Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
47 results about "Data Authentication Algorithm" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
The Data Authentication Algorithm (DAA) is a former U.S. government standard for producing cryptographic message authentication codes. DAA is defined in FIPS PUB 113, which was withdrawn on September 1, 2008. The algorithm is not considered secure by today's standards.
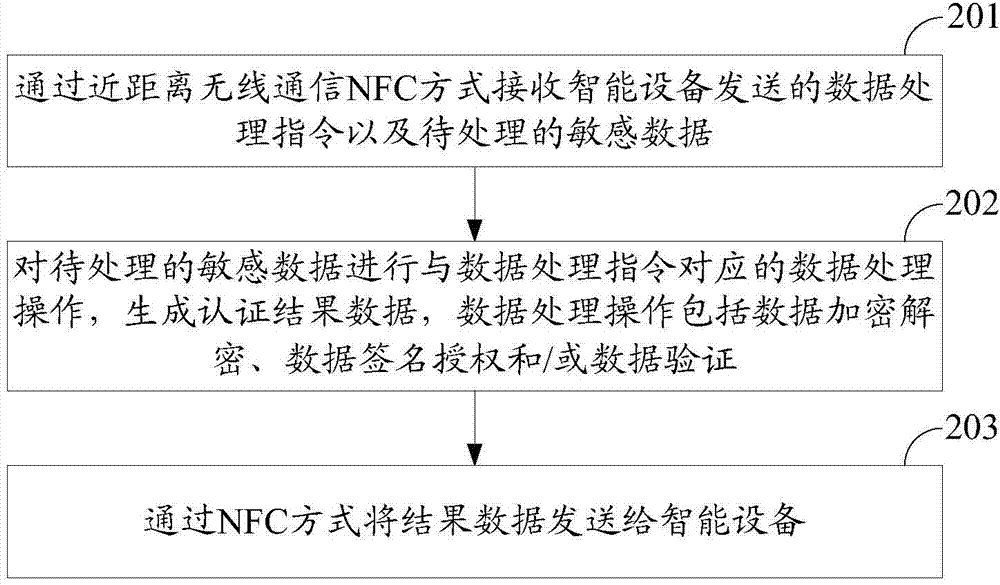
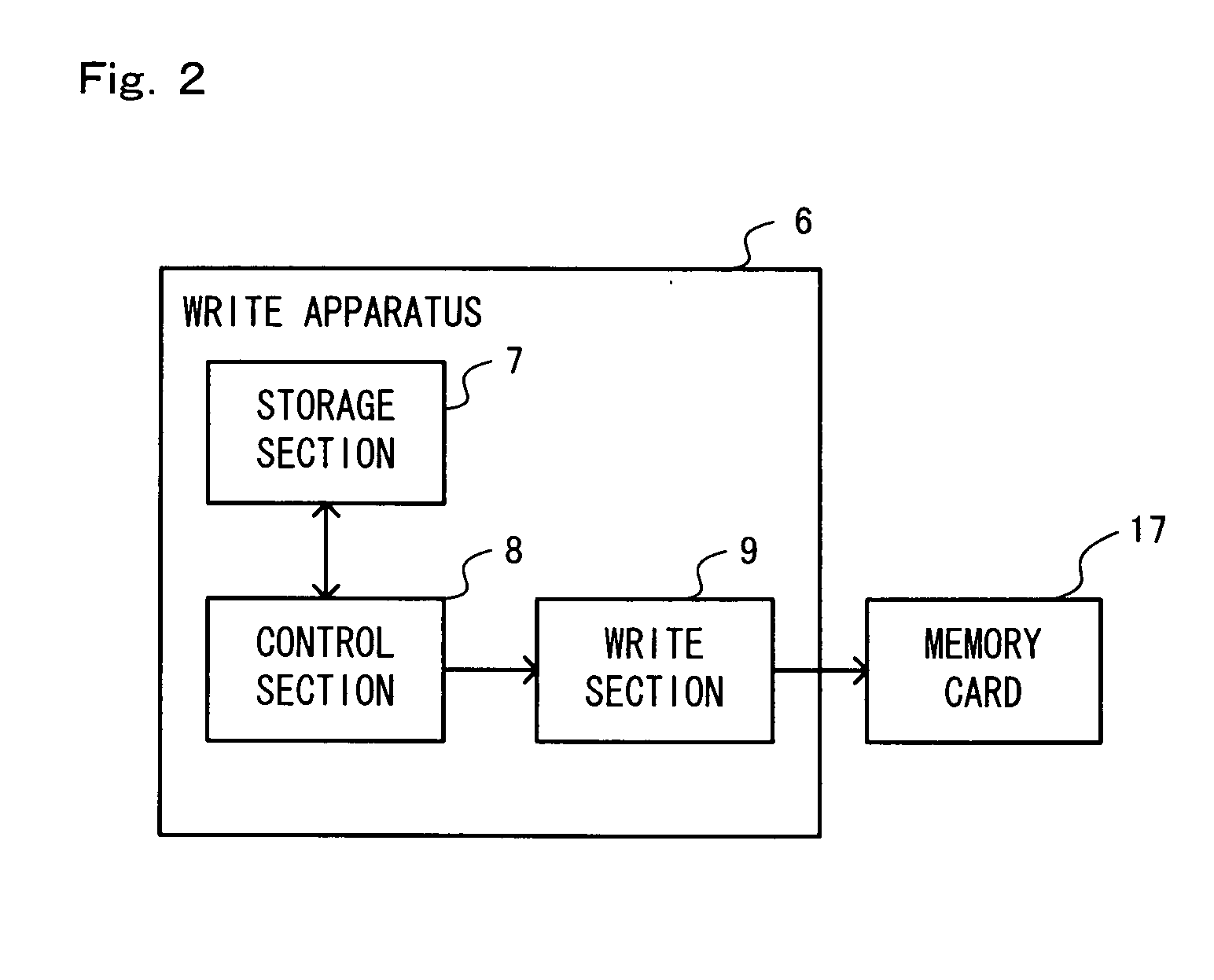
Data authentication method and device
InactiveCN103701605AEnsure safetyUser identity/authority verificationNear-field systems using receiversData validationSource Data Verification
The invention discloses a data authentication method, which can be used for realizing the data authentication process of a mobile terminal. The method comprises the following steps that sensitive data to be processed and data processing instructions sent by intelligent equipment are received in an NFC (near field communication) mode; the sensitive data to be processed is subjected to the data processing operation corresponding to the data processing instructions, authentication result data is generated, and the data processing operation comprises the data encryption and decryption, data signature authorization and data verification; the result data is sent to the intelligent equipment in the NFC mode. The invention also discloses a data authentication device.
Owner:WATCHDATA SYST
Data encryption transmission method and system
InactiveCN102333093AImprove securityFast encryption and decryptionEncryption apparatus with shift registers/memoriesUser identity/authority verificationCiphertextNetwork communication
The invention is applicable to the field of network communication, and provides a data encryption transmission method and system. The data encryption transmission method comprises the following steps: A. a server dynamically generates a DES (data encryption standard) key based on a data encryption algorithm (DEA), and encrypts the DES key by an RSA (Rivest, Shamir and Adleman) public key which is dynamically generated by a client side so as to generate an RSA encrypted ciphertext; B. the client side decrypts the received RSA encrypted ciphertext so as to obtain the DES key; and C. a message transferred between the server and the client side is compressed according to a ZLIB algorithm, and then the DES key encrypts the compressed message. The data encryption transmission method has the beneficial effects that the RSA and DES encryption algorithms are combined together, namely the message is encrypted according to the DES algorithm and meanwhile the DES key is encrypted according to the RSA algorithm so as to integrate the advantage of fast encryption and decryption speed of the DES algorithm and the advantage of high safety of the RSA algorithm; and meanwhile the message is compressed according to the ZLIB algorithm so as to realize safe and efficient data encryption transmission.
Owner:SHENZHEN SEG SCI NAVIGATIONS CO LTD
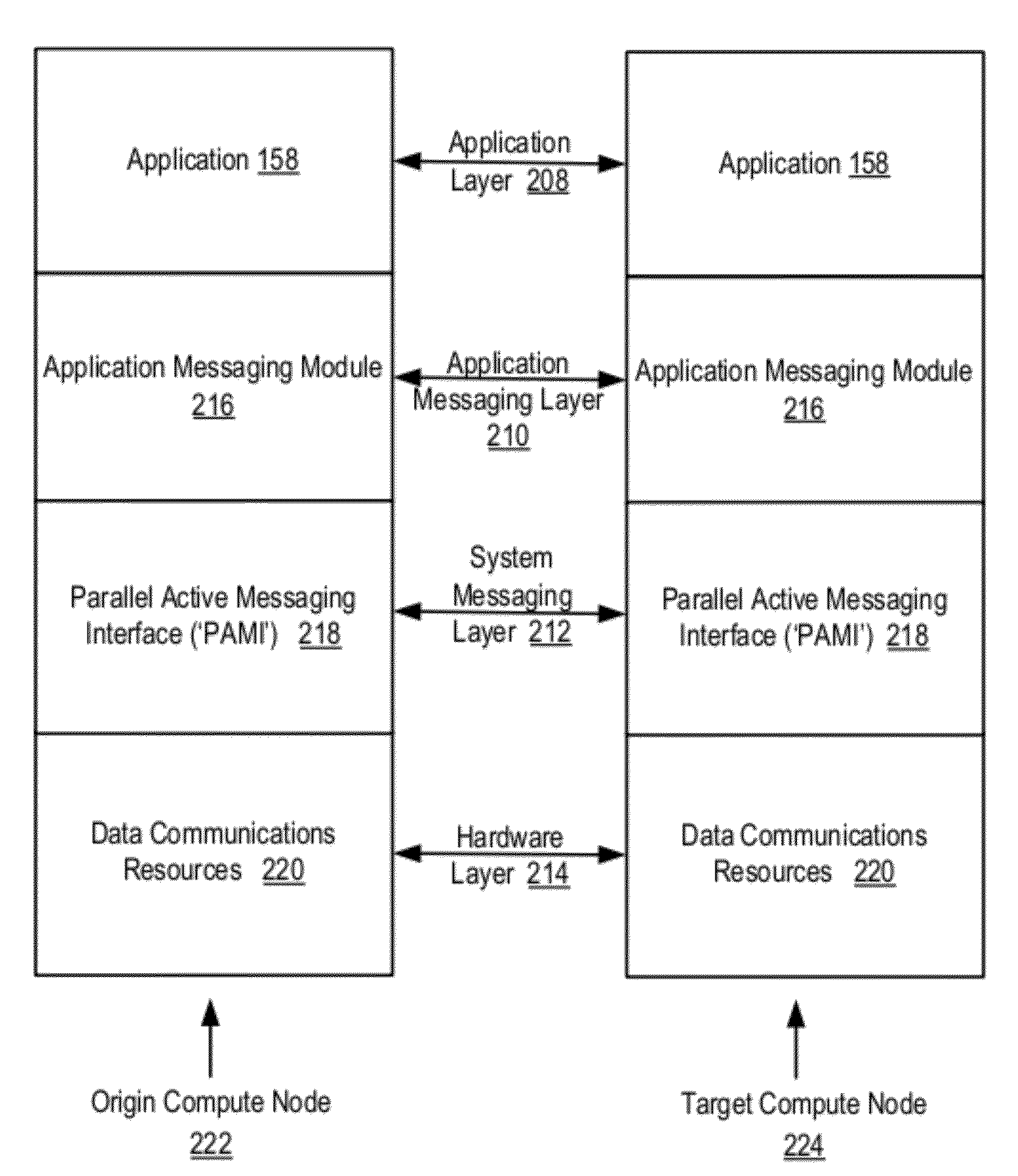
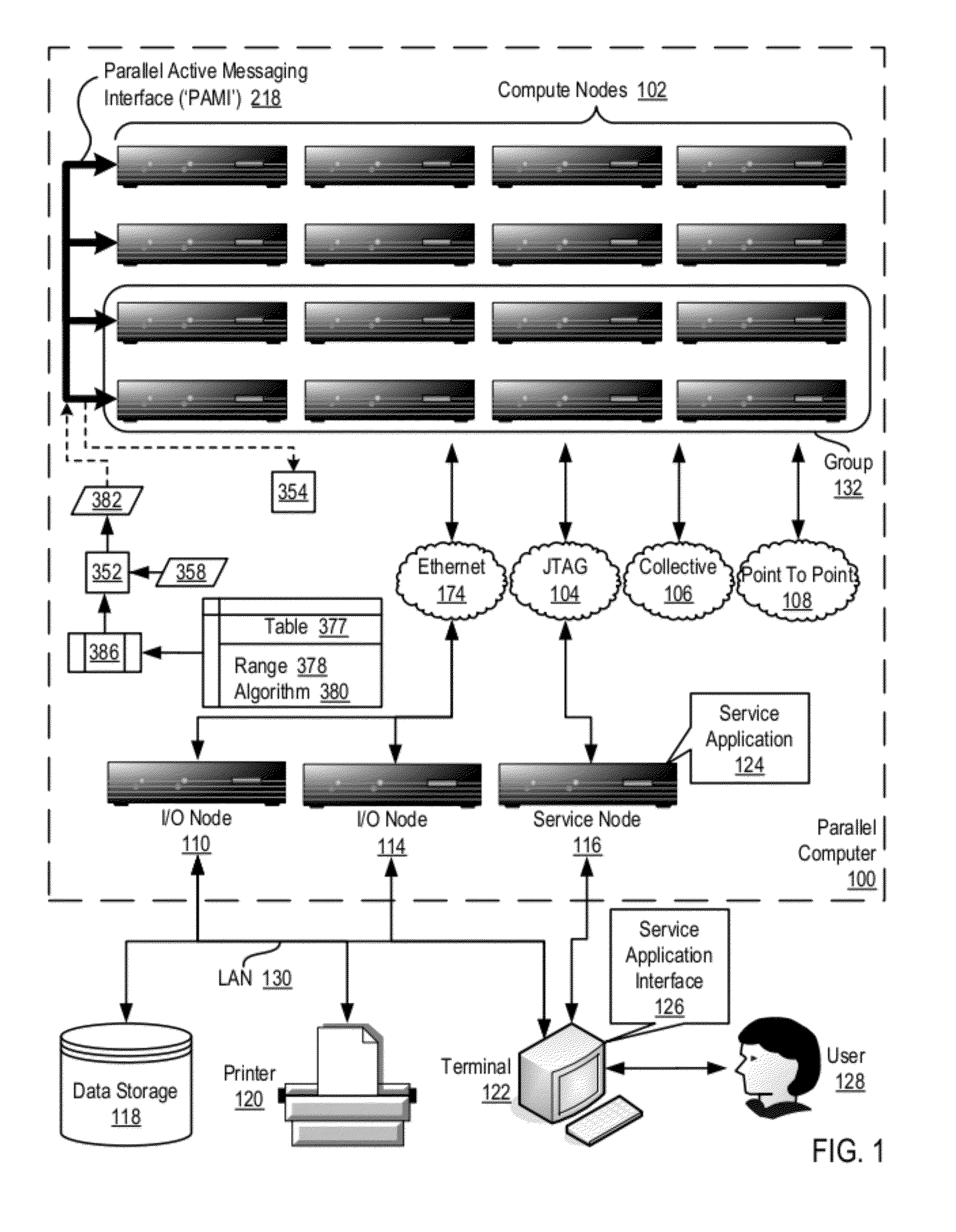
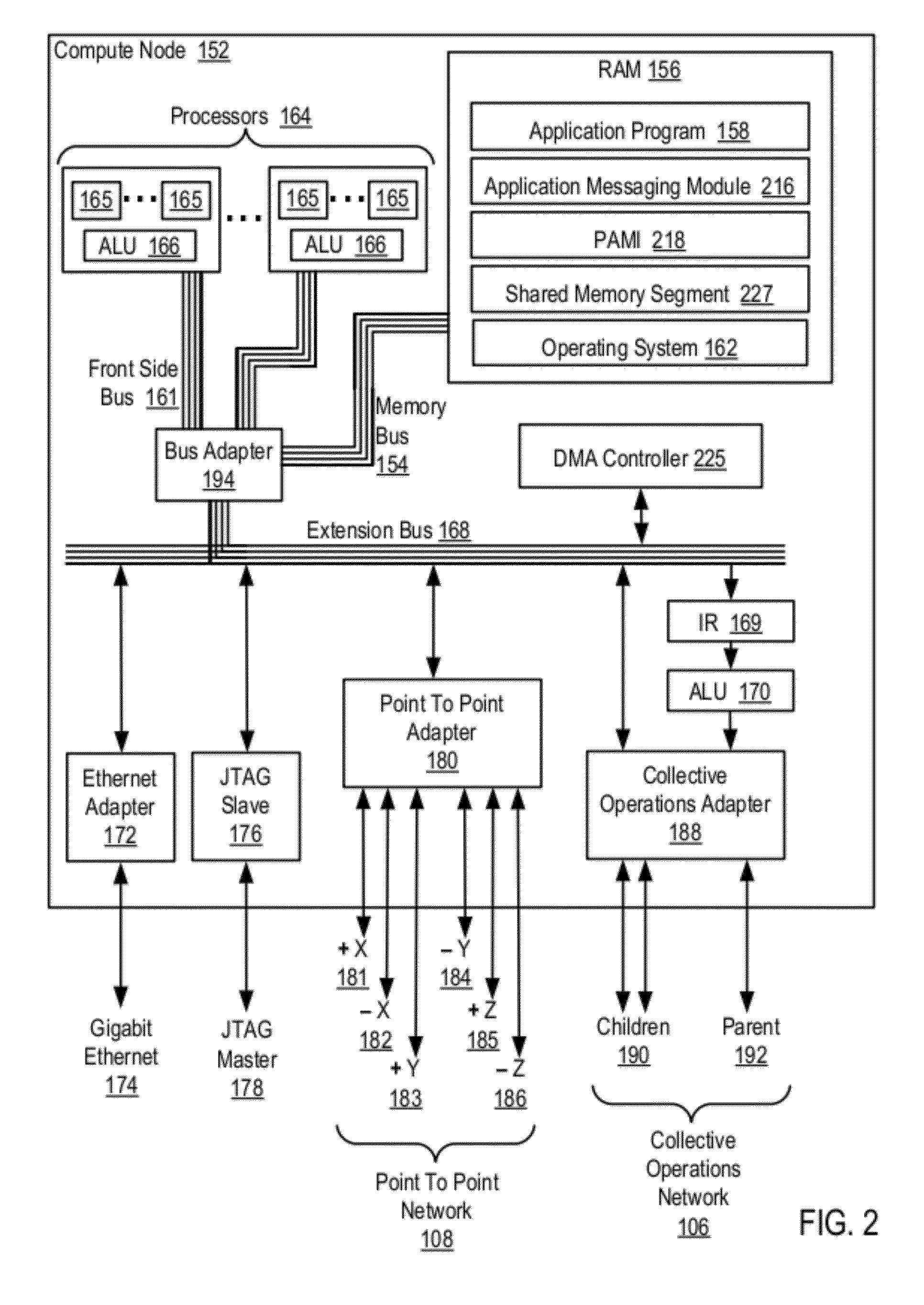
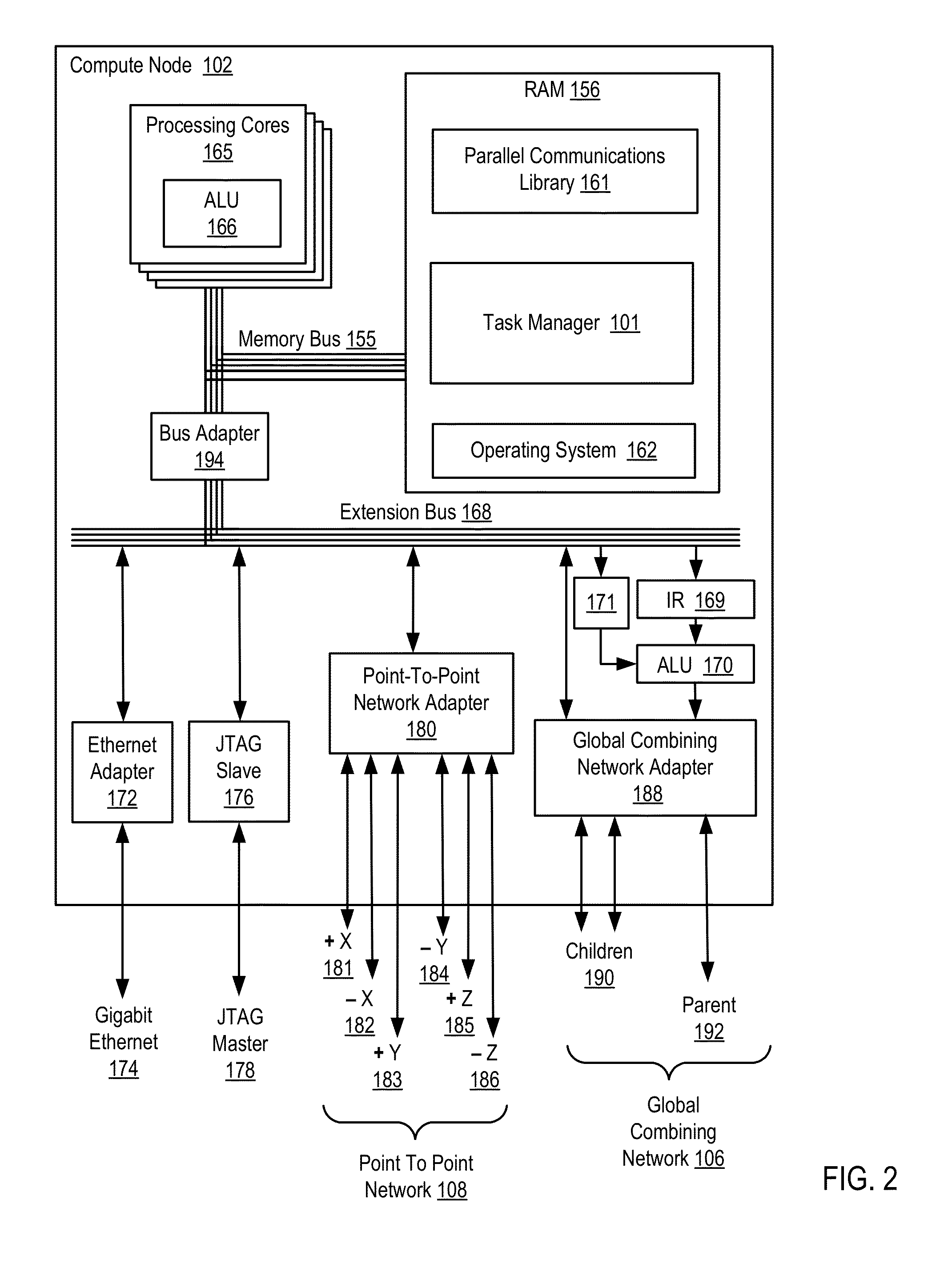
Data Communications In A Parallel Active Messaging Interface Of A Parallel Computer
InactiveUS20120144400A1Digital computer detailsMultiprogramming arrangementsCommunication endpointParallel computing
Algorithm selection for data communications in a parallel active messaging interface (‘PAMI’) of a parallel computer, the PAMI composed of data communications endpoints, each endpoint including specifications of a client, a context, and a task, endpoints coupled for data communications through the PAMI, including associating in the PAMI data communications algorithms and ranges of message sizes so that each algorithm is associated with a separate range of message sizes; receiving in an origin endpoint of the PAMI a data communications instruction, the instruction specifying transmission of a data communications message from the origin endpoint to a target endpoint, the data communications message characterized by a message size; selecting, from among the associated algorithms and ranges, a data communications algorithm in dependence upon the message size; and transmitting, according to the selected data communications algorithm from the origin endpoint to the target endpoint, the data communications message.
