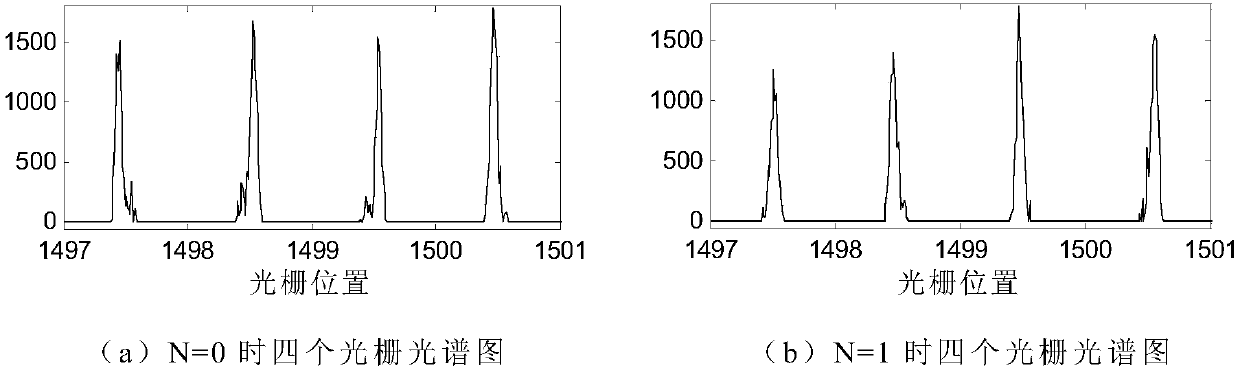
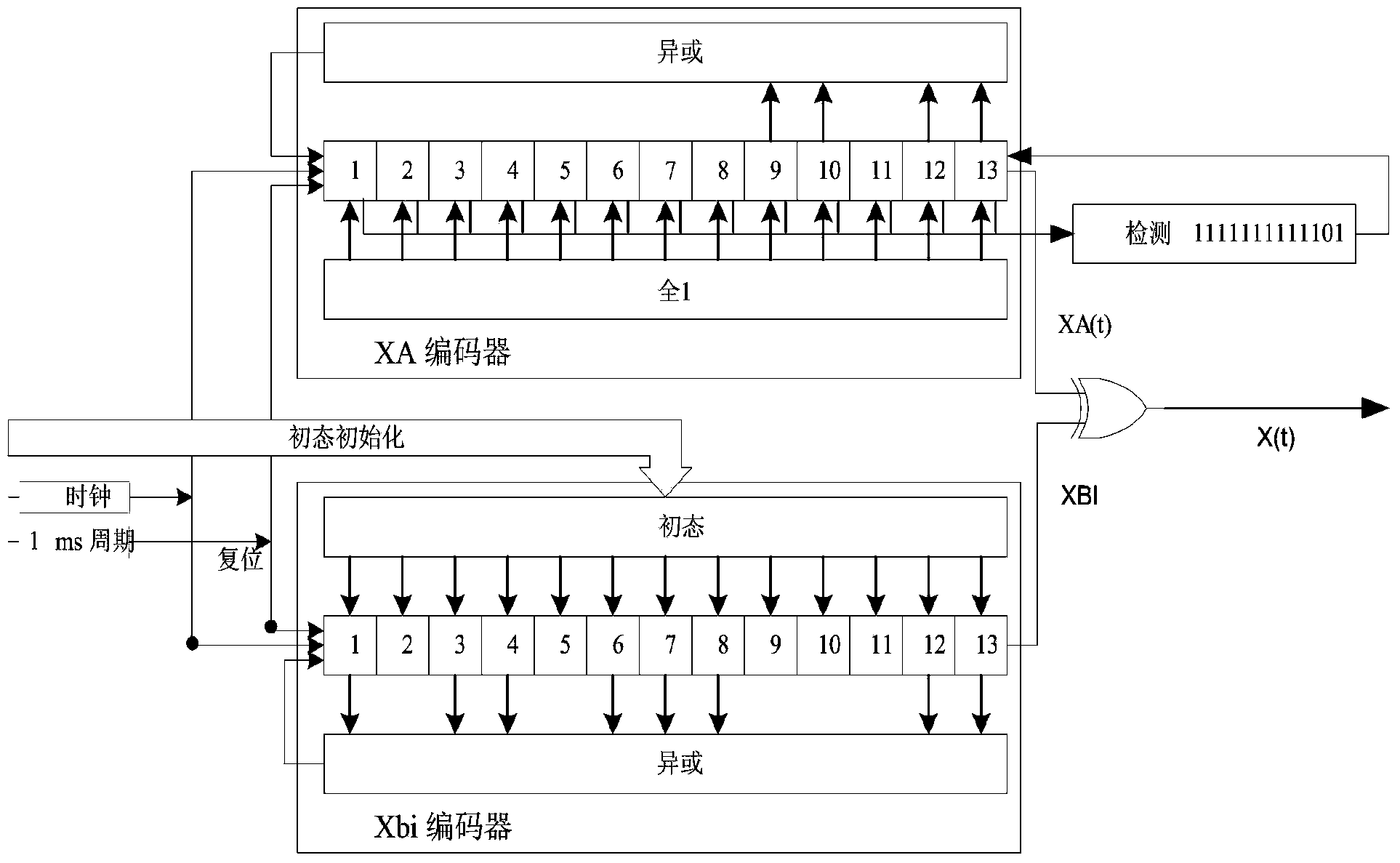
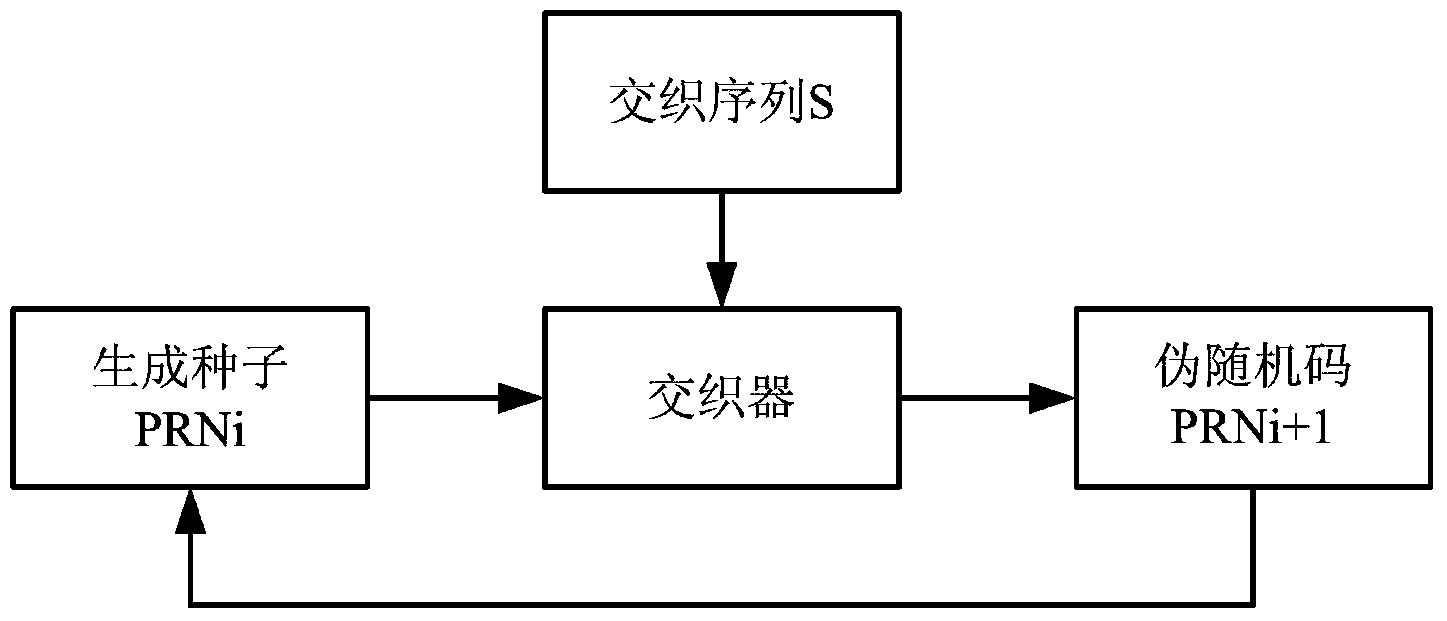
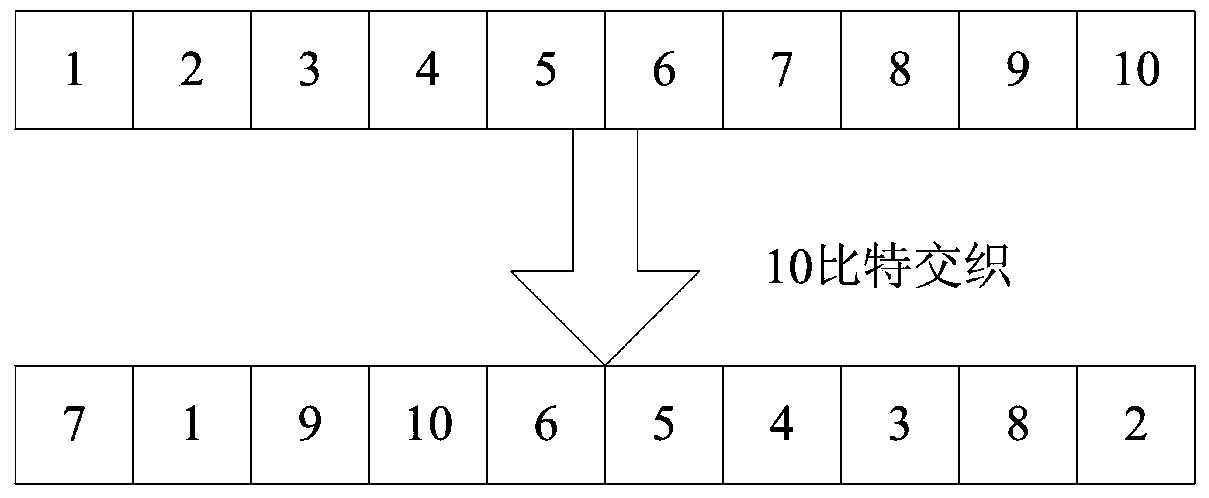
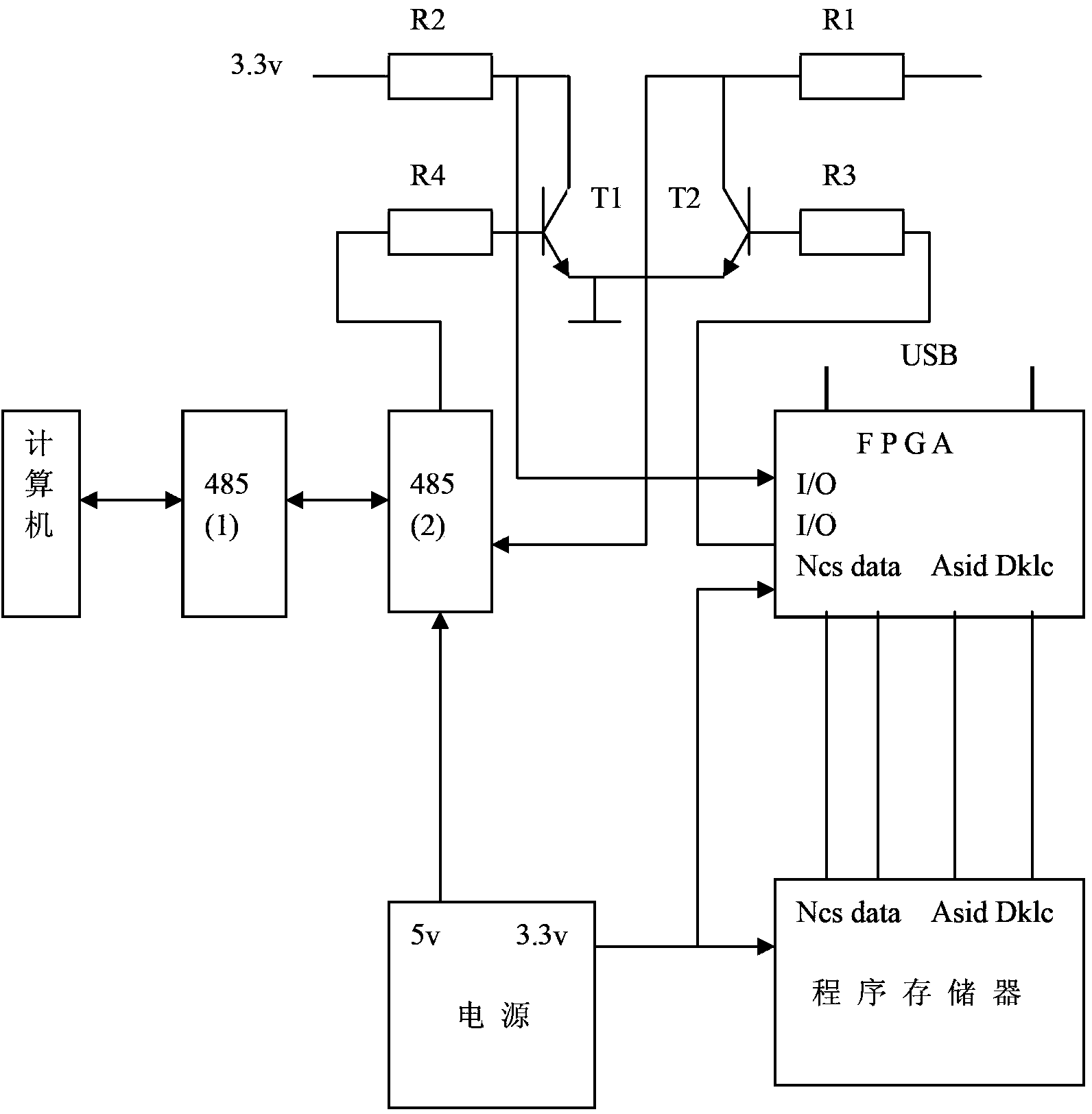
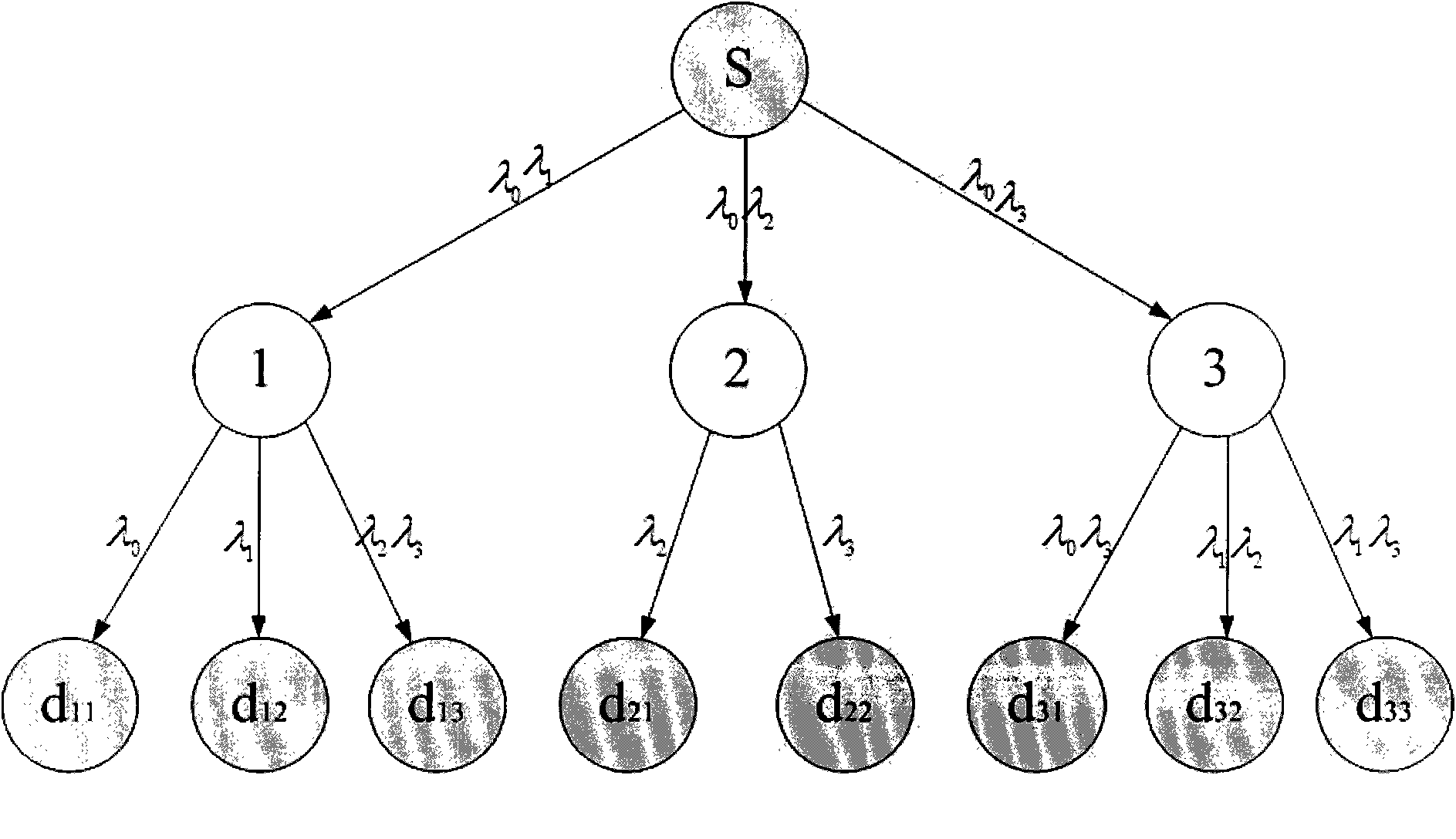
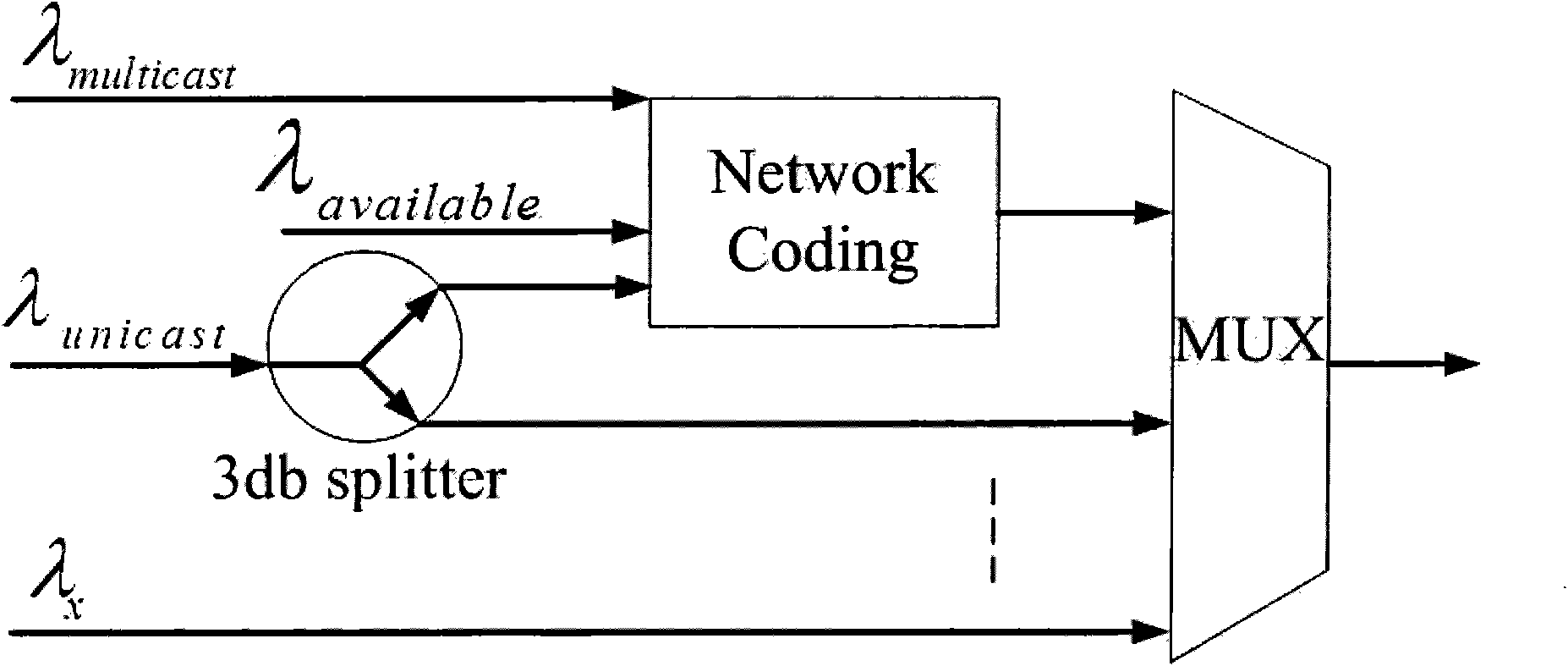
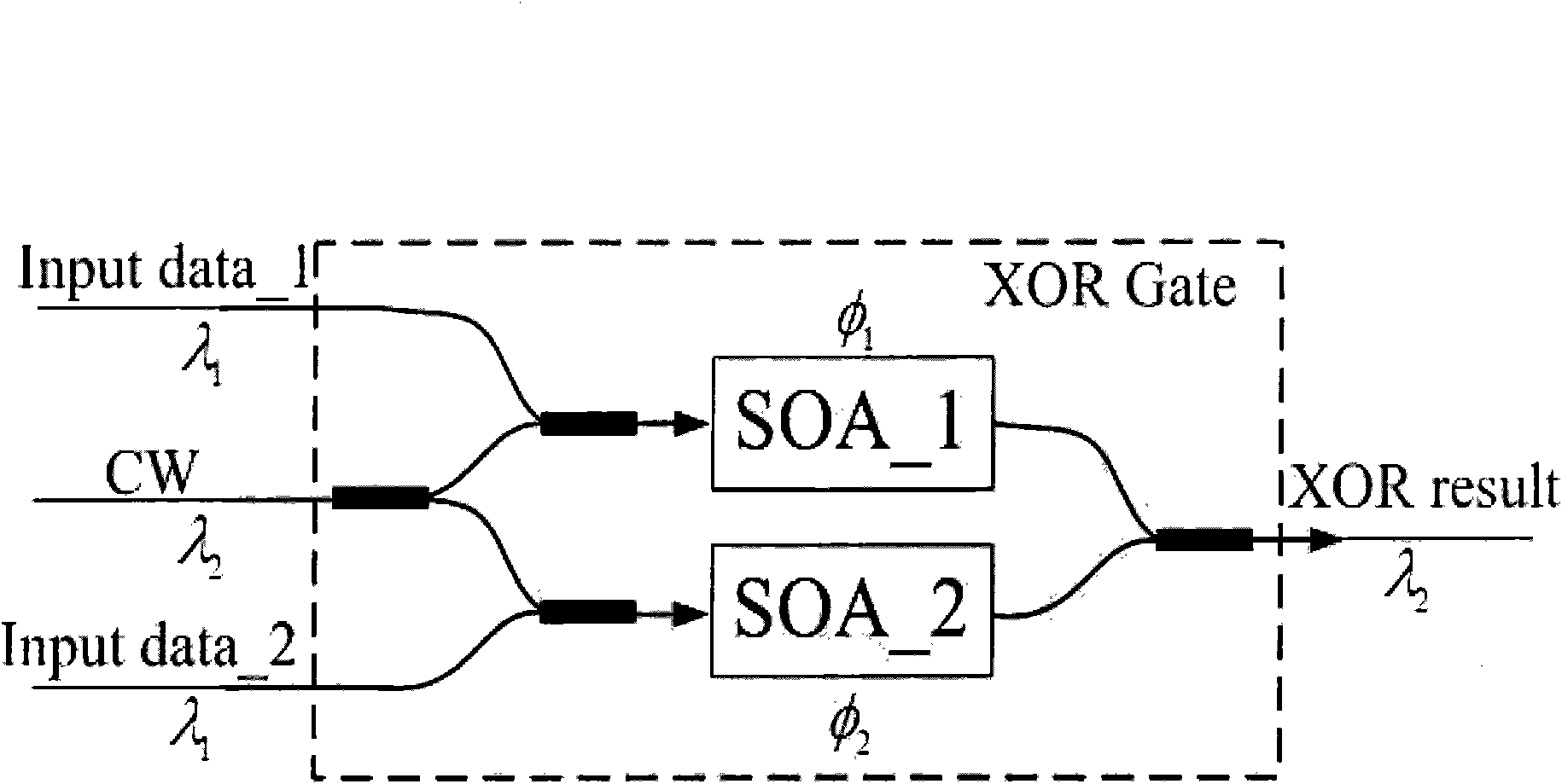
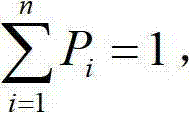Patents
Literature
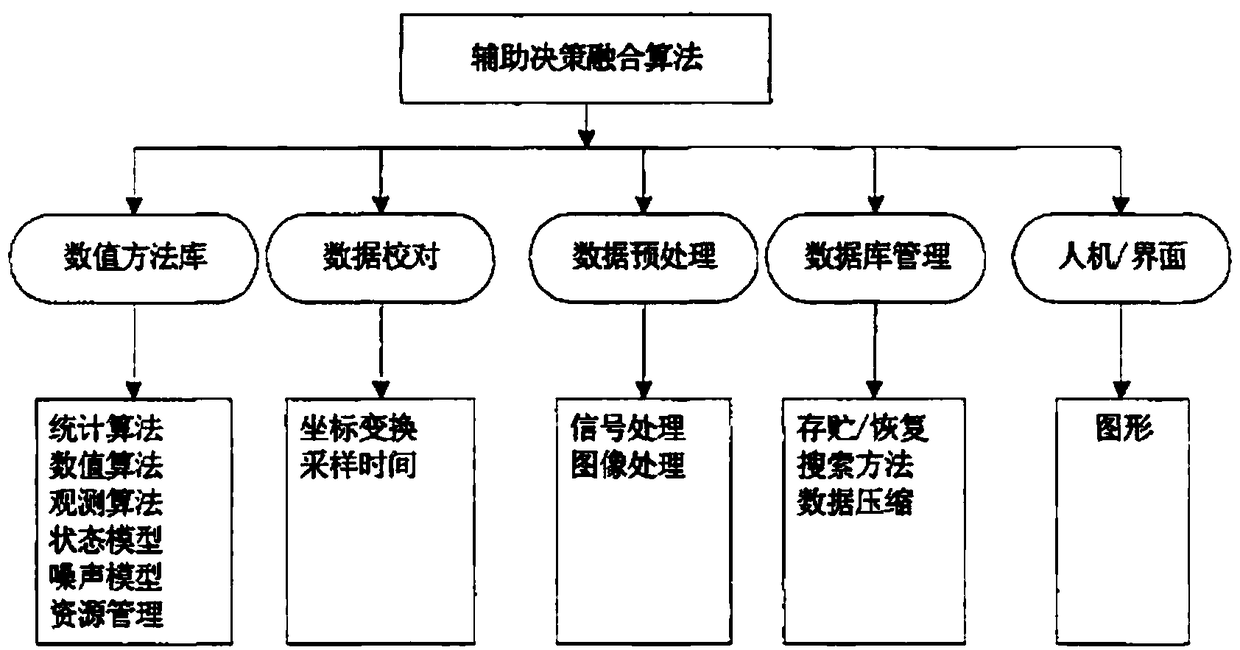
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
64 results about "Coding theory" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Coding theory is the study of the properties of codes and their respective fitness for specific applications. Codes are used for data compression, cryptography, error detection and correction, data transmission and data storage. Codes are studied by various scientific disciplines—such as information theory, electrical engineering, mathematics, linguistics, and computer science—for the purpose of designing efficient and reliable data transmission methods. This typically involves the removal of redundancy and the correction or detection of errors in the transmitted data.
