not AdvertisementsCommerceSpecial data processing applicationsCandidate keyAd serving
Owner:TENCENT TECH (SHENZHEN) CO LTD
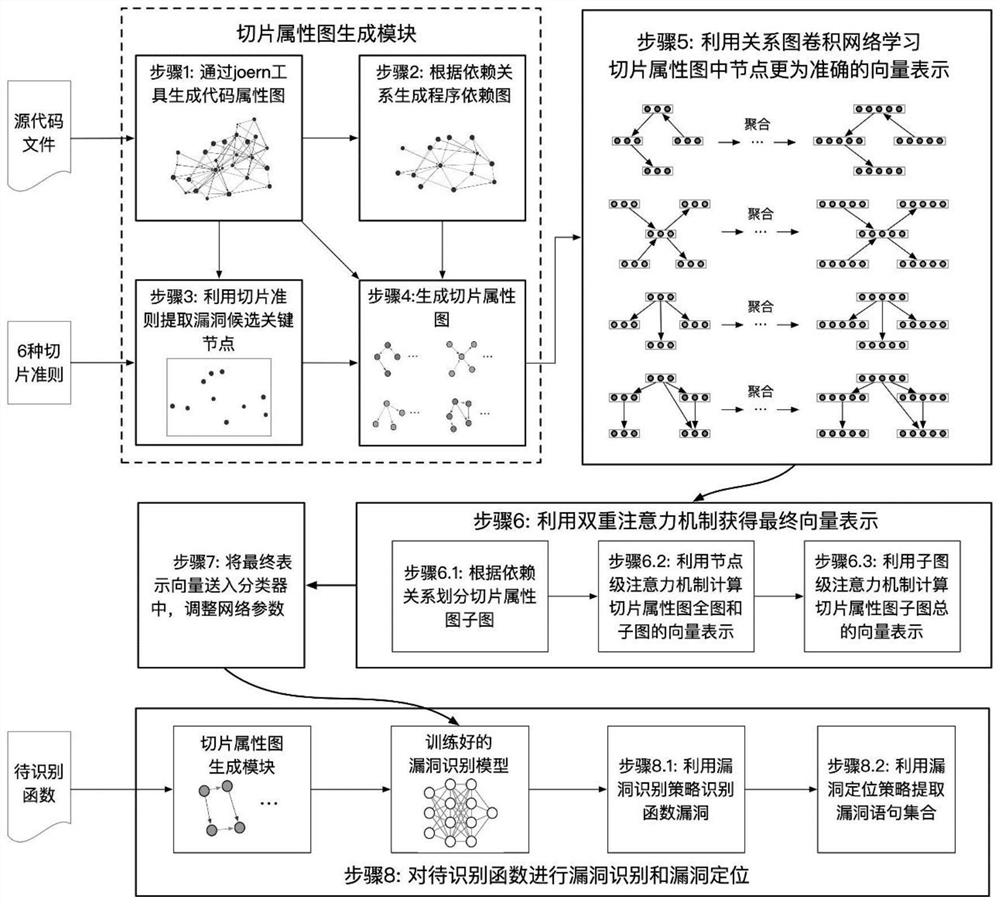
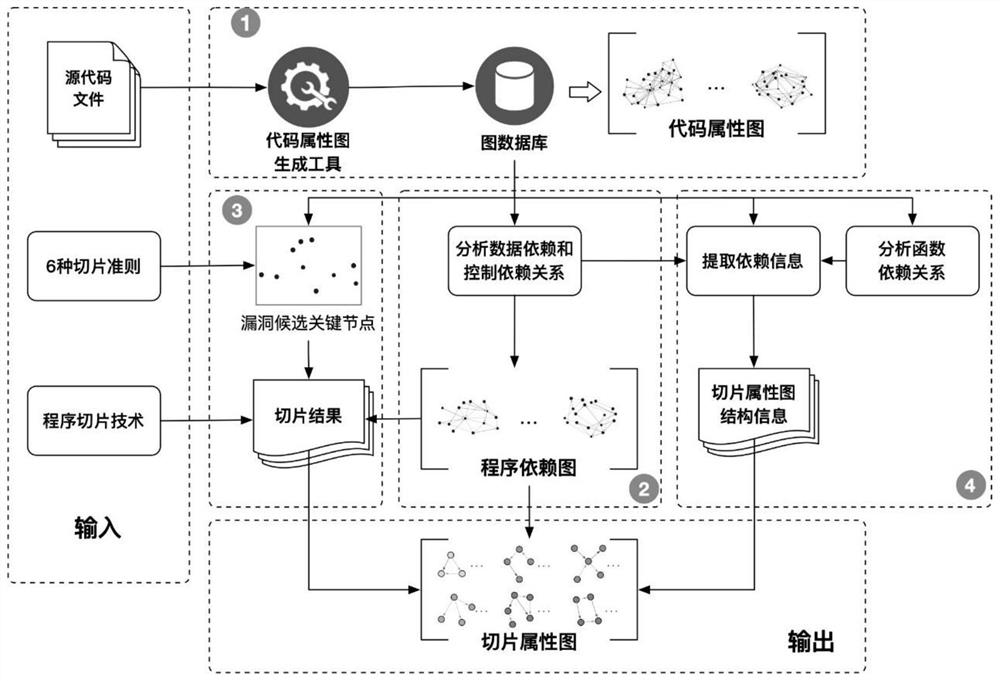
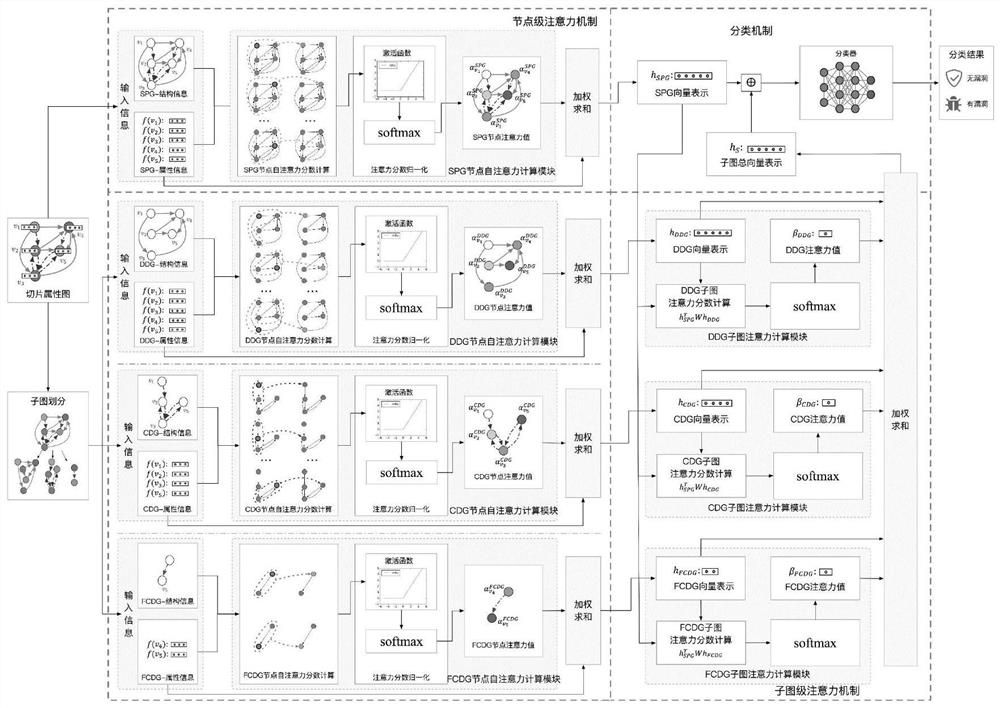
Function-level code vulnerability detection method based on slice attribute graph representation learning
ActiveCN112699377AIncrease coverageReduce false positivesPlatform integrity maintainanceRelation graphProgram slicing
The invention discloses a function-level code vulnerability detection method based on slice attribute graph representation learning, and the method comprises the steps: firstly introducing a new slice criterion, proposing the concept of a slice attribute graph, and generating a slice attribute graph of a code based on the slice criterion and a program slice technology; extracting graph structure information, node attribute information and code context information which have a dependency relationship with the vulnerability candidate key points; then, performing representation learning on the slice attribute graph by utilizing a relation graph convolutional neural network and combining a dual attention mechanism based on nodes and sub-graphs so as to learn a more comprehensive and accurate vulnerability mode; and finally, fusing the vulnerability identification results of the slice attribute graphs to realize function-level vulnerability detection, and determining a set of vulnerability candidate statements and grammatical elements associated with vulnerabilities. More vulnerability candidate key points can be covered, structures, attributes and context information related to vulnerabilities are fully learned and expressed, and the vulnerability detection accuracy is improved.
