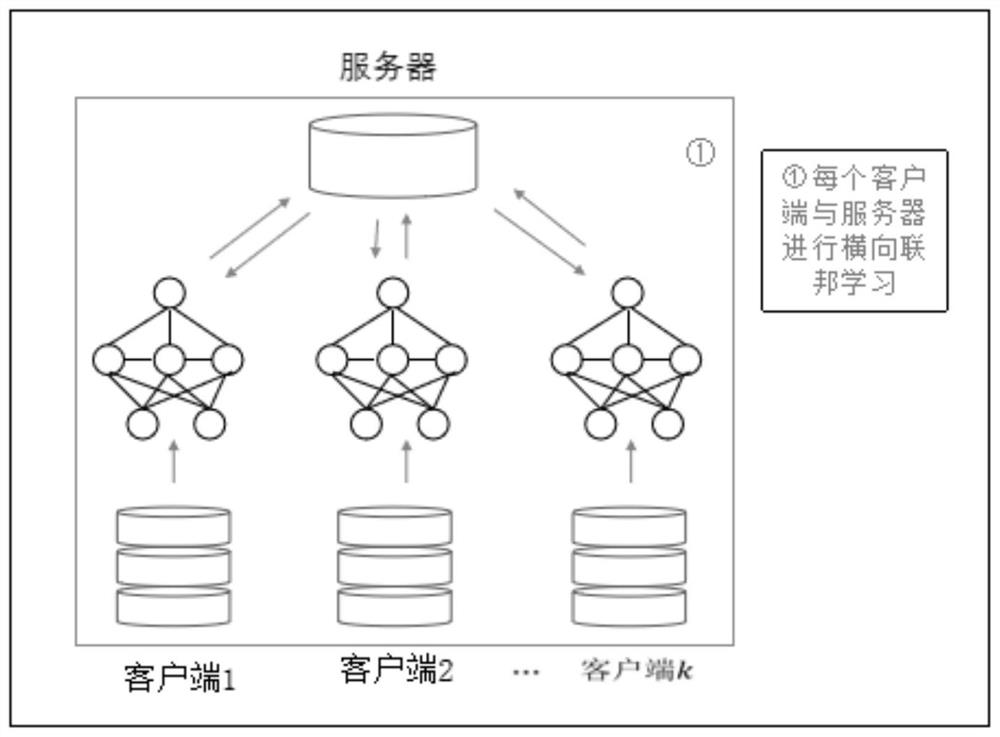
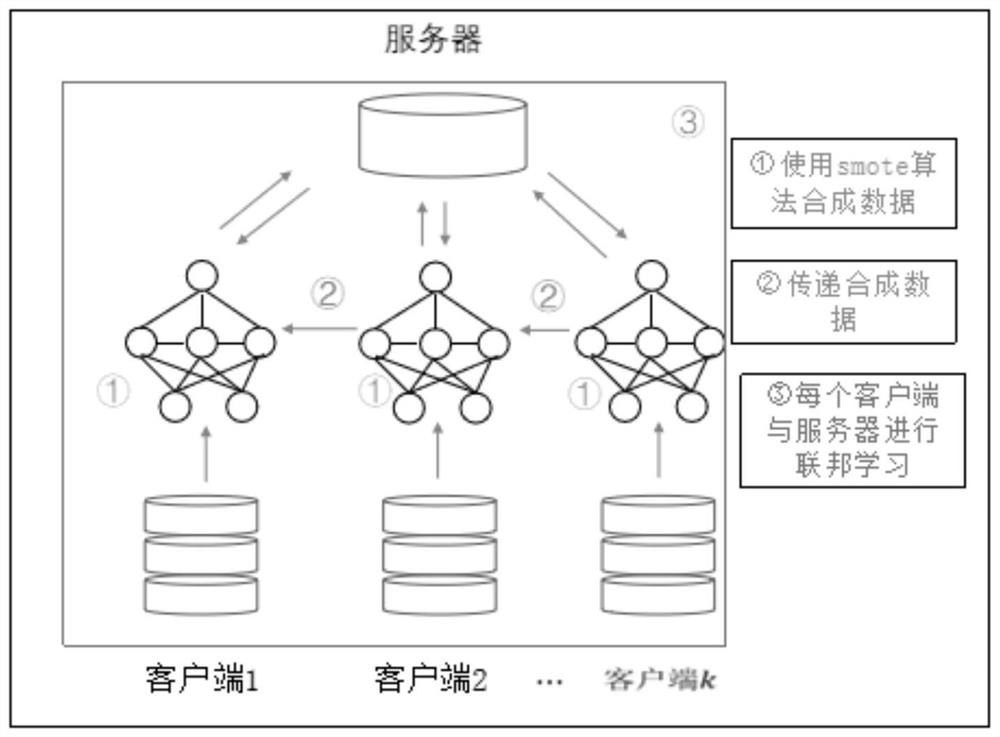
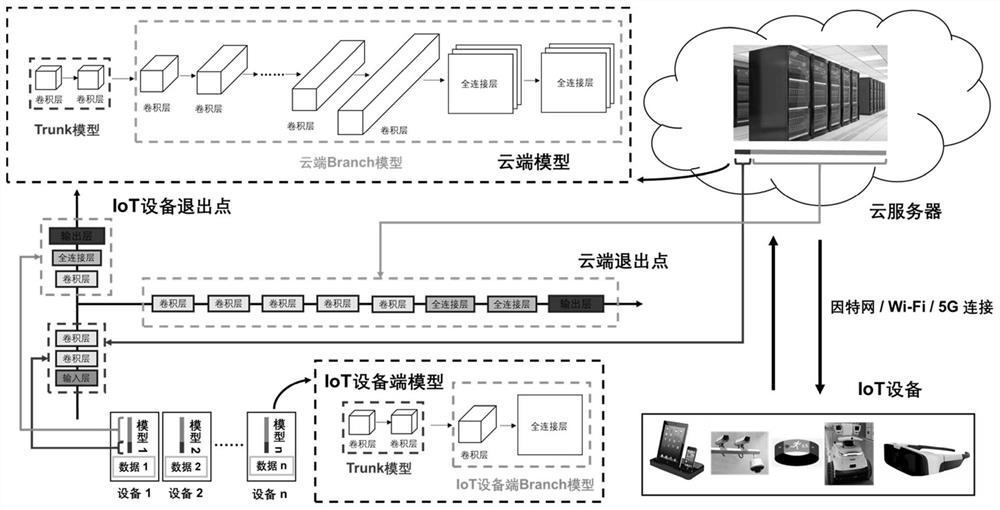
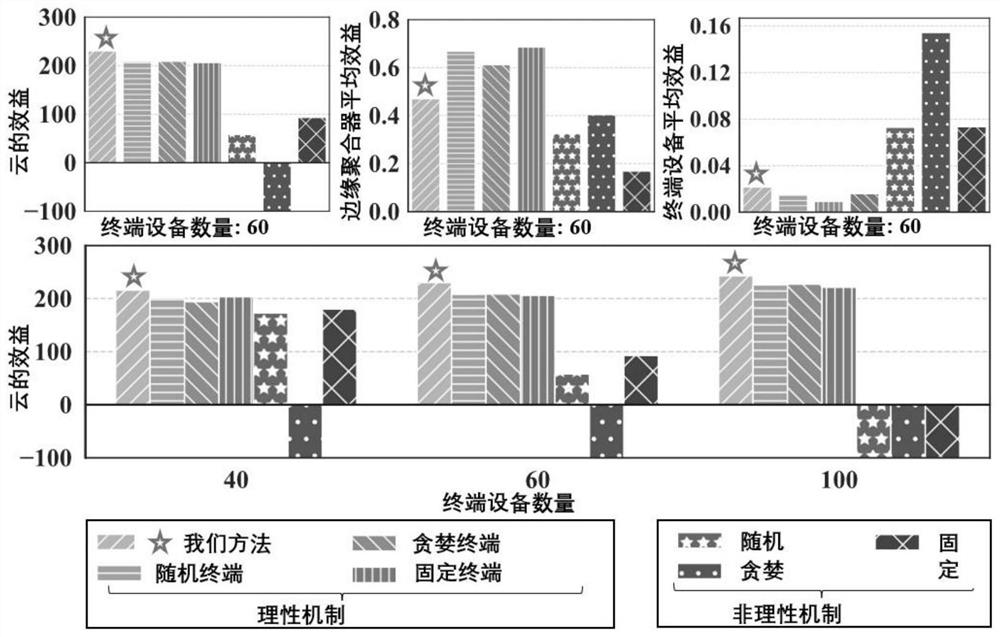
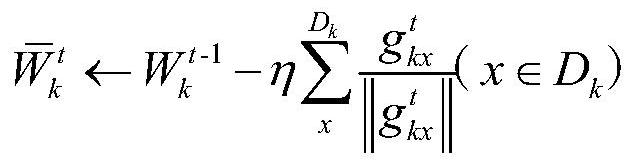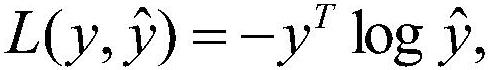Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
240results about How to "Protect data privacy" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
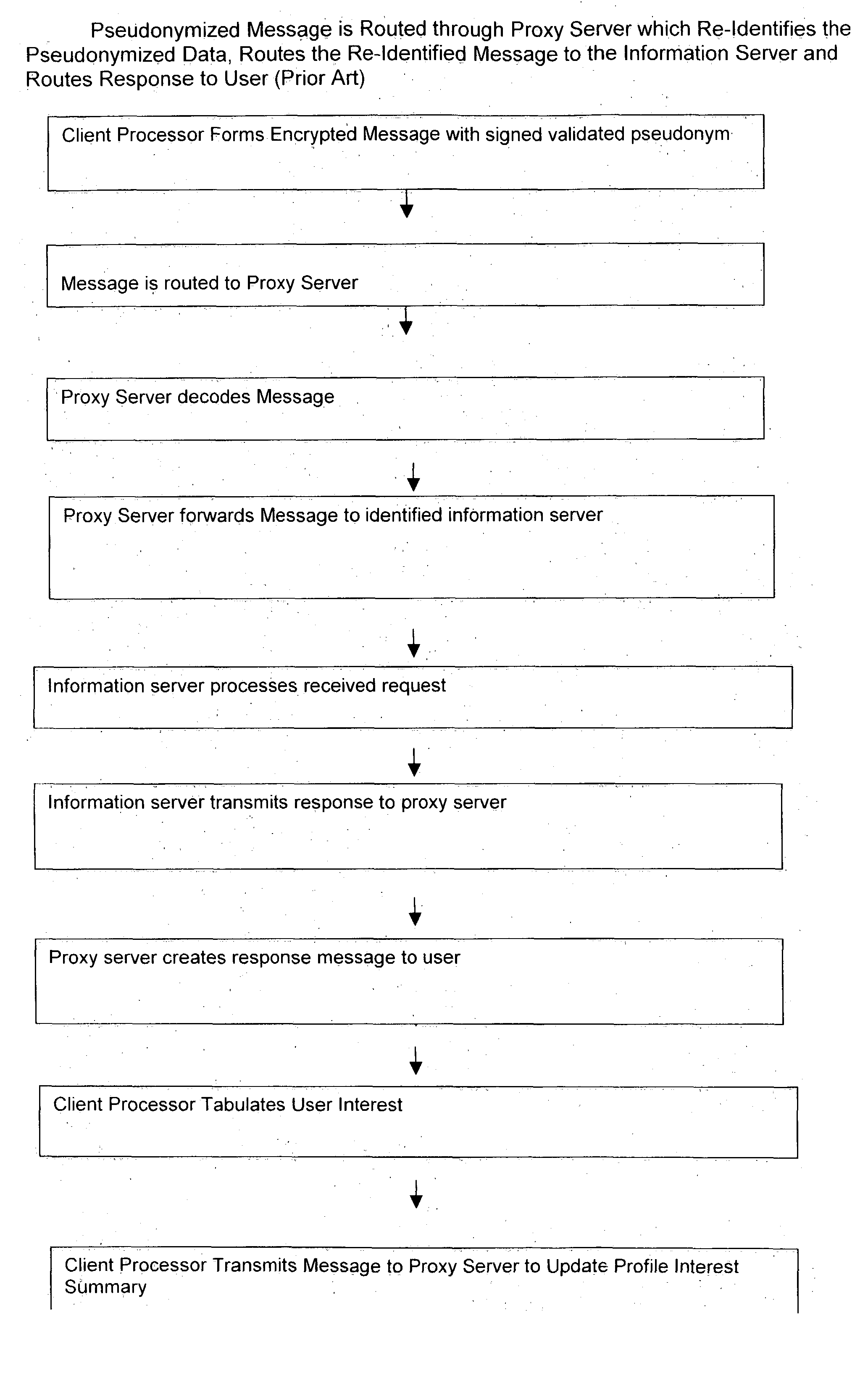
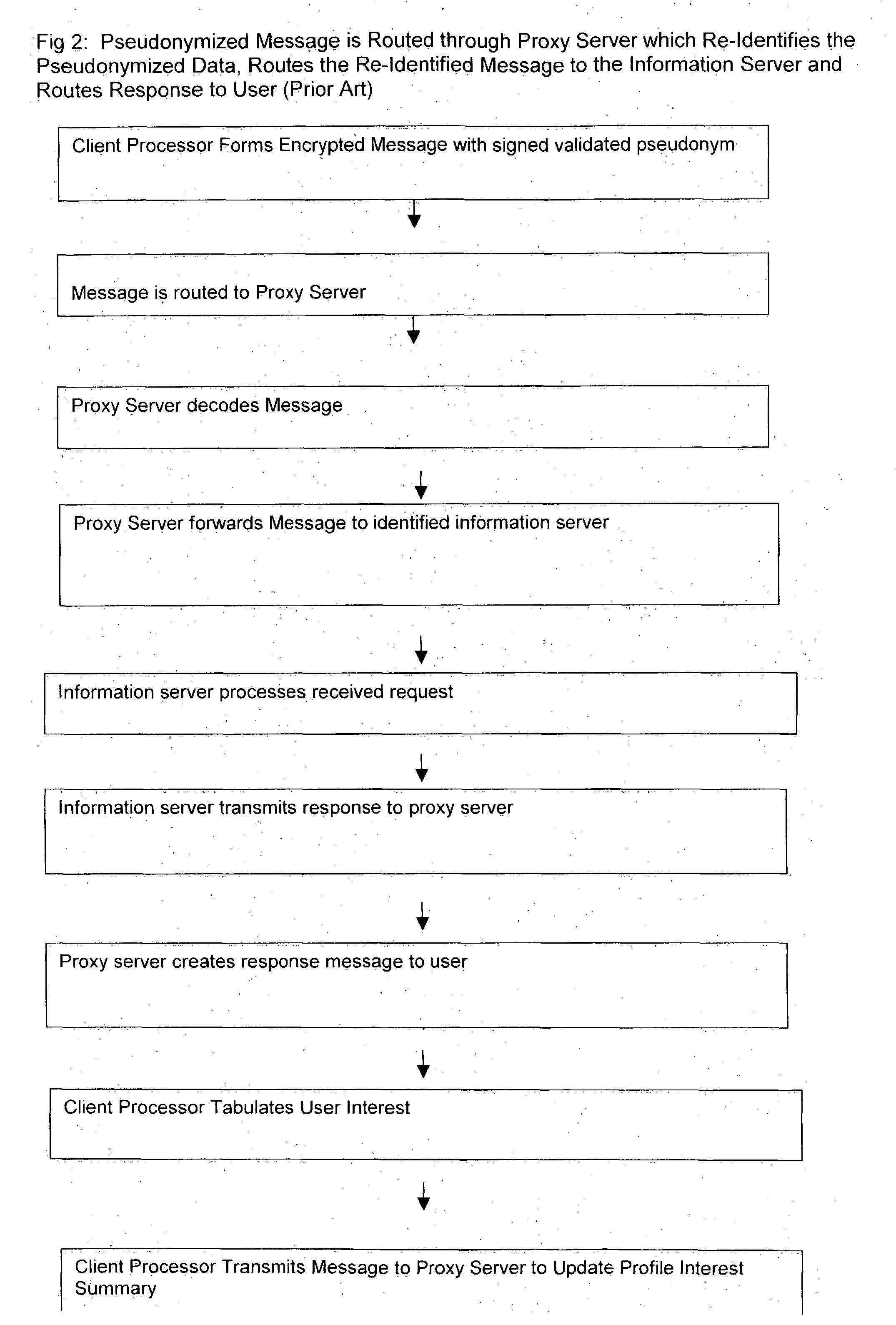
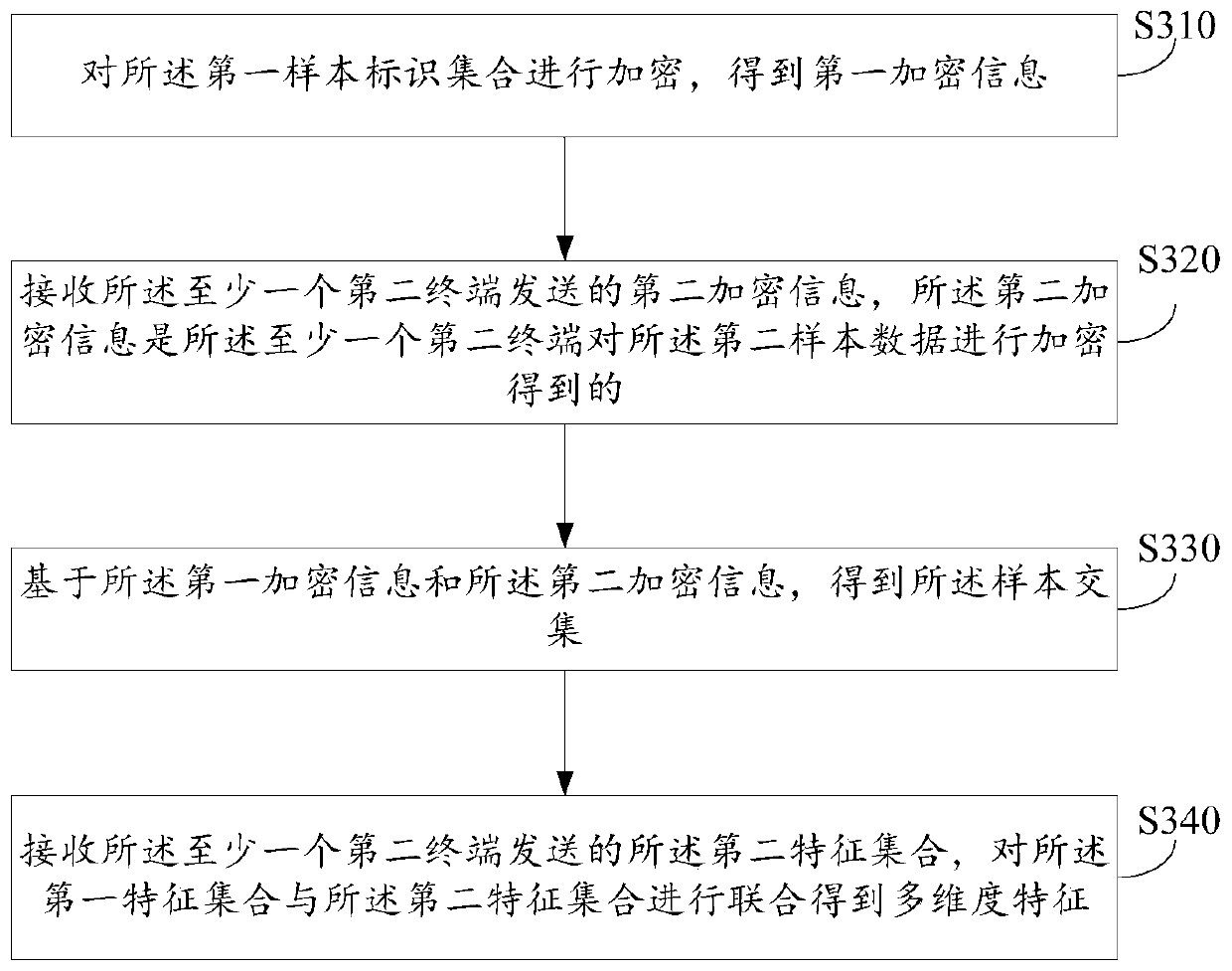
Use of proxy servers and pseudonymous transactions to maintain individual's privacy in the competitive business of maintaining personal history databases
InactiveUS20060031301A1Protect data privacyPrivacy can be assuredComputer security arrangementsMultiple digital computer combinationsInternet privacyData access
A system is provided that preserves data privacy for the Individual—I and Private Data Owner (PDO) while granting data access to the User-U and Accessor who need such data to perform their usual and customary business functions. The method and system completely control the User's access to the Private Data Owner's Private Data by replacing Identifying Information for the User—U, Individual—I, Accessor and PDO with pseudonyms. This assures the overall privacy of individuals, throughout the course of collecting, storing, accessing, analyzing and sharing detailed private records among different organizations engaged in providing and / or consuming services and / or products. Access Control Rule Sets (“ACRS”) consist of instructions which prescribe the terms and conditions for permitting Users to access the PDO's Pseudonymized and Actual Private data in accordance with the rules governing their authorization to access such data.
