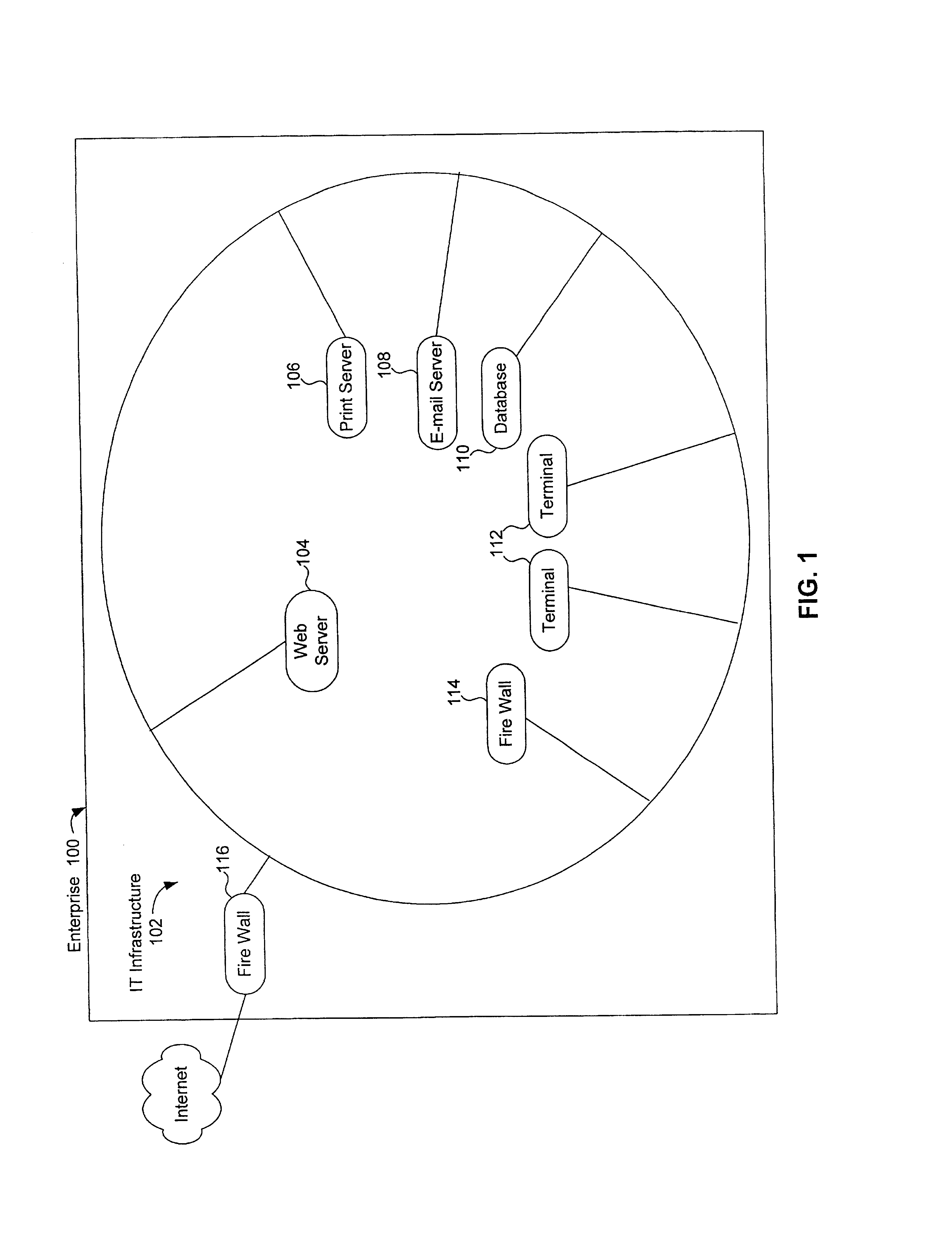
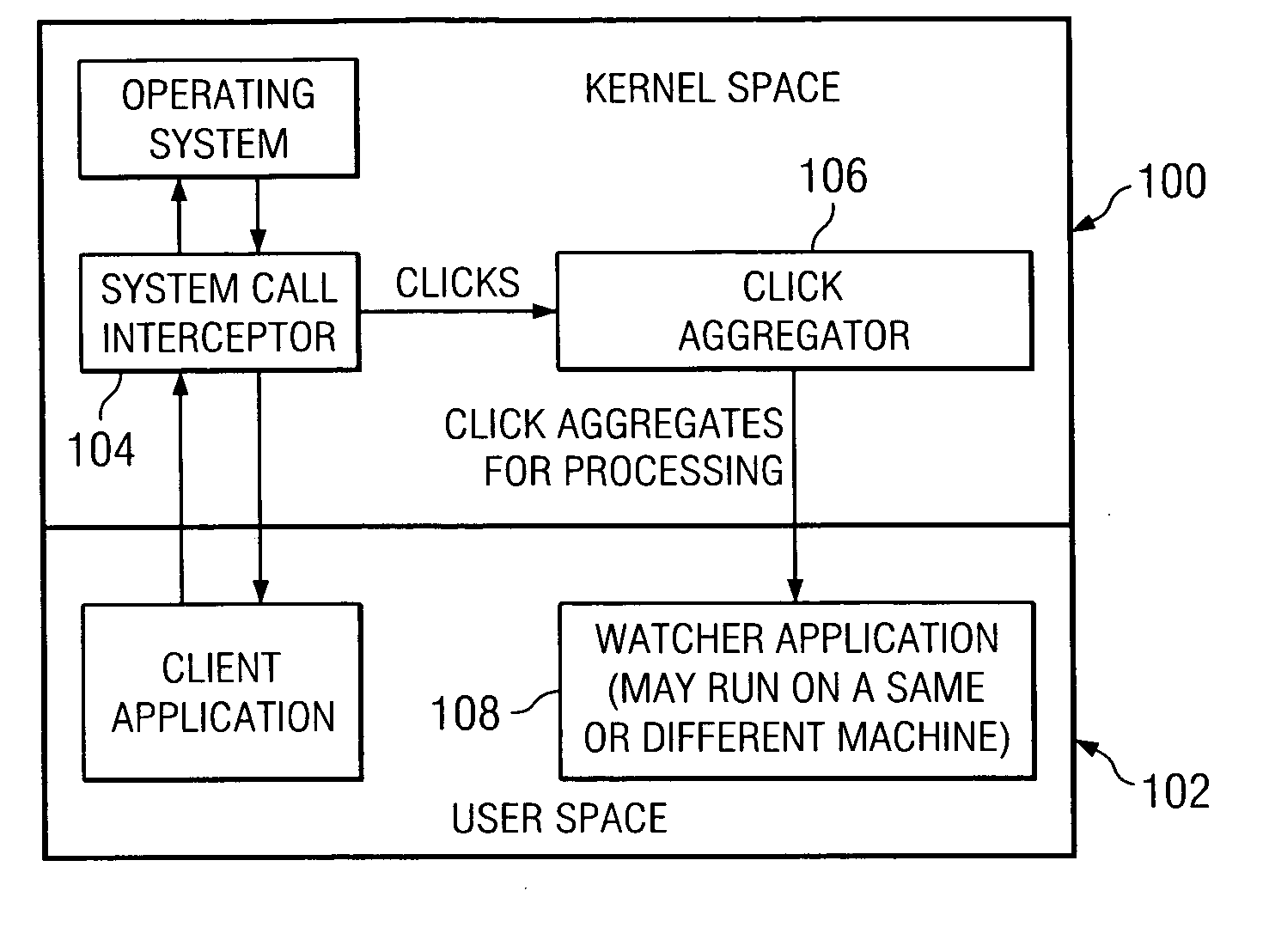
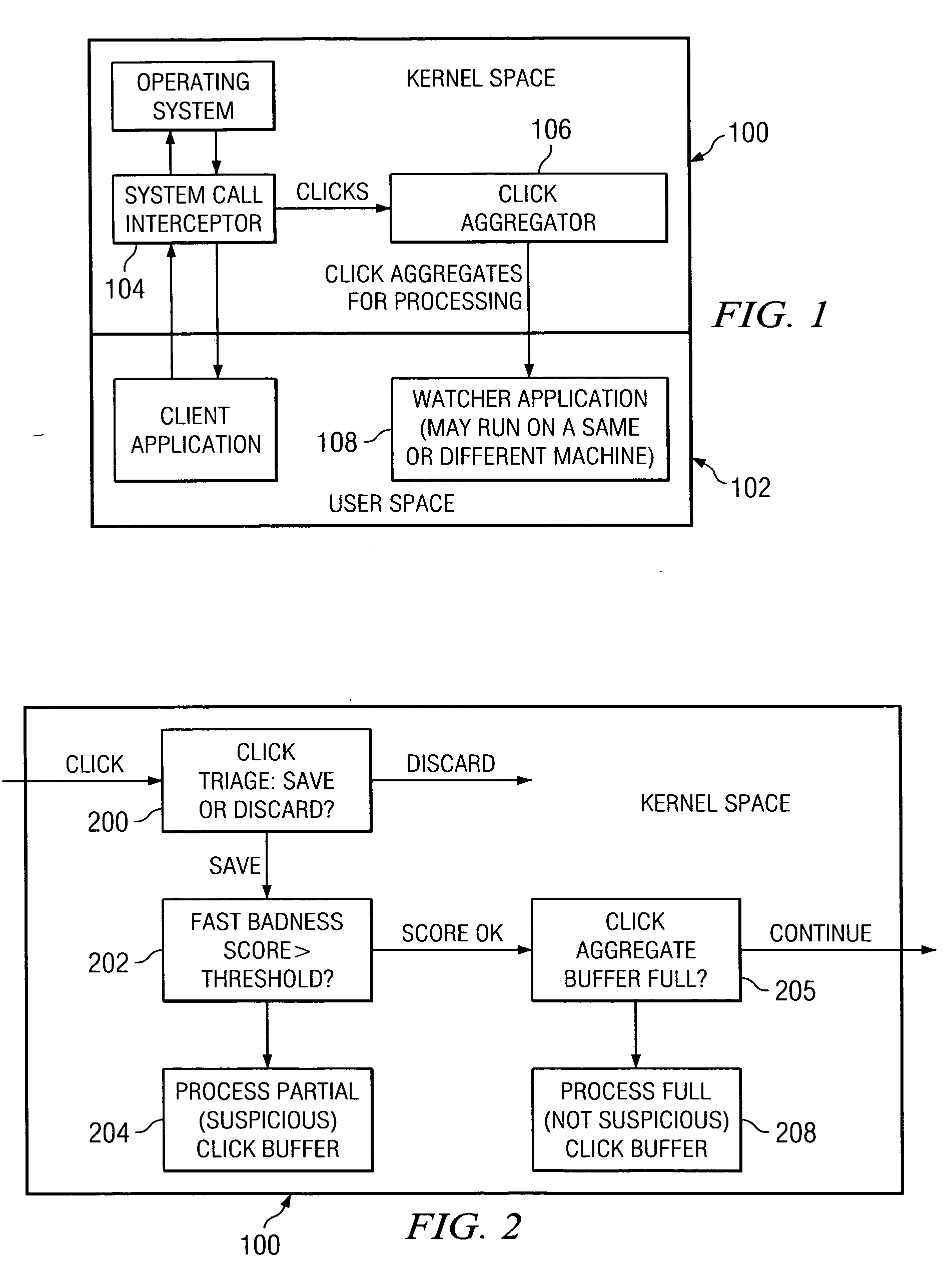
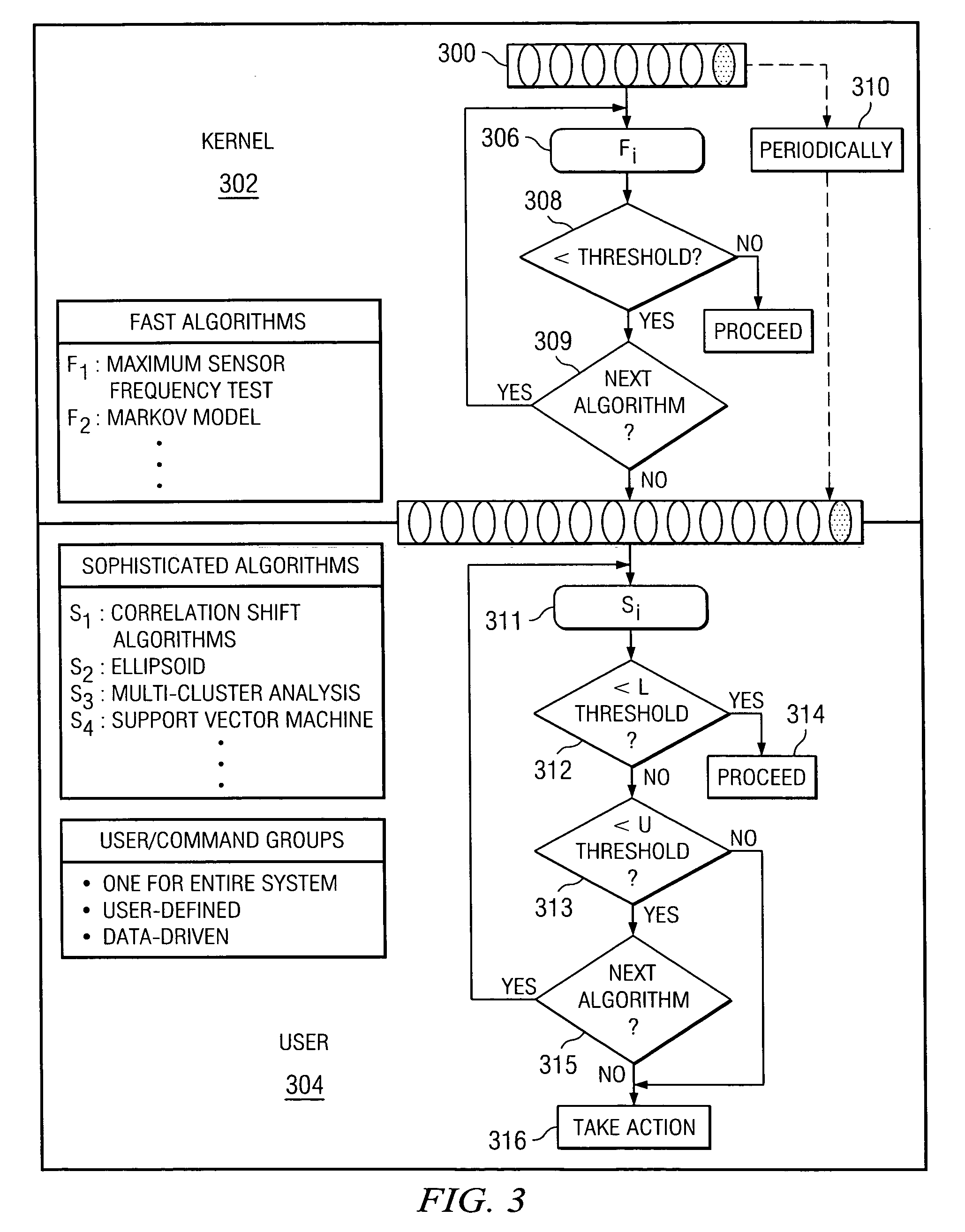
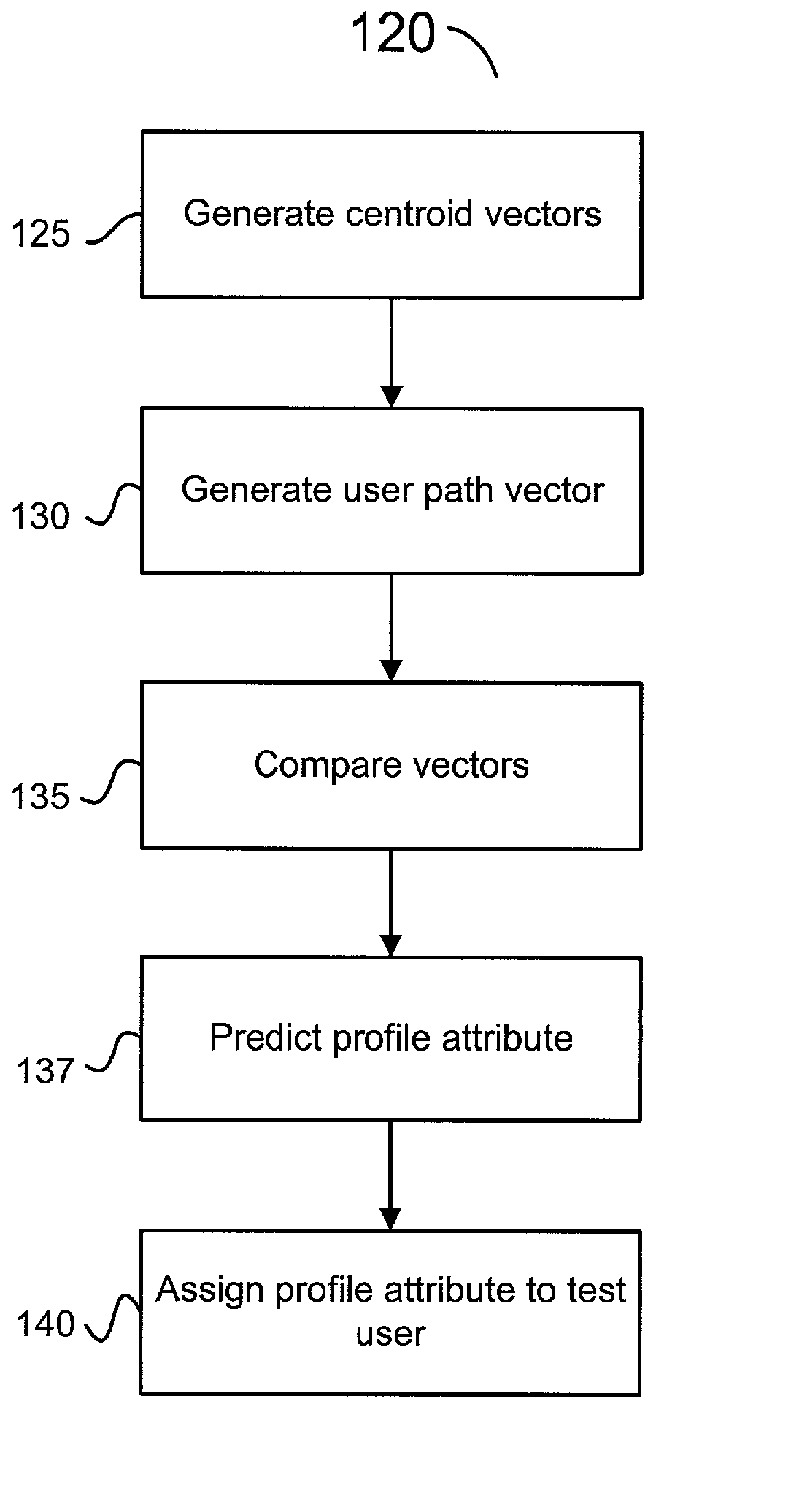
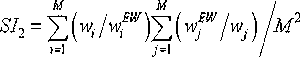Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
401 results about "Combined result" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
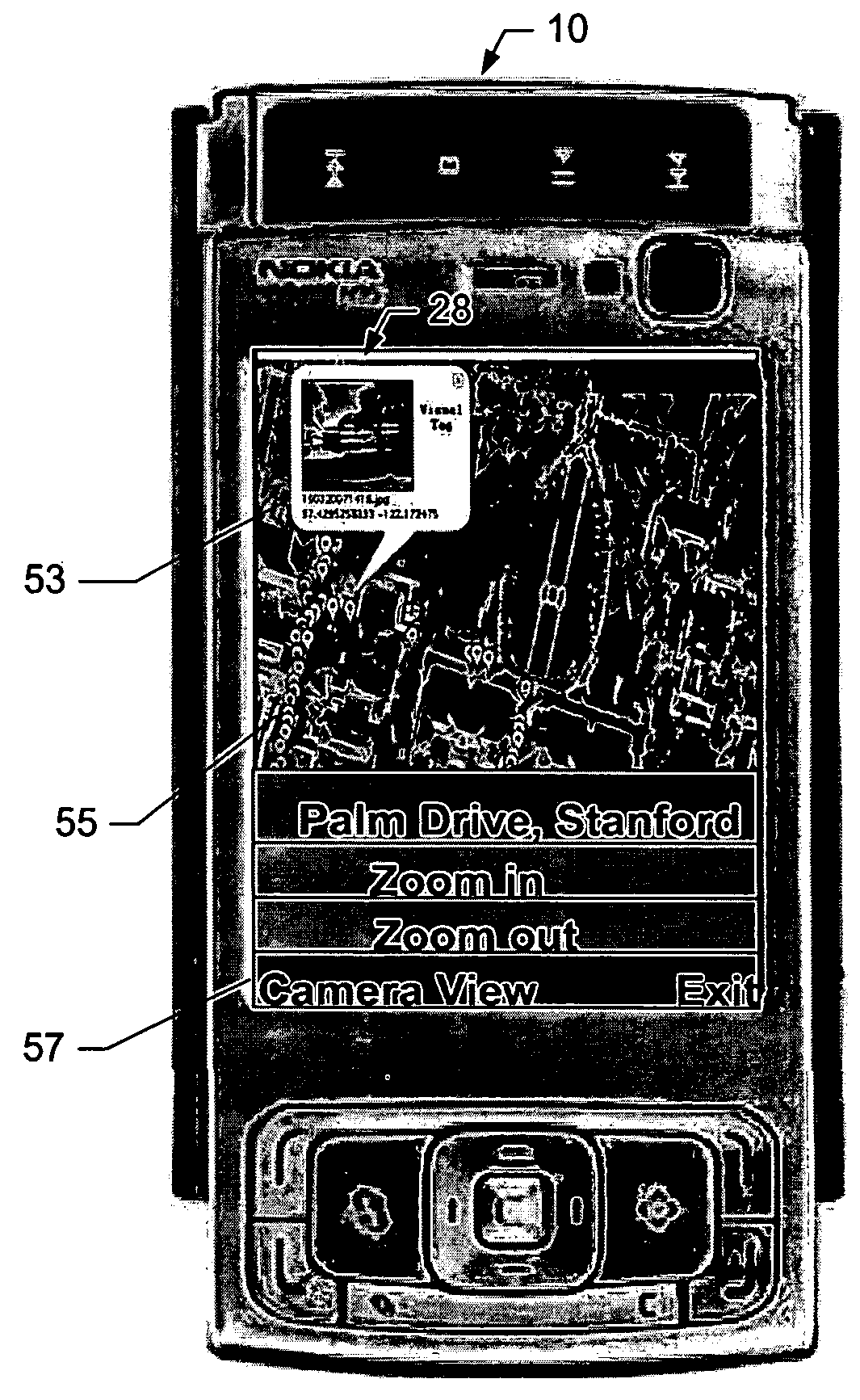
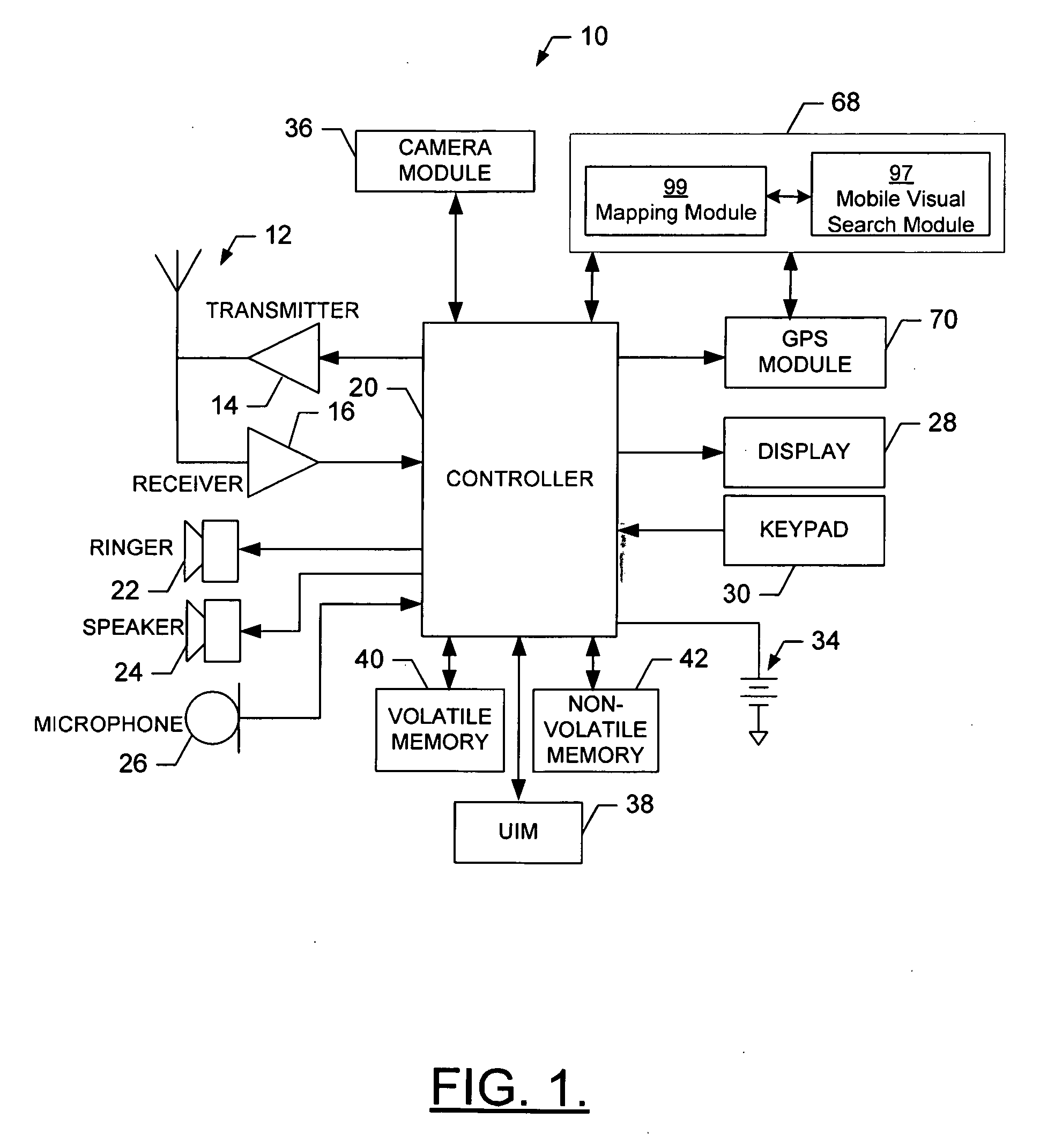
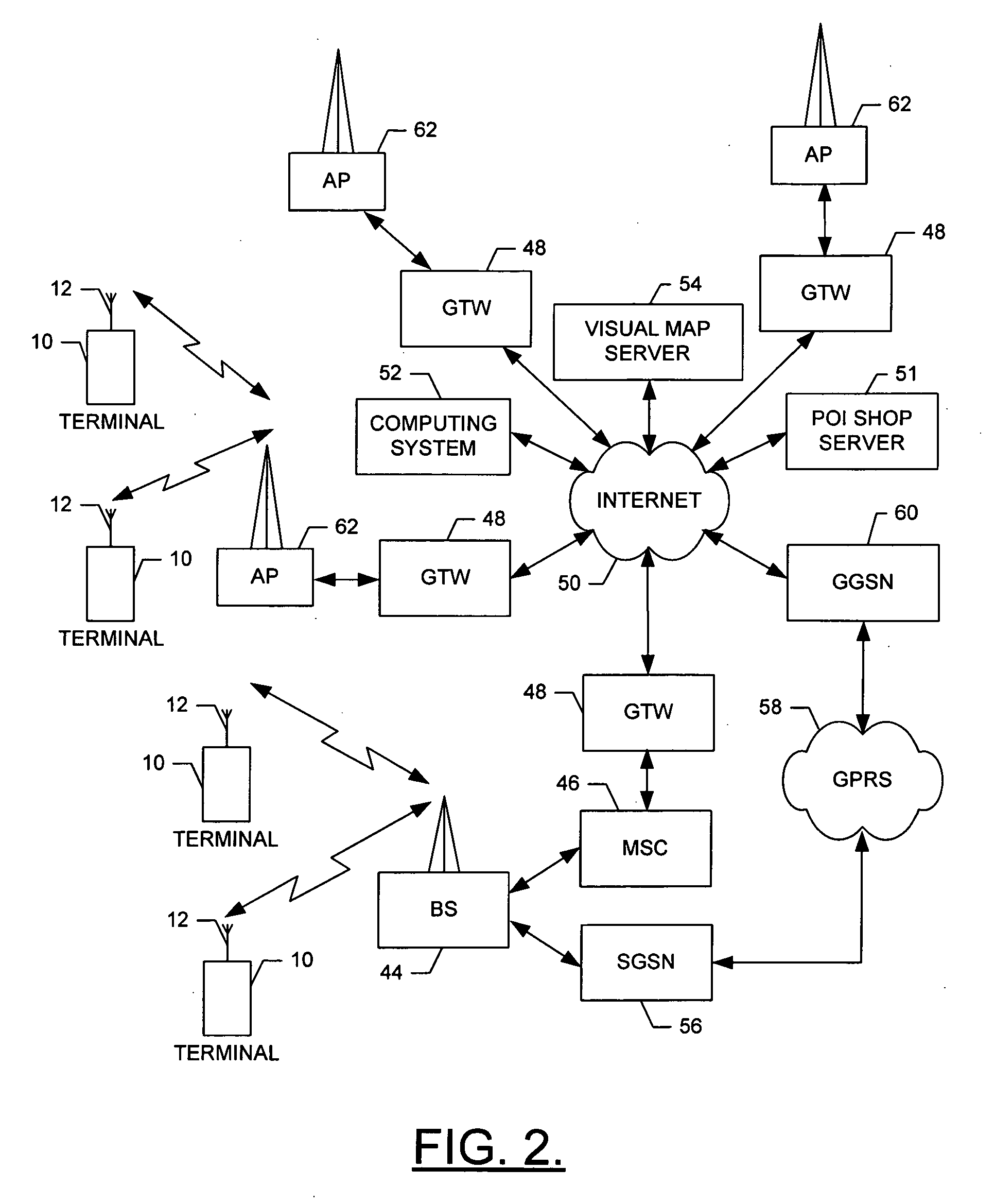
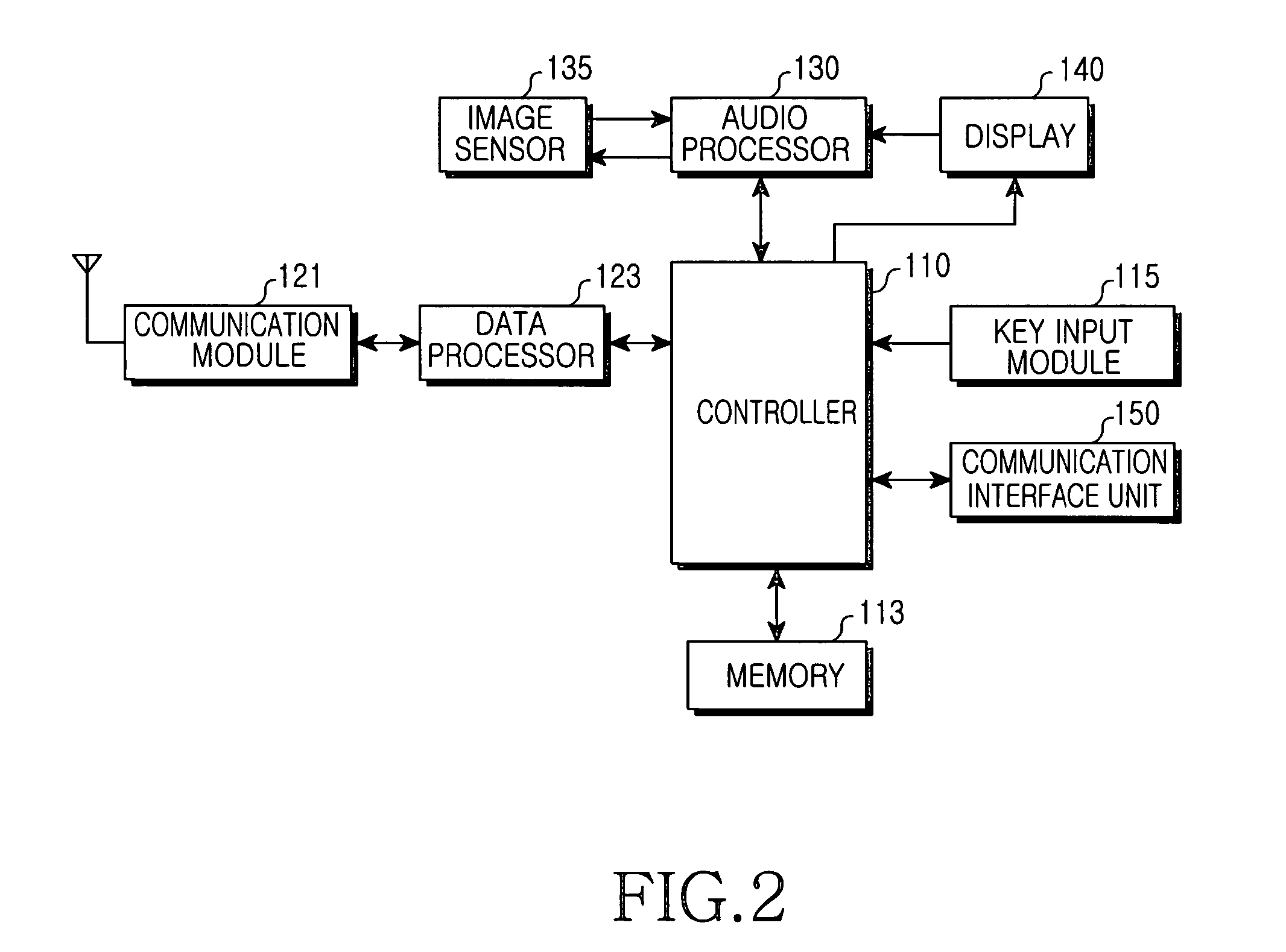
Method, Device, Mobile Terminal, and Computer Program Product for a Point of Interest Based Scheme for Improving Mobile Visual Searching Functionalities
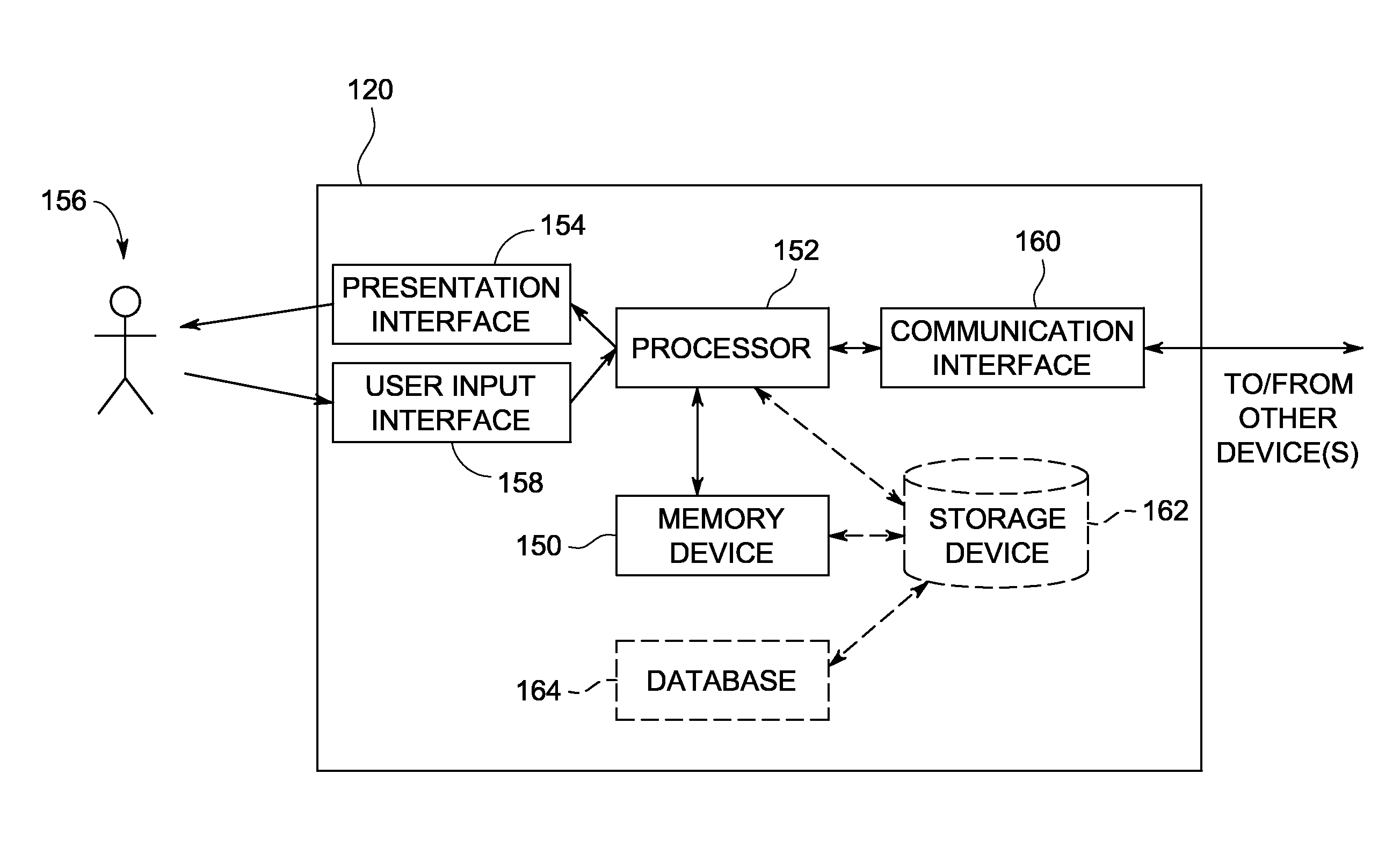
InactiveUS20080268876A1Easy accessImprove experienceSubstation equipmentRadio/inductive link selection arrangementsInformation resourceMobile vision
Owner:NOKIA TECHNOLOGLES OY
Method, system and computer program product for assessing information security
A method, system and computer program product for assessing information security interviews users regarding technical and non-technical issues. In an embodiment, users are interviewed based on areas of expertise. In an embodiment, information security assessments are performed on domains within an enterprise, the results of which are rolled-up to perform an information security assessment across the enterprise. The invention optionally includes application specific questions and vulnerabilities and / or industry specific questions and vulnerabilities. The invention optionally permits users to query a repository of expert knowledge. The invention optionally provides users with working aids. The invention optionally permits users to execute third party testing / diagnostic applications. The invention, optionally combines results of executed third party testing / diagnostic applications with user responses to interview questions, to assess information security. A system in accordance with the invention includes an inference engine, which may include a logic based inference engine, a knowledge based inference engine, and / or an artificial intelligence inference engine. In an embodiment, the invention includes an application specific tailoring tool that allows a user to tailor the system to assess security of information handled by a third party application program.
