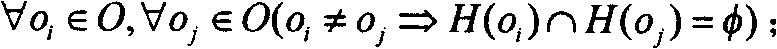Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
221 results about "Is security" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Security+ is a certification sponsored by CompTIA, the Computing Technology Industry Association. The Security+ Certification shows that you have the competence required to apply knowledge of security concepts, tools, and procedures to react to security incidents, as well as anticipating security risks and guarding against them before they occur.
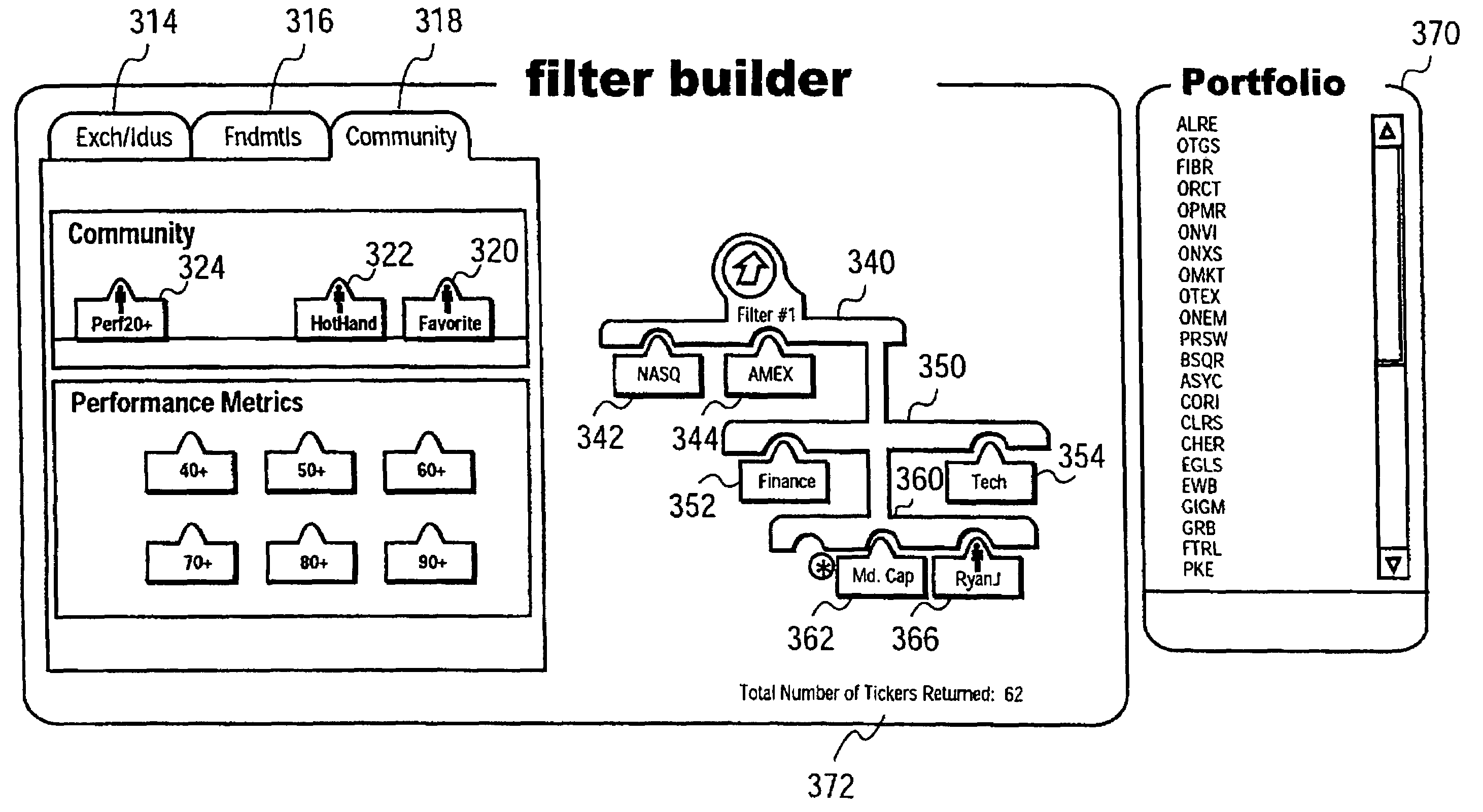
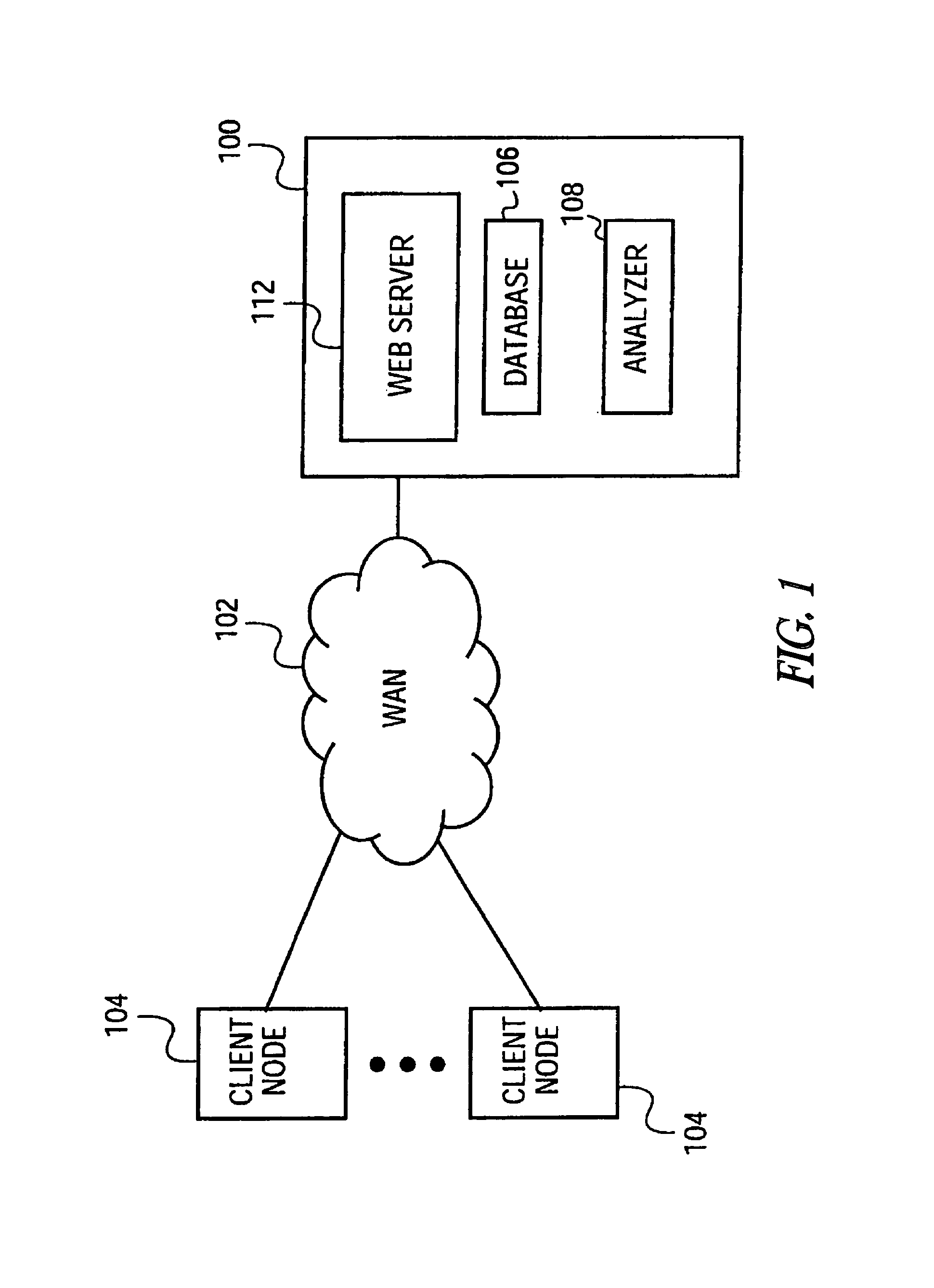
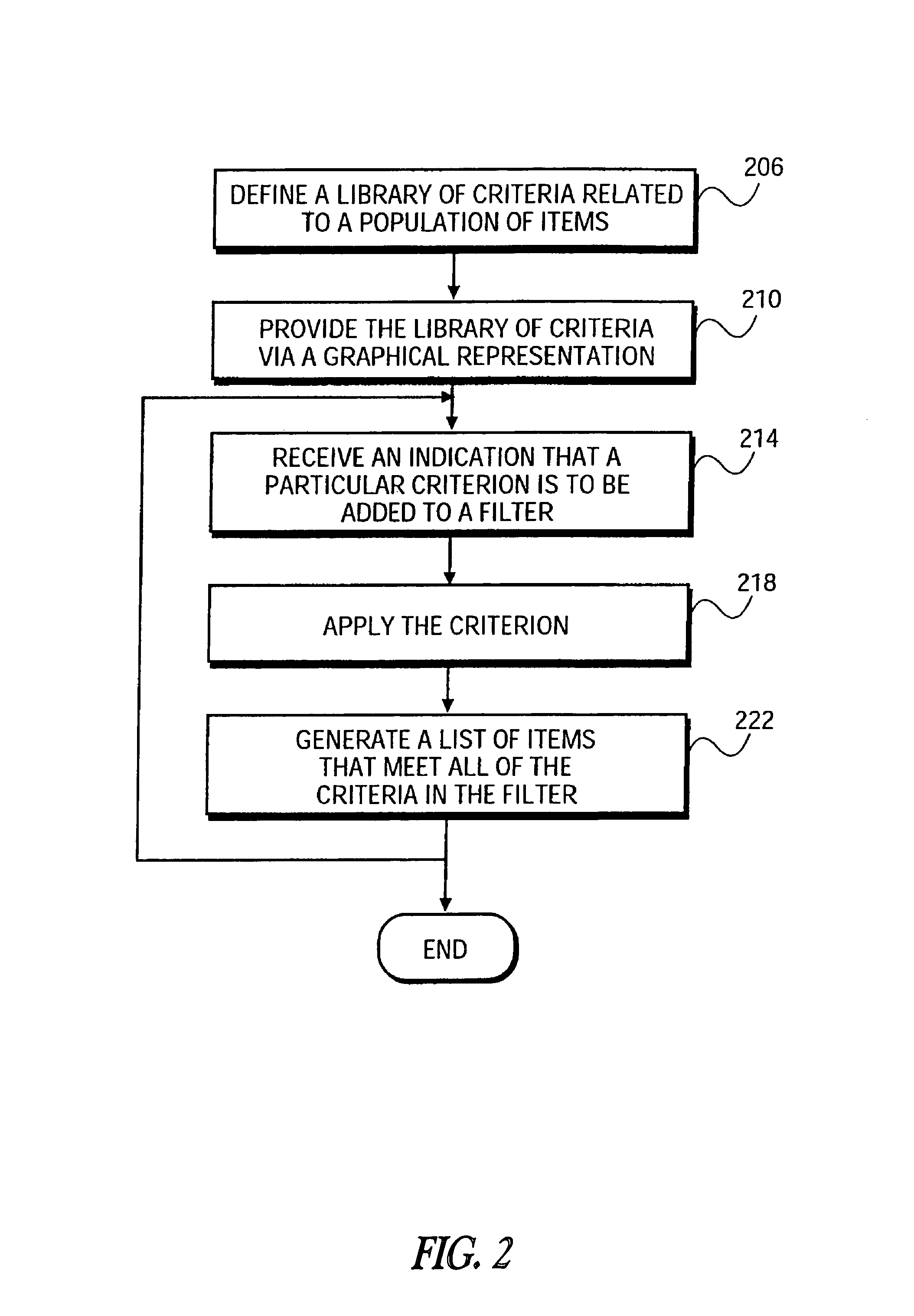
Graphical user interface for filtering a population of items
Graphical user interface for filtering a population of items. The graphical user interface may be implemented as a method on a system comprising a computer server or other computing device. The system defines a library of available criteria to be used in filtering a population of items to identify items of interest. Each criterion has a graphical representation. The system receives an indication of at least one of the criterion to be applied to the population as a filter and also accepts an indication of a tier of the filter to which the selected criterion is to be associated. The system identifies a list of items of interest satisfying a current set of criteria defining the filter. A graphical representation of the filter is displayed by the system while it is being constructed by the user. In one embodiment, the items are securities such as stocks.
Owner:EBAY INC +2
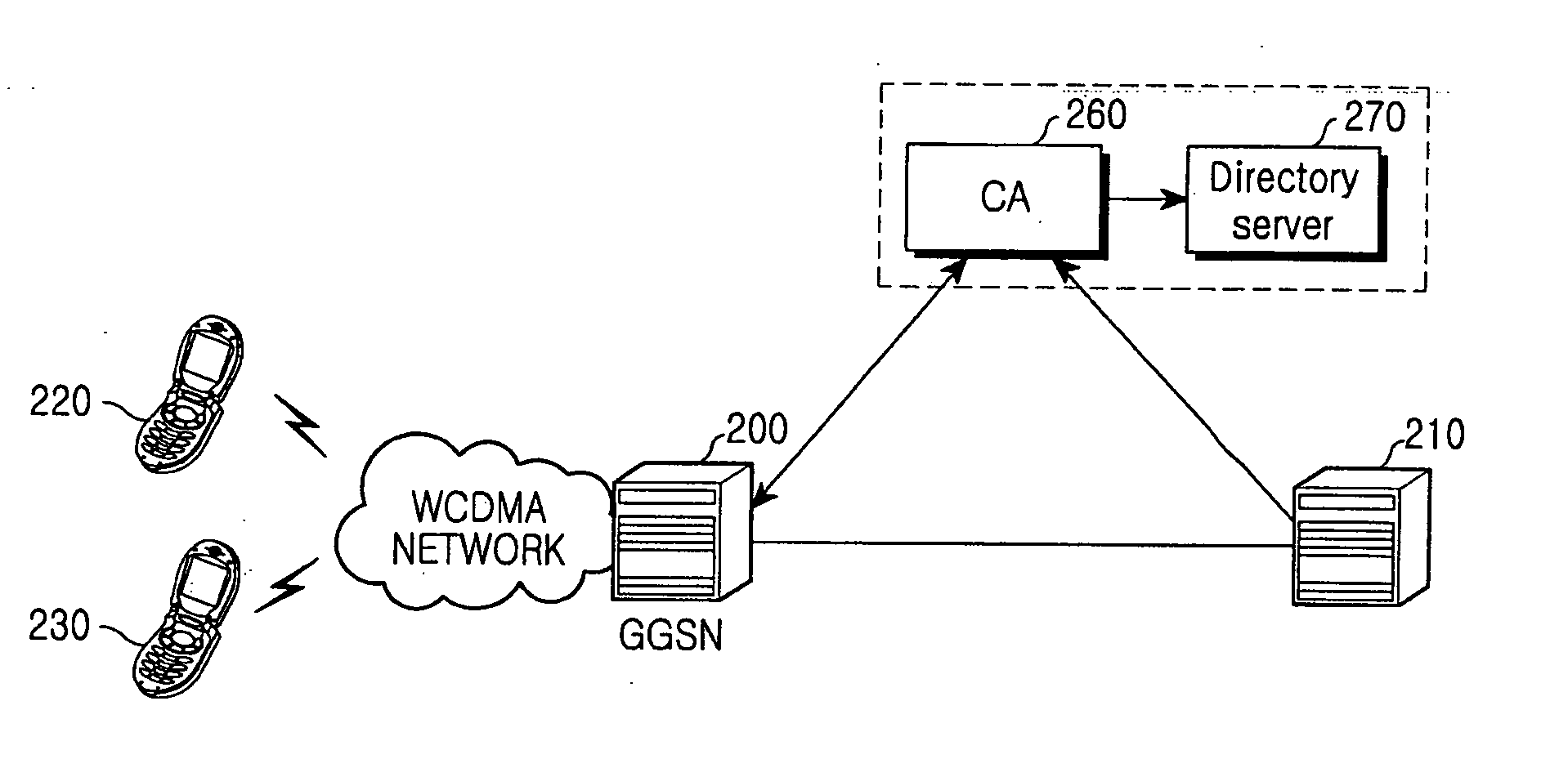
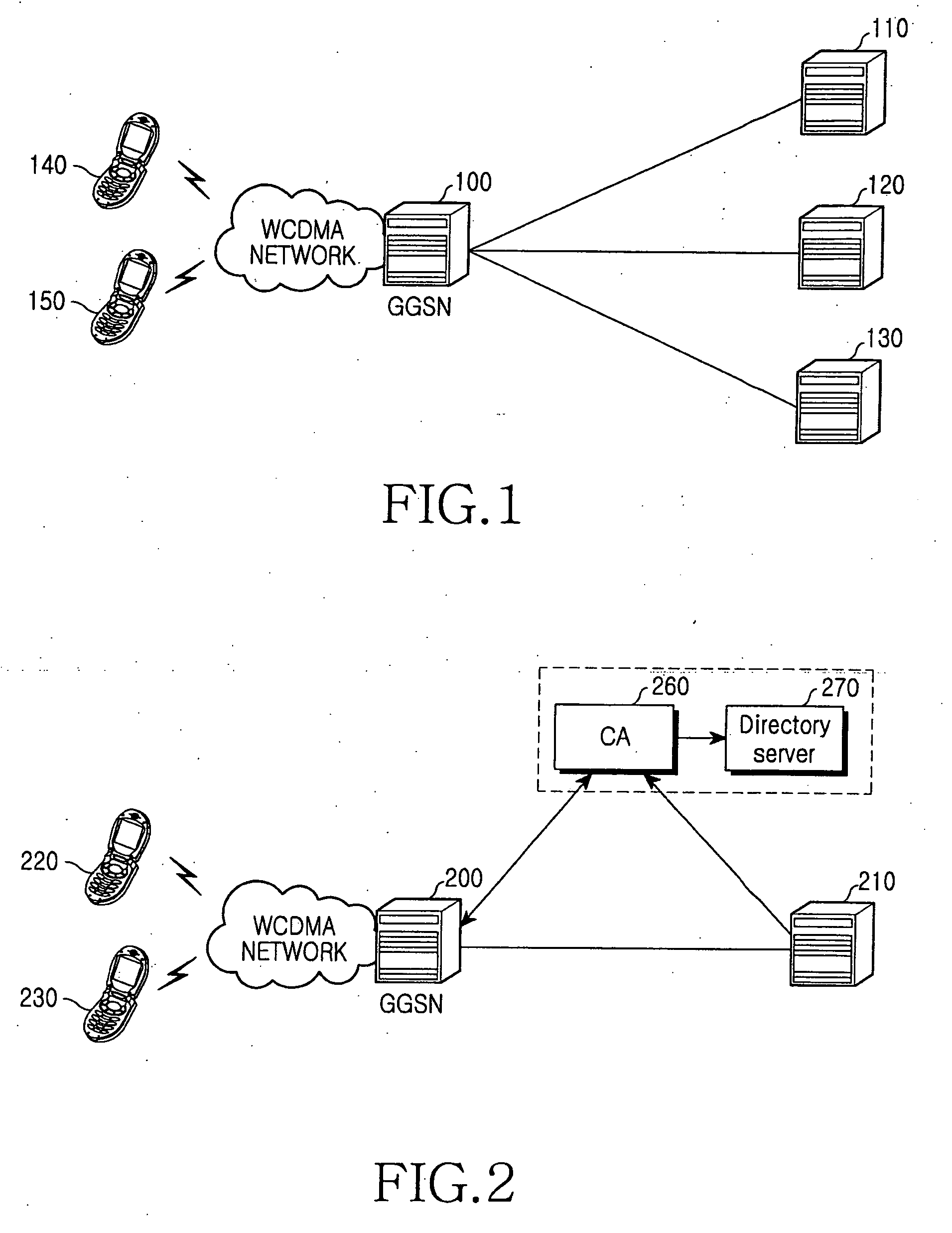
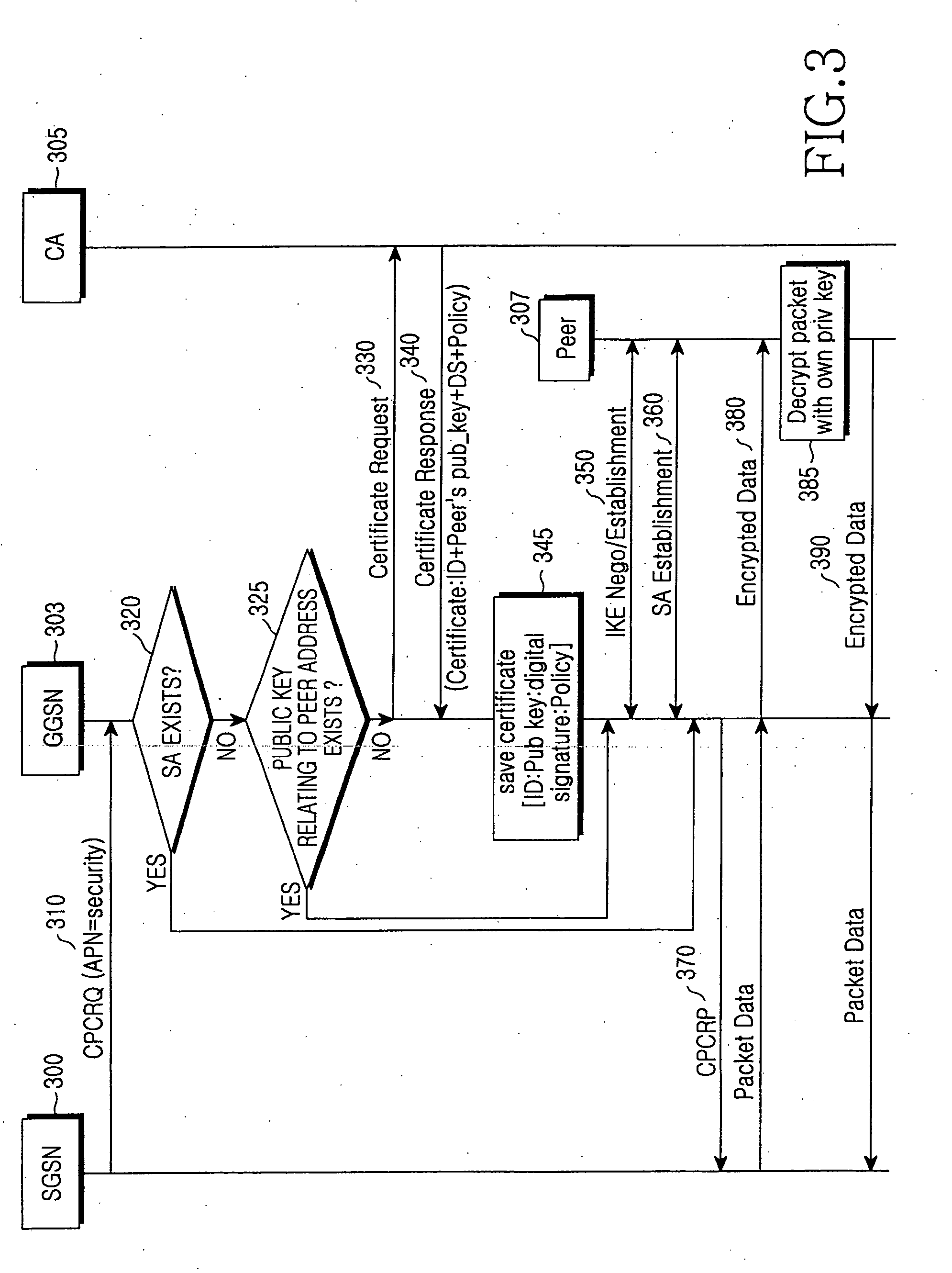
Method and apparatus for security of IP security tunnel using public key infrastructure in mobile communication network
InactiveUS20060105741A1Applied load reductionUnauthorised/fraudulent call preventionEavesdropping prevention circuitsKey exchangeInternet Key Exchange
A method and apparatus is provided for security of an IP security tunnel using public key infrastructure, including the steps of receiving a request message which relates to a security service requested by a mobile node, determining if there is security association (SA) for the security service and determining if there is a public key related to a peer address when the SA does not exist, sending a certificate request message to a certificate authority (CA) when the public key does not exist and receiving a certificate response message which has a certificate that includes a public key. The method further includes the steps of performing an internet key exchange and SA establishment procedure with a peer corresponding to the peer address by using the certificate, completing the internet key exchange and the SA establishment, and encrypting a packet received from the mobile node, transmitting the encrypted packet to the peer, decrypting a packet received from the peer, and transmitting the decrypted packet to the mobile node.
