Multi-party joint privacy data processing method and device
A technology of privacy data and data parties, which is applied in electronic digital data processing, digital data protection, secure communication devices, etc., can solve problems such as leakage of user privacy data and damage to user interests, so as to protect data privacy and efficiently combine data computing and processing. , the effect of reducing the amount of communication
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0079] The solutions provided in this specification will be described below in conjunction with the accompanying drawings.
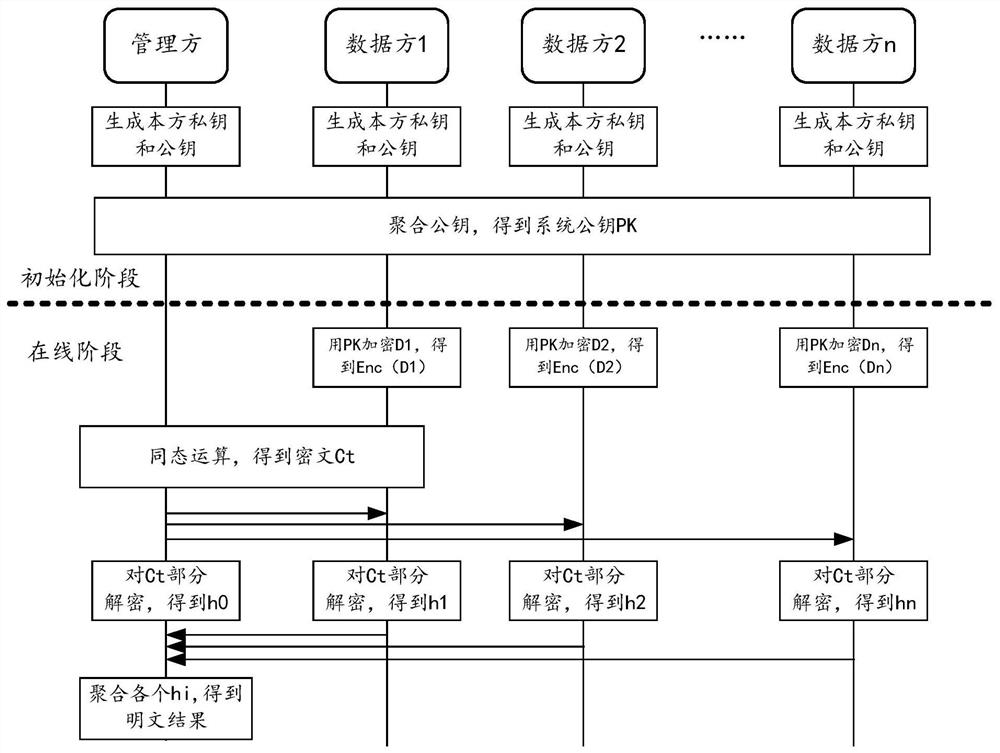
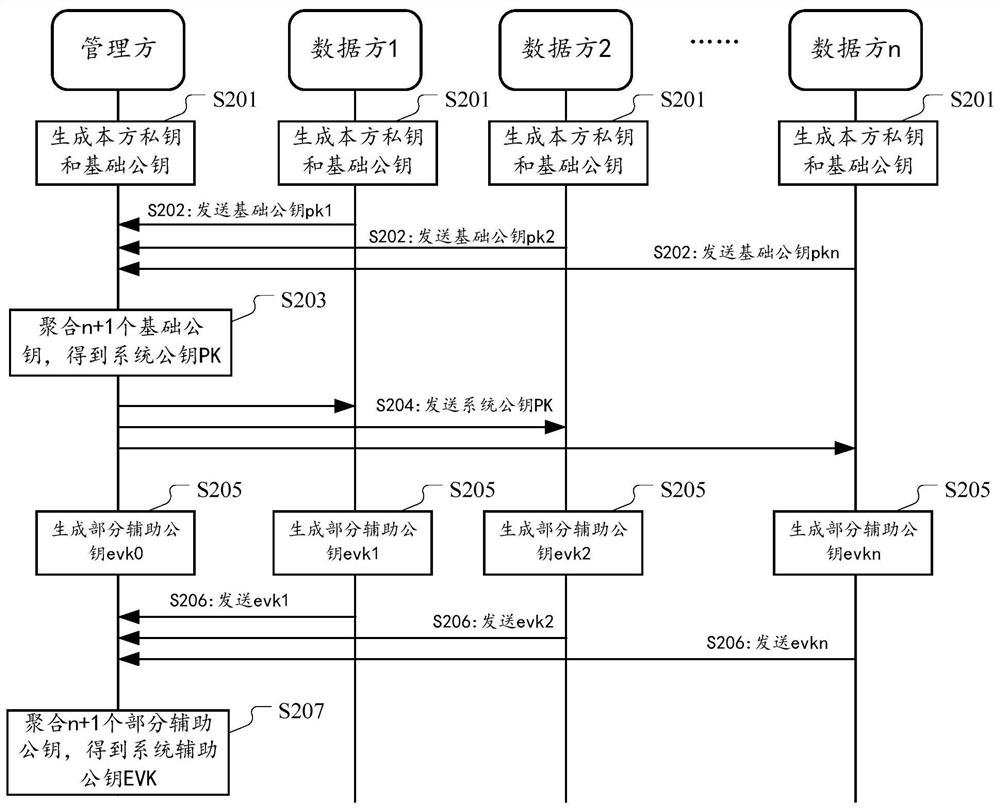
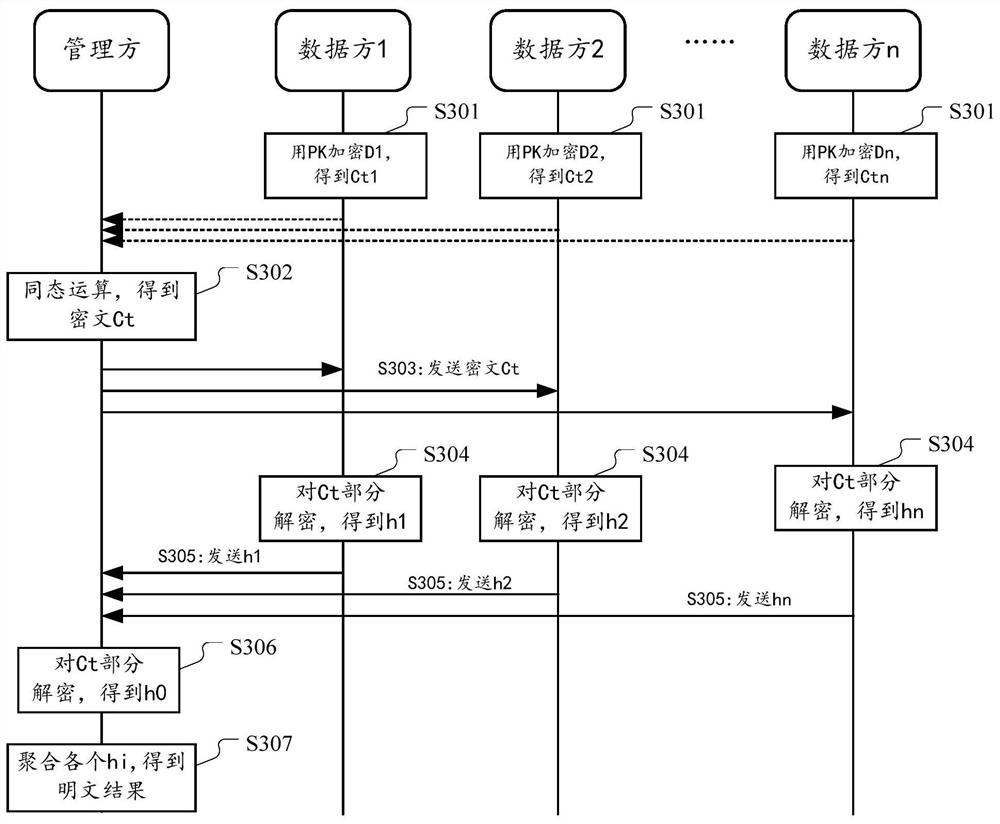
[0080] In order to protect the data privacy of each data party in the process of joint data processing by multiple parties, this manual provides a multi-key fully homomorphic encryption scheme. According to this scheme, in a distributed scenario involving multiple participants, each participant executes an asymmetric key generation algorithm to generate its own public key and private key. The system aggregates the public keys of each participant to generate a system public key and distributes it to each participant. Data parties holding private data use such a system public key to encrypt their own private data, and broadcast the encrypted ciphertext data. One or several of the parties perform homomorphic operations on the ciphertext data of each data party to obtain the ciphertext operation results. Each participant uses its own private key to partial...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com