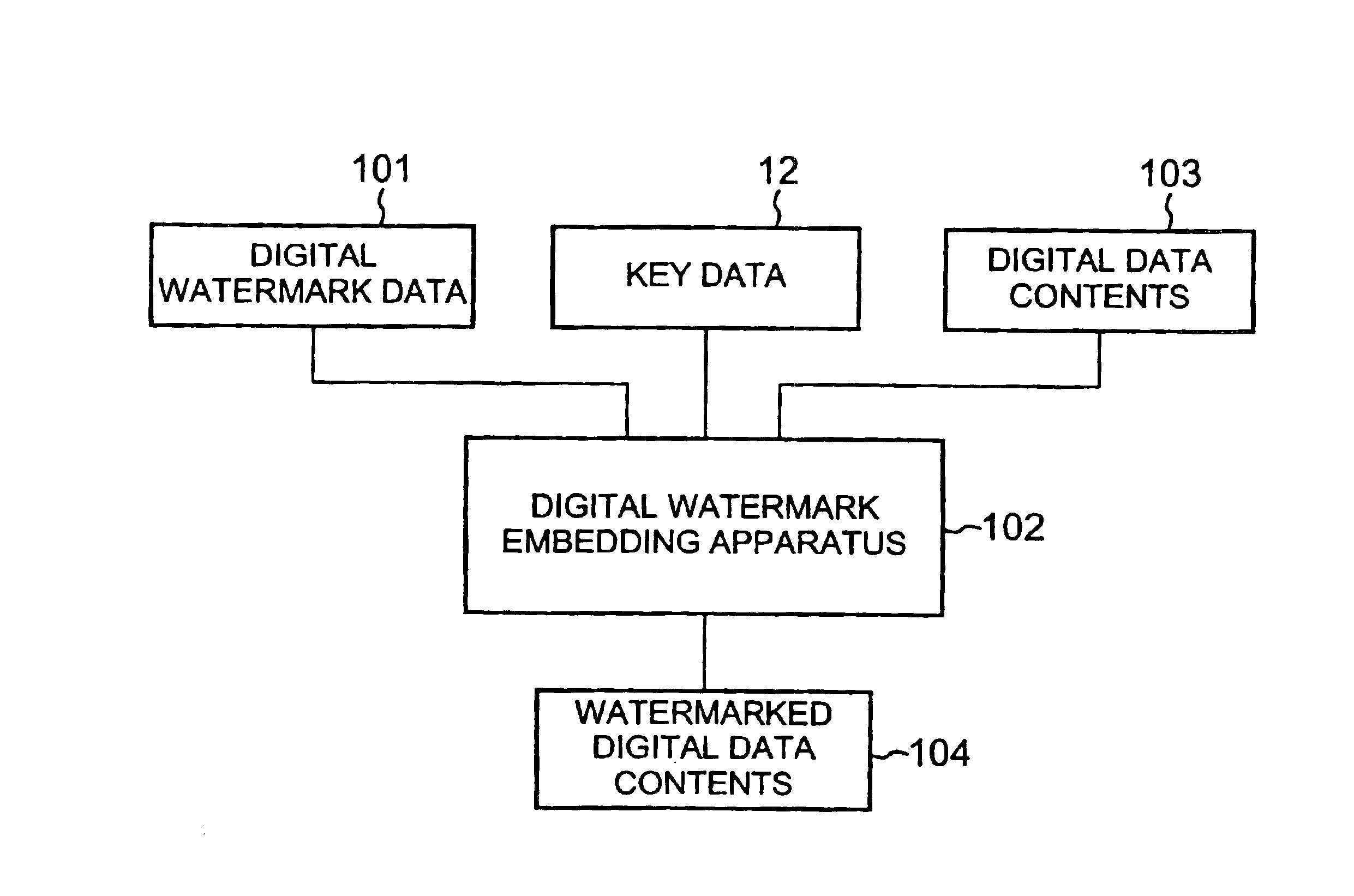
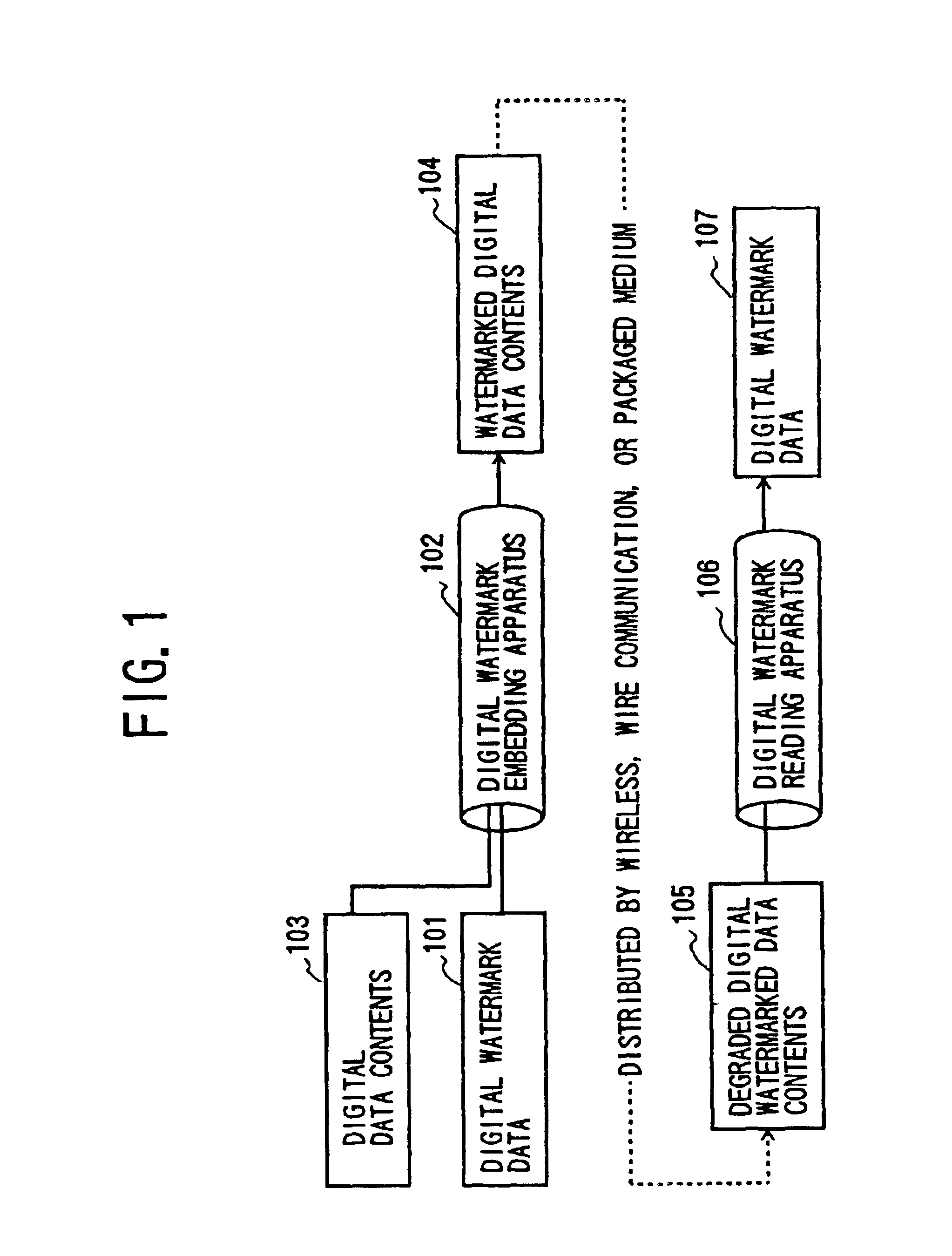
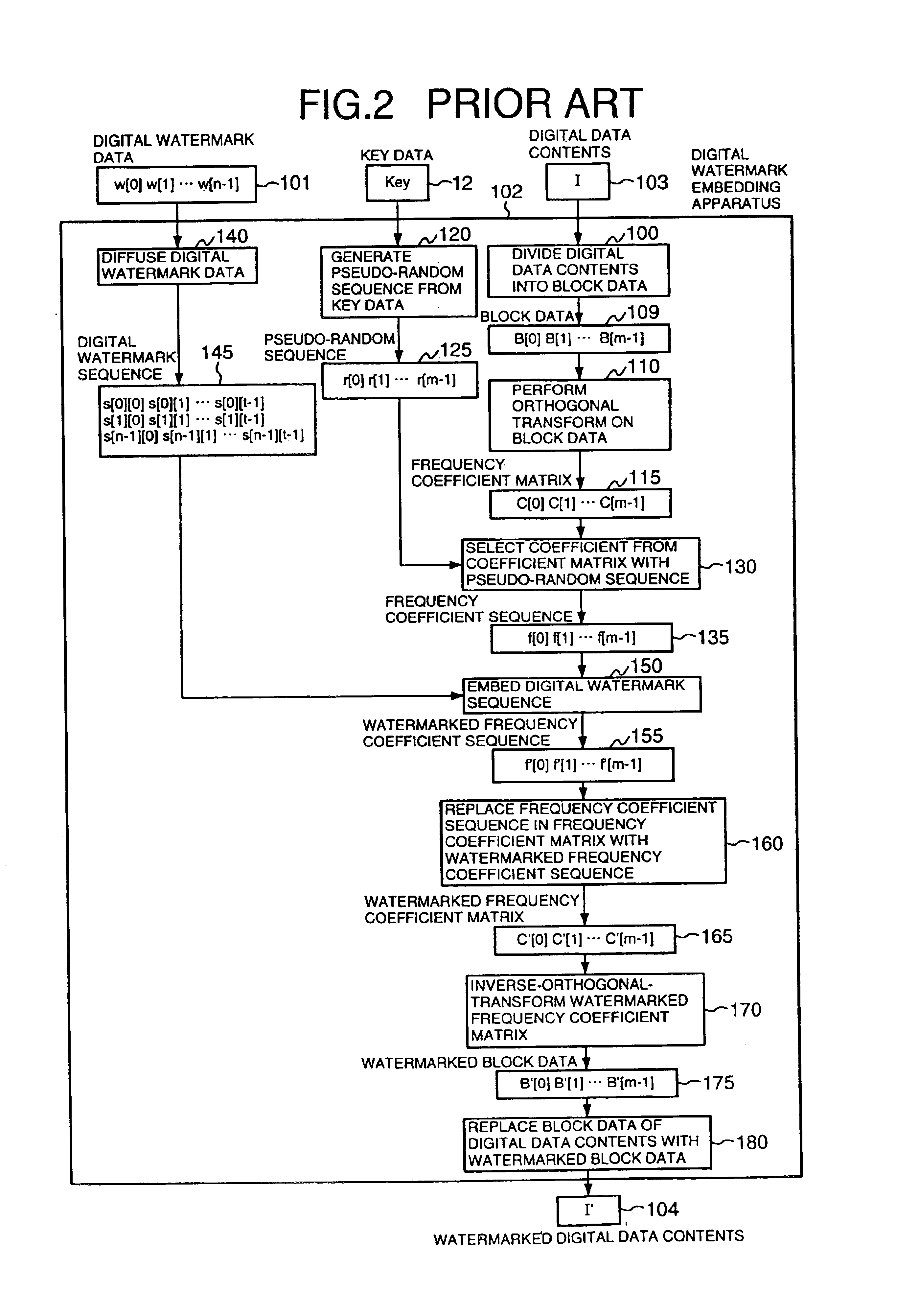
Method and apparatus for digital watermarking
InactiveUS7072492B2Quality improvementIncreased durabilityUser identity/authority verificationCharacter and pattern recognitionDigital dataDigital watermarking
Owner:NIPPON TELEGRAPH & TELEPHONE CORP
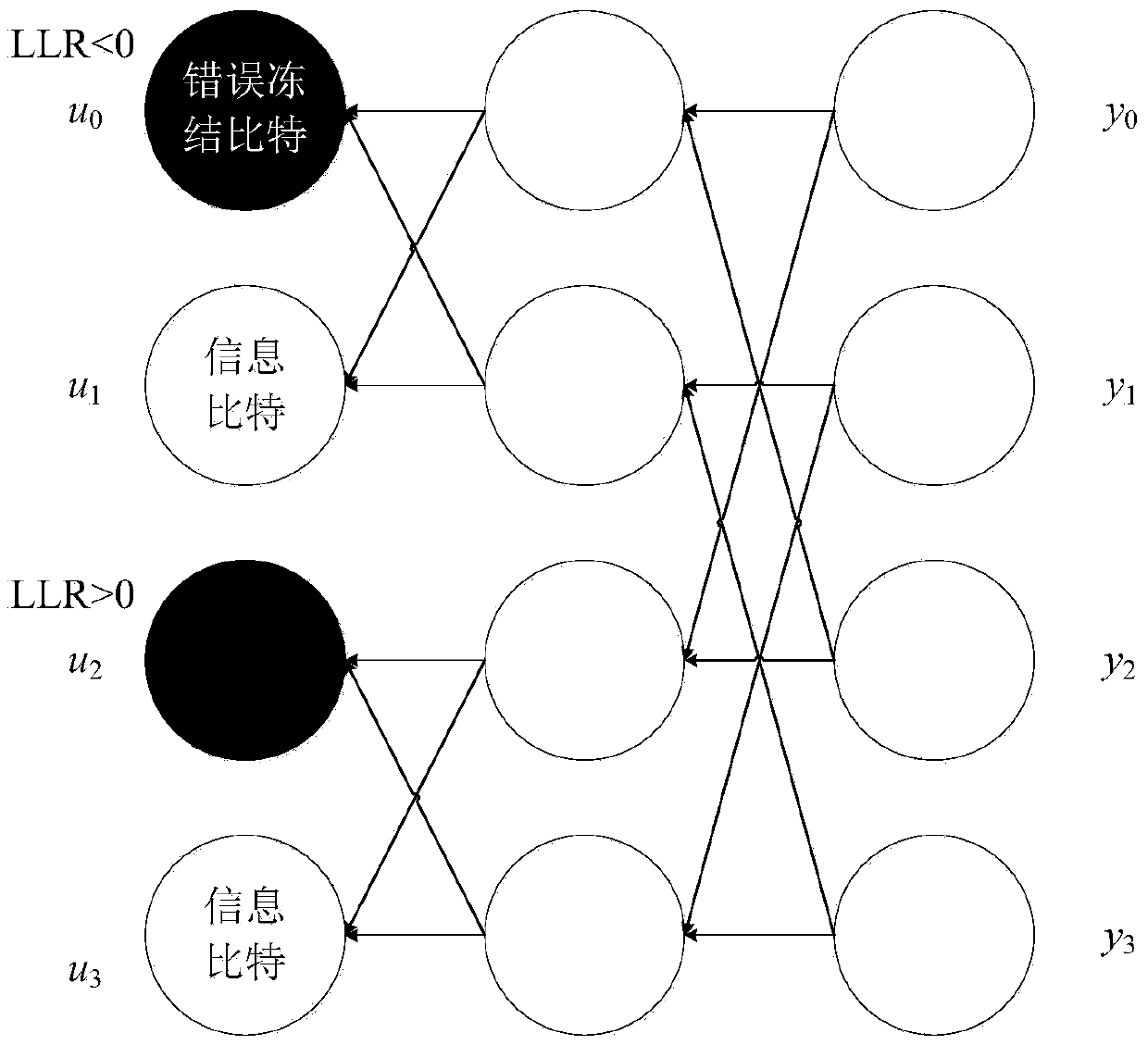
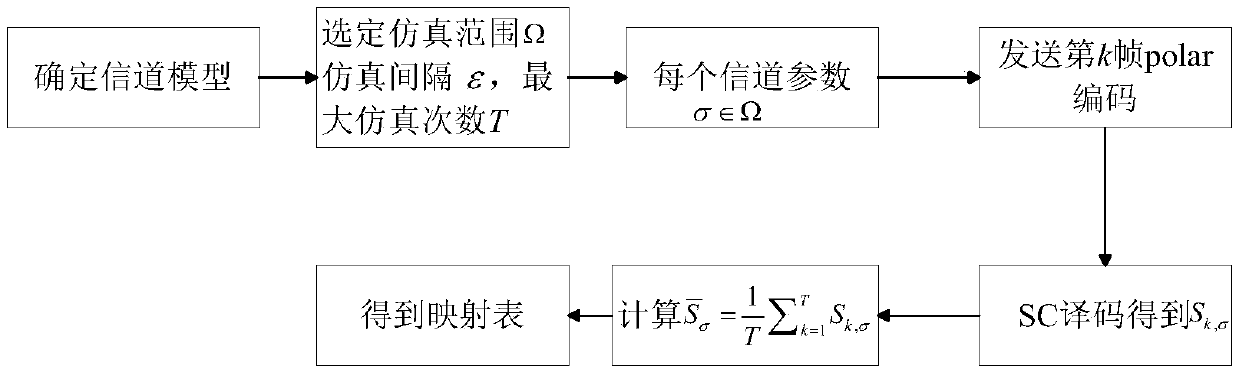
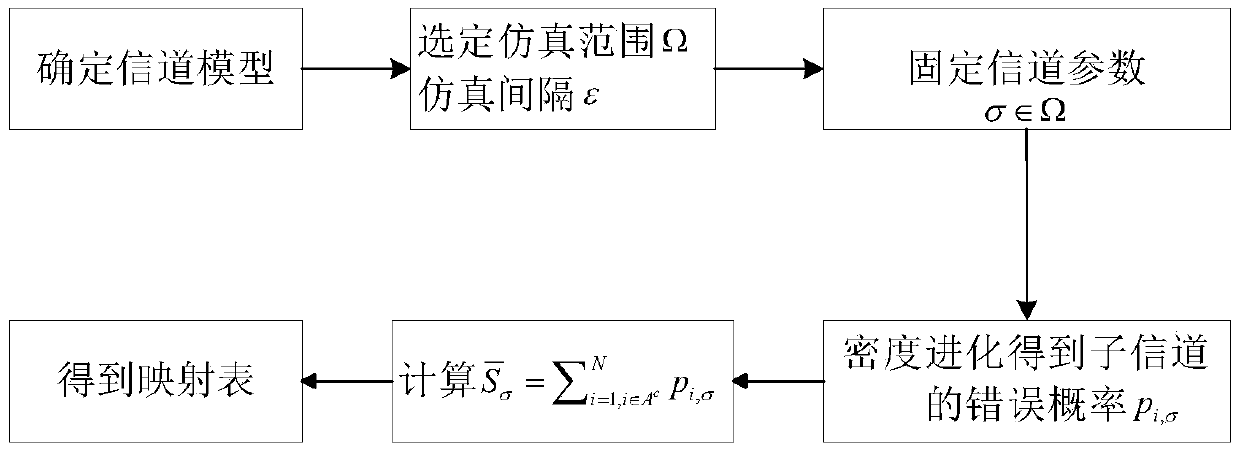
Channel estimation method based on polar code
ActiveCN105553892AReduce complexityBaseband system detailsCode conversionRound complexityEstimation methods
The invention provides a channel estimation method based on a polar code, and belongs to the field of communication. The method provided by the invention is applicable to estimating a univariate channel; firstly a mapping table between the mean value of the number of error freezing bits and a channel parameter to be estimated is obtained, and then the channel estimation is performed. The mapping table is obtained by using a limited code Monte Carlo method or a limited code theory calculation method. The mean value of the number of the error freezing bits in the SC decoding result of an L frame polar code is counted, and the corresponding channel parameter is obtained through contrasting the mapping table. According to the channel estimation method provided by the invention, the concept of the error freezing bits is creatively provided, and the channel code is joined with the channel estimation, thus the complexity is reduced, and the more accurate channel parameter can be obtained with the smaller complexity.