Owner:IBM CORP
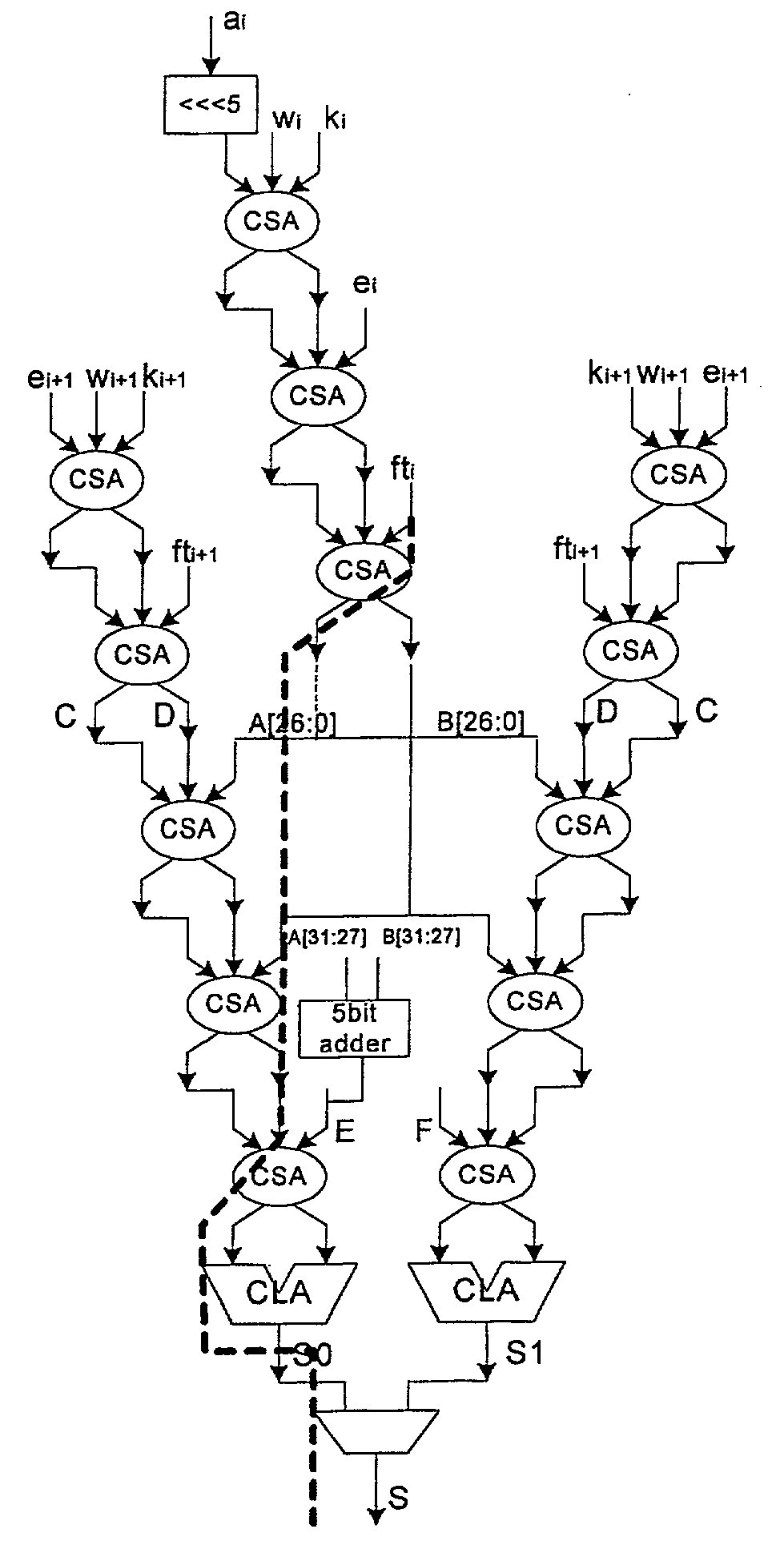
Fast SHA1 implementation
InactiveUS7299355B2Improve performanceIncrease speedRandom number generatorsPublic key for secure communicationCombined useIPsec
Provided is an architecture (hardware implementation) for an authentication engine to increase the speed at which SHA1 multi-loop and / or multi-round authentication algorithms may be performed on data packets transmitted over a computer network. As described in this application, the invention has particular application to the variant of the SHA1 authentication algorithms specified by the IPSec cryptography standard. In accordance with the IPSec standard, the invention may be used in conjunction with data encryption / encryption architecture and protocols. However it is also suitable for use in conjunction with other non-IPSec cryptography algorithms, and for applications in which encryption / decryption is not conducted (in IPSec or not) and where it is purely authentication that is accelerated. Among other advantages, an authentication engine in accordance with the present invention provides improved performance with regard to the processing of short data packets.
Owner:AVAGO TECH WIRELESS IP SINGAPORE PTE
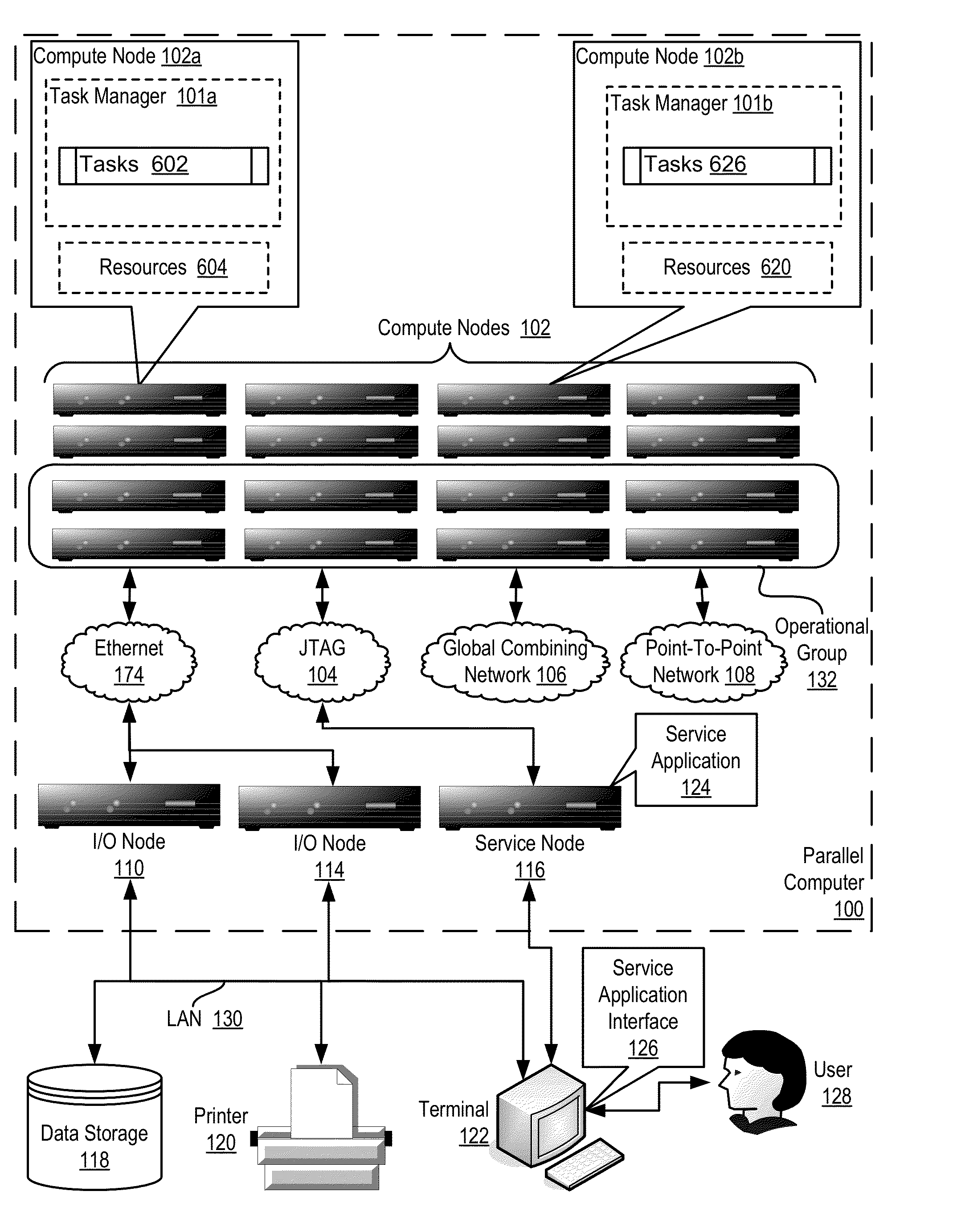
Topology Mapping In A Distributed Processing System
InactiveUS20130024866A1Multiprogramming arrangementsMultiple digital computer combinationsTopology mappingData Authentication Algorithm
Topology mapping in a distributed processing system, the distributed processing system including a plurality of compute nodes, each compute node having a plurality of tasks, each task assigned a unique rank, including: assigning each task to a geometry defining the resources available to the task; selecting, from a list of possible data communications algorithms, one or more algorithms configured for the assigned geometry; and identifying, by each task to all other tasks, the selected data communications algorithms of each task in a single collective operation.
Owner:IBM CORP
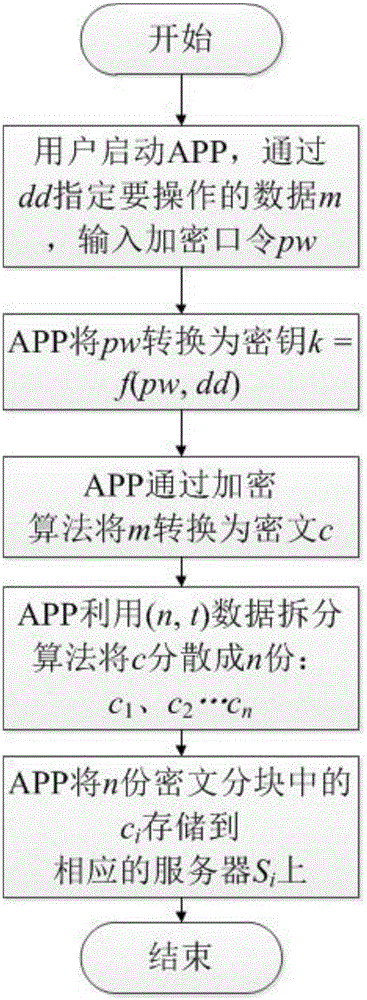
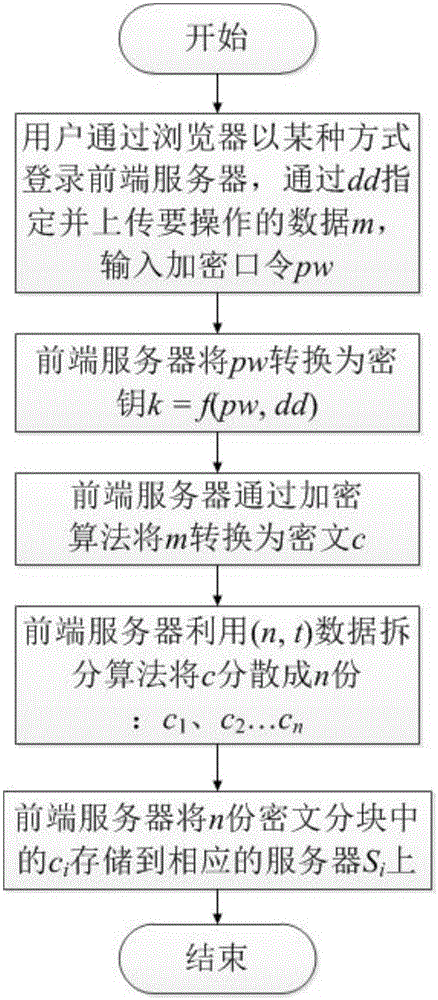
Data storage method for privacy protection based on encryption password and data fractionation
The invention relates to a data storage method for privacy protection based on an encryption password and data fractionation. A user specifies data to be operated on a client and inputs the encryption password, the client converts the encryption password into a key for encrypting a plaintext and converts the plaintext into a ciphertext by use of an encryption algorithm, then the client divides the ciphertext into n parts by use of a (n, t) data fractionation algorithm and respectively stores the n parts of the ciphertext on a plurality of servers; when the user needs to recover the data, the clients takes back t parts of the n parts of ciphertext sub-blocks and recovers the ciphertext by use of a recovering algorithm corresponding to the data fractionation algorithm; and the client converts the encryption password input by the user into a key and coverts the ciphertext into a plaintext by use of a corresponding decryption algorithm. The data storage method provided by the invention can be used for effectively protecting the data privacy of the user without adding additional equipment, thereby facilitating system deployment and user application.
