Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
47 results about "Unsafe environment" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
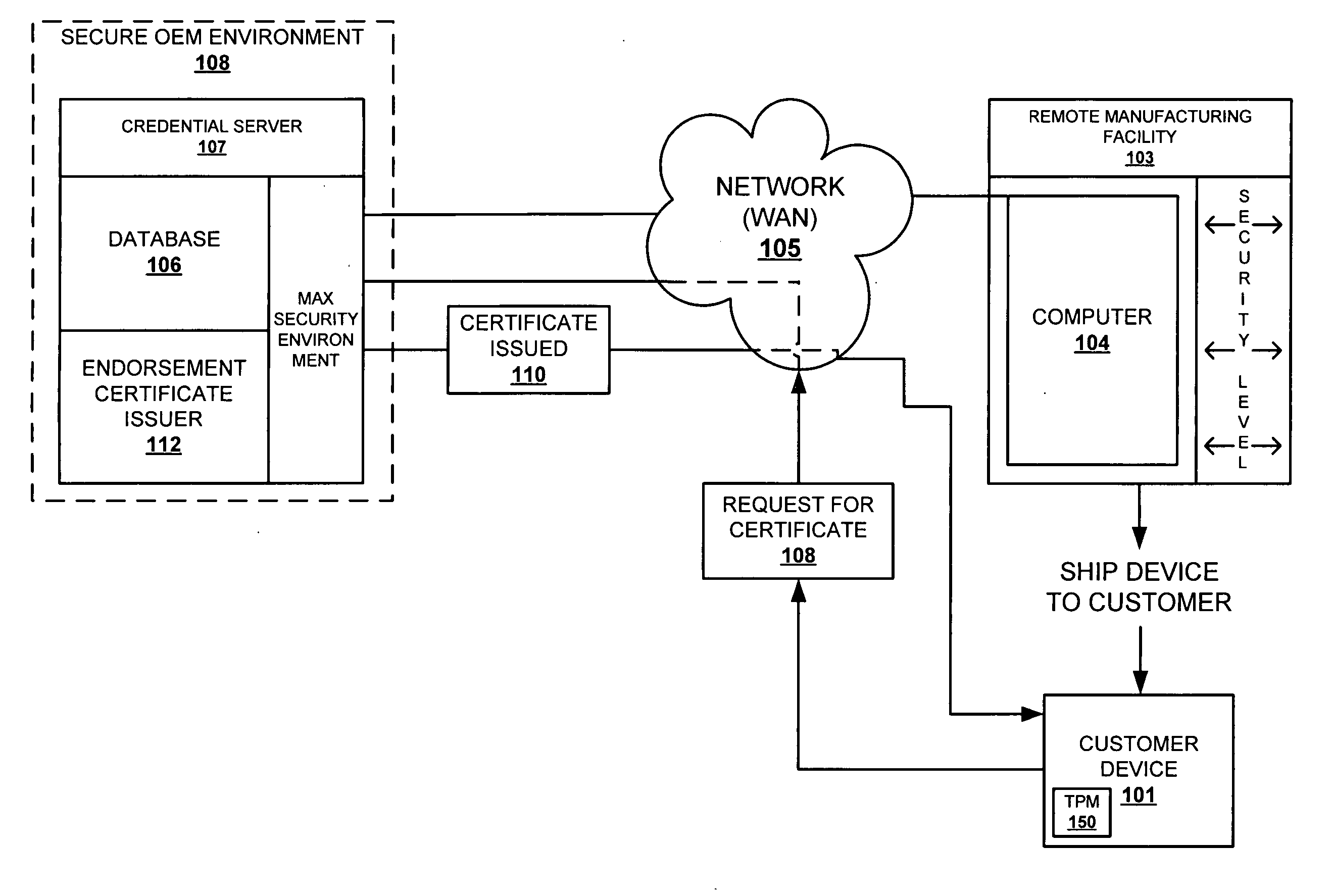
Method for securely creating an endorsement certificate in an insecure environment
InactiveUS20050144440A1Low costKey distribution for secure communicationUser identity/authority verificationByteUnsafe environment
A method and system for ensuring security-compliant creation and signing of endorsement keys of manufactured TPMs. The endorsement keys are generated for the TPM. The TPM vendor selects an N-byte secret and stores the N-byte secret in the TPM along with the endorsement keys. The secret number cannot be read outside of the TPM. The secret number is also provided to the OEM's credential server. During the endorsement key (EK) credential process, the TPM generates an endorsement key, which comprises both the public key and a hash of the secret and the public key. The credential server matches the hash within the endorsement key with a second hash of the received public key (from the endorsement key) and the vendor provided secret. The EK certificate is generated and inserted into the TPM only when a match is confirmed.
Owner:IBM CORP
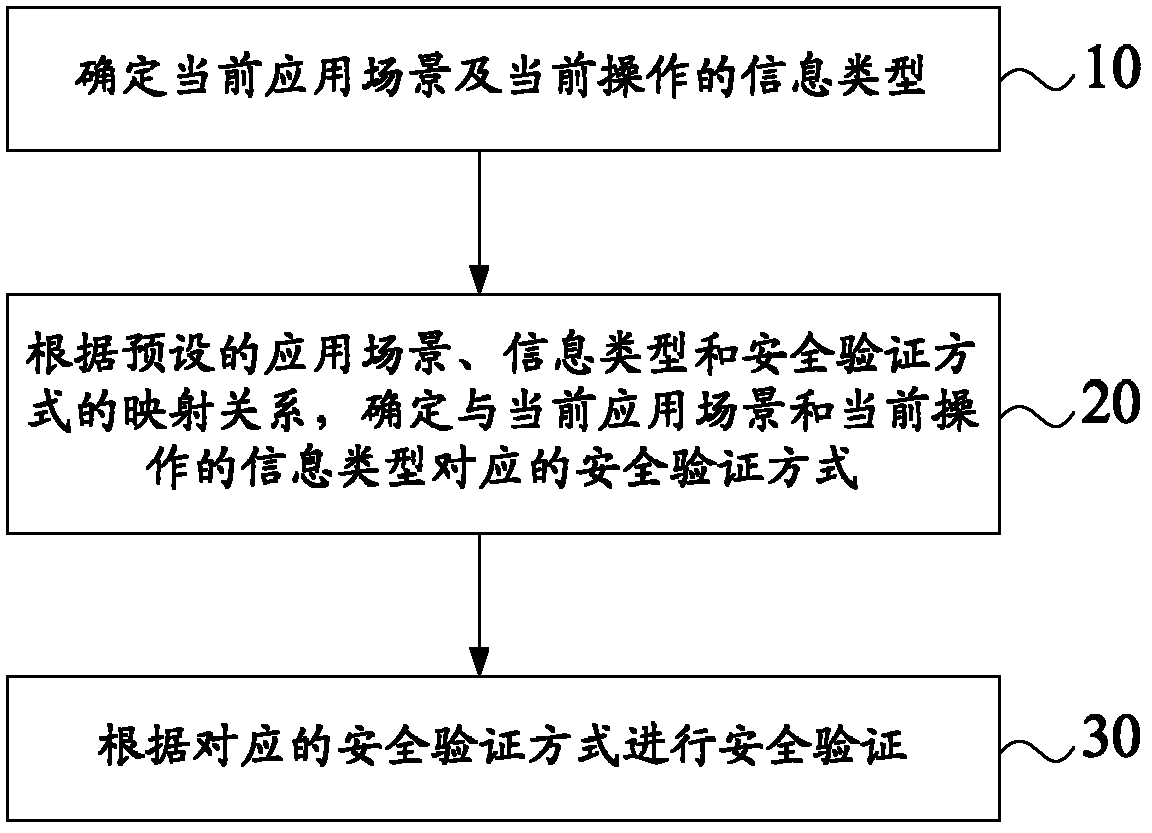
Safety verification method and equipment
InactiveCN102685106AImprove operational convenienceProtection securityUser identity/authority verificationSpeech analysisInformation typeUnsafe environment
The invention provides a safety verification method and equipment. The safety verification method comprises the following steps of: determining a current application scene and an information type of current operation; determining a safety verification mode corresponding to the current application scene and the information type of the current operation according to a mapping relation among the pre-supposed application scene, the information type and the safety verification mode; and performing safety verification according to the corresponding safety verification mode. By adopting the technical scheme, the pre-supposed safety verification mode matched with the current application scene is selected according to the application scene in which a user is located. According to the dynamic safety verification mode, the operation convenience of the user in a safe environment can be enhanced, and the safety of private information and data of the user in an unsafe environment can also be protected as far as possible.