Owner:HERZ FREDERICK S M +2
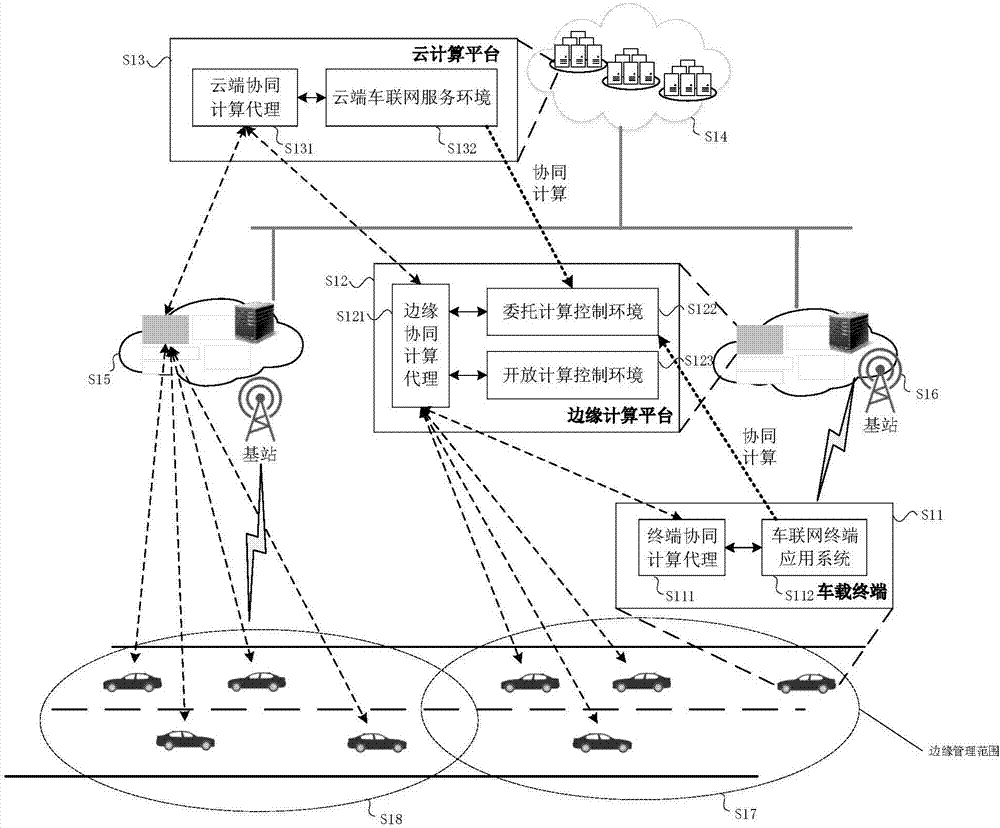
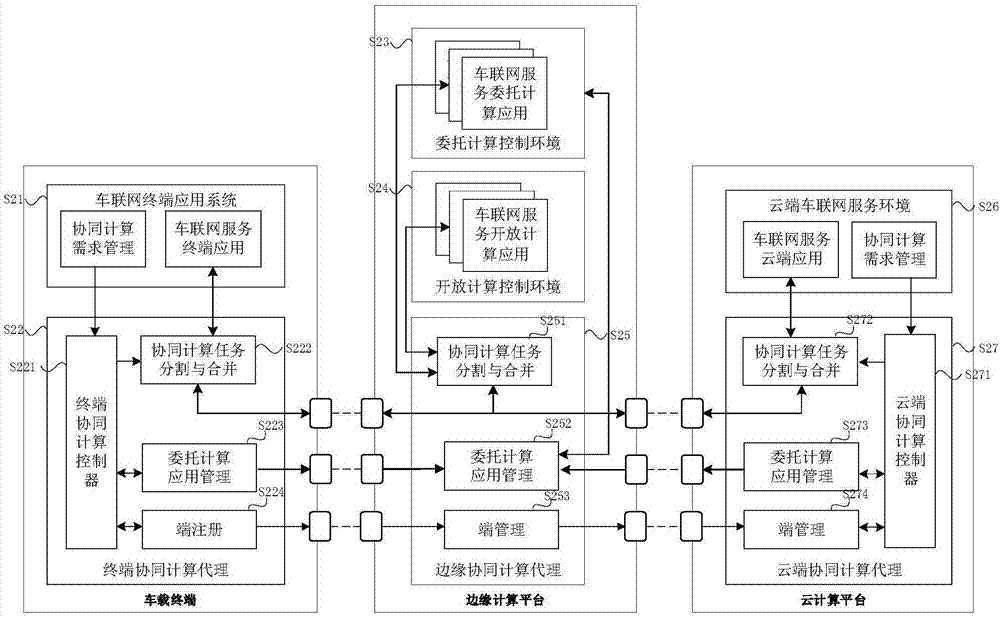
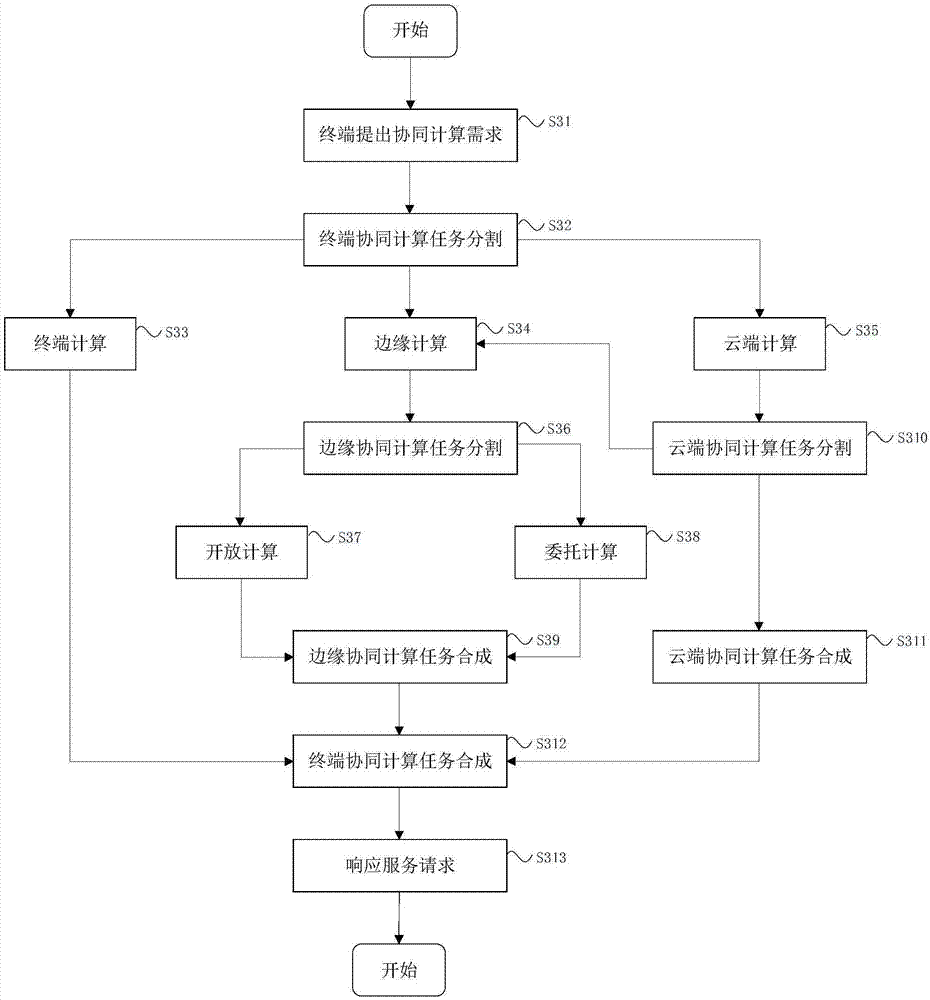
IoV (Internet of Vehicles) service cooperative computation method and system based on cloud end, edge end and vehicle end
ActiveCN107959708AComputing Process SecuritySolve the lack of computing powerTransmissionServices computingThe Internet
The invention discloses an IoV (Internet of Vehicles) service cooperative computation method and system based on a cloud end, an edge end and a vehicle end, and belongs to the field of cloud computation and intelligent driving. According to the computation system and the computation method, firstly, a vehicle-mounted terminal responds to an IoV service request proposed by an IoV terminal application system. A cloud computation platform implements cooperative interactive computation with the vehicle-mounted terminal and an edge computation platform, and provides a service computation resource or a cloud service request by a cloud IoV service environment module. The edge computation platform implements cooperative interactive computation with the vehicle-mounted terminal and the cloud computation platform by an edge cooperative computation agent module, and takes charge of integrating feedback results of a delegation computation control environment module and an open computation controlenvironment module. According to the invention, the unilateral problems of insufficient computation ability of the vehicle end, limited computation resources of the edge end and large data delay of the cloud end are solved, computation efficiency is improved, and user experience is optimized.
Owner:BEIJING UNIV OF POSTS & TELECOMM
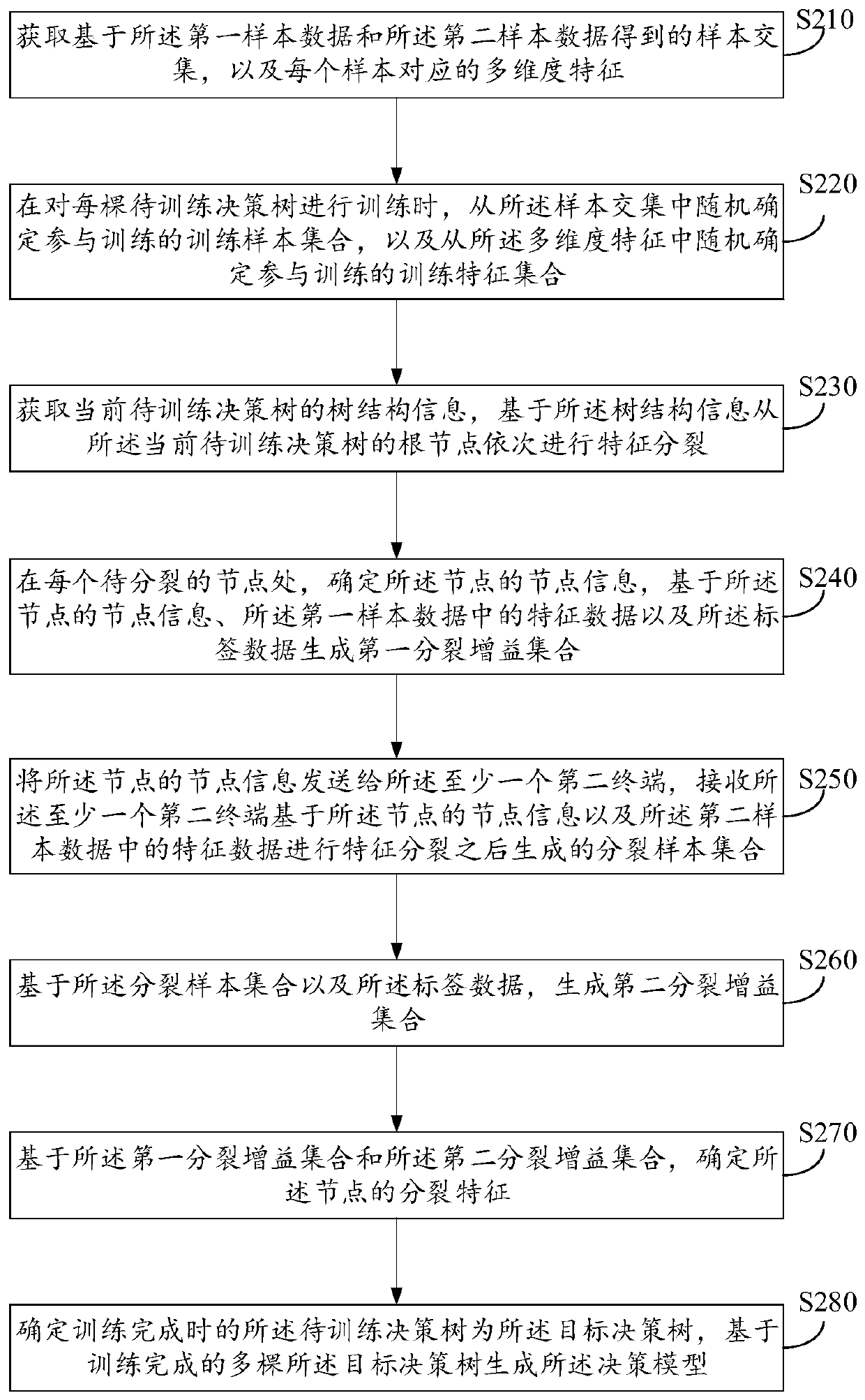
Decision model training method, prediction method and device based on longitudinal federation learning
ActiveCN111598186AAvoid safety hazardsAvoid leaked issuesCharacter and pattern recognitionDecision modelFeature set
The invention relates to a decision model training method, prediction method and device based on longitudinal federated learning. The training method comprises the steps that a training sample set participating in training and a training feature set are randomly determined; at each node of the current decision tree to be trained, determining node information of the node, and generating a first split gain set; receiving a split sample set generated by at least one second terminal; generating a second split gain set based on the split sample set and the label data; determining a splitting feature of the node based on the first splitting gain set and the second splitting gain set; and generating the decision model based on the plurality of trained target decision trees. According to the method and the device, the problem that the label data is leaked in the transmission process can be avoided, the safety of the node data of each participant is improved, and the data privacy of each participant node is protected.
Owner:TENCENT TECH (SHENZHEN) CO LTD
Use of proxy servers and pseudonymous transactions to maintain individual's privacy in the competitive business of maintaining personal history databases
InactiveUS7844717B2Protect data privacyPrivacy can be assuredComputer security arrangementsMultiple digital computer combinationsData accessProxy server
A system is provided that preserves data privacy for the Individual-I and Private Data Owner (PDO) while granting data access to the User-U and Accessor who need such data to perform their usual and customary business functions. The method and system completely control the User's access to the Private Data Owner's Private Data by replacing Identifying Information for the User-U, Individual-I, Accessor and PDO with pseudonyms. This assures the overall privacy of individuals, throughout the course of collecting, storing, accessing, analyzing and sharing detailed private records among different organizations engaged in providing and / or consuming services and / or products. Access Control Rule Sets (“ACRS”) consist of instructions which prescribe the terms and conditions for permitting Users to access the PDO's Pseudonymized and Actual Private data in accordance with the rules governing their authorization to access such data.
Owner:HERZ FREDERICK S M +2
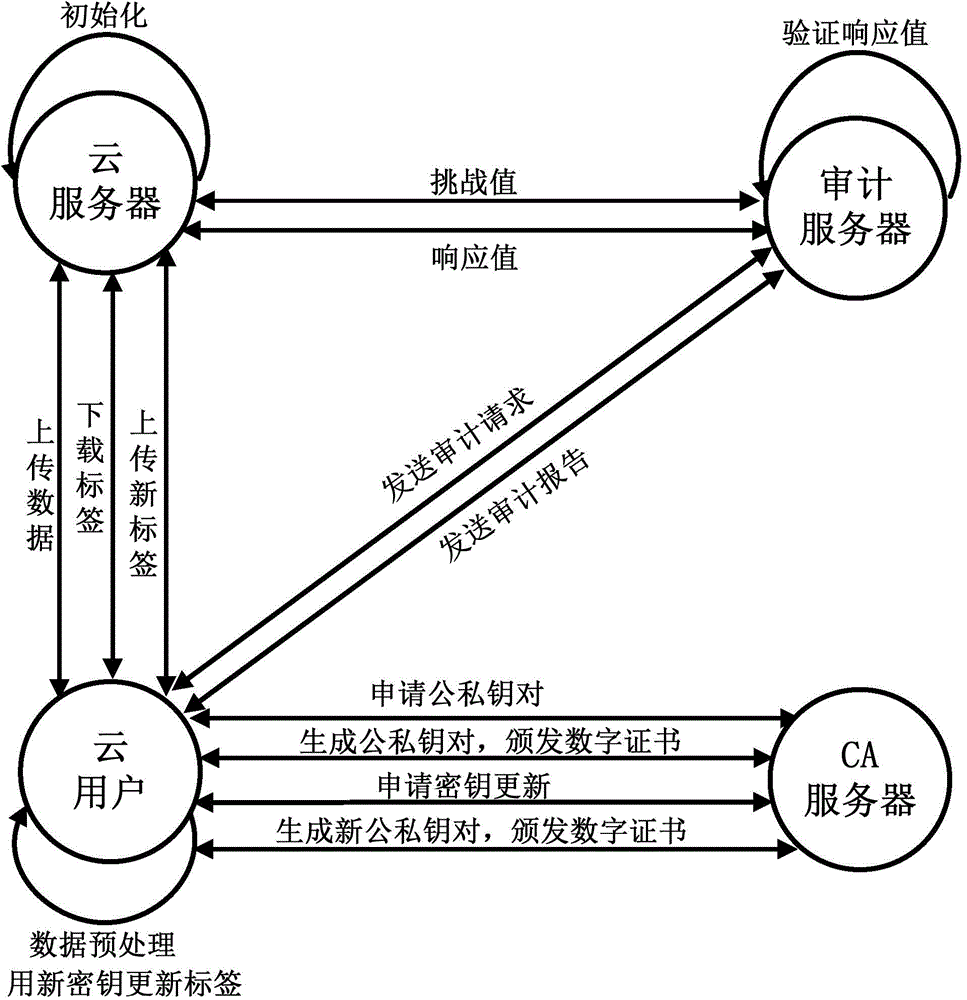
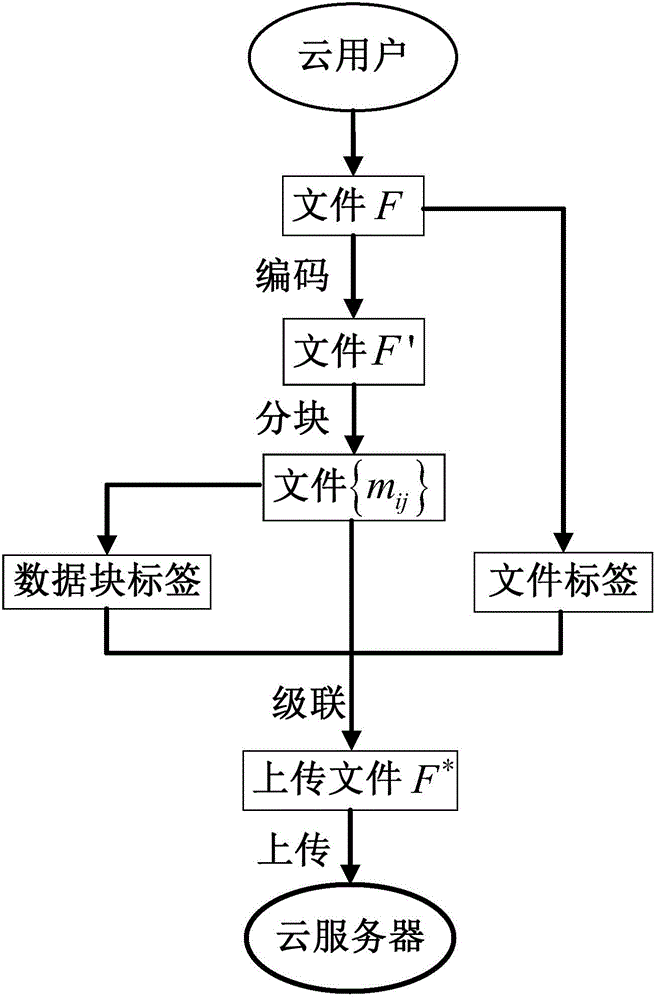
Secret key updating method for cloud storage and implementation method of cloud data auditing system
InactiveCN104811300AReduce trafficNo need to consume bandwidthKey distribution for secure communicationCloud userCloud data
The invention discloses a secret key updating method for cloud storage and an implementation method of a cloud data auditing system, and belongs to the technical field of network security. The secret key updating method for cloud storage comprises the steps that when a cloud user needs to update a secret key, a CA server is requested to generate a new secret key, and a new file label and a new data block label are generated based on a file label and a data block label downloaded from a cloud server, the old secret key and the new secret key at present, are uploaded to the cloud server, and are used for replacing the corresponding old file label and the corresponding old data block label in the cloud server. Meanwhile, the invention further discloses the implementation method of the cloud data auditing system on the basis of zero-knowledge verification. When the cloud user needs to update the secret key, the corresponding file label and the corresponding data block label on the cloud server are updated based on the secret key updating method for cloud storage. The secret key updating method for cloud storage and the implementation method of the cloud data auditing system are used in a cloud network, the communication cost, caused by changing of the secret key, between the cloud server and the cloud user can be remarkably reduced, the calculation cost of the operation that the cloud user calculates the labels again is reduced, and the data privacy can be effectively protected in the auditing process.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
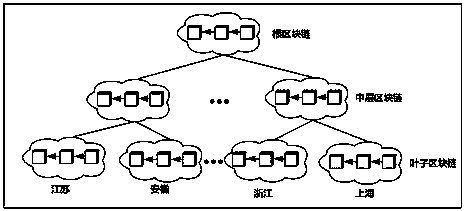
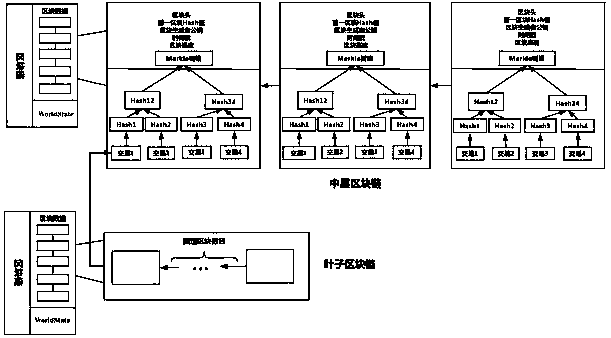
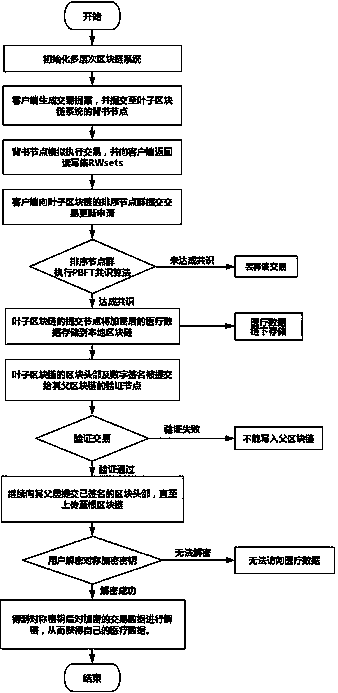
Intelligent medical data storage method based on multi-level blockchain system architecture
ActiveCN110727737AImprove efficiency andHigh robustness and fault toleranceDatabase distribution/replicationDigital data protectionBlockchainEncryption system
The invention discloses an intelligent medical data storage method based on a multi-level blockchain system architecture. According to the method, an existing single-chain or double-layer blockchain system design is abandoned, a multi-layer blockchain system architecture is provided based on a Hyperledger Fabric platform to solve the storage problem of medical data, efficient management of large-scale medical data is achieved, and the efficiency and expandability of the system are greatly improved. Meanwhile, a dual-key encryption system combining public key encryption and symmetric encryptionis adopted, storage and sharing of medical data are achieved under the condition that privacy of the patient is protected, and great convenience is provided for medical institutions, patients and scientific research institutions.