Owner:INST OF INFORMATION ENG CAS +1
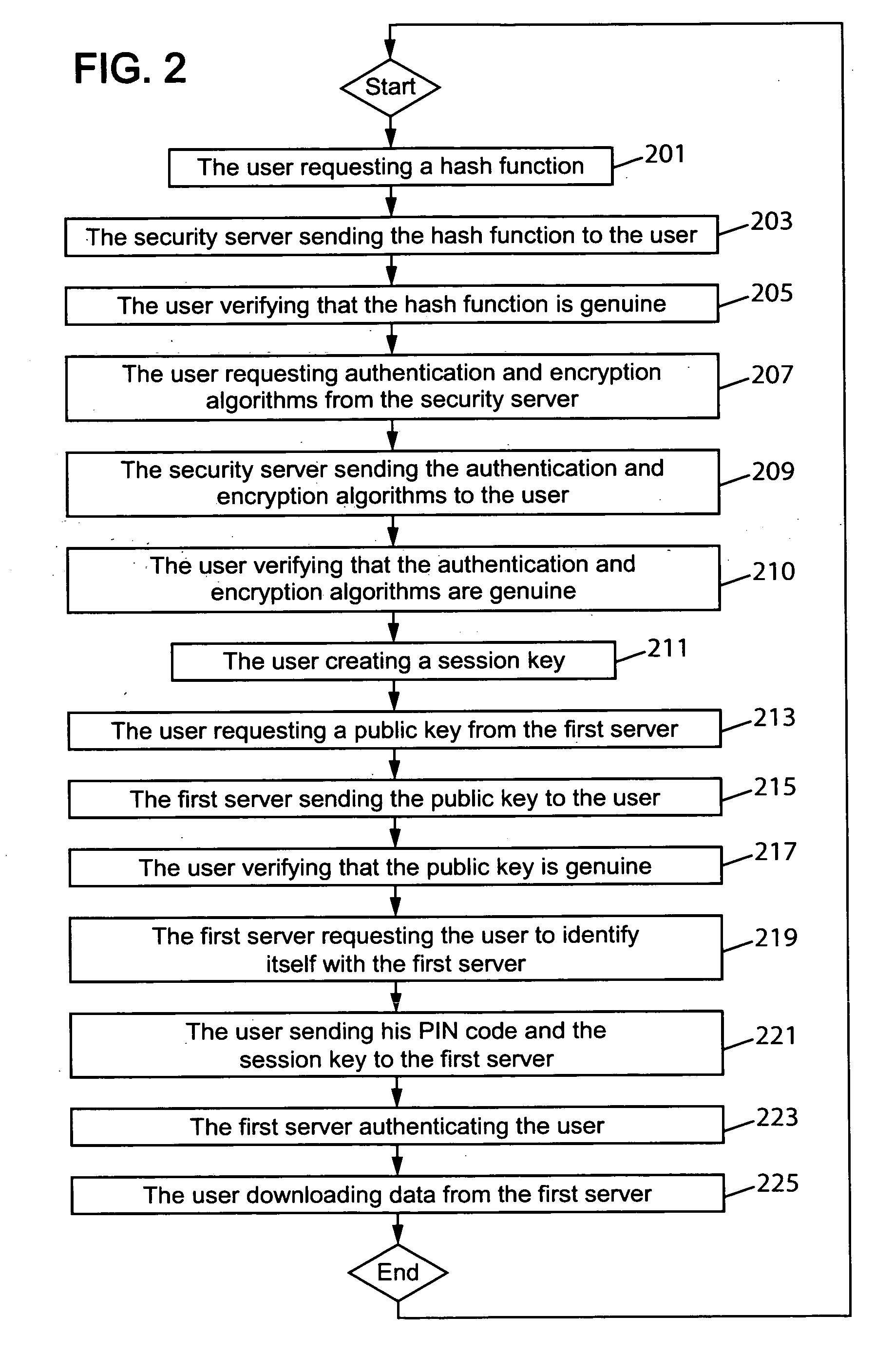
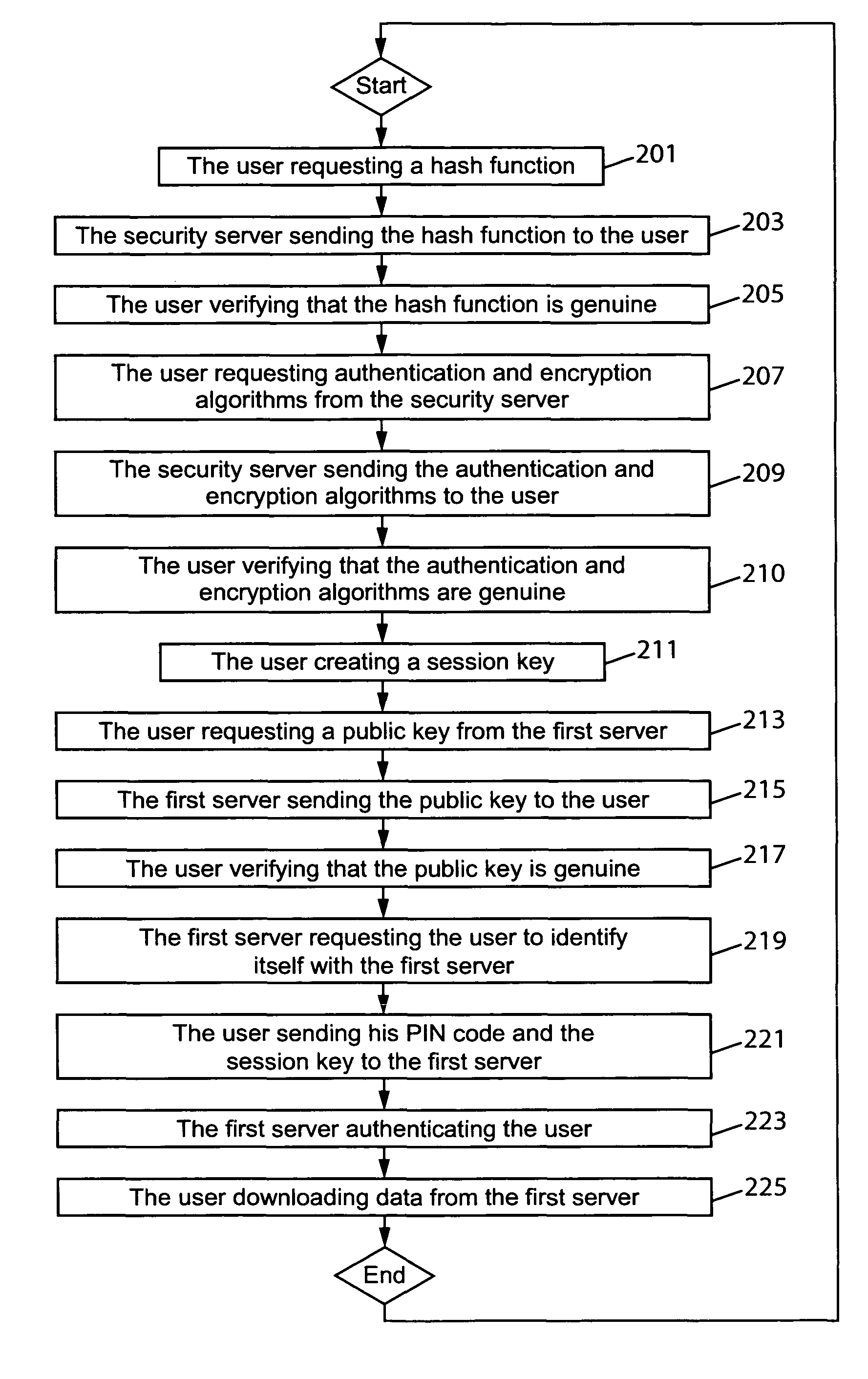
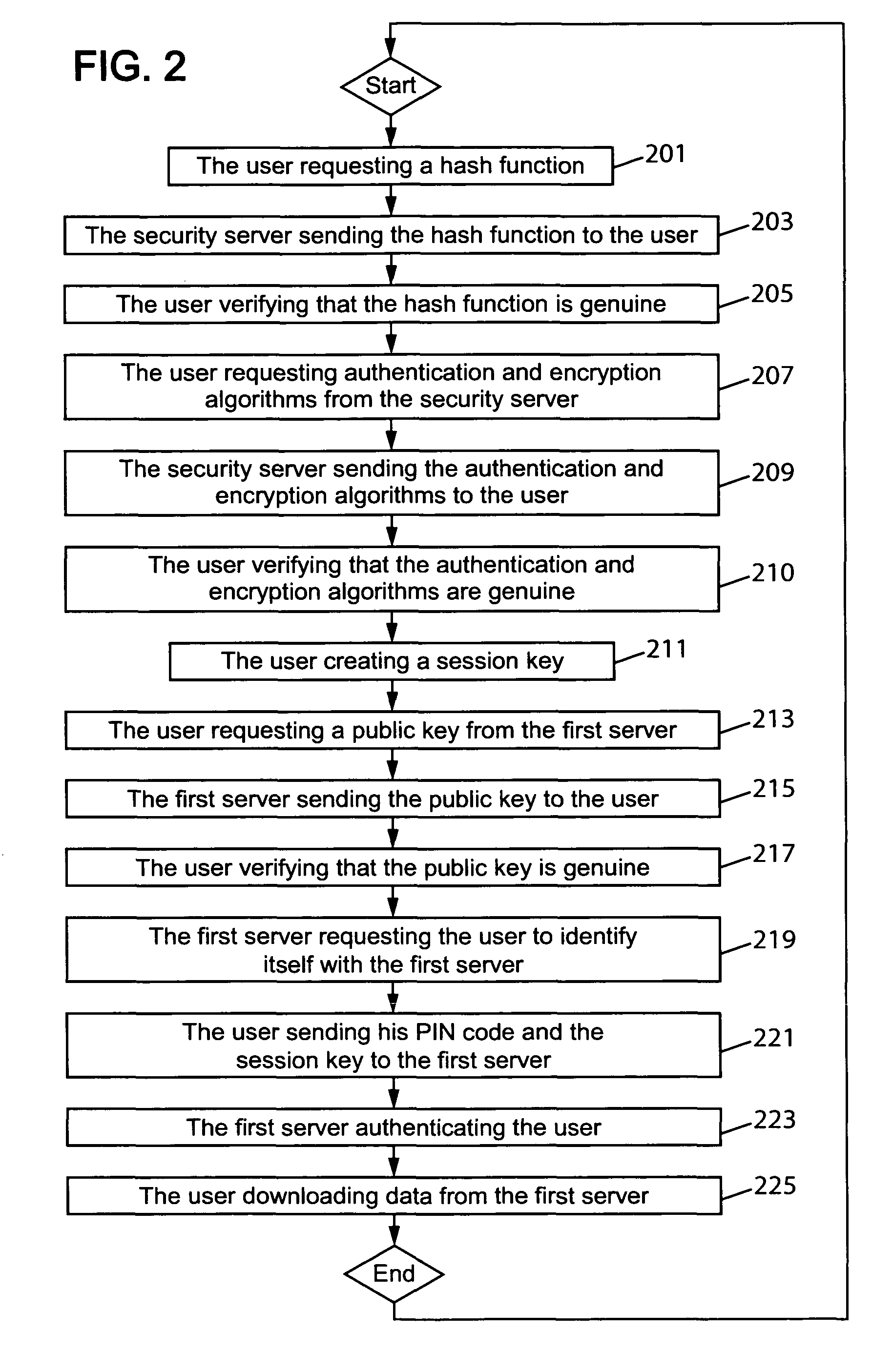
Establishing a secured communication session
ActiveUS20080148043A1Authentication securityUser identity/authority verificationSecret communicationSecure communicationCommunications system
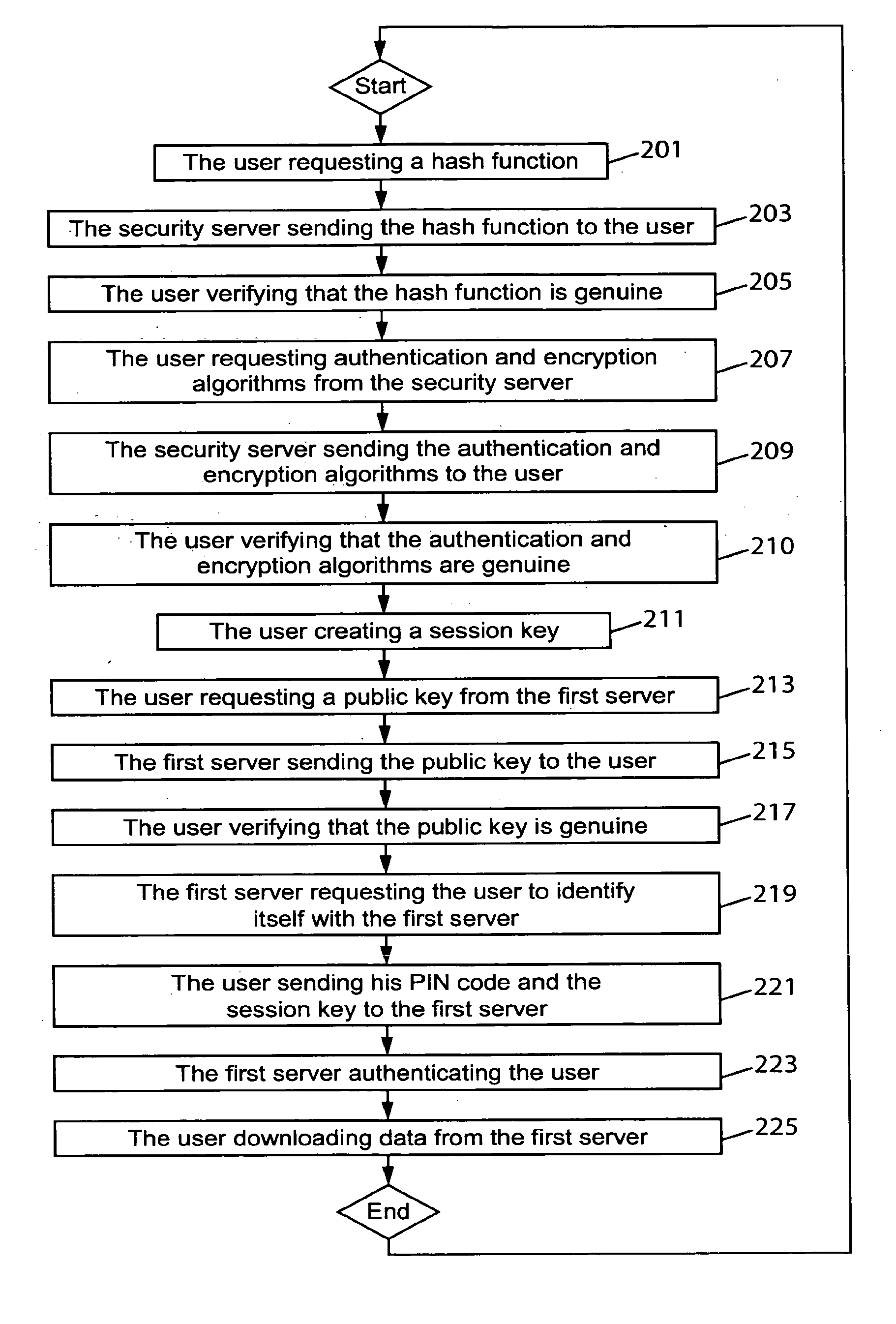
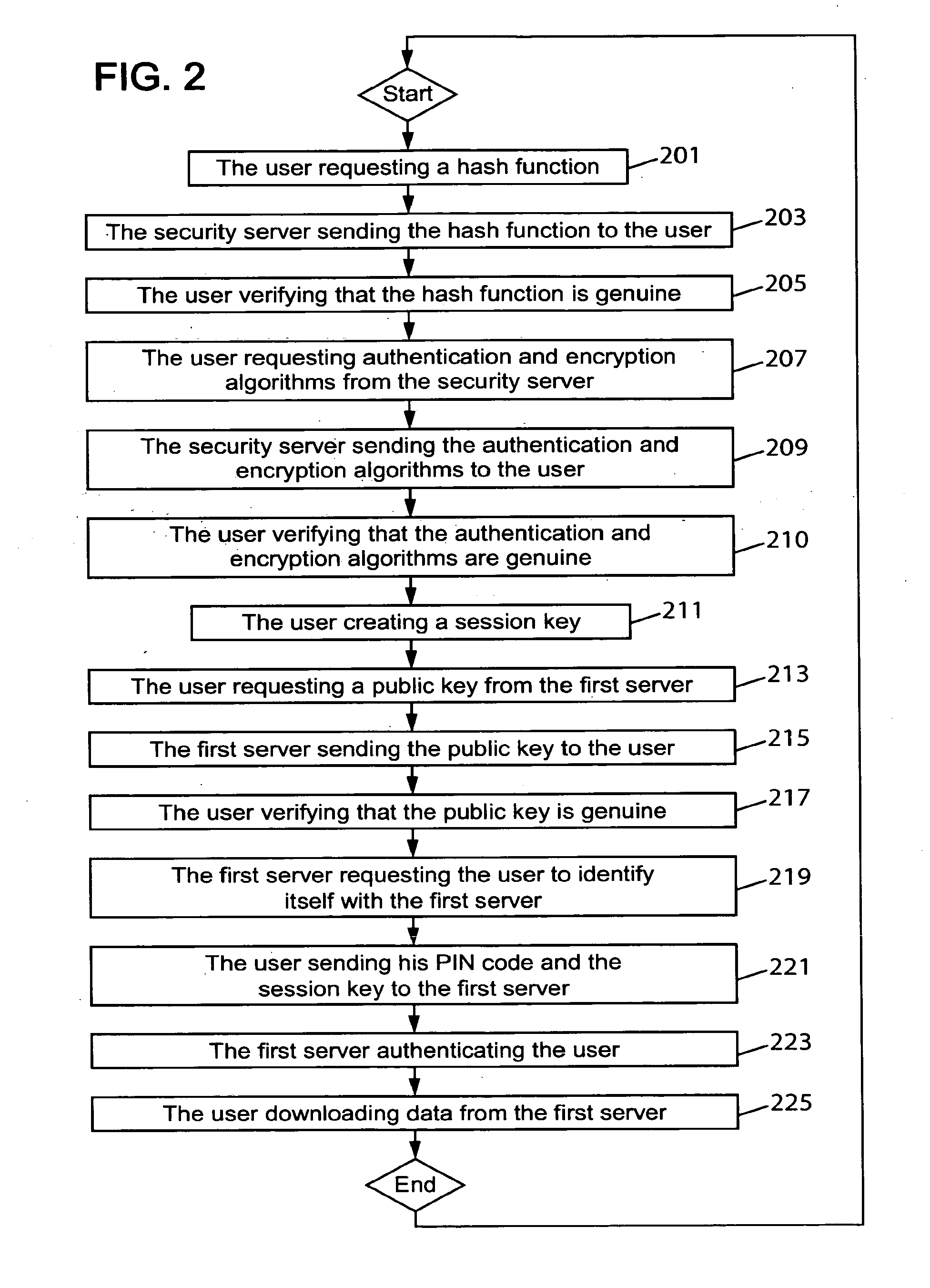
The present invention relates to a method for establishing a secured communication session in a communication system between a user using an untrusted device and a server. According to the present invention the user first obtains an authentication algorithm and an encryption algorithm and then creates a session key. Next the user obtains a public key of the server and sends a personal identity number to the server for authentication by using the authentication algorithm, the personal identity number being encrypted by using the encryption algorithm and the public key of the server. The user also sends the session key to the server for encrypting purpose between the user and the server, the session key being encrypted by using the encryption algorithm and the public key of the server.
