Security authentication method combining multiple algorithms
A security authentication, multi-algorithm technology, applied in key distribution, can solve the problems of short brute force cracking theory time and information security threats, achieve the effect of small extra overhead and reduce the threat of key brute force cracking
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
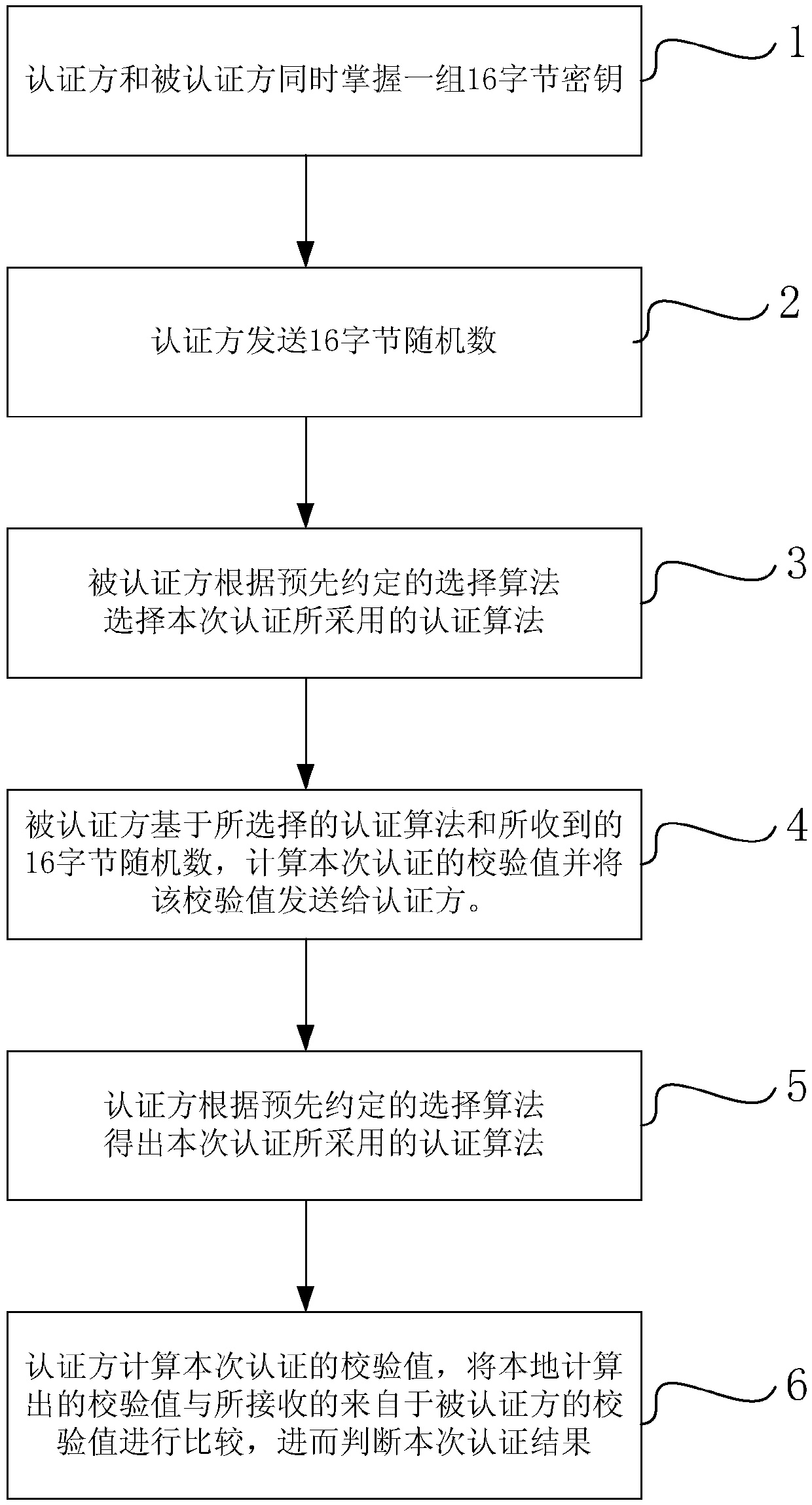
[0025] According to an embodiment of the present invention, a security authentication method combining the national secret SM4 algorithm and the 3DES algorithm is provided.
[0026] For the convenience of description, the following first analyzes the principle of the national secret SM4 algorithm and 3DES algorithm. In principle, these two algorithms have the following characteristics:
[0027] 1. The key length of the two algorithms is the same: the key length of the national secret SM4 algorithm and the 3DES algorithm are both 16 bytes, although the actual effective key length of the 3DES algorithm is 112 bits, but due to the actual application of the key The setting is in bytes, and the 3DES key is usually a 16-byte value.
[0028] 2. In the two algorithms, the lengths of plaintext and ciphertext data blocks are integer multiples. The length of the plaintext and ciphertext data blocks of the SM4 algorithm is 16 bytes, and the length of the 3DES algorithm plaintext and cip...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com