Owner:SAFEOPERATIONS
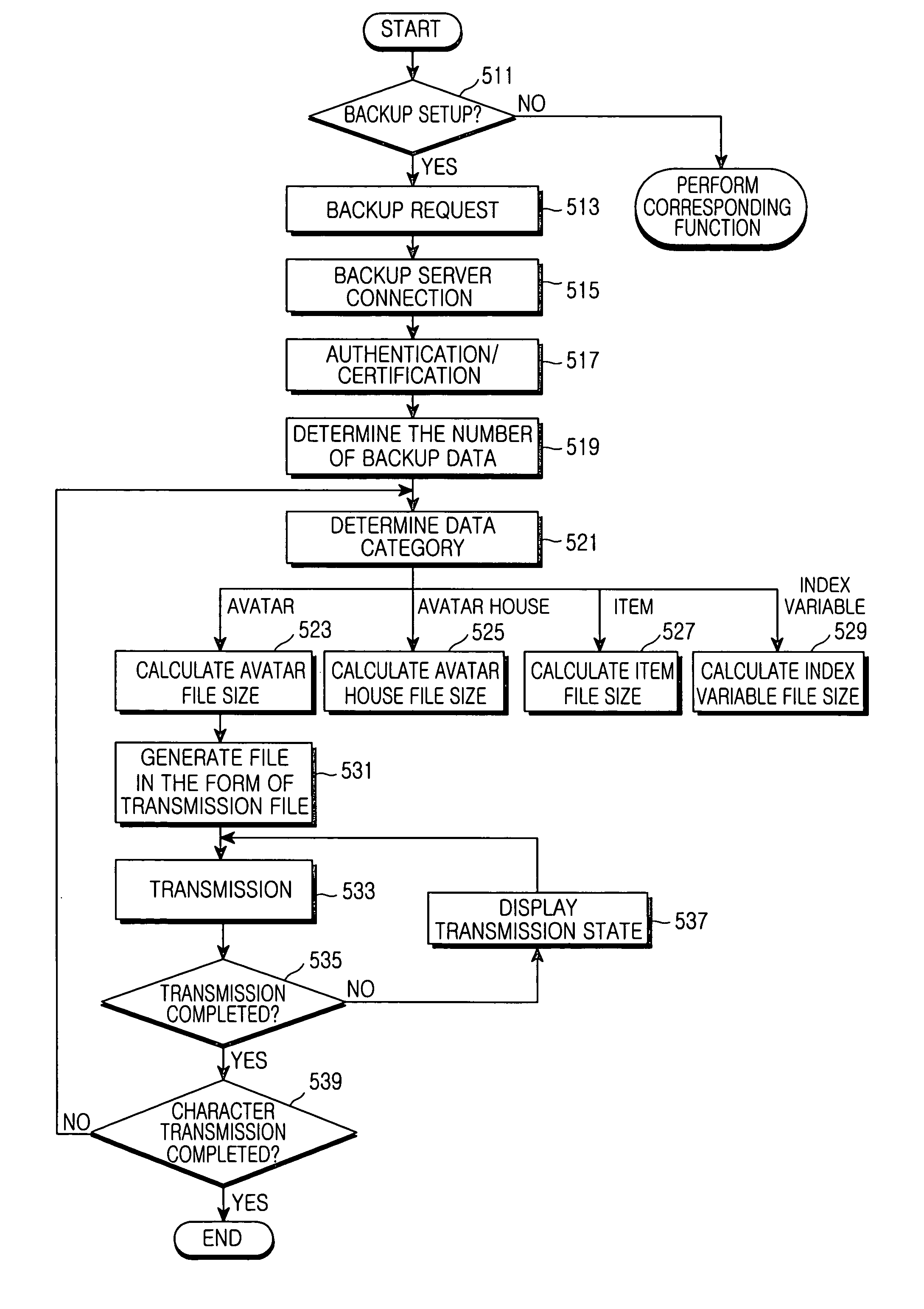
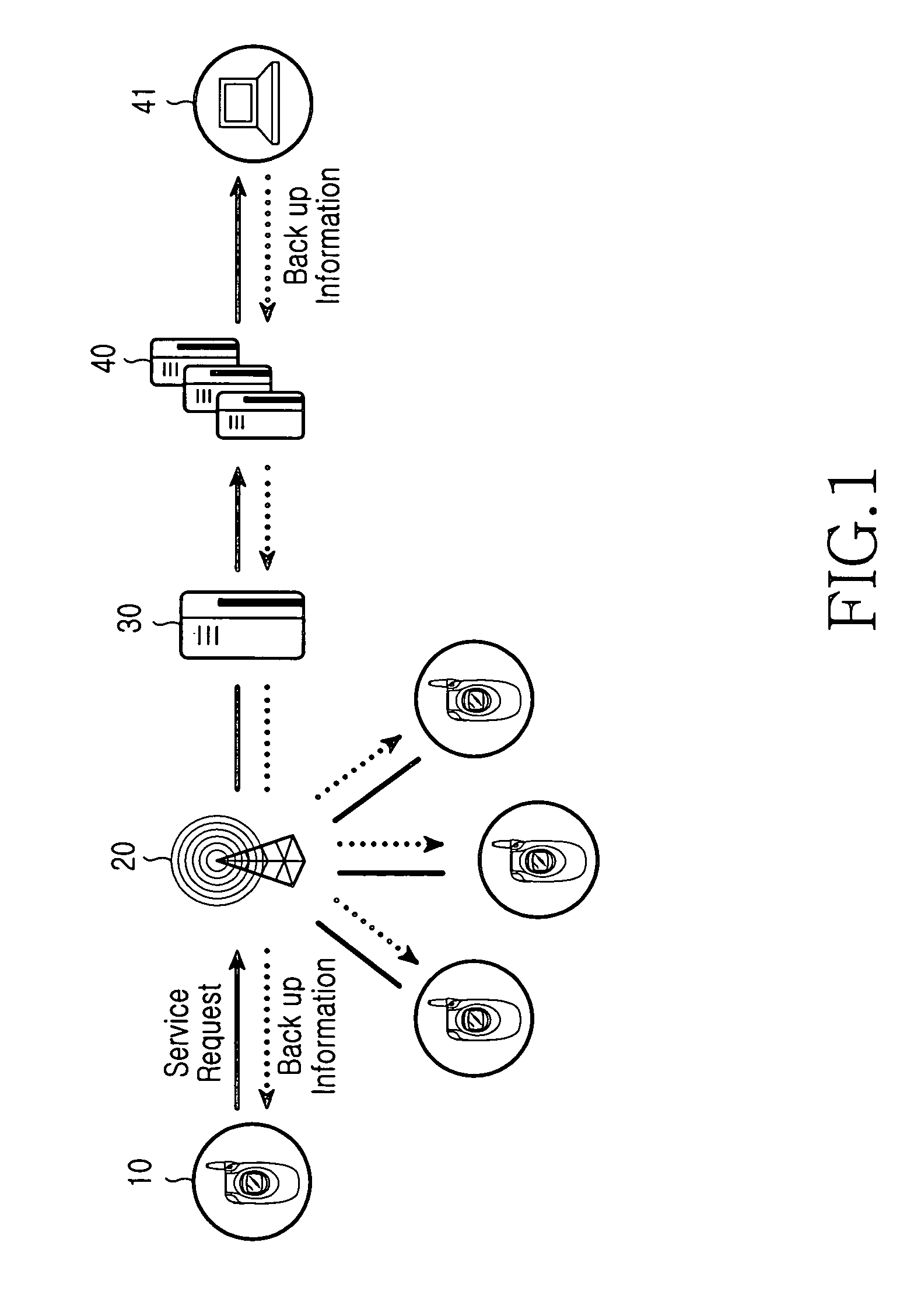
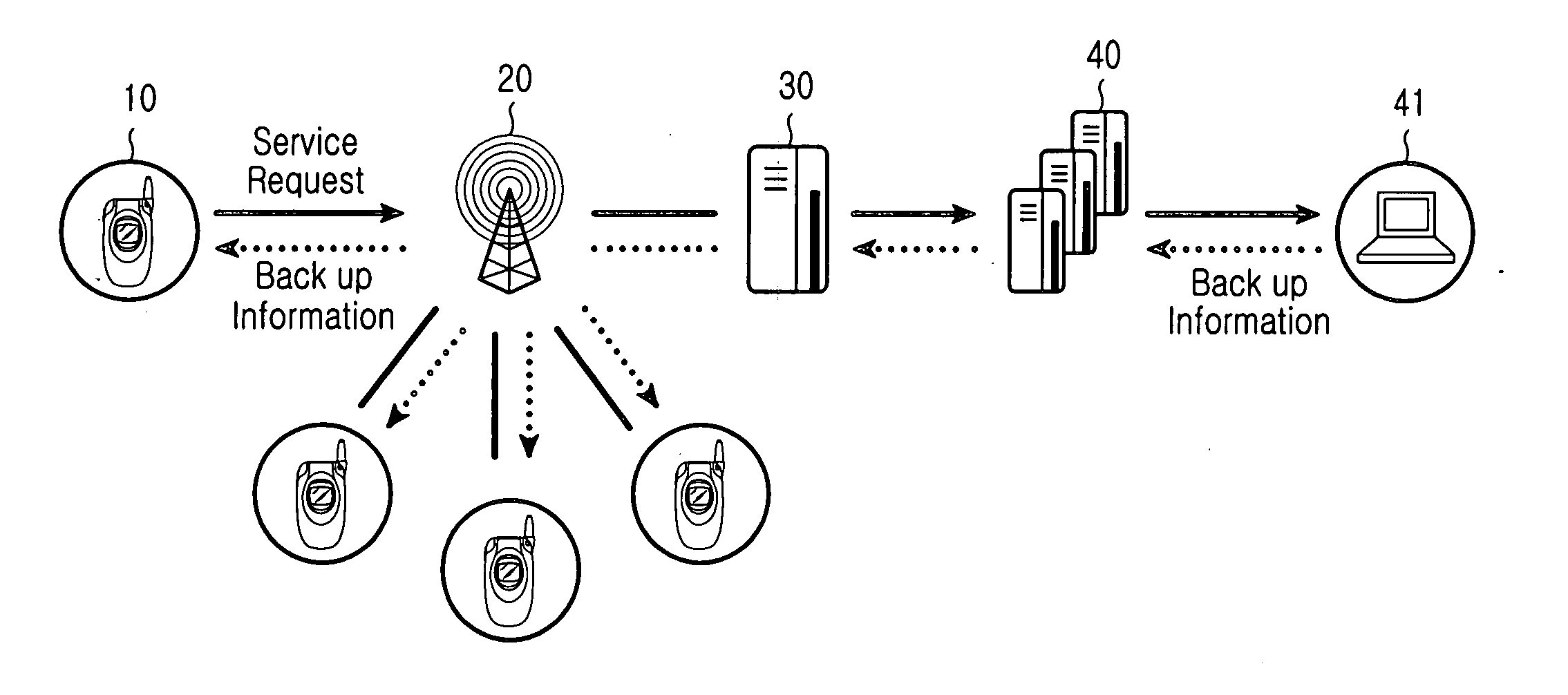
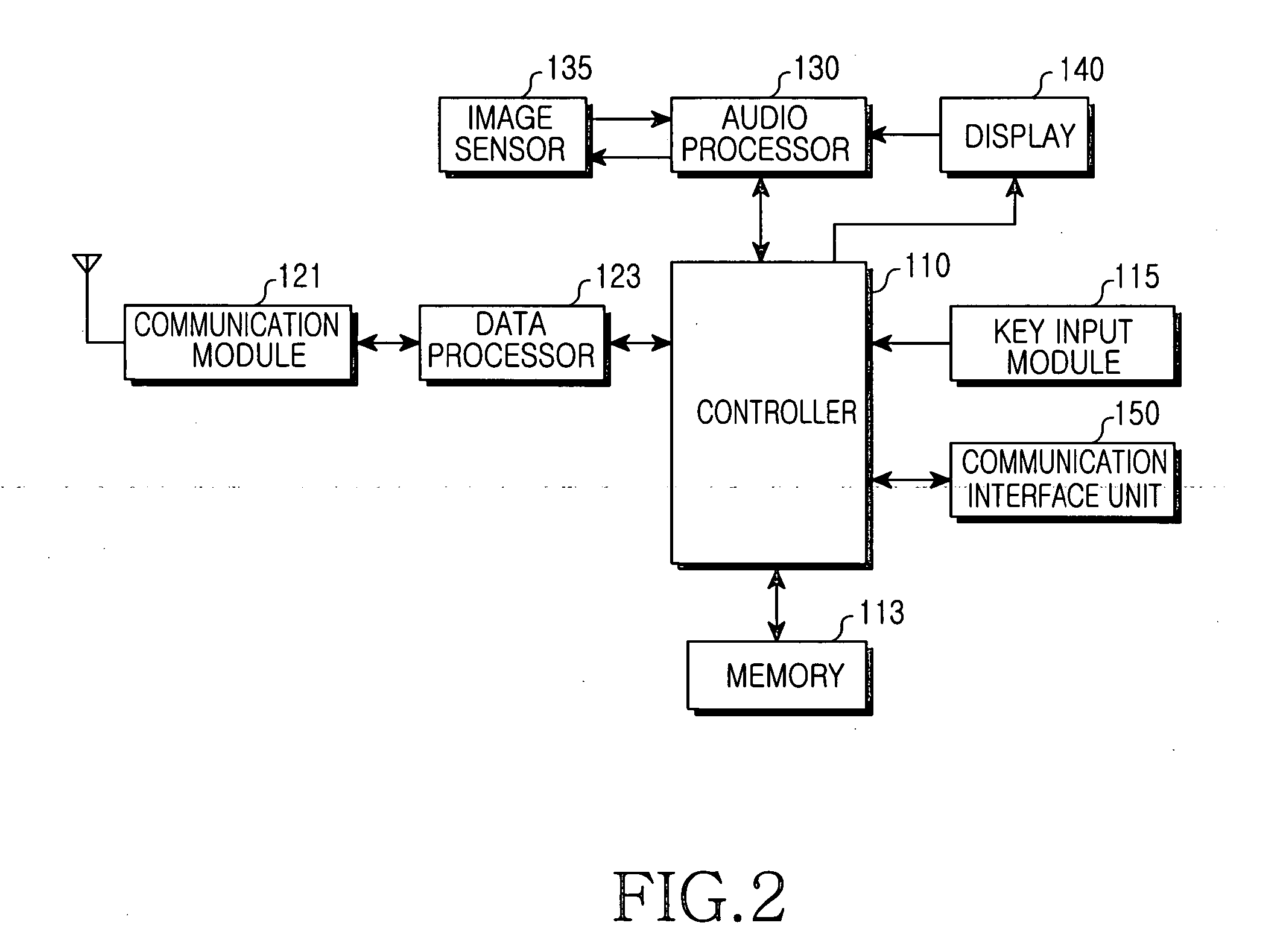
Apparatus and method for processing a data backup service for use in a mobile terminal
InactiveUS7885931B2Digital data processing detailsRadio/inductive link selection arrangementsData synchronizationResource information
An apparatus and method for processing a data backup service of a mobile terminal. The apparatus and method backs-up data files stored in a mobile terminal in a backup server over a wireless Internet. The backup server is capable of backing-up resource information of the mobile terminal. The apparatus and method comprise a) checking setup backup resources during a backup setup procedure, and attempting to establish a connection to the backup server; b) analyzing category information of data to be transmitted to the backup server after connecting to the backup server, determining the number of references if the data category is equal to data including iterative information, and determining a division interval on the basis of a file size and performing data synchronization if the data category is equal to data including binary data. The apparatus and method further comprise c) separately storing the synchronization data serving as the iterative information and combining the separately-stored results when the synchronization data is determined to be iterative information, or divisionally storing the synchronization data, combining the divisionally-stored results, and transmitting the combined result when the synchronization data is determined to be divisionally-designated data; and d) terminating a backup operation of the mobile terminal when the backup server generates a response signal after the data is transmitted to the backup server.
Owner:SAMSUNG ELECTRONICS CO LTD
User profile classification by web usage analysis
InactiveUS7162522B2Web data retrievalDigital data processing detailsInternet usersWeb usage analysis
Owner:XEROX CORP
Method and system for detecting intrusive anomalous use of a software system using multiple detection algorithms
InactiveUS20060085854A1Improve detection accuracyAccurate detectionMemory loss protectionDetecting faulty computer hardwareCountermeasureSoftware system
A method of detecting an intrusion into (or an anomaly in a behavior of) a target software system begins by instrumenting the target software system to generate behavior data representing a current observation or observation aggregate. The method then determines whether the current observation or observation aggregate warrants a second level examination; preferably, this determination is made by processing the current observation or observation aggregate through a first level detection algorithm that provides a first, provisional indication of a possible intrusion. If a result of executing the first level detection algorithm indicates that the current observation or observation aggregate warrants a second level examination, the method continues by processing the current observation or observation aggregate through at least one or more second level detection algorithms to provide a second, more definite, fine grain indication of a possible intrusion. The observation aggregates used by the first and second level detection algorithms may be the same or different. The first and second level detection algorithms may be executed in the same or different systems, machines or processors. The target software system operation may be suspended as the current observation or observation aggregate is processed through the one or more second level detection algorithms. A given action (e.g., sending an alert, logging the event, activating a countermeasure, or the like) may be taken if the result of the second level examination indicates a possible intrusion. Multiple algorithms may be executed together within a single examination level, with the individual results then analyzed to obtain a composite result or output indicative of intrusive or anomalous behavior.
Owner:STRATACLOUD
User profile classification by web usage analysis
ActiveUS20030101024A1Web data retrievalMultiple digital computer combinationsWeb usage analysisInternet users
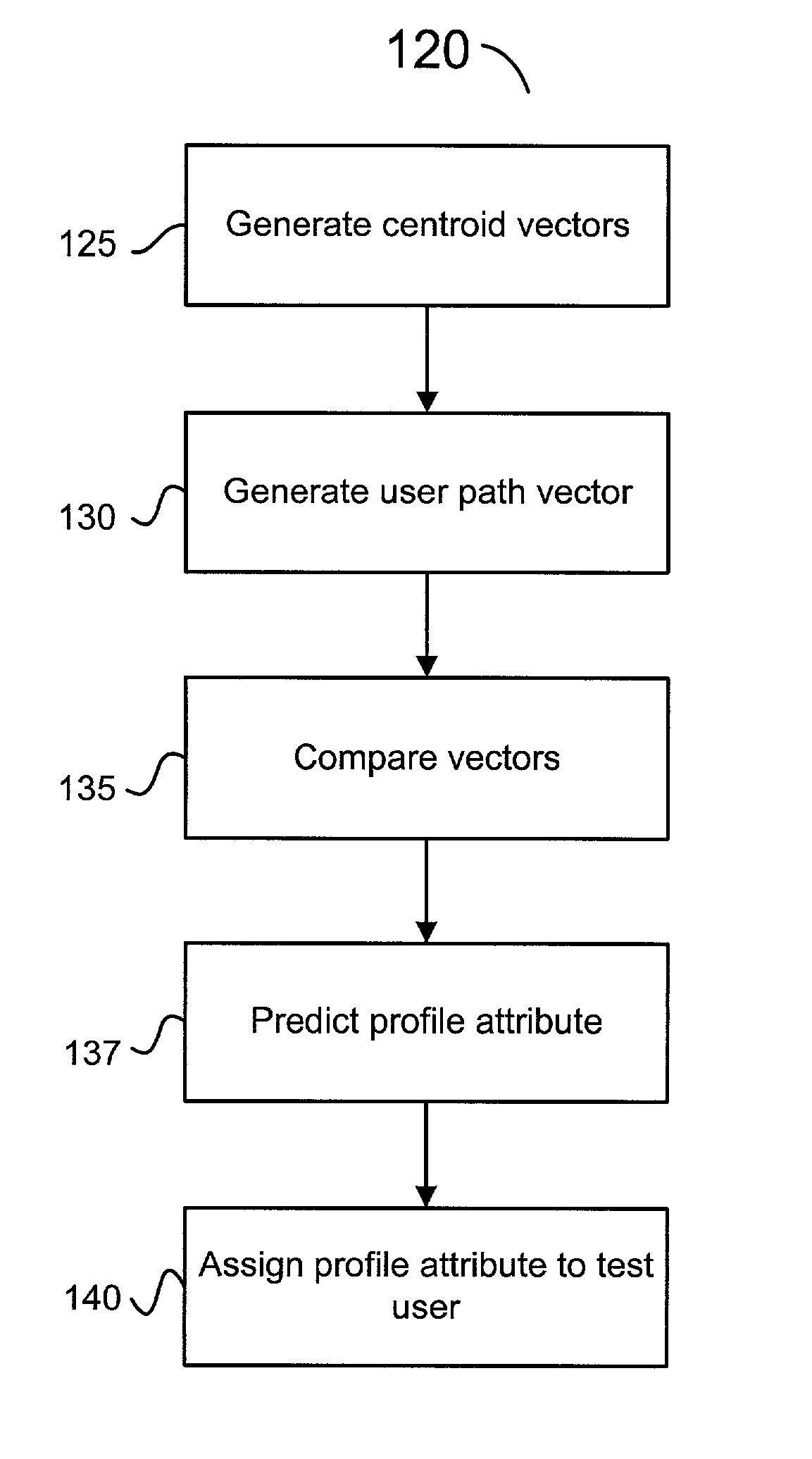
Demographic information of an Internet user is predicted based on an analysis of accessed web pages. Web pages accessed by the Internet user are detected and mapped to a user path vector which is converted to a normalized weighted user path vector. A centroid vector identifies web page access patterns of users with a shared user profile attribute. The user profile attribute is assigned to the Internet user based on a comparison of the vectors. Bias values are also assigned to a set of web pages and a user profile attribute can be predicted for an Internet user based on the bias values of web pages accessed by the user. User attributes can also be predicted based on the results of an expectation maximization process. Demographic information can be predicted based on the combined results of a vector comparison, bias determination, or expectation maximization process.