Owner:SAMSUNG ELECTRONICS CO LTD
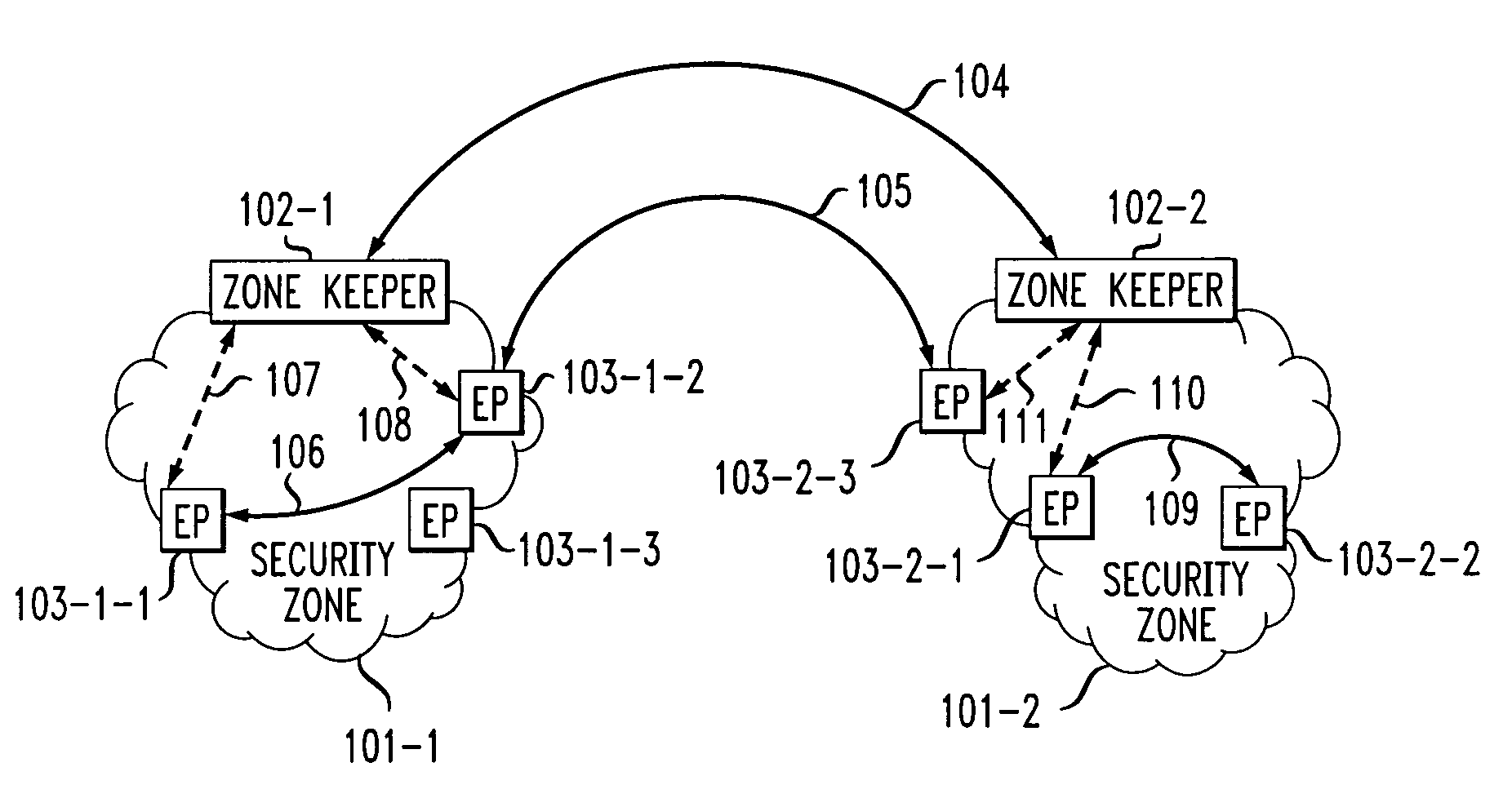
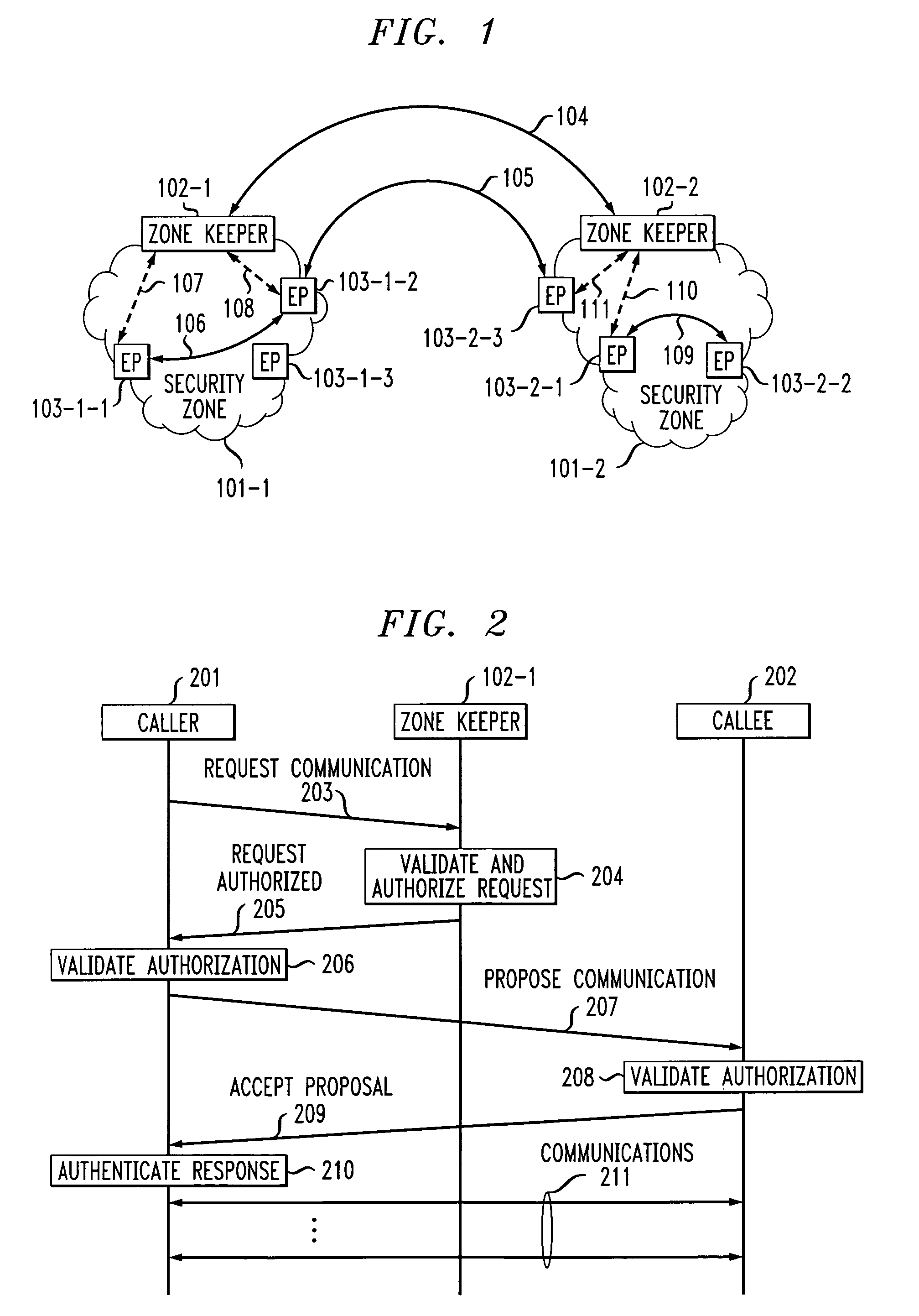
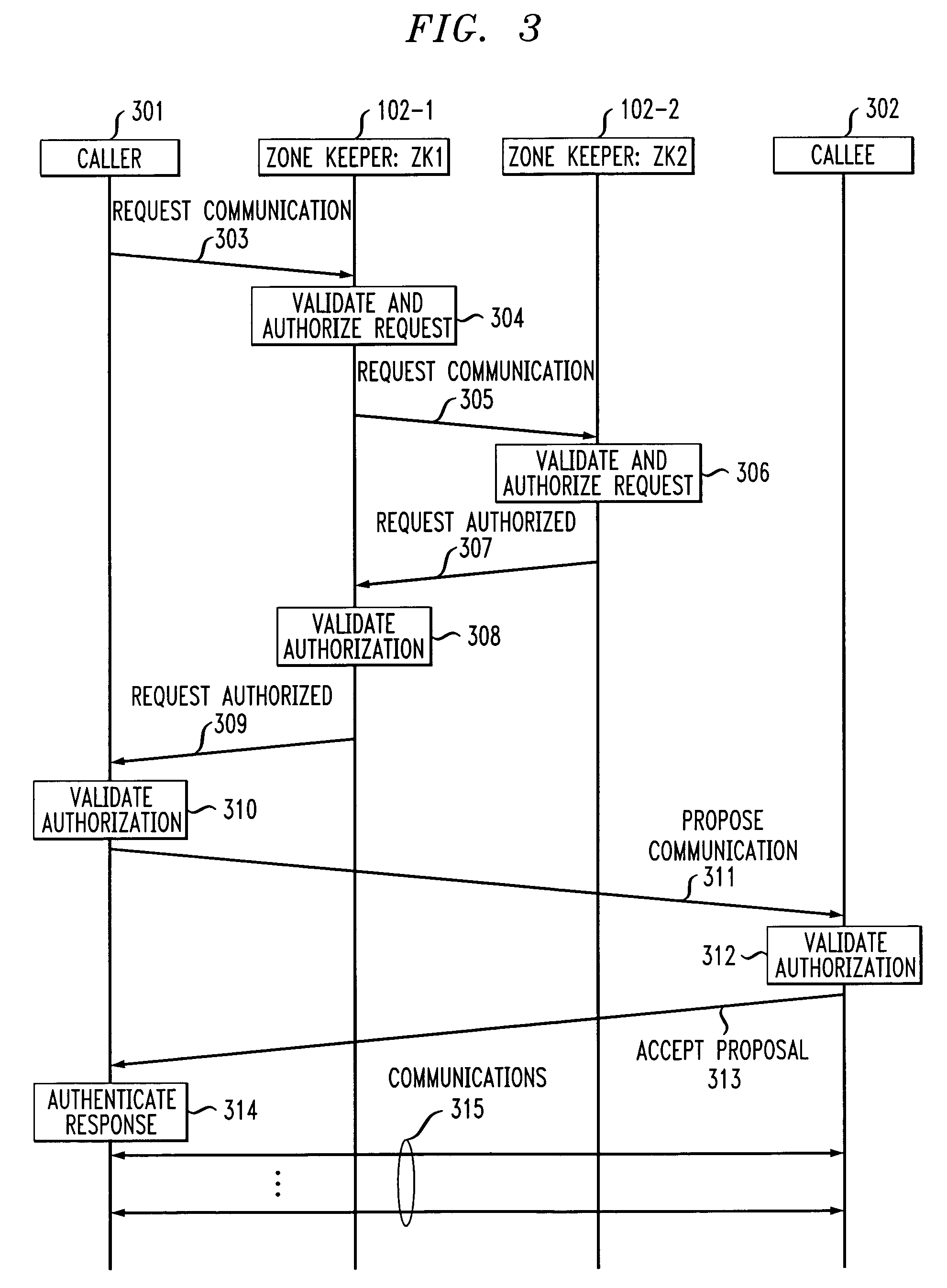
Dual-tier security architecture for inter-domain environments
InactiveUS6996716B1Communication securityUser identity/authority verificationDigital computer detailsCost effectivenessSecurity information
A two-tier security architecture that provides balance between the use of public and secret-key cryptography to realize cost-effectiveness and scalability of security. One tier is an intra-zone tier and the other tier is an inter-zone tier. The intra-zone tier addresses communication between users employing endpoints within a prescribed Security Zone and is designed to achieve cost-effectiveness. The inter-zone tier specifies how communication between users employing endpoints from different Security Zones can be established and is designed to provide scalability for intra-enterprise and / or inter-enterprise communications. Specifically, each Security Zone has a “Zone Keeper” and one or more endpoints that may be employed by users. The Zone Keeper authenticates, i.e., validates, users employing an endpoint in the Security Zone and determines whether a caller and a callee are security compatible. When setting up a communication, the caller provides the Zone Keeper security information in order for the caller to prove its identity. The callee supplies to the caller information confirming its identity. A proposal on how the communication is to be Set-up is sent from the caller to the callee, and if they agree to the proposal and their security is authenticated, the communication is started. For inter-zone, inter-domain, communications, the caller provides information as described above to its Zone Keeper. Then, the caller's Zone Keeper forwards the caller's request to the Zone Keeper of the security associated with the callee. Additionally, the caller's Zone Keeper also supplies the callee's Zone Keeper with its security identity so that the callee's Zone Keeper may authenticate that the request is from the caller's Zone Keeper. Then, the callee's Zone Keeper sends back an authorization to the Caller's Zone Keeper. This authorization includes the callee's Zone Keeper security identity so that the caller's Zone Keeper can authenticate that the authorization is from the callee's Zone Keeper.
Owner:AVAYA INC
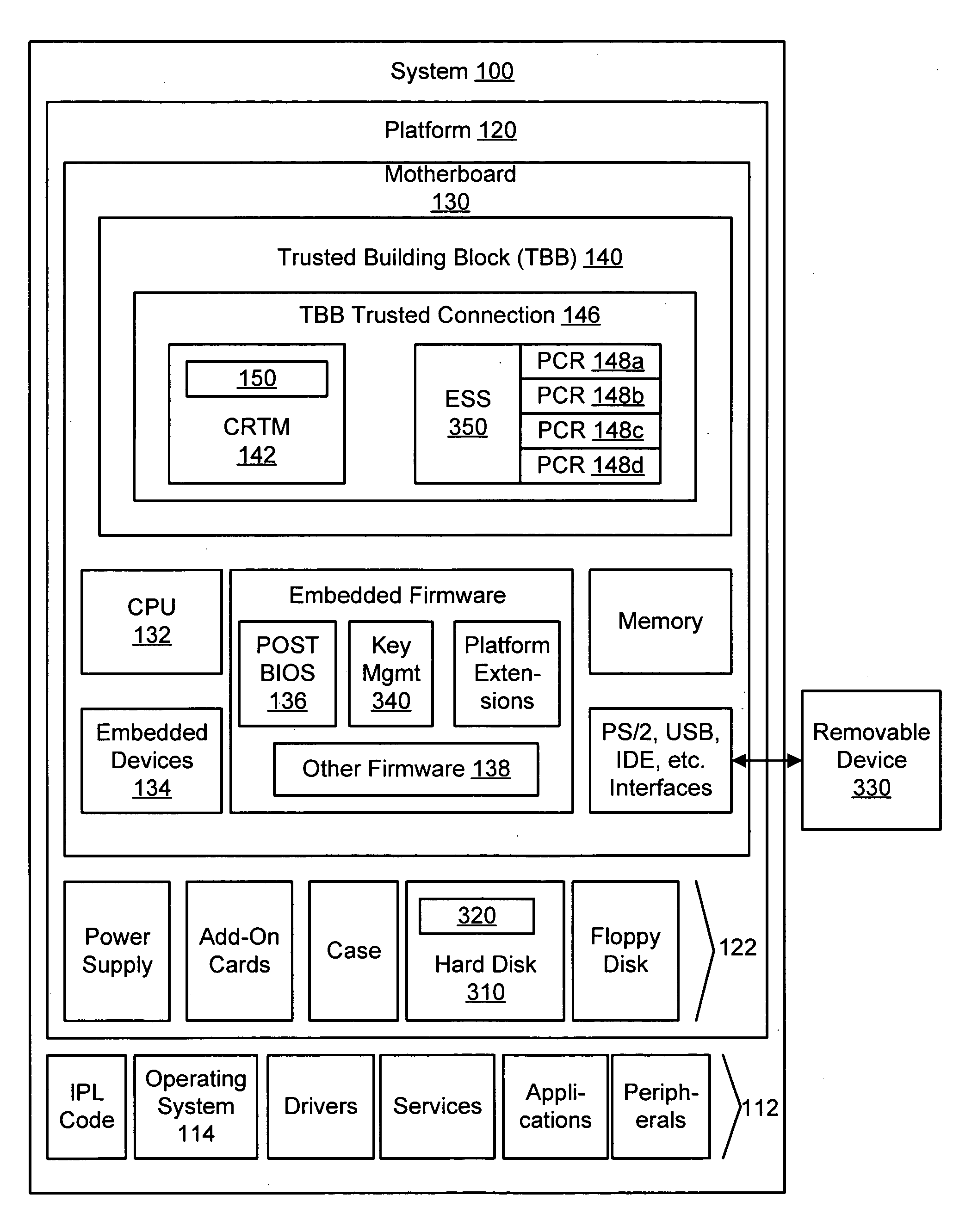
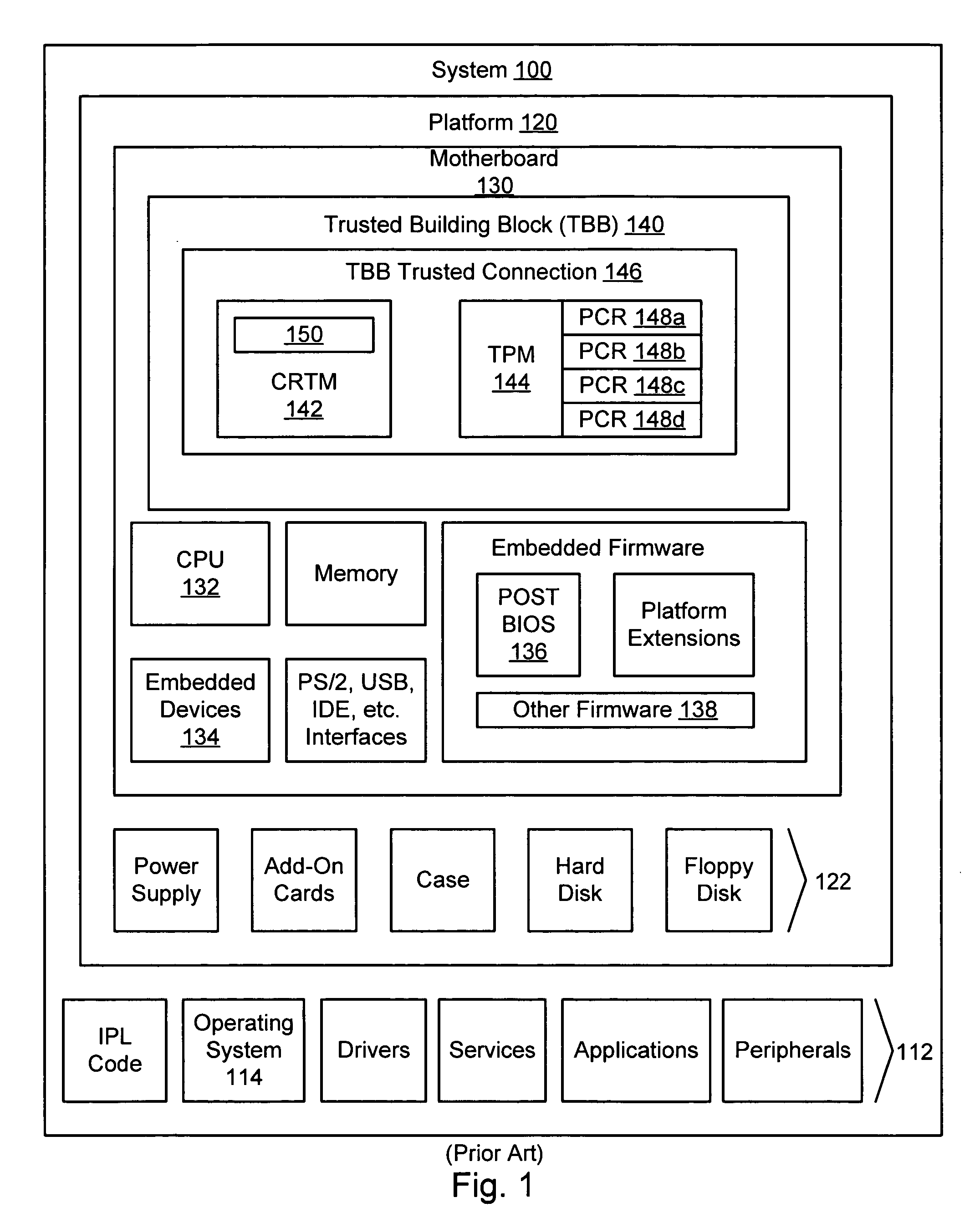
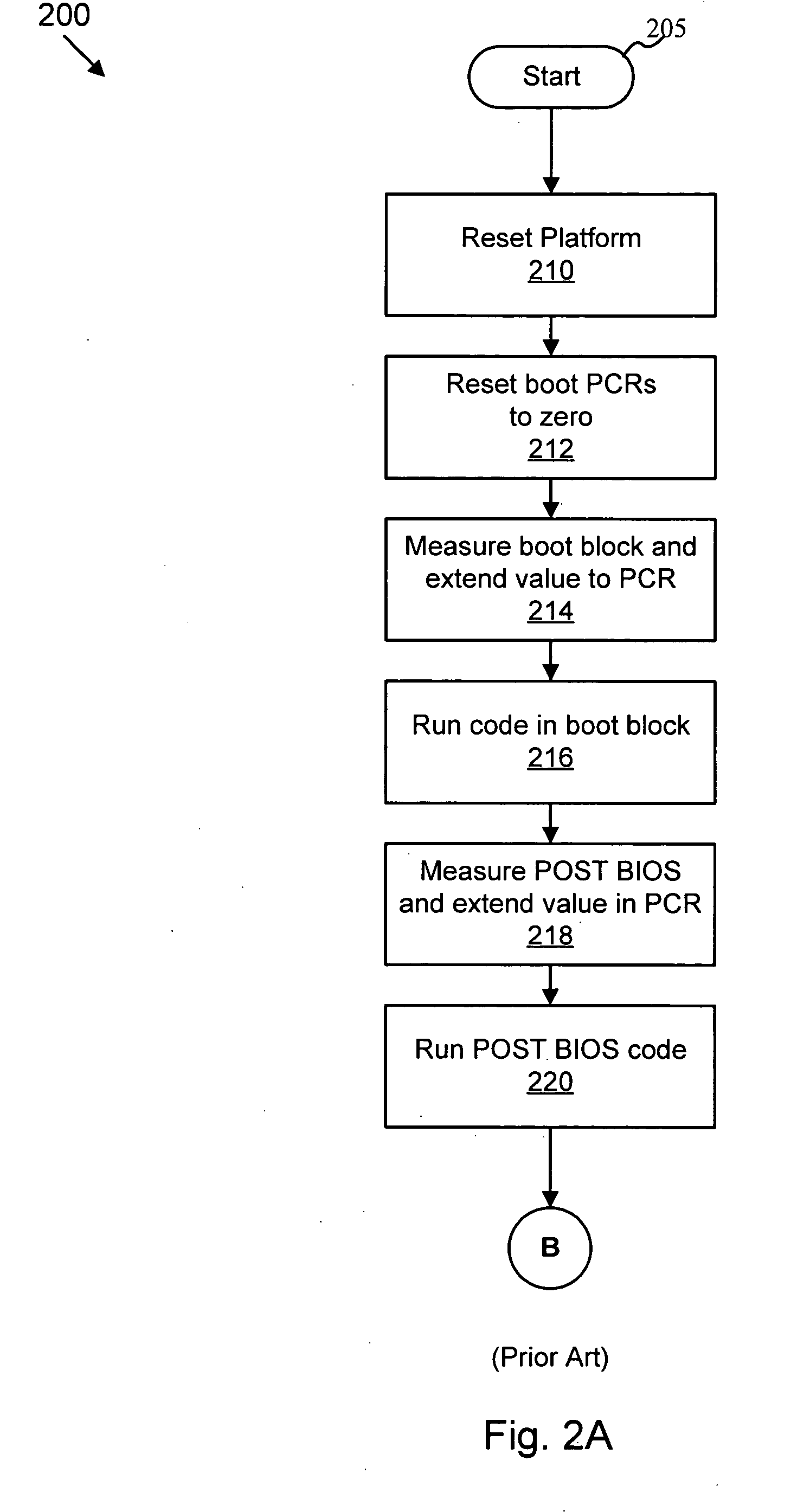
Apparatus, system, and method for sealing a data repository to a trusted computing platform
ActiveUS20050141717A1Improve securityUnauthorized memory use protectionHardware monitoringTrusted ComputingSystem configuration
An apparatus, method, and system to seal a data repository to a trusted computing platform is described. The data repository may be sealed by encrypting the data on the repository and sealing a cryptographic key to a specific set of platform resources. With the data repository sealed to the platform, the system boot sequence will fail if the system configuration is compromised, for example by insertion of “snoopware” or a modified BIOS. Additionally, if the computer containing the data repository is lost or stolen, the encrypted data remains secure even if the repository is attached to a system modified to bypass normal safeguards.
Owner:LENOVO PC INT
Method for implementing mandatory access control mechanism of security operating system
InactiveCN101727545ALower threshold requirementsInternal/peripheral component protectionInformation processingOperational system
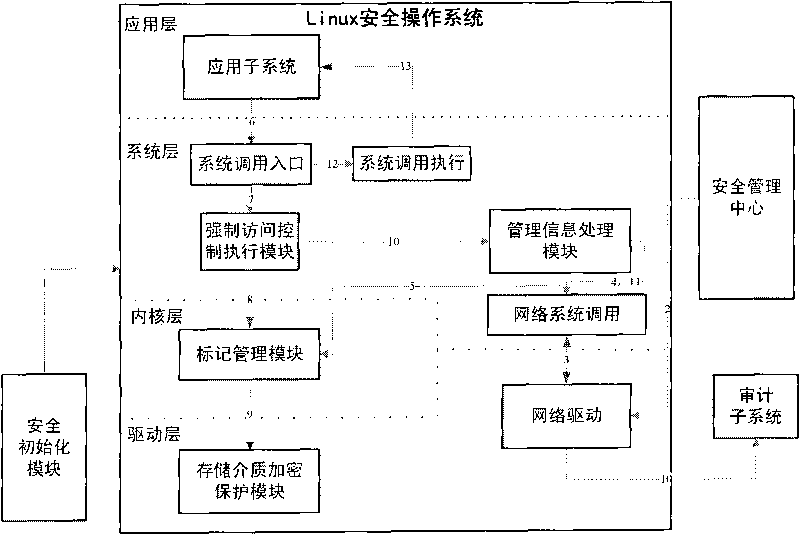
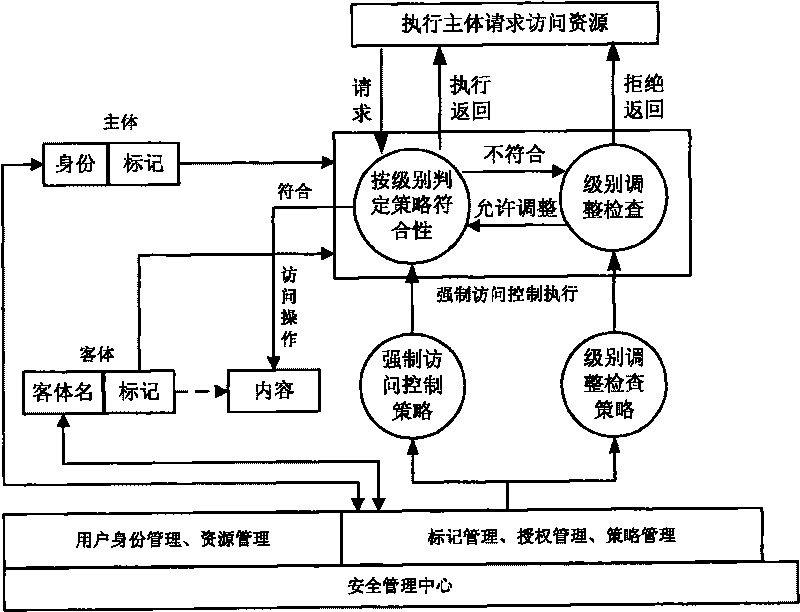
The invention relates to a method for implementing a mandatory access control mechanism of a security operating system, which belongs to the field of the design and implementation of a security operating system. The subject of the security operating system is a security system structure and an access control process. The security system structure requires an operation system to support the mandatory access control mechanism, describe the dependency relationship between hierarchical division and modules in design, be divided into a driving layer, an inner nuclear layer, a system layer and an application layer from the bottom to the top in implementation method and comprise a mandatory access control execution module, a mark management module, a management information processing module, a security initialization module and a storage medium encipherment protection module. The mandatory access control process determines the time and process precedence relationship for implementing the mandatory access control in the security operation system. A support model, a data structure and a hook function specify the details of the implementation. The mandatory access control mechanism is a necessary security function of a high-security operation system. The method can be widely used in the design of high-security operation system.