Owner:BEIHANG UNIV
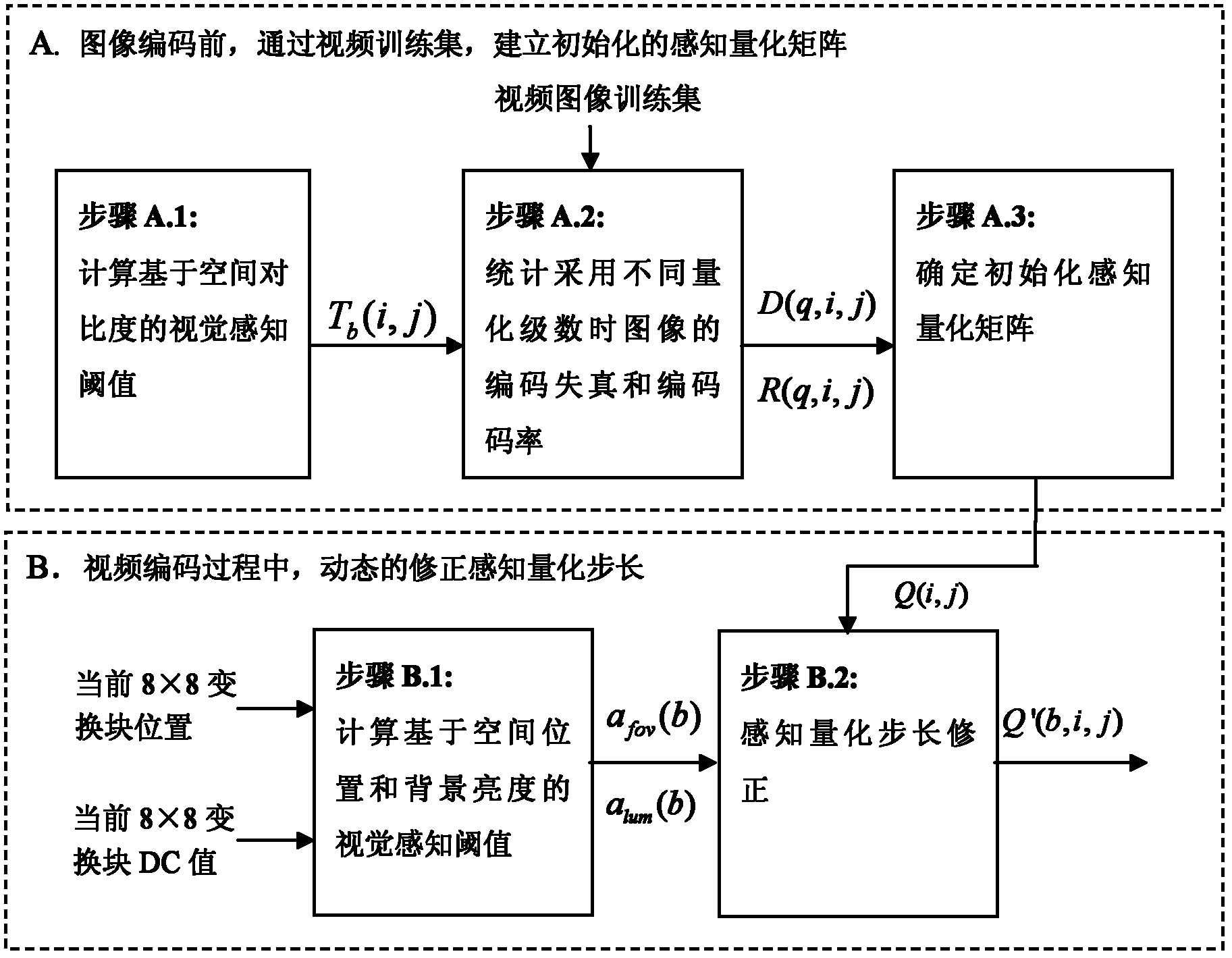
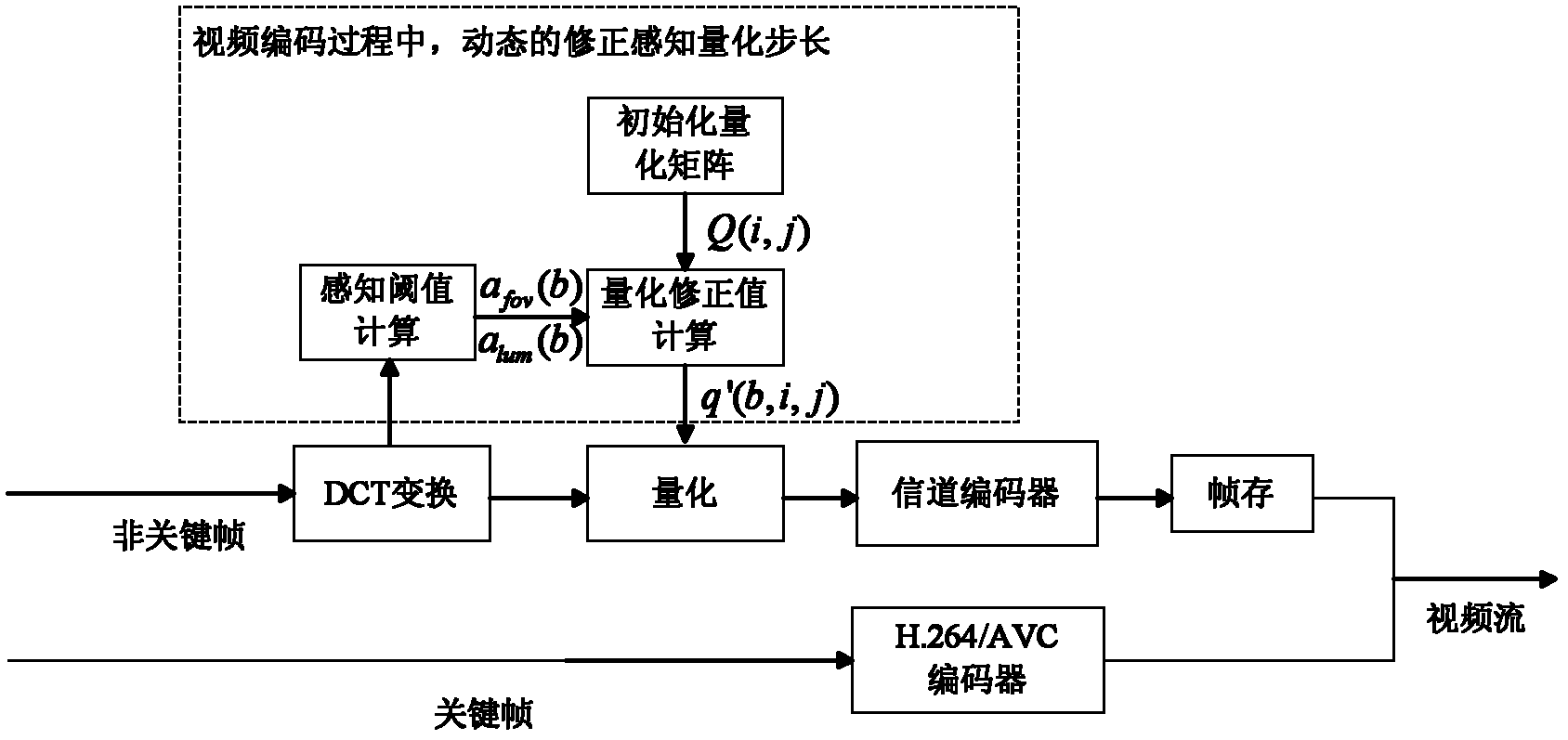
A quantization method based on visual perception characteristics in distributed video coding
InactiveCN102281446AReduce code rateImprove encoding performanceTelevision systemsDigital video signal modificationBase codeComputer architecture
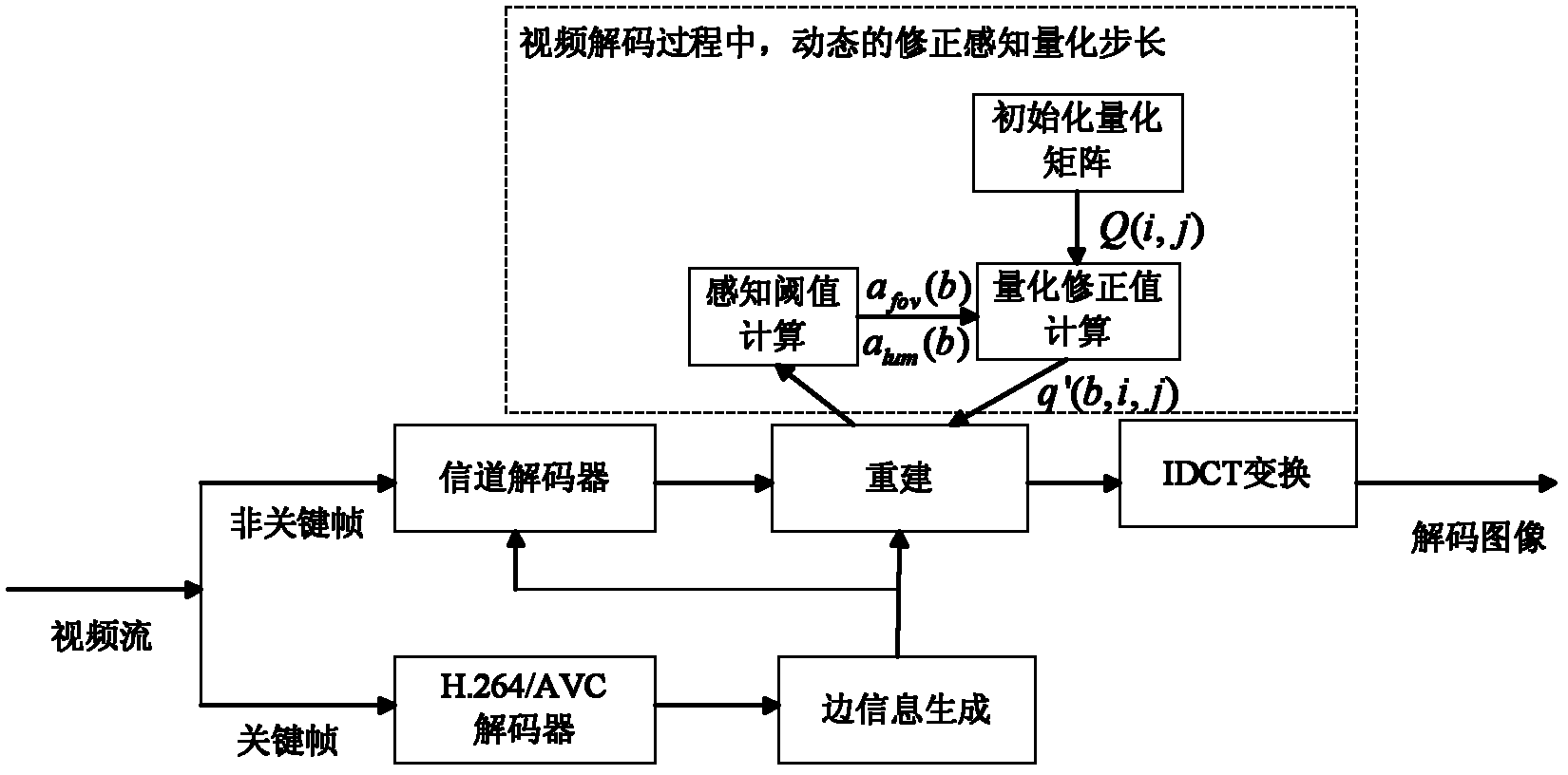
The invention discloses a visual-perception-characteristic-based quantification method in distributed video coding. A distributed video coding characteristic is combined with a visual perception characteristic, a perception quantification matrix is initialized before coding, and two steps of perception quantification strategies for quantifying the step length are dynamically adjusted in the coding process. The visual perception characteristic of the human eye is fully utilized, selective coding / decoding is realized according to different sensitivity of the human eye on image contents, errors which cannot be observed by the human eye in the original image and the side information are prevented from being coded and decoded, and the distributed video coding rate is effectively reduced on thepremise that the subjective quality of the coded image is not affected. The method can be compatible with the conventional research results for improving the distributed video coding performance; andby the method, the coding performance of the distributed video is further improved, and a more efficient distributed video coding strategy is realized. The method is suitable for multiple distributed-video-coding-theory-based coding frameworks of single view point, third dimension, multiple view points and the like, and has good universality.
Owner:SOUTHWEST JIAOTONG UNIV
Method for fountain codes under binary erasure channel
ActiveCN103888225AReasonable designImprove confidentialityError prevention/detection by using return channelFountain codeData stream
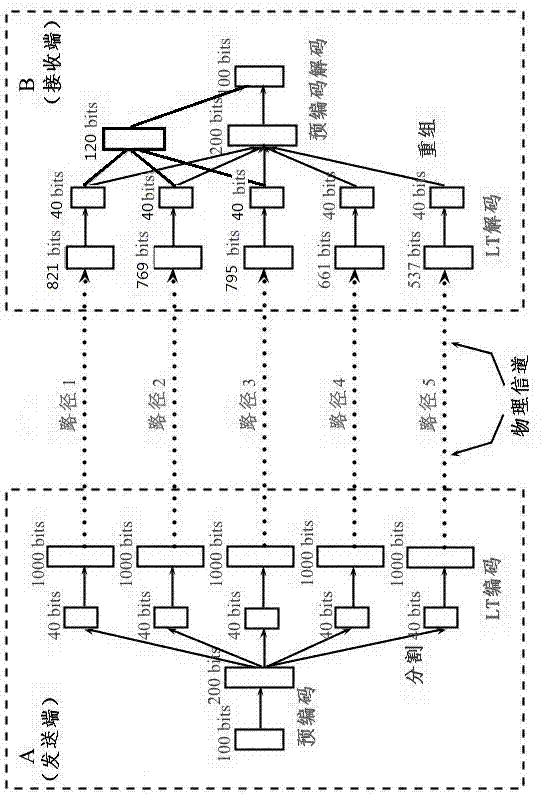
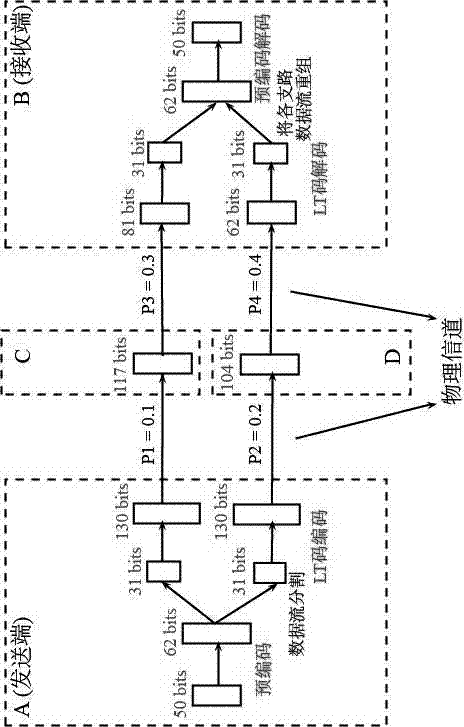
The invention provides a method for fountain codes under a binary erasure channel. According to the method, basic LT code precoding is carried out on an original data flow; segmentation processing is carried out on the coded data flow, and the coded data flow is divided into several branch information flows according to needs; basic LT code precoding is carried out on each branch information flow; the branch information flows are sent according to a routing scheme made in advance; the branch information flow the first to reach is decoded by means of a maximum likelihood method at the decoding end; the compiled branch information flows are regrouped according to an original segmentation scheme; the regrouped information flows are compiled through a maximum likelihood decoding method to obtain the original data flow, and original data are correctly and completely compiled. The method is reasonable in design, confidentiality, integrity and availability can be basically achieved during information transmission, and it is guaranteed that correct decoding can be achieved by a decoding side. The method lays a foundation for secure transmission of information and has a great significance in coding theory and network information security architecture construction.
Owner:HUAIHAI INST OF TECH
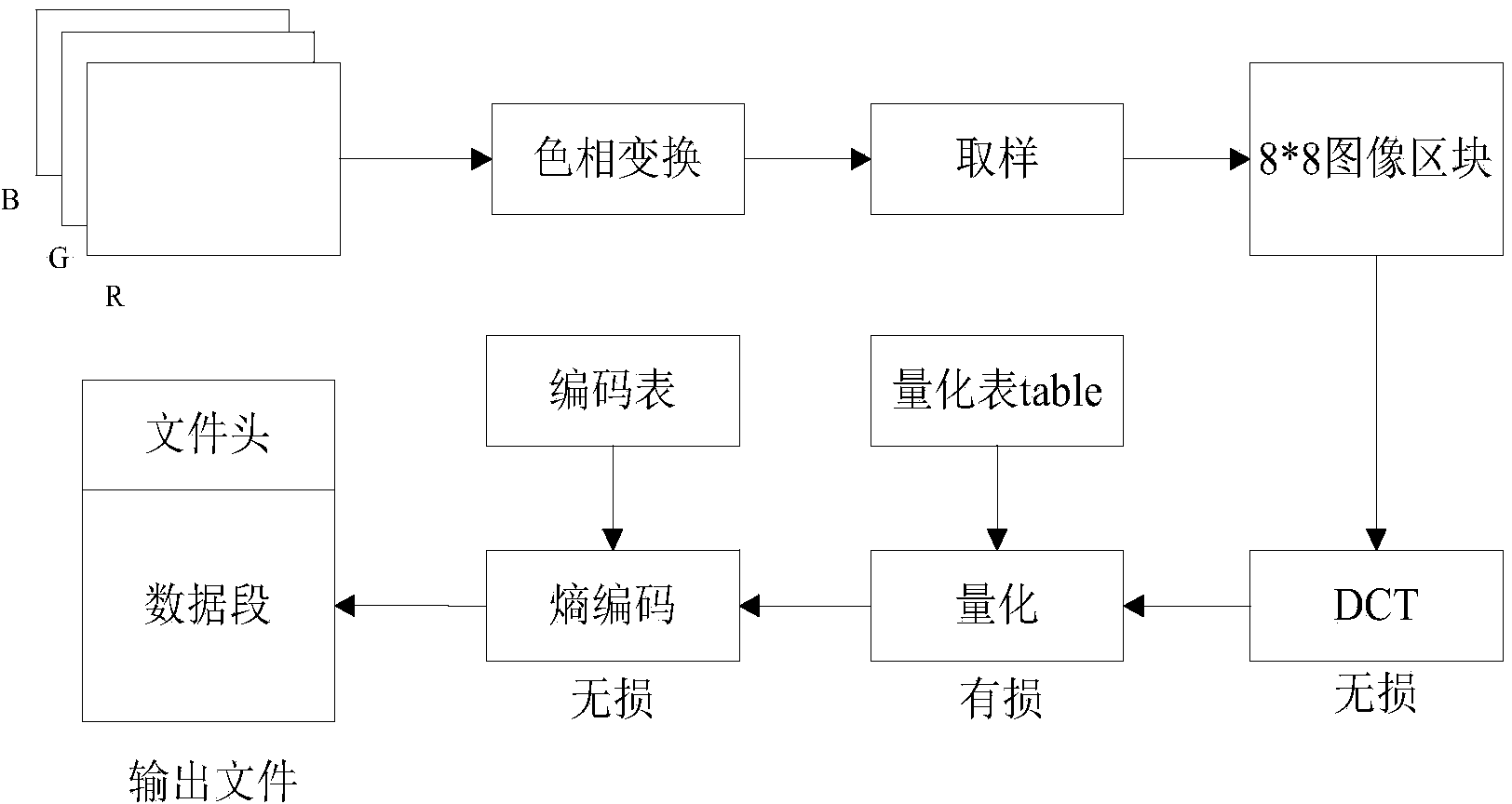
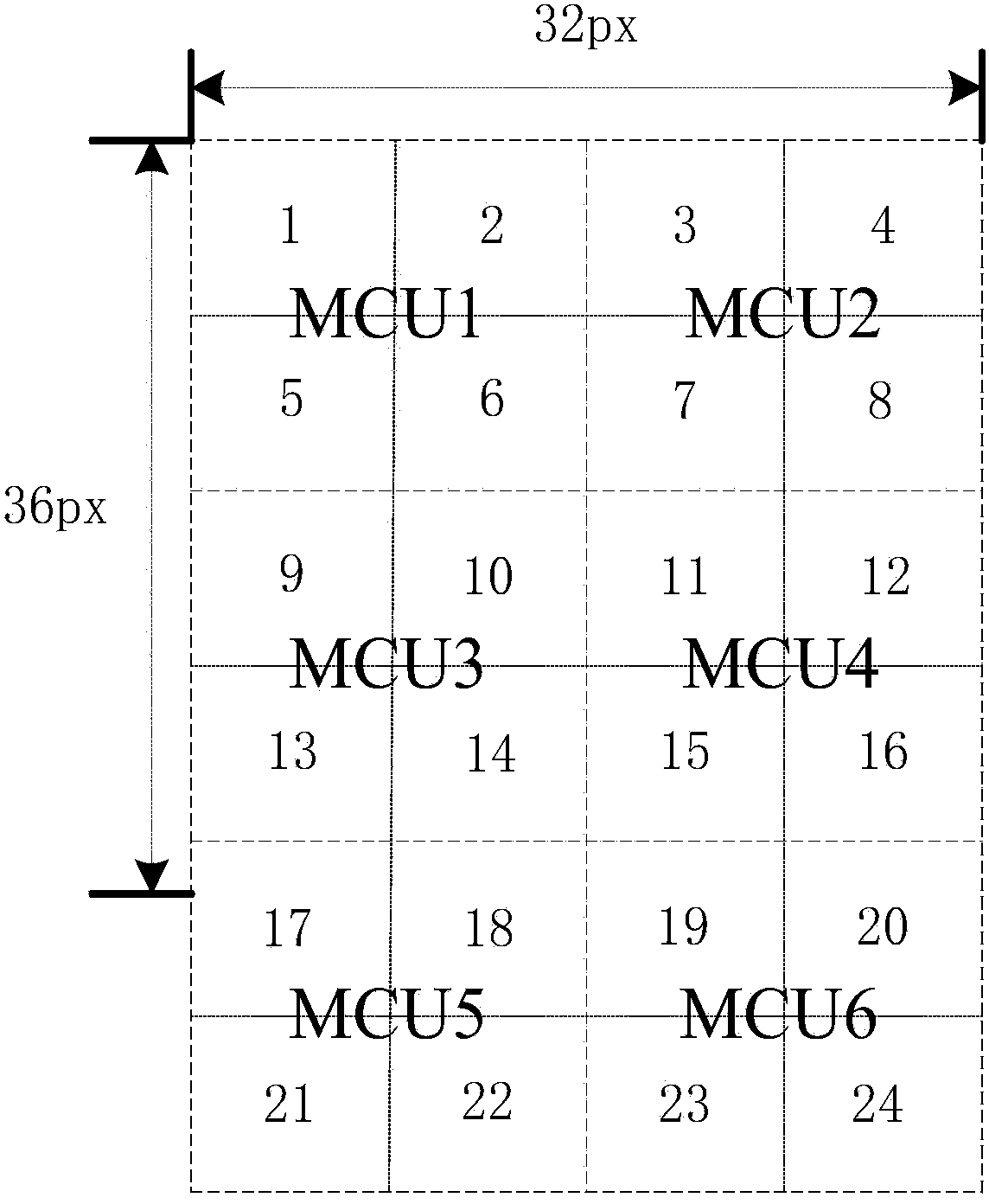
Picture segmentation method based on JPEG document flow
ActiveCN103778631ASolve the problem of consuming a lot of memorySolve efficiency problemsImage analysisImage memory managementSize differenceData stream
The invention discloses a picture segmentation method based on JPEG document flow. The method comprises the following steps: the step 1 in which the picture size, re-entry interval and sampling factor information can be acquired according to the JPEG coding theory and the data stream format thereof; the step 2 in which the picture segmentation number is calculated according to the JPEG picture size and read re-entry interval number; and the step 3 in which segmentation is performed on a JPEG picture according to the segmentation number, and segmentation reading is performed on the JPEG picture circularly. According to the method of the invention, the problem of size difference and especially problems of large memory usage, large time consumption and low efficiency with oversized pictures can be effectively solved, and advantages of less memory usage and stability can be realized.