Owner:NANJING UNIV OF POSTS & TELECOMM
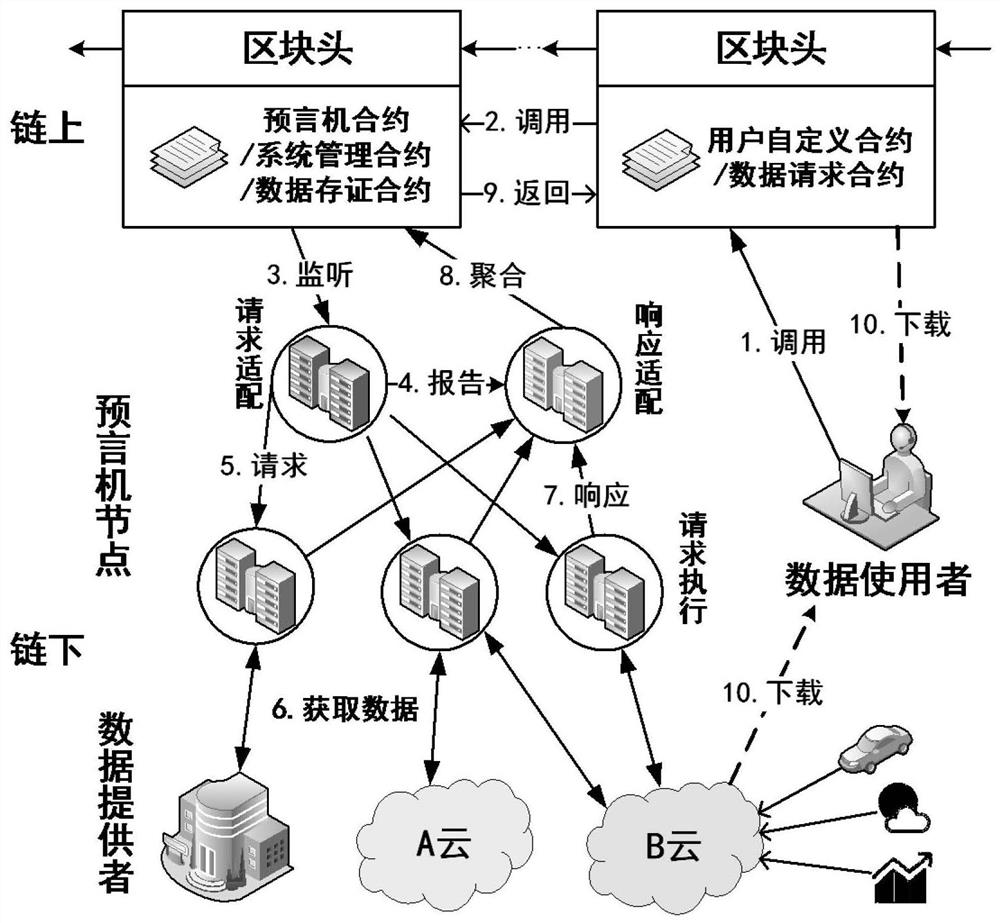
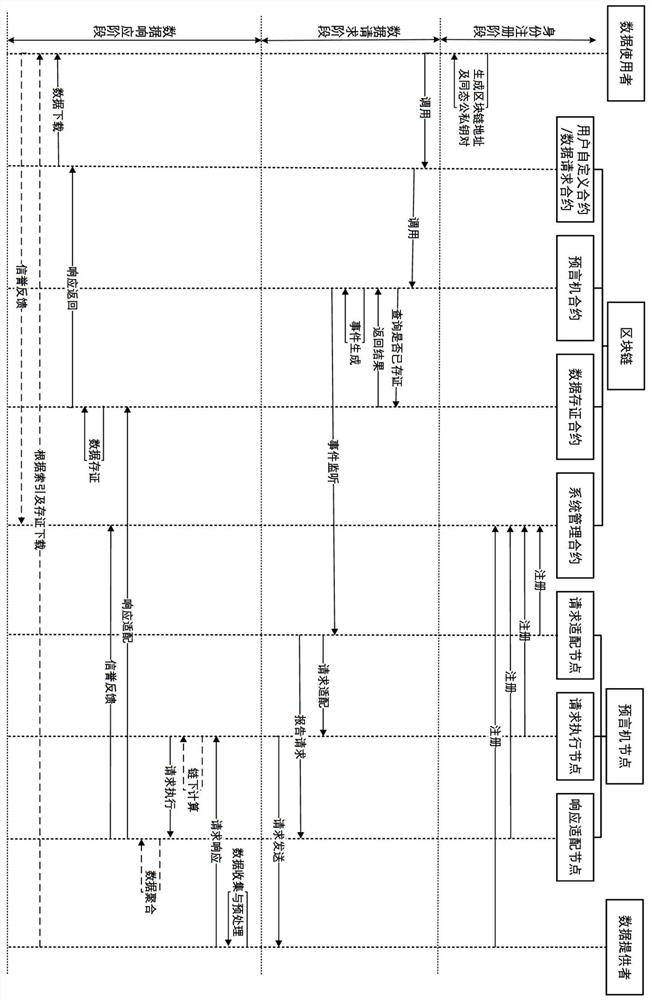
On-chain and off-chain data sharing scheme based on distributed oracle machine and homomorphic encryption
ActiveCN112016105ATake the initiative to obtainImprove timelinessDigital data protectionCommunication with homomorphic encryptionData integrityData provider
The invention belongs to the technical field of block chains. The scheme comprises four kinds of entities including a data user, a block chain, an oracle machine node and a data provider, and the block chain deploys a system management contract, an oracle machine contract, a data storage contract, a data request contract and a user-defined contract; wherein the oracle machine node comprises a request adaptation node, a response adaptation node and a request execution node; according to the scheme, cooperative sharing of the on-chain data and the off-chain data is realized by using the distributed oracle machine, the network bandwidth and the on-chain storage space demand are reduced, and the data integrity can be verified through the on-chain evidence storage; according to the scheme, homomorphic encryption is used for protecting data privacy in the processing process of the oracle machine and realizing basic under-chain computing capacity, better universality and verifiable safety areachieved. Meanwhile, data aggregation operation is set under a chain, and the processing performance is improved compared with on-chain aggregation.
Owner:东北大学秦皇岛分校
Federation prediction method based on federation learning
ActiveCN112364943AImprove performanceIncrease aggregation weightForecastingCharacter and pattern recognitionDifferential privacyNetwork model
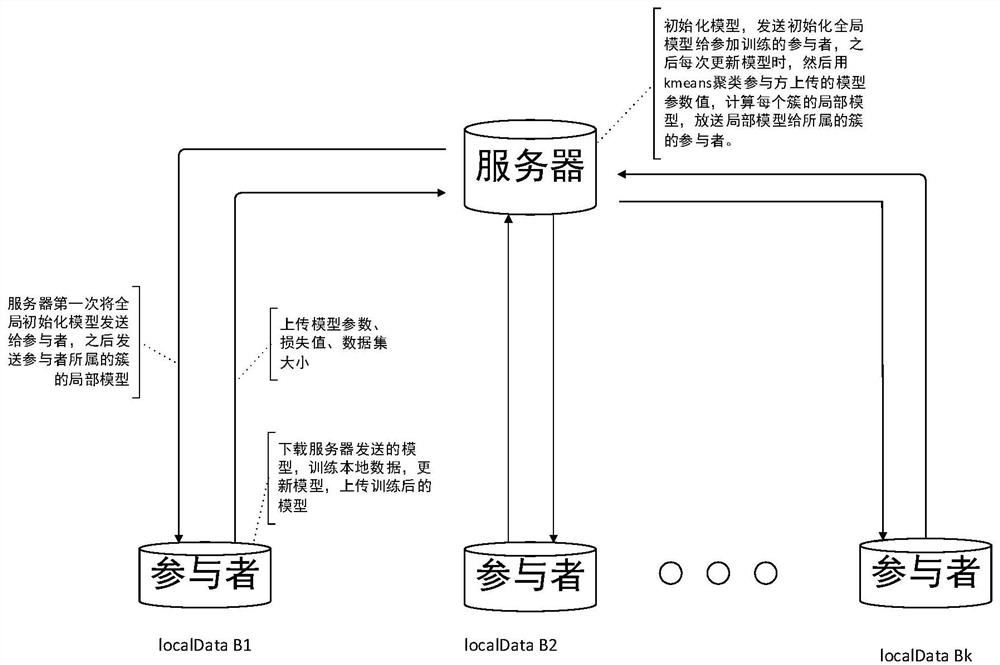
The invention discloses a federation prediction method based on federation learning, and the method enables the parameter change of a neural network model updated by a single participant to have onlydirection difference and no size difference through the unitization of a locally updated gradient vector, thereby protecting the data privacy, and avoiding the use of homomorphic and differential privacy or other encryption technologies. Under the condition of not losing data precision, the communication cost between the equipment and the server is greatly reduced. Besides, considering that the difference of data in a federated learning scene is large, the performance of a local participant can be improved by increasing the local information of the data, the uploaded neural network model parameters are clustered by utilizing a k-means algorithm to obtain similar neural network model parameters, the neural network model parameter aggregation weight is improved. The method is more suitable for the data scene of the participant.
Owner:GUANGXI NORMAL UNIV
Cloud data safe auditing method based on multi-Agent
InactiveCN103124293AProtection securityProtect transmission securityData switching networksGraphical user interfaceApplication programming interface
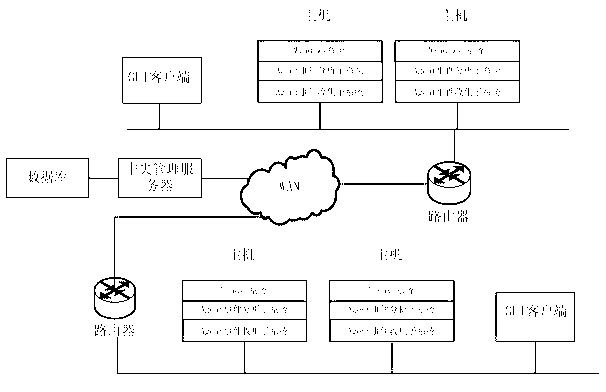
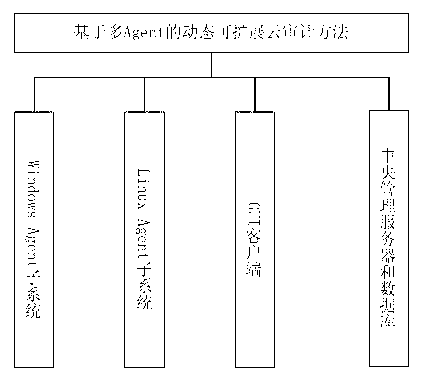
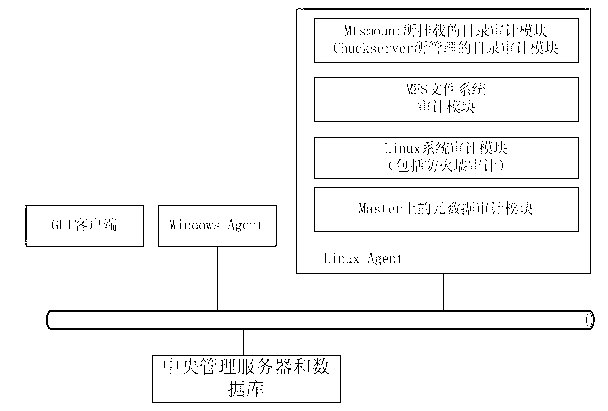
The invention discloses a dynamically extensible cloud auditing method based on multi-Agent. The method includes steps that every host loads and operates an Agent event collection subsystem and an Agent event analysis subsystem; the collection subsystem and the analysis subsystem serve as background processes to collect and analyze auditing information in a monitored cloud auditing system, and transmit data to a central administrator server; a GUI (Graphical User Interface)client-side is used for checking status of every host; the central administrator server and a data base are used for receiving data and reports from the hosts, controlling communication information of the whole cloud auditing system, and analyzing and store received safe auditing events; a Windows Agent subsystem bottom calls application programming interface of the system to access to contents of Windows events, then the contents are normalized to system log events to be sent to the Agent event analysis subsystem; and an Linux Agent system bottom uses an event collection module to collect data.
Owner:PLA UNIV OF SCI & TECH
Identity-based privacy protection integrity detection method and system in cloud storage
ActiveCN107948143AReduce overheadReduce public key certificate management workUser identity/authority verificationThird partyData integrity
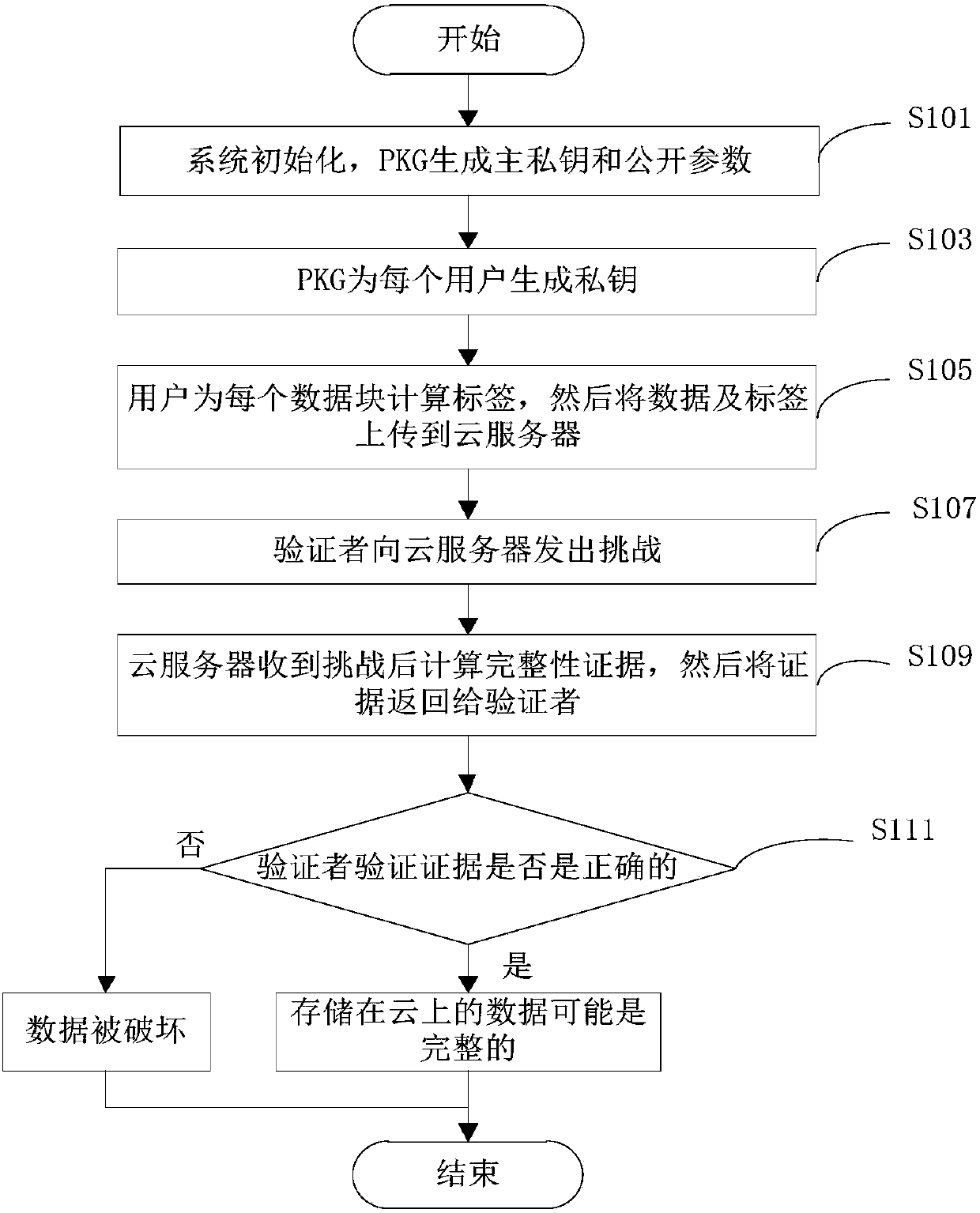
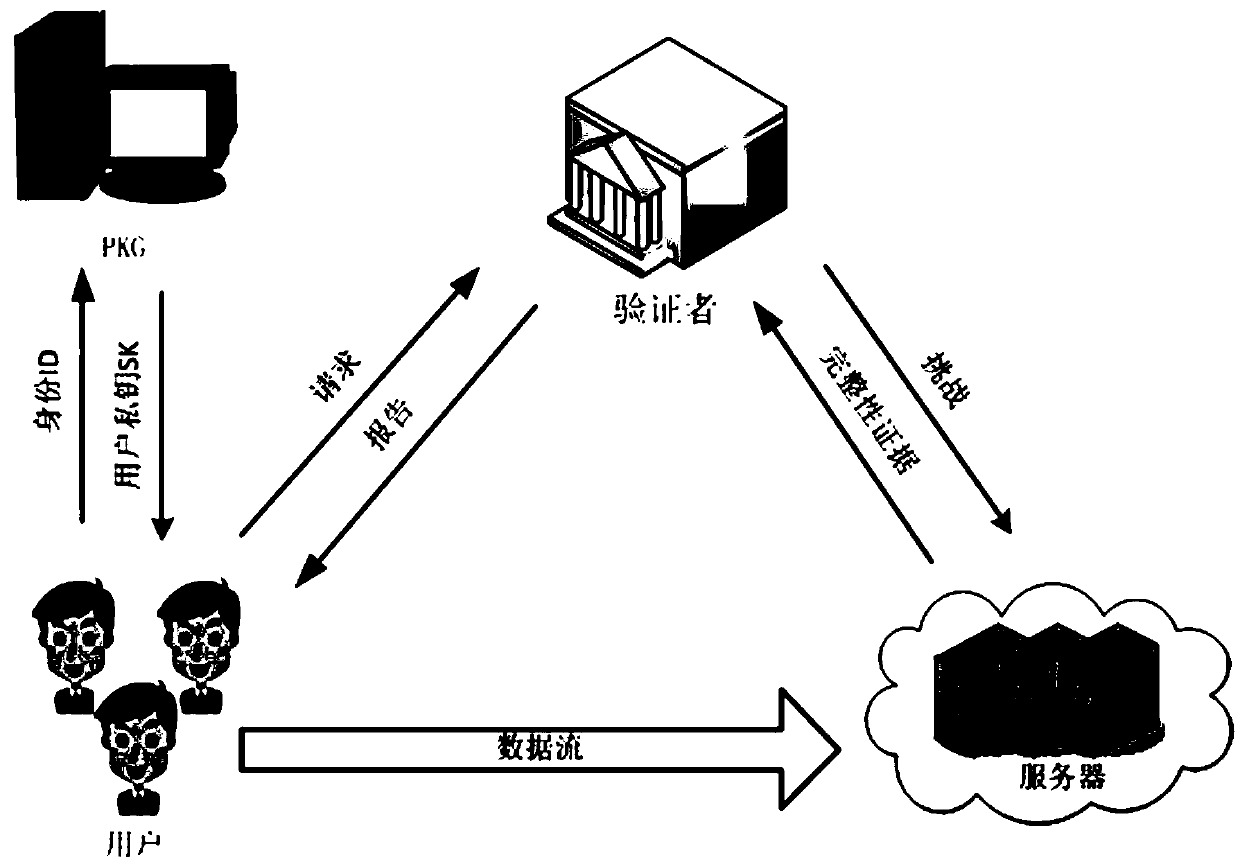
The invention discloses an identity-based privacy protection integrity detection method and system in a cloud storage. The method comprises the following steps of (1) a system initialization stage that a trusted third-party PKG generates a main private key and a public parameter; (2) a secret key extraction stage that the trusted third-party PKG generates a private key for a user according to useridentity; (3) a label generation stage that the user generates a data label for each data block by using the private key and uploads data and the corresponding data label to a cloud server; (4) a challenge inquiry stage that a verifier sends a challenge to the cloud server; (5) an evidence generation stage that the cloud server computes an integrity evidence according to challenge information andreturns the integrity evidence to the verifier; and (6) a verification stage that the verifier verifies the data integrity according to the evidence. According to the method and the system, the public key certificate management and calculation cost of the system is reduced based on an identity signature, and meanwhile, the identity privacy and the data privacy of the user are protected in a process of verifying the data integrity, and the safety of the system is improved.
Owner:ANHUI UNIVERSITY
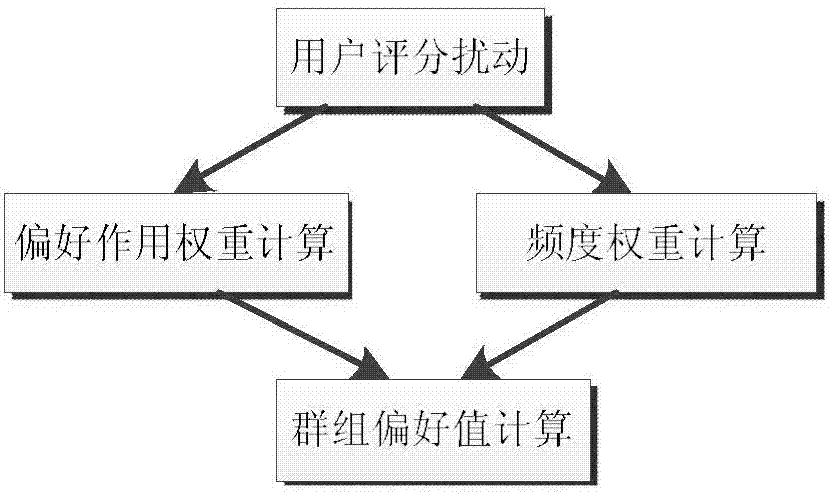
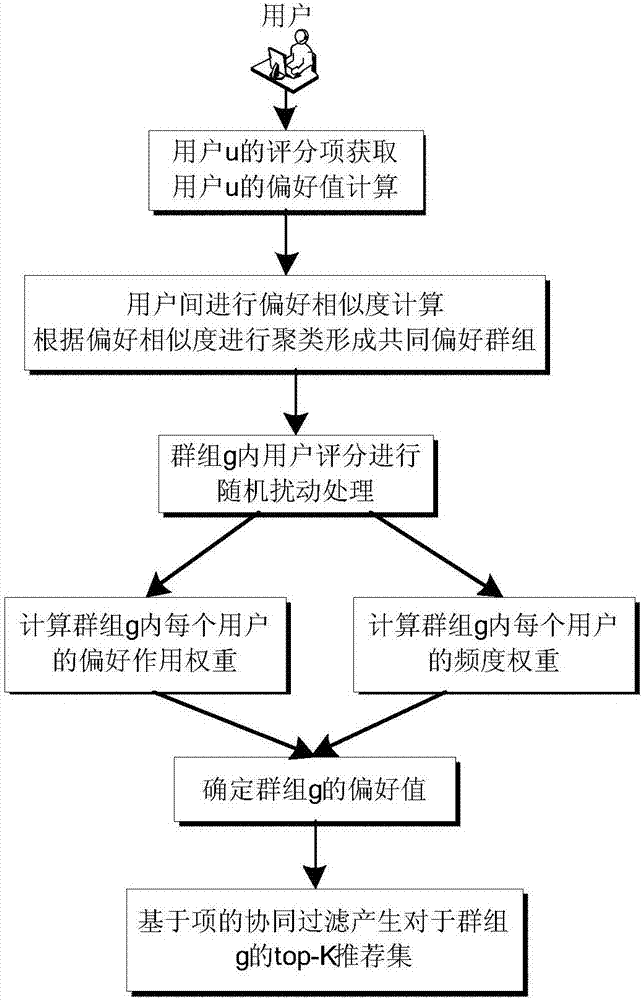
Collaborative filtering group recommendation method based on stochastic disturbance technology
ActiveCN106909607AEffective reflection of interestProtect data privacySpecial data processing applicationsUser privacyPrivacy protection
The invention discloses a collaborative filtering group recommendation method based on a stochastic disturbance technology, mainly aims at solving the problem that a user is likely to expose private information in a collaborative filtering group recommendation process, and provides a privacy protection group recommendation method. The collaborative filtering group recommendation method based on the stochastic disturbance technology mainly includes the steps that user initial score data disturbance processing, user interest and preference values, preference action weight and frequency weight are provided, through the stochastic disturbance technology, user initial score data is processed to protect private data of users, common preference groups are formed through the user interest and preference values, group preference values are obtained through the preference action weight and the frequency weights, and on the basis of collaborative filtering of items, forecast scores of the common preference groups are obtained. The requirement is met that the groups are recommended and the private data of the users in the groups is protected at the same time.