Owner:BEIJING BENY WAVE SCI & TECH
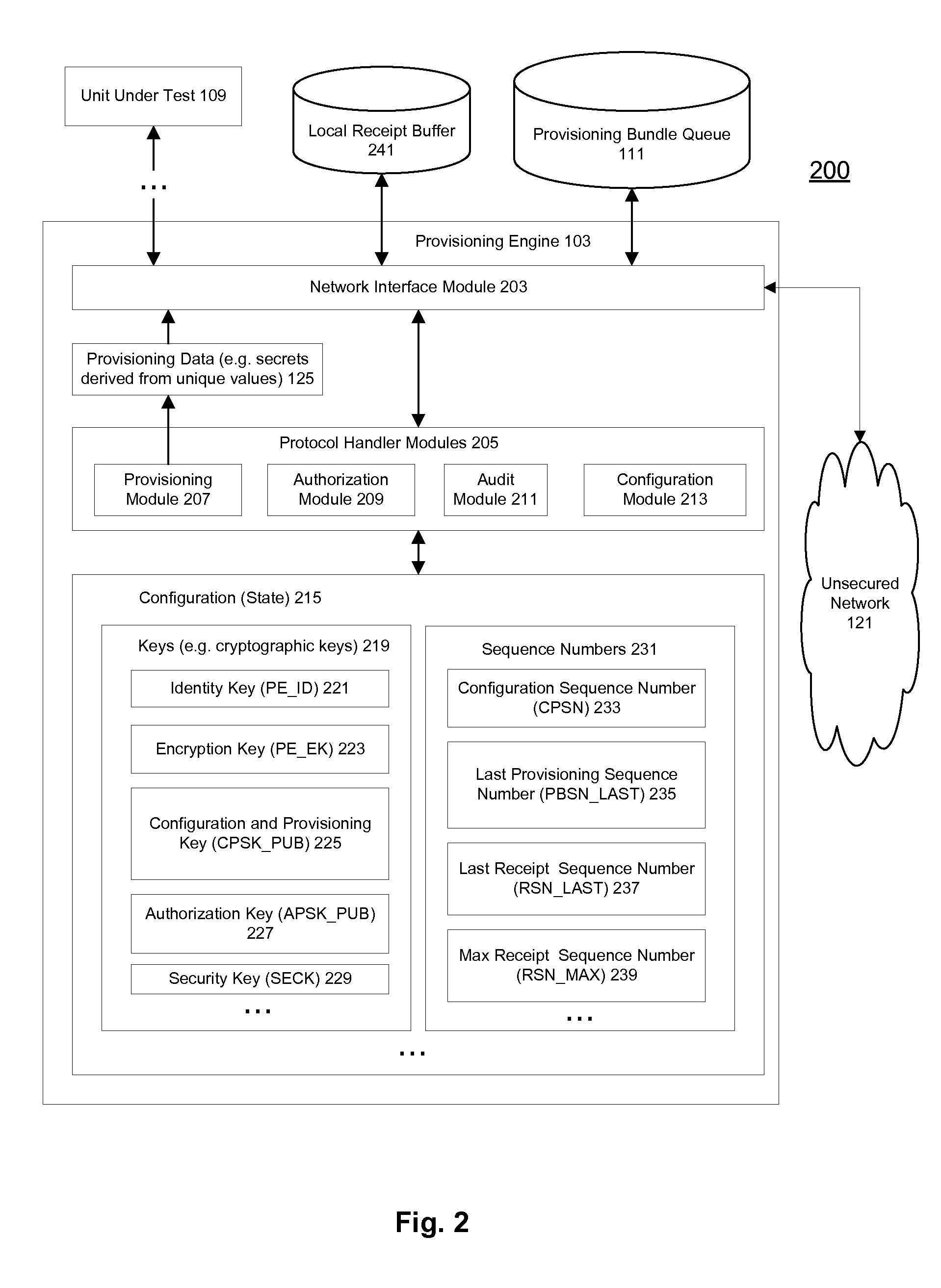
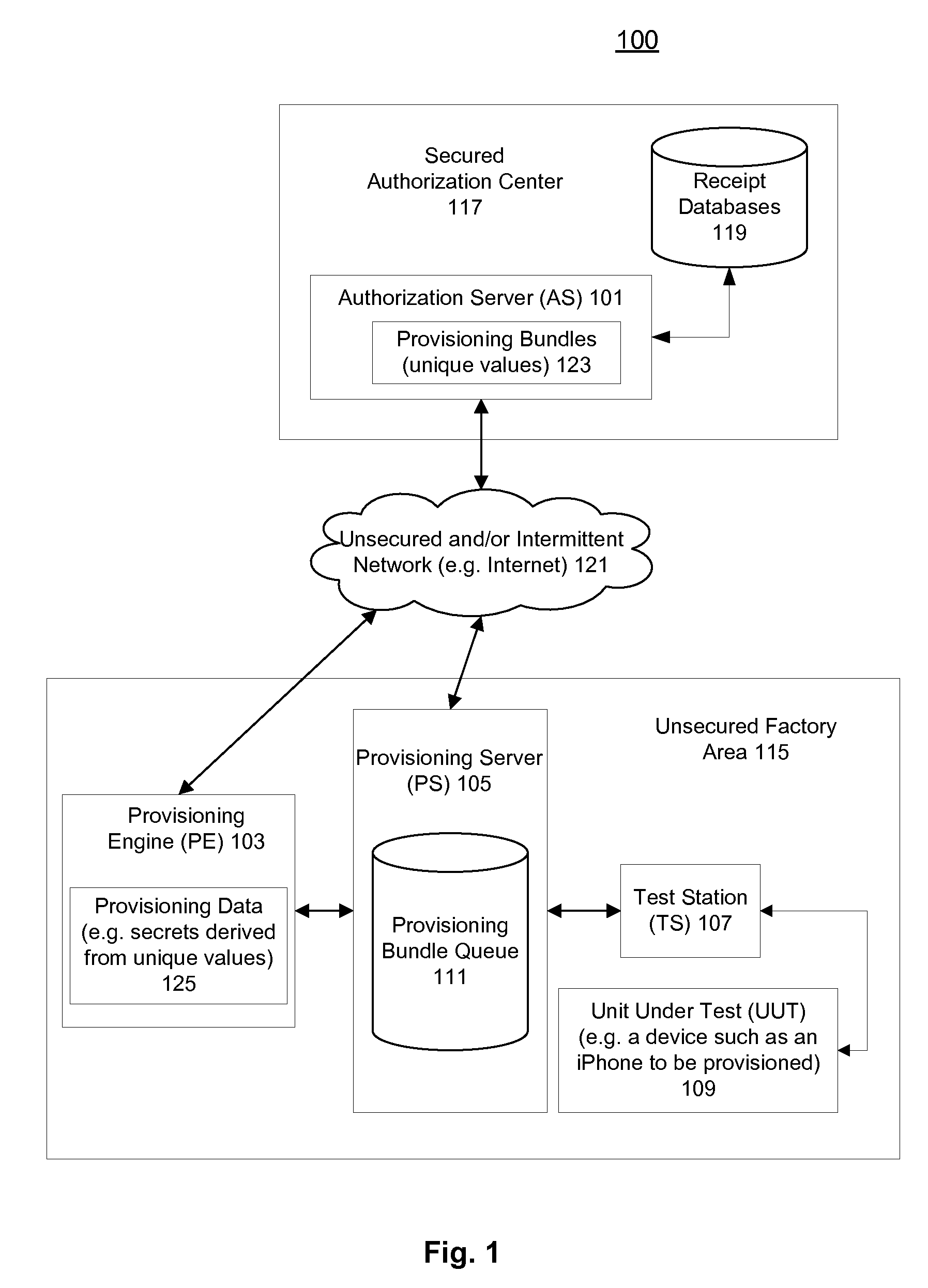
Provisioning secrets in an unsecured environment
ActiveUS20090300758A1Key distribution for secure communicationDigital data processing detailsPersonalizationComputer hardware
A method and apparatus for generating provisioning data to provision a device are described. A provisioning bundle is validated according to a relationship between a configuration and a bundle sequence number identifying the provisioning bundle. A provisioning request includes a device hardware identifier identifying the device. An authorization for the provisioning request is determined for generating provisioning data including the provisioning bundle personalized by the device hardware identifier for the device.