Owner:西安博易智能科技有限公司
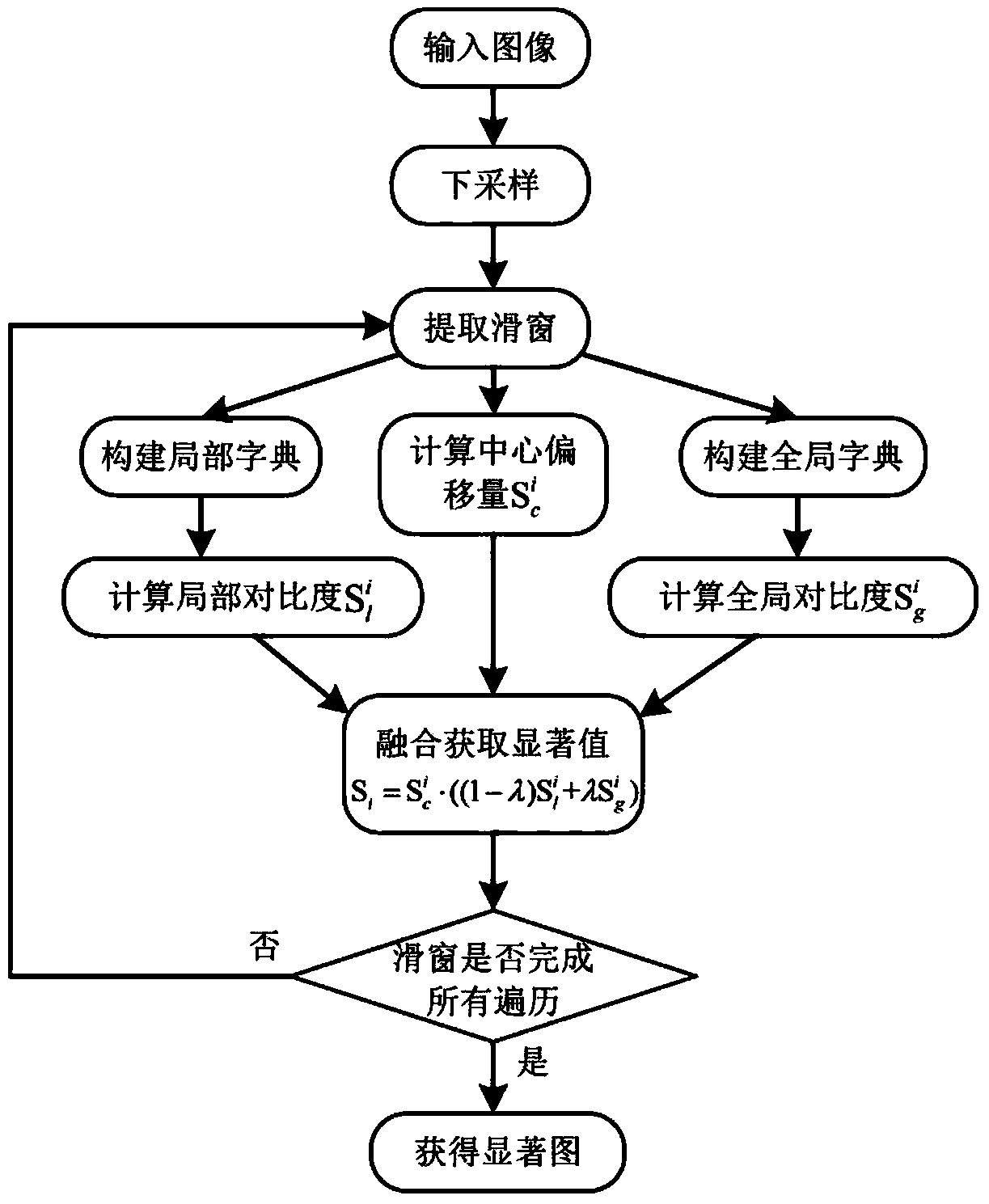
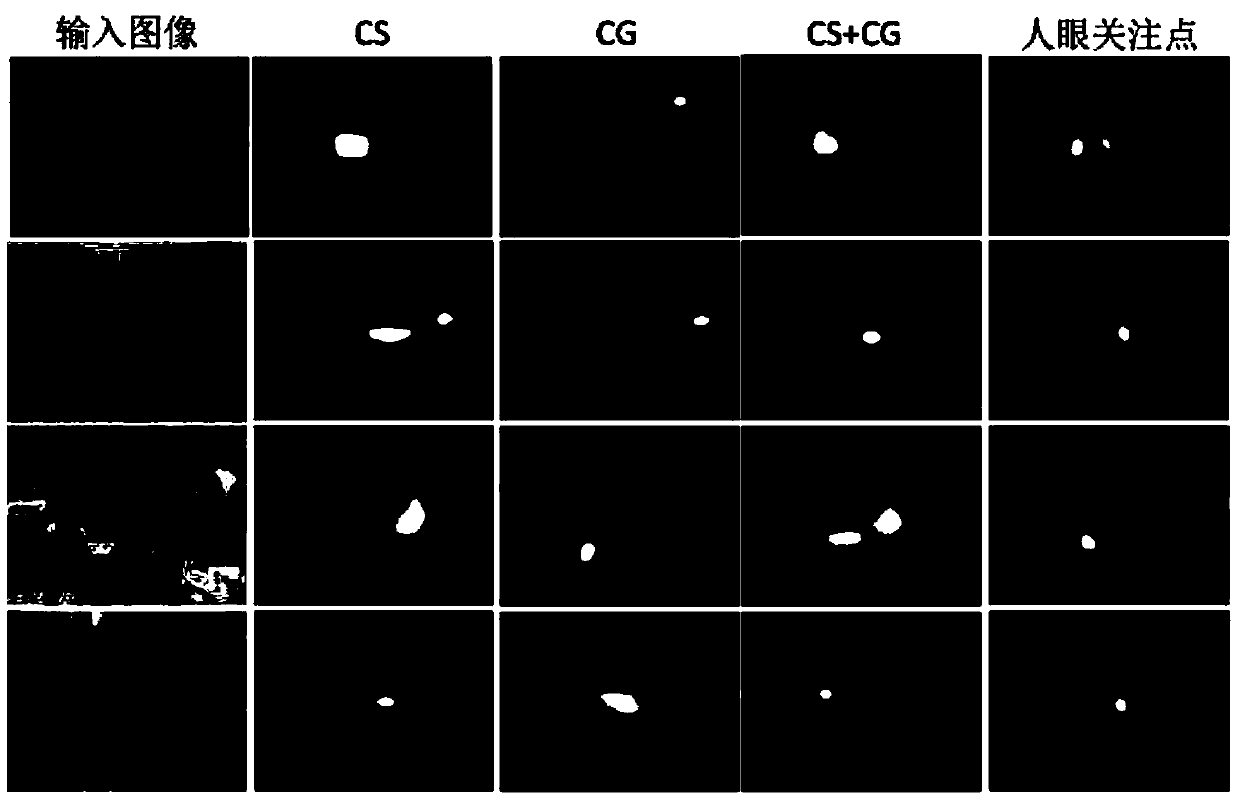
Bottom-up visual saliency generating method fusing local-global contrast ratio
InactiveCN103996040AAccurateRobustImage analysisCharacter and pattern recognitionPattern recognitionVisual saliency
The invention provides a bottom-up visual saliency generating method fusing the local-global contrast ratio. According to the method, firstly, the local contrast ratio between a certain image block in an image and the other image blocks in a neighbor domain and the global contrast ratio between the image block and the remaining image blocks in the image are calculated based on the sparse coding theory, then, the two kinds of comparative information are organically combined together, the center offset is added into the two kinds of comparative information, finally, fusion of the local contrast ratio and the global contrast ratio is achieved, and a visual saliency calculation model with better accuracy and visual is built.
Owner:NORTHWESTERN POLYTECHNICAL UNIV
Forward error correction-based method for reliably transmitting network coding multicast data stream
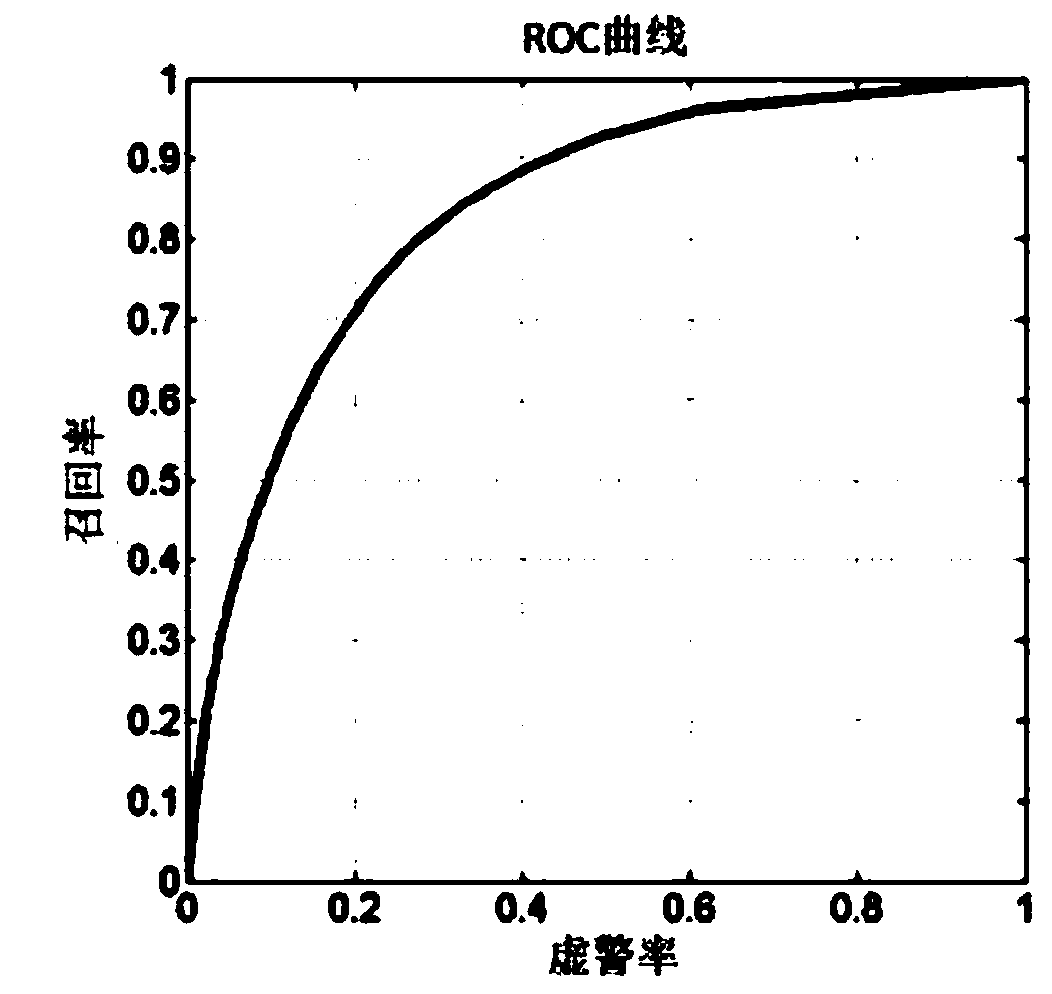
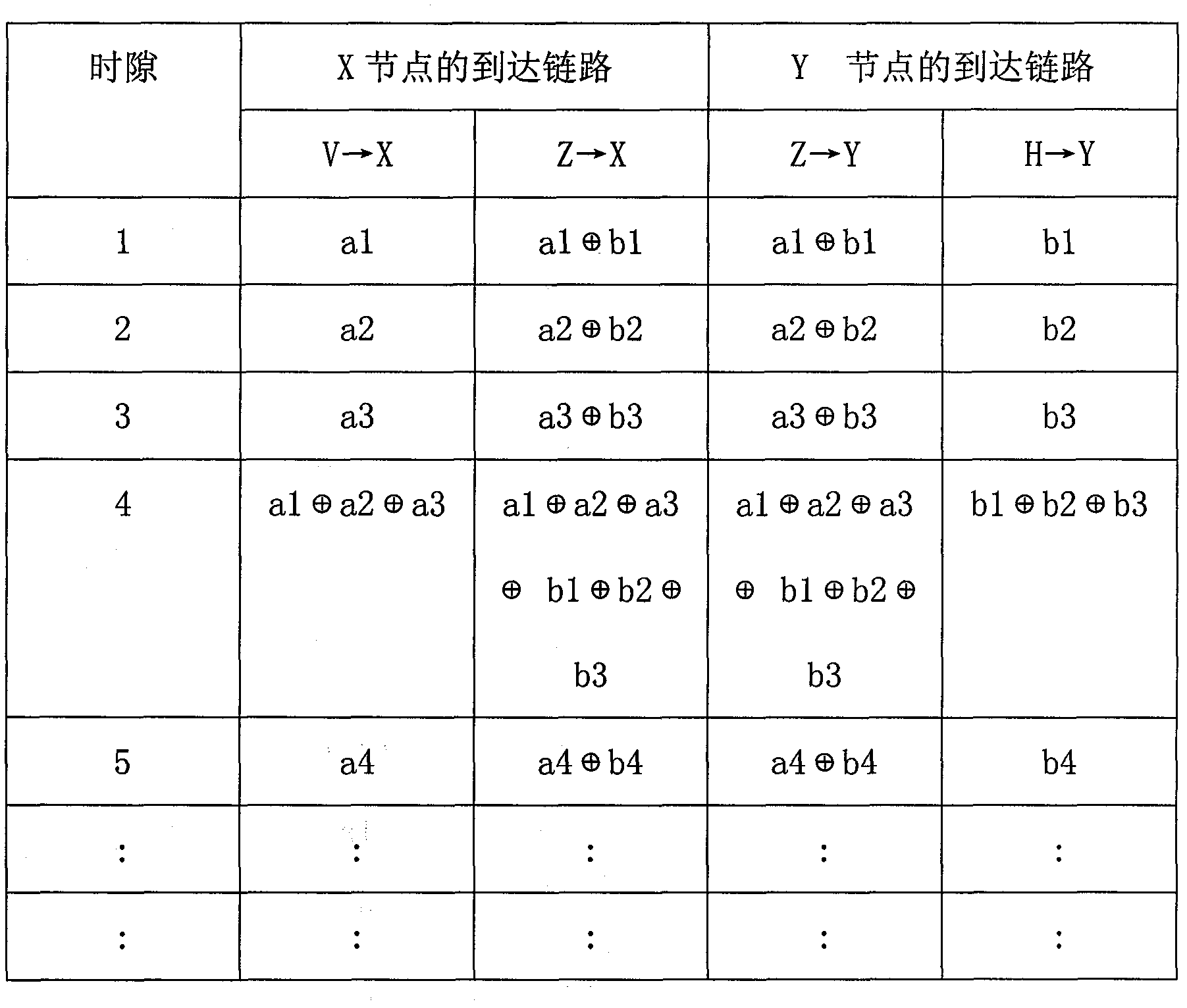
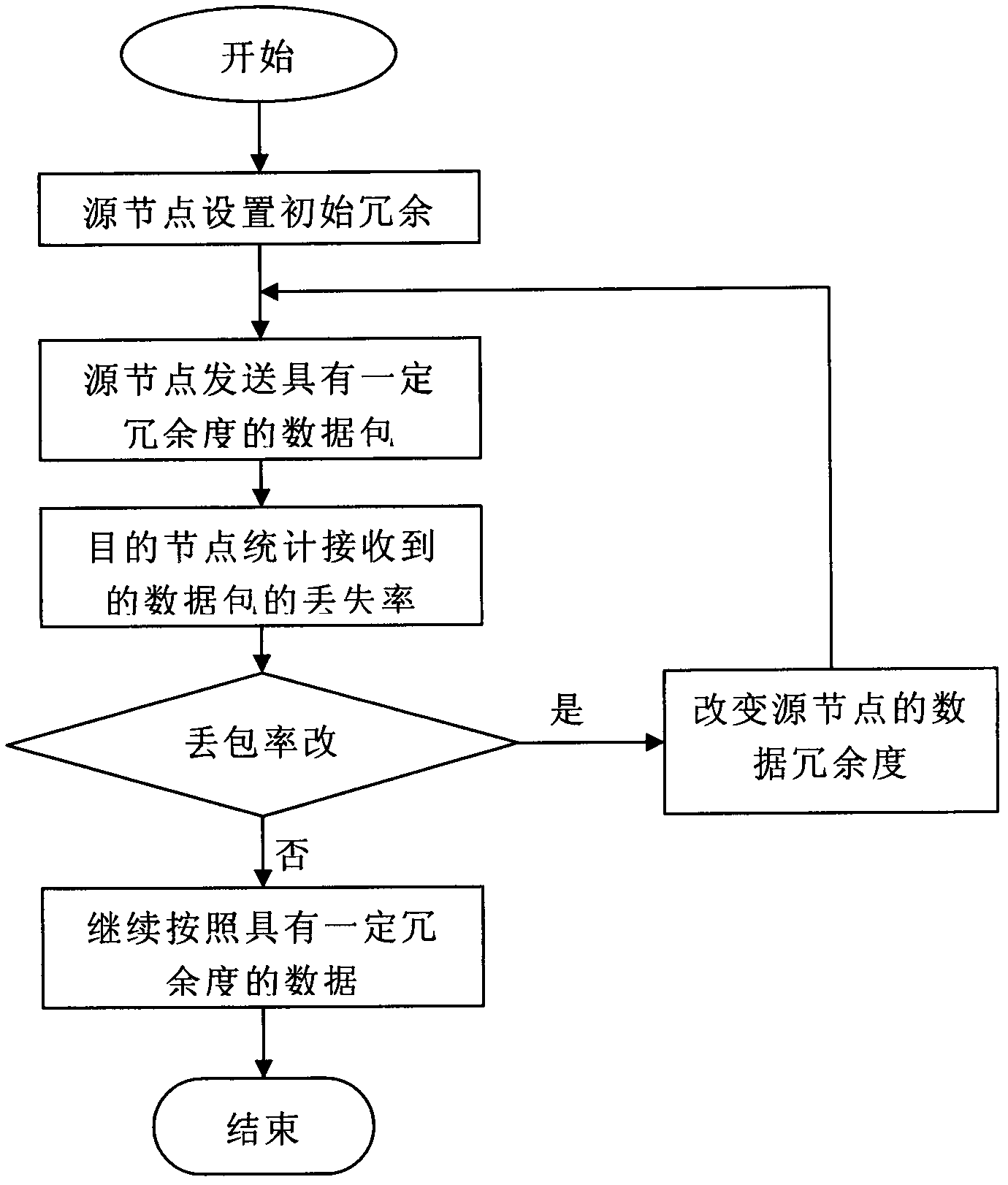
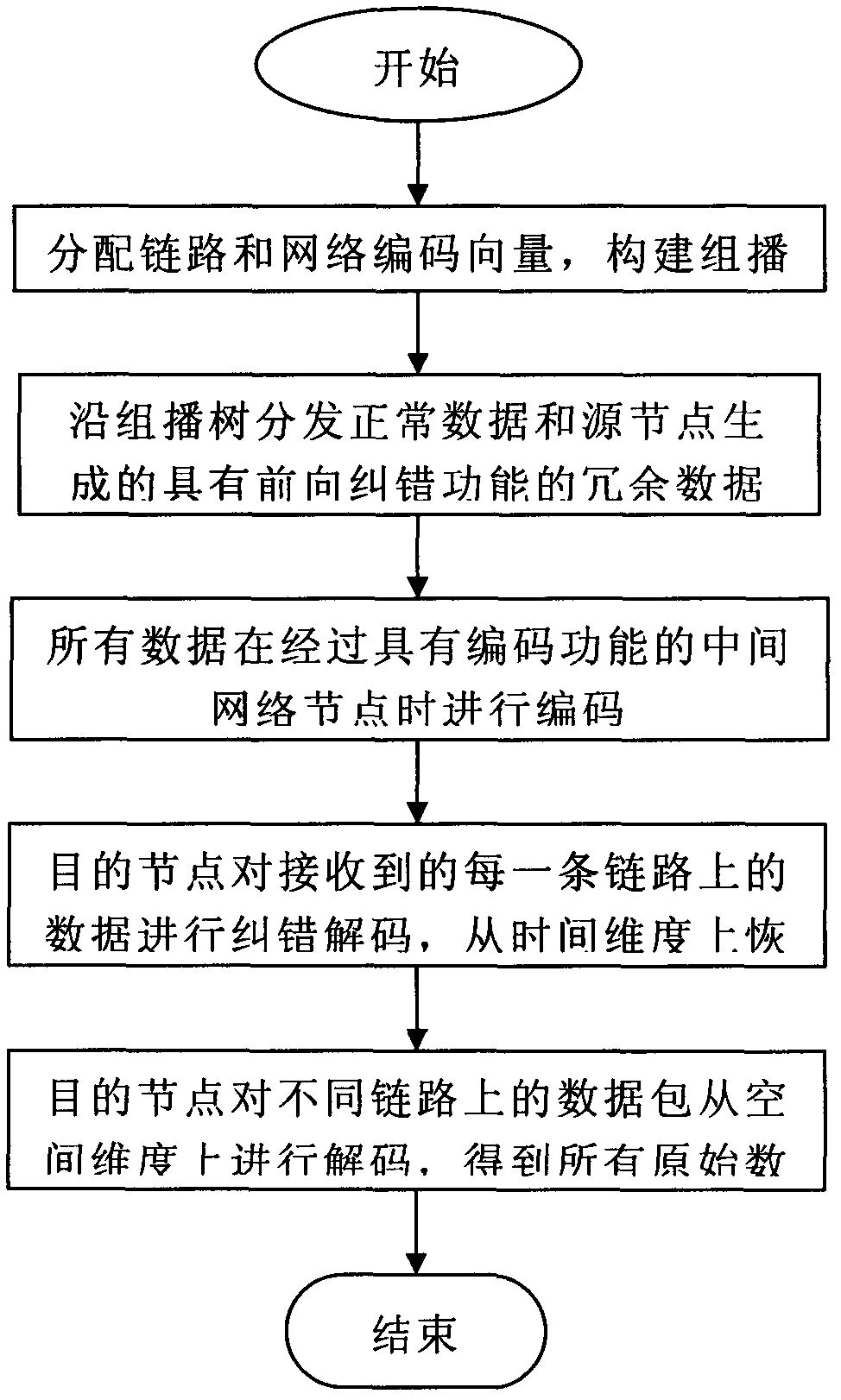
The invention is provided based on a classical network coding theory, and provides a novel forward error correction-based method for reliably transmitting a network coding multicast data stream by fusing the existing forward error correction technology and a network coding technology to solve the problem of data packet dropout. In the method, redundant data with the forward error correction function is added into each parallel data stream on a network coding multicast path, and is commanded to code according to a coding vector the same as original data when passing through a node with a network coding function; and a source node can regulate the redundancy of the data stream in real time according to the size of packet dropout which is fed back by a target node. According to the method, redundancy protection to transmission data on any link in a multicast tree can be realized, namely, in a certain packet dropout, all target nodes can be recovered from received data to establish the original data, even packet dropout happens on any one or more links in the multicast path simultaneously, so that the defect that a plurality of target nodes are influenced due to that single coding data is lost in the classical network coding multicast network can be overcome. Therefore, the capability of data loss tolerance of the multicast network based on the network coding can be improved.
Owner:BEIJING UNIV OF POSTS & TELECOMM
Network coding method oriented to peer-to-peer communication in tree topology structure
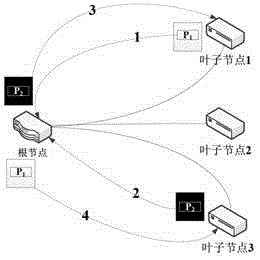
ActiveCN103188048AMaintain master-slave relationshipImprove exchange efficiencyError preventionTraffic capacityNetwork code
The invention discloses a network coding method oriented to peer-to-peer communication in a tree topology structure. According to the network coding method, a root node and leads and participates in the discovery of paired leaves of network coding as well as establishment and removal of paired connection, and each leaf node only participates in a cooperative manner; and each leaf node is used for marking and caching data frames which are possible to participate in network coding, the root node is used for correspondingly caching and coding the data frames which participate in the network coding as well as marking and issuing the data frames subjected to the network coding, and each leaf node is used for carrying out decoding and corresponding caching emptying on the received coded data frames. According to the network coding method, a detailed and particular implementation scheme is provided aiming at the network coding in the peer-to-peer communication in the tree topology structure, a network coding theory theoretically reaching a maximum flow is implemented in the tree topology structure network in a detailed and complete manner, and the master-slave relation on signaling transceiving and data processing between the root node and each leaf node in the tree structure network is kept, and therefore, the exchange efficiency of local peer-to-peer traffic in the tree structure network is improved.