Owner:XEROX CORP
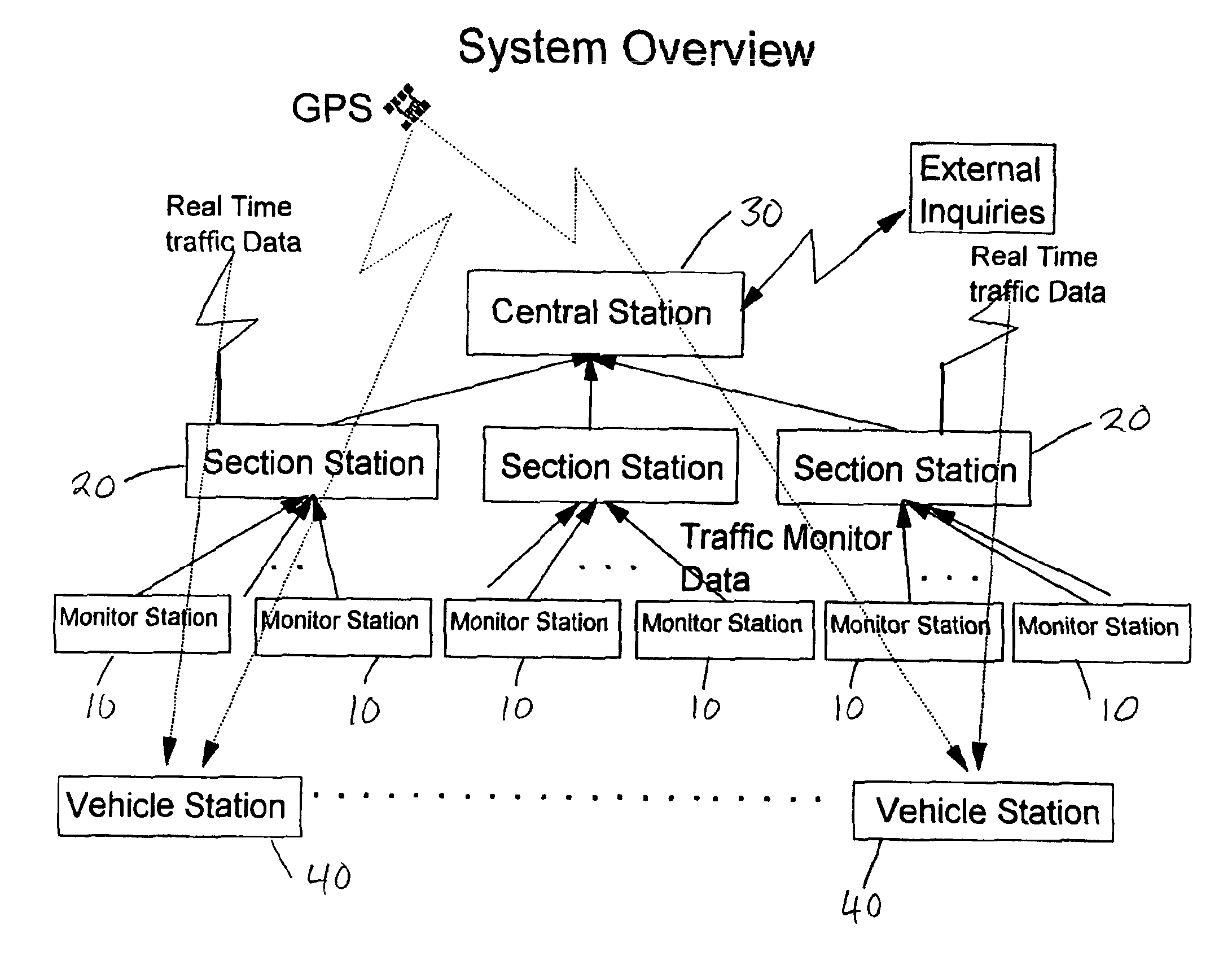
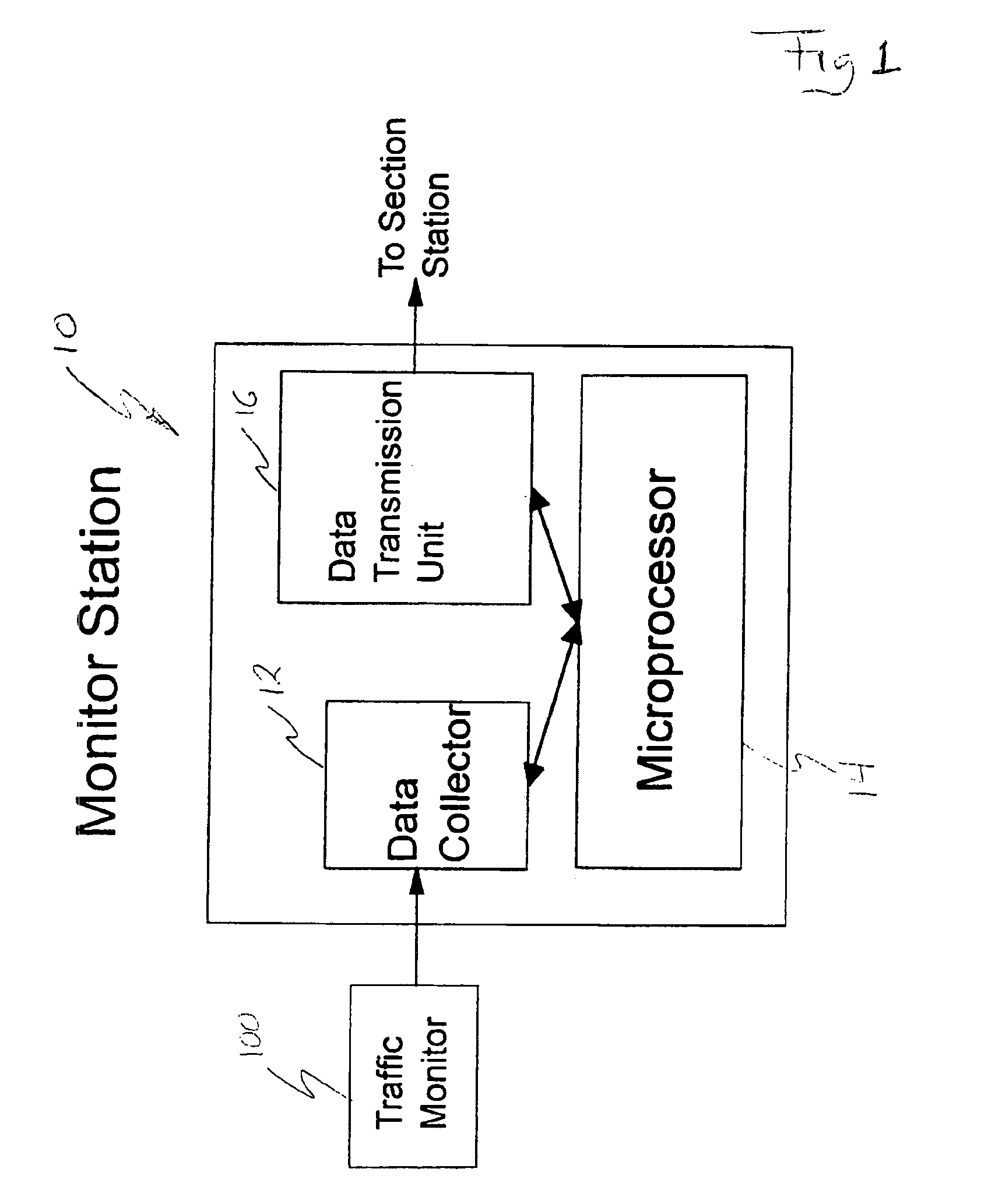
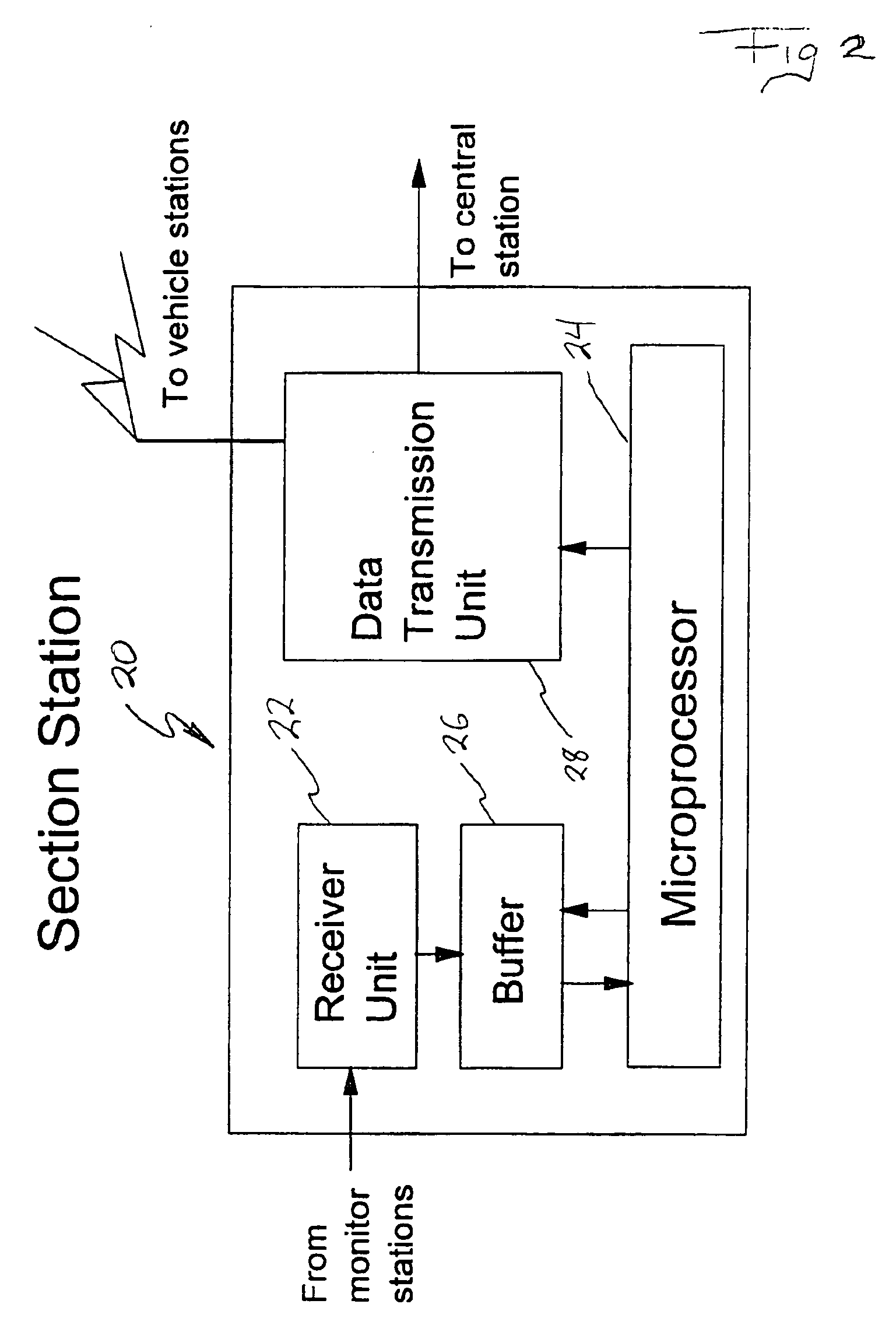
Traffic flow and route selection display system for routing vehicles
InactiveUS6911918B2Easy to displayReduce complexity and densityAnalogue computers for vehiclesInstruments for road network navigationTraffic capacityRoad map
A real-time vehicular traffic flow display system employs groups of monitor stations positioned at spaced-apart locations along vehicular roadways, to sense the speed of traffic flow on a given portion of a route. Individual section stations each serve a sequential group of different monitor stations. Each monitor station senses the speed of vehicular traffic a given road portion and transmits corresponding information to an associated section station; each section station processes the received signals, and transmits them to display stations on board vehicles in addition to sending the signals to an optional geographic area central station. The signals transmitted to vehicles present information concerning traffic speed for each monitored portion of a road in addition to identifying the road portion; traffic speed information is processed to identify predetermined ranges of average speed in selected colors. Each vehicle station includes a Global Positioning System (GPS) receiver and visual display device with access to both the GPS including a database of local area road maps for display. All portions of each monitored route on a displayed map are shown in a color corresponding to the average speed of traffic monitored on the corresponding route portion. The current position of the vehicle station is shown on the map, and a “preferred” route from that location to an optionally selected destination is highlighted; both functions are accomplished in accordance with known GPS technology. An optional geographic area central station stores information not usually available in the on-board vehicle station, such as wide-area maps, and also receives traffic condition signals from various section stations including those beyond the range of the vehicle station. The central station correlates these two sources of information and makes the combined results available for separate access by users of the system.
Owner:CHEN SHAWFU
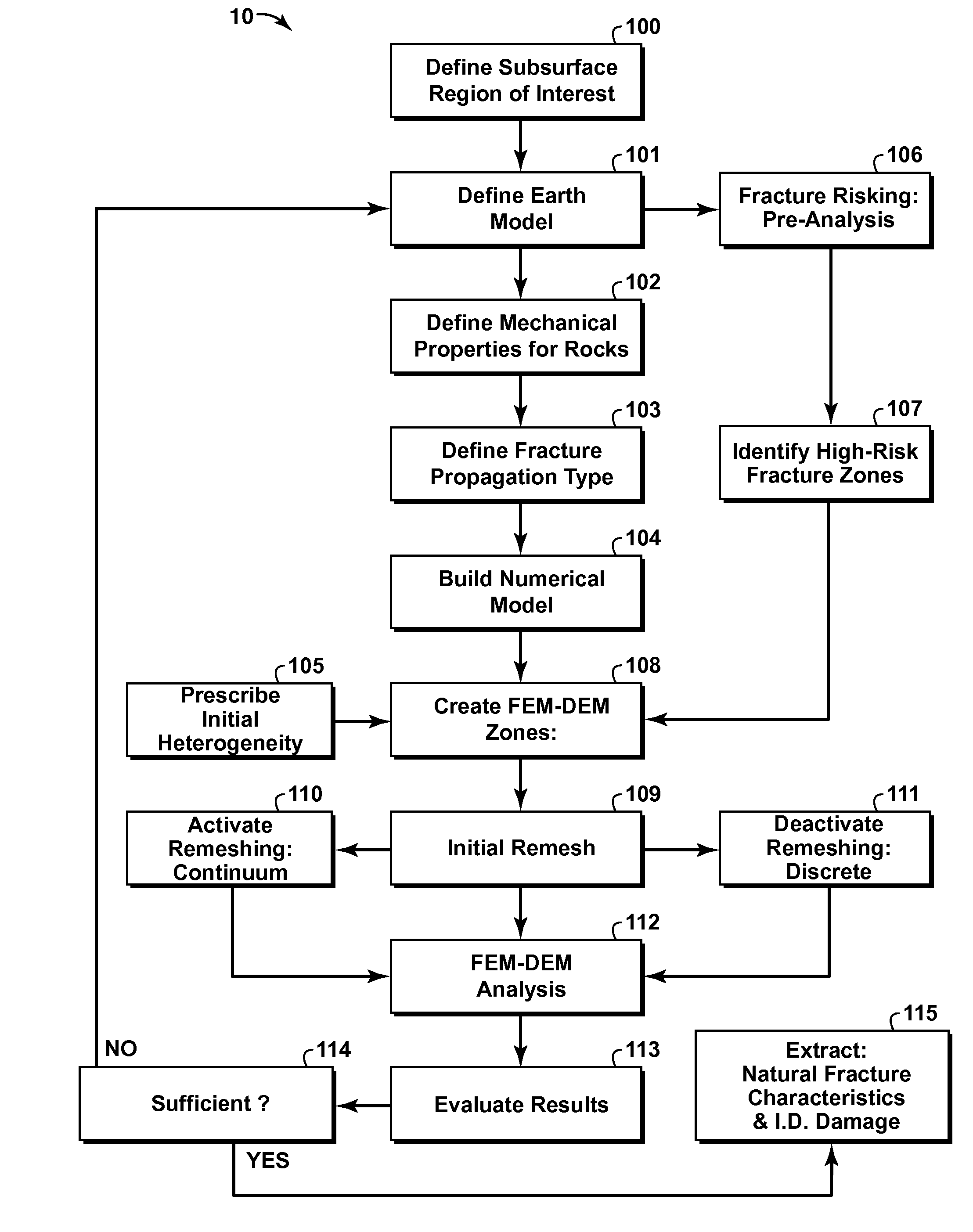
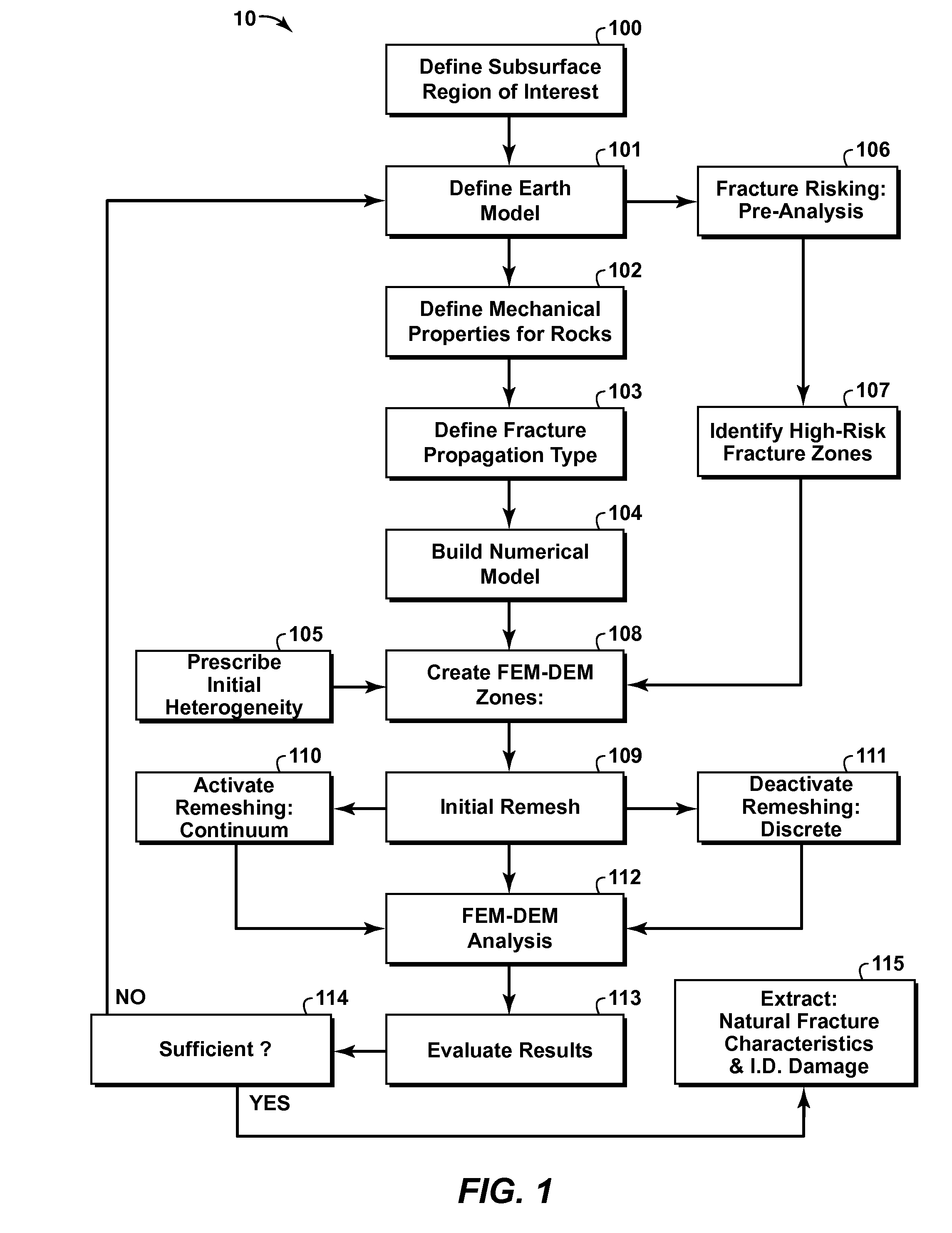
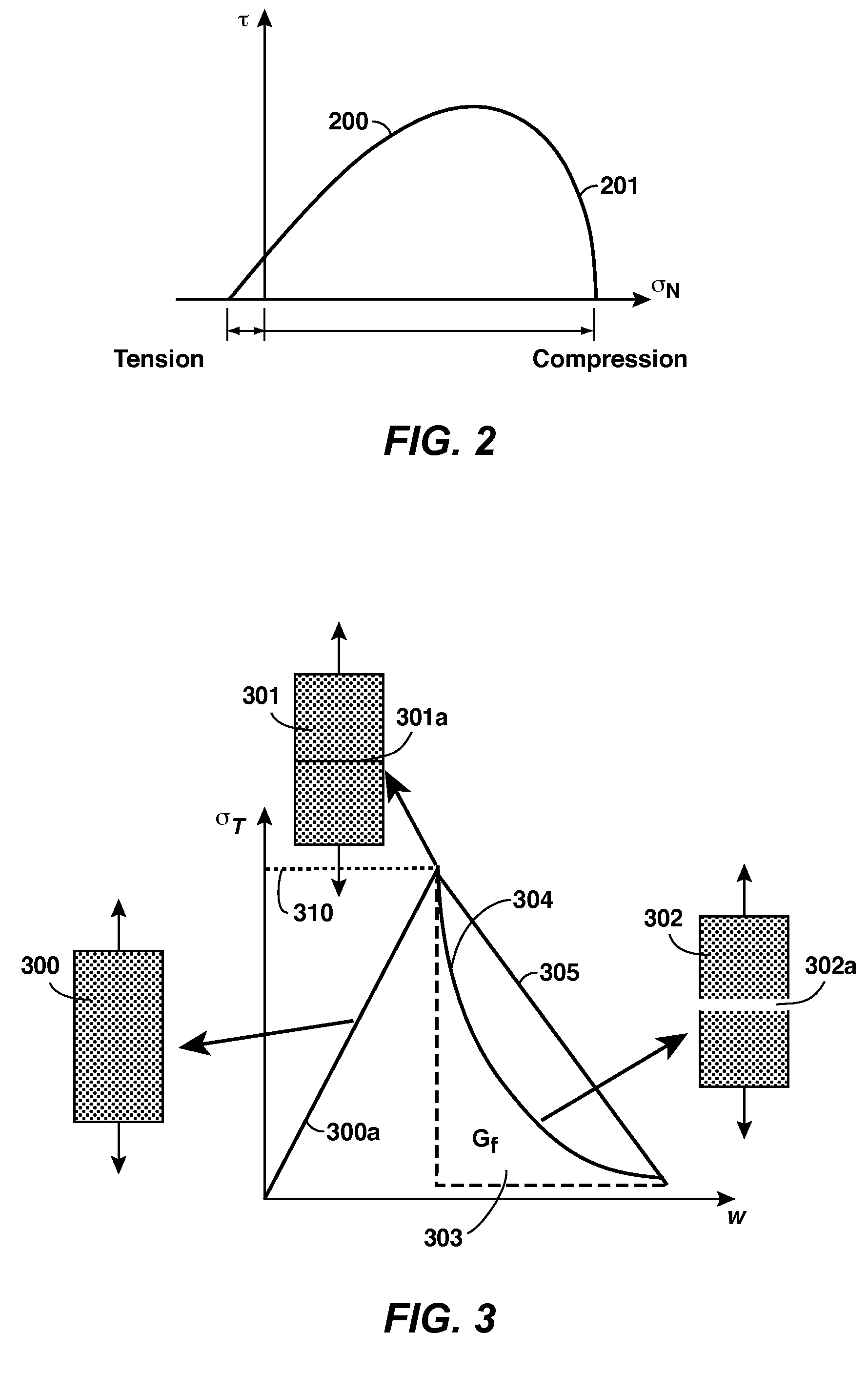
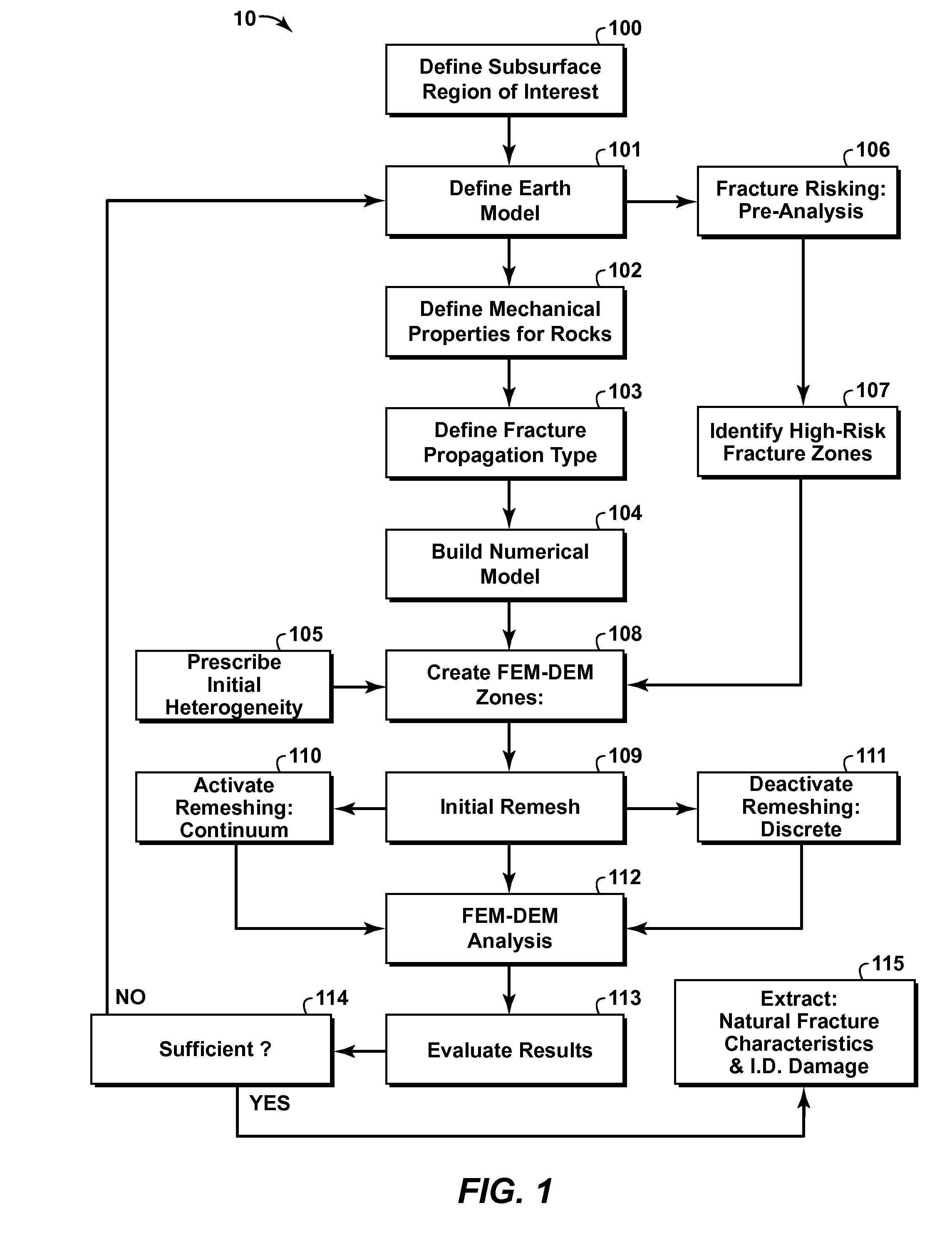
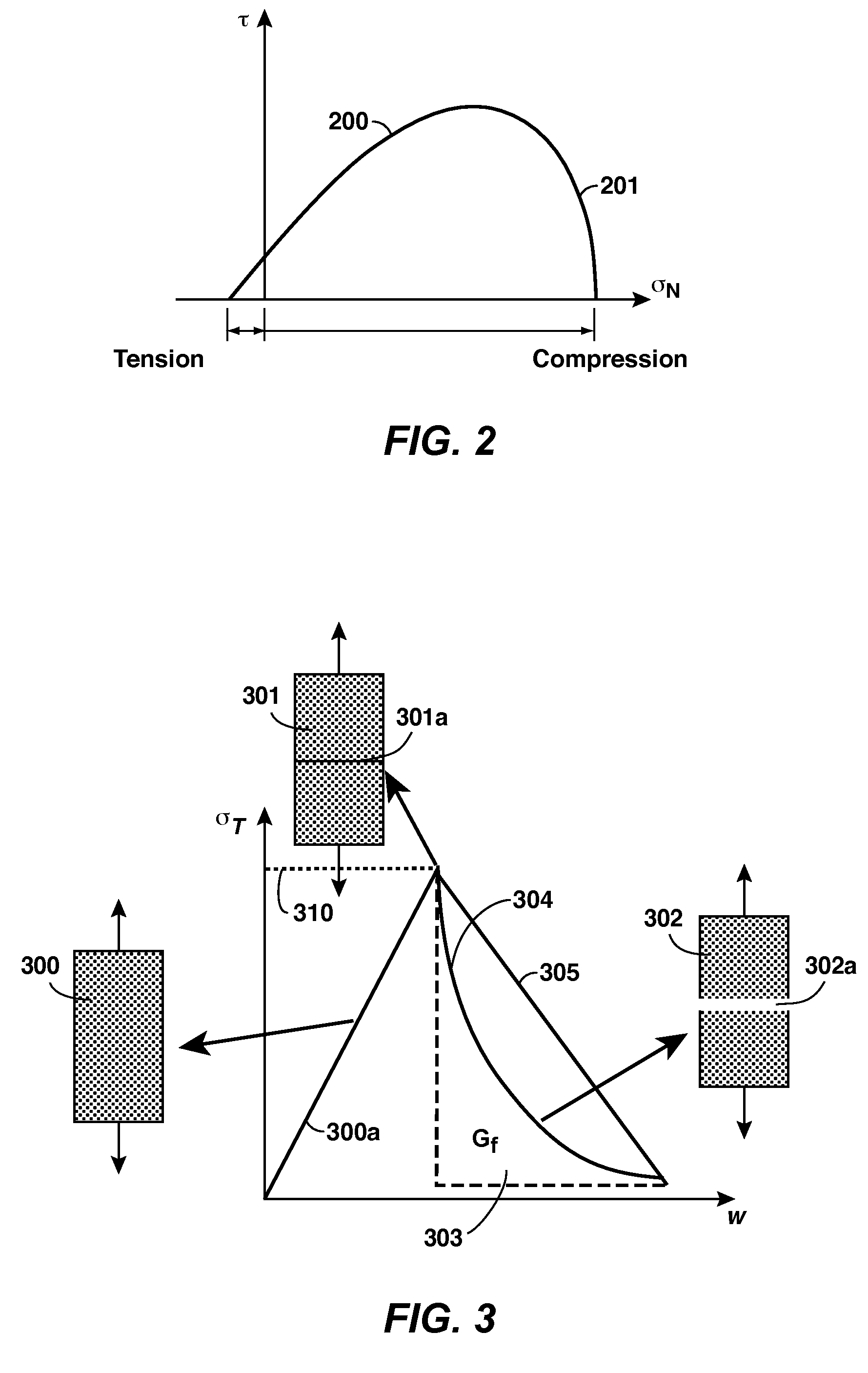
Method of Predicting Natural Fractures And Damage In A Subsurface Region
InactiveUS20110077918A1Limiting predictive capabilityComputation using non-denominational number representationDesign optimisation/simulationAnalysis toolsFracture risk
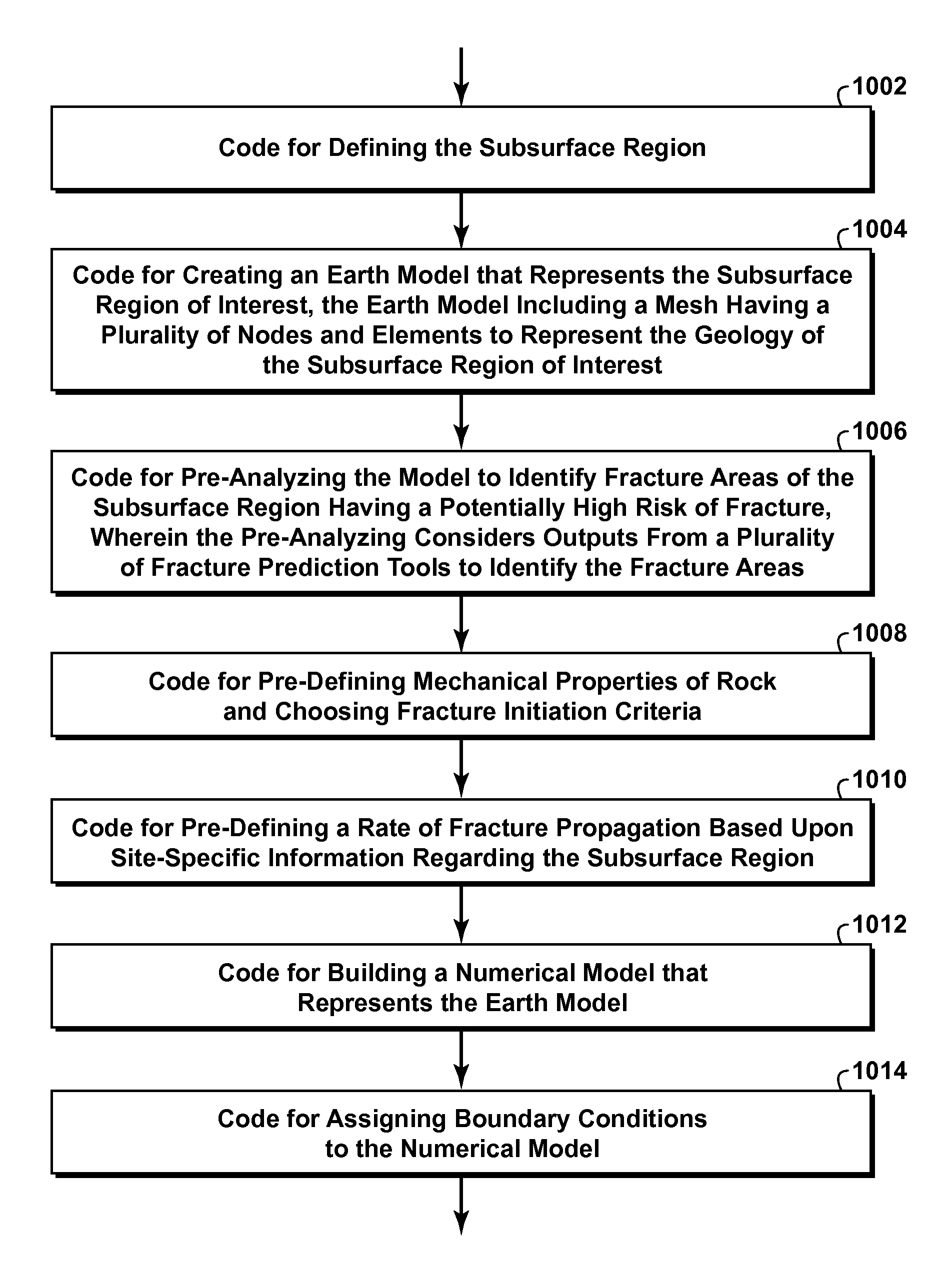
A method for predicting localized damage and naturally occurring fractures in a subsurface region is provided. This invention uses a hybrid FEM-DEM (i.e. finite-discrete element) framework combined with a fracture risking analysis and fracture initiation and propagation criteria, to model the transition of rock from a state of continuum to discontinuum. The risking analysis combines results from other natural fracture prediction tools (e.g. displacement discontinuity method, restoration analyses, curvature analysis, analytical solutions, continuum analysis) to augment FEM-DEM solutions, such as by providing remote and local boundary conditions and identifying potential regions of anticipated damage and fracturing. Natural fractures and damage information is extracted from the modeling results and may be used directly for predictions or used as input into other fracture analysis tools or techniques. The FEM-DEM and risking techniques can be incorporated into a variety of numerical simulation software packages that use a finite-discrete method solver.