Owner:HARBIN INST OF TECH
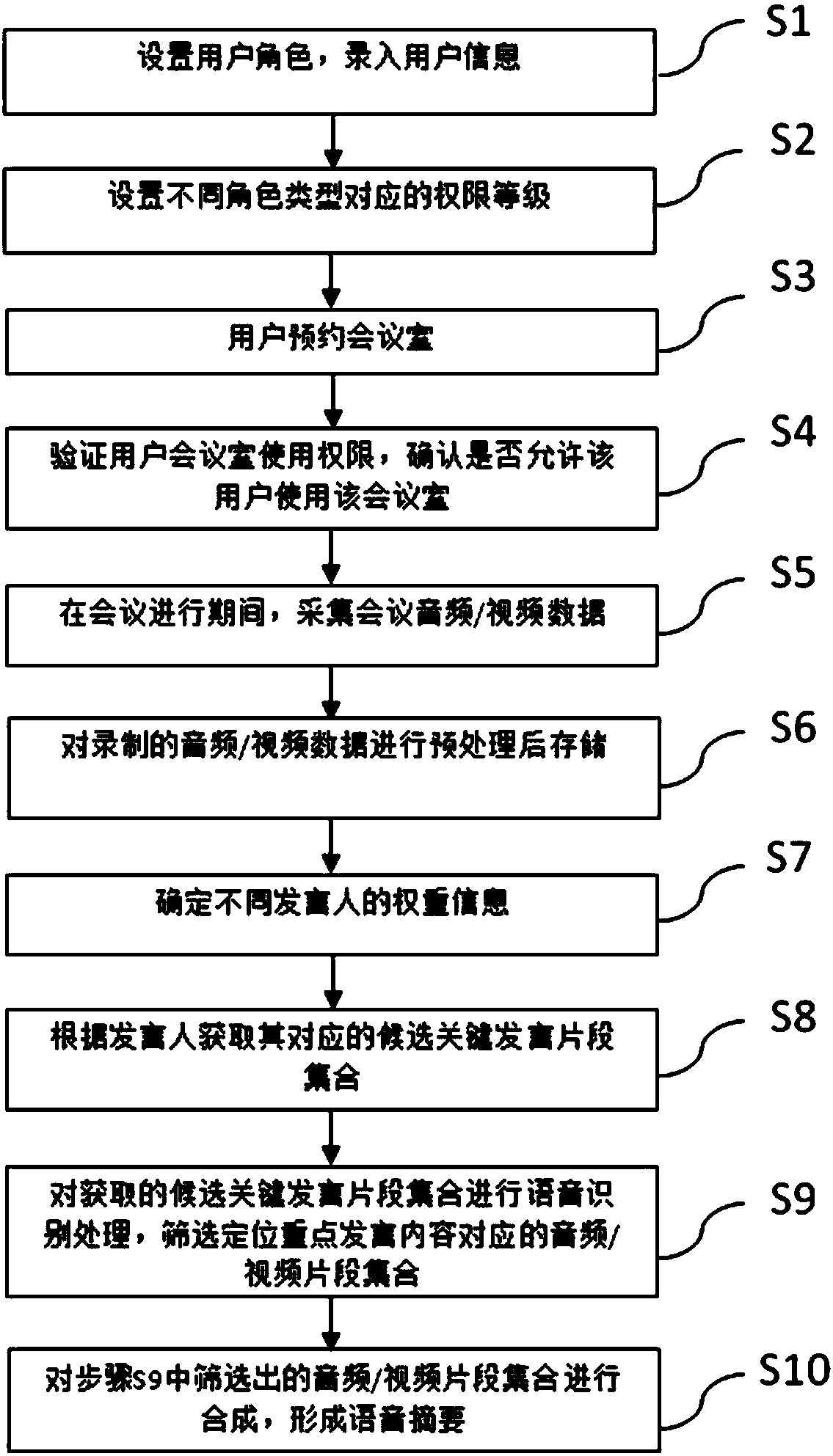
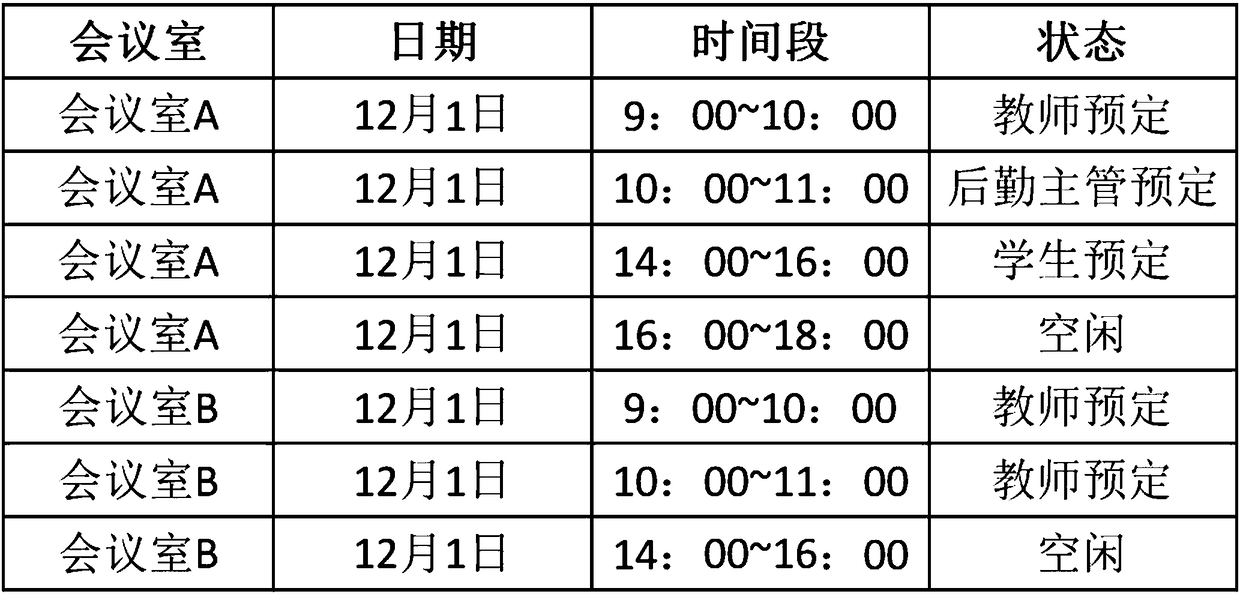
Conference intelligent management method and system
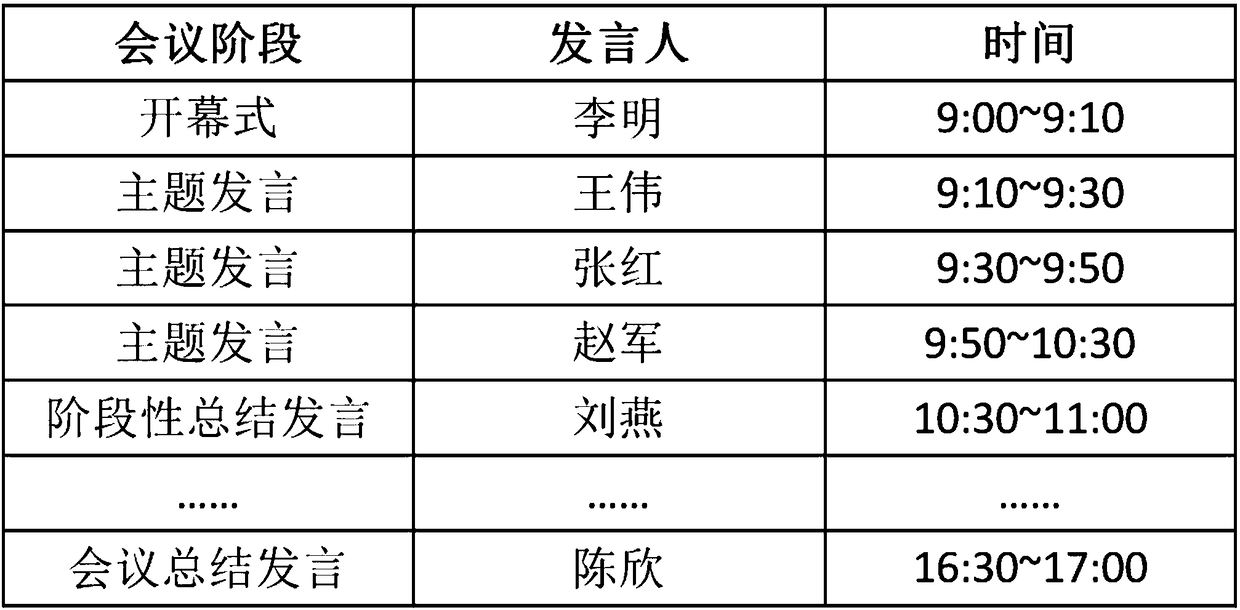
ActiveCN108346034AAvoid out-of-order useEasy to manageReservationsSpecial service for subscribersWeight coefficientPersonal details
The invention discloses a conference intelligent management method and system, and relates to the field of intelligent management. The method, by the distinguishing user roles and user authorities, changes a reservation result of a reserved conference room in different ways, facilitates the management of the conference and coordinates the emergency situations; determines, by analyzing the speakingposition, the identity information, and personal information of a speaker in the conference, the weight coefficient of the speaker so as to obtain candidate key speech segments corresponding to different speakers according to the weight coefficients by using different preset strategies, and further intercept a candidate key speech segment set according to the characteristics of the speech content, processes the intercepted candidate key speech segment set to obtain the audio / video