Owner:APPLE INC
Anonymous Authentication Algorithm for Remote Attestation on Trusted Platforms
ActiveCN102291396AMeet authenticationReduce the number of timesPublic key for secure communicationUser identity/authority verificationAnonymous authenticationData Authentication Algorithm
Owner:HANGZHOU SUNYARD DIGITAL SCI
Differentiated authentication method and differentiated authentication device
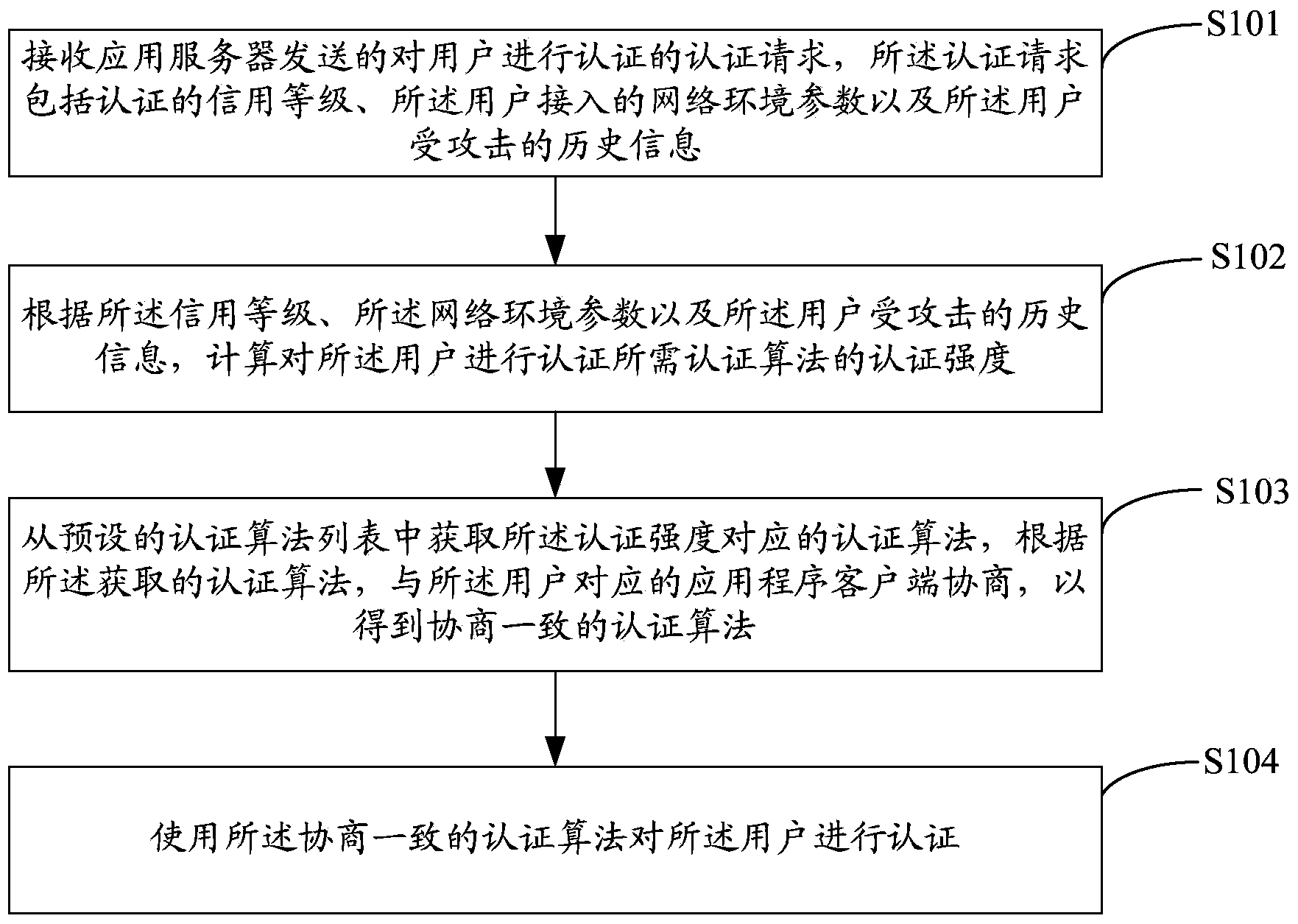
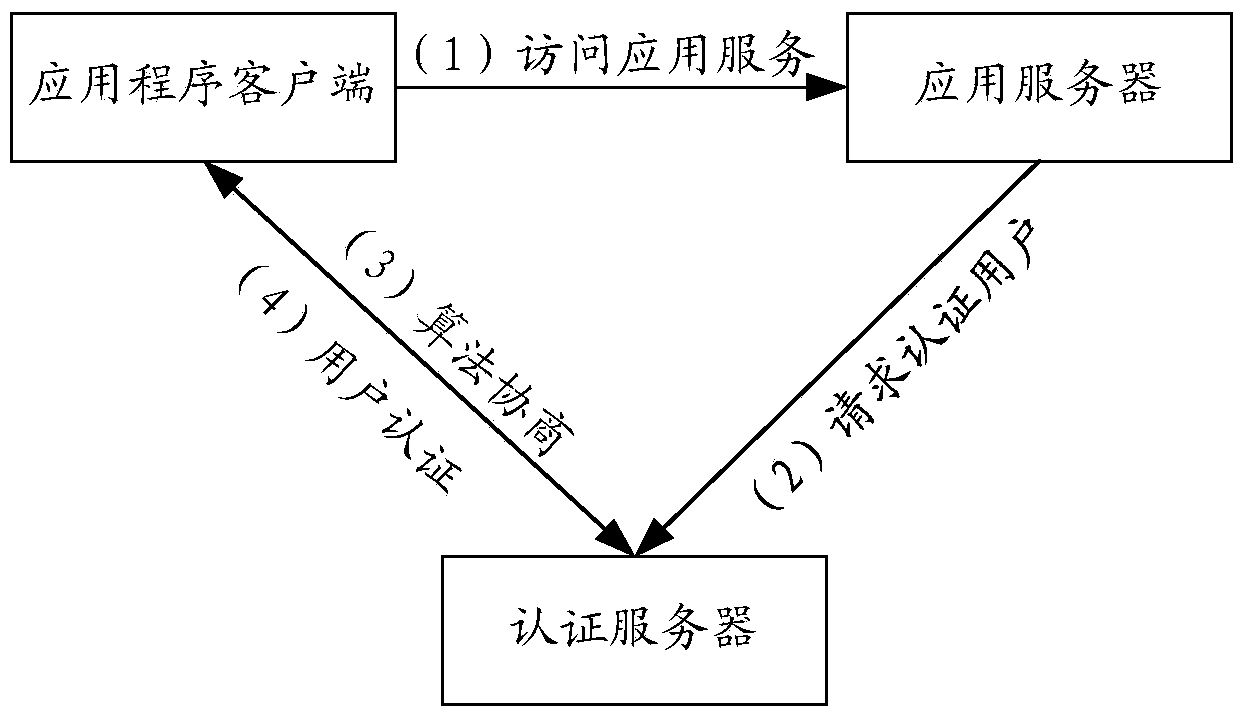
ActiveCN103685244AAchieving a safe stateImprove securityUser identity/authority verificationApplication serverSecure state
The invention provides a differentiated authentication method and a differentiated authentication device and is applicable to the technical field of computers. The differentiated authentication method includes receiving an authentication request to users from an application server, calculating authentication strength of an authentication algorithm required for authentication of the user according to lever of assurance, network environmental parameter and attack history information of the user, acquiring the authentication algorithm corresponding to the authentication strength from a preset authentication algorithm list, consulting with an application program client side corresponding to the user to acquire the consensus authentication algorithm according to the acquired authentication algorithm, and authenticating the user by the consensus authentication algorithm, thereby performing differentiated authentication to the user according to security status when the user has access to the application server. Security of the application server is improved. The authentication request includes the authentication lever of assurance, the parameter of network environment accessed by the user and the attack history information of the user.
Owner:SHENZHEN UNIV
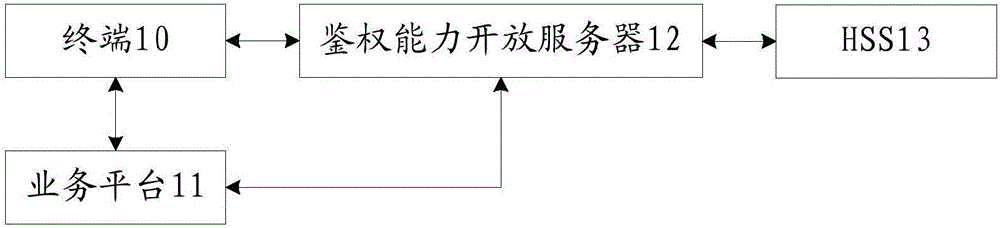
Service authentication method and authentication capability opening server
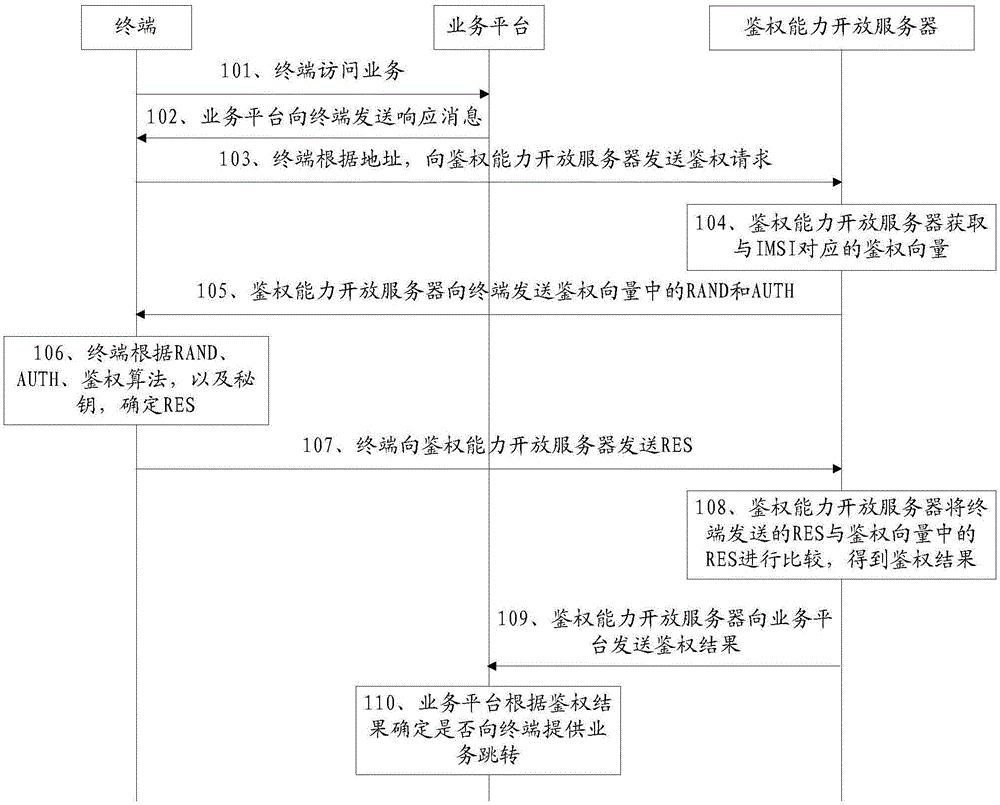
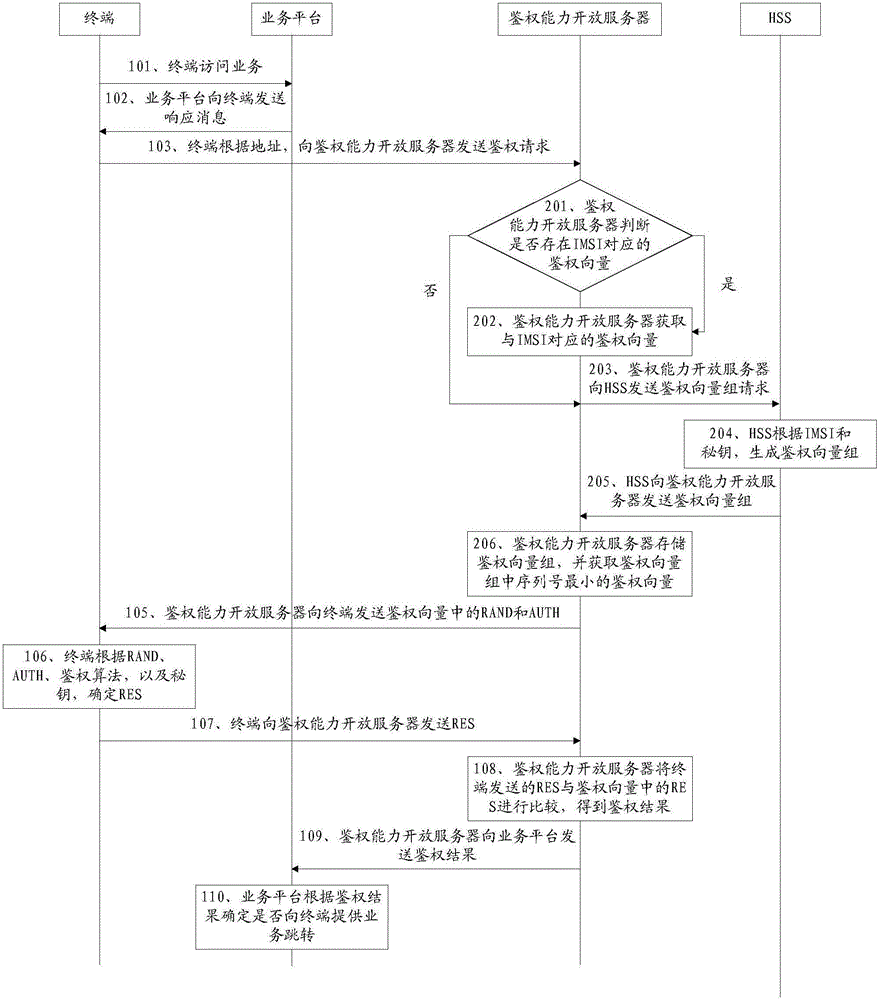
The invention discloses a service authentication method and an authentication capability opening server, and relates to the field of communication technology. An authentication capability of a service provider can be opened, and the burden in constructing an authentication system and developing real-name subscribers of the service side is reduced. The method comprises that after accessing a service, a terminal sends an authentication request with IMSI to the authentication capability opening server according to an address back fed by a service platform; the authentication capability open server obtains an authentication vector corresponding to the IMSI, and sends RAND and AUTH in the authentication vector to the terminal; according to the RAND, AUTH, an authentication algorithm and a secret key, the terminal determines a response RES, and sends the RES to the authentication capability opening server; the authentication capability opening server compares the received RES with an RES in the authentication vector, obtains an authentication result, and sends the authentication result to the service platform; and the service platform determines whether to provide service jump to the terminal according to the authentication result. The service authentication method and the authentication capability opening server are suitable for a service authentication process.
Owner:CHINA UNITED NETWORK COMM GRP CO LTD
Data authentication method, apparatus and system
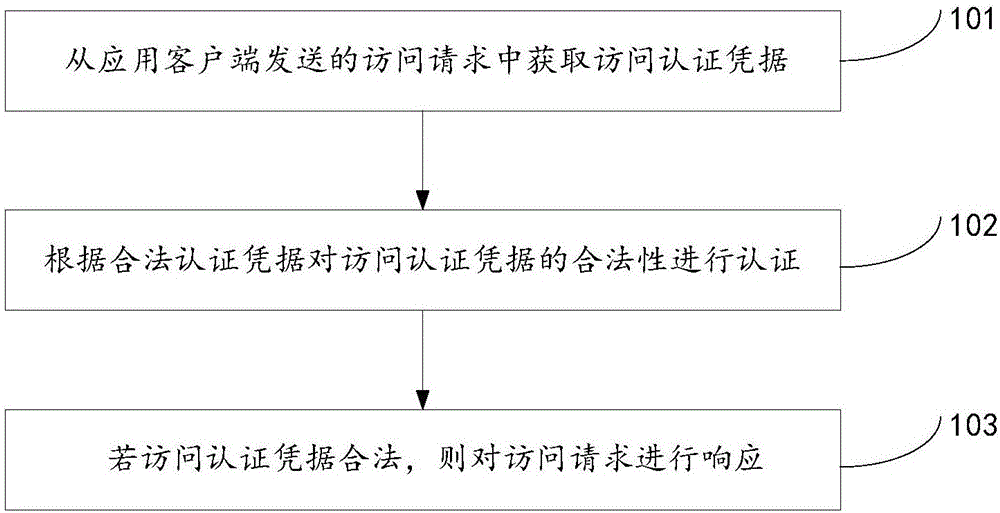
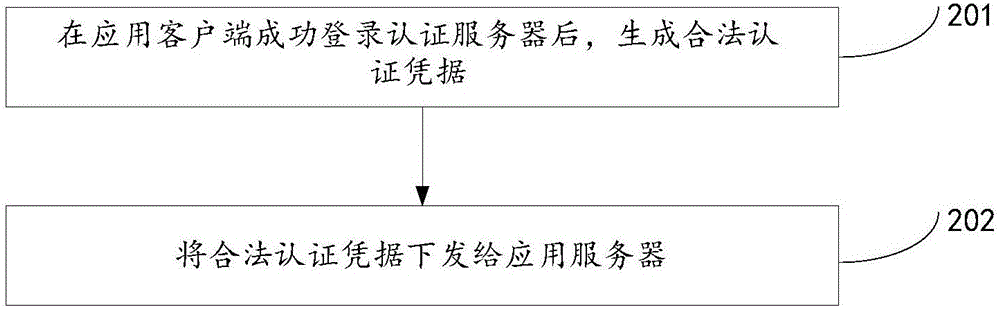
The invention discloses a data authentication method, apparatus and system, and relates to the technical field of the Internet. The problem that a CAS authentication method in the existing single-point login system brings a very large pressure to an authentication server is solved. The method disclosed by the invention comprises the following steps: obtaining access authentication evidence from an access request sent by an application client, wherein the access authentication evidence is the evidence of the application client to access an application server; authenticating the validity of the access authentication evidence according to valid authentication evidence, wherein the valid authentication evidence is released by the authentication server to the application server; and if the access authentication evidence is valid, making response to the access request. The data authentication method, apparatus and system disclosed by the invention is used in a CAS authentication process.