Owner:EXXONMOBIL UPSTREAM RES CO
Techniques for automatically tracking and archiving transactional data changes
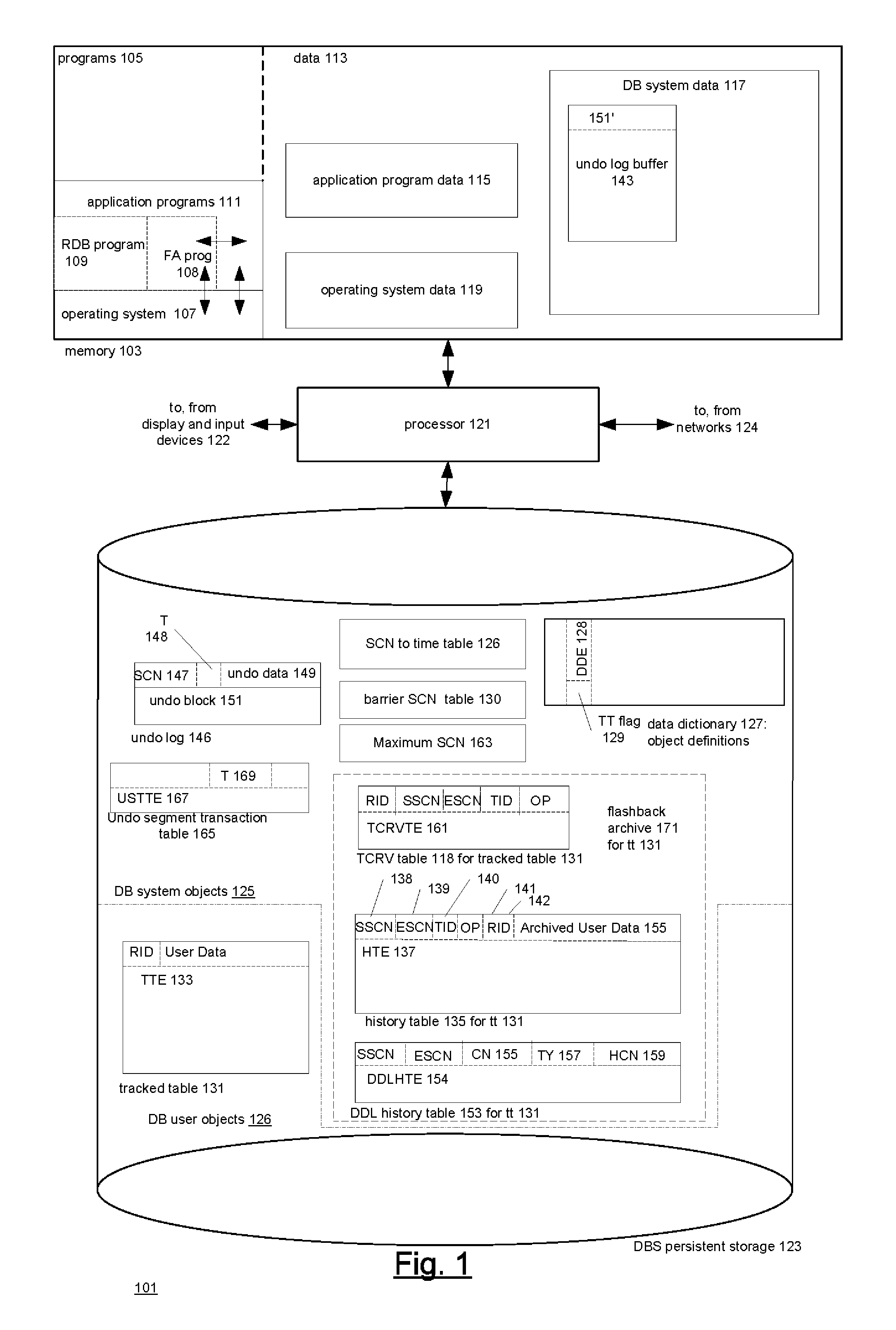
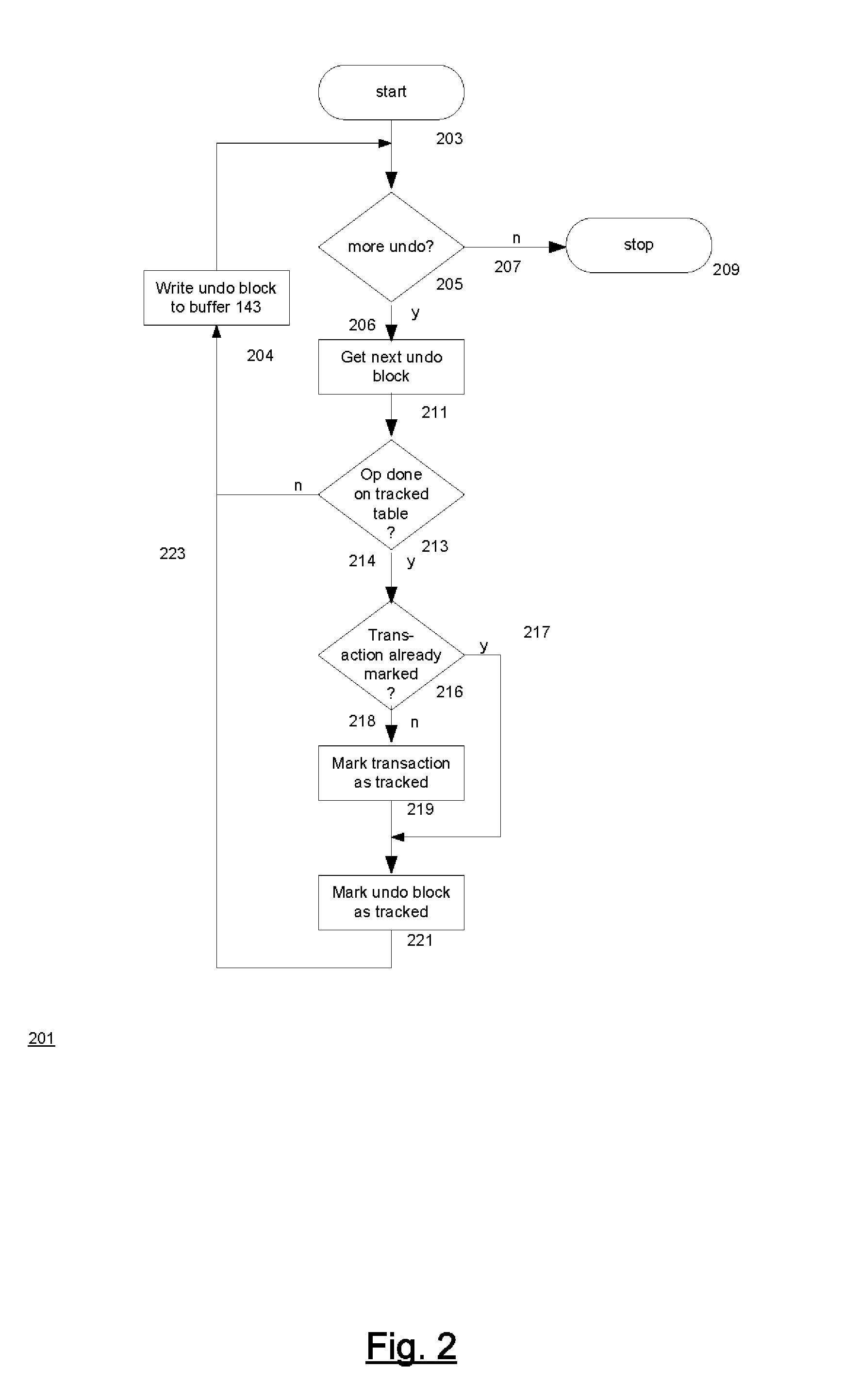
ActiveUS20080098045A1Error detection/correctionDigital data processing detailsBackground processManagement system
A technique for making versions of rows of a user-defined tracked table temporally queryable. The database management system of the technique permits temporal queries of user-defined tables. The queries return versions of rows in the user-defined table that are currently in an undo log maintained by the database system. Associated with the tracked table are a system history table which contains versions of the rows and temporal metadata indicating when the versions were in the tracked table and a system form history table which contains versions of the form of the tracked table and metadata indicating when the tracked table had the form. These tables are created and maintained by a background process in the database management system. A temporal query on the tracked table combines results from the undo log with results from the system history table. The results' form is determined by the system form history table.
Owner:ORACLE INT CORP
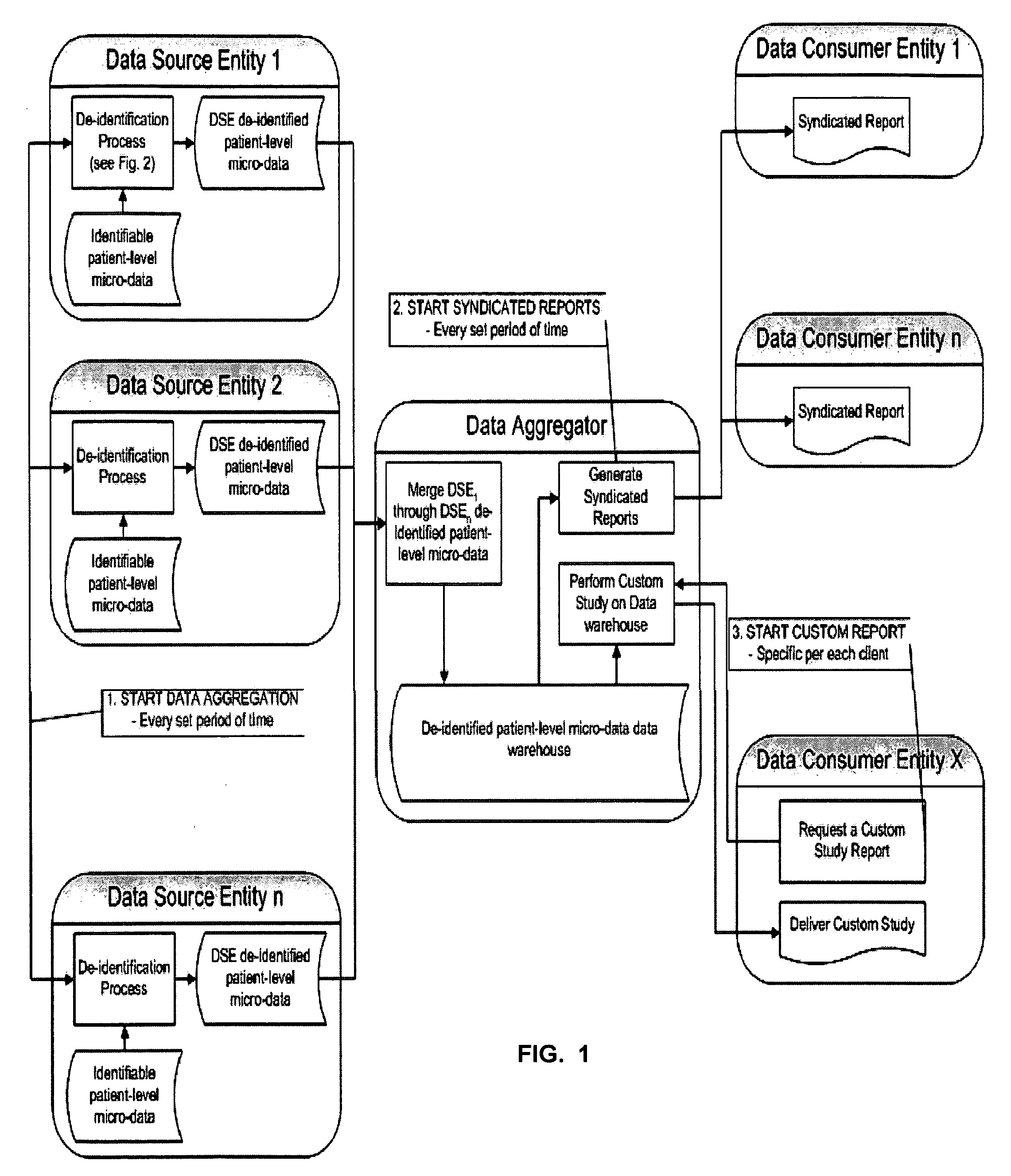
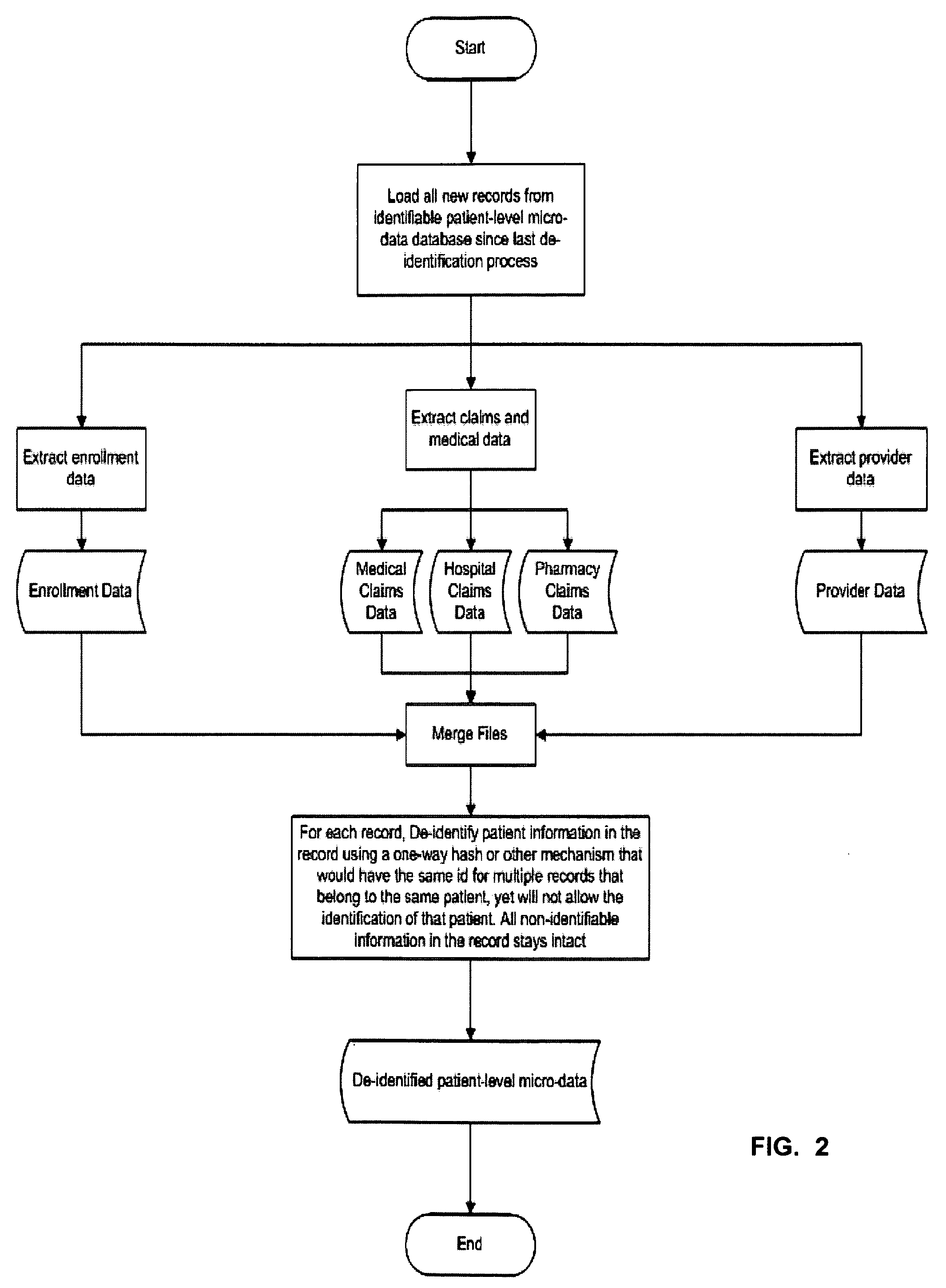
Double Blinded Privacy-Safe Distributed Data Mining Protocol
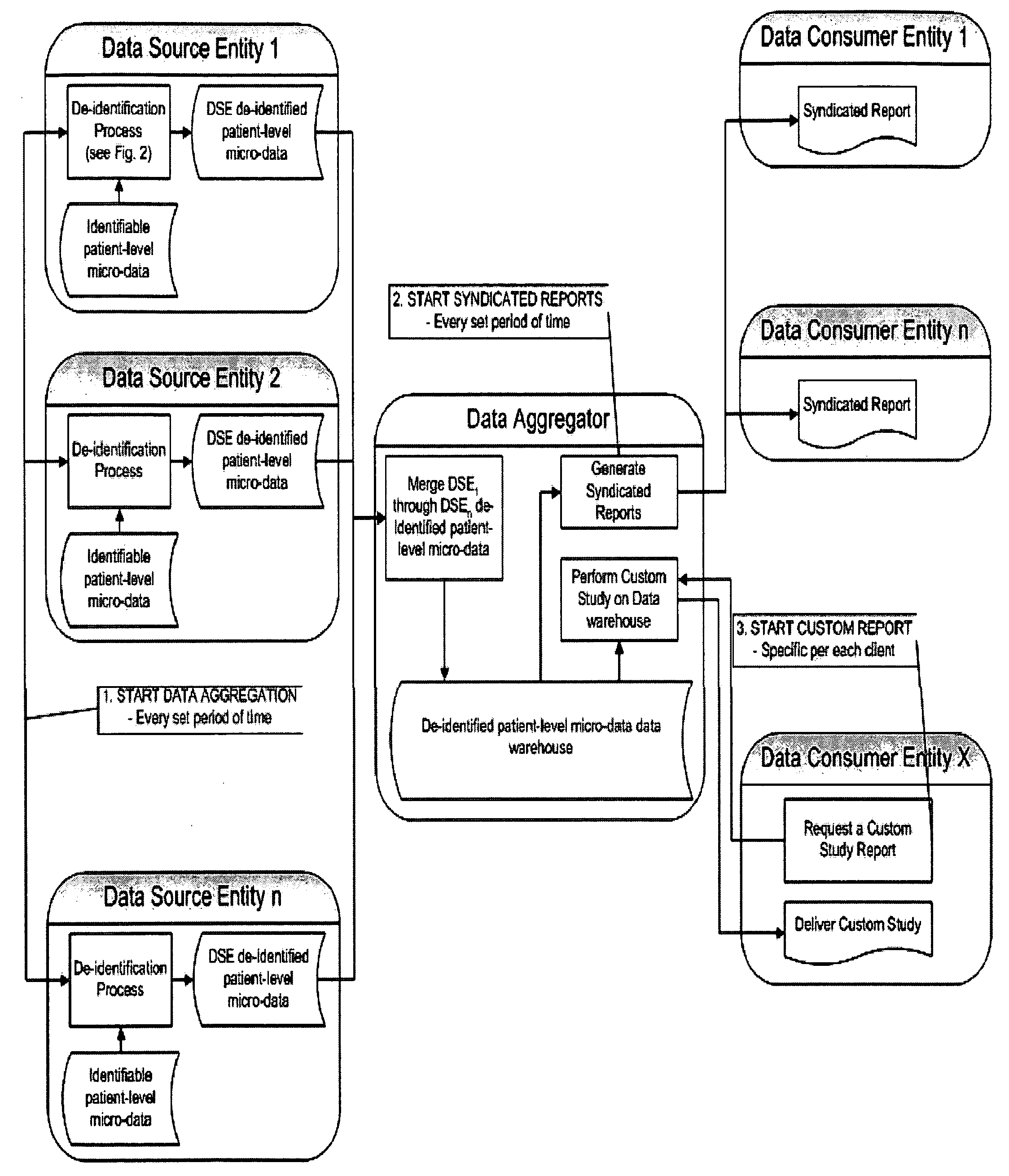
ActiveUS20090150362A1Easy to analyzeImplementation is particularly straightforwardMedical data miningDigital data processing detailsDouble blindData source
A Double Blinded Privacy-Safe Distributed Data Mining Protocol is disclosed, among an aggregator, a data consumer entity having privacy-sensitive information, and data source entities having privacy-sensitive information. The aggregator does not have access to the privacy-sensitive information at either the data consumer entity or the data source entities. The aggregator formulates a query without using privacy-sensitive information, and sends the query to the data consumer entity. The data consumer entity generates a list of specific instances that meet the conditions of the query and sends the list, encrypted, to the data source entities either directly or through the aggregator. The data source entities match the list against transactional data, de-identify the matched results, and send them to the aggregator. The aggregator combines results from data source entities and sends the combined result to the data consumer entity. This allows for privacy-safe data mining where both the data consumer entity and data source entities have privacy-sensitive information not available for the aggregator to see or use.
Owner:VEEVA SYST
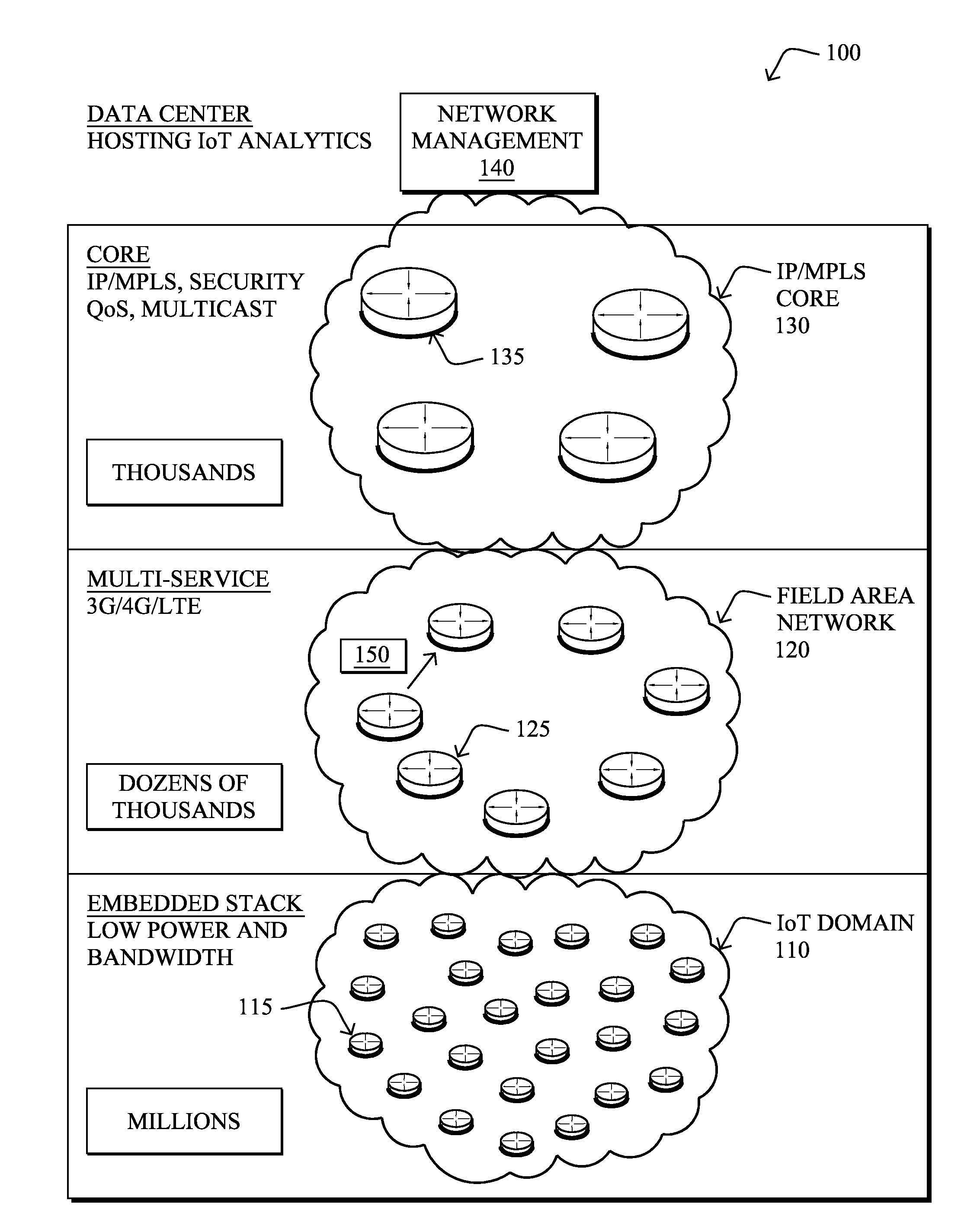
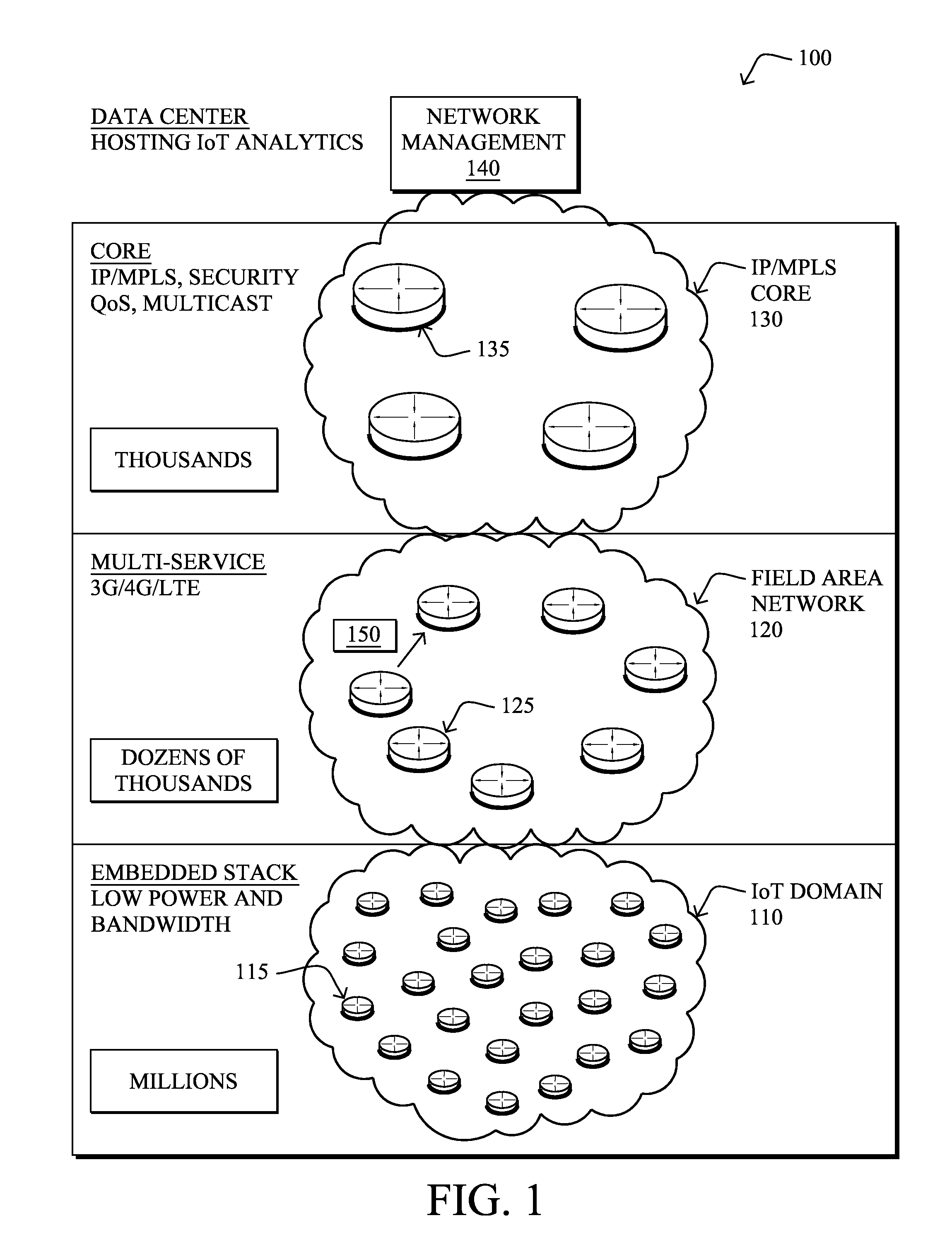
Assisted intelligent routing for minimalistic connected object networks
ActiveUS20130159550A1Digital computer detailsTransmissionService-level agreementDistributed intelligence
In one embodiment, a distributed intelligence agent (DIA) collects local state information from a plurality of minimalistic connected objects (MCOs) in a computer network, the local state information for each MCO comprising a corresponding neighbor list and a selected next-hop for the respective MCO, where one or more of the MCOs are configured to select their next-hop without any self-optimization. The DIA may then analyze a current routing topology, which is the combined result of the selected next-hops, in comparison to a computed optimal routing topology, and (optionally) in light of required service level agreement (SLA), to determine whether to optimize the current routing topology. In response to determining that the current routing topology should be optimized, the DIA may transmit a unicast routing instruction to one or more individual MCOs to instruct those individual MCOs how to optimize the current routing topology, accordingly.