Owner:APPLE INC
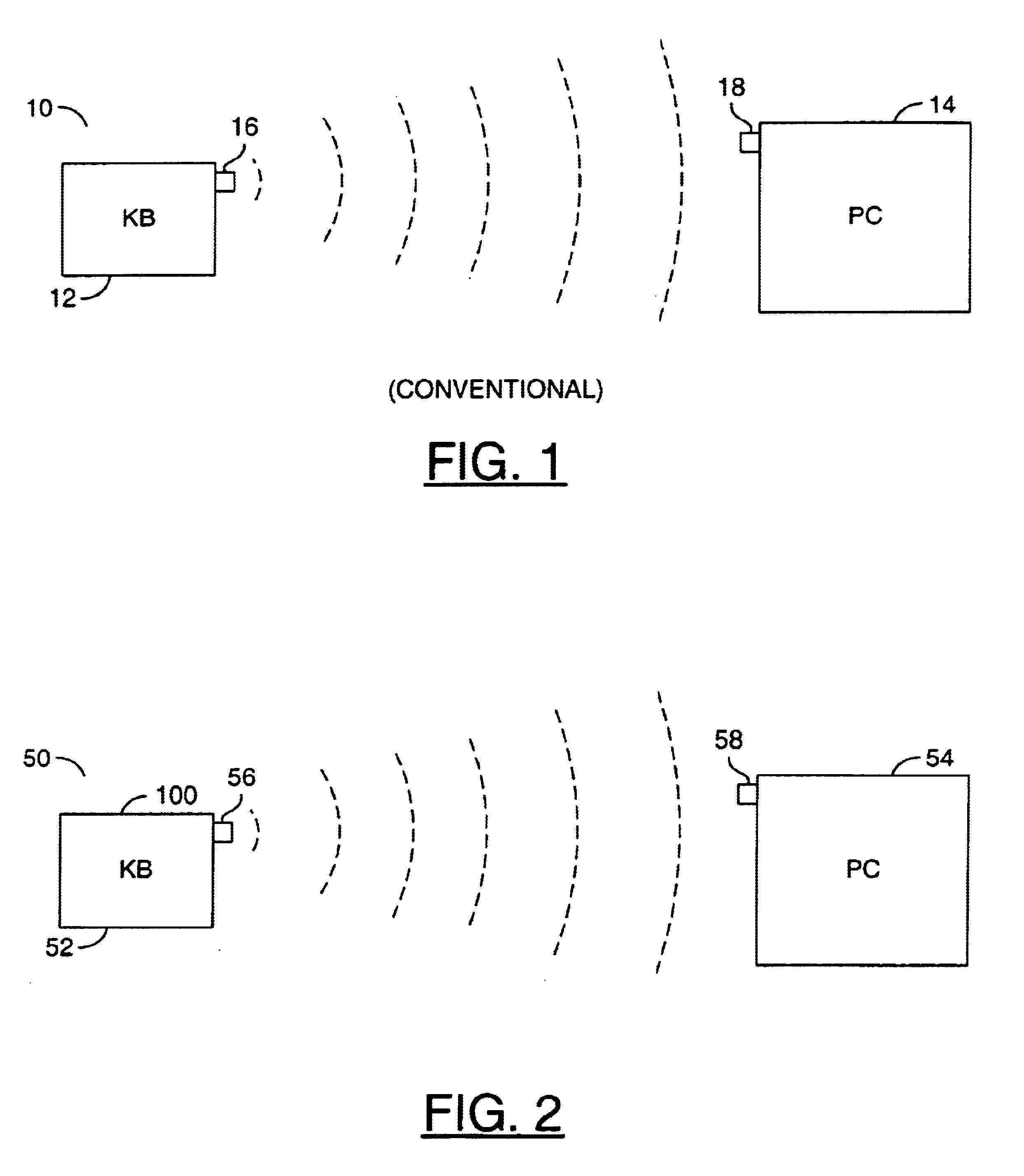
Method and/or apparatus for implementing security in keyboard-computer communication
InactiveUS6912605B1Reduce vulnerabilityIncrease probabilityDigital data processing detailsElectronic switchingKeyboard computerHuman–computer interaction
A method for altering timing between transmissions of an input device comprising the steps of (A) receiving a plurality of inputs from the input device, (B) altering the timing between the inputs and (C) presenting the altered inputs in a potentially insecure environment.
Owner:CYPRESS SEMICON CORP
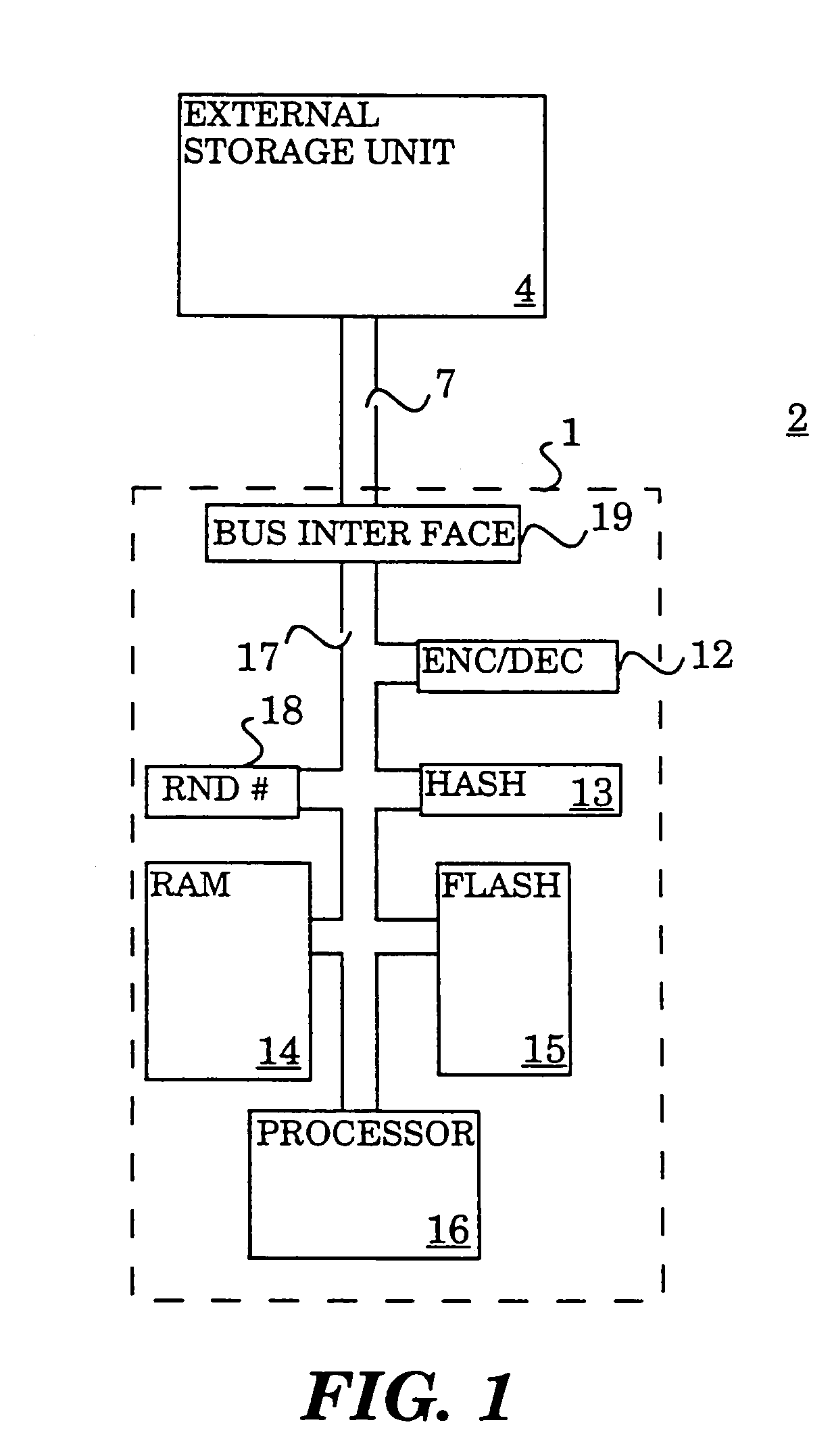
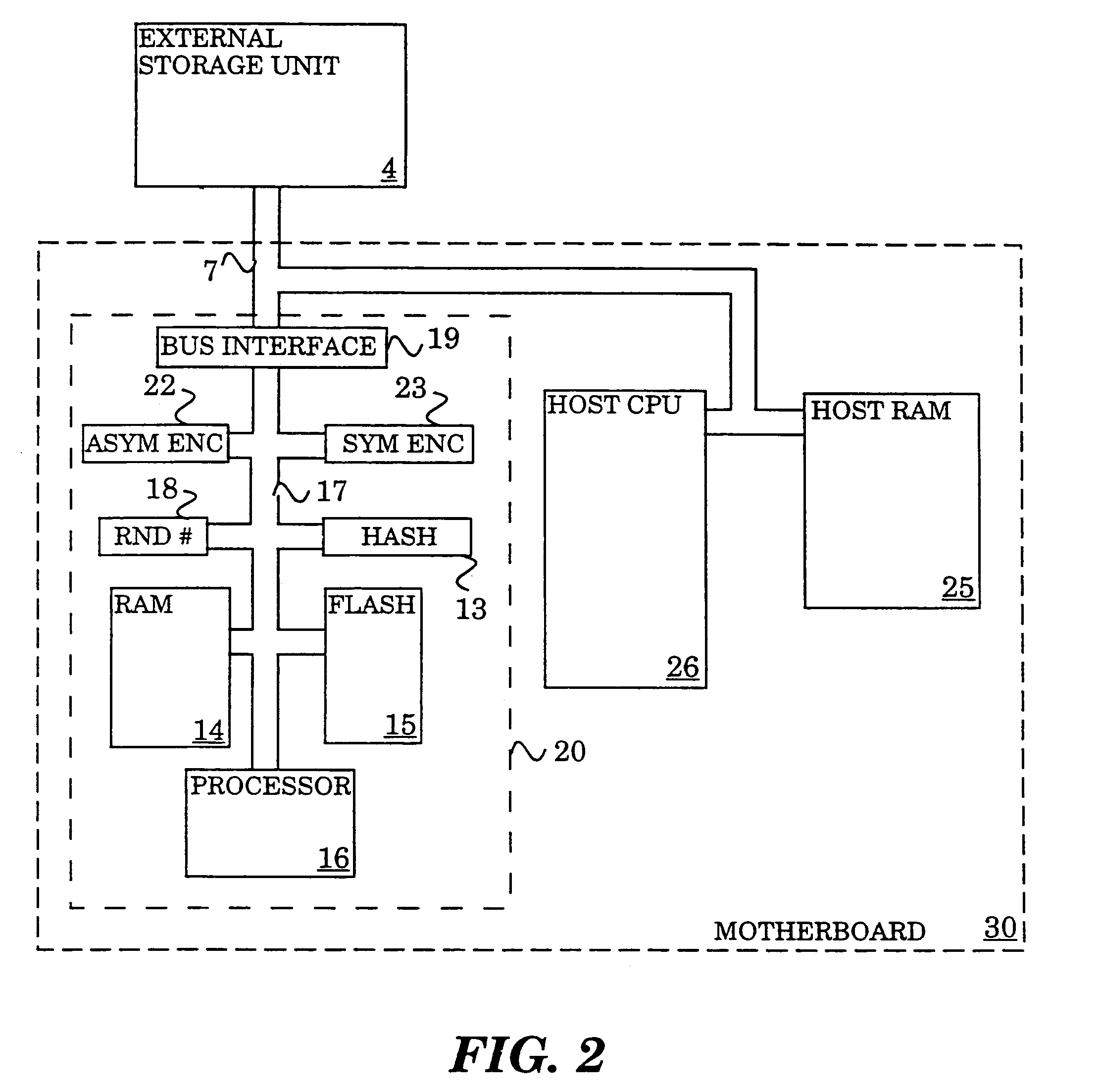
Cryptographically protected paging system
InactiveUS7149901B2Maintain confidentialityMaintain integrityMemory architecture accessing/allocationDigital data processing detailsHash functionPhysical security
A method and system for maintaining integrity and confidentiality of pages paged to an external storage unit from a physically secure environment. An outgoing page is selected to be exported from a physically secure environment to an insecure environment. An integrity check value is generated and stored for the outgoing page. In one embodiment, this takes the form of taking a one-way hash of the page using a well-known one-way hash function. The outgoing page is then encrypted using a cryptographically strong encryption algorithm. Among the algorithms that might be used in one embodiment of the invention are IDEA and DES. The encrypted outgoing page is then exported to the external storage. By virtue of the encryption and integrity check, the security of the data on the outgoing page is maintained in the insecure environment.
