Safety verification method and equipment
A technology of security verification and verification method, applied in the field of security verification method and equipment, can solve the problem of inability to take into account the convenience of operation and user information security, and achieve the effect of increasing the convenience of operation and protecting the security.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
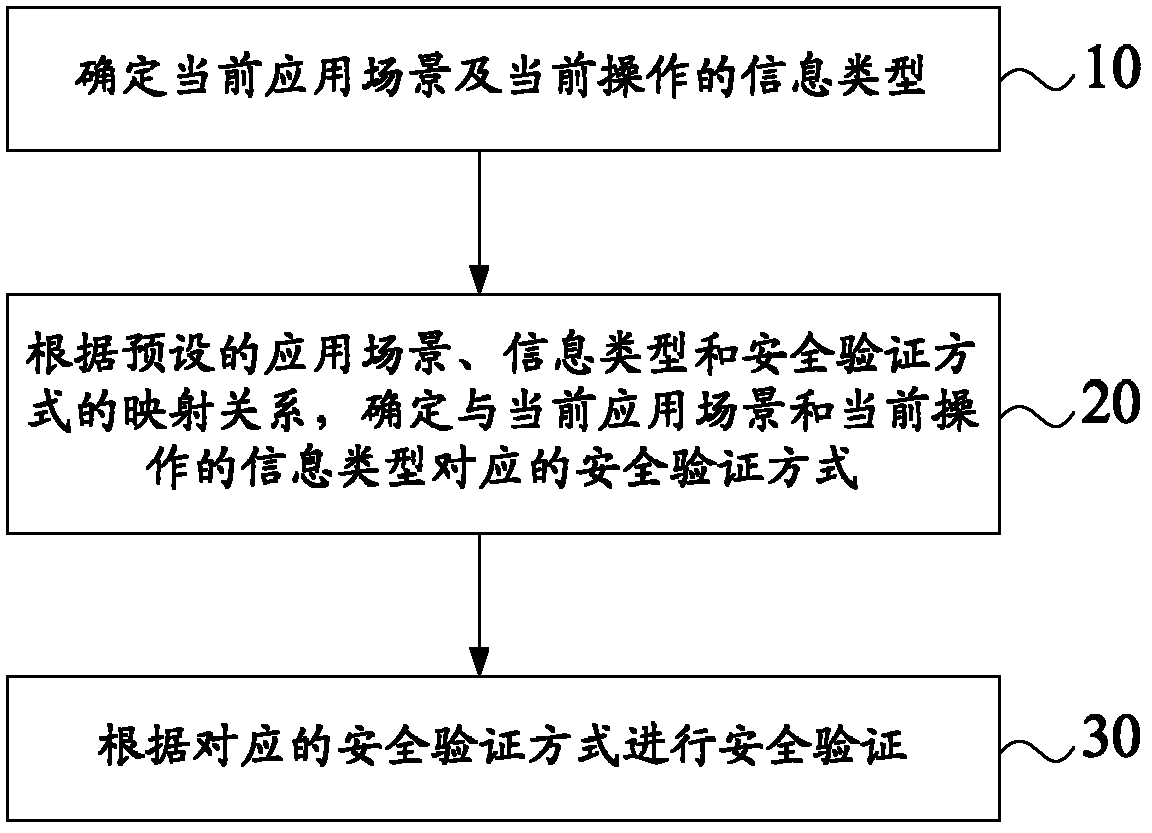
[0054] figure 1 It is a schematic flowchart of a security verification method provided by an embodiment of the present invention. This method is applicable to devices and various mobile terminals, such as mobile phones and tablet computers, whose application environments may change. Such as figure 1 As shown, the security verification method includes:
[0055] Step 10: Determine the current application scenario and the information type of the current operation.
[0056] For example, the security verification device determines the current application scenario and the information type of the current operation. The current application scene is the current application scene of the device. For example, the application scene can be divided into several categories such as work scene, family scene, entertainment scene, etc., and can also be classified in other ways according to actual needs. The type of information currently operated is the type of information currently operated by...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com