Owner:CISCO TECH INC
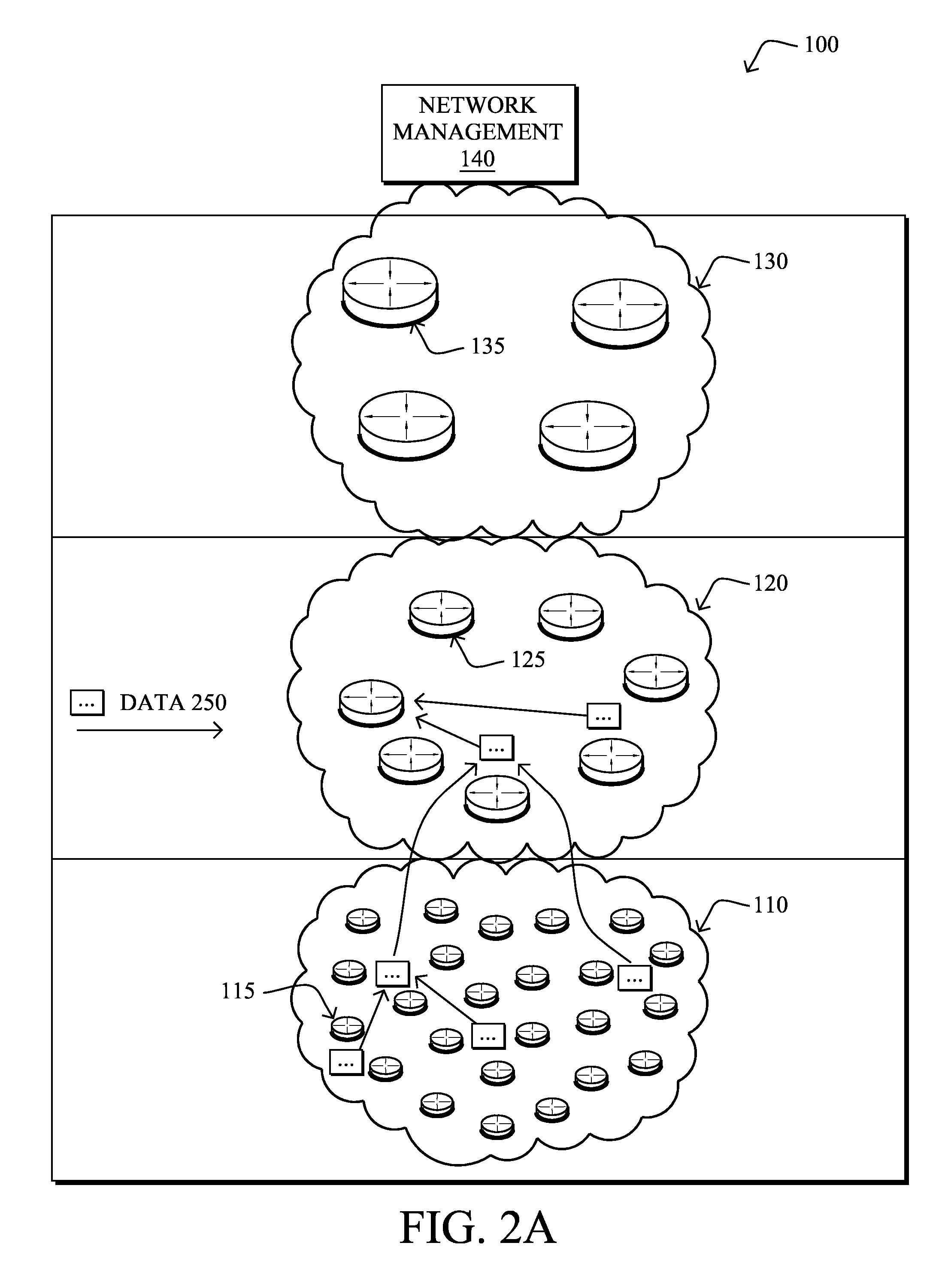
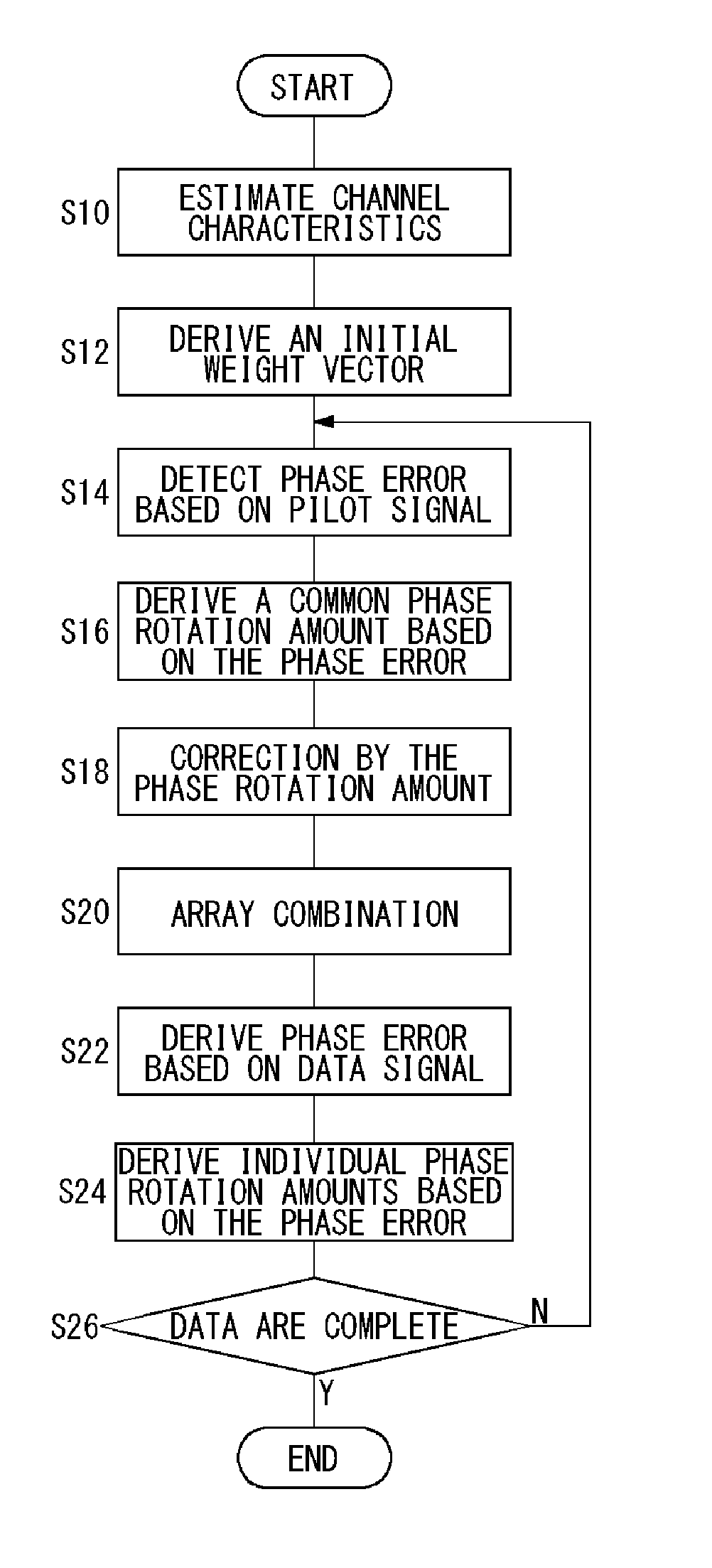
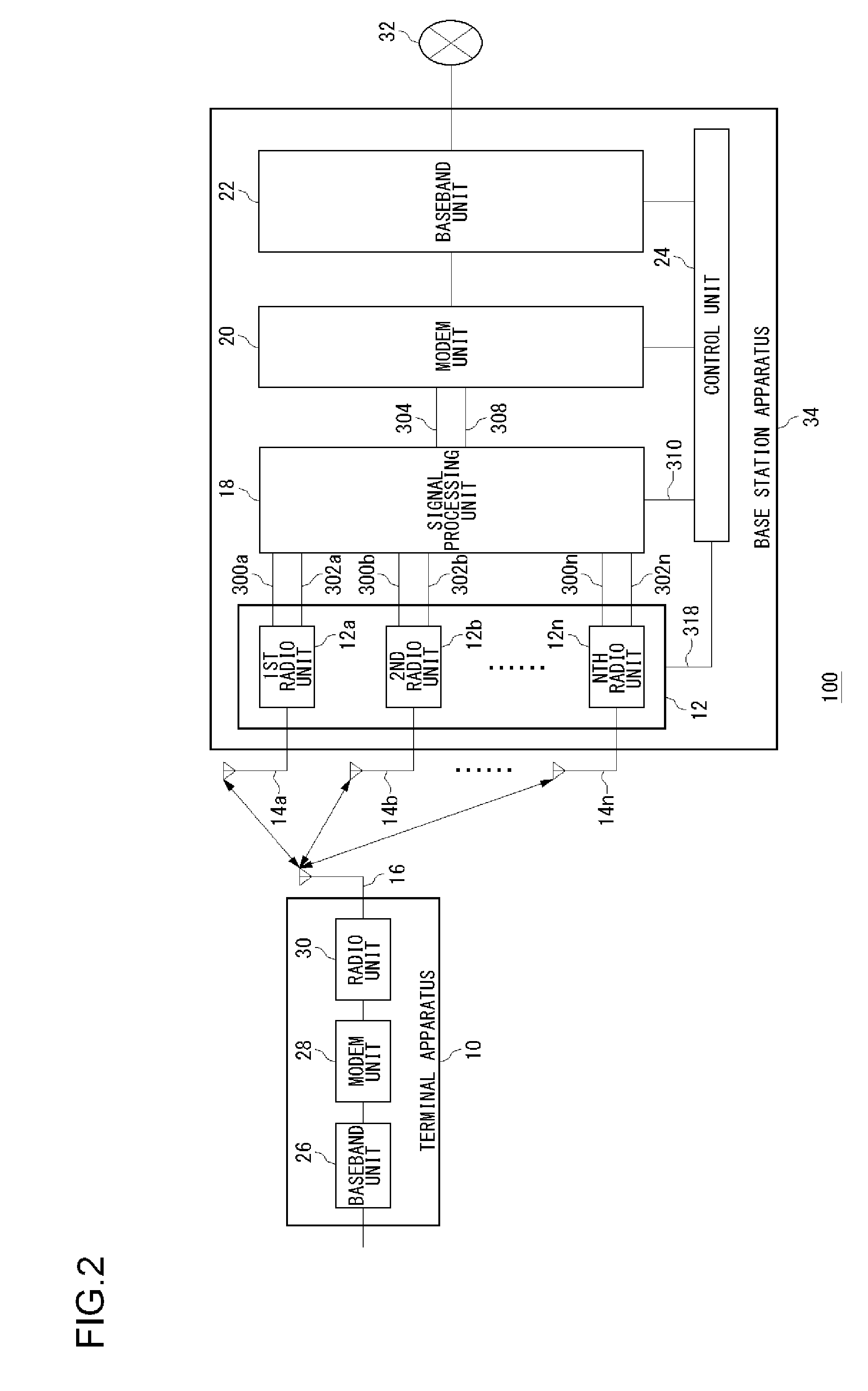
Receiving method for receiving signals by a plurality of antennas, and a receiving apparatus and a radio apparatus using the same
InactiveUS20080063012A1Improve Phase AccuracyImprove accuracyTransmission control/equlisationModulated-carrier systemsPhase differenceEngineering
A weight vector computing unit derives amounts of phase rotation for a plurality of multicarrier signals, respectively, and rotates the phase of a weight vector. A combining unit weights respectively a plurality of multicarrier signals with the phase-rotated weight vector, combines weighting results, and determines a combined result. A receiving weight vector computing unit remodulates the determined result and derives a first phase difference between the plurality of multicarrier signals and a result of the remodulation. The receiving weight vector computing unit remodulates the values of pilot signals and derives a second phase difference between the plurality of multicarrier signals and a result of the remodulation. Further, the receiving weight vector derives phase rotation amounts based on the first phase difference and the second phase difference.
Owner:HERA WIRELESS
Apparatus and method for processing a data backup service for use in a mobile terminal
InactiveUS20050050117A1Digital data processing detailsRadio/inductive link selection arrangementsData synchronizationResource information
An apparatus and method for processing a data backup service of a mobile terminal. The apparatus and method backs-up data files stored in a mobile terminal in a backup server over a wireless Internet. The backup server is capable of backing-up resource information of the mobile terminal. The apparatus and method comprise a) checking setup backup resources during a backup setup procedure, and attempting to establish a connection to the backup server; b) analyzing category information of data to be transmitted to the backup server after connecting to the backup server, determining the number of references if the data category is equal to data including iterative information, and determining a division interval on the basis of a file size and performing data synchronization if the data category is equal to data including binary data. The apparatus and method further comprise c) separately storing the synchronization data serving as the iterative information and combining the separately-stored results when the synchronization data is determined to be iterative information, or divisionally storing the synchronization data, combining the divisionally-stored results, and transmitting the combined result when the synchronization data is determined to be divisionally-designated data; and d) terminating a backup operation of the mobile terminal when the backup server generates a response signal after the data is transmitted to the backup server.
Owner:SAMSUNG ELECTRONICS CO LTD
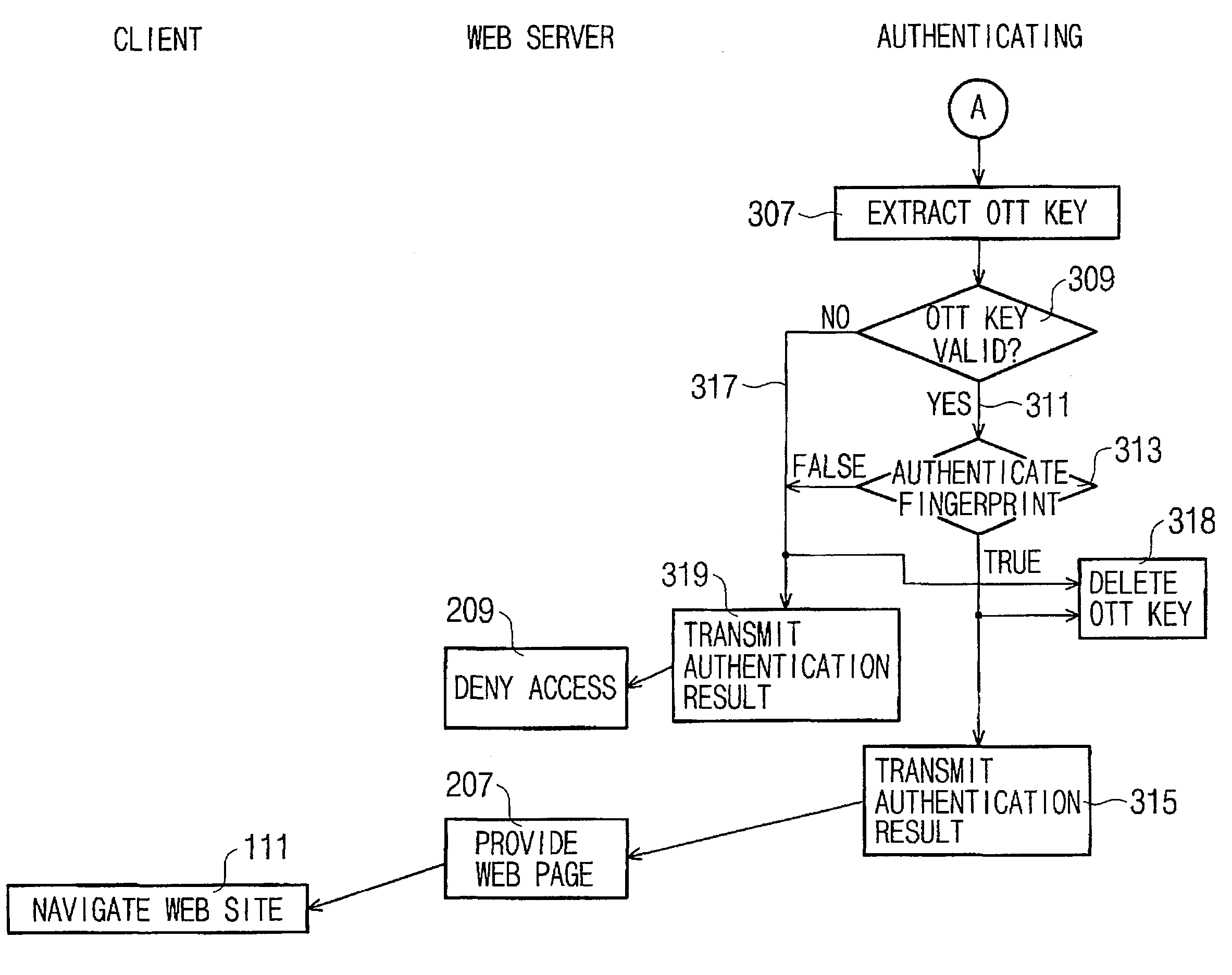
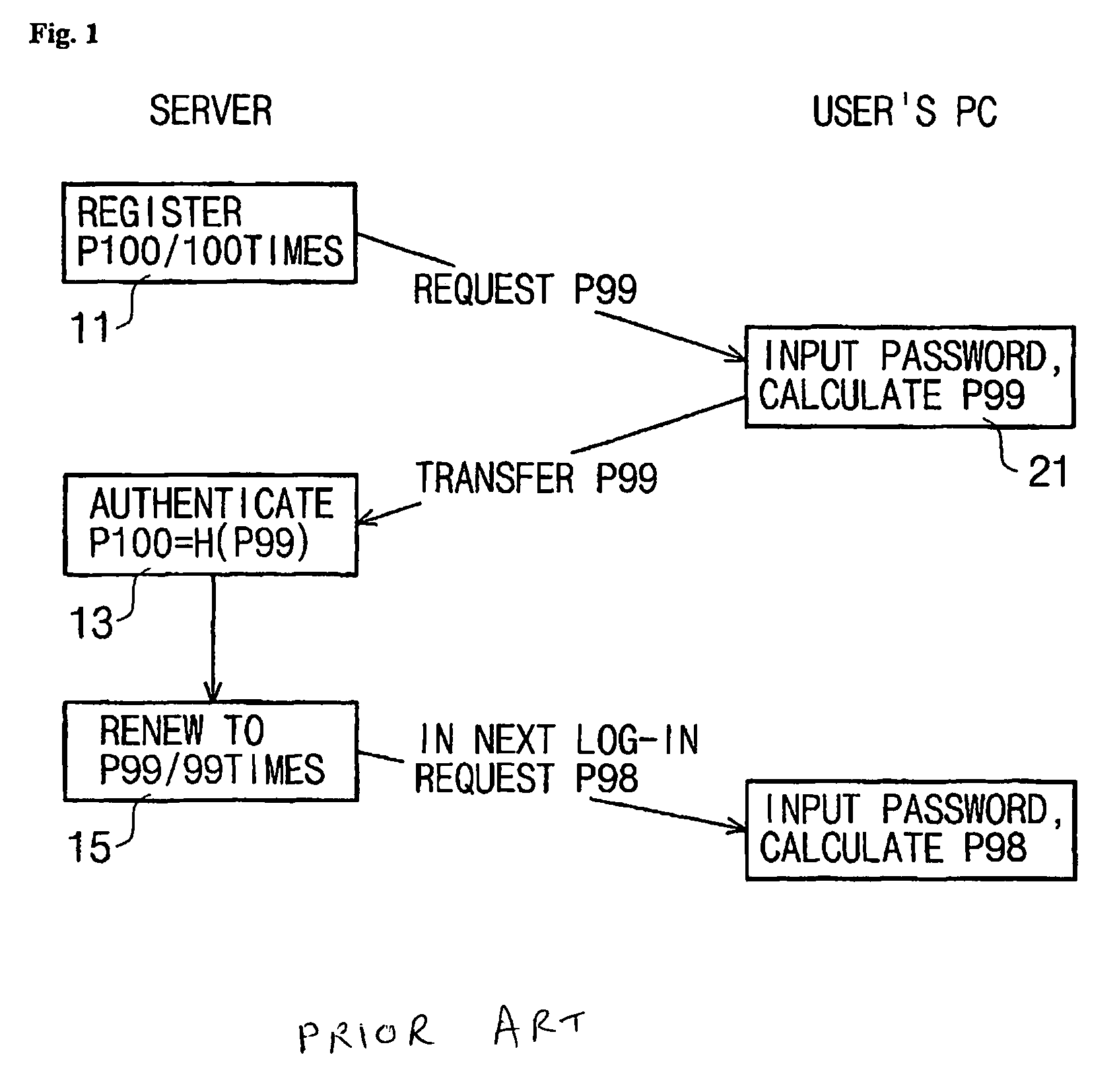
User authenticating system and method using one-time fingerprint template
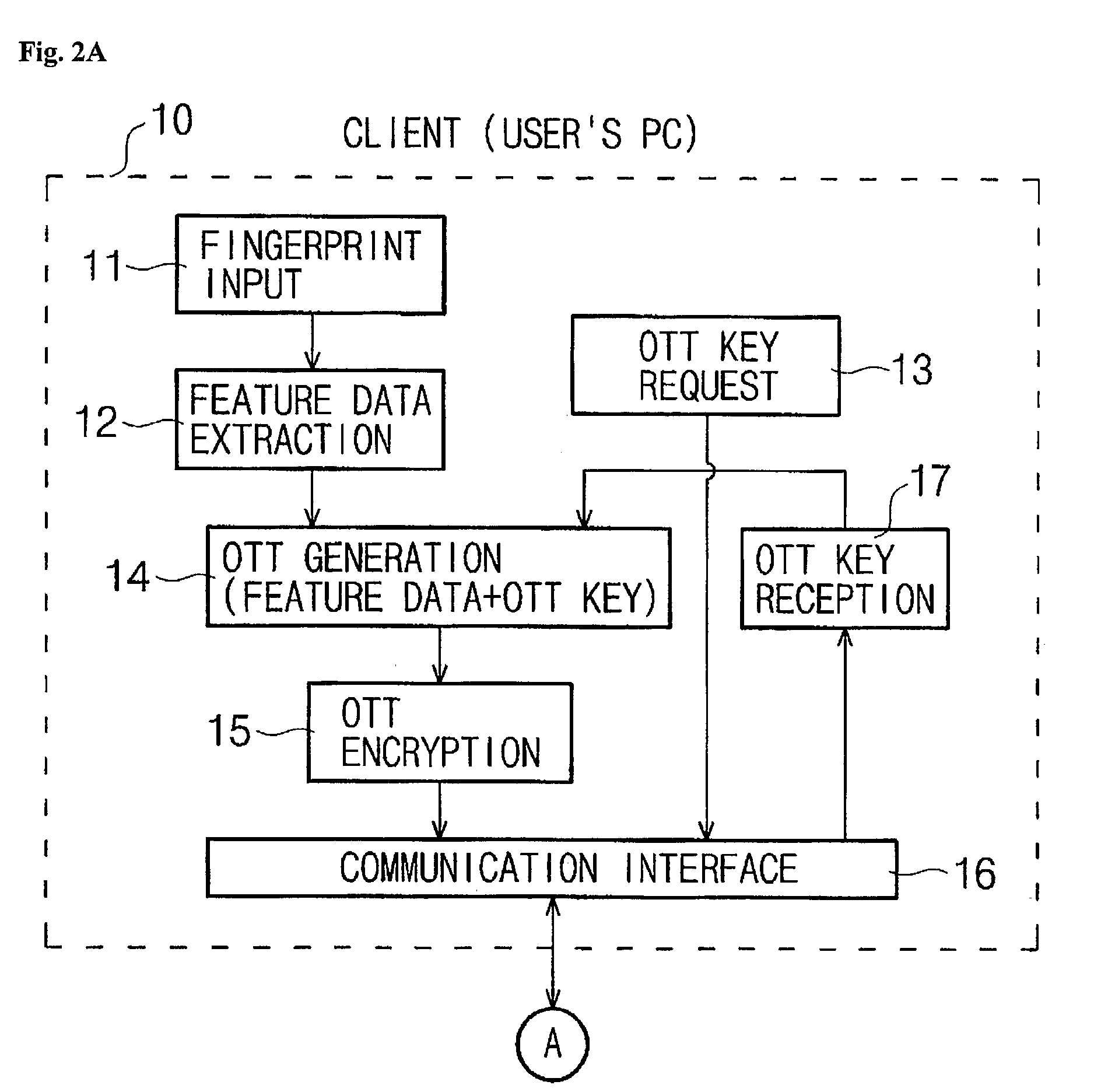
InactiveUS7035442B2Avoid authenticationElectric signal transmission systemsKey distribution for secure communicationUser authenticationFeature data
This invention relates to a user authenticating system and a method using aone-time fingerprint template. The system and the method according to the invention are improvements of the conventional user authentication based on the manner of comparing the fingerprint feature data only, for the purpose of preventing a false authentication by misusing fingerprint feature data, if exposed in the course of transfer thereof. In the system and the method according to the invention, fingerprint feature data of a user are combined with an OTT key transferred from a server. The combined result is encoded and transferred to an authenticating server. The authenticating server then confirms validity of the OTT key and authenticates the user based on the fingerprint. Thus, the present invention has an advantage of preventing a false authentication through hacking, etc., even if the OTT key is exposed to a network, because the OTT key is used only once for authentication.
