Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
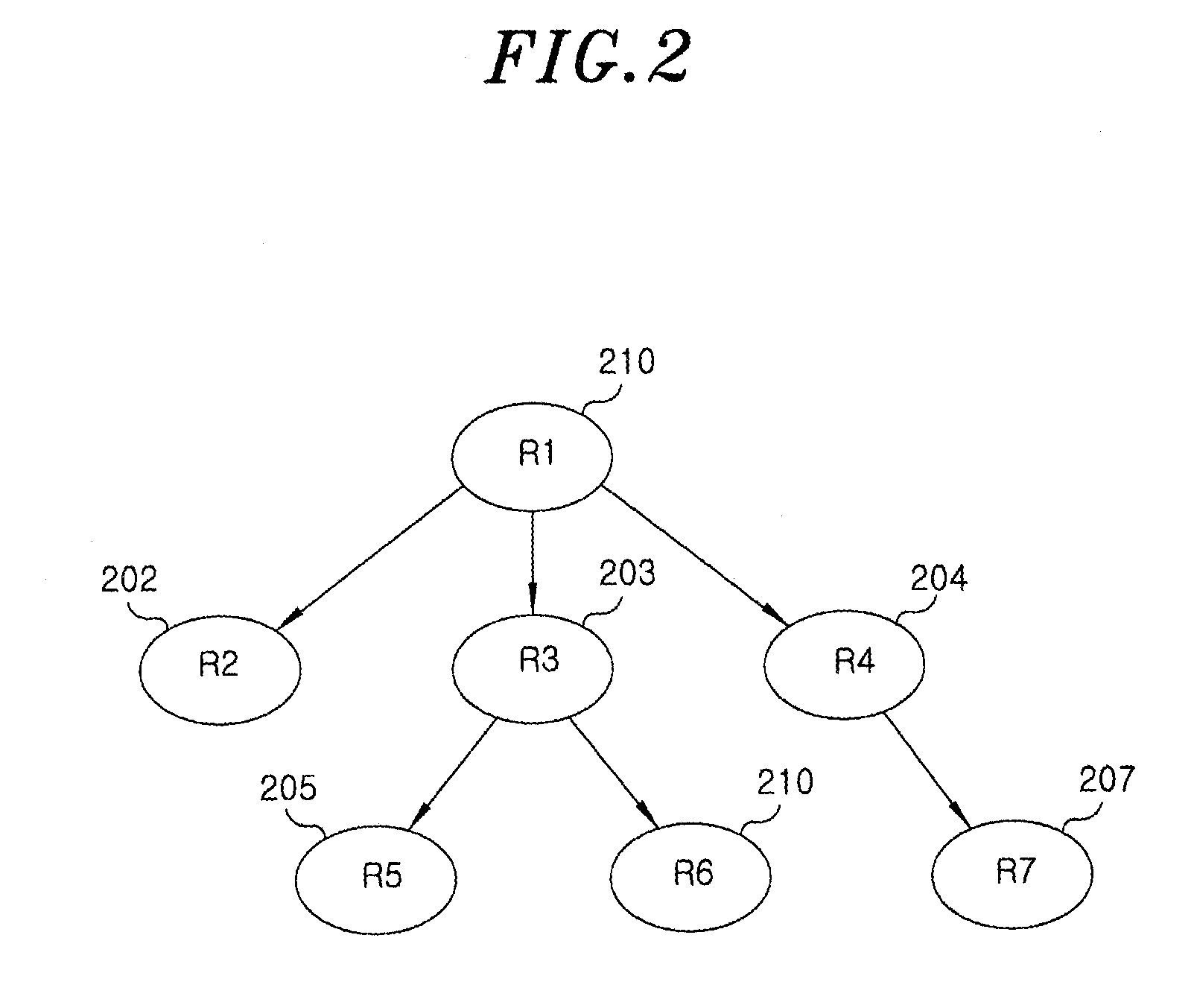
55 results about "Role-based access control" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
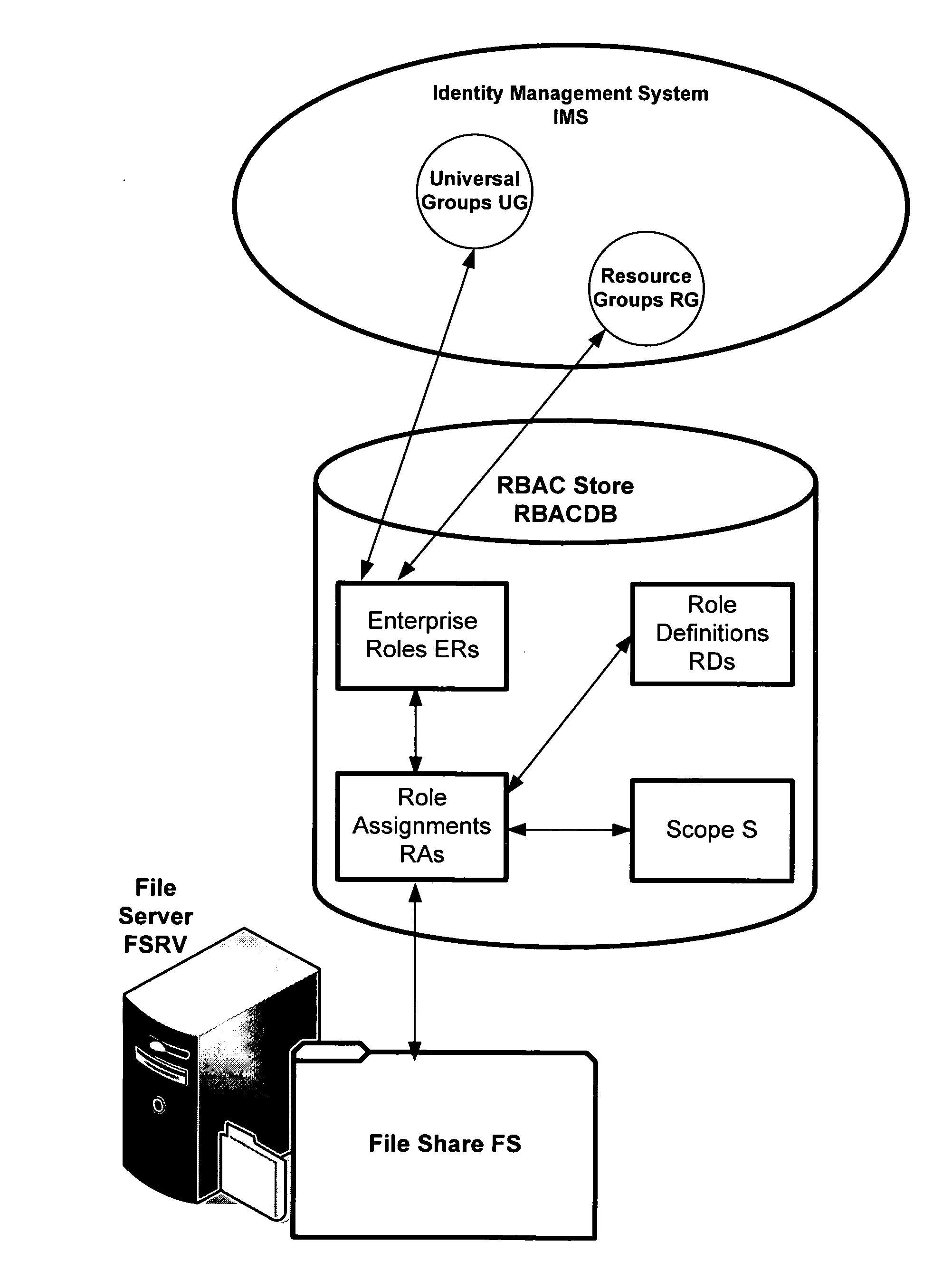
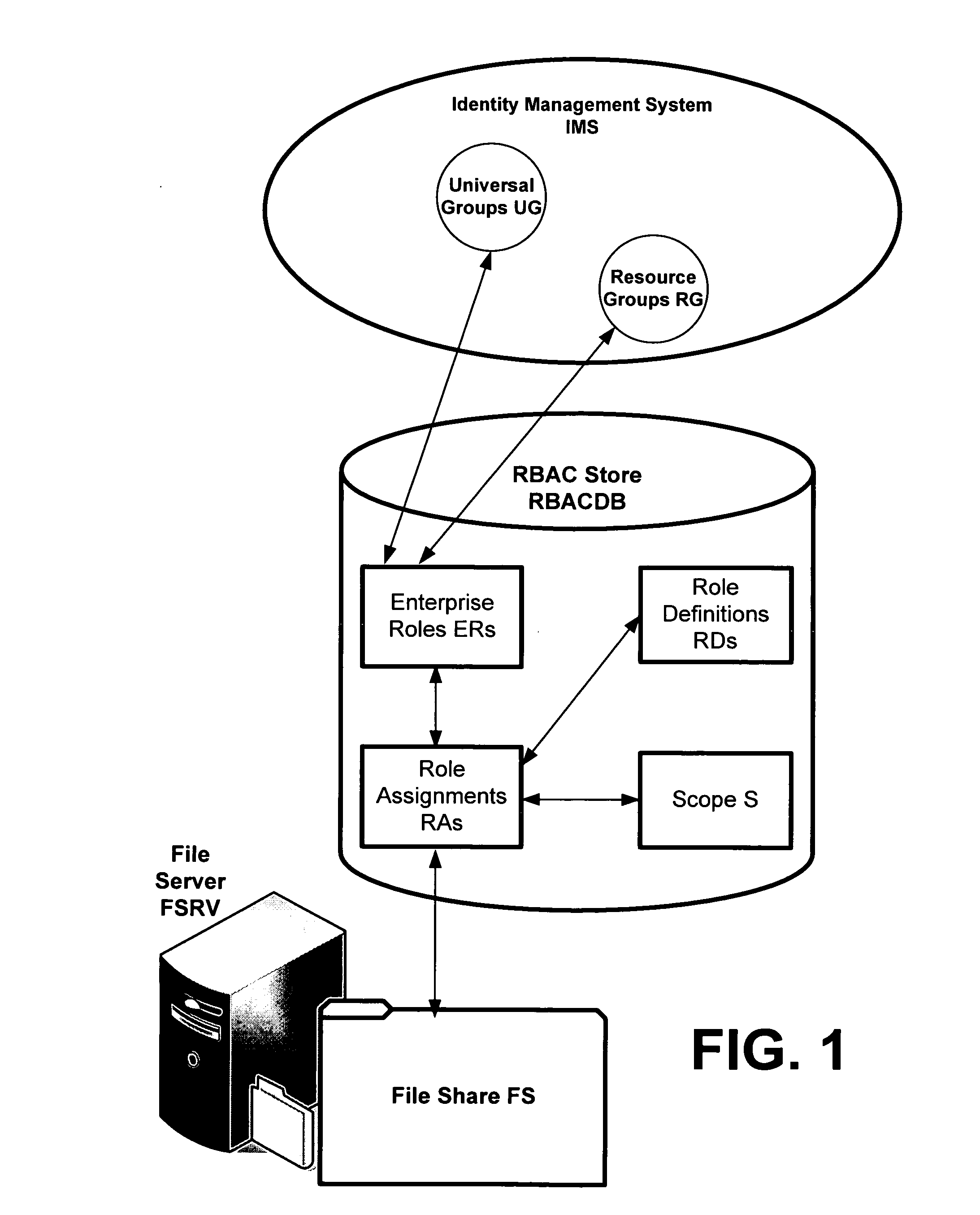
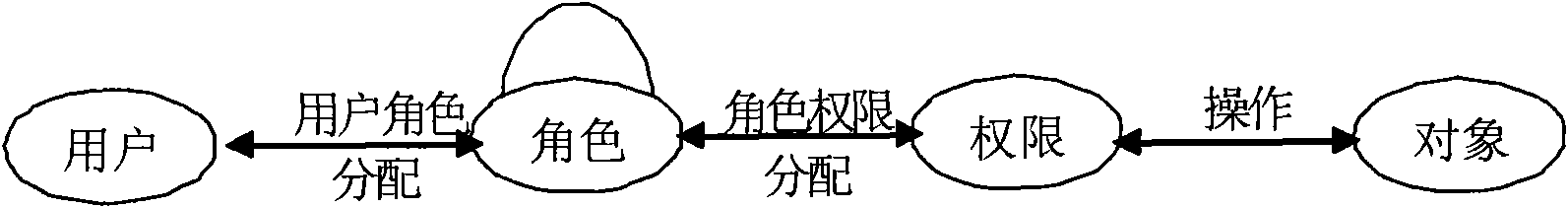
In computer systems security, role-based access control (RBAC) or role-based security is an approach to restricting system access to authorized users. It is used by the majority of enterprises with more than 500 employees, and can implement mandatory access control (MAC) or discretionary access control (DAC).
Translating role-based access control policy to resource authorization policy
ActiveUS20070283443A1Program control using stored programsDigital data processing detailsFile systemManaged object
Translation of role-based authoring models for managing RBAC “roles” to resource authorization policy (RAP), such as ACL-based applications, is provided. A generic RBAC system is defined from which mappings to other authorization enforcement mechanism make possible the translation of RBAC “roles” to resource authorization policies applied to resources managed by a resource manager, e.g., a file system resource manager. An implementation is described that uses Windows Authorization Manager as a storage mechanism and object model to manage object types and relationships translated from an RBAC system.
