Differentiated authentication method and differentiated authentication device
An authentication method and a differentiated technology, applied in the computer field, can solve the problems of differentiated security services, low security of application servers, inability to provide application services, etc., and achieve the effect of improving security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
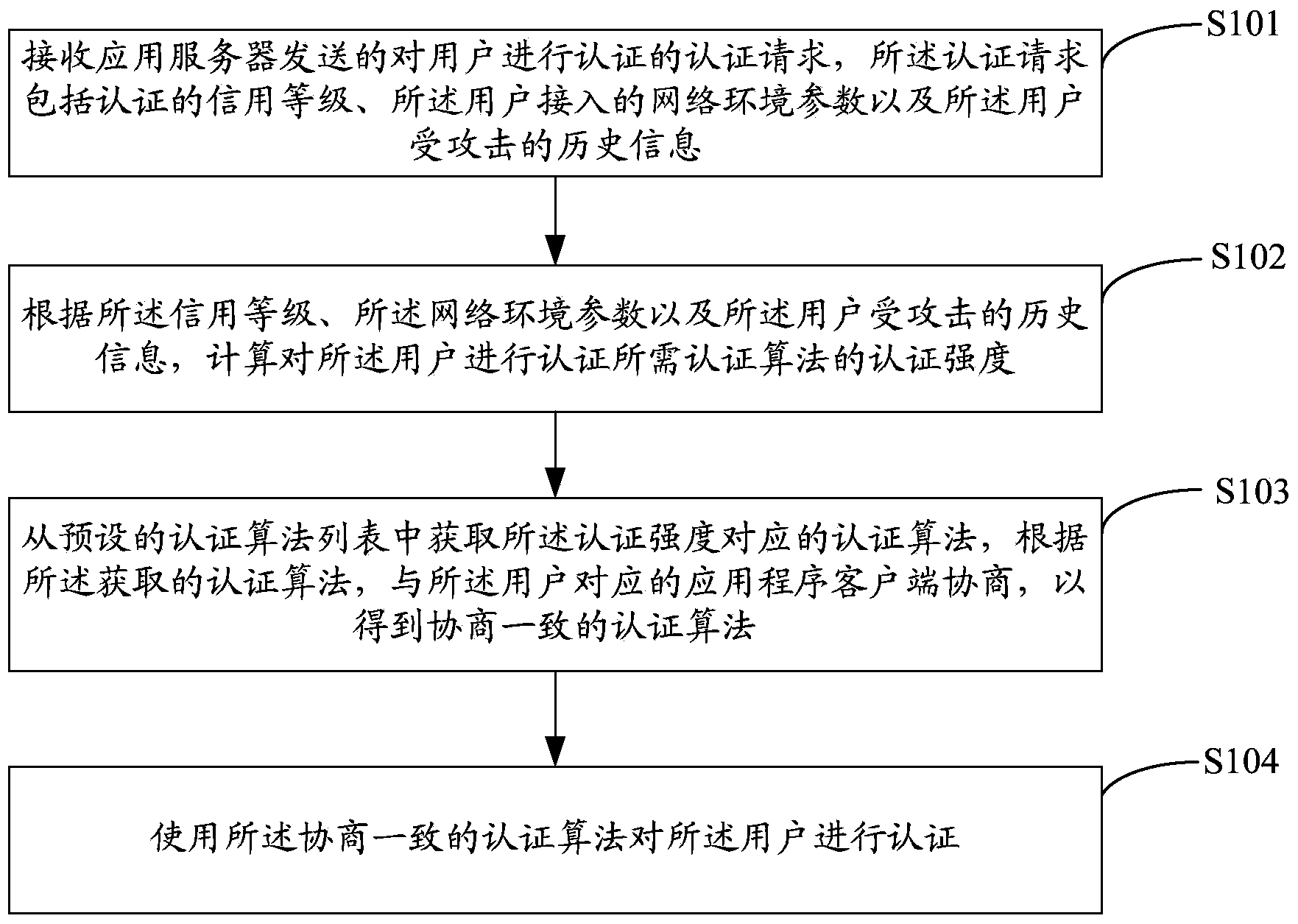
[0022] figure 1 The implementation flow of the differentiated authentication method provided by Embodiment 1 of the present invention is shown, and the details are as follows:
[0023] In step S101, an authentication request for authenticating a user sent by an application server is received, and the authentication request includes an authentication credit level, network environment parameters accessed by the user, and attack history information of the user.