Owner:GRADUATE SCHOOL OF THE CHINESE ACAD OF SCI GSCAS
Methods that provide dispatchers in power grid control centers with a capability to manage changes
InactiveUS20110071690A1Easy to manageMechanical power/torque controlLevel controlProgram planningPower grid
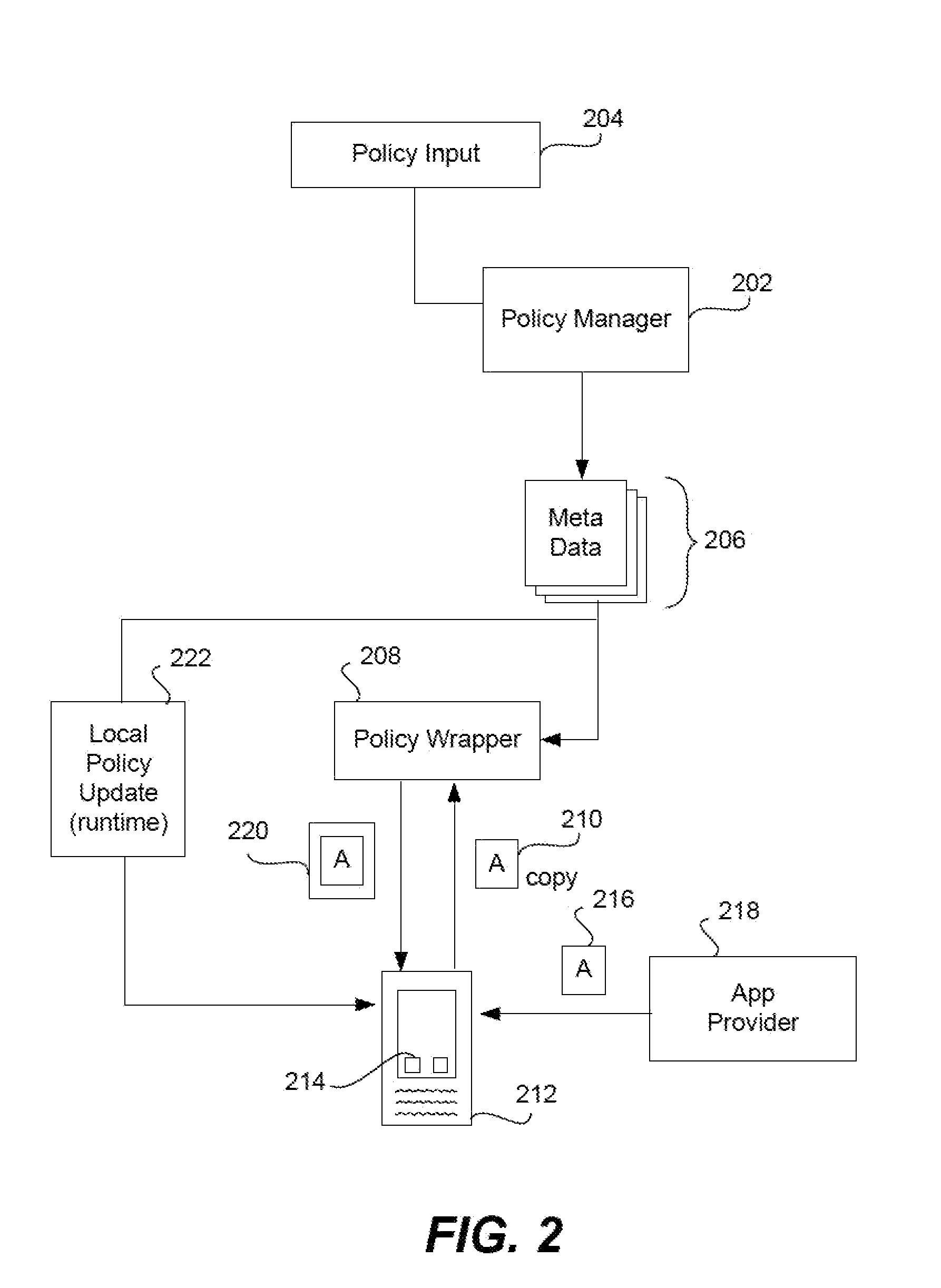
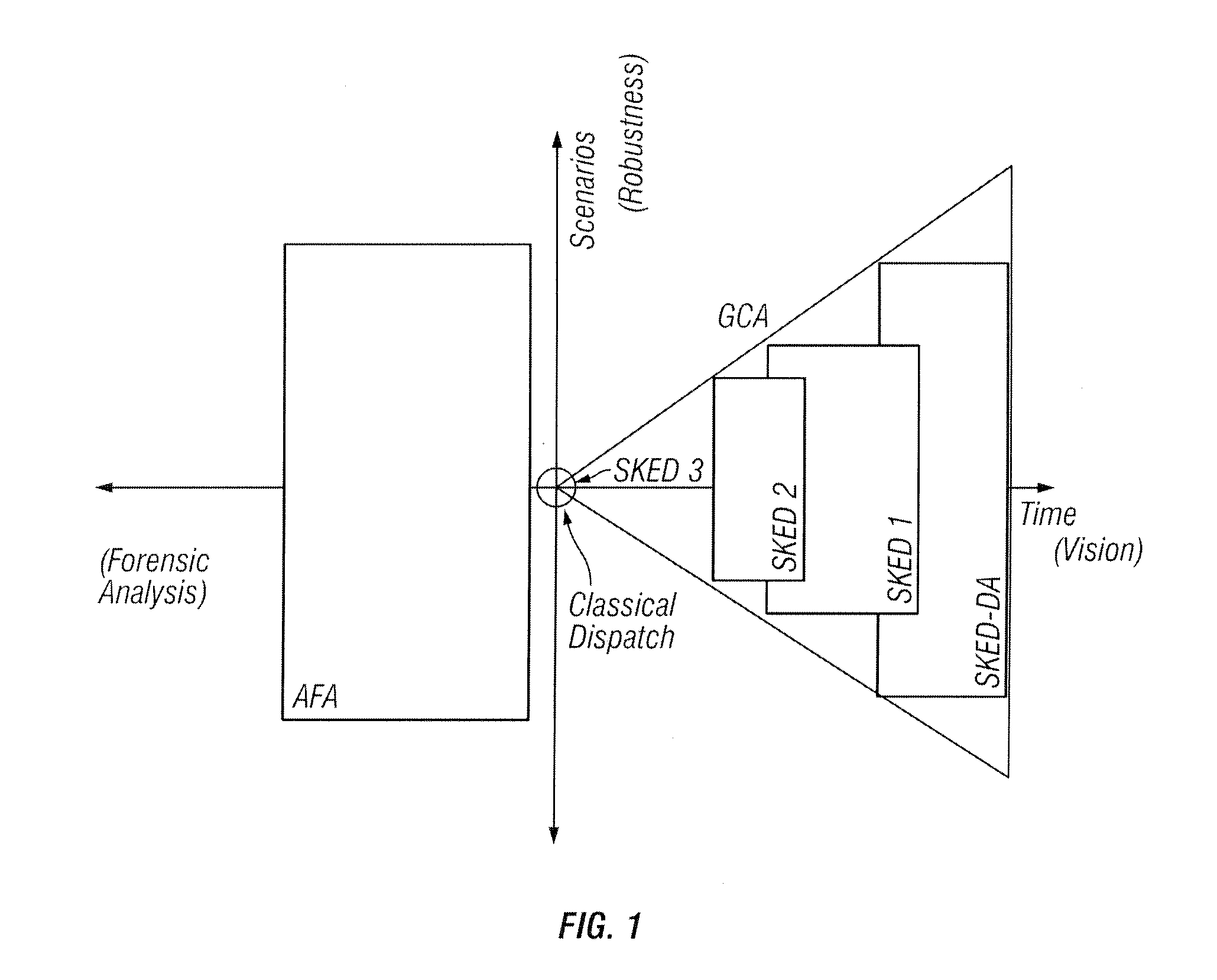
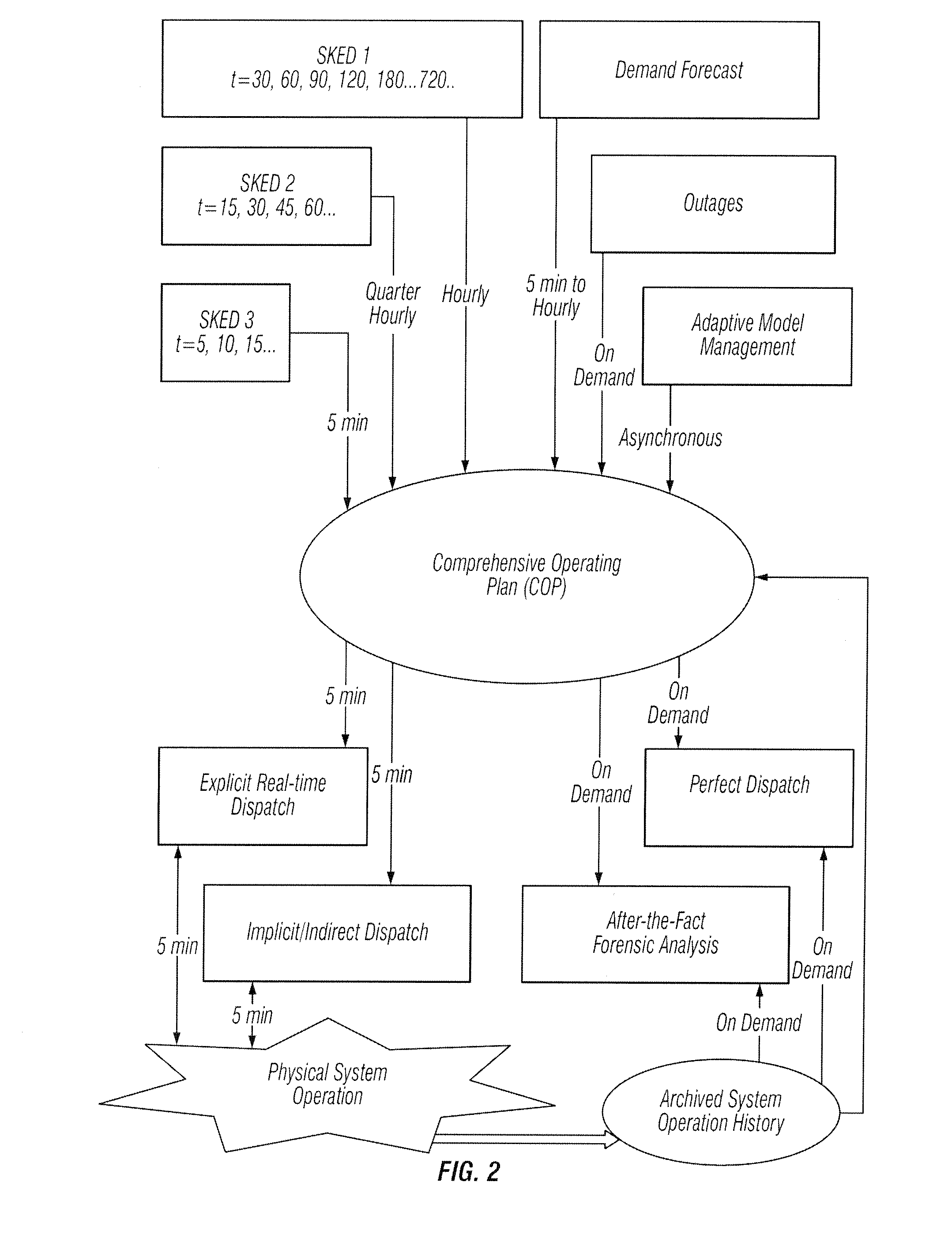
Methods are provided that enable dispatchers in power grid control centers to manage changes. A comprehensive operating plan is provided with multiple, security constrained economic dispatch engines 1, 2 and 3. The scheduler engines are security constrained unit commitments and economic dispatch sequences with different look-ahead periods. The comprehensive operation plan is configured to integrate scheduler engines into a unified scheduling system. The comprehensive operating plan includes a repository of all operating plans in a multi-stage decision process.
Owner:ALSTOM TECH LTD
Model based systems management in virtualized and non-virtualized environments
ActiveUS20110138441A1Well formedDigital computer detailsPlatform integrity maintainanceVirtualizationSystems management
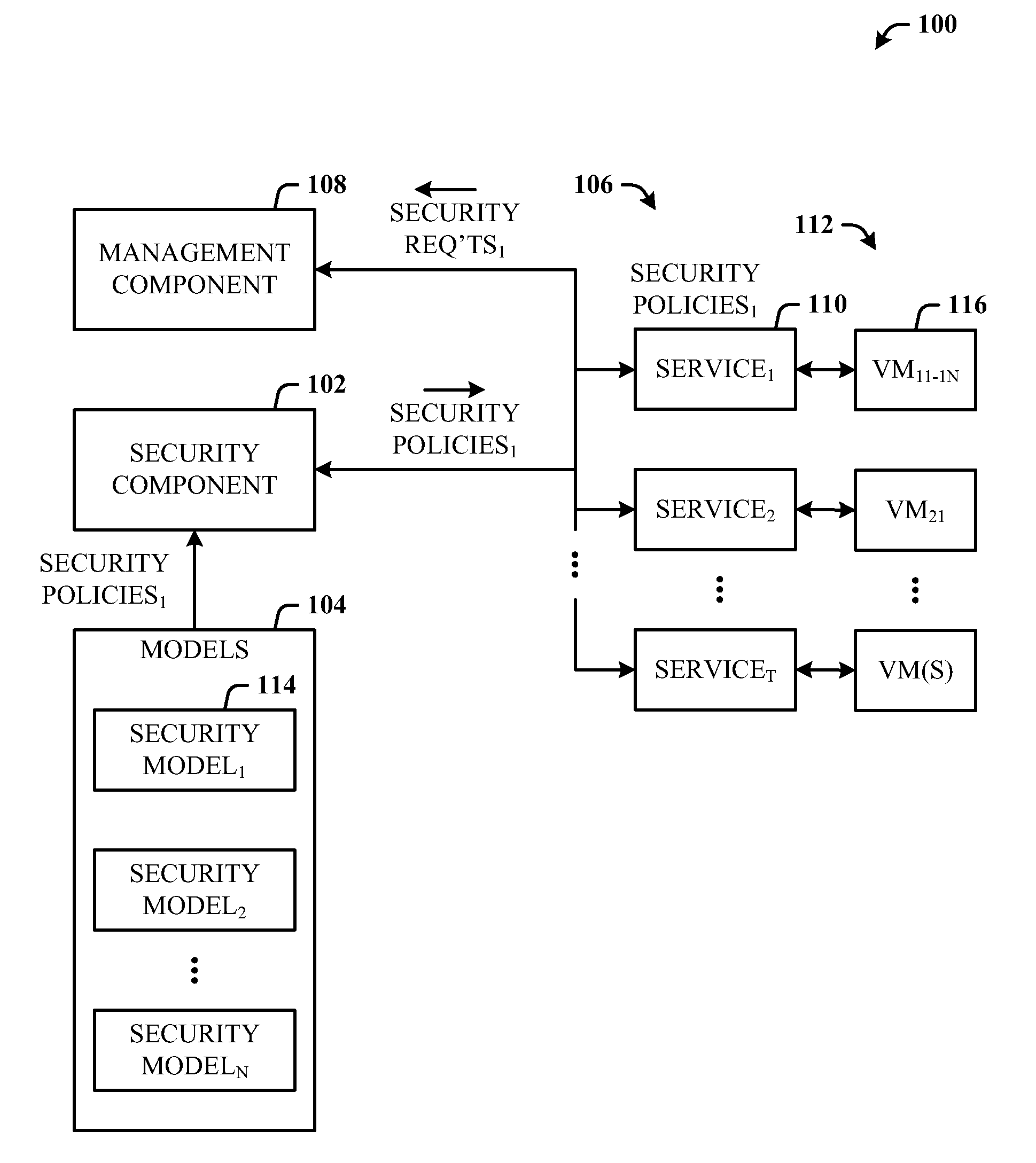
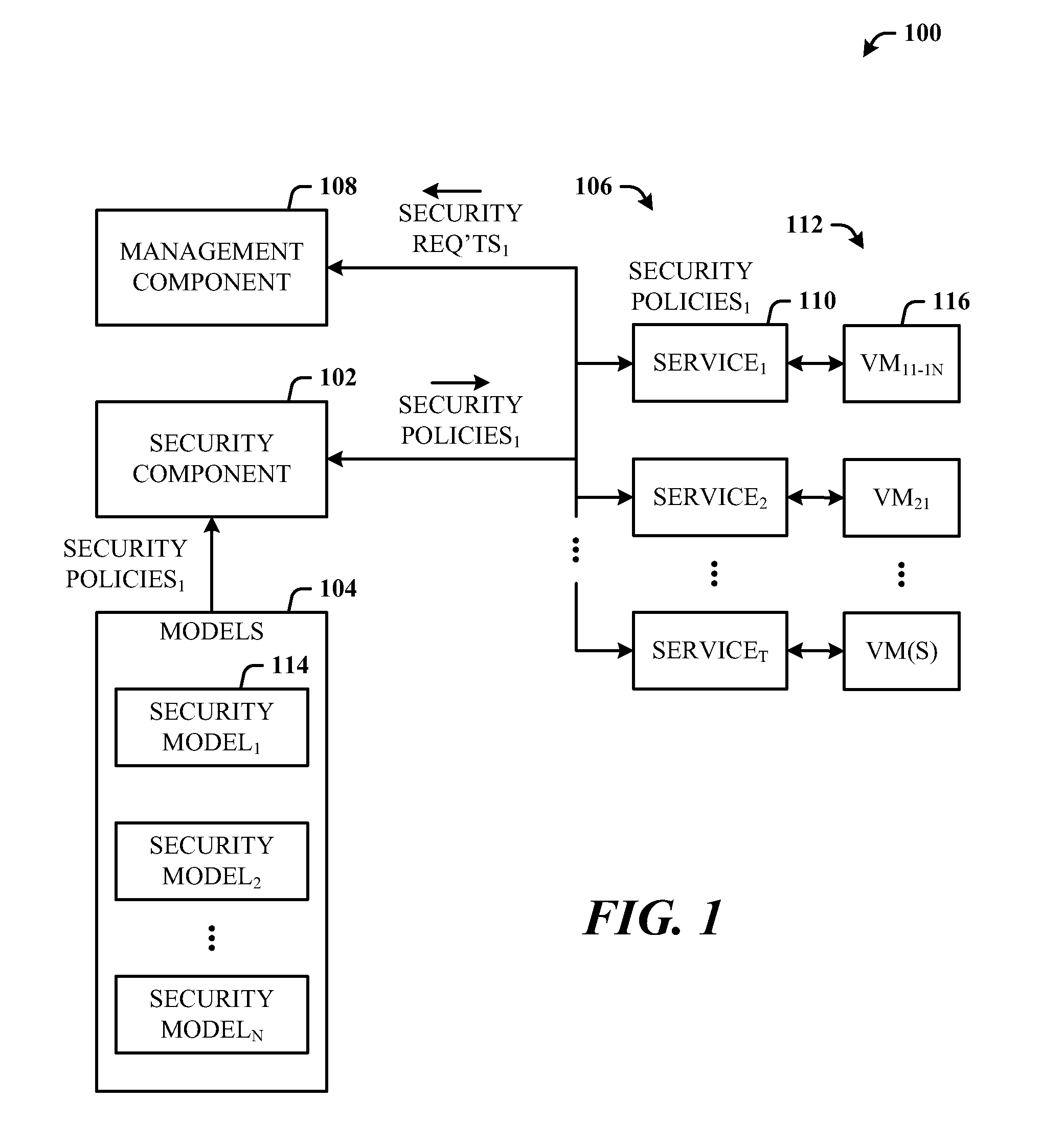
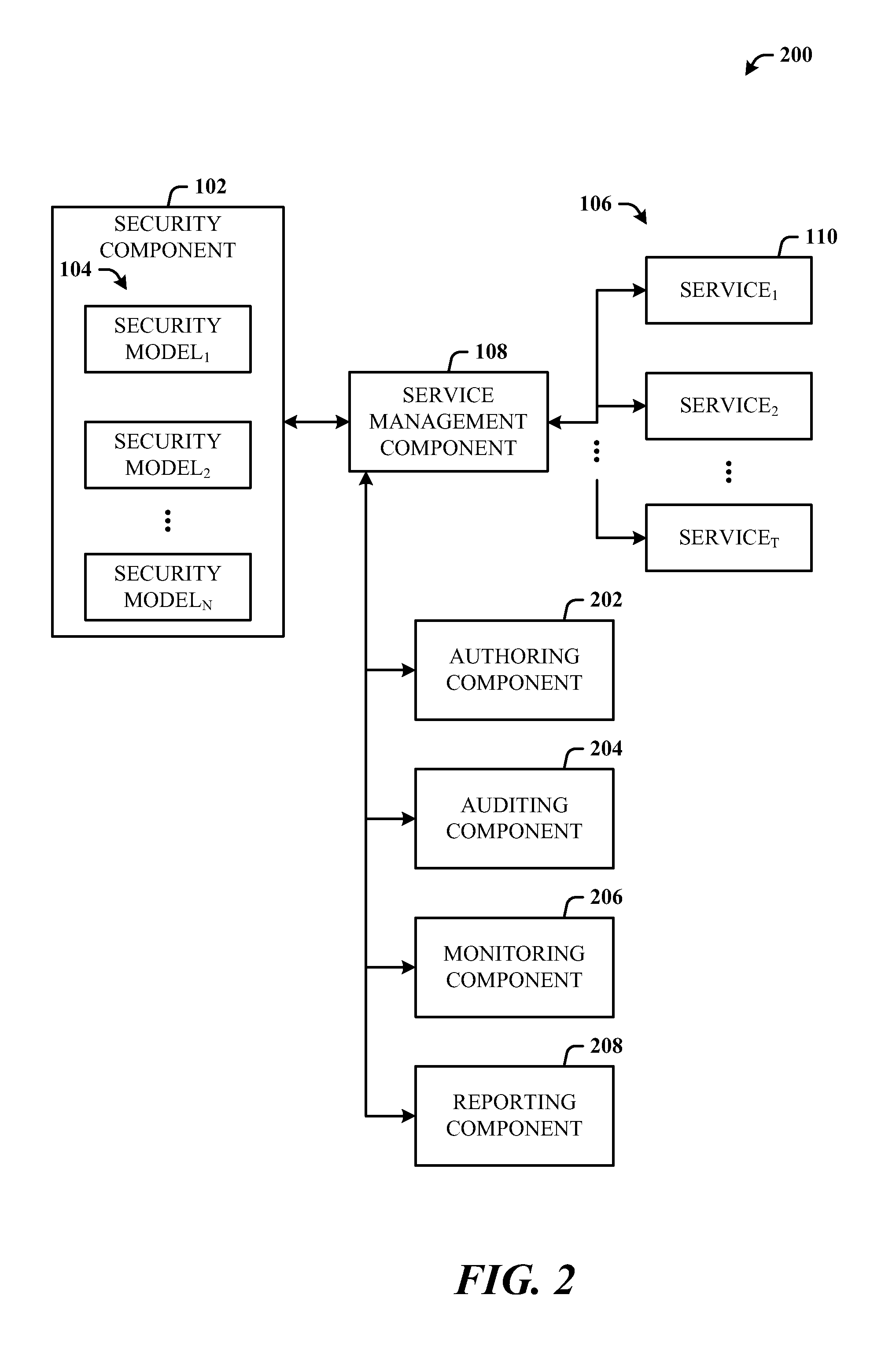
Architecture that provides model-based systems management in virtualized and non-virtualized environments. A security component provides security models which define security requirements for services. A management component applies one or more of the security models during the lifecycle of virtual machines and services. The lifecycle can include initial deployment, expansion, moving servers, monitoring, and reporting. The architecture creates a formal description model of how a virtual machine or a service (composition of multiple virtual machines) is secured. The security requirements information can also be fed back to the general management system which uses this information in its own activities such as to guide the placement of workloads on servers can be security related.
Owner:MICROSOFT TECH LICENSING LLC
Method and apparatus for detecting vulnerabilities and bugs in software applications
InactiveUS20080184208A1Computer security arrangementsSpecific program execution arrangementsApplication softwareComputer software
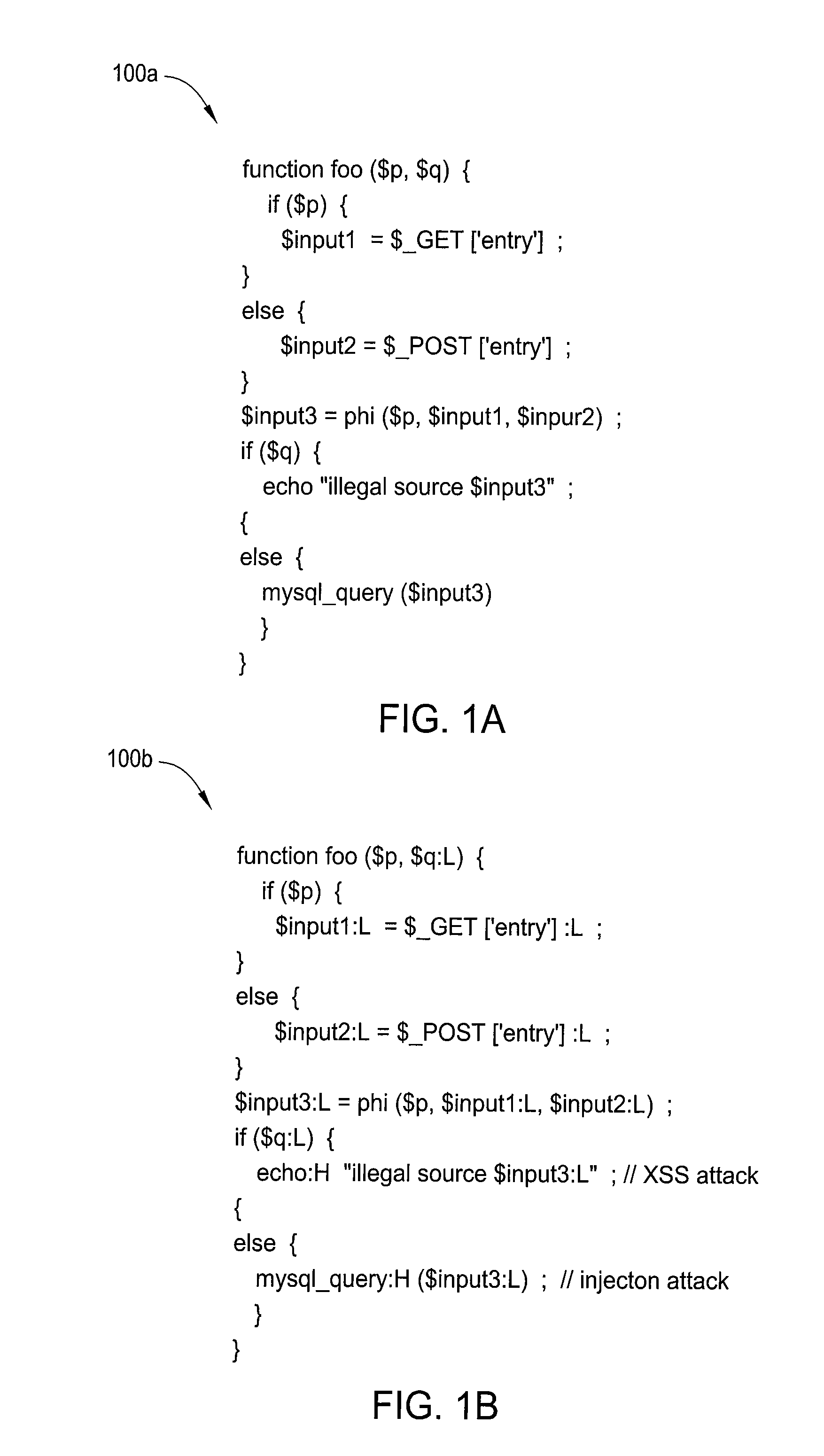
In one embodiment, the present invention is a method and apparatus for detecting vulnerabilities and bugs in software applications. One embodiment of a method for detecting a vulnerability in a computer software application comprising a plurality of variables that have respective values and include data and functions includes detecting at least one piece of data that is tainted, tracking the propagation of the tainted data through the software application, and identifying functions that are security sensitive and that are reached by the tainted data its the propagation.