Owner:MICROSOFT TECH LICENSING LLC
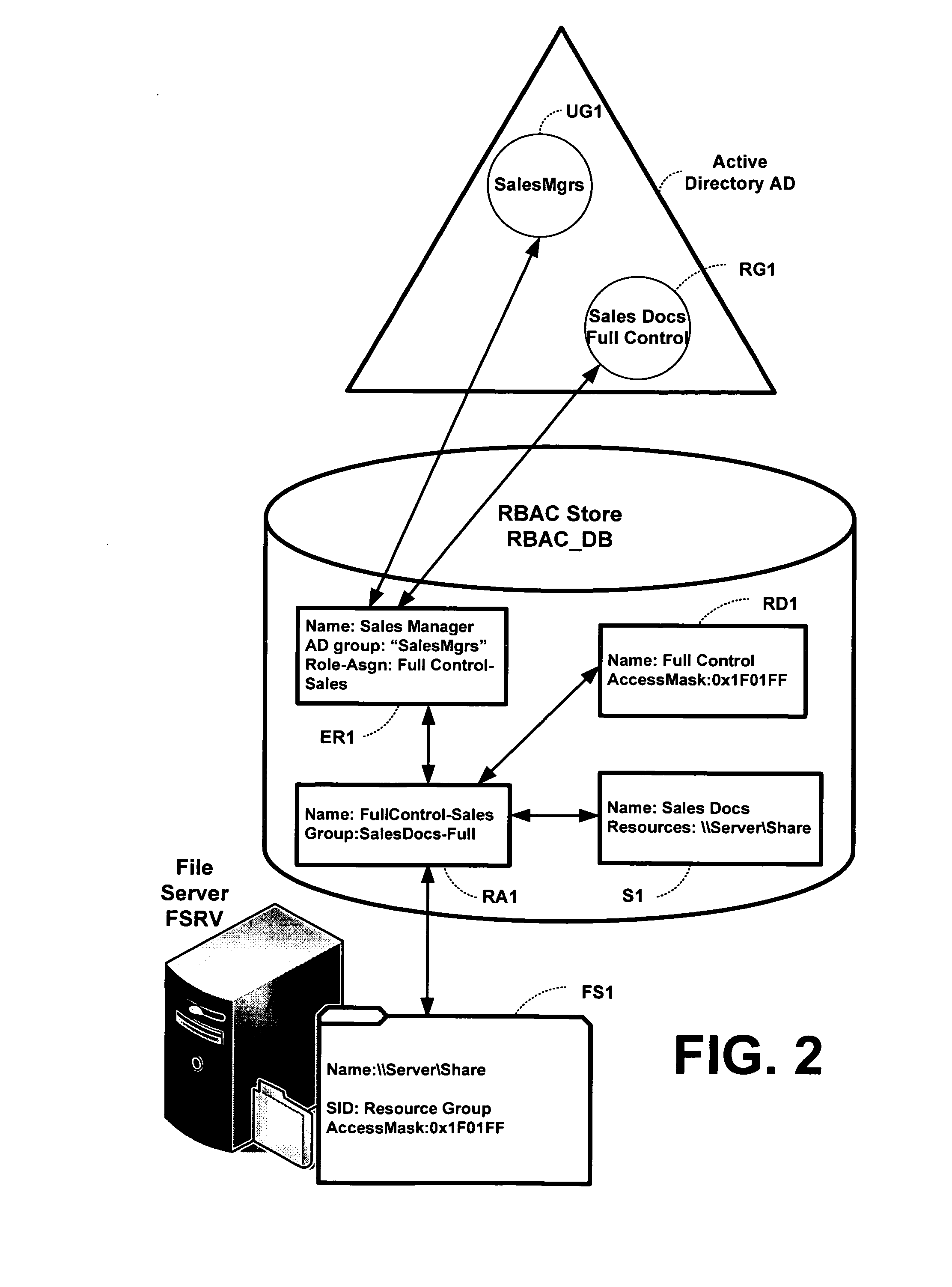
Resource level role based access control for storage management
InactiveUS20080120302A1Computer security arrangementsTransmissionRole-based access controlResource based
A method, apparatus, and system for providing role-based access control (RBAC) for storage management are described herein. Resource-identifying information is stored in a role-based access database for a network storage system, in association with role-identifying information for each of a plurality of roles and operation-identifying information. The operation-identifying information indicates one or more authorized operations for each of the plurality of roles and the resource-identifying information identifies specific resources maintained by the network storage system. The role-identifying information, data indicating one or more authorized operations for at least one of the roles, and resource-specific identifying information in the role-based access database are used to determine whether to allow or deny a request from a network storage client to access a resource maintained by the network storage system.
Owner:NETWORK APPLIANCE INC
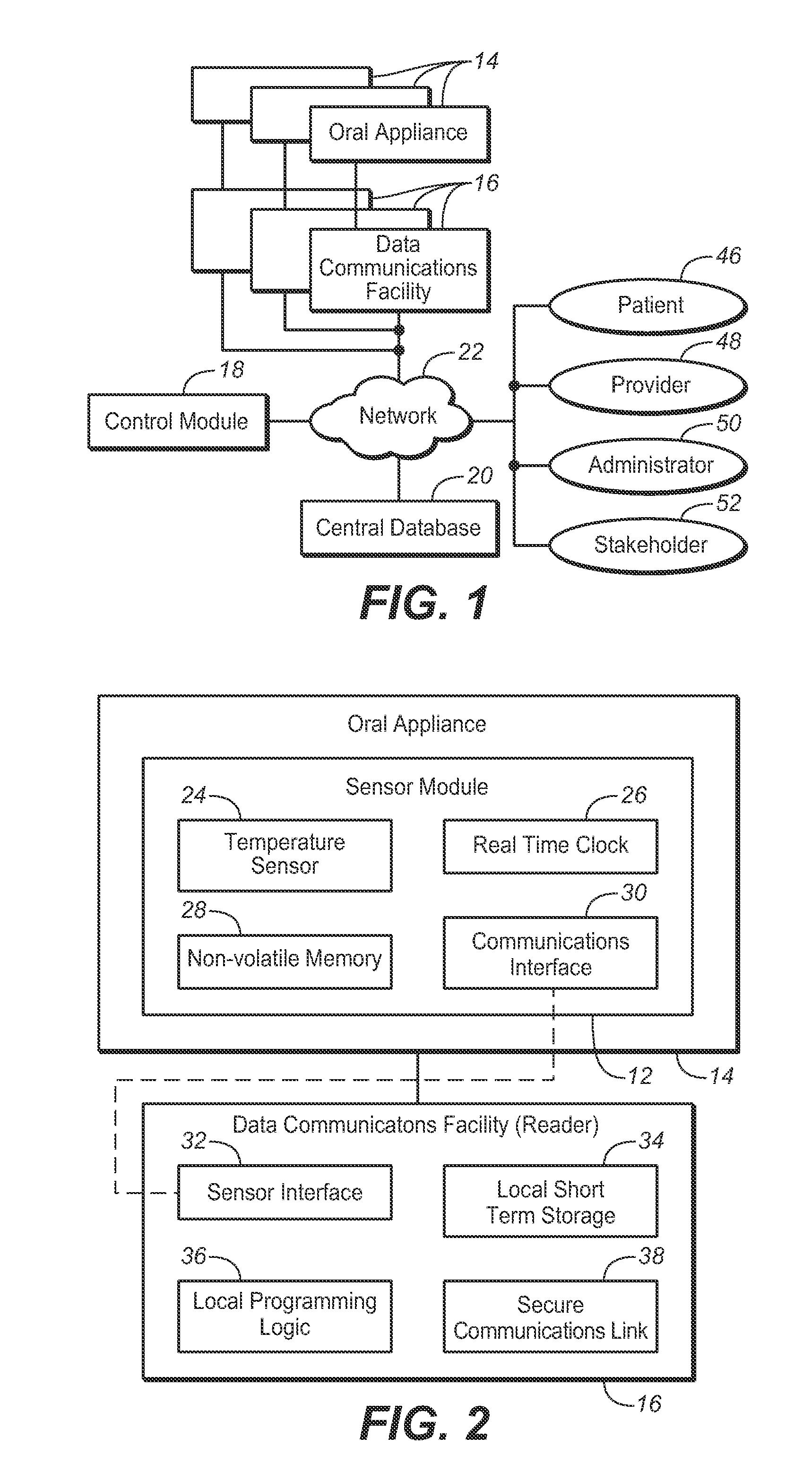
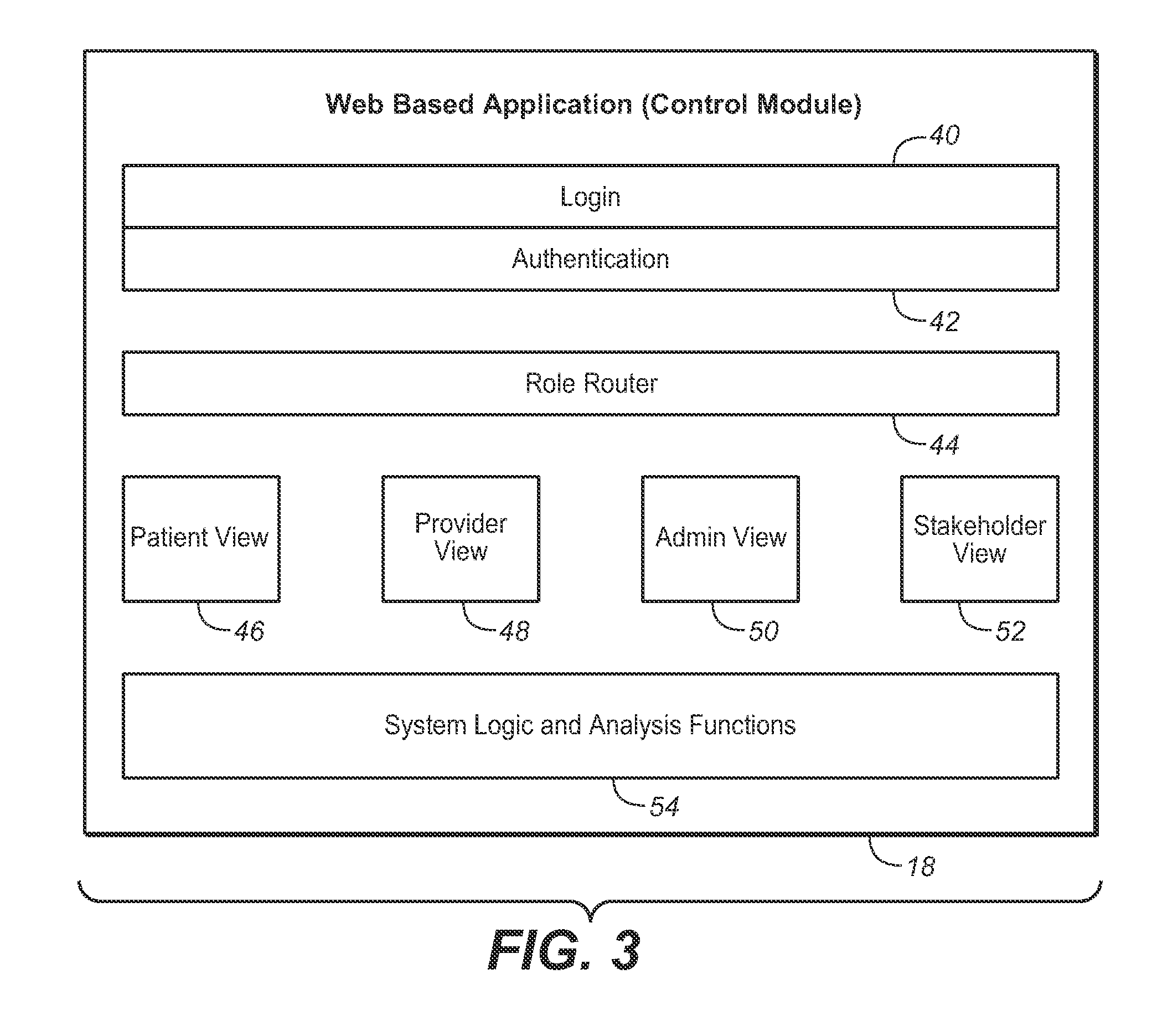
System for monitoring of and managing compliance with treatment for obstructive sleep apnea using oral appliance therapy and method therfor
InactiveUS20100312484A1Respiratory organ evaluationSensorsNetwork connectionRole-based access control
A system and method for monitoring of and managing compliance with treatment for obstructive sleep apnea using oral appliance therapy comprises a sensor module installed in an oral appliance, a data communications facility for communicating with the oral appliance, a control module, and a central database for storing data. Data stored on the sensor module is transferred to the data communications facility for local storage. The control module validates the locally stored temperature data and uploads the validated data into the central database. Temperature data stored in the central database may be viewed remotely via a secure computer network connection in graphical form by authorized users using role-based access controls. Authorized users may include the patient, the patient's provider, system administrators, and stake holders including insurance carriers providing medical coverage for OAT.
Owner:DUHAMEL JAMES B +1
Defining consistent access control policies
ActiveUS7921452B2Computer security arrangementsSpecial data processing applicationsRole-based access control
A method of defining policies for controlling access to resources of a system. Authorization requirements for the system are modeled to obtain a model expressing each of a plurality of access control policies as a constraint. From the model is generated a single policy set in an authorization markup language that captures the requirements. This method can be used to define role-based access control policies in a format that can be adapted for input to a variety of access control mechanisms. This generative approach to access control design allows maintenance to be performed at the requirements level.