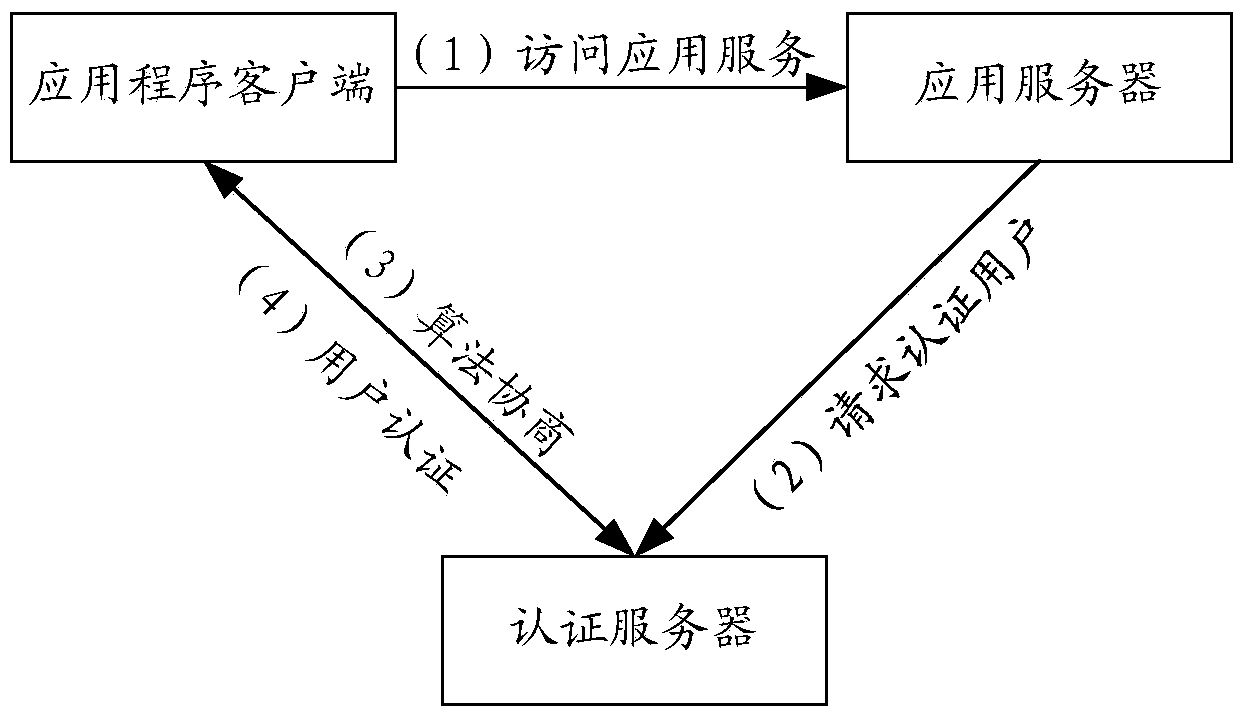
[0024] In the embodiment of the present invention, the application server is used to provide application services, and when the user requests to access the application server through the application program client, the application server requests the authentication server to authenticate the user. The authentication server is an authentication service provider trusted by the application service provider / application server, for example, a CA center and the like.
[0025] In the embodiment of the present invention, the re...