Owner:IBM CORP
Network security method
InactiveUS20060010485A1Avoid communicationDigital data processing detailsMultiple digital computer combinationsIs securitySoftware
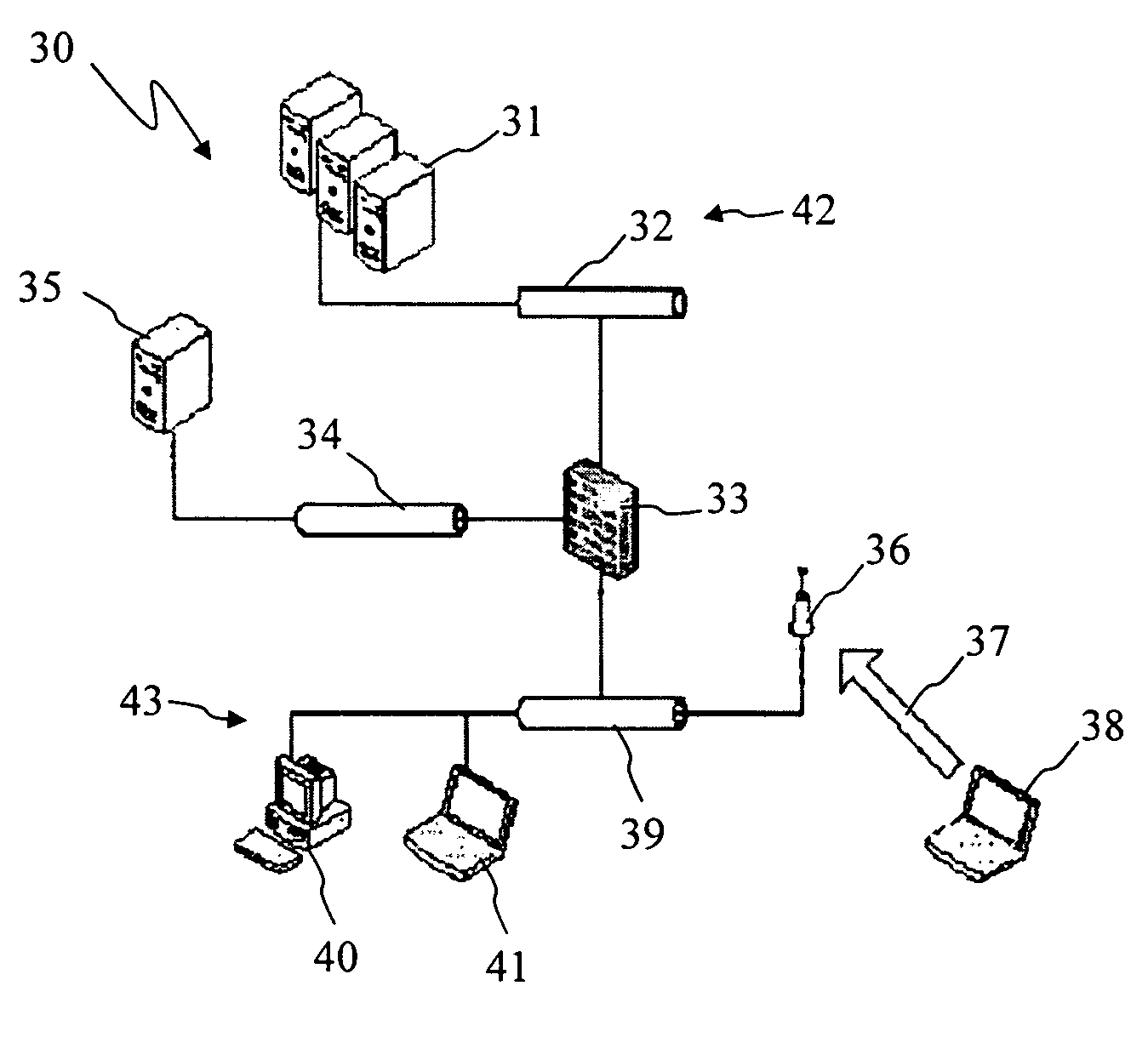
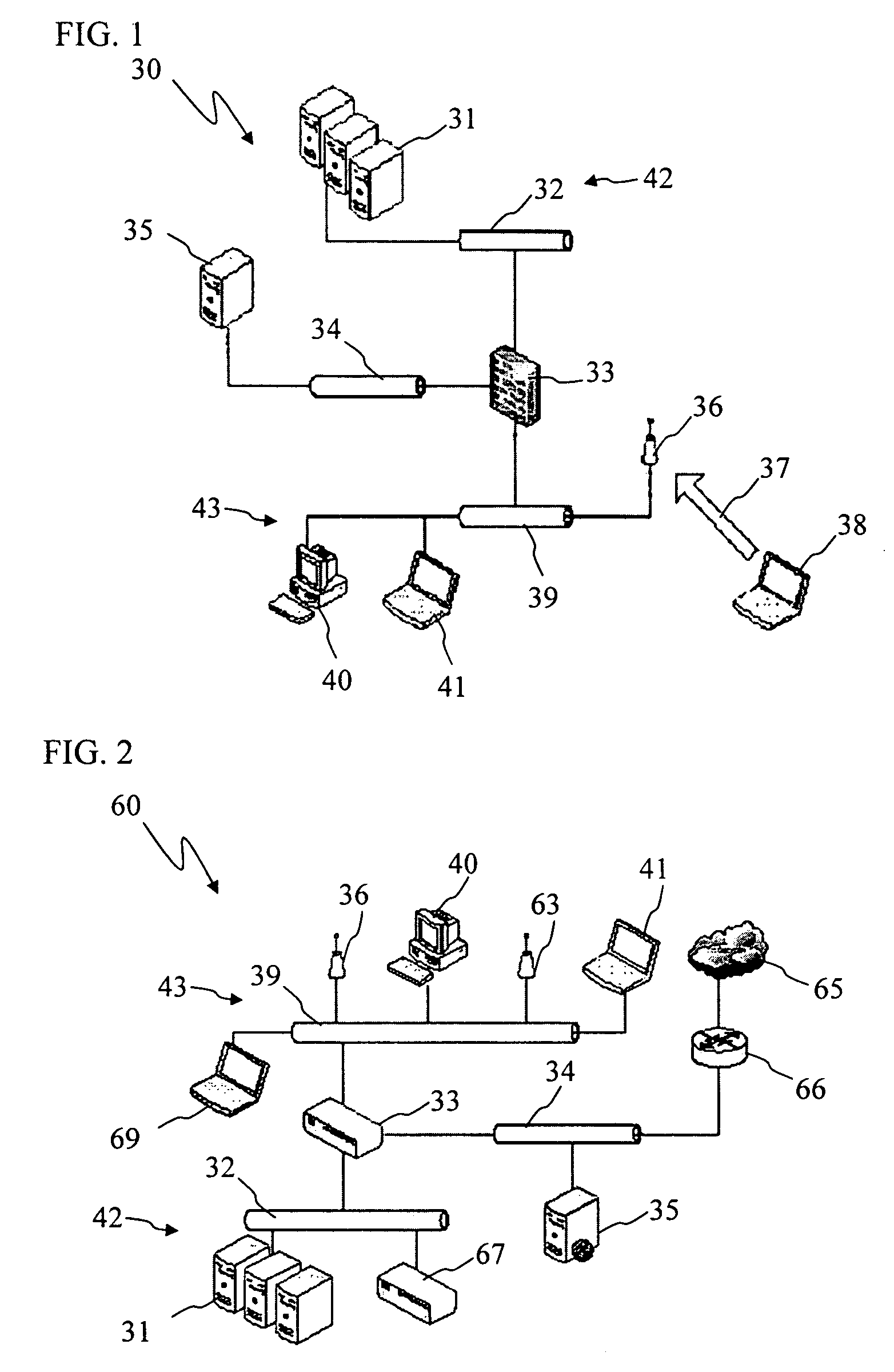
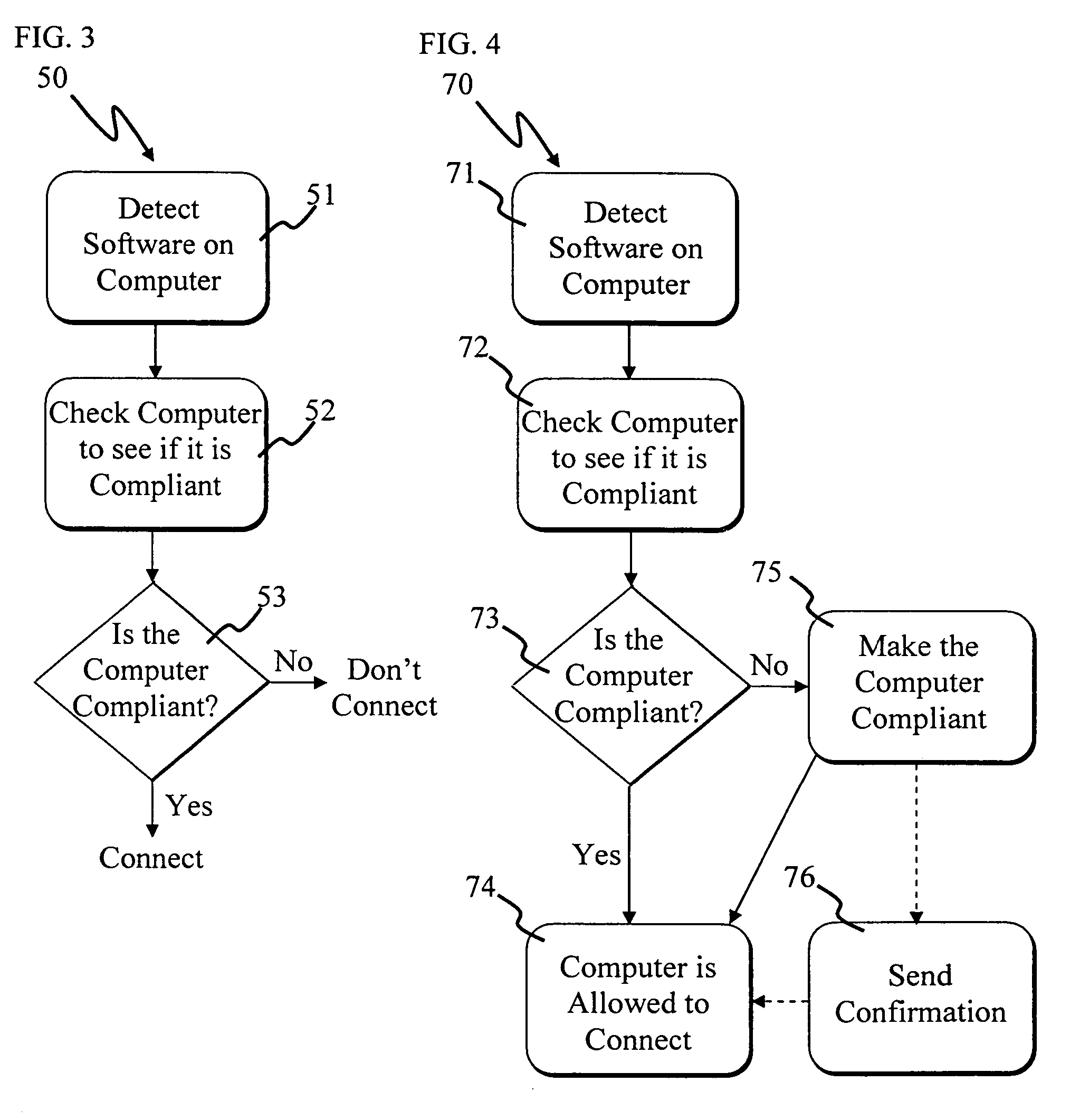
A method includes detecting software installed on a first computer; checking the software to see if it is security compliant; preventing the first computer from communicating with a second computer if the software is security non-compliant; and allowing the first computer to communicate with a third computer, the third computer making the first computer security compliant.
Owner:GORMAN JIM
Personal computer based on wireless human-machine interactive device and method of transmitting data thereof
InactiveUS20050015528A1Secure and reliable data transmissionReduce the burden onDigital data processing detailsSpeech analysisData streamWireless transmission
Method for transmitting data in a personal computer based on wireless human-machine interactive device, comprising at least following steps: inputting event information by user via an external device connected to the wireless human-machine interactive device and; capturing the information stream by host system and stimulating burst the event received from input of user; converting and compressing the image and voice data of the burst event by host system, and transmitting to interactive device in manner of wireless; the wireless interactive device reverts the data stream and outputs to display and voice device. The host system is separated from display device and external device, the transmission manner is wireless and the transmission is security and credibility. The burden of network is low and architecture is flexible. The strong function of software and hardware of computer host can be fully used for providing mobile official business and wireless entertainment to users. The radio of performance and price is high and easy to extend for new application of wireless multimedia.
Owner:LENOVO (BEIJING) CO LTD
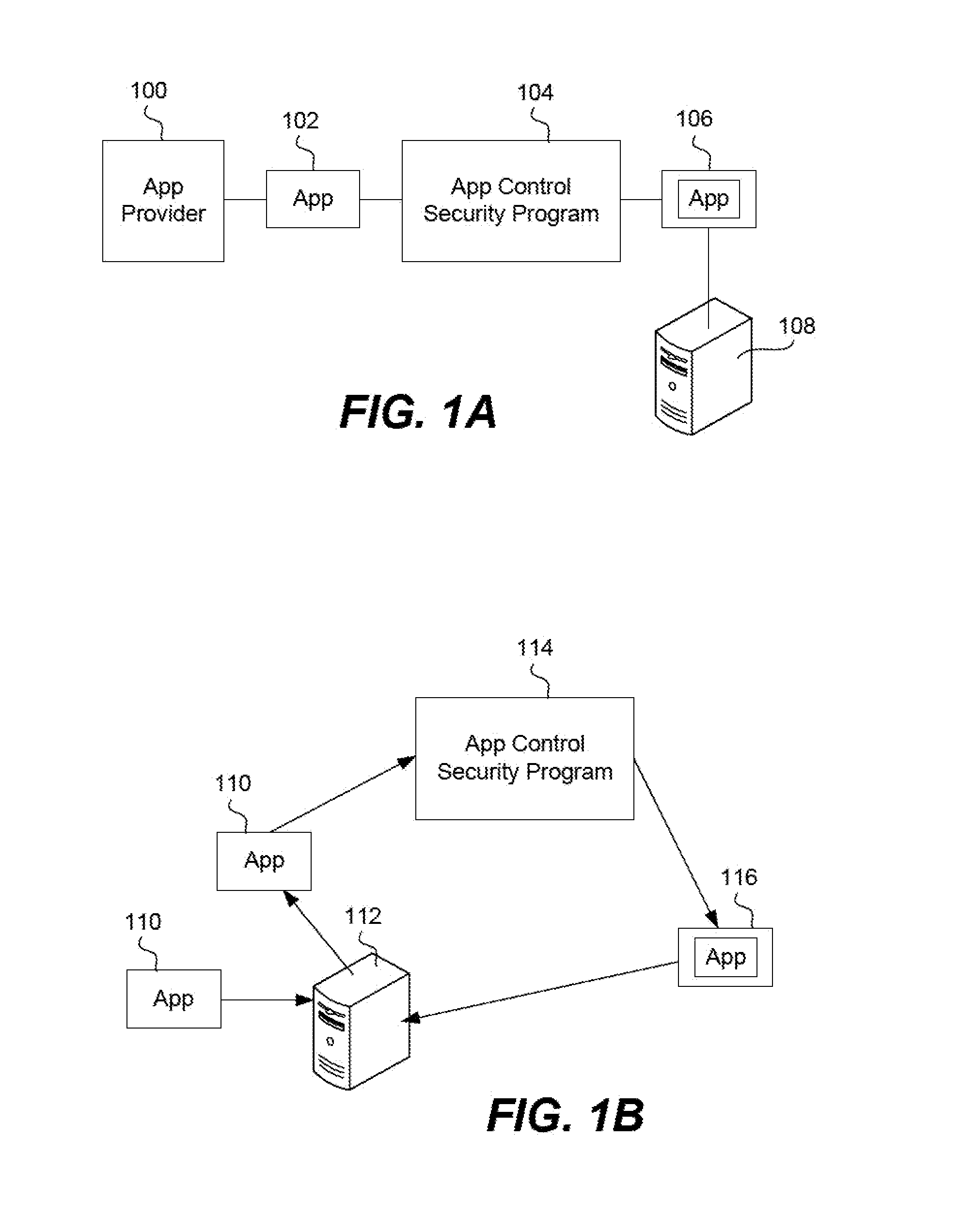
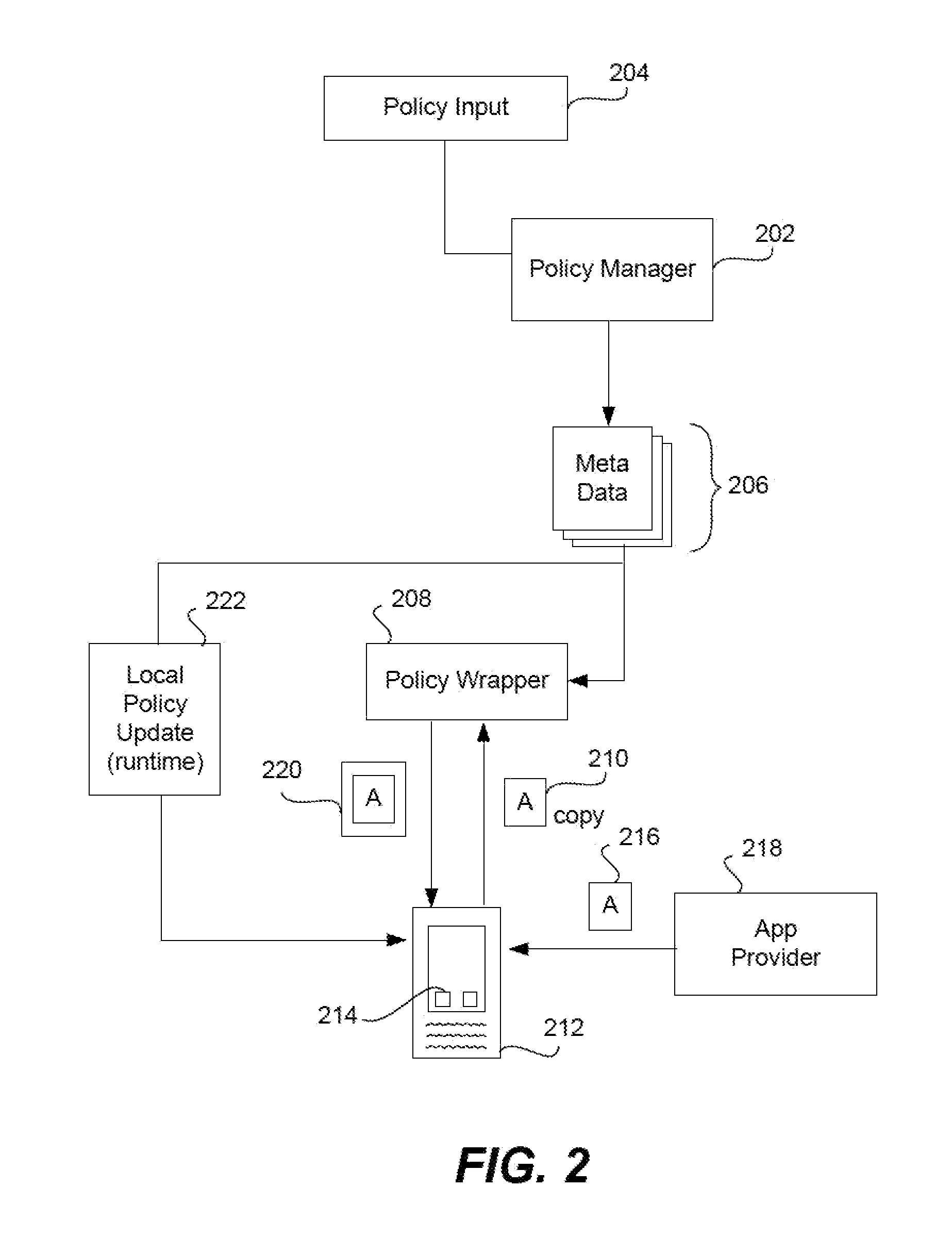
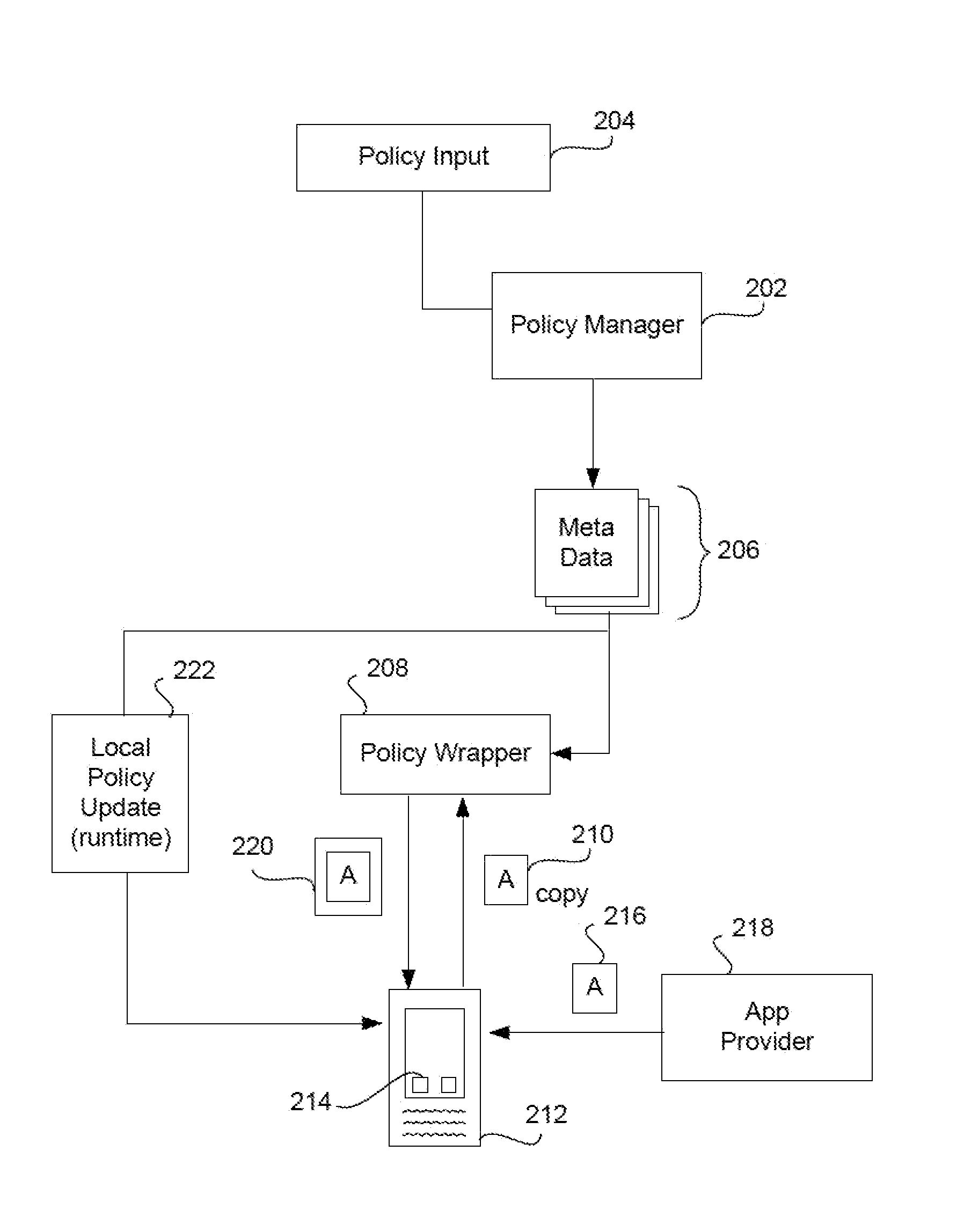
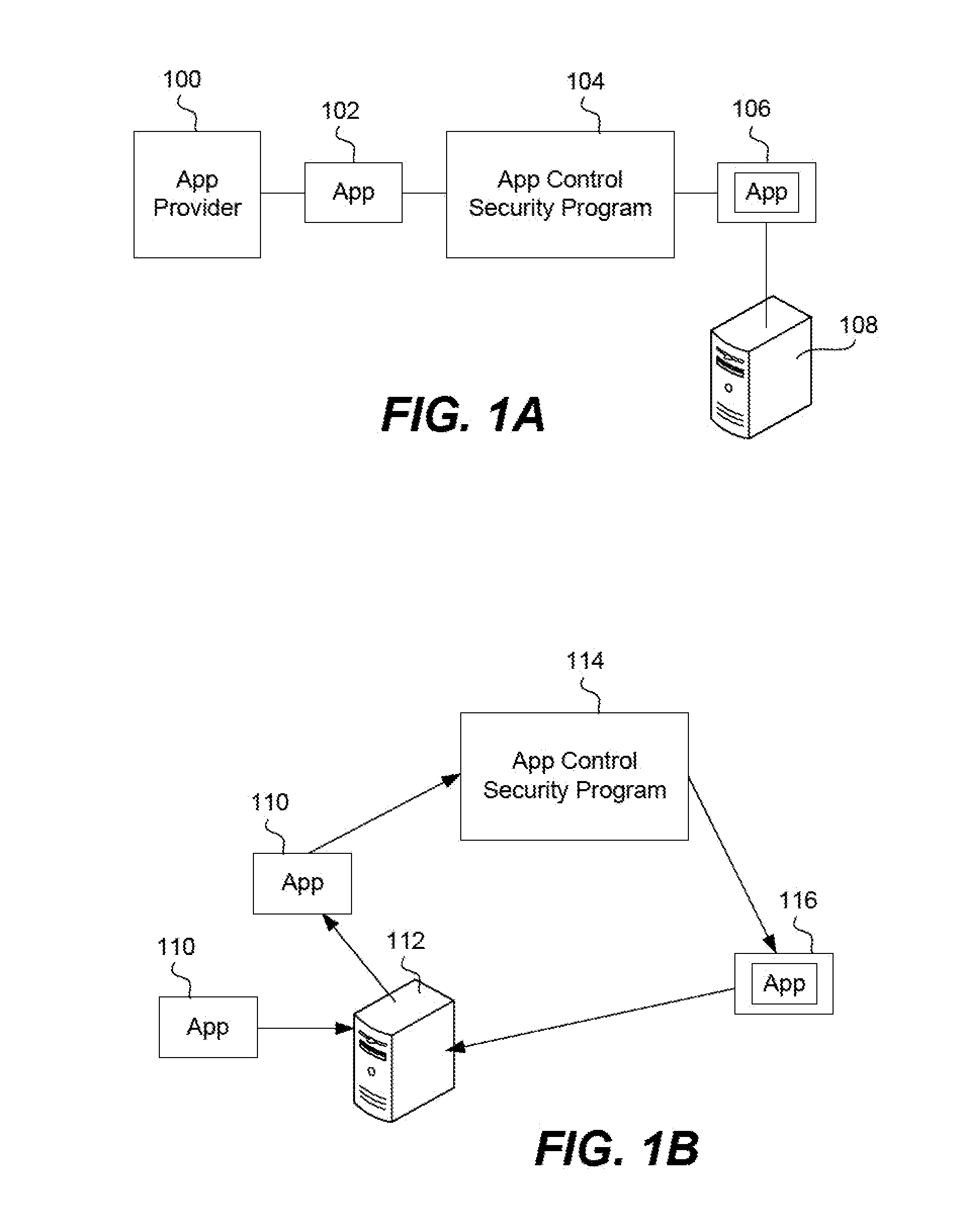
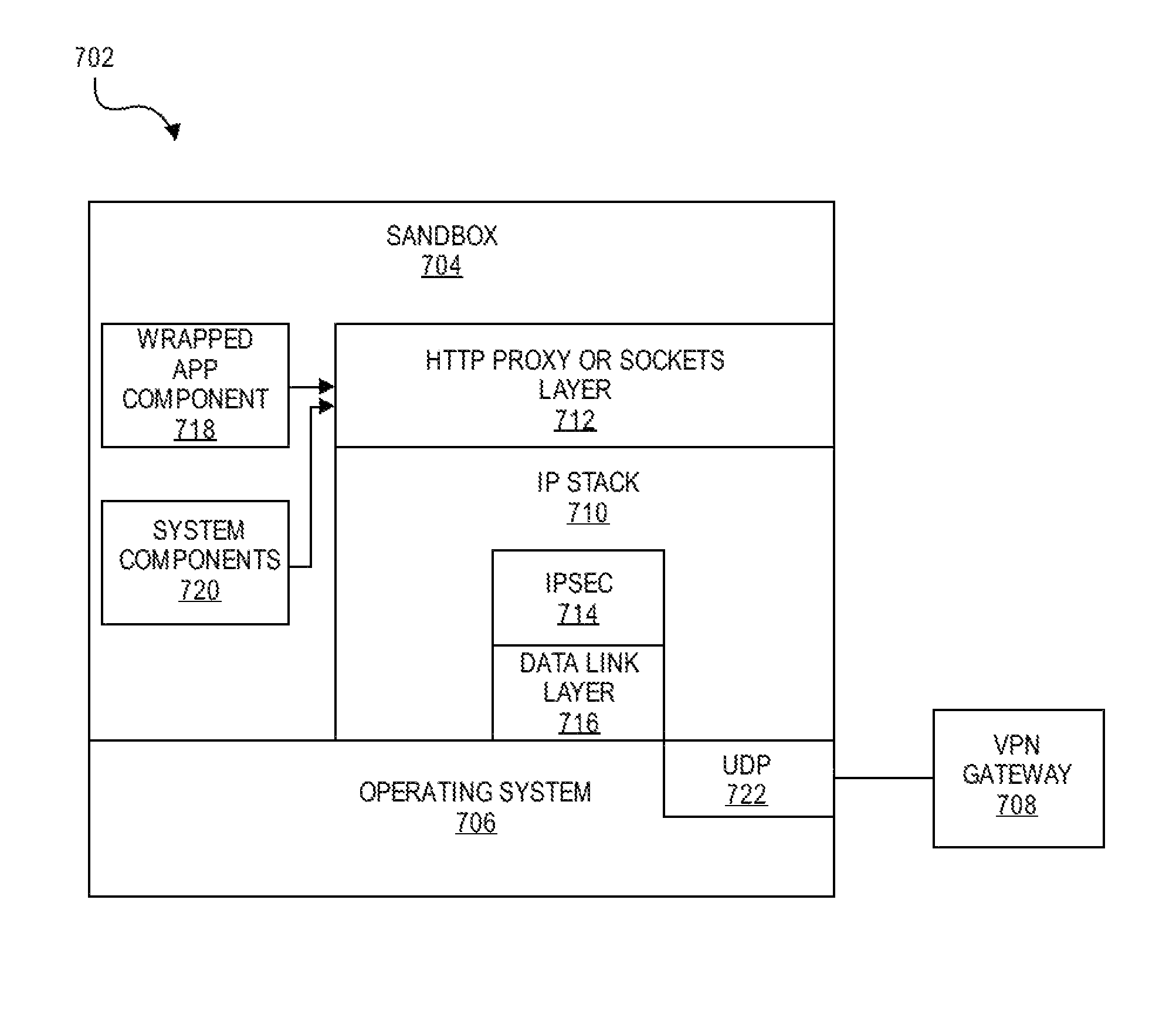
Creating a virtual private network (VPN) for a single app on an internet-enabled device or system
ActiveUS20130247147A1More secureDigital data processing detailsData switching by path configurationComputer hardwareOperational system
An Internet-enabled device, such as a smartphone, tablet, PC, wearable sensor, or household appliance, executes an application (or “app”) has its own VPN connection with a VPN gateway device. The app does not use the device-level or system VPN to connect with the gateway. The app, which may be security wrapped, is made more secure by having its own VPN tunnel with the gateway, wherein the VPN tunnel is not used by other apps running on the device. The conventional (or device-level) VPN connection is not used by the app(s). The app has its own IP stack, an HTTP proxy layer, an IPsec module, and a virtual data link layer which it uses to build IP packets, encapsulate them, and transmit them to a transport module in the device operating system, for example, a UDP module.