Owner:NANJING UNIV OF POSTS & TELECOMM
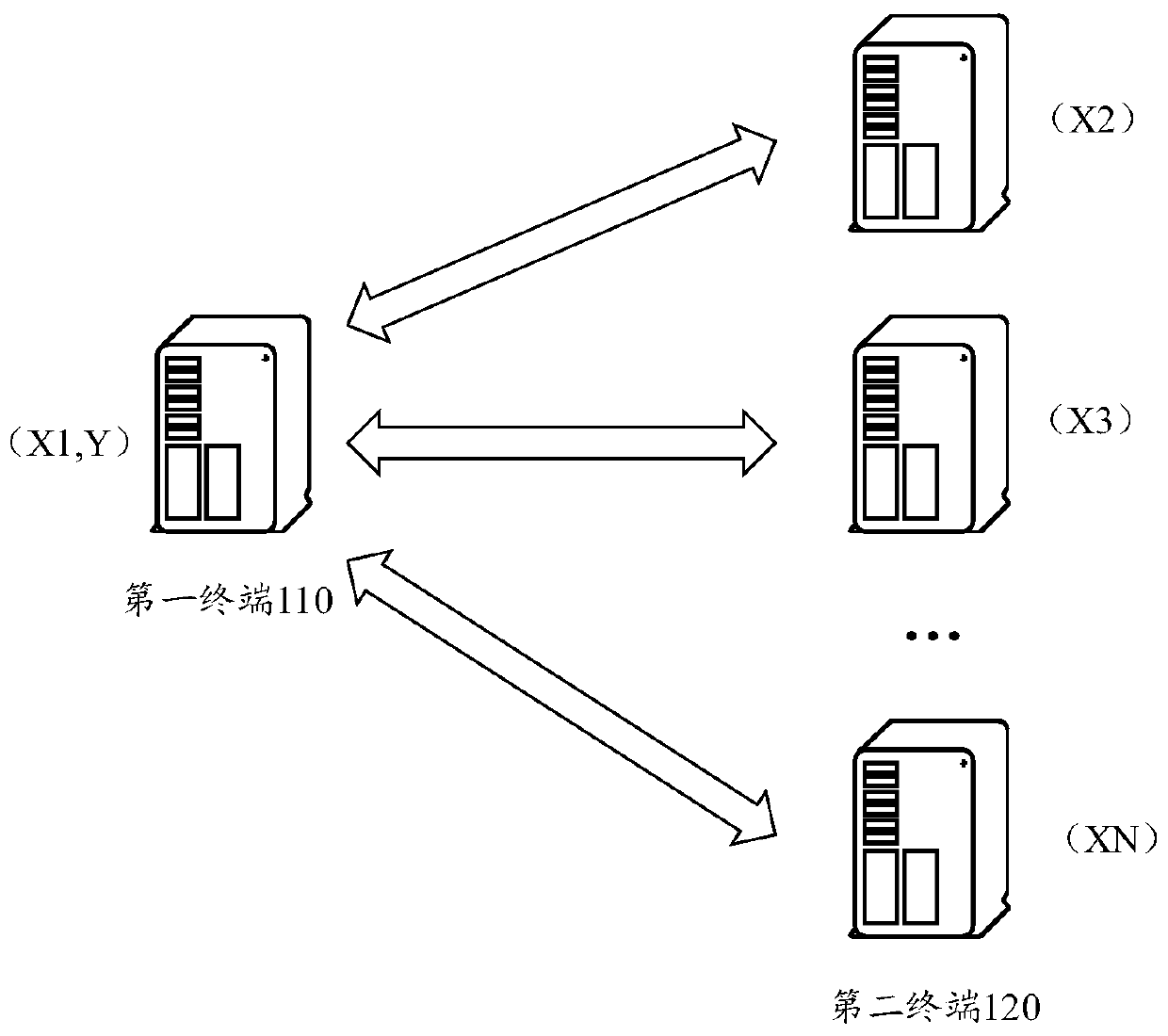
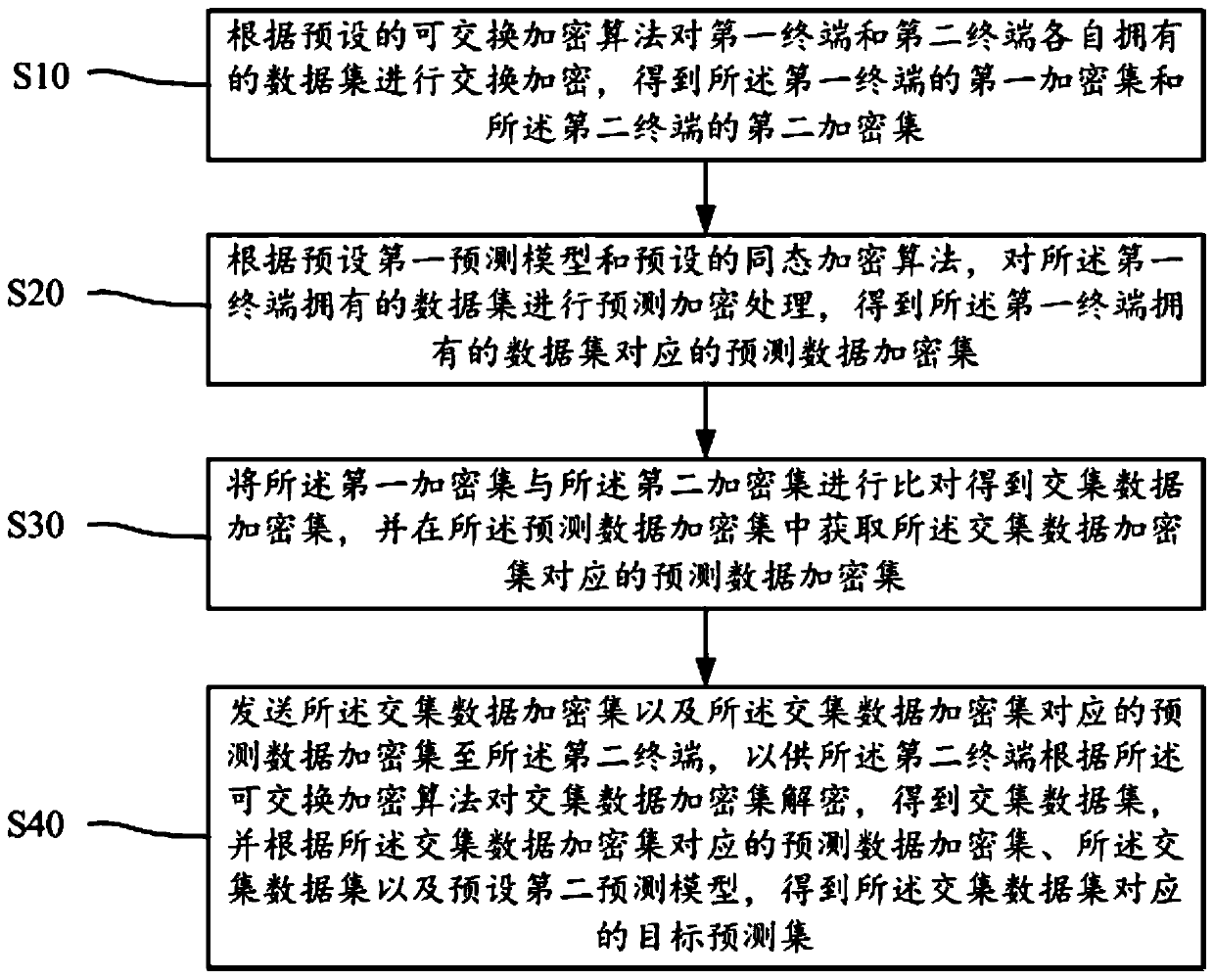
Sensitive information processing method and device and readable storage medium
ActiveCN110851869AImprove securityProtect data privacyDigital data protectionInformation processingData set
The invention discloses a sensitive information processing method. The method comprises the following steps: exchanging and encrypting data sets of the first terminal and the second terminal accordingto an exchangeable encryption algorithm; obtaining a first encryption set of the first terminal and a second encryption set of the second terminal, according to the first prediction model, a data setowned by the first terminal and a homomorphic encryption algorithm, obtaining prediction data encryption set, obtaining intersection data encryption set of the first encryption set and the second encryption set, and acquiring prediction data encryption set of intersection data encryption set, and sending the intersection data encryption set and prediction data encryption set of the intersection data encryption set to the second terminal, so that the second terminal obtains a target prediction set corresponding to the intersection data set. The invention further discloses equipment and a readable storage medium. The multi-model joint prediction value corresponding to the intersection data can be obtained without disclosing respective data sets between the terminals, so that the data privacy is protected, and the information security is improved.
Owner:WEBANK (CHINA)
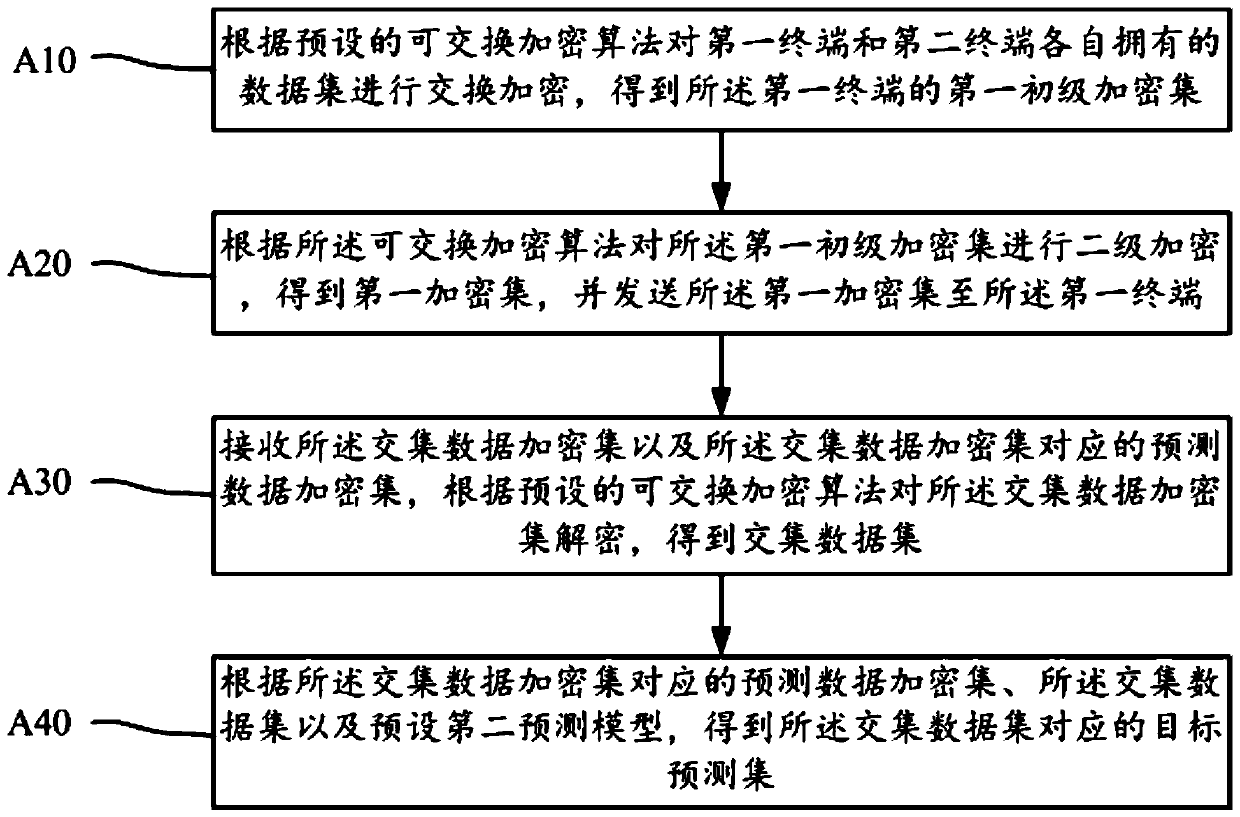
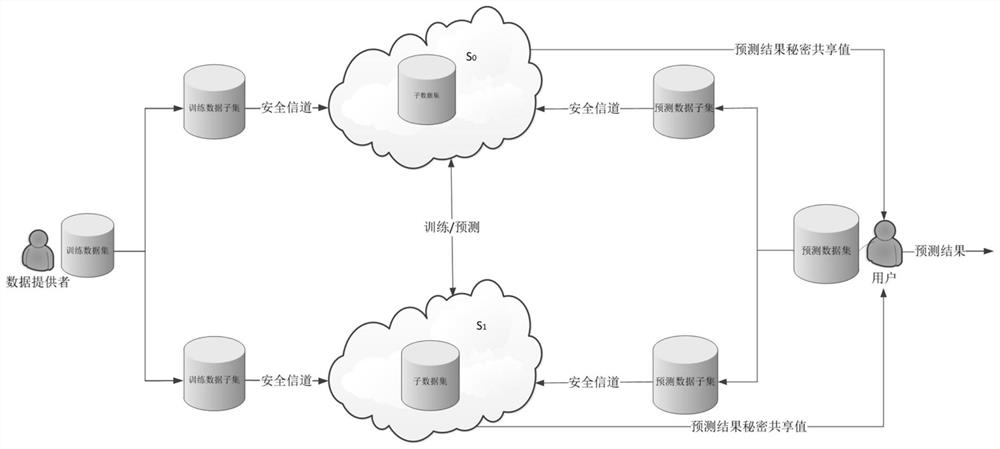
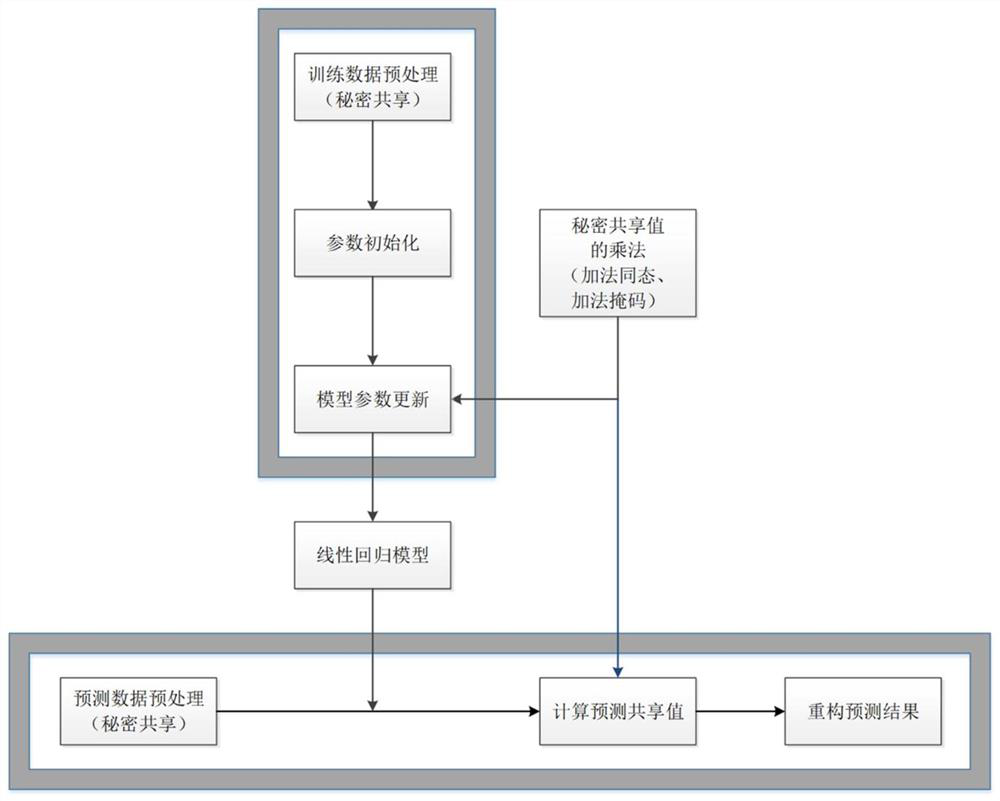
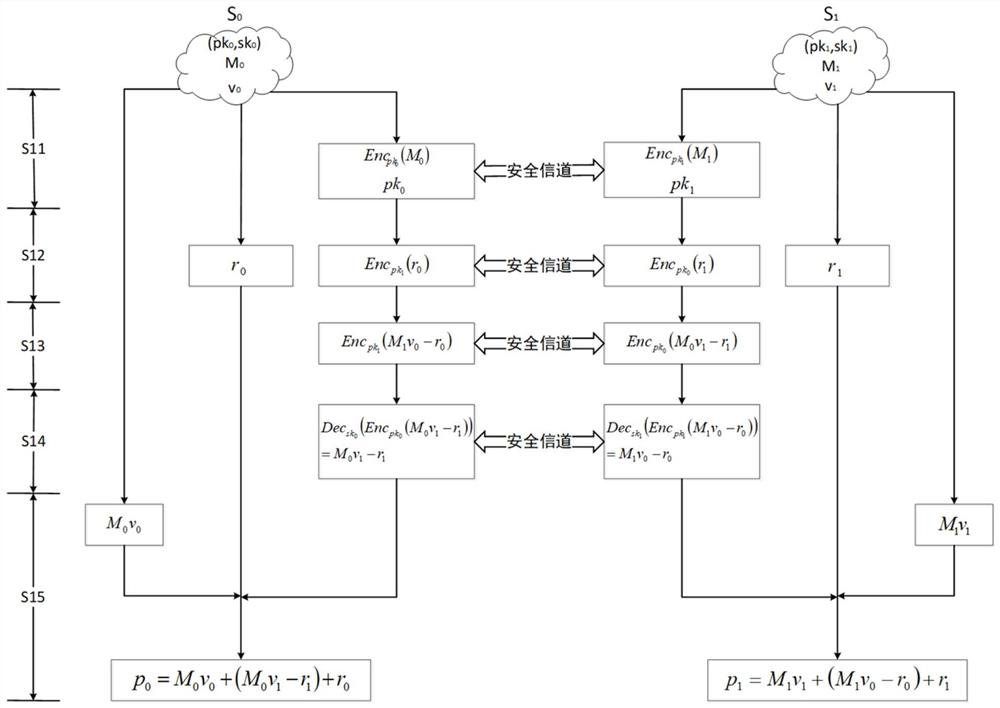
Data privacy protection system based on secure two-party calculation linear regression algorithm
PendingCN112182649ARealize privacy protectionPrivacy protectionKey distribution for secure communicationDigital data protectionData predictionEngineering
The invention discloses a linear regression algorithm based on secure two-party calculation. The method comprises the following steps: S1, adopting multiplication of a secret sharing value; S2, preprocessing the training data; S3, initializing parameters; S4, updating model parameters; S5, preprocessing the prediction data; S6, calculating a prediction sharing value; and S7, reconstructing a prediction result. According to the scheme, the privacy of data and model parameters is not leaked, and meanwhile, the required communication overhead is lower. According to the method, privatization is carried out on original training data and model parameters, and a linear regression algorithm for protecting data privacy is realized by virtue of convenience of cloud service under the condition that acloud server cannot obtain the original training data and intermediate parameters and cannot deduce the model parameters. On the basis, a regression prediction task can be safely executed, and when computing and storing resources of the cloud server are utilized, training and data prediction of a linear regression model can be efficiently and accurately carried out.