Owner:INTEL CORP
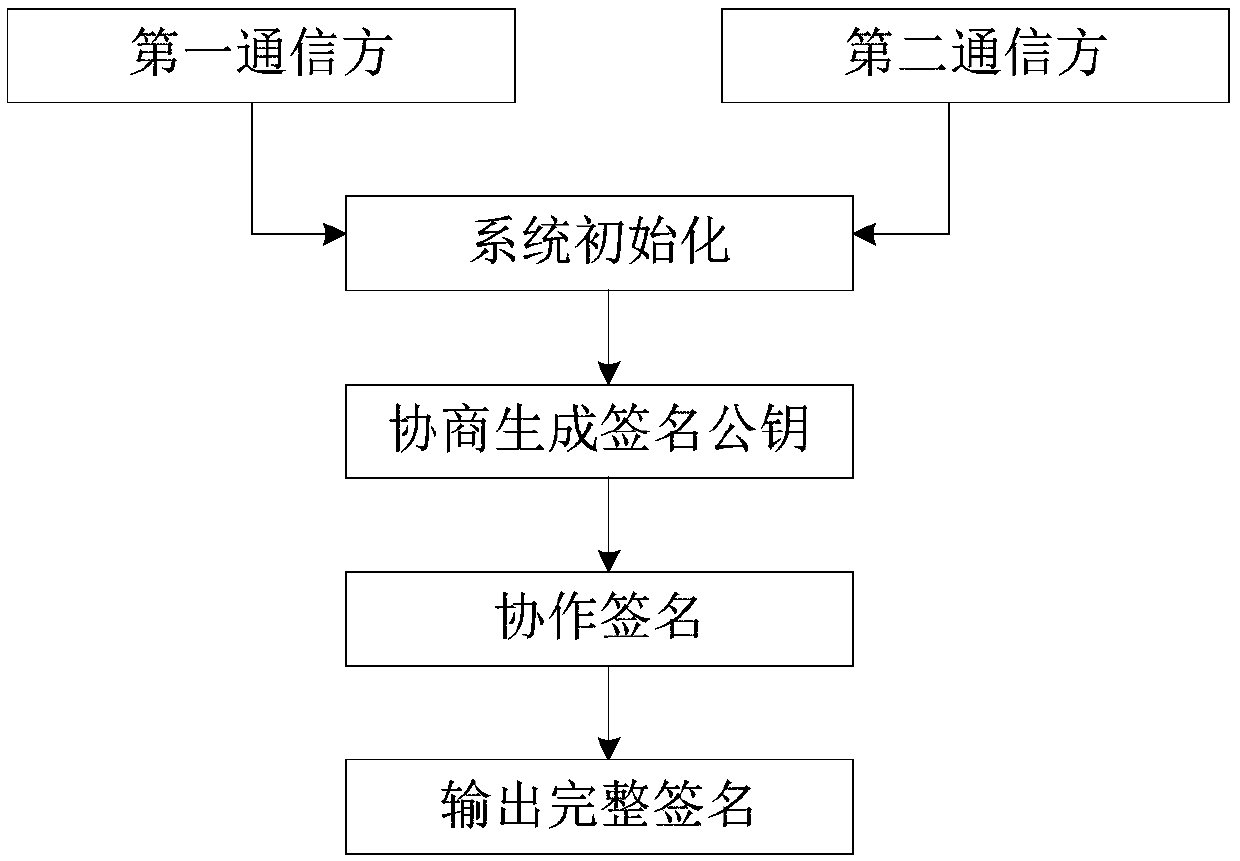
Secure two-party collaboration SM2 signature method
ActiveCN108667626AAvoid attackImprove securityKey distribution for secure communicationPublic key for secure communicationPlaintextMan-in-the-middle attack
The invention provides a secure two-party collaboration SM2 signature method consisting of steps of system initialization, negotiation generation of a signature public key, collaborative signature andoutput of a complete signature. According to the secure two-party collaboration SM2 signature method provided by the invention, prior to the negotiation of the signature public key and the collaborative signature, the both communication parties authenticate the identity of the opposite party by using the zero knowledge proof technology, the correctness of outputting the complete signature is ensured by using the promise technology, it is ensured that the first communication party does not need to decrypt a received ciphertext by using the homomorphic encryption technology, the operation of the corresponding ciphertext can be realized, and a timestamp mechanism is added to ensure that the both communication parties can output the complete signature only when the identity of the first communication party, the current time and the position information of the first communication party are consistent, so that the security of the system is greatly improved, the loss caused by the leakage ofa signature private key is reduced, and the man-in-the-middle attack can be prevented. The secure two-party collaboration SM2 signature method provided by the invention has higher security and can beused in an environment in which a communication channel is not safe.
Owner:SHAANXI NORMAL UNIV +1
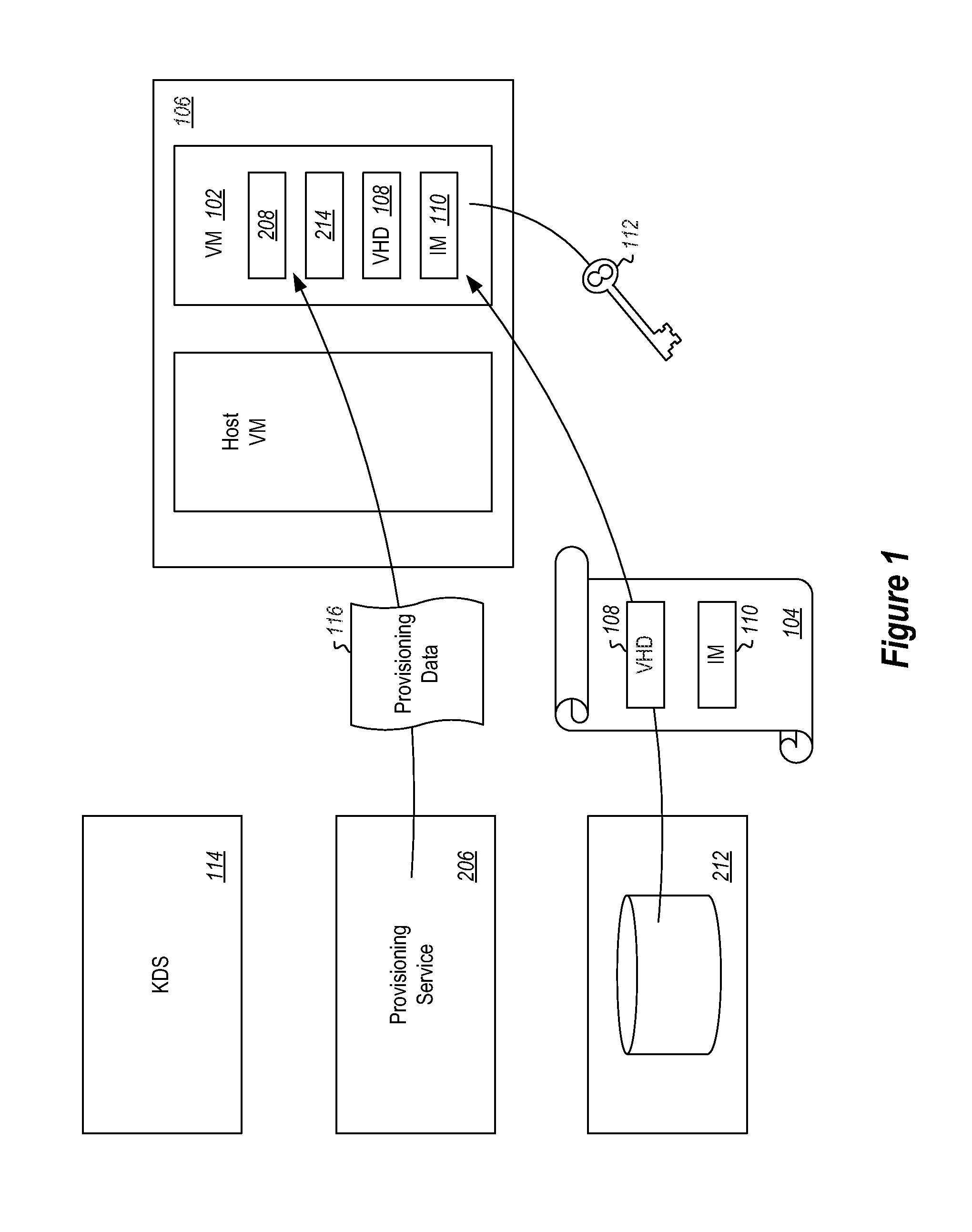
Secure Creation of Encrypted Virtual Machines from Encrypted Templates
ActiveUS20160140343A1Well formedDigital computer detailsPlatform integrity maintainanceUnsafe environmentBooting
Booting a machine in a secure fashion in a potentially unsecure environment. The method includes a target machine beginning a boot process. The method further includes the target machine determining that it needs provisioning data to continue booting. The target machine contacts a secure infrastructure to obtain the provisioning data. The target machine provides an identity claim that can be verified by the secure infrastructure. As a result of the secure infrastructure verifying the identity claim, the target machine receives a request from the secure infrastructure to establish a key sealed to the target machine. The target machine provides the established key to the secure infrastructure. The target machine receives the provisioning data from the secure infrastructure. The provisioning data is encrypted to the established key. The target machine decrypts the encrypted provisioning data, and uses the provisioning data to finish booting.