Owner:THE BOEING CO
Method and computer program product for creating enterprise management systems
ActiveUS20160328217A1Software maintainance/managementModel driven codeDashboardRole-based access control
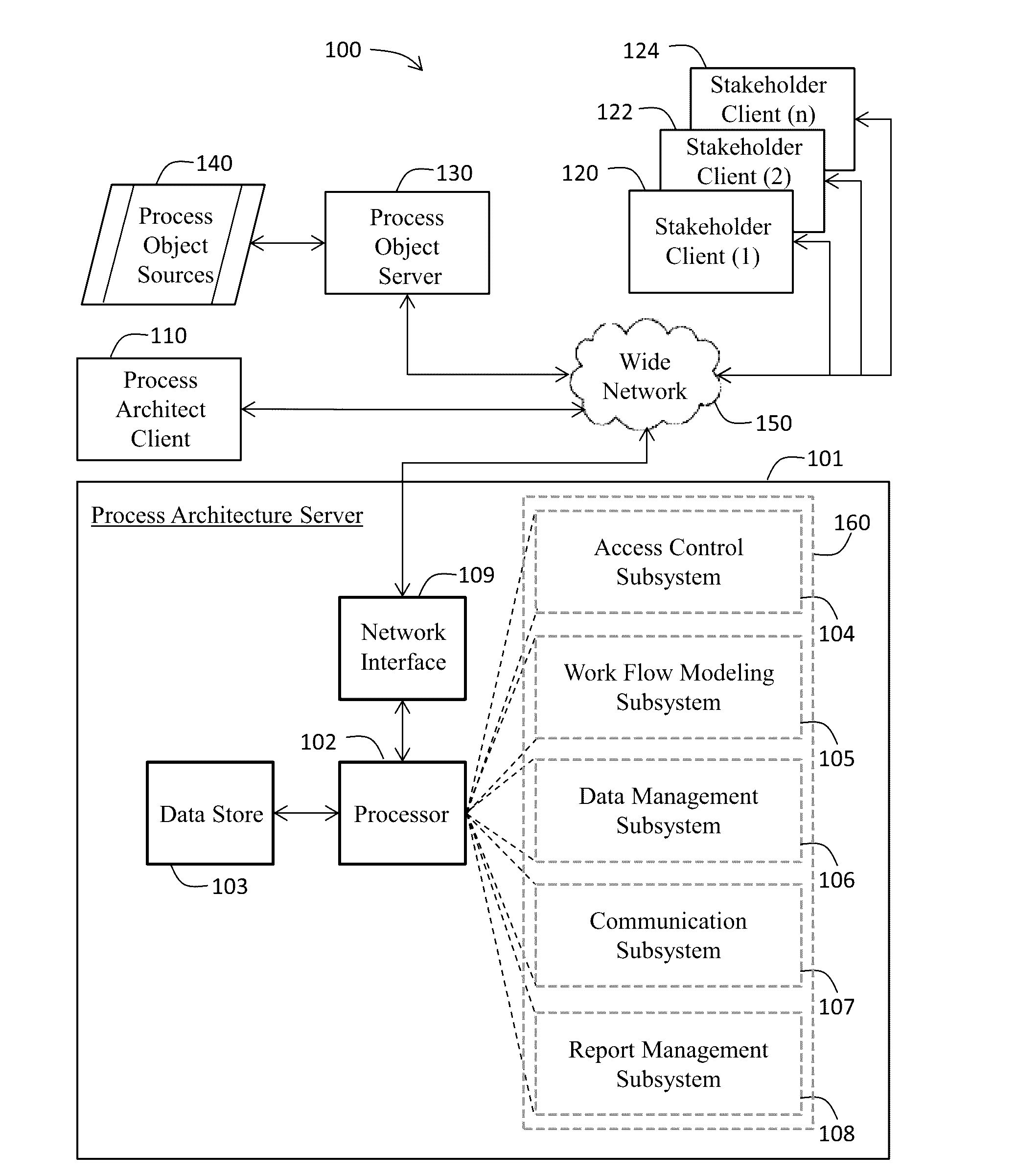
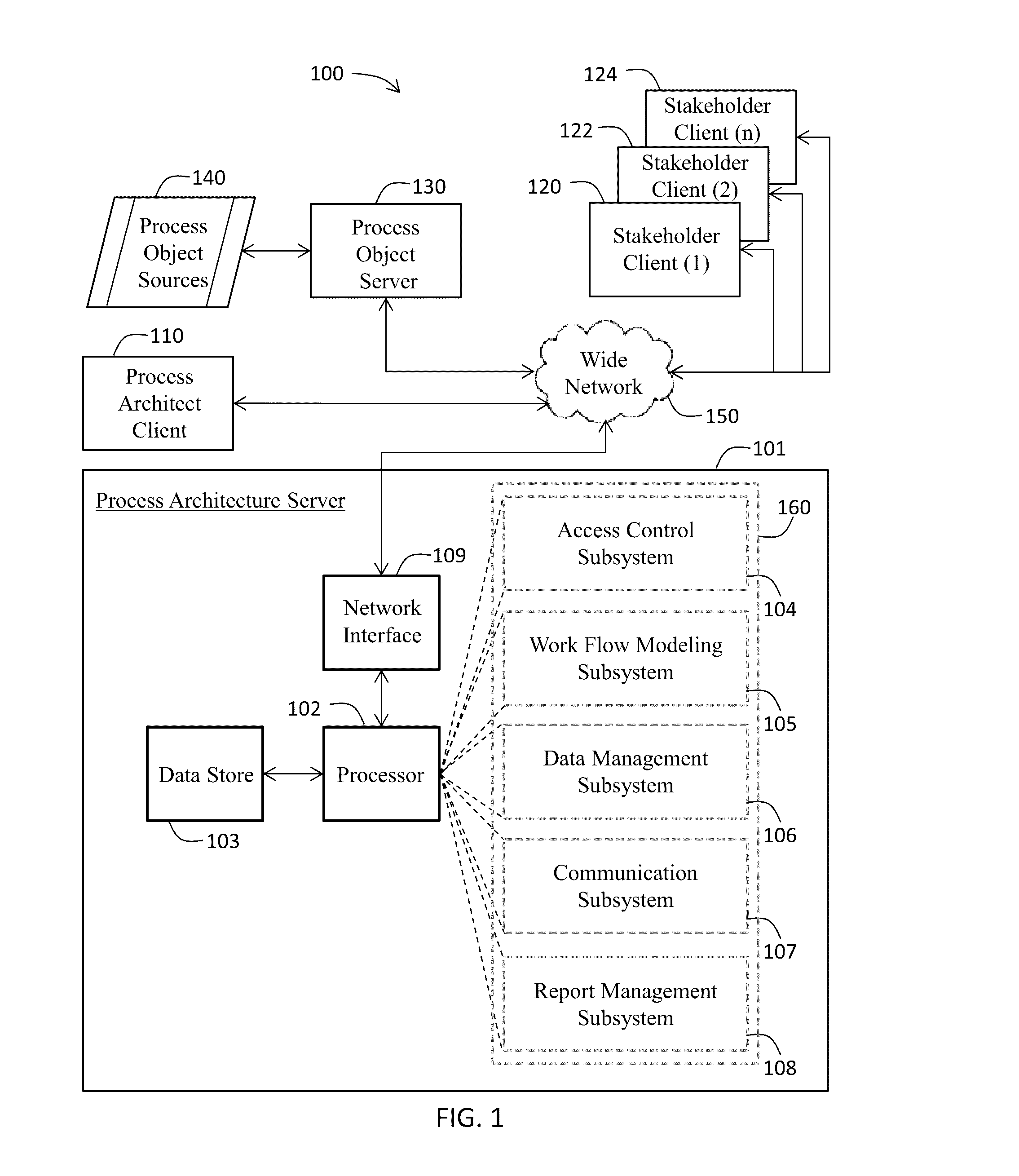
A computer program product for creating an enterprise management dashboard program, and comprising a process architecture server, a process architect client, a stakeholder client, and / or a process object server. The process architecture server includes a compiler characterized by an access control subsystem (receives role-base access control definition data), a work flow modeling subsystem (receives process model definition data), a data management subsystem (receives data structure definition data), a communication subsystem (receives communication protocol definition data), and a report management subsystem (receives report content definition data). The compiler uses the aforementioned data to create executable computer code for the enterprise management dashboard program based on modeling constructs including project sites, task pages, interface templates, report templates, and / or third-party process content. The resultant enterprise management dashboard program may be used to create and save process objects such as projects, tasks, artifacts (e.g., digital files), and process metrics.
Owner:CRAIG TECHNICAL CONSULTING INC
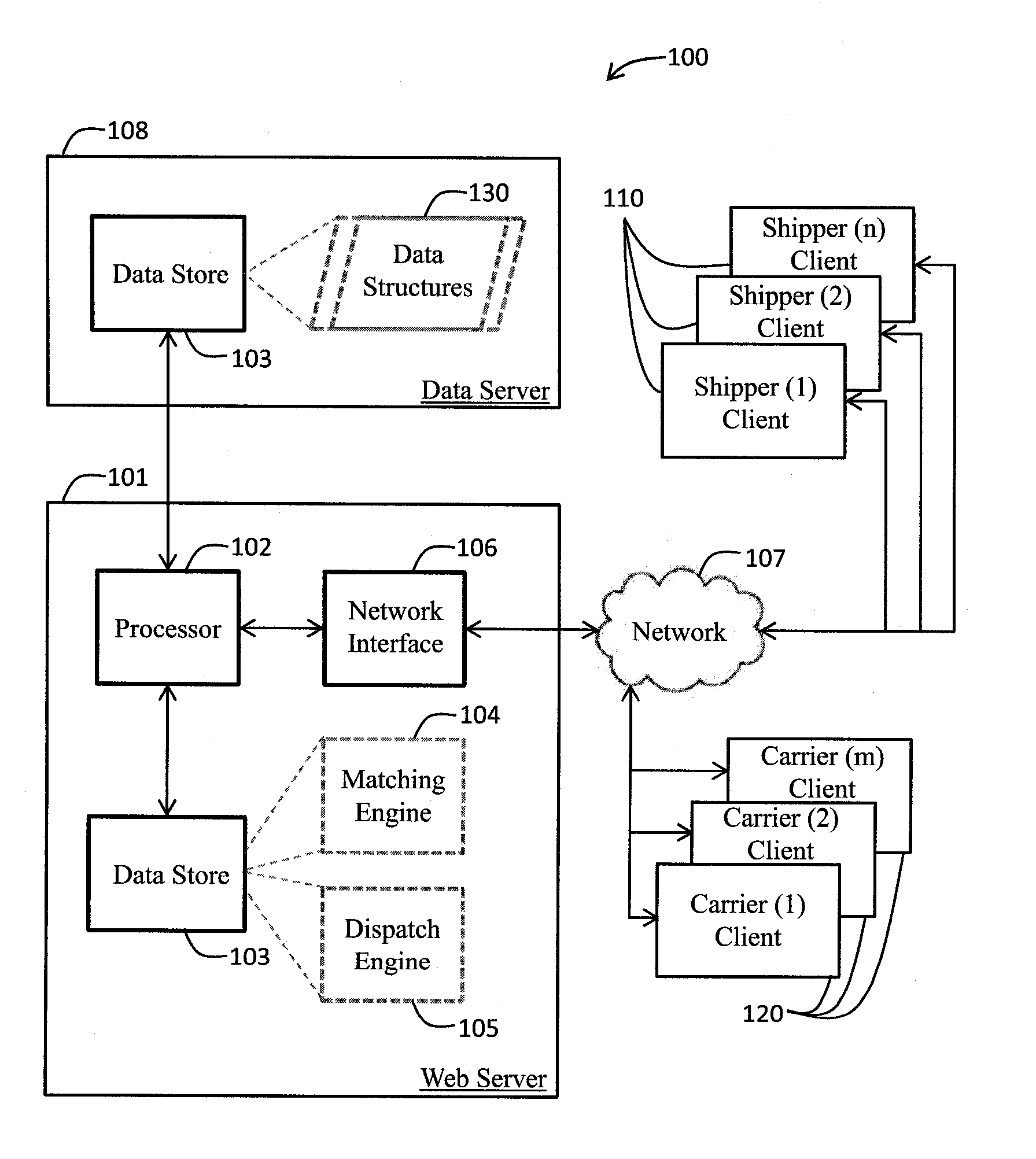
Freight services marketplace system and methods
InactiveUS20140324633A1Quick and efficientEasy to handleBuying/selling/leasing transactionsLogisticsVisibilityPayment
A computer system and associated methods for implementing an online freight services marketplace. Freight service offerings posted to the marketplace by carriers are matched to freight service requests from shippers. Compound service offerings are formed from freight service offerings having service parameters (lane, space, transit time, availability, price, and status) that accommodate load parameters (origin, destination, size, and weight) of the freight service request. Compound service offerings selected by the shipper are provisioned and reserved for subsequent dispatch. Role-based access controls within the marketplace restrict visibility of confidential information, such as carrier pricing and shipper identity. Automatic freight transaction facilitation includes shipper payment processing and shipping document generation. Status tracking capability may be augmented with alert messaging and / or in-transit re-planning to minimize the impact of common issues that threaten to defeat a shipment in progress.