Owner:BEIJING UNIV OF POSTS & TELECOMM
Use-case-based tacit knowledge visualization method
InactiveCN103020441APromote disseminationEasy to learnSpecial data processing applicationsTacit knowledgeDual-coding theory
Owner:STATE GRID CORP OF CHINA +1
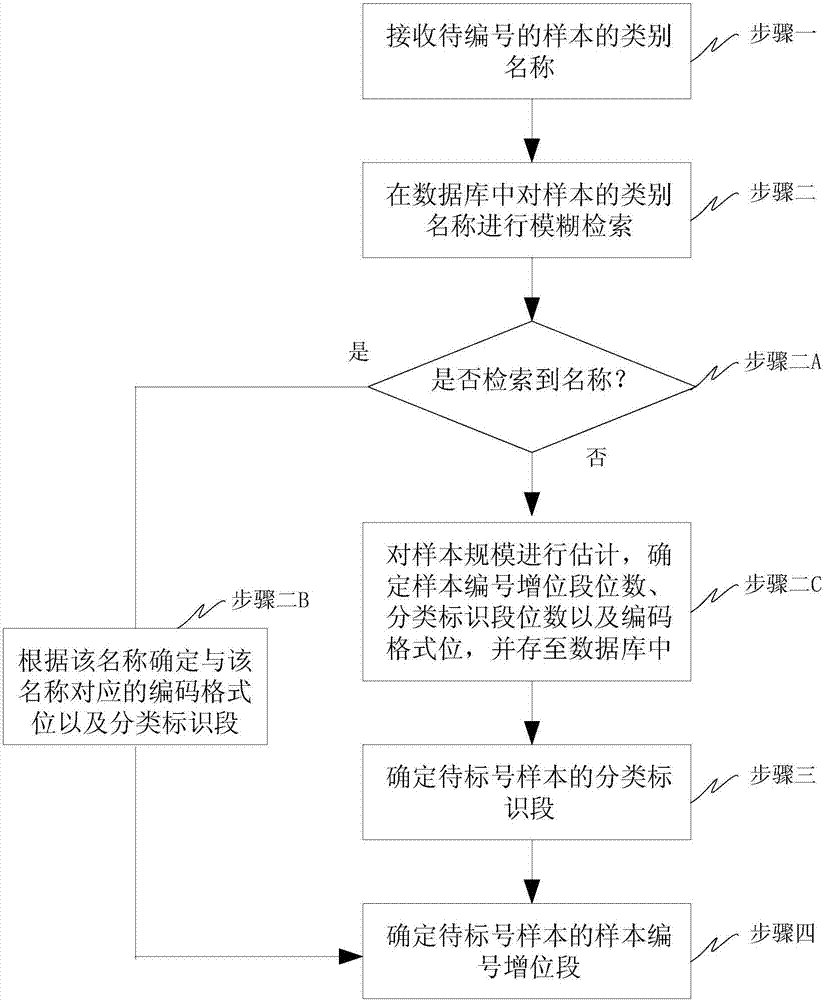
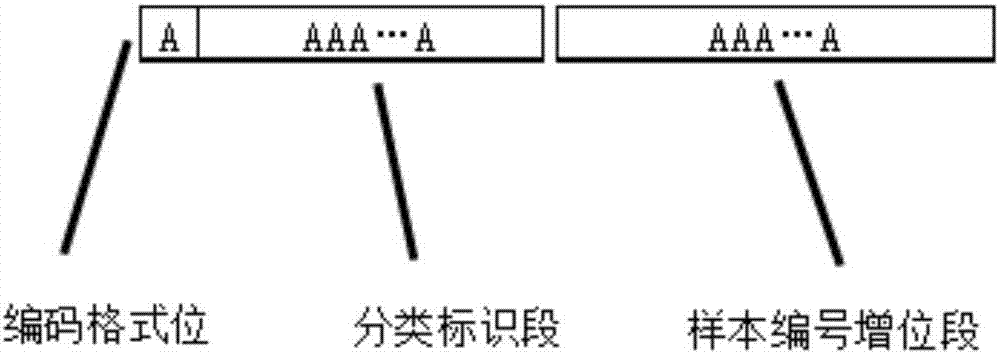
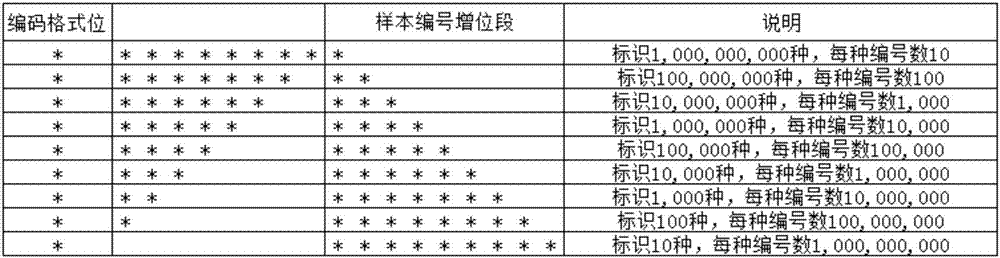
Classification information-containing ID numbering method
InactiveCN107515919AReduce the proportionReduce labor costsStructured data retrievalSpecial data processing applicationsCode spaceComputer science
The invention relates to a classification information-containing numbering method, in particular to a classification information-containing ID numbering method according to different sources and different sample quantities. The invention provides the classification information-containing ID numbering method for overcoming the shortcomings that meanings and digits of fields in existing codes are relatively fixed and difficult to flexibly set, and the same code quantities can be formed by the codes with the same lengths theoretically, but practical situations are not considered to fully utilize existing code spaces. The method comprises the steps of receiving type names of to-be-numbered samples; performing fuzzy retrieval on the types of the sample names in a database; determining classification identification sections of the to-be-numbered samples; and determining sample number digit addition sections of the to-be-numbered samples. The method is suitable for a sample source information-containing sample code system.
Owner:黑龙江然得基尔医学科技发展有限公司
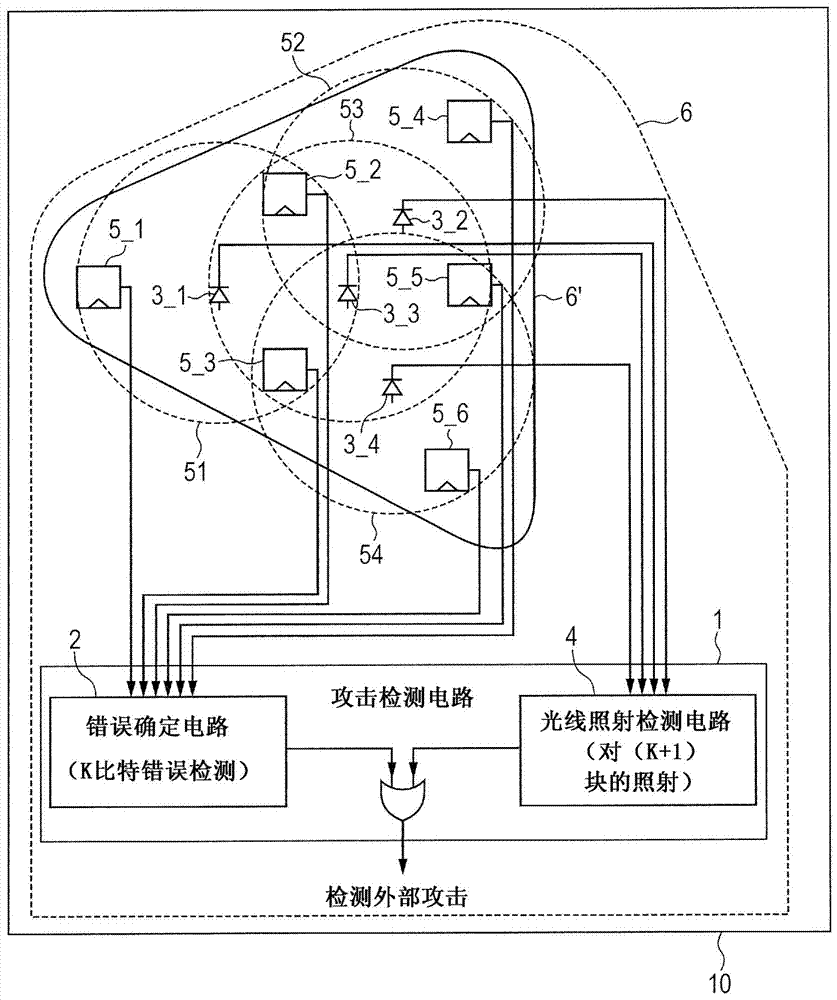
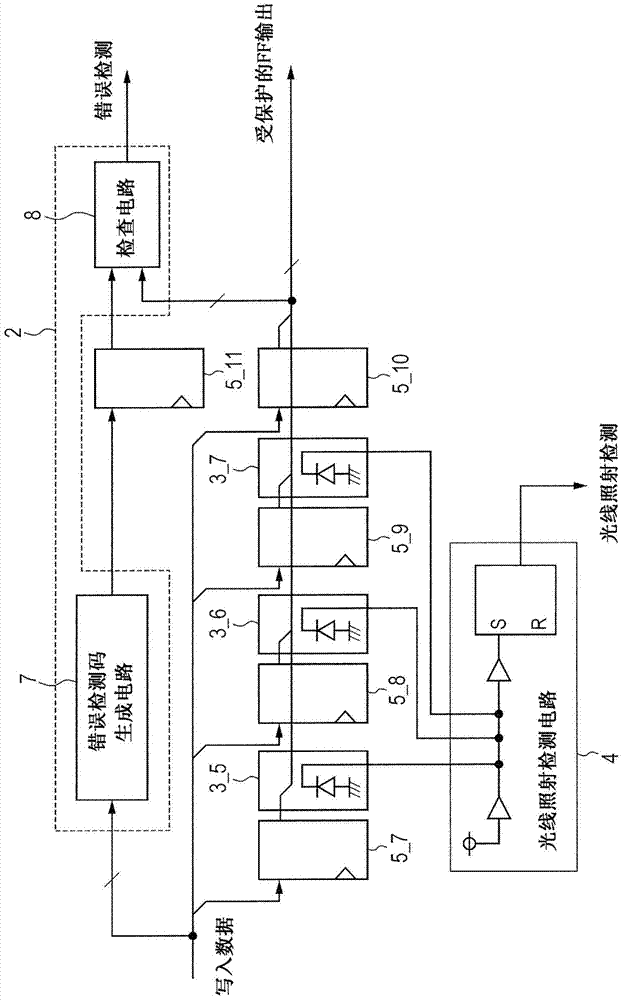
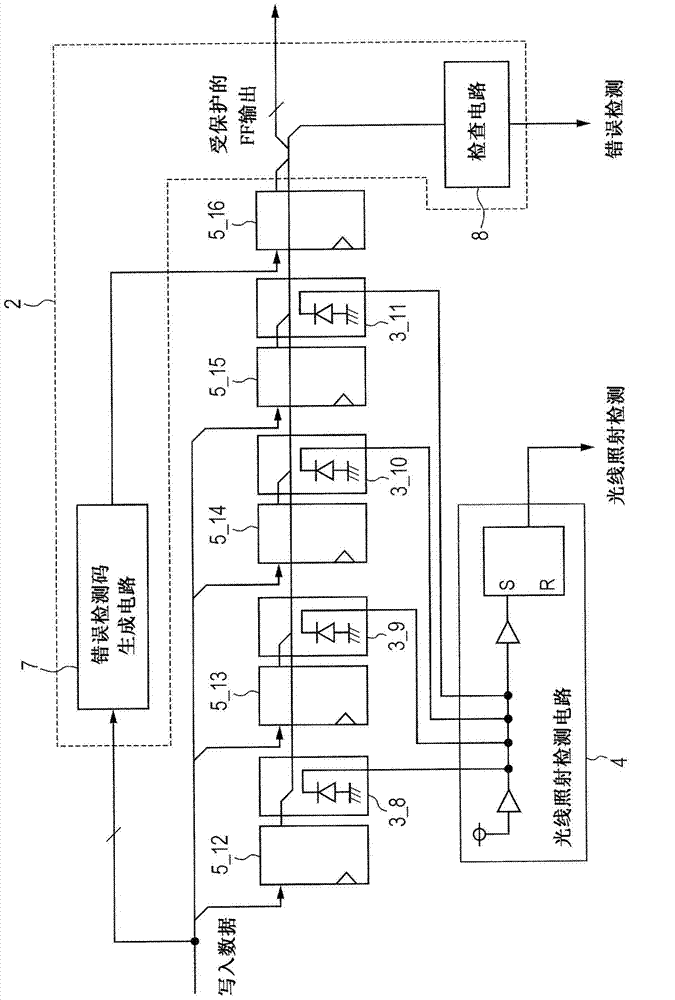
Semiconductor integrated circuit
InactiveCN103679011AReliability increasing modificationsDigital data protectionComputer hardwareLight irradiation
The invention relates to a semiconductor integrated circuit. Confidential information stored in an LSI can be protected against laser attacks for the purpose of obtaining or forging confidential information through breakdown of the LSI. Laser attacks are detected whatever the number of error bits caused by laser attacks in multi-bit storage elements. Provided is an attack detection circuit for detecting multi-bit storage elements contained in a logic circuit. The attack detection circuit includes an error determination circuit capable of detection through a logic operation such as a code theory and a light irradiation detection circuit having light detection elements, and the light detection elements are arranged so that the light irradiation detection circuit can detect errors of the number of bits beyond the detection limit of the error determination circuit. Due to error detection by the error determination circuit and light irradiation detection by the light irradiation detection circuit, the circuits complementarily detect fault attacks from outside.
Owner:RENESAS ELECTRONICS CORP
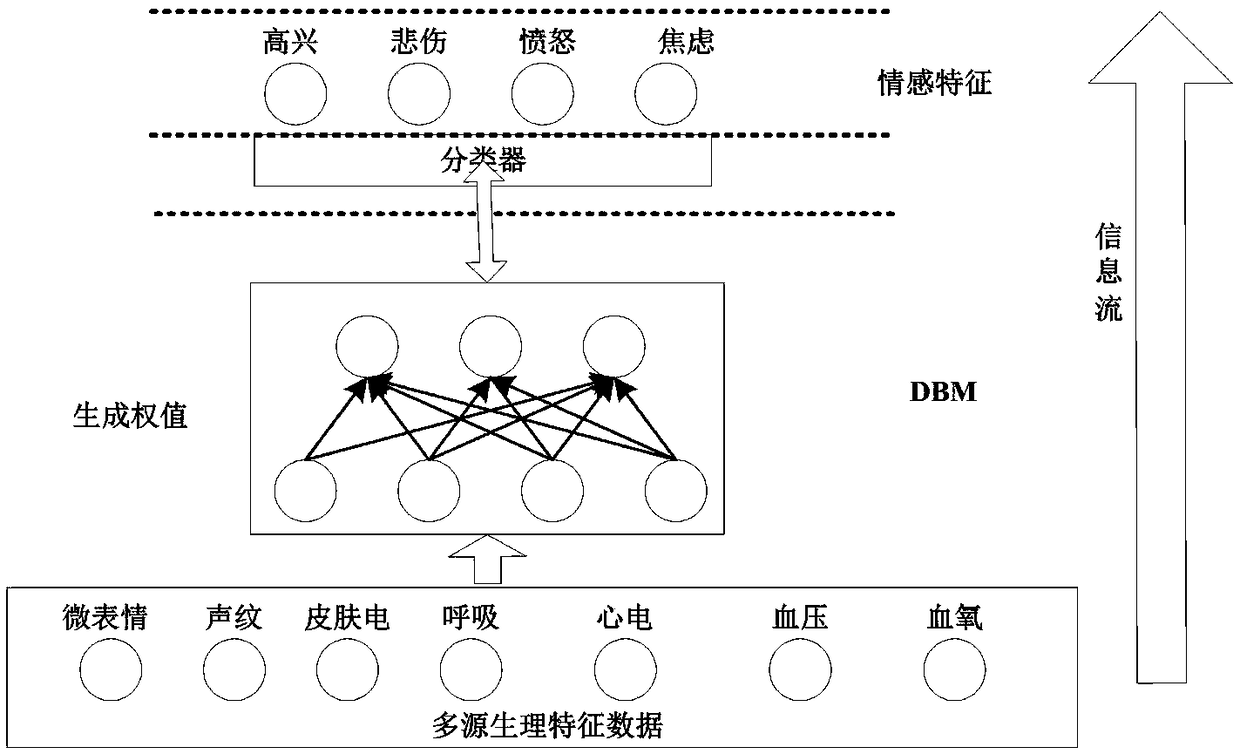
Depth neural network multi-source data fusion method using micro-expression multi-input information
InactiveCN109190550AImprove fault toleranceStable and reliable outputBiometric pattern recognitionNeural architecturesMulti inputAlgorithm
The invention discloses a depth neural network multi-source data fusion method using micro-expression multi-input information. A deep neural network learning architecture combining micro-expression and multi-input information is used to reconstruct the characteristic weights of a specific affective analysis model through unsupervised greedy layer-by-layer training method for multi-source data in front of affective computation, and then the values are transferred to the hidden layer to reconstruct the original input data. In order to obtain the true expression of emotional characteristics, thebidirectional data layer and the hidden layer are iterated many times. Through the top-level data eigenvector fusion, high-precision heterogeneous multi-dimensional data fusion target information is formed. The invention provides a sparse coding based on the SAE structure, which reduces the dimension of the high-dimensional physiological feature vector through the bottom-up sparse coding theory, so that fewer over-complete physiological feature data base vectors can accurately represent the original high-dimensional feature.
Owner:SHENYANG CONTAIN ELECTRONICS SCI & TECH CO LTD
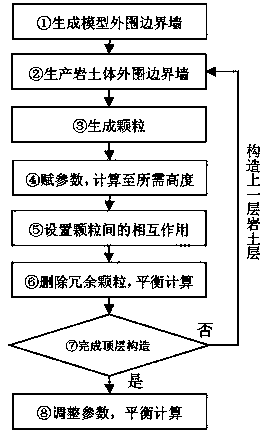
Method for simulating rock masses with surfaces of unconformity
InactiveCN103823946AClose to the actual damage characteristicsSpecial data processing applicationsParticle flowMATLAB
The invention discloses a method for simulating rock masses with surfaces of unconformity. According to the method, the influence of the surfaces of unconformity of rock stratums on simulation is taken into account, PFC3D based on the particle flow code theory is used as a simulation platform, and contact situations of the different rock stratums in the underground rock masses are simulated respectively, wherein the contact situations comprise conformity, parallel unconformity and angular unconformity. The method includes the following steps that a rock mass coordinate system is defined, key coordinate points of the trend of contact surfaces are determined, trend curves are fitted through MATLAB, curve parameters are acquired, the rock stratums are constructed through a drop method, and the contact surfaces are formed through FISH according to the parameters of the trend curves. By the adoption of the method, the underground rock masses can be accurately modeled, and the method is used for constructing the rock masses mingled with the contact surfaces of different forms.
Owner:陈善乐
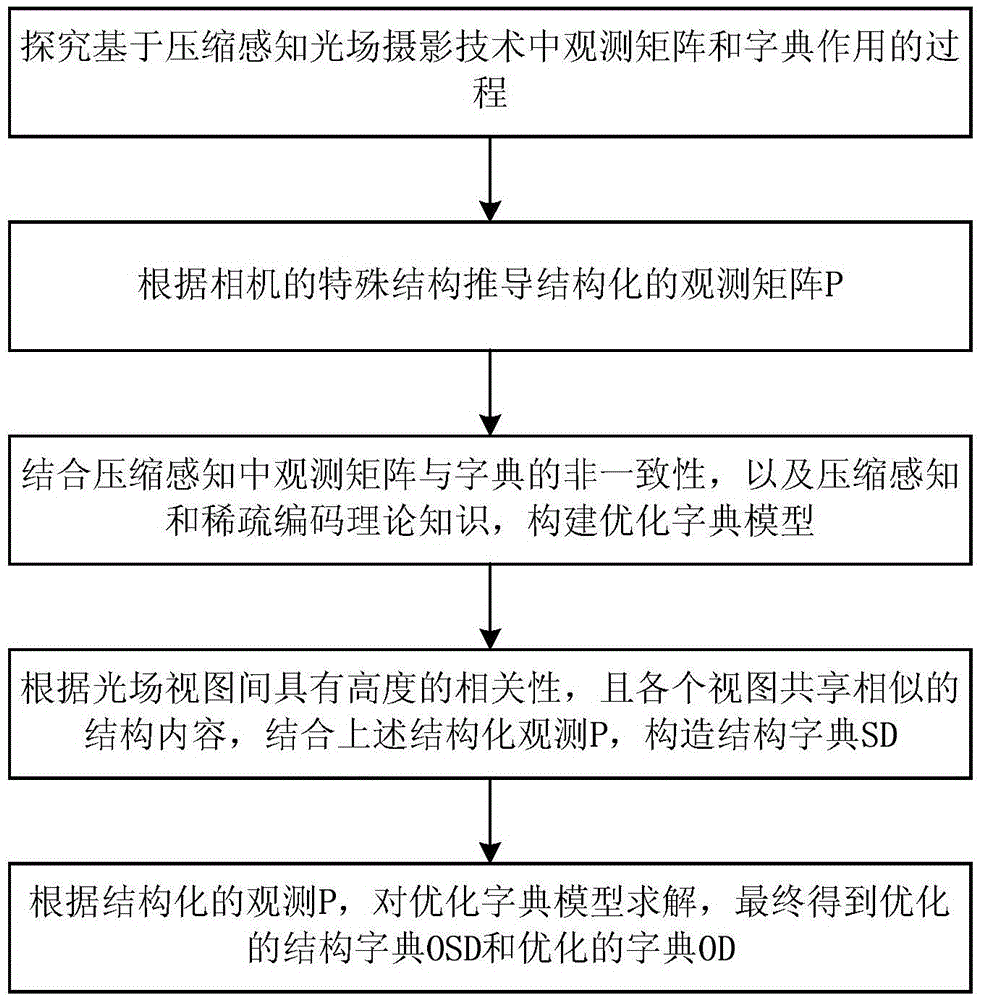
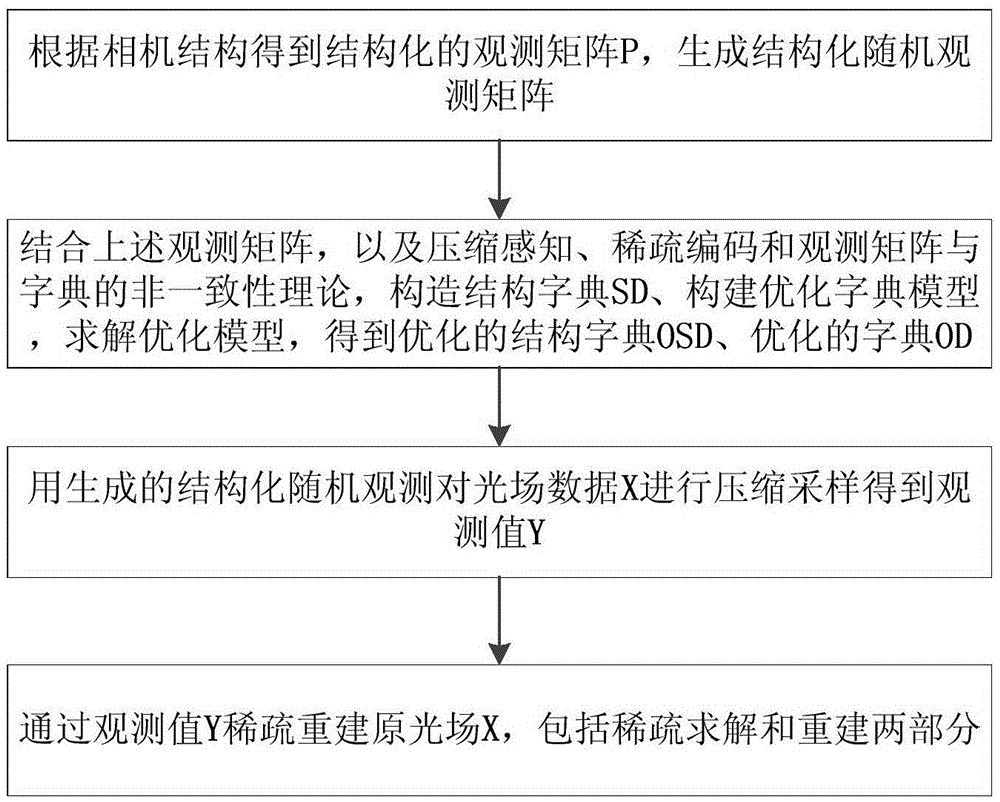
Dictionary optimization method
ActiveCN105654119AEasy to trainSave storage spaceCharacter and pattern recognitionObservation matrixLight field
The invention discloses a dictionary optimization method. The structural features of light field data can be better carried, storage space for a dictionary can be reduced and reconstruction quality of a light field image can be obviously enhanced. The method comprises the steps that (1) the affecting process of an observation matrix and the dictionary based on a compressed sensing light field photography is researched; (2) a structured observation matrix P is derived according to the structure of a camera; (3) an optimized dictionary model is constructed through combination of inconsistency of the observation matrix and the dictionary in compressed sensing and compressed sensing and the sparse coding theory knowledge; (4) a structural dictionary SD is constructed according to high correlation between light field views and the similar structural content shared by all the views with combination of the structured observation P; and (5) the optimized dictionary model is solved according to the structured observation P, and finally an optimized structural dictionary OSD and an optimized dictionary OD are obtained.