Owner:SECUGEN CORP
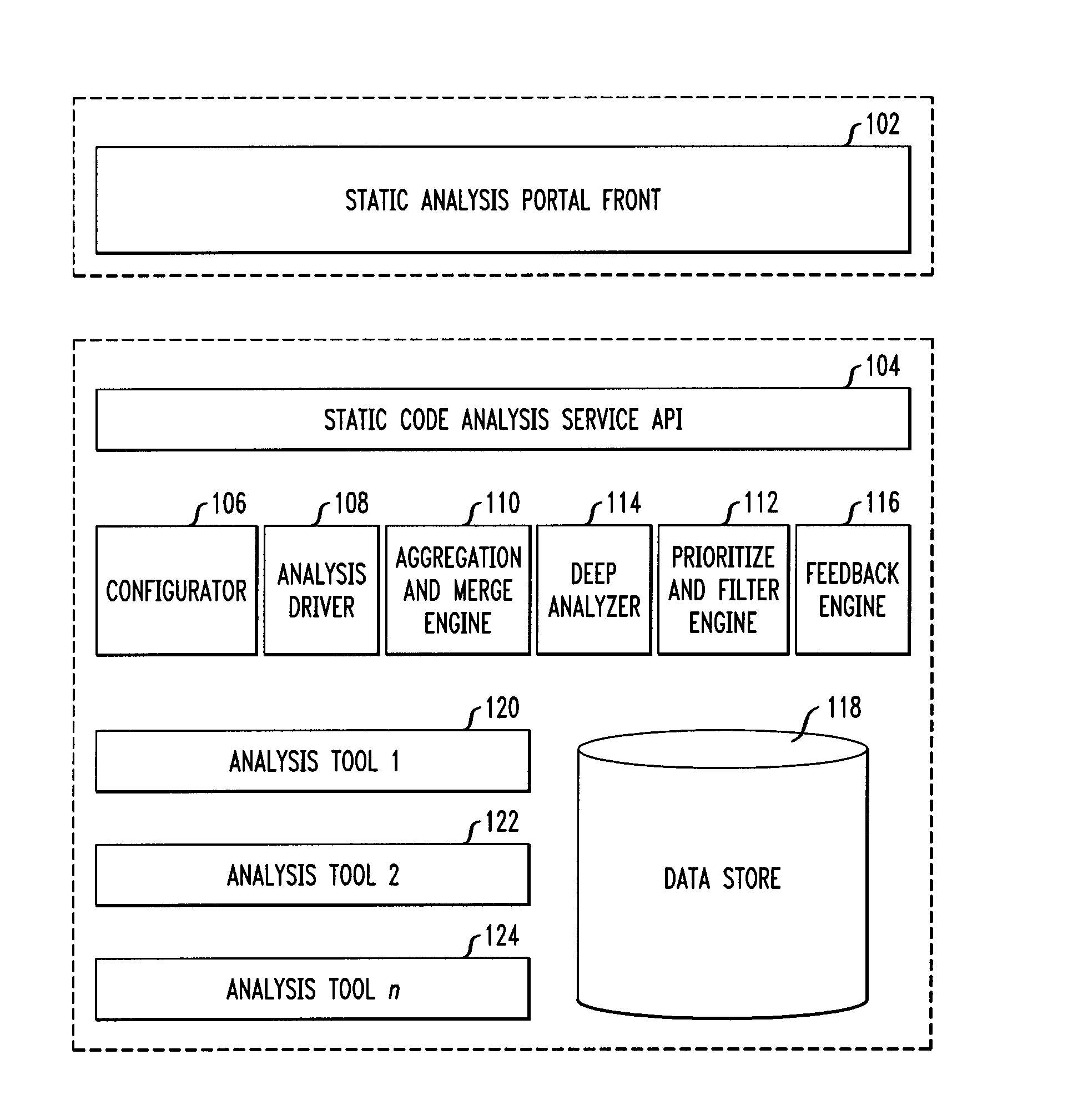
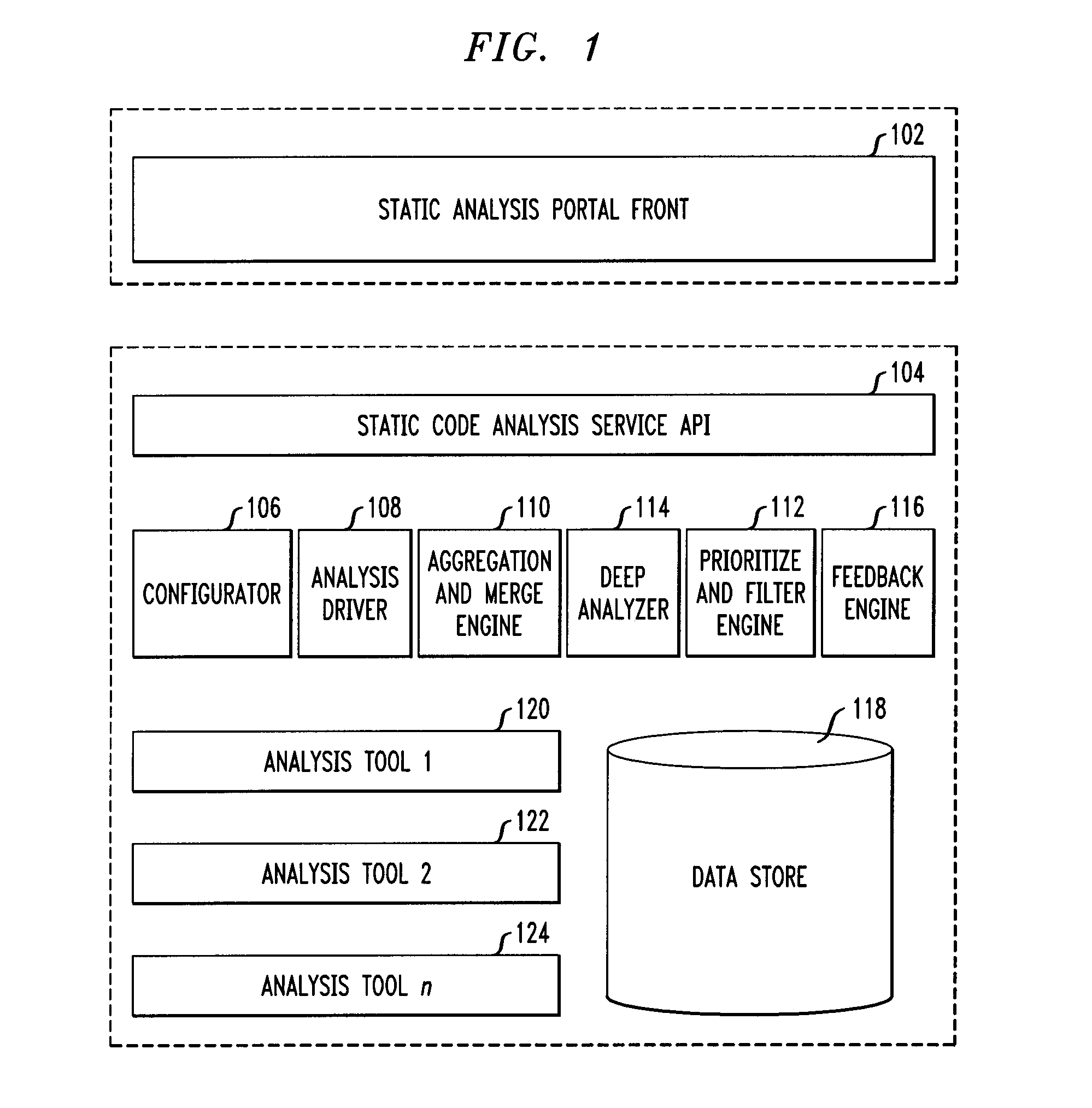
Static code analysis
InactiveUS20100333069A1Reverse engineeringSpecific program execution arrangementsAnalysis toolsStatics
Techniques for static code analysis are provided. The techniques include routing a code analysis request to a set of one or more static code analysis tools based on a context of the request, merging one or more tool-specific outputs of the code analysis, wherein merging the one or more tool-specific outputs comprises using one or more tool-specific mappings to one or more static code analysis abstractions and one or more source linkages of one or more static code analysis defects, performing a deep analysis on a set of one or more defect categories, and combining results of the merging with the deep analysis to filter out one or more false-positives and to add one or more new true positives to create an optimal set of defects.
Owner:IBM CORP
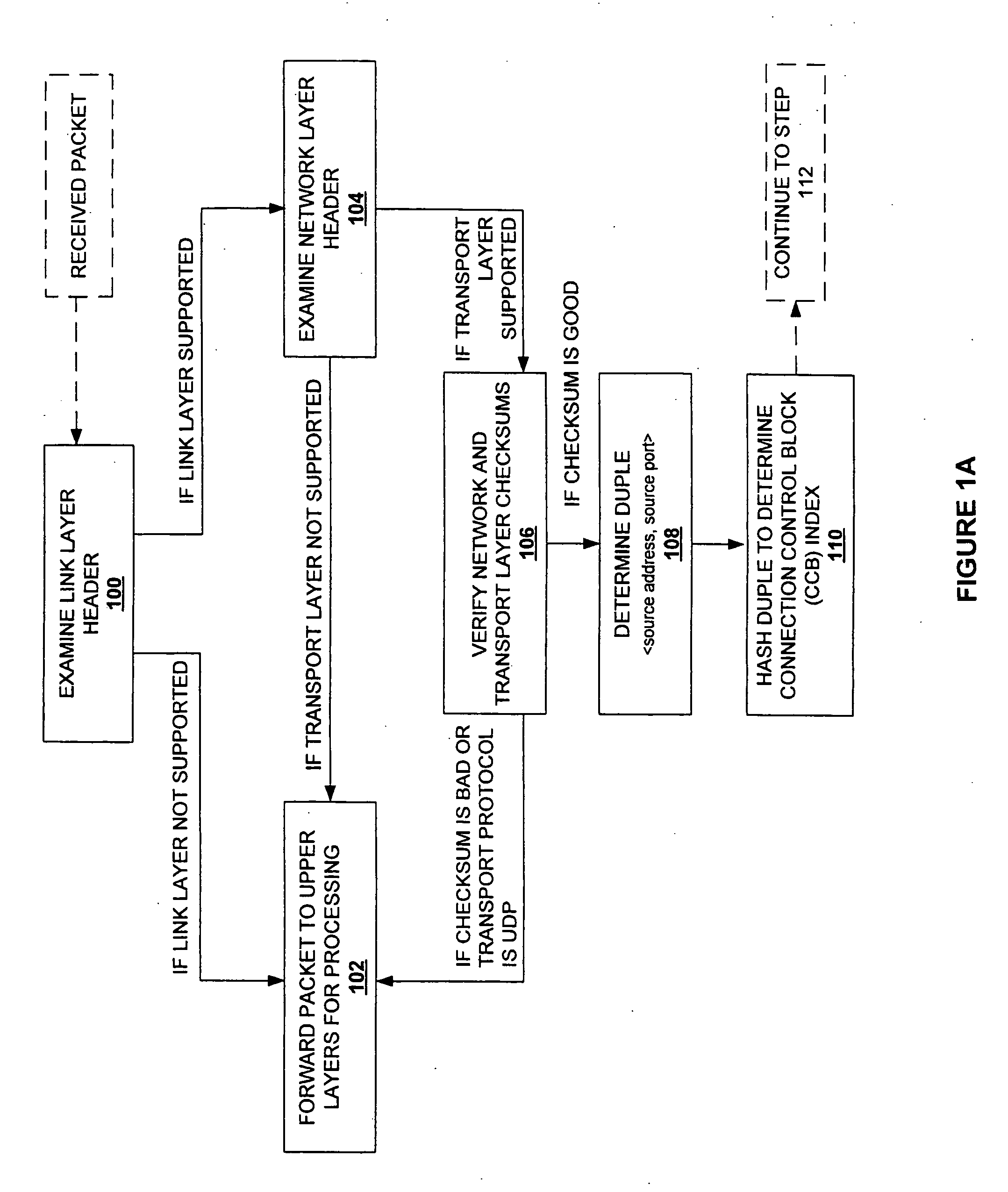
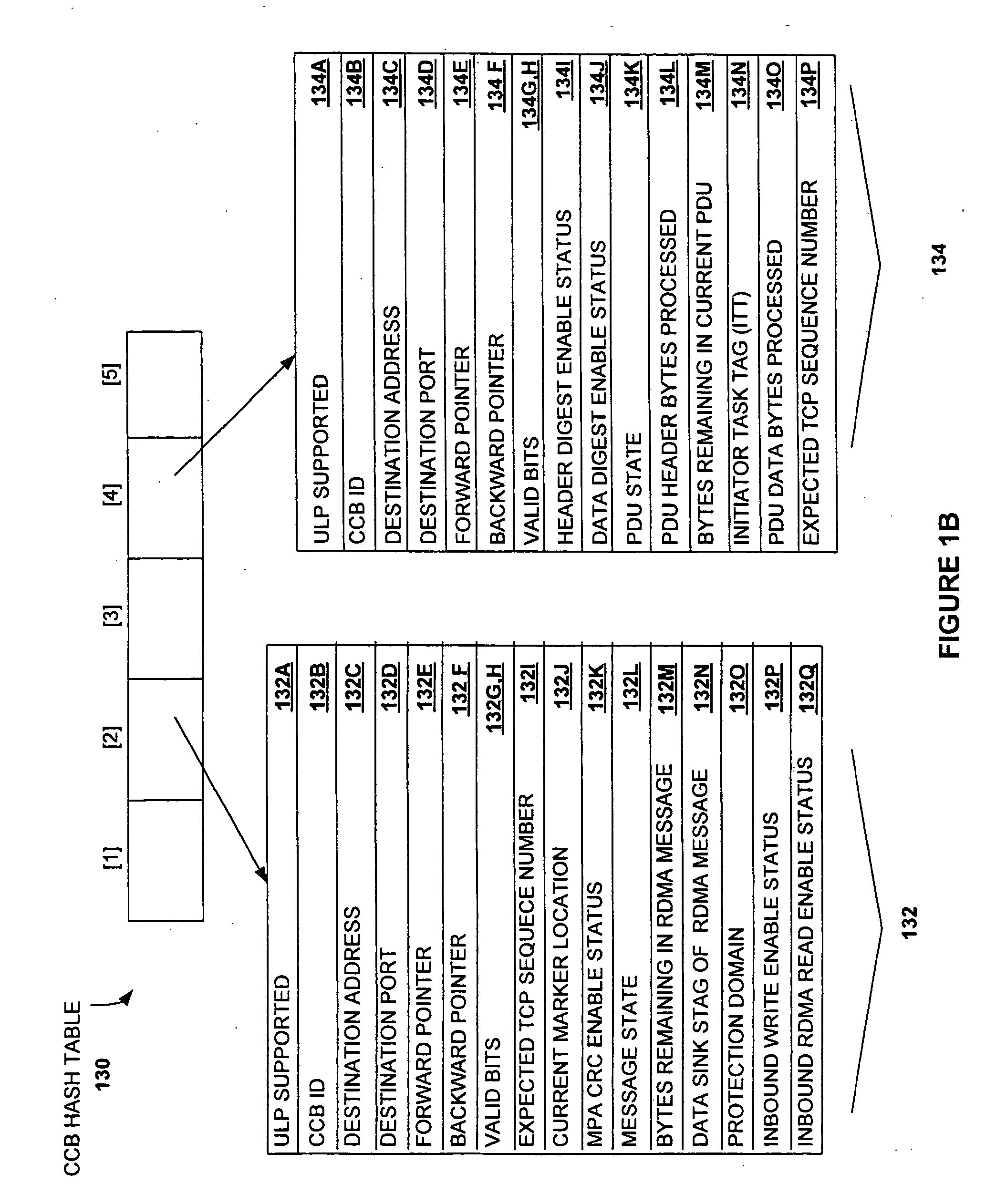
Method and system for providing direct data placement support
InactiveUS20060034283A1Reduction of CPU processing overheadReduced space requirementsTime-division multiplexData switching by path configurationWire speedZero-copy
A system and method for reducing the overhead associated with direct data placement is provided. Processing time overhead is reduced by implementing packet-processing logic in hardware. Storage space overhead is reduced by combining results of hardware-based packet-processing logic with ULP software support; parameters relevant to direct data placement are extracted during packet-processing and provided to a control structure instantiation. Subsequently, payload data received at a network adapter is directly placed in memory in accordance with parameters previously stored in a control structure. Additionally, packet-processing in hardware reduces interrupt overhead by issuing system interrupts in conjunction with packet boundaries. In this manner, wire-speed direct data placement is approached, zero copy is achieved, and per byte overhead is reduced with respect to the amount of data transferred over an individual network connection. Movement of ULP data between application-layer program memories is thereby accelerated without a fully offloaded TCP protocol stack implementation.
Owner:IBM CORP
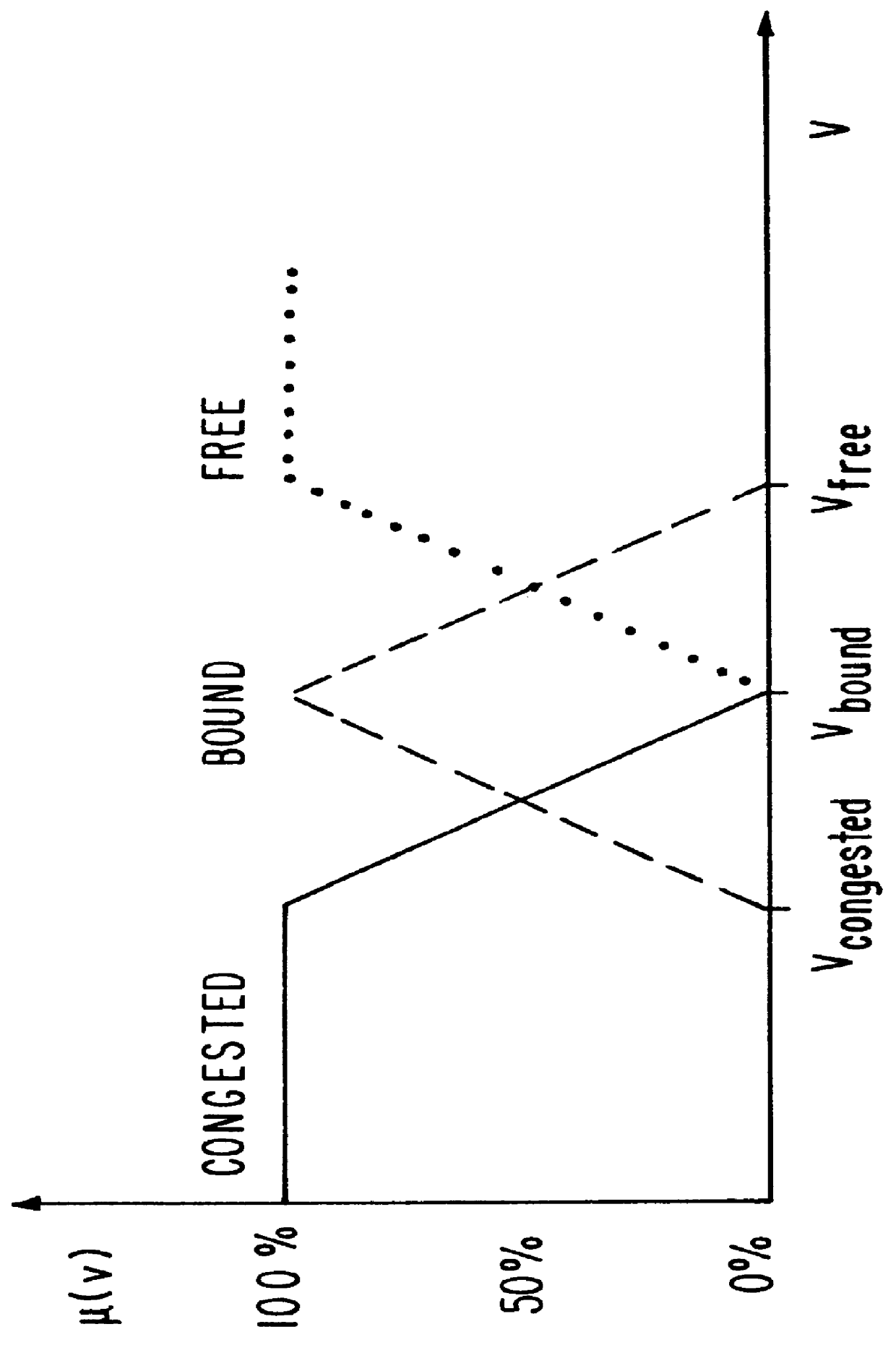
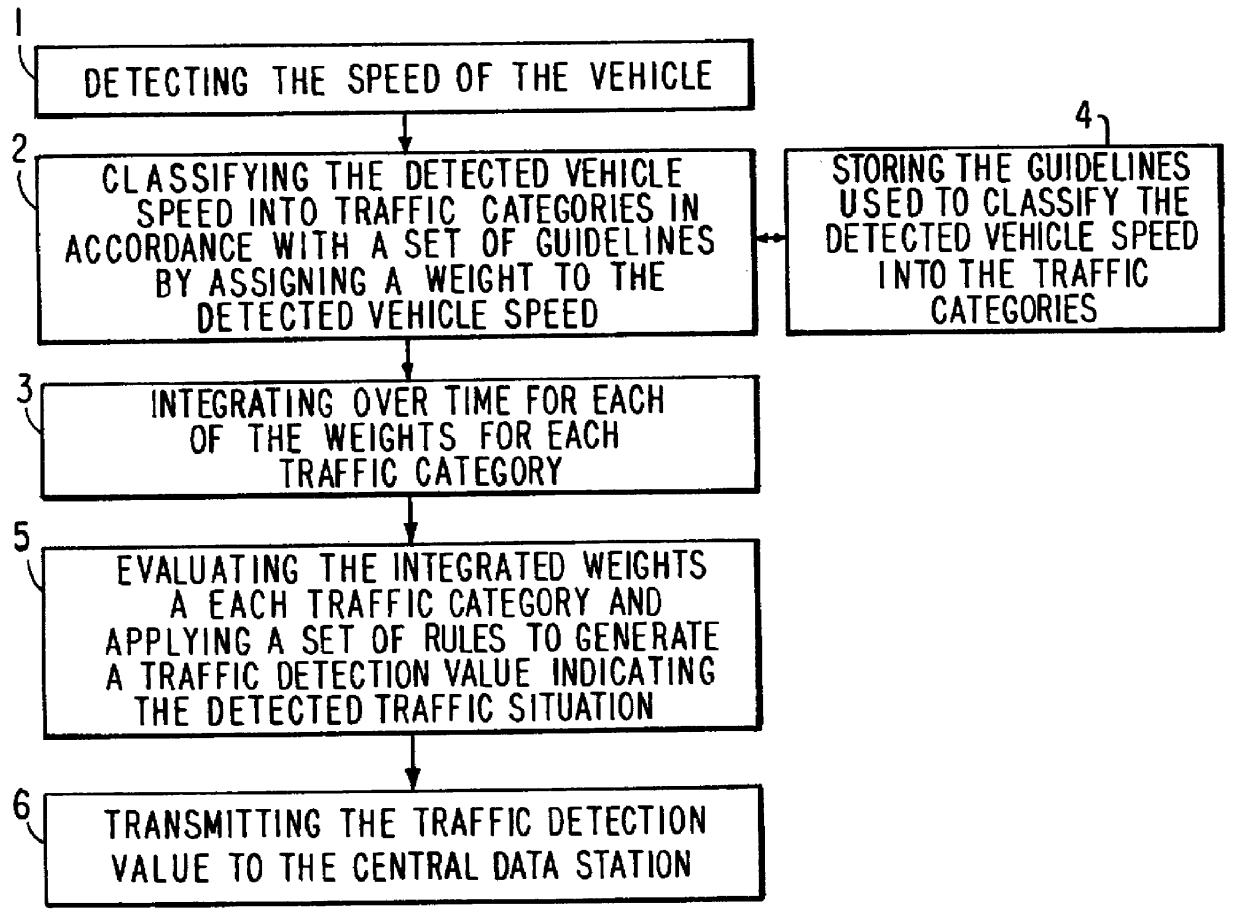
Vehicle-autonomous detection of traffic backup
InactiveUS6131064AAnalogue computers for vehiclesArrangements for variable traffic instructionsTraffic capacityGuideline
A process for automated vehicle-autonomous detection of a particular traffic situation by continuously detecting an instantaneous vehicle speed onboard a vehicle. The detected vehicle speeds are classified using guidelines which may be based on rigid values or on fuzzy logic relationships, into one or more of a plurality of traffic categories by assigning a weight for that detected vehicle speed to each of the traffic categories. Thereafter, for each traffic category the weights associated with the detected speed values are integrated over time to calculate an integrated result for each traffic category. The integrated results of the traffic categories are then evaluated based on predetermined rules or criteria to generate a probabilistically-based traffic detection value indicating the traffic category representing the vehicles' current traffic situation. The traffic categories and guidelines or membership functions or relationships are defined for use with a particular type of road.
Owner:MANNESMANN AG
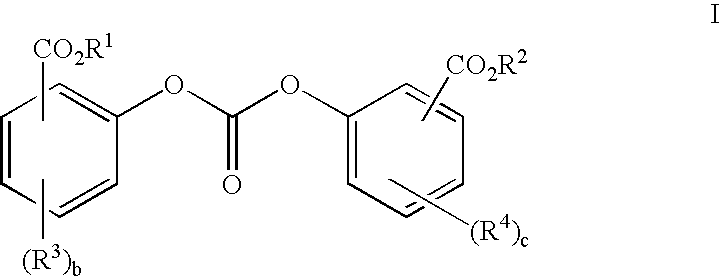
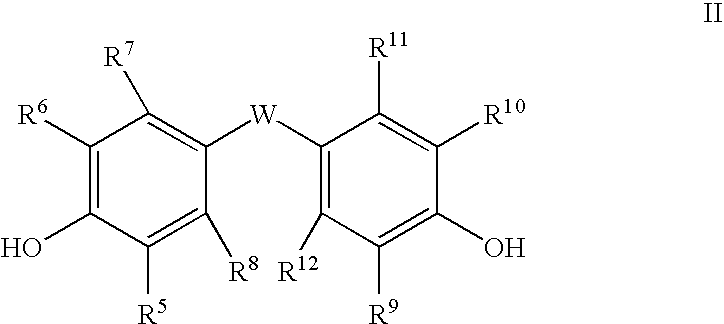
Method of polycarbonate preparation
InactiveUS20050261460A1Low levelImprove the level ofCeramic shaping apparatusFries rearrangementHydroquinone Compound
Polycarbonates containing low or undetectable levels of Fries rearrangement products and comprising repeat units derived from one or more of resorcinol, hydroquinone, methylhydroquinone, bisphenol A, and 4,4′-biphenol have been prepared by the melt reaction of one or more of the aforementioned dihydroxy aromatic compounds with an ester-substituted diaryl carbonate such as bis-methyl salicyl carbonate. Low, or in many instances undetectable, levels of Fries rearrangement products are found in the product polycarbonates obtained as the combined result of a highly effective catalyst system which suppresses the Fries reaction and the use of lower melt polymerization temperatures relative to temperatures required for the analogous polymerization reactions using diphenyl carbonate.
Owner:SABIC INNOVATIVE PLASTICS IP BV
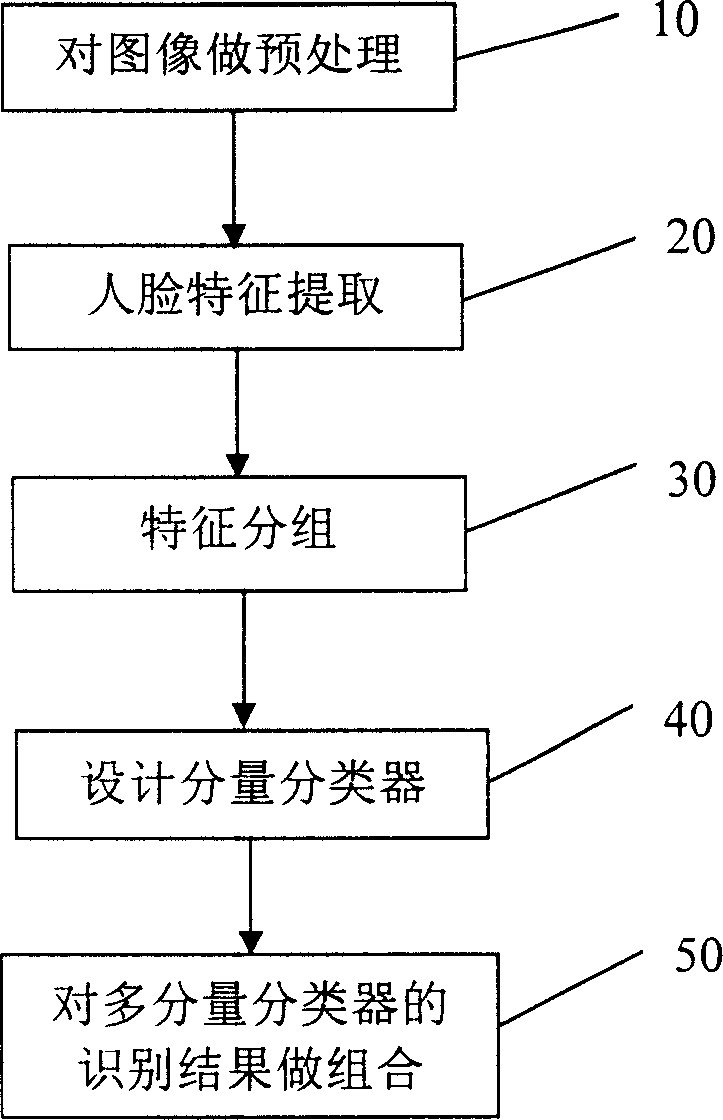
Feature classification based multiple classifiers combined people face recognition method
ActiveCN1908960AReduce computational complexityAvoid the curse of dimensionalityCharacter and pattern recognitionComputation complexityCurse of dimensionality
The disclosed multi-classifier combination face recognition method based on feature sorting comprises: extracting face area from initial image for pre-process and feature extraction; feature sorting to obtain different face feature groups; designing component classifier for every group to recognize face and combine results for optimal effect. This invention overcomes dimension disaster, reduces algorithm complexity, and improves recognition performance.
Owner:INST OF COMPUTING TECH CHINESE ACAD OF SCI
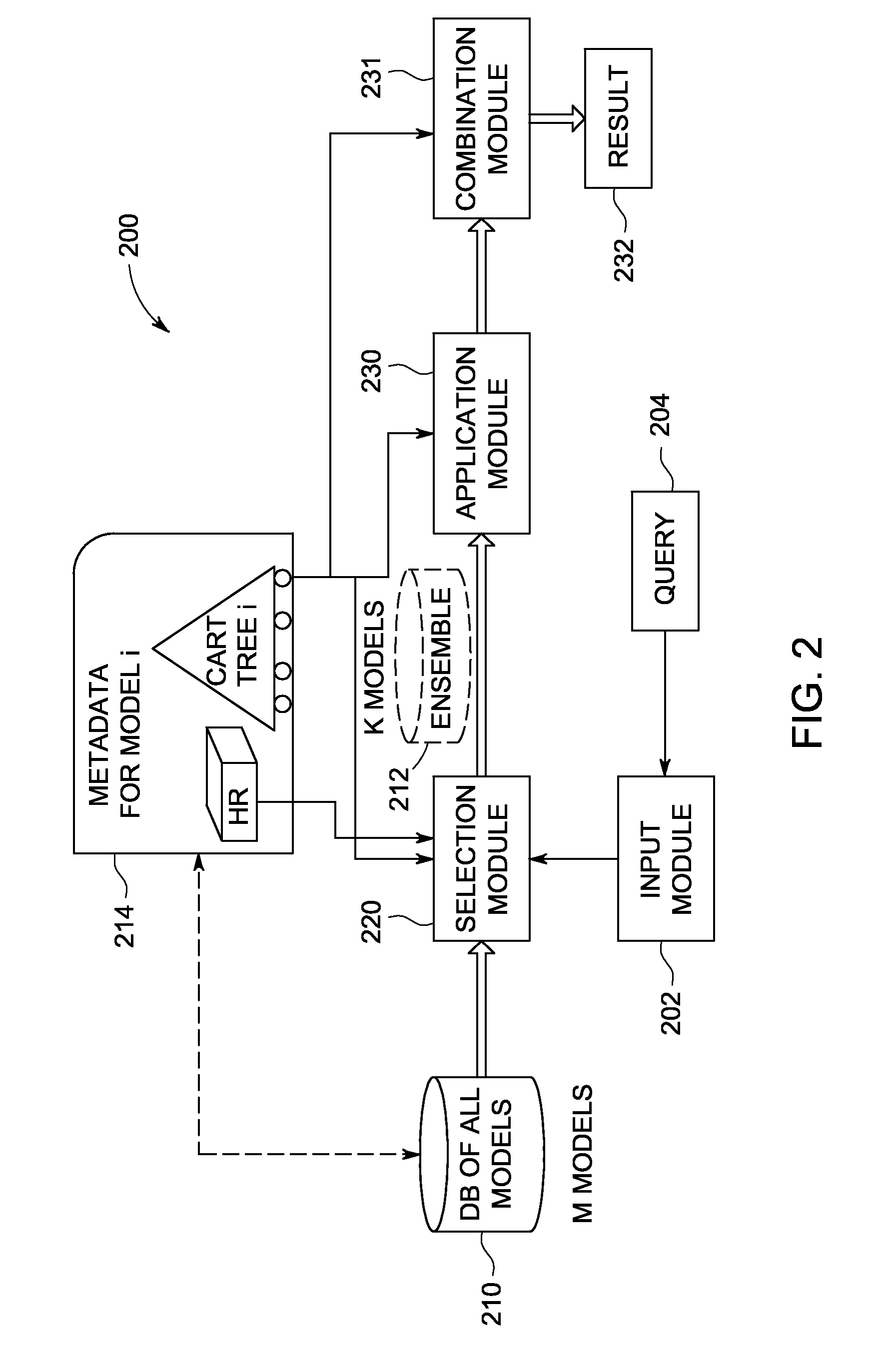
System and Method For Creating Customized Model Ensembles On Demand
A computer-implemented system for creating customized model ensembles on demand is provided. An input module is configured to receive a query. A selection module is configured to create a model ensemble by selecting a subset of models from a plurality of models, wherein selecting includes evaluating an aspect of applicability of the models with respect to answering the query. An application module is configured to apply the model ensemble to the query, thereby generating a set of individual results. A combination module is configured to combine the set of individual results into a combined result and output the combined result, wherein combining the set of individual results includes evaluating performance characteristics of the model ensemble relative to the query.