Owner:SHANGHAI OCEAN UNIV
Attribute-based online/offline keyword search method in mobile cloud environment and cloud computing application system thereof
InactiveCN107547530AImplement searchReduce computational costKey distribution for secure communicationEncryption apparatus with shift registers/memoriesCiphertextMobile cloud
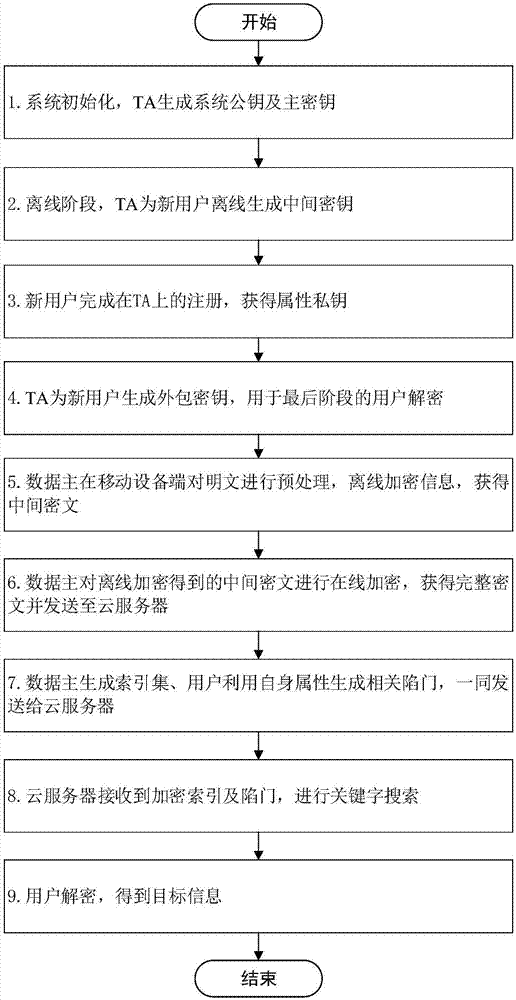
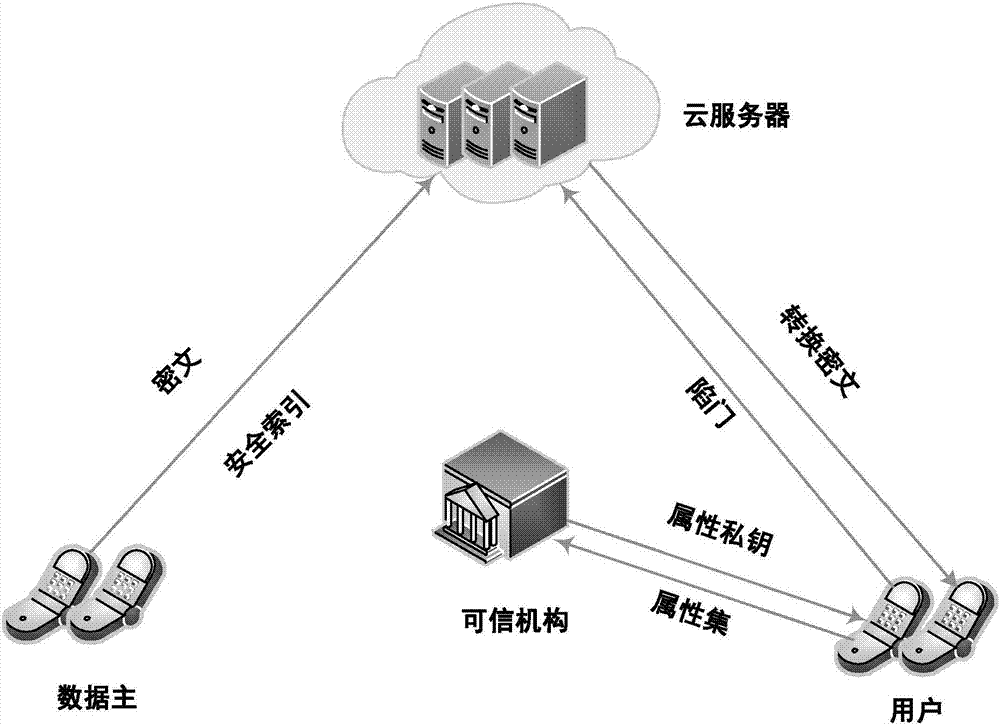
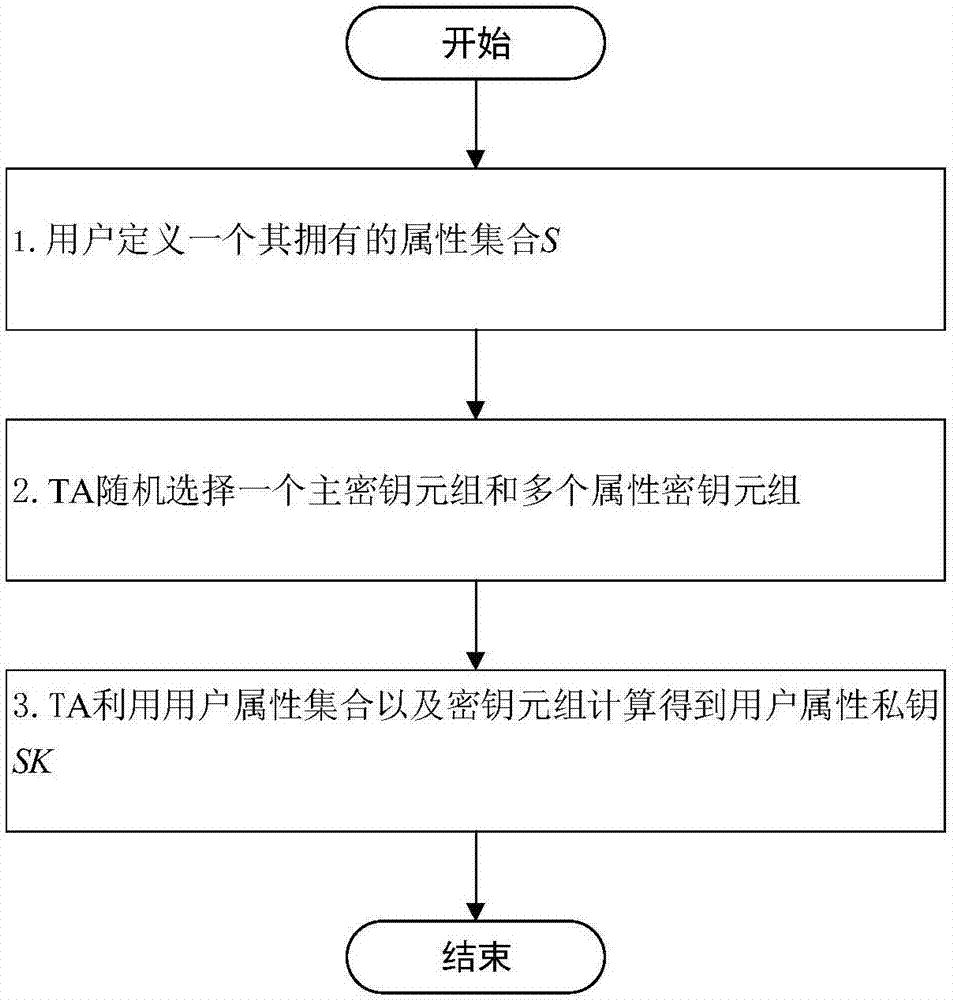
The invention discloses an attribute-based online / offline keyword search method and its cloud computing application system in a mobile cloud environment, comprising the following steps: system initialization, TA generates a public key and a master key; TA generates an intermediate key offline for a new user After the new user completes the registration, TA generates its attribute private key; TA generates an outsourced key for the new user; the data master encrypts the information offline on the mobile device side to obtain the intermediate ciphertext;) the data master encrypts the intermediate ciphertext online to obtain the complete ciphertext The data master generates an index set, and the user uses its own attributes to generate relevant trapdoors, and sends them to the cloud server together; the cloud server receives the encrypted index and trapdoor, and searches for keywords; the user decrypts to obtain the target information. The present invention realizes searchable encryption based on an attribute encryption mechanism and online / offline technology, protects user privacy, and greatly reduces user expenses.
Owner:ANHUI UNIVERSITY
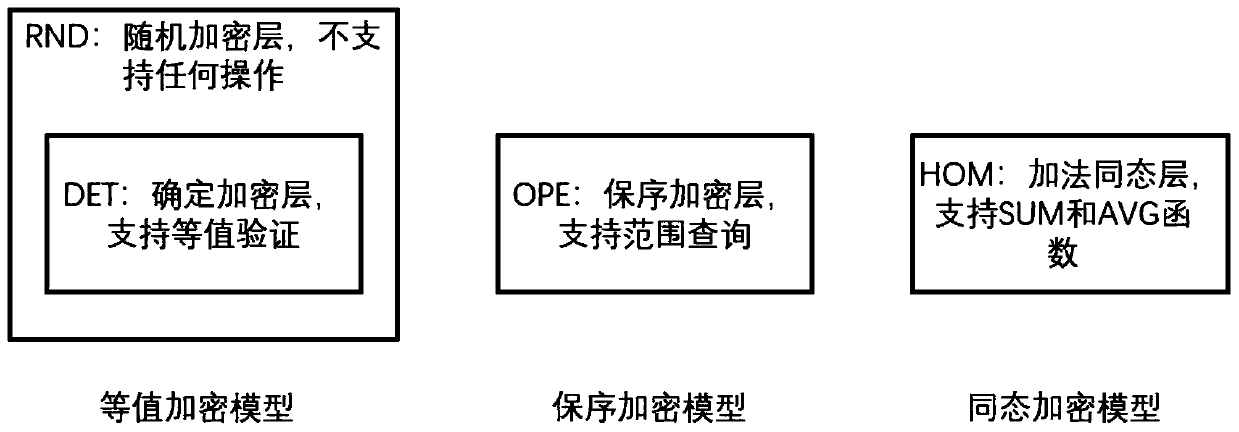
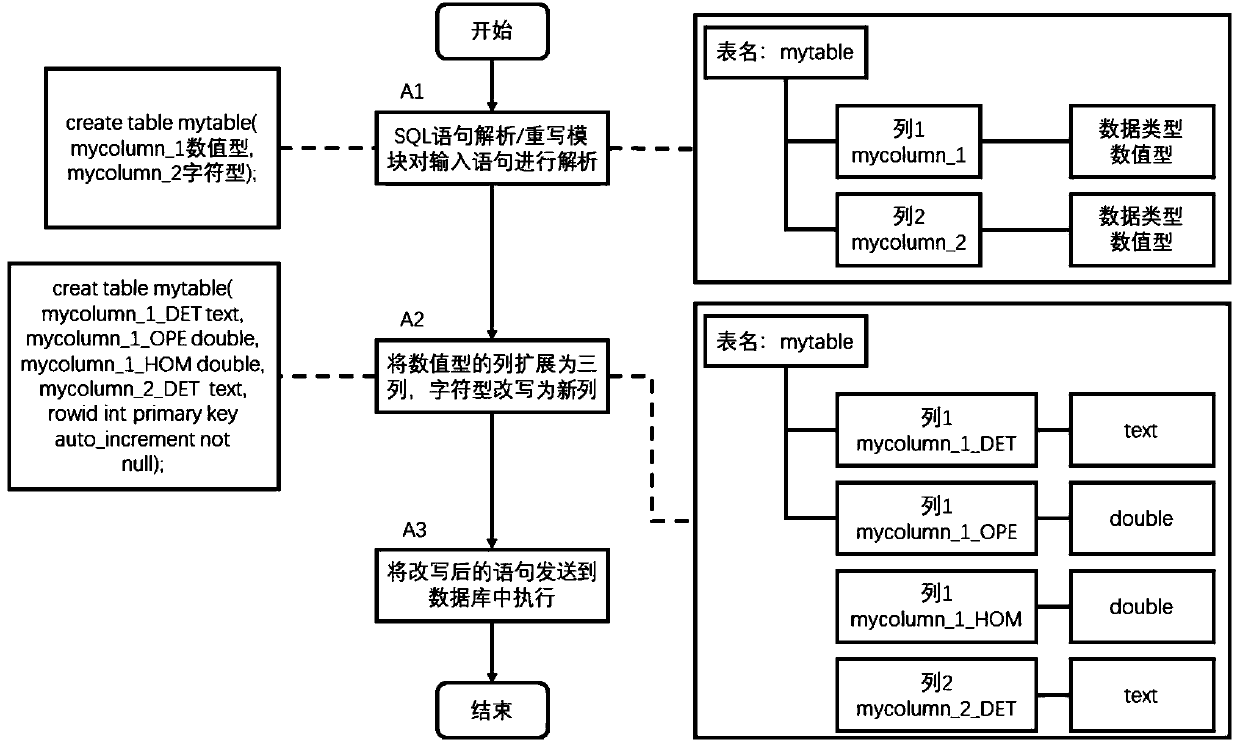
A searchable database security encryption system
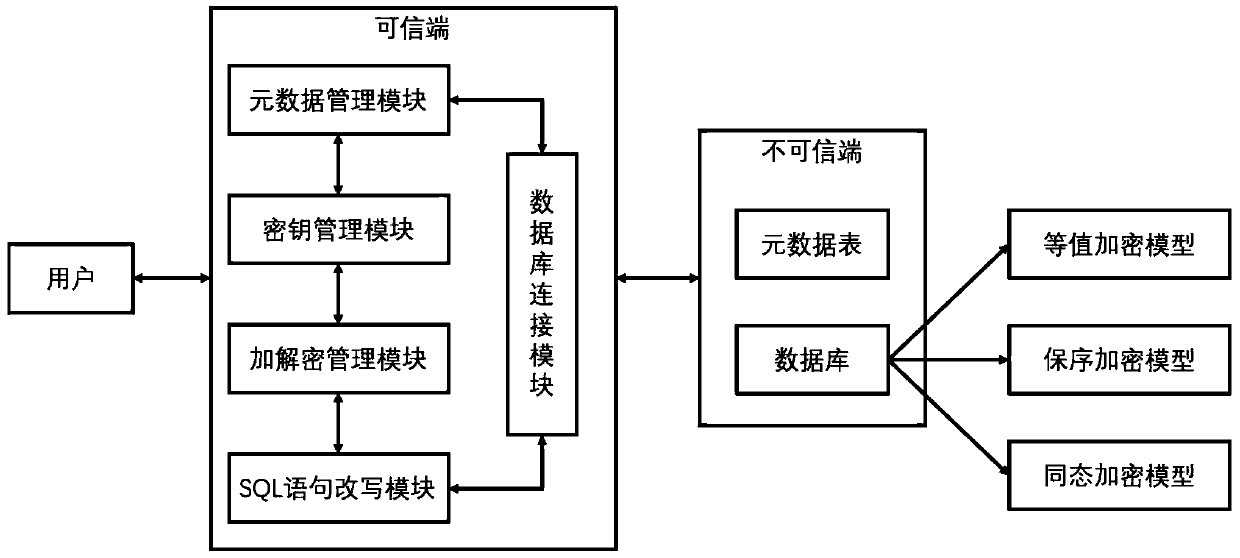
InactiveCN109815719AAvoid exposureProtect data privacyDigital data information retrievalDigital data protectionPlaintextMetadata management
The invention discloses a searchable database security encryption system. The system comprises a metadata management module, a key management module, an encryption and decryption module, an SQL statement rewriting module, a database connection module, a metadata table and an encryption model. According to the searchable database security encryption system, the encryption layer is dynamically adjusted in the statement execution process, so that a complex SQL statement is directly executed on a ciphertext, an untrusted database server is prevented from exposing plaintext data, and the data privacy is protected.
Owner:GUANGDONG POWER GRID CO LTD INFORMATION CENT
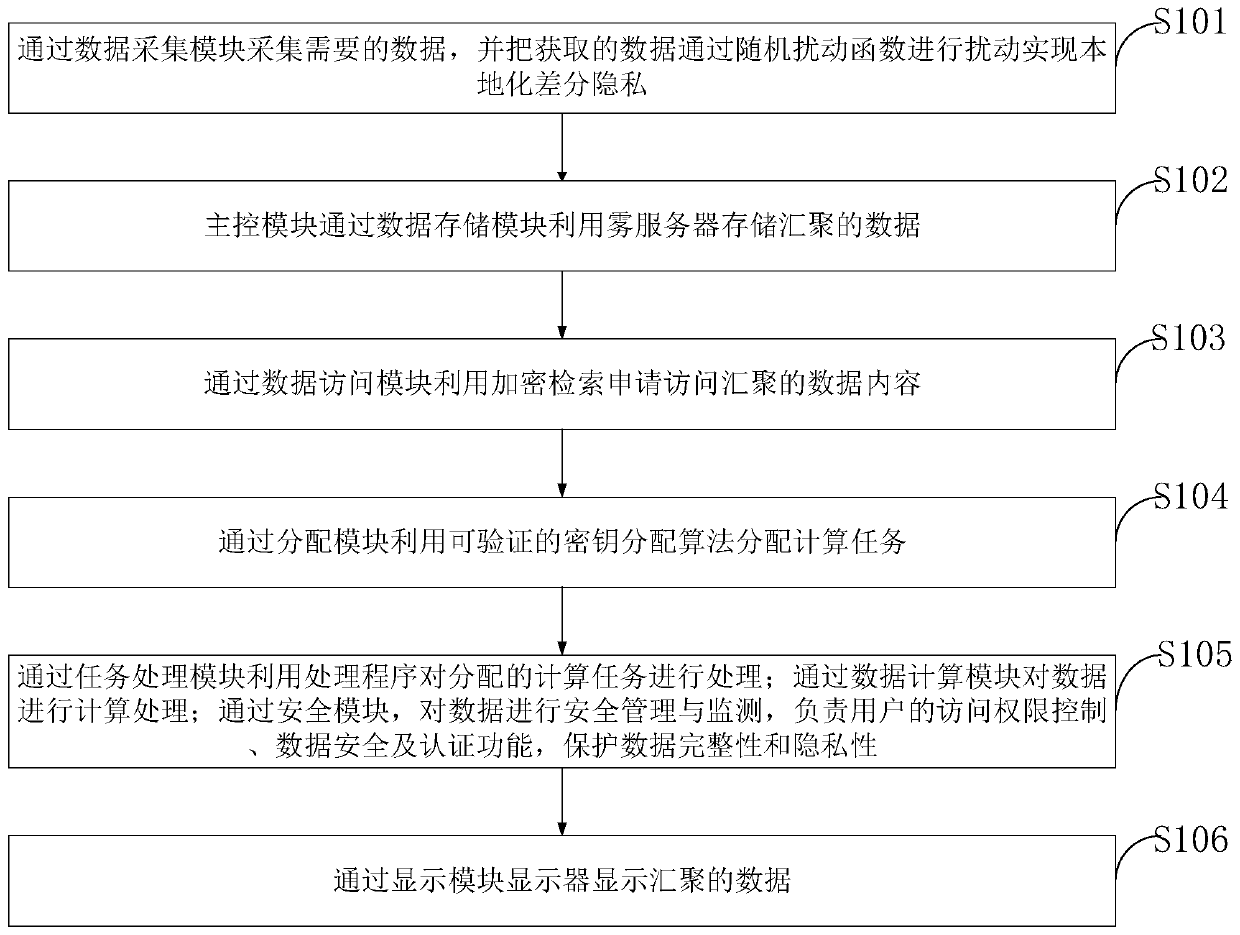
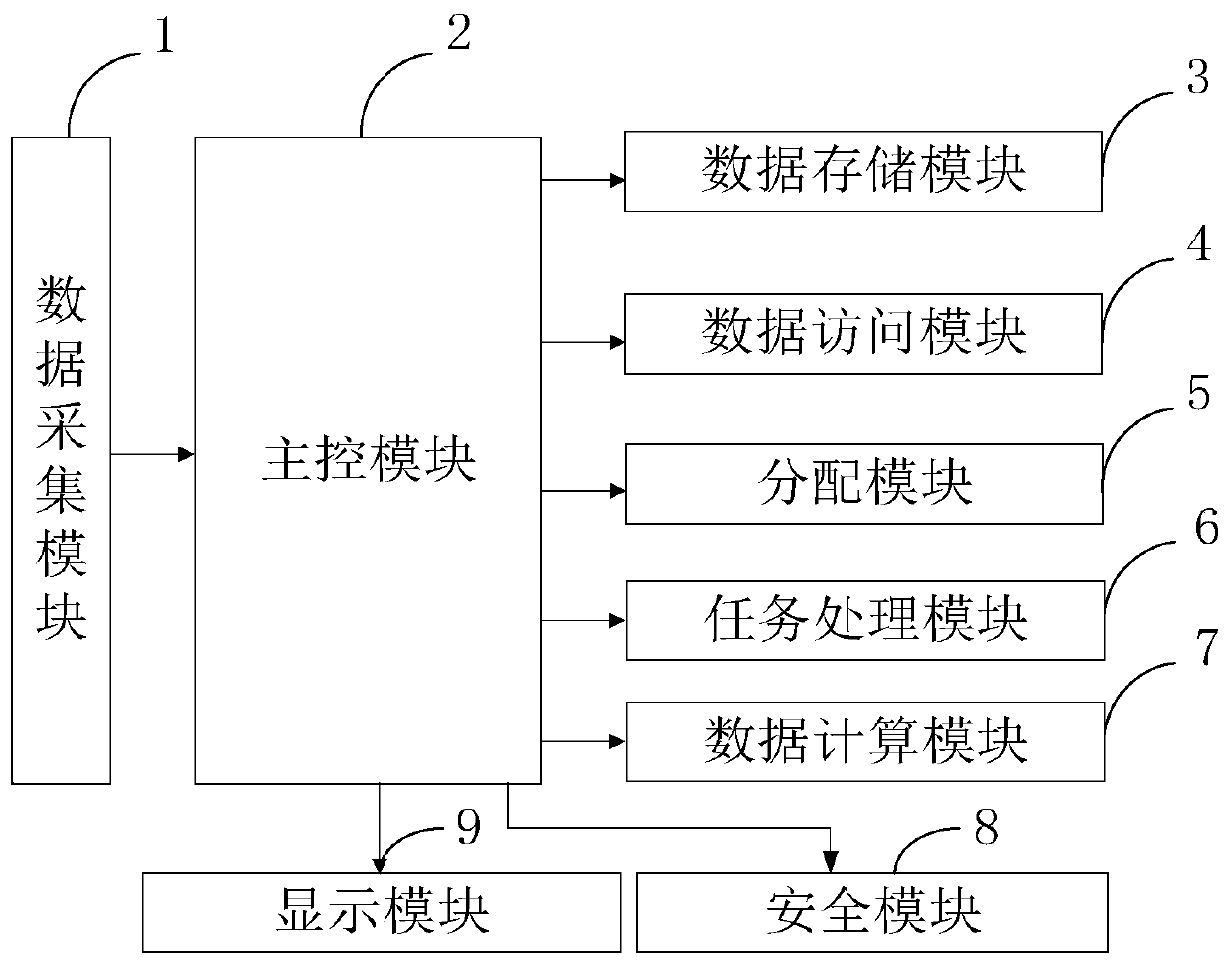
Security data storage and computing method based on Internet of Things fog computing-edge computing
ActiveCN110213036AProtection securityEnsure safetyKey distribution for secure communicationCommunication with homomorphic encryptionEncryptionData store
The invention belongs to the technical field of data storage and computing, and discloses a security data storage and computing method based on Internet of Things fog computing-edge computing. Localized Epsilon differential privacy is achieved through the data collection module, data encryption is achieved at fog nodes, and the safety of local area data is protected; the data storage module is used for storing encrypted data and protecting the privacy of the data on the fog server; the data access module is used for realizing data security decryption and protecting data information security sharing; the distribution module uploads own distribution task to the scheduler, so that the privacy of the computing terminal can be effectively protected; meanwhile, the computing tasks are decomposedthrough the task processing module, and parallel computing is conducted on the multiple decomposed computing subtasks. According to the invention, while the processing speed of the computing task isimproved, the data security and data privacy of the whole system are ensured.
Owner:XIDIAN UNIV +1
Automobile maintenance data storage method based on alliance chain
ActiveCN111159750AAchieve sharingAvoid the problem of too large blocksFinanceDigital data protectionCloud storageData store
The invention provides an automobile maintenance data storage method based on an alliance chain. At present, a traditional storage mode of the automobile maintenance data mainly adopts paper materialsand scattered local database storage, and the storage mode shows many defects in the aspects of integrity and usability of the maintenance data. According to the invention, a blockchain technology taking an alliance chain as a main part and a cloud storage technology are used, logic blockchain storage and physical cloud storage of maintenance data are realized, so that real maintenance data cannot be tampered and traceable once generated and submitted to a verification node and written into a block by a P-DPoS consensus mechanism, and a user can know the integrity of submitted data in time through a Merkle root verification method. Meanwhile, related cryptography technologies such as a public key encryption algorithm, a proxy re-encryption algorithm, an SOK protocol and the like are adopted, so that disclosure and sharing of part of maintenance data are realized under the condition of ensuring that personal identity privacy is not leaked, and great convenience is provided for a claimprocess of a user.