Owner:FREIGHTOPOLIS
Database access control method on basis of multi-strategy integration
ActiveCN104484617AEnsure safetyQuick Action SupportDigital data protectionElectronic systemsRole-based access control
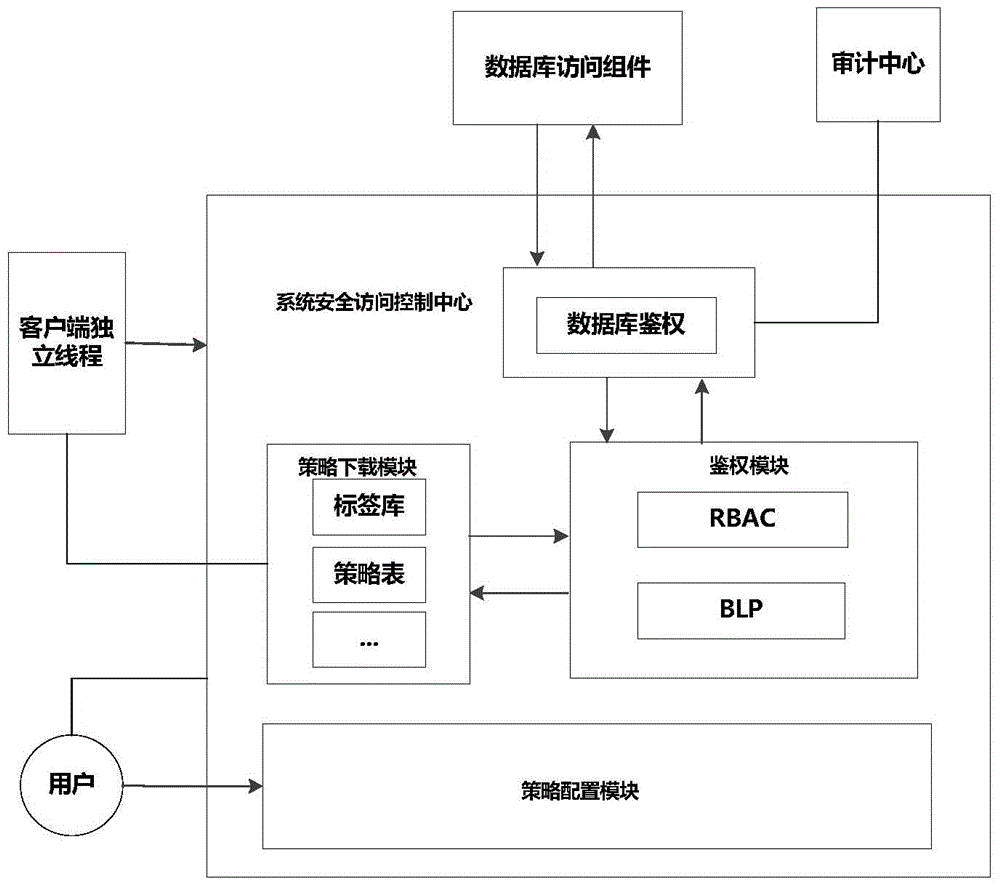
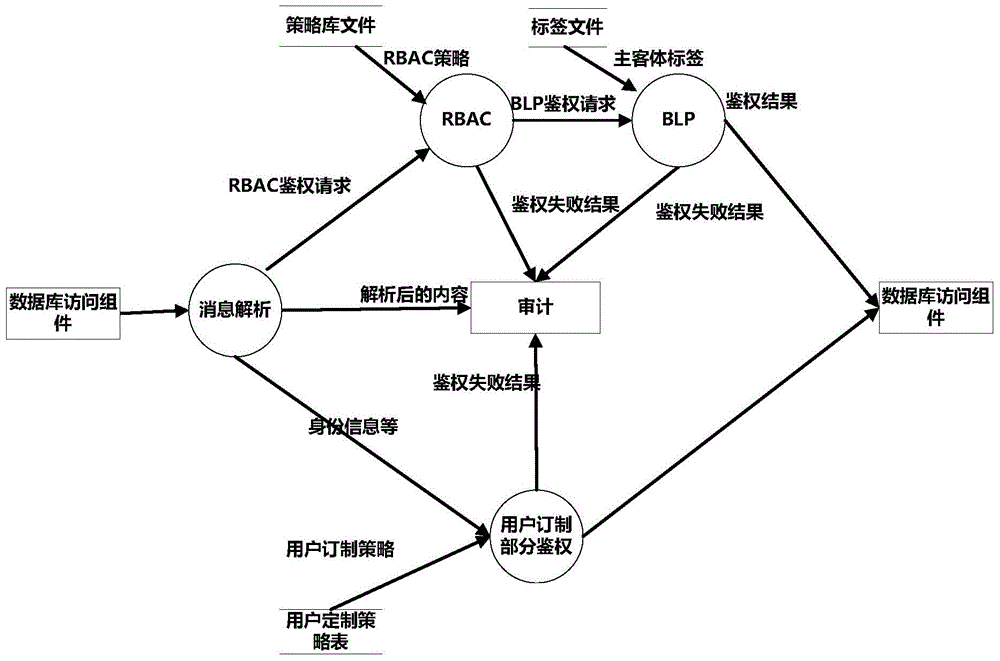
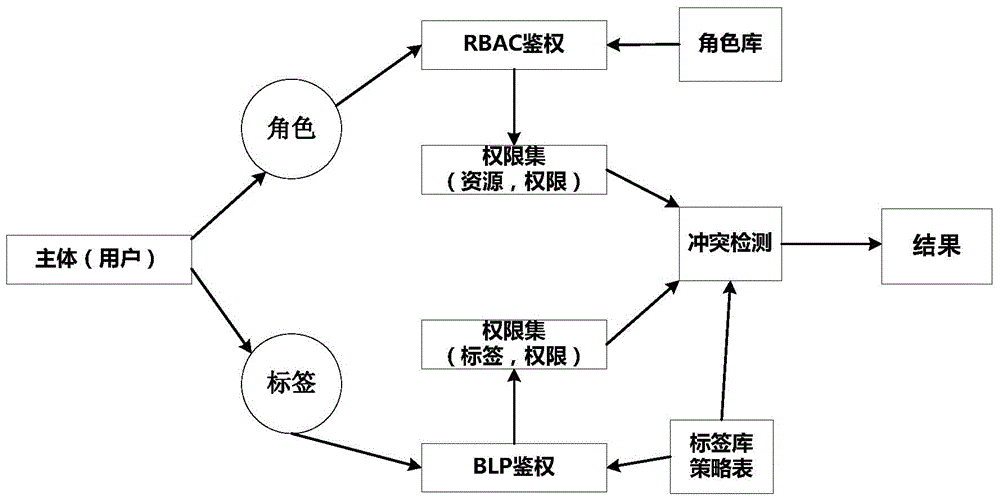
The invention provides a database access control method on the basis of multi-strategy integration. The database access control method aims to solve widespread problems in the aspect of security access to databases of comprehensive electronic systems. The database access control method includes enabling an RBAC (role-based access control) module to judge whether roles corresponding to users have access permission corresponding to required-to-be-accessed database tables or not; denying access if the roles do not have the access permission; enabling a BLP (Bell-La Padula) module to judge operation permission of the users for fields in the required-to-be-accessed database tables if the roles have the access permission. The database access control method has the advantages that various security levels of information in databases can be assuredly effectively accessed, the security of the databases can be protected on table levels and even field levels, permission of subjective bodies and objective bodies can be effectively customized according to actual conditions, and corresponding access control strategies can be provided for the subjective bodies of the different roles.
Owner:AVIC NO 631 RES INST
Role access control-based information system data storage layer and building method
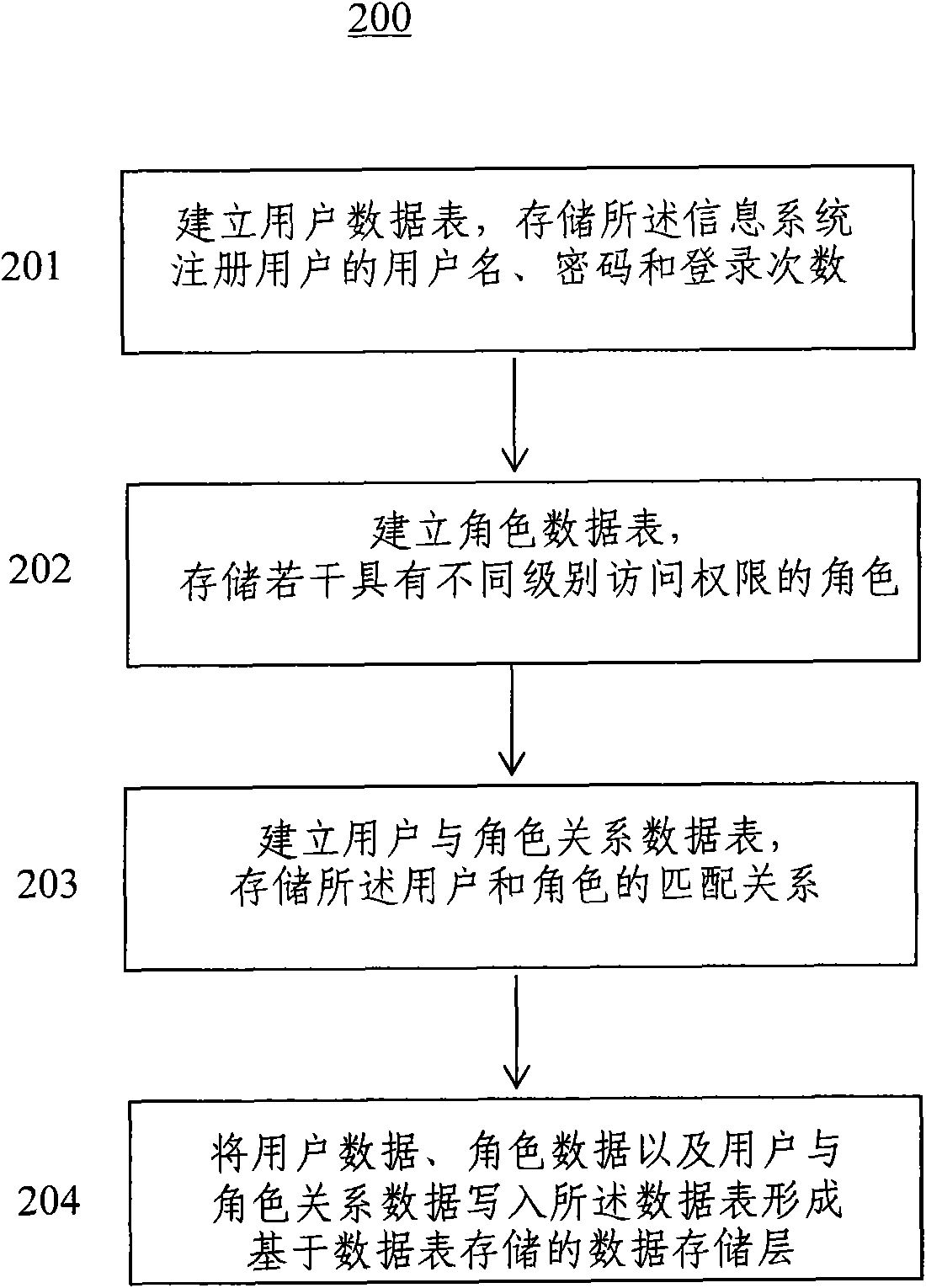
InactiveCN102004868AAchieve matchingImplement modificationDigital data authenticationSpecial data processing applicationsPasswordRole-based access control
The invention discloses a role access control-based information system data storage layer and a building method. User name, password and login times of information system registered users are stored through a user data table; a plurality of roles with access authorities of different levels are stored through a role data table; and a matching relationship between the users and the roles is stored through a user and role relationship data table. The data tables of the data storage layer are called by an information system to realize modification of system user information and matching between the users and the roles and further fulfill the purpose of endowing and controlling the access authorities of the users.