segment set forming a speech abstract, extracts more content for important speech, extracts relatively less content for unimportant speech, and finally forms the reasonable abstract content and provides users with effective help.
Owner:SHENZHEN EAGLESOUL TECH CO LTD
Exclusive preshared key authentication
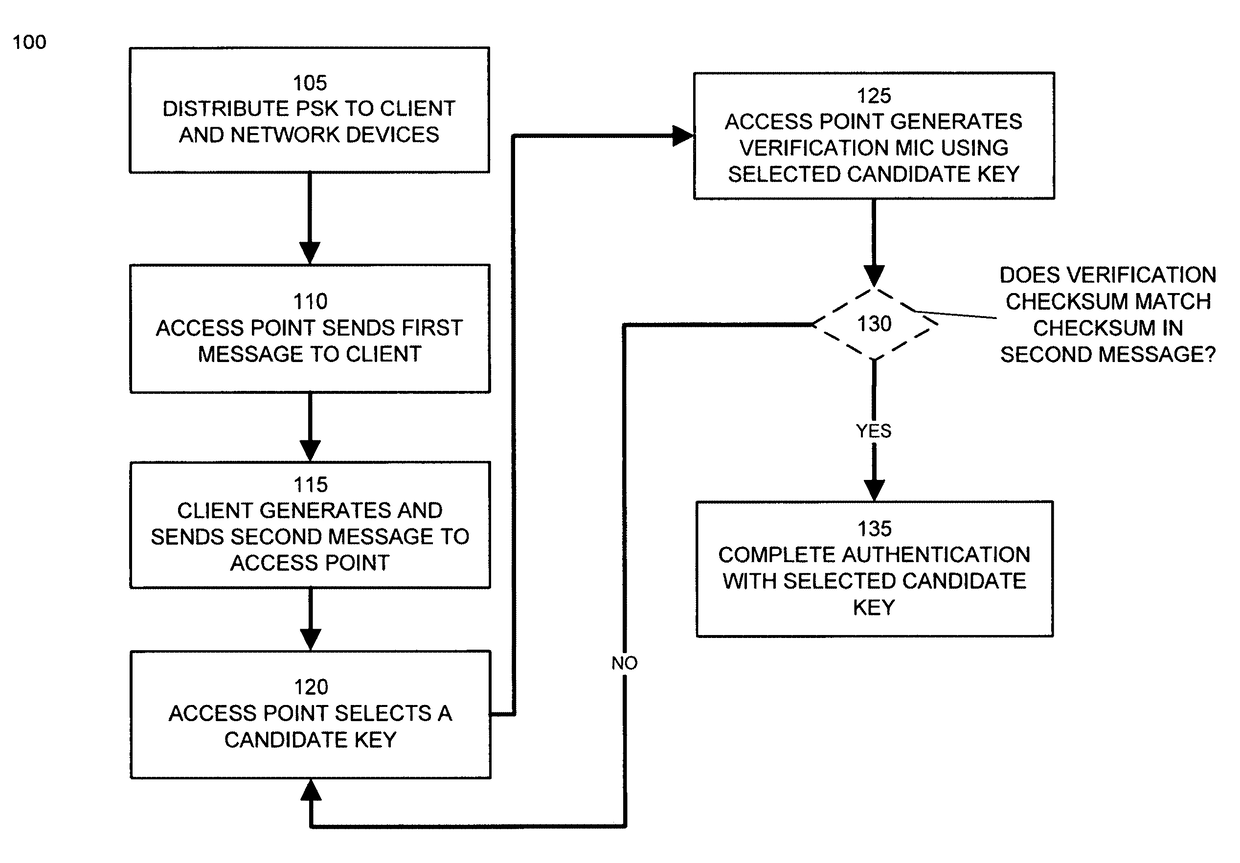
ActiveUS9674892B1Same controlSame flexibilityUser identity/authority verificationSecurity arrangementNetwork connectionChecksum
Preshared keys are assigned to client devices, users, or user groups. The set of valid preshared keys or keys derived therefrom is distributed to network devices such as wireless access points. A client device attempts to establish a secure network connection with a network device using its assigned preshared key. A network device identifies the client device's preshared key by selecting a candidate key from its set of valid preshared keys. The network device determines a validation cryptographic checksum based on the selected candidate key. If the validation cryptographic checksum matches the client's cryptographic checksum, the network device establishes a secure network connection with the client device using this candidate key. If the