Data authentication method and apparatus
A data and authentication technology, applied in the field of data processing, can solve the problems of long authentication time, low efficiency, and waiting for the authentication result.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 2
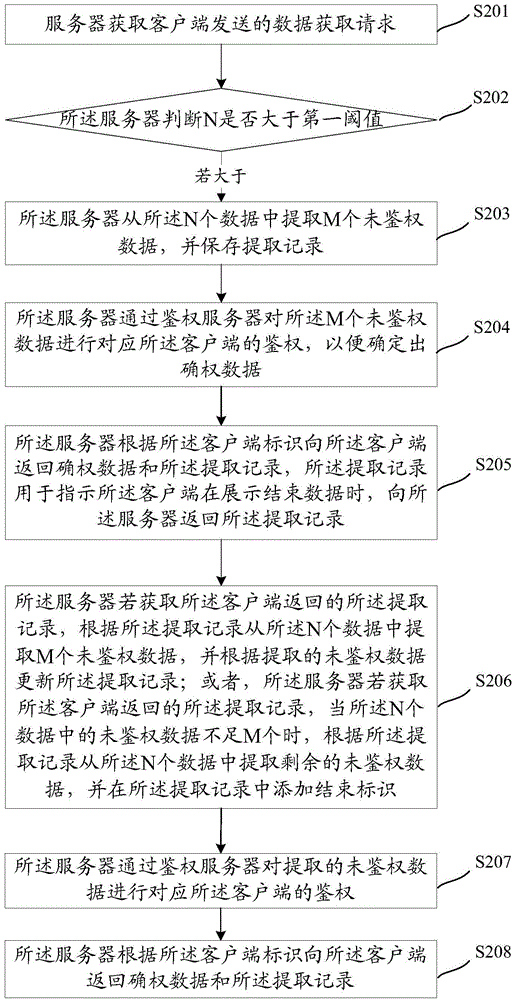
[0123] image 3 A device structure diagram of a data authentication device provided by an embodiment of the present invention, the device includes:
[0124] The acquisition unit 301 originally acquires a data acquisition request sent by a client, the data acquisition request includes a client identifier and a data set requested to be acquired, the data set includes N data, and N is greater than or equal to 2.
[0125] The first judging unit 302 is configured to judge whether N is greater than a first threshold, and if so, trigger the extraction unit.
[0126] The extraction unit 303 is configured to extract M pieces of unauthenticated data from the N pieces of data, and save the extraction record, and the unauthenticated data is the data that has not been corresponding to the client through the authentication server by the server For the authenticated data, the extraction record is used to record the data information of the extracted data, M<N.
[0127] The authentication un...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com