Owner:MICROSOFT TECH LICENSING LLC
Protecting users from accidentally disclosing personal information in an insecure environment
ActiveUS8347380B1Less privilegeMemory loss protectionDigital data processing detailsVirtualizationInternet privacy
A method and system for protecting users from accidentally disclosing personal information in an insecure environment. In one embodiment, the method includes monitoring I / O device input data associated with a guest operating system on a virtualization platform. The guest operating system has less privilege than a privileged operating system on the virtualization platform. The method further includes determining whether the I / O device input data corresponds to personal information of a user, and delaying or blocking the transfer of the I / O device input data to the guest operating system if the I / O device input data corresponds to the personal information of the user.
Owner:CA TECH INC
Annular steel structure supporting construction method with open type TBM (tunnel boring machine)
InactiveCN103557013AAvoid manual cleaningReduce dependenceUnderground chambersTunnel liningGratingSlag
An open state is formed behind a shield of an open type TBM (tunnel boring machine), so that bolting and shotcreting with wire mesh and the like can be realized, when unfavorable geological conditions such as crushed zones are encountered, broken surrounding rock collapses and falls, which not only threatens the safety of operating personnel and equipment, but also greatly lowers the construction efficiency. The invention discloses an annular steel structure supporting construction method with the open type TBM. The supporting TBM is provided with a shield which has an annular steel structure installation space. When the unfavorable geological conditions are encountered, the annular steel structure can be fast erected in an assembly line mode under the protection of the shield, the shield is replaced with the annular steel structure for supporting the surrounding rock as the TBM tunnels; under the protection of the annular steel structure, an annular steel grating and a steel mesh hollow structure are used for carrying out the bolting and shotcreting supporting and the like, the previous extensive construction is changed to controllable standardized operation, the original open type unsafe environment is changed to a closed protected operation zone; the construction method disclosed by the invention is different from the passive supporting which is carried out after the surrounding rock collapses and falls; the annular steel structure actively close off the broken surrounding rock, then the surrounding rock becomes a part of the supporting structure, the work amount for backfilling concrete and removing slag is greatly reduced, and thus the method is more efficient and safer, the cost is reduced and the operation is easy to realize.
Owner:王静
Interaction between secured and unsecured environments
InactiveUS20110010755A1Acutation objectsDigital data processing detailsComputer networkUnsafe environment
A method comprising: receiving a data structure including an identifier identifying a process for performance by a secured environment; and identifying to an unsecured environment the process identified by the data structure.A method comprising: receiving at a secured environment a data structure including an identifier identifying a process for performance by the secured environment; and controlling at the secured environment performance of the identified process in dependence upon a signal received from an unsecured environment.
Owner:NOKIA TECHNOLOGLES OY
Method of cleaning vessels in a refinery
InactiveUS6893509B2Lighting and heating apparatusHollow article cleaningContaminated equipmentCompound (substance)
Disclosed is a novel process for interior cleaning and by cleaning, removing noxious gas and / or restoring the operating efficiency of organically contaminated hydrocarbon processing equipment in a safe and effective manner and in a very short period of time, without a need to manually enter an unsafe environment and mechanically remove organic contaminants. Used is a formulation of non-aqueous, monocyclic saturated terpene mixed with a non-ionic surfactant package. The terpene-based chemical is injected into organically contaminated equipment using a novel process involving high-pressure steam to form a very effective cleaning vapor.
Owner:REFINED TECH
16-wheel SM4-128/128 white box password implementation method
InactiveCN110278072AImprove computing efficiencyIntegrity guaranteedEncryption apparatus with shift registers/memoriesComputer hardwarePassword
In an unsafe environment, a cryptographic analyzer can implement attacks on an algorithm and a secret key by tracking a binary system operated by a program, reading the secret key in a memory and a program execution intermediate result, carrying out static analysis and the like, and a white-box cryptographic algorithm can protect the secret key in the unsafe environment. The invention discloses a 16-round SM4-128 / 128 white box password implementation method, which describes a new mode of improving an SM4 password algorithm when the encryption round number is 16, and the mode improves the structure of a round function, namely the iterative process of the encryption algorithm. An improved SM4 white-box cryptographic algorithm is provided, and the whole encryption and decryption process can be converted into a form of calculating randomly selected affine transformation and lookup tables. The principle is that the internal state of a coding hiding algorithm is input and output scrambled, the secret key is embedded into a lookup table in a coding mode, and meanwhile, a block matrix is used for reducing the scale of the lookup table.
