Data storage method for privacy protection based on encryption password and data fractionation
A data and password technology, applied in the field of data security, can solve the problems of easy enumeration of keys and leakage of user privacy, and achieve the effect of protecting data privacy and facilitating system deployment and user use.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0031] In order to make the object, technical solution and advantages of the present invention clearer, the present invention will be described in detail below in conjunction with specific embodiments and with reference to the accompanying drawings.
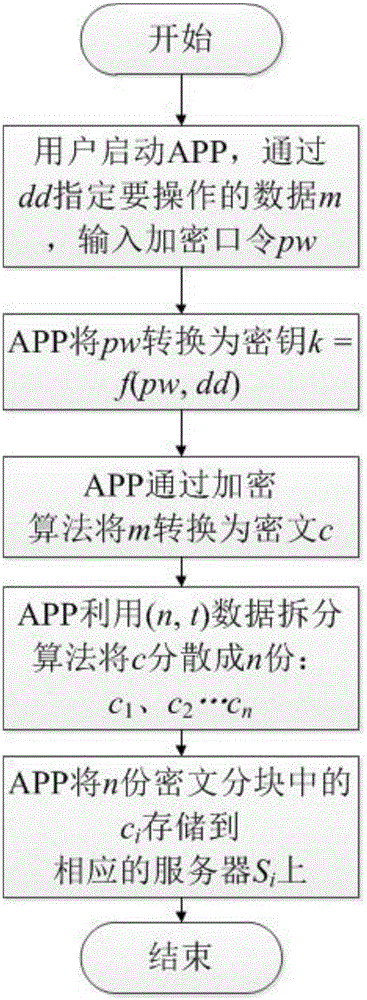
[0032] In the present invention, the user disperses the ciphertext c of data m into n parts and stores them on n servers as an example for illustration, wherein the key derivation function f used is SHA-256, and the encryption and decryption algorithm is AES-256, (n , t) The data splitting algorithm is the Shamir secret sharing algorithm, and the corresponding data descriptor of m is dd (such as the file name, etc.).
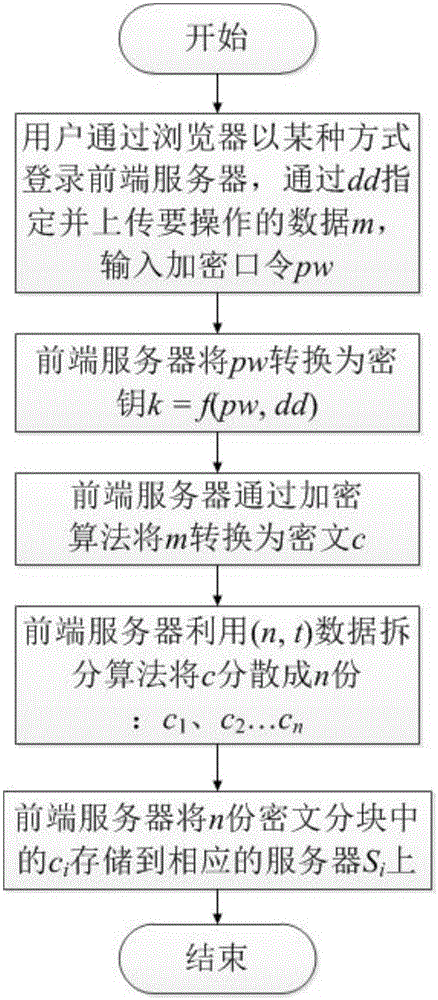
[0033] An application scenario during the specific implementation of the present invention is that the application program (APP) on the mobile smart terminal realizes all client functions, and the processes of storing data and restoring data are as follows: figure 1 with figure 2 shown.
[0034] figure 1 In the...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com