Owner:GENERAL ELECTRIC CO
Apparatus and method for electrocardiogram-assisted blood pressure measurement
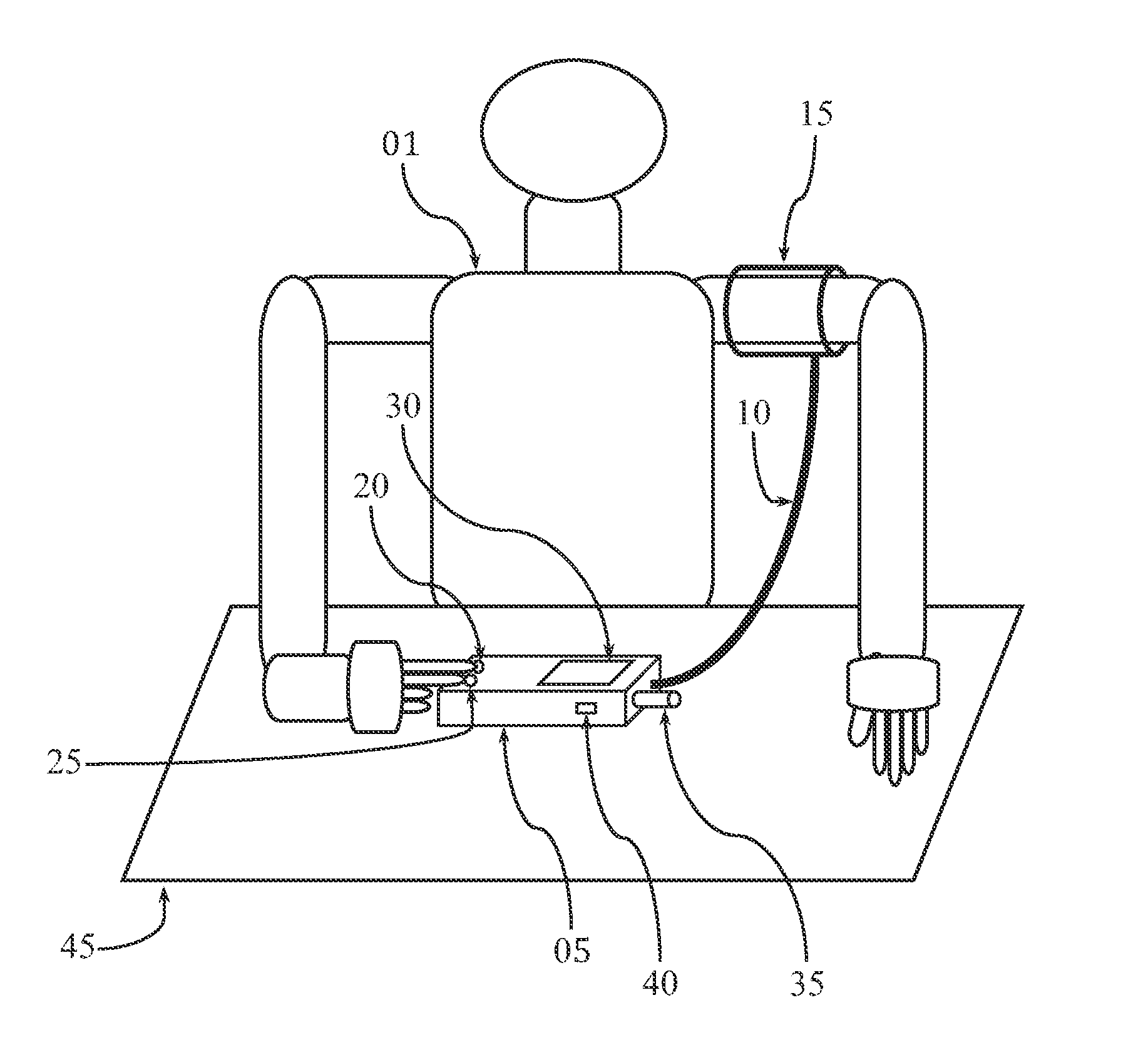
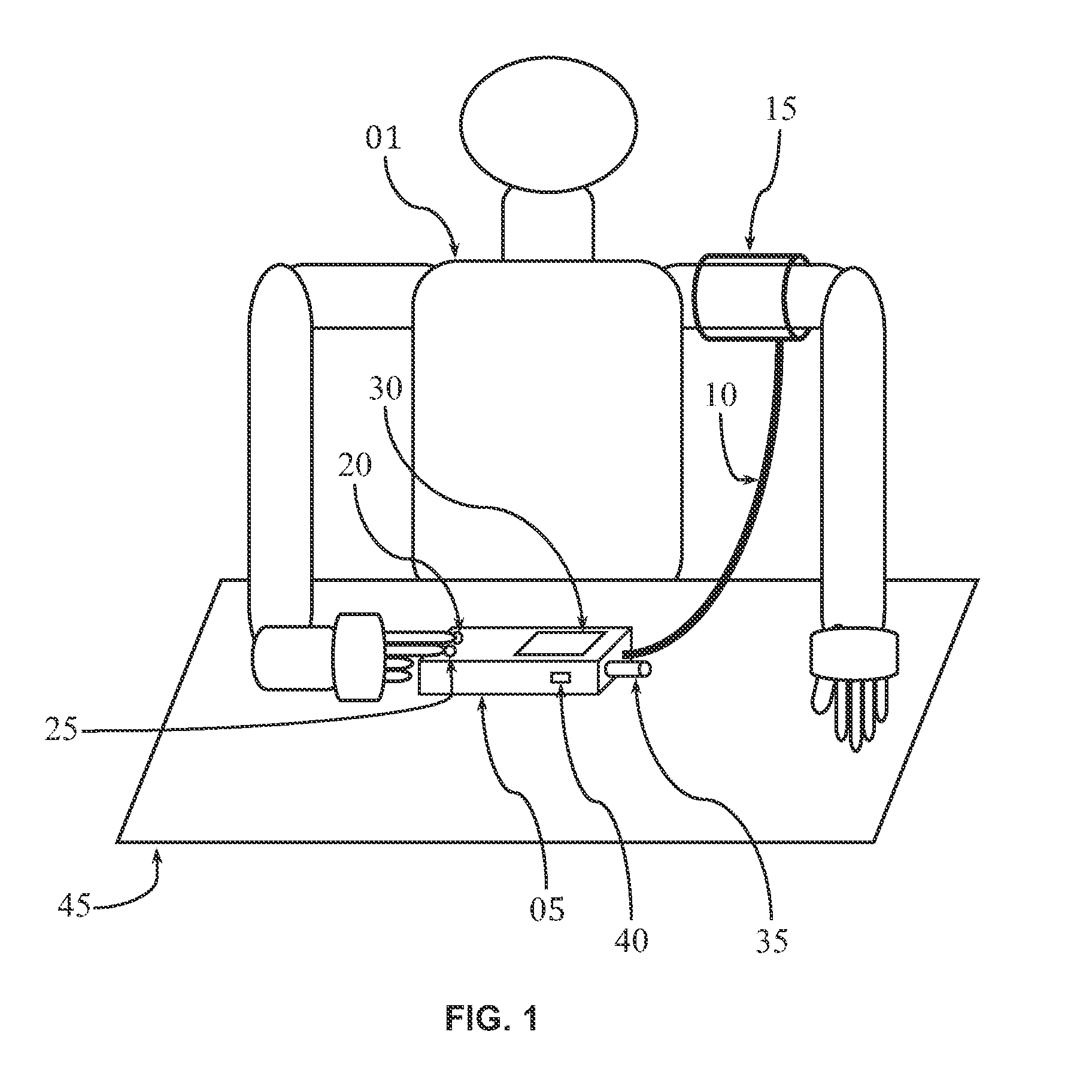
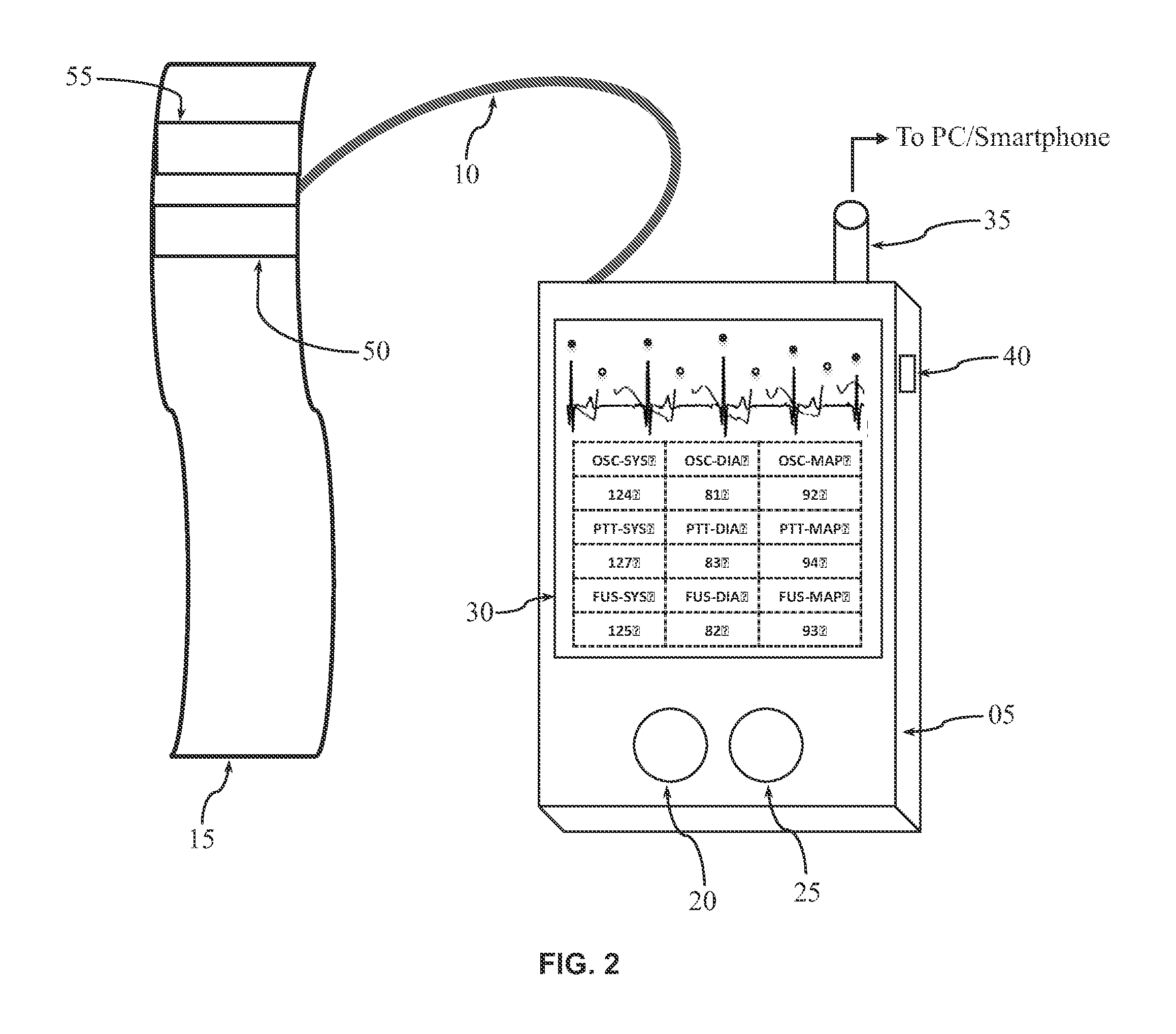
InactiveUS20120283583A1Reduce noiseReduce transmission noiseEvaluation of blood vesselsCatheterPatient managementNon invasive
Apparatus, method, and software for electrocardiogram-assisted non-invasive arterial blood pressure d stiffness measurement is disclosed including brachial cuff with flexible electrodes, control box with rigid electrodes, and associated hardware / software. Cuff is wrapped around upper arm while electrodes on device are touched with fingers of other hand. Device acquires simultaneous ECG / oscillometric data during cuff deflation. Processing unit determines ECG R-peak positions to isolate arterial pulses and calculate pulse transit time. Change in pulse amplitude as function of cuff pressure is used for constructing oscillometric envelope and calculating blood pressure using empirical coefficients. Change in pulse transit time as function of cuff pressure is used independently for constructing pulse transit time envelopes and finding blood pressure with / without empirical coefficients. Fusion algorithm combines results for robust blood pressure and vessel stiffness evaluation. Device sends physiological information to personal computer / smartphone wirelessly, for further analysis. Computer / smartphone transmits information to third party for patient management.
Owner:BATKIN IZMAIL +5
System and method for locating inspection robot in petrochemical plant
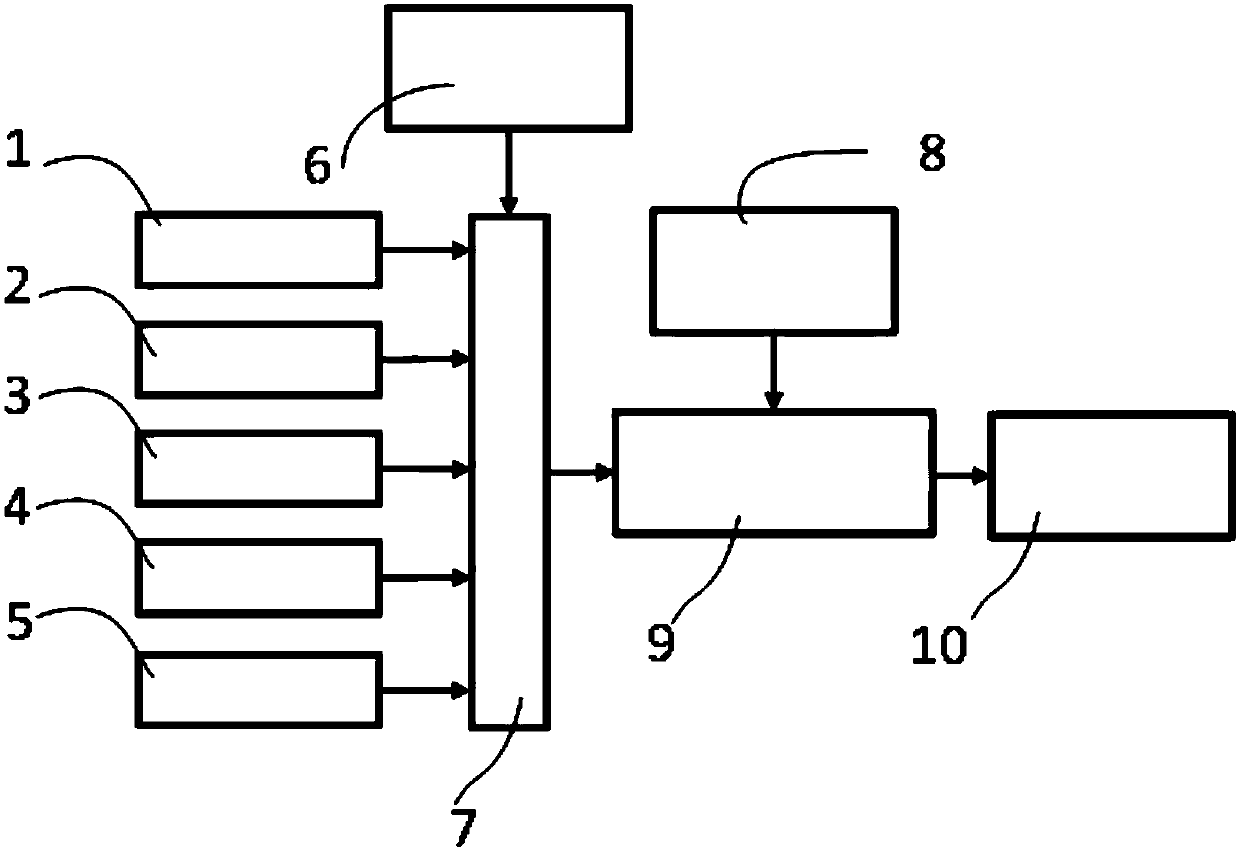
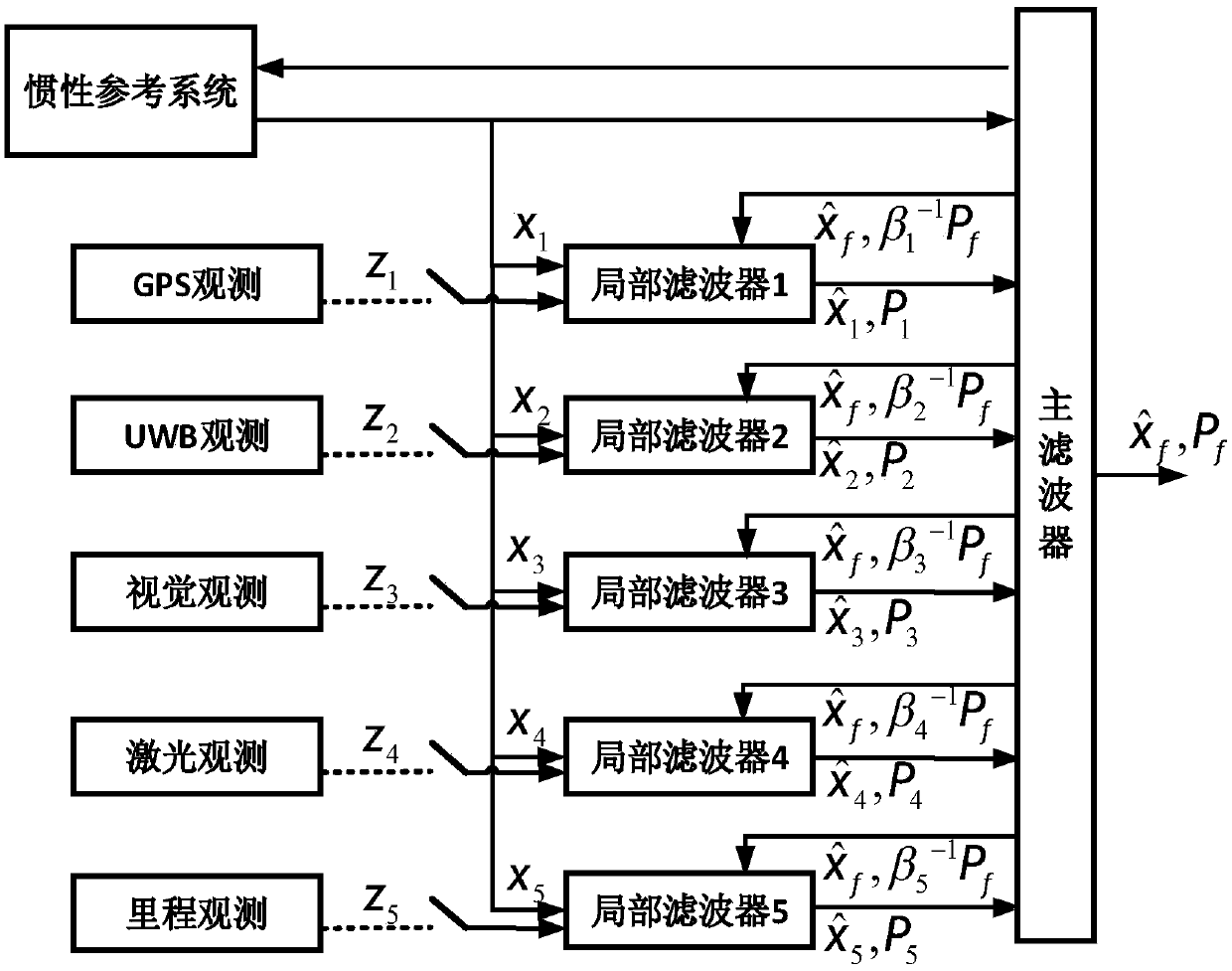
ActiveCN108225302AGuaranteed seamless positioningObservation synchronizationNavigation by speed/acceleration measurementsSatellite radio beaconingPetrochemicalGlobal Positioning System
The invention discloses a system and a method for locating an inspection robot in a petrochemical plant. The system comprises a global positioning system (GPS) observation unit, an ultra-wide bandwidth (UWB) observation unit, a visual observation unit, a laser observation unit, a mileage observation unit, a combination decision module, an inertial state estimation module, an available positioningobservation / strapdown inertial navigation system (SINS) combination module, and a positioning information fusion module. The GPS observation unit, the UWB observation unit, the visual observation unit, the laser observation unit and the mileage observation unit acquire the respective observation data and send same to the combination decision module; the combination decision module performs multi-layer map-based positioning by combining an environmental map model stored in an environmental model prior information module so as to determine available observation types; the available positioning observation / SINS combination module combines available observation data with a corresponding motion equation established by an inertial state estimation module, and the combined result is sent to the positioning information fusion module for carrying out final integrated pose estimation. The system and the method solve the problem of seamless positioning of the inspection robot which runs in various complicated regions of the petrochemical plant, and guarantee the continuity of a positioning process and the stability of the positioning result.
Owner:CHINA UNIV OF MINING & TECH +1
Multispectral face detection method based on graphics processing unit (GPU)
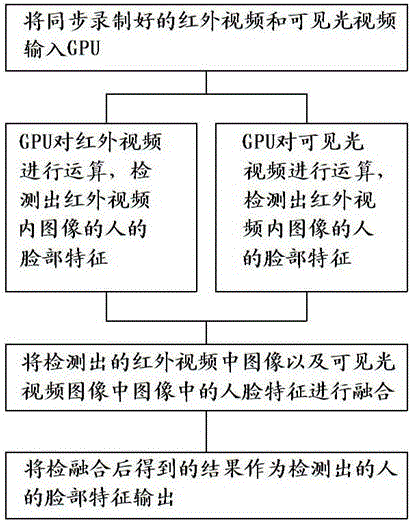
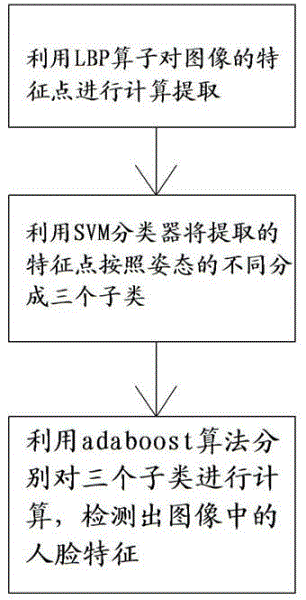
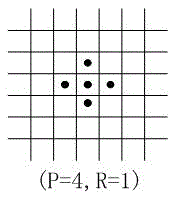
InactiveCN102622589ABreak the limitation of only being able to detect positive facesCharacter and pattern recognitionFace detectionSvm classifier
The invention discloses a multispectral face detection method based on a graphics processing unit (GPU). The GPU based on compute unified device architecture (CUDA) is used for calculating an infrared light video and a visible light video which are recorded synchronously, so that features of a face in an infrared light image and a visible light image are detected respectively; and an infrared light detection result and a visible light detection result are combined synchronously, and a combined result is used as a face feature of a human and output. According to the multispectral face detection method, the face detection results based on the infrared light image and the visible light image are combined. The detection method is not influenced by light, and a detected face image is an accurate visible light image; and a face in an image can be detected under a severe environment. During detection, a support vector machine (SVM) classifier for classifying attitudes of faces is constructed; and due to the classification of the attitude classifier, face detection based on an adaboos detection algorithm is performed on sub types of infrared images. According to the technology, faces with various attitudes in the infrared images can be detected; and the limitation that only front faces in the infrared images can be detected is broken through.
Owner:陈遇春
Steam-electric generating set rotor thermal bending unbalance fault real time diagnostic method
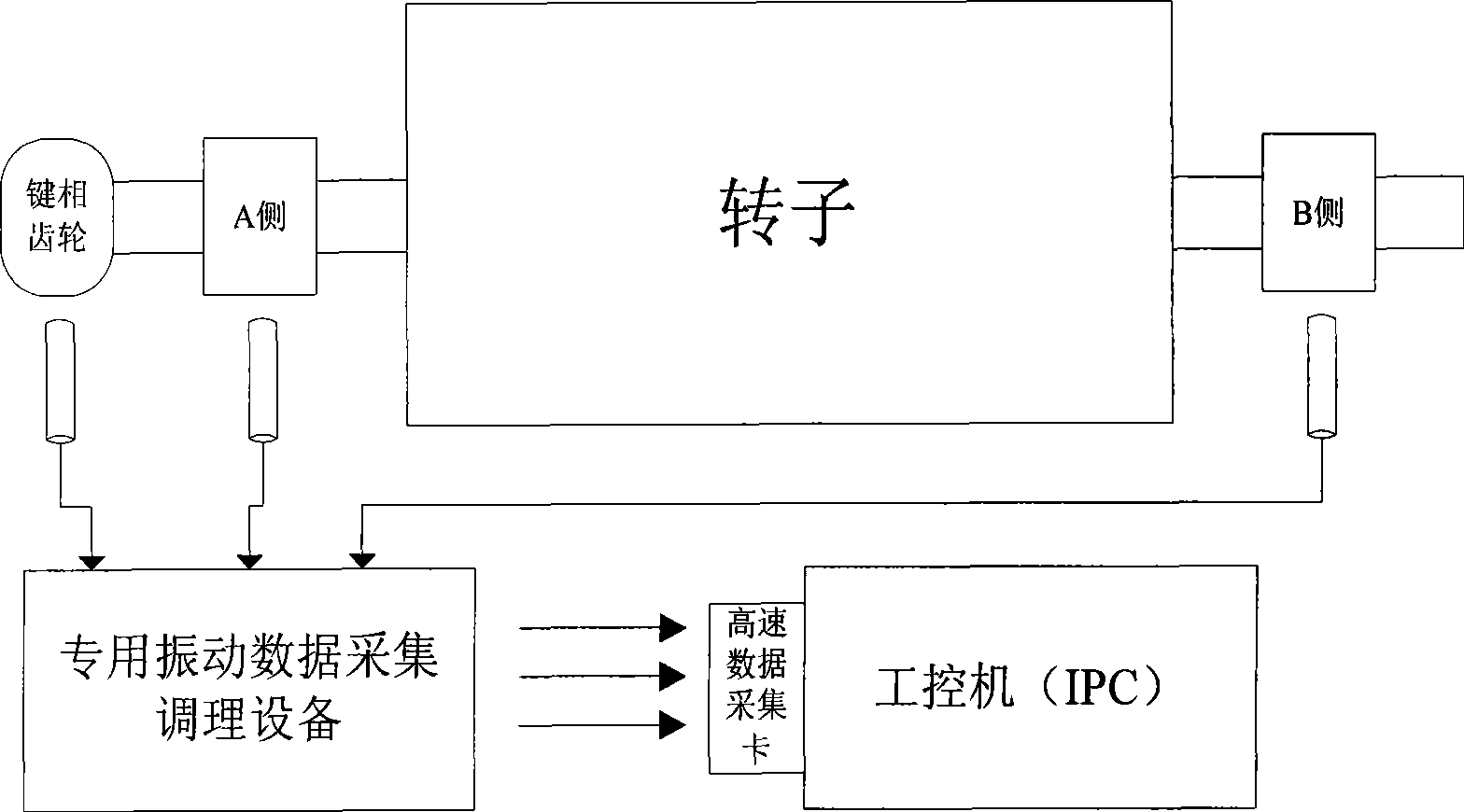
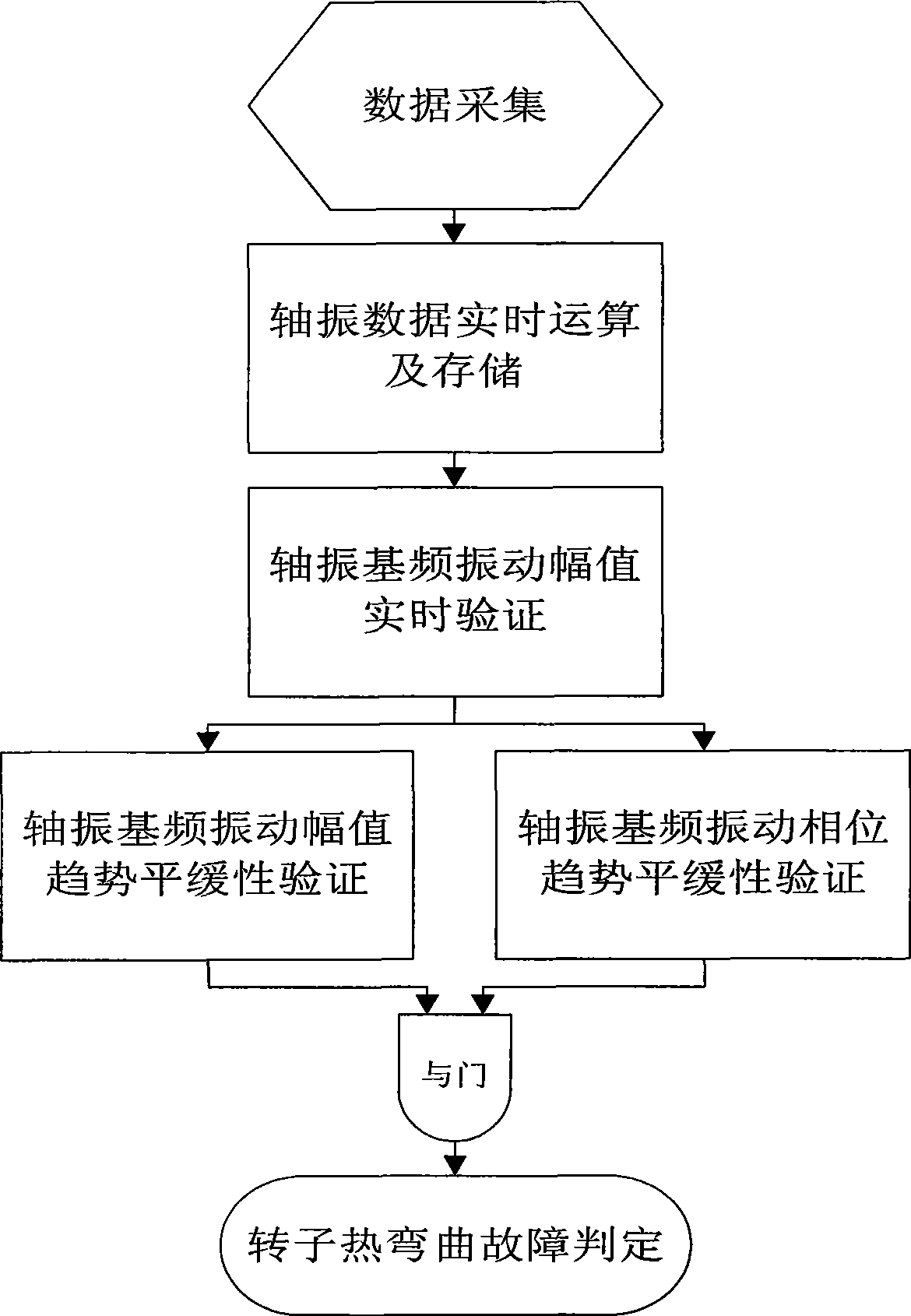
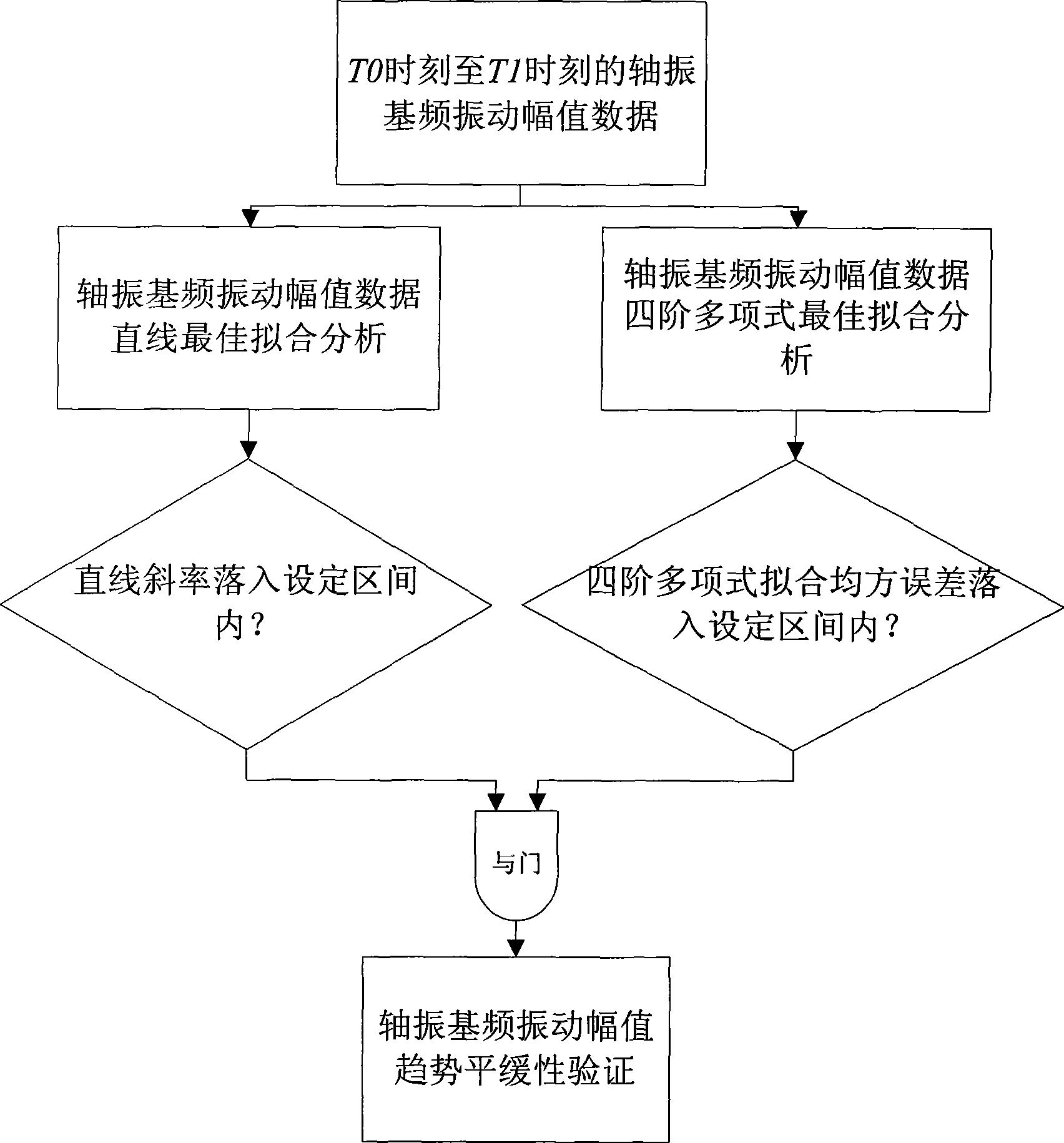
InactiveCN101451898AMethod scienceConclusion scienceStatic/dynamic balance measurementVibration amplitudeAxial vibration
The invention discloses a real time diagnosing method for turbo unit rotor thermal bending malfunctions. The method processes the calculation, analysis and judgments for the vibrating data via collecting the rotor vibrating signals of the turbo unit; and the method processes the real-time calculation of storage on both sides of the rotor shaft relative vibration frequency of vibration amplitude and phase values, and real-time axis vibration frequency of vibration amplitude in real-time authentication, determine any side of the rotor shaft vibration amplitude of the vibration frequency is greater than the vibration amplitude threshold. Then the method is combined with least square method, based on the axial vibration frequency of vibration data axis vibration frequency of the vibration amplitude of the trend of flat-based authentication and shaft vibration frequency vibration phase of verification, such as the trend of moderate real-time quantitative calculation and analysis. Calculated in real-time quantitative analysis based on the combined results of the verification, automatic real-time diagnosis of whether units imbalance rotor thermal bending failure. The invention has the advantages of scientific method; reliable conclusions can automatically real-time online monitoring, fault diagnosis and so on.