Owner:NANJING UNIV OF POSTS & TELECOMM
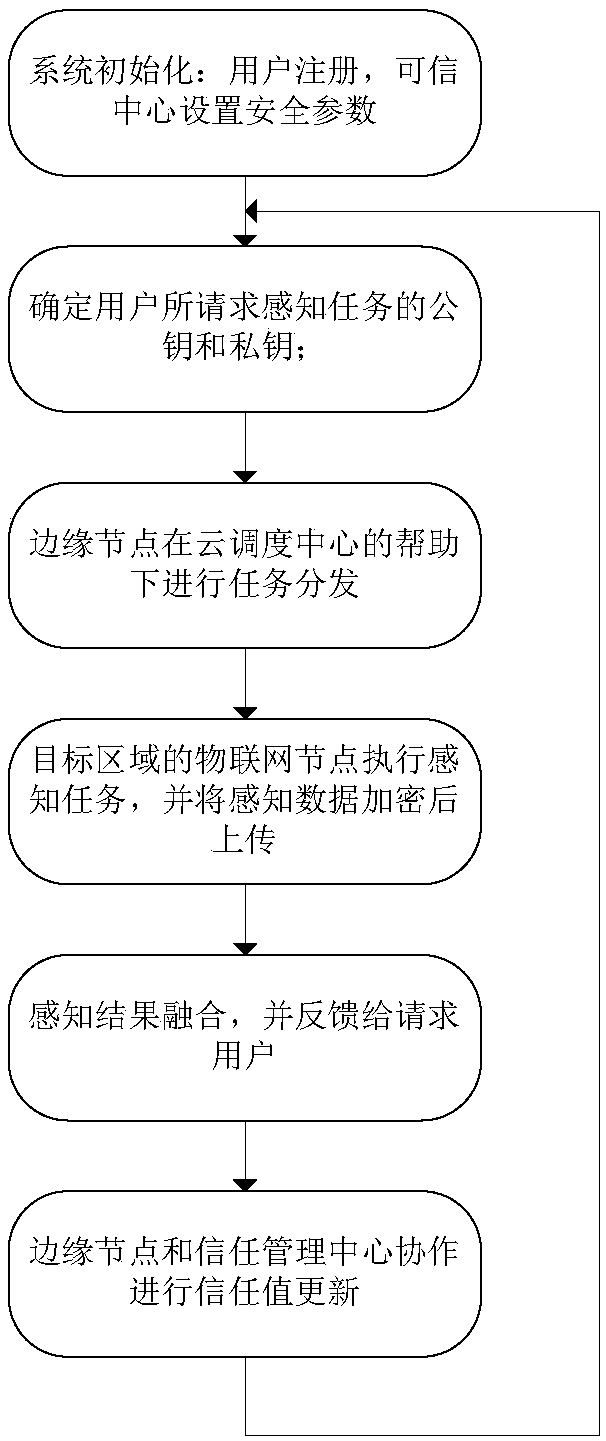
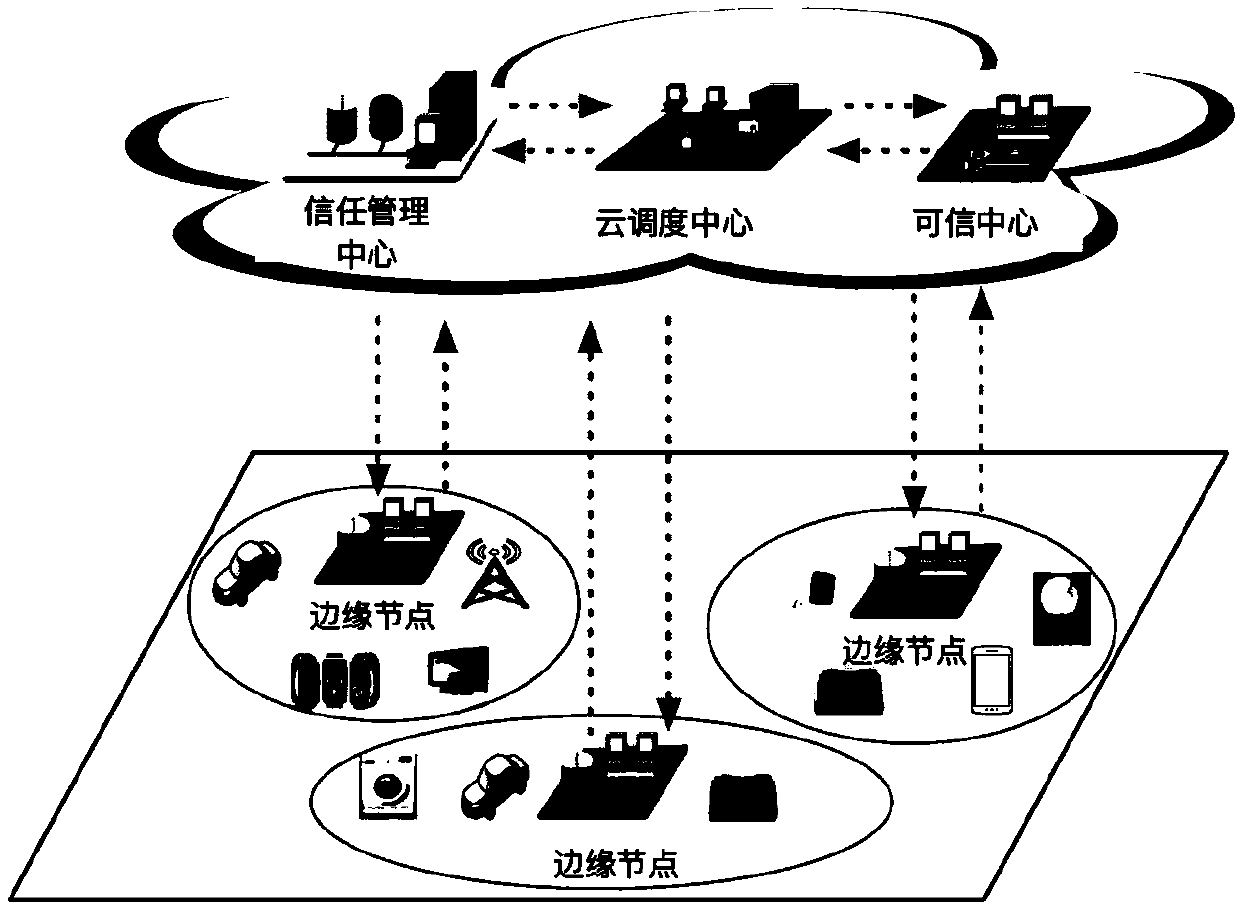
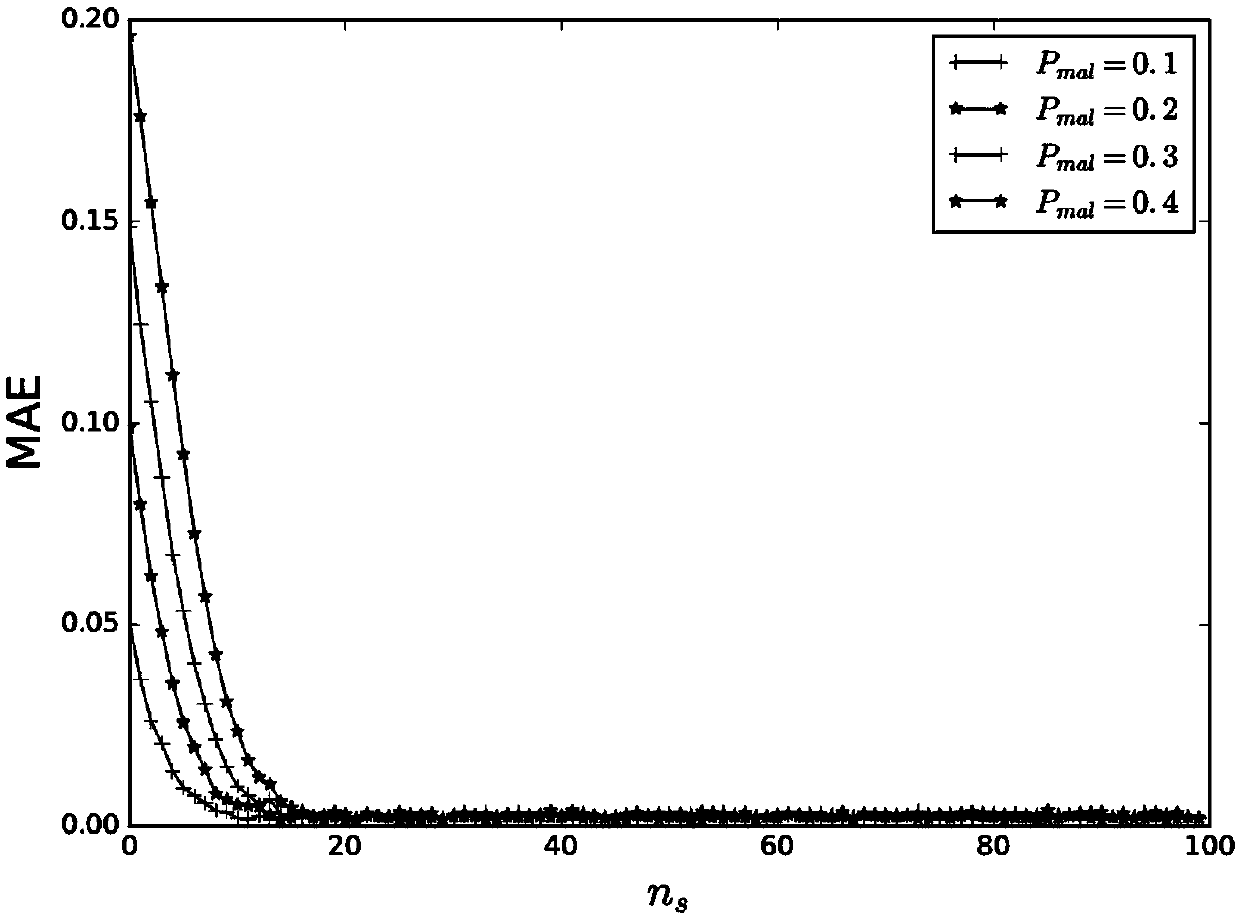
Method for protecting privacy of user and resisting to malicious user in Internet of Things on basis of edge computing
ActiveCN108924081AImprove reliabilityLose weightCommunication with homomorphic encryptionOriginal dataInternet privacy
The invention belongs to the field of information security and discloses a method for protecting privacy of a user and resisting to a malicious user in Internet of Things on the basis of edge computing, comprising the following steps: introducing an SHE homomorphic cryptosystem, on the basis of protecting the privacy of the user, calculating and updating a trust value of the user, and resisting the malicious user and injection of malicious data; and loading a complex ciphertext operation to an edge node by utilizing an edge computing mode, and protecting the privacy of the user, including thesteps of executing a perception task and updating the trust value of a user executing the perception task under cooperation of a target area edge node and a trust management center. The method disclosed by the invention introduces an emerging edge computing mode, better accords with the actual network demand and can estimate reliability of data without leaking the original data, so that resistanceto the malicious user is realized by introducing a trust management mechanism on the basis of protecting privacy of user data.
Owner:深圳中泰智丰物联网科技有限公司
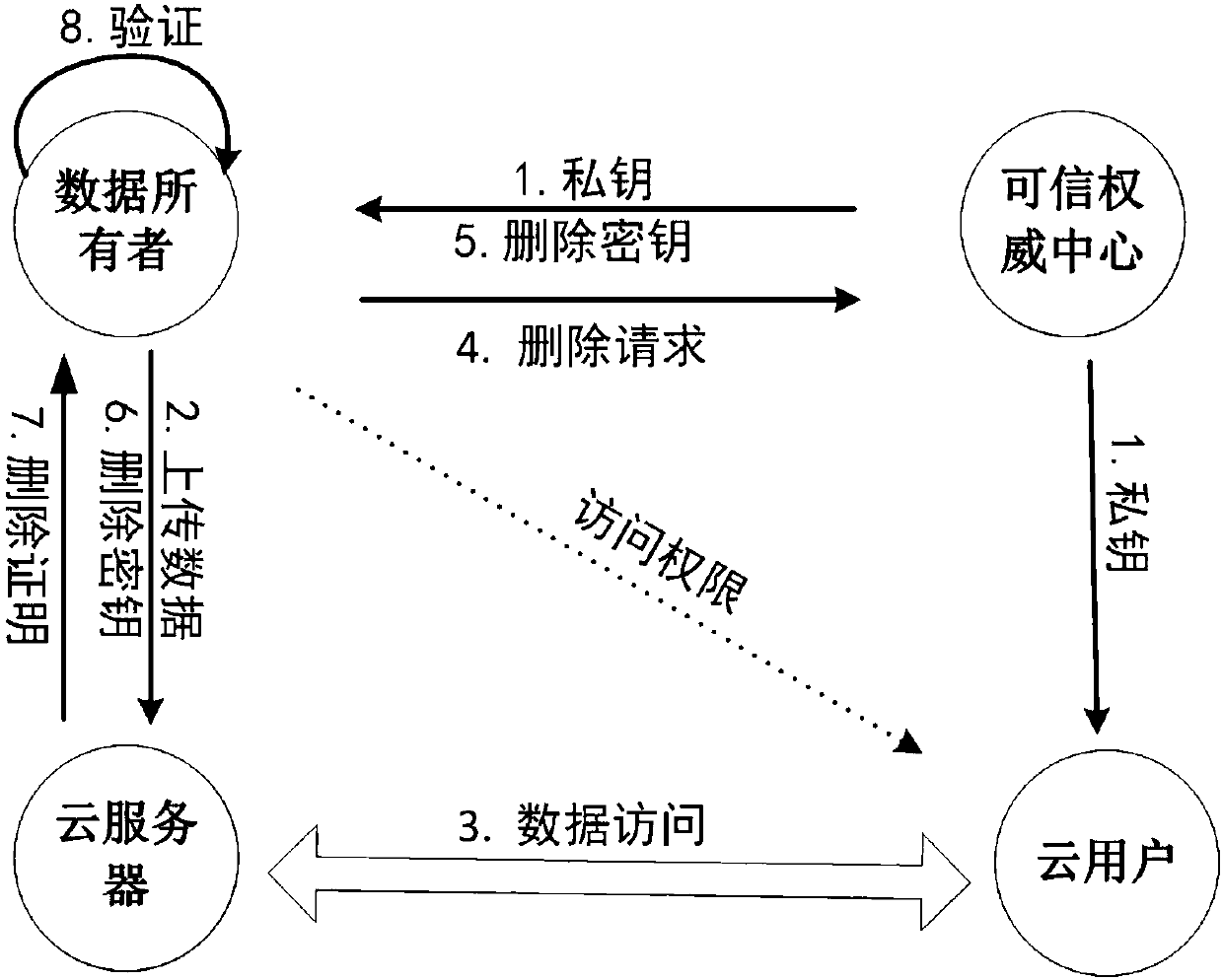
Cloud data deterministic deletion method for supporting fine-grained access
ActiveCN108600171ADecrypted correctlyWon't leakUser identity/authority verificationRevocationPrivacy protection
The invention relates to a cloud data deterministic deletion method for supporting fine-grained access, comprising the following steps: a data owner encrypts data and outsources the encrypted data toa cloud server, so that only the user who meets an access requirement can decrypt the data; when the data owner wants to delete the data stored in the cloud server, the owner first sends a deletion request to a trusted authority center, which returns a deletion key, namely, a re-encrypted key to the data owner, the data owner sends the deletion key to the cloud server, and the cloud server carriesout a deletion operation on the data; after performing the deletion operation, the cloud server returns a certificate to the data owner, and the data owner verifies that the target data has been deleted through a Merkle hash tree. The cloud data deterministic deletion method in the invention utilizes attribute revocation and the Merkle hash tree to realize verifiable data deletion, supports fine-grained access control to achieve the purpose of privacy protection, and greatly improves the use ratio of the cloud server.
Owner:SHAANXI NORMAL UNIV
Cloud Data Sharing Method Based on Block Chain to Realize Data Tampering Resistance and User Collusion
ActiveCN109145612AEffective traceabilityEnsure safetyDigital data protectionTransmissionTamper resistanceConfidentiality
In recent years, with the application of cloud more and more widely, the problem of privacy leakage of cloud sharing data is constantly occurring at home and abroad. Privacy leakage in cloud data sharing has become the focus of attention, and relevant solutions are constantly proposed. Most of the existing schemes are composed of a single shareholder or a specific user. However, in actual data sharing scenarios, the shared data is usually provided by multiple data owners, which brings a series of new problems to protect the privacy of the data, such as malicious tampering of the shared data, collusion between malicious users, and collusion between users and cloud service providers. The invention provides a cloud data sharing method based on block chain for realizing data tampering prevention and user conspiracy. The method realizes that the data is not tampered with by malicious users when sharing by adopting the method of public bookkeeping and intelligent contract in the block chain,and realizes the confidentiality of the shared data by adopting a (p, t) threshold Paillier cryptosystem, thereby avoiding the problem that malicious users collude to steal the shared data.