Owner:BLUE CEDAR NETWORKS INC
Secure unlocking and recovery of a locked wrapped app on a mobile device
InactiveUS20140040622A1Key distribution for secure communicationUnauthorised/fraudulent call preventionPassphraseApplication software
A security-wrapped app that is locked and inaccessible is unlocked and recovered using a secure and user-friendly protocol. Apps that are security wrapped are passphrase protected. The app security keystore on the device becomes locked. The keystore is encrypted with a recovery key which is only in an encrypted form on the device and cannot be decrypted or otherwise accessed by the user. As such, the user cannot unlock the keystore on the device and therefore is not able to unlock the app. The app can be unlocked using a recovery mechanism that is highly secure in all communications between the mobile device and the service provider server. At the same time the recovery mechanism is easy for the end user to carry out.
Owner:BLUE CEDAR NETWORKS INC
System tools that provides dispatchers in power grid control centers with a capability to make changes
InactiveUS20110029142A1Mechanical power/torque controlData processing applicationsEngineeringUser interface
A system tool provides dispatchers in power grid control centers with a capability to manage changes. A user interface and a plurality of scheduler engines are provided. A comprehensive operating plan has multiple dispatch engines that are security constrained unit commitments and economic dispatch sequences with different look-ahead periods. The comprehensive operating plan is configured to integrate the dispatch engines into a unified scheduling system. The comprehensive operating plan has a data structure for capturing scheduling data, transaction scheduling, load forecast and time series data. The comprehensive operating plan is configured to coordinate scheduling data to and from power grid system applications and present a comprehensive, synchronized and harmonized view of scheduling data to at least one of, applications, power grid system operators and other stakeholders for power grid system operations.
Owner:ALSTOM TECH LTD
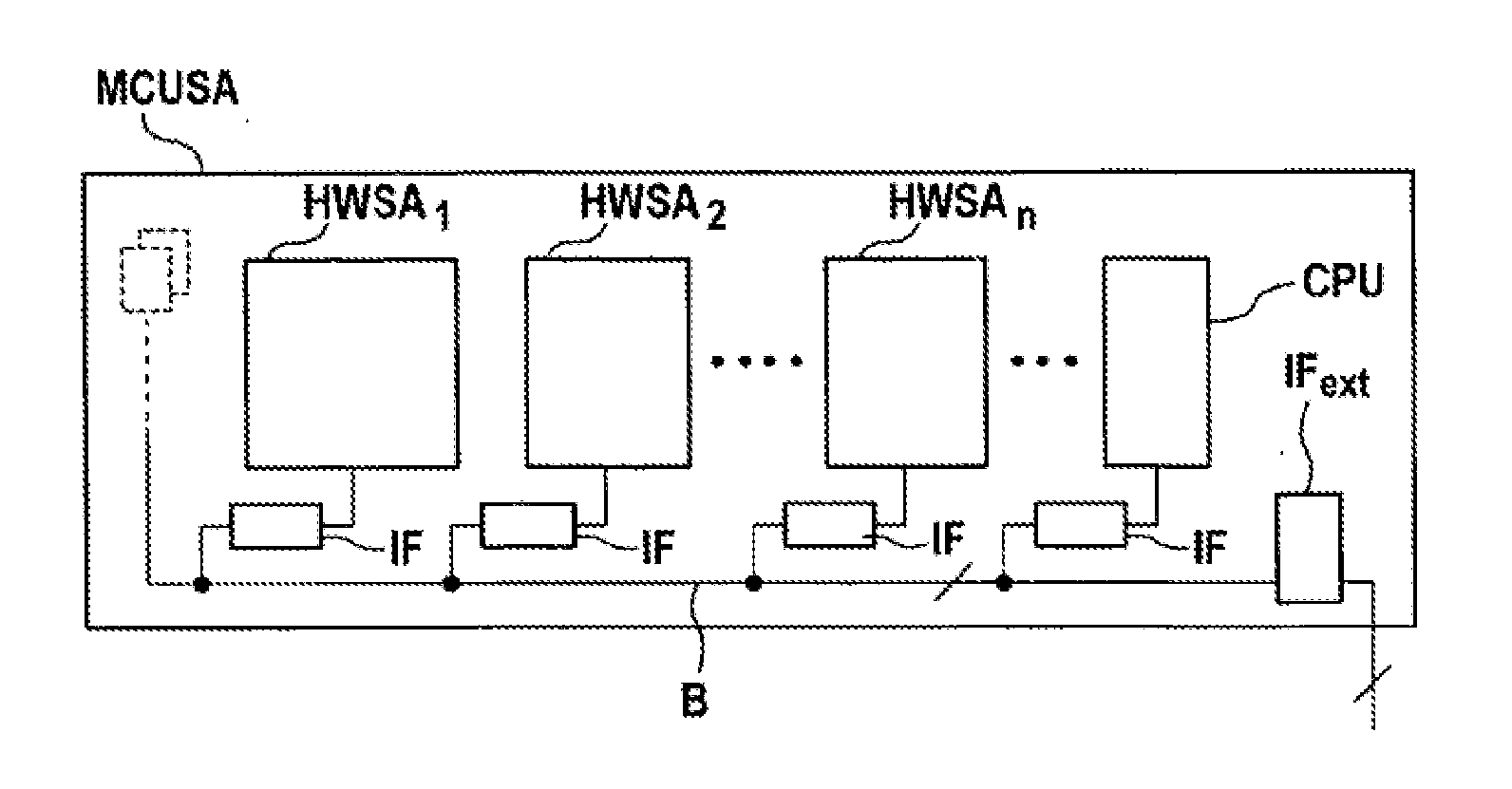
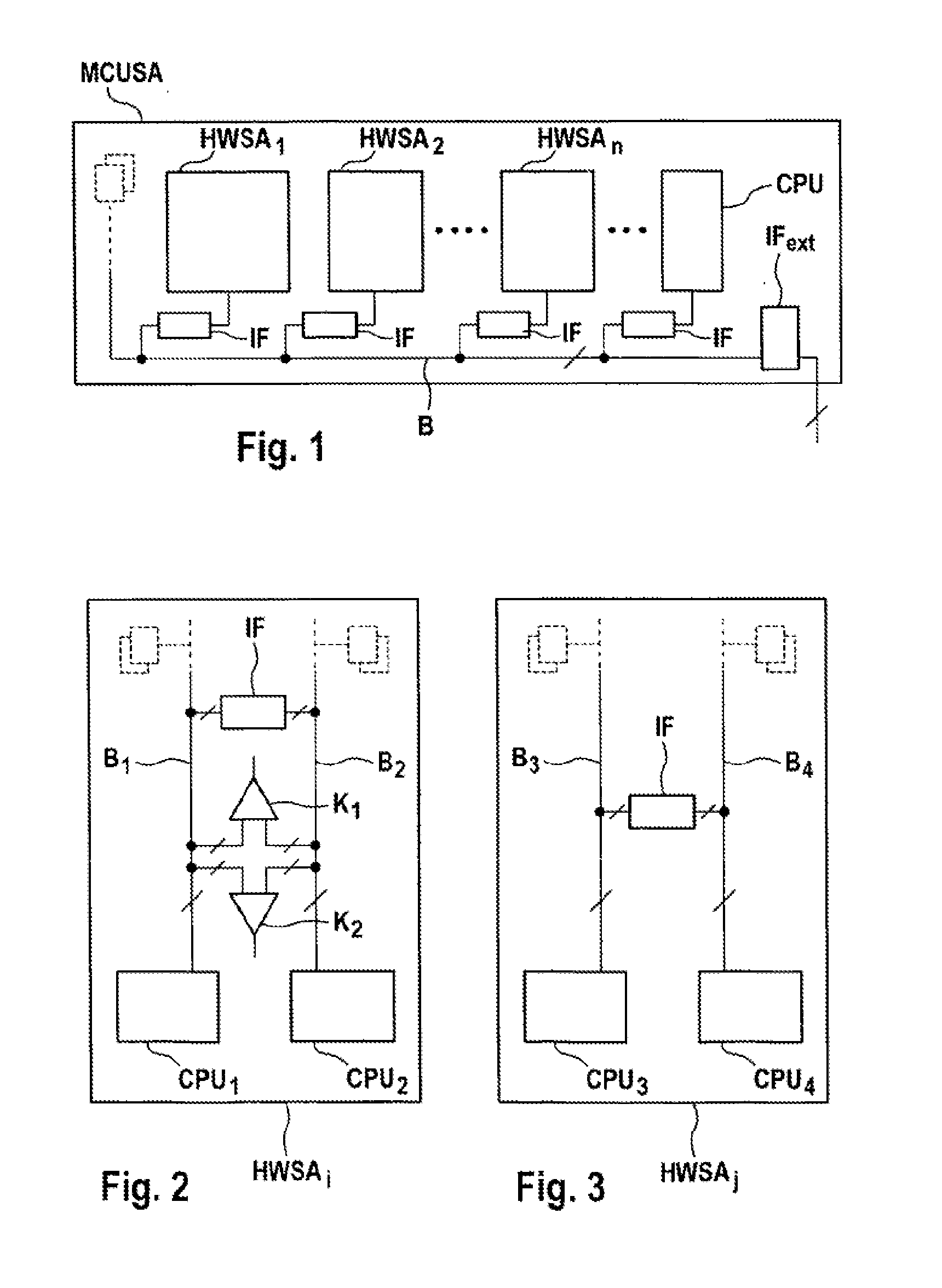
Microprocessor System Having Fault-Tolerant Architecture
InactiveUS20130268798A1Improve robustnessFurther-increased robustnessSafety arrangmentsError avoidanceFault tolerant architectureIntrinsic safety
The invention relates to a microprocessor system for executing software modules, at least some of which are security critical, within the scope of controlling functions or tasks assigned to the software modules, comprising an intrinsically safe microprocessor module having at least two microprocessor cores. At least one further intrinsically safe microprocessor module having at least two microprocessor cores is provided. At least two microprocessor modules are connected via a bus system, at least two software modules are provided which execute functions, at least some of which overlap, the software modules having at least partially overlapping functions are distributed on a microprocessor module or n at least two microprocessor modules, and means for comparing or arbitrating events generated with the software modules for the identical functions are provided in order to detect software or hardware faults.
Owner:CONTINENTAL TEVES AG & CO OHG
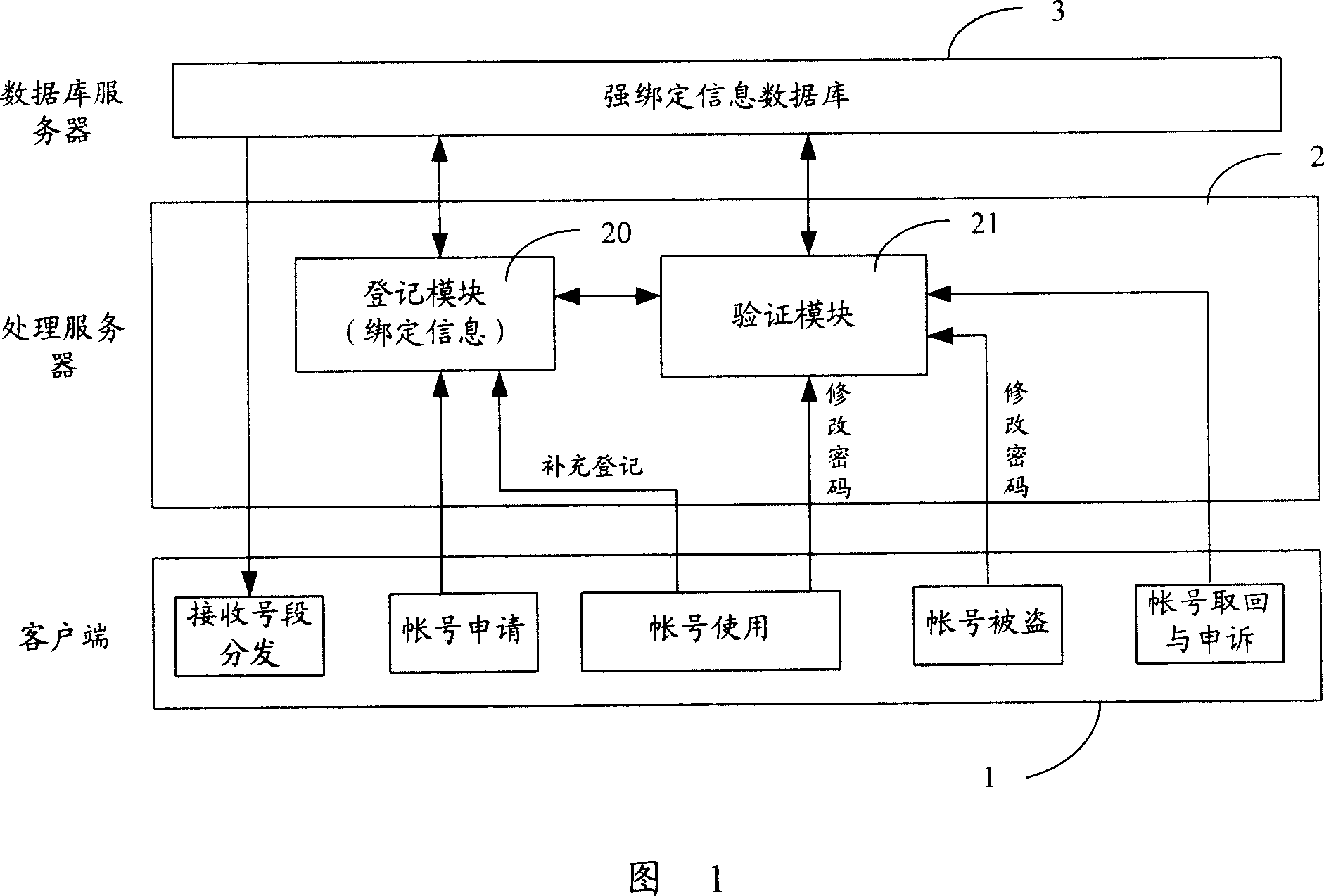
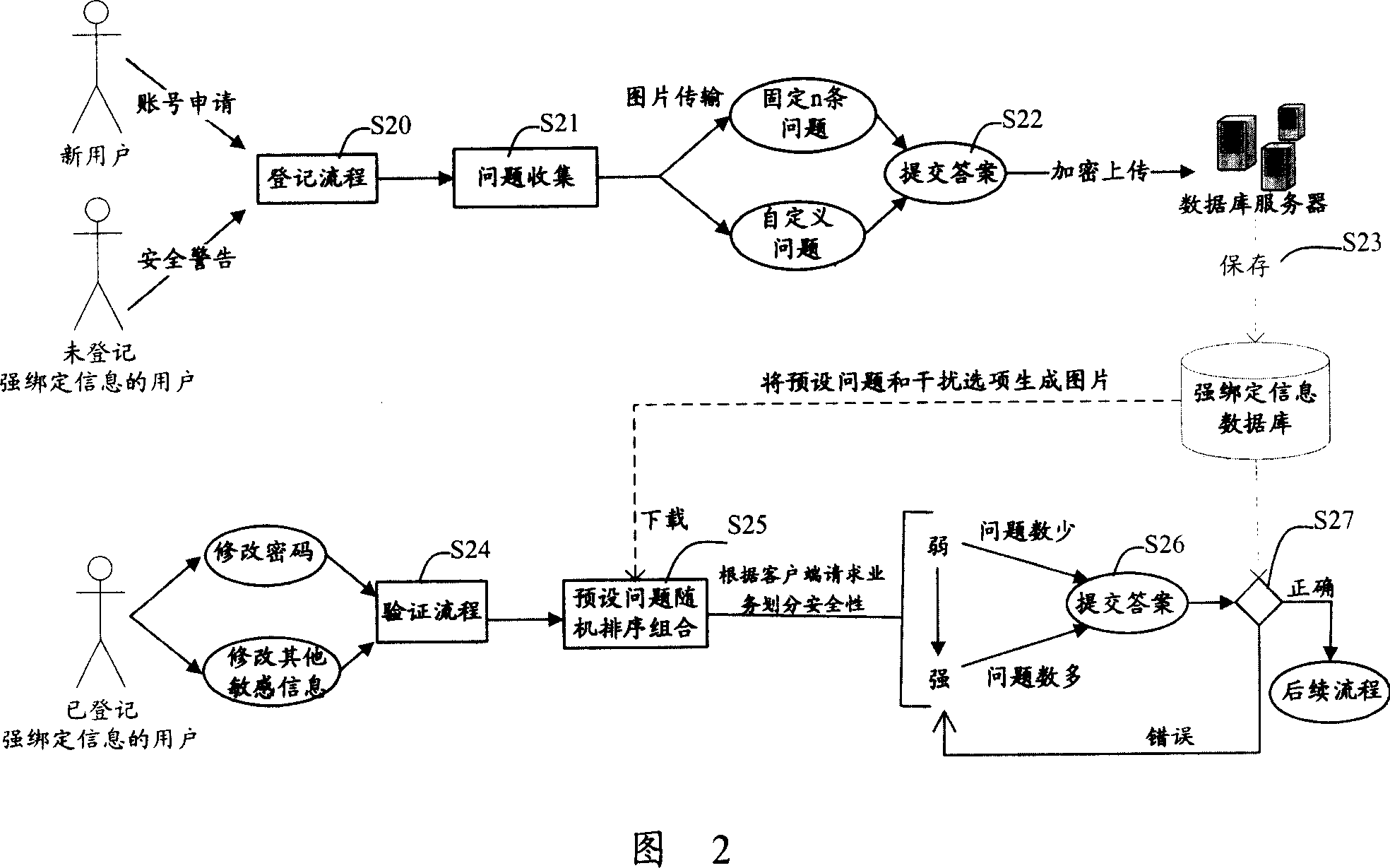
Instant-communication-based accounts security management system and method
ActiveCN101035116ARaise the barLower memory thresholdData switching networksSafety management systemsDatabase server
This invention discloses an account based on the IM security management system, including client, server and database server processing, the server covers the processing server modules at least including a registration and verification module, the processing server modules covers the registration module for the client to receive from the account of the strong bonding registration information, and the strong bonding of the registration information transmitted to the database server; which stores module from the register corresponding to each account of the strong bonding information, the validating modules in the client's business is requested , calling the request of business-grade counterparts bundled information send information generated test to the client, who used to verify the identity of legitimacy. The present invention also provides a real-time communications based on the account of safety management methods. The present invention to improve or revise stolen passwords or sensitive account information threshold; meanwhile, the account holders more easily recover passwords, difficult to verify the information was intercepted, and strong safety.