validation cryptographic checksum does not match the cryptographic checksum provided by the client device, the network device repeats this comparison using different candidate keys selected from its set of valid preshared keys until a match is found.
Owner:EXTREME NETWORKS INC
Character input device and method
InactiveUS20010040517A1Without increasing key operation frequencyInput/output for user-computer interactionElectronic switchingNull characterAlgorithm
Texts including required message are entered with a small number of keys such as those of a cellular telephone. In this case, a conversion table is unnecessary and the number of key operations is reduced. The number of input characters or input character strings composed by sequentially selecting one from a plurality of alphabets distributed to sequentially entered keys is relevant to the number of operation keys (N) raised to the number of distributed character (M) power (-NM) including meaningless characters or character strings and, with respect to these, character conversion is executed by referring to a dictionary means, through the operation of the conversion / next candidate key. The dictionary means stores numeric strings and words of meaningful characters or character strings among the said characters and character strings.
Owner:FUJITSU TOSHIBA MOBILE COMM LTD
Popular song key segment pick-up method for music listening
The method of extracting popular songs' key section is used in the music audition and belongs to the field of music signal analysis. It adopts the music signal of the WAV format with its sampling rate of 11025Hz and quantizing digit of 8 as the object, divides the music data stream into a series of frequency segments with fixed length, extracts the short time energy of every segment, groups the frequency segments in according to the time, counts the threshold value of the short time energy crossing the response curve, binarizates it, extracts the candidate key sections on the basis, puts the candidate key sections with appropriate length into the muster and finally chooses the highest average short time energy in the muster as the final popular songs' key section. Dealing with the 5-minute popular song in the Pentium IV 1,500M HZ CPU machine only needs 470 milliseconds. Except for the time of reading the data, the execution time only is 90 milliseconds, which realizes the aim to extract the key sections online and real time.