Owner:NORTH CHINA ELECTRIC POWER UNIV (BAODING)
Vehicle navigation system with high safety and guiding method thereof
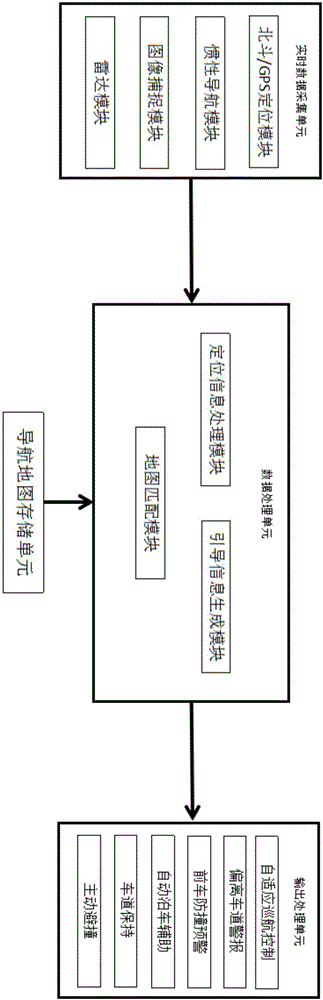
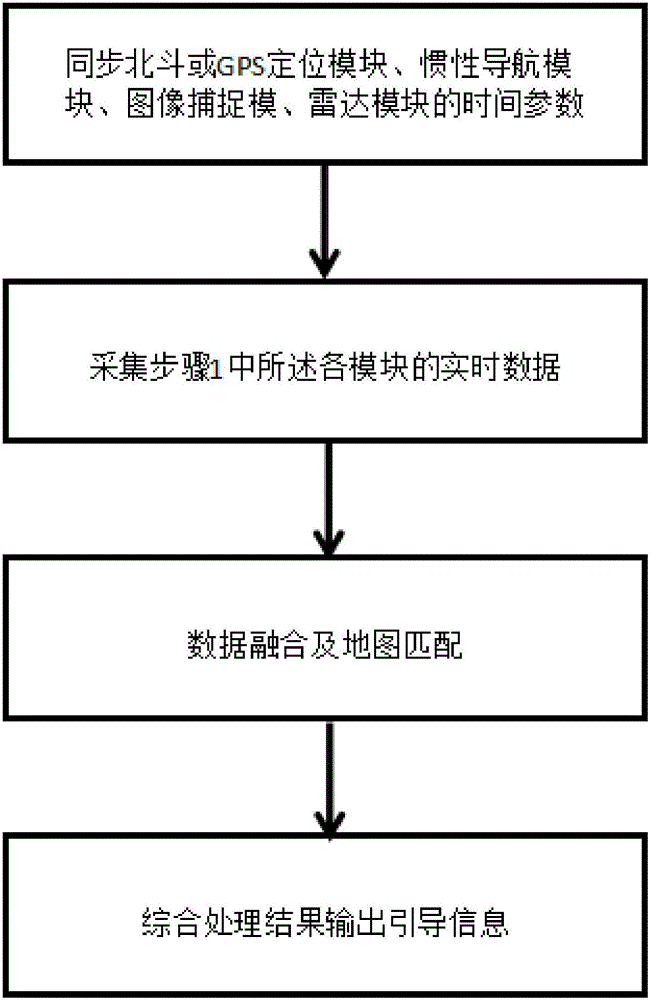
InactiveCN106225789AHigh precisionIncrease initiativeInstruments for road network navigationNavigation by speed/acceleration measurementsReal-time dataRadar
The invention discloses a vehicle navigation system with the high safety and a guiding method thereof. The vehicle navigation system comprises a real-time data collection unit, a data processing unit, a navigation map storage unit and an output reminding unit; the data processing unit receives real-time data collected by the real-time data collection unit, the real-time data is matched with map data provided by the navigation map storage unit after being processed, and then guiding information is output by the output reminding unit. Accordingly, the driving safety is promoted through sensor recognition results, sensors comprise a high-precision map, a binocular camera and a radar, the characteristics of all the sensors are combined, targeted screening and filtering are conducted, and after the results are integrated, the safety guiding information is output.
Owner:WUHAN UNIV OF TECH +1
Network selecting method based on multi-attribute decision-making and group decision-making
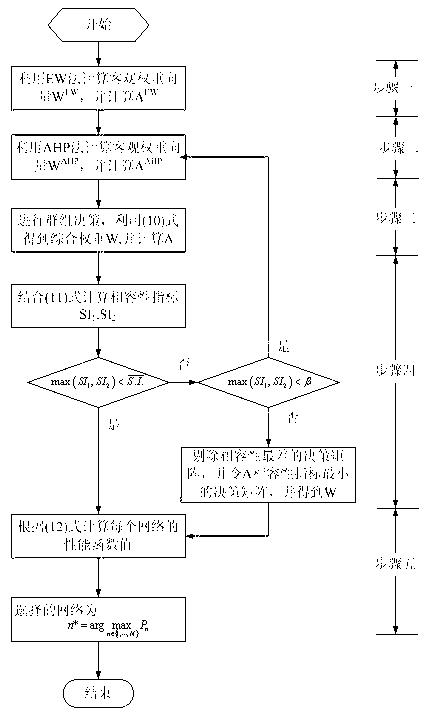
InactiveCN102781072AReduce switching timesAssess restrictionWireless resource managementQuality of service
Network selecting is a key problem of wireless resource management under a heterogeneous network scene. The invention provides a network selecting method based on multi-attribute decision-making and group decision-making. First, a subjective decision-making result and an objective decision-making result are obtained through a multi-attribute decision-making method, the subjective decision-making result and the objective decision-making result are obtained through a level analysis method and an entropy weight method respectively, then the subjective decision-making result and the objective decision-making result are combined through the group decision-making, compatible theory in the group decision-making is adopted for judging rationality of the combined result, whether the combined result has rationality is judged, if the result is not reasonable, decision-making is required, and combination is conducted again. The decision-making is conducted for a network according to the combined result, and a suitable network is selected for users. The network selecting method not only gives consideration to objective attribute, but also gives consideration to preference of the users, and the users can not select some networks with poor performance according to preference of the users. The network selecting method not only can effectively reduce times of switching, but also can provide satisfactory service quality for the users.
Owner:NANJING UNIV OF POSTS & TELECOMM
Method for evaluating video quality
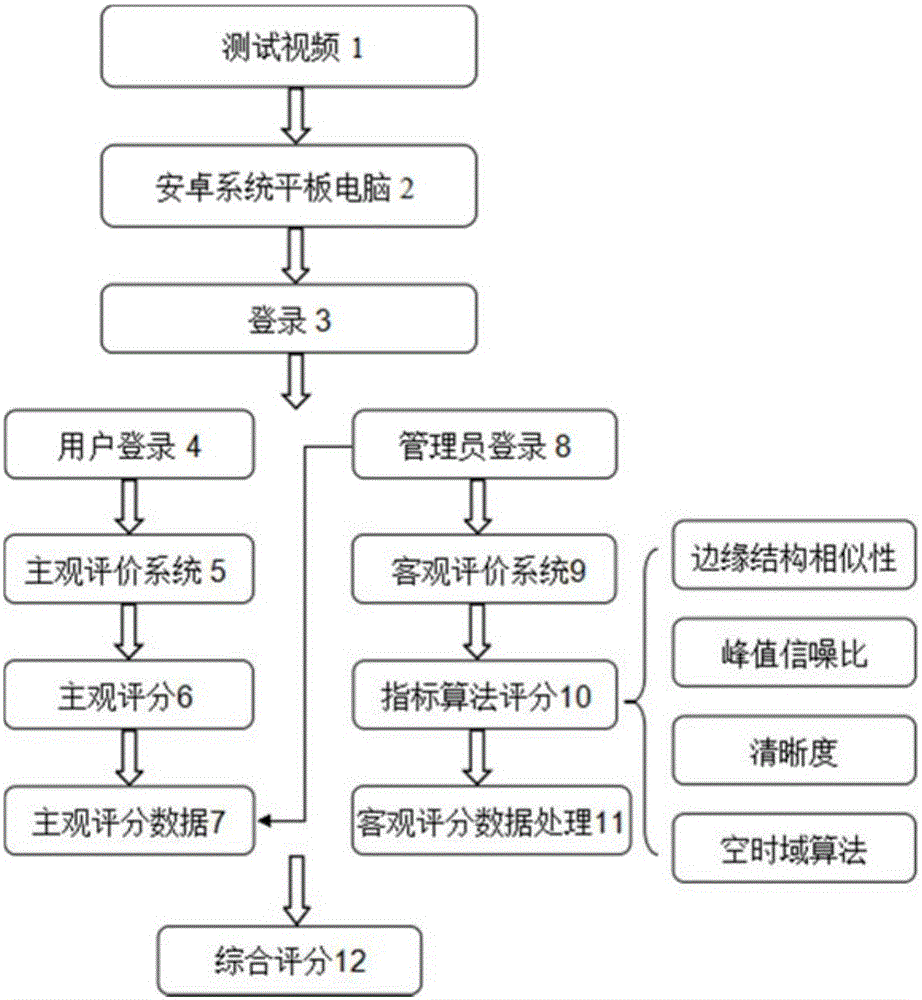
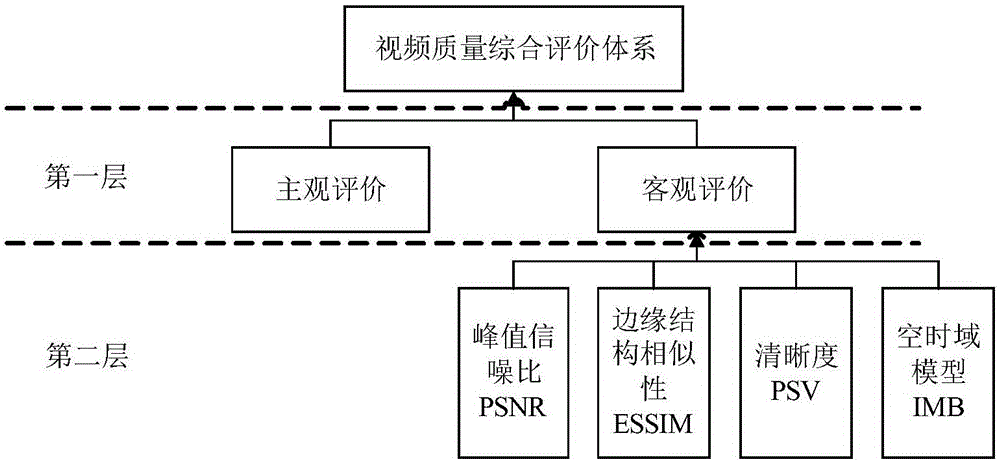
ActiveCN105100789AGuaranteed accuracyEffective evaluationTelevision systemsPattern recognitionTime domain
The invention relates to a method for evaluating video quality. The method includes a first step of subjectively evaluating the video quality in nine scoring level, calculating average subjective scores of each scene among a plurality of video scenes, and finishing subjective evaluation of video quality to obtain a subjectively evaluating result; a second step of carrying out objective evaluating pretreatment on video quality, including peak value signal-to-noise ratio processing, edge structure similarity processing, sharpness processing and spatial-time domain value processing; a third step of objectively evaluating the video quality to obtain an objective evaluating result; and a fourth step of comprehensively evaluating the video quality. In the fourth step, subjective evaluating result and the objective evaluating result are combined to obtain a comprehensive result through comprehensive calculation. The accuracy of the video evaluation result is effectively improved, and high-efficient evaluation is realized.
Owner:TIANJIN UNIV OF SCI & TECH
Method of predicting natural fractures and damage in a subsurface region
InactiveUS8494827B2Computation using non-denominational number representationDesign optimisation/simulationAnalysis toolsFracture risk
A method for predicting localized damage and naturally occurring fractures in a subsurface region is provided. This invention uses a hybrid FEM-DEM (i.e. finite-discrete element) framework combined with a fracture risking analysis and fracture initiation and propagation criteria, to model the transition of rock from a state of continuum to discontinuum. The risking analysis combines results from other natural fracture prediction tools (e.g. displacement discontinuity method, restoration analysis, curvature analysis, analytical solutions, continuum analysis) to augment FEM-DEM solutions, such as by providing remote and local boundary conditions and identifying potential regions of anticipated damage and fracturing. Natural fractures and damage information is extracted from the modeling results and may be used directly for predictions or used as input into other fracture analysis tools or techniques. The FEM-DEM and risking techniques can be incorporated into a variety of numerical simulation software packages that use a finite-discrete method solver.
Owner:EXXONMOBIL UPSTREAM RES CO
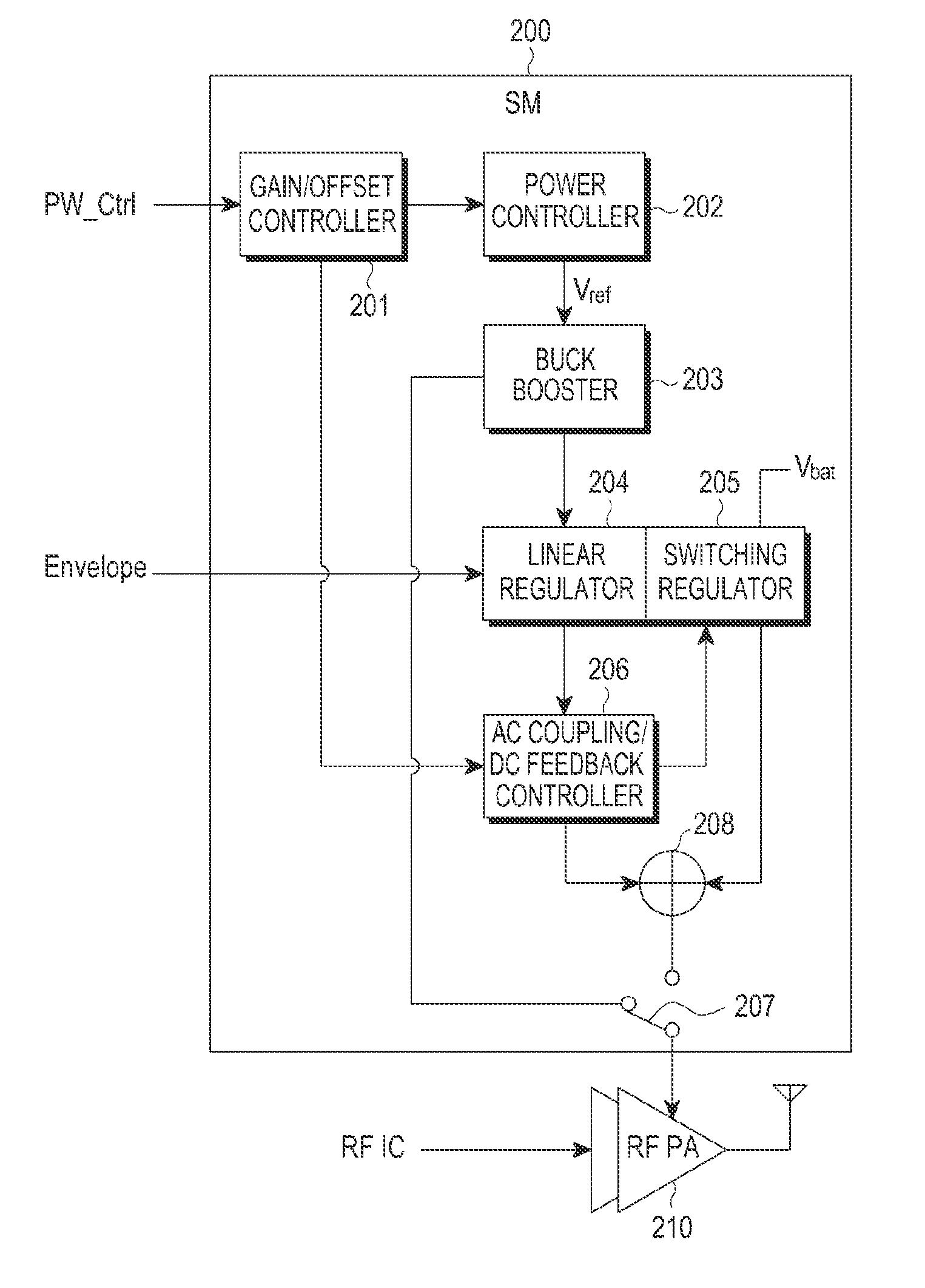
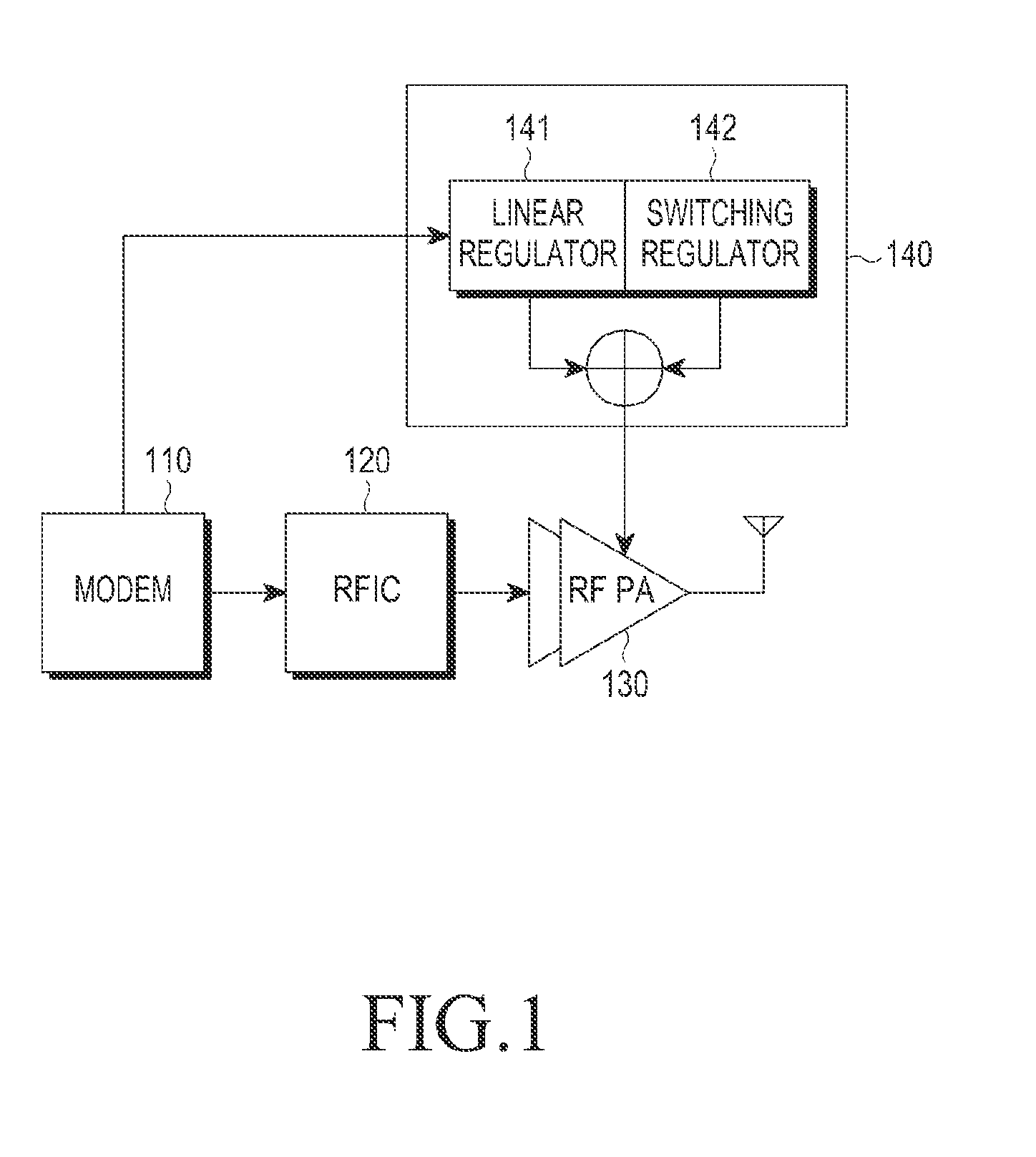
Method and apparatus for supplying power to a radio frequency power amplifier
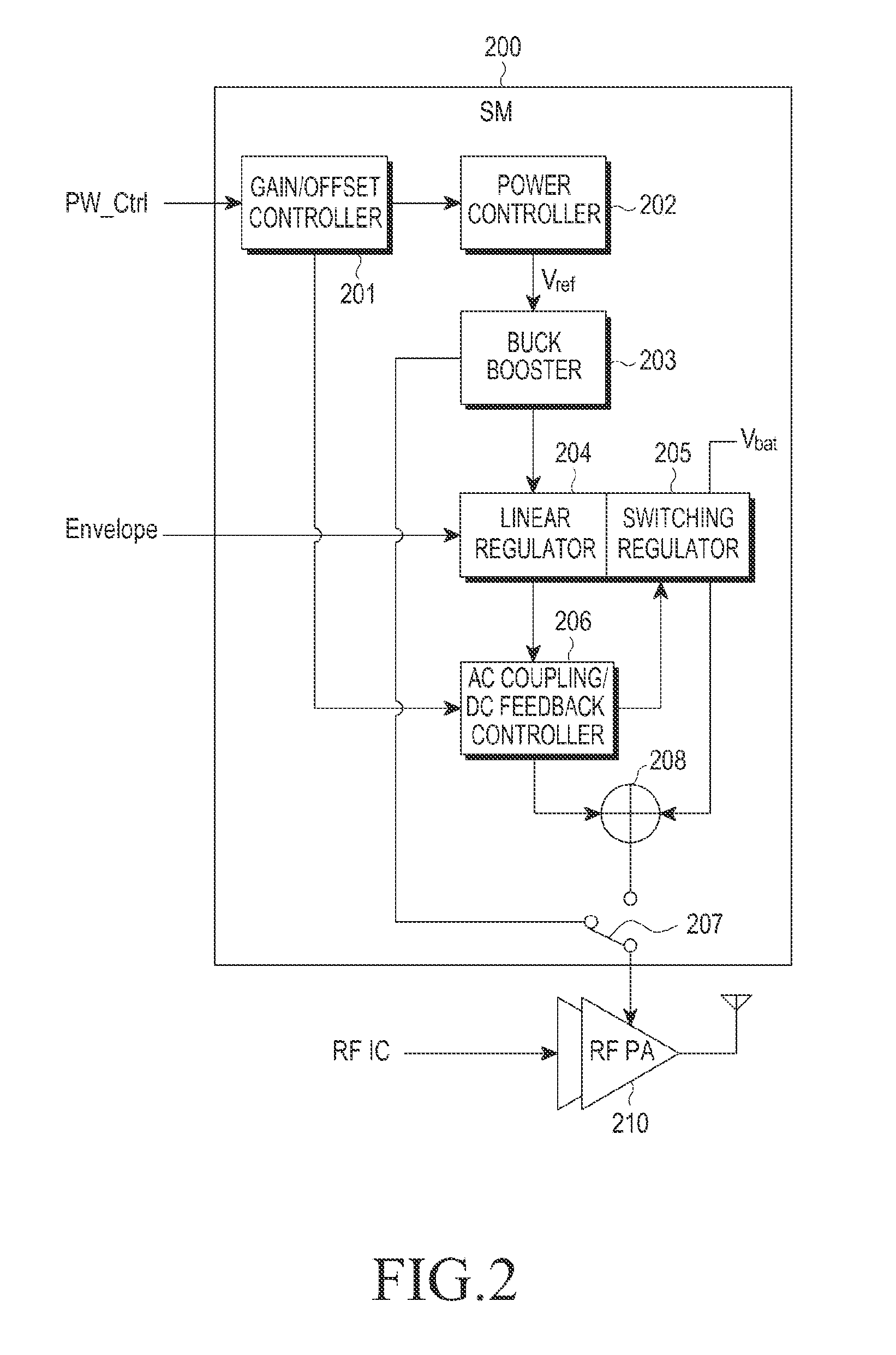
ActiveUS20160065139A1Improving respective efficiencyHigh frequency amplifiersGain controlLinear regulatorModem device
A method and a supply modulator (SM) are provided for supplying power from a wireless transmitter to a radio frequency (RF) power amplifier. A power control signal input from a modem is received. A reference voltage is determined. An operating mode of the SM is changed by controlling a level of the reference voltage. A voltage is determined based on the level of a reference voltage. When the operating mode of the SM is an ET mode, a first output signal from a linear regulator and a second output signal from a switching regulator are combined to obtain a combined result, and the combined result is output. The first output signal is based on the voltage. When the operating mode of the SM is an APT mode, the voltage based on the reference voltage is output.
Owner:SAMSUNG ELECTRONICS CO LTD
Method and apparatus for iterative computer-mediated collaborative synthesis and analysis
InactiveUS20070226296A1Multiple digital computer combinationsOffice automationData scienceCombined result
Owner:SRI INTERNATIONAL
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com