Owner:SANDA UNIVERSITY
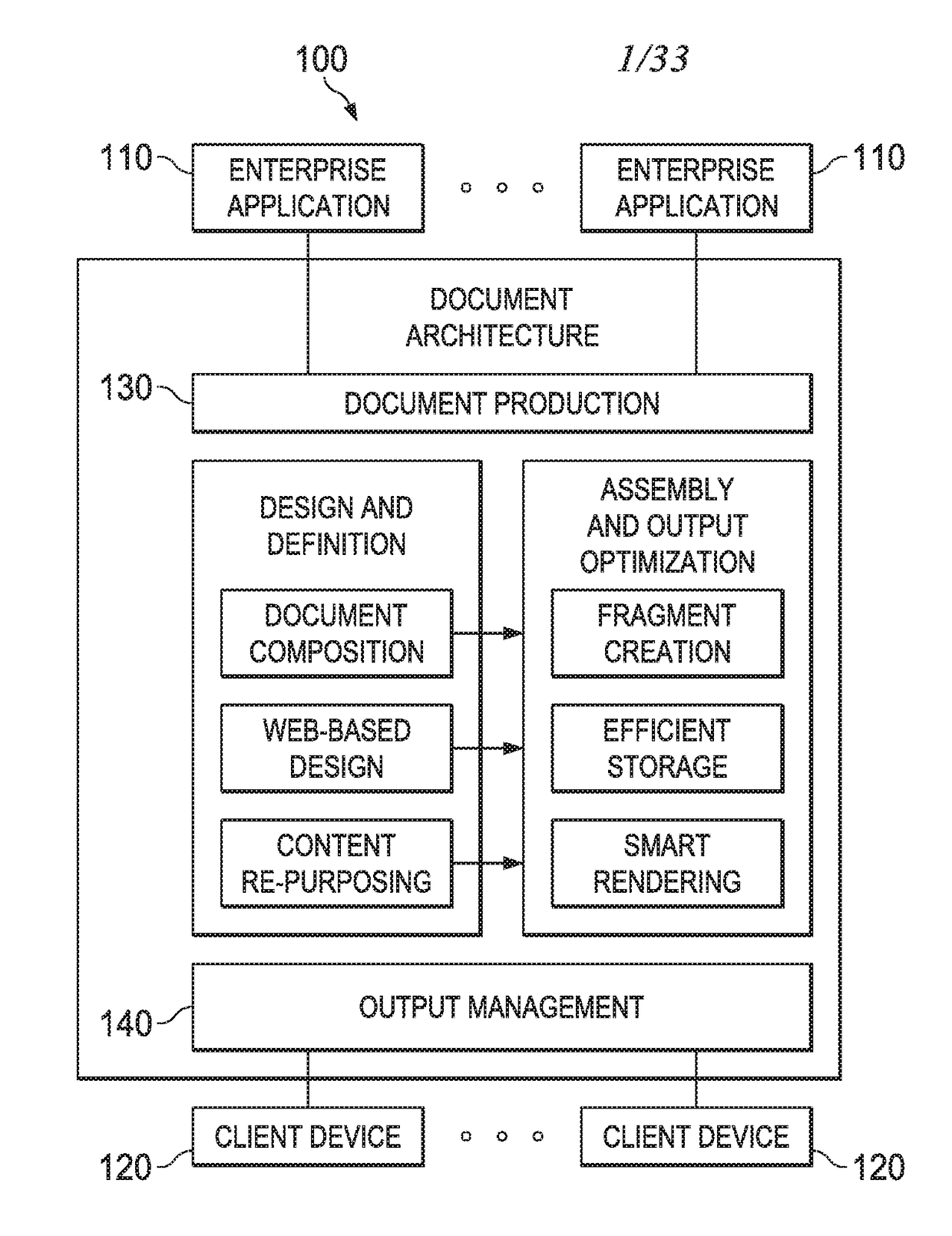
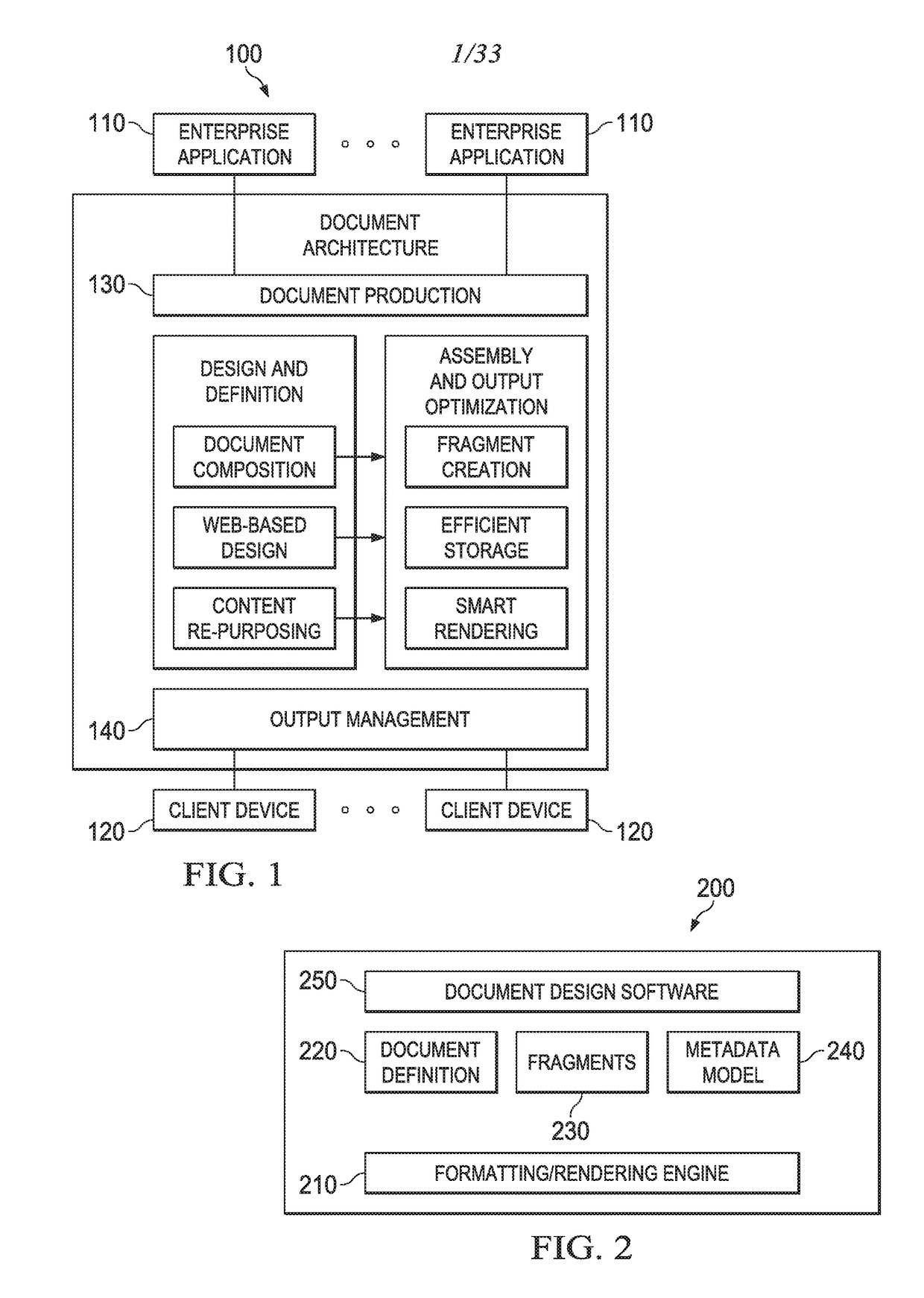
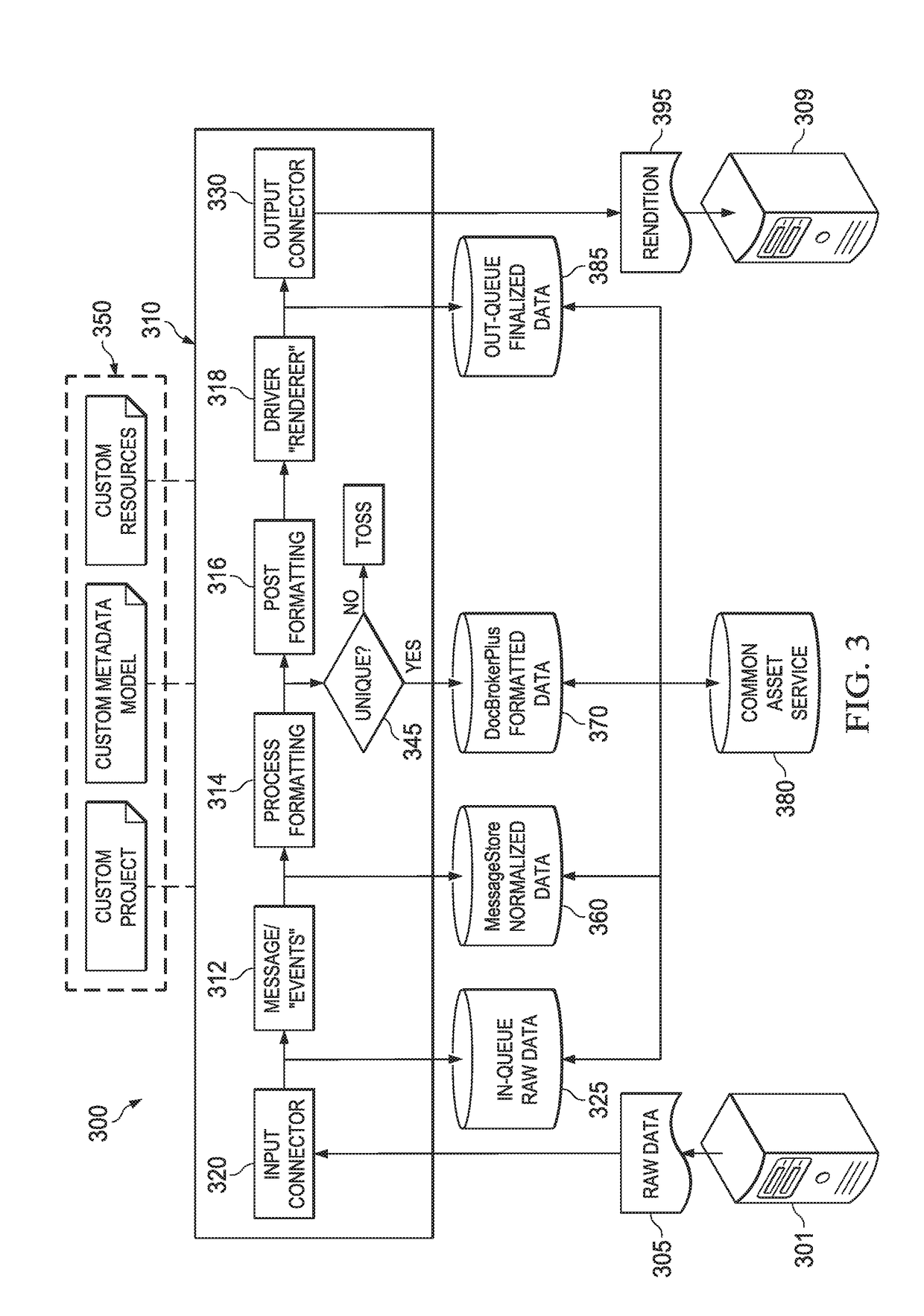
Document architecture with fragment-driven role-based access controls
ActiveUS20170346828A1Increase flexibilityFine granularityDigital data protectionNatural language data processingRole-based access controlEngineering
A document production system may construct a document from fragments based on a theme associated with the document. The theme may contain section(s), each section having an access control list (ACL) associated therewith. The ACL may specify role-based user group(s) and permission(s) for the role-based user group(s). The system may evaluable rules applicable to the document. At least one rule may pertain to the ACL(s). The evaluation may include, at least in part, utilizing user login information received over a network from a client device. In constructing the document, the system may assemble the document in accordance with the rules and utilizing the fragments and meta information that describes the document. The system may render the document thus assembled utilizing the ACL, generate a view of the document, and communicate the view of the document over the network to the client device for presentation on the client device.
Owner:OPEN TEXT SA ULC
Role access control system and method based on block chain smart contract
ActiveCN110348202ANot easy to tamper withWith traceability functionDigital data protectionDigital data authenticationRole-based access controlControl system
The invention provides a role access control system based on a block chain smart contract. According to RBAC rule setting, the role access control system based on the block chain smart contract is logically divided into a data layer, an access control layer and a presentation layer, and the role access control system based on the block chain smart contract is divided into a user module, a role module and an authority module according to function modules. The invention further provides a role access control method. Contract deployment, administrator initialization and role and authority configuration need to be completed before the access control system is used; and then, the user can perform login, a manager can do works such as audit and role distribution. The role access control method comprises the following steps: 1, deploying an intelligent contract of a role access control system based on a block chain intelligent contract in a block chain system; 2, configuring permission and roles; 3, the user registering an account; 4, auditing user registration; 5, the administrator allocating roles to the users; and 6, the user logging in and accesses the system by using the secret key.
Owner:BEIJING WUZI UNIVERSITY
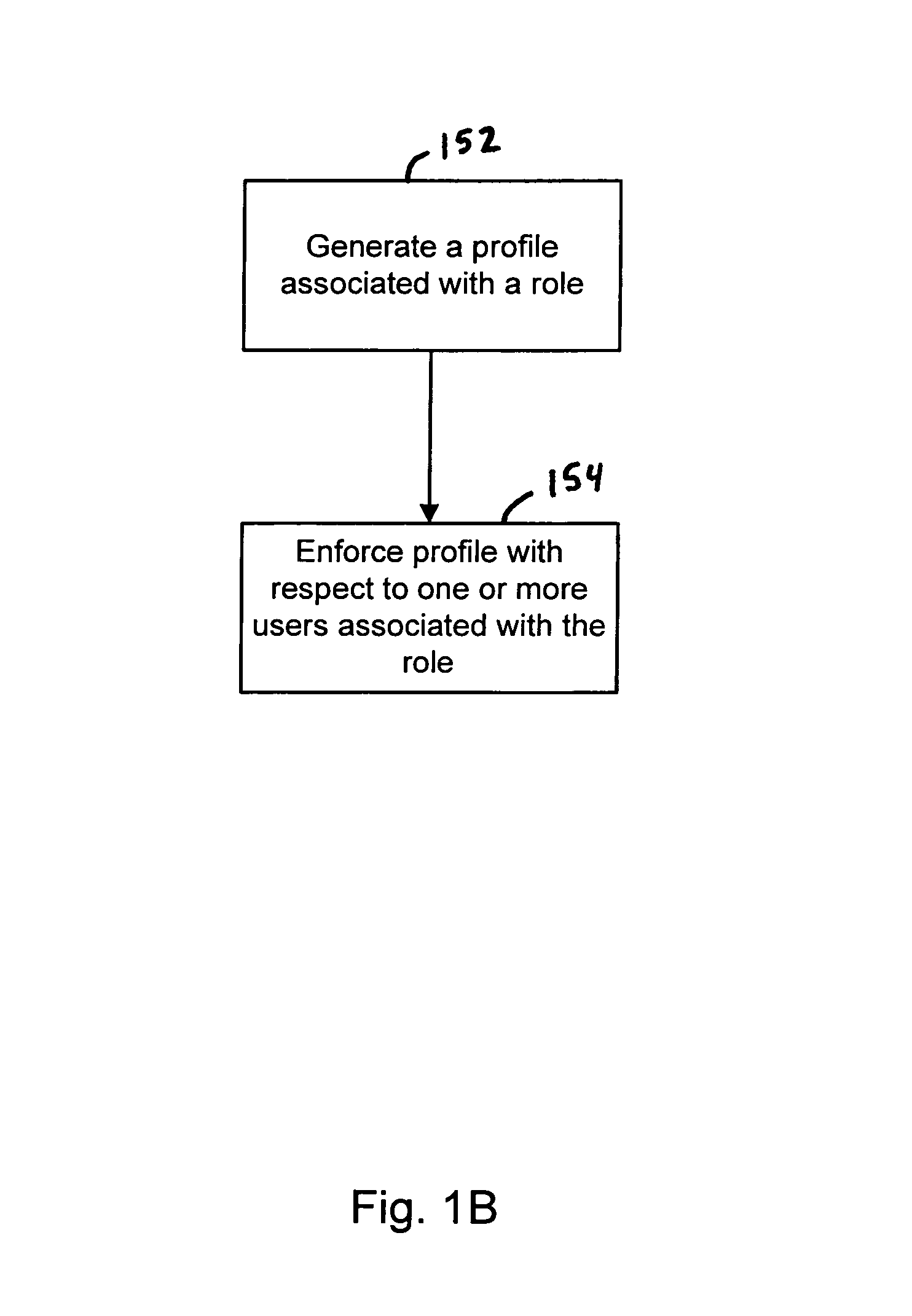
Role based access controls
ActiveUS8214398B1Digital data processing detailsComputer security arrangementsRole-based access controlComputerized system
Role-based access controls improve user access in a computer system. A profile associated with a role is generated. The profile is enforced with respect to one or more users associated with the role. Optionally, the profile is generated based at least in part on a user interaction.