Owner:NEUSOFT CORP
Multi-target data association algorithm based on feature matching matrix
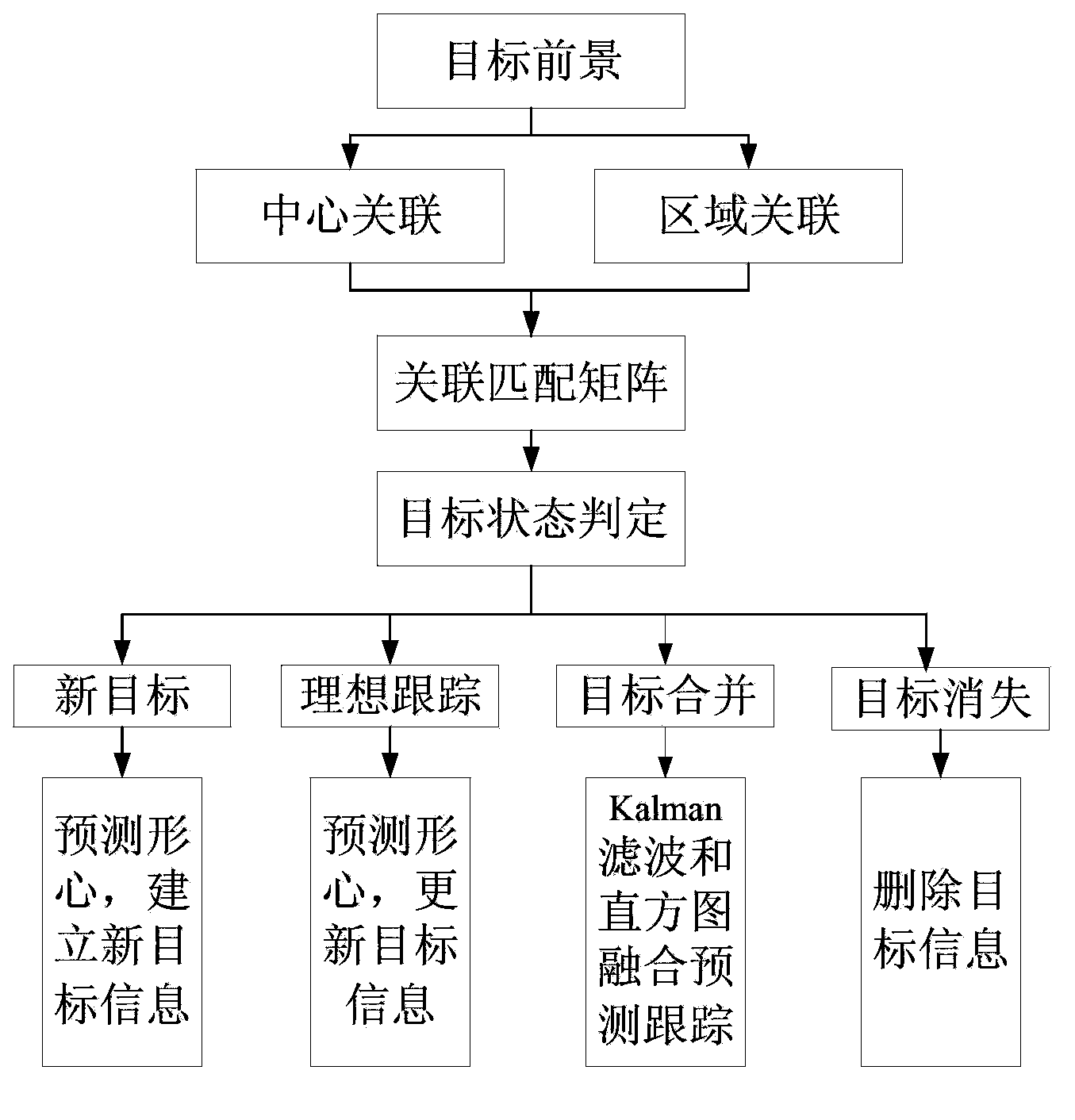
The invention belongs to the technical field of photoelectricity, and particularly relates to a multi-target data association algorithm based on a feature matching matrix. The algorithm includes the following steps that a current video sequence image is collected in the stationary state of shooting equipment; a target, closest to the center of a moving target at the moment of t-1, in the center of a jth moving area at the moment of t is calculated, and the closest matching distance is recorded as d (i, j); the intersecting area of a moving target at a t-1 frame and a moving target at a t frame is calculated, and if the intersecting area of a target at the moment t and a target in the current area is larger than a certain threshold, the intersecting area is recorded as s (i, j); when the center association distance and the area intersecting area are both larger than a certain threshold, an element R (i, j) of the matching matrix is set as 1; an association matching matrix is judged, and association tracking is performed on emerged new targets and an ideal tracking state through a centroid matching algorithm; when combination of the targets occurs, movement information and color information before combination of the targets are reserved respectively, and combination tracking of Kalman filtering and histogram fusion is performed. According the multi-target data association algorithm based on the feature matching matrix, multi-target data association under the condition of sheltering can be achieved.
Owner:中国航天科工集团第二研究院二〇七所
Encrypted communication apparatus and control method therefor
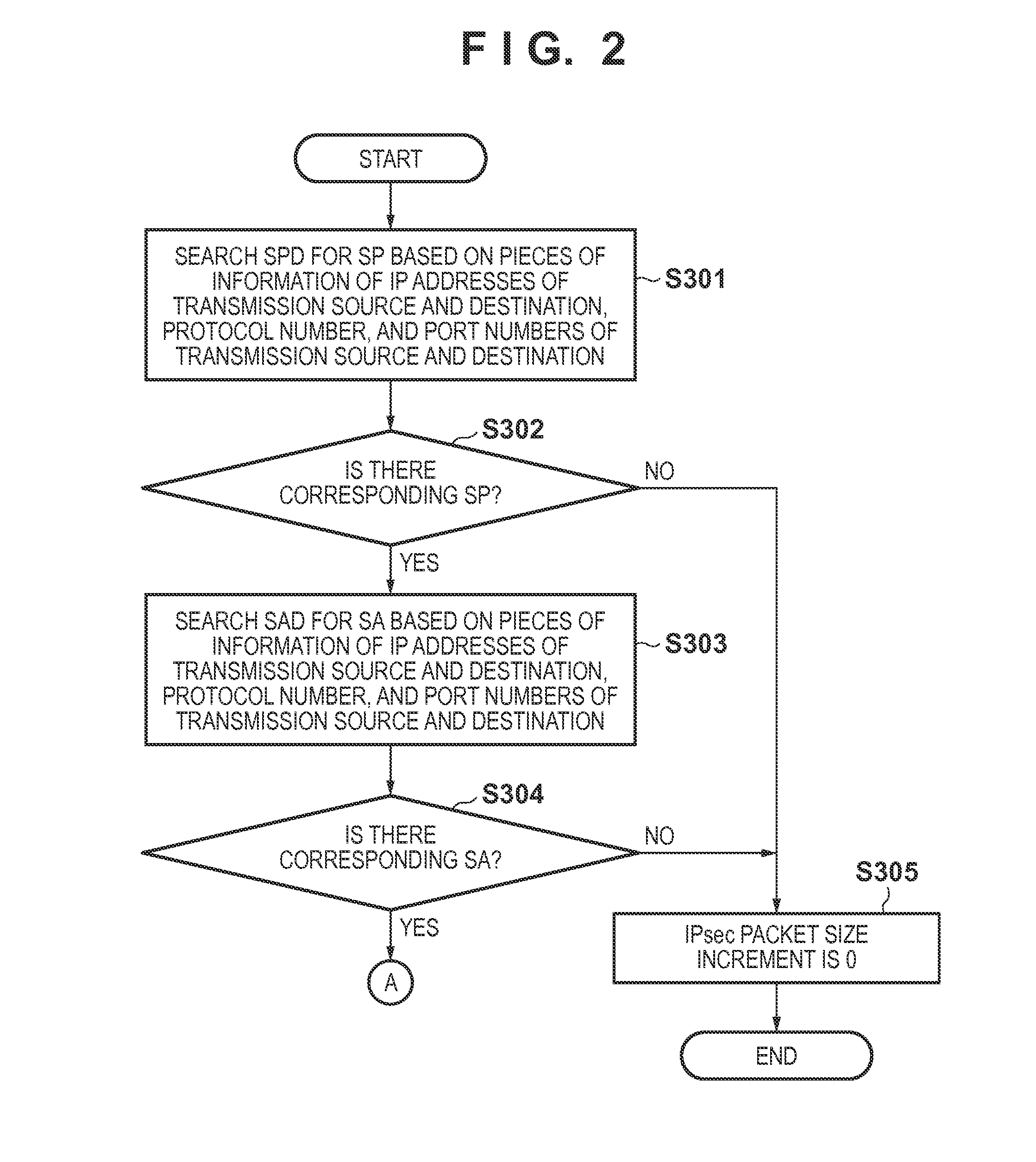
ActiveUS20140101435A1Minimizes calculation amount of calculationMaximize sizeTransmissionIPsecCryptographic protocol
An encrypted communication apparatus determines a security protocol in IPsec to be applied to an IP packet, and calculates, based on the determined security protocol, a packet size which prevents the IP packet from being fragmented even if IPsec is applied to the IP packet. The packet size to be calculated is independent of an encryption algorithm and authentication algorithm which are actually specified by the determined security protocol.
Owner:CANON KK
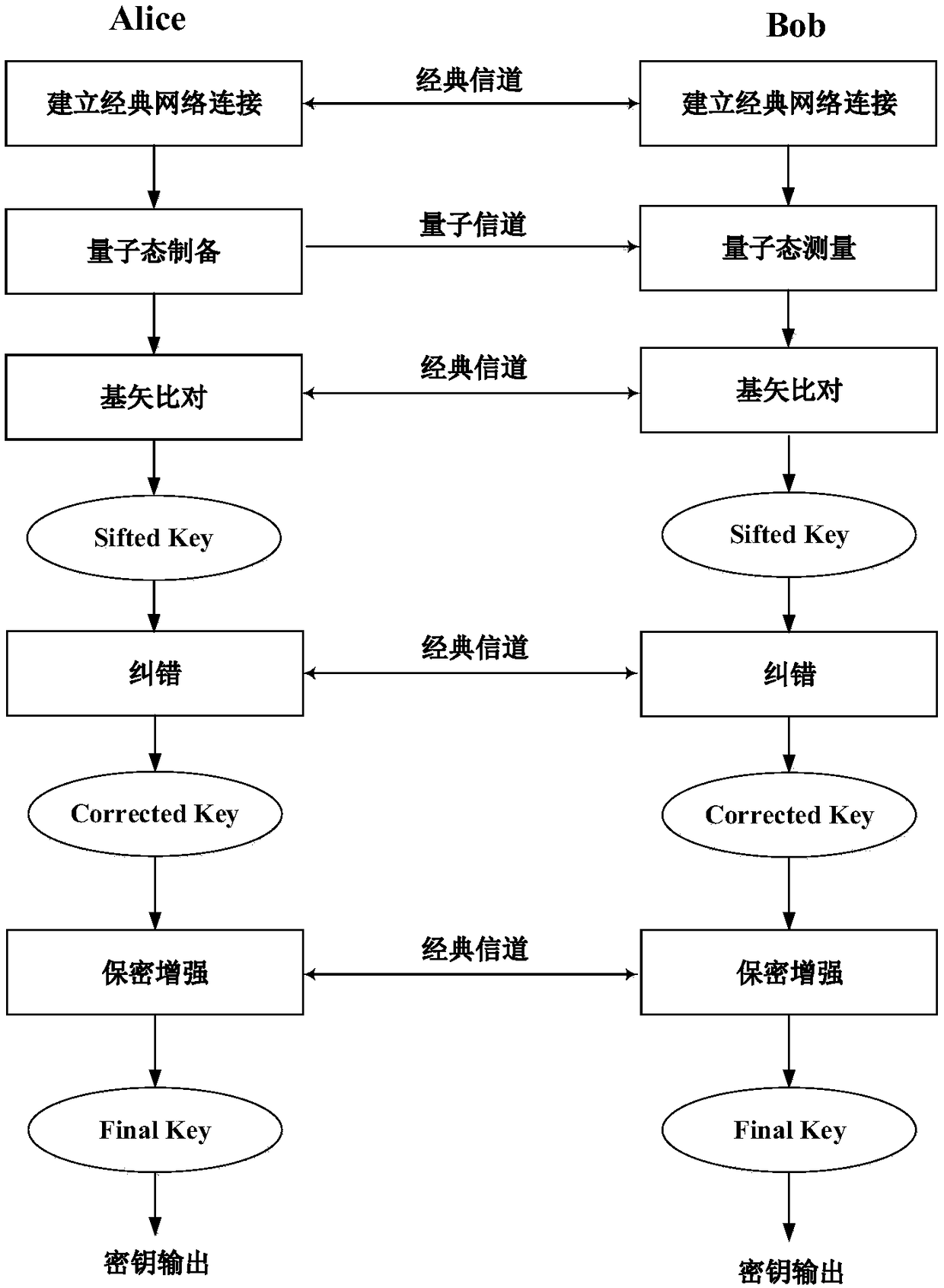
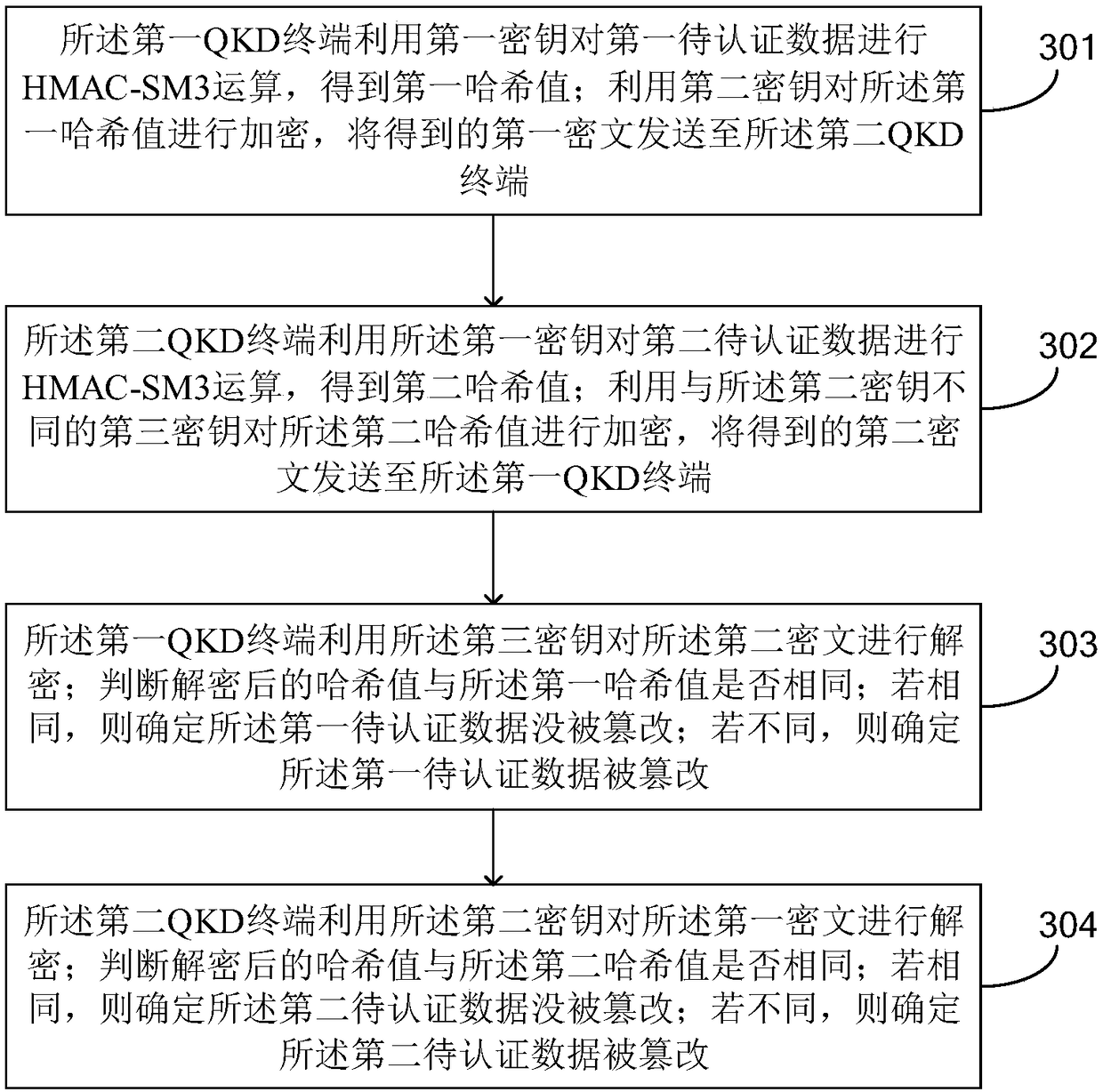
Data authentication method based on HMAC-SM3 algorithm and quantum key distribution system
ActiveCN109274480AImprove accuracyImprove securityKey distribution for secure communicationEncryption apparatus with shift registers/memoriesData integrityTransfer procedure
The present application discloses a data authentication method based on a HMAC-SM3 algorithm and a quantum key distribution system. For two quantum key distribution QKD terminals communicating througha classic network, the two QKD terminals use the same key and adopt HMAC-SM3 algorithm The to perform hashing operation on the terminal interaction data in the same time period to obtain a hash valuerespectively, wherein, the terminal interaction data comprises data sent by two QKD terminals to opposite terminals respectively,. If the interactive data of the terminal is not tampered with while passing through the classic network, the hash values obtained by the two QKD terminals from the peers are the same as the hash values calculated by the two QKD terminals themselves. The hash value obtained by the HMAC-SM3 algorithm has higher security and is not easy to be cracked in the transmission process, which improves the accuracy of data integrity authentication.