Owner:BEIJING ELECTRONICS SCI & TECH INST
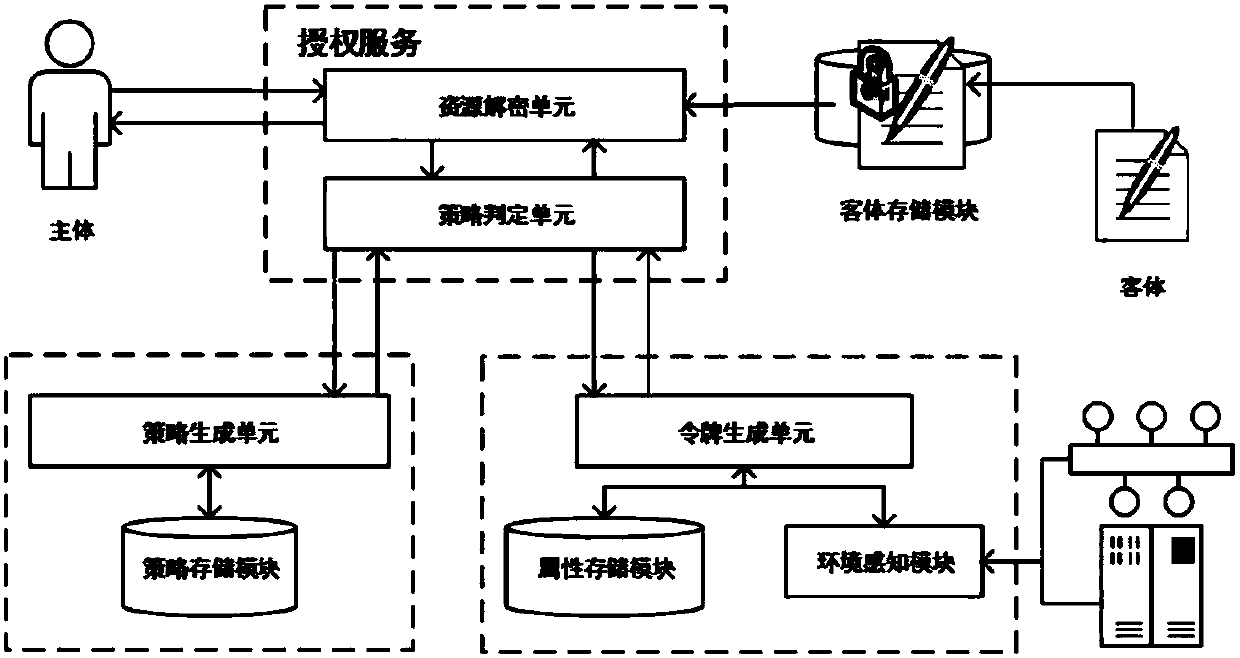
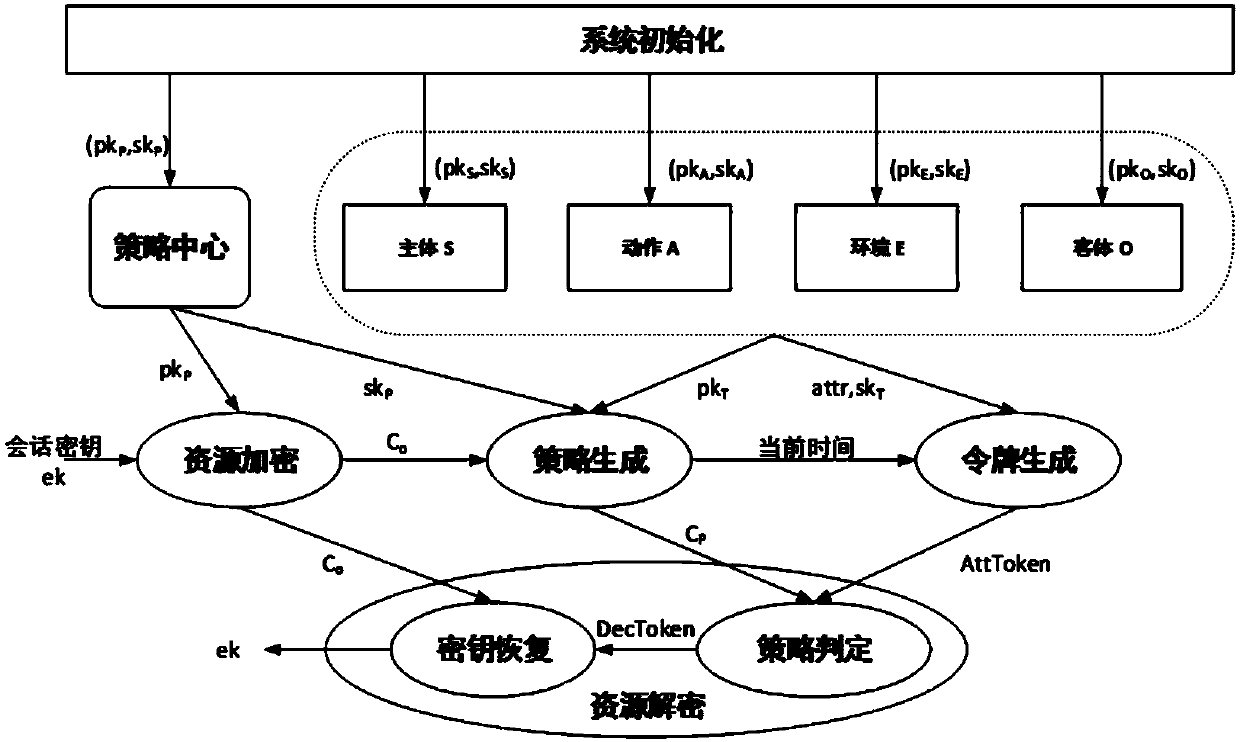
Cryptography attribute-based access control method and system based on dynamic rule
ActiveCN107864139AHigh security requirementsGuaranteed unforgeabilitySecuring communicationExtensibilityUnsafe environment
The invention relates to a cryptography attribute-based access control method and system based on a dynamic rule, mainly belonging to the technical field of information. In the cryptography attribute-based access control system based on the dynamic rule, protected objects are stored in a encrypted form, and only the requests satisfying the requirements of access policies in the attribute-based access control can be authorized to decrypt the objects, therefore, it can be ensured that data in an unsafe environment can be accessed with authorization according to a security policy, and meanwhile,the extensibility of the policies and the dynamic acquisition of the attributes are also supported. The cryptography attribute-based access control method and system based on the dynamic rule are divorced from the traditional encryption system framework, and are a new attribute-based access control model, method and system supporting the cryptography decision. The cryptography attribute-based access control method and system based on the dynamic rule can achieve more secure, diversified, dynamic and flexible access authorization, which are suitable for large-scale organizations or informationsystems, and can be applied to the environments such as cloud computing, grid computing, distributed computing, and so on.
Owner:UNIV OF SCI & TECH BEIJING
Secure creation of encrypted virtual machines from encrypted templates
Booting a machine in a secure fashion in a potentially unsecure environment. The method includes a target machine beginning a boot process. The method further includes the target machine determining that it needs provisioning data to continue booting. The target machine contacts a secure infrastructure to obtain the provisioning data. The target machine provides an identity claim that can be verified by the secure infrastructure. As a result of the secure infrastructure verifying the identity claim, the target machine receives a request from the secure infrastructure to establish a key sealed to the target machine. The target machine provides the established key to the secure infrastructure. The target machine receives the provisioning data from the secure infrastructure. The provisioning data is encrypted to the established key. The target machine decrypts the encrypted provisioning data, and uses the provisioning data to finish booting.
Owner:MICROSOFT TECH LICENSING LLC
Method for determining inquiry answer type bidirectional identification and business, and encipher device applying the method
InactiveCN101471770AGet rid of vulnerabilityGet rid of spying passiveCommerceSecuring communicationSecure communicationThe Internet
The invention relates to a secure communication device and a method, in particular to a device and a method for sending and receiving a code by adopting a special manner. In the question answering mutual identity and transaction confirmation method and the device adopting the method, the confirmation method comprises identity verification and transaction content confirmation, and has the characteristic of mutual authentication. An encryption device is separated from the outside completely, and has no electronic connecting interface, so that the hacker attack can be avoided, and the device can also be used in the environment of no personal computer. In the device and the method, not only does a server identify a client in a unilateralism manner, but the client also discriminates the validity of the server through checking the validity of a quenstion and answers the quenstion after confirming the validity of the quenstion only, thereby effectively resisting fishing trap. By adopting the method and the encryption device, identity verification and electronic transaction can be performed safely in unsafe environments such as an Internet bar, etc.
Owner:毛华
Mobile storage medium management method and mobile storage medium management device
The invention discloses a special formatting method and a special formatting device for mobile storage equipment, and aims to solve the problem that data of mobile storage equipment leak in an unsafe environment. The mobile storage equipment comprises first system data and second system data. The special formatting method for the mobile storage equipment comprises the following steps of judging whether redirection operation is performed only or not, judging whether the current environment is a safe environment or not if the redirection operation is not performed only, prompting that special formatting cannot be carried out if the current environment is not safe, and then quitting; constructing and updating the first system data of the mobile storage equipment; judging whether the redirection operation is performed only or not, formatting the mobile storage equipment if the redirection operation is performed only, then performing redirection operation on the first system data and the second system data of the mobile storage equipment, and quitting; performing redirection operation on the first system data if the redirection operation is not performed only, setting an encryption completion status, setting an encryption key, formatting data of various partitions of the mobile storage equipment, and performing redirection operation on the second system data of the various partitions.
Owner:北京明朝万达科技股份有限公司
Domain-aware device protection via cross-validation among spatially-adjacent devices
ActiveUS9854445B1Unauthorised/fraudulent call preventionConnection managementUnsafe environmentMobile device
Protecting a mobile device is provided. A first set of IoT devices in a first domain at a first geographic location is established by communicating with respective members of the first set of IoT devices. Respective ones of the first set of IoT devices are identified within the first domain as registered to a user corresponding to a mobile device based on a list of registered devices generating a registered subset of IoT devices that includes the mobile device. It is determined that the mobile device is in an unsecure environment based on establishing proximity to unknown IoT devices that are not members of the registered subset of IoT devices. A self-protection mode of operation is launched on the mobile device in response to determining that the mobile device is in the unsecure environment based on establishing proximity to the unknown IoT devices.
Owner:IBM CORP
Server-based trust detection method and device
InactiveCN107798246AAvoid startingImprove reliabilityPlatform integrity maintainanceUnsafe environmentCost savings
The invention provides a server-based trust detection method and device. The method includes the steps that a power-on request is sent to a server, a server MB CPLD receives a power-on signal, and meanwhile, whether or not a system is in a trusted state is judged through a BMC trusted input / output interface signal; if not, the MB CPLD refuses the power-on request; if yes, the server system is powered on. According to the method, the server system cannot be started unless a BMC detects that the server system is in a trusted state, so that it is avoided that the server is started in an unsafe environment, and the reliability of the server system is improved; by using software for encrypting the system, the cost is reduced.
Owner:ZHENGZHOU YUNHAI INFORMATION TECH CO LTD
Closed space device inspection method and apparatus
ActiveCN108830256ARealize automatic inspectionImprove inspection efficiencyCharacter and pattern recognitionPoint cloudCloud data
The embodiments of the present invention disclose a closed space device inspection method and device. According to the closed space device inspection method and apparatus of the invention, point clouddata collection is performed on devices in different regions in a closed space; after splicing and de-noising processing is performed on the point cloud data of the devices in each region, and the de-noised point cloud data are matched with each point cloud data model in a point cloud data model library, so that the first attribute information of each device, which is represented by the de-noisedpoint cloud data, can be determined; the de-noised point cloud data and the first attribute information are saved in an associated manner; the de-noised point cloud data are compared with historicalpoint cloud data associated with the first attribute information, so that abnormality analysis can be performed on the devices which are represented by the de-noised point cloud data; and therefore, the automatic inspection of the devices in the enclosed space can be realized, the inspection efficiency of the devices in the enclosed space can be improved, and the probability that inspection personnel are exposed to an unsafe environment such as lack of oxygen and water can be lowered.
