Method for protecting privacy of user and resisting to malicious user in Internet of Things on basis of edge computing
A user privacy and edge computing technology, applied in the field of information security, can solve problems such as traffic accidents, impact of IoT data fusion process, endangering personal and property safety, etc., to achieve the effect of improving reliability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
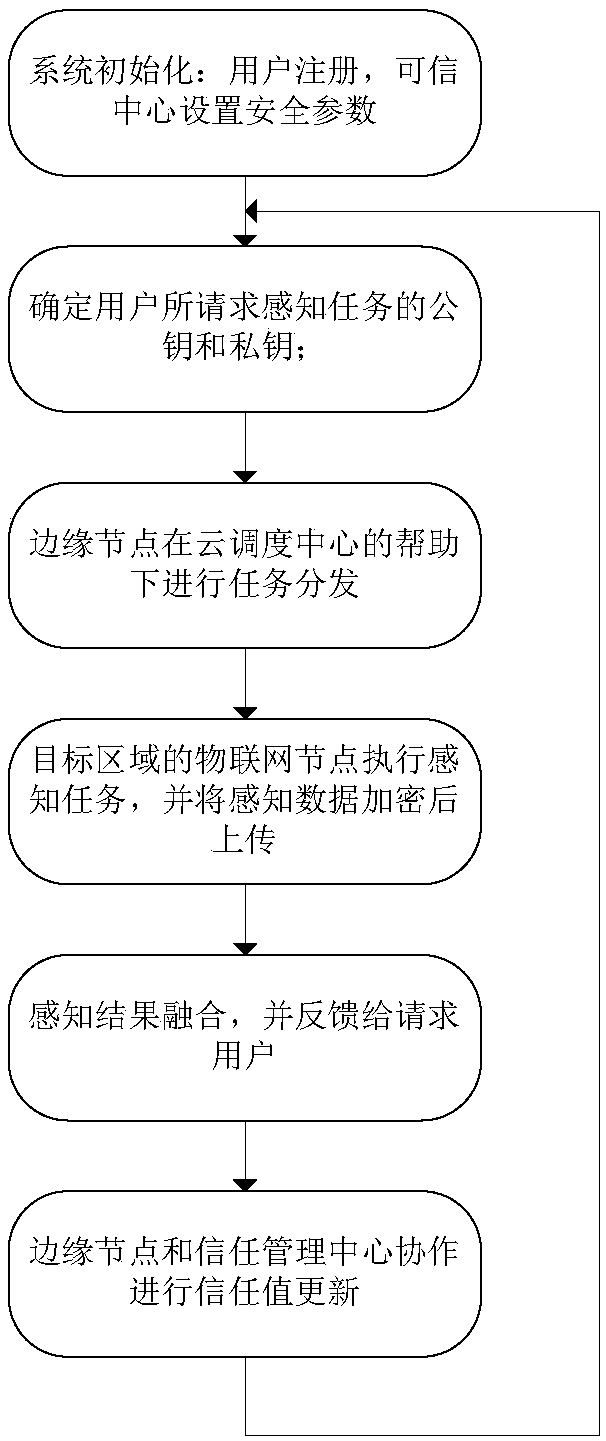
[0061] In order to make the object, technical solution and advantages of the present invention more clear, the present invention will be further described in detail below in conjunction with the examples. It should be understood that the specific embodiments described here are only used to explain the present invention, not to limit the present invention.