Owner:QUANTUMCTEK
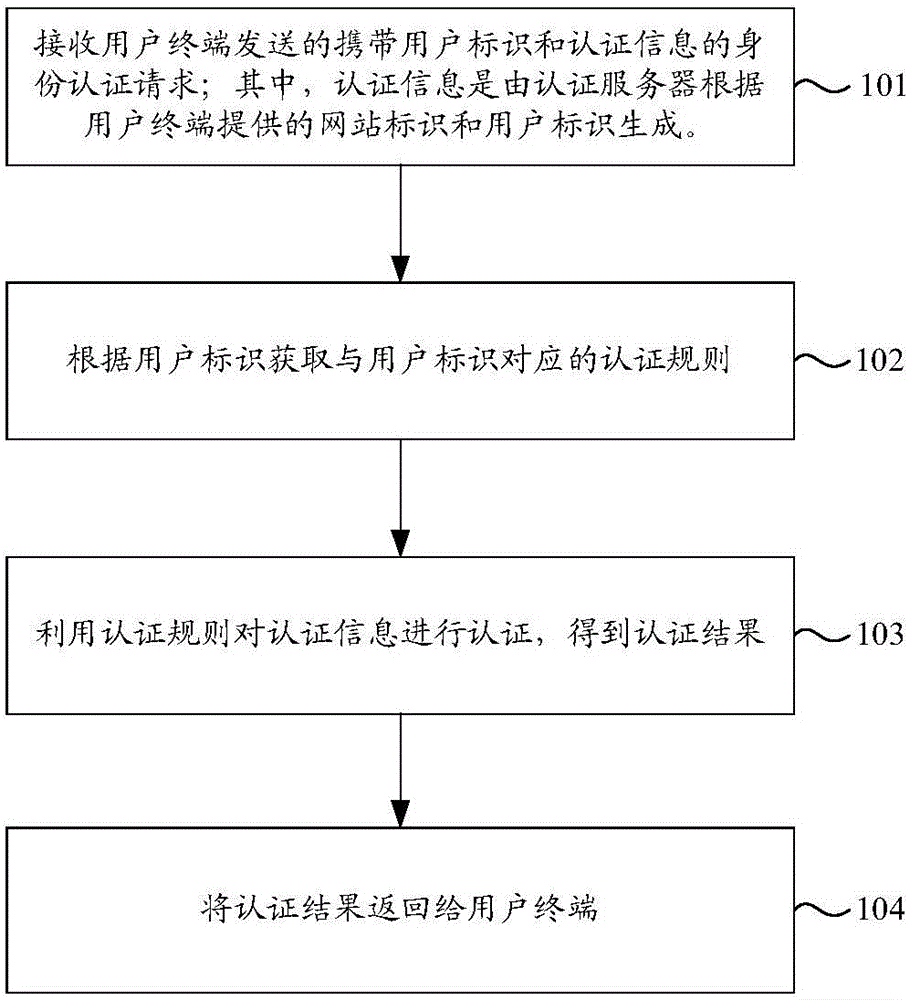
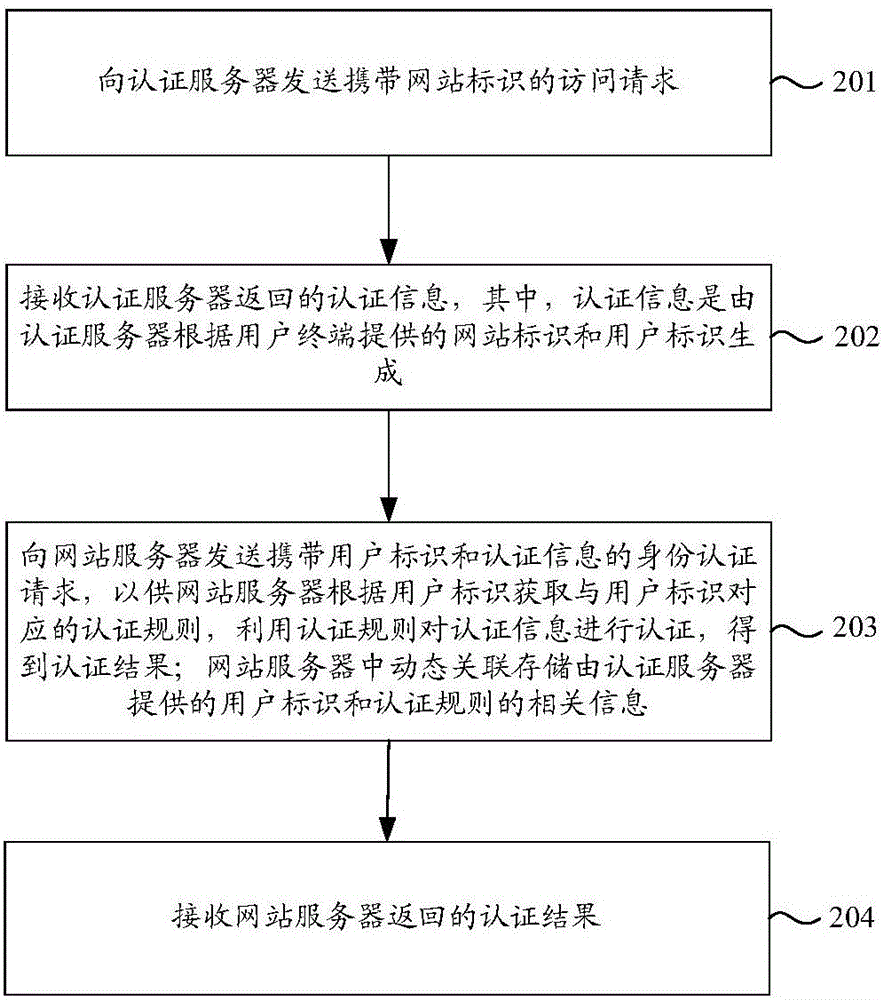
Identity authentication method and system, user terminal and website server
ActiveCN106534150AImprove securityGuarantee information securityTransmissionInternet privacyComputer terminal
The invention discloses an identity authentication method and system, a user terminal and a website server, and relates to the technical field of electronic information. The method comprises the following steps: dynamically and associatively storing related information of a user identifier and an authentication rule provided by an authentication server on the side of the website server; receiving an authentication request carrying the user identifier and authentication information sent by the user terminal, wherein the authentication information is generated by the authentication server according to a website identifier and the user identifier provided by the user terminal; obtaining the authentication rule corresponding to the user identifier according to the user identifier; authenticating the authentication information; and finally returning an authentication result to the user terminal. According to the identity authentication method and system, the user terminal and the website server provided by the invention, the authentication server can dynamically change the authentication algorithm of the website server to a user, the potential safety hazard caused by the fixed presence of the algorithm between the authentication server and the website server is avoided, the security of the identity authentication system is improved, and the information security of the users and the websites is ensured.
Owner:JIANGSU PAYEGIS TECH CO LTD
Establishing a secured communication session
ActiveUS8285989B2Authentication securityUser identity/authority verificationSecret communicationCommunications systemData Authentication Algorithm
The present invention relates to a method for establishing a secured communication session in a communication system between a user using an untrusted device and a server. According to the present invention the user first obtains an authentication algorithm and an encryption algorithm and then creates a session key. Next the user obtains a public key of the server and sends a personal identity number to the server for authentication by using the authentication algorithm, the personal identity number being encrypted by using the encryption algorithm and the public key of the server. The user also sends the session key to the server for encrypting purpose between the user and the server, the session key being encrypted by using the encryption algorithm and the public key of the server.
Owner:APPLE INC
Security authentication method combining multiple algorithms
InactiveCN107566125AReduce threatReduce overheadKey distribution for secure communicationEncryption apparatus with shift registers/memoriesData Authentication AlgorithmSecurity authentication
Owner:GIESECKE & DEVRIENT (CHINA) INFORMATION TECH CO LTD
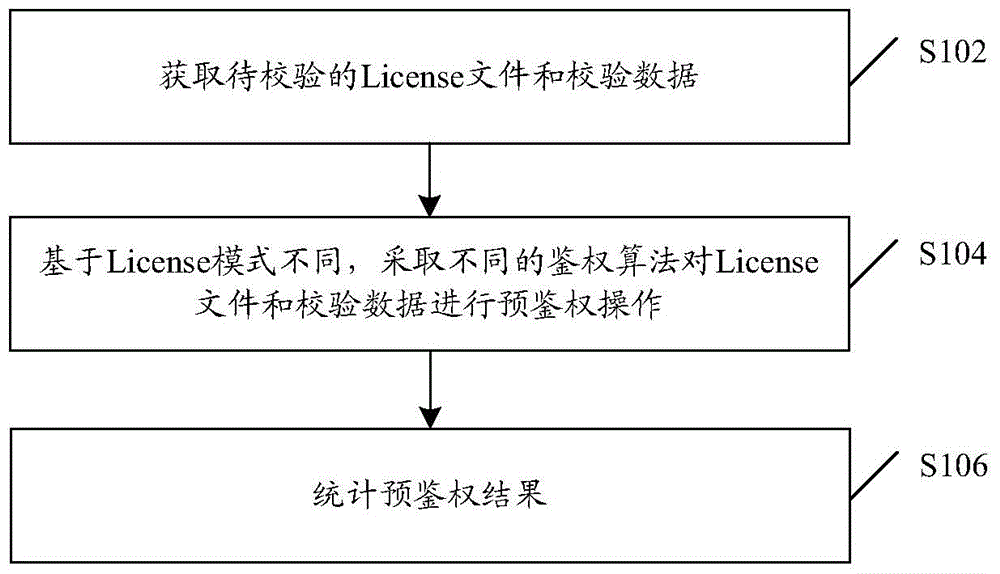
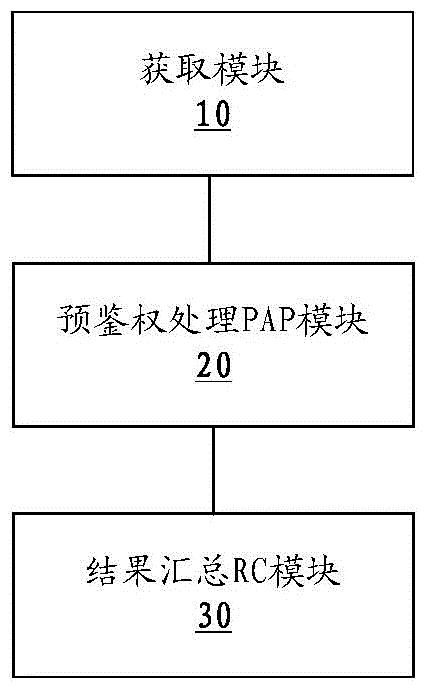
License pre-authentication method, device and system
InactiveCN105790943AAchieve decouplingImprove operation and maintenance efficiencyUser identity/authority verificationSecurity arrangementData Authentication AlgorithmNetwork administrator
The invention discloses a License pre-authentication method, device and system; wherein the method comprises following steps of obtaining to-be-checked License files and checking data; based on different License modes, using different authentication algorithms to carry out pre-authentication operations to the to-be-checked License files and checking data; and carrying out statistics to pre-authentication results. Through adoption of the invention, the problem of lacking pre-authentication in the License solving scheme in the prior art is solved; the realization method of pre-authentication is provided; the network operation and maintenance efficiency is improved; moreover, through adoption of ideals such as using cross-platform language to develop the authentication algorithms, packaging the authentication algorithms and dynamic loading, provided by the invention, a network administrator and the version of a base station are decoupled, the system is more reliable, and the maintenance and development costs of software are greatly reduced.
Owner:ZTE CORP
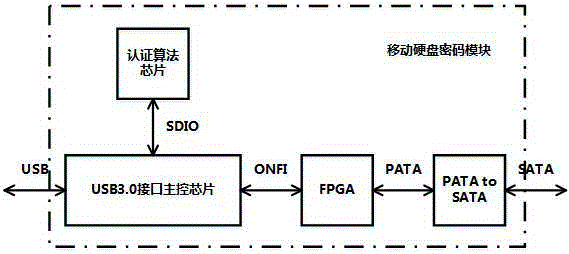
Mobile hard disk password module
InactiveCN105205416AAvoid unsafe hazardsPrevent theftInternal/peripheral component protectionPasswordData Authentication Algorithm
The invention discloses a mobile hard disk password module, and relates to the field of data security. The mobile hard disk password module comprises a USB3.0 interface main control chip, an authentication algorithm chip, an FPGA and a PATA-to-SATA bridge sheet, wherein the USB3.0 interface main control chip is suitable for being connected with a USB interface, and communicates with both the authentication algorithm chip and the FPGA; the FPGA communicates with the PATA-to-SATA bridge sheet; and the PATA-to-SATA bridge sheet is suitable for being connected with storage equipment. The authentication algorithm chip realizes identity authentication; after authentication, user data are encrypted and decrypted through the FPGA, and finally the PATA-to-SATA bridge sheet is used for writing or reading data into or out of storage equipment. The mobile hard disk password module can effectively prevent the data in a storage system from being stolen, tampered or damaged by personnel concerned, so that the completeness and the security of the user data can be guaranteed.
Owner:INSPUR GROUP CO LTD
Method of updating an authentication algorithm in a computer system
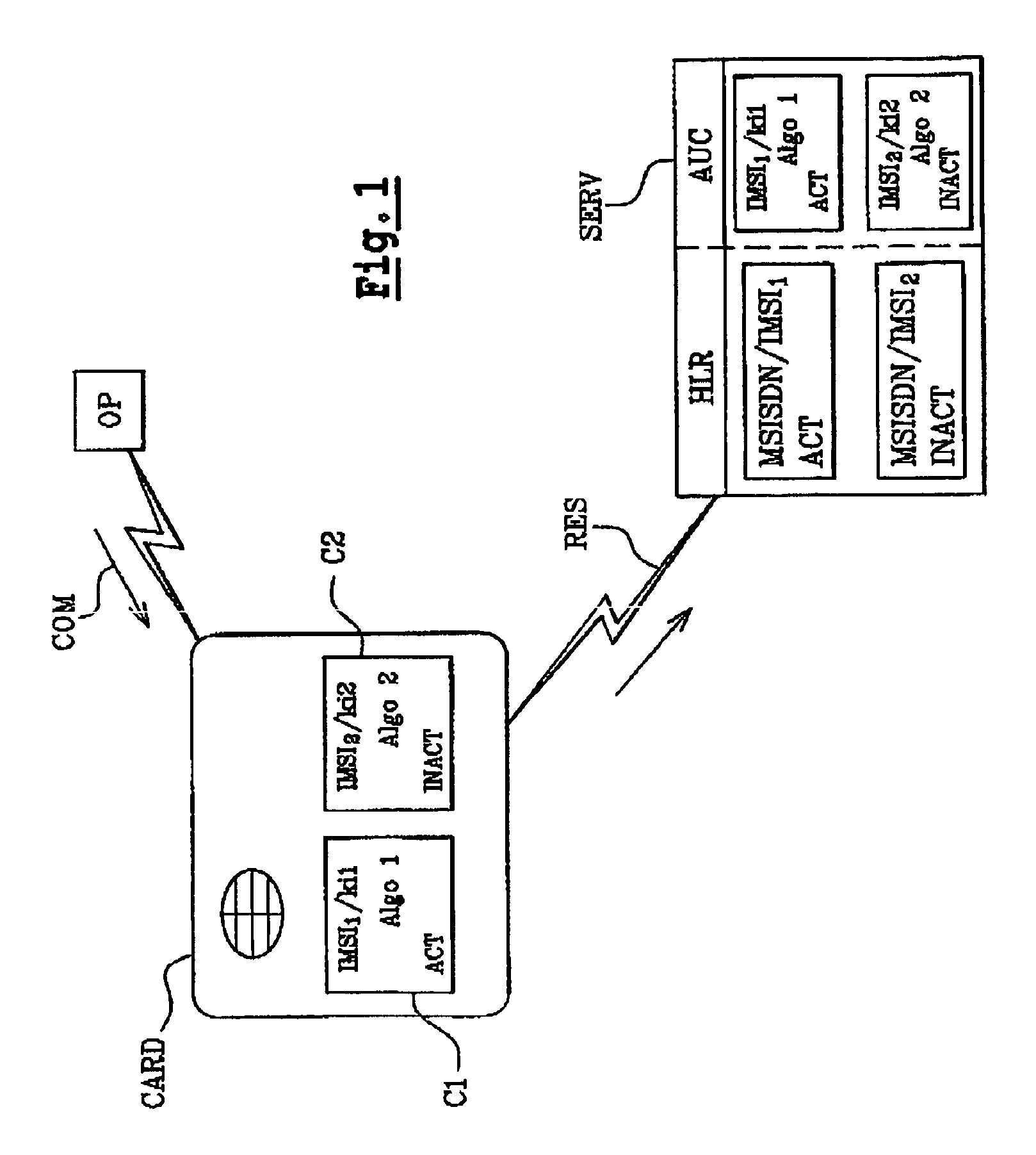
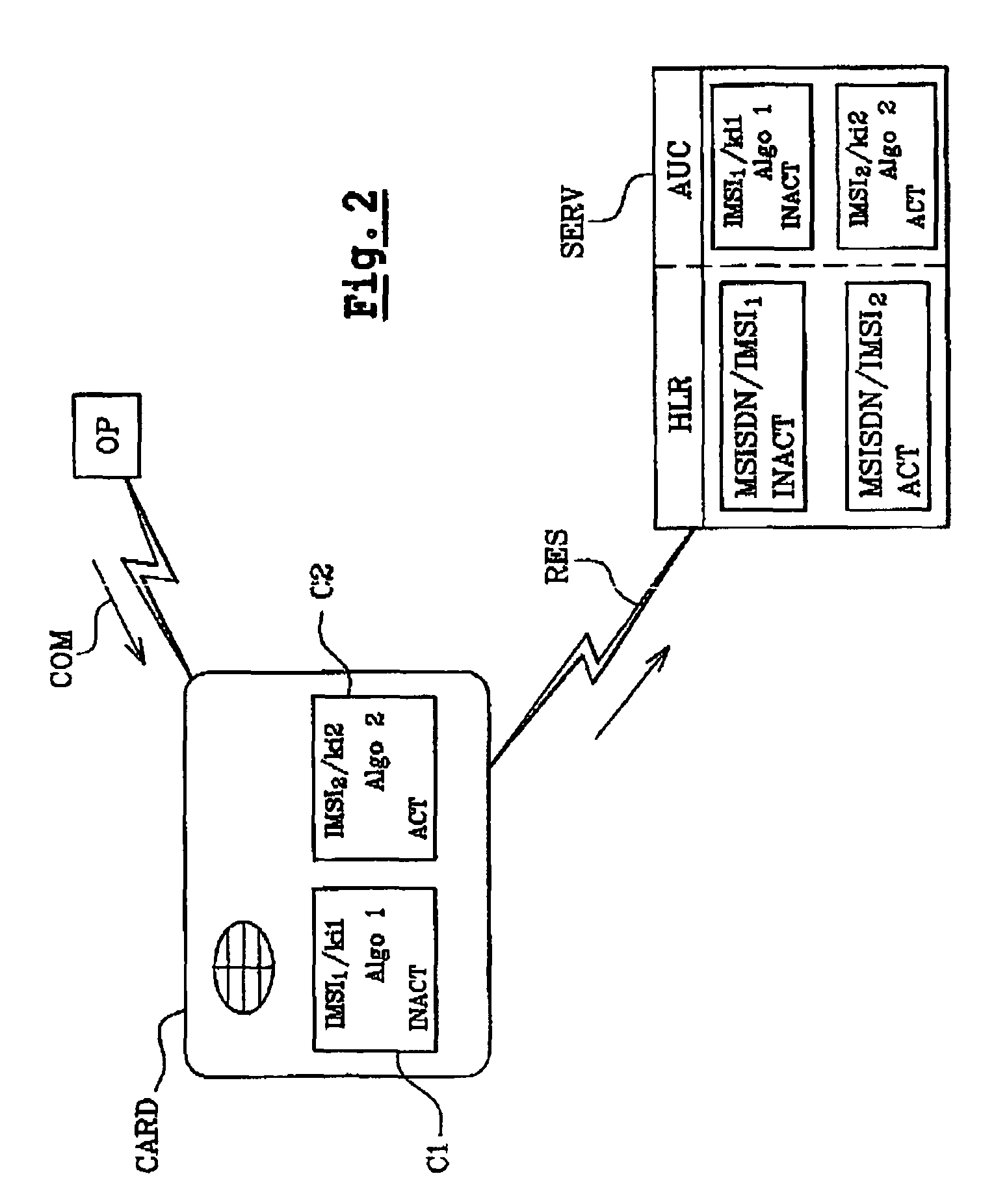
ActiveUS8031871B2Shorten the timeUnauthorised/fraudulent call preventionMultiple keys/algorithms usageComputer hardwareComputerized system
The invention relates to a method of updating an authentication algorithm in at least one data processing device (CARD, SERV) which can store a subscriber identity (IMSI1) which is associated with an authentication algorithm (Algo1) in a memory element of said device (CARD, SERV). The inventive method comprises the following steps, namely: a step whereby a second inactive (Algo2) authentication algorithm is pre-stored in a memory element of the device and a step for switching from the first algorithm (Algo1) to the second algorithm (Algo2) which can inhibit the first algorithm (Algo1) and activate the second (Algo2).