Owner:STATE GRID INTELLIGENCE TECH CO LTD
Method and system for wireless transmission of content
ActiveUS20130251149A1Quickly and safely obtainedEnsure safetySecret communicationSecurity arrangementWireless transmissionComputer network
The invention discloses a method and a system for wireless transmission of content. The present invention relates generally to wireless network technology, Problems solved by the invention is that, the method for manually entering the shared key is neither convenient nor secure, while the method for transmitting the shared key over the wireless network also makes the shared key exposed to an unsafe environment. Embodiments of the invention provide the program as follows: a method and a system for wireless transmission of content, wherein, capturing shared key, using the shared key to encrypt the content, and then transmitting the encrypted content over the wireless network. Embodiments of the invention are suitable for terminals and devices wirelessly connected, and so on.
Owner:NVIDIA CORP
Data security protection method of safe mobile storage equipment
The invention belongs to the data security field of mobile storage equipment, in particular to a data security protection method of safe mobile storage equipment, which is used for solving the problems of data security of the mobile storage equipment when the mobile storage equipment is crosswise used among different host computer environments. The safe mobile storage equipment adopts a single-equipment and multi-data view design so that the same safe mobile storage equipment provide a single or a plurality of different data views according to the different applied external host computer environments (different safe environments or different unsafe environments). The different data views correspond to different physical storage zones or logical storage zones isolated from each other. The safe mobile storage equipment invention has the benefits advantages that the safe mobile storage equipment adopts the single-equipment and multi-data view design, realizes the data ferry of the storage zones in the unsafe environments through a special safe browser in a safe environment and automatic identification design on external host computer systems in the unsafe environments and adopts an encryption mode to store data in safety mobile storage equipment.
Owner:WUHAN TIANYU INFORMATION IND
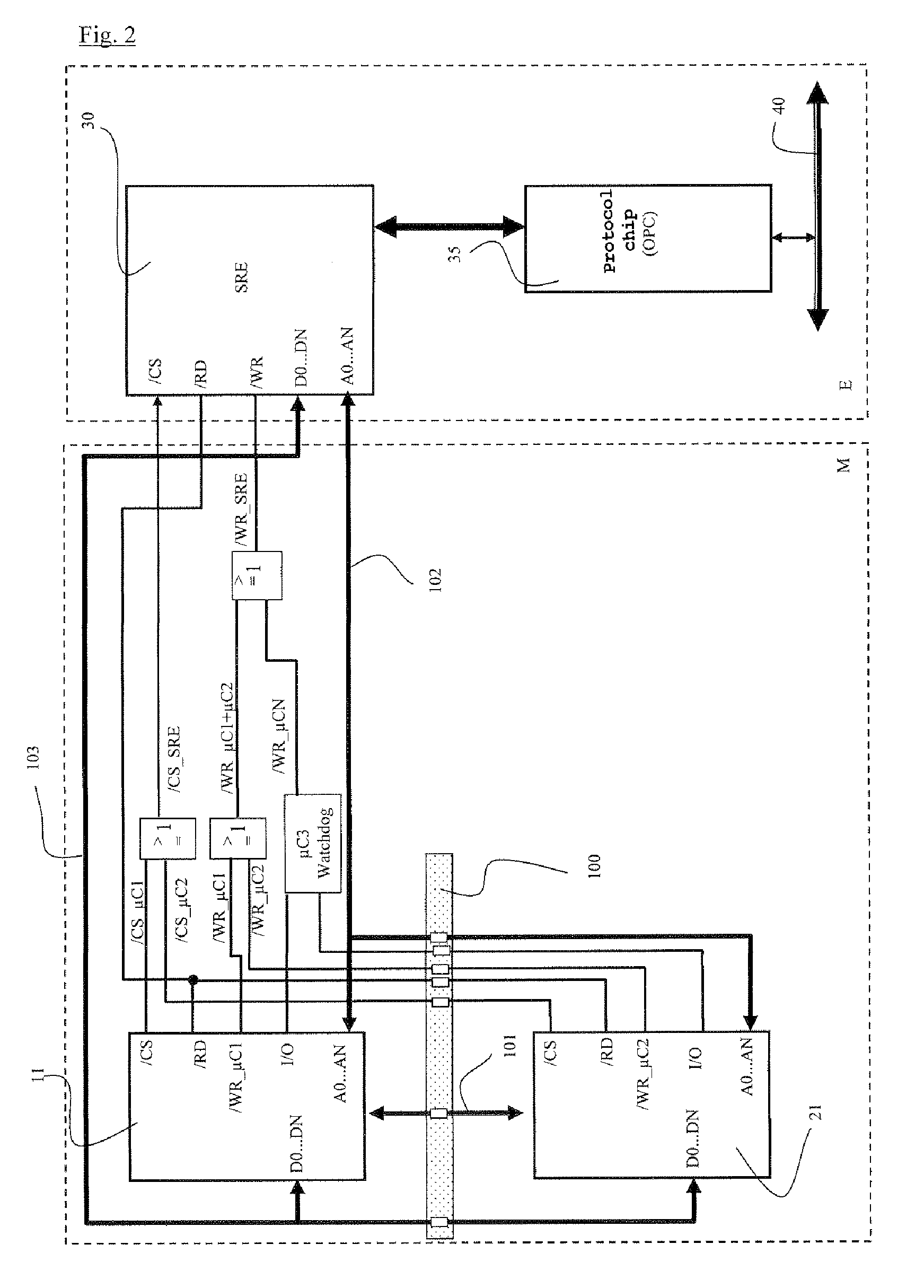
Method and equipment for transferring multi-channel information into single channel safety information
ActiveCN101078922AImprove securityQuick connectionProgramme controlTransmission systemsProcessor registerCoupling
The invention relates to a method and to an apparatus, which has been adapted to carry out the method, for the coupling of a safety-critical process from a safe environment, which has at least two redundant processing channels, to an environment which is not safe or to an environment which is safe but has fewer processing channels. To this end, provision is made of a method which processes a data record which is relevant to the safety-critical process, in particular on a protocol-specific basis, to form a respective safe protocol ( 14, 24 ) using at least two redundant processing channels ( 1, 2 ) in accordance with identical laws, and forms a common safe protocol taking into account at least two redundant safe coupling protocols ( 14, 24 ), to be precise by accessing a common (buffer) register ( 30 ) using each of the processing channels ( 1, 2 ), in which case a write authorization is allocated only once for each register location, and, when writing at least elements ( 14 ') of the common safety-based protocol using a processing channel ( 1 ) with write authorization, at least one further processing channel ( 2 ) is first of all used to check ( 25 ) whether these elements ( 14 ') are identical to one another, and access to the common buffer register for the purpose of storing these elements is enabled only when they are identical to one another.
Owner:PHOENIX CONTACT GMBH & CO KG
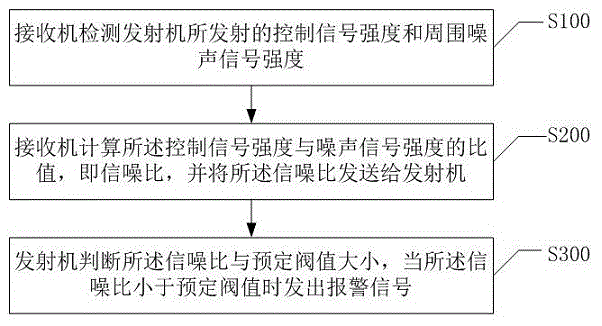
Remote alarming method and system based on detection of signal-to-noise ratio
InactiveCN105139591AAccurate detectionDetection intelligenceAlarmsSignal-to-noise ratio (imaging)Control signal
The invention discloses a remote alarming method and system based on detection of signal-to-noise ratio. The method includes the following steps: a receiver detects the intensity of a control signal sent by a transmitter and the intensity of ambient noise; the receiver calculates the ratio between the intensity of the control signal and the intensity of the noise signal, i.e., the signal-to-noise ratio, and the receiver sends the signal-to-noise ratio to the transmitter; the transmitter determines the size of the signal-to-noise ratio and a predetermined threshold value, and when the signal-to-noise ratio is smaller than the predetermined threshold value, an alarming signal is sent. According to the invention, multiple factors which impact remote operations are fully taken into consideration, such as the noise factor and the factors of the remote model, so that detection for a remote operation environment is more accurate and smart. When unsafe environment is detected, an alarm can be sent in time to alert an operator and reduce operation risks. The receiver can perform real-time detection, real-time transmission, and guarantee the timeliness and accuracy of data.
Owner:FLYSKY TECH CO LTD
Method and apparatus for converting multichannel messages into a single-channel safe message
ActiveUS7945818B2Simple and cost-effectiveEasy to implementError detection/correctionData switching networksEngineeringUnsafe environment
A method and an apparatus are disclosed for the coupling of a safety-critical process from a safe environment to an environment that is not safe or to an environment that is safe but has fewer processing channels. To this end, provision is made of a method which processes a data record that is relevant to the safety-critical process to form a respective safe protocol using at least two redundant processing channels in accordance with identical laws, and forms a common safe protocol taking into account at least two redundant safe coupling protocols. When writing at least elements of the common safety-based protocol using a processing channel with write authorization, another processing channel is used to check whether these elements are identical to one another. Access to a common buffer register for the purpose of storing these elements is enabled only when they are identical to one another.
