Safety protection method for mobile terminal, mobile terminal, safety system and application method
A mobile terminal and security protection technology, applied in the field of security zone systems, can solve the problems of low correlation of personal attributes, easy to be bypassed, easy to steal information, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0107] The present invention will be further described in detail below in conjunction with specific embodiments. However, it should not be understood that the scope of the above subject matter of the present invention is limited to the following embodiments, and all technologies realized based on the content of the present invention belong to the scope of the present invention.
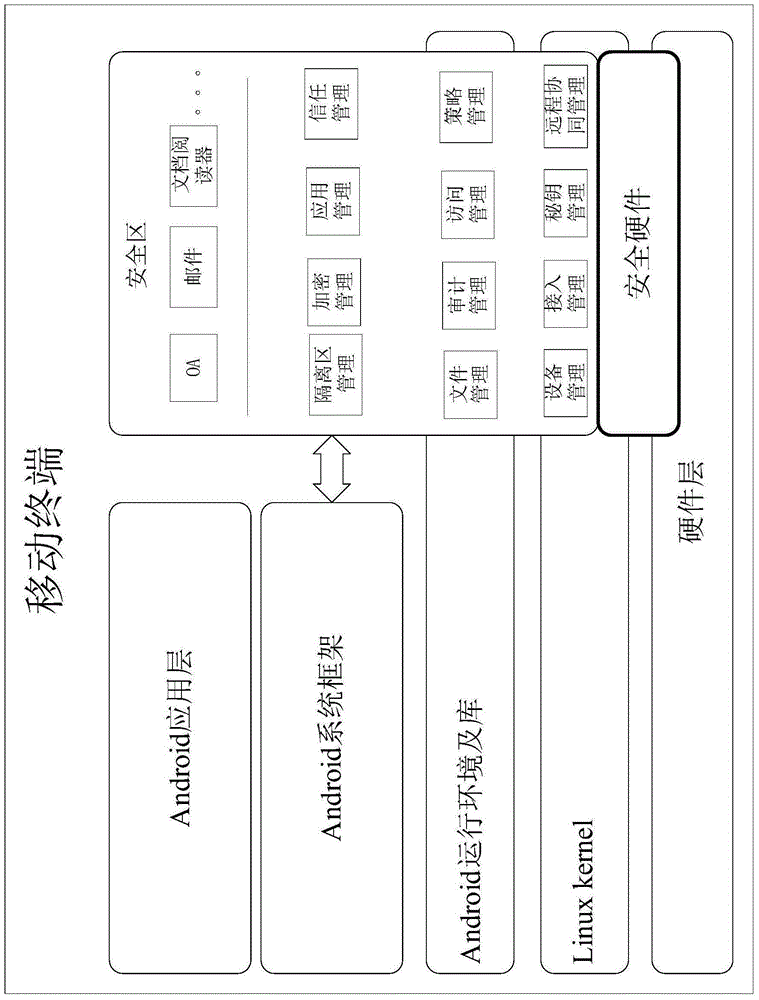
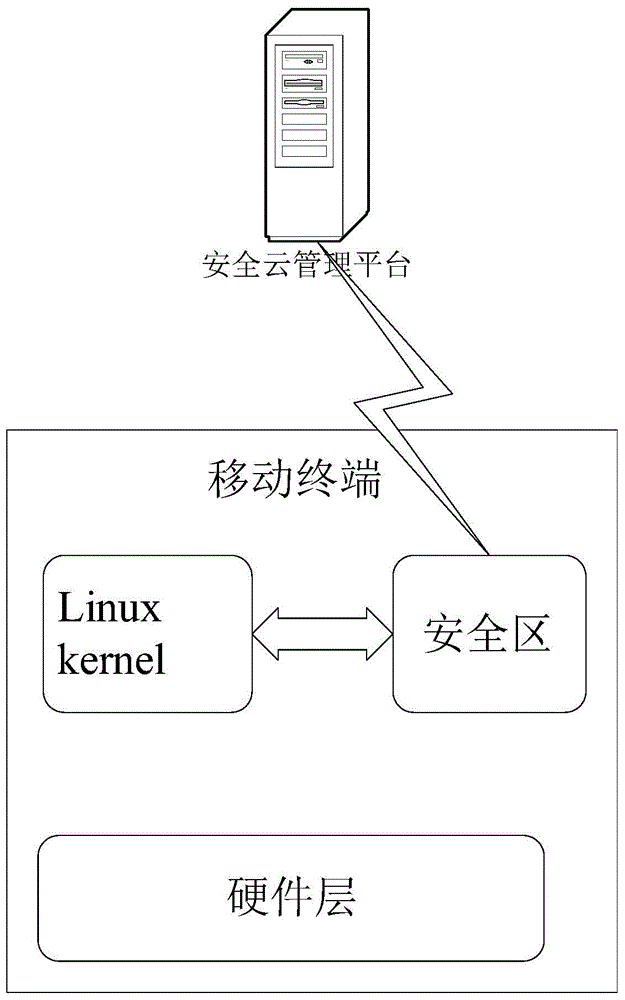
[0108] The present invention provides a mobile terminal security protection method based on an isolated area, which mainly isolates a separate area on the mobile terminal as a safe area, and then puts the application / data to be protected in the safe area, and the user Access to applications and / or data in this security zone is required after security verification. In this way, one machine can be used for two purposes, which not only ensures the normal use of applications in the common area, but also provides higher security protection for applications in the safe area, and solves the problem of trustw...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com