Owner:THALES DIS FRANCE SA
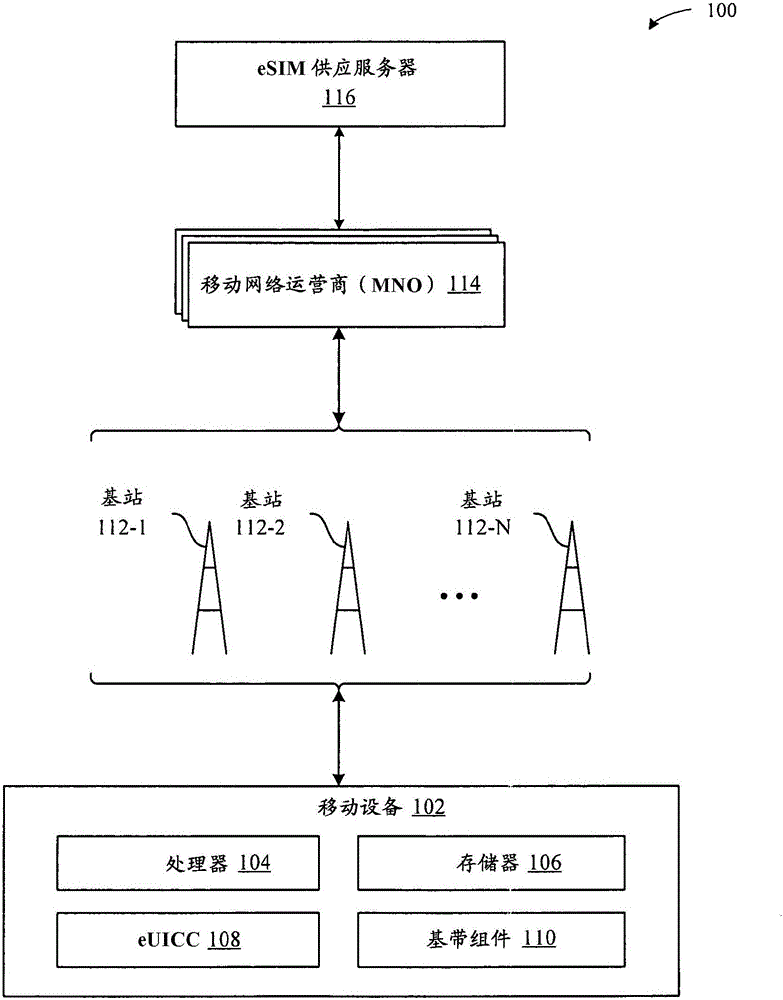
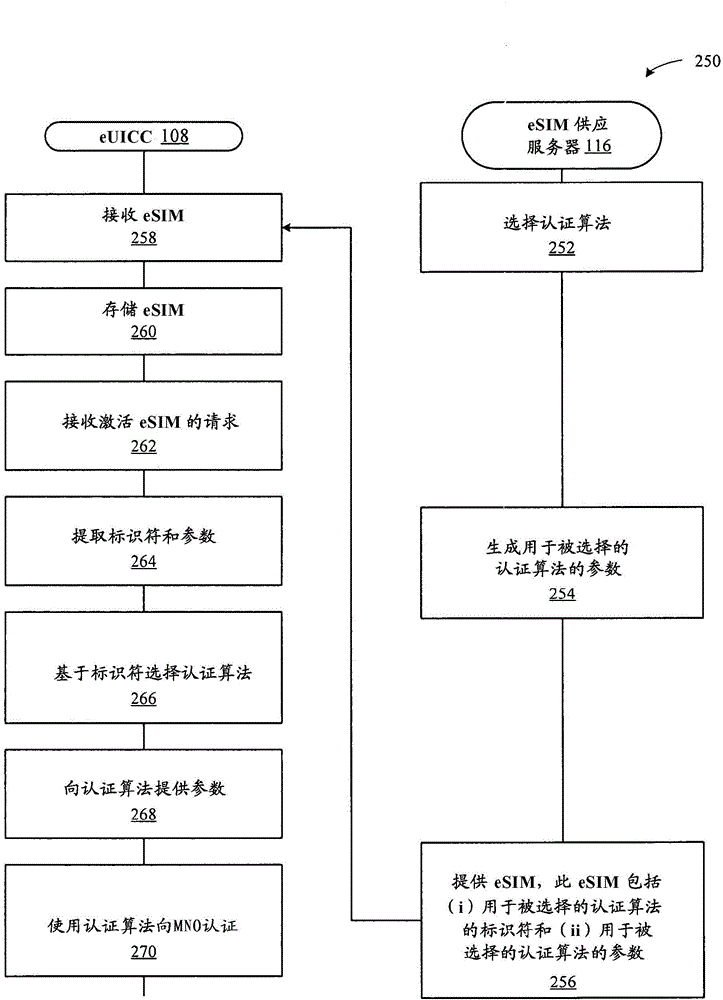
Techniques for dynamically supporting different authentication algorithms
Disclosed herein are different techniques for enabling a mobile device to dynamically support different authentication algorithms. A first technique involves configuring an eUICC included in the mobile device to implement various authentication algorithms that are utilized by MNOs (e.g., MNOs with which the mobile device can interact). Specifically, this technique involves the eUICC storing executable code for each of the various authentication algorithms. According to this technique, the eUICC is configured to manage at least one eSIM, where the eSIM includes (i) an identifier that corresponds to one of the various authentication algorithms implemented by the eUICC, and (ii) authentication parameters that are compatible with the authentication algorithm. A second technique involves configuring the eUICC to interface with an eSIM to extract (i) executable code for an authentication algorithm used by an MNO that corresponds to the eSIM, and (ii) authentication parameters that are compatible with the authentication algorithm.
Owner:APPLE INC
Data authentication method and apparatus
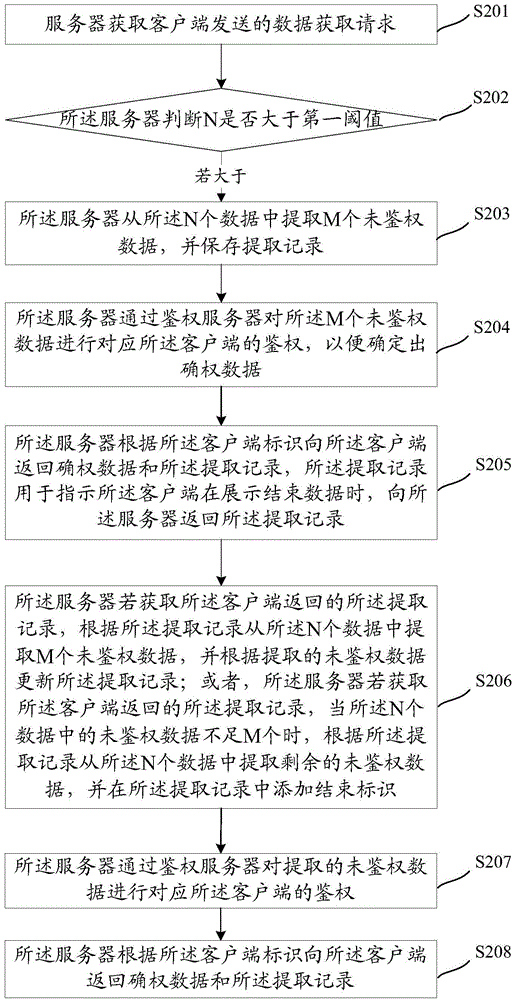
The embodiments of the invention disclose a data authentication method and apparatus. The method comprises the following steps: obtaining by a server the data obtaining request sent from a customer terminal wherein the data obtaining request includes customer terminal identification and a data set requested to be obtained and the data set includes N data; determining whether N is greater than a first threshold value or not; and if N is greater, extracting M unauthenticated data from the N data and recording the extraction record; using the authentication server to conduct authentication to the M unauthenticated data from the corresponding customer terminal so as to determine the right confirmation data; and based on the customer terminal identification, returning to the customer terminal the right confirmation data and the extraction record wherein the extraction record is used to indicate the extraction record returned to the server when the customer terminal completes data display. Therefore, all that needs to be done is authenticate some parts of the data and then, right confirmation data can be returned to the customer terminal, reducing the time of the customer terminal to wait for an authentication result and increasing the user's use experience.
Owner:ALIBABA GRP HLDG LTD
Establishing a Secured Communication Session
ActiveUS20130046984A1Authentication securityUser identity/authority verificationSecret communicationCommunications systemData Authentication Algorithm
The present invention relates to a method for establishing a secured communication session in a communication system between a user using an untrusted device and a server. According to the present invention the user first obtains an authentication algorithm and an encryption algorithm and then creates a session key. Next the user obtains a public key of the server and sends a personal identity number to the server for authentication by using the authentication algorithm, the personal identity number being encrypted by using the encryption algorithm and the public key of the server. The user also sends the session key to the server for encrypting purpose between the user and the server, the session key being encrypted by using the encryption algorithm and the public key of the server.
Owner:APPLE INC
Intelligent card applicable to special mobile communication requirements and security control method thereof
ActiveCN102612026AFlexible configurationRecord carriers used with machinesSecurity arrangementOperation modeSmart card
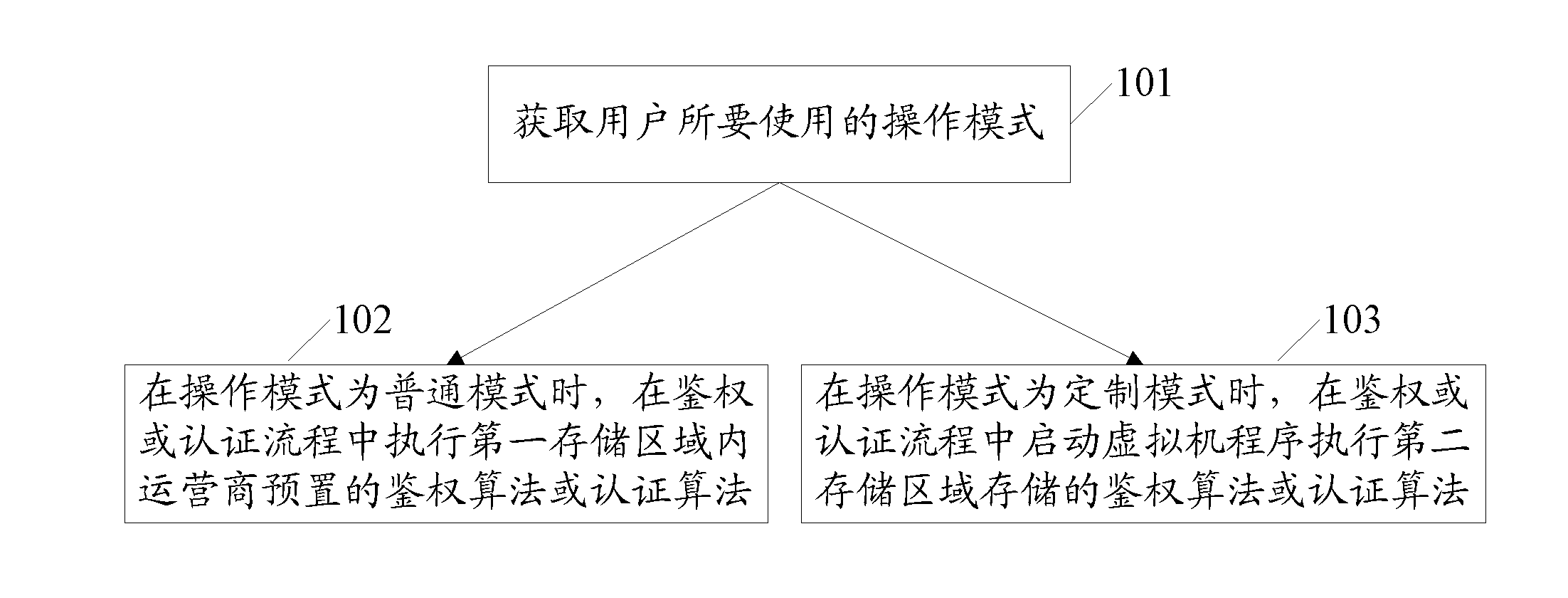
The invention provides a security control method and system of an intelligent card applicable to special mobile communication requirements. According to the method, a storage area in the intelligent card is divided into a first storage area and a second storage area, wherein the first storage area stores an authentication algorithm and an identification algorithm which are preset by an operator before the intelligent card is issued, and is used when the operation mode is a common mode; the second storage area stores the authentication algorithm and / or the identification algorithm which are / is customized by a user after the intelligent card is issued; the intelligent card is used for acquiring the operation mode about to be used by the user, actuating the authentication algorithm or the identification algorithm, which is preset by the operator in the first storage area, in the process of authentication or identification when the operation mode is a common mode, and starting a virtual machine program to actuate the authentication algorithm or the identification algorithm in the process of authentication or identification when the operation mode is a customization mode.
Owner:DATANG MICROELECTRONICS TECH CO LTD
Authentication method and authentication server of access request
ActiveCN109379344AImprove accuracyIncrease flexibilityTransmissionData Authentication AlgorithmAuthentication server
The embodiment of the invention relates to the technical field of the data processing, and discloses an authentication method and authentication server of an access request. The authentication methodof the access request disclosed by the embodiment of the invention is applied to an authentication server, and comprises the following steps: receiving an authentication request from a CDN node server, determining a corresponding authentication algorithm type according to the authentication request; authenticating the authentication request according to the determined authentication algorithm typecorresponding to the authentication request, and generating an authentication result; and sending the authentication result to the CDN node server so that the CDN node server can make response on a resource access request of a user terminal according to the authentication result. Through the authentication method disclosed by the embodiment of the invention, the authentication accuracy and security are improved, the misjudgment is greatly reduced, and the authentication is hard to be counterfeited.
Owner:CHINANETCENT TECH
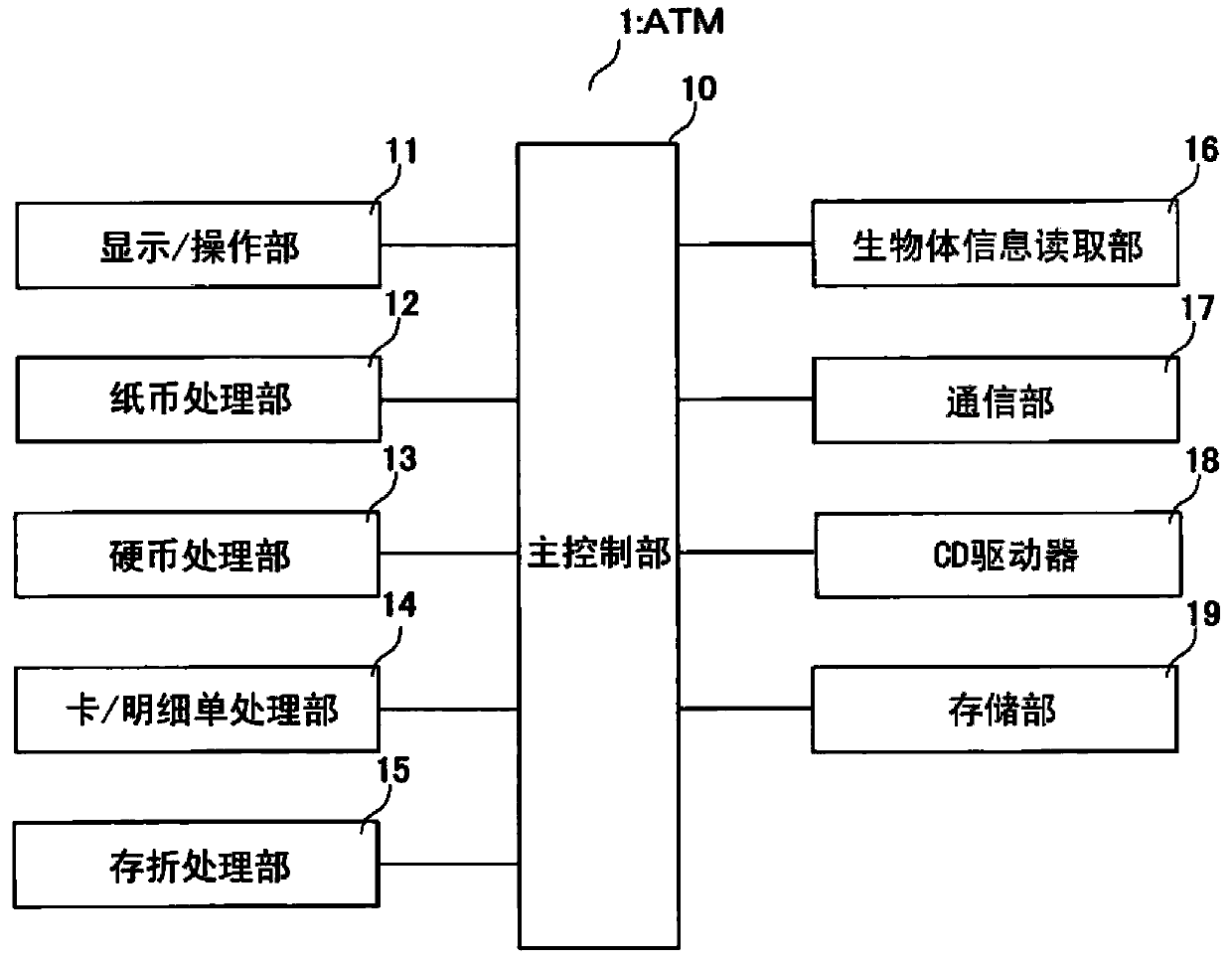
Paper processing device and authentication algorithm updating program
InactiveCN102789659BImprove processing efficiencyCharacter and pattern recognitionData Authentication AlgorithmBlack list
The invention provides a paper processing device, which can ensure paper authentication accuracy and can inhibit the increase of a false coupon list and inhibit the decrease of authentication processing efficiency based on a serial number. A main control part (10) reads an authentication algorithm (s21) from a CD disposed in a CD driver (18) and installs the authentication algorithm (s22). If the CD is recorded with a deletion list, the main control part (10) reads the deletion list (s24) from the CD. The main control part (10) reads the serial number and currency registered in the deletion list one by one. If a serial number black list is registered with serial numbers and currency which are consistent with the above serial numbers and currency, the serial numbers (s25-s28) will be deleted from the serial number black list.