Owner:EMC IP HLDG CO LLC
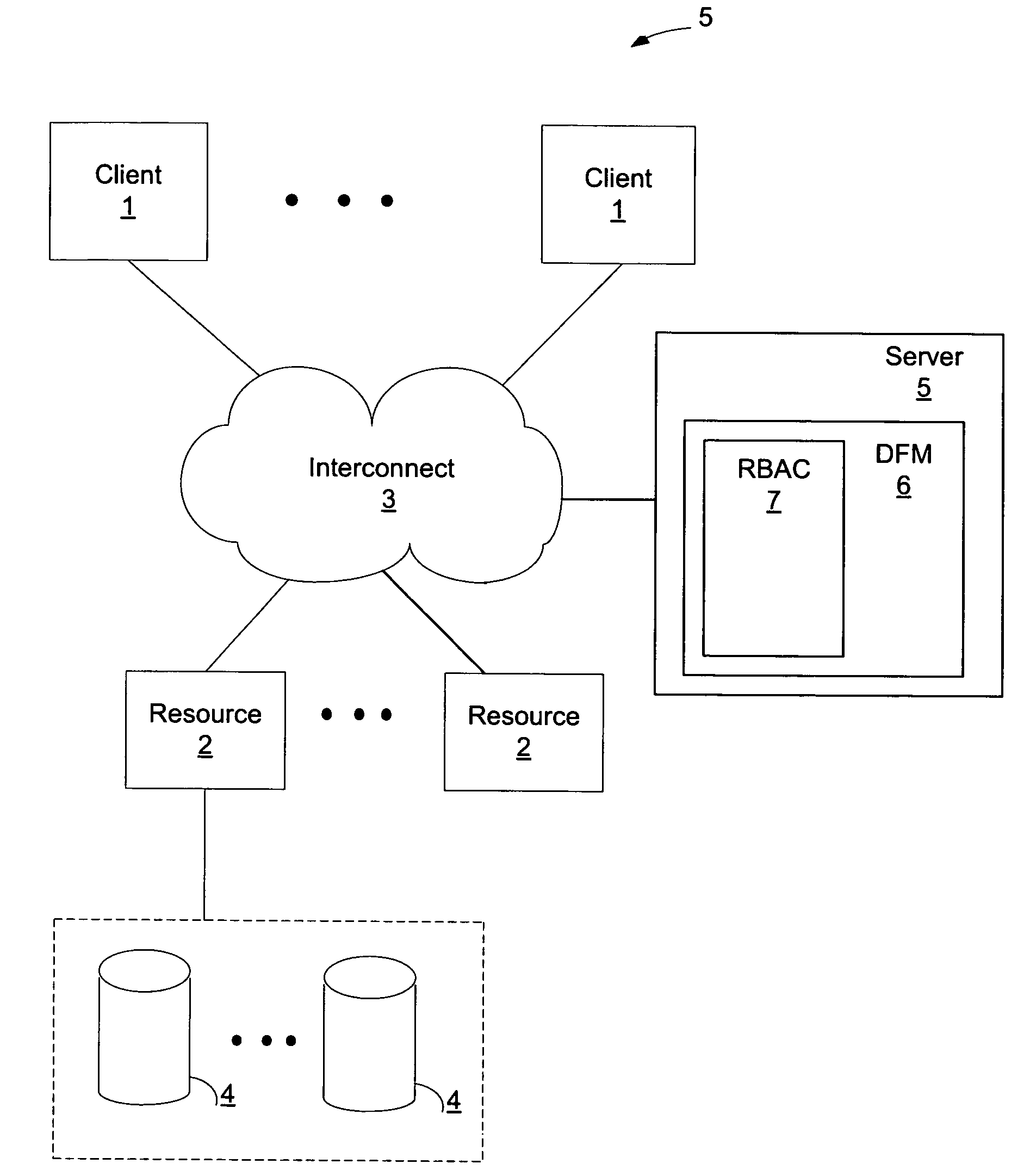
Methods and apparatus for scoped role-based access control
InactiveUS20080005115A1Computer security arrangementsTransmissionRole-based access controlControl system
Methods and apparatus for providing role-based access control of a resource by a subject in an access control system are provided. The system comprises one or more roles capable of association with one or more subjects, and a plurality of permission sets. One or more of the plurality of permission sets are associated with each of the one or more roles. The system further comprises a plurality of resources. One or more of the plurality of resources are associated with each of the one or more permission sets, and each of the plurality of resources is associated with a set of one or more subjects. A given subject in a set of one or more subjects for a given resource and having a role-permission association with the given resource is provided access control of the given resource.
Owner:IBM CORP
Business events process synergic modeling method based on role authority control
InactiveCN101226615AAvoid Concurrent Access ViolationsIntegrity guaranteedMultiprogramming arrangementsResourcesProcess integrationRole-based access control
Provided is an enterprise business synergic modeling approach based on roles access control in the technical field of enterprise engineering and information, which is mainly in view of the characteristics of multi-phase, multi-step and multi-level of process of modern enterprise business and by means of thoughts of system access control based on roles and harmonizing theory and bringing in novel synergic access mechanism, the invention coordinates the modeling personnel of multi-department, different level and different profession to conduct parallel and exotically model building for the process of the enterprise business. The core is based on the roles of modeling personnel in business process access control mechanism RBPMPC and concurrent access control of the model is conducted in the process of synergic modeling by two different sub-procedure operation locks and four locking rules. The invention consults the decomposable process of the process of the enterprise business and decomposes the modeling task by employing top-down manner and manner of refining down step by step, which mainly includes three basic steps of primary decomposition, refining modeling and sub-procedure integration and the like.
Owner:BEIHANG UNIV
System and method for selective authentication when acquiring a role
InactiveUS7890998B2Digital data processing detailsUnauthorized memory use protectionRole-based access controlPassword
A system, method, and program product is provided that provides authentication on a per-role basis in a Role-Based Access Control (RBAC) environment. When a user attempts to acquire a role, the improved RBAC system determines whether (a) no authentication is required (e.g., for a non-sensitive role such as accessing a company's product catalog), (b) a user-based authentication (e.g., password) is required, or (c) a role-based authentication (e.g., role-specific password is required).
Owner:INT BUSINESS MASCH CORP
Role-based access control
A user interface and a processor coupled to the user interface wherein the processor receives access requests through the user interface and authorizes access through the user interface. The processor associates a rights request with a role based policy to determine access rights, modifies the determined access rights in accordance with an exception list related to particular users and records, and authorizes access to a record based upon the modified determined access rights.
Owner:KONINKLIJKE PHILIPS ELECTRONICS NV
Safety exchange method for MMS specification application layer
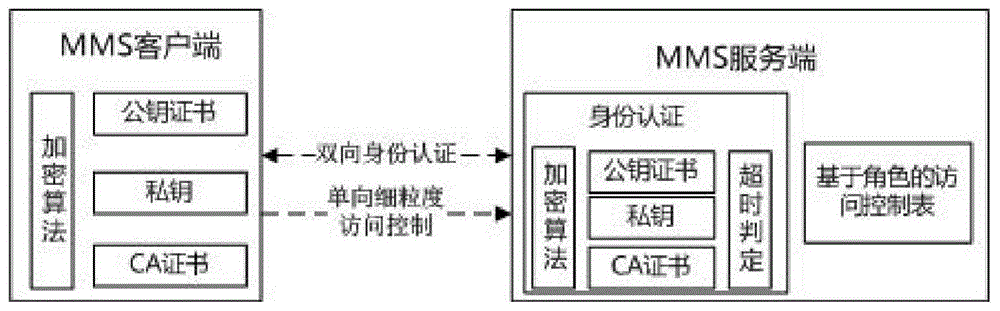
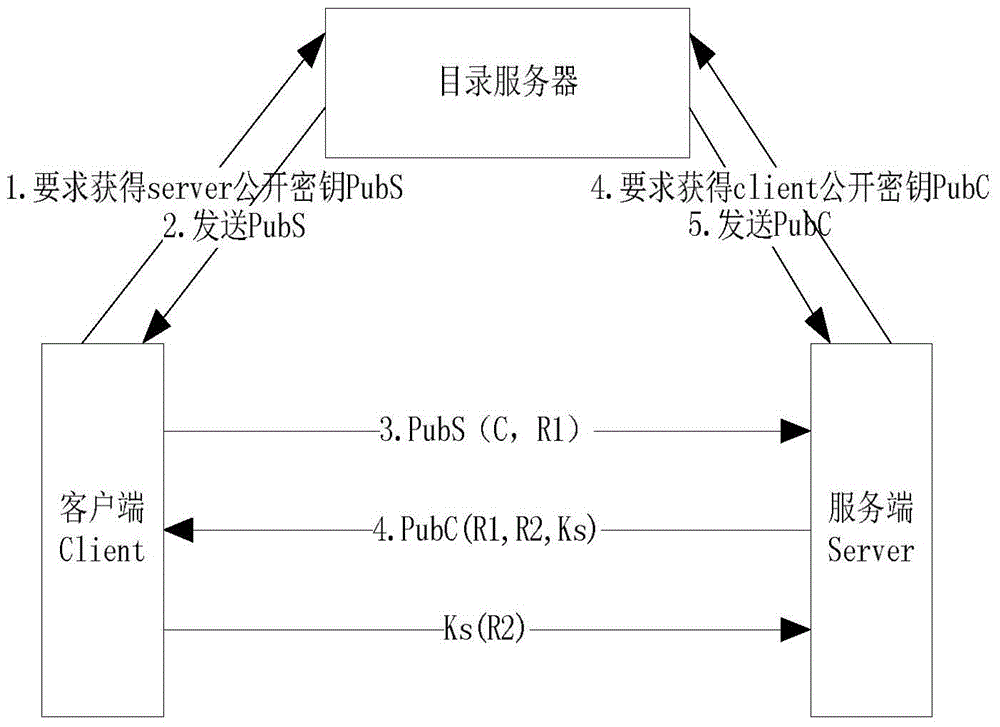
InactiveCN104702599AEnsure safetyEnhanced authenticationUser identity/authority verificationSmart substationProtocol Application
The invention discloses a safety exchange method for an MMS specification application layer. When an intelligent substation device uses MMS message communication, the MMS application layer safety reinforcing exchange method enables both MMS protocol communication sides to perform identity authentication at the application through carrying out safety improvement on the MMS application layer and controls the access authority of an MMS client through using role-based access based on the authentication. The safety exchange method for the MMS specification application layer includes steps that 1) starting an MMS association authorization function, and extending authorization data structure; 2) through extending the authorization data structure, using a public encryption algorithm to carry out identity authorization on the association process of the MMS application layer, and at the same time, performing relay attack protection; 3) using a role-based access control technology to construct the access control relationship between the MMS client and MMS service, after passing the association authentication, allowing an MMS server to use a configured access control relation table to carry out fine-grained access control on the MMS client, if the MMS client meets the demand, allowing the MMS client to access the corresponding service, otherwise, refusing to provide service.
Owner:CHINA SOUTHERN POWER GRID COMPANY
Methods and Apparatus for Scoped Role-Based Access Control
InactiveUS20080243856A1Digital data processing detailsAnalogue secracy/subscription systemsRole-based access controlControl system
Methods and apparatus for providing role-based access control of a resource by a subject in an access control system are provided. The system comprises one or more roles capable of association with one or more subjects, and a plurality of permission sets. One or more of the plurality of permission sets are associated with each of the one or more roles. The system further comprises a plurality of resources. One or more of the plurality of resources are associated with each of the one or more permission sets, and each of the plurality of resources is associated with a set of one or more subjects. A given subject in a set of one or more subjects for a given resource and having a role-permission association with the given resource is provided access control of the given resource.
Owner:IBM CORP
Network-Oriented Matrix Sharing For Genealogy And Social Networks Through Network-Role-Based Access Controls
InactiveUS20120233666A1Simple and safe processDigital data processing detailsComputer security arrangementsRole-based access controlSocial web
A computer-implemented method for displaying social media content items using a network based browser. The method includes displaying a plurality of networks from a social media content database, the database including social media content items organized into networks, receiving a selection of a network from the plurality of networks from a user, comparing access control information for the selected network including determining role types authorized to view social media content items in the network to a role type associated with the user for that network, identifying a plurality of social media content items that can be displayed on the comparison, and displaying the identified social media content items.