Owner:TENCENT TECH (SHENZHEN) CO LTD
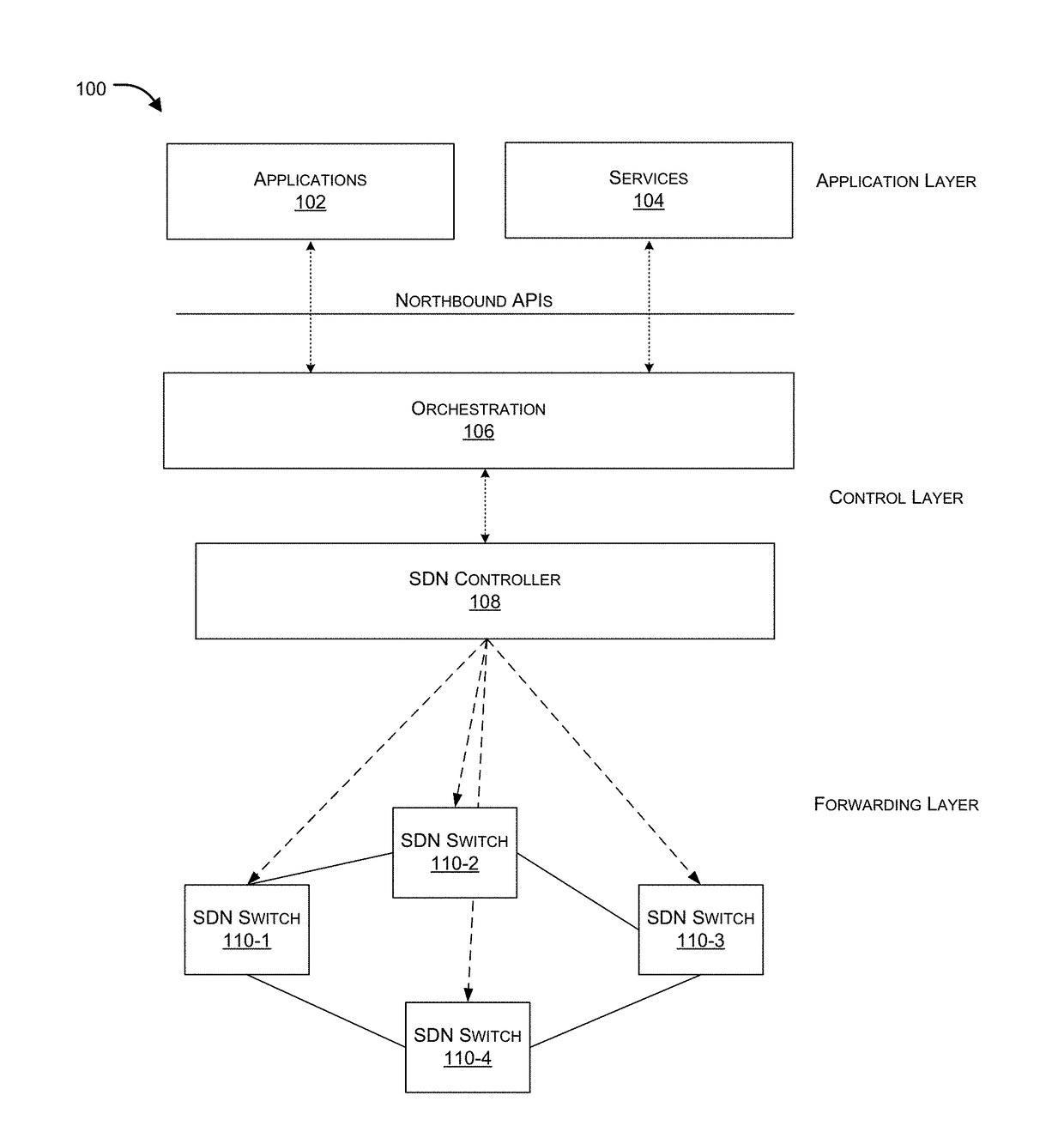
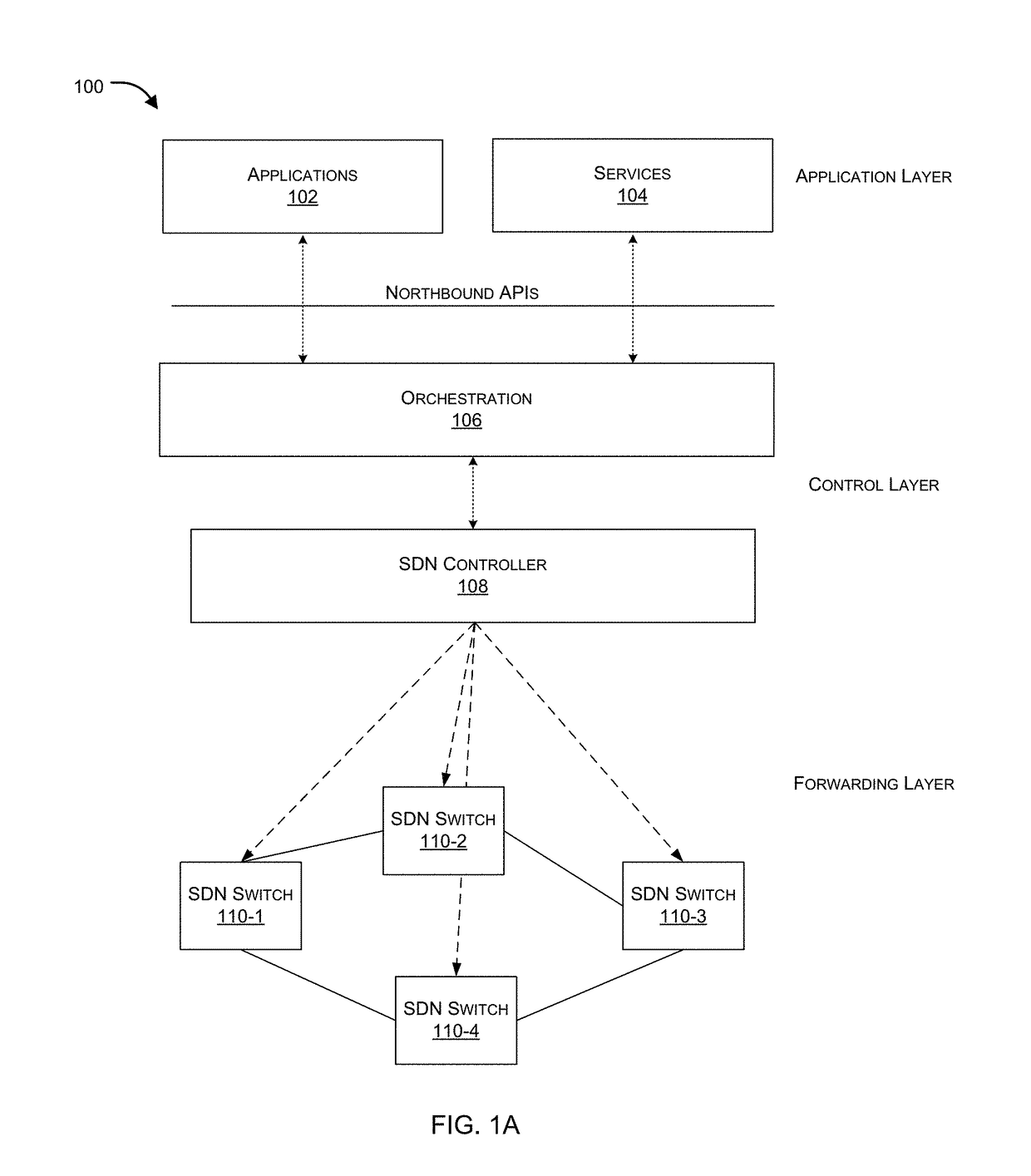
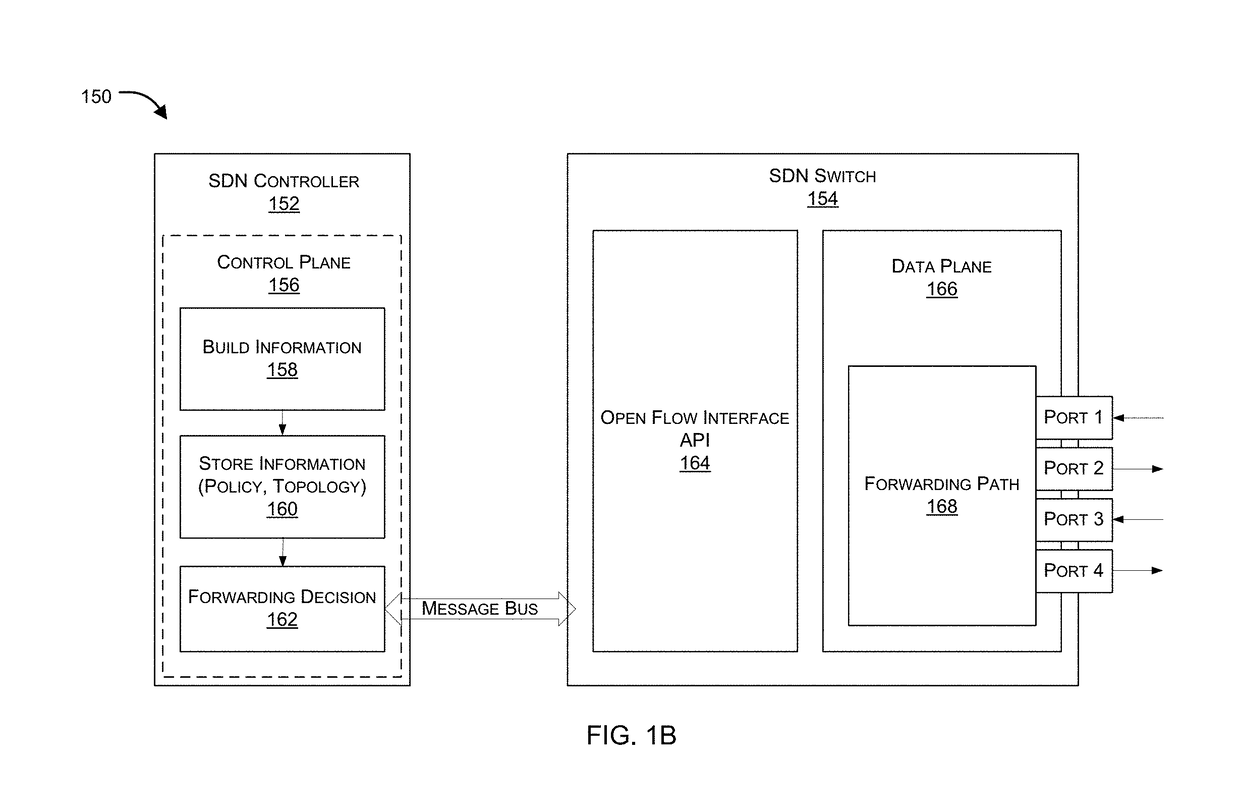
Sequentially serving network security devices using a software defined networking (SDN) switch
Systems and methods for an SDN switch that provides service group chaining for sequentially serving multiple network security devices are provided. According to one embodiment, a packet received by the switch is processed by a first FPU based on a first set of rules and forwarded conditionally to a first security device. The packet is security processed, including dropping it or forwarding it to an egress port or forwarding it to a second FPU. When forwarded to the second FPU, the packet is processed based on a second set of rules by forwarding it to a second security device or dropping it or forwarding it to the egress port. When forwarded to the second security device, the packet is security processed, including dropping it or forwarding it to the egress port or conditionally forwarding it to a third FPU to be sequentially forwarded to a third security device.
Owner:FORTINET
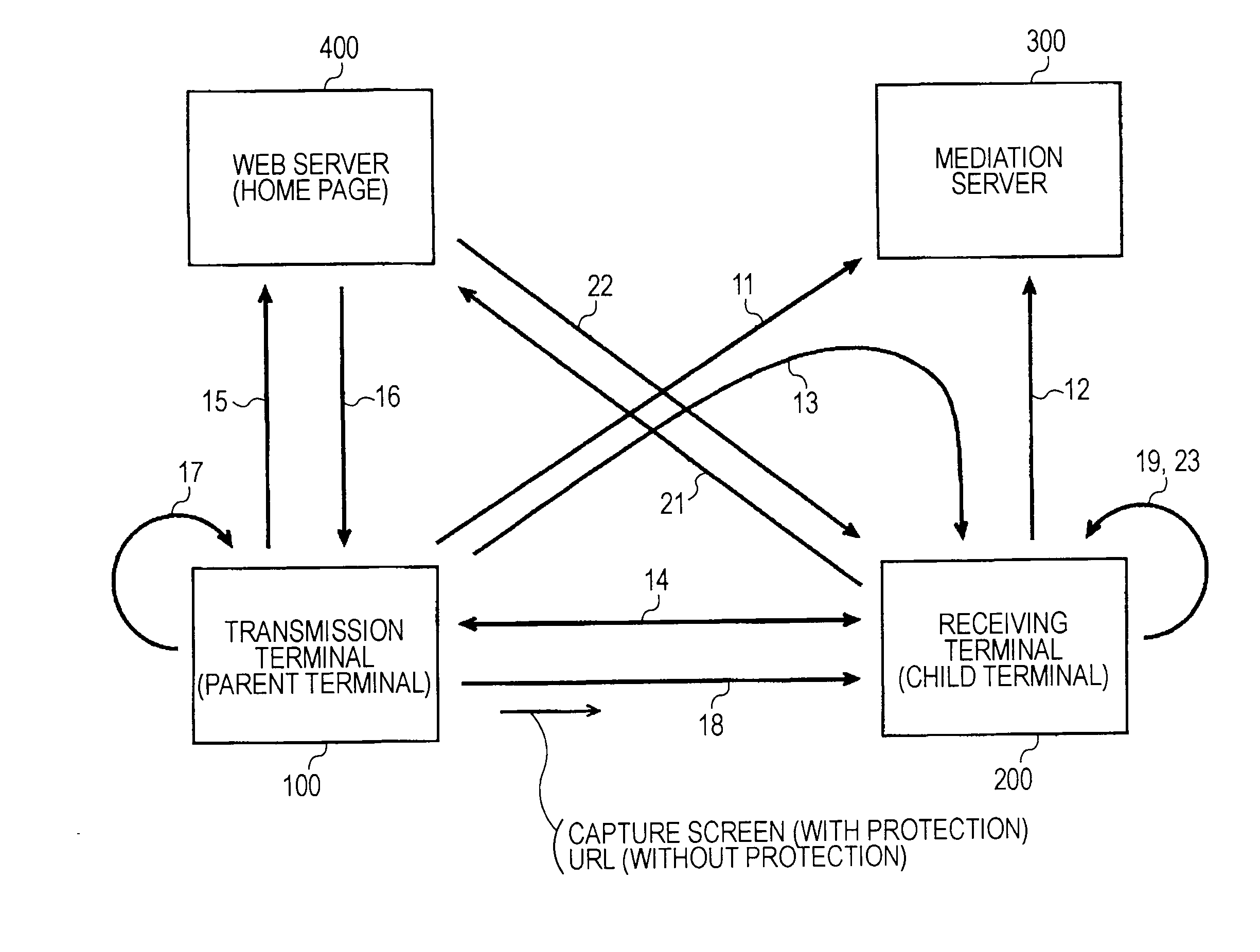
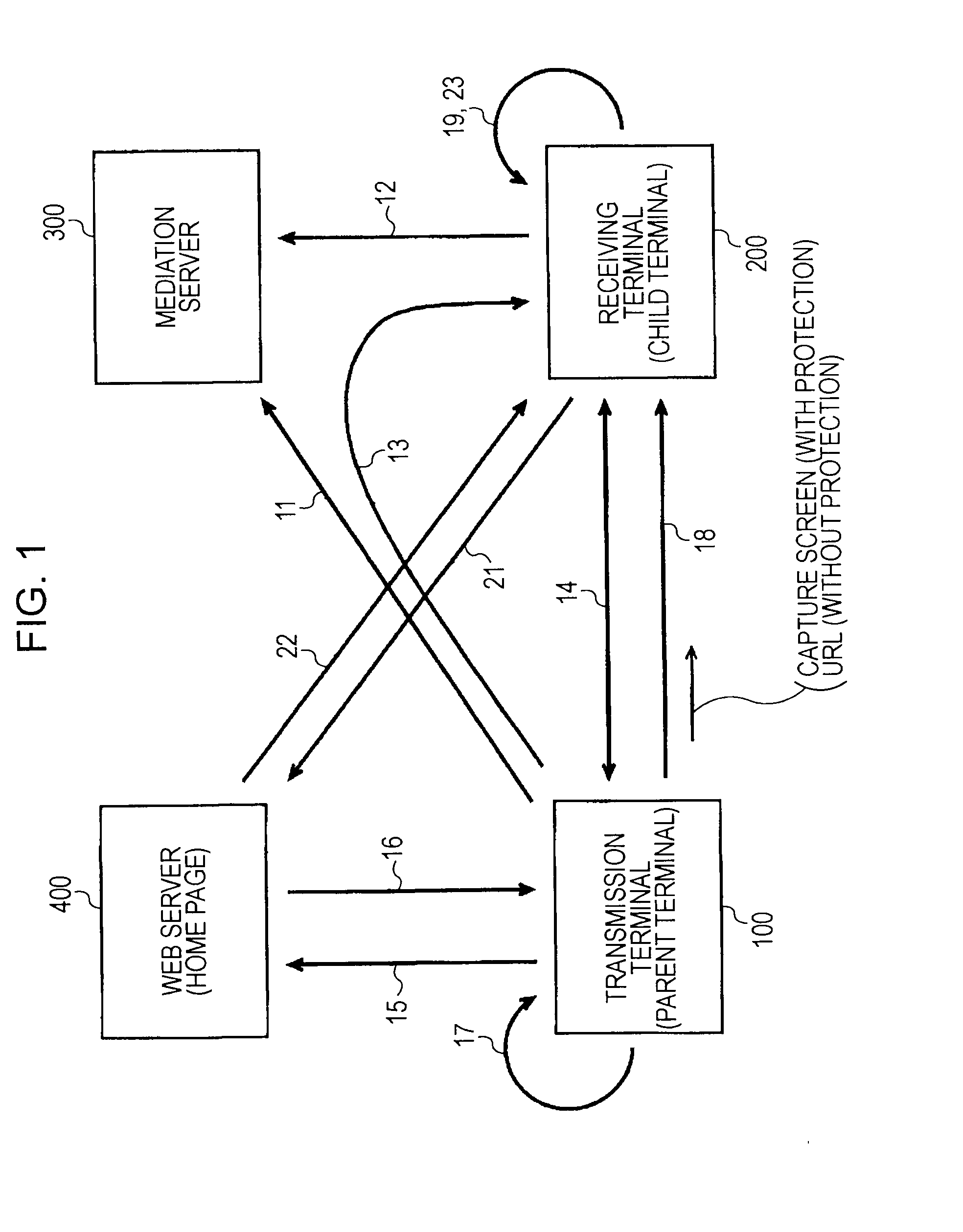
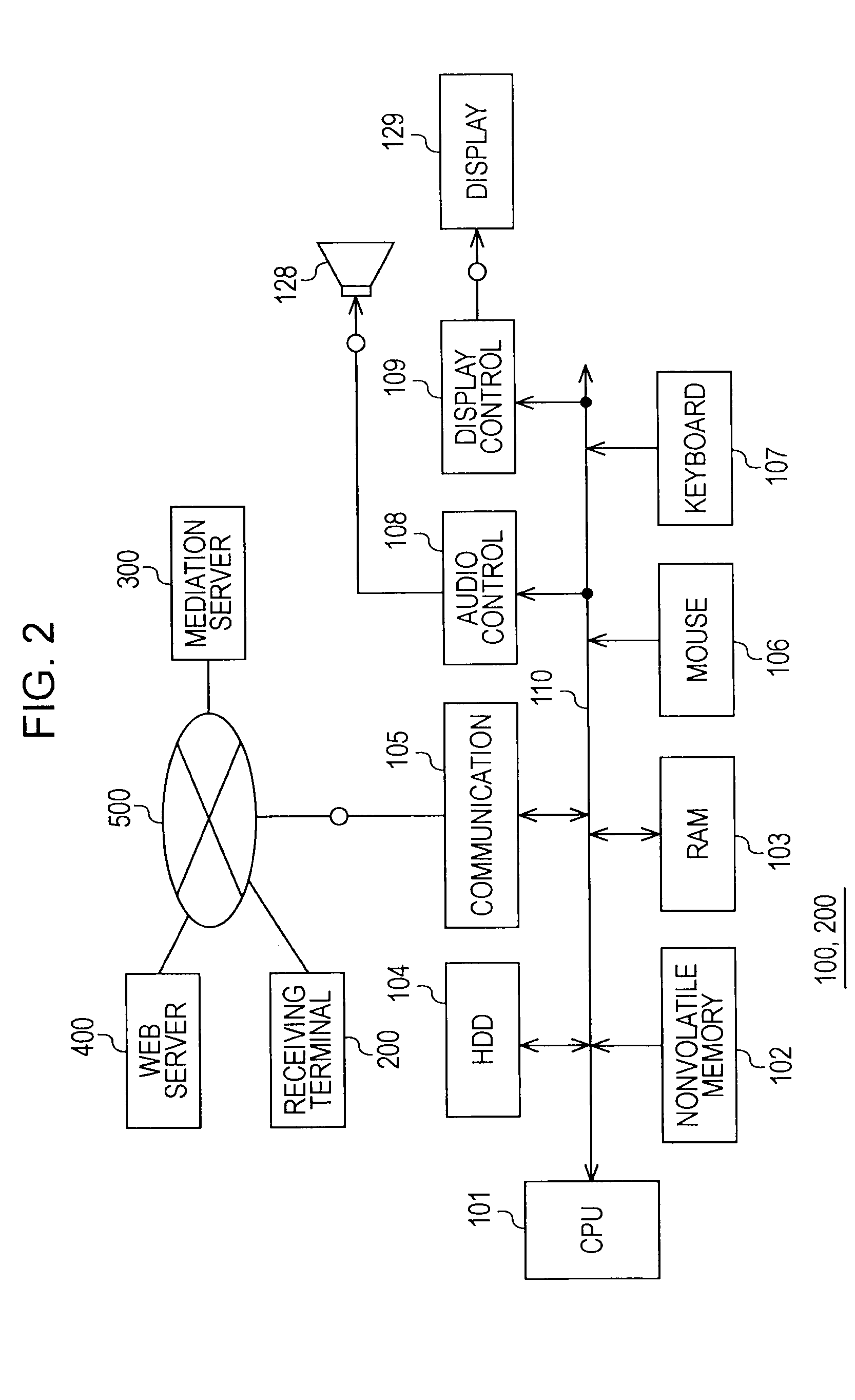
Web-screen sharing system, web-screen sharing terminals, and sharing program thereof
InactiveUS20090119602A1Multiple digital computer combinationsInternal/peripheral component protectionScreen sharingUniform resource locator
A Web-screen sharing system including a first and a second terminals, and a mediation server. The system includes: the terminals exchanging addresses through the mediation server; connecting the terminals using the addresses; when the first terminal is connected to any Web server, detecting whether a content in the Web server is security-protected; if protected, performing predetermined authentication processing with the Web server; when the authentication is successful, the Web server transmitting a content following the authentication processing to the first terminal; the first terminal displaying the content as a Web screen, and capturing the Web screen; transmitting an image file of the Web screen to the second terminal to display the screen on the second terminal, if not protected, the first terminal receiving the content from the Web server, and transmitting a URL at that time to the second terminal to display the Web screen.
Owner:SONY CORP
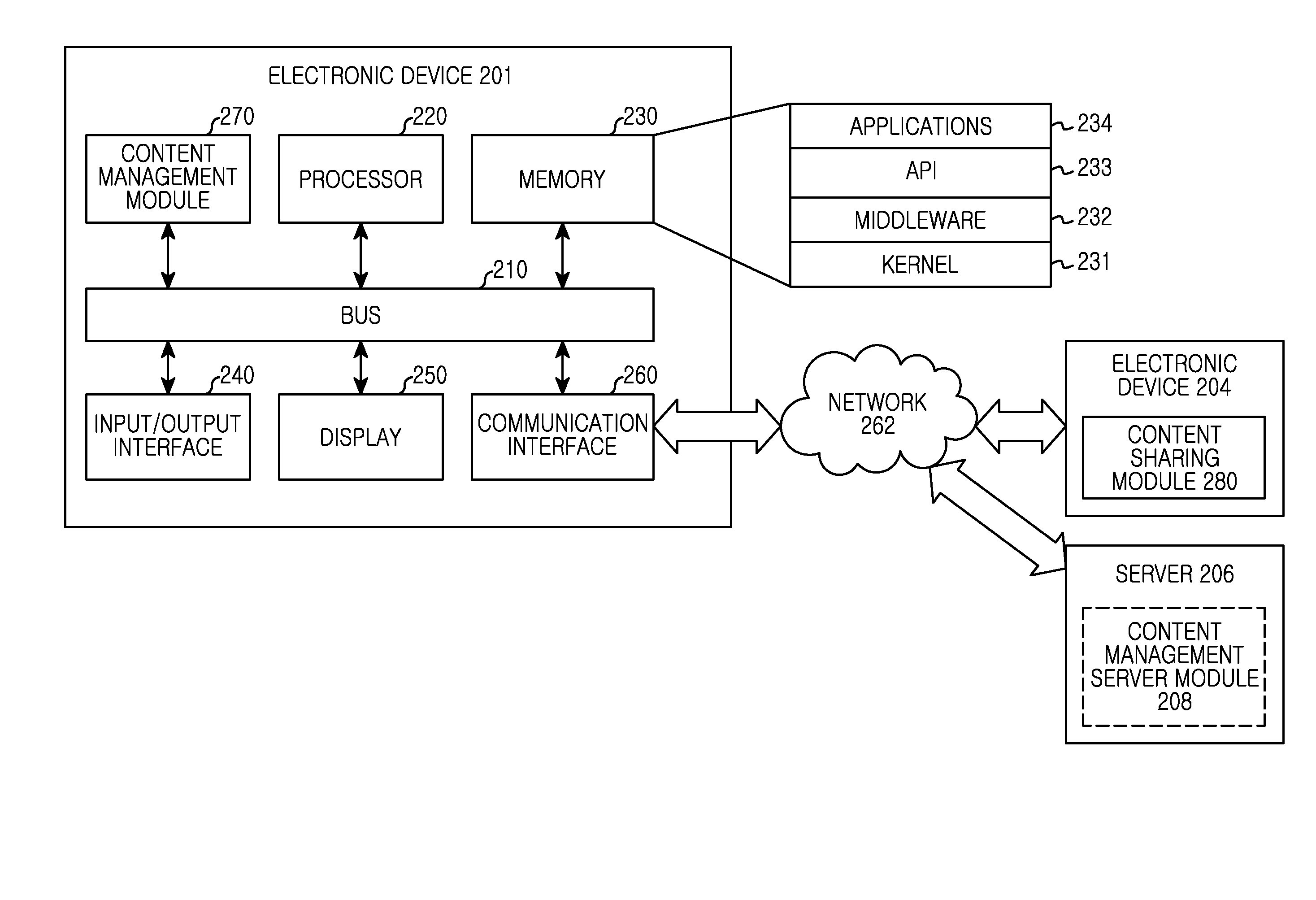
Method and apparatus for sharing content between electronic devices
ActiveUS20150324605A1Key distribution for secure communicationDigital data processing detailsSignal responseComputer network
A method of a first device and an electronic device are provided. The method includes receiving a request signal related to contents stored in the first device from a second device communicatively coupled to the first device; transmitting the contents to the second device in response to the request signal, wherein the contents are security applied contents; and releasing the security of the contents by authenticating a user related to the contents.
Owner:SAMSUNG ELECTRONICS CO LTD
Shipping container monitoring system
InactiveUS20080129493A1Increase probabilityMinimize false alarm rateLogisticsElectric signalling detailsSensor arrayRisk level
The present invention provides a method and apparatus for using a sensor array that detects environmental changes in or around a shipping container. Sensors detect NBC materials and detect tampering with the container (such as broken seals and open doors). The sensors are monitored remotely. The sensors are tracked for determining risk levels and communicating the risks to receiving ports, customs officials, shipping companies, and other interested entities. The sensors can also detect environmental conditions that may be important to the protection of cargo that may not be security-sensitive, but may require special conditions (such as perishable food). The system may categorize cargo into various levels of risk (such as mandatory inspection, occasional inspection, and random inspection).