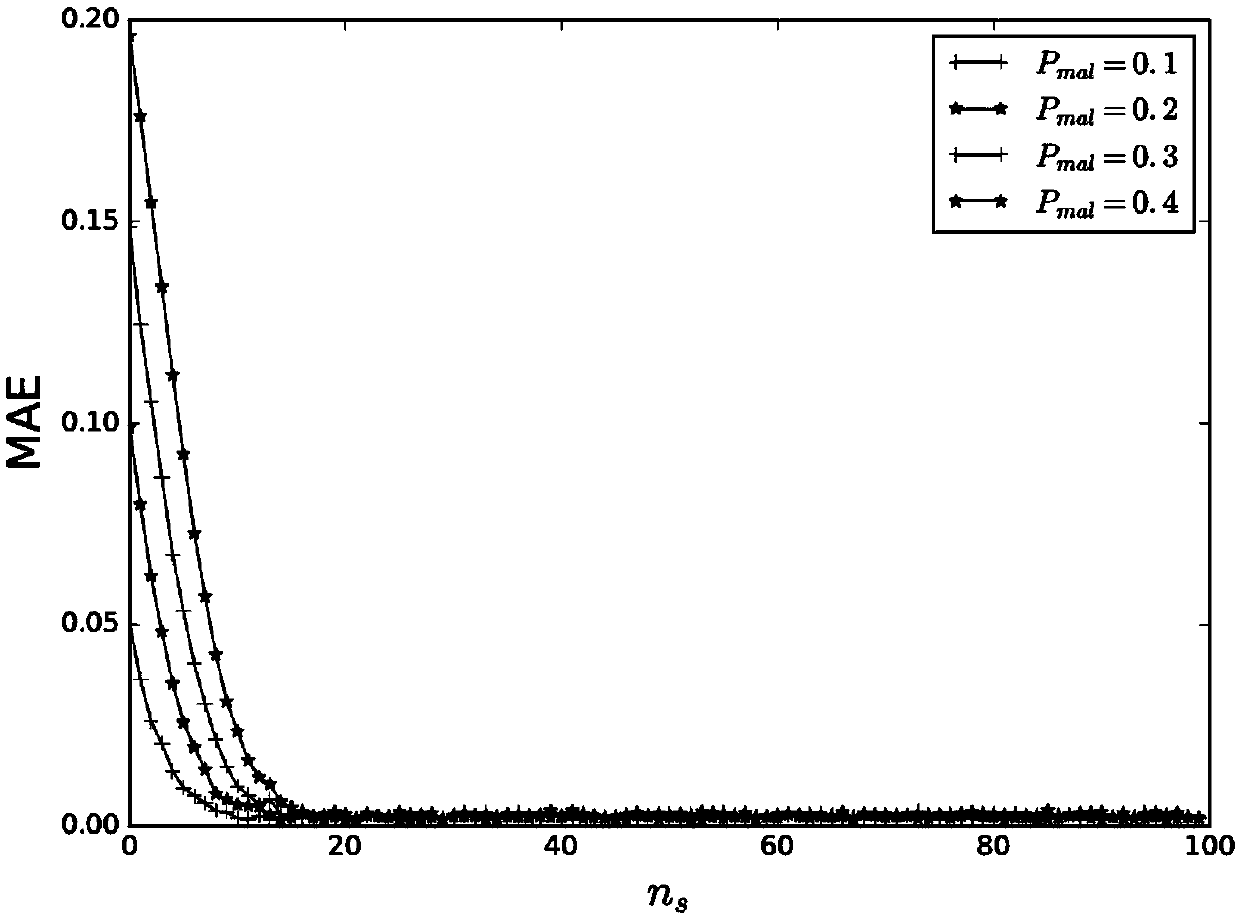
[0062] By introducing the SHE homomorphic encryption system, the present invention realizes the calculation and update of the user's trust value on the basis of protecting the user's privacy, and finally realizes resisting malicious users from injecting malicious data. In addition, by using the edge computing mode to load complex ciphertext operations to edge nodes, the load on users when implementing privacy protection is reduced, which has strong practicability.
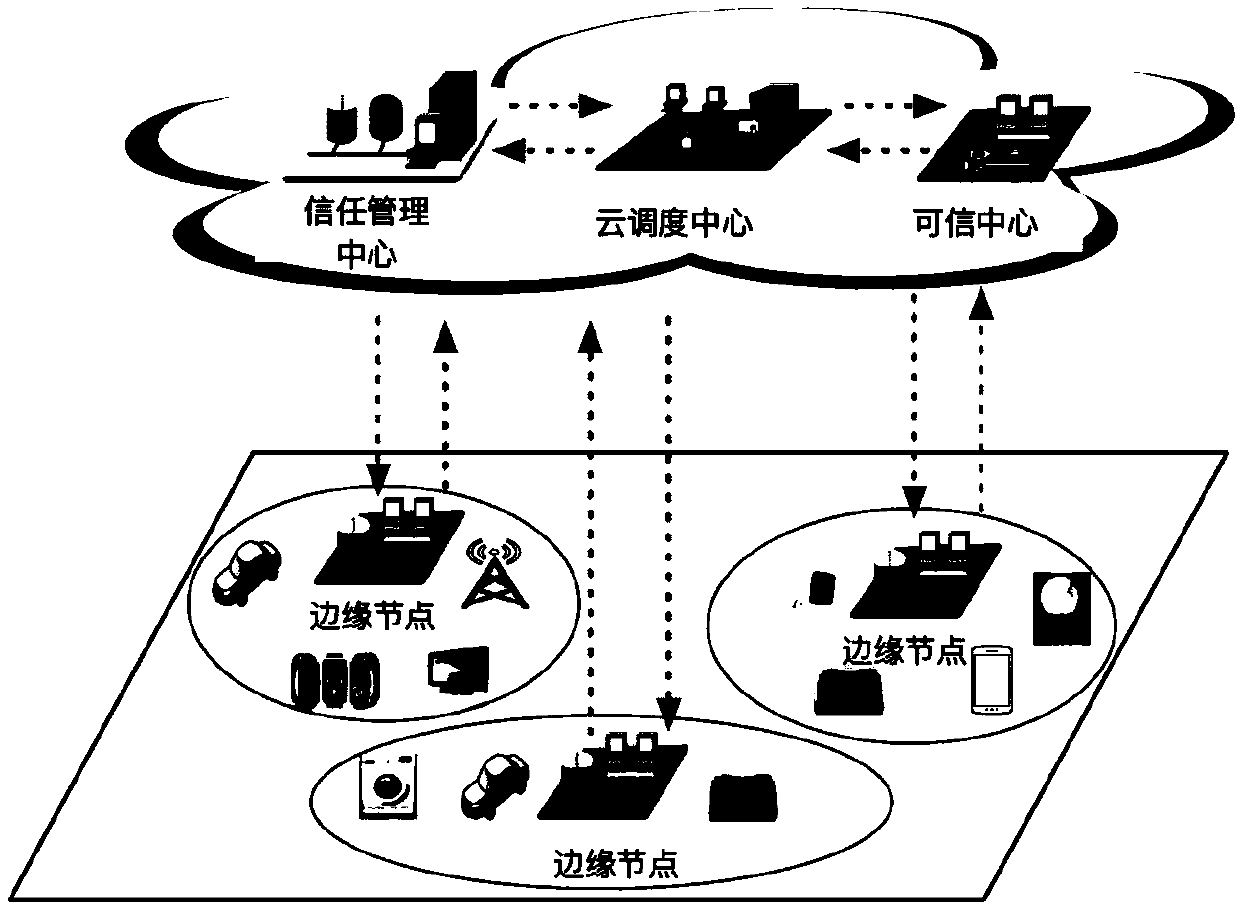
[0063] The application scenario of the present invention is the Internet of Things based on the edge computing mode, such as figure 2 , users in the network c...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com