Owner:GU SHENG HE
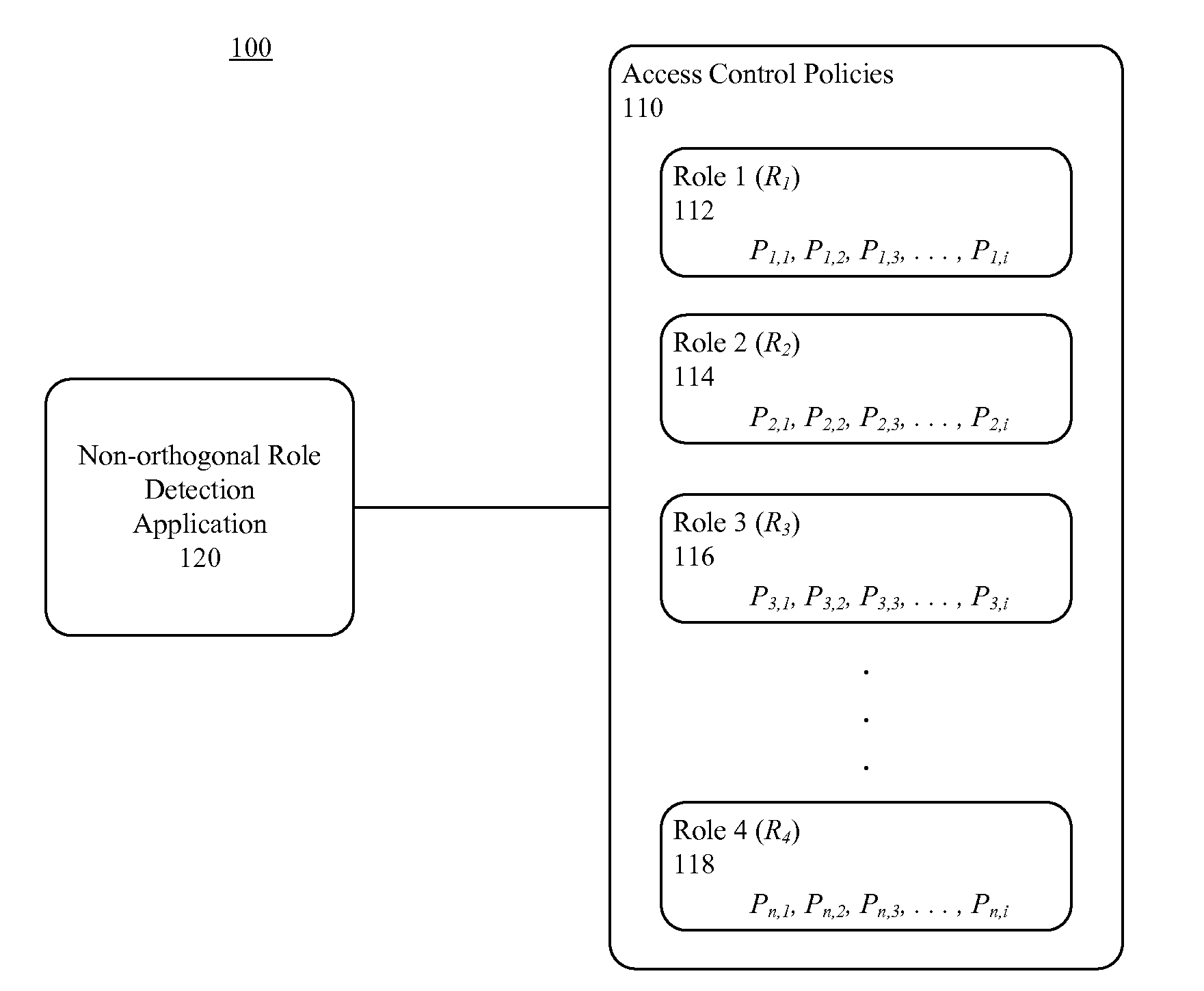
Identifying non-orthogonal roles in a role based access control system
InactiveUS20080295145A1Computer security arrangementsTransmissionControl systemRole-based access control
A method for identifying non-orthogonal roles (112, 114, 116, 118) in an access control system (100). The method can include, for at least one policy (Pn,i) defined for a first role (112) in the access control system, automatically determining whether there is at least one policy (Pm,j) defined in a second role that conflicts with the policy defined in the first role. The method also can include, responsive to determining that the policy defined in the second role conflicts with the policy defined in the first role, providing a conflict indicator.
Owner:MOTOROLA INC
Freight services marketplace system and methods
InactiveUS20160071055A1Quick and efficientEasy to handleFinancePayment architectureVisibilityPayment
A computer system and associated methods for implementing an online freight services marketplace. Freight service offerings posted to the marketplace by carriers are matched to freight service requests from shippers. Compound service offerings are formed from freight service offerings having service parameters (lane, space, transit time, availability, price, and status) that accommodate load parameters (origin, destination, size, and weight) of the freight service request. Compound service offerings selected by the shipper are provisioned and reserved for subsequent dispatch. Role-based access controls within the marketplace restrict visibility of confidential information, such as carrier pricing and shipper identity. Automatic freight transaction facilitation includes shipper payment processing and shipping document generation. Status tracking capability may be augmented with alert messaging and / or in-transit re- planning to minimize the impact of common issues that threaten to defeat a shipment in progress.
Owner:FREIGHTERA LOGISTICS INC
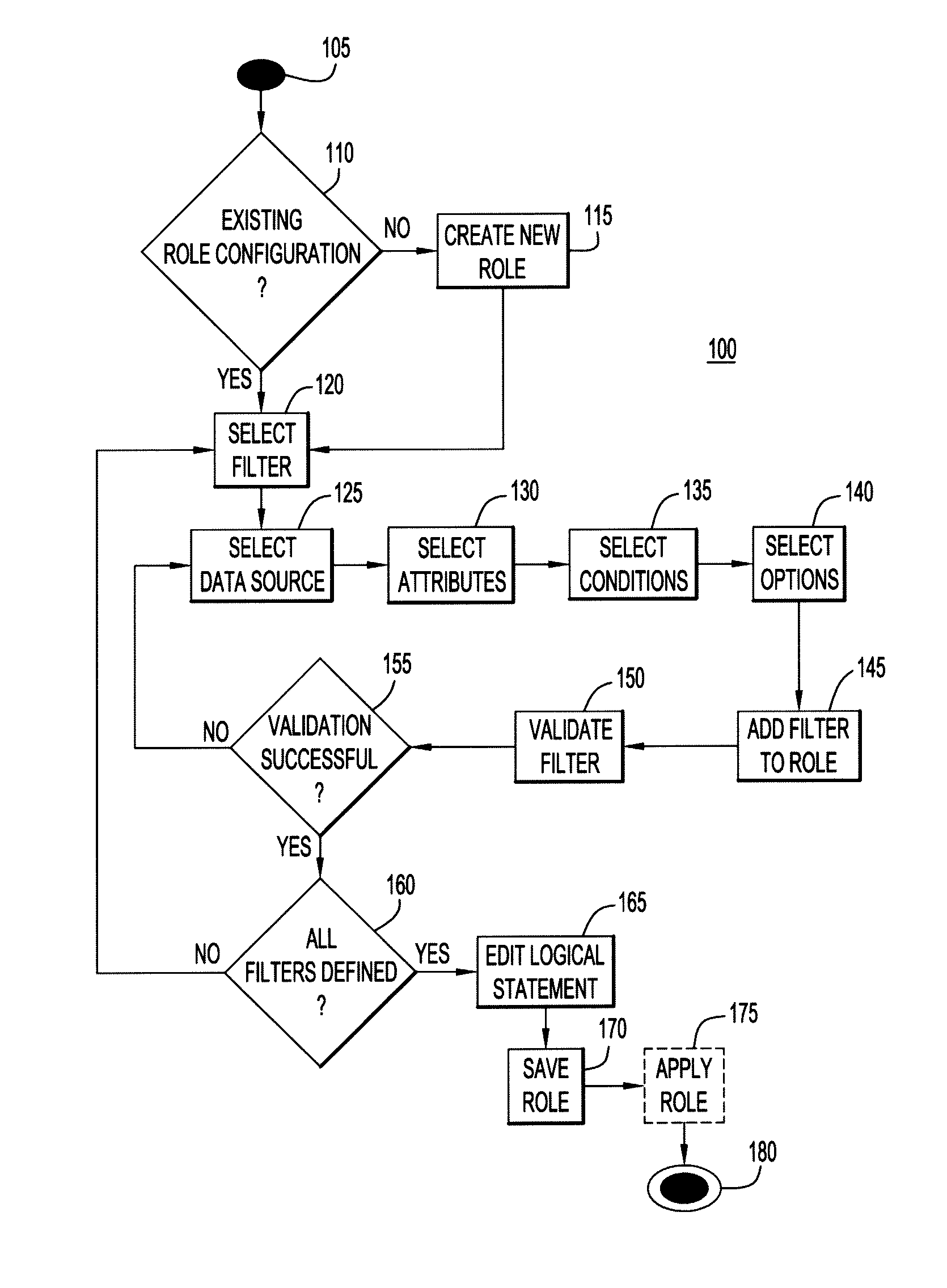
Dynamic management of role membership
ActiveUS8832774B2Digital data processing detailsUnauthorized memory use protectionWeb serviceControl system
A method and system for dynamically managing entity membership in a role, using role configurations that comprise one or more dynamic role filters, which are linked to data sources such as databases or web services. The role filters are dynamic because, each time a role membership is queried, the role configuration and its component role filters must be evaluated with respect to the current information in the linked data sources. The roles may be used in role-based access control systems or entity identification systems.
Owner:PERATON INC
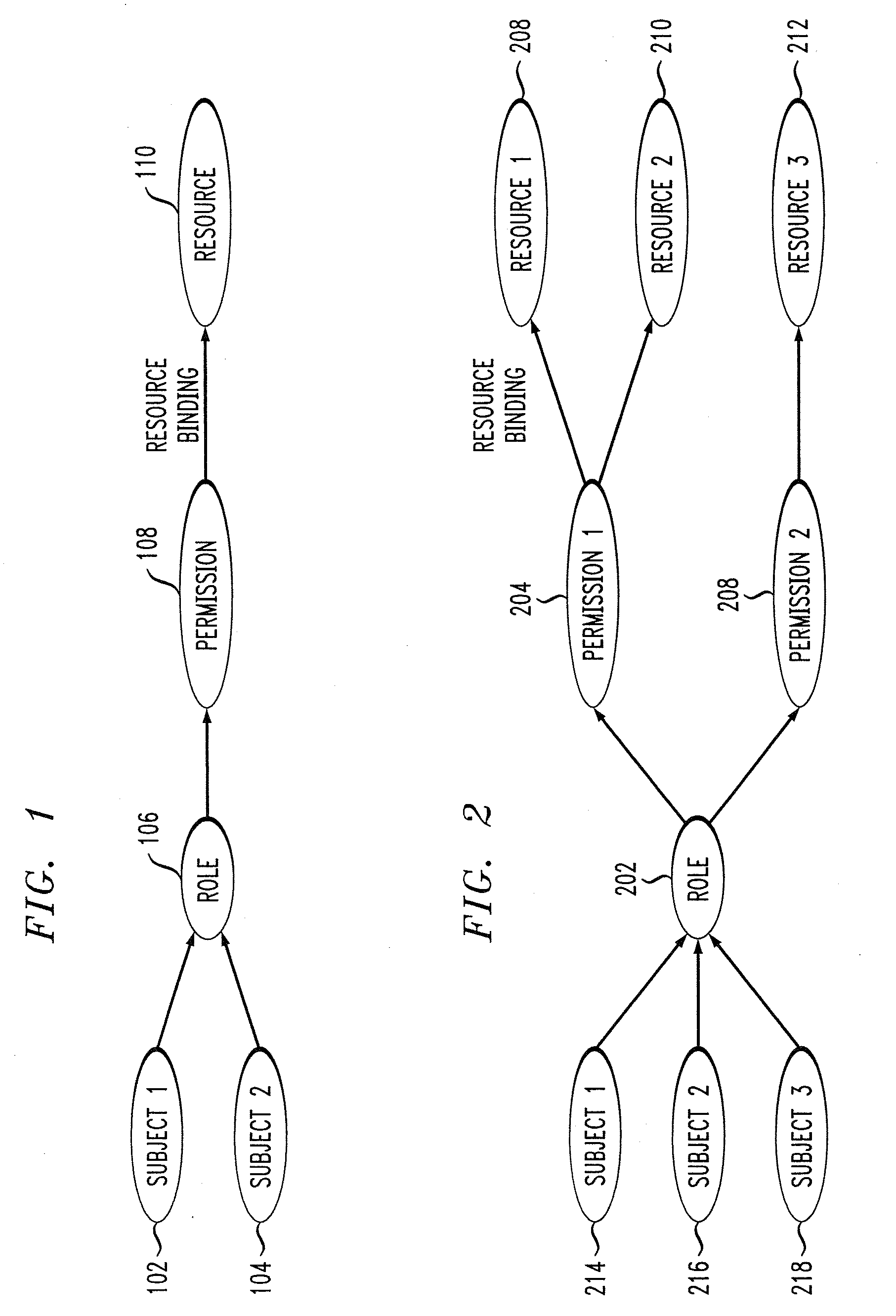
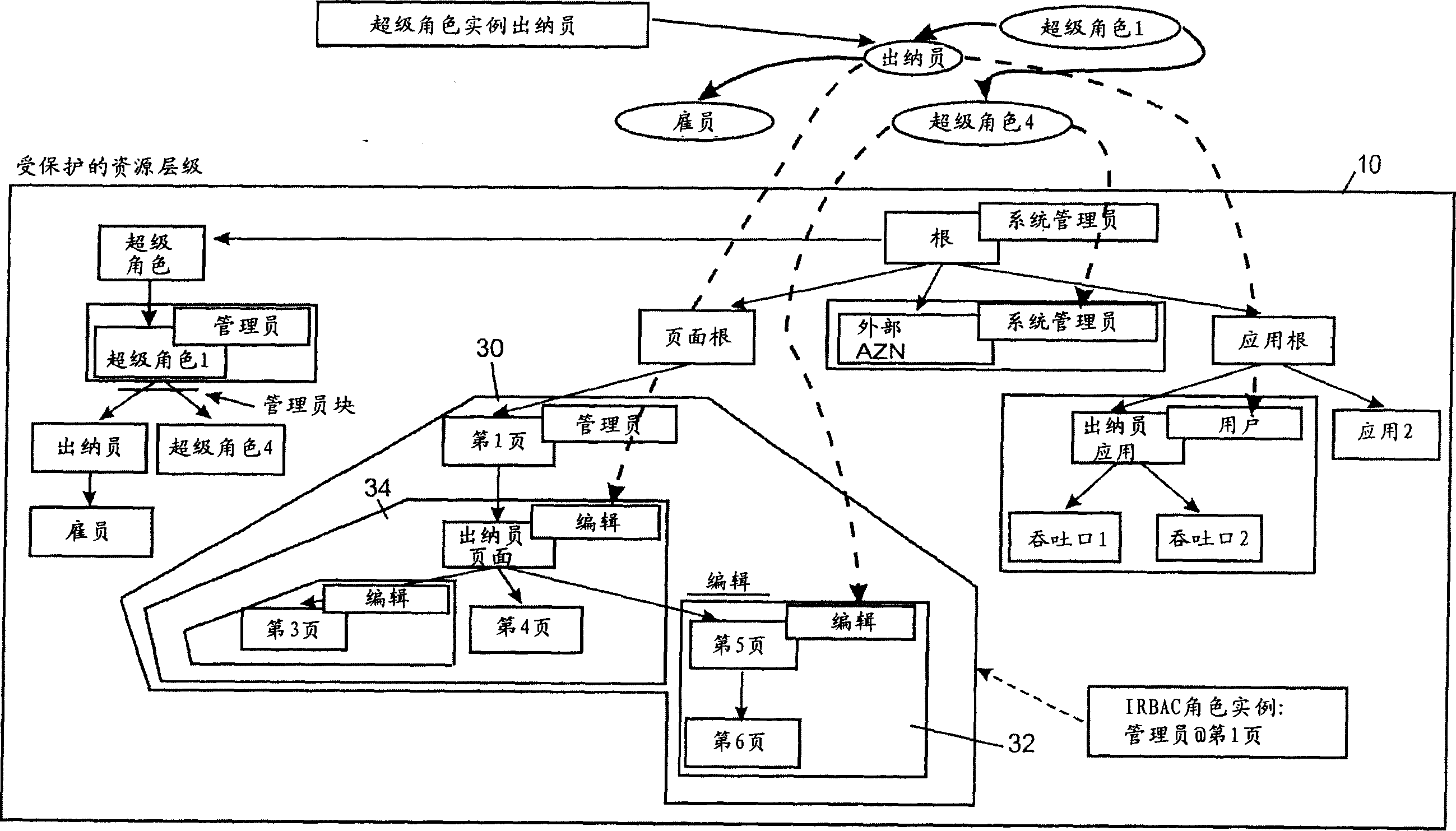
Role-based access control system, method and computer program product
ActiveCN1763761AReduce complexityLess quantityDigital data processing detailsComputer security arrangementsControl systemMedia access control
The invention relates to a role-based access control system, including: a role definition system, used to define roles as permission sets on individual resources, and thus form role instances respectively; and a super role definition system, used to define a set of roles by Role instance grouping defines at least one super role into a super role, where one super role contains all permissions contained in the grouped resource instances. Furthermore, the invention relates to a suitable method, computer program and computer program product.