Owner:BEIJING UNIV OF TECH
Image encryption algorithm based on quantum chaotic mapping and DNA encoding
The invention provides an image encryption algorithm based on quantum chaotic mapping and DNA encoding, in combination with a quantum chaotic system and a DNA coding theory, in order to ensure the safety of image information. Firstly, generating a random sequence by using a quantum Logistic chaotic to cyclically shift and scramble images; then performing dynamic DNA encoding on the images by usinga quantum chaos mapping; then performing DNA addition by using Lorenz chaotic, or diffusing the images; and finally, performing DNA decoding on the image by using quantum chaos to obtain a cipher-image. The image encryption algorithm is obtained by the combination of the above portions, which can encrypt the images by the giving different chaotic primary values.
Owner:NORTHEAST FORESTRY UNIVERSITY
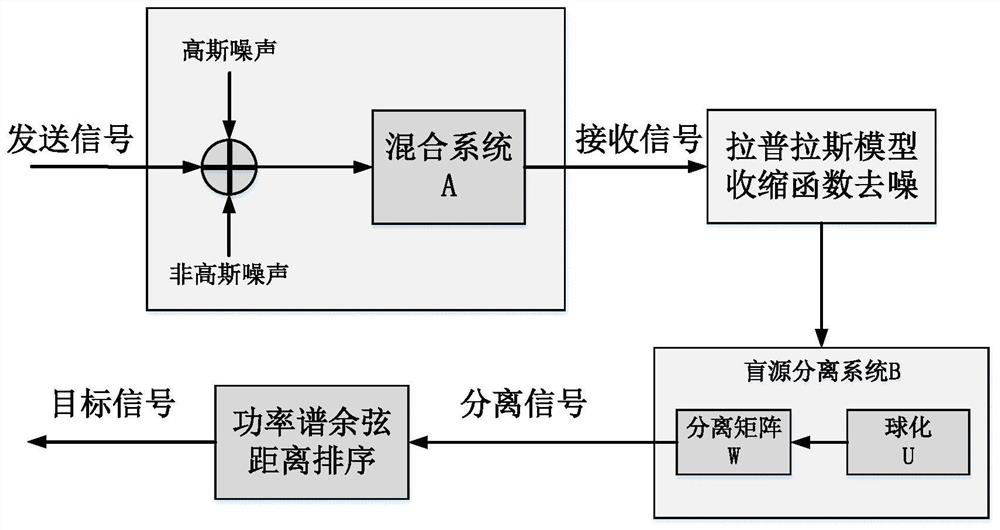
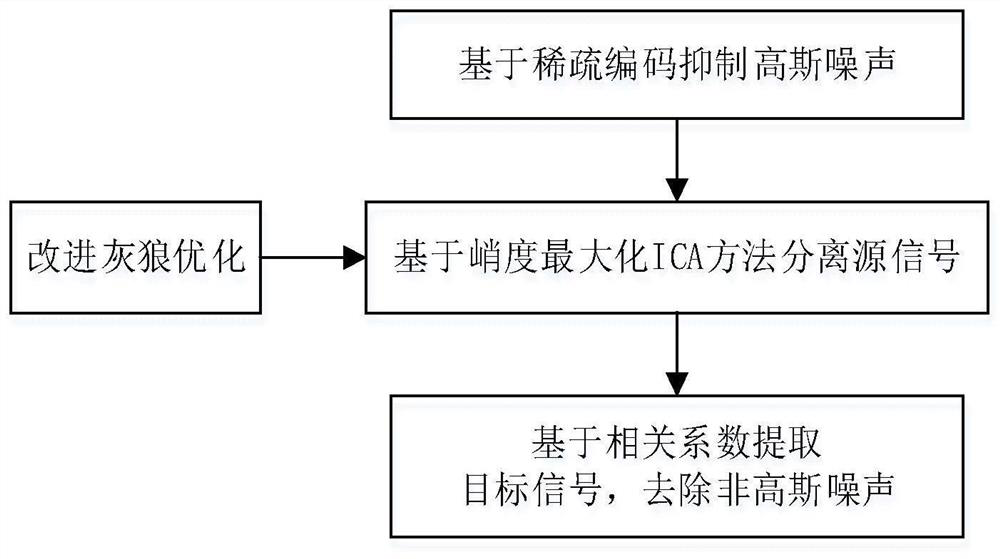
Underwater acoustic signal Gaussian/non-Gaussian noise suppression method based on blind source separation
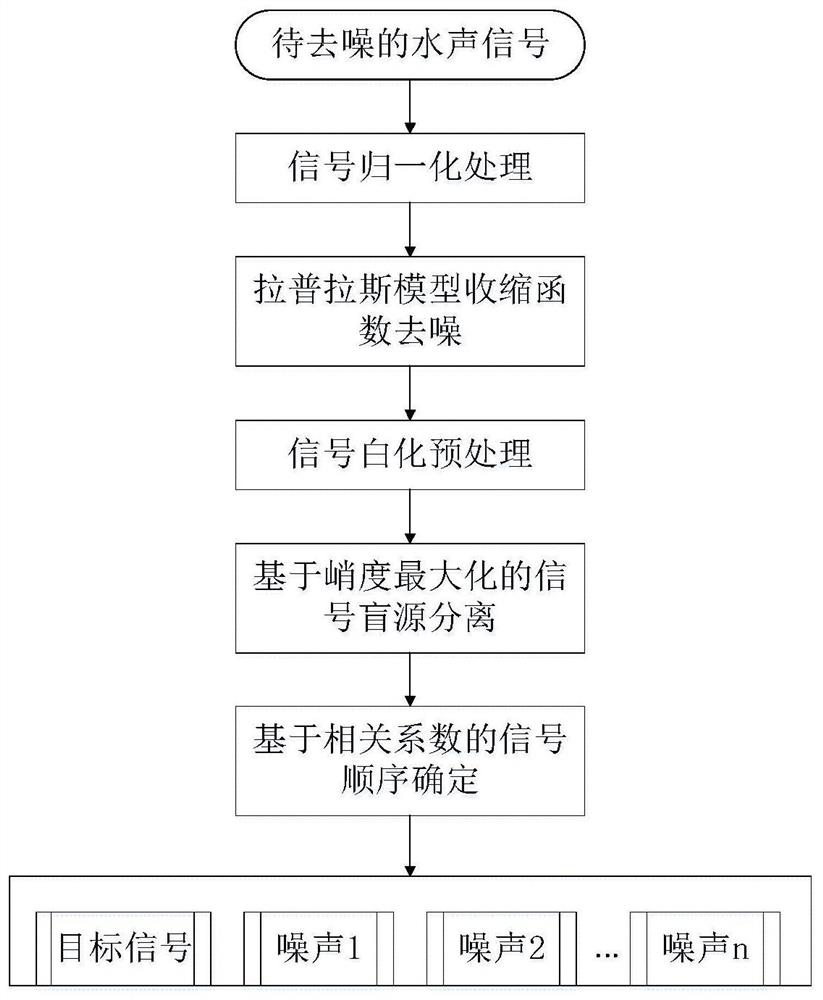
ActiveCN112133321AImprove received signal qualityEfficient removalSpeech analysisArtificial lifeTarget signalNoise
The invention discloses an underwater acoustic signal Gaussian / non-Gaussian noise suppression method based on blind source separation. The method is used for underwater acoustic communication signal denoising. Firstly, Gaussian noise is removed in advance by adopting a sparse coding theory based on underwater acoustic signal sparse characteristics, including constructing a sparse penalty functionbased on a Laplace distribution model and solving a sparse component under the condition of maximum likelihood estimation; and then based on the non-Gaussian characteristic of the underwater acousticsignal, the non-Gaussian random noise is regarded as a source signal, and based on an improved grey wolf optimization algorithm, solving the blind source separation problem of the underwater acousticsignal; and finally, a target signal is extracted based on the correlation coefficient matrix between the separated signal and the received signal, and non-Gaussian noise is removed. According to themethod, Gaussian and non-Gaussian noise in a complex underwater acoustic environment can be effectively suppressed, and the underwater acoustic signal receiving quality is improved.
Owner:QINGDAO UNIV OF SCI & TECH
Quantum image encryption algorithm based on chaotic system and DNA dynamic coding
In order to guarantee the security of quantum information, the invention provides a quantum image encryption algorithm based on chaotic mapping and DNA coding in combination with a chaotic system anda DNA coding theory. According to the algorithm, first, quantum coding is performed on an image; second, a sequence generated in Logistic chaos is utilized to scramble the quantum image; third, Lorenzchaos is utilized to perform dynamic DNA coding and DNA additive operation to diffuse the quantum image; and finally the quantum image is measured to obtain a ciphertext image. Through combination ofthe parts, the quantum encryption algorithm is obtained, and through the algorithm, the quantum image can be encrypted by giving different chaotic initial values.
Owner:NORTHEAST FORESTRY UNIVERSITY
Secure multi-user pilot authentication method based on hierarchical two-dimensional feature coding
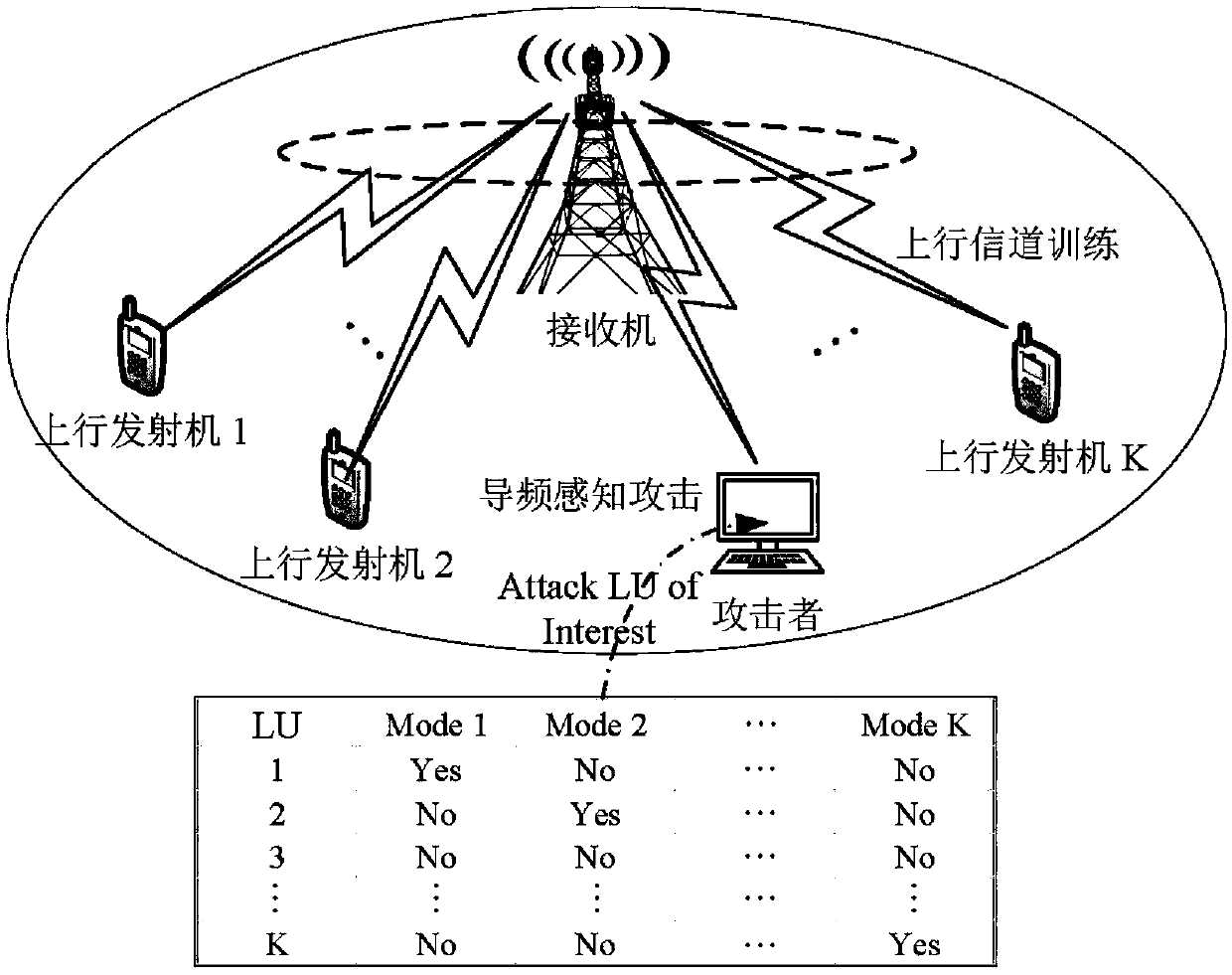
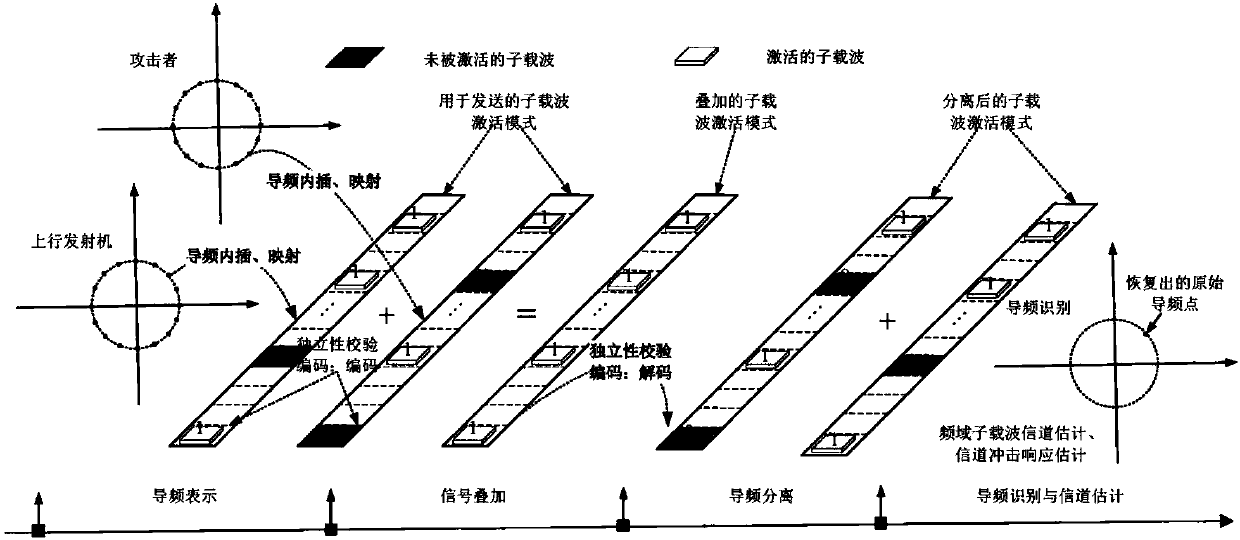
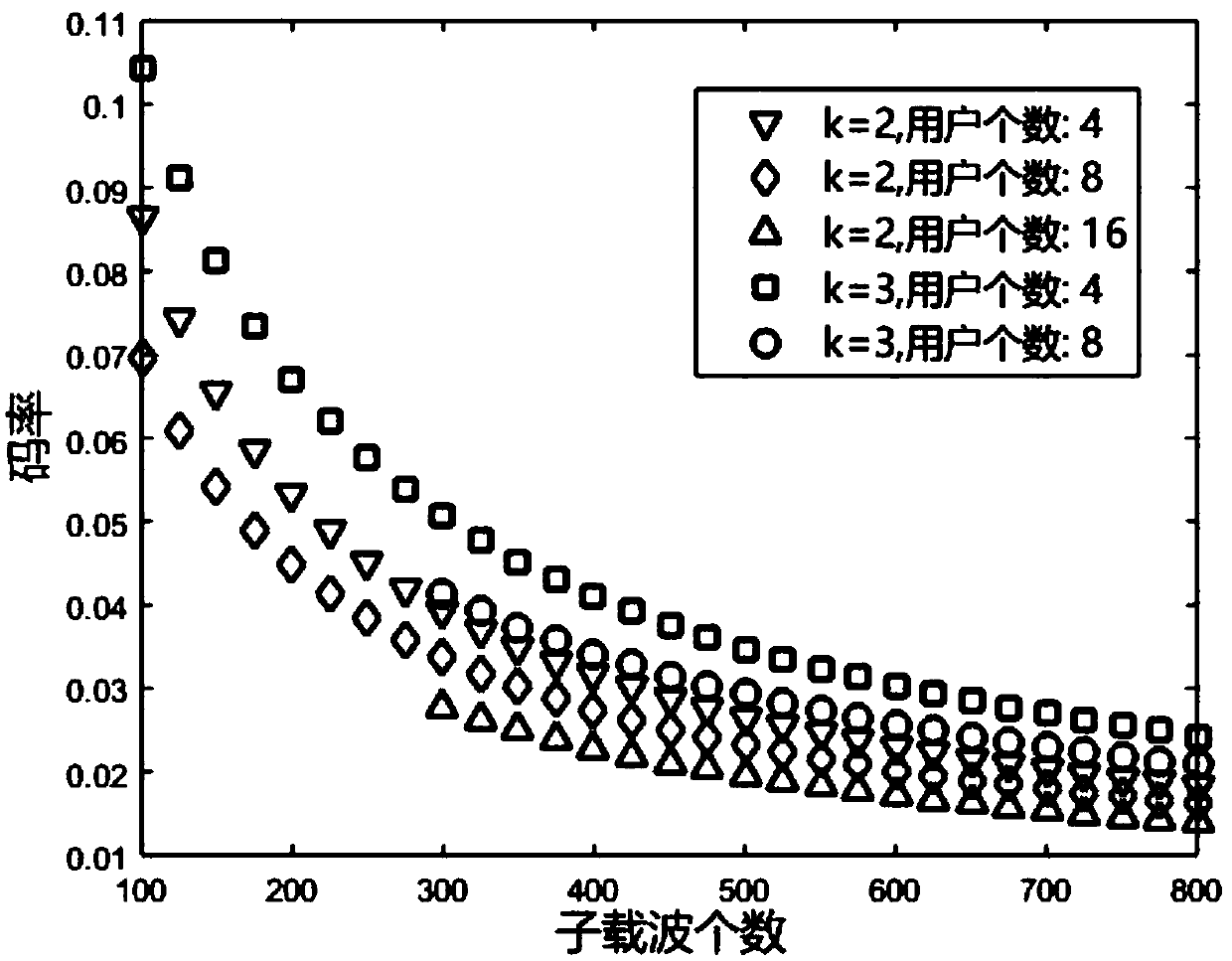
A secure multi-user pilot authentication method based on hierarchical two-dimensional feature coding is provided. Original pilot signals specified by each legitimate user (LU) are now randomized and coded into subcarrier activation modes (SAPs). Although these coded SAPs are covered by malicious signals and overlap and interfere with each other in a wireless environment, the coded SAPs can still be separated, identified and reliably decoded into codewords and ultimately converted into corresponding pilot signals, thereby ensuring SMPA. A five-layer hierarchical decoding (HD) model for SMPA isconstructed to demonstrate the principles of feature coding and decoding. A reliability constrained contraction (RBC) theory is proposed to narrow the constraint interval, which is completed by a codebook partitioning technology for H2DF. By optimizing the number of sub-codebooks, the upper and lower IEP boundaries shrink and coincide. Supported by the H2DF coding theory, the method can show goodstability in terms of SMPA.
