Information security technology based on prime number coding theory
A technology of information security and coding theory, applied in the direction of preventing unauthorized use of memory, protecting stored content from loss, etc., can solve the hidden dangers of information security, cannot achieve security and effectiveness, cannot realize encryption and decryption control, management and distribution, etc. Achieve the effect of super anti-interference and shortened time
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0019] The present invention will be further described in detail below in conjunction with the accompanying drawings and embodiments.
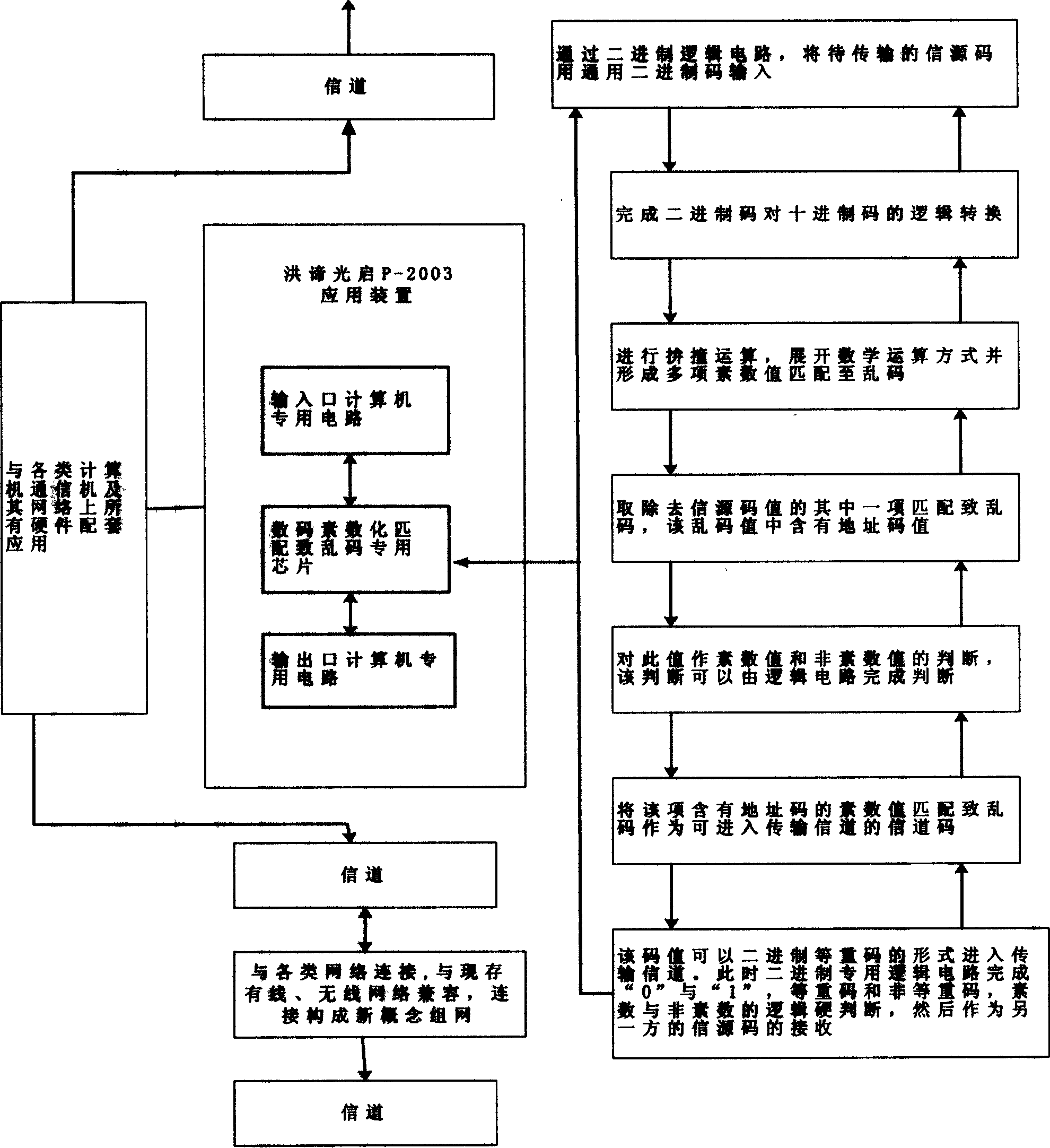
[0020] like figure 1 Shown is a block diagram of network channel codes implemented by hardware-specific binary logic circuits according to the present invention, and discloses a method for transmitting information processed by the method of the present invention in a computer network system.
[0021] First, through the binary logic circuit, the source code to be transmitted is input with universal binary code. And complete the logical conversion of binary code to decimal code. Then carry out colliding operation, expand the mathematical operation mode and form multiple prime values to match to garbled codes. In the process of implementing prime number logical reasoning and colliding operations again and again, the characteristics similar to concepts such as "soliton" and "single group" are produced, thereby forming discontinuous prime numbe...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com