Owner:INT BUSINESS MASCH CORP
Key tree construction and key distribution method for hierarchical role-based access control
InactiveUS8447037B2Efficient executionReduce consumptionKey distribution for secure communicationMultiple keys/algorithms usageRole-based access controlKey distribution
A key tree construction and key distribution method for hierarchical role-based access control, includes: constructing a key tree including relationships between a hierarchical structure of role groups and data; performing encryption and decryption of data keys and role keys; and generating a key table, in which the data keys required to decrypt encrypted data and the role keys required to decrypt encrypted data keys are stored, with reference to the key tree. Further, the key tree construction and key distribution method for hierarchical role-based access control includes performing management such that a specific role group can obtain a data key by performing decryption based on its own role key by using both the key tree and the key table.
Owner:ELECTRONICS & TELECOMM RES INST
Intrusion detection system and method based on role access control
ActiveCN109150853AGuaranteed confidentialityVersatileTransmissionRole managementRole-based access control
The present invention provides an intrusion detection system and method based on role access control. The system comprises a network environment detection module which is used for performing intrusionsecurity detection on the access of a user and / or filtering and purifying the application information of the user, a role management module which is used for judging whether the operation of the userexceeds an authority assigned by a role assigned to the user, a system resource allocation module which is used for allocating system resources to the user according to the role of the user, and a monitoring module which is used for judging whether the working in the system is normal or not according to abnormal activities in the network environment detection module, the role management module and / or the system resource allocation module. According to the intrusion detection system based on role access control, the function of an intrusion detection system is further improved, the probabilityof occurrence of errors is reduced, and the security of the system is ensured.
Owner:喻伟
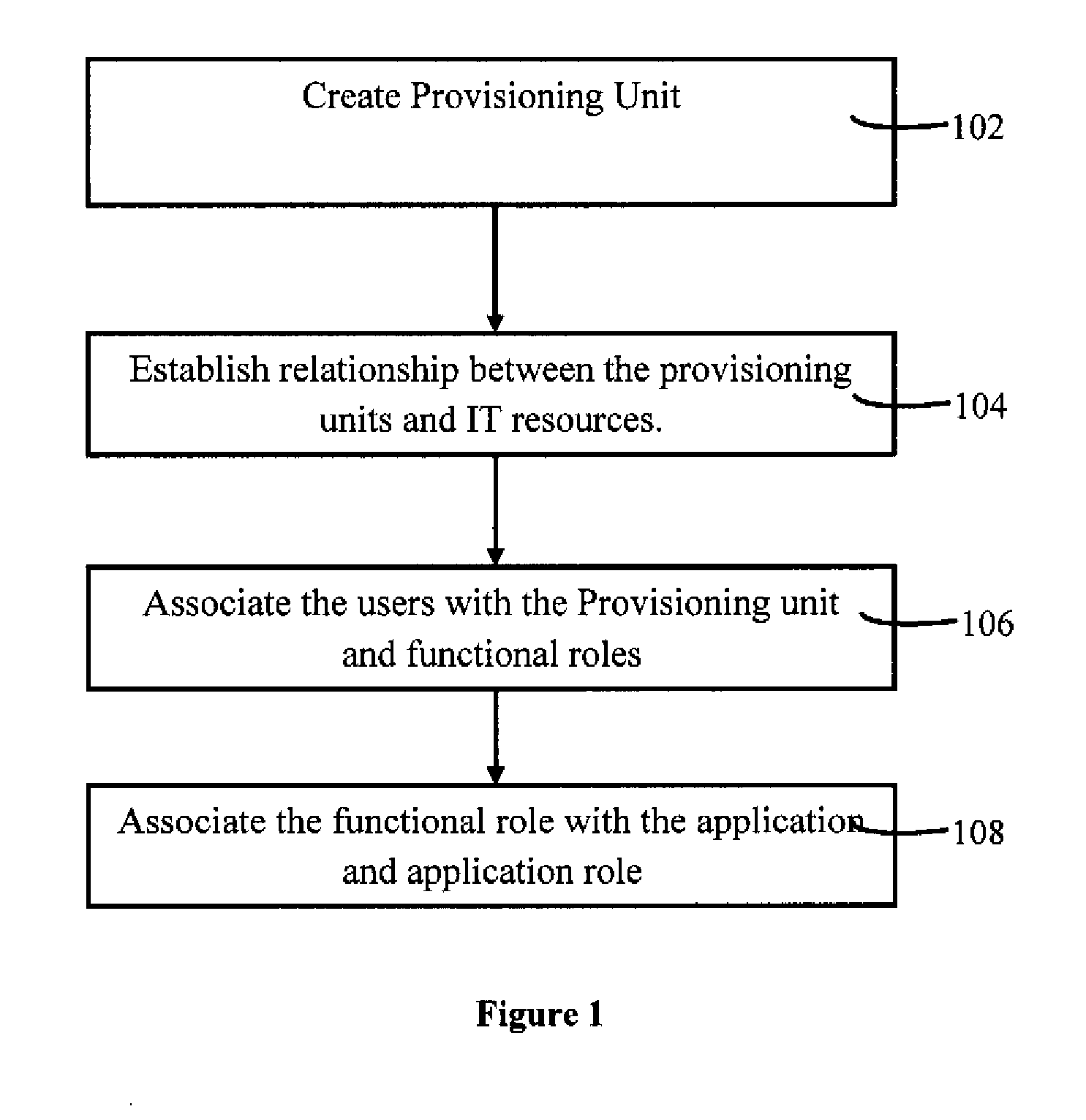
System and Method for Managing Role Based Access Controls of Users
ActiveUS20140090026A1Digital data processing detailsComputer security arrangementsRole-based access controlMultiple applications
A method and system for role based access control for a plurality of users in a heterogeneous enterprise environment, comprising: establishing a functional relationship between a plurality of provisioning unit using a provision unit module. The users are mapped with the provisioning unit based on attributes of the users. Events are captured via the provision unit module. The users needed to be re-mapped are determined upon the event completion. Application role defined in context of an application embedded in an application registry module is mapped with the provisioning unit. Call back service is executed for the re-mapped users having entitlement associated with each of the application stored in a roles registry module. An application role is determined and defined for a new user for the plurality of the application enabling managing of the role based access control.
Owner:TATA CONSULTANCY SERVICES LTD
Revision control server with self-hosting multi-level access controls and user notifications
InactiveUS8990249B1Digital data processing detailsSpecial data processing applicationsSelf-hostingRole-based access control
Described is a system for managing a multi-user revision control repository which provides multi-level access control. The present invention describes creating configuration files which describe a set of management states of management areas of a repository. The configuration files describe access control to a set of management areas, and the set of management states is stored in the repository to create a self-hosting management implementation. A new commit is processed to the repository by contacting a revision control repository server with a client software, communicating a user's new revision to the revision control repository server, verifying the user's authentication and authorization prior to collecting a new revision with the revision control repository server, and executing a custom script configured to run on the revision control repository server.
Owner:HRL LAB
Multi-strategy access control login method and device, computer equipment and storage medium
ActiveCN111800440AImprove securityMulti-Strategy Access ImplementationUser identity/authority verificationRole-based access controlDatabase
The invention discloses a multi-strategy access control login method and a device thereof, computer equipment and a storage medium, which relate to the techniques of cloud security, wherein the resource access control in a server is to select at least two from role-based access control strategies, user group-based access control strategies, rule-based access control strategies, user attribute-based access control strategies and user-based access control strategies; and the token data of the user is analyzed to obtain corresponding authority information when the user logs in later, and if the authority information corresponds to the access authority, the corresponding authority data of the to-be-accessed resource is sent to the user side. The invention also relates to a blockchain technology, which realizes multi-control strategy access, adapts to more access control scenes, and improves resource data security.
Owner:PINGAN INT SMART CITY TECH CO LTD
Operation and maintenance service subsystem
The invention discloses an operation and maintenance service subsystem technology. According to the operation and maintenance service subsystem key technology, based on user management and authorization management, role-based access control (RBAC) which is popular currently is adopted for design, each permission is bound with the role independently, and a permission combination for the user is realized through one-to-multiple or multiple-to-multiple mapping between users and roles. Besides, according to a hierarchical relationship of the roles, inclusion weighting on a lower-level role by an upper-level role is achieved, the permission management has flexibility and scalability, multiple API interfaces and data interfaces which are developed secondarily are developed through operation service, an application developer in a fourth party can develop multiple plug-in expansion platform functions according to the interfaces, the data interfaces can allow an authorized user to communicate with an external system with the user personal information and process recording information in the platform, such as sharing user activities, community logs and friend information with a social website.
Owner:BEIJING OPEN DISTANCE EDUCATION CENT
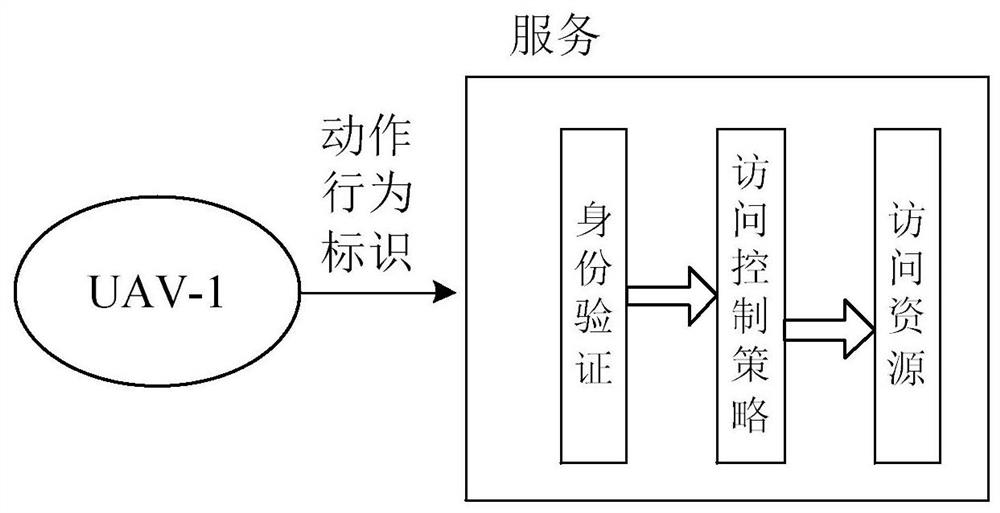
UAV cluster access control method and device based on block chain, equipment and medium
PendingCN113609509AAvoid churnSolve the problem of incomplete acquisitionDigital data protectionDigital data authenticationRole-based access controlControl engineering
The invention relates to a UAV cluster access control method and device based on a block chain, equipment and a medium. The method comprises the steps of: registering a current UAV into a UAV cluster network of a UAV-VCM control framework constructed based on a block chain; obtaining and verifying the longest block chain in the UAV cluster network; utilizing a priority role distribution contract set in an intelligent contract of the UAV-VCM control framework, and reading and reserving state information of a bifurcated block corresponding to a maximum block while the maximum block is accessed; and updating the block chain, and issuing the latest state information of all UAVs in the UAV cluster network. The block chain technology is applied to the UAV cluster, a role-based access control mechanism model is improved, and a priority role allocation contract is set, so that the problem of incomplete acquisition of combat information caused by block bifurcation when the block chain technology is applied to the UAV cluster is solved, and information loss caused by block bifurcation is avoided.
Owner:NAT UNIV OF DEFENSE TECH
Improved sub-tree access control in network architectures
InactiveCN101755427AComputer security arrangementsTransmissionControl systemRole-based access control
Access control system in a diretory accessed by a diretory access protocol. The system has a security protocol adaptation module (1215) configured to review a data request from a requesting entity (1203) received in a directory operations server (1213) and to locate a security rule pertaining to the requesting entity. Also, the security protocol adaption module modifies the data request so that the data request appears to originate from one of a first security user (1207) having a read permission or from a second security user (1209) having a read and write permission.
Owner:APERTIO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com