Owner:HITACHI OMRON TERMINAL SOLUTIONS CORP
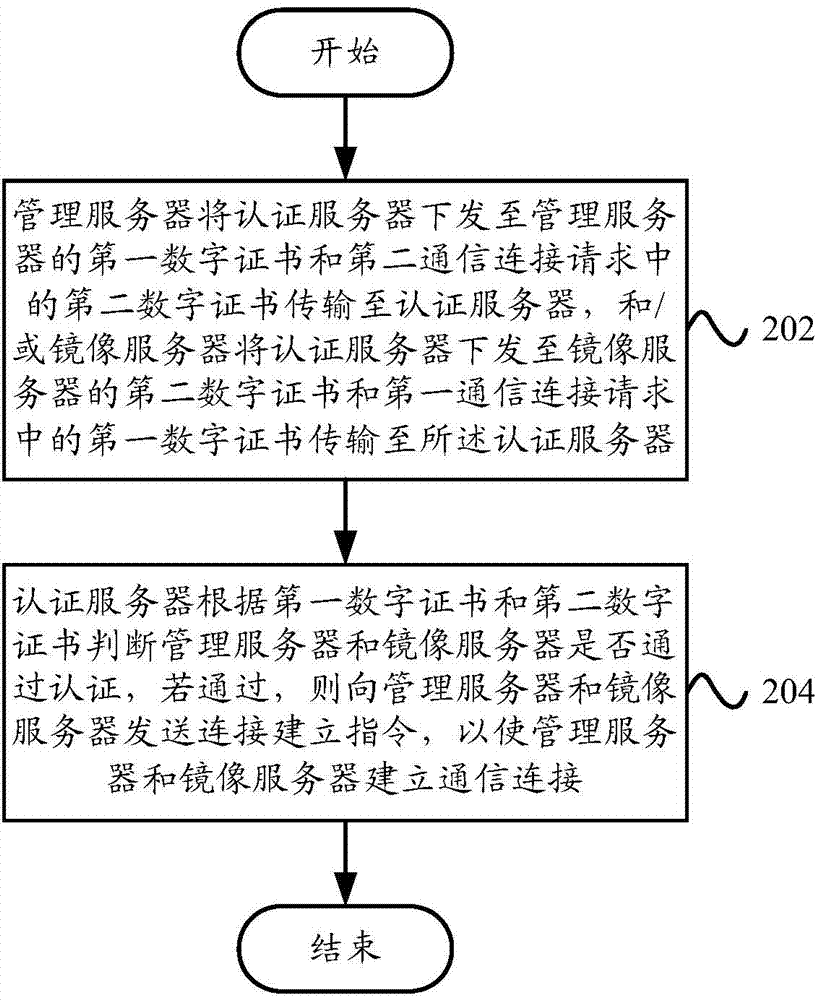
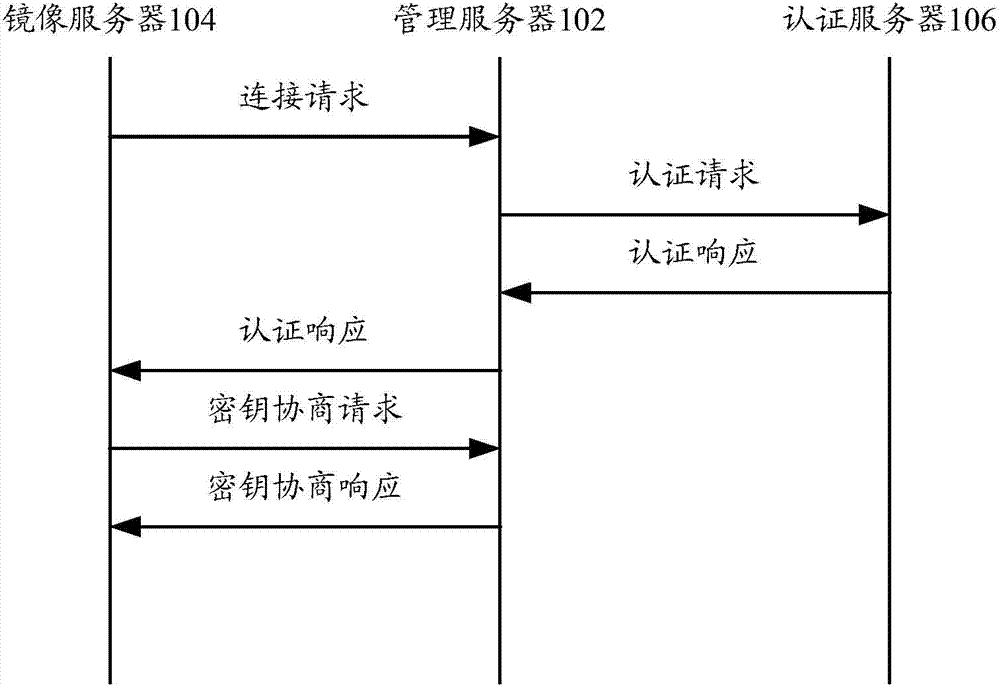
Data authentication system and data authentication method
ActiveCN103501230AEnsure safetyPrevent illegal readingUser identity/authority verificationData Authentication AlgorithmAuthentication server
The invention provides a data authentication system, which comprises a management server, at least one mirror image server and an authentication server, wherein the management server is used for receiving a first communication connection request, and transmitting a first digital certificate and a second digital certificate in the first communication connection request to the authentication server; the at least one mirror image server is used for receiving a second communication connection request, and transmitting the second digital certificate and the first digital certificate in the second communication connection request to the authentication server; the authentication server is used for judging whether the management server and the at least one mirror image server pass authentication or not, and if the management server and the at least one mirror image server pass the authentication, a communication connection is allowed to be established between the management server and the at least one mirror image server. The invention also provides a data authentication method. According to the technical scheme provided by the invention, the safety of patient information in the management server and the at least one mirror image server can be ensured, and therefore, the patient information in the management server and the at least one mirror image server is prevented from being illegally read, and illegal information is prevented from being written in the management server or the at least one mirror image server.
Owner:PKU HEALTHCARE IT
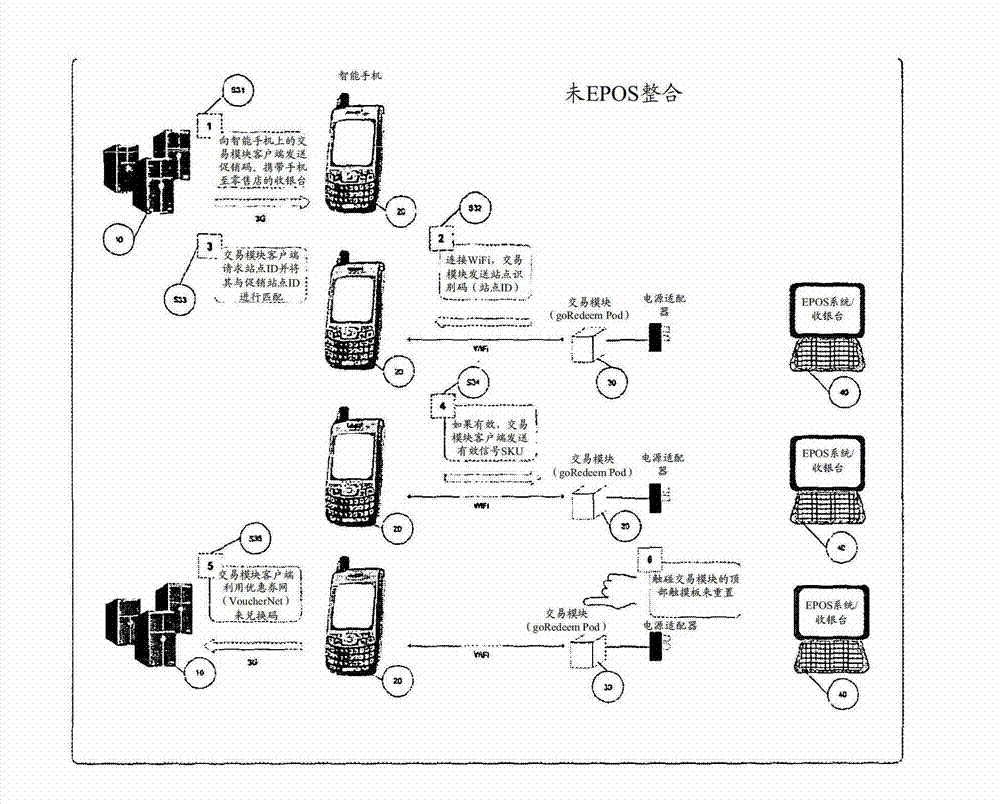
Electronic transaction method and system
InactiveCN103250170ADiscounts/incentivesBuying/selling/leasing transactionsSecure Electronic TransactionComputer module
Consumer with a token incorporating a transaction code on their Smartphone brings their Smartphone to a retailer equipped with a transaction module. When purchasing an article, connection is established between the Smartphone and the transaction module and the transaction module transmits its identity code to the Smartphone. The Smartphone subsequently runs the transaction code and identity code through an authentication algorithm. If authenticated, the Smartphone sends authentication signal to the transaction module and a transaction report to a transaction server. Upon receipt of the authentication signal, the transaction module outputs a corresponding validity indication. This enables any retailer possessing a transaction module to process an electronic transaction without directly altering the retailers system. This therefore provides a simpler and potentially cheaper way of implementing electronic transactions at a wide variety of unrelated retail outlets.
Owner:2ERGO
Data authentication method and data authentication system
ActiveUS20080010462A1Efficiently performing checking processReduce memory capacityUser identity/authority verificationDigital data protectionComputer hardwareDigital signature
A storage means which can be accessed by an authentication apparatus stores content data, a first digest table including primary digest values corresponding to a plurality of data portions constituting the content data, a second digest table including secondary digest values corresponding to a plurality of data portions of the first digest table, and a digital signature generated from the second digest table. In a first reading step, the second digest table and the digital signature are read out from the storage means into a memory of the authentication apparatus. In a first authentication step, the authenticity of the content data is verified using the digital signature read out into the memory and the second digest table read out into the memory.
Owner:NINTENDO CO LTD
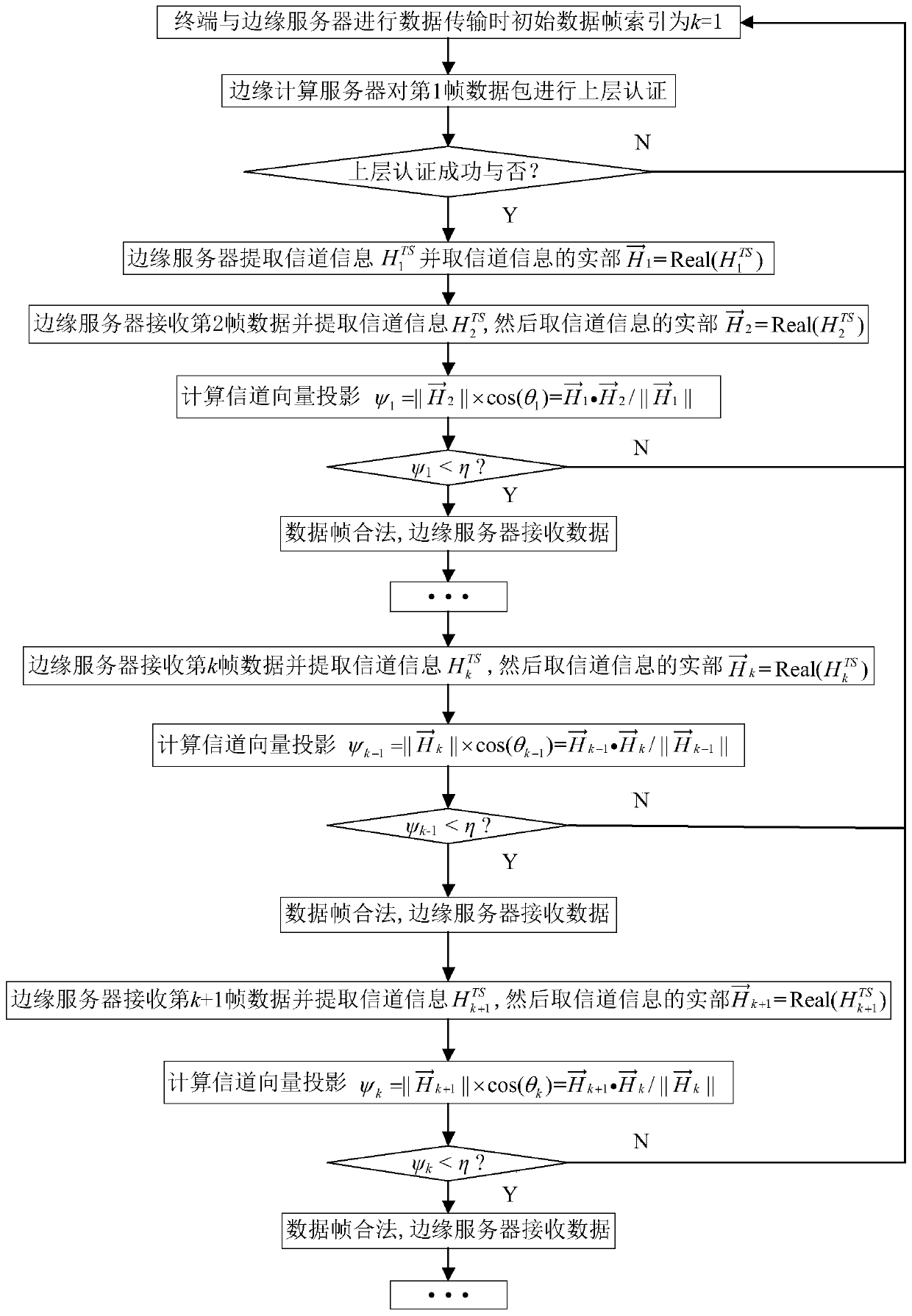
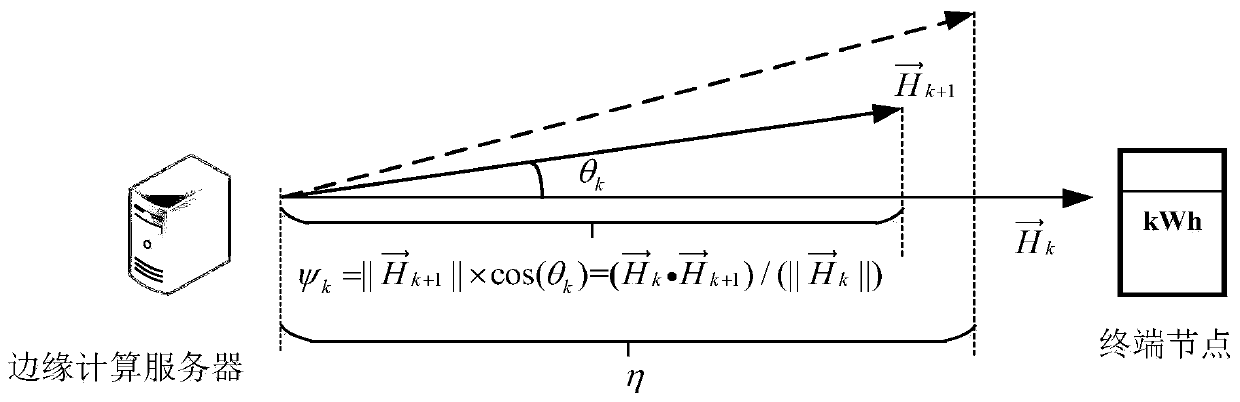
Data transmission safety authentication method and system based on edge calculation and vector projection
ActiveCN110493256AAccurate verificationReduce computational complexityTransmissionReference vectorComputation complexity
The invention discloses a data transmission safety authentication method and a data transmission safety authentication system based on edge calculation and vector projection. The method comprises thefollowing steps: S1, initial authentication: when a terminal node performs data transmission with an edge computing server, the edge computing server performs upper-layer authentication on an initialdata packet, and extracts a corresponding channel information vector as a reference vector for data packet authentication; S2, calculating the vector projection of the channel information: when the edge calculation server receives a new continuous data frame, extracting the channel information of the current data frame and calculating the vector projection of the channel information correspondingto the previous frame of data packet; and S3, judging the legality of the continuous data frames: checking the legality of the continuous data frames through binary hypothesis. According to the invention, the calculation complexity of the edge calculation server is reduced, and the safety and the data authentication rate of the system authentication data are improved.
Owner:SHENZHEN POWER SUPPLY BUREAU +1
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com