Embodiment 2
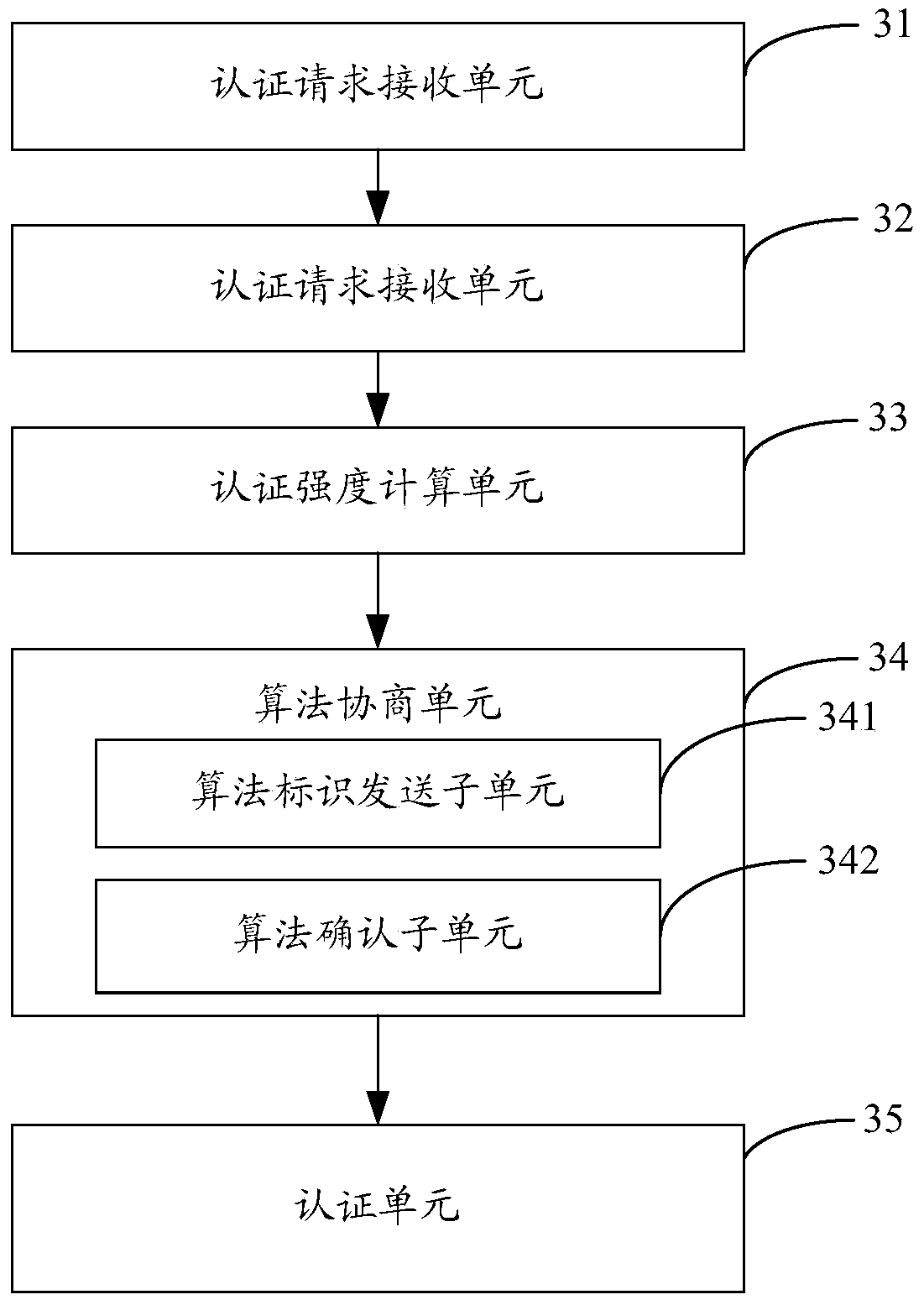
[0038] image 3 The structure of the differentiated authentication device provided by the second embodiment of the present invention is shown, and for the convenience of description, only the parts related to the embodiment of the present invention are shown.
[0039] The algorithm configuration unit 31 is configured to configure corresponding authentication algorithms for different preset authentication strengths.
[0040] An authentication request receiving unit 32, configured to receive an authentication request sent by the application server to authenticate the user, the authentication request including the credit level of authentication, the network environment parameters accessed by the user, and the attack history information of the user;
[0041] An authentication strength calculation unit 33, configured to calculate the authentication strength of the authentication algorithm required for authenticating the user according to the credit rating, the network environment p...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com