Owner:TSINGHUA UNIV
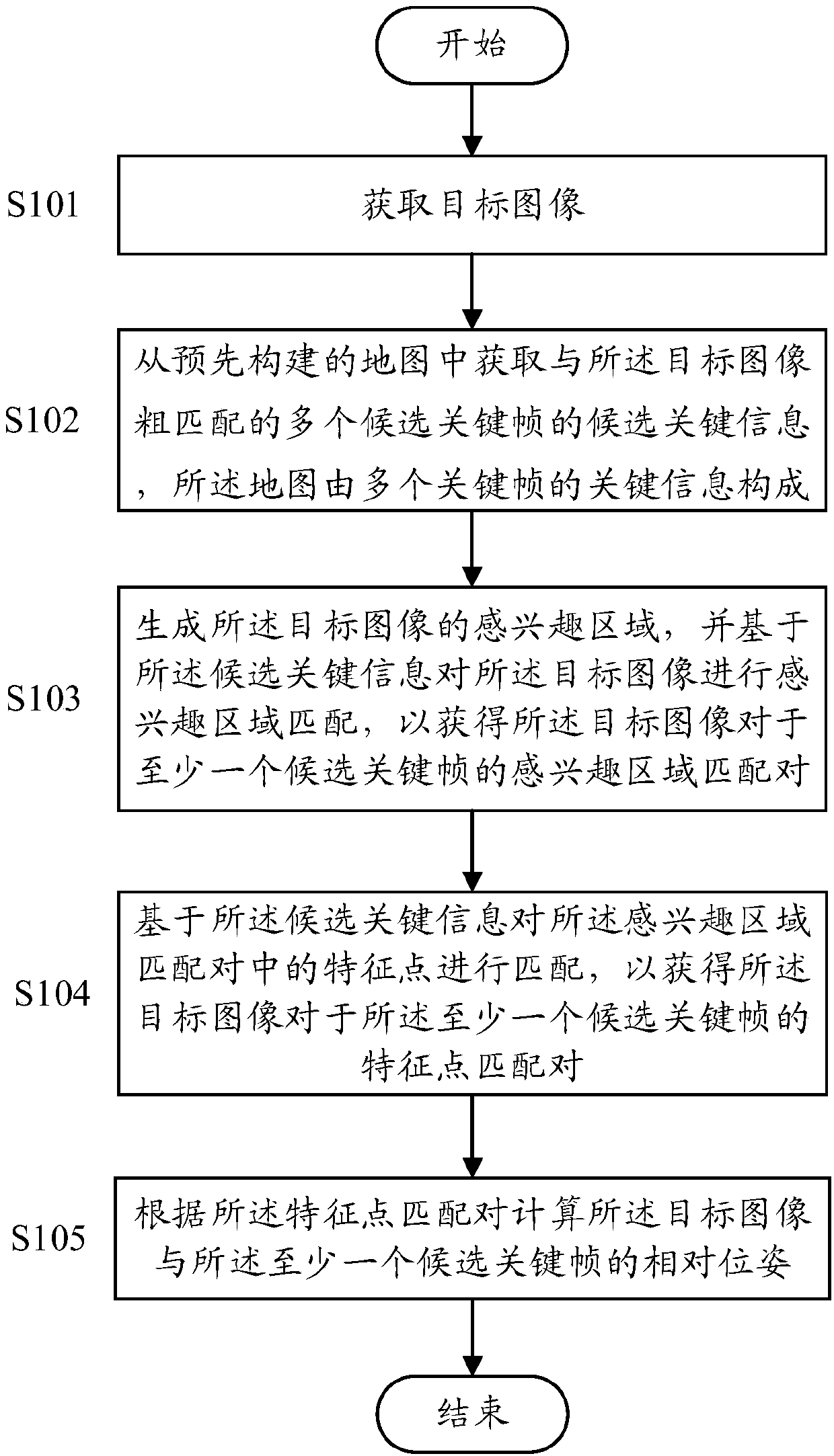
Positioning method, positioning device and readable storage medium
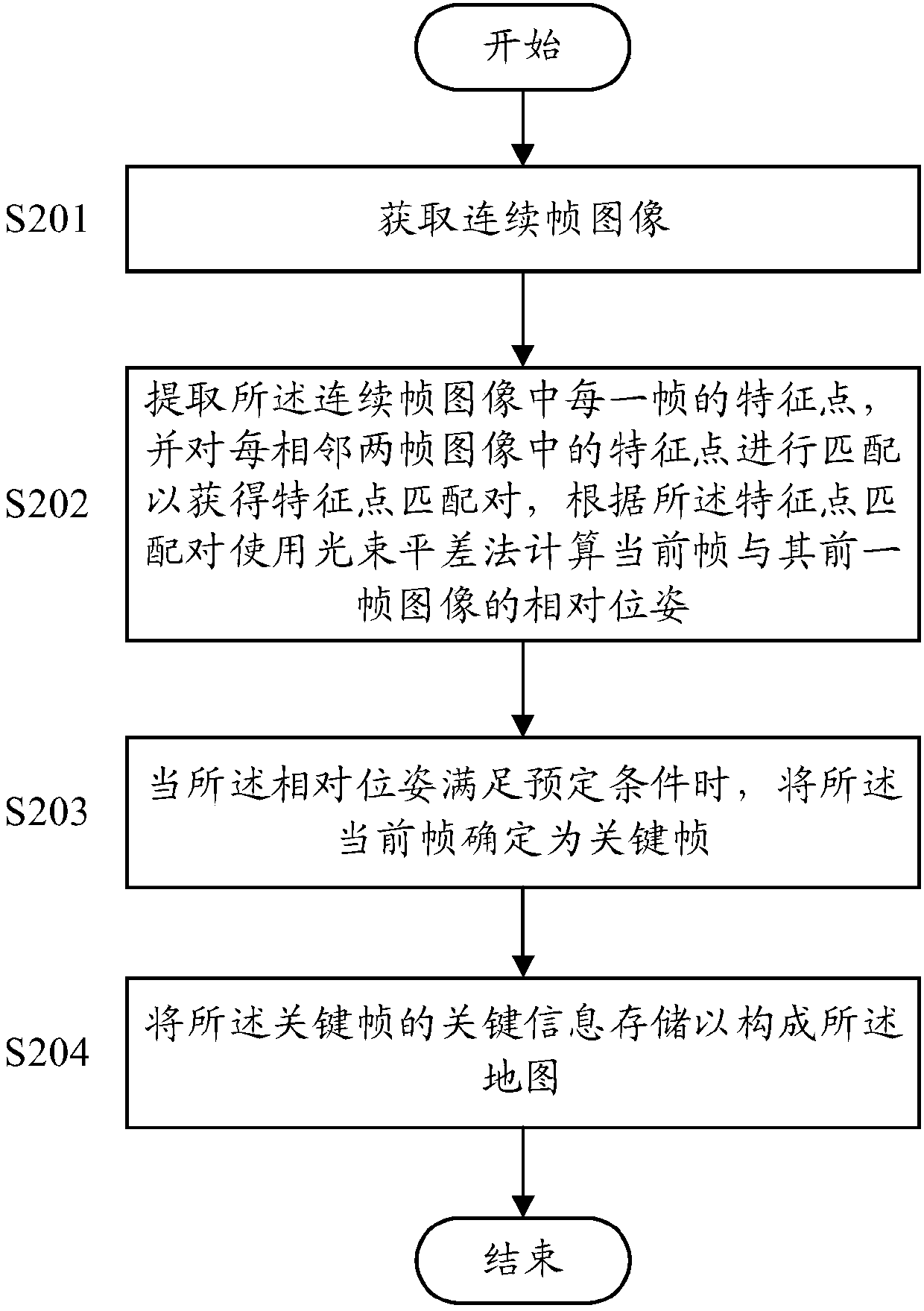
PendingCN110097045AAvoid duplicate fetchesCharacter and pattern recognitionKey frameFeature point matching
The invention discloses a positioning method. The positioning method comprises the following steps of obtaining a target image; obtaining the candidate key information of a plurality of candidate keyframes coarsely matched with the target image from a pre-constructed map, wherein the map is composed of the key information of the plurality of key frames; generating a region-of-interest (ROI) of the target image, and performing the region-of-interest matching on the target image based on the candidate key information to obtain a region-of-interest matching pair of the target image for at leastone candidate key frame; matching the feature points in the region-of-interest matching pair based on the candidate key information to obtain a feature point matching pair of the target image for theat least one candidate key frame; and calculating the relative pose of the target image and the at least one candidate key frame according to the feature point matching pair.
Owner:RICOH KK
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com