Owner:XI AN JIAOTONG UNIV
Network coding connection management method based on peer-to-peer communication flow triggering
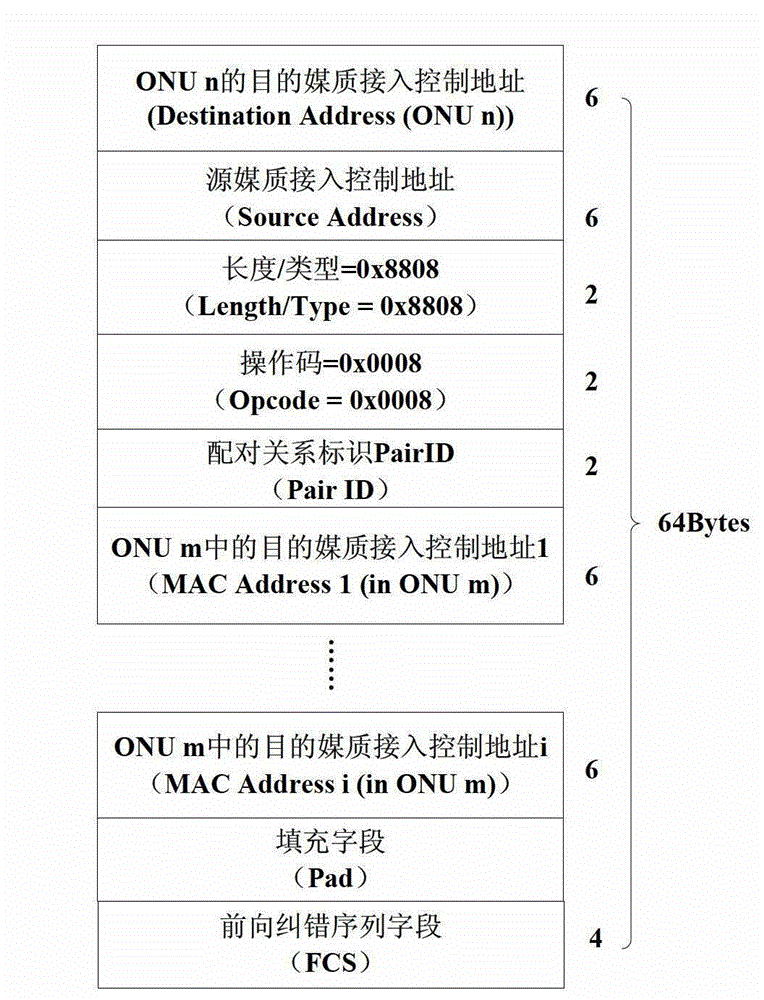
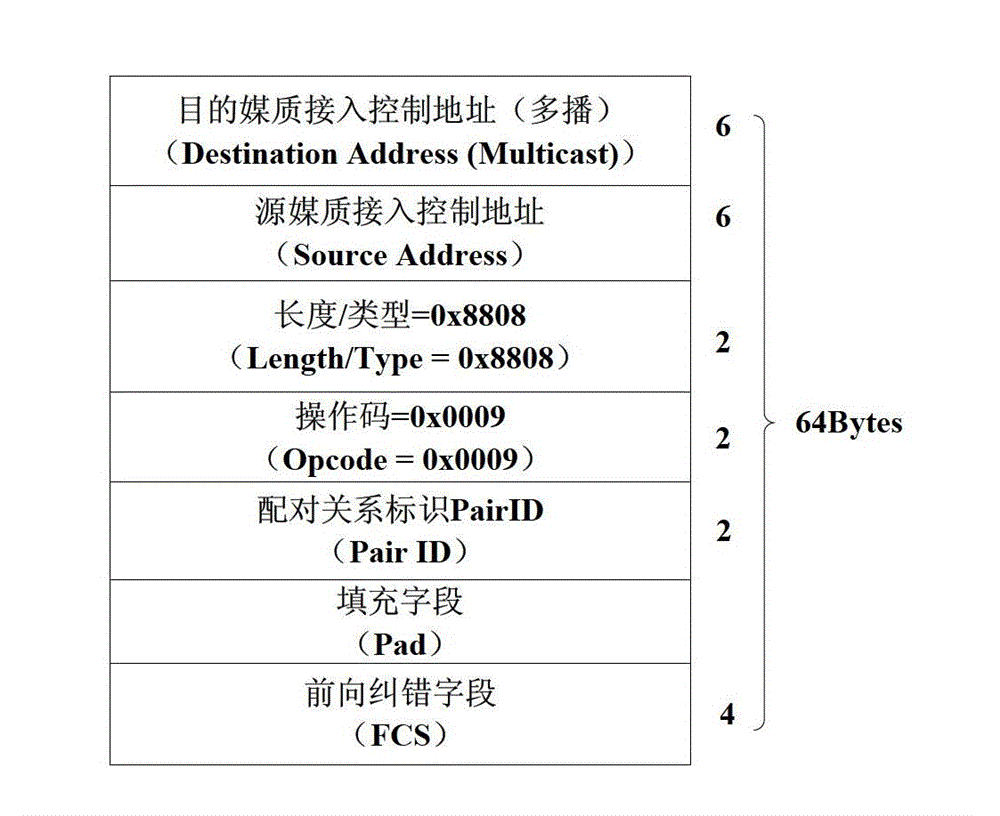
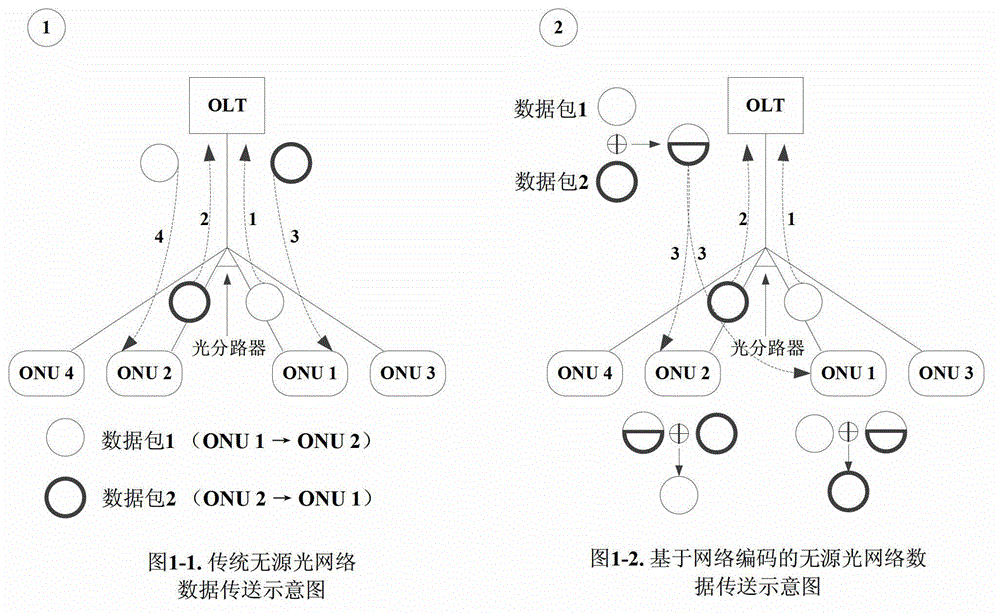
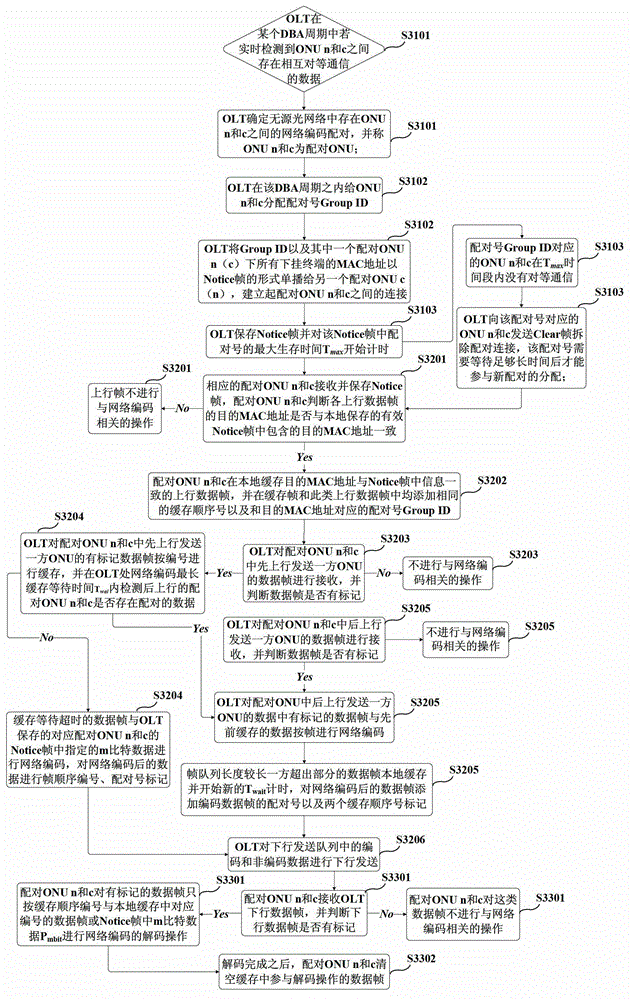
The invention discloses a network coding connection management method based on peer-to-peer communication flow triggering. The network coding connection management method based on the peer-to-peer communication flow triggering includes the steps: finding optical network units (ONU) where peer-to-peer communication flow exists by an optical line terminal (OLT) and carrying out building and removing of network code pairing connection on the ONU, wherein each ONU is only involved collaboratively; marking and caching data frames which are probably involved in network coding by the ONU, carrying out corresponding caching and coding on network code data frames by an optical line input (OLI), and carrying out marking and sending on the data frames which are through the network coding; and carrying out network decoding and corresponding cache clearing on the received data frames which are coded by the ONU. According to the network coding connection management method based on the peer-to-peer communication flow triggering, master-slave relation between the OLT and the ONU is kept, each ONU is not need to carry out learning of logical link identifiers (LLID) and media access control (MAC) addresses on downlink data frames locally and not need to maintain a paring table of LLID of the whole network ONU and the MAC addresses of an under-link host machine. The network coding connection management method based on the peer-to-peer communication flow triggering is further capable of enabling a network coding theory to be specifically and fully applied in tree-shaped topological passive optical networks and being compatible with the existing passive optical networks.
Owner:BEIJING UNIV OF POSTS & TELECOMM
Gray-code-based large-scale fiber grating sensing network demodulating system and method
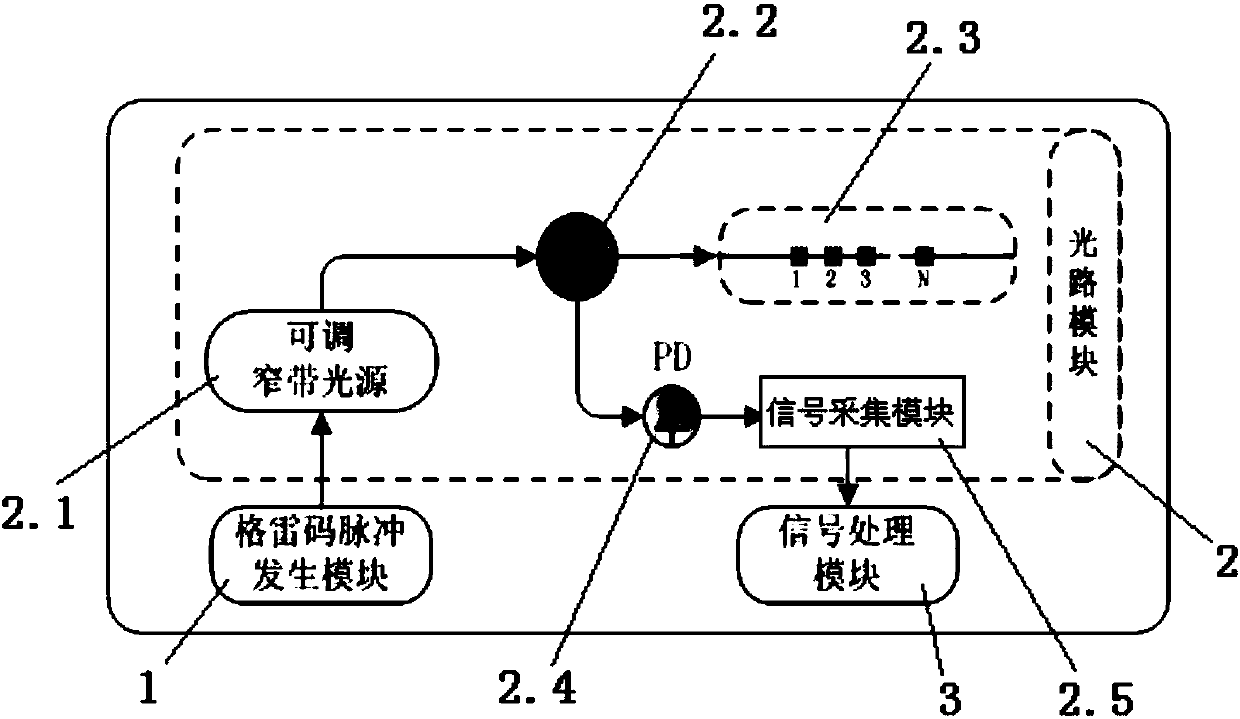
ActiveCN107782346AIncrease distanceImprove signal-to-noise ratioConverting sensor output opticallyFiberGrating
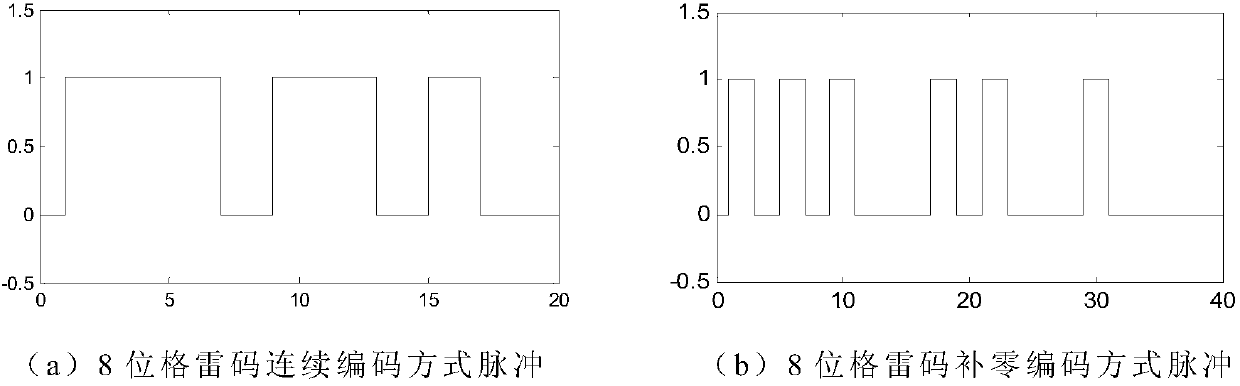
The invention discloses a Gray-code-based large-scale fiber grating sensing network demodulating system. A signal output end of a Gray code pulse generation module is connected with a control signal input end of an adjustable narrow band light source, a signal output end of the adjustable narrow band light source is connected with a first interface of an optical coupler, a second interface of theoptical coupler accesses a grating sensing network, a third interface of the optical coupler is connected with a signal input end of a signal collecting module through a photoelectric converter, and asignal output end of the signal collecting module is connected with a signal input end of a signal processing module. Accordingly, a Gray code coding theory is cited, fiber grating sensing network characteristics are combined, and pulse coding and decoding modes special for the fiber grating sensing network are provided.
Owner:WUHAN UNIV OF TECH
Method for constructing pseudo-random code based on interleaver
ActiveCN103929278AUnlimited quantityPerfectly balancedError preventionComputation complexityError correcting
The invention discloses a method for constructing a pseudo-random code based on an interleaver. According to the method, an interleaver technology and a pseudo-random code construction method in an error correcting code theory are effectively combined. According to the interleaver technology, a large pseudo-random code candidate set is constructed. The method overcomes the defects that an existing pseudo-random code construction method is poor in code length flexibility, limited in code set number, and high in computing complexity in the construction process.
Owner:NO 54 INST OF CHINA ELECTRONICS SCI & TECH GRP
Multiparameter three-dimensional digital encryption method
InactiveCN103401684AIncrease the difficulty of decryptionOvercoming complexitySecuring communicationOriginal dataXML Encryption
The invention relates to the field of computer scrambling coding theory and communication, and provides a multiparameter three-dimensional digital encryption method, which includes the following steps: based on original data in a computer storage and according to the arbitrary carry number and integer computational formula, a plurality of encryption keys of original data can be obtained through the FPGA, then the original data can be stored in a three-dimensional coordinate enciphered data represented by encryption keys, and besides an encryption key and original data storage sequence linear list is formed and communicated with enciphered data through a network, so that the data encryption is realized. The encryption method adopts a simple computational formula, has many encryption parameters and great difficulty in decryption, and overcomes the deficiencies that the former asymmetric encryption computational formula is complex, is limited to word length and causes high possibility of forming decimals as no decimal is formed in the calculating parameters.
Owner:DALIAN UNIV OF TECH
Network coding based wavelength conflict solution in WDM (Wavelength Division Multiplex) multicast network
InactiveCN101877804AMultiplex system selection arrangementsWavelength-division multiplex systemsFault toleranceNetwork on
The invention discloses a method for solving wavelength conflicts in a WDM (Wavelength Division Multiplex) network on the basis of a network coding technology and an implementation process thereof. The network coding technology derives from a classic network coding theory but is different from the traditional network coding theory and lays an extra emphasis on improving the network property and providing protection and fault tolerance functions for a network, and in the invention, the idea of the network coding technology is firstly utilized to provide a brand new solution and approach for the wavelength conflict problems among different services in the WDM multicast network. The core idea for solving the wavelength conflicts among different services in the WDM network by adopting the network coding technology is that different service signals with conflicts are converted into a new code signal after a network coding operation, and the code signal can be borne by any available wavelength and carries out code restoration on the original signals at a next-hop node or a target node so as to complete the operation.
Owner:BEIJING UNIV OF POSTS & TELECOMM
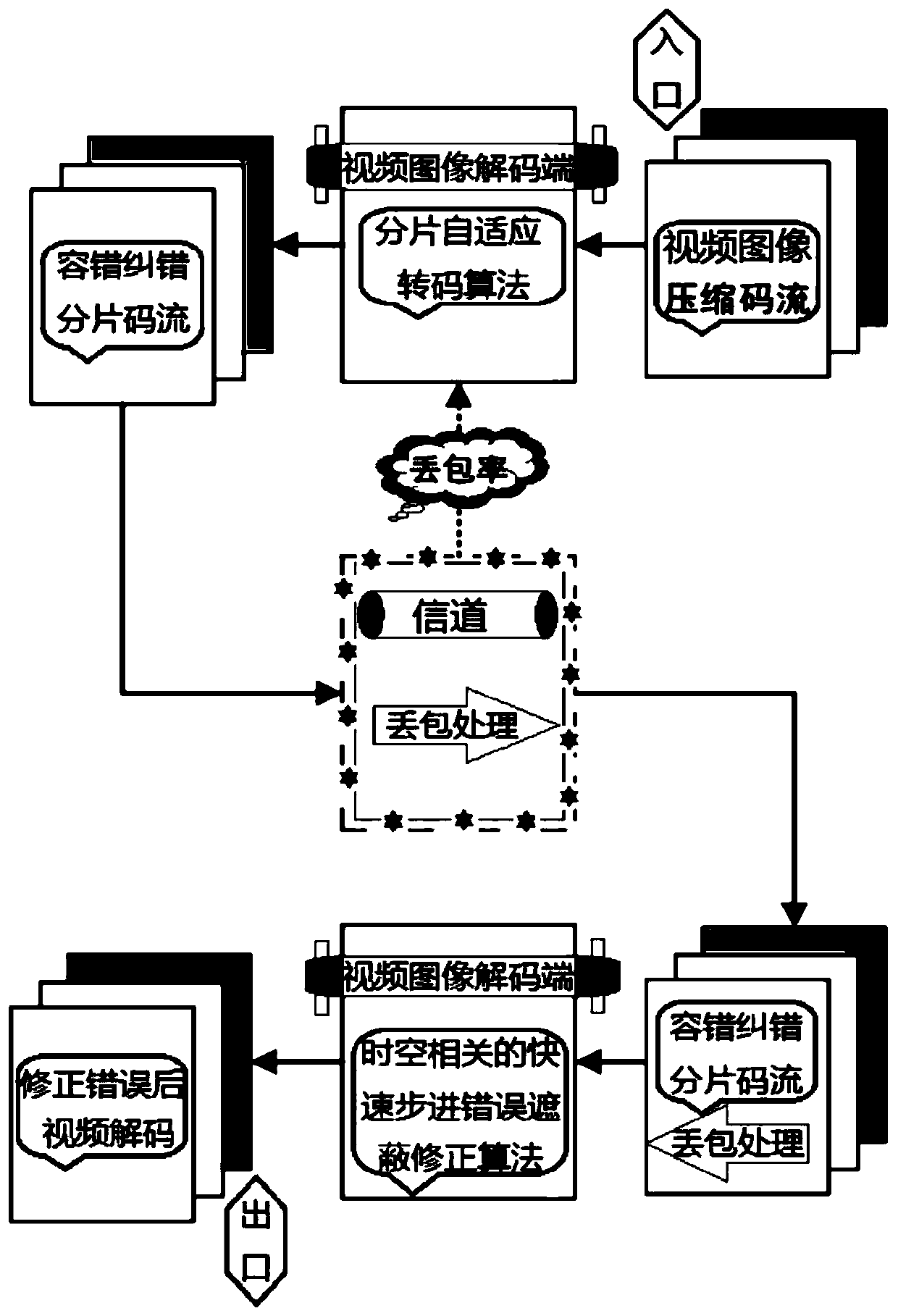
Video image high-quality transcoding method with excellent error code resistance
PendingCN111510722AExcellent anti-error performanceImprove objective qualityDigital video signal modificationCorrection algorithmSource encoding
The invention provides a video image high-quality transcoding method with excellent error code resistance. According to the video image high-quality transcoding method, a fragmentation adaptive transcoding algorithm is provided for optimizing distortion-limited information source coding at a video image transcoding end, the fragmentation adaptive transcoding algorithm is based on a fragmentation technology of MPEG-4 advanced video coding, combines a distortion limiting information source coding theory, establishes a uniform fragmentation number limit distortion information source coding model,and adopts a strategy of adaptively adjusting the fragment number of each frame of image to consider the code rate and the fault-tolerant performance; and at a video image decoding end, a space-timerelated rapid stepping error masking correction algorithm is provided, on the basis of a rapid stepping image error recovery method, the space-time related rapid stepping error masking correction algorithm is used for correcting a video residual error, and recovers a whole macro block in combination with time domain information of a video image. Experimental results show that the two fault-tolerant algorithms can effectively enhance the fault-tolerant performance of the video image.
Owner:王程
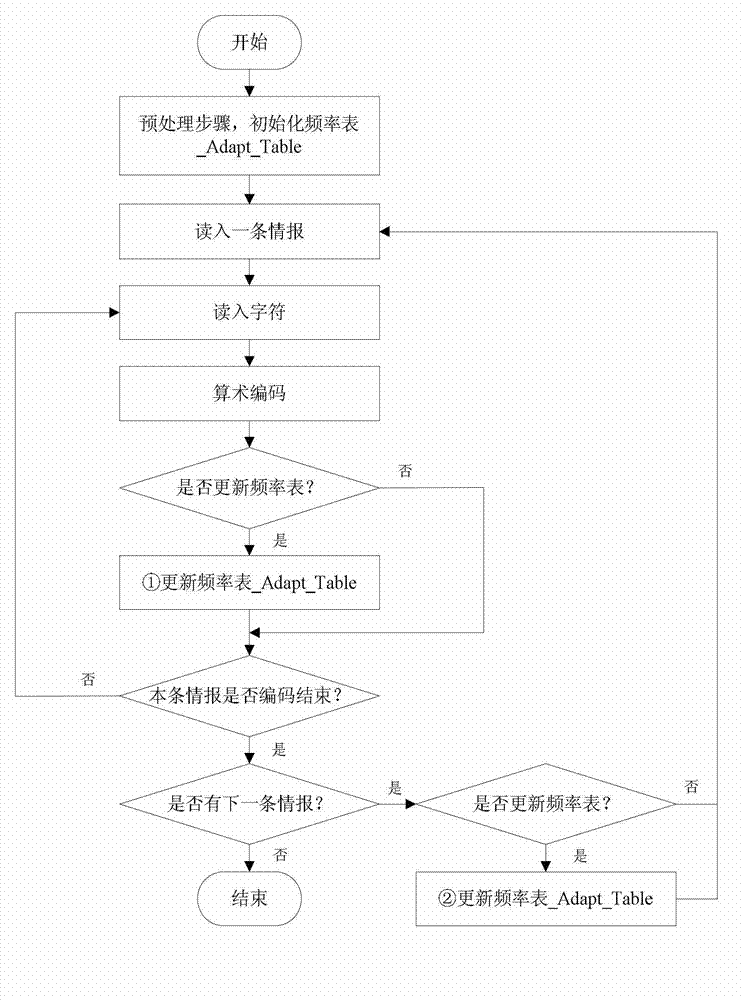
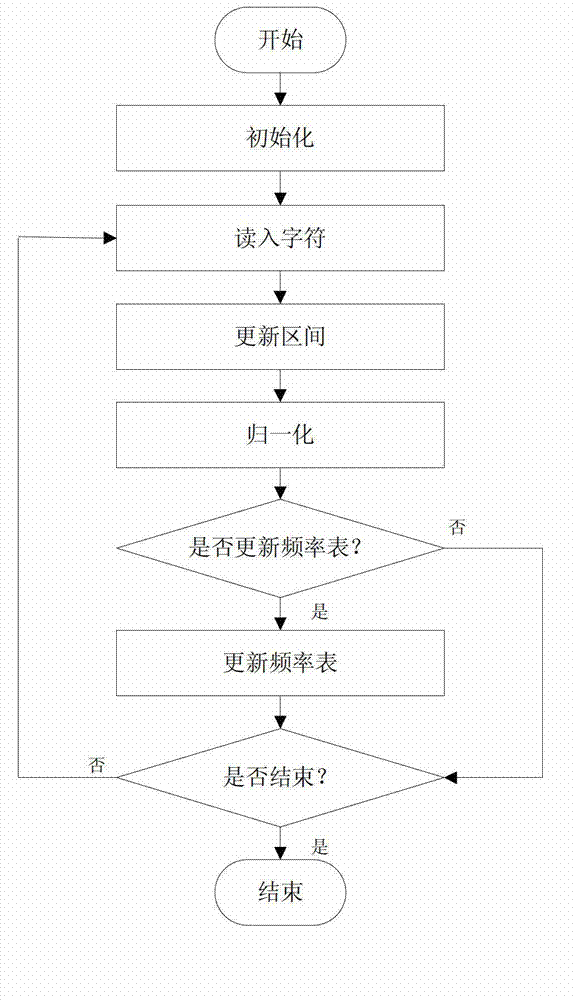
Character-type message compression method
ActiveCN102811113AIncrease the compression ratioImprove efficiencyError preventionArithmetic codingSelf adaptive
The invention discloses a character-type message compression method, and provides an optimized self-adaptive updating method for updating a frequency table. The method is characterized in that updating is conducted character by character in a coding process, i.e. the frequency table is updated after each character is arithmetically coded in a current message. The updating of the frequency table occupies certain calculation quantity, and if the calculation resource is limited, a first way cannot be adaptive. The invention adopts the other way, i.e. the updating of the frequency table is conducted by adopting a plurality of messages as a unit, only the appearance times of each character is recorded after a single message is arithmetically coded character by character, and the updating of the frequency table is conducted according to a record situation after the coding of the messages reaching the set quantity is ended. Due to the adoption of the character-type message compression method, the nondestructive compression of the message can be effectively realized, the problems such as long delay, occupation of surplus bandwidth, occupation of vast storage resource and the like in the application process such as message sharing, storage, allocation and the like can be solved, so that the compression ratio approximates or reaches a maximal value of entropy coding theory.
