Secure multi-user pilot authentication method based on hierarchical two-dimensional feature coding
A two-dimensional feature, multi-user technology, applied in the baseband system, multi-frequency code system, baseband system components, etc., can solve the problems of interference pilot sharing mechanism, affecting channel estimation, and difficult data recovery of legitimate transceivers.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0067] The present invention is further described below in conjunction with accompanying drawing:
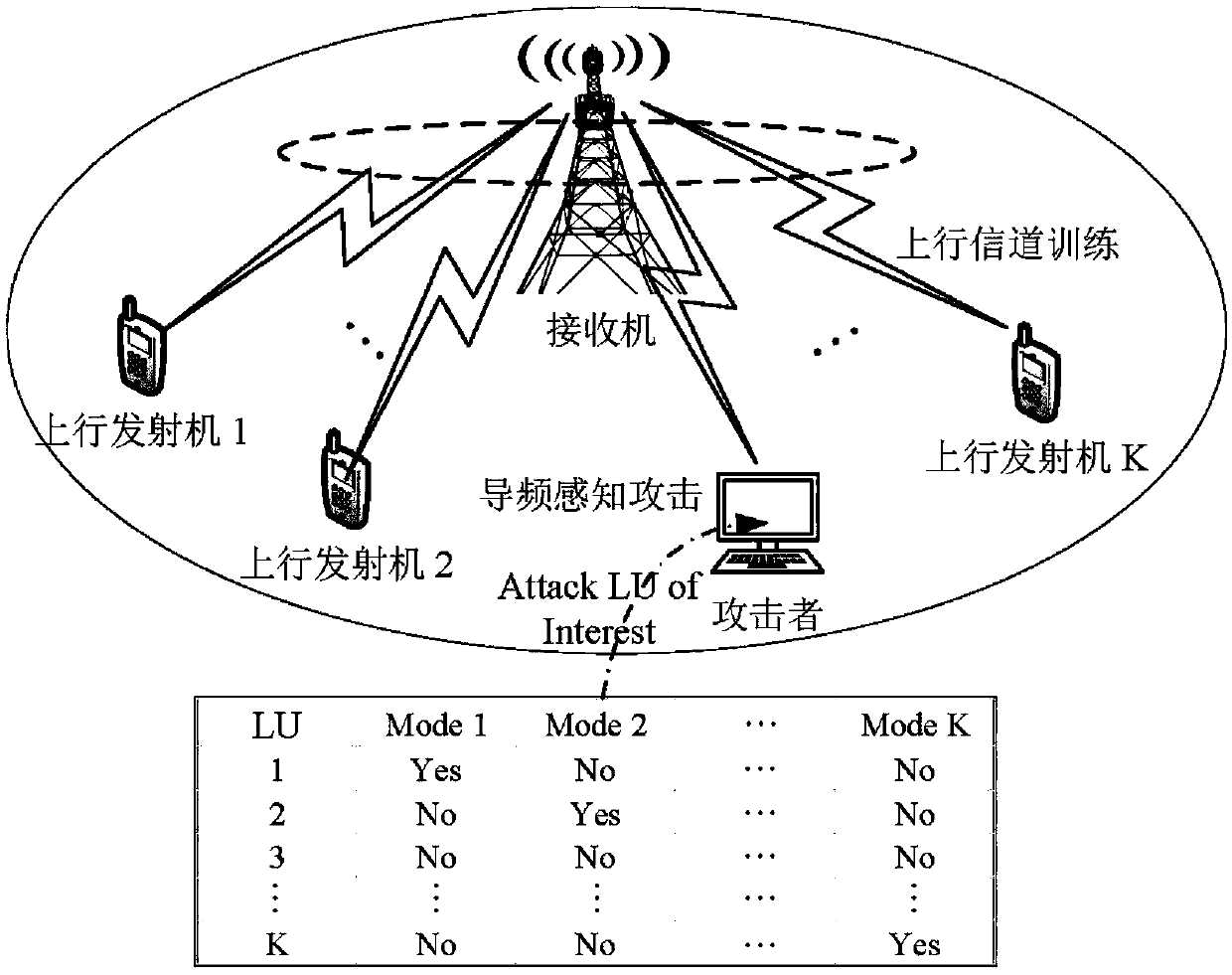
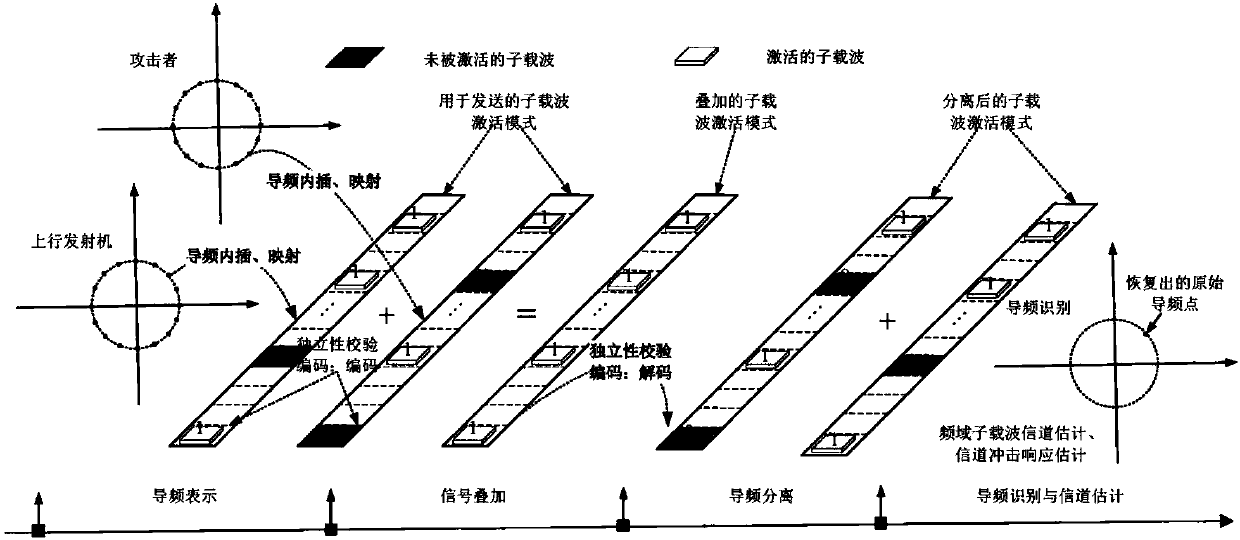
[0068] figure 1 Given the system model diagram, considering K uplink transmitters, a receiver and a pilot-aware attacker, a total of K+1 uplink communication links are generated, which are uplink transmitter→receiver, and pilot-aware attacker → Receiver. The receiver has N T The root antenna, the uplink transmitter and the pilot-aware attacker are all single-antenna. In the frequency domain, each antenna of each uplink occupies N subcarriers in each OFDM symbol. In the time domain, each communication link samples L paths, and the channel model is: Represents the channel impulse response between the mth uplink transmitter and the ith receiving antenna of the receiver, Represents the power delay spectrum of the lth path; represents the channel impulse response between the pilot-aware attacker and the i-th receiving antenna of the receiver, and is independent of Represe...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com