Owner:FUENTES LAZARO +1
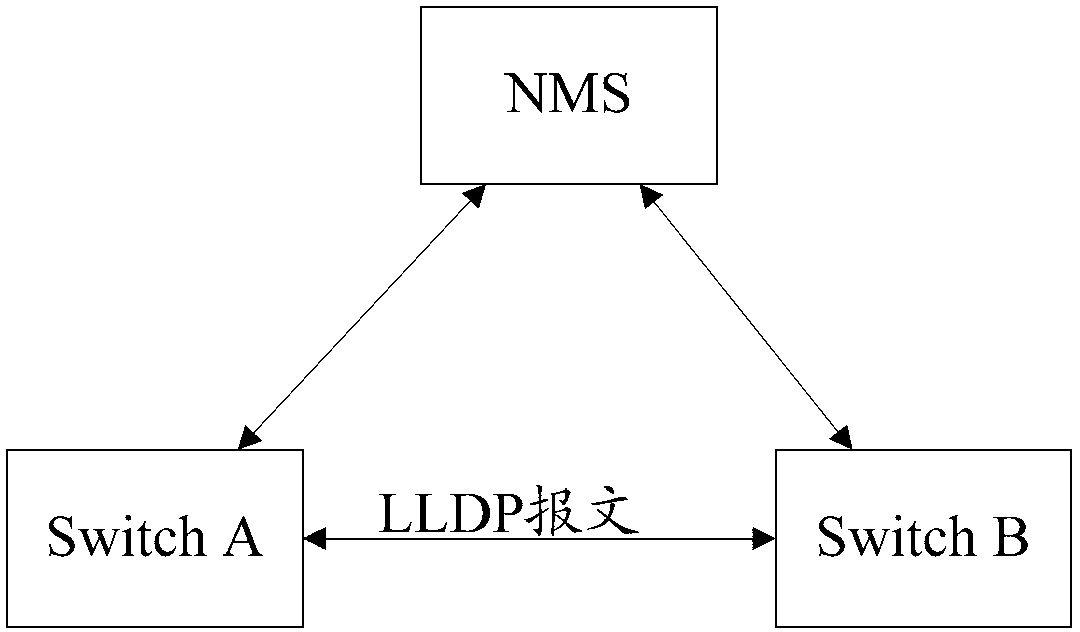
Link discovery method and device
ActiveCN103236941AReduce leakageReduce overheadEnergy efficient ICTHybrid transportDevice typeNetwork management
The invention discloses link discovery method and device, and belongs to the technical field of network management. The link discovery method includes determining security level of a network device according to authentication TLV (type, length and value) when a first LLDP (link layer discovery protocol) message sent by a directly connected device is received by a network device; and if the security level of the network device is security, determining the device type of the directly connected device, and sending a second LLDP message to the directly connected device according to corresponding relationship between the device type of the directly connected device and the TLV. According to the link discovery method, the security level of the network device is determined, when the security level of the network device is security, the device type of the directly connected device is determined, and corresponding TLV is selected to send according to the device type of the directly connected device, so that the situation that all types of TLVs are sent to the directly connected device in the prior art is avoided, possibility of device information linkage is reduced, the sent LLDP message is more reasonable, and link cost is saved.
Owner:HUAWEI TECH CO LTD
Quarantine Method and System
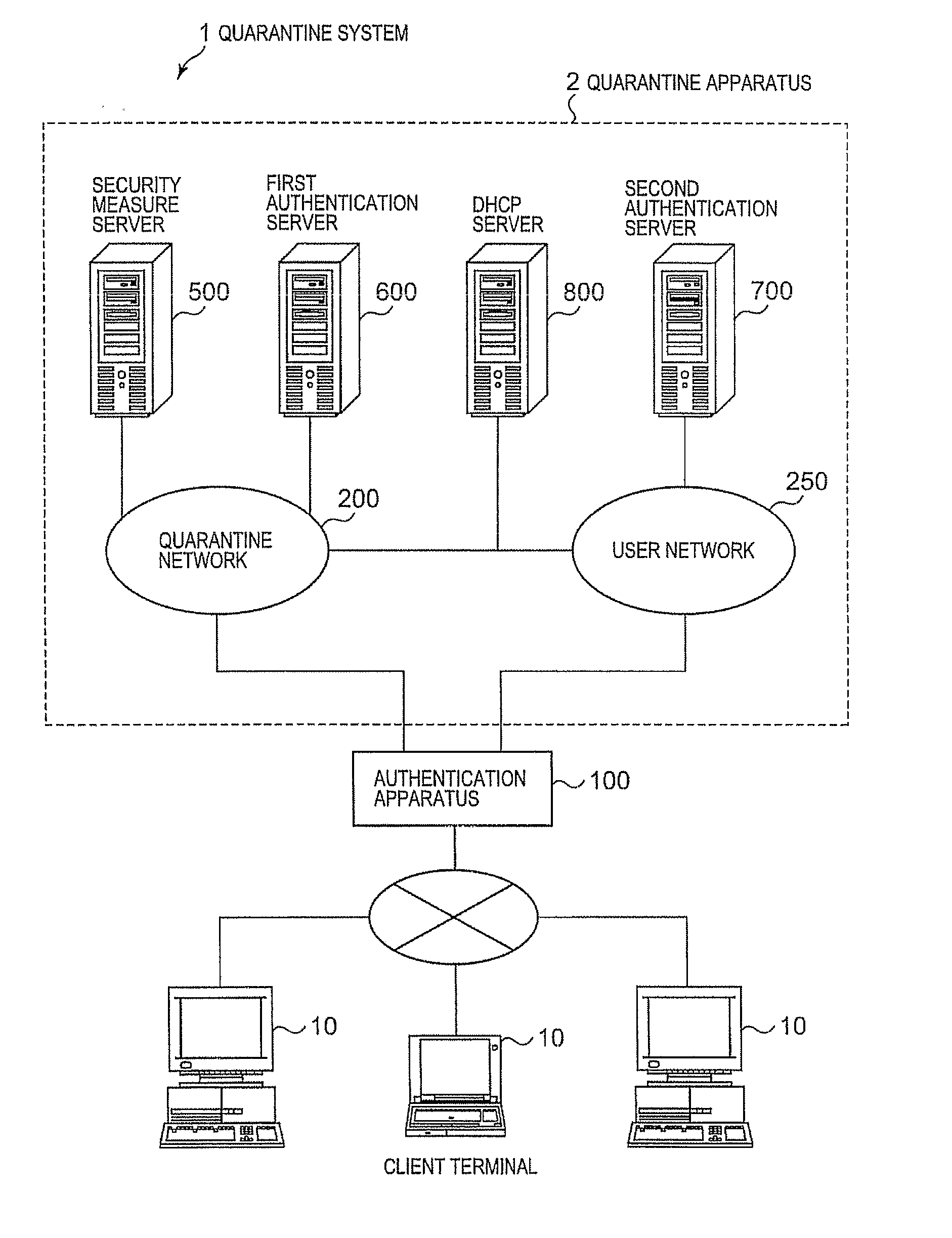
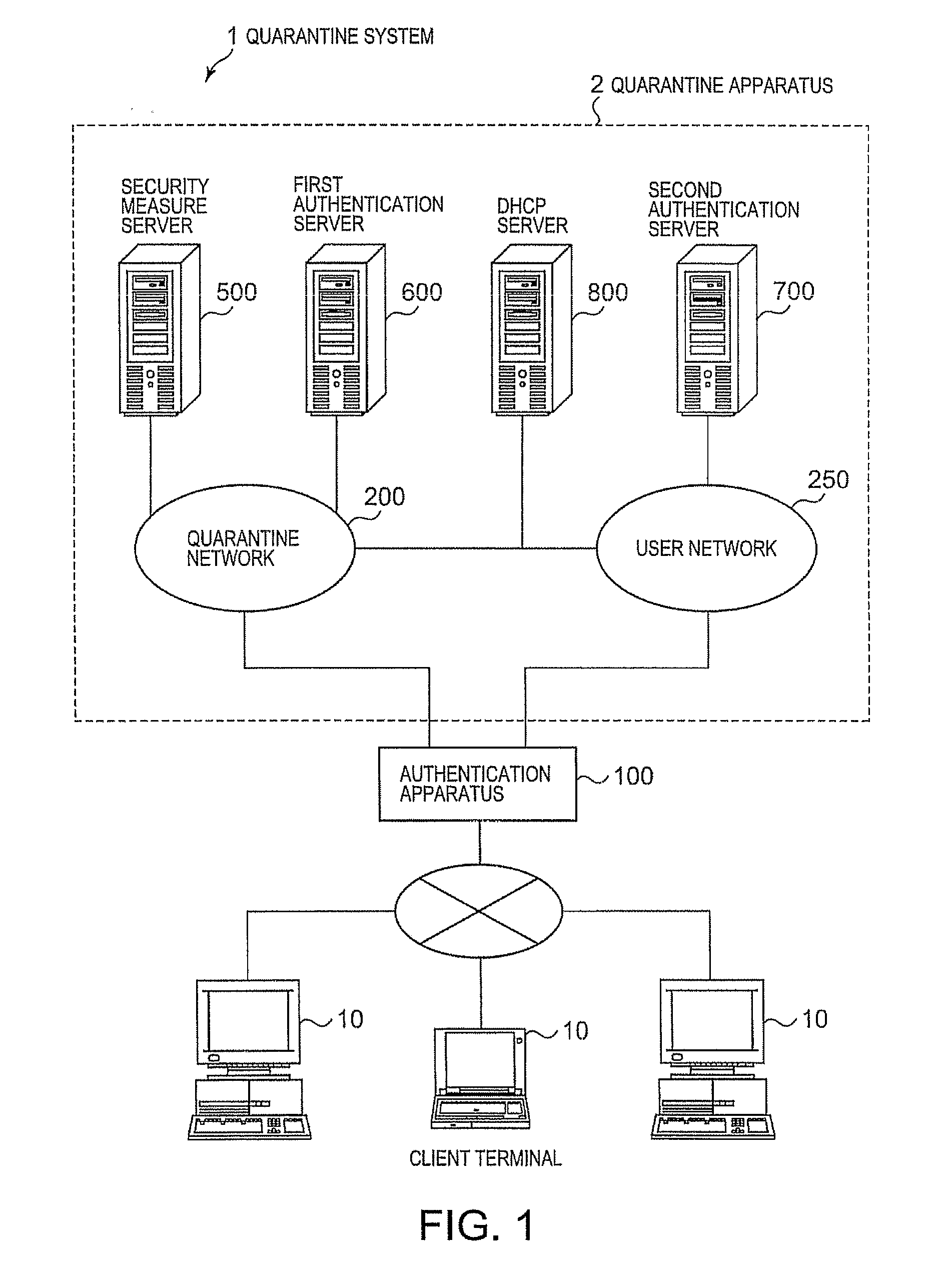
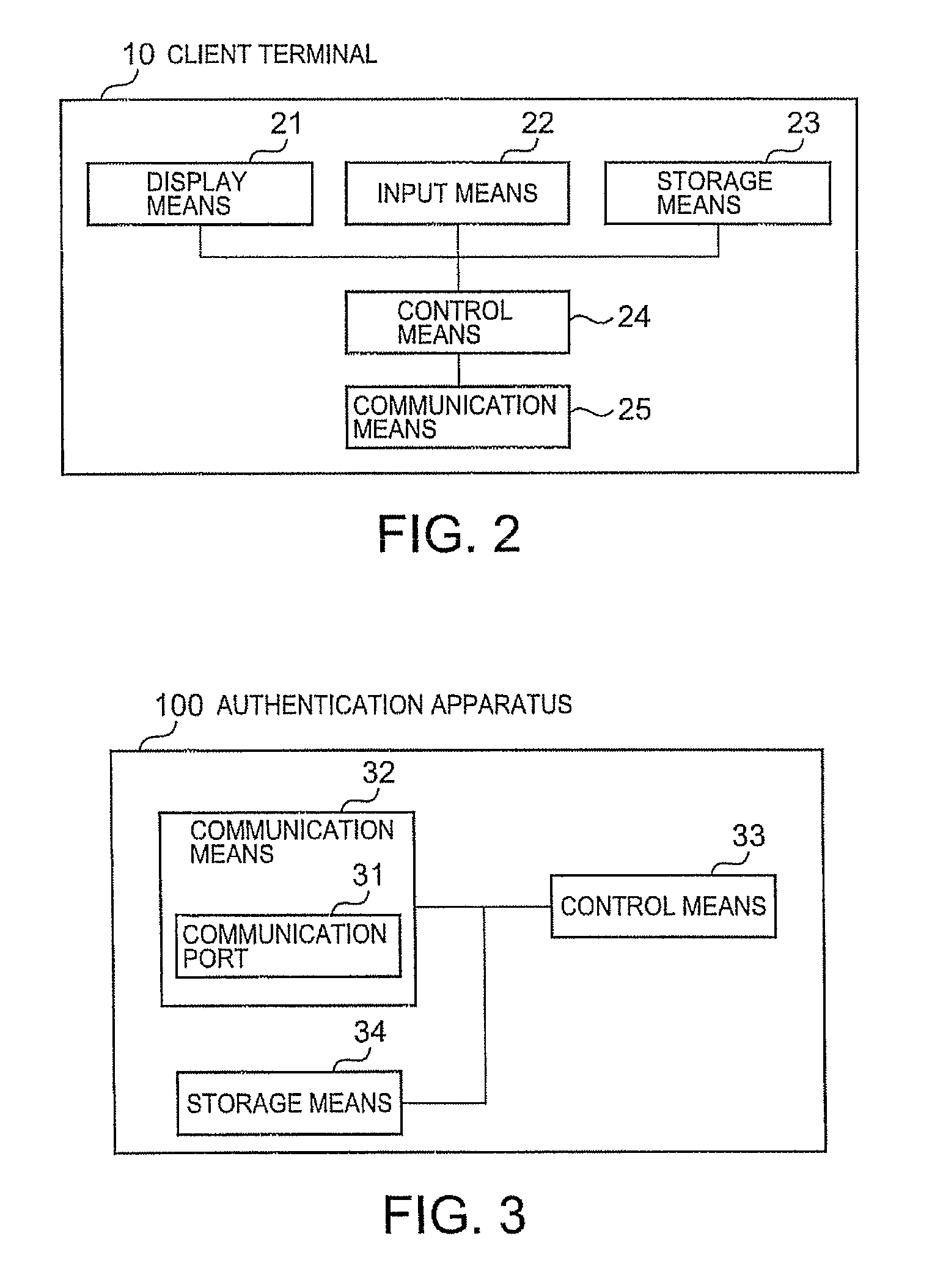
ActiveUS20080040785A1Imposing burdenSatisfy the security levelDigital data processing detailsUser identity/authority verificationSecurity MeasureSecurity check
A quarantine method and system for allowing a client terminal to connect to a user network. An authentication apparatus recognizes that a communication means of the client terminal has been activated. The authentication apparatus is connected to a quarantine network, to the user network, and to the client terminal. The client terminal is permitted to connect to the quarantine network by confirming a common certificate for the client terminal followed by storing the common certificate in the client terminal. The client terminal is security checked to determine whether each check item of a plurality of check items has a violation. For each check item having a violation, a security measure is performed to improve the check item with respect to the violation. The client terminal is allowed to connect to the user network by confirming a user certificate for the client terminal followed by storing the user certificate in the client terminal.
Owner:KYNDRYL INC
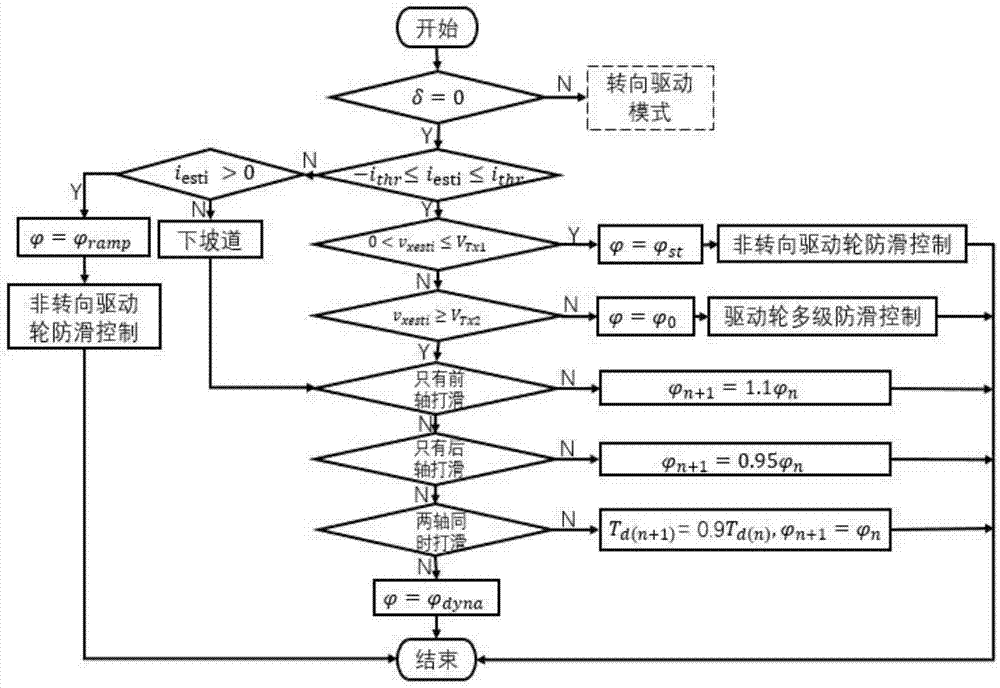
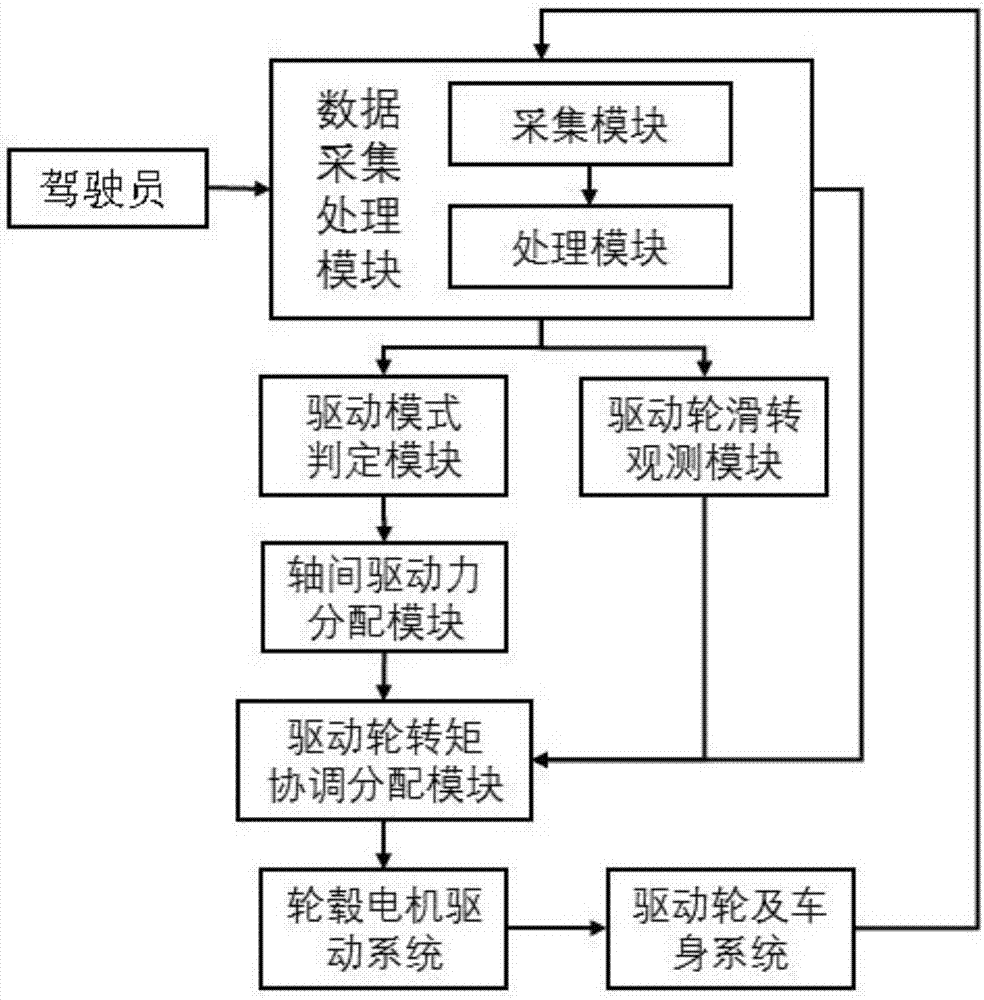
Driving force control method for whole wheel hub motor driving vehicle
InactiveCN107953801AImprove stabilityIncrease profitSpeed controllerElectric devicesMotor driveDrive wheel
Disclosed is a driving force control method for a whole wheel hub motor driving a vehicle, and belongs to the field of vehicle driving force control. The driving force control method for the whole wheel hub motor driving the vehicle comprises the following steps that manipulation information of a driver and operation parameters of the vehicle are collected by a data acquisition and processing module, and pretreatment is carried out, the manipulation information of the driver and parameter information of the vehicle are obtained to be sent to a driving mode determination module, a driving wheeltrackslip observation module, and a driving wheel torque coordination allocation module; turning intention of the driver is determined and an target torque obtained by the driver driving pedals is analyzed; a driving cycle of the vehicle is determined according to operation information of the vehicle, according to the purpose of driving control under each working condition is security or dynamicproperty to determine driving force control targets, and driving force control methods such as limiting the target torque, adjusting diving force allocation of a front shaft and a rear shaft, and driving skid resistance are reasonably used. The driving force control method for the whole wheel hub motor driving the vehicle aims to overcome the problem that an existing wheel hub motor fails to achieve good coordination and control to lead to reduction of practicability, and the applicability of the existing vehicles driven by a wheel hub motor.
Owner:JILIN UNIV
Creating a virtual private network (VPN) for a single app on an internet-enabled device or system
ActiveUS8990920B2Digital data processing detailsData switching by path configurationOperational systemPrivate network
An Internet-enabled device, such as a smartphone, tablet, PC, wearable sensor, or household appliance, executes an application (or “app”) has its own VPN connection with a VPN gateway device. The app does not use the device-level or system VPN to connect with the gateway. The app, which may be security wrapped, is made more secure by having its own VPN tunnel with the gateway, wherein the VPN tunnel is not used by other apps running on the device. The conventional (or device-level) VPN connection is not used by the app(s). The app has its own IP stack, an HTTP proxy layer, an IPsec module, and a virtual data link layer which it uses to build IP packets, encapsulate them, and transmit them to a transport module in the device operating system, for example, a UDP module.
Owner:BLUE CEDAR NETWORKS INC
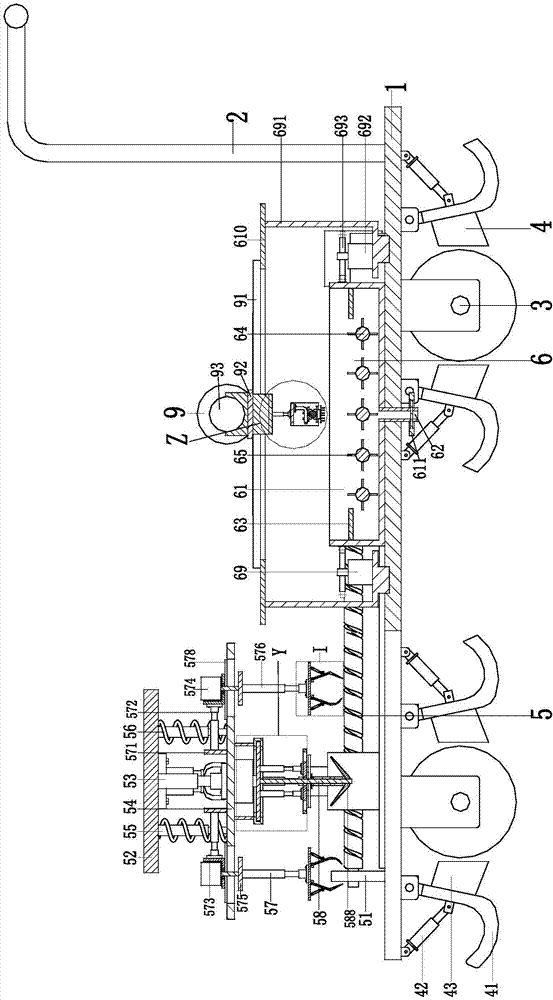
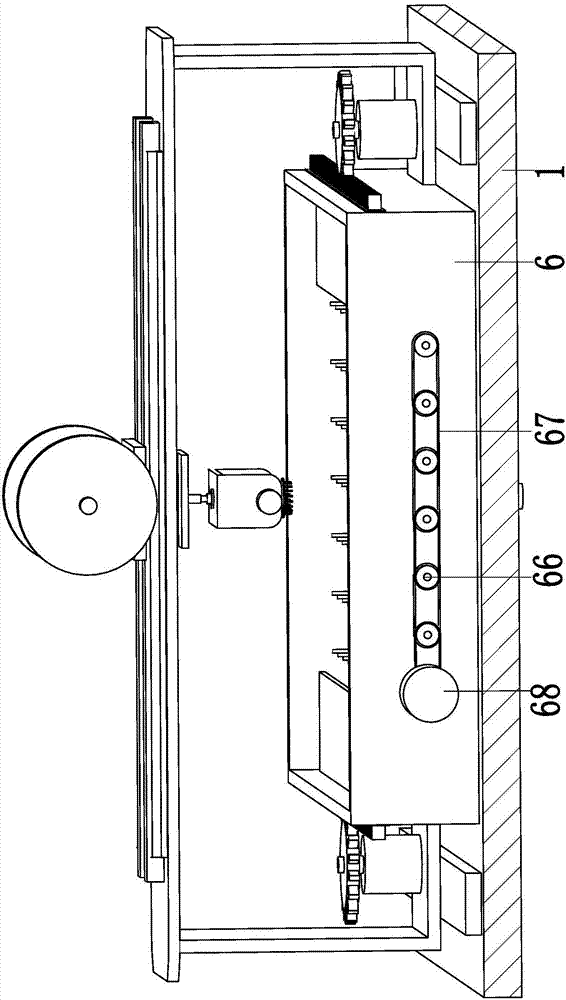
Equipment for peeling, slicing and drying rhizoma dioscoreae being traditional Chinese medicine for treating chronic enteritis
InactiveCN107549832AEasy to controlExtended drying timeConveyorsDrying gas arrangementsEngineeringUltimate tensile strength
The invention relates to a drying equipment for peeling and slicing Chinese medicinal yams for treating chronic enteritis, which comprises a bottom plate, a feeding device, a peeling device, a slicing device and a drying device. device, slicing device and drying device. The present invention can solve the problems of manual operation, potential safety hazards, low work efficiency, high labor intensity, incomplete peeling and other problems existing in the existing yam processing technology, and can realize automatic peeling, slicing and drying of yams. Without manual operation, it has the advantages of high work efficiency, low labor intensity, complete peeling, sufficient drying, good safety, and automatic adjustment.
Owner:潘学勇
Security devices, their production and use
Security documents, such as passports, bank notes and credit cards, often incorporate security devices that are difficult to replicate by conventional printing or copying techniques. Disclosed herein are security devices and methods for their production. In selected embodiments, the security devices may be used with polymer core materials in such a way that they simulate the appearance of known security devices more traditionally used with paper core materials.
Owner:FORTRESS OPTICAL FEATURES
Automatic assembly and disassembly and washing device of sewage checking well lid for ventilation of municipal pipe system
InactiveCN107338853ARealize the function of automatic assembly, disassembly and cleaningEasy to operateSewer cleaningSewer pipelinesMunicipal sewageWater well
The invention relates to an automatic installation, disassembly and cleaning equipment for sewage inspection manhole covers for municipal pipeline system ventilation. device. The present invention can solve the problems existing in the assembly, disassembly and cleaning process of the existing sewage inspection manhole cover, the need to manually assemble and disassemble the sewage inspection manhole cover with the help of existing lifting equipment, the need to manually clean up the stains on the sewage inspection manhole cover, and the need to manually flush the sewage Inspecting the manhole cover, manual assembly and disassembly of the sewage manhole cover with the help of existing lifting equipment is complicated. During the assembly and disassembly process, the sewage manhole cover is easy to shake, posing a safety hazard. The sewage generated during the process of manually flushing the sewage and inspecting the manhole cover will not be discharged anywhere to affect the environment. Manually clean the sewage In order to solve the problems of low labor intensity and low work efficiency for checking the stains on the manhole cover, it can realize the function of automatic assembly, disassembly and cleaning of the manhole cover for sewage inspection.