Owner:THE 28TH RES INST OF CHINA ELECTRONICS TECH GROUP CORP
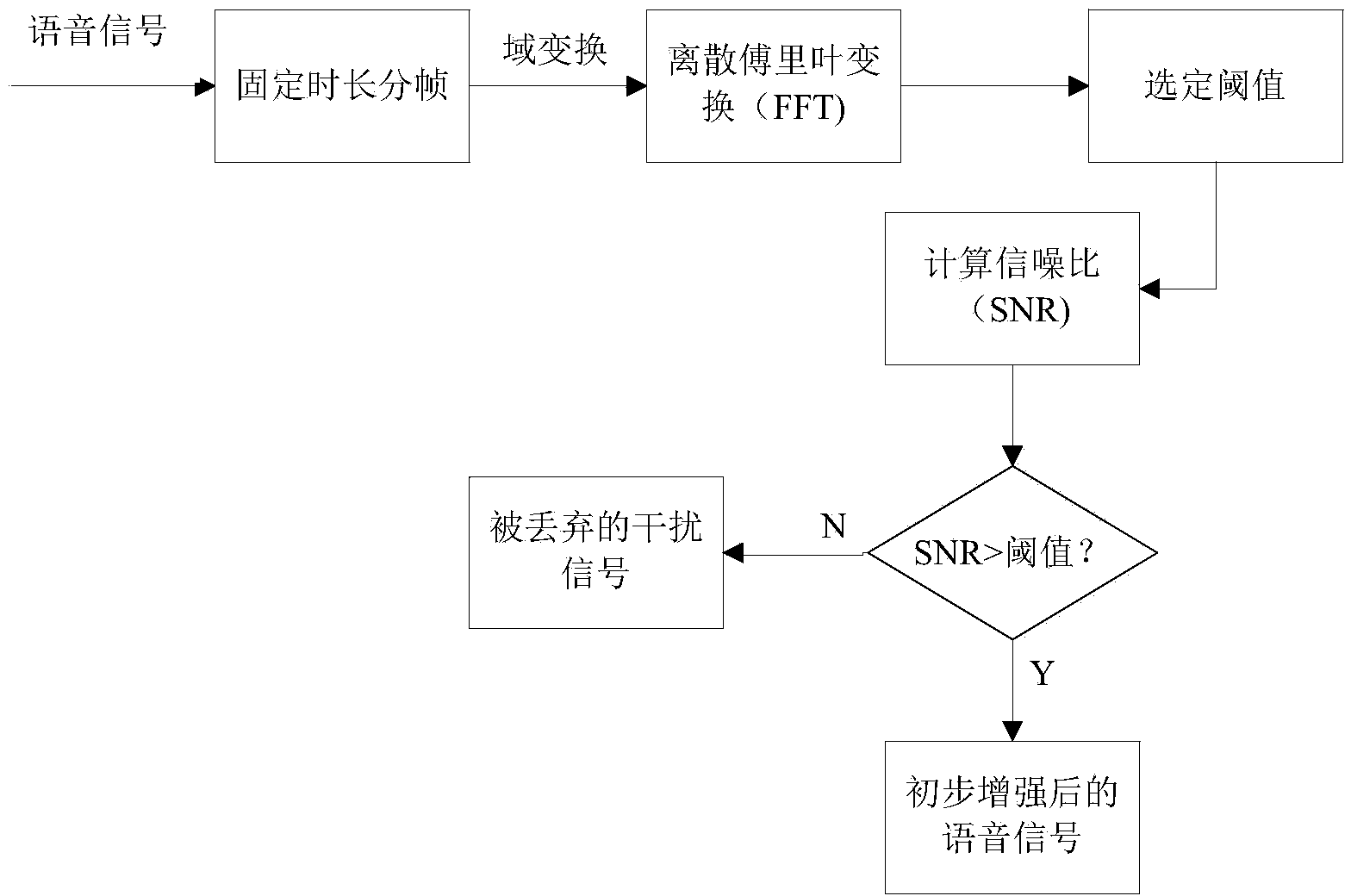
Voice enhancement method based on combination of sparse code and ideal binary system mask
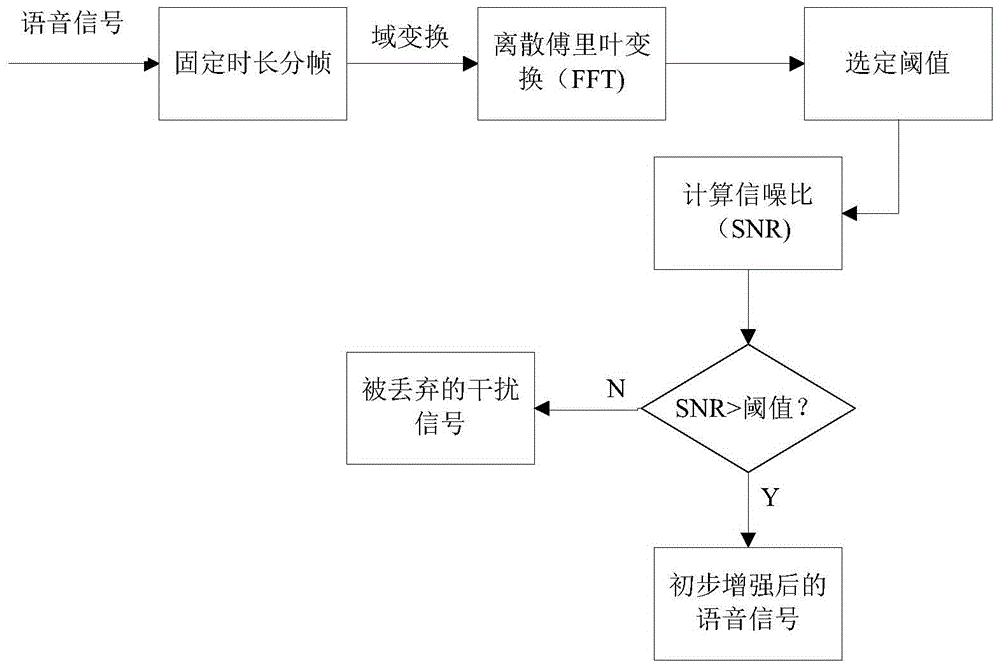
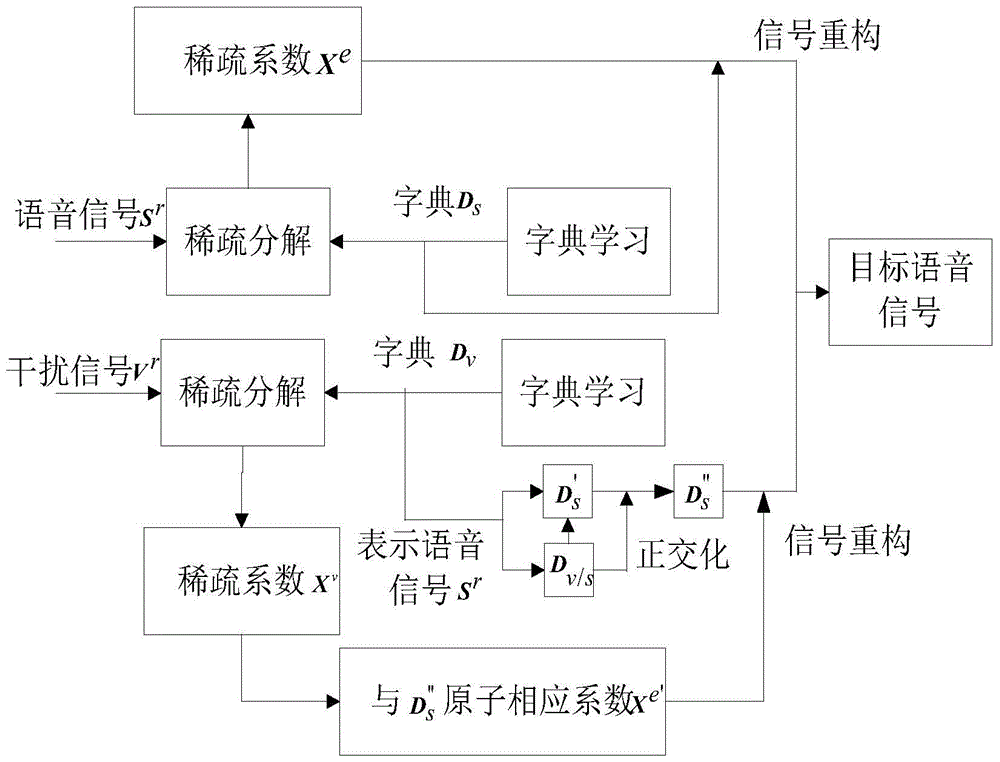
InactiveCN104240717AImprove intelligibilityQuality improvementSpeech analysisTime domainImproved algorithm
The invention discloses a voice enhancement method based on combination of a sparse code and an ideal binary system mask. The method is an improved algorithm for overcoming the defects of noise residue and voice element losses in a traditional ideal binary system mask algorithm. The method includes the steps that a time domain voice signal is converted to be a frequency domain signal by the utilization of the short-time Fourier transform; in the frequency domain, primary denoising processing is carried out on the voice signal according to the ideal binary system mask method; further denoising processing is carried out on the primarily-denoised voice signal through a sparse coding theory, and effective voice elements are extracted from a signal perceived as an interference signal, so that the effect of voice enhancement is achieved. Compared with the prior art, the method has the advantages of being good in denoising performance, high in voice intelligibility and the like.
Owner:HOHAI UNIV CHANGZHOU
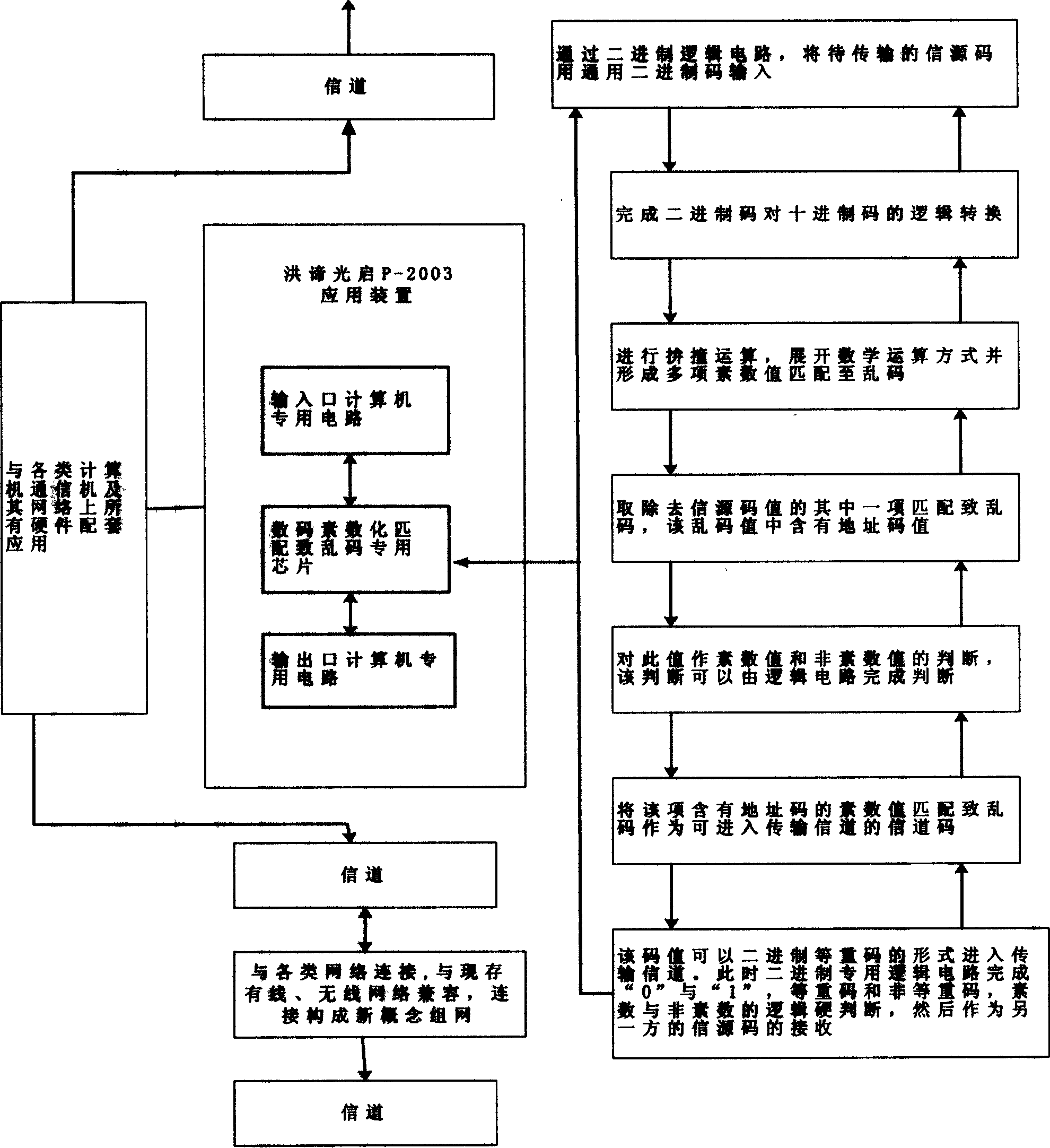
Information security technology based on prime number coding theory
InactiveCN1567253AShorten the timeValue-added speedMemory loss protectionUnauthorized memory use protectionNetwork communicationInformation security
This invention provides a kind of new information security technique that based on prime number encoding theory. During the information transmission, first, it matches the signal source code and encodes them to clobber by prime number encoding theory. The prime number matched clobber is served as channel code to enter the transmission channel. It executes channel error detection during channel transmission, and decodes the channel code at the receiving end. The clobber generating method comprises: during the conversion by executing the prime number logical reasoning and clash calculation, it generates the feature of isolated seed and single cluster, so to form non-linear function discontinuous prime number encoding reasoning clobber. This invention can ensure the complete match of network communication data to prime number data, so the information data can arrive timely, reliably, availably.
Owner:SHANGHAI HONGDI DIGITAL TECH
Color blind watermarking method based on Hamming code, eigenvalue decomposition and image correction
ActiveCN111223035AImprove robustnessWatermark is invisibleImage data processing detailsPattern recognitionColor image
The invention discloses a color blind watermarking method based on Hamming codes, eigenvalue decomposition and image correction by combining a Hamming coding theory and eigenvalue decomposition. Firstly, all characteristic values of a pixel block are obtained according to characteristics of characteristic value decomposition, and embedding and blind extraction of a digital watermark are completedby quantizing the sum of absolute values of the characteristic values; secondly, according to the geometric attributes of the image containing the watermark, the image after various geometric attackscan be corrected. According to the method, the digital watermark of the color image can be embedded into the color host image, so that the method not only has better watermark concealment and higher safety, but also has stronger robustness and larger embedding capacity, and is suitable for occasions of copyright protection of high-capacity color digital images with strong robustness.
Owner:上海瑞盛联信息科技有限公司
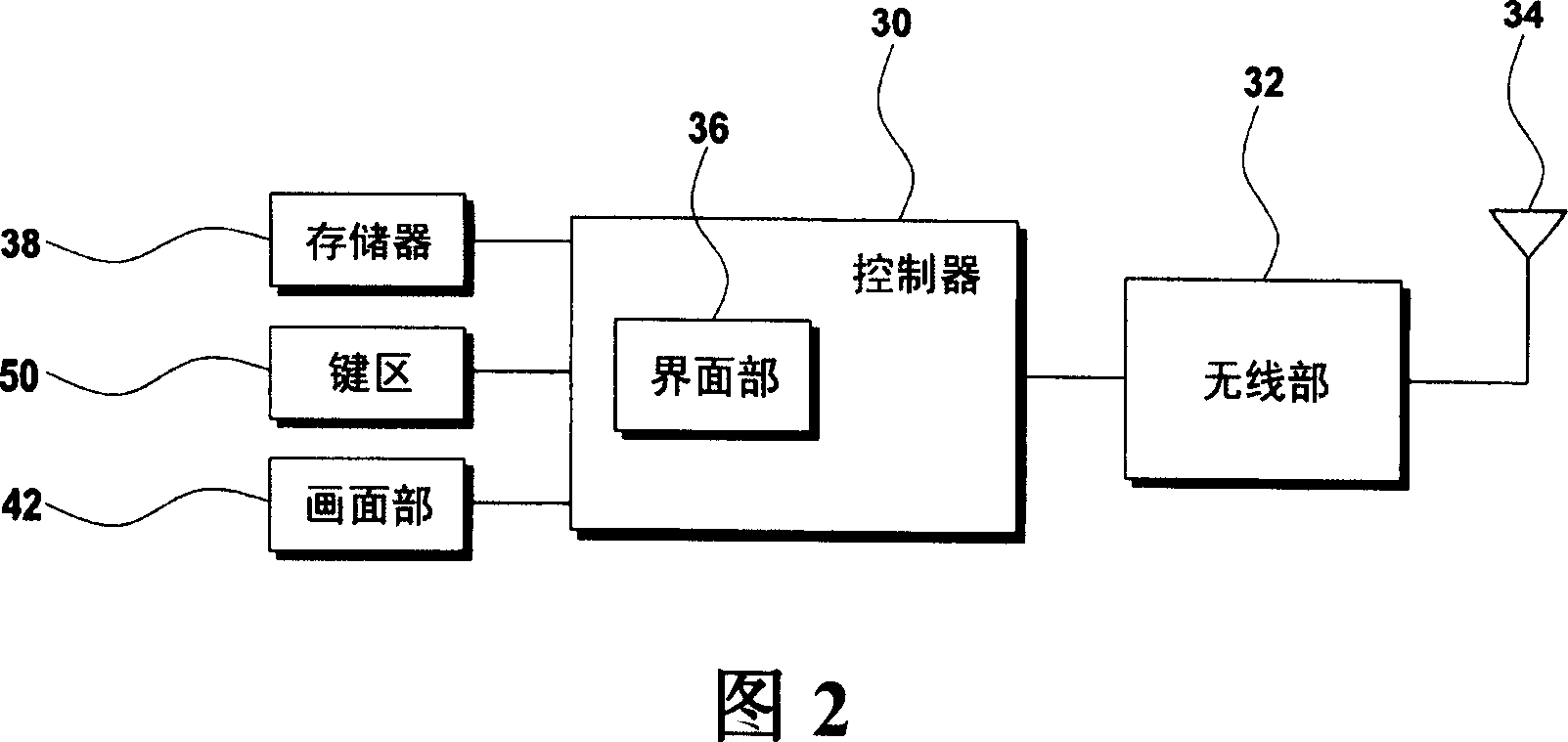
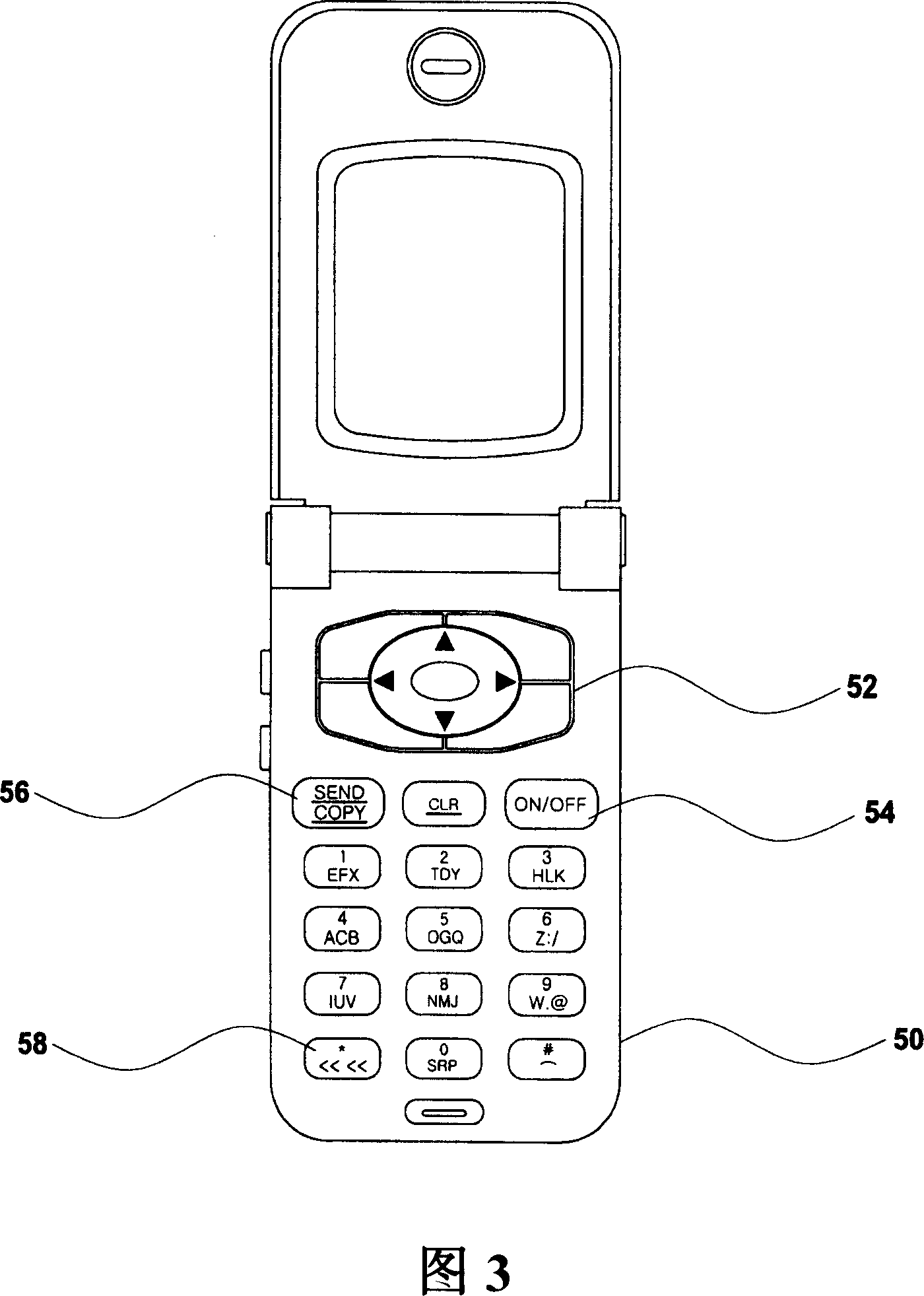
Keypad device of mobile communication terminal and input method thereof
InactiveCN1960549ASimple inputEasy to enterRadio/inductive link selection arrangementsMessaging/mailboxes/announcementsUniform resource locatorLettering
The present invention relates to a keypad device of a mobile communication terminal and an input method thereof. In the present invention, in order to improve the speed of inputting the english characters, english characters having a higher frequency are provided in positions where characters are convenient to be input by analysing english character frequency based on the code theory, and in order to make the input of URL easy, an additional function for inputting special characters and continuous characters easily is provided. In the present invention, the english characters are allocated according to that if the position of the key is easy to be input based on the occuring frequency of the english characters in the code theory, and in the positions of the keys 3, 6, 9, # which are not convenient for inputting are allocated with english characters having lower frequency to make the input of english characters more convenient for the users of the mobile communication terminal. Furthermore, blank space key is provided in the keypad through which blank space can be input, also a copy key is provided for inputting through copy when users input characters, and a reverse key is also provided for inputting characters in the reverse order of the english characters allocated according to the figure keys. As a result, the input operation of processing english characters is more effective.
Owner:LG ELECTRONICS (CHINA) R&D CENT CO LTD
Speech Enhancement Method Based on Combination of Sparse Coding and Ideal Binary Mask
InactiveCN104240717BImprove intelligibilityQuality improvementSpeech analysisTime domainImproved algorithm
The invention discloses a voice enhancement method based on combination of a sparse code and an ideal binary system mask. The method is an improved algorithm for overcoming the defects of noise residue and voice element losses in a traditional ideal binary system mask algorithm. The method includes the steps that a time domain voice signal is converted to be a frequency domain signal by the utilization of the short-time Fourier transform; in the frequency domain, primary denoising processing is carried out on the voice signal according to the ideal binary system mask method; further denoising processing is carried out on the primarily-denoised voice signal through a sparse coding theory, and effective voice elements are extracted from a signal perceived as an interference signal, so that the effect of voice enhancement is achieved. Compared with the prior art, the method has the advantages of being good in denoising performance, high in voice intelligibility and the like.
Owner:HOHAI UNIV CHANGZHOU
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com