Owner:DONGHUA UNIV
Method and device for outsourced data query verification, electronic equipment and readable storage medium
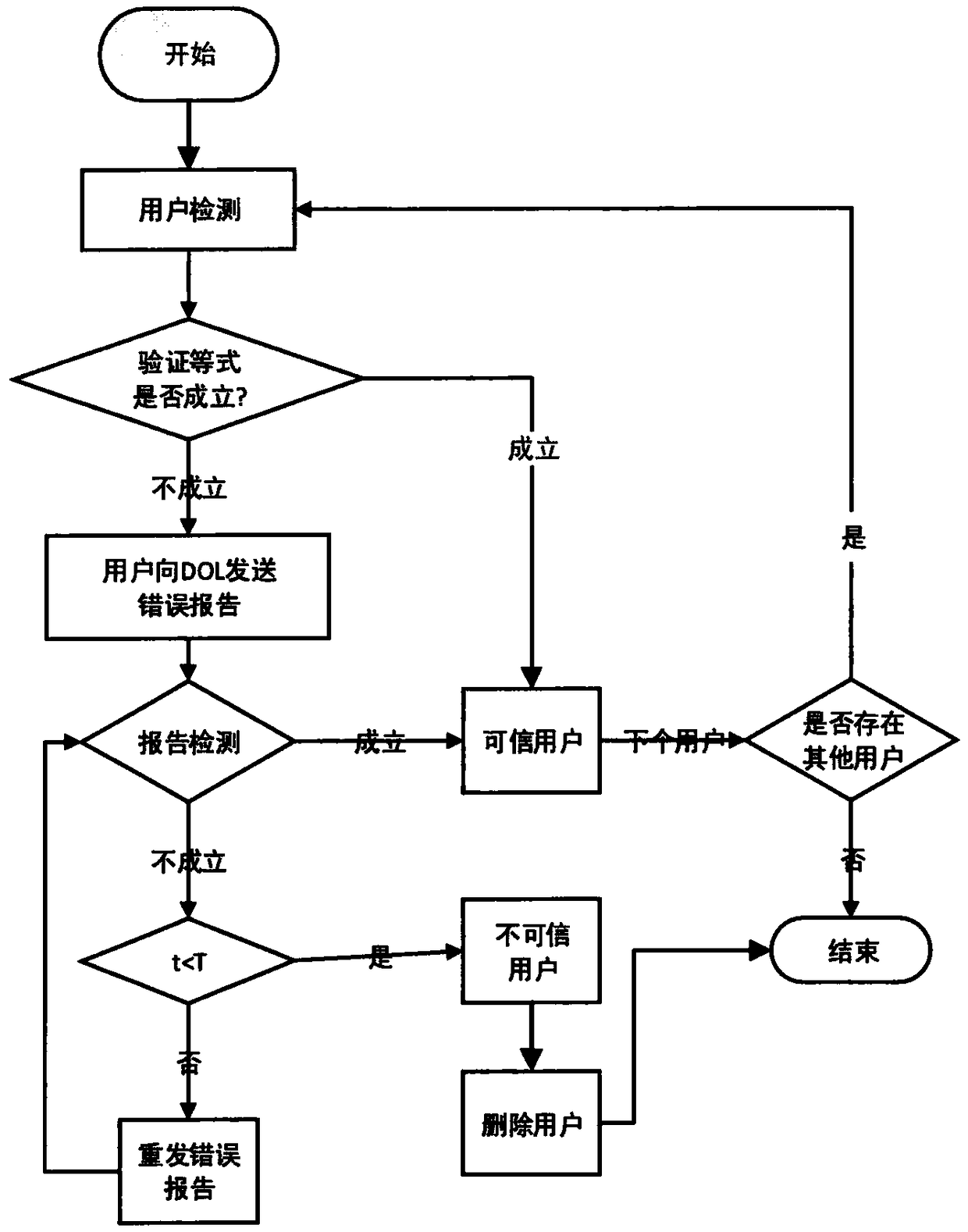
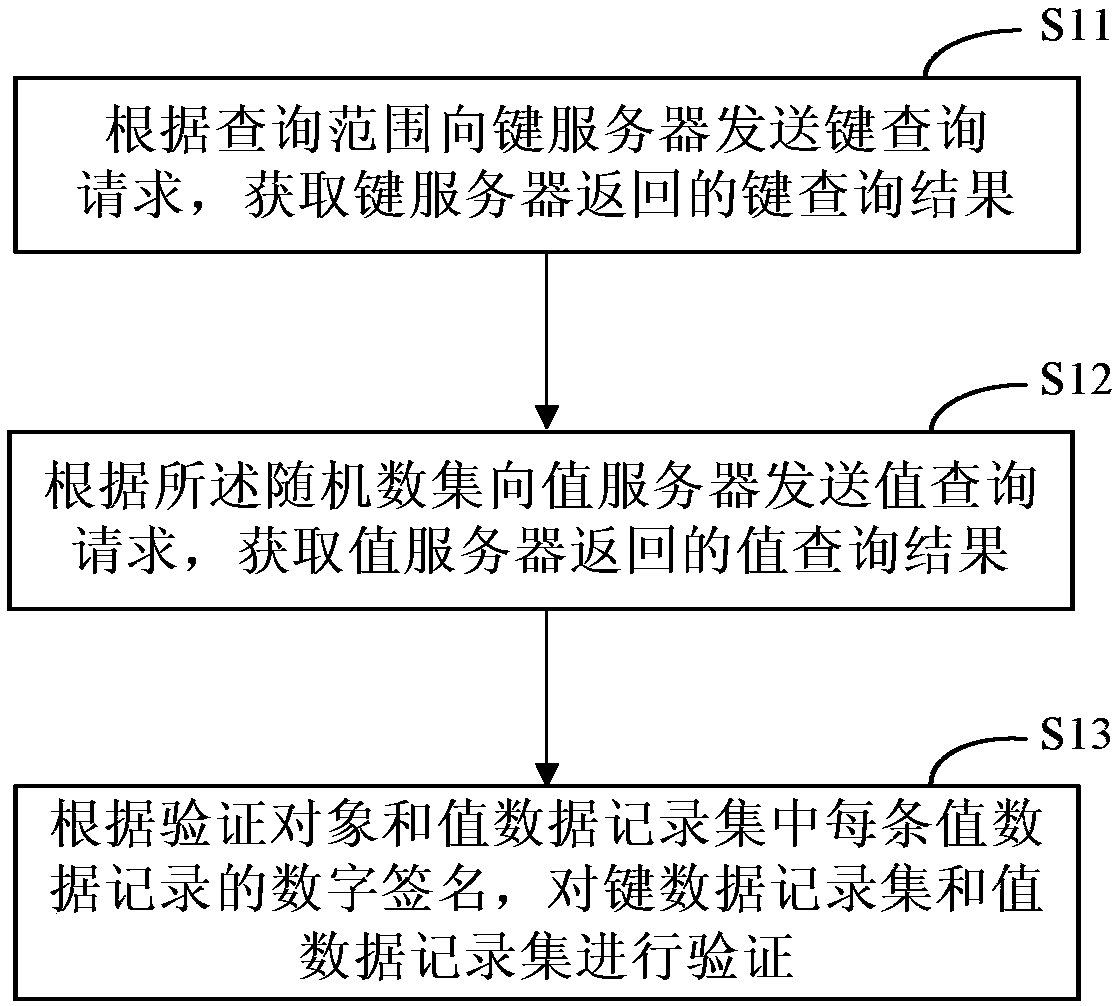
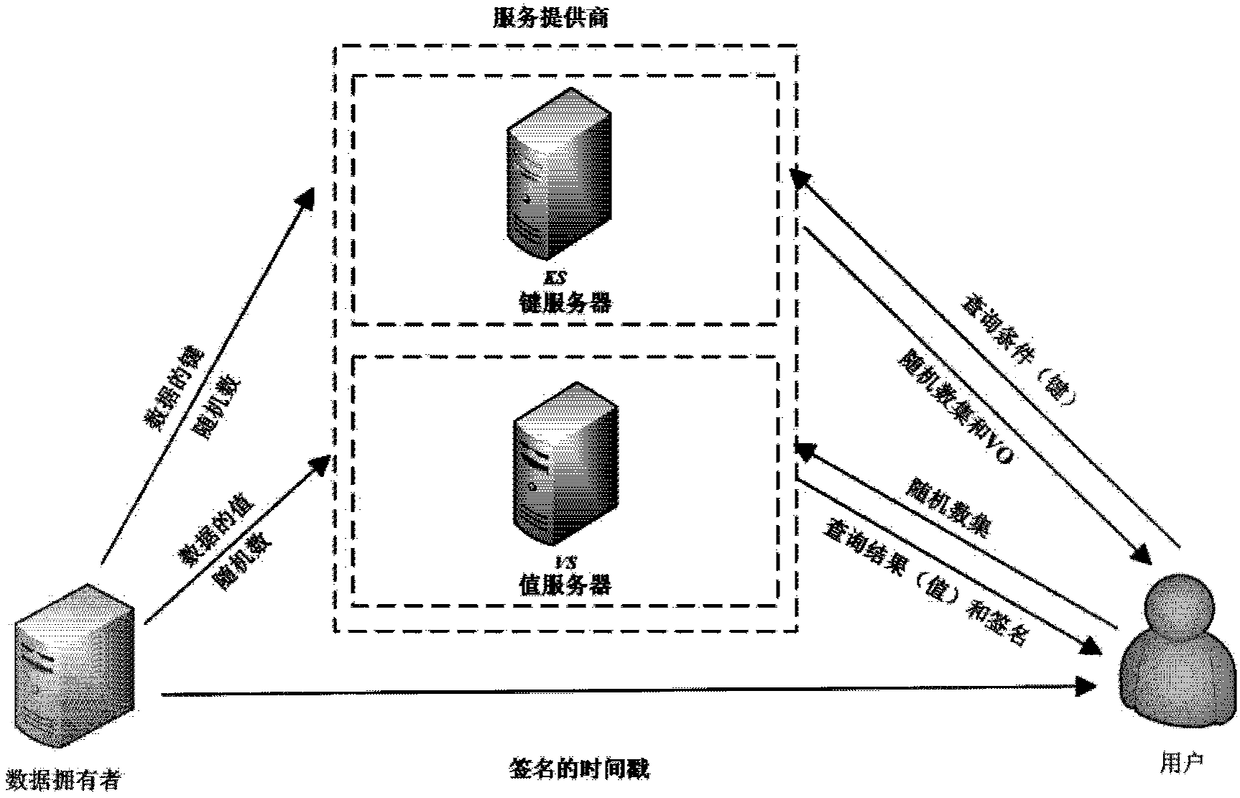
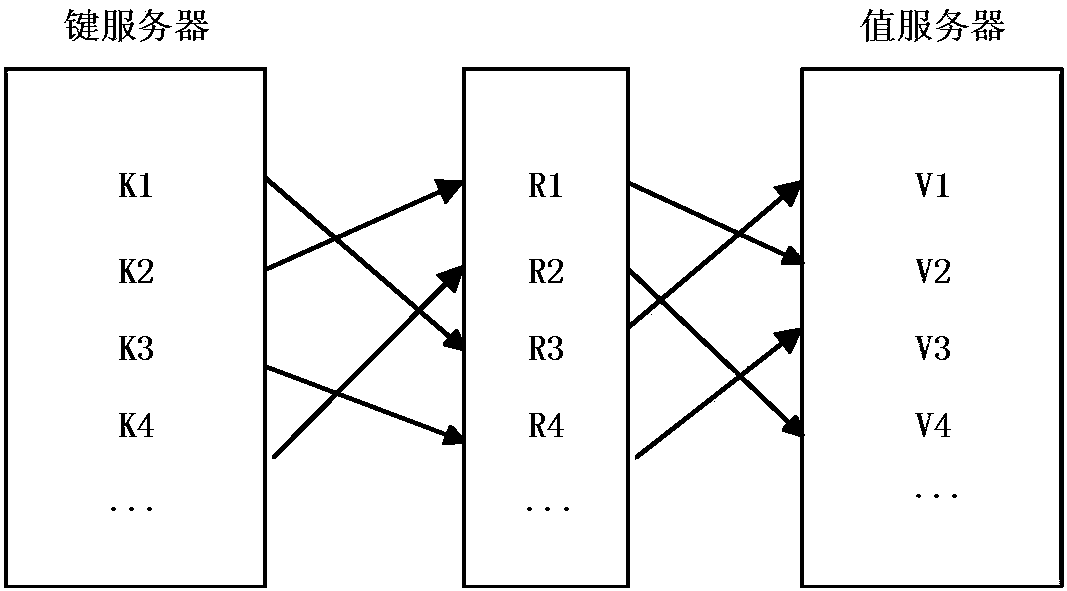
InactiveCN108733710AVerify TimelinessOvercoming query validation issuesSpecial data processing applicationsRecordsetDigital signature
The embodiment of the invention provides a method and a device for outsourced data query verification, electronic equipment and a readable storage medium, which can solve a problem of query verification under outsourced Key-Value storage and can solve a problem of being difficult to construct a query verification object under a condition of protecting data privacy. The method comprises the following steps: sending a key query request to a key server according to a query range, acquiring a key query result returned back by the key server, wherein the key query result comprises a verification object, a key data record set and a random number set corresponding to the key data record set; sending a value query request to a value server according to the random number set, acquiring a value query result returned back by the value server, wherein the value query result comprises a value data record set and a digital signature of each value data record in the value data record set; and according to the verification object and the digital signature of each value data record in the value data record set, verifying the key data record set and the value data record set.
Owner:BEIJING JINGDONG SHANGKE INFORMATION TECH CO LTD +1
Ciphertext retrieval method
InactiveCN103927340AImplement the sort functionImprove efficiencySpecial data processing applicationsSecuring communicationCiphertextDocumentation
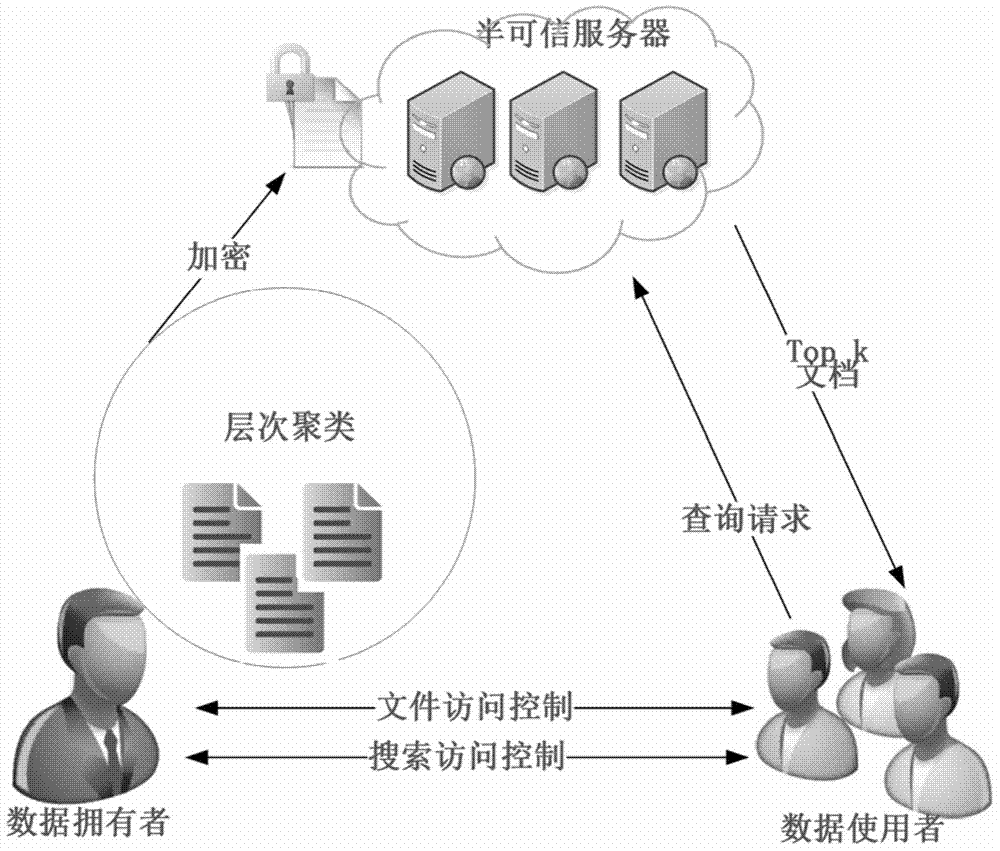
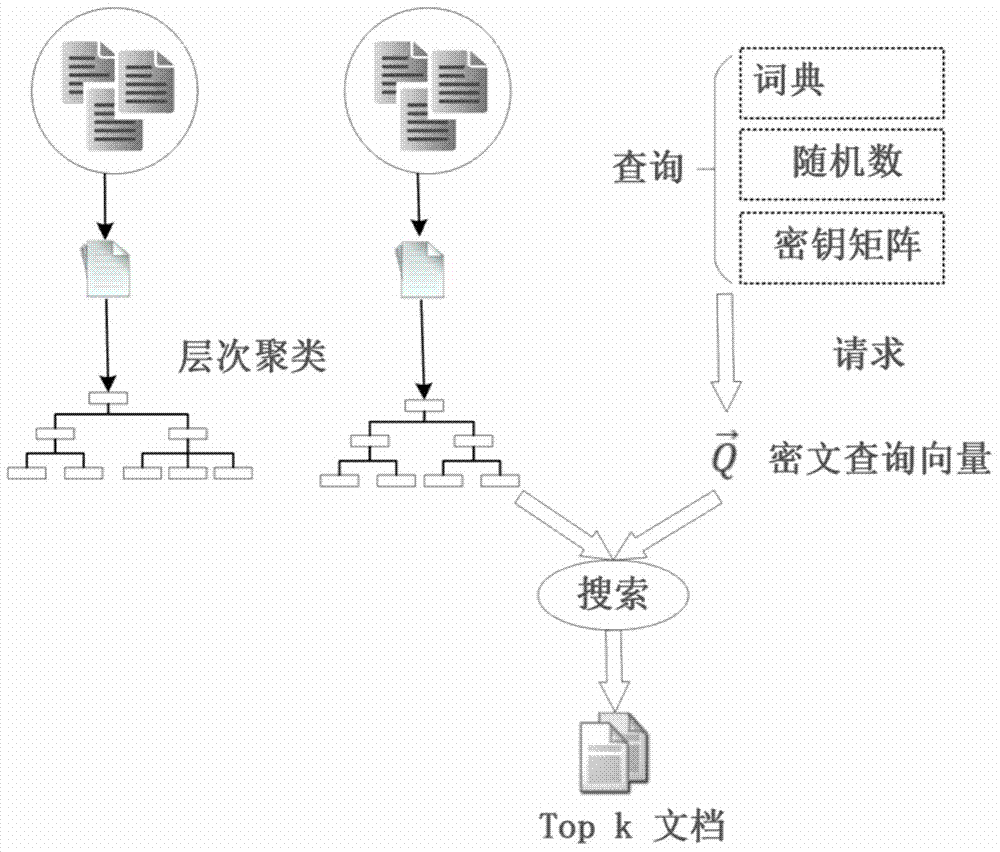
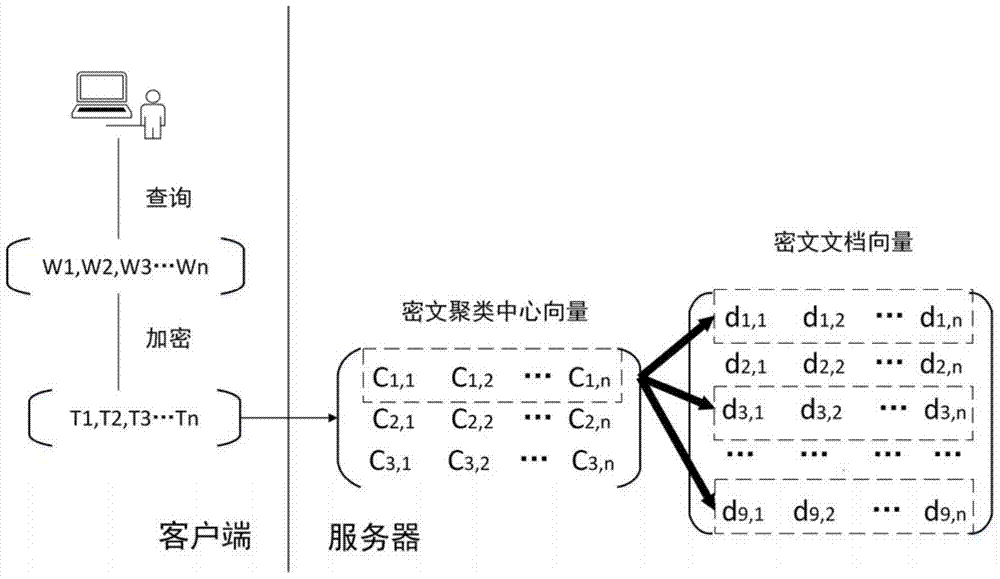
The invention discloses a ciphertext retrieval method. Hierarchical clustering creation and index encryption are performed in a client; a receiver receives a ciphertext query vector; scores of correlation between document vectors and the query vector can be calculated through the ciphertext index based on hierarchical clustering; a document ranking function is achieved according to the scores of correlation; ciphertext document vectors are not all queried in the querying process, instead document vectors in specific clusters are retrieved, and accordingly, query time is greatly shortened and ciphertext retrieval efficiency is improved. The ciphertext retrieval method supports retrieving multi-keyword rankable ciphertext and supports retrieving ciphertext with big data, and data privacy is protected effectively.
Owner:INST OF INFORMATION ENG CAS
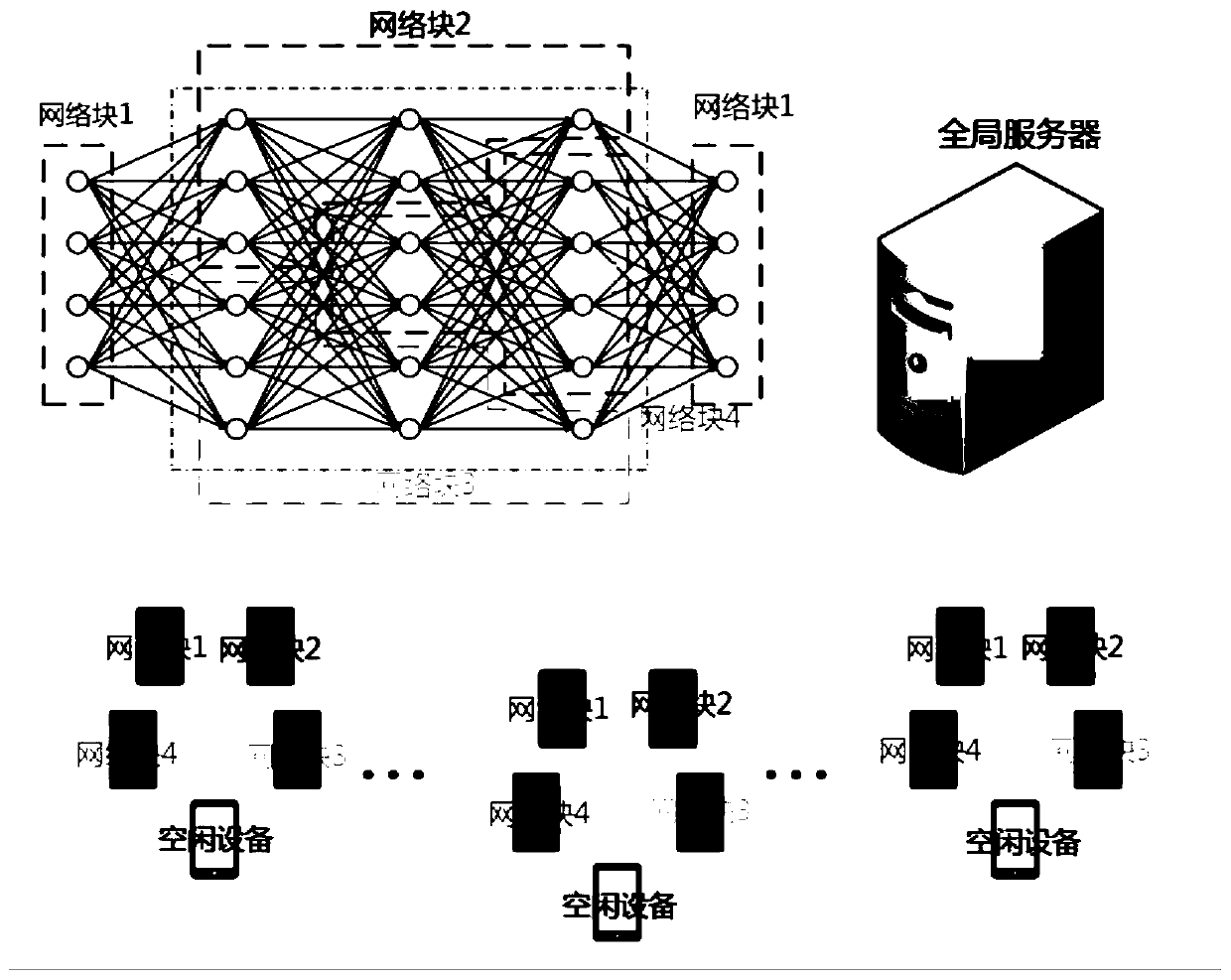
Distributed deep learning training method based on mobile device for protecting data privacy
InactiveCN110263928AProtect data privacyAbsolute controlNeural learning methodsService provisionInternet privacy
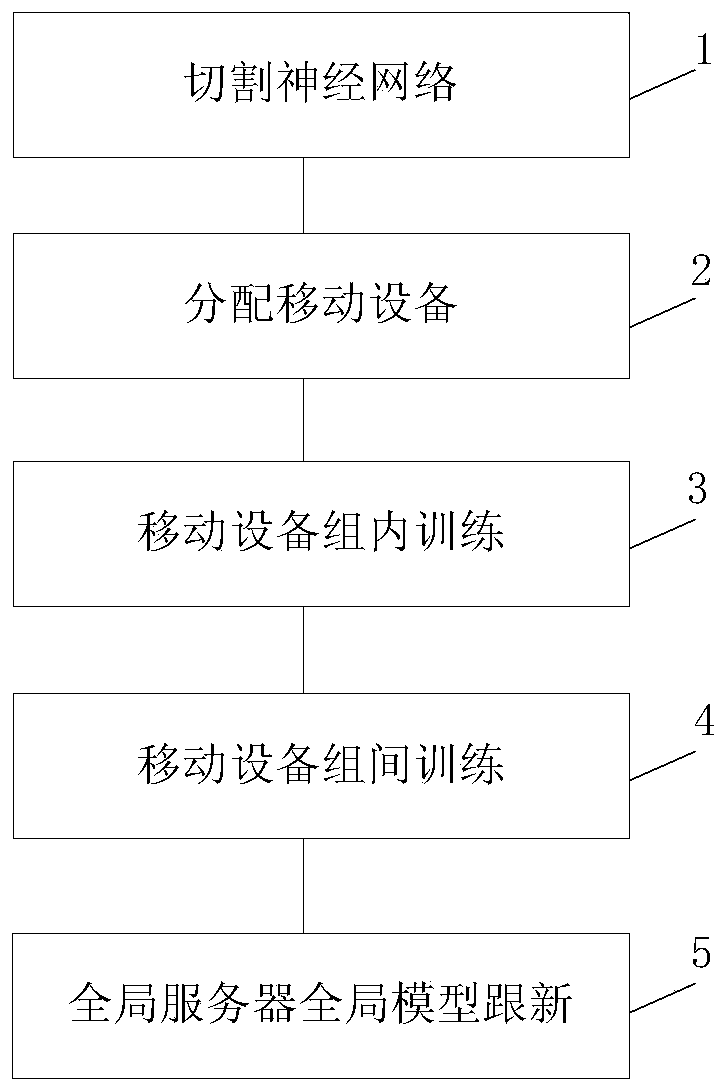
The invention discloses a distributed deep learning training method based on a mobile device for protecting data privacy. The method comprises the following steps of 1, cutting a neural network; 2, distributing the mobile device; 3, training in a mobile device group; 4, training among the mobile device groups; and 5, updating a global model of a global server. According to the distributed deep learning training method, the purposes of protecting the data privacy of the user and enabling the training model to achieve high performance are achieved, the user enjoys the absolute control right for the training data generated by the user, and the problem that a service provider can maliciously use, violate and leak the user data privacy under the traditional centralized deep learning, is solved.