Owner:PHOENIX CONTACT GMBH & CO KG
Security scanning method and system
The invention provides a security scanning method and system. The method includes steps: performing security scanning on a data exchange environment to obtain a scanning result; determining whether a first authentication mode is valid according to the scanning result; if yes, prompting the fact that the data exchange environment is a safe environment, and receiving a password input by a user in order to perform authentication; and if not, prompting the fact that the data exchange environment is an unsafe environment, receiving the selection for the first authentication mode and a second authentication mode by the user, enabling the corresponding authentication mode to be valid according to the authentication mode selected by the user, and receiving the password input by the user in order to perform authentication. According to the method and system, through the setting of various authentication modes, the content for security scanning is diversified and transparent, and the user interface and the operation are more visual.
Owner:TENCENT TECH (SHENZHEN) CO LTD
Data safety ferrying system and matched method thereof
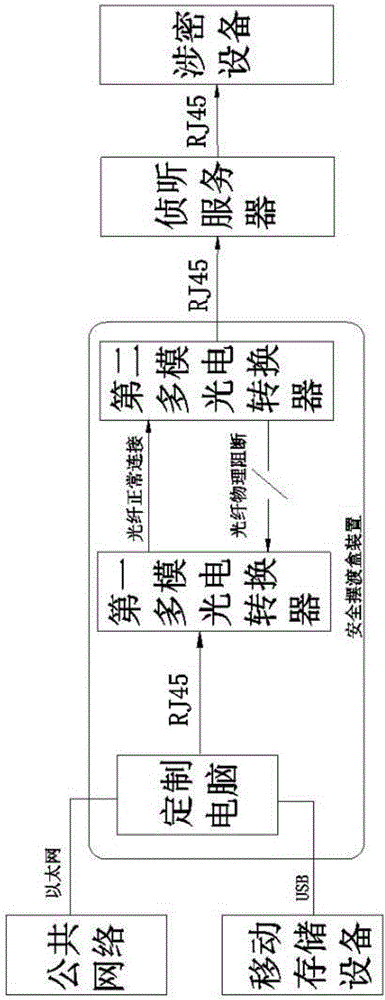
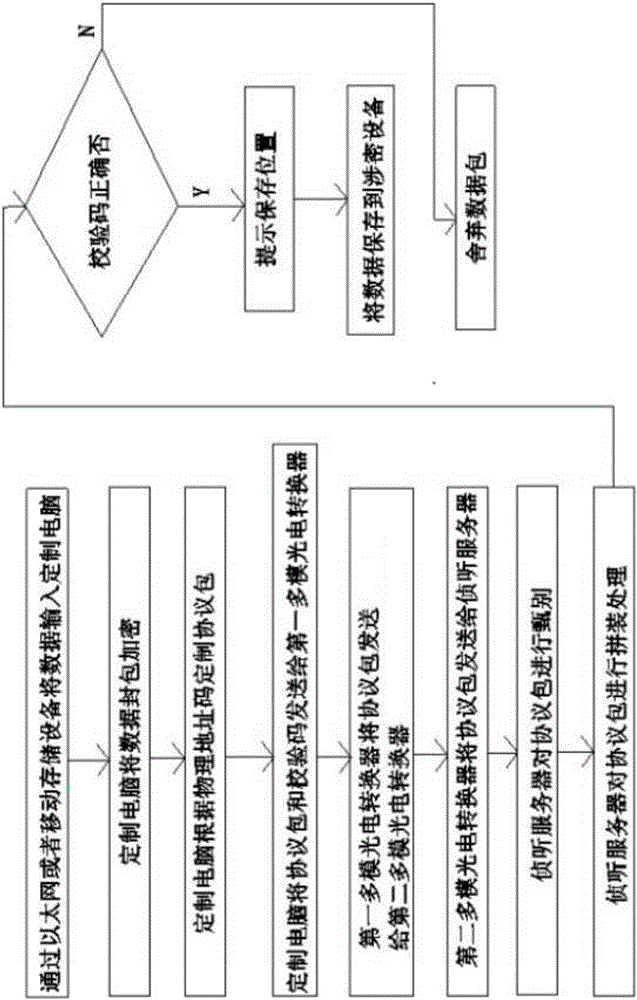
InactiveCN107437034AResolve transmissionChange is not free and embarrassingDigital data protectionData switching by path configurationMatching methodsData transmission
The invention discloses a data safety ferrying system and a matched method thereof, and belongs to the technical field of data transmission safety. The method comprises a safety ferrying box device, an interception server and a secret-related device. The problem about confidential data transmission is solved, files can be easily imported in a self-service mode in secret-related enterprises, and queuing for CD burning is not needed any more; the system can become a safe one-way file obtaining access port in an unsafe environment where the portable secret-related device is located, and embarrassment that outside office work handling of the secret-related device is not free is changed.
Owner:南京水晶石数字科技有限公司
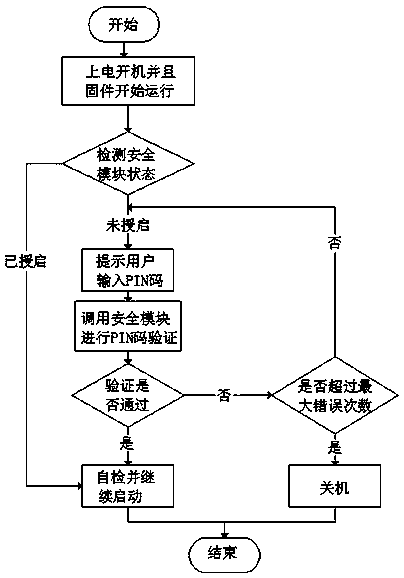
Firmware starting method based on PIN code authorization
PendingCN109992933AAvoid startingAvoid exposurePlatform integrity maintainanceProgram loading/initiatingComputer resourcesUser input
The invention discloses a firmware starting method based on PIN code authorization. The method comprises the following steps that 1, a TCM security card is used in a computer integrated with the TCM security card; step 2, starting up and electrifying, and detecting the TCM security card by the security firmware; 3, when it is detected that the state of the security card is normal and the firmwareflag bit is not started, the screen pops up a prompt box to prompt a user to input a PIN code; 4, the user inputs the PIN code in a manual input mode or in a mode of reading the file from the storagedevice; step 5, the firmware sends the received PIN code to the TCM for verification; and step 6, after the verification is passed, the firmware starts the mark position and continues to start the system, and if the verification is not passed, prompts re-input and prompts the remaining input times, and shuts down when the maximum fault-tolerant times are exceeded. The method can prevent TCM resources from being exposed in an unsafe environment, prevent the computer from being started in the unsafe environment and use the computer resources, and is better in safety.
Owner:昆仑太科(北京)技术股份有限公司
Provisioning secrets in an unsecured environment
ActiveUS8752165B2Key distribution for secure communicationDigital data processing detailsPersonalizationComputer hardware
A method and apparatus for generating provisioning data to provision a device are described. A provisioning bundle is validated according to a relationship between a configuration and a bundle sequence number identifying the provisioning bundle. A provisioning request includes a device hardware identifier identifying the device. An authorization for the provisioning request is determined for generating provisioning data including the provisioning bundle personalized by the device hardware identifier for the device.
Owner:APPLE INC
Keytote component
InactiveUS7958355B2Key distribution for secure communicationUser identity/authority verificationCommunication interfaceMan-in-the-middle attack
Systems and methods that facilitate introducing devices having digital characteristics to one another, to mitigate a man-in-the-middle attack. A keytote component supplies initial session keys for communication between devices, and includes a plurality of interfaces that can facilitate such communication. The keytote component can receive a key from a first device via one of a plulrality of communication interfaces associated with the keytote component. The user can then physically carry the keytote component to the vicinity of a second device for transferring the key thereto. As such, a man-in-the-middle attack can be mitigated, as an encrypted channel can be established in an insecure environment.
Owner:MICROSOFT TECH LICENSING LLC
Method and device for reducing risk of financial transaction
ActiveCN108198332AAvoid exposurePrevent leakagePayment protocolsCoded identity card or credit card actuationPasswordCiphertext
The invention discloses a method and device for reducing the risk of a financial transaction. The method comprises the steps that a card reader chip prepares a data source to be sent to a financial ICchip, and a request for generating application authentication ciphertext including the data source is generated; the card reader chip sends the request for generating the application authentication ciphertext to the financial IC chip; the card reader chip receives response data, containing the application authentication ciphertext, returned by the financial IC chip; the card reader chip conductscompression, scrambling and conversion on the response data to obtain a dynamic password; the card reader chip outputs the dynamic password to complete the financial transaction. The method and devicehave the advantages that the transaction password can be prevented from being exposed in an unsafe environment in the process of using a financial IC for transactions, the transaction password is prevented from being leaked, the transaction risk is reduced, and the transaction security is improved.
Owner:FEITIAN TECHNOLOGIES
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com