Owner:俞樑兵
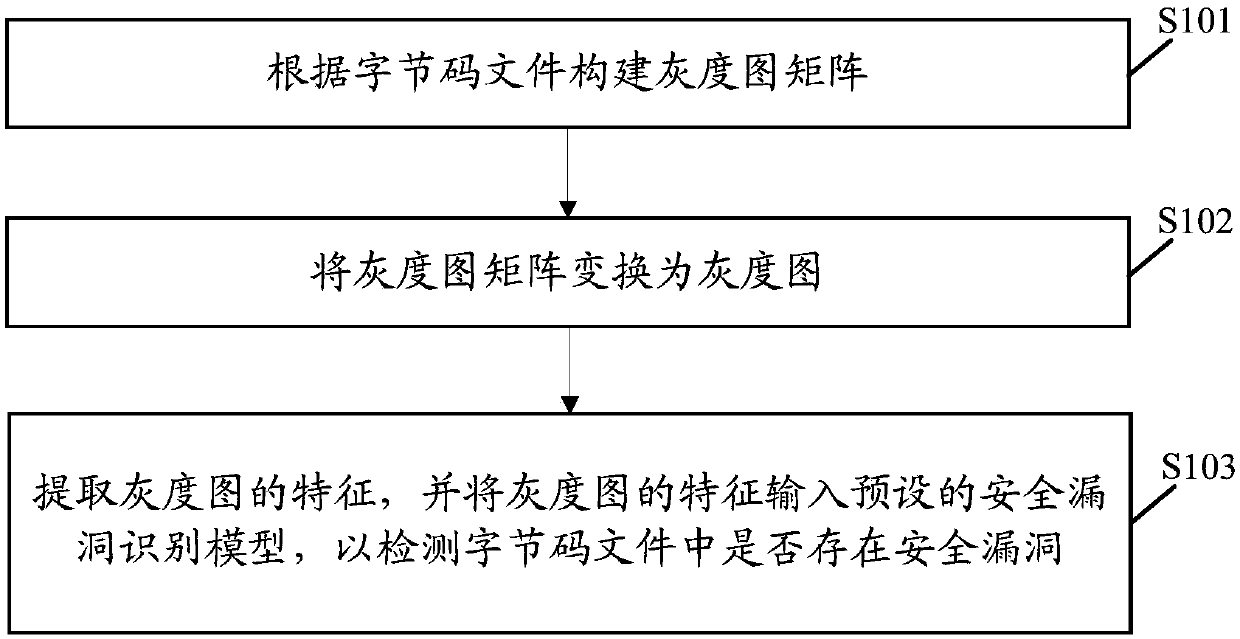
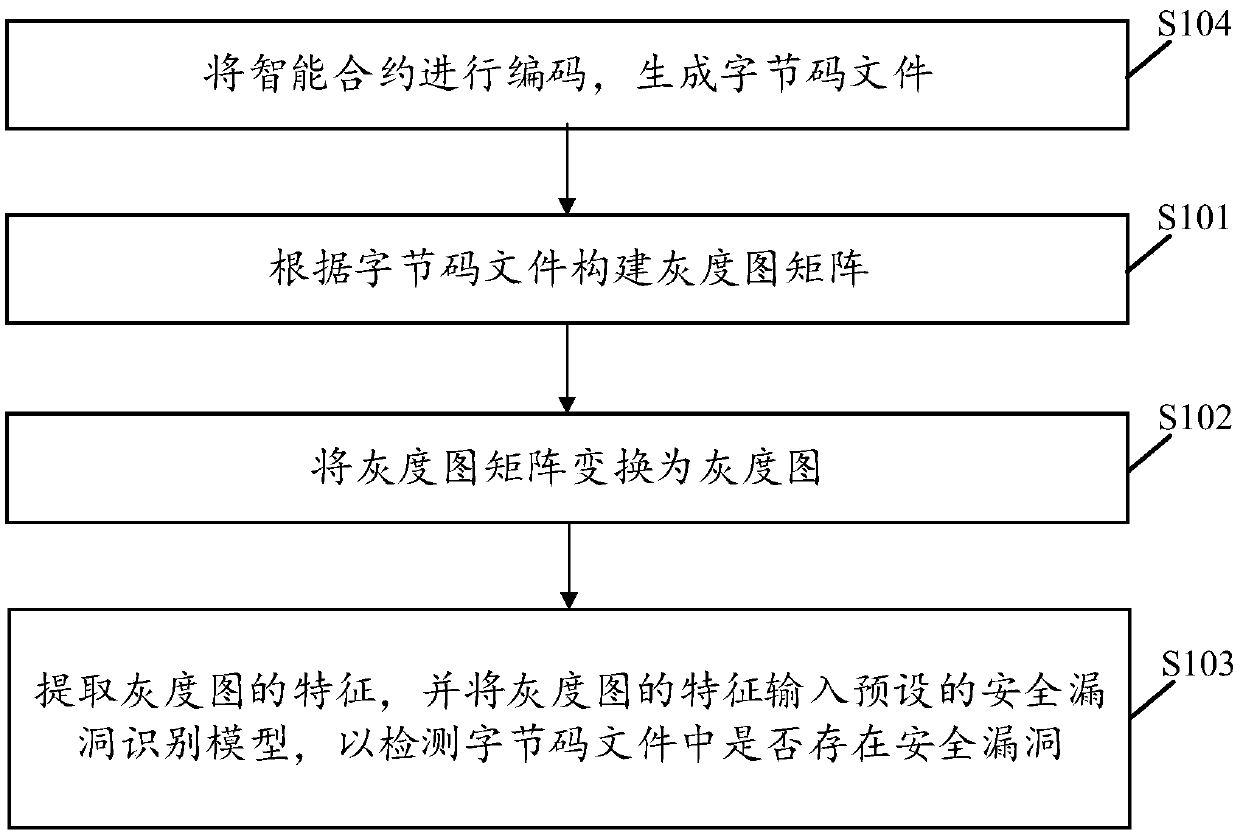
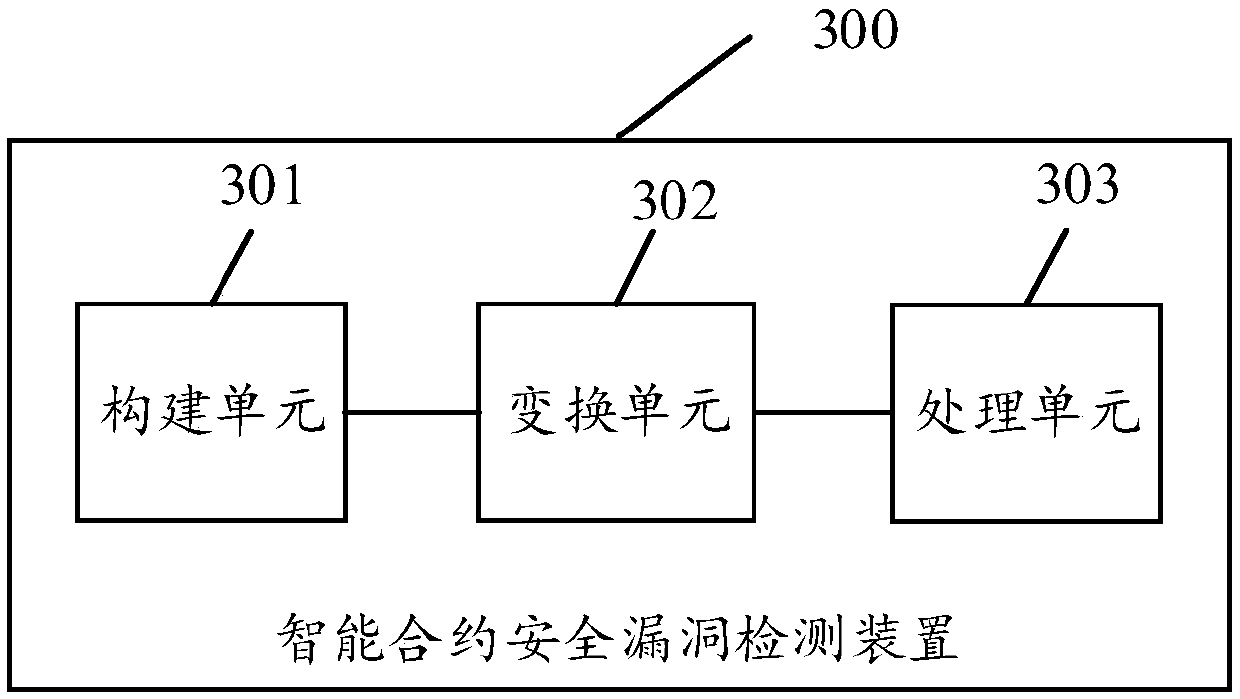
Intelligent contract security vulnerability detection method and device, terminal and storage medium
ActiveCN108985066AHigh precisionImprove accuracyImage analysisCharacter and pattern recognitionSmart contractIs security
The embodiment of the invention discloses an intelligent contract security vulnerability detection method and device, a terminal and a storage medium, wherein the method comprises the following steps:constructing a gray image matrix according to a byte code file; transforming the gray image matrix into a gray image; extracting the features of the gray image and inputting the features into the preset security vulnerability identification model to detect whether there are security vulnerabilities in the bytecode file. The implementation of the application can detect the security holes existingin the intelligent contract, and can improve the detection accuracy of detecting the security holes at the same time.
Owner:BEIJING KINGSOFT INTERNET SECURITY SOFTWARE CO LTD
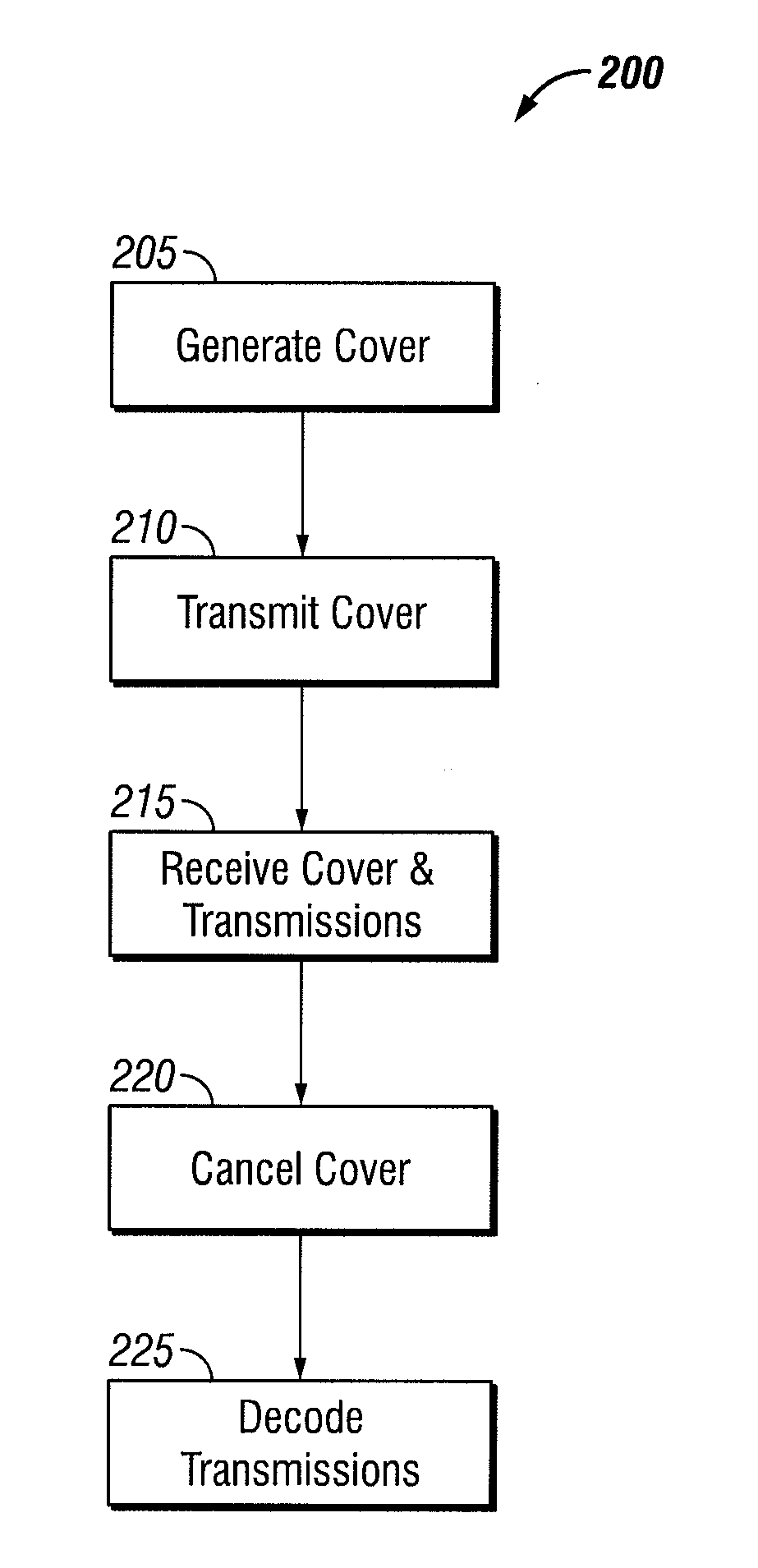
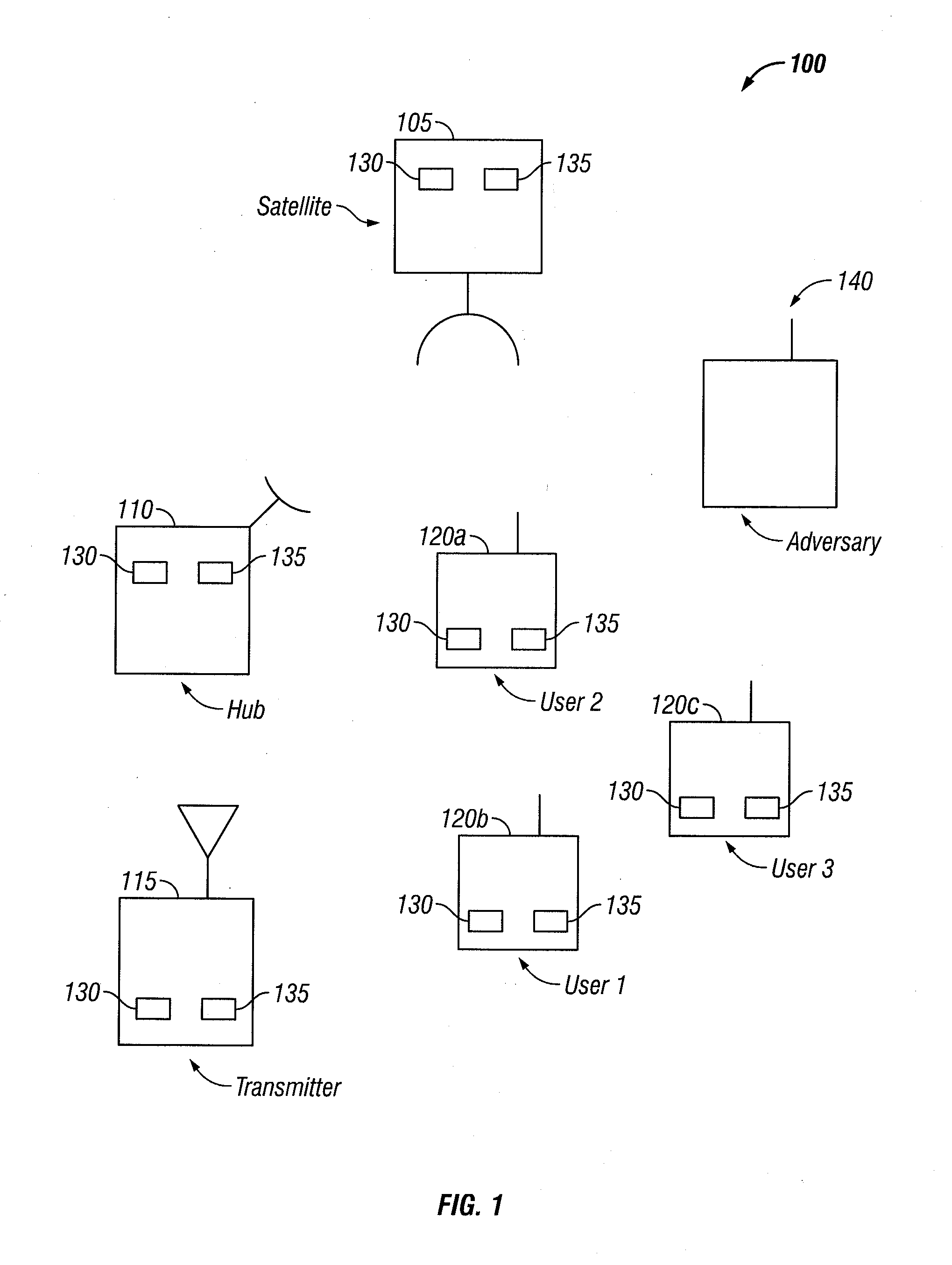
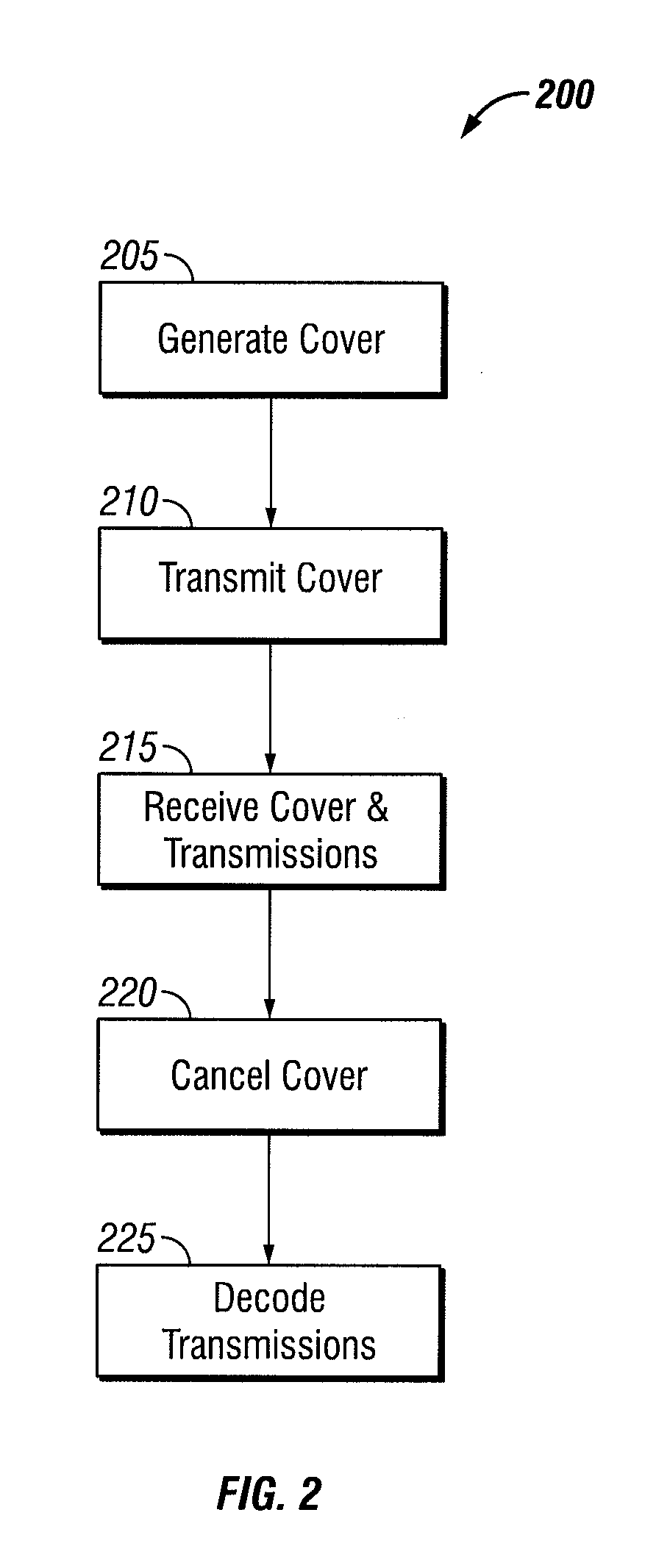
Traffic flow analysis mitigation using a cover signal
ActiveUS8711688B1Preventing traffic flow analysis attackAvoid attackError preventionTransmission systemsTraffic capacitySelf interference
Network communications face security issues including traffic flow analysis attacks. Such attacks include deduction of information about networks through analysis of transmitted traffic volume or statistics, even if the traffic is encrypted. For example, an adversary may deduce operational information from traffic volume, or its timing. Described herein are security techniques that can provide transmission security with an obfuscating “cover” signal for any contention-based multiple access system by employing signal interference cancellation techniques, but are not so limited. The cover signal is transmitted on the same frequency band used by terminals on the network. Using “known-signal” and / or self-interference cancellation techniques, the cover signal can be removed by authorized terminals that have appropriate cover signal information and timing synchronization. An adversary cannot distinguish between real traffic and the cover signal while authorized terminals can recover transmissions without impact to network capacity.
Owner:VIASAT INC
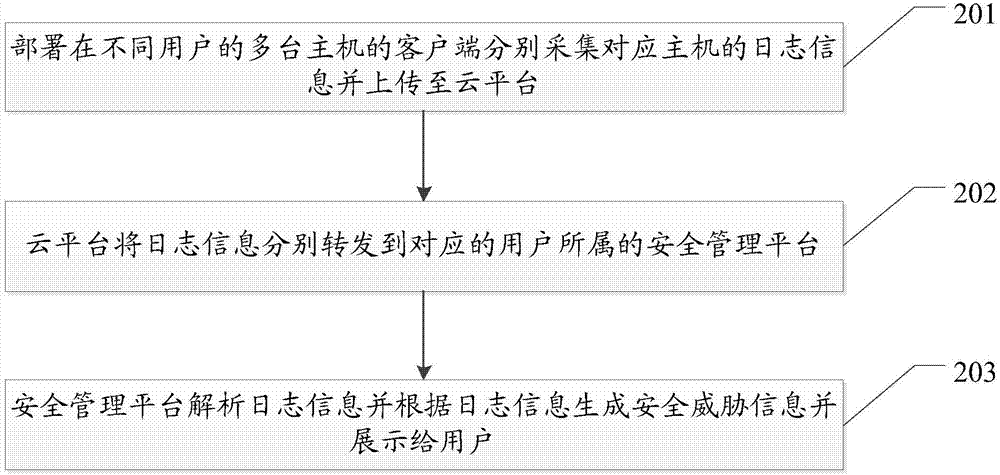
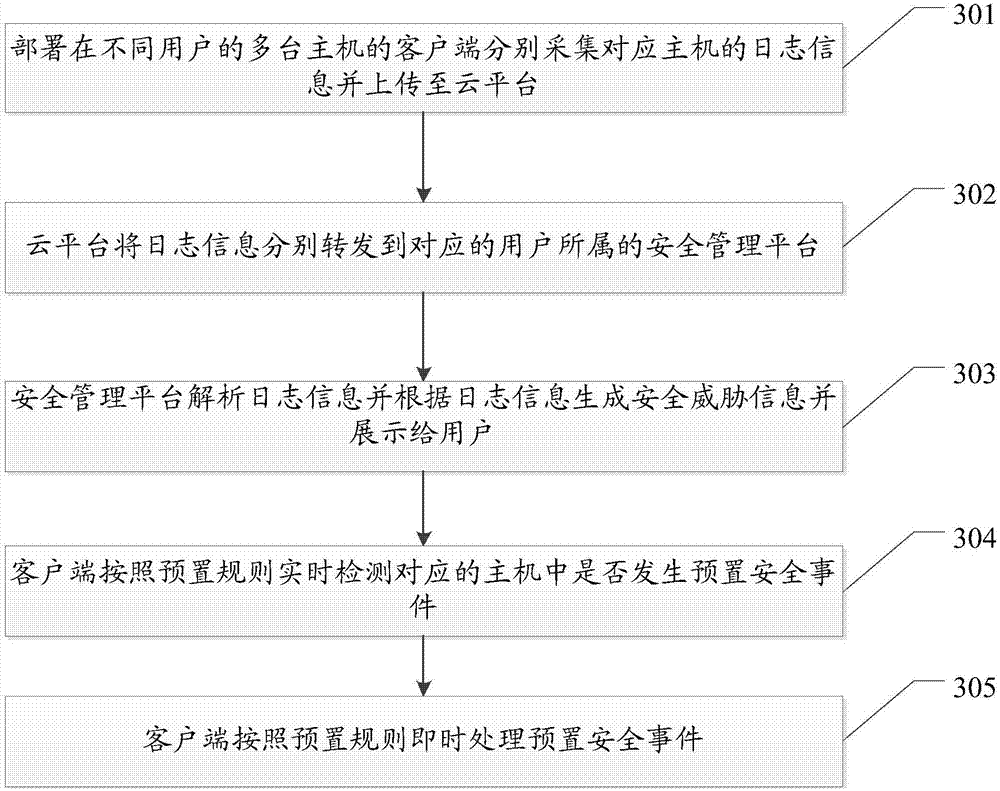
Host security detection method and system based on central management
ActiveCN107295021AReduce resource overheadImprove Security Monitoring EfficiencyTransmissionInformation security managementCentralized management
The embodiment of the invention provides a host security detection method and system based on central management, and the method and system are used for improving the efficiency of host security detection based on central management. The method comprises the steps: clients in multiple hosts of different users separately acquire log information of corresponding hosts and upload to a cloud platform, the cloud platform is arranged in public network, and one client is arranged on each to-be-security detected host; the cloud platform separately forwards the log information security management platforms which users corresponding to the log information belong, and the cloud platform comprises at least one security management platform; and the security management platforms separately analyze the log information and generate security threat information according to the log information and display to the users.
Owner:SANGFOR TECH INC
Special heat dissipation apparatus for box-type substation
InactiveCN107306018AOvercome immobilityOvercoming easily damagedSubstation/switching arrangement cooling/ventilationDistribution substationsElectric power systemOperating temperature
The invention relates to a substation in an electric power system, in particular to a special heat dissipation device for a box-type substation with convenient operation and good use effect. The heat dissipation device of the present invention includes a ventilation window and a heat dissipation window. A heat dissipation fan is provided through the bracket, and the ventilation window is provided with blades whose opening and closing angles are controlled by the stepping motor and the transmission device. It is easy to be damaged and has potential safety hazards. Setting ventilation windows on the box-type substation to control the working temperature in the substation can not only meet the heat dissipation and ventilation needs of the substation, but also prevent the open box door or window sash from being unable to adapt to bad weather. problems, making the heat dissipation and ventilation process of the substation more intelligent, energy-saving and safe.
Owner:WEIHAI WENDENG POWER SUPPLY CO OF STATE GRID SHANDONG ELECTRIC POWER CO
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com