Owner:UNIV OF SCI & TECH OF CHINA
A privacy protection data publishing method based on conditional probability distribution
ActiveCN109543445AAvoiding the choice problemProtect data privacyDigital data protectionData setPrivacy protection
The invention belongs to the technical field of information security and privacy protection, and is a privacy protection data publishing method based on conditional probability distribution. Accordingto the conditional probability distribution, an attacker's prior knowledge is modeled so that the attacker has different prior knowledge in different transactions. Then using the constructed model and quasi-identifier attribute value, the sensitive attribute value of each record is predicted, and the original value is replaced with the predicted value, and then published. There is no direct correlation between the predicted values of the published sensitive attributes and the original values, which effectively protects the privacy of user data. The predicted distribution of sensitive attribute values is similar to the real distribution, which effectively controls the distribution error and ensures the availability of the published dataset better than that of the generalized and stochasticresponse method. The invention can provide privacy protection mechanism for data release in various social fields such as medical treatment, finance, credit generation, transportation and the like, and provides support for application of data in scientific research and social service while protecting user data privacy.
Owner:FUDAN UNIV
Optimization method for transverse federated learning
PendingCN112734032AGood effectEffectively handle data heterogeneityNeural learning methodsEvaluation resultEngineering
The invention belongs to the technical field of federated learning and big data, and particularly relates to an optimization method for transverse federated learning, which comprises the following steps: S1, enabling a client to acquire data and preprocess the data; s2, processing the data of the client through an SMOTE-Non-IID model; s3, performing SMOTE-Non-IID model training through a client server architecture in transverse federated learning in combination with a data generation environment; s4, obtaining an optimization model of the SMOTE-Non-IID, and obtaining an evaluation result through prediction; according to the invention, each client synthesizes the data by adopting the SMOTE algorithm and receives the synthesized data from other clients at the same time, so that the problem of data heterogeneity in federated learning is effectively solved, and relatively high prediction accuracy can be ensured.
Owner:HANGZHOU DIANZI UNIV
Joint learning framework based on cooperation of cloud server and IoT equipment
ActiveCN111625361AImprove forecast accuracyProtect data privacyResource allocationNeural architecturesEngineeringMachine learning
The invention discloses a joint learning framework based on cooperation of a cloud server and IoT equipment. The method is characterized in that a cloud server and IoT equipment collaborative joint learning framework of a distributed AI system architecture is adopted, and the method specifically comprises the steps of cloud offline training, IoT equipment and cloud collaborative online joint training, IoT equipment and cloud collaborative reasoning and the like. Compared with the prior art, the joint learning framework has the advantages that the method adapts to different IoT use environmentsor use preferences of users, better performance effects of the local equipment model and the cloud model are realized, prediction accuracy and average reasoning execution time of the neural network in the IoT equipment are effectively improved, data privacy of local equipment users is protected, and the method is especially suitable for distributed application scenes with diversified data distribution.
Owner:EAST CHINA NORMAL UNIV
Incentive method and system for hierarchical federated learning under end-side cloud architecture and complete information
ActiveCN113992676AProtect data privacyImprove training effectMachine learningNeural architecturesTerminal equipmentEngineering
The invention discloses an incentive method and system for hierarchical federated learning under an end-side cloud architecture and complete information. The method comprises the following steps: establishing a three-layer game model among terminal equipment, an edge aggregator and a cloud server based on a Stackelberg game; enabling the terminal equipment to download the power data learning model in the cloud server through the edge aggregator; constructing a model evolution function based on a hierarchical federated learning algorithm; solving an optimal strategy of three parties by utilizing Nash equilibrium, so the utility of the terminal equipment, the utility of the edge aggregator and the utility of the cloud server are maximized; enabling the terminal terminal to send the model updated based on the optimal strategy to the edge aggregator, enabling the edge aggregator to carry out excitation issuing on the terminal device based on the optimal strategy and sending the aggregated model to the cloud server; and enabling the cloud server to carry out excitation issuing on the edge aggregator based on the optimal strategy and carry out re-aggregation on the model. According to the invention, rewards can be provided for the terminal equipment and the edge aggregator, and reasonable and fair income distribution is realized.
Owner:TIANJIN UNIV
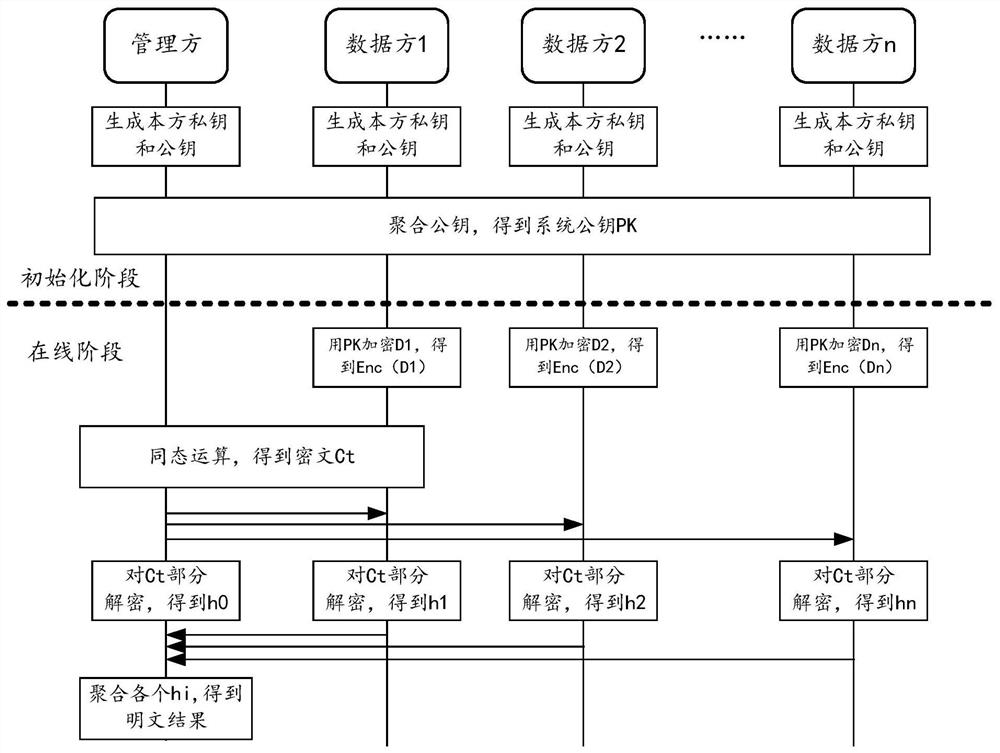
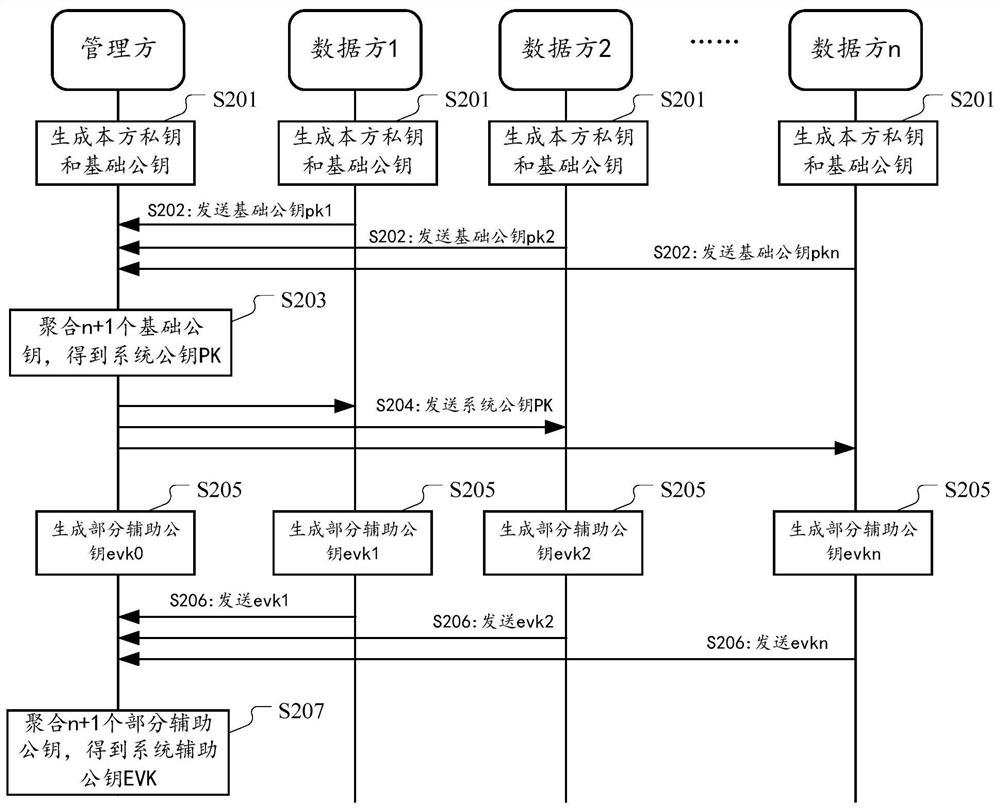
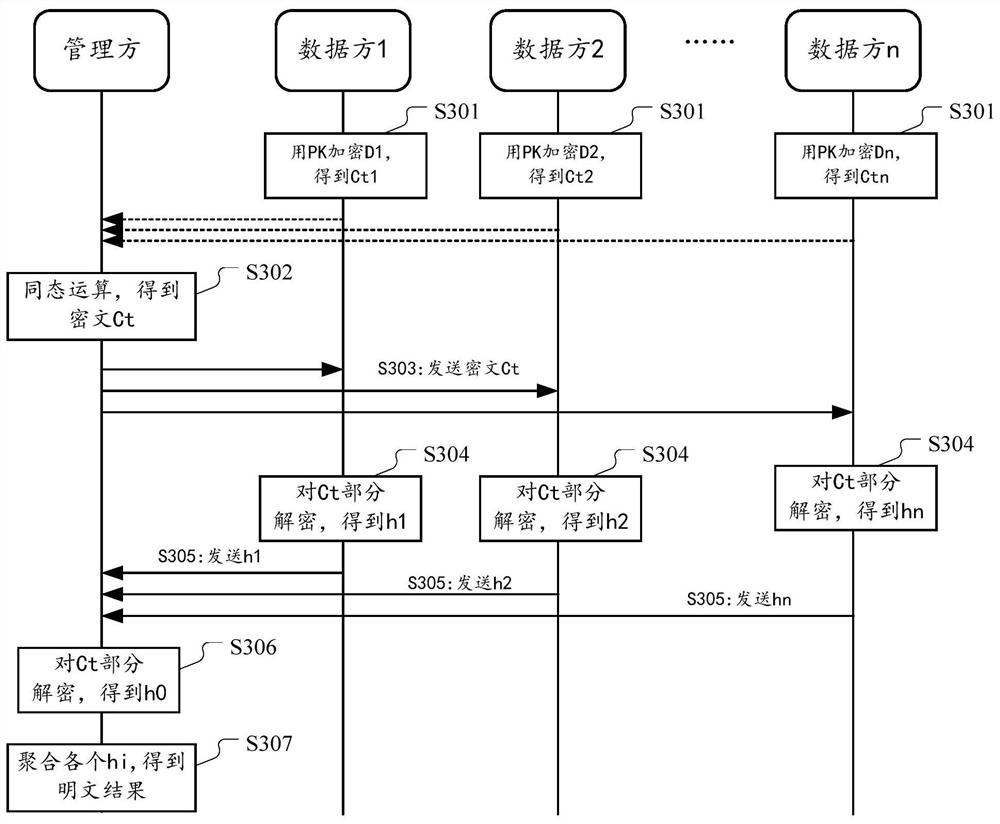
Multi-party joint privacy data processing method and device
ActiveCN112989368ASimplify complexityReduce trafficDigital data protectionCommunication with homomorphic encryptionPlaintextCiphertext
The embodiment of the invention provides a method and a system for processing private data through combination of multiple parties, the multiple parties comprise a management party and n data parties, and the method comprises the following steps. Each data party encrypts the original privacy data held by the data party by using the system public key and adopting an agreed homomorphic encryption algorithm to obtain corresponding ciphertext data, wherein the system public key is obtained by aggregating n + 1 basic public keys respectively corresponding to multiple parties. And then at least one of the multiple parties performs homomorphic operation on the n parts of ciphertext data according to a preset rule to obtain a ciphertext operation result. And each participant performs partial decryption on the ciphertext operation result by using the private key of the participant to obtain a partial plaintext result. And the management party performs aggregation operation on the plaintext result of each part to obtain a plaintext operation result.
Owner:ALIPAY (HANGZHOU) INFORMATION TECH CO LTD
Efficient query processing method for protecting location privacy and query privacy
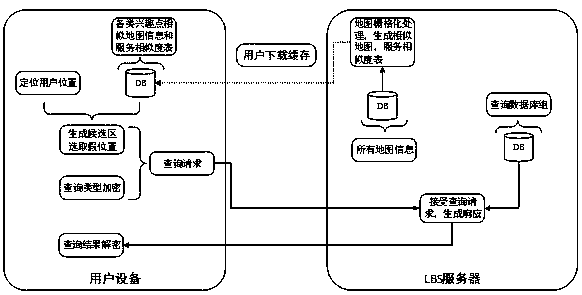
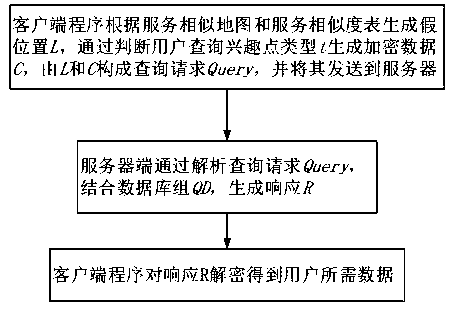
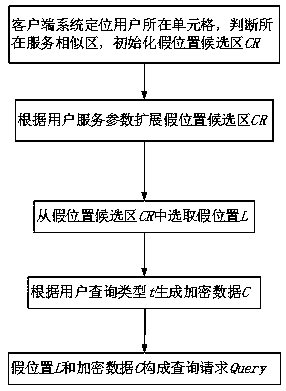
ActiveCN111083631AProtect data privacyReduce time complexityDigital data information retrievalDigital data protectionQuality of serviceMobile device
An efficient query processing method for protecting location privacy and query privacy specifically comprises the following steps: (1) a user selecting a false location through a cached service similarity map and a service similarity table by using mobile equipment at a client; generating encrypted data according to the interest point types to be queried by the user and the total number of the interest point types; forming a query request by the false position and the encrypted data, and sending the query request to an LBS (Location Based Service) server; (2) according to the received query request, generating a response by using a stored database by the server, and returning the response to the client; and (3) the client decrypting the data in the response returned by the server to obtainthe data required by the user. According to the method, the false position is selected by utilizing the existing service similarity, so that certain service quality is ensured while the position privacy is protected. The type inquired by the user is encrypted by utilizing homomorphic encryption, so that the server can return data required by the user under the condition that the inquiry type of the user is not exposed.
Owner:LANZHOU JIAOTONG UNIV
Hybrid cloud-oriented multi-keyword Top-k ciphertext retrieval method and system of privacy protection
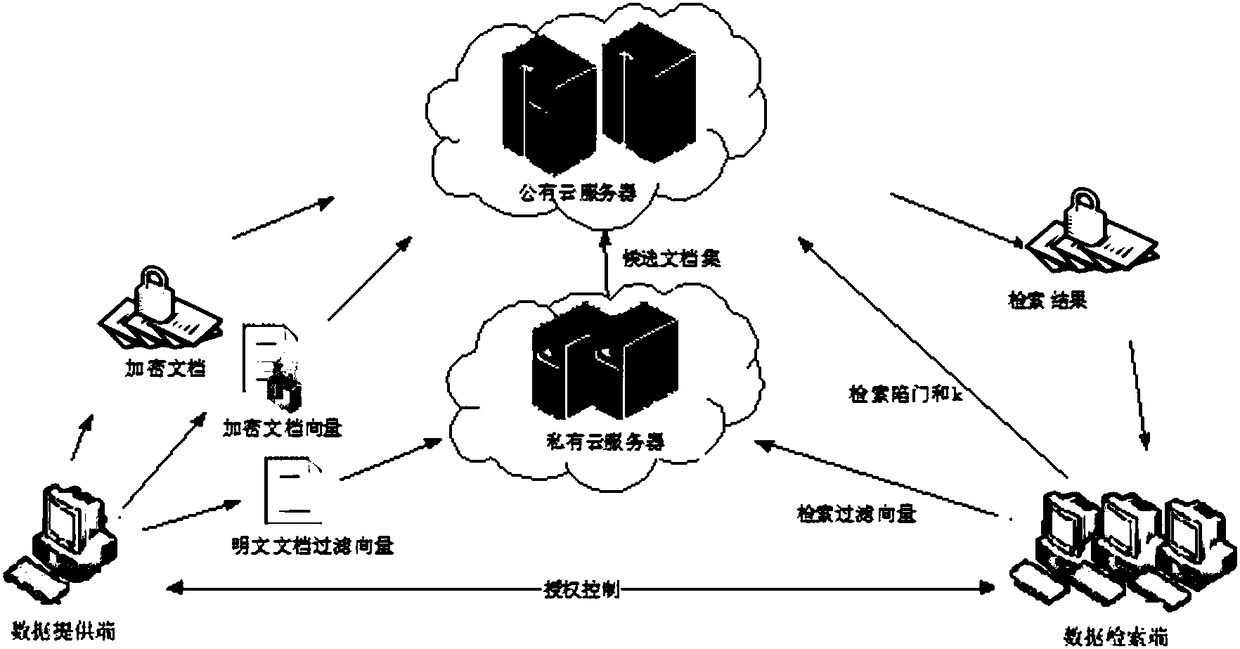
ActiveCN108363689AImprove securityProtect data privacySemantic analysisCharacter and pattern recognitionCiphertextPrivacy protection
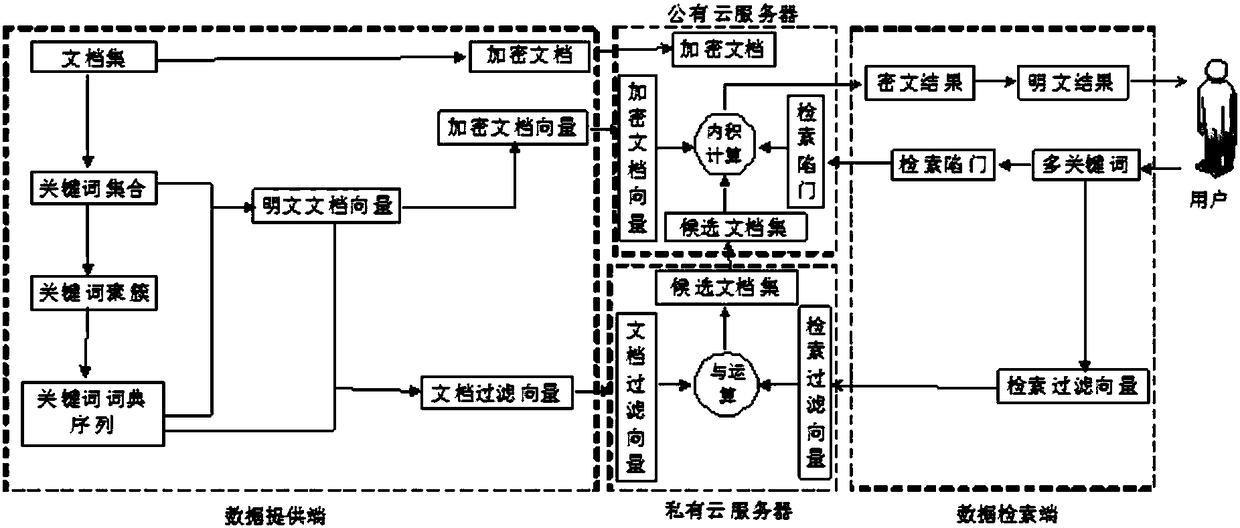
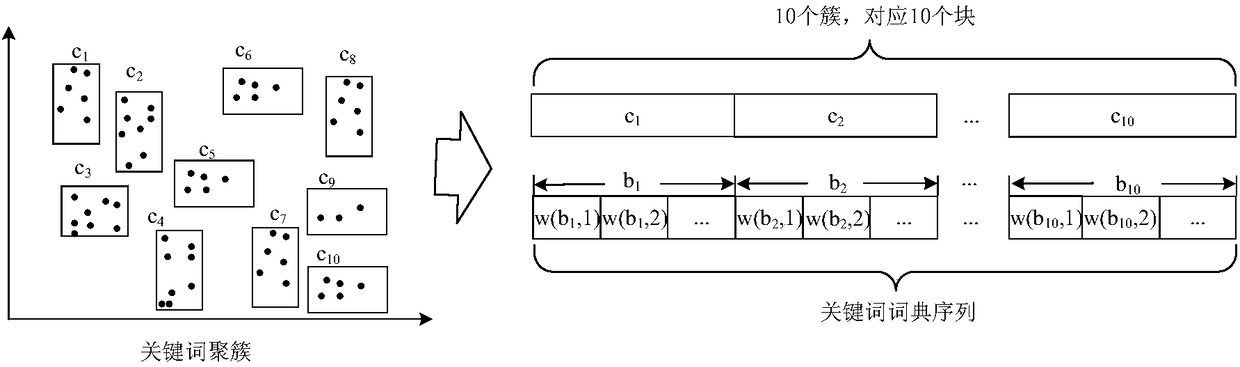
The invention discloses a hybrid cloud-oriented multi-keyword Top-k ciphertext retrieval method and system of privacy protection. The method and system mainly solve the problem that retrieval efficiency is low. A scheme thereof includes: utilizing correlation relationships among keywords by a data providing end to generate a keyword dictionary sequence through clustering technology; and generatinga high-dimensional document vector and low-dimensional document filtering vectors by each document, then outsourcing ciphertext documents and encrypted document vectors to an unauthentic public cloudserver, and storing the plaintext document filtering vectors to an authentic private cloud server. In retrieval, a candidate document set is firstly calculated through the private cloud server, and then retrieval result Top-k document calculation is realized through the public cloud server. Aggregation characteristics of the correlation keywords in the keyword dictionary sequence improve a filtering effect of the private cloud server, and compress a size of the candidate document set. According to the method, a process is simple, security is high, realization is easy, and highly-efficient multi-keyword ciphertext retrieval processing can be realized in a hybrid-cloud environment through lower calculation overheads.
Owner:NANJING UNIV OF POSTS & TELECOMM
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com